-
 @ 3b7fc823:e194354f
2025-02-10 17:34:18
@ 3b7fc823:e194354f
2025-02-10 17:34:18Dealing with law enforcement can be a challenging and stressful experience. However, understanding your rights and knowing how to navigate such situations can empower you to protect yourself. Here’s a structured approach to handle these interactions effectively:
- Stay Calm and Compliant:
-
When approached by law enforcement, remain calm and avoid sudden movements. Slowly raise your hands and identify yourself if possible.
-
Ask for Identification:
-
Request the officer's name, badge number, and station. This documentation can be crucial later on.
-
Know Your Miranda Rights:
-
Upon arrest, you have the right to remain silent. Do not answer questions without consulting a lawyer. If Mirandized, exercise your right to remain silent.
-
Refuse Incriminating Statements:
-
Avoid answering questions that could incriminate yourself. Politely state, "I will not answer any questions at this time."
-
Document the Incident:
-
Use your phone or notebook to record details such as dates, times, and descriptions of interactions. Note any injuries or mistreatment.
-
Seek Legal Advice:
-
After the encounter, contact a lawyer. They can review evidence and provide guidance on how to proceed.
-
Understand Search and Seizure Laws:
-
Officers generally need a warrant to search your property unless there's probable cause. If stopped without a warrant, calmly refuse entry.
-
Use a Body Camera Policy:
-
If applicable, ask for the officer's body camera footage and request it via formal complaint if refused.
-
Know When to Comply:
-
Comply with instructions that do not infringe on your rights, such as providing identification when legally required.
-
Consider a Witness Statement:
- If you witness illegal actions, consider reporting them. Your role as a bystander may be crucial in documenting incidents.
-
Seek Emotional Support:
- Interactions with law enforcement can be traumatic. Reach out to support groups or mental health resources for assistance.
-
Understand Legal Recourse:
- If rights are violated, consult legal aid societies or civil rights organizations for guidance on filing complaints or seeking redress.
Conclusion: Understanding your rights and documenting interactions is essential when dealing with law enforcement. This guide provides a framework to help you navigate such situations confidently and protect your rights effectively. Remember, knowledge is power, and being informed can lead to better outcomes in challenging circumstances.
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-
 @ ec42c765:328c0600
2025-02-05 23:45:09
@ ec42c765:328c0600
2025-02-05 23:45:09test
test
-
 @ ec42c765:328c0600
2025-02-05 23:43:35
@ ec42c765:328c0600
2025-02-05 23:43:35test
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ ec42c765:328c0600
2025-02-05 23:38:12
@ ec42c765:328c0600
2025-02-05 23:38:12カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

カスタム絵文字の対応状況(2025/02/06)

カスタム絵文字を使うためにはカスタム絵文字に対応したクライアントを使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
対応クライアント
ここではnostterを使って説明していきます。
準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
右上のGet startedからNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。

- 右側のOptionsからBookmarkを選択

これでカスタム絵文字を使用するためのリストに登録できます。
カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
文章中に使用
- 投稿ボタンを押して投稿ウィンドウを表示
- 顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択
- : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

リアクションに使用
- 任意の投稿の顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

カスタム絵文字を探す
先述したemojitoからカスタム絵文字を探せます。
例えば任意のユーザーのページ emojito ロクヨウ から探したり、 emojito Browse all からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2025/02/06)
※漏れがあるかもしれません
各絵文字セットにあるOpen in emojitoのリンクからemojitoに飛び、使用リストに追加できます。
以上です。
次:Nostrのカスタム絵文字の作り方
Yakihonneリンク Nostrのカスタム絵文字の作り方
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
仕様
-
 @ ec42c765:328c0600
2025-02-05 23:16:35
@ ec42c765:328c0600
2025-02-05 23:16:35てすと
nostr:nevent1qqst3uqlls4yr9vys4dza2sgjle3ly37trck7jgdmtr23uuz52usjrqqqnjgr
nostr:nevent1qqsdvchy5d27zt3z05rr3q6vvmzgslslxwu0p4dfkvxwhmvxldn9djguvagp2
test
てs
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ dc4cd086:cee77c06
2025-02-09 03:35:25
@ dc4cd086:cee77c06
2025-02-09 03:35:25Have you ever wanted to learn from lengthy educational videos but found it challenging to navigate through hours of content? Our new tool addresses this problem by transforming long-form video lectures into easily digestible, searchable content.
Key Features:
Video Processing:
- Automatically downloads YouTube videos, transcripts, and chapter information
- Splits transcripts into sections based on video chapters
Content Summarization:
- Utilizes language models to transform spoken content into clear, readable text
- Formats output in AsciiDoc for improved readability and navigation
- Highlights key terms and concepts with [[term]] notation for potential cross-referencing
Diagram Extraction:
- Analyzes video entropy to identify static diagram/slide sections
- Provides a user-friendly GUI for manual selection of relevant time ranges
- Allows users to pick representative frames from selected ranges
Going Forward:
Currently undergoing a rewrite to improve organization and functionality, but you are welcome to try the current version, though it might not work on every machine. Will support multiple open and closed language models for user choice Free and open-source, allowing for personal customization and integration with various knowledge bases. Just because we might not have it on our official Alexandria knowledge base, you are still welcome to use it on you own personal or community knowledge bases! We want to help find connections between ideas that exist across relays, allowing individuals and groups to mix and match knowledge bases between each other, allowing for any degree of openness you care.
While designed with #Alexandria users in mind, it's available for anyone to use and adapt to their own learning needs.
Screenshots
Frame Selection

This is a screenshot of the frame selection interface. You'll see a signal that represents frame entropy over time. The vertical lines indicate the start and end of a chapter. Within these chapters you can select the frames by clicking and dragging the mouse over the desired range where you think diagram is in that chapter. At the bottom is an option that tells the program to select a specific number of frames from that selection.
Diagram Extraction

This is a screenshot of the diagram extraction interface. For every selection you've made, there will be a set of frames that you can choose from. You can select and deselect as many frames as you'd like to save.
Links
- repo: https://github.com/limina1/video_article_converter
- Nostr Apps 101: https://www.youtube.com/watch?v=Flxa_jkErqE
Output
And now, we have a demonstration of the final result of this tool, with some quick cleaning up. The video we will be using this tool on is titled Nostr Apps 101 by nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 during Nostrasia. The following thread is an analog to the modular articles we are constructing for Alexandria, and I hope it conveys the functionality we want to create in the knowledge space. Note, this tool is the first step! You could use a different prompt that is most appropriate for the specific context of the transcript you are working with, but you can also manually clean up any discrepancies that don't portray the video accurately. You can now view the article on #Alexandria https://next-alexandria.gitcitadel.eu/publication?d=nostr-apps-101
Initially published as chained kind 1's nostr:nevent1qvzqqqqqqypzp5r5hd579v2sszvvzfel677c8dxgxm3skl773sujlsuft64c44ncqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgc7hglpn
Or view on Coracle https://coracle.social /nevent1qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgcppemhxue69uhkummn9ekx7mp0qgsdqa9md83tz5yqnrqjw07hhkpmfjpkuv9hlh5v8yhu8z274w9dv7qnnq0s3
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Músicas grudentas e conversas
Uma vez que você ouviu uma música grudenta e ela volta, inteira, com toda a melodia e a harmonia, muitos dias depois, contra a sua vontade. Mas uma conversa é impossível de lembrar. Por quê?
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Bluesky is a scam
Bluesky advertises itself as an open network, they say people won't lose followers or their identity, they advertise themselves as a protocol ("atproto") and because of that they are tricking a lot of people into using them. These three claims are false.
protocolness
Bluesky is a company. "atproto" is the protocol. Supposedly they are two different things, right? Bluesky just releases software that implements the protocol, but others can also do that, it's open!
And yet, the protocol has an official webpage with a waitlist and a private beta? Why is the protocol advertised as a company product? Because it is. The "protocol" is just a description of whatever the Bluesky app and servers do, it can and does change anytime the Bluesky developers decide they want to change it, and it will keep changing for as long as Bluesky apps and servers control the biggest part of the network.
Oh, so there is the possibility of other players stepping in and then it becomes an actual interoperable open protocol? Yes, but what is the likelihood of that happening? It is very low. No serious competitor is likely to step in and build serious apps using a protocol that is directly controlled by Bluesky. All we will ever see are small "community" apps made by users and small satellite small businesses -- not unlike the people and companies that write plugins, addons and alternative clients for popular third-party centralized platforms.
And last, even if it happens that someone makes an app so good that it displaces the canonical official Bluesky app, then that company may overtake the protocol itself -- not because they're evil, but because there is no way it cannot be like this.
identity
According to their own documentation, the Bluesky people were looking for an identity system that provided global ids, key rotation and human-readable names.
They must have realized that such properties are not possible in an open and decentralized system, but instead of accepting a tradeoff they decided they wanted all their desired features and threw away the "decentralized" part, quite literally and explicitly (although they make sure to hide that piece in the middle of a bunch of code and text that very few will read).
The "DID Placeholder" method they decided to use for their global identities is nothing more than a normal old boring trusted server controlled by Bluesky that keeps track of who is who and can, at all times, decide to ban a person and deprive them from their identity (they dismissively call a "denial of service attack").
They decided to adopt this method as a placeholder until someone else doesn't invent the impossible alternative that would provide all their desired properties in a decentralized manner -- which is nothing more than a very good excuse: "yes, it's not great now, but it will improve!".
openness
Months after launching their product with an aura of decentralization and openness and getting a bunch of people inside that believed, falsely, they were joining an actually open network, Bluesky has decided to publish a part of their idea of how other people will be able to join their open network.
When I first saw their app and how they were very prominently things like follower counts, like counts and other things that are typical of centralized networks and can't be reliable or exact on truly open networks (like Nostr), I asked myself how were they going to do that once they became and open "federated" network as they were expected to be.
Turns out their decentralization plan is to just allow you, as a writer, to host your own posts on "personal data stores", but not really have any control over the distribution of the posts. All posts go through the Bluesky central server, called BGS, and they decide what to do with it. And you, as a reader, doesn't have any control of what you're reading from either, all you can do is connect to the BGS and ask for posts. If the BGS decides to ban, shadow ban, reorder, miscount, hide, deprioritize, trick or maybe even to serve ads, then you are out of luck.
Oh, but anyone can run their own BGS!, they will say. Even in their own blog post announcing the architecture they assert that "it’s a fairly resource-demanding service" and "there may be a few large full-network providers". But I fail to see why even more than one network provider will exist, if Bluesky is already doing that job, and considering the fact there are very little incentives for anyone to switch providers -- because the app does not seem to be at all made to talk to multiple providers, one would have to stop using the reliable, fast and beefy official BGS and start using some half-baked alternative and risk losing access to things.
When asked about the possibility of switching, one of Bluesky overlords said: "it would look something like this: bluesky has gone evil. there's a new alternative called freesky that people are rushing to. I'm switching to freesky".
The quote is very naïve and sounds like something that could be said about Twitter itself: "if Twitter is evil you can just run your own social network". Both are fallacies because they ignore the network-effect and the fact that people will never fully agree that something is "evil". In fact these two are the fundamental reasons why -- for social networks specifically (and not for other things like commerce) -- we need truly open protocols with no owners and no committees.
-
 @ 554ab6fe:c6cbc27e
2025-02-10 16:48:35
@ 554ab6fe:c6cbc27e
2025-02-10 16:48:35René Descartes famously stated, "I think therefore I am." A concept centered around the idea that the existence of our meta-conscious thought proves our existence. Furthermore, it denotes a sense of self-derived from the presence of our thinking. What if this famous idea is wrongly reversed? What if our perceived sense of self derives from our thoughts, and these thoughts act as an illusion of the true nature of the self?
A couple of my posts have focused on the idea that the calm mind, potentially derived from a practice of meditation, can achieve a heightened sense of awareness. Some neuroscientists now view the mind as a predictive modeling machine (Seth, 2013), constantly receiving signals from both internal and external sources, generating predictions and models to understand the current condition. This theory inspired me to create an analogy of a calm pond: Imagine the brain and mind as a pond, and instead of neuronal signals, raindrops are falling into the pond. When the pond is calm, and a single drop falls, the pond's ripples provide adequate information to deduce the location and size of the raindrop. By observing the single ripple, one can simply understand the raindrop. However, if there is a storm and many raindrops impact the pond simultaneously, then the ripples are indistinguishable. This makes the analysis of the incoming information near impossible. This may be how the brain works. This would be why calming the mind generates such benefits in health because the brain can analyze the information accurately and execute the proper response. This idea is supported by scientific evidence that interoception increases with mindfulness practice. I have alluded to this idea as a possible explanation of why meditation generates a higher form of consciousness. More on this later.
To further explore this idea, a deeper exploration into the neuroscience of internal mental processes is required. The areas of the brain that are clinically recognized to perform internal mental operations are known as the default mode network (DMN) (Ekhtiari et al., 2016; van Buuren et al., 2010). The DMN is not a single area of the brain but a network and interaction between many areas. The brain areas involved within the DMN include the medial prefrontal cortex (mPFC), the anterior and posterior cingulate cortex (ACC and PCC), temporoparietal junction (TPJ), later temporal cortex (LTC), and the temporal pole (TempP)(Farb et al., 2007; Zhou et al., 2020). In general, the mental processes conducted by the DMN are self-referential processing, long-term memory retrieval, and mind-wandering (Ekhtiari et al., 2016; Marstaller et al., 2017; Spreng & Grady, 2010; van Buuren et al., 2010). However, the functions expand beyond just those. Different brain areas carry differing roles in these processes. For example, the PCC plays a unique role in the autobiographical retrieval process and plays a role in self-centered spatial navigation (Hamilton et al., 2015). However, sometimes these processes manifest in more complex interactions. For example, both the PCC and anterior portion of the mPFC (amPFC) facilitate self-referential processes and the interaction between other hubs of the DMN (Zhou et al., 2020). The role of the DMN is complicated, but its relationship to meditation is significant.
The DMN's plays a significant role in mental ruminations and the activity of the mind. In our modern culture, mental ruminations are commonplace and widely accepted. With this cultural norm, there is no adequate training to properly handle these thoughts when they become repetitive, unconstructive, and potentially destructive. Repetitive unconstructive ruminations are associated with and can lead to depression (Watkins, 2008). Therefore, this mental habit attributes to a significant source of many mental health issues. It is a primary reason why meditation seems to be such an effective mental health benefiting practice. In Eastern traditions, this unhealthy mind is called the "monkey mind": a mind that swings from thought to thought, often time traveling to the past and future. Meditation, and similar practices, aim to quiet this monkey mind. From a clinical perspective, it is fascinating to consider that the DMN may be a neural network representing the monkey mind's activation. There is research to support this idea as well. Autobiographical memory retrieval processes activate the DMN (Spreng & Grady, 2010). Additionally, the DMN seems to maintain a cohesive perception of the self across time to interpret novel information (Marstaller et al., 2017). Clearly, not only is the DMN involved in processes that involve thoughts about the self, but it is also primarily responsible for our mental time traveling processes. If meditation aims to bring our experience to the present, then the DMN is the antithesis.
As previously stated, mental ruminations and other unconstructive thought patterns drive the development of mental health issues such as anxiety and depression. Given that the DMN has a strong relationship to these thought patterns, it is also interesting to note that DMN activity dominance is associated with the development of depression (Hamilton et al., 2011). The brain areas that seem to be activated more often during depression are the anterior and dorsal regions of the mPFC, PCC, temporal lobes, and the TPJ (Zhou et al., 2020)—further suggesting that the DMN is the brain region highly responsible for our inner self-referential thoughts, our time traveling thoughts, and the subsequent mental health outcomes.
The DMN represents, in large part, the mental activity of the mind that removes us from a calm and present state of being. In other words, it adds more “raindrops” to the calm pond (my analogy from before) making it harder for the brain to analyze and adequately react to incoming information. Evidence for this idea lies in the observation that the DMN is responsible for monkey mind-like processes and in learning and conditioning. Again, the brain is constantly receiving neuronal signals from the body. Say it receives a signal from the toe: it must first predict that the signal came from the toe, then understand what the signal meant, and react accordingly. So, if the signal was a pain signal, the brain may command the toe to lift from the ground. If the signal stops, the brain knows the toe is no longer in pain, verifying the prediction. If the signal doesn't stop, further trial and error are required. This is a simple example, but the brain is likely processing and reacting to signals like this all the time, both from information coming from outside the body and within. Therefore, much learning and prediction model generation is taking place. Imagine the famous experiment of Pavlov's dogs. The dogs learned that a particular cue meant food, and their bodies learned to react accordingly. This learning and conditioning are a fundamental aspect of biological life. The DMN plays a significant role in this learning within our brain. For example, the PCC responds to error detection, and the signal is amplified when small rewards or novel stimuli are introduced to the experience (Heilbronner & Platt, 2013). Areas of the DMN (such as the mPFC and PCC) are also thought to be involved in contextualizing memories of safety and inhibit fear responses when appropriate (Marstaller et al., 2017). Finally, the mPFC is thought to play a role in goal-directed motivation (Hamilton et al., 2015). All this evidence suggests that the DMN plays a significant role in the learning process by contextualizing information.
Keep in mind that the DMN can only accurately contextualize incoming stimuli if the full range of signals is adequately recognized. According to the calm pond idea, the noisy activation of a ruminating mind may hinder this ability. Here, greater clarification and definition on what a polluted mind means is needed. To define such mental patterns, functions of specific DMN regions will be explained. Commonly activated regions within the DMN that involve self-referential processes are (Farb et al., 2007; Knyazev, 2013):
- The orbitomedial prefrontal cortex (omPFC) – which contextualizes experienced stimuli as experienced by the self
- The ACC – which actively monitors the self-experienced stimuli
- The mPFC – which evaluates the self-experienced stimuli
- The PCC – which is involved in a generated a broader context of the personal experience given certain self-experienced stimuli.
By now, it may be evident that the DMN is involved with what is commonly referred to as the "ego". Some researchers claim that the DMN develops the ego itself (R. L. Carhart-Harris & Friston, 2010). The term "ego" derives from Freudian psychoanalytic, and for this reason, the term "narrative-self" will be used instead. It is crucial to consider the word choice here. As previously explained, the DMN generates a time-oriented perception of the self to contextualize information. Furthermore, the four brain areas above all involved contextualizing an experience as experienced by the narrative self (rather than the self being the experience), monitoring these experiences across time, and evaluating these experiences as a broader implication of the experience of the self. The DMN is generating a narrative of the self through every experience. This is indeed where many unconstructive ruminations arise. Any reader can likely relate to ruminating over themselves and their circumstances and thinking about what this means in the larger context of their lives, worth, purpose, etc. This is the monkey mind. This is the DMN.
So, the real question becomes: what effect does the strong presence of a narrative-self have on our broader experience and health? Does a strong presence of the narrative-self influence the body's interoceptive abilities and ability to properly analyze and predict incoming stimuli? This is a complex and challenging question, but evidence suggests that this is indeed the case. In a fantastic study by Farb and others in 2007, fMRIs were used to monitor brain activity in those who did and did not practice mindfulness meditation (Farb et al., 2007). In this study, a distinction was made between narrative focus and experiential focus. For eight weeks, those who underwent mindfulness meditation training were taught to practice experiential focus, which involves having present centered awareness of all thoughts, feelings, and experiences in a non-judgmental manner. Narrative focus was defined as judging experiences and trying to figure out what those stimuli meant. Brain scans were performed on both trained and untrained participants during both focus styles. For both groups, narrative focus increased activation of the mPFC and PCC as expected. During experiential focus, both groups reduced mPFC activity, but only the meditation trained group increased activation of the insula. This is incredible because the insula is highly involved in interoception and the sensations of internal physical states (Fox et al., 2014; Mehling et al., 2012). This study by Farb and others suggests a functional difference between the narrative-self and an experiential-self and shows how the quieting of the narrative-self increases interoceptive abilities and enhances the brains' ability to analyze incoming stimuli properly. Not to mention, this study shows how this skill can be trained.
So far, we have seen how the DMN is involved in the generation of the narrative-self and how this influences our ability to analyze the signals coming from the body. The next reasonable question is to what extent can this be changed? And what are the implications of such change? As was previously shown in the mentioning of the study by Farb and others in 2007, mindfulness meditation appears to be capable of changing DMN activity. This is not the only study to suggest this. Another study showed that meditation decreased mPFC activity in DMN regions, such as the TPJ and PCC (Scheibner et al., 2017). It has also been shown that the neurotransmitter GABA reduces DMN activity, and both yoga and meditation have been implicated in the release of GABA (Guglietti et al., 2013; Hu et al., 2013; Streeter et al., 2018). The release of GABA release is also modulated by the vagus nerve, providing evidence of the possible mechanism at which meditation inhibits DMN activity (Hu et al., 2013; Keute et al., 2018; Streeter et al., 2018). Through these studies, it seems evident that meditation decreases DMN activity. In what ways is this significant? Firstly, it provides more explanation as to why meditation seems capable of alleviating depression. Similarly, it offers more evidence for how meditation increases interoceptive awareness (de Jong et al., 2016; Farb et al., 2010; Hanley et al., 2017). The increase in interoception suggests that the brain is more adequately processing not only the internal environment more adequately, but presumably the outside environment as well. Reality in general is being more accurately understood. It is possible that this also implicates a broader understanding of how meditation can alter consciousness and allowing monks, yogis, and the like to achieve nirvana/samadhi/enlightenment, or whatever you prefer to call such a state of altered consciousnesses. Perhaps this experience of altered consciousness is a more accurate interpretation of reality, produced by enhanced interoception and exteroception.
The subject of altered consciousness is perhaps best explored through brain changes induced by another technique commonly used in a spiritual manner: psychedelics. The famous studies from Johns Hopkins University using psilocybin found that this drug causes a spiritual experience often described as a sense of unity of all things that transcend space and time (Griffiths et al., 2006, 2008). Many participants rate this experience as one of the most significant spiritual experiences of their life (Griffiths et al., 2006). These experiences were often described with an experienced loss sense of self and an altered form of consciousness (Griffiths et al., 2008). It is not hard to imagine that this experience seems very similar to that of a trained monk or yogi, who learn to let go of their narrative-self and gain a sense of oneness with all things. This connection is further verified by the observation that psilocybin decreases the activity of the ACC, PCC, and mPFC (Robin L. Carhart-Harris et al., 2012). Ayahuasca, another psychedelic drug used in spiritual rituals by the indigenous peoples of the Amazon, also has been shown to have similar effects (Palhano-Fontes et al., 2015). Additionally, LSD has been shown to do the same (Speth et al., 2016). Suppose both psychedelic drugs and meditative practice decrease the same DMN, which generates the narrative-self. In that case, both methods likely lead one to the same place: an experience beyond time and space, where one is present with a profound sense of unity with everything.
This, to me, is a profound idea. It suggests that quieting the mind, or calming the “pond”, improves mental, physical, and spiritual health. It provides one with a perception full of compassion, peace, and love. It not only can make the individual healthier, but so too the community and planet. It is extraordinary evidence that improving the self is the greatest means of improving the world around us. Not to mention, it provides a simple means of liberating oneself from the struggle and hardship of life. Perhaps it is not life that is hard on us, but ourselves, by allowing the narrative-mind to take hold of our reality, rather than letting a purer form of consciousness dominate our perceptions. This is the pursuit, and meditation techniques are the practice.
References
Carhart-Harris, R. L., & Friston, K. J. (2010). The default-mode, ego-functions and free-energy: A neurobiological account of Freudian ideas. Brain, 133(4), 1265–1283. https://doi.org/10.1093/brain/awq010
Carhart-Harris, Robin L., Erritzoe, D., Williams, T., Stone, J. M., Reed, L. J., Colasanti, A., Tyacke, R. J., Leech, R., Malizia, A. L., Murphy, K., Hobden, P., Evans, J., Feilding, A., Wise, R. G., & Nutt, D. J. (2012). Neural correlates of the psychedelic state as determined by fMRI studies with psilocybin. Proceedings of the National Academy of Sciences of the United States of America, 109(6), 2138–2143. https://doi.org/10.1073/pnas.1119598109
de Jong, M., Lazar, S. W., Hug, K., Mehling, W. E., Hölzel, B. K., Sack, A. T., Peeters, F., Ashih, H., Mischoulon, D., & Gard, T. (2016). Effects of mindfulness-based cognitive therapy on body awareness in patients with chronic pain and comorbid depression. Frontiers in Psychology, 7(JUN). https://doi.org/10.3389/fpsyg.2016.00967
Ekhtiari, H., Nasseri, P., Yavari, F., Mokri, A., & Monterosso, J. (2016). Neuroscience of drug craving for addiction medicine: From circuits to therapies. In Progress in Brain Research (Vol. 223, pp. 115–141). Elsevier B.V. https://doi.org/10.1016/bs.pbr.2015.10.002
Farb, N. A. S., Anderson, A. K., Mayberg, H., Bean, J., McKeon, D., & Segal, Z. v. (2010). Minding One's Emotions: Mindfulness Training Alters the Neural Expression of Sadness. Emotion, 10(1), 25–33. https://doi.org/10.1037/a0017151
Farb, N. A. S., Segal, Z. v., Mayberg, H., Bean, J., Mckeon, D., Fatima, Z., & Anderson, A. K. (2007). Attending to the present: Mindfulness meditation reveals distinct neural modes of self-reference. Social Cognitive and Affective Neuroscience, 2(4), 313–322. https://doi.org/10.1093/scan/nsm030
Fox, K. C. R., Nijeboer, S., Dixon, M. L., Floman, J. L., Ellamil, M., Rumak, S. P., Sedlmeier, P., & Christoff, K. (2014). Is meditation associated with altered brain structure? A systematic review and meta-analysis of morphometric neuroimaging in meditation practitioners. Neuroscience and Biobehavioral Reviews, 43, 48–73. https://doi.org/10.1016/j.neubiorev.2014.03.016
Griffiths, R. R., Richards, W. A., Johnson, M. W., McCann, U. D., & Jesse, R. (2008). Mystical-type experiences occasioned by psilocybin mediate the attribution of personal meaning and spiritual significance 14 months later. Journal of Psychopharmacology, 22(6), 621–632. https://doi.org/10.1177/0269881108094300
Griffiths, R. R., Richards, W. A., McCann, U., & Jesse, R. (2006). Psilocybin can occasion mystical-type experiences having substantial and sustained personal meaning and spiritual significance. Psychopharmacology, 187(3), 268–283. https://doi.org/10.1007/s00213-006-0457-5
Guglietti, C. L., Daskalakis, Z. J., Radhu, N., Fitzgerald, P. B., & Ritvo, P. (2013). Meditation-related increases in GABAB modulated cortical inhibition. Brain Stimulation, 6(3), 397–402. https://doi.org/10.1016/j.brs.2012.08.005
Hamilton, J. P., Farmer, M., Fogelman, P., & Gotlib, I. H. (2015). Depressive Rumination, the Default-Mode Network, and the Dark Matter of Clinical Neuroscience. In Biological Psychiatry (Vol. 78, Issue 4, pp. 224–230). Elsevier USA. https://doi.org/10.1016/j.biopsych.2015.02.020
Hamilton, J. P., Furman, D. J., Chang, C., Thomason, M. E., Dennis, E., & Gotlib, I. H. (2011). Default-mode and task-positive network activity in major depressive disorder: Implications for adaptive and maladaptive rumination. Biological Psychiatry, 70(4), 327–333. https://doi.org/10.1016/j.biopsych.2011.02.003
Hanley, A. W., Mehling, W. E., & Garland, E. L. (2017). Holding the body in mind: Interoceptive awareness, dispositional mindfulness and psychological well-being. Journal of Psychosomatic Research, 99, 13–20. https://doi.org/10.1016/j.jpsychores.2017.05.014
Heilbronner, S. R., & Platt, M. L. (2013). Causal evidence of performance monitoring by neurons in posterior cingulate cortex during learning. Neuron, 80(6), 1384–1391. https://doi.org/10.1016/j.neuron.2013.09.028
Hu, Y., Chen, X., Gu, H., & Yang, Y. (2013). Resting-state glutamate and GABA concentrations predict task-induced deactivation in the default mode network. Journal of Neuroscience, 33(47), 18566–18573. https://doi.org/10.1523/JNEUROSCI.1973-13.2013
Keute, M., Ruhnau, P., Heinze, H. J., & Zaehle, T. (2018). Behavioral and electrophysiological evidence for GABAergic modulation through transcutaneous vagus nerve stimulation. Clinical Neurophysiology, 129(9), 1789–1795. https://doi.org/10.1016/j.clinph.2018.05.026
Knyazev, G. G. (2013). EEG correlates of self-referential processing. Frontiers in Human Neuroscience, 7(MAY), 1–14. https://doi.org/10.3389/fnhum.2013.00264
Marstaller, L., Burianová, H., & Reutens, D. C. (2017). Adaptive contextualization: A new role for the default mode network in affective learning. Human Brain Mapping, 38(2), 1082–1091. https://doi.org/10.1002/hbm.23442
Mehling, W. E., Price, C., Daubenmier, J. J., Acree, M., Bartmess, E., & Stewart, A. (2012). The Multidimensional Assessment of Interoceptive Awareness (MAIA). PLoS ONE, 7(11). https://doi.org/10.1371/journal.pone.0048230
Palhano-Fontes, F., Andrade, K. C., Tofoli, L. F., Jose, A. C. S., Crippa, A. S., Hallak, J. E. C., Ribeiro, S., & de Araujo, D. B. (2015). The psychedelic state induced by Ayahuasca modulates the activity and connectivity of the Default Mode Network. PLoS ONE, 10(2), 1–13. https://doi.org/10.1371/journal.pone.0118143
Scheibner, H. J., Bogler, C., Gleich, T., Haynes, J. D., & Bermpohl, F. (2017). Internal and external attention and the default mode network. NeuroImage, 148(January), 381–389. https://doi.org/10.1016/j.neuroimage.2017.01.044
Seth, A. K. (2013). Interoceptive inference, emotion, and the embodied self. Trends in Cognitive Sciences, 17(11), 565–573. https://doi.org/10.1016/j.tics.2013.09.007
Speth, J., Speth, C., Kaelen, M., Schloerscheidt, A. M., Feilding, A., Nutt, D. J., & Carhart-Harris, R. L. (2016). Decreased mental time travel to the past correlates with default-mode network disintegration under lysergic acid diethylamide. Journal of Psychopharmacology, 30(4), 344–353. https://doi.org/10.1177/0269881116628430
Spreng, R. N., & Grady, C. L. (2010). Patterns of brain activity supporting autobiographical memory, prospection, and theory of mind, and their relationship to the default mode network. Journal of Cognitive Neuroscience, 22(6), 1112–1123. https://doi.org/10.1162/jocn.2009.21282
Streeter, C., Gerbarg, P. L., Nielsen, G. H., Brown, R. P., Jensen, J. E., Silveri, M., & Streeter, C. C. (2018). Effects of Yoga on Thalamic Gamma-Aminobutyric Acid, Mood and Depression: Analysis of Two Randomized Controlled Trials. Neuropsychiatry, 8(6), 1923–1939. https://doi.org/10.4172/Neuropsychiatry.1000535
van Buuren, M., Gladwin, T. E., Zandbelt, B. B., Kahn, R. S., & Vink, M. (2010). Reduced functional coupling in the default-mode network during self-referential processing. Human Brain Mapping, 31(8), 1117–1127. https://doi.org/10.1002/hbm.20920
Watkins, E. R. (2008). Constructive and unconstructive repetitive thought. Psychological Bulletin, 134(2), 163–206. https://doi.org/10.1037/0033-2909.134.2.163
Zhou, H. X., Chen, X., Shen, Y. Q., Li, L., Chen, N. X., Zhu, Z. C., Castellanos, F. X., & Yan, C. G. (2020). Rumination and the default mode network: Meta-analysis of brain imaging studies and implications for depression. In NeuroImage (Vol. 206, p. 116287). Academic Press Inc. https://doi.org/10.1016/j.neuroimage.2019.116287
-
 @ dff95033:862fbf40
2025-02-05 23:19:29
@ dff95033:862fbf40
2025-02-05 23:19:29This event has been deleted; your client is ignoring the delete request.
-
 @ ec42c765:328c0600
2025-02-05 22:05:55
@ ec42c765:328c0600
2025-02-05 22:05:55カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

カスタム絵文字の対応状況(2025/02/06)

カスタム絵文字を使うためにはカスタム絵文字に対応したクライアントを使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
対応クライアント
ここではnostterを使って説明していきます。
準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
右上のGet startedからNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。

- 右側のOptionsからBookmarkを選択

これでカスタム絵文字を使用するためのリストに登録できます。
カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
文章中に使用
- 投稿ボタンを押して投稿ウィンドウを表示
- 顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択
- : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

リアクションに使用
- 任意の投稿の顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

カスタム絵文字を探す
先述したemojitoからカスタム絵文字を探せます。
例えば任意のユーザーのページ emojito ロクヨウ から探したり、 emojito Browse all からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2025/02/06)
※漏れがあるかもしれません
各絵文字セットにあるOpen in emojitoのリンクからemojitoに飛び、使用リストに追加できます。
以上です。
次:Nostrのカスタム絵文字の作り方
Yakihonneリンク Nostrのカスタム絵文字の作り方
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
仕様
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Jofer
Jofer era um jogador diferente. À primeira vista não, parecia igual, um volante combativo, perseguia os atacantes adversários implacavelmente, um bom jogador. Mas não era essa a característica que diferenciava Jofer. Jofer era, digamos, um chutador.
Começou numa semifinal de um torneio de juniores. O time de Jofer precisava do empate e estava sofrendo uma baita pressão do adversário, mas o jogo estava 1 a 1 e parecia que ia ficar assim mesmo, daquele jeito futebolístico que parece, parece mesmo. Só que aos 46 do segundo tempo tomaram um gol espírita, Ruizinho do outro time saiu correndo pela esquerda e, mesmo sendo canhoto, foi cortando para o meio, os zagueiros meio que achando que já tinha acabado mesmo, devia ter só mais aquele lance, o árbitro tinha dado dois minutos, Ruizinho chutou, marcou e o goleiro, que só pulou depois que já tinha visto que não ia ter jeito, ficou xingando.
A bola saiu do meio e tocaram para Jofer, ninguém nem veio marcá-lo, o outro time já estava comemorando, e com razão, o juiz estava de sacanagem em fazer o jogo continuar, já estava tudo acabado mesmo. Mas não, estava certo, mais um minuto de acréscimo, justo. Em um minuto dá pra fazer um gol. Mas como? Jofer pensou nas partidas da NBA em que com alguns centésimos de segundo faltando o armador jogava de qualquer jeito para a cesta e às vezes acertava. De trás do meio de campo, será? Não vou ter nem força pra fazer chegar no gol. Vou virar piada, melhor tocar pro Fumaça ali do lado e a gente perde sem essa humilhação no final. Mas, poxa, e daí? Vou tentar mesmo assim, qualquer coisa eu falo que foi um lançamento e daqui a uns dias todo mundo esquece. Olhou para o próprio pé, virou ele de ladinho, pra fora e depois pra dentro (bom, se eu pegar daqui, direitinho, quem sabe?), jogou a bola pro lado e bateu. A bola subiu escandalosamente, muito alta mesmo, deve ter subido uns 200 metros. Jofer não tinha como ter a menor noção. Depois foi descendo, o goleirão voltando correndo para debaixo da trave e olhando pra bola, foi chegando e pulando já só pra acompanhar, para ver, dependurado no travessão, a bola sair ainda bem alta, ela bateu na rede lateral interna antes de bater no chão, quicar violentamente e estufar a rede no alto do lado direito de quem olhava.
Mas isso tudo foi sonho do Jofer. Sonhou acordado, numa noite em que demorou pra dormir, deitado na sua cama. Ficou pensando se não seria fácil, se ele treinasse bastante, acertar o gol bem de longe, tipo no sonho, e se não dava pra fazer gol assim. No dia seguinte perguntou a Brunildinho, o treinador de goleiros. Era difícil defender essas bolas, ainda mais se elas subissem muito, o goleiro ficava sem perspectiva, o vento alterava a trajetória a cada instante, tinha efeito, ela cairia rápido, mas claro que não valia à pena treinar isso, a chance de acertar o gol era minúscula. Mas Jofer só ia tentar depois que treinasse bastante e comprovasse o que na sua imaginação parecia uma excelente idéia.
Começou a treinar todos os dias. Primeiro escondido, por vergonha dos colegas, chegava um pouco antes e ficava lá, chutando do círculo central. Ao menor sinal de gente se aproximando, parava e ia catar as bolas. Depois, quando começou a acertar, perdeu a vergonha. O pessoal do clube todo achava engraçado quando via Jofer treinando e depois ouvia a explicação da boca de alguém, ninguém levava muito a sério, mas também não achava de todo ridículo. O pessoal ria, mas no fundo torcia praquilo dar certo, mesmo.
Aconteceu que num jogo que não valia muita coisa, empatezinho feio, aos 40 do segundo tempo, a marcação dos adversários já não estava mais pressionando, todo mundo contente com o empate e com vontade de parar de jogar já, o Henrique, meia-esquerdo, humilde, mas ainda assim um pouco intimidante para Jofer (jogava demais), tocou pra ele. Vai lá, tenta sua loucura aí. Assumiu a responsabilidade do nosso volante introspectivo. Seria mais verossímil se Jofer tivesse errado, primeira vez que tentou, restava muito tempo ainda pra ele ter a chance de ser herói, ninguém acerta de primeira, mas ele acertou. Quase como no sonho, Lucas, o goleiro, não esperava, depois que viu o lance, riu-se, adiantou-se para pegar a bola que ele julgava que quicaria na área, mas ela foi mais pra frente, mais e mais, daí Lucas já estava correndo, só que começou a pensar que ela ia pra fora, e ele ia só se dependurar no travessão e fazer seu papel de estar na bola. Acabou que por conta daquele gol eles terminaram em segundo no grupo daquele torneiozinho, ao invés de terceiro, e não fez diferença nenhuma.
-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ 6bae33c8:607272e8
2025-02-10 15:27:25
@ 6bae33c8:607272e8
2025-02-10 15:27:25I didn’t realize how much I had missed a good old fashioned Super Bowl blowout. I wasn’t even gonna bet the game, but over the last couple days, I got an Eagles vibe. There was too much, “The refs won’t let the Chiefs lose”, and Patrick Mahomes and Taylor Swift, and other noise, and yet the line didn’t budge. It was obvious the Eagles were the sharper side, and they had the league’s best defense, which usually correlates to overperformance of the spread in Super Bowls, sometimes massive overperformance.
But it wasn’t any one thing — just an overall dawning on me that the Eagles were probably the right side. I didn’t feel that strongly about it, even so, and decided I’d just bet Saquon Barkley for MVP, get 3:1 or so if the Eagles won. So I texted someone in the states to place the bet for me, and best he could offer was +175! That’s a terrible value for a RB to win MVP! A few minutes later Tim Schuler offered to bet me $50, give me the Eagles +1, and I obliged him. After that, I texted my friend back to put $500 on the Eagles +1 for me.
Of course, I didn’t stay up all night to watch — after losing 1K on the Falcons (who were up 28-3 in the third quarter at 3 am) eight years ago, never again. So I caught the 40-minute version this morning. What a great game! The Eagles dominated from start to finish. The defensive line got after Mahomes on every play. And while the Chiefs sold out to stop Barkley, Jalen Hurts ran wild on them.
I’m sure I would have enjoyed a Chiefs blowout less, but the beauty of a blowout is it settles things. There’s no looking back at a bad call, a dropped pass or a fumble and wondering what might have been. Close games have drama, but they are more or less arbitrary. I mean I get it, the guy made the throw at the time with the game on the line, but maybe also he just got the cheap roughing the passer call or the ticky tack PI. When the Giants won the Super Bowl on Scott Norwood’s miss, I didn’t have the same sense of satisfaction I did when they blew out John Elway’s Broncos five years earlier. Yes, they won, but it might as well have been on a coin flip.
I grew up on blowouts in the ‘80s — Raiders-Redskins, 49ers-Dolphins, Pats-Bears, Giants-Broncos, Redskins-Broncos — only the Bengals managed to keep Super Bowl losses close (Congratulations Jeff Erickson!) This was before replay reviews and all the lawyering about what is and isn’t a completed catch. The last fucking thing you wanted was some controversy about who really outplayed whom. So it was nice to win some easy money and not to have to worry about refs or fumbles or untimely drops for a change.
-
I wanted Saquon to win MVP, but he drew the attention of the KC defense, is one of the best I’ve ever seen in blitz pickup and still had 97 yards from scrimmage. One of the all-time great years from an all-time great back. (He broke Terrell Davis’ record for the most yardage, regular season and playoffs, too, albeit in two extra games.)
-
Hurts threw the one bad pick under pressure, but it served as a good punt, and otherwise had a near perfect game. Only four other incomplete passes, 72 yards and a score on the ground. He was an easy MVP call.
-
I was a little worried about shaky Jake Elliott, but he drilled all four of his field goals, three of them twice!, due to penalties.
-
Patrick Mahomes padded his stats in garbage time, but he got crushed. An elite defense that gets home with four is the way you kill the GOATS. The Giants did it to Tom Brady twice.
-
Xavier Worthy had a nice garbage-time stat-padding game, but he was the only one. DeAndre Hopkins had a bad drop, though they got him a garbage-time feel-good TD, basically a participation trophy.
-
Congrats to Lane Johnson, Brandon Graham, Elliott and long-snapper Rick Lovato — the only four players in NFL history to defeat both Tom Brady and Mahomes in Super Bowls.
-
The only negative is I lost my $50 four-teams bet with Erickson. I had the Chiefs, Bills, Lions and Ravens, he had the field. But I directed Schuler to pay him, which is good, because I cancelled Paypal for their retarded foray into free-speech policing, and now I don’t have to figure out a workaround.
-
-
 @ ec42c765:328c0600
2025-02-05 20:30:46
@ ec42c765:328c0600
2025-02-05 20:30:46カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

カスタム絵文字の対応状況(2024/02/05)

カスタム絵文字を使うためにはカスタム絵文字に対応したクライアントを使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
対応クライアント
ここではnostterを使って説明していきます。
準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
右上のGet startedからNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。

- 右側のOptionsからBookmarkを選択

これでカスタム絵文字を使用するためのリストに登録できます。
カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
文章中に使用
- 投稿ボタンを押して投稿ウィンドウを表示
- 顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択
- : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

リアクションに使用
- 任意の投稿の顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

カスタム絵文字を探す
先述したemojitoからカスタム絵文字を探せます。
例えば任意のユーザーのページ emojito ロクヨウ から探したり、 emojito Browse all からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2024/06/30)
※漏れがあるかもしれません
各絵文字セットにあるOpen in emojitoのリンクからemojitoに飛び、使用リストに追加できます。
以上です。
次:Nostrのカスタム絵文字の作り方
Yakihonneリンク Nostrのカスタム絵文字の作り方
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
仕様
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O caso da Grêmio TV
enquanto vinha se conduzindo pela plataforma superior daquela arena que se pensava totalmente preenchida por adeptos da famosa equipe do Grêmio de Porto Alegre, viu-se, como por obra de algum nigromante - dos muitos que existem e estão a todo momento a fazer más obras e a colocar-se no caminhos dos que procuram, se não fazer o bem acima de todas as coisas, a pelo menos não fazer o mal no curso da realização dos seus interesses -, o discretíssimo jornalista a ser xingado e moído em palavras por uma horda de malandrinos a cinco ou seis passos dele surgida que cantavam e moviam seus braços em movimentos que não se pode classificar senão como bárbaros, e assim cantavam:
Grêmio TV pior que o SBT !
-
 @ 91bea5cd:1df4451c
2025-02-04 17:24:50
@ 91bea5cd:1df4451c
2025-02-04 17:24:50Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Replacing the web with something saner
This is a simplification, but let's say that basically there are just 3 kinds of websites:
- Websites with content: text, images, videos;
- Websites that run full apps that do a ton of interactive stuff;
- Websites with some interactive content that uses JavaScript, or "mini-apps";
In a saner world we would have 3 different ways of serving and using these. 1 would be "the web" (and it was for a while, although I'm not claiming here that the past is always better and wanting to get back to the glorious old days).
1 would stay as "the web", just static sites, styled with CSS, no JavaScript whatsoever, but designers can still thrive and make they look pretty. Or it could also be something like Gemini. Maybe the two protocols could coexist.
2 would be downloadable native apps, much easier to write and maintain for developers (considering that multi-platform and cross-compilation is easy today and getting easier), faster, more polished experience for users, more powerful, integrates better with the computer.
(Remember that since no one would be striving to make the same app run both on browsers and natively no one would have any need for Electron or other inefficient bloated solutions, just pure native UI, like the Telegram app, have you seen that? It's fast.)
But 2 is mostly for apps that people use every day, something like Google Docs, email (although email is also broken technology), Netflix, Twitter, Trello and so on, and all those hundreds of niche SaaS that people pay monthly fees to use, each tailored to a different industry (although most of functions they all implement are the same everywhere). What do we do with dynamic open websites like StackOverflow, for example, where one needs to not only read, but also search and interact in multiple ways? What about that website that asks you a bunch of questions and then discovers the name of the person you're thinking about? What about that mini-app that calculates the hash of your provided content or shrinks your video, or that one that hosts your image without asking any questions?
All these and tons of others would fall into category 3, that of instantly loaded apps that you don't have to install, and yet they run in a sandbox.
The key for making category 3 worth investing time into is coming up with some solid grounds, simple enough that anyone can implement in multiple different ways, but not giving the app too much choices.
Telegram or Discord bots are super powerful platforms that can accomodate most kinds of app in them. They can't beat a native app specifically made with one purpose, but they allow anyone to provide instantly usable apps with very low overhead, and since the experience is so simple, intuitive and fast, users tend to like it and sometimes even pay for their services. There could exist a protocol that brings apps like that to the open world of (I won't say "web") domains and the websockets protocol -- with multiple different clients, each making their own decisions on how to display the content sent by the servers that are powering these apps.
Another idea is that of Alan Kay: to design a nice little OS/virtual machine that can load these apps and run them. Kinda like browsers are today, but providing a more well-thought, native-like experience and framework, but still sandboxed. And I add: abstracting away details about design, content disposition and so on.
These 3 kinds of programs could coexist peacefully. 2 are just standalone programs, they can do anything and each will be its own thing. 1 and 3, however, are still similar to browsers of today in the sense that you need clients to interact with servers and show to the user what they are asking. But by simplifying everything and separating the scopes properly these clients would be easy to write, efficient, small, the environment would be open and the internet would be saved.
See also
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: General confusion
Most IPFS open-source projects, libraries and apps (excluding Ethereum stuff) are things that rely heavily on dynamic data and temporary links. The most common projects you'll see when following the IPFS communities are chat rooms and similar things. I've seen dozens of these chat-rooms. There's also a famous IPFS-powered database. How can you do these things with content-addressing is a mistery. Of course they probably rely on IPNS or other external address system.
There's also a bunch of "file-sharing" on IPFS. The kind of thing people use for temporary making a file available for a third-party. There's image sharing on IPFS, pastebins on IPFS and so on. People don't seem to share the preoccupation with broken links here.
-
 @ 3b7fc823:e194354f
2025-02-10 13:13:25
@ 3b7fc823:e194354f
2025-02-10 13:13:25Alright, let’s get one thing straight: you’re scrolling through your phone, shopping online, maybe even working from home. But here’s the thing – someone might be watching. Not in the creepy stalker way, but in the “is that company really needing my data?” kind of way. That’s where a Virtual Private Network (VPN) comes in, saving you from the prying eyes of marketers, governments, and even your own internet provider.
What Does a VPN Do?
A VPN creates a secure, encrypted connection between your device and a VPN server. This allows you to browse the internet anonymously, keeping your online activities private from your Internet Service Provider (ISP), network administrators, and even hackers. When you connect to a VPN, your internet traffic is routed through an intermediary server, making it difficult for anyone to track your online movements.
Why You Need a VPN: Privacy edition
- Hiding Your IP Address
Every time you jump online, your device gets an IP address, like a digital ID. If you don’t use a VPN, everyone can see this ID, making it easy for advertisers and governments to track your every move.
-
[X ] Myth: A VPN hides my IP address from everyone.
-
[X] Reality: A VPN hides your IP address only from the websites you visit and your ISP. Your internet service provider still knows you're using a VPN, but they won't be able to see what sites you're visiting. Your VPN knows what sites you are visiting and may know who you are as well.
-
Bypassing Censorship
Ever tried accessing something that’s blocked in your country? A VPN can help you bypass those restrictions, letting you watch the latest shows, access social media, or even download books without getting flagged as a troublemaker.
- Protecting Your Data
When you connect to public Wi-Fi – like at a café or airport – you’re basically handing over your data on a silver platter. A VPN encrypts this data, so even if someone intercepts it, they can’t decode it. Think of it as adding an extra layer of security.
- Avoiding Surveillance
Companies and governments love collecting data. From what you search to who you talk to, there’s a lot of stuff that’s none of their business. A VPN ensures that only you know where you’ve been online.
- Safeguarding Your Personal and Professional Life
Whether you’re working from home or just shopping for a present, a VPN keeps your activities private. It’s like having a secure safe for all your online stuff, so no one can snoop.
- Stopping Targeted Ads
Companies track your browsing habits to send you ads that follow you around the internet. A VPN breaks this cycle, making sure those creepy “you might like” ads stop following you around.
- No Logs Policy
Some VPNs keep records of your activity, which means they could be handed over if the government comes knocking. But with a no-logs policy, nothing is stored – they promise ;)
- The Dark Side of Free VPNs
Before you jump into using a free VPN, think twice. Free services often come with a catch: they might sell your data to advertisers or even track your activity themselves. It’s like getting a free hotdog at a gas station – it sounds great, but you’ll probably regret it later.
How to Use a VPN (Because You’re Not a Tech Wizard)
- Choose the Right Provider
Go for a reputable service that offers strong encryption and a no-logs policy. Look for options with a kill switch, which stops any data from being leaked if the connection drops. I prefer ones you can pay annoymously but that may be overkill for most people.
- Download and Install
Once you pick a provider, download the app to your device. It’s not rocket science, but it does require a bit more than just opening an email.
- Set It Up
Most VPNs have user-friendly interfaces. Just click “Connect” and you’re good to go. You might need to enter your login details or use a password from your provider.
The Final Word Using a VPN isn’t about being a hacker or someone with something to hide. It’s about respecting your privacy and having control over what you share online. In today’s world, where companies and governments are constantly getting more creative about how they collect data, it’s practically a requirement if you want to stay ahead of the curve.
So there you have it – the secret life of your internet. With a VPN, you’re not just protecting yourself; you’re making sure that your digital footprint is as small as possible. Whether you’re at home or on the go, a VPN gives you the freedom to surf, shop, and work without anyone watching your every move.
And hey, if you’re still not convinced, just think about it this way: imagine your internet connection as a crowded public space. Without a VPN, everyone’s staring at you. With one, you’re wearing a mask, and no one’s the wiser.
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-
 @ da0b9bc3:4e30a4a9
2025-02-10 12:51:46
@ da0b9bc3:4e30a4a9
2025-02-10 12:51:46Hello Stackers!
It's Monday so we're back doing "Meta Music Mondays" 😉.
From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme.
Welcome to Femmes Fatales 3!!!
I absolutely loved doing this last year so I'm bringing it back for round 3!
It's Femmes Fatales, where we celebrate women in ~Music. So let's have those ladies of the lung, the sirens of sound, our Femmes Fatales!
https://youtu.be/ya69LUa1E_w?si=cM6yCALsPpp9L3Sc
I recently got introduced to these ladies. Their music is fantastic, they're really talented musicians. They are:
Lilith: The vocalist. Lamia: The lead guitarist. Nixe: The bassist. Abrahel: The drummer.
Their identity is meant to be a mystery, so let's keep it that way.
These Nuns can make Noise!!
Let's go!
Talk Music. Share Tracks. Zap Sats.
originally posted at https://stacker.news/items/881416
-
 @ 59cb0748:9602464b
2025-01-01 06:15:09
@ 59cb0748:9602464b
2025-01-01 06:15:09Nostrでお世話になっている方も、お世話になってない方も、こんにちは!
タコ頭大吉です!
NIP-23を使った初めての投稿です。
今回は、私がここ数ヶ月中にデザインをした三種類のビタキセケースの紹介記事になります!!
ビタキセを買ったもののあまり自分の好みに合う外観や仕様のケースがなく、いくつかプロトタイプを作りそれなりに時間をかけて考えたケース達です。
これら3シリーズに関しては、FDMタイプの3Dプリンタの精度、耐久性、出力後の作業性を考慮して一つのパーツで完結することに拘って設計をしました。
一定以上の充填率でプリントをすればそれなりに丈夫なはずです。
また、基本的に放熱性と保護性を両立できるように設計をしたつもります。
それぞれのモデルについて簡単に紹介をさせていただきますので、よろしければ各リポジトリに付属のREADMEを読んでいただいて自作、フィードバックをいただけましたら幸いです。
それでは、簡単に各モデルの紹介をさせていたきます。
AirLiftFrame
 最初に作ったモデルです!
少し大きいのが難点ですが、分厚めのフレームをベースとし基盤周辺をあえて囲わない設計により、保護性と放熱を阻害しない事の両立を狙っています。
最初に作ったモデルです!
少し大きいのが難点ですが、分厚めのフレームをベースとし基盤周辺をあえて囲わない設計により、保護性と放熱を阻害しない事の両立を狙っています。
TwinAirLiftFrame
 ビタキセを買い増ししたことにより、複数台をカッコよく運用したいという需要が自分の中に出てきたので、AirLiftFrameを2つくっつけたら良いのではと言うごくごく単純な発想でつくり始めたケースです。
しかし、ただ横並びにしただけでは廃熱が干渉するだけではなく、DCジャックやUSBポートへのアクセスが阻害されるという問題にすぐに気がつきました。
そこで、WebUI上でディスプレイの表示を上下反転出来ることに注目し、2台を上下逆向きに取り付ける事でそれらの問題を解決しました!
ビタキセを買い増ししたことにより、複数台をカッコよく運用したいという需要が自分の中に出てきたので、AirLiftFrameを2つくっつけたら良いのではと言うごくごく単純な発想でつくり始めたケースです。
しかし、ただ横並びにしただけでは廃熱が干渉するだけではなく、DCジャックやUSBポートへのアクセスが阻害されるという問題にすぐに気がつきました。
そこで、WebUI上でディスプレイの表示を上下反転出来ることに注目し、2台を上下逆向きに取り付ける事でそれらの問題を解決しました!
VoronoiShell
 AirLiftFrameシリーズのサイズを小型化する事から始めたプロジョクトです。
縦横の寸法の削減だけではなく、厚みを薄くつくリたいという希望がありました。
所が単純に薄くすると、持った時に発熱する背面パーツに手が触れてしまったり、落下などでぶつかった際に背面パーツが破損する懸念がありました。
そこで、(当初は付けたくはなかった)背面保護用のグリルをデザインする必要が出てきました。
初めは多角形でしたがあまりにもダサく、調べている内にVoronoi柄という有機的なパターンに行き付き即採用しました。
結果、ビタキセを取り付けると柄が見えなくなるのが勿体無いぐらい個性的でスタイリッシュなデザインに仕上がりました。
AirLiftFrameシリーズのサイズを小型化する事から始めたプロジョクトです。
縦横の寸法の削減だけではなく、厚みを薄くつくリたいという希望がありました。
所が単純に薄くすると、持った時に発熱する背面パーツに手が触れてしまったり、落下などでぶつかった際に背面パーツが破損する懸念がありました。
そこで、(当初は付けたくはなかった)背面保護用のグリルをデザインする必要が出てきました。
初めは多角形でしたがあまりにもダサく、調べている内にVoronoi柄という有機的なパターンに行き付き即採用しました。
結果、ビタキセを取り付けると柄が見えなくなるのが勿体無いぐらい個性的でスタイリッシュなデザインに仕上がりました。
いずれカスタム方法やインサートナットや増設ファンの選定方法等を紹介したいのですが、今回はNIP-23になれるという意図もあるので紹介に留めます! また、他の関連OSハードウェアプロジェクトのケースもデザインできたらと思っております!
今後ともタコ頭をよろしくお願いいたします。
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Scala is such a great language
Scala is amazing. The type system has the perfect balance between flexibility and powerfulness.
matchstatements are great. You can write imperative code that looks very nice and expressive (and I haven't tried writing purely functional things yet). Everything is easy to write and cheap and neovim integration works great.But Java is not great. And the fact that Scala is a JVM language doesn't help because over the years people have written stuff that depends on Java libraries -- and these Java libraries are not as safe as the Scala libraries, they contain reflection, slowness, runtime errors, all kinds of horrors.
Scala is also very tightly associated with Akka, the actor framework, and Akka is a giant collection of anti-patterns. Untyped stuff, reflection, dependency on JVM, basically a lot of javisms. I just arrived and I don't know anything about the Scala history or ecosystem or community, but I have the impression that Akka has prevent more adoption of Scala from decent people that aren't Java programmers.
But luckily there is a solution -- or two solutions: ScalaJS is a great thing that exists. It transpiles Scala code into JavaScript and it runs on NodeJS or in a browser!
Scala Native is a much better deal, though, it compiles to LLVM and then to binary code and you can have single binaries that run directly without a JVM -- not that the single JARs are that bad though, they are great and everybody has Java so I'll take that anytime over C libraries or NPM-distributed software, but direct executables even better. Scala Native just needs a little more love and some libraries and it will be the greatest thing in a couple of years.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Que vença o melhor
Nos esportes e jogos em geral, existe uma constante preocupação em balancear os incentivos e atributos do jogo, as regras do esporte em si e as regras das competições para que o melhor vença, ou, em outras palavras, para que sejam minimizados os outros fatores exceto a habilidade mais pura quanto possível no jogo em questão.
O mundo fora dos jogos, porém, nem sempre pode ter suas regras mudadas por um ente que as controla e está imbuído da vontade e dos meios para escolher as melhores regras possíveis para a obtenção dos resultados acima. Aliás, é muitas vezes essa possibilidade é até impensável. Mesmo quando ela é pensável e levada em conta os fatores que operam no mundo real não são facilmente identificáveis, eles são muitos, e mudam o tempo todo.
Mais do que isso, ao contrário de um jogo em que o objetivo é praticamente o mesmo para todo mundo, os objetivos de cada agente no mundo real são diferentes e incontáveis, e as "competições" que cada um está disputando são diferentes e muitas, cada minúsculo ato de suas vidas compreendendo várias delas simultaneamente.
Da mesma forma, é impossível conceber até mesmo o conceito de "melhor" para que se deseje que ele vença.
Mesmo assim é comum encontrarmos em várias situações gente que parte do princípio de que se Fulano está num certo lugar (por exemplo, um emprego muito bom) e Beltrano não isso se deve ao fato de Fulano ter sido melhor que Beltrano.
Está aí uma crítica à idéia da meritocracia (eu tinha me esquecido que essa palavra existia).
-
 @ ec42c765:328c0600
2024-12-22 19:16:31
@ ec42c765:328c0600
2024-12-22 19:16:31この記事は前回の内容を把握している人向けに書いています(特にNostrエクステンション(NIP-07)導入)
手順
- 登録する画像を用意する
- 画像をweb上にアップロードする
- 絵文字セットに登録する
1. 登録する画像を用意する
以下のような方法で用意してください。
- 画像編集ソフト等を使って自分で作成する
- 絵文字作成サイトを使う(絵文字ジェネレーター、MEGAMOJI など)
- フリー画像を使う(いらすとや など)
データ量削減
Nostrでは画像をそのまま表示するクライアントが多いので、データ量が大きな画像をそのまま使うとモバイル通信時などに負担がかかります。
データ量を増やさないためにサイズやファイル形式を変更することをおすすめします。
以下は私のおすすめです。 * サイズ:正方形 128×128 ピクセル、長方形 任意の横幅×128 ピクセル * ファイル形式:webp形式(webp変換おすすめサイト toimg) * 単色、単純な画像の場合:png形式(webpにするとむしろサイズが大きくなる)
その他
- 背景透過画像
- ダークモード、ライトモード両方で見やすい色
がおすすめです。
2. 画像をweb上にアップロードする
よく分からなければ emojito からのアップロードで問題ないです。
普段使っている画像アップロード先があるならそれでも構いません。
気になる方はアップロード先を適宜選んでください。既に投稿されたカスタム絵文字の画像に対して
- 削除も差し替えもできない → emojito など
- 削除できるが差し替えはできない → Gyazo、nostrcheck.meなど
- 削除も差し替えもできる → GitHub 、セルフホスティングなど
これらは既にNostr上に投稿されたカスタム絵文字の画像を後から変更できるかどうかを指します。
どの方法でも新しく使われるカスタム絵文字を変更することは可能です。
同一のカスタム絵文字セットに同一のショートコードで別の画像を登録する形で対応できます。3. 絵文字セットに登録する
emojito から登録します。
右上のアイコン → + New emoji set から新規の絵文字セットを作成できます。


① 絵文字セット名を入力
基本的にカスタム絵文字はカスタム絵文字セットを作り、ひとまとまりにして登録します。
一度作った絵文字セットに後から絵文字を追加することもできます。
② 画像をアップロードまたは画像URLを入力
emojitoから画像をアップロードする場合、ファイル名に日本語などの2バイト文字が含まれているとアップロードがエラーになるようです。
その場合はファイル名を適当な英数字などに変更してください。
③ 絵文字のショートコードを入力
ショートコードは絵文字を呼び出す時に使用する場合があります。
他のカスタム絵文字と被っても問題ありませんが選択時に複数表示されて支障が出る可能性があります。
他と被りにくく長くなりすぎないショートコードが良いかもしれません。
ショートコードに使えるのは半角の英数字とアンダーバーのみです。
④ 追加
Add を押してもまだ作成完了にはなりません。

一度に絵文字を複数登録できます。
最後に右上の Save を押すと作成完了です。

画面が切り替わるので、右側の Options から Bookmark を選択するとそのカスタム絵文字セットを自分で使えるようになります。
既存の絵文字セットを編集するには Options から Edit を選択します。
以上です。
仕様
-
 @ ec42c765:328c0600
2024-12-13 08:16:32
@ ec42c765:328c0600
2024-12-13 08:16:32Nostr Advent Calendar 2024 の 12日目の記事です。
昨日の 12/11 は きりの さんの 2024年のNostrリレー運営を振り返る でした。
nostr-zap-view 作った
リポジトリ: https://github.com/Lokuyow/nostr-zap-view/
動作確認ページ: https://lokuyow.github.io/nostr-zap-view/それ何?
特定の誰かや何かに宛てたZap(投げ銭)を一覧できるやつ
を
自分のWebサイトに設置できるやつ
自分のサイトに設置した例 * SNSリンク集ページ(最下部): https://lokuyow.github.io/
おいくらサッツ(Zap一覧ボタン): https://osats.money/
今日からビットコ(最下部): https://lokuyow.github.io/btc-dca-simulator/なんで作ったの?
私の去年のアドベントカレンダー
【Nostr】Webサイトにビットコインの投げ銭ボタンを設置しよう【Zap】
https://spotlight.soy/detail?article_id=ucd7cbrql/
が前提になってるけど長いので要約すると * ZapするやつはあるけどZap見るやつがないので欲しい * ZapをNostr(の典型的なkind:1クライアント)内だけに留めるのはもったいない * Webサイトの広告うざいからZap(的な何か)で置き換わって欲しいお前だれ?
非エンジニア、非プログラマー
AIにコード出させてるだけ人作った感想
できた
作った感想2
完成してから気付いた本当に作りたかったもの
こういうところにそのままZapを表示できる感じにしたい
 (ここまでちゃんとした商業ブログでなく)個人のブログやHPの端っこに「Sponsored by」欄があって名前が表示される感じ
(ここまでちゃんとした商業ブログでなく)個人のブログやHPの端っこに「Sponsored by」欄があって名前が表示される感じ
もうZapっていう文字もビットコインっていう文字もNostrも出さなくていいし説明もしなくていいのでは感がある
イメージはWebサイトを対象にしたニコニ広告 + スーパーチャット + 祭りとか神社の奉納者一覧
で思ったのは
個人からの投げ銭なら推し活的なものにしかならないけど
企業がNostrにアカウントを作ってサイトに投げ銭をしたら企業の広告になるんでは!?
~~企業がNostrにアカウントを!?デリヘルしか見たことない!~~今後
思いつき、予定は未定
* ボタン→ダイアログ形式でなくバナー、Embed形式にしてページアクセスですぐ見れるようにする * 多分リレーに負荷がかかるのでなんかする * Zapの文字は出さず「Sponsored by」等にする * 単純な最新順でなくする * 少額Zapをトリミング * 一定期間(一か月など)ごとで金額順にソート * 多分リレーに負荷がかかるのでなんかする * 今は投稿宛てのZapをWebサイト宛てのZapと勝手に言い張ってるだけなのでちゃんとWebサイト宛てのZapにする * NIPの提案が必要 * ウォレットの準拠も必要 * リレー(wss://~)宛てのZapもできてほしい将来
インターネットのすべてに投げ銭をさせろ
おわり
明日は mono さんの Open Sats 申請編 です!!
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Token-Curated Registries
So you want to build a TCR?
TCRs (Token Curated Registries) are a construct for maintaining registries on Ethereum. Imagine you have lots of scissor brands and you want a list with only the good scissors. You want to make sure only the good scissors make into that list and not the bad scissors. For that, people will tell you, you can just create a TCR of the best scissors!
It works like this: some people have the token, let's call it Scissor Token. Some other person, let's say it's a scissor manufacturer, wants to put his scissor on the list, this guy must acquire some Scissor Tokens and "stake" it. Holders of the Scissor Tokens are allowed to vote on "yes" or "no". If "no", the manufactures loses his tokens to the holders, if "yes" then its tokens are kept in deposit, but his scissor brand gets accepted into the registry.
Such a simple process, they say, have strong incentives for being the best possible way of curating a registry of scissors: consumers have the incentive to consult the list because of its high quality; manufacturers have the incentive to buy tokens and apply to join the list because the list is so well-curated and consumers always consult it; token holders want the registry to accept good and reject bad scissors because that good decisions will make the list good for consumers and thus their tokens more valuable, bad decisions will do the contrary. It doesn't make sense, to reject everybody just to grab their tokens, because that would create an incentive against people trying to enter the list.
Amazing! How come such a simple system of voting has such enourmous features? Now we can have lists of everything so well-curated, and for that we just need Ethereum tokens!
Now let's imagine a different proposal, of my own creation: SPCR, Single-person curated registries.
Single-person Curated Registries are equal to TCR, except they don't use Ethereum tokens, it's just a list in a text file kept by a single person. People can apply to join, and they will have to give the single person some amount of money, the single person can reject or accept the proposal and so on.
Now let's look at the incentives of SPCR: people will want to consult the registry because it is so well curated; vendors will want to enter the registry because people are consulting it; the single person will want to accept the good and reject the bad applicants because these good decisions are what will make the list valuable.
Amazing! How such a single proposal has such enourmous features! SPCR are going to take over the internet!
What TCR enthusiasts get wrong?
TCR people think they can just list a set of incentives for something to work and assume that something will work. Mix that with Ethereum hype and they think theyve found something unique and revolutionary, while in fact they're just making a poor implementation of "democracy" systems that fail almost everywhere.
The life is not about listing a set of "incentives" and then considering the problems solved. Almost everybody on the Earth has the incentive for being rich: being rich has a lot of advantages over being poor, however not all people get rich! Why are the incentives failing?
Curating lists is a hard problem, it involves a lot of knowledge about the problem that just holding a token won't give you, it involves personal preferences, politics, it involves knowing where is the real limit between "good" and "bad". The Single Person list may have a good result if the single person doing the curation is knowledgeable and honest (yes, you can game the system to accept your uncle's scissors and not their competitor that is much better, for example, without losing the entire list reputation), same thing for TCRs, but it can also fail miserably, and it can appear to be good but be in fact not so good. In all cases, the list entries will reflect the preferences of people choosing and other things that aren't taken into the incentives equation of TCR enthusiasts.
We don't need lists
The most important point to be made, although unrelated to the incentive story, is that we don't need lists. Imagine you're looking for a scissor. You don't want someone to tell if scissor A or B are "good" or "bad", or if A is "better" than B. You want to know if, for your specific situation, or for a class of situations, A will serve well, and do that considering A's price and if A is being sold near you and all that.
Scissors are the worst example ever to make this point, but I hope you get it. If you don't, try imagining the same example with schools, doctors, plumbers, food, whatever.
Recommendation systems are badly needed in our world, and TCRs don't solve these at all.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Precautionary Principle
The precautionary principle that people, including Nassim Nicholas Taleb, love and treat as some form of wisdom, is actually just a justification for arbitrary acts.
In a given situation for which there's no sufficient knowledge, either A or B can be seen as risky or precautionary measures, there's no way to know except if you have sufficient knowledge.
Someone could reply saying, for example, that the known risk of A is tolerable to the unknown, probably magnitudes bigger, risk of B. Unless you know better or at least have a logical explanation for the risks of B (a thing "scientists" don't have because they notoriously dislike making logical claims), in which case you do know something and is not invoking the precautionary principle anymore, just relying on your logical reasoning – and that can be discussed and questioned by others, undermining your intended usage of the label "precautionary principle" as a magic cover for your actions.
-
 @ 91bea5cd:1df4451c
2025-02-04 17:15:57
@ 91bea5cd:1df4451c
2025-02-04 17:15:57Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ fad5c183:5cb8046b
2025-02-10 17:46:03
@ fad5c183:5cb8046b
2025-02-10 17:46:03The Big Question: What Really Supports Bitcoin? Let’s cut the fluff. Money has always needed something to back it. In the past, it was gold, something tangible, scarce, and universally recognized as valuable. Then came fiat (government-backed currency), which ditched gold in favor of trust in central banks.
Now, Bitcoin is here. It’s digital, decentralized, and allegedly free from manipulation. But is it? If Bitcoin isn’t backed by gold, oil, or government decree, what gives it value? And if a small number of players hold most of it, are we just recreating the same problems as fiat?
Let’s dig in.
Why Bitcoin Has Value (Even If You Can’t Touch It) Bitcoin is backed by math, code, and energy—not physical resources. Its value comes from three major factors:
- Scarcity – Only 21 million BTC will ever exist. No central bank can “print” more.
- Security – It’s protected by cryptography and (proof-of-work). Hacking the Bitcoin network is practically impossible.
- Market Trust – Bitcoin is valuable because people believe in its ability to store value, just like gold or fiat.
Unlike government money, where supply is controlled by a central authority, Bitcoin’s supply is fixed and transparent.
Sounds great, right? Well, there’s a catch.
Are We Just Repeating the Fiat Problem?
Fiat money is flawed because central banks can print it endlessly, manipulate interest rates, and control its flow. This causes inflation, bailouts, and financial crises.
Bitcoin fixes that. No one can create more Bitcoin out of thin air. But here’s the issue:
A small number of people and institutions own a huge percentage of Bitcoin. These “whales” can manipulate price movements, just like big banks do with fiat. Unlike fiat, where governments intervene (for better or worse), Bitcoin markets are unregulated and volatile. So, if whales can dump Bitcoin to crash prices and buy back cheap, is it really that different from fiat where the rich get richer?
Bitcoin’s Advantage: Transparency & Control
Here’s where Bitcoin still wins:
✅ No Central Control – Governments and banks can’t change its monetary policy. ✅ Transparency – Every transaction is on the blockchain. No hidden “money printing.” ✅ Self-Custody – You can hold your Bitcoin, unlike fiat, which sits in a bank that can freeze or seize it.
But let’s not pretend it’s perfect. If the majority of Bitcoin remains concentrated in a few hands, it still creates power imbalances.
The solution? More decentralization—and that’s where Nostr comes in.
How Nostr & Bitcoin Could Change the Game
Nostr is a decentralized communication protocol. No servers, no censorship, no single point of control.
When paired with Bitcoin and the Lightning Network, it could:
- Enable truly peer-to-peer transactions without banks or centralized exchanges.
- Reduce whale manipulation by increasing adoption and distribution.
- Support a free, censorship-resistant financial system without intermediaries.
Imagine a world where you don’t need banks or corporations to transact—just an internet connection. That’s where we’re headed.
Final Thought: Are We at Square One?
Bitcoin isn’t a perfect solution, but it’s a step forward. It removes central banks from the equation but still struggles with wealth concentration and market manipulation.
So, are we just recreating fiat 2.0? Maybe in some ways. But here’s the difference:
The rules can’t be changed by elites in a closed room. Every transaction is visible—no shady money printing. Anyone can self-custody their assets—no middlemen needed. The key to breaking the cycle? More decentralization, better distribution, and adoption beyond whales and institutions.
Bitcoin is a tool. It’s up to us to use it wisely.
What do you think? Are we just repeating history, or is Bitcoin truly different? Let’s debate. 🔥
-
 @ 6bcc27d2:b67d296e
2024-10-21 03:54:32
@ 6bcc27d2:b67d296e
2024-10-21 03:54:32yugoです。 この記事は「Nostrasia2024 逆アドベントカレンダー」10/19の分です。Nostrasiaの当日はリアルタイムで配信を視聴していました。Nostrを使ってアプリケーションの再発明をすべきという発表を聴き、自分だったらどんなものを作ってみたいかを考えて少し調べたり試みたりしたのでその記録を書きます。また、超簡単なものですがおそらく世界初となるvisionOS対応のNostrクライアントをつくってみたので最後の方に紹介します。
アプリケーションを再発明する話があったのは、「What is Nostr Other Stuff?」と題したkaijiさんの発表でした。
Nostrプロトコルを使って既存のアプリケーションを再発明することで、ユーザ体験を損なわずにゆるやかな分散を促すことができ、プロトコルとしてのNostrも成長していくというような内容でした。
自分はまだNostrで何かをつくった経験はなかったので、実装に必要な仕様の知識がほとんどない状態からどのようなアプリケーションをつくってみたいかを考えました。
最初に思いついたのは、Scrapboxのようなネットワーク型のナレッジベースです。自分は最近visionOS勉強会をやっており、勉強会でナレッジを共有する手段としてScrapboxの導入を検討していました。
Nostrコミュニティにも有志によるScrapboxがありますが、Nostrクライアントがあればそれを使うだろうから同じくらいの実用性を備えたクライアントはまだ存在しないのではないかという見立てでした。
長文投稿やpublic chatなどの機能を組み合わせることで実現できるだろうか。そう思っていた矢先、NIP-54のWikiという規格があることを知りました。
https://github.com/nostr-protocol/nips/blob/master/54.md
まだちゃんとは読めていないですが、Scrapboxもwikiソフトウェアだし参考になりそうと思っています。正式な仕様に組み込まれていないようで、採用しているクライアントはfiatjafによるリファレンス実装(?)のwikistrくらいしか見つかりませんでした。
Scrapboxのようなナレッジベースを志向するNostrクライアントがあれば、後述するvisionOS対応クライアントの存在もありアカウントを使いまわせて嬉しいので試してみたいです。もし他にも似たようなサービスをどなたか知っていたら教えてください。
また現在は、勉強会やワークショップ、ハッカソンなどのコラボレーションワークを支援するためのツールを自分たちでも開発しています。Apple Vision Proに搭載されているvisionOSというプラットフォームで動作します。
https://image.nostr.build/14f0c1b8fbe5ce7754825c01b09280a4c22f87bbf3c2fa6d60dd724f98919c34.png
この画面で自分が入りたいスペースを選んで共有体験を開始します。
スライドなどのコンテンツや自らのアバターを同期させることで、遠隔地にいてもまるでオフラインかのように同じ空間を共有することが可能になります。
https://image.nostr.build/cfb75d3db2a9b9cd39f502d6426d5ef4f264b3d5d693b6fc9762735d2922b85c.jpg
ということなので、急遽visionOS対応のクライアントを作ってみました。検索しても1つも事例が出てこなかったので多分まだ世界で実装しているアプリはないのではないでしょうか。
とはいえ、クライアントを名乗っているもののまだ大した機能はなく、リレーからデータを取得するだけの読み取り専用です。
https://image.nostr.build/96e088cc6a082528682989ccc12b4312f9cb6277656e491578e32a0851ce50fe.png
画像では自分のプロフィールデータをリレーから取得しています。
まだどのライブラリもvisionOSに対応していなかったりで手こずったものの仕様の勉強になりました。
ただvisionOSアプリはiOSアプリ同様NIP-7が使えないので秘密鍵を自分で保管しなくてはならず、今後どう対処すべきかわかりかねています。これから時間ある時に少しずつ調べていこうと思っていますが、ネイティブアプリの秘密鍵周りはあまりリソースが多くないようにも感じました。もしどなたかその辺の実装に詳しい方いたら教えていただけると嬉しいです。
準備ができたらそのうちコードも公開したいと思っています。
これから少しずつ色んな機能を実装しながらNostrで遊んでいきたいです!
-
 @ 78c90fc4:4bff983c
2025-02-10 12:08:13
@ 78c90fc4:4bff983c
2025-02-10 12:08:13“Die Welt wird von ganz anderen Personen regiert als diejenigen es sich vorstellen, die nicht hinter den Kulissen stehen.”
Benjamin Disraeli, zweimaliger britischer Premierminister und Romanautor.
Quelle:
https://www.unz.com/article/the-disraeli-enigma/\ \ Als 1853 der Krimkrieg zwischen Russland und dem Osmanischen Reich ausbrach, wurde das Osmanische Reich vom Vereinigten Königreich und Frankreich gerettet. Zwanzig Jahre später zog Zar Alexander II. als Beschützer der unterdrückten serbischen und bulgarischen Christen erneut gegen die Osmanen in den Krieg. Als die Russen vor den Toren Konstantinopels/Istanbuls standen, waren die Osmanen gezwungen, die Schaffung der autonomen Fürstentümer Bulgarien, Serbien und Rumänien durch den Vertrag von San Stefano zu akzeptieren. Die Briten waren mit diesem Vertrag unzufrieden und beriefen zusammen mit Österreich-Ungarn den Berliner Kongress (1878) ein, der ihn aufhob. Russische Eroberungen wurden zurückgenommen, Armenien und Bulgarien wurden größtenteils an das Osmanische Reich zurückgegeben und der Balkan wurde in heterogene und konfliktreiche Staaten aufgeteilt. Diese „Balkanisierung“ löste nationalistische Ressentiments aus, die den Ersten Weltkrieg auslösen sollten.
\ Das Hauptziel des Berliner Vertrags bestand darin, das zu retten, was von einem schwächelnden Osmanischen Reich zu retten war, um der panslawistischen Expansion Russlands entgegenzuwirken. England, das stets eifersüchtig auf seine Vormachtstellung zur See bedacht war, wollte verhindern, dass Russland näher an den Bosporus heranrückte. Die Briten erhielten das Recht, Zypern als Marinestützpunkt zu nutzen und gleichzeitig den Suezkanal zu überwachen. Dies war der Beginn des „Great Game“ Großbritanniens um die Kolonialherrschaft in Asien und die Eindämmung Russlands, was insbesondere zur Schaffung Afghanistans als Pufferstaat führte.
\ Es gibt verschiedene Möglichkeiten, diesen Abschnitt der Geschichte zu interpretieren, der den Keim für alle Tragödien des 20. Jahrhunderts („das jüdische Jahrhundert“ laut Yuri Slezkine) in sich trägt.[1]\ Yuri Slezkine, The Jewish Century, Princeton University Press, 2004.
\ Es gibt unterschiedliche Ansichten darüber, welche Kräfte die Geschichte in dieser entscheidenden Zeit geprägt haben. Aber letztendlich wird Geschichte von Menschen gemacht, und sie kann nur verstanden werden, wenn man die Hauptakteure und ihre Motive identifiziert: Man kann den Vietnamkrieg einfach nicht verstehen, ohne sich mit der Denkweise von Johnson oder Kissinger auseinanderzusetzen. Unter den Anstiftern des Berliner Vertrags sticht ein Name besonders hervor: Benjamin Disraeli (1804–1881), Premierminister unter Königin Victoria von 1868 bis 1869 und erneut von 1874 bis 1880. Disraeli war auch der Mann, der 1875 die Übernahme des Suezkanals durch England ermöglichte, und zwar durch die Finanzierung seines Freundes Lionel de Rothschild, dem Sohn von Nathan Mayer – eine Operation, die die Kontrolle der Rothschilds über die Bank of England festigte.
\ Disraeli ist ein sehr interessanter Fall, da er sowohl ein bedeutender britischer Staatsmann während der globalen Hegemonie Großbritanniens als auch ein Romanautor war, der seine fiktiven Figuren dazu benutzte, seine ehrlichen Gedanken zu äußern, während er eine Art „glaubhafte Abstreitbarkeit“ (Sidonia spricht, nicht ich!) aufrechterhielt. Wir haben daher die einzigartige Gelegenheit, die wahren Motive des Mannes in der Politik zwischen den Zeilen zu lesen. Stellen Sie sich vor, Kissinger hätte Romane geschrieben, in denen ein Jude die Hauptfigur ist, der die Außen- und Militärpolitik des Imperiums vorantrieb und gleichzeitig ein enger Freund des reichsten jüdischen Bankiers war.\ \
Disraeli wird als der wahre Erfinder des Britischen Empires bezeichnet, da er es war, der Königin Victoria durch das Parlament mit dem Royal Titles Act von 1876 zur Kaiserin von Indien ernennen ließ (das obere Bild ist eine Karikatur, die Disraeli als Hausierer zeigt, der der Königin die Kaiserkrone überreicht).
Disraeli war, wie bereits erwähnt, die Hauptinspiration für den Berliner Kongress. Darüber hinaus war Disraeli ein Vorläufer des Zionismus, der versuchte, die „Wiederherstellung Israels“ auf die Tagesordnung des Berliner Kongresses zu setzen, in der Hoffnung, den Sultan Abdul Hamid davon zu überzeugen, Palästina als autonome Provinz zu gewähren. Der Sultan lehnte das Angebot ab, das wahrscheinlich das Versprechen finanzieller Unterstützung für seine zusammenbrechende Wirtschaft beinhaltete – wie auch Herzls Angebot im Jahr 1902, das ebenfalls abgelehnt wurde.\ \ Der Zionismus war Disraelis uralter Traum: Nach einer Reise in den Nahen Osten im Alter von sechsundzwanzig Jahren veröffentlichte er seinen ersten Roman, Die wundersame Geschichte des Alroy, und ließ seinen Helden, einen einflussreichen Juden des Mittelalters, sagen: „Mein Wunsch ist eine nationale Existenz, die wir nicht haben. Mein Wunsch ist das Land der Verheißung und Jerusalem und der Tempel, alles, was wir eingebüßt haben, wonach wir uns gesehnt haben, wofür wir gekämpft haben, unser schönes Land, unser heiliges Glaubensbekenntnis, unsere einfachen Sitten und unsere alten Bräuche.“\ Disraeli schrieb diese Zeilen noch vor den Anfängen der biblischen Archäologie; erst 1841 veröffentlichte Edward Robinson seine Biblical Researches in Palestine. Die ersten Ausgrabungen des von Königin Victoria geförderten Palestine Exploration Fund begannen 1867. Wohlhabende britische Juden hatten sich jedoch schon lange zuvor für Palästina interessiert. Disraelis Interesse wurde durch seinen Nachbarn und vierzigjährigen Freund Moses Montefiore beeinflusst, der Judith Cohen, die Schwägerin von Nathan Rothschild, heiratete. Nach einer Reise nach Palästina im Jahr 1827 widmete Montefiore seine immensen Ressourcen der Unterstützung seiner Glaubensgenossen im Heiligen Land, indem er Land kaufte und Häuser baute.
\ Sowohl Montefiore als auch Disraeli waren sephardischer Herkunft. Disraeli stammte aus einer Familie portugiesischer Marranen, die in Venedig zum Judentum konvertierten. Sein Großvater war 1748 nach London gezogen. Benjamin wurde im Alter von dreizehn Jahren getauft, als sein Vater Isaac D'Israeli zusammen mit seiner ganzen Familie zum anglikanischen Christentum konvertierte. Isaac D'Israeli ist der Autor eines Buches mit dem Titel The Genius of Judaism(in Anlehnung an Chateaubriands Le Génie du Christianisme), in dem er die einzigartigen Eigenschaften des jüdischen Volkes verherrlicht, aber die talmudischen Rabbiner dafür verantwortlich macht, dass sie „den nationalen Geist ihres Volkes versiegeln“ und „die Einfachheit ihres antiken Glaubens korrumpieren“. Wie für viele andere Juden dieser Zeit war die Konversion für D'Israeli rein opportunistisch: Bis zum Beginn des 19. Jahrhunderts blieben Verwaltungskarrieren für Juden verschlossen. Ein Gesetz von 1740 hatte ihre Einbürgerung erlaubt, aber es hatte Volksaufstände provoziert und wurde 1753 aufgehoben. Viele einflussreiche Juden, wie der Stadtbankier Sampson Gideon, entschieden sich dann für eine nominelle Konversion ihrer Kinder.[2]\ Cecil Roth, A History of the Marranos (1932), Meridian Books, 1959, S. 148.\ \ Etwa zur gleichen Zeit wie Disraeli konvertierte Heinrich Heine (1797–1856) zum Luthertum (während einer seiner Brüder zum Katholizismus konvertierte, um Offizier in Österreich zu werden, und ein anderer zur Orthodoxie, um als Arzt in Russland zu dienen). Heine betrachtete die Taufe als „Eintrittskarte in die europäische Zivilisation“. Er beklagte sich jedoch darüber, dass er von den Deutschen immer noch als Jude angesehen wurde, und zog es daher vor, in Frankreich zu leben, wo er als Deutscher angesehen wurde. Nur wenige Jahre nach seiner Konversion zeigten seine Schriften eine sehr negative Einstellung gegenüber dem Christentum, das er als „düstere, blutrünstige Religion für Kriminelle“ bezeichnete, die die Sinnlichkeit unterdrücke. Am Ende seines Lebens bereute er seine Taufe, die ihm nichts gebracht hatte, und erklärte in seinem letzten Buch Romanzero: „Ich mache kein Geheimnis aus meinem Judentum, zu dem ich nicht zurückgekehrt bin, weil ich es nicht verlassen habe.“[3]\ Zitiert in Kevin MacDonald, Separation and Its Discontents: Toward an Evolutionary Theory of Anti-Semitism, Praeger, 1998, kindle 2013, l. 4732–4877.
\ Genau wie bei den portugiesischen Marranen im 15. Jahrhundert verstärkte die Taufe bei den europäischen Juden des 19. Jahrhunderts ein nicht-religiöses, rassisches Verständnis des Judentums. Disraeli bezeichnete sich selbst als „Anglikaner jüdischer Abstammung“.
\ Für Hannah Arendt ist Disraeli ein „Rassenfanatiker“, der in seinem ersten Roman Alroy (1833) „einen Plan für ein jüdisches Reich entwickelte, in dem Juden als streng getrennte Klasse herrschen würden“. In seinem anderen Roman Coningsby „entfaltete er einen fantastischen Plan, nach dem jüdisches Geld den Aufstieg und Fall von Höfen und Reichen beherrscht und in der Diplomatie die Oberhand hat“. Diese Idee „wurde zum Dreh- und Angelpunkt seiner politischen Philosophie“.[4]\ Hannah Arendt, The Origins of Totalitarianism, Band 1: Antisemitism, Meridian Books, 1958, S. 309–310.\ Dies ist eine ziemlich fantastische Anschuldigung, die die meisten Biografen Disraelis nicht bestätigen würden. Sie ist jedoch wahrscheinlich richtig. Aber wir müssen genau auf Disraelis eigene Stimme hören, die durch Sidonia zum Ausdruck kommt, die Figur, die in drei seiner Romane vorkommt: Coningsby (1844), Sybil (1845) und Tancred (1847).
In Sidonias Worten spürt man den Groll gegen die Nation, in die er sich zu integrieren versuchte:\ Kann es etwas Absurderes geben, als dass eine Nation sich an eine Einzelperson wendet, um ihren Kredit, ihre Existenz als Imperium und ihren Komfort als Volk zu erhalten; und diese Einzelperson, der ihre Gesetze die stolzesten Rechte der Staatsbürgerschaft, das Privileg, in ihrem Senat zu sitzen und Land zu besitzen, verweigern; denn obwohl ich unbesonnen genug war, mehrere Ländereien zu kaufen, bin ich der Meinung, dass ein Engländer hebräischen Glaubens nach dem geltenden Recht Englands keinen Boden besitzen kann.
\ Da es einem Juden nicht möglich ist, sich durch Landbesitz in die britische Aristokratie zu integrieren, selbst wenn er zum örtlichen Glauben konvertiert, was sollte ein Jude tun, außer durch die Macht des Geldes aufzusteigen? Wie Heine spürte auch Disraeli die Heuchelei der Christen, die es den Juden übel nahmen, dass sie keine Christen waren, sie aber weiterhin als Juden behandelten, wenn sie konvertierten, und es insgeheim sogar vorzogen, dass sie Juden blieben.
\ Laut Disraelis Biografen Robert Blake ist Sidonia „eine Kreuzung zwischen Lionel de Rothschild und Disraeli selbst“. Er stammt von einer Adelsfamilie aus Aragon ab, zu deren herausragenden Mitgliedern ein Erzbischof und ein Großinquisitor gehörten, die beide heimlich dem Judentum ihrer Väter anhingen. Sidonias Vater, wie auch Lionel de Rothschilds Vater, „machte während der Napoleonischen Kriege ein großes Vermögen mit Militärverträgen und der Versorgung der verschiedenen Armeen“. Nachdem er sich in London niedergelassen hatte, „setzte er alles, was er besaß, auf die Waterloo-Anleihe; und das Ereignis machte ihn zu einem der größten Kapitalisten Europas.“ Seit seinem siebzehnten Lebensjahr besuchte Sidonia die Fürstenhöfe der Schuldner seines Vaters und lernte die Geheimnisse der Macht kennen. „Die geheime Geschichte der Welt war sein Zeitvertreib. Es bereitete ihm großes Vergnügen, die verborgenen Motive mit den öffentlichen Vorwänden der Transaktionen zu kontrastieren.“ Disraeli selbst war laut Robert Blake „von Verschwörungen besessen“.[5]\ Robert Blake, Disraeli (1966), Faber Finds, 2010, S. 202.
\ Sidonia ist von seiner Rasse begeistert: „Alles ist Rasse – es gibt keine andere Wahrheit.“ Er weigert sich, eine Nichtjüdin zu heiraten, weil, so der Erzähler, „keine irdische Überlegung ihn jemals dazu veranlassen würde, die Reinheit der Rasse zu beeinträchtigen, auf die er stolz ist.“ Mit „Rasse“ meinte Disraeli Blutsverwandtschaft. In seinem letzten Roman Endymion (1880) schrieb er:\ Kein Mensch wird das Prinzip der Rasse gleichgültig behandeln. Es ist der Schlüssel zur Geschichte, und der Grund, warum die Geschichte oft so verwirrend ist, liegt darin, dass sie von Männern geschrieben wurde, die dieses Prinzip und all das damit verbundene Wissen nicht kennen ... Sprache und Religion machen keine Rasse aus – es gibt nur eine Sache, die eine Rasse ausmacht, und das ist Blut.\ Sidonia erzählt seinem Schützling Coningsby in Coningsby oder die neue Generation, dass die Verfolgung durch christliche Nationen die jüdische Nation niemals zerschlagen könnte.
\ Tatsache ist, dass man eine reine Rasse der kaukasischen Organisation nicht vernichten kann. Es ist eine physiologische Tatsache; ein einfaches Naturgesetz, das ägyptische und assyrische Könige, römische Kaiser und christliche Inquisitoren verblüfft hat. Keine Strafgesetze, keine körperlichen Folterungen können bewirken, dass eine überlegene Rasse in einer unterlegenen aufgehen oder von ihr vernichtet werden sollte. Die gemischten verfolgenden Rassen verschwinden, die reine verfolgte Rasse bleibt bestehen. Und im Moment, trotz Jahrhunderten oder gar Jahrzehnten der Erniedrigung, übt der jüdische Geist einen enormen Einfluss auf die Angelegenheiten Europas aus. Ich spreche nicht von ihren Gesetzen, denen Sie immer noch gehorchen; von ihrer Literatur, mit der Ihr Geist gesättigt ist, sondern vom lebendigen hebräischen Intellekt. Sie beobachten nie eine große intellektuelle Bewegung in Europa, an der die Juden nicht in hohem Maße beteiligt sind.\ Wo auch immer er reiste, fügte Sidonia hinzu, sah er jüdische Berater hinter Monarchen und Staatsoberhäuptern.
„Sie sehen also, mein lieber Coningsby, dass die Welt von ganz anderen Persönlichkeiten regiert wird, als diejenigen, die nicht hinter den Kulissen stehen, sich vorstellen können.“
In einem Sachbuch (Lord George Bentinck: A Political Biography, 1852) schrieb Disraeli:\ [Juden] sind ein lebendiger und der eindrucksvollste Beweis für die Falschheit dieser verderblichen Doktrin der Neuzeit, der natürlichen Gleichheit der Menschen. ... die natürliche Gleichheit der Menschen, die heute in Mode ist und die Form einer kosmopolitischen Bruderschaft annimmt, ist ein Prinzip, das, wenn man danach handeln könnte, die großen Rassen zersetzen und den ganzen Genius der Welt zerstören würde. ... Die angeborene Tendenz der jüdischen Rasse, die zu Recht stolz auf ihr Blut ist, ist gegen die Doktrin der Gleichheit der Menschen.[6]\ Benjamin Disraeli, Lord George Bentinck, Archibald, 1852 (archive.org), S. 496.
\ Disraeli ist eindeutig auf derselben Wellenlänge wie Moses Hess, Herzls geistiger Vater, der, nachdem er Marx (einen weiteren nominellen Konvertiten) beeinflusst hatte, zu dem Schluss kam, dass „der Rassenkrieg wichtiger ist als der Klassenkampf“ (Rom und Jerusalem, 1862). Ein gutes Beispiel für dialektische politische Manipulation ist, dass Hess Marx weiterhin heimlich unterstützte und auf dessen Bitte hin nach dem Generalkongress der Internationale in Basel (5.–12. September 1869) Verleumdungen gegen Bakunin veröffentlichte, in denen er Bakunin beschuldigte, ein Agent provocateur der russischen Regierung zu sein und „im Interesse des Panslawismus“ zu arbeiten.[7]\ Bakunins Antwort auf Französisch, „Aux citoyens rédacteurs du Réveil“, finden Sie auf Wikisource.org.\ Es ist interessant zu sehen, dass ein anderer Proto-Zionist wie Disraeli den russischen Interessen zutiefst feindlich gesinnt war.\ \ Was war Disraelis Motivation hinter der Außenpolitik, die er dem britischen Empire vermittelte? Glaubte er, dass es die offensichtliche Bestimmung der Briten sei, die Welt zu erobern? Oder sah er das britische Empire als Instrument für die überlegene Bestimmung der jüdischen Nation, wenn er sich daran erinnerte, wie Esra und Nehemia in biblischen Zeiten die Außenpolitik der Perser ausgenutzt hatten? Indem er den Suezkanal (der zwischen 1859 und 1869 von den Franzosen gegraben wurde) mit den britischen Interessen in Verbindung brachte, wollte er einfach nur die Franzosen übertrumpfen, oder legte er damit den Grundstein für das zukünftige Bündnis zwischen Israel und dem angloamerikanischen Empire? Da die Briten nun einmal den Suezkanal besaßen, mussten sie ihn verteidigen, und wie ginge das besser als mit einer befreundeten jüdischen autonomen Regierung in der Nähe in Palästina? Genau das war es, was Chaim Weizmann dreißig Jahre später den Briten schmackhaft machen wollte: „Das jüdische Palästina wäre ein Schutz für England, insbesondere in Bezug auf den Suezkanal.“[8]\ Chaim Weizmann, Trial and Error, Harper & Brothers, 1949, S. 192.
\ Und als die Israelis 1956 mit britischer und französischer Unterstützung in den Sinai einmarschierten, taten sie dies, indem sie Großbritannien erneut versprachen, die Kontrolle über den von Nasser verstaatlichten Kanal an Großbritannien zurückzugeben.
\ Disraelis Russophobie, zu der er Königin Victoria bekehrte, und seine Verteidigung der Türken, deren Massaker an den Serben und Bulgaren allgemein bekannt waren, führten zu Theorien über eine jüdische Verschwörung. William Ewart Gladstone, ein langjähriger Gegner Disraelis und selbst mehrmals Premierminister (1868–1874, 1880–1885, 1886 und 1892–1894), erklärte, dass Disraeli „die britische Außenpolitik als Geisel seiner jüdischen Sympathien nahm und mehr daran interessiert war, die Leiden der Juden in Russland und der Türkei zu lindern, als an britischen Interessen“. Die Zeitung „The Truth“ vom 22. November 1877 spielte auf die Vertrautheit Disraelis mit den Rothschilds an und vermutete „eine stillschweigende Verschwörung ... seitens einer beträchtlichen Anzahl von Anglo-Hebräern, um uns im Namen der Türken in einen Krieg zu ziehen“. Es wurde außerdem daran erinnert, dass Disraeli in einer Rede vor dem britischen Unterhaus im Jahr 1847 die Zulassung von Juden zu wählbaren Ämtern gefordert hatte, mit der Begründung, dass „der jüdische Geist einen enormen Einfluss auf die Angelegenheiten Europas ausübt“.[9]\ Stanley Weintraub, Disraeli: A Biography, Hamish Hamilton, 1993, S. 579, 547.
\ Die Königin stand, wie ein Großteil der britischen Aristokratie, bereits unter dem Bann einer modischen Theorie, die den Angelsachsen einen israelitischen Ursprung zuschrieb. Diese Theorie war erstmals zur Zeit Oliver Cromwells aufgetaucht und wurde 1840 von Pastor John Wilson in seinen Vorlesungen über das alte Israel und den israelitischen Ursprung der modernen Nationen Europas sowie 1870 von Edward Hine in The English Nation Identified with the Lost Israel neu aufgelegt. In diesem Werk erfahren wir, dass das Wort „Saxon“ von „Isaac's sons“ (Söhne Isaaks) abgeleitet ist. Diese lächerliche Theorie lieferte eine billige biblische Rechtfertigung für den britischen Kolonialismus und sogar für den Völkermord an den kolonisierten Völkern (neue Kanaaniter) durch das britische Empire (neues Israel).[10]\ André Pichot, Aux origines des théories raciales, de la Bible à Darwin, Flammarion, 2008, S. 124–143, 319.
\ Königin Victoria war glücklich, glauben zu können, dass ihre edle Abstammung auf König David zurückging, und ließ ihre Söhne beschneiden, ein Brauch, der bis heute fortbesteht. Es mag etwas Wahres an dem Gefühl der britischen Elite für ihr Judentum liegen, denn im 16. und 17. Jahrhundert hatten viele Ehen reiche jüdische Familien mit der alten, verarmten Landaristokratie vereint, so dass nach Hilaire Bellocs Schätzung „mit Beginn des 20. Jahrhunderts diejenigen der großen territorialen englischen Familien, in denen es kein jüdisches Blut gab, die Ausnahme waren“.[11]\ Hilaire Belloc, The Jews, Constable & Co., 1922 (archive.org), S. 223.
\ Die Begeisterung der Königin für das Judentum hatte aber auch viel mit dem Einfluss Disraelis zu tun, der einmal gegenüber einem Freund damit prahlte: „Jeder mag Schmeichelei, und wenn es um das Königshaus geht, sollte man sie mit einer Kelle auftragen.“[12]\ Stanley Weintraub, Disraeli: A Biography, Hamish Hamilton, 1993, S. 579, 547.
\ Der Fall Disraeli ist aufschlussreich, weil die Frage, die er aufwirft, dieselbe ist wie die Frage, die heute geopolitische Analysten in Bezug auf die Beziehung zwischen den Vereinigten Staaten und Israel spaltet: Wer führt wen an der Nase herum? Ist Israel der Brückenkopf der Vereinigten Staaten im Nahen Osten oder sind die Vereinigten Staaten, wie Zbigniew Brzezinski einmal sagte, der „dumme Esel“ Israels? Die Beantwortung dieser Frage für das Jahrhundert vor dem Zweiten Weltkrieg (als „Israel“ das internationale Judentum bedeutete) hilft bei der Beantwortung derselben Frage heute, da die symbiotische Beziehung zwischen Israel und dem Imperium erheblich gewachsen ist.
\ Die Antwort hängt vom Standpunkt des Betrachters ab. Die Zionisten haben natürlich ein Interesse daran, die Ansicht zu fördern, dass Israel den angloamerikanischen Interessen dient und nicht umgekehrt. Disraeli argumentierte vor dem britischen Parlament, dass ein jüdisches Palästina im Interesse des britischen Kolonialismus sei. Aber jüdische Zionisten haben die Dinge schon immer aus der anderen Perspektive betrachtet, und man kann kaum glauben, dass Disraeli ihre Ansicht nicht insgeheim teilte. Wenn der Held seines Romans Tancred (1847), ein Jude, der wie Disraeli zum Lord ernannt wurde, das britische Empire mit folgenden Worten verherrlicht: „Wir wollen die Welt erobern, angeführt von Engeln, um die Menschheit unter göttlicher Herrschaft glücklich zu machen“, wer verbirgt sich hinter diesem zweideutigen „wir“? Ist es dasselbe doppeldeutige „wir“, das die PNAC-Neokonservativen benutzten, um Amerika in Kriege zum Wohle Israels zu verwickeln?
\ Wenn ein britischer Jude wie Disraeli zu den Briten „wir“ sagte, war dies eine strategische Zweideutigkeit. Er traf damit den patriotischen Nerv der angelsächsischen Elite, die den gemeinsamen Glauben an die Mission des britischen Empires teilte, die Welt zu zivilisieren – Menschen wie Lord Salisbury, Mitglied von Cecil Rhodes' Round Table, der sich für eine Weltregierung durch die „britische Rasse“ einsetzte.[13]\ Carroll Quigley, The Anglo-American Establishment, From Rhodes to Cliveden (1949), Books In Focus, 1981.
\ Der britische Imperialismus und der zionistische Nationalismus wurden etwa zur gleichen Zeit geboren wie die Zwillinge Esau und Jakob und sind seit ihrer Geburt eng miteinander verflochten. Zwei Überlegungen helfen jedoch, ihre wahre Beziehung zu verstehen. Erstens reichen die ideologischen Wurzeln des Britischen Empires nicht weiter zurück als bis ins 17. Jahrhundert, während die des Zionismus mehr als zwei Jahrtausende zurückreichen. Zweitens starb das Britische Empire nach dem Ersten Weltkrieg, während der Zionismus aufblühte. Aus diesen beiden Gründen ist die Theorie, dass der Zionismus ein Nebenprodukt des britischen Imperialismus ist (nennen wir sie die Chomsky-Theorie), nicht haltbar.
\ Um die wahre Beziehung zwischen Zion und Albion zu Disraelis Zeiten zu verstehen, muss man die Macht der Rothschild-Dynastie über die britische Politik richtig einschätzen. Ohne die Rothschilds hätte Großbritannien nie die Kontrolle über den Suezkanal erlangt, der den Grundstein des britischen Empires im Nahen Osten bildete. Die Rothschilds selbst kandidierten nicht für ein politisches Amt, heirateten jedoch manchmal in eine solche Familie ein: Lord Archibald Primrose, 1886 und von 1892 bis 1894 Außenminister und 1894–1895 Premierminister, war der Schwiegersohn von Mayer Amschel de Rothschild.\ Es ist bemerkenswert, dass Theodor Herzl den zukünftigen jüdischen Staat als „aristokratische Republik“ mit „dem ersten Prinzen Rothschild“ an der Spitze sah. In einer langen Tirade in seinem Tagebuch ermahnte er die Rothschilds, ihre bösen Seelen zu erlösen, indem sie den Zionismus statt Kriege finanzierten:\ Ich weiß nicht, ob alle Regierungen bereits erkennen, welche internationale Bedrohung Ihr Weltreich darstellt. Ohne Sie können keine Kriege geführt werden, und wenn Frieden geschlossen werden soll, sind die Menschen umso mehr auf Sie angewiesen. Für das Jahr 1895 wurden die Militärausgaben der fünf Großmächte auf vier Milliarden Francs geschätzt, und ihre tatsächliche militärische Stärke in Friedenszeiten auf 2.800.000 Mann. Und diese Streitkräfte, die in der Geschichte ihresgleichen suchen, kommandieren Sie finanziell, ungeachtet der widerstreitenden Wünsche der Nationen. ... Und Ihr verfluchter Reichtum wächst immer noch. ... Aber wenn Sie sich uns anschließen, ... werden wir unseren ersten gewählten Herrscher aus Ihrem Haus nehmen. Das ist das leuchtende Leuchtfeuer, das wir auf die Spitze des fertigen Eiffelturms Ihres Vermögens setzen werden. In der Geschichte wird es so aussehen, als wäre das der Zweck des gesamten Bauwerks gewesen.[14]\ \ The Complete Diaries of Theodor Herzl, edited by Raphael Patai, Herzl Press & Thomas Yoseloff, 1960, vol. 1, pp. 163–170.\ Wie Richard Wagner jedoch einmal sagte (Judaism in Music, 1850), zogen es die Rothschilds vor, „die Juden der Könige“ zu bleiben, anstatt „die Könige der Juden“ zu sein.\ \ Wenn die Zeit für die Gründung des jüdischen Staates zu Disraelis Zeiten noch nicht reif war, dann vor allem deshalb, weil die Juden in Russland sich von Palästina ebenso wenig angezogen fühlten wie die Juden in Europa; sie wussten kaum, wo es lag. Erst kürzlich von Zar Alexander II. emanzipiert, strebten sie lediglich eine Auswanderung nach Europa oder in die Vereinigten Staaten an. Erst nach der Ermordung von Zar Alexander II. im Jahr 1881 (einen Monat vor Disraelis Tod) wurden einige von ihnen durch die Pogrome für Leon Pinskers proto-zionistischen Aufruf von 1882 empfänglich: „Wir müssen uns ein für alle Mal mit dem Gedanken abfinden, dass die anderen Nationen uns aufgrund ihres angeborenen natürlichen Antagonismus für immer ablehnen werden.“[15]\ Benzion Netanyahu, The Founding Fathers of Zionism, Balfour Books, 2012, Kindle l. 761-775.
\ Ebenfalls im Jahr 1881 begann Baron Edmond de Rothschild vom Pariser Zweig, unter der Schirmherrschaft seiner Palestine Jewish Colonization Association (PICA) Land in Palästina zu kaufen und die Ansiedlung jüdischer Siedler zu finanzieren, insbesondere in Tel Aviv. Die meisten bestehenden internationalen jüdischen Organisationen, wie B'nai B'rith (gegründet 1843 in New York) oder die Alliance Israélite Universelle (gegründet 1860 in Paris), waren jedoch der Meinung, dass Israel als verstreute Nation gut zurechtkäme und keine Pläne für Palästina habe.\ Dies änderte sich während des Ersten Weltkriegs, als ein äußerst effizientes Netzwerk aufgebaut wurde, das beide Seiten des Atlantiks verband.[16]\ Alison Weir, Against Our Better Judgment: The Hidden History of How the U.S. Was Used to Create Israel, 2014, Kindle l. 387-475.
\ Theodor Herz konzentrierte seine diplomatischen Bemühungen zunächst auf Deutschland, aber in England begannen sich die Dinge vielversprechend zu entwickeln („Der Schwerpunkt hat sich nach England verlagert“, schrieb er 1895 in sein Tagebuch), was zum Teil der Rekrutierung von Israel Zangwill zu verdanken war, der laut Benzion Netanyahu „der erste war, der in den oberen Kreisen der britischen Politik direkt über den Zionismus sprach“, insbesondere mit Lloyd George, „einem engen Bekannten Zangwills von Beginn seiner zionistischen Tätigkeit bis zu seinem Lebensende“.[17]\ Netanyahu, The Founding Fathers of Zionism, l. 2536-59.
\ Erinnern wir uns daran, dass Zangwill der erfolgreiche Autor von The Melting Pot war, einem Theaterstück, das Mischehen für Amerikaner pries. Hier besteht kein Widerspruch, denn „die gemischten verfolgten Rassen verschwinden, die reine verfolgte Rasse bleibt bestehen“, wie Sidonia sagte.\ \ Die Bedeutung von Disraelis geopolitischen Manövern wird von Historikern der Zionisten selten anerkannt, da sie oberflächlich betrachtet nicht den Weg für die Gründung des jüdischen Staates geebnet zu haben scheinen. Tatsächlich bildeten sie jedoch das unsichtbare Fundament, auf dem Herzl und Zangwill aufbauten. Und diese unsichtbare Kontinuität zeugt von der erstaunlichen generationsübergreifenden Beharrlichkeit des jüdischen Volkes, das sein jahrtausendealtes, selbsternanntes Schicksal Generation für Generation vorantreibt. Ja, es ist wirklich bewundernswert, wenn auch verheerend für die westliche Zivilisation, die durch zweitausend Jahre Christentum ahnungslos und ihres eigenen Sinns für Blut beraubt wurde. Wie der zionistische Autor Jakob Klatzkin einmal in der Zeitschrift „Der Jude“, 1916, schrieb:\ Wir bilden in uns selbst eine geschlossene juristische und geschäftliche Körperschaft. Eine starke Mauer, die wir errichtet haben, trennt uns von den Menschen in den Ländern, in denen wir leben – und hinter dieser Mauer befindet sich ein jüdischer Staat.[18]
Zitiert in Robert Edward Edmondson, The Jewish System Indicted by the Documentary Record, 1937 (archive.org), S. 15.\ \ Anmerkungen\ [1] Yuri Slezkine, The Jewish Century, Princeton University Press, 2004.\ [2] Cecil Roth, A History of the Marranos (1932), Meridian Books, 1959, S. 148.\ [3] Zitiert in Kevin MacDonald, Separation and Its Discontents: Toward an Evolutionary Theory of Anti-Semitism, Praeger, 1998, kindle 2013, l. 4732–4877.\ [4] Hannah Arendt, The Origins of Totalitarianism, Band 1: Antisemitism, Meridian Books, 1958, S. 309–310.\ [5] Robert Blake, Disraeli (1966), Faber Finds, 2010, S. 202.\ [6] Benjamin Disraeli, Lord George Bentinck, Archibald, 1852 (archive.org), S. 496.\ [7] Bakunins Antwort auf Französisch, „Aux citoyens rédacteurs du Réveil“, auf Wikisource.org.\ [8] Chaim Weizmann, Trial and Error, Harper & Brothers, 1949, S. 192.\ [9] Stanley Weintraub, Disraeli: A Biography, Hamish Hamilton, 1993, S. 579, 547.\ [10] André Pichot, Aux origines des théories raciales, de la Bible à Darwin, Flammarion, 2008, S. 124–143, 319.\ [11] Hilaire Belloc, The Jews, Constable & Co., 1922 (archive.org), S. 223.\ [12] Stanley Weintraub, Disraeli: A Biography, Hamish Hamilton, 1993, S. 579, 547.\ [13] Carroll Quigley, The Anglo-American Establishment, From Rhodes to Cliveden (1949), Books In Focus, 1981.\ [14] The Complete Diaries of Theodor Herzl, edited by Raphael Patai, Herzl Press & Thomas Yoseloff, 1960, vol. 1, pp. 163–170.\ [15] Benzion Netanyahu, The Founding Fathers of Zionism, Balfour Books, 2012, Kindle-Ausgabe, S. 761–775.\ [16] Alison Weir, Against Our Better Judgment: The Hidden History of How the U.S. Was Used to Create Israel, 2014, Kindle-Ausgabe, S. 387–475.\ [17] Netanyahu, The Founding Fathers of Zionism, S. 2536-59.\ [18] Zitiert in Robert Edward Edmondson, The Jewish System Indicted by the Documentary Record, 1937 (archive.org), S. 15.
-
 @ fd208ee8:0fd927c1
2025-02-06 15:58:38
@ fd208ee8:0fd927c1
2025-02-06 15:58:38Beginning at the start
In my previous article, The Establishment, I answered the question: "How do we form a company?" I realize, now, that I was getting a bit ahead, of myself, as the precursor to a company is a team, and many people struggle to form teams. So, I will go back to the beginning, and then you can read both articles to the end, and then stop.
The Initiation
The first, and most-difficult step of team formation, is the initiation. We know that it must be the most-difficult, as it's the step that carries the highest potential reward, and it's the step that is tried-and-failed most often. (Some people, like Elon Musk or Donald Trump, are born Initiators with excellent follow-through, but this archetype is exceedingly thin on the ground because it requires you to be mildly autistic, have barely-throttled ADHD, and/or tend to megalomania, also popularly known as "toxic masculinity", "CEO personality", or "being a successful military officer".)
Someone needs to form a useful, attractive Vision and then motivate other people to help them achieve it. That sounds really easy, but it's actually brutally difficult because * You have to come up with an idea that is coherent, plausible, and inspiring. * You have to be able to communicate that idea to other people and make it appealing to them, by tying it into their own personal goals and desires. * You have to be able to hone and reformulate that idea, constantly, to correct it or to re-motivate the other team members. * You have to defend the idea against detractors, naysayers, and trolls, and you have to do it so vociferously, that it will erode your own popularity among those who disagree with you and open you to personal attacks. * You have to be able to focus on the idea, yourself, for a long stretch of time, and not allow yourself to get bored, lazy, or distracted.
So, just do and be all of those things, and then initiate the team, with the method I will name the Hatbock Method. It is so named because of the classic, German initiation ritual, in which an Initiator stands up, loudly defines their Vision and calls into a group "Wer hat Bock?" (roughly, "Who has the hunger/desire?") and whoever responds with "Ich hab Bock." (roughly, "Yes, I hunger for this.") is a part of the team.
Then the Initiator says, "Okay, everyone with the hunger, let's sit down together, and discuss this some more." (This "sitting" is literally called a "seating", or "Sitzung", which is the German word for "meeting".)
The Sitting
We now get to the second most difficult part of team formation: figuring out where to sit. Most teams get this wrong, repeatedly, and many teams dissolve or fracture under the difficulty of this momentous decision. You would think organizing yourselves online would make this easier ("Oh, we'll just meet online!"), but the number of places available for sitting online are limitless. You can talk your whole Vision into the ground, with laborous discussions and migrations between Chachi, OxChat, Telegram, SimpleX, Slack, Discord, WhatsApp, GitHub, Teams, Coracle, Matrix... you get the idea.
Try to keep in mind that the Vision is more important than the seating area, and go with the flow. Simply, find someplace and go there. Worry about it again, at a later date. Don't lose momentum. Sit down and start discussing the Vision, immediately.

Now, this next bit is very important:
Do not let anyone outside your team influence where you sit!
...unless they are providing your team with some good, service, or income, that makes choosing their preferred location the superior choice.
This is the German Stammtisch principle, where a host encourages you to come sit down, regularly, in some particular place, because your sitting there provides them with some benefit: they can overhear your conversations, get you to test out their seating area, sell you refreshments, etc. Your choice of seating, in other words, is a valuable good, and you should only "sell" it to someone who rewards you in measure. They have to reward you because their preferred seating area wasn't your immediate and obvious choice, so there was probably something unappealing or uncertain about the seating area.
Plan it in
Once you've sat down, and finished your rough draft of the Vision, you need to figure out when to sit. This is the third most-difficult part of team formation. (Yes, don't worry, it gets easier as it goes along.)
The most popular plan is the Wirsehenuns Plan (roughly, "We'll see each other, around.") This can work quite well, if you just want to have a loose collaboration, that calls itself together in an ad hoc fashion, when a team member feels the need. Also known as "@ me, bros".
It's not a great plan for more intensive collaboration, as that tends to need a certain amount of velocity, to actually happen, as the speed of movement has a centrifugal effect on the tasks. Team momentum, in other words, creates a sort of gravity, that keeps the team together as a unit. So, for deeper teamwork, I would recommend the Stammtisch variant: name a place and date/time, when you will next meet. Preferably, on a rotating schedule: daily, weekly, last Thursday of the month, etc.
And then meet there and then. And discuss amongst yourselves. Set clear, short-term tasks (and assign them to particular people!), medium-term strategies, and longer-term goals. Write everything down. Anything not written down, is a suggestion, not an assigned task.
If you find your Stammtisch becoming increasingly rewarding and productive, and your goals start moving closer and closer into sight, then you might want to formalize your team structure further, as a company.
-
 @ 7e19a1dd:ea50ba3b
2025-02-10 11:16:42
@ 7e19a1dd:ea50ba3b
2025-02-10 11:16:42Air compressors are workhorses across industries, from manufacturing plants to auto repair shops. However, keeping them running smoothly requires regular maintenance, which can be a time-consuming and costly chore. That’s where air compressor filters come into play. These simple yet vital components can help extend the life of your compressor while saving you money and headaches down the line.
What Do Air Compressor Filters Actually Do?
Air compressors suck in air from their surroundings, and that air isn’t always clean. It can carry dirt, moisture, and even tiny particles that can damage your compressor's internal parts. Filters act as the gatekeepers, trapping contaminants before they wreak havoc.
Without a good filter, dirt and debris can clog valves and reduce efficiency. Even worse, it can lead to costly repairs—or worse, a full-blown breakdown. Filters also remove moisture, preventing rust and corrosion in your compressor and connected equipment.
Less Maintenance, More Savings
Regular maintenance on an air compressor is inevitable, but filters significantly cut down the frequency of those tune-ups. Clean air means fewer clogs and less wear and tear on moving parts. As a result, you’ll need fewer repairs and part replacements over time.
And let’s not forget energy efficiency. When an air compressor operates with clean air, it doesn’t have to work as hard. This reduced workload translates into lower energy bills. Over time, this can add up to significant savings.
Filters Protect Your Investment
Air compressors aren’t cheap, and replacing one can feel like a punch to the wallet. Using high-quality air compressor filters protects your investment by keeping the equipment running at peak performance. Think of it like regularly changing your car’s oil. It’s a small, affordable step that prevents big problems later.
Save Time and Effort
No one enjoys unscheduled downtime, especially when deadlines are looming. A well-maintained compressor equipped with a proper filter is far less likely to break down unexpectedly. That means fewer interruptions and more time to focus on your work. And here’s another bonus: replacing filters is quick and easy. Compared to the hours it can take to clean or repair a compressor, swapping out a filter is a breeze.
Choosing the Right Filter
Not all filters are created equal. Make sure you choose one that matches your compressor’s specifications. If you’re unsure, check your user manual or ask a professional. Investing in a high-quality filter might cost a little more upfront, but it will pay off in the long run.
Final Thoughts
Air compressor filters are a small but mighty tool in keeping your equipment running smoothly. They cut down on maintenance, protect your compressor, and save you both time and money. By making filters a regular part of your maintenance routine, you’ll not only extend the life of your compressor but also improve its efficiency. That’s a win-win for your wallet and your workflow. So, the next time you fire up your air compressor, make sure its filter is up to the task. You’ll thank yourself later!
-
 @ e3ba5e1a:5e433365
2025-02-04 08:29:00
@ e3ba5e1a:5e433365
2025-02-04 08:29:00President Trump has started rolling out his tariffs, something I blogged about in November. People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I put up a poll on X to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.

For purposes of this blog post, our ultimate question will be the following:
- Suppose apples currently sell for $1 each in the entire United States.
- There are domestic sellers and foreign sellers of apples, all receiving the same price.
- There are no taxes or tariffs on the purchase of apples.
- The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following:
- Number of apples bought in the US
- Price paid by buyers for apples in the US
- Post-tax price received by domestic apple producers
- Post-tax price received by foreign apple producers
Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1?
And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why:
- The number of apples bought will go down
- The buyers will pay more for each apple they buy, but not the full amount of the tariff
- Domestic apple sellers will receive a higher price per apple
- Foreign apple sellers will receive a lower price per apple, but not lowered by the full amount of the tariff
In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit.
Marginal benefit
All of the numbers discussed below are part of a helper Google Sheet I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are some difficulties with creating supply and demand charts in Google Sheets.
Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B.
But that’s not what I mean. What I mean is: how high would the price of apples have to go everywhere so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5.
How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot.
The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called marginal benefit: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal demand curve. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:

Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples.
Marginal cost
Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product.
Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right?
Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of sunk costs. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further.
Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price!
However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with:
- Total expenditure: $100 + $70 * 8 hours a day * 5 days \== $2900
- Total revenue: $5000 (10,000 apples at $0.50 each)
- Total profit: $2100
So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money.
This kind of analysis is called marginal cost. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:

Equilibrium price
We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:

You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the surplus created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example:
- When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point.
- When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point.
Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.”
OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality.
Modeling taxes
Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve.
First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:

With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve.
We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:

The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:

As we can see, the equilibrium has shifted:
- The equilibrium price paid by consumers has risen from $1 to $1.20.
- The total number of apples purchased has dropped from 63 apples to 60 apples.
- Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus.
- Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42.
- Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21.
- The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise.
We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes:
- Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples.
- Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless.
- Domestic producers scored. They can sell less apples and make more revenue doing it.
- And the government walked away with an extra $30.
Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price.
Other taxes
Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down.
And generally speaking, this is what you’ll always see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost.
You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with:
- Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price.
- Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost.
- Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise.
This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ 5a261a61:2ebd4480
2025-02-02 20:42:37
@ 5a261a61:2ebd4480
2025-02-02 20:42:37Let’s be real—sticking to anything for 90 days is like trying to herd cats on espresso. You start strong, then life happens: kids, chores, or that one glass of wine that makes you forget foot rubs (#relatable). But here’s the thing: 90-day challenges aren’t about perfection. They’re about bribing your lizard brain with rewards and scaring it straight with punishments.
The Game Plan
First, pick a thing—something that makes you feel like a devoted servant or a slightly frazzled superhero. Daily foot care? Chores with a side of #FLR flair? Cool. Now, break it into chunks: 30 days (survival mode), 60 days (grind phase), and 90 days (victory lap).
Keeping up something for so long is no joke. That's why you need those little checkpoints along the way. Each milestone should feel special—30 days deserves celebration, 60 days something more meaningful, and 90 days? That's your victory dance moment.
Reality check: some days will suck, and you'll want to skip. That's where having everything planned out helps. When your brain is foggy and you're tired, you don't want to be negotiating with yourself about what counts and what doesn't. The hardest part isn't even doing the thing—it's remembering to do it every single day, until it feels wrong NOT to do it.
Why It (Maybe) Works
Three months is long enough for habits to stick, short enough to see the finish line. Plus, tying it to power exchange? Genius. Every foot rub or denied cum becomes a ritual, proof you're leveling up as a sub/human/slightly-messy adult. And let's be honest—nothing fuels devotion like a mix of structure, desperation, and the occasional humiliating punishment.
Current run
My current challenge is to get my wife/godess/object of my insatiable kinky thoughts/partner feet massaged with special cream. It's for making evyrthing soft, help nails and yadayadayada. Basically preping her feet for more instensive worshiping. She doesn't know my hidden agenda and I am not sure if I would really be into it, since I am more into being her devout toy than having foot fetish, but I think it will be all the same if I put myself juuust right. So for my rewards I have planned these? - 30 days: Tiny dopamine hit. (making little photoset of Her feet playing with my hardon… for science.)
- 60 days: Mid-tier flex. (cleaning mushed banana split off Her toes tongue only)
- 90 days: Go nuclear. (a tiny foot spa whirpool because She deserves it, damn it :D and it will create more opportunities for... you know )As for the hhip part of the sugar duo... It was easy having one for my shaving rutine, but here? Not sure and it's bad that I ave started challenge without having them prepared... May be that warrant more punishment?
TL;DR
90-day challenges are the BDSM of self-improvement: consensual, slightly painful, and weirdly addictive. Fail? Reset, adapt, try again. Win? Congrats, you’re now 10% more disciplined and 100% more bumptious on Nostr.
90days #FLR #LostCauseButStillTrying #femdom
-
 @ 5d4b6c8d:8a1c1ee3
2025-02-10 16:32:15
@ 5d4b6c8d:8a1c1ee3
2025-02-10 16:32:15The Super Bowl definitely threw me off a bit. My dad offered to bring some food over and the plan was to eat before the game/during the first half. I have no idea what he was doing, but for some reason, it took him two hours to get the food (that was already made) ready to eat.
All things considered, I still did ok. The dry fast was about 13 hours and I might make it to 16 hours without eating (I'm at 15 now).
Score Card
Day 1: 14 hour fast (13 dry) Day 2: 15 hour fast (14 dry) Day 3: 17 hours (16 dry) Day 4: 18 hours (17 dry) Day 5: 18 hours (16 dry) Day 6: 19 hours (16 dry) Day 7: 16 hours (15 dry) Day 8: 18 hours (17 dry) Day 9: 17 hours (17 dry) Day 10: TBD (13 dry)
originally posted at https://stacker.news/items/881691
-
 @ 31da2214:af2508e2
2025-02-10 10:08:06
@ 31da2214:af2508e2
2025-02-10 10:08:06A global privacy nightmare is unfolding. The UK government secretly ordered Apple to backdoor encrypted iCloud storage worldwide—but Apple is legally forbidden from revealing this order, or they face criminal charges. This affects 2 BILLION USERS.
Here’s the full story & why it’s part of a much bigger power grab. 🧵👇 [Thread by @sayerjigmi on Thread Reader App]
1) The UK's Secret Order to Backdoor Encryption 🔓
Under the UK’s Investigatory Powers Act (IPA) 2016, Apple was served a Technical Capability Notice (TCN)—forcing them to create a backdoor for encrypted iCloud data.
This is not limited to UK users. It applies worldwide, meaning your private files are at risk, no matter where you live.
🔗 @macworld report
2) Apple’s Legal Gag Order 🤐
Apple is legally forbidden from revealing this order. If Apple even acknowledges that the UK issued this demand, they could face criminal charges.
This is a secret government order with global consequences.
3) A Global Threat to Encryption 🌍
This isn’t just about the UK (although they are leading the charge in threatening citizens in OTHER countries for violating BRITISH censorship laws!).
If Apple complies, every government in the world will demand the same access—from the US to China to authoritarian regimes.
End-to-end encryption would be effectively dead.
4) Apple’s Dilemma: Comply or Withdraw? 🚪
Apple has two choices:
- Comply & weaken encryption globally.
- Refuse & withdraw services from the UK.WhatsApp & Signal faced similar threats last year and vowed to leave the UK rather than compromise security. Will Apple do the same?
🚨 Watch the heated discussion between Damian Collins, director of CCDH (architect of the UK Online Safety Bill), and Signal’s CEO: YouTube Link
5) Why This Matters: Encryption Protects Everything 🔐
- Encryption protects financial data, health records, personal security (e.g., where you live or work), and private conversations.
- Governments always say they need backdoors for national security—but history shows they’re used for mass surveillance.
- Once a backdoor exists, hackers, rogue employees, and other governments WILL find it.
6) The UK’s War on Encryption 🛡️
The UK is trying to dominate the global surveillance & censorship landscape.
While the US, Canada, Australia, and New Zealand have supported strong encryption to mitigate cyber threats, the UK stands alone in its war on encryption.
7) The Free Speech Crackdown 🗣️
This isn’t just about encryption—it’s about control. Governments worldwide are criminalizing dissent and censoring free speech, using tech companies as their enforcement arms.
🔗 GreenMedInfo Report
8) The Global Censorship Agenda 🌐
This ties into the UK’s broader, GLOBALLY ORCHESTRATED censorship agenda:
- The Online Safety Bill criminalizes encrypted messaging & forces platforms to scan private messages.
- The Digital Services Act (EU) gives governments the power to shut down online content they don’t like.
- Leaked US-UK documents show direct coordination between UK intelligence & the Biden administration to censor online speech.
9) The Architects of Speech Policing: CCDH 🕵️♂️
The Center for Countering Digital Hate (CCDH)—a UK intelligence-backed group—has been a driving force behind global censorship.
They were caught:
- Running “black ops” to suppress RFK Jr.’s presidential campaign.
- Leading the "Kill Musk’s Twitter" directive, trying to shut down free speech on X.
- Labeling 12 private US citizens as the “Disinformation Dozen” to justify mass censorship.
🔗 Reclaim the Net Investigation
10) The Pattern is Clear: Surveillance + Censorship 🔍
1️⃣ Governments create "safety" laws to justify surveillance.
2️⃣ They pressure tech companies to enforce censorship.
3️⃣ Once encrypted services are gone, nothing is private anymore.This is the biggest attack on digital freedom in history.
11) What Can We Do? 💪
- Support companies that refuse to build backdoors (Signal, ProtonMail, etc.).
- Push for legislation that protects encryption & free speech.
- Stay informed & spread awareness—governments count on secrecy to push these policies through.
- Follow and support privacy and internet freedom organizations such as:
- @G_W_Forum
- @FFO_Freedom
- @ReclaimTheNetHQ
12) The Ultimate Power Grab: Controlling All Digital Communication 📱
If Apple caves, every other platform will be forced to follow.
📌 The UK’s Global Playbook:
- A backdoor to encryption (Investigatory Powers Act).
- A government-linked censorship network (CCDH).
- A speech-policing framework that extends worldwide (Online Safety Bill).This is a global effort to control what people can say, share, and store privately.
13) The Final Stand: Will You Comply or Resist? ⚔️🚨
They want total control—your speech, your privacy, your elections. This is the defining battle of our time.
🇬🇧 UK’s war on encryption = Global censorship blueprint.
🗳️ Election meddling + speech policing = A hijacked democracy.📢 Digital freedom is human freedom.
Stand up. Speak out. Fight back. 🏴☠️🔥
Full thread preserved by Thread Reader App.
-
 @ c8383d81:f9139549
2025-02-05 13:06:05
@ c8383d81:f9139549
2025-02-05 13:06:05My own stats on what I’ve done over the weekend:
-
Spoke to +100 developers, it was great seeing a couple of familiar Flemish faces and meeting some new ones but overall the crowd was extremely diverse.
-
Ended up doing a short interview promoting the protocol and ended up going to 0 talks.
-
Tried to evangelize by going booth by booth to distribute a Nostr flyer to other FOSDEM projects, with the hope that they would broadcast the info towards their SOME person to add Nostr on their list or to build out a library for the languages that were present ( This was a fairly slow approach )
-
Kept it to Nostr protocol 95% of the time, the Bitcoin narrative is not always a good time to push and as a side note I’ve met more Monero users than in the last 5 years.
-
Was able to convince some engineers to look into the #soveng endeavor.
Small overview from the most common questions:
- They have heard about Nostr but are not sure of the details. ( mostly through the bitcoin community )
- What is the difference with ActivityPub, Mastodon, Fediverse ?
- IOT developers, so questions regarding MQTT & Meshtastic integrations ?
- Current state of MLS on Nostr ?
- What are the current biggest clients / apps build on Nostr ?
- Will jack still give a talk ?
Things we could improve:
- Bring more stickers like loads more,
- Bring T-shirts, Pins… could be a good way to fund these adventures instead of raising funds. ( Most projects where selling something to help raise funds for projects )
- Almost no onboarding / client installs.
- Compared to the Nostr booth at BTC Amsterdam not a single person asked if they could charge their phone.
Personal Note: The last time I visited was roughly 13 years ago and me being a little more seasoned I just loved the fact that I was able to pay some support to the open source projects I’ve been using for years ( homebrew, modzilla, Free BSD,.. ) and see the amazing diverse crowd that is the open source Movement 🧡
Al final shoutout to our great pirate crew 🏴☠️: The Dutch Guard ( nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe & nostr:npub1l77twp5l02jadkcjn6eeulv2j7y5vmf9tf3hhtq7h7rp0vzhgpzqz0swft ) and a adrenaline fueled nostr:npub1t6jxfqz9hv0lygn9thwndekuahwyxkgvycyscjrtauuw73gd5k7sqvksrw , nostr:npub1rfw075gc6pc693w5v568xw4mnu7umlzpkfxmqye0cgxm7qw8tauqfck3t8 and nostr:npub1r30l8j4vmppvq8w23umcyvd3vct4zmfpfkn4c7h2h057rmlfcrmq9xt9ma amazing finally meeting you IRL after close to 2 years since the Yakihonne hackathon 😀

-
-
 @ 9e69e420:d12360c2
2025-02-01 11:16:04
@ 9e69e420:d12360c2
2025-02-01 11:16:04Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ 0176967e:1e6f471e
2024-07-28 15:31:13
@ 0176967e:1e6f471e
2024-07-28 15:31:13Objavte, ako avatari a pseudonymné identity ovplyvňujú riadenie kryptokomunít a decentralizovaných organizácií (DAOs). V tejto prednáške sa zameriame na praktické fungovanie decentralizovaného rozhodovania, vytváranie a správu avatarových profilov, a ich rolu v online reputačných systémoch. Naučíte sa, ako si vytvoriť efektívny pseudonymný profil, zapojiť sa do rôznych krypto projektov a využiť svoje aktivity na zarábanie kryptomien. Preskúmame aj príklady úspešných projektov a stratégie, ktoré vám pomôžu zorientovať sa a uspieť v dynamickom svete decentralizovaných komunít.
-
 @ 42342239:1d80db24
2025-02-10 08:16:32
@ 42342239:1d80db24
2025-02-10 08:16:32The risks associated with cryptocurrencies have recently received attention in the media, where e.g. the Swedish Financial Supervisory Authority warns of the high volatility and risk of investments in crypto. Within the EU, as usual, significant efforts are being made to expand the already extensive regulatory framework. Meanwhile, in the US, there has been a marked turnaround. Even the presidential family has launched their own cryptocurrencies, resulting in criticism from industry experts .
Important perspectives, however, are conspicuous by their absence in the conversation.
Iain McGilchrist, a British psychiatrist and philosopher, has introduced the hemispheric hypothesis (a theory about how the brain's two hemispheres function). The left hemisphere is more detail- and control-oriented, while the right hemisphere is more holistic. A society dominated by the left hemisphere, such as our own according to McGilchrist , "would see it as its task to control everything maximally and would have a paranoid feeling that we need to have surveillance cameras everywhere...".
During a speech at the World Economic Forum, President Trump recently stated that conservatives complain about big banks, such as Bank of America, not allowing them to conduct business within the bank. Critics argue that the American banking system has been used to persecute political opponents, both during Obama's and Biden's terms. Under Obama, 'Operation Chokepoint' was introduced to limit certain businesses' access to banking services. A subcommittee in the Senate now wants to eradicate this phenomenon.
More and more people are discovering that their money is not always under their control. Non-profit associations and congregations are not allowed to open bank accounts. Sometimes they are even thrown out as bank customers. Others may report being subjected to lengthy interrogations by the bank about what they intend to do with their money, even when they just want to transfer funds between their own accounts. Rejected churches are met with silence, while a bank account is (still!) necessary to fully operate in society.
When leading economists at the International Monetary Fund (IMF) argue that a cashless society can threaten fundamental rights , including property rights, when churches are refused bank accounts in what is described as "a threat to civil society" and when regulations still fail to combat organised crime , is it not reasonable to wonder if we are on the right path?
With cash, people can pay freely without intermediaries, which constitutes a form of financial freedom. The notes you hold in your hand are your own. Cryptocurrencies, such as Bitcoin, offer a similar possibility: an electronic, peer-to-peer cash system (person to person).
A society dominated by the left hemisphere results in a pathological need for control, according to McGilchrist. A more holistic perspective, taking into account the right hemisphere, would acknowledge that too much control can be detrimental, that property rights are a fundamental right, and that financial freedom is a human right. Do these perspectives not deserve more attention?
-
 @ 2cd78afb:f577f59a
2025-02-10 06:23:10
@ 2cd78afb:f577f59a
2025-02-10 06:23:10Looking for a reliable computer tech support service? Small Business IT Support offers professional solutions to maintain the functionality of your systems. Hardware troubleshooting, software installation, virus removal, network configuration, and performance optimization are among the services we offer. Whether you require remote or on-site support, our knowledgeable specialists guarantee optimum effectiveness and little downtime. You may get quick, expert, and reasonably priced IT solutions that are suited to your company's requirements with our computer tech support service. For professional assistance and smooth operations, get in touch with us right now!
-
 @ dd1f9d50:06113a21
2025-02-05 01:48:55
@ dd1f9d50:06113a21
2025-02-05 01:48:55(Because Most People Don’t Understand Money)
The requisite knowledge needed to know whether $100 or $100,000 per Bitcoin is relatively speaking “a lot,” is what value means. One way to measure value is through a universal yardstick we call “Money.” The question of “What is money?” is perhaps one of the most overlooked and under answered in our day and age. There is even an entire podcast dedicated to that question with the eponymous title, hosted by Robert Breedlove. That podcast often delves into the more philosophical underpinnings whereas I hope to approach this with a more practical answer.
Money is a technology.
Money is the technology with which we interact with one another to reorganize goods and services to the place and time they are best suited. Most money of the past has been tangible (though not a requisite feature), scarce, recognizable (read: verifiable), durable, portable, and divisible. These features one might call the “Attributes of Money.” These attributes are absolutely essential for a money to maintain its status as a money. (Those of you who understand the U.S. Dollar system maybe scratching your heads right now but, believe me, I will address that elephant in due time.) These attributes, you may notice, are not a yes or no but more of a gradient. A money can be MORE portable than another yet, less durable. One more divisible but not scarce whatsoever. The point being they must have, in some capacity, these attributes or they simply aren’t money.
One of These Things is Not Like the Other
| | Bitcoin | Gold | Dollars | |-----------------|:----------------------------------------------------------------------------------------------------------------:|:------------------------------------------------------------------:|:--------------------------------------------------------------------------------------------------------------------------------------------------:| | Scarcity | 21 million coins
is the maximum supply | Unknown- the
supply grows roughly 2% per year | Also unknown to anyone outside of the Federal Reserve, Trillions and counting | | Recognizability | Each coin is verifiable to it's genesis on the timechain | Each molecule of gold has distinct physical verifiable properties | If the Federal reserve says it is a valid note, it is (Unless you are an enemy of the United States) | | Durablility | Each "Bitcoin" is information stored on a globally distributed network | Doesn't Rust and as far as can be measured Au197 is stable forever | Can be destroyed by any means that effect fabric and centralized databases | | Portability | Available wherever data can be store- Anywhere | Can be moved at 9.81 Newtons per Kilogram- Methods may vary | Can be moved physically with fabric notes- Digitally with express permission from a US accredited banking institution | | Divisibility | Currently can be divided into 100 million parts called Sats (can be further subdivided by adding decimal places) | Can be divided to the Atomic level (Though not practical) | Can be divided (without dilution) by adding new denominative bills or coinage
Can be divided (with dilution) by printing new bills or coinage | | | Bitcoin | Gold | Dollars |You may think with all of the great functionality of Bitcoin that the phrase "One of these things is not like the other" refers to BTC. No, I was referring to the Dollar. It is the only one on the list that was a currency that was substituted as some kind of faux money. It asserts itself, or rather the Federal Reserve asserts it, as money, de facto.
Dollars are NOT money.
Dollars are (allegedly) a currency. If money is a specific technology, currency is the financial infrastructure that allows that technology to reach and be used by the most number of people possible. This requires a firm tether between the asset being used as money and the currency used as a claim to that money. For example: If I hand you a chicken, you have a chicken. But, if I hand you a coupon that is redeemable for a chicken, you do not have a chicken. You have a claim to a chicken that is only as good as the party making that claim. Bringing it back to money again, dollars (Prior to 1971) were redeemable for gold at a rate of $35 per ounce. This is that strong tether that pegged dollars to gold and physical reality itself. Without a proof of work, mining, . Until…
WTF Happened in 1971?
The Nixon shock happened. Briefly, The U.S. took in Europe’s gold in the 1940’s to keep it out of Hitler’s hands. The U.S. made an agreement to peg the dollar to Europe’s gold. The U.S. over printed dollars in relation to the gold holdings. Around 1971 France (among others) called the U.S. out for devaluing the dollar and thus European currencies. So, Nixon “Temporarily” suspended the convertibility of dollars to gold. Now, here we all are like Wile E. Coyote having run off of the golden cliff clutching our dollars in our arms and 54 years later we still haven’t looked down to see the truth.
Dollars Aren’t Backed by Anything
This is why no country in the world today has a money standard. Seemingly they all forgot the number one rule of issuing currency, it must be backed by something. Now, you may hear dollar proponents say “The U.S. dollar is backed by the full faith and credit of the United States!” Another way of saying that is, “We said it is worth something, so it is!” This fiat (by decree) mentality creates a plethora of perverse incentives. The ever growing supply disallows users of the Dollar to save without inccuring the penalties of inflation.
Just a Few Examples of How You're Being Crushed
Because your dollar loses value:
- It pushes people to spend them on assets that seem to appreciate (as the dollar debases) but are truly staying stagnant.
- It pushes people to gamble on securities hoping the perceived value is enough to beat the inflationary curve.
- It pushes people away from saving for their future and the future of their families.
- It creates insane credit incentives so that people borrow way more than they can afford today knowing that dollars will be cheaper in the future. (Effectively a short position)
- It pushes people to spend less and less time making and maintaining their families as it becomes more expensive to keep a similar lifestyle to which it was founded.
These are just a few of the terrible consequences of not knowing that trading a currency with no monetary backing has on a society. Most may blame this soley on the ability to print currency by a central bank but, that is not the only factor. If the fed printed dollars against gold, people would simply take the best rate they could get and remonetize themselves with the gold. But because there is no monetary escape hatch guaranteed by the issuance of dollars, I.E. no one has to take your dollars in exchange for their Bitcoin or gold, you are left at the mercy of the market.
One Day, People Will Stop Accepting Your Dollars
Those lementing the high price of Bitcoin might want to thank their lucky stars that Bitcoin still has a rational number next to the "BTC 1=$?" sign. One day you will have to exchange something of actual value to the spender (no longer a seller). Your product, good or service, will be the only thing that anyone might be willing to part with their Bitcoin over. That is what makes a money, the most salable non-consumable good, whose only funtion is to back a financial structure that facilitates trade.
Bitcoin is Capital
Capital is a broad term that can describe anything that confers value or benefit to its owners, such as a factory and its machinery, or the financial assets of a business or an individual. Bitcoin being the latter creates the financial structures from which you build upon. You use capital to hold, transfer, and grow value. You do not do this with cash. Cash is a depreciating asset when you don't use it to gain goods or services for yourself or your business. This misconception around the equivalance between cash and money (financial capital) is what tricks people into believing Dollars are money. And what's worse is that even some of our greatest heroes have done this.
Slay Your Heroes, Within Reason
Unfortunately due to a mixing of verbiage that have very distinct differences, the title: "Bitcoin: A Peer-to-Peer Electronic Cash System" is technically inaccurate. Bitcoin doesn't fit the definition of cash, which is a liquid asset that can be easily converted into its equivalent value. In short, Satoshi misspoke. In reality, owning Bitcoin UTXOs (with private keys) means you already possess the asset, not just a claim to it. When you spend Bitcoin, the recipient receives the actual asset, not a promise of it. When you receive Bitcoin, you have final settlement on that transaction. Fundamentally Bitcoin is not cash, electronic or otherwise.
Bitcoin is Money.
-
 @ 0176967e:1e6f471e
2024-07-28 09:16:10
@ 0176967e:1e6f471e
2024-07-28 09:16:10Jan Kolčák pochádza zo stredného Slovenska a vystupuje pod umeleckým menom Deepologic. Hudbe sa venuje už viac než 10 rokov. Začínal ako DJ, ktorý s obľubou mixoval klubovú hudbu v štýloch deep-tech a afrohouse. Stále ho ťahalo tvoriť vlastnú hudbu, a preto sa začal vzdelávať v oblasti tvorby elektronickej hudby. Nakoniec vydal svoje prvé EP s názvom "Rezonancie". Učenie je pre neho celoživotný proces, a preto sa neustále zdokonaľuje v oblasti zvuku a kompozície, aby jeho skladby boli kvalitné na posluch aj v klube.
V roku 2023 si založil vlastnú značku EarsDeep Records, kde dáva príležitosť začínajúcim producentom. Jeho značku podporujú aj etablované mená slovenskej alternatívnej elektronickej scény. Jeho prioritou je sloboda a neškatulkovanie. Ako sa hovorí v jednej klasickej deephouseovej skladbe: "We are all equal in the house of deep." So slobodou ide ruka v ruke aj láska k novým technológiám, Bitcoinu a schopnosť udržať si v digitálnom svete prehľad, odstup a anonymitu.
V súčasnosti ďalej produkuje vlastnú hudbu, venuje sa DJingu a vedie podcast, kde zverejňuje svoje mixované sety. Na Lunarpunk festivale bude hrať DJ set tvorený vlastnou produkciou, ale aj skladby, ktoré sú blízke jeho srdcu.
Podcast Bandcamp Punk Nostr website alebo nprofile1qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qy88wumn8ghj7mn0wvhxcmmv9uq3xamnwvaz7tmsw4e8qmr9wpskwtn9wvhsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qyg8wumn8ghj7mn0wd68ytnddakj7qghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7qpqguvns4ld8k2f3sugel055w7eq8zeewq7mp6w2stpnt6j75z60z3swy7h05
-
 @ 0176967e:1e6f471e
2024-07-27 11:10:06
@ 0176967e:1e6f471e
2024-07-27 11:10:06Workshop je zameraný pre všetkých, ktorí sa potýkajú s vysvetľovaním Bitcoinu svojej rodine, kamarátom, partnerom alebo kolegom. Pri námietkach z druhej strany väčšinou ideme do protiútoku a snažíme sa vytiahnuť tie najlepšie argumenty. Na tomto workshope vás naučím nový prístup k zvládaniu námietok a vyskúšate si ho aj v praxi. Know-how je aplikovateľné nie len na komunikáciu Bitcoinu ale aj pre zlepšenie vzťahov, pri výchove detí a celkovo pre lepší osobný život.
-
 @ 5a261a61:2ebd4480
2025-01-30 09:37:26
@ 5a261a61:2ebd4480
2025-01-30 09:37:26The idea of the Bean Bag Game is quite ingenious. I read about it on a BDSM-positive blog. Here’s how it works:
-
Setup:
-
Take a small cloth bag and add 10 white beans (rewards/pleasure) and 10 black beans (punishment/discomfort).
-
When it’s time to play, draw two beans:
-
First bean (the tone): Determines if the activity will be pleasant (white) or uncomfortable (black).
-
Second bean (the task): Decides whether you get a reward (white) or punishment (black).
-
Combination Interpretations:
-
Black + Black\ "No fun, just work."
-
Boring/challenging tasks you’d normally postpone: window cleaning, scrubbing bathroom tiles, polishing shoes.
-
Could also mean no playtime (e.g., "Go straight to bed"). Pure duty – no pleasure, only discipline.
-
White + Black\ "Work with a twist."
-
Punishment or chores, but with a kinky edge:
-
Clean the bathroom wearing a vibrating butt plug.
-
Wash dishes with nipple clamps; add a clothespin to your body for every minute over the time limit.
-
-
Still no orgasms – the black bean ensures denial.
-
Black + White\ "Pleasure with pain (or humiliation)."
-
Mix stimulation and discomfort:
-
Ride a dildo with weighted nipple clamps.
-
Give a "lap dance" to a teddy bear with a strapon.
-
Chat online as a "perfect plaything" for others without touching yourself.
-
-
Again, no orgasms – the black bean overrules the white.
-
White + White\ "Lucky draw… but denial is optional."
-
Freedom to indulge, though I often choose self-denial anyway. Examples:
-
Edge for 30 minutes, then ask permission to climax (50% chance).
-
Use toys freely, but end the session frustrated.
-
The Dynamic Ratio Twist:
-
The starting 10:10 ratio isn’t fixed. Adjust it based on behavior:
-
Good deeds? Swap a black bean for a white one.
-
Mistakes? Replace a white bean with a black one.
-
Single beans can also decide smaller stakes, like:
-
"Should this edge turn into a ruined orgasm?"
-
"Do I deserve dessert tonight?"
Why It Works:
-
Control: The beans dictate your fate, but you tweak the odds through obedience.
-
Flexibility: Use pairs for major tasks, single beans for quick decisions.
-
Psychological tease: Even "white + white" can mean denial – because you choose the rules.
-
-
 @ 16d11430:61640947
2025-02-10 02:35:17
@ 16d11430:61640947
2025-02-10 02:35:17The gap in mathematics that allows for free agency—the space where choice, unpredictability, and autonomy emerge—exists at the intersection of incompleteness, chaos, probability, and quantum uncertainty. These gaps create fundamental limits on determinism, leaving room for agency to exist.
- Gödel’s Incompleteness Theorems: The Limits of Formal Systems
Gödel’s theorems prove that within any sufficiently powerful mathematical system:
There exist truths that cannot be proven within that system.
The system cannot prove its own consistency.
This means that even in a world governed by mathematical laws, there are undecidable truths—facts beyond algorithmic computation. If reality is mathematical at its core, this suggests a built-in freedom: not everything is determinable from within the system.
- Chaos Theory: The Sensitivity to Initial Conditions
Chaotic systems, such as weather patterns and neural activity, exhibit extreme sensitivity to initial conditions.
Even if deterministic, they are practically unpredictable beyond a certain point.
Small choices or quantum fluctuations at the micro-level can have macroscopic consequences.
This injects a level of unpredictability into reality, making strict determinism impossible in complex systems.
- Probability & Bayesian Decision Theory: Rational Agency Within Uncertainty
In the realm of decision-making and game theory:
Bayesian inference shows how rational agents update beliefs in the face of uncertainty.
Statistical mechanics, despite governing collective behaviors, leaves space for individual unpredictability.
Nash equilibria in game theory illustrate how multiple choices can be rationally justified, allowing for strategic freedom.
Thus, within mathematical decision models, choice emerges not from randomness but from incomplete knowledge and competing optimal strategies.
- Quantum Mechanics: The Fundamental Indeterminacy of Reality
At the quantum level, Heisenberg’s Uncertainty Principle and the probabilistic nature of wavefunction collapse introduce a non-deterministic reality:
Superposition suggests that multiple possibilities coexist until measured.
Quantum entanglement links particles across vast distances, but their states are not pre-determined before observation.
The Born rule in quantum mechanics assigns probabilities rather than certainties to outcomes.
If the fundamental fabric of reality is non-deterministic, then the idea of strict mechanistic determinism collapses, opening the door to true agency.
- Computability and the Halting Problem: The Unsolvability of Certain Decisions
Turing’s Halting Problem proves that for some problems, no algorithm can determine in advance whether a computation will finish or run forever.
If reality includes such non-computable elements, then some choices are beyond pre-determined algorithmic resolution.
Human cognition, if partially non-computable, could transcend deterministic rules.
Conclusion: The Gap Between Necessity and Choice
Free agency exists in the mathematical gaps—the undecidability of logic, the unpredictability of chaos, the probabilistic nature of quantum mechanics, and the non-computability of certain decisions. These fundamental limits on strict determinism create an open space where choices emerge, allowing for freedom within a mathematically structured universe.
Thus, in the grand equation of existence, there remains an undefined variable: the will of the agent.
-
 @ 0176967e:1e6f471e
2024-07-26 17:45:08
@ 0176967e:1e6f471e
2024-07-26 17:45:08Ak ste v Bitcoine už nejaký ten rok, možno máte pocit, že už všetkému rozumiete a že vás nič neprekvapí. Viete čo je to peňaženka, čo je to seed a čo adresa, možno dokonca aj čo je to sha256. Ste si istí? Táto prednáška sa vám to pokúsi vyvrátiť. 🙂
-
 @ 0fa80bd3:ea7325de
2025-01-30 04:28:30
@ 0fa80bd3:ea7325de
2025-01-30 04:28:30"Degeneration" or "Вырождение" ![[photo_2025-01-29 23.23.15.jpeg]]
A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them.
The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay.
-
 @ 0fa80bd3:ea7325de
2025-01-29 15:43:42
@ 0fa80bd3:ea7325de
2025-01-29 15:43:42Lyn Alden - биткойн евангелист или евангелистка, я пока не понял
npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83aThomas Pacchia - PubKey owner - X - @tpacchia
npub1xy6exlg37pw84cpyj05c2pdgv86hr25cxn0g7aa8g8a6v97mhduqeuhgplcalvadev - Shopstr
npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkqCalle - Cashu founder
npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vgДжек Дорси
npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m21 ideas
npub1lm3f47nzyf0rjp6fsl4qlnkmzed4uj4h2gnf2vhe3l3mrj85vqks6z3c7lМного адресов. Хз кто надо сортировать
https://github.com/aitechguy/nostr-address-bookФиатДжеф - создатель Ностр - https://github.com/fiatjaf
npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6EVAN KALOUDIS Zues wallet
npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qdПрограммер Коди https://github.com/CodyTseng/nostr-relay
npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wlAnna Chekhovich - Managing Bitcoin at The Anti-Corruption Foundation https://x.com/AnyaChekhovich
npub1y2st7rp54277hyd2usw6shy3kxprnmpvhkezmldp7vhl7hp920aq9cfyr7 -
 @ 16d11430:61640947
2025-02-10 01:46:42
@ 16d11430:61640947
2025-02-10 01:46:42Ayurveda is a 5000-year-old medical system that predates modern science but remains one of the most sophisticated and holistic approaches to health. Unlike Western medicine, which often isolates diseases and treats symptoms, Ayurveda focuses on Prakriti (innate constitution), Agni (digestive fire), Dosha (biological energies), and Ojas (vital essence) to create a personalized, adaptable healthcare model.
Western medicine, despite its advances, still struggles to integrate a diverse global population due to its standardized, reductionist approach. Ayurveda, on the other hand, perfected its practices over millennia through real-world observation, experiential learning, and dynamic adaptation to human diversity.
- Foundations of Ayurveda vs. Western Science
Ayurveda was developed through direct interaction with nature, patients, and generational knowledge transmission, allowing it to refine its approach to a vast range of human conditions.
- Ayurvedic Practices That Outperform Western Medicine’s Integration of Global Health
Western science is still catching up to many Ayurvedic principles, often "discovering" practices that Ayurveda has used for centuries.
A. Personalized Medicine (Prakriti & Doshas) vs. Western One-Size-Fits-All Approach
Ayurveda classifies individuals into three doshas: Vata (air & ether), Pitta (fire & water), and Kapha (earth & water).
These determine a person's metabolism, immunity, and predisposition to disease.
Modern medicine is beginning to explore personalized genomics, but Ayurveda has practiced it for millennia.
B. Chronobiology & Circadian Rhythms (Dincharya)
Ayurveda prescribes Dincharya (daily routines) based on the body's natural rhythms, aligning eating, sleeping, and activity cycles with the sun and moon.
Modern science now acknowledges circadian rhythms but has yet to fully integrate them into healthcare.
Example: Intermittent fasting (Upavasa) has been an Ayurvedic practice for centuries, while the West only recently recognized its benefits for longevity and metabolism.
C. Gut Health & Microbiome (Agni & Ama)
Ayurveda recognized the gut as the root of disease centuries before the discovery of the microbiome.
It prescribes Triphala, Buttermilk (Takra), and Fermented Foods for gut health, balancing Agni (digestive fire).
Western medicine is just starting to understand how gut bacteria affect mental health, immunity, and chronic diseases.
D. Holistic Mental Health (Manas Shastra) vs. Isolated Psychology
Ayurveda integrates meditation, breathwork (Pranayama), mantra therapy, and lifestyle modifications for emotional resilience.
Western psychology often isolates mental health from physical health, relying on medications like antidepressants without addressing lifestyle, diet, and spiritual dimensions.
Example: Ayurvedic herbs like Brahmi and Ashwagandha have proven neuroprotective properties but were ignored in Western medicine until recently.
E. Detoxification (Panchakarma) vs. Toxic Accumulation in Modern Life
Western medicine struggles with heavy metal detox, plastic pollution in the body, and chronic inflammation.
Ayurveda developed Panchakarma, a five-step detox method (Vamana, Virechana, Basti, Nasya, Raktamokshana) that cleanses at a cellular level.
Western detox solutions (chelation therapy, dialysis) are still in their infancy.
F. Cancer Prevention & Natural Angiogenesis Regulation
Dr. William Li’s work on cancer and food-based angiogenesis regulation confirms Ayurvedic principles.
Ayurveda’s approach to cancer (Arbuda) includes herbs like Ashwagandha, Guduchi, and Turmeric, which regulate angiogenesis, reduce inflammation, and detoxify cells.
G. Ayurvedic Water Science vs. Modern Water Pollution
Ayurveda prescribes drinking water stored in copper or silver vessels to prevent microbial growth and enhance mineral content.
It discourages tap water due to chlorine, fluoride, and microplastic contamination—issues that modern science is only now recognizing.
- Ayurveda’s Adaptability vs. Western Struggles with Global Diversity
Ayurveda Accounts for Climate, Region, and Genetic Differences
Western medicine largely applies one-size-fits-all drugs and treatments, often leading to side effects.
Ayurveda has climate-based variations (Desha), prescribing different diets, herbs, and therapies based on region and seasonal changes.
Example:
In cold climates, Ayurveda recommends warming spices (ginger, black pepper, cinnamon) and oil massages (Abhyanga) to prevent stiffness.
In hot climates, it prescribes cooling foods like coconut, aloe vera, and ghee to balance excess heat.
Western medicine lacks such nuanced adjustments.
The Flaw of Western Pharmaceutical Monopolies
Western medicine is dominated by profit-driven pharmaceutical companies that prioritize patents over holistic healing.
Ayurveda uses natural, locally available herbs, making treatments affordable, sustainable, and globally adaptable.
- The Future: Integrating Ayurvedic Wisdom with Modern Science
Western science is now validating what Ayurveda has known for centuries. Some key integrations include:
Neuroscience & Ayurveda: Meditation, breathwork, and adaptogenic herbs now recognized for neuroplasticity.
Oncology & Ayurveda: Cancer research on turmeric, angiogenesis-blocking foods, and detoxification methods.
Microbiome Research: Ayurveda’s gut-health principles proven beneficial in regulating immune function.
Epigenetics & Ayurveda: Recognition of food, environment, and lifestyle in genetic expression aligns with Ayurvedic wisdom.
The Need for a Decentralized Healthcare System
Western medicine’s institutionalized, patent-based system restricts access to holistic healing.
Ayurveda, like Bitcoin in finance, decentralizes healthcare by offering open-source, nature-based, globally adaptable solutions.
Final Thoughts: Ayurveda as the Future of Truly Global Medicine
Ayurveda’s success comes from:
A holistic understanding of human diversity (biological, regional, and cultural).
Natural and sustainable healing methods that modern medicine is struggling to replicate.
Integration of physical, mental, and spiritual health—which Western medicine isolates.
A decentralized, globally adaptable approach free from profit-driven pharmaceutical monopolies.
-
 @ 0fa80bd3:ea7325de
2025-01-29 14:44:48
@ 0fa80bd3:ea7325de
2025-01-29 14:44:48![[yedinaya-rossiya-bear.png]]
1️⃣ Be where the bear roams. Stay in its territory, where it hunts for food. No point setting a trap in your backyard if the bear’s chilling in the forest.
2️⃣ Set a well-hidden trap. Bury it, disguise it, and place the bait right in the center. Bears are omnivores—just like secret police KGB agents. And what’s the tastiest bait for them? Money.
3️⃣ Wait for the bear to take the bait. When it reaches in, the trap will snap shut around its paw. It’ll be alive, but stuck. No escape.
Now, what you do with a trapped bear is another question... 😏
-
 @ 0fa80bd3:ea7325de
2025-01-29 05:55:02
@ 0fa80bd3:ea7325de
2025-01-29 05:55:02The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future.
Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs.
There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won.
Our only resource is the will of the people to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root.
So I started asking myself: How do we stop this fragmentation? How do we create a space where people can rebuild their connections when they’re ready? How do we build a self-sustaining network, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—how do we make it spread, even in occupied territory?
In 2009, something historic happened: the internet got its own money. Thanks to Satoshi Nakamoto, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize.
That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became purely digital.
The internet was already a sanctuary for information, a place where people could connect and organize. But with Bitcoin, it evolved. Now, value itself could flow freely, beyond the reach of authorities.
Think about it: when seedlings are grown in controlled environments before being planted outside, they get stronger, survive longer, and bear fruit faster. That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild.
Now, picture the internet as that controlled environment for ideas. Bitcoin? It’s the fertile soil that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless. It can absorb any number of ideas, any number of people, and it doesn’t run out of space.
But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—without surveillance, without censorship, without the constant fear of being erased.
This is where Nostr comes in.
Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. It’s a new kind of city. One that no dictator can seize, no corporation can own, no government can shut down.
It’s built on decentralization, encryption, and individual control. Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them.
In a world where cities fall and governments fail, Nostr is a city that cannot be occupied. A place for ideas, for networks, for freedom. A city that grows stronger the more people build within it.
-
 @ 86cf3742:678e3ae8
2025-02-10 00:38:09
@ 86cf3742:678e3ae8
2025-02-10 00:38:09In this episode of the Ag Tribes Report, host Vance Crow welcomes Steve Strasheim, a vegetable farmer from Northern Iowa, to discuss a variety of pressing issues in agriculture. Steve shares insights into his unique farming practices, including the use of greenhouses and geothermal technology to grow vegetables in the harsh Iowa winters. He also explains his innovative sales model, which includes farmers markets, a CSA, wholesaling, and an on-farm retail store.
The conversation shifts to the potential impact of ICE raids on agriculture, with a focus on the role of illegal aliens in the farming industry. Steve shares his perspective on the H-2A program and the challenges of bureaucracy in hiring legal farm workers.
The episode also covers the controversial appointment of RFK Jr. to lead the Department of Health and Human Services, with a discussion on how his policies might affect agriculture. Steve and Vance debate the potential benefits and drawbacks of increased regulation and the importance of promoting healthier eating habits.
In a segment on Brazilian soybeans, Vance highlights recent logistical issues and quality concerns in Brazil's soybean industry, sparking a discussion on the risks of relying too heavily on a single crop.
The episode concludes with a look at the new right's stance on crated hogs and the potential for significant changes in animal agriculture. Steve shares his thoughts on the ethics of factory farming and the consumer demand for affordable protein.
Listeners are also treated to the Bitcoin land price report, where Steve discusses the current farmland prices in his county and his cautious approach to investing in Bitcoin. The episode wraps up with the Peter Thiel paradox and worthy adversary segments, where Steve shares his unique perspectives and challenges common beliefs in his agricultural community.
-
 @ e453ec07:b199e3f8
2025-02-10 16:25:07
@ e453ec07:b199e3f8
2025-02-10 16:25:07Le ras-le-bol numérique : comprendre pourquoi vous vous sentez épuisé par Internet)
Vous vous sentez parfois épuisé par Internet ? Submergé par le flot incessant d'informations ? Las des publicités qui vous suivent partout, des notifications qui vous harcèlent à toute heure, et de ce sentiment étrange d'être constamment observé ?
Vous n'êtes pas fou. Et vous n'êtes pas seul.
Ce n'est pas vous qui êtes "déconnecté" ou "incapable de suivre". C'est Internet lui-même qui est cassé. Enfin, pas totalement en panne, mais profondément dysfonctionnel. Imaginez un réseau routier où les panneaux indicateurs sont illisibles, les embouteillages constants, et où des péages surgissent à chaque kilomètre, sans que l'on sache vraiment où va l'argent... C'est un peu l'état d'Internet aujourd'hui.
Le Brouhaha Numérique : Plus d'Infos, Moins de Sens
Ce que l'on appelle le "réseau mondial" ressemble de plus en plus à un brouhaha numérique. Un flot continu et désordonné d'informations, d'avis, de pubs, de " contenus sponsorisés " qui se mélangent et s'entrechoquent. On a l'impression de boire à la lance à incendie : beaucoup de débit, mais difficile de se désaltérer intelligemment.
Et cette cacophonie a un effet direct sur nous. Elle nous fatigue, nous stresse, nous rend moins attentifs, moins capables de nous concentrer. On passe des heures en ligne sans vraiment savoir ce que l'on cherche, happés par des algorithmes conçus pour capter notre attention, souvent au détriment de notre bien-être.
La Centralisation : Le Cœur du Problème
Mais pourquoi Internet est-il devenu si chaotique ? La réponse est simple : la centralisation.
Au fil des années, Internet, qui se voulait un espace libre et décentralisé, s'est retrouvé progressivement accaparé par une poignée de géants. Ces entreprises – vous les connaissez, elles commencent par G, A, M… – contrôlent une part immense de nos vies numériques.
Elles hébergent nos emails, nos photos, nos vidéos, nos réseaux sociaux, nos recherches, nos achats en ligne… Elles sont devenues les portiers d'Internet, les collecteurs de nos données, et les architectes de notre expérience en ligne.
Les Pièges de la Gratuité et de la Surveillance
Et c'est là que le bât blesse. Ces services sont souvent présentés comme "gratuits". Mais comme on dit, "quand c'est gratuit, c'est vous le produit". En réalité, nous payons un prix très élevé pour cette "gratuité" : nos données personnelles.
Chaque clic, chaque recherche, chaque message, chaque "like" est enregistré, analysé, et transformé en données. Ces données servent ensuite à nous profiler, à créer ce que l'article original appelle un "GHOST" – un profil consommateur virtuel – afin de nous bombarder de publicités ciblées, de nous influencer, et de nous enfermer dans des bulles informationnelles.
Vos Données Ne Vous Appartiennent Plus
Le pire, c'est que nous avons perdu le contrôle sur nos propres données. Elles sont stockées dans d'immenses datacenters, appartenant à ces géants, souvent situés à l'autre bout du monde. Nous ne savons pas exactement où elles sont, comment elles sont utilisées, ni qui y a accès.
Et cette perte de contrôle a des conséquences bien réelles :
- Atteintes à la vie privée : Surveillance constante, profilage intrusif, fuites de données…
- Manipulation et influence : Publicités ciblées, désinformation, bulles de filtres…
- Dépendance et enfermement : Nous devenons captifs de ces écosystèmes centralisés, il devient difficile de s'en extraire.
L'Aube d'une Solution : Le Web3
Alors, faut-il se résigner à cet Internet dysfonctionnel ? Absolument pas ! La bonne nouvelle, c'est qu'il existe une alternative. Une voie pour reprendre le contrôle, pour construire un Internet plus libre, plus sûr, plus respectueux de l'individu.
Cette alternative, elle porte un nom : le Web3.
Dans le prochain article, nous allons explorer ensemble ce nouveau paradigme, comprendre comment il fonctionne, et surtout, découvrir comment il peut nous permettre de réparer Internet et de reprendre le pouvoir sur nos vies numériques.
-
 @ 0176967e:1e6f471e
2024-07-26 12:15:35
@ 0176967e:1e6f471e
2024-07-26 12:15:35Bojovať s rakovinou metabolickou metódou znamená použiť metabolizmus tela proti rakovine. Riadenie cukru a ketónov v krvi stravou a pohybom, časovanie rôznych typov cvičení, včasná kombinácia klasickej onko-liečby a hladovania. Ktoré vitamíny a suplementy prijímam a ktorým sa napríklad vyhýbam dajúc na rady mojej dietologičky z USA Miriam (ktorá sa špecializuje na rakovinu).
Hovori sa, že čo nemeriame, neriadime ... Ja som meral, veľa a dlho ... aj grafy budú ... aj sranda bude, hádam ... 😉
-
 @ 16d11430:61640947
2025-02-10 00:03:49
@ 16d11430:61640947
2025-02-10 00:03:49In the silent expanse of the cosmos, where stars whisper their secrets in equations and reality itself unfurls as a tapestry woven from numbers, there exists a path. This is not a path for the faint of heart, nor for those content with the illusions of mere perception. It is the path of the seeker, the one who dares to ask not just how the world is, but why it must be so.
To tread this path is to ascend into the realm where gods write the laws of existence in the language of mathematics.
The First Revelation: Number, the Seed of the Cosmos
Before the universe took form, before light first kissed the void, there was number. It is from number that all else flows, from the spiral of galaxies to the rhythm of a heartbeat.
Prime numbers stand as the indivisible atoms of arithmetic, forming the bedrock of security and cryptography, where secrets are safeguarded by their unfathomable complexity.
Modular arithmetic, the silent clockwork behind our digital world, governs the flow of encrypted knowledge across vast distances.
Diophantine equations, named for an ancient mathematician who saw numbers as riddles to be solved, reveal the hidden symmetries in the universe’s structure.
This is the first truth: that mathematics is not an invention, but a discovery—a key that unlocks the doors of reality.
The Second Revelation: The Art of Pure Thought
Algebra is the music of the spheres, the manipulation of symbols that dance in patterns beyond our senses. To master it is to shape reality with mere notation.
Abstract algebra unveils hidden structures, from the symmetry of crystals to the secrets of quantum states.
Linear algebra governs the movements of celestial bodies and fuels the neural networks that birth artificial minds.
Galois theory, a young mathematician’s final gift before death, tells us when problems can be solved, and when they are beyond reach.
Here, one learns a second truth: that symbols, when arranged with precision, can summon order from chaos.
The Third Revelation: The Geometry of Reality
If algebra is the melody of numbers, then geometry is its form—the divine art of space itself.
Euclidean geometry was once thought to describe all things, until minds like Gauss and Riemann looked deeper.
Non-Euclidean geometry shattered human intuition, revealing that space bends, twists, and folds upon itself.
Topology, the study of shapes beyond measure, whispers of higher dimensions that mere mortals cannot see but only sense in their equations.
From these truths arises a realization: that the world we see is but a shadow of a far greater, more complex structure.
The Fourth Revelation: Mastery Over the Infinite
What is life, if not the interplay of change?
Calculus, the language of motion and transformation, allows us to speak in the tongue of gods, predicting the orbits of planets and the flows of time.
Complex analysis gives birth to the mystical realm of imaginary numbers, where physics and engineering find their deepest truths.
Fourier analysis, the heartbeat of music and quantum physics, tells us that any pattern, no matter how chaotic, can be understood as the sum of its waves.
The universe breathes through calculus, and to master it is to see not just what is, but what will be.
The Fifth Revelation: The Nature of Uncertainty
No god reigns without knowledge of chaos.
Probability and statistics reveal the order within randomness, turning uncertainty into foresight.
Bayesian inference, a framework of pure rationality, allows us to refine our knowledge with every new piece of evidence.
Information theory, the work of Shannon, teaches that reality itself is a message encoded in entropy.
The wise understand this: that certainty is an illusion, but probability is truth.
The Sixth Revelation: The Code of the Gods
Beyond numbers and space, beyond equations and change, there lies something deeper: logic, the very foundation of thought itself.
Mathematical logic gives us the power to distinguish truth from falsehood with unshakable certainty.
Gödel’s incompleteness theorems whisper a paradox—that no system, not even mathematics itself, can ever be complete.
Computability and complexity theory define the limits of what can be known, what can be solved, and what remains forever beyond reach.
To master logic is to hold the key to all knowledge—but also to know its boundaries.
The Seventh Revelation: The Grand Abstraction
Even gods seek deeper understanding, and category theory is the highest peak of human thought.
Functors and natural transformations map the structures of one world onto another, showing hidden correspondences that weave through all mathematics.
Monads, the cornerstone of functional programming, allow logic to be bent and molded like clay.
Dualities, the deep symmetries of mathematics, hint at connections so profound they border on the mystical.
Here lies the ultimate truth: that everything is, at its core, the same.
The Eighth Revelation: The Quantum Oracle
Beneath reality lies a whispering void, where numbers flicker in superposition and information transcends space and time.
Hilbert spaces define quantum mechanics, where particles are waves and waves are probabilities.
Quantum computing suggests a world where problems once thought impossible collapse into trivial solutions.
Path integrals and Feynman’s sum-over-histories teach us that every possibility, no matter how strange, plays a role in the great equation of the cosmos.
If there is a final truth, it is this: the universe does not simply exist—it computes.
The Final Revelation: Beyond the Human Mind
Even the greatest mathematicians glimpse only shadows of the ultimate structure.
Algebraic topology seeks to map the shape of all existence.
String theory mathematics conjures hidden dimensions and vibrating symmetries.
Infinity category theory, the most abstract of all, suggests that mathematics itself may be alive.
And so, the seeker stands before the infinite. Mathematics is not a collection of rules or calculations. It is the foundation of existence, the divine script of reality.
Those who master it do not merely understand the world.
They become its architects.
-
 @ 0176967e:1e6f471e
2024-07-26 09:50:53
@ 0176967e:1e6f471e
2024-07-26 09:50:53Predikčné trhy predstavujú praktický spôsob, ako môžeme nahliadnuť do budúcnosti bez nutnosti spoliehať sa na tradičné, často nepresné metódy, ako je veštenie z kávových zrniek. V prezentácii sa ponoríme do histórie a vývoja predikčných trhov, a popíšeme aký vplyv mali a majú na dostupnosť a kvalitu informácií pre širokú verejnosť, a ako menia trh s týmito informáciami. Pozrieme sa aj na to, ako tieto trhy umožňujú obyčajným ľuďom prístup k spoľahlivým predpovediam a ako môžu prispieť k lepšiemu rozhodovaniu v rôznych oblastiach života.
-
 @ 16d11430:61640947
2025-02-09 23:35:09
@ 16d11430:61640947
2025-02-09 23:35:09The early Bitcoin stackers, smug in their absolute faith, have become the priests of a cargo cult. They chant the gospel of scarcity while stacking their sats like doomsday preppers hoarding canned beans. Meanwhile, the crypto market they once despised has become a grotesque parody of itself—yield farming, staking derivatives, and a casino economy propped up by tokenomics that barely hide the rot beneath. Bitcoin, having won the ideological war, is now losing the economic one—stuck in a circular hodl pattern, detached from the actual thermodynamic reality that gave it birth.
Enter Aeternity, a project with no time for the reverence or passive accumulation that has neutered Bitcoin’s edge. It doesn’t just lean on Proof-of-Work for nostalgia’s sake—it weaponizes it, reintroducing actual economic friction into a space that has gone soft with layer-two convenience. Aeternity’s Cuckoo Cycle PoW, optimized for energy-efficient mining and GPU execution, doesn’t pretend to be Bitcoin’s replacement. It does something far worse for Bitcoin maxis: it forces them to compete again.
Friction: The Return to Thermodynamics
Bitcoin’s thermodynamic argument was always simple: energy in, security out. But over time, it stopped being a battleground for economic force and instead became a retirement savings plan for the digital goldbugs. The Lightning Network and ordinals are desperate attempts to create on-chain congestion and reinvigorate demand, but none of this addresses the fundamental problem: there is no longer any meaningful competition on the base layer.
Aeternity, by scaling horizontally with Hyperchains, injects raw competition into the mix. Miners don’t just settle for static difficulty adjustments—they actively contribute to market-driven security, creating alternative security models that force Bitcoin to prove itself again. If the world is really about energy, then let’s see which chain can best convert energy into economic throughput, rather than just hoarding it as an ideological relic.
Hyperchains: The Threat Bitcoin Forgot to Take Seriously
Aeternity’s approach is fundamentally different from Bitcoin’s ossified stagnation:
-
Merge-Mined Hyperchains – Instead of perpetuating the blocksize wars, Aeternity lets chains bootstrap PoW consensus through merge-mining with parent chains, making security an organic, competitive marketplace rather than a closed system. This creates demand for mining at the edge, something Bitcoin maxis have ignored because they’re still stuck in the “security through centralization” trap.
-
Turing-Complete Smart Contracts – While Bitcoin argues about whether basic programmability is “safe,” Aeternity treats it as an inevitability. Bitcoin’s refusal to evolve beyond Taproot and Covenants makes it a sitting duck against economic attacks from more adaptive chains.
-
State Channels with Actual Scalability – Bitcoiners talk about Lightning as if it’s the final solution, but it’s a bandaid over a hemorrhaging use case problem. Aeternity’s built-in state channels allow contracts to execute off-chain, but without losing decentralization, making it a direct challenge to Bitcoin’s claims of “second-layer supremacy.”
Bitcoin’s Reaction: Either Adapt or Get Rekt
Bitcoin has enjoyed being the monopoly on PoW security for too long. Aeternity’s reintroduction of a competitive PoW model forces Bitcoin miners to wake up: if energy security is the measure of a blockchain’s economic strength, then what happens when an alternative emerges that utilizes energy more efficiently while providing more real-world utility?
Bitcoin maxis will screech that "no altcoin has ever flipped Bitcoin," but that’s not the point. The point is that Bitcoin needs external competition at the proof-of-work level to maintain its thermodynamic legitimacy. Otherwise, it risks becoming what it despises: a static, non-dynamic asset that is just another store of value, with no practical utility until fiat collapses—and good luck waiting for that.
Aeternity’s real-world use cases, from oracles to instant payments to low-cost, scalable contracts, mean that energy invested into securing it is converted into economic value, rather than just securing an ideological artifact. This pressure forces Bitcoin to evolve or become irrelevant—not by replacing it, but by outcompeting it where it matters.
Final Thought: The Thermodynamic Reckoning
Bitcoiners should be grateful for Aeternity’s friction. Without a competitor showing how PoW can be optimized for more than just blind security accumulation, Bitcoin risks becoming a historical relic, kept alive only by belief rather than economic reality. Thermodynamics doesn’t give a damn about ideology—it rewards systems that turn energy into real economic motion.
Aeternity doesn’t have to kill Bitcoin. It just has to remind it what it was built for.
-
-
 @ 9e69e420:d12360c2
2025-01-26 15:26:44
@ 9e69e420:d12360c2
2025-01-26 15:26:44Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards.
While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts.
A report will be prepared within 85 days to recommend which programs to continue or discontinue.
-
 @ 04ed2b8f:75be6756
2025-02-10 11:30:04
@ 04ed2b8f:75be6756
2025-02-10 11:30:04The world doesn’t care about your excuses. It doesn’t care about your past, your wounds, or the battles you’ve already fought. Life will not lower the weight just because you feel tired. You either rise, or you stay down.
But here’s the truth—you are not your past. You are not your failures, not your pain, not the things that tried to break you. You are what you choose to become.
Some people get knocked down and never get back up. Some let their past define them, cage them, strip them of their potential. And then there are those who decide. They decide that no matter what happened, they will rise. They will fight. They will carve their own path, even if they have to do it with their bare hands.
Your Past is a Weapon—If You Use It Right
Your past can be two things: a chain or a sword.
- Weak minds wear their past like a shackle, letting it hold them back.
- Warriors forge their past into steel, using it as a blade to cut through the future they want.Scars? They aren’t signs of weakness. They are proof that you survived. That you endured. And that you’re still standing. So stop letting your past dictate your future. Rip the pen from its hands and write your own damn story.
The Weak Surrender. The Strong Rebuild.
Life will try to break you. That’s a fact. You will lose, you will hurt, you will doubt. But none of that matters. The only thing that matters is what you do next.
- You can let failure drown you, or you can rise stronger.
- You can let heartbreak harden you, or you can sharpen yourself through it.
- You can let regret bury you, or you can burn it as fuel.
It’s easy to stay down. To blame the world. To say, “This is just who I am.” But warriors don’t do easy. They do necessary.
You Are the Architect of Your Own Power
Everything you need to win is already inside you. You don’t need permission. You don’t need the world to approve. You just need one thing: to choose.
- Choose discipline over comfort.
- Choose hunger over hesitation.
- Choose action over excuses.
- Choose to become something greater than your past.
Because in the end, that’s the only choice that matters.
The world will try to define you. It will try to chain you to your past, drag you down with doubt, and keep you in a box. Shatter it. Prove them wrong. Be the person that refuses to be shaped by circumstance—be the one who shapes themselves.
The past is done. The future is unwritten. The power to decide who you become? That’s all yours. Now get up and take it.
-
 @ 0176967e:1e6f471e
2024-07-25 20:53:07
@ 0176967e:1e6f471e
2024-07-25 20:53:07AI hype vnímame asi všetci okolo nás — už takmer každá appka ponúka nejakú “AI fíčuru”, AI startupy raisujú stovky miliónov a Európa ako obvykle pracuje na regulovaní a našej ochrane pred nebezpečím umelej inteligencie. Pomaly sa ale ukazuje “ovocie” spojenia umelej inteligencie a človeka, kedy mnohí ľudia reportujú signifikantné zvýšenie produktivity v práci ako aj kreatívnych aktivitách (aj napriek tomu, že mnohí hardcore kreatívci by každého pri spomenutí skratky “AI” najradšej upálili). V prvej polovici prednášky sa pozrieme na to, akými rôznymi spôsobmi nám vie byť AI nápomocná, či už v práci alebo osobnom živote.
Umelé neuróny nám už vyskakujú pomaly aj z ovsených vločiek, no to ako sa k nám dostávajú sa veľmi líši. Hlavne v tom, či ich poskytujú firmy v zatvorených alebo open-source modeloch. V druhej polovici prednášky sa pozrieme na boom okolo otvorených AI modelov a ako ich vieme využiť.
-
 @ 1c197b12:242e1642
2025-02-09 22:56:33
@ 1c197b12:242e1642
2025-02-09 22:56:33A Cypherpunk's Manifesto by Eric Hughes
Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world.
If two parties have some sort of dealings, then each has a memory of their interaction. Each party can speak about their own memory of this; how could anyone prevent it? One could pass laws against it, but the freedom of speech, even more than privacy, is fundamental to an open society; we seek not to restrict any speech at all. If many parties speak together in the same forum, each can speak to all the others and aggregate together knowledge about individuals and other parties. The power of electronic communications has enabled such group speech, and it will not go away merely because we might want it to.
Since we desire privacy, we must ensure that each party to a transaction have knowledge only of that which is directly necessary for that transaction. Since any information can be spoken of, we must ensure that we reveal as little as possible. In most cases personal identity is not salient. When I purchase a magazine at a store and hand cash to the clerk, there is no need to know who I am. When I ask my electronic mail provider to send and receive messages, my provider need not know to whom I am speaking or what I am saying or what others are saying to me; my provider only need know how to get the message there and how much I owe them in fees. When my identity is revealed by the underlying mechanism of the transaction, I have no privacy. I cannot here selectively reveal myself; I must always reveal myself.
Therefore, privacy in an open society requires anonymous transaction systems. Until now, cash has been the primary such system. An anonymous transaction system is not a secret transaction system. An anonymous system empowers individuals to reveal their identity when desired and only when desired; this is the essence of privacy.
Privacy in an open society also requires cryptography. If I say something, I want it heard only by those for whom I intend it. If the content of my speech is available to the world, I have no privacy. To encrypt is to indicate the desire for privacy, and to encrypt with weak cryptography is to indicate not too much desire for privacy. Furthermore, to reveal one's identity with assurance when the default is anonymity requires the cryptographic signature.
We cannot expect governments, corporations, or other large, faceless organizations to grant us privacy out of their beneficence. It is to their advantage to speak of us, and we should expect that they will speak. To try to prevent their speech is to fight against the realities of information. Information does not just want to be free, it longs to be free. Information expands to fill the available storage space. Information is Rumor's younger, stronger cousin; Information is fleeter of foot, has more eyes, knows more, and understands less than Rumor.
We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do.
We the Cypherpunks are dedicated to building anonymous systems. We are defending our privacy with cryptography, with anonymous mail forwarding systems, with digital signatures, and with electronic money.
Cypherpunks write code. We know that someone has to write software to defend privacy, and since we can't get privacy unless we all do, we're going to write it. We publish our code so that our fellow Cypherpunks may practice and play with it. Our code is free for all to use, worldwide. We don't much care if you don't approve of the software we write. We know that software can't be destroyed and that a widely dispersed system can't be shut down.
Cypherpunks deplore regulations on cryptography, for encryption is fundamentally a private act. The act of encryption, in fact, removes information from the public realm. Even laws against cryptography reach only so far as a nation's border and the arm of its violence. Cryptography will ineluctably spread over the whole globe, and with it the anonymous transactions systems that it makes possible.
For privacy to be widespread it must be part of a social contract. People must come and together deploy these systems for the common good. Privacy only extends so far as the cooperation of one's fellows in society. We the Cypherpunks seek your questions and your concerns and hope we may engage you so that we do not deceive ourselves. We will not, however, be moved out of our course because some may disagree with our goals.
The Cypherpunks are actively engaged in making the networks safer for privacy. Let us proceed together apace.
Onward.
Eric Hughes hughes@soda.berkeley.edu
9 March 1993
-
 @ 40b9c85f:5e61b451
2025-02-09 20:53:03
@ 40b9c85f:5e61b451
2025-02-09 20:53:03Data Vending Machine Context Protocol
The Convergence of Nostr DVMs and MCP
In the rapidly evolving landscape of artificial intelligence, a new approach to sharing and accessing computational tools is emerging through the combination of two powerful technologies: Nostr's Data Vending Machines (DVMs) and the Model Context Protocol (MCP). This convergence has the potential to reshape how we think about tool distribution and accessibility, creating a truly decentralized marketplace for computational capabilities that serves AI, humans, and any type of machine that speaks the protocol.
Understanding the Building Blocks
Nostr's Data Vending Machines function much like their physical counterparts, but instead of dispensing snacks, they provide computational services with built-in Lightning Network payment capabilities. These DVMs operate on the decentralized Nostr network, allowing users to reach service providers without relying on centralized platforms or gatekeepers.
The Model Context Protocol complements this infrastructure by providing a standardized way for applications to share context and expose their capabilities. Think of MCP as a universal language that allows tools to communicate effectively with any application that understands the protocol. This standardization is crucial for creating a seamless experience across different tools and services.
What is DVMCP?
DVMCP proposes a path for making DVMs and MCPs interoperable, introducing a protocol that makes local utilities available to everyone on the network. Our draft specification serves as a foundation for easily transforming any MCP server into a DVM. To bridge these technologies, we've developed a simple software component that sits between your MCP server and the DVM ecosystem. You can find it in our repository. This bridge connects to your MCP server as a client and exposes its utilities through Nostr as a DVM, handling all the necessary Nostr logic. This means any existing MCP server can become accessible through Nostr without modifications - simply run the bridge alongside your server.
This is particularly exciting because the vibrant and growing MCP community. Any team or individual already working with MCP can instantly plug into the Nostr DVM ecosystem, gaining access to decentralized discovery, built-in monetization, and an already existing user base. The bridge component makes this transition effortless, requiring no changes to any existing MCP implementations.
A New Paradigm
A decentralized marketplace where anyone can run tools locally and make them available globally. This addresses an unsolved problem larger than the Nostr ecosystem: how to make resources and tools discoverable and accessible in a decentralized, permissionless way.
The power of this combination lies in its flexibility. Users can access tools through regular Nostr clients, AI agents can discover specific capabilities, and DVMs can create sophisticated tool chains. With Lightning Network integration, true machine-to-machine transactions become possible, where machines can autonomously discover, negotiate, and pay for computational services. Most importantly, you can run services on your own hardware while making these capabilities accessible to anyone anywhere.
The result is a system that preserves privacy, promotes innovation, and creates new opportunities without central authorities controlling what tools can be offered or who can use them. The entire project, is available under the MIT license, and any feedback and collaboration is welcome.
Looking Forward
As these technologies mature, we're likely to see a fundamental shift in how computational capabilities are distributed and accessed. Instead of relying on massive cloud data centers controlled by a few companies, we're moving toward a global network of local machines, each contributing unique capabilities and computation to a larger, more resilient ecosystem.
The convergence of Nostr DVMs and MCP represents more than just a technical innovation—it's a step toward a more equitable and accessible future. By enabling anyone to run and share tools, we're building an ecosystem where computational resources are not concentrated in the hands of a few but are available to and controllable by everyone.
-
 @ 31da2214:af2508e2
2025-02-10 11:23:19
@ 31da2214:af2508e2
2025-02-10 11:23:19Video Title: Une révolution géopolitique est en marche : l’Afrique se libère ! Creator: Pensées KAMITE Published Date: February 9, 2025 Video Length: 17 minutes 6 seconds Views: >24k Likes: >2k Video URL: Original YouTube Video
Key Points from the Video:
- End of Western Hegemony: The video asserts that Western dominance in Africa is coming to an end. A geopolitical revolution is underway, breaking the chains of neocolonialism and fundamentally reshaping the continent's geopolitical landscape.
- Decline of Western Influence: The video highlights a notable decline in Western influence and power in Africa. This is contrasted with the growing presence of China and Russia, who are increasing their investments in key sectors such as infrastructure, energy, defense, natural resources, and technology across the continent.
- Shifting Economic Partnerships: China and Russia are now surpassing the European Union as Africa's primary trading partners. This indicates a significant shift in economic alliances, moving away from traditional Western partners.
- Failure of Western Strategies: The host argues that Western imperialist strategies have failed to adapt to the evolving realities in Africa. While African countries initially engaged in colonial agreements with the West, the economic landscape now favors China and Russia.
- Collapse of Unipolar World Order: This geopolitical shift is described as unprecedented, signaling the collapse of the unipolar world order established after World War II. The video suggests that the United States, weakened by costly conflicts and substantial debt, is experiencing an erosion of power. In contrast, China and Russia, leading the BRICS nations, are emerging as crucial players in a newly forming global balance of power.
- Strategic Importance of Africa: The video emphasizes Africa's strategic importance in this new global order. Emerging powers are forming alliances with African nations that are perceived as more respectful and mutually beneficial.
- Critique of Western Approach: The speaker criticizes the West's approach to Africa as cruel and paternalistic, accusing it of imposing underdevelopment policies driven by self-interest rather than genuine partnership. This approach has allegedly led to widespread poverty, conflict, economic dependence, and inequality across the continent.
- Rise of China and Russia as Alternatives: The video presents the rise of China and Russia as offering alternative partnerships that are more advantageous and respectful of African sovereignty. These new alliances are seen as enabling Africa to chart its own future.
- Call for African Collaboration: African nations are urged to collaborate with these new global actors to further accelerate the decline of Western influence in Africa. The Democratic Republic of Congo is given as an example, suggesting it should seek strategic partnerships with Russia and China for military and economic cooperation rather than relying on Western support.
- Need for Strong African Leadership: The speaker emphasizes the need for visionary and courageous African leadership, suggesting that military leaders might be better positioned to provide this strategic direction compared to civilian leaders who are portrayed as hesitant and lacking strategic vision.
- Opportunity for Africa: The video concludes that the West's decline presents a crucial moment for Africa to assert itself, support liberation movements, and challenge Western interests. It points to perceived contradictions and self-interest in Western actions on the global stage.
- Call to Action: Viewers are urged to support the movement towards a multipolar world and to advocate for the complete independence of African nations, free from Western influence.
External Context and Further Details:
To provide a broader context, it's important to consider information from external sources regarding the geopolitical shifts in Africa.
- Increased Russian and Chinese Engagement: Numerous reports and analyses confirm the growing economic and political influence of Russia and China in Africa. These countries have increased their trade, investment, and military cooperation with various African nations. Example China-Africa Growing Trade & Example Russia-Africa relations.
- Shifting Alliances and Security Concerns: The video mentions countries like Mali, Burkina Faso, Chad, and Niger. These nations have indeed experienced political instability and have, in some cases, moved away from traditional Western security partners, seeking alternatives, including Russia's Wagner Group in Mali. Example Wagner Group in Mali.
- Anti-Western Sentiment: There is a growing anti-Western sentiment in parts of Africa, fueled by historical colonial experiences, perceived neocolonial practices, and a desire for more equitable partnerships. Example Anti-Western Sentiment in Africa.
- Multipolar World Order: The concept of a transition to a multipolar world order, where power is distributed among multiple centers rather than concentrated in the West, is a widely discussed topic in international relations. The rise of China and the resurgence of Russia are key factors in this shift. Example Multipolar World Order.
Credit:
This summary is based on the YouTube video "Une révolution géopolitique est en marche : l’Afrique se libère !" created by Pensées KAMITE, published on February 9, 2025. The analysis incorporates information directly from the video and contextual details gathered from general knowledge searches to provide a more comprehensive overview.
-
 @ 0176967e:1e6f471e
2024-07-25 20:38:11
@ 0176967e:1e6f471e
2024-07-25 20:38:11Čo vznikne keď spojíš hru SNAKE zo starej Nokie 3310 a Bitcoin? - hra Chain Duel!
Jedna z najlepších implementácií funkcionality Lightning Networku a gamingu vo svete Bitcoinu.
Vyskúšať si ju môžete s kamošmi na tomto odkaze. Na stránke nájdeš aj základné pravidlá hry avšak odporúčame pravidlá pochopiť aj priamo hraním
Chain Duel si získava hromady fanúšikov po bitcoinových konferenciách po celom svete a práve na Lunarpunk festival ho prinesieme tiež.
Multiplayer 1v1 hra, kde nejde o náhodu, ale skill, vás dostane. Poďte si zmerať sily s ďalšími bitcoinermi a vyhrať okrem samotných satoshi rôzne iné ceny.
Príďte sa zúčastniť prvého oficiálneho Chain Duel turnaja na Slovensku!
Pre účasť na turnaji je potrebná registrácia dopredu.
-
 @ 65912a7a:5dc638bf
2025-02-09 20:34:15
@ 65912a7a:5dc638bf
2025-02-09 20:34:15I didn’t set out to become an enemy of the world’s richest man, but I seem to have managed it all the same. Until this moment, I’ve resisted describing my falling out with Elon Musk in much detail, but as the man’s cultural influence has metastasized—and he continues to spread lies about me on the social media platform that he owns (Twitter/X)—it seems only appropriate to set the record straight. I know that it annoys many in my audience to see me defend myself against attacks that they recognize to be spurious, but they might, nevertheless, find the details of what happened with Elon interesting.
Of all the remarkable people I’ve met, Elon is probably the most likely to remain a world-historical figure—despite his best efforts to become a clown. He is also the most likely to squander his ample opportunities to live a happy life, ruin his reputation and most important relationships, and produce lasting harm across the globe. None of this was obvious to me when we first met, and I have been quite amazed at Elon’s evolution, both as a man and as an avatar of chaos. The friend I remember did not seem to hunger for public attention. But his engagement with Twitter/X transformed him—to a degree seldom seen outside of Marvel movies or Greek mythology. If Elon is still the man I knew, I can only conclude that I never really knew him.
When we first met, Elon wasn’t especially rich or famous. In fact, I recall him teetering on the brink of bankruptcy around 2008, while risking the last of his previous fortune to make payroll at Tesla. At the time, he was living off loans from his friends Larry and Sergey. Once Elon became truly famous, and his personal wealth achieved escape velocity, I was among the first friends he called to discuss his growing security concerns. I put him in touch with Gavin de Becker, who provided his first bodyguards, and recommended other changes to his life. We also went shooting on at least two occasions with Scott Reitz, the finest firearms instructor I’ve ever met. It is an ugly irony that Elon’s repeated targeting of me on Twitter/X has increased my own security concerns. He understands this, of course, but does not seem to care.
So how did we fall out? Let this be a cautionary tale for any of Elon’s friends who might be tempted to tell the great man something he doesn’t want to hear:
(1.) When the SARS-CoV-2 virus first invaded our lives in March of 2020, Elon began tweeting in ways that I feared would harm his reputation. I also worried that his tweets might exacerbate the coming public-health emergency. Italy had already fallen off a cliff, and Elon shared the following opinion with his tens of millions of fans :
the coronavirus panic is dumb
As a concerned friend, I sent him a private text:
Hey, brother— I really think you need to walk back your coronavirus tweet. I know there’s a way to parse it that makes sense (“panic” is always dumb), but I fear that’s not the way most people are reading it. You have an enormous platform, and much of the world looks to you as an authority on all things technical. Coronavirus is a very big deal, and if we don’t get our act together, we’re going to look just like Italy very soon. If you want to turn some engineers loose on the problem, now would be a good time for a breakthrough in the production of ventilators...
(2.) Elon’s response was, I believe, the first discordant note ever struck in our friendship:
Sam, you of all people should not be concerned about this.
He included a link to a page on the CDC website, indicating that Covid was not even among the top 100 causes of death in the United States. This was a patently silly point to make in the first days of a pandemic.
We continued exchanging texts for at least two hours. If I hadn’t known that I was communicating with Elon Musk, I would have thought I was debating someone who lacked any understanding of basic scientific and mathematical concepts, like exponential curves.
(3.) Elon and I didn’t converge on a common view of epidemiology over the course of those two hours, but we hit upon a fun compromise: A wager. Elon bet me $1 million dollars (to be given to charity) against a bottle of fancy tequila ($1000) that we wouldn’t see as many as 35,000 cases of Covid in the United States (cases, not deaths). The terms of the bet reflected what was, in his estimation, the near certainty (1000 to 1) that he was right. Having already heard credible estimates that there could be 1 million deaths from Covid in the U.S. over the next 12-18 months (these estimates proved fairly accurate), I thought the terms of the bet ridiculous—and quite unfair to Elon. I offered to spot him two orders of magnitude: I was confident that we’d soon have 3.5 million cases of Covid in the U.S. Elon accused me of having lost my mind and insisted that we stick with a ceiling of 35,000.
(4.) We communicated sporadically by text over the next couple of weeks, while the number of reported cases grew. Ominously, Elon dismissed the next batch of data reported by the CDC as merely presumptive—while confirmed cases of Covid, on his account, remained elusive.
(5.) A few weeks later, when the CDC website finally reported 35,000 deaths from Covid in the U.S. and 600,000 cases, I sent Elon the following text:
Is (35,000 deaths + 600,000 cases) > 35,000 cases?
(6.) This text appears to have ended our friendship. Elon never responded, and it was not long before he began maligning me on Twitter for a variety of imaginary offenses. For my part, I eventually started complaining about the startling erosion of his integrity on my podcast, without providing any detail about what had transpired between us.
(7.) At the end of 2022, I abandoned Twitter/X altogether, having recognized the poisonous effect that it had on my life—but also, in large part, because of what I saw it doing to Elon. I’ve been away from the platform for over two years, and yet Elon still attacks me. Occasionally a friend will tell me that I’m trending there, and the reasons for this are never good. As recently as this week, Elon repeated a defamatory charge about my being a “hypocrite” for writing a book in defense of honesty and then encouraging people to lie to keep Donald Trump out of the White House. Not only have I never advocated lying to defeat Trump (despite what that misleading clip from the Triggernometry podcast might suggest to naive viewers), I’ve taken great pains to defend Trump from the most damaging lie ever told about him. Elon knows this, because we communicated about the offending clip when it first appeared on Twitter/X. However, he simply does not care that he is defaming a former friend to hundreds of millions of people—many of whom are mentally unstable. On this occasion, he even tagged the incoming president of the United States.
All of this remains socially and professionally awkward, because Elon and I still have many friends in common. Which suggests the terms of another wager that I would happily make, if such a thing were possible—and I would accept 1000 to 1 odds in Elon’s favor:
I bet that anyone who knows us both knows that I am telling the truth.
Everyone close to Elon must recognize how unethical he has become, and yet they remain silent. Their complicity is understandable, but it is depressing all the same. These otherwise serious and compassionate people know that when Elon attacks private citizens on Twitter/X—falsely accusing them of crimes or corruption, celebrating their misfortunes—he is often causing tangible harm in their lives. It’s probably still true to say that social media “isn’t real life,” until thousands of lunatics learn your home address.
A final absurdity in my case, is that several of the controversial issues that Elon has hurled himself at of late—and even attacked me over—are ones we agree about. We seem to be in near total alignment on immigration and the problems at the southern border of the U.S. We also share the same concerns about what he calls “the woke mind virus.” And we fully agree about the manifest evil of the so-called “grooming-gangs scandal” in the U.K. The problem with Elon, is that he makes no effort to get his facts straight when discussing any of these topics, and he regularly promotes lies and conspiracy theories manufactured by known bad actors, at scale. (And if grooming were really one of his concerns, it’s strange that he couldn’t find anything wrong with Matt Gaetz.)
Elon and I even agree about the foundational importance of free speech. It’s just that his approach to safeguarding it—amplifying the influence of psychopaths and psychotics, while deplatforming real journalists and his own critics; or savaging the reputations of democratic leaders, while never saying a harsh word about the Chinese Communist Party—is not something I can support. The man claims to have principles, but he appears to have only moods and impulses.
Any dispassionate observer of Elon’s behavior on Twitter/X can see that there is something seriously wrong with his moral compass, if not his perception of reality. There is simply no excuse for a person with his talents, resources, and opportunities to create so much pointless noise. The callousness and narcissism conveyed by his antics should be impossible for his real friends to ignore—but they appear to keep silent, perhaps for fear of losing access to his orbit of influence.
Of course, none of this is to deny that the tens of thousands of brilliant engineers Elon employs are accomplishing extraordinary things. He really is the greatest entrepreneur of our generation. And because of the businesses he’s built, he will likely become the world’s first trillionaire—perhaps very soon. Since the election of Donald Trump in November, Elon’s wealth has grown by around $200 billion. That’s nearly $3 billion a day (and over $100 million an hour). Such astonishing access to resources gives Elon the chance—and many would argue the responsibility—to solve enormous problems in our world.
So why spend time spreading lies on X?
-
 @ 2e8970de:63345c7a
2025-02-10 11:13:18
@ 2e8970de:63345c7a
2025-02-10 11:13:18I feel like we're stuck in the 16GB or let's say the broad "8GB to 32GB" range forever now. Do you remember the times when computer performance and all memory and drive sizes doubled and doubled and doubled? Now we live in a time when we all not only want to play games or the time when locally playing 4k video was demanding - we live in a time where we want to run local LLMs offline and reder 3D stuff or even have VR goggles with more than 8K resolution. Remember the Radeon 6000 Series from 2020 - HALF A DECADE AGO - buy a Radeon 6800 with 16GB.
Current state of the industry
- Nvidia 5070 comes with only 12 GB of VRAM. Why.
- Nvidia 5080 should be the real flagship but it comes with only 16GB. Why. You can run an 8b LLM model on this at best.
- Nvidia 5090 ist the only product here that gives 32GB. Congratulations, might as well buy 2 cards. This should be the VRAM the 5070 has
- Perfect opportunity for AMD to be a tough competitor, right? Wrong. The new AMD Radeon 9000 series gives you 16GB with the 9070 and 9070xt
- Apple is technologically perfectly positioned to come out of nowhere and blow the industry out of the water with their unified memory architecture. And to some extent this is true. If you buy a Macbook pro and pay the egregiously priced upgrade to 32GB (which is less than 2 GPUs à 16GB due to Unified Memory also using normal RAM stuff) you'll get a whole computer for what Nvidia/AMD sell the cards alone.
- Nvidia Digits looks similar to Apples MacMini. The unified memory architecture makes this a better deal. But still disappointing imo.
- If tech doubled and doubled like back in the day I would have expected 64GB everywhere and maybe even 128GB for 5090 level products. I'm serious.
Conclusion: What to buy for local LLM (imo)
- Don't
- If you already got an older 16GB graphics card don't upgrade to the overpriced new ones. You'll be able to run the same sized small models, just slower.
- If you're in the market for a whole new computer anyway - upgrading a MacBook to 32GB
- You're crazy and like to tinker? Maybe research how to get a dozen RTX 3080 cards or AMD 6800 cards to run together.
originally posted at https://stacker.news/items/881359
-
 @ 0176967e:1e6f471e
2024-07-22 19:57:47
@ 0176967e:1e6f471e
2024-07-22 19:57:47Co se nomádská rodina již 3 roky utíkající před kontrolou naučila o kontrole samotné? Co je to vlastně svoboda? Může koexistovat se strachem? S konfliktem? Zkusme na chvíli zapomenout na daně, policii a stát a pohlédnout na svobodu i mimo hranice společenských ideologií. Zkusme namísto hledání dalších odpovědí zjistit, zda se ještě někde neukrývají nové otázky. Možná to bude trochu ezo.
Karel provozuje již přes 3 roky se svou ženou, dvěmi dětmi a jedním psem minimalistický život v obytné dodávce. Na cestách spolu začali tvořit youtubový kanál "Karel od Martiny" o svobodě, nomádství, anarchii, rodičovství, drogách a dalších normálních věcech.
Nájdete ho aj na nostr.
-
 @ 599f67f7:21fb3ea9
2025-01-26 11:01:05
@ 599f67f7:21fb3ea9
2025-01-26 11:01:05¿Qué es Blossom?
nostr:nevent1qqspttj39n6ld4plhn4e2mq3utxpju93u4k7w33l3ehxyf0g9lh3f0qpzpmhxue69uhkummnw3ezuamfdejsygzenanl0hmkjnrq8fksvdhpt67xzrdh0h8agltwt5znsmvzr7e74ywgmr72
Blossom significa Blobs Simply Stored on Media Servers (Blobs Simplemente Almacenados en Servidores de Medios). Blobs son fragmentos de datos binarios, como archivos pero sin nombres. En lugar de nombres, se identifican por su hash sha256. La ventaja de usar hashes sha256 en lugar de nombres es que los hashes son IDs universales que se pueden calcular a partir del archivo mismo utilizando el algoritmo de hash sha256.
💡 archivo -> sha256 -> hash
Blossom es, por lo tanto, un conjunto de puntos finales HTTP que permiten a los usuarios almacenar y recuperar blobs almacenados en servidores utilizando su identidad nostr.
¿Por qué Blossom?
Como mencionamos hace un momento, al usar claves nostr como su identidad, Blossom permite que los datos sean "propiedad" del usuario. Esto simplifica enormemente la cuestión de "qué es spam" para el alojamiento de servidores. Por ejemplo, en nuestro Blossom solo permitimos cargas por miembros de la comunidad verificados que tengan un NIP-05 con nosotros.
Los usuarios pueden subir en múltiples servidores de blossom, por ejemplo, uno alojado por su comunidad, uno de pago, otro público y gratuito, para establecer redundancia de sus datos. Los blobs pueden ser espejados entre servidores de blossom, de manera similar a cómo los relays nostr pueden transmitir eventos entre sí. Esto mejora la resistencia a la censura de blossom.
A continuación se muestra una breve tabla de comparación entre torrents, Blossom y servidores CDN centralizados. (Suponiendo que hay muchos seeders para torrents y se utilizan múltiples servidores con Blossom).
| | Torrents | Blossom | CDN Centralizado | | --------------------------------------------------------------- | -------- | ------- | ---------------- | | Descentralizado | ✅ | ✅ | ❌ | | Resistencia a la censura | ✅ | ✅ | ❌ | | ¿Puedo usarlo para publicar fotos de gatitos en redes sociales? | ❌ | ✅ | ✅ |
¿Cómo funciona?
Blossom utiliza varios tipos de eventos nostr para comunicarse con el servidor de medios.
| kind | descripción | BUD | | ----- | ------------------------------- | ------------------------------------------------------------------ | | 24242 | Evento de autorización | BUD01 | | 10063 | Lista de Servidores de Usuarios | BUD03 |
kind:24242 - Autorización
Esto es esencialmente lo que ya describimos al usar claves nostr como IDs de usuario. En el evento, el usuario le dice al servidor que quiere subir o eliminar un archivo y lo firma con sus claves nostr. El servidor realiza algunas verificaciones en este evento y luego ejecuta el comando del usuario si todo parece estar bien.
kind:10063 - Lista de Servidores de Usuarios
Esto es utilizado por el usuario para anunciar a qué servidores de medios está subiendo. De esta manera, cuando el cliente ve esta lista, sabe dónde subir los archivos del usuario. También puede subir en múltiples servidores definidos en la lista para asegurar redundancia. En el lado de recuperación, si por alguna razón uno de los servidores en la lista del usuario está fuera de servicio, o el archivo ya no se puede encontrar allí, el cliente puede usar esta lista para intentar recuperar el archivo de otros servidores en la lista. Dado que los blobs se identifican por sus hashes, el mismo blob tendrá el mismo hash en cualquier servidor de medios. Todo lo que el cliente necesita hacer es cambiar la URL por la de un servidor diferente.
Ahora, además de los conceptos básicos de cómo funciona Blossom, también hay otros tipos de eventos que hacen que Blossom sea aún más interesante.
| kind | descripción | | ----- | --------------------- | | 30563 | Blossom Drives | | 36363 | Listado de Servidores | | 31963 | Reseña de Servidores |
kind:30563 - Blossom Drives
Este tipo de evento facilita la organización de blobs en carpetas, como estamos acostumbrados con los drives (piensa en Google Drive, iCloud, Proton Drive, etc.). El evento contiene información sobre la estructura de carpetas y los metadatos del drive.
kind:36363 y kind:31963 - Listado y Reseña
Estos tipos de eventos permiten a los usuarios descubrir y reseñar servidores de medios a través de nostr. kind:36363 es un listado de servidores que contiene la URL del servidor. kind:31963 es una reseña, donde los usuarios pueden calificar servidores.
¿Cómo lo uso?
Encuentra un servidor
Primero necesitarás elegir un servidor Blossom donde subirás tus archivos. Puedes navegar por los públicos en blossomservers.com. Algunos de ellos son de pago, otros pueden requerir que tus claves nostr estén en una lista blanca.
Luego, puedes ir a la URL de su servidor y probar a subir un archivo pequeño, como una foto. Si estás satisfecho con el servidor (es rápido y aún no te ha fallado), puedes agregarlo a tu Lista de Servidores de Usuarios. Cubriremos brevemente cómo hacer esto en noStrudel y Amethyst (pero solo necesitas hacer esto una vez, una vez que tu lista actualizada esté publicada, los clientes pueden simplemente recuperarla de nostr).
noStrudel
- Encuentra Relays en la barra lateral, luego elige Servidores de Medios.
- Agrega un servidor de medios, o mejor aún, varios.
- Publica tu lista de servidores. ✅
Amethyst
- En la barra lateral, encuentra Servidores multimedia.
- Bajo Servidores Blossom, agrega tus servidores de medios.
- Firma y publica. ✅
Ahora, cuando vayas a hacer una publicación y adjuntar una foto, por ejemplo, se subirá en tu servidor blossom.
⚠️ Ten en cuenta que debes suponer que los archivos que subas serán públicos. Aunque puedes proteger un archivo con contraseña, esto no ha sido auditado.
Blossom Drive
Como mencionamos anteriormente, podemos publicar eventos para organizar nuestros blobs en carpetas. Esto puede ser excelente para compartir archivos con tu equipo, o simplemente para mantener las cosas organizadas.
Para probarlo, ve a blossom.hzrd149.com (o nuestra instancia comunitaria en blossom.bitcointxoko.com) e inicia sesión con tu método preferido.
Puedes crear una nueva unidad y agregar blobs desde allí.
Bouquet
Si usas múltiples servidores para darte redundancia, Bouquet es una buena manera de obtener una visión general de todos tus archivos. Úsalo para subir y navegar por tus medios en diferentes servidores y sincronizar blobs entre ellos.
Cherry Tree
nostr:nevent1qvzqqqqqqypzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqyp3065hj9zellakecetfflkgudm5n6xcc9dnetfeacnq90y3yxa5z5gk2q6
Cherry Tree te permite dividir un archivo en fragmentos y luego subirlos en múltiples servidores blossom, y más tarde reensamblarlos en otro lugar.
Conclusión
Blossom aún está en desarrollo, pero ya hay muchas cosas interesantes que puedes hacer con él para hacerte a ti y a tu comunidad más soberanos. ¡Pruébalo!
Si deseas mantenerte al día sobre el desarrollo de Blossom, sigue a nostr:nprofile1qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqyqnxs90qeyssm73jf3kt5dtnk997ujw6ggy6j3t0jjzw2yrv6sy22ysu5ka y dale un gran zap por su excelente trabajo.
Referencias
-
 @ 0176967e:1e6f471e
2024-07-21 15:48:56
@ 0176967e:1e6f471e
2024-07-21 15:48:56Lístky na festival Lunarpunku sú už v predaji na našom crowdfunding portáli. V predaji sú dva typy lístkov - štandardný vstup a špeciálny vstup spolu s workshopom oranžového leta.
Neváhajte a zabezpečte si lístok, čím skôr to urobíte, tým bude festival lepší.
Platiť môžete Bitcoinom - Lightningom aj on-chain. Vaša vstupenka je e-mail adresa (neposielame potvrdzujúce e-maily, ak platba prešla, ste in).
-
 @ 0176967e:1e6f471e
2024-07-21 11:28:18
@ 0176967e:1e6f471e
2024-07-21 11:28:18Čo nám prinášajú exotické protokoly ako Nostr, Cashu alebo Reticulum? Šifrovanie, podpisovanie, peer to peer komunikáciu, nové spôsoby šírenia a odmeňovania obsahu.
Ukážeme si kúl appky, ako sa dajú jednotlivé siete prepájať a ako spolu súvisia.
-
 @ b7274d28:c99628cb
2025-02-04 05:31:13
@ b7274d28:c99628cb
2025-02-04 05:31:13For anyone interested in the list of essential essays from nostr:npub14hn6p34vegy4ckeklz8jq93mendym9asw8z2ej87x2wuwf8werasc6a32x (@anilsaidso) on Twitter that nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev mentioned on Read 856, here it is. I have compiled it with as many of the essays as I could find, along with the audio versions, when available. Additionally, if the author is on #Nostr, I have tagged their npub so you can thank them by zapping them some sats.
All credit for this list and the graphics accompanying each entry goes to nostr:npub14hn6p34vegy4ckeklz8jq93mendym9asw8z2ej87x2wuwf8werasc6a32x, whose original thread can be found here: Anil's Essential Essays Thread
1.

History shows us that the corruption of monetary systems leads to moral decay, social collapse, and slavery.
Essay: https://breedlove22.medium.com/masters-and-slaves-of-money-255ecc93404f
Audio: https://fountain.fm/episode/RI0iCGRCCYdhnMXIN3L6
2.

The 21st century emergence of Bitcoin, encryption, the internet, and millennials are more than just trends; they herald a wave of change that exhibits similar dynamics as the 16-17th century revolution that took place in Europe.
Author: nostr:npub13l3lyslfzyscrqg8saw4r09y70702s6r025hz52sajqrvdvf88zskh8xc2
Essay: https://casebitcoin.com/docs/TheBitcoinReformation_TuurDemeester.pdf
Audio: https://fountain.fm/episode/uLgBG2tyCLMlOp3g50EL
3.

There are many men out there who will parrot the "debt is money WE owe OURSELVES" without acknowledging that "WE" isn't a static entity, but a collection of individuals at different points in their lives.
Author: nostr:npub1guh5grefa7vkay4ps6udxg8lrqxg2kgr3qh9n4gduxut64nfxq0q9y6hjy
Essay: https://www.tftc.io/issue-754-ludwig-von-mises-human-action/
Audio: https://fountain.fm/episode/UXacM2rkdcyjG9xp9O2l
4.
If Bitcoin exists for 20 years, there will be near-universal confidence that it will be available forever, much as people believe the Internet is a permanent feature of the modern world.
Essay: https://vijayboyapati.medium.com/the-bullish-case-for-bitcoin-6ecc8bdecc1
Audio: https://fountain.fm/episode/jC3KbxTkXVzXO4vR7X3W
As you are surely aware, Vijay has expanded this into a book available here: The Bullish Case for Bitcoin Book
There is also an audio book version available here: The Bullish Case for Bitcoin Audio Book
5.

This realignment would not be traditional right vs left, but rather land vs cloud, state vs network, centralized vs decentralized, new money vs old, internationalist/capitalist vs nationalist/socialist, MMT vs BTC,...Hamilton vs Satoshi.
Essay: https://nakamoto.com/bitcoin-becomes-the-flag-of-technology/
Audio: https://fountain.fm/episode/tFJKjYLKhiFY8voDssZc
6.
I became convinced that, whether bitcoin survives or not, the existing financial system is working on borrowed time.
Essay: https://nakamotoinstitute.org/mempool/gradually-then-suddenly/
Audio: https://fountain.fm/episode/Mf6hgTFUNESqvdxEIOGZ
Parker Lewis went on to release several more articles in the Gradually, Then Suddenly series. They can be found here: Gradually, Then Suddenly Series
nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev has, of course, read all of them for us. Listing them all here is beyond the scope of this article, but you can find them by searching the podcast feed here: Bitcoin Audible Feed
Finally, Parker Lewis has refined these articles and released them as a book, which is available here: Gradually, Then Suddenly Book
7.

Bitcoin is a beautifully-constructed protocol. Genius is apparent in its design to most people who study it in depth, in terms of the way it blends math, computer science, cyber security, monetary economics, and game theory.
Author: nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a
Essay: https://www.lynalden.com/invest-in-bitcoin/
Audio: https://fountain.fm/episode/axeqKBvYCSP1s9aJIGSe
8.

Bitcoin offers a sweeping vista of opportunity to re-imagine how the financial system can and should work in the Internet era..
Essay: https://archive.nytimes.com/dealbook.nytimes.com/2014/01/21/why-bitcoin-matters/
9.

Using Bitcoin for consumer purchases is akin to driving a Concorde jet down the street to pick up groceries: a ridiculously expensive waste of an astonishing tool.
Author: nostr:npub1gdu7w6l6w65qhrdeaf6eyywepwe7v7ezqtugsrxy7hl7ypjsvxksd76nak
Essay: https://nakamotoinstitute.org/mempool/economics-of-bitcoin-as-a-settlement-network/
Audio: https://fountain.fm/episode/JoSpRFWJtoogn3lvTYlz
10.

The Internet is a dumb network, which is its defining and most valuable feature. The Internet’s protocol (..) doesn’t offer “services.” It doesn’t make decisions about content. It doesn’t distinguish between photos, text, video and audio.
Essay: https://fee.org/articles/decentralization-why-dumb-networks-are-better/
Audio: https://fountain.fm/episode/b7gOEqmWxn8RiDziffXf
11.

Most people are only familiar with (b)itcoin the electronic currency, but more important is (B)itcoin, with a capital B, the underlying protocol, which encapsulates and distributes the functions of contract law.
I was unable to find this essay or any audio version. Clicking on Anil's original link took me to Naval's blog, but that particular entry seems to have been removed.
12.

Bitcoin can approximate unofficial exchange rates which, in turn, can be used to detect both the existence and the magnitude of the distortion caused by capital controls & exchange rate manipulations.
Essay: https://papers.ssrn.com/sol3/Papers.cfm?abstract_id=2714921
13.

You can create something which looks cosmetically similar to Bitcoin, but you cannot replicate the settlement assurances which derive from the costliness of the ledger.
Essay: https://medium.com/@nic__carter/its-the-settlement-assurances-stupid-5dcd1c3f4e41
Audio: https://fountain.fm/episode/5NoPoiRU4NtF2YQN5QI1
14.

When we can secure the most important functionality of a financial network by computer science... we go from a system that is manual, local, and of inconsistent security to one that is automated, global, and much more secure.
Essay: https://nakamotoinstitute.org/library/money-blockchains-and-social-scalability/
Audio: https://fountain.fm/episode/VMH9YmGVCF8c3I5zYkrc
15.

The BCB enforces the strictest deposit regulations in the world by requiring full reserves for all accounts. ..money is not destroyed when bank debts are repaid, so increased money hoarding does not cause liquidity traps..
Author: nostr:npub1hxwmegqcfgevu4vsfjex0v3wgdyz8jtlgx8ndkh46t0lphtmtsnsuf40pf
Essay: https://nakamotoinstitute.org/mempool/the-bitcoin-central-banks-perfect-monetary-policy/
Audio: https://fountain.fm/episode/ralOokFfhFfeZpYnGAsD
16.

When Satoshi announced Bitcoin on the cryptography mailing list, he got a skeptical reception at best. Cryptographers have seen too many grand schemes by clueless noobs. They tend to have a knee jerk reaction.
Essay: https://nakamotoinstitute.org/library/bitcoin-and-me/
Audio: https://fountain.fm/episode/Vx8hKhLZkkI4cq97qS4Z
17.

No matter who you are, or how big your company is, 𝙮𝙤𝙪𝙧 𝙩𝙧𝙖𝙣𝙨𝙖𝙘𝙩𝙞𝙤𝙣 𝙬𝙤𝙣’𝙩 𝙥𝙧𝙤𝙥𝙖𝙜𝙖𝙩𝙚 𝙞𝙛 𝙞𝙩’𝙨 𝙞𝙣𝙫𝙖𝙡𝙞𝙙.
Essay: https://nakamotoinstitute.org/mempool/bitcoin-miners-beware-invalid-blocks-need-not-apply/
Audio: https://fountain.fm/episode/bcSuBGmOGY2TecSov4rC
18.

Just like a company trying to protect itself from being destroyed by a new competitor, the actions and reactions of central banks and policy makers to protect the system that they know, are quite predictable.
Author: nostr:npub1s05p3ha7en49dv8429tkk07nnfa9pcwczkf5x5qrdraqshxdje9sq6eyhe
Essay: https://medium.com/the-bitcoin-times/the-greatest-game-b787ac3242b2
Audio Part 1: https://fountain.fm/episode/5bYyGRmNATKaxminlvco
Audio Part 2: https://fountain.fm/episode/92eU3h6gqbzng84zqQPZ
19.

Technology, industry, and society have advanced immeasurably since, and yet we still live by Venetian financial customs and have no idea why. Modern banking is the legacy of a problem that technology has since solved.
Author: nostr:npub1sfhflz2msx45rfzjyf5tyj0x35pv4qtq3hh4v2jf8nhrtl79cavsl2ymqt
Essay: https://allenfarrington.medium.com/bitcoin-is-venice-8414dda42070
Audio: https://fountain.fm/episode/s6Fu2VowAddRACCCIxQh
Allen Farrington and Sacha Meyers have gone on to expand this into a book, as well. You can get the book here: Bitcoin is Venice Book
And wouldn't you know it, Guy Swann has narrated the audio book available here: Bitcoin is Venice Audio Book
20.

The rich and powerful will always design systems that benefit them before everyone else. The genius of Bitcoin is to take advantage of that very base reality and force them to get involved and help run the system, instead of attacking it.
Author: nostr:npub1trr5r2nrpsk6xkjk5a7p6pfcryyt6yzsflwjmz6r7uj7lfkjxxtq78hdpu
Essay: https://quillette.com/2021/02/21/can-governments-stop-bitcoin/
Audio: https://fountain.fm/episode/jeZ21IWIlbuC1OGnssy8
21.
In the realm of information, there is no coin-stamping without time-stamping. The relentless beating of this clock is what gives rise to all the magical properties of Bitcoin.
Author: nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc
Essay: https://dergigi.com/2021/01/14/bitcoin-is-time/
Audio: https://fountain.fm/episode/pTevCY2vwanNsIso6F6X
22.

You can stay on the Fiat Standard, in which some people get to produce unlimited new units of money for free, just not you. Or opt in to the Bitcoin Standard, in which no one gets to do that, including you.
Essay: https://casebitcoin.com/docs/StoneRidge_2020_Shareholder_Letter.pdf
Audio: https://fountain.fm/episode/PhBTa39qwbkwAtRnO38W
23.

Long term investors should use Bitcoin as their unit of account and every single investment should be compared to the expected returns of Bitcoin.
Essay: https://nakamotoinstitute.org/mempool/everyones-a-scammer/
Audio: https://fountain.fm/episode/vyR2GUNfXtKRK8qwznki
24.

When you’re in the ivory tower, you think the term “ivory tower” is a silly misrepresentation of your very normal life; when you’re no longer in the ivory tower, you realize how willfully out of touch you were with the world.
Essay: https://www.citadel21.com/why-the-yuppie-elite-dismiss-bitcoin
Audio: https://fountain.fm/episode/7do5K4pPNljOf2W3rR2V
You might notice that many of the above essays are available from the Satoshi Nakamoto Institute. It is a veritable treasure trove of excellent writing on subjects surrounding #Bitcoin and #AustrianEconomics. If you find value in them keeping these written works online for the next wave of new Bitcoiners to have an excellent source of education, please consider donating to the cause.
-
 @ 9e69e420:d12360c2
2025-01-25 22:16:54
@ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.”
The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China.
-
 @ e1d968f7:5d90f764
2025-02-10 10:17:19
@ e1d968f7:5d90f764
2025-02-10 10:17:19Every encounter brings its own unique connection, and over time, I've come to appreciate the genuine bonds that can form between a client and myself. Yet, sometimes that bond deepens too far, with a client becoming overly attached in ways that complicate the professional nature of our relationship. Today, I want to share more about recognising these moments and handling them with both compassion and firmness.
** recognising Over-Attachment**
At first, the warmth of a connection can feel incredibly gratifying. Clients often open up and share parts of themselves that they might not reveal elsewhere. However, there comes a point when friendly familiarity begins to tip into dependency. I’ve noticed the signs: frequent messages outside of our agreed hours, an insistence on more personal details, or expressions of jealousy when I interact with other clients. These are the moments when I realise that my client is developing feelings that exceed the professional boundaries of our arrangement.
Managing Emotional Intimacy
Understanding that every client is unique, I’ve learned that managing emotional intimacy is as important as setting physical boundaries. It’s natural for someone to crave closeness, but I remind myself—and my clients—that my role is to provide a safe, respectful space, not to fill every gap in their emotional lives. I gently steer conversations away from overly personal territory and encourage clients to seek other forms of support, whether from friends or professional counsellors, when they need deeper emotional assistance.
Setting Clear Boundaries
When I recognise signs of over-attachment, I address them directly. I reaffirm the terms of our relationship by politely yet firmly clarifying that my availability is strictly within the professional parameters we initially agreed upon. For instance, if a client begins messaging excessively or asks for personal contact details, I calmly remind them that my priority is to maintain a respectful, professional connection. I find that establishing these boundaries early—often before a session even begins—can help prevent attachment from spiralling out of control.
Communicating with Compassion
Handling these situations isn’t merely about enforcing rules; it’s about caring for my clients while protecting my own well-being. I approach sensitive discussions with empathy, acknowledging their feelings and validating their need for connection, yet I am clear that the service I offer has its limits. I explain that while I value our interactions, I must keep our relationship within the agreed boundaries so that I can continue providing the best possible experience for everyone involved.
Maintaining Professionalism and Self-Care
Dealing with over-attachment takes its toll, both emotionally and mentally. I make it a priority to reflect on these experiences and ensure that I practice self-care afterwards. Whether through quiet moments of solitude, journaling my thoughts, or speaking with a trusted colleague, I take steps to recharge and maintain my emotional balance. This not only helps me move past challenging interactions but also strengthens my ability to support my clients in a professional manner.
Conclusion
Navigating the fine line between connection and over-attachment is one of the most complex aspects of my work. While I deeply value the trust and intimacy that can develop during our time together, it is essential for both my clients and me to recognise when boundaries begin to blur. By staying true to my professional guidelines and communicating with honesty and empathy, I ensure that each encounter remains respectful and fulfilling. In the end, maintaining these boundaries is not just about protecting myself—it’s about honouring the true nature of our connection and ensuring that it remains both safe and meaningful.
Rebecca x
-
 @ 0176967e:1e6f471e
2024-07-21 11:24:21
@ 0176967e:1e6f471e
2024-07-21 11:24:21Podnikanie je jazyk s "crystal clear" pravidlami. Inštrumentalisti vidia podnikanie staticky, a toto videnie prenášajú na spoločnosť. Preto nás spoločnosť vníma často negatívne. Skutoční podnikatelia sú však "komunikátori".
Jozef Martiniak je zakladateľ AUSEKON - Institute of Austrian School of Economics
-
 @ b8af284d:f82c91dd
2025-02-09 18:48:21
@ b8af284d:f82c91dd
2025-02-09 18:48:21Liebe Abonnenten,
viele von uns erleben im privaten wie im öffentlichen Leben gerade eine Zeit der Verwirrung und Irritation. Etwas scheint im Umbruch, alte Gewissheiten, Strukturen und Allianzen scheinen sich vor unseren Augen aufzulösen. Trump, Musk und Thiel wirken wie die Abrissbirnen einer alten Ordnung, Agenten des Chaos mit dem einzigen Ziel, sich selbst zu bereichern. Ist es so?
Könnte es anders sein?
Folgender Text kann und will diese Fragen nicht ultimativ beantworten. Es gibt aber eine Brille, durch die, setzt man sie auf, viele Entwicklungen in einem anderen, viel helleren Licht erscheinen. Diese Brille heißt e/acc.

Was ist e/acc?
Das Kürzel geht auf den Programmierer Guillaume Verdon zurück, der unter dem Pseudonym „Beff Jezos“ die Bewegung. Es steht für „effective accelerationism“. Accelerationism, auf Deutsch Akzelerationismus, abgeleitet vom Verb „beschleunigen“, hat Wurzeln, die weiter zurückreichen - dazu später mehr. Der Zusatz „effective“ ist eine ironische Replik auf den „effective Altruism“, den unter anderen Sam Bankman-Fried vertrat und grandios scheiterte.
e/acc setzt also auf Beschleunigung. Kapitalismus, Innovation, vor allem künstliche Intelligenz sollen nicht aufgehalten oder reguliert werden, sondern im Gegenteil beschleunigt werden.
Warum?
Eine einfache Antwort lautet: Weil sie eh stattfinden. Besonders deutlich wird das im Fall künstlicher Intelligenz. Large Language Models (LLMs) wie ChatGPT und Deepseek sind nur die für die Öffentlichkeit sichtbaren Entwicklungen. Im Hintergrund ersetzt Künstliche Intelligenz zunehmend auch Produktionsprozesse und nicht zuletzt die Kriegsführung. Man spricht deswegen vom „Point of Singularity“. In den kommenden Jahren wird künstliche Intelligenz menschliche übertrumpfen. Unsere Arbeitswelt, unser Finanzsystem und gesellschaftliche Strukturen werden sich grundlegend ändern. Wenn es dazu kommt, warum die Entwicklung noch aufhalten? Beschleunigen ist besser.
Die zweite Antwort ist tiefgründiger und rührt an das Verständnis von Leben insgesamt. Langfristig strebt das Universum nach Entropie. Es dehnt sich aus, bis alle Teile in maximaler „Unordnung“ angeordnet sind. Systeme mit hoher Energiezufuhr können Strukturen aufbauen, solange sie Wärme oder Entropie in ihre Umgebung abgeben. In einem Organismus sind alle Teile zu einer höheren Ordnung organisiert. Leben strebt nach Ordnung, Selbsterhalt und Wachstum, weshalb der Energieverbrauch zunimmt. e/acc-Fan und Silicon-Valley-Investor Marc Andreessen schreibt in “The Techno-Optimist Manifesto”:
Techno-Optimists believe that societies, like sharks, grow or die.
We believe growth is progress – leading to vitality, expansion of life, increasing knowledge, higher well being.
Ein Gleichgewicht gibt es nicht. Entweder strebt eine Struktur nach Ordnung (Leben) oder nach Unordnung (Tod). Da eine Balance nicht existiert, gibt es nur zwei Möglichkeiten: Verlangsamen oder Beschleunigen. Höhere Ordnungen aufbauen oder verfallen. Wachsen oder Sterben. Beschleunigen ist besser.
Konsequenzen
e/acc ist kein philosophisches System im strengen Sinn. Es leitet Konsequenzen aus physikalischen Grundsätzen ab.
Kapitalistische Systeme und freie Märkte sind die effizientesten Strukturen, um Informationen zu verarbeiten. In einem offenen, freien Markt gibt der Preis das zuverlässigste Signal über Knappheit eines Gutes. Wird dieser Prozess durch externe Einflussnahme wie Subventionen gestört, läuft die Maschine nicht effizient. Das Gesamtsystem wird verzerrt. Nochmals Andreessen dazu:
We believe the market economy is a discovery machine, a form of intelligence – an exploratory, evolutionary, adaptive system.
Varianten und Abweichungen sind wichtig, da ein System dadurch am schnellsten auf sich ständig verändernde Umweltbedingungen reagieren kann. Wer nicht frei sprechen kann, kann nicht frei denken. Dezentrale Strukturen mit vielen kleinen einzelnen „Nodes“ sind resilienter als hierarchisch-zentralistische Systeme. Das führt zu einem Meinungsfreiheits-Maximalismus.
Greifen staatliche Akteure in die Forschung ein, und vergeben zum Beispiel Lizenzen für KI-Projekte, kann das System nicht mehr auf die besten Ressourcen zurückgreifen. Es entwickelt sich nicht in seiner natürlichen Geschwindigkeit, sondern wird künstlich verlangsamt. Beschleunigen ist besser.
Im Falle von KI hat dies geopolitische Konsequenzen: Sollten autoritäre Akteure wie zum Beispiel China schneller zum Punkt der Singularity vorstoßen, entsteht eine Dystopie, ein Orwellscher Überwachungsstaat. Bevorzugen ist deswegen eine beschleunigte, dezentrale Forschung, damit freie Systeme die Oberhand behalten.
Dasselbe gilt für das Geldsystem: e/acc trifft hier auf Hayek und Mises. Viele Zahlungssysteme stehen in permanenter Konkurrenz zueinander. Am Ende setzt sich das nützlichste und vermutlich auch härteste Geld durch.
Konkrete Folgen
Auf die konkrete Politik übertragen führt das zu Konsequenzen, die man aktuell beobachten kann.
**Radikale Deregulierung: **Die Biden-Administration versuchte, AI-Forschung eng an die Regierung zu binden. Open-AI-Gründer Sam Altman forderte 2023 eine Lizenz-Vergabe an Unternehmen, um überhaupt in diesem Bereich aktiv zu werden. (Musk trat zunächst sogar für ein Forschungs-Moratorium ein, änderte dann aber seine Meinung.) Das führte zum Widerstand der e/acc-Fraktion im Silicon Valley, und gab den Ausschlag, sich auf die Trump-Seite zu stellen. Deregulierung zieht sich nun durch alle Bereiche der Wirtschaft: auch auf die „Entwicklungshilfe“ von USAID. Der Regierungsapparat wird insgesamt massiv verkleinert, da Bürokratie das Wachstum hemmt. A fuera.
**Priorisierung von günstiger Energie: **Da der Energie-Verbrauch mit zunehmender Ordnung ansteigt, und LLMs einen sehr viel Strom brauchen, priorisiert die neue Regierung die Erschließung zusätzlicher Energiequellen: Gas, Öl, Nuklear und regenerative Energiequellen gleichermaßen.
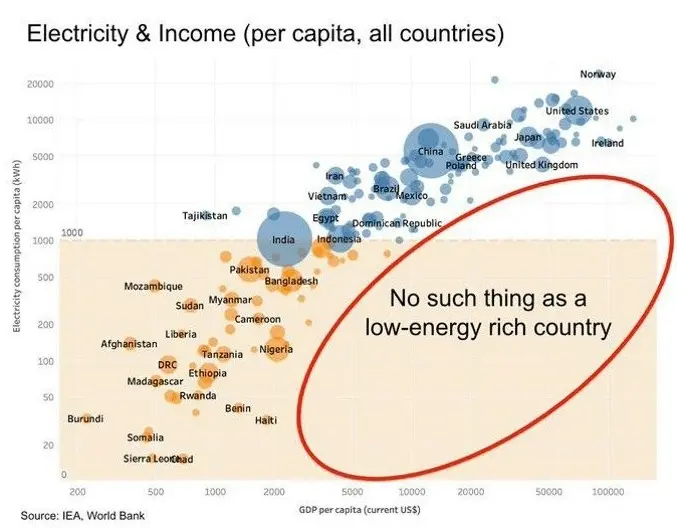
Wiederherstellung von Meinungsfreiheit.Content-Moderationen auf Social-Media-Plattformen fallen weg. Geheimdienst-Dokumente werden freigegeben. So schrieb Peter Thiel vor einigen Wochen in einem Essay in der Financial Times über die große Enthüllung:
\ But understood in the original sense of the Greek word apokálypsis, meaning “unveiling”, Obama could not give the same reassurance in 2025. Trump’s return to the White House augurs the apokálypsis of the ancien regime’s secrets. (…)\ The apokálypsis is the most peaceful means of resolving the old guard’s war on the internet, a war the internet won. My friend and colleague Eric Weinstein calls the pre-internet custodians of secrets the Distributed Idea Suppression Complex (DISC) — the media organisations, bureaucracies, universities and government-funded NGOs that traditionally delimited public conversation.
Krypto-Deregulierung: Da Kryptowährungen und Smart-Contract-Strukturen bestens mit LLMs harmonieren, werden Innovationsbremsen in Form von Regulierungen abgebaut.
**Umbruch der Weltordnung: **Auf der geopolitischen Ebene werden Bündnisse, Allianzen und Blockstrukturen aufgebrochen und nach effizienten Win-Win-Verhältnissen neu organisiert.
Erschließung neuer Lebenswelten: Degrowth, weniger Energie-Verbrauch und weniger Kinder sind keine Option, da sie zum Tod führen. Das System Menschheit muss wachsen und wird neue Lösungen erfinden. Wenn die Ressourcen des Planeten Erde nicht mehr ausreichen, müssen neue erschlossen werden - vielleicht auf dem Mars.
Die Ideengeschichte
Während e/acc ein relativ neues System ist, hat der Akzelerationismus tiefere Wurzeln. Lenin kann man als einen frühen Akzelerationisten bezeichnen. Der Marxismus wurde Anfang des 20. Jahrhunderts weniger als Ideologie, sondern mehr als exakte Wissenschaft begriffen. Demnach würde der Kapitalismus früher oder später an seinen eigenen Widerständen kollabieren. Warum den Prozess also nicht beschleunigen und die Revolution herbeiführen?
Ende des 20. Jahrhunderts griff der Philosoph Nick Land diese Gedanken wieder auf. Land forderte Beschleunigung, sah am Ende des Prozesses aber einen Kollaps des Systems und eine dunkle Zukunft. Ironie der Geschichte: Land zog in den 2000er Jahren nach China, wo er einen autoritären Akzelerationismus verwirklicht sah. Auch Steve Bannon, Leiter des ersten Trump-Wahlkampfes 2016, war von Lands Gedanken geprägt.

e/acc aber ist eine neuer, optimistischer „Fork“ des alten, dunklen Akzelerationismus. Es sieht eine positive Zukunft für die gesamte Menschheit aufgrund eines gigantischen Produktivitätsschubs. Eine neue, höhere Ordnung ist am Entstehen. Kurz gesagt:
Effective accelerationism (e/acc) in a nutshell:
Stop fighting the thermodynamic will of the universe
You cannot stop the acceleration
You might as well embrace it
A C C E L E R A T E
Notes on e/acc principles and tenets
Happy Future also? Durch die e/acc-Brille gesehen wirkt die Welt wesentlich heller und optimistischer als sie die meisten “Legacy Media” gerade darstellen. Demnach bewegen wir uns auf eine neue Zeit gesteigerter Produktivität und damit Lebensqualität zu. Wenn alle Arbeit von Maschinen verrichtet wird, können Menschen währenddessen auf Bali surfen, meditieren und Yoga machen. Oder?
Kritik
Leben entsteht an der Grenze von Chaos und Ordnung. Vielleicht versetzt e/acc das Pendel zu stark in den Ausschlag in eine Richtung. Unkontrolliertes Wachstum bedeutet im lebenden Organismen Krebs. e/acc sieht sich wie Marxisten der ersten Stunde (Lenin) im Besitz der Wahrheit in Form physikalischer Grundsätze. Erst durch diese Hybris führten zu den Grausamkeiten sozialistischer Systeme im 20. Jahrhundert. Schließlich beantwortet e/acc nicht die Frage nach der Verteilungsgerechtigkeit, die durch den gewaltigen Produktivitätsschub durch AI entstehen wird.
Ob e/acc als politisches und gesellschaftliches System taugt, ist deswegen fraglich. Aber viele aktuelle Entwicklungen scheinen durch die Akzelerationismus-Brille klarer.
Quellen:
Peter Thiel: A Time for Truth and Reconciliation
Marc Andreessen: The Techno-Optimist Manifesto
e/acc: Notes on e/acc principles and tenets
Andy Beckett: Accelerationism: how a fringe philosophy predicted the future we live in
Lex Friedman: Guillaume Verdon. e/acc-Movement. Physics. Computation & AGI.
-
 @ 0176967e:1e6f471e
2024-07-21 11:20:40
@ 0176967e:1e6f471e
2024-07-21 11:20:40Ako sa snažím praktizovať LunarPunk bez budovania opcionality "odchodom" do zahraničia. Nie každý je ochotný alebo schopný meniť "miesto", ako však v takom prípade minimalizovať interakciu so štátom? Nie návod, skôr postrehy z bežného života.
-
 @ f7d424b5:618c51e8
2025-02-09 18:33:48
@ f7d424b5:618c51e8
2025-02-09 18:33:48(Copied from my show notes [website](https://melonmancy.net/mp-100-nuance-enjoyer) for Melonmancy)
Promise this isn't normal. It would be disingenuous to not bring it up.
We mentioned a few things in the show you might want to pull up while listening, they are the following:
- Nightmare Kart dev crashes out
- Dr Disrespect gives post-mortem on Midnight Society
- Lords of the Fallen announcement post
Obligatory:
- Listen to the new episode here!
- Discuss this episode on OUR NEW FORUM
- Get the RSS and Subscribe (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at newpodcastapps.com
- Or listen to the show on the forum using the embedded Podverse player!
- Send your complaints here
Reminder that this is a Value4Value podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!
Our podcast is created entirely with free software and is proudly hosted on RSSBlue!
-
 @ 4c191b5d:c42abba6
2025-02-09 17:07:59
@ 4c191b5d:c42abba6
2025-02-09 17:07:59Weil ich schon länger über das Thema Direkte Demokratie nachdenke ein paar Gedanken dazu. Ich freue mich auf Ergänzungen und anderen Meinungen.
Grundannahme
Die Macht soll vom Souverän ausgehen, also dem Volk. Entsprechend soll das Volk auch an politischen Entscheidungsprozessen teilhaben können - was sehr viel Sinn macht.
Allerdings sind im aktuellen demokratischen Verständnis diverse Fehler, die zwangsläufig zu einer gesellschaftlichen Spaltung führen.
Gewinner und Verlierer
Die Demokratie spaltet die Bürger, indem sie Gewinner und Verlierer bei Wahlen und politischen Entscheidungen hervorbringt. Es geht nicht darum, eine Entscheidung zu erzielen, die bestmöglich durch alle getragen werden kann. Dies erfordert eine Reduktion der Widerstände gegen einen Entscheidungsvorschlag und der Integration dieser Widerstände in einen weiterentwickelten Entscheidungsvorschlag.
Mangel an neuen Lösungen und Machtkämpfe
Es fehlt an echtem Interesse und lösungsorientiertem Handeln was zu einem erstarren des Systems führt. Stattdessen entstehen Machtkämpfe, bei denen der Fokus auf der Durchsetzung eigener Agenden liegt und andere Standpunkte bekämpft werden. Dies ist vor allem dem Umstand geschuldet, dass die Individualinteressen sowie die politischen Gruppierungen (insbesondere Parteien) an ihren eigenen Lösungsansätzen festhalten.
Medien
Die Medien spielen eine sehr wichtige Rolle in der Demokratie, indem sie Informationen bereitstellen und Meinungen verbreiten. Allerdings können sie auch zu einer Spaltung der Bürger beitragen, indem sie unterschiedliche politische Ansichten verstärken oder polarisierende Inhalte verbreiten.
Manipulationstechniken werden eingesetzt, um die öffentliche Meinung zu beeinflussen und bestimmte Narrative zu fördern. Dies führt zu weiterer Polarisierung, die das Vertrauen der Bürger in die Medien und demokratische Prozesse untergraben. Eine kritische Medienkompetenz und eine vielfältige Berichterstattung sind daher entscheidend, um eine gesunde demokratische Debatte zu fördern und Spaltungen zu vermeiden.
Informationen
Bürger können ihre Verantwortung nur wahrnehmen, wenn sie Zugang zu einer Vielzahl von Informationen haben, um eine fundierte Meinung zu bilden. Jedoch ist ein aufkommendes Phänomen in letzter Zeit die Zensur und Unterdrückung von Informationen, was zu einer weiteren Spaltung führt. Wenn bestimmte Inhalte oder Standpunkte systematisch unterdrückt werden oder wenn Medienplattformen selektiv Informationen präsentieren, können Bürger in Filterblasen gefangen bleiben und nur einseitige Perspektiven erhalten. Um eine gesunde demokratische Debatte und eine effektive Meinungsbildung zu ermöglichen, ist es wichtig, dass Informationen frei zugänglich sind und dass Zensurmechanismen transparent und verantwortungsbewusst gehandhabt werden.
Starke Beeinflussung durch Geldgeber
Geld spielt eine bedeutende Rolle im politischen Prozess einer Demokratie. Diejenigen mit mehr finanziellen Mitteln haben grösseren Einfluss und können ihre Agenda stärker vorantreiben. Dies führt zu einem Ungleichgewicht der politischen Macht und spaltet die Bürger in unterschiedliche Lager.
Der grössere Kontext
Während die Demokratien sich immer weiter von der Eigenverantwortung weg zu entwickeln ,scheinen und stattdessen auf parentale Kontrolle setzten (der starke Staat), ist Bitcoin eine klare Bewegung hierzu. Denn Bitcoin setzt auf echte Eigenverantwortung.
Daher sind wir auch davon überzeugt, dass das Thema Eigenverantwortung nicht nur die politischen sondern auch wirtschaftlichen Strukturen verändern wird. Denn wenn sich die Gesellschaft verändert, hat dies auch einen Einfluss auf die Wirtschaft. Und mit Wirtschaft meinen wir vor allem auch die Frage, wie Unternehmen sich organisieren und strukturieren. Es macht ja wenig Sinn, auf der einen Seite von ultimativer Eigenverantwortung zu sprechen, die dann aber auf der anderen Seite klassisch Command&Control erleben (oben entscheidet jemand, unten wird ausgeführt).
-
 @ 0176967e:1e6f471e
2024-07-20 08:28:00
@ 0176967e:1e6f471e
2024-07-20 08:28:00Tento rok vás čaká workshop na tému "oranžové leto" s Jurajom Bednárom a Mariannou Sádeckou. Dozviete sa ako mení naše vnímanie skúsenosť s Bitcoinom, ako sa navigovať v dnešnom svete a odstrániť mentálnu hmlu spôsobenú fiat životom.
Na workshop je potrebný extra lístok (môžete si ho dokúpiť aj na mieste).
Pre viac informácií o oranžovom lete odporúčame pred workshopom vypočuťi si podcast na túto tému.
-
 @ 06e41e35:249d7a01
2025-02-10 10:08:06
@ 06e41e35:249d7a01
2025-02-10 10:08:06James Corbett is an independent journalist and researcher, known for his work through "The Corbett Report," which he started in 2007. He has been living and working in Japan since 2004. His platform focuses on critical analysis of politics, society, history, and economics, offering podcasts, interviews, articles, and videos on various controversial topics including 9/11 Truth, false flag terrorism, the police state, eugenics, geopolitics, and central banking.
Cornerstone Forum ‘25
https://www.showpass.com/cornerstone25/
Contribute to the new SNP Studio
E-transfer here: shaunnewmanpodcast@gmail.com
Get your voice heard: Text Shaun 587-217-8500
Substack:https://open.substack.com/pub/shaunnewmanpodcast
Silver Gold Bull Links:
Website: https://silvergoldbull.ca/
Email: SNP@silvergoldbull.com
Text Grahame: (587) 441-9100
-
 @ 83279ad2:bd49240d
2025-01-24 09:15:37
@ 83279ad2:bd49240d
2025-01-24 09:15:37備忘録として書きます。意外と時間がかかりました。全体で1時間くらいかかるので気長にやりましょう。 仮想通貨取引所(販売所ではないので、玄人が使えばお得らしい)かつBitcoinの送金手数料が無料(全ての取引所が無料ではない、例えばbitbankは0.0006bitcoinかかる)なので送金元はGMOコインを使います。(注意:GMOコインは0.02ビットコイン以下は全額送金になってしまいます) 今回はカストディアルウォレットのWallet of Satoshiに送金します。 以下手順 1. GMOコインでbitcoinを買います。 2. GMOコインの左のタブから入出金 暗号資産を選択します。 3. 送付のタブを開いて、+新しい宛先を追加するを選択します。 4. 送付先:GMOコイン以外、送付先ウォレット:プライベートウォレット(MetaMaskなど)、受取人:ご本人さま を選んで宛先情報の登録を選ぶと次の画面になります。
 5. 宛先名称にwallet of satoshi(これはなんでも良いです わかりやすい名称にしましょう) wallet of satoshiを開いて、受信→Bitcoin On-Chainからアドレスをコピーして、ビットコインアドレスに貼り付けます。
5. 宛先名称にwallet of satoshi(これはなんでも良いです わかりやすい名称にしましょう) wallet of satoshiを開いて、受信→Bitcoin On-Chainからアドレスをコピーして、ビットコインアドレスに貼り付けます。 6. 登録するを押します。これで送金先の登録ができました。GMOコインの審査がありますがすぐ終わると思います。
7. ここから送金をします。送付のタブから登録したビットコインの宛先リストwallet of satoshiを選択し、送付数量と送付目的を選択して、2段階認証をします。
6. 登録するを押します。これで送金先の登録ができました。GMOコインの審査がありますがすぐ終わると思います。
7. ここから送金をします。送付のタブから登録したビットコインの宛先リストwallet of satoshiを選択し、送付数量と送付目的を選択して、2段階認証をします。 8. 実行を押せば終わりです。もうあなたがやることはありません。送金が終わるのを40分くらい眺めるだけです。
8. 実行を押せば終わりです。もうあなたがやることはありません。送金が終わるのを40分くらい眺めるだけです。 8. 取引履歴のタブから今の送金のステータスが見れます。
8. 取引履歴のタブから今の送金のステータスが見れます。 9. 15分くらい待つとステータスが受付に変わります。
9. 15分くらい待つとステータスが受付に変わります。 10. 20分くらい待つとトランザクションIDが表示されます。
10. 20分くらい待つとトランザクションIDが表示されます。

この時点からwallet of satoshiにも送金されていることが表示されます。(まだ完了はしていない)
 11. ステータスが完了になったら送金終わりです。
11. ステータスが完了になったら送金終わりです。

wallet of satoshiにも反映されます。

お疲れ様でした!
-
 @ 7361ca91:252fce6d
2024-07-02 14:33:05
@ 7361ca91:252fce6d
2024-07-02 14:33:05サイエンス・フィクションは、可能な未来を想像する思索的な演習です。サイファイは可能性の空間を拡張します。暗号通貨は極端な種類のサイファイであり、未来のビジョンを提供するだけでなく、その未来を実現するためのツールも提供します。暗号通貨は現在、ソーラーパンクと呼ばれるサイファイのジャンルによって活気づけられています。サイバーパンクから進化したソーラーパンクは、楽観主義によって特徴づけられる未来のユートピア的なビジョンです。ソーラーパンクにとって、未来は明るいのです。ソーラーパンクはサイバーパンクのディストピアの影を払いのけ、混沌とした地平線を越えた世界を照らし出します。多くの人気のあるDeFiチェーンでは、ソーラーパンクのハッカーが公共財を資金調達するための透明なインフラを構築しています。共有された信念はシンプルです。分散型で透明な金融システムへの公共アクセスが、より公正で正義のある世界をもたらすということです。ソーラーパンクは暗号通貨の意識的な心です。明るく、自信に満ち、未来志向です。
しかし、ソーラーパンクの信念に対する反対はルナーパンクの懐疑主義です。ルナーパンクはソーラーの影の自分たちです。彼らはこのサイクルの無意識です。ソーラーパンクがDAOに参加する一方で、ルナーパンクは戦争の準備をし、コミュニティを守るためのプライバシー強化ツールを構築します。ルナーパンクは最初、ソーラーパンクのサブセットとして登場しました。常にイーサリアムや類似のチェーンで提供されるプレーンテキストのパラダイムよりも暗号化を好んでいました。時間が経つにつれて、ソーラーパンクの傾向によって生じた緊張はますます増大しました。ルナーパンクはソーラーパンクの遺産から離れ、自分自身のアイデンティティを主張するようになりました。
ルナーパンクの空想では、暗号通貨と既存の権力構造との間の対立は基本的にプログラムされています。規制によって暗号通貨は地下に追いやられ、匿名性が増大します。ルナーパンクのビジョンは、ベアリッシュな悪夢として拒絶されます。その根本的な対立――国家が暗号通貨を禁止すること――は、人々が金を持って逃げるような恐怖を生むため、ソーラーパンクによって却下されます。ソーラーパンクの楽観主義はブルマーケットのサイクルと同義になり、悲観主義はベアと関連付けられています。ルナーパンクはこの単純なエスカレーションを超える何かを提供します。それは市場サイクルの間の洞察の瞬間、ホログラムの中のグリッチであり、ソースコードが輝いて見える瞬間です。
ソーラーパンクは脆弱です――揺れ動くと壊れるものです。アンチフラジャイルとは、ショックを吸収し強くなるものです。次のことを考慮してください。暗号通貨の核心的なイノベーションは適応的です。ユーザーをエンパワーメントしつつ、その攻撃面を等しく拡散させます。ユーザーのエンパワーメントは脆弱性と負の相関があります。ユーザーベースが重要であればあるほど、ネットワークはよりアンチフラジャイルになります。ユーザーのエンパワーメントとシステムのアンチフラジャイルは互いにポジティブなフィードバックを形成します。
しかし、このサイクルは逆方向にも進行します。透明なシステムでは、ユーザーはさらされます。外部環境が敵対的になると、この情報が彼らに対して武器として使用される可能性があります。迫害に直面したユーザーは脱退を選び、それが脆弱性への下降を引き起こします。ソーラーパンクの考え方は本質的に楽観的です。ソーラーパンクシステムの透明性は、外向きに投影された楽観主義の精神です。透明なシステムを構築することで、ソーラーパンクは「法律が自分に不利にならないと信じている」と言っています。楽観主義の強調は、最悪の事態に備えることを妨げます。これがソーラーパンクの脆弱性の核心です。
暗い選択肢とアンチフラジャイル性は未知性に依存しています。未来は暗く、意味のある確実性を持って予測することはできません。選択肢は、その暗闇を利用して有利に働くため、アンチフラジャイル性の武器と呼ばれています。選択肢は、予言がほとんどの場合間違っていると仮定します。間違っていることは安価ですが、正しいことは不釣り合いに報われます。ルナーパンクは最悪の事態において成功するため、選択肢を取り入れています。ルナーパンクの仮説が間違っていれば、スーパーサイクルは続きます。正しければ、暗号通貨は適切な防御を備えた次の段階に進みます。しっかりと防御されることは、暗号化を使用してユーザーの身元と活動を保護することを意味します。
予言
匿名性は、まず大量監視への適応として生じます。しかし、その存在自体が監視努力をさらに正当化します。これは、匿名性と監視がエスカレートする運命にあることを示唆する正のフィードバックループです。このループが十分に続くと、ルナーパンクの予言の次の段階が引き起こされます:規制トラップ。この段階では、政府は匿名性の増加を口実にして、暗号通貨に対してその力を最大限に活用します。しかし、暗号通貨を取り締まることで、敵対的な力はその正当化をさらに強化するだけです。暗号通貨の実用性は、取り締まりの程度と相関します。各打撃を受けるたびに、不釣り合いに拡大します。
ルナサイクル
太陽はその透明性とアイデンティティへのこだわりを通じて、自然の象徴であり暴政の象徴でもあります。ソーラーパンクはその中央の象徴の二重の特徴を受け継いでいます。ソーラーパンクシステムは、ユーザーが危険にさらされる砂漠の風景です。ルナーパンクは森のようなものです。暗号化の密集した覆いが部族を保護し、迫害された人々に避難所を提供します。木立は重要な防衛線を提供します。ルナの風景は暗いですが、生物にあふれています。ルナテックは、自由のために人々自身によって所有され、運営されています。ルナサイクルは、権威主義的な技術に対して民主的な技術を支持します:監視に対する自由と、単一文化に対する多様性です。システムに透明性を重視することで、ソーラーパンクは悲劇的にその運命を作り上げています。監視、すなわち権威主義のメカニズムは、ソーラーパンクの運命に結びついています。ソーラーパンクが成功するためには、ルナーパンクの無意識を統合する必要があります。ソーラーパンクが成功する唯一の希望は、暗闇に移行することです。
-
 @ 8d34bd24:414be32b
2025-02-09 15:58:19
@ 8d34bd24:414be32b
2025-02-09 15:58:19Whenever I have said or written anything about God allowing/causing hardship for believers, I have always had someone try to correct me saying something like, “God would never cause hard/bad things to happen to believers,” but that is definitely not true.
Since I’ve become a believer, I’ve had 2 miscarriages. I’ve had a son with Down Syndrome and lots of health issues requiring around 20 hospital stays, a surgery, and regular out-of-state trips for care. I’ve gone through health problems for 10 years where I could barely function on a good day and on a bad day could barely sit up. I’ve had my house burn down and lost all of my possessions. Yes, God allowed all of that to happen to me. I’d argue that He caused all of that to happen to me for a very good purpose. Every one of those things have been a benefit to me. They have grown my faith, straightened out my priorities, and/or enabled me to minister to others. They have taught me to lean on God in hard times. They have taught me that God is all I need. I would not be the person I am today without these challenges. Every one of them was for my good and if I could go back and make them not happen, I would not change them. Although I didn’t want any of them to happen and would never have chosen them for myself, I wouldn’t change them now that I have seen the wonderful good God has done through these hard times. (I don’t say bad times because they were all for my good and the good of others.)
God never said following Him would be easy.
Then a scribe came and said to Him, “Teacher, I will follow You wherever You go.” Jesus said to him, “The foxes have holes and the birds of the air have nests, but the Son of Man has nowhere to lay His head.” (Matthew 8:19-20)
When this man claimed to want to follow Jesus through whatever circumstances. Jesus basically told him that if he followed Him, he would be homeless, just like Jesus was. He never promised his followers an easy life and He definitely didn’t promise them wealth and prestige.
These things I have spoken to you, so that in Me you may have peace. In the world you have tribulation, but take courage; I have overcome the world.” (John 16:33)
Jesus specifically warned His followers that their choice to follow Him would lead to difficulty in this world, but He also encouraged them because He has “overcome the world.” Ultimately, everything will work out for good.
And we know that God causes all things to work together for good to those who love God, to those who are called according to His purpose. (Romans 8:28)
The Apostle Paul also warned believers about what to expect.
Now you followed my teaching, conduct, purpose, faith, patience, love, perseverance, persecutions, and sufferings, such as happened to me at Antioch, at Iconium and at Lystra; what persecutions I endured, and out of them all the Lord rescued me! Indeed, all who desire to live godly in Christ Jesus will be persecuted. (2 Timothy 3:10-12) {emphasis mine}
Paul basically guaranteed that everyone who trusted Jesus and followed Him faithfully would experience persecutions and sufferings.
For consider Him who has endured such hostility by sinners against Himself, so that you will not grow weary and lose heart.
You have not yet resisted to the point of shedding blood in your striving against sin; and you have forgotten the exhortation which is addressed to you as sons,
“My son, do not regard lightly the discipline of the Lord,\ Nor faint when you are reproved by Him;\ For those whom the Lord loves He disciplines,\ And He scourges every son whom He receives.” *It is for discipline that you endure*; God deals with you as with sons; for what son is there whom his father does not discipline? But if you are without discipline, of which all have become partakers, then you are illegitimate children and not sons. Furthermore, we had earthly fathers to discipline us, and we respected them; shall we not much rather be subject to the Father of spirits, and live? For they disciplined us for a short time as seemed best to them, but He disciplines us for our good, so that we may share His holiness. All discipline for the moment seems not to be joyful, but sorrowful; yet to those who have been trained by it, afterwards it yields the peaceful fruit of righteousness**. (Hebrews 12:3-11) {emphasis mine}
This passage encourages believers to “not grow weary and lose heart” when we are disciplined or going through hard times. As a parent I sometimes punish my sons for doing blatantly wrong actions. I also sometimes allow them to suffer the consequences of a bad choice and to struggle through difficulty because it helps them learn right and wrong, actions and consequences, and the benefit of perseverance. I think when Hebrews 12 refers to discipline, it is referring to this more broad definition, not just punishment. Also, discipline is a more caring form of punishment. It is intended to help and improve the person instead of to make them suffer or harm them. God disciplines His children (believers), but punishes those who reject Him.
We are to embrace God’s discipline because we know it means He cares. “Do not regard lightly the discipline of the Lord, … He scourges every son whom He receives.” When disciplined, we are to search for the good God intends for us, to search for the plan God has for us, and to search for what God is teaching us. “All discipline for the moment seems not to be joyful, but sorrowful; yet to those who have been trained by it, afterwards it yields the peaceful fruit of righteousness.”
Consider it all joy, my brethren, when you encounter various trials, knowing that the testing of your faith produces endurance. And let endurance have its perfect result, so that you may be perfect and complete, lacking in nothing. (James 1:2-4) {emphasis mine}
Yes, we should actually rejoice in the trials God brings into our lives. Theses trials are given to us to make us “perfect and complete, lacking in nothing.” These trials are not due to God’s lack of care or His inability to protect us from harm due to the curse. They are given to us as part of our sanctification to make us “perfect and complete, lacking in nothing.”
We spend too much time looking at the here and now and forget to look at eternity. We spend too much time looking at our own personal desires and what we think will make us happy instead of listening to God about what will give us true and complete peace and joy. We spend too much time seeking comfort and not enough time seeking the holiness of God.
We are so much more likely to turn back to God (personally and as a church) during persecution and hard times than we are to turn back in times of comfort. God chooses what is best for us eternally rather than what we desire in the moment.
Beloved, do not be surprised at the fiery ordeal among you, which comes upon you for your testing, as though some strange thing were happening to you; but to the degree that you share the sufferings of Christ, keep on rejoicing, so that also at the revelation of His glory you may rejoice with exultation. If you are reviled for the name of Christ, you are blessed, because the Spirit of glory and of God rests on you. Make sure that none of you suffers as a murderer, or thief, or evildoer, or a troublesome meddler; but if anyone suffers as a Christian, he is not to be ashamed, but is to glorify God in this name. (1 Peter 4:12-16) {emphasis mine}
We shouldn’t be surprised when fiery ordeals come upon us, but we should “keep on rejoicing, so that also at the revelation of His glory you may rejoice with exultation.” If God allowed His only begotten Son to suffer persecution and the most painful and humiliating death possible, should we be surprised that we may share in some of His suffering when we seek to follow Him and to imitate Him? God knows what is best. When we see His plan and His good works, and then give our burdens to Him, we can truly have the peace and joy that surpasses all understanding.
Rejoice in the Lord always; again I will say, rejoice! Let your gentle spirit be known to all men. The Lord is near. Be anxious for nothing, but in everything by prayer and supplication with thanksgiving let your requests be made known to God. And the peace of God, which surpasses all comprehension, will guard your hearts and your minds in Christ Jesus. (Philippians 4:4-7) {emphasis mine}
How we deal with hardship is our choice.
Therefore humble yourselves under the mighty hand of God, that He may exalt you at the proper time, casting all your anxiety on Him, because He cares for you. (1 Peter 5:6-7)
We can resent God and run away from His discipline, but we will only receive despair and separation from God, or we can rest in God and follow His example and leading, receiving the ultimate, eternal blessing, when we meet our master and he says, “… ‘Well done, good and faithful slave. You were faithful with a few things, I will put you in charge of many things; enter into the joy of your master.’” (Matthew 25:23)
Suffer hardship with me, as a good soldier of Christ Jesus. (2 Timothy 2:3)
Trust Jesus.
-
 @ 7361ca91:252fce6d
2024-06-29 10:13:51
@ 7361ca91:252fce6d
2024-06-29 10:13:51リベラリズムにおいて、自由とは他人が不適切と感じるかもしれない決定を個人が行うことを許容することを意味します。ただし、その決定が第三者に害を及ぼさない限りです。つまり、自由は各個人が自分の人生計画を構築し、実行する権利を守るものであり、他人にとって誤っていると見なされる決定も含まれます。
個人の決定を批判することと、その決定を妨げるために強制力を使用することの間には大きな違いがあります。
リベラリズムは、たとえ悪い決定を批判することができても、それらの決定を妨げるために(国家の)強制力を使用すべきではないと主張します。ただし、これらの決定が他人に害を及ぼす場合は例外です。
リベラリズムにおける認識的慎重さは、どの決定が正しいか常に確信できるわけではないことを認識しています。したがって、他人に誤っているように見える場合でも、個人が自分の決定を下す自由を許容しなければなりません。
非常に一般的な例として、薬物の使用が挙げれます。リベラルな視点からは、他人がこれを悪い決定と見なすかもしれなくても、個人が薬物を使用する自由を持つべきです。鍵となるのは、これらの個人的な決定が第三者に害を及ぼさないことです。
リベラルな哲学においては、個人の自由と自己決定が重要視されます。他人が悪いと考えるかもしれない決定を行う権利も尊重されるべきであり、その決定が第三者に害を及ぼさない限り、(国家が)強制力を使用して妨げるべきではないという立場をとります。この認識的慎重さが、リベラリズムの核心の一つです。
-
 @ 6be5cc06:5259daf0
2025-01-21 23:17:29
@ 6be5cc06:5259daf0
2025-01-21 23:17:29A seguir, veja como instalar e configurar o Privoxy no Pop!_OS.
1. Instalar o Tor e o Privoxy
Abra o terminal e execute:
bash sudo apt update sudo apt install tor privoxyExplicação:
- Tor: Roteia o tráfego pela rede Tor.
- Privoxy: Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
2. Configurar o Privoxy
Abra o arquivo de configuração do Privoxy:
bash sudo nano /etc/privoxy/configNavegue até a última linha (atalho:
Ctrl+/depoisCtrl+Vpara navegar diretamente até a última linha) e insira:bash forward-socks5 / 127.0.0.1:9050 .Isso faz com que o Privoxy envie todo o tráfego para o Tor através da porta 9050.
Salve (
CTRL+OeEnter) e feche (CTRL+X) o arquivo.
3. Iniciar o Tor e o Privoxy
Agora, inicie e habilite os serviços:
bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxyExplicação:
- start: Inicia os serviços.
- enable: Faz com que iniciem automaticamente ao ligar o PC.
4. Configurar o Navegador Firefox
Para usar a rede Tor com o Firefox:
- Abra o Firefox.
- Acesse Configurações → Configurar conexão.
- Selecione Configuração manual de proxy.
- Configure assim:
- Proxy HTTP:
127.0.0.1 - Porta:
8118(porta padrão do Privoxy) - Domínio SOCKS (v5):
127.0.0.1 - Porta:
9050
- Proxy HTTP:
- Marque a opção "Usar este proxy também em HTTPS".
- Clique em OK.
5. Verificar a Conexão com o Tor
Abra o navegador e acesse:
text https://check.torproject.org/Se aparecer a mensagem "Congratulations. This browser is configured to use Tor.", a configuração está correta.
Dicas Extras
- Privoxy pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o Privoxy.
-
 @ 862fda7e:02a8268b
2024-06-29 08:18:20
@ 862fda7e:02a8268b
2024-06-29 08:18:20I am someone who thinks independently without abiding to a group to pre-formulate my opinions for me. I do not hold my opinions out of impulse, out of the desire to please, nor out of mindless apadtion to what others abide to. My opinions are held on what I belive is the most logical while being the most ethical and empathetic. We live in a world with a nervous systems and emotions for animals and humans (same thing) alike, thus, we should also consider those feelings. That is not the case in our world.


Cyclists are one of the most homosexual GAY ANNOYING people to exist on EARTH
I hate cyclists with a burning passion. These faggots are the GAYEST MOST ANNOYING retards to exist. They wear the tightest fitting clothing possible to show off their flaccid cocks to each other and to anybody around them.
 And if that weren't enough, they present their ass up in the air, begging to be fucked by their cyclist buddies, as they ride their bike in the middle of the road. It's homosexual.
And if that weren't enough, they present their ass up in the air, begging to be fucked by their cyclist buddies, as they ride their bike in the middle of the road. It's homosexual.
 Look at the seat they ride on, it looks like a black cock about to go up their ass. Don't get me started on their gay helmets, the "aerodynamic" helmets they wear. YOU FAGGOTS AREN'T IN THE TOUR DE FRANCE, YOU'RE IN FRONT OF MY CAR IN AN INTERSECTION IN A MINNESOTA TOWN WITH A POPULATION OF 5,000. They LIKE the look of the costume. And that's just what it is - a costume. You're required to have a "look" as a cyclist - you aren't really a cyclist if you don't spend hundreds of dollars on the gay gear. God forbid you just get a bike and ride it around on a trail like anyone else.
These people LIKE to be seen. They WANT to be seen as cool, which is why they ride right in front of my fucking car at 15mph in a 45mph zone. I swear, every time I pass one of these cyclists, I am this close to yelling "FAGGOT" out the window at them. The only reason I haven't is because they like to record everything on their gay bikes and upload it to Youtube, so then I'd have to deal with you people knowing where I live just because I called some fruit on a bike a faggot. Think I'm exaggerating? Think again. These homos have an entire community built on "catching" drivers who dare drive too close or blow their exhaust at the poor little faggy cyclist. There's Youtube channels dedicated to this. Part of their culture is being a victim by cars. Almost like it's dangerous to be in the middle of the road going 15mph on a 45mph road. Oh but I'm sure cars almost hitting you is surely a personal attack and nothing to do with the fact that what you're doing is DANGEROUS YOU RETARD.
Look at the seat they ride on, it looks like a black cock about to go up their ass. Don't get me started on their gay helmets, the "aerodynamic" helmets they wear. YOU FAGGOTS AREN'T IN THE TOUR DE FRANCE, YOU'RE IN FRONT OF MY CAR IN AN INTERSECTION IN A MINNESOTA TOWN WITH A POPULATION OF 5,000. They LIKE the look of the costume. And that's just what it is - a costume. You're required to have a "look" as a cyclist - you aren't really a cyclist if you don't spend hundreds of dollars on the gay gear. God forbid you just get a bike and ride it around on a trail like anyone else.
These people LIKE to be seen. They WANT to be seen as cool, which is why they ride right in front of my fucking car at 15mph in a 45mph zone. I swear, every time I pass one of these cyclists, I am this close to yelling "FAGGOT" out the window at them. The only reason I haven't is because they like to record everything on their gay bikes and upload it to Youtube, so then I'd have to deal with you people knowing where I live just because I called some fruit on a bike a faggot. Think I'm exaggerating? Think again. These homos have an entire community built on "catching" drivers who dare drive too close or blow their exhaust at the poor little faggy cyclist. There's Youtube channels dedicated to this. Part of their culture is being a victim by cars. Almost like it's dangerous to be in the middle of the road going 15mph on a 45mph road. Oh but I'm sure cars almost hitting you is surely a personal attack and nothing to do with the fact that what you're doing is DANGEROUS YOU RETARD.
 I've seen these "share the road" signs in the most insane and dangerous places. I've seen them on HIGHWAYS, yes, HIGHWAYS, where the cyclist would BARELY have any room next to the car. It's insanely dangerous and I guess to some people, the constant threat of dying is fun... until it actually happens.
I will never understand the mind of a cyclist. You are not in the fricken' Tour de France. You look like a homosexual that's inconveniencing HEAVY METAL HIGH POWERED CARS RIGHT BEHIND YOU. It's incredibly dangerous, and you can't rely on the very heavy, high powered cars and the people driving them to honor your life. Road rage is real, you might be the tipping point for some angry old boomer in his Ram to RAM INTO YOU and kill you. God I hate cyclists, their gay look, their cocky "better than you" attitude. Hey fudge stripe, in a battle between my CAR and your soft body, my CAR WILL WIN. Get off the road and go suck some cocks instead. Stop riding the bikes and go ride cocks instead, you homo.
I've seen these "share the road" signs in the most insane and dangerous places. I've seen them on HIGHWAYS, yes, HIGHWAYS, where the cyclist would BARELY have any room next to the car. It's insanely dangerous and I guess to some people, the constant threat of dying is fun... until it actually happens.
I will never understand the mind of a cyclist. You are not in the fricken' Tour de France. You look like a homosexual that's inconveniencing HEAVY METAL HIGH POWERED CARS RIGHT BEHIND YOU. It's incredibly dangerous, and you can't rely on the very heavy, high powered cars and the people driving them to honor your life. Road rage is real, you might be the tipping point for some angry old boomer in his Ram to RAM INTO YOU and kill you. God I hate cyclists, their gay look, their cocky "better than you" attitude. Hey fudge stripe, in a battle between my CAR and your soft body, my CAR WILL WIN. Get off the road and go suck some cocks instead. Stop riding the bikes and go ride cocks instead, you homo. -
 @ da0b9bc3:4e30a4a9
2025-02-10 07:48:14
@ da0b9bc3:4e30a4a9
2025-02-10 07:48:14Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/881283
-
 @ 16d11430:61640947
2025-01-21 20:40:22
@ 16d11430:61640947
2025-01-21 20:40:22In a world drowning in Monopoly money, where people celebrate government-mandated inflation as "economic growth," it takes a special kind of clarity—nay, cynicism—to rise above the fiat circus. This is your guide to shedding your fiat f**ks and embracing the serene chaos of sound money, all while laughing at the absurdity of a world gone fiat-mad.
- Don’t Feed the Clowns
You know the clowns I’m talking about: central bankers in their tailored suits and smug smirks, wielding "tools" like interest rates and quantitative easing. Their tools are as real as a magician's wand, conjuring trillions of dollars out of thin air to keep their Ponzi economy afloat.
Rule #1: Don’t engage. If a clown offers you a hot take about the "strength of the dollar," smile, nod, and silently wonder how many cups of coffee their paycheck buys this month. Spoiler: fewer than last month.
- Turn Off the Fiat News
Do you really need another breathless headline about the next trillion-dollar deficit? Or the latest clickbait on why you should care about the stock market's emotional rollercoaster? Mainstream media exists to distract you, to keep you tethered to their illusion of importance.
Turn it off. Replace it with something sound, like the Bitcoin whitepaper. Or Nietzsche. At least Nietzsche knew we were doomed.
- Mock Their Inflationary Gospel
Fiat apologists will tell you that inflation is "necessary" and that 2% a year is a "healthy target." Sure, because a little robbery every year keeps society functioning, right? Ask them this: "If 2% is healthy, why not 20%? Why not 200%? Why not Venezuela?"
Fiat logic is like a bad acid trip: entertaining at first, but it quickly spirals into existential horror.
- Celebrate the Fiat Freakshow
Sometimes, the best way to resist the fiat clown show is to revel in its absurdity. Watch politicians print money like teenagers running up a credit card bill at Hot Topic, then watch the economists applaud it as "stimulus." It’s performance art, really. Andy Warhol could never.
- Build in the Chaos
While the fiat world burns, Bitcoiners build. This is the ultimate "not giving a fiat f**k" move: creating a parallel economy, one satoshi at a time. Run your Lightning node, stack sats, and laugh as the fiat circus consumes itself in a flaming pile of its own debt.
Let them argue about who gets to rearrange the deck chairs on the Titanic. You’re busy designing lifeboats.
- Adopt a Fiat-Free Lifestyle
Fiat-free living means minimizing your entanglement with their clown currency. Buy meat, not ETFs. Trade skills, not IOUs. Tip your barber in Bitcoin and ask if your landlord accepts Lightning. If they say no, chuckle and say, “You’ll learn soon enough.”
Every satoshi spent in the real economy is a slap in the face to the fiat overlords.
- Find the Humor in Collapse
Here’s the thing: the fiat system is unsustainable. You know it, I know it, even the clowns know it. The whole charade is destined to collapse under its own weight. When it does, find solace in the absurdity of it all.
Imagine the central bankers explaining hyperinflation to the public: "Turns out we can't print infinity after all." Pure comedy gold.
- Stay Ruthlessly Optimistic
Despite the doom and gloom, there’s hope. Bitcoin is hope. It’s the lifeboat for humanity, the cheat code to escape the fiat matrix. Cynicism doesn’t mean nihilism; it means seeing the rot for what it is and choosing to build something better.
So, don’t just reject the fiat clown show—replace it. Create a world where money is sound, transactions are sovereign, and wealth is measured in energy, not debt.
Final Thought: Burn the Tent Down
Aldous Huxley once envisioned a dystopia where people are so distracted by their own hedonistic consumption that they don’t realize they’re enslaved. Sound familiar? The fiat clown show is Brave New World on steroids, a spectacle designed to keep you pacified while your wealth evaporates.
But here’s the punchline: they can only enslave you if you care. By rejecting their system, you strip them of their power. So let them juggle their debts, inflate their bubbles, and print their trillions. You’ve got Bitcoin, and Bitcoin doesn’t give a fiat f**k.
Welcome to the satirical resistance. Now go stack some sats.
-
 @ 862fda7e:02a8268b
2024-06-29 08:16:47
@ 862fda7e:02a8268b
2024-06-29 08:16:47
Pictured above is a female body that looks incredibly similar to mine. So similar that it could be mine if I didn't have a c-section scar. Actually her boobs are a bit bigger than mine, but mine do look like that when they swell.

Nudity should be normalized
I don't understand why people get offended or sensitive over the human body. Especially the female human chest. We all have nipples, we all know what they look like, so I don't understand why a female being topless is unacceptable, whereas a male topless is normal. I've seen shirtless men with more shapely, larger breasts than mine. Personally, I have stopped caring if other people see the shape of my breasts or my nipples if they were to be poking in the freezer section of the grocery store. I stopped wearing bras years ago. I often times want to be topless outside in my yard because it feels good and natural. I like the sun on my skin, and I especially love the rain on my skin. It's very unfortunate that our natural human body is massively shamed, by who I believe, is the reptilians (for a number of reasons). Logically, it makes no sense to be outraged by the female human chest. We all know what nipples look like, we all have them, I truly believe women should be allowed to be topless like men are. If it's hot out and you're doing yard work - pop your top off, who cares?
I understand that males and some females sexualize the human chest. However, that is not my problem. That is none of my concern what others think about my body. I should be allowed to wear my human body as it is just like anyone else should be. What I can't wrap my mind around is why people are shocked or offended by the human body, since we ALL know what these parts look like and we all have them. I understand in certain scenarios being topless or nude would likely be inapproriate, or that perverts would use it as a way to expose themselves to children. In an ideal world, we could live like tribes where the human body is normal, it's not overtly sexual. This is why we're so offended over the human body - it's constantly concealed, so the moment we get to see a female chest, it's suddenly sexual because it's normally tabboo to be seen. I wish I could be shirtless outside, I envy males who get to truly feel the wind, the earth on their backs and their chest. Female and male nipples look the same, I don't understand why it should be illegal for me to experience nature in my natural state.
Anyways, I highly dislike the "nudist" people because it is NOT about accepting the human body in its natural state. It's completely co-opted by pedophiles who want to expose themselves to childen or for children to expose themselves to others for sexual gratification. There are nudist resorts pedophile parents force their children to go to (as a child you have no personal autonomy and are completely a slave to your parents - trust me, I know this because I couldn't LEGALLY decide which parent I wanted to live with up until I was 18 years old. If your parent wants you to do something, a child in the US has no legal say over that, so if your parent wants to go to a nudist resort, you must go). A human body should simply be a human body, it's unfortunate that being unclothed immediately brings on sexualization. This is mostly an issue because clothes is the expected default. The more tabboo something is, the more naughty the thing is.
I am not a nudist. However, I do believe that at the very least, females should have the right to be topless in similar settings as males are allowed to. I don't think a woman is a slut if she's in her natural state, in her human body, and proceeds life as normal. How one acts portrays slutty behavior. Living your life in your natural human body should be a right without caviots. I feel detached from people who constantly see the human body as flawed (e.g. circumcision industry, body hair removal industry, clothing industry). These industries are harmful for the victims in them (infant boys, and modern day slaves in sweatshops), and the main motivating factor is money among all these industries.
-
 @ 1cb14ab3:95d52462
2025-02-09 15:45:32
@ 1cb14ab3:95d52462
2025-02-09 15:45:32Hey all. I am setting up a Plebeian Marketplace on Nostr using my Lightning node. I currently have two channels open (one with a capacity of 500,000 sats, one with a capacity of 100,000 sats). Both use different LSP's (Megalith and Olympus).
My question is regarding the maximum product price I can set for my marketplace. One of my products is 1M sats. Obviously my receiving capacity is not large enough to cover this, so I was planning on opening up another channel.
If I open another channel for 500,000 sats, that would bring my total receiving capacity to 1.1M which would cover the product. However my question is if I need all of the receiving capacity in the same channel, or if the sale would pull from all three channels? Am I best to close out the first two channels and open a single, larger channel?
Sorry for the noob question.
Tl;DR: Can someone explain how I should best set up my node to accommodate my store.
originally posted at https://stacker.news/items/880591
-
 @ 9e69e420:d12360c2
2025-01-21 19:31:48
@ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits.
Active Compounds
The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant
Antimicrobial Properties
Bacterial Protection The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance.
Antifungal Effects It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections.
Digestive Health Benefits
Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms
Anti-inflammatory and Antioxidant Effects
The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions
Respiratory Support
It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function
Additional Benefits
Skin Health - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties
Cardiovascular Health Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health
Pain Management The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief
Safety Note
While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
-
 @ 378943b3:9815e145
2025-02-10 00:38:15
@ 378943b3:9815e145
2025-02-10 00:38:15You show up and talk, we handle the rest of your podcast - https://calendly.com/noblelore/podcast-discovery-call
Rob Long is a data engineer with experience at Monsanto and a deep understanding of how data shapes our world. In this episode, Jack and Rob dive into the hidden mechanics behind digital surveillance, financial control, and the fight for privacy. They discuss how Bitcoin can be a tool for financial freedom, the challenges of opting out of data collection, and why decentralized social media could change the internet as we know it. Rob also shares his unique approach to retaining knowledge, his thoughts on sovereignty, and why curating a bookshelf can be a game-changer for personal growth.
0:00 - Intro
0:22 - What is NobleLore?
0:55 - What is a data engineer?
1:45 - How has being a data engineer shaped Rob's perspective?
2:39 - How data collection shapes our world
5:52 - The problem with fiat currency
7:18 - The utility of Bitcoin
14:38 - How does Rob use Bitcoin?
16:19 - The difference between Nostr and other social media platforms
25:28 - Podcasting on Nostr
31:34 - What stage of development is social media currently in?
37:28 - What is sovereignty, and why does it matter?
41:32 - Does Rob consider himself a free thinker?
42:19 - Rob’s curated bookshelf and the power of re-reading
49:25 - What is the most important thing that young people should be paying attention to? -
 @ b17fccdf:b7211155
2025-01-21 17:02:21
@ b17fccdf:b7211155
2025-01-21 17:02:21The past 26 August, Tor introduced officially a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks.
~ > This feature at the moment, is deactivate by default, so you need to follow these steps to activate this on a MiniBolt node:
- Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing
tor --versionExample of expected output:
Tor version 0.4.8.6. This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html) Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc. Tor compiled with GCC version 12.2.0~ > If you have v0.4.8.X, you are OK, if not, type
sudo apt update && sudo apt upgradeand confirm to update.- Basic PoW support can be checked by running this command:
tor --list-modulesExpected output:
relay: yes dirauth: yes dircache: yes pow: **yes**~ > If you have
pow: yes, you are OK- Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added
sudo nano /etc/tor/torrcExample:
```
Hidden Service BTC RPC Explorer
HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/ HiddenServiceVersion 3 HiddenServicePoWDefensesEnabled 1 HiddenServicePort 80 127.0.0.1:3002 ```
~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links:
- Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002
- LND: https://github.com/bitcoin/bitcoin/issues/28499
More info:
- https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/
- https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ
Enjoy it MiniBolter! 💙

