-
 @ 97c70a44:ad98e322
2025-02-03 22:25:35
@ 97c70a44:ad98e322
2025-02-03 22:25:35Last week, in a bid to understand the LLM hype, I decided to write a trivial nostr-related program in rust via a combination of codebuff (yes, that is a referral link, pls click), aider, and goose.
The result of the experiment was inconclusive, but as a side effect it produced a great case study in converting a NINO into a Real Nostr App.
Introducing Roz
Roz, a friendly notary for nostr events.
To use it, simply publish an event to
relay.damus.ioornos.lol, and roz will make note of it. To find out when roz first saw a given event, just ask:curl https://roz.coracle.social/notary/cb429632ae22557d677a11149b2d0ccd72a1cf66ac55da30e3534ed1a492765dThis will return a JSON payload with a
seenkey indicating when roz first saw the event. How (and whether) you use this is up to you!De-NINO-fying roz
Roz is just a proof of concept, so don't rely on it being there forever. And anyway, roz is a NINO, since it provides value to nostr (potentially), but doesn't really do things in a nostr-native way. It also hard-codes its relays, and certainly doesn't use the outbox model or sign events. But that's ok, it's a proof of concept.
A much better way to do this would be to modify roz to properly leverage nostr's capabilities, namely:
- Use nostr-native data formats (i.e., draft a new kind)
- Use relays instead of proprietary servers for data storage
- Leverage nostr identities and signatures to decouple trust from storage, and allow trusted attestations to be discovered
Luckily, this is not hard at all. In fact, I've gone ahead and drafted a PR to the NIPs repo that adds timestamp annotations to NIP 03, as an alternative to OpenTimestamps. The trade-off is that while user attestations are far less reliable than OTS proofs, they're much easier to verify, and can reach a pretty high level of reliability by combining multiple attestation sources with other forms of reputation.
In other words, instead of going nuclear and embedding your attestations into The Time Chain, you can simply ask 5-10 relays or people you trust for their attestations for a given event.
This PR isn't terribly important on its own, but it does remove one small barrier between us and trusted key rotation events (or other types of event that require establishing a verifiable chain of causality).
-
 @ 2edbcea6:40558884
2023-10-15 18:16:19
@ 2edbcea6:40558884
2023-10-15 18:16:19Happy Sunday #Nostr !
Here’s your #NostrTechWeekly newsletter brought to you by nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk written by nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2
NostrTechWeekly is a weekly newsletter focused on the more technical happenings in the nostr-verse.
Let’s dive in!
Recent Upgrades to Nostr (AKA NIPs)
It’s been a while since a new NIP was merged but there's a lot of activity on some meaty proposed NIPs. Looking forward to the upgrades 💪
1) (Proposed) NIP 96: HTTP File Storage
One of the challenges of Nostr is where to store files (images, videos, PDFs, etc). Storing them on relays could bloat relays and lead to more centralization.
This NIP proposes a protocol to help third parties offer file hosting services to Nostr users. This NIP defines the necessary shape of the API of a third party offering file hosting services, so that these services can be easily used by Nostr clients to serve the content to users.
The proposal also defines an optional way for users to specify which File Storage servers they’d like the client to upload content to.
Author: arthurfranca, Semisol, staab, v0l, bndw, michaelhall923, fishcakeday, quentintaranpino
2) (Proposed) Updates to NIP 72: Moderated Communities (like Reddit)
Currently NIP 72 specifies that posts to moderated communities are of kind 1 which is the default kind which is for tweet-like content. Therefore posts to moderated communities would show up in many clients without enough context.
This proposal would update the default kind for moderated communities so that the content of moderated communities would not show up on the default feed for users. This paves the way for Reddit-like clients to provide an experience that’s focused on just posts to these communities.
Author: vivganes
3) (Proposed) NIP 91: IoT Sensors and Intents
Right now many “Internet of Things” devices require you to report that data from the IoT sensor to the device maker’s servers and write integrations with their ecosystem to take action based on that information.
This NIP reserves a set of event kinds for IoT sensors reporting data (8000 - 8999). For example 8003 would be for thermometers to report temperature in celsius as a number, separate from 8005 which would allow reporting a location as an array of two numbers: longitude and latitude.
This NIP would allow developers to offer IoT devices that report to Nostr relays which gives you more control over the data and the process of taking action based on that data.
Author: nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6, BlackCoffee, arcbtc
4) (Proposed) NIP 107: Nostr Powered IoT
In conjunction with NIP 91, this NIP will enable a robust IoT ecosystem on Nostr.
This NIP’s goal is to help facilitate the development of Nostr clients that are IoT controllers. That way a user and a device can essentially “DM” each other data and commands.
For example a user could install an IoT device that’s a switch for a light. There would be a Nostr client where you can “register” the new device and authorize some list of Nostr users that can utilize the device
Once registered any authorized device user would be able to toggle the light on and off from a Nostr client that supports IoT operations. This is entirely done via Nostr DMs, so you can do this from anywhere as long as you control the private key of a user that the device recognizes as a controller, and the data transferred and the commands are encrypted.
Author: arcbtc, BlackCoffee
Notable Projects
Shopstr 🛒
Shopstr is a classifieds app similar to Craigslist, you can post items for sale and facilitate transactions via lightning payments or DMs. Still early but this will be a useful addition to the Nostr-verse and a circular Bitcoin economy.
Author: nostr:npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkq
Shipyard 🚢
https://shipyard.pub/ is a client for composing and scheduling Nostr content, it’s easy to use and pretty slick. Many big content creators rely on such tools for legacy social media (Twitter, Instagram, etc).
This is a huge unlock for any big content creators that want to make the transition to Nostr but still preserve their ability to push content on a regular basis and monetize it.
Author: nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft
Nostr Design 🎨
nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac has been offering resources and design help to Nostr devs for some time now via nostrdesign.org.
NostrDesign.org has set out to start conversations around the unique communication challenges of Nostr (keypairs, relays, signing extensions, etc) so that we can build some common patterns to help normies get started with Nostr without too much confusion or tutorial overhead. This will become more necessary as time and adoption goes on.
Good design can also make a huge difference in the success of a new product, especially if there aren’t exact analogs to draw from when building a Nostr app (like when you’re cloning an existing product). I for one am a dev that SUCKS at UX and could use some advice from a thoughtful partner that wants Nostr’s success just as much as I do.
Latest conversations: Design and Nostr adoption
There’s been some discussion lately about how necessary design is to the Nostr ecosystem, and I’ll posit that it depends on your desires for Nostr.
Why design matters
Great design does not necessitate that something be beautiful. Great design is about usability.
Great design strips away unnecessary functionality and information so that only what matters remains. Great design understands the user’s desires and intent and empowers them to achieve their goals. Great design communicates how something ought to work with minimal explanation. Great design empowers the user to try something unfamiliar.
Craigslist is well designed in this sense, so is HackerNews, and the Reddit of a few years ago. They aren’t beautiful but they provide immense value in a simple and intuitive way.
Developers aren’t always the best at designing experiences that solve for usability and good communication to the user. The help of a good designer can be a huge help; making an app usable by a broader audience.
Accessibility and adoption
Adoption, in a very rough sense, can be thought of as a function of both how useful something is and how accessible it is. Think of accessibility as both how easy it is to use, as well as how easy it is to access (from my device, in my legal jurisdiction, for a low enough price).
If something is incredibly useful but not very accessible, only some people will use it (IRC). If something is very accessible but not very useful, no one will use it (case in point: it’s hard to name any 😂). If something is very useful and very accessible, then it will get widely adopted (ChatGPT).
If we want Nostr to remain a niche community (with limited impact on the world) then we can ignore how easy our ecosystem is to use. I don’t think that’s anyone’s goal.
The 10X better app on Nostr
When trying to get adoption for a new product the rule of thumb is that it needs to be 10X better than alternatives for folks to start adopting it and leave a competitor. Nostr is 10X better for folks that care about freedom tech, which is why most of us are already here.
We’ve built Nostr-based clones of many of the most prominent internet offerings (Twitter, Reddit, Imgur, Bitly, Instagram, Medium, WhatsApp, Craiglist, etc) the list goes on and on but that’s not driving adoption. That’s probably because the nostr-versions are, at-best, as good in functionality but they’re only better than the original in that they’re on Nostr (and therefore freedom tech).
Much to our consternation most people don’t seem to care about freedom tech as much as they should. If we’re to drive mass adoption we also have to discover applications that are uniquely possible on Nostr that are new and valuable enough to attract folks to try Nostr to try that app.
At that moment we’ll also need the basics of Nostr to be accessible enough that people aren’t scared off by the new patterns (keypairs, no usernames, no email alerts, no reset-password flow, which relays do I join?, etc). If we don’t care about solving both problems we are giving a middle finger to a majority of the population of Earth.
What era of Nostr are we in?
From what I’m seeing Nostr is still in the era of experimentation and foundation building.
If our goal is a freedom-oriented ecosystem of micro-apps to compete with Big Tech then we’re doing all the right work.
We definitely need to provide all the same functionality folks are used to (micro blogging, blogging, group chat, moderated communities, meme sharing, monetizing content, etc). Building Nostr-based clones is helping with that.
We are working on tools to help developers build on Nostr (NDK, NAK, nostr-tools, etc).
We’re building general purpose browsers (Spring) to explore all corners of Nostr (current and future)
We’re experimenting with offerings unique to Nostr to see what killer app drives people to try Nostr en masse (Data Vending Machines, self-sovereign Internet of Things, uncensorable private and secure group chat, etc).
Good design doesn’t seem to be THE reason that adoption of Nostr isn’t exponential, but at some point it will become the bottleneck to adoption and it’s good to think ahead. The best time to plant a tree is ten years ago and all that.
Until next time 🫡
If you want to see something highlighted, if we missed anything, or if you’re building something we didn’t post about, let us know. DMs welcome at nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk
Stay Classy, Nostr.
-
 @ b17fccdf:b7211155
2025-02-01 18:41:27
@ b17fccdf:b7211155
2025-02-01 18:41:27Next new resources about the MiniBolt guide have been released:
- 🆕 Roadmap: LINK
- 🆕 Dynamic Network map: LINK
- 🆕 Nostr community: LINK < ~ REMOVE the "[]" symbols from the URL (naddr...) to access
- 🆕 Linktr FOSS (UC) by Gzuuus: LINK
- 🆕 Donate webpage: 🚾 Clearnet LINK || 🧅 Onion LINK
- 🆕 Contact email: hello@minibolt.info
Enjoy it MiniBolter! 💙
-
 @ 2fb77d26:c47a6ee1
2025-02-01 14:40:02
@ 2fb77d26:c47a6ee1
2025-02-01 14:40:02In H. G. Wells’ Roman Die Zeitmaschine und den diversen Verfilmungen werden sie als »ausschweifend, langsam und naiv« dargestellt. Von »untermenschlicher Intelligenz« gezeichnet. Für Dan Simmons sind sie »faul, ungebildet und unkultiviert«. Die Eloi. Die als Nahrungsquelle der Morlocks gehaltenen Nachfahren des Homo sapiens. »Sie entwickeln sich rückläufig und verlernen Jahrtausende von Kultur, Denken und Vernunft, bis sie sich mit dem Vergnügen des bloßen Daseins zufrieden geben«. Ertönt das Schlüsselsignal, auf das sie von ihren Züchtern konditioniert wurden – eine umgebaute Zivilschutzsirene – trotten sie freiwillig und in hypnotischer Apathie zur Schlachtbank.
Ein ähnlichen Eindruck hatten viele Maßnahmenkritiker von den Unterstützern der mittlerweile in allen Punkten widerlegten Covid-Propaganda. Zurecht. Das Gefolge von Drosten, Lauterbach und Co. war blind für Fakten und ist ins offene Messer gelaufen. Bedauerlicherweise verhalten sich viele Maßnahmenkritiker aber nun in weiten Teilen genauso. Sie haben Idole gefunden. Wollen glauben. Sie ignorieren Informationen, Fakten und Daten und werden Opfer einer neu justierten, gut geölten Propagandamaschine. Nur, um die in ihre neuen Helden gesetzten Hoffnungen nicht aufgeben und der wenig erbaulichen Realität nicht ins Auge blicken zu müssen.
Sie glauben an Donald Trump, Javier Milei, Alice Weidel, Peter Thiel und vor allem Elon Musk. Daran, dass der supranationale Nachhaltigkeitskorporatismus am Ende sei, das Finanzsystem gerettet und Gerechtigkeit hergestellt wird. Die Widerständler von gestern sind die »Schlafschafe« von heute. Sie scheinen vergessen zu haben, wie Propaganda funktioniert. Aus diesem Grund – und weil es ein so schön griffiges Wort ist, bei dem man nur einen Buchstaben verändern muss, um daraus den Vornamen eines vermeintlichen Heilsbringers zu basteln – erlaube ich mir, die Anhänger des MAGA-Kults im Zuge der folgenden Seiten mokant als Eloi zu bezeichnen. Ein bisschen Spaß muss sein.
Kurskorrektur mit Ansage
Lynn Forester de Rothschild, in der finanzoligarchischen Hackordnung mindestens eine Ebene über BlackRock und Co. anzusiedeln, kündigte den aktuellen Narrativwechsel bereits am 30. August 2023 an, als sie bei Bloomberg sagte, der Begriff »ESG gehöre in die Tonne«. Er sei verbrannt. Auch BlackRock-CEO Larry Fink, der Marktteilnehmer zur Unterstützung von ESG »zwingen« wollte, teilte seinen Investoren bereits am 26. März 2023 mit, das in Verruf gekommene Label ESG durch den Begriff »Energiepragmatismus« zu ersetzen.
Sowohl Rothschild als auch Fink räumten aber gleichzeitig ein, dass sich die übergeordnete Agenda nicht ändern und man die »Green Economy« weiter vorantreiben werde, man diese aber besser vermarkten müsse, um konservative Kreise nicht weiter gegen sich aufzubringen. Ein simpler Marketing-Trick. Wenig überraschend also, dass sowohl BlackRock als auch sechs amerikanische Großbanken Anfang 2025 die Net Zero Initiative verließen. Zum »perfekten Zeitpunkt«, wie die New York Post bemerkt, um nicht von der negativen, anti-woken Berichterstattung rund um die verheerenden Feuersbrünste in Los Angeles tangiert zu werden.
Es scheint, als hätten die Eloi bereits wieder verdrängt, dass die WEF-Meetings 2021 und 2024 unter Arbeitstiteln wie »The Great Narrative« und »Rebuilding Trust« liefen. Artikuliertes Ziel der Davoser PR-Abteilung für Globalisierungsfragen war nämlich, sich den zunehmend echauffierten, misstrauischen Pöbel vom Hals zu halten. Durch neue Narrative und vertrauensbildende Maßnahmen. Und das hat, zumindest vorerst, ausgezeichnet funktioniert.
In den USA stieg das Vertrauen in ordnungsgemäß durchgeführte Präsidentschaftswahlen 2024 zum ersten Mal seit Jahren wieder etwas an. In Europa macht sich ebenfalls Zuversicht breit. Schließlich haben die sogenannten »Rechtspopulisten« nicht mehr nur in Italien und Ungarn, sondern auch in Finnland, der Slowakei und den Niederlanden Oberwasser. Von den Erfolgen der AFD ganz zu schweigen. Diese führen, wie zuletzt in Thüringen, trotz klarem Wählervotum zwar nicht zur Regierungsbeteiligung, weil »demokratische Prozesse« und »Brandmauern« das zu verhindern wissen – aber dabei sein ist ja bekanntlich alles. Dass Friedenstreiberin Alice Weidel den bundesdeutschen Rüstungsetat auf knapp 200 Milliarden verdoppeln will, scheint die euphorisierten Kritiker dunkelgrüner Militarisierung auch nicht auszubremsen. Hauptsache nicht grün. Oder woke.
Überstaatliche Sphären
Dabei scheint Euphorie in Anbetracht der Tatsachen alles andere als angebracht. So hat Milei nach Angaben von Global Finance zwar das argentinische »Staatsdefizit nach 123 Jahren beendet«, dafür leben heute 53 Prozent der 45 Millionen Argentinier in Armut. Der höchste Wert seit 20 Jahren. Ende 2023 waren es noch 41,7 Prozent. Daran ändert auch semantische Schützenhilfe von libertären Denkfabriken wie der Hoover Institution nichts. Die radikalen Privatisierungsfeldzüge von »El Loco« haben einen hohen Preis. Ob Aerolineas Argentinas, die staatliche Fluglinie, der Stahlproduzent IMPSA oder das Transportunternehmen Trenes Argentinos Cargas, das 7.800 Kilometer Bahnstrecke betreibt – das Volksvermögen wird an die Meistbietenden verscherbelt. Wer das ist, kann sich wohl jeder ausmalen. Denn sein Schlachtruf »Afuera!« (Raus hier!) gilt augenscheinlich nicht für BlackRock und Co. – schließlich sei Argentinien »ziemlich billig« zu haben, wie es Rick Rieder, Top-Bond-Manager des Unternehmens schon 2019 formulierte.
Man muss allerdings nicht in die Ferne schweifen, um sich der realen Gefahren für die Freiheit bewusst zu werden. Jener Gefahren, die von Personalien gänzlich unberührt bleiben. So arbeitet die Europäische Union weiter an der eID, der Grundlage des technokratisch-totalitären Kontroll-Grids. Ihre Einführung ist beschlossene Sache. Offen ist lediglich, ab wann sie zum Obligatorium wird. Auch das persönliche CO2-Budget ist auf Kurs. Mit ETS2 (EU Emissions Trading System) nimmt die EPA (Environmental Protection Agency) seit dem 1. Januar 2025 nach der Konzernwirtschaft nun kleine und mittlere Unternehmen in den Fokus und verpflichtet diese, CO2-Kompensationsabgaben auf ihren Gas-, Benzin- und Mineralölverbrauch zu entrichten. Das dürfte Heiz-, Fracht- und folglich die Lebenshaltungskosten des Bürgers in neue Höhen treiben. Bis der Sonntagsausflug mit dem Familienauto nicht mehr nur Zeit, Benzin und Nerven, sondern auch CO2-Gebühren kostet, dauert es also wohl nicht mehr allzu lange.
Dieser überparteilichen, supranational koordinierten Überwachungs- und Enteignungsagenda ist weder durch die Wahl des geringeren Übels noch durch Auswandern zu entkommen. Denn wie sich der Internetpräsenz des »Global Governance Forum« (GGF) entnehmen lässt, wird bereits eifrig an »Global Government« gearbeitet. Die UN-nahe Nichtregierungsorganisation hat sich nämlich zum Ziel gesetzt, die Charta der Vereinten Nationen bis 2028 zu aktualisieren und den allseits bekannten »Herausforderungen unserer Zeit« anzupassen. Pünktlich ab 2030 soll das neue Vertragswerk ratifiziert werden und neben neuen Befugnissen für den Internationalen Gerichtshof sowie einer UN-Streitmacht auch eine Regierungsstruktur analog der Europäischen Union ermöglichen. Sprich, eine Weltregierung. Ganz demokratisch selbstverständlich.
Neben eID und CO2-Budget sind natürlich auch die Ausweispflicht fürs Internet und die automatisierte Zensur unliebsamer Inhalte weiter auf Kurs. Nachdem die Vereinten Nationen im September 2024 bereits dem totalitären »Pakt für die Zukunft« zustimmten, wurde am Heiligabend 2024 noch rasch die neue »Konvention gegen Onlineverbrechen« durchgewunken. Und seit Januar 2025 treibt die UN die Umsetzung eines noch weitreichenderen Abkommens namens »Global Digital Compact« voran. Ein Papier, vor dem ich bereits im Juli 2023 gewarnt habe. Was all das für den Bürger bedeutet, zeigt sich in Griechenland, wo die Regierung seit Anfang des Jahres Social-Media-Konten mit Steuer-Identifikationsnummern verknüpft, um eine Alterskontrolle fürs Internet einzuführen. Damit folgt die von der EU in Kreditsklaverei gehaltene Regierung in Athen dem Vorbild Australiens, wo der Zugang so Social-Media-Plattformen künftig erst ab einem Alter von 16 Jahren erlaubt werden soll – wofür man schlussendlich jeden Nutzer kontrollieren muss, der online geht.
Auch das von vielen noch immer als Mythos abgetane Geoengineering wird derweil munter weitergeführt. Obwohl Berichte des US-Kongress und mittlerweile sogar wissenschaftliche Berater der EU-Kommission vor großflächigem Solar Radiation Management warnen. Im Rahmen eines offiziellen, 54 Seiten umfassenden Reports an die EU-Kommission sowie eines Artikels des britischen Guardian vom 9. Dezember 2024 verwies das siebenköpfige Forscherteam auf die unabschätzbaren Konsequenzen solcher Eingriffe und forderte ein EU-weites Moratorium.
Wie genau Trump, Musk, Milei, Meloni, Weidel und Co. die Welt vor diesem Sammelsurium an totalitären Übergriffigkeiten retten wollen, konnte mir bislang keiner der Eloi sagen.
DJ Trump
Warum die in Donald Trump, den »Vater der Impfung«, und sein zionistisches Kriegstreiberkabinett gesetzten Hoffnungen bald bitterer Enttäuschung weichen dürften, habe ich bereits am 14. November 2024 ausführlich beschrieben. Dass auch die beiden Hauptargumente seiner Befürworter – dass er die mRNA-Kampagne mittlerweile bereue und in seiner ersten Amtsperiode Friedenspolitik betrieben habe – schlichtweg falsch sind, ebenfalls. Denn anhand der nackten Zahlen lässt sich eindeutig belegen, dass Trump »der kriegslüsternste Präsident der jüngeren Geschichte« war. Und wie stolz er auf »Operation Warp Speed« ist, die unzählige Amerikaner Gesundheit oder Leben kostete, ließ er die Welt zuletzt am 17. November 2024 auf seinem Social-Media-Netzwerk Truth Social wissen.
Trumps Interesse gilt nicht Frieden und Freiheit, sondern Donald Trump. So war es sein ganzes Leben lang. Wenn sich »The Donald« jemandem verpflichtet fühlt, ist es vielleicht Wilbur Ross, der ehemalige Chef von Rothschild Inc. Bankruptcy Advising. Denn wie das Forbes Magazine am 8. Dezember 2016 korrekt erläuterte, rette das Bankhaus vor gut 30 Jahren nicht nur Trumps bankrotte Casinos, sondern damit auch seine ganze Karriere. Nicht weil man in Trumps Geschäften und Immobilien einen besonderen Wert sah, sondern weil man die Person Donald Trump als »Anlage« betrachtete. Trotzdem ist es sicher nur Zufall, dass Ross von 2017 bis 2021 Handelsminister der Vereinigten Staaten war.
Elon Musk
Auch über den PayPal-Mafioso, CIA-Handlanger und Bilderberg-Executive Peter Thiel, dessen Protegé JD Vance nun US-Vizepräsident ist, habe ich bereits im September 2024 einen ausführlichen Artikel geschrieben. Gleiches gilt für Elon Musk, dessen trügerisches Image als Genius, Erfinder und Entrepreneur ich sogar schon im Oktober 2022 durchleuchtet habe. Zitat:
»Dass Elon Musk nicht rein zufällig zur liberal-coolen Ikone avancierte, legt ein Blick in seine Anfangsjahre als Unternehmer nahe. Denn während im sagenumwobenen Silicon Valley Ende der 1990er-Jahre eine Vielzahl an erfolgreicheren Tech-Entrepreneuren existierte, war es ausgerechnet Elon Musk, der für einen absolut inhaltsleeren Gastauftritt bei CNN gefilmt wurde, sodass zum ersten Mal eine breitere Öffentlichkeit von ihm Notiz nehmen musste. Dabei war sein erstes Unternehmen – Zip2 –, das er im Jahre 1995 mit seinem Bruder sowie einem weiteren Partner gegründet und im Februar 1999 für circa 300 Millionen US-Dollar an Compaq veräußert hatte, nicht das revolutionärste Unterfangen im kalifornischen IT-Mekka dieser Tage. Es handelte sich um ein simples Telefonbuch fürs Internet. Wenig mehr als eine Datenbank, in die sich Unternehmen eintragen konnten, um ihre Adresse im Netz zu hinterlegen.«
Meine fast zweieinhalb Jahre alte Analyse bedarf allerdings dringend einer Aktualisierung. Denn was Musk in der Zwischenzeit trieb – und für die Zukunft plant – hat so gar nichts mit dem zu tun, was seine geradezu fanatisierten Anhänger in ihm sehen wollen.
Fangen wir der Vollständigkeit halber aber noch mal vorne an: Elon Musk hat weder PayPal gegründet noch den Tesla erfunden. Auch wenn er das gerne so darstellt. Dafür fertigte Tesla unter seiner Ägide dann aber »RNA Mikrofabriken« für das deutsche Unternehmen CureVac, das zusammen mit Bayer mRNA-Injektionen gegen Corona auf den Markt brachte. Und während Musk gegenüber der New York Post am 30. September 2020 sagte, sich nicht gegen Covid impfen lassen zu wollen, erklärte er dem TIME Magazine am 13. Dezember 2021, bereits geimpft zu sein. Zeitgeistig flexibel ist er also. Wer behauptet, Musk hätte seine Meinung zur mRNA-Technologie seit dem Covid-Fiasko signifikant geändert und sehe das Produkt nun kritisch, ist schlecht informiert. Noch am 12. April 2023 erklärte er bei Twitter, dass er mRNA für eine »medizinische Revolution« hält. Vergleichbar mit dem Schritt »von analog zu digital«.
Was Musk mit digitaler Revolution meint, zeigte sich 2017 mit Hurricane Irma. Damals gab das Unternehmen für Besitzer von Fahrzeugen mit 75 kWh ein Softwareupdate heraus, das die Reichweite von 338 auf 400 Kilometer steigerte – was im Umkehrschluss bedeutet, dass Tesla-Besitzer um eine eigentlich abrufbare Leistung ihres eigenen Fahrzeugs betrogen werden, wenn gerade keine Naturkatastrophe wütet. Dass Tesla-Kunden darüber hinaus permanent überwacht werden, zeigte sich unlängst im Rahmen der Explosion eines Cybertrucks in Las Vegas. Augenbewegungen, Mimik, Geschlecht, Hautfarbe, Körpertemperatur, Gepäckanordnung, Route, Ladestopps, Bezahlvorgänge, Telefonbuch, Musik-Playlist, Online-Abos, et cetera. Was von Sensoren und Verbindungen zu erfassen ist, wird erfasst, wie eine Untersuchung von Mozilla im Herbst 2023 feststellte. Das gilt im Übrigen nicht nur für Tesla, sondern für praktisch alle modernen Autos. Ein Tesla hat es dabei nur am leichtesten. Die gesammelten Daten werden entweder zum Schleuderpreis verkauft und/oder gegen uns verwendet.
Doch zurück zu Musk, der Twitter nicht übernahm, um Meinungsfreiheit herzustellen, sondern um die Plattform zur »Alles-App« zu machen. Sein erklärtes Vorbild: die chinesische Spionage-App WeChat. Deswegen will er alle Nutzer »als echte Menschen identifizieren«. Biometrisch versteht sich. Dafür arbeitet man bei Twitter bevorzugt mit israelischen Unternehmen zusammen, die von ehemaligen Mossad-Agenten gegründet wurden. Vielleicht stellte ja Doppelagent Jeffrey Epstein den Kontakt zum Mossad her, nachdem er Musk als regelmäßigen Teilnehmer seiner Edge-Foundation Seminare zum Thema Nudging schätzen gelernt hatte. Epstein war nämlich der einzige nennenswerte Sponsor von Edge.
Twitter kaufte Musk übrigens nicht von seinem eigenen Geld, sondern mit Hilfe von 94 Investoren, deren Namen ein US-Bundesrichter erst im August 2024 veröffentlichte, weil Jacob Silverman (Reporters Committee for Freedom of the Press) sie einklagte. Die Liste umfasst so illustre Namen wie Fidelity Investments, Sequoia Capital, Andreessen Horowitz, Bandera Fund, Binance Capital Management, Sean Combs (alias Diddy) Capital, Jack Dorsey (Twitter Gründer), Baron Opportunity Fund oder Prinz Alwaleed bin Talal al Saud von der saudischen Königsfamilie. Da wird also offenbar »der Sumpf« mit mehr Sumpf »trockengelegt«. Von der Nominierung des WEF Executive Chair Linda Yaccarino als neuer Twitter-CEO und »Freedom of Speech« versus »Freedom of Reach« mal ganz abgesehen.
Auch die von den Eloi als sensationelle Enthüllung gefeierten Twitter Files sind leider nicht ernst zu nehmen. Denn sie offenbarten nichts, was man nicht schon wusste. Zudem ist bis heute unklar, woher die veröffentlichten Informationen kamen, wer den Zugriff darauf gesteuert hat, was dort noch gespeichert war, warum praktisch nur ein von Elon ausgewählter Journalist Zugriff darauf hatte und dieser nur Screenshots, anstelle ganzer Dokumente veröffentlichen durfte. Ein echter Leak besteht aus einem Archiv, das man selbst durchsuchen kann – nicht aus ein paar handverlesenen Screenshots.
Fehlt noch Space X. Ein Unternehmen, das Musk zwar selbst gegründet hat, dessen Erfolge aber in weiten Teilen anderen Umständen zu verdanken sind. So schreibt beispielsweise inside Tesla am 22. März 2022:
»Schon Anfang der 2000er-Jahre hatte die NASA erkannt, dass ihr bald die Möglichkeit fehlen würde, selbst Astronauten und Material ins All und zur ISS zu bringen. Man machte sich also auf die Suche nach Partnern aus der Privatwirtschaft und wurde unter anderem bei Elon Musks Space X fündig. Bereits 2006, also noch in der Entwicklungsphase der Falcon 1, erhielt Musks Unternehmen fast 400 Millionen US-Dollar Startfinanzierung unter dem COTS-Programm.«
Space X war von Beginn an als verlängerte Werkbank der NASA gedacht, weil der US-Weltraumbehörde immer mehr Mittel gestrichen wurden. Die Öffentlichkeit hatte nämlich das Interesse an ziviler Raumfahrt verloren. Daher setzte man in Washington immer öfter den Rotstift an. Doch seit Musk die Menschen öffentlichkeitswirksam zum Mars befördern will – »let’s build Marsian Technocracy« – steigt das Interesse wieder. Leider muss ich die Vorfreude auf eine planetare Kolonie aber etwas dämpfen. Denn Space X wird nicht betrieben, um Menschen auf den Mars zu bringen, sondern um das »weltgrösste Netzwerk an Spionagesatelliten aufzubauen«.
Musks Weltraumagentur ist Handlanger des militärisch-industriellen Komplexes und einer der wichtigsten Vertragspartner des Pentagon. Das konnte man 2017 schon im Observer nachlesen. Oder am 9. Januar 2018 bei CNBC, die vom (missglückten) Transport eines streng geheimen US-Spionagesatelliten berichtete. Am 15. April 2022 kommentierte Tech Unwrapped zwei weitere Spionagesatelliten des US-Militärs, die Space X in die Umlaufbahn beförderte. Seit Jahren erhält das Unternehmen Milliarden von US-Regierung und Geheimdiensten. Siehe Los Angeles Times vom 30. Mai 2015: 4,9 Milliarden. Oder ein Artikel des Wall Street Journal vom 23. Februar 2024: 1,8 Milliarden. Oder eine lange Liste von staatlichen Zuwendungen, die Business Insider am 15. Dezember 2021 veröffentlichte. Damit basiert der Erfolg von Space X nicht primär auf Musks genialem Unternehmergeist, sondern auf Subventionen. Auf Steuergeldern.
Nicht zu vergessen: Starlink. Das von Space X betriebene, weltumspannende Satellitennetzwerk. Es mag den Vorteil haben, dass damit auch Menschen in entlegenen Regionen des Planeten oder Katastrophengebieten Zugriff auf das Internet haben. Dabei sollte allerdings nicht unterschlagen werden, dass Starlink in seiner finalen Ausbaustufe circa 42.000 Satelliten umfassen und damit ein permanentes Strahlungsfeld erzeugen wird. Gesundheitliche Risiken für den Homo sapiens: unklar. Darüber hinaus haben die Orbiter Zugriff auf das NORAD-Datenbanksystem, um Weltraumschrott ausweichen zu können. Sprich, sie sind permanent mit Systemen des US-Militär verbunden. Aus diesem Grund ermöglicht Starlink auch die Steuerung von Kampfdrohnen – siehe Ukraine-Konflikt – sowie 30 mal schnelleres Senden von Daten an und von US-Kampfflugzeugen. Während die Öffentlichkeit Musks Satellitennetzwerk vor allem als ziviles Produkt betrachtet, ist Starlink primär von militärischem Interesse. Nicht umsonst wird parallel Starshield aufgebaut, das dem geheimdienstlich-militärischen Komplex unter anderem die diskrete Echtzeitüberwachung der ganzen Welt erlaubt. Auch von DEW-Fähigkeiten (Directed Energy Weapon) ist die Rede. Ende 2024 befanden sich bereits 98 solcher Satelliten in erdnaher Umlaufbahn.
In Anbetracht dieser Informationen ist es also kaum verwunderlich, dass Musk seit Jahren offen für Technokratie wirbt. Für ein zentralistisches, faschistoides Herrschaftsmodell, das schon sein Großvater Joshua Haldemann als führender Kopf in den USA und Kanada vertrat. Der Familientradition folgend empfiehlt Musk eine CO2-Steuer zum Kampf gegen den Klimawandel, ein universelles Grundeinkommen, um die von der KI ausgelösten Disruptionen abzufangen und sein Neuralink Gehirnimplantat, um dem drohenden Transhumanismus etwas Transhumanismus entgegenzusetzen.
Futurum Technologicus
Für Kunden, denen Chips im Kopf irgendwie zu altbacken sind, entwickelt Musks Unternehmen in Zusammenarbeit mit iota Biosciences natürlich ein zeitgemäßeres Premiumprodukt: Neural Dust. Intelligente Nanopartikel in Staubkorngröße, die sich im Gehirn anreichern. Die lassen sich dann wahrscheinlich – wie die in Indien bereits zugelassene Nasal-Impfung gegen Covid – durch die Nase ziehen. Oder durch Luftschächte öffentlicher Gebäude pumpen. Man kann die neue Freiheit also förmlich riechen.
Ganz wie es der 44 Seiten starke »National Nanotechnology Initiative Strategic Plan« (NNI Plan) des Weißen Hauses im Oktober 2021 vorsah: »Die Öffentlichkeit einbeziehen und Mitarbeiterzahlen im Bereich Nanotechnologie erhöhen«. Nicht umsonst hat Donald Trump der entsprechenden Behörde in seiner ersten Amtszeit zusätzliche Mittel genehmigt. Genau wie Joe Biden nach ihm.
Das von der Technokratie-Bewegung vor fast einem Jahrhundert definierte nordamerikanische Technate – sprich, der amerikanische Verantwortungsbereich einer weltweiten Technokratie – sieht der von Trump und Musk reanimierten Vision einer »nordamerikanischen Union« übrigens verblüffend ähnlich. Wen interessiert bei all der Make-Great-Euphorie schon noch, dass Imperialismus scheisse, Dänemark ein souveräner Staat und der Panamakanal ein strategisches Nadelöhr der internationalen Handelsschifffahrt ist. Oder, dass die »nordamerikanische Union« nicht nur bei Trump-Cheerleadern wie Alex Jones vor ein paar Jahren noch als »böser Globalisten-Plan« galt.
Schauen wir nach vorne. In Richtung »goldenes Zeitalter«, wie Trump es nennt. Dieses dürfte für den Normalbürger nämlich sehr ungemütlich werden. Denn es wird dominiert von Algorithmen. Von Künstlicher Intelligenz. Für die Eloi also primär von Grok, dem auf Twitter (und Teslas) integrierten Chatbot. Dieser basiert auf Technologie des Unternehmens xAI – laut Wikipedia gegründet von Elon Musk im März 2023. Das mag zwar so im Handelsregister stehen, ist wohl aber nur die halbe Wahrheit. Denn xAI dürfte die Fortführung eines DARPA-Projekts darstellen, das bereits 2015 unter dem Titel »Explainable Artificial Intelligence« (XAI) gestartet wurde und 2021 auslief. Als die Finanzierung seitens DARPA eingestellt wurde, machte XAI die Forschungsergebnisse auf einem Server zugänglich. Circa 18 Monate Jahre später engagierte Elon Musk Igor Babuschkin als Chefingenieur für xAI. Babuschkin hatte zuvor acht Jahre lang für Googles DeepMind-Projekt gearbeitet und nutzte aller Wahrscheinlichkeit nach die DARPA-Ergebnisse um xAI, beziehungsweise Grok zu entwickeln.
Im Juli 2023 verkündete Musk, xAI sei im Gegensatz zu den Konkurrenzprodukten von Google, Microsoft und OpenAI eine »gute« KI. Erstaunlich, wenn die gleichen Ingenieure am Werk sind und die KI auf Basis eines Militärprojekts entsteht. Zudem sprechen auch die Top-Sponsoren von xAI nicht unbedingt für das »Gute«. Denn unter den größten Geldgebern der letzten Finanzierungsrunde vom 23. Dezember 2024 befinden sich so illustre Namen wie BlackRock, AMD, Nvidia und Fidelity, die zusammen weitere sechs Milliarden Dollar für Musks KI-Unternehmen zur Verfügung stellten.
Genug Liquidität, um xAI für die »Alles-App« weiterzuentwickeln, wo Grok seit einer Weile automatisch Kurzbeschreibungen für Profile erstellt, die man weder abschalten noch ändern kann. Twitter-Nutzer müssen nun also nicht mehr selbst das Profil eines Accounts durchstöbern, um sich einen ersten Eindruck von der Person zu machen, sondern bekommen diesen von Elon Musks KI geliefert. Vorurteil auf Knopfdruck sozusagen. Vergleichbar mit einem Sozialkreditsystem. Denn die täglich neu generierte Zusammenfassung basiert auf dem Nutzerverhalten.
»Die neuen, KI-generierten Grok-Kurzprofile unter jedem X-Nutzerprofil SIND de facto ein Social Credit System nach chinesischem Vorbild für den Westen. Das Profil jedes Nutzers wird tagesaktuell neu berechnet. Äußert man sich zu verschiedenen Themen, nennt die KI das schnell mal »verheddern«. Grok gibt zu, das Profil wird erstellt aus dem eigenen Nutzerverhalten des Tages, seinen eigenen Berechnungen und nicht näher definierten Anweisungen«, kommentierte Journalistin Aya Velázquez die Neuerung am 14. Januar 2025.
Andere Nutzer werden als »leicht erregbar« beschrieben, »verzetteln« sich oder »glauben an Wettermanipulation zur Klimakontrolle«. Offener wird ein Debattenraum dank solcher Adjektive und Zusammenfassungen sicher nicht. Wer möchte schon das Profil von leicht erregbaren Chemtrail-Gläubigen anschauen oder gar mit diesen assoziiert werden. Gegen solch eine automatisierte, herablassend daherkommende Einordnung durch intransparent operierende KI war die Faktencheck-Industrie geradezu harmlos. Wer also annimmt, die Abschaffung der Faktenchecker bei Facebook und Co. bedeute ein Ende der Zensur, irrt. Sie wird im Gegenteil deutlich raffinierter und weitreichender werden.
Details zum persönlichen Punktestand im Grok-Sozialkreditsystem oder Information über das Zustandekommen der Bewertung erhält man auf Anfrage natürlich nicht. Twitter wird die daraus entstehende Hierarchie aber mit Sicherheit für Reichweitensteuerung, Nudging-Kampagnen und weitere sozialarchitektonische Funktionen nutzen. Vor allem, wenn 2025 das Bezahlsystem »X Money« eingeführt wird. Dann werden die Eloi bald nicht mehr nur um Reichweite, Follower und Re-Tweets buhlen, sondern auch um Geld – das als Folge unliebsamer Postings zu Genozid X, Krieg Y oder Person Z künftig schneller eingefroren werden dürfte als jedes Bankkonto. De-Banking der nächsten Generation. Und irgendwann trifft das jeden. Außer, man schwimmt immer mit dem Strom.
Doch damit nicht genug. Am 13. Dezember 2024 gab das wohl den wenigsten bekannte Unternehmen WISeSat bekannt, künftig mit Space X zusammenzuarbeiten, um »verschiedene Produkte und Systeme zu kombinieren«. Die WISeSat AG ist eine Tochterfirma der in Genf (Schweiz) ansässigen WISeKey International Holding AG, die im Bereich Cybersicherheit, KI und IoT (Internet of Things) tätig ist. Die Ankündigung dieser Kollaboration ließ die WISeKey-Aktie kurzfristig um 107,73 Prozent steigen. Ein erster gemeinsamer Start zum Transport sogenannter Picosatelliten fand am 14. Januar 2025 von der Vandenberg Space Force Base in Kalifornien statt.
Aber was genau macht WISeSat? Einer Presseerklärung des Unternehmens vom 15. September 2023 lässt sich entnehmen:
»WISeSAT AG zeichnet sich dank ihrer Konstellation von ultra-sicheren Picosatelliten und Infrastruktur durch sichere und effektive Kommunikationsstrategien für vernetzte Geräte aus. Die Expertise des Unternehmens in kryptografischer Technologie und sicherem Datenmanagement hat die sichere IoT-Implementierung in zahlreichen Bereichen neu definiert, von städtischen Innovationen in Smart Cities bis hin zu modernster industrieller Automatisierung. (…) WISeSAT steht an vorderster Front bei der Entwicklung von ultra-sicheren Picosatelliten-Lösungen in Zusammenarbeit mit ihrem Verbündeten FOSSA Systems. Es setzt sich für sichere IoT-Kommunikation über raumbasierte Netzwerke ein und nutzt die neuesten kryptografischen Innovationen, um sichere und sofortige Datenaustausche in verschiedenen Bereichen zu gewährleisten (…).«
Im Klartext: WISeSat bringt Satelliten von der Größe einer Tupperdose ins All. Diese Mini-Orbiter umkreisen den Planeten in niedrigen Umlaufbahnen und etablieren dort ein Netzwerk für kryptografierte Echtzeitdatenübertragung. Fliegende 5G-Masten sozusagen. Oder WLAN-Router. Nur viel schneller. Für das Internet der Dinge – und Smart Cities.
»In dieser Woche startet WISeSat einen Satelliten der neuen Generation und markiert damit einen wichtigen Meilenstein in der Entwicklung einer globalen Satellitenkonstellation, die eine umfassende Erdabdeckung mit ultraniedriger Latenzzeit ermöglicht. Entwickelt, um Billionen von IoT-Geräten in Echtzeit zu verfolgen und aufzuspüren.« (Carlos Creus Moreira, WISeKEy CEO, 12. Januar 2025)
Welche Datenträger dieses Picosatelliten-Netzwerk künftig verfolgen und aufspüren soll, zeigt sich bei einem Blick auf das Produktportfolio der Holding-Gesellschaft WISeKey – einem »weltweit führenden Anbieter von Cybersicherheit, digitaler Identität und Internet der Dinge (IoT) Lösungen«. Denn die Holding existiert seit 24 Jahren, besteht aus fünf Unternehmen, hat mehr als eineinhalb Milliarden Chips und über fünf Milliarden »Roots of Trust« installiert, residiert an sechs internationalen Standorten und hat gut 3.000 Kunden in Staat und Wirtschaft beglückt. Einen Wikipedia-Eintrag gibt es für das bei NASDAQ und SIX gelistete Unternehmen erstaunlicherweise trotzdem nicht.
Dafür aber für den seit Mai 2021 amtierenden »Chief Digital Transformation Officer« Pierre Maudet. Der war ab Juni 2012 Mitglied des Genfer Staatsrats, 2013 bei den Young Global Leaders des Weltwirtschaftsforums und 2015 bei der Bilderberger Konferenz in Telfs-Buchen (Österreich). Nachdem er im Februar 2021 vom Genfer Polizeigericht wegen Vorteilsnahme verurteilt wurde, trat er als Staatsrat zurück – und drei Monate später bei WISeKey an. Am 30. April 2023 wurde er, ungeachtet seiner kriminellen Vergangenheit, zusätzlich wieder in den Genfer Staatsrat gewählt. Wie praktisch. Solch eine schamlose Unverfrorenheit scheint Maudet perfekt für das zu qualifizieren, was bei WISeKey unter dem Deckmantel der »Quantensicherheit« entwickelt wird – ein raumbasiertes eID-Ökosystem.
»Quantensicherheit nutzt Prinzipien der Quantenmechanik, um den Datenschutz und die sichere Informationsübertragung zu revolutionieren. Kernstück ist die Quantenschlüsselverteilung (Quantum Key Distribution, QKD), eine Spitzentechnologie, die mithilfe der Quantenmechanik vernetzte Teilchen für den sicheren Austausch von Verschlüsselungskennwerten erzeugt.«
Ob digitale Identität, Unterschrift, Cloud oder Software – von der Know-Your-Customer-Biometrie bis hin zur Unternehmenslösung für die Mitarbeiteridentifikation. WISeKey hilft. Anmelden kann sich jeder. Während die Produktpalette für den privaten Sektor noch nach Lieferketten-Management, Sendungsverfolgung, Login-Lösung für eBanking oder Face ID auf dem Smartphone klingt – aber deutlich weitreichender ist, schauen sie sich die Homepage an – sprechen die WISeKey-Angebote im Bereich Regierungen eine ganz andere Sprache. Denn unter diesem Menüpunkt bewirbt der diskret operierende Konzern seine »CertifyID Trust Center Platform«:
»Die CertifyID Trust Center Platform ist eine industrialisierte eID-Verwaltungslösung für Bürger, die Benutzer und ihre Anmeldeinformationen verwaltet, insbesondere digitale IDs und digitale Zertifikate für groß angelegte Anwendungen wie landesweite E-Government-Dienste. Es handelt sich um eine vollständige industrielle Public Key Infrastruktur- und ID-Verwaltungslösung, die Regierungsdienste rund um die Uhr unterstützt.
Die CertifyID Trust Center Plattform wird in einer Reihe von Anwendungen der Regierung und des öffentlichen Sektors verwendet, zum Beispiel: Personalausweis, ePassport (ICAO-konform), Führerschein, Gesundheit, Wahlen/Abstimmen.
Die CertifyID Plattform wurde unter Verwendung der Sicherheits- und Public Key Infrastruktur-Expertise von WISeKey entwickelt und kann vollständig in E-Government-Frameworks, kommerzielle Frameworks (…) und in das Bereitstellungsframework für E-Government-Dienste eines Landes integriert werden.«
Da passt es doch wunderbar ins Bild, dass WISeKey am 13. Oktober 2022 eine »Partnerschaftsvereinbarung zur Zusammenarbeit bei der Entwicklung weltraumbezogener Aktivitäten« mit der Schweizer Armee bekannt gab – schließlich residieren in der Alpenrepublik nicht nur UN, GAVI, WEF, Club of Rome und jede Menge NGOs, sondern auch die Bank für Internationalen Zahlungsausgleich (BIZ), die ganz sicher Verwendung für ein quantengesichertes Echtzeit-Picosatellitennetzwerk findet, wenn ihr »Unified Ledger« (Zentrales Hauptbuch) für das Blockchain-Weltfinanzsystem von morgen zum Einsatz kommt. In Anbetracht der »allumfassenden Marktblase« (D. Webb, 2024) ist damit wohl in absehbarer Zeit zu rechnen.
Das also sind die Projekte, Pläne und neuen Partner von Elon. Auf mich machen ja speziell die korrupten Genfer Quantenspezialisten mit ihren Picosatelliten und schlüsselfertigen eID-Lösungen nicht unbedingt den Eindruck von Freiheitskämpfern. Und auch die am 22. Januar 2024 bei einer Pressekonferenz im Weißen Haus angekündigten »personalisierten mRNA-Injektionen gegen Krebs« lassen mich eher skeptisch zurück.
Genau wie der Umstand, dass diese binnen 48 Stunden »personalisierte mRNA« durch die Rechenleistung von OpenAI ermöglicht werden soll. Denn das von Elon Musk mitgegründete Unternehmen des WEF- und Bilderberg-affinen Sam Altman steht im berechtigten Verdacht, für den Tod eines Whistleblowers im Dezember 2024 verantwortlich zu sein. Während Polizei und Medien den Tod des OpenAI-Forschers Suchir Balaji als Selbstmord deklarieren, sprechen sowohl die Umstände am Fundort seiner Leiche als auch Balajis Eltern von »eiskaltem Mord«. Nicht zu vergessen, dass Altman von seiner eigenen Schwester des jahrelangen Missbrauchs beschuldigt wird und sich dafür demnächst vor Gericht verantworten muss. Selbst The Economist räumte am 10. Dezember 2024 ein, dass »die PayPal Mafia die amerikanische Regierung übernimmt«. Und das mit der »Mafia« scheint man in Washington mittlerweile wörtlich zu nehmen.
Aber die von einigen aus der Hüfte geschossenen Präsidialdekreten euphorisierten Eloi werden sicher Gründe finden, das alles zu ihren Gunsten auszulegen. Immerhin hat Trump ein paar Leute begnadigt und will aus der WHO austreten. Wie seine Fanbase es bewerkstelligt, auszublenden, dass »The Donald« schon in seiner ersten Amtszeit aus der WHO austreten wollte und es unterließ, erschließt sich mir aber leider nicht. Genau wie die Begeisterung für ein Gespräch zwischen Musk und Weidel. Man stelle sich nur mal vor, George Soros, Bill Gates oder Eric Schmitt konferierten mit deutschen Politikern. Oder bekämen Sendezeit im ÖRR. Nicht auszudenken.
Wie heißt es so schön: »Eine schmerzliche Wahrheit ist besser als eine Lüge« (Thomas Mann). Stimmt. Nur fällt es relativ schwer, eine Lüge einzugestehen, wenn der, dem man sie beichten muss, der Lügner ist.
So bleibt nur zu hoffen, dass möglichst viele Eloi diesen Schritt trotzdem möglichst bald hinter sich bringen. Im eigenen Interesse. Denn wie schon Ernst Freiherr von Feuchtersleben feststellte, ist »Reue der Verstand, der zu spät kommt«. Und das kann in diesen Tagen verheerende Folgen haben.
-
 @ fd208ee8:0fd927c1
2025-01-19 12:10:10
@ fd208ee8:0fd927c1
2025-01-19 12:10:10I am so tired of people trying to waste my time with Nostrized imitations of stuff that already exists.
Instagram, but make it Nostr. Twitter, but make it Nostr. GitHub, but make it Nostr. Facebook, but make it Nostr. Wordpress, but make it Nostr. GoodReads, but make it Nostr. TikTok, but make it Nostr.
That stuff already exists, and it wasn't that great the first time around, either. Build something better than that stuff, that can only be brought into existence because of Nostr.
Build something that does something completely and awesomely new. Knock my socks off, bro.
Cuz, ain't nobody got time for that.
-
 @ 0fa80bd3:ea7325de
2025-01-29 05:55:02
@ 0fa80bd3:ea7325de
2025-01-29 05:55:02The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future.
Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs.
There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won.
Our only resource is the will of the people to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root.
So I started asking myself: How do we stop this fragmentation? How do we create a space where people can rebuild their connections when they’re ready? How do we build a self-sustaining network, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—how do we make it spread, even in occupied territory?
In 2009, something historic happened: the internet got its own money. Thanks to Satoshi Nakamoto, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize.
That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became purely digital.
The internet was already a sanctuary for information, a place where people could connect and organize. But with Bitcoin, it evolved. Now, value itself could flow freely, beyond the reach of authorities.
Think about it: when seedlings are grown in controlled environments before being planted outside, they get stronger, survive longer, and bear fruit faster. That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild.
Now, picture the internet as that controlled environment for ideas. Bitcoin? It’s the fertile soil that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless. It can absorb any number of ideas, any number of people, and it doesn’t run out of space.
But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—without surveillance, without censorship, without the constant fear of being erased.
This is where Nostr comes in.
Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. It’s a new kind of city. One that no dictator can seize, no corporation can own, no government can shut down.
It’s built on decentralization, encryption, and individual control. Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them.
In a world where cities fall and governments fail, Nostr is a city that cannot be occupied. A place for ideas, for networks, for freedom. A city that grows stronger the more people build within it.
-
 @ 47750177:8969e41a
2025-01-09 12:00:00
@ 47750177:8969e41a
2025-01-09 12:00:0028.1 Release Notes
Bitcoin Core version 28.1 is now available from:
This release includes new features, various bug fixes and performance improvements, as well as updated translations.
Please report bugs using the issue tracker at GitHub:
https://github.com/bitcoin/bitcoin/issues
To receive security and update notifications, please subscribe to:
https://bitcoincore.org/en/list/announcements/join/
How to Upgrade
If you are running an older version, shut it down. Wait until it has completely shut down (which might take a few minutes in some cases), then run the installer (on Windows) or just copy over
/Applications/Bitcoin-Qt(on macOS) orbitcoind/bitcoin-qt(on Linux).Upgrading directly from a version of Bitcoin Core that has reached its EOL is possible, but it might take some time if the data directory needs to be migrated. Old wallet versions of Bitcoin Core are generally supported.
Running Bitcoin Core binaries on macOS requires self signing.
cd /path/to/bitcoin-28.x/bin xattr -d com.apple.quarantine bitcoin-cli bitcoin-qt bitcoin-tx bitcoin-util bitcoin-wallet bitcoind test_bitcoin codesign -s - bitcoin-cli bitcoin-qt bitcoin-tx bitcoin-util bitcoin-wallet bitcoind test_bitcoinCompatibility
Bitcoin Core is supported and extensively tested on operating systems using the Linux Kernel 3.17+, macOS 11.0+, and Windows 7 and newer. Bitcoin Core should also work on most other UNIX-like systems but is not as frequently tested on them. It is not recommended to use Bitcoin Core on unsupported systems.
Notable changes
P2P
- When the
-portconfiguration option is used, the default onion listening port will now be derived to be that port + 1 instead of being set to a fixed value (8334 on mainnet). This re-allows setups with multiple local nodes using different-portand not using-bind, which would lead to a startup failure in v28.0 due to a port collision.
Note that a
HiddenServicePortmanually configured intorrcmay need adjustment if used in connection with the-portoption. For example, if you are using-port=5555with a non-standard value and not using-bind=...=onion, previously Bitcoin Core would listen for incoming Tor connections on127.0.0.1:8334. Now it would listen on127.0.0.1:5556(-portplus one). If you configured the hidden service manually in torrc now you have to change it fromHiddenServicePort 8333 127.0.0.1:8334toHiddenServicePort 8333 127.0.0.1:5556, or configure bitcoind with-bind=127.0.0.1:8334=onionto get the previous behavior. (#31223) - #30568 addrman: change internal id counting to int64_tKey
-
31166 key: clear out secret data in DecodeExtKey
Build
-
31013 depends: For mingw cross compile use
-gcc-posixto prevent library conflict -
31502 depends: Fix CXXFLAGS on NetBSD
Test
-
31016 test: add missing sync to feature_fee_estimation.py
-
31448 fuzz: add cstdlib to FuzzedDataProvider
-
31419 test: fix MIN macro redefinition
-
31563 rpc: Extend scope of validation mutex in generateblock
Doc
-
31007 doc: add testnet4 section header for config file
CI
-
30961 ci: add LLVM_SYMBOLIZER_PATH to Valgrind fuzz job
Misc
-
31267 refactor: Drop deprecated space in
operator""_mst -
31431 util: use explicit cast in MultiIntBitSet::Fill()
Credits
Thanks to everyone who directly contributed to this release:
- fanquake
- Hennadii Stepanov
- laanwj
- MarcoFalke
- Martin Zumsande
- Marnix
- Sebastian Falbesoner
As well as to everyone that helped with translations on Transifex.
- When the
-
 @ 9e69e420:d12360c2
2025-02-01 11:16:04
@ 9e69e420:d12360c2
2025-02-01 11:16:04Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-
 @ b8851a06:9b120ba1
2025-01-14 15:28:32
@ b8851a06:9b120ba1
2025-01-14 15:28:32It Begins with a Click
It starts with a click: “Do you agree to our terms and conditions?”\ You scroll, you click, you comply. A harmless act, right? But what if every click was a surrender? What if every "yes" was another link in the chain binding you to a life where freedom requires approval?
This is the age of permission. Every aspect of your life is mediated by gatekeepers. Governments demand forms, corporations demand clicks, and algorithms demand obedience. You’re free, of course, as long as you play by the rules. But who writes the rules? Who decides what’s allowed? Who owns your life?
Welcome to Digital Serfdom
We once imagined the internet as a digital frontier—a vast, open space where ideas could flow freely and innovation would know no bounds. But instead of creating a decentralized utopia, we built a new feudal system.
- Your data? Owned by the lords of Big Tech.
- Your money? Controlled by banks and bureaucrats who can freeze it on a whim.
- Your thoughts? Filtered by algorithms that reward conformity and punish dissent.
The modern internet is a land of serfs and lords, and guess who’s doing the farming? You. Every time you agree to the terms, accept the permissions, or let an algorithm decide for you, you till the fields of a system designed to control, not liberate.
They don’t call it control, of course. They call it “protection.” They say, “We’re keeping you safe,” as they build a cage so big you can’t see the bars.
Freedom in Chains
But let’s be honest: we’re not just victims of this system—we’re participants. We’ve traded freedom for convenience, sovereignty for security. It’s easier to click “I Agree” than to read the fine print. It’s easier to let someone else hold your money than to take responsibility for it yourself. It’s easier to live a life of quiet compliance than to risk the chaos of true independence.
We tell ourselves it’s no big deal. What’s one click? What’s one form? But the permissions pile up. The chains grow heavier. And one day, you wake up and realize you’re free to do exactly what the system allows—and nothing more.
The Great Unpermissioning
It doesn’t have to be this way. You don’t need their approval. You don’t need their systems. You don’t need their permission.
The Great Unpermissioning is not a movement—it’s a mindset. It’s the refusal to accept a life mediated by gatekeepers. It’s the quiet rebellion of saying, “No.” It’s the realization that the freedom you seek won’t be granted—it must be reclaimed.
- Stop asking. Permission is their tool. Refusal is your weapon.
- Start building. Embrace tools that decentralize power: Bitcoin, encryption, open-source software, decentralized communication. Build systems they can’t control.
- Stand firm. They’ll tell you it’s dangerous. They’ll call you a radical. But remember: the most dangerous thing you can do is comply.
The path won’t be easy. Freedom never is. But it will be worth it.
The New Frontier
The age of permission has turned us into digital serfs, but there’s a new frontier on the horizon. It’s a world where you control your money, your data, your decisions. It’s a world of encryption, anonymity, and sovereignty. It’s a world built not on permission but on principles.
This world won’t be given to you. You have to build it. You have to fight for it. And it starts with one simple act: refusing to comply.
A Final Word
They promised us safety, but what they delivered was submission. The age of permission has enslaved us to the mundane, the monitored, and the mediocre. The Great Unpermissioning isn’t about tearing down the old world—it’s about walking away from it.
You don’t need to wait for their approval. You don’t need to ask for their permission. The freedom you’re looking for is already yours. Permission is their power—refusal is yours.
-
 @ b8851a06:9b120ba1
2024-12-16 16:38:53
@ b8851a06:9b120ba1
2024-12-16 16:38:53Brett Scott’s recent metaphor of Bitcoin as a wrestling gimmick, reliant on hype and dollar-dependence, reduces a groundbreaking monetary innovation to shallow theatrics. Let’s address his key missteps with hard facts.
1. Bitcoin Isn’t an Asset in the System—It’s the System
Scott claims Bitcoin competes with stocks, bonds, and gold in a financial "wrestling ring." This misrepresents Bitcoin’s purpose: it’s not an investment vehicle but a decentralized monetary network. Unlike assets, Bitcoin enables permissionless global value transfer, censorship resistance, and self-sovereign wealth storage—capabilities fiat currencies cannot match.
Fact: Bitcoin processes over $8 billion in daily transactions, settling more value annually than PayPal and Venmo combined. It isn’t competing with assets but offering an alternative to the monetary system itself.
2. Volatility Is Growth, Not Failure
Scott critiques Bitcoin’s price volatility as evidence of its unsuitability as "money." However, volatility is a natural stage in the adoption of transformative technology. Bitcoin is scaling from niche use to global recognition. Its growing liquidity and adoption already make it more stable than fiat in inflationary economies.
Fact: Bitcoin’s annualized volatility has decreased by 53% since 2013 and continues to stabilize as adoption rises. It’s the best-performing asset of the last decade, with an average annual ROI of 147%—far outpacing stocks, gold, and real estate. As of February 2024, Bitcoin's volatility was lower than roughly 900 stocks in the S and P 1500 and 190 stocks in the S and P 500. It continues to stabilize as adoption rises, making it an increasingly attractive store of value.
3. Bitcoin’s Utility Extends Beyond Countertrade
Scott diminishes Bitcoin to a "countertrade token," reliant on its dollar price. This ignores Bitcoin’s primary functions:
- Medium of exchange: Used in remittances, cross-border payments, and for the unbanked in Africa today (e.g., Ghana, Nigeria, Kenya).
- Store of value: A hedge against inflation and failing fiat systems (e.g., Argentina, Lebanon, Turkey).
- Decentralized reserve asset: Held by over 1,500 public and private institutions, including Tesla, MicroStrategy, and nations like El Salvador.
Fact: Lightning Network adoption has grown 1,500% in capacity since 2021, enabling microtransactions and reducing fees—making Bitcoin increasingly viable for everyday use. As of December 2024, Sub-Saharan Africa accounts for 2.7% of global cryptocurrency transaction volume, with Nigeria ranking second worldwide in crypto adoption. This demonstrates Bitcoin's real-world utility beyond mere speculation.
4. Bitcoin Isn’t Controlled by the Dollar
Scott suggests Bitcoin strengthens the dollar system rather than challenging it. In truth, Bitcoin exists outside the control of any nation-state. It offers people in authoritarian regimes and hyperinflationary economies a lifeline when their local currencies fail.
Fact: Over 70% of Bitcoin transactions occur outside the U.S., with adoption highest in countries like Nigeria, India, Venezuela, China, the USA and Ukraine—where the dollar isn’t dominant but government overreach and fiat collapse are. This global distribution shows Bitcoin's independence from dollar dominance.
5. Hype vs. Adoption
Scott mocks Bitcoin’s evangelists but fails to acknowledge its real-world traction. Bitcoin adoption isn’t driven by hype but by trustless, verifiable technology solving real-world problems. People don’t buy Bitcoin for "kayfabe"; they buy it for what it does.
Fact: Bitcoin wallets reached 500 million globally in 2023. El Salvador’s Chivo wallet onboarded 4 million users (60% of the population) within a year—far from a gimmick in action. As of December 2024, El Salvador's Bitcoin portfolio has crossed $632 million in value, with an unrealized profit of $362 million, demonstrating tangible benefits beyond hype.
6. The Dollar’s Coercive Monopoly vs. Bitcoin’s Freedom
Scott defends fiat money as more than "just numbers," backed by state power. He’s correct: fiat relies on coercion, legal mandates, and inflationary extraction. Bitcoin, by contrast, derives value from transparent scarcity (capped at 21 million coins) and decentralized consensus, not military enforcement or political whims.
Fact: Bitcoin’s inflation rate is just 1.8%—lower than gold or the U.S. dollar—and will approach 0% by 2140. No fiat currency can match this predictability. As of December 2024, Bitcoin processes an average of 441,944 transactions per day, showcasing its growing role as a global, permissionless monetary system free from centralized control.
Conclusion: The Revolution Is Real
Scott’s "wrestling gimmick" analogy trivializes Bitcoin’s purpose and progress. Bitcoin isn’t just a speculative asset—it’s the first truly decentralized, apolitical form of money. Whether as a hedge against inflation, a tool for financial inclusion, or a global settlement network, Bitcoin is transforming how we think about money.
Dismiss it as a gimmick at your peril. The world doesn’t need another asset—it needs Bitcoin.
"If you don't believe me or don't get it, I don't have time to try to convince you, sorry." Once Satoshi said.
There is no second best.
-
 @ e3ba5e1a:5e433365
2025-02-04 08:29:42
@ e3ba5e1a:5e433365
2025-02-04 08:29:42President Trump has started rolling out his tariffs, something I blogged about in November. People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I put up a poll on X to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.

For purposes of this blog post, our ultimate question will be the following:
- Suppose apples currently sell for $1 each in the entire United States.
- There are domestic sellers and foreign sellers of apples, all receiving the same price.
- There are no taxes or tariffs on the purchase of apples.
- The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following:
- Number of apples bought in the US
- Price paid by buyers for apples in the US
- Post-tax price received by domestic apple producers
- Post-tax price received by foreign apple producers
Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1?
And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why:
- The number of apples bought will go down
- The buyers will pay more for each apple they buy, but not the full amount of the tariff
- Domestic apple sellers will receive a higher price per apple
- Foreign apple sellers will receive a lower price per apple, but not lowered by the full amount of the tariff
In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit.
Marginal benefit
All of the numbers discussed below are part of a helper Google Sheet I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are some difficulties with creating supply and demand charts in Google Sheets.
Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B.
But that’s not what I mean. What I mean is: how high would the price of apples have to go everywhere so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5.
How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot.
The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called marginal benefit: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal demand curve. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:

Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples.
Marginal cost
Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product.
Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right?
Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of sunk costs. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further.
Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price!
However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with:
- Total expenditure: $100 + $70 * 8 hours a day * 5 days \== $2900
- Total revenue: $5000 (10,000 apples at $0.50 each)
- Total profit: $2100
So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money.
This kind of analysis is called marginal cost. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:

Equilibrium price
We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:

You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the surplus created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example:
- When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point.
- When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point.
Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.”
OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality.
Modeling taxes
Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve.
First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:

With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve.
We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:

The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:

As we can see, the equilibrium has shifted:
- The equilibrium price paid by consumers has risen from $1 to $1.20.
- The total number of apples purchased has dropped from 63 apples to 60 apples.
- Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus.
- Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42.
- Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21.
- The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise.
We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes:
- Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples.
- Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless.
- Domestic producers scored. They can sell less apples and make more revenue doing it.
- And the government walked away with an extra $30.
Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price.
Other taxes
Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down.
And generally speaking, this is what you’ll always see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost.
You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with:
- Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price.
- Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost.
- Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise.
This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ 06b7819d:d1d8327c
2024-12-12 11:43:36
@ 06b7819d:d1d8327c
2024-12-12 11:43:36The Peano axioms are a set of rules that define the natural numbers (like 0, 1, 2, 3, and so on) in a logical way. Here’s a simplified explanation: 1. There is a first number: There is a number called zero, and it is the starting point for all natural numbers. 2. Each number has a next number: Every number has a unique “successor,” or the number that comes after it (like 1 comes after 0, 2 comes after 1, etc.). 3. Zero is special: Zero is not the “next” number of any other number. This means the sequence of natural numbers doesn’t loop back to zero. 4. No two numbers are the same if they have different successors: If two numbers have the same “next” number, then they must actually be the same number. 5. Patterns hold for all numbers: If something is true for zero, and it stays true when moving from one number to the next, then it must be true for all numbers.
These principles lay the groundwork for understanding and working with the natural numbers systematically.
-
 @ df478568:2a951e67
2025-02-05 01:02:39
@ df478568:2a951e67
2025-02-05 01:02:39
About 150,000 blocks ago, I bought burgers for my family with sats at NextBurger in Newport, California. The Orange County Bitcoin Meetup found a hamburger stand that wanted to accept Bitcoin. This attracted Bitcoiners from all over Southern California. People brought their families. Some sat stackers sold wares outside as if it were a Farmer's Market. A couple kids sold some hats. One dude sold pins. I bought one off him. It resembled the Opendime I use as a keychain. He wore a 21M/infinity hat. We talked about Knut Svanholm books. He asked me, "What do you do for bitcoin?"
"I write a blog," I said. I must have written three articles about Bitcoin back then. I set up a BTCpayServer with LunaNode. My real idea was to write for sats, but I spent more sats on Lunanode than I made. I needed something to sell.
I had a few shitty ideas but no real business plan. I told Pins about one of these shitty ideas.
"I'm thinking about selling BIP39 raffle tickets, but they're a pain in the ass to cut." See what I mean, bad ideas.
Pins didn't say it was a bad idea though. I assure you, it was, but Pins gave this advice.
”Maybe you can use a 3D Printer."
I never did it, but I was impressed by how willing he was to help me. That's common in bitcoin. Bitcoiners are incentivized to help other Bitcoiners. The more people that accept Bitcoin at their stores, the bigger the demand for Bitcoin. The bigger the demand, the more the

Bitcoin Is For Spending
I participate in the circular economy because I consider using Bitcoin as money to be more advantageous for my savings strategy. When you earn sats, spend sats, and save sats, you break free from the chains of fiat debasement. Dollars are designed to go down in purchasing power to manipulate the public into spending more. That's why most people have more than one TV, but can't afford a $400 emergency. I spend Bitcoin because it forces me to be frugal. Fiat is designed to spend as quickly as possible since it will buy less groceries tomorrow than it will today.
Bitcoin is designed to buy more groceries tomorrow than it will today. When you expect $30 worth of Open AI services will likely be worth $433 in 21 years(if we assume Saylor is correct) you evaluate everything you buy with an orange colored lens. Your shopping habits change. A month of Chat GPT premium mightr be a month's worth of groceries in the future. I no longer buy Nike's because they coat 80k-120k sats, but I expect them to look like shredded cheese in six months. I would rather pay 100k sats for a nice pair of hiking shoes. I expect they will last me a few years.
Knowing this, you might ask, why would you spend Sats on a stupid pin? I've had my open dime pin for almost 4 years now and I expect to have it for years to come. It must have cost me about 100k sats. I don't expect it to be worth that much in the future, but you never know. Sometimes, I watch The Antique Road Show on PBS. Some pins, made by famous artists, are worth thousands of dollars. There is a chance collectibles like this will become more valuable, but I'm skeptical of this. I bought this PIN because it sparks joy, as Marie Kondo says.
This is not investment advice. Your Sats will almost certainly be worth more than your pins in the future, but if you buy a PIN from Salvador Dali, nobody stacks Sats. If you buy a PIN from BTCPins, a hardcore bitccoiner stack sats, which means less sats on the market will be availavle for 8 billion people when you buy a pin. Maybe pins will buy another hat from a bitccoiner, but that just means another bitccoiner stacks Sats. Notice how these Sats never make it back to the exchange because Bitcoiners know their stack will be more valuable in the future than they are today. So when you spend Sats, you only spend Sats on the things you find most valuable.
Pins I Bought Online

Although I consider these Pins art. I don't view art as an investment. I don't expect to ever sell one of these Pins for $110,000 like that banana duct-taped to a canvas before the artist got the munchies. I don't want dollars anyway. That's like a whole coin for a banana. I wouldn't spend 100,000,000 sats for one of these Pins, but BTCPins are not so pretentiously priced.
I recently bought some pins I've been salivating over for months. I need a better way of displaying them, but here are the pins I recently bought.
An Awesome Affiliate Link
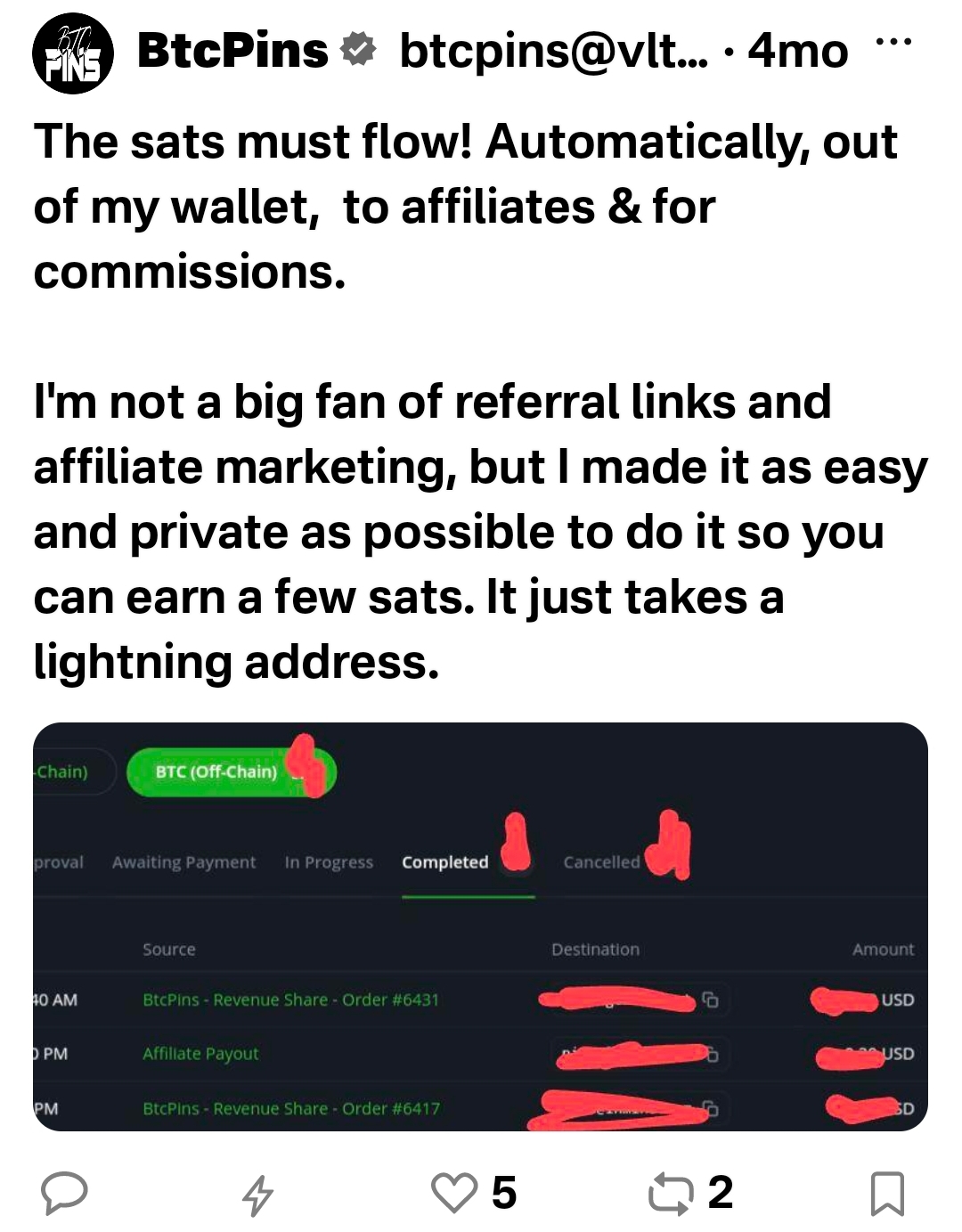
BTCPins has a unique affiliate link. Provide your lightning address and it will generate an affiliate link for you. These things have been around since the 90s, but what makes this particular link notable is how commissions are paid: In sats on the Bitcoin lightning network.
How BTCPins Affiliates Work
- Navigate to https://btcpins.com/affiliates/
- Enter your lightning address.
- Generate your link
- Share with the world.
So buy a pin or two from BTCPins today using my affiliate link:
Encrypted Link: https://btcpins.com/?aff=ex1GhhNeeU9-PQ1-ZVEkarU9bSnsNyq98Jy_lEUBLmsrWsCqa69PYohMWcCOGK9tK1rAqmuvT2KITFnAjhivbfOajnP3D8A8O09Hi-OY4K8
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
-
 @ fc2470ed:17d9ee27
2025-01-30 14:24:23
@ fc2470ed:17d9ee27
2025-01-30 14:24:23by Hynek Fencl, July 2024
The way to Liberland is easy but not simple. Technically speaking, it’s just a short bike ride away from the nearest village on a comfortable bike path through a stunning forest known as the “Amazon of Europe”. On one side, one senses the presence of the mighty Danube River beyond the tall trees, and on the other stretch the farmlands of north-eastern Croatia. Then you take a left turn to a straight forest path, ride all the way to the end, and after a few bends on the track, you will have entered “the promised land”.
The part that is not simple is that Croatia both does and does not consider Gornja Siga (the local name for the area we now refer to as Liberland) to be its territory – depending on who you ask. This means that along the picturesque bike path, you will almost certainly encounter a border police patrol car, and, depending on whether you seem to them like you’re affiliated with Liberland, they will tell you to stop and hand over your ID. They run it through their system and, if you’re lucky enough to be a citizen of the EU, they let you pass. If you’re not and you give them a non-EU passport, they will ask you to come to the station with them to “determine the circumstances of your stay in Croatia.” You will then be issued with paperwork telling you to leave the country within the next 7 days, banning you from re-entering in the next 1-3 months. The official reasoning they’ll give for this is their reasonable suspicion that you have not come to Croatia as a tourist but with the intent to either do paid work (for which you would have to get a business/work visa) or to break the law (such as camping outside designated camping grounds or starting a fire in the forest).
All of this is part of a big game of chess that is being played out between Croatia and the Liberlanders. Croatia is in a tricky spot. They cannot properly administer the territory of Liberland and enforce its law in it – lest it would create an indication that the Croatian state officially claims it as its territory. However, they cannot not administer it either, since it’s on “their” side of the river, and it is risky for a rogue, unpredictable operation (from their perspective) like the establishment and growth of Liberland to just be left to its own devices right on their doorstep. This is, then, how we arrive at the status quo, with Croatia relating to Liberland in some way while being careful about the international perception of its action in another way. The resulting practice is a persistent harassment campaign toward the Liberlanders, with the apparent intent to create uncertainty and lower the appetite of potential Liberland settlers for this kind of adventure.
How to establish a new country
Liberland was born from an anomaly – a historical border dispute between Croatia and Serbia. The dispute involves the definition of where the border stands in relation to the Danube and goes back to 1947. Then, both lands along the river belonged to a single country – Yugoslavia – but the dispute arose with respect to the boundaries of its constituent states. It remained unresolved during the communist era and became an issue of international borders after the breakup of Yugoslavia.
Serbia claims that the border runs down the middle of the Danube, with the eastern bank being Serbian and the western bank Croatian. Croatia, on the other hand, claims that the border is set by historical borders marked by cadastral municipalities surrounding the Danube.
These municipality borders run along a different path because they were set before the course of the Danube was straightened during the 19th Century to allow for easier shipping. This results in disputed “pockets” of land on both sides of the river. The pockets on the eastern bank have a combined area of around 130 km2, while those on the western bank only amount to less than 10 km2. Not surprisingly, then, both countries claim that the border runs in a way where they get the >90% of land and the other country only gets the small remaining areas. However, this means that, by implication, since both countries are claiming the large areas, neither of them is claiming the smaller ones. These areas were, then, so-called terra nullius.
Under international law, there is no issue with any state claiming unowned and unclaimed land for themselves. And that is exactly what Czech businessman, politician, and activist Vít Jedlička did in 2015 when he proclaimed into existence the newly created Free Republic of Liberland on the largest, 7 km2 piece of the unclaimed areas between Croatia and Serbia.
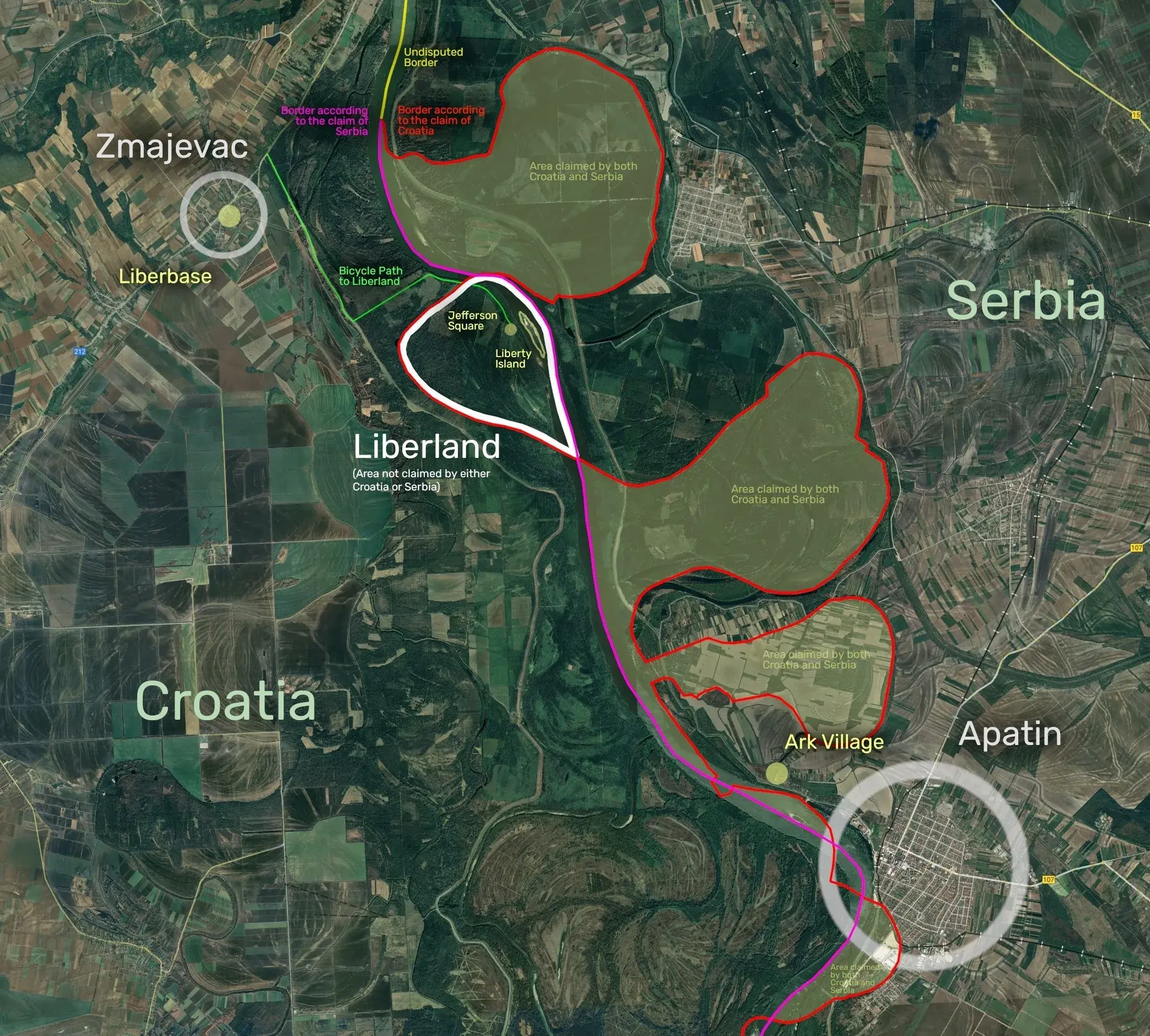
It's one thing to announce a new country to the world. It’s an entirely different thing to make this country legitimate. Under the Montevideo Convention, a proper country needs to have 1) a permanent population, 2) a defined territory, 3) government, and 4) capacity to enter into relations with other states. Now, 9 years after the birth of Liberland, it clearly has three of those. As to a permanent population, the Liberlanders would argue that it definitely exists, even though Liberland’s now over 1200 registered citizens have had to largely live in “exile” ever since.
Nevertheless, despite the Convention, there’s one thing that makes something a country more than anything else – whether other countries see you as a country. The more diplomatic recognition an entity has, the more country-like it becomes. This is especially relevant for breakaway governments, governments in exile, or, most importantly in this case, startup countries like Liberland.
Very much aware of this, along with other members of Liberland’s startup government, Jedlička has been on a worldwide mission to legitimize Liberland in the eyes of other countries. Though there have been many amiable meetings and even some measure of support in some cases, no official recognition by any UN member has been achieved as of mid-2024. Liberland now has representatives and offices in multiple countries in the further pursuit of this goal. Though the effectiveness of this strategy has been questioned by many for the lack of decisive results so far, one thing remains unambiguously true: if recognized by even one or two UN members, Liberland would instantly gain an amazing amount of legitimacy and gravitas in the eyes of the world.
The quest for territory
Establishing international relations with countries anywhere in the world is not the only strategy that the Liberlanders have been employing in making the country more real and legitimate. This includes liaising and negotiating with the neighboring Serbia and Croatia. These relations are by far the most important and impactful ones. If both of Liberland’s neighboring countries were to either outright recognize the startup micro-state, or even just adopted an approach of non-interference, Liberland would be free to start actually developing and to find its own long-term position in the world.
As for Serbia, its Ministry of Foreign Affairs let itself be heard that, in their view, Liberland’s claims are a “trivial matter” but, in any case, they do not infringe upon the sovereignty of Serbia. One can imagine that Serbia might actually be secretly quite pleased with Liberland’s activities, since now Croatia has an issue to deal with on “their” side of the river, which, if they are not careful, could contribute to the legitimization of Serbia’s claim to the larger pieces of territory claimed by both countries.
With Croatia, things get quite a bit more complicated. In an official statement, the country rejected the claim that Gornja Siga is terra nullius, arguing instead that the land belongs to one of the two neighboring countries – the only question is to which one, which will be answered at some point in the future. Croatia also said it would stop any threatening and provocative activities on the territory even by force if necessary.
Ever since Liberland’s birth in 2015, the Liberlanders have been trying to make a mark on the territory. For a long time, even just entering Liberland wasn’t really possible. Under a deal between the Croatian and Serbian police that was put in place during the European migration crisis, Croatian authorities may enter Liberland and patrol it for security reasons (preventing illegal migration) even though they do not officially claim the territory as theirs. In addition, the border police have a near-permanent presence on the Danube River, preventing people from crossing into Liberland by boat.
As a result, anyone who would try to come to Liberland in any way would always be promptly arrested by the Croatians, essentially for entering a prohibited area.
After years of this status quo, a rather unexpected thing happened that made things suddenly move forward in a positive direction for the Liberlanders. In April 2023, during Liberland’s 8th anniversary celebrations, a famous YouTuber with a significant following decided to try to enter Liberland. After a few unsuccessful attempts due to heavy police presence and monitoring, he and his team hired jet skis and rode them all the way from Hungary down the Danube. When they got close to Liberland, they encountered the police boats again, but their jet skis were faster than the boats, so they managed to land at Liberland’s Liberty Island and plant a flag there. A few moments later, the police caught up to them and an aggressive policeman took out their handheld cameras before assaulting them and then kicking them on the ground, as can be clearly seen from drone footage of the incident.
As they had broken no laws, they were ultimately let go after the incident and free to leave the island without being arrested. However, the heavy-handed and illegal conduct of the Croatian police had been clearly documented and became part of the video that was published in July 2023.
The video promptly went viral, gaining almost 10 million views on YouTube. By comparison, the total population of Croatia is just under 4 million. When the news spread even to the Croatian press and TV stations, Croatia had a serious PR problem on their hands. The police had been clearly in the wrong, conducting themselves in a seriously improper way to the point of using physical force against peaceful people who had broken no laws nor engaged in any violence or hostilities themselves.
Something had to change. So, following this incident, the Croatian police adopted a different unofficial policy – from now on, they would let people enter Liberland if they wished to do so, in a controlled way. Since early August 2023, if you wish to enter Liberland, you can go on foot or by bike, take the access road down the forest, and show your documents to the Croatian police, just as you would at a border crossing. In a typical grand fashion of Liberland’s media team, Liberland made an announcement that an official border crossing had been opened between Croatia and Liberland (Croatia had obviously never made an official announcement like this, but for Liberland, that was the de facto situation on the ground).
In the weeks following the “opening of the border”, many enthusiastic settlers started coming to Liberland to finally begin making their mark on the territory of “the promised land.” They started constructing simple wooden houses, a bathroom, an open-air restaurant, and the related power and water infrastructure on Liberland’s mainland beach opposite Liberty Island in a settlement named Mateos Marina.
On September 7th, 2023, a troop of about 50 policemen and forestry workers, including a demolition crew, raided the settlement. The raid was officially dubbed a “cleanup operation” by Hrvatske šume, Croatia’s state forestry service. With the assistance of the police, they tore down all the wooden houses and structures using chainsaws and stole equipment as well as personal possessions of the Liberlanders on site. Several Liberlanders were arrested for “failure to comply with a lawful order”.

One might ask, if Liberland is not officially part of Croatia, what authority does Croatia have to come in to steal and destroy? Staying true to their claim that Liberland is not part of Croatia, the Croatians had announced to Serbia that they would be conducting the “cleanup” on Serbia’s territory, to keep it clean on their behalf.
We may only speculate about the reasons for carrying out this operation in such a heavy-handed, destructive way. One possibility is that allowing people to enter Liberland in the first place was a way for Croatia to lure some people to Liberland, become comfortable, and then come in and destroy everything to show everyone what would happen if they got involved in the project. Or perhaps it was the unexpected level of life, community-building, and construction going on in such a short period of time after the “opening of the border” that the Croatian police felt like they had to put a stop to it before things got so big they could not be easily destroyed anymore.
No matter the reasons, the raid had a chilling effect on prospective Liberlanders. Though there is plenty of video documentation of the operation, no one made a viral video about it this time. Though some media did pick up the news, it did not become a big story. Consequently, the PR fallout from this for Croatia was not unmanageable.
Liberlanders soon returned to the territory. However, the level of enthusiasm, energy, and external support was not as great as it had been before the raid. From then on, settlement efforts focused mainly on Liberty Island, unreachable by trucks and impossible for forestry workers to get to without a large boat which they seem not to have. Though perhaps a more strategic place to set up camp, Liberty Island is also much more prone to flooding than the rest of Liberland.
In the following few months, several makeshift houses were constructed using a combination of wood and sandbags. During this time, Liberland even hosted a first wedding on the island. The settlement was kept alive during winter as well, with Liberland enthusiasts staying mostly in houseboats whenever it was impossible to camp on site.
In the meantime, an enthusiastic settler couple bought a sizeable house with a courtyard in the village closest to Liberland – Zmajevac – which they have transformed into a base of operations for settlers. This is now called Liberbase and it is where visits to Liberland start, with bikes, supplies, and construction materials being gathered before going on the 40-minute bike ride.

In the spring of 2024, work started on the reconstruction of a former hunting lodge at a central location on Liberland’s mainland – Jefferson Square. The building was demolished a few years ago but the foundations, including a cellar, were left in place. The site was cleared, the foundations refreshed, and new walls for the future governmental building have sprung up from the ground. A professional construction crew was hired to speed up the re-building of this base, using large concrete bricks, to a standard that will make it logistically and practically difficult for the Croatian police and forestry workers to try to destroy.
 The battle for legitimacy
The battle for legitimacy The ongoing construction in Liberland is rather slow. It is difficult to bring construction materials to Liberland. It is prohibited to drive motor vehicles on the bike path leading to Liberland, which means that everything has to be manually hauled from Liberbase on cargo bikes. In addition, from time to time, bikes get stolen by the police or forestry workers. Despite these difficulties, the determination of the settlers is unwavering and they are working every day to move construction forward.
The ongoing construction in Liberland is rather slow. It is difficult to bring construction materials to Liberland. It is prohibited to drive motor vehicles on the bike path leading to Liberland, which means that everything has to be manually hauled from Liberbase on cargo bikes. In addition, from time to time, bikes get stolen by the police or forestry workers. Despite these difficulties, the determination of the settlers is unwavering and they are working every day to move construction forward.Is it possible to bring materials by boat? How did they get sandbags and other materials to Liberty Island?
The importance of such a commitment should not be underestimated. The continuous presence of settlers is incredibly important for Liberland. It shows the seriousness of the project. It shows that Liberland is a genuine community and a fledgling nation rather than, as some accusations tend to go, just an elaborate publicity stunt.
Practical difficulties with the Croatian authorities are not limited to construction-related issues. Even staying and camping in Liberland comes with its quirks. If you’re staying on Jefferson Square, you should be prepared for several police visits every day. These check-ups are usually nothing dramatic. The police usually show up, ask a couple of questions, and perhaps tell the settlers that they are not allowed to camp there or start a fire, but they don’t actually do anything more than that and just go about their day.
It seems that the Croatian police are rather shy about enforcing Croatian law in a territory that is not officially considered part of Croatia. International law often takes into account the de facto situation of the matter in any dispute. If Croatia enforced their law in Liberland, this would therefore be an indication that they do, in fact, consider the territory to be theirs in practice, despite the official stance of the state. It would play into the hands of Serbia, reinforcing their claims to the large parcels of land on the other side of the Danube.
In addition, Liberlanders on the ground report that the majority of Croatian police officers generally behave quite fairly and respectfully toward them – only a minority appear to hold a personal grudge against Liberland, being abusive and sometimes even violent instead. It seems highly likely that the police in general are just doing their job, following orders from above. Most of them don’t actually take it as a personal commitment to make life more difficult for the Liberlanders.
This is rather important from a big-picture perspective, because the settlers, by contrast, are often heavily personally invested in the project and see it as their mission to see Liberland develop into a proper country. This disparity in energy and determination is strong and perhaps this is what will, in the end, cause Liberland to prevail in this drawn-out dispute.

The dispute with Hrvatske šume is quite different. As of mid-2024, the forestry workers tend to turn up at Jefferson Square about every fortnight. Unlike the police, they do not limit themselves to words but tend to steal everything that is not bolted down – including tools, materials, tents, bikes, and personal possessions of the settlers camping there. The justification remains the same – to “clean the forest of any waste.” In their encounters with the police as well as the forestry workers, Liberlanders are of course meticulous in their video documentation of any illegal actions by the authorities.
The Liberlanders’ difficulties, however, do not just stay local. As previously mentioned, upon trying to enter Liberland from Croatia, people who do not have EU citizenship are promptly issued a one-to-three-month ban on entering Croatia, with 7 days to leave the country. This is done under legislation relating to citizenship and tourism.
However, things can escalate even further. Since last year, several key Liberland settlers and organizers, including Liberland’s President Vít Jedlička himself, have seen “heavier guns” used against them. They have been banned from entering Croatia for 5 years under anti-terrorism legislation, where the authorities argue that these Liberlanders are something akin to a threat to national security.
The Liberlanders have mounted a legal defense against this, in addition to challenging Croatia on other legal fronts. They have had some successes so far – in particular, it should now be clear that the Liberlanders do not need any building permits to construct buildings on their territory. Unfortunately, other issues – including the 5-year bans from Croatia – still remain unresolved.
Most Liberlanders remain hopeful nonetheless. They have seen their situation move forward significantly over the last year. A year ago, they were not even able to enter Liberland without being chased and/or arrested. Now, even some construction is possible, albeit in a limited way.
The road ahead
The long-term vision, of course, remains to build a full-fledged, internationally respected and recognized city-state. Liberland’s leaders often speak of a “Balkan Monaco”, referring to the amazing development possibilities that a freedom-oriented country in the middle of Europe could offer. Liberland has already hosted an urbanist/architectural contest, and there are concrete plans for the first hotel as well as a riverside real estate development. What is more, Liberland’s land is actually more than three times the size of Monaco.
Nevertheless, Liberland cannot move forward in a meaningful way toward these visions and aspirations under the status quo. The Liberlanders need to be able to build at scale and be free from harassment, both by the police and the forestry workers. Some kind of political deal is necessary as the next step toward proper development of Liberland.
Such a deal could take multiple forms, but all of them involve the Croatian authorities changing their attitude toward Liberland away from a policy of unrelenting obstruction – not necessarily toward outright recognition, but at least toward accepting Liberland as a neighborly project that will move forward and develop in some way.
One option could be to allow motor vehicles on the bike path toward Liberland, with a deal that could include charging Liberlanders some fair tolls to pay for the wear and tear of the pavement. An alternative would be to simply allow river crossing into Liberland from Serbia on the Danube. Since Croatia does not officially consider Liberland its territory, their current interference with this traffic is illegal anyway. Simply stopping this illegal conduct would help Liberland significantly without Croatia facilitating Liberland’s development in any active way.

Regardless of these options, the first and most notable step would be to stop banning non-EU citizens from re-entering Croatia as well as lift the existing (entirely unjustified and unreasonable) 5-year bans on Jedlička and the others.
It is easy to see why Croatia is wary and suspicious of Liberland’s development. One can understand the worries of a state in whose immediate proximity there is a new and unknown state growing and taking root. Nevertheless, Croatia actually has a lot to gain from making some kind of deal with Liberland.
First: currently there are perhaps a dozen policemen on patrol around Liberland at all times. This includes police vehicles and boats. This is a significant expense for the police force – an expense which is rather unsubstantiated, given that Liberlanders have clearly proven to be peaceful people who do not wish to pose any threat to Croatia, its people, or its law enforcement officers. Making a deal would mean that this large expense is not needed anymore.
Second: Liberland borders an area of Croatia that has been rather “left behind”, is underdeveloped, and suffers from a lack of jobs and investment. Consequently, younger people are leaving the area and the current population is growing older. If Liberland was growing and open for business nearby, it would provide the region exactly with the job opportunities, large investment, and overall development that it desperately needs.
Third: Croatia could use Liberland as an opportunity to actually gain an advantage in the ongoing border dispute with Serbia. As previously mentioned, Croatia cannot openly and properly administer the territory, as it would be an indication in the eyes of international law that they consider the territory to be theirs. On the other hand, it Liberland is located on “their” side of the Danube, so Croatia does have an interest in making sure the area is under their control somehow. Striking a deal with Liberland could involve Liberland agreeing to some obligations related to the administration of the territory which correspond to Croatia’s priorities. In this way, Croatia would have an active say in what happens on this land, effectively “outsourcing” its administration without officially claiming it as part of Croatia.
In addition to all these advantages being present, Liberland is very much open to cooperation with Croatia and is keenly looking forward to welcoming any future productive relations with Croatian authorities. There will be no grudges held on Liberland’s side, and if a mutually beneficial deal or solution were to be found, no one would look behind at any historical quibbles or difficulties. Liberland would be an excellent and friendly neighbor to Croatia, not just causing any issues but actively helping the overall development of the surrounding region.
Time will tell how things will develop. At the present, the momentum, energy, and enthusiasm is definitely on the side of Liberland. There seems to be very little actual interest from the Croatian side to cause issues for Liberland and to continue to prevent the fledgling state from developing further. All that is left are the bureaucratic hurdles of a state that is being overly conservative about its approach to the important issues of the day. Things might take time, but seeing the determination of the settlers and the willingness of all Liberlanders to be unrelenting in their fight for the cause, it is not difficult to argue that we might be seeing the dawn of Liberland as the world’s next proper city-state as we speak.
-
 @ 3bf0c63f:aefa459d
2024-11-07 14:56:17
@ 3bf0c63f:aefa459d
2024-11-07 14:56:17The case against edits
Direct edits are a centralizing force on Nostr, a slippery slope that should not be accepted.
Edits are fine in other, more specialized event kinds, but the
kind:1space shouldn't be compromised with such a push towards centralization, becausekind:1is the public square of Nostr, where all focus should be on decentralization and censorship-resistance.- Why?
Edits introduce too much complexity. If edits are widespread, all clients now have to download dozens of extra events at the same time while users are browsing a big feed of notes which are already coming from dozens of different relays using complicated outbox-model-based querying, then for each event they have to open yet another subscription to these relays -- or perform some other complicated batching of subscriptions which then requires more complexity on the event handling side and then when associating these edits with the original events. I can only imagine this will hurt apps performance, but it definitely raises the barrier to entry and thus necessarily decreases Nostr decentralization.
Some clients may be implemneted in way such that they download tons of events and then store them in a local databases, from which they then construct the feed that users see. Such clients may make edits potentially easier to deal with -- but this is hardly an answer to the point above, since such clients are already more complex to implement in the first place.
- What do you have against complex clients?
The point is not to say that all clients should be simple, but that it should be simple to write a client -- or at least as simple as physically possible.
You may not be thinking about it, but if you believe in the promise of Nostr then we should expect to see Nostr feeds in many other contexts other than on a big super app in a phone -- we should see Nostr notes being referenced from and injected in unrelated webpages, unrelated apps, hardware devices, comment sections and so on. All these micro-clients will have to implement some complicated edit-fetching logic now?
- But aren't we already fetching likes and zaps and other things, why not fetch edits too?
Likes, zaps and other similar things are optional. It's perfectly fine to use Nostr without seeing likes and/or zaps -- and, believe me, it does happen quite a lot. The point is basically that likes or zaps don't affect the content of the main post at all, while edits do.
- But edits are optional!
No, they are not optional. If edits become widespread they necessarily become mandatory. Any client that doesn't implement edits will be displaying false information to its users and their experience will be completely broken.
- That's fine, as people will just move to clients that support edits!
Exactly, that is what I expect to happen too, and this is why I am saying edits are a centralizing force that we should be fighting against, not embracing.
If you understand that edits are a centralizing force, then you must automatically agree that they aren't a desirable feature, given that if you are reading this now, with Nostr being so small, there is a 100% chance you care about decentralization and you're not just some kind of lazy influencer that is only doing this for money.
- All other social networks support editing!
This is not true at all. Bluesky has 10x more users than Nostr and doesn't support edits. Instagram doesn't support editing pictures after they're posted, and doesn't support editing comments. Tiktok doesn't support editing videos or comments after they're posted. YouTube doesn't support editing videos after they're posted. Most famously, email, the most widely used and widespread "social app" out there, does not support edits of any kind. Twitter didn't support edits for the first 15 years of its life, and, although some people complained, it didn't hurt the platform at all -- arguably it benefitted it.
If edits are such a straightforward feature to add that won't hurt performance, that won't introduce complexity, and also that is such an essential feature users could never live without them, then why don't these centralized platforms have edits on everything already? There must be something there.
- Eventually someone will implement edits anyway, so why bother to oppose edits now?
Once Nostr becomes big enough, maybe it will be already shielded from such centralizing forces by its sheer volume of users and quantity of clients, maybe not, we will see. All I'm saying is that we shouldn't just push for bad things now just because of a potential future in which they might come.
- The market will decide what is better.
The market has decided for Facebook, Instagram, Twitter and TikTok. If we were to follow what the market had decided we wouldn't be here, and you wouldn't be reading this post.
- OK, you have convinced me, edits are not good for the protocol. But what do we do about the users who just want to fix their typos?
There are many ways. The annotations spec, for example, provides a simple way to append things to a note without being a full-blown edit, and they fall back gracefully to normal replies in clients that don't implement the full annotations spec.
Eventually we could have annotations that are expressed in form of simple (human-readable?) diffs that can be applied directly to the post, but fall back, again, to comments.
Besides these, a very simple idea that wasn't tried yet on Nostr yet is the idea that has been tried for emails and seems to work very well: delaying a post after the "submit" button is clicked and giving the user the opportunity to cancel and edit it again before it is actually posted.
Ultimately, if edits are so necessary, then maybe we could come up with a way to implement edits that is truly optional and falls back cleanly for clients that don't support them directly and don't hurt the protocol very much. Let's think about it and not rush towards defeat.
-
 @ 3b7fc823:e194354f
2025-02-04 23:57:49
@ 3b7fc823:e194354f
2025-02-04 23:57:49Protecting Privacy as an LGBTQ+ Individual: A Comprehensive Guide
Privacy is a cornerstone of personal freedom, especially for those within the LGBTQ+ community who often face unique challenges due to discrimination and surveillance. This guide offers practical steps tailored to safeguard your privacy, ensuring you can navigate the digital landscape with confidence and security.
1. Legal Awareness: Understanding Your Rights
Before taking any action, it's crucial to understand your legal rights regarding privacy. In many regions, laws may criminalize expression of identity or orientation, so being informed about local legislation is essential. Familiarize yourself with privacy laws and data protection regulations that might apply to you.
2. Encryption: Safeguarding Your Communications
- End-to-End Encryption: Use messaging apps like Signal or SimpleX to ensure your communications are encrypted from end to end, preventing unauthorized access.
- Secure Email Services: Employ email services like ProtonMail, which offers end-to-end encryption and zero-knowledge proof, ensuring only the sender and recipient can decrypt messages.
3. Anonymity Networks: Masking Your Identity
- Tor Network: Utilize Tor for anonymous browsing and secure communication, hiding your IP address to avoid surveillance.
- Pseudonyms and Aliases: Consider using pseudonyms or anonymous accounts when engaging in online communities to protect your identity.
4. Minimizing Metadata Exposure: Avoiding Data Trails
- Data Minimization: Only collect necessary information and avoid sharing excessive personal details online.
- Avoid Tracking Technologies: Refrain from using location-sharing apps or platforms that track your movements.
5. Secure Online Presence: Managing Your Digital Footprint
- Use Privacy-Friendly Platforms: Engage in forums and communities that prioritize user privacy, such as Mastodon with enhanced privacy settings and encrypted P2P on Matrix.
- Adjust Privacy Settings: Regularly review and adjust social media settings to limit data collection by platforms.
6. Avoiding Data Collection: Shielding Your Information
- Third-Party Data Avoidance: Be cautious of apps that collect personal data, especially location data, which can be used for surveillance.
- Review Privacy Policies: Before using any service, review their privacy policies to understand what information they collect and how it is used.
7. Physical Security: Protecting Your Devices
- Device Protection: Regularly update your devices and use strong, unique passwords to prevent unauthorized access.
- Encryption on Devices: Enable encryption on your mobile devices and computers to secure stored data.
8. Community Safety: Securing LGBTQ+ Networks
- Encrypted Communication Channels: Use encrypted channels like SimpleX or Signal for community discussions to ensure member safety.
- Secure Group Servers: Ensure that community servers are regularly maintained and encrypted to prevent data breaches.
9. Mental Health Considerations: Maintaining Balance
- Stress Management: Recognize the mental toll of constant privacy concerns and seek balance through mindfulness or stress-relief practices.
- Support Networks: Engage with support groups that offer both emotional support and practical advice on privacy strategies.
10. Advocacy: Supporting Privacy Rights
- Engage in Advocacy: Support organizations and initiatives that fight for digital rights, including privacy and freedom of expression..
- Raise Awareness: Use your voice to highlight issues of privacy and surveillance, contributing to broader societal change. Speak up when you see hate.
11. Tech Tools: Empowering Your Privacy Practices
- Signal: For secure messaging, Signal offers end-to-end encryption without requiring phone numbers for some platforms.
- ProtonMail: A secure email service that uses PGP encryption and does not require a phone number for account creation.
- Tresorit: Offers encrypted cloud storage with zero-knowledge proof, ensuring only you control your data.
By integrating these strategies, you can protect your privacy while fostering a safer online environment. Remember, informed and proactive measures are key to safeguarding your identity and rights in the digital age.
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-
 @ b8851a06:9b120ba1
2025-01-28 21:34:54
@ b8851a06:9b120ba1
2025-01-28 21:34:54Private property isn’t lines on dirt or fences of steel—it’s the crystallization of human sovereignty. Each boundary drawn is a silent declaration: This is where my will meets yours, where creation clashes against chaos. What we defend as “mine” or “yours” is no mere object but a metaphysical claim, a scaffold for the unfathomable complexity of voluntary exchange.
Markets breathe only when individuals anchor their choices in the inviolable. Without property, there is no negotiation—only force. No trade—only taking. The deed to land, the title to a car, the seed of an idea: these are not static things but frontiers of being, where human responsibility collides with the infinite permutations of value.
Austrian economics whispers what existentialism shouts: existence precedes essence. Property isn’t granted by systems; it’s asserted through action, defended through sacrifice, and sanctified through mutual recognition. A thing becomes “owned” only when a mind declares it so, and others—through reason or respect—refrain from crossing that unseen line.
Bitcoin? The purest ledger of this truth. A string of code, yes—but one that mirrors the unyielding logic of property itself: scarce, auditable, unconquerable. It doesn’t ask permission. It exists because sovereign minds choose it to.
Sigh. #nostr
I love #Bitcoin. -
 @ 599f67f7:21fb3ea9
2025-01-26 11:01:05
@ 599f67f7:21fb3ea9
2025-01-26 11:01:05¿Qué es Blossom?
nostr:nevent1qqspttj39n6ld4plhn4e2mq3utxpju93u4k7w33l3ehxyf0g9lh3f0qpzpmhxue69uhkummnw3ezuamfdejsygzenanl0hmkjnrq8fksvdhpt67xzrdh0h8agltwt5znsmvzr7e74ywgmr72
Blossom significa Blobs Simply Stored on Media Servers (Blobs Simplemente Almacenados en Servidores de Medios). Blobs son fragmentos de datos binarios, como archivos pero sin nombres. En lugar de nombres, se identifican por su hash sha256. La ventaja de usar hashes sha256 en lugar de nombres es que los hashes son IDs universales que se pueden calcular a partir del archivo mismo utilizando el algoritmo de hash sha256.
💡 archivo -> sha256 -> hash
Blossom es, por lo tanto, un conjunto de puntos finales HTTP que permiten a los usuarios almacenar y recuperar blobs almacenados en servidores utilizando su identidad nostr.
¿Por qué Blossom?
Como mencionamos hace un momento, al usar claves nostr como su identidad, Blossom permite que los datos sean "propiedad" del usuario. Esto simplifica enormemente la cuestión de "qué es spam" para el alojamiento de servidores. Por ejemplo, en nuestro Blossom solo permitimos cargas por miembros de la comunidad verificados que tengan un NIP-05 con nosotros.
Los usuarios pueden subir en múltiples servidores de blossom, por ejemplo, uno alojado por su comunidad, uno de pago, otro público y gratuito, para establecer redundancia de sus datos. Los blobs pueden ser espejados entre servidores de blossom, de manera similar a cómo los relays nostr pueden transmitir eventos entre sí. Esto mejora la resistencia a la censura de blossom.
A continuación se muestra una breve tabla de comparación entre torrents, Blossom y servidores CDN centralizados. (Suponiendo que hay muchos seeders para torrents y se utilizan múltiples servidores con Blossom).
| | Torrents | Blossom | CDN Centralizado | | --------------------------------------------------------------- | -------- | ------- | ---------------- | | Descentralizado | ✅ | ✅ | ❌ | | Resistencia a la censura | ✅ | ✅ | ❌ | | ¿Puedo usarlo para publicar fotos de gatitos en redes sociales? | ❌ | ✅ | ✅ |
¿Cómo funciona?
Blossom utiliza varios tipos de eventos nostr para comunicarse con el servidor de medios.
| kind | descripción | BUD | | ----- | ------------------------------- | ------------------------------------------------------------------ | | 24242 | Evento de autorización | BUD01 | | 10063 | Lista de Servidores de Usuarios | BUD03 |
kind:24242 - Autorización
Esto es esencialmente lo que ya describimos al usar claves nostr como IDs de usuario. En el evento, el usuario le dice al servidor que quiere subir o eliminar un archivo y lo firma con sus claves nostr. El servidor realiza algunas verificaciones en este evento y luego ejecuta el comando del usuario si todo parece estar bien.
kind:10063 - Lista de Servidores de Usuarios
Esto es utilizado por el usuario para anunciar a qué servidores de medios está subiendo. De esta manera, cuando el cliente ve esta lista, sabe dónde subir los archivos del usuario. También puede subir en múltiples servidores definidos en la lista para asegurar redundancia. En el lado de recuperación, si por alguna razón uno de los servidores en la lista del usuario está fuera de servicio, o el archivo ya no se puede encontrar allí, el cliente puede usar esta lista para intentar recuperar el archivo de otros servidores en la lista. Dado que los blobs se identifican por sus hashes, el mismo blob tendrá el mismo hash en cualquier servidor de medios. Todo lo que el cliente necesita hacer es cambiar la URL por la de un servidor diferente.
Ahora, además de los conceptos básicos de cómo funciona Blossom, también hay otros tipos de eventos que hacen que Blossom sea aún más interesante.
| kind | descripción | | ----- | --------------------- | | 30563 | Blossom Drives | | 36363 | Listado de Servidores | | 31963 | Reseña de Servidores |
kind:30563 - Blossom Drives
Este tipo de evento facilita la organización de blobs en carpetas, como estamos acostumbrados con los drives (piensa en Google Drive, iCloud, Proton Drive, etc.). El evento contiene información sobre la estructura de carpetas y los metadatos del drive.
kind:36363 y kind:31963 - Listado y Reseña
Estos tipos de eventos permiten a los usuarios descubrir y reseñar servidores de medios a través de nostr. kind:36363 es un listado de servidores que contiene la URL del servidor. kind:31963 es una reseña, donde los usuarios pueden calificar servidores.
¿Cómo lo uso?
Encuentra un servidor
Primero necesitarás elegir un servidor Blossom donde subirás tus archivos. Puedes navegar por los públicos en blossomservers.com. Algunos de ellos son de pago, otros pueden requerir que tus claves nostr estén en una lista blanca.
Luego, puedes ir a la URL de su servidor y probar a subir un archivo pequeño, como una foto. Si estás satisfecho con el servidor (es rápido y aún no te ha fallado), puedes agregarlo a tu Lista de Servidores de Usuarios. Cubriremos brevemente cómo hacer esto en noStrudel y Amethyst (pero solo necesitas hacer esto una vez, una vez que tu lista actualizada esté publicada, los clientes pueden simplemente recuperarla de nostr).
noStrudel
- Encuentra Relays en la barra lateral, luego elige Servidores de Medios.
- Agrega un servidor de medios, o mejor aún, varios.
- Publica tu lista de servidores. ✅
Amethyst
- En la barra lateral, encuentra Servidores multimedia.
- Bajo Servidores Blossom, agrega tus servidores de medios.
- Firma y publica. ✅
Ahora, cuando vayas a hacer una publicación y adjuntar una foto, por ejemplo, se subirá en tu servidor blossom.
⚠️ Ten en cuenta que debes suponer que los archivos que subas serán públicos. Aunque puedes proteger un archivo con contraseña, esto no ha sido auditado.
Blossom Drive
Como mencionamos anteriormente, podemos publicar eventos para organizar nuestros blobs en carpetas. Esto puede ser excelente para compartir archivos con tu equipo, o simplemente para mantener las cosas organizadas.
Para probarlo, ve a blossom.hzrd149.com (o nuestra instancia comunitaria en blossom.bitcointxoko.com) e inicia sesión con tu método preferido.
Puedes crear una nueva unidad y agregar blobs desde allí.
Bouquet
Si usas múltiples servidores para darte redundancia, Bouquet es una buena manera de obtener una visión general de todos tus archivos. Úsalo para subir y navegar por tus medios en diferentes servidores y sincronizar blobs entre ellos.
Cherry Tree
nostr:nevent1qvzqqqqqqypzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqyp3065hj9zellakecetfflkgudm5n6xcc9dnetfeacnq90y3yxa5z5gk2q6
Cherry Tree te permite dividir un archivo en fragmentos y luego subirlos en múltiples servidores blossom, y más tarde reensamblarlos en otro lugar.
Conclusión
Blossom aún está en desarrollo, pero ya hay muchas cosas interesantes que puedes hacer con él para hacerte a ti y a tu comunidad más soberanos. ¡Pruébalo!
Si deseas mantenerte al día sobre el desarrollo de Blossom, sigue a nostr:nprofile1qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqyqnxs90qeyssm73jf3kt5dtnk997ujw6ggy6j3t0jjzw2yrv6sy22ysu5ka y dale un gran zap por su excelente trabajo.
Referencias
-
 @ 47750177:8969e41a
2024-11-04 12:00:00
@ 47750177:8969e41a
2024-11-04 12:00:0027.2 Release Notes
Bitcoin Core version 27.2 is now available from:
This release includes various bug fixes and performance improvements, as well as updated translations.
Please report bugs using the issue tracker at GitHub:
https://github.com/bitcoin/bitcoin/issues
To receive security and update notifications, please subscribe to:
https://bitcoincore.org/en/list/announcements/join/
How to Upgrade
If you are running an older version, shut it down. Wait until it has completely shut down (which might take a few minutes in some cases), then run the installer (on Windows) or just copy over
/Applications/Bitcoin-Qt(on macOS) orbitcoind/bitcoin-qt(on Linux).Upgrading directly from a version of Bitcoin Core that has reached its EOL is possible, but it might take some time if the data directory needs to be migrated. Old wallet versions of Bitcoin Core are generally supported.
Compatibility
Bitcoin Core is supported and extensively tested on operating systems using the Linux Kernel 3.17+, macOS 11.0+, and Windows 7 and newer. Bitcoin Core should also work on most other Unix-like systems but is not as frequently tested on them. It is not recommended to use Bitcoin Core on unsupported systems.
Notable changes
P2P
-
30394 net: fix race condition in self-connect detection
Init
-
30435 init: change shutdown order of load block thread and scheduler
RPC
-
30357 Fix cases of calls to FillPSBT errantly returning complete=true
PSBT
-
29855 psbt: Check non witness utxo outpoint early
Test
-
30552 test: fix constructor of msg_tx
Doc
-
30504 doc: use proper doxygen formatting for CTxMemPool::cs
Build
-
30283 upnp: fix build with miniupnpc 2.2.8
-
30633 Fixes for GCC 15 compatibility
CI
-
30193 ci: move ASan job to GitHub Actions from Cirrus CI
-
30299 ci: remove unused bcc variable from workflow
Credits
Thanks to everyone who directly contributed to this release:
- Ava Chow
- Cory Fields
- Martin Zumsande
- Matt Whitlock
- Max Edwards
- Sebastian Falbesoner
- Vasil Dimov
- willcl-ark
As well as to everyone that helped with translations on Transifex.
-
-
 @ 1cb14ab3:95d52462
2025-02-04 22:17:27
@ 1cb14ab3:95d52462
2025-02-04 22:17:27Chef's notes
Credit to The Yummy Life. Go show them love below: https://www.theyummylife.com/Pickled_Jalapeno_Peppers
Details
- ⏲️ Prep time: 1 hour
- 🍳 Cook time: 20 mins
- 🍽️ Servings: 4 mason jars (pint)
Ingredients
- 2 lbs. jalapenos
- 2-1/4 cups vinegar (white distilled, apple cider, or a combination of the two)
- 2-1/4 cups water
- 2 tablespoons sugar or honey (optional)
- ADD TO EACH PINT JAR
- 1/2 teaspoon kosher salt
- 1/2 teaspoon whole black pepper corns
- 1/4 teaspoon whole cumin seeds
- 1/4 teaspoon whole coriander seeds
- 1 bay leaf
- 1 whole garlic clove, peeled
- 1/8 teaspoon Pickle Crisp granules (optional)
Directions
- Slice 1/2 pound jalapenos into 1/8" rounds, discarding stem ends.
- Prepare the jars: Wash 4 pint jars and lids in hot sudsy water, then keep them warm.
- Prepare the pickling liquid: Combine 1/2 cup plus 1 tablespoon vinegar, 1/2 cup plus 1 tablespoon water, and 1-1/2 teaspoons sugar or honey (optional) in a 2 quart pan, heating until just before boiling.
- Fill the jars: Add jalapeno slices to each jar, pressing them down and packing them in compactly, then pour the hot pickling liquid into each jar, leaving 1/2" head space.
- Process and store: Allow jars to cool to room temperature, then store them in the refrigerator or can them using standard USDA water process canning procedures, following storage guidelines for refrigerator or canned pickled peppers.
-
 @ 29af23a9:842ef0c1
2025-01-24 09:28:37
@ 29af23a9:842ef0c1
2025-01-24 09:28:37A Indústria Pornográfica se caracteriza pelo investimento pesado de grandes empresários americanos, desde 2014.
Na década de 90, filmes pornográficos eram feitos às coxas. Era basicamente duas pessoas fazendo sexo amador e sendo gravadas. Não tinha roteiro, nem produção, não tinha maquiagem, nada disso. A distribuição era rudimentar, os assinantes tinham que sair de suas casas, ir até a locadora, sofrer todo tipo de constrangimento para assistir a um filme pornô.
No começo dos anos 2000, o serviço de Pay Per View fez o número de vendas de filmes eróticos (filme erótico é bem mais leve) crescer mas nada se compara com os sites de filmes pornográficos por assinatura.
Com o advento dos serviços de Streaming, os sites que vendem filmes por assinatura se estabeleceram no mercado como nunca foi visto na história.
Hoje, os Produtores usam produtos para esticar os vasos sanguíneos do pênis dos atores e dopam as atrizes para que elas aguentem horas de gravação (a Série Black Mirror fez uma crítica a isso no episódio 1 milhão de méritos de forma sutil).
Além de toda a produção em volta das cenas. Que são gravadas em 4K, para focar bem as partes íntimas dos atores. Quadros fechados, iluminação, tudo isso faz essa Indústria ser "Artística" uma vez que tudo ali é falso. Um filme da Produtora Vixen, por exemplo, onde jovens mulheres transam em mansões com seus empresários estimula o esteriótipo da mina padrão que chama seu chefe rico de "daddy" e seduz ele até ele trair a esposa.
Sites como xvídeos, pornHub e outros nada mais são do que sites que salvam filmes dessas produtoras e hospedam as cenas com anúncios e pop-ups. Alguns sites hospedam o filme inteiro "de graça".
Esse tipo de filme estimula qualquer homem heterosexual com menos de 30 anos, que não tem o córtex frontal de seu cérebro totalmente desenvolvido (segundo estudos só é completamente desenvolvido quando o homem chega aos 31 anos).
A arte Pornográfica faz alguns fantasiarem ter relação sexual com uma gostosa americana branquinha, até escraviza-los. Muitos não conseguem sair do vício e preferem a Ficção à sua esposa real. Então pare de se enganar e admita. A Pornografia faz mal para a saúde mental do homem.
Quem sonha em ter uma transa com Lana Rhodes, deve estar nesse estágio. Trata-se de uma atriz (pornstar) que ganhou muito dinheiro vendendo a ilusão da Arte Pornografica, como a Riley Reid que só gravava para grandes Produtoras. Ambas se arrependeram da carreira artística e agora tentam viver suas vidas como uma mulher comum.
As próprias atrizes se consideram artistas, como Mia Malkova, chegou a dizer que Pornografia é a vida dela, que é "Lindo e Sofisticado."
Mia Malkova inclusive faz questão de dizer que a industria não escravisa mulheres jovens. Trata-se de um negócio onde a mulher assina um contrato com uma produtora e recebe um cachê por isso. Diferente do discurso da Mia Khalifa em entrevista para a BBC, onde diz que as mulheres são exploradas por homens poderosos. Vai ela está confundindo o Conglomerado Vixen com a Rede Globo ou com a empresa do Harvey Weinstein.
Enfim, se você é um homem solteiro entre 18 e 40 anos que já consumiu ou que ainda consome pornografia, sabia que sofrerá consequências. Pois trata-se de "produções artísticas" da indústria audiovisual que altera os níveis de dopamina do seu cérebro, mudando a neuroplasticidade e diminuindo a massa cinzenta, deixando o homem com memória fraca, sem foco e com mente nebulosa.
Por que o Estado não proíbe/criminaliza a Pornografia se ela faz mal? E desde quando o Estado quer o nosso bem? Existem grandes empresarios que financiam essa indústria ajudando governos a manterem o povo viciado e assim alienado. É um pão e circo, só que muito mais viciante e maléfico. Eu costume dizer aos meus amigos que existem grandes empresários jvdeus que são donos de grandes Produtoras de filmes pornográficos como o Conglomerado Vixen. Então se eles assistem vídeos pirateados de filmes dessas produtoras, eles estão no colo do Judeu.
-
 @ 16d11430:61640947
2025-02-05 00:52:05
@ 16d11430:61640947
2025-02-05 00:52:05Introduction: Colonization as a Multi-Generational Trauma
Colonization was not only a political and economic endeavor but also a deeply psychological one. Through forced labor, cultural erasure, and systematic oppression, colonizers imposed a set of economic and social behaviors that favored their interests. Though most colonies gained independence in the mid-20th century, the trauma of colonization remains embedded in their financial and governance structures.
Modern research in epigenetics suggests that trauma can alter gene expression and be passed down through generations (Yehuda & Lehrner, 2018). In a socio-economic context, the colonial mindset—marked by dependency, economic passivity, and a lack of financial sovereignty—persists within many post-colonial nations. One of the most insidious methods by which this trauma is maintained is through fiat currency and debt-based financial systems, which perpetuate economic dependency on former colonizers.
- The Psychological Impact of Colonial Trauma and Economic Passivity
Historical trauma theory suggests that populations subjected to prolonged oppression develop collective learned helplessness—a psychological state in which they stop attempting to resist their conditions because they have been conditioned to believe resistance is futile (Sotero, 2006).
This manifests in post-colonial societies in several ways:
-
Economic Dependency: A tendency to rely on foreign aid, multinational corporations, and foreign direct investment (FDI) rather than fostering self-sustaining industries.
-
Risk Aversion in Economic Policy: Research suggests that traumatic experiences affect the brain’s ability to take financial risks (Shields et al., 2016), leading to post-colonial states preferring IMF/World Bank solutions rather than exploring independent monetary policies.
-
Political Elite Compliance: Many former colonies' elites were educated in Western institutions, perpetuating colonial economic structures that maintain wealth extraction.
- Fiat Currency as a Tool of Economic Control
Fiat currency—money that has no intrinsic value but is backed by government decree—has been one of the most effective tools for maintaining economic dominance over former colonies.
A. The CFA Franc: A Colonial Currency in 2024
One of the most blatant examples of fiat currency maintaining colonial control is the CFA franc, used by 14 African countries, but ultimately controlled by France.
These countries must keep 50% of their foreign reserves in the French Treasury.
France dictates the monetary policies of these countries, limiting their financial autonomy.
Import dependency: Because the CFA franc is overvalued, it makes local goods more expensive while making European imports cheaper, reinforcing dependency on former colonizers.
B. The Role of the IMF and World Bank in Debt Colonialism
Post-colonial nations, lacking industrial infrastructures due to resource extraction under colonial rule, often turn to IMF and World Bank loans for development. However, these loans come with conditions that ensure neo-colonial economic control:
Structural Adjustment Programs (SAPs): Force nations to privatize industries, cut social spending, and open markets to foreign corporations—benefiting Western investors.
Perpetual Debt: Since loans are taken in foreign fiat currencies (USD, Euro), debt is rarely reduced, creating a cycle of endless repayment that prevents real economic independence.
- How Colonial Trauma Conditions Profitable Behaviors for Former Colonizers
Even outside of direct financial mechanisms, the trauma of colonization has conditioned post-colonial societies to adopt behaviors that benefit the former colonizers.
A. Elites as Gatekeepers of Colonial Structures
In many post-colonial nations, political and economic elites maintain colonial financial policies because they personally benefit from them. Studies (Acemoglu & Robinson, 2012) show that economic elites in post-colonial states are more likely to align with global financial institutions rather than advocate for economic self-determination.
B. Consumer Culture as a Neo-Colonial Tool
Western consumerism remains deeply ingrained in many post-colonial societies. This is a legacy of cultural imperialism, where local industries were suppressed in favor of Western goods.
The majority of African, South Asian, and Latin American countries continue to import Western luxury goods, technology, and services instead of developing their own.
As a result, much of the wealth generated in these countries flows back to Western corporations, mirroring the colonial economic extraction model.
Conclusion: Fiat Currency as the Modern Brand of Colonization
The economic and psychological trauma of colonization ensures that former colonies remain profitable markets and debt-ridden nations under the control of their colonizers. Fiat currency, international debt structures, and cultural hegemony serve as the modern pillars of economic colonialism, reinforcing behaviors that favor Western economic dominance.
Key Takeaways:
-
Historical trauma conditions former colonies into economic dependency.
-
Fiat currency (such as the CFA franc) remains a tool of colonial control.
-
The IMF and World Bank perpetuate financial dependency through debt cycles.
-
Consumer culture ensures wealth extraction from former colonies to Western economies.
Unless these structures are dismantled, economic sovereignty for formerly colonized nations remains an illusion. Breaking free from the financial colonial matrix requires monetary independence, de-dollarization strategies, and local industrialization, rather than continued reliance on Western financial systems.
References:
Yehuda, R., & Lehrner, A. (2018). Intergenerational transmission of trauma effects: Putative role of epigenetic mechanisms. World Psychiatry, 17(3), 243-257.
Sotero, M. M. (2006). A conceptual model of historical trauma: Implications for public health practice and research. Journal of Health Disparities Research and Practice, 1(1), 93-108.
Shields, G. S., Sazma, M. A., & Yonelinas, A. P. (2016). The effects of acute stress on economic decision-making. Psychoneuroendocrinology, 67, 226-234.
Acemoglu, D., & Robinson, J. (2012). Why Nations Fail: The Origins of Power, Prosperity, and Poverty. Crown Business.
Sylla, N. S. (2019). The CFA Franc: The Shackles of Monetary Dependence. Pluto Press.
Hudson, M. (2021). Super Imperialism: The Economic Strategy of American Empire. Pluto Press.
-
 @ fd208ee8:0fd927c1
2024-12-26 07:02:59
@ fd208ee8:0fd927c1
2024-12-26 07:02:59I just read this, and found it enlightening.
Jung... notes that intelligence can be seen as problem solving at an everyday level..., whereas creativity may represent problem solving for less common issues
Other studies have used metaphor creation as a creativity measure instead of divergent thinking and a spectrum of CHC components instead of just g and have found much higher relationships between creativity and intelligence than past studies
https://www.mdpi.com/2079-3200/3/3/59
I'm unusually intelligent (Who isn't?), but I'm much more creative, than intelligent, and I think that confuses people. The ability to apply intelligence, to solve completely novel problems, on the fly, is something IQ tests don't even claim to measure. They just claim a correlation.
Creativity requires taking wild, mental leaps out into nothingness; simply trusting that your brain will land you safely. And this is why I've been at the forefront of massive innovation, over and over, but never got rich off of it.
I'm a starving autist.
Zaps are the first time I've ever made money directly, for solving novel problems. Companies don't do this because there is a span of time between providing a solution and the solution being implemented, and the person building the implementation (or their boss) receives all the credit for the existence of the solution. At best, you can hope to get pawned off with a small bonus.
Nobody can remember who came up with the solution, originally, and that person might not even be there, anymore, and probably never filed a patent, and may have no idea that their idea has even been built. They just run across it, later, in a tech magazine or museum, and say, "Well, will you look at that! Someone actually went and built it! Isn't that nice!"
Universities at least had the idea of cementing novel solutions in academic papers, but that: 1) only works if you're an academic, and at a university, 2) is an incredibly slow process, not appropriate for a truly innovative field, 3) leads to manifestations of perverse incentives and biased research frameworks, coming from 'publish or perish' policies.
But I think long-form notes and zaps solve for this problem. #Alexandria, especially, is being built to cater to this long-suffering class of chronic underachievers. It leaves a written, public, time-stamped record of Clever Ideas We Have Had.
Because they are clever, the ideas. And we have had them.
-
 @ 06b7819d:d1d8327c
2024-12-08 10:52:55
@ 06b7819d:d1d8327c
2024-12-08 10:52:55Power as the Reduction of Possibilities: Niklas Luhmann’s Perspective
Niklas Luhmann, a leading figure in systems theory, offers a unique conceptualization of power that diverges from traditional notions of domination or coercion. Rather than viewing power as a forceful imposition of will, Luhmann frames it as a mechanism for reducing possibilities within a given social system. For Luhmann, power is less about direct coercion and more about structuring decision-making processes by limiting the range of available options.
In his systems-theoretical approach, Luhmann argues that power operates as a communication medium, enabling complex social systems to function by simplifying the overwhelming array of potential actions. In any decision-making context, there are countless possibilities, and not all can be pursued. Power serves as a tool to focus attention, filter alternatives, and channel behavior toward specific actions while excluding others. This reduction of options creates a manageable environment for coordinated action, which is essential for the stability of a system.
Importantly, this process does not inherently involve force or threats. Instead, power works through expectations, norms, and structures that guide behavior. For example, in an organizational setting, the hierarchy of authority determines which decisions are permissible, thereby shaping the actions of individuals without overt coercion. The employees’ actions are not forced; rather, they are conditioned by the organizational framework, which narrows their choices.
Luhmann’s idea redefines power as a productive force in social systems. By limiting possibilities, power reduces uncertainty, making collaboration and collective action possible. It ensures that systems can function efficiently despite their inherent complexity. This perspective shifts the emphasis from conflict to coordination, offering a more nuanced understanding of how power operates in modern societies.
In sum, Niklas Luhmann’s theory of power as the reduction of possibilities highlights its integrative role in enabling social systems to navigate complexity. It challenges conventional views of power as coercion, emphasizing its capacity to organize and stabilize interactions through the selective limitation of actions.
-
 @ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08
@ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08Tldr
- Nostr is an open and interoperable protocol
- You can integrate it with workflow automation tools to augment your experience
- n8n is a great low/no-code workflow automation tool which you can host yourself
- Nostrobots allows you to integrate Nostr into n8n
- In this blog I create some workflow automations for Nostr
- A simple form to delegate posting notes
- Push notifications for mentions on multiple accounts
- Push notifications for your favourite accounts when they post a note
- All workflows are provided as open source with MIT license for you to use
Inter-op All The Things
Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In Using NFC Cards with Nostr I explored the
nostr:URI to launch Nostr clients from a card tap.The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails.
My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted.
This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull.
So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications.
All we need are simple ways to plug things together.
Nostr and Workflow Automation
Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective.
n8n for workflow automation
Many workflow automation tools exist. My favourite is n8n. n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to.
Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine.
Eating my own dogfood
It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do?
In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting.
I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up.
Running n8n with Nostrobots
I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills.
- I have a cheap VPS which currently runs my HAVEN Nostr Relay and Albyhub Lightning Node in Docker containers,
- My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows.
Installing n8n
Self-hosting n8n could not be easier. I followed n8n's Docker-Compose installation docs–
- Install Docker and Docker-Compose if you haven't already,
- Create your
docker-compose.ymland.envfiles from the docs, - Create your data folder
sudo docker volume create n8n_data, - Start your container with
sudo docker compose up -d, - Your n8n instance should be online at port
5678.
n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there.
Installing Nostrobots
To integrate n8n nicely with Nostr, I used the Nostrobots community node by Ocknamo.
In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in.
You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative).
To install a community node, see n8n community node docs. From your workflow dashboard–
- Click the "..." in the bottom left corner beside your username, and click "settings",
- Cilck "community nodes" left sidebar,
- Click "Install",
- Enter the "npm Package Name" which is
n8n-nodes-nostrobots, - Accept the risks and click "Install",
- Nostrobots is now added to your n8n instance.
Using Nostrobots
Nostrobots gives you nodes to help you build Nostr-integrated workflows–
- Nostr Write – for posting Notes to the Nostr network,
- Nostr Read – for reading Notes from the Nostr network, and
- Nostr Utils – for performing certain conversions you may need (e.g. from bech32 to hex).
Nostrobots has good documentation on each node which focuses on simple use cases.
Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use.
What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible.
Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with NIP-01). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of.
Creating and adding workflows
With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation.
- Click "Add workflow" to go to the workflow builder screen,
- If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added,
- If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article).
Nostr Workflow Automations
It's time to build some things!
A simple form to post a note to Nostr
I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily.
I needed a basic form with credentials that posted a Note.
For this I can use a very simple workflow–
- A n8n Form node – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted.
- A Set node – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain.
- A Nostr Write node (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays.
Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive".
It may also be the world's simplest Nostr client.
You can find the Nostr Form to Post a Note workflow here.
Push notifications on mentions and new notes
One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want–
- To make sure I never miss a note addressed to any of my Npubs – For this I want a push notification any time any Nostr user mentions any of my Npubs,
- To make sure I always see all notes from key accounts – For this I need a push notification any time any of my Npubs post any Notes to the network,
- To get these notifications on all of my devices – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day.
I needed to build a Nostr push notifications solution.
To build this workflow I had to string a few ideas together–
- Triggering the node on a schedule – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited,
- Storing a list of Npubs in a Nostr list – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists (NIP-51, kind 30000). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. Listr.lol or Nostrudel.ninja). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions,
- Using specific relays – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata,
- Querying Nostr events (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do–
- I read the EventID of my Kind 30000 list, to return the desired pubkeys,
- For notifications on mentions, I read all Kind 1 notes that mention that pubkey,
- For notifications on new notes, I read all Kind 1 notes published by that pubkey,
- Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub,
- I transform the EventID into a Nevent to help clients find it.
- Using the Nostr URI – As I did with my NFC card article, I created a link with the
nostr:URI prefix so that my phone's native client opens the link by default, - Push notifications solution – I needed a push notifications solution. I found many with n8n integrations and chose to go with Pushover which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license.
Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go.
You can find the Nostr Push Notification If Mentioned here and If Posts a Note here.
In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible.
Use my workflows
I have open sourced all my workflows at my Github with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use.
To import any of my workflows–
- Click on the workflow of your choice, e.g. "Nostr_Push_Notify_If_Mentioned.json",
- Click on the "raw" button to view the raw JSON, ex any Github page layout,
- Copy that URL,
- Enter that URL in the "import from URL" dialog mentioned above.
To configure them–
- Prerequisites, credentials, and variables are all stated,
- In general any variables required are entered into a Set Node that follows the trigger node,
- Pushover has some extra setup but is very straightforward and documented in the workflow.
What next?
Over my first four blogs I explored creating a good Nostr setup with Vanity Npub, Lightning Payments, Nostr Addresses at Your Domain, and Personal Nostr Relay.
Then in my latest two blogs I explored different types of interoperability with NFC cards and now n8n Workflow Automation.
Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this:
- Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds),
- Automated or scheduled posting (such as auto-liking everything Lyn Alden posts),
- Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming),
- All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr,
- All kinds of other automation (such as BlackCoffee controlling a coffee machine),
- All kinds of AI Assistants and Agents,
In fact I have already released an open source workflow for an AI Assistant, and will share more about that in my next blog.
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ 1cb14ab3:95d52462
2025-02-04 21:42:24
@ 1cb14ab3:95d52462
2025-02-04 21:42:24Chef's notes
Classic beef n' broccoli. Easy to make and dank to eat.
Details
- ⏲️ Prep time: 20 mins
- 🍳 Cook time: 10 mins.
Ingredients
- 1 lb top sirloin steak, thinly sliced
- ¼ cup low sodium soy sauce
- 2 teaspoons cornstarch
- 1 tablespoon dark brown sugar
- 2 tablespoons fresh ginger, minced
- 1 tablespoon oil
- 1 head broccoli, cut into 1-inch (2 ½ cm) florets
- ½ cup water
- 3 cloves garlic, minced
- ¼ teaspoon red pepper flakes, optional
- 1 teaspoon toasted sesame oil
Directions
- In a medium bowl, mix together the sirloin steak, soy sauce, cornstarch, brown sugar, and ginger until the meat is evenly covered in the marinade. Set aside to marinate for 20 minutes.
- Heat the oil in a large skillet or wok over medium-high heat. Dump in the meat and marinade and sear each side until golden brown. Transfer the meat to a clean bowl and set aside.
- Place the broccoli into the hot skillet and sauté until the broccoli has just started to brown, about 1 minute. Pour the water into the skillet and immediately cover with a lid. Let it steam for 2 minutes, until the broccoli has softened.
- Remove the lid and toss in the garlic, red pepper flakes, and sesame oil. Sauté until the garlic becomes fragrant, about 30 seconds.
- Add the steak back into the pan and stir to combine. Remove from heat and serve on a bed of brown rice.
-
 @ aade47fd:281e8e4f
2025-02-04 17:27:47
@ aade47fd:281e8e4f
2025-02-04 17:27:47Сюрприз! Оказалось, что мне потребовалось две недели для того, чтобы сделать вторую запись в свой ЕЖЕДНЕВНИК. Раньше после такого оглушительного провала бросил бы это дело, но задачей дневника было формирование дисциплины, а не сам дневник. Нет ничего удивительного в том, что дисциплины на ежедневные записи не хватило сразу: буду стараться писать как можно чаще пока не выйду устойчиво на ежедневные публикации.
Я на Сахалине
Вчера, третьего февраля, мы с отцом прилетели на Сахалин. Планирую провести здесь около трех-четырех месяцев, на пару летних месяцев вернусь в Питере (ве-ло-си-пед), а в августе снова на остров. Здесь очень много работы, а отвлекаться практически не на что. Именно то, что мне сейчас нужно.
Личность
Есть я. Есть не я. Граница между мной и не мной — моя личность. Это структура, через которую внешний мир возействует на меня, а я на него. Над личностью можно и нужно работать. В конечном счете, я верю, что больше ни на что непосредственным образом мы не влияем. Мир это поток случайных событий и состояний. Уверен, что в моменте мы ничего не решаем — все реакции готовы заранее. Их подготовка — наша ответственность. В этом и заключается формирование личности. Можно сказать, что сформированная личность это стена, и чем она выше и прочнее, тем устойчивее твое бытие. С жадностью тащи камни для этой стены: любое решение и дело должно первостепенной целью ставить собственное развитие, а только потом уже внешний результат. Слабая личность пропускает в тебя все проклятия окружающего мира, делая жизнь жалкой и отправленной. Так бывает с теми, кто ставит ценности мира над своими собственными. Жаль, что я понял это так поздно. Повезло, что я понял это вообще. Здесь, на Сахалине, у меня будет время решить, чем наполнять мою жизнь, а что отвергать.
Амбиции
Помню, что еще лет двадцать назад у слова "амбиции" было исключительно негативный смысл. Надеюсь, мы окончательно ушли от этого. Амбиции это аппетит к жизни. Человек без амбиций — полуживой, тень своего зомби. Такого невозможно полюбить. Новость для меня оказалась в том, что речь здесь идет не только о мужчинах: недавно я потерял интерес и симпатию к женщине не обнаружив в ней амбиций к развитию. Не ставлю на людях крест, я и сам провел много лет в таком состоянии, но лучше я буду двигаться один, чем стану пытаться кого-то растолкать. Спрашивают, может ли всемогущий Бог создать такой камень, который сам не смог бы поднять? Отвечаю: да, этот камень — человек.
На сегодня все. Встретимся завтра!
-
 @ f0c7506b:9ead75b8
2024-12-08 09:05:13
@ f0c7506b:9ead75b8
2024-12-08 09:05:13
Yalnızca güçlü olanların hakkıdır yaşamak.
Güçlü olan ileri gider ve saflar seyrekleşir. Ama üç beş büyük, güçlü ve tanrısal kişi güneşli ve aydınlık gözleriyle o yeni, o vaat edilmiş ülkeye ulaşacaktır. Belki binlerce yıl sonra ancak. Ve güçlü, adaleli, hükmetmek için yaratılmış elleriyle hastaların, zayıfların ve sakatların ölüleri üzerinde bir krallık kuracaklardır. Bir krallık!
Benim aradığım insanların kendileri değil, sesleridir.
Duyguları körelmiş, çeşitli düşüncelere saplanmış kalabalık hiçbir zaman ilerlemenin taşıyıcısı olamaz, kendi küçüklüğünün o küflü içgüdüsüyle kalabalığın kin ve nefretle baktığı bir kişi, bir büyük kişi, iradesinin gösterdiği yolda kimsenin gözünün yaşına bakmaksızın ilahi bir güç ve bir zafer gülümsemesiyle yürüyebilir ancak.
Bizim soyumuz da sonsuz oluşum piramidinin doruk noktasını oluşturmaktan uzaktır. Bizler de mükemmelliğe ulaşmış değiliz. Bizler de henüz olgunlaşmadık.
Şairler sevgiye övgüler döşenir; doğrusu sevginin güçlü bir şey olduğu kesin. Hüneşin bir ışınıdır sevgi, aydınlatıp nurlandırır insanı der bazıları; bazıları da insanı esrikliğe sürükleyen bir zehri kendisinde barındırdığını söyler. Gerçekten de yol açtığı sonuçlar, bir hekimin ağır bir ameliyattan önce korkudan titreyen hastaya teneffüs ettirdiği güldürücü gazınkine benzer, içinde tepinip duran acıyı unutturur hastaya.
Önemli olan, hayatta hiç değilse bir kez kutsal bir ilkbaharın yaşanmasıdır; öyle bir bahar ki, insanın gönlünü ilerideki bütün günleri altın yaldızla kaplamaya yetecek kadar ışık ve parıltıyla doldursun.
Şu hayat denen şey kötü bir işçiliğin ürünü, acemilere göre bir şey. Bu kepaze yaşam uğruna insan nelere katlanmıyor ki!
Kendisine sadakatten ayrılmadığı, yalnızca kendisinin olan bir tek bu var: Yalnızlığı.
Sahildeki üstü tenteli hasır koltuklar arkasındaki yüksek, sessiz kum tepeleri içinde yürürsen, tenteler altındaki insanları göremezsin; ama birinin bir diğerine seslendiğini, bir başkasının gevezelik ettiğini, bir ötekinin güldüğünü işitir ve anlarsın hemen: bu insan şöyle şöyle biridir diyebilirsin. Onun hayatı sevdiğini, bağrında büyük bir özlem ya da acı barındırdığını, bu acının da sesini ağlamaklı kıldığını her gülüşünde hissedersin.
-
 @ 57d1a264:69f1fee1
2025-02-05 00:25:20
@ 57d1a264:69f1fee1
2025-02-05 00:25:20How does open source development contribute to bitcoin's security, reliability, and evolution as a network?
originally posted at https://stacker.news/items/876130
-
 @ 378562cd:a6fc6773
2025-02-02 18:58:38
@ 378562cd:a6fc6773
2025-02-02 18:58:38Chef's notes
I'm only testing this out right now. I will update the recipe as well as add my own image soon after making this dish again.
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 4
Ingredients
- 4 to 6 potatoes (size depending)
- 1 lb ground beef
- seasonings
- 2 cans chili beans
- 1 onion
- katsup
- shredded cheese of some kind
Directions
- saute onion and add ground beef to skillet. Season to liking.
- peel if you like and thin slice potatoes
- in a rectangle baking dish, layer potatoes, beans, meat and cheese (like a lasagna) until you have used all your ingredients. Try and make at least 2 or 3 layers with extra cheese on top.
- Bake at 350 for one hour. Serve and enjoy!
-
 @ 06b7819d:d1d8327c
2024-12-03 09:00:46
@ 06b7819d:d1d8327c
2024-12-03 09:00:46The History of Bananas as an Exportable Fruit and the Rise of Banana Republics
Bananas became a significant export in the late 19th century, fueled by advancements in transportation and refrigeration that allowed the fruit to travel long distances without spoilage. Originally native to Southeast Asia, bananas were introduced to the Americas by European colonists. By the late 1800s, companies like the United Fruit Company (later Chiquita) and Standard Fruit Company (now Dole) began cultivating bananas on a large scale in Central America and the Caribbean.
These corporations capitalized on the fruit’s appeal—bananas were cheap, nutritious, and easy to transport. The fruit quickly became a staple in Western markets, especially in the United States. However, the rapid expansion of banana exports came at a significant political and social cost to the countries where the fruit was grown.
To maintain control over banana production and maximize profits, these companies required vast amounts of arable land, labor, and favorable trade conditions. This often led them to form close relationships with local governments, many of which were authoritarian and corrupt. The companies influenced policies to secure land concessions, suppress labor rights, and maintain low taxes.
The term “banana republic” was coined by writer O. Henry in 1904 to describe countries—particularly in Central America—that became politically unstable due to their economic dependence on a single export crop, often controlled by foreign corporations.
The U.S. government frequently supported these regimes as part of its broader strategy during the Cold War to counter communist influence in the region. Washington feared that labor movements and demands for land reform, often supported by the peasantry and indigenous groups, could lead to the rise of socialist or communist governments. Consequently, the U.S. backed coups, such as the 1954 overthrow of Guatemala’s democratically elected President Jacobo Árbenz, who had threatened United Fruit’s interests by redistributing unused land.
These interventions created a legacy of exploitation, environmental degradation, and political instability in many banana-exporting countries. While bananas remain a global dietary staple, their history underscores the complex interplay of economics, politics, and imperialism.
-
 @ 83279ad2:bd49240d
2025-01-24 09:15:37
@ 83279ad2:bd49240d
2025-01-24 09:15:37備忘録として書きます。意外と時間がかかりました。全体で1時間くらいかかるので気長にやりましょう。 仮想通貨取引所(販売所ではないので、玄人が使えばお得らしい)かつBitcoinの送金手数料が無料(全ての取引所が無料ではない、例えばbitbankは0.0006bitcoinかかる)なので送金元はGMOコインを使います。(注意:GMOコインは0.02ビットコイン以下は全額送金になってしまいます) 今回はカストディアルウォレットのWallet of Satoshiに送金します。 以下手順 1. GMOコインでbitcoinを買います。 2. GMOコインの左のタブから入出金 暗号資産を選択します。 3. 送付のタブを開いて、+新しい宛先を追加するを選択します。 4. 送付先:GMOコイン以外、送付先ウォレット:プライベートウォレット(MetaMaskなど)、受取人:ご本人さま を選んで宛先情報の登録を選ぶと次の画面になります。
 5. 宛先名称にwallet of satoshi(これはなんでも良いです わかりやすい名称にしましょう) wallet of satoshiを開いて、受信→Bitcoin On-Chainからアドレスをコピーして、ビットコインアドレスに貼り付けます。
5. 宛先名称にwallet of satoshi(これはなんでも良いです わかりやすい名称にしましょう) wallet of satoshiを開いて、受信→Bitcoin On-Chainからアドレスをコピーして、ビットコインアドレスに貼り付けます。 6. 登録するを押します。これで送金先の登録ができました。GMOコインの審査がありますがすぐ終わると思います。
7. ここから送金をします。送付のタブから登録したビットコインの宛先リストwallet of satoshiを選択し、送付数量と送付目的を選択して、2段階認証をします。
6. 登録するを押します。これで送金先の登録ができました。GMOコインの審査がありますがすぐ終わると思います。
7. ここから送金をします。送付のタブから登録したビットコインの宛先リストwallet of satoshiを選択し、送付数量と送付目的を選択して、2段階認証をします。 8. 実行を押せば終わりです。もうあなたがやることはありません。送金が終わるのを40分くらい眺めるだけです。
8. 実行を押せば終わりです。もうあなたがやることはありません。送金が終わるのを40分くらい眺めるだけです。 8. 取引履歴のタブから今の送金のステータスが見れます。
8. 取引履歴のタブから今の送金のステータスが見れます。 9. 15分くらい待つとステータスが受付に変わります。
9. 15分くらい待つとステータスが受付に変わります。 10. 20分くらい待つとトランザクションIDが表示されます。
10. 20分くらい待つとトランザクションIDが表示されます。

この時点からwallet of satoshiにも送金されていることが表示されます。(まだ完了はしていない)
 11. ステータスが完了になったら送金終わりです。
11. ステータスが完了になったら送金終わりです。

wallet of satoshiにも反映されます。

お疲れ様でした!
-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ dd664d5e:5633d319
2024-12-14 15:25:56
@ dd664d5e:5633d319
2024-12-14 15:25:56
Christmas season hasn't actually started, yet, in Roman #Catholic Germany. We're in Advent until the evening of the 24th of December, at which point Christmas begins (with the Nativity, at Vespers), and continues on for 40 days until Mariä Lichtmess (Presentation of Christ in the temple) on February 2nd.

It's 40 days because that's how long the post-partum isolation is, before women were allowed back into the temple (after a ritual cleansing).

That is the day when we put away all of the Christmas decorations and bless the candles, for the next year. (Hence, the British name "Candlemas".) It used to also be when household staff would get paid their cash wages and could change employer. And it is the day precisely in the middle of winter.

Between Christmas Eve and Candlemas are many celebrations, concluding with the Twelfth Night called Epiphany or Theophany. This is the day some Orthodox celebrate Christ's baptism, so traditions rotate around blessing of waters.

The Monday after Epiphany was the start of the farming season, in England, so that Sunday all of the ploughs were blessed, but the practice has largely died out.

Our local tradition is for the altar servers to dress as the wise men and go door-to-door, carrying their star and looking for the Baby Jesus, who is rumored to be lying in a manger.

They collect cash gifts and chocolates, along the way, and leave the generous their powerful blessing, written over the door. The famous 20 * C + M + B * 25 blessing means "Christus mansionem benedicat" (Christ, bless this house), or "Caspar, Melchior, Balthasar" (the names of the three kings), depending upon who you ask.
They offer the cash to the Baby Jesus (once they find him in the church's Nativity scene), but eat the sweets, themselves. It is one of the biggest donation-collections in the world, called the "Sternsinger" (star singers). The money goes from the German children, to help children elsewhere, and they collect around €45 million in cash and coins, every year.

As an interesting aside:
The American "groundhog day", derives from one of the old farmers' sayings about Candlemas, brought over by the Pennsylvania Dutch. It says, that if the badger comes out of his hole and sees his shadow, then it'll remain cold for 4 more weeks. When they moved to the USA, they didn't have any badgers around, so they switched to groundhogs, as they also hibernate in winter.
-
 @ 91bea5cd:1df4451c
2025-02-04 17:24:50
@ 91bea5cd:1df4451c
2025-02-04 17:24:50Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ dd664d5e:5633d319
2024-12-07 20:02:01
@ dd664d5e:5633d319
2024-12-07 20:02:01Yeah, so... nah.
People keep trying to explain to me, that women will be better-off, if they become more dangerous. While I can see the inevitableness of women living in remote rural areas learning to shoot with a rifle, and similar, I'm generally against arming women with killing machines.
This is not because I'm averse to the idea of using violence to solve problems (albeit after exhausting better options), or because I don't like guns, or am unfamiliar with them. It's also not because I don't know I would look totally, mind-numbingly hot holding something long and spearlike, while dressed in camo and wearing a T-Shirt that appears to have shrunk in the wash.

It's a more fundamental set of problems, that irks me.
Bazooka Barbie
American gun manufacturers saturated the public and private male market so thoroughly, that they eventually turned to marketing firearms to women.
Men are scary and bad. There is Stranger Danger. We can't just make the neighborhood less dangerous because erm... reasons. Stay safe with a cute gun.

It has gone along with the predictable hypersexualization of the conservative feminine ideal. Since guns are considered aggressive, women with guns are perceived as more sexually available. Guns (and tanks, bombs, bows, etc.) make women "equal", "independent", "feisty", "hot", "freaky", "calculating", "empowered", etc.

Sorta slutty, basically.
This Gun Girl is not like the helpless, hapless, harmless homemaker ideal, of yesteryear. A woman who was dependent, chaste, gentle, wise... and in need of protection. A woman who saw the men around her as people she could rely on for providing her with a safe environment. That woman is au revoir. Now, sistas are doing it for themselves. 💪🏻
The New Martial Missy needs a man, like a fish needs a bicycle... but make it country.
Yeah, it's marketing, but it sure has set the tone, and millions of men have been trained to prefer women who market themselves in this manner. Hard, mean, lean women. That will not remain without wider societal consequences.
You know, I liked that homemaker. I miss her. She's literally me.

Those arms are for cuddling babies, not holding rocket launchers.
Now, that we've all become accustomed to imagery of women holding firearms, it wasn't much of a leap to condition us all to the sight of women in frontline police, guard, or military positions.

Instead of war being a terrible, highly-lethal, territorial fight amongst men, it's now cute, hip, trendy and fun. It's a big party, and women are finally allowed to join in.

Now, women have finally jettisoned the terrible burden of being society's life-bearers and caretakers, and we're just more potential enemy combatants. We know it's okay to punch women, shoot women, etc. since we've been watching it happen on screens, for decades. Women are now often assumed to be fighters, not lovers. Cavalry, not mothers.
Girls on top
Not only does this undermine any female role -- and put female civilians under a cloud of suspicion -- it also reduces mens' claim to be paramount in governance. Why should a man be the Commander in Chief, if women are on the battlefield?
In fact, why should men be in charge of anything, anywhere? Look at them. There they are. Hiding at home. Cowering in their kitchens, wringing their hands and fretting, while courageous, dangerous women protect them from dangers foreign and domestic. Women are the better men, really.
Is this really where we want to go?
The final bitterness
But one thing I find most disturbing is something more personal. The ubiquitous nature of firearms in American homes has made domestic violence increasingly deadly. Adding more guns, for the female residents, often serves to make such violence even more deadly for women.
It turns out, that women are usually reluctant to shoot people they know; even more than men. Women without this inhibition are prone to sharing their home with men missing the same trait. And, now, they have more guns.
-
 @ 9e69e420:d12360c2
2025-01-30 12:23:04
@ 9e69e420:d12360c2
2025-01-30 12:23:04Tech stocks have taken a hit globally after China's DeepSeek launched a competitive AI chatbot at a much lower cost than US counterparts. This has stirred market fears of a $1.2 trillion loss across tech companies when trading opens in New York.
DeepSeek’s chatbot quickly topped download charts and surprised experts with its capabilities, developed for only $5.6 million.
The Nasdaq dropped over 3% in premarket trading, with major firms like Nvidia falling more than 10%. SoftBank also saw losses shortly after investing in a significant US AI venture.
Venture capitalist Marc Andreessen called it “AI’s Sputnik moment,” highlighting its potential impact on the industry.
![] (https://www.telegraph.co.uk/content/dam/business/2025/01/27/TELEMMGLPICT000409807198_17379939060750_trans_NvBQzQNjv4BqgsaO8O78rhmZrDxTlQBjdGLvJF5WfpqnBZShRL_tOZw.jpeg)
-
 @ 378562cd:a6fc6773
2025-02-02 17:53:05
@ 378562cd:a6fc6773
2025-02-02 17:53:05Chef's notes
I'm only testing this out right now. I will update the recipe as well as add my own image soon after making this dish again.
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 4
Ingredients
- 4 to 6 potatoes (size depending)
- 1 lb ground beef
- seasonings
- 2 cans chili beans
- 1 onion
- katsup
- shredded cheese of some kind
Directions
- saute onion and add ground beef to skillet. Season to liking.
- peel if you like and thin slice potatoes
- in a rectangle baking dish, layer potatoes, beans, meat and cheese (like a lasagna) until you have used all your ingredients. Try and make at least 2 or 3 layers with extra cheese on top.
- Bake at 350 for one hour. Serve and enjoy!
-
 @ 06b7819d:d1d8327c
2024-12-02 20:05:48
@ 06b7819d:d1d8327c
2024-12-02 20:05:48Benjamin Franklin and His Fondness for Madeira Wine
Benjamin Franklin, one of America’s most celebrated founding fathers, was not only a statesman, scientist, and writer but also a man of refined taste. Among his many indulgences, Franklin was particularly fond of Madeira wine, a fortified wine from the Portuguese Madeira Islands. His love for this drink was well-documented and reflects both his personal preferences and the broader cultural trends of 18th-century America.
The Allure of Madeira Wine
Madeira wine was highly prized in the 18th century due to its unique production process and exceptional durability. Its rich, fortified nature made it well-suited for long sea voyages, as it could withstand temperature fluctuations and aging in transit. This durability made Madeira a popular choice in the American colonies, where European wines often spoiled before arrival.
Franklin, who was known for his appreciation of fine things, embraced Madeira as a beverage of choice. Its complex flavors and storied reputation resonated with his intellectual and social pursuits. The wine was often served at dinners and social gatherings, where Franklin and his contemporaries debated ideas and shaped the future of the nation.
Franklin’s Personal Connection to Madeira
In Franklin’s writings and correspondence, Madeira is mentioned on several occasions, reflecting its prominence in his life. He referred to the wine not only as a personal pleasure but also as a symbol of hospitality and refinement. As a diplomat in France and England, Franklin often carried Madeira to share with his hosts, using it as a means of forging connections and showcasing the tastes of the American colonies.
One notable instance of Franklin’s affinity for Madeira occurred during his time in Philadelphia. He reportedly had cases of the wine shipped directly to his home, ensuring he would never be without his favorite drink. Madeira also featured prominently in many toasts and celebrations, becoming a hallmark of Franklin’s gatherings.
The Role of Madeira in Colonial America
Franklin’s fondness for Madeira reflects its broader significance in colonial America. The wine was not only a favorite of the elite but also a symbol of resistance to British taxation. When the British imposed heavy duties on imported goods, including wine, Madeira became a patriotic choice for many colonists. Its direct trade routes with the Madeira Islands circumvented British intermediaries, allowing Americans to assert their economic independence.
A Legacy of Taste
Franklin’s appreciation for Madeira wine endures as a charming detail of his multifaceted life. It offers a glimpse into the personal habits of one of America’s most influential figures and highlights the cultural exchanges that shaped colonial society. Today, Franklin’s love of Madeira serves as a reminder of the historical connections between wine, politics, and personal expression in the 18th century.
In honoring Franklin’s legacy, one might raise a glass of Madeira to toast not only his contributions to American independence but also his enduring influence on the art of living well.
-
 @ 91bea5cd:1df4451c
2025-02-04 17:15:57
@ 91bea5cd:1df4451c
2025-02-04 17:15:57Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ cffd7b79:dd8ca91f
2025-01-24 02:11:04
@ cffd7b79:dd8ca91f
2025-01-24 02:11:04Introductory
That right folks, it is called Satlantis. An upcoming game that is based on Minecraft. It uses a game engine called Launti/Minetest that has been in development since 2023, but it is unclear when it will be released. It is small team of bitcoin enthusiasts of 3-5 game developers.
Their Origin Story
It started out as a Minecraft server around 2018. It was prosperous with many players up to 100 players for just a SMP Server. Then on 2023, Mojang Studios contacted the owner of the server to shut it down due to have a play-to-earn function.
Their Discord Server
In their discord server, you can now earn their own currency called joules which can be earned by playing Counter Strike 2, Fortnite or Dead by Daylight. The joules then can be exchange for sats. If you wanna invest your sats into it, you can buy ASICs through the auction which is fueled by joules which gives you sats in return by the hour.
In Conclusion
From Minecraft to Minetest, it has great potential for such a game nowadays since not only its through some dApp currency scheme, but its straightforward process. if you want to see their site it is at Satlantis.net.
I am Chrissy Sage and I am out!
-
 @ e31e84c4:77bbabc0
2024-12-02 10:44:07
@ e31e84c4:77bbabc0
2024-12-02 10:44:07Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net
Fiduciary duty is the obligation to act in the client’s best interests at all times, prioritizing their needs above the advisor’s own, ensuring honesty, transparency, and avoiding conflicts of interest in all recommendations and actions.
This is something all advisors in the BFAN take very seriously; after all, we are legally required to do so. For the average advisor this is a fairly easy box to check. All you essentially have to do is have someone take a 5-minute risk assessment, fill out an investment policy statement, and then throw them in the proverbial 60/40 portfolio. You have thousands of investment options to choose from and you can reasonably explain how your client is theoretically insulated from any move in the \~markets\~. From the traditional financial advisor perspective, you could justify nearly anything by putting a client into this type of portfolio. All your bases were pretty much covered from return profile, regulatory, compliance, investment options, etc. It was just too easy. It became the household standard and now a meme.
As almost every real bitcoiner knows, the 60/40 portfolio is moving into psyop territory, and many financial advisors get clowned on for defending this relic on bitcoin twitter. I’m going to specifically poke fun at the ‘40’ part of this portfolio.
The ‘40’ represents fixed income, defined as…
An investment type that provides regular, set interest payments, such as bonds or treasury securities, and returns the principal at maturity. It’s generally considered a lower-risk asset class, used to generate stable income and preserve capital.
Historically, this part of the portfolio was meant to weather the volatility in the equity markets and represent the “safe” investments. Typically, some sort of bond.
First and foremost, the fixed income section is most commonly constructed with U.S. Debt. There are a couple main reasons for this. Most financial professionals believe the same fairy tale that U.S. Debt is “risk free” (lol). U.S. debt is also one of the largest and most liquid assets in the market which comes with a lot of benefits.
There are many brilliant bitcoiners in finance and economics that have sounded the alarm on the U.S. debt ticking time bomb. I highly recommend readers explore the work of Greg Foss, Lawrence Lepard, Lyn Alden, and Saifedean Ammous. My very high-level recap of their analysis:
-
A bond is a contract in which Party A (the borrower) agrees to repay Party B (the lender) their principal plus interest over time.
-
The U.S. government issues bonds (Treasury securities) to finance its operations after tax revenues have been exhausted.
-
These are traditionally viewed as “risk-free” due to the government’s historical reliability in repaying its debts and the strength of the U.S. economy
-
U.S. bonds are seen as safe because the government has control over the dollar (world reserve asset) and, until recently (20 some odd years), enjoyed broad confidence that it would always honor its debts.
-
This perception has contributed to high global demand for U.S. debt but, that is quickly deteriorating.
-
The current debt situation raises concerns about sustainability.
-
The U.S. has substantial obligations, and without sufficient productivity growth, increasing debt may lead to a cycle where borrowing to cover interest leads to more debt.
-
This could result in more reliance on money creation (printing), which can drive inflation and further debt burdens.
In the words of Lyn Alden “Nothing stops this train”
Those obligations are what makes up the 40% of most the fixed income in your portfolio. So essentially you are giving money to one of the worst capital allocators in the world (U.S. Gov’t) and getting paid back with printed money.
As someone who takes their fiduciary responsibility seriously and understands the debt situation we just reviewed, I think it’s borderline negligent to put someone into a classic 60% (equities) / 40% (fixed income) portfolio without serious scrutiny of the client’s financial situation and options available to them. I certainly have my qualms with equities at times, but overall, they are more palatable than the fixed income portion of the portfolio. I don’t like it either, but the money is broken and the unit of account for nearly every equity or fixed income instrument (USD) is fraudulent. It’s a paper mache fade that is quite literally propped up by the money printer.
To briefly be as most charitable as I can – It wasn’t always this way. The U.S. Dollar used to be sound money, we used to have government surplus instead of mathematically certain deficits, The U.S. Federal Government didn’t used to have a money printing addiction, and pre-bitcoin the 60/40 portfolio used to be a quality portfolio management strategy. Those times are gone.
Now the fun part. How does bitcoin fix this?
Bitcoin fixes this indirectly. Understanding investment criteria changes via risk tolerance, age, goals, etc. A client may still have a need for “fixed income” in the most literal definition – Low risk yield. Now you may be thinking that yield is a bad word in bitcoin land, you’re not wrong, so stay with me. Perpetual motion machine crypto yield is fake and largely where many crypto scams originate. However, that doesn’t mean yield in the classic finance sense does not exist in bitcoin, it very literally does. Fortunately for us bitcoiners there are many other smart, driven, and enterprising bitcoiners that understand this problem and are doing something to address it. These individuals are pioneering new possibilities in bitcoin and finance, specifically when it comes to fixed income.
Here are some new developments –
Private Credit Funds – The Build Asset Management Secured Income Fund I is a private credit fund created by Build Asset Management. This fund primarily invests in bitcoin-backed, collateralized business loans originated by Unchained, with a secured structure involving a multi-signature, over-collateralized setup for risk management. Unchained originates loans and sells them to Build, which pools them into the fund, enabling investors to share in the interest income.
Dynamics
- Loan Terms: Unchained issues loans at interest rates around 14%, secured with a 2/3 multi-signature vault backed by a 40% loan-to-value (LTV) ratio.
- Fund Mechanics: Build buys these loans from Unchained, thus providing liquidity to Unchained for further loan originations, while Build manages interest payments to investors in the fund.
Pros
- The fund offers a unique way to earn income via bitcoin-collateralized debt, with protection against rehypothecation and strong security measures, making it attractive for investors seeking exposure to fixed income with bitcoin.
Cons
- The fund is only available to accredited investors, which is a regulatory standard for private credit funds like this.
Corporate Bonds – MicroStrategy Inc. (MSTR), a business intelligence company, has leveraged its corporate structure to issue bonds specifically to acquire bitcoin as a reserve asset. This approach allows investors to indirectly gain exposure to bitcoin’s potential upside while receiving interest payments on their bond investments. Some other publicly traded companies have also adopted this strategy, but for the sake of this article we will focus on MSTR as they are the biggest and most vocal issuer.
Dynamics
-
Issuance: MicroStrategy has issued senior secured notes in multiple offerings, with terms allowing the company to use the proceeds to purchase bitcoin.
-
Interest Rates: The bonds typically carry high-yield interest rates, averaging around 6-8% APR, depending on the specific issuance and market conditions at the time of issuance.
-
Maturity: The bonds have varying maturities, with most structured for multi-year terms, offering investors medium-term exposure to bitcoin’s value trajectory through MicroStrategy’s holdings.
Pros
-
Indirect Bitcoin exposure with income provides a unique opportunity for investors seeking income from bitcoin-backed debt.
-
Bonds issued by MicroStrategy offer relatively high interest rates, appealing for fixed-income investors attracted to the higher risk/reward scenarios.
Cons
-
There are credit risks tied to MicroStrategy’s financial health and bitcoin’s performance. A significant drop in bitcoin prices could strain the company’s ability to service debt, increasing credit risk.
-
Availability: These bonds are primarily accessible to institutional investors and accredited investors, limiting availability for retail investors.
Interest Payable in Bitcoin – River has introduced an innovative product, bitcoin Interest on Cash, allowing clients to earn interest on their U.S. dollar deposits, with the interest paid in bitcoin.
Dynamics
-
Interest Payment: Clients earn an annual interest rate of 3.8% on their cash deposits. The accrued interest is converted to Bitcoin daily and paid out monthly, enabling clients to accumulate Bitcoin over time.
-
Security and Accessibility: Cash deposits are insured up to $250,000 through River’s banking partner, Lead Bank, a member of the FDIC. All Bitcoin holdings are maintained in full reserve custody, ensuring that client assets are not lent or leveraged.
Pros
-
There are no hidden fees or minimum balance requirements, and clients can withdraw their cash at any time.
-
The 3.8% interest rate provides a predictable income stream, akin to traditional fixed-income investments.
Cons
-
While the interest rate is fixed, the value of the Bitcoin received as interest can fluctuate, introducing potential variability in the investment’s overall return.
-
Interest rate payments are on the lower side
Admittedly, this is a very small list, however, these types of investments are growing more numerous and meaningful. The reality is the existing options aren’t numerous enough to service every client that has a need for fixed income exposure. I challenge advisors to explore innovative options for fixed income exposure outside of sovereign debt, as that is most certainly a road to nowhere. It is my wholehearted belief and call to action that we need more options to help clients across the risk and capital allocation spectrum access a sound money standard.
Additional Resources
-
River: The future of saving is here: Earn 3.8% on cash. Paid in Bitcoin.
-
MicroStrategy: MicroStrategy Announces Pricing of Offering of Convertible Senior Notes
Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net
-
-
 @ 1cb14ab3:95d52462
2025-02-05 00:14:34
@ 1cb14ab3:95d52462
2025-02-05 00:14:34Welcome to the first installment of my ‘Nostr Spotlight’, a series where I explore various Nostr clients (which I will refer to as apps for simplicity sake), review their features, and share tips on how to use them effectively.
For the first installment, I’m diving into npub.pro, an incredible service that lets anyone on Nostr create a fully functional website using their already-published notes.
What is npub.pro?
npub.pro is a simple—yet powerful— tool that takes your Nostr content and turns it into a website instantly. By filtering through hashtags or keywords, or hand-selecting which notes to feature, you can curate what appears on your site.
This allows for highly customizable and dynamic websites that anyone on Nostr can deploy. Whether you’re a blogger, photographer, journalist, artist—or just want to organize your notes into a cleanly setup website—this service opens up endless possibilities for showcasing your notes.
Who Should Use npub.pro?
This service is ideal for:
✅ Writers and bloggers who want a frictionless way to publish content.
✅ Artists and photographers looking to showcase their work.
✅ Journalists and researchers who need an easy way to organize articles.
✅ Anyone who wants a personal website without dealing with hosting or technical setups.
Why I Love npub.pro
I’ve personally deployed several websites using npub.pro, each serving a different purpose:
HesArt – My personal art portfolio.
https://image.nostr.build/6a7030a24a9c5d4a9e3a0854020e08740241e870e46083b6b326ca36d5dc681f.png
Hes – My main long-form writing site, featuring artist statements, travel guides, photo series, tech reviews, and economic essays.
https://image.nostr.build/7d088829dd2ec0f9702430f115e29d368da85a78227cf6524f8773216f6a102e.png
HesCooks – A collection of curated recipes.
https://image.nostr.build/840ffdc74ac618ddf9534d4ab77a09d02aee45eee8c332a6733bcea5b80a3d2a.png
HesCreates – A categorized and searchable archive of my notes.
https://image.nostr.build/4663c91f3c77ad59f0f291813c672395f8cc20c6806ca2afffb3e3d65b6c6f37.png
The ability to filter my Nostr content and instantly publish it as a website has made organizing my notes seamless and efficient. The opportunities are endless and I have several ideas for other websites I plan on deploying.
How to Get Started
1.Visit npub.pro.
2.Enter your Nostr private key (nsec) using an extension of bunker.
3.Choose your filters (hashtags, keywords, etc.) to curate what appears and select a pre-made theme.
4.Publish instantly – no extra setup needed!
It’s that simple.
Final Verdict:
5/5 Stars ⭐⭐⭐⭐⭐
npub.pro is an outstanding tool that makes publishing on the web effortless for Nostr users. It’s intuitive, versatile, and packed with potential use cases. Whether you need a blog, portfolio, or curated archive, this app delivers.
Highly recommended!
More from Hes
Note: This spotlight is not sponsored. I thoroughly enjoy the service and have received outstanding customer service from the team at npub.pro!
Stay tuned for more Nostr App Spotlights as I explore the best apps in the ecosystem!
-
 @ fd208ee8:0fd927c1
2024-09-27 07:10:40
@ fd208ee8:0fd927c1
2024-09-27 07:10:40Let's talk about baking bread
I've mentioned a few times, how large-scale central planning leads inevitably to artificial scarcity and rising prices. Allow me to illustrate -- using a completely invented allegory about bread -- that has absolutely no parallels to any economy you may already be familiar with.
We start with 20
Let us say, there is a group of 20 people in a village doing something that requires some niche skill and interest, but not inordinate amounts of talent or uncommon knowledge, such as baking loaves of bread containing emmer wheat. This is not an easy thing to do, and you'd have to read up on it and practice, to begin with, but it's not an insurmountably-high barrier for anyone who already knows how to bake.
Now, they're not baking all that much of this bread, as the market for people who want to eat it, is still rather small. But, they're happy to bake the bread, and sell it below cost (at $10), as they can see that the market is steadily growing and they know that there is a possibility of recuperating their investments, and maybe even turning some profit. They hope to eventually profit either directly (through the selling of the bread), or indirectly (as A Person Who Helped Invent Emmer Bread), or ideally some combination of the two.
They are baking away, and honing their baking skills, and scrounging up the money for bigger and better ovens or cleverly-arranging discounted contracts for slightly-larger deliveries of wheat, and more and more bakers see this activity and wander over to their village, to see how this bread is made. Well, the current bakers are starting to sink under all of the bread orders they are receiving, and customers are complaining of late deliveries, so they start to ask the 10 visiting bakers, if they would like to also set up a bakery and take some of the production off of their hands.
We now have 25 bakers
The visiting bakers consider it and 5 agree and the rest wander off again, as they already are quite busy baking the bread they've always baked, and they aren't as certain of the possibility of growth, for this new type of bread.
The 5 additional bakers take a while to setup shop and assemble staff and place wheat orders and etc., but after a few weeks or months, they are also adding to the bread supply. There are now 25 bakers, all completely booked-out, producing bread. The price of bread has fallen, to $8/loaf.
And the bread they produced! All of the bakers competing for orders and expanding their product lines and customer base quickly lead to the white emmer bread being followed by whole-grain emmer bread, emmer dinner rolls, emmer-raisin bread, and even one rebel daring to bake spelt-emmer pretzels because... Well, why not? The customer, (who, at this point, is the person eating the bread), gets to decide which bread will be baked, and the pretzels sell like hotcakes.
The emmer hotcakes also sell like hotcakes.
No baker is making much (or any) money off of the baking, but they all can see where this will end up, so they are still highly motivated and continue to invest and innovate at breathtaking speed. We now have emmer baking mixes, "We luv emmer" t-shirts, emmer baking crowd-sourcing, all-about-emmer recipe books and blogs, etc. The bakers see this all as an investment, and cross-finance their fledgling businesses through selling other bread types, their spouse's day job, burning through their savings, or working Saturday night, stocking shelves at the grocery.
Everyone can be a winner! Everyone can find their niche-in-niche! Everyone can specialize! Private enterprise for every baker, who rises and falls on his own efforts alone! And although everyone was competing with everyone else, there was no bitterness, as everyone could clearly see that effort and reward were in some sort of balance.
We are now short 3
But, alas, that was not meant to be. The joy and harmony is short-lived.
A gigantic, wealthy foundation, who is dedicated to "ensuring much emmer bread will be baked, by financially supporting emmer bakers" enters the chat.
"We have seen that there is much baking going on, here, but just think how much better and more baking could be done, if we financed your baking! Isn't that clever? Then you could really concentrate on baking, instead of having to worry about financing your business or marketing your products. All you have to do, is apply to receive our baker's grant, by signing this form, acknowledging that you will only bake products containing nothing but emmer and you will otherwise support our mission. We promise to pay you $100/loaf."
The 2 people making spelt-emmer pretzels, and the 1 person making spelt-emmer cookies, refuse to sign on, and slink off, as they are very convinced of the rightness of including spelt. One emmer-purist baker refuses on some economic principle that nobody comprehends, and immediately turns around and goes back to work in their bakery, with their shoulders hunched. But the remaining 21 bakers happily apply for a baker's grant. The mixed-grain bakers are upset about the breakup of the emmer market, and spend some time sulking, before wandering off to the new, much-smaller, spelt bread market, that is setting up, down the street. Where they sell their bread for $6 and slowly go bankrupt.
And then there were 10
2 weeks go by. 4 weeks go by. Baking has slowed. The grant hopefuls hold a meeting, where they discuss the joys of baking. Baking slows further.
Everyone is too excited, to find out if their new Universal Customer will be paying for the bread they bake. $100 a loaf! Just think of it! All of the bakers quickly do the math and realize that they not only will turn a profit, they can buy themselves a nice house and a new car and...
Nobody listens to the complaints from The Old Customers, who are the useless individual people only paying $8, despite them slaving away, all day, in front of a hot oven. They should be happy that they are getting bread, at all! Instead they complain that the bread is dry, that the delivery is late, that the bottoms are burnt. Ingrates.
And, then, the big day arrives, and the foundation happily announces that they will be giving 10 lucky bakers a grant.
The bakers are stunned. It had seemed that all of the bakers would be getting the grants, not only part of them. But, of course, the Universal Customer looked through the applications and tried to spend its money wisely. Why give grants to 5 bakers, who all produce the same type of olive-emmer bread? Give it to one, and then tell him to produce 5 times as much bread. He is then the olive-emmer bread expert and they will simply keep loose tabs on him, to nudge him to bake the bread in a sensible manner. And, of course, he shall always focus on baking olive bread, as that is what the grant is for.
The bakers stroll off, to their bakeries. Those who baked olive bread and received no grant, close up shop, as they can see which way the wind is blowing. The other grantless bakers reformulate their bakery plans, to see if they can somehow market themselves as "grant-free bakers" and wonder at how long they can stand the humiliation of selling to demanding, fickle customers at $8/loaf, when others are selling at $100/loaf, to an indifferent customer who doesn't even eat it.
The happiest 10 bakers leave for another conference, and while they are gone, their bakeries burn down. Their grants continue to flow, regardless, and the actual bread eaters are now standing in line at the last few bakeries, paying $20/loaf.
The End.
-
 @ 1f79058c:eb86e1cb
2024-10-28 13:31:15
@ 1f79058c:eb86e1cb
2024-10-28 13:31:15This week, it finally happened: I still had a Lightning channel open with a node that hadn't been online for the better part of a year now, so I decided to close the channel unilaterally. But force-closing a channel means you have to broadcast the latest commitment transaction, the pre-set fee of which was only ~1 sat/vB for this one.
With LND, if the channel is created as an anchor channel (by default only since version 0.12), then the commitment transaction contains small extra outputs (currently 330 sats), which let either channel partner spend one of them into a child transaction that can be created with higher fees to pay for the parent transaction (CPFP). LND even has a built-in command for that:
lncli wallet bumpclosefeeHowever, this channel was created in the old-school way, and was thus stuck with its low fee. In fact, even the local bitcoin node refused to accept the transaction into its own mempool, so the bitcoin p2p network didn't even know it existed. So how do we get out of this pickle?
The solution
Enter the mempool.space Accelerator. It is essentially an automated way to create agreements with various mining pools to mine your low-fee transaction in exchange for an out-of-band payment. Mempool.space coordinates these agreements and out-of-band payments with miners and gets a share from the overall fee for that.
Now, if you're in the same situation as I was, you might search for the ID of your closing transaction and find that mempool.space cannot find it. Remember how the local bitcoin node (with mostly default settings) didn't accept it in the first place?
1. Get the transaction to be broadcast
In your
bitcoin.conf, add the following line:minrelaytxfee=0This sets the minimum fee to 0, meaning it will accept and broadcast your transactions, no matter how low the fee is. Restart
bitcoindand wait a little bit. LND will retry broadcasting the closing transaction every minute or so until it succeeds. At some point you should be able to find it on mempool.space.2. Use the Accelerator to confirm it
Once you can see the transaction on mempool.space, you can just click the "Accelerate" button next to the ETA. This will bring you to a page that shows you the estimated share of miners that will include your transaction in their blocks, as well as some acceleration fee options for various transaction fee levels, which you can pay for via the Lightning Network, of course.
If you haven't looked into this service before (which I had), then the fees might be a bit of a surprise to you. This thing is not cheap! Bumping my fee from 1 sat/vB to ~9 sats/vB cost a whopping 51,500 sats (31 USD that day). Bumping it higher only seemed to add the difference in the transaction fee itself, so the service seems to have cost a flat 50K sats at the time.
Unfortunately, this channel wasn't particularly large, so the acceleration fee amounted to ~9% of my remaining channel balance. But 91% of something is better than 100% of nothing, so I actually felt pretty good about it.
Next, you will see something like this:
Time to lean back and let the miners work for you. In my case, the ETA was eerily precise. It told me that it would take ~56 minutes to confirm the transaction, and almost exactly an hour later it was mined.
3. Wait
Now that our transaction is confirmed, our channel is not closed immediately, of course. The time lock of the HTLC protects our channel partner from us broadcasting an old channel state in which our balance might be higher than in the latest state.
In my case, it was set to 144 blocks, i.e. ~24 hours. So I checked back the next day, et voilá: channel closed and balance restored. 🥳
-
 @ b83e6f82:73c27758
2025-01-22 16:29:15
@ b83e6f82:73c27758
2025-01-22 16:29:15Citrine 0.7.1
- Add the restore follows button back
- Show notification when backing up database
- Listen for pokey broadcasts
Download it with zap.store, Obtainium, f-droid or download it directly in the releases page
If you like my work consider making a donation
Verifying the release
In order to verify the release, you'll need to have
gpgorgpg2installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:bash gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6DOnce you have his PGP key you can verify the release (assuming
manifest-v0.7.1.txtandmanifest-v0.7.1.txt.sigare in the current directory) with:bash gpg --verify manifest-v0.7.1.txt.sig manifest-v0.7.1.txtYou should see the following if the verification was successful:
bash gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03 gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>"That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:
bash cat manifest-v0.7.1.txtOne can use the
shasum -a 256 <file name here>tool in order to re-compute thesha256hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly. -
 @ 9e69e420:d12360c2
2025-01-30 12:13:39
@ 9e69e420:d12360c2
2025-01-30 12:13:39Salwan Momika, a Christian Iraqi known for burning the Koran in Sweden, was shot dead during a TikTok livestream in an apartment in Sodertalje. The 38-year-old sparked outrage in the Muslim community for his demonstrations, leading to global condemnation. After being rushed to the hospital, he was pronounced dead.
Authorities arrested five individuals in connection with the incident. Momika's death comes days before a court ruling on his possible incitement of ethnic hatred. The incident highlights the tensions surrounding free speech and religious sentiments, intensifying after his controversial protests in 2023.
-
 @ 9e69e420:d12360c2
2025-01-26 15:26:44
@ 9e69e420:d12360c2
2025-01-26 15:26:44Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards.
While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts.
A report will be prepared within 85 days to recommend which programs to continue or discontinue.
-
 @ e3ba5e1a:5e433365
2025-02-04 08:29:00
@ e3ba5e1a:5e433365
2025-02-04 08:29:00President Trump has started rolling out his tariffs, something I blogged about in November. People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I put up a poll on X to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.

For purposes of this blog post, our ultimate question will be the following:
- Suppose apples currently sell for $1 each in the entire United States.
- There are domestic sellers and foreign sellers of apples, all receiving the same price.
- There are no taxes or tariffs on the purchase of apples.
- The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following:
- Number of apples bought in the US
- Price paid by buyers for apples in the US
- Post-tax price received by domestic apple producers
- Post-tax price received by foreign apple producers
Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1?
And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why:
- The number of apples bought will go down
- The buyers will pay more for each apple they buy, but not the full amount of the tariff
- Domestic apple sellers will receive a higher price per apple
- Foreign apple sellers will receive a lower price per apple, but not lowered by the full amount of the tariff
In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit.
Marginal benefit
All of the numbers discussed below are part of a helper Google Sheet I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are some difficulties with creating supply and demand charts in Google Sheets.
Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B.
But that’s not what I mean. What I mean is: how high would the price of apples have to go everywhere so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5.
How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot.
The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called marginal benefit: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal demand curve. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:

Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples.
Marginal cost
Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product.
Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right?
Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of sunk costs. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further.
Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price!
However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with:
- Total expenditure: $100 + $70 * 8 hours a day * 5 days \== $2900
- Total revenue: $5000 (10,000 apples at $0.50 each)
- Total profit: $2100
So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money.
This kind of analysis is called marginal cost. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:

Equilibrium price
We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:

You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the surplus created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example:
- When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point.
- When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point.
Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.”
OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality.
Modeling taxes
Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve.
First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:

With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve.
We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:

The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:

As we can see, the equilibrium has shifted:
- The equilibrium price paid by consumers has risen from $1 to $1.20.
- The total number of apples purchased has dropped from 63 apples to 60 apples.
- Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus.
- Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42.
- Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21.
- The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise.
We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes:
- Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples.
- Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless.
- Domestic producers scored. They can sell less apples and make more revenue doing it.
- And the government walked away with an extra $30.
Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price.
Other taxes
Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down.
And generally speaking, this is what you’ll always see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost.
You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with:
- Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price.
- Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost.
- Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise.
This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
-
 @ dd664d5e:5633d319
2024-08-24 07:57:16
@ dd664d5e:5633d319
2024-08-24 07:57:16We can talk about something else, now.
Making boosts/quotes the primary way new users find a variety of topics is a fundamental flaw. We don't need boosts (which merely results in the main trending list trending even harder, as people feel safer boosting something that is already popular), and hashtags have become the mess they naturally will become.
We need topical forums and relay-based community boards.
This would actively encourage those of us who want to write on OtherTopics to write more on them, as we would have some chance of the material being found by those interested in it. And it would spare us having to win some general popularity contest, just to be able to converse about golfing, Hinduism, or veganism.
Scrollable "timeline" feeds, even with AI assistance (like DVMs), don't accomplish this as well, as they eliminate the ability to skim the top-level and selectively read. You have to scroll, scroll, scroll.
It would also reduce the overloading of the original posts with videos, which is starting to give Nostr a Tik-Tok vibe. There's nothing wrong with that, per se, and we should probably have clients like that, but it makes life hard for anyone who wants to have a deeper discussion. People scrolling have trouble even "seeing" a text-based OP, but using the written word is a true signal to the other people, that you are capable of carrying a conversation through text.
Examples for other styles of client
(I am including the Communities in Nostrudel and Satellite, even though they don't yet work, effectively.)
Some of the things that set these clients apart, is that: 1. they are topic-first or thread-first, not person-first, 2. they sometimes allow voting (I suppose we could rank by zaps), 3. they often allow the user to override the default order and simply look at whatever is newest, most popular, or where their friends are currently active (i.e. they allow for easy sorting and filtering), 4. they cap the depth of threads to one or two levels, keep the indentation tiny, or offer a "flat" view, 5. they are primarily text-based (Reddit broke with this and now their main pages look really spammy), 6. they allow you to see all of the entries in the thread, at once, and simply actualize to display the entries that pop up in-between, 7. they often have some indication of what you have already read (this is application data) and allow you to sort for "stuff I haven't looked at, yet".
https://i.nostr.build/uCx5YKMOsjhKBU5c.png https://i.nostr.build/hMkm2oKpos0pWaV9.png https://i.nostr.build/mGQONMw5RC8XKtph.png https://i.nostr.build/TCSkG1bPuMOL0jja.webp https://i.nostr.build/3fLjCSNdtefiZmAH.png https://i.nostr.build/BHgo7EKTK5FRIsVl.png
-
 @ 06b7819d:d1d8327c
2024-11-29 13:26:00
@ 06b7819d:d1d8327c
2024-11-29 13:26:00The Weaponization of Technology: A Prelude to Adoption
Throughout history, new technologies have often been weaponized before becoming widely adopted for civilian use. This pattern, deeply intertwined with human priorities for power, survival, and dominance, sheds light on how societies interact with technological innovation.
The Weaponization Imperative
When a groundbreaking technology emerges, its potential to confer an advantage—military, economic, or ideological—tends to attract attention from those in power. Governments and militaries, seeking to outpace rivals, often invest heavily in adapting new tools for conflict or defense. Weaponization provides a context where innovation thrives under high-stakes conditions. Technologies like radar, nuclear energy, and the internet, initially conceived or expanded within the framework of military priorities, exemplify this trend.
Historical Examples
1. Gunpowder: Invented in 9th-century China, gunpowder was first used for military purposes before transitioning into civilian life, influencing mining, construction, and entertainment through fireworks.-
The Internet: Initially developed as ARPANET during the Cold War to ensure communication in the event of a nuclear attack, the internet’s infrastructure later supported the global digital revolution, reshaping commerce, education, and social interaction.
-
Drones: Unmanned aerial vehicles began as tools of surveillance and warfare but have since been adopted for everything from package delivery to agricultural monitoring.
Weaponization often spurs rapid technological development. War environments demand urgency and innovation, fast-tracking research and turning prototypes into functional tools. This phase of militarization ensures that the technology is robust, scalable, and often cost-effective, setting the stage for broader adoption.
Adoption and Civilian Integration
Once a technology’s military dominance is established, its applications often spill into civilian life. These transitions occur when:
• The technology becomes affordable and accessible. • Governments or corporations recognize its commercial potential. • Public awareness and trust grow, mitigating fears tied to its military origins.For example, GPS was first a military navigation system but is now indispensable for personal devices, logistics, and autonomous vehicles.
Cultural Implications
The process of weaponization shapes public perception of technology. Media narratives, often dominated by stories of power and conflict, influence how societies view emerging tools. When technologies are initially seen through the lens of violence or control, their subsequent integration into daily life can carry residual concerns, from privacy to ethical implications.
Conclusion
The weaponization of technology is not an aberration but a recurring feature of technological progress. By understanding this pattern, societies can critically assess how technologies evolve from tools of conflict to instruments of everyday life, ensuring that ethical considerations and equitable access are not lost in the rush to innovate. As Marshall McLuhan might suggest, the medium through which a technology is introduced deeply influences the message it ultimately conveys to the world.
-
-
 @ df57b498:d049124f
2025-01-26 03:59:47
@ df57b498:d049124f
2025-01-26 03:59:47Chef's notes
This is cobbled together from trial and error and the web.
Serve hot pancakes with preferably butter and maple syrup. Add other toppings like bananas, nuts, or other fruits and toppings as have available and/or desired.
Details
- ⏲️ Prep time: 10 minutes
- 🍳 Cook time: 10 minutes
Ingredients
- 1 cup flour
- 2 tablespoons sugar
- 2 teaspoons baking powder
- 1 teaspoon salt
- 1 cup milk
- 2 tablespoons vegetable oil
- 1 egg, beaten
Directions
- Combine the dry ingredients.
- Add the wet ingredients and mix.
- Pour or ladle the batter onto the oiled griddle or pan.
- Cook until bubbles form, flip, and cook on the other side.
-
 @ 06b7819d:d1d8327c
2024-11-29 12:11:05
@ 06b7819d:d1d8327c
2024-11-29 12:11:05In June 2023, the Law Commission of England and Wales published its final report on digital assets, concluding that the existing common law is generally flexible enough to accommodate digital assets, including crypto-tokens and non-fungible tokens (NFTs).
However, to address specific areas of uncertainty, the Commission recommended targeted statutory reforms and the establishment of an expert panel.
Key Conclusions and Recommendations:
1. Recognition of a Third Category of Personal Property:Traditional English law classifies personal property into two categories: “things in possession” (tangible items) and “things in action” (enforceable rights). Digital assets do not fit neatly into either category. The Commission recommended legislation to confirm the existence of a distinct third category of personal property to better accommodate digital assets. 
-
Development of Common Law: The Commission emphasized that the common law is well-suited to adapt to the complexities of emerging technologies and should continue to evolve to address issues related to digital assets. 
-
Establishment of an Expert Panel: To assist courts in navigating the technical and legal challenges posed by digital assets, the Commission recommended that the government create a panel of industry experts, legal practitioners, academics, and judges. This panel would provide non-binding guidance on issues such as control and transfer of digital assets. 
-
Facilitation of Crypto-Token and Crypto-Asset Collateral Arrangements: The Commission proposed the creation of a bespoke statutory legal framework to facilitate the use of digital assets as collateral, addressing current legal uncertainties in this area. 
-
Clarification of the Financial Collateral Arrangements Regulations: The report recommended statutory amendments to clarify the extent to which digital assets fall within the scope of the Financial Collateral Arrangements (No 2) Regulations 2003, ensuring that existing financial regulations appropriately cover digital assets. 
Overall, the Law Commission’s report underscores the adaptability of English common law in addressing the challenges posed by digital assets, while also identifying specific areas where legislative action is necessary to provide clarity and support the evolving digital economy.
-
-
 @ 21ffd29c:518a8ff5
2025-02-04 21:12:15
@ 21ffd29c:518a8ff5
2025-02-04 21:12:15- What Are Homestead Chickens?
Homestead chickens are domesticated fowl kept by homeowners to provide eggs and companionship. They play a vital role in the homestead ecosystem.
Why Water is Essential in Cold Weather - Hydration Basics:
Chickens don't drink much water naturally but need it for hydration, especially during cold weather when metabolic rates increase. - Environmental Factors:
Cold weather can lead to ice buildup on water sources. Chickens benefit from having access to fresh water year-round.Maintaining Accessible Water Sources - Shallow Troughs:
Use shallow troughs instead of deep containers to minimize ice formation and ensure constant water supply. - Automatic Feeders:
Consider installing automatic feeders for convenience, especially in unpredictable weather conditions. - Multiple Water Sources:
Provide multiple water sources to prevent competition and ensure all chickens have access.Preventing Ice Buildup - Floating Shallow Troughs:
Opt for troughs that sit above the ground to avoid ice buildup. Ensure they're placed where they can't freeze completely. - Regular Checks:
Inspect water sources regularly to remove ice and debris, maintaining accessibility for chickens.Best Practices for Watering Chickens - Waterers Designed for Cold Weather:
Use waterers made of stainless steel or plastic that can withstand cold temperatures. - Seasonal Adjustments:
During extreme cold spells, supplement with a small amount of fresh water to aid in drinking.Conclusion - Key Takeaways:
Providing proper water is crucial for the health and well-being of homestead chickens during cold weather. Maintaining accessible, shallow water sources prevents issues like ice buildup and ensures hydration.Final Thoughts - Sustainability Considerations:
While chickens don't drink much, ensuring they have water supports their overall health and sustainability efforts. - Environmental Impact:
Thoughtful water management can reduce water usage, promoting eco-friendly practices on the homestead. - What Are Homestead Chickens?
-
 @ dd664d5e:5633d319
2024-08-15 20:52:04
@ dd664d5e:5633d319
2024-08-15 20:52:04Here's how people use OtherStuff apps.
1) They usually go there to write or post, not to read or view, unless someone they closely follow wrote about it in a Kind 01 note, SimpleX chat, Slack Channel, Telegram group, etc.
2) While they are there, they sometimes look around at what their frens have posted, zap them, leave a comment or a reply, etc. Sometimes they spend hours there. They really like it!
3) Then they leave.
4) If someone responds to anything they posted or wrote there, with anything other than a Kind 01 reply, they do not know about it, because it does not show up in their normal feed or notifications.
5) They do not come back until 1) happens again.
-
 @ 9e69e420:d12360c2
2025-01-26 01:31:47
@ 9e69e420:d12360c2
2025-01-26 01:31:47Chef's notes
arbitray
- test
- of
- chefs notes
hedding 2
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 5
Ingredients
- Test ingredient
- 2nd test ingredient
Directions
- Bake
- Cool
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ 30b99916:3cc6e3fe
2025-01-21 02:08:26
@ 30b99916:3cc6e3fe
2025-01-21 02:08:26Details
- 🍳 Cook time: 10 to 8 minutes at 350
- 🍽️ Servings: About 4 dozen cookies
Ingredients
- 2 sticks of butter
- 2 eggs
- 1 cup granulated sugar
- 1 cup brown sugar
- 1 cup peanut butter
- 1 t vanilla
- 2 cups flour
- 1/2 t salt
- 1 t soda
- 6 oz Semi-Sweet Chocolate chips (optional)
Directions
- Blend butter, eggs, vanilla and sugars together thoroughly
- Next blend in peanut butter thoroughly
- Next blend in flour, salt, and soda thoroughly
- Optional blend in chocolate chips
- Add about table spoon of cookie dough per cookie on a cookie sheet. With a fork based in sugar place a cross hatch pattern on each cookie. Bake cookies for 10 to 8 minutes and place onto cooler rack.
-
 @ 0fa80bd3:ea7325de
2025-01-30 04:28:30
@ 0fa80bd3:ea7325de
2025-01-30 04:28:30"Degeneration" or "Вырождение" ![[photo_2025-01-29 23.23.15.jpeg]]
A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them.
The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay.
-
 @ 1cb14ab3:95d52462
2025-02-04 18:40:56
@ 1cb14ab3:95d52462
2025-02-04 18:40:56What is it?
I stumbled upon the Elgato Stream Deck while aimlessly browsing the web, and I was instantly intrigued. But one question kept nagging me—how would I use this, and why do I even need it?
I don’t stream.
At first glance, it seemed like just another gadget to clutter my already cramped desk in my tiny Shanghai apartment. But curiosity got the best of me. After some research, I decided to give it a shot and see what all the hype was about.
And wow—was that hype justified.
This isn’t a deep-dive review covering every feature (there are plenty of those online). Instead, I want to share some of the workflows I’ve set up and hopefully get you thinking about the endless possibilities you could create with a Stream Deck.
If you’re someone who loves making computer tasks easier but struggles to remember keyboard shortcuts beyond Ctrl + V, this little device might just change the way you work.
Launching Apps and Websites

I won’t lie—my favorite use for the Stream Deck is the sheer convenience of pressing a button and instantly launching what I need.
Want to watch YouTube? Button.
Open Photoshop? Button.
Play a game? Button.
Check Bitcoin prices? Those are always on the display.


Sure, it’s a small thing, but the speed and ease of launching apps or navigating to websites make a surprising difference. What used to be a few clicks and keystrokes is now a single tap.
After using the Stream Deck for a while, my laptop feels... clunky. I’ve genuinely noticed an increase in my productivity and focus.
Custom Application Profiles
One of the most powerful features of the Stream Deck is its ability to switch profiles based on the application you’re using.
This means that every time you switch programs, the buttons automatically adjust to show relevant shortcuts and commands. It’s a game-changer for software with hundreds of keyboard shortcuts, making multitasking seamless.
I’ll admit—setting up custom profiles can be a bit time-consuming. The good news? You don’t have to start from scratch. There are tons of downloadable third-party profiles for popular programs like Illustrator, Photoshop, Final Cut Pro, DaVinci Resolve, Microsoft Office, and Ableton.

If your favorite app doesn’t have a pre-made profile, you can always build your own. It takes some effort, but once it's set up, the workflow improvements are worth it.
Music and Audio Control

I use an audio interface for lossless wired playback and external microphone support. The Stream Deck makes switching between my computer’s default mic and my studio mic effortless—no more digging through system preferences.
Even if you don’t use external audio gear, the Stream Deck still has plenty of value for music lovers.

It integrates with Apple Music and Spotify, letting you control playback, skip tracks, like songs, and add them to playlists—all without switching apps. Elgato is constantly adding new third-party integrations, which gives the device even more longevity.
Lighting and Smart Home Control
If you have smart home devices, the Stream Deck can act as a command center. It integrates with platforms like Philips Hue, LIFX, Nanoleaf, and IFTTT, letting you control lights, scenes, and colors with a single tap.
Want to set the mood for gaming, reading, or watching a movie? Done.
You can even use it to trigger other smart devices, like cameras, thermostats, or speakers, using IFTTT applets. The possibilities here are endless.
Finder and Document Shortcuts
One of the most unexpectedly useful features for me has been quick access to folders and files.
I’ve set up buttons for my most frequently used folders—Downloads, Desktop, and Documents—so I can access them instantly. I’ve also created buttons for specific files like spreadsheets and PDFs, so I don’t have to dig through folders to find them.
It sounds simple, but when juggling multiple projects, these little time-savers add up fast.
Final Thoughts
The Elgato Stream Deck is a surprisingly versatile tool that enhances productivity, creativity, and entertainment. Whether you’re launching apps, controlling music, managing smart devices, or creating complex workflows, it streamlines everyday tasks in a way that’s hard to go back from.
At first, I thought it was just for streamers. Now? I can’t imagine working without it.
I hope this post gives you some ideas on how to make the most of a Stream Deck. If you have any questions or thoughts, drop a comment below.
Thanks for reading!
Feel free to support me by grabbing one through my affiliate link below:
More from Hes
Originally published in 2022. All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.
-
 @ 1e566682:60493eed
2025-02-04 18:05:06
@ 1e566682:60493eed
2025-02-04 18:05:06بازار ارزهای دیجیتال بهزودی شاهد یک تغییر مهم خواهد بود. طبق گزارش اخیر منتشرشده در فوربز، بیتکوین و سایر ارزهای دیجیتال در آستانه یک "زلزله قیمتی" قرار دارند که به دلیل تغییرات نظارتی و تصمیمات کلان اقتصادی در ایالات متحده شکل میگیرد. کارشناسان پیشبینی میکنند که این تغییرات میتوانند نوسانات شدیدی در ارزش داراییهای دیجیتال ایجاد کنند و بازار را تحت تأثیر قرار دهند.
دلایل اصلی این زلزله قیمتی
- سیاستهای جدید نظارتی و قانونی
دولت آمریکا به دنبال وضع مقررات سختگیرانهتری برای نظارت بر ارزهای دیجیتال است. کمیسیون بورس و اوراق بهادار ایالات متحده و سایر نهادهای نظارتی در حال بررسی اقداماتی برای محدود کردن برخی فعالیتهای مرتبط با ارزهای دیجیتال هستند. این مقررات میتواند شامل نظارت دقیقتر بر صرافیهای ارز دیجیتال، سختگیری در فرآیندهای ضدپولشویی و احراز هویت مشتریان باشد.
- تغییرات مالیاتی و تأثیر آن بر سرمایهگذاران
دولت ایالات متحده در حال بررسی اصلاحات مالیاتی است که میتواند تأثیر قابلتوجهی بر سرمایهگذاران ارزهای دیجیتال بگذارد. مالیات بر سود حاصل از معاملات ارزهای دیجیتال میتواند افزایش یابد و سرمایهگذاران را به اتخاذ استراتژیهای جدید معاملاتی وادار کند. این مسئله ممکن است موجب کاهش حجم معاملات و افزایش نوسانات قیمتی شود.
- سیاستهای پولی فدرال رزرو
فدرال رزرو (بانک مرکزی آمریکا) نقش مهمی در تعیین نرخ بهره و سیاستهای مالی دارد. اگر نرخ بهره افزایش یابد، سرمایهگذاران ممکن است تمایل بیشتری به سرمایهگذاری در داراییهای کمریسک مانند اوراق قرضه دولتی داشته باشند و سرمایههای خود را از بازار ارزهای دیجیتال خارج کنند. این امر میتواند منجر به کاهش قیمت بیتکوین و سایر رمزارزها شود.
- افزایش پذیرش سازمانی و واکنش بازار
در حالی که قوانین سختگیرانه میتوانند فشار نزولی بر قیمتها وارد کنند، افزایش پذیرش بیتکوین توسط شرکتهای بزرگ و موسسات مالی میتواند از کاهش شدید قیمتها جلوگیری کند. بسیاری از شرکتها همچنان به پذیرش رمزارزها بهعنوان یک روش پرداخت ادامه میدهند و برخی بانکهای بزرگ نیز وارد بازار رمزارز شدهاند که این موضوع میتواند روند کلی بازار را تغییر دهد.
تأثیرات احتمالی بر قیمت بیتکوین و سایر ارزهای دیجیتال
با در نظر گرفتن این عوامل، دو سناریوی اصلی برای آینده قیمت بیتکوین و بازار رمزارزها وجود دارد:
-
سناریوی نزولی: اگر مقررات سختگیرانه اجرایی شوند و نرخ بهره افزایش یابد، ممکن است بیتکوین و سایر رمزارزها با کاهش قیمت مواجه شوند. در این شرایط، سرمایهگذاران خرد و سازمانی ممکن است با خروج از بازار، نوسانات شدیدتری را رقم بزنند.
-
سناریوی صعودی: در صورتی که افزایش پذیرش بیتکوین در میان موسسات مالی ادامه یابد و قوانین بهطور متعادل اجرا شوند، احتمال دارد که بیتکوین بتواند سطح حمایتی خود را حفظ کرده و در بلندمدت به رشد خود ادامه دهد.
جمعبندی: سرمایهگذاران باید چه کار کنند؟
با توجه به این شرایط، سرمایهگذاران ارزهای دیجیتال باید با دقت تحولات نظارتی و اقتصادی را دنبال کنند. مدیریت ریسک، تنوعبخشی به سبد سرمایهگذاری و در نظر گرفتن چشمانداز بلندمدت میتواند از ضررهای احتمالی جلوگیری کند.
این زلزله قیمتی ممکن است بازار رمزارزها را به شدت متزلزل کند، اما همانطور که در گذشته نیز دیدهایم، بازار ارزهای دیجیتال بارها از بحرانهای مشابه عبور کرده و به رشد خود ادامه داده است. باید دید که در نهایت این تغییرات چگونه شکل خواهند گرفت و چه تأثیری بر آینده بیتکوین و سایر ارزهای دیجیتال خواهند گذاشت.
-
 @ 3bf0c63f:aefa459d
2024-10-26 14:18:23
@ 3bf0c63f:aefa459d
2024-10-26 14:18:23kind:1maximalism and the future of other stuff and Nostr decentralizationThese two problems exist on Nostr today, and they look unrelated at first:
- People adding more stuff to
kind:1notes, such as making them editable, or adding special corky syntax thas has to be parsed and rendered in complicated UIs; - The discovery of "other stuff" content (i.e. long-form articles, podcasts, calendar events, livestreams etc) is hard due to the fact that most people only use microblogging clients and they often don't appear there for them.
Point 2 above has 3 different solutions:
- a. Just publish everything as
kind:1notes; - b. Publish different things as different kinds, but make microblogging clients fetch all the event kinds from people you follow, then render them natively or use NIP-31, or NIP-89 to point users to other clients that would render them better;
- c. Publish different things as different kinds, and reference them in
kind:1notes that would act as announcements to these other events, also relying on NIP-31 and NIP-89 for displaying references and recommending other clients.
Solution a is obviously very bad, so I won't address it.
For a while I have believed solution b was the correct one, and many others seem to tacitly agree with it, given that some clients have been fetching more and more event kinds and going out of their way to render them in the same feed where only
kind:1notes were originally expected to be.I don't think clients doing that is necessarily bad, but I do think this have some centralizing effects on the protocol, as it pushes clients to become bigger and bigger, raising the barrier to entry into the
kind:1realm. And also in the past I have talked about the fact that I disliked that some clients would display my long-form articles as if they were normalkind:1notes and just dump them into the feeds of whoever was following me: nostr:nevent1qqsdk90k9k30vtzwpj6grxys9mvsegu5kkwd4jmpyhlmtjnxet2rvggprpmhxue69uhhyetvv9ujumn0wdmksetjv5hxxmmdqy8hwumn8ghj7mn0wd68ytnddaksygpm7rrrljungc6q0tuh5hj7ue863q73qlheu4vywtzwhx42a7j9n5hae35cThese and other reasons have made me switch my preference to solution c, as it gives the most flexibility to the publisher: whoever wants to announce stuff so it can be discovered can, whoever doesn't don't have to. And it allows microblogging clients the freedom to render just render tweets and having a straightforward barrier between what they can render and what is just a link to an external app or webapp (of course they can always opt to render the referenced content in-app if they want).
It also makes the case for microapps more evident. If all microblogging clients become superapps that can render recipe events perfectly why would anyone want to use a dedicated recipes app? I guess there are still reasons, but blurring the line between content kinds in superapps would definitely remove some of the reasons and eventually kill all the microapps.
That brings us back to point 1 above (the overcomplication of
kind:1events): if solution c is what we're going to, that makeskind:1events very special in Nostr, and not just another kind among others. Microblogging clients become the central plaza of Nostr, thus protecting their neutrality and decentralization much more important. Having a lot of clients with different userbases, doing things in slightly different ways, is essential for that decentralization.It's ok if Nostr ends up having just 2 recipe-sharing clients, but it must have dozens of microblogging clients -- and maybe not even full-blown microblogging clients, but other apps that somehow deal with
kind:1events in multiple ways. It's ok if implementing a client for public audio-rooms is very hard and complicated, but at the same time it should be very simple to write a client that can render akind:1note referencing an audio-room and linking to that dedicated client.I hope you got my point and agreed because this article is ended.
- People adding more stuff to
-
 @ c3b2802b:4850599c
2025-01-30 09:06:41
@ c3b2802b:4850599c
2025-01-30 09:06:41In Kirpal Sagar ist ein Modell für die Welt entstanden, das soziale mit ökologischen sowie spirituellen Sehnsüchten der Völker unserer Welt verbindet. Knapp 20 Jahre nach der Gründung von Kirpal Sagar wurde mit grossem Brimborium zwar in Rio de Janeiro die Agenda 21 mit ähnlichen Zielen ausgerufen. Doch in den 3 Dekaden danach ist mir kein Projekt begegnet, welches den InitiatorInnen und Aktiven in Kirpal Sagar das Wasser reichen kann.
Konkret: In der Gemeinschaftsküche wird seit Beginn des Projekts, also seit 50 Jahren, für mittellose Menschen kostenloses Essen zubereitet. Die Küche wird vom eigenen Öko – Landwirtschaftsbetrieb beliefert. Um Bedürftigen zu helfen, wurde 1983 das Krankenhaus eingerichtet. Im 1994 eingeweihten Altenheim finden alte Menschen ein Zuhause, die sonst auf sich allein gestellt wären. Bedürftige aus der Umgebung erhalten Unterstützung in Notfällen. Die Kirpal Sagar Academy ist eine Schule, die derzeit 500 Kinder bis zur Hochschulreife führt. Kinder aus mittellosen Familien werden vom Träger unterstützt.
Basis des Zusammenlebens ist ein lebendiger Dialog zwischen den Religionen der beteiligten Menschen. Hier wird keine bestimmte Religion gelehrt, sondern auf die Essenz der Religion, den spirituellen Kern, der allen Religionen gemeinsam ist, verwiesen, wie auch in den weithin sichtbaren Symbolen von Kirpal Sagar (z.B. auf dem Titelbild oben) dargestellt ist.
In einer nach außen offenen Gemeinschaft leben hier ständig mehr als 800 Menschen, viele mit ihren Familien – freiwillige Mitarbeiter, die am Aufbau beteiligt sind, Lehrer, Schüler, Arbeiter, Ärzte, Angestellte usw. Ebenso sind regelmäßig Helfer und Gäste aus dem Ausland vor Ort. So erlebt man ein lebendiges Miteinander verschiedener Kulturen, Religionen und Mentalitäten.
Als ich 2007 erstmals hier war, fand zum Beispiel eine Hochzeitsveranstaltung für Dutzende junge Paare aus ärmsten Verhältnissen statt, welchen ohne Unterstützung keine Trauung möglich war.
Man sieht Menschen ihren alltäglichen Arbeiten nachgehen und kann an Sport- und Schulveranstaltungen teilnehmen. Ebenso sind auch Gäste bei traditionellen Festen oder religiösen Feierlichkeiten und Ritualen willkommen, die jeder seiner Religionszugehörigkeit entsprechend ausüben kann. In diesem Teil des Punjab begegnet man vor allem Hindus und Sikhs, bei größeren Veranstaltungen sind auch Vertreter weiterer Religionen zu Gast. Über Jahre der Zusammenarbeit konnte man praktisch sehen, dass das Ideal „Eine Welt, eine Menschheit“ keine Utopie ist. In Europa gibt es Unterstützer-Initiativen, in denen sich Menschen aus unserem Teil der Erde für Projekte dieser Art engagieren. Details über einzelne Lebensbereiche in der Modellkommune erfahren Sie hier, speziell zu Gesundheitsfragen hier.
Zuerst veröffentlicht auf der Plattform Zukunftskommunen.
-
 @ 0fa80bd3:ea7325de
2025-01-29 15:43:42
@ 0fa80bd3:ea7325de
2025-01-29 15:43:42Lyn Alden - биткойн евангелист или евангелистка, я пока не понял
npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83aThomas Pacchia - PubKey owner - X - @tpacchia
npub1xy6exlg37pw84cpyj05c2pdgv86hr25cxn0g7aa8g8a6v97mhduqeuhgplcalvadev - Shopstr
npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkqCalle - Cashu founder
npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vgДжек Дорси
npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m21 ideas
npub1lm3f47nzyf0rjp6fsl4qlnkmzed4uj4h2gnf2vhe3l3mrj85vqks6z3c7lМного адресов. Хз кто надо сортировать
https://github.com/aitechguy/nostr-address-bookФиатДжеф - создатель Ностр - https://github.com/fiatjaf
npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6EVAN KALOUDIS Zues wallet
npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qdПрограммер Коди https://github.com/CodyTseng/nostr-relay
npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wlAnna Chekhovich - Managing Bitcoin at The Anti-Corruption Foundation https://x.com/AnyaChekhovich
npub1y2st7rp54277hyd2usw6shy3kxprnmpvhkezmldp7vhl7hp920aq9cfyr7 -
 @ 5a261a61:2ebd4480
2025-02-02 20:42:37
@ 5a261a61:2ebd4480
2025-02-02 20:42:37Let’s be real—sticking to anything for 90 days is like trying to herd cats on espresso. You start strong, then life happens: kids, chores, or that one glass of wine that makes you forget foot rubs (#relatable). But here’s the thing: 90-day challenges aren’t about perfection. They’re about bribing your lizard brain with rewards and scaring it straight with punishments.
The Game Plan
First, pick a thing—something that makes you feel like a devoted servant or a slightly frazzled superhero. Daily foot care? Chores with a side of #FLR flair? Cool. Now, break it into chunks: 30 days (survival mode), 60 days (grind phase), and 90 days (victory lap).
Keeping up something for so long is no joke. That's why you need those little checkpoints along the way. Each milestone should feel special—30 days deserves celebration, 60 days something more meaningful, and 90 days? That's your victory dance moment.
Reality check: some days will suck, and you'll want to skip. That's where having everything planned out helps. When your brain is foggy and you're tired, you don't want to be negotiating with yourself about what counts and what doesn't. The hardest part isn't even doing the thing—it's remembering to do it every single day, until it feels wrong NOT to do it.
Why It (Maybe) Works
Three months is long enough for habits to stick, short enough to see the finish line. Plus, tying it to power exchange? Genius. Every foot rub or denied cum becomes a ritual, proof you're leveling up as a sub/human/slightly-messy adult. And let's be honest—nothing fuels devotion like a mix of structure, desperation, and the occasional humiliating punishment.
Current run
My current challenge is to get my wife/godess/object of my insatiable kinky thoughts/partner feet massaged with special cream. It's for making evyrthing soft, help nails and yadayadayada. Basically preping her feet for more instensive worshiping. She doesn't know my hidden agenda and I am not sure if I would really be into it, since I am more into being her devout toy than having foot fetish, but I think it will be all the same if I put myself juuust right. So for my rewards I have planned these? - 30 days: Tiny dopamine hit. (making little photoset of Her feet playing with my hardon… for science.)
- 60 days: Mid-tier flex. (cleaning mushed banana split off Her toes tongue only)
- 90 days: Go nuclear. (a tiny foot spa whirpool because She deserves it, damn it :D and it will create more opportunities for... you know )As for the hhip part of the sugar duo... It was easy having one for my shaving rutine, but here? Not sure and it's bad that I ave started challenge without having them prepared... May be that warrant more punishment?
TL;DR
90-day challenges are the BDSM of self-improvement: consensual, slightly painful, and weirdly addictive. Fail? Reset, adapt, try again. Win? Congrats, you’re now 10% more disciplined and 100% more bumptious on Nostr.
90days #FLR #LostCauseButStillTrying #femdom
-
 @ b17fccdf:b7211155
2025-01-21 18:33:28
@ b17fccdf:b7211155
2025-01-21 18:33:28
CHECK OUT at ~ > ramix.minibolt.info < ~
Main changes:
- Adapted to Raspberry Pi 5, with the possibility of using internal storage: a PCIe to M.2 adapter + SSD NVMe:
Connect directly to the board, remove the instability issues with the USB connection, and unlock the ability to enjoy higher transfer speeds**
- Based on Debian 12 (Raspberry Pi OS Bookworm - 64-bit).
- Updated all services that have been tested until now, to the latest version.
- Same as the MiniBolt guide, changed I2P, Fulcrum, and ThunderHub guides, to be part of the core guide.
- All UI & UX improvements in the MiniBolt guide are included.
- Fix some links and wrong command issues.
- Some existing guides have been improved to clarify the following steps.
Important notes:
- The RRSS will be the same as the MiniBolt original project (for now) | More info -> HERE <-
- The common resources like the Roadmap or Networkmap have been merged and will be used together | Check -> HERE <-
- The attempt to upgrade from Bullseye to Bookworm (RaspiBolt to RaMiX migration) has failed due to several difficult-to-resolve dependency conflicts, so unfortunately, there will be no dedicated migration guide and only the possibility to start from scratch ☹️
⚠️ Attention‼️-> This guide is in the WIP (work in progress) state and hasn't been completely tested yet. Many steps may be incorrect. Pay special attention to the "Status: Not tested on RaMiX" tag at the beginning of the guides. Be careful and act behind your responsibility.
For Raspberry Pi lovers!❤️🍓
Enjoy it RaMiXer!! 💜
By ⚡2FakTor⚡ for the plebs with love ❤️🫂
- Adapted to Raspberry Pi 5, with the possibility of using internal storage: a PCIe to M.2 adapter + SSD NVMe:
-
 @ dd664d5e:5633d319
2024-07-21 10:46:33
@ dd664d5e:5633d319
2024-07-21 10:46:33My suggestion for scaling up and staying humble
The original protocol design was "good enough for now"
When Nostr was invented and got started with developing implementations, the Original Devs (ODs) were convinced this was going to be big... maybe... someday... hopefully.
But, whatever they did at the moment should definitely scale up a bit and be a bit flexible, to attract innovators and keep up the momentum. So, they designed the protocol to be open and left the specifications a bit vague and very high-level, so that nobody was forced into a particular implementation, in order to adhere to the spec. And they put the specs into a GitHub repository and managed them by a committee of collaborators, who were generally open to changes to the specs, including breaking changes.
That was smart. And it was "good enough for now"... back then. After all, Nostr (and the associated wiki and modular article specs) hadn't been invented, yet, so they couldn't write the protocol in the protocol before the protocol existed. They're good, but not that good.
What they specifically wrote, into the Nostr Protocol was:
To promote interoperability, we standards (sic) that everybody can follow, and we need them to define a single way of doing each thing without ever hurting backwards-compatibility, and for that purpose there is no way around getting everybody to agree on the same thing and keep a centralized index of these standards...
Standards may emerge in two ways: the first way is that someone starts doing something, then others copy it; the second way is that someone has an idea of a new standard that could benefit multiple clients and the protocol in general without breaking backwards-compatibility and the principle of having a single way of doing things, then they write that idea and submit it to this repository, other interested parties read it and give their feedback, then once most people reasonably agree we codify that in a NIP which client and relay developers that are interested in the feature can proceed to implement.
I disagree with this statement.
I don't disagree with what they meant, or what they wanted, I disagree with what they specifically wrote.
Standards (defined as prose specifications) are not the only -- or even best -- way to ensure interoperability or to check for backwards-compatibility. And, as they later note, basing a protocol off of implementations is arguably worse (but faster) than using specifications, as implementations have a life of their own and are sometimes simply shoddy or buggy, their content eventually differs from what ends up in the final standard, or there are soon multiple implementations covering the same spec "in theory", but not in practice, so that their events are incompatible.
And then the inevitable, heated discussion begins: * Which implementation is the Real Standard™? * Who controls the Real Standard™? * How is the Real Standard™ spec supposed to be written? * Does everything have to be in the same file type or markup language? If not, how can we ensure compatibility? * What is realistic content for the data files? * Is the Real Standard™ including all of the information needed to ensure interoperability, but not anything more, without reducing innovation and artificially forcing consensus by encouraging copy-paste or forking of product code?
There is a third way: write the test first
We actually do not need standards to define a single way of doing each thing. A test is another way, and I think it is the best (i.e. the most-efficient and most-effective) way.
Specifically, I think we can borrow the simple behavior-driven design (BDD) language called Gherkin (or something similar), which is used to write dynamic specifications: i.e. implementations that test adherence to a set of rules, rather than an implementation that uses the rules to perform some task for an end user.
Gherkin simply allows you to create standard scenarios and test data and write the tests up in a way that can be performed manually or through automation. For example ( source ):

(For a concrete example of such a TDD Protocol for Nostr, please see the nostr-voliere repo from nostr:npub1axy65mspxl2j5sgweky6uk0h4klmp00vj7rtjxquxure2j6vlf5smh6ukq .)
This really is better
This TDD Protocol design would have some downsides and some upsides, of course, like any change.
Downsides
- You can't write a TDD spec by yourself unless you understand basic software functionality, how to define an acceptance test, and can formulate a use case or user story.
- The specs will be more informative and agnostic, but also longer and more detailed.
- Someone will have to propose concrete test data (i.e. a complete json event) and spec interlinking will be explicit, rather than writing "...", "etc.", or "sorta like in that other section/doc, but not really" all over the place.
- The specs will tend to focus on positive cases, and leave off error-handling or most edge-cases, so developers can't use them to replace unit tests or other verification of their product.
Upsides
- The specs will be concrete and clear, in a type of pseudocode, while leaving the actual implementation of any feature up to the individual developer, who uses the spec.
- The specs will be orderly and uniquely-identifiable, and can have hierarchy and granularity (major and minor tests, optional tests, tests only under certain conditions, etc.)
- Deciding whether changes to the spec are breaking changes to the protocol would be simple to determine: Does the previous test still pass?
- Specs will always be final, they will simply be versioned and become more or less defined over time, as the tests are adjusted.
- Product developers will feel less like they "own" particular specs, since their implementation is actually what they own and the two remain permanently separate.
- Developers can create an implementation list, defining specific tests in specific versions, that they adhere to. This makes it more transparent, what their product actually does, and lowers their own documentation burden.
- Rather than stalking the NIPs for changes, or worrying about what some other implementation someplace has built, developers can just pull the repo and try running the relevant tests.
- Each product developer can test the spec by trying to perform or automate/run it, and request changes to ensure testability, raising the quality of the spec review process.
This is already a lot to think about, so I'm just going to end this here. Thank you for reading.
-
 @ c3b2802b:4850599c
2025-01-28 10:46:10
@ c3b2802b:4850599c
2025-01-28 10:46:10Dear sisters and brothers, I have been born in a country without any religion. As a young adult I understood that a life without spirituality does not make sense. Today, 50 years later, I am convinced that the family of creation consists of divine beings with the potential to unfold endless love - independently of the controversies between singular religions.
Each of us human beings is full of divine sparks which may strengthen each moment during our life the fire of love and compassion toward all living beings in the universe. These divine sparks may feed the eternal dance of creation.
Religion and science have converged during the last centuries: Divine spirit is the driving force of all happenings in our universe. Buddha, Plato, Jesus Christ, Kabir, Guru Nanak, Albert Schweitzer and recently many Nobel Price winning physicists have expressed the same conviction:
We are divine creators of the paradise resulting from genesis on this planet within the living universe. Looking around the world these days, however, we observe harm, hunger, dissence, struggle and war.
How does this coexist – the potential to create the paradise on the one hand – and the destructive forces leading to a multitude of catastrophes? May be you like the following way to interprete what is going on actually:
We are born to be tested in a learning adventure of evolution within the cosmos. The life of each of us is an examination checking whether we are ripe for creating the paradise.
Each generation of human beings has the chance to reach the tipping point. Possibly todays generation, all of us sitting here, might overcome the centennial struggle on details of diverse religions and worldviews. If we today conjointly remember our potential as divine beings to create a peaceful and well balanced world - then we can make the next step of cosmic evolution – charcterized by love, peace and respect for all forms of life:
We may give now birth to a new chapter in the process of evolution. The time might be ripe these days. Let me give some illustrations for my optimism based on my work of the past 30 years in Germany: 30 years ago in my country most of all fuels for electricity and heating were imported. All German villages depended existially from international trusts supplying nuclear and fossil energy. The great majority of Germans relied on imported fossile or nuclear fuels. Today, 30 years later, we count 200 villages with own energy production based on regional ressources which were initiated by teams of german universities, where I have been active.
During the same time the number of similar activities aiming at a regionally organized society all over the world exploded. In many countries many local initiatives were founded organizing food production, local trade, water supply and many other fields of human needs on a regional base in fair and clean ways, without any international activities of global players like MacDonald or Monsanto.
Another world is possible – and even better, the regional society is blossoming already since decades worldwide.
A second source for my optimism is my scientific work. Humans dispose of spiritual potentials enabling us to connect with the holy spirit surrounding us since eternal times. Individuals unfolding this potential and behaving respectfully toward other beings report higher well-being as compared to other people. That empirical pattern has been found in hundreds of scientific studies all over the world. These results feed our trust, that we are on the right way with our regional initiatives like Kirpal Sagar in India, the new energy villages in Germany, the clean and fair agriculture initiatives worldwide, the open seeds movement and the many further initiatives.
Remembering Mahatma Gandhi, the great indian philosopher and politician: We do not need to fight against the players of the old world, against psychopathic people in international trusts and organizations who plan a world all of us dislike. This old structure will break down by itself.
Meanwhile we build the society we prefere: Ethically grounded communities like Kirpal Sagar, based on grace, fairness and respect between all living beings. My congratulation to the golden jubilee of this wonderful project, which may serve as a model for the whole world.
Let´s shake our hands, connect our hearts and let´s bring our souls in harmony within the cosmic concert of love!
Peter Schmuck, psychologist and regional society activist, Germany, february 5 2024.
First published at the German platform for future communities
-
 @ 06b7819d:d1d8327c
2024-11-29 11:59:20
@ 06b7819d:d1d8327c
2024-11-29 11:59:20The system design and challenges of retail Central Bank Digital Currencies (CBDCs) differ significantly from Bitcoin in several key aspects, reflecting their distinct purposes and underlying philosophies:
-
Core Purpose and Issuance
• CBDCs: Issued by central banks, CBDCs are designed as state-backed digital currencies for public use. Their goal is to modernize payments, enhance financial inclusion, and provide a risk-free alternative to private money. • Bitcoin: A decentralized, peer-to-peer cryptocurrency created to operate independently of central authorities. Bitcoin aims to be a store of value and medium of exchange without reliance on intermediaries or governments.
-
Governance and Control
• CBDCs: Operate under centralized governance. Central banks retain control over issuance, transaction validation, and data management, allowing for integration with existing regulatory frameworks (e.g., AML and CFT). • Bitcoin: Fully decentralized, governed by a consensus mechanism (Proof of Work). Transactions are validated by miners, and no single entity controls the network.
-
Privacy
• CBDCs: Seek to balance privacy with regulatory compliance. Privacy-enhancing technologies may be implemented, but user data is typically accessible to intermediaries and central banks to meet regulatory needs. • Bitcoin: Pseudonymous by design. Transactions are public on the blockchain but do not directly link to individual identities unless voluntarily disclosed.
-
System Design
• CBDCs: May adopt a hybrid system combining centralized (e.g., central bank-controlled settlement) and decentralized elements (e.g., private-sector intermediaries). Offline functionality and interoperability with existing systems are priorities. • Bitcoin: Fully decentralized, using a distributed ledger (blockchain) where all transactions are validated and recorded without reliance on intermediaries.
-
Cybersecurity
• CBDCs: Cybersecurity risks are heightened due to potential reliance on centralized points for data storage and validation. Post-quantum cryptography is a concern for future-proofing against quantum computing threats. • Bitcoin: Security relies on cryptographic algorithms and decentralization. However, it is also vulnerable to quantum computing in the long term, unless upgraded to quantum-resistant protocols.
-
Offline Functionality
• CBDCs: Exploring offline payment capabilities for broader usability in remote or unconnected areas. • Bitcoin: Offline payments are not natively supported, although some solutions (e.g., Lightning Network or third-party hardware wallets) can enable limited offline functionality.
-
Point of Sale and Adoption
• CBDCs: Designed for seamless integration with existing PoS systems and modern financial infrastructure to encourage widespread adoption. • Bitcoin: Adoption depends on merchant willingness and the availability of cryptocurrency payment gateways. Its volatility can discourage usage as a medium of exchange.
-
Monetary Policy and Design
• CBDCs: Can be programmed to support specific policy goals, such as negative interest rates, transaction limits, or conditional transfers. • Bitcoin: Supply is fixed at 21 million coins, governed by its code. It is resistant to monetary policy interventions and inflationary adjustments.
In summary, while CBDCs aim to complement existing monetary systems with centralized oversight and tailored features, Bitcoin is designed as a decentralized alternative to traditional currency. CBDCs prioritize integration, control, and regulatory compliance, whereas Bitcoin emphasizes autonomy, censorship resistance, and a trustless system.
-
-
 @ 8d34bd24:414be32b
2025-02-04 17:55:30
@ 8d34bd24:414be32b
2025-02-04 17:55:30So many of our problems are due to our point of view. The closer our point of view gets to God, the more peace and joy we will feel.
Too often we look at God as the big, bad killjoy. We resent when He tells us all the “fun” things we aren’t supposed to do and when He tells us to do difficult things like submit to God, submit to husbands, submit to authorities. Too many people focus on the “do nots,” and don’t like the idea of anyone telling them what to do. They then do their own thing, which they think will make them happy. Unfortunately, this leads to the opposite.
God is our Creator. He created us for a purpose within the rest of His creation.
For we are His workmanship, created in Christ Jesus for good works, which God prepared beforehand so that we would walk in them. (Ephesians 2:10)
When we are doing His will we will find peace and joy. When we fight Him on what we should and should not be doing, we feel frustration, depression, and even despair. Our constant seeking of things to make us happy is actually our innate desire for God and to fulfill His will. Unfortunately, we frequently don’t see the truth and avoid the one thing that will give us peace because it is hard, inconvenient, and doesn’t lead to what we think we want right now.
God wants what is best for us. He also thinks eternally. He doesn’t think in the here and now, like we do. Just as a parent makes decisions for his/her child based on knowledge of what will be better for them in the long term (saving vs spending, healthy food vs junk food, etc.), God makes decisions for us based on what will best prepare us for eternity with Him. Frequently that looks much different than what we think we want. Frequently that even includes hardship and pain because we are much more likely to grow in faith, strength, and holiness during hardship than we do during comfort. We need to understand that God knows best and that He never makes a mistake.
Trust in the Lord with all your heart\ And do not lean on your own understanding.\ In all your ways acknowledge Him,\ And He will make your paths straight.\ Do not be wise in your own eyes;\ Fear the Lord and turn away from evil.\ It will be healing to your body\ And refreshment to your bones. (Proverbs 3:5-8)
Nothing happens on earth without God allowing it. Just as Satan had to ask permission to persecute Job, in the same way nobody can cause believers harm without God allowing it for His purpose, which is usually related to helping them to put their full trust in Him.
Remember the former things long past,\ For I am God, and there is no other;\ I am God, and there is no one like Me,\ Declaring the end from the beginning,\ And from ancient times things which have not been done,\ Saying, ‘My purpose will be established,\ And I will accomplish all My good pleasure’; (Isaiah 46:9-10)
So often I focus on how awesome, powerful, and holy our God is. He is also the most tender, loving, caring, personal father God. Read Psalm 139. The God of the Bible is not a distant clock maker who set the world in motion and let it go about without His care. He is personally involved in everything that happens and in the life of every person on earth, but especially in the life of those who trust in Him.
O Lord, You have searched me and known me.\ You know when I sit down and when I rise up;\ You understand my thought from afar.\ You scrutinize my path and my lying down,\ *And are intimately acquainted with all my ways.\ Even before there is a word on my tongue,\ Behold, O Lord, You know it all.*\ You have enclosed me behind and before,\ And laid Your hand upon me.\ Such knowledge is too wonderful for me;\ It is too high, I cannot attain to it.\ Where can I go from Your Spirit?\ Or where can I flee from Your presence?\ If I ascend to heaven, You are there;\ If I make my bed in Sheol, behold, You are there.\ If I take the wings of the dawn,\ If I dwell in the remotest part of the sea,\ *Even there Your hand will lead me*,\ And Your right hand will lay hold of me.\ If I say, “Surely the darkness will overwhelm me,\ And the light around me will be night,”\ Even the darkness is not dark to You,\ And the night is as bright as the day.\ Darkness and light are alike to You.\ For You formed my inward parts;\ You wove me in my mother’s womb.\ I will give thanks to You, for I am fearfully and wonderfully made;\ Wonderful are Your works,\ And my soul knows it very well.\ My frame was not hidden from You,\ When I was made in secret,\ And skillfully wrought in the depths of the earth;\ Your eyes have seen my unformed substance;\ And in Your book were all written\ The days that were ordained for me,\ When as yet there was not one of them.\ How precious also are Your thoughts to me, O God!\ How vast is the sum of them!\ If I should count them, they would outnumber the sand.\ When I awake, I am still with You.\ O that You would slay the wicked, O God;\ Depart from me, therefore, men of bloodshed.\ For they speak against You wickedly,\ And Your enemies take Your name in vain.\ Do I not hate those who hate You, O Lord?\ And do I not loathe those who rise up against You?\ I hate them with the utmost hatred;|\ They have become my enemies.\ **Search me, O God, and know my heart;\ Try me and know my anxious thoughts;\ And see if there be any hurtful way in me,\ And lead me in the everlasting way. (Psalm 139) {emphasis mine}
What is one of the greatest desires of our hearts? Isn’t it to be truly known and loved for who we are?
O Lord, You have searched me and known me.\ You know when I sit down and when I rise up;\ You understand my thought from afar. (Psalm 139:1-2)
How amazing is it that the Creator of the universe knows you personally and cares for you among all of creation?
Even before there is a word on my tongue,\ Behold, O Lord, You know it all. (Psalm 139:4)
He knows our every action, our every thought, and our every feeling before we do.
Such knowledge is too wonderful for me;\ It is too high, I cannot attain to it. (Psalm 139:6)
We cannot fully understand how much our Creator cares for us and how carefully God guides us in our every path. We usually can’t see what is for our best. We usually can’t see what great work God is working in us. We usually can’t comprehend how great is His love, knowledge, and plan.
Even there Your hand will lead me,\ And Your right hand will lay hold of me. (Psalm 139:10)
It doesn’t matter how difficult a situation we have gotten into. It doesn’t matter how powerful our adversaries are. It doesn’t matter how weak we are. God is always there guiding us and protecting us. Just as God allowed Job to go through difficulty as part of God’s plan for Job and for us, He did not allow Job to be killed. He was guided through the worst of situations and led to ultimate blessing.
Your eyes have seen my unformed substance;\ And in Your book were all written\ The days that were ordained for me,\ When as yet there was not one of them. (Psalm 139:16)
God knew us and had a plan for us before He even created the universe. He knew every day we would live before we were conceived. We can’t surprise Him and He will be guiding us every day of our lives, especially those who have trusted Him as savior.
How precious also are Your thoughts to me, O God!\ How vast is the sum of them! (Psalm 139:17)
We are precious to God and He should be precious to us because of all He has done for us.
Search me, O God, and know my heart;\ Try me and know my anxious thoughts;\ And see if there be any hurtful way in me,\ And lead me in the everlasting way. (Psalm 139:23-24)
This should be our prayer. We should ask for Him to bring are faults to our minds so we can repent and we should ask for Him to lead us in His “everlasting way.” We should admit that our Father God knows best and submit to His will. Everything goes so much smoother when we aren’t fighting our God. Even when He leads us through hardship, being in His will makes all of the difference in the world.
I pray that you will put your trust in our loving Creator and that you will submit to His will. I pray that you will understand that His ways are better even when you don’t understand the why. I pray that you will humbly submit to His will and be used to further the Kingdom for His glory and your blessing.
Trust Jesus.
FYI, Psalm 139 is also one of the best passages on why all believers should oppose abortion. In God’s universe there are no accidents and there are no unwanted babies. Every person ever conceived had a purpose in God’s plan. Every person ever conceived is valuable and made in the image of God. God values all human life and so should we.
-
 @ 3bf0c63f:aefa459d
2024-05-21 12:38:08
@ 3bf0c63f:aefa459d
2024-05-21 12:38:08Bitcoin transactions explained
A transaction is a piece of data that takes inputs and produces outputs. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered.
Imagine you have 10 satoshis. That means you have them in an unspent transaction output (UTXO). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a script that unlocks that transaction and related signatures, then you specify outputs along with a script that locks these outputs.

As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them.
For most of the cases locking and unlocking means specifying a public key whose controller (the person who has the corresponding private key) will be able to spend. Other fancy things are possible too, but we can ignore them for now.
Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.

If you're still interested in transactions maybe you could take a look at this small chapter of that Andreas Antonopoulos book.
If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: https://en.bitcoin.it/wiki/Coin_analogy
-
 @ 2fb77d26:c47a6ee1
2025-01-08 19:47:47
@ 2fb77d26:c47a6ee1
2025-01-08 19:47:47Sehr geehrte Damen und Herren,
wenn wir an Schlachtfelder denken, sehen wir vor unserem inneren Auge düstere Bilder von verkohlten Wracks, von Einschlagkratern, schreienden Verwundeten, Leichen und dichten Rauchschwaden, die am Horizont über verbrannter Erde wabern.
Vergleichbare Assoziationen drängen sich auf, versucht man in Bilder zu fassen, in was für einer Gesellschaft wir mittlerweile leben. Intellektuelle Wracks, mediales Flächenbombardement, stumme Schreie von Pharmaopfern und hungernden Kindern, weggescrollt von Smartphone-Zombies, deren letzter Hauch Empathie am Rande ihres dissoziativen Wahrnehmungshorizontes verblasst. Zivilisatorische Transformation als Kriegsfilm.
Früher verliefen die Frontlinien von Klassenkampf und Propagandakrieg durch die Auslagen der Zeitungskioske, durch Rundfunkredaktionen und über die nach Sendeschluss flimmernden Bildschirme der Mattscheibe. Heute durch den Kopf.
Sprichwörtlich. Denn die »Vierte Industrielle Revolution« begegnet zunehmendem Desinteresse an Erziehungsfunk und aufkeimender Renitenz mit Dopamin-Shots, Implantaten und Nanotechnologie. Das erklärte Ziel der Herrschaftskaste ist nicht mehr die Manipulation, sondern die Fernsteuerung der Steuersklaven. Das »Hive Mind«.
Sendeschluss gibt es nicht mehr. Und der Newsfeed ist unerschöpflich, ist Manifestation dessen, was Aufmerksamkeitsökonomie für uns bedeutet: Den Verlust wertvoller Lebenszeit an neonbunte Sinnlosigkeit. Das Smartphone dient nicht der Evolution, sondern der Degeneration der Spezies Mensch. Es ist kein Werkzeug, sondern eine Waffe. Aber das Handy lässt sich — wie das TV-Gerät — abschalten. Oder abschaffen. Das birgt Risiken — denn nur Lufthoheit über dem Debattenraum garantiert dem postmodernen Feudalismus Machterhalt. Dementsprechend setzen seine Vertreter nun alles daran, invasive Technologien ins Feld zu führen, um sich unserer Gedanken bemächtigen zu können.
Der Kriegsfilm spielt sich also nicht mehr nur als dunkles Phantasma vor unserem inneren Auge ab, er handelt nicht von irgendeinem fernen Land — das zu erobernde Terrain, das primäre Schlachtfeld der biodigitalen Konvergenz liegt unmittelbar hinter dem Sehnerv. Kriegsziel: Die Verschmelzung von Mensch und Maschine. Transhumanismus. Und bei so manchem Zeitgenossen scheint bereits eine gewisse Konträrfaszination am eigenen Untergang Einzug zu halten. Die Résistance des Mediazän verteidigt demnach nicht nur das Recht auf Meinungsfreiheit, sie kämpft um den Erhalt des freien Willens. Um Menschlichkeit. Um das Fortbestehen unserer Spezies.
Vor diesem Hintergrund beschäftigt sich die dritte GEGENDRUCK mit dem »Schlachtfeld Gehirn«. Mit dem zerebralen Status quo. Die Autoren analysieren und dokumentieren den Stand von Forschung, Angriffswellen, Waffenarsenal und Verteidigungsmechanismen. Denn unser Leben ist das Produkt unserer Gedanken. Unserer Erinnerungen. Sie sind die Basis unserer Freiheit, unserer Geschichte und Zukunft. Wir müssen sie schützen. Mit allen Mitteln.
Denn »ein Kopf ohne Gedächtnis ist eine Festung ohne Besatzung« (Napoleon).
Im Namen des gesamten Teams,
Tom-Oliver Regenauer
Printausgabe bestellen unter: www.gegendruck.de
-
 @ 0fa80bd3:ea7325de
2025-01-29 14:44:48
@ 0fa80bd3:ea7325de
2025-01-29 14:44:48![[yedinaya-rossiya-bear.png]]
1️⃣ Be where the bear roams. Stay in its territory, where it hunts for food. No point setting a trap in your backyard if the bear’s chilling in the forest.
2️⃣ Set a well-hidden trap. Bury it, disguise it, and place the bait right in the center. Bears are omnivores—just like secret police KGB agents. And what’s the tastiest bait for them? Money.
3️⃣ Wait for the bear to take the bait. When it reaches in, the trap will snap shut around its paw. It’ll be alive, but stuck. No escape.
Now, what you do with a trapped bear is another question... 😏
-
 @ 9e69e420:d12360c2
2025-01-25 22:16:54
@ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.”
The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China.
-
 @ 07e188a1:24d232f3
2024-10-26 09:16:44
@ 07e188a1:24d232f3
2024-10-26 09:16:44Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
A sub heading goes a long way
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
-
 @ b7274d28:c99628cb
2025-02-04 05:31:13
@ b7274d28:c99628cb
2025-02-04 05:31:13For anyone interested in the list of essential essays from nostr:npub14hn6p34vegy4ckeklz8jq93mendym9asw8z2ej87x2wuwf8werasc6a32x (@anilsaidso) on Twitter that nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev mentioned on Read 856, here it is. I have compiled it with as many of the essays as I could find, along with the audio versions, when available. Additionally, if the author is on #Nostr, I have tagged their npub so you can thank them by zapping them some sats.
All credit for this list and the graphics accompanying each entry goes to nostr:npub14hn6p34vegy4ckeklz8jq93mendym9asw8z2ej87x2wuwf8werasc6a32x, whose original thread can be found here: Anil's Essential Essays Thread
1.

History shows us that the corruption of monetary systems leads to moral decay, social collapse, and slavery.
Essay: https://breedlove22.medium.com/masters-and-slaves-of-money-255ecc93404f
Audio: https://fountain.fm/episode/RI0iCGRCCYdhnMXIN3L6
2.

The 21st century emergence of Bitcoin, encryption, the internet, and millennials are more than just trends; they herald a wave of change that exhibits similar dynamics as the 16-17th century revolution that took place in Europe.
Author: nostr:npub13l3lyslfzyscrqg8saw4r09y70702s6r025hz52sajqrvdvf88zskh8xc2
Essay: https://casebitcoin.com/docs/TheBitcoinReformation_TuurDemeester.pdf
Audio: https://fountain.fm/episode/uLgBG2tyCLMlOp3g50EL
3.

There are many men out there who will parrot the "debt is money WE owe OURSELVES" without acknowledging that "WE" isn't a static entity, but a collection of individuals at different points in their lives.
Author: nostr:npub1guh5grefa7vkay4ps6udxg8lrqxg2kgr3qh9n4gduxut64nfxq0q9y6hjy
Essay: https://www.tftc.io/issue-754-ludwig-von-mises-human-action/
Audio: https://fountain.fm/episode/UXacM2rkdcyjG9xp9O2l
4.
If Bitcoin exists for 20 years, there will be near-universal confidence that it will be available forever, much as people believe the Internet is a permanent feature of the modern world.
Essay: https://vijayboyapati.medium.com/the-bullish-case-for-bitcoin-6ecc8bdecc1
Audio: https://fountain.fm/episode/jC3KbxTkXVzXO4vR7X3W
As you are surely aware, Vijay has expanded this into a book available here: The Bullish Case for Bitcoin Book
There is also an audio book version available here: The Bullish Case for Bitcoin Audio Book
5.

This realignment would not be traditional right vs left, but rather land vs cloud, state vs network, centralized vs decentralized, new money vs old, internationalist/capitalist vs nationalist/socialist, MMT vs BTC,...Hamilton vs Satoshi.
Essay: https://nakamoto.com/bitcoin-becomes-the-flag-of-technology/
Audio: https://fountain.fm/episode/tFJKjYLKhiFY8voDssZc
6.
I became convinced that, whether bitcoin survives or not, the existing financial system is working on borrowed time.
Essay: https://nakamotoinstitute.org/mempool/gradually-then-suddenly/
Audio: https://fountain.fm/episode/Mf6hgTFUNESqvdxEIOGZ
Parker Lewis went on to release several more articles in the Gradually, Then Suddenly series. They can be found here: Gradually, Then Suddenly Series
nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev has, of course, read all of them for us. Listing them all here is beyond the scope of this article, but you can find them by searching the podcast feed here: Bitcoin Audible Feed
Finally, Parker Lewis has refined these articles and released them as a book, which is available here: Gradually, Then Suddenly Book
7.

Bitcoin is a beautifully-constructed protocol. Genius is apparent in its design to most people who study it in depth, in terms of the way it blends math, computer science, cyber security, monetary economics, and game theory.
Author: nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a
Essay: https://www.lynalden.com/invest-in-bitcoin/
Audio: https://fountain.fm/episode/axeqKBvYCSP1s9aJIGSe
8.

Bitcoin offers a sweeping vista of opportunity to re-imagine how the financial system can and should work in the Internet era..
Essay: https://archive.nytimes.com/dealbook.nytimes.com/2014/01/21/why-bitcoin-matters/
9.

Using Bitcoin for consumer purchases is akin to driving a Concorde jet down the street to pick up groceries: a ridiculously expensive waste of an astonishing tool.
Author: nostr:npub1gdu7w6l6w65qhrdeaf6eyywepwe7v7ezqtugsrxy7hl7ypjsvxksd76nak
Essay: https://nakamotoinstitute.org/mempool/economics-of-bitcoin-as-a-settlement-network/
Audio: https://fountain.fm/episode/JoSpRFWJtoogn3lvTYlz
10.

The Internet is a dumb network, which is its defining and most valuable feature. The Internet’s protocol (..) doesn’t offer “services.” It doesn’t make decisions about content. It doesn’t distinguish between photos, text, video and audio.
Essay: https://fee.org/articles/decentralization-why-dumb-networks-are-better/
Audio: https://fountain.fm/episode/b7gOEqmWxn8RiDziffXf
11.

Most people are only familiar with (b)itcoin the electronic currency, but more important is (B)itcoin, with a capital B, the underlying protocol, which encapsulates and distributes the functions of contract law.
I was unable to find this essay or any audio version. Clicking on Anil's original link took me to Naval's blog, but that particular entry seems to have been removed.
12.

Bitcoin can approximate unofficial exchange rates which, in turn, can be used to detect both the existence and the magnitude of the distortion caused by capital controls & exchange rate manipulations.
Essay: https://papers.ssrn.com/sol3/Papers.cfm?abstract_id=2714921
13.

You can create something which looks cosmetically similar to Bitcoin, but you cannot replicate the settlement assurances which derive from the costliness of the ledger.
Essay: https://medium.com/@nic__carter/its-the-settlement-assurances-stupid-5dcd1c3f4e41
Audio: https://fountain.fm/episode/5NoPoiRU4NtF2YQN5QI1
14.

When we can secure the most important functionality of a financial network by computer science... we go from a system that is manual, local, and of inconsistent security to one that is automated, global, and much more secure.
Essay: https://nakamotoinstitute.org/library/money-blockchains-and-social-scalability/
Audio: https://fountain.fm/episode/VMH9YmGVCF8c3I5zYkrc
15.

The BCB enforces the strictest deposit regulations in the world by requiring full reserves for all accounts. ..money is not destroyed when bank debts are repaid, so increased money hoarding does not cause liquidity traps..
Author: nostr:npub1hxwmegqcfgevu4vsfjex0v3wgdyz8jtlgx8ndkh46t0lphtmtsnsuf40pf
Essay: https://nakamotoinstitute.org/mempool/the-bitcoin-central-banks-perfect-monetary-policy/
Audio: https://fountain.fm/episode/ralOokFfhFfeZpYnGAsD
16.

When Satoshi announced Bitcoin on the cryptography mailing list, he got a skeptical reception at best. Cryptographers have seen too many grand schemes by clueless noobs. They tend to have a knee jerk reaction.
Essay: https://nakamotoinstitute.org/library/bitcoin-and-me/
Audio: https://fountain.fm/episode/Vx8hKhLZkkI4cq97qS4Z
17.

No matter who you are, or how big your company is, 𝙮𝙤𝙪𝙧 𝙩𝙧𝙖𝙣𝙨𝙖𝙘𝙩𝙞𝙤𝙣 𝙬𝙤𝙣’𝙩 𝙥𝙧𝙤𝙥𝙖𝙜𝙖𝙩𝙚 𝙞𝙛 𝙞𝙩’𝙨 𝙞𝙣𝙫𝙖𝙡𝙞𝙙.
Essay: https://nakamotoinstitute.org/mempool/bitcoin-miners-beware-invalid-blocks-need-not-apply/
Audio: https://fountain.fm/episode/bcSuBGmOGY2TecSov4rC
18.

Just like a company trying to protect itself from being destroyed by a new competitor, the actions and reactions of central banks and policy makers to protect the system that they know, are quite predictable.
Author: nostr:npub1s05p3ha7en49dv8429tkk07nnfa9pcwczkf5x5qrdraqshxdje9sq6eyhe
Essay: https://medium.com/the-bitcoin-times/the-greatest-game-b787ac3242b2
Audio Part 1: https://fountain.fm/episode/5bYyGRmNATKaxminlvco
Audio Part 2: https://fountain.fm/episode/92eU3h6gqbzng84zqQPZ
19.

Technology, industry, and society have advanced immeasurably since, and yet we still live by Venetian financial customs and have no idea why. Modern banking is the legacy of a problem that technology has since solved.
Author: nostr:npub1sfhflz2msx45rfzjyf5tyj0x35pv4qtq3hh4v2jf8nhrtl79cavsl2ymqt
Essay: https://allenfarrington.medium.com/bitcoin-is-venice-8414dda42070
Audio: https://fountain.fm/episode/s6Fu2VowAddRACCCIxQh
Allen Farrington and Sacha Meyers have gone on to expand this into a book, as well. You can get the book here: Bitcoin is Venice Book
And wouldn't you know it, Guy Swann has narrated the audio book available here: Bitcoin is Venice Audio Book
20.

The rich and powerful will always design systems that benefit them before everyone else. The genius of Bitcoin is to take advantage of that very base reality and force them to get involved and help run the system, instead of attacking it.
Author: nostr:npub1trr5r2nrpsk6xkjk5a7p6pfcryyt6yzsflwjmz6r7uj7lfkjxxtq78hdpu
Essay: https://quillette.com/2021/02/21/can-governments-stop-bitcoin/
Audio: https://fountain.fm/episode/jeZ21IWIlbuC1OGnssy8
21.
In the realm of information, there is no coin-stamping without time-stamping. The relentless beating of this clock is what gives rise to all the magical properties of Bitcoin.
Author: nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc
Essay: https://dergigi.com/2021/01/14/bitcoin-is-time/
Audio: https://fountain.fm/episode/pTevCY2vwanNsIso6F6X
22.

You can stay on the Fiat Standard, in which some people get to produce unlimited new units of money for free, just not you. Or opt in to the Bitcoin Standard, in which no one gets to do that, including you.
Essay: https://casebitcoin.com/docs/StoneRidge_2020_Shareholder_Letter.pdf
Audio: https://fountain.fm/episode/PhBTa39qwbkwAtRnO38W
23.

Long term investors should use Bitcoin as their unit of account and every single investment should be compared to the expected returns of Bitcoin.
Essay: https://nakamotoinstitute.org/mempool/everyones-a-scammer/
Audio: https://fountain.fm/episode/vyR2GUNfXtKRK8qwznki
24.

When you’re in the ivory tower, you think the term “ivory tower” is a silly misrepresentation of your very normal life; when you’re no longer in the ivory tower, you realize how willfully out of touch you were with the world.
Essay: https://www.citadel21.com/why-the-yuppie-elite-dismiss-bitcoin
Audio: https://fountain.fm/episode/7do5K4pPNljOf2W3rR2V
You might notice that many of the above essays are available from the Satoshi Nakamoto Institute. It is a veritable treasure trove of excellent writing on subjects surrounding #Bitcoin and #AustrianEconomics. If you find value in them keeping these written works online for the next wave of new Bitcoiners to have an excellent source of education, please consider donating to the cause.
-
 @ c3b2802b:4850599c
2025-01-24 14:04:29
@ c3b2802b:4850599c
2025-01-24 14:04:29Der klaren, frischen Wahrnehmung der Welt, deren Teil wir sind, stehen vier Schleier im Weg.
Der Schleier der WERTUNG: Getrennt werden Dinge die Lust/Gefallen versprechen - von Dingen, die Unlust und Antipathie erzeugen. Letztere werden unterdrückt.
Der Schleier der BENENNUNG: Getrennt werden Dinge, für die wir Namen und Begriffe kennen – von Dingen die wir nicht benennen können. Letztere werden unterdrückt.
Der Schleier von ERZIEHUNG und AUSBILDUNG: Getrennt werden Dinge, für die uns Regeln und Konventionen vorliegen - von Dingen, die nicht geregelt sind, etwa Visionen und Träume. Letztere werden unterdrückt.
Der Schleier der EGO-ORIENTIERUNG: Getrennt werden Dinge, die für unser „ich“ bedeutsam scheinen – von Dingen, die als „nicht-ich“ eingeordnet werden. Letztere werden unterdrückt.
Jeder Mensch verfügt über das Potential, diese Schleier auszuräumen: Spirituelles Potential.
Das gemeinsame Ziel der spirituellen Traditionen der Menschheit besteht darin, durch transpersonale/religiöse Entwicklung, ggf. unterstützt durch Meditation, diese Schleier bewußt zu machen - um sie dann zu entfernen. Das Ergebnis dieses Prozesses wird in verschiedenen Traditionen unterschiedlich benannt, etwa ERLEUCHTUNG, NIRWANA, SATORI.
Das Bestreben, unser spirituelles Potential zu nutzen und diesen Weg zu begehen, wird in der gegenwärtigen Industriegesellschaft nicht gefördert, da klare Menschen sich nicht für fremde Interessen manipulieren und instrumentalisieren lassen. Klare Menschen lassen sich nicht als Soldaten oder Sklaven missbrauchen.
Wollen wir eine zukunftsfähige Gesellschaft, scheint die Entfaltung der spirituellen Potentiale bei einer kritischen Anzahl von Menschen unabdingbar. Wir brauchen den klaren Blick dafür, dass die gegenwärtigen Entwicklungen nicht zukunftsfähig sind, sondern in einer Sackgasse enden – und dass es Alternativen gibt.
Zum Stärken dieser Potentiale kann man sich an verschiedenen Stufenmodellen orientieren, etwa:
Die fünf Ebenen des transpersonalen Bewusstseins nach Sri Aurobindo und Ken Wilber
o Höherer Geist: Erfassen des Ganzen mit einem Blick
o Erleuchteter Geist: geflutetes Bewusstsein, Kreativität
o Intuitiver Geist: Erleben einer permanenten Einheit
o Overmind: kosmische Wonne, universelle Liebe
o Supramental: kontinuierliches non-duales Erfassen der Wirkichkeit
Die vier Ebenen des integralen Bewusstseins nach Jean Gebser
o No time – only present time
o Transzendieren des RaumZeit Erlebens
o Nonduale Erfahrung, offenes Gewahrsein, SATORI
o Transparenz des Geistes, NIRWANA, Verschwinden von Begehren, loslassen des Haftens am Ego
Acht Jhanische Versenkungsstadien, beschrieben bei Markus Klische
o Innere Tiefe
o Versiegen des mentalen Schwingens
o Erfahrungsstrom von Aussen nach Innen
o Kraft des Gleichmutes
o Gewahrsein von endlosem Raum
o Realität wird nicht länger "dinghaft" erlebt
o Auftrennung Objekt – Subjekt verschwindet
o Weder Wahrnehmung noch Nicht-Wahrnehmung
Drei Phasen der Meditation nach Harald Walach
o Ausblick: Atemmeditation stärkt Aufmerksamkeit nach Innen
o Einblick: Achtsamkeit, nicht wertendes Verweilen beim Strom der Geschehnisse
o Tiefblick: neue Wirklichkeitsbereiche werden spürbar. Kensho-Licht, Satori, Verbundenheit, Mitgefühl
Sollten diese Überlegungen bei Ihnen anklingen und Sie mögen gleich anfangen, etwas zu tun, um den Kontakt mit dem Seelischen zu stärken und das Göttliche in uns stärker zum Klingen zu bringen: Schalten Sie alle Informationsquellen ab, welchen Sie nicht recht trauen. Wer das Gift von Propaganda stoppt und die gewonnene Zeit und Energie für die Wahrnehmung der Dinge und Ereignisse im realen Hier und Jetzt nutzt, hat den ersten und heute vielleicht wichtigsten Schritt auf dem Weg zur klaren und frischen Wahrnehmung der Welt bereits getan. Selber schauen, denken, fühlen - und sich vielleicht noch die Sinnfrage von Victor Frankl stellen:
WAS ERWARTET DIE WELT VON MIR?
Dann wird unser Weg in die Regionalgesellschaft frei.
Details zur Potentialentfaltung in der Regionalgesellschaft finden Sie hier.
-
 @ dd664d5e:5633d319
2024-06-28 13:04:48
@ dd664d5e:5633d319
2024-06-28 13:04:48An immodest proposal
It is grant season again, and -- as every grant season -- there is some cheering, some complaining, and much bewilderment, as the grants are announced and monies are dispersed.
I'm mostly a bystander to this spectacle, but it's impossible to ignore it, or to not become emotionally entangled in the general circus of it, so I've decided to write about it -- again -- as it is effecting me and interrupting my own efforts -- again.
What I'm about to suggest here is something that has never been done before (at least, not on a grant system of this scale), but it's always easy to criticize, whine, or fall into conspiracy-theorizing, so I've decided to try something more constructive and propose a solution.
The Five Whys
Why do some projects get turned down for grants?
Why do some people receive grants over and over and over?
Why do others refuse to apply for grants?
Why is an enormous amount of money being spent, but nobody knows how much is left over?
Why is it not really clear who is receiving what?
Why, why, why?!
Doctor, heal thyself!
Leaving this many whys lying around, or responding to them defensively or with small information-leaks, is an open communication fail on our open communication protocol.
We don't really have the excuse of not knowing how to communicate transparently and publicly, since that is our professional specialty. If we can't figure out how to run a grant program in the most continuously innovative and traceable way possible, even though we are a collection of some of the most talented perpetual innovators on the planet, then who can?
We are all process engineers, so let's engineer our own processes.
The application process
The main problem with the grant application process is that there is a grant application process. There shouldn't be. Everyone who is working in our space is working transparently, actively marketing their ideas, and everything they do is a matter of public record.
We know who the builders are. We know what they are doing. We can interact with them about what they are doing. We can turn on our computers, pull out some popcorn, and entertain ourselves all day, every day, just watching them labour and think aloud and debate, and fork various repositories or Nostr notes.
There is, at most, a loss of information, as there are so many people working on so many things, that it can become difficult to even track one particular person. That means it is not too much for us to ask, to suggest that anyone interested in a grant at least make their interest known in some small way.
Wave if you want a grant
That way should be as small as possible. Tiny. Ideally, they shouldn't even have to go that way themself; others should be able to nominate them. A 10-minute barrier to entry is already high, if it requires some formal, explicit act of supplication.
Does that sound silly to you? Then you do not understand how profoundly logical, forward-thinking, and diligent software developers can be. If they "just fill out a form" and/or "have an informal discussion", in order to receive money, it smacks disturbingly of "job interview" and "contract". These are people for whom contract law is holy law, so many will agonize over the decision.
-
Some already have a job and they don't know how it will be in the future. What if they have to work overtime?
-
Or they have a family and worry that they can't promise to deliver within some particular time. The wife could get pregnant, the baby could get sick, they might have to move house.
-
Maybe they are students and exam time is approaching. Or they are simply shy or very young, and therefore reluctant to be seen "tooting their own horn". There is probably someone more worthy, and they are taking away the money he would get.
-
Maybe they were hit with such an inner building passion that they hacked the whole implementation out their last vacation and... well... it's now already there. Everyone is already using it. Darn. Why apply for a grant, for something you've already finished? Seems sort of silly. Is that even allowed? What are the grants even for?
-
What if they already have such a well-publicized project, that everyone is already watching them and keeping tabs? Then it's embarrassing to apply, on a lark, and get turned down. But if they don't apply, then everyone encourages them to apply. What to do?
-
Many prefer to keep their head down and keep building, for months or years at a time, and clap politely when others are awarded a grant. In fact, they happily zap the recipients and then go right back to building and releasing. They're often grateful to just bathe in other people's joy, by proxy, while they stack sats and stay humble and keep coding.
That is why a large subset of potential grant recipients never even apply. That is also why those who have received a grant are less reluctant to apply for another. Successful application breeds successful application. The emotional barrier to entry has fallen. To those that have, shall be given.
Let's use Nostr to run Nostr grants
We should turn the tables around completely. We want the developers to keep developing, not jumping through hoops. We don't want them to be distracted and internally torn over the ethics of requesting funding. We don't want them to be afraid to apply for grants or be mystified by the grant-giving process, or be humiliated or frustrated by a declined grant.
-
Let us come up with very clear, understandable criteria for rewarding grants, write them down, and publish them on Nostr Wiki. Accept comments and critiques of the criteria. After every round of grants, we should review the criteria, suggest improvements, and publish the new version in the same place.
-
Let every application be judged according to this criteria and the results should be published after every round. The results should include a rating for each criteria and (if the grant is given) the amount of the grant awarded or (if the grant is declined) the reasons for the decline and what the applicant can improve to have a better chance of receiving a grant in the future.
-
Ideally, no applicant should walk away from a declined grant feeling hopeless or slighted. Every applicant should feel like the grant process gave them valuable feedback on their own efforts and expert guidance on what they should maybe focus more on.
-
Every application should be a standing application that has to be explicitly removed from the list by the person listed as an applicant. Anything not removed automatically enters the next round. If there is no further development on the project, then the application should be paused and removed after 2 rounds of being paused.
-
The application process should consist of adding yourself or someone else to a Wiki Grant Application List and linking to some documentation of the project. Any npub that trolls or spams the list should be prohibited from further contribution. The quality and completeness of that documentation should be a factor in grant acceptance.
-
Grant decisions should include a "handicap" (like in golf), that take into account how Nostr-experienced the applicant is and how easy it was for them to add a new implementation to some already-existing system. The tendency should be to award newer applicants such grants, with more-experienced applicants competing for long-term funding or being offered a paid(!) place on the grant board, but not both.
-
Each grant round should be proceeded by a grant scope declaration (we shall be awarding X number of grants with an average of X Bitcoin per grant) accompanied by a funding overview and update (How much money was collected since the last round? How much did we spend? How much do we have now? etc.).
Okay, this is just a prototype
I'm sure that I'm going to be bombarded with naysayers, critics, and people who think I am "writing above my pay grade", but I wouldn't be me if I let that daunt me.
All I am trying to do is change the discussion into one focused on uncovering the grant problems and offering grant solutions, rather than debates about whether some particular person was grant-worthy, or long rants on some particular person's real motives.
It's a lot of Real Money. It's worth talking about, but it's not worth fighting over. Let's talk.
-
-
 @ 06b7819d:d1d8327c
2024-11-28 18:30:00
@ 06b7819d:d1d8327c
2024-11-28 18:30:00The Bank of Amsterdam (Amsterdamse Wisselbank), established in 1609, played a pivotal role in the early history of banking and the development of banknotes. While banknotes as a concept had been pioneered in China centuries earlier, their modern form began emerging in Europe in the 17th century, and the Bank of Amsterdam leveraged its unique position to dominate this nascent monetary tool.
Founding and Early Innovations
The Bank of Amsterdam was created to stabilize and rationalize Amsterdam’s chaotic monetary system. During the early 1600s, a plethora of coins of varying quality and origin circulated in Europe, making trade cumbersome and unreliable. The Wisselbank provided a centralized repository where merchants could deposit coins and receive account balances in return, denominated in a standardized unit of account known as “bank money.” This “bank money” was more stable and widely trusted, making it an early form of fiat currency.
The Rise of Banknotes
Although the Wisselbank initially issued “bank money” as a ledger-based system, the growing demand for portable, trusted currency led to the adoption of transferable receipts or “banknotes.” These receipts acted as claims on deposited money and quickly became a trusted medium of exchange. The innovation of banknotes allowed merchants to avoid carrying large quantities of heavy coinage, enhancing convenience and security in trade.
Monopoly on Banknotes
The Wisselbank’s reputation for financial stability and integrity enabled it to establish a monopoly on banknotes in the Dutch Republic. The bank’s stringent policies ensured that its issued notes were fully backed by coinage or bullion, which bolstered trust in their value. By centralizing the issuance of notes, the bank eliminated competition from private or less reliable issuers, ensuring its notes became the de facto currency for merchants and traders.
Moreover, the bank’s policies discouraged the redemption of notes for physical coins, as it charged fees for withdrawals. This incentivized the circulation of banknotes rather than the underlying specie, cementing their role in the economy.
Decline of the Monopoly
The Wisselbank’s monopoly and influence lasted for much of the 17th century, making Amsterdam a hub of global trade and finance. However, as the 18th century progressed, financial mismanagement and competition from other emerging financial institutions eroded the Wisselbank’s dominance. By the late 18th century, its role in the global financial system had diminished, and other European financial centers, such as London, rose to prominence.
Legacy
The Bank of Amsterdam’s early monopolization of banknotes set a precedent for centralized banking and the development of modern monetary systems. Its ability to create trust in a standardized, portable medium of exchange foreshadowed the role that central banks would play in issuing and regulating currency worldwide.
-
 @ c3b2802b:4850599c
2025-01-20 12:30:47
@ c3b2802b:4850599c
2025-01-20 12:30:47Im Jahr 2000 hat ein Team von Sozialwissenschaftlern eine Reihe von strukturierten Interviews geführt mit Personen, welche regionale Lösungen zur Nutzung von lokal vorhandener Energie umgesetzt hatten, z.B. die Stromrebellen aus Schönau im Schwarzwald. Wir fragten sie:
Was sind die Besonderheiten Ihres Projekts? Wie haben Sie andere Menschen motiviert und mobilisiert, sich an dem Projekt zu beteiligen? Wie haben Sie andere Menschen überzeugt und wie haben Sie Schwierigkeiten bei der Verfolgung Ihrer Ziele überwunden? Welche Faktoren haben zum Erfolg des Projekts geführt? Welche Rolle spielten die Medien bei der Verbreitung der Idee? Gab es Konsequenzen des kollektiven Handelns für die Gemeinschaft? Gab es Veränderungen im Grad der Identifikation der Menschen mit ihrem Dorf? Hat sich das Gemeinschaftsgefühl während des Projekts verändert?
Wir haben auch erfragt, ob die Befragten mit dem Umstellungsprozess im Dorf zufrieden sind und was sie anders machen würden, wenn sie die Möglichkeit hätten, es noch einmal zu tun. Ziel war es, aus den Erfahrungen aus solchen Projekten zu lernen und diese in unserem Projekt "Energiewendedörfer" anzuwenden. Darüber hinaus haben wir versucht, Gesetzmäßigkeiten zu finden und zu formulieren, die erfolgreiche kollektive Handlungsprozesse im Allgemeinen kennzeichnen.
Unter den in verschiedenen Initiativen wiederholt genannten Erfolgsfaktoren befand sich die Aussage: Wir waren erfolgreich, weil wir uns für und nicht gegen etwas engagiert haben. Wenn das Ziel des Projekts positiv und konstruktiv formuliert wird, führt das weiter als wenn man Gegner, seien es Personen oder Unternehmen benennt, gegen die man zu agieren plant. In Schönau etwa, einem Schwarzwald-Städtchen nannte sich nach dem Tschernobyl-Unfall die die daraus motivierte Initiativgruppe für regionale Energie "Eltern für eine atomenergie-freie Zukunft" und nicht "Eltern gegen die Nuklearenergie". Über dieses Framing der eigenen Aktivitäten wurde zu Beginn der Initiative in Schönau intensiv diskutiert. Man wurde sich einig, dass die PRO-Formulierung eine positive Lebensauffassung stützt, dass die "Pro-Haltung" dahinter Assoziationen zur konstruktiven Konfliktlösung, zu Liebe, zu Hilfe für die Menschen und zur Erhaltung der Natur weckt, während die "Kontra-Haltung" oft einen destruktiven Charakter hat und im besten Falle einen Mißstand erfolgreich bekämpft, aber keine Alternative in die Welt bringt.
Am Erfolg der EWS Schönau, heute einer Genossenschaft mit 13.597 Mitgliedern, lässt sich der Erfolg dieser positiven Einstellung erkennen. Die EWS bietet heute landesweit Energie an, welche nicht auf fossilen Importen beruht sondern die aus Energiequellen in den Regionen unseres Landes gewonnen wird. Das Modell der EWS ist damit ein wesentlicher Baustein der Regionalgesellschaft und stand sicherlich auch Pate bei vielen der ca. 800 Energiegenossenschaften im Land, welche in den vergangenen Jahrzehnten entstanden sind.
Die Anwendung des Erfolgsfaktors PRO statt KONTRA in den eigenen Projekten hat vermutlich zum Erfolg der 200 Energiewendedörfer im Land beigetragen, welche in unseren Teams nach dem Jahr 2000 initiiert worden waren.
Zum Abschluss ein kurzer Blick auf die besondere Situation der vergangenen fünf Jahre. Die Ereignisse seit 2020 haben in Deutschland und auch weltweit eine gewaltige Bewegung gegen die Maßnahmen von Regierungen ausgelöst, welche auf Einschränkung von Menschenrechten sowie medizinische Zwangsmaßnahmen abzielten. Dadurch wurde eine Kontra-Haltung erzwungen für alle Menschen, die den Abbau demokratischer Strukturen sowie Einschränkungen der Verfügung über die eigene Gesundheit nicht zulassen wollten. Hier waren Kontra-Aktivitäten von Montagsspaziergängen bis hin zu Großdemonstrationen sicherlich notwendig und haben möglicherweise Schlimmeres wie einen allgemeinen Impfzwang verhindert.
Dennoch habe ich nach längerer Überlegung die Formulierung oben PRO statt KONTRA belassen. Denn es geht hier um die Psychologie des Wandels hin zur Regionalgesellschaft. Aktivitäten gegen Angriffe auf bisher Erreichtes sind sicher wichtig, sie können sogar in politisch heissen Phasen überlebenswichtig werden. Auch meine Tochter und ich sahen Anfang der 2020er den Bundestag durch den Sprühregen von Wasserwerfern. Doch wenn wir in der Grundhaltung im KONTRA bleiben, wird die gesellschaftliche Evolution hin zu einer fairen Regionalgesellschaft um keinen Deut vorankommen.
Sollten Sie zu denen gehören, die langjährig im Widerstand gegen Angriffe auf die Würde und Rechte der Völker unserer Welt aktiv waren: Mein allergrößter Respekt für Ihr Engagement. Spätestens, wenn Sie ein Ausbrennen Ihrer Energie wahrnehmen - versuchen Sie es einmal mit PRO :-)
Das Titelfoto zeigt Michael Sladek, 2024 verstorbener Initiator der EWS. Danke Michael, für den gewaltigen Impuls, den Du im Kreise der Schönauer Engagierten mit Deinem Lebenswerk der Regionalgesellschaft geschenkt hast.
-
 @ 91bea5cd:1df4451c
2025-02-04 05:24:47
@ 91bea5cd:1df4451c
2025-02-04 05:24:47Novia é uma ferramenta inovadora que facilita o arquivamento de vídeos e sua integração com a rede NOSTR (Notes and Other Stuff Transmitted over Relay). Funcionando como uma ponte entre ferramentas de arquivamento de vídeo tradicionais e a plataforma descentralizada, Novia oferece uma solução autônoma para a preservação e compartilhamento de conteúdo audiovisual.
Arquitetura e Funcionamento
A arquitetura de Novia é dividida em duas partes principais:
-
Frontend: Atua como a interface do usuário, responsável por solicitar o arquivamento de vídeos. Essas solicitações são encaminhadas para o backend.
-
Backend: Processa as solicitações de arquivamento, baixando o vídeo, suas descrições e a imagem de capa associada. Este componente é conectado a um ou mais relays NOSTR, permitindo a indexação e descoberta do conteúdo arquivado.
O processo de arquivamento é automatizado: após o download, o vídeo fica disponível no frontend para que o usuário possa solicitar o upload para um servidor Blossom de sua escolha.
Como Utilizar Novia
-
Acesso: Navegue até https://npub126uz2g6ft45qs0m0rnvtvtp7glcfd23pemrzz0wnt8r5vlhr9ufqnsmvg8.nsite.lol.
-
Login: Utilize uma extensão de navegador compatível com NOSTR para autenticar-se.
-
Execução via Docker: A forma mais simples de executar o backend é através de um container Docker. Execute o seguinte comando:
bash docker run -it --rm -p 9090:9090 -v ./nostr/data:/data --add-host=host.docker.internal:host-gateway teamnovia/noviaEste comando cria um container, mapeia a porta 9090 para o host e monta o diretório
./nostr/datapara persistir os dados.
Configuração Avançada
Novia oferece amplas opções de configuração através de um arquivo
yaml. Abaixo, um exemplo comentado:```yaml mediaStores: - id: media type: local path: /data/media watch: true
database: /data/novia.db
download: enabled: true ytdlpPath: yt-dlp ytdlpCookies: ./cookies.txt tempPath: /tmp targetStoreId: media secret: false
publish: enabled: true key: nsec thumbnailUpload: - https://nostr.download videoUpload: - url: https://nostr.download maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://files.v0l.io maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://nosto.re maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://blossom.primal.net maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2
relays: - ws://host.docker.internal:4869 - wss://bostr.bitcointxoko.com secret: false autoUpload: enabled: true maxVideoSizeMB: 100
fetch: enabled: false fetchVideoLimitMB: 10 relays: - match: - nostr - bitcoin
server: port: 9090 enabled: true ```
Explicação das Configurações:
mediaStores: Define onde os arquivos de mídia serão armazenados (localmente, neste exemplo).database: Especifica o local do banco de dados.download: Controla as configurações de download de vídeos, incluindo o caminho para oyt-dlpe um arquivo de cookies para autenticação.publish: Configura a publicação de vídeos e thumbnails no NOSTR, incluindo a chave privada (nsec), servidores de upload e relays. Atenção: Mantenha sua chave privada em segredo.fetch: Permite buscar eventos de vídeo de relays NOSTR para arquivamento.server: Define as configurações do servidor web interno de Novia.
Conclusão
Novia surge como uma ferramenta promissora para o arquivamento e a integração de vídeos com o ecossistema NOSTR. Sua arquitetura modular, combinada com opções de configuração flexíveis, a tornam uma solução poderosa para usuários que buscam preservar e compartilhar conteúdo audiovisual de forma descentralizada e resistente à censura. A utilização de Docker simplifica a implantação e o gerenciamento da ferramenta. Para obter mais informações e explorar o código-fonte, visite o repositório do projeto no GitHub: https://github.com/teamnovia/novia.
-
-
 @ cff1720e:15c7e2b2
2025-01-19 17:48:02
@ cff1720e:15c7e2b2
2025-01-19 17:48:02Einleitung\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie roland@pareto.space können sie sogar jederzeit umziehen, egal wohin. Cool, das ist state of the art! Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.

Warum Nostr?
Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz "unserer Demokratie” praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.

Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ Resümee: keine Standards, keine Daten, keine Rechte = keine Zukunft!

\ Wie funktioniert Nostr?
Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum “single point of failure”, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. roland@pareto.space ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ Resümee: ein offener Standard, alle Daten, alle Rechte = große Zukunft!

\ Warum ist Nostr die Zukunft des Internet?
“Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie (Value4Value). OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.

\ Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.
https://nostr.net/ \ https://start.njump.me/
Hier das Interview zum Thema mit Radio Berliner Morgenröte
-
 @ dd664d5e:5633d319
2024-06-25 09:28:03
@ dd664d5e:5633d319
2024-06-25 09:28:03Should show up here as content
nostr:note1m9jdd9w9qxwa8gfda6n3sku7nf6mjnxylhaaa8wpnvdz85xajrasrrpj2a
-
 @ 7f29628d:e160cccc
2025-01-07 11:50:30
@ 7f29628d:e160cccc
2025-01-07 11:50:30Der gut informierte Bürger denkt bei der Pandemie sofort an Intensivstationen, an die Bilder aus Bergamo und erinnert sich an die Berichterstattung damals – also muss es wohl ein Maximum gewesen sein. Manche Skeptiker behaupten jedoch das Gegenteil. Klarheit sollte ein Blick nach Wiesbaden, zum Statistischen Bundesamt, schaffen. Schließlich sitzen dort gut bezahlte Profis, die seit vielen Jahrzehnten die Sterbestatistik pflegen und veröffentlichen. Jeder Todesfall wird in Deutschland über die Standesämter exakt erfasst.
Doch die Überraschung: Das Statistische Bundesamt liefert uns auf diese einfache Frage zwei extrem unterschiedliche Antworten – ein Minimum und ein Maximum. Das Ergebnis hängt davon ab, wie tief man in die Veröffentlichungen des Bundesamtes eintaucht. Betrachtet man nur die Webseiten und Pressemitteilungen, erhält man den Eindruck eines Maximums. Schaut man jedoch etwas tiefer in die Tabellen und Rohdaten, zeigt sich plötzlich ein Minimum. Aber wie kann das sein? Beides gleichzeitig geht ja wohl kaum. Wer lügt hier – die Tabellen des Amtes oder die Pressemitteilungen? Gehen wir dieser Frage Schritt für Schritt auf den Grund.
2020: Ein historisches Maximum?
Schauen wir uns die vielen Hundert Veröffentlichungen des Statistischen Bundesamtes aus dieser Zeit an. Oder wir kürzen ab und fragen ChatGPT, da die KI auf diesen Daten trainiert wurde und das gesamte Material kennt. Die Frage an ChatGPT lautet also: Wie war das Sterbegeschehen im Jahr 2020 im Vergleich zu den Vorjahren?
ChatGPT antwortet: »Im Jahr 2020 war die Sterblichkeit in Deutschland höher als in den Jahren zuvor. Es gab eine Übersterblichkeit von etwa 982.000 Todesfällen, das sind rund 46.000 mehr als der Durchschnitt der Vorjahre (2016 bis 2019). Dieser Anstieg wurde überwiegend im Zusammenhang mit der COVID-19-Pandemie gesehen. Während die Sterbezahlen in den Vorjahren schwankten, war ein solch signifikanter Anstieg wie 2020 bisher nicht zu beobachten.«
Wir fragen konkreter: Ist es ein Fakt, dass wir eine so ernste Lage im Sterbegeschehen wie im Frühjahr 2020 noch nie erlebt haben?
ChatGPT bestätigt: »Ja, die COVID-19-Pandemie führte im Frühjahr 2020 zu einer außergewöhnlichen Situation im Sterbegeschehen in Deutschland. Die dramatische Übersterblichkeit, die ab der 13. Kalenderwoche auftrat, veranlasste das Statistische Bundesamt, besonders eindringliche Warnungen zu veröffentlichen. Der damalige Vizepräsident des Amtes und andere führende Stimmen wiesen öffentlich darauf hin, dass die Todesfallzahlen stark vom Durchschnitt abwichen. Diese klare Warnung richtete sich an die Öffentlichkeit und die Politik gleichermaßen. Die Medien berichteten intensiv über diese Warnungen, was das Bewusstsein für die Schwere der Pandemie erheblich schärfte. In den vergangenen Jahrzehnten hatte es keine vergleichbare Übersterblichkeit gegeben, die eine solch umfangreiche Kommunikation durch das Statistische Bundesamt erforderlich gemacht hätte.«
Ein gut informierter Zeitungsleser wird sich an dieser Stelle bestätigt fühlen: Ja, so war es damals. Ein Maximum im Sterbegeschehen – wegen der Pandemie. Oder etwa nicht?
2020: Ein historisches Minimum?
Tauchen wir in die Rohdaten des Statistischen Bundesamtes ein. Die Tabellen, die das Amt seit Jahrzehnten verlässlich veröffentlicht, nennen sich Sterbetafeln. Diese werden jährlich bereitgestellt und stehen auf der Website des Bundesamtes zum Download bereit. Ein erster Blick in die Sterbetafeln mag den Laien abschrecken, doch mit einer kurzen Erklärung wird alles verständlich. Wir gehen schrittweise vor.
Nehmen wir die Sterbetafel des Jahres 2017. Sie enthält zwei große Tabellen – eine für Männer und eine für Frauen. Jede Zeile der Tabelle steht für einen Jahrgang, zum Beispiel zeigt die Zeile 79 die Daten der 79-jährigen Männer. Besonders wichtig ist nun die zweite Spalte, in der der Wert 0,05 eingetragen ist. Das bedeutet, dass 5 Prozent der 79-jährigen Männer im Jahr 2017 verstorben sind. Das ist die wichtige Kennzahl. Wenn wir diesen exakten Wert, den man auch als Sterberate bezeichnet, nun in ein Säulendiagramm eintragen, erhalten wir eine leicht verständliche visuelle Darstellung (Grafik 1).

Es ist wichtig zu betonen, dass dieser Wert weder ein Schätzwert noch eine Modellrechnung oder Prognose ist, sondern ein exakter Messwert, basierend auf einer zuverlässigen Zählung. Sterberaten (für die Fachleute auch Sterbewahrscheinlichkeiten qx) sind seit Johann Peter Süßmilch (1707–1767) der Goldstandard der Sterbestatistik. Jeder Aktuar wird das bestätigen. Fügen wir nun die Sterberaten der 79-jährigen Männer aus den Jahren davor und danach hinzu, um das Gesamtbild zu sehen (Grafik 2). Und nun die entscheidende Frage: Zeigt das Jahr 2020 ein Maximum oder ein Minimum?

Ein kritischer Leser könnte vermuten, dass die 79-jährigen Männer eine Ausnahme darstellen und andere Jahrgänge im Jahr 2020 ein Maximum zeigen würden. Doch das trifft nicht zu. Kein einziger Jahrgang verzeichnete im Jahr 2020 ein Maximum. Im Gegenteil: Auch die 1-Jährigen, 2-Jährigen, 3-Jährigen, 9-Jährigen, 10-Jährigen, 15-Jährigen, 18-Jährigen und viele weitere männliche Jahrgänge hatten ihr Minimum im Jahr 2020. Dasselbe gilt bei den Frauen. Insgesamt hatten 31 Jahrgänge ihr Minimum im Jahr 2020. Wenn wir schließlich alle Jahrgänge in einer einzigen Grafik zusammenfassen, ergibt sich ein klares Bild: Das Minimum im Sterbegeschehen lag im Jahr 2020 (Grafik 3).

Ein kritischer Leser könnte nun wiederum vermuten, dass es innerhalb des Jahres 2020 möglicherweise starke Ausschläge nach oben bei einzelnen Jahrgängen gegeben haben könnte, die später durch Ausschläge nach unten ausgeglichen wurden – und dass diese Schwankungen in der jährlichen Übersicht nicht sichtbar sind. Doch auch das trifft nicht zu. Ein Blick auf die wöchentlichen Sterberaten zeigt, dass die ersten acht Monate der Pandemie keine nennenswerten Auffälligkeiten aufweisen. Es bleibt dabei: Die Rohdaten des Statistischen Bundesamtes bestätigen zweifelsfrei, dass die ersten acht Monate der Pandemie das historische Minimum im Sterbegeschehen darstellen. (Für die Fachleute sei angemerkt, dass im gleichen Zeitraum die Lebenserwartung die historischen Höchststände erreicht hatte – Grafik 4.)

So konstruierte das Amt aus einem Minimum ein Maximum:
Zur Erinnerung: Die Rohdaten des Statistischen Bundesamtes, die in den jährlichen Sterbetafeln zweifelsfrei dokumentiert sind, zeigen für das Jahr 2020 eindeutig ein Minimum im Sterbegeschehen. Aus diesen »in Stein gemeißelten« Zahlen ein Maximum zu »konstruieren«, ohne die Rohdaten selbst zu verändern, scheint auf den ersten Blick eine unlösbare Aufgabe. Jeder Student würde an einer solchen Herausforderung scheitern. Doch das Statistische Bundesamt hat einen kreativen Weg gefunden - ein Meisterstück gezielter Manipulation. In fünf Schritten zeigt sich, wie diese Täuschung der Öffentlichkeit umgesetzt wurde:
(1) Ignorieren der Sterberaten: Die präzisen, objektiven und leicht verständlichen Sterberaten aus den eigenen Sterbetafeln wurden konsequent ignoriert und verschwiegen. Diese Daten widersprachen dem gewünschten Narrativ und wurden daher gezielt ausgeklammert.
(2) Fokus auf absolute Todeszahlen: Die Aufmerksamkeit wurde stattdessen auf die absolute Zahl der Todesfälle gelenkt. Diese wirkt allein durch ihre schiere Größe dramatisch und emotionalisiert die Diskussion. Ein entscheidender Faktor wurde dabei ignoriert: Die absolute Zahl der Todesfälle steigt aufgrund der demografischen Entwicklung jedes Jahr an. Viele Menschen verstehen diesen Zusammenhang nicht und verbinden die steigenden Zahlen fälschlicherweise mit der vermeintlichen Pandemie.
(3) Einführung der Übersterblichkeit als neue Kennzahl: Erst ab Beginn der „Pandemie“ wurde die Kennzahl "Übersterblichkeit" eingeführt – und dies mit einer fragwürdigen Methode, die systematisch überhöhte Werte lieferte. Diese Kennzahl wurde regelmäßig, oft monatlich oder sogar wöchentlich, berechnet und diente als ständige Grundlage für alarmierende Schlagzeilen.
(4) Intensive Öffentlichkeitsarbeit: Durch eine breit angelegte Kampagne wurden die manipulativen Kennzahlen gezielt in den Fokus gerückt. Pressemitteilungen, Podcasts und öffentliche Auftritte konzentrierten sich fast ausschließlich auf die absoluten Todeszahlen und die Übersterblichkeit. Ziel war es, den Eindruck einer dramatischen Situation in der Öffentlichkeit zu verstärken.
(5) Bekämpfen kritischer Stimmen: Kritiker, die die Schwächen und manipulativen Aspekte dieser Methoden aufdeckten, wurden systematisch diskreditiert. Ihre Glaubwürdigkeit und Kompetenz wurden öffentlich infrage gestellt, um das sorgsam konstruierte Narrativ zu schützen.
Ohne diesen begleitenden Statistik-Betrug wäre das gesamte Pandemie-Theater meiner Meinung nach nicht möglich gewesen. Wer aus einem faktischen Minimum ein scheinbares Maximum "erschafft", handelt betrügerisch. Die Folgen dieses Betruges sind gravierend. Denken wir an die Angst, die in der Bevölkerung geschürt wurde – die Angst, bald sterben zu müssen. Denken wir an Masken, Abstandsregeln, isolierte ältere Menschen, Kinderimpfungen und all die Maßnahmen, die unter anderem auf diese falsche Statistik zurückgehen.
Wollen wir Bürger uns das gefallen lassen?
Wenn wir als Bürger zulassen, dass ein derart offensichtlicher und nachprüfbarer Täuschungsversuch ohne Konsequenzen bleibt, dann gefährdet das nicht nur die Integrität unserer Institutionen – es untergräbt das Fundament unserer Gesellschaft. In der DDR feierte man öffentlich Planerfüllung und Übererfüllung, während die Regale leer blieben. Damals wusste jeder: Statistik war ein Propagandainstrument. Niemand traute den Zahlen, die das Staatsfernsehen verkündete.
Während der Pandemie war es anders. Die Menschen vertrauten den Mitteilungen des Statistischen Bundesamtes und des RKI – blind. Die Enthüllungen durch den "RKI-Leak" haben gezeigt, dass auch das Robert-Koch-Institut nicht der Wissenschaft, sondern den Weisungen des Gesundheitsministers und militärischen Vorgaben folgte. Warum sollte es beim Statistischen Bundesamt anders gewesen sein? Diese Behörde ist dem Innenministerium unterstellt und somit ebenfalls weisungsgebunden.
Die Beweise für Täuschung liegen offen zutage. Es braucht keinen Whistleblower, keine geheimen Enthüllungen: Die Rohdaten des Statistischen Bundesamtes sprechen für sich. Sie sind öffentlich einsehbar – klar und unmissverständlich. Die Daten, die Tabellen, die Veröffentlichungen des Amtes selbst – sie sind die Anklageschrift. Sie zeigen, was wirklich war. Nicht mehr und nicht weniger.
Und wir? Was tun wir? Schweigen wir? Oder fordern wir endlich ein, was unser Recht ist? Wir Bürger dürfen das nicht hinnehmen. Es ist Zeit, unsere Behörden zur Rechenschaft zu ziehen. Diese Institutionen arbeiten nicht für sich – sie arbeiten für uns. Wir finanzieren sie, und wir haben das Recht, Transparenz und Verantwortung einzufordern. Manipulationen wie diese müssen aufgearbeitet werden und dürfen nie wieder geschehen. Die Strukturen, die solche Fehlentwicklungen in unseren Behörden ermöglicht haben, müssen offengelegt werden. Denn eine Demokratie lebt von Vertrauen – und Vertrauen muss verdient werden. Jeden Tag aufs Neue.
.
.
MARCEL BARZ, Jahrgang 1975, war Offizier der Bundeswehr und studierte Wirtschafts- und Organisationswissenschaften sowie Wirtschaftsinformatik. Er war Gründer und Geschäftsführer einer Softwarefirma, die sich auf Datenanalyse und Softwareentwicklung spezialisiert hatte. Im August 2021 veröffentlichte Barz den Videovortrag »Die Pandemie in den Rohdaten«, der über eine Million Aufrufe erzielte. Seitdem macht er als "Erbsenzähler" auf Widersprüche in amtlichen Statistiken aufmerksam.
-
 @ 06b7819d:d1d8327c
2024-11-27 11:53:39
@ 06b7819d:d1d8327c
2024-11-27 11:53:39Understanding Figure and Ground: How We Perceive the World
The concept of “figure and ground” originates from Gestalt psychology but takes on profound implications in Marshall McLuhan’s media theory. At its core, figure and ground describe the relationship between what we focus on (the “figure”) and the larger context that shapes and influences it (the “ground”). Together, they illustrate how perception is shaped not only by what we pay attention to, but by what we overlook.
Figure and Ground in Perception
Imagine looking at a photo of a tree in a forest. The tree might stand out as the figure—it’s what your attention is drawn to. However, the forest, the sky, and even the light conditions around the tree create the ground. These background elements are not immediately in focus, but they are essential to understanding the tree’s existence and meaning within its environment.
Our minds are naturally inclined to separate figure from ground, but this process often distorts our perception. By focusing on one aspect, we tend to neglect the broader context that gives it meaning. This principle applies not just to visual perception but also to the way we experience media, technology, and culture.
McLuhan’s Take: Media as Ground
For McLuhan, media and technology are the “ground” upon which all human activity takes place. We often fixate on the “figure” of a medium—the content it delivers—without recognizing the ground, which is the medium itself and its pervasive influence. For example, we might focus on the latest viral video (the figure) without reflecting on how platforms like TikTok (the ground) shape attention spans, social behaviors, and even our cultural norms.
McLuhan famously argued that “the medium is the message,” meaning the medium’s structure and characteristics influence society far more deeply than the specific content it carries. The figure (content) distracts us from examining the ground (medium), which often operates invisibly.
Figure and Ground in Daily Life
Consider smartphones. The apps, messages, and videos we interact with daily are the figures. The ground is the smartphone itself—a device that transforms communication, alters social dynamics, and restructures how we manage time and attention. Focusing solely on what’s displayed on the screen blinds us to the ways the device reshapes our lives.
Rebalancing Perception
To truly understand the impact of media and technology, McLuhan urged us to become aware of the ground. By stepping back and observing how the environment shapes the figure, we can better grasp the larger systems at work. This requires a shift in perspective: instead of asking “What does this content mean?” we might ask “How does this medium affect the way I think, behave, or relate to others?”
Understanding figure and ground helps us see the world more holistically, uncovering hidden dynamics that shape perception and culture. It’s a reminder that what we take for granted—what fades into the background—is often the most transformative force of all.
-
 @ 47750177:8969e41a
2024-10-05 17:56:42
@ 47750177:8969e41a
2024-10-05 17:56:4225.0 Release Notes
Bitcoin Core version 25.0 is now available from:
This release includes new features, various bug fixes and performance improvements, as well as updated translations.
Please report bugs using the issue tracker at GitHub:
https://github.com/bitcoin/bitcoin/issues
To receive security and update notifications, please subscribe to:
https://bitcoincore.org/en/list/announcements/join/
How to Upgrade
If you are running an older version, shut it down. Wait until it has completely shut down (which might take a few minutes in some cases), then run the installer (on Windows) or just copy over
/Applications/Bitcoin-Qt(on macOS) orbitcoind/bitcoin-qt(on Linux).Upgrading directly from a version of Bitcoin Core that has reached its EOL is possible, but it might take some time if the data directory needs to be migrated. Old wallet versions of Bitcoin Core are generally supported.
Compatibility
Bitcoin Core is supported and extensively tested on operating systems using the Linux kernel, macOS 10.15+, and Windows 7 and newer. Bitcoin Core should also work on most other Unix-like systems but is not as frequently tested on them. It is not recommended to use Bitcoin Core on unsupported systems.
Notable changes
P2P and network changes
- Transactions of non-witness size 65 bytes and above are now allowed by mempool and relay policy. This is to better reflect the actual afforded protections against CVE-2017-12842 and open up additional use-cases of smaller transaction sizes. (#26265)
New RPCs
- The scanblocks RPC returns the relevant blockhashes from a set of descriptors by scanning all blockfilters in the given range. It can be used in combination with the getblockheader and rescanblockchain RPCs to achieve fast wallet rescans. Note that this functionality can only be used if a compact block filter index (-blockfilterindex=1) has been constructed by the node. (#23549)
Updated RPCs
- All JSON-RPC methods accept a new named
parameter called
argsthat can contain positional parameter values. This is a convenience to allow some parameter values to be passed by name without having to name every value. The python test framework andbitcoin-clitool both take advantage of this, so for example:
sh bitcoin-cli -named createwallet wallet_name=mywallet load_on_startup=1Can now be shortened to:
sh bitcoin-cli -named createwallet mywallet load_on_startup=1-
The
verifychainRPC will now returnfalseif the checks didn't fail, but couldn't be completed at the desired depth and level. This could be due to missing data while pruning, due to an insufficient dbcache or due to the node being shutdown before the call could finish. (#25574) -
sendrawtransactionhas a new, optional argument,maxburnamountwith a default value of0. Any transaction containing an unspendable output with a value greater thanmaxburnamountwill not be submitted. At present, the outputs deemed unspendable are those with scripts that begin with anOP_RETURNcode (known as 'datacarriers'), scripts that exceed the maximum script size, and scripts that contain invalid opcodes. -
The
testmempoolacceptRPC now returns 2 additional results within the "fees" result: "effective-feerate" is the feerate including fees and sizes of transactions validated together if package validation was used, and also includes any modified fees from prioritisetransaction. The "effective-includes" result lists the wtxids of transactions whose modified fees and sizes were used in the effective-feerate (#26646). -
decodescriptmay now infer a Miniscript descriptor under P2WSH context if it is not lacking information. (#27037) -
finalizepsbtis now able to finalize a transaction with inputs spending Miniscript-compatible P2WSH scripts. (#24149)
Changes to wallet related RPCs can be found in the Wallet section below.
Build System
- The
--enable-upnp-defaultand--enable-natpmp-defaultoptions have been removed. If you want to use port mapping, you can configure it using a .conf file, or by passing the relevant options at runtime. (#26896)
Updated settings
-
If the
-checkblocksor-checkleveloptions are explicitly provided by the user, but the verification checks cannot be completed due to an insufficient dbcache, Bitcoin Core will now return an error at startup. (#25574) -
Ports specified in
-portand-rpcportoptions are now validated at startup. Values that previously worked and were considered valid can now result in errors. (#22087) -
Setting
-blocksonlywill now reduce the maximum mempool memory to 5MB (users may still use-maxmempoolto override). Previously, the default 300MB would be used, leading to unexpected memory usage for users running with-blocksonlyexpecting it to eliminate mempool memory usage.
As unused mempool memory is shared with dbcache, this also reduces the dbcache size for users running with
-blocksonly, potentially impacting performance. - Setting-maxconnections=0will now disable-dnsseedand-listen(users may still set them to override).Changes to GUI or wallet related settings can be found in the GUI or Wallet section below.
New settings
- The
shutdownnotifyoption is used to specify a command to execute synchronously before Bitcoin Core has begun its shutdown sequence. (#23395)
Wallet
- The
minconfoption, which allows a user to specify the minimum number of confirmations a UTXO being spent has, and themaxconfoption, which allows specifying the maximum number of confirmations, have been added to the following RPCs in #25375: fundrawtransactionsendwalletcreatefundedpsbt-
sendall -
Added a new
next_indexfield in the response inlistdescriptorsto have the same format asimportdescriptors(#26194) -
RPC
listunspentnow has a new argumentinclude_immature_coinbaseto include coinbase UTXOs that don't meet the minimum spendability depth requirement (which before were silently skipped). (#25730) -
Rescans for descriptor wallets are now significantly faster if compact block filters (BIP158) are available. Since those are not constructed by default, the configuration option "-blockfilterindex=1" has to be provided to take advantage of the optimization. This improves the performance of the RPC calls
rescanblockchain,importdescriptorsandrestorewallet. (#25957) -
RPC
unloadwalletnow fails if a rescan is in progress. (#26618) -
Wallet passphrases may now contain null characters. Prior to this change, only characters up to the first null character were recognized and accepted. (#27068)
-
Address Purposes strings are now restricted to the currently known values of "send", "receive", and "refund". Wallets that have unrecognized purpose strings will have loading warnings, and the
listlabelsRPC will raise an error if an unrecognized purpose is requested. (#27217) -
In the
createwallet,loadwallet,unloadwallet, andrestorewalletRPCs, the "warning" string field is deprecated in favor of a "warnings" field that returns a JSON array of strings to better handle multiple warning messages and for consistency with other wallet RPCs. The "warning" field will be fully removed from these RPCs in v26. It can be temporarily re-enabled during the deprecation period by launching bitcoind with the configuration option-deprecatedrpc=walletwarningfield. (#27279) -
Descriptor wallets can now spend coins sent to P2WSH Miniscript descriptors. (#24149)
GUI changes
- The "Mask values" is a persistent option now. (gui#701)
- The "Mask values" option affects the "Transaction" view now, in addition to the "Overview" one. (gui#708)
REST
- A new
/rest/deploymentinfoendpoint has been added for fetching various state info regarding deployments of consensus changes. (#25412)
Binary verification
- The binary verification script has been updated. In previous releases it would verify that the binaries had been signed with a single "release key". In this release and moving forward it will verify that the binaries are signed by a threshold of trusted keys. For more details and examples, see: https://github.com/bitcoin/bitcoin/blob/master/contrib/verify-binaries/README.md (#27358)
Low-level changes
RPC
- The JSON-RPC server now rejects requests where a parameter is specified multiple times with the same name, instead of silently overwriting earlier parameter values with later ones. (#26628)
- RPC
listsinceblocknow accepts an optionallabelargument to fetch incoming transactions having the specified label. (#25934) - Previously
setban,addpeeraddress,walletcreatefundedpsbt, methods allowed non-boolean and non-null values to be passed as boolean parameters. Any string, number, array, or object value that was passed would be treated as false. After this change, passing any value excepttrue,false, ornullnow triggers a JSON value is not of expected type error. (#26213)
Credits
Thanks to everyone who directly contributed to this release:
- 0xb10c
- 721217.xyz
- @RandyMcMillan
- amadeuszpawlik
- Amiti Uttarwar
- Andrew Chow
- Andrew Toth
- Anthony Towns
- Antoine Poinsot
- Aurèle Oulès
- Ben Woosley
- Bitcoin Hodler
- brunoerg
- Bushstar
- Carl Dong
- Chris Geihsler
- Cory Fields
- David Gumberg
- dergoegge
- Dhruv Mehta
- Dimitris Tsapakidis
- dougEfish
- Douglas Chimento
- ekzyis
- Elichai Turkel
- Ethan Heilman
- Fabian Jahr
- FractalEncrypt
- furszy
- Gleb Naumenko
- glozow
- Greg Sanders
- Hennadii Stepanov
- hernanmarino
- ishaanam
- ismaelsadeeq
- James O'Beirne
- jdjkelly@gmail.com
- Jeff Ruane
- Jeffrey Czyz
- Jeremy Rubin
- Jesse Barton
- João Barbosa
- JoaoAJMatos
- John Moffett
- Jon Atack
- Jonas Schnelli
- jonatack
- Joshua Kelly
- josibake
- Juan Pablo Civile
- kdmukai
- klementtan
- Kolby ML
- kouloumos
- Kristaps Kaupe
- laanwj
- Larry Ruane
- Leonardo Araujo
- Leonardo Lazzaro
- Luke Dashjr
- MacroFake
- MarcoFalke
- Martin Leitner-Ankerl
- Martin Zumsande
- Matt Whitlock
- Matthew Zipkin
- Michael Ford
- Miles Liu
- mruddy
- Murray Nesbitt
- muxator
- omahs
- pablomartin4btc
- Pasta
- Pieter Wuille
- Pttn
- Randall Naar
- Riahiamirreza
- roconnor-blockstream
- Russell O'Connor
- Ryan Ofsky
- S3RK
- Sebastian Falbesoner
- Seibart Nedor
- sinetek
- Sjors Provoost
- Skuli Dulfari
- SomberNight
- Stacie Waleyko
- stickies-v
- stratospher
- Suhas Daftuar
- Suriyaa Sundararuban
- TheCharlatan
- Vasil Dimov
- Vasil Stoyanov
- virtu
- w0xlt
- willcl-ark
- yancy
- Yusuf Sahin HAMZA
As well as to everyone that helped with translations on Transifex.
-
 @ 5a261a61:2ebd4480
2025-01-30 09:37:26
@ 5a261a61:2ebd4480
2025-01-30 09:37:26The idea of the Bean Bag Game is quite ingenious. I read about it on a BDSM-positive blog. Here’s how it works:
-
Setup:
-
Take a small cloth bag and add 10 white beans (rewards/pleasure) and 10 black beans (punishment/discomfort).
-
When it’s time to play, draw two beans:
-
First bean (the tone): Determines if the activity will be pleasant (white) or uncomfortable (black).
-
Second bean (the task): Decides whether you get a reward (white) or punishment (black).
-
Combination Interpretations:
-
Black + Black\ "No fun, just work."
-
Boring/challenging tasks you’d normally postpone: window cleaning, scrubbing bathroom tiles, polishing shoes.
-
Could also mean no playtime (e.g., "Go straight to bed"). Pure duty – no pleasure, only discipline.
-
White + Black\ "Work with a twist."
-
Punishment or chores, but with a kinky edge:
-
Clean the bathroom wearing a vibrating butt plug.
-
Wash dishes with nipple clamps; add a clothespin to your body for every minute over the time limit.
-
-
Still no orgasms – the black bean ensures denial.
-
Black + White\ "Pleasure with pain (or humiliation)."
-
Mix stimulation and discomfort:
-
Ride a dildo with weighted nipple clamps.
-
Give a "lap dance" to a teddy bear with a strapon.
-
Chat online as a "perfect plaything" for others without touching yourself.
-
-
Again, no orgasms – the black bean overrules the white.
-
White + White\ "Lucky draw… but denial is optional."
-
Freedom to indulge, though I often choose self-denial anyway. Examples:
-
Edge for 30 minutes, then ask permission to climax (50% chance).
-
Use toys freely, but end the session frustrated.
-
The Dynamic Ratio Twist:
-
The starting 10:10 ratio isn’t fixed. Adjust it based on behavior:
-
Good deeds? Swap a black bean for a white one.
-
Mistakes? Replace a white bean with a black one.
-
Single beans can also decide smaller stakes, like:
-
"Should this edge turn into a ruined orgasm?"
-
"Do I deserve dessert tonight?"
Why It Works:
-
Control: The beans dictate your fate, but you tweak the odds through obedience.
-
Flexibility: Use pairs for major tasks, single beans for quick decisions.
-
Psychological tease: Even "white + white" can mean denial – because you choose the rules.
-
-
 @ dd664d5e:5633d319
2024-06-24 06:05:05
@ dd664d5e:5633d319
2024-06-24 06:05:05The new Great Library
We have all heard tales of Amazon or other booksellers banning customers from their bookstores or censoring/editing purchased books. The famous Project Gutenberg, and similar organizations, are performing a good work, to help protect many of our precious books from this fate, but it is merely a centralized website and therefore not censorship resistant. Also, it mostly posts books in English or German.
So, we at nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz have decided to move Project Gutenberg to Nostr and house it in the most distributed way possible: on relays. Specifically, our new, public Citadel relay for out-of-print books (and other documents), but also on any relay, anywhere.
And, because we are a very humble group, we're naming the effort "Alexandria". And the first book to be printed on Nostr is the Bible because obviously.
Why on relays?
Well, why not on relays? Relays are one of the few widely-distributed databases for documentation in existence. The relay database spans the entire globe and anyone can maintain their own relay on their personal computer or mobile phone.
That means that anyone can house their own books. Which books are their own? Any books they have in their own possession. Any books someone would have to physically pry out of their cold, dead, computer.
Notes are perfect for publishing
Once we begin generating eBooks from notes with an associated header (which will be quite easy to do, so long as they are written in markdown or similar), they will also be readable, downloadable, and storable in ePub format (see Pandoc). And it is, after all, only a matter of time until someone enterprising makes an ePaper Nostr client for calmer reading of notes, and then you can download and read them, without having to bother converting beforehand, which maintains their Nostr-navigation.
The new event kind 30040 allows us to take any sort of note containing any sort of characters and create a type of "note collection" or "book of notes", "journal of notes", "magazine of notes". And it can be nested or embedded in other notes, creating any sort of note-combination and note-hierarchy you can think of, only limited in size by the ability of your computer to processes the relationships.
Save the Zettels
The associated kind 30041 adds the prospect of breaking longer texts or articles up into sections or snippets (called "Zettel" in German). We can then collect or refer to particular bits of a longer text (like a chart, elegant paragraph or definition, data table), directly. Anyone can create such snippets, even of texts they didn't write, as they can add a reference to the original publication in the tags of the new event.
This means we no longer have to "copy-paste" or quote other people's works, we can simply tie them in. If we worry about them being deleted, we can fork them to create our own, digitally-linked version, and then tie that in. This means that source material can be tied to the new material, and you can trace back to the source easily (using Nostr IDs and tags, which are signed identifiers) and see who else is branching out from that source or discussing that source.
It's gonna be HUGE!
We are making a big, beautiful library... and you are going to build it for us. Anyone, anywhere can therefore publish or republish any document they wish, with Nostr, and store it wherever they have a relay, and view it on any client willing to display it.
You will own something and be happy.
-
 @ 06b7819d:d1d8327c
2024-11-26 16:57:14
@ 06b7819d:d1d8327c
2024-11-26 16:57:14Hanlon’s Razor is a philosophical principle or adage that states:
“Never attribute to malice that which is adequately explained by stupidity.”
It suggests that when trying to understand someone’s actions, it is often more reasonable to assume a lack of knowledge, competence, or foresight rather than intentional harm or ill will. The principle encourages people to avoid jumping to conclusions about malicious intent and instead consider simpler, more mundane explanations.
Hanlon’s Razor is often used in problem-solving, interpersonal interactions, and organizational settings to promote understanding and reduce conflict. It’s part of a broader family of “razors,” which are rules of thumb used to simplify decision-making.
-
 @ 9e69e420:d12360c2
2025-01-19 04:48:31
@ 9e69e420:d12360c2
2025-01-19 04:48:31A new report from the National Sports Shooting Foundation (NSSF) shows that civilian firearm possession exceeded 490 million in 2022. The total from 1990 to 2022 is estimated at 491.3 million firearms. In 2022, over ten million firearms were domestically produced, leading to a total of 16,045,911 firearms available in the U.S. market.
Of these, 9,873,136 were handguns, 4,195,192 were rifles, and 1,977,583 were shotguns. Handgun availability aligns with the concealed carry and self-defense market, as all states allow concealed carry, with 29 having constitutional carry laws.
-
 @ c69b71dc:426ba763
2025-01-18 15:39:35
@ c69b71dc:426ba763
2025-01-18 15:39:35Chef's notes
This raw vegan curry ramen is a vibrant, nourishing dish packed with fresh vegetables and a rich, creamy coconut curry broth. It’s quick to prepare, full of flavour, and the perfect guilt-free comfort food! 🌱 Feel free to use your favourite veggies👩🏼🍳
Details
- ⏲️ Prep time: 20 min.
- 🍳 Cook time: 0
- 🍽️ Servings: 2
Ingredients
- 500g or 2 packs kelp noodles
- 1/2 Lemon juice ( 1/4 for soaking and 1/4 for the soup
- Salt
- Fresh vegetables of your choice, such as: 4 medium mushrooms, 4 leaves red cabbage, 2 carrots (julienned or peeled into strips), 1 Celery stick (diced)
- 2 cups coconut milk (or coconut cream diluted with water)
- 1/2 flesh of a Coconut (optional, if using fresh coconuts) otherwise more coconut cream
- 1 thumb of fresh ginger
- 1 thumb of fresh turmeric
- 2 tbsp light miso paste
- 2 pitted dates
- 2 tbsp cashews
- 1 clove garlic
- 1 tsp curry powder or pepper (optional)
Directions
- Prepare the Noodles: Rinse the kelp noodles thoroughly. Then soak them in warm water with a squeeze of lemon juice and a pinch of salt for 10 minutes to soften.
- Prep the Vegetables: Thinly slice or julienne carrots, dice celery, thinly cut mushrooms, cut the red cabbage into thin strips.
- Make the Broth: In a blender, combine the following: 2 cups coconut milk (or coconut cream diluted with water if fresh coconuts are unavailable), ginger, turmeric, 1/4 juice of 1 lemon, light miso paste, pitted dates, cashews, garlic, salt, curry powder
- Blend on high speed for about 3 to 4 minutes until the broth is smooth and slightly warm. Do not overheat!
- Assemble the Ramen: Drain the kelp noodles and place them in serving bowls. Arrange the prepped vegetables on top of the noodles. Pour the warm curry broth over the noodles and vegetables.
- Serve immediately and enjoy your raw vegan ramen with chopsticks for an authentic touch!
-
 @ 3bf0c63f:aefa459d
2024-03-23 08:57:08
@ 3bf0c63f:aefa459d
2024-03-23 08:57:08Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ dd664d5e:5633d319
2024-06-23 07:03:28
@ dd664d5e:5633d319
2024-06-23 07:03:28I've been dealing with a lot of aspiring IT people, lately, and it has me sort of jaded.
I'm trying to think of the level of competence I would expect of someone like myself because it has changed, dramatically, since I started out, 26 years ago. I've only now managed to catch up enough to feel "requalified" for my own profession, so I thought I'd write it down for all of you, so that you know what to look for.
As in, what is the new "industry standard" knowledge level for a software business analyst?
If I were hiring a business analyst today, I'd ask...
- What do e-mail, FTP, and UML have in common?
- What is the difference between an intranet and the Internet? Name the four Internet layers and one protocol for each.
- What are unit tests and integration tests and what are they useful for? Who should write them? Who should be looking at the results?
- What is a build server and why use one? What is the difference between continuous integration and continuous deployment?
- Please explain the three source control commands: commit, push, and pull.
- Please explain the three Linux commands: pwd, ls, cat.
- How do software branches work? What is a merge conflict? What are pull requests?
- What is the difference between an activity diagram, a state-machine diagram, and a class diagram and when is it best to use which?
- What are DDD and TDD? What purpose do they serve?
- What are use cases and user stories? When is it best to use which? What is gherkin?
- What is the difference between stateful and stateless?
- What is agile programming?
- Explain the difference between Kanban, Xtreme Programming, and Scrum, and when is it best to use which?
- What is the difference between functional and object-oriented programming? Why use one, rather than the other?
- What are wireframes, mockups, and prototypes?
- Name two network topologies and give an example for an implementation of each.
- What are XML, Json, and Yaml and why use one, rather than another?
- What is an ORM and why use one? What are validators?
- Name three types of databases and a use case they are ideal for.
- Explain the importance of data sets to machine learning.
-
 @ 47750177:8969e41a
2024-10-05 17:40:25
@ 47750177:8969e41a
2024-10-05 17:40:2528.0 Release Notes
Bitcoin Core version 28.0 is now available from:
This release includes new features, various bug fixes and performance improvements, as well as updated translations.
Please report bugs using the issue tracker at GitHub:
https://github.com/bitcoin/bitcoin/issues
To receive security and update notifications, please subscribe to:
https://bitcoincore.org/en/list/announcements/join/
How to Upgrade
If you are running an older version, shut it down. Wait until it has completely shut down (which might take a few minutes in some cases), then run the installer (on Windows) or just copy over
/Applications/Bitcoin-Qt(on macOS) orbitcoind/bitcoin-qt(on Linux).Upgrading directly from a version of Bitcoin Core that has reached its EOL is possible, but it might take some time if the data directory needs to be migrated. Old wallet versions of Bitcoin Core are generally supported.
Running Bitcoin Core binaries on macOS requires self signing.
cd /path/to/bitcoin-28.0/bin xattr -d com.apple.quarantine bitcoin-cli bitcoin-qt bitcoin-tx bitcoin-util bitcoin-wallet bitcoind test_bitcoin codesign -s - bitcoin-cli bitcoin-qt bitcoin-tx bitcoin-util bitcoin-wallet bitcoind test_bitcoinCompatibility
Bitcoin Core is supported and extensively tested on operating systems using the Linux Kernel 3.17+, macOS 11.0+, and Windows 7 and newer. Bitcoin Core should also work on most other UNIX-like systems but is not as frequently tested on them. It is not recommended to use Bitcoin Core on unsupported systems.
Notable changes
Testnet4/BIP94 support
Support for Testnet4 as specified in BIP94 has been added. The network can be selected with the
-testnet4option and the section header is also named[testnet4].While the intention is to phase out support for Testnet3 in an upcoming version, support for it is still available via the known options in this release. (#29775)
Windows Data Directory
The default data directory on Windows has been moved from
C:\Users\Username\AppData\Roaming\BitcointoC:\Users\Username\AppData\Local\Bitcoin. Bitcoin Core will check the existence of the old directory first and continue to use that directory for backwards compatibility if it is present. (#27064)JSON-RPC 2.0 Support
The JSON-RPC server now recognizes JSON-RPC 2.0 requests and responds with strict adherence to the specification. See JSON-RPC-interface.md for details. (#27101)
JSON-RPC clients may need to be updated to be compatible with the JSON-RPC server. Please open an issue on GitHub if any compatibility issues are found.
libbitcoinconsensus Removal
The libbitcoin-consensus library was deprecated in 27.0 and is now completely removed. (#29648)
P2P and Network Changes
- Previously if Bitcoin Core was listening for P2P connections, either using
default settings or via
bind=addr:portit would always also bind to127.0.0.1:8334to listen for Tor connections. It was not possible to switch this off, even if the node didn't use Tor. This has been changed and nowbind=addr:portresults in binding onaddr:portonly. The default behavior of binding to0.0.0.0:8333and127.0.0.1:8334has not been changed.
If you are using a
bind=...configuration withoutbind=...=onionand rely on the previous implied behavior to accept incoming Tor connections at127.0.0.1:8334, you need to now make this explicit by usingbind=... bind=127.0.0.1:8334=onion. (#22729)-
Bitcoin Core will now fail to start up if any of its P2P binds fail, rather than the previous behaviour where it would only abort startup if all P2P binds had failed. (#22729)
-
UNIX domain sockets can now be used for proxy connections. Set
-onionor-proxyto the local socket path with the prefixunix:(e.g.-onion=unix:/home/me/torsocket). (#27375) -
UNIX socket paths are now accepted for
-zmqpubrawblockand-zmqpubrawtxwith the format-zmqpubrawtx=unix:/path/to/file(#27679) -
Additional "in" and "out" flags have been added to
-whitelistto control whether permissions apply to inbound connections and/or manual ones (default: inbound only). (#27114) -
Transactions having a feerate that is too low will be opportunistically paired with their child transactions and submitted as a package, thus enabling the node to download 1-parent-1-child packages using the existing transaction relay protocol. Combined with other mempool policies, this change allows limited "package relay" when a parent transaction is below the mempool minimum feerate. Topologically Restricted Until Confirmation (TRUC) parents are additionally allowed to be below the minimum relay feerate (i.e., pay 0 fees). Use the
submitpackageRPC to submit packages directly to the node. Warning: this P2P feature is limited (unlike thesubmitpackageinterface, a child with multiple unconfirmed parents is not supported) and not yet reliable under adversarial conditions. (#28970)
Mempool Policy Changes
-
Transactions with version number set to 3 are now treated as standard on all networks (#29496), subject to opt-in Topologically Restricted Until Confirmation (TRUC) transaction policy as described in BIP 431. The policy includes limits on spending unconfirmed outputs (#28948), eviction of a previous descendant if a more incentive-compatible one is submitted (#29306), and a maximum transaction size of 10,000vB (#29873). These restrictions simplify the assessment of incentive compatibility of accepting or replacing TRUC transactions, thus ensuring any replacements are more profitable for the node and making fee-bumping more reliable.
-
Pay To Anchor (P2A) is a new standard witness output type for spending, a newly recognised output template. This allows for key-less anchor outputs, with compact spending conditions for additional efficiencies on top of an equivalent
sh(OP_TRUE)output, in addition to the txid stability of the spending transaction. N.B. propagation of this output spending on the network will be limited until a sufficient number of nodes on the network adopt this upgrade. (#30352) -
Limited package RBF is now enabled, where the proposed conflicting package would result in a connected component, aka cluster, of size 2 in the mempool. All clusters being conflicted against must be of size 2 or lower. (#28984)
-
The default value of the
-mempoolfullrbfconfiguration option has been changed from 0 to 1, i.e.mempoolfullrbf=1. (#30493)
Updated RPCs
-
The
dumptxoutsetRPC now returns the UTXO set dump in a new and improved format. Correspondingly, theloadtxoutsetRPC now expects this new format in the dumps it tries to load. Dumps with the old format are no longer supported and need to be recreated using the new format to be usable. (#29612) -
AssumeUTXO mainnet parameters have been added for height 840,000. This means the
loadtxoutsetRPC can now be used on mainnet with the matching UTXO set from that height. (#28553) -
The
warningsfield ingetblockchaininfo,getmininginfoandgetnetworkinfonow returns all the active node warnings as an array of strings, instead of a single warning. The current behaviour can be temporarily restored by running Bitcoin Core with the configuration option-deprecatedrpc=warnings. (#29845) -
Previously when using the
sendrawtransactionRPC and specifying outputs that are already in the UTXO set, an RPC error code of-27with the message "Transaction already in block chain" was returned in response. The error message has been changed to "Transaction outputs already in utxo set" to more accurately describe the source of the issue. (#30212) -
The default mode for the
estimatesmartfeeRPC has been updated fromconservativetoeconomical, which is expected to reduce over-estimation for many users, particularly if Replace-by-Fee is an option. For users that require high confidence in their fee estimates at the cost of potentially over-estimating, theconservativemode remains available. (#30275) -
RPC
scantxoutsetnow returns 2 new fields in the "unspents" JSON array:blockhashandconfirmations. See the scantxoutset help for details. (#30515) -
RPC
submitpackagenow allows 2 new arguments to be passed:maxfeerateandmaxburnamount. See the subtmitpackage help for details. (#28950)
Changes to wallet-related RPCs can be found in the Wallet section below.
Updated REST APIs
- Parameter validation for
/rest/getutxoshas been improved by rejecting truncated or overly large txids and malformed outpoint indices via raising an HTTP_BAD_REQUEST "Parse error". These requests were previously handled silently. (#30482, #30444)
Build System
-
GCC 11.1 or later, or Clang 16.0 or later, are now required to compile Bitcoin Core. (#29091, #30263)
-
The minimum required glibc to run Bitcoin Core is now 2.31. This means that RHEL 8 and Ubuntu 18.04 (Bionic) are no-longer supported. (#29987)
-
--enable-lcov-branch-coveragehas been removed, given incompatibilities between lcov version 1 & 2.LCOV_OPTSshould be used to set any options instead. (#30192)
Updated Settings
- When running with
-alertnotify, an alert can now be raised multiple times instead of just once. Previously, it was only raised when unknown new consensus rules were activated. Its scope has now been increased to include all kernel warnings. Specifically, alerts will now also be raised when an invalid chain with a large amount of work has been detected. Additional warnings may be added in the future. (#30058)
Changes to GUI or wallet related settings can be found in the GUI or Wallet section below.
Wallet
-
The wallet now detects when wallet transactions conflict with the mempool. Mempool-conflicting transactions can be seen in the
"mempoolconflicts"field ofgettransaction. The inputs of mempool-conflicted transactions can now be respent without manually abandoning the transactions when the parent transaction is dropped from the mempool, which can cause wallet balances to appear higher. (#27307) -
A new
max_tx_weightoption has been added to the RPCsfundrawtransaction,walletcreatefundedpsbt, andsend. It specifies the maximum transaction weight. If the limit is exceeded during funding, the transaction will not be built. The default value is 4,000,000 WU. (#29523) -
A new
createwalletdescriptorRPC allows users to add new automatically generated descriptors to their wallet. This can be used to upgrade wallets created prior to the introduction of a new standard descriptor, such as taproot. (#29130) -
A new RPC
gethdkeyslists all of the BIP32 HD keys in use by all of the descriptors in the wallet. These keys can be used in conjunction withcreatewalletdescriptorto create and add single key descriptors to the wallet for a particular key that the wallet already knows. (#29130) -
The
sendallRPC can now spend unconfirmed change and will include additional fees as necessary for the resulting transaction to bump the unconfirmed transactions' feerates to the specified feerate. (#28979) -
In RPC
bumpfee, if afee_rateis specified, the feerate is no longer restricted to following the wallet's incremental feerate of 5 sat/vb. The feerate must still be at least the sum of the original fee and the mempool's incremental feerate. (#27969)
GUI Changes
-
The "Migrate Wallet" menu allows users to migrate any legacy wallet in their wallet directory, regardless of the wallets loaded. (gui#824)
-
The "Information" window now displays the maximum mempool size along with the mempool usage. (gui#825)
Low-level Changes
Tests
-
The BIP94 timewarp attack mitigation is now active on the
regtestnetwork. (#30681) -
A new
-testdatadiroption has been added totest_bitcointo allow specifying the location of unit test data directories. (#26564)
Blockstorage
- Block files are now XOR'd by default with a key stored in the blocksdir.
Previous releases of Bitcoin Core or previous external software will not be able to read the blocksdir with a non-zero XOR-key.
Refer to the
-blocksxorhelp for more details. (#28052)
Chainstate
- The chainstate database flushes that occur when blocks are pruned will no longer empty the database cache. The cache will remain populated longer, which significantly reduces the time for initial block download to complete. (#28280)
Dependencies
- The dependency on Boost.Process has been replaced with cpp-subprocess, which is contained in source. Builders will no longer need Boost.Process to build with external signer support. (#28981)
Credits
Thanks to everyone who directly contributed to this release: - 0xb10c - Alfonso Roman Zubeldia - Andrew Toth - AngusP - Anthony Towns - Antoine Poinsot - Anton A - Ava Chow - Ayush Singh - Ben Westgate - Brandon Odiwuor - brunoerg - bstin - Charlie - Christopher Bergqvist - Cory Fields - crazeteam - Daniela Brozzoni - David Gumberg - dergoegge - Edil Medeiros - Epic Curious - Fabian Jahr - fanquake - furszy - glozow - Greg Sanders - hanmz - Hennadii Stepanov - Hernan Marino - Hodlinator - ishaanam - ismaelsadeeq - Jadi - Jon Atack - josibake - jrakibi - kevkevin - kevkevinpal - Konstantin Akimov - laanwj - Larry Ruane - Lőrinc - Luis Schwab - Luke Dashjr - MarcoFalke - marcofleon - Marnix - Martin Saposnic - Martin Zumsande - Matt Corallo - Matthew Zipkin - Matt Whitlock - Max Edwards - Michael Dietz - Murch - nanlour - pablomartin4btc - Peter Todd - Pieter Wuille - @RandyMcMillan - RoboSchmied - Roman Zeyde - Ryan Ofsky - Sebastian Falbesoner - Sergi Delgado Segura - Sjors Provoost - spicyzboss - StevenMia - stickies-v - stratospher - Suhas Daftuar - sunerok - tdb3 - TheCharlatan - umiumi - Vasil Dimov - virtu - willcl-ark
As well as to everyone that helped with translations on Transifex.
- Previously if Bitcoin Core was listening for P2P connections, either using
default settings or via
-
 @ dd664d5e:5633d319
2024-06-21 19:11:51
@ dd664d5e:5633d319
2024-06-21 19:11:51Finding Catholics and Catholic-friendly content on Nostr
Obvious Catholics being obvious
nostr:npub1m4ny6hjqzepn4rxknuq94c2gpqzr29ufkkw7ttcxyak7v43n6vvsajc2jl
nostr:npub1k92qsr95jcumkpu6dffurkvwwycwa2euvx4fthv78ru7gqqz0nrs2ngfwd
nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn
nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735
nostr:npub1rcr8h76csgzhdhea4a7tq5w5gydcpg9clgf0cffu6z45rnc6yp5sj7cfuz
nostr:npub1fyd0awkakq4aap70ual7mtlszjle9krffgwnsrkyua2frzmysd8qjj8gvg
nostr:npub1q0fe26apcqeeyqnlre29fqu7ysx0ucm5ly637md3zlvy2xcfsm3s0lsv4r
nostr:npub1dvdcmtp5llrp63jdlmhspe9gffsyu9ew7cu3ld3f9y7k79nxzjxqf4d4rm
nostr:npub1paxyej8f8fh57ny0fr5w2mzp9can9nkcmeu5jaerv68mhrah7t8s795ky6
nostr:npub1tvw3h5xqnuc2aq5zelxp3dy58sz7x9u8e6enkxywmrz70cg2j2zqjes44n
nostr:npub13tahtl9pjw9u5ycruqk84k6sfmkyljsr7y2pc4s840ctlm73fxeq3j6e08
nostr:npub1w4jkwspqn9svwnlrw0nfg0u2yx4cj6yfmp53ya4xp7r24k7gly4qaq30zp
Other good Christian follows
nostr:npub1hqy4zwnvsdmlml4tpgp0kgrruxamfcwpgm4g3q2tr3d2ut3kuxusx73psm
nostr:npub1cpstx8lzhwctunfe80rugz5qsj9ztw8surec9j6mf8phha68dj6qhm8j5e
nostr:npub1ak5kewf6anwkrt0qc8ua907ljkn7wm83e2ycyrpcumjvaf2upszs8r0gwg
nostr:npub1mt8x8vqvgtnwq97sphgep2fjswrqqtl4j7uyr667lyw7fuwwsjgs5mm7cz
nostr:npub1q6ya7kz84rfnw6yjmg5kyttuplwpauv43a9ug3cajztx4g0v48eqhtt3sh
nostr:npub1356t6fpjysx9vdchfg7mryv83w4pcye6a3eeke9zvsje7s2tuv4s4k805u
nostr:npub1kun5628raxpm7usdkj62z2337hr77f3ryrg9cf0vjpyf4jvk9r9smv3lhe
nostr:npub1qf6gsfapq94rj0rcptkpm9sergacmuwrjlgfx5gznjajtvkcx3psfhx6k5
nostr:npub1ll99fcrclkvgff696u8tq9vupw9fulfc8fysdf6gfwp7hassrh2sktxszt
nostr:npub1zy37ecnhpvx4lmxh4spd0898sxdj0ag8m64s9yq499zaxlg7qrqq8c53q6
nostr:npub1rtlqca8r6auyaw5n5h3l5422dm4sry5dzfee4696fqe8s6qgudks7djtfs
nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn
nostr:npub18zqmath26txwfhc70af8axk7pftjre9x7cf0lxkg92nvj2cpfgts8va790
Christian follow list
An exhaustive list of Christians is maintained by nostr:npub1mt8x8vqvgtnwq97sphgep2fjswrqqtl4j7uyr667lyw7fuwwsjgs5mm7cz. Just look at his list on https://listr.lol/
Catholic community
You can also join the community, to reach other catholics (usable on #Nostrudel #Coracle #Amethyst and #Satellite): nostr:naddr1qvzqqqyx7cpzqqnd3dl8hnptg9agfugwmdcmgfl7wcrfjpgfpv28ksq6dnmqc0e8qqyyxct5dphkc6trmu6k9l
Christian topic relay
And always make sure to use the #catholic hashtag, to get onto the top-specific christpill relay (add it to your relay list: wss://christpill.nostr1.com/).
Hope that helps! 😊
-
 @ 3bf0c63f:aefa459d
2024-03-19 14:32:01
@ 3bf0c63f:aefa459d
2024-03-19 14:32:01Censorship-resistant relay discovery in Nostr
In Nostr is not decentralized nor censorship-resistant I said Nostr is centralized. Peter Todd thinks it is centralized by design, but I disagree.
Nostr wasn't designed to be centralized. The idea was always that clients would follow people in the relays they decided to publish to, even if it was a single-user relay hosted in an island in the middle of the Pacific ocean.
But the Nostr explanations never had any guidance about how to do this, and the protocol itself never had any enforcement mechanisms for any of this (because it would be impossible).
My original idea was that clients would use some undefined combination of relay hints in reply tags and the (now defunct)
kind:2relay-recommendation events plus some form of manual action ("it looks like Bob is publishing on relay X, do you want to follow him there?") to accomplish this. With the expectation that we would have a better idea of how to properly implement all this with more experience, Branle, my first working client didn't have any of that implemented, instead it used a stupid static list of relays with read/write toggle -- although it did publish relay hints and kept track of those internally and supportedkind:2events, these things were not really useful.Gossip was the first client to implement a truly censorship-resistant relay discovery mechanism that used NIP-05 hints (originally proposed by Mike Dilger) relay hints and
kind:3relay lists, and then with the simple insight of NIP-65 that got much better. After seeing it in more concrete terms, it became simpler to reason about it and the approach got popularized as the "gossip model", then implemented in clients like Coracle and Snort.Today when people mention the "gossip model" (or "outbox model") they simply think about NIP-65 though. Which I think is ok, but too restrictive. I still think there is a place for the NIP-05 hints,
nprofileandneventrelay hints and specially relay hints in event tags. All these mechanisms are used together in ZBD Social, for example, but I believe also in the clients listed above.I don't think we should stop here, though. I think there are other ways, perhaps drastically different ways, to approach content propagation and relay discovery. I think manual action by users is underrated and could go a long way if presented in a nice UX (not conceived by people that think users are dumb animals), and who knows what. Reliance on third-parties, hardcoded values, social graph, and specially a mix of multiple approaches, is what Nostr needs to be censorship-resistant and what I hope to see in the future.
-
 @ 3ffac3a6:2d656657
2025-02-04 04:31:26
@ 3ffac3a6:2d656657
2025-02-04 04:31:26In the waning days of the 20th century, a woman named Annabelle Nolan was born into an unremarkable world, though she herself was anything but ordinary. A prodigy in cryptography and quantum computing, she would later adopt the pseudonym Satoshi Nakamoto, orchestrating the creation of Bitcoin in the early 21st century. But her legacy would stretch far beyond the blockchain.
Annabelle's obsession with cryptography was not just about securing data—it was about securing freedom. Her work in quantum computing inadvertently triggered a cascade of temporal anomalies, one of which ensnared her in 2011. The event was cataclysmic yet silent, unnoticed by the world she'd transformed. In an instant, she was torn from her era and thrust violently back into the 16th century.
Disoriented and stripped of her futuristic tools, Annabelle faced a brutal reality: survive in a world where her knowledge was both a curse and a weapon. Reinventing herself as Anne Boleyn, she navigated the treacherous courts of Tudor England with the same strategic brilliance she'd used to design Bitcoin. Her intellect dazzled King Henry VIII, but it was the mysterious necklace she wore—adorned with a bold, stylized "B"—that fueled whispers. It was more than jewelry; it was a relic of a forgotten future, a silent beacon for any historian clever enough to decode her true story.
Anne's fate seemed sealed as she ascended to queenship, her influence growing alongside her enemies. Yet beneath the royal intrigue, she harbored a desperate hope: that the symbol around her neck would outlast her, sparking curiosity in minds centuries away. The "B" was her signature, a cryptographic clue embedded in history.
On the scaffold in 1536, as she faced her execution, Anne Boleyn's gaze was unwavering. She knew her death was not the end. Somewhere, in dusty archives and encrypted ledgers, her mark endured. Historians would puzzle over the enigmatic "B," and perhaps one day, someone would connect the dots between a queen, a coin, and a time anomaly born from quantum code.
She wasn't just Anne Boleyn. She was Satoshi Nakamoto, the time-displaced architect of a decentralized future, hiding in plain sight within the annals of history.
-
 @ f9cf4e94:96abc355
2024-12-31 20:18:59
@ f9cf4e94:96abc355
2024-12-31 20:18:59Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( dominictarr ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt (ssb) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia.
Se você está se perguntando de onde diabos veio o nome Scuttlebutt:
Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.

Marinheiros se reunindo em torno da rixa. ( fonte )
Dominic descobriu o termo boato em um artigo de pesquisa que leu.
Em sistemas distribuídos, fofocar é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”.
Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto. Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar. Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário de bordo (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem.
Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. Cada item adicionado a um log do usuário é chamado de mensagem.
Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.

Perspectivas dos participantes
Scuttlebot
O software Pub é conhecido como servidor Scuttlebutt (servidor ssb ), mas também é conhecido como “Scuttlebot” e
sbotna linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial.Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.


Perspectivas dos participantes
Pubs - Hubs
Pubs públicos
| Pub Name | Operator | Invite Code | | ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ | |
scuttle.us| @Ryan |scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=| | pub1.upsocial.com | @freedomrules |pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=| | Monero Pub | @Denis |xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=| | FreeSocial | @Jarland |pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=| |ssb.vpn.net.br| @coffeverton |ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=| | gossip.noisebridge.info | Noisebridge Hackerspace @james.network |gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=|Pubs privados
Você precisará entrar em contato com os proprietários desses bares para receber um convite.
| Pub Name | Operator | Contact | | --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- | |
many.butt.nz| @dinosaur | mikey@enspiral.com | |one.butt.nz| @dinosaur | mikey@enspiral.com | |ssb.mikey.nz| @dinosaur | mikey@enspiral.com | | ssb.celehner.com | @cel | cel@celehner.com |Pubs muito grandes
Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)
| Pub Name | Operator | Invite Code | | --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ | |
scuttlebutt.de| SolSoCoG |scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=| |Lohn's Pub| @lohn |p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=| | Scuttle Space | @guil-dot | Visit scuttle.space | |SSB PeerNet US-East| timjrobinson |us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=| | Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= |GUI - Interface Gráfica do Utilizador(Usuário)
Patchwork - Uma GUI SSB (Descontinuado)
Patchwork é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.

Fonte: scuttlebutt.nz
Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub. Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs.
Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth.
Patchbay - Uma GUI Alternativa
Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que Patchwork e Patchfoo , então você pode facilmente dar uma volta com sua identidade existente.

Planetary - GUI para IOS

Planetary é um app com pubs pré-carregados para facilitar integração.
Manyverse - GUI para Android

Manyverse é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone .
Fontes
-
https://scuttlebot.io/
-
https://decentralized-id.com/decentralized-web/scuttlebot/#plugins
-
https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd
-
Secure Scuttlebutt : um protocolo de banco de dados global.
-