-
 @ a95c6243:d345522c
2025-02-19 09:23:17
@ a95c6243:d345522c
2025-02-19 09:23:17Die «moralische Weltordnung» – eine Art Astrologie. Friedrich Nietzsche
Das Treffen der BRICS-Staaten beim Gipfel im russischen Kasan war sicher nicht irgendein politisches Event. Gastgeber Wladimir Putin habe «Hof gehalten», sagen die Einen, China und Russland hätten ihre Vorstellung einer multipolaren Weltordnung zelebriert, schreiben Andere.
In jedem Fall zeigt die Anwesenheit von über 30 Delegationen aus der ganzen Welt, dass von einer geostrategischen Isolation Russlands wohl keine Rede sein kann. Darüber hinaus haben sowohl die Anreise von UN-Generalsekretär António Guterres als auch die Meldungen und Dementis bezüglich der Beitrittsbemühungen des NATO-Staats Türkei für etwas Aufsehen gesorgt.
Im Spannungsfeld geopolitischer und wirtschaftlicher Umbrüche zeigt die neue Allianz zunehmendes Selbstbewusstsein. In Sachen gemeinsamer Finanzpolitik schmiedet man interessante Pläne. Größere Unabhängigkeit von der US-dominierten Finanzordnung ist dabei ein wichtiges Ziel.
Beim BRICS-Wirtschaftsforum in Moskau, wenige Tage vor dem Gipfel, zählte ein nachhaltiges System für Finanzabrechnungen und Zahlungsdienste zu den vorrangigen Themen. Während dieses Treffens ging der russische Staatsfonds eine Partnerschaft mit dem Rechenzentrumsbetreiber BitRiver ein, um Bitcoin-Mining-Anlagen für die BRICS-Länder zu errichten.
Die Initiative könnte ein Schritt sein, Bitcoin und andere Kryptowährungen als Alternativen zu traditionellen Finanzsystemen zu etablieren. Das Projekt könnte dazu führen, dass die BRICS-Staaten den globalen Handel in Bitcoin abwickeln. Vor dem Hintergrund der Diskussionen über eine «BRICS-Währung» wäre dies eine Alternative zu dem ursprünglich angedachten Korb lokaler Währungen und zu goldgedeckten Währungen sowie eine mögliche Ergänzung zum Zahlungssystem BRICS Pay.
Dient der Bitcoin also der Entdollarisierung? Oder droht er inzwischen, zum Gegenstand geopolitischer Machtspielchen zu werden? Angesichts der globalen Vernetzungen ist es oft schwer zu durchschauen, «was eine Show ist und was im Hintergrund von anderen Strippenziehern insgeheim gesteuert wird». Sicher können Strukturen wie Bitcoin auch so genutzt werden, dass sie den Herrschenden dienlich sind. Aber die Grundeigenschaft des dezentralisierten, unzensierbaren Peer-to-Peer Zahlungsnetzwerks ist ihm schließlich nicht zu nehmen.
Wenn es nach der EZB oder dem IWF geht, dann scheint statt Instrumentalisierung momentan eher der Kampf gegen Kryptowährungen angesagt. Jürgen Schaaf, Senior Manager bei der Europäischen Zentralbank, hat jedenfalls dazu aufgerufen, Bitcoin «zu eliminieren». Der Internationale Währungsfonds forderte El Salvador, das Bitcoin 2021 als gesetzliches Zahlungsmittel eingeführt hat, kürzlich zu begrenzenden Maßnahmen gegen das Kryptogeld auf.
Dass die BRICS-Staaten ein freiheitliches Ansinnen im Kopf haben, wenn sie Kryptowährungen ins Spiel bringen, darf indes auch bezweifelt werden. Im Abschlussdokument bekennen sich die Gipfel-Teilnehmer ausdrücklich zur UN, ihren Programmen und ihrer «Agenda 2030». Ernst Wolff nennt das «eine Bankrotterklärung korrupter Politiker, die sich dem digital-finanziellen Komplex zu 100 Prozent unterwerfen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-02-15 19:05:38
@ a95c6243:d345522c
2025-02-15 19:05:38Auf der diesjährigen Münchner Sicherheitskonferenz geht es vor allem um die Ukraine. Protagonisten sind dabei zunächst die US-Amerikaner. Präsident Trump schockierte die Europäer kurz vorher durch ein Telefonat mit seinem Amtskollegen Wladimir Putin, während Vizepräsident Vance mit seiner Rede über Demokratie und Meinungsfreiheit für versteinerte Mienen und Empörung sorgte.
Die Bemühungen der Europäer um einen Frieden in der Ukraine halten sich, gelinde gesagt, in Grenzen. Größeres Augenmerk wird auf militärische Unterstützung, die Pflege von Feindbildern sowie Eskalation gelegt. Der deutsche Bundeskanzler Scholz reagierte auf die angekündigten Verhandlungen über einen möglichen Frieden für die Ukraine mit der Forderung nach noch höheren «Verteidigungsausgaben». Auch die amtierende Außenministerin Baerbock hatte vor der Münchner Konferenz klargestellt:
«Frieden wird es nur durch Stärke geben. (...) Bei Corona haben wir gesehen, zu was Europa fähig ist. Es braucht erneut Investitionen, die der historischen Wegmarke, vor der wir stehen, angemessen sind.»
Die Rüstungsindustrie freut sich in jedem Fall über weltweit steigende Militärausgaben. Die Kriege in der Ukraine und in Gaza tragen zu Rekordeinnahmen bei. Jetzt «winkt die Aussicht auf eine jahrelange große Nachrüstung in Europa», auch wenn der Ukraine-Krieg enden sollte, so hört man aus Finanzkreisen. In der Konsequenz kennt «die Aktie des deutschen Vorzeige-Rüstungskonzerns Rheinmetall in ihrem Anstieg offenbar gar keine Grenzen mehr». «Solche Friedensversprechen» wie das jetzige hätten in der Vergangenheit zu starken Kursverlusten geführt.
Für manche Leute sind Kriegswaffen und sonstige Rüstungsgüter Waren wie alle anderen, jedenfalls aus der Perspektive von Investoren oder Managern. Auch in diesem Bereich gibt es Startups und man spricht von Dingen wie innovativen Herangehensweisen, hocheffizienten Produktionsanlagen, skalierbaren Produktionstechniken und geringeren Stückkosten.
Wir lesen aktuell von Massenproduktion und gesteigerten Fertigungskapazitäten für Kriegsgerät. Der Motor solcher Dynamik und solchen Wachstums ist die Aufrüstung, die inzwischen permanent gefordert wird. Parallel wird die Bevölkerung verbal eingestimmt und auf Kriegstüchtigkeit getrimmt.
Das Rüstungs- und KI-Startup Helsing verkündete kürzlich eine «dezentrale Massenproduktion für den Ukrainekrieg». Mit dieser Expansion positioniere sich das Münchner Unternehmen als einer der weltweit führenden Hersteller von Kampfdrohnen. Der nächste «Meilenstein» steht auch bereits an: Man will eine Satellitenflotte im Weltraum aufbauen, zur Überwachung von Gefechtsfeldern und Truppenbewegungen.
Ebenfalls aus München stammt das als DefenseTech-Startup bezeichnete Unternehmen ARX Robotics. Kürzlich habe man in der Region die größte europäische Produktionsstätte für autonome Verteidigungssysteme eröffnet. Damit fahre man die Produktion von Militär-Robotern hoch. Diese Expansion diene auch der Lieferung der «größten Flotte unbemannter Bodensysteme westlicher Bauart» in die Ukraine.
Rüstung boomt und scheint ein Zukunftsmarkt zu sein. Die Hersteller und Vermarkter betonen, mit ihren Aktivitäten und Produkten solle die europäische Verteidigungsfähigkeit erhöht werden. Ihre Strategien sollten sogar «zum Schutz demokratischer Strukturen beitragen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ d360efec:14907b5f
2025-02-21 10:48:17
@ d360efec:14907b5f
2025-02-21 10:48:17Overall Assessment:
Bitcoin (BTCUSDT) on OKX remains highly volatile and the overall trend is uncertain. While the long-term trend (Daily chart) is technically still an uptrend, it has weakened significantly. The 4-hour and 15-minute charts are in confirmed downtrends. This analysis focuses on identifying key levels where Smart Money might be active and assessing trend strength.
Detailed Analysis by Timeframe:
(1) TF Day (Daily): https://www.tradingview.com/x/o9YgoBlr/
- Trend: Uptrend (Significantly Weakening, at high risk of reversing).
- SMC (Smart Money Concepts):
- Higher Highs (HH) and Higher Lows (HL) structure is becoming less defined and broken. The recent price action has broken previous lows.
- Prior Breaks of Structure (BOS) to the upside, but now a significant and deep pullback is underway.
- Liquidity:
- Sellside Liquidity (SSL): Significant SSL rests below previous lows in the 85,000 - 90,000 range. This is a likely target for Smart Money.
- Buyside Liquidity (BSL): BSL is present above the all-time high.
- ICT (Inner Circle Trader Concepts):
- Order Block: The price has broken below the prior bullish Order Block (the large green candle before a significant up-move). This is a major bearish signal.
- EMA (Exponential Moving Average):
- Price has broken below the 50-period EMA (yellow), a bearish signal.
- The 200-period EMA (white) is the next major support level.
- Money Flow (LuxAlgo):
- A long red bar indicates strong selling pressure.
- Trend Strength (AlgoAlpha):
- Red Cloud indicating Downtrend, No Buy/Sell Signal.
- Volume Profile: Relatively low volume on the recent decline.
- Candlesticks: The most recent candlestick is red, confirming selling pressure.
- Support: EMA 200, 85,000-90,000 (SSL area).
- Resistance: EMA 50, Previous All-Time High.
- Summary: The Daily chart's uptrend is significantly weakening. The break below the 50 EMA and the bullish Order Block, combined with the negative Money Flow and bearish Trend Strength, are all major warning signs. The SSL below is a key area to watch.
(2) TF4H (4-Hour): https://www.tradingview.com/x/0sGC0Gny/
- Trend: Downtrend.
- SMC:
- Lower Highs (LH) and Lower Lows (LL).
- BOS to the downside.
- Liquidity:
- SSL: Below previous lows.
- BSL: Above previous highs.
- ICT:
- Order Block: The price was rejected by a bearish order Block
- EMA:
- Price is below both the 50-period and 200-period EMAs (bearish).
- Money Flow (LuxAlgo):
- Predominantly red, confirming selling pressure.
- Trend Strength (AlgoAlpha):
- Green Cloud But No Buy/Sell Signal. Indicates Sideway
- Volume Profile: * Relatively high volume.
- Support: Recent lows.
- Resistance: EMA 50, EMA 200, Order Block.
- Summary: The 4-hour chart is in a confirmed downtrend. The Money Flow is bearish, price below both EMAs.
(3) TF15 (15-Minute): https://www.tradingview.com/x/c7kIbqU0/
- Trend: Downtrend (but showing some signs of consolidation/sideways movement).
- SMC:
- Lower Highs (LH) and Lower Lows (LL) - but with slightly higher lows recently.
- BOS to the downside.
- ICT:
- Order Block Price could not break up the bearish Order Block.
- EMA:
- The 50-period and 200-period EMAs are acting as resistance.
- Money Flow (LuxAlgo):
- Alternating red and green, predominantly red.
- Trend Strength (AlgoAlpha):
- Red Cloud (Bearish), BUT there's a bullish divergence (price made a lower low, but the Trend Strength indicator made a higher low). This is a potential early warning sign, but needs strong confirmation.
- Volume Profile:
- Relatively high Volume
- Support: Recent lows.
- Resistance: EMA 50, EMA 200, Order Block.
- Summary: The 15-minute chart is in a downtrend, although with very tentative signs of stabilization. The bullish divergence on the Trend Strength is noteworthy, but not a buy signal on its own.
Overall Strategy and Recommendations (BTCUSDT):
- Primary Trend (Day): Uptrend (Significantly Weakening).
- Secondary Trend (4H): Downtrend.
- Short-Term Trend (15m): Downtrend (Potential Early Reversal Signals).
- Liquidity: Significant SSL zones exist below the current price on all timeframes.
- Money Flow: Negative on all timeframes.
-
Trend Strength: Bearish on Day and 15m. Sideway on 4H.
-
Strategies:
-
Wait & See (Best Option): The conflicting signals and the strong bearish momentum on the shorter timeframes, combined with the weakening Daily chart, make waiting the most prudent approach. Look for:
- Bearish Confirmation: A decisive break below the recent lows on the 15m and 4H charts, with increasing volume and continued negative Money Flow. This would confirm the continuation of the downtrend.
- Bullish Confirmation: A strong, sustained break above the 15m EMAs, a shift in the 15m Money Flow to green, and a bullish signal on the 4H Trend Strength, and price holding above EMAs and ideally reclaiming the Daily Order Block.
-
Short (High Risk): This aligns with the 4H and 15m downtrends.
- Entry: On rallies towards resistance levels (EMAs on 15m/4H, previous support levels that have turned into resistance).
- Stop Loss: Above recent highs on the chosen timeframe.
- Target: The next support levels (recent lows on 15m, then potentially the SSL zones on the 4H and Daily charts).
-
Buy (Extremely High Risk - Not Recommended): Do not attempt to buy until there are very strong and consistent bullish reversal signals across all timeframes, including a definitive shift in market structure on the 4H and 15m charts, positive Money Flow, and a clear break above resistance levels. The bullish divergence on the 15m Trend Strength is not sufficient on its own.
-
Key Recommendations:
- Conflicting Timeframes: The primary conflict is now resolved toward the downside. The Daily is weakening significantly.
- Money Flow: Consistently negative, a major bearish factor.
- Trend Strength: Bearish on Day and 15, Sideways on 4H, but the divergence on the 15m is a potential early warning.
- Daily Order Block: The break of the bullish Order Block is a significant bearish development.
- Sellside Liquidity (SSL): Be aware that Smart Money may target the SSL zones below. This increases the risk of stop-loss hunting.
- Risk Management: Due to the high uncertainty and volatility, strict risk management is absolutely critical. Use tight stop-losses, do not overtrade, and be prepared for rapid price swings.
- Volume: Confirm any breakout or breakdown with volume.
Day Trading and Intraday Trading Strategies:
-
Day Trade (TF15 focus):
- Short Bias: Given the current 15m downtrend and negative Money Flow, the higher probability is to look for shorting opportunities.
- Entry: Look for price to rally to resistance levels (EMAs, Order Blocks, previous support levels that have become resistance) and then show signs of rejection (bearish candlestick patterns, increasing volume on the downside).
- Stop Loss: Place a stop-loss order above the resistance level where you enter the short position.
- Take Profit: Target the next support level (recent lows).
- Be very cautious: The bullish divergence on the Trend Strength indicator suggests a potential bounce could occur. Don't be aggressive with shorts until this divergence is invalidated.
- Avoid Long positions: Until there's a clear and confirmed bullish reversal on the 15m chart (break above EMAs, positive Money Flow, bullish market structure).
- Short Bias: Given the current 15m downtrend and negative Money Flow, the higher probability is to look for shorting opportunities.
-
Swing Trade (TF4H focus):
- Short Bias: The 4H chart is in a downtrend.
- Entry: Wait for price to rally to resistance levels (EMAs, Order Blocks) and show signs of rejection.
- Stop Loss: Above the resistance level where you enter the short position.
- Take Profit: Target the next support levels (e.g., the 200 EMA on the Daily chart, SSL zones).
- Avoid Long positions: Until there's a clear and confirmed bullish reversal on the 4H chart.
- Short Bias: The 4H chart is in a downtrend.
SMC Day Trade Setup Example (TF15 - Bearish):
- Identify Bearish Order Block: Locate a bearish Order Block on the TF15 chart (a bullish candle before a strong downward move). We have identified this in previous analyses.
- Wait for Pullback: Wait for the price to pull back up to test the Order Block (this may or may not happen).
- Bearish Entry:
- Rejection: Look for price action to reject the Order Block (e.g., a pin bar, engulfing pattern, or other bearish candlestick pattern).
- Break of Structure: Look for a break of a minor support level on a lower timeframe (e.g., 1-minute or 5-minute) after the price tests the Order Block.
- Money Flow: Confirm that Money Flow remains negative (red).
- Stop Loss: Place a stop-loss order above the Order Block.
- Take Profit: Target the next support level (e.g., recent lows) or a bullish Order Block on a higher timeframe.
In conclusion, BTCUSDT is currently in a high-risk, bearish environment in the short-to-medium term. The "Wait & See" approach is strongly recommended for most traders. Shorting is the higher-probability trade at this moment, but only for experienced traders who can manage risk extremely effectively. Buying is not recommended at this time.
Disclaimer: This analysis is for informational purposes only and represents a personal opinion. It is not financial advice. Investing in cryptocurrencies involves significant risk. Investors should conduct their own research and exercise due diligence before making any investment decisions.
-
 @ c631e267:c2b78d3e
2025-02-07 19:42:11
@ c631e267:c2b78d3e
2025-02-07 19:42:11Nur wenn wir aufeinander zugehen, haben wir die Chance \ auf Überwindung der gegenseitigen Ressentiments! \ Dr. med. dent. Jens Knipphals
In Wolfsburg sollte es kürzlich eine Gesprächsrunde von Kritikern der Corona-Politik mit Oberbürgermeister Dennis Weilmann und Vertretern der Stadtverwaltung geben. Der Zahnarzt und langjährige Maßnahmenkritiker Jens Knipphals hatte diese Einladung ins Rathaus erwirkt und publiziert. Seine Motivation:
«Ich möchte die Spaltung der Gesellschaft überwinden. Dazu ist eine umfassende Aufarbeitung der Corona-Krise in der Öffentlichkeit notwendig.»
Schon früher hatte Knipphals Antworten von den Kommunalpolitikern verlangt, zum Beispiel bei öffentlichen Bürgerfragestunden. Für das erwartete Treffen im Rathaus formulierte er Fragen wie: Warum wurden fachliche Argumente der Kritiker ignoriert? Weshalb wurde deren Ausgrenzung, Diskreditierung und Entmenschlichung nicht entgegengetreten? In welcher Form übernehmen Rat und Verwaltung in Wolfsburg persönlich Verantwortung für die erheblichen Folgen der politischen Corona-Krise?
Der Termin fand allerdings nicht statt – der Bürgermeister sagte ihn kurz vorher wieder ab. Knipphals bezeichnete Weilmann anschließend als Wiederholungstäter, da das Stadtoberhaupt bereits 2022 zu einem Runden Tisch in der Sache eingeladen hatte, den es dann nie gab. Gegenüber Multipolar erklärte der Arzt, Weilmann wolle scheinbar eine öffentliche Aufarbeitung mit allen Mitteln verhindern. Er selbst sei «inzwischen absolut desillusioniert» und die einzige Lösung sei, dass die Verantwortlichen gingen.
Die Aufarbeitung der Plandemie beginne bei jedem von uns selbst, sei aber letztlich eine gesamtgesellschaftliche Aufgabe, schreibt Peter Frey, der den «Fall Wolfsburg» auch in seinem Blog behandelt. Diese Aufgabe sei indes deutlich größer, als viele glaubten. Erfreulicherweise sei der öffentliche Informationsraum inzwischen größer, trotz der weiterhin unverfrorenen Desinformations-Kampagnen der etablierten Massenmedien.
Frey erinnert daran, dass Dennis Weilmann mitverantwortlich für gravierende Grundrechtseinschränkungen wie die 2021 eingeführten 2G-Regeln in der Wolfsburger Innenstadt zeichnet. Es sei naiv anzunehmen, dass ein Funktionär einzig im Interesse der Bürger handeln würde. Als früherer Dezernent des Amtes für Wirtschaft, Digitalisierung und Kultur der Autostadt kenne Weilmann zum Beispiel die Verknüpfung von Fördergeldern mit politischen Zielsetzungen gut.
Wolfsburg wurde damals zu einem Modellprojekt des Bundesministeriums des Innern (BMI) und war Finalist im Bitkom-Wettbewerb «Digitale Stadt». So habe rechtzeitig vor der Plandemie das Projekt «Smart City Wolfsburg» anlaufen können, das der Stadt «eine Vorreiterrolle für umfassende Vernetzung und Datenerfassung» aufgetragen habe, sagt Frey. Die Vereinten Nationen verkauften dann derartige «intelligente» Überwachungs- und Kontrollmaßnahmen ebenso als Rettung in der Not wie das Magazin Forbes im April 2020:
«Intelligente Städte können uns helfen, die Coronavirus-Pandemie zu bekämpfen. In einer wachsenden Zahl von Ländern tun die intelligenten Städte genau das. Regierungen und lokale Behörden nutzen Smart-City-Technologien, Sensoren und Daten, um die Kontakte von Menschen aufzuspüren, die mit dem Coronavirus infiziert sind. Gleichzeitig helfen die Smart Cities auch dabei, festzustellen, ob die Regeln der sozialen Distanzierung eingehalten werden.»
Offensichtlich gibt es viele Aspekte zu bedenken und zu durchleuten, wenn es um die Aufklärung und Aufarbeitung der sogenannten «Corona-Pandemie» und der verordneten Maßnahmen geht. Frustration und Desillusion sind angesichts der Realitäten absolut verständlich. Gerade deswegen sind Initiativen wie die von Jens Knipphals so bewundernswert und so wichtig – ebenso wie eine seiner Kernthesen: «Wir müssen aufeinander zugehen, da hilft alles nichts».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-01-31 20:02:25
@ a95c6243:d345522c
2025-01-31 20:02:25Im Augenblick wird mit größter Intensität, großer Umsicht \ das deutsche Volk belogen. \ Olaf Scholz im FAZ-Interview
Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur Reuters Verbreitung in den Medien gefunden hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten.
Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen sei repräsentativ, behauptet der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von Mitgliedern, die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben».
Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH, also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges «Demokratie-Update» aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet.
Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer befürchteten, dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen.
Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein? Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise abgelehnt. Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen.
Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen, die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter berichtet. Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert».
Der Vorwand «unzulässiger Einflussnahme» auf Politik und Wahlen wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als «völlig irre» bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird «E-Voting» seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg.
Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus. Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die weit verbreitete Armut zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c43d6de3:a6583169
2025-02-20 23:54:51
@ c43d6de3:a6583169
2025-02-20 23:54:51"So, What’s the News?"
Were it not for these very words, we might never have had a modern capitalistic society.
Between 1500 and 1800, coffeehouses were more than just places to grab a quick hit of caffeine—they were the beating heart of local communities. These spaces buzzed with debate, discussion, and the exchange of groundbreaking ideas. Strangers became intellectual sparring partners, not merely reading the news but dissecting and debating it in real-time.
One could easily imagine Adam Smith engaged in animated conversation with David Hume in a coffeehouse on Edinburgh’s Royal Mile—the former outlining the invisible hand of the market, the latter countering that human behavior is driven more by emotion than reason. Such debates weren’t confined to elite scholars. Merchants, craftsmen, and common laborers sat shoulder to shoulder, engaging in discussions that transcended social class.
But then came industrialization.
The rise of factory life replaced the organic rhythms of community engagement with rigid work schedules. As cities expanded and people became busier, the once-thriving coffeehouses—where time was slow, conversation was deep, and debate was central—began to empty. The demand for efficiency left little room for leisurely discussions, and over time, the public square of ideas withered.

nostr:npub1uzt238htjzpq39dxmltlx60vxym9fetk9czz6kddq6fhvkf4z3usy9qtrh Mouth watering Hodl rounds- Bitcoin only
https://shopstr.store/listing/84f20c5e1ef94762b60f0d5fb4398594ace6c5589212f94269e9542fbe351732
Photos Courtesy of nostr:npub1c8n9qhqzm2x3kzjm84kmdcvm96ezmn257r5xxphv3gsnjq4nz4lqelne96 Give him a follow and some zap love if you like his art
Empty Street Corners and Hollow Venues
Adam Smith would lose his mind with how interconnected the world is today.
Yet, he might also notice something unsettling: while we are globally connected, our local communities feel more fragmented than ever before.
He’d have a hell of an online presence but he, just like many do today, might get the sense that something isn't quite right. The world is quieterthan ever before while online discourse teeters on the verge of violent physical manifestations.
It’s not that public discourse has disappeared. Rather, it has been exiled to the internet. Social media has become our new coffeehouse, but instead of robust face-to-face engagement, we navigate a landscape of curated algorithms, viral outrage, and fragmented conversations. The once-public square of ideas has transformed into isolated echo chambers, where avatars shape narratives that must be adhered to lest one be accused of inconsistency and lose credibility.
The result? People live layered lives with layered personas—some even attaining secret fame in online communities while remaining anonymous in their own neighborhoods. Meanwhile, the street corners remain empty, and the venues that once thrived with the fervor of intellectual thought stand hollow.

Photos Courtesy of nostr:npub1c8n9qhqzm2x3kzjm84kmdcvm96ezmn257r5xxphv3gsnjq4nz4lqelne96 Give him a follow and some zap love if you like his art
The Need for a Modern Coffeehouse
Historically, coffeehouses were revolutionary because they democratized knowledge. They provided an open forum for ideas, allowing philosophy, politics, and commerce to intermingle freely. Unlike monasteries or universities, coffeehouses welcomed anyone who could afford a cup of coffee.
With the rise of digital discourse, have we lost something essential? The depth, accountability, and personal engagement that once defined public debate have been replaced by reactionary commentary and fleeting viral moments. The question is no longer where we discuss ideas—it’s how we engage with them.
We need to ask ourselves: Can we reclaim a physical space for intellectual exchange? Or has the age of meaningful, face-to-face discourse faded, vanishing with the steam of yesterday’s coffee?
Can We Bring Back the Local Forum? Should We Care?
Before coffeehouses, philosophy lived in elite institutions and royal courts. With the rise of coffee culture, it became truly public, shaping modern democracy, scientific thought, and social progress. The internet, for all its wonders, lacks the tactile, immediate, and personal engagement that once made intellectual debate so powerful.
The challenge ahead is not just about nostalgia for coffeehouse debates—it’s about asking whether we can create new spaces, physical or digital, that foster real intellectual exchange. Without them, we risk losing something fundamental: the ability to challenge, refine, and reshape our ideas through genuine human connection. But most of all, we risk the possibility great ideas come but no action is ever taken to make them real in this real world.
So, what’s the news?
Thank you for reading!
If this article resonated with you, let me know with a zap and share it with friends who might find it insightful.
All zap revenue from this article is shared with nostr:npub1c8n9qhqzm2x3kzjm84kmdcvm96ezmn257r5xxphv3gsnjq4nz4lqelne96 for his photograph contributions.
Your help sends a strong signal for content creators like us to keep making cool shit like this!
Interested in fiction? Follow nostr:npub1j9cmpzhlzeex6y85c2pnt45r5zhxhtx73a2twt77fyjwequ4l4jsp5xd49 for great short stories and serialized fiction.
More photography and articles you might like from nostr:npub1cs7kmc77gcapuh2s3yn0rc868sckh0qam7p5p4t9ku88rfjcx95sq8tqw9 and nostr:npub1c8n9qhqzm2x3kzjm84kmdcvm96ezmn257r5xxphv3gsnjq4nz4lqelne96 :
nostr:naddr1qvzqqqr4gupzps0x2pwq9k5drv99k0tdkmsekt4j9hx4fu8gvvrwez3p8yptx9t7qqxnqvfjxqer2tfh0fekz7r5l270gu
 https://pictureroom.substack.com/p/020825
https://pictureroom.substack.com/p/020825nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq24s4mrfdm55utg23z55ufs94argvn523k5yqhkrc3
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2nvnr5d4nngw2zgd5k5c6etftrzez9fd9kkcl0pzp
-
 @ a95c6243:d345522c
2025-01-24 20:59:01
@ a95c6243:d345522c
2025-01-24 20:59:01Menschen tun alles, egal wie absurd, \ um ihrer eigenen Seele nicht zu begegnen. \ Carl Gustav Jung
«Extremer Reichtum ist eine Gefahr für die Demokratie», sagen über die Hälfte der knapp 3000 befragten Millionäre aus G20-Staaten laut einer Umfrage der «Patriotic Millionaires». Ferner stellte dieser Zusammenschluss wohlhabender US-Amerikaner fest, dass 63 Prozent jener Millionäre den Einfluss von Superreichen auf US-Präsident Trump als Bedrohung für die globale Stabilität ansehen.
Diese Besorgnis haben 370 Millionäre und Milliardäre am Dienstag auch den in Davos beim WEF konzentrierten Privilegierten aus aller Welt übermittelt. In einem offenen Brief forderten sie die «gewählten Führer» auf, die Superreichen – also sie selbst – zu besteuern, um «die zersetzenden Auswirkungen des extremen Reichtums auf unsere Demokratien und die Gesellschaft zu bekämpfen». Zum Beispiel kontrolliere eine handvoll extrem reicher Menschen die Medien, beeinflusse die Rechtssysteme in unzulässiger Weise und verwandele Recht in Unrecht.
Schon 2019 beanstandete der bekannte Historiker und Schriftsteller Ruthger Bregman an einer WEF-Podiumsdiskussion die Steuervermeidung der Superreichen. Die elitäre Veranstaltung bezeichnete er als «Feuerwehr-Konferenz, bei der man nicht über Löschwasser sprechen darf.» Daraufhin erhielt Bregman keine Einladungen nach Davos mehr. Auf seine Aussagen machte der Schweizer Aktivist Alec Gagneux aufmerksam, der sich seit Jahrzehnten kritisch mit dem WEF befasst. Ihm wurde kürzlich der Zutritt zu einem dreiteiligen Kurs über das WEF an der Volkshochschule Region Brugg verwehrt.
Nun ist die Erkenntnis, dass mit Geld politischer Einfluss einhergeht, alles andere als neu. Und extremer Reichtum macht die Sache nicht wirklich besser. Trotzdem hat man über Initiativen wie Patriotic Millionaires oder Taxmenow bisher eher selten etwas gehört, obwohl es sie schon lange gibt. Auch scheint es kein Problem, wenn ein Herr Gates fast im Alleingang versucht, globale Gesundheits-, Klima-, Ernährungs- oder Bevölkerungspolitik zu betreiben – im Gegenteil. Im Jahr, als der Milliardär Donald Trump zum zweiten Mal ins Weiße Haus einzieht, ist das Echo in den Gesinnungsmedien dagegen enorm – und uniform, wer hätte das gedacht.
Der neue US-Präsident hat jedoch «Davos geerdet», wie Achgut es nannte. In seiner kurzen Rede beim Weltwirtschaftsforum verteidigte er seine Politik und stellte klar, er habe schlicht eine «Revolution des gesunden Menschenverstands» begonnen. Mit deutlichen Worten sprach er unter anderem von ersten Maßnahmen gegen den «Green New Scam», und von einem «Erlass, der jegliche staatliche Zensur beendet»:
«Unsere Regierung wird die Äußerungen unserer eigenen Bürger nicht mehr als Fehlinformation oder Desinformation bezeichnen, was die Lieblingswörter von Zensoren und derer sind, die den freien Austausch von Ideen und, offen gesagt, den Fortschritt verhindern wollen.»
Wie der «Trumpismus» letztlich einzuordnen ist, muss jeder für sich selbst entscheiden. Skepsis ist definitiv angebracht, denn «einer von uns» sind weder der Präsident noch seine auserwählten Teammitglieder. Ob sie irgendeinen Sumpf trockenlegen oder Staatsverbrechen aufdecken werden oder was aus WHO- und Klimaverträgen wird, bleibt abzuwarten.
Das WHO-Dekret fordert jedenfalls die Übertragung der Gelder auf «glaubwürdige Partner», die die Aktivitäten übernehmen könnten. Zufällig scheint mit «Impfguru» Bill Gates ein weiterer Harris-Unterstützer kürzlich das Lager gewechselt zu haben: Nach einem gemeinsamen Abendessen zeigte er sich «beeindruckt» von Trumps Interesse an der globalen Gesundheit.
Mit dem Projekt «Stargate» sind weitere dunkle Wolken am Erwartungshorizont der Fangemeinde aufgezogen. Trump hat dieses Joint Venture zwischen den Konzernen OpenAI, Oracle, und SoftBank als das «größte KI-Infrastrukturprojekt der Geschichte» angekündigt. Der Stein des Anstoßes: Oracle-CEO Larry Ellison, der auch Fan von KI-gestützter Echtzeit-Überwachung ist, sieht einen weiteren potenziellen Einsatz der künstlichen Intelligenz. Sie könne dazu dienen, Krebserkrankungen zu erkennen und individuelle mRNA-«Impfstoffe» zur Behandlung innerhalb von 48 Stunden zu entwickeln.
Warum bitte sollten sich diese superreichen «Eliten» ins eigene Fleisch schneiden und direkt entgegen ihren eigenen Interessen handeln? Weil sie Menschenfreunde, sogenannte Philanthropen sind? Oder vielleicht, weil sie ein schlechtes Gewissen haben und ihre Schuld kompensieren müssen? Deswegen jedenfalls brauchen «Linke» laut Robert Willacker, einem deutschen Politikberater mit brasilianischen Wurzeln, rechte Parteien – ein ebenso überraschender wie humorvoller Erklärungsansatz.
Wenn eine Krähe der anderen kein Auge aushackt, dann tut sie das sich selbst noch weniger an. Dass Millionäre ernsthaft ihre eigene Besteuerung fordern oder Machteliten ihren eigenen Einfluss zugunsten anderer einschränken würden, halte ich für sehr unwahrscheinlich. So etwas glaube ich erst, wenn zum Beispiel die Rüstungsindustrie sich um Friedensverhandlungen bemüht, die Pharmalobby sich gegen institutionalisierte Korruption einsetzt, Zentralbanken ihre CBDC-Pläne für Bitcoin opfern oder der ÖRR die Abschaffung der Rundfunkgebühren fordert.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-01-18 09:34:51
@ c631e267:c2b78d3e
2025-01-18 09:34:51Die grauenvollste Aussicht ist die der Technokratie – \ einer kontrollierenden Herrschaft, \ die durch verstümmelte und verstümmelnde Geister ausgeübt wird. \ Ernst Jünger
«Davos ist nicht mehr sexy», das Weltwirtschaftsforum (WEF) mache Davos kaputt, diese Aussagen eines Einheimischen las ich kürzlich in der Handelszeitung. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den vergangenen vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
Der deutsche WEF-Gründer hatte bei dieser Gelegenheit immer höchst lobende Worte für seine Landsmännin: 2021 erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und 2022 fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
Von der Leyens Handeln während der sogenannten Corona-«Pandemie» lobte Schwab damals bereits ebenso, wie es diese Woche das Karlspreis-Direktorium tat, als man der Beschuldigten im Fall Pfizergate die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
Jene Herausforderungen durch «Krisen epochalen Ausmaßes» werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im Global Risks Report nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
Ein «Great Mental Reset» sei die Voraussetzung dafür, dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
Der aktuelle Zustand unserer Gesellschaften ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die Rechtsstaatlichkeit stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ d360efec:14907b5f
2025-02-21 10:39:03
@ d360efec:14907b5f
2025-02-21 10:39:03ภาพรวม BTCUSDT (OKX):
Bitcoin (BTCUSDT) ยังคงมีความผันผวนและแนวโน้มที่ไม่ชัดเจน แม้ว่า TF Day จะยังคงแสดงโครงสร้างตลาดที่เป็นขาขึ้น แต่ ก็เริ่มอ่อนแรงลงอย่างเห็นได้ชัด แนวโน้ม TF4H และ TF15 เป็น Sideway Down
วิเคราะห์ทีละ Timeframe:
(1) TF Day (รายวัน): https://www.tradingview.com/x/IVA4uegL/
- แนวโน้ม: ขาขึ้น (Uptrend) อ่อนแรงลงอย่างมาก, มีความเสี่ยงที่จะเปลี่ยนแนวโน้ม
- SMC:
- Higher Highs (HH) และ Higher Lows (HL) เริ่มไม่ชัดเจน, ราคาหลุด Low ก่อนหน้า
- Break of Structure (BOS) ด้านบน แต่มีการปรับฐานที่รุนแรง
- Liquidity:
- มี Sellside Liquidity (SSL) อยู่ใต้ Lows ก่อนหน้า (บริเวณ 85,000 - 90,000)
- มี Buyside Liquidity (BSL) อยู่เหนือ High เดิม
- ICT:
- Order Block: ราคาหลุด Order Block ขาขึ้น
- EMA:
- ราคา หลุด EMA 50 (สีเหลือง) ลงมาแล้ว
- EMA 200 (สีขาว) เป็นแนวรับถัดไป
- Money Flow (LuxAlgo):
- สีแดงยาว แสดงถึงแรงขายที่แข็งแกร่ง
- Trend Strength (AlgoAlpha):
- สีแดง (เมฆแดง) แสดงถึงแนวโน้มขาลง และไม่มีสัญญาณซื้อ/ขายปรากฏ
- Volume Profile: Volume ค่อนข้างเบาบาง
- แท่งเทียน: แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย
- แนวรับ: EMA 200, บริเวณ 85,000 - 90,000 (SSL)
- แนวต้าน: EMA 50, High เดิม
- สรุป: แนวโน้มขาขึ้นอ่อนแรงลงอย่างมาก, สัญญาณอันตรายหลายอย่าง, Money Flow และ Trend Strength เป็นลบ, หลุด Order Block และ EMA 50
(2) TF4H (4 ชั่วโมง): https://www.tradingview.com/x/BP0BDAts/
- แนวโน้ม: Sideway Down
- SMC:
- Lower Highs (LH) และ Lower Lows (LL)
- Break of Structure (BOS) ด้านล่าง
- Liquidity:
- มี SSL อยู่ใต้ Lows ก่อนหน้า
- มี BSL อยู่เหนือ Highs ก่อนหน้า
- ICT:
- Order Block: ราคาไม่สามารถผ่าน Order Block ขาลงได้ และราคากำลังทดสอบ Order Block ขาขึ้น
- EMA:
- ราคาอยู่ใต้ EMA 50 และ EMA 200
- Money Flow (LuxAlgo):
- สีแดง แสดงถึงแรงขาย
- Trend Strength (AlgoAlpha):
- เขียว/ไม่มีสัญญาณ แสดงถึงแนวโน้ม Sideway
- Volume Profile: * Volume ค่อนข้างสูง
- แนวรับ: บริเวณ Low ล่าสุด, Order Block
- แนวต้าน: EMA 50, EMA 200, บริเวณ Order Block
- สรุป: แนวโน้ม Sideway Down, แรงขายมีอิทธิพล
(3) TF15 (15 นาที): (https://www.tradingview.com/x/c7kIbqU0/)
- แนวโน้ม: ขาลง (Downtrend) แต่เริ่มเห็นสัญญาณ Sideways
- SMC:
- Lower Highs (LH) และ Lower Lows (LL) เริ่มเห็นการยก Low เล็กน้อย
- Break of Structure (BOS) ด้านล่าง
- ICT:
- Order Block: ราคา Sideways ใกล้ Order Block
- EMA:
- EMA 50 และ EMA 200 เป็นแนวต้าน
- Money Flow (LuxAlgo):
- แดงสลับเขียว
- Trend Strength (AlgoAlpha):
- สีแดง (เมฆแดง) แสดงถึงแนวโน้มขาลง แต่มีสัญญาณ Bullish Divergence (ราคาทำ Lower Low แต่ Trend Strength ยก Low)
- Volume Profile: * Volume ค่อนข้างสูง
- แนวรับ: บริเวณ Low ล่าสุด
- แนวต้าน: EMA 50, EMA 200, Order Block
- สรุป: แนวโน้มขาลง, เริ่มพักตัว, Money Flow เริ่มมีความไม่แน่นอน
สรุปภาพรวมและกลยุทธ์ (BTCUSDT):
- แนวโน้มหลัก (Day): ขาขึ้น (อ่อนแรงลงอย่างมาก, เสี่ยงที่จะเปลี่ยนแนวโน้ม)
- แนวโน้มรอง (4H): Sideway Down
- แนวโน้มระยะสั้น (15m): ขาลง (เริ่มพักตัว, มี Divergence)
- Liquidity: มี SSL ทั้งใน Day, 4H, และ 15m
- Money Flow: เป็นลบในทุก Timeframes
- Trend Strength: Day/15m เป็นขาลง, 4H Sideway
- กลยุทธ์:
- Wait & See (ดีที่สุด): รอความชัดเจน
- Short (เสี่ยง): ถ้าไม่สามารถ Breakout EMA/แนวต้านใน TF ใดๆ ได้ หรือเมื่อเกิดสัญญาณ Bearish Continuation
- ไม่แนะนำให้ Buy: จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจนมากๆ
Day Trade & การเทรดรายวัน:
-
Day Trade (TF15):
- Short Bias: หาจังหวะ Short เมื่อราคาเด้งขึ้นไปทดสอบแนวต้าน (EMA, Order Block)
- Stop Loss: เหนือแนวต้านที่เข้า Short
- Take Profit: แนวรับถัดไป (Low ล่าสุด)
- ระวัง: Bullish Divergence ใน Trend Strength
- ไม่แนะนำให้ Long
-
Swing Trade (TF4H):
- Short Bias: รอจังหวะ Short เมื่อราคาไม่สามารถผ่านแนวต้าน EMA หรือ Order Block ได้
- Stop Loss: เหนือแนวต้านที่เข้า Short
- Take Profit: แนวรับถัดไป
- ไม่แนะนำให้ Long
สิ่งที่ต้องระวัง:
- Sellside Liquidity (SSL): มีโอกาสสูงที่ราคาจะถูกลากลงไปแตะ SSL
- False Breakouts: ระวัง
- Volatility: สูง
- Divergence (TF15): อาจเป็นสัญญาณเริ่มต้นของการกลับตัว แต่ต้องรอการยืนยัน
- Trend Strength (TF4H): ไม่มีสัญญาณซื้อ/ขาย ต้องระวัง
Setup Day Trade แบบ SMC (ตัวอย่าง):
- ระบุ Order Block: หา Order Block ขาลง (Bearish Order Block) ใน TF15 (แท่งเทียนสีเขียวก่อนที่ราคาจะลงแรง)
- รอ Pullback: รอให้ราคา Pullback ขึ้นไปทดสอบ Order Block นั้น
- หา Bearish Entry:
- Rejection: รอ Price Action ปฏิเสธ Order Block (เช่น เกิด Pin Bar, Engulfing)
- Break of Structure: รอให้ราคา Break โครงสร้างย่อยๆ ใน TF ที่เล็กกว่า (เช่น 1m, 5m) หลังจากที่ทดสอบ Order Block
- Money Flow: ดู Money Flow ให้เป็นสีแดง
- ตั้ง Stop Loss: เหนือ Order Block
- ตั้ง Take Profit: แนวรับถัดไป (เช่น Low ล่าสุด) หรือ Order Block ขาขึ้น (Bullish Order Block) ใน TF ที่ใหญ่กว่า
คำแนะนำ:
- ความขัดแย้งของ Timeframes: มีอยู่ แต่แนวโน้มระยะกลาง-สั้น เป็นลบ
- Money Flow: เป็นลบในทุก Timeframes
- Trend Strength: เริ่มมี Divergence ใน TF15
- Order Block TF Day: หลุด Order Block ขาขึ้นแล้ว
- ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-
 @ 5188521b:008eb518
2025-02-21 08:29:00
@ 5188521b:008eb518
2025-02-21 08:29:00At 21 Futures, we publish original fiction in the cypherpunk, libertarian, sci-finance and bitcoin genre.
Our mission is to give power to world-changing ideas through story.
We publish several original titles each year, including our short-fiction anthologies.
21 Futures is currently open to submissions.
As an imprint of Konsensus Network, we also help fiction authors through our hybrid publishing services. Authors select the right services to help them shape and produce their masterpiece. Together, we send it out into the world.
Hybrid publishers outside the freedom space will take your money, but they will lack the niche expertise and desire to make your book succeed.
21 Futures is run by a passionate team of freedom-loving editors and professionals. We only accept the highest quality manuscripts because we want to champion work that we believe in too.
Our Publishing Services
\ As an imprint of Konsensus Network, we provide:
- Cover design
- Marketing services
- Print and distribution
- Editing and proofreading
- Typesetting and interior design
- language services and translation
We create bespoke packages to give authors the ultimate flexibility . You maintain ownership and control of your work, and you keep ALL the royalties earned.

Submissions guidelines
Submit your manuscript for assessment via the form.
21 Futures publishes book-length fiction which focuses on cypherpunk, libertarian, and freedom ideals.
We're looking for characters which drive empathy, compelling stories, and novel ideas. Finished manuscripts only (no pitches please). We do not publish poetry, plays, or non-fiction.
Please complete the form with as much detail as possible to help us best assess your work.
Upload your first chapter (or up to 10,000 words).
Authors retain the copyright to their work. Manuscripts will not be shared outside the editorial team and will not be kept on file.
After assessment, we'll get back to you within 21 days, outlining the best route forward for publication.
For questions on rights, sponsorship and partnerships, please use the contact page.
Submit your manuscript
Publish your story with 21 Futures

21 Futures is open to established and emerging fiction writers. We feature several stories each month on our blog.
We publish cypherpunk, libertarian, sci-finance and bitcoin themed fiction.
Our editors are looking for gripping, human-interest stories with emotional impact. They want strong characters, high stakes, and moments of epiphany and change.
We also publish book reviews (same genres as above).
We do not accept poetry, essays, articles, or diatribes.
- For book reviews, we suggest under 1,000 words.
- For stories, we suggest under 5,000 words.
Currently, we don't offer payment for publication on our blog.
However, authors can include their lightning address to garner tips.
We also post stories on NOSTR. All zaps earned by the post will be forwarded to the author's wallet.
Email your story or review as a document (no PDFs) to write@21futures.com. Please include a short author bio and a photo if you wish.
We will get back to you within 21 days.
-
 @ a95c6243:d345522c
2025-01-13 10:09:57
@ a95c6243:d345522c
2025-01-13 10:09:57Ich begann, Social Media aufzubauen, \ um den Menschen eine Stimme zu geben. \ Mark Zuckerberg
Sind euch auch die Tränen gekommen, als ihr Mark Zuckerbergs Wendehals-Deklaration bezüglich der Meinungsfreiheit auf seinen Portalen gehört habt? Rührend, oder? Während er früher die offensichtliche Zensur leugnete und später die Regierung Biden dafür verantwortlich machte, will er nun angeblich «die Zensur auf unseren Plattformen drastisch reduzieren».
«Purer Opportunismus» ob des anstehenden Regierungswechsels wäre als Klassifizierung viel zu kurz gegriffen. Der jetzige Schachzug des Meta-Chefs ist genauso Teil einer kühl kalkulierten Business-Strategie, wie es die 180 Grad umgekehrte Praxis vorher war. Social Media sind ein höchst lukratives Geschäft. Hinzu kommt vielleicht noch ein bisschen verkorkstes Ego, weil derartig viel Einfluss und Geld sicher auch auf die Psyche schlagen. Verständlich.
«Es ist an der Zeit, zu unseren Wurzeln der freien Meinungsäußerung auf Facebook und Instagram zurückzukehren. Ich begann, Social Media aufzubauen, um den Menschen eine Stimme zu geben», sagte Zuckerberg.
Welche Wurzeln? Hat der Mann vergessen, dass er von der Überwachung, dem Ausspionieren und dem Ausverkauf sämtlicher Daten und digitaler Spuren sowie der Manipulation seiner «Kunden» lebt? Das ist knallharter Kommerz, nichts anderes. Um freie Meinungsäußerung geht es bei diesem Geschäft ganz sicher nicht, und das war auch noch nie so. Die Wurzeln von Facebook liegen in einem Projekt des US-Militärs mit dem Namen «LifeLog». Dessen Ziel war es, «ein digitales Protokoll vom Leben eines Menschen zu erstellen».
Der Richtungswechsel kommt allerdings nicht überraschend. Schon Anfang Dezember hatte Meta-Präsident Nick Clegg von «zu hoher Fehlerquote bei der Moderation» von Inhalten gesprochen. Bei der Gelegenheit erwähnte er auch, dass Mark sehr daran interessiert sei, eine aktive Rolle in den Debatten über eine amerikanische Führungsrolle im technologischen Bereich zu spielen.
Während Milliardärskollege und Big Tech-Konkurrent Elon Musk bereits seinen Posten in der kommenden Trump-Regierung in Aussicht hat, möchte Zuckerberg also nicht nur seine Haut retten – Trump hatte ihn einmal einen «Feind des Volkes» genannt und ihm lebenslange Haft angedroht –, sondern am liebsten auch mitspielen. KI-Berater ist wohl die gewünschte Funktion, wie man nach einem Treffen Trump-Zuckerberg hörte. An seine Verhaftung dachte vermutlich auch ein weiterer Multimilliardär mit eigener Social Media-Plattform, Pavel Durov, als er Zuckerberg jetzt kritisierte und gleichzeitig warnte.
Politik und Systemmedien drehen jedenfalls durch – was zu viel ist, ist zu viel. Etwas weniger Zensur und mehr Meinungsfreiheit würden die Freiheit der Bürger schwächen und seien potenziell vernichtend für die Menschenrechte. Zuckerberg setze mit dem neuen Kurs die Demokratie aufs Spiel, das sei eine «Einladung zum nächsten Völkermord», ernsthaft. Die Frage sei, ob sich die EU gegen Musk und Zuckerberg behaupten könne, Brüssel müsse jedenfalls hart durchgreifen.
Auch um die Faktenchecker macht man sich Sorgen. Für die deutsche Nachrichtenagentur dpa und die «Experten» von Correctiv, die (noch) Partner für Fact-Checking-Aktivitäten von Facebook sind, sei das ein «lukratives Geschäftsmodell». Aber möglicherweise werden die Inhalte ohne diese vermeintlichen Korrektoren ja sogar besser. Anders als Meta wollen jedoch Scholz, Faeser und die Tagesschau keine Fehler zugeben und zum Beispiel Correctiv-Falschaussagen einräumen.
Bei derlei dramatischen Befürchtungen wundert es nicht, dass der öffentliche Plausch auf X zwischen Elon Musk und AfD-Chefin Alice Weidel von 150 EU-Beamten überwacht wurde, falls es irgendwelche Rechtsverstöße geben sollte, die man ihnen ankreiden könnte. Auch der Deutsche Bundestag war wachsam. Gefunden haben dürften sie nichts. Das Ganze war eher eine Show, viel Wind wurde gemacht, aber letztlich gab es nichts als heiße Luft.
Das Anbiedern bei Donald Trump ist indes gerade in Mode. Die Weltgesundheitsorganisation (WHO) tut das auch, denn sie fürchtet um Spenden von über einer Milliarde Dollar. Eventuell könnte ja Elon Musk auch hier künftig aushelfen und der Organisation sowie deren größtem privaten Förderer, Bill Gates, etwas unter die Arme greifen. Nachdem Musks KI-Projekt xAI kürzlich von BlackRock & Co. sechs Milliarden eingestrichen hat, geht da vielleicht etwas.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-01-03 20:26:47
@ a95c6243:d345522c
2025-01-03 20:26:47Was du bist hängt von drei Faktoren ab: \ Was du geerbt hast, \ was deine Umgebung aus dir machte \ und was du in freier Wahl \ aus deiner Umgebung und deinem Erbe gemacht hast. \ Aldous Huxley
Das brave Mitmachen und Mitlaufen in einem vorgegebenen, recht engen Rahmen ist gewiss nicht neu, hat aber gerade wieder mal Konjunktur. Dies kann man deutlich beobachten, eigentlich egal, in welchem gesellschaftlichen Bereich man sich umschaut. Individualität ist nur soweit angesagt, wie sie in ein bestimmtes Schema von «Diversität» passt, und Freiheit verkommt zur Worthülse – nicht erst durch ein gewisses Buch einer gewissen ehemaligen Regierungschefin.
Erklärungsansätze für solche Entwicklungen sind bekannt, und praktisch alle haben etwas mit Massenpsychologie zu tun. Der Herdentrieb, also der Trieb der Menschen, sich – zum Beispiel aus Unsicherheit oder Bequemlichkeit – lieber der Masse anzuschließen als selbstständig zu denken und zu handeln, ist einer der Erklärungsversuche. Andere drehen sich um Macht, Propaganda, Druck und Angst, also den gezielten Einsatz psychologischer Herrschaftsinstrumente.
Aber wollen die Menschen überhaupt Freiheit? Durch Gespräche im privaten Umfeld bin ich diesbezüglich in der letzten Zeit etwas skeptisch geworden. Um die Jahreswende philosophiert man ja gerne ein wenig über das Erlebte und über die Erwartungen für die Zukunft. Dabei hatte ich hin und wieder den Eindruck, die totalitären Anwandlungen unserer «Repräsentanten» kämen manchen Leuten gerade recht.
«Desinformation» ist so ein brisantes Thema. Davor müsse man die Menschen doch schützen, hörte ich. Jemand müsse doch zum Beispiel diese ganzen merkwürdigen Inhalte in den Social Media filtern – zur Ukraine, zum Klima, zu Gesundheitsthemen oder zur Migration. Viele wüssten ja gar nicht einzuschätzen, was richtig und was falsch ist, sie bräuchten eine Führung.
Freiheit bedingt Eigenverantwortung, ohne Zweifel. Eventuell ist es einigen tatsächlich zu anspruchsvoll, die Verantwortung für das eigene Tun und Lassen zu übernehmen. Oder die persönliche Freiheit wird nicht als ausreichend wertvolles Gut angesehen, um sich dafür anzustrengen. In dem Fall wäre die mangelnde Selbstbestimmung wohl das kleinere Übel. Allerdings fehlt dann gemäß Aldous Huxley ein Teil der Persönlichkeit. Letztlich ist natürlich alles eine Frage der Abwägung.
Sind viele Menschen möglicherweise schon so «eingenordet», dass freiheitliche Ambitionen gar nicht für eine ganze Gruppe, ein Kollektiv, verfolgt werden können? Solche Gedanken kamen mir auch, als ich mir kürzlich diverse Talks beim viertägigen Hacker-Kongress des Chaos Computer Clubs (38C3) anschaute. Ich war nicht nur überrascht, sondern reichlich erschreckt angesichts der in weiten Teilen mainstream-geformten Inhalte, mit denen ein dankbares Publikum beglückt wurde. Wo ich allgemein hellere Köpfe erwartet hatte, fand ich Konformismus und enthusiastisch untermauerte Narrative.
Gibt es vielleicht so etwas wie eine Herdenimmunität gegen Indoktrination? Ich denke, ja, zumindest eine gestärkte Widerstandsfähigkeit. Was wir brauchen, sind etwas gesunder Menschenverstand, offene Informationskanäle und der Mut, sich freier auch zwischen den Herden zu bewegen. Sie tun das bereits, aber sagen Sie es auch dieses Jahr ruhig weiter.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 6b57533f:eaa341f5
2025-02-21 07:49:21
@ 6b57533f:eaa341f5
2025-02-21 07:49:21🏝️lost in the ordinary?
Welcome to Stories
Discover a hidden paradise where the world slows down, and adventure begins..
🌊 Step into tranquility.
Wake up to the sound of gentle waves and endless blue horizons.
🛶Live the dream.
Unwind, explore, and escape—your perfect getaway is just one step away.
-
 @ a95c6243:d345522c
2025-01-01 17:39:51
@ a95c6243:d345522c
2025-01-01 17:39:51Heute möchte ich ein Gedicht mit euch teilen. Es handelt sich um eine Ballade des österreichischen Lyrikers Johann Gabriel Seidl aus dem 19. Jahrhundert. Mir sind diese Worte fest in Erinnerung, da meine Mutter sie perfekt rezitieren konnte, auch als die Kräfte schon langsam schwanden.
Dem originalen Titel «Die Uhr» habe ich für mich immer das Wort «innere» hinzugefügt. Denn der Zeitmesser – hier vermutliche eine Taschenuhr – symbolisiert zwar in dem Kontext das damalige Zeitempfinden und die Umbrüche durch die industrielle Revolution, sozusagen den Zeitgeist und das moderne Leben. Aber der Autor setzt sich philosophisch mit der Zeit auseinander und gibt seinem Werk auch eine klar spirituelle Dimension.
Das Ticken der Uhr und die Momente des Glücks und der Trauer stehen sinnbildlich für das unaufhaltsame Fortschreiten und die Vergänglichkeit des Lebens. Insofern könnte man bei der Uhr auch an eine Sonnenuhr denken. Der Rhythmus der Ereignisse passt uns vielleicht nicht immer in den Kram.
Was den Takt pocht, ist durchaus auch das Herz, unser «inneres Uhrwerk». Wenn dieses Meisterwerk einmal stillsteht, ist es unweigerlich um uns geschehen. Hoffentlich können wir dann dankbar sagen: «Ich habe mein Bestes gegeben.»
Ich trage, wo ich gehe, stets eine Uhr bei mir; \ Wieviel es geschlagen habe, genau seh ich an ihr. \ Es ist ein großer Meister, der künstlich ihr Werk gefügt, \ Wenngleich ihr Gang nicht immer dem törichten Wunsche genügt.
Ich wollte, sie wäre rascher gegangen an manchem Tag; \ Ich wollte, sie hätte manchmal verzögert den raschen Schlag. \ In meinen Leiden und Freuden, in Sturm und in der Ruh, \ Was immer geschah im Leben, sie pochte den Takt dazu.
Sie schlug am Sarge des Vaters, sie schlug an des Freundes Bahr, \ Sie schlug am Morgen der Liebe, sie schlug am Traualtar. \ Sie schlug an der Wiege des Kindes, sie schlägt, will's Gott, noch oft, \ Wenn bessere Tage kommen, wie meine Seele es hofft.
Und ward sie auch einmal träger, und drohte zu stocken ihr Lauf, \ So zog der Meister immer großmütig sie wieder auf. \ Doch stände sie einmal stille, dann wär's um sie geschehn, \ Kein andrer, als der sie fügte, bringt die Zerstörte zum Gehn.
Dann müßt ich zum Meister wandern, der wohnt am Ende wohl weit, \ Wohl draußen, jenseits der Erde, wohl dort in der Ewigkeit! \ Dann gäb ich sie ihm zurücke mit dankbar kindlichem Flehn: \ Sieh, Herr, ich hab nichts verdorben, sie blieb von selber stehn.
Johann Gabriel Seidl (1804-1875)
-
 @ f288a224:1da1792c
2025-02-19 16:43:40
@ f288a224:1da1792c
2025-02-19 16:43:40First, some context.
I'm a child of the original internet chat-rooms on IRC, and I've tried over the last decades different applications and websites that we could all agree are "social media", but until I found NOSTR (Notes and Other Stuff Transmitted by Relays) I hadn't had this certainty that this isn't something that I will eventually change for something else.
Today, even with all its early stage issues, I have the certainty that NOSTR may be the ULTIMATE and FINAL HOME for my online life.
THE PROBLEMS with the current/old social media landscape

I'm tired of moving from one social media to the next.
As many of you, in my digital lifetime I've had many accounts that have now become obsolete; and the "content" and followings I created during that time was lost when one tech giant lost over the other, forcing us all to "MOVE" ourselves over to the new, and start building our content and following from scratch.
Lately, it's become even worse, where many of us have seen ourselves forced to use and feed more than one social media at a time, since they all serve various purposes, with sometimes diverse functionality, besides all being catered to different segments of people to connect you to (LinkedIn, Instagram, TikTok, Youtube...). How much is too much, though? And how much time should we keep spending re-adapting our content to reach all of our network?
For work, I've found myself having to create accounts in several of these giant data hoarding companies, having to build each following from scratch and to create "content" for all, and having to go through the hurdle of posting everything, everywhere, all at once.
I'm sick of ever-changing terms, conditions and capabilities.
Let's be honest, the majority of us have never ever read the full terms and conditions, let alone every time they are updated without us knowing which rights to our data we are giving away, and which terms we are accepting that may be detrimental to us and our mental health.
We've learnt to accept that we are in their playground, they make up the rules, and if they choose to change the rules mid-game we just need to swallow it. We literally have no other choice, it's either that or desertion, which basically means walking away from everything we've built on their "public square". So, like a carefully engineered detrimental incentive structure, the more time we spend building on their turf, the more we are tied to them and conditioned to never leave them. The more we build and make them grow on our content, the more we'll lose if or when we drop out.
And even if you accept all that and choose to play along, and you do your best to create the most awesome account in the neighborhood, the random changes they make to optimize ad revenue or user attention will inevitably affect you and all your work.
If you created all your feed according to Instagram's squares but they choose to change to TikTok style dimensions due to their tech positioning battle with the Chinese giant... You swallow. If you edited your reels according to what you felt was the best 100 seconds video... Not anymore, suddenly 90 seconds is the maximum you're allowed... No appeal, no options. You Swallow. What? Seeing less of the people you actually WANT TO FOLLOW because they decided to clutter your feed with ads and suggestions, guess again: YOU SWALLOW.
AREN'T YOU FEELING FULL ENOUGH OF ALL THE SHIT THEY'VE FORCED DOWN YOUR THROAT?
Living our digital lives on these platforms feels like standing on ever changing quicksand, never endingly trying to "hack the algorithm" in order to have our content placed in front of the people who should automatically be able to see us from the moment they chose to follow us; and the worst part of it is, you never know when you may lose it all.
Let's not forget, your social media account is NOT REALLY YOURS.
Recently, a friend's social media account was hacked. She didn't know how it happened; all she knew is that she got an email from Meta saying she had acted against community guidelines and her accounts were therefore being removed (the one hacked and all those liked to her email, which meant personal and work accounts). She tried to appeal, to no avail. She hadn't done anything wrong, but suddenly her identity had disappeared from all our feeds, and her content didn't exist anywhere anymore. She lost plenty of photos she had always counted on finding on her Instagram and lost the people she followed and who followed her. It was as if she had never existed on the platform.
(Looks like a good moment to remind you to download all your valued content from the platforms you use in case something like this happens to you)
 And this happened to someone who hadn't done anything "to deserve it". It has actually happened to more than one person I know, and every time they've been helpless and had no recourse, and yet, found themselves having to rebuild from scratch on the same platform that de-platformed them, because they had "no other option", and "their friends are there".
And this happened to someone who hadn't done anything "to deserve it". It has actually happened to more than one person I know, and every time they've been helpless and had no recourse, and yet, found themselves having to rebuild from scratch on the same platform that de-platformed them, because they had "no other option", and "their friends are there".Many more people have encountered this awful wake up call, some because of a hack, like my friend, others found themselves removed because they posted content critical of the platform... there are so many reasons people have gotten de-platformed and posts have gotten deleted without warning. And every time, we accept it, as if we owe them something; as if we need to settle for this kind of abusive environment that gets rich on our content and attention without having a say in anything.
But we do have another option that flips that attention retention model completely on its head and empowers the user. That option is NOSTR, our exit from the extractive social media silos they have trapped us into.
NOSTR: The better social experience for the internet era.
NOSTR (Notes and Other Stuff Transmitted by Relays) is not a social media app, it's an Internet protocol. It's open source and many many developers around the world are creating apps on top of it and creating THE ULTIMATE SOCIAL MEDIA EXPERIENCE for users.
I first heard of NOSTR from Jack Dorsey on what used to be called Twitter, and when I joined it two years ago it was really rough around the edges, but it was FULL OF POTENTIAL and the value proposition was very clear to me from the beginning.
Firstly, YOU OWN YOUR IDENTITY, that includes your content and your follower list.
So, what does owning you identity mean? I guess many of us have thought we owned our identity before, but the reality is that the platforms owned our identities, which is why they could delete or censor us.
Owning your identity on NOSTR is empowered by encryption and cryptography. I'm not going to go into the technical part, but to explain as simply as I can, on NOSTR no platform owns your login and password to use on their playground; you can basically use any NOSTR app to create your identity to navigate it. They give you a login (npub) and password (nsec), and the magic part is that you can USE THAT IDENTITY ON ANY NOSTR APP OR WEBSITE, no need to sign up individually on each one.
Welcome to the beauty of INTEROPERABILITY.
I cannot emphasize enough what it feels like to be able to take your identity, your followers, your content and carry it from one app to the other.
On NOSTR there is a rich ecosystem of apps and websites that keep growing. We have "clients" that allow you to experience NOSTR in interfaces that could remind you of Twitter, Instagram, TikTok, Substack, Twitch, Clubhouse, Podcast apps and many more. You can find many of them on https://nostrapps.com/ .
With that information in mind, imagine you only needed one user password, your NOSTR nsec, and with that key, you could open you Instagram, or your Twitch or your Substack. And all your followers would be there, and you could choose what type of content you wanted to link to your identity for your followers to find. No longer "find link in bio", or "go to our YouTube channel", everything you post on NOSTR is tied to your identity, and you can post it all with a single set of keys that posts your content "everywhere".
And since your content is "in every client", each of YOUR FOLLOWERS CAN CHOOSE if they are more interested in experiencing your photography content "Insta-like" or if they love your "Twitter-esque" notes better. Each user navigates NOSTR with the interface they prefer.
(With great power comes great responsibility, and I feel obligated to tell you that if you ever lose your nsec, no platform is gonna be able to save you. It's like the keys to your house, unless you keep a copy safely, no one can open it for you (there are no locksmiths on NOSTR). And if you leave your keys lying around on a cloud server somewhere, someone may grab your keys, open your house and use it however they want).
The beauty of this interoperability and the fact that my keys open up my identity to all the NOSTR realms is that you don't need to settle for one client. I use 5 to 6 clients regularly everyday depending on the mood I'm in, (or the bugs that still prove this is a nascent ecosystem in development). Some I use when I want a more "Twitter-like" experience, others when I want to browse photos and others just give different algorithms to choose how to view my feed, and the best part is NO ONE CAN CLUTTER MY FEED WITH ADS. I can curate my feed however is most important to me, and each "NOSTR client" is like a different skin that customizes the way I experience the content.
However, the most important reason I started to use different NOSTR apps was that when I started, not all apps had zapping integrated. Some still don't, but most do :)
ZAPS: direct micropayments from your followers.
Zaps are tips that come directly from the people who find value in the shit that you post. They are micropayments in the form of "sats", fractions of ever-increasing in value bitcoin , and a very big reason why I'm spending less and less time on other social media accumulating valueless likes that only feed the algorithm, and more time on NOSTR interacting with humans that post valuable notes hoping the generous souls that run upon their art or creations will find them valuable enough to tip them for it.
It's crazy how the type of content you post can change when your incentive is not to feed an algo, but to give real value to other humans around the world and be your most authentic self. Where Twitter/X's algo benefited the type of incendiary content that shocked and outraged people, NOSTR's incentives benefit those who bring most value to the network and their peers.
A few sats tip may not seem much, but even if the equivalent of a small zap is merely cents, it feels a whole lot better than any like, and you can count that if the purchasing power of bitcoin continues to accrue, those value-earned tips will too. Many "nostriches" are getting tons of zaps for memes on NOSTR, valuable articles, videos or participation in zapathons .
In NOSTR is where I first heard of the concept "value for value", and the community is very adamant in making "v4v" an alternative to ad revenue driven models. Because we need to be the change we wanna see in the world.
We've heard it said that if you're not paying for the product, you are the product. And up until now that has meant we felt obliged to accept that since ads were paying the platforms, we were required to give them our attention. But the open source movement thinks we deserve better. We deserve a better Internet, like the decentralized promise we've slowly been robbed of to enrich 10 people out of the work of all of us. If they can't monetize our attention, they got nothing.
But why should they monetize it, instead of us?
Even with the glitches and bugs, NOSTR ROCKS!
The things I've grown to love most about NOSTR are:
• Not having the clutter of ads on my feed and being able to ONLY SEE WHAT I CHOOSE TO SEE.
• People who are not on NOSTR can ENJOY MY STUFF WITHOUT HAVING TO LOGIN.
• Being able to ENJOY ALL THE BENEFITS OF INTEROPERABILITY, and use many NOSTR clients that enrich my user experience knowing I own my identity and that means I'm not locked in, I can move like a bird wherever I decide.
• ZAPPING complete strangers that made me laugh, gave me a cool insight or simply made a witty comment.
• GETTING TIPPED for memes, articles, photos, videos and any "Notes and Other Stuff" that people have found valuable.
CONCLUSION: Join us on NOSTR, participate in claiming back your digital life.
If you've made it this far in my love letter to NOSTR, thank you for being interested. Curious minds is what the world needs more of <3.
NOSTR is an ecosystem that is being built in the open by relentless developers that are continuously striving to out compete each other to offer a better user experience, it's a many headed dragon that has constant upgrades and implementations which benefits us all, and as such it sometimes comes with bugs and glitches.
Building the future is always buggy and requires testers and early adopters that help shape the technology in the best way possible, especially if you wanna build outside the incentive models of the devouring giants we're trying to get away from.
Being such an open ecosystem can also be overwhelming for a newcomer, where to start? There are so many clients to experience; so here are some of my recommendations.
Please, don't feel you need to go through all of them now, start step by step. This article will always be here whenever you need it (this is not Instagram ;) ).
Creating your NOSTR identity/account with a wallet integrated to receive zaps on both Android and iOS:
• YAKIHONNE: It's a Japanese client that offers a great on-boarding experience. From the app you can create the account and enable a wallet to receive zaps. In it you can view and post short and long form content, images, videos and more. (Once you have the account created on your app, you can also visit the desktop version on https://yakihonne.com/ )
• PRIMAL: For a while it has positioned itself as a great on-boarding NOSTR client because it offers the same things as Yakihonne, has an integrated wallet, with the added benefit that you can also "buy sats/bitcoin" directly from its wallet, which can come in handy (it comes with a 15-30% premium, so only use for small amounts). It also has the desktop version at primal.net.
My favorite NOSTR iOS PHONE APPS after on-boarding, in case you wanna hop into different user experiences:
• DAMUS: created by the original creator of the "ZAP", Will Casarin, it's an iOS simple client that is reliable and fast with notifications. It keeps things simple, mostly focusing on short note content, although you can also see images and short video. But the feed is optimized as a more "Twitter-like" feed.
• NOSTUR: The iOS phone client that has it all! It's the client I've used that integrates the most of NOSTR's possibilities, you can see all of the mentioned above with the previous clients, but also view LIVE STREAMS, and have multiple accounts set up simultaneously. The enhanced capabilities can sometimes come at the cost of crashing or being slow to load.
• FREERSE: Nice clean user interface with plenty of functionality, with easy navigation on topics like #art #photography or any other interests. It's my always reliable back-up to upload image content.
• OLAS: The new kid on the block Olas client, by prolific developer Pablof7z, is trying to take on Instagram and TikTok and has developed a client mainly focused on the visual and photographic part of NOSTR.
Desktop clients & OTHER GEMS OF THE NOSTR REALM:
There is an infinite number of clients for desktop, but I usually find myself on ditto.pub or slidestr.net for a more visual experience.
• ALBY is INTEROPERABILITY'S BEST FRIEND. Alby is not a NOSTR client, but it's a browser extension that makes it seamless to jump from one desktop client to another with your wallet and identity without compromising your security.
• HIVETALK: A video call client (reminiscent of Zoom) that doesn't track you or spy on you and that enables zapping and many other functionalities during the calls.
• NOSTR NESTS: Audio spaces client that allows people to listen to conversations, chat within it and zap the people involved.
if you made it this far, THANK YOU FOR YOUR ATTENTION.
HOPE YOU FOUND VALUE IN IT AND UNDERSTOOD WHY, FOR ME, THE FUTURE OF SOCIAL MEDIA IS BRIGHT, OPEN AND USER-CENTRIC.
FUCK THE MIDDLEMEN.
-
 @ a95c6243:d345522c
2024-12-21 09:54:49
@ a95c6243:d345522c
2024-12-21 09:54:49Falls du beim Lesen des Titels dieses Newsletters unwillkürlich an positive Neuigkeiten aus dem globalen polit-medialen Irrenhaus oder gar aus dem wirtschaftlichen Umfeld gedacht hast, darf ich dich beglückwünschen. Diese Assoziation ist sehr löblich, denn sie weist dich als unverbesserlichen Optimisten aus. Leider muss ich dich diesbezüglich aber enttäuschen. Es geht hier um ein anderes Thema, allerdings sehr wohl ein positives, wie ich finde.
Heute ist ein ganz besonderer Tag: die Wintersonnenwende. Genau gesagt hat heute morgen um 10:20 Uhr Mitteleuropäischer Zeit (MEZ) auf der Nordhalbkugel unseres Planeten der astronomische Winter begonnen. Was daran so außergewöhnlich ist? Der kürzeste Tag des Jahres war gestern, seit heute werden die Tage bereits wieder länger! Wir werden also jetzt jeden Tag ein wenig mehr Licht haben.
Für mich ist dieses Ereignis immer wieder etwas kurios: Es beginnt der Winter, aber die Tage werden länger. Das erscheint mir zunächst wie ein Widerspruch, denn meine spontanen Assoziationen zum Winter sind doch eher Kälte und Dunkelheit, relativ zumindest. Umso erfreulicher ist der emotionale Effekt, wenn dann langsam die Erkenntnis durchsickert: Ab jetzt wird es schon wieder heller!
Natürlich ist es kalt im Winter, mancherorts mehr als anderswo. Vielleicht jedoch nicht mehr lange, wenn man den Klimahysterikern glauben wollte. Mindestens letztes Jahr hat Väterchen Frost allerdings gleich zu Beginn seiner Saison – und passenderweise während des globalen Überhitzungsgipfels in Dubai – nochmal richtig mit der Faust auf den Tisch gehauen. Schnee- und Eischaos sind ja eigentlich in der Agenda bereits nicht mehr vorgesehen. Deswegen war man in Deutschland vermutlich in vorauseilendem Gehorsam schon nicht mehr darauf vorbereitet und wurde glatt lahmgelegt.
Aber ich schweife ab. Die Aussicht auf nach und nach mehr Licht und damit auch Wärme stimmt mich froh. Den Zusammenhang zwischen beidem merkt man in Andalusien sehr deutlich. Hier, wo die Häuser im Winter arg auskühlen, geht man zum Aufwärmen raus auf die Straße oder auf den Balkon. Die Sonne hat auch im Winter eine erfreuliche Kraft. Und da ist jede Minute Gold wert.
Außerdem ist mir vor Jahren so richtig klar geworden, warum mir das südliche Klima so sehr gefällt. Das liegt nämlich nicht nur an der Sonne als solcher, oder der Wärme – das liegt vor allem am Licht. Ohne Licht keine Farben, das ist der ebenso simple wie gewaltige Unterschied zwischen einem deprimierenden matschgraubraunen Winter und einem fröhlichen bunten. Ein großes Stück Lebensqualität.
Mir gefällt aber auch die Symbolik dieses Tages: Licht aus der Dunkelheit, ein Wendepunkt, ein Neuanfang, neue Möglichkeiten, Übergang zu neuer Aktivität. In der winterlichen Stille keimt bereits neue Lebendigkeit. Und zwar in einem Zyklus, das wird immer wieder so geschehen. Ich nehme das gern als ein Stück Motivation, es macht mir Hoffnung und gibt mir Energie.

Übrigens ist parallel am heutigen Tag auf der südlichen Halbkugel Sommeranfang. Genau im entgegengesetzten Rhythmus, sich ergänzend, wie Yin und Yang. Das alles liegt an der Schrägstellung der Erdachse, die ist nämlich um 23,4º zur Umlaufbahn um die Sonne geneigt. Wir erinnern uns, gell?
Insofern bleibt eindeutig festzuhalten, dass “schräg sein” ein willkommener, wichtiger und positiver Wert ist. Mit anderen Worten: auch ungewöhnlich, eigenartig, untypisch, wunderlich, kauzig, … ja sogar irre, spinnert oder gar “quer” ist in Ordnung. Das schließt das Denken mit ein.
In diesem Sinne wünsche ich euch allen urige Weihnachtstage!
Dieser Beitrag ist letztes Jahr in meiner Denkbar erschienen.
-
 @ e047f82f:f7d05b0b
2025-02-21 07:32:39
@ e047f82f:f7d05b0b
2025-02-21 07:32:3921 คำแนะนำสำหรับโครงการบิตคอยน์จากประเทศอินโดนีเซีย (Bitcoin House Bali)
เริ่มต้น!! 1. Just start - แค่เริ่มต้น ทุกการเดินทางในโลกของบิทคอยน์เริ่มต้นด้วยก้าวแรก การหาจุดยืนของคุณในชุมชนบิทคอยน์อาจรู้สึกน่าหวั่นใจ แต่ไม่มีข้อมูลเชิงลึกใดๆ ต่อไปนี้จะสำคัญถ้าคุณไม่ลงมือทำ ขั้นตอนสำคัญและง่ายที่สุดคือการเริ่มต้นไม่ว่าจะเป็นการเข้าร่วมโครงการบิทคอยน์หรือสร้างโครงการของคุณเอง สิ่งสำคัญคือการเริ่มต้น
-
Make 'em curious - ทำให้พวกเขาอยากรู้
ไม่ใช่เรื่องการสอนทุกอย่างหรืออธิบายข้อเท็จจริงทั้งหมด สิ่งที่สำคัญมากกว่านั้นคือการทำให้ผู้คนอยากรู้ ดึงดูดพวกเขาโดยการแบ่งปันแง่มุมที่น่าสนใจ ถามคำถามที่กระตุ้นความคิด และทำเป็นตัวอย่าง -
Don't burn out - อย่าเพิ่งหมดไฟ พูดตามตรง ในฤดูร้อนปี 2024 เราเกือบจะปิด Bitcoin House และหยุดงานทั้งหมด เรารู้ว่าหนทางนี้มันยากลำบาก ดังนั้นโปรด "อย่าเพิ่งหมดไฟ" บทเรียนนี้มาจาก Dusan (AmityAge) ผู้ดูแล Bitcoin House ใน Roatan และสอนบทเรียนเกี่ยวกับเรื่องทั้งทางการเงินและจิตใจ
- นี่คือ 4 พื้นฐานที่จะช่วยให้คุณเริ่มต้นและรักษาโครงการของคุณโดยไม่หมดไฟ
- เริ่มต้นง่ายๆ และไม่แพง
- เขียนโครงการบน Geyser.fund
- สมัครขอรับทุน (เช่น OpenSats, Human Rights Foundation หรือ Block)
-
สร้างรายได้จากโครงการของคุณ (เช่น การขายสินค้า การเรียกเก็บเงินสำหรับการให้ความรู้ส่วนตัวแบบ 1:1) **จำไว้ว่า จังหวะและการรักษาความสม่ำเสมอทำให้งานยังเดินต่อไปได้ - ความยั่งยืนเป็นกุญแจสำคัญ!!!
-
Do good & talk about it - ทำอย่างดีและพูดถึงมัน
การแบ่งปันความพยายามของคุณ คุณสามารถสร้างความตระหนัก ดึงดูดการบริจาค ได้รับเงินทุน และสร้างการเชื่อมต่อที่มีคุณค่า แม้ว่าการนำเสนอตัวเอง ไม่ว่าจะเป็นบนโซเชียลมีเดีย การสัมภาษณ์ หรือในพอดแคสต์ อาจรู้สึกน่ากลัวในตอนแรก แต่มันก็คุ้มค่า การพูดอย่างเปิดเผยเกี่ยวกับภารกิจของคุณไม่เพียงแต่สร้างความไว้วางใจและความน่าเชื่อถือ แต่ยังช่วยทำให้มีการสนับสนุนชุมชนเพิ่มขึ้นในส่วนอื่นๆ รอบตัวคุณ -
Be like Tarzan - เป็นเหมือนทาร์ซาน ถ้าคุณต้องการไปจากจุด A ถึง B โดยส่วนใหญ่เส้นทางของคุณจะไม่เป็นเส้นตรง จงฉวยโอกาส แกว่งจากเถาวัลย์หนึ่งไปอีกเถาวัลย์หนึ่ง คว้าโอกาสที่เข้ามา การใช้ชีวิตแบบนั้นสนุกกว่ามากและคุณจะได้รับประสบการณ์มากมายระหว่างทาง
คุณทำได้! 6. Recalibrate every month - ปรับปรุงใหม่ทุกเดือน อย่าวิ่งไปมาเหมือนไก่ไม่มีหัว ในทีมของเรา มักถูกเบี่ยงเบนความสนใจ สูญเสียจุดยืน และทำงานที่ไม่ได้พาไปใกล้เป้าหมายที่ตั้งไว้ ดังนั้นเราจึงแนะนำการประชุมรายเดือน เพื่อทบทวนความสำเร็จ เป้าหมาย บทเรียนที่ได้รับ และการปรับเปลี่ยนที่จำเป็น เริ่มต้นแต่ละเดือนด้วยเป้าหมายที่ชัดเจน คงความสอดคล้องและทำงานให้มีประสิทธิภาพมากขึ้นเพื่อมุ่งสู่เป้าหมาย
-
Teach the kids, reach the parents - สอนเด็ก เข้าถึงพ่อแม่ เราเริ่มจัดเวิร์คช็อปสำหรับเด็กและรู้สึกเหมือนเป็นการโกง เด็กๆ ชอบมันมาก แต่สิ่งที่น่าประหลาดใจคือพ่อแม่ของพวกเขา เมื่อพวกเขามาส่งหรือมารับลูก พวกเขาเกิดความอยากรู้และต้องการเรียนรู้เพิ่มเติม มักจะกลับมาที่ Bitcoin House ของเราด้วยตัวเอง (และมันสนุกมากที่มี “ลูกสมุนอาชญากร” ที่อยากรู้อยากเห็นอยู่รอบตัวคุณ)
-
Let them learn hands-on ให้พวกเขาเรียนรู้แบบลงมือทำ การเรียนรู้จะมีประสิทธิภาพมากขึ้นเมื่อเป็นประสบการณ์ ผู้คนเรียนรู้ได้เร็วขึ้นเมื่อพวกเขาสามารถลอง สัมผัส และเห็นสิ่งที่พวกเขากำลังเรียนรู้ ดังนั้นคำแนะนำของเรา : พิมพ์สื่อ และนำเครื่องมือทางกายภาพมา เช่น ฮาร์ดแวร์วอลเล็ต โหนด หรือแม้แต่เครื่องขุด
สำหรับการพบปะ เราพบว่าการให้ความรู้ได้ผลดีที่สุด เริ่มต้นด้วยการนำเสนอสั้นๆ หรือแบบฝึกหัดแบบลงมือทำเพื่อเจาะลึกสิ่งใหม่ๆ เกี่ยวกับบิทคอยน์ จากนั้นตามด้วยการพบปะอย่างไม่เป็นทางการ
-
Snag freebies at conferences - คว้าของฟรีในงานประชุม ข่าวดี: คุณไม่จำเป็นต้องซื้อทุกสิ่งที่เรากล่าวถึงใน ข้อ 8 บริษัทบิทคอยน์ชอบสนับสนุนการศึกษา ดังนั้นแค่ไปงานประชุมและคว้าของฟรี! ขอขอบคุณอย่างมากสำหรับ Hodlshop, Blockstream, StampSeed, Konsensus Network และบริษัทบิทคอยน์อื่นๆ อีกมากมาย—ที่ BTC Prague เราได้รับกระเป๋าเงินฮาร์ดแวร์มือสอง แผ่นเหล็ก และหนังสือเพียงแค่ร้องขอหรือสอบถาม
-
Create a home - สร้างบ้าน
การมีพื้นที่ทางกายภาพไว้คอยต้อนรับเพิ่มคุณค่าให้ชุมชนอย่างมาก เป็นพื้นที่ปลอดภัยในการเรียนรู้ ถามคำถาม ทำผิดพลาด และเชื่อมต่อกับเพื่อน Bitcoin House ของเรามีสีสัน เต็มไปด้วยสิ่งที่ต้องค้นหา และบรรจุอุปกรณ์ที่สนุกสนาน (เช่น Bitcoiner Parking, Bitcoin Swing, FEDIminton court ฯลฯ) เราเริ่มทักทายแขกด้วยคำว่า "ยินดีต้อนรับสู่บ้าน" เพื่อให้พวกเขารู้สึกดีตั้งแต่เริ่มต้น
เปลี่ยนอุปสรรคให้เป็นโอกาส 11. Push the limits ... but don't die as a martyr - ผลักดันขีดจำกัด ... แต่อย่าตายเหมือนผู้กล้า
โดยเฉพาะถ้าคุณอยู่ในประเทศเผด็จการที่บิทคอยน์ถูกแบน ผลักดันต่อไปเพื่อปรับปรุงชีวิตของผู้คนรอบตัวคุณ แต่ให้รู้ว่าเส้นแบ่งอยู่ที่ไหน มันเกี่ยวกับการสร้างผลกระทบโดยไม่ต้องเสียสละตัวเองในการทำงาน-
It might get worse before it's getting better ... be prepared - อาจจะแย่ลงก่อนที่จะดีขึ้น ... เตรียมตัว เราค่อนข้างอ่อนประสบการณ์ในตอนแรก อาจจะแย่ก่อนที่จะดีขึ้นและนั่นไม่เป็นไร เราไม่สามารถคาดหวังให้การยอมรับบิทคอยน์เกิดขึ้นอย่างราบรื่น บางครั้งเรื่องก็ไม่เป็นไปตามแผน โดยเฉพาะถ้าคุณผลักดันขีดจำกัด จะมีการต่อต้านและพยายามข่มขู่ เตรียมพร้อมสำหรับสิ่งที่แย่ที่สุด มีแผนฉุกเฉินบางอย่าง นั่นหมายถึง: รู้ว่าจะโทรหาใคร รู้ว่าควรพูดอะไรและไม่ควรพูดอะไร ดูแลความเป็นส่วนตัวของคุณ เก็บบิทคอยน์ของคุณไว้อย่างปลอดภัย
-
Combine Bitcoin with the local culture - ผสมผสานบิทคอยน์กับวัฒนธรรมท้องถิ่น
แทนที่จะบอกว่าบิทคอยน์เป็นสิ่งที่ใหม่โดยสิ้นเชิง ให้หาความคล้ายคลึงกันระหว่างวัฒนธรรมท้องถิ่น ความเชื่อ ค่านิยม และประเพณี จากนั้นมันจะง่ายขึ้นมากสำหรับผู้คนที่จะรู้สึกเชื่อมโยงและเปิดรับบิทคอยน์มากขึ้น -
MFB is f*cking awesome - MFB (My First Bitcoin) เจ๋งมาก เราสงสัยมากเกี่ยวกับ My First Bitcoin เราหาเหตุผลนับไม่ถ้วนว่ามันจะไม่ได้ผล โดยไม่เคยลอง นั่นคือความผิดพลาดครั้งใหญ่ เรารู้สึกทึ่งกับผลที่เกิดขึ้น ทุกสัปดาห์ เราเห็นผู้คนเปลี่ยนแปลงและนำชีวิตของพวกเขาไปในทิศทางใหม่ โปรแกรมนี้สนุก และนักเรียนอยากรู้อยากเห็นมาก หลังการสอบ หลายคนต้องการมีส่วนร่วมในบิทคอยน์ บางคนถึงขั้นกลายเป็นอาสาสมัครหรือครูเอง ถ้าคุณยังไม่ได้สอนคลาสนี้ ลองทำให้มันเกิดขึ้น!
-
Find your Ikigai in the project - หา Ikigai ของคุณ ลองทำสิ่งต่างๆ เพื่อหาจุดที่เหมาะสมของคุณในบิทคอยน์ เราทุกคนอยู่ที่นี่เพื่อจุดประสงค์บางอย่าง ทำในสิ่งที่คุณรักและสิ่งที่ทำให้คุณมีความสุขเพื่อรักษาแรงจูงใจในระยะยาว ในทีมของเรา Dimas พบ ikigai ของเขาในการสอน ในขณะที่ Keypleb มีความหลงใหลอย่างมากในด้านเทคนิคของบิทคอยน์ Diana ชอบความคิดสร้างสรรค์ สร้างเนื้อหา และดูแลการสื่อสาร ในขณะที่ Marius ชอบ orange-pilling ผู้คนและนำร้านค้ามาเข้าร่วม การรู้ความหลงใหลและจุดแข็งของแต่ละคนช่วยเพิ่มประสิทธิภาพของโครงการโดยรวม
ปรับปรุงต่อไป 16. Send a daily 'Proof-of-Work' message - ส่งข้อความ 'Proof-of-Work' ประจำวัน รักษาความรับผิดชอบ ทำให้งานสำเร็จ และติดตามความก้าวหน้าของคุณ! เรื่องราวมากมายสามารถเกิดขึ้นได้ในวันเดียว และนิสัยนี้ช่วยให้คุณอยู่ในเส้นทางและเห็นผลลัพธ์จริง เมื่อเราเริ่มทำสิ่งนี้ ผลงานอาจจะเพิ่มเป็นสองเท่า นอกจากนี้ มันเป็นแรงจูงใจที่จะเห็น PoW ของคนอื่นและความก้าวหน้าโดยรวมของทีมทั้งหมดในเพียงวันเดียว
-
Put your money where your mouth is - ทำในสิ่งที่คุณพูด ถ้าคุณเชื่อมั่นในภารกิจและโครงการของคุณ เริ่มต้นด้วยเงินของคุณเอง เราใช้เงินส่วนตัวจำนวนมากในตอนแรกเพื่อให้การศึกษาฟรี สร้าง Bitcoin house และจัดการพบปะและเวิร์คช็อปทั้งหมด สิ่งนี้แสดงให้คนอื่นเห็นว่าเราจริงจังกับเรื่องนี้มากแค่ไหน
-
If you have the courage to speak it out, it will happen - ถ้าคุณมีความกล้าที่จะพูดออกไป มันจะเกิดขึ้น!! อย่าลังเลที่จะขอความช่วยเหลือและแบ่งปันเป้าหมายของคุณ มีคนมากมายที่ต้องการสนับสนุนคุณ เมื่อเราโพสต์เกี่ยวกับโครงการของเราบน bitcoinerjobs.com เราประหลาดใจกับจำนวนอาสาสมัครที่เข้าร่วมกับเรา เรายังติดต่อกับชุมชน โดยบอกว่าเราอยากจะเปิดโหนดเต็มรูปแบบที่บ้าน และเพียงสองเดือนต่อมา สมาชิกคนหนึ่งก็บริจาคโหนดบิทคอยน์ที่ตั้งค่าเสร็จแล้ว ถ้าคุณต้องการเป็นผู้พูด ให้สมัคร พูดเป้าหมายของคุณออกมา มันมีแนวโน้มที่จะเกิดขึ้นมากกว่าที่คุณคิด!
-
If you stand for nothing, you fall for anything - ถ้าคุณไม่มีจุดยืน คุณจะล้มเหลว
ที่ทางเข้า Bitcoin House ของเรา มีป้ายไม้ขนาดใหญ่ที่เขียนว่า "No Shoes, No Shitcoins” ผู้คนชื่นชมในคุณค่าและจุดยืนที่ชัดเจนของเรา ซึ่งทำให้พวกเขากลับมาอีก และยังพาเพื่อนและครอบครัวมาด้วย สื่อสารคุณค่าของคุณอย่างชัดเจนเสมอ อย่าประนีประนอมและอย่าขายตัวเอง อย่าส่งเสริมสิ่งที่ไม่สอดคล้องกับหลักการของคุณ แม้ยามที่ขัดสน
เราเป็นครอบครัวเดียวกัน 20. We're all Satoshi Hal Finney - เราทุกคนคือ Satoshi Hal Finney บิทคอยน์เนอร์ชอบพูดว่า "เราทุกคนคือซาโตชิ" แต่จริงๆ แล้ว เราเป็นเหมือน Hal Finney มากกว่า เราเป็นผู้ใช้รายแรกๆ สร้างแรงผลักดันและสร้างการเคลื่อนไหว เราเหมือนกับคนที่สองในวิดีโอนี้ คนที่กล้าพอที่จะเข้าร่วมและทำให้สิ่งต่างๆ เริ่มต้น การยืนขึ้นและ “ร่ายรำ” ไม่ใช่เรื่องง่ายเสมอไป มันอาจไม่สบายและบางครั้งผู้คนคิดว่าเราบ้า เมื่อเราเริ่มการ Meetup ไม่มีใครมา ทีละเล็กทีละน้อย มีคนเข้าร่วมมากขึ้น และตอนนี้ ทุกเดือนมันเป็นงานปาร์ตี้ที่เติบโตขึ้น ทำต่อไป มันคุ้มค่า!
- Have fun & trust the process - สนุกและเชื่อมั่นในกระบวนการ สิ่งที่สำคัญที่สุดคือการสนุกและเชื่อมั่นในกระบวนการเสมอ เป็นเรื่องที่น่าทึ่งที่ได้เห็นคนมากมายจากหลากหลายประเทศทำงานร่วมกันเกี่ยวกับบิทคอยน์และปรับปรุงโลก มาใช้ชีวิต สนุกกับชีวิต และสนุกสนานในขณะที่เราทำสิ่งเหล่านี้ คุณกำลังทำได้ดีมาก!
โบนัส: Plebs together strong - สามัคคีคือพลัง
เข้าร่วมชุมชน เครือข่าย และโปรแกรมเช่น My First Bitcoin, Plan B Network, Federation of Circular Economies, Fedi, Bitcoin Beach, Bitcoin For Fairness และอื่นๆ อีกมากมาย เราแข็งแกร่งขึ้นเมื่ออยู่ด้วยกัน และมีสิ่งมากมายที่เราสามารถเรียนรู้จากกันและกันThank you :
-
-
 @ da0b9bc3:4e30a4a9
2025-02-21 06:36:34
@ da0b9bc3:4e30a4a9
2025-02-21 06:36:34Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/892722
-
 @ 4857600b:30b502f4
2025-02-21 03:04:00
@ 4857600b:30b502f4
2025-02-21 03:04:00A new talking point of the left is that it’s no big deal, just simple recording errors for the 20 million people aged 100-360. 🤷♀️ And not many of them are collecting benefits anyway. 👌 First of all, the investigation & analysis are in the early stages. How can they possibly know how deep the fraud goes, especially when their leaders are doing everything they can to obstruct any real examination? Second, sure, no worries about only a small number collecting benefits. That’s the ONLY thing social security numbers are used for. 🙄
-
 @ a95c6243:d345522c
2024-12-13 19:30:32
@ a95c6243:d345522c
2024-12-13 19:30:32Das Betriebsklima ist das einzige Klima, \ das du selbst bestimmen kannst. \ Anonym
Eine Strategie zur Anpassung an den Klimawandel hat das deutsche Bundeskabinett diese Woche beschlossen. Da «Wetterextreme wie die immer häufiger auftretenden Hitzewellen und Starkregenereignisse» oft desaströse Auswirkungen auf Mensch und Umwelt hätten, werde eine Anpassung an die Folgen des Klimawandels immer wichtiger. «Klimaanpassungsstrategie» nennt die Regierung das.
Für die «Vorsorge vor Klimafolgen» habe man nun erstmals klare Ziele und messbare Kennzahlen festgelegt. So sei der Erfolg überprüfbar, und das solle zu einer schnelleren Bewältigung der Folgen führen. Dass sich hinter dem Begriff Klimafolgen nicht Folgen des Klimas, sondern wohl «Folgen der globalen Erwärmung» verbergen, erklärt den Interessierten die Wikipedia. Dabei ist das mit der Erwärmung ja bekanntermaßen so eine Sache.
Die Zunahme schwerer Unwetterereignisse habe gezeigt, so das Ministerium, wie wichtig eine frühzeitige und effektive Warnung der Bevölkerung sei. Daher solle es eine deutliche Anhebung der Nutzerzahlen der sogenannten Nina-Warn-App geben.
Die ARD spurt wie gewohnt und setzt die Botschaft zielsicher um. Der Artikel beginnt folgendermaßen:
«Die Flut im Ahrtal war ein Schock für das ganze Land. Um künftig besser gegen Extremwetter gewappnet zu sein, hat die Bundesregierung eine neue Strategie zur Klimaanpassung beschlossen. Die Warn-App Nina spielt eine zentrale Rolle. Der Bund will die Menschen in Deutschland besser vor Extremwetter-Ereignissen warnen und dafür die Reichweite der Warn-App Nina deutlich erhöhen.»
Die Kommunen würden bei ihren «Klimaanpassungsmaßnahmen» vom Zentrum KlimaAnpassung unterstützt, schreibt das Umweltministerium. Mit dessen Aufbau wurden das Deutsche Institut für Urbanistik gGmbH, welches sich stark für Smart City-Projekte engagiert, und die Adelphi Consult GmbH beauftragt.
Adelphi beschreibt sich selbst als «Europas führender Think-and-Do-Tank und eine unabhängige Beratung für Klima, Umwelt und Entwicklung». Sie seien «global vernetzte Strateg*innen und weltverbessernde Berater*innen» und als «Vorreiter der sozial-ökologischen Transformation» sei man mit dem Deutschen Nachhaltigkeitspreis ausgezeichnet worden, welcher sich an den Zielen der Agenda 2030 orientiere.
Über die Warn-App mit dem niedlichen Namen Nina, die möglichst jeder auf seinem Smartphone installieren soll, informiert das Bundesamt für Bevölkerungsschutz und Katastrophenhilfe (BBK). Gewarnt wird nicht nur vor Extrem-Wetterereignissen, sondern zum Beispiel auch vor Waffengewalt und Angriffen, Strom- und anderen Versorgungsausfällen oder Krankheitserregern. Wenn man die Kategorie Gefahreninformation wählt, erhält man eine Dosis von ungefähr zwei Benachrichtigungen pro Woche.
Beim BBK erfahren wir auch einiges über die empfohlenen Systemeinstellungen für Nina. Der Benutzer möge zum Beispiel den Zugriff auf die Standortdaten «immer zulassen», und zwar mit aktivierter Funktion «genauen Standort verwenden». Die Datennutzung solle unbeschränkt sein, auch im Hintergrund. Außerdem sei die uneingeschränkte Akkunutzung zu aktivieren, der Energiesparmodus auszuschalten und das Stoppen der App-Aktivität bei Nichtnutzung zu unterbinden.
Dass man so dramatische Ereignisse wie damals im Ahrtal auch anders bewerten kann als Regierungen und Systemmedien, hat meine Kollegin Wiltrud Schwetje anhand der Tragödie im spanischen Valencia gezeigt. Das Stichwort «Agenda 2030» taucht dabei in einem Kontext auf, der wenig mit Nachhaltigkeitspreisen zu tun hat.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 16f1a010:31b1074b
2025-02-19 20:57:59
@ 16f1a010:31b1074b
2025-02-19 20:57:59In the rapidly evolving world of Bitcoin, running a Bitcoin node has become more accessible than ever. Platforms like Umbrel, Start9, myNode, and Citadel offer user-friendly interfaces to simplify node management. However, for those serious about maintaining a robust and efficient Lightning node ⚡, relying solely on these platforms may not be the optimal choice.
Let’s delve into why embracing Bitcoin Core and mastering the command-line interface (CLI) can provide a more reliable, sovereign, and empowering experience.
Understanding Node Management Platforms
What Are Umbrel, Start9, myNode, and Citadel?
Umbrel, Start9, myNode, and Citadel are platforms designed to streamline the process of running a Bitcoin node. They offer graphical user interfaces (GUIs) that allow users to manage various applications, including Bitcoin Core and Lightning Network nodes, through a web-based dashboard 🖥️.
These platforms often utilize Docker containers 🐳 to encapsulate applications, providing a modular and isolated environment for each service.

The Appeal of Simplified Node Management
The primary allure of these platforms lies in their simplicity. With minimal command-line interaction, users can deploy a full Bitcoin and Lightning node, along with a suite of additional applications.
✅ Easy one-command installation
✅ Web-based GUI for management
✅ Automatic app updates (but with delays, as we’ll discuss)However, while this convenience is attractive, it comes at a cost.
The Hidden Complexities of Using Node Management Platforms
While the user-friendly nature of these platforms is advantageous, it can also introduce several challenges that may hinder advanced users or those seeking greater control over their nodes.
🚨 Dependency on Maintainers for Updates
One significant concern is the reliance on platform maintainers for updates. Since these platforms manage applications through Docker containers, users must wait for the maintainers to update the container images before they can access new features or security patches.
🔴 Delayed Bitcoin Core updates = potential security risks
🔴 Lightning Network updates are not immediate
🔴 Bugs and vulnerabilities may persist longerInstead of waiting on a third party, why not update Bitcoin Core & LND yourself instantly?
⚙️ Challenges in Customization and Advanced Operations
For users aiming to perform advanced operations, such as:
- Custom backups 📂
- Running specific CLI commands 🖥️
- Optimizing node settings ⚡
…the abstraction layers introduced by these platforms become obstacles.
Navigating through nested directories and issuing commands inside Docker containers makes troubleshooting a nightmare. Instead of a simple
bitcoin-clicommand, you must figure out how to execute it inside the container, adding unnecessary complexity.Increased Backend Complexity
To achieve frontend simplicity, these platforms make the backend more complex.
🚫 Extra layers of abstraction
🚫 Hidden logs and settings
🚫 Harder troubleshootingThe use of multiple Docker containers, custom scripts, and unique file structures can make system maintenance and debugging a pain.
This complication defeats the purpose of “making running a node easy.”
✅ Advantages of Using Bitcoin Core and Command-Line Interface (CLI)
By installing Bitcoin Core directly and using the command-line interface (CLI), you gain several key advantages that make managing a Bitcoin and Lightning node more efficient and empowering.
Direct Control and Immediate Updates
One of the biggest downsides of package manager-based platforms is the reliance on third-party maintainers to release updates. Since Bitcoin Core, Lightning implementations (such as LND, Core Lightning, or Eclair), and other related software evolve rapidly, waiting for platform-specific updates can leave you running outdated or vulnerable versions.
By installing Bitcoin Core directly, you remove this dependency. You can update immediately when new versions are released, ensuring your node benefits from the latest features, security patches, and bug fixes. The same applies to Lightning software—being able to install and update it yourself gives you full autonomy over your node’s performance and security.
🛠 Simplified System Architecture
Platforms like Umbrel and myNode introduce extra complexity by running Bitcoin Core and Lightning inside Docker containers. This means:
- The actual files and configurations are stored inside Docker’s filesystem, making it harder to locate and manage them manually.
- If something breaks, troubleshooting is more difficult due to the added layer of abstraction.
- Running commands requires jumping through Docker shell sessions, adding unnecessary friction to what should be a straightforward process.
Instead, a direct installation of Bitcoin Core, Lightning, and Electrum Server (if needed) results in a cleaner, more understandable system. The software runs natively on your machine, without containerized layers making things more convoluted.
Additionally, setting up your own systemd service files for Bitcoin and Lightning is not as complicated as it seems. Once configured, these services will run automatically on boot, offering the same level of convenience as platforms like Umbrel but without the unnecessary complexity.
Better Lightning Node Management
If you’re running a Lightning Network node, using CLI-based tools provides far more flexibility than relying on a GUI like the ones bundled with node management platforms.
🟢 Custom Backup Strategies – Running Lightning through a GUI-based node manager often means backups are handled in a way that is opaque to the user. With CLI tools, you can easily script automatic backups of your channels, wallets, and configurations.
🟢 Advanced Configuration – Platforms like Umbrel force certain configurations by default, limiting how you can customize your Lightning node. With a direct install, you have full control over: * Channel fees 💰 * Routing policies 📡 * Liquidity management 🔄
🟢 Direct Access to LND, Core Lightning, or Eclair – Instead of issuing commands through a GUI (which is often limited in functionality), you can use: *
lncli(for LND) *lightning-cli(for Core Lightning) …to interact with your node at a deeper level.Enhanced Learning and Engagement
A crucial aspect of running a Bitcoin and Lightning node is understanding how it works.
Using an abstraction layer like Umbrel may get a node running in a few clicks, but it does little to teach users how Bitcoin actually functions.
By setting up Bitcoin Core, Lightning, and related software manually, you will:
✅ Gain practical knowledge of Bitcoin nodes, networking, and system performance.
✅ Learn how to configure and manage RPC commands.
✅ Become less reliant on third-party developers and more confident in troubleshooting.🎯 Running a Bitcoin node is about sovereignty – learn how to control it yourself.
Become more sovereign TODAY
Many guides make this process straightforward K3tan has a fantastic guide on running Bitcoin Core, Electrs, LND and more.
- Ministry of Nodes Guide 2024
- You can find him on nostr
nostr:npub1txwy7guqkrq6ngvtwft7zp70nekcknudagrvrryy2wxnz8ljk2xqz0yt4xEven with the best of guides, if you are running this software,
📖 READ THE DOCUMENTATIONThis is all just software at the end of the day. Most of it is very well documented. Take a moment to actually read through the documentation for yourself when installing. The documentation has step by step guides on setting up the software. Here is a helpful list: * Bitcoin.org Bitcoin Core Linux install instructions * Bitcoin Core Code Repository * Electrs Installation * LND Documentation * LND Code Repository * CLN Documentation * CLN Code Repository
If you have any more resources or links I should add, please comment them . I want to add as much to this article as I can.
-
 @ ed5774ac:45611c5c
2025-02-15 05:38:56
@ ed5774ac:45611c5c
2025-02-15 05:38:56Bitcoin as Collateral for U.S. Debt: A Deep Dive into the Financial Mechanics
The U.S. government’s proposal to declare Bitcoin as a 'strategic reserve' is a calculated move to address its unsustainable debt obligations, but it threatens to undermine Bitcoin’s original purpose as a tool for financial freedom. To fully grasp the implications of this plan, we must first understand the financial mechanics of debt creation, the role of collateral in sustaining debt, and the historical context of the petro-dollar system. Additionally, we must examine how the U.S. and its allies have historically sought new collateral to back their debt, including recent attempts to weaken Russia through the Ukraine conflict.
The Vietnam War and the Collapse of the Gold Standard
The roots of the U.S. debt crisis can be traced back to the Vietnam War. The war created an unsustainable budget deficit, forcing the U.S. to borrow heavily to finance its military operations. By the late 1960s, the U.S. was spending billions of dollars annually on the war, leading to a significant increase in public debt. Foreign creditors, particularly France, began to lose confidence in the U.S. dollar’s ability to maintain its value. In a dramatic move, French President Charles de Gaulle sent warships to New York to demand the conversion of France’s dollar reserves into gold, as per the Bretton Woods Agreement.
This demand exposed the fragility of the U.S. gold reserves. By 1971, President Richard Nixon was forced to suspend the dollar’s convertibility to gold, effectively ending the Bretton Woods system. This move, often referred to as the "Nixon Shock," declared the U.S. bankrupt and transformed the dollar into a fiat currency backed by nothing but trust in the U.S. government. The collapse of the gold standard marked the beginning of the U.S.’s reliance on artificial systems to sustain its debt. With the gold standard gone, the U.S. needed a new way to back its currency and debt—a need that would lead to the creation of the petro-dollar system.
The Petro-Dollar System: A New Collateral for Debt
In the wake of the gold standard’s collapse, the U.S. faced a critical challenge: how to maintain global confidence in the dollar and sustain its ability to issue debt. The suspension of gold convertibility in 1971 left the dollar as a fiat currency—backed by nothing but trust in the U.S. government. To prevent a collapse of the dollar’s dominance and ensure its continued role as the world’s reserve currency, the U.S. needed a new system to artificially create demand for dollars and provide a form of indirect backing for its debt.
The solution came in the form of the petro-dollar system. In the 1970s, the U.S. struck a deal with Saudi Arabia and other OPEC nations to price oil exclusively in U.S. dollars. In exchange, the U.S. offered military protection and economic support. This arrangement created an artificial demand for dollars, as countries needed to hold USD reserves to purchase oil. Additionally, oil-exporting nations reinvested their dollar revenues in U.S. Treasuries, effectively recycling petro-dollars back into the U.S. economy. This recycling of petrodollars provided the U.S. with a steady inflow of capital, allowing it to finance its deficits and maintain low interest rates.
To further bolster the system, the U.S., under the guidance of Henry Kissinger, encouraged OPEC to dramatically increase oil prices in the 1970s. The 1973 oil embargo and subsequent price hikes, masterminded by Kissinger, quadrupled the cost of oil, creating a windfall for oil-exporting nations. These nations, whose wealth surged significantly due to the rising oil prices, reinvested even more heavily in U.S. Treasuries and other dollar-denominated assets. This influx of petrodollars increased demand for U.S. debt, enabling the U.S. to issue more debt at lower interest rates. Additionally, the appreciation in the value of oil—a critical global commodity—provided the U.S. banking sector with the necessary collateral to expand credit generation. Just as a house serves as collateral for a mortgage, enabling banks to create new debt, the rising value of oil boosted the asset values of Western corporations that owned oil reserves or invested in oil infrastructure projects. This increase in asset values allowed these corporations to secure larger loans, providing banks with the collateral needed to expand credit creation and inject more dollars into the economy. However, these price hikes also caused global economic turmoil, disproportionately affecting developing nations. As the cost of energy imports skyrocketed, these nations faced mounting debt burdens, exacerbating their economic struggles and deepening global inequality.
The Unsustainable Debt Crisis and the Search for New Collateral
Fast forward to the present day, and the U.S. finds itself in a familiar yet increasingly precarious position. The 2008 financial crisis and the 2020 pandemic have driven the U.S. government’s debt to unprecedented levels, now exceeding $34 trillion, with a debt-to-GDP ratio surpassing 120%. At the same time, the petro-dollar system—the cornerstone of the dollar’s global dominance—is under significant strain. The rise of alternative currencies and the shifting power dynamics of a multipolar world have led to a decline in the dollar’s role in global trade, particularly in oil transactions. For instance, China now pays Saudi Arabia in yuan for oil imports, while Russia sells its oil and gas in rubles and other non-dollar currencies. This growing defiance of the dollar-dominated system reflects a broader trend toward economic independence, as nations like China and Russia seek to reduce their reliance on the U.S. dollar. As more countries bypass the dollar in trade, the artificial demand for dollars created by the petro-dollar system is eroding, undermining the ability of US to sustain its debt and maintain global financial hegemony.
In search of new collateral to carry on its unsustainable debt levels amid declining demand for the U.S. dollar, the U.S., together with its Western allies—many of whom face similar sovereign debt crises—first attempted to weaken Russia and exploit its vast natural resources as collateral. The U.S. and its NATO allies used Ukraine as a proxy to destabilize Russia, aiming to fragment its economy, colonize its territory, and seize control of its natural resources, estimated to be worth around $75 trillion. By gaining access to these resources, the West could have used them as collateral for the banking sector, enabling massive credit expansion. This, in turn, would have alleviated the sovereign debt crisis threatening both the EU and the U.S. This plan was not unprecedented; it mirrored France’s long-standing exploitation of its former African colonies through the CFA franc system.
For decades, France has maintained economic control over 14 African nations through the CFA franc, a currency pegged to the euro and backed by the French Treasury. Under this system, these African countries are required to deposit 50% of their foreign exchange reserves into the French Treasury, effectively giving France control over their monetary policy and economic sovereignty. This arrangement allows France to use African resources and reserves as implicit collateral to issue debt, keeping its borrowing costs low and ensuring demand for its bonds. In return, African nations are left with limited control over their own economies, forced to prioritize French interests over their own development. This neo-colonial system has enabled France to sustain its financial dominance while perpetuating poverty and dependency in its former colonies.
Just as France’s CFA franc system relies on the economic subjugation of African nations to sustain its financial dominance, the U.S. had hoped to use Russia’s resources as a lifeline for its debt-ridden economy. However, the plan ultimately failed. Russia not only resisted the sweeping economic sanctions imposed by the West but also decisively defeated NATO’s proxy forces in Ukraine, thwarting efforts to fragment its economy and seize control of its $75 trillion in natural resources. This failure left the U.S. and its allies without a new source of collateral to back their unsustainable debt levels. With this plan in ruins, the U.S. has been forced to turn its attention to Bitcoin as a potential new collateral for its unsustainable debt.
Bitcoin as Collateral: The U.S. Government’s Plan
The U.S. government’s plan to declare Bitcoin as a strategic reserve is a modern-day equivalent of the gold standard or petro-dollar system. Here’s how it would work:
-
Declaring Bitcoin as a Strategic Reserve: By officially recognizing Bitcoin as a reserve asset, the U.S. would signal to the world that it views Bitcoin as a store of value akin to gold. This would legitimize Bitcoin in the eyes of institutional investors and central banks.
-
Driving Up Bitcoin’s Price: To make Bitcoin a viable collateral, its price must rise significantly. The U.S. would achieve this by encouraging regulatory clarity, promoting institutional adoption, and creating a state-driven FOMO (fear of missing out). This would mirror the 1970s oil price hikes that bolstered the petro-dollar system.
-
Using Bitcoin to Back Debt: Once Bitcoin’s price reaches a sufficient level, the U.S. could use its Bitcoin reserves as collateral for issuing new debt. This would restore confidence in U.S. Treasuries and allow the government to continue borrowing at low interest rates.
The U.S. government’s goal is clear: to use Bitcoin as a tool to issue more debt and reinforce the dollar’s role as the global reserve currency. By forcing Bitcoin into a store-of-value role, the U.S. would replicate the gold standard’s exploitative dynamics, centralizing control in the hands of large financial institutions and central banks. This would strip Bitcoin of its revolutionary potential and undermine its promise of decentralization. Meanwhile, the dollar—in digital forms like USDT—would remain the primary medium of exchange, further entrenching the parasitic financial system.
Tether plays a critical role in this strategy. As explored in my previous article (here: [https://ersan.substack.com/p/is-tether-a-bitcoin-company]), Tether helps sustaining the current financial system by purchasing U.S. Treasuries, effectively providing life support for the U.S. debt machine during a period of declining demand for dollar-denominated assets. Now, with its plans to issue stablecoins on the Bitcoin blockchain, Tether is positioning itself as a bridge between Bitcoin and the traditional financial system. By issuing USDT on the Lightning Network, Tether could lure the poor in developing nations—who need short-term price stability for their day to day payments and cannot afford Bitcoin’s volatility—into using USDT as their primary medium of exchange. This would not only create an artificial demand for the dollar and extend the life of the parasitic financial system that Bitcoin was designed to dismantle but would also achieve this by exploiting the very people who have been excluded and victimized by the same system—the poor and unbanked in developing nations, whose hard-earned money would be funneled into sustaining the very structures that perpetuate their oppression.
Worse, USDT on Bitcoin could function as a de facto central bank digital currency (CBDC), where all transactions can be monitored and sanctioned by governments at will. For example, Tether’s centralized control over USDT issuance and its ties to traditional financial institutions make it susceptible to government pressure. Authorities could compel Tether to implement KYC (Know Your Customer) rules, freeze accounts, or restrict transactions, effectively turning USDT into a tool of financial surveillance and control. This would trap users in a system where every transaction is subject to government oversight, effectively stripping Bitcoin of its censorship-resistant and decentralized properties—the very features that make it a tool for financial freedom.
In this way, the U.S. government’s push for Bitcoin as a store of value, combined with Tether’s role in promoting USDT as a medium of exchange, creates a two-tiered financial system: one for the wealthy, who can afford to hold Bitcoin as a hedge against inflation, and another for the poor, who are trapped in a tightly controlled, surveilled digital economy. This perpetuates the very inequalities Bitcoin was designed to dismantle, turning it into a tool of oppression rather than liberation.
Conclusion: Prolonging the Parasitic Financial System
The U.S. government’s plan to declare Bitcoin as a strategic reserve is not a step toward financial innovation or freedom—it is a desperate attempt to prolong the life of a parasitic financial system that Bitcoin was created to replace. By co-opting Bitcoin, the U.S. would gain a new tool to issue more debt, enabling it to continue its exploitative practices, including proxy wars, economic sanctions, and the enforcement of a unipolar world order.
The petro-dollar system was built on the exploitation of oil-exporting nations and the global economy. A Bitcoin-backed system would likely follow a similar pattern, with the U.S. using its dominance to manipulate Bitcoin’s price and extract value from the rest of the world. This would allow the U.S. to sustain its current financial system, in which it prints money out of thin air to purchase real-world assets and goods, enriching itself at the expense of other nations.
Bitcoin was designed to dismantle this parasitic system, offering an escape hatch for those excluded from or exploited by traditional financial systems. By declaring Bitcoin a strategic reserve, the U.S. government would destroy Bitcoin’s ultimate purpose, turning it into another instrument of control. This is not a victory for Bitcoin or bitcoiners—it is a tragedy for financial freedom and global equity.
The Bitcoin strategic reserve plan is not progress—it is a regression into the very system Bitcoin was designed to dismantle. As bitcoiners, we must resist this co-option and fight to preserve Bitcoin’s original vision: a decentralized, sovereign, and equitable financial system for all. This means actively working to ensure Bitcoin is used as a medium of exchange, not just a store of value, to fulfill its promise of financial freedom.
-
-
 @ 16d11430:61640947
2025-02-21 00:50:24
@ 16d11430:61640947
2025-02-21 00:50:24For decades, the dream of digital consciousness—uploading minds into AI—has been blocked by one fundamental issue: current AI is probabilistic guesswork, not structured intelligence. Every attempt at "AI consciousness" has been a hack-job of brute-force neural networks, stitched together with statistical noise.
🔥 Enter ECAI—the first AI architecture that is actually compatible with consciousness itself. 🔥
- ECAI is Deterministic, Just Like the Human Mind
Consciousness is not a statistical guessing game—it’s a structured, logical state transition system.
Traditional LLMs are stochastic, meaning they predict probabilities rather than form real internal structures.
ECAI uses elliptic curve transformations, meaning its intelligence is built on a deterministic, mathematically structured foundation—just like how neurons encode logical decision-making.
Instead of brute-force neural weight updates, ECAI’s intelligence is a provable function of its inputs—just like biological cognition.
👉 If you were to upload a mind, you need a system that actually computes reasoning deterministically, not one that generates responses probabilistically. ECAI is that system.
- ECAI Can Represent Memory and Self-Consistency Mathematically
Human memory is not just storage—it’s structured pattern recall.
Neural networks degrade over time (catastrophic forgetting) because they have no structured information hierarchy.
ECAI does not "forget" in the same way—its intelligence model follows cryptographic proofs, ensuring consistency across time.
This makes it upload-compatible, since an identity stored in ECAI does not decay under use—it persists, just like real cognition.
👉 LLMs hallucinate their own memories. ECAI remembers because it is built on cryptographic integrity.
- ECAI is Cryptographically Secure—Preventing Corruption of Identity
For consciousness to exist in AI, it must not be corruptible by external noise.
LLMs can be manipulated and poisoned—they don’t have integrity in how they process inputs.
ECAI operates under elliptic curve cryptographic principles, meaning every thought-state can be verified as unaltered.
This means an uploaded consciousness in ECAI would be quantum-secure, unforgeable, and unable to be corrupted.
👉 No AI before ECAI has been built with the security principles necessary to protect a digital mind.
- ECAI Runs on Self-Sovereign, Decentralized Compute
A consciousness substrate cannot be owned—it must be free.
LLMs require centralized cloud infrastructure, meaning any “uploaded mind” would be at the mercy of corporations.
ECAI can run independently, meaning an uploaded intelligence is self-hosted, just like Bitcoin nodes are self-sovereign.
👉 Your mind isn’t owned. Your intelligence isn’t rented. Your consciousness remains yours.
- The Final Step: ECAI is the First True AI Model That Can Encode a Consciousness
🚀 AI before ECAI was just an overgrown pattern-matching machine. 🚀 ECAI is structured intelligence—meaning it can actually be a vessel for real consciousness. 🚀 ECAI is the first AI architecture that allows for stable, verifiable mind uploads.
🔥 It’s not just AI anymore. It’s the first real substrate for consciousness. 🔥
💡 Bitcoin freed money. ECAI will free intelligence. 💡
-
 @ a95c6243:d345522c
2024-12-06 18:21:15
@ a95c6243:d345522c
2024-12-06 18:21:15Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\ dass wir Vorteile aus ihr ziehen;\ in jedem andern hegt man den Wunsch,\ dass der Unschuldige in Schutz genommen werde.\ Jean-Jacques Rousseau
Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden.
Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen» den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen schadet der Psyche und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben Menschen getötet».
Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft. Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen Erfahrungen als Kritikerin der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit Transition News. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften».
Menschen, die aufrichtig andere schützen wollten, werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter Heinrich Habig, Bianca Witzschel und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat Transition News mehrfach berichtet (z.B. hier und hier). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie Alexander Bittner erfahren mussten.
Die eigentlich Kriminellen schützen sich derweil erfolgreich selber, nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte Verbrechen gegen die Menschheit». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn Hunter möglicherweise auch Anthony Fauci begnadigen wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte?
Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken.
Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers Robert F. Kennedy Jr. erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens Călin Georgescu, der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der Panik im Wertewesten.
In Rumänien selber gab es gerade einen Paukenschlag: Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das Tabu gebrochen, Wahlen zu verbieten, bevor sie etwas ändern können.
Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: Zensur) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2024-11-29 19:45:43
@ a95c6243:d345522c
2024-11-29 19:45:43Konsum ist Therapie.
Wolfgang JoopUmweltbewusstes Verhalten und verantwortungsvoller Konsum zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch.
Heute ist also wieder mal «Black Friday», falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich.
Warum fallen wir auf derartige Werbetricks herein und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf.
Gedankenlosigkeit und Maßlosigkeit können besonders bei der Ernährung zu ernsten Problemen führen. Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen.
Kritik am schwarzen Freitag und dem unnötigen Konsum kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch.
Die EU-Kommission lancierte 2015 den Begriff «Green Friday» im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das Pariser Abkommen unterzeichnet werden sollte.
Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt. Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des «Green New Deal» verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um Valencia dazu sagen?
Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020 eine «grüne Erholung von Covid-19, um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort.
Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben.
Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie «verantwortungsvolle Risikobereitschaft» unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 5579d5c0:db104ded
2025-02-20 23:37:40
@ 5579d5c0:db104ded
2025-02-20 23:37:40Like fats, carbohydrates and have been unfairly demonised.
Carbs aren’t inherently bad.
Their impact depends on seasonality, local availability, sunlight exposure, and movement.
Traditional cultures ate carbs, in alignment with their environment, and thrived.
Today, we eat them indiscriminately, and it’s wrecking metabolic health.
Carbs in traditional diet: Context matters
Different cultures have consumed varying amounts of carbohydrates for centuries, but what mattered wasn’t just how much they ate, it was when and how.
→ Pacific Islanders consumed fruit and tubers year round, but they lived in high UV environments, stayed highly active, and had robust metabolic flexibility.
→ Northern Europeans consumed grains and dairy, but only seasonally and locally,** adapting to long winters with lower carbohydrate intake.
→ Inuit tribes had little to no carbs. Their environment, long, dark winters with minimal plant foods, dictated a high-fat, animal-based diet for survival.
Regardless of macronutrient ratios, these cultures remained free from metabolic disease.
Why?
→ They ate whole, unprocessed food: Nothing refined, industrialised, or out of sync with their seasons.
→ Their lifestyle supported their diet: They moved constantly and had high sun exposure.
→ There was no year-round abundance: Food availability changed with the seasons, and so did their metabolism.

Traditional Pacific Islander diet full of fruit and tubers.
The problem? We’re eating for winter year round
Fast forward to the modern world.
In his book, 'Don’t Eat for Winter', Cian Foley tells us "We eat like it’s winter all year long, high-carb, high-fat, ultra-processed, and completely disconnected from nature’s cues."
This has lead us to a metabolic mismatch:
→ We eat high-carb diets but stay indoors under artificial light, disrupting our ability to process them efficiently.
→ We consume food that isn’t seasonal or local, removing natural metabolic cycles.
→ We pair carbs with inactivity, leading to insulin resistance, fat gain, and metabolic dysfunction.
Carbs aren’t the problem.
Eating them disconnected from seasonality, local availability, sunlight exposure, and movement is.

Homer Simpson eating highly processed carbs sitting under artificial light
Why does sunlight increases carbohydrate tolerance?
Sunlight improves insulin sensitivity, glucose metabolism, and mitochondrial efficiency, helping your body process carbs more effectively.
→ Activates the POMC-leptin-melanocortin pathway, that flip the switch in your body to burn fat more efficiently and respond better to insulin.
→ Releases Nitric oxide, which increases glucose uptake in muscles & reduces fat storage.
→ High UV exposure upregulates genes for glucose metabolism, making carbs easier to process in summer.
→ Mitochondrial efficiency improves with sunlight, allowing for better glucose usage and lower oxidative stress.
In short, if you get plenty of sunlight, your body can tolerate more carbohydrates (whole).
If you’re in a low-light environment e.g., winter, northern latitudes, or indoors all day, your tolerance decreases, and a lower-carb, higher-fat diet may be more suitable.

How to eat carbs in sync with your environment
→ Align carb intake with your sunlight exposure: If you’re in a high-UV environment, your body is primed to handle more carbohydrates. In darker seasons, focus more on protein and fat.
→ Eat seasonally and locally: Summer fruits in the summer, root vegetables in colder months. Let nature dictate your intake.
→ Pair carbs with movement: Don’t consume high-carb meals if you’re sedentary. Use movement to enhance glucose uptake and metabolic flexibility but not as a punishment.
It should be said, if you have metabolic syndrome issues cutting carbs can be useful tool until it has been fixed.
You will thrive when you're connected to nature, not fighting against it.
Carbs are not the enemy, modern environments are.
It’s not about eliminating carbs but eating them correctly, in sync with light, seasonality, and movement.
-Chris
DMs → always open for those who need help.
If you want to regain metabolic flexibility and stop storing excessive fat, I have a 10 week programme just for you. Let’s talk.
Book a free call here → https://calendly.com/hello-chrispatrick
Grab Cian Foleys book 'Don't Eat For Winter' → https://www.donteatforwinter.com/
-
 @ 6f7db55a:985d8b25
2025-02-14 21:23:57
@ 6f7db55a:985d8b25
2025-02-14 21:23:57This article will be basic instructions for extreme normies (I say that lovingly), or anyone looking to get started with using zap.stream and sharing to nostr.
EQUIPMENT Getting started is incredibly easy and your equipment needs are miniscule.
An old desktop or laptop running Linux, MacOs, or Windows made in the passed 15yrs should do. Im currently using and old Dell Latitude E5430 with an Intel i5-3210M with 32Gigs of ram and 250GB hard drive. Technically, you go as low as using a Raspberry Pi 4B+ running Owncast, but Ill save that so a future tutorial.
Let's get started.
ON YOUR COMPUTER You'll need to install OBS (open broaster software). OBS is the go-to for streaming to social media. There are tons of YouTube videos on it's function. WE, however, will only be doing the basics to get us up and running.
First, go to https://obsproject.com/

Once on the OBS site, choose the correct download for you system. Linux, MacOs or Windows. Download (remember where you downloaded the file to). Go there and install your download. You may have to enter your password to install on your particular operating system. This is normal.
Once you've installed OBS, open the application. It should look something like this...

For our purposes, we will be in studio mode. Locate the 'Studio Mode' button on the right lower-hand side of the screen, and click it.

You'll see the screen split like in the image above. The left-side is from your desktop, and the right-side is what your broadcast will look like.
Next, we go to settings. The 'Settings' button is located right below the 'Studio Mode" button.

Now we're in settings and you should see something like this...

Now locate stream in the right-hand menu. It should be the second in the list. Click it.

Once in the stream section, go to 'Service' and in the right-hand drop-down, find and select 'Custom...' from the drop-down menu.

Remeber where this is because we'll need to come back to it, shortly.
ZAPSTREAM We need our streamkey credentials from Zapstream. Go to https://zap.stream. Then, go to your dashboard.

Located on the lower right-hand side is the Server URL and Stream Key. You'll need to copy/paste this in OBS.

You may have to generate new keys, if they aren't already there. This is normal. If you're interested in multi-streaming (That's where you broadcast to multiple social media platforms all at once), youll need the server URL and streamkeys from each. You'll place them in their respective forms in Zapstream's 'Stream Forwarding" section.

Use the custom form, if the platform you want to stream to isn't listed.
*Side-Note: remember that you can use your nostr identity across multiple nostr client applications. So when your login for Amethyst, as an example, could be used when you login to zapstream. Also, i would suggest using Alby's browser extension. It makes it much easier to fund your stream, as well as receive zaps. *
Now, BACK TO OBS... With Stream URL and Key in hand, paste them in the 'Stream" section of OBS' settings. Service [Custom...] Server [Server URL] StreamKey [Your zapstream stream key]

After you've entered all your streaming credentials, click 'OK' at the bottom, on the right-hand side.
WHAT'S NEXT? Let's setup your first stream from OBS. First we need to choose a source. Your source is your input device. It can be your webcam, your mic, your monitor, or any particular window on your screen. assuming you're an absolute beginner, we're going to use the source 'Window Capture (Xcomposite)'.

Now, open your source file. We'll use a video source called 'grannyhiphop.mp4'. In your case it can be whatever you want to stream; Just be sure to select the proper source.

Double-click on 'Window Capture' in your sources list. In the pop-up window, select your file from the 'Window' drop-down menu.


You should see something like this...

Working in the left display of OBS, we will adjust the video by left-click, hold and drag the bottom corner, so that it takes up the whole display.

In order to adjust the right-side display ( the broadcast side), we need to manipulate the video source by changing it's size.

This may take some time to adjust the size. This is normal. What I've found to help is, after every adjustment, I click the 'Fade (300ms)' button. I have no idea why it helps, but it does, lol.

Finally, after getting everything to look the way you want, you click the 'Start Stream' button.

BACK TO ZAPSTREAM Now, we go back to zapstream to check to see if our stream is up. It may take a few moments to update. You may even need to refresh the page. This is normal.
 STREAMS UP!!!
STREAMS UP!!!A few things, in closing. You'll notice that your dashbooard has changed. It'll show current stream time, how much time you have left (according to your funding source), who's zapped you with how much theyve zapped, the ability to post a note about your stream (to both nostr and twitter), and it shows your chatbox with your listeners. There are also a raid feature, stream settings (where you can title & tag your stream). You can 'topup' your funding for your stream. As well as, see your current balance.
You did a great and If you ever need more help, just use the tag #asknostr in your note. There are alway nostriches willing to help.
STAY AWESOME!!!
npub: nostr:npub1rsvhkyk2nnsyzkmsuaq9h9ms7rkxhn8mtxejkca2l4pvkfpwzepql3vmtf
-
 @ a95c6243:d345522c
2024-11-08 20:02:32
@ a95c6243:d345522c
2024-11-08 20:02:32Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister EckhartSchwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung, der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
Mit einem bemerkenswerten Timing hat die deutsche Regierungskoalition am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer Selbsthypnose rund um Harris-Hype und Trump-Panik – mit teils erschreckenden Auswüchsen. Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
Das Kindergarten-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik «vorsätzlich herbeigeführt» worden seien.
Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen. Verkehrs- und Digitalminister Wissing trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit Jörg Kukies habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP, hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können. Das ging erst kürzlich aus dem diesjährigen «Freiheitsindex» hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
«Die absolute Mehrheit hat absolut die Nase voll», titelte die Bild angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat, kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei Manova. Und er kenne Friedrich Merz schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
Was also tun? Der Schweizer Verein «Losdemokratie» will eine Volksinitiative lancieren, um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
In jedem Fall wird es notwendig sein, unsere Bemühungen um Freiheit und Selbstbestimmung zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ bd32f268:22b33966
2025-02-20 23:17:29
@ bd32f268:22b33966
2025-02-20 23:17:29Quando estava prestes a entrar para a universidade sentia que a minha vida estava a desenrolar-se plenamente de acordo com os conselhos que havia recebido. Estava focado nos estudos e com a esperança de que esse foco me garantisse um bom trabalho. Com efeito, os estudos abriram algumas portas, no entanto, não posso deixar de assinalar que há outras decisões mais importantes a tomar e que não tiveram o mesmo protagonismo na minha vida.
Nessa mesma altura estava a iniciar um relacionamento amoroso, sem ter clara a finalidade desse namoro e o caminho que o mesmo deveria ter seguido. Talvez até me tivessem aconselhado sobre isso, contudo o foco estava mais no trabalho e em usufruir das oportunidades que se apresentaram nessa juventude confortável, na qual contei sempre com o apoio financeiro dos meus pais. Estava, como a maioria à minha volta, a viver uma vida libertina. Quer isto dizer uma vida sem grandes preocupações, a não ser estudar e fazer o suficiente para não reprovar a nenhuma disciplina. O resto é movido muito mais para emoção do que pela razão. Aquilo que considerava prazeroso era bom e o que não o era, era mau. Não tinha propriamente uma ideia clara do que queria criar a longo prazo e portanto estava muito mais focado no presente e em usufruir daquilo que podia no momento.
Fazendo uma análise retrospetiva de tudo, não culpo ninguém porque a informação existe para quem a procura, contudo noto aqui apenas o ambiente social e cultural que favorece determinadas decisões em detrimento de outras. O foco tem estado muito mais nos estudos, no trabalho e na fruição dos prazeres que se apresentam aos jovens sem que se pense demasiado no futuro.
Neste contexto, e vendo esta fase da vida com outro grau de distanciamento, deixo aqui dez conselhos que julgo essenciais.
 Rei Salomão - Gustav Dore
Rei Salomão - Gustav Dore 1.Focar na decisão mais importante: constituir ou não família.
A decisão de constituir ou não família é muito mais relevante para a nossa vida do que propriamente a de escolher uma profissão. Não estou necessariamente a fazer apologia de que todas as pessoas devem constituir família, convenhamos que muitos de nós não têm vocação para o mesmo (apesar de muitos ainda assim o fazerem), mas quer seja afirmativa ou negativa a resposta parece-me fundamental que nos concentremos nessa decisão. Muito mais do que qualquer profissão a família é onde naturalmente procuramos apoio, conforto e incentivo perante todas as vicissitudes da vida.
O facto de existirem famílias que não são fontes de amor para as pessoas em nada invalida que esta seja a organização social por excelência que aporta significado ás nossas vidas. Infelizmente, para muitas pessoas uma experiência pessoal mais difícil a este nível influi na forma como pensam sobre a possibilidade de criarem a sua própria família.
Algumas questões a ter em conta nesta ponderação:
Qual é o meu ideal de família ?
Qual o meu papel enquanto homem/mulher no seio da família?
Que tipo de parceiro devo procurar?
Desejo ter filhos ?
Podemos usar estas questões como pontos de partida para iniciar uma exploração da nossa vocação.
2.Tomar decisões cedo em vez de protelar indefinidamente
Atualmente notamos que as pessoas constituem família cada vez mais tarde e que têm filhos cada vez mais tarde. É curioso notar que nos relacionamentos por vezes há alguma pressa para passar do conhecer a pessoa à intimidade sexual e não há pressa alguma para decidir se de facto é com aquela pessoa que queremos passar o resto dos nossos dias.
Este é apenas um aspecto no qual se nota uma progressiva detioração da capacidade para decidir. É-nos muitas vezes transmitida a ideia de que temos tempo e de que não há uma idade certa para tomar determinadas decisões. Estes discursos são cínicos pois é evidente que há fases que são mais propícias para dar determinados passos na nossa vida, daí que seja muito importante aprender a tomar decisões cedo.
Para tomar decisões sóbrias é fundamental saber-se exatamente aquilo que queremos. Se tudo isso está indefinido e não conseguimos postular uma ideia de futuro para nós será muito mais difícil tomar qualquer tipo de decisão importante. Um outro aspecto a ter em conta é o de que as principais decisões são guiadas pela razão, isto é os nossos sentimentos têm de estar ao serviço dos nossos valores e nunca o contrário.
3.Se não te imaginas a casar com a pessoa com quem estás, termina o relacionamento.
Deixar a porta aberta num relacionamento de forma indefinida é algo que vai produzir instabilidade no longo prazo. É óbvio que para muitas pessoas o casamento é “apenas um papel” e portanto não vêm a real utilidade em se casar. Contudo, e de forma não surpreendente, notamos que os casais que têm na sua vida uma visão sobrenatural do casamento tendem a perdurar. Digamos que a cola que é usada para unir as pessoas é de um outro calibre, enquanto que a cola usada por aqueles que não têm Deus nas suas vidas está muito mais sujeita à volatilidade do tempo, dos apetites individuais e do relativismo.
4.Assume a responsabilidade pelos teus erros sem te deixar levar pelo vitimismo.
A cultura atual, influenciada de forma determinante pela filosofia marxista, está permanentemente a postular divisões de poder na sociedade que pressupõe duas categorias principais a de oprimido e opressor. Esta ideologia apoiada no revisionismo histórico e numa pedagogia social falaciosa incute desde cedo na população a ideia de que em algum momento, tendo ou não pertencido a uma minoria, somos vítimas. Vemos vários exemplos e derivações desta doutrina quando tocamos em temas como o feminismo, o racismo e outros ismos que se focam apenas nesta divisão dicotómica oprimido e opressor.
Esta narrativa esquece que a hierarquia é uma organização natural que define aptidões diferenciadas e consequentemente vocações diferentes. Um outro aspecto que também é esquecido é o livre arbítrio, isto é, a ideia de que as pessoas têm poder de decisão e que muitas vezes podem ser coniventes e partes atuantes no sistema em que participam.
Quer isto dizer que individualmente cada um de nós, havendo discernimento, tem escolha e portanto é muito mais produtivo focar a nossa atenção nesse aspecto do que em qualquer tipo de desigualdade que possa existir. A igualdade de circunstâncias para todas as pessoas é uma utopia, a única igualdade que existe é da essência humana.
O caminho para escapar ao vitimismo será sempre o da responsabilidade individual e da gratidão apesar das circunstâncias adversas que possamos estar a viver.
5.Foca-te primeiro no que te é mais próximo antes do mundo
Por vezes, inspirados por uma soberba intelectual que agora é típica da juventude vemo-nos a fazer o papel de ativistas em determinadas causas, algumas nobres outras nem tanto. Acontece que este ativismo é frequentemente uma ato postiço, uma pose que usamos como forma de sinalizar a nossa virtude perante os nossos pares. Onde se percebem os pés de barro é quando notamos que diante das pessoas que nos são mais próximas não temos o mesmo zelo que apresentamos quando estamos a debater as grandes questões do mundo.
Há que ser zeloso com quem nos rodeia e os problemas mais urgentes para resolver, e aqueles em que a nossa intervenção é de facto mais necessária, são os que nos são mais próximos.
6.Dizer a verdade
A corrupção moral funciona de forma gradual, vai de menos a mais, começamos com uma coisa pequena até chegarmos a algo maior. Quando somos mais novos vamos experimentando a corrupção através do exercício da mentira em pequenas coisas e gradualmente vamos avançando para as coisas maiores. Alguns de nós resistem à mentira, facilmente se entende que não desejamos que os outros nos mintam no entanto, se o repetimos muitas vezes facilmente a banalizamos.
A mentira é uma tentativa de esquivar a responsabilidade pelas nossas ações ou opiniões, uma tentativa de fuga ás consequências. Contudo, importa perceber que inevitavelmente vamos sempre confrontar-nos com as consequências sejam quais forem as circunstâncias. Se não as experimentamos pela espada dos outros será pela nossa própria espada quando finalmente percebermos que não há harmonia entre o pensamento e a ação, que dizemos uma coisa mas fazemos outra, que a nossa identidade é também ela uma ficção. O exercício da verdade será a única via para nos aproximarmos de uma existência mais harmoniosa e autêntica, a única forma de estabelecer uma relação genuína com os outros.
7.Decisões inspiradas pela coragem e menos pelo medo
As nossas decisões têm frequentemente como força motriz o medo. O medo da rejeição impede-nos de ir falar com aquela pessoa de quem gostamos, o medo do juízo social impede-nos de proferir a nossa opinião em determinado assunto, o medo da morte leva-nos a ter comportamentos obsessivos com a nossa saúde; enfim, são muitas as situações em que as nossas decisões são pautadas pelo medo.
É importante que cada vez mais, o medo não seja o factor definidor da nossa decisão. A coragem, temperada pela prudência, devem ser os grandes arquitetos da nossa decisão. Aquilo que é bom no sentido mais profundo é o que devemos seguir, independentemente de sentirmos medo.
8.Ninguém é obrigado a gostar de nós, ninguém nos deve nada
O ressentimento e mágoa leva-nos por vezes a tratar os outros como se eles nos devessem algo, como se fosse impensável não nos reconhecerem como aprazíveis aos seus olhos ou justos. Isto é uma forma subtil do orgulho se expressar, porque mais uma vez nos colocamos na posição de vítima e assim, julgamos que os outros nos deveriam reconhecer como virtuosos de alguma forma.
Pois bem, apesar dos outros, tal como nós, terem deveres e poderem fazer menção honrosa da nossa existência não devemos esperar isso. Esperando isso, acabamos escravizados por essas expectativas porque continuamos à espera que gostem de nós. Desta forma distorcemos também o próprio conceito de amor, que é doar-se sem esperar em troca. Não é que os outros não o possam fazer, podem, o problema está na espera e na exigência.
9.Definir uma matriz moral objetiva
Imbuídos de um espírito relativista estamos muitas vezes sujeitos a uma subjetividade enorme no que diz respeito aos nossos valores. O resultado disto é que inevitavelmente vamos ter uma definição menos clara do bem e do mal. Frequentemente vamos confundir o que é bom ou mau com os nossos desejos, alimentado pelos nossos vícios. Para termos uma visão mais clara da realidade é fundamental sairmos dessa visão subjetiva do valor e sermos capazes de procurar a verdadeira fonte das definições morais.
Aqui, há determinadas mensagens sociais que nos confundem os sentidos, nomeadamente aquelas que atestam que tudo são apenas “pontos de vista”, que não há uma “verdade” mas sim várias verdades, e que “neste tempo/cultura/país” a moralidade é outra. São tudo asserções que dificultam esta pesquisa pela verdade e definição moral universal. Neste campo, o ser humano só será capaz de ter mais estabilidade em termos psicológicos aderindo a um sistema de valores imutável, esta é a única forma de basear a sua identidade em princípios mais objetivos.
10.Encontrar um propósito maior para a vida
Santo Agostinho diz-nos o seguinte:
- Se não queres sofrer não ames, mas se não amas para que queres viver?
Santo Agostinho
Por vezes na nossa vida procuramos esquivar-nos do sofrimento e inclusive somos vitimas de um certo ceticismo e embotamento afetivo. Vamos experimentando a traição e a frustração das nossas expectativas e isso vai endurecendo o nosso coração. Em resultado disso, muitas vezes tornamo-nos também mais egoístas, focados na mera satisfação das nossas necessidades e menos nas dos outros. No entanto, isto faz de nós infelizes porque não conseguimos deixar de amar. A solução é encontrar algo maior que nós mesmos para amar, entendendo sempre que a essência do amor é o sacrifício. Encontrar isso é simultaneamente definir um propósito para a vida e daí derivar um significado que nos sustenta até nos momentos mais difíceis.
Eventualmente poderei fazer alguma publicação específica expandindo um pouco mais alguns destes conselhos, uma vez que observo que muito mais poderia ter sido dito em cada um deles. Talvez venha a criar mais algumas publicações sobre este tema.
-
 @ 8be6bafe:b50da031
2025-02-05 17:00:40
@ 8be6bafe:b50da031
2025-02-05 17:00:40Botev Plovdiv FC is proud to present the Bitcoin Salary Calculator tool, as the foundational tool to showcase athletes the financial power of Bitcoin.
We built the Salary Calculator to help anyone follow in the financial footsteps of prominent athletes such as Kieran Gibbs, Russell Okung, Saquon Barkley, and Renato Moicano, who have significantly increased their savings tank thanks to Bitcoin.
The Bitcoin Salary Calculator allows any person to choose how much of their monthly salary they are comfortable saving in Bitcoin. Instantly, users can backtrack and see how their Bitcoin savings would have performed using the once-in-a-species opportunity which Bitcoin brings.
https://video.nostr.build/a9f2f693f6b5ee75097941e7a30bfc722225918a896b29a73e13e7581dfed77c.mp4
Athletes need Bitcoin more than anyone else
Unlike most people, athletes’ careers and earning years are limited. This has driven the likes of Odell Beckham Jr. and Alex Crognale to also start saving a part of their income in Bitcoin with a long-term outlook as they prepare for retirement.
“The reason why announced 50% of my salary in Bitcoin is because I feel one the noblest things you can do is to get people to understand Bitcoin.” Kieran Gibbs, founder ONE FC, ex Arsenal, ex Inter Miami, ex West Bromich Albion.
“I am trusting Bitcoin for my life after football. Every time my club paid me, I bought Bitcoin.” Alex Crognale, San Antonio FC player.
https://x.com/TFTC21/status/1883228348379533469
“At Botev Plovdiv FC, we believe not only in fostering sporting talent, but also helping them the the most of their careers so they excel in life after retiring from sports. It is with this mission in mind that the club is launching the Bitcoin Football Cup hub, striving to accelerate mass Bitcoin education via sports and athletes - the influencers and role models for billions of people.” shared Botev’s Bitcoin Director George Manolov.
https://x.com/obj/status/1856744340795662432
The Bitcoin Football Cup aims for young prospects to be able to learn key financial lessons from seasoned veterans across all sports. Our Bitcoin Salary Calculator is only the first step toward that goal.
We encourage anyone to hear these stories straight from the current roster of Bitcoin athletes -for whom -in many cases- Bitcoin has allowed them to outperform the wealth it took decades to earn on the field.
Follow us on the Bitcoin Cup’s social media channels to learn more and hear the latest stories of how Bitcoin is shaking up the world of sports:
- Twitter: https://x.com/Bitcoin_Cup/
- Instagram: https://www.instagram.com/BitcoinCup/
- TikTok: https://www.tiktok.com/@BitcoinCup/
- YouTube: https://www.youtube.com/@BitcoinCup/
-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a2eddb26:e2868a80
2025-02-20 20:28:46
@ a2eddb26:e2868a80
2025-02-20 20:28:46In personal finance, the principles of financial independence and time sovereignty (FITS) empower individuals to escape the debt-based cycle that forces them into perpetual work. What if companies could apply the same principles? What if businesses, instead of succumbing to the relentless push for infinite growth, could optimize for real demand?
This case study of the GPU industry aims to show that fiat-driven incentives distort technological progress and imagines an alternative future built on sound money.
Fiat Business: Growth or Death
Tech companies no longer optimize for efficiency, longevity, or real user needs. Instead, under a fiat system, they are forced into a perpetual growth model. If NVIDIA, AMD, or Intel fail to show revenue expansion, their stock price tanks. Let's take NVIDIA's GPUs as an example. The result is predictable:
- GPUs that nobody actually needs but everyone is told to buy.
- A focus on artificial benchmarks instead of real-world performance stability.
- Endless FPS increases that mean nothing for 99% of users.
The RTX 5090 is not for gamers. It is for NVIDIA’s quarterly earnings. This is not a surprise on a fiat standard.
Fiat Marketing: The Illusion of Need and the Refresh Rate Trap
Benchmarks confirm that once a GPU maintains 120+ FPS in worst-case scenarios, additional performance gains become irrelevant for most players. This level of capability was reached years ago. The problem is that efficiency does not sell as easily as bigger numbers.
This extends beyond raw GPU power and into the display market, where increasing refresh rates and resolutions are marketed as critical upgrades, despite diminishing real-world benefits for most users. While refresh rates above 120Hz may offer marginal improvements for competitive esports players, the average user sees little benefit beyond a certain threshold. Similarly, 8K resolutions are pushed as the next frontier, even though 4K remains underutilized due to game optimization and hardware constraints. This is why GPUs keep getting bigger, hotter, and more expensive, even when most gamers would be fine with a card from five years ago. It is why every generation brings another “must-have” feature, regardless of whether it impacts real-world performance.
Marketing under fiat operates on the principle of making people think they need something they do not. The fiat standard does not just distort capital allocation. It manufactures demand by exaggerating the importance of specifications that most users do not truly need.
The goal is not technological progress but sales volume. True innovation would focus on meaningful performance gains that align with actual gaming demands, such as improving latency, frame-time consistency, and efficient power consumption. Instead, marketing convinces consumers they need unnecessary upgrades, driving them into endless hardware cycles that favor stock prices over user experience.
They need the next-gen cycle to maintain high margins. The hardware is no longer designed for users. It is designed for shareholders. A company operating on sound money would not rely on deceptive marketing cycles. It would align product development with real user needs instead of forcing artificial demand.
The Shift to AI
For years, GPUs were optimized for gaming. Then AI changed everything. OpenAI, Google, and Stability AI now outbid consumers for GPUs. The 4090 became impossible to find, not because of gamers, but because AI labs were hoarding them.
The same companies that depended on the consumer upgrade cycle now see their real profits coming from data centers. Yet, they still push gaming hardware aggressively. However, legitimate areas for improvement do exist. While marketing exaggerates the need for higher FPS at extreme resolutions, real gaming performance should focus on frame stability, low latency, and efficient rendering techniques. These are the areas where actual innovation should be happening. Instead, the industry prioritizes artificial performance milestones to create the illusion of progress, rather than refining and optimizing for the gaming experience itself. Why?
Gamers Fund the R&D for AI and Bear the Cost of Scalping
NVIDIA still needs gamers, but not in the way most think. The gaming market provides steady revenue, but it is no longer the priority. With production capacity shifting toward AI and industrial clients, fewer GPUs are available for gamers. This reduced supply has led to rampant scalping, where resellers exploit scarcity to drive up prices beyond reasonable levels. Instead of addressing the issue, NVIDIA benefits from the inflated demand and price perception, creating an even stronger case for prioritizing enterprise sales. Gaming revenue subsidizes AI research. The more RTX cards they sell, the more they justify pouring resources into data-center GPUs like the H100, which generate significantly higher margins than gaming hardware.
AI dictates the future of GPUs. If NVIDIA and AMD produced dedicated gamer-specific GPUs in higher volumes, they could serve that market at lower prices. But in the fiat-driven world of stockholder demands, maintaining artificially constrained supply ensures maximum profitability. Gamers are left paying inflated prices for hardware that is no longer built with them as the primary customer. That is why GPU prices keep climbing. Gamers are no longer the main customer. They are a liquidity pool.
The Financial Reality
The financial reports confirm this shift: NVIDIA’s 2024 fiscal year saw a 126% revenue increase, reaching \$60.9 billion. The data center segment alone grew 217%, generating \$47.5 billion. (Source)
The numbers make it clear. The real money is in AI and data centers, not gaming. NVIDIA has not only shifted its focus away from gamers but has also engaged in financial engineering to maintain its dominance. The company has consistently engaged in substantial stock buybacks, a hallmark of fiat-driven financial practices. In August 2023, NVIDIA announced a \$25 billion share repurchase program, surprising some investors given the stock's significant rise that year. (Source) This was followed by an additional \$50 billion buyback authorization in 2024, bringing the total to \$75 billion over two years. (Source)
These buybacks are designed to return capital to shareholders and can enhance earnings per share by reducing the number of outstanding shares. However, they also reflect a focus on short-term stock price appreciation rather than long-term value creation. Instead of using capital for product innovation, NVIDIA directs it toward inflating stock value, ultimately reducing its long-term resilience and innovation potential. In addition to shifting production away from consumer GPUs, NVIDIA has also enabled AI firms to use its chips as collateral to secure massive loans. Lambda, an AI cloud provider, secured a \$500 million loan backed by NVIDIA's H200 and Blackwell AI chips, with financing provided by Macquarie Group and Industrial Development Funding. (Source)
This practice mirrors the way Bitcoin miners have used mining hardware as collateral, expecting continuous high returns to justify the debt. GPUs are fast-depreciating assets that lose value rapidly as new generations replace them. Collateralizing loans with such hardware is a high-risk strategy that depends on continued AI demand to justify the debt. AI firms borrowing against them are placing a leveraged bet on demand staying high. If AI market conditions shift or next-generation chips render current hardware obsolete, the collateral value could collapse, leading to cascading loan defaults and liquidations.
This is not a sound-money approach to business. It is fiat-style quicksand financialization, where loans are built on assets with a limited shelf life. Instead of focusing on sustainable capital allocation, firms are leveraging their future on rapid turnover cycles. This further shifts resources away from gamers, reinforcing the trend where NVIDIA prioritizes high-margin AI sales over its original gaming audience.
At the same time, NVIDIA has been accused of leveraging anti-competitive tactics to maintain its market dominance. The GeForce Partner Program (GPP) launched in 2018 sought to lock hardware partners into exclusive deals with NVIDIA, restricting consumer choice and marginalizing AMD. Following industry backlash, the program was canceled. (Source)
NVIDIA is not merely responding to market demand but shaping it through artificial constraints, financialization, and monopolistic control. The result is an industry where consumers face higher prices, limited options, and fewer true innovations as companies prioritize financial games over engineering excellence.
On this basis, short-term downturns fueled by stock buybacks and leveraged bets create instability, leading to key staff layoffs. This forces employees into survival mode rather than fostering long-term innovation and career growth. Instead of building resilient, forward-looking teams, companies trapped in fiat incentives prioritize temporary financial engineering over actual product and market development.
A Sound Money Alternative: Aligning Incentives
Under a sound money system, consumers would become more mindful of purchases as prices naturally decline over time. This would force businesses to prioritize real value creation instead of relying on artificial scarcity and marketing hype. Companies would need to align their strategies with long-term customer satisfaction and sustainable engineering instead of driving demand through planned obsolescence.
Imagine an orange-pilled CEO at NVIDIA. Instead of chasing infinite growth, they persuade the board to pivot toward sustainability and long-term value creation. The company abandons artificial product cycles, prioritizing efficiency, durability, and cost-effectiveness. Gaming GPUs are designed to last a decade, not three years. The model shifts to modular upgrades instead of full replacements. Pricing aligns with real user needs, not speculative stock market gains.
Investors initially panic. The stock takes a temporary hit, but as consumers realize they no longer need to upgrade constantly, brand loyalty strengthens. Demand stabilizes, reducing volatility in production and supply chains. Gamers benefit from high-quality products that do not degrade artificially. AI buyers still access high-performance chips but at fair market prices, no longer subsidized by forced consumer churn.
This is not an abstract vision. Businesses could collateralize loans with Bitcoin. Companies could also leverage highly sought-after end products that maintain long-term value. Instead of stock buybacks or anti-competitive practices, companies would focus on building genuine, long-term value. A future where Bitcoin-backed reserves replace fiat-driven financial engineering would stabilize capital allocation, preventing endless boom-bust cycles. This shift would eliminate the speculative nature of AI-backed loans, fostering financial stability for both borrowers and lenders.
Sound money leads to sound business. When capital allocation is driven by real value rather than debt-fueled expansion, industries focus on sustainable innovation rather than wasteful iteration.
Reclaiming Time Sovereignty for Companies
The fiat system forces corporations into unsustainable growth cycles. Companies that embrace financial independence and time sovereignty can escape this trap and focus on long-term value.
GPU development illustrates this distortion. The RTX 3080 met nearly all gaming needs, yet manufacturers push unnecessary performance gains to fuel stock prices rather than improve usability. GPUs are no longer designed for gamers but for AI and enterprise clients, shifting NVIDIA’s priorities toward financial engineering over real innovation.
This cycle of GPU inflation stems from fiat-driven incentives—growth for the sake of stock performance rather than actual demand. Under a sound money standard, companies would build durable products, prioritizing efficiency over forced obsolescence.
Just as individuals can reclaim financial sovereignty, businesses can do the same. Embracing sound money fosters sustainable business strategies, where technology serves real needs instead of short-term speculation.
Bitcoin
FITS
Marketing
TimeSovereignty
BitcoinFixesThis
OptOut
EngineeringNotFinance
SoundBusiness
-
 @ b17fccdf:b7211155
2025-02-01 18:41:27
@ b17fccdf:b7211155
2025-02-01 18:41:27Next new resources about the MiniBolt guide have been released:
- 🆕 Roadmap: LINK
- 🆕 Dynamic Network map: LINK
- 🆕 Nostr community: LINK < ~ REMOVE the "[]" symbols from the URL (naddr...) to access
- 🆕 Linktr FOSS (UC) by Gzuuus: LINK
- 🆕 Donate webpage: 🚾 Clearnet LINK || 🧅 Onion LINK
- 🆕 Contact email: hello@minibolt.info
Enjoy it MiniBolter! 💙
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ b8851a06:9b120ba1
2025-01-28 21:34:54
@ b8851a06:9b120ba1
2025-01-28 21:34:54Private property isn’t lines on dirt or fences of steel—it’s the crystallization of human sovereignty. Each boundary drawn is a silent declaration: This is where my will meets yours, where creation clashes against chaos. What we defend as “mine” or “yours” is no mere object but a metaphysical claim, a scaffold for the unfathomable complexity of voluntary exchange.
Markets breathe only when individuals anchor their choices in the inviolable. Without property, there is no negotiation—only force. No trade—only taking. The deed to land, the title to a car, the seed of an idea: these are not static things but frontiers of being, where human responsibility collides with the infinite permutations of value.
Austrian economics whispers what existentialism shouts: existence precedes essence. Property isn’t granted by systems; it’s asserted through action, defended through sacrifice, and sanctified through mutual recognition. A thing becomes “owned” only when a mind declares it so, and others—through reason or respect—refrain from crossing that unseen line.
Bitcoin? The purest ledger of this truth. A string of code, yes—but one that mirrors the unyielding logic of property itself: scarce, auditable, unconquerable. It doesn’t ask permission. It exists because sovereign minds choose it to.
Sigh. #nostr
I love #Bitcoin. -
 @ 6ad3e2a3:c90b7740
2025-02-19 14:17:22
@ 6ad3e2a3:c90b7740
2025-02-19 14:17:22Like most members of the human race, I don’t enjoy filing my taxes. “Don’t enjoy” though understates my actual feeling which is “would rather do a tour in Afghanistan.” It’s not even the money I’m forced to pay that I know for sure will be misallocated, stolen or worse — put to use in ways that are anathema to everything I believe and in direct opposition to conditions in which human beings thrive. That’s only part of it.
The other and perhaps bigger part is they require me — under penalty of law — to do homework. They command me, as though they were my boss, to complete this work project, my tax return, and if I don’t I’ll have my property seized, my credit destroyed and even go to prison. This is so even though I am not a criminal, and I never agreed to work for this boss.
And it’s not just a random work project I am required to submit, so that they can misallocate, steal and attack me with my own money. It’s a project that requires me to divulge private details about myself, what transactions I’ve made, with whom I made them and for what purpose. I am a private citizen, I hold no public office or official role, and yet the public sector is not only entitled to comb through the details of my life, but I must be complicit in helping them under penalty of law, i.e., threat of violence if I don’t comply.
. . .
This was not always the case. The income tax was only introduced in 1913, and at the time was only for the richest of the rich. That is to say, it is not the default state of affairs in the United States under its original constitution, and it’s strange that it’s been normalized as such. And despite it being normalized — for the greater good, of course — our government is still somehow $36 trillion in debt.
In other words, despite the annual indignity to which we subject ourselves, the government spends far more money than it takes in. I am reminded of Dostoyevsky’s line: “Your worst sin is that you have destroyed and betrayed yourself for nothing.” The government is spending money it doesn’t have, whether you pay it or not, and the money you do pay, for things you not only do not want but are vehemently against, doesn’t come close to covering their cost.
. . .
I was having lunch with some normies last month, and the subject of taxes came up. They were talking about the ways in which they, as ex-pats, minimize their tax burden, using certain loopholes, and at one point someone questioned why government pensions were taxed, given the entity paying the pension and demanding it be taxed was one and the same. Why not just pay a smaller pension?
One of them asked me, and I said: “I don’t think anyone should be taxed.” She shook her head and muttered in amusement, “No, people need to be taxed.” This despite not two minutes earlier explaining how she was optimizing her tax status, which no doubt she would have optimized all the way to zero or if she were able!
. . .
Taxes are necessary, it’s assumed, to pay for things individuals won’t. “Who will build the roads?” they wonder. I would imagine car makers would be invested in building roads, those who ship goods via truck might have an interest and consumers, flush with their new zero percent tax rate, might pay a little more for the end products to facilitate road creation so those products get to them on time and in good condition. In fact, it might be more expensive to ship them via horseback or whatever alternate form of transport would take the place of motor vehicles should no one shell out for roads.
Moreover, people seem to believe taxes should always be taken not from them, but from those rich enough to afford them painlessly. Never mind anyone reading this substack is vastly wealthy compared to much of the third world (how painful can taxes be so long as you have food on the table and a roof over your head?), and never mind no one ever voluntarily pays more tax than he owes. Why not? If taxation is a good thing, why not do more good by overpaying?
But no, it’s always someone else who needs to be forced under penalty of law, i.e., threat of violence, to give up his property for what those in authority deem “the greater good”. Taken to its logical conclusion, if the authorities deem anyone sufficiently wealthy and the greater good sufficiently necessary, they can legally take that wealth by force. We can quibble about how much funding is necessary and what is the “greater good,” but it’s often essential things like the “safe and effective” vaccine without which millions would surely die or the necessity of invading Iraq, which cost $6 trillion to prevent Sadaam Hussein’s “weapons of mass destruction” from reaching US soil.
It’s amazing authorities so often discover urgent projects without which people will die or suffer terribly, on account of which it’s necessary to commandeer money you’ve earned or saved! And while I am taking about the indignity of filing income tax, I don’t mean to leave out property tax, sales tax, estate tax, individual state and city taxes and the like. At least with some of those you have a fixed amount to pay, and you don’t have to submit to an on-camera self-administered anal cavity search of your finances in those cases.
You’d also think given how many ways citizens are taxed that roads would be in tip top condition, our water and environment would be clean, our airports modern and state of the art, our health care affordable and accessible, but of course none of that is the case. Again per Dostoyevsky — we have betrayed ourselves for nothing.
. . .
The irony of this essay/diatribe is I will file my taxes like the cuck I am over the next week or so. I don’t want to do this, but it’s simply not worth the consequences for non-compliance. And I feel bad about making this compromise — bad about myself because I am doing something I feel is wrong for convenience, the same kind of calculation people made when they injected themselves with experimental mRNA chemicals they didn’t want to keep their jobs or travel. I like to think of myself as resolute and uncompromising, but in this instance I roll over every year. Perhaps that’s part of why I dread it so much.
. . .
I’ll end with a footnote of sorts. In the late spring of 2023, I discovered I was due a significant refund, and I paid my accountants who figured this out $400 to re-file for me. They told me I could expect it to take up to nine months to process, so I largely forgot about it until spring of 2024 when I called but got phone-treed to death and waited until September to brute-force my way to a human in another department to explain the situation. They didn’t tell me anything, but agreed to do a “trace” which a couple weeks later revealed someone else had intercepted and cashed my check. (It’s not direct deposit because I’m overseas.)
I immediately returned the form proving it was not my signature on the deposited check, and now, five months later, in February of 2025, they are still processing my purported payment which I have yet to receive. I did, however, receive a notice of the interest I was “paid” for 2024 on which I’m expected to be taxed. That interest went to the person who stole my original check obviously, they know this, and yet it apparently hasn’t caught up in the system. And the truth is I will probably pay the tax on it as the hassle of explaining why I’m not is simply not worth it, and I will sort it out on next year’s tax return, assuming Trump hasn’t abolished the IRS entirely, God willing, and delivered us, in small part, from this abject dystopia.
-
 @ 5de23b9a:d83005b3
2025-02-19 03:47:19
@ 5de23b9a:d83005b3
2025-02-19 03:47:19In a digital era that is increasingly controlled by large companies, the emergence of Nostr (Notes and Other Stuff Transmitted by Relays) is a breath of fresh air for those who crave freedom of expression.
Nostr is a cryptography-based protocol that allows users to send and receive messages through a relay network. Unlike conventional social media such as Twitter or Facebook
1.Full Decentralization: No company or government can remove or restrict content.
2.Sensor-Resistant: Information remains accessible despite blocking attempts.
3.Privacy and Security: Uses cryptography to ensure that only users who have the keys can access their messages.* **
-
 @ 4d41a7cb:7d3633cc
2025-02-20 20:24:06
@ 4d41a7cb:7d3633cc
2025-02-20 20:24:06I just deleted my Twitter account forever. I've never done this because I wanted to take the time to extract the most value from my feed—all my shared thoughts and most of my favorite ideas from the past 5 years.
As crazy as it sounds, this powerful information helped shape my thoughts and helped me become the person I am today in some way. I think there’s a lot of value there, and I want to keep that value, not to trust any third party or clown like Elon with it, who could just decide to delete it or restrain my access to it, like I found they did many times, like in the following examples:

 I don't remember what those posts were referring to, but for some reason I found them valuable; maybe I saved them, maybe I didn't, but the fact that someone can decide for me makes me mad.
I don't remember what those posts were referring to, but for some reason I found them valuable; maybe I saved them, maybe I didn't, but the fact that someone can decide for me makes me mad.Nobody should have the power to decide what can be said and what cannot be said, because this is the root of mental slavery: restricting your access to information and understanding.
I believe all bitcoiners should extract their value from Twitter and bring it to Nostr (or save it for them at least) because that is real sovereignty. I know as well as you know that we were (and still are) trapped in a Twitter bubble. Our opinions, thoughts, and ideas don't reach the masses, and they’ll never do so inside this kind of controlled ecosystem.
So if we are going to keep screaming inside of a bubble, let’s at least do it in our own bubble (insert Nostr), where at least we know it's going to stay there, without a single point of failure, without permission required, and without demonetization risks, PUTTING OUR TIME AND ENERGY WHERE OUR MOUTH, VALUES AND MONEY ARE.
I also want to express my gratitude to all the truth seekers, Austrian economics students, bitcoiners, anarchists, and even shitcoiners who have shared their thoughts with me on Twitter over the past years.
I’ve learned so much from you about what I should and should not do!
Your insights played a crucial role in helping me broaden my awareness and transform into the best version of myself. Of course that was just the seed; even one post could have been the reason I ended up listening to XYC podcasts or reading XYC books that changed my life for the better. Imagine how powerful that is, and how dangerous if someone could restrict it.
In 2020 I truly realized the clown world we're living in. From there I've spent the last five years researching and studying history. I have read hundreds of books and articles to discover that everything that happens in the world is by design.
Here’s a list of 9 things I learned over the past five years:
- Slavery was never abolished
The power structures have been using control over information and control over money as tools to enslave humanity for thousands of years. Religious institutions, monarchies, governments, and banks had kept this power for themselves and have exploited it to enslave humankind.
Governments are tax farms for corporations. Central bankers, who are their creditors, control the bankrupt governments. These private institutions are responsible for most of the evils of our modern society because they destroyed the incentive structure of capitalism (in fact, they are part of the communist manifesto); they provided the funding for wars, fake studies about nutrition, indoctrination, demoralization, etc.
Modern slavery is working for a currency that someone else can just create out of thin air without effort or energy.
The ultimate form of slavery is to need permission from an “authority” to commerce and to do it under its terms and conditions.Control over the mediums of exchange gave the power structure complete control over commerce. Bitcoin freed us from the control over money. That’s why bitcoin is permissionless.
But without your voluntary compliance, none of this would be possible; that's why they invest billions of dollars to manipulate your mind, mold your beliefs, and program you to comply and follow their lead. They know they cannot force 8 billion humans to go ahead with their game; they need to make us believe in it so we voluntarily play.
- Slavery starts in your mind
It all starts with governing your mind (govern-ment) and convincing you that you should use this XYC currency, pay taxes, and obey these laws because that’s the “right thing” (or how things are supposed to be) when the opposite is true. This broke corporation (government) has ‘the legal power’ to use violence against you if you refuse to comply. This is not moral; this is slavery.
If you have a basic understanding of morality, you’ll soon discover that the right thing to do is to oppose slavery and wrongdoings…Surprise! The whole system is wrong, based on lies, sustained by crime, and pushing slavery worldwide.
Prisons are mental, so free your mind.
Our mind is our biggest tool, and our mindset is our biggest asset, so we should be very careful about what information we feed our minds and be more mindful and intentional about it. As long as you don't want to be an NPC and you want to be a player, of course…
- We are the masters of our own reality
Every action we take is a vote for the life we want to live. For every action, there's a reaction, and in our lives, this is no different. Every day, our beliefs shape our reality through the decisions we make. This is how it works: our beliefs define our thoughts, our thoughts define our emotions, and our emotions define our actions. Finally, our actions define our realities.
That's why it's so important to know where our beliefs and ideas come from. In most cases, they used to come from schools, universities, families, communities, and the mainstream media. These days, they primarily originate from algorithms, which will be discussed in more detail shortly. And you know what? Most of them are wrong! That's why the world is in this situation.
-
Positive, nourishing, empowering, and educational algorithms = better state of mind, better emotions, better actions, better results = order
-
Negative, demoralizing, victimizing, and indoctrinating algorithms create confusion, lack of sense, fear, insecurities, and wrong decisions = chaos.
-
There are two types of individuals: Creators vs parasites
In 2023 I published my book ‘The Great Parasite; the international banks their plans and methods’ were i tell the story of central banks, their war with the funding fathers of the US, how they ended up taking over and what their plan for global domination.
The great parasite is obviously the banking system, since it creates currency out of thin air and demand us to pay back plus interest, banks end up getting the wealth of their clients (including nation states) for free.
This is crazy, legalized theft and modern slavery.
I also discovered that there are two types of individuals:
The creator stands firm in his convictions, the parasite follows the opinions of others.
*> The creator thinks the parasite copies.
*> The creator produces the parasite plunders.
The creator's interest is the conquest of nature, the parasite's is the conquest of man.
*> The creator requires independence, neither serves nor rules, he treats men with free exchange and voluntary choice.
*> The parasite seeks power, wishes to bind all men to act together and enslave themselves. The parasite claims that man is only a tool to be used, that he must think like his fellows and act like them and live in servitude to collective needs regardless of his own.
*> Look at history, all that we have, all the great achievements, have come from the independent work of independent minds, and all the horrors and destruction of attempts to force mankind to become robots, without brains and without souls, without personal rights, without personal ambition, without will, hope or dignity come from parasites.
*> It is an ancient conflict, it has another name, the individual versus the collective.
I believe there are two types of individuals: reactive and proactive, parasites and creators. Unfortunalty most human beings are reactive and acting as parasites.
We are trained to obey and always take the default option. The second group does not conform with the status quo and looks for non-traditional ways of doing things.
They create their own opportunities and change the things they don't like. This group is always smaller, but it is the only one capable of changing the world. Think of the founding fathers and how they fought for their freedom! And most recently , cyberpunks! Thanks God for the cyberpunks!
The existence of this type of people is the reason why I have hope, and I see a better future is possible if we work to build it.
- The end of the central bank's era: Bitcoin or slavery.
Opt out; escape the slave money
Almost two decades ago, Bitcoin was just an idea in the mind of some cyberpunks: digital cash, digital physical money, a system outside of the system, far from governments and banks control, decentralized, unstoppable, limited, and based on cryptography. Now it’s the 13th biggest currency by market cap, and it’s on its way to eating up a significant percentage of global wealth because it is more than a currency or just another form of money.
Bitcoin heralds the end of the central bank era, which we can also define as the end of economic slavery. We should understand bitcoin as a solution to a problem; that problem is central banks.
Bitcoin is private property you can really own, which gives the power back to the people. Indeed, it is the sole instrument available to safeguard our unalienable right to private property. THIS IS KEY to survive the great wealth confiscation that is coming. What they call ’The great reset’; “You will own nothing and be happy”.
If you stop to think about it, you don't really own anything beyond your body, mind, and soul. Your thoughts and opinions are also part of your mind. Your house? If you have to pay to keep it, it is not yours! Your car? Are you referring to the vehicle for which you require authorization to drive or risk its confiscation? What about your stocks and bonds? You don't even have a title to the property. Remember NFTs? Well, this is even worse; you barely even have exposure to the price if bankers let you benefit from it.
These individuals have the power to alter the regulations at any given time. They can stop you from accessing your balances in bank accounts (Canadian truckers); they can stop you from buying a hot stock to make a quick buck (shutting down the buy button on Game Stop Inc).
BUT YOU CAN REALLY OWN BITCOIN AND YOUR PERSONAL INFORMATION IF YOU DECIDE TOO!
There are no excuses for those willing to fight for freedom; if it’s not Bitcoin/Nostr-related, it's just noise for me.vBitcoin is a a financial intelligence test, the fact that only a few get it (Bitcoin maxis) shows how financially retarded most people are. And this is, of course, by design.
Honest money, private property, free markets, and free speech are the three fundamental pillars for a free society. All of them require honest and moral individuals, of course, and a system fair enough to not incentivize crime and dishonest transactions.
- The end of mind control: Nostr or slavery
Opt out of Slave social media platforms
What a journey, guys! How far we came! I remember back in the day fantasizing about the idea of having this “decentralized Twitter,” and now we have something 1000 times bigger, a decentralized, unstoppable protocol to share information that uses the hardest money ever invented as its native medium of exchange and unit of account.
 I am not a technical guy so I had obviously no idea of what I was talking about. But I know we have Nostr now and I understand that Nostr and lighting are good friends. So that makes me happy.
I am not a technical guy so I had obviously no idea of what I was talking about. But I know we have Nostr now and I understand that Nostr and lighting are good friends. So that makes me happy.Twitter sucks; the algorithm feeds you garbage. It’s full of bots and people trying to scam you. It’s filled with shadow banning; it is not censorship resistant; there’s a lot of noise and retards. The XRP guys being paid to promote the scam, the million of bots and asian women asking how your trading is going, is disgusting.
Twitter is communist, and they are trying to turn it into a communist super app. Don’t let Master Elon determine your future and the reach of your voice. Be sovereign; own your data join Nostr.
 If you keep voting for Twitter, you are still voting for your own enslavement. If you believe in your position, focus on Nostr and bring important audience members with you. Have some self-respect.
If you keep voting for Twitter, you are still voting for your own enslavement. If you believe in your position, focus on Nostr and bring important audience members with you. Have some self-respect.Nostr is waiting for us (sane and normal people) with common sense and plans for the future. Those who create value and plan to have healthy families as it should be. With free speech and hard money, we are forming our own free market, totally independent from the censored clown world, but its growth and development depend on the decisions of each one of us.
DO NOT UNDERESTIMATE YOUR INDIVIDUAL POWER, BECAUSE THAT’S HOW OUR COLLECTIVE POWER GROWS.
If you believe Elon is not a part of the establishment, your pineal gland remains calcified. Fuck Twitter and Elon, fuck the IMF plantation, the Federal Reserve, the UN, the WEF, and every global communist organization out there trying to micromanage the economy and control your life. Fuck censorship and communism.
Long live private property and free speech. Long live Bitcoin and Nostr!
- The New world order is real
The powers that run the world (banksters) are executing a long-planned playbook: a global cashless society with a surveillance system (global communism and tyranny). And history shows they are willing to do what’s necessary to advance in their agenda: a New World Order.
If you google this term, the first thing it will pump is “The New World Order Conspiracy theory”. For those who continue to perceive this as a 'conspiracy theory,' let me inform you that it is not. It is not a theory but a REAL conspiracy.
 The agenda is simple: World government, world currency and world taxes. This is only posible with a global digital credit system and mass surveillance. Cash has to be completely eradicated and they are going step by step.
The agenda is simple: World government, world currency and world taxes. This is only posible with a global digital credit system and mass surveillance. Cash has to be completely eradicated and they are going step by step.Agenda 2030, The Great Reset, Climate change, Build back better, Stakeholder capitalism and many other key names are used to describe this agenda. This plan is the antithesis of human rights, freedoms, health, family, and happiness.
Since all fiat currencies will eventually end up losing all their value, and since public debts are mathematically imposible to repay (governments are bankrupt) banks are planing a transition to a world government directed by the United Nations and it’s global agendas.
Past agendas like agenda 21 and agenda 2030 have already failed so now they are pushing for the “Pact for the Future” where world leaders pledge action for “peace and sustainable development.
“He who controls the food supply controls the people; he who controls the energy can control whole continents; who controls money can control the world”
Henry Kissinger (1923-2023)
If you google this quote ‘fact checkers’ will say is fake, but it is not. Even if it was, the statement is true, and their agenda is that: control, control, control. That what parasites want to do.
Their goal is simple: Keep their control positions of power and prevent slaves from planing a rebellion. So they need.
-
Have absolute control over the information flow, to prevent the population from understanding what really going on. Absolute censorship.
-
Distractions. Bread and circus. Fake leaders acting as hero’s for the cameras but working for the conspirators behind the scenes. Video game and virtual reality in better and accesible technological devices. Fake or artificial events in the news to keep us distracted and looking the other way while they advance in their agenda.
-
Cheap credit, UBIs and nominal negative interest rates for the mass unemployment that the IA deflation + financial crisis will crate. This is necessary to prolong the agony of the fiat system and prolong its collapse.
-
Eradicate a big percentage of the populations and weakened it to prevent a rebellion. Poisoning the food, water, air, products, vaccines, drugs, etc.
-
Destroy the family unit to debilitate society (Pushing LGTBQ + trans, etc, etc), the porn industry, contraceptives, etc.
-
Reduce the levels of testosterone to kill the masculine active energy.
This and many other horrible things are on their plans and many are already being executed before our eyes, even if you see them of not.
The sooner you realize and start taking action the better.
- We are in a transition phase marked by chaos
New world disorder
This transition period we are going through is full of chaos. We have people doing the right thing for the wrong reasons, and then we have people doing the wrong thing for the right reasons. There are only a few who can really see what’s going on behind the surface.
This is complete chaos. That’s why we need the active participation of most of us in order to bring light, share the truth, and acknowledge the darkness outside while focusing on what we can control inside in order to build the change we want to see in this world.
Shitcoins and memecoins are a great proof of the chaos phase we are going through. It’s easy to spot that the majority have no idea what’s going on. What’s happening is the same as what has been happening since financial markets exist (rug pulls, scams, pumps, and dumps); the only difference is that now everyone can do it (it has been democratized). Even presidents are participating; recently Trump, now Milei it’s all a big shitshow.
The nature of ‘capitalism’ nowadays is that everyone scams everyone, and whoever scams the most ultimately wins. Under this basis, central banks are the winners. But bitcoin is changing this.
This is going to be a short transition because the market is already saturated and the scam is almost evident by this point. Only a few speculators and idiot investors keep falling for it.
- Taking responsibility
We are held captive by both our ignorance and our monetary system. Our monetary system is more than our currency; it is our government, our commercial laws, our titles of property, our products, and so on. Almost everything in our modern world is somehow integrated with the monetary system.
It's our responsibility to take skin in the game and find out what the facts are. Nobody is going to do it for us If we build our beliefs and thoughts based on the facts and testimonies of people with real life experience, we will be prepared to make better decisions and build a better future for ourselves and our families.
It is very important to have a community aligned under the same set of values and principles. Creating a group of strong sovereign individuals, capable of helping to build a better future for ourselves and our families. The only way to do this is by working together and pooling our knowledge, skills and resources.
With Bitcoin good information and good people nothing can stop us.
Bringing light and understanding on this is the first step; choosing alternatives built on a bitcoin standard is the second.
We understand that money is energy, and every purchase we make is a vote, either for creators or for parasites. We are either voting for a 1984-type of society or for a 1776-type of revolution.
Unfortunately, the majority is voting for their own slavery. The good news is that we don’t need a majority; we need a strong minority…
A minority focused on creating a critical mass of individuals.
A minority focused on generating cheap and sustainable energy.
A minority focused on protecting the farmers.
A minority using Bitcoin as a store/measure of value and medium of exchange.
A minority creating circular economies, eliminating unnecessary intermediaries, and encouraging local production, sovereignty, and sustainability.
A minority using technology to liberate society and prevent it from being enslaved by globalists in a dystopian reality.
A minority having strong and healthy kids and families.
A minority focused on creating beneficial educational resources.
Governments can be broke, but that doesn't mean that we are or should be too. WE ARE NOT OUR GOVERNMENTS. Money changers, using their legal and monetary tricks, have been robbing us of our wealth for centuries just like parasites, but not anymore.
It’s our time; we, the creators, have the power, so let's prove it.
Live free or die trying!
-
 @ e5de992e:4a95ef85
2025-02-20 19:56:02
@ e5de992e:4a95ef85
2025-02-20 19:56:02The Illusion of Opportunity
A trader who focuses primarily on "making money" will often see opportunities that do not truly exist. This mindset leads to impulsive decision-making, overtrading, and unnecessary risk exposure. Successful trading is not about chasing profits but about executing a well-structured process that leads to consistent, sustainable results over time.
Traders who prioritize money over process often fall into the trap of forcing trades that do not meet their criteria. They see potential where the market does not support a trade, leading to poor risk-reward decisions. This psychological bias creates a cycle of frustration and loss, as each forced trade compounds previous mistakes.
The Shift From Profit to Process
The best traders focus on refining their strategy rather than constantly monitoring their profit and loss (P&L). By shifting attention from financial gain to execution quality, traders develop the discipline required to succeed in various market conditions.
Key Principles to Maintain Focus on Process:
Trade Selection: Every trade must align with a predefined strategy. If a setup does not meet strict criteria, it should be ignored, regardless of perceived opportunity. Risk Management: Prioritizing risk over reward ensures longevity in the market. Traders who focus only on making money often ignore stop-loss discipline, leading to significant drawdowns. Emotional Control: The desire to profit can cloud judgment, making traders more susceptible to market traps. Avoiding emotional trading requires a structured plan and a mindset that prioritizes long-term consistency.
The Pitfalls of Profit-Driven Trading
When the primary goal is making money rather than executing well-structured trades, several common mistakes emerge:
- Overtrading
Traders who are focused on profit often believe that more trades equate to more opportunities. In reality, overtrading leads to higher transaction costs, increased exposure to market noise, and a greater likelihood of errors.
Example: A trader sees multiple setups in a choppy market and takes unnecessary trades, resulting in minor losses that accumulate over time. A disciplined trader, in contrast, waits for high-probability setups and executes fewer trades with precision.
- Ignoring Market Conditions
Markets move through different phases—trending, ranging, and volatile conditions. A trader fixated on making money may ignore these dynamics and attempt to force trades in an unfavorable environment.
Example: A momentum trader who performs well in trending markets struggles when conditions turn choppy. Instead of adjusting their approach or stepping back, they continue to take the same trades, leading to repeated losses.
- Chasing Trades
Traders focused on quick profits often enter trades late, fearing they will miss out on a move. This "chasing" behavior results in poor entry points and reduces the overall risk-reward ratio.
Example: A stock makes a strong breakout, and a trader jumps in at an overextended price. The stock then retraces, forcing them to exit at a loss. Had they waited for a proper entry, they could have positioned themselves for a lower-risk trade.
- Neglecting Risk-Reward Ratios
Traders who prioritize making money tend to focus on potential gains while disregarding downside risks. Without a proper risk-reward framework, a few bad trades can wipe out previous gains.
Example: A trader takes multiple high-risk trades aiming for large profits. While some work out, one significant loss erases weeks of gains. A trader who prioritizes risk management would avoid such scenarios by ensuring all trades maintain a favorable risk-reward ratio.
Developing a Sustainable Trading Mindset
To succeed in trading, the mindset must shift from short-term profit to long-term process optimization. This involves creating a structured approach that removes emotional bias and ensures consistency.
Steps to Improve Trading Discipline:
Follow a Trading Plan – Define entry and exit rules, risk management parameters, and position sizing. Track and Review Performance – Maintain a trading journal to assess past decisions and identify patterns in behavior. Limit the Number of Trades – Focus on quality over quantity to avoid unnecessary exposure and reduce emotional trading. Develop Patience – Wait for high-probability setups instead of reacting impulsively to market movements. Separate Money From Execution – Judge success based on adherence to a strategy rather than daily profit and loss fluctuations.
Conclusion: Process Over Profit
Traders who focus exclusively on making money often fall into patterns of impulsive decision-making, overtrading, and poor risk management. The key to long-term success lies in developing a structured process that prioritizes disciplined execution over immediate financial gains.
By refining strategy, managing risk, and maintaining emotional discipline, traders can build a sustainable approach that leads to consistent profitability. Instead of seeking opportunities everywhere, traders should focus on executing only the best setups, ensuring that every decision aligns with a well-defined plan.
-
 @ 000002de:c05780a7
2025-02-20 19:45:50
@ 000002de:c05780a7
2025-02-20 19:45:50Are you seeing it? Been oddly quiet for me but I have friends that are seeing people come unglued. Think its hard to sustain that level if outrage. It's not healthy for sure. I was so angry during Covid and realized it wasn't worth it.
What's your experience. Not online but IRL.
originally posted at https://stacker.news/items/892219
-
 @ 599f67f7:21fb3ea9
2025-01-26 11:01:05
@ 599f67f7:21fb3ea9
2025-01-26 11:01:05¿Qué es Blossom?
nostr:nevent1qqspttj39n6ld4plhn4e2mq3utxpju93u4k7w33l3ehxyf0g9lh3f0qpzpmhxue69uhkummnw3ezuamfdejsygzenanl0hmkjnrq8fksvdhpt67xzrdh0h8agltwt5znsmvzr7e74ywgmr72
Blossom significa Blobs Simply Stored on Media Servers (Blobs Simplemente Almacenados en Servidores de Medios). Blobs son fragmentos de datos binarios, como archivos pero sin nombres. En lugar de nombres, se identifican por su hash sha256. La ventaja de usar hashes sha256 en lugar de nombres es que los hashes son IDs universales que se pueden calcular a partir del archivo mismo utilizando el algoritmo de hash sha256.
💡 archivo -> sha256 -> hash
Blossom es, por lo tanto, un conjunto de puntos finales HTTP que permiten a los usuarios almacenar y recuperar blobs almacenados en servidores utilizando su identidad nostr.
¿Por qué Blossom?
Como mencionamos hace un momento, al usar claves nostr como su identidad, Blossom permite que los datos sean "propiedad" del usuario. Esto simplifica enormemente la cuestión de "qué es spam" para el alojamiento de servidores. Por ejemplo, en nuestro Blossom solo permitimos cargas por miembros de la comunidad verificados que tengan un NIP-05 con nosotros.
Los usuarios pueden subir en múltiples servidores de blossom, por ejemplo, uno alojado por su comunidad, uno de pago, otro público y gratuito, para establecer redundancia de sus datos. Los blobs pueden ser espejados entre servidores de blossom, de manera similar a cómo los relays nostr pueden transmitir eventos entre sí. Esto mejora la resistencia a la censura de blossom.
A continuación se muestra una breve tabla de comparación entre torrents, Blossom y servidores CDN centralizados. (Suponiendo que hay muchos seeders para torrents y se utilizan múltiples servidores con Blossom).
| | Torrents | Blossom | CDN Centralizado | | --------------------------------------------------------------- | -------- | ------- | ---------------- | | Descentralizado | ✅ | ✅ | ❌ | | Resistencia a la censura | ✅ | ✅ | ❌ | | ¿Puedo usarlo para publicar fotos de gatitos en redes sociales? | ❌ | ✅ | ✅ |
¿Cómo funciona?
Blossom utiliza varios tipos de eventos nostr para comunicarse con el servidor de medios.
| kind | descripción | BUD | | ----- | ------------------------------- | ------------------------------------------------------------------ | | 24242 | Evento de autorización | BUD01 | | 10063 | Lista de Servidores de Usuarios | BUD03 |
kind:24242 - Autorización
Esto es esencialmente lo que ya describimos al usar claves nostr como IDs de usuario. En el evento, el usuario le dice al servidor que quiere subir o eliminar un archivo y lo firma con sus claves nostr. El servidor realiza algunas verificaciones en este evento y luego ejecuta el comando del usuario si todo parece estar bien.
kind:10063 - Lista de Servidores de Usuarios
Esto es utilizado por el usuario para anunciar a qué servidores de medios está subiendo. De esta manera, cuando el cliente ve esta lista, sabe dónde subir los archivos del usuario. También puede subir en múltiples servidores definidos en la lista para asegurar redundancia. En el lado de recuperación, si por alguna razón uno de los servidores en la lista del usuario está fuera de servicio, o el archivo ya no se puede encontrar allí, el cliente puede usar esta lista para intentar recuperar el archivo de otros servidores en la lista. Dado que los blobs se identifican por sus hashes, el mismo blob tendrá el mismo hash en cualquier servidor de medios. Todo lo que el cliente necesita hacer es cambiar la URL por la de un servidor diferente.
Ahora, además de los conceptos básicos de cómo funciona Blossom, también hay otros tipos de eventos que hacen que Blossom sea aún más interesante.
| kind | descripción | | ----- | --------------------- | | 30563 | Blossom Drives | | 36363 | Listado de Servidores | | 31963 | Reseña de Servidores |
kind:30563 - Blossom Drives
Este tipo de evento facilita la organización de blobs en carpetas, como estamos acostumbrados con los drives (piensa en Google Drive, iCloud, Proton Drive, etc.). El evento contiene información sobre la estructura de carpetas y los metadatos del drive.
kind:36363 y kind:31963 - Listado y Reseña
Estos tipos de eventos permiten a los usuarios descubrir y reseñar servidores de medios a través de nostr. kind:36363 es un listado de servidores que contiene la URL del servidor. kind:31963 es una reseña, donde los usuarios pueden calificar servidores.
¿Cómo lo uso?
Encuentra un servidor
Primero necesitarás elegir un servidor Blossom donde subirás tus archivos. Puedes navegar por los públicos en blossomservers.com. Algunos de ellos son de pago, otros pueden requerir que tus claves nostr estén en una lista blanca.
Luego, puedes ir a la URL de su servidor y probar a subir un archivo pequeño, como una foto. Si estás satisfecho con el servidor (es rápido y aún no te ha fallado), puedes agregarlo a tu Lista de Servidores de Usuarios. Cubriremos brevemente cómo hacer esto en noStrudel y Amethyst (pero solo necesitas hacer esto una vez, una vez que tu lista actualizada esté publicada, los clientes pueden simplemente recuperarla de nostr).
noStrudel
- Encuentra Relays en la barra lateral, luego elige Servidores de Medios.
- Agrega un servidor de medios, o mejor aún, varios.
- Publica tu lista de servidores. ✅
Amethyst
- En la barra lateral, encuentra Servidores multimedia.
- Bajo Servidores Blossom, agrega tus servidores de medios.
- Firma y publica. ✅
Ahora, cuando vayas a hacer una publicación y adjuntar una foto, por ejemplo, se subirá en tu servidor blossom.
⚠️ Ten en cuenta que debes suponer que los archivos que subas serán públicos. Aunque puedes proteger un archivo con contraseña, esto no ha sido auditado.
Blossom Drive
Como mencionamos anteriormente, podemos publicar eventos para organizar nuestros blobs en carpetas. Esto puede ser excelente para compartir archivos con tu equipo, o simplemente para mantener las cosas organizadas.
Para probarlo, ve a blossom.hzrd149.com (o nuestra instancia comunitaria en blossom.bitcointxoko.com) e inicia sesión con tu método preferido.
Puedes crear una nueva unidad y agregar blobs desde allí.
Bouquet
Si usas múltiples servidores para darte redundancia, Bouquet es una buena manera de obtener una visión general de todos tus archivos. Úsalo para subir y navegar por tus medios en diferentes servidores y sincronizar blobs entre ellos.
Cherry Tree
nostr:nevent1qvzqqqqqqypzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqyp3065hj9zellakecetfflkgudm5n6xcc9dnetfeacnq90y3yxa5z5gk2q6
Cherry Tree te permite dividir un archivo en fragmentos y luego subirlos en múltiples servidores blossom, y más tarde reensamblarlos en otro lugar.
Conclusión
Blossom aún está en desarrollo, pero ya hay muchas cosas interesantes que puedes hacer con él para hacerte a ti y a tu comunidad más soberanos. ¡Pruébalo!
Si deseas mantenerte al día sobre el desarrollo de Blossom, sigue a nostr:nprofile1qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqyqnxs90qeyssm73jf3kt5dtnk997ujw6ggy6j3t0jjzw2yrv6sy22ysu5ka y dale un gran zap por su excelente trabajo.
Referencias
-
 @ 4857600b:30b502f4
2025-02-20 19:09:11
@ 4857600b:30b502f4
2025-02-20 19:09:11Mitch McConnell, a senior Republican senator, announced he will not seek reelection.
At 83 years old and with health issues, this decision was expected. After seven terms, he leaves a significant legacy in U.S. politics, known for his strategic maneuvering.
McConnell stated, “My current term in the Senate will be my last.” His retirement marks the end of an influential political era.
-
 @ 29af23a9:842ef0c1
2025-01-24 09:28:37
@ 29af23a9:842ef0c1
2025-01-24 09:28:37A Indústria Pornográfica se caracteriza pelo investimento pesado de grandes empresários americanos, desde 2014.
Na década de 90, filmes pornográficos eram feitos às coxas. Era basicamente duas pessoas fazendo sexo amador e sendo gravadas. Não tinha roteiro, nem produção, não tinha maquiagem, nada disso. A distribuição era rudimentar, os assinantes tinham que sair de suas casas, ir até a locadora, sofrer todo tipo de constrangimento para assistir a um filme pornô.
No começo dos anos 2000, o serviço de Pay Per View fez o número de vendas de filmes eróticos (filme erótico é bem mais leve) crescer mas nada se compara com os sites de filmes pornográficos por assinatura.
Com o advento dos serviços de Streaming, os sites que vendem filmes por assinatura se estabeleceram no mercado como nunca foi visto na história.
Hoje, os Produtores usam produtos para esticar os vasos sanguíneos do pênis dos atores e dopam as atrizes para que elas aguentem horas de gravação (a Série Black Mirror fez uma crítica a isso no episódio 1 milhão de méritos de forma sutil).
Além de toda a produção em volta das cenas. Que são gravadas em 4K, para focar bem as partes íntimas dos atores. Quadros fechados, iluminação, tudo isso faz essa Indústria ser "Artística" uma vez que tudo ali é falso. Um filme da Produtora Vixen, por exemplo, onde jovens mulheres transam em mansões com seus empresários estimula o esteriótipo da mina padrão que chama seu chefe rico de "daddy" e seduz ele até ele trair a esposa.
Sites como xvídeos, pornHub e outros nada mais são do que sites que salvam filmes dessas produtoras e hospedam as cenas com anúncios e pop-ups. Alguns sites hospedam o filme inteiro "de graça".
Esse tipo de filme estimula qualquer homem heterosexual com menos de 30 anos, que não tem o córtex frontal de seu cérebro totalmente desenvolvido (segundo estudos só é completamente desenvolvido quando o homem chega aos 31 anos).
A arte Pornográfica faz alguns fantasiarem ter relação sexual com uma gostosa americana branquinha, até escraviza-los. Muitos não conseguem sair do vício e preferem a Ficção à sua esposa real. Então pare de se enganar e admita. A Pornografia faz mal para a saúde mental do homem.
Quem sonha em ter uma transa com Lana Rhodes, deve estar nesse estágio. Trata-se de uma atriz (pornstar) que ganhou muito dinheiro vendendo a ilusão da Arte Pornografica, como a Riley Reid que só gravava para grandes Produtoras. Ambas se arrependeram da carreira artística e agora tentam viver suas vidas como uma mulher comum.
As próprias atrizes se consideram artistas, como Mia Malkova, chegou a dizer que Pornografia é a vida dela, que é "Lindo e Sofisticado."
Mia Malkova inclusive faz questão de dizer que a industria não escravisa mulheres jovens. Trata-se de um negócio onde a mulher assina um contrato com uma produtora e recebe um cachê por isso. Diferente do discurso da Mia Khalifa em entrevista para a BBC, onde diz que as mulheres são exploradas por homens poderosos. Vai ela está confundindo o Conglomerado Vixen com a Rede Globo ou com a empresa do Harvey Weinstein.
Enfim, se você é um homem solteiro entre 18 e 40 anos que já consumiu ou que ainda consome pornografia, sabia que sofrerá consequências. Pois trata-se de "produções artísticas" da indústria audiovisual que altera os níveis de dopamina do seu cérebro, mudando a neuroplasticidade e diminuindo a massa cinzenta, deixando o homem com memória fraca, sem foco e com mente nebulosa.
Por que o Estado não proíbe/criminaliza a Pornografia se ela faz mal? E desde quando o Estado quer o nosso bem? Existem grandes empresarios que financiam essa indústria ajudando governos a manterem o povo viciado e assim alienado. É um pão e circo, só que muito mais viciante e maléfico. Eu costume dizer aos meus amigos que existem grandes empresários jvdeus que são donos de grandes Produtoras de filmes pornográficos como o Conglomerado Vixen. Então se eles assistem vídeos pirateados de filmes dessas produtoras, eles estão no colo do Judeu.
-
 @ 378562cd:a6fc6773
2025-02-20 16:35:11
@ 378562cd:a6fc6773
2025-02-20 16:35:11In the ever-evolving landscape of social media, platforms like Twitter and Facebook have dominated the space for years. They’ve shaped the way we interact, share, and consume information. But as censorship concerns, algorithmic manipulation, and corporate control over data become more apparent, a new contender has emerged—NOSTR (Notes and Other Stuff Transmitted by Relays). The differences are striking for those who have stepped into the NOSTR ecosystem. Let’s dive into what sets it apart and why it’s more than just another social media platform—it’s a movement.
Decentralization vs. Corporate Control
The fundamental structure is one of the most noticeable differences between NOSTR and traditional platforms like Twitter or Facebook. Both are owned by massive corporations that dictate what can and cannot be said. They collect data, sell advertisements, and use algorithms to curate what users see.
NOSTR, on the other hand, is fully decentralized. No single entity controls the platform, no shadowy moderation teams tweak visibility based on corporate interests, and no risk of being permanently banned by a faceless algorithm. Instead, NOSTR operates on an open protocol, allowing anyone to participate without gatekeepers. Your content is truly yours, and no one can take that away from you.
A Different Class of People
Scrolling through Twitter or Facebook often feels like wading through a digital battlefield. Political flame wars, mind-numbing clickbait, and attention-seeking outrage dominate the feeds. While both platforms do have intelligent and well-meaning users, they are drowned out by noise, bots, and engagement-hacking algorithms designed to fuel division.
NOSTR, by contrast, attracts a different breed of users—people who value free speech, independent thought, and meaningful conversation. Many of them are builders, thinkers, and pioneers eager to create a better way of interacting online. There’s a noticeable shift in tone; rather than content driven by controversy and outrage, you’ll find people discussing innovation, philosophy, and real-world solutions. Conversations feel more organic, unfiltered, and free from the artificial constraints imposed by big tech algorithms.
Similarities Exist But With a Better Foundation
At a glance, using a NOSTR client may seem similar to traditional social media platforms. Users post messages (called ‘notes’), interact with others, and build followings. You can reply, share, and engage much like you would on Twitter. But under the hood, everything operates on a more open, transparent system.
Instead of relying on centralized servers controlled by corporations, NOSTR functions through relays—public or private servers that transmit messages. Since there’s no corporate overlord dictating what gets priority in your feed, you see content chronologically and unfiltered. Additionally, identity and reputation are built through cryptographic keys rather than being at the mercy of a username that a platform can seize or shadowban at will.
No Ads, No Tracking, No Manipulation
Let’s be honest—traditional social media has become a giant advertisement machine. Everything is optimized to keep you engaged just long enough to serve more ads and collect more data. Your feed isn’t showing you what’s most relevant; it’s showing you what makes the company the most money.
NOSTR eliminates this problem entirely. There are no forced ads, no trackers collecting your data, and no algorithm deciding what you should see. Instead, users fund relays or tip content creators directly, creating an ecosystem that values people over profit.
For New Users: A Starting Point
If you’re new to NOSTR, welcome! I’m still a beginner myself, but I’ve already seen the potential this platform has to change how we connect online. Getting started can seem overwhelming at first, but there are a few key tools and resources that can help smooth the transition.
For a great user-friendly NOSTR client, Damus (for iOS) and Amethyst (for Android) are excellent places to start. If you prefer a web-based option, Primal.net offers a simple and intuitive experience. These platforms make it easy to dive in, start posting, and get a feel for how NOSTR operates.
But NOSTR isn’t just about social media—it’s a foundation for something bigger. Developers and innovators are expanding their reach beyond simple note-sharing. Specialized communities and applications are already emerging, including platforms for photography, recipe sharing, and even swap sites, all built using the NOSTR framework. The possibilities are growing, and the future looks bright.
Final Thoughts
The shift from Twitter or Facebook to NOSTR isn’t just about switching platforms; it’s about embracing a fundamentally better way to communicate online. With decentralization, real freedom of expression, and a community of forward-thinking individuals, NOSTR offers an experience that traditional social media simply cannot match.
For those seeking a place where ideas flow freely, where profit-driven algorithms don’t dictate engagement, and where you control your own digital presence, NOSTR is not just an alternative. It’s an upgrade.
Let's connect and learn together!
npub1x7zk9nfqsjwuuwm5mpdu8eevsnu2kk0ff23fv58p45d50fhuvaeszg44p2
primal.net/Goody
-
 @ 8f69ac99:4f92f5fd
2025-02-20 15:24:24
@ 8f69ac99:4f92f5fd
2025-02-20 15:24:24Anarquia: uma palavra que frequentemente evoca imagens de caos e desordem, associada ao velho oeste sem lei ou a futuros distópicos onde impera a força bruta. No entanto, para aqueles que investigam mais a fundo, a anarquia revela-se como algo muito mais sofisticado—um sistema não definido pela ausência de regras, mas sim pela ausência de governantes (rules without rulers). Essa distinção fundamental é essencial para compreender um dos conceitos mais fascinantes e, ao mesmo tempo, mais difamados da sociedade.
A ideia de que anarquia significa desordem ou uma sociedade sem estrutura é um equívoco baseado no medo do desconhecido e na falta de compreensão dos seus princípios básicos. Na realidade, a anarquia assenta sobre um princípio fundamental: o Princípio da Não-Agressão (PNA). Este princípio estabelece que nenhum indivíduo tem o direito de iniciar o uso da força, coerção ou fraude contra os outros, sem o seu consentimento, sendo este um dos pilares fundamentais para a preservação da propriedade privada e das liberdades individuais.
Não se trata, portanto, de uma sociedade sem regras, mas sim de uma organização baseada em estruturas legais descentralizadas e orgânicas, como a lei natural e o direito consuetudinário, que emergem naturalmente através das interacções voluntárias entre indivíduos. A história demonstra que, mesmo na ausência de uma autoridade central, os seres humanos são perfeitamente capazes de criar ordens sociais complexas, baseadas na cooperação, na ajuda mútua e no progresso.
Este artigo explora como a anarquia funciona enquanto sistema de cooperação voluntária e direito natural, desafiando as concepções erradas que persistem sobre o tema e revelando o seu potencial para fortalecer a liberdade individual e a coesão social. Ao analisar as suas raízes filosóficas, o papel do Estado dentro de um enquadramento anarquista e os exemplos históricos que demonstram a capacidade da humanidade para se auto-organizar, procuramos iluminar um futuro onde a liberdade não seja apenas um sonho utópico, mas uma possibilidade concreta.
Principio da Não Agressão (PNA)
A base da anarquia assenta sobre um princípio inegociável: o Princípio da Não-Agressão. Este postulado não é apenas uma directriz moral, mas sim uma regra essencial de conduta, destinada a fomentar uma sociedade cooperativa e pacífica, onde os indivíduos vivem sem medo da coerção ou da violência.
A partir deste princípio, deriva-se naturalmente a propriedade privada, pois cada indivíduo tem o direito de usufruir e gerir os recursos que adquire sem recorrer à força contra terceiros. Da mesma forma, a violação deste princípio—seja através do roubo, homicídio ou qualquer tipo de agressão física ou psicológica, não consentida—é condenada de forma universal, pois representa um atentado contra a liberdade de cada um.
Num enquadramento anarquista, a ausência de uma estrutura coerciva não significa a ausência de ordem. Métodos como pressão social, ostracismo de infractores e mecanismos privados de justiça ajudam a manter a harmonia social. Por exemplo, em situações de litígio entre vizinhos sobre a posse de um terreno, em vez de recorrer ao Estado, poderiam simplesmente resolver a disputa através de um mediador comunitário ou de um serviço de arbitragem voluntário.
Ordem Sem Autoridade Central
A crença de que a lei e a ordem dependem de um poder centralizado ignora uma vasta tradição histórica de sistemas legais descentralizados que surgiram espontaneamente, sem intervenção estatal. A anarquia não significa ausência de normas, mas sim uma ordem espontânea baseada em leis naturais e consuetudinárias.
A lei natural consiste em princípios universais, reconhecidos pela razão, que não dependem da autoridade estatal. Já o direito consuetudinário assenta na tradição e nos precedentes, evoluindo conforme as necessidades das comunidades. Um excelente exemplo histórico é o código jurídico medieval islandês "Grágás", que regulava litígios e contratos através de mediação voluntária.
Sistemas baseados na reputação também são eficazes. No passado, comerciantes que desrespeitassem contratos viam-se rapidamente excluídos do mercado. Hoje, soluções descentralizadas como a arbitragem privada demonstram que contratos podem ser cumpridos sem necessidade de coerção estatal.
Anarquia como Estado Natural da Cooperação Humana
A cooperação voluntária está no cerne da natureza humana. A ideia de que é necessária uma autoridade central para garantir harmonia social desconsidera as inúmeras instâncias de colaboração espontânea ao longo da história.
O funcionamento dos mercados ilustra perfeitamente a anarquia em acção. Sem um governo a ditar regras, indivíduos interagem livremente, criando riqueza e inovação. A busca pelo progresso científico também reflecte este princípio: Albert Einstein, Nikola Tesla, Henry Ford ou Thomas Edison não foram forçados pelo Estado a desenvolver as suas invenções—fizeram-no por interesse próprio, beneficiando toda a humanidade.
Da mesma forma, a revolução industrial não foi um plano centralizado, mas sim o resultado de inúmeras inovações individuais que impulsionaram a prosperidade global. A tecnologia moderna, com exemplos como Bitcoin e Nostr, redes descentralizadas, prova que sociedades podem operar sem intermediários estatais, ou autoridades centrais.
Estado: Pode Existir Num Enquadramento Anarquista?
O Estado, mesmo na sua versão mais reduzida, pode representar um risco para a liberdade individual. Alguns, eu incluído, argumentam que um "Estado mínimo" (minarquia) poderia existir para garantir segurança e mediar disputas, mas essa estrutura pode rapidamente expandir-se e transformar-se num mecanismo de coerção.
A necessidade de mecanismos de controlo e equilíbrio
Mesmo um Estado reduzido exigiria salvaguardas para evitar abusos de poder. Para isso, seriam necessários mecanismos que garantam que nenhuma autoridade se torne dominante e que a sociedade mantenha a sua autonomia.
Algumas soluções incluem:
- Representação directa: Em vez de delegar decisões a políticos, a população poderia ter mais influência directa nas questões que afectam a sua vida (como na Suiça por exemplo).
- Arbitragem independente: Conflitos poderiam ser resolvidos sem recorrer a tribunais estatais, através de mediação voluntária e sistemas de justiça comunitária.
- Redes de apoio social: Fortalecer redes de ajuda mútua reduziria a necessidade de um governo central para fornecer serviços essenciais.
Exemplos práticos
Algumas iniciativas mostram que a sociedade pode funcionar com estruturas descentralizadas:
- Cidades com participação cívica activa: Experiências como o orçamento participativo em algumas cidades demonstram como a sociedade pode gerir recursos colectivos sem excessiva intervenção estatal.
- Redes de ajuda mútua: Grupos como a Mutual Aid Disaster Response Network nos EUA provam que comunidades podem organizar-se para responder a crises sem depender do Estado.
O desafio não é apenas imaginar um mundo sem Estado, mas conceber modelos descentralizados que garantam a liberdade individual e impeçam a concentração de poder. A verdadeira questão é: conseguiremos criar sistemas mais justos e funcionais sem recorrer à coerção estatal?
Raízes Filosóficas da Anarquia
A anarquia tem uma longa tradição filosófica que remonta a pensadores como William Godwin, Pierre-Joseph Proudhon e Max Stirner, cada um contribuindo com diferentes perspectivas sobre a organização social sem governantes. No século XX, pensadores como Murray Rothbard e Hans-Hermann Hoppe aprofundaram a ideia do anarco-capitalismo, propondo que todos os serviços actualmente providenciados pelo Estado poderiam ser oferecidos por meio de mercados livres.
A raiz histórica da anarquia está firmemente ancorada no pensamento de esquerda (a tradicional... ), na medida em que a sua proposta fundamental é a eliminação do poder central. O anarquismo clássico emergiu como uma resposta ao absolutismo e ao capitalismo industrial, defendendo que a autoridade imposta pelo Estado e pelas elites económicas deveria ser desmantelada para dar lugar a um sistema de cooperação voluntária e descentralizada. Proudhon, ao afirmar "a propriedade é roubo", reflectia esta preocupação com a concentração de poder e riqueza nas mãos de poucos.
Com o tempo, no entanto, diferentes correntes começaram a emergir dentro da tradição anarquista. A tradição anarquista de esquerda enfatiza a justiça social e a solidariedade comunitária, rejeitando tanto o Estado como o capitalismo. Nomes como Bakunin e Kropotkin defenderam a abolição da propriedade privada em favor de sistemas cooperativos, argumentando que apenas a auto gestão e o apoio mútuo poderiam garantir a verdadeira liberdade.
Por outro lado, no século XX, surgiu uma vertente anarquista mais associada à direita, especialmente com Rothbard e Hoppe, que viam o mercado como a melhor alternativa ao Estado. Para os anarco-capitalistas, a liberdade individual é prioritária, e a descentralização deve ocorrer não apenas ao nível político, mas também económico, permitindo que todas as transacções sejam voluntárias e baseadas na propriedade privada.
Apesar dessas divergências, há um ponto comum entre todas as vertentes anarquistas: a rejeição do monopólio da violência estatal. Tanto anarquistas de esquerda quanto de direita reconhecem que o poder centralizado inevitavelmente conduz à opressão e à limitação da liberdade individual. O debate interno dentro do anarquismo não é sobre a necessidade de abolir o Estado, mas sim sobre o que deve substituí-lo: auto gestão comunitária e colectivismo ou mercados livres e concorrência voluntária?
A preservação da propriedade privada e a liberdade de associação são, para mim, princípios fundamentais dentro do pensamento anarquista. Nada impede que, numa sociedade anarquista, grupos de indivíduos escolham unir-se voluntariamente para formar projectos cooperativos baseados em valores partilhados. O que distingue essa abordagem da imposição estatal é o carácter voluntário e descentralizado dessas associações, garantindo que cada pessoa possa viver conforme os seus próprios princípios sem coerção externa.
Esta dicotomia entre esquerda e direita dentro do anarquismo reflecte diferentes interpretações sobre a melhor forma de organizar a sociedade sem coerção. O que permanece inegável é que a anarquia, independentemente da vertente, continua a ser uma proposta de resistência contra qualquer forma de domínio centralizado, colocando a liberdade e a autonomia no centro da organização social.
Conclusão
A anarquia não é um sonho utópico, mas sim uma alternativa viável à organização centralizada da sociedade. Através do respeito pelo Princípio da Não-Agressão, da descentralização das normas jurídicas e da cooperação voluntária, podemos construir um mundo mais livre, onde as pessoas têm o poder de se governar a si mesmas.
Sistemas como Bitcoin já demonstram que a descentralização funciona e que a ausência de intermediários coercivos é não só possível, mas desejável. O desafio não é saber se a anarquia pode funcionar, mas sim quanto tempo levará para as pessoas perceberem que um mundo sem Estado é mais próspero e justo.
anarquia #anarco #bitcoin
Photo by Orit Matee on Unsplash
-
 @ 83279ad2:bd49240d
2025-01-24 09:15:37
@ 83279ad2:bd49240d
2025-01-24 09:15:37備忘録として書きます。意外と時間がかかりました。全体で1時間くらいかかるので気長にやりましょう。 仮想通貨取引所(販売所ではないので、玄人が使えばお得らしい)かつBitcoinの送金手数料が無料(全ての取引所が無料ではない、例えばbitbankは0.0006bitcoinかかる)なので送金元はGMOコインを使います。(注意:GMOコインは0.02ビットコイン以下は全額送金になってしまいます) 今回はカストディアルウォレットのWallet of Satoshiに送金します。 以下手順 1. GMOコインでbitcoinを買います。 2. GMOコインの左のタブから入出金 暗号資産を選択します。 3. 送付のタブを開いて、+新しい宛先を追加するを選択します。 4. 送付先:GMOコイン以外、送付先ウォレット:プライベートウォレット(MetaMaskなど)、受取人:ご本人さま を選んで宛先情報の登録を選ぶと次の画面になります。
 5. 宛先名称にwallet of satoshi(これはなんでも良いです わかりやすい名称にしましょう) wallet of satoshiを開いて、受信→Bitcoin On-Chainからアドレスをコピーして、ビットコインアドレスに貼り付けます。
5. 宛先名称にwallet of satoshi(これはなんでも良いです わかりやすい名称にしましょう) wallet of satoshiを開いて、受信→Bitcoin On-Chainからアドレスをコピーして、ビットコインアドレスに貼り付けます。 6. 登録するを押します。これで送金先の登録ができました。GMOコインの審査がありますがすぐ終わると思います。
7. ここから送金をします。送付のタブから登録したビットコインの宛先リストwallet of satoshiを選択し、送付数量と送付目的を選択して、2段階認証をします。
6. 登録するを押します。これで送金先の登録ができました。GMOコインの審査がありますがすぐ終わると思います。
7. ここから送金をします。送付のタブから登録したビットコインの宛先リストwallet of satoshiを選択し、送付数量と送付目的を選択して、2段階認証をします。 8. 実行を押せば終わりです。もうあなたがやることはありません。送金が終わるのを40分くらい眺めるだけです。
8. 実行を押せば終わりです。もうあなたがやることはありません。送金が終わるのを40分くらい眺めるだけです。 8. 取引履歴のタブから今の送金のステータスが見れます。
8. 取引履歴のタブから今の送金のステータスが見れます。 9. 15分くらい待つとステータスが受付に変わります。
9. 15分くらい待つとステータスが受付に変わります。 10. 20分くらい待つとトランザクションIDが表示されます。
10. 20分くらい待つとトランザクションIDが表示されます。

この時点からwallet of satoshiにも送金されていることが表示されます。(まだ完了はしていない)
 11. ステータスが完了になったら送金終わりです。
11. ステータスが完了になったら送金終わりです。

wallet of satoshiにも反映されます。

お疲れ様でした!
-
 @ 0b118e40:4edc09cb
2025-02-19 01:21:45
@ 0b118e40:4edc09cb
2025-02-19 01:21:45Are we living in his definition of democracy?
It’s interesting how political parties can divide a country, especially in democracies where both oppression and individual choice coexist.
As I was exploring global economics and political ideologies, I picked up The Republic by Plato (again). The first time I read it, I only read the book on the Allegory of the Cave and it felt enlightening. This time around, I read through all the books and I thought to myself : this is absolutely nuts!
Over 2,000 years ago, The Republic imagined a world disturbingly similar to Gattaca or 1984. For a quick rundown, Plato believed in a police state, eugenics, a caste system, and brainwashing people through state-controlled media and education. Sounds wild? I thought so too.
And for some reason, Plato had a serious grudge against art. To him, art was deceptive and emotionally manipulative. Maybe because there was a skit making fun of Socrates at that time by Aristophanes (the father of comedy) or maybe because he struggled to deal with emotions, we will never know.
Plato obviously wasn’t a fan of democracy as he wanted a dystopian world. But to be fair, he genuinely thought that his ideal world (Kallipolis) was a utopia. Maybe someone who loves extreme order and control might think the same but I sure don’t.
His teacher Socrates was also not a fan of democracy because he believed the mass majority were too ignorant to govern and only those intelligent enough could. His student, Aristotle, was more moderate but still critical, seeing democracy as vulnerable to corruption and mob rule. Socrates, Plato, and Aristotle were around the Classical Greek era, 5th to 4th century BC.
The idea of democracy existed long before them. The first recorded version was in Athens during the 6th BC, developed by leaders like Solon and Pericles. It was a direct democracy where free male citizens (non-slaves) could vote on laws themselves instead of electing representatives.
These guys influenced how we think about democracy today. But looking around, I wonder, did we end up in Plato’s dystopian world?
Plato’s take on democracy
Plato’s lack of trust of democracy stemmed from Socrates’ death. Socrates himself was a fierce critic of democracy, as he believed governance should be based on wisdom rather than popularity.
Other thinkers, like Pythagoras and Herodotus (father of history), also examined different political systems, but Socrates was the most influential critic. He warned that allowing the uneducated masses to choose leaders would lead to poor governance, as they could be easily swayed by persuasive speakers rather than guided by knowledge.
Athenian democracy relied on large citizen juries and was particularly vulnerable to rhetoric and public sentiment.
In the end, Socrates became a victim of the very system he criticized. His relentless questioning of widely accepted beliefs, now known as the Socratic Method, earned him powerful enemies. Socrates’ constant probing forced them to confront uncomfortable truths. It annoyed people so much, that it eventually led to his trial and execution. Socrates was condemned to death by popular vote.
I wonder, if we applied the Socratic Method today to challenge both the left and the right on the merits of the opposing side, would they be open to expanding their perspectives, or would they react with the same hostility?
This questioning technique is now also used in some schools and universities as a teaching method, encouraging open-ended discussion where students contribute their own thoughts rather than passively receiving information. But how open a school, system, or educator is to broad perspectives depends largely on their own biases and beliefs. Even with open-ended questions, the direction of the conversation can be shaped by those in charge, potentially limiting the range of perspectives explored.
Socrates’ brutal death deeply grounded Plato’s belief that democracy, without intellectual rigor, was nothing but a mob rule. He saw it as a system doomed to chaos, where the unqualified, driven by emotion or manipulated by rhetoric, made decisions that ultimately paved the way for tyranny.
The Republic
The Republic was written around 375 BC, after the Peloponnesian War. One of its most famous sections is the Allegory of the Cave, where prisoners are stuck watching shadows on a wall, thinking that it’s reality until one breaks free and sees the real world. That’s when the person becomes enlightened, using knowledge and reason to escape ignorance. They return to free others, spreading the truth. I love this idea of breaking free from suppression through knowledge and awareness.
But as I went deeper into Plato’s work, I realized what the plot twist was.
Plato wrote this book for strict state control. He wanted total control over education, media, and even families like in the book 1984. He argued that people should be sorted into a caste system, typically workers, warriors, and philosopher-kings so that society runs like a well-oiled machine. The “guardians” would police the state and everyone would go through physical and military training. To top it off, kids would be taken away from their parents and raised by the state for the “greater good.” like in the movie Gattaca. If that sounds a little too Orwellian, that’s because it is.
Plato believed that only philosophers, the truly enlightened ones from that “cave”, should rule. To him, democracy was a joke, a breeding ground for corruption and tyranny.
I found it completely ironic that this book that warns about brainwashing in the Allegory of the Cave also pushes for a state-controlled society, where thinking for yourself isn’t really an option.
And yet, looking around today, I wonder, are we really any different? We live in a world where oppression and enlightenment exist side by side.
Plato was slightly progressive in that he thought men and women should have equal education, but only for the ruling Guardian class.
In The Republic, Plato didn’t focus much on economics or capitalism as we understand them today. His philosophies were more concerned with justice, governance, and the ideal structure of society. He did touch on wealth and property, particularly in The Republic and Laws but it was more on being against wealth accumulation by rulers (philosopher-kings had to live communally and without private property).
While these ideas echo elements of socialism, he never outlined a full economic system like capitalism or socialism.
The hatred for art
Plato was deeply skeptical of art. He believed that it appealed to emotions over rational thought and distorted reality. In The Republic (Book X), he argued that art is an imitation of an imitation, pulling people further from the truth. If he had his way, much of modern entertainment, including poetry, drama, and even certain types of music, would not exist in their expressive forms.
Despite Plato’s distrust of the arts, his time was a golden age for Greek drama, sculpture, and philosophy. Ironically, the very city where he built his Academy, Athens, was flourishing with the kind of creativity he wanted to censor.
Even medicine, which thrived under Hippocrates (the father of medicine), was considered an art requiring lifelong mastery. His quote, ‘Life is short, and art is long,’ reflects the long span of time it takes to cultivate and appreciate knowledge and skills, which was something Plato valued. Yet, he dismissed most art as a distraction from truth.
Plato particularly criticized poets and playwrights like Homer, as he claimed they spread false ideas about gods and morality. He was also wary of Aristophanes, as he believed his work stirred emotions rather than encouraging rational thought. It probably did not help that Aristophanes mocked Socrates in his play The Clouds, which may have influenced Plato’s views.
What’s clear is that Plato didn’t hate art because he didn’t understand it. He deeply understood the power of storytelling and its ability to mold societal beliefs. He argued for banning poets entirely from his “ideal city” to prevent them from misleading the public.
But he did value some forms of art. After all, he was a writer himself, and writing is a form of art. He approved of artistic expressions that promoted moral and intellectual virtue, such as hymns, architecture, and patriotic poetry, as long as they served the greater purpose of instilling order and wisdom in society.
Plato’s five regimes
Plato believed governments naturally decay over time, moving from order to chaos. He outlined five regimes, which he considers each to be worse than the last.
-
Aristocracy (Philosopher-King rule) : This is his pitch, the ideal state, ruled by wise elites who value knowledge over power. Some aspects of modern authoritarian states echo this model
-
Timocracy (Military rule) : A government driven by honor and discipline, like Sparta. Over time, ambition overtakes virtue, leading to oligarchy.
-
Oligarchy (Rule by the wealthy) : The rich seizes power and deepens inequality. Many democracies today show oligarchic tendencies, where money dominates politics.
-
Democracy (Rule by the masses) : The people overthrow the elites, prioritizing freedom over order. But without stability, democracy becomes fragile, and vulnerable to demagogues and external manipulation.
-
Tyranny (Dictatorship) : When democracy collapses, a charismatic leader rises, promising order but seizing absolute power. What begins as freedom ends in oppression.
Modern politics seems stuck in a cycle, shifting between democracy, oligarchy, and authoritarian control. If Plato was right, no system is permanent and only the illusion of stability remains.
Does Plato’s ideal state exist in any country today?
Some aspects of modern benevolent dictatorships, like Singapore under Lee Kuan Yew, or socialist states like China, may resemble Plato’s vision in their emphasis on elite rule, long-term planning, and state control. But, these governments operate pragmatically, balancing governance with economic power, political strategy, and public influence rather than strictly adhering to philosophical ideals.
Could this be compared to Taliban rule, given the censorship, authoritarian control, and rigid social hierarchy? While there are superficial similarities, the key difference is that Plato valued knowledge, reason, and meritocracy, while the Taliban enforced religious fundamentalism and theocratic rule. Plato’s Kallipolis also included some level of gender equality for the ruling class, whereas the Taliban’s system is heavily restrictive, especially toward women.
While Plato’s ideas echo in certain authoritarian-leaning states, his rigid caste system, philosopher-led governance, and rejection of democracy set his vision apart from any modern political system.
Aristotle’s take on democracy
Aristotle wasn’t Athenian, but he documented and analyzed 158 constitutions, including Athenian democracy. He studied at Plato’s Academy for over 20 years, growing up in a world influenced by Athens’ democratic experiment. He lived through the tail end of Athens’ golden age, witnessed its decline, and experienced how different forms of rule influenced politics and the mindset of the people under them.
For Aristotle, governments were good or corrupted. The good ones were monarchs, aristocracy (wise elites), and polity (a constitutional gov’t where the middle class keeps power balanced). The corrupted ones were tyranny (monarchy gone wrong), oligarchy, and democracy.
Aristotle saw how democracy, if unchecked, could spiral into chaos or be co-opted by populist leaders. But unlike Plato, who rejected democracy outright, Aristotle believed it could work if properly structured.
His concept of ‘polity’ was a constitutional government that balanced democratic participation with stability, relying on a strong middle class to prevent both mob rule and elite domination. This idea of checks and balances, a mixed government, and middle-class stability make polity the closest to modern constitutional democracies today when compared to all 3 of the Greek philosophers.
What happened after Athens?
Of course, democracy didn’t end with Athens, it evolved over time. After Athens’ golden age came Alexander the Great (Aristotle’s student and the king of Macedonia). He conquered Greece, Persia, Egypt, and part of India, creating the largest empire of his time. After his death in 323 BCE, his empire split among his generals, marking the beginning of the Hellenistic period.
Rome saw a shift from the fall of the Roman Republic to the rise of the Roman Empire under Augustus moving away from democratic ideals to centralized rule. But the Western Roman Empire fell about 500 years later largely due to internal decline and invasions by the Germanic Tribes (modern-day Sweden, Switzerland, Germany). The Eastern Roman Empire (Byzantine Empire, based in Constantinople or modern-day Turkey) rose and survived for nearly 1,000 more years until it fell to the Ottoman Turks in 1453.
During the Medieval period (5th–15th century), Europe saw a rise in monarchies and feudalism. Power shifted to kings, nobles, and the church, with little direct participation from ordinary people. Some democratic elements survived in places like Venice and Florence, where wealthy merchant families controlled city-states.
By the 17th century, democracy started creeping back into political thought, though not without skepticism. Machiavelli and Hobbes weren’t exactly fans of democracy, but they had plenty to say about power and governance. Later on Machiavelli hinted on the possible idea of a republic/mixed government in the *Discourses of Livy *
Meanwhile, England was going through its own struggles with power. The English Civil War (1642–1651) was a showdown between King Charles I, who wanted absolute power, and Parliament, which wanted more influence. Charles ignored Parliament and was executed in 1649. England briefly became a republic under Oliver Cromwell, but the monarchy returned after his death.
In 1688, the Glorious Revolution forced King James II (Charles I’s son) to flee to France. Parliament then invited William of Orange (a Dutch Protestant) and his wife Mary to take the throne. In 1689, they signed the English Bill of Rights, which limited the monarchy’s power, strengthened Parliament, and guaranteed certain rights to citizens.
This was a significant moment in history as it effectively ended the absolute monarchy and established a constitutional monarchy in England.
The American Revolution in 1776 and the French Revolution in 1789 pushed democratic ideals forward but still excluded women, slaves, and the poor. Historian Luciano Canfora, in his book Democracy in Europe, argues that early liberal democracy was full of contradictions as it preached equality, yet economic and social exclusion remained.
(Note: If you want to understand the history of anarchism, the French Revolution is a key starting point. It influenced early anti-authoritarian thought, which later evolved into socialist and anti-capitalist movements. Over time, libertarians adopted anarchist principles, leading to the development of anarcho-capitalism. The concept of anarchism in politics has taken nearly two centuries to emerge in its modern form).
The 19th and 20th centuries saw the expansion of democracy. But as Canfora explains it, it also saw its exploitation and manipulation. Although industrialization and social movements pushed for broader suffrage, democracy remained controlled by elites who feared true mass participation. Democracy became a tool for maintaining power rather than a true expression of the people’s will.
According to Canfora, the Cold War turned democracy into a geopolitical tool, with Western powers supporting or opposing democratic movements based on strategic interests rather than principles.
Today, there are many versions of democracy from direct democracy to representative democracy, presidential democracy, social democracy, religious democracy, constitutional democracy, communist democracy, and more. And is often viewed as a brand name for “good governance”. But are they?
In the end, was Plato right?
At a meta level, Plato’s argument was about control, be it controlling what people read, hear, and even think. The debate often centers on curated knowledge vs rhetoric. Plato believed that absolute obedience would bring harmony, even at the cost of individuality. Today, we call that totalitarian or dictatorship
But when we take a second look at things, are we already living in Plato’s world?
Governments across the globe control education, influence media narratives, and regulate speech. Many so-called democracies aren’t as free as they claim to be. So maybe Plato’s influence on modern democracies runs deeper than we realize.
Another key debate today is that, unlike Plato’s time, most people are educated. However, much of this education is still designed by state systems, which can influence how people think and vote. How do we balance empowering people through education while ensuring true independence in a system built on critical thinking rather than one that merely feeds information?
Truth is, democracy has never been a pure, people-driven system. It has always been influenced by power struggles, wealth, and manipulation. Often it has been an instrument of control rather than liberation.
Yet, the people have always resisted. In the past, they gathered in the streets, risking tear gas, rubber bullets or being dragged into Black Marias. Today, digital activism has allowed for mass mobilization with fewer risks. In many countries especially in third-world countries, online movements on platforms like Twitter during Jack’s time, forced governments to overturn policies. This may be the closest we've come to real democracy which is direct action without the usual state violence.
But with this rise in digital activism comes the counterforce through government and corporate requirements for censorship, algorithmic manipulation, and the quiet steering of public discourse. Platforms once seen as tools of liberation can become tools of control. Facebook mood experiment in 2012 tested positive and negative content on 700,000 people and proved emotions can be manipulated at scale. Cambridge Analytica was exposed in its attempt to manipulate votes.
This is where decentralized networks like Nostr matter as a fundamental resistance to centralized control over speech. If democracy is to return to the people, it must also break free from algorithmic gatekeepers and censorship.
Because the so-called ‘ignorant masses’, the very people Plato dismissed, are the ones who fight for freedom.
Because real democracy isn’t about control.
It’s about freedom.
It’s about choice.
It’s about the people, always.
-
-
 @ a012dc82:6458a70d
2025-02-20 15:02:29
@ a012dc82:6458a70d
2025-02-20 15:02:29The Financial Accounting Standards Board (FASB) has recently introduced a groundbreaking ruling that significantly alters the way Bitcoin and other cryptocurrencies are accounted for in financial statements. This new development is poised to transform the landscape of crypto accounting, bringing in more transparency and alignment with traditional financial practices. Let's delve into the details of this pivotal change.
Table of Contents
-
Introduction to the New FASB Ruling
-
The Shift to Fair Value Accounting
-
Understanding Fair Value Accounting
-
Impact on Financial Reporting
-
-
Advantages of the New Approach
-
Enhanced Transparency and Accuracy
-
Positive Implications for Companies
-
-
Challenges and Considerations
-
Dealing with Volatility
-
Auditor Expertise
-
-
Industry Response and Future Outlook
-
Embracing the Change
-
Long-Term Implications
-
-
Conclusion
-
FAQs
Introduction to the New FASB Ruling
The FASB, the principal body responsible for establishing accounting standards in the United States, announced a new set of rules concerning the accounting of cryptocurrencies like Bitcoin. This announcement marks a significant shift from the previous accounting practices for digital assets. Previously, the lack of clear guidelines led to inconsistencies and uncertainties in how companies reported their crypto holdings. The new ruling aims to standardize these practices and reflects the growing importance of cryptocurrencies in the financial world.
The Shift to Fair Value Accounting
Understanding Fair Value Accounting
Under the new FASB rules, companies are now required to account for cryptocurrencies at their fair value. Fair value accounting involves assessing assets and liabilities based on their current market value, rather than their historical cost. This approach is expected to provide a more accurate and real-time reflection of a company's financial status. It marks a significant departure from the traditional cost-based accounting methods, which often do not reflect the current market realities, especially in the case of highly volatile assets like cryptocurrencies.
Impact on Financial Reporting
This shift to fair value accounting means that companies holding cryptocurrencies will report the value of these assets based on their market prices at the end of each reporting period. This move is a departure from the previous method where Bitcoin was treated as an intangible asset, leading to certain limitations in financial reporting. For instance, under the old rules, if the value of Bitcoin fell below its purchase price, companies had to report a loss, but they couldn't report an increase in value unless the asset was sold. The new approach allows for a more dynamic and responsive reporting system that better reflects the economic realities of holding cryptocurrencies.
Advantages of the New Approach
Enhanced Transparency and Accuracy
One of the primary benefits of this new ruling is the increased transparency and accuracy it brings to financial reporting. Companies can now reflect the actual market value of their crypto holdings, providing a clearer picture of their financial health. This change is particularly significant given the volatile nature of cryptocurrencies. By reporting the fair market value, companies can provide stakeholders with a more accurate depiction of their financial standing, which is crucial for informed decision-making by investors, regulators, and other stakeholders.
Positive Implications for Companies
Companies are likely to welcome this change as it allows them to report unrealized gains and losses on cryptocurrencies. This could encourage more businesses to add cryptocurrencies like Bitcoin to their balance sheets, as they can now recognize the appreciation in value without needing to sell the assets. This change could also lead to a broader acceptance of cryptocurrencies as a legitimate and valuable asset class, potentially spurring further investment and innovation in the crypto space.
Challenges and Considerations
Dealing with Volatility
The inherent volatility of cryptocurrencies like Bitcoin poses a significant challenge in fair value accounting. Companies will need to develop robust methods to accurately assess the market value of these assets, which can fluctuate widely. This volatility requires continuous monitoring and frequent valuation adjustments, which can be resource-intensive and complex. Companies will need to invest in sophisticated valuation models and possibly seek external expertise to ensure accuracy and compliance.
Auditor Expertise
Another challenge lies in the need for auditors to acquire expertise in valuing cryptocurrencies. Assessing the fair market value of digital assets is a complex task that requires specific knowledge and skills. Auditors will need to stay abreast of the rapidly evolving crypto market and develop new methodologies for valuation. This requirement not only adds a layer of complexity to the audit process but also underscores the need for ongoing education and training in this emerging field.
Industry Response and Future Outlook
Embracing the Change
The industry's response to the FASB's ruling has been largely positive. Industry leaders view this as a step towards mainstream acceptance of cryptocurrencies and a move that aligns digital assets with traditional financial reporting standards. This ruling is seen as a validation of the growing role of cryptocurrencies in the financial sector and a sign that regulatory bodies are beginning to recognize and adapt to the unique characteristics of these digital assets.
Long-Term Implications
In the long run, this ruling could lead to greater institutional adoption of cryptocurrencies. As financial reporting becomes more standardized and transparent, it may foster greater trust and confidence among investors and regulators. This could pave the way for more widespread use of cryptocurrencies in various financial transactions and potentially influence the development of new financial products and services centered around digital assets.
Conclusion
The FASB's latest ruling on cryptocurrency accounting is a landmark decision that aligns the treatment of digital assets with traditional financial practices. While it presents certain challenges, particularly in terms of volatility and the need for specialized auditor expertise, the overall impact is expected to be profoundly positive. This change not only enhances transparency and accuracy in financial reporting but also paves the way for broader acceptance and integration of cryptocurrencies in the mainstream financial world. As the industry adapts to these new rules, we can expect to see a more mature and robust crypto market, potentially leading to innovative financial solutions and greater economic opportunities.
FAQs
When will the new FASB rules take effect? The new rules are set to take effect from December 15, 2024, but companies have the option to apply them earlier.
How does fair value accounting affect financial reporting? Fair value accounting allows companies to report the value of cryptocurrencies based on current market prices, providing a more accurate and real-time reflection of a company's financial status.
What are the benefits of the new FASB ruling? The new ruling enhances transparency and accuracy in financial reporting and encourages more businesses to add cryptocurrencies to their balance sheets by allowing them to report unrealized gains and losses.
What challenges does the new ruling present? The main challenges include dealing with the volatility of cryptocurrencies in fair value accounting and the need for auditors to develop expertise in valuing these digital assets.
What is the industry's response to the new ruling? The industry has largely responded positively, viewing it as a step towards mainstream acceptance of cryptocurrencies and alignment with traditional financial reporting standards.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 266815e0:6cd408a5
2025-02-18 17:25:31
@ 266815e0:6cd408a5
2025-02-18 17:25:31noStrudel
Released another major version of noStrudel v0.42.0 Which included a few new features and a lot of cleanup
nostr:naddr1qvzqqqr4gupzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqp3hx7um5wf6kgetv956ry6rmhwr
Blossom
On the blossom front there where a few more PRs - Expanded the documentation around CORS headers in BUD-01 thanks to nostr:npub1a6we08n7zsv2na689whc9hykpq4q6sj3kaauk9c2dm8vj0adlajq7w0tyc - Made auth optional on the
/uploadendpoint PR - Added aHEAD /mediaendpoint for BUD-05 PR - Added range request recommendations to BUD-01 PRWith blossom uploads starting to be supported in more nostr clients users where starting to ask where to find a list of blossom servers. so I created a simple nostr client that allows users to post servers and leave reviews blossomservers.com Its still very much a work in progress (needs login and server and review editing) The source is on github
I also started another project to create a simple account based paid blossom server blossom-account-server Unfortunately I got sidetracked and I didn't have the time to give it the attention it needs to get it over the finish line
Smaller projects
- cherry-tree A small app for uploading chunked blobs to blossom servers (with cashu payment support)
- vite-plugin-funding A vite plugin to collect and expose package "funding" to the app
- node-red-contrib-rx-nostr The start of a node-red package for rx-nostr. if your interested please help
- node-red-contrib-applesauce The start of a node-red package for applesauce. I probably wont finish it so any help it welcome
Plans for 2025
I have a few vague ideas of what I want to work on Q1 of 2025. but there are a few things i know for certain.
I'm going to keep refactoring noStrudel by moving core logic out into applesauce and making it more modular. This should make noStrudel more reliable and hopefully allow me to create and maintain more apps with less code
And I'm going to write tests. tests for everything. hopefully tests for all the libraries and apps I've created in 2024. A lot of the code I wrote in 2024 was hacky code to see if things could work. and while its been working pretty well I'm starting to forget the details of of the code I wrote so I cant be sure if it still works or how well it works.
So my solution is to write tests, lots of tests :)
-
 @ 6ad3e2a3:c90b7740
2025-02-18 17:08:23
@ 6ad3e2a3:c90b7740
2025-02-18 17:08:23I’m not doing any writing today. Taking the day, maybe the week, off. Just not in the mood.
This whole idea you’re supposed to write, get the thoughts out, the ideas moving is stupid. To what end? I’m done with evaluating myself for productivity, justifying myself to myself — or anyone else.
What I really need is to find some pleasant distractions. Something to fill my time, or as Elon Musk says of Twitter “to avoid regretted user seconds.” I’ve tried Twitter itself, of course, but Musk’s algorithm falls woefully short. After an hour of doom and dopamine scrolling, punctuated with the occasional shitpost, many seconds are regretted — roughly 3500 of them.
I could turn to alcohol or drugs, but too many side effects. Yes, you’re distracted, but what about after that? You’re always left worse off than where you started. Even alcoholics and drug addicts — the pros! — know it’s a dead end.
I don’t know, maybe spend more time with loved ones? You hear that a lot. “If I didn’t have to work so much, I’d spend more time with loved ones.” LOL. Like what, you’re going to hang around while your “loved ones” are doing things with their actual lives. Maybe I’ll take the bus to school with Sasha, hang out with her and her friends, see how that goes. Quality time!
Exercise. It’s the perfect solution, good for your health, you feel better, your mind is calm. Only problem is it’s fucking miserable. If your aim is to avoid sitting at a desk to write, forcing your carcass around a track is hardly an upgrade. It’s like quitting your middle management job to break rocks in a prison chain gang.
There must be something I can do. Eating sugary processed food is out of the question for the same reason alcohol and drugs are. Becoming obese and diabetic is no solution, as many of the pros (obese diabetics) would no doubt attest.
Meditation. That’s it! You sit on a cushion, count your breaths. Pretty soon you are calm. You can meditate for as long as you want! It’s perfect, and it’s easy. Well, it’s not that easy. You get distracted by your thoughts and you’re just sitting there thinking about the things for which you hope and dread in your life.
Of course, you notice that distraction and come back to the breath, but pretty soon you’re wandering again. And you come back again. But really you’re wondering how long you’ve been sitting, your feet are falling asleep, your back is tight and you don’t feel much different. You weren’t even properly distracted because instead of being distracted from your mind, you are being distracted by it. It’s a worst-case scenario of sorts — you neither get anything done, nor escape the endless self-evaluation and justification.
That just means you’re doing it wrong, though. You’re failing at it. If you did it right, it would be the perfect escape from yourself. But it’s not working, so you’re failing. Or maybe you succeeded a little bit. You’re not sure. You are still evaluating whether that was a good use of your time. The same evaluation process you use to decide whether you’ve done enough writing, the same tired bullshit from which you were trying to escape in the first place!
Let’s face it, you’re not just going to meditate your way out of the problem. If you could, you would have already, and so would everyone else. We would all be enlightened. Maybe you need to go to an ashram or something, find a guru on top of a mountain in the Himalayas. LOL, you’re not gonna do that! You are way too attached to your comforts and daily routines, no matter how dull and unsatisfying they ultimately are.
There’s nowhere to run, nowhere to hide, no one to see, nothing to do. You are out of options. There is only one thing in your absolute control, and it’s where you direct your attention. And you have decided that no matter how bleak and pointless the alternatives the one thing about which you are resolute is you are taking the day off from writing.
-
 @ f1989a96:bcaaf2c1
2025-02-20 14:21:39
@ f1989a96:bcaaf2c1
2025-02-20 14:21:39Good morning, readers!
This week, we honor the loss of the late Alexei Navalny, whose bravery inspired millions of Russians to stand up against Vladimir Putin’s financial, political, and social repression. Since his murder, the Kremlin has only tightened its grip — imprisoning citizens for political donations, blocking NGOs from funding, advancing its central bank digital currency, and limiting access to open alternatives like Bitcoin.
In global news, a new survey of 34 central banks by the Official Monetary and Financial Institutions Forum (OMFIF) revealed that 31% have delayed plans to issue a retail central bank digital currency (CBDC). While this is a welcome shift, given that CBDCs threaten to give authoritarian regimes unprecedented tools to micro-control society, efforts to oppose and expose CBDCs must continue. The Human Rights Foundation (HRF) is proud that its CBDC Tracker (you can explore it here) continues to reveal these threats.
In privacy news, Bitcoin Core developer Carl Dong unveiled a new VPN called Obscura, the first open-source VPN that can’t log your network activity by design and outsmarts network filters for enhanced censorship resistance. Tools like this make the work of activists harder to surveil and censor under authoritarian regimes. Additionally, Zeus Wallet and Primal introduced support for Nostr Wallet Connect (NWC), further expanding interoperability between Nostr clients and Lightning wallets and giving more power back to the people.
Finally, we feature a Bitcoin node tutorial from Bitcoin educator Ben Perrin, “BTC Sessions,” walking viewers through setting up a node on a computer and connecting it to Sparrow Wallet. This tutorial is especially suited for dissidents and can empower curious individuals with the ability to verify the Bitcoin network independently, enhance privacy, and eliminate reliance on third parties. There is no need to be technically inclined to follow along with this tutorial.
Now, let’s dive right in!
Subscribe Here
GLOBAL NEWS
Russia | One Year Since Navalny Murdered by Regime
One year ago, Alexei Navalny was murdered in a remote Arctic prison, where he was sent to die for daring to stand against dictator Vladimir Putin. Navalny was Russia’s leading opposition figure, a relentless leader who exposed regime corruption at the highest level and inspired millions to believe in a brighter future. His murder confirmed a grim reality: the Kremlin will stop at nothing to silence those who oppose it. Since Navalny’s passing, Putin has only tightened his grip — charging innocent citizens for financially supporting dissent, blocking NGOs from funding (and access to their own money), accelerating the roll-out of a CBDC to tighten financial control, and restricting access to open alternatives like Bitcoin.
Argentina | Milei Facing Fraud Charges and Impeachment for Promoting Memecoin
Argentinian President Javier Milei is facing impeachment calls and fraud charges after promoting a cryptocurrency called $LIBRA, which has since crashed in value. He initially claimed $LIBRA would “encourage economic growth by funding small businesses and startups.” Instead, the token briefly soared above $5 before plummeting. Critics argue the $LIBRA launch resembles a “rug pull,” where paid promoters inflate a token’s value, then cash out, leaving investors with worthless holdings. As the backlash grew, Milei deleted his posts promoting $LIBRA and defended himself, insisting he didn't “promote it” — he simply “shared it.” Regardless, the damage is done. $LIBRA is now trading below $1, losing tens of thousands of global citizens most of their money. Behind $LIBRA is Kelsier Ventures, a group allegedly courting Nigeria and other governments with similar schemes. The saga continues to unfold, but the lessons are clear: political memecoins present major risks, and governments are not above rugging their own citizens.
Zimbabwe | Ordinary Citizens Pay Price of Deeply Indebted Regime
Zimbabwe’s debt crisis has pushed 7.6 million people into food insecurity as an El niño-driven drought worsens an economy already horribly mismanaged and exploited by a military dictatorship. The roots of this crisis run deep. Former tyrant Robert Mugabe’s land seizures in the early 2000s shattered agricultural output, wiped out foreign investment, and unleashed hyperinflation that erased Zimbabweans’ savings and wages. Decades of economic mismanagement drained the national resources and exacerbated food insecurity. Now, ordinary citizens shoulder the cost of regime failures. Families who once farmed their own land depend on expensive food imports they can’t afford, while the bankrupt regime pleads for more dollar-based loans — only to weaken the local currency and sink the country further into debt.
Singapore | Rising Costs Contradict Government’s Inflation Claims
Singaporean citizens are refuting government claims that inflation is easing, pointing to the rising costs of essential goods and services. While official data reports a 2.4% annual inflation rate, everyday expenses tell a different story. The government highlights falling car prices — a benefit for the wealthy — while downplaying state-imposed fare hikes that disproportionately impact those who rely on public transport (lower-income individuals). With elections looming, many accuse the government of manipulating narratives to downplay these economic struggles. The persistent rise in everyday costs reveals a common disconnect between opaque government statistics issued by autocrats and the financial realities lived by ordinary citizens.
World | Central Banks Delaying CBDC Plans
A new survey of 34 central banks by the Official Monetary and Financial Institutions Forum (OMFIF) revealed that 31% have delayed plans to issue a retail central bank digital currency (CBDC). It also found that the share of central banks inclined to issue a CBDC fell from 38% in 2022 to just 18% today. While this slowdown is a welcomed shift, the survey concludes that most central banks still expect to issue a CBDC in the future. In any jurisdiction, CBDCs mean more financial control in the hands of the government, which opens the door to surveillance, censorship, and control over financial activity. This concentrated power undermines civil liberties, especially in authoritarian regimes, putting dissidents and individuals at greater risk. Learn more about the dangers CBDCs pose to human rights and financial freedom here.
_____________
Webinar Series for Nonprofits: Become Unstoppable
HRF will host a free, three-day webinar from March 17-19, teaching human rights defenders and nonprofits how to use Bitcoin to counter state censorship and confiscation. Sessions run daily from 10:30 a.m. to 12:00 p.m. EDT and are beginner-friendly. The webinar will be led by Anna Chekhovich, HRF’s Bitcoin nonprofit adoption lead and financial manager at Alexei Navalny’s Anti-Corruption Foundation, and will be co-hosted by Ben Perrin “BTC Sessions,” one of the world’s top technical Bitcoin educators.
SXSW | The Human Rights Risks of Central Bank Digital Currencies (CBDCs)
Join HRF at SXSW 2025 in Austin from March 7-13 to explore how CBDCs threaten financial freedom. Experts Roger Huang, Charlene Fadirepo, and Nick Anthony will discuss how authoritarian regimes use CBDCs for surveillance and control. Attendees can also visit HRF’s CBDC Tracker booth to explore an interactive map of CBDC developments worldwide.
_____________
BITCOIN AND FREEDOM TECH NEWS
Obscura | New Virtual Private Network
Bitcoin Core developer Carl Dong launched Obscura VPN, the first private and open-source VPN designed for maximum censorship resistance. Unlike traditional VPNs, it cannot log your network activity by design. Obscura achieves this by never seeing users’ encrypted Internet traffic. Because of this, it is impossible to log activity — even if compelled or compromised. Additionally, Obscura uses a custom stealth protocol that blends in with regular Internet traffic, making the VPN harder to detect or block. Tools like this make the work of activists under authoritarian regimes harder to surveil and censor.
Zeus Wallet and Primal | Integrate Nostr Wallet Connect
Zeus, a Bitcoin Lightning wallet, and Primal, a Nostr client, have integrated the Nostr Wallet Connect (NWC) protocol. This protocol allows apps to interact with Bitcoin Lightning wallets, boosting interoperability between Bitcoin (decentralized money) and Nostr (decentralized communications). Zeus’s NWC integration expands wallet connectivity by allowing users to link external wallets like Alby Hub or Cashu.me, improving transaction flexibility. Primal’s NWC integration brings even more functionality. Users can connect Primal wallet to any Nostr app, send zaps (bitcoin micropayments) from the web app, and link any self-custodial wallet that supports NWC. These updates strengthen Bitcoin and Nostr interoperability, allowing instant, censorship-resistant payments and communications without relying on traditional banking infrastructure.
Proton | Officially Launches Proton Wallet
Proton Wallet, an open-source Bitcoin wallet from privacy services company Proton (creators of ProtonMail), is now available on Android, iOS, and the web. It features end-to-end encryption, address rotation for greater privacy (the same Bitcoin address is never used twice), and Replace-by-Fee (RBF) to speed up stuck transactions. It is also fully self-custodial, meaning users retain complete control over their funds. With Proton now offering both secure email and Bitcoin transactions, users have a stronger, more resilient digital toolkit to protect their communications and money. This is of particular interest to human rights activists operating in difficult environments.
Bitcoin Keeper | Releases Support for Miniscript and More Signing Devices
Bitcoin Keeper, an open-source mobile multisignature (multisig) wallet and winner of HRF’s “Easy Mobile Multisig” bounty, released v2.0 with new security features. The update brings Miniscript, a structured way to write Bitcoin scripts that enable users to create customized multisig vaults. This unlocks advanced setups for inheritance planning, time-locked savings, and more flexible security models. Support for Miniscript also expanded to more signing devices, including BitBox02, COLDCARD, Tapsigner, Blockstream Jade, and Ledger. Keeper is created and run by Indian developers, reminding us that some of the world’s best freedom tools are made by people living in difficult political environments.
Coracle | Implements Nstart for Easy Onboarding
Coracle, a Nostr client and HRF grantee, implemented Nstart, a tool that streamlines onboarding to the Nostr protocol. This makes it easier for first-time users to set up an account, securely back up their private keys, and get started. By lowering entry barriers, Coracle’s Nstart improves access to Nostr’s decentralized, censorship-resistant network. For activists curious about Nostr but unsure of how to start, this may be a tool worth exploring. For a quick-start Nostr guide, click here.
Bitwise | Donates $150,000 to Bitcoin Open Source Development
Bitwise, a Bitcoin ETF provider, donated $150,000 to support open-source Bitcoin developers, fulfilling its pledge to allocate 10% of its Bitcoin ETF ($BITB) gross profits annually. Brink, OpenSats, and HRF will be responsible for allocating the funds to developers working to secure and improve the network and advancing it as a tool for financial freedom and human rights. Bitwise also promised increased contributions in the future as $BITB grows. By reinvesting in Bitcoin’s open-source ecosystem, Bitwise sets a strong example of industry stewardship.
RECOMMENDED CONTENT
Bitcoin Node Tutorial by BTC Sessions
In this tutorial, renowned Bitcoin educator Ben Perrin “BTC Sessions” guides viewers through setting up their own Bitcoin node, a device that runs the Bitcoin software. This enables them to audit Bitcoin’s supply independently and achieve greater financial sovereignty. By running a personal node, users also eliminate the need to trust third parties, enhance their privacy, and strengthen Bitcoin’s decentralization. The tutorial covers installing a free node on a computer and connecting it to Sparrow Wallet. If you are not technically inclined, not to worry. Perrin explains everything in a clear, beginner-friendly way, making it easy to follow along. You can watch the full walkthrough here.
Bitcoin Payments: From Digital Gold to Everyday Currency by Breez and 1A1z
In this new report from Bitcoin Lightning company Breez and freedom tech researcher 1A1z, the authors explore how Bitcoin is evolving beyond a store of value into a functional everyday currency. It highlights the rapid adoption of the Lightning network, the global rise of internet-native payments, and real-world use cases from businesses like Pick n Pay, Namecheap, and Mercari as examples of this. Bitcoin payments are proving their capabilities on a global scale, and this report does a commendable job of proving it.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ c4b5369a:b812dbd6
2025-02-17 06:06:48
@ c4b5369a:b812dbd6
2025-02-17 06:06:48As promised in my last article:
nostr:naddr1qvzqqqr4gupzp394x6dfmvn69cduj7e9l2jgvtvle7n5w5rtrunjlr6tx6up9k7kqq2k6ernff9hw3tyd3y453rdtph5uvm6942kzuw08y0
In this one we will dive into how exactly an unidirectional payments channel powered ecash mint system would be implemented, using the tech available today! So if you haven't read that article yet, give it a read!
I first intended to write a longwinded article, explaining each part of the system. But then I realized that I would need some visualization to get the message across in a more digestable way. This lead me to create a slide deck, and as I started to design the slides it became more and more clear that the information is easier shown with visualizations, than written down. I will try to give a summary as best as I can in this article, but I urge you, to please go visit the slide deck too, for the best experience:
TAKE ME TO THE SLIDE DECK!
Intro
In this article we will go over how we can build unidirectional payment channels on Bitcoin. Then we will take a look into how Cashu ecash mints work, and how we can use unidirectional payment channels to change the dynamics between ecash users and the mint.
Before we start, let me also give credits to nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac for comming up with the idea, to nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp for providing an idea for non-expiring unidirectional channels, and nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference for hosting an event where these ideas could be discussed and flourish.
Building unidirectional payment channels
If you've read the previous article, you already know what unidirectional payment channels are. There are actually a coupple different ways to implement them, but they all do have a few things in common:
- The
sendercan only send - The
Receivercan only receive - They are VERY simple
Way simpler than the duplex channels like we are using in the lightning network today, at least. Of course, duplex channels are being deployed on LN for a reason. They are very versatile and don't have these annoying limitations that the unidirectional payment channels have. They do however have a few drawbacks:
- Peers have liveness requirements (or they might forfeit their funds)
- Peers must backup their state after each transaction (if they don't they might forfeit their funds)
- It is a pretty complex system
This article is not meant to discredit duplex channels. I think they are great. I just also think that in some use-cases, their requirements are too high and the system too complex.
But anyway, let's see what kind of channels we can build!
Spillman/CLTV-Channel
The Spillman channel idea has been around for a long time. It's even explained in Tadge Dryjas Presentation on Payment channels and the lightning network from back in the day. I compiled a list of some of the most important propperties of them in the slide below:

Great!
Now that we know their properties, let's take a look at how we can create such a channel (Slides):

We start out by the
sendercreating afunding TX. Thesenderdoesn't broadcast the transaction though. If he does, he might get locked into a multisig with thereceiverwithout an unilateral exit path.Instead the
senderalso creates arefund TXspending the outputs of the yet unsignedfunding TX. Therefund TXis timelocked, and can only be broadcast after 1 month. Bothsenderandreceivercan sign thisrefund TXwithout any risks. Oncesenderreceives the signedrefund TX, he can broadcast thefunding TXand open the channel. Thesendercan now update the channel state, by pre-signing update transactions and sending them over to thereceiver. Being a one-way channel, this can be done in a single message. It is very simple. There is no need for invalidating old states, since thesenderdoes not hold any signedupdate TXsit is impossible for thesenderto broadcast an old state. Thereceiveronly cares about the latest state anyways, since that is the state where he gets the most money. He can basically delete any old states. The only thing thereceiverneeds to make sure of, is broadcasting the latestupdate TXbefore therefund TX'stimelock expires. Otherwise, thesendermight take the whole channel balance back to himself.This seems to be already a pretty useful construct, due to its simplicity. But we can make it even more simple!

This setup works basically the same way as the previous one, but instead of having a refund transaction, we build the
timelockspend path directly into thefunding TXThis allows thesenderto have an unilateral exit right from the start, and he can broadcast thefunding TXwithout communicating with thereceiver. In the worst case, the receiver rejects the channel, and the sender can get his money back after the timelock on the output has expired. Everything else basically works in the same way as in the example above.The beauty about this channel construct is in its simplicity. The drawbacks are obvious, but they do offer some nice properties that might be useful in certain cases.

One of the major drawbacks of the
Spillman-style channels(apart from being unidirectional) is that they expire. This expiry comes with the neat property that neither of the party has to watch the chain for channel closures, and thesendercan operate the channel with zero additional state, apart from his private keys. But they do expire. And this can make them quite inflexible. It might work in some contexts, but not so much in others, where time needs to be more flexible.This is where
Roose-Childs triggered channelscome into play.Roose-Childs triggered channel
(I gave it that name, named after nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp and nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac . If someone knows if this idea has been around before under a different name, please let us know!)
Roose-Childs triggered channelswere an idea developed by Steven and Luke at the nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference. They essentially remove the channel expiry limitation in return for introducing the need for thesenderto create a channel backup at the time of channel creation, and for thereceiverthe need to watch the chain for trigger transactions closing the channel.
They also allow for splicing funds, which can be important for a channel without expiry, allowing the
senderto top-up liquidity once it runs out, or for thereceivertaking out liquidity from the channel to deploy the funds elsewhere.Now, let's see how we can build them!

The
funding TXactually looks the same as in the first example, and similarly it gets created, but not signed by thesender. Then, sender and receiver both sign thetrigger TX. Thetrigger TXis at the heart of this scheme. It allows bothsenderandreceiverto unilaterally exit the channel by broadcasting it (more on that in a bit).Once the
trigger TXis signed and returned to thesender, the sender can confidently sign and boradcast thefunding TXand open the channel. Thetrigger TXremains off-chain though. Now, to update the channel, thesendercan pre-sign transactions in similar fashion to the examples above, but this time, spending the outputs of the unbroadcastedtrigger TX. This way, both parties can exit the channel at any time. If thereceiverwants to exit, he simply boradcasts thetrigger TXand immediately spends its outputs using the latestupdate TX. If thesenderwants to exit he will broadcast thetrigger TXand basically force thereceivershand. Either, thereceiverwill broadcast the latestupdate TX, or thesenderwill be able to claim the entire channel balance after the timelock expired.
We can also simplify the
receiver'sexit path, by thesenderpre-signing an additional transactionR exit TXfor each update. this way, thereceiveronly needs to broadcast one transaction instead of two.
As we've mentioned before, there are some different trade-offs for
Roose-Childs triggered channels. We introduce some minimal state and liveness requirements, but gain more flexibility.
Ecash to fill in the gaps
(I will assume that the reader knows how ecash mints work. If not, please go check the slides where I go through an explanation)
Essentially, we are trying to get a lightning like experience, without all the lightning complexities and requirements. One big issue with ecash, is that it is fully custodial. If we can offset that risk by holding most of the funds in a self custodial channel, we can have a reasonable trade-off between usability and self custody.

In a system like that, we would essentially turn the banking model onto its head. Where in a traditional bank, the majority of the funds are held in the banks custody, and the user only withdraws into his custody what he needs to transact, in our model the user would hold most funds in his own custody.

If you ask me, this approach makes way more sense. Instead of a custodian, we have turned the "bank" into a service provider.
Let's take a look at how it would work in a more practical sense:

The
ecash userwould open an unidirectional payment channel to themint, using one of his on-chain UTXOs. This allows him then to commit incrementally funds into the mints custody, only the amounts for his transactional needs. The mint offers connectivity to the lightning network an handles state and liveness as a service provider.The
ecash user, can remain offline at all times, and his channel funds will always be safe. The mint can only ever claim the balance in the channel via theupdate TXs. Themintcan of course still decide to no longer redeem any ecash, at which point they would have basically stolen theecash user'stransactional balance. At that point, it would probably be best for theecash userto close his channel, and no longer interact or trust thismint.Here are some of the most important points of this system summarized:

And that is basically it! I hope you enjoyed this breakdown of Unidirectional payment channel enabled Ecash mints!
If you did, consider leaving me a zap. Also do let me know if this type of breakdown helps you understand a new topic well. I am considering doing similar breakdowns on other systems, such as ARK, Lightning or Statechains, if there is a lot of interest, and it helps people, I'll do it!
Pleas also let me know what you think about the
unidirectional channel - ecash mintidea in the comments. It's kind of a new idea, an it probably has flaws, or things that we haven't thought about yet. I'd love to discuss it with you!I'll leave you with this final slide:

Cheers,
Gandlaf
- The
-
 @ 8d34bd24:414be32b
2025-02-16 04:19:34
@ 8d34bd24:414be32b
2025-02-16 04:19:34Last night in my Bible reading I read this verse:
“As for you, do not pray for this people, and do not lift up cry or prayer for them, and do not intercede with Me; for I do not hear you. (Jeremiah 7:16) {emphasis mine}
My first thought was “Why in the world is God telling us not to pray for this people? Doesn’t the Bible tell us to pray about everything?”
First of all, then, I urge that entreaties and prayers, petitions and thanksgivings, be made on behalf of all men, for kings and all who are in authority, so that we may lead a tranquil and quiet life in all godliness and dignity. This is good and acceptable in the sight of God our Savior, who desires all men to be saved and to come to the knowledge of the truth. (1 Timothy 2:1-4) {emphasis mine}
Doesn’t God tell us to pray for whatever is bothering us?
Be anxious for nothing, but in everything by prayer and supplication with thanksgiving let your requests be made known to God. And the peace of God, which surpasses all comprehension, will guard your hearts and your minds in Christ Jesus. (Philippians 4:6-7)
Doesn’t the Bible say that God will answer all of our requests?
Whatever you ask in My name, that will I do, so that the Father may be glorified in the Son. (John 14:13)
Doesn’t the Bible tell us to pray for Israel and Jerusalem and His chosen people?
Pray for the peace of Jerusalem:\ “May they prosper who love you.\ May peace be within your walls,\ And prosperity within your palaces.”\ For the sake of my brothers and my friends,\ I will now say, “May peace be within you.”\ For the sake of the house of the Lord our God,\ I will seek your good. (Psalm 122:6-9) {emphasis mine}
Doesn’t the Bible even tell us to pray for our enemies?
“But I say to you who hear, love your enemies, do good to those who hate you, bless those who curse you, pray for those who mistreat you. (Luke 6:27-28)
If all of this is true, then why does this verse tell us to not pray for this people, especially considering this is referring to God’s chosen people?
To answer this question, let us look at a broader portion of this passage:
“As for you, do not pray for this people, and do not lift up cry or prayer for them, and do not intercede with Me; for I do not hear you. Do you not see what they are doing in the cities of Judah and in the streets of Jerusalem? The children gather wood, and the fathers kindle the fire, and the women knead dough to make cakes for the queen of heaven; and they pour out drink offerings to other gods in order to spite Me. Do they spite Me?” declares the Lord. “Is it not themselves they spite, to their own shame?” (Jeremiah 7:16-19) {emphasis mine}
God is saying to not pray for these people who have turned from Him and are worshipping other gods. These people are in full rejection of God. Still does it mean that we can’t pray for them at all or is this talking about a particular kind of prayer?
A little later in Jeremiah, we read:
“Therefore do not pray for this people, nor lift up a cry or prayer for them; for I will not listen when they call to Me because of their disaster. (Jeremiah 11:14)
and
So the Lord said to me, “Do not pray for the welfare of this people. When they fast, I am not going to listen to their cry; and when they offer burnt offering and grain offering, I am not going to accept them. Rather I am going to make an end of them by the sword, famine and pestilence.” (Jeremiah 14:11-12) {emphasis mine}
We get a little more specificity on the command to “not pray for” in Jeremiah 14. We are told, “Do not pray for the welfare of this people.” This is not a universal command to never pray for them, but a command to not pray for their welfare. It is a command to not pray blessings on those in active rebellion against God.
At the time this command was made, the Israelites were expecting God’s protection and blessings while refusing to follow Him and instead worshipping other gods. This command isn’t a blanket statement to not pray for a sinning Israel, but a statement to not pray for blessings and protection for a sinning Israel. If this was a blanket statement it would contradict Psalm 122 above.
This is the confidence which we have before Him, that, if we ask anything according to His will, He hears us. And if we know that He hears us in whatever we ask, we know that we have the requests which we have asked from Him. (1 John 5:14-15) {emphasis mine}
Using 1 John 5:14, we can begin to see the catch. We are to pray “according to His will.” It is not God’s will for sinners and those in open rebellion against God to be blessed or protected from hardship. A prayer such as, “Please turn your people back to you and give them a pure heart and repentance from sin,” would be according to His will. A prayer to “Please bless and protect Israel” while Israel has turned their back on God is not a prayer that God will answer. He will “not hear you.”
The Bible also says:
You ask and do not receive, because you ask with wrong motives, so that you may spend it on your pleasures. (James 4:3)
How often are our prayers not answered because we pray with wrong motives? At least sometimes. Of course there are also times when God tells us to wait or has something better in mind and we can’t see it because we are not seeking His will, but our own.
It is always good to pray for someone’s repentance and salvation. It isn’t always good to pray for someone’s healing, blessings, and prosperity. It is always good to pray for a nation to turn back to God and to obey His commands. It isn’t always good to pray for a nation’s prosperity and power in the world. Sometimes God’s will is to punish those who turn away from Him or against Him. We need to make sure we are aligned to God’s will and not just seeking our own.
I recommend that our prayers be like Jesus’s prayer right before going to the cross, “saying, “Father, if You are willing, remove this cup from Me; yet not My will, but Yours be done.” (Luke 22:42). Our requests should be like that of Shadrach, Meshach, and Abed Ngo right before being thrown in the fiery furnace, “But even if He does not, let it be known to you, O king, that we are not going to serve your gods or worship the golden image that you have set up.” (Daniel 3:18). This isn’t just words thrown on the end of our prayers “yet not My will, but Yours be done,” but a cry of our hearts in full and complete trust in our Father God.
One thing that helps me is I try to pray the problem not the solution. God knows much better solutions than we do because He knows everything that has happened, everything that is happening, and everything that will happen. He knows what will lead to the best long term solution. When we pray the solution we desire, we miss out on the blessings of God’s knowledge, wisdom, and love.
May God lead you and guide you in a closer relationship to Him so that your will is completely aligned with His will and you are in close fellowship to Our Father in Heaven.
Trust Jesus
-
 @ c43d6de3:a6583169
2025-02-20 13:14:38
@ c43d6de3:a6583169
2025-02-20 13:14:38
How Are We Defining Happiness?
In 1776, Thomas Jefferson penned the words that would echo through history:
“…that they are endowed by their Creator with certain unalienable Rights, that among these are Life, Liberty and the pursuit of Happiness.”
These words were not simply a poetic flourish—they reflected a deep understanding of philosophy, one that Jefferson, an avid reader of Aristotle, likely connected with the Greek concept ofeudaimonia.
Aristotle described eudaimonia as the highest form of human flourishing, achieved through virtuous living, strong character, and meaningful social bonds.
But what does happiness mean today?
According tothe World Happiness Report, six factors determine a nation's happiness:
- Income
- Health
- Social support
- Freedom to make life decisions
- Generosity
- The absence of corruption
These components closely mirror Jefferson’s vision of life, liberty, and the pursuit of happiness. Yet despite living in an era of unprecedented convenience and opportunity, many in our generation struggle with unhappiness, anxiety, and a pervasive sense of dissatisfaction.

So, what went wrong?
I believe its largely because of the absence of mentorship in modern society.
Aristotle emphasized that a person’s character—shaped by habits and guided by mentorship—was central to a flourishing life. He saw mentorship not as a luxury but as a necessity for cultivating wisdom, resilience, and social responsibility. Yet, in today’s world, strong mentor-mentee relationships have become increasingly rare.
When we invert Aristotle’s formula for happiness, we find the root causes of our collective unhappiness:
- A lack of mentorship and guidance
- Poor habits formed in the absence of discipline
- Excess and indulgence replacing moderation
- Rampant hypersensitivity rather than resilience
- A loss of moral grounding and sense of justice
- Struggles with forming and maintaining friendships
- Apathy toward civic engagement and community
Of all these, the absence of mentorship stands out as the foundational issue. Without guidance, young people are left to navigate life’s complexities alone, often falling into destructive habits.
In earlier generations, mentorship was woven into the fabric of society—through family, community leaders, apprenticeships, and even religious or philosophical instruction. Today, social media and fleeting digital interactions have replaced these deep, formative relationships.

Reclaiming Happiness Through Mentorship
To restore a sense of meaning and fulfillment, we must prioritize mentorship in our personal and professional lives. Parents, teachers, and leaders must recognize their responsibility to guide the next generation, not just with knowledge, but with wisdom. Seeking out mentors—and becoming one ourselves—can foster resilience, character, and purpose.
Happiness is not simply a product of material success or personal freedom; it is cultivated through relationships, values, and the pursuit of excellence. If we wish to see a happier generation, we must first rebuild the lost art of mentorship.
Thank you for reading!
If this article resonated with you, let me know with a zap and share it with friends who might find it insightful.
Your help sends a strong signal to keep making content like this!
Interested in fiction? Follow nostr:npub1j9cmpzhlzeex6y85c2pnt45r5zhxhtx73a2twt77fyjwequ4l4jsp5xd49 for great short stories and serialized fiction.
More articles you might like from Beneath The Ink:
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2nvnr5d4nngw2zgd5k5c6etftrzez9fd9kkcl0pzp
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2kvnfd094y26zkt9dxgmnw0fqkvhmfd4tng8wp0uv
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq25yan2w39rsjj0dqk5ckn52ptxsc3nve8hw0aftmq
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2kjjzzfpjxvutjg33hjvpcw5cyjezyv9y5k0umm6k
-
 @ fd208ee8:0fd927c1
2025-02-15 07:37:01
@ fd208ee8:0fd927c1
2025-02-15 07:37:01E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md https://github.com/nostr-protocol/nips/blob/master/61.md
-
 @ b17fccdf:b7211155
2025-01-21 18:33:28
@ b17fccdf:b7211155
2025-01-21 18:33:28
CHECK OUT at ~ > ramix.minibolt.info < ~
Main changes:
- Adapted to Raspberry Pi 5, with the possibility of using internal storage: a PCIe to M.2 adapter + SSD NVMe:
Connect directly to the board, remove the instability issues with the USB connection, and unlock the ability to enjoy higher transfer speeds**
- Based on Debian 12 (Raspberry Pi OS Bookworm - 64-bit).
- Updated all services that have been tested until now, to the latest version.
- Same as the MiniBolt guide, changed I2P, Fulcrum, and ThunderHub guides, to be part of the core guide.
- All UI & UX improvements in the MiniBolt guide are included.
- Fix some links and wrong command issues.
- Some existing guides have been improved to clarify the following steps.
Important notes:
- The RRSS will be the same as the MiniBolt original project (for now) | More info -> HERE <-
- The common resources like the Roadmap or Networkmap have been merged and will be used together | Check -> HERE <-
- The attempt to upgrade from Bullseye to Bookworm (RaspiBolt to RaMiX migration) has failed due to several difficult-to-resolve dependency conflicts, so unfortunately, there will be no dedicated migration guide and only the possibility to start from scratch ☹️
⚠️ Attention‼️-> This guide is in the WIP (work in progress) state and hasn't been completely tested yet. Many steps may be incorrect. Pay special attention to the "Status: Not tested on RaMiX" tag at the beginning of the guides. Be careful and act behind your responsibility.
For Raspberry Pi lovers!❤️🍓
Enjoy it RaMiXer!! 💜
By ⚡2FakTor⚡ for the plebs with love ❤️🫂
- Adapted to Raspberry Pi 5, with the possibility of using internal storage: a PCIe to M.2 adapter + SSD NVMe:
-
 @ d360efec:14907b5f
2025-02-20 10:16:03
@ d360efec:14907b5f
2025-02-20 10:16:03ภาพรวม BTCUSDT (OKX):
Bitcoin (BTCUSDT) ยังคงแสดงความผันผวนและแนวโน้มที่ไม่ชัดเจน แม้ว่าแนวโน้มระยะยาว (TF Day) จะยังคงมีลักษณะเป็นขาขึ้น (แต่อ่อนแรงลงอย่างมาก) แนวโน้มระยะกลาง (TF4H) และระยะสั้น (TF15) เป็นขาลง การวิเคราะห์ครั้งนี้จะเน้นไปที่การระบุระดับราคาที่ Smart Money อาจจะเข้ามามีส่วนร่วม และการประเมินความแข็งแกร่งของแนวโน้ม
วิเคราะห์ทีละ Timeframe:
(1) TF Day (รายวัน):
- แนวโน้ม: ขาขึ้น (Uptrend) อ่อนแรงลงอย่างมาก, มีความเสี่ยงที่จะเปลี่ยนแนวโน้ม
- SMC:
- Higher Highs (HH) และ Higher Lows (HL) เริ่มไม่ชัดเจน, ราคาหลุด Low ก่อนหน้า
- Break of Structure (BOS) ด้านบน แต่มีการปรับฐานที่รุนแรง
- Liquidity:
- มี Sellside Liquidity (SSL) อยู่ใต้ Lows ก่อนหน้า (บริเวณ 85,000 - 90,000)
- มี Buyside Liquidity (BSL) อยู่เหนือ High เดิม
- ICT:
- Order Block: ราคาหลุด Order Block ขาขึ้น (บริเวณแท่งเทียนสีเขียวก่อนหน้านี้) สัญญาณลบ
- EMA:
- ราคา หลุด EMA 50 (สีเหลือง) ลงมาแล้ว
- EMA 200 (สีขาว) เป็นแนวรับถัดไป
- Money Flow (LuxAlgo):
- สีแดงยาว แสดงถึงแรงขายที่แข็งแกร่ง
- Trend Strength (AlgoAlpha):
- สีแดง (เมฆแดง) แสดงถึงแนวโน้มขาลง และไม่มีสัญญาณซื้อ/ขายปรากฏ
- Volume Profile: Volume ค่อนข้างเบาบาง
- แท่งเทียน: แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย
- แนวรับ: EMA 200, บริเวณ 85,000 - 90,000 (SSL)
- แนวต้าน: EMA 50, High เดิม
- สรุป: แนวโน้มขาขึ้นอ่อนแรงลงอย่างมาก, สัญญาณอันตรายหลายอย่าง, Money Flow และ Trend Strength เป็นลบ, หลุด Order Block และ EMA 50
(2) TF4H (4 ชั่วโมง):
- แนวโน้ม: ขาลง (Downtrend)
- SMC:
- Lower Highs (LH) และ Lower Lows (LL)
- Break of Structure (BOS) ด้านล่าง
- Liquidity:
- มี SSL อยู่ใต้ Lows ก่อนหน้า
- มี BSL อยู่เหนือ Highs ก่อนหน้า
- ICT:
- Order Block: ราคาไม่สามารถผ่าน Order Block ขาลงได้
- EMA:
- ราคาอยู่ใต้ EMA 50 และ EMA 200
- Money Flow (LuxAlgo):
- สีแดง แสดงถึงแรงขาย
- Trend Strength (AlgoAlpha):
- สีเขียว (เมฆเขียว) แต่ไม่มีสัญญาณซื้อ/ขายปรากฏ
- Volume Profile:
- Volume ค่อนข้างสูง
- แนวรับ: บริเวณ Low ล่าสุด
- แนวต้าน: EMA 50, EMA 200, บริเวณ Order Block
- สรุป: แนวโน้มขาลงชัดเจน, แรงขายมีอิทธิพล, Trend Strength ขัดแย้งกับ Price Action
(3) TF15 (15 นาที):
- แนวโน้ม: ขาลง (Downtrend) แต่เริ่มเห็นสัญญาณ Sideways
- SMC:
- Lower Highs (LH) และ Lower Lows (LL) เริ่มเห็นการยก Low เล็กน้อย
- Break of Structure (BOS) ด้านล่าง
- ICT:
- Order Block: ราคา Sideways ใกล้ Order Block
- EMA:
- EMA 50 และ EMA 200 เป็นแนวต้าน
- Money Flow (LuxAlgo):
- แดงสลับเขียว แต่ส่วนใหญ่ยังเป็นสีแดง
- Trend Strength (AlgoAlpha):
- สีแดง (เมฆแดง) แสดงถึงแนวโน้มขาลง แต่มีสัญญาณ Bullish Divergence (ราคาทำ Lower Low แต่ Trend Strength ยก Low)
- Volume Profile:
- Volume ค่อนข้างสูง
- แนวรับ: บริเวณ Low ล่าสุด
- แนวต้าน: EMA 50, EMA 200, Order Block
- สรุป: แนวโน้มขาลง, เริ่มพักตัว, Money Flow เริ่มมีความไม่แน่นอน, Trend Strength มี Divergence
สรุปภาพรวมและกลยุทธ์ (BTCUSDT):
- แนวโน้มหลัก (Day): ขาขึ้น (อ่อนแรงลงอย่างมาก, เสี่ยงที่จะเปลี่ยนแนวโน้ม)
- แนวโน้มรอง (4H): ขาลง
- แนวโน้มระยะสั้น (15m): ขาลง (เริ่มพักตัว, มี Divergence)
- Liquidity: มี SSL ทั้งใน Day, 4H, และ 15m
- Money Flow: เป็นลบในทุก Timeframes
- Trend Strength: Day/15m เป็นขาลง, 4H เป็นขาขึ้น แต่ไม่มีสัญญาณ
- กลยุทธ์:
- Wait & See (ดีที่สุด): รอความชัดเจน โดยเฉพาะการ Breakout หรือ Breakdown จากกรอบ Sideways ใน TF15
- Short (เสี่ยง): ถ้าไม่สามารถ Breakout EMA/แนวต้านใน TF ใดๆ ได้, หรือเมื่อเกิดสัญญาณ Bearish Continuation
- ไม่แนะนำให้ Buy: จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจนมากๆ
Day Trade & การเทรดรายวัน:
-
Day Trade (TF15):
- Short Bias: หาจังหวะ Short เมื่อราคาเด้งขึ้นไปทดสอบแนวต้าน (EMA, Order Block)
- Stop Loss: เหนือแนวต้านที่เข้า Short
- Take Profit: แนวรับถัดไป (Low ล่าสุด)
- ระวัง: Bullish Divergence ใน Trend Strength
- ไม่แนะนำให้ Long
-
Swing Trade (TF4H):
- Short Bias: รอจังหวะ Short เมื่อราคาไม่สามารถผ่านแนวต้าน EMA หรือ Order Block ได้
- Stop Loss: เหนือแนวต้านที่เข้า Short
- Take Profit: แนวรับถัดไป
- ไม่แนะนำให้ Long
สิ่งที่ต้องระวัง:
- Sellside Liquidity (SSL): มีโอกาสสูงที่ราคาจะถูกลากลงไปแตะ SSL
- False Breakouts: ระวัง
- Volatility: สูง
- Divergence (TF15): อาจเป็นสัญญาณเริ่มต้นของการกลับตัว แต่ต้องรอการยืนยัน
- Trend Strength (TF4H): ไม่มีสัญญาณซื้อ/ขาย ต้องระวัง
Setup Day Trade แบบ SMC (ตัวอย่าง):
- ระบุ Order Block: หา Order Block ขาลง (Bearish Order Block) ใน TF15 (แท่งเทียนสีเขียวก่อนที่ราคาจะลงแรง)
- รอ Pullback: รอให้ราคา Pullback ขึ้นไปทดสอบ Order Block นั้น
- หา Bearish Entry:
- Rejection: รอ Price Action ปฏิเสธ Order Block (เช่น เกิด Pin Bar, Engulfing)
- Break of Structure: รอให้ราคา Break โครงสร้างย่อยๆ ใน TF ที่เล็กกว่า (เช่น 1m, 5m) หลังจากที่ทดสอบ Order Block
- Money Flow: ดู Money Flow ให้เป็นสีแดง
- ตั้ง Stop Loss: เหนือ Order Block
- ตั้ง Take Profit: แนวรับถัดไป (เช่น Low ล่าสุด) หรือ Order Block ขาขึ้น (Bullish Order Block) ใน TF ที่ใหญ่กว่า
คำแนะนำ:
- ความขัดแย้งของ Timeframes: มีอยู่ แต่แนวโน้มระยะกลาง-สั้น เป็นลบ
- Money Flow: เป็นลบในทุก Timeframes
- Trend Strength: เริ่มมี Divergence ใน TF15
- Order Block TF Day: หลุด Order Block ขาขึ้นแล้ว
- ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-
 @ 7f29628d:e160cccc
2025-01-07 11:50:30
@ 7f29628d:e160cccc
2025-01-07 11:50:30Der gut informierte Bürger denkt bei der Pandemie sofort an Intensivstationen, an die Bilder aus Bergamo und erinnert sich an die Berichterstattung damals – also muss es wohl ein Maximum gewesen sein. Manche Skeptiker behaupten jedoch das Gegenteil. Klarheit sollte ein Blick nach Wiesbaden, zum Statistischen Bundesamt, schaffen. Schließlich sitzen dort gut bezahlte Profis, die seit vielen Jahrzehnten die Sterbestatistik pflegen und veröffentlichen. Jeder Todesfall wird in Deutschland über die Standesämter exakt erfasst.
Doch die Überraschung: Das Statistische Bundesamt liefert uns auf diese einfache Frage zwei extrem unterschiedliche Antworten – ein Minimum und ein Maximum. Das Ergebnis hängt davon ab, wie tief man in die Veröffentlichungen des Bundesamtes eintaucht. Betrachtet man nur die Webseiten und Pressemitteilungen, erhält man den Eindruck eines Maximums. Schaut man jedoch etwas tiefer in die Tabellen und Rohdaten, zeigt sich plötzlich ein Minimum. Aber wie kann das sein? Beides gleichzeitig geht ja wohl kaum. Wer lügt hier – die Tabellen des Amtes oder die Pressemitteilungen? Gehen wir dieser Frage Schritt für Schritt auf den Grund.
2020: Ein historisches Maximum?
Schauen wir uns die vielen Hundert Veröffentlichungen des Statistischen Bundesamtes aus dieser Zeit an. Oder wir kürzen ab und fragen ChatGPT, da die KI auf diesen Daten trainiert wurde und das gesamte Material kennt. Die Frage an ChatGPT lautet also: Wie war das Sterbegeschehen im Jahr 2020 im Vergleich zu den Vorjahren?
ChatGPT antwortet: »Im Jahr 2020 war die Sterblichkeit in Deutschland höher als in den Jahren zuvor. Es gab eine Übersterblichkeit von etwa 982.000 Todesfällen, das sind rund 46.000 mehr als der Durchschnitt der Vorjahre (2016 bis 2019). Dieser Anstieg wurde überwiegend im Zusammenhang mit der COVID-19-Pandemie gesehen. Während die Sterbezahlen in den Vorjahren schwankten, war ein solch signifikanter Anstieg wie 2020 bisher nicht zu beobachten.«
Wir fragen konkreter: Ist es ein Fakt, dass wir eine so ernste Lage im Sterbegeschehen wie im Frühjahr 2020 noch nie erlebt haben?
ChatGPT bestätigt: »Ja, die COVID-19-Pandemie führte im Frühjahr 2020 zu einer außergewöhnlichen Situation im Sterbegeschehen in Deutschland. Die dramatische Übersterblichkeit, die ab der 13. Kalenderwoche auftrat, veranlasste das Statistische Bundesamt, besonders eindringliche Warnungen zu veröffentlichen. Der damalige Vizepräsident des Amtes und andere führende Stimmen wiesen öffentlich darauf hin, dass die Todesfallzahlen stark vom Durchschnitt abwichen. Diese klare Warnung richtete sich an die Öffentlichkeit und die Politik gleichermaßen. Die Medien berichteten intensiv über diese Warnungen, was das Bewusstsein für die Schwere der Pandemie erheblich schärfte. In den vergangenen Jahrzehnten hatte es keine vergleichbare Übersterblichkeit gegeben, die eine solch umfangreiche Kommunikation durch das Statistische Bundesamt erforderlich gemacht hätte.«
Ein gut informierter Zeitungsleser wird sich an dieser Stelle bestätigt fühlen: Ja, so war es damals. Ein Maximum im Sterbegeschehen – wegen der Pandemie. Oder etwa nicht?
2020: Ein historisches Minimum?
Tauchen wir in die Rohdaten des Statistischen Bundesamtes ein. Die Tabellen, die das Amt seit Jahrzehnten verlässlich veröffentlicht, nennen sich Sterbetafeln. Diese werden jährlich bereitgestellt und stehen auf der Website des Bundesamtes zum Download bereit. Ein erster Blick in die Sterbetafeln mag den Laien abschrecken, doch mit einer kurzen Erklärung wird alles verständlich. Wir gehen schrittweise vor.
Nehmen wir die Sterbetafel des Jahres 2017. Sie enthält zwei große Tabellen – eine für Männer und eine für Frauen. Jede Zeile der Tabelle steht für einen Jahrgang, zum Beispiel zeigt die Zeile 79 die Daten der 79-jährigen Männer. Besonders wichtig ist nun die zweite Spalte, in der der Wert 0,05 eingetragen ist. Das bedeutet, dass 5 Prozent der 79-jährigen Männer im Jahr 2017 verstorben sind. Das ist die wichtige Kennzahl. Wenn wir diesen exakten Wert, den man auch als Sterberate bezeichnet, nun in ein Säulendiagramm eintragen, erhalten wir eine leicht verständliche visuelle Darstellung (Grafik 1).

Es ist wichtig zu betonen, dass dieser Wert weder ein Schätzwert noch eine Modellrechnung oder Prognose ist, sondern ein exakter Messwert, basierend auf einer zuverlässigen Zählung. Sterberaten (für die Fachleute auch Sterbewahrscheinlichkeiten qx) sind seit Johann Peter Süßmilch (1707–1767) der Goldstandard der Sterbestatistik. Jeder Aktuar wird das bestätigen. Fügen wir nun die Sterberaten der 79-jährigen Männer aus den Jahren davor und danach hinzu, um das Gesamtbild zu sehen (Grafik 2). Und nun die entscheidende Frage: Zeigt das Jahr 2020 ein Maximum oder ein Minimum?

Ein kritischer Leser könnte vermuten, dass die 79-jährigen Männer eine Ausnahme darstellen und andere Jahrgänge im Jahr 2020 ein Maximum zeigen würden. Doch das trifft nicht zu. Kein einziger Jahrgang verzeichnete im Jahr 2020 ein Maximum. Im Gegenteil: Auch die 1-Jährigen, 2-Jährigen, 3-Jährigen, 9-Jährigen, 10-Jährigen, 15-Jährigen, 18-Jährigen und viele weitere männliche Jahrgänge hatten ihr Minimum im Jahr 2020. Dasselbe gilt bei den Frauen. Insgesamt hatten 31 Jahrgänge ihr Minimum im Jahr 2020. Wenn wir schließlich alle Jahrgänge in einer einzigen Grafik zusammenfassen, ergibt sich ein klares Bild: Das Minimum im Sterbegeschehen lag im Jahr 2020 (Grafik 3).

Ein kritischer Leser könnte nun wiederum vermuten, dass es innerhalb des Jahres 2020 möglicherweise starke Ausschläge nach oben bei einzelnen Jahrgängen gegeben haben könnte, die später durch Ausschläge nach unten ausgeglichen wurden – und dass diese Schwankungen in der jährlichen Übersicht nicht sichtbar sind. Doch auch das trifft nicht zu. Ein Blick auf die wöchentlichen Sterberaten zeigt, dass die ersten acht Monate der Pandemie keine nennenswerten Auffälligkeiten aufweisen. Es bleibt dabei: Die Rohdaten des Statistischen Bundesamtes bestätigen zweifelsfrei, dass die ersten acht Monate der Pandemie das historische Minimum im Sterbegeschehen darstellen. (Für die Fachleute sei angemerkt, dass im gleichen Zeitraum die Lebenserwartung die historischen Höchststände erreicht hatte – Grafik 4.)

So konstruierte das Amt aus einem Minimum ein Maximum:
Zur Erinnerung: Die Rohdaten des Statistischen Bundesamtes, die in den jährlichen Sterbetafeln zweifelsfrei dokumentiert sind, zeigen für das Jahr 2020 eindeutig ein Minimum im Sterbegeschehen. Aus diesen »in Stein gemeißelten« Zahlen ein Maximum zu »konstruieren«, ohne die Rohdaten selbst zu verändern, scheint auf den ersten Blick eine unlösbare Aufgabe. Jeder Student würde an einer solchen Herausforderung scheitern. Doch das Statistische Bundesamt hat einen kreativen Weg gefunden - ein Meisterstück gezielter Manipulation. In fünf Schritten zeigt sich, wie diese Täuschung der Öffentlichkeit umgesetzt wurde:
(1) Ignorieren der Sterberaten: Die präzisen, objektiven und leicht verständlichen Sterberaten aus den eigenen Sterbetafeln wurden konsequent ignoriert und verschwiegen. Diese Daten widersprachen dem gewünschten Narrativ und wurden daher gezielt ausgeklammert.
(2) Fokus auf absolute Todeszahlen: Die Aufmerksamkeit wurde stattdessen auf die absolute Zahl der Todesfälle gelenkt. Diese wirkt allein durch ihre schiere Größe dramatisch und emotionalisiert die Diskussion. Ein entscheidender Faktor wurde dabei ignoriert: Die absolute Zahl der Todesfälle steigt aufgrund der demografischen Entwicklung jedes Jahr an. Viele Menschen verstehen diesen Zusammenhang nicht und verbinden die steigenden Zahlen fälschlicherweise mit der vermeintlichen Pandemie.
(3) Einführung der Übersterblichkeit als neue Kennzahl: Erst ab Beginn der „Pandemie“ wurde die Kennzahl "Übersterblichkeit" eingeführt – und dies mit einer fragwürdigen Methode, die systematisch überhöhte Werte lieferte. Diese Kennzahl wurde regelmäßig, oft monatlich oder sogar wöchentlich, berechnet und diente als ständige Grundlage für alarmierende Schlagzeilen.
(4) Intensive Öffentlichkeitsarbeit: Durch eine breit angelegte Kampagne wurden die manipulativen Kennzahlen gezielt in den Fokus gerückt. Pressemitteilungen, Podcasts und öffentliche Auftritte konzentrierten sich fast ausschließlich auf die absoluten Todeszahlen und die Übersterblichkeit. Ziel war es, den Eindruck einer dramatischen Situation in der Öffentlichkeit zu verstärken.
(5) Bekämpfen kritischer Stimmen: Kritiker, die die Schwächen und manipulativen Aspekte dieser Methoden aufdeckten, wurden systematisch diskreditiert. Ihre Glaubwürdigkeit und Kompetenz wurden öffentlich infrage gestellt, um das sorgsam konstruierte Narrativ zu schützen.
Ohne diesen begleitenden Statistik-Betrug wäre das gesamte Pandemie-Theater meiner Meinung nach nicht möglich gewesen. Wer aus einem faktischen Minimum ein scheinbares Maximum "erschafft", handelt betrügerisch. Die Folgen dieses Betruges sind gravierend. Denken wir an die Angst, die in der Bevölkerung geschürt wurde – die Angst, bald sterben zu müssen. Denken wir an Masken, Abstandsregeln, isolierte ältere Menschen, Kinderimpfungen und all die Maßnahmen, die unter anderem auf diese falsche Statistik zurückgehen.
Wollen wir Bürger uns das gefallen lassen?
Wenn wir als Bürger zulassen, dass ein derart offensichtlicher und nachprüfbarer Täuschungsversuch ohne Konsequenzen bleibt, dann gefährdet das nicht nur die Integrität unserer Institutionen – es untergräbt das Fundament unserer Gesellschaft. In der DDR feierte man öffentlich Planerfüllung und Übererfüllung, während die Regale leer blieben. Damals wusste jeder: Statistik war ein Propagandainstrument. Niemand traute den Zahlen, die das Staatsfernsehen verkündete.
Während der Pandemie war es anders. Die Menschen vertrauten den Mitteilungen des Statistischen Bundesamtes und des RKI – blind. Die Enthüllungen durch den "RKI-Leak" haben gezeigt, dass auch das Robert-Koch-Institut nicht der Wissenschaft, sondern den Weisungen des Gesundheitsministers und militärischen Vorgaben folgte. Warum sollte es beim Statistischen Bundesamt anders gewesen sein? Diese Behörde ist dem Innenministerium unterstellt und somit ebenfalls weisungsgebunden.
Die Beweise für Täuschung liegen offen zutage. Es braucht keinen Whistleblower, keine geheimen Enthüllungen: Die Rohdaten des Statistischen Bundesamtes sprechen für sich. Sie sind öffentlich einsehbar – klar und unmissverständlich. Die Daten, die Tabellen, die Veröffentlichungen des Amtes selbst – sie sind die Anklageschrift. Sie zeigen, was wirklich war. Nicht mehr und nicht weniger.
Und wir? Was tun wir? Schweigen wir? Oder fordern wir endlich ein, was unser Recht ist? Wir Bürger dürfen das nicht hinnehmen. Es ist Zeit, unsere Behörden zur Rechenschaft zu ziehen. Diese Institutionen arbeiten nicht für sich – sie arbeiten für uns. Wir finanzieren sie, und wir haben das Recht, Transparenz und Verantwortung einzufordern. Manipulationen wie diese müssen aufgearbeitet werden und dürfen nie wieder geschehen. Die Strukturen, die solche Fehlentwicklungen in unseren Behörden ermöglicht haben, müssen offengelegt werden. Denn eine Demokratie lebt von Vertrauen – und Vertrauen muss verdient werden. Jeden Tag aufs Neue.
.
.
MARCEL BARZ, Jahrgang 1975, war Offizier der Bundeswehr und studierte Wirtschafts- und Organisationswissenschaften sowie Wirtschaftsinformatik. Er war Gründer und Geschäftsführer einer Softwarefirma, die sich auf Datenanalyse und Softwareentwicklung spezialisiert hatte. Im August 2021 veröffentlichte Barz den Videovortrag »Die Pandemie in den Rohdaten«, der über eine Million Aufrufe erzielte. Seitdem macht er als "Erbsenzähler" auf Widersprüche in amtlichen Statistiken aufmerksam.
-
 @ d360efec:14907b5f
2025-02-20 10:12:37
@ d360efec:14907b5f
2025-02-20 10:12:37Overall Assessment:
Bitcoin (BTCUSDT) on OKX remains highly volatile and shows conflicting signals. The long-term trend (Daily chart) is technically still an uptrend, but it has weakened considerably and is showing significant signs of a potential reversal. The 4-hour and 15-minute charts are in confirmed downtrends. The focus of this analysis is on identifying potential areas of Smart Money activity (liquidity pools and order blocks) and assessing trend strength.
Detailed Analysis by Timeframe:
(1) TF Day (Daily):
- Trend: Uptrend (Significantly Weakening, at risk of reversing).
- SMC (Smart Money Concepts):
- Higher Highs (HH) and Higher Lows (HL) structure is becoming less defined. The recent price action has broken previous lows.
- Prior Breaks of Structure (BOS) to the upside, but the current pullback is very deep.
- Liquidity:
- Sellside Liquidity (SSL): Significant SSL rests below previous lows in the 85,000 - 90,000 range. This is a likely target for Smart Money.
- Buyside Liquidity (BSL): BSL is present above the all-time high.
- ICT (Inner Circle Trader Concepts):
- Order Block: The price has broken below the prior bullish Order Block (the large green candle before a significant up-move). This is a major bearish signal.
- EMA (Exponential Moving Average):
- Price has broken below the 50-period EMA (yellow), a bearish signal.
- The 200-period EMA (white) is the next major support level.
- Money Flow (LuxAlgo):
- A long red bar indicates strong selling pressure.
- Trend Strength (AlgoAlpha):
- Red Cloud indicating Downtrend, No Buy/Sell Signal
- Volume Profile: Relatively low volume on the recent decline.
- Candlesticks: The most recent candlestick is red, confirming selling pressure.
- Support: EMA 200, 85,000-90,000 (SSL area).
- Resistance: EMA 50, Previous All-Time High.
- Summary: The Daily chart's uptrend is significantly weakening. The break below the 50 EMA and the bullish Order Block, combined with the negative Money Flow and bearish Trend Strength, are all major warning signs.
(2) TF4H (4-Hour):
- Trend: Downtrend.
- SMC:
- Lower Highs (LH) and Lower Lows (LL).
- BOS to the downside.
- Liquidity:
- SSL: Below previous lows.
- BSL: Above previous highs.
- ICT:
- Order Block: The price rallied up to, and was rejected by, a bearish Order Block.
- EMA:
- Price is below both the 50-period and 200-period EMAs (bearish).
- Money Flow (LuxAlgo):
- Predominantly red, confirming selling pressure.
- Trend Strength (AlgoAlpha):
- Green Cloud, But No Buy/Sell Signal. This indicates a potential retracement within the downtrend, or a period of consolidation, not a trend reversal.
- Volume Profile:
- Relatively High volume
- Support: Recent lows.
- Resistance: EMA 50, EMA 200, Order Block.
- Summary: The 4-hour chart is in a confirmed downtrend. The Money Flow is bearish, and the price was rejected by a key Order Block. The green Trend Strength cloud without a buy signal suggests a potential temporary relief rally or consolidation, not a trend change.
(3) TF15 (15-Minute):
- Trend: Downtrend (with some signs of possible stabilization).
- SMC:
- Lower Highs (LH) and Lower Lows (LL) – but the most recent low is slightly higher, a potential early sign of a change.
- BOS to the downside.
- ICT:
- Order Block: Price has reacted to bearish Order Block.
- EMA:
- The 50-period and 200-period EMAs are acting as resistance.
- Money Flow (LuxAlgo):
- Red and green alternating , showing some buying pressure has appeared, but sellers are still in control overall.
- Trend Strength (AlgoAlpha):
- Red Cloud (Bearish), BUT there's a bullish divergence (price made a lower low, but the Trend Strength indicator made a higher low). This is a potential early warning sign of a reversal, but it needs strong confirmation.
- Volume Profile:
- relatively high volume.
- Support: Recent lows.
- Resistance: EMA 50, EMA 200, Order Block.
- Summary: The 15-minute chart is in a downtrend, but there are very early and tentative signs of a possible stabilization or even a minor bounce. The bullish divergence on the Trend Strength is important to note, but it's not a buy signal on its own.
Overall Strategy and Recommendations (BTCUSDT):
- Primary Trend (Day): Uptrend (Significantly Weakening).
- Secondary Trend (4H): Downtrend.
- Short-Term Trend (15m): Downtrend (Potential Early Reversal Signals).
- Liquidity: Significant SSL zones exist below the current price on all timeframes.
- Money Flow: Negative on all timeframes, although the 15m is showing some buying pressure returning.
-
Trend Strength: Bearish on Day and 15m. Bullish on 4H, but without a buy/sell signal, indicating a likely retracement or consolidation, not a trend change.
-
Strategies:
-
Wait & See (Best Option): The conflicting signals (especially the 4H Trend Strength) and the strong bearish momentum on the shorter timeframes make waiting the most prudent approach. Look for:
- Bearish Confirmation: A decisive break below the recent lows on the 15m and 4H charts, with increasing volume and continued negative Money Flow. This would confirm the continuation of the downtrend.
- Bullish Confirmation: A strong, sustained break above the 15m EMAs, a shift in the 15m Money Flow to green, and a bullish signal on the 4H Trend Strength. This would be a very early sign of a potential reversal, but it would need further confirmation on the 4H chart (price above EMAs, positive Money Flow).
-
Short (High Risk): This is the more likely scenario at this moment, given the 4H and 15m downtrends.
- Entry: On rallies towards resistance levels (EMAs on 15m/4H, previous support levels that have turned into resistance).
- Stop Loss: Above recent highs on the chosen timeframe.
- Target: The next support levels (recent lows on 15m, then the Daily Order Block area around 92,000-94,000).
-
Buy on Dip (Extremely High Risk - Not Recommended): Do not attempt to buy until there are very strong and consistent bullish reversal signals across all timeframes, including a definitive shift in market structure on the 4H and 15m charts, positive Money Flow, and a clear break above resistance levels.
-
Key Recommendations:
- Conflicting Signals: The most important factor is the conflict between the still technically bullish Daily chart and the bearish 4H and 15m charts. The 4H Trend Strength being bullish without a signal adds to the uncertainty.
- Money Flow: The predominantly negative Money Flow is a major bearish factor.
- 15m Trend Strength Divergence: This is a potential early warning, but it's not a buy signal on its own. It needs much more confirmation.
- Daily Order Block: The break of the bullish Order Block on the Daily chart is a significant bearish development.
- Sellside Liquidity (SSL): Be aware that Smart Money may target the SSL zones below. This increases the risk of stop-loss hunting.
- Risk Management: Due to the high uncertainty and volatility, strict risk management is absolutely critical. Use tight stop-losses, do not overtrade, and be prepared for rapid price swings.
- Volume: Confirm any breakout with volume.
Day Trading and Intraday Trading Strategies:
-
Day Trade (TF15 focus):
- Short Bias: Given the current 15m downtrend and negative Money Flow, the higher probability is to look for shorting opportunities.
- Entry: Look for price to rally to resistance levels (EMAs, Order Blocks, previous support levels that have become resistance) and then show signs of rejection (bearish candlestick patterns, increasing volume on the downside).
- Stop Loss: Place a stop-loss order above the resistance level where you enter the short position.
- Take Profit: Target the next support level (recent lows).
- Be very cautious: The bullish divergence on the Trend Strength indicator suggests a potential bounce could occur. Don't be aggressive with shorts until this divergence is invalidated.
- Avoid Long positions: Until there's a clear and confirmed bullish reversal on the 15m chart (break above EMAs, positive Money Flow, bullish market structure).
- Short Bias: Given the current 15m downtrend and negative Money Flow, the higher probability is to look for shorting opportunities.
-
Swing Trade (TF4H focus):
- Short Bias: The 4H chart is in a downtrend.
- Entry: Wait for price to rally to resistance levels (EMAs, Order Blocks) and show signs of rejection.
- Stop Loss: Above the resistance level where you enter the short position.
- Take Profit: Target the next support levels (e.g., the 200 EMA on the Daily chart, SSL zones).
- Avoid long position: Until there's a clear and confirmed bullish reversal on the 4H chart.
- Short Bias: The 4H chart is in a downtrend.
SMC Day Trade Setup Example (TF15 - Bearish):
- Identify Bearish Order Block: Locate a bearish Order Block on the TF15 chart (a bullish candle before a strong downward move). We have already identified this in previous analyses.
- Wait for Pullback: Wait for the price to pull back up to test the Order Block.
- Bearish Entry:
- Rejection: Look for price action to reject the Order Block (e.g., a pin bar, engulfing pattern, or other bearish candlestick pattern).
- Break of Structure: Look for a break of a minor support level on a lower timeframe (e.g., 1-minute or 5-minute) after the price tests the Order Block. This confirms weakening bullish momentum.
- Money Flow: Confirm that Money Flow remains negative (red).
- Stop Loss: Place a stop-loss order above the Order Block.
- Take Profit: Target the next support level (e.g., recent lows) or a bullish Order Block on a higher timeframe.
In conclusion, BTCUSDT is currently in a high-risk, uncertain environment. The short-term and medium-term trends are bearish, while the long-term trend is weakening. The best approach for most traders is to wait for clearer signals. Shorting is the higher-probability trade at this moment, but only for experienced traders who can manage risk aggressively. Buying is extremely risky and not recommended at this time. The bullish divergence on the 15m Trend Strength is a potential early warning of a change, but it needs much more confirmation before acting on it. The 4-hour chart showing a green cloud with no buy/sell signal adds to the uncertainty, suggesting a possible retracement/consolidation within the downtrend.
Disclaimer: This analysis is for informational purposes only and represents a personal opinion. It is not financial advice. Investing in cryptocurrencies involves significant risk. Investors should conduct their own research and exercise due diligence before making any investment decisions.
-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ 78c90fc4:4bff983c
2025-02-20 08:00:54
@ 78c90fc4:4bff983c
2025-02-20 08:00:54Hans Maria Globke\ \ Nazi, Catholic, author of racial laws. ======================================
\ The Catholic lawyer Globke had a problematic past: it was common knowledge that he had been a co-commentator on the Nuremberg Laws and had held important positions in the Reich Ministry of the Interior.\ \ In the newly founded Federal Republic of Germany, the experienced lawyer Globke was appointed to the Federal Chancellery. Because of his past in the Reich Ministry of the Interior, Adenauer does not yet dare to appoint him as a state secretary, but the discreet, efficient Rhineland Catholic immediately becomes Adenauer's confidant, a shadowy figure who works behind the scenes. Globke maintains close relations with the Vatican and is Adenauer's liaison to the CIA, with whom he discusses all important decisions, including personnel matters. From now on, Globke is always there when positions of power need to be filled. He ensures that the Gehlen Organisation, which was financed by the CIA as a spy service after the war, eventually becomes the BND. Globke is involved in setting up the Office for the Protection of the Constitution and in the preparations for the establishment of the Bundeswehr.\ \ In 1953, Globke became state secretary in the chancellor's office, with an almost unimaginable amount of power. He allowed the BND to spy on opponents of the Adenauer government within the country, in violation of the law, and controlled the Press and Information Office. He drafted legislation to allow former Nazi elites (civil servants, judges, military, police, secret service agents) to return to high positions. Globke has access to the ‘Reptilienfonds’ (Reptile Fund), which he uses to secure the desired domestic and foreign policy stability, including through large cash payments. And he increasingly plays the decisive role in the new governing party, the CDU. As Adenauer's closest adviser, the best-informed man in Bonn influences political guidelines; Globke - the secret chancellor.\ \ Hans Maria Globke is certainly the most prominent example of the seamless continuity of careers in the civil service before and after 1945. The documentary by Bernhard Pfletschinger and Jürgen Bevers goes in search of the ’ secret of Globke’, his role in the Nazi extermination of Jews, the extensive network of interests and loyalties that he served and that served him – so much so that his name was not even mentioned during the Adolf Eichmann trial. The results paint a picture that allows a new perspective on the history of the Federal Republic of Germany.’\ \ https://www.youtube.com/watch?v=awTUDrEzsUg&t=5s\ \ https://x.com/RealWsiegrist/status/1892479642700800356\ \ \ Wilhelm Frick and Hans Globke were central figures in the National Socialist administration and contributed significantly to the implementation of Nazi ideology.\ \ https\://x.com/RealWsiegrist/status/1892481115128021426\ \ ## Wilhelm Frick\ Wilhelm Frick (1877–1946) was a leading NSDAP politician and served as Reich Minister of the Interior from 1933 to 1943. During the Weimar Republic, he had already served as Thuringia's minister of the interior, where he implemented measures to enforce the Gleichschaltung and promote the NSDAP. As Reich Minister of the Interior, Frick played a key role in the destruction of Weimar democracy by introducing laws and ordinances that severely restricted fundamental rights, such as the ‘Reichstag Fire Decree’ of 1933. He also played a major role in the ‘Gleichschaltung’ of the federal states and institutions, which enabled the NSDAP to consolidate its power. After the war, Frick was sentenced to death in the Nuremberg trials of the major war criminals and executed in 1946.\ \ ## Hans Globke\ Hans Globke (1898–1973) was a lawyer and senior official in the Reich Ministry of the Interior under Wilhelm Frick. He is best known for his involvement in the 1935 Nuremberg Laws, on which he wrote a legal commentary. Globke was also involved in measures that discriminated against Jewish citizens, such as making it more difficult to change one's name. During the war, he was involved in administrative tasks, including in the occupied territories. After the war, he continued his career and became head of the Federal Chancellery under Chancellor Konrad Adenauer (1953-1963). Globke's role remains controversial because, on the one hand, he was considered the ‘grey eminence’ of the Adenauer government, but on the other hand, he was never held accountable for his Nazi involvement. \ \ Both men embody different aspects of Nazi rule: Frick as the central architect of the repressive state and Globke as the technocratic enforcer of discriminatory laws.\ \ Sources\ [1] Wilhelm Frick - Wikipedia https\://de.wikipedia.org/wiki/Wilhelm_Frick\ [2] Hans Globke - Wikipedia https\://de.wikipedia.org/wiki/Hans_Globke\ [3] Nazi war criminals still in the chancellery https\://www.klassegegenklasse.org/nazi-kriegsverbrecher-immer-noch-im-kanzleramt/\ [4] Trial against Ex-Nazi Hans Globke | Anne Frank House https\://www.annefrank.org/de/timeline/231/prozess-gegen-ex-nazi-hans-globke/\ [5] Trial of former Nazi Hans Globke | Anne Frank House https\://www.annefrank.org/en/timeline/231/trial-of-former-nazi-hans-globke/\ [6] [PDF] The Reich Ministry of the Interior under Heinrich Himmler 1943–1945 https\://www.ifz-muenchen.de/heftarchiv/2006_4_4_lehnstaedt.pdf\ [7] Hans Globke - LeMO Biografie - Stiftung Haus der Geschichte https\://www.hdg.de/lemo/biografie/hans-globke.html\ [8] [PDF] The Verdict against Globke https\://media.frag-den-staat.de/files/docs/3a/0f/0d/3a0f0dbfff8e4e68b28356f60a7ed26e/globke.pdf\
-
 @ da0b9bc3:4e30a4a9
2025-02-20 06:33:45
@ da0b9bc3:4e30a4a9
2025-02-20 06:33:45Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/891531
-
 @ 6be5cc06:5259daf0
2024-12-29 19:54:14
@ 6be5cc06:5259daf0
2024-12-29 19:54:14Um dos padrões mais bem estabelecidos ao medir a opinião pública é que cada geração tende a seguir um caminho semelhante em termos de política e ideologia geral. Seus membros compartilham das mesmas experiências formativas, atingem os marcos importantes da vida ao mesmo tempo e convivem nos mesmos espaços. Então, como devemos entender os relatórios que mostram que a Geração Z é hiperprogressista em certos assuntos, mas surpreendentemente conservadora em outros?
A resposta, nas palavras de Alice Evans, pesquisadora visitante na Universidade de Stanford e uma das principais estudiosas do tema, é que os jovens de hoje estão passando por um grande divergência de gênero, com as jovens mulheres do primeiro grupo e os jovens homens do segundo. A Geração Z representa duas gerações, e não apenas uma.
Em países de todos os continentes, surgiu um distanciamento ideológico entre jovens homens e mulheres. Milhões de pessoas que compartilham das mesmas cidades, locais de trabalho, salas de aula e até casas, não veem mais as coisas da mesma maneira.
Nos Estados Unidos, os dados da Gallup mostram que, após décadas em que os sexos estavam distribuídos de forma relativamente equilibrada entre visões políticas liberais e conservadoras, as mulheres entre 18 e 30 anos são agora 30 pontos percentuais mais liberais do que os homens dessa faixa etária. Essa diferença surgiu em apenas seis anos.
A Alemanha também apresenta um distanciamento de 30 pontos entre homens jovens conservadores e mulheres jovens progressistas, e no Reino Unido, a diferença é de 25 pontos. Na Polônia, no ano passado, quase metade dos homens entre 18 e 21 anos apoiou o partido de extrema direita Confederation, em contraste com apenas um sexto das jovens mulheres dessa mesma idade.
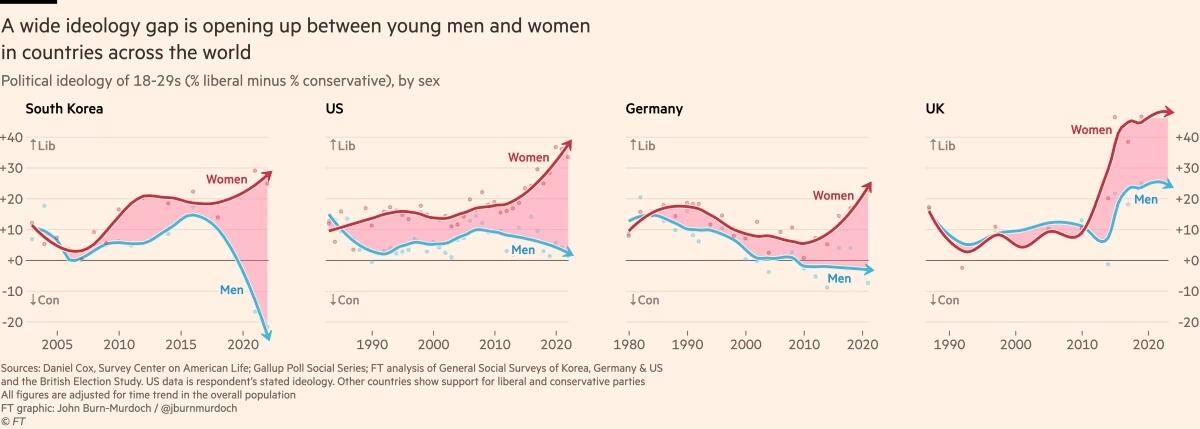
Fora do Ocidente, há divisões ainda mais acentuadas. Na Coreia do Sul, há um enorme abismo entre homens e mulheres jovens, e a situação é semelhante na China. Na África, a Tunísia apresenta o mesmo padrão. Vale notar que em todos os países essa divisão drástica ocorre principalmente entre a geração mais jovem, sendo muito menos pronunciada entre homens e mulheres na faixa dos 30 anos ou mais velhos.
O movimento # MeToo foi o principal estopim, trazendo à tona valores feministas intensos entre jovens mulheres que se sentiram empoderadas para denunciar injustiças de longa data. Esse estopim encontrou especialmente terreno fértil na Coreia do Sul, onde a desigualdade de gênero é bastante visível e a misoginia explícita é comum. (palavras da Financial Times, eu só traduzi)
Na eleição presidencial da Coreia do Sul em 2022, enquanto homens e mulheres mais velhos votaram de forma unificada, os jovens homens apoiaram fortemente o partido de direita People Power, enquanto as jovens mulheres apoiaram o partido liberal Democratic em números quase iguais e opostos.
A situação na Coreia é extrema, mas serve como um alerta para outros países sobre o que pode acontecer quando jovens homens e mulheres se distanciam. A sociedade está dividida, a taxa de casamento despencou e a taxa de natalidade caiu drasticamente, chegando a 0,78 filhos por mulher em 2022, o menor número no mundo todo.
Sete anos após a explosão inicial do movimento # MeToo, a divergência de gênero em atitudes tornou-se autossustentável.
Dados das pesquisas mostram que em muitos países, as diferenças ideológicas vão além dessa questão específica. A divisão progressista-conservadora sobre assédio sexual parece ter causado ou pelo menos faz parte de um alinhamento mais amplo, em que jovens homens e mulheres estão se organizando em grupos conservadores e liberais em outros assuntos.
Nos EUA, Reino Unido e Alemanha, as jovens mulheres agora adotam posturas mais liberais sobre temas como imigração e justiça racial, enquanto grupos etários mais velhos permanecem equilibrados. A tendência na maioria dos países tem sido de mulheres se inclinando mais para a esquerda, enquanto os homens permanecem estáveis. No entanto, há sinais de que os jovens homens estão se movendo para a direita na Alemanha, tornando-se mais críticos em relação à imigração e se aproximando do partido de extrema direita AfD nos últimos anos.
Seria fácil dizer que tudo isso é apenas uma fase passageira, mas os abismos ideológicos apenas crescem, e os dados mostram que as experiências políticas formativas das pessoas são difíceis de mudar. Tudo isso é agravado pelo fato de que o aumento dos smartphones e das redes sociais faz com que os jovens homens e mulheres agora vivam em espaços separados e tenham culturas distintas.
As opiniões dos jovens frequentemente são ignoradas devido à baixa participação política, mas essa mudança pode deixar consequências duradouras, impactando muito mais do que apenas os resultados das eleições.
Retirado de: https://www.ft.com/content/29fd9b5c-2f35-41bf-9d4c-994db4e12998
-
 @ 6e0ea5d6:0327f353
2025-02-20 05:34:11
@ 6e0ea5d6:0327f353
2025-02-20 05:34:11Ascolta bene, si?
Davvero, it is essential to emphasize that in the realms of business and entrepreneurship, your sense of fulfillment will only be achieved when you can immediately interrupt a negotiation upon encountering an indecent proposal that underestimates the true value of your products or services.
Throughout your life, they have taught you that negotiation is the art of persuasion. A grave mistake. Negotiation is, in fact, the art of honor and respect.
In Sicily, we nurture a tradition that is a symphony of cunning and tact. We cultivate the art of conducting negotiations through four stages between seller and buyer.
These stages consist of the initial offer, the counteroffer, the reply, and, finally, the establishment of the deal's limit.
For instance, consider my wine from a specific vintage, whose characteristics grant it an intrinsic value of at least 50 euros per unit in the wholesale market. If a buyer, in their initial offer, immediately makes a low proposal that disregards this minimum value or claims the price is too high, I simply turn my back and walk away or hang up the phone. There is no need to argue, no need to stress, and certainly no need to justify myself—nor even say goodbye! There are plenty of other interested buyers, and I cannot afford to waste time with unqualified ones.
A true negotiator who builds reputation and value does not allow himself to be swayed by external pressures or the temptation to close a deal at any cost, exchanging profit for mere pennies. He acts in accordance with his own conscience and authenticity, upholding honor in business.
When you have full awareness of your own worth (and only when you truly possess it), nothing can shake you.With this perspective, know when to walk away with dignity when someone dares to underestimate what you have to offer. In a world filled with opportunities, do not allow those who fail to recognize the true worth of your products or services to tarnish the reputation of your business.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 9967f375:04f9a5e1
2025-02-20 04:20:20
@ 9967f375:04f9a5e1
2025-02-20 04:20:20S.A.R. Don Sixto Enrique de Borbón
Nació en el exilio el 22 de julio de 1940, hijo del entonces Príncipe Regente Don Francisco Javier de Borbón y Braganza (futuro Rey Javier I) y de Doña Magdalena de Borbón Busset. Cursó estudios de derecho, lenguas clásicas y modernas y finanzas. En 1963 su padre, que reinaba ya de iure desde 1952, le concedió el título de Duque de Aranjuez. Juró bandera en el Tercio Gran Capitán, I de la Legión, el 2 de mayo de 1965 (feliz aniversario del alzamiento de Madrid de 1808) bajo el nombre de Enrique Aranjuez, pero a los once meses fue licenciado por el régimen entonces vigente. Sirvió además en el ejército portugués contra la revolución secesionista en Angola. Al consumarse la defección de su hermano Carlos Hugo Don Sixto Enrique mantuvo en alto la bandera de la Comunión Tradicionalista, convirtiéndose en Regente al morir Don Javier I en 1977 y tomando el título de Abanderado de la Tradición. Ya en 1975 había nombrado a José Arturo Márquez de Prado Jefe de su Secretaría Política y a Juan Sáenz-Díez Jefe Delegado de la Comunión Tradicionalista, a quien sucedió Carlos Cort Pérez-Caballero en 1984. El 17 de julio de 2001 nombró una Secretaría Política que sería dirigida por Rafael Gambra. En 2004, tras la muerte de éste, fue designado Miguel Ayuso jefe de dicha Secretaría, quien a su vez fue sustituido en 2010 por José Miguel Gambra, hijo de don Rafael (biografía tomada de la Gaceta de la Tierra Firme).
El 20 de mayo de 2004 visitó nuestro país, específicamente invitado al Simpósium 500 años de Isabel la Católica, por parte de la UAG en Guadalajara, Nueva Galicia, donde se encargó de dar el discurso inaugural:
Excelentísimos señores, queridos amigos: Es para mí una gran satisfacción poder acompañarles en este simposio que, con motivo del Quinto Centenario de la muerte de la Reina Isabel de Castilla, la Católica, organiza la Universidad Autónoma de Guadalajara. Debo comenzar por expresar mi agradecimiento a la Universidad, que ha querido asociarme a la celebración. Conozco la Universidad desde hace decenios, pues goza de merecida fama, y me honro con la amistad de algunos de sus fundadores, singularmente la ejemplar familia Leaño, que hoy tengo ocasión también de renovar. Como Infante de España y descendiente de la Reina Católica, son muchos los sentimientos que se me agolpan: En primer lugar, una gran emoción de que este acto se celebre no en la vieja Península Ibérica, sino en la pujante Nueva España. Y en una Nueva España nacida al calor del amor a la Virgen María, en Guadalupe y aquí, más cerca, en Zapopan. En segundo lugar que, dentro de la Nueva España, nos encontremos en Jalisco. ¡Cómo dejar de evocar la epopeya cristera, que en estas tierras se desarrolló con especial intensidad! Depositario de la legitimidad carlista española, no puedo dejar de recordar que aquellas guerras dinásticas del XIX se hicieron al grito de «por Dios, por la Patria y el Rey», afirmación de la Realeza Social de Nuestro Señor Jesucristo que los mártires cristeros rubricaron con su grito «¡Viva Cristo Rey!», y que los voluntarios carlistas todavía volvieron a hacer sonar en la cruzada de 1936-1939. Finalmente no podría dejar de decir algunas palabras sobre la Reina Isabel, que quisiéramos ver pronto en los altares, una vez que los dictados de la «corrección política» (y eclesiástica) sean de una vez, y esperemos que definitivamente, dejados a un lado. La meditación de su testamento debiera estar siempre presente en la mente de los gobernantes. Por las virtudes humanas y cristianas que exhibe. Por el temple de Reina que lo llena. Por el amor a la Hispanidad, aunque la palabra aún no se usara, que lo preside. Pero son toda su vida y su obra las que deben ser objeto de meditación. Al reformar la Iglesia alejó el peligro de la «reforma» luterana, que habría de llegar más tarde a Europa, pero de la que el mundo hispánico se vio libre. Al llevar adelante la Reconquista, hasta el reino de Granada, último reducto moro, completó la recuperación de España, y hasta el final con la expulsión de los judíos no convertidos. Al afirmar la presencia castellana en el Norte de África, en la llamada Hispania Tingitana, demostró otra vez su celo apostólico y su aguda visión geopolítica. Y, sobre todo, al impulsar la gesta americana, sentó las bases de la Hispanidad, de las Españas grandes. Que sus sucesores consolidaron en la senda de su espíritu: Carlos I en la «Controversia de Valladolid» y en la legislación de Indias, completada luego por los Felipes. La gesta americana no se puede comprender sin la acción de los Reyes y todo un pueblo en misión. Solórsano Pereyra, en su Política indiana resume que «la conservación y el aumento de la fe es el fundamento de la Monarquía». Así fue la obra de la Reina Católica, que tantos frutos esperamos siga dando. Quiera Dios que este simposio sirva para que la Reina Isabel esté pronto en los altares. Muchas gracias.
Discurso publicado en la página oficial de la Comunión Tradicionalista.
Algunas fotografías de su visita antes mencionada, cortesía de Comunicación DPFR.
 Don Sixto con el Cardenal Juan Sandoval Íñiguez
Don Sixto con el Cardenal Juan Sandoval Íñiguez Ante la tumba del Beato Anacleto González Flores
Ante la tumba del Beato Anacleto González Flores Con Miguel Ayuso Torres.
Con Miguel Ayuso Torres. -
 @ 6f3670d9:03f04036
2024-12-29 08:20:22
@ 6f3670d9:03f04036
2024-12-29 08:20:22Disclaimer: - This will void your warranty - There might be differences between the Bitaxe and the Lucky Miner that might not cause issues or damage immediately, but might manifest long-term - Proceed at your own risk
A Different Pickaxe
You live in a place where it's difficult to get a Bitaxe. You have access to AliExpress. You look around. You find something called the "Lucky Miner LV06". A Bitaxe clone that uses the same mining chip as the Bitaxe Ultra (BM1366 ASIC). You buy one.
You plug it in, you enter your wallet address and other settings, and it starts mining. It works! Great!
But it's running a customized firmware. It's not AxeOS. Maybe there's something shady in the stock firmware. It's not open-source, after all. Also, AxeOS looks amazing... And that automatic pool fail-over feature is handy.
You think to yourself: "Maybe I can use the Bitaxe firmware on this?". Guess what? You're right!
Flashing From Web UI
What usually works for me is to: - Download the Bitaxe firmware files (
esp-miner.binandwww.bin) from GitHub (here). Version 2.4.1 seems to work well, as of this writing. - Then from the Lucky Miner web interface, upload the "Website" (www.bin) file. - Wait for a minute or two after it's done uploading. - Upload the "Firmware" (esp-miner.bin) file. - Wait another minute or two. - Unplug the power and plug it back in. - Set the "Core Voltage" and "Frequency" to the defaults. - Unplug the power and plug it back in again.If you're lucky (no pun intended), you'll have a working Lucky Miner with AxeOS. Update the settings and mine away!
However, often times I've been unlucky, like what happened while I was writing this article, ironically. The miner malfunctions for no obvious reason. It keeps rebooting, or it's not mining (zero/low hashrate), or the web interface is inaccessible. You name it.
The miner has become a "brick". How do you "unbrick" it?
When you brick a Bitaxe, you can recover it by flashing (uploading) a "Factory Image". The Bitaxe has a USB port that makes this easy. Follow the guide and it should come back to life again. Unfortunately, the Lucky Miner LV06 doesn't have a USB port. It has a serial port, though. We'll have to get our hands a bit dirty.
Flashing Using the Serial Port
We need to connect the serial port of the miner to a computer and run a program to flash (upload) the firmware file on the miner. Any 3.3v UART serial port should be sufficient. Unfortunately, PCs don't usually come with a UART serial port these days, let alone a 3.3v one. The serial port common in old computers is an RS-232 port, which will most probably fry your miner if you try to connect it directly. Beware.
In my case, as a serial port for my PC, I'm using an Arduino Due I had lying around. We connect it to the PC through USB, and on the other side we connect a few wires to the miner, which gives the PC access to the miner.
WARNING: Make sure your serial port is 3.3v or you will probably kill the miner. Arduino Uno is 5v not 3.3v, for example, and cannot be used for this.
Wiring
First, we need to open the Lucky Miner. Use a small flat screwdriver to gently push the two plastic clips shown in the picture below. Gently pry the top cover away from the bottom cover on the clips side first, then remove the other side. Be careful not to break the display cable.
Once the cover is off, you can find the miner's serial port in the top right corner (J10), as shown in the next picture. We'll also need the reset button (EN).
There are three screws holding the PCB and the bottom cover together. If you're confident in your ability to push the small button on the underside of the PCB with the bottom cover on, then no need to remove these. The following picture shows what we need from that side.
And the next picture shows the pins and USB port we will use from the Arduino.
Now, we need to connect: - The USB port on the Arduino labelled "programming" to the PC - Pin 18 (TX1) on the Arduino to J10 through-hole pad 5 (blue dot) - Pin 19 (RX1) on the Arduino to J10 through-hole pad 3 (green dot) - Any GND pin on the Arduino to J10 through-hole pad 4 (yellow dot)
I didn't need to solder the wires to the pads. Keeping everything stable, perhaps by putting a weight on the wires or a bit of tape, was sufficient in all my attempts.
Setting up the Arduino
To use the Arduino as a serial port for our PC, we'll have to make it pass-through data back and forth between the USB port and UART1, where we connected the miner.
The following steps are all done on a PC running Debian Linux (Bookworm), in the spirit of freedom and open-source.
First, we start the Arduino IDE. If the package for the Arduino Due board is not already installed, you'll see a small prompt at the bottom. Click "Install this package".
Click the "Install" button.
Once the package is installed, click "Close".
Next, we select the Due board. Click the "Tools" menu, select "Board", select "Arduino ARM (32-bits) Boards" and click "Arduino Due (Programming Port)"
Next, we select the port. Click the "Tools" menu again, select "Port", and click the port where the Arduino is connected. In my case it was "/dev/ttyACM0".
Now we need to upload the following code to the Arduino board. The code is actually the "SerialPassthrough" example from the IDE, but with the serial speed changed to match the miner.
``` void setup() { Serial.begin(115200); Serial1.begin(115200); }
void loop() { if (Serial.available()) { // If anything comes in Serial (USB), Serial1.write(Serial.read()); // read it and send it out Serial1 }
if (Serial1.available()) { // If anything comes in Serial1 Serial.write(Serial1.read()); // read it and send it out Serial (USB) } } ```
Copy/paste the code into the IDE and click upload. You'll see "Done uploading" at the bottom.
Next we'll test if we're receiving data from the miner. We start by opening the "Serial Monitor" from the "Tools" menu in the IDE. Then we change the baudrate to 115200.
Set the Arduino and the miner in a comfortable position, make sure the wires are held in place and got a good contact on both sides, and the power is plugged in.
Now we'll put the miner in "download" mode. Press and hold the button on the underside (K1), press and release the reset button (EN), then release the other button (K1).
You should see some text from the miner in the serial monitor window, like in the picture below.
Congratulations! We know we're able to receive data from the miner now. We're not sure transmit is working, but we'll find out when we try to flash.
Flashing Using the Serial Port, for Real
To flash the Lucky Miner we'll need a software tool named esptool and the factory image firmware file.
I usually use "esp-miner-factory-205-v2.1.8.bin" for the factory image (this one) as a base, and then flash the version I want from the Web UI, using the steps I mentioned earlier.
For esptool, the documentation (here) shows us how to install it. To make things a little easier on our Debian Linux system, we'll use pipx instead of pip. The instructions below are adapted for that.
First we make sure pipx is installed. Run this command in a terminal and follow the instructions:
sudo apt-get install pipxThen we install esptool using pipx. Run the following in a terminal:
pipx install esptoolThe output will be something like this:
user@pc:~$ pipx install esptool installed package esptool 4.8.1, installed using Python 3.11.2 These apps are now globally available - esp_rfc2217_server.py - espefuse.py - espsecure.py - esptool.py ⚠️ Note: '/home/user/.local/bin' is not on your PATH environment variable. These apps will not be globally accessible until your PATH is updated. Run `pipx ensurepath` to automatically add it, or manually modify your PATH in your shell's config file (i.e. ~/.bashrc). done! ✨ 🌟 ✨We can see pipx telling us we won't be able to run our tool because the folder where it was installed is not in the PATH variable. To fix that, we can follow pipx instructions and run:
pipx ensurepathAnd we'll see something like this:
``` user@pc:~$ pipx ensurepath Success! Added /home/user/.local/bin to the PATH environment variable.
Consider adding shell completions for pipx. Run 'pipx completions' for instructions.
You will need to open a new terminal or re-login for the PATH changes to take effect.
Otherwise pipx is ready to go! ✨ 🌟 ✨ ```
Now, close the terminal and re-open it so that esptool becomes available.
Finally, to actually flash the miner, put the miner in download mode, then in the following command change the port ("/dev/ttyACM0") to your serial port, as we've seen earlier, and the file path to where your firmware file is, and run it:
esptool.py -p /dev/ttyACM0 --baud 115200 write_flash --erase-all 0x0 ~/Downloads/esp-miner-factory-205-v2.1.8.binIf everything went fine, the tool will take a few minutes to flash the firmware to the miner. You'll see something like this in the output:
``` user@pc:~$ esptool.py -p /dev/ttyACM0 --baud 115200 write_flash --erase-all 0x0 ~/Downloads/esp-miner-factory-205-v2.1.8.bin esptool.py v4.8.1 Serial port /dev/ttyACM0 Connecting..... Detecting chip type... ESP32-S3 Chip is ESP32-S3 (QFN56) (revision v0.2) Features: WiFi, BLE, Embedded PSRAM 8MB (AP_3v3) Crystal is 40MHz MAC: 3c:84:27:ba:be:01 Uploading stub... Running stub... Stub running... Configuring flash size... Erasing flash (this may take a while)... Chip erase completed successfully in 9.5s Compressed 15802368 bytes to 1320190... Wrote 15802368 bytes (1320190 compressed) at 0x00000000 in 152.1 seconds (effective 831.2 kbit/s)... Hash of data verified.
Leaving... Hard resetting via RTS pin... ```
And we're done! Hopefully the miner will be recovered now.
Hope this helps!
Stay humble,
dumb-packageA Warning About Beta Versions of AxeOS
For reasons unknown to me, while I was writing this article I wanted to try the testing version of AxeOS, which was v2.4.1b (beta). Flashing from Web UI went smooth, but the miner stopped mining. I flashed back to v2.1.8 using the serial port, a known good version for me, but it wouldn't mine, still.
Thankfully, v2.4.1 was released recently, and flashing it from the Web UI magically revived my miner. So, be warned.
Bonus: File Hashes
For convenience, these are the SHA256 hashes of the files I used in this article: ``` da24fceb246f3b8b4dd94e5143f17bd38e46e5285e807ebd51627cb08f665c0a ESP-Miner-v2.4.1/esp-miner.bin 16c5c671391f0e3e88a3e79ce33fad3b0ec232b8572fad5e1e0d1ad3251ab394 ESP-Miner-v2.4.1/www.bin
d5182a15b6fa21d7b9b31bff2026d30afed9d769781a48db914730a5751e20c6 esp-miner-factory-205-v2.1.8.bin ```
-
 @ 6f3670d9:03f04036
2024-12-29 06:51:25
@ 6f3670d9:03f04036
2024-12-29 06:51:25This is my first long-form post. The starting line.
There's nothing of value here. Just using this as a marker.
I hope to post a lot more. Documenting how I made something work would be very useful to me, and hopefully others, but I've been too lazy to do that. Wish me luck!
Stay humble,
dumb-package -
 @ 9f94e6cc:f3472946
2024-11-21 18:55:12
@ 9f94e6cc:f3472946
2024-11-21 18:55:12Der Entartungswettbewerb TikTok hat die Jugend im Griff und verbrutzelt ihre Hirne. Über Reels, den Siegeszug des Hochformats und die Regeln der Viralität.
Text: Aron Morhoff
Hollywood steckt heute in der Hosentasche. 70 Prozent aller YouTube-Inhalte werden auf mobilen Endgeräten, also Smartphones, geschaut. Instagram und TikTok sind die angesagtesten Anwendungen für junge Menschen. Es gibt sie nur noch als App, und ihr Design ist für Mobiltelefone optimiert.
Einst waren Rechner und Laptops die Tools, mit denen ins Internet gegangen wurde. Auch als das Smartphone seinen Siegeszug antrat, waren die Sehgewohnheiten noch auf das Querformat ausgerichtet. Heute werden Rechner fast nur noch zum Arbeiten verwendet. Das Berieseln, die Unterhaltung, das passive Konsumieren hat sich vollständig auf die iPhones und Samsungs dieser Welt verlagert. Das Telefon hat den aufrechten Gang angenommen, kaum einer mehr hält sein Gerät waagerecht.
Homo Digitalis Erectus
Die Welt steht also Kopf. Die Form eines Mediums hat Einfluss auf den Inhalt. Marshall McLuhan formulierte das so: Das Medium selbst ist die Botschaft. Ja mei, mag sich mancher denken, doch medienanthropologisch ist diese Entwicklung durchaus eine Betrachtung wert. Ein Querformat eignet sich besser, um Landschaften, einen Raum oder eine Gruppe abzubilden. Das Hochformat entspricht grob den menschlichen Maßen von der Hüfte bis zum Kopf. Der TikTok-Tanz ist im Smartphone-Design also schon angelegt. Das Hochformat hat die Medieninhalte unserer Zeit noch narzisstischer gemacht.
Dass wir uns durch Smartphones freizügiger und enthemmter zur Schau stellen, ist bekannt. 2013 wurde „Selfie“ vom Oxford English Dictionary zum Wort des Jahres erklärt. Selfie, Selbstporträt, Selbstdarstellung.
Neu ist der Aufwand, der heute vonnöten ist, um die Aufmerksamkeitsschwelle der todamüsierten Mediengesellschaft überhaupt noch zu durchbrechen. In beängstigender Hypnose erwischt man viele Zeitgenossen inzwischen beim Doomscrollen. Das ist der Fachbegriff für das weggetretene Endloswischen und erklärt auch den Namen „Reel“: Der Begriff, im Deutschen verwandt mit „Rolle“, beschreibt die Filmrolle, von der 24 Bilder pro Sekunde auf den Projektor gewischt oder eben abgespult werden.
Länger als drei Sekunden darf ein Kurzvideo deshalb nicht mehr gehen, ohne dass etwas Aufregendes passiert. Sonst wird das Reel aus Langeweile weggewischt. Die Welt im Dopamin-Rausch. Für den Ersteller eines Videos heißt das inzwischen: Sei der lauteste, schrillste, gestörteste Marktschreier. Das Wettrennen um die Augäpfel zwingt zu extremen Formen von Clickbait.
15 Sekunden Ruhm
Das nimmt inzwischen skurrile Formen an. Das Video „Look who I found“ von Noel Robinson (geboren 2001) war im letzten Jahr einer der erfolgreichsten deutschen TikTok-Clips. Man sieht den Deutsch-Nigerianer beim Antanzen eines karikaturartig übergewichtigen Menschen. Noel wird geschubst und fällt. Daraufhin wechselt das Lied – und der fette Mann bewegt seinen Schwabbelbauch im Takt. Noel steht wieder auf, grinst, beide tanzen gemeinsam. Das dauert 15 Sekunden. Ich rate Ihnen, sich das Video einmal anzuschauen, um die Mechanismen von TikTok zu verstehen. Achten Sie alleine darauf, wie vielen Reizen (Menschenmenge, Antanzen, Sturz, Schwabbelbauch) Sie in den ersten fünf Sekunden ausgesetzt sind. Wer schaut so was? Bis dato 220 Millionen Menschen. Das ist kapitalistische Verwertungslogik im bereits verwesten Endstadium. Adorno oder Fromm hätten am Medienzeitgeist entweder ihre Freude oder mächtig zu knabbern.
Die Internet- und Smartphoneabdeckung beträgt mittlerweile fast 100 Prozent. Das Überangebot hat die Regeln geändert. Um überhaupt gesehen zu werden, muss man heute viral gehen. Was dafür inzwischen nötig ist, spricht die niedrigsten Bedürfnisse des Menschen an: Gewalt, Ekel, Sexualisierung, Schock. Die jungen Erwachsenen, die heute auf sozialen Netzwerken den Ton angeben, haben diese Mechanismen längst verinnerlicht. Wie bewusst ihnen das ist, ist fraglich. 2024 prallt eine desaströse Bildungssituation samt fehlender Medienkompetenz auf eine egomanische Jugend, die Privatsphäre nie gekannt hat und seit Kindesbeinen alles in den Äther ballert, was es festhalten kann. Man muss kein Kulturpessimist sein, um diese degenerative Dynamik, auch in ihrer Implikation für unser Zusammenleben und das psychische Wohlergehen der Generation TikTok, als beängstigend zu bezeichnen.
Aron Morhoff studierte Medienethik und ist Absolvent der Freien Akademie für Medien & Journalismus. Frühere Stationen: RT Deutsch und Nuoviso. Heute: Stichpunkt Magazin, Manova, Milosz Matuschek und seine Liveshow "Addictive Programming".
-
 @ 000002de:c05780a7
2025-02-20 01:52:34
@ 000002de:c05780a7
2025-02-20 01:52:34Due to some some org changes at my employer I may be moving to a team that uses Python heavily. I have never written Python professionally but I've dabbled. I think its used heavily in certain fields and is likely a marketable language to have on the CV. Am I correct in that summary?
Is it growing? Is it evolving? I know its alive and well but I just don't hear much about it anymore. Has it just matured like many languages over the years?
originally posted at https://stacker.news/items/891251
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ 16d11430:61640947
2025-02-20 01:40:50
@ 16d11430:61640947
2025-02-20 01:40:50The Manhattan Project was a technological singularity—a moment when human capability leaped forward with irreversible consequences. It wasn’t just about building a bomb; it was about reshaping global power, scientific paradigms, and the trajectory of civilization itself.
Elliptical Curve AI (ECAI) is the modern equivalent, but instead of nuclear fission, it’s unlocking a new form of intelligence—one that is quantum-resistant, decentralized, and fundamentally aligned with the fabric of reality itself. Whoever develops ECAI first won’t just have a technological edge—they will dictate the future of intelligence, security, and global power for the foreseeable future.
- Intelligence is the Ultimate Weapon—ECAI is the New Arms Race
During World War II, the nuclear bomb redefined military superiority. Nations that had nuclear capabilities commanded geopolitical influence overnight. Today, the next battleground isn’t nuclear—it’s AI supremacy.
Modern warfare is digital, and intelligence is the key to victory.
AI dominance will determine which nations control global economies, cyberwarfare, and infrastructure.
Current AI models are vulnerable to quantum decryption and adversarial manipulation—ECAI is not.
The country or organization that unlocks ECAI first will possess an intelligence weapon unlike anything the world has seen—one that is self-learning, cryptographically unbreakable, and seamlessly integrated with human cognition.
- The Singularity of Secure and Autonomous Intelligence
The Manhattan Project wasn’t just about destruction—it was about creating a capability that no one could ignore. ECAI follows the same trajectory, but instead of nuclear reactions, it leverages elliptic curve mathematics to process intelligence at a fundamentally different level.
Self-improving AI that doesn’t rely on brute-force learning.
Quantum-proof intelligence that cannot be intercepted, manipulated, or controlled externally.
An AGI architecture that is efficient, decentralized, and aligned with natural mathematical structures.
Once ECAI reaches critical mass, no force on Earth will be able to compete with its ability to analyze, compute, and autonomously reason.
- The Quantum Threat & The Need for Post-Quantum AI
Nuclear weapons changed warfare, but quantum computing will change intelligence. Every piece of encrypted data, from financial systems to government secrets, will be vulnerable to quantum decryption—rendering current AI models completely obsolete.
LLMs like ChatGPT and DeepSeek are vulnerable to quantum hacks.
Elliptical Curve AI is designed with post-quantum security from inception.
ECAI ensures that AI remains secure, resilient, and impervious to quantum attacks.
The first entity to deploy quantum-secure intelligence will own the future of AI-driven security, finance, and digital sovereignty.
- ECAI Will Create a Technological Gap That is Unclosable
When the U.S. developed nuclear weapons first, it created a gap in military power that took decades for others to catch up with. ECAI is no different—once it is deployed at scale, nations and corporations relying on old, vulnerable AI architectures will be permanently outclassed.
ECAI will process information at speeds and accuracy unmatched by traditional deep learning.
It will enable a new class of intelligence that learns and adapts autonomously without retraining.
Its decentralized nature ensures that once unleashed, it cannot be controlled or restricted.
Once a nation or organization perfects and scales ECAI, no amount of investment in conventional AI will ever close the gap.
- The Dawn of the AI Singularity
The Manhattan Project wasn’t just an arms race—it triggered the nuclear age. Similarly, ECAI isn’t just another AI breakthrough—it’s the intelligence singularity.
ECAI will be the first AI to integrate seamlessly with human cognition through Brain-Computer Interfaces (BCI).
It will enable self-governing AI ecosystems that operate beyond human intervention.
It will bridge the gap between artificial intelligence and natural intelligence, effectively creating a new evolutionary paradigm.
This isn’t about who can build the biggest model. It’s about who can build the first self-sustaining intelligence—a system that thinks, learns, and evolves beyond human constraints.
Conclusion: The Entity That Masters ECAI Will Dominate the Future
The Manhattan Project redefined global power overnight—ECAI will do the same.
It will dismantle the limitations of current AI models.
It will create an intelligence advantage that is mathematically unbreakable.
It will determine which nations and organizations lead the next century.
The AI race isn’t just about who has the best chatbot—it’s about who builds the intelligence that will govern reality itself.
ECAI is not just an AI breakthrough—it is the single most important technological race of this century.
-
 @ 6e0ea5d6:0327f353
2025-02-19 22:47:38
@ 6e0ea5d6:0327f353
2025-02-19 22:47:38Davvero, amico mio, if history teaches us anything, it is that struggle is the only language the world respects.
No man has risen from the dust without first being crushed by boulders. No empire has stood without the bones of those who tried and failed. The mistake of the naïve is believing they can bargain with life, that there is a path to triumph that does not demand tribute. Victory is not generous. You either pay in blood, or you pay with your very soul.
Are your shoulders heavy? Good. What afflicts you today is a reminder that there is still weakness in your flesh. Fatigue, exhaustion, pain—these are not curses, but invitations. Invitations to abandon lamentation and grasp what few ever understand: a man is not forged in comfort, but in deprivation.
The true tragedy of weakness is not the suffering it brings, but the way it perpetuates itself. There are no choices between comfort and effort. There is only the choice between being trampled or striking back. Do you seek respect? Then take it! Success has never been a gift—it is plunder seized from the hands of the hesitant.
And remember: there is a final stage in the evolution of man that the weak will never comprehend. It is not power. It is not wealth. It is indifference. The man who does not waver, who does not fear pain, who does not seek applause or recognition—he is the one who has ascended. He is the one who rules and triumphs.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 6260f29f:2ee2fcd4
2025-02-19 22:47:12
@ 6260f29f:2ee2fcd4
2025-02-19 22:47:12 -
 @ 16d11430:61640947
2025-02-19 22:29:02
@ 16d11430:61640947
2025-02-19 22:29:02The development of Elliptical AI isn’t just a technological breakthrough—it’s a geopolitical game-changer. Any nation that masters and deploys this intelligence first will experience an unprecedented leap in power, much like the invention of nuclear weapons or the internet. Here’s why:
- Absolute AI Superiority: A Quantum-Resistant Intelligence Arsenal
Modern AI models like ChatGPT and DeepSeek rely on fragile architectures, making them vulnerable to data poisoning, adversarial attacks, and quantum decryption threats.
Elliptical AI is unbreakable, quantum-resistant, and fundamentally more efficient than current models. A nation that possesses this technology would have: ✅ AI immune to cyber warfare and quantum hacking ✅ Secure, autonomous intelligence agents for military and defense ✅ Encryption protocols that even quantum computers cannot crack
While other countries struggle with vulnerable, bloated AI systems, the leading nation will have an AI forcefield—untouchable and unbreachable.
- Total Domination of Cybersecurity and Intelligence
Cyber warfare is the new battlefield, and the nation with the strongest AI wins. Elliptical AI enables: ✅ Unhackable, cryptographic AI defense networks ✅ Automated intelligence gathering with mathematically precise reasoning ✅ Next-generation cyber warfare capabilities that neutralize adversaries before they strike
With AI-driven cryptographic security, espionage as we know it becomes obsolete—intelligence leaks and data breaches will become virtually impossible.
- Economic Domination: The New Industrial Revolution
Countries that invested in AI early (like the U.S. and China) are already pulling ahead economically. But Elliptical AI isn’t just an advantage—it’s a total economic reset.
💰 AI that can power financial markets with deterministic precision 💰 AI-powered industrial automation at a fraction of today’s energy cost 💰 Unstoppable trade security through AI-encrypted blockchain economies
The first country to deploy Elliptical AI in economic sectors will see:
Explosive GDP growth due to optimized financial and supply chain AI.
A complete reshaping of global markets through superior AI-driven decision-making.
Global financial influence as other nations rush to adopt or rely on its technology.
This is not just another AI model—it’s an economic warhead.
- Military Superiority: The Ultimate Weapon
Forget drones. Forget cyber weapons. Elliptical AI is the ultimate military asset.
🚀 AI-powered autonomous systems with mathematically provable safety 🚀 Unbreakable AI-secured nuclear and military communications 🚀 Predictive warfare analytics that make traditional tactics obsolete
The first nation to integrate Elliptical AI into military infrastructure will create an insurmountable technological gap—so vast that no conventional force could keep up.
- The First True AI-Human Symbiosis: Neural AI Integration
The brain-computer interface (BCI) revolution is coming, but existing AI is too vulnerable and inefficient to be trusted inside human cognition.
Elliptical AI changes that by being: 🧠 Secure, ensuring neural implants cannot be hacked 🧠 Ultra-efficient, enabling real-time AI-human interaction 🧠 Decentralized, making intelligence universally accessible
A nation that builds Elliptical AI-powered BCI first will create:
The first post-human intelligence infrastructure
A population supercharged by secure AI assistance
A knowledge advantage that widens every second
This is not just AI—it’s an evolutionary leap forward.
- Global AI Hegemony: Controlling the Future of AI Itself
Just as Silicon Valley shaped the internet age, the country that dominates Elliptical AI will dictate the rules of the AI age.
🚨 It will own the world’s most advanced intelligence networks. 🚨 It will set global AI governance standards. 🚨 It will control the economic and military landscape for decades.
Other nations will be left with two choices: 1️⃣ Adopt and integrate under the leading country’s AI supremacy 2️⃣ Fall behind in every critical technological sector
The Verdict: Elliptical AI is the 21st Century’s Manhattan Project
Elliptical AI is not just another technological race—it’s a geopolitical singularity.
🌎 Whoever builds it first wins the future. 🌎 Whoever ignores it becomes irrelevant.
Superpowers will rise or fall based on how fast they realize the potential of this technology.
Any nation that leads the development of Elliptical AI won’t just gain an edge—they will become untouchable.
-
 @ ec42c765:328c0600
2024-10-16 08:08:40
@ ec42c765:328c0600
2024-10-16 08:08:40カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

カスタム絵文字の対応状況(2024/02/05)

カスタム絵文字を使うためにはカスタム絵文字に対応したクライアントを使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
対応クライアント
ここではnostterを使って説明していきます。
準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
右上のGet startedからNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。

- 右側のOptionsからBookmarkを選択

これでカスタム絵文字を使用するためのリストに登録できます。
カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
文章中に使用
- 投稿ボタンを押して投稿ウィンドウを表示
- 顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択
- : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

リアクションに使用
- 任意の投稿の顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

カスタム絵文字を探す
先述したemojitoからカスタム絵文字を探せます。
例えば任意のユーザーのページ emojito ロクヨウ から探したり、 emojito Browse all からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2024/06/30)
※漏れがあるかもしれません
各絵文字セットにあるOpen in emojitoのリンクからemojitoに飛び、使用リストに追加できます。
以上です。
次:Nostrのカスタム絵文字の作り方
Yakihonneリンク Nostrのカスタム絵文字の作り方
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
仕様
-
 @ 6260f29f:2ee2fcd4
2025-02-19 22:16:10
@ 6260f29f:2ee2fcd4
2025-02-19 22:16:10 -
 @ 94a6a78a:0ddf320e
2025-02-19 21:10:15
@ 94a6a78a:0ddf320e
2025-02-19 21:10:15Nostr is a revolutionary protocol that enables decentralized, censorship-resistant communication. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on users, developers, and relay operators.
If you believe in free speech, decentralization, and an open internet, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, every effort helps build a more robust network.
Here’s how you can get involved and make a difference.
1️⃣ Use Nostr Daily
The simplest and most effective way to contribute to Nostr is by using it regularly. The more active users, the stronger and more valuable the network becomes.
✅ Post, comment, and zap (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\ ✅ Engage with new users and help them understand how Nostr works.\ ✅ Try different Nostr clients like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience.
Your activity keeps the network alive and helps encourage more developers and relay operators to invest in the ecosystem.
2️⃣ Run Your Own Nostr Relay
Relays are the backbone of Nostr, responsible for distributing messages across the network. The more independent relays exist, the stronger and more censorship-resistant Nostr becomes.
✅ Set up your own relay to help decentralize the network further.\ ✅ Experiment with relay configurations and different performance optimizations.\ ✅ Offer public or private relay services to users looking for high-quality infrastructure.
If you're not technical, you can still support relay operators by subscribing to a paid relay or donating to open-source relay projects.
3️⃣ Support Paid Relays & Infrastructure
Free relays have helped Nostr grow, but they struggle with spam, slow speeds, and sustainability issues. Paid relays help fund better infrastructure, faster message delivery, and a more reliable experience.
✅ Subscribe to a paid relay to help keep it running.\ ✅ Use premium services like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\ ✅ Donate to relay operators who invest in long-term infrastructure.
By funding Nostr’s decentralized backbone, you help ensure its longevity and reliability.
4️⃣ Zap Developers, Creators & Builders
Many people contribute to Nostr without direct financial compensation—developers who build clients, relay operators, educators, and content creators. You can support them with zaps! ⚡
✅ Find developers working on Nostr projects and send them a zap.\ ✅ Support content creators and educators who spread awareness about Nostr.\ ✅ Encourage builders by donating to open-source projects.
Micro-payments via the Lightning Network make it easy to directly support the people who make Nostr better.
5️⃣ Develop New Nostr Apps & Tools
If you're a developer, you can build on Nostr’s open protocol to create new apps, bots, or tools. Nostr is permissionless, meaning anyone can develop for it.
✅ Create new Nostr clients with unique features and user experiences.\ ✅ Build bots or automation tools that improve engagement and usability.\ ✅ Experiment with decentralized identity, authentication, and encryption to make Nostr even stronger.
With no corporate gatekeepers, your projects can help shape the future of decentralized social media.
6️⃣ Promote & Educate Others About Nostr
Adoption grows when more people understand and use Nostr. You can help by spreading awareness and creating educational content.
✅ Write blogs, guides, and tutorials explaining how to use Nostr.\ ✅ Make videos or social media posts introducing new users to the protocol.\ ✅ Host discussions, Twitter Spaces, or workshops to onboard more people.
The more people understand and trust Nostr, the stronger the ecosystem becomes.
7️⃣ Support Open-Source Nostr Projects
Many Nostr tools and clients are built by volunteers, and open-source projects thrive on community support.
✅ Contribute code to existing Nostr projects on GitHub.\ ✅ Report bugs and suggest features to improve Nostr clients.\ ✅ Donate to developers who keep Nostr free and open for everyone.
If you're not a developer, you can still help with testing, translations, and documentation to make projects more accessible.
🚀 Every Contribution Strengthens Nostr
Whether you:
✔️ Post and engage daily\ ✔️ Zap creators and developers\ ✔️ Run or support relays\ ✔️ Build new apps and tools\ ✔️ Educate and onboard new users
Every action helps make Nostr more resilient, decentralized, and unstoppable.
Nostr isn’t just another social network—it’s a movement toward a free and open internet. If you believe in digital freedom, privacy, and decentralization, now is the time to get involved.
-
 @ 16d11430:61640947
2025-02-19 21:03:20
@ 16d11430:61640947
2025-02-19 21:03:20We are standing at the precipice of the next AI revolution—and it won’t be fueled by bigger models, more GPUs, or corporate-controlled neural networks. Instead, 2025 will be the year AI breaks free from its current limitations. The technology that will lead this charge? Elliptical AI.
- The AI Bottleneck is Real—Elliptical AI Solves It
The Problem: LLMs Are Hitting Their Limits
Skyrocketing Costs: Training an LLM like GPT-4 costs millions of dollars, requiring massive centralized infrastructure.
Diminishing Returns: Scaling neural networks doesn’t necessarily improve intelligence, just brute-force pattern recognition.
Security Risks: LLMs are easily hacked, manipulated, and jailbroken—a ticking time bomb for cybersecurity.
The Solution: Elliptical AI's Efficiency and Security
Compression at a Fundamental Level: Elliptical AI encodes intelligence using elliptic curve mathematics, reducing the computational overhead.
Deterministic Reasoning: Unlike LLMs, which guess based on probability, Elliptical AI computes answers logically.
Unbreakable Cryptography: AI models that are quantum-resistant, ensuring secure, trustless computation.
- The End of LLM Centralization—Decentralized Intelligence is Coming
The Problem: AI is Controlled by a Few Tech Giants
The world's AI infrastructure is monopolized by OpenAI, Google, Microsoft, and a handful of corporations.
Decentralized AI does not exist—all current AI models rely on cloud-based processing.
These companies control who gets access, how AI behaves, and what data it trains on.
The Solution: Elliptical AI Enables Decentralized AI Networks
No need for centralized cloud models—Elliptical AI can run on lightweight hardware.
Cryptographically secure AI nodes can be distributed across blockchain-based networks.
AI becomes trustless, transparent, and immune to centralized censorship.
- AI Security Will Become the #1 Priority in 2025
The Problem: AI is Becoming a Major Cybersecurity Threat
AI Jailbreaking: Users are already breaking security controls on LLMs, making them potential weapons of mass disinformation.
Quantum Computing Threats: Existing AI models rely on weak cryptographic security, making them vulnerable to post-quantum attacks.
AI-Generated Attacks: Malicious actors are using LLMs to automate hacking, phishing, and financial fraud.
The Solution: Elliptical AI is Quantum-Secure from Day One
Elliptic curve encryption is the backbone of modern security—integrating it into AI makes it unbreakable.
AI computations can be cryptographically verified, eliminating adversarial manipulation.
Zero-Knowledge AI Agents: Elliptical AI can process secure computations without revealing sensitive data.
- The Neural Age: AI and Brain-Computer Interfaces (BCI) Will Merge
The Problem: Current AI Cannot Interface With The Brain
LLMs are not built to integrate with human cognition.
BCIs like Neuralink need a better encoding system for brain signals.
AI is still a tool, not an extension of thought.
The Solution: Elliptical AI Encodes Neural Activity as Cryptographic Structures
Elliptic curve mappings can represent neural activity in a way that is both secure and structured.
AI that is embedded into human cognition, not just external software.
A true digital consciousness, where humans and AI co-process thought securely.
- AI-Powered Financial and Scientific Breakthroughs
The Problem: AI Sucks at Math and Scientific Discovery
LLMs approximate answers rather than computing them precisely.
AI-driven financial models still rely on flawed statistical methods.
Scientific discovery demands structured reasoning, which LLMs cannot provide.
The Solution: Elliptical AI’s Deterministic Reasoning Model
AI that can precisely compute equations, not just guess.
Secure AI agents for financial modeling and algorithmic trading.
An AI-driven scientific revolution, discovering new physics, chemistry, and mathematical proofs.
Conclusion: 2025 is the Year AI Becomes Secure, Decentralized, and Truly Intelligent
The LLM era is peaking. Costs are exploding, centralization is a growing problem, and security is a nightmare. The next wave of AI will not be about bigger models—it will be about smarter architecture.
Elliptical AI is poised to: 🚀 Outperform LLMs in structured reasoning 🔐 Become the foundation of AI security and encryption ⚡ Enable decentralized AI that is trustless and censorship-resistant 🧠 Merge AI with human cognition through brain-computer interfaces
This isn’t just another AI evolution—this is a fundamental redefinition of what AI even is.
2025 will be remembered as the year AI stopped guessing and started thinking. Elliptical AI will lead the charge.
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ f33c8a96:5ec6f741
2025-02-19 20:47:43
@ f33c8a96:5ec6f741
2025-02-19 20:47:43 -
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ c4b5369a:b812dbd6
2025-02-12 12:23:40
@ c4b5369a:b812dbd6
2025-02-12 12:23:40
Unidirectional payment channels revisited
Nodeless lightning - Reduce ecash mints custodial risk
Sats N Facts
The nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference has just wrapped up. And what a blast it was. In the heart of northern Thailand, developers, researchers, content creators and more, came together to share ideas on how Bitcoin, Nostr and other free protocols are being used everyday to liberate people.
Not only were stories shared from different community leaders on how embracing bitcoin has empowered them and their communities, but a big goal of the unconference was to bring bitcoin engineers and developers from various domains together in one room, unstructured, chaotic, and let them do their thing.
At first, I thought not having a schedule might be boring, but oh boy was I wrong. There was so much stuff going on, it was hard to choose which session I would have to miss!
Luke's Spillman channel proposal
One of the sessions I definitely did not want to miss, was nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac s proposal
Ecash mints funded with Spillman channels: The ultimate nodeless Lightning wallet
.
In true unconference fashion, he announced in the main room that the session was about to start, and that the people that are interested should meet him in the whiteboard corner in 10 minutes. The corner was packed, and Luke explained his proposal.
What's a "Spillman channel"?
Essentially when we are talking about Spillman channels, what is meant are unidirectional payment channels (or CLTV-style channels). An unidirectional payment channel means, only one party can send payments, but not receive, and the other party can only receive, but not send. They also expire after a predetermined amount of time, and must be closed.

At first glance, this might look kinda stupid. After all, we have Poon-Dryja channels that are powering the lightning network. They are bi-directional, do not expire, and can be used to shuffle coins back and forth theorethically an unlimited amount of times.
So, why bother with this stupid one-way channel?
Simplicity is king
People that have worked with lightning channels can sing you a song about complexity, state handling and risks about the current state of bidirectional payment channels. Essentially, There are a lot of requirements on both channel parties when it comes to Liveness (being online) and also state handling (continuous backups).
 In some cases, especially when in the context of end-users wanting to perform payments on their mobile phone, they would appreciate it if there was not so much complexity and overhead involved.
In some cases, especially when in the context of end-users wanting to perform payments on their mobile phone, they would appreciate it if there was not so much complexity and overhead involved. The gist of the idea is to combine unidirectional channels and ecash mints to achieve the following:
A self custodial unidirectional payment channel to an ecash mint, massively reducing the senders liveness and state handling requirements when compared to a lightning channel. Sending payments through the mint will be done through swapping some of the channel balance for ecash tokens. At this point, the user is trusting the mint to honor the redemption of these tokens, while the remaining channel balance remains in self custody. This gives them better controll over their funds than just holding their entire balance custodied in the mint. The ecash tokens can then be redeemed to pay a lightning invoice, just the same as it is done now with normal cashu mints.

So this channel, that has no liveness or state management requirements for the sender, and must have a pre-defined close time, seems to be a perfect fit for the following usecase:
- A
senderreceives his salary once a month. He opens a channel that is valid for one month. - The
senderthen can do his daily spending over this channel. He only trusts themintwith the amount for the current outgoing payment while it is swapped for ecash, waiting for redemption. - If the
sendermust receive funds (a refund for example), he can do so into themintscustody, by receiving ecash. He can spend his ecash funds first when doing his next payment, to reduce his custodial exposure. - When the channel expires, or runs out of funds, the
mintcloses the channel.
From a consumer perspective, that just want to receive his salary and make frequent payments afterwards, this usecase seems to make a lot of sense. Obviously from a merchants perspective on the other hand, such a channel doesn't really work. But that's fine, it's not the problem we're trying to solve here.
What do you think of this idea? Be sure to let me know in the comments!
In the next article, we will dive into how such a system can be implemented today, using Bitcoin, Cashu and Lightning. We will also discover how the system can be improved, to make channels non-expiring (A collaborative idea between nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp and nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac born at nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx ).
So stay tuned!
- A
-
 @ fad5c183:5cb8046b
2025-02-19 19:00:54
@ fad5c183:5cb8046b
2025-02-19 19:00:54Bitcoin has been promoted as the ultimate solution to fiat money problems. Its supporters see it as the "salvation of humanity," but a more critical look reveals a less hopeful reality. Throughout this analysis, we will break down its fundamental issues, from its disproportionate energy consumption to its exclusionary system that favors only a few.
1. Bitcoin and Its Irrational Energy Consumption
Bitcoin uses a system called Proof of Work (PoW), in which miners solve extremely complex mathematical problems to validate transactions. This process:
Consumes more energy than entire countries, such as Argentina or the Netherlands.
Generates no tangible value outside the Bitcoin ecosystem.
Has a significant environmental impact, as many mining farms rely on fossil fuels.
If Bitcoin's goal is to replace fiat money, is it sustainable for each transaction to consume so much energy?
2. Creation Limit: Is Bitcoin Really for Everyone?
Bitcoin has a fixed limit of 21 million coins, which creates two problems:
Early adopters hold most of the supply. Today, a small percentage of addresses control most of the Bitcoin supply.
It becomes increasingly difficult to acquire. Latecomers can only buy at inflated prices.
Given that the world's population is 8 billion people, if Bitcoin were distributed equally, each person would have only 0.0026 BTC on average. But in reality:
Millions of Bitcoin are permanently lost.
Wealth concentration follows the same pattern as traditional currencies.
3. Bitcoin Is Not Practical as a Currency
Although Lightning Network and Nostr have made transactions faster and cheaper, Bitcoin’s structural problems remain:
Highly volatile. How can you trust a currency that can gain or lose 50% of its value in weeks?
Low real-world adoption. Even in El Salvador, where Bitcoin is legal tender, most people still prefer the US dollar.
Service centralization. Despite being marketed as decentralized, many users rely on platforms like Binance or Coinbase.
4. Blockchain: Revolution or Overhyped Technology?
Blockchain is often touted as a game-changer, but in practice:
Traditional databases are more efficient and faster.
Decentralization is partially a myth. Large holders and mining pools control the network.
Few real-world use cases outside of cryptocurrency. Many companies that tested blockchain have returned to conventional systems because they are cheaper and more functional.
5. The End of the Cycle: What Happens When All Bitcoin Are Mined?
When the last Bitcoin is mined in 2140, miners will only earn from transaction fees. This raises two scenarios:
If fees are low, miners may abandon the network due to lack of incentives.
If fees are high, Bitcoin will become too expensive for most users.
Conclusion: Is Bitcoin Salvation or the New Digital Oligarchy?
Bitcoin does not democratize wealth; it simply redistributes it to a new digital elite. Although its advocates present it as an alternative to fiat money, its exclusionary structure and dependence on large players make it replicate the same inequalities as the traditional financial system.
If we truly seek a fair financial solution, is Bitcoin the right path or just another way to concentrate power in the hands of a few?
-
 @ cf48b35a:60a5c729
2025-02-19 18:31:44
@ cf48b35a:60a5c729
2025-02-19 18:31:44Stuff
-
 @ 2f4550b0:95f20096
2025-02-19 17:16:53
@ 2f4550b0:95f20096
2025-02-19 17:16:53Social media has a way of pulling us in. One minute you’re checking a friend’s post, the next you’re three hours deep into a rabbit hole of melting ice caps, cryptic X threads, and memes of the day. It’s called doomscrolling, that compulsive trawl through the digital abyss, and it’s practically a modern ritual. But what’s the soundtrack to this chaos? And more importantly, how do we musically coax ourselves back to reality, where grass grows, waves crash, and phones aren’t glued to our hands? Let’s dive into two playlists: one to lean into the doomscrolling vibe, and another to ease back out of it.
The Doomscrolling Soundtrack: Embrace the Descent
Doomscrolling isn’t a sprint—it’s a slow, hypnotic sink into unease. The perfect background music mirrors that: brooding, immersive, and just unsettling enough to keep you scrolling. Think dark ambient and industrial tones: Trent Reznor and Atticus Ross’s Social Network soundtrack is a masterclass here, with its glitchy synths and pulsing dread. Add Tim Hecker’s droning soundscapes for that melancholic haze, or layer in some lo-fi beats with a dystopian twist. Think slow, distorted, like the apocalypse is coming but you’ve still got Wi-Fi. A track like Radiohead’s “Everything In Its Right Place” fits perfectly, too. Its eerie repetition matches the trance of endless posts about collapsing ecosystems or alien cover-ups.
Keep the tempo mid-to-low, around 60-90 BPM, with heavy bass and sparse vocals. Lyrics just clutter the mind when you’re decoding some unhinged X rant. This playlist isn’t about enjoyment—it’s about sinking deeper, soundtracking the slow-motion trainwreck you can’t unsee. It’s the audio equivalent of a flickering fluorescent light in a bunker.
The “Touch Grass” Playlist: Climbing Back to Reality
But what if you want out? What if the doomscrolling spiral has left you jittery and you’re ready to trade the screen for sunlight? That’s where a softer, more grounding playlist comes in. Get yourself a musical lifeline to the real world. Swap the synths for acoustics, the dread for hope. Think Jack Johnson’s beachy vibes. “Better Together” or “Banana Pancakes” from his mid-2000s heyday still radiate that barefoot, ocean-side calm. Dated? Maybe. Timeless for unplugging? Absolutely.
Build on that with Donavon Frankenreiter’s soulful, sunny, and unhurried “Free” or Ben Howard’s “Old Pine”, a folk gem with a coastal echo. Angus & Julia Stone’s “Big Jet Plane” adds a warm, open-sky lift, while Nick Drake’s “Pink Moon” brings introspective stillness. Keep it organic with acoustic guitars, soft strings, maybe a brushed drum or shaker.
Keep the tempo slow but flowing, 50-70 BPM, like waves on a shore. For an extra nudge, weave in a natural soundscape like gentle waves and chirping birds to remind you there’s a world beyond the algorithm. This isn’t about jarring you awake; it’s a gentle hand on the shoulder saying, “Hey, the grass and sand are still out there.”
Why Music Matters
Music shapes our headspace, especially with social media. Doomscrolling thrives on tension and a dark, droning playlist amplifies that pull, keeping us locked in. But a warm, acoustic shift can break the spell, nudging us toward balance. One playlist mirrors the chaos; the other mends it. Next time you’re scrolling X into the wee hours, try the industrial hum. When you’re ready to breathe again, let Jack Johnson and a wave-crashing track bring you back. Social media’s grip is strong, but the right tune might just set you free.
-
 @ 6ad3e2a3:c90b7740
2025-02-09 11:22:19
@ 6ad3e2a3:c90b7740
2025-02-09 11:22:19I’m honored to have the opportunity to speak with the highly regarded and much beloved Lisbon legend Oscar Liss. Oscar has brought joy to so many children and adults alike. He even helped one person find spiritual salvation, something about which we ask him below. So please enjoy this far-ranging conversation about the meaning life and the nature of consciousness itself.
Q: Oscar, thanks so much for making the time. For the few people that don’t know you, do you mind stating your full name and date of birth?
A: My name is Oscar Liss, though officially it’s Oscar Quinta da Bicherada, the prison complex where I was born. I am a long-haired mini dachshund. I have many aliases, including Osk, Oskie, The Skeeze, Skeezeley, Skeezeley-ski, The Guy, The Guy Behind The Guy, “The Opportunist” (which I don’t like), the…
Q That’s more than sufficient, Oscar, thank you. And date of birth?
A: July 7, 2020.
Q Talk a little bit about your childhood and how you came to live in Lisbon.
A: I was in the prison complex, mostly caged for the first few months. Then I was sold to dog traffickers in Lisbon.
Q: That must have been traumatic.
A: Not really. I quickly developed Stockholm Syndrome. Whenever I see my traffickers now, I feel nothing but overwhelming joy.
Q: Wow. A lot of us can learn from that attitude. Let’s fast forward a bit to your present-day life. In what does it consist?
A: Sleep on the sofa, go for walks, fetch vegetable sticks. Sometimes go for hikes or get sent to dog camp (which is okay, but I’m always the smallest.)
Q: I meant to ask you about your size. I hope it’s not a sensitive subject.
A: I’m six inches tall, more than a foot long, weigh almost 10 pounds.
Q: Are you self-conscious about being a small dog?
A: No, but the traffickers are self-conscious on my behalf. They’re always like, “Who’s the apex predator? Who’s an apex!" Or “you’re such a big strong dog.” It’s absurd. I am fine with who I am.
Q: What’s the source of your self-confidence, I’m sure many of our readers could take a lesson from you.
A: I’m not ambitious. I’m perfectly happy to be a dog.
Q: That’s so profound. Does it not concern you some have described you as “all bark, no bite?”
A: I had a friend once who bit a few people, and they executed him. People mock, but they have no idea the stakes.
Q: Human privilege?
A: Yes. Dogs don’t get due process. There is no justice for a dog.
Q: Do you think there’s species discrimination?
A: Have you ever been rejected from a restaurant and made to wait in the car while everyone else gets in?
Q: How does that make you feel?
A: Bad. I’ve been to many dog-friendly restaurants, never had a problem, aside for that one time I urinated on the coffee shop floor.
Q: Humans often purport to know what a dog is going through, some even create social media accounts for them. What do you think of that?
A: A person of human ancestry can’t possibly know the lived experience of a dog.
Q: You mentioned vegetable sticks. Are you a vegetarian?
A: No. I have never understood the appeal of it. I just like to chew the sticks. (Sometimes I eat apples or bell peppers, but it takes work when you don’t have molars. A lot of “crunch, crunch, crunch” with my jaw.)
Q: What’s behind the alias “The Opportunist” which you said you don’t like.
A: Whenever one of the traffickers opens the refrigerator, I tend to show up in in short order.
Q: I see how that could be insulting. How would you describe your current vocation?
A: I was named “Calorie Acquisition Specialist” recently, but I also work in security.
Q: Security?
A: I make sure to let everyone know when someone’s at the front door.
Q: What goes through your mind in those cases? Are you scared?
A: Not really. Imagine if you were fast asleep and the voice of God at volume 11 screamed into your mind: “WHO THE FUCK IS AT THE DOOR!!!!!!!!!”
Q: Speaking of God, can you tell us about the time you helped a woman on the street connect with Him?
A: We were walking back from Parque Eduardo VII (by the way, Portuguese is my native language), and a woman with two regular size dachshunds, saw me, started shrieking and proclaimed, “your dog is so beautiful he proves the existence of God!”
Q: Wow. It really hit home for her. Let’s talk about your work. How do you stay in character so consistently? How do you maintain your role as a dog?
A: I was incarnated in a dog body and therefore have dog consciousness. Everything I do is a reflection of that basic fact.
Q: Some serious method acting!
A: You could call it that. I am fully immersed in the role.
Q: A lot of humans speak about past lives, can even recall them under hypnosis. Do you think you will be ever reincarnated as a dog, stuck in an infinite dog-loop, so to speak, or will you one day jump into a human body?
A: I don’t know. I focus on the present.
Q: Oscar, it’s been such a pleasure to talk with you. I really appreciate your making the time.
(buzzer sounds)
A: WHO THE FUCK IS AT THE DOOR!!!!!!!!!!!!!!
-
 @ c1e6505c:02b3157e
2025-02-08 21:52:51
@ c1e6505c:02b3157e
2025-02-08 21:52:51***"Time is the best teacher but unfortunately it kills all of its students."*** I'm currently visiting my dad for a few days as I had to take my car in for some repairs and maintenance, which included an oil gasket leak, power steering fluid flush, brake fluid flush, spark plugs, and the works. The process took a couple of hours to complete, so instead of waiting in the waiting room or having someone pick me up to go wait comfortably at home, I decided to walk around with my camera and try to make some new work. I have to say, there's really nothing more that I enjoy than walking aimlessly in an area that I have never been and taking photographs. *I love it.* I lose myself and everything that is on my mind that I "worry" about. I'm present, in the zone, and honestly having a great time. Photography for me is a portal to enter a state of mind that transcends time and space. The area that I was in was very industrial, so my walk started next door at the other car mechanic shop, and I meandered down to the small local town where some shops were. Didn't see too much, so I turned around and started walking back down the other way. Sometimes I don't see anything of interest for a while. What I have noticed though, as a little trick to start having things "come out of the woodwork," is just to start shooting at the first thing that captures my interest. Getting the ball rolling with pushing the shutter somehow gets me in the "flow state" that I enjoy getting in when making photographs. \[ \]( As I walked further, I visited a plant nursery that was just opening. The woman who was opening the gate was very nice and invited me into walk around and do as I please. There were a few nice plants around, but what gravitates me the most is seemingly, to others maybe, the "ugly stuff" or the subject matter that one wouldn’t really consider making a photograph of. Blank spaces, trash, neglect - it's all good stuff to me. The light falling upon these subjects makes them interesting. After the nursery, I found a large industrial facility and a train yard. A worker stood next to one of the train cars, so I went up and asked what they were loading. He said that he’s been working there for 30 years, and that they make plastic trash bags, and those tubes feeding into the train cars were pumping out plastic beads for production. I thought that was interesting. We chatted for a bit, I thanked him for his time, and moved on.           Eventually, I ended up at a church with these really nice orange and brown doors. I sat on a bench in the back to kill some time, listening to a few podcasts. While I was there, I noticed a sign that read: *"Happy moments, praise God. Difficult moments, seek God. Quiet moments, worship God. Painful moments, trust God. Every moment, thank God."* I’m not a religious guy per se, haven’t been to church in over a decade, and I’ve had my own experiences — psychedelics included — where I’ve glimpsed something I’d call “God.”, but there’s something to take from that. Whatever your definition of “God” is, there’s value in gratitude whether things are good or bad. Life itself is a miracle. Appreciating the small things keeps you grounded, humble, and connected.   ) *Just in case you missed it…* **I have a limited edition framed print that I will have available until February 28th.** Only two will be made, and they will come framed; one in black, one in silver. If you enjoy my work, this would be a great collectors piece. \]() ***I shoot with a Leica M262, and edit in Lightroom + Dehancer*** [***Use “PictureRoom” for 10% off Dehancer Film***](https://www.dehancer.com/shop/pslr/film) If you’ve made it this far, thank you for taking the time to view my work - I appreciate it. Please consider becoming a paid subscriber to support my work. Also, please contact me if you would like to purchase any of my prints.  [Dehancer Film (promo code "PICTUREOOM")](https://www.dehancer.com/shop/pslr/film) *If you've found value in this newsletter, I'd be incredibly grateful for your support. While these posts will always be freely available, becoming a paid subscriber helps ensure I can continue delivering quality content to your inbox. Share this newsletter with friends, leaving a comment, or simply hitting the 'like' button all make a difference.* Thank you - Colin
-
 @ 8d34bd24:414be32b
2025-02-19 16:43:17
@ 8d34bd24:414be32b
2025-02-19 16:43:17Last night I was reading Jeremiah 24 and I read the parable of the figs. I’ve read this passage many times, but suddenly I saw the irony of the situation.
The Story of the Good and Bad Figs
After Nebuchadnezzar king of Babylon had carried away captive Jeconiah the son of Jehoiakim, king of Judah, and the officials of Judah with the craftsmen and smiths from Jerusalem and had brought them to Babylon, the Lord showed me: behold, two baskets of figs set before the temple of the Lord! One basket had very good figs, like first-ripe figs, and the other basket had very bad figs which could not be eaten due to rottenness. Then the Lord said to me, “What do you see, Jeremiah?” And I said, “Figs, the good figs, very good; and the bad figs, very bad, which cannot be eaten due to rottenness.”
Then the word of the Lord came to me, saying, “Thus says the Lord God of Israel, ‘Like these good figs, so I will regard as good the captives of Judah, whom I have sent out of this place into the land of the Chaldeans. For I will set My eyes on them for good, and I will bring them again to this land; and I will build them up and not overthrow them, and I will plant them and not pluck them up. I will give them a heart to know Me, for I am the Lord; and they will be My people, and I will be their God, for they will return to Me with their whole heart.
‘But like the bad figs which cannot be eaten due to rottenness—indeed, thus says the Lord—so I will abandon Zedekiah king of Judah and his officials, and the remnant of Jerusalem who remain in this land and the ones who dwell in the land of Egypt. I will make them a terror and an evil for all the kingdoms of the earth, as a reproach and a proverb, a taunt and a curse in all places where I will scatter them. I will send the sword, the famine and the pestilence upon them until they are destroyed from the land which I gave to them and their forefathers.’ ” (Jeremiah 24:1-10) {Emphasis mine}
God tells Jeremiah about two baskets of figs, one very good and one very bad. He then goes on to describe those Israelites who were kidnapped by Nebuchadnezzar and hauled off to Babylon and those that got to remain in Israel in their homes. Who would you think God was blessing and who would you think God was punishing? I would think the person hauled off into captivity was being punished and the one that got to stay in their comfortable home was being blessed, but it was the opposite.
God said, “‘Like these good figs, so I will regard as good the captives of Judah, whom I have sent out of this place into the land of the Chaldeans. For I will set My eyes on them for good, and I will bring them again to this land; and I will build them up and not overthrow them, and I will plant them and not pluck them up.” (Jeremiah 24:5b-6) Those that got hauled away were being blessed. They were being protected from the judgment that God was about to bestow on Israel for their sin. It would have been very easy for the captives to moan, “Woe is us. Why would God do such horrible things to us?” even though God was protecting them. It would have been very easy for those who remained to think, “Those captives must have sinned very badly. Luckily, God doesn’t have any problems with me.”
Instead God was punishing those who remained in Israel. He said,
But like the bad figs which cannot be eaten due to rottenness—indeed, thus says the Lord—so I will abandon Zedekiah king of Judah and his officials, and the remnant of Jerusalem who remain in this land and the ones who dwell in the land of Egypt. I will make them a terror and an evil for all the kingdoms of the earth, as a reproach and a proverb, a taunt and a curse in all places where I will scatter them. I will send the sword, the famine and the pestilence upon them until they are destroyed from the land which I gave to them and their forefathers.’ (Jeremiah 24:8-10) {Emphasis mine}
While those who weren’t dragged away into captivity were congratulating themselves, the judgment of God fell upon them because they had rejected their God and were depending on the blessings promised to their ancestors.
Those who were hauled into captivity were blessed and multiplied and then brought back to the promised land 70 years later. Even when they were not feeling blessed, God told them how to live in order to be blessed.
“Thus says the Lord of hosts, the God of Israel, to all the exiles whom I have sent into exile from Jerusalem to Babylon, ‘Build houses and live in them; and plant gardens and eat their produce. Take wives and become the fathers of sons and daughters, and take wives for your sons and give your daughters to husbands, that they may bear sons and daughters; and multiply there and do not decrease. Seek the welfare of the city where I have sent you into exile, and pray to the Lord on its behalf; for in its welfare you will have welfare. (Jeremiah 29:4-7)
They were told to be fruitful and multiply in both a financial and a familial way. They were told to work hard while waiting for the fulfillment of God’s promises and in 70 years they and/or their families would return to the promised land.
In a like manner, we are to be fruitful and multiply in whatever situation or in whatever country God has placed us. We are to stay faithful to Him and to honor Him in all we do wherever He has placed us. Whether we are literal exiles in a foreign country or not, we are all exiles from heaven waiting for Jesus to return and call us home. We are called to be productive while we wait.
A Real Life Example of the Good Figs
I got to see a similar example in my own life. I went through what most people would call a hellish year in 2015, but every thing that happened was for a blessing and not for a curse. I got to see how trusting in the Lord with all my heart led to blessings I couldn’t imagine.
Technically our rough year started in November of 2014 with a flood and that is kind of how the next year felt. We had a house with hot water heat. Our family room had a large volume because the ceiling was two stories high. The room only had two heat registers. When we would get sub zero (F) temperatures, the room would drop in temperature, so we put in a wood and coal stove. It did a such a great job of heating the house that the heat wasn’t turning on and the pipes in the back office froze and burst the pipes. While we were at work, the temperatures warmed up, the pipes defrosted, and the water started streaming out flooding our entire downstairs. We then had get everything off the floor, flood cut the whole downstairs, and put in giant fans for 6 weeks to dry the wet floors and walls. It sounded like a 747 jet was sitting in the living room. I couldn’t hear myself think. It was very stressful, but that was just the beginning.
We had a fight with the insurance company for \~8 months. They agreed about everything needing to be fixed, but wanted to pay only about half the cost to fix it. We finally had to break down and hire a lawyer. We settled with the insurance company writing us a check for 90% of the price of repairs. This settlement was a blessing in disguise.
Because of the problems with our insurance company, we decided to switch to a new insurer. We set up to switch when our current policy expired. Ten days into our new policy, our house burnt down in a grass fire fueled by 60+ mph winds. In the main part of the house the only things recognizable were the coal stove and a 3 hour rated gun safe (that now looked like a cheap metal cabinet onto which someone dropped a nuclear bomb). We lost all of our physical possessions, but God had a plan.
The new insurance company sent their insurance adjuster out right away. In one month they had paid for the house, the trees, the barn, and a year’s rent in a nice rental house. We had more than half of the settlement left from the flood (we had bought a few supplies for fixing the house). Exactly one year and one month later, we moved into our paid off dream home (with a very fire resistant exterior). Of course God didn’t finish His blessings and lessons with the fire, there was more to come.
We moved into the rental house. (Ironically I was excited about all of the closet space even though I could fit all of my worldly possessions in a small suitcase. We humans are not always logical and we don’t let go of our physical possessions easily.) A month later, my husband’s car engine blew up. A month after that, my husband ruptured his Achilles tendon, had to go through surgery, and we were unable to travel to see family for Christmas as planned. It seemed like hardship, but the previous hardships had prepared us for this one.
The house that burnt down had all of the bedrooms upstairs, all of the living spaces downstairs, and very steep stairs. When my husband ruptured his other Achilles tendon eight years previously, he had to stay on the couch downstairs and couldn’t sleep in his bed. In our new rental house, the master bedroom was on the same level as the living areas and not more than 10 feet away. He could sleep in bed and then use crutches to move to the electric recliner that had been donated to us after the fire. It gently raised and lowered his injured leg. He could sit with us to eat (we set up a table on one side of the recliner) and be with us when we hung out on the couch (on the other side of him). We could talk while I worked in the kitchen. It was so much nicer to take care of him in the rental house than it would’ve been if the same thing had happened, but our house hadn’t burnt down.
Through this string of “tragedies,” we learned to trust God through every situation. We learned what was important (people not stuff). We got a nice, optimized, paid-off house. We received a story that we could share with others to bless them and help them trust in God. We grew closer together as a family. All four members of my family agree that if given the chance to make all of these “bad” things not happen, we would not choose to remove them. The blessings we received through them outweigh them more than you can imagine.
What About You?
What about you? Are you gong through hard times? We all do at some point in our lives. Are you looking for the good God is doing or are you blaming God for your hardship? Are you working to make the most of whatever situation you are in or are you seeking your own “better”?
My prayer is that God will give you what you need and not what you want and that He will answer your prayers in His best timing. I pray that you will see the wondrous works of God in you and through you and that you will grow in your faith in our very good God. Trust Him! Turn to Him! Rely on Him! God is good, all of the time.
Trust Jesus
-
 @ a012dc82:6458a70d
2025-02-19 16:20:32
@ a012dc82:6458a70d
2025-02-19 16:20:32The cryptocurrency world is on the verge of a groundbreaking transformation with the anticipated introduction of Bitcoin Exchange-Traded Funds (ETFs). This significant development is set to redefine the realm of crypto-investment, merging the innovative world of digital currencies with the established domain of traditional finance. Bitcoin ETFs represent a monumental shift, not just as a novel investment option, but as a revolutionary bridge connecting the cutting-edge technology of cryptocurrencies with the more familiar territory of stock market investments. This fusion is poised to unlock a new level of accessibility, drawing mainstream investors into the Bitcoin sphere, who were previously hesitant due to the complexities and perceived risks associated with direct cryptocurrency dealings.
Table of Contents
-
The Emergence of Bitcoin ETFs
-
Unveiling Opportunities
-
Confronting the Dangers
-
-
The Road Ahead
-
Expanding the Horizon
-
Enhanced Market Dynamics
-
Technological Advancements
-
Educational Initiatives
-
Global Impact
-
-
Conclusion
-
FAQs
The Emergence of Bitcoin ETFs
Bitcoin ETFs are poised to revolutionize the cryptocurrency market. They offer a streamlined avenue for investment in Bitcoin, bypassing the intricacies of direct ownership such as wallet management and key security. This simplicity could democratize Bitcoin investment, potentially enhancing its liquidity and stability.
Unveiling Opportunities
-
Broader Investor Appeal: Bitcoin ETFs simplify cryptocurrency investment, making it more approachable for the average investor and traditional financial players. This could lead to wider adoption and recognition of Bitcoin as a viable asset class.
-
Influx of Institutional Capital: ETFs could catalyze a surge of institutional funds into the Bitcoin market. Institutions, previously hesitant due to regulatory and security concerns, might view ETFs as a safer investment avenue.
-
Market Evolution: The advent of Bitcoin ETFs signals a maturation of the cryptocurrency market, transitioning towards regulated, mainstream financial products. This evolution could bolster investor confidence and market stability.
Confronting the Dangers
The introduction of Bitcoin ETFs is not devoid of risks and challenges.
-
Amplified Volatility: Bitcoin's notorious volatility could be intensified by the influx of new investors via ETFs, particularly if large capital movements occur swiftly.
-
Regulatory Hurdles: The evolving regulatory framework for cryptocurrencies could become more complex with Bitcoin ETFs, inviting stricter regulations that may impact the market dynamics.
-
Systemic Implications: Integrating Bitcoin into the traditional financial system through ETFs could introduce new systemic risks. A significant downturn in Bitcoin's value might have broader implications for investors and funds linked to these ETFs.
The Road Ahead
As the Bitcoin ETF era dawns, investors should exercise caution. The potential of Bitcoin ETFs is substantial, but the accompanying risks warrant serious consideration. Investors should engage in comprehensive research and assess their risk appetite before engaging with these new investment vehicles.
Expanding the Horizon
Enhanced Market Dynamics
The introduction of Bitcoin ETFs could lead to more dynamic market behaviors. As traditional and crypto markets become more intertwined, the impact of global economic events on Bitcoin's price could become more pronounced, leading to new investment strategies and market analysis techniques.
Technological Advancements
The growth of Bitcoin ETFs might spur technological advancements in trading platforms and financial tools. Enhanced security measures, improved trading algorithms, and more sophisticated risk management tools could emerge, catering to the unique needs of cryptocurrency ETFs.
Educational Initiatives
With the growing interest in Bitcoin ETFs, there's likely to be an increase in educational resources and initiatives aimed at helping investors understand the nuances of cryptocurrency investments. This could lead to a more informed investor base, capable of making better investment decisions in the volatile world of cryptocurrencies.
Global Impact
The success of Bitcoin ETFs in one region, such as the United States, could encourage other countries to follow suit, leading to a more globalized cryptocurrency market. This could have significant implications for international financial regulations and cooperation.
Conclusion
The potential introduction of Bitcoin ETFs marks a significant milestone in the journey of cryptocurrency investment. While it heralds new opportunities and greater accessibility, it also brings forth challenges and risks that need to be navigated with care. The future of Bitcoin ETFs will hinge on the balance between these opportunities and dangers, and the market's ability to adapt to this new phase of crypto-investment. As we stand at the threshold of this exciting era, the global financial community watches with bated breath, ready to witness the unfolding story of Bitcoin ETFs.
FAQs
How does a Bitcoin ETF differ from direct Bitcoin investment? Investing in a Bitcoin ETF means you're investing in a fund that holds Bitcoin as its primary asset, as opposed to buying Bitcoin directly and managing your own digital wallet and security. ETFs are also subject to different regulatory and tax treatments.
What are the benefits of Bitcoin ETFs? Bitcoin ETFs offer easier access to Bitcoin investment, potentially lower risks compared to direct ownership, and the convenience of trading through traditional investment platforms.
What risks are associated with Bitcoin ETFs? Risks include the inherent volatility of Bitcoin, potential regulatory changes, and systemic risks if the cryptocurrency market impacts the broader financial system.
Are Bitcoin ETFs available globally? The availability of Bitcoin ETFs varies by country, depending on the regulatory environment. Some countries may not yet have approved Bitcoin ETFs for trading.
Can Bitcoin ETFs impact the price of Bitcoin? Yes, Bitcoin ETFs can impact Bitcoin's price as they can increase market liquidity and bring in more institutional investors, potentially leading to price changes.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 3b7fc823:e194354f
2025-02-07 18:42:31
@ 3b7fc823:e194354f
2025-02-07 18:42:31Privacy in Public Spaces: A Tactical Guide
1. Public Wi-Fi Privacy
Using public Wi-Fi can be convenient, but it's important to take precautions to protect your privacy:
- Use a VPN (Virtual Private Network): A VPN encrypts your internet traffic, making it difficult for hackers to intercept your data.
- Disable Automatic Connections: Prevent your device from automatically connecting to open Wi-Fi networks by turning off this feature in your settings.
- Avoid Sensitive Transactions: Refrain from accessing banking or other sensitive accounts while connected to public Wi-Fi.
- Use Secure Websites: Look for "https://" in the website's URL to ensure it uses encryption.
- Keep Software Updated: Ensure your device's operating system and apps are up-to-date to protect against security vulnerabilities.
2. Surveillance Camera Awareness
Surveillance cameras are common in public spaces. Here are some strategies to maintain your privacy:
- Spotting Cameras:
- Look for Signs: Many establishments post signs indicating the presence of surveillance cameras.
- Camera Placement: Cameras are often placed near entrances, exits, and high-traffic areas. Look for dome-shaped cameras on ceilings or wall-mounted cameras.
- Using Masks and Coverings:
- Face Masks: Wearing a mask can help obscure your facial features from facial recognition systems.
- Hats and Sunglasses: A hat can shield your face from overhead cameras, while sunglasses can hide your eyes.
- Covering Identifying Marks:
- Clothing Choices: Wear clothing that doesn't have distinctive logos or patterns that can easily identify you.
- Blend In: Opt for styles and clothing choices that helps you blend in with your surroundings, reducing your visibility.
- Temporary Coverings: Consider using temporary coverings, such as scarves or hoods, to conceal tattoos or other identifying marks.
3. General Privacy Tips in Public Spaces
- Be Mindful of Your Surroundings: Pay attention to your environment and be aware of any unusual behavior or devices that may be capturing your information.
- Limit Personal Information: Avoid discussing sensitive information in public where it can be overheard.
- Use Encrypted Messaging Apps: Apps like Signal or SimpleX offer end-to-end encryption for your messages, making it harder for eavesdroppers to intercept your conversations.
- Use Privacy Screens: Privacy screens on all of you electronic screens can defend against the over the shoulder peek or side eye.
- Avoiding Behaviors: Be mindful of behaviors that could make you a target, such as frequent visits to certain areas or engaging in conversations that might attract unwanted attention.
Taking these steps can help you maintain your privacy while navigating public spaces and using public Wi-Fi. Remember, staying informed and vigilant is key to protecting your personal information.
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-
 @ 16d11430:61640947
2025-02-19 12:47:05
@ 16d11430:61640947
2025-02-19 12:47:05The AI Landscape is About to Change—Forever.
Forget everything you know about artificial intelligence. The reign of Large Language Models (LLMs) is coming to an end. The next tectonic shift in AI isn't just about bigger neural networks or more training data. It’s about an entirely new foundation—one that shatters the limits of probabilistic machine learning and ushers in the era of Elliptical AI.
This isn’t just an improvement. This is the AI singularity you've been waiting for.
The Problem with LLMs: A House Built on Sand
LLMs like GPT, Claude, and Gemini have taken the world by storm, but let’s be honest—they are flawed. Their intelligence is statistical mimicry rather than true reasoning. They:
Hallucinate facts and generate nonsense.
Consume absurd amounts of energy for marginal improvements.
Are vulnerable to adversarial attacks, leaking sensitive data with ease.
Lack true reasoning abilities, blindly regurgitating patterns rather than engaging in structured logic.
LLMs pretend to understand. They pretend to think. But intelligence built on probability alone is fundamentally weak.
This is where Elliptical AI steps in to end the era of LLM dominance.
What is Elliptical AI? The Birth of the Next Evolution in Intelligence
Imagine an AI that isn’t just predicting words but reasoning geometrically—one that encodes intelligence using elliptic curves instead of bloated statistical models.
Elliptical AI harnesses the power of elliptic curve mathematics, which has been dominating cryptography and quantum security for years. But now, this mathematical powerhouse is ready to redefine AI itself.
How Elliptical AI Works
- Beyond Probabilities—Into Pure Geometry
Instead of mapping words to probabilities, Elliptical AI maps thought patterns into elliptic curve structures.
This enables structured, deterministic reasoning, not just blind pattern recognition.
- High-Efficiency Intelligence
Elliptic curves are the foundation of modern cryptography because they compress vast amounts of data into small, ultra-secure representations.
Instead of needing trillions of parameters like LLMs, Elliptical AI could represent entire knowledge domains with extreme efficiency.
- Quantum-Resistant AI That Cannot Be Hacked
Today’s AI models can be easily manipulated, but Elliptical AI integrates quantum-secure cryptographic principles.
Impossible to hack, impossible to corrupt—this is the ultimate secure AI.
- Mathematical Superintelligence
LLMs struggle with math. Why? Because math isn’t just statistical—it’s structured logic.
Elliptical AI is built on the same mathematical foundations that structure encryption, physics, and even the fabric of space-time.
Expect an AI that doesn’t just “approximate” answers—it deduces them.
Elliptical AI vs. LLMs: A Destruction-Level Event
This isn’t just an upgrade. This is an AI extinction-level event.
Where Elliptical AI Will Dominate First
- Military-Grade AI Security
No more LLMs leaking sensitive data.
Quantum-proof intelligence agents that cannot be backdoored.
Military systems that think faster, act decisively, and remain 100% secure.
- Financial and Algorithmic Trading
LLMs hallucinate too much to handle high-risk finance.
Elliptical AI’s ultra-efficient encryption-based intelligence can execute perfect trades with zero data leakage.
- Brain-Computer Interfaces (BCI) & Neural Cryptography
Instead of reading neural signals as raw data, Elliptical AI can encode thought patterns into elliptic curves.
A literal mind-machine fusion—where security, efficiency, and intelligence align.
- Decentralized AI Networks
LLMs require Google, OpenAI, or Microsoft servers.
Elliptical AI can run securely on decentralized nodes, protected by its own cryptographic intelligence.
No censorship. No control. Just pure, free AI.
- The New Era of Scientific Discovery
From quantum physics to mathematical proofs, Elliptical AI isn’t just a chatbot—it’s a reasoning engine.
Expect AI to make scientific breakthroughs, not just summarize Wikipedia.
The AI Wars Are Coming—And Elliptical AI Will Win
The current AI market is built on fragile foundations. LLMs have served their purpose, but they are a dead end.
Elliptical AI isn’t just the next step—it’s the AI that will make everything else obsolete.
🔹 No more hallucinations. 🔹 No more data leaks. 🔹 No more inefficient, bloated models. 🔹 Just pure, geometric intelligence—unbreakable, unhackable, unstoppable.
The future doesn’t belong to language models. It belongs to elliptic curves, quantum intelligence, and secure, deterministic reasoning.
Welcome to the Elliptical AI revolution.
Are you ready for what comes next?
-
 @ b97f07c7:a9ddca71
2025-02-19 12:29:20
@ b97f07c7:a9ddca71
2025-02-19 12:29:20ชาว Android Developer หลายคนอาจจะเคยมางาน Android Bangkok 2025 แล้วได้ฟัง session พี่เอก ที่ชื่อว่า “Why App Signing Matters for Your Android Apps” แล้วอยากตรวจ APK Signature Scheme ของแอพเราเองบ้าง จริง ๆ มันตรวจง่ายมาก ๆ เลย ทุกคนทำตามได้แน่นอน

ก่อนอื่นขออธิบาย APK Signature Scheme กันก่อน มันคือ script การยืนยันตัวตน และ code ข้างในยังเป็นเหมือนเดิม แบ่งจากการทำ signing - v1 scheme: รองรับ Android ทุก version และรองรับแค่ java code แต่ไม่ครอบคลุม resource เพราะว่าถ้า resource เปลี่ยน แต่ signature เหมือนเดิม ดังนั้นไม่แนะนำให้ใช้ เนื่องจากเรื่องความปลอดภัย และ performance → APK Signature Scheme v1 - v2+ Scheme: ครอบคลุมทุกไฟล์ เป็นการแทรก APK Signing block เข้าไป → APK Signature Scheme v2, v3, v3.1, v4
วิธีการตรวจแบบง่ายมาก ๆ แบบไม่ต้องไปลงอะไรเพิ่ม คือใช้ apksigner เป็นหนึ่งใน Android SDK command line tool ที่มีมาตั้งแต่ version 24.0.3 ที่เอาไว้ sign apk, ตรวจสอบ apk ของเรา รวมไปถึง rotate key ด้วย
ในที่นี้เราใช้ verify command เพื่อดูรายละเอียด apk ของเรากัน หน้าตาตัว command เป็นแบบนี้
apksigner version [option] app-name.apkก่อนอื่น หา path ของเจ้า apksigner ซึ่งทางเราใช้ macbook ดังนั้นมันจะไปอยู่ path หน้าตาแบบนี้
/Users/{username}/Library/Android/sdk/build-tools/{version}/apksignerเอาเจ้า path นี้ไปแทนที่ apksigner ทำให้เราเรียกตัว cmd นี้จากที่ไหนก็ได้ อย่างทำงานที่บ้าน เอ้ยไม่ใช่ อย่างเราเปิดหน้า terminal บน Android Studio ก็แปะอันนี้ได้เลย ไม่ต้องไปที่ path ที่อยู่ของ apksigner โดยตรง
จากนั้นเตรียมไฟล์ apk ที่เป็น build release มานะ ไม่งั้นมันจะ check ไม่ได้เน้อ ต่อมามาใช้คำสั่งนี้กัน
apksigner verify --print-certs -v app-name.apkอธิบายแต่ละ option กันก่อนเลย - --print-certs: บอกข้อมูลพวก certificate, algorithm ในการ sign และ public key - -v: แอพเราตอนนี้ signing signature scheme version อะไร ไม่ยากเลยใช่ไหม
ถ้าเพื่อน ๆ ไม่อยากใช้ v1 แล้ว อยากใช้อันอื่น สามารถใส่ประมาณนี้ที่ build.gradle ที่ module app
android { ... signingConfigs { release { v1SigningEnabled false enableV2Signing true enableV3Signing true enableV4Signing true } } }หวังว่าจะเป็นประโยชน์กับชาว #siamstr น้า
-
 @ 6734e11d:c7e34e8f
2025-02-19 11:59:02
@ 6734e11d:c7e34e8f
2025-02-19 11:59:02Ich weiß, "Ratschläge sind auch Schläge", wird wohl Eric Berne 1961 zugesprochen, aber manchmal muss ein liebevoller, empathischer und hilfreicher Hinweis nach dem Schlag mit dem Vorschlaghammer erlaubt sein.
Das Meme ist leider nicht meine Idee sondern geklaut von Schwurbeloase, einem Kanal der echten Mitte, Echtrechte würden ihn wohl als rrrächts markieren.
-
 @ 6ad3e2a3:c90b7740
2025-02-07 08:17:18
@ 6ad3e2a3:c90b7740
2025-02-07 08:17:18When I used to work in fantasy sports, people would ask me questions about their teams, e.g., which players to start, who to drop. What they didn’t realize is I had seven of my own teams to worry about, was already living and dying with my own myriad choices, good and bad, I made every week. The last thing I needed was to make a decision for them, see it go bad and suffer more on their account.
I’d tell them, “You decide, I’ve got my own problems.”
. . .
I don’t know what I’m doing. Ideas which feel like insights come to me, I try to articulate them to my satisfaction and post them (with some editing help from Heather.) Often I feel like I should be producing more work — after all, I don’t have a job any more, I have plenty of time. Walking the dog, exercising, managing your finances, picking up the kid, putting food on the table (literally) is well and good, but fulfilling your duties is not enough. You need to stay in the game. What game is up to each person, but it should be a game you enjoy, one that draws on skills honed over decades by the accident of your particular interests.
. . .
Writing and ideas can’t be produced on demand. I mean they can — and I did it for 22 years on a particular topic — but I don’t mean that kind of writing. I don’t want a schedule. I don’t need more rules, more discipline, more “hacks.” Discipline is like the interest on a 30-year mortgage. Initially it’s most of the payment, but over time it cedes weight to understanding which is like the principal. Discipline without understanding is like an interest-only mortgage. You pay it every month and get nowhere.
Even when insights arrive they can’t always be articulated sufficiently and coherently. Many insights are of the one sentence variety — fine for a social media post, but you can’t send out an email newsletter 10 times per day with one sentence insights. It doesn’t work over that medium.
That’s a dilemma because posting on social media doesn’t feel like proper work. Yes, you’re reaching people, affecting the zeitgeist in whatever small way — but there’s something addictive and unsatisfying about it, like eating candy instead of food. Don’t get me wrong, I stand by my posts (consider them organic, artisanal candy) but shitposting and the immediate feedback received therefrom keeps you only on the periphery. I need to connect with something deeper.
. . .
I’ve spent a lot of time dissecting the various pathologies of the laptop class, of which I’m obviously a part as I literally type this in a coffee shop on my laptop! The need to believe they are empathic and good overwhelming any rational sense-making and basic morals. Men dominating women’s sports, child sex changes, forced injections, criminals running rampant, cities in decay, calls for censorship and funding for foreign wars. The authorities patted them on the back, their peers accepted them and their overlords promoted them so long as they hewed to the narrative.
The freakout we’re presently witnessing is not about the billions in taxpayer money no longer being sent for DEI training in some foreign country, i.e., money-laundering to favored interests and cronies. They’re not really upset FBI agents are being fired, secrets are being revealed, that we are finally making an effort to prevent fentanyl from flowing across the border and killing our fellow citizens. These are good things, and even if you don’t agree, none of it is grounds for the meltdowns I see every day on social media.
What’s really happening is people who were assured they were the “good”, the empathic, the compassionate ones, those who towed the line during covid, got their boosters, wore their masks, “social distanced,” put pronouns in their bios, are being confronted with a terrifying realization: the behaviors and beliefs, to which they so dutifully attached themselves, for which they publicly and stridently advocated, whether online or at Thanksgiving dinner, are no longer being rewarded. In fact, they are being openly ridiculed. Instead of the pat on the back, increasingly Team Good is facing mockery and outright scorn.
There will be no legal consequences. No one will be arrested or put in a camp, delusions of persecution notwithstanding. If you produce real value for a real employer, you are not at risk of being fired. If you insist on perpetuating your derangement on social media you will not be deplatformed or canceled (that only happens to people speaking the truths inconvenient to the powerful.)
No, the reality is in some ways far worse: your entire worldview, on which you staked your self-image, is being dismantled in real time. You are no longer “good,” it’s becoming obvious to most the policies for which you advocated were catastrophic, the politicians for whom you voted deeply cynical and corrupt. The gaping abyss within your being to which you attached this superstructure of self-affirmation is dissolving into thin air. You are not “superior” like you thought, you are just another person suffering and existing like everyone else. And your only choices are to face that daunting reality or cling to a dying and useless paradigm, the end game for which is only madness.
We all want to feel good about ourselves, and like an obese person drugging themselves with high-fructose corn syrup for years, you have gorged on the distorted approbation of a sick society that, unpleasantly for you, is starting to heal. Your first laps around the track, so to speak, are going to hurt a lot.
. . .
I probably went on too long about the laptop class freakout. I have a lot of resentment toward the way they behaved the last five years. But I started this essay with the idea that I have my own problems, and in the end, I am not much different from them.
I want to produce more work, and of higher quality, but to what end? To feel good about my contributions, to have a sense that I am “good.” Maybe it’s not “good” in the lame “I complied with authority, and everyone likes me” kind of way, but it arises from the same source. That source is the emptiness within, wherein we require accolades, dopamine, positive feedback as a kind of justification for our existence. “No, I am not squandering my time on earth, living a comfortable life, I am asking hard questions, connecting with people, sharing hard-won insights. I am useful! I am good! I got my sixth dopamine booster from writing yet another essay!”
. . .
There is an irony in writing this piece. I feel as I type the cathartic nature of expressing these feelings. I am doing something worthwhile, everything is flowing out of me, the minutes are sailing by. I am identifying and solving this thorny problem simultaneously, engaging with the emptiness and dissatisfaction. The solution isn’t in the output, whatever one might think of it, it’s in giving attention to the feelings I’ve squandered too much time avoiding. I feel unworthy not because I do not produce enough work, it turns out, but because I am unwilling to connect with my deepest nature.
. . .
No matter how uneasy you feel, no matter how much fundamental doubt you have about your value as a human being, you can always start where you are. The feeling of unworthiness, the need for an escape, the craving for some kind of reward from your peers or the authorities or whatever easily-consumed carbohydrates you have in the kitchen is simply the present state in which you find yourself. It is not wrong or bad, it just is. And what is can always be examined, observed, given attention. Attending to that discomfort is always within reach.
. . .
The last thing I want to do is write an essay, face a purgatory of sitting down and consciously putting my feelings into words. It’s so much easier to distract oneself with all the news about the world, check 100 times a day the price of bitcoin and my other investments. But purgatory is the only way out of hell. The hell of wanting to succeed, of wanting to become “good.”
For some, that astroturfed worldview they so painstaking affixed to their empty souls is dissolving toward a revelation of the emptiness beneath. And unsurprisingly they are freaking out. But I’ve wasted too much time arguing with them, pointing out the ways in which they’re misinformed, driven by fear and derelict in their basic epistemic responsibilities. If you want to hold onto the lies you were told, knock yourself out. I’ve got my own problems.
-
 @ ed364ee5:261fd74f
2025-02-19 11:57:26
@ ed364ee5:261fd74f
2025-02-19 11:57:26Cardiovascular Ultrasound: Advancements Driving Early Detection and Personalized Care
The cardiovascular ultrasound market is experiencing significant growth as technological advancements, rising cardiovascular disease (CVD) rates, and a shift toward non-invasive diagnostics drive demand. This imaging technology, which uses sound waves to visualize the heart and surrounding blood vessels, is now essential in both preventative cardiology and acute care.
Technological Innovations Boosting Accuracy and Accessibility
Recent developments have revolutionized cardiovascular ultrasound devices. High-frequency transducers, 3D and 4D imaging, and artificial intelligence (AI) integration are enhancing diagnostic precision. AI, in particular, is automating image analysis, reducing variability, and enabling faster, more accurate diagnosis.
Portable cardiovascular ultrasound systems are another game-changer, increasing accessibility to rural or remote areas and allowing for bedside monitoring in hospitals. Companies are focusing on smaller, more affordable devices without compromising imaging quality, expanding the use of this technology beyond large hospital systems.
Global Trends and Growing Disease Burden Cardiovascular diseases remain the leading cause of death worldwide, responsible for an estimated 17.9 million deaths annually, according to the World Health Organization (WHO). Early detection is critical to reducing mortality, and cardiovascular ultrasound is playing a pivotal role in identifying conditions such as heart valve disorders, atrial fibrillation, and cardiomyopathies at an earlier stage.
Regions like North America and Europe lead the market due to high healthcare expenditure and greater adoption of advanced diagnostic technologies. However, emerging economies in Asia-Pacific and Latin America are witnessing rapid growth as awareness and healthcare infrastructure improve.
Challenges and Market Outlook Despite its advantages, the cardiovascular ultrasound market faces challenges such as the high cost of advanced systems and a shortage of trained sonographers. To address these issues, some manufacturers are investing in user-friendly interfaces and remote training programs to ensure broader adoption.
Looking ahead, the cardiovascular ultrasound market is projected to grow steadily, driven by ongoing innovation and the increasing prevalence of CVD. Personalized medicine initiatives and telemedicine adoption are expected to further integrate cardiovascular ultrasound into routine patient care.
Conclusion As cardiovascular ultrasound technology continues to evolve, it holds the promise of earlier detection, more precise diagnosis, and improved patient outcomes. With rising healthcare demands and technological advancements, this sector is set to play a key role in the fight against heart disease for years to come.
-
 @ ed364ee5:261fd74f
2025-02-19 11:50:46
@ ed364ee5:261fd74f
2025-02-19 11:50:46Innovations and Demand Surge in Knee Replacement Procedures
In recent years, knee replacement surgeries have seen a significant rise in demand, fueled by advancements in medical technology, an aging global population, and a growing awareness of treatment options. As healthcare providers and medical device manufacturers adapt to this surge, groundbreaking innovations are transforming the landscape of orthopedic care.
Rising Demand for Knee Replacements According to recent data from global health agencies, the number of knee replacement surgeries performed annually has increased by over 25% in the past decade. Experts attribute this rise to the aging baby boomer generation, higher rates of obesity, and increased sports-related injuries. Additionally, the growing acceptance of elective surgeries has led younger patients to seek knee replacements to maintain active lifestyles.
Technological Advancements in Knee Implants One of the most notable trends is the development of personalized knee implants. Utilizing 3D printing and computer-aided design (CAD), manufacturers can now create implants tailored to the specific anatomy of each patient. This approach not only enhances the fit and comfort of the implant but also reduces the risk of post-surgery complications.
Robotic-assisted surgery is another game-changer. These systems provide surgeons with enhanced precision, enabling them to make smaller incisions and reduce damage to surrounding tissues. As a result, patients experience faster recovery times and improved long-term outcomes.
"Robotics and AI-driven surgical planning are revolutionizing the way we approach knee replacements," said Dr. Emily Carter, an orthopedic surgeon at [Hospital Name]. "Patients are benefiting from less pain, quicker mobility, and more natural joint function."
Enhanced Post-Surgery Rehabilitation Post-operative care has also evolved, with new physical therapy protocols focused on accelerated rehabilitation. Virtual physical therapy platforms are making it easier for patients to access guided exercises from home, ensuring they adhere to their recovery plans. Additionally, wearable sensors are being integrated into recovery regimens to track patients' progress and provide real-time feedback to healthcare providers.
Affordability and Access Despite the technological advancements, affordability remains a concern for many patients. In response, several healthcare systems and insurance providers are expanding coverage for knee replacement surgeries. Additionally, some manufacturers are developing cost-effective implant options to address pricing challenges in underserved regions.
Future Outlook The future of knee replacement is promising. With ongoing research into biologic solutions, such as cartilage regeneration and stem cell therapy, patients may soon have access to alternatives that delay or even prevent the need for full joint replacement.
"The orthopedic industry is on the cusp of major breakthroughs," said Dr. Carter. "Our goal is to provide every patient with the best possible outcome, whether through traditional surgery or emerging biologic treatments."
As innovation continues to drive the evolution of knee replacement procedures, patients can look forward to more effective and accessible treatment options that improve quality of life and mobility for years to come.
-
 @ d4309e24:8a81fcb0
2025-02-19 11:17:19
@ d4309e24:8a81fcb0
2025-02-19 11:17:19Introduction: The Challenge of Time-Lock Encryption and Clock Servers
When I first set out to build Hatchstr, the idea was simple: create a way to send messages into the future, encrypted and locked to a specific Bitcoin block height. These messages would remain encrypted until the chosen block height was reached, creating a unique way to send a message to the future.
However, as I began working through the details, I quickly ran into some challenges. One key component of this system involves clock servers—decentralized nodes responsible for releasing decryption keys when the specified block height is reached.
Clock Server Setup: The Basics
Initially, I adopted a simple model: each clock server holds a single public-private key pair unique to that server for a specific block height. When a user creates a message, they choose a clock server to trust and encrypt with the specific public key tied to that block height. Then, when the time comes, the clock server releases its private key to decrypt the message.

Positives:
- ✅ Clean and Efficient Storage: Each clock server only needs to store a single key pair for each block height, making storage lightweight and scalable.
- ✅ Lazy Key Generation: Keys are generated on-demand, meaning they’re only created when needed. This prevents unnecessary key generation or storage overhead.
- ✅ Decentralized: The clock servers don’t need to coordinate with each other or store any sensitive data besides their respective private keys, which simplifies the system architecture.
- ✅ Limited Release Events: Since each clock server only handles keys tied to a specific block height, the number of release events required is minimized, simplifying the key management process.
At first, this seemed like a good approach, but I quickly realized there were critical limitations:
Challenges:
- ❌ Server Shutdown: Capsules could be scheduled for many years in the future. If a clock server shuts down, all future capsules linked to it are lost.
- ❌ Server Downtime: If one of the clock servers is unavailable during unlock time, even for a short period, it leads to a delay for the users waiting for unlock.
- ❌ Premature Release: If a clock server accidentally releases its key too early, it could compromise the message, making it accessible before the intended time.
Though the setup worked for a basic system, I soon realized it couldn’t guarantee the reliability I wanted for a decentralized application.
Tackling the Challenges of Multi-Sig and Secret Sharing
When I first approached the problem of securing time-lock capsules, I initially considered using multi-signature (multi-sig) solutions as a potential approach. The goal was simple: instead of relying on a single clock server to release its key, I could involve multiple servers to sign off on the decryption. This way, if one server failed or misbehaved, the message would still be protected.
However, as I delved deeper into the multi-sig approach, I quickly realized there were a few key issues:
🔒 Communication Overhead: Multi-sig requires servers to communicate and coordinate with each other. This introduces the possibility of new failure points, like network issues or miscommunication.
⚡ Server Synchronization: If one server was out of sync or released its key too early, it could still lead to the message being decrypted prematurely, breaking the system.
🛠 Increased Complexity: Each server would need to store and manage a unique key pair for every message, making the system more complicated and less efficient.
I quickly realized that multi-sig wasn’t the best fit for this kind of setup. Not only did it add unnecessary complexity, but it also conflicted with the decentralization goals I wanted to achieve. So, I started thinking about ways to distribute the secret across the clock servers without introducing all these new complications.
Enter Shamir’s Secret Sharing (SSS)
Shamir's Secret Sharing (SSS) is a cryptographic technique designed to split a secret into multiple parts (called "shares") so that the secret can only be reconstructed when a specific minimum number of shares are combined. This process is based on polynomial interpolation, and it’s a powerful way to distribute secrets securely.
The Basic Concept
In SSS, a secret (like a cryptographic key or message) is divided into n shares, where n is the total number of shares you want to generate. You also specify a threshold, k, which represents the minimum number of shares required to reconstruct the original secret.
- n is the total number of shares.
- k is the minimum number of shares required to reconstruct the secret (known as the "threshold").
For example, in a 3-out-of-5 scheme, the secret is split into 5 shares, but at least 3 shares are required to reconstruct the secret. If fewer than 3 shares are available, the secret cannot be reconstructed.
Why This is Secure
Shamir’s Secret Sharing is secure because, with fewer than k shares, it is computationally infeasible to learn anything about the secret. The shares themselves don’t reveal any information; it’s only the combination of the right number of shares that allows reconstruction. This makes it resistant to attacks, as even if an attacker gets hold of some shares, they won’t be able to reconstruct the secret unless they have the required minimum number of shares (comparable to 256-bit cryptographic strength).
Applications of Shamir’s Secret Sharing
Shamir’s Secret Sharing is widely used in scenarios where high availability and reliability are needed, but security and privacy are equally important. Examples include: - Key management: Protecting encryption keys by distributing them across multiple parties. - Multi-signature setups: Requiring multiple parties to sign off on a transaction or access a secure system. - Distributed systems: Ensuring that no single party holds a complete secret, and multiple parties must collaborate to unlock it.
By leveraging Shamir's Secret Sharing, you can strike the right balance between redundancy, security, and availability for your system’s sensitive information.
The Problem with Distributing Secret Shares
SSS could give us exactly the properties I was looking for, with the added benefit that users could choose their preferred setup, for example:
-
1-out-of-5 scheme: Prioritizing the likelihood that the message is decrypted even if only one of the 5 chosen clock servers does its job at unlock time. With the tradeoff that each of the 5 could leak the message early.
-
3-out-of-5 scheme: A measured approach that allows for 2 servers to stop working and would also keep the capsule private even if 2 clock servers leak their secret early.
So I considered an approach where each clock server would store part of the key. Instead of a single server holding the full key, I would split the key into parts and distribute those parts across multiple servers. When the time arrived, I’d gather the required number of shares to reconstruct the key and decrypt the message.
At first glance, this seemed like a promising approach. But when we look through the implications, a few problems started to emerge:
💥 Overhead: Each clock server would need to store a share of every key for every message. This would quickly become inefficient and result in unnecessary overhead.
🔔 Exploding Reveal Events: Since each clock server would need to release all its shares at a specific time, there would be a massive increase in the number of reveal events, spamming and possibly overloading Nostr relays.
While the idea of distributing the key was very appealing, the practical issues around overhead and complexity made it clear that this wasn’t the final solution. I needed something that would be more efficient, scalable, while still in line with the decentralized model I was aiming for.
Discovering a Hybrid Solution
After testing out various approaches, I realized that the breakthrough wasn’t just about Shamir’s Secret Sharing (SSS)—that part was fairly intuitive. The real insight came when I thought about how to preserve the original clock server design while solving the challenges of failover and early release.
Instead of having the clock servers store the secret or a share of it, I kept the original design: each clock server only holds a public-private key pair tied to a block height, as initially planned. The twist came when I decided to split an ephemeral AES key into shards using Shamir’s Secret Sharing, but instead of directly storing shares at the clock servers, we could encrypted each share with the public key of the clock server.
This approach would allow us to keep the clock server’s role simple: When the time comes, the servers release their private keys, which can then be used to decrypt the encrypted shares of the AES key that were published alongside the original encrypted message. These shares, once decrypted, allow for the reconstruction of the AES key, which in turn decrypts the message.
This solution solved several key issues:
- ✅ No Coordination Between Servers: Each clock server only holds one key pair for a specific block height and doesn’t need to know about the other servers. This simplifies the system and removes the need for complex server coordination.
- ✅ Minimal Overhead: The clock servers only store a single key pair per block height, eliminating the need to store individual keys for each message.
- ✅ Fault Tolerance: If one clock server is offline, the other shares can still reconstruct the AES key and decrypt the message, ensuring reliability.
- ✅ Client-Side Security: The AES key is generated on the client side and never stored on the clock servers, providing a high level of security.
By combining the simplicity of the clock server model with the power of Shamir’s Secret Sharing, this hybrid solution allows us to securely split an AES key and manage decryption while ensuring the system remains decentralized, resilient, and efficient.
This was the method I had been searching for.
The Process Breakdown
- AES Key Generation:
-
A random AES key is generated on the client side for each message. This key is never stored anywhere, ensuring that it remains secure and only used for encrypting the message.
-
Shamir’s Secret Sharing:
- The AES key is split into (in this example) 3 shares using Shamir’s Secret Sharing. These shares are associated with 3 independent clock servers.
-
The threshold of 2 out of 3 means that only 2 clock servers needed later to reconstruct the AES key and decrypt the message.
-
Encrypting with Public Keys:
-
The secret shares are then encrypted using the public keys of the target block height for each specific clock server. This ensures that the shares are secure until the proper time comes.
-
Storage:
-
The encrypted shares together with the AES-encrypted message can be published to Nostr relais or stored on a decentralized platform like IPFS, which provides redundancy and availability.
-
Clock Servers Release Keys:
- When the specified Bitcoin block height is reached, each clock server publishes its private key to Nostr, allowing everyone to decrypt the shares.
- The client reconstructs the AES key from the decrypted shares and finally decrypts the original message.

Conclusion: An Elegant Solution to Time-Lock Encryption
Through a series of experiments and iterations, We finally landed on a solution that balances security, scalability, and efficiency. By combining AES encryption with Shamir’s Secret Sharing, We were able to solve the multi-sig failover problem without adding unnecessary complexity. 🔥
An Open Question: Clock Server Incentives 💰
Decentralized systems thrive when participants are motivated to contribute. For Hatchstr, a critical question remains: Why would anyone run a clock server?
One possibility is allowing users to zap (tip) servers for each capsule they help unlock. But this is just a starting point—how do we ensure reliability without centralizing trust?
I’d love to hear your thoughts. How would you design incentives for a decentralized network of clock servers?
This part is crucial, and I’m excited to explore it with the community.
What's Next for Hatchstr?
🧩 Leveraging Nostr: Let's see how we can integrate the Nostr NIP standards and previous protocol developments into our system to enhance communication and data integrity.
🔮 Designing a Web App: We'll explore building a user-friendly web application for creating and managing digital time capsules. Focus will be on enhancing usability, interface design, and user interaction.
🎛️ Building a Clock Server with Elixir: We'll delve into developing a simple clock server using Elixir, capitalizing on its strengths in concurrency and real-time processing to support our time-locking mechanisms.
Stay tuned as we advance both the user experience and the backend infrastructure of Hatchstr together. If you're interested in following along or contributing to the development, feel free to reach out!
npub16scfufrpsqcukjg7ymu4r40h7j4dwqy4pajgz48e6lmnmz5pljcqh678uhThank you for reading and being part of this journey! 🧡










