-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ 434f9799:2d548c15
2025-01-23 23:15:34
@ 434f9799:2d548c15
2025-01-23 23:15:34如果你在乎你网上的内容, 请为它们附上版权声明. 如果你在共享你的内容, 请表明你的意图. 否则不要抱怨别人为何不按你的意愿使用, 因为你从没有表明过它.
同样身为创作者, 但还没有能自诩 "艺术家" 的程度, 从自己生产内容然后公开的开始就是希望被別人看到自己的作品, 并且要让别人知道「这是我创造的东西」, 然后才会有原创, 抄袭和借鉴的争论. 我是从最开始也是从 UGC 平台上逐渐转移到拥有自己 "平台" (从博客开始) 的人, 当时只为了追求所谓「自由」, 自己想写什么就写什么, 这是我的博客凭什么你来指指点点? 然后逐渐意识到当自己的身份从创作者用户过渡到创作者平台, 必须要考虑的事情就会变多, 这也是权利和义务的无条件对等结果, 我自己一个人就要成为平台. 到这时, 能对我指指点点人只会变得更多, 体量只会更大, 范围也会扩大到全世界, 因为这是互联网. 那么生活在在 UGC 平台的人难道就没有这个烦恼吗? 不是的, 只不过是平台已经帮我做了决定, 因为我必须同意他们的使用政策和隐私协议我才能使用, 包括其中顺带同意的版权声明.
作为小到自己都不想称之为一个 "平台" 的独立博客, 也要用自己身为平台应该要做的事情, 我的博客用户是谁? 是所有能够访问到我的博客的人, 机器人甚至伪装为人的机器人.
所以我需要:
-
如果我用了 Google Analytics 而我如果要面向的用户当地存在个人数据法, 那就要加上一个 cookie 知情确认通知.
-
如果有机器人来我的博客, 而我不想让它们进来, 那我应该声明 robots.txt.
-
如果我的用户, 我的读者希望能够轻松自如地帮我分享内容而不用时时刻刻都向我发消息确认转发请求, 那么我应该声明版权许可, 那至少也是 CC-BY 的等级.
-
如果我不希望我的内容在沒有许可的情况下被复制, 被重新演绎, 被用作商业用途盈利; 要么实行事后责任制, 请一个版权律师和版权机器人帮我给这些讨厌的东西发律师函, 发给对方的 ASN 管理员, DNS 解析服务器管理员, 域名管理局或者其他所有为它提供基础设施服务的服务商, 期盼他们能够遵守「自己的」法律.
-
如果我不希望某些用户访问我的博客, 我需要使用 WAF 屏蔽他们.
但可惜, 这互联网上最著名的版权法案 DMCA 也存在 "合理使用" 裁定, 各国各地对互联网著作权的处理也不尽相同, 如此大费周章并不能就让所有我想要不能使用我内容的人放弃使用我的内容. 那么真的没有办法了?
没有问题, 还可以同时实行事前责任制, 因为我还有 DRM, 也就是数字版权管理. 我能自己购买, 租用甚至自己开发一套版权管理系统, 只有在我的平台上才能看到我的内容, 别人想要复制我的内容会变得无比艰难, 但也只止步于 "无比艰难" 而已.
我作为平台, 需要这么努力吗? 或者说有必要这么麻烦吗? 手段的升级只会消耗更多的时间和金钱, 我只是一个小小的独立博客, 我只能用上 CC 和 robots.txt, 最多给内容加点水印. 我只是想保护我的内容而已, OpenAI 一众很可能已经在不知不觉中掠夺过我的东西了, 治不了大公司还治不了你吗?!
恭喜你, 你已经拥有成为一个平台的觉悟了.
说点实际的
我能在此如此大放厥词完全因为我实际拥有这个博客, 不用担心我会因为一两句话就破坏某些平台的狗屁 "社区守则" 乃至它们左右摇摆的政治立场, 没有别的意思, 这里的「政治」只不过是对于这些平台在社会中所扮演角色的简称.
如果你同意我说的, 那么下面是作为多个「独立平台」管理员对平台管理员的一些建议:
- 如果你愿意为你的内容负责, 请至少为你的独立平台附上版权声明, 哪怕是在页脚加一个 "Copyright © CC-BY" 甚至 "Copyright © All rights reserved". 当然前提是你的内容全部出自你的手, 或者你的平台有其他用户并且他们同意你的声明.
- 如果你希望或者不希望被机器人或者某些机器人自动抓取内容, 请为你的独立平台添加 robots.txt. 所有的机器人都能声称自己是真实的用户代理(User-Agent), 在如今的互联网上, 所有人都默认在没有 robots.txt 声明的情况下机器人可以随意进出你的平台, 尝试获取你的平台内容.
如果你已经是平台内的用户了, 或者你的独立平台需要使用其他平台的内容, 以下对于内容创作者的建议:
- 不要尝试使用任何没有版权声明的平台里的实际内容. 它们比 "保留所有权利" 甚至带有 DRM 的内容更加不确定, 因为它们的创作者不愿意主动表露自己对他人使用自己内容的意图. 除非你愿意到处查找内容创作者或者平台的联系方式, 然后联系上他们请求使用他们的东西. 当然, 直接不使用实际内容就行了, 你可以引用来源乃至完全重新演绎它们, 就像 ChatGPT 一样.
- 好好阅读平台的版权声明, 使用许可和隐私政策, 大多数时候你的东西是不是你的取决于平台而不是你, 甚至包括你的隐私. 实际上, 我们处于社会化状态下是被动着去使用某些平台, 要么你说服别人或者强迫别人去使用你想用的平台, 而这又对于追求「人人平等」的现代社会是不可接受的, 除非这种对等关系被打破. 知悉这些条款并且在乎自己内容的创作者能够控制自己可以在这里产生什么东西, 或者是在平台上借助自己的内容和平台达成交易换取自己想要的东西.
结语
创作者或者是艺术家的世界对于版权这种事情看起来很在乎, 但实际上没有几个人是亲自去执行的, 大多都是依附于创作平台或者版权公司, 让它们代行自己的权利, 让自己能够专心于创作, 然后拿到自己想要的.
然而在计算机和互联网融合的世界, 构建这个数字世界的 "艺术家" 们早就已经发起了一场颠覆这种局面的政治运动, 名字叫作 "开源", 赋予开源权利的许可叫做 "开源许可", 成就他们理想的叫做 "自由软件", 自由软件基金会和 GPL 许可证由此诞生, 始于 1989 年.
而现实世界的艺术家们呢? 他们创作文学, 绘画, 音乐乃至影片在互联网上获得全世界范围的传播, 但可惜依旧遵守着老一套的规矩, 把自己的作品交给平台, 交给公司管理. 自由软件基金会诞生后的 12 年, 知识共享(Creative Commons, CC)才出现在互联网. 那么在这之前的 12 年间, 互联网上的艺术家们生产的内容难道都是默认公共领域的吗? 我想更多是即使想要保留部分权利但根本没有意识到要声明自己的意图.
而二十多年后的今天, 依旧如此. "书呆子" 程序员无人不知开源, 知道自己的创造的东西需要让别人知道自己的作品能够被如何使用, 即使是 "Copyleft", 是 "All rights reversed" 放弃了全部权利, 也是知道自己一开始就有权利可以对自己的东西这么做.
而那些迷失在意识洪流中的疯狂艺术家们, 对待自己的作品如何被别人使用上还是模棱两可, 暧昧不清. 即使是 CC 和 robots.txt 也都是可有可无地充满艺术感, 他们确实在乎自己的作品, 但是更在乎自己.
PS: 本文属一时兴起一笔写完, 可能有很多奇怪的地方, 如果需要转载, 请首先遵守本站/账户的版权许可. 欢迎指正和纠错.
封面
Photo by Aaron Burden on Unsplash
-
-
 @ 0d97beae:c5274a14
2025-01-23 21:05:12
@ 0d97beae:c5274a14
2025-01-23 21:05:12History is written by the victor.
There is very little we can know about our history. We can have written literature and physical evidence, yet it is rarely possible to know the facts of something without having been there at the time. Even in the court of law, testimonies can be falsified, evidence can be misinterpreted, and stories can be spun to provide an alternative account of events.
In a world where history is shaped by perspective and bias, it might seem impossible to ever construct an account of events that is entirely free from distortion; not without a central arbiter who is entrusted to preserve the truth. We often rely on records of agreements to help settle disputes; however, as the degree of risk increases - such as when purchasing a house, for example - we need to involve licensed third parties who can be trusted to keep and preserve a historical record of our agreements, ensuring that penalties can be enforced if either party breaks the terms therein.
Of course, these agreements are often still vague enough to allow for re-interpretation, and, with enough corruption, nothing prevents the very institutions that were supposed to protect the sanctity of the agreement from altering the records. Fortunately, the system has worked well and has served its purpose truthfully most of the time.
Relating back to Bitcoin
Bitcoin is able to do something remarkable: it can create a historical record of events that cannot be altered or revised in any way. However, it does not solve the problem of people and institutions re-interpreting records or choosing not to apply enforcement; this technology cannot be used to replace any and everything, it has a very specific use case. Bitcoin is designed to capture transaction records and enforce the criteria that they must meet before accepting them. They enforce that they do not inflate the supply of bitcoin units, and that they have included all of the necessary information required to be fully verifiable.
As well as enforcing transaction rules strictly, Bitcoin uses a process to fossilise these records into history through two core technical innovations: "proof of work" and "difficulty adjustment". Proof of work introduces the cost of energy, while difficulty adjustment enforces the cost of time. Together, Bitcoin effectively uses time and energy to ensure that history can never be rewritten.
To break it down a bit more, people can still create alternative chains of events, but each candidate must include the relevant time and energy data to make comparisons possible. Additionally, the "proof of work" technology ensures that the energy data is impossible to fabricate. The chain that has clearly spent the most time and energy will stand out immediately, meaning the chain produced by the largest global community will always emerge as the victor, without the need for inconclusive debates or corruptible authority figures to make the call.
The magic lies in how data produced by Bitcoin is fully self verifiable. It is not just the transaction data that can be verified, it is the complete historical order of events that were observed and fossilised in real-time through a fair and neutral, yet irreversible process.
Why we run Bitcoin nodes
Bitcoin does not run by itself. Beyond needing users to create and submit transactions, it also requires people to provide energy for its proof of work, and it requires people to participate by collecting, verifying, and storing the information in as many places as possible, all around the world.
If Bitcoin had an Achilles' heel, it would be the loss of its recorded data. If the data were lost, then there would be nothing to stop an alternative set of records from taking its place and rewriting history. By running a node, we ensure that there are plentiful copies of this data.
From a self-serving perspective, running a Bitcoin node ensures that we are always able to access first-hand data about the state of Bitcoin and our wallets. If we rely on third parties to inform us of this information, we introduce a layer of risk and place our trust in someone else. If that trust is abused, we could be fooled into believing we have received bitcoin when in fact this was not the case. While a Bitcoin node does collect its data from online sources, since it collects data from multiple sources and it is able to validate and identify any discrepant data, it is more likely to provide you with the latest and most accurate information available.
We also help in situations where connectivity is limited, such as the time when Australia was cut off from the world wide internet for some time. In this case, users in Australia were inconvenienced for some time:
- With limited connectivity, miners in Australia could not share their work quickly enough to compete effectively with the greater global network.
- Users might see their transactions remain unconfirmed for longer periods of time.
- Users may even see their transactions transition from confirmed to unconfirmed as nodes struggle to keep up with the chain of events being agreed upon by the greater network.
By operating a node in Australia, you were helping to link and share data in real-time with the rest of the network, and if you had a connection to the greater network, you would be helping to bridge the connection.
Once the internet was restored, your node would help to keep track of all the unconfirmed transactions in your country and share them with the greater global network so that they can be processed.
It should be noted that Bitcoin network does not need any sort of manual intervention to come to a shared agreement about the legitimate chain of events and continue operating as normal.
-
 @ 3b70689a:c1e351eb
2025-01-22 23:47:36
@ 3b70689a:c1e351eb
2025-01-22 23:47:36来自西班牙的公司 Liberux 最近推出了他们的新手机 Liberux NEXX 众筹计划. 根据目前主页上的介绍, 这款设备将会搭载基于 Debian 13 ARM 构建的 LiberuxOS 操作系统, 并且还提供一个受限的(jailed)的 Android 子系统.

Liberux 的 Fediverse 主页
Liberux 硬件开发工程师 Carlos Rodríguez 的 Fediverse 主页
Carlos Rodríguez 说, 目前网站上的 NEXX 是最初版本, 目前仍然在努力制造第一台原型机, 并且所有的硬件和软件设计都将免费(公开).
WOW, I think our little secret has been revealed, we hope that in a short time you will be able to see the first functional prototypes. We are working very hard on it, by the way, all our designs, both hardware and software, will be free. At the moment the web is a first version, some things will be modified.
硬件参数
-
CPU: 瑞芯微 RK3588s (八核心, 8nm, 2.4Ghz, 2022Q1)
-
GPU: ARM Mali-G610 (4 核心, 2021Q2)
- 存储: 32GB LPDDR4x RAM, 256GB eMMC ROM
- 电池: 5300mAh (可拆卸)
- 接口: 3.5mm 耳机 * 1, USB-C 3.1 * 2
- 扩展: microSD 插槽 (2TB Max)
- 屏幕: 6.34 吋, OLED, 2400*1080
- 相机: 后置 32MP, 前置 13MP
- 通讯: 高通骁龙 X62 基带 (2021Q1), 海华 AW-CM256SM 无线网卡 (Wi-Fi 5, 蓝牙 5.0)
- 传感器: 昇佳 STK3311-X 环境光传感器, 美新 MMC3630KJ 三轴磁传感器, 应美盛 ICM-42670-P 加速度计/陀螺仪
- 其他: 内置 DAC 和功放芯片 (瑞昱 ALC5640-VB-CG, 艾为 AW8737SCSR)
其他特点
设备目前公布的外观设计均是渲染效果, 最终交付的设备很可能会与这些渲染图片有很大出入. 但仍然可以通过这些效果图理解 Liberux 的最初意图.
- 摄像头 & 麦克风, 蓝牙 & WLAN, 数据网络功能模块的物理开关(位于顶部).

- 后置指纹解锁, 无摄像模组凸起.
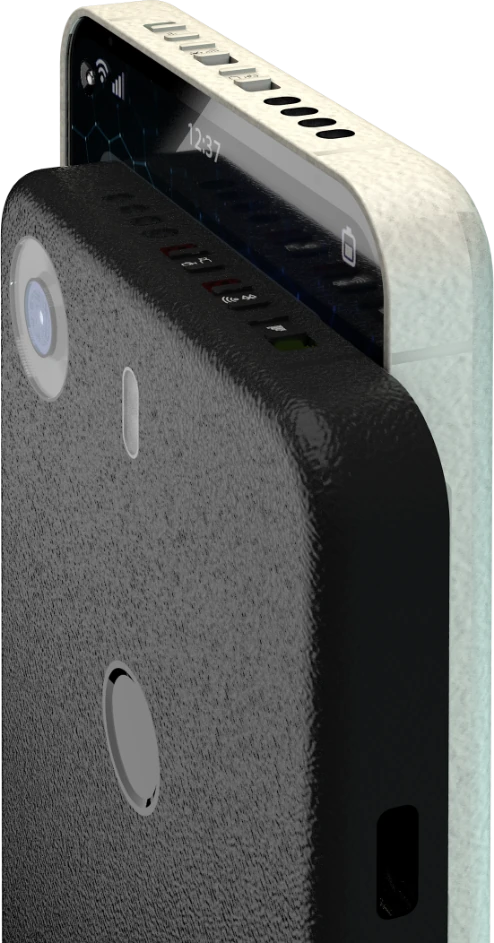
- 左上角挖孔前置摄像头.

- 电源键位于侧边右下角.
其他报道
- Liberux Nexx: New Linux smartphone with 32GB RAM, 2TB storage, 5G and more - NotebookCheck.net News
- Смартфон Liberux Nexx получил ОС Linux и поддержку 2 ТБ памяти - 4PDA (讨论)
- Smartfon z Linuksem? Oto Liberux NEXX. Ekran OLED, 32 GB RAM i system oparty na Debianie. Ciekawy model, choć nie bez wad | PurePC.pl (讨论)
- LINux on MOBile: "The Liberux Nexx (https://libe…" - Fosstodon (Fediverse, 讨论, 工程师回复)
-
-
 @ 0d97beae:c5274a14
2025-01-11 16:52:08
@ 0d97beae:c5274a14
2025-01-11 16:52:08This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs
The reason why we have broken money
Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world.
In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes.
However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore.
Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too.
Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it.
Bitcoin overcomes the "transfer of hard money" problem
Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design.
Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it.
Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive.
Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold.
Bitcoin blurs the line between commodity and technology
Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules.
At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable.
Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases.
The dangers of derivatives
A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold.
In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin.
Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense.
Learn for yourself
If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody".
There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance.
-
 @ 8f69ac99:4f92f5fd
2025-01-06 17:11:58
@ 8f69ac99:4f92f5fd
2025-01-06 17:11:58Os humanos evoluíram para contar maçãs, não estrelas. Estamos programados para compreender números pequenos e tangíveis com facilidade, mas, no momento em que atingimos centenas ou milhares, os nossos cérebros começam a ter dificuldades. Esta limitação desempenha um papel significativo na fricção que as pessoas sentem ao tentar compreender Bitcoin, desde os seus fundamentos de segurança até ao seu sistema monetário.
A natureza abstracta de Bitcoin é construída sobre conceitos matemáticos complexos, incluindo criptografia e números grandes. No entanto, estes elementos podem ser esmagadores para muitos potenciais utilizadores, investidores e até especialistas. Neste artigo, vamos explorar porque é que os humanos têm dificuldade com números grandes e como esta limitação afecta a nossa compreensão de Bitcoin.
Porque é que os humanos têm dificuldade com números grandes
O nosso cérebro está programado para pensar de forma linear e processar números pequenos com facilidade. No entanto, quando se trata de números grandes, tudo começa a parecer confuso. Limitações evolutivas significam que fomos desenvolvidos para contar maçãs, não estrelas. Para além de algumas dezenas, os números começam a parecer "muitos" em vez de quantidades específicas.
Por exemplo, considere o número de chaves privadas possíveis em Bitcoin. Com 256 bits usados para encriptação, isto traduz-se em aproximadamente
$$2^{256}$$chaves únicas. Embora este número seja impressionante, a maioria das pessoas tem dificuldade em compreender a sua enormidade. Para colocar em perspectiva: - Existem mais átomos no universo observável do que grãos de areia em todas as praias da Terra.Além disso, o nosso cérebro frequentemente luta para entender fenómenos exponenciais, que desempenham um papel crucial no sucesso de Bitcoin. O crescimento da população mundial ou o número de hashes efectuados por segundo pelos mineradores de Bitcoin podem parecer incompreensíveis devido à sua natureza rápida.
Finalmente, a falta de pontos de referência do dia a dia dificulta a compreensão de conceitos complexos como chaves privadas e hashrate. Por exemplo, dizer "100 biliões" pode significar algo para si, mas decompor isso em números mais pequenos e manejáveis é uma história completamente diferente.
A História do Tabuleiro de Xadrez e o Grão de Arroz - uma pequena explicação didáctica sobre exponenciais.
Certa vez, um matemático indiano inventou o jogo de xadrez e apresentou-o ao rei local (frequentemente chamado de Maharaja). O rei ficou tão impressionado com o jogo que ofereceu recompensar o matemático com qualquer coisa que ele desejasse.
O matemático humildemente pediu um único grão de arroz para ser colocado na primeira casa do tabuleiro de xadrez, e que a quantidade de arroz fosse duplicada em cada casa seguinte. O rei, pensando que este era um pedido modesto, concordou imediatamente.
O processo começou: - 1 grão na primeira casa,
- 2 grãos na segunda,
- 4 grãos na terceira,
- 8 grãos na quarta, e assim por diante.Mas, à medida que avançavam, os números começaram a crescer rapidamente. Na 20.ª casa, já eram necessários mais de 1 milhão de grãos de arroz. Na 40.ª casa, o total ultrapassava 1 bilião de grãos. Na 64.ª e última casa, o total era um espantoso 18 quintiliões de grãos de arroz (
$$2^{64} - 1$$).Esta quantidade era tão vasta que exigiria mais arroz do que poderia ser cultivado na Terra naquela época. O rei, ao perceber que subestimara o pedido do matemático, foi forçado a admitir derrota ou, em algumas versões da história, puniu o matemático pela sua astúcia.
Bitcoin e Números Grandes: A Tecnologia Incompreendida
A complexidade de Bitcoin reside na sua dependência de criptografia e números imensos. Vamos explorar três áreas chave onde estes conceitos podem criar atrito.
A Segurança Incompreensível das Chaves Privadas
A segurança de Bitcoin assenta na escala absoluta do seu espaço de chaves privadas. Existem
$$2^{256}$$chaves possíveis — um número tão grande que tentar adivinhar uma chave não é apenas improvável, é praticamente impossível. É como se lhe pedisse para adivinhar o número em que estou a pensar entre 1 e 115792089237316195423570985008687907853269984665640564039457584007913129639936!Para colocar isto em perspectiva: - Imagine que existem mais estrelas no universo observável do que grãos de areia nas praias da Terra. Mesmo que combinasse todos os grãos de areia e estrelas, o número resultante ainda seria inferior a ```$$2^{256}$$```.
Esta escala impressionante garante a robustez da segurança criptográfica de Bitcoin, mas pode parecer esmagadora para os recém-chegados.
O Hashrate de 1 Zettahash/s
Recentemente, a mineração de Bitcoin ultrapassou a marca de 1 zettahash por segundo (
$$10^{21}$$hashes por segundo). Esta medida de poder computacional destaca a escala imensa da segurança da rede.Para ilustrar: - Imagine tentar adivinhar um número biliões de vezes por segundo, por pessoa, para todos os humanos na Terra. Mesmo com todo este esforço combinado, mal arranharíamos a superfície do actual hashrate de Bitcoin.
Este poder computacional imenso é o que garante que, uma vez adicionada uma transacção à timechain (ou blockchain se preferir) de Bitcoin, seja praticamente impossível alterá-la.
A Barreira da Criptografia
A criptografia de curva elíptica, ECC, um elemento chave em Bitcoin, utiliza matemática avançada que pode parecer abstracta para não especialistas. Baseia-se em "funções unidireccionais," onde gerar uma chave pública a partir de uma chave privada é fácil, mas reverter o processo é quase impossível.
O recente medo da computação quântica (apenas FUD), mostra bem esta segurança na matemática. O Willow, o computador da quântico da Google, com 105 qubits, resolveu um problema de benchmark em 5 minutos, que levaria a um super computador 10 septiliões de anos a resolver (mais tempo que a idade do universo, 13.8 mil milhões de anos).
Para conseguir encontrar a chave privada a partir de uma chave publica, seriam necessários cerca de 124000 Willows para o fazer em 1 dia, ou cerca de 340 para o fazer em 1 ano. E mesmo assim, apenas os endereços mais antigos, P2PK (Pay to Public Key) estariam vulneráveis, os endereços P2PKH (Pay to Public Key Hash) tem mais um nível de segurança, o hash.
O Willow teria que ter milhões ou milhares de milhões de qubits para conseguir descobrir uma chave privada a partir da chave publica. Não temos ainda tecnologia para isso...
Para simplificar: - Pense nisso como uma fechadura que só pode ser aberta com uma chave única. Uma vez trancada, o processo é irreversível sem essa chave, proporcionando uma segurança incomparável.
O Obstáculo Psicológico: Viés de Unidade
Além dos aspectos técnicos, a psicologia desempenha um papel importante na forma como as pessoas percebem o valor, ou melhor o preço, de bitcoin. O viés da unidade — a tendência de preferir números inteiros — pode criar uma barreira emocional.
O Problema do "Preço Alto" de bitcoin
Ver o preço de bitcoin em dezenas (centenas?) de milhares de euros pode dissuadir potenciais investidores, que podem sentir que é demasiado caro ou inacessível. Esta percepção persiste, embora bitcoin possa ser dividido em unidades mais pequenas.
Satoshis como Solução
A menor unidade de bitcoin, o satoshi (1/100.000.000 BTC), oferece uma solução para este viés. Apresentar bitcoin em termos de satoshis permite pontos de preço mais compreensíveis. Por exemplo: - "1.000 sats custam €1,00" soa muito mais acessível do que "€100.000 por bitcoin."
O uso de satoshis reformula o valor de bitcoin, facilitando a sua compreensão e acessibilidade. E sim, pode comprar €1,00 de bitcoin, ou até mesmo menos de €0,01!
Conclusão
A dificuldade com números grandes não é única de Bitcoin, mas a sua natureza digital e abstracta amplifica o desafio. Desde a escala incompreensível das chaves privadas até à enorme hashrate e ao obstáculo psicológico do viés de unidade, estas barreiras podem dificultar a compreensão e adopção.
No entanto, ao: 1. Simplificar conceitos criptográficos,
2. Usar analogias compreensíveis, e
3. Promover os satoshis como unidade padrão,podemos tornar Bitcoin mais acessível para a pessoa comum. Assim como a sociedade aprendeu a abraçar a electricidade sem precisar entender os electrões, também podemos abraçar Bitcoin sem compreender completamente cada número por trás dele.
bitcoin #quantum
Photo by Greg Rakozy on Unsplash
-
 @ 2efaa715:3d987331
2024-12-21 16:54:55
@ 2efaa715:3d987331
2024-12-21 16:54:55More than you wanted to know about a little-understood but important aspect of diet and health, explained in a nontechnical manner, with oversimplifications abound.
Your cells need some kind of fuel to function. this fuel can only come (ultimately) from the outside world as food. AKA "diet". your blood carries the fuel to the cells so they can do their work. on most diets, the main fuel for cells is glucose, which the body derives from sugar or carbohydrates (which are basically sugar + some complexity). on other diets, the main fuel for cells is fat. on these diets, fat/lipid particles are carried on little blood ferries called lipoproteins (the final "L" in LDL and HDL). LDL carries lipids to your cells so they can use it, HDL carries unused lipids away from your cells (to the liver) so they can be disposed of. (on both very high carb and very low carb diets, your cells will still use some amount of both glucose and fat for energy, but the ratio will change dramatically).
Naturally, if you have a lot of these ferries in your blood (because you are using fat as cell-fuel), your LDL and HDL counts ("total cholesterol") will be high on basic blood tests.LDL - the ferries that carry fats to your cells to burn - come in two varieties: - small + dense - large + fluffy
both carry fuel to your cells, but the small/dense ones have an unfortunate side-effect of slamming into artery walls, penetrating them, and accidentally depositing their lipids there. This is the "plaque" of cardiovascular disease fame. The large, fluffy particles do not penetrate the arterial walls as readily - they bounce off and keep going on to their destinations. their effect on arterial plaque is not zero, but far less impactful than small, dense particles.In either case, the HDL particles are always good: they remove excess lipids from the body. this is why HDL is "the good cholesterol". There are advanced blood tests available which measure particle size (so, like, an acutally useful test), but odds are your doctor will refuse to order this test. Strange!
We didn't mention Triglycerides yet. Suffice it to say that more triglycerides = smaller, denser LDL particles = more arterial wall penetration = more cardiovascular risk. To finish off our triglycerides sidebar, the dietary patterns that increase triglycerides (bad!) are: excess calories from carbohydrates, added sugars and refined carbohydrates, low fiber intake, low omega-3 intake (especially in combination with excess seed oil intake), high trans fats consumption (more on trans fat in a moment).
Back to finish up cholesterol: this is why a diet that is high in good fats (again, more in a moment) will increase "total cholesterol" - you have more fat boats fueling your cells - but doesn't indicate greater cardiovascular risk: because the large, fluffy particles are not damaging your arteries and the large number of HDL particles are protective!
Furthermore, if you reconsider the sidebar on triglycerides you'll notice that avoiding refined carbohydrates and sugars has the added effect of lowering triglycerides, which keeps the LDL particles even healthier. You'll often see the simple recommendation to keep the HDL/Triglycerides ratio high. this is why. HDL good, triglycerides bad.We didn't even get into insulin sensitivity - one of the most important factors in metabolic health... another time.
A last word on dietary fat types: Not all fats are created equally. You can look into monounsaturated and polyunsaturated on your own, but I want to mention two others here: Trans fat and Saturated fat.
Trans fats mostly come from artificial sources, like processed vegetable or seed oils. most often found in ultra-processed, packaged foods. yuck. trans fat lowers HDL, increases inflammation and increases proportion of small, dense LDL particles. These are all the bad things we discussed above.
Saturated fat is mainly found in meat, dairy and coconut oil. It increases LDL particle size and raises HDL. These are the good things we discussed above.
So, yes, while someone's total cholesterol may go up when eating saturated fats, it doesn't necessarily mean their cardiovascular risk has increased.Now that you understand how cholesterol works, compare moderate saturated fat intake to eating a diet full of refined carbohydrates, sugars, processed vegetable/seed oils, and all the other items we explained above...
Ok really now, the last last word: the "cholesterol" you see on a food label has less impact on blood cholesterol than you thought. the details are too squirrely to go into here, but the takeway is: the fat content discussed above is the lion's share of the impact, with the number you see next to "cholesterol" on your food label having a negligible effect.
diet #paleo #keto #health #healthstr #foodstr #carnivore #cholesterol
-
 @ 3b7fc823:e194354f
2025-02-02 22:55:32
@ 3b7fc823:e194354f
2025-02-02 22:55:32The Secret to Staying Private in the Digital Wild West: A Guide to Using Encryption
You’re scrolling through social media, and suddenly you realize your phone’s been tracking your location and displaying it on your profile for months. You’re not even sure how that happened. Or maybe you’ve noticed that every time you shop online, the item you looked for follows you around with ads wherever you go. Sound familiar? Yeah, welcome to the digital world—where your data is basically a free buffet for anyone who knows how to ask.
But here’s the thing: you don’t have to sit back and take it. Encryption is like the secret weapon that lets you lock up your data and keep those prying eyes out. It’s not just for hackers or spies—it’s for regular people who want to take control of their privacy in a world that’s increasingly looking like a reality show where everyone’s a contestant.
What Is Encryption, and Why Should You Care?
Encryption is like a secure box that only you can open. When you use encryption, your data is scrambled in a way that’s hard for anyone else to read, even if they try. Think of it as putting on a metaphorical cloak that makes your online activity invisible to just about everyone except the people you want to see it.
For example, when you browse the internet, your connection is often not encrypted by default. That’s why websites start with “https” to indicate a secure connection—it’s saying, “Hey, we’re using encryption here!” Without that little green padlock, anyone on the same WiFi could potentially spy on what you’re doing.
So, encryption isn’t just for tech geeks or government agencies. It’s for everyone who wants to protect their data from being sold, stolen, or misused without their consent. And guess what? You’re already using it without realizing it. Every time you use a password-protected account or send an encrypted message, you’re reaping the benefits of encryption.
The Privacy Advantages of Encryption for Regular People
Let’s break down why encryption is your best friend when it comes to privacy:
-
Financial Transactions
When you pay online or use a banking app, encryption keeps your financial info safe from hackers. It ensures that only the banks and businesses you’re dealing with can access your money—no one else can. -
Online Accounts
Your email, social media, and other accounts often use encryption to protect your login details. That’s why you see those little “lock” icons when you’re logging in. Without encryption, someone could potentially intercept your password and gain unauthorized access to your account. -
Data Breaches
Encryption can often prevent data breaches from being useful. Even if hackers manage to steal your information, the encryption makes it unreadable, so the stolen data is basically worthless to the attackers. -
Location Data
If you’re worried about apps tracking your every move, encryption can help limit how much of that data is accessible. Some apps use encryption to protect location data, making it harder for companies to sell your movements without your consent. -
Privacy Protection
Encryption acts as a layer of protection against invasive technologies. For example, some apps use tracking software that follows you around the internet based on your browsing history. With encryption, these trackers can be blocked or limited, giving you more control over what information is collected about you.
How to Use Encryption Like a Pro
Now that you know why encryption is essential for privacy, let’s talk about how to use it effectively:
-
Use Strong Passwords
Encryption works only if your passwords are strong and unique. Don’t reuse passwords from one account to another, and avoid using easily guessable information like “password123” or your birth year. Use a password manager if you need help keeping track of them. -
Enable HTTPS Everywhere
Install browser extensions like HTTPS Everywhere to automatically encrypt your connections to websites that don’t support encryption by default. This ensures that even if you’re not actively thinking about it, your data is still protected. -
Look for the Lock Icon
Whenever you’re on a website or app, look for the lock icon in the URL bar. Make sure it’s encrypted before you input any personal information. -
Use Encrypted Communication Tools
For private conversations, use apps like Signal or SimpleX, which are designed with encryption in mind. These tools ensure that only the sender and recipient can read your messages, keeping them safe from prying eyes. -
Enable Two-Factor Authentication (2FA)
This isn’t exactly encryption, but it’s a close second. 2FA adds an extra layer of security by requiring you to provide two forms of verification—like your password and a code sent to your phone—to access your account. While not encryption itself, it works alongside encryption to keep your accounts secure. -
Use Encrypted Storage and Backup
When storing sensitive files or data, use encrypted cloud storage or external drives. Tools like BitLocker (for Windows) or AES-256 encryption can protect your files from unauthorized access. -
Stay Updated
Encryption technology is always evolving, so it’s important to keep your software and apps updated. Outdated systems are often easy targets for hackers, leaving you vulnerable to attacks.
Final Thoughts: Your Data Is Your Power
In a world where data is a commodity, encryption is your weapon against the invasive tactics of corporations and hackers alike. It empowers you to control what information you share and protects you from having it used against you. So, whether you’re shopping online, using your favorite apps, or just browsing the web, remember that encryption is there to help you stay private and in control of your own data.
And if you ever feel overwhelmed by all the privacy stuff, just remember this: you’re not alone. Millions of people are fighting for stronger privacy protections every day. So, do your part by using encryption wisely—your data and your privacy are worth it. Let’s make sure no one can take that away from you.
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-
-
 @ 8f69ac99:4f92f5fd
2024-12-13 15:20:32
@ 8f69ac99:4f92f5fd
2024-12-13 15:20:32O recente vídeo do "Cor do Dinheiro", do Camilo Lourenço, na rubrica "Pé de Meia" é um exemplo claro de como a desinformação e uma compreensão superficial continuam a prejudicar as discussões públicas sobre Bitcoin. Os convidados, Francisco Louro e Antonio Mello Campello, regurgitaram argumentos ultrapassados e falaciosos com uma confiança que faria Dunning e Kruger sentirem orgulho. Desde descartar Bitcoin como mera especulação até confundi-lo com moedas meme e actividades criminosas, as suas alegações destacam não apenas a ignorância, mas também a sua recusa em compreender objectivamente esta tecnologia revolucionária. Este artigo visa desmontar algumas das suas afirmações, expondo as suas perspectivas superficiais enquanto apresenta Bitcoin como a inovação transformadora que realmente é.
Nem vou comentar a historia da blockchain, ja escrevi sobre isso num outro artigo que podem encontrar aqui.
Bitcoin: É Apenas Especulação?
Antonio Mello Campello começa com o argumento ultrapassado de que Bitcoin é puramente especulativo, desprovido de "valor real". Este argumento é risível, considerando a adopção de Bitcoin por nações como El Salvador e empresas como a MicroStrategy. Se Bitcoin fosse apenas especulativo, por que entidades bilionárias e governos o integrariam nas suas estratégias financeiras?
A sua ignorância torna-se ainda mais evidente na incapacidade de compreender que todas as tecnologias revolucionárias enfrentam cepticismo inicial. A internet já foi vista como uma curiosidade de nicho que desapareceria como o fax, e aqui estamos, usando-a para espalhar opiniões mal informadas sobre Bitcoin. A incapacidade do convidado, e devo dizer do apresentador também, de reconhecer este paralelo revela a sua falta de perspectiva histórica e tecnológica.
O Valor de Bitcoin: O Mito do Valor Intrínsecos
“Bitcoin não tem valor intrínseco porque não gera dividendos ou retornos,” afirmam. Por esta lógica, o ouro, que também não gera dividendos, deve ser igualmente sem valor. A verdade é que o valor de Bitcoin reside nas suas propriedades: escassez, descentralização e segurança. Com um limite de fornecimento de 21 milhões e um registo inviolável, Bitcoin oferece um nível de transparência e fiabilidade incomparável a qualquer moeda fiduciária.
A afirmação também ignora o uso de Bitcoin como protecção contra a inflação e instabilidade económica. Ao contrário do euro, que o Banco Central Europeu inflacionou até à exaustão, Bitcoin oferece previsibilidade e independência face a políticas monetárias irresponsáveis. A compreensão superficial dos apresentadores demonstra a sua incapacidade de valorizar como as propriedades únicas de Bitcoin desafiam o status quo dominado pelas moedas fiduciárias.
Confundir Bitcoin com Memecoins
Equiparar o Bitcoin ao Dogecoin não é apenas ignorância; é absolutamente ridículo. Enquanto a Dogecoin prospera em memes e tweets de Musk, Bitcoin é um sistema monetário robusto construído com mais de uma década de descentralização, segurança e adopção global. Esta equivalência falsa mina qualquer credibilidade que os participantes do vídeo poderiam esperar manter.
Dogecoin carece da escassez, segurança e descentralização que tornam Bitcoin revolucionário. Comparar os dois é como comparar um carro de luxo a um carrinho de pedais infantil. Um é projectado para utilidade no mundo real; o outro é uma brincadeira passageira.
Volatilidade: Uma Característica, Não Um Problema
Outra crítica ultrapassada: a volatilidade de Bitcoin. Sim, o preço da bitcoin oscila, mas o mesmo aconteceu com as acções e mesmo o ouro nos seus primeiros dias. A volatilidade é uma fase natural de uma classe de activos emergente. Apesar disso, a bitcoin tem proporcionado retornos de longo prazo incomparáveis, recompensando aqueles que compreendem o seu potencial e permanecem pacientes.
A ironia é gritante: enquanto desconsideram Bitcoin pela sua volatilidade, falham em mencionar a lenta erosão de valor do euro ou os crashes periódicos dos mercados de acções. A volatilidade de Bitcoin é o preço da inovação, e, à medida que a adopção cresce, a estabilidade seguir-lhe-á. A incapacidade dos participantes de reconhecer esta dinâmica demonstra o seu pensamento de curto prazo e a falta de visão do panorama maior.
A Narrativa do Crime: Um Argumento Preguiçoso
Afirmar que Bitcoin é principalmente usado para actividades criminosas, ou teóricos da conspiração, é talvez o argumento mais preguiçoso de todos. Dados mostram consistentemente que transacções ilícitas representam menos de 1% do uso total de bitcoin. Enquanto isso, o dinheiro em espécie, cash, continua a ser a ferramenta preferida dos criminosos em todo o mundo. Devemos banir euros e dólares também?
Ironicamente, a transparência de Bitcoin torna-se uma péssima escolha para criminosos. Ferramentas de análise de blockchain tornaram-se inestimáveis para as autoridades, permitindo-lhes rastrear e capturar infractores. A incapacidade dos participantes de reconhecer este facto reflecte ignorância deliberada ou preguiça intelectual — ou talvez ambos.
Aplicações Práticas: Reduzindo a Desigualdade Financeira
“Bitcoin não tem casos de uso no mundo real,” dizem eles, ignorando os milhões que dependem dele para remessas, inclusão financeira e protecção contra hiperinflação. Iniciativas como a Praia Bitcoin no Brasil e o Bitcoin Ekasi na África do Sul, entre muitos outros, mostram como Bitcoin capacita comunidades ignoradas pelos sistemas financeiros tradicionais.
Ao permitir transacções baratas, rápidas e sem fronteiras, Bitcoin resolve problemas reais para pessoas reais. Descartar esses casos de uso como triviais não é apenas ignorância, mas também um exemplo gritante de privilégio financeiro. A incapacidade dos comentadores de reconhecer isso destaca o quão desconectados estão dos desafios enfrentados por aqueles fora de suas bolhas confortáveis.
Bitcoin vs. Activos Tradicionais: Uma Falsa Dicotomia
Os convidados argumentam que activos tradicionais, como acções e imobiliário, são investimentos superiores. Isto perde totalmente o ponto. Bitcoin não é (apenas?) um investimento; é um novo paradigma monetário. A sua portabilidade, divisibilidade e resistência à censura fazem dele um activo único, complementar aos investimentos tradicionais.
Imobiliário, ou terreno, podem ser confiscados, ou sujeitos a depreciação por factores ambientais ou sociais, e acções estão sujeitas a má gestão corporativa. Bitcoin, em contrapartida, é inalienável e opera independentemente de erros humanos. A incapacidade dos participantes de compreender esta diferença fundamental fala muito sobre a sua compreensão limitada do potencial transformador de Bitcoin.
O Limite de Fornecimento: Um "Gimmick" que Redefine o Dinheiro
Descrever o limite de fornecimento de 21 milhões de bitcoin como um "truque" é tanto desinformado quanto risível. A escassez sempre impulsionou o valor, como visto com o ouro, ou autocolantes do CR7. O fornecimento fixo de Bitcoin garante que ele não pode ser desvalorizado por políticas monetárias arbitrárias — uma característica, não uma falha.
Enquanto bancos centrais inundam economias com moeda fiduciária, erodindo o poder de compra das pessoas, a previsibilidade de Bitcoin oferece um porto seguro. A rejeição desta característica crítica pelos participantes revela uma falta de literacia económica e uma recusa em compreender os princípios fundamentais de Bitcoin.
Independência dos Bancos Centrais: A Proposta de Bitcoin
A noção de que a falta de apoio dos bancos centrais enfraquece Bitcoin é ridícula. Bancos centrais, com o seu histórico de políticas inflacionárias e crises financeiras, estão longe de serem exemplos de confiabilidade. A independência de Bitcoin protege-o de manipulações e garante a sua integridade. Essa é, alias, a grande proposta de valor de Bitcoin, inscrita no bloco genesis!
O argumento dos participantes reflecte um apego profundo a sistemas tradicionais que repetidamente falharam mas, do qual provavelmente beneficiam. A transparência, previsibilidade e descentralização de Bitcoin fazem deste activo uma alternativa superior, expondo as suas críticas como infundadas.
Conclusão: Ignorância Não é Argumento
O programa falha redondamente a premissa inicial com que o Camilo Lourenço abre o video. Reduzir a ignorância sobre Bitcoin. Os participantes do vídeo demonstraram uma falta chocante de compreensão sobre o assunto, repetindo argumentos ultrapassados e comparações falaciosas sem se darem ao trabalho de debater criticamente com o tema. O seu descarte de Bitcoin como especulativo, volátil e criminoso ignora evidências esmagadoras da sua utilidade, resiliência e potencial transformador.
Bitcoin representa uma mudança de paradigma em como pensamos sobre dinheiro, valor e inclusão financeira. É hora de os críticos irem além de argumentos superficiais e reaccionários e inteirarem-se com Bitcoin pelos seus méritos. Até lá, as suas críticas não passam de ecos de ignorância perante a inovação e alvo de chacota na comunidade.
Admiro bastante o Camilo Lourenço e o seu trabalho mas, desta vez, não esteve bem. Não só não houve contraditório como os convidados não entregaram aquilo que foi prometido no inicio do video.
-
 @ 8f69ac99:4f92f5fd
2024-12-13 11:49:05
@ 8f69ac99:4f92f5fd
2024-12-13 11:49:05A conversa global sobre Bitcoin entrou numa nova fase, saindo do campo da especulação para o centro das decisões estratégicas. A proposta do Presidente-eleito Donald Trump para criar uma reserva nacional de Bitcoin, a votação iminente dos acionistas da Microsoft sobre Bitcoin como investimento corporativo e a análise da Amazon para usar Bitcoin como activo de reserva mostram como a teoria dos jogos está a influenciar decisões reais.
No centro destas iniciativas está o conceito de vantagem do first-mover. Os primeiros a agir — sejam empresas ou nações — têm a oportunidade de colher benefícios desproporcionais, desde domínio financeiro até influência global. No entanto, essas acções obrigam os concorrentes a reagir, criando um efeito dominó em várias indústrias e fronteiras. Com apenas ~1.206.000 bitcoins restantes para serem minerados, a corrida começou, e os stakes não poderiam ser mais altos.
A Reserva de Bitcoin de Trump: Uma Estratégia de Estado-Nação
Em julho de 2024, Donald Trump surpreendeu o mundo financeiro ao anunciar planos para estabelecer uma reserva nacional de Bitcoin. Em novembro, mais detalhes foram revelados no projecto de lei proposto pela senadora Cynthia Lummis, “Bitcoin Act of 2024,” que prevê a aquisição de um milhão de bitcoins ao longo de cinco anos, financiada pela realocação de activos do Federal Reserve, evitando aumento da dívida pública.
O plano não é apenas uma protecção contra a inflação; é uma jogada geopolítica. Tornando-se a primeira potência a adoptar Bitcoin nesta escala, os EUA buscam consolidar a sua liderança na economia global em transformação. Esta medida obriga outras nações, como China ou Rússia — que já estão a discutir também integrar Bitcoin nas suas economias — a repensarem as suas estratégias.
A proposta de Trump introduz uma dinâmica de jogo de soma zero. Se os EUA acumularem uma reserva significativa enquanto outras nações ficam para trás, o país ganha soberania financeira, maior influência global e o poder de moldar o futuro. Contudo, essa acção pode desencadear uma corrida global, com países a competir para garantir o máximo de Bitcoin possível antes que sua oferta finita se esgote.
A Proposta de Bitcoin da Microsoft: Pressão sobre Gigantes Corporativos
Em outubro de 2024, os acionistas da Microsoft receberam uma proposta solicitando que a empresa explorasse Bitcoin como investimento corporativo. Com a votação marcada para 10 de dezembro, a decisão terá um impacto que ultrapassa a própria Microsoft. Uma votação a favor pode desencadear uma reacção em cadeia entre outras gigantes tecnológicas, enquanto uma recusa pode abrir espaço para que empresas como Google ou Apple se posicionem como líderes no sector.
Nota: a votacao foi negativa, apenas 0.55% dos accionistas da Microsoft votaram a favor! Caso para dizer que a Microsoft teve um momento Kodak! #HFSP
Michael Saylor, presidente executivo da MicroStrategy, tem estado na linha da frente, defendendo a adopção corporativa de Bitcoin, apresentando-o não apenas como um activo financeiro, mas como uma oportunidade transformadora. A administração da Microsoft recomendou a rejeição da proposta, citando processos de investimento já existentes. No entanto, a pressão está a aumentar. O desempenho impressionante de Bitcoin, com ganhos anuais de 131% e um preço recorde acima de $104.000, torna cada vez mais difícil para as empresas ignorarem a oportunidade.
Para a Microsoft, os stakes são claros: agir cedo permitiria que a empresa se posicionasse como líder na integração de Bitcoin na estratégia corporativa, pressionando concorrentes como Google, Apple e Meta a fazerem o mesmo ou arriscarem ficar para trás. Uma entrada tardia, por outro lado, pode resultar em custos mais elevados e oportunidades perdidas, à medida que o preço de Bitcoin continua a subir com a crescente procura institucional.
A Aposta da Amazon em Bitcoin
A Amazon, a maior retalhista online do mundo, está agora numa encruzilhada. No dia 8 de dezembro de 2024, a empresa recebeu uma proposta dos accionistas para alocar 5% das suas reservas de $88 mil milhões em Bitcoin. Este movimento acompanha uma tendência crescente de interesse institucional, com fundos negociados em bolsa de Bitcoin a atraírem milhares de milhões de dólares em entradas na última semana.
Se a Amazon aprovar a proposta na Assembleia Geral Anual de 2025, o impacto será sísmico. A decisão da empresa enviará um sinal claro ao mercado, validando Bitcoin como um activo de reserva legítimo. Além disso, colocará uma pressão significativa sobre rivais como Walmart, Google e Alibaba para seguirem o exemplo. À medida que mais empresas entram no mercado, a oferta finita de Bitcoin será ainda mais pressionada, elevando seu preço e recompensando aqueles que agiram primeiro.
A possível adopção de Bitcoin pela Amazon também reforça a ideia do efeito de sinalização na teoria dos jogos. Ao abraçar Bitcoin, a Amazon demonstraria confiança no futuro do activo, incentivando outros participantes do mercado a fazerem o mesmo. A decisão provavelmente aceleraria um efeito dominó em várias indústrias, dificultando cada vez mais para os concorrentes permanecerem inertes.
Efeito Dominó
As movimentações estratégicas de Trump, Microsoft e Amazon não existem isoladamente — são catalisadores de uma corrida mais ampla. El Salvador e Butão já se posicionaram como adoptantes iniciais, mas a proposta de Trump eleva a adopção de Bitcoin a um novo patamar. Se os EUA agirem de forma decisiva, é provável que aliados e concorrentes façam o mesmo, desencadeando uma corrida por reservas de Bitcoin que poderá assemelhar-se a uma corrida armamentista em intensidade. Como já se começa a ver no Canada, Rússia, Alemanha, etc...
O mesmo se aplica às corporações. À medida que líderes como MicroStrategy, Tesla e, potencialmente, Microsoft e Amazon tomam posições, os concorrentes enfrentarão uma pressão crescente para agir ou arriscar a irrelevância. Cada novo participante no mercado reduz a oferta disponível de Bitcoin, criando uma urgência crescente para os retardatários.
Os números reforçam a aposta: apenas ~1.206.000 bitcoins permanecem para serem minerados e apenas cerca de 2.000.000 em exchanges. Com a adopção institucional e nacional a acelerar, a luta por este recurso limitado provavelmente impulsionará ainda mais os preços, transformando Bitcoin de um "activo especulativo" para um imperativo estratégico.
Conclusão: O Jogo de Bitcoin Está em Curso
A dinâmica de adopção de Bitcoin ilustra a teoria dos jogos em acção que podemos observar em tempo real. A vantagem dos pioneiros não é apenas um conceito teórico — é uma vantagem tangível na corrida por Bitcoin, oferecendo recompensas desproporcionais aos primeiros a agir e forçando outros a reagirem. A proposta de Trump para uma reserva nacional de Bitcoin define o palco para uma corrida geopolítica, enquanto gigantes corporativos como Microsoft e Amazon enfrentam decisões que moldarão os seus futuros e pondo pressão nos seus concorrentes.
À medida que a oferta de Bitcoin diminui e o seu preço reflecte a crescente procura, a pressão para agir cedo só aumentará. Seja no palco nacional ou corporativo, as decisões tomadas hoje definirão o panorama económico de amanhã. O jogo de Bitcoin está em curso, e os jogadores que compreendem os riscos — e agem estrategicamente — têm o potencial de moldar a próxima era das finanças globais.
bitcoin #gameTheory
-
 @ 378562cd:a6fc6773
2025-02-02 18:58:38
@ 378562cd:a6fc6773
2025-02-02 18:58:38Chef's notes
I'm only testing this out right now. I will update the recipe as well as add my own image soon after making this dish again.
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 4
Ingredients
- 4 to 6 potatoes (size depending)
- 1 lb ground beef
- seasonings
- 2 cans chili beans
- 1 onion
- katsup
- shredded cheese of some kind
Directions
- saute onion and add ground beef to skillet. Season to liking.
- peel if you like and thin slice potatoes
- in a rectangle baking dish, layer potatoes, beans, meat and cheese (like a lasagna) until you have used all your ingredients. Try and make at least 2 or 3 layers with extra cheese on top.
- Bake at 350 for one hour. Serve and enjoy!
-
 @ df8f0a64:057d87a5
2024-11-29 13:58:48
@ df8f0a64:057d87a5
2024-11-29 13:58:482024年下半期の振り返り
あんまり変化はないんですが、進捗ありません!で終わっても仕方ないのでちょっとは無理やりでも振り返りましょう
0. 退職した
上半期時点で決まってはいたんですが、 6年間ほど勤務した会社を退職しました
退職直前まで爆発物取扱みたいなタスクをこなして、なかなかひやひやした退職プロセス
静かに退職したいので送別会の類のイベントは無しにしてくれというお願いをきいてくれた各メンバーに感謝です
1. 公開していたNostrリレーの設定を変更した
日本のみに公開していたリレーを、全世界に公開しました
当初はCloudflareでリレーをホストしていたのが、利用していたnosflareもcfrelayもクライアントに対してイベントを配布するコードがなく(R2だけではできない)
さてどうしたものかと悩んでいたタイミングで、Umbrelのおひとり様リレーのポートを公開する対応をしました。リレーのお引越し
で、公開してしばらくしたら、すごい勢いで日本国外からの投稿が着信するようになり大困惑
調べてみたら、Mutiny wallet(現在はサービス終了)が運営しているblastr.mutinywallet.com(たぶんまだ稼働している)が原因でした
Nostr.watchのAPIを利用して、世の中にあるNostrリレーすべてにイベントを送り込む凶悪な思想犯です
ヘッダー情報などでブロックできなかったので、blastrがホストされてるCloudflareのIPを全てブロックする力技で対処しました
ちなみに、nosflareもいつのまにかblastrのようなものをホストしているようです
なんなんでしょうね、Nostrの白人さんたちの、過激なほど分散というか対検閲をしようとするお節介さは
2. 公開していたNostrリレーを潰した
上記のように折角いろいろやったリレーを潰しました
Reply guyというbotが猛威をふるった時期、クソみたいなイベントをばら撒かれてくることに私がキレたからです。クソが
NostrとしてはこれをきっかけにWoTを組み込んだリレーが開発されたりして、スパム対策が一歩前進した感があります。クソが
スパムばら撒きをBostrが助長してるみたいな批難を受けて、作者のYonleさんがブチ切れ、全Nostr関連リポジトリのメンテを放棄する事態も発生
ちょうどMutiny walletでGOXしたご本人の機嫌が悪かった時期に、クソスパムがぶつかったことによる悲しい出来事でした。ほんとクソ
3. おわりに
他にもこまいことはいくつかあるんですが、主にはこんなとこでしょうか。来年も楽しくNostrしたいですね
-
 @ 378562cd:a6fc6773
2025-02-02 17:53:05
@ 378562cd:a6fc6773
2025-02-02 17:53:05Chef's notes
I'm only testing this out right now. I will update the recipe as well as add my own image soon after making this dish again.
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 4
Ingredients
- 4 to 6 potatoes (size depending)
- 1 lb ground beef
- seasonings
- 2 cans chili beans
- 1 onion
- katsup
- shredded cheese of some kind
Directions
- saute onion and add ground beef to skillet. Season to liking.
- peel if you like and thin slice potatoes
- in a rectangle baking dish, layer potatoes, beans, meat and cheese (like a lasagna) until you have used all your ingredients. Try and make at least 2 or 3 layers with extra cheese on top.
- Bake at 350 for one hour. Serve and enjoy!
-
 @ 97c70a44:ad98e322
2024-11-22 22:36:31
@ 97c70a44:ad98e322
2024-11-22 22:36:31This week I finally released Flotilla, a discord/slack-like client I've been working on for about three months. This project began as a NIP 29 client, and after 3 PRs, lots of discussion, a podcast, and a partial implementation, I decided to go my own way.
This of course means that I broke compatibility with all the NIP 29 group clients out there, but I did it for good reasons. In this post I hope to explain those reasons, and speculate on how best to move forward with "relay-based" groups on nostr.
To give you some quick context, NIP 29 and my approach to groups (which I'll dub "relays-as-groups" for clarity) are very similar, with a fundamental difference. Both have chat, join requests, group metadata, membership, moderation, etc. However, the basic unit of a NIP 29 group is a random group id string, while the basic unit of a Flotilla group is a relay itself.
I believe this design difference emerged in part because of what we were attempting to build. NIP 29 groups tend to be more telegram-like, where groups function more like chat rooms, and users join each one individually. On flotilla, groups function more like Discord servers, or Slack workspaces, and users join an entire group of chat rooms at once.
"Relays as groups" has four major advantages over "groups hosted by relays".
Decentralization
First, using relays as groups supports decentralization better than hosting user-managed groups on relays.
(To be clear here, I'm not referring to client-managed groups, which is a whole different approach that we've experimented with in the past, both with NIP 72 communities and with NIP 87 encrypted groups. Both NIP 29 and relays-as-groups solve many of the consistency problems associated with attempting to have a linear, synchronous conversation across multiple relays. While both alternatives have a story for migrating or mirroring a group, both rely heavily on the host relay to not censor user messages.)
I know what you're thinking. How can reducing the number of relays improve decentralization? Relays were originally introduced in order to create redundancy and spread trust across many actors, creating censorship resistance. This model was difficult for many bitcoiners to wrap their heads around, because it's a very different kind of decentralization than what a blockchain delivers.
Communities are an essentially different use case from a broadcast network where content is delivered based on author or recipient relay selections. Every message to a community would have to be delivered to all members of the community. Sending each message to all members' personal inbox relays just doesn't make sense; there has to be some other inbox for the community to work off of.
Additionally, online communities almost always have moderators and admins. This is even true of very public, open types of communities, like subreddits. The only type of community that doesn't have moderators is one that emerges naturally from social clustering. And even in that case there is loose consensus about who is in and who isn't, based on the actions/follows/mutes of the participants, whether these clusters are huge or tiny. Socially-emergent groups are served well by chat applications or broadcast networks.
But the subset of online communities that do prefer to confer moderator status on certain members are essentially centralized. In other words, centralization and control is a feature, not a bug.
Now, that doesn't mean there don't need to be considerations around credible exit and removing/adding moderators over time. But the fact is that moderator-led communities are always under the oversight of the moderators at any given time, even if the identity of those moderators changes and their power is limited.
What this implies is that decentralization for moderator-led groups looks very different from decentralization for a broadcast network. There is nothing at all wrong with giving moderators full control over the group's communications (qua the group; DMs and public broadcast content between group members should happen outside the group's infrastructure, just as people also exist outside the communities they are a part of). What is important is that no one has control over groups that they aren't nominally the admin of.
In concrete terms, what this all means is that community moderators should self-host their infrastructure. This is the same principle as motivates self-custody and home servers, but applied to communities. If community leaders manage their own relays, this means that no hosting company or relay admin can de-platform their community. Centralization of network infrastructure in this case aligns with the trust structure of the group.
Applying this to our group dilemma, it's easy to see that NIP 29 groups are more vulnerable to censorship or data harvesting attacks by malicious relay admins, since many unrelated groups might live on a single relay. In contrast, if you treat relays as groups themselves, every group is forced to live on a separate relay, spreading risk across more hosting providers.
Now, this doesn't necessarily mean that many "relays" aren't "virtual relays" managed by the same hosting provider. So I'll admit that even "relay-based" groups don't completely solve this problem. But I think it will tend to nudge community organizers toward thinking about community infrastructure in a more self-sovereign (or community-sovereign) way.
Investment in Relays
While both NIP 29 and relays-as-groups rely heavily on relays to implement the features that support each specification, there's an important difference between the feature sets. In NIP 29, relay support is specific only to groups, and isn't applicable to other use cases. In contrast, every protocol feature added to support the "relays as groups" can be re-purposed for other types of relays.
Take join requests for example. NIP 29's kind
9021events allow users to request access to a group, and that's all. Kind28934join requests on the other hand allow users to request access to relays. Which in the relays-as-groups model means group access, but it also means custom feed access, inbox relay access, maybe even blossom server access. In fact, kind28934was originally proposed at the beginning of this year in order to support a different version of hosted groups, but remains as relevant as it ever was despite iteration on groups.The orthogonality of features added to relays to any specific use case will long-term result in simpler specs, and more interesting relay-based use cases being possible. Join requests are only one example. The same is true of 1984-based moderation, the proposed LIMITS command, AUTH, NIP 11 relay metadata, etc.
We already have web of trust relays, feed relays, archival relays, and many more. Being able to request access to closed versions of these is useful. Being able to signal federation between multiple instances of these, run by different people, is useful. And of course, relay metadata, reports, and LIMITS are self-evidently useful for normal relays, since they pre-date Flotilla.
I've always said that relays are some of the coolest and most under-appreciated parts of nostr. This doesn't mean that we should add every possible feature to them, but features related to data curation and access control fit really well with what relays are good for. For more on the role of relays and what features should be added to them, see my nostrasia talk Functional Relays.
Declarative vs Imperative
A common paradigm in programming is that of declarative vs imperative programming. Imperative programming focuses on "how" to achieve a given result, leaving "what" the code is doing to be inferred by the programmer. Declarative programming instead focuses on the "what", and allows some underlying implementation to solve the how. A good balance between these paradigms (and knowing when to use one over the other) allows programmers to work faster, make fewer mistakes, and produce less code.
Another way to look at this is that a specification should contain as much ambiguity as possible, but without compromising the system attributes the specification is supposed to guarantee. It can get complex when figuring out what attributes are core to the specification, since sometimes the "how" does actually matter a lot.
However, nostr in particular falls pretty far along the "declarative" end of this spectrum because of its decentralized nature. The only person who can say anything with any authority is the person who signs an event. This event is a "declaration", and any effects it has are necessarily up to the relays, clients, and people interpreting the event. However, what others do with an event is an expectation that must be taken into account by the publisher, forming a feedback loop. This dialectic is what creates stability in the protocol.
In more concrete terms, no one can "tell" anyone else what they have to do by publishing an event like you might in a traditional, centralized RPC-type system. Any event whose semantics are a "command" rather than a "fact" or "request" is broken unless the counter party is fully committed to carrying out the command. An example of a "command" scenario on nostr is NIP 46 remote signing, in which the bunker is the agent of the user making the request. If the bunker implementation fails to carry out a valid command initiated by the user, its interpretation of that event is objectively incorrect.
NIP 29 applies this same paradigm to relays, particularly in the area of moderation, membership edits, and group metadata. In other words, there are several "commands" which instruct the relay to do something.
This isn't necessarily a bad thing, but it does increase the number of things the interface between the client and relay have to agree on. A regular relay may accept an
add-userrequest, but then do nothing with it, violating the contract it has implicitly accepted with the user. The solution to this is feature detection, which is a whole other API to be specified and implemented.My ideal solution to this problem is to shift the semantics of events away from "commands" to "facts" - in other words, to make the interface more declarative.
In fact, we already have an interface for moderation that works like this. Many clients support kind
1984"report" events. Users sending these reports have no expectations about how they will be used. They are a "fact", a declaration of opinion with certain semantics. Other actors in the network may choose whether or not to pay attention to these.This same model is easily applied to communities. Without having to implement any feature detection (either for the relay's implementation, or for the user's role on that relay), anyone can simply send a "report". This goes into the black hole of the relay, and may subsequently be ignored, broadcasted, or acted on.
The really nice thing about this model is that because there is no expectation for "how" reports are to be interpreted, any approach to moderation can be used depending on relay policy or client implementation. In NIP 29, if you issue a
delete-event, it either happens or it doesn't and if it doesn't, you have to explain the failure to the user somehow.In the relays-as-groups model, e-tagging an event in a kind
1984requires no user feedback, and therefore it can be interpreted however the relay prefer. This can result in insta-banning, manual review, thresholds based on number of reporters, a leaky-bucket social score algorithm, shadow banning, temporary banning, soft-moderation by allowing clients to request reports and respond to them by changing user interface elements, or anything else you can think of.The reason I think this is important is that community moderation is a very hard problem, and baking certain semantics into the specification can result in the complete failure of the spec. NIP 72 should be considered an example of what not to do. Some NIP 72 communities have survived due to the dedication of the moderators, but many more have failed because of the rigid moderation model. We should try not to make the same mistake again.
Conclusion
Now, having said all that, I think there is actually a lot of value to NIP 29. What finally clicked for me this week after releasing Flotilla is that the two approaches are actually complementary to one another. One of the most common feature requests I've already heard for flotilla is to have more complete support for rooms, which are currently implemented as not much more than hashtags. Better rooms (i.e., "nested groups") would require: authentication, membership, moderation, and pretty much everything else that exists for the top-level group.
As much as I believe the relays-as-groups approach is superior to NIP 29 for top-level groups, it doesn't make any sense to try to "nest" relays to create sub-groups. Something like NIP 29 is needed in order to fully support rooms anyway, so I think the convergence of the two approaches is all but inevitable. In fact, fiatjaf has already merged a PR which will allow me to use the same event kinds in flotilla as exist already in NIP 29 clients.
There are just a few more changes that are necessary in order for me to fully adopt NIP 29 in Flotilla:
- NIP 29 feature detection
- Opaque ids for unmanaged groups prevent unmanaged groups from having human-readable names
- We need a mechanism for building membership lists without relay support
- Better handling for
9021group join requests
I've opened PRs for each of these (linked above). Hopefully we can work through these issues and combine our powers to become the Captain Planet of group implementations.
-
 @ 97c70a44:ad98e322
2024-11-18 17:57:17
@ 97c70a44:ad98e322
2024-11-18 17:57:17So I have this cool new product, which for about two weeks has been ready to release, if I could just solve one thing. I have recently moved away from storing user keys in my apps due to the ease with which they could (and have) been put at risk. In doing so, I've discovered that despite its downsides, pasting your nsec into an app is a pretty straightforward operation which even non-technical people can pull off. In contrast, pretty much no other key management solution is.
Just to state the obvious, and to kick off this survey of nostr key management options, let me just state that asking users to paste their nsec into your app is a bad idea. However good your intentions, this opens your users up to all kinds of attack vectors, including clipboard hijacking attacks, exposing keys to insecure communication channels, exposing keys to many different apps, supply chain attacks, XSS attacks, and yes, bugs that cause your software to send keys to analytics or error reporting backends.
The era of nsec-pasting is over.
I've committed to embracing the pain and removing nsec login from Coracle, and I encourage other devs to do the same. The sooner we treat key management with the urgency it deserves, the sooner we can come up with a secure and convenient key management solution.
As an aside,
ncryptsecis a great innovation for securely transporting keys, but it still doesn't protect against exposure to apps that need to use keys. It has its place though; in fact I'm of the opinion thatnsecand seed words should be deprecated, and support for them should be removed. Giving friendly names and human-readable representations to data that is essentially private is a really bad idea (unless you're memorizing your key). But I digress.Signer Comparisons
Let's go through a few existing options for key management, and compare their relative merits. I've tried to list them in the order they appeared on the scene, which also helps to clarify the logic of how signers have evolved. Throughout, I will be focusing on what kinds of user experience each approach unlocks for non-technical users, since my goal is to build products that work for regular people.
Extension Signers
The first signer application (that I know of) was nos2x, by fiatjaf. As I understand it, this was a proof-of-concept of how users might protect their keys without releasing custody of them. And it works really well! In fact, even though there have been many forks and imitators, I still use nos2x when using nostr on my desktop browser.
Extension signers offer a great user experience, along a narrow happy path. Setting up a browser extension is a relatively familiar process for normal users, and once it's done you don't really have to think about it. In theory, extensions can also include their own onboarding process and key backup strategies as well, allowing users to get started in a single place. Plus, there's very little latency involved in making calls to the signer extension.
This positive experience breaks down quickly though once a user wants to use a desktop or mobile application. When this happens, users have to start over essentially from scratch. Nothing they did to set up the extension helps them move to another signer application.
While it's technically possible to use extension signers on mobile via e.g. the Kiwi browser, this doesn't work for native apps or apps installed as PWAs. Instead, you either have to revert to pasting keys, or use some other solution.
One slight permutation of extension signers is browser signers, like Spring. Instead of adding a signer to your browser, Spring allows you to install a browser that holds your keys and allows you to use any nostr web application. But this has all the same basic limitations that extension signers do.
Hardware Signers
Hardware signers came around shortly after extension signers. I'm not going to spend much time talking about them here, because although they're about as far along the spectrum towards security as you can go, they're also not very convenient. Non-technical users aren't going to onboard by buying (or building) a device which they have to connect to their desktop via USB whenever they want to sign a message. Hardware signers have their place, but onboarding isn't it.
The only hardware signer I'm aware of (although I'm sure I've heard of others) is from LNBits, and is usually used via a browser extension like horse. This of course means that it has all the same limitations that browser extensions have, and then some (although mobile and desktop apps would likely be able to find a way to talk directly to the signer).
Hosted Signers
Remote signers (aka "bunkers") use the Nostr Connect protocol (also known as NIP 46) for remote signing.
Hosted signers in particular are one example of a NIP 46 remote signer, which lives on "somebody else's computer". Because they use a legacy web architecture, they can be built to be very familiar and convenient to users. It's trivial to build a hosted signer that offers email/password login along with 2FA, password resets, session revokation, the whole shebang. But they have one fatal flaw, which is that they are custodial. This means that not only do users have to relinquish exclusive control over their keys, but hosted signers also can become a target for hackers.
Desktop Signers
Several projects exist which allow users to run their own bunker, on their own hardware. These include nostr clients like Gossip, as well as command-line utilities like nak. This approach is mostly an improvement over extension signers, because it widens the scope of applications that can conveniently access the signer from those that run in the browser to those that run on the desktop computer the signer lives on. The downside is that they have to communicate via relays, which either introduces latency or requires an additional component to be running locally.
While it's technically possible to use desktop signers to log in on other computers or mobile apps, I don't think that's going to be very practical for most people. Mobile apps by definition are more portable than regular computers. Anyone who wants to access their nostr account on more than one device will have to either set up separate solutions, or go with another kind of remote signer. This isn't a huge obstacle for people highly invested in nostr, but it's a significant amount of friction for a new user.
Mobile Signers
Mobile signers solve the problem introduced by desktop signers of not always having access to your signer (or of your signer not having access to you, due to being powered down or disconnected from the internet). Mobile devices are generally more available than desktop devices, and also have better push notifications. This means that users can approve signer requests from any device as easily as tapping a notification.
Mobile signers on Android can also upgrade their UX by taking advantage of NIP 55 to avoid the round trip to relays, reducing latency and making it possible to sign things offline. Amber has been a pioneer in this area, and other projects like Nostrum and Alby's nostr-signer have been prototyped.
To date, there unfortunately haven't been any signer applications released for iOS, which leaves the mobile signer story incomplete. In my opinion, this is probably the most promising solution for end users, although it's currently under-developed.
Web Signers
One interesting alternative that combines the benefits of hosted, desktop, and mobile wallets is nsec.app. This is a web application frontend which keeps keys in the browser, so that they are never shared with a third party. Using web push notifications and a healthy sprinkle of black magic, nsec.app is able to respond to signer requests by opening itself in a browser window.
This works generally pretty well for desktop web applications, less well on android, still less well for android PWAs, and (to my understanding) not at all on iOS. Artur from nostr.band is working on these problems using a variety of approaches, one of which is embedding nsec.app in an iframe and communicating using
postMessage.This approach also makes it possible to sync keys between your phone and desktop, simulating a hosted UX by making them accessible from either location by signing in to nsec.app. This is done by encrypting user keys and storing them on the nsec.app server. In theory this should be secure, but it's something to consider.
I'm cautiously optimistic about this approach. If successful, it would enable a single brand to exist on every platform, which is important to reduce unnecessary configuration and cognitive overhead for users.
Multisig Signers
Another experimental approach is multi-sig. Promenade is a project by fiatjaf exploring this possibility. This would allow users to split their keys across different custodians and require all (or some majority of them) to approve an event signature before it would be valid.
The downsides of this are an increase in complexity (more moving parts for users to deal with) and latency (more parties to coordinate with to sign events). I'm also not clear on whether encryption is possible using multi-signature keys. If not, that would preclude not only existing direct messages (which will hopefully end up on MLS eventually anyway), but also things like private lists, mutes, and application settings. I think multi-signature signers are promising, but are definitely a long-term project.
Self-Hosted Signers
Coming nearly full circle, self-hosted signers are a special case of hosted signers, but, you know, self-hosted. These signers might live on a home server like a Start9 and be accessible for signer request approvals via tor, or they might live on a server run by the user (or an Uncle Jim). This would be an extremely convenient approach for anyone willing to deal with the complexities of hosting the infrastructure.
A good candidate for NIP 46 support might be AlbyHub, which is already one of the easiest self-hosted wallets to set up and use. Adding signer suppport to AlbyHub would allow users to have their wallet and nostr keys stored in the same place, and accessible anywhere either via the web interface or via AlbyGo.
Omniplatform Signers
This leads me to, finally, "omniplatform" signers. This isn't really a new architecture, but a combination of several. User choice is great, but nostr has a very tight complexity budget when onboarding new users. If a brand can manage to get new users set up with a very simple but sub-optimal solution, then grow them into a more complete integration into the nostr ecosystem, that would be a huge win.
I think Alby has a great shot at doing this, if it's something they want to prioritize. Bitwarden would also be a great candidate, since they already have apps on every platform, as well as a self-hosted option (Vaultwarden). If users could start with a mobile app, and incrementally set up a browser extension, self-hosted vault, and hardware signer as needed, that I think would be an ideal path.
Nostr Connect: broken, but promising
If you can't tell from the above comparison, I'm partial to NIP 46 as the best, most flexible way to build high-quality user experiences. Remote key management means a reduction in moving keys, hosting keys, and software installation and administration. If we can get users to the point where their keys live in only two places (their password manager and their signer), we'll be doing good.
There are however many ways to implement NIP 46. Implementing all of them in a single client (or signer) would be burdensome for developers, and introduce a lot of UI complexity to users. Here's a quick survey of flows that currently exist.
Signer -> Client
The simplest way to connect a client and a bunker is for a user to explicitly authorize the connection by copying a
bunker://URL from their signer application to their client. This allows the bunker to generate and validate a secret embedded in the URL without the client having to do anything other than pass it along in the initialconnectrequest.This is a great UX for people who know what they're doing, but isn't at all friendly to newcomers. Someone signing in for the first time isn't going to know what a bunker link is, and even if they do they're immediately confronted with the problem of picking a signer, setting it up, and finding out where in that app they can obtain a bunker link. This can be marginally smoothed out using things like protocol handlers and QR codes, but these won't apply in all (or even most) cases.
Client -> Signer
The reverse flow is similar. This relies on the user to explicitly authorize the connection by copying a
nostrconnect://url from the client into the signer app. In technical terms, this requires one fewer step, since in NIP 46 the connection is always initiated by the client. In this case, the pasting of the URL replaces theconnectrequest. The client listens for a response containing a client-generated secret embedded in thenostrconnect://url. This step isn't currently supported by all signer apps, some of which return anackinstead. This can result in session hijacking, where an attacker can intercept signing requests (although they can't do anything that would require the user's key, like decrypting messages).While at first glance
nostrconnectseems functionally identical tobunkerlinks, the UX has the potential to be much better. The reason for this has to do with how people use which devices, and where a client or signer application is most likely to be run. This requires making some assumptions, but in my mind the most common scenario is that a user will want to host their signer on their phone, since that is the device that is most universally available for authorizations (apart from an always-online hosted signer on the open internet). In other words, users generally have their phones with them when they're using their computer, but often don't have a desktop available when using their phone. This idea is validated by (for example) the prevalence of SMS-based 2FA, which assumes the presence of a phone.Assuming the signer is on the user's phone, QR-scan flows for client authorization make a lot more sense if the client is the one generating the link, since they can simply scan a code generated on another device with their camera, or copy/paste or use a protocol handler for a client on the same device. In contrast, when using a
bunkerlink users might find themselves in the awkward position of having to copy a link from their phone to their desktop. Whether this is done via QR code or by sending yourself a link via DM/text/email, it's an awkward flow most people aren't really prepared for.Auto-Connect
Some enhancements have been made to the bunker flow which allow clients to send an initial
connectrequest without asking the user to copy links between apps. These allow clients to do away with opaque magic strings entirely and provide the idealized "just one click" flow. However, after trying to make this flow work over the course of a couple weeks, I've come to the opinion that the additional complexity involved in automating the flow just isn't worth it.There are a few variants of this "auto-connect" flow:
- Signer NIP-05: Signers can register a NIP 05 address for a user's pubkey on their domain, allowing users to enter their address rather than their pubkey on login. Unfortunately, this address has no relation to their actual NIP 05 address, which can result in a lot of confusion.
- User NIP-05: To solve this problem, fiatjaf has proposed a new version which allows users to enter their own NIP 05 in at login instead of the one provided by the signer. The client would then look up the user's
10046event and follow the signer pubkey listed there. - Nostrconnect handler: Signers may publish a NIP 89 handler which includes a handler url that clients can send
nostrconnecturls to. This isn't currently specified anywhere, but it is supported by nsec.app. This bypasses the NIP 05 address requirement entirely, allowing users to simply pick a signer and click a button.
Each of these flows have their own strengths and weaknesses, but all of them share a dependency on some external source of truth for routing a user to the correct bunker.
In the first case, this is done by remembering the NIP 05 address assigned by the signer, which relies on DNS and on users to not forget which address they're using.
In the second case, this is done by relying on the user having done a significant amount of configuration (setting up a NIP 05, adding it to their kind 0, and having published a
10046event) which may or may not exist. This forces clients to gracefully degrade to some alternative login method anyway, and adds UX friction since users have to choose which interface will work for them.The final method bypasses the need for users to remember their NIP 05 address, but it does require either the client or the user to select a trusted signer. If poorly implemented, this could result in users choosing an untrustworthy signer on signup (risking their keys), or the wrong signer on login resulting in a broken session.
For all these reasons, I've opted to go with the vanilla bunker/nostrconnect flow, which allows me to display a simple interface to users. Presenting a QR code without comment assumes that users know what to do with it, but the benefit is that it makes explicit the signer selection step which the auto-connect flows try to paper over. This is actually a good thing, because instead of using heuristics like addresses or lists of signers presented by a client to make the decision, users can choose based on which app they actually have installed, which is a richer mnemonic device.
Making NIP 46 Work
The bottom line here is that while NIP 46 is the best baseline for signer support, it doesn't currently work very well at all. There are a variety of reasons for this:
- The specification itself isn't clear, and is constantly changing. This leads to incompatibilities between apps and signers (or explosive complexity in trying to handle every case).
- Extensions to the basic bunker flow (both in terms of signer implementation and signer discovery) are worth researching, but each one creates another dimension of possible incompatibility. Signers will be incentivized to support every possible login flow, creating complexity for users and increasing attack surface area. Clients will have to implement fallbacks to their preferred signup flows, again resulting in UX complexity.
- Clients don't currently deal well with latency. In order for NIP 46 to work smoothly, clients will have to implement better loading, debouncing, optimistic updates, publish status, and "undo". There are downsides to this, but many of these features endu up being built by mature software products anyway, so supporting these patterns may actually improve rather than degrade UX.
- There's currently no easy and secure way for users to store keys in a single signer which they can access anywhere. This means that users have to set up multiple bunkers depending where they're sitting, or resort to alternative login methods like NIP 07 or 55. These are great upgrades, since they reduce latency and bandwidth use, but shouldn't be required for new users to learn.
- There's no unified experience across platforms. If a user signs up on their desktop, how do they safely transfer their keys to their Android signer app? If they're given seed words, how can they import them as an nsec? Consensus on best practices would be an improvement, but I think only a unified UX across platforms for a single signer can really solve this.
- As nice as it might be to bypass app stores and built-in push notifications, shunning traditional platforms drastically increases the friction for users. To my knowledge, no signer app currently exists in traditional app stores, or supports built-in push notifications. If we want nostr to be accessible to non-technical folks, we can't ask them to start by downloading Obtanium or zap.store and a UnifiedPush distributor for their platform.
As I mentioned above, I don't think NIP 46 will ever be the only solution for signers. But I do think it's a great baseline on which to build a kind of "progressive enhancement" approach. For example, clients should support at least nostrconnect/bunker links, and encourage users once they've logged in to upgrade to NIP 55 or NIP 07 signers. Signers should exist in the mainstream app store and use native push notifications, with an option to install elsewhere or opt-in to UnifiedPush.
The goal here is to balance user experience and security. The number one rule for this is to reduce attack vectors for obtaining user keys. This points to (ideally) a single non-custodial signer, easily accessible to the user, and a simple protocol for using that signer from any app. Progressive enhancement is fine, but we should always be able to fall back to this baseline.
-
 @ 3bf0c63f:aefa459d
2024-11-07 14:56:17
@ 3bf0c63f:aefa459d
2024-11-07 14:56:17The case against edits
Direct edits are a centralizing force on Nostr, a slippery slope that should not be accepted.
Edits are fine in other, more specialized event kinds, but the
kind:1space shouldn't be compromised with such a push towards centralization, becausekind:1is the public square of Nostr, where all focus should be on decentralization and censorship-resistance.- Why?
Edits introduce too much complexity. If edits are widespread, all clients now have to download dozens of extra events at the same time while users are browsing a big feed of notes which are already coming from dozens of different relays using complicated outbox-model-based querying, then for each event they have to open yet another subscription to these relays -- or perform some other complicated batching of subscriptions which then requires more complexity on the event handling side and then when associating these edits with the original events. I can only imagine this will hurt apps performance, but it definitely raises the barrier to entry and thus necessarily decreases Nostr decentralization.
Some clients may be implemneted in way such that they download tons of events and then store them in a local databases, from which they then construct the feed that users see. Such clients may make edits potentially easier to deal with -- but this is hardly an answer to the point above, since such clients are already more complex to implement in the first place.
- What do you have against complex clients?
The point is not to say that all clients should be simple, but that it should be simple to write a client -- or at least as simple as physically possible.
You may not be thinking about it, but if you believe in the promise of Nostr then we should expect to see Nostr feeds in many other contexts other than on a big super app in a phone -- we should see Nostr notes being referenced from and injected in unrelated webpages, unrelated apps, hardware devices, comment sections and so on. All these micro-clients will have to implement some complicated edit-fetching logic now?
- But aren't we already fetching likes and zaps and other things, why not fetch edits too?
Likes, zaps and other similar things are optional. It's perfectly fine to use Nostr without seeing likes and/or zaps -- and, believe me, it does happen quite a lot. The point is basically that likes or zaps don't affect the content of the main post at all, while edits do.
- But edits are optional!
No, they are not optional. If edits become widespread they necessarily become mandatory. Any client that doesn't implement edits will be displaying false information to its users and their experience will be completely broken.
- That's fine, as people will just move to clients that support edits!
Exactly, that is what I expect to happen too, and this is why I am saying edits are a centralizing force that we should be fighting against, not embracing.
If you understand that edits are a centralizing force, then you must automatically agree that they aren't a desirable feature, given that if you are reading this now, with Nostr being so small, there is a 100% chance you care about decentralization and you're not just some kind of lazy influencer that is only doing this for money.
- All other social networks support editing!
This is not true at all. Bluesky has 10x more users than Nostr and doesn't support edits. Instagram doesn't support editing pictures after they're posted, and doesn't support editing comments. Tiktok doesn't support editing videos or comments after they're posted. YouTube doesn't support editing videos after they're posted. Most famously, email, the most widely used and widespread "social app" out there, does not support edits of any kind. Twitter didn't support edits for the first 15 years of its life, and, although some people complained, it didn't hurt the platform at all -- arguably it benefitted it.
If edits are such a straightforward feature to add that won't hurt performance, that won't introduce complexity, and also that is such an essential feature users could never live without them, then why don't these centralized platforms have edits on everything already? There must be something there.
- Eventually someone will implement edits anyway, so why bother to oppose edits now?
Once Nostr becomes big enough, maybe it will be already shielded from such centralizing forces by its sheer volume of users and quantity of clients, maybe not, we will see. All I'm saying is that we shouldn't just push for bad things now just because of a potential future in which they might come.
- The market will decide what is better.
The market has decided for Facebook, Instagram, Twitter and TikTok. If we were to follow what the market had decided we wouldn't be here, and you wouldn't be reading this post.
- OK, you have convinced me, edits are not good for the protocol. But what do we do about the users who just want to fix their typos?
There are many ways. The annotations spec, for example, provides a simple way to append things to a note without being a full-blown edit, and they fall back gracefully to normal replies in clients that don't implement the full annotations spec.
Eventually we could have annotations that are expressed in form of simple (human-readable?) diffs that can be applied directly to the post, but fall back, again, to comments.
Besides these, a very simple idea that wasn't tried yet on Nostr yet is the idea that has been tried for emails and seems to work very well: delaying a post after the "submit" button is clicked and giving the user the opportunity to cancel and edit it again before it is actually posted.
Ultimately, if edits are so necessary, then maybe we could come up with a way to implement edits that is truly optional and falls back cleanly for clients that don't support them directly and don't hurt the protocol very much. Let's think about it and not rush towards defeat.
-
 @ 8f69ac99:4f92f5fd
2024-10-30 14:54:26
@ 8f69ac99:4f92f5fd
2024-10-30 14:54:26Nos últimos anos, a narrativa dominante retrata a mineração de Bitcoin como um consumidor voraz de energia, com impactos ambientais desproporcionais. Embora a mineração de Bitcoin exija uma quantidade significativa de energia, esta visão ignora um ponto crucial: o seu potencial para promover a sustentabilidade ambiental e remodelar a integração de energias renováveis.
Este artigo vai além dos debates convencionais sobre a pegada de carbono, explorando como a mineração de Bitcoin pode mitigar os impactos ambientais e catalisar uma transição energética sustentável, transformando o que alguns consideram uma inutilidade num aliado contra a dependência dos combustíveis fósseis e a adversidade climática.
Desafios da Energia Renovável
Alcançar um futuro sustentável depende da adopção de fontes de energia renovável, mas estas enfrentam desafios únicos. Gerir o excesso de energia produzido durante períodos de baixa procura e lidar com as limitações da actual tecnologia de baterias são obstáculos significativos. Além disso, a transmissão de energia a longas distâncias permanece ineficiente, o que impede que recursos renováveis remotos alcancem mercados mais amplos.
Por exemplo, as linhas de corrente contínua de alta tensão (HVDC) perdem aproximadamente 3% de potência por cada 1.000 km, enquanto as linhas de corrente alternada de alta tensão (HVAC) perdem cerca de 7% por cada 1.000 km. Isto significa que, por cada quilómetro, as linhas HVDC perdem cerca de 0,003%, e as linhas HVAC perdem cerca de 0,007% (as linhas de alta tensão são projectadas para diminuir perdas, as perdas são ainda maiores na media tensão). Estas perdas, aliadas à dificuldade de transportar energia de parques renováveis remotos, sublinham a necessidade de soluções localizadas.
Por exemplo, em 2018, cerca de 6,5 milhões de MWh de produção de energia solar fotovoltaica foram descartados, ou "mandados fora", no Chile, na China, na Alemanha e nos Estados Unidos conjuntamente. É importante notar que, à medida que a capacidade de energia renovável continua a crescer rapidamente (com o aumento das adições de capacidade renovável global anual em quase 50%, para quase 510 gigawatts em 2023), a quantidade absoluta de energia desperdiçada é susceptível de aumentar, a menos que se façam melhorias significativas na infraestrutura da rede, no armazenamento de energia e na gestão da procura.
Monetizar o Excesso de Energia através da Mineração de Bitcoin
Fontes de energia renovável, como a solar e a eólica, muitas vezes geram mais electricidade do que a rede necessita em determinados momentos, criando um excedente de energia que normalmente é desperdiçado. Este excesso permanece subutilizado porque:
- As soluções de armazenamento em grande escala são limitadas e dispendiosas ou mesmo inexistentes;
- A capacidade de transmissão muitas vezes não é suficiente para distribuir energia a longas distâncias;
- E a procura nem sempre coincide com os períodos de produção máxima de energia renovável.
A mineração de Bitcoin apresenta uma solução apelativa, ao actuar como um consumidor de energia flexível, capaz de ajustar rapidamente o seu consumo para se alinhar com a oferta. Operações de mineração localizadas perto de instalações de energia renovável — como centrais hidroeléctricas ou parques solares — podem absorver o excesso de energia que, de outra forma, seria desperdiçado, monetizando-o. Esta configuração não só reduz o desperdício de energia renovável, como também proporciona fontes de rendimento fiáveis para projectos renováveis, incentivando o investimento em infraestruturas verdes.
Mineração de Bitcoin como Consumidor Flexível
As operações de mineração de Bitcoin podem ajustar dinamicamente o seu consumo de energia, actuando como uma "carga flexível" na rede. As principais vantagens incluem:
- Escalabilidade Rápida: Os equipamentos de mineração podem aumentar ou diminuir o seu consumo de energia quase instantaneamente, respondendo às flutuações na disponibilidade de energia.
- Independência Geográfica: A mineração de Bitcoin pode ser realizada em qualquer local com ligação à internet, permitindo que os mineradores se situem perto das fontes renováveis, independentemente da infraestrutura da rede.
- Capacidade Modular: O equipamento de mineração é altamente escalável, permitindo que os produtores de energia desenhem sistemas modulares que se adaptem à capacidade energética disponível.
Incentivos Económicos e Benefícios
A utilização do excedente de energia para a mineração de Bitcoin permite que os produtores de energia renovável gerem receitas a partir de energia que, de outra forma, seria desperdiçada. Este impulso económico aumenta a rentabilidade dos projectos de energia renovável, tornando-os mais atractivos para os investidores. Os benefícios adicionais incluem:
- Estabilização da Rede: As operações de mineração ajudam a equilibrar a oferta e a procura na rede, contribuindo para a resiliência e estabilidade da mesma.
- Redução do Desperdício: Ao consumir electricidade excedente, a mineração de Bitcoin reduz significativamente a quantidade de energia renovável desperdiçada.
- Aumento do Financiamento para Renováveis: Os lucros provenientes da mineração de Bitcoin podem ser reinvestidos em novos projectos de energia renovável, soluções de armazenamento e infraestrutura de rede, criando um ciclo positivo de reforço para a energia verde.
Aplicações no Mundo Real
Vários exemplos ilustram como a mineração de Bitcoin monetiza eficazmente o excedente de energia:
- No Texas, os mineradores de Bitcoin aproveitam o excesso de energia eólica, apoiando a rede através de programas de resposta à procura que aumentam a fiabilidade da rede durante períodos de alta e baixa procura.
- No Quebec, o excesso de energia hidroeléctrica é canalizado para operações de mineração de Bitcoin, o que ajuda a estabilizar a rede e a reduzir o desperdício de energia renovável.
- Um estudo da Universidade de Cornell descobriu que projectos de energia renovável nos EUA poderiam gerar milhões de dólares ao minerar Bitcoin durante estágios pré-comerciais, demonstrando a viabilidade económica desta abordagem.
Potencial Impacto na Transição para Energias Renováveis
Ao monetizar o excedente de energia através da mineração de Bitcoin, esta abordagem acelera a transição para energias renováveis. Os benefícios incluem:
- Viabilidade Económica para Renováveis: A monetização da energia desperdiçada torna os projectos renováveis mais rentáveis e, portanto, mais atractivos para investidores.
- Flexibilidade da Rede: A mineração de Bitcoin fornece uma fonte de procura escalável e adaptável, ajudando os operadores de rede a gerir as flutuações de oferta.
- Pegada de Carbono Reduzida: Ao utilizar fontes renováveis, o impacto ambiental da mineração de Bitcoin diminui, alinhando-se com os objectivos de sustentabilidade.
- Adopção Acelerada de Energias Renováveis: A maior rentabilidade e a redução do desperdício incentivam um maior investimento, impulsionando a adopção de tecnologias de energia renovável.
Essencialmente, a mineração de Bitcoin oferece uma solução única para os desafios da produção intermitente de energia renovável, criando uma procura flexível e independente da localização para a electricidade excedente que, de outra forma, seria desperdiçada. À medida que mais projectos renováveis adoptam este modelo, a mineração de Bitcoin pode desempenhar um papel crucial na promoção de um panorama energético sustentável e descentralizado.
Fornecimento de Energia a Regiões Isoladas e Subdesenvolvidas
Um dos impactos mais promissores da mineração de Bitcoin é a capacidade de levar electricidade a regiões remotas e subdesenvolvidas. Pequenas centrais hidroeléctricas e instalações solares são opções cada vez mais viáveis para comunidades isoladas que não têm acesso a redes tradicionais. Mineradores de Bitcoin, em busca de energia barata e excedente, podem apoiar e financiar estas instalações, reduzindo a lacuna energética e permitindo o acesso a energia limpa para estas comunidades.
Por exemplo, aldeias em África que anteriormente não tinham electricidade podem agora operar escolas, clínicas e empresas, graças a pequenos projectos de energia renovável apoiados pela mineração de Bitcoin. Este acesso catalisa o crescimento económico, criando um ciclo virtuoso onde a energia leva a investimentos, educação e melhor saúde — elevando comunidades inteiras para fora da pobreza.
Redução de Emissões através da Mitigação de Metano
A mineração de Bitcoin também contribui para a redução das emissões de metano — um gás de efeito estufa com um potencial de aquecimento global 28 a 34 vezes superior ao do CO₂ num período de 100 anos. As emissões de aterros sanitários, resíduos agrícolas e poços de petróleo abandonados representam uma ameaça climática significativa, mas a mineração de Bitcoin oferece uma solução única ao converter este poluente em energia.
Quando o metano é queimado para gerar electricidade, é convertido em CO₂ e vapor de água, que, embora também sejam gases de efeito estufa, são muito menos potentes do que o metano. Na verdade, o metano é responsável por cerca de 25% do aquecimento global que experimentamos actualmente, apesar da sua concentração relativamente baixa na atmosfera. Ao capturar e utilizar o metano, as operações de mineração de Bitcoin transformam um dano ambiental numa fonte de energia produtiva, reduzindo as emissões globais de gases de efeito estufa e criando novas fontes de rendimento.
Por exemplo, nos EUA, o metano de poços de petróleo abandonados está a ser capturado para alimentar a mineração de Bitcoin, criando um sistema fechado que evita que o metano seja queimado ou liberado directamente na atmosfera. Esta abordagem não só mitiga as emissões, como também apoia o crescimento económico em regiões com recursos de metano não aproveitados.
Resiliência e Flexibilidade da Rede
A integração de fontes renováveis, como a eólica e a solar, introduziu desafios para a estabilidade das redes eléctricas. Com as renováveis, os operadores de rede enfrentam flutuações de frequência mais frequentes e uma resposta inercial reduzida — as renováveis não fornecem a mesma resposta inercial que as centrais térmicas tradicionais, tornando a rede mais susceptível a mudanças rápidas.
A flexibilidade da mineração de Bitcoin pode desempenhar um papel fundamental na estabilização das redes eléctricas. Durante a tempestade de inverno Uri, no Texas, os mineradores de Bitcoin reduziram o seu consumo de energia para libertar capacidade para serviços essenciais, mostrando o papel da mineração de Bitcoin como uma carga flexível e reactiva de energia.
Ao ajustar o consumo de energia com base na disponibilidade de oferta, os mineradores de Bitcoin podem ajudar a equilibrar as redes com elevada penetração de renováveis. Esta sinergia com energias renováveis e nucleares fornece uma solução robusta para a gestão da procura energética, especialmente à medida que a rede transita para fontes de baixo carbono.
Impacto Ambiental de Longo Prazo
A mineração de Bitcoin tem o potencial de revolucionar a produção e o consumo de energia. Ao integrar energias renováveis, aproveitar o metano e oferecer gestão flexível da carga, o Bitcoin pode desempenhar um papel fundamental num futuro energético sustentável e descentralizado. Inovação política, responsabilidade industrial e colaboração intersectorial são essenciais para concretizar o potencial do Bitcoin na transição verde.
Diante dos desafios ambientais actuais, a mineração de Bitcoin oferece mais do que inovação financeira. Representa um poderoso aliado na construção de um futuro sustentável e equitativo — onde os objectivos digitais e ambientais alinham-se para criar uma economia global mais limpa e resiliente.
Bitcoin #mining #greenEnergy #renewables
-
 @ 3bf0c63f:aefa459d
2024-10-26 14:18:23
@ 3bf0c63f:aefa459d
2024-10-26 14:18:23kind:1maximalism and the future of other stuff and Nostr decentralizationThese two problems exist on Nostr today, and they look unrelated at first:
- People adding more stuff to
kind:1notes, such as making them editable, or adding special corky syntax thas has to be parsed and rendered in complicated UIs; - The discovery of "other stuff" content (i.e. long-form articles, podcasts, calendar events, livestreams etc) is hard due to the fact that most people only use microblogging clients and they often don't appear there for them.
Point 2 above has 3 different solutions:
- a. Just publish everything as
kind:1notes; - b. Publish different things as different kinds, but make microblogging clients fetch all the event kinds from people you follow, then render them natively or use NIP-31, or NIP-89 to point users to other clients that would render them better;
- c. Publish different things as different kinds, and reference them in
kind:1notes that would act as announcements to these other events, also relying on NIP-31 and NIP-89 for displaying references and recommending other clients.
Solution a is obviously very bad, so I won't address it.
For a while I have believed solution b was the correct one, and many others seem to tacitly agree with it, given that some clients have been fetching more and more event kinds and going out of their way to render them in the same feed where only
kind:1notes were originally expected to be.I don't think clients doing that is necessarily bad, but I do think this have some centralizing effects on the protocol, as it pushes clients to become bigger and bigger, raising the barrier to entry into the
kind:1realm. And also in the past I have talked about the fact that I disliked that some clients would display my long-form articles as if they were normalkind:1notes and just dump them into the feeds of whoever was following me: nostr:nevent1qqsdk90k9k30vtzwpj6grxys9mvsegu5kkwd4jmpyhlmtjnxet2rvggprpmhxue69uhhyetvv9ujumn0wdmksetjv5hxxmmdqy8hwumn8ghj7mn0wd68ytnddaksygpm7rrrljungc6q0tuh5hj7ue863q73qlheu4vywtzwhx42a7j9n5hae35cThese and other reasons have made me switch my preference to solution c, as it gives the most flexibility to the publisher: whoever wants to announce stuff so it can be discovered can, whoever doesn't don't have to. And it allows microblogging clients the freedom to render just render tweets and having a straightforward barrier between what they can render and what is just a link to an external app or webapp (of course they can always opt to render the referenced content in-app if they want).
It also makes the case for microapps more evident. If all microblogging clients become superapps that can render recipe events perfectly why would anyone want to use a dedicated recipes app? I guess there are still reasons, but blurring the line between content kinds in superapps would definitely remove some of the reasons and eventually kill all the microapps.
That brings us back to point 1 above (the overcomplication of
kind:1events): if solution c is what we're going to, that makeskind:1events very special in Nostr, and not just another kind among others. Microblogging clients become the central plaza of Nostr, thus protecting their neutrality and decentralization much more important. Having a lot of clients with different userbases, doing things in slightly different ways, is essential for that decentralization.It's ok if Nostr ends up having just 2 recipe-sharing clients, but it must have dozens of microblogging clients -- and maybe not even full-blown microblogging clients, but other apps that somehow deal with
kind:1events in multiple ways. It's ok if implementing a client for public audio-rooms is very hard and complicated, but at the same time it should be very simple to write a client that can render akind:1note referencing an audio-room and linking to that dedicated client.I hope you got my point and agreed because this article is ended.
- People adding more stuff to
-
 @ 8d34bd24:414be32b
2025-02-02 21:31:11
@ 8d34bd24:414be32b
2025-02-02 21:31:11This Sunday our pastor had to give a sermon with very little preparation. He was leading an elders’ retreat and one of the elders was supposed to preach in his place. The elder who had prepared a sermon ended up in the hospital, so our pastor had to prep fast. He did a great thing. He preached on a passage, but also used that passage to demonstrate how he studies scripture. It was a great sermon. The passage he preached on reminded me of a time in my past when I learned some important lessons.
Almost 20 years ago, I was leading a high school girls Bible study. They picked out a book about Mary and Martha to study. Initially, I wasn’t thrilled with their choice, but didn’t have a theological problem with it, so I agreed for us to study this book. (I don’t remember the name of the book and all my books burnt up when my house burnt down almost 10 years ago). In the end, I probably got more out of the study than any of the girls because I have a definite tendency to be a Martha. What was Martha’s error? Let’s check out the passage:
Now as they went on their way, Jesus entered a village. And a woman named Martha welcomed him into her house. And she had a sister called Mary, who sat at the Lord’s feet and listened to his teaching. But Martha was distracted with much serving. And she went up to him and said, “Lord, do you not care that my sister has left me to serve alone? Tell her then to help me.” But the Lord answered her, “Martha, Martha, you are anxious and troubled about many things, but one thing is necessary. Mary has chosen the good portion, which will not be taken away from her.” (Luke 10:38-42 ESV)
Jesus visited two sisters who welcomed Him into their home. Mary sat at Jesus’s feet and listened to His teaching. Martha spent her time serving everyone and taking care of everyone’s physical needs.
Is taking care of their home and the needs of their guests a bad thing? Of course not, but is it the best?
To make things much worse, Martha then got upset because her sister Mary wasn’t helping her. She was just sitting there taking in every word that Jesus said. Most of us would think Martha’s sacrifices to take care of everyone was better than Mary’s choice to just sit at Jesus’s feet, but did Martha really choose the better path?
Martha then showed that her heart wasn’t focused right and she wasn’t putting the most important things first. She complained to Jesus about her sister’s failure to help and even commanded her Creator, “Tell her then to help me.” Instead of focusing on the words of Jesus, her frustration led her to command her God to act in the way she desired. She was so busy with cooking, cleaning, and serving, that she missed the most important things — spending time with and listening to her God, who was right there in her house with her. This was an opportunity that shouldn’t be missed due to busyness.
How often do we all do this same thing? How often are busy doing good things and miss the most important things? How often are we busy doing ministry that we forget about the reason for the ministry? I don’t know about you, but this happens to me a lot more often than I would like to admit. My biggest sins are usually not what most people think of as sins. My biggest sins are getting so busy that I leave God out of my life. I am so busy serving God that I forget to follow His leading. I am so busy doing what most people would consider good things, but if God is not part of them, they are not worth much. Because I am focusing on getting things done, worry and stress overtake me harming my health and my relationship with Jesus.
I don’t think this is taking Scripture out of context:
We have come to know and have believed the love which God has for us. God is love, and the one who abides in love abides in God, and God abides in him. (1 John 4:16) {emphasis mine}
Knowing that God is love, read the following passage replacing love with God.
If I speak with the tongues of men and of angels, but do not have love, I have become a noisy gong or a clanging cymbal. If I have the gift of prophecy, and know all mysteries and all knowledge; and if I have all faith, so as to remove mountains, but do not have love, I am nothing. And if I give all my possessions to feed the poor, and if I surrender my body to be burned, but do not have love, it profits me nothing. (1 Corinthians 13:1-3)
If I do not include God in my every action, “it profits me nothing.”
In reality it shouldn’t be allowing God to join me in my works, but me joining God in His works. It should be me listening to God’s word and the leading of the Holy Spirit, looking and seeing what God is doing around me, and me joining in His great works. It should be me allowing God to use me as a tool.
There are times that God speaks clearly and directly to us about what He desires for our lives, but most of the time, He speaks through His word — the Bible. Knowing the Bible helps us to know His will and His eternal plan, so we can follow Him and join Him in His work. Knowing the Bible helps us to differentiate between what is good and what is God’s best. It helps us to prioritize what is really important.
And this I pray, that your love may abound still more and more in real knowledge and all discernment, so that you may approve the things that are excellent, in order to be sincere and blameless until the day of Christ; having been filled with the fruit of righteousness which comes through Jesus Christ, to the glory and praise of God. (Philippians 1:9-11) {emphasis mine}
We can’t obey God, imitate Christ, or follow Him if we refuse to listen and that means spending time in the Bible and time in prayer with Him.
“Listen to Me, you stubborn-minded, Who are far from righteousness.” (Isaiah 46:12)
Come, you children, listen to me; I will teach you the fear of the Lord . (Psalm 34:11)
“Now therefore, O sons, listen to me, For blessed are they who keep my ways. (Proverbs 8:32)
But seek first His kingdom and His righteousness, and all these things will be added to you. (Matthew 6:33)
Our focus on Jesus/God must go beyond knowing Him. It is equally important to obey.
And He [Jesus] said to another, “Follow Me.” But he said, “Lord, permit me first to go and bury my father.” But He said to him, “Allow the dead to bury their own dead; but as for you, go and proclaim everywhere the kingdom of God.” (Luke 9:59-60) [clarification mine]
Once we know what He wants from us, we need to instantly drop what we are doing and follow Him. We can’t put other things ahead of obeying God.
For amazement had seized him and all his companions because of the catch of fish which they had taken; and so also were James and John, sons of Zebedee, who were partners with Simon. And Jesus said to Simon, “Do not fear, from now on you will be catching men.” When they had brought their boats to land, they left everything and followed Him. (Luke 5:9-11) {emphasis mine}
We should be like these apostles, that, after their most successful catch of fish in their entire career as fishermen, “they left everything and followed Him.” We need to let go of what we think is important and obey Him. We need to change our priorities to match God’s priorities.
That may mean we change careers to one that allows more free time for ministry or even going into full time ministry. It may mean letting go on keeping the perfect, clean house, so there is time for ministry, Bible study, or discipling our kids. It may mean changing your habits from watching TV with your family to reading the Bible with your family. For each of us, it will look different, but we need to be like Mary and choose to sit “at the Lord’s feet and listened to his teaching.” We need to be like the apostles who “left everything and followed Him.” We need to choose to put Jesus’s plans before our own. We need to choose to make God’s values our values.
But this is what I commanded them, saying, ‘Obey My voice, and I will be your God, and you will be My people; and you will walk in all the way which I command you, that it may be well with you.’ (Jeremiah 7:23)
Like so many things, it is simple, but it isn’t necessarily easy. We have to change the way we think in order to obey faithfully.
If anyone serves Me, he must follow Me; and where I am, there My servant will be also; if anyone serves Me, the Father will honor him. (John 12:26)
We have to change our priorities to God’s priorities.
Then Jesus said to His disciples, “If anyone wishes to come after Me, he must deny himself, and take up his cross and follow Me. (Matthew 16:24)
We need to seek God, His word, and His presence.
As the deer pants for the water brooks,\ So my soul pants for You, O God.\ My soul thirsts for God, for the living God;\ When shall I come and appear before God? (Psalm 42:1-2)
We need to be in God’s word daily, so we know who God is and what He desires from us.
How can a young man keep his way pure?\ By keeping it according to Your word.\ With all my heart I have sought You;\ Do not let me wander from Your commandments.\ *Your word I have treasured in my heart*,\ That I may not sin against You.\ Blessed are You, O Lord;\ Teach me Your statutes.\ With my lips I have told of\ All the ordinances of Your mouth.\ I have rejoiced in the way of Your testimonies,\ As much as in all riches.\ *I will meditate on Your precepts*\ And regard Your ways.\ I shall delight in Your statutes;\ I shall not forget Your word. (Psalm 119:9-16) {emphasis mine}
We need to read the Bible cover to cover so we know the whole word of God. Once we have read through the Bible multiple times, we need to spend time studying the Bible in more depth, so we can know the details, see how the different parts relate to each other, and grow in our knowledge of God. We need to study the Bible and use this knowledge to guide every decision in life — big and small.
Yet they did not listen or incline their ears, but stiffened their necks in order not to listen or take correction. (Jeremiah 17:23)
Just reading the Bible or sitting in church listening to sermons will not make a difference if we don’t truly listen and internalize God’s word, so we can apply it in our every day life. God knows what is best for us and we will never be truly at peace or have true joy until we are living our lives in the light of God’s word and direction.
My prayer for you and for me is that we will have the heart of Mary rather than the heart of Martha and that we will faithfully seek and follow God all of the days of our lives.
Trust Jesus.
-
 @ 8f69ac99:4f92f5fd
2024-10-25 09:49:56
@ 8f69ac99:4f92f5fd
2024-10-25 09:49:56O recente relatório do Banco Central Europeu, As Consequências Distribucionais do Bitcoin, recicla a velha narrativa de que o Bitcoin é um activo especulactivo que causa desigualdade de riqueza sem oferecer benefícios económicos tangíveis. Os autores, Ulrich Bindseil e Jürgen Schaaf, desfilam as críticas de sempre, afirmando que o Bitcoin falhou como sistema de pagamento global e que se transformou numa bolha, enriquecendo os primeiros utilizadores à custa da sociedade. Também lançam uma pitada de alarmismo ambiental e argumentam que o Bitcoin ameaça a democracia.
Como era de esperar, o BCE continua apegado às mesmas concepções erradas que já foram desmentidas inúmeras vezes. O que este relatório não percebe, de forma espectacular, é que o Bitcoin não é apenas mais um activo; é uma tábua de salvação para aqueles desiludidos com os sistemas fiduciários inflacionários e governos corruptos. Ao longo desta análise, vamos desmontar os argumentos do BCE, expondo não só o seu profundo desconhecimento sobre o Bitcoin, mas também a ignorância gritante em relação ao seu potencial de conceder soberania financeira a milhões de pessoas em todo o mundo. O BCE retrata o Bitcoin como uma ferramenta elitista, mas ignora como as suas próprias políticas têm sistematicamente enriquecido alguns poucos à custa da maioria. Vamos então entrar no assunto.
1. Deturpam o Papel do Bitcoin como Sistema de Pagamentos
"O Bitcoin nunca foi usado em grande escala para transacções legais no mundo real."
Que originalidade. Os autores descartam a utilidade de pagamento do Bitcoin com um gesto, mostrando que não compreendem a Lightning Network, que facilita transacções rápidas, baratas e escaláveis a nível global. Certamente, talvez os europeus ainda não estejam a comprar os seus cafés com Bitcoin, mas isso é irrelevante. O Bitcoin é uma tábua de salvação financeira em locais como El Salvador e em inúmeras outras regiões que sofrem com sistemas fiduciários em colapso.
Esta visão eurocêntrica, como se todo o mundo partilhasse das mesmas condições económicas, reflecte uma total falta de perspectiva. Os autores seleccionam dados a dedo para encaixar na sua narrativa anti-Bitcoin, enquanto convenientemente ignoram os milhões que utilizam o Bitcoin para escapar à hiperinflação e a regimes autoritários. A afirmação de que o Bitcoin não é usado para transacções "legais" é não só enganosa, como revela a sua ignorância sobre as necessidades reais de quem vive fora da sua bolha privilegiada.
2. Deturpam o Bitcoin como activo Especulactivo
"O Bitcoin não gera qualquer fluxo de caixa (como o imobiliário), juros (como as obrigações) ou dividendos (como as ações)."
Parabéns, BCE, acabaram de perder o ponto fulcral do Bitcoin. Esta afirmação mostra uma falta de entendimento fundamental do que torna o Bitcoin único. Ao contrário de imóveis ou obrigações, o Bitcoin é uma forma alternativa de dinheiro—não algum esquema de rendimento passivo.
O valor do Bitcoin não depende de gerar dividendos ou juros, mas advém da sua escassez, descentralização e resistência à censura. Ao reduzir o Bitcoin a modelos de activos tradicionais, o BCE ignora o paradigma económico revolucionário que este oferece: uma escapatória aos sistemas fiduciários inflacionários, particularmente para os milhares de milhões de pessoas presas em sistemas financeiros corruptos.
Ao tentar enquadrar o Bitcoin em modelos convencionais, os autores revelam a sua preguiça intelectual. A utilidade do Bitcoin reside no seu potencial como dinheiro sólido, e não como um veículo de investimento para especuladores atrás de rendimento.
3. Deturpam os Custos Ambientais e Sociais da Mineração
"A mineração de Bitcoin consome muita energia e causa danos ecológicos e sociais."
Ah sim, o argumento gasto sobre o consumo energético. Enquanto a mineração de Bitcoin realmente requer energia, os autores omitem convenientemente os enormes avanços que a indústria fez em direcção à sustentabilidade. Cada vez mais, os mineradores de Bitcoin recorrem a fontes de energia renovável e, em alguns casos, estão até a ajudar a financiar infraestruturas de energia verde.
A ironia aqui é que o BCE, uma instituição que fomenta políticas que inflam bolhas imobiliárias e de acções, de repente está preocupado com os custos sociais e ambientais. E mais, ignoram como a procura de energia barata por parte do Bitcoin incentiva realmente o desenvolvimento de soluções energéticas sustentáveis. Num mundo onde os sistemas fiduciários alimentam a ganância corporativa e a degradação ambiental, o Bitcoin está posicionado para impulsionar uma verdadeira inovação na energia verde.
4. Visão Deturpada da Redistribuição de Riqueza
"Os efeitos de riqueza do Bitcoin beneficiam os primeiros utilizadores à custa dos que chegam mais tarde e dos que não o possuem."
Isto é pura comédia. Aparentemente, o BCE acabou de descobrir que os primeiros investidores em qualquer activo beneficiam mais do que os que chegam depois. Não é assim que os mercados funcionam? Os primeiros investidores em acções, imóveis e ouro beneficiam de forma desproporcional—mas, curiosamente, isto só se torna um problema quando se trata de Bitcoin.
O que o BCE realmente teme é que o Bitcoin democratize a riqueza de uma maneira que eles não conseguem controlar. Com o Bitcoin, não precisas de acesso privilegiado para participar. Não precisas de um corretor XPTO ou de permissão dos guardiões financeiros. Ao contrário das próprias políticas do BCE—concebidas para inflacionar a riqueza dos já ricos através de bolhas imobiliárias e do mercado de acções—Bitcoin oferece um campo de jogo nivelado para qualquer pessoa com uma ligação à internet.
5. Sensacionalismo: a Ameaça à Democracia
"O aumento perpétuo do preço do Bitcoin empobrece o resto da sociedade e põe em risco a democracia."
Aqui, os autores entram no melodrama, avisando que o aumento do preço do Bitcoin põe em risco a democracia. É fascinante como ignoram a verdadeira ameaça à democracia: as suas próprias políticas inflacionárias.
Na realidade, os sistemas fiduciários, através da inflação incessante e do quantitative easing, erodem sistematicamente a riqueza dos mais pobres e da classe média. Os ricos, com as suas carteiras de acções e imóveis, conseguem resistir à tempestade. Mas o trabalhador comum, cujo salário compra cada vez menos a cada ano, é esmagado. Se há algo que ameaça a democracia, é o poder descontrolado do BCE de desvalorizar a moeda que as pessoas usam para viver. Bitcoin, por outro lado, dá às pessoas uma reserva de valor incorruptível e descentralizada, imune aos caprichos dos banqueiros centrais.
6. Percepção "Equivocada" da Escalabilidade do Bitcoin
"As transações em Bitcoin na blockchain são lentas e caras."
Esta crítica ignora a realidade do progresso tecnológico. As transacções on-chain de Bitcoin nunca foram pensadas para compras diárias—para isso é que serve a Lightning Network. Os autores agarram-se a esta crítica desactualizada, como se o Bitcoin fosse uma entidade estática que não evoluiu na última década.
Soluções de segunda camada como a Lightning Network permitem transacções quase instantâneas e de baixo custo, tornando o Bitcoin escalável de maneiras que o BCE se recusa a reconhecer. Mas porque deixar que os factos estraguem uma boa história de medo?
7. Ignoram o Impacto Económico Global do Bitcoin
"O Bitcoin não tem casos de uso benéficos para a sociedade."
Esta afirmação é tão limitada que é quase impressionante. A utilidade do Bitcoin não se trata de conveniência para os ocidentais comprarem café; trata-se de sobrevivência para as pessoas em países como a Venezuela, o Líbano ou a Nigéria.
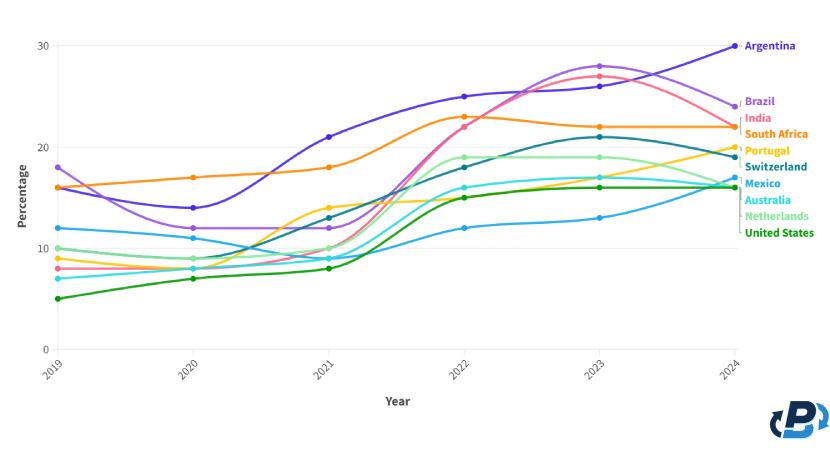
Quando as moedas locais colapsam e as pessoas não podem confiar nos seus bancos, o Bitcoin oferece uma saída. Ao descartar o impacto real de Bitcoin sobre os milhares de milhões (mais de metade da população mundial) de pessoas que vivem sob regimes opressivos e em hiperinflação, o BCE revela um embaraçoso viés ocidental e falta de empatia. O Bitcoin é mais do que apenas um activo alternativo, é uma tábua de salvação para pessoas em todo o mundo que sofrem com sistemas fiduciários falhados.
Conclusão
O relatório do BCE recicla críticas desactualizadas e já desmentidas, não conseguindo ver o panorama geral. Aplica modelos financeiros antigos a uma nova forma de dinheiro, ignorando o potencial de Bitcoin para democratizar o acesso a um sistema financeiro justo, descentralizado e incorruptível. Enquanto os bancos centrais, como o BCE, continuam a desvalorizar moedas e a inflacionar bolhas de activos (e parece que vem ai mais...), Bitcoin oferece às pessoas um caminho para a soberania financeira.
O verdadeiro valor de Bitcoin não se encontra nas críticas superficiais e eurocêntricas do BCE. O seu valor reside na capacidade de fornecer liberdade financeira a indivíduos em todo o mundo, libertos da má gestão de governantes e banqueiros centrais. Se há algo que ameaça a democracia, é o historial do BCE de enriquecer alguns poucos à custa de muitos. Bitcoin, por outro lado, oferece um futuro mais justo—um onde são os indivíduos, e não as instituições, que têm o poder.
Alguma literatura: - Universidade de Cornell - Bitcoin pode impulsionar o desenvolvimento de energias renovaveis - Aldeias em Africa com electricidade atraves de Bitcoin - Relatorio de 2023 sobre a Lightning Network da River - Adopcao de Bitcoin por Pais
Photo by Taras Chernus on Unsplash
Bitcoin #BCE
-
 @ df8f0a64:057d87a5
2024-10-10 15:18:39
@ df8f0a64:057d87a5
2024-10-10 15:18:39書き散らす動機
残暑続きからの急な気温低下で鼻炎がひどくなる今日この頃、皆様お元気でしょうか
株主への抗議のために退職してから2ヶ月半、流石に暇を持て余してきました 時間がある上に能動的に働く気も起きず、ひたすらボーッとしたりうねうね考え事をする日々です 幸いにして人生も折り返しにさしかかる頃になり、時折「今、人生が終わって構わないのでは?」というようなことも考えたりします (鬱病既往歴ありますが私は元気です)
子どものお迎えを終えて、いつもどおり夕食をとり、またうねうねしているうちに ふと、6年前の年末に急死された、仕事でお世話になったTさんのことを思い出しました
子を寝かしつけてもまだ頭の中をぐるぐるしていたので、ここに吐き出してすっきりしようという魂胆です
Tさんとの出会い
私のキャリアの(ほぼ)スタートはVC(ベンチャーキャピタル)でした 誰のせいでもないとある経緯もあり、周囲からは警戒され避けられ、わずか6年ではありますが、 インナーサークルに入り込めない時期を過ごし、当時の上司と二人、とにかくやれることをやり続ける毎日でした
いつものようにピッチイベントに参加しているとき、近くの席にいたスーツ姿の3人組と目が一瞬合います
「事業会社の人だ」
協調投資やファンド出資のきっかけを掴むべく、その3人に話かけます
「よろしければ弊社投資先のご紹介や御社の...」
ひととおりの挨拶を済ませ、この人たちにも避けられるんだろうと思いながらも要件を切り出します
「是非やりましょう」
いつもとは違う嬉しい返事をくれたのがTさんでした
面倒見の良い他社の先輩
そのときの3人組であるMさん・Iさん・Tさんには、私の仕事人生の中で最もお世話になったと言っても過言ではありません
ファンドの営業を受けていただき、協調投資を行い、VCからの転職後にも協業相手として他部署のキーマンをご紹介いただき...
社会人になったばかりの私の、今思い返せば恥ずかしい(部下がこんな提案したら卒倒する)レベルの提案を、 誰もが知る一流企業の多忙な役職持ちであるにも関わらず、毎回一時間も割いて丁寧に対応してくださる心の広い方でした
当時、VCと接点をもつような事業会社の対スタートアップ部隊は、本業でご活躍されている方が兼任で取り組むパターンが多く、Mさん・Iさん・Tさんももちろんそう
その後も昇進され、最後には本社の取締役に。今年遂に退任され、所謂「あがり」でしょうか、子会社の取締役に異動 長い社会人人生をほぼ走りきり、有終の美を飾ろうとする時期にさしかかっています
でもTさんはそこにはいません
残される側
冒頭触れたとおり、Tさんは6年前のこの時期に急死されました 死因については、Tさんのご友人がFBに投稿していた文章を読んでも、Iさんに聞いてもわからない
悲しいかな、四十年近く生きていると、死因が明かされない理由がわかるようになる機会が一度や二度はあります Tさんもおそらくそうだったのでしょう
直前まで、Iさんと一緒にベイエリアに出張され、楽しそうなコメントと共に写真を投稿されていたのに 晩婚なのか再婚なのか、とにかくご結婚されて一年ちょっと。お子様も生まれたばかりだったのに Tさんは近い人間に心中を隠して、静かにこの世を去りました
あなたの快い返事に、どれほど私が救われたのか 転職後の提案のとき、受付で顔を出してすぐ「元気?」と声をかけてくださったことがどれほど私を安心させてくれたか あなたが声をかけてくれる度、私の社会人としての成果が生まれたことに、私は十分に感謝を伝えられていません
まだしばらく残る理由
振り返って、Tさんのように誰かの人生をenhanceできたのか?と自分に問うと、まだできたとは思えません。残念ですが
今ここで死んでも私は構わないけど、まだもうちょっと頑張るべきかな、老いてから誰かに感謝をしてもらうまで生きてみてもいいかな
そうふと思い直しているうちに日付が変わりました
-
 @ 5a261a61:2ebd4480
2025-02-02 20:42:37
@ 5a261a61:2ebd4480
2025-02-02 20:42:37Let’s be real—sticking to anything for 90 days is like trying to herd cats on espresso. You start strong, then life happens: kids, chores, or that one glass of wine that makes you forget foot rubs (#relatable). But here’s the thing: 90-day challenges aren’t about perfection. They’re about bribing your lizard brain with rewards and scaring it straight with punishments.
The Game Plan
First, pick a thing—something that makes you feel like a devoted servant or a slightly frazzled superhero. Daily foot care? Chores with a side of #FLR flair? Cool. Now, break it into chunks: 30 days (survival mode), 60 days (grind phase), and 90 days (victory lap).
Keeping up something for so long is no joke. That's why you need those little checkpoints along the way. Each milestone should feel special—30 days deserves celebration, 60 days something more meaningful, and 90 days? That's your victory dance moment.
Reality check: some days will suck, and you'll want to skip. That's where having everything planned out helps. When your brain is foggy and you're tired, you don't want to be negotiating with yourself about what counts and what doesn't. The hardest part isn't even doing the thing—it's remembering to do it every single day, until it feels wrong NOT to do it.
Why It (Maybe) Works
Three months is long enough for habits to stick, short enough to see the finish line. Plus, tying it to power exchange? Genius. Every foot rub or denied cum becomes a ritual, proof you're leveling up as a sub/human/slightly-messy adult. And let's be honest—nothing fuels devotion like a mix of structure, desperation, and the occasional humiliating punishment.
Current run
My current challenge is to get my wife/godess/object of my insatiable kinky thoughts/partner feet massaged with special cream. It's for making evyrthing soft, help nails and yadayadayada. Basically preping her feet for more instensive worshiping. She doesn't know my hidden agenda and I am not sure if I would really be into it, since I am more into being her devout toy than having foot fetish, but I think it will be all the same if I put myself juuust right. So for my rewards I have planned these? - 30 days: Tiny dopamine hit. (making little photoset of Her feet playing with my hardon… for science.)
- 60 days: Mid-tier flex. (cleaning mushed banana split off Her toes tongue only)
- 90 days: Go nuclear. (a tiny foot spa whirpool because She deserves it, damn it :D and it will create more opportunities for... you know )As for the hhip part of the sugar duo... It was easy having one for my shaving rutine, but here? Not sure and it's bad that I ave started challenge without having them prepared... May be that warrant more punishment?
TL;DR
90-day challenges are the BDSM of self-improvement: consensual, slightly painful, and weirdly addictive. Fail? Reset, adapt, try again. Win? Congrats, you’re now 10% more disciplined and 100% more bumptious on Nostr.
90days #FLR #LostCauseButStillTrying #femdom
-
 @ d57360cb:4fe7d935
2025-02-02 16:33:16
@ d57360cb:4fe7d935
2025-02-02 16:33:16Beauty and art function beyond the mind.
When you’re not thinking, when the mind reaches its natural silence. When it quiets down.
You begin to experience and actually experience how things are.
There is no more narration. Things happen as if by magic. Everything is in its place happening and grooving.
Every act, every movement feels like jazz.
We’re better doers than we are thinkers. But the world thinks otherwise.
-
 @ 6b57533f:eaa341f5
2025-02-02 15:46:41
@ 6b57533f:eaa341f5
2025-02-02 15:46:41🏝️lost in the ordinary?
Welcome to Stories
Discover a hidden paradise where the world slows down, and adventure begins..
🌊 Step into tranquility.
Wake up to the sound of gentle waves and endless blue horizons.
🛶Live the dream.
Unwind, explore, and escape—your perfect getaway is just one step away.
-
 @ 8f69ac99:4f92f5fd
2024-09-30 15:06:03
@ 8f69ac99:4f92f5fd
2024-09-30 15:06:03À medida que a automação continua a moldar as indústrias e milhões enfrentam a ameaça do desemprego, o Rendimento Básico Incondicional (RBI) surgiu como uma das soluções mais debatidas para abordar a pobreza, a desigualdade e a insegurança económica. No seu cerne, o RBI propõe uma quantia regular e incondicional de dinheiro para os indivíduos, visando fornecer estabilidade financeira independentemente do estado de emprego. Este artigo explora os resultados de um estudo recente que testou os efeitos do RBI em economias desenvolvidas, revelando resultados surpreendentes que desafiam as narrativas optimistas em torno da política.
O que é o RBI?
O RBI é um sistema financeiro onde todos recebem uma quantia fixa de dinheiro, independentemente do rendimento ou do estado de emprego. Não é uma ideia nova. Desde o tempo de Júlio César em Roma até economistas modernos como Milton Friedman, o conceito evoluiu. No século XX, Friedman defendeu o conceito de um imposto negativo sobre o rendimento, enquanto mais recentemente, o "Dividendo da Liberdade" de Andrew Yang trouxe a ideia do RBI para a arena política mainstream.
O objectivo do RBI é simples: dar aos indivíduos os meios para cobrir as suas necessidades básicas, para que possam concentrar-se no desenvolvimento pessoal, na educação e na melhoria da sua posição económica. Os defensores argumentam que poderia revolucionar o sistema de bem-estar social, simplificar a burocracia e encorajar o empreendedorismo, dando às pessoas a liberdade de correr riscos sem medo de ruína financeira.
Os Benefícios Teóricos do RBI: Preferência Temporal e Necessidades Essenciais
Um dos conceitos-chave no coração dos potenciais benefícios do RBI é a preferência temporal, que se refere à inclinação de um indivíduo para valorizar recompensas presentes em detrimento das futuras. Uma preferência temporal alta significa priorizar necessidades e gratificação imediatas, enquanto uma preferência temporal baixa sugere uma disposição para adiar recompensas em favor de ganhos a longo prazo. Economicamente, aqueles com alta preferência temporal tendem a tomar decisões financeiras de curto-prazo—gastando em consumo imediato em vez de investir em educação, habilidades ou activos que levariam a uma maior riqueza ao longo do tempo. Socialmente, isso muitas vezes perpetua ciclos de pobreza, uma vez que famílias com alta preferência temporal lutam para escapar do modo de sobrevivência do dia-a-dia, limitando as suas oportunidades de mobilidade ascendente. Por exemplo, as famílias podem usar o seu rendimento para cobrir necessidades imediatas como renda ou alimentos, em vez de investir em educação ou iniciar um negócio.
O RBI, em teoria, poderia ajudar a reduzir a alta preferência temporal dos indivíduos ao aliviar a pressão financeira imediata das necessidades básicas de sobrevivência. Quando as pessoas não precisam mais se preocupar em conseguir o essencial como comida, renda de casa ou cuidados de saúde, podem mudar para uma preferência temporal baixa, focando-se em investimentos em educação, formação ou outras actividades económicas a longo prazo. Esta mudança é crucial para romper o ciclo da pobreza, onde as famílias ficam presas a resolver necessidades de curto prazo em detrimento da prosperidade futura.
No entanto, é essencial reconhecer o papel significativo de atender às necessidades humanas básicas antes que qualquer progresso económico a longo prazo possa ser alcançado. Sem resolver primeiro essas questões fundamentais—como habitação, nutrição e cuidados de saúde—não se pode esperar que os indivíduos prosperem ou sequer considerem o auto aperfeiçoamento. Qualquer esforço para elevar a sociedade a padrões de vida mais altos deve começar por proporcionar a estabilidade e a segurança que permitem aos indivíduos planear o futuro. Sem resolver esses desafios imediatos, a perspectiva de elevar uma sociedade como um todo permanece inatingível.
Vale a pena notar que os governos, ao propor sistemas como o RBI para ajudar ostensivamente os seus cidadãos, muitas vezes criam dependência de programas de assistência social. Com o tempo, isso pode incentivar comportamentos de alta preferência temporal, ao fomentar a dependência de ajuda a curto prazo em vez de incentivar o crescimento auto-sustentável a longo prazo. Em muitos casos, os programas de segurança social perpetuam involuntariamente (ou não), a pobreza ao prender as pessoas em ciclos de dependência, em vez de capacitá-las a se libertar da insegurança financeira.
O conhecido provérbio, "Dê um peixe a um homem e alimentá-lo-á por um dia; ensine um homem a pescar e alimentá-lo-á por toda a vida," captura a essência deste argumento. Embora fornecer ajuda financeira imediata através do RBI possa ajudar a curto prazo, sem incentivos adequados e sistemas de apoio que incentivem a autossuficiência, há o risco de que a política ofereça apenas um alívio temporário sem fomentar verdadeiras soluções a longo prazo para a melhoria económica.
Em resumo, enquanto o RBI promete aliviar a pressão financeira e mudar as pessoas para um planeamento a longo prazo, o contexto social mais amplo e a participação do governo na criação de dependência devem ser examinados criticamente para garantir que leve genuinamente a um progresso económico duradouro.
Estudo Recente sobre o RBI: Configuração e Principais Métricas
Um estudo realizado entre 2020 e 2023 procurou entender como o RBI impacta o bem-estar financeiro em economias desenvolvidas, particularmente nos EUA. O estudo centrou-se em 3.000 famílias de Dallas no Texas, e Chicago no Illinois, dividindo-as em dois grupos:
- Grupo 1: 1.000 famílias receberam $1.000 por mês durante três anos ($36.000 no total).
- Grupo 2: 2.000 famílias receberam $50 por mês durante três anos ($1.800 no total).
O estudo mediu rendimento, património líquido, emprego e bem-estar geral para avaliar como o RBI afectou a saúde financeira dos participantes e as suas oportunidades de melhoria económica.
Principais Descobertas: Os Resultados Surpreendentes do RBI
Queda nos Rendimentos
Contrariando as expectativas, os participantes que receberam $1.000 por mês ganharam, em média, $1.500 a menos anualmente do que aqueles do grupo de controlo. Em vez de usar o rendimento adicional para investir em educação ou formação profissional, os beneficiários reduziram as suas horas de trabalho em 1,3 a 1,4 horas por semana, passando mais tempo em actividades de lazer em vez de em actividades que poderiam melhorar o seu potencial de rendimento a longo prazo.
Nenhuma Melhoria no Capital Humano
Outra expectativa chave do RBI é que ajudaria os beneficiários a investir em habilidades e educação. No entanto, o estudo não encontrou melhorias significativas no capital humano. Apesar de receber apoio financeiro, os beneficiários não procuraram educação superior ou formação profissional em maiores taxas do que o grupo de controlo, deixando a promessa central do RBI não realizada.
Impacto Negativo no Património Líquido
Talvez o resultado mais surpreendente tenha sido o efeito sobre o património líquido. Os participantes que receberam $36.000 terminaram com $1.000 a menos em património líquido do que aqueles que receberam apenas $1.800. Isso levanta sérias questões sobre como os beneficiários do RBI geriram as suas finanças, uma vez que o dinheiro adicional deveria ter ajudado a poupar ou a investir em activos.
Falta de Resiliência Financeira
O RBI também falhou em melhorar a capacidade dos participantes de lidar com choques financeiros. Não houve mudanças significativas no acesso ao crédito, na morosidade ou nas taxas de falência entre os beneficiários, sugerindo que o RBI não proporcionou a estabilidade financeira ou a resiliência que os defensores esperavam.
A Mídia Retratou Incorretamente os Resultados
Apesar destes resultados surpreendentes, a cobertura da mídia sobre o estudo focou em resultados secundários, como a flexibilidade aumentada ou pequenas melhorias no estilo de vida, como visitas mais frequentes ao dentista. Esta reportagem selectiva é provavelmente devido às motivações dos que financiaram a pesquisa.
O estudo foi realizado pela Open Research, uma empresa fundada por Sam Altman, CEO da OpenAI. Altman tem interesse em promover o RBI como uma solução para o desemprego em massa esperado como resultado da ascensão da IA e da automação. Ao focar em melhorias marginais e enquadrar o RBI como um caminho para a flexibilidade, a mídia minimizou as descobertas principais do estudo: os beneficiários do RBI terminaram mais pobres e menos financeiramente seguros do que seus homólogos.
À medida que a IA continua a evoluir, o seu potencial para substituir empregos em várias indústrias torna-se cada vez mais claro. Na agricultura, por exemplo, onde tarefas intensivas em mão-de-obra como arar campos, plantar e colher uma vez exigiram muitos trabalhadores, máquinas e automação impulsionadas por IA estão a tornar possível que um único operador realize o trabalho de dez pessoas. Por exemplo, tractores autónomos equipados com IA podem arar e semear vastos campos com um mínimo de intervenção humana. Da mesma forma, ceifeiras controladas por IA podem optimizar a colheita de culturas como morangos ou uvas, reduzindo drasticamente a necessidade de mão-de-obra manual.
Esta tendência não se limita à agricultura. Os empregos de colarinho azul na manufactura, construção e logística também estão em risco. Robôs automatizados em fábricas podem agora montar produtos mais rapidamente e com maior precisão do que os trabalhadores humanos, e sistemas geridos por IA podem gerir cadeias de abastecimento com uma eficiência que supera as capacidades humanas. Mesmo os empregos tradicionalmente vistos como seguros contra a automação, como a condução de camiões ou veículos de entrega, estão a ser ameaçados pela ascensão de veículos autónomos.
À medida que estas tecnologias se tornam mais generalizadas, muitas pessoas podem ver-se deslocadas do mercado de emprego tradicional, levando a uma crescente divisão económica. O RBI é frequentemente proposto como uma rede de segurança para prevenir a pobreza generalizada causada por esta mudança. No entanto, sem abordar as mudanças estruturais subjacentes e as oportunidades de requalificação para os trabalhadores, o RBI por si só pode não ser suficiente para fechar a lacuna criada pelas perdas de empregos induzidas pela IA. É por isso que Altman e outros na indústria da IA têm interesse em apresentar o RBI como uma solução inovadora para a crise iminente da automação.
Desafios e Limitações do Estudo
Há vários factores a considerar ao interpretar estes resultados. O estudo ocorreu durante a pandemia global de COVID-19, um período de severas perturbações económicas. Isso levanta questões sobre se as descobertas podem ser totalmente generalizadas para condições económicas mais típicas.
Outra limitação chave é o modelo de RBI testado—pagamentos mensais de $1.000. Esta estrutura pode não ser a maneira mais eficaz de entregar o RBI. Os pagamentos mensais podem incentivar os beneficiários a tratar o RBI como rendimento suplementar, levando a gastos de curto prazo em vez de investimentos a longo prazo em capital humano.
Explorando Abordagens Alternativas ao RBI
Uma alternativa é um modelo de pagamento em lump-sum, onde os beneficiários recebem um grande pagamento de uma só vez em vez de parcelas mensais mais pequenas. Isso poderia permitir que fizessem investimentos significativos, como a compra de um veículo ou a liquidação de dívidas, que teriam um impacto a longo prazo no seu bem-estar financeiro.
Num experimento de RBI realizado na Libéria, por exemplo, os beneficiários usaram os pagamentos em lump-sum para melhorar as suas casas, passando de telhados de erva para telhados de metal, Evitando assim reparações e custos, tempo e dinheiro, todos os anos. Esses investimentos levaram a economias a longo prazo e aumentaram a qualidade de vida, demonstrando os potenciais benefícios de pagamentos grandes e antecipados.
Outra abordagem é integrar o RBI com o sistema fiscal, proporcionando alívio fiscal (ou vouchers) para aqueles que optam por não utilizar serviços públicos, como educação ou saúde. Isso mudaria o RBI de um subsídio directo para um sistema mais flexível que recompensa a responsabilidade pessoal, enquanto ainda fornece alívio financeiro.
Conclusão: O Futuro do RBI e o Cepticismo
O estudo recente coloca dúvidas sobre a eficácia do RBI na sua forma actual. Embora o conceito tenha potencial, particularmente na abordagem da pobreza, as descobertas do estudo sugerem que os pagamentos mensais podem não levar às melhorias financeiras a longo prazo que os defensores esperavam. Os beneficiários do estudo trabalharam menos, ganharam menos e terminaram com um património líquido inferior, desafiando a premissa central do RBI. O estado da economia também tem um papel importante no sucesso dos programas. O sucesso na Libéria contrasta com o menos sucedido estudo nos Estado Unidos.
No entanto, isso não significa que o RBI seja um conceito falhado. Em vez disso, destaca a necessidade de mais pesquisa e experimentação com diferentes modelos, como distribuições em lump-sum ou RBI baseado em impostos. À medida que a IA e a automação moldam a economia, encontrar soluções eficazes para a insegurança económica permanece crucial, e o RBI, de alguma forma, ainda poderia desempenhar um papel nesse futuro.
Photo by Erik Mclean on Unsplash
-
 @ 8f69ac99:4f92f5fd
2024-09-27 13:19:59
@ 8f69ac99:4f92f5fd
2024-09-27 13:19:59É o imobiliário realmente a melhor forma de fazer crescer e proteger a sua riqueza, ou existem melhores alternativas que a maioria das pessoas está a ignorar? Durante séculos, as pessoas têm visto o imobiliário como um refúgio seguro para investimentos—baseando-se na estabilidade histórica e na segurança percebida. Possuir uma casa tem sido há muito considerado um pilar na construção de riqueza e na garantia do futuro de alguém. No entanto, enquanto comprar uma casa para viver pode ser um bom investimento para a vida, o que dizer de investir em imobiliário para preservação de riqueza, arrendamento ou especulação? Poderá esta estratégia ter armadilhas ocultas que levam os investidores a cometer erros?
Se alguém, por qualquer razão, tem dinheiro disponível, esse capital precisa ser alocado ou corre o risco de perder valor devido à inflação. No entanto, a falta de alternativas visíveis, o desconhecimento de opções mais modernas ou uma aversão ao risco, levam muitas pessoas a pensarem imediatamente no imobiliário como a solução. Esta é a escolha natural para o investidor comum, que pode não estar ciente dos desafios envolvidos.
Para muitos, a suposição é que o imobiliário irá sempre superar outras classes de activos. Mas, por trás desta estratégia aparentemente infalível, existe uma teia de desafios e incertezas. As realidades financeiras do investimento imobiliário são frequentemente ignoradas, e aqueles que se aventuram na propriedade sem uma compreensão adequada podem enfrentar despesas inesperadas, volatilidade de mercado e perdas financeiras.
As Realidades Financeiras do Investimento Imobiliário
Ao considerar o imobiliário como uma estratégia de investimento, é essencial distinguir entre a posse de casa para habitação e o investimento em propriedades. Enquanto comprar uma casa para viver pode ser um óptimo investimento para a vida, o imobiliário para fins de investimento é muito mais complexo.
Custos Ocultos da Propriedade
Investir em imobiliário envolve custos iniciais e contínuos significativos, incluindo:
- Entrada: Tipicamente 10% do preço de compra, que poderia ser melhor gasto em outro lugar.
- Custos de fecho: Taxas associadas à compra e venda de propriedades, que variam entre 2-5% do preço de compra.
- Impostos sobre propriedades: Pagamentos anuais ou semestrais aos governos locais (IMI por exemplo), que podem aumentar com o tempo.
- Seguro: Prémios para seguros de edifícios e responsabilidade civil.
- Manutenção: Custos contínuos, que geralmente representam entre 1-3% do valor da propriedade anualmente.
Comparação: Verdadeiras Despesas da Propriedade vs. Arrendamento
O arrendamento muitas vezes evita os custos iniciais substanciais, impostos e taxas de manutenção associados à posse de uma casa. Para muitos, especialmente em mercados habitacionais voláteis, isso torna o arrendamento mais financeiramente viável no curto a médio prazo. Possuir propriedades pode bloquear capital que poderia ser melhor investido noutro lugar.
Riscos de Alavancagem e Dívida
Os investimentos imobiliários geralmente requerem dívida, amplificando tanto os ganhos potenciais quanto as perdas. Uma pequena queda no valor da propriedade pode ter um impacto significativo na sua equidade. Se os valores das propriedades diminuírem, os investidores podem encontrar-se em dificuldades financeiras.
Os Fardos Ocultos do Imobiliário
Embora frequentemente visto como um investimento de baixo risco, o imobiliário traz fardos ocultos. Muitos presumem que é um investimento passivo, mas gerir propriedades—lidar com manutenção e inquilinos—é tudo menos passivo.
Externalidades e Consequências Secundárias
Ao comprar uma propriedade, você também assume: - Custos de manutenção: Desde pequenos reparos até grandes renovações. - Gestão de inquilinos: Encontrar inquilinos fiáveis e lidar com questões relacionadas com inquilinos. - Mudanças de vizinhança: Dinâmicas de vizinhança em mudança podem afectar os valores das propriedades. - Preocupações ambientais: Desastres naturais ou mudanças ambientais locais podem impactar as propriedades.
Imprevisibilidade e Risco do Mercado
O mercado imobiliário está sujeito a bolhas e recessões. As bolhas de propriedades, as quedas de mercado e as mudanças nas regulamentações podem ter efeitos severos sobre o valor do imobiliário.
Liquidez
O imobiliário é um activo altamente ilíquido, muitas vezes levando meses a ser vendido. Em contraste, activos mais líquidos podem ser vendidos rapidamente quando necessário, tornando o imobiliário menos atractivo para aqueles que buscam flexibilidade.
O Impacto Social do Investimento Imobiliário
A forma como a sociedade vê o imobiliário impacta a acessibilidade e a disponibilidade de habitação.
A Crise de Acessibilidade à Habitação
Investir em propriedades para armazenar riqueza ou gerar rendimento passivo eleva os preços e reduz a disponibilidade de habitação para famílias de baixos e médios rendimentos. O “prémio monetário” associado ao investimento imobiliário aumenta a procura, empurrando os preços para cima e exacerbando a escassez de habitação em grandes cidades europeias.
Prémio Monetário
O prémio monetário no contexto do imobiliário refere-se ao valor extra que os investidores atribuem às propriedades não apenas pela sua utilidade como casas, mas como investimentos que podem armazenar, ou preservar, riqueza. Isso significa que as pessoas estão dispostas a pagar mais pelo imobiliário porque o veem como uma forma de preservar e aumentar o seu dinheiro, em vez de apenas um lugar para viver.
Por exemplo, se uma casa vale €200,000 com base na sua utilização real (como espaço habitacional), mas os investidores estão dispostos a pagar €250,000 porque acreditam que ela irá valorizar ao longo do tempo, a diferença de €50,000 é o prémio monetário. Este aumento da procura por parte dos investidores pode elevar os preços das habitações, dificultando a vida às pessoas que precisam de casas acessíveis. Em essência, o prémio monetário reflecte a ideia de que algumas propriedades são valorizadas mais pelo seu potencial como activos financeiros do que pela sua função como lares.
Preço vs. Valor Utilitário
Se o imobiliário fosse visto apenas pela sua utilidade—proporcionar abrigo—os preços das habitações reflectiriam melhor o seu valor real, melhorando a acessibilidade. O modelo actual, que prioriza o investimento em propriedades em detrimento da sua função como casa, promove a gentrificação e o deslocamento.
Bom vs. Mau Investimento numa Casa
Enquanto comprar uma casa para viver é um investimento sensato, usar o imobiliário para preservação de riqueza, arrendamento ou especulação pode ter consequências sociais negativas, perpetuando a desigualdade e reduzindo as opções de habitação para aqueles que mais precisam.
Finanças Tradicionais vs. Imobiliário
Em contraste com o imobiliário, os mercados financeiros tradicionais proporcionam uma forma mais dinâmica e eficiente de armazenar valor.
Mercado de Acções e Índices como Melhores Alternativas
Historicamente, os índices do mercado de acções, como o S&P 500 e o Euro Stoxx 50, superaram o imobiliário em termos de retornos. Estes índices oferecem diversificação e exposição de baixo custo ao crescimento a longo prazo. No entanto, mesmo estes mercados têm limitações, especialmente quando se considera a inflação. Por exemplo, o retorno composto histórico do S&P 500 é de cerca de 7% por ano uma vez ajustado pela inflação. Em alguns casos, pode mesmo resultar em perdas ao considerar a inflação real.
Custos e Barreiras de Entrada
Para as pessoas comuns, aceder ao mercado de acções requer um corretor, o que adiciona camadas de complexidade e taxas. Muitas pessoas, especialmente aquelas que trabalham em empregos "9 às 5", encontram-se numa posição em que são quase forçadas a aprender sobre o mercado de acções e investimentos tradicionais apenas para proteger o seu dinheiro, arduamente ganho, da inflação. Esta não é uma tarefa simples, pois investir em acções ou índices requer pesquisa, monitorização e conhecimento que a maioria das pessoas não tem tempo ou desejo de adquirir.
Além disso, a taxa de inflação real que as pessoas enfrentam muitas vezes difere das métricas oficiais, como o Índice de Preços ao Consumidor (IPC). A verdadeira inflação sentida pelas pessoas é melhor reflectida no aumento de preços dos bens e serviços que compram regularmente. Assim, mesmo o S&P 500, uma vez ajustado para esta inflação do mundo real, pode não ser tão seguro ou lucrativo quanto parece.
Uma Alternativa Mais Simples
Para aqueles que procuram uma opção de investimento mais directa, existe uma alternativa moderna: Bitcoin. Ao contrário das acções e do imobiliário, que requerem conhecimento significativo e gestão, Bitcoin pode ser comprado e mantido com esforço mínimo. Isso torna-o uma escolha atraente para indivíduos que não têm tempo para navegar pelas complexidades das finanças tradicionais.
Por Que Bitcoin É um Armazenamento de Valor Superior
1. Custos Baixos e Sem Externalidades
Bitcoin não tem impostos sobre propriedades, custos de manutenção ou seguros. A sua natureza descentralizada e baixas taxas de transacção tornam-no uma forma de armazenamento de valor eficaz em termos de custo.
2. Liquidez e Segurança
Bitcoin é um activo altamente líquido e facilmente transferível, tornando-o superior ao imobiliário, que leva tempo a vender. Além disso, a tecnologia descentralizada e segura do Bitcoin oferece protecção contra manipulação e confiscação.
3. Sem Necessidade de Especialização
Ao contrário do mercado de acções ou do imobiliário, Bitcoin pode ser mantido e gerido sem conhecimento especializado, tornando-o ideal para pessoas ocupadas ou aquelas novas no investimento.
4. Melhor que o Ouro
A natureza digital de Bitcoin faz com que seja mais transportável e acessível do que activos físicos como o ouro. É sem fronteiras e pode ser armazenado de forma segura, ao contrário do ouro ou do imobiliário, que exigem medidas de segurança física.
Conclusão: Repensar a Estratégia de Investimento
-
A Armadilha do Imobiliário: Muitos veem o imobiliário como um investimento de baixo risco e padrão, mas esta mentalidade é errada. Os custos ocultos, os impactos sociais e as questões de liquidez tornam-no menos atraente quando analisado criticamente.
-
Alternativas das Finanças Tradicionais: Investimentos tradicionais como acções e índices oferecem retornos superiores e escalabilidade em comparação com o imobiliário, proporcionando uma opção melhor para preservação de riqueza.
-
A Ascensão de Bitcoin: Bitcoin oferece uma forma ainda mais directa e eficiente de armazenar valor, livre das complexidades e custos tanto do imobiliário quanto das finanças tradicionais, enquanto proporciona liquidez, segurança e facilidade de uso.
-
Um Futuro Mais Brilhante: Ao movermo-nos além das estratégias tradicionais centradas no imobiliário e abraçar alternativas modernas, podemos desbloquear um futuro mais equitativo e rentável para a preservação de riqueza.
Photo by Tierra Mallorca on Unsplash
-
 @ 3b7fc823:e194354f
2025-02-02 13:39:49
@ 3b7fc823:e194354f
2025-02-02 13:39:49Why You Should Only Run DeepSeek Locally: A Privacy Perspective and how to
In an era where AI tools promise immense utility, the decision to run DeepSeek locally is not merely about functionality but also about safeguarding privacy and security. Here's the rationale why:
-
Control Over Data Access: Running DeepSeek locally ensures that data processing occurs on your own machine or server, allowing you to have full control over who can access the system. This reduces the risk of unauthorized access and misuse.
-
Data Privacy: By keeping computations local, you ensure that personal data does not leave your control, minimizing the risk of exposure through cloud-based services.
-
Security Measures: Local operation provides an additional layer of security. You can implement access controls, monitor usage, and respond to incidents more effectively, which might be harder or impossible when relying on third-party platforms.
-
Practical Implementation: Tools like Ollama and OpenWebUI facilitate setting up a local environment, making it accessible even for those with limited technical expertise. This setup empowers individuals to leverage AI capabilities while maintaining privacy.
-
Right to Control Data: Privacy is a fundamental right, and running DeepSeek locally respects this by allowing users to decide what data they share and how it's accessed. This empowers individuals to make informed choices about their personal data.
For those prioritizing privacy, this approach is not just beneficial—it's essential.
Running DeepSeek Locally: A Guide for Individual Home Users
DeepSeek is a powerful AI search engine that can help with various tasks, but running it locally gives you greater control over your data and privacy. Here’s how you can set it up at home.
What You’ll Need
- A Computer: A desktop or laptop with sufficient processing power (at least 4GB RAM).
- Python and pip: To install and run DeepSeek.
- Ollama: An open-source tool that allows you to run AI models locally.
- OpenWebUI: A simple web interface for interacting with Ollama.
Step-by-Step Guide
1. Install the Prerequisites
- Python: Download and install Python from https://www.python.org.
- pip: Use pip to install Python packages.
bash pip install --upgrade pip - Ollama:
bash pip install ollama - OpenWebUI: Visit https://github.com/DeepSeek-LLM/openwebui and follow the instructions to install it.
2. Set Up Ollama
- Clone the official Ollama repository:
bash git clone https://github.com/OllamaAI/Ollama.git cd Ollama - Follow the installation guide on https://ollama.ai to set it up.
3. Run DeepSeek Locally
- Use OpenWebUI as your interface:
bash # Start OpenWebUI (open a terminal and run this): python openwebui.py --model deepseek-llm-v0.2-beta - A web browser will open, allowing you to interact with DeepSeek.
Tips for Optimization
- Reduce Memory Usage: Use smaller models like
deepseek-llm-v0.2-betaif your computer has limited resources. - Limit Model Access: Only allow authorized users to access the system by restricting IP addresses or using a VPN.
- Regular Updates: Keep all software up to date to protect against vulnerabilities.
Why Run DeepSeek Locally?
- Privacy: Your data stays on your local machine, reducing the risk of unauthorized access.
- Flexability: Running locally allows you to build specific models for specific uses and provide them with RAG data.
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
-
-
 @ fbf0e434:e1be6a39
2025-02-02 13:32:12
@ fbf0e434:e1be6a39
2025-02-02 13:32:12本文原载于《CERN Courier》,是由欧洲核子研究中心(CERN,全称Conseil Européen pour la Recherche Nucléaire)出版的权威科学期刊,专注于报道全球物理学、技术及创新领域的前沿动态。以下正文内容是对全球开源开发者激励平台DoraHacks的创始人张剑南的专访报道,探讨了黑客松如何成为科技创新的重要推动力以及DoraHacks在其中扮演的角色。
万维网(World Wide Web)、人工智能(Artificial Intelligence)与量子计算(Quantum Computing)——这些划时代的技术有何共同之处?DoraHacks创始人张剑南认为,它们都源于“Hacks(黑客精神)”。“当万维网在欧洲核子研究中心(CERN)诞生时,它向我们证明了一件事:要想改变并提高人类的生活方式和工作效率,关键在于以创新的思维利用现有的技术以实现突破。”张剑南解释道,“如果总是从零开始,我们永远无法取得实质性的进步。这恰恰就是开源运动和黑客马拉松的核心价值。”
十年前,张剑南参与筹办了CERN Webfest 2013,这是一场致力于探索如何以创新方式运用技术来服务科学与社会的黑客马拉松活动。通过Webfest,张剑南不仅实现了编程技能与物理学知识的跨学科融合,还与来自世界各地、背景各异的hackers建立了持久深厚的联系。随着参与黑客松次数的增多,他的“黑客精神”愈发强烈,最终驱使他创立了自己的公司。2024年,张剑南重返Webfest,但这次他不再是参与者,而是作为DoraHacks的首席执行官来见证这场盛会。
黑客马拉松是一种持续数天的社交编程活动,具有高度的包容性和开放性——参与者无需学术机构或企业背景即可加入。这种特性吸引了众多才华横溢的个体参与其中。活动中,hackers以团队形式合作,结合各自的技能,通过软件、硬件或商业计划等来解决技术难题。这不仅让物理学家、计算机科学家、工程师和企业家齐聚一堂,各展所长,也让年轻的开发者们有机会突破传统研究框架,提升技能、积累作品集,并拓展职业人脉。
“如果你对某件事充满热情,就应该能够立即投入其中并全力以赴,”张剑南强调,“追求梦想并不需要特定的学历或背景。”
对于在某个领域刚起步的研究者来说,黑客松的意义远不止于技术挑战。它为进入一个研究或行业领域提供了另一种途径,弥合了学术理论与实际应用之间的鸿沟。很多由大学举办的黑客松往往能够吸引到企业的赞助,这些赞助除了作为奖金来激励开发者持续开发,也会用来租赁大型场馆,以容纳数百甚至上千名参与者。
“正是这些大规模的黑客松吸引了众多行业猎头和导师的关注,”张剑南解释道,“他们把这类活动看作他们的人才库。通过黑客松,参与者们能够与大公司的人直接交流,加速职业发展,同时也能在实践中提升他们的编程能力。”
在2010年代,张剑南经常在周末参加黑客松,这也成为他创业的基石。“我曾经坐在计算机科学学院的公共休息室里,埋头研究我的黑客项目。我的大多数朋友也是在那里认识的,”张剑南回忆道,“但后来我意识到,如果想做出真正伟大的东西,必须有效地组织人力与资金。然后我就开始‘逃课’,不去上计算机系的课程,而是偷偷溜进商学院的教室里。”张剑南常常在商学院的教室后排听课,一边听课一边谋划自己的创业计划。他每天都与同行交流,评估各种不同的商业模式。“在创业过程中,要把工程知识与商业理论结合起来思考,”他补充道,“这是比较有趣的一点,让整个过程也轻松了一些。”
然而,从科学研究转向创业并非易事。“创业初期必须亲力亲为,要自己去学习然后完成各种任务。”张剑南坦言,“好处是能够接触到许多新技能和新朋友,但同时也得强迫自己去做那些原本不擅长的事情。”
这种经历也反映了许多创业者的共同困境:选择自己从头学习新技能,还是寻找合适的创业伙伴然后把任务分配出去?可是找到值得信赖的合作伙伴也不是一件容易的事,错误的决策甚至可能阻碍公司的发展。因此,从一开始就明确公司的愿景和使命显得尤为重要。
“解决方案其实很简单,”张剑南表示,“重点是要投入足够多的时间,亲自完成关键里程碑,以确保产品真正具备可行性。只要有了明确的商业计划和愿景,就能获得来自各方的支持。”
去中心化的社区治理
很多黑客马拉松参与者在活动结束后就会放弃自己的项目,但张剑南创立DoraHacks的初衷并非如此。他希望为全球的黑客团队提供一个平台,让他们能够将创意转化为成熟产品。“我希望黑客马拉松不仅仅是一个招聘工具,”他解释道,“它更应该推动开源开发和去中心化的社区治理。比如现在,来自坦桑尼亚的黑客可以与美国的黑客团队远程协作,然后获得持续的支持,以开发出真正有影响力的产品。这种模式让技术领域变得更多样化,同时也能够让更多人接触到不同的领域。”
DoraHacks通过帮助组织者降低后勤成本,为参与者提供更可靠的资金支持机制,使黑客松超越学术机构的限制,吸引更多对创新充满热情的个体研究者参与。然后不断发展整个社区,让年轻一代的开发者、研究者们能够在自己的职业初期,接触到比以往更多的机遇和机会。
“商业模式正在发生根本的变化,”张剑南指出,黑客马拉松正在发展成为新兴技术的基石,尤其是在量子计算、区块链和人工智能等以开源形式起步的领域。“产品创造的过程将会迎来重大变革。未来的技术发展不再依赖于孤立封闭的产品开发,而是基于黑客们可以共同贡献的平台和基础设施。”
如今,黑客马拉松的意义已不仅限于编程或建立人脉——它们更关乎突破技术边界、创造有意义的解决方案,并开辟新的职业道路。黑客马拉松是创意孵化器,并且能够对这些创意产生持久的影响力。张剑南希望帮助这些创意变为现实。“未来创新的方式一定是协作完成的,是开源的,”他再次强调,“在传统社会环境里,企业的发展依赖于在闭源技术周围筑起的护城河,这种技术更新方式的效率低下且不容易实现。而真正创新的未来,将以开放平台技术为核心,让全球开发者能够在现有项目的基础上不断迭代更新。这样的开放协作精神正是Hacker Movement(开源极客运动)如此重要的原因。”
采访者:Alex Epshtein(编辑助理)。 原文链接:https://cerncourier.com/wp-content/uploads/2025/01/CERNCourier2025JanFeb-digitaledition.pdf
-
 @ ddf03aca:5cb3bbbe
2025-02-02 13:09:27
@ ddf03aca:5cb3bbbe
2025-02-02 13:09:27We’re thrilled to announce the stable release of Cashu-TS v2.2! Although this update is a minor version bump, it brings significant improvements under the hood that enhance the overall developer experience. We’ve spent several weeks testing and refining these changes.
What’s New in v2.2?
While there are no breaking changes in this release, there are many internal changes. If you spot any regressions or unexpected behavior, please let us know. Here’s a rundown of the major updates:
- Enhanced Proof Creation: The way proofs are created internally has been revamped.
- User-Controlled Outputs: You now have full control over how outputs are created.
- Improved Bundling: We’ve switched our bundling tool to vite for faster and more modern builds.
- Updated Testing Tools: Our testing framework has migrated to vitest and msw, with added browser testing via Playwright.
New Flexibility with OutputData
In previous versions of Cashu-TS, the creation of outputs (or BlindedMessages) was hidden away. Even though there were options to tweak the process (like deterministic secrets or P2PK), you were always limited to the built-in logic.
What’s Changed?
In v2.2, we’ve introduced a public interface that not only streamlines output creation but also lets you plug in your own custom logic when needed. With the new
outputDataoption available on all output-creating methods, you can now bypass the automatic process and provide your own outputs.For example, you can create two proofs tied to different public keys in a single mint operation:
ts const data1 = OutputData.createP2PKData({ pubkey: "key1" }, 10, keys); const data2 = OutputData.createP2PKData({ pubkey: "key2" }, 10, keys); const { keep, send } = await wallet.send(20, proofs, { outputData: { send: [...data1, ...data2] }, });Customization Made Easy
The
outputDataoption now accepts anything that conforms to theOutputDataLikeinterface. This means you can introduce your own output creation logic—even if it’s not natively supported by Cashu-TS yet. Here’s what the interface looks like:```ts export interface OutputDataLike { blindedMessage: SerializedBlindedMessage; blindingFactor: bigint; secret: Uint8Array;
toProof: (signature: SerializedBlindedSignature, keyset: MintKeys) => Proof; } ```
Introducing OutputData Factories
While having full control is empowering, it also means you’ll need to handle tasks like fee calculation and amount selection manually. To strike a balance between control and convenience, we now support OutputData Factories.
A factory is simply a function that takes an amount and
MintKeysas input and returns anOutputDataLikeobject. This way, you can define a blueprint for your output data without worrying about the nitty-gritty details. For instance, you can create separate factories for amounts you keep versus those you send:```ts function keepFactory(a: number, k: MintKeys) { return OutputData.createSingleP2PKData({ pubkey: "keepPk" }, a, k.id); }
function sendFactory(a: number, k: MintKeys) { return OutputData.createSingleP2PKData({ pubkey: "sendPk" }, a, k.id); }
const { send, keep } = await wallet.send(amount, proofs, { outputData: { send: createFactory("send"), keep: createFactory("keep") }, }); ```
Plus, you can now instantiate a
CashuWalletwith a defaultkeepFactory, ensuring that all change amounts automatically lock to your key—streamlining your workflow even further.
Bundling Improvements with Vite
Starting with v2.2, we’ve transitioned from using
tscto vite for transpiling and bundling the library code. Although this change is mostly behind the scenes, it brings several benefits:- Modern Build Target: We’ve updated our build target to ES6.
- Updated Exports: The package exports now reflect the latest JavaScript standards.
- Standalone Build Soon: We’re working on a standalone build that bundles Cashu-TS along with all its dependencies. This will let you import Cashu-TS directly into your HTML.
If you encounter any issues with the new bundling setup, please let us know.
A Nod to Vitest
In addition to our bundling improvements, we’ve migrated our testing framework from Jest (with nock) to vitest combined with msw. This switch gives us more flexibility in testing and mocking, plus we’ve added browser testing based on Playwright—thanks to the tip from nostr:npub16anjdksmvn5x08vtden04n64rw5k7fsjmedpw8avsx8wsh8ruhlq076pfx!
In Conclusion
Although Cashu-TS v2.2 is a minor version update, it comes packed with improvements that enhance both the developer experience and the flexibility of the library. We’re excited to see how you’ll use these new features in your projects! Thanks to all the amazing contributors that add to this library.
Thank you for being a part of the Cashu-TS community. As always, if you have any questions, suggestions, or issues, don’t hesitate to reach out to us.
-
 @ 8f69ac99:4f92f5fd
2024-09-27 08:55:34
@ 8f69ac99:4f92f5fd
2024-09-27 08:55:34Os Millennials e a Geração Z estão a sentir a pressão. Dívidas estudantis esmagadoras, o aumento do custo de vida e salários estagnados têm levado muitos a questionar o futuro. Ao navegarem num sistema que parece estar contra eles, não é surpresa que um número crescente procure soluções que prometem intervenção governamental ou até mesmo o socialismo, na esperança de encontrar alívio.
Mas e se o problema não for o capitalismo ou o livre mercado, como muitos são levados a acreditar? E se a verdadeira solução estiver noutro lugar — algo que oferece tanto liberdade financeira como clareza moral?
Entra Bitcoin. Mais do que uma moeda digital, Bitcoin representa um novo caminho — um que pode proporcionar poder económico ao mesmo tempo que nos liberta da corrupção e do controlo do sistema actual. Vamos explorar como Bitcoin pode oferecer aos Millennials e à Geração Z a liberdade financeira, moral e espiritual que têm procurado.
As Lutas Económicas dos Millennials e da Geração Z
Num mundo que celebra a inovação e a educação, por que é que os Millennials e a Geração Z estão a lutar mais do que qualquer outra geração anterior? Apesar de serem os grupos mais educados e tecnologicamente avançados da história, os jovens na casa dos 20 e 30 anos enfrentam desafios financeiros que ameaçam as suas perspectivas de longo prazo.
Desafios Financeiros da Geração Z
A Geração Z, nascida entre o final da década de 1990 e o início da década de 2010, está a enfrentar uma verdadeira tempestade financeira. Dados recentes revelam que:
- Declínio do rendimento: O rendimento médio para jovens de 22-24 anos no 4.º trimestre de 2023 era de 45.493 dólares, uma queda de quase 12% em relação aos 51.852 dólares no 4.º trimestre de 2013.
- Dívida crescente: A relação dívida-rendimento para a Geração Z aumentou para 16,05%, enquanto a dívida média de cartão de crédito é agora de 2.834 dólares.
- Stress financeiro: Um impressionante 45% vive de salário em salário, e apenas cerca de um quarto acredita que se reformará de forma confortável.
As principais causas incluem o aumento dos custos de vida, dívidas estudantis que rondam os 31.300 dólares e a inflação, que tem corroído o poder de compra.
Desafios Económicos dos Millennials
Da mesma forma, os Millennials, nascidos entre 1981 e 1996, enfrentam as suas próprias lutas:
- Cicatrizes da recessão: Ao entrarem no mercado de trabalho durante a Grande Recessão, muitos ainda enfrentam insegurança no emprego e salários mais baixos.
- Dificuldades habitacionais: Tal como a Geração Z, confrontam-se com a escalada dos preços das habitações, sendo que muitos não conseguem encontrar habitação acessível.
- Incerteza na carreira: A economia dos “gig” cria um ambiente de trabalho precário, dificultando a estabilidade.
Estes desafios são exacerbados pela desigualdade de riqueza, dinâmicas laborais em mudança e a pesada dívida estudantil.
Factores Contribuintes
As forças por detrás destes desafios económicos incluem:
- Aumento dos custos de vida: Os preços das habitações aumentaram mais de 50% na última década, o que pressiona as finanças dos jovens.
- Dívida estudantil: Níveis elevados de dívida continuam a sobrecarregar ambas as gerações.
- Inflação: A erosão dos salários reduz ainda mais o rendimento disponível para investir no futuro.
Estas dificuldades económicas são sintomas de uma mudança cultural mais ampla. À medida que mergulhamos mais profundamente nos próximos capítulos, exploraremos como estas transformações estão a redefinir as noções tradicionais de trabalho, riqueza e segurança.
O Apelo das Narrativas Marxistas, Socialistas e Globalistas
Nos últimos anos, os Millennials e a Geração Z têm sido inundados com uma cacofonia de narrativas económicas que culpam o capitalismo pelas suas dificuldades financeiras. Esta narrativa tem ganhado tracção nas redes sociais, nas instituições de ensino e até entre alguns políticos. No entanto, e se esta perspectiva for fundamentalmente falaciosa? Este capítulo defende que os verdadeiros culpados pelas dificuldades económicas destas gerações não são o capitalismo em si, mas sim as políticas e instituições que governam a nossa economia.
Culpar Erradamente: Compreender as Verdadeiras Causas das Dificuldades Económicas
Os Millennials e a Geração Z enfrentam desafios financeiros como nenhuma geração anterior — dívidas estudantis esmagadoras, habitação inacessível e salários estagnados estão entre as principais barreiras à estabilidade financeira. No entanto, muitos são atraídos por narrativas que fazem do capitalismo o bode expiatório para as suas dificuldades.
Políticos e elites frequentemente afirmam que a social-democracia e a intervenção estatal são as respostas para os nossos problemas económicos. Argumentam que o capitalismo é um sistema falhado, culpando-o pela desigualdade e pela pobreza, ao mesmo tempo que apresentam o socialismo e o controlo governamental como soluções necessárias. Esta perspectiva, contudo, simplifica em demasia uma questão complexa.
Na realidade, os Millennials e a Geração Z não enfrentam um problema de concentração excessiva de riqueza nas mãos de poucos. Enfrentam, sim, uma falta de mobilidade económica e de segurança para todos. O problema não é que o capitalismo seja injusto; é que a nossa social-democracia actual gerou disparidades no acesso a recursos e oportunidades.
A Realidade: Não Vivemos num Mercado Livre
A narrativa de que os Millennials e a Geração Z enfrentam dificuldades financeiras devido aos defeitos do capitalismo é fundamentalmente errada. Na realidade, a nossa sociedade opera sob um sistema de social-democracia, não sob princípios verdadeiros de mercado livre.
Sistema Actual: Social-Democracia, Não Capitalismo
A sociedade hoje está mais alinhada com a social-democracia do que com um verdadeiro mercado livre. Temos uma forte intervenção governamental, proteccionismo e capitalismo de compadrio que favorecem grandes corporações e elites políticas em detrimento de pequenos empreendedores e negócios. O planeamento central das políticas monetárias, das regulações e do controlo dos mercados frequentemente leva a desigualdade e instabilidade económica.
Culpa Errada no Capitalismo
Os desafios que os Millennials e a Geração Z enfrentam — como a crise da dívida estudantil, a inflação e a habitação inacessível — não são produtos do livre mercado, mas sim da intervenção governamental, de políticas fiscais falhadas e de medidas proteccionistas. A crise da dívida estudantil, por exemplo, resulta de políticas governamentais que incentivaram o endividamento e, ao mesmo tempo, inflacionaram o custo da educação.
Da mesma forma, a inflação e a habitação inacessível são frequentemente causadas por políticas governamentais que favorecem certas indústrias ou corporações em detrimento de outras, levando à distribuição desigual de recursos e oportunidades económicas.
Bitcoin como Solução Económica
Bitcoin oferece uma alternativa ao sistema falido que os Millennials e a Geração Z herdaram. Como moeda digital descentralizada, Bitcoin opera fora dos sistemas financeiros tradicionais e oferece um conjunto único de benefícios que podem ajudar a enfrentar os desafios económicos enfrentados por estas gerações.
Princípios de Dinheiro Forte
A oferta limitada de 21 milhões de unidades de bitcoin faz com que seja imune às práticas inflacionárias dos bancos centrais. Ao contrário das moedas fiduciárias, que podem ser impressas indefinidamente, a escassez do Bitcoin assegura que este preserve o seu valor ao longo do tempo. Este princípio de dinheiro forte oferece uma protecção contra a inflação e ajuda a proteger a riqueza individual numa economia onde as moedas controladas pelo governo perdem valor.
Preservação da Riqueza
Bitcoin também é uma poderosa ferramenta para a preservação da riqueza, especialmente num ambiente económico volátil. Enquanto investimentos tradicionais, como acções e obrigações, flutuam com as condições de mercado, o valor de Bitcoin é, em grande parte, independente das políticas dos bancos centrais e das economias nacionais. A sua natureza deflacionária significa que, à medida que mais pessoas adoptam Bitcoin, o seu valor tende a aumentar, proporcionando uma protecção contra crises económicas.
Bitcoin como Solução Moral e Espiritual
Para além de ser uma ferramenta económica, Bitcoin oferece uma solução moral e espiritual para aqueles que estão desiludidos com o sistema actual.
Descentralização e Ética
A natureza descentralizada do Bitcoin proporciona um caminho para que as pessoas controlem as suas vidas financeiras sem depender de autoridades centrais. Esta descentralização promove transparência, justiça e resistência à corrupção — valores muitas vezes ausentes nas instituições financeiras centralizadas de hoje.
Uma Solução para a Corrupção
O protocolo incorruptível de Bitcoin impede que qualquer entidade o manipule. Ao contrário dos sistemas tradicionais, que podem ser influenciados por interesses especiais, a blockchain, e a prova de trabalho de Bitcoin asseguram a transparência e a integridade em todas as transacções. Isto torna Bitcoin uma alternativa moral aos sistemas que estão sujeitos a corrupção e exploração.
Bitcoin como Visão de Liberdade a Longo Prazo
Bitcoin é mais do que uma solução temporária para os problemas económicos — representa uma visão de liberdade financeira e pessoal a longo prazo.
Liberdade Financeira
Bitcoin liberta os indivíduos dos ciclos inflacionários e das armadilhas da dívida criadas pelos sistemas monetários tradicionais. A sua oferta limitada assegura que o valor é preservado, oferecendo um futuro financeiro estável e seguro. Ao possuir Bitcoin, as pessoas podem escapar ao ciclo de dependência das moedas fiduciárias controladas pelo governo e proteger a sua riqueza contra a desvalorização.
Soberania Espiritual
Bitcoin não se trata apenas de acumulação de riqueza; trata-se de recuperar o controlo sobre o próprio destino. Ao permitir que as pessoas tomem decisões financeiras autónomas, Bitcoin proporciona soberania espiritual — a capacidade de viver de acordo com os próprios valores, sem estar dependente de instituições centralizadas.
Conclusão: Recuperar a Liberdade com Bitcoin
As dificuldades económicas enfrentadas pelos Millennials e pela Geração Z não são resultado do capitalismo de mercado livre, mas sim de um sistema corrompido pela intervenção governamental e pelo proteccionismo. Bitcoin oferece uma alternativa revolucionária — uma que permite que os indivíduos recuperem o controlo das suas finanças, do seu futuro e da sua liberdade.
Bitcoin representa mais do que estabilidade financeira — é um movimento em direcção à libertação moral e espiritual. Para os Millennials, a Geração Z e todos os que estão desiludidos com o sistema actual, Bitcoin oferece uma forma de romper com o status quo e construir um futuro sustentável baseado na liberdade pessoal, na integridade e na responsabilidade.
Photo by Emil Kalibradov on Unsplash
-
 @ fe41d17e:28df7452
2025-02-02 13:04:38
@ fe41d17e:28df7452
2025-02-02 13:04:38Um es vorab klarzustellen, die einzigen Gesetze an die du dich wirklich halten musst sind die Naturgesetze, es ist deine eigene Entscheidung ob du einer einseitig vom Staat beschlossenen Auflage zustimmst oder nicht, solange du bereit bist, falls du erwischt wirst, die Konsequenzen über dich ergehen zu lassen.
Wenn du diese Unterdrückung nicht mehr haben möchtest braucht es eine Revolution um den Staat irrelevant werden zu lassen und um ihm seine Grundlage (das Geld) zu entziehen ohne dabei wie er selbst zu unmoralischen Methoden zu greifen.
Diese Revolution nennt sich Agorismus, sie wird dich unabhängig vom Staat machen und den Staat langfristig schwach/überflüssig werden lassen sobald es dir genug Leute gleichtun.
Die Revolution wird nicht leicht, sie wird dir nicht die sofortige Genugtuung verschaffen, die du möglicherweise empfindest, wenn du einen Zettel in die Wahlurne wirfst und dabei das Gefühl hast, etwas verändert zu haben. Eigentlich hast du nur denselben Leuten Macht verliehen, die seit Jahrhunderten die Politiker kontrollieren, dich ausrauben und unterdrücken. Garnichts hast du damit verändert.
Es wird schwierig werden. Es wird Eigeninitiative und Veränderungen in deinem Leben erfordern. Es wird ein zermürbender, unbefriedigender Weg sein, den viele als zu hart bezeichnen werden. Es wird Jahre über Jahre dauern, in denen die Leute dich dafür schief ansehen und du kaum Anerkennung bekommen wirst.
Hier ein paar wichtige Punkte um dich mit Agorismus vertraut zu machen:
-Wenn du bereits ein Libertärer bist, lies zuerst „Das neue Libertäre Manifest“ von Samuel Edward Konkin III. Es hat nur 30 Seiten, und wenn du damit nicht zumindest deinen Horizont erweitern kannst, dann kannst du genauso gut eine britische Flagge in Amerika schwenken, Tribut zollen und einen König fordern.
-Wenn du kein Libertärer bist, lies „Eine neue Freiheit: das libertäre Manifest“ von Murray Rothbard und anschließend „Das neue Libertäre Manifest“ von SEK3.
-Konzentriere dich in deinem Leben darauf, weniger bis keine Steuern zu zahlen.
-Finde Alternativen zum Fiatgeld und sei deine eigene Bank.
-Finde lokale Quellen für Lebensmittel und Produkte.
-Handel P2P auf freien Märkten.
-Suche nach Lösungen, die auf Dezentralisierung ausgerichtet sind.
-Baue eine gewisse Menge an Lebensmitteln an, auch wenn es nur Mikrogrün ist. Dafür sind keine großen Flächen erforderlich und du kannst diese gegen andere Lebensmittel eintauschen.
-Baue dein eigenes Unternehmen außerhalb von Konzernstrukturen auf.
-Konzentriere dich auf den Handel mit anderen Agoristen.
-Nutze jede Gelegenheit um deine Verachtung gegenüber dem Staat zu äußern.
-Verbreite Agorismus.
-Beschaffe dir Waffen.
-Vertraue nur agoristischen Medien, die unpolitisch sind. Denn jeder Journalist, der dich ermutigt, zu wählen oder innerhalb des Systems zu arbeiten, könnte gekauft oder kontrolliert sein. Agoristen, die behaupten, dass Politik nicht die Antwort ist, sind die einzigen, die die Menschen wirklich von den Kontrolleuren wegführen.
Die Herrscher dieser Welt sind sich durchaus darüber im Klaren, dass das Informationszeitalter ihren Interessen schadet. Daher arbeiten sie unermüdlich an der Schaffung psychologischer Operationen (PsyOps), kontrollierter Opposition, False-Flag-Aktionen und Ablenkungsmanövern, lass dich nicht täuschen.
Erstveröffentlichung am 12. Januar auf meinem X Profil; @realbunki
-
 @ 8f69ac99:4f92f5fd
2024-09-26 11:08:21
@ 8f69ac99:4f92f5fd
2024-09-26 11:08:21As revoluções muitas vezes começam com os membros mais jovens da sociedade—adolescentes, idealistas e cheios de energia, ansiosos por causar mudanças. No entanto, no mundo de hoje, a noção de revolução foi sequestrada por forças que procuram controlar e manipular, em vez de empoderar os indivíduos. A chamada "revolução woke" é um exemplo claro, impulsionada por uma agenda que polariza a sociedade ao longo das linhas da política identitária. Esta distracção desvia a atenção dos verdadeiros problemas: a desigualdade económica e o autoritarismo. Mas há uma alternativa melhor, uma que prioriza a liberdade e a soberania em vez da divisão e do controlo—Bitcoin.
A "Revolução Woke" Globalista e a Agenda da Polarização
Uma das tácticas mais insidiosas da "revolução woke" é a polarização deliberada da sociedade. Ao criar narrativas que colocam as pessoas umas contra as outras com base em raça, género, religião e política, aqueles no poder mantêm o controlo e desviam a atenção dos problemas mais profundos que realmente importam. Esta estratégia é orwelliana: ao criar uma mentalidade de "nós contra eles", fabricam uma cultura de conflito perpétuo.
Em vez de promover uma mudança significativa, a "revolução woke" prende as pessoas num ciclo de indignação e divisão, distraindo-as de enfrentar as verdadeiras estruturas de poder—como a desigualdade económica e o excesso de controlo estatal. Esta fragmentação enfraquece os laços entre as pessoas, tornando a sociedade mais vulnerável à manipulação pelas autoridades centralizadas.
Esta polarização serve os interesses daqueles que estão no poder. Quando as pessoas estão demasiado ocupadas a lutar entre si, são menos propensas a questionar os sistemas que realmente as controlam. A "revolução woke" torna-se menos uma questão de progresso genuíno e mais uma forma de manter o status quo através da divisão e da distracção.
Por Que a Polarização é Incentivada
A polarização não é acidental—é uma estratégia calculada com o objectivo de controlar. Dividindo as pessoas em campos opostos, a sociedade fragmenta-se, tornando mais difícil para os indivíduos unirem-se contra adversários comuns ou combaterem políticas que beneficiam as elites.
Esta divisão serve também como uma distracção poderosa. Enquanto as pessoas estão consumidas por batalhas ideológicas, os sistemas financeiros centralizados e o controlo governamental expandem-se silenciosamente. Os meios de comunicação, muitas vezes controlados pelos mesmos poderes, alimentam estas divisões, mantendo as pessoas focadas em conflitos internos enquanto ocultam as verdadeiras ameaças à liberdade.
A polarização também corrói as liberdades individuais. Quando as pessoas estão envolvidas em batalhas ideológicas intermináveis, são menos propensas a notar a erosão gradual dos seus direitos. Isto é precisamente o que os poderes estabelecidos desejam—uma população distraída e dividida, demasiado ocupada para desafiar o desmantelamento lento das suas liberdades pessoais.
O Resultado da Polarização
O resultado desta polarização deliberada é uma sociedade mais preocupada com a pureza ideológica do que com a garantia das suas verdadeiras liberdades. As pessoas ficam presas na política identitária, priorizando a lealdade ao grupo em detrimento da autonomia individual. Isto promove uma mentalidade de "pensamento de grupo", onde questionar a narrativa dominante é desencorajado.
Entretanto, a desigualdade económica aprofunda-se à medida que os poderes centralizados continuam a consolidar o controlo. Os sistemas que deveriam promover equidade tornam-se cada vez mais manipulados, beneficiando os poucos em detrimento dos muitos. A verdadeira liberdade—especialmente a liberdade financeira—torna-se mais difícil de alcançar, com os indivíduos presos em sistemas concebidos para beneficiar uma minoria poderosa.
No final, a "revolução woke" apenas reforça as mesmas estruturas que afirma combater. Ao dividir as pessoas e distraí-las dos verdadeiros problemas, os poderes estabelecidos mantêm o seu controlo, enquanto as liberdades pessoais e financeiras da maioria continuam a ser corroídas.
Bitcoin: A Verdadeira Revolução
Em contraste com a "revolução woke", que divide, Bitcoin oferece uma verdadeira revolução—uma que empodera os indivíduos em vez de os separar. Bitcoin proporciona soberania financeira, retirando poder dos governos autoritários e das instituições centralizadas.
Bitcoin permite que os indivíduos controlem a sua própria riqueza, eliminando a necessidade de intermediários como bancos ou governos. As pessoas já não estão sujeitas a entidades que restringem a sua liberdade financeira. Com Bitcoin, podem criar, armazenar e transferir valor de forma segura, transparente e acessível.
Isto não se trata apenas de economia—é sobre recuperar a liberdade. A natureza descentralizada do Bitcoin permite que as pessoas tomem decisões financeiras sem interferência do estado ou de entidades corporativas.
Porque é Que o Bitcoin é Revolucionário
A verdadeira natureza revolucionária do Bitcoin reside no seu design e princípios, que rompem com os sistemas de controlo enraizados. Eis algumas razões pelas quais o Bitcoin é transformador:
-
Aberto e Sem Fronteiras: O Bitcoin transcende fronteiras, permitindo que pessoas de todo o mundo participem igualmente no sistema financeiro. Quebra barreiras baseadas em nacionalidade ou geografia, permitindo uma participação económica global.
-
Resistente à Censura: Nenhum governo ou empresa pode parar uma transacção em Bitcoin, dando às pessoas a liberdade de transferir valor sem medo de interferências ou retaliações. Esta é a forma definitiva de autonomia financeira.
-
Sem Permissão: O Bitcoin não requer aprovação de nenhuma autoridade. Ao contrário dos sistemas financeiros tradicionais, não há porteiros a controlar quem pode participar, tornando o Bitcoin uma ferramenta para a verdadeira auto-soberania financeira.
-
Neutro: O Bitcoin é imparcial. Não se importa com raça, género, religião ou política. Num mundo onde a política identitária é usada para dividir, o Bitcoin trata todos de forma igual, oferecendo um sistema financeiro inclusivo que transcende essas divisões.
Bitcoin como o Antídoto para a Polarização
O Bitcoin oferece uma solução para a divisão criada pela polarização. Transcende a política identitária ao tratar todos de forma igual, independentemente da sua origem ou crenças. A neutralidade do Bitcoin garante que nenhum grupo ou facção pode manipulá-lo para impor as suas visões sobre os outros.
Bitcoin permite que os indivíduos se libertem das narrativas divisivas e tomem controlo dos seus destinos financeiros. Promove a cooperação em vez do conflito, capacitando as pessoas a focarem-se em objectivos comuns, em vez de batalhas ideológicas.
O Bitcoin não é apenas uma moeda—é uma força unificadora, oferecendo esperança àqueles que estão cansados da divisão e das lutas pelo poder. Representa uma mudança para práticas financeiras inclusivas que priorizam a autonomia individual em detrimento do controlo centralizado.
Um Apelo à Acção
Para os jovens que sonham em criar uma mudança real: se querem liderar uma revolução que verdadeiramente empodere os indivíduos e quebre as cadeias do controlo centralizado, então é hora de abraçar o Bitcoin.
Esta revolução não é sobre seguir uma agenda predefinida ou alinhar-se com ideologias divisivas. Trata-se de criar um futuro de sistemas financeiros abertos, onde todos têm a liberdade de participar igualmente.
A cor desta revolução é laranja, simbolizando o logótipo do Bitcoin e o movimento em direcção à liberdade financeira. Representa a esperança para aqueles que querem escapar das restrições dos sistemas tradicionais e criar um mundo descentralizado e empoderado.
Conclusão
Estamos à beira de uma revolução financeira. A juventude tem uma escolha: seguir as narrativas pré-definidas dos sistemas ultrapassados ou tomar controlo dos seus próprios destinos através de redes financeiras descentralizadas e abertas.
O Bitcoin é a verdadeira revolução. É um movimento impulsionado pelo desejo de liberdade, autonomia e inclusão. Juntem-se à revolução, sejam parte de algo maior, e ajudem a construir um mundo onde o poder é descentralizado, as oportunidades são iguais e o futuro é brilhante e laranja—a cor da liberdade financeira.
Photo by Tarik Haiga on Unsplash
-
-
 @ 3bf0c63f:aefa459d
2024-09-18 10:37:09
@ 3bf0c63f:aefa459d
2024-09-18 10:37:09How to do curation and businesses on Nostr
Suppose you want to start a Nostr business.
You might be tempted to make a closed platform that reuses Nostr identities and grabs (some) content from the external Nostr network, only to imprison it inside your thing -- and then you're going to run an amazing AI-powered algorithm on that content and "surface" only the best stuff and people will flock to your app.
This will be specially good if you're going after one of the many unexplored niches of Nostr in which reading immediately from people you know doesn't work as you generally want to discover new things from the outer world, such as:
- food recipe sharing;
- sharing of long articles about varying topics;
- markets for used goods;
- freelancer work and job offers;
- specific in-game lobbies and matchmaking;
- directories of accredited professionals;
- sharing of original music, drawings and other artistic creations;
- restaurant recommendations
- and so on.
But that is not the correct approach and damages the freedom and interoperability of Nostr, posing a centralization threat to the protocol. Even if it "works" and your business is incredibly successful it will just enshrine you as the head of a platform that controls users and thus is prone to all the bad things that happen to all these platforms. Your company will start to display ads and shape the public discourse, you'll need a big legal team, the FBI will talk to you, advertisers will play a big role and so on.
If you are interested in Nostr today that must be because you appreciate the fact that it is not owned by any companies, so it's safe to assume you don't want to be that company that owns it. So what should you do instead? Here's an idea in two steps:
- Write a Nostr client tailored to the niche you want to cover
If it's a music sharing thing, then the client will have a way to play the audio and so on; if it's a restaurant sharing it will have maps with the locations of the restaurants or whatever, you get the idea. Hopefully there will be a NIP or a NUD specifying how to create and interact with events relating to this niche, or you will write or contribute with the creation of one, because without interoperability this can't be Nostr.
The client should work independently of any special backend requirements and ideally be open-source. It should have a way for users to configure to which relays they want to connect to see "global" content -- i.e., they might want to connect to
wss://nostr.chrysalisrecords.com/to see only the latest music releases accredited by that label or towss://nostr.indiemusic.com/to get music from independent producers from that community.- Run a relay that does all the magic
This is where your value-adding capabilities come into play: if you have that magic sauce you should be able to apply it here. Your service -- let's call it
wss://magicsaucemusic.com/-- will charge people or do some KYM (know your music) validation or use some very advanced AI sorcery to filter out the spam and the garbage and display the best content to your users who will request the global feed from it (["REQ", "_", {}]), and this will cause people to want to publish to your relay while others will want to read from it.You set your relay as the default option in the client and let things happen. Your relay is like your "website" and people are free to connect to it or not. You don't own the network, you're just competing against other websites on a leveled playing field, so you're not responsible for it. Users get seamless browsing across multiple websites, unified identities, a unified interface (that could be different in a different client) and social interaction capabilities that work in the same way for all, and they do not depend on you, therefore they're more likely to trust you.
Does this centralize the network still? But this a simple and easy way to go about the matter and scales well in all aspects.
Besides allowing users to connect to specific relays for getting a feed of curated content, such clients should also do all kinds of "social" (i.e. following, commenting etc) activities (if they choose to do that) using the outbox model -- i.e. if I find a musician I like under
wss://magicsaucemusic.comand I decide to follow them I should keep getting updates from them even if they get banned from that relay and start publishing onwss://nos.lolorwss://relay.damus.ioor whatever relay that doesn't even know anything about music.The hardcoded defaults and manual typing of relay URLs can be annoying. But I think it works well at the current stage of Nostr development. Soon, though, we can create events that recommend other relays or share relay lists specific to each kind of activity so users can get in-app suggestions of relays their friends are using to get their music from and so on. That kind of stuff can go a long way.
-
 @ df57b498:d049124f
2025-01-26 03:59:47
@ df57b498:d049124f
2025-01-26 03:59:47Chef's notes
This is cobbled together from trial and error and the web.
Serve hot pancakes with preferably butter and maple syrup. Add other toppings like bananas, nuts, or other fruits and toppings as have available and/or desired.
Details
- ⏲️ Prep time: 10 minutes
- 🍳 Cook time: 10 minutes
Ingredients
- 1 cup flour
- 2 tablespoons sugar
- 2 teaspoons baking powder
- 1 teaspoon salt
- 1 cup milk
- 2 tablespoons vegetable oil
- 1 egg, beaten
Directions
- Combine the dry ingredients.
- Add the wet ingredients and mix.
- Pour or ladle the batter onto the oiled griddle or pan.
- Cook until bubbles form, flip, and cook on the other side.
-
 @ 77be3409:5c7c2736
2025-02-02 12:48:25
@ 77be3409:5c7c2736
2025-02-02 12:48:25RMD Law - Personal Injury Lawyers is excited to announce the launch of its new scholarship program, designed to empower students and highlight the values of responsibility, resilience, and learning from life’s unexpected moments. This $2,500 scholarship aims to support students in their educational journeys while encouraging creativity and personal growth.
Scholarship Details
Award Amount: $2,500 Submission Deadline: December 30, 2025 Winner Announced: January 15, 2026
Eligibility Requirements To apply, students must meet the following criteria: - Be at least 16 years old and a permanent legal resident of the United States. - Be currently enrolled in a U.S. college, university, or trade school OR graduating from high school in 2025. - Have a cumulative GPA of 3.0 or higher. - Follow RMD Law on social media to see the winner announcement. - Submit all required materials by the December 30, 2025, deadline
Application Requirements Applicants are required to submit:
- A copy of their most recent high school or college transcript.
- A creative and thoughtful essay (up to 1,000 words) responding to the following prompt:
Essay Prompt: “Oops, That Was Close!”
Tell us about a moment when you narrowly avoided disaster—whether it was a hilarious mishap, an embarrassing accident, or a close call with serious consequences. - What did you learn (if anything) from the experience? - Who was at fault and why? - What would the appropriate restitution (if any) be in that situation?
Note: Applicants are encouraged to use creativity, levity, and personal insights to share their story. Let your unique voice shine through!
Selection Criteria The winner will be chosen based on: - Originality and creativity in their essay. - Relevance to the prompt. - Clarity and thoughtfulness of their response. The scholarship recipient will be announced on January 15, 2026.
How to Apply 1. Students can submit their application materials through the official RMD Law scholarship webpage: https://www.rmdlaw.com/scholarship/ 2. Follow RMD Law on social media to stay updated on the announcement and other initiatives.
About RMD Law
RMD Law is a leading personal injury law firm committed to providing exceptional legal services and making a positive impact in the communities it serves. Through initiatives like the scholarship program, RMD Law seeks to empower individuals and foster the next generation of leaders.
-
 @ 9e69e420:d12360c2
2025-01-26 01:31:47
@ 9e69e420:d12360c2
2025-01-26 01:31:47Chef's notes
arbitray
- test
- of
- chefs notes
hedding 2
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 5
Ingredients
- Test ingredient
- 2nd test ingredient
Directions
- Bake
- Cool
-
 @ 0463223a:3b14d673
2025-02-02 12:22:46
@ 0463223a:3b14d673
2025-02-02 12:22:46I’m totally wasted! I don’t mean off my head on drugs, I mean absolutely physically and mentally exhausted.
Lugging heavy PA equipment up and down stairs, plus mixing shows is a lot and at my age I’m struggling with it. Yesterday was a write off due to exhaustion. My wife and I went to the cinema, and I slept through the film. A shame, it was something I wanted to see but I was toast. I went to bed at 8pm and slept for over 12 hours. I still feel wrecked today.
Live sound was always a sort of plan B. For a number of years teaching and performing with a band or a DJ was enough to get by on. I was comfortable, financially speaking. That was until about between 2012-14, that’s when we really felt the effects of the post 2008 crash. While a lot of noise was made about the initial event, reality for the likes of me was a slow and steady decline. At that time I was leading workshops with kids with difficult backgrounds, many kids in care due to abuse and neglect. That was a solid 40% of my income, another 30% came from teaching Sound Production at a local university and the final 30% from shows.
2014 cutbacks ripped services to shreds and a few friends lost jobs. Since then, doing live sound kept the rent and bills paid but fast forward to 2025 and I’m way too tired for this shit! I hate admitting it but my earnings probably peaked around 2008 with a bump in tours from 2017 till Covid. Since then earnings have been steady in £'s but getting wiped out by inflation. In fact I had decent acounts this year but every month I'm broke by the time bills and basics have been taken care of. I LOVE mixing live music and I’m pretty good at it. I’ve had musicians call me ‘musical’ which is the highest compliment but I’m totally fucked still 2 days after Friday’s show. It's unsustainable.
I’m quitting live sound unless some touring comes up again, touring is different, living on a bus for 3 weeks pays the same as 3 months of local work and I just mix, no lifting gear. The band I tour with are based in the US and only come to the UK/EU every couple of years. I get odd trips away with other artists but they’re usually fly out EU gigs. 1 or 2 shows then fly home, plus they're irregular.
Right now I’m more interested to learn ways of making income online, I started the Kali Mera Show to learn self hosting content. Committing to a project each morning has done wonders for my mental health, cutting down on morning doom scrolling. It’s been highly successful in that regard but not so much financially. However this is jst phase 1. I’m learning the tech, learning the production and making as many mistakes as possible while the stakes are low. I’m very happy 10 or so people enjoy the show on a daily basis. Tiny numbers but I don’t fuck with YouTube or the other big tech platforms. Fuck them!
Phase 2 involves getting premises and broadening the services I can produce, focussing on content for others, getting some opportunities happening for young talent, arranging meet ups and setting up a hub to bring together the crazy, talented people I know. It’s going to be tough, I’m in a run down area, there’s not much money here (relatively speaking) but it’s an area I really dig and want to make better.
Why am I telling you this? I’m writing this as a means of getting my brain straight and sharing it because I’m open to improving myself. I see people doing interesting shit here and that helps with motivation and confidence. My only social media for the last 6 years has been the Fediverse and much as I love it, there’s a gloomier outlook there. The world is a strange place with so much bad shit but out of 8 or so billion people, I can only take on so much. Building shit in my own local community and provide facilities for online wins sounds way more productive and helpful in some small way.
I accept we’re all going to hell in a handcart but may as well enjoy the ride…
There’s much to learn, I’ve only ever been ‘in business’ for a short time in my life (despite always being freelance) and I sort of gave up on my previous attempt. Had I paid more attention I could’ve built a strong YouTube presence but I’m not into being a vehicle for companies to push their products, nor do I want to teach people music online. That market is now heavily saturated and very, very boring as far as I’m concerned. My heart wasn’t in it, even back in 2015. I’m not an influencer.
With a real life space there’s premises, business rates, and investors to consider, as well as developing services that people are actually happy to part cash with. It’s going to be hard but different hard to physically lifting sub-bass speakers up and down winding staircases! I don’t want to talk too much game, it’s results that matter but wasting days to exhaustion doesn’t help. It’s time to hang up my headphones and focus (FOCUS YOU FUCKING FUCK!).
Maybe you’re reading this and thought ‘shit, this guy’s totally deluded’. That’s cool. Tell me. I value feedback. A fair few cats here give life advice so I’ll assume you might know what you’re talking about...
-
 @ 30b99916:3cc6e3fe
2025-01-21 02:08:26
@ 30b99916:3cc6e3fe
2025-01-21 02:08:26Details
- 🍳 Cook time: 10 to 8 minutes at 350
- 🍽️ Servings: About 4 dozen cookies
Ingredients
- 2 sticks of butter
- 2 eggs
- 1 cup granulated sugar
- 1 cup brown sugar
- 1 cup peanut butter
- 1 t vanilla
- 2 cups flour
- 1/2 t salt
- 1 t soda
- 6 oz Semi-Sweet Chocolate chips (optional)
Directions
- Blend butter, eggs, vanilla and sugars together thoroughly
- Next blend in peanut butter thoroughly
- Next blend in flour, salt, and soda thoroughly
- Optional blend in chocolate chips
- Add about table spoon of cookie dough per cookie on a cookie sheet. With a fork based in sugar place a cross hatch pattern on each cookie. Bake cookies for 10 to 8 minutes and place onto cooler rack.
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ c69b71dc:426ba763
2025-01-18 15:39:35
@ c69b71dc:426ba763
2025-01-18 15:39:35Chef's notes
This raw vegan curry ramen is a vibrant, nourishing dish packed with fresh vegetables and a rich, creamy coconut curry broth. It’s quick to prepare, full of flavour, and the perfect guilt-free comfort food! 🌱 Feel free to use your favourite veggies👩🏼🍳
Details
- ⏲️ Prep time: 20 min.
- 🍳 Cook time: 0
- 🍽️ Servings: 2
Ingredients
- 500g or 2 packs kelp noodles
- 1/2 Lemon juice ( 1/4 for soaking and 1/4 for the soup
- Salt
- Fresh vegetables of your choice, such as: 4 medium mushrooms, 4 leaves red cabbage, 2 carrots (julienned or peeled into strips), 1 Celery stick (diced)
- 2 cups coconut milk (or coconut cream diluted with water)
- 1/2 flesh of a Coconut (optional, if using fresh coconuts) otherwise more coconut cream
- 1 thumb of fresh ginger
- 1 thumb of fresh turmeric
- 2 tbsp light miso paste
- 2 pitted dates
- 2 tbsp cashews
- 1 clove garlic
- 1 tsp curry powder or pepper (optional)
Directions
- Prepare the Noodles: Rinse the kelp noodles thoroughly. Then soak them in warm water with a squeeze of lemon juice and a pinch of salt for 10 minutes to soften.
- Prep the Vegetables: Thinly slice or julienne carrots, dice celery, thinly cut mushrooms, cut the red cabbage into thin strips.
- Make the Broth: In a blender, combine the following: 2 cups coconut milk (or coconut cream diluted with water if fresh coconuts are unavailable), ginger, turmeric, 1/4 juice of 1 lemon, light miso paste, pitted dates, cashews, garlic, salt, curry powder
- Blend on high speed for about 3 to 4 minutes until the broth is smooth and slightly warm. Do not overheat!
- Assemble the Ramen: Drain the kelp noodles and place them in serving bowls. Arrange the prepped vegetables on top of the noodles. Pour the warm curry broth over the noodles and vegetables.
- Serve immediately and enjoy your raw vegan ramen with chopsticks for an authentic touch!
-
 @ d1795b1a:15ab2129
2025-02-02 11:45:38
@ d1795b1a:15ab2129
2025-02-02 11:45:38The Ego is an Illusion – and Yet, We Can Shape It
Carl Jung spoke of the Shadow Self—the repressed parts of our psyche that unconsciously influence our lives. Buddhism, on the other hand, teaches that there is no self at all—our ego is an illusion, a fleeting construct that we cling to out of fear of emptiness.
These two perspectives seem to contradict each other. One tells us to integrate our hidden self, the other to dissolve it completely. But what if both are only half the picture?
I believe the Self is neither a fixed reality nor a mere illusion—it is a shapeable construct. If that is true, then the path is not to destroy the Ego-Self or blindly follow it, but to consciously shape it.
Between the Shadow and Emptiness
Our Ego-Self is our conscious identity—our thoughts, memories, and beliefs. Jung describes the Self as the totality of both the conscious and unconscious mind. Hidden in this unconscious space is the Shadow Self, containing everything we deny, suppress, or refuse to acknowledge. For Jung, the path to wholeness is integration—bringing light into the dark corners of the psyche.
Buddhism, however, goes further. It questions whether the Self exists at all. Our thoughts and emotions arise and disappear, our self-image is ever-changing—so why do we cling to something so impermanent?
Both views seem to offer opposite solutions: \ • Jung: Become WHOLE by integrating your Shadow. \ • Buddha: Become FREE by seeing the Self as an illusion.
But what if the synthesis of both is the key?
The Self as a Shapeable Reality
If the Self is not fixed but fluid, then the path forward is neither pure integration nor total dissolution but conscious creation. \ \ • Acknowledge the Shadow Self instead of fighting it. \ • See the Ego-Self not as absolute truth but as a flexible tool. \ • Engage the Solar Plexus—the center of the Unconscious Mind—through breathwork and self-awareness. \ • Use the Vagus Nerve as a bridge between conscious thought and unconscious emotion, actively shaping our beliefs and behaviors.
This aligns with New Thought philosophy, which suggests that our thoughts shape not only our perception but our reality itself. If we embrace this, the question is no longer “Who am I?” but rather: “Who do I want to be—and how can I create that Self?”
The Art of Shaping Yourself
Perhaps the Self is neither a rigid entity nor a complete illusion but a story we tell ourselves—a story we can rewrite. The key is not to destroy the Ego-Self but to use it consciously, rather than being used by it.
So the real question is not: “Does the Self exist?”
But rather: “How aware are we of the fact that we are shaping it every moment?”
-
 @ d1b118c6:4985b38d
2025-01-16 17:39:47
@ d1b118c6:4985b38d
2025-01-16 17:39:47Chef's notes
Let me know how it goes for you https://maria.omg.lol
Details
- ⏲️ Prep time: 5-20 minutes
- 🍳 Cook time: 20-40 minutes
- 🍽️ Servings: As many as you want omg!!!!
Ingredients
- Spaghetti/whatever pasta you want
- Garlic/smashed or diced as much as you want
- Tomatoes/ diced or more liquid state whatever you want
- Scallops/ I use the frozen bagged mini kind and just do a couple handfuls as many as you want
- Butter and/or olive oil but the butter is v good imo but also I used both
- Bacon/ make it extra crispy and then crumble up as much as you want
- Whatever seasonings
Directions
- Set oven to 400° or so
- Put all your bacon 🥓 strips onto tin foil lined baking sheet/s and then put the trays in the oven for 15-20 min
- Boil up your pasta in salty water
- Pull the bacon out when done
- In a pan cook up the scallops real quick like 5-10 min idk
- Sauté the tomatoes and garlic and whatever use whatever seasons and lots of butter
- Strain the pasta when it’s ready
- Mix pasta and sautéed sauce
- Add more crumbled bacon on top #garnish
-
 @ 30b99916:3cc6e3fe
2025-01-13 22:17:08
@ 30b99916:3cc6e3fe
2025-01-13 22:17:08Chef's notes
Recipe modified from a recipe published from a school cookbook in 1963.
Details
- 🍳 Cook time: 8 to 10 Minutes at 400
- 🍽️ Servings: 3 dozen or so depending on cookie size
Ingredients
- 2 sticks of butter
- 1 1/2 Cup sugar
- 2 eggs
- 1 t. vanilla (optional but recommended)
- 2 3/4 cups flour
- 2 t. Cream of tartar
- 1 t. Soda
- 1/4 t. Salt
Directions
-
- Heat over to 400
-
- Mix butter, sugar, eggs, and vanilla thoroughly.
-
- Sift together flour, cream of tartar, soda, salt and blend into mixture.
-
- Form small dough balls and roll in sugar/cinnamon
-
- Place each cookie dough ball 2" apart on a cookie sheet
-
 @ fd208ee8:0fd927c1
2025-02-02 10:33:19
@ fd208ee8:0fd927c1
2025-02-02 10:33:19GitCitadel Development Operations
We, at GitCitadel, have been updating, moving, and rearranging our servers, for quite some time. As a rather large, complex, sprawling project, we have the infrastructure setup to match, so we've decided to give you all a quick run-down of what we are doing behind-the-scenes.
Supplier Coordination

Our first task, this week, was figuring out who would host what where. We have four different locations, where our infra is stored and managed, including two locations from our suppliers. We got that straightened out, quickly, and it's all slowly coming together and being connected and networked. Exciting to watch our DevOps landscape evolve and all of the knowledge-transfer that the interactions provide.
OneDev Implementation

Our biggest internal infra project this week was the migration of all of our issues from Jira, build scripts from Jenkins, and repos from GitHub to a self-hosted OneDev instance. In the future, all of our internal build, test, issue, patch/PR, etc. effort will take place there. We also have a separate repo there for communicating with external developers and suppliers.
Our team's GitHub projects will be demoted to mirrors and a place for external devs to PR to. Public issues and patches will continue to be managed over our self-hosted GitWorkshop instance.
We're especially glad to finally escape the GitHub Gulag, and avoid being bled dry by Jira fees, without having to give up the important features that we've come to know and love. So, yay!
Next Infrasteps
Automated Testing
Now, that we have everything tied up in one, neat, backed-up package, we can finally move on to the nitty-gritty and the dirty work. So, we're rolling up our sleeves and writing the Selenium smoke test for our Alexandria client. We'll be running that in Docker containers containing different "typical Nostr" images, such as Chrome browser with Nostr Connect signing extension, or Firefox browser with Nos2x-fox extension. Once we get the Nsec Bunker and Amber logins going, we'll add test cases and images for them, as well. (Yes, we can do Bunker. I hope you are in awe at our powers).
We are also designing an automated infrastructure test, that will simply rattle through all the various internal and external websites and relays, to make sure that everything is still online and responsive.
After that, a Gherkin-based Behave feature test for Alexandria is planned, so that we can prevent regression of completed functionality, from one release to the next.
The Gherkin scenarios are written and attached to our stories before development begins (we use acceptance tests as requirements), a manual test-execution is then completed, in order to set the story to Done. These completed scenarios will be automated, following each release, with the resulting script linked to from the origin story.

Automated Builds
As the crowning glory of every DevOps tool chain stands the build automation. This is where everything gets tied together, straightened out, configured, tested, measured, and -- if everything passes the quality gates -- released. I don't have to tell you how much time developers spend staring at the build process display, praying that it all goes through and they can celebrate a Green Wave.

We are currently designing the various builds, but the ones we have defined for the Alexandria client will be a continuous delivery pipeline, like so:

This will make it easier for us to work and collaborate asynchronously and without unnecessary delays.
Expanding the Status Page

And, finally, we get to the point of all of this busyness: reporting.
We are going to have beautiful reports, and we are going to post them online, on our status page. We will use bots, to inform Nostriches of the current status of our systems, so go ahead and follow our GitCitadel DevOps npub, to make sure you don't miss out on the IT action.
Building on stone
All in all, we're really happy with the way things are humming along, now, and the steady increase in our productivity, as all the foundational work we've put in starts to pay off. It's getting easier and easier to add new team members, repos, or features/fixes, so we should be able to scale up and out from here. Our GitCitadel is built on a firm foundation.
Happy building!
-
 @ 8f69ac99:4f92f5fd
2024-08-26 15:52:41
@ 8f69ac99:4f92f5fd
2024-08-26 15:52:41No mundo das bandas desenhadas, poucos personagens são tão icónicos como Astérix e Capitão América. Estes dois heróis, oriundos de culturas e épocas muito diferentes, representam atitudes marcadamente distintas em relação ao poder e à autoridade. Astérix, o astuto gaulês de uma pequena aldeia que se opõe de forma destemida ao Império Romano, encarna o espírito de resistência e independência. Em contraste, Capitão América, frequentemente retratado como o soldado patriótico, simboliza lealdade, dever e conformidade com a autoridade governamental, especialmente nas suas primeiras representações.
Estes personagens contrastantes oferecem mais do que apenas entretenimento; reflectem valores e atitudes sociais mais profundos em relação à autoridade. Enquanto Astérix e os seus compatriotas usam a sua astúcia e uma poção misteriosa para manter a sua autonomia, o Capitão América frequentemente actua dentro dos limites de um sistema, esforçando-se para proteger o status quo. Estas diferenças podem servir como uma lente através da qual examinamos questões modernas de poder, controlo e resistência.
O Espírito de Astérix
Astérix é mais do que uma série de banda desenhada; é um fenómeno cultural que cativou audiências em todo o mundo desde a sua estreia em 1959. Criada pela brilhante dupla de escritor René Goscinny e ilustrador Albert Uderzo, a série fez a sua primeira aparição na revista francesa Pilote a 29 de Outubro de 1959. Ambientada em 50 a.C., Astérix segue as aventuras de uma pequena, mas indomável aldeia gaulesa que ousa resistir à ocupação romana. No coração destas histórias estão Astérix, um guerreiro astuto e engenhoso, e o seu melhor amigo Obélix, que possui uma força sobre-humana graças a uma poção mágica preparada pelo druida da aldeia, Panoramix.
A poção mágica é um elemento central na série, concedendo aos aldeãos habilidades sobre-humanas temporárias que lhes permitem repelir as poderosas forças romanas lideradas por Júlio César. No entanto, não é apenas a poção que mantém os romanos à distância; é o espírito indomável dos aldeãos, a sua astúcia e a sua unidade que os tornam uma força formidável. A resistência desta pequena aldeia contra o poder de Roma é simbólica dos temas maiores de liberdade, independência e desafio que permeiam a série.
Os personagens principais da série, incluindo Astérix, Obélix, Panoramix e o chefe da aldeia Vitalstatistix, contribuem cada um para o rico enredo de resistência e liberdade pessoal. Astérix, apesar de pequeno em estatura, é um herói astuto e corajoso que frequentemente usa a sua inteligência para superar os romanos. Obélix, com a sua inocência infantil e força imensa, proporciona tanto alívio cómico como músculo, enquanto a poção mágica de Panoramix serve como um símbolo da resiliência e engenho dos aldeãos.
Os temas de Astérix—resistência à opressão, busca pela liberdade pessoal e o poder da unidade—são tão relevantes hoje em dia quanto eram quando a série foi criada pela primeira vez. A luta dos aldeãos para manter a sua independência sem procurar derrubar o sistema romano reflecte um desejo de paz e autodeterminação, em vez de dominação. Neste sentido, a luta dos gauleses pode ser vista como uma metáfora para qualquer pequeno grupo desafiador que busca viver nos seus próprios termos, livre do controlo de uma entidade maior e mais poderosa.
No final, Astérix não é apenas uma história sobre um grupo de aldeãos resistindo ao domínio romano; é uma narrativa atemporal sobre o desejo universal de liberdade e a coragem de enfrentar probabilidades esmagadoras. Este espírito de resistência e independência é o que torna Astérix não apenas uma série de banda desenhada adorada, mas também um poderoso símbolo de liberdade pessoal e desafio à autoridade.
A Conformidade do Capitão América
O Capitão América, uma das figuras mais icónicas da história dos quadrinhos americanos, nasceu numa época em que o mundo estava mergulhado em conflito. Criado pelo escritor Joe Simon e pelo artista Jack Kirby, o Capitão América fez a sua estreia na Captain America Comics #1, publicada a 20 de dezembro de 1940, pela Timely Comics, antecessora do que hoje conhecemos como Marvel Comics. O personagem, cuja identidade civil é Steve Rogers, foi apresentado como um jovem frágil do Brooklyn, Nova Iorque, transformado em um super-soldado através de um soro experimental. Esta transformação permitiu-lhe tornar-se um símbolo do patriotismo americano e uma arma potente contra as potências do Eixo durante a Segunda Guerra Mundial.
Desde o seu início, o Capitão América foi concebido para ser mais do que um super-herói; ele era uma figura representativa dos ideais e valores americanos durante um período de guerra. A sua edição de estreia retratou-o famosamente a socar Adolf Hitler na capa, uma afirmação audaciosa que ressoou fortemente com o público americano. A série rapidamente se tornou uma sensação, vendendo mais de um milhão de cópias por edição, e estabeleceu o Capitão América como uma figura de destaque na luta contra a tirania, tendo o agente nazi Caveira Vermelha como seu principal adversário. Ao lado do seu parceiro, Bucky Barnes, o Capitão América embarcou em inúmeras missões que personificavam os temas de justiça, dever e patriotismo.
Os primeiros quadrinhos do Capitão América eram diretos na sua representação do bem contra o mal, refletindo a moralidade clara da época. Steve Rogers era retratado como o soldado ideal—leal, obediente e firme no seu compromisso de proteger o modo de vida americano. A sua força residia não apenas na sua destreza física, aprimorada pelo soro do super-soldado, mas também na sua fortaleza moral e disposição para seguir ordens, mesmo quando o caminho era difícil.
Apesar de alguns momentos de desafio, a identidade central do Capitão América permanece enraizada no seu papel como símbolo dos ideais americanos—lealdade, dever e a defesa da ordem estabelecida. Ele é um personagem que, durante grande parte da sua história, encarnou a conformidade com a autoridade governamental, muitas vezes trabalhando dentro do sistema para manter o status quo. Mesmo quando desafia a autoridade, como visto na história de "O Capitão," as acções de Rogers são impulsionadas pelo desejo de proteger os princípios sobre os quais o sistema é fundado, em vez de desmantelá-lo completamente.
O legado duradouro do Capitão América é um testemunho do seu papel como ícone cultural, representando as virtudes do heroísmo, resiliência e uma crença profunda no sonho americano. No entanto, esse legado também sublinha uma abordagem mais conformista à autoridade, uma que contrasta fortemente com o espírito rebelde representado por personagens como Astérix. Embora a narrativa do Capitão América se tenha certamente tornado mais complexa ao longo do tempo, a sua jornada muitas vezes retorna a uma lealdade fundamental aos ideais e estruturas da governança americana.
Um Paralelo Moderno
A Poção Secreta dos Gauleses
No mundo de Astérix, a resistência da pequena aldeia gaulesa contra o poderio do Império Romano assenta num segredo poderoso — a sua poção mágica. Esta poção, preparada pelo druida Panoramix, confere aos aldeões uma força extraordinária, permitindo-lhes resistir à dominação romana apesar do seu reduzido número. A poção é mais do que um simples instrumento de fortalecimento físico; simboliza a feroz independência dos aldeões e a sua recusa em ser subjugados por uma força mais poderosa. A poção permite aos gauleses equilibrar as forças, tornando possível a sua resistência face a probabilidades esmagadoras. É a essência da sua autonomia, um elixir mágico que protege o seu modo de vida do controlo externo.
Bitcoin como uma "Poção Secreta" dos Tempos Modernos
Semelhante à poção secreta dos gauleses, Bitcoin representa uma ferramenta moderna de resistência contra uma estrutura de poder dominante e centralizada. Uma moeda digital descentralizada, oferece a indivíduos e pequenos grupos a capacidade de realizar transacções e armazenar valor fora dos sistemas financeiros tradicionais controlados por governos e bancos centrais. É uma ferramenta financeira que, tal como a poção dos gauleses, empodera o indivíduo contra o poder da autoridade centralizada.
Assim como os romanos não podiam controlar os gauleses enquanto eles tinham acesso à sua poção, os estados modernos e as instituições financeiras acham desafiante exercer controlo total sobre indivíduos que utilizam o Bitcoin. Ele opera numa rede peer-to-peer, livre da supervisão de qualquer entidade única, tornando-o resistente à censura, à inflação e aos caprichos das autoridades centrais. Bitcoin, neste sentido, é o equivalente moderno da poção dos gauleses — uma forma de resistência que permite aos indivíduos manter a sua autonomia financeira face à crescente centralização.
Capitão América, Moeda Fiat e Controlo Estatal do Dinheiro
Em contraste, a representação inicial do Capitão América alinha-se mais de perto com os princípios da moeda fiat e o controlo centralizado do dinheiro pelo estado. Moedas fiat, como o dólar americano, o euro, yen, etc..., são emitidas e regulamentadas pelos governos, representando uma forma de autoridade que os cidadãos devem confiar e obedecer. Assim como o Capitão América muitas vezes é visto como um símbolo de lealdade ao estado, as moedas fiat exigem uma forma de confiança no poder centralizado. O estado controla a oferta de dinheiro, regulamenta o seu uso e detém a autoridade para impor políticas monetárias, tal como o Capitão América defende os valores e directrizes do seu governo.
Este controlo centralizado é ainda mais exemplificado no conceito das Moedas Digitais de Banco Central (CBDCs). As CBDCs representam a evolução máxima do dinheiro controlado pelo estado — totalmente digital, gerido centralmente e capaz de ser monitorizado e controlado a um nível sem precedentes. Os paralelos com o Capitão América são claros: ambos representam um sistema onde a autoridade é centralizada, onde o indivíduo deve confiar e obedecer às decisões tomadas por aqueles no poder.
No entanto, assim como a lealdade inquestionável do Capitão América ao estado contrasta fortemente com a defiance de Astérix, as moedas fiat e as CBDCs estão em oposição marcante à natureza descentralizada e resistente de Bitcoin. Enquanto o Capitão América pode representar o status quo, onde os indivíduos operam dentro de um sistema desenhado e controlado pelo estado, Bitcoin, como Astérix, simboliza um desafio a esse sistema — uma forma de os indivíduos afirmarem a sua independência e resistirem à intrusão do poder centralizado.
Traçar Paralelos
A comparação entre Astérix e Bitcoin, e entre Capitão América e o dinheiro controlado pelo estado, revela uma narrativa mais profunda sobre poder, controlo e resistência. Assim como os gauleses utilizam a sua poção para resistir à ocupação romana, os indivíduos modernos podem usar o Bitcoin para resistir ao controlo exercido pelos governos e instituições financeiras através das moedas fiat e das CBDCs. A poção secreta em Astérix não é apenas uma ferramenta física, mas um símbolo de liberdade e a capacidade de viver nos próprios termos. Da mesma forma, Bitcoin oferece um meio de liberdade financeira, permitindo aos indivíduos operar fora dos sistemas tradicionais de controlo.
Num mundo onde as autoridades centrais estão a consolidar cada vez mais o poder, o espírito de Astérix, encarnado no uso de Bitcoin, oferece uma alternativa poderosa ao conformismo e à obediência frequentemente representados pelo Capitão América. É um lembrete de que a verdadeira liberdade muitas vezes exige resistir ao status quo, questionar a autoridade e encontrar novas maneiras de manter a autonomia face a um poder avassalador.
A Necessidade de Mais Astérix e Menos Capitão América
À medida que o mundo evoluiu, também evoluíram os leitores que antes devoravam as aventuras de Astérix e Capitão América. As gerações que cresceram com estas bandas desenhadas agora encontram-se num mundo em rápida transformação, onde os poderes do Estado se expandiram, frequentemente à custa das liberdades individuais. O que outrora era domínio da ficção distópica—vigilância, censura e erosão da privacidade—tornou-se uma realidade que muitos aceitam com um encolher de ombros. Esta complacência, esta deriva subtil para a conformidade, é precisamente a razão pela qual precisamos mais do espírito de Astérix e menos da adesão inicial do Capitão América à autoridade.
O Capitão América, especialmente nas suas primeiras encarnações, era um símbolo de lealdade, dever e confiança inabalável nas instituições de poder. Ele lutava não apenas pelo povo, mas pelos ideais consagrados por aqueles no poder—ideais que, com o tempo, têm vindo a ser cada vez mais comprometidos. No mundo actual, onde os governos justificam a vigilância em massa em nome da segurança e restringem liberdades sob o pretexto do bem público, o tipo de patriotismo do Capitão América pode facilmente deslizar para a cumplicidade. Este não é o herói que precisamos agora.
Contrastemos isto com Astérix—uma figura pequena, astuta e ferozmente independente que, juntamente com seus conterrâneos, se recusa a curvar-se perante o poder do Império Romano. Os gauleses não procuram derrubar Roma; eles simplesmente querem viver livres nas suas próprias condições, resistindo às forças opressoras que tentariam privá-los da sua autonomia. Este espírito de desafio, esta recusa em aceitar a dominação de um poder centralizado, é o que o mundo de hoje carece desesperadamente. A poção secreta dos gauleses, um símbolo do seu poder e independência, é uma metáfora para as ferramentas que temos à nossa disposição—ferramentas como o Bitcoin—que nos permitem resistir ao crescente autoritarismo que está a enraizar-se na Europa e no mundo Ocidental.
Estamos a viver numa época em que os próprios alicerces da democracia estão a ser erodidos por aqueles que afirmam protegê-los. Os governos ultrapassam cada vez mais os seus limites, as corporações exploram, e os cidadãos, anestesiados pela conveniência e pelo medo, conformam-se. O resultado? Uma sociedade mais condescendente do que nunca, mais disposta a trocar liberdade por uma falsa sensação de segurança. Mas este não é o caminho inevitável; é uma escolha. E é uma escolha que Astérix nunca faria.
O que o mundo precisa agora é de um ressurgimento do espírito gaulês—uma disposição para questionar, resistir e afirmar os nossos direitos contra o poder estatal que avança. Precisamos ser mais como Astérix, prontos para defender a nossa autonomia com todas as ferramentas disponíveis, seja através da desobediência civil, das moedas criptográficas, ou simplesmente recusando aceitar as narrativas alimentadas por aqueles no poder. Isto não se trata apenas de proteger os nossos direitos; é sobre preservar a própria essência do que significa ser livre.
Portanto, para aqueles que cresceram com Astérix e Capitão América, é hora de se perguntarem: Qual herói vocês vão querer ser à medida que o mundo se torna mais escuro? Serão o soldado diligente, contente por seguir ordens e manter um sistema que já não serve o povo? Ou vão canalizar o espírito irreverente e indomável de Astérix, lutando não por poder, mas pelo simples direito de viver livre e independentemente? A escolha é sua, e pode muito bem definir o futuro das nossas sociedades.
Num mundo cada vez mais dominado pelo poder centralizado e pelo autoritarismo crescente, não precisamos de mais Capitães América. Precisamos de mais Astérixes—mais rebeldes, mais pensadores livres, mais pessoas que se recusam a se curvar ao inevitável. O momento de escolher é agora, antes que a poção acabe e seja tarde demais para reagir.
Conclusão
As histórias contrastantes de Astérix e Capitão América oferecem mais do que entretenimento; apresentam-nos duas maneiras distintas de lidar com o poder e a autoridade. Astérix incorpora um espírito de rebelião, independência e uma recusa em aceitar a dominação, enquanto o Capitão América, especialmente nos seus primeiros anos, simboliza lealdade à ordem estabelecida e conformidade com a autoridade. Estes personagens, enraizados nas suas culturas e épocas, ressoam profundamente com as gerações que cresceram lendo as suas aventuras.
Mas à medida que essas gerações enfrentam agora um mundo onde o poder estatal está a crescer sem controle e as liberdades individuais estão cada vez mais ameaçadas, é hora de reconsiderar qual desses heróis devemos olhar para inspiração. Numa era de vigilância em massa, censura e erosão das normas democráticas, o espírito de Astérix—desafiador, inteligente e inflexível—é mais relevante do que nunca. Precisamos canalizar esse espírito nas nossas próprias vidas, resistindo ao autoritarismo crescente que ameaça a nossa autonomia.
Bitcoin, tal como a poção secreta dos gauleses, representa uma das ferramentas que temos para afirmar a nossa independência neste novo cenário. Mas ferramentas sozinhas não são suficientes; também devemos adoptar uma mentalidade que questiona, desafia e se recusa a conformar-se com estruturas de poder injustas. Num mundo que cada vez mais exige conformidade, a chamada para abraçar o espírito de Astérix não é apenas uma nostalgia pelo passado—é uma postura necessária para salvaguardar o nosso futuro.
À medida que navegamos por estes tempos desafiantes, lembremos a lição que Astérix nos ensina: a verdadeira liberdade vale a pena lutar, mesmo contra probabilidades avassaladoras. Numa época em que o mundo parece precisar de mais soldados conformistas, escolhemos em vez disso ser os gauleses irreprimíveis, ousando viver nas nossas próprias condições. O futuro pertence não àqueles que simplesmente seguem, mas àqueles que ousam resistir.
-
 @ ccc8ee23:9f3d9783
2024-12-23 22:03:15
@ ccc8ee23:9f3d9783
2024-12-23 22:03:15Chef's notes
Indulge in tender, golden-fried chicken breast, crunchy with every bite. Nestled on a bed of steamed rice, this dish is elevated by a rich, velvety curry sauce, infused with the warmth of fragrant spices and the umami depth of soy.
Paired with vibrant vegetables for a harmonious balance of textures and flavors, this comforting classic promises to delight your soul.
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 2
Ingredients
- Chicken Fillet 250 grams
- Potato 100 grams
- Egg 1 pc
- Curry block 2 pcs or 20 grams
- breadcrumbs 100 grams / 2 cups
- flour 20 grams
- Cooking oil (for frying)
- chicken or vegetable stock 500ml
- soy sauce 1 tbsp
- Seasoning
- onion 1 pc, finely chopped
- garlic cloves 2 pcs, minced
- carrot 1 pc, chopped
Directions
- Chicken Katsu: Pound the chicken breasts until about 1/2 inch thick. Season with salt and pepper. Coat each piece in flour, then dip in beaten egg, and finally coat with breadcrumbs. Heat oil in a pan and fry the chicken for about 3-4 minutes on each side, until golden brown and fully cooked. Place on paper towels to drain.
- Make Curry Sauce: In a pan, sauté the onion, garlic, add potato and carrot until soft. Gradually add curry block and the stock, stir well. Simmer for 5-10 minutes until thickened. Add seasoning and soy sauce to taste.
- Plating: Slice the cooked chicken katsu and place it over a bed of steamed rice. Pour the curry sauce on the side or over the chicken. Garnish with chopped green chilies.
-
 @ 8f69ac99:4f92f5fd
2024-08-26 14:59:24
@ 8f69ac99:4f92f5fd
2024-08-26 14:59:24Num mundo cada vez mais digital, a relação entre o dinheiro e o controlo estatal tem sido alvo de escrutínio, especialmente com o surgimento de tecnologias financeiras descentralizadas como o Bitcoin. Tradicionalmente, os governos detêm as rédeas dos sistemas monetários, emitindo e regulando moedas para manter a estabilidade económica e o controlo. No entanto, essa centralização de poder também gerou preocupações sobre a ingerência governamental, má gestão financeira e a erosão das liberdades individuais.
Simultaneamente, governos e bancos centrais estão a explorar as Moedas Digitais de Bancos Centrais (CBDCs) como uma forma de modernizar o sistema financeiro e manter o controlo na era digital. Embora as CBDCs prometam eficiência e inclusão financeira, também levantam preocupações significativas sobre privacidade, vigilância governamental e um controlo estatal aumentado sobre as actividades financeiras individuais.
Entra o Bitcoin – uma moeda digital revolucionária que opera de forma independente de qualquer autoridade central. Nascido da crise financeira de 2008, o Bitcoin oferece uma alternativa tanto ao dinheiro tradicional controlado pelo estado quanto às CBDCs, prometendo transparência, segurança e o potencial para liberdade económica em escala global. Neste artigo, exploraremos o conceito de separar o dinheiro do estado, examinando como o Bitcoin poderia servir como uma alternativa viável. Argumentaremos que, ao desafiar o sistema monetário tradicional, o Bitcoin oferece um novo sistema de freios e contrapesos, capacitando indivíduos enquanto promove responsabilidade fiscal e inovação.
Separar o Dinheiro do Estado
Contexto Histórico
A relação entre o dinheiro e o poder estatal tem uma longa e complexa história. Durante séculos, os governos exerceram controlo sobre os sistemas monetários, desde o uso de moeda nas civilizações antigas até o estabelecimento de bancos centrais nos tempos modernos. Historicamente, o dinheiro muitas vezes era lastreado por activos tangíveis, como o ouro, que proporcionava um freio sobre os gastos e a expansão monetária do governo. O Padrão Ouro, que atava a moeda a uma quantidade fixa de ouro, foi um desses sistemas que limitou a capacidade dos estados de manipular suas moedas.
No entanto, a transição para o dinheiro fiduciário no século XX marcou uma mudança significativa. O dinheiro fiduciário, que é emitido pelo governo e não lastreado por uma mercadoria física, depende exclusivamente da confiança e da autoridade do estado emissor. Essa mudança deu aos governos um controlo sem precedentes sobre seus sistemas monetários, permitindo-lhes imprimir dinheiro à vontade e exercer mais influência sobre a economia. Embora esse sistema permitisse maior flexibilidade na resposta a crises económicas, também abriu a porta para potenciais abusos, inflação e a erosão da riqueza individual.
Importância da Separação
À luz desses desenvolvimentos, a ideia de separar o dinheiro do estado ganhou força, particularmente no contexto de preocupações crescentes sobre a ingerência governamental, instabilidade financeira e até a capacidade do estado de travar guerras sem a aprovação directa dos cidadãos. Há várias razões-chave pelas quais essa separação é crucial:
-
Prevenir a Ingerência Governamental: Quando os governos controlam o sistema monetário, podem manipulá-lo para fins políticos, como financiar guerras, expandir programas sociais ou influenciar eleições. Esse poder descontrolado permite que os governos persigam políticas que podem não ter apoio popular, sem enfrentar restrições financeiras imediatas. Separar o dinheiro do estado pode limitar essa manipulação política, criando um ambiente económico mais estável e previsível.
-
Limitar a Capacidade de Travar Guerras: Na história recente, os governos frequentemente confiaram na capacidade de imprimir dinheiro para financiar guerras, contornando a necessidade de tributação directa ou aprovação pública. Isso leva a guerras sendo travadas sem o consentimento explícito da população, que mais tarde arca com os custos através da inflação e da dívida. Ao restringir a capacidade do estado de criar dinheiro do nada, uma separação entre dinheiro e estado exigiria que os governos financiassem guerras através de impostos ou empréstimos. Isso tornaria mais difícil para os estados se envolverem em conflitos prolongados sem o apoio claro dos seus cidadãos, uma vez que aumentar impostos ou tomar empréstimos geralmente requer debate público e aprovação democrática.
-
Promover a Responsabilidade Fiscal: Sem a capacidade de imprimir dinheiro para cobrir défices, os governos seriam forçados a manter orçamentos mais equilibrados e tomar decisões financeiras mais responsáveis. Isso poderia reduzir a probabilidade de crises de dívida e inflação descontrolada, uma vez que a disciplina fiscal (os gastos do estado) se tornaria uma necessidade e não uma escolha.
-
Proteger a Riqueza Individual: As moedas fiduciárias são propensas à inflação, que corrói o poder de compra das poupanças ao longo do tempo. Em contraste, um sistema monetário que é independente do controlo estatal—como o Bitcoin, com sua oferta fixa—pode proteger a riqueza dos indivíduos contra a desvalorização e a deterioração. Em tal sistema, a capacidade do governo de corroer a riqueza através de políticas inflacionárias seria severamente limitada.
-
Incentivar a Liberdade Económica: Quando o dinheiro está livre do controlo estatal, permite que as forças do mercado determinem seu valor. Isso promove uma economia mais dinâmica e competitiva, onde indivíduos e empresas têm maior liberdade para inovar e transaccionar sem interferência governamental.
-
Reduzir a Corrupção e o Clientelismo: Sistemas monetários controlados pelo estado podem criar oportunidades para corrupção, onde indivíduos ou corporações politicamente conectados ganham vantagens financeiras injustas. Separar o dinheiro do estado reduz o potencial para tal clientelismo, promovendo um campo de jogo mais nivelado.
-
Fomentar a Inovação: Um sistema monetário descentralizado pode possibilitar inovações financeiras que não estão restritas por autoridades centrais. Isso pode levar ao desenvolvimento de novas tecnologias, serviços e produtos financeiros que beneficiam a sociedade como um todo.
O conceito de separar o dinheiro do estado desafia as estruturas de poder tradicionais que governaram as economias durante séculos. Ao limitar a influência do estado sobre o dinheiro, podemos criar um sistema que promove maior liberdade individual, responsabilidade fiscal e inovação. Além disso, ao restringir a capacidade do estado de financiar guerras através da expansão monetária, tal sistema também pode servir como um freio ao poder governamental, assegurando que decisões tão importantes quanto a guerra devem ser tomadas com a aprovação explícita do povo. Bitcoin, como uma moeda digital descentralizada, incorpora essa visão, oferecendo um caminho potencial para redefinir a relação entre o dinheiro e o poder estatal.
Proposta de Valor de Bitcoin
Bitcoin emergiu como uma inovação financeira revolucionária, desafiando o sistema monetário tradicional e oferecendo um novo paradigma para o dinheiro na era digital. Suas características únicas destacam-no tanto das moedas fiduciárias quanto de outros activos digitais, posicionando-o como uma ferramenta poderosa para preservar a riqueza, promover a liberdade económica e resistir à ingerência governamental. Vamos explorar os principais aspectos da proposta de valor de Bitcoin e por que tem ganho destaque como uma alternativa viável ao dinheiro controlado pelo estado.
Escassez Digital
Uma das características mais definidoras de Bitcoin é sua oferta fixa de 21 milhões de moedas. Esta escassez digital está codificada no protocolo de Bitcoin, garantindo que não serão criados mais do que 21 milhões de bitcoins. Ao contrário das moedas fiduciárias, que podem ser impressas em quantidades ilimitadas pelos bancos centrais, a oferta de Bitcoin é finita, tornando-o uma protecção robusta contra a inflação e a desvalorização da moeda. À medida que governos em todo o mundo se envolvem em políticas monetárias expansionistas, frequentemente levando à inflação e à perda do poder de compra, a escassez de Bitcoin fornece uma reserva de valor que é imune a tais riscos.
Descentralização e Resistência à Censura
Bitcoin opera numa rede descentralizada de computadores (nós) espalhados pelo mundo. Esta descentralização assegura que nenhuma entidade ou governo possa controlar ou manipular a rede Bitcoin. As transacções são verificadas por um mecanismo de consenso chamado proof-of-work, que adiciona camadas de segurança e evita a censura. Esta resistência à censura é crucial num mundo onde as transacções financeiras podem ser bloqueadas ou revertidas por governos ou instituições financeiras. Com Bitcoin, os indivíduos têm o poder de enviar e receber dinheiro sem interferência, ou permissão, promovendo uma maior autonomia financeira.
Transacções Globais e Sem Permissões
Bitcoin permite transacções peer-to-peer sem a necessidade de intermediários como bancos ou processadores de pagamentos. Isso torna possível enviar dinheiro através de fronteiras rapidamente, com segurança e a um custo relativamente baixo. Ao contrário dos sistemas financeiros tradicionais que frequentemente exigem permissões, documentação e intermediários, Bitcoin opera de forma sem permissões, o que significa que qualquer pessoa com uma conexão à internet pode participar na rede. Isso abre oportunidades para indivíduos em regiões não cobertas pelo sistema bancário (os "sem banco") acederem a serviços financeiros e participar na economia global.
Reserva de Valor vs. Volatilidade de Preços
Um dos desafios em compreender o valor de Bitcoin reside em separar o conceito de valor e preço. Enquanto o preço de Bitcoin pode ser altamente volátil, flutuando devido ao comércio especulativo e ao sentimento do mercado, seu valor intrínseco como um activo descentralizado, escasso e resistente à censura permanece. Valor, neste contexto, refere-se à capacidade de Bitcoin de preservar a riqueza, oferecer soberania financeira e fornecer uma protecção contra a inflação e o controlo autoritário. Preço, por outro lado, reflecte dinâmicas de mercado e pode iludir aqueles que equacionam flutuações de curto prazo com potencial de longo prazo. Compreender essa distinção é crucial para reconhecer o verdadeiro valor de Bitcoin além de sua natureza especulativa.
Impacto de Bitcoin em Países em Desenvolvimento
Enquanto Bitcoin é frequentemente visto como um investimento especulativo ou uma ferramenta para "tech bros" no Ocidente, o seu impacto em países em desenvolvimento, particularmente na África e na América do Sul, é profundo. Em regiões onde o acesso a serviços financeiros tradicionais é limitado e onde regimes autoritários controlam a economia, Bitcoin oferece uma tábua de salvação. Permite aos indivíduos armazenar valor em um activo estável, realizar transacções sem interferência governamental e contornar sistemas financeiros corruptos. Observadores ocidentais devem reconhecer seu privilégio financeiro e considerar como o Bitcoin está a capacitar milhões em países mais pobres que carecem de serviços bancários básicos e enfrentam constante incerteza económica.
A Realidade do Autoritarismo e Exclusão Financeira
De acordo com a Fundação para os Direitos Humanos (HRF), 54% da população mundial—aproximadamente 4,2 mil milhões de pessoas—vive sob regimes autoritários. Estes governos frequentemente restringem liberdades básicas, incluindo a autonomia financeira, e controlam o acesso dos cidadãos à economia global. Além disso, muitos desses indivíduos estão "desbancarizados", significando que não têm acesso a serviços bancários tradicionais. Esta falta de inclusão financeira, combinada com a regra autoritária, cria barreiras significativas à liberdade económica e à segurança pessoal. Bitcoin oferece uma solução para esses desafios ao fornecer uma forma de dinheiro descentralizada e resistente à censura, acessível a qualquer pessoa, independentemente do seu ambiente político.
Efeitos de Rede
À medida que mais pessoas adoptam Bitcoin, a sua utilidade e valor aumentam através dos efeitos de rede. A crescente adopção de Bitcoin por indivíduos, empresas e até investidores institucionais fortalece sua posição como uma alternativa viável às moedas tradicionais. Com cada novo participante, a rede torna-se mais robusta, segura e valiosa. Esse ciclo positivo ajuda a consolidar o status de Bitcoin como uma moeda digital global e uma reserva de valor credível.
Protecção Contra Riscos das Políticas Monetárias
Bitcoin também serve como uma possível protecção contra os riscos associados às políticas monetárias expansionistas, como a flexibilização quantitativa (QE) e as taxas de juros negativas. Essas políticas, frequentemente implementadas para estimular o crescimento económico, podem levar à inflação, desvalorização da moeda e instabilidade financeira. Bitcoin, com sua oferta fixa e natureza descentralizada, fornece uma salvaguarda contra tais riscos, funcionando como uma "apólice de seguro" para indivíduos e instituições que buscam proteger sua riqueza dos efeitos adversos das políticas monetárias controladas pelo governo.
Em resumo, a proposta de valor de Bitcoin reside na sua capacidade de oferecer uma alternativa descentralizada, escassa e resistente à censura ao dinheiro tradicional. Sua oferta fixa, acessibilidade global e rede crescente fazem desta uma ferramenta poderosa para preservar a riqueza e promover a liberdade económica num mundo cada vez mais incerto. À medida que mais pessoas reconhecem seu potencial, particularmente em regiões que sofrem com controlo autoritário e exclusão financeira, Bitcoin continua a consolidar o seu papel como uma força revolucionária no sistema financeiro global.
Implicações das Moedas Digitais de Banco Central (CBDCs)
À medida que os bancos centrais em todo o mundo avançam no desenvolvimento das Moedas Digitais de Banco Central (CBDCs), é essencial examinar criticamente as verdadeiras motivações por trás dessas iniciativas. Embora as CBDCs sejam frequentemente promovidas como ferramentas para modernizar o sistema financeiro e melhorar a eficiência, uma análise mais profunda revela que elas visam, na verdade, consolidar o controlo e o poder nas mãos dos governos e das elites globais. Em contraste, Bitcoin já oferece uma alternativa descentralizada, transparente e eficiente que aborda muitos dos desafios que as CBDCs afirmam resolver — sem os riscos de intervenção estatal e controlo autoritário.
Introdução às CBDCs
As CBDCs são versões digitais das moedas nacionais emitidas e reguladas pelos bancos centrais. Ao contrário das criptomoedas descentralizadas, como o Bitcoin, que operam de forma independente de qualquer autoridade central, as CBDCs são totalmente controladas pelo estado. Essa centralização do poder faz com que elas sejam fundamentalmente diferentes de Bitcoin e levanta questões importantes sobre seu verdadeiro propósito — nomeadamente, a ampliação do controlo governamental sobre os sistemas financeiros e as liberdades individuais.Benefícios Potenciais
Os defensores das CBDCs argumentam que elas podem melhorar a eficiência dos pagamentos e aumentar a inclusão financeira. As moedas digitais podem facilitar transacções mais rápidas, baratas e seguras, tanto no âmbito nacional quanto internacional. Também prometem proporcionar acesso a serviços financeiros para aqueles que actualmente não têm conta bancária, ajudando a preencher a lacuna entre os marginalizados e a economia formal.No entanto, é importante reconhecer que esses benefícios já podem ser alcançados através das tecnologias existentes, particularmente o Bitcoin. Bitcoin oferece transacções globais, sem permissão, que são seguras, eficientes e acessíveis a qualquer pessoa com uma conexão à internet. A verdadeira questão, então, é por que os governos estão pressionando por CBDCs quando uma solução melhor já existe. A resposta reside nas dinâmicas de poder e controlo que as CBDCs podem oferecer aos governos e às elites.
Preocupações e Riscos
Os riscos associados às CBDCs vão muito além das considerações técnicas e económicas — eles ameaçam fundamentalmente as liberdades e a autonomia individuais. A introdução das CBDCs poderia marcar uma expansão perigosa do controlo governamental sobre todos os aspectos da vida financeira.-
Exclusão Intencional e Controlo Social:
As CBDCs poderiam facilmente tornar-se ferramentas de controlo social. Os governos poderiam excluir selectivamente indivíduos ou grupos do sistema financeiro com base em critérios arbitrários, como crenças políticas ou comportamento social. Em regimes autoritários, esse poder poderia ser usado para suprimir a dissidência e forçar a conformidade com os mandatos do estado. Mesmo em nações democráticas, o potencial de abuso é real, à medida que políticos e burocratas — frequentemente influenciados por elites poderosas — buscam consolidar o controlo sobre a sociedade. -
Restrições de Gastos:
As CBDCs poderiam permitir que os governos imponham restrições sobre onde e como o dinheiro pode ser gasto, controlando efectivamente o comportamento dos cidadãos. Imagine um cenário em que um governo pudesse bloquear transacções relacionadas a actividades que considera indesejáveis, como protestos políticos, mídia alternativa ou negócios independentes. Esse nível de controlo daria aos políticos e burocratas o poder de moldar a sociedade de acordo com seus próprios interesses, marginalizando aqueles que resistem à sua agenda. -
Limites de Quantidade e Remuneração Escalonada:
Alguns designs de CBDCs propõem tectos sobre quanto indivíduos podem manter ou impor taxas de juros negativas sobre valores acima de certos limites. Isso poderia limitar as economias pessoais e forçar as pessoas a gastar ou investir seu dinheiro de maneiras que estejam alinhadas com os objectivos do governo. Essa forma de repressão financeira é um ataque directo à soberania financeira individual e uma ferramenta para os governos manipularem o comportamento económico em seu benefício. -
Anonimato Reduzido:
Ao contrário do dinheiro físico ou das criptomoedas descentralizadas como bitcoin, as CBDCs não teriam verdadeiro anonimato. Cada transacção poderia ser rastreada e registada pelo governo, dando aos políticos e burocratas uma visibilidade sem precedentes sobre as actividades financeiras dos cidadãos. Esse nível de vigilância não é apenas uma violação da privacidade — abre a porta para formas mais directas de controlo e coerção, à medida que o estado ganha mais poder sobre as decisões financeiras dos indivíduos. -
Repressão Financeira e Expropriação de Riqueza:
A capacidade de impor taxas de juros negativas sobre as CBDCs é outra forma de controlo governamental, onde o estado pode efectivamente tributar a riqueza sem aprovação legislativa. Isso poderia ser usado para redistribuir riqueza ou financiar programas governamentais sem a necessidade de transparência ou supervisão democrática. Tais políticas prejudicariam desproporcionalmente aqueles que buscam preservar sua riqueza e poderiam levar a uma erosão gradual da segurança financeira individual.
China e o Yuan Digital
O desenvolvimento do yuan digital pela China exemplifica os perigos potenciais das CBDCs nas mãos de um regime autoritário. A falta de freios e contrapesos no sistema político da China, combinada com a estreita relação entre o banco central e o Partido Comunista, levanta sérias preocupações de que o yuan digital poderia se tornar uma poderosa ferramenta de controlo social. Ao integrar a CBDC com seu sistema de crédito social existente, a China pode restringir ainda mais as liberdades com base em critérios definidos pelo governo, utilizando o controlo financeiro como meio de impor conformidade e lealdade ao estado.
Implicações para a UE e Além
Mesmo em democracias como a UE, a pressão por CBDCs levanta sinais de alerta. O desenvolvimento do euro digital pelo Banco Central Europeu (BCE), actualmente na fase de preparação, em Novembro de 2023, pode parecer benigno à primeira vista. No entanto, sem as devidas salvaguardas, essa moeda digital também se poderá tornar uma ferramenta de controlo estatal, particularmente se políticos e burocratas — movidos pelos seus próprios interesses e pelos das elites globais — decidirem usá-la para impor restrições à liberdade financeira e privacidade. O euro digital, como outras CBDCs, poderá ser projectado para priorizar a supervisão estatal sobre a autonomia individual.
Bitcoin: A Solução Existente
A realidade é que não há necessidade de uma CBDC. Bitcoin já oferece uma solução que proporciona os benefícios que as CBDCs afirmam entregar — eficiência, segurança e inclusão financeira — sem os riscos de controlo governamental. Bitcoin é descentralizado, transparente e resistente à censura, tornando-o uma ferramenta poderosa para a liberdade individual e a soberania financeira. Ao contrário das CBDCs, Bitcoin não serve aos interesses dos governos ou das elites globais — pois capacita os indivíduos a assumir o controlo de seus próprios destinos financeiros.
A pressão por CBDCs não se trata de resolver problemas que Bitcoin já não tenha abordado. Trata-se de poder — centralizando-o nas mãos dos governos e das elites que os influenciam. Políticos e burocratas, muitas vezes motivados por interesses próprios e pelas agendas de poderosos actores globais, veem as CBDCs como uma forma de expandir seu controlo sobre a sociedade. Em contraste, Bitcoin representa um caminho para a descentralização, autonomia e verdadeira liberdade financeira.
À medida que governos e bancos centrais avançam para implementar as CBDCs, é crucial reconhecer as verdadeiras motivações por trás dessas iniciativas. Embora as CBDCs sejam frequentemente apresentadas como inovações necessárias, elas são, em última análise, sobre controlo — ampliando o poder do estado e das elites globais às custas da liberdade individual. Bitcoin, por outro lado, oferece uma alternativa descentralizada que preserva a privacidade, a autonomia e a soberania financeira. O futuro do dinheiro deve ser um onde os indivíduos, e não os governos ou elites, detenham o poder.
Adoptar um Padrão Bitcoin
À medida que o mundo enfrenta as consequências das moedas fiduciárias controladas pelo estado—que vão desde a inflação até a instabilidade financeira—Bitcoin apresenta uma alternativa convincente: a adopção de um padrão Bitcoin. Semelhante ao Padrão Ouro do passado, que forneceu uma base monetária estável ao vincular a moeda a uma oferta fixa de ouro, um padrão Bitcoin oferece uma solução moderna baseada em princípios de dinheiro sólido. No entanto, Bitcoin vai além do que o ouro alguma vez poderia, trazendo consigo inovações tecnológicas únicas, acessibilidade global e a promessa de soberania financeira.
Comparação com o Padrão Ouro
O Padrão Ouro, que dominou grande parte dos séculos XIX e início do século XX, ofereceu uma estrutura onde o dinheiro em papel estava directamente vinculado a uma oferta finita de ouro. Este sistema restringia os gastos do governo e a inflação, pois a oferta monetária não podia ser expandida arbitrariamente. Da mesma forma, a oferta fixa de 21 milhões de moedas em Bitcoin impõe um limite rígido à expansão monetária, fornecendo uma base para um sistema monetário estável e deflacionário.
No entanto, ao contrário do ouro, Bitcoin não está sobrecarregado por limitações físicas ou centralização. Enquanto o ouro exigia armazenamento seguro e frequentemente era controlado por autoridades centrais, Bitcoin é digital e descentralizado, tornando-o mais acessível e resistente à confiscação. Além disso, a capacidade de Bitcoin de facilitar transacções instantâneas e globais dá-lhe uma vantagem sobre o ouro na economia moderna.
Benefícios de um Padrão Bitcoin
1. Princípios de Dinheiro Sólido:
No cerne de um padrão Bitcoin está o princípio do dinheiro sólido. A oferta fixa e sua natureza deflacionária incentivam um comportamento económico responsável, planeamento de longo prazo e estabilidade. Ao contrário das moedas fiduciárias, que podem ser desvalorizadas por meio da impressão infinita, a escassez de Bitcoin garante que o seu valor seja preservado ao longo do tempo. Essa previsibilidade promove um ambiente económico estável onde empresas e indivíduos podem tomar decisões com base numa reserva de valor confiável.2. Protecção Contra a Desvalorização da Moeda:
Uma das vantagens mais significativas de um padrão Bitcoin é sua protecção contra a desvalorização da moeda. Num sistema fiduciário, os governos frequentemente recorrem à impressão de mais dinheiro para financiar déficits, levando à inflação e à perda do poder de compra. A oferta fixa de Bitcoin previne tal manipulação, protegendo a riqueza dos indivíduos dos efeitos erosivos da inflação. Sob um padrão Bitcoin, as pessoas podem ter a certeza de que suas economias manterão valor a longo prazo, livres das oscilações dos bancos centrais e políticos.3. Soberania Financeira:
Um padrão Bitcoin capacita tanto indivíduos quanto nações ao fornecer dinheiro resistente à censura. Num mundo onde os sistemas financeiros são cada vez mais controlados e monitorizados por governos e instituições, Bitcoin oferece uma forma de dinheiro que não pode ser arbitrariamente apreendida ou congelada. Esta soberania financeira é particularmente crucial para aqueles que vivem sob regimes opressivos ou em países com moedas instáveis. Bitcoin permite que os indivíduos mantenham controlo sobre sua riqueza, independentemente das pressões políticas externas.4. Inclusão Financeira Global:
A natureza descentralizada de Bitcoin e as baixas barreiras à entrada tornam-no uma ferramenta ideal para a inclusão financeira global. Ao contrário dos sistemas bancários tradicionais, que frequentemente excluem os "sem banco" ou impõem altas taxas em transacções internacionais, Bitcoin pode ser acedido por qualquer pessoa com uma conexão à internet. Esta inclusividade estende-se às remessas, onde a capacidade de Bitcoin de facilitar transferências instantâneas e de baixo custo pode reduzir significativamente o fardo financeiro para aqueles que enviam dinheiro para familiares no exterior. Ao adoptar um padrão Bitcoin, o mundo poderia ver uma redução dramática na exclusão financeira e a democratização das oportunidades económicas.Inovação Tecnológica A adopção de um padrão Bitcoin também desencadearia uma onda de inovação tecnológica. Uma das tecnologias subjacentes de Bitcoin, a blockchain, permite uma ampla gama de aplicações além da moeda. A Lightning Network, por exemplo, oferece uma solução para escalar Bitcoin, permitindo transacções mais rápidas e baratas. Esta inovação abre portas para microtransações e poderia revolucionar indústrias como jogos, criação de conteúdo e finanças descentralizadas (DeFi).
Além disso, a programabilidade de Bitcoin através de contratos inteligentes fornece uma base para a construção de aplicações descentralizadas que operam sem a necessidade de intermediários. Essas inovações não apenas aumentam a funcionalidade de Bitcoin como moeda, mas também criam novas oportunidades para crescimento e eficiência económica.
Implicações Geopolíticas
1. Redução da Manipulação da Moeda:
Um padrão Bitcoin limitaria significativamente a capacidade dos governos de manipular moedas para vantagem geopolítica. Hoje, as nações frequentemente envolvem-se em desvalorização da moeda ou ajustes na política monetária para obter uma vantagem competitiva no comércio ou exercer influência no cenário global. Sob um padrão Bitcoin, com sua oferta fixa e natureza descentralizada, tais tácticas tornariam-se muito mais difíceis. Isso poderia levar a um campo de jogo mais nivelado no comércio internacional e reduzir o potencial de conflitos económicos impulsionados por guerras de moedas.2. Igualdade de Condições para Países Mais Pobres:
Para países pobres, ou mais pequenos, adoptar um padrão Bitcoin poderia oferecer protecção contra a dominação económica de países maiores. Ao usar uma moeda neutra e descentralizada, economias menores poderiam isolar-se das políticas de grandes bancos centrais, como o Federal Reserve ou o Banco Central Europeu, que frequentemente têm impactos desproporcionais nos mercados globais. Essa mudança poderia capacitar nações menores, permitindo-lhes participar da economia global em termos mais equitativos e reduzindo sua vulnerabilidade a choques monetários externos.Adoptar um padrão Bitcoin oferece um caminho para a estabilidade económica, soberania financeira e inclusão global. Ao basear-se nos princípios do dinheiro sólido, Bitcoin pode proteger contra as armadilhas da desvalorização da moeda, promovendo a inovação e nivelando o campo de jogo geopolítico. À medida que o mundo enfrenta os desafios do século XXI, Bitcoin surge como uma alternativa viável que promove a liberdade individual e a resiliência económica, oferecendo um futuro onde o dinheiro verdadeiramente pertence ao povo.
Controlo sobre o Abuso de Poder Governamental através de um Padrão Bitcoin
A adopção de um padrão Bitcoin representa mais do que uma simples mudança na política monetária; funciona como um poderoso controlo sobre o abuso de poder governamental. Num mundo onde os governos frequentemente manipulam as moedas, restringem a liberdade financeira e utilizam a política monetária como uma ferramenta de controlo, Bitcoin oferece uma alternativa descentralizada e resistente à censura que devolve o poder ao indivíduo. Este capítulo explora como um padrão Bitcoin poderia limitar o abuso de poder governamental ao impor disciplina fiscal, prevenir acções financeiras arbitrárias e capacitar os cidadãos com soberania financeira.
Restaurar a Disciplina Fiscal Uma das consequências mais significativas de um sistema monetário baseado em moeda fiduciária é a erosão da disciplina fiscal. Os governos, sem a restrição de um padrão de dinheiro sólido, podem imprimir dinheiro à vontade para financiar déficits, levando à inflação, acumulação de dívida e instabilidade económica. Sob um padrão Bitcoin, a capacidade de imprimir dinheiro seria eliminada, forçando os governos a viver dentro dos seus meios.
Com um fornecimento fixo de 21 milhões de moedas, Bitcoin impõe uma limitação natural à expansão monetária. Os governos já não seriam capazes de inflacionar a sua dívida ou desvalorizar a sua moeda para cobrir gastos excessivos. Em vez disso, teriam de equilibrar os seus orçamentos, priorizar os gastos e garantir que as suas decisões financeiras são sustentáveis a longo prazo. Este retorno à disciplina fiscal poderia reduzir os riscos de crises económicas causadas por políticas monetárias irresponsáveis e restaurar a confiança no sistema financeiro.
Prevenir Acções Financeiras Arbitrárias No sistema fiduciário actual, os governos e bancos centrais têm o poder de congelar contas, apreender activos e restringir o acesso a serviços financeiros com pouca supervisão ou responsabilidade. Esta concentração de poder pode ser usada para visar dissidentes políticos, suprimir activismo ou controlar o comportamento público. Um padrão Bitcoin, com a sua natureza descentralizada e resistente à censura, oferece uma defesa robusta contra tais acções financeiras arbitrárias.
A rede descentralizada de Bitcoin opera fora do controlo governamental, tornando quase impossível para qualquer entidade única congelar ou confiscar fundos unilateralmente. As transacções na rede Bitcoin são seguras, transparentes e irreversíveis, garantindo que os indivíduos mantenham o controlo sobre a sua riqueza. Esta protecção é especialmente importante para aqueles que vivem sob regimes autoritários ou em regiões politicamente instáveis, onde a repressão financeira é uma ferramenta comum de poder estatal.
Ao impedir que os governos apreendam arbitrariamente activos ou restrinjam a actividade financeira, um padrão Bitcoin protege os direitos e liberdades individuais. Limita a capacidade do Estado de usar os sistemas financeiros como um meio de coerção ou punição, garantindo que o dinheiro continue a ser uma ferramenta de capacitação em vez de controlo.
Capacitar os Cidadãos No seu cerne, um padrão Bitcoin capacita os cidadãos ao dar-lhes controlo directo sobre os seus activos financeiros. Ao contrário das moedas fiduciárias, que estão sujeitas às políticas governamentais, decisões de bancos centrais e à influência de elites poderosas, Bitcoin opera numa rede descentralizada onde nenhuma autoridade única tem influência. Esta mudança de controlo do Estado para o indivíduo é uma alteração profunda, com implicações abrangentes para a liberdade pessoal e autonomia económica.
Os indivíduos podem armazenar e transferir riqueza sem depender de instituições financeiras tradicionais, frequentemente entrelaçadas com interesses governamentais. Esta soberania financeira significa que as pessoas estão menos vulneráveis às restrições impostas pelo governo, inflação e manipulação económica. Numa era em que a privacidade e a autonomia estão cada vez mais ameaçadas, Bitcoin oferece uma forma de proteger a independência financeira dos indivíduos.
Além disso, a natureza global e sem permissões de Bitcoin permite que qualquer pessoa, independentemente da localização ou status, participe no sistema financeiro. Esta inclusão é um contra-peso poderoso ao controlo centralizado exercido por governos e grandes instituições financeiras. Ao adoptar um padrão Bitcoin, cidadãos de todo o mundo podem recuperar a sua liberdade financeira e participar numa economia verdadeiramente descentralizada que prioriza os direitos individuais em vez do poder estatal.
Protege Contra controlos de Capital Um exemplo concreto do poder de Bitcoin para controlar o abuso de poder governamental é a sua capacidade de contornar controlos de capital. Em muitos países, os governos impõem regulamentações rigorosas sobre o fluxo de dinheiro através das fronteiras, limitando a capacidade dos cidadãos de mover activos para fora do país. Estes controlos são frequentemente usados para sustentar moedas em dificuldade ou prevenir a fuga de capitais durante crises económicas, mas também aprisionam os cidadãos num sistema financeiro instável e desvalorizado.
Bitcoin oferece uma forma de contornar essas restrições. Como opera numa rede descentralizada, as transacções não podem ser facilmente bloqueadas ou monitorizadas pelos governos. Os indivíduos podem mover a sua riqueza através das fronteiras sem depender dos sistemas bancários tradicionais, que estão sujeitos ao controlo estatal. Esta capacidade é crucial para proteger os activos pessoais da interferência governamental e garantir que as pessoas mantenham acesso à sua riqueza, mesmo em tempos de turbulência económica.
Implicações a Longo Prazo para a Governança Democrática Um padrão Bitcoin também poderia ter implicações profundas para a governança democrática. Ao limitar a capacidade do Estado de manipular dinheiro e finanças, Bitcoin força uma maior transparência e responsabilidade nas acções governamentais. Quando os governos já não podem contar com políticas inflacionárias para encobrir a má gestão fiscal, são forçados a tomar decisões mais responsáveis e transparentes.
Além disso, a descentralização do dinheiro alinha-se com princípios democráticos ao reduzir a concentração de poder nas mãos de poucos. Numa sistema fiduciário, bancos centrais e governos exercem uma enorme influência sobre a economia e os meios de subsistência individuais. Um padrão Bitcoin redistribui este poder, tornando o sistema financeiro mais democrático e alinhado com os interesses da população em geral.
Um padrão Bitcoin oferece um poderoso controlo sobre o abuso de poder governamental ao restaurar a disciplina fiscal, prevenir acções financeiras arbitrárias e capacitar os cidadãos com soberania financeira. Numa era onde os governos buscam cada vez mais controlar e monitorizar as actividades financeiras, Bitcoin oferece uma alternativa descentralizada que prioriza a liberdade individual e a autonomia económica. Ao adoptar um padrão Bitcoin, as sociedades podem criar um sistema financeiro mais transparente, responsável e democrático que serve os interesses do povo, em vez do Estado.
Conclusão
O argumento central é claro: Bitcoin oferece um sistema descentralizado, resistente à censura e transparente que pode proteger a riqueza individual, promover a liberdade económica e servir como um controlo sobre o poder governamental. Ao contrário das moedas fiduciárias, que são susceptíveis à inflação, manipulação e controlo central, o fornecimento fixo e a natureza descentralizada de Bitcoin garantem que este permaneça fora do alcance dos governos e das elites.
Ao adoptar um padrão Bitcoin, as sociedades podem beneficiar dos princípios do dinheiro sólido que encorajam a responsabilidade fiscal, protegem contra a desvalorização da moeda e capacitam os indivíduos com soberania financeira. As inovações tecnológicas que Bitcoin traz, desde a Lightning Network até contratos inteligentes, ampliam ainda mais o seu potencial como um sistema financeiro global que é inclusivo e acessível a todos.
A ascensão das CBDCs, por outro lado, apresenta riscos significativos para a privacidade, liberdade financeira e governança democrática. Embora estas moedas digitais sejam frequentemente apresentadas como soluções modernas para desafios financeiros, elas servem, em última análise, para centralizar o controlo e expandir o poder estatal sobre as vidas financeiras dos indivíduos. Em contraste, Bitcoin oferece um caminho para a descentralização, onde o poder é distribuído e os indivíduos controlam o seu próprio destino financeiro.
A adopção de um padrão Bitcoin poderia remodelar fundamentalmente o sistema financeiro global ao impor controlos e equilíbrios sobre o abuso de poder governamental, promover a inovação e fomentar a liberdade financeira individual. Representa uma mudança do controlo centralizado do dinheiro pelos governos para um futuro financeiro mais democrático, transparente e resiliente. Numa era em que os sistemas financeiros são cada vez mais usados como armas por estados e elites, Bitcoin ergue-se como um farol de esperança para aqueles que valorizam a liberdade, a autonomia e a justiça.
À medida que o debate sobre o futuro do dinheiro se intensifica, é crucial que indivíduos, legisladores e empresas considerem as implicações destas ideias. O potencial papel de Bitcoin na remodelação do sistema financeiro global não deve ser subestimado. É tempo de explorar e abraçar as oportunidades que o dinheiro sólido e descentralizado oferece e desafiar o status quo que permitiu aos governos e elites exercerem um controlo desproporcionado sobre os sistemas financeiros mundiais.
Ao educarmo-nos, advogar pela soberania financeira e adoptar o Bitcoin como padrão, podemos ajudar a construir um futuro onde o dinheiro serve os interesses do povo, e não do Estado. O caminho a seguir pode ser desafiante, mas as recompensas — um mundo mais livre, justo e próspero — valem bem o esforço.
Photo by Aedrian Salazar on Unsplash
-
-
 @ 006532cb:fd8f28b4
2025-02-02 09:50:56
@ 006532cb:fd8f28b4
2025-02-02 09:50:56I am new to #NOSTR and not a #Dev; however, npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn's article inspired me to research and understand further. As a result, I have condensed my learnings into 10 bullet points that seem to embody the spirit of being a nostrich and the qualities we should all strive for when engaging with one another making software choices and avoiding NINO's.
- You shall not compromise on security: Prioritize the security and integrity of user data, using best practices and Nostr's built-in features to protect against unauthorized access and malicious activity.
- You shall prioritize user agency: Respect users' mute lists, use their web of trust to filter out spam, and prioritize user control over their data.
- You shall be decentralized and open: Do not hardcode relay URLs or depend on specific relay implementations, ensuring that your platform is truly decentralized and open.
- You shall leverage Nostr's technical aspects: Take advantage of Nostr's features, such as self-authenticating data, event handlers, and relays, to build a robust and decentralized platform.
- You shall use native Nostr solutions: Prefer Nostr-native solutions to solve problems, rather than relying on legacy web services, promoting a more decentralized and resilient ecosystem.
- You shall prioritize interoperability: Implement NIP 89 (Recommended Application Handlers) to enable seamless interactions with other Nostr apps, promoting a unified and decentralized ecosystem.
- You shall engage with the community: Share knowledge, contribute to the growth of the ecosystem, and collaborate with other Nostr developers to promote a unified and thriving community.
- You shall be transparent and accountable: Be transparent in your development processes, and accountable for your actions and decisions, promoting trust and confidence in the Nostr ecosystem.
- You shall innovate and evolve: Continuously innovate and improve your platform, staying up-to-date with the latest developments in the Nostr protocol and ecosystem, to ensure the best possible experience for users.
- Embody Nostr: Your application should truly represent the Nostr protocol, using its features and network to provide unique value to users.
I am excited for the future. In Eric S. Raymond's book "The Cathedral and the Bazaar" he comments;
"...and the robust doesn't care too much"
Nostr embodies the spirit of the Bazaar, a vibrant and eclectic marketplace where the robust thrive, all are welcomed and empowered to become strong.
/GN!
-
 @ da0b9bc3:4e30a4a9
2025-02-02 08:18:39
@ da0b9bc3:4e30a4a9
2025-02-02 08:18:39Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/873174
-
 @ ccc8ee23:9f3d9783
2024-12-21 06:38:47
@ ccc8ee23:9f3d9783
2024-12-21 06:38:47Chef's notes
Enjoy these Chocolate Sprinkle Cookies, a delightful combination of buttery richness, velvety chocolate, and a crunchy sprinkle finish
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 90 min
- 🍽️ Servings: 10
Ingredients
- Plain flour 250 grams
- Margarine 100 grams
- Butter 100 grams
- Vanilla essence 1 tsp
- Milk powder 1 tbsp
- Sugar 40 grams
- Chocolate bar - 80 grams, melted
- Chocolate sprinkles - for decoration
Directions
- Make the Dough: Combine the plain flour, margarine, butter, milk powder, sugar, and vanilla essence in a mixing bowl. Knead the mixture by hand until smooth and well combined.
- Shape and divide the dough into small balls, weighing approximately 8 grams each.
- Preheat the oven to 175°C. Arrange the dough balls on a baking tray and bake for about 30 minutes, or until the cookies are dry and fully cooked.
- Coat with Chocolate: Melt the chocolate bar using a double boiler or microwave. Once the cookies have cooled completely, dip each cookie into the melted chocolate, ensuring they are evenly coated.
- Place the coated cookies onto paper cups.
- While the chocolate coating is still wet, sprinkle chocolate sprinkles on top of each cookie.
- Allow the chocolate to dry completely, then arrange the cookies in a decorative airtight container for storage.
-
 @ ccc8ee23:9f3d9783
2024-12-21 06:03:28
@ ccc8ee23:9f3d9783
2024-12-21 06:03:28Chef's notes
Celebrating seasons🎉
Kastengel Chocolate-Dip, where the savoury richness of cheese meets the decadent sweetness of chocolate. A perfect flavours in every bite!
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 90 min
- 🍽️ Servings: 10
Ingredients
- Plain Flour 250 grams
- Margarine - 100 grams
- Butter 100 grams
- Egg yolk 1 pc
- Sugar 20 grams
- Grated cheese 100 grams (half for the dough, half for garnish, adjustable)
- Chocolate bar 80 grams, melted
Directions
- Make the Dough: Combine the plain flour, margarine, butter, sugar, and half of the grated cheese in a bowl. Knead the mixture with your hands until smooth and well incorporated. Roll out the dough using a rolling pin and cut into desired shapes for cookies.
- Beat the egg yolk. Brush the shaped cookies with the egg yolk mixture and sprinkle the remaining grated cheese on top.
- Bake the cookies 175’C for about 30 minutes, or until they are dry and perfectly cooked.
- Melt the chocolate bar in a double boiler or microwave until smooth.
- Dip in Chocolate: Once the cookies have cooled completely, dip both the top and bottom ends of each cookie into the melted chocolate.
- Place the dipped cookies on a wire rack or a cookie drying tray to allow the chocolate to harden and set.
- Arrange the cookies neatly in an airtight container.
-
 @ 57d1a264:69f1fee1
2025-02-02 05:47:57
@ 57d1a264:69f1fee1
2025-02-02 05:47:57Hey there, as a result of the recent SN Media Kit updated, I'll try to create few simple marketing assets for ~Stackers_Stocks territory to be spread across the web.
Feel free to share in the comments below: - Few visual references you'd like the assets to be inspired on - If visuals are not your thing, a description of your idea will help too - A slogan, or some words/concepts that express the territory's values
@BlokchainB you start, let's see how we go!
originally posted at https://stacker.news/items/873112
-
 @ ac8bb9b0:70278acc
2024-12-20 18:48:36
@ ac8bb9b0:70278acc
2024-12-20 18:48:36Details
- ⏲️ Prep time: 5
- 🍳 Cook time: 10
- 🍽️ Servings: 4
Ingredients
- 1 lb large shrimp, peeled and deveined
- 1 tablespoon extra virgin olive oil
- 3 cloves garlic, chopped
- 1/4 cup white wine, dry
- 14 oz can petite diced tomatoes, drained
- 1/2 cup half and half
- 1/2 teaspoon dried oregano
- kosher salt and fresh black pepper, to taste
- 1 teaspoon lemon juice
- 1/4 cup fresh parsley, chopped
- 8 ounces angel hair pasta, whole wheat, gluten-free or high fiber
Directions
- Boil water with salt in a large pot for the pasta. Cook pasta al dente according to package directions.
- Meanwhile, season shrimp with 1/4 teaspoon salt, black pepper and oregano.
- Heat a large skillet over medium heat. Add the oil, when warm add the shrimp and garlic and cook about 2 minutes on each side.
- Add tomatoes, wine, salt and pepper and cook an additional minute.
- Remove from heat and stir in half and half. Add lemon juice and parsley and serve over pasta.
- Divide equally in 4 plates or shallow bowls.
-
 @ 57d1a264:69f1fee1
2025-02-02 05:36:57
@ 57d1a264:69f1fee1
2025-02-02 05:36:57Hey there, as a result of the recent SN Media Kit updated, I'll try to create few simple marketing assets for ~Construction_and_Engineering territory to be spread across the web.
Feel free to share in the comments below: - Few visual references you'd like the assets to be inspired on - If visuals are not your thing, a description of your idea will help too - A slogan, or some words/concepts that express the territory's values
@BlokchainB you start, let's see how we go!
originally posted at https://stacker.news/items/873104
-
 @ ccc8ee23:9f3d9783
2024-12-19 12:46:00
@ ccc8ee23:9f3d9783
2024-12-19 12:46:00Chef's notes
Salmon Mentai Rice. Create your own layers of fluffy, seasoned rice are topped with tender, pan-seared chicken or salmon and a creamy, spicy mentai sauce made with spicy Japanese mayo .
Torched to golden perfection, it’s finished with nori and tobiko for a burst of texture and flavor. A simple tasty Japanese fusion delight that’s perfect🤩
Subtitude of Tobiko, white sesame seeds as economical option will add a nutty flavor and subtle crunch to the dish for texture and visual appeal.
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 2
Ingredients
- Steamed Rice 400 grams
- Rice vinegar 1 tbsp
- Sugar 1 tsp
- chicken breast / thighs 250 grams
- soy sauce 1 tbsp
- oyster sauce 1 tbsp
- sesame oil 1 tsp
- garlic powder 1 tsp
- cooking oil 1 tbsp
- mayonnaise (e.g., Kewpie) 4 tbsp
- sriracha or any chili sauce 1 tbsp
- tobiko if any or white sesame as optional, for texture, 2 tsp only
Directions
- Prepared the Rice: mixed in bowl 2 cups steam rice, 1 tbsp rice vinegar, 1 tsp sugar and 1/2 tsp salt. Set a side.
- Cook the Chicken: 1. Marinate the chicken pieces with 1 tsp soy sauce, 1 tsp oyster sauce, 1 tsp sesame oil, 1 tsp garlic powder for 15–20 minutes. 2. Heat cooking oil in a pan over medium heat and stir-fry the chicken until fully cooked and slightly caramelized. Remove from heat.
- Make the Mentai Sauce 1. In a small bowl, combine 4 tbsp mayonnaise, 1 tbsp chili sauce, and 1 tsp sesame oil. Add tobiko if desired for texture. Mix well.
- Assemble the Mentai Rice 1. In a heatproof bowl or tray, layer the seasoned rice as the base. 2. Add a layer of cooked chicken on top of the rice. 3. Spread the mentai sauce evenly over the chicken layer.
- Grill or Broil: Use a kitchen torch or place the dish under a broiler for 2–3 minutes until the sauce is slightly charred and bubbly.
- Garnish with white sesame or nori strips, or extra tobiko.
-
 @ 3b7fc823:e194354f
2025-02-02 03:16:40
@ 3b7fc823:e194354f
2025-02-02 03:16:40Why Privacy Matters and How to Protect It
Privacy is about control. It’s not about hiding yourself but deciding what others can see about you. Just as you don’t share everything when buying a magazine, technology shouldn’t force you to reveal more than needed.
Why Privacy is Important
-
Personal Control: Privacy lets you choose what parts of your life are visible. You shouldn’t have to share everything just to use a service.
-
Security Against Exploitation: Without privacy, people and groups can be targeted by companies or governments. This abuse can lead to data breaches or unnecessary surveillance.
-
Building Trust: Privacy is key to trust in relationships and communities. When your info is safe, you can transact and communicate without fear of misuse.
How to Protect Your Privacy 1. Think Before You Share: Only share what’s necessary and know why you’re doing it. 2. Use Encryption: Encrypt sensitive communications like emails or messages. 3. Control Data Sharing: Avoid oversharing personal details online. 4. Enable Privacy Tools: Use VPNs or privacy settings on social media to shield your data. 5. Be Mindful of Metadata: Understand that metadata (like location data) can reveal more about you than the content itself. 6. Support Privacy-Focused Brands: Choose services that prioritize privacy, like encrypted messaging apps. 7. Read Privacy Policies: Know what data you’re sharing and with whom. 8. Tools like privacy.io can help visualize your digital footprint. 9. Block Trackers: Use tools like DoNotTrackMe or uBlock Origin to stop trackers from collecting your data.
Conclusion
Protecting privacy is a vital step in safeguarding your personal freedoms. By taking proactive measures, you can control what information is accessible and ensure that your rights are respected. Remember, you are your own best advocate for privacy—trust no one but yourself to protect your data and identity.
Join the movement to champion privacy as a fundamental human right. Advocate for stronger laws and encourage others to take action, so we can all enjoy safer, more secure digital environments.
-
-
 @ ccc8ee23:9f3d9783
2024-12-19 05:55:09
@ ccc8ee23:9f3d9783
2024-12-19 05:55:09Chef's notes
Dare to taste the bold? One bite of Jengkol Balado and you’ll be hooked
Spicy Jengkol Balado - Betawi Style A traditional dish from Betawi (Jakarta), Jengkol Balado is nutty bold and aromatic delicacy made with jengkol beans. This version uses thinly sliced jengkol for a delightful texture.
Serve it with a plate of steamed fragrant white rice and a side of crunchy cucumber for a complete meal that satisfies on every level.
Details
- 🍳 Cook time: 40 min
- 🍽️ Servings: 2
Ingredients
- Jengkol 250 grams
- Chilli 100 grams
- Shallot 5 cloves
- Garlic 2 cloves
- Tomato 1 clove (small)
- Bay leaves 2
- Galangal 2cm. Bruished
- Veggie oil 20ml or 4 tsp
- Seasoning
Directions
- Prepare the Jengkol Wash the jengkol thoroughly and slice it thinly. Boil the slices in water with the bay leaves for 10–15 minutes to soften and reduce their strong odour. Drain and set aside.
- Make the Balado Paste. Blend chillies, shallots, garlic, candlenut and tomatoes into a slightly coarse paste using a blender
- Heat oil in a pan and sauté the balado paste until fragrant and the oil starts to separate. Add the galangal, bay leaves, salt, sugar, and seasoning. Stir well
- Add jengkol to the pan. Mix until jengkol are fully coated in the balado paste.
- If the mixture seems too dry, add a splash of water and let it simmer on low heat to allow the flavours to infuse.
- Taste the dish and adjust the seasoning with more salt or sugar if needed.
- Remove from heat and serve hot with steamed rice.
-
 @ ac8bb9b0:70278acc
2024-12-18 21:18:57
@ ac8bb9b0:70278acc
2024-12-18 21:18:57Details
- ⏲️ Prep time: 10
- 🍳 Cook time: 20
- 🍽️ Servings: 5
Ingredients
- 8 ounces uncooked linguine
- 1 pound chicken breast, cut into strips
- 1-2 tsp Cajun seasoning, or more to taste
- 1 tsp garlic powder
- 1 tbsp extra virgin olive oil
- 1 medium red bell pepper, thinly sliced
- 1 medium yellow bell pepper, thinly sliced
- 8 oz fresh mushrooms, sliced
- 1/2 red onion, sliced
- 3 cloves garlic, minced
- 2 tomatoes, diced
- 1 cup low sodium chicken broth
- 1/3 cup skim milk
- 1 tbsp flour
- 3 tbsp light cream cheese
- fresh cracked pepper
- 2 scallions, chopped
- kosher salt to taste
- avocado oil spray
Directions
- Prep all your vegetables.
- In a small blender make a slurry by combining milk, flour and cream cheese. Set aside.
- Season chicken generously with Cajun seasoning, garlic powder and salt.
- Prepare pasta in salted water according to package directions.
- Heat a large heavy nonstick skillet over medium-high heat; spray with oil and add half of the chicken.
- Sauté 5 to 6 minutes or until done, set aside on a plate and repeat with the remaining chicken. Set aside.
- Add olive oil to the skillet and reduce to medium; add bell peppers, onions, and garlic to skillet, sauté 3-4 minutes.
- Add mushrooms and tomatoes and sauté 3-4 more minutes or until vegetables are tender.
- Season with 1/4 tsp salt, garlic powder and fresh cracked pepper to taste.
- Reduce heat to medium-low; add chicken broth and pour in slurry stirring about 2 minutes.
- Return chicken to skillet; adjust salt and Cajun seasoning to taste, cook another minute or two until hot, then add linguine; toss well to coat.
- Top with chopped scallions and enjoy!
-
 @ 57d1a264:69f1fee1
2025-02-02 00:03:39
@ 57d1a264:69f1fee1
2025-02-02 00:03:39Welcome to the latest updated version of Stacker News Media Kit & Brand Guidelines
v1.2, a pivotal location where all the visual elements find place and help us understand how to use them to have our communications cohesive. SN brand identity is built on simplicity, trust, innovation and a taste of Texas's Wild West. With the following guidelines, as promised, I'll try to outline the essential elements of SN visual language to be easily usable internally and externally.As third interaction from the previous discussion, here below you will find all the media assets in PNG and SVG downloadable from this zip file. BTW: I've been using
Nostr🌸 Blossom Serverservers check them out, it's a really cool idea! In case the file will be not available we can always upload it in other servers. Just let me know if any issue downloading it, ideally I made three copies available from: - https://nosto.re/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip - https://blossom.poster.place/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip - https://nostr.download/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zipThe source file of all these assets still are the same Figma file and the PenPot file. This last one, has many issues and does not allow yet the same flexibility as Figma. Both files are open for contributions and comments, just need to register a dummy/anonymous account for each of the tools.
Note: To use these assets across SN, just copy-paste the image relative code, i.e.:
Stacker News Logotype
SN logo is the most recognizable visual identifier of Stacker News. It captures the essence of its brand and is to be used across the platform and other marketing materials consistently. Find below all the possible variations and colors. Ideally you should stick with it to maintain SN identity coherent, or propose something new if you feel like. If you have any question on how to place or use the logo, DO ask below, and we'll help sort it out.
| Avatar on transparent BG | Avatar on BG | Logo Extended | Logo Vertical |#| |---|---|---|---|---| |
||||Oil Black| ||||| Golden Yellow | |||||With Shadow |Stacker News Typography
This is the typography SN had used to create its logo. Download LightningVolt OpenType Font file.otf designed by Honey&Death, install it in your computer and play with it.
Typography is essential to identify, increase readability and create consistency of brands. SN uses the default
font-family:sans-serif;of your device's OS, usually are the most common and already installed in your device:system-ui, "Segoe UI", Roboto, "Helvetica Neue", "Noto Sans", "Liberation Sans", Arial, sans-serif, "Apple Color Emoji", "Segoe UI Emoji", "Segoe UI Symbol", "Noto Color Emoji". Those are mostly used for:Example Header H1
Example Header H2
Example Header H3
Example Header H4
Example Header H5
Example paragraph text The fonts selected will help to communicate the personality of the brand and provide maximum legibility for both print and screen.
Example <code>For code, the approach is the same. Let's the device OS select its defaultmonospaceone. For example, on Mac will be one of the following:SFMono-Regular, Menlo, Monaco, Consolas, "Liberation Mono", "Courier New",`Stacker News Colors
A thoughtfully curated color palette gives SN trust, professionalism, and approachability. Colors play a key role in creating consistent visual experiences through digital and print communications. Make sure you are using the right color codes below:
| # | Name | HEX code | RGB code | HLS | |---|---|---|---|---| |
| Bitcoin-only |
#F6911D|rgb(246,145,29)|hsl(32,92.3%,53.9%)| || Blackr |
#000000|rgb(0,0,0)|hsl(0,0%,0%)| || Dark |
#121214|rgb(18,18,20)|hsl(240,5.3%,7.5%)| || Gold |
#FADA5E|rgb(250,218,94)|hsl(48,94%,67.5%)| || Gray |
#969696|rgb(150,150,150)|hsl(0,0%,58.8%)| || Light |
#F0F0F0|rgb(240,240,240)|hsl(0,0%,94.1%)| || Nostrch |
#8C25F4|rgb(140,37,244)|hsl(270,90.4%,55.1%)| || Pinkish |
#E685B5|rgb(230,133,181)|hsl(330,66%,71.2%)| || Ruby |
#C03221|rgb(192,50,33)|hsl(6,70.7%,44.1%)| || Sky Hover |
#007CBE|rgb(0,124,190)|hsl(201,100%,37.3%)| || Sky Links |
#2E99D1|rgb(46,153,209)|hsl(201,63.9%,50%)| || Sky Visited |
#56798E|rgb(86,121,142)|hsl(203,24.6%,44.7%)| || So Fiat |
#5C8001|rgb(92,128,1)|hsl(77,98.4%,25.3%)|Stacker News Icons
SN utilizes a set of bespoke icons that support its communication internally across the platform. Icons help bring instant, intuitive cues for various types of content and features. We share them here for you so you can use as you wish and satisfy your creative needs.
|
||[Bounty](https://m.stacker.news/75607)|[Caret](https://m.stacker.news/75608)|[Cowboy](https://m.stacker.news/75609)|[Sun](https://m.stacker.news/75610)| |---|---|---|---|---|---| |[Edit](https://m.stacker.news/75611)|[Gun](https://m.stacker.news/75612)|[Horse](https://m.stacker.news/75613)|[Info](https://m.stacker.news/75614)|[Moon](https://m.stacker.news/75615)|[Lightning](https://m.stacker.news/75616)| |[Bald Lost Hat](https://m.stacker.news/75617)|[Markdown](https://m.stacker.news/75618)|[Nostr](https://m.stacker.news/75619)|[Referral](https://m.stacker.news/75620)|[Rewards](https://m.stacker.news/75621)|[Horse Lost Saddle](https://m.stacker.news/75622)|[Search](https://m.stacker.news/75623)| |[Shoot](https://m.stacker.news/75624)|[Texas](https://m.stacker.news/75625)|[Upload](https://m.stacker.news/75626)|[Zap Zap](https://m.stacker.news/75627)|||Stacker News Banners
Banners are important visual elements used in our digital platforms and marketing materials. They help to highlight key stories, features or announcements while maintaining our brand aesthetic.
Here below you'll find custom banners for Sn and for individial territories. I try to build those that I follow most, for now @AGORA is the only one that designed its own banners. Comment below if you'd like some banners for your territory!
SN Dark background
|970x250| |---| |
||||728x90| |---| |
|SN Gold background
|970x250| |---| |
||250x250|300x250|300x600| |---|---|---| |
||||728x90| |---| |
|SN by @Jon_Hodl
|970x250| |---| |
||250x250|300x250|300x600| |---|---|---| |
||||728x90| |---| |
|~AGORA territory
The SN P2P Marketplace |970x250| |---| |
||250x250|300x250|300x600| |---|---|---| |
||||728x90| |---| |
|~alter_native territory
|970x250| |---| |
||250x250|300x250|300x600| |---|---|---| |
||||728x90| |---| |
|~bitcoin_beginners
|970x250| |---| |
||250x250|300x250|300x600| |---|---|---| |
||||728x90| |---| |
|~Design territory
|970x250| |---| |
||250x250|300x250|300x600| |---|---|---| |
||||728x90| |---| |
|~Music territory
|970x250| |---| |
||250x250|300x250|300x600| |---|---|---| |
||||728x90| |---| |
|Anything else we could add?
If you feel something is missing, or you know a better tool to manage this media kit for SN in a collaborative and FOSS way then, DO share it in a comment below
Territory owners [^1], do you need banners for your territory? Feel free to edit the figma file liked above or comment below sharing your needs or ideas, I'll try to do something for you.
By following these guidelines, we ensure consistency and professionalism in every case where Stacker News is represented here internally to stackers or to our audience in the KYC internet, reinforcing SN credibility as a trusted source for data-driven journalism.
[^1]: FYI: @Aardvark @AGORA @anna @antic @AtlantisPleb @Bell_curve @benwehrman @bitcoinplebdev @Bitter @BlokchainB @ch0k1 @davidw @ek @elvismercury @frostdragon @grayruby @HODLR @inverselarp @Jon_Hodl @k00b @marks @MaxAWebster @mega_dreamer @niftynei @nout @OneOneSeven @OT @PlebLab @Public_N_M_E @RDClark @realBitcoinDog @roytheholographicuniverse @siggy47 @softsimon @south_korea_ln @theschoolofbitcoin @TNStacker @UCantDoThatDotNet @Undisciplined
originally posted at https://stacker.news/items/872925
-
 @ ac8bb9b0:70278acc
2024-12-16 19:37:12
@ ac8bb9b0:70278acc
2024-12-16 19:37:12Details
- ⏲️ Prep time: 10
- 🍳 Cook time: 20
- 🍽️ Servings: 6
Ingredients
- 2 tablespoons extra virgin olive oil
- 1 1/2 pounds ground chicken
- 1 yellow onion, chopped
- 2 tablespoons taco seasoning
- salt and black pepper
- 2 1/2 cups salsa or enchilada sauce
- 1 chipotle chili in adobo, chopped
- 2 cups fresh corn
- 4 ounces cream cheese, at room temperature
- 1/4 cup plain greek yogurt
- 1 teaspoon chili powder
- 1 1/2 cups shredded Mexican cheese blend
- 2 cups tortilla chips
- avocado, cilantro, and green onions, for serving
Directions
- Preheat the oven to 400° F.
- In a large oven-safe skillet, combine the olive oil, chicken, onion, salt, and pepper. Set the skillet over high heat. Cook, breaking up the meat as it cooks, until browned all over, 5 minutes. Add the taco seasoning, cook another 2 minutes. Then add 1/2 cup water. Stir in the salsa/enchilada sauce and chipotle. Simmer 5 minutes. Remove from the heat and add in the cilantro.
- In a bowl, combine the corn, cream cheese, yogurt, chili powder, and salt. Stir in 1/2 cup cheese.
- Dollop 1/3 of the corn mix over the skillet. Add the tortilla chips on top, pressing them gently into the skillet. Add the remaining corn mix by spoonfuls on top of the chips (like nachos). Top with the remaining cheese. Bake for 15 minutes, until the cheese is melted.
- Serve topped as desired with avocado, cilantro, green onion, and cotija/feta cheese.
-
 @ e0e92e54:d630dfaa
2025-02-01 22:32:51
@ e0e92e54:d630dfaa
2025-02-01 22:32:51When a Client Wants Out…& A Yellow Flag Appears
This week was an interesting one with a client that wants to exit our agreement early.
(Totally fine. It happens and usually when one or both parties want to part ways, unless it's marriage, then it's at minimum a Yellow Flag if not a Red Flag that should be observed).
I tend to work with clients that have multiple irons in the fire, hence why they need someone like me to come along side them and provide guidance and help root them in the area they must focus on.
There is a strong parallel with this irregardless of whether it's #business #life or #impact
This client had big goals, but like many business owners, they defaulted to reactionary decisions instead of a structured plan. That’s when the Yellow Flag turned into a pattern I’ve seen before—Random Acts of X.
The Cost of Random Acts of X
If your solution is:
A. Throw money at it, and/or
B. Fire, Aim, Ready...instead of Ready, Aim, Fire
This WILL result in Random Acts of X (wherein X is whatever your are focused on, ie Marketing...aka Random Acts of Marketing essentially equates to the proverbial "throw spaghetti on the wall")
Is that really a thing? Like do Italians or some other cultures actually throw spaghetti on the wall to see if it "sticks"? Inquiring minds want to know! 🤷♂️
As I mentioned, my clients tend to have a lot of things they are trying to accomplish at once. This leads to fragmented efforts and lack luster results.
That being said, I approach everything as a relationship. Afterall, I believe:
Leadership = Relationships!
With this particular client there was one project he abruptly ended. Again, that's fine...it's their business...
Since I'm there to help them lead well, I reminded them this is a relationship and asked "What's next that you want me to focus on?"
We got on the same page with the new project and not even 2 days later that's where the Yellow Flag appeared in the form of issue A (just throw money at it).
Shortcuts Lead to Ghost Towns (Buying Followers Won’t Work)
You see, they wanted me to lead a marketing campaign to build relationships with people their company could sponsor. BUT they just wanted to "buy followers".
When I noticed one of their social accounts has 28k followers and on average only 14 impressions per post...
I asked "How's that working out for ya?"
You see folks, real relationships take time!
One cannot simply "throw money at it" and expect sound, sustainable results.
If you’re buying an audience instead of building one, you won’t have a community—you'll have a ghost town.
What Fake Engagement Looks Like in Business & Family
Think of it this way...
Imagine all you did in your family's relationships was throw money at it. You just "bought followers" in the form of taking this trip, buying that thing for them; and you totally avoided the time investment the relationship requires?
Sure...you might have been physically there...but were you present?
I run into this often with my son. He wants me to watch him play a video game. And during that time together what is he doing? He keeps looking over his shoulder to make sure I'm paying attention to HIM and not clandestinely on my phone.
Same goes for his Basketball...he wants me there rebounding for him...not sitting in a chair idly watching.
Are You Present or Just Physically There?
Business Owners and Leaders!
Husbands, Wives, and Parents!
People whom desire to have an impact!
The Process is the Shortcut!
Play silly games. Win silly prizes.
Intentionally build relationships. Reap rewards forever.
It's...
That...
Simple...
Easy? Not really...especially for someone like me whom is just as keen to spend time in nature or chillaxing with a cup of coffee on the back porch, thinking (and wishing my garden was growing better LOL).
But simple? Yes!
Create the process, execute the process, refine the process, and repeat.
The Process is the Shortcut...
Your Next Step: Cut the Shortcuts. Build the Process.
So—where do you need to refine your process today?
💡 What’s one way you can be more present in a relationship this week?
💡 What can you eliminate to move you closer to real impact—instead of just chasing more?
🔹 Drop your answer below 👇
Jason Ansley* is the founder of Above The Line Leader*, where he provides tailored leadership support and operational expertise to help business owners, entrepreneurs, and leaders thrive.
Want to strengthen your leadership and enhance operational excellence? Connect with Jason at https://abovethelineleader.com/contact
📌 This article first appeared on Nostr. You can also find more Business Leadership Articles and content at: 👉 https://abovethelineleader.com/business-leadership-articles

-
 @ dbb19ae0:c3f22d5a
2025-02-01 21:51:44
@ dbb19ae0:c3f22d5a
2025-02-01 21:51:44List of Wordpress articles:
- https://alashazam.wordpress.com/2024/07/01/python-nostr/
- https://alashazam.wordpress.com/2024/07/02/python-nostr-2/
- https://alashazam.wordpress.com/2024/07/03/python-nostr-second-program/
- https://alashazam.wordpress.com/2024/07/04/python-nostr-sdk/
- https://alashazam.wordpress.com/2024/07/04/python-nostr-third-program/
- https://alashazam.wordpress.com/2024/07/05/python-nostr-guessing-the-npub/
- https://alashazam.wordpress.com/2024/07/06/python-nostr_sdk-fetching-metadata/
- https://alashazam.wordpress.com/tag/python/
```python
!/usr/bin/env python3
""" Fetches the joined date from a Nostr profile and calculates the days since account creation.
Usage: python fetch_joined_date.py [npub]
Arguments: npub : The public key of the user (in npub format).
Requirements: - nostr_sdk library - Python 3.x
Example: python fetch_joined_date.py npub1... """
import argparse import time import ssl import json import uuid import logging from datetime import datetime from nostr.event import EventKind from nostr.relay_manager import RelayManager from nostr.key import PublicKey from nostr.filter import Filter, Filters from nostr.message_type import ClientMessageType
Configure logging
logging.basicConfig(level=logging.INFO, format="%(levelname)s: %(message)s")
RELAY_URL = "wss://relay.damus.io"
def fetch_metadata(npub): """Fetches metadata from a Nostr profile given an npub key.""" pub_key = PublicKey.from_npub(npub) filters = Filters([Filter(authors=[pub_key.hex()], kinds=[EventKind.SET_METADATA])]) subscription_id = uuid.uuid1().hex request = [ClientMessageType.REQUEST, subscription_id, *filters.to_json_array()]
relay_manager = RelayManager() relay_manager.add_relay(RELAY_URL) relay_manager.add_subscription(subscription_id, filters) try: relay_manager.open_connections({"cert_reqs": ssl.CERT_NONE}) time.sleep(1) # Allow time for connection relay_manager.publish_message(json.dumps(request)) time.sleep(1) # Allow time for response while relay_manager.message_pool.has_events(): event_msg = relay_manager.message_pool.get_event() metadata = json.loads(event_msg.event.content) return metadata except Exception as e: logging.error(f"Error fetching metadata: {e}") finally: relay_manager.close_connections() return Nonedef fetch_joined_date(npub): """Retrieves the joined date of a Nostr profile and calculates days since creation.""" metadata = fetch_metadata(npub) if not metadata or "created_at" not in metadata: logging.warning("Could not retrieve metadata or 'created_at' field is missing.") return
try: created_at = int(metadata["created_at"]) created_date = datetime.utcfromtimestamp(created_at) days_since_creation = (datetime.utcnow() - created_date).days logging.info(f"Account created on: {created_date.strftime('%Y-%m-%d %H:%M:%S UTC')}") logging.info(f"Days since account creation: {days_since_creation}") except (ValueError, TypeError): logging.error("Invalid 'created_at' timestamp.")if name == "main": parser = argparse.ArgumentParser(description="Fetch the joined date from a Nostr profile.") parser.add_argument("npub", type=str, help="The public key of the user (in npub format).") args = parser.parse_args()
fetch_joined_date(args.npub)```
-
 @ 07804b78:c375c543
2024-12-15 12:56:05
@ 07804b78:c375c543
2024-12-15 12:56:05Japanese follows. 日本語はあとで。
This article is for the 14th day of Nostr Advent Calendar 2024 (relay blogging). The article for the 13th day was "Open Sats 申請編" (Applying for Open Sats) by mono-san. The article for the 14th day will be "Nostrはじめました。" (I started Nostr) by bro-san.
Thinking of Thingstr
I've come up with an idea for Other Staff that I think is interesting (at least, for me), so I'm going to write about it. I actually wanted to show you the implementation and brag about it, but it's not solid enough to be implemented yet.
The key idea is just “add a reaction to the WikiData ID”.
WikiData
There is a service called WikiData. It is a knowledge base that provides structured data. You may be wondering what it is, but the important thing to understand here is that WikiData assigns identifiers to a fairly wide range of “objects” and “things”.
So, if you can react to this, you can think of various applications just by thinking of it for a moment, right?
For example, the anime series “There are too many losing heroines!” is assigned the ID
Q123819103. The corresponding page is https://www.wikidata.org/wiki/Q123819103 .(NOTE: The canonical URI for entities on Wikidata is http://www.wikidata.org/entity/Q1142841. This is in accordance with Semantic Web conventions, and is not https, but http. Also, this URI does not necessarily match the actual address of the correspnding web page. Just an identifier. In most cases, it will redirect).
What can wd do?
For example, what about a website that records your anime viewing history? You can record what you want to watch with 👀, what you've already watched with ✅, and your favorites with ☆. You can also express your “likes” for production companies, staff, voice actors, etc. In this way, you can see what a particular user likes.
This could be a movie, a book, a comic, an author, music, an idol group, a place, or food (Someone likes pork cutlet
Q1142841). The fact that you can record everything in the same framework is what makes it interesting.What form of event should it be recorded as?
There is probably room for discussion about how to record this information in a concrete way. The simplest way would be to use NIP-25's "Reactions to a website" kind:17 (a.k.a. Makibishi). How about something like this?
json [ ["i", "wd:Q123819103", "http://www.wikidata.org/entity/Q123819103"], ]Since NIP-73 has External Content IDs, it would be good if we could include WikiData here so that we could write
wd:Q123819103. Actually,isbn:and other identifiers have already been defined, so it is possible to use the current NIP range to describe books (however, the authors do not have IDs. If we use WikiData as an ID, we can also describe reactions related to the author). Of course, it is not a matter of choosing one or the other, and it is also fine to add the ISBN tag at the same time as the WikiData tag for books.Search for recorded reactions
So far, this is all very simple, but it would be inconvenient if we didn't include tags to mark subsets of reactions (for example, only those related to anime) so that we can query them together. When we try to create a site that is specialized for a certain purpose, we need to be able to extract the reactions that are necessary.
On Wikidata, the predicate
wdt:P31(instance of) is used to group together concepts that represent the same thing. For example, how about including this in theltag? "There are too many losing heroines!" is a "Japanese television anime series (Q63952888)", so:json [ ["i", "wd:Q1142841", "http://www.wikidata.org/entity/Q1142841"], ["l", "wdt:P31 wd:Q63952888"] ]UPDATE(2024-12-15): rnurachue-san suggested that
#lor#Lmight be better for labeling (the first version used#a). I think that's a good idea, so I've updated the article. nostr:nevent1qgswamu0rsela0kwhj87p24ueapxdp04vzz7ar0pp6lfyq923t3l02cqyr9786635s60ra0f973nwv2sln2l74lqx4twdlgxfz2jgevpvsgtc9zwn6dHowever, when you think about creating an anime website, you may want to query both TV anime and anime films. This makes things more complicated. "Japanese TV anime series (
Q63952888)" is a subclass (subclass of;wdt:P279) of "Anime series (Q117467261)", which is in turn a subclass of "Anime (Q1107)". However, if you were to embed this hierarchy in each reaction, it would waste a lot of space. The following query will get all the superclasses of "Japanese TV anime series (Q63952888)", but there are 54 of them.https://query.wikidata.org/#%23%20Subclass%20hierarchy%20traversal%20for%20Q63952888%0ASELECT%20%3Fitem%20%3FitemLabel%20%3Fsuperclass%20%3FsuperclassLabel%0AWHERE%20%7B%0A%20%20%23%20Starting%20class%0A%20%20wd%3AQ63952888%20wdt%3AP279%2a%20%3Fsuperclass%20.%0A%20%20BIND%28wd%3AQ63952888%20AS%20%3Fitem%29%0A%20%20SERVICE%20wikibase%3Alabel%20%7B%20bd%3AserviceParam%20wikibase%3Alanguage%20%22%5BAUTO_LANGUAGE%5D%2Cen%22.%20%7D%0A%7D%0AORDER%20BY%20%3Fsuperclass%0A
So, I think it should be okay for practical purposes to embed
P31s of the reaction target. In other words, if you search for "anime seriesQ63952888" and "anime movieQ20650540", that should be enough. Fortunately, the conditions for single-character tags work with OR, so you can query multiple tags at once. we'll have to try it to see how well it works in practice, though.Discussion: Which kind should I use?
So far we have considered using kind:17, but we have not yet decided whether it is a good idea to mix Thingstr events with reactions to web pages.
Also, there may be a debate over whether to record regular events or addressable events, depending on the purpose of use. For example, if you want to record the transition of viewing results and impressions on an anime viewing site, you should use regular events, and if you want to maintain the viewing status, you should use addressable events.
What do you think?
Other ideas
If we can react to Nodes on OpenStreetMap using the same framework, we might be able to create something like Swarm. Since the views you want to see will differ depending on the purpose, it would be good to create various sites while having a consistent way of recording. Wouldn't that be the most Nostr-like thing?
Summary
I discussed how to use WikiData and OpenStreetMap as an ID infrastructure and realize various check-in and review services with a unified data model by using them on Nostr. Please let us know if you have any feedback. Or why not try implementing it?
この記事は Nostr Advent Calendar 2024 の14日目の記事です。13日目の記事はmonoさんによる「Open Sats 申請編」でした。15日目の記事はbroさんによる「Nostrはじめました。」です。
Thingstrについて考えた
面白そうな(と勝手に思ってる) Other Staff のアイディアを思いついたので、書いてみます。 本当は実装を持ってきて自慢したかったのですが、まだふわっとしていて実装に落ちていません。
コアになるアイディアは「WikiData の ID に対して、Reactionをつける」これだけです。
WikiData
WikiData というサービスがあります。構造化データを提供する知識ベースです。 なにそれ?という感じですが、ここで大事なのはWikiDataはかなり広範な「もの」「こと」に識別子(Identifier)を付与している、ということです。
だから、これにリアクションできれば、ぱっと思いつくだけでもいろいろな応用ができそうじゃないですか。
例えば、アニメシリーズ「負けヒロインが多すぎる!」には
Q123819103というIDが振られています。これに対応するページとして https://www.wikidata.org/wiki/Q123819103 があります。(ただし、WikiData のエンティティに対する canonical な URI は http://www.wikidata.org/entity/Q1142841 であることには注意が必要です。セマンティックウェブの作法で https ではなく http になっています。そして、このURIは必ずしもWebページのアドレス一致しません。大抵の場合はリダイレクトされます)。
なにができるの
たとえば、アニメの視聴記録サイトはどうでしょう。👀は見たい作品、✅は視聴済み、☆はお気に入り、みたいに記録していく。制作会社、スタッフ、声優、...に対してLikeを表明したりできそうです。そうすると、あるユーザが何にLikeしているかわかります。
これが映画でもいいし、書籍、漫画、作家でもいいし、音楽でもいいし、アイドルグループでもいいし、場所でもいいし、食べ物でもいい(とんかつ
Q1142841が好き、とか)。全部同じ枠組みで記録できるのが面白そうなところです。どういうNostrイベントで記録する?
具体的な記録の仕方には議論の余地があるでしょう。一番単純なのは、NIP-25の "Reactions to a website" kind:17 (Makibishi) を使う方法でしょうか。こんなのはどうでしょう。
json [ ["i", "wd:Q123819103", "http://www.wikidata.org/entity/Q123819103"], ]NIP-73にExternal Content IDsがあるので、ここにWikiDataを入れられるようにして
wd:Q123819103と書けるとよさそうです。実はisbn:などはすでに定義されているので、書籍に関しては現行のNIPの範囲でもうまいことできます(ただ、著者にはIDが振られていません。WikiDataをIDに使うと著者に関するリアクションも記述できます)。もちろん、どちらか一方を選ぶというものでもなくて、書籍にはWikiDataのタグと当時にISBNのタグを付与しておいてもいいと思います。記録されたリアクションを検索する
ここまではシンプルでよいのですが、リアクションの部分集合(たとえばアニメに関連するものだけ、とか)をまとめてクエリできるように、目印となるタグを入れておかないと不便です。ある目的に特化したサイトを作ろうとしたとき、必要になるリアクションが抽出できるようにしておかないといけません。
WikiData では
wdt:P31(instance of) という述語で、ある概念が何を表しているかをグルーピングしてくれています。例えばこれをlタグとかに含めておくのはどうでしょうか。負けヒロインが多すぎる!は「日本のテレビアニメシリーズ(
Q63952888)」なので、json [ ["i", "wd:Q1142841", "http://www.wikidata.org/entity/Q1142841"], ["l", "wdt:P31 wd:Q63952888"] ]みたいな感じで付与します。
UPDATE(2024-12-15): rnurachueさんからラベル付けには
#lまたは#Lのほうがよいかもという提案をいただきました。最初のバージョンでは#aを使用していました。そのとおりだと思ったので更新しました。 nostr:nevent1qgswamu0rsela0kwhj87p24ueapxdp04vzz7ar0pp6lfyq923t3l02cqyr9786635s60ra0f973nwv2sln2l74lqx4twdlgxfz2jgevpvsgtc9zwn6dただ、アニメサイトを作ることを考えると、テレビアニメも劇場版アニメも両方クエリしたいこともありそうですよね。そうなると話が複雑になってきます。
「日本のテレビアニメシリーズ(
Q63952888)」は「アニメシリーズ(Q117467261)」のサブクラス(subclass of;wdt:P279)で、それがさらに「アニメ(Q1107)」 のサブクラスになっています。ただ、この階層をいちいちリアクションに埋め込むのと大変なことになります。以下のようなクエリで「日本のテレビアニメシリーズ(Q63952888)」のすべての上位クラスが取れるのですが、54件もあります。https://query.wikidata.org/#%23%20Subclass%20hierarchy%20traversal%20for%20Q63952888%0ASELECT%20%3Fitem%20%3FitemLabel%20%3Fsuperclass%20%3FsuperclassLabel%0AWHERE%20%7B%0A%20%20%23%20Starting%20class%0A%20%20wd%3AQ63952888%20wdt%3AP279%2a%20%3Fsuperclass%20.%0A%20%20BIND%28wd%3AQ63952888%20AS%20%3Fitem%29%0A%20%20SERVICE%20wikibase%3Alabel%20%7B%20bd%3AserviceParam%20wikibase%3Alanguage%20%22%5BAUTO_LANGUAGE%5D%2Cen%22.%20%7D%0A%7D%0AORDER%20BY%20%3Fsuperclass%0A
なので、リアクション対象の
P31を埋め込む、くらいで実用上は問題ないような気がします。つまり、検索するときに 「アニメシリーズQ63952888」と「アニメ映画Q20650540」を対象にすれば、十分では、ということです。幸い、一文字タグの条件はORで効くので、複数を並べて一度にクエリできます。実際にどのくらいうまく行くかはやってみないとわからないですが。議論: どの kind を使うべきか?
一旦 kind 17 を使うことを考えてきましたが、Thingstr のイベントが Web ページに対するリアクションと混ざるのが良いことなのか、いまいち判断がついていません。
また、用途によって regular event で記録するべきか、それとも addressable event で記録すべきか、という議論もありそうです。 アニメ視聴サイトを例にあげるなら、視聴実績とか感想の変遷を記録したいならば regular event でしょうし、視聴の状態を保持したいならば addressable とするのがよさそうです。
どう思いますか?
他のアイディア
これと同じ枠組みで OpenStreetMap の Node に対してリアクションできるようにすれば Swarm のようなものも実現できるかもしれません。
用途ごとに見たいビューは違うだろうから、一貫した記録の仕方を持ちつつ、色々なサイトを作ったらいいんじゃないでしょうか。それって最高にNostrっぽくないですか?
まとめ
WikiDataやOpenStreetMapをID基盤として活用し、Nostr上でreactすることで、様々なチェックインサービス、レビューサービスを統一的なデータモデルで実現する方法について議論しました。フィードバックがあったら教えてください。むしろ実装してみてください。
-
 @ 8f69ac99:4f92f5fd
2024-08-20 14:15:40
@ 8f69ac99:4f92f5fd
2024-08-20 14:15:40O conceito de minarquia apresenta um cenário político intrigante, no qual existe um estado mínimo com o foco em salvaguardar as liberdades individuais, ao mesmo tempo que fornece serviços essenciais como a aplicação da lei, defesa militar e funções judiciais. Esta introdução explora os princípios fundamentais e as principais características da minarquia, preparando o terreno para examinar como ela contrasta com várias ideologias e quais implicações essa filosofia pode ter na formação de uma sociedade que defende a liberdade pessoal sem sacrificar as protecções necessárias.
O minarquismo propõe uma alternativa tanto às estruturas governamentais maiores quanto às doutrinas libertárias, como o anarcocapitalismo, ao defender a menor interferência possível do estado, mantendo ao mesmo tempo suas funções fundamentais. Ao compararmos a minarquia com outras ideologias, torna-se claro que esta filosofia se distingue na sua abordagem à responsabilidade individual, à economia de mercado livre e à tributação mínima — todos estes aspectos têm como objectivo ampliar as liberdades pessoais sem uma presença excessiva do governo.
Com uma compreensão clara dos princípios fundamentais da minarquia, exploramos como as sociedades podem transitar para essa ideologia.
Princípios do Minarquismo
O minarquismo é uma filosofia política que defende um estado mínimo, priorizando os direitos individuais, como a vida, a liberdade e a propriedade. O papel do governo é limitado a funções essenciais, como defesa nacional, aplicação da lei e manutenção da justiça, permitindo que os indivíduos façam suas próprias escolhas e exerçam maior responsabilidade e autonomia pessoal.
O minarquismo está enraizado na crença de que a liberdade individual é a chave para o florescimento humano. Ao minimizar a intervenção do governo, os minarquistas argumentam que as pessoas têm mais controle sobre suas vidas e podem perseguir seus objectivos sem regulamentações ou impostos desnecessários. Esta filosofia enfatiza a importância da tomada de decisões individuais e os potenciais efeitos negativos, como ineficiências, restrições à liberdade e consequências indesejadas, quando o governo intervém.
Diferenças Fundamentais com a Social-Democracia
O minarquismo difere significativamente da social-democracia, que enfatiza a intervenção do governo na economia e nos serviços sociais. Num sistema minarquista, as instituições privadas, as organizações comunitárias e a cooperação voluntária desempenham um papel crucial no atendimento às necessidades sociais, reduzindo a dependência da intervenção estatal. Em contraste, as social-democracias dependem fortemente da regulamentação e provisão de serviços pelo governo.
O Apelo da Minarquia
O minarquismo atrai aqueles que valorizam a liberdade pessoal e são cépticos quanto ao poder do governo. Seus defensores argumentam que um governo menor reduz o risco de corrupção, ineficiência e excesso de autoridade, ao mesmo tempo que promove uma sociedade mais dinâmica e próspera. Ao limitar o papel do estado às suas funções mais essenciais, a minarquia busca criar um sistema em que os indivíduos sejam livres para buscar a sua própria felicidade e sucesso sem o controle excessivo do governo.
Compreender a minarquia exige uma mudança de pensamento sobre o papel do governo. Em vez de ver o estado como provedor e protector em todos os aspectos da vida, o minarquismo vê o governo como uma instituição necessária, mas limitada, focada unicamente na protecção dos direitos individuais. Ao comparar a minarquia com a social-democracia, podemos ver as diferenças distintas na forma como esses sistemas abordam a governação, a gestão económica e os serviços sociais. Essa compreensão fundamental ajudará a explorar em mais detalhe os benefícios e desafios potenciais da minarquia.
As Implicações Económicas do Minarquismo
O minarquismo, que defende um estado mínimo, provoca mudanças significativas na forma como a economia de um país funciona. Este capítulo explora como uma nação pode transitar para um sistema minarquista, examinando os efeitos nos seus mercados internos, relações comerciais e sistemas financeiros. Ao reduzir a intervenção do governo, o minarquismo promove um ambiente onde as empresas são livres para operar com mínimas restrições, incentivando a concorrência e a inovação. Também discutiremos os potenciais desafios de transitar de uma economia mais regulamentada para uma minarquista e como a escolha do consumidor e a concorrência podem manter práticas justas e estabilidade económica, mesmo com menor supervisão governamental.
A Abordagem Minarquista aos Mercados Nacionais
Num sistema minarquista, o governo de um país foca-se na proteção dos direitos individuais e na garantia de que os contratos são respeitados, ao mesmo tempo que se afasta da intervenção directa na economia. Isso significa que as empresas no país operam com menos regulamentações, permitindo-lhes maior liberdade para inovar e competir. Diferentemente dos ambientes fortemente regulamentados, onde as regras governamentais podem, por vezes, sufocar a concorrência e proteger os actores estabelecidos, uma abordagem de mercado livre incentiva a entrada de novos participantes e o florescimento de ideias.
Para um país em transição para a minarquia, isso pode envolver a redução gradual das regulamentações e a transferência de responsabilidades do estado para o sector privado. À medida que as empresas ganham mais autonomia, os monopólios são menos propensos a formar-se porque a concorrência e a escolha do consumidor naturalmente mantêm o poder sob controle. Se uma empresa dentro do país não agir de forma responsável — seja em relação aos clientes, ao meio ambiente ou aos seus funcionários — outras empresas que ofereçam alternativas melhores provavelmente a superarão, promovendo um mercado mais dinâmico e ético.
Os acordos comerciais com outros países, num quadro minarquista, focar-se-iam na simplicidade e na justiça. Uma nação que adopta a minarquia negociaria acordos que priorizam benefícios mútuos sem a intervenção pesada do governo, levando a relações comerciais internacionais mais abertas e dinâmicas. No entanto, o foco principal continua a ser a forma como o país individual gere o seu próprio cenário económico.
Redefinindo os Sistemas Financeiros Nacionais
O minarquismo também reformularia o sistema financeiro de um país. O papel tradicional dos bancos centrais, que controlam a oferta monetária e as taxas de juros, poderia ser reduzido ou reformado, permitindo que as instituições bancárias privadas assumam um papel maior. Nesse ambiente, os mercados financeiros dentro do país seriam mais autorregulados, guiados pelos princípios da oferta e da procura, em vez de políticas governamentais.
Para um país que adopta a minarquia, isso poderia significar afastar-se das políticas monetárias conduzidas pelo governo e permitir que as forças do mercado determinem a estabilidade cambial e as práticas financeiras. Embora isso possa levar a mais flutuações no valor da moeda, também abre caminho para soluções financeiras inovadoras, como o uso de moedas digitais descentralizadas.
O investimento dentro do país e além das suas fronteiras provavelmente aumentaria, à medida que menos restrições e menores barreiras à entrada incentivassem o fluxo de capital de forma mais livre. Isso cria uma economia mais interconectada, onde empresas e investidores podem aproveitar oportunidades, tanto a nível doméstico quanto internacional.
Desafios e Oportunidades na Transição para a Minarquia
Para um país em transição para a minarquia, uma das principais oportunidades é que a concorrência, impulsionada pela escolha do consumidor, torna-se o regulador principal do mercado. Num mercado verdadeiramente livre, as empresas devem manter um bom comportamento — seja ambiental, social ou economicamente — ou correm o risco de serem superadas por outras que o façam. Esta estrutura de incentivos naturais pode ser mais eficaz do que a regulamentação governamental na promoção de um comportamento empresarial responsável, já que as empresas que priorizam a sustentabilidade e a justiça tendem a ser recompensadas pelos consumidores.
A estabilidade económica num país minarquista baseia-se nos princípios da responsabilidade pessoal e da cooperação voluntária. Em tempos de crise, soluções privadas, como sociedades de ajuda mútua ou seguros privados, podem substituir as redes de segurança governamentais. Essa abordagem descentralizada pode ser mais adaptável e responsiva, oferecendo soluções adaptadas às necessidades específicas de diferentes regiões dentro do país.
A protecção ambiental é outra área onde as soluções baseadas no mercado podem prosperar. Num sistema minarquista, as empresas podem adoptar práticas sustentáveis para atender à demanda dos consumidores ou ganhar uma vantagem competitiva. Por exemplo, as empresas que reduzem a sua pegada de carbono ou usam materiais ambientalmente amigáveis podem atrair mais clientes e aumentar a sua participação no mercado. Esta abordagem alinha os incentivos empresariais com os objectivos ambientais, criando uma situação vantajosa para ambas as partes, sem a necessidade de mandatos governamentais.
Exemplos do Mundo Real: A Influência do Minarquismo nas Economias Nacionais
Exemplos históricos e modernos fornecem uma visão de como o minarquismo pode influenciar as economias nacionais. Por exemplo, Hong Kong, antes de sua devolução à China em 1997, operava com uma intervenção governamental mínima em muitos sectores, levando a um rápido crescimento económico. Da mesma forma, as políticas de baixos impostos e pró-negócios de Singapura fizeram dela um centro financeiro global. Esses exemplos mostram que um estado mínimo pode fomentar o sucesso económico, mas também destacam a importância de manter o equilíbrio certo entre liberdade e responsabilidade dentro da nação.
Ao comparar o minarquismo com sistemas mais intervencionistas, os benefícios de uma abordagem de mercado livre a nível nacional tornam-se claros. Enquanto as economias fortemente regulamentadas frequentemente enfrentam ineficiências e um crescimento mais lento, o minarquismo promove um ambiente dinâmico e competitivo onde a inovação prospera. No entanto, é essencial reconhecer que essa abordagem exige uma cultura de responsabilidade e participação activa das empresas e consumidores dentro do país.
O minarquismo oferece uma visão de uma economia onde a liberdade, a inovação e a concorrência impulsionam a prosperidade nacional. Ao reduzir o papel do governo, essa abordagem abre caminho para uma economia mais dinâmica e eficiente a nível nacional. Embora existam desafios, particularmente em garantir estabilidade e equidade durante a transição, os incentivos naturais de um mercado livre — guiados pela escolha do consumidor e pela concorrência — podem enfrentar essas preocupações. À medida que os países consideram a transição para um sistema minarquista, compreender o seu impacto potencial nas suas relações económicas internas e internacionais é fundamental para moldar políticas que equilibrem abertura com crescimento responsável.
Um Roteiro para a Minarquia
Em muitas democracias sociais, o governo desempenha um papel significativo na prestação de serviços como saúde, educação e bem-estar social. No entanto, alternativas privadas já existem e muitas vezes competem com esses serviços públicos. O desafio na transição para a minarquia não é apenas introduzir opções privadas, mas reduzir a dominância do estado e a dependência dos serviços públicos. Este capítulo delineia um roteiro prático para gradualmente deslocar o equilíbrio da provisão estatal para a privada, reduzindo a intervenção governamental, os gastos públicos e os impostos de uma forma que permita uma transição suave e sustentada. À medida que o estado se retira de certas áreas, os indivíduos experimentarão uma redução na sua carga tributária, conduzindo a uma maior liberdade financeira e a um equilíbrio mais saudável para a economia.
Incentivar o Crescimento das Alternativas Privadas
Em muitas democracias sociais, alternativas privadas em setores como saúde, educação e seguros coexistem com os serviços prestados pelo estado. No entanto, essas opções privadas muitas vezes têm dificuldades para competir porque os cidadãos são obrigados a pagar impostos que financiam os serviços públicos, fazendo com que as opções fornecidas pelo estado pareçam "gratuitas" ou significativamente mais baratas.
O primeiro passo na transição para a minarquia é nivelar o campo de jogo entre os prestadores públicos e privados. Uma abordagem eficaz é oferecer incentivos fiscais ou créditos às pessoas que optam por serviços privados. Por exemplo, se alguém optar por um seguro de saúde ou educação privada, poderá receber um crédito fiscal que compense o custo desses serviços. Isso não só torna as alternativas privadas mais acessíveis, mas também reduz gradualmente a carga tributária do indivíduo à medida que depende menos dos serviços fornecidos pelo estado.
À medida que mais pessoas migram para serviços privados, a demanda pelos serviços públicos diminuirá, permitindo que o governo reduza os gastos nessas áreas. Essa redução nos gastos pode ser repassada directamente aos contribuintes através de impostos mais baixos, aumentando ainda mais o apelo das alternativas privadas e promovendo um equilíbrio mais saudável entre os sectores público e privado.
Reduzir a Dominância do Estado Através da Privatização Gradual
À medida que as alternativas privadas ganham força, o próximo passo é reduzir a dominância do estado em certos sectores. Isso pode ser alcançado através da privatização gradual de empresas e serviços estatais, garantindo que a transição não interrompa o acesso a serviços essenciais.
Por exemplo, no sector de saúde, o governo poderia começar terceirizando certos serviços para prestadores privados ou permitindo que mais hospitais privados operem ao lado dos públicos. Com o tempo, à medida que o sector privado se mostrar capaz de atender a mais necessidades de saúde, o estado pode reduzir sua participação directa, eventualmente limitando seu papel a fornecer uma rede de segurança para aqueles que não podem pagar por opções privadas.
A privatização deve ser feita de forma transparente e cuidadosa para garantir que os serviços permaneçam acessíveis e que a concorrência impeça a formação de monopólios. À medida que o governo recua e reduz seus gastos, essas economias podem ser traduzidas em impostos mais baixos para indivíduos e empresas, tornando a economia mais dinâmica e dando aos cidadãos mais controle sobre seus recursos financeiros.
Descentralização dos Serviços Públicos
Outro passo importante na transição para a minarquia é descentralizar os serviços públicos. Mesmo com a redução do papel do estado, os governos locais e as comunidades podem assumir mais responsabilidades. A descentralização permite uma tomada de decisão mais localizada, que pode reflectir melhor as necessidades e preferências de diferentes regiões.
Por exemplo, os governos locais poderiam ter mais controle sobre como os serviços públicos são prestados, permitindo que experimentem diferentes modelos, incluindo parcerias com empresas privadas. Isso também poderia envolver a transferência de certos serviços públicos do governo nacional para as autoridades locais, que estão mais bem equipadas para gerenciá-los de forma eficiente e responsiva.
À medida que a descentralização reduz a carga sobre o governo central, as economias realizadas podem ser repassadas aos contribuintes. O controle local muitas vezes requer menos recursos do que a supervisão nacional, e à medida que o custo geral do governo diminui, os cidadãos devem ver uma redução correspondente em suas obrigações fiscais.
Reformas Legais e Fiscais
A transição para um sistema minarquista requer reformas legais e fiscais que apoiem a mudança da provisão pública para a privada de serviços. Uma área crítica é a reforma tributária. À medida que as alternativas privadas assumem mais responsabilidades e o estado reduz sua participação em vários sectores, o sistema tributário deve ser ajustado para reflectir essa mudança.
Créditos fiscais ou deduções para o uso de serviços privados podem reduzir a pressão financeira sobre os indivíduos, incentivando-os a optar por serviços privados em vez dos fornecidos pelo estado. Com o tempo, à medida que o governo reduz os gastos em áreas como saúde, educação e bem-estar social, as taxas de imposto podem ser gradualmente reduzidas. Essa redução de impostos aumentará a renda disponível para indivíduos e famílias, permitindo-lhes fazer escolhas mais independentes e investir nos serviços privados que melhor atendam às suas necessidades.
Além disso, as leis que restringem a concorrência ou favorecem os serviços públicos em detrimento dos privados devem ser gradualmente reformadas ou revogadas. As reformas legais devem se concentrar em criar um campo de jogo nivelado onde os prestadores privados possam competir de forma justa, garantindo que os consumidores tenham mais escolhas e que as empresas sejam motivadas a oferecer melhores serviços.
Ao alinhar a redução de impostos com a diminuição dos gastos públicos, a transição para a minarquia pode levar a um equilíbrio mais saudável para a economia, onde os indivíduos têm mais controle sobre suas finanças e o estado só arrecada o necessário para cumprir suas funções essenciais.
Redução dos Gastos Públicos e Transição para a Auto-suficiência
O passo final na transição para a minarquia é reduzir gradualmente os gastos públicos à medida que os serviços privados se tornam mais estabelecidos e amplamente utilizados. Isso pode ser feito reduzindo gradualmente os programas governamentais que têm alternativas privadas viáveis. Por exemplo, à medida que as opções de saúde e educação privadas se tornam mais acessíveis e acessíveis, o financiamento público para essas áreas pode ser reduzido.
Ao mesmo tempo, promover a auto-suficiência e os sistemas de apoio comunitário pode ajudar a reduzir a dependência dos programas de bem-estar do estado. Incentivar a caridade privada, as sociedades de ajuda mútua e as iniciativas comunitárias locais pode fornecer redes de segurança para os necessitados sem exigir uma intervenção governamental extensiva.
À medida que os gastos públicos diminuem, o governo pode reduzir ainda mais os impostos, permitindo que os cidadãos mantenham mais de sua renda. Isso cria um ciclo virtuoso onde impostos mais baixos e menor intervenção governamental levam ao aumento da actividade do sector privado, maior autonomia individual e uma economia mais equilibrada e eficiente.
O objectivo é criar uma sociedade onde indivíduos e comunidades sejam capacitados a cuidar de suas próprias necessidades, reduzindo o papel do estado às suas funções mais essenciais. Ao gerenciar cuidadosamente a redução dos gastos públicos e alinhá-la com cortes de impostos, a transição pode ser suave e sustentável, garantindo que ninguém fique sem apoio durante o processo.
A transição da democracia social para a minarquia é um processo complexo que requer planeamento cuidadoso e implementação gradual. Ao focar no incentivo às alternativas privadas, reduzir a dominância do estado através da privatização, descentralizar os serviços públicos, implementar reformas legais e fiscais e reduzir gradualmente os gastos públicos e os impostos, um país pode realizar com sucesso a mudança para um estado mínimo. Essa abordagem garante que a transição seja suave e sustentável, permitindo que indivíduos e organizações privadas assumam um papel maior na sociedade enquanto reduzem a dependência da intervenção governamental. Em última análise, este roteiro oferece um caminho para uma maior liberdade pessoal, eficiência económica e um equilíbrio mais saudável entre responsabilidades públicas e oportunidades privadas.
Implementação Prática do Minarquismo em Áreas-Chave
Enquanto o capítulo anterior delineou os passos gerais necessários para a transição para um sistema minarquista, este capítulo foca em como esses princípios podem ser aplicados a áreas específicas de governança e serviços públicos. Ao examinar sectores como a saúde, economia, bem-estar social, educação e defesa, podemos explorar estratégias práticas para reduzir a intervenção do governo, garantindo que as funções essenciais sejam mantidas e até mesmo melhoradas por meio de alternativas privadas e comunitárias. A ênfase estará na criação de uma transição equilibrada que promova a concorrência, melhore a qualidade e maximize a liberdade individual.
Saúde: Transição do Público para o Privado
A saúde é frequentemente uma das áreas mais controversas nas discussões sobre a redução da intervenção governamental. Em muitos países, os sistemas públicos de saúde coexistem com prestadores privados, mas o domínio dos serviços financiados pelo governo pode criar desequilíbrios. Para transitar para um modelo mais minarquista de saúde, é essencial uma redução gradual dos programas governamentais de saúde.
Uma estratégia é introduzir incentivos fiscais para indivíduos que optem por cuidados de saúde ou seguros privados. Isso reduz a dependência do sistema público de saúde, ao mesmo tempo que alivia o fardo financeiro de manter ambos os sistemas. Com o tempo, o governo pode retirar-se progressivamente do envolvimento directo na saúde, focando-se em fornecer uma rede de segurança para aqueles que não podem pagar por cuidados privados.
Incentivar a concorrência no mercado de saúde é outro passo crítico. Ao reduzir as regulamentações que limitam os prestadores privados, o mercado pode tornar-se mais competitivo, reduzindo os custos e melhorando a qualidade do serviço. Além disso, promover a inovação através da desregulamentação permite que os prestadores de saúde desenvolvam novos tratamentos e serviços que melhor atendam às necessidades da população.
Economia: Adoptar Princípios de Laissez-Faire e Reforma Fiscal
Um princípio central do minarquismo é a crença de que a economia funciona melhor quando livre de intervenção governamental excessiva. Na transição para um estado mínimo, é crucial reduzir as regulamentações em todos os sectores. Ao permitir que as forças de mercado ditem as actividades económicas, as empresas podem operar de forma mais eficiente, responder mais rapidamente às demandas dos consumidores e fomentar a inovação.
A reforma fiscal é outro aspecto crítico desta transição. Conforme delineado no capítulo anterior, a redução do gasto público permite uma correspondente redução nos impostos. O objectivo é implementar impostos mais simples e baixos que financiem apenas as funções essenciais do governo, como defesa, policiamento e o sistema judicial. Um sistema tributário mais simples não só reduz o fardo financeiro sobre indivíduos e empresas, mas também elimina a complexidade e ineficiências associadas a um código tributário inflado.
Além disso, proteger os direitos de propriedade é fundamental para uma economia próspera. Garantir uma estrutura legal robusta que defenda a propriedade privada e faça cumprir os contratos criará um ambiente estável para o investimento e o empreendedorismo. Esta base legal é vital para incentivar o crescimento económico numa sociedade minarquista.
Estado Social: Passar de Programas Governamentais para Apoio Voluntário
A assistência social é outra área onde a transição para um estado mínimo exige um planeamento cuidadoso. O objectivo é eliminar gradualmente os programas sociais fornecidos pelo governo e substituí-los por caridade privada, apoio comunitário e auto-suficiência.
Uma abordagem é promover e incentivar a ajuda voluntária através de benefícios fiscais para doações de caridade. Incentivar o crescimento de organizações privadas e instituições de caridade para apoiar os necessitados pode reduzir a dependência da acção social governamental. Isso não só capacita as comunidades a cuidarem de si mesmas, mas também fomenta um senso de solidariedade e responsabilidade compartilhada.
À medida que os programas sociais governamentais são eliminados, a promoção da literacia financeira e da auto-suficiência torna-se essencial. Ao fornecer educação e recursos para ajudar os indivíduos a gerirem as suas finanças e planear o futuro, uma sociedade minarquista pode garantir que os cidadãos estão preparados para prosperar sem o apoio governamental extensivo.
Educação: Expandir a Escolha e Reduzir o Controle Governamental
A educação é uma área crítica onde os princípios do minarquismo podem ser aplicados com grande efeito. Em muitas democracias sociais, os sistemas de educação pública dominam, com escolas privadas e opções de ensino doméstico disponíveis, mas muitas vezes financeiramente inacessíveis para muitas famílias. Para transitar para uma abordagem mais minarquista, o papel do governo na educação deve ser reduzido, enquanto as opções para pais e estudantes são ampliadas.
Uma estratégia eficaz é introduzir vouchers ou créditos fiscais para escolas privadas e ensino doméstico. Isso permite que os pais escolham a melhor opção educacional para os seus filhos, seja uma escola pública, instituição privada ou ensino doméstico, sem serem penalizados financeiramente por optarem por sair do sistema público.
Ao reduzir o controle governamental sobre a educação e permitir mais concorrência, a qualidade da educação provavelmente melhorará à medida que as escolas competem para atrair estudantes. Esse ambiente competitivo promove a inovação nos métodos de ensino, desenvolvimento curricular e resultados gerais dos alunos. Com o tempo, o governo pode reduzir o seu envolvimento, focando-se em garantir que os padrões básicos sejam cumpridos, em vez de gerenciar directamente as escolas.
Defesa e Manutenção da Ordem: Foco em Funções Essenciais
Em uma sociedade minarquista, o papel do governo é limitado às suas funções mais essenciais, sendo a defesa e a manutenção da ordem entre as mais cruciais. No entanto, mesmo dentro dessas áreas, há espaço para reduzir o excesso de intervenção governamental e introduzir alternativas privadas.
Para a defesa nacional, o governo deve manter uma força militar forte e capaz para proteger a soberania da nação. No entanto, isso não impede o uso de contratantes privados para funções não combatentes, como logística, manutenção e serviços de apoio. Ao terceirizar essas funções, o governo pode concentrar os seus recursos nas necessidades essenciais de defesa, enquanto reduz os gastos gerais.
Na aplicação da lei, o governo deve priorizar a manutenção da ordem pública e garantir a justiça através de um sistema legal justo. No entanto, certas funções não essenciais, como serviços de segurança, podem ser terceirizadas para empresas privadas onde for viável. Isso permite que a polícia e o judiciário se concentrem em suas responsabilidades primárias, ao mesmo tempo que encorajam um uso mais eficiente dos recursos.
Desafios e Aproveitamento das Oportunidades do Minarquismo
A transição para um sistema minarquista, como delineado em capítulos anteriores, envolve uma abordagem cuidadosa e sustentada para reduzir a intervenção do governo e os gastos públicos. No entanto, essa jornada não está isenta de desafios. Este capítulo explora os possíveis obstáculos que um país pode enfrentar durante a transição para o minarquismo e como superá-los. Além disso, destaca as oportunidades únicas que surgem com a adopção de um estado mínimo. Ao abordar esses desafios de forma ponderada e aproveitar as oportunidades de forma eficaz, um país pode garantir uma transição bem-sucedida que beneficie os seus cidadãos e a sua economia.
Superando a Resistência Pública e os Equívocos
Um dos principais desafios na transição para o minarquismo é superar a resistência pública e os equívocos sobre o que um estado mínimo implica. Muitas pessoas, especialmente aquelas habituadas à intervenção governamental nas suas vidas, podem recear que a redução do papel do estado as deixe vulneráveis ou sem serviços essenciais.
Para lidar com essas preocupações, é fundamental uma comunicação clara e educação. O governo e os defensores do minarquismo devem articular os benefícios de um estado mínimo, como maior liberdade pessoal, redução de impostos e serviços mais eficientes. Campanhas públicas, debates e fóruns podem ajudar a dissipar mitos e fornecer exemplos concretos de como a transição será gerida para garantir que ninguém seja deixado para trás. Destacar transições bem-sucedidas noutras regiões ou países, ou apontar alternativas privadas que já prosperam, pode ajudar a construir confiança no processo.
Também é importante envolver o público no processo de tomada de decisões, garantindo que as suas vozes sejam ouvidas e que a transição reflicta as necessidades e os desejos da população. Ao promover um sentido de propriedade e participação, o governo pode mitigar a resistência e construir um apoio alargado para a mudança para o minarquismo.
Garantindo uma Transição Suave em Serviços Essenciais
À medida que o governo reduz o seu papel em áreas como saúde, educação e apoio social, garantir que as alternativas privadas estejam prontas para atender à procura é crucial. A transição deve ser gerida cuidadosamente para evitar interrupções nos serviços essenciais.
Uma estratégia é implementar transições graduais, onde os serviços públicos reduzem gradualmente o seu âmbito à medida que os prestadores privados expandem as suas ofertas. Esta abordagem faseada permite ajustes conforme necessário e garante que não surjam lacunas nos serviços. Por exemplo, na área da saúde, os hospitais públicos podem começar a fazer parcerias com entidades privadas para partilhar responsabilidades, com um calendário claro para que o sector privado assuma totalmente o controlo.
Outro ponto importante a considerar é a acessibilidade. Para evitar desigualdade na prestação de serviços, é vital garantir que as alternativas privadas permaneçam acessíveis e que existam mecanismos, como subsídios ou preços escalonados, para apoiar aqueles que não podem pagar pelas opções privadas de imediato. Esta abordagem está alinhada com o objectivo de reduzir os gastos públicos, garantindo que os serviços essenciais permaneçam disponíveis para todos os cidadãos.
Desigualdade Económica
Uma preocupação comum com a redução da intervenção governamental é o potencial aumento da desigualdade económica. Críticos do minarquismo frequentemente argumentam que, sem programas de apoio do estado, a diferença entre ricos e pobres poderia aumentar. Abordar este desafio requer uma combinação de soluções orientadas pelo mercado e sistemas de apoio comunitário.
Uma forma de mitigar a desigualdade é promovendo uma economia vibrante e competitiva, onde as oportunidades de progresso estejam disponíveis para todos. À medida que as regulamentações governamentais diminuem, as barreiras ao empreendedorismo e à criação de negócios são reduzidas, permitindo que mais pessoas participem na economia e gerem riqueza. Além disso, promover a educação e a formação de competências através de iniciativas privadas pode ajudar a garantir que os indivíduos estejam preparados para ter sucesso num mercado mais livre.
Organizações de caridade privadas e grupos comunitários também desempenham um papel crucial no apoio àqueles que, de outra forma, poderiam ficar desamparados. Ao incentivar uma cultura de filantropia e ajuda mútua, uma sociedade minarquista pode fornecer redes de segurança sem depender de programas extensivos de assistência governamental. Incentivos fiscais para doações de caridade podem fortalecer ainda mais este sector, garantindo que a ajuda esteja disponível para aqueles que necessitam.
Estabilidade Económica
Outro desafio na transição para o minarquismo é manter a estabilidade económica, especialmente em tempos de crise. Num sistema onde a intervenção governamental é mínima, mecanismos alternativos devem estar em vigor para prevenir e responder a choques económicos.
Uma abordagem é promover o desenvolvimento de instituições financeiras privadas que possam fornecer suporte durante recessões. Por exemplo, esquemas de seguros privados, fundos de investimento e modelos de cooperativas bancárias podem oferecer segurança financeira sem a necessidade de resgates governamentais. Incentivar práticas financeiras responsáveis e promover um sector privado resiliente são essenciais para manter a estabilidade numa economia minarquista.
O comércio internacional e a cooperação também podem desempenhar um papel estabilizador. Ao entrar em relações comerciais abertas e mutuamente benéficas, um país minarquista pode diversificar a sua economia e reduzir a sua vulnerabilidade a choques domésticos. Além disso, manter uma política monetária flexível e adaptável, possivelmente através de sistemas financeiros descentralizados, pode ajudar a amortecer o impacto das flutuações económicas globais.
Oportunidades para Inovação e Crescimento
Embora os desafios da transição para o minarquismo pareçam significativos, as oportunidades que esta apresenta para inovação e crescimento são igualmente atraentes. Um estado mínimo cria um ambiente onde o empreendedorismo e a criatividade podem prosperar, livres das restrições de regulamentações pesadas e da supervisão burocrática.
À medida que o governo se retira de áreas como regulamentação da indústria e serviços públicos, as empresas privadas são incentivadas a inovar e encontrar formas mais eficientes de atender às necessidades dos consumidores. Isto pode levar a avanços em tecnologia, saúde, educação e outros sectores que melhoram a qualidade de vida e impulsionam o crescimento económico.
Além disso, a redução de impostos e dos gastos governamentais liberta recursos para que indivíduos e empresas invistam em novos empreendimentos. Com mais rendimento disponível e menos burocracia, as pessoas são incentivadas a seguir as suas ideias empreendedoras, levando a uma economia mais dinâmica e competitiva. Isto, por sua vez, cria empregos, aumenta a produtividade e promove uma cultura de auto-suficiência e inovação.
A transição para um sistema minarquista apresenta tanto desafios como oportunidades. Ao abordar as preocupações públicas, garantir uma transição suave nos serviços essenciais, enfrentar a desigualdade económica e manter a estabilidade, um país pode navegar com sucesso o caminho para um estado mínimo. Ao mesmo tempo, ao aproveitar as oportunidades para inovação, crescimento e maior liberdade pessoal, pode-se levar a uma sociedade mais dinâmica e próspera. Ao gerir cuidadosamente estes desafios e aproveitar as oportunidades, um sistema minarquista pode oferecer um futuro mais promissor, onde os indivíduos são livres para prosperar com mínima intervenção governamental.
Estudos de Caso e Exemplos Históricos
Embora nenhum país tenha adoptado plenamente o minarquismo na sua forma mais pura, várias nações implementaram políticas que se alinham de perto com os ideais de governo limitado e liberdade económica. Estes países fornecem estudos de caso valiosos que ilustram tanto os sucessos como os desafios de reduzir a intervenção do Estado. Ao examinar estes exemplos, podemos obter insights sobre como os princípios minarquistas podem ser aplicados na prática e os potenciais resultados dessas políticas.
Hong Kong: Um Modelo de Liberdade Económica
Historicamente, Hong Kong tem sido um exemplo de destaque de governo limitado e liberdade económica. Apesar das recentes mudanças políticas, a sua abordagem de longa data à governação oferece um estudo de caso valioso sobre a eficácia de um estado mínimo. Hong Kong é conhecida pelo seu sistema fiscal simples, com taxas baixas e complexidade mínima. Isto permitiu que empresas e indivíduos mantivessem mais dos seus rendimentos, impulsionando o crescimento económico e o investimento.
O compromisso de Hong Kong com o livre comércio é outro marco da sua abordagem. Com muito poucas barreiras comerciais, a região tornou-se um centro global de comércio, atraindo empresas de todo o mundo. A intervenção governamental nos negócios foi tradicionalmente mínima, permitindo que o sector privado prosperasse sem regulamentações excessivas. Estas políticas colocaram consistentemente Hong Kong no topo dos índices globais de liberdade económica, demonstrando os benefícios de uma abordagem de governo limitado.
No entanto, é importante reconhecer que, mesmo em Hong Kong, o equilíbrio entre liberdade económica e intervenção governamental tem sido sujeito a mudanças, especialmente nos últimos anos. Isto sublinha o desafio contínuo de manter um estado mínimo num ambiente político e económico dinâmico.
Singapura: Combina Eficiência com Governo Limitado
Singapura é frequentemente citada como uma história de sucesso pela sua combinação de liberdade económica e governação eficiente. Classificada em primeiro lugar no Índice de Liberdade Económica de 2023, Singapura cultivou um ambiente favorável aos negócios que atrai investimentos e promove a inovação. O seu sistema regulatório é conhecido por ser eficiente e simplificado, reduzindo os obstáculos burocráticos que frequentemente retardam a actividade económica em outros países.
Uma das estratégias-chave de Singapura tem sido manter taxas de imposto baixas, concebidas para serem competitivas a nível global. Esta abordagem não só incentiva as empresas a estabelecer operações em Singapura, como também permite que os cidadãos mantenham mais do seu rendimento, promovendo a independência financeira.
Embora o governo de Singapura desempenhe um papel mais activo em certos sectores em comparação com um modelo minarquista puro, a ênfase do país na liberdade económica, regulamentação mínima e impostos baixos serve como um exemplo convincente de como um governo limitado pode impulsionar a prosperidade. Este equilíbrio entre envolvimento estatal e liberdade de mercado oferece um modelo que outros países podem aprender, mesmo que busquem um estado mais mínimo.
Suíça: Descentralização e Federalismo
A Suíça é conhecida pela sua estrutura governamental descentralizada, que distribui o poder entre os seus 26 cantões. Esta abordagem federalista limita a autoridade do governo central e capacita os governos locais a tomar decisões que melhor sirvam as suas comunidades. Esta descentralização alinha-se com os princípios minarquistas, garantindo que a governação esteja o mais próxima possível das pessoas, reduzindo o alcance do controlo centralizado.
A Suíça também ocupa uma posição elevada em liberdade económica, graças em parte ao seu ambiente favorável aos negócios e regulamentação limitada. O sistema fiscal competitivo do país e o seu sector financeiro estável fizeram dele um centro global para bancos e investimentos.
A abordagem da Suíça demonstra como um país pode combinar governo limitado com uma governação local forte, proporcionando uma alta qualidade de vida enquanto mantém a liberdade económica. Este equilíbrio entre autonomia local e estabilidade nacional oferece lições valiosas para aqueles que defendem uma transição para o minarquismo.
Nova Zelândia: Desregulamentação e Privatização
A jornada da Nova Zelândia em direcção à redução da intervenção governamental começou com reformas significativas nas décadas de 1980 e 1990. O país abraçou a desregulamentação, removendo muitas das restrições sobre empresas e mercados financeiros. Estas mudanças abriram a economia, fomentando a concorrência e a inovação.
Além da desregulamentação, a Nova Zelândia realizou um esforço de privatização em larga escala, vendendo empresas estatais a investidores privados. Esta mudança reduziu o papel do governo na economia e aumentou a eficiência em sectores anteriormente dominados pela propriedade pública.
Classificada em quinto lugar no Índice de Liberdade Económica de 2023, a Nova Zelândia demonstra os benefícios de reduzir o controlo estatal sobre a economia. Embora o país ainda mantenha alguns serviços sociais, a sua abordagem à desregulamentação e privatização oferece um roteiro para outras nações que procuram implementar gradualmente os princípios minarquistas.
Estónia: Inovação Digital e Liberdade Económica
A Estónia destaca-se como um exemplo moderno de como a tecnologia pode apoiar a transição para um governo mais limitado. A adopção de serviços digitais pelo país reduziu significativamente a burocracia, facilitando a interação dos cidadãos e das empresas com o Estado. As iniciativas de governo electrónico da Estónia simplificam processos como a declaração de impostos, votação e registo de empresas, reduzindo a necessidade de uma grande força de trabalho governamental.
Além das suas inovações digitais, a Estónia implementou um imposto de renda único, que simplifica o sistema fiscal e alinha-se com os ideais minarquistas de justiça e simplicidade. Classificada em sexto lugar no Índice de Liberdade Económica de 2023, a Estónia mostrou como a adopção de tecnologia e políticas de mercado livre podem reduzir a intervenção governamental, mantendo um elevado nível de confiança e eficiência pública.
O exemplo da Estónia destaca o potencial das ferramentas digitais para melhorar a transição para um estado mínimo, tornando o governo mais eficiente e menos intrusivo na vida dos cidadãos.
Movimentos Modernos: A Ascensão de Sistemas Descentralizados e Bitcoin
Para além destes exemplos nacionais, os movimentos modernos em direcção à descentralização oferecem novas possibilidades para reduzir a intervenção do governo. Um dos desenvolvimentos mais notáveis nos últimos anos é a ascensão do Bitcoin. A moeda digital descentralizada desafia os sistemas financeiros tradicionais ao operar sem autoridade central, alinhando-se com os princípios minarquistas de redução do controlo estatal.
O Bitcoin oferece uma alternativa às moedas emitidas pelo governo, permitindo que indivíduos realizem transacções financeiras sem depender de bancos ou outras instituições regulamentadas pelo Estado. Esta inovação não só proporciona mais liberdade financeira, como também reduz a necessidade de supervisão governamental na economia. À medida que o Bitcoin continua a evoluir, pode desempenhar um papel significativo no apoio aos princípios do minarquismo a nível global.
Estes movimentos modernos, juntamente com os estudos de caso de países que adoptaram elementos de governo limitado, ilustram a relevância contínua das ideias minarquistas. Embora nenhum país tenha adoptado completamente o minarquismo, os sucessos e desafios destes exemplos oferecem insights valiosos para aqueles que procuram reduzir a intervenção governamental e promover a liberdade económica.
Conclusão
A jornada em direcção ao minarquismo oferece a promessa de uma sociedade onde a liberdade individual, a responsabilidade pessoal e a eficiência económica ocupam o centro do palco. Ao reduzir a intervenção governamental e focar nas funções essenciais, o minarquismo apresenta um caminho para uma sociedade mais dinâmica e inovadora. A transição, conforme delineado nos capítulos anteriores, exige um planeamento cuidadoso, uma implementação gradual e um compromisso em manter a estabilidade, enquanto se capacita o sector privado e as comunidades a assumirem papéis mais relevantes.
Fundamental para este processo é garantir que as alternativas privadas aos serviços governamentais não sejam apenas disponíveis, mas também competitivas, permitindo que os cidadãos beneficiem de impostos mais baixos e de um mercado mais ágil. Ao abraçar a desregulamentação, a descentralização e a privatização, e ao aproveitar ferramentas modernas, como plataformas digitais e uma moeda descentralizada e global como o Bitcoin, as nações podem reduzir a presença do estado, enquanto melhoram a qualidade dos serviços e das oportunidades para os seus cidadãos.
Os estudos de caso apresentados no capítulo anterior, desde Hong Kong até à Estónia, ilustram tanto os sucessos como os desafios de se mover em direcção a um estado mínimo. Estes exemplos fornecem lições valiosas para qualquer nação que considere tal transição, demonstrando que a liberdade económica e o governo limitado podem coexistir com prosperidade e estabilidade.
Obrigado por ter lido até aqui e por explorar comigo as ideias do minarquismo. Gostaria muito de ouvir as suas opiniões—estas ideias ressoam consigo? O que pensa sobre a possibilidade de uma transição para um estado mínimo? Quer concorde, discorde ou tenha perguntas, os seus comentários são valiosos.
Photo by Jon Tyson on Unsplash
-
 @ ac8bb9b0:70278acc
2024-12-11 20:10:29
@ ac8bb9b0:70278acc
2024-12-11 20:10:29Details
- ⏲️ Prep time: 15
- 🍳 Cook time: 1 hour 30 minutes
- 🍽️ Servings: 10
Ingredients
- 1 lb. ground beef
- 1 cup celery diced
- 1 cup carrots diced
- 1 medium onion diced
- 2 medium potatoes diced
- 5 cups beef broth
- 1 15 oz. can corn, drained
- 1 8 oz. can tomato sauce
- 1 28 oz. can diced tomatoes
- 1 teaspoon salt
- 1 teaspoon Italian seasoning
- 1 bay leaf
Directions
- In a large dutch oven (I used a 6-quart), over medium heat brown the ground beef until done. Spoon off the excess fat.
- Add the remaining ingredients and stir. Bring to a boil and reduce the heat. Allow to simmer for 1 to 1 ½ hours (with the lid on, but tilted so steam can release) or until the vegetables are tender.
- Remove the bay leaf and serve.
-
 @ fa984bd7:58018f52
2024-08-19 08:23:31
@ fa984bd7:58018f52
2024-08-19 08:23:31 -
 @ 20e17dd0:2ae504d7
2025-02-01 21:14:41
@ 20e17dd0:2ae504d7
2025-02-01 21:14:411. Hardware Selection
It is important to select adequately the hardware that will be used to build your Node. The Node will be running 24h /7 days and will countain your lightning channels. It is important to use high quality hardware and spend the extra dollars for it.
At the time of building my Node, there was a shortage of Raspberry Pi and I was looking for an optimal alternative. I have decided to go ahead and purchase a used Mac Mini (late 2012).
It is recommended NOT to purchase a Mac Mini newer than 2012 (i.e 2014 and up) because Apple started to solder the RAM to the Logic Board after 2012. The Mac Mini Late 2012 is the last model that is fully customizable with SSD and RAM upgrades.
Here is the list of hardware that will be used in this build:
- 2 x 8G DDR3L Sodim 1600Mhz 1.35V
- 1 x Mac Mini (Late 2012) 2.5Ghz
- 1 x Samsung Evo 870 1Tb SSD ^
^ Note: As discussed earlier, it is important to select hardware of quality. I had initially purchased a low cost 2Tb SSD but it failed while trying to download the Bitcoin blockchain.
2. Hardware Upgrade
To facilitate the upgrade of the hardware, you will need the proper tools to remove some T6 & T8 screws.
Here are the steps to dismount the few components of the Mac Mini to upgrade the hardware:
- Unplug the Mac Mini.
- Turn it upside down with the black cover facing up.
-
Put your thumbs in the 2 grooves of the cover and turn the piece counterclockwise.

-
Remove the cover.
- Remove 3 x T6 screws holding the fan.

- Lift the fan and disconnect the connector by pulling gently straight up the wires.
- Remove 1x T6 screw at the bottom of the shroud (black plastic piece on the left of the fan).

-
Remove the shroud by holding the top right part with your fingers and turning it clockwise.

-
Remove 4 x T8 screws of the grill WIFI cover.

- The top of the grill is mounted under the Mac Mini case. Lift gently the bottom of the grill and pull towards yourself to remove the grill.
- Move the grill aside, you do not have to disconnect the WIFI sensor, just be careful.
2.1 Upgrading the RAM
The RAM is visible and accessible from the moment you remove the cover. Simply release each RAM by releasing the clips on the side. Once disengaged, the RAM will spring in a 45-degree angle. Remove it and put back the upgraded RAM at a 45 degree angle and push it down for it to clip.
2.2 Upgrading the SSD
It is important to note that the Mac Mini has 2 SSD bay. They are referred to as the “upper bay” and “lower bay”. Since we have flipped the Mac Mini upside down to remove the bottom cover, the “upper bay” is located under the “lower bay”.
The “upper bay” is mounted with an expansion kit that holds the SSD in position whereas the “lower bay” SSD is simply resting on top of the “upper bay” SSD.
One important aspect is that the connecting cables for the “lower bay” and “upper bay” SSD are not the same. The “upper bay” SSD connects on the logic board on the right and the “lower bay” SSD cable connects on the left. Removing the “upper bay” SSD requires removing the logic board therefore requires more work. It is recommended to install the new SSD in the “lower” bay. Here are the 2 scenarios:
1.Your Mac Mini has already a Hard Drive installed in the “lower” bay. In that case insert a credit card under the HD and gently pry it upwards. You will be able to slide it out of the bay. The reason to pry it gently is because since there is no “upper” bay drive, The HD is being held in the air by 2 screws on the side that are aligned in 2 holes in the Mac Mini case. Once the HD is removed, transfer the connecting cable and the 2 screws to the new SSD. To put back the new SSD, it is easier to rotate the Mac Mini 90 degree and have the mounting holes at the bottom and use the gravity to get the 2 mounting screws in the holes. After, connect the connector to the logic board.
- Your Mac Mini has already a Hard Drive installed in the “upper bay”? Leave it there, you do not need mounting screws, but you need a new connecting cable. You will have to buy a “lower bay connector”. Once installed on the SSD, slide the SSD on top of the original one. The connector will plug on the logic board on the left of the “upper bay” SSD connector.
A good preparation would be to go in “Disk Utility” menu on MacOS and search for “upper” or “lower” position before starting to disassemble.
Reassemble everything and you are done.
-
 @ f0c7506b:9ead75b8
2024-12-08 09:05:13
@ f0c7506b:9ead75b8
2024-12-08 09:05:13
Yalnızca güçlü olanların hakkıdır yaşamak.
Güçlü olan ileri gider ve saflar seyrekleşir. Ama üç beş büyük, güçlü ve tanrısal kişi güneşli ve aydınlık gözleriyle o yeni, o vaat edilmiş ülkeye ulaşacaktır. Belki binlerce yıl sonra ancak. Ve güçlü, adaleli, hükmetmek için yaratılmış elleriyle hastaların, zayıfların ve sakatların ölüleri üzerinde bir krallık kuracaklardır. Bir krallık!
Benim aradığım insanların kendileri değil, sesleridir.
Duyguları körelmiş, çeşitli düşüncelere saplanmış kalabalık hiçbir zaman ilerlemenin taşıyıcısı olamaz, kendi küçüklüğünün o küflü içgüdüsüyle kalabalığın kin ve nefretle baktığı bir kişi, bir büyük kişi, iradesinin gösterdiği yolda kimsenin gözünün yaşına bakmaksızın ilahi bir güç ve bir zafer gülümsemesiyle yürüyebilir ancak.
Bizim soyumuz da sonsuz oluşum piramidinin doruk noktasını oluşturmaktan uzaktır. Bizler de mükemmelliğe ulaşmış değiliz. Bizler de henüz olgunlaşmadık.
Şairler sevgiye övgüler döşenir; doğrusu sevginin güçlü bir şey olduğu kesin. Hüneşin bir ışınıdır sevgi, aydınlatıp nurlandırır insanı der bazıları; bazıları da insanı esrikliğe sürükleyen bir zehri kendisinde barındırdığını söyler. Gerçekten de yol açtığı sonuçlar, bir hekimin ağır bir ameliyattan önce korkudan titreyen hastaya teneffüs ettirdiği güldürücü gazınkine benzer, içinde tepinip duran acıyı unutturur hastaya.
Önemli olan, hayatta hiç değilse bir kez kutsal bir ilkbaharın yaşanmasıdır; öyle bir bahar ki, insanın gönlünü ilerideki bütün günleri altın yaldızla kaplamaya yetecek kadar ışık ve parıltıyla doldursun.
Şu hayat denen şey kötü bir işçiliğin ürünü, acemilere göre bir şey. Bu kepaze yaşam uğruna insan nelere katlanmıyor ki!
Kendisine sadakatten ayrılmadığı, yalnızca kendisinin olan bir tek bu var: Yalnızlığı.
Sahildeki üstü tenteli hasır koltuklar arkasındaki yüksek, sessiz kum tepeleri içinde yürürsen, tenteler altındaki insanları göremezsin; ama birinin bir diğerine seslendiğini, bir başkasının gevezelik ettiğini, bir ötekinin güldüğünü işitir ve anlarsın hemen: bu insan şöyle şöyle biridir diyebilirsin. Onun hayatı sevdiğini, bağrında büyük bir özlem ya da acı barındırdığını, bu acının da sesini ağlamaklı kıldığını her gülüşünde hissedersin.
-
 @ be41636e:e55c4909
2025-02-01 18:51:52
@ be41636e:e55c4909
2025-02-01 18:51:52Will Quantum Computers Kill Bitcoin? The Truth May Surprise You
One of the biggest fears around Bitcoin is that quantum computers (QCs) will render it obsolete. But is this really a legitimate concern, or just another doomsday myth?
The Real Threat: Not All Quantum Computers Are Equal
First, let’s get one thing straight: quantum computers already exist. The first notable ones appeared in the 1990s, built by IBM and Stanford. So why hasn’t Bitcoin already been hacked? Because it’s not about whether quantum computers exist—it’s about how powerful they need to be.
Are All Bitcoin Addresses at Risk?
No! If you’ve entered Bitcoin after 2010 or use a wallet backed up with 12 or 24 words (BIP-39, introduced in 2013), your funds are safe from quantum threats for a very long time—centuries, at least.
But why?
Understanding How Bitcoin’s Security Works
Bitcoin security is based on private keys. (These are represented by the 12-24 words you write down when setting up a wallet.) From this private key, a public key is created. In Bitcoin’s early days, people shared public keys directly to receive payments. But in 2010, Bitcoin introduced an extra layer of security: hashed addresses.
Now, instead of sharing your public key, your wallet generates a Bitcoin address, which is actually a hash of your public key. This adds an extra step for an attacker: before they can find your private key, they must first break the hash to reveal your public key.
Two Steps to Breaking Bitcoin
To steal Bitcoin using quantum computing, an attacker must:
- Break the hash (Bitcoin address → public key) using Grover’s algorithm.
- Break the elliptic curve cryptography (public key → private key) using Shor’s algorithm.
Where Do Quantum Computers Stand Today?
Let’s put things in perspective. Google’s Willow processor, which made headlines recently, has 105 physical qubits. But breaking Bitcoin’s elliptic curve cryptography (step 2 above) requires about 2,330 logical qubits, running for minutes to hours.
So how does 105 physical qubits compare to 2,330 logical qubits? It’s not even in the same league. To get 2,330 logical qubits, we'd likely need millions of physical qubits—a technology that is still decades away.
Now, even if we magically reached 2,330 logical qubits tomorrow, that only breaks public keys. It still wouldn't be enough to break Bitcoin addresses (step 1), which would take centuries with current quantum algorithms.
Who Should Be Worried?
- People who used Bitcoin before 2010 and still have funds sitting in old public-key-based addresses (P2PK addresses). Their funds could be stolen in minutes to hours if a powerful enough quantum computer emerged.
- People who reuse addresses—this exposes the public key, making it vulnerable to a quantum attack, even when you are using more modern addresses. (Many wallets, including Trust Wallet, SafePal, Exodus, and Atomic Wallet, still allow this bad practice!)
Who Can Sleep Soundly?
- Anyone using modern Bitcoin addresses (P2PKH, SegWit, Taproot). Their addresses are hashed, meaning an attacker would need centuries to break the first layer of protection before even getting to the public key.
- Anyone moving their coins periodically—since modern Bitcoin wallets generate new addresses for each transaction, public keys remain hidden.
The Concrete Wall Analogy
Think of your Bitcoin private key as being locked inside a massive vault. The first layer of protection is your Bitcoin address, which acts like a thick concrete wall. Cracking through this wall with current quantum algorithms would take centuries. Even if someone managed to break through, they would still face a second, much thinner barrier—your public key. This one would take only minutes to hours to breach. But by then, Bitcoin security upgrades would likely already be in place, leaving attackers empty-handed.
But What If We Make a Huge Quantum Leap?
Yes, it’s possible that new quantum algorithms emerge, or that quantum hardware advances faster than expected. But Bitcoin’s development community isn’t sitting idle, waiting to get wrecked. There are already proposals for quantum-resistant Bitcoin addresses, and they can be implemented before quantum computers reach a dangerous level.
The Bottom Line
🚀 Quantum computers won’t kill Bitcoin anytime soon.
📌 If you’re using a modern Bitcoin wallet, your funds are safe from quantum threats for the foreseeable future.
📌 If you reuse addresses, stop! It exposes your public key and makes you vulnerable much sooner.
📌 Bitcoin developers are already preparing for a quantum-resistant future.
So, no, quantum computers won’t be the end of Bitcoin. But they might be the end of bad security practices! 🔐
-
 @ 65912a7a:5dc638bf
2024-12-08 05:33:02
@ 65912a7a:5dc638bf
2024-12-08 05:33:02Chef's notes
This is my late partner's award winning Cajun rice & beans recipe. It's an updated take on the traditional Cajun comfort food.
Chef Darin was a classically trained chef who spent 30+ years in the kitchen perfecting his recipes, and delivering authentic Cajun and Creole food to his patrons. This is a 5-star dish that will earn the respect of the most discerning Cajun afficionado. You won't be disappointed.
I suggest making this recipe exactly as directed the first time, and then make whatever adjustments you want for future batches. Also, don't cheap out on the Andouille. No Johnsonville or Hillshire Farms. Chef Aidelle's is a good choice, as is Silva's from Whole Foods. They cost a few extra bucks, but it's absolutely worth it.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 3 hours
- 🍽️ Servings: 12
Ingredients
- 16oz small red beans, dry
- 2 cups long grain white rice
- 14-16oz andouille sausage, sliced
- 8oz ham, cubed
- 1 large yellow onion, chopped
- 1 green bell pepper, chopped
- 2-3 stalks celery, chopped
- 2 tbsp garlic (12 cloves), minced
- 7 cups water
- ¼ cup olive oil
- 2 large bay leaves
- 1 tbsp parsley, dried
- 1 tsp thyme, dried
- 1 tsp Cajun seasoning
- ½ tsp cayenne pepper, dried
- ¼ tsp sage, rubbed
- 1½ tsp salt (more or less to taste)
Directions
- Soak beans in a large pot of water overnight.
- Heat oil in a large stockpot over medium heat. Cook onion, bell pepper, celery, garlic in olive oil for 3 to 4 minutes (until onion is translucent).
- Add beans, bay leaves, parsley, thyme, salt, MSG, Cajun seasoning, cayenne pepper, Sage, and water. Stir, bring to a boil, and then reduce heat to medium-low (btwn 2-3). Cover and simmer for 2½ hours.
- Remove bay leaves. Mash some of the beans. Stir Andouille and ham into beans, and simmer uncovered for an additional 30 minutes.
- Meanwhile, prepare the rice. Bring water and rice to a boil in a saucepan. Reduce heat, cover, and simmer for 20 minutes.
- Serve beans over steamed white rice.
-
 @ b17fccdf:b7211155
2025-02-01 18:41:27
@ b17fccdf:b7211155
2025-02-01 18:41:27Next new resources about the MiniBolt guide have been released:
- 🆕 Roadmap: LINK
- 🆕 Dynamic Network map: LINK
- 🆕 Nostr community: LINK < ~ REMOVE the "[]" symbols from the URL (naddr...) to access
- 🆕 Linktr FOSS (UC) by Gzuuus: LINK
- 🆕 Donate webpage: 🚾 Clearnet LINK || 🧅 Onion LINK
- 🆕 Contact email: hello@minibolt.info
Enjoy it MiniBolter! 💙
-
 @ be41636e:e55c4909
2025-02-01 18:35:06
@ be41636e:e55c4909
2025-02-01 18:35:06One of the biggest fears around Bitcoin is that quantum computers (QCs) will render it obsolete. But is this really a legitimate concern, or just another doomsday myth?
The Real Threat: Not All Quantum Computers Are Equal
First, let’s get one thing straight: quantum computers already exist. The first notable ones appeared in the 1990s, built by IBM and Stanford. So why hasn’t Bitcoin already been hacked? Because it’s not about whether quantum computers exist—it’s about how powerful they need to be.
Are All Bitcoin Addresses at Risk?
No! If you’ve entered Bitcoin after 2010 or use a wallet backed up with 12 or 24 words (BIP-39, introduced in 2013), your funds are safe from quantum threats for a very long time—centuries, at least.
But why?
Understanding How Bitcoin’s Security Works
Bitcoin security is based on private keys. (These are represented by the 12-24 words you write down when setting up a wallet.) From this private key, a public key is created. In Bitcoin’s early days, people shared public keys directly to receive payments. But in 2010, Bitcoin introduced an extra layer of security: hashed addresses.
Now, instead of sharing your public key, your wallet generates a Bitcoin address, which is actually a hash of your public key. This adds an extra step for an attacker: before they can find your private key, they must first break the hash to reveal your public key.
Two Steps to Breaking Bitcoin
To steal Bitcoin using quantum computing, an attacker must:
- Break the hash (Bitcoin address → public key) using Grover’s algorithm.
- Break the elliptic curve cryptography (public key → private key) using Shor’s algorithm.
Where Do Quantum Computers Stand Today?
Let’s put things in perspective. Google’s Willow processor, which made headlines recently, has 105 physical qubits. But breaking Bitcoin’s elliptic curve cryptography (step 2 above) requires about 2,330 logical qubits, running for minutes to hours.
So how does 105 physical qubits compare to 2,330 logical qubits? It’s not even in the same league. To get 2,330 logical qubits, we'd likely need millions of physical qubits—a technology that is still decades away.
Now, even if we magically reached 2,330 logical qubits tomorrow, that only breaks public keys. It still wouldn't be enough to break Bitcoin addresses (step 1), which would take centuries with current quantum algorithms.
Who Should Be Worried?
- People who used Bitcoin before 2010 and still have funds sitting in old public-key-based addresses (P2PK addresses). Their funds could be stolen in minutes to hours if a powerful enough quantum computer emerged.
- People who reuse addresses—this exposes the public key, making it vulnerable to a quantum attack, even when you are using more modern addresses. (Many wallets, including Trust Wallet, SafePal, Exodus, and Atomic Wallet, still allow this bad practice!)
Who Can Sleep Soundly?
- Anyone using modern Bitcoin addresses (P2PKH, SegWit, Taproot). Their addresses are hashed, meaning an attacker would need centuries to break the first layer of protection before even getting to the public key.
The Concrete Wall Analogy
Think of your Bitcoin private key as being locked inside a massive vault. The first layer of protection is your Bitcoin address, which acts like a thick concrete wall. Cracking through this wall with current quantum algorithms would take centuries. Once one breaks through this wall, they would face a second wall, which is a much thinner barrier—your public key. This one would take only minutes to hours to breach.
But What If We Make a Huge Quantum Leap?
Yes, it’s possible that new quantum algorithms emerge, or that quantum hardware advances faster than expected. But Bitcoin’s development community isn’t sitting idle, waiting to get wrecked. There are already proposals for quantum-resistant Bitcoin addresses, and they can be implemented before quantum computers reach a dangerous level.
The Bottom Line
🚀 Quantum computers won’t kill Bitcoin anytime soon.
📌 If you’re using a modern Bitcoin wallet, your funds are safe from quantum threats for the foreseeable future.
📌 If you reuse addresses, stop! It exposes your public key and makes you vulnerable much sooner.
📌 Bitcoin developers are already preparing for a quantum-resistant future.
So, no, quantum computers won’t be the end of Bitcoin. But they might be the end of bad security practices! 🔐
-
 @ 3bf0c63f:aefa459d
2024-12-06 20:37:26
@ 3bf0c63f:aefa459d
2024-12-06 20:37:26início
"Vocês vêem? Vêem a história? Vêem alguma coisa? Me parece que estou tentando lhes contar um sonho -- fazendo uma tentativa inútil, porque nenhum relato de sonho pode transmitir a sensação de sonho, aquela mistura de absurdo, surpresa e espanto numa excitação de revolta tentando se impôr, aquela noção de ser tomado pelo incompreensível que é da própria essência dos sonhos..."
Ele ficou em silêncio por alguns instantes.
"... Não, é impossível; é impossível transmitir a sensação viva de qualquer época determinada de nossa existência -- aquela que constitui a sua verdade, o seu significado, a sua essência sutil e contundente. É impossível. Vivemos, como sonhamos -- sozinhos..."
- Livros mencionados por Olavo de Carvalho
- Antiga homepage Olavo de Carvalho
- Bitcoin explicado de um jeito correto e inteligível
- Reclamações
-
 @ 8f69ac99:4f92f5fd
2024-08-16 16:12:36
@ 8f69ac99:4f92f5fd
2024-08-16 16:12:36O comunismo, tal como idealizado por Karl Marx e Friedrich Engels, prometia uma sociedade utópica, livre de divisões de classe, onde os recursos seriam partilhados de forma equitativa e o Estado acabaria por desaparecer. No entanto, apesar de várias tentativas de implementar esta ideologia em diferentes países, o sonho do "verdadeiro" comunismo nunca se concretizou. Uma das principais razões para esse fracasso reside no factor humano—um aspecto que Marx e Engels não consideraram completamente no seu quadro teórico. Além disso, a implementação de controlos de preços, frequentemente utilizada em economias comunistas e planificadas centralmente, tem repetidamente levado a consequências económicas não intencionais e frequentemente desastrosas. Este artigo explora os desafios inerentes à concretização do verdadeiro comunismo e o papel que os controlos de preços desempenham em minar os próprios objectivos que deveriam apoiar.
A Visão do Verdadeiro Comunismo
O Quadro Ideológico de Marx e Engels
Karl Marx e Friedrich Engels, nas suas obras revolucionárias, como "O Manifesto Comunista" e "O Capital", lançaram as bases para o que se tornaria uma das ideologias mais influentes dos séculos XIX e XX: o comunismo. No seu cerne, o comunismo é uma crítica ao capitalismo, que Marx e Engels viam como um sistema intrinsecamente explorador, onde a burguesia (a classe capitalista) se enriquece ao extrair mais-valia do proletariado (a classe trabalhadora). A sua visão para o futuro era a de uma revolução que derrubasse as estruturas capitalistas, levando à criação de uma sociedade sem classes e sem Estado.
Nesta sociedade ideal, os meios de produção—fábricas, terras e recursos—seriam colectivamente detidos pelo povo. O motivo do lucro, que impulsiona o capitalismo, seria substituído pela produção para uso, garantindo que bens e serviços fossem distribuídos com base na necessidade, em vez da capacidade de pagar. O Estado, que Marx e Engels viam como um instrumento de opressão de classe, acabaria por "definhar" à medida que a necessidade de estruturas de poder coercitivo desaparecesse. Isto levaria a uma sociedade onde a igualdade, a cooperação e a propriedade comunal seriam a norma, e a exploração de uma classe por outra deixaria de existir.
Marx e Engels acreditavam que esta transição do capitalismo para o comunismo seria alcançada através de uma série de etapas. Inicialmente, a classe trabalhadora tomaria o poder político e estabeleceria uma "ditadura do proletariado", onde o Estado serviria para desmantelar o sistema capitalista e redistribuir riqueza e recursos. Com o tempo, à medida que os vestígios do capitalismo fossem eliminados e as distinções de classe dissolvidas, o próprio Estado se tornaria desnecessário e gradualmente desapareceria, deixando para trás uma sociedade verdadeiramente comunista.
Embora esta visão fosse revolucionária e tenha inspirado muitos movimentos em todo o mundo, ela baseava-se em várias suposições—particularmente em relação à natureza humana e às dinâmicas sociais—que se revelariam problemáticas na prática.
O Factor Humano: O Que Marx e Engels Não Previram
Um dos erros críticos na teoria de Marx e Engels é a subestimação da complexidade do comportamento e das motivações humanas. A sua visão de uma sociedade harmoniosa e sem classes assume que, uma vez alterada a estrutura económica, a natureza humana se adaptaria em conformidade. No entanto, a realidade mostrou-se muito mais complicada.
Os seres humanos não são apenas actores económicos movidos por condições materiais. Eles também são motivados por ambições pessoais, desejos de poder e status, e pela necessidade de reconhecimento individual. Embora Marx e Engels reconhecessem o papel da luta de classes na formação da história, eles não consideraram plenamente o quão profundamente enraizadas estão as hierarquias sociais e as dinâmicas de poder, mesmo em sociedades que afirmam ter abolido as distinções de classe.
Em todas as tentativas de implementar o comunismo, novas elites surgiram, muitas vezes compostas por oficiais do partido e burocratas que detinham poder e privilégios significativos. Estas elites, longe de personificarem os ideais igualitários do comunismo, frequentemente perpetuaram as mesmas desigualdades que deveriam eliminar. A concentração de poder no Estado, que deveria ser uma medida temporária durante a transição do capitalismo, tornou-se entrincheirada e autoritária. Em vez de definhar, o Estado frequentemente cresceu em poder e opressão, à medida que aqueles no controle procuravam manter as suas posições.
Além disso, a abolição da propriedade privada, embora teoricamente destinada a eliminar a exploração, removeu muitos dos incentivos que impulsionam a inovação e a produtividade. Em economias comunistas, onde o emprego e as necessidades básicas eram garantidos independentemente do esforço individual, o absentismo, a ineficiência e a falta de motivação tornaram-se generalizados. O desejo humano de realização pessoal e recompensa, algo que Marx e Engels não abordaram completamente, desempenhou um papel significativo na estagnação económica que muitos sistemas comunistas experimentaram.
Outro aspecto crítico que Marx e Engels não previram é a importância da flexibilidade e adaptabilidade nos sistemas económicos. O planeamento económico centralizado, uma marca dos estados comunistas, frequentemente lutou para responder às mudanças nas condições económicas e nas exigências dos consumidores. Sem os mecanismos de feedback proporcionados pelos preços de mercado, os planificadores tiveram dificuldade em alocar recursos de forma eficiente. Esta rigidez levou a persistente escassez de bens, produtos de baixa qualidade e à incapacidade de satisfazer as necessidades da população—um cenário muito distante da abundância e igualdade prometidas pela ideologia comunista.
Em resumo, embora Marx e Engels tenham delineado uma visão convincente de uma sociedade livre da exploração e das desigualdades do capitalismo, subestimaram os desafios colocados pela natureza humana e pelas complexidades da organização social e económica. O factor humano—abrangendo as motivações individuais, a persistência das hierarquias sociais e a necessidade de sistemas económicos flexíveis e adaptáveis—tem consistentemente minado as tentativas de alcançar o "verdadeiro" comunismo. Esta falha tem sido uma razão fundamental pela qual o sonho de uma sociedade sem Estado e sem classes tem permanecido ilusório em todas as implementações reais da ideologia comunista.
Tentativas Históricas de Comunismo
Ao longo do século XX, várias nações tentaram implementar o comunismo com base nos princípios marxistas. Esses esforços resultaram numa ampla gama de resultados económicos e sociais, mas nenhum conseguiu alcançar a sociedade sem classes e sem Estado idealizada por Marx e Engels.
A União Soviética e a Europa de Leste
A União Soviética foi a primeira e a maior tentativa de implementar o comunismo. Estabelecida na sequência da Revolução Bolchevique de 1917, o Estado soviético rapidamente adoptou o planeamento económico centralizado e nacionalizou indústrias. Sob o comando de Joseph Stalin, a URSS embarcou numa rápida industrialização, com realizações significativas na indústria pesada e no poder militar. O modelo soviético foi posteriormente exportado para a Europa de Leste após a Segunda Guerra Mundial, onde os estados satélites adoptaram sistemas de planeamento centralizado semelhantes.
Embora a União Soviética tenha inicialmente registado alguns sucessos, particularmente na transformação de uma sociedade predominantemente agrária numa potência industrial, essas conquistas tiveram um custo significativo. A natureza rígida e centralizada do planeamento económico soviético levou a ineficiências generalizadas. A ausência de sinais de mercado dificultou a alocação eficaz de recursos, resultando em escassez crónica de bens de consumo e produtos de baixa qualidade. O controlo de preços foi uma ferramenta chave no sistema soviético, destinado a manter os bens básicos acessíveis, mas muitas vezes resultou em mercados distorcidos e actividade no mercado negro.
Politicamente, o regime soviético tornou-se cada vez mais repressivo. A concentração de poder no Partido Comunista criou uma nova classe de elite composta por burocratas e funcionários, minando os ideais igualitários do comunismo. A dissidência foi severamente reprimida, e a falta de competição política fez com que o sistema fosse resistente a reformas, mesmo perante problemas económicos crescentes. Na década de 1980, a economia soviética estava em estagnação, e as tentativas de reforma, como a Perestroika de Mikhail Gorbachev, chegaram tarde demais para salvar o regime. Em 1991, a União Soviética colapsou, e os seus estados satélites na Europa de Leste rapidamente abandonaram o comunismo em favor de reformas orientadas para o mercado.
China e Vietname: Reformas de Mercado e Capitalismo de Estado
A China apresenta um caso único na história do comunismo. Após o Partido Comunista chegar ao poder em 1949, a China inicialmente seguiu o modelo soviético de planeamento centralizado e controlo estatal da economia. No entanto, esta abordagem levou a resultados desastrosos, sendo o mais notável o Grande Salto em Frente, que resultou numa fome generalizada e na morte de milhões de pessoas. Reconhecendo a necessidade de mudança, a liderança chinesa, sob Deng Xiaoping, iniciou uma série de reformas de mercado no final da década de 1970 que transformaram profundamente a economia.
Essas reformas, frequentemente chamadas de "socialismo com características chinesas", introduziram mecanismos de mercado e permitiram a iniciativa privada, mantendo, no entanto, o controlo político do Partido Comunista. A economia da China experimentou um crescimento sem precedentes, com uma média de quase 10% de crescimento anual do PIB durante várias décadas. No entanto, esse sucesso foi alcançado à custa do abandono de muitos dos princípios fundamentais do marxismo. O sistema da China é melhor descrito como "capitalismo de estado", onde o estado mantém o controlo sobre indústrias-chave, mas as forças de mercado desempenham um papel significativo na economia mais ampla.
O Vietname seguiu um caminho semelhante. Após a Guerra do Vietname e a reunificação do país sob o domínio comunista, o Vietname inicialmente seguiu uma economia planeada centralmente. No entanto, como a China, também enfrentou dificuldades económicas, o que levou à introdução de reformas orientadas para o mercado na década de 1980, conhecidas como Đổi Mới. Essas reformas impulsionaram um rápido crescimento económico e tiraram milhões da pobreza, mas também marcaram um afastamento da ideologia comunista tradicional.
Tanto a China como o Vietname demonstram que o sucesso económico sob um governo comunista é possível quando os mecanismos de mercado são introduzidos. No entanto, esse sucesso representa uma desvio significativo da visão comunista original, destacando os desafios de alcançar o verdadeiro comunismo na prática.
Cuba: Um Legado Misto
A experiência comunista de Cuba oferece uma perspectiva diferente, focando-se mais em realizações sociais do que no sucesso económico. Desde a Revolução Cubana de 1959, o país tem mantido um governo comunista sob a liderança de Fidel Castro e seus sucessores. A economia de Cuba tem sido longamente caracterizada pelo planeamento centralizado e controlo estatal, com o controlo de preços desempenhando um papel significativo em manter os bens básicos acessíveis.
Apesar das suas dificuldades económicas, Cuba fez progressos notáveis em áreas como a saúde e a educação. O sistema de saúde do país, em particular, é frequentemente elogiado pela sua acessibilidade e resultados, com uma expectativa de vida e taxas de mortalidade infantil comparáveis às de nações muito mais ricas. A educação é outra área onde Cuba se destacou, alcançando altas taxas de alfabetização e amplo acesso à escolarização.
No entanto, esses sucessos sociais tiveram um custo de estagnação económica. Cuba classifica-se baixo em liberdade económica em comparação com outros países das Américas, e a sua economia tem sido marcada por escassez persistente de bens básicos, em parte devido aos controlos de preços que distorcem a dinâmica do mercado. O país também dependeu fortemente de apoio externo, particularmente de petróleo subsidiado de aliados como a União Soviética e, mais tarde, a Venezuela. À medida que esses apoios externos diminuíram, as dificuldades económicas de Cuba aprofundaram-se.
Politicamente, Cuba manteve um estado unipartidário, com pouca tolerância para a dissidência. Como outros estados comunistas, viu a emergência de uma nova classe de elite, com funcionários do partido e líderes militares a usufruírem de privilégios não disponíveis aos cidadãos comuns. Embora as conquistas sociais de Cuba sejam significativas, não foram suficientes para superar os desafios económicos inerentes ao seu sistema.
Ao examinar as tentativas históricas de comunismo, torna-se claro que, embora alguns estados comunistas tenham alcançado sucessos notáveis — seja na industrialização, nos serviços sociais ou no crescimento económico —, nenhum conseguiu criar a sociedade sem classes e sem Estado idealizada por Marx e Engels. O factor humano, as ineficiências económicas e as consequências não intencionais de políticas como os controlos de preços minaram consistentemente esses esforços. Seja através do colapso da União Soviética, das reformas de mercado na China e no Vietname, ou das lutas contínuas em Cuba, a história do comunismo é marcada pela tensão entre a ideologia e a realidade.
O Impacto Económico do Controle de Preços
Os controles de preços, frequentemente implementados em economias comunistas e planeadas centralmente, são ferramentas usadas pelos governos para regular os preços de bens e serviços essenciais. Embora estes controles sejam normalmente introduzidos com a intenção de proteger os consumidores, garantir a acessibilidade e manter a equidade social, eles frequentemente levam a distorções económicas significativas. Em sistemas comunistas, onde o controlo estatal sobre a economia é primordial, os controles de preços têm sido uma característica central da política económica. No entanto, as consequências desses controles têm sido muitas vezes prejudiciais, resultando em ineficiências de mercado, redução da inovação e encargos sociais e fiscais não intencionais.
Distorções na Oferta e na Procura
Uma das consequências económicas mais significativas dos controles de preços é a interrupção do equilíbrio natural entre a oferta e a procura. Em sistemas comunistas, os tectos de preços (preços máximos) são frequentemente estabelecidos em bens essenciais para garantir a acessibilidade. No entanto, quando os preços são mantidos artificialmente baixos, a procura normalmente excede a oferta, levando a escassez crónica. Este era um fenómeno comum na União Soviética, onde bens de consumo básicos como alimentos, vestuário e itens domésticos eram frequentemente escassos. A falta de sinais de mercado, como o aumento dos preços para indicar uma maior procura, impedia a alocação eficiente de recursos, exacerbando as carências.
Por outro lado, os "pisos" de preços (preços mínimos) podem levar a excedentes. Nos sectores agrícolas, por exemplo, a fixação de preços acima do nível de equilíbrio de mercado pode resultar em superprodução. Isto leva ao desperdício de recursos e ineficiências, pois o governo deve ou comprar o excesso de oferta ou deixá-lo desperdiçar. Estas distorções ilustram o desafio fundamental do planeamento central: sem os mecanismos autorreguladores de um mercado livre, as economias têm dificuldades em equilibrar eficazmente a produção com o consumo.
Redução do Investimento e da Inovação
Os controles de preços também podem ter um efeito desmotivador sobre o investimento e a inovação. Quando os governos impõem tectos de preços, eles frequentemente reduzem as margens de lucro para os produtores. Em economias comunistas, onde o Estado controla a maior parte da produção, isso pode desencorajar o investimento interno e a actividade empresarial. A ausência de incentivos baseados no mercado para a inovação leva à estagnação, pois há pouca motivação para melhorar a eficiência ou desenvolver novos produtos.
Esta falta de inovação era evidente na União Soviética e em outras economias planeadas centralmente, onde os avanços tecnológicos ficaram atrás dos países capitalistas. As indústrias que eram fortemente controladas por preços, como bens de consumo e produtos farmacêuticos, sofreram com baixa produtividade e tecnologia desactualizada. Em sectores como o farmacêutico, os controles de preços reduziram os incentivos para a investigação e desenvolvimento, potencialmente limitando futuras inovações médicas. O efeito a longo prazo desta redução do investimento é o menor crescimento económico e a diminuição da competitividade no cenário global.
Deterioração da Qualidade
Outra consequência dos controles de preços é a deterioração da qualidade. Quando os preços são estabelecidos demasiado baixos, os produtores frequentemente procuram maneiras de cortar custos para manter a rentabilidade. Isto resulta frequentemente em bens e serviços de menor qualidade. Em economias comunistas, onde a escolha do consumidor é limitada e a concorrência é suprimida, há pouca pressão sobre os produtores para manter altos padrões. O resultado é que os consumidores ficam com produtos inferiores, deteriorando ainda mais o padrão de vida.
Por exemplo, na União Soviética, o foco na quantidade em detrimento da qualidade na fabricação levou a produtos mal feitos que muitas vezes não atendiam às necessidades dos consumidores. Em sectores como a habitação, os controles de rendas mantinham os preços baixos, mas a qualidade do parque habitacional deteriorava-se, uma vez que havia pouco incentivo para a manutenção ou melhoria. Esta troca entre preços baixos e baixa qualidade destaca uma das falhas principais dos controles de preços na prática.
Mercados Negros e Economias Informais
As ineficiências criadas pelos controles de preços frequentemente levam ao surgimento de mercados negros, onde os bens são vendidos a preços superiores aos níveis estabelecidos pelo governo. Em economias comunistas, onde as carências são comuns, os mercados negros tornam-se um mecanismo crucial para obter bens escassos. Estes mercados ilegais minam o controlo do governo sobre a economia e criam uma economia paralela que opera fora do sistema oficial.
Na União Soviética e na Europa Oriental, os mercados negros prosperavam à medida que os consumidores procuravam aceder a bens que estavam indisponíveis ou eram de baixa qualidade nas lojas estatais. A existência destes mercados também destaca o fracasso dos controles de preços em atingir os seus objectivos pretendidos, pois as mesmas pessoas que deveriam beneficiar de preços baixos acabavam por pagar preços muito mais altos no sector informal.
Racionamento e Filas
Quando os controles de preços levam à escassez, os governos muitas vezes recorrem a sistemas de racionamento para distribuir os suprimentos limitados. O racionamento, embora assegure que todos recebam uma parte dos bens escassos, também introduz ineficiências e iniquidades. Filas longas para necessidades básicas tornaram-se uma visão comum em muitos países comunistas, com pessoas a gastar horas à espera de itens que frequentemente estavam em falta.
Este sistema não só desperdiçava tempo valioso, como também evidenciava as falhas do planeamento central. O racionamento e as filas são uma consequência directa dos controles de preços que impedem os mercados de se ajustarem naturalmente. Em vez de permitir que os preços subam e incentivem o aumento da produção, os governos mantêm preços artificialmente baixos, resultando em escassez crónica e frustração generalizada entre a população.
Encargo Fiscal e Consequências Sociais
Manter controles de preços frequentemente requer uma intervenção governamental significativa, incluindo subsídios aos produtores para compensar os custos dos preços baixos. Isto cria um encargo fiscal que pode sobrecarregar os orçamentos governamentais, especialmente em economias que já enfrentam ineficiências. Em alguns casos, o custo de manter os controles de preços pode superar os benefícios, levando a políticas económicas insustentáveis.
Além disso, os controles de preços podem levar a consequências sociais não intencionais. Embora sejam destinados a ajudar as populações mais vulneráveis, eles podem, por vezes, beneficiar aqueles que não precisam de assistência. Por exemplo, os controles de rendas destinados a proporcionar habitação acessível podem acabar por beneficiar indivíduos mais ricos que têm acesso a apartamentos com rendas controladas, enquanto os indivíduos de baixos rendimentos continuam a enfrentar dificuldades com a acessibilidade habitacional.
Além disso, os controles de preços podem empurrar a actividade económica para o sector informal, reduzindo as receitas fiscais e a supervisão regulatória. Esta informalidade enfraquece a capacidade do Estado de gerir a economia de forma eficaz e cria distorções adicionais.
Crescimento Económico a Longo Prazo e Impactos Específicos por Sector
A longo prazo, as distorções causadas pelos controles de preços podem levar a uma redução do crescimento económico. Ao interferir nos sinais de mercado, os controles de preços desencorajam o investimento, a inovação e a produtividade, todos essenciais para o desenvolvimento económico sustentado. Ao longo do tempo, isso pode resultar em estagnação, como visto em muitas economias comunistas onde o crescimento abrandou ou até mesmo retrocedeu.
Sectores específicos, como o farmacêutico e o agrícola, podem ser particularmente afectados pelos controles de preços. No sector farmacêutico, por exemplo, os tectos de preços podem reduzir o incentivo para as empresas investirem em investigação e desenvolvimento, potencialmente limitando futuras inovações médicas. Na agricultura, os pisos de preços podem levar à superprodução, desperdício e à necessidade de intervenções governamentais onerosas.
Os Benefícios a Curto Prazo e Potenciais Justificativas
Embora os controles de preços sejam geralmente vistos de forma negativa devido às suas consequências a longo prazo, podem haver alguns benefícios a curto prazo, especialmente em tempos de crise. Por exemplo, durante emergências, os controles de preços podem impedir a exploração de preços e garantir que bens essenciais permaneçam acessíveis às populações vulneráveis. Nestes casos, os controles de preços podem fornecer alívio temporário e proteger os consumidores de abusos.
No entanto, esses benefícios a curto prazo são muitas vezes superados pelos custos a longo prazo. Mesmo em situações de crise, os efeitos distorcionários dos controles de preços podem criar mais problemas do que resolvem, tornando-os uma ferramenta que deve ser usada com cautela.
Os controles de preços, embora destinados a proteger os consumidores e promover a equidade social, frequentemente levam a consequências económicas, de mercado e sociais não intencionais. Em sistemas comunistas, onde o controlo estatal sobre a economia é central, estes controles exacerbaram ineficiências, sufocaram a inovação e criaram uma série de resultados negativos, desde mercados negros até encargos fiscais. Embora possa haver situações onde os controles de preços sejam justificados a curto prazo, o seu impacto a longo prazo é geralmente prejudicial, minando os próprios objectivos que pretendem alcançar. Compreender o legado complexo dos controles de preços nas economias comunistas fornece lições valiosas para os formuladores de políticas que procuram equilibrar a estabilidade económica com a equidade social.
Consequências do Planeamento Centralizado e do Controlo de Preços
Autoritarismo e a Concentração de Poder
Uma das consequências políticas mais significativas do planeamento económico centralizado e do controlo de preços é a concentração de poder dentro do aparelho de Estado. Em teoria, o comunismo idealiza uma sociedade sem Estado, mas na prática, a implementação desses sistemas muitas vezes exige uma autoridade central forte para aplicar as directivas económicas e manter o controlo. Esta concentração de poder frequentemente leva ao autoritarismo, como se vê em numerosos regimes comunistas.
A centralização do poder permite que um pequeno grupo de líderes ou um único partido domine a vida política, muitas vezes suprimindo a oposição e restringindo as liberdades individuais. Sem pesos e contrapesos, estes regimes podem impor controlos rigorosos na economia e na sociedade, levando a uma repressão generalizada. A natureza autoritária desses governos é frequentemente justificada como um meio necessário para proteger a revolução e manter a ordem social, mas resulta na erosão dos princípios democráticos e na marginalização das vozes dissidentes.
Além disso, a concentração de poder no Estado mina os próprios ideais do comunismo. Em vez de uma sociedade sem classes, emerge uma nova classe dominante de funcionários do partido e burocratas, que gozam de privilégios e autoridade muito além do cidadão comum. Esta dinâmica de poder não só contradiz os objectivos igualitários do comunismo, como também perpetua a desigualdade dentro do sistema.
Desigualdade Social e o Surgimento de Novas Elites
Apesar do objectivo teórico de eliminar as classes sociais, os sistemas comunistas muitas vezes testemunham o surgimento de novas elites. Estas elites, compostas por líderes do partido, burocratas do Estado e oficiais militares, gozam de privilégios significativos que os distinguem da população em geral. Este fenómeno reflecte o desafio inerente de alcançar uma verdadeira igualdade num sistema onde o poder está concentrado nas mãos de poucos.
Em muitos casos, essas novas elites tornam-se enraizadas, criando um fosso entre os governantes e os governados que espelha as divisões de classe que o comunismo pretendia eliminar. Os privilégios e o poder desfrutados por essas elites frequentemente levam à corrupção e ao clientelismo, corroendo ainda mais a confiança pública no sistema. O descontentamento resultante entre a população pode levar a agitação, à medida que as pessoas percebem que a igualdade prometida é inatingível dentro da estrutura política existente.
A Supressão de Dissidência e Suas Consequências Económicas
A supressão da dissidência é uma característica marcante de muitos regimes comunistas, impulsionada pela necessidade de manter o controlo tanto sobre a economia quanto sobre a sociedade. Na prática, essa supressão assume várias formas, incluindo censura, vigilância e perseguição de oponentes políticos. A falta de competição política e de debate aberto sufoca a inovação e o feedback crítico, que são essenciais para uma economia dinâmica e adaptável.
Sem a capacidade de expressar preocupações ou propor políticas alternativas, os regimes comunistas muitas vezes lutam para responder de forma eficaz aos desafios económicos. A natureza rígida do planeamento centralizado, combinada com a supressão da dissidência, cria um ciclo vicioso em que os problemas são ignorados ou exacerbados, levando a um maior declínio económico. A ausência de dissidência também significa que as reformas necessárias são adiadas ou bloqueadas, à medida que as elites no poder priorizam os seus próprios interesses em detrimento do bem comum.
As consequências a longo prazo dessa supressão são profundas. Economias que carecem de flexibilidade para se adaptar às mudanças ou enfrentar ineficiências tornam-se estagnadas, levando a escassez, declínio na produtividade e uma queda no padrão de vida da população. A supressão da dissidência não só prejudica o desempenho económico, mas também enfraquece o tecido social, à medida que a confiança no governo se deteriora e as pessoas se sentem cada vez mais alienadas do sistema político.
Autoritarismo nas Sociedades Ocidentais: Uma Preocupação Crescente
Nos últimos anos, o aumento do autoritarismo nas sociedades ocidentais tornou-se uma preocupação crescente, manifestando-se através de várias tendências chave que ecoam algumas das dinâmicas observadas em regimes comunistas. Embora as democracias ocidentais estejam longe de um autoritarismo pleno, a concentração de poder, o crescimento das desigualdades sociais, o surgimento de novas elites e a supressão da dissidência sugerem um desvio preocupante dos princípios democráticos liberais.
Tem havido uma crescente centralização do poder em muitos países ocidentais, muitas vezes manifestada através do excesso de autoridade executiva e da expansão do poder presidencial ou do primeiro-ministro. O enfraquecimento dos mecanismos de pesos e contrapesos entre os ramos do governo e as tentativas de minar a independência judicial e o estado de direito são indicadores claros desta tendência. Esta concentração de poder corrói as normas e instituições democráticas ao longo do tempo, tornando mais difícil responsabilizar os líderes.
A crescente desigualdade económica tem alimentado o descontentamento e movimentos populistas em muitos países ocidentais. O aumento da disparidade de riqueza entre as elites e a população em geral, os salários estagnados para as classes média e trabalhadora e a redução da mobilidade social contribuíram para um crescente sentimento de desilusão com os sistemas democráticos tradicionais. Esta disparidade económica criou um terreno fértil para líderes com tendências autoritárias, que prometem resolver esses problemas, mas muitas vezes concentram ainda mais o poder.
O surgimento de novas estruturas de poder e grupos de elites, como os oligarcas da tecnologia e as elites empresariais ligadas à política, tem desafiado os mecanismos tradicionais de responsabilização democrática. Estas novas elites frequentemente exercem uma influência significativa sobre a informação, o discurso e a política, operando fora do alcance das instituições democráticas. Líderes populistas, que cultivam cultos de personalidade, também contribuem para esta mudança, enfraquecendo ainda mais os processos democráticos.
As preocupações sobre restrições à liberdade de expressão e ao debate aberto estão a crescer nas sociedades ocidentais. Embora não sejam equivalentes à censura autoritária vista em regimes comunistas, tendências como a "cultura do cancelamento", a vigilância governamental e a repressão de protestos têm um efeito dissuasor sobre o discurso aberto. A autocensura devido ao medo de retaliações online ou de consequências profissionais está a tornar-se mais comum, limitando a diversidade de pontos de vista no debate público.
A fé pública nos pilares centrais da democracia — governos, partidos políticos e funcionários eleitos — tem-se deteriorado em muitos países ocidentais. O cepticismo em relação aos meios de comunicação tradicionais e ao conhecimento especializado também aumentou, enquanto a integridade dos sistemas eleitorais é cada vez mais questionada. Esta perda de confiança cria oportunidades para líderes com tendências autoritárias ganharem apoio, enfraquecendo ainda mais as instituições democráticas.
O aumento do autoritarismo nas sociedades ocidentais, embora ainda não comparável ao controlo centralizado visto em regimes comunistas, sinaliza uma mudança preocupante em relação aos princípios da democracia liberal. A concentração de poder, o crescimento das desigualdades sociais, o surgimento de novas elites e a supressão da dissidência são todos factores que espelham os problemas enfrentados pelos estados comunistas históricos, embora em formas diferentes. Estas tendências, se não forem controladas, podem levar a uma erosão gradual das normas e instituições democráticas, minando os próprios alicerces de sociedades livres e abertas.
Os paralelos entre os desafios enfrentados pelos regimes comunistas e as tendências actuais nas democracias ocidentais destacam a importância de abordar essas questões subjacentes. Assim como o planeamento económico centralizado e o controlo de preços levaram a ineficiências e agitação social nos estados comunistas, a concentração de poder e a desigualdade no Ocidente ameaçam enfraquecer os sistemas democráticos por dentro. A supressão da dissidência e a diminuição da confiança nas instituições democráticas agravam ainda mais esses problemas, criando um ambiente onde o autoritarismo pode ganhar terreno.
É crucial que as sociedades ocidentais reforcem as normas e instituições democráticas. Isso envolve garantir que os pesos e contrapesos entre os ramos do governo sejam mantidos, protegendo a independência judicial e salvaguardando o estado de direito. Abordar a desigualdade económica também é essencial, pois é um dos principais impulsionadores dos sentimentos populistas e autoritários. Políticas que promovam a mobilidade social, salários justos e oportunidades económicas podem ajudar a reconstruir a confiança nos sistemas democráticos.
Além disso, promover um discurso público aberto e inclusivo é vital para prevenir a supressão da dissidência. Isso significa defender a liberdade de expressão, encorajar a diversidade de pontos de vista e resistir à tentação de silenciar opiniões impopulares através de pressão social ou governamental. Ao criar uma cultura que valoriza o debate e respeita perspectivas diferentes, as sociedades ocidentais podem resistir ao desvio para o autoritarismo.
Finalmente, reconstruir a confiança nas instituições democráticas exige transparência, responsabilização e capacidade de resposta por parte dos governos e líderes políticos. Os funcionários eleitos devem ser vistos a agir no interesse público, e as instituições devem ser percepcionadas como justas e eficazes. Restaurar a confiança nos sistemas eleitorais e nos meios de comunicação também é essencial para contrariar a ascensão do populismo e do autoritarismo.
Embora os desafios enfrentados pelas democracias ocidentais hoje sejam distintos dos que atormentaram os regimes comunistas, as dinâmicas subjacentes de poder, desigualdade e dissidência partilham algumas semelhanças preocupantes. Ao reconhecer e aprender com os fracassos do comunismo e ao abordar estas questões de frente, as sociedades ocidentais podem fortalecer as suas fundações democráticas e evitar o deslizamento para o autoritarismo.
Conclusão
Em resumo, os fracassos do verdadeiro comunismo e os efeitos prejudiciais dos controles de preços não são meramente notas de rodapé históricas, mas lições duradouras que continuam a ressoar hoje em dia. O colapso de inúmeros regimes comunistas e as persistentes dificuldades económicas em países que ainda tentam aderir aos princípios comunistas destacam as falhas fundamentais da ideologia. O factor humano—motivações individuais, o desejo de liberdade pessoal e as complexidades da governação—continuamente perturbam a visão utópica de uma sociedade sem classes e sem estado. O planeamento centralizado e os controles de preços, longe de criar igualdade e estabilidade, têm consistentemente levado a ineficiências económicas, escassez e regimes autoritários.
No entanto, estas lições não são apenas relevantes para o passado. As sociedades ocidentais de hoje enfrentam os seus próprios riscos, à medida que a esquerda se inclina cada vez mais para políticas autoritárias sob o disfarce de equidade e justiça social. A pressão por mais controlo estatal, juntamente com uma crescente intolerância à dissidência, espelha os estágios iniciais dos mesmos sistemas que levaram à tirania e ditadura no passado. O marxismo cultural, um movimento que busca remodelar a sociedade promovendo a ideologia marxista através das instituições culturais, está a ganhar força, particularmente no meio académico e nos meios de comunicação. Esta mudança ideológica está a corroer as fundações da liberdade individual e da liberdade económica que têm definido o Ocidente.
De forma alarmante, muitos jovens no Ocidente estão a louvar cada vez mais a ideologia marxista e o comunismo, muitas vezes sem compreender plenamente as realidades históricas desses sistemas. Esta tendência reflecte uma perigosa ignorância das atrocidades e do sofrimento que ocorreram sob os regimes comunistas. A romantização do comunismo ignora as duras verdades da história—a repressão, o colapso económico e a perda de liberdades pessoais que têm consistentemente acompanhado as tentativas de implementar esta ideologia.
É crucial manter-se vigilante contra estas tendências. As lições da história devem servir de alerta para aqueles que procuram replicar sistemas falhados. Embora a busca por uma sociedade mais justa e equitativa seja um objectivo nobre, não pode vir à custa das liberdades individuais e dos benefícios comprovados de uma economia baseada no mercado. As sociedades ocidentais devem proteger-se contra o fascínio do autoritarismo, seja na forma de comunismo declarado ou de formas mais subtis de controlo estatal. Garantir que a próxima geração compreenda a verdadeira natureza dessas ideologias é essencial para preservar as liberdades e a prosperidade que foram arduamente conquistadas ao longo de séculos.
Photo by Mick Haupt on Unsplash
-
 @ b17fccdf:b7211155
2025-02-01 18:28:39
@ b17fccdf:b7211155
2025-02-01 18:28:39
Check out the MiniBolt guide -> HERE <-
- Core guides
- System
- Bitcoin
- Bitcoin client (Bitcoin Core)
- Electrum server (Fulcrum)
- Desktop signing app (Sparrow Wallet)
- Blockchain explorer (BTC RPC Explorer)
- Lightning
- Lightning client (LND)
- Channel backup
- Web app (ThunderHub)
- Mobile app (Zeus)
- Bonus guides
- System bonus guide
- Dashboard & Appearance
- System Administration
- Install / Update / Uninstall common languages
- Databases
- Security
- Resilience
- Hardware
- Bitcoin bonus guides
- Electrum servers
- Signing apps
- Desktop
- Electrum Wallet Desktop
- Decentralized exchange
- Resilience
- Fun
- Testnet
- Payment processors
- Nostr bonus guides
- Relays
- Nostr relay
🏗️ Roadmap | 🌐 Dynamic Network map | 🔧 Issues | 📥 Pull requests | 🗣️ Discussions
By ⚡2FakTor⚡
Last updated: 22/12/2024
-
 @ fa984bd7:58018f52
2024-08-16 13:22:12
@ fa984bd7:58018f52
2024-08-16 13:22:12 -
 @ 434f9799:2d548c15
2024-08-12 13:39:00
@ 434f9799:2d548c15
2024-08-12 13:39:00一般来说, AdGuard 和 uBlock Origin 用的这种 Adblock Plus 风格的语法非常适合用于匹配 URL, 但是也会存在一些极其少见的情况必须要用到正则来匹配.
比如小红书的网页版, 主页使用参数来定位贴文频道位置:
https://www.xiaohongshu.com/explore?channel_id=homefeed_recommend
而具体的贴文则是:
https://www.xiaohongshu.com/explore/xxxxx?xsec_token=xxxxx
如果我们要清理小红书的贴文的参数, 一般就会写这样的规则:
text ||www.xiaohongshu.com/explore^$removeparam但是这条规则不仅仅匹配到了贴文, 还匹配到了主页, 导致主页用来定位的参数会在刷新后命中规则, 然后被清理.
除非去详细指定要清理的参数键, 类似这样:
text ||www.xiaohongshu.com/explore^$removeparam=/^(p1|p2|p3)=/这样能避开 channel_id 这样的主页参数被意外清理, 但是要最大限度清理参数非常繁琐(要显式指定每一个目标参数键), 当然也能排除特定的不需要清理(或者说不能)的参数键:
text ||www.xiaohongshu.com/explore^$removeparam=~channel_id但问题又来了, 我们没办法确定 "不能" 清理的参数键在意外匹配到的页面上是否与实际我们要清理的贴文的 URL 有重合, 很可能一个参数在首页就是重要的, 但在贴文中就是无用的(大多数社媒的贴文页面参数基本都是无用的).
另外一个例子是新浪微博, 用户资料页是:
https://weibo.com/u/xxxxx?tabtype=feed
微博贴文页是:
https://weibo.com/123456/XrcXwXTWX?from=xxxxx
如果要清理微博贴文 URL 中的全部参数而直接用这条规则:
text ||weibo.com/*/*^$removeparam很显然就会误伤到用户资料页的参数, 除非我们再写一条规则排除掉资料页:
text @@||weibo.com/u^$removeparam这种情况在用户侧实际上很多, 我们没办法观测黑盒里全部可以和不可以清理的参数, 只知道部分可以清理的和部分必要的参数. 这种匹配不精准的情况, 要么尽可能探明可以清理的参数精准指定, 要么尽量把规则的匹配范围限定在更加具体的 URL 上只保留部分必要的参数.
本来 "精准匹配" 就是写这类规则的首要考虑目标, 现在既然发现了容易被 "误伤" 的页面, 那就只能退而求其次选择更原始的正则匹配了:
-
小红书贴文:
text /https?:\/\/www\.xiaohongshu\.com\/explore\/[0-9a-z]+/$removeparam=~xsec_token -
微博贴文:
text /https?:\/\/weibo\.com\/[0-9]+\/[0-9a-zA-Z]+/$removeparam
使用正则需要更加注意匹配范围的精确性, AdGuard 里的正则匹配性能相对一般过滤器规则表达式要差(虽然人也没办法非常直观地感受到).
How to create your own ad filters | AdGuard Knowledge Base - Regular expressions support
-
 @ d57360cb:4fe7d935
2025-02-01 18:22:10
@ d57360cb:4fe7d935
2025-02-01 18:22:10What is life but a preparation for the grand finale.
Think of your life up to this point. You’ve been living in the midst of death whether you pay attention to it or not.
Your youth faded, the years go by, relationships fail, careers fail, people die, the ones close to you and those you hardly know. Civilizations wiped out, total species completely gone with no trace.
Here you are in the midst of death. A vortex of change wiping everything in its path. Creating space for the unknown and new. Nothing lasts, nothing stays the same, everything ends. Ending gives great significance to life.
How will you be in the presence of someone you love knowing they or you will vanish one day?
What wouldn’t you put off if you were aware your time was slipping and there’s nothing you can do.
What would you stop doing?
What would you let go of?
Who would you forgive?
Life comes with a bullet and it has your name on it. You don’t know when it’ll happen.
Don’t believe you ever have time it’s always a fantasy. Death will knock you on your feet when you least expect it.
Use death as a doorway to a deep meaningful life.
-
 @ 148755e6:450c107f
2024-12-05 10:09:32
@ 148755e6:450c107f
2024-12-05 10:09:32突然荒野に行きたくなったので行ってきたエントリーです
まずは練習。高尾山へ
Nostrは古今東西ありとあらゆるオフ会が生えており、
まるで荒野に行きたいという私の意志を完全に汲み取ったかのように「紅葉を見にいこうようオフ」がそこに生えていたので参加した。(しおんさんご主催ありがとうございました)
前半1時間くらいの坂道がマジきつかったです。前半キツすぎて後半足痛かった。。 終始人がいっぱいいて渋谷かと思った。
確かに道がかなり整備されていて、逆にコンクリート故に足が疲れたのかもしれない。隣の人は途中の急な坂道で足を滑らせてて、横で転倒事故が起きるかと思いました。
山頂に行っても人がたくさんいて、迷子になりかけた。あそこはスクランブル交差点や。 そして山頂の先にあるもみじ台まで歩くと人がまばらで、まったりして蕎麦食べたりしながら休憩して下山。
登りは暑くて汗かきましたが、山頂でまったりしてると汗も引いてきて少し冷えました。
下山はスイスイ。16時近くで結構暗かったので、冬の間は早めの登頂・下山がおすすめですね。
登り2時間・下り1時間半で概ね見込み通りって感じでした。
高尾山は登ってると景色が変わります。ちょっと開けた場所に出て下の街が見えたり、草木があったり、階段があったり、参道があったり。。そういう意味では退屈しない2時間でした。
ビギナー山とはいえ、革靴やヒールのある靴で登ってる人がいてびっくり。ツルッと滑ることあると思いますので、スニーカーで登ることをお勧めします。
舐めプしてたとはいえめちゃくちゃキツかったおもひで。
更なる練習。小浅間山へ
さて私は荒野に行きたいワケなのですが、高尾山に荒野はありませんでした。更なる練習として小浅間山へ。
前日(か前々日)に雪が降ったようで、山に雪が残っておりました。
それでも都内の汚れてべちゃっとした感じの雪ではなく、粉砂糖がちょっと積もってるみたいな感じで綺麗だった。
登り前半の30分くらい、景色や道が変わらず、ずっと歩きっぱなしになってしまいました。時間みて休憩しながら行けばよかったなあ。
登るにつれて気温が下がっていくのか、積雪が厚くなっていく。
40分くらいは割と平坦な道が続きますが、突然山頂っぽいものが現れて、「これを登れっていうのかい...?」とビビるほどピーンと急な道が出てきました。(写真だと分かりづらいですね)
ただ、高尾山のコンクリート道に比べると足の疲れはそこまででした。雪道なので気をつけて歩くという意味では疲れましたが、春〜秋とかは快適に登れるんじゃないでしょうか。
山頂に到着するとドーンと浅間山が見えて圧巻。
風が強くて飛ばされる恐怖はありましたが、なんとか無事でいられました。あったかいお茶美味しかった〜。
なぜかギャルの看板があって、謎でした。写真はひとまずありません。
山頂が2箇所あって、それぞれで眺めを満喫していたら結構時間が経ってました。
小さい背丈くらいの木や足元にちょっとした植物があったり、自分的にはかなり理想の荒野に近かったです。(植物に対する解像度が低すぎる) 往復で2時間程度の山らしいんですが、なんやかんやと2時間半強くらいいた気がします。
荒野ビギナーは小浅間山に往け
というわけで、荒野に行きたい人はまずは小浅間山を登ると良いと思います。 また登りたい。
荒野部部長
一緒に高尾山・小浅間山に登ってくれた方、ありがとうございました! 個人的には来年の春までに秩父多摩甲斐国立公園に行き、来年の秋までに大山隠岐国立公園に行くという目標を立ててるんですが、 少々時間が空くので次どこに行こうかしらと考えているところです。
ヒントとしては、火山で、あまり高低差のないところだとビギナーの私にちょうど良さそうです。
とある情報筋によると伊豆大島が良さそうなので、次の機会に行けたらと思っています。
みんなで荒野に行こう!
-
 @ 0d97beae:c5274a14
2024-08-10 00:47:04
@ 0d97beae:c5274a14
2024-08-10 00:47:04** takes deep breath **
Bitcoin mining is often simplified to the point where the definition is basically meaningless. I will try to explain it as simply as possible but first we need to unlearn some unhelpful things.
The goal of Bitcoin mining is NOT to earn bitcoin
If we start with the premise that the goal of mining is to earn bitcoin, it makes everything 100x harder to explain. It's a nuanced point however, miners DO mine to earn bitcoin, but in the grand scheme of things, the main goal of mining is not to create or earn bitcoin.
I like to think of Bitcoin as a complex clock or watch, there are many small moving parts all coming together to keep the system working flawlessly. Take out one small part and the whole thing might fall apart. The goal of mining is to provide "immutability" and "finality" to all the events that occur on the Bitcoin network.
Understanding the anatomy of Bitcoin
Before we can understand the purpose of Bitcoin mining, we must first understand a little about the anatomy of Bitcoin and some of the properties it must uphold to be useful.
Consider your bank account; there is a balance associated with your name, but what gives that data integrity? Usually it is the fact that the data is coming from an authoritative source, a trusted third party. If I could get a copy of the bank's database, would you trust that the same data sourced from my machine was correct? Could I have modified the records before showing it to you?
Bitcoin does not rely on any authority. This is a very important part of its design and it is what allows Bitcoin to remain independent of any company or government. To achieve this, it relies on checks and balances to be embedded within the data that it contains. Bitcoin is fully transparent in order to ensure that anyone can audit its data. The most important thing to check, of course, is that the books are balanced, but beyond that, Bitcoin introduced personal digital signatures to ensure that records are authorised by individuals directly, and it introduced an ordering system.
Digital signatures not only prove that a record was created by the owner of the bitcoin being spent, but if the record is ever altered, the signature no longer matches; this means that we don't need to trust anyone to execute our requests faithfully.
Order is important to ensure that everybody can agree with which payments are valid and which are not. Imagine I write two identical cheques to give all of my bank balance to two different people. One will settle, the other will bounce. With a traditional bank, one banker will decide which came first and will decide which settles and which bounces. In a decentralised (not centralised) system like Bitcoin, we need to be able to introduce a robust and reliable ordering system that does not rely on a trusted authority. Beyond just ordering, there also needs to be some integrity to the data so that not only an order can be agreed upon, but also there can be no re-ordering. Determining an order without preventing re-ordering is basically useless.
Ordering records
You may have heard of the "blockchain". This technology is just a data format, but Bitcoin uses this technology to help lock in an order into the record system. In a blockchain, records are grouped into blocks, and each block must have a link back to its previous block, creating a chain of blocks; pretty self explanatory in hindsight.
Imagine somebody deciding to become part of the Bitcoin network, they wish to get a copy of all the bitcoin records, but there is a problem:
- One person shows a series of records that fully balances, has all the other checks and balances, and it shows a payment from me to you.
- Another person provides a similar series of records that also fully balances but it does not show that payment from me to you, it shows a payment from me to me in its place.
Which one is correct? Both pass all checks, but if I choose the first set of records, then the payment from me to me becomes invalid because it attempts to spend money that has already been spent, while if I take the second set of records, the inverse becomes true.
The blockchain allows us to declare an order, but we still need a way to lock that order in, such that if someone provides an alternative set of records with a different order of events, we can all use some robust and reliable set of rules to choose the same record set without needing to coordinate with one another or rely on some trusted authoritative source.
This solution also needs to be resistant to being gamed; one elephant in the room is the idea of relying on dates and times, but computers are terrible at agreeing on time and although data can travel at the speed of electrons, there are still bottlenecks that can lead to data arriving in a different order between different computers.
Using a game of chance to prevent changes
The most fair way to make an arbitrary decision such as this, where there is no real right or wrong answer (remember "date sent" can be gamed, so we can't base any decisions on that), but a decision still needs to be made is by introducing something that is statistically hard to undo.

You may know the game of Boggle. This is a game where you have a set of dice inside a tray with letters on the sides instead of numbers; you place a box cover over it, shake it, and then allow the dice to fall into a mould at the bottom so that they are all sitting alongside each other in a square formation (usually 4x4) with one letter facing up per die. Let's re-imagine that the goal of the game was simply to shake the box, align the dice and remove the cover and if there was a 4 letter word on each row, you win, and if not you must shake again.
This is analogous to Bitcoin mining. It is a pure game of chance, and if we had a bunch of them, we could turn the game into a race: who can create the longest chain of winning boggle shakes in a row!
To illustrate how the blockchain creates links between blocks, we can add an additional rule that the first die in a Boggle tray (we will call them blocks going forward) must match the last die in the previous block. This way, we know that the order of blocks cannot change as the link is being built up.
Here is an illustration of a chain from this game:

Finally, let's make it more interesting: the goal is to have as many blocks as you can on the longest chain. If you notice that someone else has a pretty long chain, you can abandon your own and start to build blocks for their chain instead. If you create a block that satisfies the rules and your first letter matches the last letter of their last block, your block can go on top.
We will start to notice the following things:
- People will quite quickly start to abandon their own chains and work on top of one faster growing chain.
- The chain with the most people working on it will naturally grow at a faster pace.
- Those competing too hard to maximise the number of blocks they have in a chain will see their chain fall behind the fastest growing chain.
- It takes a non-negligable time between rounds and usually one person wins at a time, there are rarely any moments where two people create a valid block for the same chain within moments of one another.
Using forks to change history

It gets interesting when someone notices something like an offensive word in the chain, let's call it "DUCK". A lot of people don't care, but a large group of individuals do, so they choose to "fix" the rules, making that block and all the blocks after it invalid too (because they all eventually link back to the invalid block).
They create a new block that continues off from the block before the offensive one, creating what we call a "fork". This new chain will inherit the same past as the original chain, but it will still be shorter than the original chain because during the time it took to create this alternative block to replace the offensive one, the rest of the players continued to build blocks on the original chain as normal.
Since this game is mostly based on chance, the chain that grows the fastest will be the one that has the most players contributing to it. Even if the smaller group appears faster for some time, over a long enough time, statistics will prevail; it is the same as how over enough coin flips, we will observe that there really is a 50/50 chance of heads over tails, even if the first few flips were mostly all heads.
If enough players are motivated to contribute to the shorter, profanity-free chain, then that chain will grow faster and eventually become, and remain, the longest chain. The other indifferent players will then jump ship and join the new longest chain in order to maximise the number of their blocks in the new longest and faster growing chain.
Fortunately, the more likely scenario is that the offended group is a minority and the original chain remains the longest and fastest growing chain. This natural phenomenon ensures that the history of events cannot easily be changed for simply arbitrary reasons. On a global scale, this phenomenon is ever more present, because not even laws, politics, nor what is considered moral can be agreed across the world.
Cheating
In a game like the one above, there are opportunities to cheat. Maybe you could choose not to shake your box, but place the dice by hand. Unless someone is constantly watching you, no one would ever know.
With Bitcoin mining, there are simply no such shortcuts. The fastest and cheapest way to produce a block is to play fairly. Let's dive into what Bitcoin mining really is.
What exactly is Bitcoin mining?
People often use analogies to describe mining; "it's like a lottery", "miners solve complex mathematical problems", "miners guess random numbers". The problem with analogies are that they tend to omit key details that ultimately mislead the reader.
Miners perform a series of tasks repetitively, simplified:
- Collect the records that users create and compose them into a file.
- Add a reference to the previous block.
- Add a random number to the end.
- Check if the file satisfies a certain special criteria.
- If not, replace the random number with a new random number and repeat from step 3.
To check if a file satisfies our special criteria, we pass the file through a special program called "SHA256" and the program reveals a large unpredictable unique number. We check to see if that number is below a pre-determined target and if so, it has satisfied the criteria (i.e. given SHA256(FILE1) = 123 and TARGET = 20, is 123 < 20?).
SHA256 is a known as a mathematical "hash function". Although its output is unpredictable, it is also "deterministic", which means that given the same input file, it will always produce the same number. It is unpredictable because given the same file with even a small change will produce a completely different number altogether. We use these type of algorithms to give our files identifiers that make them resistant to tampering; it is very useful when downloading from torrents, where files can be downloaded in parallel, from multiple places, be reconstructed, and the file is only accepted if it resolves to the same identifier, ensuring that you get exactly what you asked for.
These files containing records are traditionally called "blocks", and once an acceptable block has been produced (aka mined), it is shared with all the online Bitcoin nodes and we all move on to mining the next block. As we observed before, attempting to ignore the latest mined block is counterproductive and would result in a fork and put you on a path of creating blocks for a new chain that no one would care about and that everyone would simply discard as invalid data.
As you can imagine, this process is very repetitive. One round is hardly power intensive, but the chances of success are so low, that it takes many cycles to find a successful block. The process of mining is very power intensive due to the nature of the process being a repetitive process with a low chance of success.
The incentives
Many people who focus on the "number guessing" and "repetitive nature" side of things tend to consider this process to be pretty arbitrary, however this repetitive chance-based system is key to ensure that it cannot be cheated. As we have discussed, it introduces order, and solidifies it to bring robustness and reliability to Bitcoin.
This process also incurs a cost. Computers draw electrical power to perform their operations, and when people are competing with one another, this power draw becomes non-negligible very quickly.
Miners do earn bitcoin when they mine. As they create blocks, they include an entry allocating bitcoin to themselves. This is their incentive to add the most number of blocks to the chain, as the more blocks they add, the more bitcoin they can earn.
The amount that a miner can allocate to themselves is based on two things:
- Transaction fees (aka fee market): users can see what transactions are waiting to be mined, what fees they are offering, and can offer a competitive fee to get their transactions prioritised. Miners will often pick the transactions that offer the highest fees to include into their blocks; this ensures that they are earning the most amount of Bitcoin that they have available to them at all times.
- Block reward: Every block can issue a fixed amount of new bitcoin which the miner can allocate to themselves. Around every four years, the amount of new bitcoin that can be issued is reduced in a controlled manner, and in the year 2140, there will be no more bitcoin left to issue, meaning that miners will need to remain profitable using transaction fees alone.
The block reward satisfies two purposes:
- Bitcoin must be distributed fairly; there are no licenses or authority based limitations that restrict who can mine bitcoin. Anyone with access to energy, a computer and internet can participate, and therefore new bitcoin can land in the hands of almost absolutely anyone around the world, based purely on fair chance.
- People must be incentivised to participate in the running of the Bitcoin network, Bitcoin is nothing without a diverse and distributed mass of people running it. Early adopters earn more, while as we get closer to the year 2140, we expect that a critical mass of people will rely on Bitcoin and a plethora of tools, technologies and infrastructure have been built to support it.
These incentives are why people think the goal of mining is to produce more Bitcoin. While for a miner, the main goal is to earn bitcoin, for the system as a whole, mining serves a very different, important and distinct role and the rewards are there merely to ensure people are motivated to do it.
The difficulty adjustment
To get a complete view of Bitcoin mining, the "difficulty adjustment" feature of Bitcoin addresses the elephant in the room: as more people compete to mine bitcoin, wouldn't blocks get produced more quickly?
Bitcoin blocks are produced every 10 minutes on average. Every 2 weeks, or more precisely, every 2016 blocks, a "difficulty target" is redetermined based on the historical production rate of the previous 2016 blocks. All the participants who help to run the Bitcoin network are able to follow this well defined rule automatically on their own computers and will come to the exact same result.
The difficulty target is a way to change the odds of the chance based game, such that we can maintain the average of 10 minutes per solve. Doing this on a regular basis, ensures that even if more miners enter, or if the hardware becomes more efficient, or if they get access to even more energy and computing power, or even if many miners exit, the network can adjust itself and ensure that the network runs smoothly and at a constant pace.
There are also many extra rules that ensure that even this part of the system cannot be gamed. Many developers, mathematicians and philosophers have evaluated Bitcoin deeply and have not found ways to easily game the system.
The 10 minute pace of the system is important for a number of reasons:
- The issuance of new bitcoin as a reward should not happen too quickly; people need time to discover and adopt bitcoin in order to ensure that bitcoin can be distributed as fairly as possible.
- Chance is unpredictable and there are cases where multiple miners do find blocks within moments of one another, and this creates forks in the system. The chances of this happening consecutively is rare, and this allows the network to very quickly settle on a single chain and continue operating without issue. Reducing the 10 minute average interval would amplify this situation, causing problems with the smooth running of the network.
- Considering that blocks can be up to 4mb in size, 10 minutes is ample time for it to be distributed to all bitcoin computers across the world wide web, even over slow network infrastructure and old hardware. 10 minute block times ensure that all computers can remain up to date and not be left eternally catching up as more blocks are being produced faster than their computers can download and validate.
With the difficulty property, the Bitcoin network can grow at a constant pace, and yet everyone can still tell which chain has had the most effort contributed towards it. When a computer comes across two chains, two versions of history, it does not look to find the "longest" chain, but it looks for the one that has the solved for the most amount of difficulty. The result is the same, the chain of data that is considered official is the one that has the most amount of man and electrical power behind it.
-
 @ ac8bb9b0:70278acc
2024-12-04 20:30:30
@ ac8bb9b0:70278acc
2024-12-04 20:30:30Chef's notes
Make Ahead: You can prepare this recipe up to one week in advance. Store it in an airtight container in the refrigerator.
To Freeze: Allow the dish to cool completely before transferring it to a freezer-safe bag. Lay the bag flat in the freezer to ensure even freezing and to save space. Thaw it in the refrigerator overnight before using it.
Details
- ⏲️ Prep time: 5
- 🍳 Cook time: 5
- 🍽️ Servings: 1
Ingredients
- ½ cup soy sauce
- 2 Tablespoons rice vinegar
- 1 Tablespoon sesame oil
- 1/4 cup + 1 Tablespoon light brown sugar
- 1 Tablespoon honey
- 3/4 teaspoon ground ginger
- 1 clove garlic , minced
- 2 teaspoons cornstarch+ 2 tsp water , mixed together to make a cornstarch slurry
- 1/4 teaspoon crushed red pepper flakes
Directions
- Make the teriyaki sauce by adding all of the sauce ingredients to a small saucepan over medium heat.
- Bring to a boil, stirring constantly, and boil for about 1 minute. The sauce should be thick enough to coat the back of the spoon.
- Serve over rice or with a stir-fry. See post above for additional ideas.
-
 @ cff1720e:15c7e2b2
2025-02-01 17:37:00
@ cff1720e:15c7e2b2
2025-02-01 17:37:00Am 4. Oktober 1957 sendete Sputnik 1 erste Signale aus dem All. Die Welt war fasziniert, die Amerikaner geschockt, da die Russen sie in der Raumfahrt technologisch überholt hatten. Es folgte der Wettlauf im All mit Apollo-Programm und Mondlandung 1969. Am 27. Januar 2025 erlebte die USA einen weiteren Sputnik-Moment, diesmal durch die chinesische KI-App deepseek R1. Diese App schoss wenige Stunden nach ihrem Start auf Platz 1 der App-Stores, vorbei an dem bisherigen KI-Spitzenreiter ChatGPT. Die Aktie des KI-Chipherstellers Nvidia verlor 17% (600 Mrd. USD Börsenwert), das war der bisher höchste Tagesverlust des US-Aktienmarktes. Marc Andreessen verwendete gar die Formulierung “Sputnik-Schock", diese einseitige Sichtweise erschwert aber eine Betrachtung aus verschiedenen Perspektiven.

Was lässt sich mit ein paar Tagen Abstand daraus schlussfolgern? Die Aktionäre haben überreagiert und die Falschen bestraft. Die Nervosität der Anleger ist aber verständlich bei einem KGV von 46 bei Nvidia und 27 bei den “Magnificent Seven” (die großen US KI-Anbieter). Normale KGVs bewegen sich um 15, d.h. wir haben es mit einer ausgeprägten KI-Blase zu tun, die in Kürze platzen dürfte. Eine weitere Blase die schon vor dem Start geplatzt ist, ist das Projekt “Stargate” der Firmen OpenAI, Oracle und Softbank. In den nächsten 4 Jahren wollen sie 500 Mrd. USD für über 10 neue KI-Rechenzentren investieren, um Amerikas vermeintliche KI-Vorherrschaft gegenüber China weiter auszubauen. Die schon vorher vorhandenen Zweifel an dem Projekt (Elon Musk auf X “sie haben das Geld gar nicht”) wurden nun durch den Erfolg von deepseek verstärkt.

deepseek hat nämlich offenbart, dass die bisherige US KI-Strategie, "wir schlagen die Chinesen mit unserer DataCenter-Power", ein fataler Irrweg ist. Den Analysten von Bernstein zufolge ist das Modell von deepseek geschätzt 20 bis 40 mal billiger zu betreiben als ähnliche Modelle von OpenAI. Die Chinesen haben ihre Innovation durch Kreativität erzielt, im Gegensatz zur Gigantomanie der US-Konzerne, die sich in einem Überbietungs-Wettbewerb der Ressourcen-Verschwendung befinden. Hunderte Milliarden an Investorengeldern und ca. 9% des nationalen Stromverbrauchs führen zwar zur Bereicherung einiger Konzerne und ihrer Besitzer, nicht aber zu adäquaten Ergebnissen. Das selbe Muster konnte man bereits bei der Rüstungsbranche beobachten, die mit dem etwa 10-fachen Budget (1 Billion USD) nicht im Stande war bessere Waffensysteme zu produzieren als Russland (Oreshnik-Schock 2024).

Wenn Donald Trump wirklich Amerika stärken möchte, dann sollte er umgehend seine technokratischen Berater entlassen und Sun Tzu lesen, ein Buch, das die Grundlagen asiatischer Strategie vermittelt und den Krieg vermeiden lehrt ("Der klügste Krieger ist der, der niemals kämpfen muss"). Die chinesischen Erfolge basieren auf exzellenter Bildung, Startup-Förderung und minimaler Regulierung, Konzepte die der Westen zwar stets gepredigt aber nie geliefert hat. “Make Amerika smart again” hieße daher Abschied von Kriegsrhetorik, Embargos, Oligarchen-Projekten und der bisherigen Großmacht-Hybris. Annektionspläne für Grönland und Kanada passen nicht in das Bild, Wiederherstellung von Meinungsfreiheit und Abbau von Regulierungen schon (Streichung von Bidens KI-Regulierung Executive Order 14110). Wohin steuert Trump die USA? Wird der deepseek-Moment dabei helfen falsche Strategieansätze zu korrigieren? Das ist noch unklar, während aber schon jetzt unzweifelhaft feststeht, dass die EU und Deutschland weder bei der KI noch in der Geostrategie eine Rolle spielen, dafür aber als unangefochtene Regulierungs-Weltmeister. Herzlichen Glückwunsch!

„Man kann zwar die Realität ignorieren, aber nicht die Folgen davon ignorieren.“ Ayn Rand
Der wirkliche Gewinner dieser Woche ist aber die OpenSource-Szene mit ihren dezentralen Lösungsansätzen. Nicht nur deepseek R1 ist OpenSource sondern auch Marco o1 von Alibaba (https://github.com/huggingface). Die Nutzung ist kostenlos (ChatGPT kostet 200 USD pro Monat), daher können sowohl die Modellbildung, die Trainingsdaten als auch die Rechenleistung von unzähligen Aktivisten weltweit verteilt erbracht werden. Dafür braucht es weder Milliarden-Budgets, Regierungsprogramme oder neue DataCenter. Das Potential der Crowd übertrifft jeden zentralistischen Ansatz. Die Ergebnisse sind besser und die Kontrolle liegt nicht in den Händen einzelner. Smarte Lösung sind verteilt, das beweisen Projekte wie Bitcoin (seit 16 Jahren), Lightning und neuerdings auch Nostr. Deshalb haben wir Pareto (https://pareto.space) auf diesen Fundamenten entwickelt (Nostr, Lightning) und in 6 Monaten mit Freiwilligen mehr erreicht als viele große IT-Unternehmen in Jahren. Die Dinosaurier sterben aus, dem Schwarm gehört die Zukunft.
-
 @ 26bb2ebe:70530958
2024-12-02 16:46:10
@ 26bb2ebe:70530958
2024-12-02 16:46:10nostterに画像最適化機能つけたよ(サーバー編)
この記事はNostr Advent Calendar 2024 の3日目の記事です。
あまり技術的な話はないので暇つぶし程度に読んでみてください。
どうしてこうなった?
そもそも認証の改善以前にNostrあんまり人が増えてないのが一番課題だよねと思ったのが始まりでした。 Nostrに人が増えないのはオーガニック検索流入が少ないからに違いないと特に根拠もなく思ったのでNostrのまとめサイト(Toggeter)のようなものを作ろうと考えました。
ところでNostrのまとめを行うアプリ自体は鎌倉さんという方がノスリというのを作成されていました。ブログ形式のイベントにTwitterライクな短文投稿をまとめるというものでまさしくToggeterですが、そこまで活用されていません。 そこでその仕組みをありがたくそのまま転用してまとめ記事を何らかの方法で量産しつつ、一つのドメインのサイトにまとめてSEOもなんかうまいことやれば検索流入増えるんじゃねという目論みです。
ところでそのまとめサイトは静的サイトジェネレータで(SSG:Static Site Generator)でつくりたいなと思いました。いや普通に考えてSSRにしてサーバ側でNostrからデータとってきたらSEO的にもよくねって感じなんですが、SSRでサーバーでウェブソケット呼ぶのだる…レイテンシを考慮すると結構不利じゃないかなと思ったわけです。うそです。そこまで考えてなくてほとんど個人的な好みです。(多分ちゃんとキャッシュきかせればそんなにレイテンシ問題にならなさそうな気がする)。ただキャッシュとかも考慮すると結構複雑な気はする。
ということで今年の6月頃にNostrのブログ記事をSSGするサイトをためしに作りました。 去年のアドベントカレンダー記事とか乗っけてます。
全然画像最適化の話になりませんね。もうちょっとです。
SSGのブログといえばGatsby(今は下火かも)とかで作成した経験があります。Gatsbyでは画像用のプラグインが公式に用意されていて生成されたブログに表示される画像はもとの画像データから変換され、表示時のサイズに最適化されたサイズにリサイズすることができます。
それだけではなくサイトの初期表示時には画像の画質を落としてぼやけた画像を表示してその後元画像が読み込まれたらきれいな画像を表示する、みたいなことができます。インラインでデータを持っているのでHTMLの表示と同時に画像の初期表示ができたりします。(その頃はよくわかってなかったがNostrのNIP-92で定義されているblurhashとかを使っていたんでしょう多分)
とにかくSSGは初期表示の速さが良い。というのが自分の頭の中にあるわけです。SSGのブログをNostrで作るとなると当然同じことがやりたい。
しかし、Nostrの画像はただのURLです。(オプショナルで画像のメタデータを定義できるimetaタグはあるが…)
基本的にSSGの画像最適化というのはローカルに存在する画像データをビルド時に変換するという流れで行われます。もしくはリモートURLに画像が置かれる場合は画像ストレージサービスやCDN上で配信されるときに最適化されることになります。
Nostrの画像はただの外部のURLですから(2回目)、ローカルの画像を変換する方法は採用できないわけです。無理やり実行するならビルド時にURLからすべての画像を一旦ダウンロードして変換するとかも考えましたが、ただの外部URLというのはつまりは一体どういうファイルなのかダウンロードしてみるまでわからない、要するに全然信頼できないということですから、よくわからないURLをかたっぱしからダウンロードするようなことは避けたいわけですね。(極端な話100GBの画像URLとかつくって攻撃されたら破綻しますよね)
ここが結構他の中央集権的なSNSと違って辛いところなのかなと思います。X(Twitter)とかであれば画像ストレージサーバは一つなので表示される画像の形式も一つに限定されるのですが、画像のアップロードが外部頼みでただのURLなので(3回目)何が来るかわからないということですね。
サーバ側で画像形式などを制限できない(imetaも信頼できるかわからない)となるとクライアント側でなんとか対応する必要があり、Nostrはクライアント側が大変なプロトコルだなあとということに思いを馳せていましたが、いろいろ考えたり調べた結果として作るべきものは画像最適化のためのプロキシサーバであるということがわかりました。
プロキシサーバというのはここでどういう働きをするのかというと、もとの画像がおいてあるサーバとクライアントのあいだに入って、もとの画像を一旦ダウンロードして圧縮したり縮小したりしてそのあとクライアントに送ってあげるという働きをします。
プロキシがないとき
[画像置き場] -> [クライアント]プロキシがあるとき
[画像置き場] -> [プロキシ] -> [クライアント]利点としてはクライアントが実際にダウンロードするのはサイズの小さな画像になるので通信量や画像の表示スピードは改善します。が、一方でサーバを経由する分通信にかかる時間(レイテンシ)が長くなります。というわけなので、当初の目的である表示速度の改善を実現するには、画像をエッジキャッシュするなどの対応が必須となります。平たく言うと一度送った画像はプロキシで保存しておいて次に要求されたらそれをすぐ返すということです。
画像をどれくらいのサイズにするか、画質はどうするかなどはプロキシに指示してあげれば良いのでクライアント側は想定通りの画像を受け取れてハッピーということになります。嘘です。ある程度はハッピーですが、プロキシ自体がエラーを返す可能性もあるし、処理できなくてもとの画像をそのまま返す場合もあります。そんなあれこれの結果、クライアントはフォールバック処理を実装する必要がありました。(それはまた別の記事で)
一方で自分はNostrのモバイルクライアントのヘビーユーザですので、Nostrの通信量の多さも解決したい課題でした。Nostrやってるとすぐギガがなくなります。 通信量の多さのボトルネックはウェブソケットで送られるNostrのイベントの通信量というよりは投稿に添付される画像のダウンロードの方ではないかという話もTLで耳にしたため(特に裏もとらず)、いっちょ画像最適化のプロキシサーバを作ってクライアントに実装してプルリクエスト投げるかと考えました。
そこで私はまずクライアントをAmethystからnostterに乗り換えることから始めました。なぜならばAmethystよりもTypeScriptとSvelteで書かれているnostterのほうがコントリビュートしやすかったという私的な事情です。
解決したい課題
遠回りしてきましたが課題はこれ。
- Nostrの画像の表示改善
- Nostrの通信量の改善
インターフェイス(設計)
画像最適化のプロキシは実装よりもインターフェースを考えるのが大変です。ここはとても苦労しそうな気がしたので、何も考えず cloudflare Imagesのインターフェースをそのまま借用することにしました。
https://developers.cloudflare.com/images/transform-images/transform-via-url/
また何かあってもcloudflare Imageに課金して乗り換えることが可能という利点もあります。
実装
とにかく時間がないので手グセでかけるTypeScriptかJS。かつ課金しないで可用性を維持できる無料枠のサーバレス環境が使いたかったので cloudflare workers に目星をつけて調査したところ、非常に素晴らしい記事を見つけましたのでこのwasmのライブラリをTSから呼び出して使わせていただくことにしました。
自分の実装したところはURLのパースと、キャッシュAPIの呼び出しを行って、最後にこのライブラリを叩くだけです。 ほかはクライアントキャッシュ用のヘッダーを書き換えたりとか細かいことはやっていますが全く大したことはやっておらず、サーバは非常にリーズナブルにやりたいことを実装した形になりました。 大変助かりました。
実装したものがこちらです。
https://github.com/ocknamo/nostr-image-optimizer
実装後の課題
このプロキシただのパブリックAPIなのでDoS攻撃に弱いです。何回もAPIをたたかれたら無料枠をすぐに超えてしまうことが容易に想像できました。 無料枠超えても使えなくなるだけで破産はしないので安心ですが、しかし対策は考える必要があります。
WAF
WAFです。APIに対するリクエスト回数などに対する制限をIPごとにかけています。また攻撃された場合検知できれば特定のIPや地域をブラックリストに入れることも可能です。
細かいことを説明してギリギリを攻めて攻撃されても困るので細かく説明しませんが、当初は全力でDoS攻撃されても無料枠超えないくらいの感じで制限をかけていました。 しかしNostrのTLをちょっと早めに表示するとすぐにWAFに引っかかってエラーになるという状態になることもあり、結局アイコンの表示は画像最適化の対象にしない方針にするなどの影響がありました。
いろいろあって、前提が変わり、もう少し制限をゆるくしたのでアイコンの対応は今後は検討できるかもしれません。
まとめ
割と手抜きで作ったことがわかるかと思います。実装しててNostrへの貢献ではあるはずですが、Nostrのプロトコル(NIPsとか)全然関係ないことやってるなと思いました。
フロントについては来週書きます。
次回のアドベントカレンダーの記事は eyemono.moe さんによる”クライアント自作を通して得られた知見まとめ”ですね!楽しみです!
-
 @ e262ed3a:e147fbcb
2025-02-01 15:37:28
@ e262ed3a:e147fbcb
2025-02-01 15:37:28Feel free to develop
I got an idea while watching a video from @BTCSessions, which I personally cannot implement technically. Therefore, I would like to present it here for discussion and free implementation. It makes sense to me, but what do I know? Let the swarm intelligence decide.
The goal of the business idea is:
How can I bring as many solo miners as possible into a pool without them having to pay for the electricity for mining and their mining hardware can be amortized quickly, so they can purchase more mining hardware? How can we financially support Bitcoin and Nostr developers in the long term? How can we intensify developers for the implementation of this idea? How can we encourage non-Bitcoiners to invest in the support of the Bitcoin network? How can we get non-Bitcoin retailers to invest in the Bitcoin network?
**The answer is: PROSPECT OF WINNING
The solution lies in a kind of RAFFLE. (Not a betting website) !**
The legal difference between a BET and a RAFFLE varies from country to country. It lies in the fact that a raffle must be very transparent regarding the chances of winning and the proceeds must go to a good cause. Those involved in the implementation can, of course, be compensated (also with a profit for the individual participants). The extent to which this is allowed would have to be checked by those who want to implement this idea.
In the following, I will describe the implementation roughly. Since this is not a sales presentation, please excuse me if the following proposal is not fully structured.
**Participants in the idea are:
Consumers (ticket buyers) Bitcoin miners Retailers Non-profit company that implement the project**
What's it about? @BTCSessions has a YouTube video about the miner FutureBit. In the dashboard of the solo miner, you could see how high the hash rate was. But above all, you could see how high the chance of winning was for the solo miner in the overall network. In the case of BTCSessions FutureBit, the hash rate was around 5 TerraHash and the chance of winning was around 1:1,000,000. (Which, according to my calculations, was not correct). The power consumption was around 32 watts. When I saw that, it suddenly dawned on me.
Could it be possible to create a website/app that determines the total hash rate of a mining pool and then offers an electronic, numbered ticket for each 1 TerraHash (TH/s) of the pool for, for example, 0.1 USD? The minimum purchase amount would be 10 tickets. The customer sees the chance of winning and could even see the possible payout. The ticket is only valid for the next block (similar to roulette).
Another variant could be that the buyer can select one or more of the next 10 blocks and purchase tickets for the selected block. Since you don't know in advance how high the pool hash rate will be 5 or 10 blocks ahead, the amount of tickets to be issued for the 2nd block, for example, could only be 90% of the current pool hash rate, the 3rd block only 80%, and so on. If block 3, for example, advances to position 2, the previously unavailable 10% will be released for further tickets. (Determined by the pool hash rate at that time)
The purchase of 10 or more tickets could be automated in the customer's account on the website/app (intervals: hourly, daily, weekly, every 10 blocks, etc.). Customers could also top up their account with satoshis, enabling automatic deductions for ticket purchases. This could be facilitated by automatically issuing a Nostr npub to each customer, which would also create a wallet at Primal.net (Strike). For non-Bitcoiners, Zaprite could be used to recharge their account. Alternatively, customers could enter a NostrWalletConnection NWC to enable automatic deductions from their Lightning wallet. The project operators might also consider running their own ecash mint, which would allow them to assign an integrated ecash address to customers without a Lightning address. Tickets with ascending numbers would be allocated strictly in the order of payment receipts.
Calculations for the miners: The FutureBit miner consumed approximately 30 watts per terahash/hour. Let's assume that 10 terahash consume 300 watts per hour, then the miner consumes 50 watts per 10 minutes (per block). Let's further assume that a kilowatt-hour of electricity costs between 10 and 30 cents, then it costs the miner 3-9 cents per hour for electricity at 10 terahash mining capacity. So, 0.5-1.5 cents per block. In the case that each ticket is sold for 1 terahash for the next block, one could automatically transfer, for example, 5% of the satoshis received from ticket sales to each participating miner in the pool (proportional to the average hash rate delivered by the miner in the last block in the pools). This happens even if the block is not found. If fewer tickets are sold than the maximum possible amount, then the 5% of the sold tickets will be distributed proportionally. (See also my Excel file?
At the center of the project is a website/app that manages the raffle. Here, anyone can register and create an account. Either as a miner, retailer, or customer with or without KYC, for example, with their own nostr nsec, wallet signature, email and password or phone number and password.
Once logged into the account, Bitcoiners can enter their Lightning address and a Bitcoin on-chain address. Non-Bitcoiners enter their financial data in case they win.
Miners must enter a Bitcoin and Lightning (or ecash) address. The pooling process is also managed in the miner's account.
Tickets can be purchased (like in a regular online shop) and paid for in any way. Zaprite could be a solution here. But also Strike, Cashapp, etc. As described above, such purchases could also be automated.
Retailers can also register as such. They will then have the opportunity to sell "tickets" to their customers and collect the money in cash. To sell tickets, they must enter the customer's name and a valid email address. After payment, they must send the purchase price via Lightning to the non-profit company, which will then confirm the purchase to the ticket buyer and the retailer with all the data. This is the receipt for the buyer. In the event of a win (the mined block must have 3-6 block confirmations), the ticket buyer will receive an email explaining all the further details of how to claim the prize. This could be a link that takes them directly to the website and logs them in directly. The winner can then enter their data on how and where the money should be paid out (Bitcoin address or bank details). Alternatively, they can go to their retailer, who can assist them by entering the data in their sub-account (customer account). To prevent the retailer from falsifying the data entry, the winner will first receive an email with the entered data, which they can confirm (if correct). Since the retailer is also involved in the win, they will also be notified.
How many tickets can be offered per round (Bitcoin block)? The number of tickets depends on the hash rate in the pool. One ticket can be issued per 1 TerraHash (TH/s). How the ticket is generated per round and customer, I don't know, as I lack the technical knowledge. Maybe as a kind of NFT that contains the corresponding data (customer number (npub) of the buyer and possibly retailer, block number, ticket number). Or as a Taproot asset on Lightning? Or as a minted ecash coin? Or simply as an entry in a database that the customer can see in their account.
The maximum payout of the winnings in the event of a found block to the ticket holders could be 70%. The remaining 30% would be distributed to the miners and retailers. For example: Miners 25%, retailers 5%. The non-profit organization receives nothing from the block rewards. Instead, it receives 65% of the revenue from all ticket sales. With a mining pool hash rate of 10,000 TH/s, where all tickets are sold continuously, a daily donation of around 93,000 USD would be generated. (see Excel.file)
The revenue, after deducting the possible costs of the organization, goes directly to @opensats and/or other organizations that support the Bitcoin network after each block. Either via Lightning or Bitcoin on-chain payment.
In the attached Excel file, you can find my calculations. Here, anyone can play through different scenarios.
What I noticed was that with maximum ticket sales per block, only around 200 USD per 10 tickets would be paid out, since each participating ticket wins in the event of a found block. Since I believe that this is not a very great incentive for buying tickets, I suggest the following variants.
Winning variants: Each purchased ticket has a running number. Ticket 1 has the number 000.000, ticket 2 has the number 000.001, ticket 10.120 has the number 010.119, and so on.
If the next block is found, then this found block in the Bitcoin blockchain has a hash. For example, block 881367 has the hash 000000000000000000014b0fab24355c71c6940584d9cd5990c0b081a31d54a4
Let's now remove the letters and read only the numbers from back to front, so the last 3 numbers are 544
Instead of every participating ticket winning, in this variant, only the tickets with the ending digits 544 win.
With, for example, 11,000 tickets sold, the ticket numbers 000.544 / 001.544 / 002.544 ... 010.544 would win. So, 11 ticket participants would win. Each winner with this number would receive around 0.284 Bitcoin (3.125 BTC / 11).
One could also let the ticket numbers with the ending digits 44 win, and thus every hundredth ticket. Or even combine it.
What I also noticed was that with retailers, a special case arises. Retailers receive 5% of the block rewards in the event of a found block. But only proportionally to the tickets sold by the retailer. This means that in order for the entire 5% to be distributed to the retailers, all 10,000 tickets of 10.000 possible tickets would have to be sold by retailers. Since not all tickets will be sold by retailers, a remaining amount will be left over. This could be distributed additionally to the miners. Or any other variant.
I hope the idea finds resonance and invites discussion. Maybe I've made some mistakes in thinking, and the idea is not feasible. But if you like the idea, please forward it to developers, investors, and others you know.
Stay humble hash sats
@nostr:npub1uf3w6w3z4kxy0zc80m6a03tt9s7855c9r8kkjmkju47xtc28l09sc30gqq
-
 @ 8f69ac99:4f92f5fd
2024-07-30 16:17:35
@ 8f69ac99:4f92f5fd
2024-07-30 16:17:35A arte sempre foi um veículo para o comentário social, dissidência política e expressão cultural. No entanto, o outrora vibrante panorama da liberdade artística parece agora estar a ser ofuscado por uma indústria cada vez mais homogeneizada e politicamente orientada, que funciona mais como propaganda do que como criatividade genuína. Há uma interseção desconfortável entre a política e a arte, onde os artistas modernos se tornaram porta-vozes de ideologias de esquerda, em vez de pensadores independentes ou inovadores.
Um Breve Histórico da Dissidência Artística
No passado, artistas alinhados com movimentos políticos progressistas, como o comunismo, o socialismo e o anarquismo, eram aclamados como campeões da mudança, utilizando os seus talentos criativos para desafiar normas estabelecidas. A ideologia de esquerda oferecia uma plataforma para expressar dissidência contra sistemas opressivos no poder, defendendo as comunidades desfavorecidas e marginalizadas e promovendo a igualdade social. No entanto, esse alinhamento resultava de convicções genuínas, e não de mera conformidade política.
A Radicalização da Ideologia Moderna de Esquerda
Com o passar do tempo, as ideologias de esquerda evoluíram para manifestações mais radicais, impulsionadas pelo "virtue signaling" (sinalização de virtude), activismo performativo e apropriação cultural. Estas novas formas de pensamento de esquerda mudaram o foco de um envolvimento político genuíno para uma obsessão com auto promoção e influência nas redes sociais. Os artistas modernos são cada vez mais pressionados a alinhar-se com essas tendências para manter a relevância ou garantir apoio financeiro, contribuindo assim para uma cultura de conformidade em vez de inovação artística pelo seu próprio valor.
A Captura Intelectual pelos Estados Socialistas
Os governos socialistas têm historicamente procurado captar talentos intelectuais para servirem os seus objectivos, com os artistas a serem frequentemente cooptados para disseminar propaganda estatal. O papel do artista moderno como porta-voz da narrativa socialista evoluiu para além da mera conformidade – agora, há uma expectativa implícita de conformidade política e alinhamento cultural, abafando efetivamente vozes dissidentes dentro da comunidade artística.
A Mudança da Arte pela Beleza para a Arte pelos Subsídios
Outrora impulsionados pelo compromisso de produzir obras belas que ressoavam com o público e contribuíam economicamente através de vendas de bilhetes ou mercadorias, os artistas têm dependido cada vez mais de financiamento público como principal fonte de rendimento. Esta mudança resultou numa indústria onde as criações artísticas não são mais julgadas apenas pelo seu valor estético, mas sim pela sua correcção política e capacidade de atrair apoio governamental.
A Relação Artista-Contribuinte: Uma Questão de Parasitismo
Embora os artistas tenham tradicionalmente dependido do patrocínio de benfeitores ricos, a dependência contemporânea de financiamento público criou uma relação complicada entre os criativos e os seus cidadãos. Numa era em que os fundos públicos são cada vez mais escassos para apoiar várias iniciativas, alguns críticos argumentam que a arte financiada por impostos não passa de um comportamento parasitário – utilizando o trabalho árduo das pessoas comuns para produzir obras que pouco servem para esses mesmos indivíduos. No entanto, é importante notar que alguns argumentam que o financiamento público pode ajudar a apoiar artistas emergentes ou a preservar o património cultural, acrescentando nuance a este debate.
Conclusão: Reivindicando a Verdadeira Independência Criativa
À luz destas preocupações, é hora de reexaminar a relação entre arte e política na sociedade contemporânea. Ao encorajar a autenticidade sobre a conformidade ideológica, promover uma gama diversificada de vozes dentro da comunidade artística e promover a transparência em torno das fontes de financiamento e afiliações políticas, para recuperar uma verdadeira independência criativa das narrativas dirigidas pelo estado. Plataformas como o Nostr, onde os criadores de conteúdo podem receber gorjetas diretamente pelo seu trabalho, fornecem um modelo para fomentar uma maior independência. Estas plataformas permitem que os artistas se conectem diretamente com o seu público, contornando os gatekeepers tradicionais e a influência estatal. Ao apoiar estas e outras iniciativas semelhantes, os artistas podem ser vistos novamente como catalisadores de mudanças positivas, em vez de meros porta-vozes numa paisagem cultural cada vez mais politizada.
Photo by Chris Czermak on Unsplash
-
 @ c230edd3:8ad4a712
2024-12-02 03:49:19
@ c230edd3:8ad4a712
2024-12-02 03:49:19Chef's notes
This recipe is not my own, but it was great and easy, so I'm moving it here. Cooking as instructed serves 2, but this could easily be adjusted to include stir fry vegetables and rice, to make this a meal for 4.
Details
- ⏲️ Prep time: 15 minutes, 1-24 hours marinating
- 🍳 Cook time: 10-15 minutes
- 🍽️ Servings: 2-4
Ingredients
- 1 Venison Heart (elk would work well, too. recipe would need to be doubled)
- 1/2 Asian Pear, grated
- 2 Cloves Garlic, grated
- 1 Tbsp Ginger, grated
- 3 Tbsp Soy Sauce
- 1 Tbsp Honey
- 1 Tbsp Onion, grated
- 1 Tbsp Toasted Sesame Oil
- 1 tsp Red Pepper Flakes
- 2 Shallots, chopped
- Sesame Seeds
- Cooking Oil
Directions
- Mix all ingredients besides heart, shallots, sesame seeds and cooking oil in a medium bowl.
- Remove arteries and excess fat from heart, cut in half and rinse
- Cut into thin slices or bite size pieces
- Add to marinade, mix and cover. Allow to soak for 1-24 hours.
- Heat oil in large frying pan over med-high to high heat
- Drain excess marinade.
- Place heart in pan and sear on both sides to desired doneness. Medium rare is ideal for heart.
- Remove from pan and garnish with chopped shallots and sesame seeds. Serve with stir fry veggies and rice, if desired.
-
 @ 8f69ac99:4f92f5fd
2024-07-29 16:09:25
@ 8f69ac99:4f92f5fd
2024-07-29 16:09:25Na sociedade actual, é comum referir-se ao governo como "o público" ou "o estado", tratando-o como uma entidade sem rosto que existe apenas para fornecer serviços. No entanto, essa abordagem pode ter consequências não intencionais. Quando os indivíduos dependem do estado para obter apoio, muitas vezes perdem o contacto com o aspecto humano da doação de ajuda. Torna-se impessoal e burocrático, tornando mais fácil para as pessoas explorarem o sistema sem sentirem qualquer verdadeiro senso de responsabilidade, ou remorso. É precisamente por isso que a assistência social deveria ser privada — não porque os necessitados não sejam merecedores, mas porque quando os indivíduos dão ajuda, é mais provável que tratem os outros com dignidade e respeito. Este fenómeno não é exclusivo dos tempos modernos; foi observado ao longo da história, onde a ascensão de governos centralizados e burocracias levou a um declínio na caridade comunitária.
Em contraste, a caridade privada, historicamente gerida por instituições comunais como a igreja por exemplo, traz um toque pessoal ao processo de ajuda. Quando a ajuda é dada por indivíduos ou grupos comunitários, promove-se um senso de responsabilidade mútua entre o doador e o receptor. Essa conexão pessoal pode alterar significativamente o comportamento daqueles que recebem ajuda, pois é mais provável que respeitem e apreciem a assistência recebida. Por exemplo, quando uma família recebe alimentos e abrigo de uma igreja local, ou uma família da comunidade, um vizinho, etc..., é mais provável que sinta gratidão e responsabilidade, para com a comunidade que a ajudou, em vez de simplesmente ver a ajuda como uma esmola de um governo sem rosto.
Além disso, a ineficiência dos programas de assistência social administrados pelo estado frequentemente resultam em má alocação de recursos e falta de apoio personalizado. Numa comunidade saudável, aqueles que são mais afortunados tendem a contribuir directa ou indirectamente para a elevação de toda a comunidade. Isto pode ser através de assistência financeira, fornecendo bens como alimentos e abrigo, ou criando oportunidades de crescimento e desenvolvimento. Por exemplo, um empresário bem-sucedido pode escolher doar uma parte dos seus lucros a um banco alimentar local, ou um profissional qualificado pode oferecer os seus serviços pro bono a uma organização comunitária. Reconhecendo que qualquer pessoa pode passar por períodos de necessidade, a caridade comunitária garante um sistema de apoio mais compassivo, localizado e eficaz.
As consequências de um sistema de bem-estar administrado pelo estado e sem rosto são profundas. Quando os indivíduos não são responsabilizados pelas suas acções, é mais provável que aproveitem o sistema, levando a uma cultura de dependência e direito adquirido. Isso pode ter efeitos devastadores sobre indivíduos, famílias e comunidades, à medida que se tornam dependentes de subsídios governamentais em vez de tomarem a iniciativa para melhorar suas circunstâncias. Além disso, a falta de conexão pessoal entre o doador e o receptor pode levar a um sentimento de desumanização, onde os indivíduos são vistos apenas como estatísticas, em vez de pessoas com dignidade e valor inerentes.
Em contraste, a caridade comunitária promove um senso de comunidade e coesão social. Quando os indivíduos estão directamente envolvidos na prestação de ajuda, é mais provável que sejam motivados a criar mudanças positivas na sua comunidade, em vez de simplesmente dependerem do estado para fornecer soluções. Isso pode levar a um sistema de apoio mais sustentável e eficaz, onde os indivíduos são capacitados a assumir a responsabilidade por suas vidas e comunidades.
Os Benefícios da Caridade Comunitária
Então, quais são os benefícios de mudar o cuidado social de um estado sem rosto para um modelo baseado na comunidade? Em primeiro lugar, promove um senso de conexão pessoal e responsabilidade entre o doador e o receptor. Isso pode levar a um suporte mais eficaz e sustentável, bem como a um maior senso de comunidade e coesão social. Além disso, a caridade comunitária encoraja os indivíduos a tomarem iniciativa e responsabilidade por suas vidas, em vez de dependerem de subsídios governamentais.
Além disso, a caridade comunitária pode levar a um suporte mais direccionado e eficaz. Quando os indivíduos estão directamente envolvidos na prestação de ajuda, é mais provável que compreendam as necessidades específicas da comunidade e ajustem o seu apoio de acordo. Isso pode levar a um uso mais eficiente dos recursos, bem como a um maior senso de satisfação e realização entre aqueles que prestam ajuda.
Conclusão
O estado levou a problemas significativos na administração de programas de protecção social, promovendo uma cultura de dependência e exploração. Em contraste, a caridade comunitária traz um toque pessoal ao processo de ajuda, promovendo um senso de responsabilidade mútua entre o doador e o receptor. Reconhecendo a importância da conexão pessoal e do envolvimento comunitário, podemos criar um sistema de apoio mais compassivo e eficaz que beneficie tanto o doador quanto o receptor. Em última análise, mudar para um modelo baseado na comunidade poderia levar a uma ajuda mais significativa e responsável, promovendo comunidades mais fortes e resilientes.
Photo by John Cameron on Unsplash
-
 @ 3369d0a7:eb020757
2024-11-28 07:41:32
@ 3369d0a7:eb020757
2024-11-28 07:41:32Chef's notes
This recipe was a staple at every thanksgiving with family and now I share it with you nostr family. Absolutely one of my favorite side dish during the holiday. The corn pudding in the photo is NOT baked, I will update it. I hate stock photos.
Details
- ⏲️ Prep time: 15-20 min
- 🍳 Cook time: 30-40 min
- 🍽️ Servings: 6-8
Ingredients
- 2 cans of creamed corn
- 2c Milk
- 1 Box of Jiffy Cornbread Mix
- 3 eggs
- 1/4-1/3c sugar
- 1/2- green bell pepper or pepper onion blend
- 1/4TBsp vanilla
- 1/2tsp Salt
- 2TBsp Butter
Directions
- Grab medium saucepan and desired baking dish at least 9x9
- Place saucepan on medium-high heat
- Add butter and sauté pepper onion blend until tender
- Combine milk, eggs, sugar and vanilla, mix well
- Lather warmed (NOT HOT) baking dish with butter
- Sprinkle half a box of Jiffy corn bread mix in the baking dish
- Add both cans of creamed corn to peppers and onions
- Pour wet ingredients into slightly cooled creamed corn mixture
- Sprinkle the other half box of jiffy mix into the baking dish
- Incorporate the wet and dry ingredients in dish so there are no dry lumps
- Let set for 10 min before placing in a 325 degree oven for 30-40 minutes, until the center is solid and the edges are golden brown.
-
 @ 8f69ac99:4f92f5fd
2024-07-18 13:08:29
@ 8f69ac99:4f92f5fd
2024-07-18 13:08:29A noção de que "os ricos estão a ficar mais ricos e os pobres estão a ficar mais pobres" tornou-se uma narrativa generalizada, frequentemente perpetuada por manchetes sensacionalistas e análises superficiais. No entanto, um exame mais detalhado revela que este mito é construído sobre uma série de equívocos sobre a natureza do capitalismo, intervencionismo governamental e progresso humano.
A Maré Alta Levanta Todos os Barcos
Embora seja verdade que a desigualdade de riqueza persiste, é essencial reconhecer que o capitalismo tem sido historicamente o único sistema económico que eleva o padrão de vida de todos, incluindo os pobres. A capacidade do mercado livre de criar incentivos, promover a inovação e alocar recursos de forma eficiente levou a um crescimento económico sem precedentes e a melhores padrões de vida.
Num sistema capitalista, a criação de riqueza não é apenas domínio dos ricos; também beneficia a classe média e os pobres. À medida que as empresas crescem e prosperam, criam novos empregos, oportunidades e serviços que podem tirar as pessoas da pobreza. A proliferação de pequenas empresas, startups e empreendedorismo na Europa, tal como nos Estados Unidos, fomentou uma cultura de inovação e auto-aperfeiçoamento que transcende classes sociais.
Considere o exemplo da Europa pós-guerra. O Plano Marshall, que injectou enormes quantias de capital em economias devastadas pela guerra, é frequentemente creditado como a base para a rápida recuperação económica e crescimento. Este boom económico viu o surgimento de uma classe média robusta e reduções significativas na pobreza em todo o continente.
Intervencionismo é uma Barreira à Mobilidade Económica
No entanto, é crucial reconhecer que não vivemos numa sociedade puramente capitalista ou numa verdadeira economia de mercado livre. O intervencionismo governamental muitas vezes desempenha um papel significativo na definição dos resultados económicos, criando barreiras que impedem os pobres e a classe média de prosperar. Esta intervenção pode distorcer a dinâmica do mercado, levando a ineficiências e oportunidades desiguais para o avanço económico.
Desde tarifas comerciais a leis laborais, as políticas governamentais podem sufocar o empreendedorismo, limitar a concorrência e reduzir a mobilidade económica. Em muitos países europeus, a elevada tributação e regulamentos rigorosos podem impedir o crescimento dos negócios e a inovação. A concentração de riqueza e poder nas mãos de poucos indivíduos ou famílias pode perpetuar desigualdades sociais e económicas, frequentemente exacerbadas por políticas governamentais que favorecem interesses estabelecidos.
Padrão de Vida Sem Precedentes
É essencial colocar o estado actual das coisas em perspectiva histórica. Comparado a apenas 100 anos atrás, as pessoas hoje são mais ricas, saudáveis e melhor educadas do que nunca. Os avanços tecnológicos em medicina, educação e comunicação melhoraram significativamente a qualidade de vida.
Tome, por exemplo, a ampla disponibilidade de smartphones, que democratizou o acesso à informação e oportunidades. Reis e rainhas de antigamente só podiam sonhar em ter tais capacidades tecnológicas ao seu dispor. De facto, muitas pessoas hoje desfrutam de um padrão de vida que anteriormente era reservado para a elite. Os avanços na saúde, como vacinas e antibióticos, aumentaram drasticamente a esperança de vida e reduziram as taxas de mortalidade.
Considere o caso da Suécia, onde inovações tecnológicas e políticas sociais têm trabalhado em conjunto para criar um dos mais altos padrões de vida do mundo. Este progresso é um testemunho de como o capitalismo, combinado com uma governação ponderada, pode melhorar a prosperidade geral.
Eficiência vs. Inflação
A inovação e os avanços tecnológicos tornaram os processos de produção muito mais eficientes, levando a aumentos significativos na produção e reduções nos custos de produção. Por exemplo, um agricultor nos anos 60 podia produzir alimentos suficientes para alimentar cerca de 25 pessoas, enquanto hoje, devido aos avanços na tecnologia agrícola, um único agricultor pode alimentar mais de 150 pessoas. Este aumento drástico na produtividade deveria resultar em preços mais baixos dos alimentos devido à natureza deflacionária da tecnologia.
No entanto, apesar destas eficiências, os preços dos bens não viram uma correspondente queda. Em vez disso, temos uma economia inflacionária, em grande parte devido à interferência do governo e às políticas dos bancos centrais. As políticas monetárias dos bancos centrais, como a flexibilização quantitativa e as baixas taxas de juros, juntamente com as intervenções governamentais, levaram a um aumento da oferta de dinheiro e a uma maior demanda, o que contribui para a inflação.
Tome o exemplo dos preços dos alimentos: enquanto os avanços tecnológicos aumentaram significativamente a produtividade agrícola, o preço dos alimentos continuou a subir. Esta discrepância pode ser atribuída a factores como subsídios, tarifas e políticas monetárias que distorcem a dinâmica do mercado e contribuem para a inflação dos preços, negando os benefícios deflacionários do progresso tecnológico.
Conclusão: Uma Perspectiva Equilibrada sobre a Distribuição de Riqueza
Em conclusão, a noção de que "os ricos estão a ficar mais ricos e os pobres estão a ficar mais pobres" é uma simplificação que ignora as complexidades do capitalismo, intervencionismo governamental e progresso humano. Embora seja verdade que a desigualdade de riqueza persiste, é essencial reconhecer os benefícios do capitalismo na promoção do crescimento económico e melhores padrões de vida.
Ao reconhecer o papel do intervencionismo governamental na definição dos resultados económicos e destacar o padrão de vida sem precedentes de que muitos desfrutam hoje, podemos trabalhar para criar uma sociedade mais equitativa e próspera para todos. É hora de ir além das narrativas simplistas e, em vez disso, focar em políticas que promovam a mobilidade económica, o empreendedorismo e a inovação – elevando assim a maré de prosperidade para todos.
-
 @ c1e6505c:02b3157e
2024-11-28 00:02:26
@ c1e6505c:02b3157e
2024-11-28 00:02:26Chef's notes
Leftover ground beef? Not sure what to do with it?
Here’s what I do with mine. I call it…
The Beef Panzone
It’s like an omelette, a calzone, and a quesadilla had a baby. I called it that for now, but hey, if you’ve got a better name, lemme hear it!
The beef’s already cooked and seasoned with sea salt, but feel free to spice it up however you like.
Watch the video here: https://video.nostr.build/ad4856d2704ab0626a1907f5da8fedcb776495080bbaa92f4472db402c9f689d.mp4
Details
- ⏲️ Prep time: 5
- 🍳 Cook time: 10
- 🍽️ Servings: 1-2
Ingredients
- ground beef
- 2-3 eggs
- water
- sea salt
- honey
- coconut oil
Directions
- Leftover ground beef – Chop it into small pieces. Trust me, the smaller, the better—it’ll cover more surface area in the pan.
- Two eggs, whipped with a dash of water.
- Heat up a small pan.
- Add coconut oil (around a tablespoon).
- Once the oil’s warmed up, throw in the beef.
- Stir it around.
- I like to add local honey here—sweeten it up to your taste.
- Mix it all around.
- Pour in the egg mixture, making sure it spreads out evenly. I use chopsticks here because they make it easier to maneuver.
- Use those chopsticks to poke through the egg and let the uncooked top flow to the pan. This speeds up cooking time.
- Cover it for 1–3 minutes.
- Optional step: Cut it down the middle.
- Fold it over like a calzone.
- Plate it up, either by flipping the pan over onto the plate or scooping it out.
- PANZONE!
-
 @ ca4e5bf2:96645a6b
2024-06-25 23:32:08
@ ca4e5bf2:96645a6b
2024-06-25 23:32:08Prismas de lightning
Un aspecto que aún está tremendamente poco utilizado es la programabilidad de bitcoin. Existen cosas simples como las transacciones programadas (agendadas, temporizadas) y los pagos múltiples automatizados, pero indudablemente seguimos atrapados en el pensamiento convencional acerca del flujo de los sats.
Quisiera proponer una idea simple que fue compartida conmigo hace unos meses, con la esperanza de que se distribuya ampliamente y, en el mejor de los casos, alguien la implemente. (O una mejor versión de ella).
Es la siguiente:
Todo el crédito a Mr. Kukks, quien está oficialmente sin tiempo[^1] para implementarla él mismo.
Prismas de lightning
Un prisma de lightning es un constructo que permite "flujos de división de valor entre direcciones de lightning", parafraseando al autor.
Básicamente, sus características son: - un prisma se identifica con una dirección de lightning (o algo similar) - un prisma tiene un o múltiples receptores - un prisma puede ser receptor de otro, es decir, formar una "cadena de prismas" - las divisiones se definen programáticamente, esto es, con código
Este constructo simple permite todo tipo de casos de uso y puede ser implementado en la capa de las aplicaciones, sin ningún cambio en los protocolos de Bitcoin o Lightning.
Un ejemplo obvio es la división de valor para artículos de blogs y formas similares de escritura de extensión considerable. Imagina si cada artículo (o capítulo de un libro) tuviera su propia dirección de Lightning, repartiendo valor entre autor, editor, ilustrador y revisores del texto automáticamente.
El concepto de esas divisiones de valor ya existe en el podcasting 2.0, donde se aplica ampliamente a podcasts y episodios. Podría argumentarse que tener un identificador separado para el constructo es la evolución natural de esa forma de compartir valor, ya que sería más fácil conceptualizarlos y encadenarlos entre sí.
Otro caso de uso obvio es compartir los zaps de Nostr. Imagina que cada tweet citado que es zappeado se divide automáticamente, pasando el 50% (o el monto configurado por el usuario) a la nota original. O imagina un prisma creado ad-hoc, repartiendo los zaps equitativamente para todos los etiquetados en una nota.
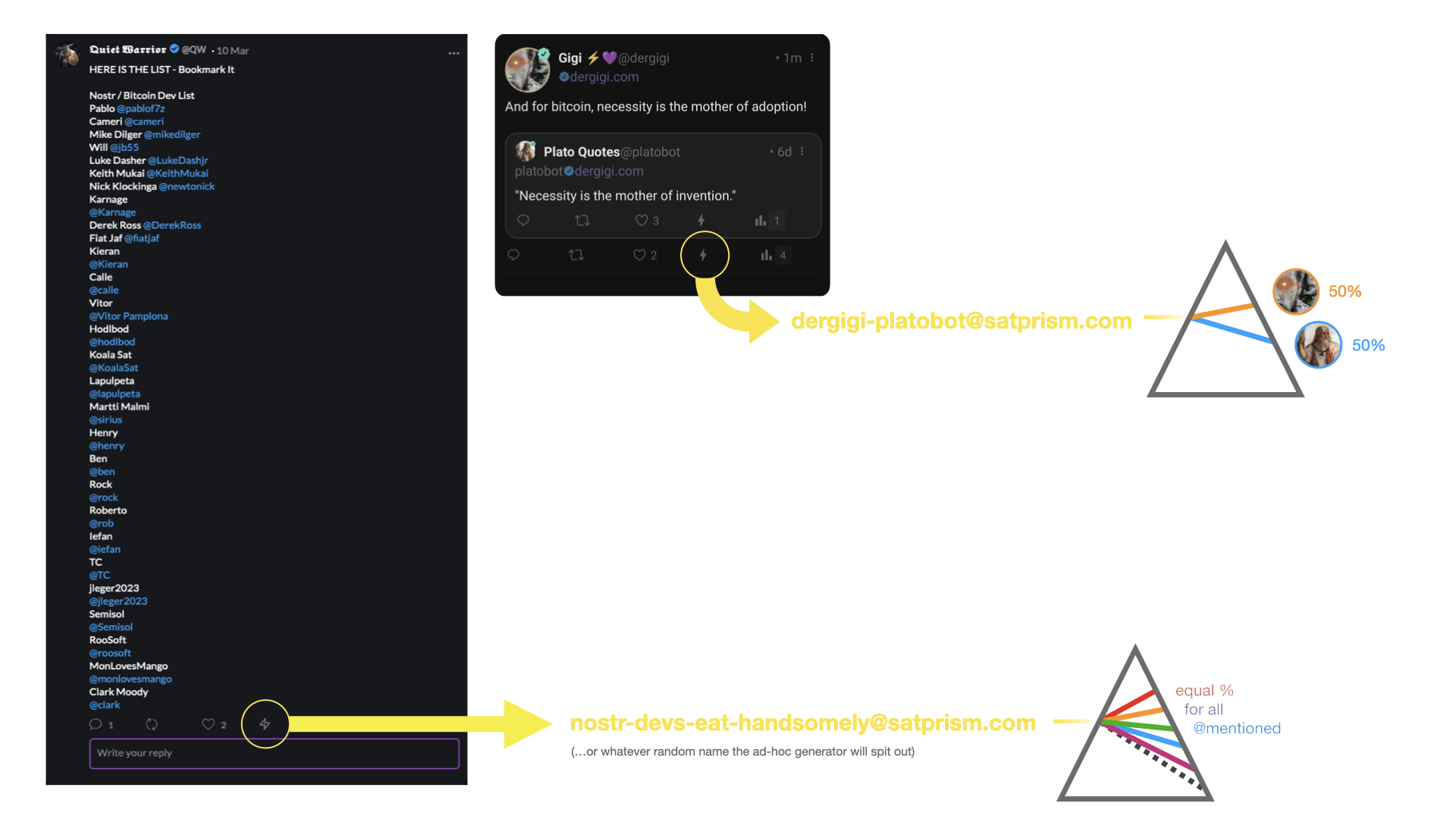 ¡Splits de sats para nostr! ¿acaso hay algo mejor?
¡Splits de sats para nostr! ¿acaso hay algo mejor?Como los pagos son redirigidos, cada prisma actúa como una especie de proxy. Esto puede ser útil tanto para organizaciones como para individuos, ya que tu identificador de pago permanece igual incluso si tu infraestructura subyacente o proveedor de billetera cambian.
Problemas y mejoras
Existen dos preocupaciones centrales: comisiones y privacidad. No sólo hay que tener en cuenta las comisiones derivadas de la división y redirección de los pagos, sino también el hecho de que las direcciones ligthning se basan en IP, lo que tiene ciertas implicaciones de privacidad. Podríamos usar LNURL sobre nostr -de nuevo, créditos para Kukks- que trae a colación la siguiente pregunta: ¿son las direcciones lightning (Lightning Addresses) el nivel de abstracción correcto para los prismas de lightning?
Al fin y al cabo, no queremos enviar sats a direcciones sino a personas. Si nostr continua tomando vuelo, podría convertirse en sí mismo en la libreta de direcciones global para ese tipo de cosas, en otras palabras, el lugar al que se acude para buscar información de pago de personas, organizaciones y otras entidades. En el futuro, un prisma podría tener múltiples identificadores
nprofileonpubcomo destinos, detrás de los cuales está la información de pago concreta.
Los identificadores no tienen que ser necesariamente direcciones lightning (Lightning Addresses). ¡
Npubso similares también pueden funcionar!En cualquier caso, en este punto, no estoy demasiado preocupado por los detalles de la implementación. Estoy preocupado por una falta de imaginación, que es a lo que este post intenta responder.
Hablando de imaginación: ¿Por qué no tenemos ninguna billetera que automáticamente mueva sats a otra a partir de un cierto umbral? Estoy más que feliz de tener dinero para el almuerzo en una billetera custodial (delegada, controlada por terceros), pero una vez que alcanza tres meses de renta ya no estoy tan cómodo. ¿Por qué no puede la billetera automáticamente enviar el excedente de sats a mi dirección lightning soberana una vez que contiene más que el monto de una cena? O hacer un loop-out mensualmente para mover mis sats a almacenamiento frío?
Bueno, divago.
Una mejora que me gustaría ver es que se provean los prismas de forma transparente. En el mejor caso, los usuarios deberían poder ver cómo los pagos se reparten, de una forma fácil de entender y verificar. Una posibilidad es transmitir un evento reemplazable parametrizado (definido por el NIP-33) cada vez que un prisma se crea o actualiza. Claro que, dependiendo del caso de uso, puede tener sentido mantener el/los lugar/es finales ocultos del público.
Estoy seguro de que existen más problemas y muchas otras mejoras, pero, como siempre, lo perfecto es enemigo de lo bueno, así que hablemos sobre soluciones prácticas que pueden ser implementadas y usadas ahora mismo.
Implementación
Los prismas basados en direcciones lightning pueden ser construidos hoy sin demasiado esfuerzo. Podrías incluso construirlo tu mismo sin ninguna experiencia programando utilizando dos extensiones de LNbits: scrub y split. Agrega satdress encima para darle a cada billetera su propia dirección lightning y ¡voilà!, tienes un prisma de lightning. Puedes incluso construir una buena interfaz sobre él, ya que todo lo anterior puede ser creado programáticamente con simples llamadas de API.
Hice todo eso (excepto el "construir una buena interfaz sobre él) para juguetear con la idea. Sí, es algo precaria y probablemente no sea la solución más estable o elegante, pero más o menos funciona y puede ser utilizada hoy.
La dirección blogpost@satprism.com mostrada arriba es un ejemplo en funcionamiento[^2]. Va a dividir los pagos 50/50 entre Kukks y yo (Gigi), dirigiendo los sats a nuestras respectivas direcciones lightning soberanas, provistas por nuestras instancias de BTCPay Server.
Imagino múltiples servicios siendo creados con una correcta implementación, cargando una pequeña comisión por dicho servicio (sic). (Tal como fue mencionado anteriormente, alguna especie de comisión será requerida por las comisiones de enrutado, ya que los pagos son redirigidos a direcciones externas).
Mi esperanza es que ese tipo de ideas y constructos novedosos se vuelvan más prevalentes mientras se van volviendo más prevalentes los zaps y pagos V4V similares, como también la red lightning en general. Claro que, en el mejor escenario, tendremos esas herramientas integradas nativamente a nivel del protocolo, pero no veo razón por la que no deberíamos experimentar un poco con lo que tenemos hoy, incluso si las soluciones son imperfectas. Hasta que el Bolt12 y similares sean ubicuos, ensamblar algo que simplemente funcione no es una idea tan terrible[^3].
Palabras finales
Espero que esta idea encuentre adopción amplia entre escritores y otros creadores de contenido, tal como la idea de "streaming sats" -y los splits de esos streams de valor- encontraron amplia adopción entre podcasters.
Lo que aún falta es adjuntar información de pago a eventos individuales (en lugar de a perfiles) para que cada contenido tenga su propia información de pago. Tal vez sea tan simple como extender la metadata del NIP-23, o tal vez tendría sentido tener este tipo de metadata para otros kinds también.
Ya veremos, y por "veremos", me refiero a ustedes: los desarrolladores que se sientan a diseñar y construir cosas.
Estaré alentándolos mientras hago shitpost en nostr.

Nota del traductor:
Todas las direcciones lightning, prismas y demás se mantuvieron fieles al post original. Si quieres colaborar conmigo, puedes hacerlo a mi lnaddres: wispy@getalby.com.
Traducciones
- Alemán por HiP0 [^1]: Le prometí a Kukks no hablar sobre ello por un par de semanas para que él pudiera adelantarse e implementarlo, pero estaba preocupado en mejorar la privacidad de todos, lo que también es muy importante. [^2]: Todos los prismas mostrados en este post son ejemplos funcionales: nostr-devs-eat-handsomely@satprism.com hace un split en partes iguales a todos los devs mencionatos en la nota de Quiet Warrior, y dergigi-platobot@satprism.com es un split entre el robot y yo. También me tomé la libertad de crear rhr@satprism.com, que hace un split entre Marty y Matt, y también einundzwanzig@satprism.com para los hablantes de alemán. [^3]: Creé los prismas de ejemplo de forma manual, así que me temo que, hasta que alguien construya una buena interfaz que permita a los usuarios crearlos por sí mismos, no habrá una explosión de prismas. Me gusta crear un montón de billeteras lnbits como a cualquiera, pero crear los splits y redirecciones es cansador después de un rato.
¿Te interesa ayudar? ¡Agrega una traducción!
Este trabajo de traducción, al igual que su fuente original tienen la licencia CC BY-SA 4.0, y se espera lo mismo de sus eventuales derivados.
-
 @ 617f0a85:b403d1ed
2024-11-27 00:35:41
@ 617f0a85:b403d1ed
2024-11-27 00:35:41Chef's notes
I got this recipe from a friend in college. I'm not sure where she came across it, but I don't think she'd mind me posting it here.
Details
- ⏲️ Prep time: 15 min
Ingredients
- 2.5 cups unbleached all-purpose flour
- 1 tsp salt
- 2 tbsp sugar
- 12 tbsp cold unsalted butter
- 0.5 cup lard
- 0.25 cup vodka
- 0.25 cup cold water
Directions
- Process 1.5 cups flour, salt, and sugar in food processor until combined, about 2 one-second pulses. Add butter and shortening and process until homogeneous dough just starts to collect in uneven clumps, about 15 seconds (dough will resemble cottage cheese curds and there should be no uncoated flour). Scrape bowl with rubber spatula and redistribute dough evenly around processor blade. Add remaining cup flour and pulse until mixture is evenly distributed around bowl and mass of dough has been broken up, 4 to 6 quick pulses. Empty mixture into medium bowl
- Sprinkle vodka and water over mixture. With rubber spatula, use folding motion to mix, pressing down on dough until dough is slightly tacky and sticks together. Divide dough into two even balls and flatten each into 4-inch disk. Wrap each in plastic wrap and refrigerate at least 45 minutes or up to 2 days.
-
 @ a012dc82:6458a70d
2025-02-01 15:17:38
@ a012dc82:6458a70d
2025-02-01 15:17:38The cryptocurrency landscape is witnessing a remarkable resurgence, with Bitcoin once again leading the charge. After a period of volatility and uncertainty, Bitcoin has reclaimed its throne as the king of cryptocurrencies, drawing renewed interest from investors and financial experts alike. This article delves into the factors behind Bitcoin's comeback, its implications for the market, and what the future might hold.
Table Of Content
-
The Remarkable Recovery of Bitcoin
-
The Ripple Effect on the Crypto Market
-
Investor Sentiment: Cautious Optimism
-
The Future Outlook: Opportunities and Challenges
-
A New Era for Bitcoin
-
Conclusion
-
FAQs
The Remarkable Recovery of Bitcoin
A Surge in Value
After a tumultuous phase marked by sharp declines and skepticism, Bitcoin has made a striking comeback. The digital currency's value has seen a significant upswing, reminding investors of its potential as a high-reward, albeit high-risk, asset. This recovery is not just a numerical increase but a symbol of resilience in the face of market adversities.
Driving Factors
Several factors have contributed to Bitcoin's resurgence. These include an increase in institutional adoption, technological advancements within the blockchain ecosystem, and a growing recognition of Bitcoin as a 'digital gold' amidst economic uncertainties. Moreover, regulatory clarity in some regions has provided a more stable environment for cryptocurrency investments.
The Ripple Effect on the Crypto Market
Boosting Market Confidence
Bitcoin's rebound has had a ripple effect across the entire cryptocurrency market. Altcoins and emerging digital assets have also seen a boost in both value and investor interest. This resurgence has rekindled the enthusiasm for decentralized finance (DeFi) and non-fungible tokens (NFTs), which had waned during the market downturn.
Impact on Blockchain Innovation
The renewed interest in Bitcoin has spurred further innovation in blockchain technology. Developers and entrepreneurs are increasingly exploring new use cases for blockchain, expanding beyond traditional financial applications to areas like supply chain management, digital identity, and more.
Investor Sentiment: Cautious Optimism
Institutional Investors' Role
Institutional investors, once wary of Bitcoin's volatility, are now more open to including it in their portfolios. This shift is partly due to the improved infrastructure and regulatory frameworks that make investing in Bitcoin less risky than in its early years.
Retail Investors' Perspective
Retail investors, who were significantly affected by the previous market downturn, are approaching Bitcoin with cautious optimism. Many are drawn by the potential for high returns but remain mindful of the risks involved.
The Future Outlook: Opportunities and Challenges
Potential for Growth
With its current momentum, Bitcoin has the potential for further growth. Its evolving role in the financial ecosystem, particularly in areas like digital payments and remittances, suggests a bright future.
Navigating Challenges
However, challenges remain. Regulatory uncertainties, potential market manipulations, and the environmental impact of Bitcoin mining are issues that need addressing. How these challenges are managed will significantly influence Bitcoin's trajectory.
A New Era for Bitcoin
A Testament to Resilience
Bitcoin's comeback is a testament to its resilience and the enduring faith of its supporters. It has not only reclaimed its position as the leading cryptocurrency but has also reinforced the belief in the potential of digital currencies.
A Dynamic Future Ahead
As investors, both institutional and retail, continue to take notice, Bitcoin's journey is far from over. Its ability to adapt, innovate, and overcome challenges will shape not just its future but also that of the broader cryptocurrency market. The current phase is just the beginning of what promises to be a dynamic and transformative era for Bitcoin and digital currencies as a whole.
Conclusion
Bitcoin's resurgence marks a significant milestone in the cryptocurrency world. Its ability to bounce back from adversity and regain its status as the leading digital currency has not only bolstered investor confidence but also highlighted the growing maturity of the crypto market. As Bitcoin continues to evolve, navigating through regulatory landscapes and technological advancements, it stands as a symbol of innovation and resilience in the ever-changing world of finance.
FAQs
Why has Bitcoin's value surged recently? Bitcoin's value has surged due to factors like increased institutional adoption, advancements in blockchain technology, and its growing recognition as a digital store of value amidst economic uncertainties.
How has Bitcoin's recovery affected the overall crypto market? Bitcoin's recovery has positively impacted the entire crypto market, boosting the value of altcoins and reigniting interest in decentralized finance (DeFi) and non-fungible tokens (NFTs).
Are institutional investors now more interested in Bitcoin? Yes, institutional investors are showing increased interest in Bitcoin, thanks to improved investment infrastructure and clearer regulatory frameworks.
What are the main challenges facing Bitcoin in the future? The main challenges include regulatory uncertainties, potential market manipulations, and the environmental impact of Bitcoin mining.
Is it safe for retail investors to invest in Bitcoin now? While Bitcoin offers potential high returns, it remains a high-risk investment. Retail investors should approach with caution and consider diversifying their investment portfolio.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ fd208ee8:0fd927c1
2025-01-23 15:31:24
@ fd208ee8:0fd927c1
2025-01-23 15:31:24Planning Alexandria
People keep asking what features nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz has planned for #Alexandria, but they're not set in stone because we're an agile project.
What we do have, is lots of tickets on our Kanban boards and a naming scheme, where we use a famous person's last name, to signify the release goals.

Gutenberg v 0.1.0
(after the inventor of the printing press) will contain the features needed to read and write NIP-62 Curated Publications, as well as encompassing the complex infrastructure, architecture, documentation, and personnel we require to make this all run smoothly and look easy.

Euler v 0.2.0
(after a mathematician credited with establishing graph theory) will contain the features for deep-searching, visually exploring, and smartly navigating the data set, wiki page display, annotating and citing the publications, exporting to other formats (like PDF, ePUB, and LaTeX), and commenting/reviewing. To help with the heavy lifting, we will be swapping out the core with our own Nostr SDK called "Aedile".

Defoe v 0.3.0
(after an author who perfected the novel format) will be all about our favorite writers. We will be focusing upon profile data, payment systems, book clubs and communities, and stylesheets.
That is everything we have planned, for the v1.0 edition, and we consider that version to be a true product.
As for after that, a teaser...

-
 @ 9f51b59f:75e7c3a2
2024-11-26 20:04:51
@ 9f51b59f:75e7c3a2
2024-11-26 20:04:51Chef's notes
Use bone in or boneless short rib. This recipe also works with ox tail and pork shoulder or any kind of meat that’s ideal for braising low and slow.
Details
- ⏲️ Prep time: 30 mins
- 🍳 Cook time: 2.5-3.5 hours
- 🍽️ Servings: 6-8
Ingredients
- 3 Tablespoons natural cooking oil (I use tallow or ghee)
- 2 lbs boneless short ribs (bone-in also works)
- Salt & Pepper
- 1 small red onion, diced
- 5 garlic cloves rough chopped
- 1 bell or poblano pepper, seeded & diced
- 2 teaspoon chili powder
- 1 teaspoon ancho chili powder
- 1 tablespoon smoked paprika
- 1 tablespoon dark coco powder
- 2 teaspoon cumin
- 1 tablespoon graham masla
- 1 teaspoon dried oregano
- 3 tablespoons apple cider vinegar
- 1/2 cup tomato puree
- 3 tablespoons chipotle adobo sauce
- 3 bay leaves
- 1.5 cups stock or water
- 2 fresh limes, juiced
- Banana leaves, optional
- Avocado, sour cream, lime juice
- Shaved red cabbage with lime juice
Directions
- Preheat oven to 315 degrees F. Using a Dutch oven or braising pan, begin heating oil over high heat on the stove top.
- Season beef with salt and pepper and begin searing in the pot. Once browned on all sides set the beef aside and add the onions, garlic, and peppers to the same pan and reduce the heat.
- Season and cook the veggies 5 to 8 minutes until they start to caramelize. Add the chili pepper, paprika, coco, cumin, marsala, and dried oregano.
- Briefly toast the spices and deglaze with the vinegar and immediately add the tomato puree.
- Add the adobo sauce, broth, and using a stick blender or blender buzz the cooking liquid. (if using banana leaves remove the cooking liquid from the pan or use a new pot with lid. Line the pot with the leaves shingled over one another, return the cooking liquid over the leaves.)
- Return the beef to the pot and cover with lid or foil (fold leaves over the meat then cover).
- Place the pot in the oven and cook for 2 hours before checking, the meat should be fork tender when done.
- Mash the avocado into the sour cream and season with lime juice or hot sauce. Serve on tortillas with the crema and cabbage.
-
 @ e237877a:dd6a20c2
2024-06-13 17:10:53
@ e237877a:dd6a20c2
2024-06-13 17:10:53This article was originally published on my blog. As an experiment, it is being syndicated here on Nostr.
There is Teflon in your bloodstream. ^1
Dupont knew about the toxicity of their chemicals since as far back as 1976, and to this day fight responsibility for their part in creating a ubiqitous chemical that does not naturally deteriorate. ^2
The chemicals used in the production of Teflon (PFOAs and PFOs) were finally deemed toxic enough that DuPont, and the 13 other producers of it, don't make it anymore - and have replaced it with New Teflon, and new chemicals. They claim these new chemicals are safe, despite the larger scientific body calling this into question^3. To quote these scientists directly:
"Whenever possible, avoid products containing, or manufactured using, PFASs. These include many products that are stain-resistant, waterproof or nonstick."
The Madrid Statement on Poly- and Perfluoroalkyl Substances
Without a doubt, using old teflon is comprimising your long-term health and the worldwide environment - Teflon is not just found in every human being on the planet, in some dosage, but every fish and mammal as well. New Teflon is still under research and speculation to its health effects - but I ask you this - do you trust DuPont chemical corporation to do the right thing if its toxic as well?
And yet, Teflon remains ubiquitous in our homes and kitchens. Much like the early days of "discovering" tobacco companies were covering up the long term health damage of their products, people are skeptical to the danger of Teflon, and moving slowly. In a way, we're addicted to the convenience - in spite of the fact that the usefulness of a Teflon pan is nothing more then a parlour trick.
Oil and Steel
The reality is, every pan is nonstick, if prepared and used properly. Teflon pans simply reinforce bad habits around your cooking - mainly using too low of temperatures to cook dishes effectively.
If you are wondering why your egg sticks in a steel pan, your pan was too cold. Here's the steps:
- Heat up the pan until it is so hot, a drop of water dances around the pan - but not so hot it immediately evaporates.
- Drop the temperature to medium-low, and add a cold oil of your choice. Crack your eggs one by one into the pan. Cook for 3-5 minutes.
- Flip when you want to flip them. Remove and serve.
But even if Stainless Steel remains intimidating as a cooking surface, alternatives remain. The current zeitgeist has turned towards cast iron, which when treated properly - and this step is far easier then people act like it is - is completely non-stick and able to handle any of your cooking needs.
https://www.youtube.com/watch?v=yGSDqXjoAsM
The counterpoint to using Cast Iron is multifold - one, that they are too heavy to cook dexterously with (flipping pancakes, omelettes, and such), and two that they are expensive - much more so then a Teflon pan, I admit.
This is where carbon steel enters the picture - long the back bone of commerical kitchens, carbon steel is the secret workhorse that makes a teflon-free kitchen as functional. Seasoned in the same way as cast iron, they are lightweight, easy to care for, and, critically, completely non-stick. [^4]
[^4]: As long as you are heating it hot enough, which, seriously, I cannot stress enough you should be doing.
Best of all, they're affordable. You can find them online for as low as $50, but the real tip is that restaurant supply stores frequently have broken cases (meaning they opened a bulk set for a client who only needed a few), and are likely selling the rest of the case at or near cost - I picked up my first pan this way for $30.
This is the strange truth of professional cookwear. The best stuff doesn't have a consumer marketing department; they sell primarily to commercial kitchens who already know what the best stuff to use is - in this case carbon steel pans, because they've been using these pans for hundreds of years with no problem - literally, carbon steel woks have a lineage all the way back to Imperial China.
-
 @ 3bf0c63f:aefa459d
2024-06-13 15:40:18
@ 3bf0c63f:aefa459d
2024-06-13 15:40:18Why relay hints are important
Recently Coracle has removed support for following relay hints in Nostr event references.
Supposedly Coracle is now relying only on public key hints and
kind:10002events to determine where to fetch events from a user. That is a catastrophic idea that destroys much of Nostr's flexibility for no gain at all.- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
kind:1s -- now that cannot work because the person who created the post doesn't have the relays specific to those communities in their outbox list; - There is a discussion happening in a niche relay, for example, a relay that can only be accessed by the participants of a conference for the duration of that conference -- since that relay is not in anyone's public outbox list, it's impossible for anyone outside of the conference to ever refer to these events;
- Some big public relays, say, relay.damus.io, decide to nuke their databases or periodically delete old events, a user keeps using that big relay as their outbox because it is fast and reliable, but chooses to archive their old events in a dedicated archival relay, say, cellar.nostr.wine, while prudently not including that in their outbox list because that would make no sense -- now it is impossible for anyone to refer to old notes from this user even though they are publicly accessible in cellar.nostr.wine;
- There are topical relays that curate content relating to niche (non-microblogging) topics, say, cooking recipes, and users choose to publish their recipes to these relays only -- but now they can't refer to these relays in the external Nostr world of
kind:1s because these topical relays are not in their outbox lists. - Suppose a user wants to maintain two different identities under the same keypair, say, one identity only talks about soccer in English, while the other only talks about art history in French, and the user very prudently keeps two different
kind:10002events in two different sets of "indexer" relays (or does it in some better way of announcing different relay sets) -- now one of this user's audiences cannot ever see notes created by him with their other persona, one half of the content of this user will be inacessible to the other half and vice-versa. - If for any reason a relay does not want to accept events of a certain kind a user may publish to other relays, and it would all work fine if the user referenced that externally-published event from a normal event, but now that externally-published event is not reachable because the external relay is not in the user's outbox list.
- If someone, say, Alex Jones, is hard-banned everywhere and cannot event broadcast
kind:10002events to any of the commonly used index relays, that person will now appear as banned in most clients: in an ideal world in which clients followednprofileand other relay hints Alex Jones could still live a normal Nostr life: he would print business cards with hisnprofileinstead of annpuband clients would immediately know from what relay to fetch his posts. When other users shared his posts or replied to it, they would include a relay hint to his personal relay and others would be able to see and then start following him on that relay directly -- now Alex Jones's events cannot be read by anyone that doesn't already know his relay.
- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
-
 @ 4dc2e570:7b8126f9
2024-11-25 17:39:37
@ 4dc2e570:7b8126f9
2024-11-25 17:39:37Chef's notes
Pickled pearl onions can usually be found at a middle eastern grocery store.
Details
- ⏲️ Prep time: 30 - 45 minutes
- 🍳 Cook time: 2 hours and 30 minutes
- 🍽️ Servings: 6
Ingredients
- 2.5 lbs stew meat
- 4 cloves Garlic
- 2 onions
- 6oz Bacon, chopped
- 4 Carrots (cut in 1/2 in pieces)
- 3 celery sticks (cut in 1 in pieces)
- 5 or so small gold potatoes, quartered
- 3ish tbps Flour
- 4 tbsp tomato paste
- 14 oz Guinness Beer
- 3 cups chicken stock
- 1 tsp Thyme
- 2 bay leaves
- Ghee
- Salt and pepper
Directions
- Pat dry then salt and pepper the beef. Melt 1/2 tbsp ghee over high med-high heat. Brown the beef on each side well, makes the stew tasty. This takes patience. Do some breath work while you're at it. :) Add ghee as necessary so browny bits on bottom dont burn. Put meat aside.
- In same pan, sauté onion and garlic for a few min. Throw in bacon till browned. Put in carrot and celery.
- Add 3tbsp flour (or a bit more, basically till oil is soaked up) and stir for a minute. Add tomato paste. Stir a couple more minutes.
- Add thin layer of beer and scrape yummy bits from bottom of pan. Mix everything well. Add rest of beer, broth, and herbs.
- Carmelize the pickled pearl onion on low med heat with a lil olive oil and stirring occasionally.
- Simmer covered for 2 hours. Add potatoes. Simmer for a further 30 minutes uncovered to let the sauce reduce a bit. Salt and pepper as you like. Add in some pearl onions. Enjoy.
-
 @ df478568:2a951e67
2025-02-01 15:07:26
@ df478568:2a951e67
2025-02-01 15:07:26
Garlic Cashew Recipe
I wrote about selling roasted cashews as an experiment in capitalism here. I make them myself and in the spirit of free and open source software, I figured I would open-source the recipe with a catch. You can get the recipe in one of two ways.
- Become a paid subscriber to my Substack and you will get a key to unlock the cipher text
- Read it in the clear(un-encrypted) on nostr. The easiest way to do this is to navigate to primal.net in your browser and search for “marc26z.” Click on my profile and *you can find all of my writing in the clear in the reads section.
I tried using PGP in another article, but it’s a little cumbersome and pretentious. Andreas Grifin said, Nostr is what PGP should have been. A web of trust with easy-to-use encryption and verification. I tend to agree. So I’m using something else.

https://8gwifi.org/CipherFunctions.jsp
Decrypt using the passphrase below the paywall.
"To encrypt is to indicate the desire for privacy, and to encrypt with weak cryptography is to indicate not too much desire for privacy.”
I do not indicate a desire for too much privacy here, but I like playing with these things. I hope you enjoy playing with them too.
How To Decrypt
- Go to https://encrypt-online.com/decrypt/ on your favorite web browser.
- Choose aes-256-cbc(this is the default setting)
- Copy and paste the cipher text into the decryption field
- enter the passphrase into the passphrase field
- press the Decrypt button
- Optional: Copy and paste the decrypted recipe into a markdown editor like https://dillinger.io/
U2FsdGVkX1+4jxMfWCc6kNsbDa0i/J3eiV81r7/z5c0Eqe73vw01M22uRFm9PjRRaj/CJN+BidtuNXQW6G3hk3S/4AoGN2gKfKkKSbzEHsONZ2LeXuoPflikratDU+lADVeR5IlsVaATyImBO0k/cXq54TOlEXBoVRCIqaA9tO8UA126GfTdmegXX14jUcdV9EISSGw8Bn5fksptm6qKyz2GsmyiKcmNczh8Nz7biyhCrnrt2hyLDbirIAjZcCTJjkAlJjrrvuLHJZx6pmq6MsMv2eHT35d/WL/+ZpBgLVh2Xq2u+J9izNKYMgvMSsJKylC7MJvj4xAOosJuq9IyGN6b/7z2UTSsR13Utc8aFeW3zxtkvAqYthh7XV1H2e1nEKOij8gOfFHvlfj10IiG0g3QbEch1nTTGq3Lncql9Q1a9QZb5pcsellPWeR4vhko3ssdxzIkLnvGz5Cjy1brMjZ97j7sSmHE9FT10L4L6ijXWuW25ikDRK0xnks0VfAvDVz75NCE+Qaz9MLPt8h0ESto3bTyuXrHFNNPOxnaEDw4TvSTN5G0tmUrqotRMmu5DadAm6aLMmJHL1OHVNGK4fH7Hb9S+7dBLEbQG3vRivz2SzpqgKFnFYwMJTQykUC3
Passphrase: implored-junker-requires
Here is the decrypted recipe if you do not wish to learn about encryption, but want to try my delicious non-vegan cashew recipe anyway.
1 LB organic raw cashews 2 TBS beef tallow 2 TBS salt 1 TBS garlic powder
Melt tallow in the microwave Brush the tallow on the nuts. Spread onto a cookie sheet.
Preheat oven 350 degrees
Bake for 10 minutes.
Let cool.
Violá!
Enjoy your garlic-roasted cashews. Or...you can pick some up at nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
881,805https://mempool.marc26z.com/block/00000000000000000000f5d9aa481b8f2555deaa8638a3c1f2eb4ffa8f474f9d
-
 @ cbaa0c82:e9313245
2025-02-01 15:07:16
@ cbaa0c82:e9313245
2025-02-01 15:07:16TheWholeGrain - #January2025
This January we really got to start the story telling of our first adventure series painted by Dakota Jernigan a.k.a. The Bitcoin Painter! The typical Singles of the month were released on Sunday along with a special Single released on the first to celebrate the New Year! Here we go, 2025! And, even with all that the monthly Concept Art, Bitcoin Art, and the newest Cover Art from Toast's Comic Collection were all still released! Not only was the first month of 2025 quite packed full of fun content, but the Bread and Toast website got a makeover! Did you notice all the explanation points!? We're all so excited we just can't help ourselves from using them!
January Sunday Singles 2025-01-01 | Sunday Single 73 Title: Happy New Year 2025 Happy New Year! What a year 2024 has been! We can’t wait to see what 2025 has in store for us! https://i.nostr.build/QFTmeR5p2FthPMXp.png
2025-01-05 | Sunday Single 074 Title: Snowflake It’s the most beautiful snowflake Toast has ever seen… until this one melts then it’s on to the next one! https://i.nostr.build/YHGeOcYv8WEP1fAf.png
2025-01-12 | Sunday Single 075 Title: Weight Lifting End-Piece has been working out since last year’s resolution. Now, time for heavy lifting! https://i.nostr.build/8lxeovAr5aK598Ze.png
2025-01-19 | Sunday Single 076 Title: Good Morning GM, Everybody! https://i.nostr.build/9jn2D2if4sFfNXzU.png
2025-01-26 | Sunday Single 077 Title: Chess When it comes to the chessboard, Bread is King. https://i.nostr.build/LZq57iL7tOWbHAKc.png
Adventure Series: Questline Bread, Toast, and End-Piece have started their journey in Grain Valley, and they have already found themselves in what used to be a village that is now been burnt to a crisp!
Writer: Daniel David (dan 🍞) Artist: Dakota Jernigan (The Bitcoin Painter)
2025-01-14 | Questline 001 - The Adventure Begins Our heroes take their first steps upon one of the oldest paths in all of Grain Valley. They can see the mountains in the background of the landscape before them. As they walk, they see in the distance ahead of them large amounts of black smoke rising until it disappears into the sky. https://i.nostr.build/ygjmYlWAZ4uPfPCn.png
2025-01-28 | Questline 002 - A Village Burned The source of smoke surrounds our heroes as their path brings them to the center of what used to be a village. It seems to be completely abandoned with no signs of life. Yet, all the remains of the village appear to have only recently burned to a crisp. What could have possibly happened here? https://i.nostr.build/BJ4L1shKh5YERzWc.png
Other Content Released in January 2025 2025-01-01 | Toast's Comic Collection Title: Iron Bread #9 "I am Iron Bread." - Tony Starch https://i.nostr.build/QJKkDCbfgc6Vqzcq.png
2025-01-08 | Concept Art Title: Second Bread Sketch A second sketch of the character Bread. Remade and cleaned up. https://i.nostr.build/4TXIRSUGA6viEaJx.png
2025-01-15 | Bitcoin Art Title: Stack Sats Toast is constantly stacking sats! https://i.nostr.build/txxkux0oJqyjNcSL.png
Thanks for checking out the fifth issue of The Whole Grain. The Whole Grain is released on the first of every month and covers all of the content released by Bread and Toast in the previous month. For all Bread and Toast content visit BreadandToast.com!
Thanks for helping us kick off 2025! Bread, Toast, and End-Piece
BreadandToast #SundaySingle #Questline #ToastsComicCollection #ConceptArt #BitcoinArt #Bread #Toast #EndPiece #Artstr #Comic #Cartoon #NostrOnly #🖼️
List of nPubs Mentioned: The Bitcoin Painter: npub1tx5ccpregnm9afq0xaj42hh93xl4qd3lfa7u74v5cdvyhwcnlanqplhd8g
dan 🍞: npub16e3vzr7dk2uepjcnl85nfare3kdapxge08gr42s99n9kg7xs8xhs90y9v6

















