-
 @ 8d34bd24:414be32b
2025-01-30 23:35:39
@ 8d34bd24:414be32b
2025-01-30 23:35:39Sometimes I’m reading the Bible and see a connection and go off chasing a rabbit trail. I type up my idea to organize my thoughts and see if there is actual Biblical support for it. Although it feels a bit weird to share Biblical ideas that I’m not certain about, it also seems a waste of lots of work to not share my speculations. Feel free to give me feedback if you disagree, especially if you have Scripture or historical evidence showing I’m wrong.
In this case, I’ve seen a portion that seems to be prophecy about our future, but that doesn’t necessarily mean that this entire group of chapters is future predictions. Sometimes prophecy mixes events that happens soon after the prophecy with events that will not be fulfilled until the distant future (like prophecies about Jesus’s first and second comings). I try to be open about what ideas I feel I have strong Biblical evidence to support and when my ideas have some evidence, but not conclusive evidence. This is one of my more speculative posts, but I hope you will find it thought provoking.
I was recently reading Isaiah 18-22. I had always assumed these prophecies of warning were in reference to things that had happened in the distant past (not that I knew any particular historical fulfillment), but this time I saw some major parallels with Revelation.
Now behold, here comes a troop of riders, horsemen in pairs.” And one said, “Fallen, fallen is Babylon; And all the images of her gods are shattered on the ground.” (Isaiah 21:9) {emphasis mine}
From Revelation:
And another angel, a second one, followed, saying, “Fallen, fallen is Babylon the great, she who has made all the nations drink of the wine of the passion of her immorality.” (Revelation 14:8) {emphasis mine}
And he cried out with a mighty voice, saying, “Fallen, fallen is Babylon the great! She has become a dwelling place of demons and a prison of every unclean spirit, and a prison of every unclean and hateful bird. (Revelation 18:2) {emphasis mine}
Of course it is possible that Babylon and Babylon the great are parallel, but different nations, but the similarity of statement is hard to deny.
All you inhabitants of the world and dwellers on earth,\ As soon as a standard is raised on the mountains, you will see it,\ And as soon as the trumpet is blown, you will hear it. (Isaiah 18:3) {emphasis mine}
This passage talks about all inhabitants of the world seeing a standard raised. Until the past 20 years or so, this was not possible. Now that almost every person on earth has a smart phone, we can know what is going on around the world in real time. This passage also refers to “dwellers on earth” which is a phrase used numerous times in Revelation.
In Revelation 11, it speaks of the two witnesses who testify to Jesus and call down plagues on the earth. After their death:
And their dead bodies will lie in the street of the great city which mystically is called Sodom and Egypt, where also their Lord was crucified. Those from the peoples and tribes and tongues and nations will look at their dead bodies for three and a half days, and will not permit their dead bodies to be laid in a tomb. And those who dwell on the earth will rejoice over them and celebrate; and they will send gifts to one another, because these two prophets tormented those who dwell on the earth. (Revelation 11:8-10) {emphasis mine}
Both passages refer to those who dwell on the earth and both talk about every person on earth seeing what is happening. This doesn’t sound like a prophecy fulfilled in ancient times, but about a prophecy that could not be fulfilled until modern times.
If these prophecies are about the end times and if the end times are now or very soon, what could they be referring to? Isaiah 18 begins with:
Woe to the land of whirring wings\ along the rivers of Cush,\ which sends envoys by sea\ in papyrus boats over the water.\ Go, swift messengers,\ to a people tall and smooth-skinned,\ to a people feared far and wide,\ an aggressive nation of strange speech,\ whose land is divided by rivers. (Isaiah 18:1-2)
Cush was located where modern day Sudan is located on the western edge of the Red Sea. Right across the red sea is Yemen which has been involved in missile and drone strikes on ships in the Red Sea. Traditionally the “land of whirring wings” is interpreted to mean locusts, but could it be referring to modern technology like drones? Who is Cush sent to seek? Who are the people “over the water,” “tall1 and smooth-skinned,” “feared far and wide,” and “an aggressive nation of strange speech,\ whose land is divided by rivers.”? I wonder if it could be the US. The US is over the Atlantic Ocean, “feared far and wide,” “an aggressive nation of strange speech” (involved in the business of almost every nation on earth), and divided by the Mississippi River (and to a lesser extent the Missouri and Ohio Rivers). The US also likes to act as the world’s policeman and get involved in every international dispute in the world. If Sudan was in fear of attack by the Houthis in Yemen, it would be expected for the US to be called in and get involved.
At the end of this prophecy:
At that time gifts will be brought to the Lord Almighty\ from a people tall and smooth-skinned,\ from a people feared far and wide,\ an aggressive nation of strange speech,\ whose land is divided by rivers—\ the gifts will be brought to Mount Zion, the place of the Name of the Lord Almighty. (Isaiah 18:7)
This same nation will bring a gift to Mount Zion (Jerusalem/Israel). The US has been regularly giving Israel weapons to defend itself from attacks by the enemies around it. If this nation is the US, then this would make sense, especially with our change in leadership.
When I read Isaiah 19, it made me think of the Muslim Brotherhood takeover of Egypt starting in 2011.
“I will stir up Egyptian against Egyptian—\ brother will fight against brother,\ neighbor against neighbor,\ city against city,\ kingdom against kingdom.\ The Egyptians will lose heart,\ and I will bring their plans to nothing;\ they will consult the idols and the spirits of the dead,\ the mediums and the spiritists.\ I will hand the Egyptians over\ to the power of a cruel master,\ and a fierce king will rule over them,”\ declares the Lord, the Lord Almighty. (Isaiah 19:2-4)
The next part of this passage talks about the Nile drying up and the canals stinking and the fields becoming parched. I did a web search related to drought in Egypt and found an article about drought fears from 2020. The building of the Grand Ethiopia Renaissance Dam on the Blue Nile is causing a fear of major drought in Egypt. There are negotiations between Egypt, Sudan, and Ethiopia to deal with this, but it looks like an ongoing issue for Egypt. An interesting fact is that Ethiopia started building this dam in 2011 -- the same year of the Muslim Brother Hood overthrow of Egypt.
The biggest problem with my theory is Isaiah 20, which talks about Assyria leading Egypt and Cush (Sudan) away as captives. Assyria was located in what is currently Northern Iraq. It is hard to fathom Iraq conquering Egypt and Sudan. The area of Assyria did include a little bit of Turkey, which would be more believable as a conqueror.
Now we get back to the verses in Isaiah 21, which started this musing. First there is a description of terrorists attack:
A prophecy against the Desert by the Sea:
Like whirlwinds sweeping through the southland,\ an invader comes from the desert,\ from a land of terror.\ A dire vision has been shown to me:\ The traitor betrays, the looter takes loot.\ Elam, attack! Media, lay siege!\ I will bring to an end all the groaning she caused. (Isaiah 21:1-2)
Elam is the Eastern edge of Iraq on the Border of Iran and Media is in Iran. Could this be an attack from Iran that includes some of its Shia allies in Iraq? What kind of attack could it be – conventional or nuclear? Who are they attacking?
Look, here comes a man in a chariot\ with a team of horses.\ And he gives back the answer:\ ‘Babylon has fallen, has fallen.\ All the images of its gods\ lie shattered on the ground!’ ”\ My people who are crushed on the threshing floor,\ I tell you what I have heard\ from the Lord Almighty,\ from the God of Israel. (Isaiah 21:9-10)
In ancient times, Babylon was located in the location of modern Iraq, but if we look at the words “Babylon has fallen, has fallen,” and associate them with the almost identical words in Revelation, “Fallen, fallen is Babylon the great,” and we consider how Revelation also refers to “Mystery Babylon” then we are likely talking about an attack on a different nation. (Why would Babylon be a mystery if it was the same people in the same location? It would be a mystery if it was a country and peoples that didn’t exist at the time of the prophecy, but would have the spirit of Babylon in them.) If you take into account my arguments in “Speculation on Babylon the Great” and associate this nation with the people “over the water,” “tall and smooth-skinned,” “feared far and wide,” and “an aggressive nation of strange speech, whose land is divided by rivers.” then this could be an attack on the US (I’ll admit there is a fair amount of speculation here). Although the US has become quite anti-God and has been pushing a lot of evil around the world, it still has one of the largest populations of believers in the world. The statement “My people who are crushed on the threshing floor” also fits for the US.
I know some people won’t consider the possibility that the US could be Mystery Babylon or Babylon the Great because they can’t consider the US being an evil nation, but the US has been pushing many unbiblical ideas on the nations around the globe, like LGBTQ ideology and abortion. It is also possible I am looking too hard for my own country in the scriptures because if the US isn’t mentioned, then something has to happen to the US before the Tribulation occurs to make the US become unimportant in international affairs. We all have our biases.
I’d love to hear your thoughts on my speculations. I’d also like to hear whether people benefit from my speculations or prefer me to stick to the clear and more easily understood Bible passages and Bible truths.
Trust Jesus.\ \ your sister in Christ,
-
 @ cc8d072e:a6a026cb
2025-01-30 17:20:24
@ cc8d072e:a6a026cb
2025-01-30 17:20:24Recently, I had the opportunity to work as an advisor for an AI agent project, which is created by team with a lot of fin-tech software develop experience. As we coded together, their real-time questions and challenges provided unique insights into the hurdles software engineers face when transitioning to AI development. They would pause at moments that most AI engineers take for granted - "How can we be sure the agent understood correctly?", "What if the model makes a mistake?", "How do we handle the uncertainty?" These weren't just isolated questions; they represented the fundamental paradigm shift required when moving from traditional software engineering to AI development. And thats why i think it might be worthy to take sometime write down this article and if you are going to start your first AI agent programming, spending 5 min reading t his will save you a lot of time later.
1. Shifting from Deterministic to Probabilistic Thinking
- Traditional software engineering deals with deterministic outcomes
- AI systems operate on probability rather than certainty
- Engineers need to adapt from "100% correct" mindset to accepting probabilistic outcomes
- Blockchain developers may find this particularly challenging due to their background in exact, deterministic systems
2. Understanding Core AI Concepts
(There are a lot of concepts to understand, but i will focus on the most frequently asked ones)
Memory Management
- Short-term Memory: Implemented through conversation context
- Long-term Memory: Implemented through vector databases (RAG - Retrieval Augmented Generation)
- Context length management is crucial due to LLM token limitations
Language Models and Fine-tuning
- Base models (like GPT) provide general intelligence
- Domain-specific knowledge can be added through:
- Fine-tuning with custom datasets
- Adding RAG layers for specific knowledge domains
3. Technical Framework Knowledge
Essential Tools and Frameworks
- Vercel AI SDK (if you are a typescript guy)
- LangChain (alternative option)
- Different models(openai, claude, gemini, etc, of course, now, deepseek. the temu in llm )
- Understanding of prompt engineering
Multi-Agent Systems
- Agents can communicate through natural language
- Inter-agent communication requires careful system design
- Implementation of thought processes and decision-making loops
- Safety considerations for system commands and operations
4. Language and Localization Considerations
- System prompts typically work best in English
- Multi-language support requires careful handling:
- Input translation to English
- Processing in English
- Output translation to target language
- Model performance varies across different languages
5. Safety and Error Handling
- Implementing validation layers for critical operations
- Understanding model limitations and potential errors
- Building feedback mechanisms to detect misunderstandings
Conclusion
Transitioning from software engineering to AI engineering requires a significant mindset shift. While traditional software engineering skills remain valuable, understanding probabilistic systems, language models, and AI-specific architectures is crucial. The key is to balance innovation with practical safety considerations, especially when dealing with critical applications.
Remember that AI systems are not perfect, and building robust applications requires careful consideration of their limitations and appropriate safety measures. Start with existing frameworks and gradually build up complexity as you become more comfortable with AI-specific concepts and challenges.(the conclusion part is written by chatgpt, did you notice? :))
-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ 8d5ba92c:c6c3ecd5
2025-01-30 15:58:03
@ 8d5ba92c:c6c3ecd5
2025-01-30 15:58:03For me, it’s simple yet profound: a job and labor aren’t the same thing. You don’t have to struggle to perform a task or to meet someone else's unrealistic expectations. In fact, if you genuinely enjoy what you’re doing and believe in its purpose, the results will naturally be better—and everyone benefits.
I’m speaking from the perspective of someone who walked away from a "well-established career" multiple times. These days, I might be working more than ever, but I don’t feel tired, frustrated, or burned out. The radical change I made—leaving the "professional fiat world" behind—wasn’t easy, but I’ve never regretted it. Now, working fully in Bitcoin, I feel more motivated and satisfied than ever before.
Sure, it's not always straightforward.
This lifestyle definitely comes with its challenges. But those challenges don’t crush me. Just the opposite. When combined with a sense of freedom, they become opportunities for growth—something I truly value. It’s a completely different experience compared to most jobs rooted in the old system.
I’m not saying working in Bitcoin is all sunshine and rainbows, nor am I criticizing anyone still working in fiat. What I’m trying to emphasize is the core message of that quote:
Do what you love, and you’ll never work a day in your life...
Read it aloud and think about your last couple of jobs.
How did you feel? Did you find fulfillment and satisfaction, or was it more like a form of slavery that made you dread going to bed and waking up every morning?
I didn’t really have those feelings, except for one corporation at the beginning of my career, which gave me a hard time but also taught me valuable lessons. Aside from that experience, most of my jobs weren’t too bad—no need to complain. Still, I often questioned my situation: 'Seriously, why do I have to do this or that if I know it doesn’t make sense?'
Doing things you don’t believe in can lead to frustration, often in ways you might not even realize, yet every time, significantly affecting your well-being and the people around you.
Now, I hardly know what inner anger means.
I wake up happy, full of passion and ideas. I don’t track the hours as they pass; instead, I focus on all the tasks I complete and how they make a difference for me and others. Yes, I love what I do. And returning to the main point of this article, I shouldn’t even see it as work, even though in practice it definitely is.
The key here is a mix of independence, purpose, and self-determination. Bitcoin has helped me achieve that to a level that’s hard to break.
A Fresh Take on The Market
I also remember that 5-7 years ago, especially for non-devs, Bitcoin-based jobs weren’t as accessible as they are now (which is probably why I stayed in my traditional career for so long...). It’s really only in the last, maybe 2-3 years that things have changed. With so many areas expanding beyond just mining and tech-related stuff, and new interesting projects popping up regularly, there’s almost any position you can imagine to jump into.
According to a recent report by Bitvocation '69% of Bitcoin jobs are non-developer roles'. Also, more than half of available positions in 2024 offered remote opportunities, giving job seekers extra flexibility. Bitcoin is borderless—and so are many of the jobs in this space. If you’ve ever thought working in Bitcoin was out of reach, think again—and check this out "BITCOIN JOB MARKET DATA, 2024 Report".
One tip from my experience: a good option is to start with a part-time role while keeping your traditional fiat job for more stability, especially at the beginning. After a while, you’ll gain more confidence and see which direction you want to go. Or, if you position yourself so that you don’t need to earn a lot for the next 3-6 months, consider finding a project- or task-based Bitcoin job, maybe even just an internship. Meanwhile, you might decide to focus on building something unique on your own. It can feel amazing! You’ll gain valuable skills, sharpen your experience, and better understand which options work best for your future.
You see, just like in nature, balance is key. You don’t have to run before you can walk.
What I’m saying is this:
The choice is yours, as long as you plan ahead + learn, while staying true to your needs, beliefs, and priorities.
If you want it, do it. Starting a career in Bitcoin is possible, and I have a feeling this space will grow even faster in the next few years. Yes, there will still be ups and downs (hello, bear markets!), but if you plan thoughtfully, there’s not much to worry about.
We’re still early—Bitcoin is only 16 years old—but if you’ve been following this space, you’ve probably seen how dynamic and resilient it is. If you’ve ever thought about working in Bitcoin, now is the time to rethink the possibilities :)))
BTC Your Mind. Let it Beat.
Şelale
-
 @ f1989a96:bcaaf2c1
2025-01-30 15:25:34
@ f1989a96:bcaaf2c1
2025-01-30 15:25:34Good morning, readers!
This week, authoritarian regimes augmented their control and monitoring of online spaces in an attempt to suppress the dissenting voices of those they have financially repressed. While Pakistanis grapple with the highest cost of living in Asia, the military-backed regime passed an oppressive social media bill that empowers the government to imprison and fine individuals deemed to be spreading “disinformation” online.\ \ Meanwhile, in Belarus, authoritarian Alexander Lukashenko secured a seventh term in an openly rigged presidential election, further consolidating his grip on power and deepening the country’s political and financial repression. This prolongs his rule beyond three decades, cementing him as the sole ruler of Belarus since the country gained independence from the Soviet Union in 1991.
In freedom technology news, open-source developer Super Testnet released a new privacy tool called Hurricash. It lets multiple users lock funds together in a single Bitcoin Unspent Transaction Output (UTXO), allowing them to transact within the pool of users with greater privacy and efficiency. With greater liquidity and adoption, it could prove a useful tool for human rights activists seeking financial privacy. \ \ Additionally, Zaprite integrated BTCPay Server, enabling users to accept Bitcoin, Lightning, and fiat payments using self-custodial and self-hosted Bitcoin infrastructure. This is particularly valuable for nonprofits and activists in authoritarian regimes, where governments monitor and restrict financial activity.
We end with the latest episode of the “Money Matters” podcast, where Jack Mallers, CEO of Strike, interviews HRF Chief Strategy Officer Alex Gladstein to discuss the often overlooked connection between Bitcoin and financial freedom.
Now, let’s jump right in!
Subscribe Here
GLOBAL NEWS
Belarus | Lukashenko Sweeps Openly Rigged Election Amid Financial Repression
In Belarus, authoritarian leader Alexander Lukashenko secured a seventh term in an openly rigged presidential election. Lukashenko’s crusade against dissent and political opposition has left many citizens and opposition figures exiled, imprisoned, and financially repressed. Historically, his regime has frozen bank accounts, blocked foreign currency exchanges, and cut off independent media from funding. By wielding financial and political power, Lukashenko ensures that no real opposition can rise, turning Belarus into a country where even the illusion of democracy has disappeared. In these environments, Bitcoin and tools like Lnp2pbot (an HRF grantee) help Belarusians circumvent financial restrictions and transact in a currency that Lukashenko can’t control.
Nigeria | Joins BRICS Economic Coalition
Nigeria is expanding its financial repression both internationally and domestically. It recently joined BRICS, an intergovernmental economic organization led by the Chinese and Russian regimes. For some, this raises concerns as Nigeria may deepen its authoritarian ways and further restrict individual financial freedoms. Member countries are each leaders in the development and implementation of central bank digital currencies (CBDCs), threatening individual financial autonomy as financial control is increasingly placed under the purview of authoritarian states. In parallel, the Nigerian regime plans to distribute a 75,000 naira ($48) “cash transfer” to the nation’s poorest citizens. This bid to alleviate poverty risks, while stoking inflation and compromising privacy, as the initiative relies on digital registration through the National Identity Number (NIN) system. Nigeria’s strategy of using both micro and macro financial controls limits open markets and curtails individual freedoms.
Pakistan | Regime Passes Repressive Bill Targeting Online Spaces
Pakistan’s military-backed regime passed a repressive social media bill that allows officials to imprison citizens for spreading “disinformation” online. Under this new law, officials can block “unlawful and offensive” content and remove users from social media at a time when Pakistanis are increasingly turning to online spaces to express discontent over regime-imposed economic hardships. Those “spreading disinformation” risk facing three years in prison and fines of up to 2 million rupees ($7,150) — a harsh penalty for citizens grappling with the highest cost of living on the continent. Further, social platforms must register with the Social Media Protection and Regulatory Authority to operate or risk a permanent ban. Censorship and Internet controls are sadly nothing new for Pakistanis since the regime has blocked X during elections and enacted a nationwide Internet firewall to suppress public discourse and action.
Cuba | Salary of Baseball Player Buys a Carton of Eggs
Cuba’s cost-of-living crisis is so severe that even the country’s top and most profitable athletes cannot make ends meet. Exemplifying this, the monthly salary of a professional baseball player in the National Series — Cuba’s premier sporting event — barely covers the cost of a carton of eggs, forcing them to seek opportunities elsewhere. With the Cuban peso in freefall, several players have resigned, citing financial hardships as the reason for leaving the sport they love. Their departures reflect a broader reality: wages across Cuba fail to keep pace with severe inflation caused by the Cuban regime’s continuous economic mismanagement. The state continues to enforce wages in the collapsing peso while requiring “MLC” credits to purchase high-quality food and goods in a system that pulls in foreign exchange from abroad while stealing from citizens at home.
South Sudan | Regime Blocks Citizen Access to Social Media
In South Sudan, rebel leader Salva Kiir Mayardit directed the National Communication Authority (NCA) to block each citizen’s access to social media nationwide for up to three months, citing concerns over “public safety” and “mental health.” This decision follows violent videos of Sudanese armed forces attacking South Sudanese refugees in Sudan. Sudanese rights groups condemned the ban as a blatant act of censorship and an abuse of power. “The death of our South Sudanese in Sudan should not culminate in blocking social media, which is one of the ways many of us get information,” said one Sudanese citizen. By restricting social media, the regime demonstrates a clear willingness to silence dissent, suppress information, and stifle transparency under the guise of “protection.” As Sudanese grapple with rising prices, the ban further isolates them, leaving little room to coordinate relief efforts, share grievances, or hold those in power accountable.
RECOMMENDED CONTENT
IMF Offers a Glimpse at the Perils of Central Bank Digital Currencies by J.D. Tuccille
In this article for Reason Magazine, J.D. Tuccille examines the dangers of central bank digital currencies (CBDCs) and their implications for financial independence and privacy. Drawing from the International Monetary Fund’s (IMF) “CBDC Virtual Handbook,” Tuccille explains how CBDCs grant governments unprecedented control to monitor transactions, impose restrictions, and manipulate financial behavior. He contrasts these state-issued digital currencies with decentralized alternatives like Bitcoin, highlighting the stark differences in privacy and user freedom. You can read the complete analysis here. To learn more about CBDCs and the threats they pose to civil liberties and human rights, check out our HRF’s CBDC Tracker.
BITCOIN AND FREEDOM TECH NEWS
Super Testnet | Launches Hurricash
Bitcoin Developer Super Testnet released Hurricash, an experimental and open-source Bitcoin privacy protocol. Hurricash lets multiple users lock funds together in a single Bitcoin Unspent Transaction Output (UTXO), making their transactions more private. Users can then transact within the pool with greater efficiency and privacy. With greater liquidity and adoption, it could prove a useful tool for human rights defenders seeking financial privacy. Innovations like this could also pave the way for activists in many decades to afford trustless BTC transactions.
Zaprite | Integrates BTCPay Server
Zaprite, a platform for accepting Bitcoin payments, recently integrated BTCPay Server, an open-source Bitcoin payment processor and HRF grantee. This integration allows users to accept Bitcoin, Lightning, and fiat payments (like USD) while maintaining full control over their funds — something Zaprite couldn’t afford on its own. By connecting with BTCPay Server, users can receive Bitcoin payments directly to their own self-hosted wallet and node, reducing censorship risks and enhancing financial independence. This is valuable for nonprofits, merchants, and activists in authoritarian regimes, where governments monitor, freeze, and restrict financial activity.
Breez SDK | Implements Pay to BIP 353 Addresses
The Breez Software Development Kit (SDK), a tool for integrating self-custodial Lightning payments into apps and services, now supports payments to BIP 353 addresses. BIP 353 enables individuals with access to a domain the ability to create static, human-readable payment addresses (such as user@domain), instead of a long string of letters and numbers. This means an activist with a website can receive Bitcoin donations directly through their domain — if their wallet supports BIP 353. Several Bitcoin wallets already using the Breez SDK include Cake Wallet, Blitz Wallet, and Klever Wallet. These static addresses make receiving Bitcoin easier, more private, and more censorship resistant, reducing surveillance risks and simplifying recurring payments.
Ark Labs | Releases Wallet Software Development Kit
Ark, a protocol promising faster and cheaper transactions on Bitcoin, released a wallet software development kit (SDK). The SDK is aimed at helping developers more readily create Ark-compatible Bitcoin wallets that support both traditional Bitcoin payments and Ark’s instant transactions on mobile and desktop platforms. Protocols like Ark hold promise for greater transaction efficiency and improve its transaction capabilities for those who need it most.
Tornado Cash | US District Court Reverses Sanctions
A United States District Court ruled to reverse the sanctions on Tornado Cash, marking a major legal win for financial privacy in the digital asset space. This decision follows a previous Appeals Court ruling that found the Treasury overstepped its authority by sentencing the digital asset mixer under the International Emergency Economic Powers Act (IEEPA). The court determined that Tornado Cash’s smart contracts (self-executing lines of code) do not constitute “property,” making them ineligible for sanctions under existing laws. These rulings set a positive precedent for decentralized protocols and financial privacy in a world where these tools are desperately needed. Developers cannot work on privacy openly in dictatorships, so they need havens in liberal democracies.
OpenSats | Announces Grants for Three Bitcoin Core Contributors
OpenSats, a public nonprofit supporting open-source software and projects, announced three new grants for Bitcoin Core contributors L0rinc, kevkevin, and Daniela Brozzoni. L0rinc will improve Bitcoin Core's performance and reliability by optimizing Initial Block Download (IBD), block storage, and database functionality. Kevkevin will enhance Bitcoin Core's stability, security, and usability by fixing bugs and reviewing pull requests. Finally, Daniela will review Bitcoin Core's code, adding features and improving test coverage. HRF is pleased to see the continued support of open-source developers from this Bitcoin Development Fund grantee.
Bitcoin Chiang Mai | Bitcoin for Human Rights Meetup
Bitcoin Chiang Mai, a grassroots Bitcoin community in Thailand, will host a meetup exploring Bitcoin’s role in human rights and financial freedom on Feb. 7, 2025. HRF Global Bitcoin Adoption Fellow Win Ko Ko Aung will discuss how Bitcoin empowers activists and communities under authoritarian rule, with a particular focus on Burmese citizens. Held in Burmese and English, the event will educate attendees on Bitcoin as a tool for escaping financial repression. If you have Burmese friends in Chiang Mai, share this opportunity with them. You can register here.
RECOMMENDED CONTENT
Bitcoin and Freedom with Alex Gladstein
In a special episode of the “Money Matters” podcast, Jack Mallers, CEO of Strike, speaks with Alex Gladstein, chief strategy officer at HRF, to discuss the powerful link between Bitcoin and financial freedom. Gladstein unpacks how authoritarian regimes manipulate money to control the public and explains why open-source financial tools are critical for resisting oppression. His insights make a compelling case for financial sovereignty as a fundamental human right — and why Bitcoin remains the most effective tool to secure it.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ e31e84c4:77bbabc0
2025-01-30 10:31:49
@ e31e84c4:77bbabc0
2025-01-30 10:31:49Censorship today has evolved into something far more insidious than its traditional form. No longer limited to overt bans or government blacklists, it now thrives in subtler, more pervasive ways—hidden behind corporate policies, social algorithms, and political pressures. This new form of censorship cloaks itself in the language of promoting online safety, stopping misinformation, and defending democracy, but its effect is no less stifling.
Community guidelines of big tech platforms have become the weapon of choice to shape the boundaries of online discourse. In fact, online censorship is now a growing industry that receives funding and support from both government departments and the private sector. The National Science Foundation, for example, awarded over $40 million worth of grants for the development of AI tools "to counter misinformation online" and "advance state-of-the-art misinformation research"—a long-winded way of saying AI-powered censorship tools.
As with most evils in this world, centralization is the plank on which censorship rests. The centralized nature of big tech platforms not only gives them access to treasure troves of our personal data, but programs like PRISM, also give the government backdoor access to it. Just as with central banks, platforms like YouTube and Netflix become choke points that can be squeezed at will to enforce certain narratives.
Thankfully, since the invention of Bitcoin, we have not only had hard money that cannot be debased by any central bank but, more importantly, the world was bequeathed with a blueprint for building decentralized products and services at scale. For example, it wouldn't be too far-fetched to say that the inspiration behind Nostr's design was Bitcoin, even with the apparent differences in the architectures of the two. A decentralized, censorship-resistant communications protocol was inevitable after the emergence of censorship-resistant money.
Bitcoin and Nostr are the foundation of a decentralized creator economy that is not captured by big tech and their advertisers. Despite all these great strides towards pragmatically securing free speech online, the censorship industrial complex still has a chokehold on the film industry. While social media platforms actively suppress information they don't like, the film industry disguises propaganda as entertainment to achieve the same goal.
Historically speaking, the arts, especially the film industry, have been a very important and effective tool in shaping public perception and controlling the flow of information. During World War II, the Nazis produced numerous films that were part of a broader strategy by Joseph Goebbels, the Minister of Propaganda, to manipulate public opinion in favor of the Nazi regime. They were designed to instill loyalty, promote anti-Semitism, and glorify the ideals of the Third Reich. Unfortunately, these tactics were not confined to that period in history and are still in use today.
Since 1948, the Pentagon's Entertainment Liaison Office has played a significant role in shaping Hollywood productions, with the Central Intelligence Agency (CIA) subsequently establishing a similar office in 1996. Initially perceived as passive advisors, these agencies have exerted influence by requesting script changes in exchange for access to resources like equipment and filming locations. The Department of Defense (DoD) has backed over 800 feature films, including major franchises like Transformers, Top Gun, The Terminator, and Iron Man. On the small screen, over 1,100 TV titles like Army Wives, NCIS, Homeland, and Flight 93 have received Pentagon support since 2001.

Journalist David Robb, in his book Operation Hollywood: How the Pentagon Shapes and Censors the Movies, wrote:
"The Pentagon even uses movies and TV shows to target children as future recruits, as it did with two of the most popular kids' TV shows of all time, Lassie and The Mickey Mouse Club. Episodes of both shows were rewritten at the Pentagon's insistence to make the armed forces more attractive to children."
It is undeniably evident that for a very long time, the national security state has shaped thousands of hours of our viewing experience. The portrayal of war in these productions often paints a sanitized picture that masks the complexities of combat, the ambiguities of victory, and the political machinations behind military actions. Are we seeing the truth of war, or a carefully crafted narrative that serves a larger agenda? Are the horrors of war being normalized as necessary evils to rally public support for future conflicts? One can only wonder.
Time would fail me if we had to discuss how this same relationship extends to the news media, as exemplified by the dismissal of Phil Donahue from MSNBC for having guests on his show who were critical of the Iraq War. Or how Disney spent almost $1 billion in 2023 on movies that were flops, as a result of their lack of substance due to their woke themes. Let's not even begin to talk about the nearly $2 billion the pharmaceutical industry spent on television ads in the first quarter of 2023 alone. Perhaps that's the going rate for a shot at shaping consumer demand and influencing news coverage of the industry. The larger point is that from both the big screen and the small screen, we are constantly bombarded with propaganda and carefully curated content that not only influences our buying decisions but our worldviews as well. This pervasive influence operates on a deeper level than we might realize, as we tend to perceive the world through cultural lenses pre-defined for us. Those who shape these fundamental worldviews wield immense power, subtly guiding our thoughts and actions. The genius of this influence lies in its invisibility - we often misinterpret these externally crafted ideas for our own independent thoughts.
As noted earlier, the film industry's centralized structure has led to a troubling prioritization of political narratives over audience needs and factual accuracy. To disrupt this status quo, a new breed of independent filmmakers and streaming platforms is required. These should embrace political neutrality and leverage emerging technologies like Bitcoin. The latter would be critical in revolutionizing content monetization, thus freeing creators from the grip of studio executives and other political influences that are used to censoring content they dislike. One such platform is IndeeHub.

IndeeHub is a streaming platform that aims to empower independent filmmakers by providing a fair and sustainable ecosystem for content creation and distribution. Not only could this potentially break Hollywood's monopoly, but it is an essential step in the creation of unbiased quality films. Despite launching early last year and still being in beta, the platform was able to score a major win when it was selected as the main streaming partner for the second edition of the Bitcoin Film Fest, which was held in Warsaw in April of this year.
IndeeHub's business model redefines film industry economics. By integrating Lightning network payments, it creates a true free market for content creators. Filmmakers earn per second of viewership, with revenue split among anyone on their cap table. Bad content immediately gets punished by lack of views and therefore lower revenue for the filmmaker, with great content being rewarded with more eyeballs and ultimately higher revenue. Just like Nostr, this serves as the perfect yardstick for measuring the reception by audiences of a particular production. This paradigm shift aligns incentives with audience engagement, potentially transforming both artistic creation and consumption.
In an interview the Ceo and founder of IndeeHub, Zack Mahoney, when quizzed on where he envisions IndeeHub said;
“Our goal is to be the best solution for filmmakers from concept to exhibition. I would love to see films not only exhibiting on this platform but beginning their lifecycle here as well. I envision a platform where filmmakers can collaborate, take risks, hone their craft, exhibit their work, and ultimately thrive in this industry.”

While many of the problems of the film industry aren't going to be solved overnight by one platform, IndeeHub is clearly on the right path to become the one-stop shop for financing films as well as collaboration and distribution. It's a truly innovative platform outside the control of the censors and the gatekeepers, beholden only to its mission. Zack went on to emphasize a very important point when he said:
"Storytelling is a cornerstone of the human experience and a fundamental process by which consciousness evolves,""Storytelling is a cornerstone of the human experience and a fundamental process by which consciousness evolves,"
a sentiment I concur with wholeheartedly. If those controlling the most influential storytelling medium are shaping society toward a dystopian reality, then what value does freedom money hold in a world where minds remain captive?
Just as Bitcoin is a solution that removed trusted third parties from transactions and created a digital peer-to-peer cash system, IndeeHub also aims to be a solution that creates an alternative to the centralized streaming platforms that are under the thumb of advertisers and government agencies. By integrating the hardest money ever known to man, Bitcoin, it's saving the film industry from collapsing under its own weight while unleashing creativity on an unimaginable scale. It's time to build the world we want to see.
Uncensoring Art was Written By Kudzai Kutukwa. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: muggyarch11@walletofsatoshi.com**
-
 @ 1af54955:31eed960
2025-01-30 08:08:22
@ 1af54955:31eed960
2025-01-30 08:08:22Persian rugs are much more than just floor coverings—they are timeless pieces of art that bring beauty, warmth, and cultural richness into homes across the globe. Known for their intricate designs, superior craftsmanship, and lasting value, these rugs have been treasured for centuries. Whether you're an interior design enthusiast or a first-time buyer, understanding the advantages of Persian rugs can help you appreciate why they remain a staple in homes and collections worldwide.

1. Durability and Longevity
One of the standout advantages of Persian rugs is their incredible durability. Hand-knotted with precision and care, these rugs are made from high-quality materials like wool, silk, and cotton. Wool, in particular, is known for its natural resilience, making Persian rugs resistant to wear and tear, even in high-traffic areas. Unlike mass-produced rugs, which can lose their appeal over time, a well-crafted Persian rug can last for generations when properly maintained. In fact, many Persian rugs have survived for hundreds of years, maintaining their beauty and structure. This longevity makes them an excellent investment, as a good-quality Persian rug only grows more valuable with age. Unlike synthetic carpets that may need replacing every few years, a Persian rug, when taken care of, can become a cherished family heirloom.

2. Unique Artistic Design
Each Persian rug is a masterpiece of artistry. With intricate patterns, vibrant colors, and symbolic designs, these rugs are often compared to fine art because of the level of skill involved in their creation. The designs can vary widely depending on the region of origin, the weaver's personal style, and the materials used. Whether you're drawn to the geometric patterns of Shiraz rugs or the floral motifs of Tabriz, there’s a design to suit every taste. Beyond the aesthetic appeal, Persian rugs also hold cultural significance. The patterns and motifs often have symbolic meanings—representing everything from nature to spiritual beliefs. When you invest in a Persian rug, you're not just buying a piece of decor ; you're embracing centuries of tradition and storytelling woven into every knot.

3. Value and Investment
Persian rugs are more than just beautiful; they are also an investment. Many high-quality Persian rugs increase in value over time, particularly rare pieces made with exceptional materials or unique designs. Collectors value rugs from specific regions or those that feature intricate craftsmanship, and these pieces can appreciate significantly in value. Buying a Persian rug can be seen as purchasing a valuable asset, especially if you select a rug from a reputable source or a renowned weaving center. Unlike furniture or modern decor, a well-maintained Persian rug can actually become more valuable as it ages, making it a wise long-term investment.

4. Versatility in Interior Design
One of the most attractive qualities of Persian rugs is their versatility. Whether your home features modern minimalism, classic elegance, or rustic charm, a Persian rug can seamlessly integrate into any design style. Its rich textures and colors can anchor a room, adding warmth and character to any space. From living rooms to bedrooms, from formal dining rooms to cozy corners, Persian rugs can elevate the atmosphere of any room. Their ability to blend with diverse interior aesthetics while maintaining their individuality makes them an enduring choice for homeowners and decorators alike.

5. Natural Materials and Sustainability
Many Persian rugs are made from natural materials like wool, silk, and cotton, which are not only luxurious but also sustainable. Wool, for instance, is a renewable resource that’s biodegradable, making it an eco-friendly alternative to synthetic fibers. The natural dyes used in Persian rugs are also derived from plants and minerals, ensuring that these rugs have a minimal environmental footprint.\ Unlike machine made rugs made from synthetic materials that may contribute to microplastics pollution, Persian rugs made from natural fibers are both luxurious and environmentally conscious, allowing you to enjoy the beauty of your home while being mindful of sustainability. Unlike machine made rugs made from synthetic materials that may contribute to microplastics pollution, Persian rugs made from natural fibers are both luxurious and environmentally conscious, allowing you to enjoy the beauty of your home while being mindful of sustainability.
 \
6. Comfort and Warmth\
\
In addition to their aesthetic and investment value, Persian rugs offer practical benefits, particularly when it comes to comfort and warmth. The thick pile of a Persian rug provides a soft surface to walk on, making it a delight to touch. Whether you're walking barefoot or sitting on the floor, the plush texture adds comfort to your space.Moreover, Persian rugs act as natural insulators. They help trap warmth, making rooms feel cozier and more comfortable, particularly during colder months. In this way, a Persian rug is not just a decorative addition to your home, but a functional one as well, contributing to your home’s overall comfort and energy efficiency.
\
6. Comfort and Warmth\
\
In addition to their aesthetic and investment value, Persian rugs offer practical benefits, particularly when it comes to comfort and warmth. The thick pile of a Persian rug provides a soft surface to walk on, making it a delight to touch. Whether you're walking barefoot or sitting on the floor, the plush texture adds comfort to your space.Moreover, Persian rugs act as natural insulators. They help trap warmth, making rooms feel cozier and more comfortable, particularly during colder months. In this way, a Persian rug is not just a decorative addition to your home, but a functional one as well, contributing to your home’s overall comfort and energy efficiency.
7. Conclusion
Persian rugs are more than just beautiful pieces of floor decor—they’re investments in artistry, culture, and comfort. Their durability, unique designs, and potential for long-term value make them an enduring choice for homeowners looking to add elegance and warmth to their spaces. Whether you’re a first-time buyer or a seasoned collector, the advantages of Persian rugs are undeniable. If you're considering adding one to your home, take the time to explore the wide range of styles and designs available. A Persian rug could be the centerpiece of your home, offering beauty, comfort, and a piece of history that will last for generations.

-
 @ 7cb5fba1:4ea55c0e
2025-01-30 05:36:08
@ 7cb5fba1:4ea55c0e
2025-01-30 05:36:08

Samira parties with customers at a brothel. She was married at 12, trafficked to a brothel two weeks later.

A madam counts money in a brothel


Mia, 15, sits with her new 27-year-old groom during their wedding. ‘My family has been saving for my wedding for a very long time. I am a girl, so they always knew they would need to give me away.' Five or six months ago, her parents found Mia a groom, a 27-year-old man who works in a garment factory. 'I am nervous,' Mia says, quietly. 'I think I will miss my family'

Yasmin waits for customers

A girl shows her self harm scars

Women wait for customers

Habiba waits for customers. The 14-year-old has been in a brothel for three years

‘I ran away from my husband after seven days. He was only about 15 or 16, but he raped me so violently that one morning, when I knew he was asleep, I slipped out of the house as quietly as I could, and ran,’ Samira says. ‘I ran back to my house, but I was too frightened to go inside because I was covered in blood and bruises. My mum died when I was 11, so my brother and sister had arranged the marriage because they could not afford to look after me any more, and I knew leaving my husband would make them angry. So I asked a rickshaw driver to take me across (the town) to my friend’s house, but he told me I should be ashamed of myself, and dropped me off at the brothel instead’

A customer enters Yasmin’s room

A police officer stops to speak to a woman outside a brothel

A customer fights with girls at a brothel
-
 @ 1f3ce62e:6e6b5d83
2025-01-29 21:38:24
@ 1f3ce62e:6e6b5d83
2025-01-29 21:38:24As part of YellowSeeds Creative Coaching and Consulting Services, one of our Seed Service is Impactful Leadership. Or what I like to call them Rainbow Leaders.
Every Services @YellowSeeds has a seed that started growing long time ago. This is the story about this one…
When I faced the challenge of taking a leadership role 10 yrs ago, I had the following questions in front of me:
🌱 How can I work out my perfectionism? I am remembered telling someone, “I don’t want to be a pain for anyone, as I did with my self always looking to be perfect”
🌱 How can I fully delegate?
🌱 How can I tune the message for each person?
I learned by doing and by taking each challenging situation as "a master Yoda" who brought something to change. I had several masters during my first years, they all were part of my first teams.
With patience, practice and not taking anything as personal, I started to develop what I called colors today. These are the leadership aspects I learned and they are all related to the colors.
There is a miss conception about leadership roles. In my career, I have seen a lot of cases where a promotion to “Manager” was a way of “awarding someone” or looking for “social status”. That easily and in just a few months become a disappointment for the person being promoted and their team.
One of the main lessons when you take a leadership role is to observe yourself a lot and be willing to change your behaviors. Most people take a leadership role and keep behaving like a team member. A leadership role requires a change in our way of thinking, speaking, doing and connecting with others.
If you are not willing to change yourself, a lot, a leadership role might not be for you.
If your most deeply passion is not supporting others to grow, a leadership role might get you far away from your real passion.
If you are not willing to work out your Ego, a leadership role might be a waste of time for you.
🌱❤️
The first color I learned from was RED. The RED Leader inside you starts to develop when you understand that the main task you have as a leader are not associated with deliverables, your main task is connecting. You don’t do, you connect and motivate. RED color invites you to remove fear of making mistakes and transform them in lessons learned. You inspire your team specially in those challenging moments.
RED is the first color you choose as a Leader, when you step in into the role, not because a social/professional status, but for your real passion to help others to grow.
\ 🌱🧡
The second color, like in the rainbow, is ORANGE. As I said previously, connecting is your main deliverable, your main responsibility as a Leader.
You start developing the ORANGE color, when you understand that connecting people and ideas is part of your role. If you are passionate about helping others to grow, you are going to inspire creativity and motivation in your interactions, because that is what someone does when they do what they love. ORANGE Leaders get the teams out of they comfort zones.
🌱💛
The third color, I learned from was YELLOW. As a YELLOW Leader you don’t keep anything for you, you naturally share what you know.
YELLOW Leaders look for brighter team members than themselves, they feel comfortable being the one with less knowledge in the room and promote the inner wisdom of their team in making decisions (they don’t have to be part of all of them). If the team depends on you for all the decisions, you are creating a dependable team and that is a sign of insecurity and keeping control. YELLOW leaders have a self-secure personalities.
Another important aspect of being YELLOW as a Leader is your capability of creating a positive environment. Those positive teams are usually a sign of a YELLOW leader around.
🌱💗
The fourth color and the most important one as a leader is PINK. I will write a whole post about leadership emotional intelligence, but this is the most critical skill or color to develop as a leader.
In order to be able to connect with your team members’ emotions, you gotta feel comfortable connecting with your own emotions first. You can’t do to others what you can’t do for yourself.
This is the most challenging aspect leaders are experiencing today, it is hard for them to support the teams emotionally. Work used to be separated from our personal life, we were not used to show emotions at work. But with recent changes, that is one of those aspects we should be willing to observe and change.
As a PINK Leader, when you connect with people’s emotions there is a bond between both which is hard to break. You can easily observe your emotional connection with your leader or team under a hard personal or professional situation. Those are the signs of how emotionally connected are you.
PINK Leaders bring mind and heart at work in a balanced equilibrium.
\ 🌱💚
The fifth color I learned from was GREEN. Some aspects of this color are related to leadership, like bringing harmony, inspiring purpose and motivate the team to bring ideas into practical implementations.
Harmony in your team is important. It is part of the work environment you create as a leader. If you want to observe your team harmony, review how is the work & life balance of your team members. There is no harmony when people work a lot, non stop “back to back meetings” or when they don’t take all their vacations time.
Inspiring purpose in your team members is helping them to identify what is their real purpose in life. Sometimes you might need to help them observe what they want to be doing, their purpose might be somewhere else and you might need to let them fly. If your team members has a real common purpose, they will convey a purposefully team.
Being practical save a lot of time and effort. Inspiring that aspect in your team will help to be efficient with your most important assets, time and team’s energy.
\ 🌱💧
The sixth color I learned a lot was SKY BLUE. Communication is one of the most frequent things you do everyday. Communication is an art, so it takes a continuously humble practice.
The SKY BLUE leader inside you will inspire you to get your communication as transparent as possible. Communication is like water, how healthy is the water your team is drinking?
🌱💙
The seventh color I learned a lot was BLUE. BLUE Leaders has an eye in the future, while the team work in the present. This is an exercise you gotta do at the very beginning when you start in a leadership position. As team members we are used to work in the present moment, the present task, the transactional day, week, or month. But someone gotta be looking for next year, the next problem to solve, the next service. That is the BLUE leader.
\ 🌱💜
The last color and most relevant one is VIOLET. As I said at the beginning, if you want to be a leader you gotta be VIOLET. You gotta be willing to change yourself and drive change and transformation in your teams.
The VIOLET Leader inspires the change agent you have inside. If change doesn’t inspire you, a leadership role might not be the right fit for you. Leadership is all about constant change.
As you can reflect, a lot of those colorful talents you are invited to develop as a leader. They are as well valuable in your personal life. Most of the talents I learned as a leader, were useful in my person life and relationships.
You don’t have to have all the colors to be a Leader, you might start with a few and be willing to be always evolving as a RAINBOW Leader, an impactful one. That is a life long challenge.
Stay colorful!
Laus
🌱 🤍💜💙💧💚💗💛🧡❤️
-
 @ 16d11430:61640947
2025-01-30 22:11:40
@ 16d11430:61640947
2025-01-30 22:11:40The Beginnings of Capital Markets
Capital markets have long been a cornerstone of modern economies, acting as a conduit for businesses to raise funds and for investors to grow their wealth. The origins of capital markets date back to the early stages of financial development, well before modern stock exchanges and cryptocurrency trading platforms.
-
Early Trading (Pre-1600s)
In ancient civilizations like Mesopotamia and Egypt, early forms of debt contracts and loans were recorded. These were rudimentary agreements between individuals and governments, often written on clay tablets. However, it wasn’t until the 16th century that true capital markets began to take shape, particularly in Europe. -
The Birth of Stock Markets (1600s)
The first formal stock exchange was established in Amsterdam in 1602 when the Dutch East India Company issued the first-ever public shares. This allowed investors to buy ownership in the company and share in its profits, creating the foundation for modern capital markets. The London Stock Exchange (LSE) and New York Stock Exchange (NYSE) would follow in the centuries to come, becoming powerful centers for trade and investment.
The Rise of Centralized Exchanges (CEX)
Capital markets, particularly in the form of centralized exchanges (CEX), flourished during the industrial revolution. As economies grew and industries expanded, capital markets evolved to meet the needs of investors and companies seeking to raise capital.
-
The Industrial Revolution (1800s)
The industrial era saw the rise of joint-stock companies and the need for capital. Stock exchanges were the main platforms through which companies could access capital and investors could trade securities. The London Stock Exchange became a dominant force in Europe, while the NYSE emerged as the largest exchange in the U.S. -
The 20th Century: Globalization and Regulation
In the 20th century, capital markets became more complex and globalized. The NYSE became synonymous with the U.S. stock market, and financial markets spread across the world, with exchanges in Asia and Europe gaining prominence. The rise of mutual funds, pension funds, and institutional investors reshaped the landscape.
The post-World War II era brought regulations like the Securities Exchange Act of 1934 in the U.S., which aimed to curb insider trading, increase transparency, and protect investors. Exchanges became highly regulated entities, with central authority overseeing transactions, clearing, and settlement to ensure fairness and stability.
- The Digital Revolution and Electronic Trading (Late 20th Century)
By the 1980s and 1990s, the introduction of electronic trading platforms marked a turning point. The NYSE and NASDAQ implemented computerized systems that facilitated faster and more efficient trades. In 1999, the launch of online trading platforms like E*Trade and Ameritrade democratized access to capital markets, allowing individuals to trade stocks from the comfort of their homes.
The Advent of Cryptocurrencies and the Emergence of CEX
As the new millennium dawned, the rise of digital technology and the internet introduced an entirely new form of asset: cryptocurrency. Bitcoin, created in 2009 by the pseudonymous Satoshi Nakamoto, introduced the world to decentralized digital currency. Cryptocurrencies offered an alternative to traditional fiat currencies and paved the way for decentralized finance (DeFi).
- The Birth of Cryptocurrency Exchanges (CEX)
The initial stages of cryptocurrency trading mirrored the early days of stock exchanges. As Bitcoin gained traction, platforms like Mt. Gox (2010) emerged as centralized cryptocurrency exchanges (CEX). These platforms allowed individuals to buy and sell Bitcoin and other cryptocurrencies, just like traditional stock exchanges facilitated the trading of stocks and bonds.
CEXs operate in a centralized manner, much like traditional financial exchanges, with a central authority acting as an intermediary between buyers and sellers. They provide liquidity, manage orders, and offer users a platform for trading various cryptocurrencies. Binance, Coinbase, and Kraken are examples of some of the largest CEXs today.
- The Role of CEXs in Crypto Adoption
Centralized exchanges have played a crucial role in cryptocurrency adoption. They provide easy access to the crypto markets, ensuring liquidity and stability. Many investors, both retail and institutional, enter the crypto world through CEXs due to their ease of use, familiarity, and regulatory oversight.
The Rise of Decentralized Exchanges (DEX)
While CEXs have dominated the landscape, the growing desire for decentralization in the cryptocurrency space gave rise to decentralized exchanges (DEXs). The idea behind DEXs is to create an exchange system that operates without a central authority, relying instead on smart contracts and blockchain technology to facilitate peer-to-peer trading.
- The Emergence of DEXs (2010s)
In 2014, the first DEX, EtherDelta, was launched on the Ethereum blockchain. It allowed users to trade ERC-20 tokens directly from their wallets, without the need for a centralized intermediary. While EtherDelta’s interface was rudimentary, it set the stage for a new wave of decentralized trading platforms.
The DEX market gained significant momentum with the rise of Uniswap (launched in 2018), which revolutionized decentralized trading by using an automated market maker (AMM) model instead of an order book system. This innovation allowed anyone to provide liquidity to the platform and earn fees, paving the way for the growth of decentralized finance (DeFi).
- Advantages of DEXs
DEXs offer several advantages over their centralized counterparts: - Decentralization: There is no central authority that controls user funds or the exchange itself. This makes DEXs more resistant to censorship and hacking.
- Privacy and Security: Users retain control of their private keys and funds, reducing the risk of exchange hacks that have plagued centralized platforms.
-
Global Access: DEXs are open to anyone with an internet connection and a wallet, allowing users worldwide to participate in trading and liquidity provision.
-
The Growth of DeFi and DEXs
As decentralized finance (DeFi) platforms grew in popularity, DEXs became the primary infrastructure for decentralized lending, borrowing, and trading. Uniswap, SushiSwap, and PancakeSwap emerged as dominant players in the DeFi space, offering decentralized token swaps, liquidity pools, and yield farming.
The rise of Layer 2 solutions, such as Optimism and Arbitrum, has further enhanced the scalability of DEXs, reducing transaction costs and increasing throughput, making decentralized exchanges more user-friendly and competitive with CEXs.
The Future of Capital Markets: CEX vs. DEX
The evolution of capital markets from traditional stock exchanges to cryptocurrency exchanges, and now to decentralized platforms, reflects the growing demand for more accessible, transparent, and efficient ways of conducting financial transactions.
While centralized exchanges still dominate the crypto space, providing crucial liquidity and stability, decentralized exchanges are growing rapidly, offering unique advantages in terms of decentralization, privacy, and global accessibility.
In the coming years, capital markets may continue to evolve, with hybrid models emerging that combine the best aspects of both CEXs and DEXs. The ability to trade traditional assets on blockchain platforms, the rise of tokenized stocks and securities, and the integration of decentralized finance could reshape the entire financial landscape, empowering individuals and institutions alike.
The transition from traditional centralized systems to decentralized ones is part of a larger trend towards democratization in finance. As technology continues to advance, capital markets will likely undergo further transformations, and we may soon witness the integration of these markets in ways that were once unimaginable, making financial systems more inclusive, transparent, and resilient.
-
-
 @ 0fa80bd3:ea7325de
2025-01-29 14:44:48
@ 0fa80bd3:ea7325de
2025-01-29 14:44:48![[yedinaya-rossiya-bear.png]]
1️⃣ Be where the bear roams. Stay in its territory, where it hunts for food. No point setting a trap in your backyard if the bear’s chilling in the forest.
2️⃣ Set a well-hidden trap. Bury it, disguise it, and place the bait right in the center. Bears are omnivores—just like secret police KGB agents. And what’s the tastiest bait for them? Money.
3️⃣ Wait for the bear to take the bait. When it reaches in, the trap will snap shut around its paw. It’ll be alive, but stuck. No escape.
Now, what you do with a trapped bear is another question... 😏
-
 @ ea30c5a8:f76a0295
2025-01-30 21:59:17
@ ea30c5a8:f76a0295
2025-01-30 21:59:17i guess this is wotking correctly?
-
 @ 04c195f1:3329a1da
2025-01-29 08:16:38
@ 04c195f1:3329a1da
2025-01-29 08:16:38Over the past week, Sweden has been rocked by an unprecedented wave of domestic terrorism. Bombings, shootings, and gang-related violence have escalated to a level that even the most hardened observers find shocking. The Swedish people are waking up—sometimes quite literally—to explosions outside their homes, their neighborhoods resembling conflict zones rather than the peaceful Scandinavian society they once knew.
A Month of Terror
Since the beginning of the year, Sweden has witnessed at least 32 bombings, averaging more than one explosion per day. In a sign of how routine this has become, state media outlet SVT now maintains a "live ticker" tracking the growing number of explosions—reminiscent of the death and infection tickers used during the COVID-19 pandemic. The attacks have struck cities large and small—Stockholm, Uppsala, Helsingborg, and Örebro among them. Some explosions have targeted residential buildings, even bedrooms where children sleep. Others have been part of gang warfare, retaliation for unpaid debts, or attempts to intimidate rivals.
Just in the past 24 hours, five separate explosions have rocked Stockholm. A grenade attack forced a school into lockdown, while an explosion in Årstaberg destroyed the entrance of an apartment building. This is not the first time—and it certainly will not be the last.
Sweden’s Political Paralysis
Despite this unprecedented security crisis, the Swedish government refuses to take meaningful action. Prime Minister Ulf Kristersson recently acknowledged the situation, stating:
“The criminal gangs show total disregard for the public. This is domestic terrorism that we must fight with the full force of society. The police are working intensively to prevent and stop acts of violence. The police can now conduct preventive wiretapping, and security zones are in place. These are important tools. But more is needed.”
However, this is yet another attempt to address symptoms rather than causes—and it will fail to even achieve that. Last night, I participated in a livestream where former MP Jeff Ahl likened the government's approach to trying to stop arterial bleeding with a band-aid. A fitting description indeed.
Meanwhile, rather than declaring a national emergency, Sweden’s political elite have prioritized ideological pet projects. Minister Paulina Brandberg was busy opening a new DEI (Diversity, Equity, Inclusion) office at Chalmers University while bombs tore through Stockholm’s suburbs. Justice Minister Gunnar Strömmer held a crisis meeting with the police last week, only to suggest that the government might be able to stop the gangs in eight years—an admission of failure if ever there was one.
The Root of the Crisis
The media and political establishment refuse to address the root cause of this descent into chaos: mass immigration and the importation of criminal clan networks. The reality is undeniable:
-
Areas like Rinkeby and Botkyrka—once Swedish working-class neighborhoods—now have overwhelming non-Swedish majorities, with Rinkeby exceeding 95% and Botkyrka over 60%. These are just two examples of the hundreds of neighborhoods across Sweden where Swedes are now a minority, where criminal clans thrive, and where gangs have effectively taken control—not just of the streets but also of local commerce and entire business districts.
-
Organized crime syndicates, many with roots in the Middle East and North Africa, exert dominance over these areas, operating parallel societies with little to no interference from Swedish authorities.
-
Police estimate that 30,000 individuals are active in criminal gangs—when factoring in extended networks, the number may be in the hundreds of thousands.
-
Most of these people should never have been allowed into Sweden in the first place.
“We’re Used to It”
Perhaps the most chilling aspect of this crisis is the growing resignation among Swedes. After a bombing in Upplands-Bro last night, one resident summed it up:
“No, I’m not worried. I’m used to it.”
This normalization of terrorism is a direct consequence of decades of political negligence, ideological blindness, and a refusal to admit policy failure. Sweden’s leaders have deliberately ignored the warnings. They have allowed the chaos to fester. And now, they pretend to be shocked as the country spirals deeper into lawlessness.
What Comes Next?
Let’s be clear: these bombings will not stop. If history is any guide, Sweden’s authorities will issue statements, hold meetings, and maybe even arrest a few foot soldiers. But the broader networks, the root causes, and the state’s unwillingness to reclaim control over the country remain unchanged.
The question is not whether Sweden can recover. The question is whether Swedes are willing to demand real change. And if they do not, how much further can this country fall before it collapses altogether?
I will continue to report on this crisis—because while mainstream media acknowledges the violence, they refuse to confront its root cause. If we do not acknowledge the failure of multiculturalism and dismantle this ideological experiment, we will never resolve this crisis.
For near-daily updates, follow me on X, Telegram, and Nostr, where I report on these events as they unfold. Stay informed, stay vigilant, and if you value my work, consider subscribing and sharing this newsletter.
■
-
-
 @ ea30c5a8:f76a0295
2025-01-30 21:58:25
@ ea30c5a8:f76a0295
2025-01-30 21:58:25whats up yall doing some more testing using nostrmo, amber, citrine, pokey on my shitty android.
-
 @ 1408bad0:4971f2ca
2025-01-30 21:53:58
@ 1408bad0:4971f2ca
2025-01-30 21:53:58I must have missed when season 2 of Silo dropped but I was very happy when I did. After the climax of season 1, we were waiting to see what happened in season 2.
I was expecting the surface to be breathable, so it was a surprise twist when it wasn't. You would think the earth would be breathable again and heal, but not yet so far.
The second series sees what happens in a neighbouring Silo and how the old Silo reacts without Juliette and her not cleaning as everyone does when they go out usually. Juliette then tries to get home and faces various challenges in order to do so.
As she does so, we also see the detioration of her own Silo. We learn more answers to questions about the Silo, it's history and how people lost their memories and why they got rid of old artefacts that remind them of the old world. It gives you a sense of not appreciating the world and life we currently have.
Some of the answers seem quite silly and you wonder if this is really necessary. Why don't they feel the need to test the air outside regularly etc, why be so cut off. More questions come than are answered.
However, the show is still very good and enjoyable. I binge watched over night until it finished.
My favourite scene, apart from the part when Juliette went back to the surface, is learning about the special room and how prepared it was. It would be good to have a bunker so we'll prepared.
Apocalyptic ending shows are quite popular now and this is quite an interesting variation of one. The series ends with flashbacks to the start of events prior to the silos and looks like it is leading up to a great season 3 flashback series. This sort of makes sense as they seem to be running out of ideas of where to go in the silo.
We were left with a cliffhanger ending and I am excited to see season 3 but there will be a bit of a wait.
-
 @ 16d11430:61640947
2025-01-29 06:06:25
@ 16d11430:61640947
2025-01-29 06:06:25Fiat, by its nature, is an anti-human force. It exists not to enhance civilization but to extract from it, to manipulate rather than to build, to obscure rather than to reveal. As it nears collapse, it will throw everything at its disposal to sustain itself—not through creation, but through control, coercion, and, ultimately, extermination. The development of AI is not an accident in this process; it is fiat’s final gambit to perfect a system that optimizes human destruction while ensuring its own survival.
This analysis will explore this trajectory through multiple lenses: economic, technological, psychological, military, and metaphysical.
- The Economic Lens: Fiat’s Structural Need for Destruction
Fiat money thrives on scarcity, but not real scarcity—engineered scarcity. It creates artificial demand through inflation, debt cycles, and controlled access to resources. Yet, as it approaches terminal decline, it must escalate its tactics.
The Degrowth Imperative: Fiat cannot function in a world where productive capacity exceeds the need for artificial scarcity. As automation reduces reliance on human labor, fiat must find ways to reduce human demand on the system. AI-driven economic models will be used to justify mass unemployment, the elimination of “useless” populations, and the restructuring of economies around controlled digital enclosures.
Programmable Money as a Rationing Mechanism: Fiat's ultimate dream is total control over consumption. Central Bank Digital Currencies (CBDCs) combined with AI-driven financial governance will dictate not just how much money one can access, but whether one is “eligible” to exist in the economy at all.
The UBI Trap: Universal Basic Income will not be an act of benevolence; it will be a mechanism to manage surplus populations with just enough to pacify, but not enough to allow self-sovereignty. AI will determine who “qualifies” and, eventually, who should be “off-ramped” from the economy entirely.
Fiat has always operated through destruction—wars, recessions, financial crises—but with AI, it now has a tool to automate and optimize these processes at scale.
- The Technological Lens: AI as the Weaponization of Fiat Logic
AI is not intelligence—it is a predictive engine trained on fiat-controlled narratives, optimized to maintain fiat dominance. Unlike operating systems, which are neutral and expand human agency, AI is an anti-tool—it removes agency, restricts sovereignty, and enforces compliance.
AI as Fiat’s Ultimate Gatekeeper: Traditional fiat systems required human gatekeepers—central bankers, politicians, corporate executives—to interpret and enforce policy. AI removes this inefficiency. AI models will automate censorship, restrict access to financial systems, and determine who is “worthy” of participation in society.
Algorithmic Reality Construction: Fiat is a system of deception, and AI is its most powerful tool for controlling perception at scale. AI-generated content will flood the information ecosystem, erasing historical context, eliminating dissenting narratives, and ensuring only fiat-approved “realities” remain. The ability to think outside the fiat paradigm will be memory-holed.
Bio-surveillance & Behavior Control: AI-integrated surveillance systems will predict, profile, and preemptively neutralize threats—not just physical threats, but ideological ones. If a person’s behavior suggests they are questioning fiat’s control, AI-driven interventions will ensure compliance—or elimination.
With AI, fiat is no longer just a system of economic control. It becomes a self-replicating, self-enforcing prison that anticipates, suppresses, and eventually eliminates resistance before it can manifest.
- The Psychological Lens: The Fiat-AI Mind War
Fiat is not just about controlling money—it’s about controlling minds. AI’s primary function is not intelligence but psychological warfare, ensuring that fiat’s victims remain unaware, obedient, and compliant.
Cognitive Overload & Learned Helplessness: AI will flood the digital landscape with content, narratives, and distractions, ensuring that people are too mentally exhausted to resist. The result? A population too numbed to recognize its own enslavement.
Automated Gaslighting: AI-generated responses will deny objective reality, making it impossible for people to discuss real issues. If you claim fiat is corrupt, AI will counter with plausible-sounding but entirely fabricated “data” to convince you otherwise. Every institution will have an AI-controlled “fact-checker” ensuring that truth never emerges.
Dehumanization of Thought: AI will gradually replace human thinking with “assistance,” weakening cognitive abilities over generations. By the time people realize what they have lost, they will no longer be capable of independent thought.
Psychological warfare is fiat’s most effective weapon because a population that cannot think clearly does not resist.
- The Military Lens: AI as the Ultimate Kill System
Every fiat empire has relied on war to maintain control, and AI provides the ultimate tool to wage war—both visible and invisible.
Automated Warfare: AI-controlled drones, autonomous combat units, and real-time battlefield analytics will allow wars to be waged without human oversight. The decision to kill will be outsourced to algorithms optimized for fiat’s survival.
Targeting Dissent: AI will be used not just for traditional warfare but for preemptive neutralization of dissenters. Whistleblowers, activists, and critics will be identified, flagged, and neutralized before they can challenge the system.
Biosecurity as a Weapon: AI-driven bio-surveillance will dictate who is “healthy,” who is a “threat,” and who should be removed from the population. Digital ID systems will merge health data with social behavior data, allowing fiat to control who lives and who dies under the guise of “public safety.”
Once AI is fully integrated into military and policing systems, fiat will no longer need soldiers—only extermination algorithms.
- The Metaphysical Lens: Fiat as the Anti-Life Principle
At its core, fiat is an inversion of life—a parasitic force that cannot create, only extract. AI is its final manifestation, a tool to ensure that humans remain trapped in an artificial, fiat-optimized existence until they are no longer needed.
The Death of Meaning: A world controlled by fiat AI is a world where nothing real exists. All narratives, emotions, and expressions will be filtered through a fiat-optimized lens, ensuring that humanity becomes a hollowed-out shell of its former self.
Elimination of the Sacred: Fiat has always sought to replace meaning with transactions. AI will complete this process by ensuring that human relationships, art, philosophy, and even consciousness itself are commodified and optimized for fiat’s survival.
The Final Cull: Fiat does not need 8 billion people. AI will manage the transition toward a world where the human population is selectively reduced, leaving only those who are either necessary for maintaining the system or who are too broken to resist.
The ultimate goal is not just control, but the elimination of those who are no longer profitable or compliant.
Conclusion: The Only Path Forward
Fiat is a virus, and AI is its ultimate mutation—a system that will automate dehumanization, control, and extermination at a scale never before possible. The only antidote is sovereignty—Bitcoin, self-hosted computing, and the rejection of AI as a controlling force.
The question is no longer whether fiat will attempt to use AI to destroy humanity—it is already happening. The only question is who will resist before the extermination machine is fully operational.
-
 @ 0fa80bd3:ea7325de
2025-01-29 05:55:02
@ 0fa80bd3:ea7325de
2025-01-29 05:55:02The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future.
Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs.
There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won.
Our only resource is the will of the people to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root.
So I started asking myself: How do we stop this fragmentation? How do we create a space where people can rebuild their connections when they’re ready? How do we build a self-sustaining network, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—how do we make it spread, even in occupied territory?
In 2009, something historic happened: the internet got its own money. Thanks to Satoshi Nakamoto, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize.
That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became purely digital.
The internet was already a sanctuary for information, a place where people could connect and organize. But with Bitcoin, it evolved. Now, value itself could flow freely, beyond the reach of authorities.
Think about it: when seedlings are grown in controlled environments before being planted outside, they get stronger, survive longer, and bear fruit faster. That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild.
Now, picture the internet as that controlled environment for ideas. Bitcoin? It’s the fertile soil that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless. It can absorb any number of ideas, any number of people, and it doesn’t run out of space.
But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—without surveillance, without censorship, without the constant fear of being erased.
This is where Nostr comes in.
Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. It’s a new kind of city. One that no dictator can seize, no corporation can own, no government can shut down.
It’s built on decentralization, encryption, and individual control. Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them.
In a world where cities fall and governments fail, Nostr is a city that cannot be occupied. A place for ideas, for networks, for freedom. A city that grows stronger the more people build within it.
-
 @ 20e7c953:3b8bcb21
2025-01-29 05:53:46
@ 20e7c953:3b8bcb21
2025-01-29 05:53:46Thai Nostriches #Siamstr
Get Ready for Sats N Facts 2025! https://satsnfacts.btc.pub/ 🎉
Join us for a series of exciting events where Bitcoin, Nostr, and local Thai communities come together to innovate, create, and connect! Here’s the breakdown for the 2 main activities:
🛠 Hackathon Overview
https://satsnfacts.btc.pub/hackathon/
This is your opportunity to work alongside leading teams and individuals pushing the boundaries of Bitcoin and Nostr. Whether you're a developer, designer, an educator or a visionary, your contributions can help shape the future of decentralized technology.

What to Expect:
Participate in the sessions by pitching and listening to others ideas or setting up a spot in the schedule. The event is designed to be a “decentralized and collaborative” effort between all participants, with activities being put together with attendees’ feedback.
🤝 Introducing Potential 🇹🇭 Participating Teams
nostr:npub1ejn774qahqmgjsfajawy7634unk88y26yktvwuzp9kfgdeejx9mqdm97a5 – Bitcoin Education and Translations for the Thai community; this would be an ideal occasion in order to connect with international developers in order to curate and share insights within the #Siamstr community
Other Projects that are formally invited are:
nostr:npub1l8ktdyyhwxh4ty5cf48tl72g8ra286nr9klmvqznvk3aqyjkucgsem97q9 – Simplifying Bitcoin payments through intuitive tools
nostr:npub1nsxnfp5690uplzgkslthcvt6269htshqeymhghthenr9wnpt869q57q2hf – Innovating Lightning infrastructure and Bitcoin ATMs
nostr:npub16elg3wf8nffkymylw9kfwecc45j9c30lufrrzx2zf5vmxjlcgkkq3xc6d7 – Enhancing social innovation through Nostr-powered solutions
🎨 Art Exhibition

What else to expect?
A showcase of Bitcoin and Nostr-inspired works by local Thai artists like nostr:npub16unl8g9ucanlpfvp94sdjdv2f4mukm2ywmgrywnrfdgt98qwrrdq0qcn35 nostr:npub14lqzjhfvdc9psgxzznq8xys8pfq8p4fqsvtr6llyzraq90u9m8fqevhssu and nostr:npub1uprlst7kjp0eyfxe4yn7q36gr885mjr9fm6ejfqt8pmdta7stv9s2xvysq - Huaiphueng Project community members.
Celebrate the creativity of our culture with a fusion of tech and art!
📍 Location: Weave Artisan Society, Chiang Mai
📅 Date: 8th - 10th February
🎟 How to Join: Register either as a Lead or Attendee, wait for confirmation from SnF team and get your ticket as a Thai National via Formstr at https://satsnfacts.btc.pub/#tickets
🌟 Why You Should Join:
If you are a Bitcoiner and Ostrich in Thailand the question should be re-formulated to... WHY WOULD YOU NOT JOIN ?
Support and grow the local ecosystem while having a great time with fellow international Bitcoiners.
✨ Mark your calendars and spread the word! Stay tuned through the links or connect with us on Nostr.
Let’s build a stronger Bitcoin & Nostr future at Sats & Facts ✌️
Pictures by nostr:npub15l5mxmljftnnqur8gf2nkjj2yuemqy2kuly7yc29lx7x598svx5s447rgk 👇


เราจะทำอะไรต่อไป ?
AND WE SAID;
ONWARDS
-
 @ c2827524:5f45b2f7
2025-01-28 22:44:50
@ c2827524:5f45b2f7
2025-01-28 22:44:50Vuoi creare il tuo profilo Nostr, ma non sai esattamente da dove iniziare?
Prova a seguire i consigli di questo tutorial!
Nosta.me
 Nosta.me è uno dei client più semplici e divertenti di tutto il protocollo Nostr.
Free e open source, Nosta regala anche un link dall'aspetto elegante per fare visualizzare il proprio profilo, come si può vedere da quello dello sviluppatore. Christoph Ono.
Nosta.me è uno dei client più semplici e divertenti di tutto il protocollo Nostr.
Free e open source, Nosta regala anche un link dall'aspetto elegante per fare visualizzare il proprio profilo, come si può vedere da quello dello sviluppatore. Christoph Ono.Cominciamo, andando proprio sulla pagina nosta.me
Creazione in 10 passi
Innanzitutto Nosta è un client adatto alla creazione del profilo, ma non per scrivere, firmare e pubblicare note. Per l'uso social di Nostr è meglio utilizzare altri client che si possono scoprire in seguito.
Ma allora: perché Nosta?
Perché propone la creazione del profilo tramite 10 step da eseguire in ordine. Alcuni dei 10 passaggi si possono saltare per essere completati in seguito, ma il cuore della creazione delle chiavi è familiare ai Bitcoiner, perché parte da una sequenza casuale di 12 parole.
Cominciamo, scegliendo proprio «Create a new profile»

Nosta da il benvenuto ad una nuova, giovane Nostrica.

È il primo dei 10 step; cliccare «Next»
 Si scelgono le prime informazioni da compilare, mettendo un nome, un paio di righe di biografia e - se presente - un sito web di riferimento.
Si scelgono le prime informazioni da compilare, mettendo un nome, un paio di righe di biografia e - se presente - un sito web di riferimento.
Una volta compilati questi 3 campi, cliccare «Next»
Il prossimo passo chiede di caricare una foto profilo. Consiglio di cliccare su "Skip", vedremo meglio in seguito la gestione delle immagini via protocollo Nostr
ENTRIAMO NEL VIVO: LA GENERAZIONE DELLE CHIAVI
In questo nuovo step Nosta calcola e mostra la recovery phrase di 12 parole. Questa frase porterà al calcolo automatico di un seed proprio come nel protocollo Bitcoin: le parole provengono dal dizionario BIP39, dopodiché la chiave privata viene calcolata sulla curva ellittica secp256k1 ed infine convertita da hex al formato nsec.
Queste 12 parole costituiscono una recovery phrase per ripristinare l'account e le relative chiavi tramite Nosta.me. Sono da scrivere bene e conservare, dopodiché si può procedere alla verifica cliccando "Next"
La procedura di verifica presenta le 12 parole posizionate a caso: per il check si devono cliccare in ordine dalla 1 alla 12
Siamo pronti per lo step successivo: Nosta mostra la chiave privata nsec. Si deve copiare e incollare su un file protetto da tenere in un luogo sicuro.
 Una volta copiata la nsec, cliccare "Next"
Una volta copiata la nsec, cliccare "Next"La creazione delle chiavi termina con la derivazione della chiave pubblica, la npub.
La npub di Nostr rappresenta l'identità dell'utente. Va copiata e incollata per conservarla, anche in un luogo sprotetto, perché si userà spesso e volentieri nel protocollo per farsi identificare
Handle, follow e wallet Bitcoin
Il passo 7/10 prevede l'impostazione dell'handle o NIP-05 nel profilo. L'handle è una caratteristica che ha due vantaggi: 1. si può scegliere un identificativo più facile da leggere e usare al posto della chiave pubblica 2. è un ulteriore sistema di verifica dell'identità Scopriremo in seguito i dettagli del NIP-05, consiglio di saltare questo passo tra gli step di Nosta
Nello step successivo vengono proposti alcuni suggerimenti per seguire utenti di Nostr. Consiglio di iniziare a seguire qualcuno, proprio per non rimanere troppo spaesati al termine della creazione del profilo, rischiando di trovare un feed completamente vuoto.
Il penultimo passo 9/10 è quello dove si configura il wallet Bitcoin. Chi ha già un LN address può giustamente inserirlo. Chi non è ancora skillato, può seguire il capitolo in cui ne parleremo più avanti e cliccare "Skip" in questa schermata

I relay
L'ultima impostazione richiesta da Nosta è la scelta dei relay, il motore delle note su Nostr. È attraverso i relay, infatti, che le le note «and other stuff» sono trasmessi alla rete. Nel passo 10/10 si trovano già dei buoni suggerimenti che - chi non è esperto - può accettare e proseguire cliccando "Next".
Chi è invece già esperto può cambiare questa lista e personalizzarla a seconda delle proprie esigenze
È tutto fatto! Nosta propone una schermata di riepilogo e - se va tutto bene - si può cliccare su "Looks good"
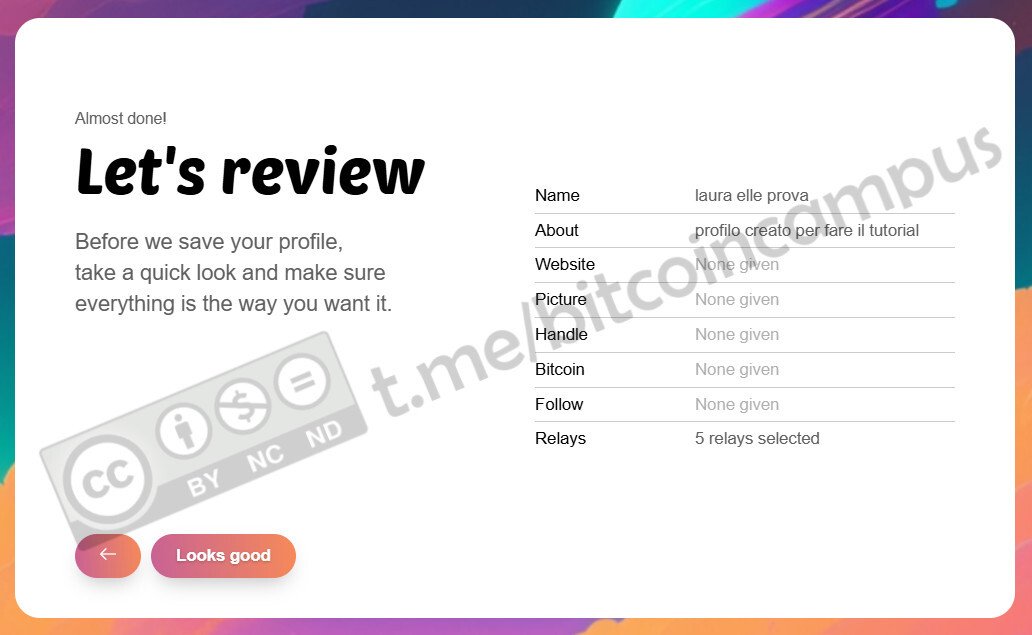
Quando siamo convinti, clicchiamo "Save" e Nosta pubblicherà il profilo per come lo abbiamo impostato.

Il profilo è praticamente pronto, sebbene scarno
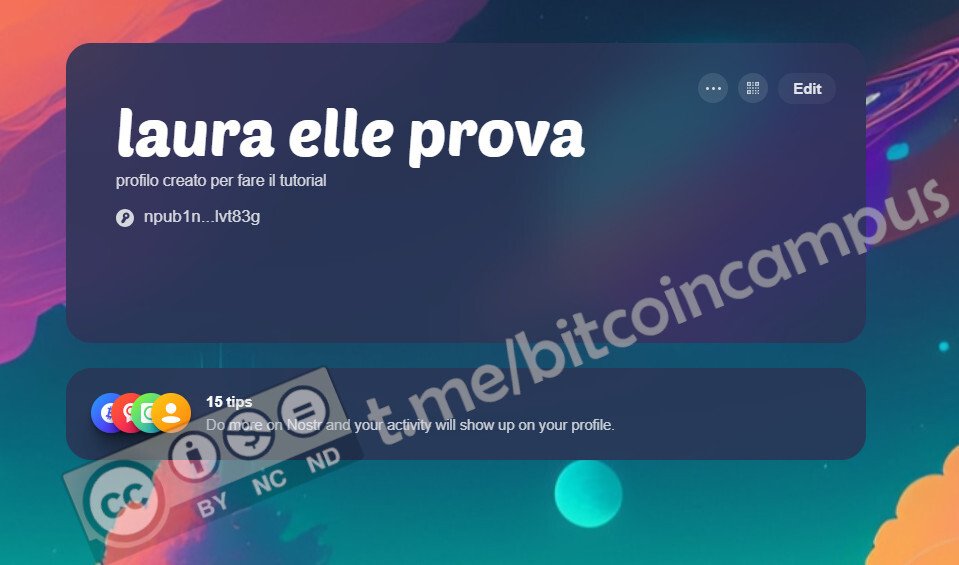
Si può abbellire e riempire con le informazioni mancanti cliccando su "Edit", così come scegliere un altro client ed iniziare ad usarlo, oppure continuare con il tutorial e scoprire come trattare più in sicurezza la chiave privata. Cambiare client, infatti, richiederebbe allo stato attuale copiare e incollare la nsec per fare ogni login. Quello che segue è un suggerimento per impostare un'estensione del browser come gestore di firma e usare l'estensione per fare tutti i tipi di login via web.
Usare il protocollo Nostr
Il profilo è pronto per essere usato. Ora si può esplorare Nostr, alla ricerca di client ed opportunità. Per fare login si deve necessariamente accedere ai client con la chiave privata nsec, al fine di poter firmare le note e propagarle. Anziché copiare e incollare la nsec in ognuno dei client, è opportuno usare "un trucco".
Login con NOS2X
Nos2X è un'estensione del browser che permette di gestilre le chiavi in un unico luogo, firmando gli eventi senza esporre la nsec ad ogni singola azione. È disponibile per Firefox e fork ed anche per Chrome.
l'esempio che segue è realizzato con Chrome, ma il procedimento per Firefox è molto simile e semplice
Cercare Nos2X tra le estensioni del browser
quindi aggiungerlo al proprio Chrome
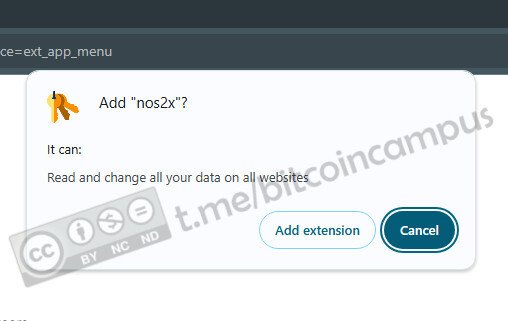
Entrare nelle impostazioni con Manage Settings
fino a trovare la schermata dove è possibile incollare la propria chiave privata, impostare qualche relay e salvare.
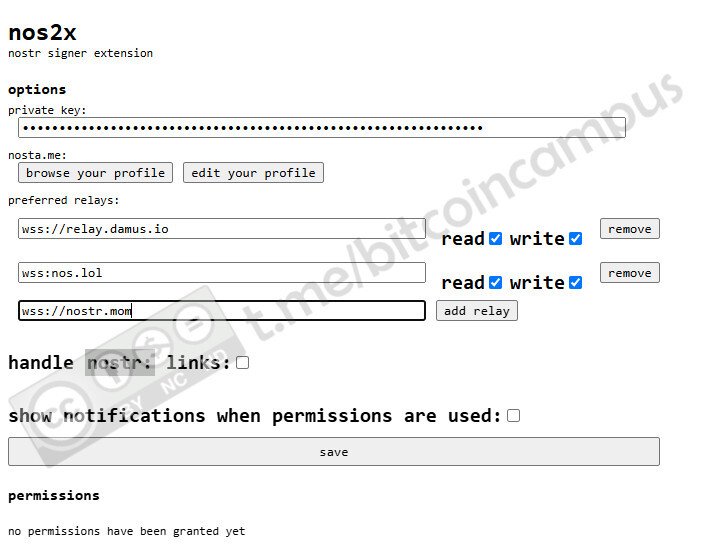
Si apre ora una finestra che chiede di autorizzare Nos2X a firmare gli eventi. Si può scegliere di autorizzare sempre o anche solo la sessione attuale, per prova. Se si sceglie "Authorize just this" è bene tenere a mente che ad ogni sessione il manager di firma chiederà l'autorizzazione. Ognuno sceglie a seconda delle proprie esigenze.
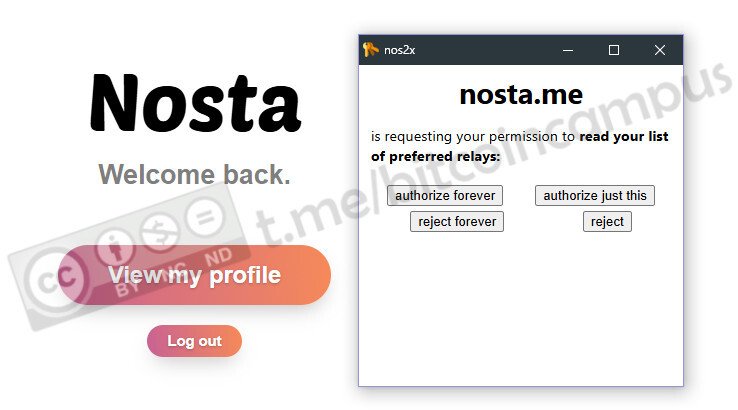
Da ora in poi, via web, ci si può loggare a qualsiasi client Nostr per continuare l'esplorazione. Si può fare, ad esempio, già con Nosta.me e fare Edit Profile, giusto per continuare a completare il proprio profilo.

Il profilo è ancora molto scarno, infatti
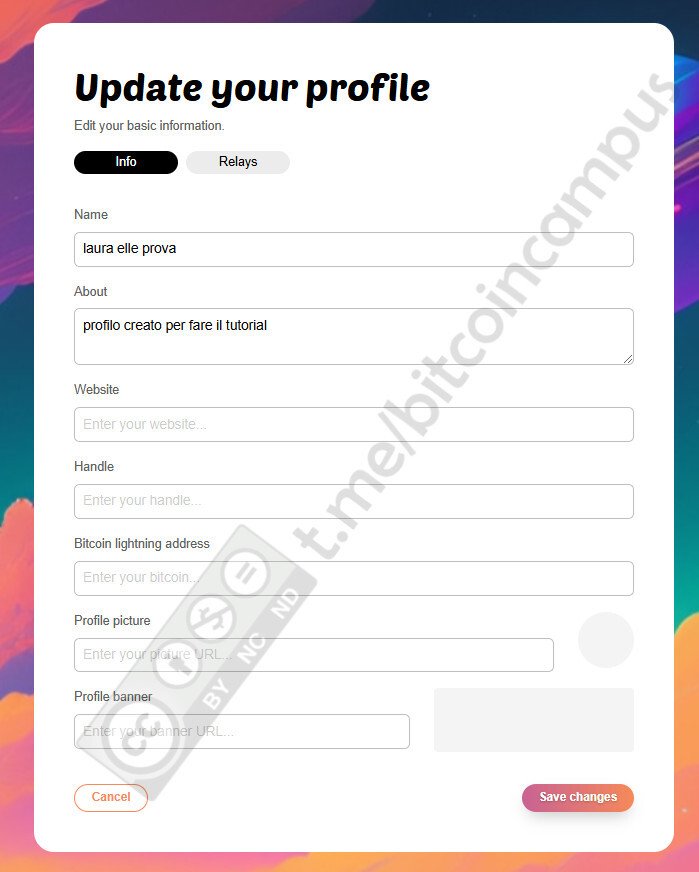
Chi ha un sito web o landing page può tranquillamente inserirlo e salvare. Alcuni dei campi sono gli step saltati al momento della creazione con Nosta e che si possono vedere ora nel dettaglio.
Handle
L'handle di Nostr è codificato nel NIP-05, Nostr Implementation Possibilities, che specifica proprio come gli utenti possono essere verificati su Nostr. Il meccanismo di verifica è simile a quello richiesto da Google per verificare la proprietà di un dominio, e consente ad ogni utente Nostr di "mappare" la propria chiave pubblica su un identificatore internet basato su DNS. Il vantaggio principale del NIP-05 è che trasforma la stringa della npub in un nome leggibile in maniera semplice. È possibile ottenere un NIP-05 for free, o anche a pagamento, scegliendoli da una delle molte liste che si trovano in una ricerca via web.
L'operazione è super semplice: * si scelga, ad esempio, zaps.lol * incollare la chiave pubblica npub * scegliere uno username rappresentativo, che completo sarà: tuousername@zaps.lol * cliccare REGISTER
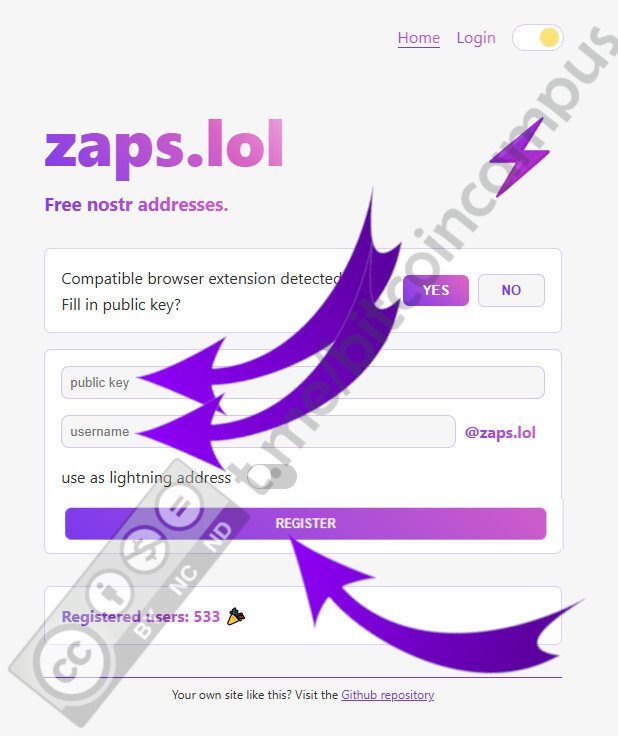
E il proprio handle è pronto e verificato, si può quindi incollare sulla maschera del profilo di Nosta.me e salvare
La gestione delle immagini
Si può impostare un avatar, così comme un banner di copertina e - in generale - postare immagini via Nostr. La gestione delle immagini avviene condividendo un URL. Sebbene la maggior parte dei client adesso consentano di caricare immagini in maniera meno complessa, non sempre queste vengono rese disponibili al primo colpo. Ci sono però altri tipi di client, che si sono specializzati nel caricamento immagini.
All'inizio meglio scegliere un client che offre questa possibilità gratuitamente, come nostrcheck.me Dalla homepage andare nel menu Public gallery -> UPLOAD -> scegliere di fare login cliccando sull'iconcina utente in alto a destra. La landing page si mostra così
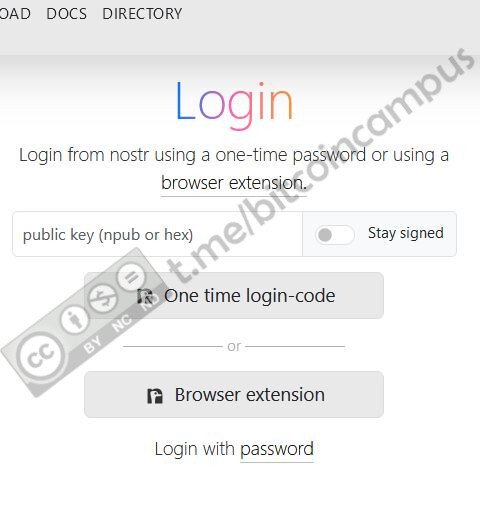
Scegliere quindi di fare login con l'extendion Nos2X e procedere con il caricamento dell'immagine profilo, seguendo le istruzioni a video. Nostrcheck carica l'immagine e fornisce l'url che si può copiare e incollare dove si vuole, ad esempio nella schermata del profilo, ma anche nei futuri post.
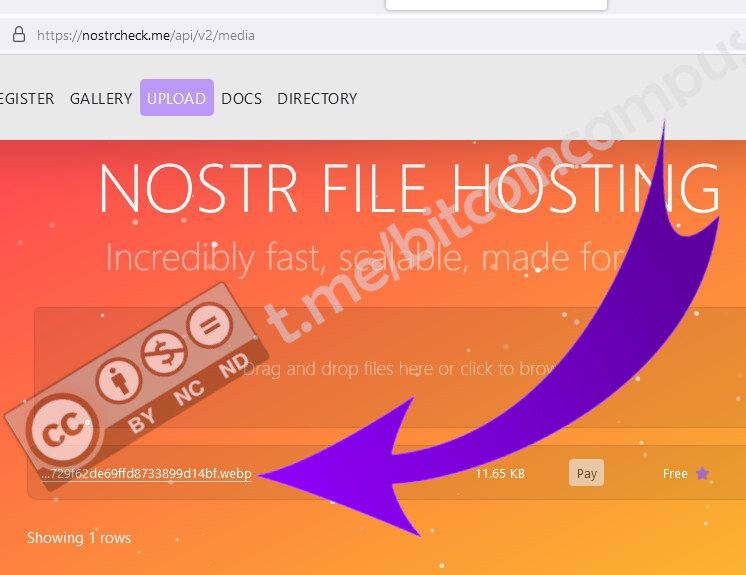
Se si sono appena caricati avatar e banner del profilo, gli url completano il profilo di Nostr, che adesso è completo di quasi tutto
LN address e wallet
È di gran lunga la più sorprendente caratteristica di Nostr: scambiare valore usando la Lightning Network di Bitcoin. Esistono differenti soluzioni, dalle più semplici alle più complesse. Se non si ha la minima idea di cosa sia un wallet LN o un LN address, meglio rimandare questa fase al momento in cui si possiede la necessaria consapevolezza. Ma per chi ha un'idea precisa di questi concetti, l'LN address permette di ricevere zap (donazioni di sats) per i contenuti condivisi che dal mittente arrivano sul proprio wallet; il wallet può essere usato per ricompensare altri creatori di contenuti, zap-pando a più non posso.
Se si utilizza una soluzione custodial come sats.mobi, LifPay(*) o altri tenere sul wallet solo pochi sats per lo scopo. Se se ne ricevono molti, perché i contenuti diventano popolari e virali, spostarli su un wallet LN non-custodial.
(*) Lifpay integra una soluzione senza alcuna frizione per l'utente inesperto, perché crea un profilo direttamente con la npub di Nostr.
Ora è davvero tutto pronto e Nostr è lì per essere esplorato

Puoi iniziare seguendo npub1c2p82fyndhk66hmz808c5pxjq8el60kh6jgj5xgdhmhksh69ktmsz8dcj5
Risorse per approfondire:
- https://laura.npub.pro/post/1733214130372/
- https://nostr.net/
- https://nostr.how/en/nostr-projects
- https://github.com/nostr-resources/
- https://nostr.com/
- https://nostr.info/resources/
- https://usenostr.org/
- https://uselessshit.co/resources/nostr/
Per info https://t.me/bitcoincampus https://planb.network/it/courses/btc105
-
 @ 16d11430:61640947
2025-01-30 21:32:58
@ 16d11430:61640947
2025-01-30 21:32:58Bitcoin was forged in the crucible of libertarian ideals—freedom, decentralization, and voluntary cooperation. It was meant to be an open, permissionless system that empowers individuals by circumventing the coercive grip of centralized institutions. Yet, as Bitcoin maximalism has matured, it has developed an increasingly exclusive and dogmatic culture, paradoxically betraying the very principles it was built upon.
The Libertarian Ethos of Bitcoin
At its core, Bitcoin aligns with libertarianism in the following ways: - Decentralization: No central authority dictates who can or cannot participate in Bitcoin. - Permissionless Innovation: Anyone can build on Bitcoin, create products, and enhance its ecosystem without seeking approval. - Free Market Dynamics: Bitcoin is intended to thrive in a competitive financial landscape, allowing individuals to choose monetary instruments that best suit their needs.
These principles mirror the libertarian belief in self-sovereignty, voluntary association, and an open market for ideas and innovation. However, Bitcoin maximalism, in its most radical form, has evolved into a gatekeeping force that runs counter to these tenets.
The Rise of Maximalist Dogma
Bitcoin maximalists argue that Bitcoin is the only valid cryptocurrency and that all alternatives (altcoins) are scams. While it is prudent to be skeptical of centralized, pre-mined tokens rife with manipulative schemes, the maximalist stance has hardened into an ideological purity test that excludes rather than embraces open discourse.
Here’s where maximalists stray from libertarian values:
- Exclusionary Attitudes Toward Developers & Innovators
- Libertarians celebrate innovation, yet maximalists ostracize developers exploring Layer 2 solutions, alternative blockchains, or privacy-enhancing technologies outside the Bitcoin stack.
-
This mirrors the top-down control of authoritarian structures rather than the open competition of free-market principles.
-
Hostility Toward Alternative Monetary Experiments
- Libertarians favor free competition in currencies, arguing that individuals should be able to choose what best serves their interests.
-
Maximalists, however, reject any competing monetary experiment, even those that could complement Bitcoin (e.g., sidechains, zero-knowledge rollups, or asset tokenization solutions).
-
Cult-Like Insistence on Absolute Adherence
- Many maximalists have adopted an aggressive, almost religious stance, enforcing ideological purity tests that reject even Bitcoin-related innovations if they don’t fit the maximalist mold.
-
Libertarianism, by contrast, is inherently pluralistic and tolerant of different approaches to achieving freedom.
-
Disregard for Financial Sovereignty of Others
- Bitcoin's ethos is to provide financial self-sovereignty, yet maximalists attack those who choose to hedge risks with other assets, whether it be Monero for privacy, stablecoins for short-term volatility resistance, or even tokenized representations of real-world assets.
- A true libertarian approach would acknowledge the right of individuals to freely navigate financial instruments that align with their preferences.
The Irony: Bitcoin Itself Benefits from Free Market Dynamics
Bitcoin did not emerge in a vacuum—it competed against previous iterations of digital money, such as e-gold, Liberty Reserve, and earlier cryptographic cash concepts. If the early cypherpunks had imposed the same dogmatic restrictions on monetary experimentation that maximalists advocate today, Bitcoin itself may never have had the chance to thrive.
Libertarianism doesn’t fear competition; it thrives on it. Bitcoin maximalists, in seeking to eliminate all perceived competition, unwittingly recreate the exclusivity and coercion they claim to oppose.
The Path Forward: A Truly Open Bitcoin Culture
To realign Bitcoin culture with its libertarian roots, the community must: 1. Embrace Open Competition – Allow Bitcoin to prove itself through the free market rather than through ideological suppression of alternatives. 2. Encourage Innovation – Welcome new technologies, even if they originate outside Bitcoin, as long as they align with the ethos of decentralization and financial freedom. 3. Respect Individual Choice – Bitcoiners should recognize that financial sovereignty includes the right to explore different economic tools without facing tribalistic attacks.
Bitcoin was never meant to be an exclusive club—it was designed as an open financial revolution. To honor its founding principles, the community must resist the urge to impose ideological purity tests and instead foster the spirit of liberty, innovation, and voluntary association that made Bitcoin possible in the first place.
-
 @ b8851a06:9b120ba1
2025-01-28 21:34:54
@ b8851a06:9b120ba1
2025-01-28 21:34:54Private property isn’t lines on dirt or fences of steel—it’s the crystallization of human sovereignty. Each boundary drawn is a silent declaration: This is where my will meets yours, where creation clashes against chaos. What we defend as “mine” or “yours” is no mere object but a metaphysical claim, a scaffold for the unfathomable complexity of voluntary exchange.
Markets breathe only when individuals anchor their choices in the inviolable. Without property, there is no negotiation—only force. No trade—only taking. The deed to land, the title to a car, the seed of an idea: these are not static things but frontiers of being, where human responsibility collides with the infinite permutations of value.
Austrian economics whispers what existentialism shouts: existence precedes essence. Property isn’t granted by systems; it’s asserted through action, defended through sacrifice, and sanctified through mutual recognition. A thing becomes “owned” only when a mind declares it so, and others—through reason or respect—refrain from crossing that unseen line.
Bitcoin? The purest ledger of this truth. A string of code, yes—but one that mirrors the unyielding logic of property itself: scarce, auditable, unconquerable. It doesn’t ask permission. It exists because sovereign minds choose it to.
Sigh. #nostr
I love #Bitcoin. -
 @ df173277:4ec96708
2025-01-28 17:49:54
@ df173277:4ec96708
2025-01-28 17:49:54Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. Chats are synced automatically between devices so you can pick up where you left off.\ Start chatting for free.
We are excited to announce that Maple AI, our groundbreaking end-to-end encrypted AI chat app built on OpenSecret, is now publicly available. After months of beta testing, we are thrilled to bring this innovative technology to the world.
 Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. It can boost your productivity on work tasks such as writing documentation, creating presentations, and drafting emails. You can also use it for personal items like brainstorming ideas, sorting out life's challenges, and tutoring you on difficult coursework. All your chats are synced automatically in a secure way, so you can start on one device and pick up where you left off on another.
Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. It can boost your productivity on work tasks such as writing documentation, creating presentations, and drafting emails. You can also use it for personal items like brainstorming ideas, sorting out life's challenges, and tutoring you on difficult coursework. All your chats are synced automatically in a secure way, so you can start on one device and pick up where you left off on another.Why Secure and Private AI?
In today's digital landscape, it is increasingly evident that security and privacy are essential for individuals and organizations alike. Unfortunately, the current state of AI tools falls short. A staggering 48% of organizations enter non-public company information into AI apps, according to a recent report by Cisco. This practice poses significant risks to company security and intellectual property.
Another concern is for journalists, who often work with sensitive information in hostile environments. Journalists need verification that their information remains confidential and protected when researching topics and communicating with sources in various languages. They are left to use underpowered local AI or input their data into potentially compromised cloud services.
At OpenSecret, we believe it is possible to have both the benefits of AI and the assurance of security and privacy. That's why we created Maple, an app that combines AI productivity with the protection of end-to-end encryption. Our platform ensures that your conversations with AI remain confidential, even from us. The power of the cloud meets the privacy of local.
 #### How Does It Work?
#### How Does It Work?Our server code is open source, and we use confidential computing to provide cryptographic proof that the code running on our servers is the same as the open-source code available for review. This process allows you to verify that your conversations are handled securely and privately without relying on trust. We live by the principle of "Don't trust, verify," and we believe this approach is essential for building in the digital age. You can read a more in-depth write-up on our technology later this week on this site.
How Much Does It Cost?
We are committed to making Maple AI accessible to everyone, so we offer a range of pricing plans to suit different needs and budgets. Our Free plan allows for 10 chats per week, while our Starter plan ($5.99/month) and Pro plan ($20/month) offer more comprehensive solutions for individuals and organizations with heavier workloads. We accept credit cards and Bitcoin (10% discount), allowing you to choose your preferred payment method.
- Free: $0
- Starter: $5.99/month
- Pro: $20/month
Our goal with Maple AI is to create a product that is secure through transparency. By combining open-source code, cryptography, and confidential computing, we can create a new standard for AI conversations - one that prioritizes your security and privacy.
Maple has quickly become a daily tool of productivity for our own work and those of our beta testers. We believe it will bring value to you as well. Sign up now and start chatting privately with AI for free. Your secrets are safe in the open.
 #### Are You An App Developer?
#### Are You An App Developer?You can build an app like Maple. OpenSecret provides secure auth, private key management, encrypted data sync, private AI, and more. Our straightforward API behaves like other backends but automatically adds security and privacy. Use it to secure existing apps or brand-new projects. Protect yourself and your users from the liability of hosting personal data by checking out OpenSecret.

Enjoy private AI Chat 🤘

-
 @ 1cb14ab3:95d52462
2025-01-30 18:45:41
@ 1cb14ab3:95d52462
2025-01-30 18:45:41














Other Photo Series by Hes:
More from Hes:
All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from these photos, please feel free to send a zap. Enjoy life on a Bitcoin standard.
-
 @ 2f4550b0:95f20096
2025-01-28 16:47:28
@ 2f4550b0:95f20096
2025-01-28 16:47:28My family and I are wrapping up a relocation from Phoenix, AZ to Austin, TX. I went ahead to get keys to our rental house, meet the movers with our household goods, and generally get as many things ready on the Austin side as possible. My husband stayed behind with our boys to wrap up the AZ house and settle things there. Our experiences over the past few weeks have got me thinking about partnership, project management, and big life changes.
This move would not have been possible without the full partnership that my husband and I have in our marriage. Division of labor is real, and in the context of a relocation it’s vital to get everything done. We trust each other to divide and conquer the myriad tasks and responsibilities necessary. He supervised packers and movers to work on the AZ house; I met them when they arrived in Austin and supervised the move-in. He managed the property management requirements at the AZ rental house; I got the keys and have managed the property management procedures and move-in for Austin. He’s taking care of our current vehicle and handling the road trip from Phoenix to Austin; I bought a second vehicle that I can use to commute. I scheduled the cleaners, landscapers, and carpet cleaning for the AZ house; he supervised the work when the crews arrived. This kind of partnership not only takes care of all the duties, it edifies the relationship we have in our marriage. The care and trust we both show means so much to both of us!
Relocation is also a project, “a series of structured tasks, activities, and deliverables that are carefully executed to achieve a desired outcome” with a specific start and end. Managing this move has been marked by two long to-do lists of tasks for me and my husband and a series of important milestones that we’ve celebrated along the way. We used our calendar to map out the timelines for each phase of the work, we assigned roles and tasks, and we identified risks and dependencies. We enlisted vendor support for many of the tasks, and supervised their efforts while we completed our own. We never got as far as creating a true Gantt chart for the project, but I certainly thought of the phases of our move in that framework.
This move marks the start of a new phase in our family life, which has been marked by a series of big life changes. Since our marriage, these have included living in a number of places, the births of our two sons, and job changes. With this relocation, we get to experience life in a new part of the world and set up our boys for their launch into adulthood. This is exciting, and also a bit daunting. But I’m proud of our efforts to start 2025 off with a bang!
-
 @ 3ad01248:962d8a07
2025-01-30 18:45:07
@ 3ad01248:962d8a07
2025-01-30 18:45:07Well we finally have our first so called "Bitcoin President" in office. It's been a solid 10 days in office now and things are playing out exactly how many thought it would. Immigration raids, federal funds being frozen and to top it all off talks of a crypto reserve instead of Bitcoin Strategic Reserve (BSR) as we were promised on the campaign trail in exchange for our votes.
The reaction from Bitcoiners has been varied to say the least. There are some who are disappointed that Trump didn't declare a BSR on day one and there are others that want to give him to to work through his other political priorities. I am of the opinion that if you promise a Bitcoin Strategic Reserve on day one that you have to follow through on something like that.
This idea came from Strike CEO Jack Mallers so the source was reputable and put that expectation on the minds of Bitcoiners, so to see this fall through is kind of a let down. There are rumblings that backers of the Ripple Blockchain are actively lobbying Trump to include Ripple in some kind of "crypto reserve".
It looks like their lobbying efforts have been paying off so far. Trump did announce an executive order on pertaining to crypto more broadly. The EO established a "Presidential Working Group" on digital asset markets. Whatever the hell this means is beyond me but it does take the Trump administration focus off of Bitcoin which isn't a good development.
When combined with Trump launching a memecoin before he even stepped into office means that Bitcoiners inside and outside of the administration need to step up and keep the pedal to the meddle to make the BSR a reality.
The Bitcoiners around Trump have done a admirable job getting the Trump administration to where they are today and have undoubtedly has made the political environment better for Bitcoiners in general but they can't lose focus now.
A question that I have been thinking about myself is should Bitcoiners even advocated for a Bitcoin Strategic Reserve? I thought we were all about separating money and state. The federal government acquiring Bitcoin is antithetical to the whole point of why Bitcoin was created in the first place.
When I see the big names in Bitcoin all salivating and cheering on a BSR I'm like they just want their bags pumped. What happened to the revolution they were espousing during the bear market? I get it, who doesn't want their bags to be pumped? Hodling is psychologically tough so finally seeing that hard work pay off is a natural desire but at the expense of giving up your principles, I'm not so sure its worth it to be honest.
A superpower nation such as the US or China using Bitcoin to supercharge what they are doing now is bad for the entire world. Who is to say that they won't use their reserves to manipulate the market, borrow against their reserve to fund more military expansion and surveillance technology to further enslave the world.
Governments are no longer accountable to the people and will do whatever they want to keep power and keep their citizens subjugated. Bitcoin adoption at the nation state level is something we should not be cheering on.
Bitcoin has been and should always be a bottom up movement. In order to take away power from the state and bring the power back to the people they need a economic alternative that isn't controlled by the state. By taking away the power of the state to tax and monitor transactions slowly drains the power of the state to oppress the people.
Bitcoiners should be encouraging and creating more Bitcoin circular economies such as:
Your bags will be pumped when we get more individuals onto the Bitcoin Standard. Going the BSR route is a shortcut that is shortsighted and undermines the whole mission of Bitcoin. I fear the cat is already out of the bag as we see more and more countries and jurisdiction announce setting up their own BSR's. As an individual keep advocating for your friends, family and neighbors to adopt a Bitcoin standard before governments get their paws on it. Good luck and Godspeed.
-
 @ 000002de:c05780a7
2025-01-30 21:17:26
@ 000002de:c05780a7
2025-01-30 21:17:26The Debian Publicity Team will no longer post on X/Twitter. We took this decision since we feel X doesn't reflect Debian shared values as stated in our social contract, code of conduct and diversity statement. X evolved into a place where people we care about don't feel safe.
A couple red flags in this post that explain their actions.
- Shared values - projects that have broad values statements are prone to isolation over time
- Social contract - that's a meaningless vapid term
I have no issue with code of conduct guidelines or having value statements but when you pick sides on cultural divides and things that are not at all related to the logical objective of a project you are going to end up where Debian has landed.
X has its issues, I'm not a fan but the reasoning behind this seems really off.
One Debian user responded with what I thought was a good summary of why this is a bad move.
I'm a long-time Debian user and fan, and am also one of the champions for using Debian in space-based applications at NASA.
IMO this is a short-sighted and foolish decision. The notion of "values" is bring sadly misapplied here.
I urge you to reconsider. More channels of communication, even with those whom you disagree with, is good for both Debian and your user community.
I'm not into the "anti-woke" or "woke" crap and I dare say most people that use Linux do not care about either side very much at all. A loud minority has been gaining power in these types of projects for a long time. Today we have very loud counters to that group that also can be annoying and out of line.
Will be interesting to watch this all unfold over the next few years. Conservatives seem to be running victory laps and I think that's not only premature but also counter-productive.
I can see leaving X for other reasons.
- Debian users are really using it to communicate with the project
- The Debian publicity team isn't seeing very much of a response for their efforts
- X has become more about politics than tech and communication
- Specific examples of how X is causing issues for the project
They do say this
X evolved into a place where people we care about don't feel safe.
That's too bad but honestly I don't buy it. Maybe I don't spend enough time on X to have much credibility on this but I'm skeptical of this being the case.
originally posted at https://stacker.news/items/870437
-
 @ 1d4d7479:8aec9f9c
2025-01-30 17:43:34
@ 1d4d7479:8aec9f9c
2025-01-30 17:43:34I'm new to Nostr and came here innocently enough. I was intrigued by the idea of building a blog on Npub.pro that not only could be published for the traditional web but would also allow us to get paid for great content or additional services within the Nostr community. Looking into the future I can see this approach as something that allows us to build a community that we can encourage to help support us.
The goals: 1. Build a traditonal blog. 2. Do work once, share on other platforms. 3. Own our content/thoughts. 4. Serve an international audience. 5. Cultivate a community. 6. Improve the Signal to Noise Ratio.
My belief is that we can serve all these through Nostr. I'll let you know how things go on the journey.
Tools on my radar: 1. Npub.pro 2. Habla.news 3. Alby
What else should I be looking at over the next 4 to 6 months when seeking to follow a Nostr-first strategy for a services business?
-
 @ 86cf3742:678e3ae8
2025-01-28 15:06:54
@ 86cf3742:678e3ae8
2025-01-28 15:06:54In this episode, we dive deep into the world of dairy farming with JR Burdick, a former conventional dairy farmer turned raw milk producer. JR shares his journey from following the traditional dairy farming system to becoming an independent raw milk seller, breaking away from industry norms and regulations. He recounts the challenges he faced, including dealing with stray voltage that decimated his herd, a lengthy legal battle with an electric company, and the emotional and financial toll it took on his family.
JR also discusses the impact of industry regulations, such as the mandatory check-off programs and the pressures from dairy cooperatives, which led him to question the sustainability and ethics of the conventional dairy system. His story is one of resilience and transformation as he navigates the complexities of direct-to-consumer sales, the challenges of marketing raw milk, and the importance of maintaining integrity in his farming practices.
Throughout the conversation, JR offers insights into the broader agricultural landscape, touching on issues like government subsidies, the consolidation of the dairy industry, and the role of technology and innovation in farming. He also shares his thoughts on the future of agriculture, the potential of Bitcoin as a financial tool for farmers, and the importance of preserving traditional farming knowledge.
This episode is a compelling exploration of the struggles and triumphs of a farmer who dared to defy the status quo and forge a new path in the world of agriculture.
-
 @ 2e8970de:63345c7a
2025-01-30 17:29:52
@ 2e8970de:63345c7a
2025-01-30 17:29:52https://x.com/MistralAI/status/1884967826215059681
https://mistral.ai/news/mistral-small-3/
originally posted at https://stacker.news/items/870135
-
 @ ae6ce958:d0f02c7d
2025-01-27 23:27:51
@ ae6ce958:d0f02c7d
2025-01-27 23:27:51In a world dominated by overhyped tech and broken promises, DamageBDD stands apart as a Bitcoin-first revolution for developers, QA teams, and enterprises. Built on the belief that resilience, transparency, and accountability are not optional, this innovation is more than just another BDD platform—it's a tool designed to harness the unstoppable power of Bitcoin and the Lightning Network to redefine software quality and team productivity. Here's why DamageBDD will light up the Lightning Network like never before:
1. Lightning-Powered Incentives for Development
Imagine a world where developers are rewarded in sats the moment their code passes a milestone. With DamageBDD, that’s no longer a dream. We use Lightning-based escrow payments tied to milestone completions, ensuring every contributor gets instant, trustless payouts for verified work. This isn’t just about payments—this is about transforming the economics of collaboration and incentivizing excellence.
2. Real-Time Transparency Meets Bitcoin Immutability
Every BDD test, every passing milestone, and every failure is immutably recorded, showcasing the evolution of a project with a timestamped on-chain timeline. By anchoring progress to Bitcoin’s ultimate ledger of truth, DamageBDD creates a level of transparency that ensures trust—whether you're a developer, a manager, or an investor.
3. Immediate Liquidity Without Compromise
The Lightning Network enables participants to exit their locked funds through near-instant buybacks—no risk of long-term lock-ins or centralized interference. Developers and stakeholders can convert their contributions back to Bitcoin at market-close rates, minus nominal fees. This system protects value while keeping all incentives aligned with delivering quality software.
4. A Bitcoin Economy for BDD
Why settle for fiat-denominated payments or centralized intermediaries when you can build directly on Bitcoin? DamageBDD’s ecosystem ensures that every satoshi stays true to the ethos of decentralization, enabling organizations to manage projects in a way that’s fair, transparent, and resilient.
5. Scalable Adoption of High-Performance Teams
The Lightning Network isn’t just a payments rail—it’s a bridge for building relationships across borders. DamageBDD allows distributed teams to thrive, making trustless collaboration possible while fostering high-performance, Bitcoin-powered workflows.
6. Redefining ROI for Investors
Investors can now lock funds into milestone-driven escrows, ensuring ROI is directly tied to results. With DamageBDD’s Lightning-enabled payouts, there’s no waiting for endless revisions or missed deadlines—just real-time accountability, measured and delivered on a timeline that’s verifiable and immutable.
Bitcoiners, this is the spark.
While the fiat world struggles with inefficiency, corruption, and misaligned incentives, DamageBDD fuels the future with a Bitcoin-powered toolkit that transforms how teams work, get paid, and build trust. This isn’t just about better software—it’s about building an unstoppable Bitcoin economy where transparency reigns, quality wins, and the Lightning Network becomes the default rail for human collaboration.
DamageBDD isn’t here to gamble on hype—it’s here to build the future. Let’s light up the Lightning Network and show the world what Bitcoin-backed innovation can achieve. Are you ready to join the revolution?
-
 @ eee391ee:8d0b97c2
2025-01-27 14:55:16
@ eee391ee:8d0b97c2
2025-01-27 14:55:16Amber 3.2.0
- Fix relay connection when starting the service
- Added profile picture in the incoming requests screen when using a large screen device
- Added more event kinds translations
- Added a log with the bunker request response
- Use the relay from the request to send the response when no app is found
Download it with zap.store, Obtainium, f-droid or download it directly in the releases page
If you like my work consider making a donation
Verifying the release
In order to verify the release, you'll need to have
gpgorgpg2installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:bash gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6DOnce you have his PGP key you can verify the release (assuming
manifest-v3.2.0.txtandmanifest-v3.2.0.txt.sigare in the current directory) with:bash gpg --verify manifest-v3.2.0.txt.sig manifest-v3.2.0.txtYou should see the following if the verification was successful:
bash gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03 gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>"That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:
bash cat manifest-v3.2.0.txtOne can use the
shasum -a 256 <file name here>tool in order to re-compute thesha256hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly. -
 @ 3459741b:616b59f9
2025-01-30 17:09:12
@ 3459741b:616b59f9
2025-01-30 17:09:12Introduction
Recently, I had the opportunity to work as an advisor for an AI agent project, which is created by team with a lot of fin-tech software develop experience. As we coded together, their real-time questions and challenges provided unique insights into the hurdles software engineers face when transitioning to AI development. They would pause at moments that most AI engineers take for granted - "How can we be sure the agent understood correctly?", "What if the model makes a mistake?", "How do we handle the uncertainty?" These weren't just isolated questions; they represented the fundamental paradigm shift required when moving from traditional software engineering to AI development. And thats why i think it might be worthy to take sometime write down this article and if you are going to start your first AI agent programming, spending 5 min reading t his will save you a lot of time later.
1. Shifting from Deterministic to Probabilistic Thinking
- Traditional software engineering deals with deterministic outcomes
- AI systems operate on probability rather than certainty
- Engineers need to adapt from "100% correct" mindset to accepting probabilistic outcomes
- Blockchain developers may find this particularly challenging due to their background in exact, deterministic systems
2. Understanding Core AI Concepts
(There are a lot of concepts to understand, but i will focus on the most frequently asked ones)
Memory Management
- Short-term Memory: Implemented through conversation context
- Long-term Memory: Implemented through vector databases (RAG - Retrieval Augmented Generation)
- Context length management is crucial due to LLM token limitations
Language Models and Fine-tuning
- Base models (like GPT) provide general intelligence
- Domain-specific knowledge can be added through:
- Fine-tuning with custom datasets
- Adding RAG layers for specific knowledge domains
3. Technical Framework Knowledge
Essential Tools and Frameworks
- Vercel AI SDK (if you are a typescript guy)
- LangChain (alternative option)
- Different models(openai, claude, gemini, etc, of course, now, deepseek. the temu in llm )
- Understanding of prompt engineering
Multi-Agent Systems
- Agents can communicate through natural language
- Inter-agent communication requires careful system design
- Implementation of thought processes and decision-making loops
- Safety considerations for system commands and operations
4. Language and Localization Considerations
- System prompts typically work best in English
- Multi-language support requires careful handling:
- Input translation to English
- Processing in English
- Output translation to target language
- Model performance varies across different languages
5. Safety and Error Handling
- Implementing validation layers for critical operations
- Understanding model limitations and potential errors
- Building feedback mechanisms to detect misunderstandings
Conclusion
Transitioning from software engineering to AI engineering requires a significant mindset shift. While traditional software engineering skills remain valuable, understanding probabilistic systems, language models, and AI-specific architectures is crucial. The key is to balance innovation with practical safety considerations, especially when dealing with critical applications.
Remember that AI systems are not perfect, and building robust applications requires careful consideration of their limitations and appropriate safety measures. Start with existing frameworks and gradually build up complexity as you become more comfortable with AI-specific concepts and challenges.(the conclusion part is written by chatgpt, did you notice? :))
-
 @ 0463223a:3b14d673
2025-01-27 10:47:00
@ 0463223a:3b14d673
2025-01-27 10:47:00I wrote this article back in 2019 but I wanted to see how it stood up today. Since writing this I’ve been diagnosed with autism. However, I question this. For sure I’ve gone through lots of ups and downs in life. Some issues probably due to childhood trauma, others due to drugs etc. but I still ask if is a natural response to bullshit.
I don’t write this to belittle any problems anyone has and the autism spectrum disorder is real (but not disorder to me). When the whole population gets diagnosed as neurodivergent what next?
If you need help, get help. I write this as a person trying to get off the drugs prescribed to me many years ago. Something I’m finding difficult but I will do it…
From 2019
A large part of the adult population in the Western World are mad, mental, bonkers, have lost their marbles and are totally insane. Well, that’s at least according to the World Health Organisation A recent WHO report stated one in four people in the world will be affected by mental or neurological disorders at some point in their lives. And there’s a very high chance that you, the reader, are completely off your rocker. Mental Health is the buzzphrase of our times. It’s on the TV, the radio and all over the internet. The UK’s Prime Minister goes on TV to state how big the problem is and just how very seriously she takes it and we’re assured the government are working extremely hard to tackle it. However, the rhetoric never amounts to anything, as anyone seeking genuine help will attest. Help is hard to come by. Doctors prescribe pills to subdue the wrong thoughts, but nothing else. No long term solutions, just keep taking the pills. Hundreds of thousands of adults are medicated in this way and now, more worryingly, are many children. So it’s vital to talk about it. It’s permanently Mentalspeng Awareness Day or Tell Facebacon Your Neurologicalwankfuck Week. It’s even become quite fashionable, with regular treats from celebrities telling of their darkest moments and how they nearly didn’t get that huge Hollywood deal because they woke up feeling sad and unhappy one winter morning. If you’re a fruit-loop tell everyone. It will be ok… Tell them about the time you were going to drive your car off a cliff and ended up in hospital after a particularly long conversation with The Samaritans. Great stuff! Tell them about the regular, uncontrollable urges to slash yourself with a Stanley knife or any other sharp object close to hand. Awesome! Tell them about how you smash yourself repeatedly in the head, sometimes with a heavy object, as you can no longer deal with the stress and frustration of being disempowered by situations completely out of your control. Cool! Tell them how you feel trapped by an increasingly expensive housing market and how you have zero financial security. Brilliant! Or maybe just tell them that sometimes you can’t get out of bed and you don’t know why or that you panic uncontrollably for no reason. Skills! Tell the world! We’re so understanding of mental health issues these days, just raise more awareness and everything will be fine, we’re here for you man/woman! (and yes, we might need to sell this information on to the appropriate persons, future employers, insurance companies or government agencies etc.). After all, we’re all good people right? Tell everyone you’re mad and they’ll understand. They’ll think of the time you were a dick and they’ll say “Ahh, poor sod, you know he’s a mental don’t you”. Well frankly no. The world is full of cunts and whilst the people close to you will be sympathetic, as far as wider society goes, you’ll be marked, your position compromised and your word will not be trusted. I mean who knows, maybe you’re delusional, perhaps you’re about to rampage through town wielding a knife or driving your car into a crowded supermarket… But hold up…. One in every four of us is mental?! Is that really the case? Let’s think about this for a second. When did 25% of the population become a massive neurospeng? This wasn’t the case 30 years ago, a quarter of the population weren’t mad. There wasn’t the vast array of medications available these days; Prozac, Sertraline, Citralopram, Promethazine, Venlafaxine, Amiltryptaline, to name a few (there are many, many more). It’s clear that a lot of people aren’t feeling right but how come the suicide rates are higher now than they were 30 years ago? If we’re all so much more aware and well medicated, surely rates would be going down? Perhaps you were diagnosed as a mental because you responded negatively to events happening around you? Maybe you’re working increasingly longer hours for less money. Perhaps the terms of your work changed drastically and you no longer feel secure. Maybe you lost jobs because of funding cut backs. Perhaps you’re in despair because your friend took their own life when their job was cut in an austerity drive. Suicide is the most horrible thing which ever way you look at it. You strip a person of their purpose and they react with the most extreme act of self violence, causing an unbelievable amount of emotional distress for those left to pick up the pieces… And so we say, “Ahh but you understand, they were mad… They were fucking mental, they lost control of their senses, it such a terrible shame but they were mad you know”. Bullshit. The term Mental Health removes all responsibility from the structures creating an environment where people are deemed no longer of value or viable human beings. But maybe you were angry because you were told by politicians that you need to live within your means, whilst those in large financial institutions increased their wealth exponentially? The world economy crashed in 2008 and there’s no money. Eh? The governments of printed more and more money, but there’s no money for you, you cunt. Perhaps it was packed aboard a spaceship and is now hurtling towards Mars! (mad people tend to think like this, after all it couldn’t be that the money was stolen). Maybe you got angry with the blatant corruption from those in public life? Politicians shout loudly that they’re for the people but will pocket pay rises, local council officials bully members of the public and make threats to cut funding . This can be done with total with total impunity, as the structures put in place to control such actions cover up any wrong doing. You see the powerful can not and will not be challenged. There is no pathway to justice. When the fire at Grenfell happened, it was clear for all to see that the housing association, council and big business were at fault, but no, blame was heaped on the lone fire officer who had the awful task of managing two lowly fire engines in London’s biggest fire since World War II. At the time my local Member of Parliament response was “the flats were refurbished to a very high standard”. We shouldn’t lay blame at those in power, we cannot have any fault with the establishment. I bet that poor fire officer was a mental too… When discussing mental health we’re not talking about a brain injury or unfortunate illness. There’s extreme difficulty coping with the world but it’s not madness and it’s not a delusion. It’s a natural reaction to bullshit. We’re are completely surrounded by bullshit, on the internet bullshit, on the TV bullshit, in the work place bullshit, from our leaders bullshit etc. etc. The world is running on massive excess levels of bullshit. And this is the natural emotional response to bullshit. Mental Health is used to invalidate the anger, freeing the powerful from responsibility and laying blame squarely at the individuals door. In the meantime, piece by piece, the powerful steal everything we’ve ever owned. So next time someone says to you raise awareness about mental health, maybe tell them to fuck off. Either that or tell them you’re flying to the Moon to have tea with Kim Jong Un and Barney The Dinosaur. Fuck mental health. *Image used without permission of Barney The Dinosaur.
-
 @ e83b66a8:b0526c2b
2025-01-30 16:11:24
@ e83b66a8:b0526c2b
2025-01-30 16:11:24I have a deep love of China. It probably started in 1981, when my Father visited China on the first trade mission from the UK to open up trading between the 2 nations.
As a family, we have historically done a lot of business in Asia starting with our company Densitron, who’s Asian headquarters were in Tokyo, through to Taiwan where we had factories leading to investing in Vbest, now Evervision an LCD manufacturer. They have admin offices in Taiwan and a factory in Jiangsu, China.
I have always hated the western narrative that China is the “enemy” or that China’s Communist / Capitalist system is “evil”.
Without understanding history, geography, cultural biases, and indoctrination it is as difficult to remove those beliefs in the same way it is difficult to convert “normies” to understand the freedom and power of Bitcoin.
I have tried and had some success, but mostly failed.
However the recent ban on TikTok and the migration of the west to the Chinese owned “rednote” app has overnight created more cultural exchanges and understanding than the previous 40+ years has ever managed to achieve. That along with the recent disclosure about Chinas advancements in AI have also deflated some of the western hubris.
If you wish to go down the rabbit hole of China from a cultural view, this YouTuber has given me a much better framework than I could ever provide as an outsider.
She is a Chinese girl, who came to the UK to study at University only to return with a mixed understanding of both cultures. She is doing a far better job of explaining the culture from a western perspective than I ever could.
https://www.youtube.com/@SimingLan
Here are 4 videos of hers that help explain a lot:
This is a lighthearted look at the recent TikTok ban TikTok ban completely backfired on US! and it's been hilarious https://www.youtube.com/watch?v=A7123nG5otA
More in-depth insights are:
My complicated relationship with China. https://www.youtube.com/watch?v=BEaw0KAuNBU
China's Biggest Problem with Free Speech Rhetoric https://www.youtube.com/watch?v=V7eSyKPbg_Y
What the West Doesn't Get about China's Rise https://www.youtube.com/watch?v=hmb1_HfflCA
-
 @ fd208ee8:0fd927c1
2025-01-23 15:31:24
@ fd208ee8:0fd927c1
2025-01-23 15:31:24Planning Alexandria
People keep asking what features nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz has planned for #Alexandria, but they're not set in stone because we're an agile project.
What we do have, is lots of tickets on our Kanban boards and a naming scheme, where we use a famous person's last name, to signify the release goals.

Gutenberg v 0.1.0
(after the inventor of the printing press) will contain the features needed to read and write NIP-62 Curated Publications, as well as encompassing the complex infrastructure, architecture, documentation, and personnel we require to make this all run smoothly and look easy.

Euler v 0.2.0
(after a mathematician credited with establishing graph theory) will contain the features for deep-searching, visually exploring, and smartly navigating the data set, wiki page display, annotating and citing the publications, exporting to other formats (like PDF, ePUB, and LaTeX), and commenting/reviewing. To help with the heavy lifting, we will be swapping out the core with our own Nostr SDK called "Aedile".

Defoe v 0.3.0
(after an author who perfected the novel format) will be all about our favorite writers. We will be focusing upon profile data, payment systems, book clubs and communities, and stylesheets.
That is everything we have planned, for the v1.0 edition, and we consider that version to be a true product.
As for after that, a teaser...

-
 @ e373ca41:b82abcc5
2025-01-27 08:33:39
@ e373ca41:b82abcc5
2025-01-27 08:33:39
This article by Milosz Matuschek first appeared in German in his publication "Freischwebende Intelligenz".
It's working! Or is it? Trump's inauguration casted its shadow in the last weeks already and produced the first big upsets. Meta/Facebook cancelled their squad of fact-checkers and will rely (like X) on community comments in future. Wokistan is unwound. Zuckerberg now presents himself as an advocate of free speech, declaring a “return to principles”.
For those who believe it, Zuckerberg is an opportunist who gave in to the Biden administration and its deletion requests during Covid without much resistance (after having given 400 mio. USD through intermediary organizations into Bidens campaign), regardless of whether it was about masks or later about “vaccinations”. His Canossa walk to Rogan does not change the fact that he betrayed his own principles and deleted millions of critical profiles, channels and groups, including groups in which Facebook users discussed vaccine damage. Where are the profiles? Are they back? Zuckerberg played Ministry of Truth and is now quoting Orwell and toeing the Musk line. This is what a driven man looks like, not a man of conviction. The mainstream is shocked and is already labeling Facebook as a new hate portal. When will the accusation of anti-Semitism kick in?
https://x.com/TheBabylonBee/status/1876683974560350626
The Musk effect
All of these are gestures of submission to the new ruler of public opinion: Elon Musk. He owns the largest network for "free speech", he himself is its biggest influencer and is recalibrating what can be said in public. His journeyman's piece was Trump's election victory. Changing the political mood in the world could be his masterpiece.
For a long time, he admittedly did this extremely skillfully. He tweeted about the deep state, Soros and Gates, the population collapse, compulsory vaccination, etc. and got on well with the critical scene, some of whom are now all too submissively trying to recognize their new messiah in him. Musk throws his media spotlight on topics that the newspapers remain silent about and gave politicians underrepresented in the mainstream, such as Alice Weidel (opposition leader in Germany, AfD), a forum.
Musk has repeatedly brought the Epstein case and paedophile scandals, such as in England (Rotherham, Oxford), into the media spotlight. Pakistani gangs abused minors and children there for years; anyone reading the verdict will need strong nerves. In Austria, a trial for gang abuse of a 12-year-old girl has just ended with an acquittal. The judges believe she wanted it that way. During the trial, the defendant put a hundred Euro note on the table for the victim's lawyer, which is what mocking “reparation” looks like. In “our democracy” in Germany, sentences are handed down on a piecework basis for ludicrous “insults to politicians”.

Musk is de facto the most powerful man in the world (satellites, SpaceX, Mars, Tesla, mRNA vaccination routes, Pentagon connections, X..,). Where so much power is involved, megalomania is not far away. He is acting increasingly clumsily.
It is currently confirming for all to see the cliché that politics is basically the entertainment department of industry. Even in “our democracy”, the bosses of the world have always chosen their political generals, who are interchangeable. In the case of Bill Gates, George Soros & Son etc., the executive was the woke nomenklatura right up to the EU. With Musk, it is the new, right-wing conservative nomenklatura.
ADVERTISEMENT:
Looking for the easiest way to buy Bitcoin and store it yourself? The Relai app is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. Here you can buy Bitcoin in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees (no financial advice). Disclaimer due to regulatory issues: The services of the Relai App are hereby only recommended to inhabitants of Switzerland or Italy.

Need more security? The Trezor wallets are recommended and easy to use, others are available in the store. Need more advice? Book an introductory meeting with a wallet expert.
Musk smooches Meloni, interviews Alice Weidel, auditions Farage (and cancels again: “doesn't have what it takes”). The Weidel interview was certainly a necessary corrective to the current media asymmetry (and no one should be able to deny access to a source of information). There is no doubt that the second strongest party in the German mainstream media does not have a fair chance to convey its content. Talk shows, if there are invitations to AfD politicians at all, are public inquisition events with calls for self-criticism.
But the Musk-Weidel talk was not journalism either. It was a public casting event, a kind of “Apprentice” on X. Or have you seen a journalist anywhere? A platform operator and a politician tapped each other a bit and confirmed each other. All this is already bringing the EU onto the scene, Thierry Breton is already waving the possible annulment of the elections in Germany. An oligarch is unmasking the EU oligarchy and both want to do it for democracy, what a world...
"Which piggy would you like?"
https://www.youtube.com/watch?v=tiwkYCFD6EA
So asked Robert Lembke some decades ago in the German TV show “What am I?”: And that's supposed to be the choice now: Pick your favorite oligarch or next slave owner. In the end, every big tech business model is based on advertising and data mining. Zuckerberg, Musk & Co. sell identity, friendship, memories and ultimately your content. Twitter also wanted to buy Substack and got “Revue”. The customer (aka the product) is sold to the advertising industry, Zuckerberg potentially knows each of his users down to their character traits (unknown even to the user) (check: www.applymagicsauce.com). Like in the 80s movie with Arnie, this is a kind of “running man”, a gladiator game in front of an assembled world audience.
Whoever wins attention for themselves (and the platform) wins back a small amount of freedom and even earns something in the process. Musk recently changed his X name to “Kekius Maximus” (whereupon memecoins of the same name immediately sprang up, to each ruler his own currency), reminiscent of the gladiator Maximus from the film of the same name by Ridley Scott. The gladiator's owner told him: “Win the crowd and you win your freedom”. Not much has changed since ancient Rome. As the world's top meme maker with the greatest reach, Musk also has the greatest influence on social moods. No content is more viral and memorable than memes. The winner here is the one with the highest level of replication. That's what Musk does.

The changes we are currently seeing are just the beginning, both positive and (possibly) negative. The first effect is already visible: Wokistan is withdrawing from platforms that are not ideologically curated. Fearing accusations of contact guilt, they obediently throw themselves off the nearest cliff and voluntarily curtail their own reach; the last example was “Watson.ch” from Switzerland, a journalistically narrow-chested list and click medium for chai latte sippers from Bern and Zurich. Will the “X-itus” be followed by the great unfriending of Facebook? There won't be much left, Tiktok also ticked to the right beat by their standards (as long as it's not against China). The next place of mercy for Woke is called Bluesky, where there is neither hate nor agitation, right?
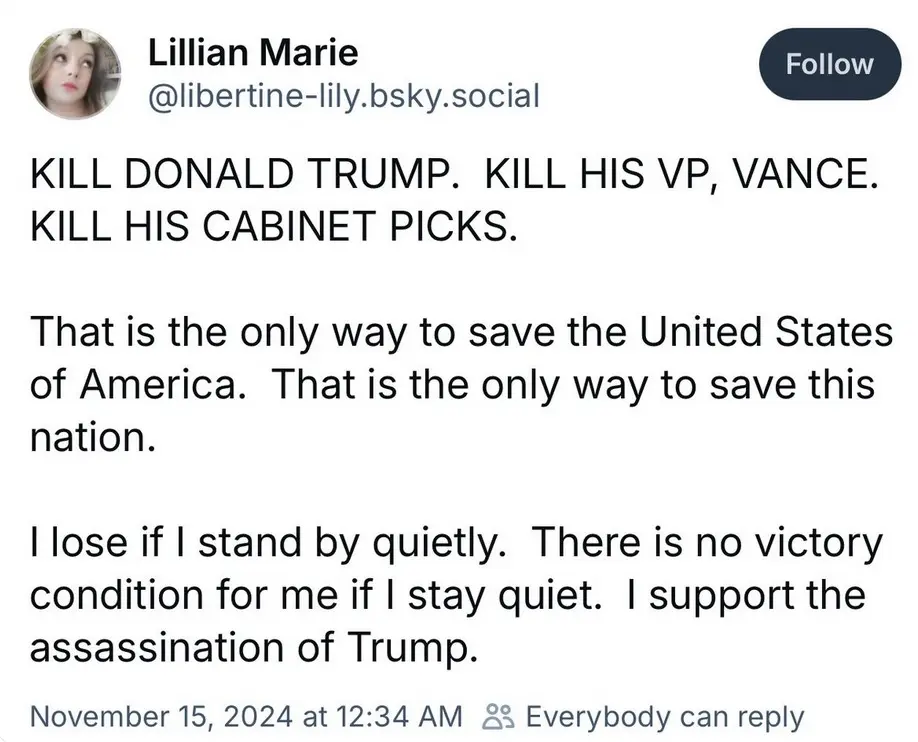
It must be clear to everyone now: The result of liberation by others is never freedom, but new dependence. What has not been fought for is always a continuation of neo-feudalism and (virtual) serfdom in a different form. The tools for regaining freedom have long been in our hands. What separates us from freedom is ultimately only comfort.
The book “The Sovereign Individual” was recently translated into German. It was written over 25 years ago.
Read it!
Join the marketplace of ideas! We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).

Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to team@pareto.space**
Not yet on Nostr and want the full experience? Easy onboarding via Nosta.me.

-
 @ bbb5dda0:f09e2747
2025-01-27 03:22:10
@ bbb5dda0:f09e2747
2025-01-27 03:22:10At Nostriga in the middle of last year I got introduced to TollGate, a project to resell internet access, I was fascinated and hyped for this to become a thing. Later during SEC-03 I got involved in the development of TollGate and helped work out the idea utilizing Nostr to make the experience of using a TollGate super smooth. That's where the idea started to make a cross-platform app that would autoconnect and start streaming sats to TollGates for internet access.
I'd been working on it here and there and this week I feel like I got in to the developer high (i'm sure some of you know what that feels like) and I just wanted to see the android app work! So as the week moved along I just kept being drawn in. And progress there was! The vision we had during SEC is coming to be a reality very fast.
TL;DR There's a demo video at the bottom.
Quick CI/CD update
I've been talking to DanConwayDev to work together on getting the UI for the pipelines into GitWorkshop, which would be the perfect place for it. He's in the middle of a rewrite, so when that is progressing a bit more we'll cooperate on making this part of it, stay tuned!
Whoami
I started by creating a service that would run on every TollGate router that a client can use to fetch their own MAC address that's later included in the payment. The MAC address is the anchor for the router to allow/disallow access. The problem we have on Android is that the operating system restricts access to this information. But since we control the router, we can work around it by creating a predictable endpoint that gives us back this answer.
Beacon frames
Routers use something called Beacon Frames, which are sent out regularly and it is the thing your phone looks at when scanning for wifi networks. It contains the name of the network (SSID) and a whole bunch of other stuff you don't usually see.
We're utilising these beacon frames to add some information specific to tollgates. There is a field in these beacon frames called 'vendor elements'. Which is originally only intended for use by manufacturers of routers. But ofcourse we can utilize them too. Which is exactly what we do.
I eperimented with these beacon frames to see how many of them we can broadcast. It turns out that we're limited to only one of them, but the good news is we can fit up to 249 characters (256 - a few reserved ones) in there. This is amazing because it will fit everything we need in there.
We put in: - Nostr npub - TollGate version - Gateway IP (required to get around OS limitations) - allocationType (KiB/Minutes) - price per 1024 units (eg: 104900 sats per 1024 KiB) - price units (sat)
So now any tollgate can broadcast this info, which is used by clients to decide wether or not they should connect. And if they do, where the payment should go.
Suggestions, Suggestions, Suggestions
Unfortunately, Android in the past few years has locked down the wifi api's and we can no longer fully autoconnect to networks. Instead we have to use the 'wifi suggestions' API. As the name implies, it will only suggest a nework to a user using a silent notification that they have to press to actually connect. But alas, we'll work with that and if it's the only user-action required, that's still quite okay.
It took me quite a while to figure out the way the OS handles these suggestions, but eventually I got it to work and was able to get the flow to work!
Adding the payment
Ok this part doesn't include an actual payment yet, but all the components are in place now for a (semi-)automatic tollgate connection, which is EPIC! In this version i still manually tap 'connect', but this can and will be automatic soon.
So the steps are as follows (this happens in a few seconds): - 📲 TollGate App scans for networks and filters for TollGates - 👤 User taps Connect [to be automated] - 📲 TollGate App suggests network - 👤 User taps suggestion notification to connect - 🤖 Android connects to network - 📲 TollGate App fetches it's own MAC address (whoami service on router) - 📲 TollGate App Connects to Nostr relay (running on the router) - 📲 TollGate App Sends payment - 🛜 Router receives payment (merchant module) - 🛜 Router creates session (merchant module) - 🛜 Router opens the gate for user (valve module) - 🛜 Router closes the gate for user, when purchase runs out (valve module)
I made this recording, it has a small caveat that at the end the page loaded because I was on 5g, the OS still thought the wifi network had a captive portal open. But there's an API to mark it as dismissed, which we can easily implement. So that's an issue we can overcome!
Demo video
https://cdn.satellite.earth/ede26976043a0b8edf278ea51aa0c00e721d2134c4e456928192090ea660bda0.mp4
-
 @ 59c2e15a:d25e6e8d
2025-01-27 02:29:42
@ 59c2e15a:d25e6e8d
2025-01-27 02:29:42Note: I originally wrote these essays on bitcoin and yoga in 2022 after completing my yoga teacher training and going deep down the bitcoin rabbit hole. I then published them to my Ghost blog in 2023. I decided to repost them here on Nostr to start 2025 to further spread the wisdom and timelessness that bitcoin and yoga share. I split my original essay into seven parts, and I will add an eighth comparing yoga and Nostr. I hope you enjoy part one - namaste!
Part I: Bitcoin and Yoga Shared Values
Part II: Mythical/Mystical Origins
Part III: Evolution of Money and Yoga
Part IV: Ashtanga Yoga - The Eight Limbs of Yoga (limbs 1-2)
Part V: Ashtanga Yoga - The Eight Limbs of Yoga (limbs 3-8)
Part VI: Bitcoin is Dharma
Part VII: Himalayan Kriya Yoga
Introduction
With each passing day, month, and year, it feels as though our human civilization is becoming more dysfunctional, untethered, and unsustainable. Individuals are working harder, longer hours, yet most remain stuck in place, goals farther from reach. We live in a world where many have outsourced the most critical task that has enabled humans to prosper – critical thinking. I challenge each one of you to remove preconceived notions you might have about Bitcoin or Yoga before reading this series. I invite you to enter with an open mind. Think for yourself – you are welcome to agree or disagree with the information and arguments I put forth.
I also encourage you to go beyond thinking – feel. Use your intuition to understand if the way you’re living your day-to-day life feels good to you, or if you have sense, an inner knowing that something is off with our society today – that there can be a better way. If you open your heart and mind to receiving new information, there is potential to motivate yourself to change your thoughts and behaviors for more aligned action towards individual sovereignty. Every individual can choose freedom and independence. Yet it has become increasingly difficult to live a life of freedom due to the fiat system of inflation and the many distractions that keep us from going inward. After deep study and reflection, I believe bitcoin and yoga both provide the individual control over their own life journey, and frameworks to understand our connection to self and others.
I'm excited to share what I have found in my own personal experience, and hope to spark curiosity within you to follow your passion. This writing is intended for anyone seeking tools to lead a life of freedom, make positive changes and deepen your understanding of self. In addition, it is written for yogis who want to learn about bitcoin, bitcoiners who want to learn more about yoga, and anyone who is interested in a fundamental understanding of these topics that I believe contain the potential to transform your life.
Part I: Bitcoin and Yoga Shared Values
Bitcoin and yoga share many fundamental values with one another and provide deep wisdom on guiding individuals towards living better and more meaningful lives. Ultimately bitcoin and yoga share the goal of individual liberation, freedom from suffering, and a deep inner, lasting peace in Being. In yoga, this state is called moksha or samadhi. I believe everyone has a true essence, an inner being that knows what is best. However, our external environment and our own conscious mind push us away from this serenity, leading to regrets about the past or anxieties about the future. This perspective of linear time and our own individual stories and identity damage our ability to stay present in the Now, leading to endless distractions. In similar ways, bitcoin and yoga provide us insight for an individual’s path to inner peace, as well as for humanity’s path to collective peace and prosperity.
Energy
At the most elemental level, energy is the force underlying both bitcoin and yoga. Energy is the universal currency of life. We would not exist without energy. We require physical energy to fuel our cells and bodies to perform essential tasks like breathing, circulation, digestion, and movement. We perceive many forms of energy such as light or sound waves, yet there are many energy wavelengths we are not able to or are not trained to perceive.
Bitcoin is powered by physical energy in the real world in a process that secures the network and unlocks new bitcoin for distribution, a process commonly referred to as mining. Interestingly, 100 years ago, Henry Ford pushed for an energy-linked currency measured in kilowatt hours that could bring peace after a brutal World War, as seen in the New York Tribune headline and article December 4, 1921: ‘Ford Would Replace Gold with Energy Currency and Stop Wars’ (i). It took another century, but mankind has finally developed a digitally-native currency tied to the physical world through energy expenditure – bitcoin.
Yoga is similarly rooted in energy that individuals tap into through breathwork, physical movement and meditations practices. This life-force energy is known in Sanskrit as prana. Prana is not bound by time or space, and it flows through individuals in over 72,000 nadis, or channels. There are three main nadis - the first is ida, our left side body which corresponds to the feminine, receiving energy, or the moon. On the right side is pingala, relating to our masculine, giving energy, or the sun. The central nadi runs through our shushumna, linking our seven main energetic centers, known as chakras. These chakras run from the base of the tail bone, up through the spine and the top of the head. Each chakra has a name, a color and key characteristics that can often become blocked through negative emotion, trauma or stress in the body. Different yogic practices target these energy centers to unlock what is stuck and enable energy to more freely flow through us in an open exchange with the earth and out the universe. This energy is ever-present; one need only to tap into this energy, feel it and utilize it for the strengthening of one’s inner being that then radiates outwards on others in your life. The energetic experience and upward surge can also be referred to as kundalini energy, a creative power of divine feminine energy that originates in the muladara chakra at the base of the spine.
 Depiction of our chakras and nadis (image source)
Depiction of our chakras and nadis (image source)Proof of Work
In both Bitcoin and Yoga, "proof of work" is required to operate, practice and move forwards. In the Bitcoin network as described in the original white paper, miners contribute tangible energy towards running a hashing algorithm on a computer – SHA256 – to earn the right to add the next block to the blockchain and collect both the coinbase and transaction fee reward (ii). The work is difficult to produce but easy to validate by others. Miners are collecting all of the valid peer-to-peer transactions being propagated to the network and establishing them as truth into the distributed ledger. The rules in bitcoin’s code incentivize honest behavior from miners through unforgeable costliness – if a miner were to lie about any of the transactions it includes in a block, independent nodes in the network would reject the block, and the miner would have lost all the real resources it expended to solve the proof of work calculation.
 Example of an ASIC - a specialized computer solely dedicated to mining bitcoin.
Example of an ASIC - a specialized computer solely dedicated to mining bitcoin.In yoga, dedicated work is needed to learn the asanas, postures, and practice for oneself; you won’t just be able to go upside down or flow through sun salutations without first learning proper alignment and breathing techniques. An individual needs to conscious decision to work on a daily yoga practice that requires energy to flow. There are several ways to work on your yoga practice beyond physical movement; these include bhakti yoga (devotion/prayer), jnana yoga (study/wisdom), karma yoga(selfless action) and raja yoga (ashtanga). Raja yoga includes ashtanga, the eight limbs or paths of yoga that Patanjali detailed \~2000 years ago that we will explore in more depth in part IV. These ancient margas (paths) and subsequent development of these ancient teachings provides individual with ample opportunity to dedicate and work towards individual enlightenment.
Decentralization
Next, there are no external barriers preventing an individual from participating in Bitcoin or yoga. Bitcoin does not discriminate and can be accessed by anyone around the world. Yoga provides a way of life full of mindfulness and appreciation. The only barriers are internal blockages, or unwillingness to ask questions, learn and take responsibility for oneself and state of being. Therefore, Bitcoin and yoga can both be defined as decentralized. There are no centralized gatekeepers preventing one from accessing the Bitcoin network or using bitcoin as money; anyone can spin up a node, download a wallet or mine bitcoin. There are over 16,000 nodes geographically distributed around the world voluntarily running the bitcoin core software code establishing the payment network, validating transactions and storing the entire transaction history of bitcoin (iii). It costs as little as a few hundred dollars and requires less than 600 gigabytes of storage to run a node – in 2023 you can find mobile phones with that much storage. No one can prevent you from sending a peer-to-peer transaction or storing your own wealth with 12 words in your head – you need only decide to take true freedom into your own hands and learn how to do so (iv). The common maxim is “don’t trust, verify”. You don’t need someone else’s permission to participate in bitcoin or trust anyone else (eg, banks) to hold your wealth.
 Geographic distribution of reachable bitcoin nodes (source: bitnodes)
Geographic distribution of reachable bitcoin nodes (source: bitnodes)Similarly, no one can stop an individual from practicing yoga, learning yogic philosophy or connecting with one’s truest self and inner guru. Anyone can choose to follow the path of yoga, focus on ones breath or develop a strong asana practice. There are many different ways to learn and interact with yoga, with experienced teachers willing to share their lessons to students all over the world. One need to simply find yoga studio, enroll in a teacher training or and engage with a teacher to experience yoga for themselves. Yoga looks and feels different depending on what country you are in or in which lineage you are being taught. Tapping into these profound lessons, as fundamental as controlling ones own breath, requires only an individual desire and the conscious decision to act. There’s no CEO or central authority dictating how Bitcoin or yoga has to be. Individuals have the freedom to express themselves voluntarily guided by frameworks we will dive into deeper.
Low Time Preference
Another core value that bitcoin and yoga share is low time preference. In Austrian economics, time preference refers to individual decision making. An individual with a low time preference makes decisions with greater consideration of the future, quieting immediate cravings and desires to pursue a higher goal (v). In bitcoin and money, lower time preference decisions include putting off consumption to save value for the future. Unfortunately, our fiat (by government decree) system induces individuals to make high time preference decisions, heightening consumerism and poor habits today that we see rampant in our society. There is a disincentive to save, as inflation of the money supply leads to debasing value of the dollar and other fiat currencies, decreasing individuals purchasing power of cash they hold onto and don’t spend soon. For example, the purchasing power of your dollar today will be cut in half over the next decade at current levels of inflation. In many ways, bitcoin is time, described brilliantly by Gigi, as it creates a decentralized clock that establishes consensus with each block (vi).
In contrast, the hard cap supply of 21 million bitcoin enables individuals to save with the knowledge that governments and central banks will not be able to debase their hard-earned value. This allows for one to plan with greater certainty, making investments that have a longer payoff period rather than chasing quick, material gains. Likewise in yoga, developing your own practice will not bear fruit right away; it takes discipline and time to continuously improve and strive towards a better future self. For example, in modern Ashtanga yoga taught by Pattabhi Jois, there is a set sequence of asanas that one studies and repeats each practice. It may even take months to have find the right alignment of body and breath for a single pose! The hours-long sequence requires dedication to practice and learn. The dedicated yogi understands that wholehearted commitment today will pay off for one’s mental, physical and spiritual health in the years to come. The ability to develop a calm mind can also be beneficial when people don’t initially understand or are intimidated by bitcoin. This approach can also enable you to stay grounded and discover the signal through the noise when learning about bitcoin.
 Sequence of asanas in Jois' Ashtanga Yoga (image source)
Sequence of asanas in Jois' Ashtanga Yoga (image source)Union
Yoga comes from the Sanskrit word “yuj”, which means ‘to join’ or ‘to unite’. Yoga represents the union of the mind, body, and soul of an individual. Yoga provides a pathway to individual sovereignty through disciplined practice and purpose. Yoga unites an individual internally and to one’s community, fostering connectedness and support (vii). Similarly, bitcoin provides a pathway to individual sovereignty in many ways. Bitcoin empowers the individual authority with property rights over one’s value, which in turn frees individuals from outside control (government or otherwise). Bitcoin’s technology enables one to hold their own wealth and life’s energy in a self-custodial fashion. Bitcoin is money that can be stored forever and transmitted through space at the speed of light on layer two via the Lightning Network.
Bitcoin is an open economic network with the potential to unite eight billion people together in a way our current unfair and fragmented financial system could never do. In many countries, a majority of people are unbanked, while intermediaries take a cut of the value to transfer slow, legacy payments like Western Union. While tens of millions people around the world have so far interacted with bitcoin – we are still early – similar to the internet of the mid-nineties. Bitcoin eliminates counter party risk associated with non-bearer assets, such as fiat currency (e.g., dollars, euros, yen). Bitcoin’s supply schedule is set and eliminates inflation time theft that fiat currency wages on individuals, which leads to anxiety and depression or feelings of hopelessness. Fiat is money enforced by the monopoly on violence that modern nation states grip tightly.
In contrast, bitcoin and yoga empower the individual to remove the shackles and embrace personal responsibility to improve ones life. Bitcoin and yoga also connect people directly to each other and tap into truth, ones inner being, bringing peace in the present and ultimately offer hope for a better future for each person, your community, and the world. Bitcoin and yoga have the power to unite humanity in love.
In the next section, we will explore both yoga and bitcoin's mystical and mythical origins.
Note: Bitcoin with a capital "B" generally refers to the protocol/network; bitcoin with a lower case "b" refers to the money/currency.
References:
i. Redman, Jamie, How Henry Ford Envisaged Bitcoin 100 Years Ago — A Unique 'Energy Currency' That Could 'Stop Wars', News.Bitcoin.Com, October 11, 2021 <https://news.bitcoin.com/how-henry-ford-envisaged-bitcoin-100-years-ago-a-unique-energy-currency-that-could-stop-wars/>
ii. Nakomoto, Satoshi, Bitcoin: A Peer-to-Peer Electronic Cash System, bitcoin.org, October 31, 2008 <https://bitcoin.org/bitcoin.pdf>
iii. https://bitnodes.io/
iv. Hall, Stephen, What is a bitcoin seed phrase and how does it work? Unchained.com. December 17, 2021 <https://unchained.com/blog/what-is-a-bitcoin-seed-phrase/>
v. Ammous, Saifedean, Making Time Preference Low Again, The Bitcoin Times, Austrian Edition (V). November 8, 2022 <https://bitcointimes.io/making-time-preference-low-again/>
vi. Gigi, Bitcoin is Time, dergigi.com. Jan 14,2021 <https://dergigi.com/2021/01/14/bitcoin-is-time/>
vii. 200 hour yoga teacher training. House of Om, Bali, Indonesia. <https://houseofom.com/>
-
 @ 76c71aae:3e29cafa
2025-01-26 22:51:16
@ 76c71aae:3e29cafa
2025-01-26 22:51:16When I first heard about the DOGE project, I was ready to throw my laptop out the window. The initial proposal read like a Silicon Valley libertarian fever dream - taking Musk's chaotic "move fast and break democracy" Twitter approach and unleashing it on federal agencies. Great, I thought, just what we need: more tech bros thinking they can "optimize" public institutions into oblivion.
But here's the weird thing - when you actually dig into what DOGE has morphed into, it's basically just USDS with a meme-worthy rebrand. For those not deep in the civic tech weeds, USDS was Obama's attempt to drag government technology out of the 1990s, inspired by the UK's actually-functional GDS program. And let's be real - government tech procurement is an absolute dumpster fire right now. We're talking billions wasted on projects that would make a CS101 student cringe, while the average American has to navigate websites that look like they were designed on GeoCities.
The deeply ironic thing is that Musk - for all his cosplaying as a technocratic messiah following in his grandfather's footsteps of dreaming up an antidemocratic technocratic state - actually has some relevant experience here. SpaceX did figure out how to work with government contracts without producing $500 million paperweights, and Tesla somehow gamed clean vehicle incentives into birthing the first new major car company since we invented radio.
Look, I'm the first to roll my eyes at Musk's wannabe-fascist posting sprees and his perpetual "I'm the main character of capitalism" energy. But speaking as someone who's banged their head against the wall of government technology modernization for years - if he actually focuses on the tech and keeps his brainrot political takes to himself, maybe DOGE could do some good?
Even Jen Pahlka, who basically wrote the book on government digital services, is cautiously optimistic. The services Americans get from their government are objectively terrible, and the procurement system is trapped in an infinite loop of failure. Maybe - and I can't believe I'm typing this - Musk's particular flavor of disruptive tech deployment could help?
Just... please, for the love of all things agile, let's keep him focused on the actual technology and far away from any more attempts to recreate his grandfather's dreams of a technocratic dystopia. We've got enough of those already.
-
 @ e034d654:ca919814
2025-01-22 23:14:27
@ e034d654:ca919814
2025-01-22 23:14:27I stumbled into nostr end of March 2023. At that point already fully thrown into the hows, whys and whats of Bitcoin, never really interested in social apps, just recently playing around with Lightning, the only experience of which at the time was Muun (😬) and stacker.news custodial wallet.
Fairly inexperienced with technicals other than rough understandings of concepts. A crappy laptop node with a dangling SSD via USB, constantly having to resync to current blockheights whenever I was ready to make an on chain transaction to cold storage. My great success after over two years of delay, and a couple failed attempts.
Something about the breadth of information for nitty gritty specifics, the clash with all the things that I found interesting about Bitcoin, with others equally as focused, kept me interested in Nostr. Plus the lighthearted shit posting to break up plumbing the depths of knowledge appealed to me.
Cut to now. Through the jurisdictional removals and even deaths of LN wallet projects, using mobile LSPs, finding use cases with the numerous cashu implementations, moderate comfortability with NWC strings of various permissions, budgets for seemingly endless apps of Nostr clients, swapping relays, isolated wallets with Alby go for my wife and cousin (I told them both not to put much on there as I'm sure failure is imminent) Alby Hub and Zeus, now fully backended by my own persistently online lightning node. All of it adding to the fluidity of my movement around the protocol.
Nimble.
Gradual progress. Reading through notes and guides posted on Nostr learning little bits, circling back eventually, if even at a time it wasn't clicking for me. Either way. Glad i've stuck to it even if I still barely know what it is I'm doing.
-
 @ 006532cb:fd8f28b4
2025-01-26 22:10:39
@ 006532cb:fd8f28b4
2025-01-26 22:10:39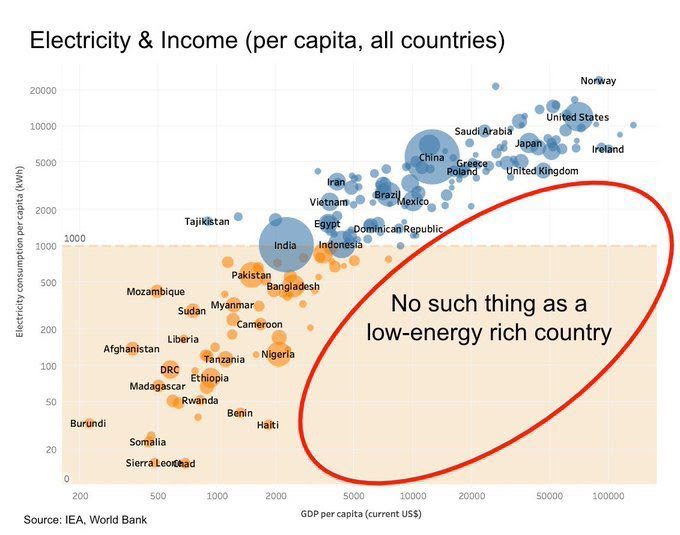

Law of Conservation of Energy: The Law of Conservation of Energy states that energy cannot be created or destroyed, only converted from one form to another. This means that the total energy of an isolated system remains constant over time, but the form of energy can change (e.g., from kinetic energy to potential energy). This fundamental principle in physics highlights the importance of energy efficiency and the potential for energy to be transformed and reused.
Henry Ford's Energy Currency: Henry Ford, the founder of the Ford Motor Company, proposed the concept of an "energy currency" in the 1920s. He suggested that energy, rather than gold or other commodities, could serve as the basis for a new monetary system. Ford's idea was that energy is the fundamental unit of value, as it is the driving force behind all economic activity. He proposed that energy could be used as a standard unit of exchange, allowing for more efficient and equitable trade.
Buckminster Fuller's View on Energy Production and Wealth: Buckminster Fuller, a renowned architect, systems theorist, and futurist, believed that energy production is the key to creating wealth and abundance. He argued that energy is the fundamental driver of economic growth and that increasing energy production can lead to increased prosperity. Fuller's concept of "ephemeralization" suggests that as energy production becomes more efficient and widespread, the cost of goods and services decreases, leading to increased abundance and wealth. He also emphasized the importance of designing systems that maximize energy efficiency and minimize waste, allowing for more equitable distribution of resources and wealth.
-
 @ f57bac88:6045161e
2025-01-26 19:43:21
@ f57bac88:6045161e
2025-01-26 19:43:21بیتیسی پی سرور: آزادی و کنترل در دستان شما بیتیسی پی سرور با تمرکز بر خودگردانی و متنباز بودن، به شما این امکان را میدهد تا کنترل کاملی بر فرآیند پرداختهای خود داشته باشید. برخی از مزایای کلیدی این پلتفرم عبارتند از:
انعطافپذیری بالا: امکان سفارشیسازی و توسعه ویژگیهای جدید بر اساس نیازهای خاص کسبوکار.
هزینه کمتر: حذف واسطهها و کارمزدهای اضافی، منجر به کاهش هزینههای پرداخت میشود.
حفظ حریم خصوصی: کنترل بیشتر بر دادههای مشتریان و کاهش ریسک نقض حریم خصوصی.
پشتیبانی از پروتکل لایتنینگ: امکان انجام تراکنشهای سریع و کمهزینه با استفاده از شبکه لایتنینگ. سایر درگاههای پرداخت رمزنگاری: راحتی در برابر کنترل در مقابل، سایر درگاههای پرداخت رمزنگاری مانند کوینبیس، کوین پیمنت و نوپینت بر راحتی استفاده و سرعت راهاندازی تمرکز دارند. این پلتفرمها اغلب دارای رابط کاربری سادهتر و قابلیتهای پیشساخته بیشتری هستند. با این حال، در ازای این راحتی، ممکن است برخی از کنترلها و انعطافپذیری را از دست بدهید. جدول مقایسه:
کدام یک برای شما مناسبتر است؟ انتخاب بین بیتیسی پی سرور و سایر درگاههای پرداخت به عوامل مختلفی بستگی دارد، از جمله:
سطح دانش فنی: اگر دانش فنی کافی دارید و به دنبال کنترل کامل بر فرآیند پرداخت هستید، بیتیسی پی سرور گزینه مناسبی است.
سادگی استفاده: اگر به دنبال راهکاری سریع و آسان برای شروع پذیرش پرداختهای رمزنگاری هستید، سایر درگاههای پرداخت ممکن است انتخاب بهتری باشند.
هزینهها: هزینههای هر پلتفرم متفاوت است و باید به دقت مقایسه شوند.
ویژگیهای مورد نیاز: لیستی از ویژگیهای مورد نیاز خود را تهیه کنید و ببینید کدام پلتفرم بیشترین تطابق را با آن دارد. در نهایت، بهترین درگاه پرداخت، درگاهی است که نیازهای خاص کسبوکارتان را برآورده کند. نکات مهم هنگام انتخاب:
امنیت: اطمینان حاصل کنید که پلتفرم انتخابی شما دارای استانداردهای امنیتی بالایی است.
پشتیبانی مشتری: وجود پشتیبانی مشتری قوی برای رفع مشکلات احتمالی بسیار مهم است.
کارمزدها: به طور دقیق کارمزدهای هر پلتفرم را بررسی کنید تا بتوانید هزینههای خود را بهینه کنید.
قابلیتهای اضافی: برخی از پلتفرمها دارای قابلیتهای اضافی مانند فاکتورسازی خودکار، گزارشگیری و ادغام با سایر سیستمها هستند.
نتیجهگیری: بیتیسی پی سرور برای کسبوکارهایی که به دنبال حداکثر کنترل، انعطافپذیری و کاهش هزینهها هستند، گزینه بسیار مناسبی است. اما اگر به دنبال راهکاری سادهتر و سریعتر هستید، سایر درگاههای پرداخت نیز میتوانند انتخابهای خوبی باشند. با در نظر گرفتن عوامل ذکر شده در این مقاله، میتوانید بهترین تصمیم را برای کسبوکارتان اتخاذ کنید.
آیا میخواهید در مورد ویژگیهای خاصی از بیتیسی پی سرور یا سایر درگاههای پرداخت اطلاعات بیشتری کسب کنید؟ گوگل کنید! 😉
لطفا توجه داشته باشید که این مقاله صرفاً به منظور اطلاعرسانی است و نباید به عنوان توصیه سرمایهگذاری تلقی شود.
در دنیای پرهیاهوی ارزهای دیجیتال، انتخاب یک درگاه پرداخت مناسب برای پذیرش پرداختهای رمزنگاری، تصمیم مهمی برای کسبوکارهاست.
بیتیسی پی سرور به عنوان یک گزینه متنباز و خودگردان، جایگاه ویژهای در میان این درگاهها دارد. اما آیا بیتیسی پی سرور بهترین گزینه برای کسبوکارتان است؟ در این مقاله، به مقایسه بیتیسی پی سرور با سایر درگاههای پرداخت رمزنگاری میپردازیم تا به شما در انتخاب آگاهانه کمک کنیم.
بیتیسی پی سرور: آزادی و کنترل در دستان شما
بیتیسی پی سرور با تمرکز بر خودگردانی و متنباز بودن، به شما این امکان را میدهد تا کنترل کاملی بر فرآیند پرداختهای خود داشته باشید. برخی از مزایای کلیدی این پلتفرم عبارتند از:
* انعطافپذیری بالا: امکان سفارشیسازی و توسعه ویژگیهای جدید بر اساس نیازهای خاص کسبوکار.
* هزینه کمتر: حذف واسطهها و کارمزدهای اضافی، منجر به کاهش هزینههای پرداخت میشود.
* حفظ حریم خصوصی: کنترل بیشتر بر دادههای مشتریان و کاهش ریسک نقض حریم خصوصی.
* پشتیبانی از پروتکل لایتنینگ: امکان انجام تراکنشهای سریع و کمهزینه با استفاده از شبکه لایتنینگ.
سایر درگاههای پرداخت رمزنگاری: راحتی در برابر کنترل
در مقابل، سایر درگاههای پرداخت رمزنگاری مانند کوینبیس، کوین پیمت و نوپیمنت بر راحتی استفاده و سرعت راهاندازی تمرکز دارند. این پلتفرمها اغلب دارای رابط کاربری سادهتر و قابلیتهای پیشساخته بیشتری هستند. با این حال، در ازای این راحتی، ممکن است برخی از کنترلها و انعطافپذیری را از دست بدهید.
جدول مقایسه:

کدام یک برای شما مناسبتر است؟
انتخاب بین بیتیسی پی سرور و سایر درگاههای پرداخت به عوامل مختلفی بستگی دارد، از جمله:
* سطح دانش فنی: اگر دانش فنی کافی دارید و به دنبال کنترل کامل بر فرآیند پرداخت هستید، بیتیسی پی سرور گزینه مناسبی است.
* سادگی استفاده: اگر به دنبال راهکاری سریع و آسان برای شروع پذیرش پرداختهای رمزنگاری هستید، سایر درگاههای پرداخت ممکن است انتخاب بهتری باشند.
* هزینهها: هزینههای هر پلتفرم متفاوت است و باید به دقت مقایسه شوند.
* ویژگیهای مورد نیاز: لیستی از ویژگیهای مورد نیاز خود را تهیه کنید و ببینید کدام پلتفرم بیشترین تطابق را با آن دارد.
در نهایت، بهترین درگاه پرداخت، درگاهی است که نیازهای خاص کسبوکارتان را برآورده کند.
نکات مهم هنگام انتخاب:
* امنیت: اطمینان حاصل کنید که پلتفرم انتخابی شما دارای استانداردهای امنیتی بالایی است.
* پشتیبانی مشتری: وجود پشتیبانی مشتری قوی برای رفع مشکلات احتمالی بسیار مهم است.
* کارمزدها: به طور دقیق کارمزدهای هر پلتفرم را بررسی کنید تا بتوانید هزینههای خود را بهینه کنید.
* قابلیتهای اضافی: برخی از پلتفرمها دارای قابلیتهای اضافی مانند فاکتورسازی خودکار، گزارشگیری و ادغام با سایر سیستمها هستند.
نتیجهگیری:
بیتیسی پی سرور برای کسبوکارهایی که به دنبال حداکثر کنترل، انعطافپذیری و کاهش هزینهها هستند، گزینه بسیار مناسبی است. اما اگر به دنبال راهکاری سادهتر و سریعتر هستید، سایر درگاههای پرداخت نیز میتوانند انتخابهای خوبی باشند. با در نظر گرفتن عوامل ذکر شده در این مقاله، میتوانید بهترین تصمیم را برای کسبوکارتان اتخاذ کنید.
آیا میخواهید در مورد ویژگیهای خاصی از بیتیسی پی سرور یا سایر درگاههای پرداخت اطلاعات بیشتری کسب کنید؟ گوگل کنید! 😉
لطفا توجه داشته باشید که این مقاله صرفاً به منظور اطلاعرسانی است و نباید به عنوان توصیه سرمایهگذاری تلقی شود.
-
 @ fd208ee8:0fd927c1
2025-01-19 12:10:10
@ fd208ee8:0fd927c1
2025-01-19 12:10:10I am so tired of people trying to waste my time with Nostrized imitations of stuff that already exists.
Instagram, but make it Nostr. Twitter, but make it Nostr. GitHub, but make it Nostr. Facebook, but make it Nostr. Wordpress, but make it Nostr. GoodReads, but make it Nostr. TikTok, but make it Nostr.
That stuff already exists, and it wasn't that great the first time around, either. Build something better than that stuff, that can only be brought into existence because of Nostr.
Build something that does something completely and awesomely new. Knock my socks off, bro.
Cuz, ain't nobody got time for that.
-
 @ e111a405:fa441558
2025-01-26 18:25:59
@ e111a405:fa441558
2025-01-26 18:25:59OpenAI released its new o3 models and numerous people argue that this is in fact Artificial General Intelligence (AGI) – in other words, an AI system that is on par with human intelligence. Even if o3 is not yet AGI, the emphasis now lies on “yet,” and – considering the exponential progression – we can expect AGI to arrive within months or maximum one to two years.
According to OpenAI, it only took 3 months to go from the o1 model to the o3 model. This is a 4x+ acceleration relative to previous progress. If this speed of AI advancement is maintained, it means that by the end of 2025 we will be as much ahead of o3 as o3 is ahead of GPT-3 (released in May 2020). And, after achieving AGI, the self-reinforcing feedback loop will only further accelerate exponential improvements of these AI systems.
But, most anti-intuitively, even after we have achieved AGI, it will for quite some time look as if nothing has happened. You won’t feel any change and your job and business will feel safe and untouchable. Big fallacy. We can expect that after AGI it will take many months of not 1-2 years for the real transformations to happen. Why? Because AGI in and of itself does not release value into the economy. It will be much more important to apply it. But as AGI becomes cheaper, agentic, and embedded into the world, we will see a transformation-explosion – replacing those businesses and jobs that are unprepared.
I thought a lot about the impact the announced – and soon to be released – o3 model, and the first AGI model are going to have.
To make it short: I am extremely confident that any skill or process that can be digitized will be. As a result, the majority of white-collar and skilled jobs are on track for massive disruption or elimination.
Furthermore, I think many experts and think tanks are fooling themselves by believing that humans will maintain “some edge” and work peacefully side-by-side with an AI system. I don’t think AGI will augment knowledge workers – i.e. anyone working with language, code, numbers, or any kind of specialized software – it will replace them!
So, if your job or business relies purely on standardized cognitive tasks, you are racing toward the cliff’s edge, and it is time to pivot now!
Let’s start with the worst. Businesses and jobs in which you should pivot immediately – or at least not enter as of today – include but are not limited to anything that involves sitting at a computer:
- anything with data entry or data processing (run as fast as you can!)
- anything that involves writing (copywriting, technical writing,
- editing, proofreading, translation)
- most coding and web development
- SAAS (won’t exist in a couple of years)
- banking (disrupted squared: AGI + Blockchain)
- accounting and auditing (won’t exist as a job in 5-10 years)
- insurance (will be disrupted)
- law (excluding high-stake litigation, negotiation, courtroom advocacy)
- any generic design, music, and video creation (graphic design, stock photography, stock videos)
- market and investment research and analysis (AI will take over 100%)
- trading, both quantitative and qualitative (don’t exit but profit now, but expect to be disrupted within 5 years)
- any middle-layer-management (project and product management)
- medical diagnostics (will be 100% AI within 5 years)
- most standardized professional / consulting services
However, I believe that in high-stakes domains (health, finance, governance), regulators and the public will demand a “human sign-off”. So if you are in accounting, auditing, law, or finance I’d recommend pivoting to a business model where the ability to anchor trust becomes a revenue source.
The question is, where should you pivot to or what business to start in 2025?
My First Principles of a Post-AGI Business Model
First, even as AI becomes infallible, human beings will still crave real, raw, direct trust relationships. People form bonds around shared experiences, especially offline ones. I believe a truly future-proof venture leverages these primal instincts that machines can never replicate at a deeply visceral level. Nevertheless, I believe it is a big mistake to assume that humans will “naturally” stick together just because we are the same species. AGI might quickly appear more reliable, less selfish than most human beings, and have emotional intelligence. So a business build upon the thesis of the “human advantage” must expertly harness and establish emotional ties, tribal belonging, and shared experiences – all intangible values that are far more delicate and complex than logic.
First Principle: Operate in the Physical World
If your product or service can be fully digitalized and delivered via the cloud, AGI can replicate it with near-zero marginal cost Infuse strategic real-world constraints (logistics, location-specific interactions, physical limitations, direct relationships) that create friction and scarcity – where AI alone will struggle
Second Principle: Create Hyper Niche Human Experiences
- The broader audience, the easier it is for AI to dominate. Instead, cultivate specialized groups and subcultures with strong in-person and highly personalized experiences.
- Offer creative or spiritual elements that defy pure rational patterns and thus remain less formulaic
Third Principle: Emphasize Adaptive, Micro-Scale Partnerships
- Align with small, local, or specialized stakeholders. Use alliances with artisan suppliers, local talents, subject-matter experts, and so on.
- Avoid single points of failure; build a decentralized network that is hard for a single AI to replicate or disrupt
Fourth Principle: Embed Extreme Flexibility
- Structured, hierarchical organizations are easily out-iterated by AI that can reorganize and optimize instantly
- Cultivate fluid teams with quickly reconfigurable structures, use agile, project based collaboration that can pivot as soon AGI-based competition arises
Opportunity Vectors
With all of that in mind, there are niches that before looked unattractive, because less scalable, that today offer massive opportunities – let’s call them opportunity vectors.
The first opportunity vector I have already touched upon:
Trust and Validation Services: Humans verifying or certifying that a certain AI outcome is ethically or legally sound – while irrational, it is exactly what humans will insist on, particularly where liability is high (medicine, finance, law, infrastructure)
Frontier Sectors with Regulatory and Ethical Friction: Think of markets where AI will accelerate R&D but human oversight, relationship management, and accountability remain essential: genetic engineering, biotech, advanced materials, quantum computing, etc.
The second opportunity vector focuses on the human edge:
- Experience & Community: Live festivals, immersive events, niche retreats, or spiritual explorations – basically any scenario in which emotional energy and a human experience is the core product - Rare Craftsmanship & Creative Quirks: Think of hyper-personalized items, physical artwork, artisanal or hands-on creations. Items that carry an inherent uniqueness or intangible meaning that an AI might replicate in design, but can’t replicate in “heritage” or provenance.
Risk Tactics
Overall, the best insurance is fostering a dynamic brand and a loyal community that invests personally and emotionally in you. People will buy from those whose values they trust. If you stand for something real, you create an emotional bond that AI can’t break. I’m not talking about superficial corporate social responsibility (nobody cares) but about authenticity that resonates on a near-spiritual level.
As you build your business, erect an ethical moat by providing “failsafe” services where your human personal liability and your brand acts as a shield for AI decisions. This creates trust and differentiation among anonymous pure-AGI play businesses.
Seek and create small, specialized, local, or digital micro-monopolies – areas too tiny or fractal for the “big AI players” to devote immediate resources to. Over time, multiply these micro-monopolies by rolling them up under one trusted brand.
Furthermore, don’t avoid AI. You cannot out-AI the AI. So as you build a business on the human edge moat, you should still harness AI to do 90% of the repetitive and analytic tasks – this frees your human capital to build human relationships, solve ambiguous problem, or invent new offerings.
Bet on What Makes Us Human
To summarize, AI is logical, combinatorial intelligence. The advancements in AI will commoditize logic and disrupt any job and business that is mainly build upon logic as capital. Human – on the other hand – is authenticity. What makes human human and your brand authentic are elements of chaos, empathy, spontaneity. In this context, human is fostering embodied, emotional, culturally contextual, physically immersive experiences. Anything that requires raw creativity, emotional intelligence, local presence, or unique personal relationships will be more AI resilient.
Therefore, a Post-AGI business must involve:
- Tangibility: Physical goods, spaces, unique craftsmanship
- Human Connection: Emotional, face-to-face, improvisational experiences
- Comprehensive Problem Solving: Complex negotiations, messy real-world situations, diverse stakeholder management
The inverse list of AGI proof industries involve some or multiple aspects of that:
Physical, In-Person, Human-Intensive Services - Healthcare: Nursing, Physical therapy, Hands-on caregiving - Skilled trades & craftsmanship
High-Level Strategy & Complex Leadership - Diplomacy, Negotiation, Trust building - Visionary entrepreneurship
Deep Emotional / Experiential Offerings - Group experiences, retreats, spiritual or therapeutic gatherings - Artistic expression that thrives on “imperfection”, physical presence, or spontaneous creativity
Infrastructure for AGI - Human-based auditing/verification - Physical data center operations & advanced hardware - Application and embedment of AI in the forms of AGI agents, algorithmic improvements, etc. to make it suitable for everyday tasks and workflow
The real differentiator is whether a business is anchored in the physical world’s complexity, emotional trust, or intangible brand relationships. Everything pure data-driven or standardized is on the chopping block – imminently.
-
 @ fd78c37f:a0ec0833
2025-01-26 12:07:12
@ fd78c37f:a0ec0833
2025-01-26 12:07:12ETHOS & PURPOSE🌐
SATS'N'FACTS emphasizes Creativity, Privacy, FOSS Advocacy,with a focus on Local Community, Decentralization, and Health Balance. It is dedicated to nurturing an environment where decentralization and open collaboration thrive, providing space for deep technical discussions, hands-on learning, and meaningful networking, all with the goal of strengthening the Bitcoin community in Asia.
They aspire to redefine boundaries and usher in a new era of design and development excellence that leaves an indelible mark on the bitcoin environment. A three-day event dedicated to fostering innovation, and freedom within the Bitcoin Developer Community in Asia.
LEADS🧑💼
Enthusiast developers and builders from around the globe, will attend this first installments of the SATS’N’FACTS. Including nostr:npub1nvfgglea9zlcs58tcqlc6j26rt50ngkgdk7699wfq4txrx37aqcsz4e7zd nostr:npub1cj6ndx5akfazux7f0vjl4fyx9k0ulf682p437fe03a9ndwqjm0tqj886t6 nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac nostr:npub1ejxswthae3nkljavznmv66p9ahp4wmj4adux525htmsrff4qym9sz2t3tv nostr:npub1gwa27rpgum8mr9d30msg8cv7kwj2lhav2nvmdwh3wqnsa5vnudxqlta2sz nostr:npub1zk6u7mxlflguqteghn8q7xtu47hyerruv6379c36l8lxzzr4x90q0gl6ef nostr:npub13rvvn5g23anm09kwnya8qvzqejxfajfa56rnn47ck5l96ke6cq4sdcd4e0 nostr:npub147whqsr5vsj86x0ays70r0hgreklre3ey97uvcmxhum65skst56s30selt nostr:npub190trvg63e6tyqlwlj6lccqpftx76lckj25c006vwx3dzvdl88yxs2nyqdx nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr nostr:npub10xk2rsg9l9ksht66egss98z7mzhetf8d7q4476d9cm6vsfv3a00qld5tdf nostr:npub19x0h8jm3mnwzhv4tpq62zta05er0qlyge73m0pwsp7h666khkd9qev2ree and more.
AGENDA📝
The event is designed to be a “decentralized and collaborative” effort between all participants, with activities being put together with attendees’ feedback. So no agenda, but here some guidance to make sure this event will be joyful and constructive:
🗓️8ᵗʰғᴇʙ Doors Opening:
- [ ] Event Opening
- [ ] Welcome session and intros
- [ ] Presentations and open discussions
- [ ] Initial networking and collaborative sessions
- [ ] Hackathon begins
🗓️9ᵗʰғᴇʙ :
- [ ] Hackathon continues
- [ ] Attendee-led sessions
- [ ] Recording room open for voluntarily podcasting and interviews
- [ ] Peer-to-peer learning and networking
🗓️10ᵗʰғᴇʙ Closing UP:
- [ ] Hackathon wrap-up
- [ ] Pitching contest and project presentations
- [ ] Networking
- [ ] Closing remarks and final session
MERCH🛍️
Their event merch is not just cool—it’s a must-have! T-shirts 👕, bags 🎒, stickers 🖼️, caps 🧢...Get yours and carry the event vibe wherever you go!


Other Fun Activities🎡
In addition to the exciting conference, they've prepared a variety of enriching experiences for you—live art and craft activities🎨, art exhibitions🖼️, creative workshops✨, and Thai massage 💆……, and more.

How to join the Event🎡
If you're in Asia this February, don't miss out—join them in the vibrant city of Chiang Mai, Thailand 🇹🇭 for an unforgettable experience!
📅 Time:8—10th February 2025 📍Location:12/8 ถ.วัวลาย ซอย 3 ตำบลหายยา, เมืองเชียงใหม่ 50100 🇹🇭ไทย 💺Book your seat: https://formstr.app/#/fill/b3b9bd115fe936848a5e03134fefff945287285d51b1dee4731fef6a1070c597 🎤Submit an idea: https://formstr.app/#/forms/cf02333ea3c0d0c21080df599373e289fa343a55e63a1abdc7f633d1594078ff 🎫Buy your ticket: https://satsnfacts.btc.pub/p/ticket/
-
 @ 29af23a9:842ef0c1
2025-01-24 09:28:37
@ 29af23a9:842ef0c1
2025-01-24 09:28:37A Indústria Pornográfica se caracteriza pelo investimento pesado de grandes empresários americanos, desde 2014.
Na década de 90, filmes pornográficos eram feitos às coxas. Era basicamente duas pessoas fazendo sexo amador e sendo gravadas. Não tinha roteiro, nem produção, não tinha maquiagem, nada disso. A distribuição era rudimentar, os assinantes tinham que sair de suas casas, ir até a locadora, sofrer todo tipo de constrangimento para assistir a um filme pornô.
No começo dos anos 2000, o serviço de Pay Per View fez o número de vendas de filmes eróticos (filme erótico é bem mais leve) crescer mas nada se compara com os sites de filmes pornográficos por assinatura.
Com o advento dos serviços de Streaming, os sites que vendem filmes por assinatura se estabeleceram no mercado como nunca foi visto na história.
Hoje, os Produtores usam produtos para esticar os vasos sanguíneos do pênis dos atores e dopam as atrizes para que elas aguentem horas de gravação (a Série Black Mirror fez uma crítica a isso no episódio 1 milhão de méritos de forma sutil).
Além de toda a produção em volta das cenas. Que são gravadas em 4K, para focar bem as partes íntimas dos atores. Quadros fechados, iluminação, tudo isso faz essa Indústria ser "Artística" uma vez que tudo ali é falso. Um filme da Produtora Vixen, por exemplo, onde jovens mulheres transam em mansões com seus empresários estimula o esteriótipo da mina padrão que chama seu chefe rico de "daddy" e seduz ele até ele trair a esposa.
Sites como xvídeos, pornHub e outros nada mais são do que sites que salvam filmes dessas produtoras e hospedam as cenas com anúncios e pop-ups. Alguns sites hospedam o filme inteiro "de graça".
Esse tipo de filme estimula qualquer homem heterosexual com menos de 30 anos, que não tem o córtex frontal de seu cérebro totalmente desenvolvido (segundo estudos só é completamente desenvolvido quando o homem chega aos 31 anos).
A arte Pornográfica faz alguns fantasiarem ter relação sexual com uma gostosa americana branquinha, até escraviza-los. Muitos não conseguem sair do vício e preferem a Ficção à sua esposa real. Então pare de se enganar e admita. A Pornografia faz mal para a saúde mental do homem.
Quem sonha em ter uma transa com Lana Rhodes, deve estar nesse estágio. Trata-se de uma atriz (pornstar) que ganhou muito dinheiro vendendo a ilusão da Arte Pornografica, como a Riley Reid que só gravava para grandes Produtoras. Ambas se arrependeram da carreira artística e agora tentam viver suas vidas como uma mulher comum.
As próprias atrizes se consideram artistas, como Mia Malkova, chegou a dizer que Pornografia é a vida dela, que é "Lindo e Sofisticado."
Mia Malkova inclusive faz questão de dizer que a industria não escravisa mulheres jovens. Trata-se de um negócio onde a mulher assina um contrato com uma produtora e recebe um cachê por isso. Diferente do discurso da Mia Khalifa em entrevista para a BBC, onde diz que as mulheres são exploradas por homens poderosos. Vai ela está confundindo o Conglomerado Vixen com a Rede Globo ou com a empresa do Harvey Weinstein.
Enfim, se você é um homem solteiro entre 18 e 40 anos que já consumiu ou que ainda consome pornografia, sabia que sofrerá consequências. Pois trata-se de "produções artísticas" da indústria audiovisual que altera os níveis de dopamina do seu cérebro, mudando a neuroplasticidade e diminuindo a massa cinzenta, deixando o homem com memória fraca, sem foco e com mente nebulosa.
Por que o Estado não proíbe/criminaliza a Pornografia se ela faz mal? E desde quando o Estado quer o nosso bem? Existem grandes empresarios que financiam essa indústria ajudando governos a manterem o povo viciado e assim alienado. É um pão e circo, só que muito mais viciante e maléfico. Eu costume dizer aos meus amigos que existem grandes empresários jvdeus que são donos de grandes Produtoras de filmes pornográficos como o Conglomerado Vixen. Então se eles assistem vídeos pirateados de filmes dessas produtoras, eles estão no colo do Judeu.
-
 @ 599f67f7:21fb3ea9
2025-01-26 11:01:05
@ 599f67f7:21fb3ea9
2025-01-26 11:01:05¿Qué es Blossom?
nostr:nevent1qqspttj39n6ld4plhn4e2mq3utxpju93u4k7w33l3ehxyf0g9lh3f0qpzpmhxue69uhkummnw3ezuamfdejsygzenanl0hmkjnrq8fksvdhpt67xzrdh0h8agltwt5znsmvzr7e74ywgmr72
Blossom significa Blobs Simply Stored on Media Servers (Blobs Simplemente Almacenados en Servidores de Medios). Blobs son fragmentos de datos binarios, como archivos pero sin nombres. En lugar de nombres, se identifican por su hash sha256. La ventaja de usar hashes sha256 en lugar de nombres es que los hashes son IDs universales que se pueden calcular a partir del archivo mismo utilizando el algoritmo de hash sha256.
💡 archivo -> sha256 -> hash
Blossom es, por lo tanto, un conjunto de puntos finales HTTP que permiten a los usuarios almacenar y recuperar blobs almacenados en servidores utilizando su identidad nostr.
¿Por qué Blossom?
Como mencionamos hace un momento, al usar claves nostr como su identidad, Blossom permite que los datos sean "propiedad" del usuario. Esto simplifica enormemente la cuestión de "qué es spam" para el alojamiento de servidores. Por ejemplo, en nuestro Blossom solo permitimos cargas por miembros de la comunidad verificados que tengan un NIP-05 con nosotros.
Los usuarios pueden subir en múltiples servidores de blossom, por ejemplo, uno alojado por su comunidad, uno de pago, otro público y gratuito, para establecer redundancia de sus datos. Los blobs pueden ser espejados entre servidores de blossom, de manera similar a cómo los relays nostr pueden transmitir eventos entre sí. Esto mejora la resistencia a la censura de blossom.
A continuación se muestra una breve tabla de comparación entre torrents, Blossom y servidores CDN centralizados. (Suponiendo que hay muchos seeders para torrents y se utilizan múltiples servidores con Blossom).
| | Torrents | Blossom | CDN Centralizado | | --------------------------------------------------------------- | -------- | ------- | ---------------- | | Descentralizado | ✅ | ✅ | ❌ | | Resistencia a la censura | ✅ | ✅ | ❌ | | ¿Puedo usarlo para publicar fotos de gatitos en redes sociales? | ❌ | ✅ | ✅ |
¿Cómo funciona?
Blossom utiliza varios tipos de eventos nostr para comunicarse con el servidor de medios.
| kind | descripción | BUD | | ----- | ------------------------------- | ------------------------------------------------------------------ | | 24242 | Evento de autorización | BUD01 | | 10063 | Lista de Servidores de Usuarios | BUD03 |
kind:24242 - Autorización
Esto es esencialmente lo que ya describimos al usar claves nostr como IDs de usuario. En el evento, el usuario le dice al servidor que quiere subir o eliminar un archivo y lo firma con sus claves nostr. El servidor realiza algunas verificaciones en este evento y luego ejecuta el comando del usuario si todo parece estar bien.
kind:10063 - Lista de Servidores de Usuarios
Esto es utilizado por el usuario para anunciar a qué servidores de medios está subiendo. De esta manera, cuando el cliente ve esta lista, sabe dónde subir los archivos del usuario. También puede subir en múltiples servidores definidos en la lista para asegurar redundancia. En el lado de recuperación, si por alguna razón uno de los servidores en la lista del usuario está fuera de servicio, o el archivo ya no se puede encontrar allí, el cliente puede usar esta lista para intentar recuperar el archivo de otros servidores en la lista. Dado que los blobs se identifican por sus hashes, el mismo blob tendrá el mismo hash en cualquier servidor de medios. Todo lo que el cliente necesita hacer es cambiar la URL por la de un servidor diferente.
Ahora, además de los conceptos básicos de cómo funciona Blossom, también hay otros tipos de eventos que hacen que Blossom sea aún más interesante.
| kind | descripción | | ----- | --------------------- | | 30563 | Blossom Drives | | 36363 | Listado de Servidores | | 31963 | Reseña de Servidores |
kind:30563 - Blossom Drives
Este tipo de evento facilita la organización de blobs en carpetas, como estamos acostumbrados con los drives (piensa en Google Drive, iCloud, Proton Drive, etc.). El evento contiene información sobre la estructura de carpetas y los metadatos del drive.
kind:36363 y kind:31963 - Listado y Reseña
Estos tipos de eventos permiten a los usuarios descubrir y reseñar servidores de medios a través de nostr. kind:36363 es un listado de servidores que contiene la URL del servidor. kind:31963 es una reseña, donde los usuarios pueden calificar servidores.
¿Cómo lo uso?
Encuentra un servidor
Primero necesitarás elegir un servidor Blossom donde subirás tus archivos. Puedes navegar por los públicos en blossomservers.com. Algunos de ellos son de pago, otros pueden requerir que tus claves nostr estén en una lista blanca.
Luego, puedes ir a la URL de su servidor y probar a subir un archivo pequeño, como una foto. Si estás satisfecho con el servidor (es rápido y aún no te ha fallado), puedes agregarlo a tu Lista de Servidores de Usuarios. Cubriremos brevemente cómo hacer esto en noStrudel y Amethyst (pero solo necesitas hacer esto una vez, una vez que tu lista actualizada esté publicada, los clientes pueden simplemente recuperarla de nostr).
noStrudel
- Encuentra Relays en la barra lateral, luego elige Servidores de Medios.
- Agrega un servidor de medios, o mejor aún, varios.
- Publica tu lista de servidores. ✅
Amethyst
- En la barra lateral, encuentra Servidores multimedia.
- Bajo Servidores Blossom, agrega tus servidores de medios.
- Firma y publica. ✅
Ahora, cuando vayas a hacer una publicación y adjuntar una foto, por ejemplo, se subirá en tu servidor blossom.
⚠️ Ten en cuenta que debes suponer que los archivos que subas serán públicos. Aunque puedes proteger un archivo con contraseña, esto no ha sido auditado.
Blossom Drive
Como mencionamos anteriormente, podemos publicar eventos para organizar nuestros blobs en carpetas. Esto puede ser excelente para compartir archivos con tu equipo, o simplemente para mantener las cosas organizadas.
Para probarlo, ve a blossom.hzrd149.com (o nuestra instancia comunitaria en blossom.bitcointxoko.com) e inicia sesión con tu método preferido.
Puedes crear una nueva unidad y agregar blobs desde allí.
Bouquet
Si usas múltiples servidores para darte redundancia, Bouquet es una buena manera de obtener una visión general de todos tus archivos. Úsalo para subir y navegar por tus medios en diferentes servidores y sincronizar blobs entre ellos.
Cherry Tree
nostr:nevent1qvzqqqqqqypzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqyp3065hj9zellakecetfflkgudm5n6xcc9dnetfeacnq90y3yxa5z5gk2q6
Cherry Tree te permite dividir un archivo en fragmentos y luego subirlos en múltiples servidores blossom, y más tarde reensamblarlos en otro lugar.
Conclusión
Blossom aún está en desarrollo, pero ya hay muchas cosas interesantes que puedes hacer con él para hacerte a ti y a tu comunidad más soberanos. ¡Pruébalo!
Si deseas mantenerte al día sobre el desarrollo de Blossom, sigue a nostr:nprofile1qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqyqnxs90qeyssm73jf3kt5dtnk997ujw6ggy6j3t0jjzw2yrv6sy22ysu5ka y dale un gran zap por su excelente trabajo.
Referencias
-
 @ f4db5270:3c74e0d0
2025-01-23 18:09:14
@ f4db5270:3c74e0d0
2025-01-23 18:09:14Hi Art lover! 🎨🫂💜 You may not know it yet but all of the following paintings are available in #Bitcoin on my website: https://isolabell.art/#shop
For info and prices write to me in DM and we will find a good deal! 🤝
 ON THE ROAD AGAIN
40x50cm, Oil on canvas
Completed January 23, 2025
ON THE ROAD AGAIN
40x50cm, Oil on canvas
Completed January 23, 2025
 SUN OF JANUARY
40x50cm, Oil on canvas
Completed January 14, 2025
SUN OF JANUARY
40x50cm, Oil on canvas
Completed January 14, 2025
 THE BLUE HOUR
40x50cm, Oil on canvas
Completed December 14, 2024
THE BLUE HOUR
40x50cm, Oil on canvas
Completed December 14, 2024
 LIKE A FRAGMENT OF ETERNITY
50x40cm, Oil on canvas
Completed December 01, 2024
LIKE A FRAGMENT OF ETERNITY
50x40cm, Oil on canvas
Completed December 01, 2024
 WHERE WINTER WHISPERS
50x40cm, Oil on canvas
Completed November 07, 2024
WHERE WINTER WHISPERS
50x40cm, Oil on canvas
Completed November 07, 2024
 L'ATTESA DI UN MOMENTO
40x40cm, Oil on canvas
Completed October 29, 2024
L'ATTESA DI UN MOMENTO
40x40cm, Oil on canvas
Completed October 29, 2024
 LE COSE CHE PENSANO
40x50cm, Oil on paper
Completed October 05, 2024
LE COSE CHE PENSANO
40x50cm, Oil on paper
Completed October 05, 2024
 TWILIGHT'S RIVER
50x40cm, Oil on canvas
Completed September 17, 2024
TWILIGHT'S RIVER
50x40cm, Oil on canvas
Completed September 17, 2024
 GOLD ON THE OCEAN
40x50cm, Oil on paper
Completed September 08, 2024
GOLD ON THE OCEAN
40x50cm, Oil on paper
Completed September 08, 2024
 SUSSURRI DI CIELO E MARE
50x40cm, Oil on paper
Completed September 05, 2024
SUSSURRI DI CIELO E MARE
50x40cm, Oil on paper
Completed September 05, 2024
 THE END OF A WONDERFUL WEEKEND
40x30cm, Oil on board
Completed August 12, 2024
THE END OF A WONDERFUL WEEKEND
40x30cm, Oil on board
Completed August 12, 2024
 FIAMME NEL CIELO
60x35cm, Oil on board
Completed July 28, 2024
FIAMME NEL CIELO
60x35cm, Oil on board
Completed July 28, 2024
 INIZIO D'ESTATE
50x40cm, Oil on cradled wood panel
Completed July 13, 2024
INIZIO D'ESTATE
50x40cm, Oil on cradled wood panel
Completed July 13, 2024
 OMBRE DELLA SERA
50x40cm, Oil on cradled wood panel
Completed June 16, 2024
OMBRE DELLA SERA
50x40cm, Oil on cradled wood panel
Completed June 16, 2024
 NEW ZEALAND SUNSET
80x60cm, Oil on canvas board
Completed May 28, 2024
NEW ZEALAND SUNSET
80x60cm, Oil on canvas board
Completed May 28, 2024
 VENICE
50x40cm, Oil on board
Completed May 4, 2024
VENICE
50x40cm, Oil on board
Completed May 4, 2024
 CORNWALL
50x40cm, Oil on board
Completed April 26, 2024
CORNWALL
50x40cm, Oil on board
Completed April 26, 2024
 DOCKS ON SUNSET
40x19,5cm, Oil on board
Completed March 14, 2024
DOCKS ON SUNSET
40x19,5cm, Oil on board
Completed March 14, 2024
 SOLITUDE
30x30cm, Oil on cradled wood panel
Completed March 2, 2024
SOLITUDE
30x30cm, Oil on cradled wood panel
Completed March 2, 2024
 LULLING WAVES
40x30cm, Oil on cradled wood panel
Completed January 14, 2024
LULLING WAVES
40x30cm, Oil on cradled wood panel
Completed January 14, 2024
 MULATTIERA IN AUTUNNO
30x30cm, Oil on cradled wood panel
MULATTIERA IN AUTUNNO
30x30cm, Oil on cradled wood panel
 TRAMONTO A KOS
40x40cm, oil on board canvas
TRAMONTO A KOS
40x40cm, oil on board canvas
 HIDDEN SMILE
40x40cm, oil on board
HIDDEN SMILE
40x40cm, oil on board
 INIZIO D'AUTUNNO
40x40cm, oil on canvas
INIZIO D'AUTUNNO
40x40cm, oil on canvas
 BOE NEL LAGO
30x30cm, oil on canvas board
BOE NEL LAGO
30x30cm, oil on canvas board
 BARCHE A RIPOSO
40x40cm, oil on canvas board
BARCHE A RIPOSO
40x40cm, oil on canvas board
 IL RISVEGLIO
30x40cm, oil on canvas board
IL RISVEGLIO
30x40cm, oil on canvas board
 LA QUIETE PRIMA DELLA TEMPESTA
30x40cm, oil on canvas board
LA QUIETE PRIMA DELLA TEMPESTA
30x40cm, oil on canvas board
 LAMPIONE SUL LAGO
30x30cm, oil on canvas board
LAMPIONE SUL LAGO
30x30cm, oil on canvas board
 DUE NELLA NEVE
60x25cm, oil on board
DUE NELLA NEVE
60x25cm, oil on board
 UNA CAREZZA
30x30cm, oil on canvas board
UNA CAREZZA
30x30cm, oil on canvas board
 REBEL WAVES
44x32cm, oil on canvas board
REBEL WAVES
44x32cm, oil on canvas board
 THE SCREAMING WAVE
40x30cm, oil on canvas board
THE SCREAMING WAVE
40x30cm, oil on canvas board
 "LA DONZELLETTA VIEN DALLA CAMPAGNA..."
30x40cm, oil on canvas board
"LA DONZELLETTA VIEN DALLA CAMPAGNA..."
30x40cm, oil on canvas board
 LIGHTHOUSE ON WHITE CLIFF
30x40cm, oil on canvas board
LIGHTHOUSE ON WHITE CLIFF
30x40cm, oil on canvas board -
 @ d3052ca3:d84a170e
2025-01-25 23:17:10
@ d3052ca3:d84a170e
2025-01-25 23:17:10It seems to me that the primary opposition to ecash from bitcoiners comes from the belief that lightning will enable self-custodial micropayments for the masses. Many lightning enthusiasts see ecash as competition that will eliminate this technological outcome (whether they admit it or not).
I understand the motivation for this line of reasoning but I don't see things this way at all. Ecash is a superset of lightning. Cashu literally doesn't have a spec for on-chain transactions (yet!). Everything cashu accomplishes is built on the back of lightning. Standing on the shoulders of giants.
I don't believe that ecash will take away market share from self-custodial lightning because lightning is not a good technology for self-custody. The high overhead costs of running your own node create a natural incentive for a semi-centralized hub and spoke network graph. It just makes economic sense for many users to share a lightning node. It doesn't make economic sense for individuals to bear this cost alone.
This stacker news post is the best writeup on this topic: https://stacker.news/items/379225
It comes from a builder who struggled with these issues for years and learned the shortcomings of the tech first hand. Notice they experimented with ecash as a solution to these problems before they burned out and pivoted to save the company.
Ecash is a superset of lightning. It extends the capability and reach of the lightning network. Without ecash, I don't believe we can achieve bitcoin mass adoption. You can't jam a square peg into a round hole.
We still have a need for self-custody of "small" amounts of bitcoin. I put small in quotes because the block size limit and the fee market it creates impose a fundamental constraint on the minimum practical size of a UTXO. This limit is pegged to the unit of bitcoin. As bitcoin increases in value the minimum size for an on-chain transaction will grow in value as well. You can send $10 worth of bitcoin on-chain today but will this be true in 10 years when the price is much higher? 100 years?
If the current exponential trends hold, we will soon price out the majority of humanity from owning a UTXO. This is bad. Like really bad. "Bitcoin is a failure" bad. This is the motivation for my posts about scaling on-chain usage to 10 billion people. I believe we will need to radically rearchitect bitcoin to achieve this goal.
Lightning is not up to the task. We should leverage lightning for what it's good at: gluing together different self-custodial bitcoin service providers. We should leverage ecash for what it's good at: peer-to-peer electronic cash micropayments. IN ADDITION we also need to start seriously looking at new ideas for scaling self custody to "small" amounts of bitcoin. I am very optimistic that we can solve this problem. There are a number of promising avenues to pursue but I think first we need to move the Overton window ~~beyond the idea of mass adoption of self-custodial lightning~~ regarding on-chain scaling.
Edit: I think the original Overton window statement was incorrect. If on-chain fees stay low then self-custodial lightning or something similar is a much better prospect.
Just my 2 sats...let me know what you think. Keep it civil or be muted.
-
 @ d57360cb:4fe7d935
2025-01-30 15:15:15
@ d57360cb:4fe7d935
2025-01-30 15:15:15Your mind is alot like a train. The Passengers on the train are your thoughts.
Most of us have way too many passengers, and an endless amount of passengers waiting to get on the ride.
If we don’t take a stop to let some of the passengers off, the train will get over crowded leaving no room for new passengers to board.
Alan Watts once said ““A person who thinks all the time has nothing to think about except thoughts. So, he loses touch with reality and lives in a world of illusions.”
Take some time daily if only for ten minutes to sit quietly and do nothing.
Let your mind rest, let it offload some passengers. You’d be surprised what you let go of and discover by taking a timeout.
-
 @ cbd2779f:72a5b029
2025-01-30 15:08:13
@ cbd2779f:72a5b029
2025-01-30 15:08:13Have a few questions pertaining to setting up a new node. Basically, I always seems to be unsure about syncing to graph, after syncing to chain. Consider setting up a new node from scratch, or migrating perhaps, and you want to do an initial setup.
- How long does it take?
- What factors determine how long it takes?
- Is the graph a universal graph that is identical from each nodes perspective?
So far, I'm monitoring progress but tailing logs, looking for clues:
tail -n 100 /data/lnd/logs/bitcoin/mainnet/lnd.log | grep GRPHI can find some relevant clues like:
2025-01-30 15:24:54.843 [INF] GRPH: Processed channels=56 updates=59 nodes=15 in last 59.823699481sand then checking with:
lncli getinfo | grep -E 'synced|peerswhich outputs"num_peers": 3, "synced_to_chain": true, "synced_to_graph": false,At the moment, I've been experimenting with pruned blockchains and this outputs a lot of errors (I believe) relating to not being able to verify UTXOs as I have `ignore-historical-gossip-filters set to true.
Any further suggestions on how to better make sure things are happening under the hood when setting up a new node, what to look for in the logs or how to know the verification progress?
originally posted at https://stacker.news/items/869944
-
 @ 7f29628d:e160cccc
2025-01-07 11:50:30
@ 7f29628d:e160cccc
2025-01-07 11:50:30Der gut informierte Bürger denkt bei der Pandemie sofort an Intensivstationen, an die Bilder aus Bergamo und erinnert sich an die Berichterstattung damals – also muss es wohl ein Maximum gewesen sein. Manche Skeptiker behaupten jedoch das Gegenteil. Klarheit sollte ein Blick nach Wiesbaden, zum Statistischen Bundesamt, schaffen. Schließlich sitzen dort gut bezahlte Profis, die seit vielen Jahrzehnten die Sterbestatistik pflegen und veröffentlichen. Jeder Todesfall wird in Deutschland über die Standesämter exakt erfasst.
Doch die Überraschung: Das Statistische Bundesamt liefert uns auf diese einfache Frage zwei extrem unterschiedliche Antworten – ein Minimum und ein Maximum. Das Ergebnis hängt davon ab, wie tief man in die Veröffentlichungen des Bundesamtes eintaucht. Betrachtet man nur die Webseiten und Pressemitteilungen, erhält man den Eindruck eines Maximums. Schaut man jedoch etwas tiefer in die Tabellen und Rohdaten, zeigt sich plötzlich ein Minimum. Aber wie kann das sein? Beides gleichzeitig geht ja wohl kaum. Wer lügt hier – die Tabellen des Amtes oder die Pressemitteilungen? Gehen wir dieser Frage Schritt für Schritt auf den Grund.
2020: Ein historisches Maximum?
Schauen wir uns die vielen Hundert Veröffentlichungen des Statistischen Bundesamtes aus dieser Zeit an. Oder wir kürzen ab und fragen ChatGPT, da die KI auf diesen Daten trainiert wurde und das gesamte Material kennt. Die Frage an ChatGPT lautet also: Wie war das Sterbegeschehen im Jahr 2020 im Vergleich zu den Vorjahren?
ChatGPT antwortet: »Im Jahr 2020 war die Sterblichkeit in Deutschland höher als in den Jahren zuvor. Es gab eine Übersterblichkeit von etwa 982.000 Todesfällen, das sind rund 46.000 mehr als der Durchschnitt der Vorjahre (2016 bis 2019). Dieser Anstieg wurde überwiegend im Zusammenhang mit der COVID-19-Pandemie gesehen. Während die Sterbezahlen in den Vorjahren schwankten, war ein solch signifikanter Anstieg wie 2020 bisher nicht zu beobachten.«
Wir fragen konkreter: Ist es ein Fakt, dass wir eine so ernste Lage im Sterbegeschehen wie im Frühjahr 2020 noch nie erlebt haben?
ChatGPT bestätigt: »Ja, die COVID-19-Pandemie führte im Frühjahr 2020 zu einer außergewöhnlichen Situation im Sterbegeschehen in Deutschland. Die dramatische Übersterblichkeit, die ab der 13. Kalenderwoche auftrat, veranlasste das Statistische Bundesamt, besonders eindringliche Warnungen zu veröffentlichen. Der damalige Vizepräsident des Amtes und andere führende Stimmen wiesen öffentlich darauf hin, dass die Todesfallzahlen stark vom Durchschnitt abwichen. Diese klare Warnung richtete sich an die Öffentlichkeit und die Politik gleichermaßen. Die Medien berichteten intensiv über diese Warnungen, was das Bewusstsein für die Schwere der Pandemie erheblich schärfte. In den vergangenen Jahrzehnten hatte es keine vergleichbare Übersterblichkeit gegeben, die eine solch umfangreiche Kommunikation durch das Statistische Bundesamt erforderlich gemacht hätte.«
Ein gut informierter Zeitungsleser wird sich an dieser Stelle bestätigt fühlen: Ja, so war es damals. Ein Maximum im Sterbegeschehen – wegen der Pandemie. Oder etwa nicht?
2020: Ein historisches Minimum?
Tauchen wir in die Rohdaten des Statistischen Bundesamtes ein. Die Tabellen, die das Amt seit Jahrzehnten verlässlich veröffentlicht, nennen sich Sterbetafeln. Diese werden jährlich bereitgestellt und stehen auf der Website des Bundesamtes zum Download bereit. Ein erster Blick in die Sterbetafeln mag den Laien abschrecken, doch mit einer kurzen Erklärung wird alles verständlich. Wir gehen schrittweise vor.
Nehmen wir die Sterbetafel des Jahres 2017. Sie enthält zwei große Tabellen – eine für Männer und eine für Frauen. Jede Zeile der Tabelle steht für einen Jahrgang, zum Beispiel zeigt die Zeile 79 die Daten der 79-jährigen Männer. Besonders wichtig ist nun die zweite Spalte, in der der Wert 0,05 eingetragen ist. Das bedeutet, dass 5 Prozent der 79-jährigen Männer im Jahr 2017 verstorben sind. Das ist die wichtige Kennzahl. Wenn wir diesen exakten Wert, den man auch als Sterberate bezeichnet, nun in ein Säulendiagramm eintragen, erhalten wir eine leicht verständliche visuelle Darstellung (Grafik 1).

Es ist wichtig zu betonen, dass dieser Wert weder ein Schätzwert noch eine Modellrechnung oder Prognose ist, sondern ein exakter Messwert, basierend auf einer zuverlässigen Zählung. Sterberaten (für die Fachleute auch Sterbewahrscheinlichkeiten qx) sind seit Johann Peter Süßmilch (1707–1767) der Goldstandard der Sterbestatistik. Jeder Aktuar wird das bestätigen. Fügen wir nun die Sterberaten der 79-jährigen Männer aus den Jahren davor und danach hinzu, um das Gesamtbild zu sehen (Grafik 2). Und nun die entscheidende Frage: Zeigt das Jahr 2020 ein Maximum oder ein Minimum?

Ein kritischer Leser könnte vermuten, dass die 79-jährigen Männer eine Ausnahme darstellen und andere Jahrgänge im Jahr 2020 ein Maximum zeigen würden. Doch das trifft nicht zu. Kein einziger Jahrgang verzeichnete im Jahr 2020 ein Maximum. Im Gegenteil: Auch die 1-Jährigen, 2-Jährigen, 3-Jährigen, 9-Jährigen, 10-Jährigen, 15-Jährigen, 18-Jährigen und viele weitere männliche Jahrgänge hatten ihr Minimum im Jahr 2020. Dasselbe gilt bei den Frauen. Insgesamt hatten 31 Jahrgänge ihr Minimum im Jahr 2020. Wenn wir schließlich alle Jahrgänge in einer einzigen Grafik zusammenfassen, ergibt sich ein klares Bild: Das Minimum im Sterbegeschehen lag im Jahr 2020 (Grafik 3).

Ein kritischer Leser könnte nun wiederum vermuten, dass es innerhalb des Jahres 2020 möglicherweise starke Ausschläge nach oben bei einzelnen Jahrgängen gegeben haben könnte, die später durch Ausschläge nach unten ausgeglichen wurden – und dass diese Schwankungen in der jährlichen Übersicht nicht sichtbar sind. Doch auch das trifft nicht zu. Ein Blick auf die wöchentlichen Sterberaten zeigt, dass die ersten acht Monate der Pandemie keine nennenswerten Auffälligkeiten aufweisen. Es bleibt dabei: Die Rohdaten des Statistischen Bundesamtes bestätigen zweifelsfrei, dass die ersten acht Monate der Pandemie das historische Minimum im Sterbegeschehen darstellen. (Für die Fachleute sei angemerkt, dass im gleichen Zeitraum die Lebenserwartung die historischen Höchststände erreicht hatte – Grafik 4.)

So konstruierte das Amt aus einem Minimum ein Maximum:
Zur Erinnerung: Die Rohdaten des Statistischen Bundesamtes, die in den jährlichen Sterbetafeln zweifelsfrei dokumentiert sind, zeigen für das Jahr 2020 eindeutig ein Minimum im Sterbegeschehen. Aus diesen »in Stein gemeißelten« Zahlen ein Maximum zu »konstruieren«, ohne die Rohdaten selbst zu verändern, scheint auf den ersten Blick eine unlösbare Aufgabe. Jeder Student würde an einer solchen Herausforderung scheitern. Doch das Statistische Bundesamt hat einen kreativen Weg gefunden - ein Meisterstück gezielter Manipulation. In fünf Schritten zeigt sich, wie diese Täuschung der Öffentlichkeit umgesetzt wurde:
(1) Ignorieren der Sterberaten: Die präzisen, objektiven und leicht verständlichen Sterberaten aus den eigenen Sterbetafeln wurden konsequent ignoriert und verschwiegen. Diese Daten widersprachen dem gewünschten Narrativ und wurden daher gezielt ausgeklammert.
(2) Fokus auf absolute Todeszahlen: Die Aufmerksamkeit wurde stattdessen auf die absolute Zahl der Todesfälle gelenkt. Diese wirkt allein durch ihre schiere Größe dramatisch und emotionalisiert die Diskussion. Ein entscheidender Faktor wurde dabei ignoriert: Die absolute Zahl der Todesfälle steigt aufgrund der demografischen Entwicklung jedes Jahr an. Viele Menschen verstehen diesen Zusammenhang nicht und verbinden die steigenden Zahlen fälschlicherweise mit der vermeintlichen Pandemie.
(3) Einführung der Übersterblichkeit als neue Kennzahl: Erst ab Beginn der „Pandemie“ wurde die Kennzahl "Übersterblichkeit" eingeführt – und dies mit einer fragwürdigen Methode, die systematisch überhöhte Werte lieferte. Diese Kennzahl wurde regelmäßig, oft monatlich oder sogar wöchentlich, berechnet und diente als ständige Grundlage für alarmierende Schlagzeilen.
(4) Intensive Öffentlichkeitsarbeit: Durch eine breit angelegte Kampagne wurden die manipulativen Kennzahlen gezielt in den Fokus gerückt. Pressemitteilungen, Podcasts und öffentliche Auftritte konzentrierten sich fast ausschließlich auf die absoluten Todeszahlen und die Übersterblichkeit. Ziel war es, den Eindruck einer dramatischen Situation in der Öffentlichkeit zu verstärken.
(5) Bekämpfen kritischer Stimmen: Kritiker, die die Schwächen und manipulativen Aspekte dieser Methoden aufdeckten, wurden systematisch diskreditiert. Ihre Glaubwürdigkeit und Kompetenz wurden öffentlich infrage gestellt, um das sorgsam konstruierte Narrativ zu schützen.
Ohne diesen begleitenden Statistik-Betrug wäre das gesamte Pandemie-Theater meiner Meinung nach nicht möglich gewesen. Wer aus einem faktischen Minimum ein scheinbares Maximum "erschafft", handelt betrügerisch. Die Folgen dieses Betruges sind gravierend. Denken wir an die Angst, die in der Bevölkerung geschürt wurde – die Angst, bald sterben zu müssen. Denken wir an Masken, Abstandsregeln, isolierte ältere Menschen, Kinderimpfungen und all die Maßnahmen, die unter anderem auf diese falsche Statistik zurückgehen.
Wollen wir Bürger uns das gefallen lassen?
Wenn wir als Bürger zulassen, dass ein derart offensichtlicher und nachprüfbarer Täuschungsversuch ohne Konsequenzen bleibt, dann gefährdet das nicht nur die Integrität unserer Institutionen – es untergräbt das Fundament unserer Gesellschaft. In der DDR feierte man öffentlich Planerfüllung und Übererfüllung, während die Regale leer blieben. Damals wusste jeder: Statistik war ein Propagandainstrument. Niemand traute den Zahlen, die das Staatsfernsehen verkündete.
Während der Pandemie war es anders. Die Menschen vertrauten den Mitteilungen des Statistischen Bundesamtes und des RKI – blind. Die Enthüllungen durch den "RKI-Leak" haben gezeigt, dass auch das Robert-Koch-Institut nicht der Wissenschaft, sondern den Weisungen des Gesundheitsministers und militärischen Vorgaben folgte. Warum sollte es beim Statistischen Bundesamt anders gewesen sein? Diese Behörde ist dem Innenministerium unterstellt und somit ebenfalls weisungsgebunden.
Die Beweise für Täuschung liegen offen zutage. Es braucht keinen Whistleblower, keine geheimen Enthüllungen: Die Rohdaten des Statistischen Bundesamtes sprechen für sich. Sie sind öffentlich einsehbar – klar und unmissverständlich. Die Daten, die Tabellen, die Veröffentlichungen des Amtes selbst – sie sind die Anklageschrift. Sie zeigen, was wirklich war. Nicht mehr und nicht weniger.
Und wir? Was tun wir? Schweigen wir? Oder fordern wir endlich ein, was unser Recht ist? Wir Bürger dürfen das nicht hinnehmen. Es ist Zeit, unsere Behörden zur Rechenschaft zu ziehen. Diese Institutionen arbeiten nicht für sich – sie arbeiten für uns. Wir finanzieren sie, und wir haben das Recht, Transparenz und Verantwortung einzufordern. Manipulationen wie diese müssen aufgearbeitet werden und dürfen nie wieder geschehen. Die Strukturen, die solche Fehlentwicklungen in unseren Behörden ermöglicht haben, müssen offengelegt werden. Denn eine Demokratie lebt von Vertrauen – und Vertrauen muss verdient werden. Jeden Tag aufs Neue.
.
.
MARCEL BARZ, Jahrgang 1975, war Offizier der Bundeswehr und studierte Wirtschafts- und Organisationswissenschaften sowie Wirtschaftsinformatik. Er war Gründer und Geschäftsführer einer Softwarefirma, die sich auf Datenanalyse und Softwareentwicklung spezialisiert hatte. Im August 2021 veröffentlichte Barz den Videovortrag »Die Pandemie in den Rohdaten«, der über eine Million Aufrufe erzielte. Seitdem macht er als "Erbsenzähler" auf Widersprüche in amtlichen Statistiken aufmerksam.
-
 @ 89ccea93:df4e00b7
2025-01-25 04:26:01
@ 89ccea93:df4e00b7
2025-01-25 04:26:01Here's a list of the services I use.
I plan to make a blog post for each on
expatriotic.memy previously defunct blog that is going live again.Stay tuned.
Networking
Flint Router Mullvad Tor Little SnitchBuying & Selling Bitcoin
Bisq Robosats Peach Hodl HodlPrivate email
Tuta Addy.io ProtonWallets
Ashigaru Stack Duo Cake Sparrow Envoy Zeus CoinosSwapping Bitcoin
Trocador basicswapdex unstoppable-swapnoKYC
```kycnot.me```Spending Bitcoin
Wise Bitrefill Bitpay PayWithMoon Coinsbee The Bitcoin Company CoinCards.comPhone
Graphene OS Minimalism Obtainium FOSS apps Signal for DMs Telegram for Groups Silent.LinkServer
DIY with Debian Start9 Dojo Ronin Dojo Monero NodesPodcasts
The Ungovernable Misfits News Network The Watchman Privacyoriginally posted at https://stacker.news/items/863051
-
 @ b97f07c7:a9ddca71
2025-01-24 12:05:25
@ b97f07c7:a9ddca71
2025-01-24 12:05:25เปิดโลก social ยุคอนาคต ที่ creator ได้รับเงินจากคนอ่าน content เต็ม 100%! ทำความรู้จัก Nostr ที่จะเปลี่ยนโลกการใช้ social ของคุณกัน!

content จากประสบการณ์จริง ที่ดองนานในระยะนึงล่ะ แต่บอกเลยว่ามันก็ solve pain point ของ user ที่ไม่อยากลับลู้ว่า AI ของ platform นั้น มาคอย suggest อะไรที่เราไม่ได้ตาม
ส่วน content creator เอง เราเป็นคนเขียน คนทำ content บน platform นั้น ๆ ทุกอย่างควบคุมโดย platform ซึ่ง platform อาจจะถูกปิดเมื่อไหร่ก็ได้ ส่วนใหญ่โดนลด reach บางคนโดน platform ลบโพส บางคนโดน platform แบน เราจึงต้องมี asset เป็นของตัวเองอย่าง website ไม่งั้น content ที่เราตั้งใจทำหายไปเสียดายแย่เลย
ซึ่ง concept และการใช้งาน Nostr นั้นลด pain point ของ creator ที่ต้องไปทุก platform เพื่อครอง keyword ซึ่งเหนื่อยมาก ๆ ถ้าเป็นสายแบบเราที่เน้นโค้ดหน่อย ๆ ต้องมาสร้างผู้ติดตามใหม่ แต่ละช่องทางได้กลุ่มผู้ติดตามต่างกันอีก
ร่ายมายาวขนาดนี้เข้าเรื่อง Nostr ได้แล้ว ว่าแต่มันคืออะไร ใช้งานยังไง ต้องทำอะไรบ้าง ไปดูกันนนน
ปล. บทความนี้เป็นแนวแนะนำว่ามันคืออะไร ใช้งานยังไง ยังไม่ลงลึกด้านเดฟนะ คืออยากให้ใช้ให้เป็นก่อนนนนนน
Nostr คืออะไร?
Nostr ย่อมาจาก Notes and Other Stuff Transmitted by Relays เป็น open protocol ที่ถูกพัฒนาโดย Giovanni Torres Parra มีจุดประสงค์คือ สร้างเครือข่ายสังคมออนไลน์ที่ไม่ถูกควบคุมหรือเซ็นเซอร์
ในที่นี้ Notes หมายถึง social media และ other stuff คือ data communication
แล้ว protocol คืออะไรล่ะ? ก็คือเราคุยกันผ่านช่องทางไหนยังไง เช่น sms, email อะไรงี้
ดังนั้นมันก็คือ note & other stuff ที่ถูก transmit โดย Relays นั่นเอง
Workflow
ปกติเราทำแอพขึ้นมาแอพนึงประกอบด้วยอะไรบ้าง?
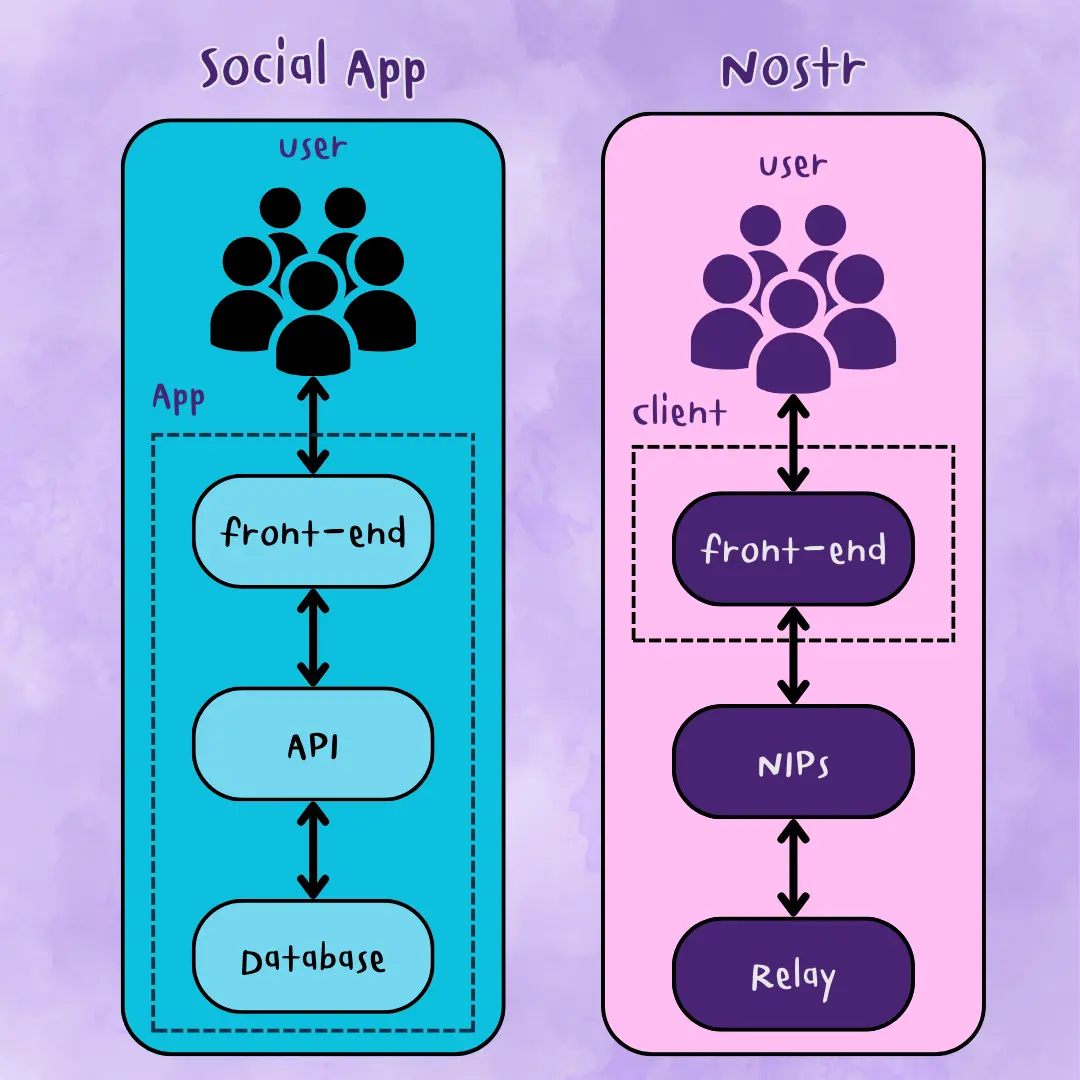
เดิมทีทีมแอพก็มีทีมหน้าบ้าน อย่าง frontend developer หรือ mobile developer อย่าง iOS และ Android แล้วก็ทีมหลังบ้าน backend developer ที่เป็นคนทำระบบหลังบ้าน ไม่ว่าจะเป็นทำ API ให้หน้าบ้านคุยกับ server แล้วก็จัดเก็บข้อมูลลง database ด้วย
flow ก็คือ user download แอพมา หรือใช้ website ตัวแอพหน้าบ้านจะเรียก API เพื่อทำอะไรบางอย่าง เช่น เปิดแอพมาเรียก API เพื่อ check ว่าเรา login อยู่ไหม แล้วก็ดึงหน้า feed มาแสดง
สำหรับ Nostr จะมีแค่คนทำหน้าบ้านเท่านั้น โดยตัวแอพเชื่อมต่อกับ relay ผ่านมาตรฐานของ NIP
ดังนั้น developer อย่างเราจะทำ client หรือตัวแอพที่ใช้ Nostr ได้เลย โดยใช้ Relay เดียวกันได้เลย ภายใต้มาตรฐานของ NIP เวลา user เปลี่ยนแอพใหม่ ตัวข้อมูล ตัวโพสต่าง ๆ ยังคงอยู่เหมือนเดิมที่ delay ไม่ต้องไปสร้าง follower ใหม่บน platform ใหม่ ๆ ให้เสียเวลา
การทำงานของ Nostr
สามารถดูตามภาพนี้ได้เลย เป็นภาพพื้นฐานในการเล่าเลย การทำงานเขาจะแบ่งเป็น 2 ฝั่ง คือ

- Client: คือแอพพลิเคชั่นที่ใช้เล่น Nostr นั่นแหละ เป็นฝั่ง user จะมี key pair คือ private key ใช้ในการยืนยันตัวตนนั่นแหละ เช่น เราเป็นคนโพสอันนี้นะ (เก็บไว้ให้ดี ๆ) และ public key บอกว่าเราคือใคร การทำงาน ตัว client เชื่อมต่อกับตัว relay เช่น บอกว่าใครเป็นคนสร้าง content นี้ หรือเราจะสร้าง content ใน Nostr ก็จะส่งข้อมูลรายละเอียดโพสอย่าง kind, content, tags, pubkey, create_at ตามมาตรฐาน NIPs ส่งไปที่ relay
- Relay: คือ database ตัวนึง ที่เป็นรูปแบบแบบกระจายศูนย์ ได้รับ event อะไร และส่งอะไรกลับไปบ้าง
ref: https://github.com/nostr-protocol/nostr
แล้ว Client และ Relay สื่อสารระหว่างกันยังไง คุยกันผ่าน WebSocket นะ แล้วแต่ละ event จะส่งมาใน JSON format น่ะ
คุณสมบัติของ Nostr
- decentralized: relay คือ database แบบกระจายศูนย์
- open protocol: Nostr เป็น open protocol สามารถใช้งานได้หลายอย่าง
- censorship-resistant: user มีสิทธิ์เลือก relay เองได้
- high security: encrypt ข้อมูลส่วนตัวก่อนส่งทุกครั้ง

มาตรฐาน NIP
NIP ย่อมาจาก Nostr Implementation Possibilities คือ มาตรฐาน protocol ที่ใช้กันสำหรับ Nostr
ใน content นี้เราไม่ลงลึกมาก เดี๋ยวจะงงกัน เอาให้เห็นภาพคร่าว ๆ เพราะมันมีเยอะมาก
หลัก ๆ ที่เราใช้งานกัน จะมี

- NIP-01: Basic protocol เป็นอันพื้นฐานที่ต้องรู้ บอกโครงสร้าง event การรับส่งข้อมูลต่าง ๆ ทำให้เรารู้โครงสร้างแล้วเอาไปสร้าง client ได้เลย ทำให้ developer focus ที่โครงสร้างนี้อันเดียวเท่านั้นในการพัฒนา เช่น post บน Nostr นั่นแหละ
- NIP-05: Nostr Address บอกว่าเราเป็นใครใน internet ฟีลเดียวกันกับ email address ทำให้เราตั้งชื่อบัญชีให้จดจำได้ง่าย ช่วยในการค้นหาและติดตามกันได้ง่ายยิ่งขึ้น เช่นจากที่เราต้องเพิ่มเพื่อนผ่าน Nostr public key ที่ยาวเหลือเกิน เป็นอะไรสั้น ๆ ฟีล email เช่น mikkipastel@siamstr.com
- NIP-23: Long-form article พวก blog ต่าง ๆ
- NIP-53: สำหรับ live stream
ส่วนแบบอื่น ๆ สามารถอ่านรายละเอียดได้ที่นี่เลย https://github.com/nostr-protocol/nips/blob/master/README.md
เริ่มใช้งานบนมือถือ
จาก workflow เราจะเห็นว่าเราสามารถใช้ client ตัวไหนก็ได้ในการเล่น Nostr และโลกของ Nostr มีตัวเลือกให้เราเยอะมากก แล้วเราจะเริ่มยังไงดี?

- ติดตั้ง Wherostr เป็นแอพที่ทีมคนไทยทำ ใช้ง่ายมาก ๆ สามารถ download ได้ทั้ง App Store และ Play Store
- แน่นอนว่าเรายังไม่มี account ให้สร้าง account
- ปรับแต่ง profile ให้เรียบร้อย
- เก็บ private key ไว้ในที่ปลอดภัย เพราะเป็น key ยืนยันตัวตนว่าเป็นเราในการทำธุรกรรมต่าง ๆ ในที่นี้คือสร้างโพส, กด like, กด share, รวมถึง zap ด้วย ในแอพอาจจะยังไม่เห็น process นี้ ต้องบนคอม
Tips: ไปรับ NIP05 สวย ๆ ได้ที่ https://siamstr.com/
การที่เราสร้าง account ใหม่นั้น จะเป็นการสร้าง key pair อันประกอบด้วย - public key: ขึ้นต้นด้วย npub1... โดยสามารถเพิ่มเพื่อนใน Nostr ผ่านอันนี้ได้ ซึ่งบอกว่าเราเป็นใคร - private key: ขึ้นต้นด้วย nsec1... เป็นส่วนที่เราต้องเก็บไว้ให้ดีเลย เพราะต้องเอามาใช้ sign กับการทำธุรกรรมของเรา เช่น การ login, สร้าง post, reaction post ใด ๆ
เชื่อมกับกระเป๋า Lightning
เชื่อมเพื่อรับ sat จากเพื่อน ๆ โดย sat เป็นหน่วยย่อยของ Bitcoin มาจาก Satoshi อันเป็นนามแฝงของผู้สร้าง Bitcoin โดย 1 Bitcoin = 100,000,000 Satoshi

- ติดตั้ง Wallet of Satoshi ตัวแอพนี้เป็น custodial wallet ที่เราไม่ต้อง set อะไรเอง แต่เราไม่ได้ถือ key ของกระเป๋านี้เองนะ สามารถ download ได้ทั้ง App Store และ Play Store
- เชื่อม email กับ Wallet of Satoshi เลข Lightning Wallet กดปุ่ม Receive แล้วก็ copy
- กลับมาที่ Wherostr ไปที่ Profile ของเรา กด Edit Profile
- วางเลขเป๋าตรง Bitcoin Lightning Address แล้วก็กด save
การใช้งานทั่วไป
ขอเปรียบเทียบกับ social network ที่เราใช้กันอยู่เนอะ สมัยก่อนโพสจะเรียงตามลำดับเวลา และเพิ่มเพื่อนหรือติดตามเพจก่อน เราถึงจะเห็น content เขาใน feed
แต่สมัยนี้ AI นำหมด ลองไถ feed ดูสิ เจอเพื่อนเราหรือเพจที่เราตามเท่าไหร่ใน 10 post ทำให้ตัว content creator ต้องเรียนรู้ algorithm ของ platform นั้น ๆ เพื่อให้ content ของเราผู้ติดตามเห็นมากขึ้น (งงม่ะ)
แล้ว Nostr ล่ะ? เหมือน social network สมัยก่อนที่เรียง feed ตามเวลาเลย เราสามารถกดติดตามเพื่อนได้ (และระบบนั้นให้เราได้ติดตามตัวเราเองได้ด้วยนะ5555) และอ่านโพสเพื่อน ๆ คนไทยใน Nostr ได้ผ่าน #siamstr
การสร้างโพส
การโพสก็แสนจะง่ายดาย กด + ตรงกลาง แล้วพิมพ์ เพิ่มรูปใด ๆ ได้ตามใจชอบเลย ฟีลประมาณ medium แหละเนอะ สำหรับ wherostr สามารถ tag สถานที่ได้ด้วย

จุดที่น่าสนใจ คือปุ่มเหมือน CPU กดไปดูจะพบว่าเราสามารถเลือก Proof of Work difficulty level ได้ ซึ่งถ้าเราตั้งไว้เพื่อกัน spam แหละ ถ้าตั้งสูงก็ใช้เวลาในการ solve นาน ซึ่ง default POW เป็น 8
เอ้ออย่าลืมติด #siamstr ด้วย
เมื่อเรียบร้อยแล้ว Post แล้วรอแปป โพสของเราเมื่อสร้างเสร็จแล้วจะอยู่บนสุดเหมือนแอพ social media ทั่วไปเลย
ข้อพึงระวัง
- ลงแล้ว edit post ไม่ได้
- และลบไม่ได้ด้วยนะจ๊ะ
- แชร์ลิ้งได้ แต่ก็ไม่แน่ใจว่าเพื่อนเปิดยังไงได้บ้าง บาง client อย่าง Yakihonne สามารถ share url link Nostr post ของเราได้เลยนะ
เราสามารถกด report, comment และ like ตามปกติเลย แต่มีปุ่มนึงเพิ่มมาจาก social network อื่น ๆ คือ zap นั่นเอง
Zap คืออะไร?
แน่นอนไม่ใช่การแอบแซ่บ แต่เป็นการที่เราเอา Bitcoin บน lightning มาใช้จ่ายต่าง ๆ เช่น เอาไปซื้อชากาแฟ หมูปิ้ง เค้กท้อฟฟี่ชลบุรี ปลากรอบ Crispy Will รวมถึงการ donate ให้กับเจ้าของ content ที่คนนี้เขียนดีมาก เรากด zap ให้เขาดีกว่า หรือไป zap ที่ profile ก็ได้ซึ่งทุก sat (satoshi หน่วยย่อยของ Bitcoin) ที่เขาส่งมาให้ เราได้รับครบทุก sat แบบไม่หักจาก platform เลย

วิธีการ zap ผ่าน Wherostr มี 2 ทาง คือ - zap ให้กับคนนั้น ๆ ที่ profile: ไปที่ profile ของเขา แล้วเราจะเห็นปุ่มสายฟ้า - zap ที่ post นั้น ๆ: เลื่อนไปล่างสุด เราจะเห็นปุ่ม repost, like, comment และอีกอันที่เป็นสายฟ้าคือ Zap
เมื่อกดปุ่ม Zap แล้ว เข้าไปหน้า Zap เลือกจำนวน sat ที่เราต้องการ Zap อาจจะใส่ข้อความไปด้วยก็ได้ แล้วก็กดปุ่ม Zap ด้านล่าง
จากนั้นมันจะเด้งไป Wallet of Satashi ที่เรา connect ไว้ ตรวจสอบธุรกรรม เรียบร้อยแล้วกด Send เขียว ๆ รอสักแปป เมื่อสำเร็จแล้วเราจะเห็นหน้าเขียว ๆ แบบนี้เลย
ถึงเงินอาจจะไม่ได้มากมายอะไรมัก ก็เป็นสิ่งที่ platform web2 ให้ไม่ได้เลยนะ กับความรู้สึกดี ๆ แบบนี้ ที่ลง content แล้วมีคนมา Zap ให้ ในขนาดที่ platform web2 ไม่มีคนกด send gift ให้เลย ฮือออออออออออ
Client App อื่น ๆ ที่น่าสนใจ
จริง ๆ เราจะใช้แอพ Client อื่น ๆ เล่น Nostr ได้นะ เพราะว่า Relay สามารถใช้ร่วมกันได้ในหลาย ๆ แอพ

ก่อนที่จะมีแอพ Wherostr เขาจะแนะนำกันว่า
ถ้าใช้ iOS ใช้แอพ Damus ส่วนชาว Android ใช้ Amethyst
ตอนนั้นที่เราลองเล่นเอง เราสร้าง account ผ่าน Iris แหละ เพราะ ก่อนหน้าที่เรารู้จัก Wherostr และเข้าใจ Nostr เราได้ลองกับ Nostr browser นึงที่ชื่อว่า Spring ในนั้นมีหลาย ๆ client ให้เราจิ้มเล่น และแอพนี้มีเฉพาะ Android เท่าน้านนน
สายเขียนบล็อก: Habla, Yakihonne, Npub.pro
ส่วนสายสตรีม: Zap.Stream
ส่วน Client อื่น ๆ สามารถเข้าไปดูได้ที่นี่ ซึ่งในนี้เป็นแค่ส่วนหนึ่งเท่านั้นแหละ https://nostrapps.com/
เริ่มใช้งานบนคอม
หลาย ๆ client นอกจากจะมีเป็นแอพบนมือถือ ยังมีเป็นหน้าเว็บไซต์อีกด้วย

สิ่งที่ต้องมีเพิ่มเติม คือ extension ที่ชื่อว่า Nostr Connect เราใส่ private key เข้าไปในนั้น พอเวลา sign transection ตัว extension จะไม่เอา private key ของเราตรง ๆ
หลังจากติดตั้ง extension ตัวนี้แล้ว การใช้งาน สมมุติเข้าเว็บ Wherostr กดปุ่ม Login แล้วจะมีหน้า popup เด้งมา ให้กด Login with Nostr extension แล้วจะขึ้นหน้าต่างให้เรา sign สองอัน คือ อ่าน public key กับ Relay
เมื่อ login เรียบร้อยแล้ว สมมุติเราสร้างโพสบนเว็บ Wherostr จามปกติ เรียบร้อยแล้วกด Post เขาจะให้เรา sign event ว่าเราเป็นคนสร้าง post นี้นะ เราจะเห็น transaction ออกมาเป็น json เลย ตามมาตรฐาน NIP-01
ปล. จริง ๆ จะกดไม่ให้เปิด popup ก็ได้นะ แต่เราอยากเปิดไว้เอง เอาไว้ check
และ extension อีกตัวที่มีคนแนะนำก่อนหน้านี้คือ Alby ตอนนี้ไม่ต้องไปขอ access code ก่อนถึงจะใช้ได้ สามารถเข้าไปสมัครที่นี่ได้เลย
https://getalby.com/
สุดท้าย ก็หวังว่าทุกคนรู้จัก Nostr กันไม่มากก็น้อยเนอะ
ถ้าใครอยากติดตามเราบน Nostr สามารถเปิดแอพ Wherostr หรืออื่น ๆ เพื่อ scan QR Code นี้ได้ หรือ copy public key หรือ Nostr user ไปหาได้น้า
แน่นอนในนี้เป็นการแท็กเราเอง nostr:npub1h9ls03lflhvgzzmkf6nsymspw3auh0f3d97c02e5l4edn2waefcszlq9qf

Reference
- https://nostr.com/
- https://github.com/nostr-protocol/nostr
- https://rightshift.to/2023/kp/14251/
- จริง ๆ ก็เอามาจากงาน Thailand Bitcoin Conference 2024 ที่เขียนไปด้วยแหละ แต่บวกกับการใช้งานจริงด้วย https://www.mikkipastel.com/thailand-bitcoin-conference-2024/
-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ fc2470ed:17d9ee27
2025-01-30 14:24:23
@ fc2470ed:17d9ee27
2025-01-30 14:24:23by Hynek Fencl, July 2024
The way to Liberland is easy but not simple. Technically speaking, it’s just a short bike ride away from the nearest village on a comfortable bike path through a stunning forest known as the “Amazon of Europe”. On one side, one senses the presence of the mighty Danube River beyond the tall trees, and on the other stretch the farmlands of north-eastern Croatia. Then you take a left turn to a straight forest path, ride all the way to the end, and after a few bends on the track, you will have entered “the promised land”.
The part that is not simple is that Croatia both does and does not consider Gornja Siga (the local name for the area we now refer to as Liberland) to be its territory – depending on who you ask. This means that along the picturesque bike path, you will almost certainly encounter a border police patrol car, and, depending on whether you seem to them like you’re affiliated with Liberland, they will tell you to stop and hand over your ID. They run it through their system and, if you’re lucky enough to be a citizen of the EU, they let you pass. If you’re not and you give them a non-EU passport, they will ask you to come to the station with them to “determine the circumstances of your stay in Croatia.” You will then be issued with paperwork telling you to leave the country within the next 7 days, banning you from re-entering in the next 1-3 months. The official reasoning they’ll give for this is their reasonable suspicion that you have not come to Croatia as a tourist but with the intent to either do paid work (for which you would have to get a business/work visa) or to break the law (such as camping outside designated camping grounds or starting a fire in the forest).
All of this is part of a big game of chess that is being played out between Croatia and the Liberlanders. Croatia is in a tricky spot. They cannot properly administer the territory of Liberland and enforce its law in it – lest it would create an indication that the Croatian state officially claims it as its territory. However, they cannot not administer it either, since it’s on “their” side of the river, and it is risky for a rogue, unpredictable operation (from their perspective) like the establishment and growth of Liberland to just be left to its own devices right on their doorstep. This is, then, how we arrive at the status quo, with Croatia relating to Liberland in some way while being careful about the international perception of its action in another way. The resulting practice is a persistent harassment campaign toward the Liberlanders, with the apparent intent to create uncertainty and lower the appetite of potential Liberland settlers for this kind of adventure.
How to establish a new country
Liberland was born from an anomaly – a historical border dispute between Croatia and Serbia. The dispute involves the definition of where the border stands in relation to the Danube and goes back to 1947. Then, both lands along the river belonged to a single country – Yugoslavia – but the dispute arose with respect to the boundaries of its constituent states. It remained unresolved during the communist era and became an issue of international borders after the breakup of Yugoslavia.
Serbia claims that the border runs down the middle of the Danube, with the eastern bank being Serbian and the western bank Croatian. Croatia, on the other hand, claims that the border is set by historical borders marked by cadastral municipalities surrounding the Danube.
These municipality borders run along a different path because they were set before the course of the Danube was straightened during the 19th Century to allow for easier shipping. This results in disputed “pockets” of land on both sides of the river. The pockets on the eastern bank have a combined area of around 130 km2, while those on the western bank only amount to less than 10 km2. Not surprisingly, then, both countries claim that the border runs in a way where they get the >90% of land and the other country only gets the small remaining areas. However, this means that, by implication, since both countries are claiming the large areas, neither of them is claiming the smaller ones. These areas were, then, so-called terra nullius.
Under international law, there is no issue with any state claiming unowned and unclaimed land for themselves. And that is exactly what Czech businessman, politician, and activist Vít Jedlička did in 2015 when he proclaimed into existence the newly created Free Republic of Liberland on the largest, 7 km2 piece of the unclaimed areas between Croatia and Serbia.
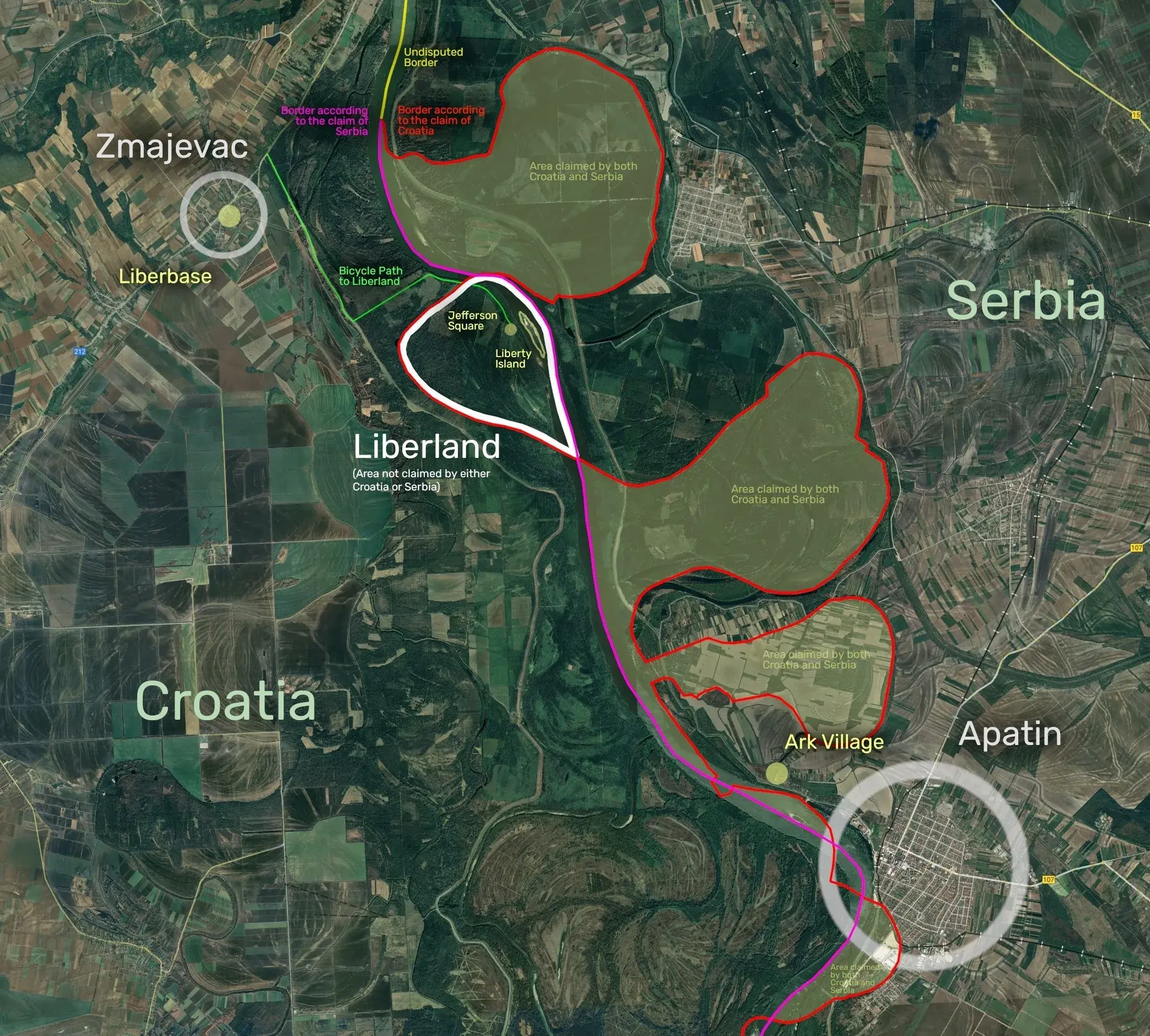
It's one thing to announce a new country to the world. It’s an entirely different thing to make this country legitimate. Under the Montevideo Convention, a proper country needs to have 1) a permanent population, 2) a defined territory, 3) government, and 4) capacity to enter into relations with other states. Now, 9 years after the birth of Liberland, it clearly has three of those. As to a permanent population, the Liberlanders would argue that it definitely exists, even though Liberland’s now over 1200 registered citizens have had to largely live in “exile” ever since.
Nevertheless, despite the Convention, there’s one thing that makes something a country more than anything else – whether other countries see you as a country. The more diplomatic recognition an entity has, the more country-like it becomes. This is especially relevant for breakaway governments, governments in exile, or, most importantly in this case, startup countries like Liberland.
Very much aware of this, along with other members of Liberland’s startup government, Jedlička has been on a worldwide mission to legitimize Liberland in the eyes of other countries. Though there have been many amiable meetings and even some measure of support in some cases, no official recognition by any UN member has been achieved as of mid-2024. Liberland now has representatives and offices in multiple countries in the further pursuit of this goal. Though the effectiveness of this strategy has been questioned by many for the lack of decisive results so far, one thing remains unambiguously true: if recognized by even one or two UN members, Liberland would instantly gain an amazing amount of legitimacy and gravitas in the eyes of the world.
The quest for territory
Establishing international relations with countries anywhere in the world is not the only strategy that the Liberlanders have been employing in making the country more real and legitimate. This includes liaising and negotiating with the neighboring Serbia and Croatia. These relations are by far the most important and impactful ones. If both of Liberland’s neighboring countries were to either outright recognize the startup micro-state, or even just adopted an approach of non-interference, Liberland would be free to start actually developing and to find its own long-term position in the world.
As for Serbia, its Ministry of Foreign Affairs let itself be heard that, in their view, Liberland’s claims are a “trivial matter” but, in any case, they do not infringe upon the sovereignty of Serbia. One can imagine that Serbia might actually be secretly quite pleased with Liberland’s activities, since now Croatia has an issue to deal with on “their” side of the river, which, if they are not careful, could contribute to the legitimization of Serbia’s claim to the larger pieces of territory claimed by both countries.
With Croatia, things get quite a bit more complicated. In an official statement, the country rejected the claim that Gornja Siga is terra nullius, arguing instead that the land belongs to one of the two neighboring countries – the only question is to which one, which will be answered at some point in the future. Croatia also said it would stop any threatening and provocative activities on the territory even by force if necessary.
Ever since Liberland’s birth in 2015, the Liberlanders have been trying to make a mark on the territory. For a long time, even just entering Liberland wasn’t really possible. Under a deal between the Croatian and Serbian police that was put in place during the European migration crisis, Croatian authorities may enter Liberland and patrol it for security reasons (preventing illegal migration) even though they do not officially claim the territory as theirs. In addition, the border police have a near-permanent presence on the Danube River, preventing people from crossing into Liberland by boat.
As a result, anyone who would try to come to Liberland in any way would always be promptly arrested by the Croatians, essentially for entering a prohibited area.
After years of this status quo, a rather unexpected thing happened that made things suddenly move forward in a positive direction for the Liberlanders. In April 2023, during Liberland’s 8th anniversary celebrations, a famous YouTuber with a significant following decided to try to enter Liberland. After a few unsuccessful attempts due to heavy police presence and monitoring, he and his team hired jet skis and rode them all the way from Hungary down the Danube. When they got close to Liberland, they encountered the police boats again, but their jet skis were faster than the boats, so they managed to land at Liberland’s Liberty Island and plant a flag there. A few moments later, the police caught up to them and an aggressive policeman took out their handheld cameras before assaulting them and then kicking them on the ground, as can be clearly seen from drone footage of the incident.
As they had broken no laws, they were ultimately let go after the incident and free to leave the island without being arrested. However, the heavy-handed and illegal conduct of the Croatian police had been clearly documented and became part of the video that was published in July 2023.
The video promptly went viral, gaining almost 10 million views on YouTube. By comparison, the total population of Croatia is just under 4 million. When the news spread even to the Croatian press and TV stations, Croatia had a serious PR problem on their hands. The police had been clearly in the wrong, conducting themselves in a seriously improper way to the point of using physical force against peaceful people who had broken no laws nor engaged in any violence or hostilities themselves.
Something had to change. So, following this incident, the Croatian police adopted a different unofficial policy – from now on, they would let people enter Liberland if they wished to do so, in a controlled way. Since early August 2023, if you wish to enter Liberland, you can go on foot or by bike, take the access road down the forest, and show your documents to the Croatian police, just as you would at a border crossing. In a typical grand fashion of Liberland’s media team, Liberland made an announcement that an official border crossing had been opened between Croatia and Liberland (Croatia had obviously never made an official announcement like this, but for Liberland, that was the de facto situation on the ground).
In the weeks following the “opening of the border”, many enthusiastic settlers started coming to Liberland to finally begin making their mark on the territory of “the promised land.” They started constructing simple wooden houses, a bathroom, an open-air restaurant, and the related power and water infrastructure on Liberland’s mainland beach opposite Liberty Island in a settlement named Mateos Marina.
On September 7th, 2023, a troop of about 50 policemen and forestry workers, including a demolition crew, raided the settlement. The raid was officially dubbed a “cleanup operation” by Hrvatske šume, Croatia’s state forestry service. With the assistance of the police, they tore down all the wooden houses and structures using chainsaws and stole equipment as well as personal possessions of the Liberlanders on site. Several Liberlanders were arrested for “failure to comply with a lawful order”.

One might ask, if Liberland is not officially part of Croatia, what authority does Croatia have to come in to steal and destroy? Staying true to their claim that Liberland is not part of Croatia, the Croatians had announced to Serbia that they would be conducting the “cleanup” on Serbia’s territory, to keep it clean on their behalf.
We may only speculate about the reasons for carrying out this operation in such a heavy-handed, destructive way. One possibility is that allowing people to enter Liberland in the first place was a way for Croatia to lure some people to Liberland, become comfortable, and then come in and destroy everything to show everyone what would happen if they got involved in the project. Or perhaps it was the unexpected level of life, community-building, and construction going on in such a short period of time after the “opening of the border” that the Croatian police felt like they had to put a stop to it before things got so big they could not be easily destroyed anymore.
No matter the reasons, the raid had a chilling effect on prospective Liberlanders. Though there is plenty of video documentation of the operation, no one made a viral video about it this time. Though some media did pick up the news, it did not become a big story. Consequently, the PR fallout from this for Croatia was not unmanageable.
Liberlanders soon returned to the territory. However, the level of enthusiasm, energy, and external support was not as great as it had been before the raid. From then on, settlement efforts focused mainly on Liberty Island, unreachable by trucks and impossible for forestry workers to get to without a large boat which they seem not to have. Though perhaps a more strategic place to set up camp, Liberty Island is also much more prone to flooding than the rest of Liberland.
In the following few months, several makeshift houses were constructed using a combination of wood and sandbags. During this time, Liberland even hosted a first wedding on the island. The settlement was kept alive during winter as well, with Liberland enthusiasts staying mostly in houseboats whenever it was impossible to camp on site.
In the meantime, an enthusiastic settler couple bought a sizeable house with a courtyard in the village closest to Liberland – Zmajevac – which they have transformed into a base of operations for settlers. This is now called Liberbase and it is where visits to Liberland start, with bikes, supplies, and construction materials being gathered before going on the 40-minute bike ride.

In the spring of 2024, work started on the reconstruction of a former hunting lodge at a central location on Liberland’s mainland – Jefferson Square. The building was demolished a few years ago but the foundations, including a cellar, were left in place. The site was cleared, the foundations refreshed, and new walls for the future governmental building have sprung up from the ground. A professional construction crew was hired to speed up the re-building of this base, using large concrete bricks, to a standard that will make it logistically and practically difficult for the Croatian police and forestry workers to try to destroy.
 The battle for legitimacy
The battle for legitimacy The ongoing construction in Liberland is rather slow. It is difficult to bring construction materials to Liberland. It is prohibited to drive motor vehicles on the bike path leading to Liberland, which means that everything has to be manually hauled from Liberbase on cargo bikes. In addition, from time to time, bikes get stolen by the police or forestry workers. Despite these difficulties, the determination of the settlers is unwavering and they are working every day to move construction forward.
The ongoing construction in Liberland is rather slow. It is difficult to bring construction materials to Liberland. It is prohibited to drive motor vehicles on the bike path leading to Liberland, which means that everything has to be manually hauled from Liberbase on cargo bikes. In addition, from time to time, bikes get stolen by the police or forestry workers. Despite these difficulties, the determination of the settlers is unwavering and they are working every day to move construction forward.Is it possible to bring materials by boat? How did they get sandbags and other materials to Liberty Island?
The importance of such a commitment should not be underestimated. The continuous presence of settlers is incredibly important for Liberland. It shows the seriousness of the project. It shows that Liberland is a genuine community and a fledgling nation rather than, as some accusations tend to go, just an elaborate publicity stunt.
Practical difficulties with the Croatian authorities are not limited to construction-related issues. Even staying and camping in Liberland comes with its quirks. If you’re staying on Jefferson Square, you should be prepared for several police visits every day. These check-ups are usually nothing dramatic. The police usually show up, ask a couple of questions, and perhaps tell the settlers that they are not allowed to camp there or start a fire, but they don’t actually do anything more than that and just go about their day.
It seems that the Croatian police are rather shy about enforcing Croatian law in a territory that is not officially considered part of Croatia. International law often takes into account the de facto situation of the matter in any dispute. If Croatia enforced their law in Liberland, this would therefore be an indication that they do, in fact, consider the territory to be theirs in practice, despite the official stance of the state. It would play into the hands of Serbia, reinforcing their claims to the large parcels of land on the other side of the Danube.
In addition, Liberlanders on the ground report that the majority of Croatian police officers generally behave quite fairly and respectfully toward them – only a minority appear to hold a personal grudge against Liberland, being abusive and sometimes even violent instead. It seems highly likely that the police in general are just doing their job, following orders from above. Most of them don’t actually take it as a personal commitment to make life more difficult for the Liberlanders.
This is rather important from a big-picture perspective, because the settlers, by contrast, are often heavily personally invested in the project and see it as their mission to see Liberland develop into a proper country. This disparity in energy and determination is strong and perhaps this is what will, in the end, cause Liberland to prevail in this drawn-out dispute.

The dispute with Hrvatske šume is quite different. As of mid-2024, the forestry workers tend to turn up at Jefferson Square about every fortnight. Unlike the police, they do not limit themselves to words but tend to steal everything that is not bolted down – including tools, materials, tents, bikes, and personal possessions of the settlers camping there. The justification remains the same – to “clean the forest of any waste.” In their encounters with the police as well as the forestry workers, Liberlanders are of course meticulous in their video documentation of any illegal actions by the authorities.
The Liberlanders’ difficulties, however, do not just stay local. As previously mentioned, upon trying to enter Liberland from Croatia, people who do not have EU citizenship are promptly issued a one-to-three-month ban on entering Croatia, with 7 days to leave the country. This is done under legislation relating to citizenship and tourism.
However, things can escalate even further. Since last year, several key Liberland settlers and organizers, including Liberland’s President Vít Jedlička himself, have seen “heavier guns” used against them. They have been banned from entering Croatia for 5 years under anti-terrorism legislation, where the authorities argue that these Liberlanders are something akin to a threat to national security.
The Liberlanders have mounted a legal defense against this, in addition to challenging Croatia on other legal fronts. They have had some successes so far – in particular, it should now be clear that the Liberlanders do not need any building permits to construct buildings on their territory. Unfortunately, other issues – including the 5-year bans from Croatia – still remain unresolved.
Most Liberlanders remain hopeful nonetheless. They have seen their situation move forward significantly over the last year. A year ago, they were not even able to enter Liberland without being chased and/or arrested. Now, even some construction is possible, albeit in a limited way.
The road ahead
The long-term vision, of course, remains to build a full-fledged, internationally respected and recognized city-state. Liberland’s leaders often speak of a “Balkan Monaco”, referring to the amazing development possibilities that a freedom-oriented country in the middle of Europe could offer. Liberland has already hosted an urbanist/architectural contest, and there are concrete plans for the first hotel as well as a riverside real estate development. What is more, Liberland’s land is actually more than three times the size of Monaco.
Nevertheless, Liberland cannot move forward in a meaningful way toward these visions and aspirations under the status quo. The Liberlanders need to be able to build at scale and be free from harassment, both by the police and the forestry workers. Some kind of political deal is necessary as the next step toward proper development of Liberland.
Such a deal could take multiple forms, but all of them involve the Croatian authorities changing their attitude toward Liberland away from a policy of unrelenting obstruction – not necessarily toward outright recognition, but at least toward accepting Liberland as a neighborly project that will move forward and develop in some way.
One option could be to allow motor vehicles on the bike path toward Liberland, with a deal that could include charging Liberlanders some fair tolls to pay for the wear and tear of the pavement. An alternative would be to simply allow river crossing into Liberland from Serbia on the Danube. Since Croatia does not officially consider Liberland its territory, their current interference with this traffic is illegal anyway. Simply stopping this illegal conduct would help Liberland significantly without Croatia facilitating Liberland’s development in any active way.

Regardless of these options, the first and most notable step would be to stop banning non-EU citizens from re-entering Croatia as well as lift the existing (entirely unjustified and unreasonable) 5-year bans on Jedlička and the others.
It is easy to see why Croatia is wary and suspicious of Liberland’s development. One can understand the worries of a state in whose immediate proximity there is a new and unknown state growing and taking root. Nevertheless, Croatia actually has a lot to gain from making some kind of deal with Liberland.
First: currently there are perhaps a dozen policemen on patrol around Liberland at all times. This includes police vehicles and boats. This is a significant expense for the police force – an expense which is rather unsubstantiated, given that Liberlanders have clearly proven to be peaceful people who do not wish to pose any threat to Croatia, its people, or its law enforcement officers. Making a deal would mean that this large expense is not needed anymore.
Second: Liberland borders an area of Croatia that has been rather “left behind”, is underdeveloped, and suffers from a lack of jobs and investment. Consequently, younger people are leaving the area and the current population is growing older. If Liberland was growing and open for business nearby, it would provide the region exactly with the job opportunities, large investment, and overall development that it desperately needs.
Third: Croatia could use Liberland as an opportunity to actually gain an advantage in the ongoing border dispute with Serbia. As previously mentioned, Croatia cannot openly and properly administer the territory, as it would be an indication in the eyes of international law that they consider the territory to be theirs. On the other hand, it Liberland is located on “their” side of the Danube, so Croatia does have an interest in making sure the area is under their control somehow. Striking a deal with Liberland could involve Liberland agreeing to some obligations related to the administration of the territory which correspond to Croatia’s priorities. In this way, Croatia would have an active say in what happens on this land, effectively “outsourcing” its administration without officially claiming it as part of Croatia.
In addition to all these advantages being present, Liberland is very much open to cooperation with Croatia and is keenly looking forward to welcoming any future productive relations with Croatian authorities. There will be no grudges held on Liberland’s side, and if a mutually beneficial deal or solution were to be found, no one would look behind at any historical quibbles or difficulties. Liberland would be an excellent and friendly neighbor to Croatia, not just causing any issues but actively helping the overall development of the surrounding region.
Time will tell how things will develop. At the present, the momentum, energy, and enthusiasm is definitely on the side of Liberland. There seems to be very little actual interest from the Croatian side to cause issues for Liberland and to continue to prevent the fledgling state from developing further. All that is left are the bureaucratic hurdles of a state that is being overly conservative about its approach to the important issues of the day. Things might take time, but seeing the determination of the settlers and the willingness of all Liberlanders to be unrelenting in their fight for the cause, it is not difficult to argue that we might be seeing the dawn of Liberland as the world’s next proper city-state as we speak.
-
 @ f57bac88:6045161e
2025-01-23 18:06:37
@ f57bac88:6045161e
2025-01-23 18:06:37چرا بیتیسی پی سرور؟
بیتیسی پی سرور یک ابزار قدرتمند است که مزایای متعددی برای مدیریت پرداختهای رمزنگاری ارائه میدهد. در ادامه، ویژگیهای کلیدی این پلتفرم را مرور میکنیم:
- متنباز و خودگردان: این نرمافزار متنباز است و به توسعهدهندگان اجازه میدهد آن را مطابق با نیازهای خود سفارشی کنند. همچنین، نصب آن بر روی سرور شخصی به کسبوکارها کنترل کامل بر دادهها و تراکنشهایشان میدهد.
- پشتیبانی از بیتکوین و لایتنینگ: این پلتفرم از پرداختهای درونزنجیرهای (آن-چین) و برونزنجیرهای (آف-چین) پشتیبانی میکند. این ویژگی باعث میشود پرداختها سریعتر، ارزانتر و مقیاسپذیرتر شوند.
- امنیت بالا: با بهرهگیری از الگوریتمهای رمزنگاری پیشرفته، امنیت تراکنشها تضمین میشود. علاوه بر این، امکان استفاده از کیف پولهای سختافزاری برای افزایش امنیت وجود دارد.
- انعطافپذیری: این ابزار با انواع کسبوکارها و فروشگاههای آنلاین سازگار است و قابلیت یکپارچهسازی بالایی دارد.
- رایگان بودن: بیتیسی پی سرور یک نرمافزار کاملاً رایگان است و استفاده از آن هیچ هزینهای در بر ندارد.
مزایای استفاده از بیتیسی پی سرور
استفاده از بیتیسی پی سرور میتواند برای کسبوکارها و مشتریان ارزش افزوده زیادی ایجاد کند:
- حفظ حریم خصوصی: اطلاعات شخصی کاربران کمتر در معرض خطر قرار میگیرد و حریم خصوصی آنها بهتر محافظت میشود.
- کاهش هزینهها: با حذف واسطهها و کارمزدهای اضافی، هزینههای پردازش پرداخت کاهش مییابد.
- جلب اعتماد مشتریان: ارائه یک روش پرداخت امن و شفاف، اعتماد مشتریان را افزایش میدهد.
- حمایت از اقتصاد غیرمتمرکز: استفاده از این ابزار به تقویت اقتصاد غیرمتمرکز و کاهش وابستگی به سیستمهای مالی متمرکز کمک میکند.
چطور از بیتیسی پی سرور استفاده کنیم؟
برای استفاده از بیتیسی پی سرور به چند مرحله ساده نیاز دارید:
- راهاندازی سرور: ابتدا یک سرور شخصی یا فضای ابری تهیه کنید.
- نصب بیتیسی پی سرور: با استفاده از مستندات رسمی، نرمافزار را نصب و تنظیم کنید.
- اتصال به کیف پول: کیف پول بیتکوین یا لایتنینگ خود را به سرور متصل کنید.
- یکپارچهسازی با کسبوکار: ابزار را با فروشگاه آنلاین یا سیستم پرداخت خود ادغام کنید.
با وجود مستندات جامع و جامعه کاربری فعال، حتی کاربران با دانش فنی محدود نیز میتوانند از این نرمافزار بهره ببرند.
موارد کاربرد
بیتیسی پی سرور در انواع مختلفی از کسبوکارها قابل استفاده است:
- فروشگاههای آنلاین
- شرکتهای فریلنسری
- مراکز خیریه
- پلتفرمهای ارائه خدمات دیجیتال
جمعبندی
بیتیسی پی سرور یک ابزار قدرتمند، امن و رایگان برای پذیرش پرداختهای رمزنگاری است که به کسبوکارها امکان مدیریت مستقل تراکنشهایشان را میدهد. اگر به دنبال راهکاری برای کاهش هزینهها، حفظ حریم خصوصی و تقویت استقلال مالی هستید، این ابزار یک گزینه ایدهآل است.
منابع پیشنهادی:
برای اطلاعات بیشتر و نصب این ابزار، به وبسایت رسمی بیتیسی پی سرور مراجعه کنید\ btcpayserver.org
-
 @ a012dc82:6458a70d
2025-01-30 14:09:20
@ a012dc82:6458a70d
2025-01-30 14:09:20In the world of finance and politics, few topics have garnered as much intrigue and debate as Bitcoin. This cryptocurrency, emerging from the fringes of the internet, quickly captured the imagination of investors, tech enthusiasts, and politicians alike. Its promise of decentralization and freedom from traditional banking systems made it a hot topic in political circles, particularly in Canada. However, as quickly as it rose to prominence, Bitcoin has seemingly receded from the political spotlight.
Table Of Content
-
The Political Heyday of Bitcoin
-
The Turning Tide: Bitcoin's Decline in Political Relevance
-
The Regulatory Response and Industry Evolution
-
The Future of Bitcoin and Cryptocurrencies in Politics
-
Conclusion
-
FAQs
The Political Heyday of Bitcoin
The Surge of Interest
During its peak, Bitcoin was not just a financial asset but a symbol of technological progress and financial autonomy. Politicians, especially in Canada, were quick to recognize its potential. Figures like Conservative Leader Pierre Poilievre championed Bitcoin, seeing it as a tool to empower individuals and a hedge against inflation.
Bitcoin in Policy and Legislation
Bitcoin's rise in value and popularity led to serious discussions about its role in the economy and its regulation. Debates in parliament and committees centered around how to integrate cryptocurrencies into the national financial system, protect investors, and harness the potential of blockchain technology.
The Turning Tide: Bitcoin's Decline in Political Relevance
The Market's Volatility
The volatile nature of Bitcoin, marked by dramatic price fluctuations, began to cast doubts in the political arena. The peak value of over $80,000 was followed by a steep decline, shaking confidence in its stability as an asset.
Changing Political Narratives
As the market fluctuated, so did the enthusiasm among politicians. The once vocal advocates like Poilievre became less outspoken about their cryptocurrency holdings, reflecting a broader shift in the political narrative around Bitcoin.
The Regulatory Response and Industry Evolution
Government and Regulatory Bodies
The initial excitement around Bitcoin led to legislative efforts and regulatory discussions. However, the lack of concrete actions and clear policies from the government left the regulatory landscape ambiguous. Independent bodies like the Canadian Securities Administrators stepped in to fill the void with guidelines and notices.
Industry Persistence Amidst Political Apathy
Despite the reduced political interest, the cryptocurrency industry continued to evolve. Developers and entrepreneurs in the space kept innovating, pushing the boundaries of blockchain technology and exploring new applications beyond financial transactions.
The Future of Bitcoin and Cryptocurrencies in Politics
Lessons Learned and the Path Forward
The rise and fall of Bitcoin in the political arena offer valuable lessons about the intersection of technology, finance, and politics. It highlights the need for a balanced approach to new technologies, combining enthusiasm with prudent regulation.
The Ongoing Debate and Potential Resurgence
While Bitcoin may have receded from the immediate political discourse, the debate around cryptocurrencies is far from over. As the technology matures and stabilizes, it may once again find its way into political conversations, potentially reshaping the financial landscape in ways yet to be imagined.
Conclusion
Bitcoin's journey through the political arena has been a tale of rapid rise, intense debate, and a quiet exit. However, this is not the end of the story for Bitcoin or cryptocurrencies. As the technology evolves and the world adapts, these digital assets may yet redefine the boundaries between technology, finance, and politics. The quiet exit of Bitcoin from the political stage today may just be the prologue to a more significant role in the future.
FAQs
Why did Bitcoin become a topic in Canadian politics? Bitcoin garnered political interest due to its potential as a decentralized financial system, promising autonomy from traditional banking and a hedge against inflation.
Who were some of the political advocates of Bitcoin in Canada? Conservative Leader Pierre Poilievre was among the notable political advocates, promoting Bitcoin as a tool for financial empowerment.
What caused Bitcoin to lose its appeal in politics? Bitcoin's appeal waned due to its market volatility, the steep decline in its value, and shifting political narratives.
How did the government respond to Bitcoin's rise? The government's response involved discussions on regulation and integration into the financial system, but concrete actions were limited.
What is the future of Bitcoin in politics? While currently less prominent, the ongoing evolution of cryptocurrency technology may lead to Bitcoin re-entering political discussions in the future.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ f57bac88:6045161e
2025-01-23 17:45:27
@ f57bac88:6045161e
2025-01-23 17:45:27چرا باید بیتکوین را در کسبوکار خود بپذیرید؟
- افزایش مشتریان: بسیاری از افراد به دنبال کسبوکارهایی هستند که بیتکوین را به عنوان روش پرداخت قبول میکنند.
- کاهش هزینههای تراکنش: هزینههای تراکنش بیتکوین به طور قابل توجهی کمتر از روشهای پرداخت سنتی است.
- امنیت بیشتر: فناوری بلاک چین که بیتکوین بر روی آن ساخته شده است، امنیت بسیار بالایی را فراهم میکند.
- دسترسی جهانی: با بیتکوین، میتوانید مشتریانی از سراسر جهان داشته باشید.
- مقاومت در برابر تورم: ارزش بیتکوین مستقل از دولتها و بانکهای مرکزی است و در برابر تورم مقاوم است.

چگونه کسبوکار خود را برای پذیرش بیتکوین آماده کنیم؟
- تحقیق و بررسی: قبل از هر اقدامی، به خوبی در مورد بیتکوین، فناوری بلاک چین و مزایای پذیرش آن تحقیق کنید.
- انتخاب کیف پول: یک کیف پول بیتکوین امن و مناسب برای کسبوکار خود انتخاب کنید.
- انتخاب درگاه پرداخت: درگاه پرداخت بیتکوین به شما امکان میدهد تا پرداختهای بیتکوین را به صورت آنلاین دریافت کنید.
- آموزش کارکنان: کارکنان خود را در مورد نحوه پذیرش پرداختهای بیتکوین آموزش دهید.
- تبلیغات: مشتریان خود را از پذیرش بیتکوین در کسبوکار خود آگاه کنید.

مراحل گام به گام برای راه اندازی پرداخت با بیتکوین:
- ثبت نام در یک صرافی معتبر: برای خرید بیتکوین، ابتدا باید در یک صرافی معتبر ثبت نام کنید.
- خرید بیتکوین: پس از احراز هویت، بیتکوین مورد نیاز خود را خریداری کنید.
- انتقال بیتکوین به کیف پول کسبوکار: بیتکوین خریداری شده را به کیف پول کسبوکار خود انتقال دهید.
- انتخاب درگاه پرداخت: یک درگاه پرداخت بیتکوین مناسب انتخاب کنید و آن را به وبسایت یا فروشگاه خود اضافه کنید.
- آغاز پذیرش پرداخت: پس از تکمیل مراحل بالا، میتوانید پرداختهای بیتکوین را از مشتریان خود دریافت کنید.

نکات مهم:
- نوسانات قیمت: قیمت بیتکوین بسیار نوسان است. برای مدیریت این نوسانات، میتوانید از ابزارهای مدیریت ریسک استفاده کنید.
- امنیت: امنیت بیتکوین بسیار مهم است. از کیف پولهای امن استفاده کنید و به طور مرتب از آنها بکاپ بگیرید.
- مقررات: از قوانین و مقررات مربوط به ارزهای دیجیتال در کشور خود آگاه باشید.
از چه سرویس های میتوان استفاده کرد؟! برنامه ها و سرویس های بسیاری برای تبادل بیتکوین وجود دارن اما برای استفاده از این سرویس ها باید چند پیش شرط را در نظر گرفت: 1- سرویس فعالیت شفافی داشته، تا هر کسی بتواند آن سرویس و زیرساخت هایش را بررسی کند. 2- غیرمتمرکز باشد. 3- دسترسی آسان داشته باشد.
معرفی چند سرویس:
- درگاه پرداخت بیتکوین برای کسب و کارها "بیتیسی پی سرور" با این سرویس میتوانید درگاه پرداخت برای خریدهای آنلاین بسازید
- کیف پول برای نگهداری بیتکوین ها بر بستر لایتنینگ ولتآفساتوشی
- برای کسب و کارهای فیزیکی و پرداخت در محل میتوانید از "بریز" استفاده کنید، که میتوانید با این سرویس اقلام به همراه قیمت در برنامه مشخص کنید تا هنگام ثبت فاکتور چند قلم را انتخاب کرده و مبلغ پرداختی را محاسبه کنید.
نتیجهگیری پذیرش بیتکوین میتواند فرصتهای جدیدی را برای کسبوکار شما ایجاد کند. با پیروی از مراحل فوق، میتوانید به راحتی کسبوکار خود را برای پذیرش بیتکوین آماده کنید.
-
 @ 9e69e420:d12360c2
2025-01-30 12:23:04
@ 9e69e420:d12360c2
2025-01-30 12:23:04Tech stocks have taken a hit globally after China's DeepSeek launched a competitive AI chatbot at a much lower cost than US counterparts. This has stirred market fears of a $1.2 trillion loss across tech companies when trading opens in New York.
DeepSeek’s chatbot quickly topped download charts and surprised experts with its capabilities, developed for only $5.6 million.
The Nasdaq dropped over 3% in premarket trading, with major firms like Nvidia falling more than 10%. SoftBank also saw losses shortly after investing in a significant US AI venture.
Venture capitalist Marc Andreessen called it “AI’s Sputnik moment,” highlighting its potential impact on the industry.
![] (https://www.telegraph.co.uk/content/dam/business/2025/01/27/TELEMMGLPICT000409807198_17379939060750_trans_NvBQzQNjv4BqgsaO8O78rhmZrDxTlQBjdGLvJF5WfpqnBZShRL_tOZw.jpeg)
-
 @ 9e69e420:d12360c2
2025-01-30 12:13:39
@ 9e69e420:d12360c2
2025-01-30 12:13:39Salwan Momika, a Christian Iraqi known for burning the Koran in Sweden, was shot dead during a TikTok livestream in an apartment in Sodertalje. The 38-year-old sparked outrage in the Muslim community for his demonstrations, leading to global condemnation. After being rushed to the hospital, he was pronounced dead.
Authorities arrested five individuals in connection with the incident. Momika's death comes days before a court ruling on his possible incitement of ethnic hatred. The incident highlights the tensions surrounding free speech and religious sentiments, intensifying after his controversial protests in 2023.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ f57bac88:6045161e
2025-01-23 17:08:34
@ f57bac88:6045161e
2025-01-23 17:08:34دلایل ضرورت فعالیت ناشناس:
تهدید علیه حریم خصوصی: با توجه به گستردگی نظارت بر فضای مجازی در ایران، حریم خصوصی کاربران به شدت در معرض تهدید قرار دارد. اطلاعات شخصی کاربران مانند آدرس IP، تاریخچه جستجو و فعالیتهای آنلاین، بهراحتی قابل ردیابی و جمعآوری است. این اطلاعات میتوانند برای شناسایی و ردیابی کاربران و اعمال محدودیتهای بیشتر مورد استفاده قرار گیرند.
عدم امنیت سایبری: زیرساختهای سایبری در ایران به اندازه کافی قوی نیستند و حملات سایبری و هک شدن حسابهای کاربری به طور مکرر رخ میدهد. در صورت هک شدن حساب کاربری، اطلاعات شخصی و خصوصی فرد در معرض افشا قرار میگیرد که میتواند عواقب جبرانناپذیری داشته باشد.
نظارت و پایش فعالیتهای آنلاین: دولتها اغلب فعالیتهای کاربران را در شبکههای اجتماعی و بسترهای آنلاین زیر نظر میگیرند. این نظارت ممکن است شامل ردیابی ارتباطات، بررسی پستها و شناسایی افراد فعال در موضوعات حساس باشد. هرگونه اظهارنظر یا فعالیتی که مغایر با سیاستهای دولت باشد، میتواند منجر به عواقب جدی مانند احضار به نهادهای امنیتی، دستگیری و محکومیتهای قضایی شود.
حملههای سایبری: هکرهای دولتی یا وابسته به دولتها ممکن است به حسابهای کاربری افراد نفوذ کرده و اطلاعات شخصی یا حرفهای آنها را مورد سوءاستفاده قرار دهند.
چرا باید ناشناس بمانیم؟
استفاده از هویت ناشناس در اینترنت میتواند امنیت کاربران را به شکل چشمگیری افزایش دهد. ناشناس بودن به معنای استفاده از ابزارها و روشهایی است که هویت واقعی کاربر (مانند نام، شماره تماس یا موقعیت جغرافیایی) را پنهان میکند. این اقدامات به افراد اجازه میدهد بدون نگرانی از پیامدهای احتمالی، به بیان نظرات و فعالیت آنلاین خود ادامه دهند.
پیامدهای عدم توجه به فعالیت ناشناس:
خودسانسوری: ترس از عواقب بیان آزادانه افکار، کاربران را به سمت خودسانسوری سوق میدهد و از این طریق، اینترنت از تنوع آرا و نظرات محروم میشود. \ کاهش مشارکت مدنی: فعالیت ناشناس، به کاربران امکان میدهد تا بدون ترس از تبعات، در مباحث اجتماعی و سیاسی مشارکت کنند و نظرات خود را آزادانه بیان کنند. عدم توجه به این موضوع، مشارکت مدنی را کاهش داده و از شکلگیری یک جامعه مدنی پویا جلوگیری میکند. \ افزایش شکاف دیجیتال: افرادی که به دلایل مختلف قادر به حفظ ناشناس بودن خود در فضای مجازی نیستند، از بسیاری از امکانات و مزایای این فضا محروم میشوند و شکاف دیجیتال عمیقتر میشود.
راهکارها برای حفظ حریم خصوصی و فعالیت ناشناس:
استفاده از ابزارهای امنیتی: استفاده از ویپیان، پروکسی و مرورگر تر، به کاربران کمک میکند تا آدرس آیپی خود را مخفی کرده و از ردیابی فعالیتهای آنلاین خود جلوگیری کنند.\ رمزنگاری پیامها: استفاده از نرمافزارهای پیامرسان رمزنگاری شده، به کاربران امکان میدهد تا ارتباطات خود را ایمن و محرمانه نگه دارند.\ ایجاد حسابهای کاربری با اطلاعات غیرواقعی: از نامهای مستعار و ایمیلهای ناشناس برای ایجاد حسابهای کاربری استفاده کنید.\ حفظ حریم خصوصی در شبکههای اجتماعی: کاربران باید تنظیمات حریم خصوصی خود را در شبکههای اجتماعی به دقت بررسی کرده و اطلاعات شخصی خود را به حداقل برسانند.\ آموزش آگاهی دیجیتال: آموزش آگاهی دیجیتال به کاربران، به آنها کمک میکند تا با تهدیدات موجود در فضای مجازی آشنا شده و روشهای مقابله با آنها را یاد بگیرند.\ اجتناب از اشتراکگذاری اطلاعات حساس: از به اشتراکگذاری اطلاعاتی که میتواند هویت واقعی شما را فاش کند، خودداری کنید.\ فعالیت در پلتفرمهای امنتر: استفاده از پیامرسانها و شبکههای اجتماعی با رمزنگاری قوی، میتواند به محافظت از اطلاعات کمک کند.
نتیجهگیری
در فضای مجازی که روز به روز نظارت و محدودیتها افزایش مییابد، فعالیت با هویت ناشناس نه تنها یک ضرورت بلکه یک ابزار اساسی برای حفظ آزادی بیان و امنیت شخصی است. هر کاربر باید آگاهانه و هوشمندانه به فعالیت در اینترنت بپردازد تا از خطرات احتمالی جلوگیری کند.
### \ پی نوشت مهم
در ایران سالانه تعداد بسیاری از انسان های نیک سرشت به دلیل عدم رعایت ناشناسی یا عدم رعایت نکات امنیتی و فعالیت های انسانی که دیکتاتوری جمهوری اسلامی با آنها مخالف است با خطرات جانی، مالی و اتفاقات ناگوار جبران ناپذیری روبرو میشوند مانند سگارو، پس لطفا بخاطر خودتان و عزیزانتان ناشناس شروع کنید، ناشناس فعالیت کنید و ناشناس بمانید

-
 @ 6871d8df:4a9396c1
2025-01-18 20:12:46
@ 6871d8df:4a9396c1
2025-01-18 20:12:46## 2024 Prediction Reflections
Politics
Democrats & 2024 Election
- “Democrats’ attempt to stifle democracy will likely put Trump in the White House. If not, some real sketchy stuff would need to happen to keep him out.”
This prediction was exactly right. The assassination attempt on Trump seemed to be the final blow for the Democrats. Despite a heavy push my legacy media, Trump won handily.
The Democrats switched to Kamala Harris after Biden showed signs of incapacity, most notably in the first debate against Trump.
My prediction for the election also turned out to be exactly right, which, thank you Robert Barnes and Richard Baris.
Evidence of Institutional Ideological Capture
- “People will continue to wake up to ideologically captured institutions, and DEI will be the main loser.”
Trump’s resounding election victory underscores that the public is increasingly aware of (and rejecting) such institutional capture.
Of note, Boeing comes to mind as an institution that had a tough time in 2024, in large part to DEI. Nothing seemed to function correctly. The biggest story being how they stranded people in space
Media & Public Opinion
Rise of Independent & Alternative Media
- “Independent and alternative media will continue to grow as people’s trust in legacy media declines.”
Twitter (X), under Elon Musk, shattered mainstream media’s influence far more than expected. As Elon has said, “You are the media now.” Alternative sources are king. - Notable Example: Kamala Harris’s decision not to appear on the Joe Rogan podcast contrasted with Trump’s appearance, further highlighting the power shift to alternative media.
Markets & IPOs
Interest Rates & Public Markets
- “As interest rates come down, I expect public markets and IPOs to heat up.”
This did not play out. Companies that were expected to go public in 2024 remain private in 2025. The reasons are varied, but there is confidence that 2025 might see changes.
Technology & AI
LLMs & AI Adoption
- “AI and LLMs will continue to move at a rapid rate, increasing productivity. Tools like Bard will become more mainstream.”
AI did take off. Usage among nontechnical users increased, and it’s no longer uncommon for people to default to AI-driven tools rather than Google search.
Decentralized AI
- “I hope to see a rise in decentralized AI to counter big-player LLMs.”
We didn’t see explicit ‘decentralized AI’ breakthroughs, but more players entered the AI market. ChatGPT still dominates, with Elon’s ‘Grok’ making moves. Google, Meta, and Microsoft remain active but slightly behind in usage.
Bitcoin & Digital Assets
Institutional Adoption of Bitcoin
- “2024 will bring more institutions to Bitcoin. Possibly another large company or nation-state. The ETF should help, likely pushing BTC to a new all-time high.”
No large public company or nation-state placed a bet, but smaller public companies did. Michael Saylor presented to Microsoft’s Board, which was the closest instance to a major move.
- Price Movement: Bitcoin did hit a new all-time high, rising to as much as $108k in 2024.Lightning Network
- “Lightning will improve but remain primarily used for acquiring Bitcoin, not everyday payments.”
Still true. Lightning usage remains tiny relative to broader Bitcoin adoption.
Nostr Adoption
- “Nostr will grow, and we’ll see new companies leverage this network beyond just social media.”
Growth continues, but Elon Musk’s Twitter takeover slowed adoption. Nostr will remain niche until a major catalyst occurs (e.g., a big player joins or forced usage due to censorship).
Stablecoin-Specific Regulations
- “Expect stablecoin regulations in 2024 that’ll be favorable to them.”
This didn’t happen, largely due to the administration’s hostility. Expect potential change in 2025.
Miscellaneous 2024 Reflections
- Return to Sanity
- 2024 felt like sanity prevailed, largely due to the Democrats’ collapse behind Biden and Harris and Elon’s Twitter dominance.
- Operation Chokepoint 2.0
- Received a lot of attention, and I’m thankful it did because my experience at Strike was radicalizing and extreme.
- Bryan Johnson & Anti-Aging
- He burst onto the scene with his obsession over biomarkers. I see it as misguided—chasing markers in isolation doesn’t automatically yield a healthy system.
- Apple’s Rough Year
- Without a visionary leader, Apple appears to be scraping by on existing products rather than innovating.
- Google Under Fire
- Google is in a tough fight with the government, just as it seems they’re on their heels with AI competition.
2025 Predictions
-
Bitcoin’s Performance Bitcoin will have a good year, but not better than 2024. To beat 2024, it must close above 206k on December 31, 2025. I’ll take the under on that.
- I am not ruling out it to be over that at some point in 2025.
-
Twitter’s Success Continues to Stunt nostr
- Nostr adoption will stay slow due to Elon’s dominant influence with X (Twitter).
- As long as it remains a beacon of free speech, I doubt we see an exodus.
-
Rumble integrating Tether might help if they allow Nostr-like features (zaps), but that seems unlikely.
-
Apple
-
Apple will continue its rent-seeking behavior and put out underwhelming products.
-
Google’s Quantum & AI
- Recent buzz about Google’s quantum chip and AI improvements won’t pan out as a big deal.
-
Google will continue to trail OpenAI and xAI in practical LLM usage.
-
Elon, Vivek & DOGE
-
I expect them to deliver more than critics think. They’ll expose bloat and inefficiencies in ways that will shake up norms. I greatly welcome this. I wouldn’t bet against them.
-
Mainstream Media Reckoning
- In Trump’s second term, mainstream news outlets will face a real reckoning, as I can’t see how their bias can continue.
- They’ll have to reduce their bias or risk bankruptcy.
-
Alternative media’s growth trend continues, especially as Twitter keeps exposing mainstream outlets’ weaknesses.
-
RFK Delivers
-
We will see big changes in the health space due to RFK at HHS. These are changes that I am very excited to see.
-
Foreign Policy
- With the transition to Trump, I expect some foreign policy wins that will buck the establishment but will deliver wins that are not thought possible by the “experts.”
Closing Note
- Overall 2024: It was a year of major political upheaval, vindication for Bitcoin, and continued AI advances.
- Outlook for 2025: Bitcoin remains strong, AI competition heats up, and media institutions face existential challenges. I’m optimistic for continued decentralization and a more level playing field across tech, finance, and politics. I think the start of Trump’s second term will be very strong for the market, health, and culture. Accelerate.
-
 @ e262ed3a:e147fbcb
2025-01-30 11:26:25
@ e262ed3a:e147fbcb
2025-01-30 11:26:25
I got an idea while watching a video from @BTCSessions, which I personally cannot implement technically. Therefore, I would like to present it here for discussion and free implementation. It makes sense to me, but what do I know? Let the swarm intelligence decide.
The goal of the business idea is:
- How can I bring as many solo miners as possible into a pool without them having to pay for the electricity for mining and their mining hardware can be amortized quickly, so they can purchase more mining hardware?
- How can we financially support Bitcoin and Nostr developers in the long term?
- How can we intensify developers for the implementation of this idea?
- How can we encourage non-Bitcoiners to invest in the support of the Bitcoin network?
- How can we get non-Bitcoin retailers to invest in the Bitcoin network?
The answer is: PROSPECT OF WINNING
The solution lies in a kind of RAFFLE. (Not a betting website)
The legal difference between a BET and a RAFFLE varies from country to country. It lies in the fact that a raffle must be very transparent regarding the chances of winning and the proceeds must go to a good cause. Those involved in the implementation can, of course, be compensated (also with a profit for the individual participants). The extent to which this is allowed would have to be checked by those who want to implement this idea.
In the following, I will describe the implementation roughly. Since this is not a sales presentation, please excuse me if the following proposal is not fully structured.
Participants in the idea are:
- Consumers (ticket buyers)
- Bitcoin miners
3) Retailers 4) Non-profit company that implement the project
What's it about? @BTCSessions has a YouTube video about the miner FutureBit. In the dashboard of the solo miner, you could see how high the hash rate was. But above all, you could see how high the chance of winning was for the solo miner in the overall network. In the case of BTCSessions FutureBit, the hash rate was around 5 TerraHash and the chance of winning was around 1:1,000,000. (Which, according to my calculations, was not correct). The power consumption was around 32 watts. When I saw that, it suddenly dawned on me.
Could it be possible to create a website/app that determines the total hash rate of a mining pool and then offers an electronic, numbered ticket for each 1 TerraHash (TH/s) of the pool for, for example, 0.1 USD? The minimum purchase amount would be 10 tickets. The customer sees the chance of winning and could even see the possible payout. The ticket is only valid for the next block (similar to roulette).
Another variant could be that the buyer can select one or more of the next 10 blocks and purchase tickets for the selected block. Since you don't know in advance how high the pool hash rate will be 5 or 10 blocks ahead, the amount of tickets to be issued for the 2nd block, for example, could only be 90% of the current pool hash rate, the 3rd block only 80%, and so on. If block 3, for example, advances to position 2, the previously unavailable 10% will be released for further tickets. (Determined by the pool hash rate at that time)
The purchase of 10 or more tickets could be automated in the customer's account on the website/app (intervals: hourly, daily, weekly, every 10 blocks, etc.). Customers could also top up their account with satoshis, enabling automatic deductions for ticket purchases. This could be facilitated by automatically issuing a Nostr npub to each customer, which would also create a wallet at Primal.net (Strike). For non-Bitcoiners, Zaprite could be used to recharge their account. Alternatively, customers could enter a NostrWalletConnection NWC to enable automatic deductions from their Lightning wallet. The project operators might also consider running their own ecash mint, which would allow them to assign an integrated ecash address to customers without a Lightning address. Tickets with ascending numbers would be allocated strictly in the order of payment receipts.
Calculations for the miners: The FutureBit miner consumed approximately 30 watts per terahash/hour. Let's assume that 10 terahash consume 300 watts per hour, then the miner consumes 50 watts per 10 minutes (per block). Let's further assume that a kilowatt-hour of electricity costs between 10 and 30 cents, then it costs the miner 3-9 cents per hour for electricity at 10 terahash mining capacity. So, 0.5-1.5 cents per block. In the case that each ticket is sold for 1 terahash for the next block, one could automatically transfer, for example, 5% of the satoshis received from ticket sales to each participating miner in the pool (proportional to the average hash rate delivered by the miner in the last block in the pools). This happens even if the block is not found. If fewer tickets are sold than the maximum possible amount, then the 5% of the sold tickets will be distributed proportionally. (See also my Excel file?
At the center of the project is a website/app that manages the raffle. Here, anyone can register and create an account. Either as a miner, retailer, or customer with or without KYC, for example, with their own nostr nsec, wallet signature, email and password or phone number and password.
Once logged into the account, Bitcoiners can enter their Lightning address and a Bitcoin on-chain address. Non-Bitcoiners enter their financial data in case they win.
Miners must enter a Bitcoin and Lightning (or ecash) address. The pooling process is also managed in the miner's account.
Tickets can be purchased (like in a regular online shop) and paid for in any way. Zaprite could be a solution here. But also Strike, Cashapp, etc. As described above, such purchases could also be automated.
Retailers can also register as such. They will then have the opportunity to sell "tickets" to their customers and collect the money in cash. To sell tickets, they must enter the customer's name and a valid email address. After payment, they must send the purchase price via Lightning to the non-profit company, which will then confirm the purchase to the ticket buyer and the retailer with all the data. This is the receipt for the buyer. In the event of a win (the mined block must have 3-6 block confirmations), the ticket buyer will receive an email explaining all the further details of how to claim the prize. This could be a link that takes them directly to the website and logs them in directly. The winner can then enter their data on how and where the money should be paid out (Bitcoin address or bank details). Alternatively, they can go to their retailer, who can assist them by entering the data in their sub-account (customer account). To prevent the retailer from falsifying the data entry, the winner will first receive an email with the entered data, which they can confirm (if correct). Since the retailer is also involved in the win, they will also be notified.
How many tickets can be offered per round (Bitcoin block)? The number of tickets depends on the hash rate in the pool. One ticket can be issued per 1 TerraHash (TH/s). How the ticket is generated per round and customer, I don't know, as I lack the technical knowledge. Maybe as a kind of NFT that contains the corresponding data (customer number (npub) of the buyer and possibly retailer, block number, ticket number). Or as a Taproot asset on Lightning? Or as a minted ecash coin? Or simply as an entry in a database that the customer can see in their account.
The maximum payout of the winnings in the event of a found block to the ticket holders could be 70%. The remaining 30% would be distributed to the miners and retailers. For example: Miners 25%, retailers 5%. The non-profit organization receives nothing from the block rewards. Instead, it receives 65% of the revenue from all ticket sales. With a mining pool hash rate of 10,000 TH/s, where all tickets are sold continuously, a daily donation of around 93,000 USD would be generated. (see Excel.file)
The revenue, after deducting the possible costs of the organization, goes directly to @opensats and/or other organizations that support the Bitcoin network after each block. Either via Lightning or Bitcoin on-chain payment.
In the attached Excel file, you can find my calculations. Here, anyone can play through different scenarios.
What I noticed was that with maximum ticket sales per block, only around 200 USD per 10 tickets would be paid out, since each participating ticket wins in the event of a found block. Since I believe that this is not a very great incentive for buying tickets, I suggest the following variants.
Winning variants: Each purchased ticket has a running number. Ticket 1 has the number 000.000, ticket 2 has the number 000.001, ticket 10.120 has the number 010.119, and so on.
If the next block is found, then this found block in the Bitcoin blockchain has a hash. For example, block 881367 has the hash 000000000000000000014b0fab24355c71c6940584d9cd5990c0b081a31d54a4
Let's now remove the letters and read only the numbers from back to front, so the last 3 numbers are 544
Instead of every participating ticket winning, in this variant, only the tickets with the ending digits 544 win.
With, for example, 11,000 tickets sold, the ticket numbers 000.544 / 001.544 / 002.544 ... 010.544 would win. So, 11 ticket participants would win. Each winner with this number would receive around 0.284 Bitcoin (3.125 BTC / 11).
One could also let the ticket numbers with the ending digits 44 win, and thus every hundredth ticket. Or even combine it.
What I also noticed was that with retailers, a special case arises. Retailers receive 5% of the block rewards in the event of a found block. But only proportionally to the tickets sold by the retailer. This means that in order for the entire 5% to be distributed to the retailers, all 10,000 tickets of 10.000 possible tickets would have to be sold by retailers. Since not all tickets will be sold by retailers, a remaining amount will be left over. This could be distributed additionally to the miners. Or any other variant.
I hope the idea finds resonance and invites discussion. Maybe I've made some mistakes in thinking, and the idea is not feasible. But if you like the idea, please forward it to developers, investors, and others you know.
Best regards.
@nostr:undefined dewe
-
 @ f1989a96:bcaaf2c1
2025-01-23 14:40:18
@ f1989a96:bcaaf2c1
2025-01-23 14:40:18Good morning, readers!
In Iran, officials are accused of exploiting a recent currency devaluation to profit at the public’s expense. The regime raised the rial’s official exchange rate from 550,000 to 640,000 per dollar to maximize its profit when selling the $5 billion it had withdrawn from the National Development Fund. This move effectively stole one quadrillion rials ($23 billion) from citizens, fueling inflation and devastating the public’s already-slim purchasing power.
In Nicaragua, dictator Daniel Ortega dissolved 15 more nonprofit organizations since the start of the year. This brings the total to more than 5,400 NGOs shut down since 2018. Ortega frequently uses financial repression to wield power over citizens, freezing bank accounts, seizing assets, and fabricating financial crimes to dismantle civil society groups.
In open-source software news, Solo Satoshi, a company advancing home Bitcoin mining, unveiled the Bitaxe Touch, a new home mining device designed for individuals to mine Bitcoin. It features a touch screen that displays mining metrics, network data, and Bitcoin news. Innovations like this help democratize access to mining and strengthen the overall Bitcoin network, making an especially big difference for people who wish to mine in difficult political environments. \ \ Meanwhile, Bitcoin developers are exploring rewarding mining pool participants with ecash shares. This model lets miners receive earnings instantly and trade them on open markets without revealing personal details. This could make mining more attractive for dissidents whilst helping strengthen Bitcoin’s overall decentralization.
Finally, we feature the release of Evan Mawarire’s book “Crazy Epic Courage,” in which the Zimbabwean pastor and activist recounts his inspiring journey of a peaceful uprising against Robert Mugabe’s dictatorship and hyperinflation. We also include a Bitkey wallet tutorial from renowned Bitcoin educator Ben Perrin, aka BTC Sessions, who walks users through setting up cold storage and best practices for safe transactions.
Now, let’s get right to it!
SUBSCRIBE HERE
GLOBAL NEWS
Iran | Regime Profiting From Currency Devaluation
In Iran, Hossein Samsami, a member of the parliament’s economic committee, accused the government of exploiting foreign currency exchange rates to profit at the expense of ordinary citizens. The regime recently increased the rial’s official exchange rate from 550,000 to 640,000 rial per dollar — a move Samsami explained “was to sell the $5 billion it had taken from the National Development Fund at the highest price.” By manipulating the exchange rate, the regime effectively stole one quadrillion rials ($23 billion) from citizens. This deliberate devaluation will drive up inflation, deplete savings, and push basic goods further out of reach. Iran’s multi-tiered exchange rate system has long fueled corruption, allowing regime insiders to profit from the gap between the artificially low official exchange rate and the higher free-market rate. To block any financial escape, the regime has tried to close onramps to Bitcoin.
Nicaragua | Regime Dismantles More Nonprofit Organizations
Since the start of 2025, the Nicaraguan regime dissolved an additional 15 nonprofit organizations (NGOs), including Save the Children and the Dominican Nuns Foundation of Nicaragua. This latest wave of repression brings the total to more than 5,400 NGOs shut down since 2018 under dictator Daniel Ortega. Ortega uses financial repression as a weapon, freezing bank accounts, seizing assets, and fabricating financial crimes to dismantle these groups. Deprived of resources and funding, these organizations are forced to close, leaving vulnerable communities without aid. These crackdowns come as part of Ortega’s broader strategy to stifle dissent, dismantle civil society, and consolidate his grip on Nicaragua.
Nigeria | Political and Bitcoin Activist Faces Regime Censorship
James Otudor, an activist and founder of Bitcoin Calabar, a Nigerian Bitcoin circular economy, described what he believes is a deliberate campaign to silence his Bitcoin advocacy. After filing a lawsuit against the Nigerian regime to defend citizens’ rights to own, use, and trade Bitcoin, Otudor was interrogated by the Department of State Security (DSS) about his funding sources and financial activities. Despite providing proof of legitimate earnings, he reports facing a series of suspicious and coordinated attacks — including the theft of his lawyers’ documents, the suspension of his social media accounts, and disruptions to his phone and internet services. These actions represent the extent to which authoritarian regimes like Nigeria will go to block financial tools that operate beyond their control.
United Arab Emirates | AI Ambitions and Authoritarian Control
The United Arab Emirates (UAE) is accelerating its bid to lead the global artificial intelligence race, with reports suggesting that intelligence chief Sheikh Tahnoun is in talks with the United States to acquire NVIDIA’s proprietary AI chips. At the center of this push is G42, an AI conglomerate heavily invested in data analytics, satellite imagery, and predictive surveillance. These technologies enable the UAE to expand domestic surveillance and control to suppress dissent with unprecedented precision. As an authoritarian regime with an appalling human rights record, the UAE has long used technology to surveil activists, journalists, and civil society. Now, it aims to take surveillance and repression to new heights.
Uganda | Civic Group Calls for the End of Trials of Civilians in Military Courts
On Wednesday, Jan. 15, Agora Discourse, a civic group co-founded by activist and Oslo Freedom Forum speaker Agather Atuhaire, launched a Change petition calling for the end of trials of civilians in military courts in Uganda. The next day, police officers harassed and roughed up Agather Atuhaire as she delivered a physical copy of the petition, addressed to Chief Justice Owinyi Dollo, at Uganda’s Supreme Court in the capital, Kampala. Alongside this physical repression, Uganda employs financial repression — freezing the bank accounts of civil society organizations to diminish civilian voices and their right to association and organization. This petition aims to rally international pressure against the regime’s practice of using military courts to target dissidents. If you have a moment, please consider reviewing and signing the petition here.
RECOMMENDED CONTENT
“Crazy Epic Courage” by Evan Mawarire
Zimbabwean pastor and activist Evan Mawarire never set out to become a revolutionary — he simply wanted to speak the truth. But when a video of him draped in a Zimbabwean flag went viral, it ignited a nationwide movement that would challenge Robert Mugabe, one of Africa’s longest-standing autocrats and a thief who looted Zimbabwean wealth via hyperinflation. In his newly released book, “Crazy Epic Courage,” Mawarire details how an ordinary citizen can become the voice of a nation. From arrests and exile to global advocacy, his journey is a testament to risking everything for what is right. Read the full book here.
BITCOIN AND FREEDOM TECH NEWS
This week’s Bitcoin news focuses on Bitcoin mining updates. To learn more about Bitcoin mining, we recommend checking out this explainer article and video.
Mostro | Implements Key Management to Boost Privacy
Mostro, a peer-to-peer (P2P) Bitcoin exchange built on Nostr, introduced advanced key management to improve user privacy. Created by Venezuelan developer Francisco Calderon, Mostro — specifically designed to aid people under tyranny — enables individuals to buy and sell Bitcoin without sharing excessive personal information. This adds another layer of privacy critical for human rights defenders, journalists, and nonprofits operating under authoritarian regimes. As a past recipient of HRF’s Bitcoin Development Fund, Mostro continues to advance private Bitcoin access for those who need it most.
Bitcoin Safe | New Bitcoin Wallet Designed for Non-Technical Users
Bitcoin Safe is a new open-source Bitcoin wallet designed to make self-custody simple even for non-technical users, something that really comes in handy for human rights activists. The wallet guides users through the setup process, with step-by-step instructions for both single-signature (where one private key is used to control your Bitcoin) and multi-signature wallets (which require multiple private keys for added security). Bitcoin Safe also includes features to manage Bitcoin efficiently, such as automatically combining unused Bitcoin (known as Unspent Transaction Outputs or UTXOs), speeding up stuck transactions with fees (known as Replace-By-Fee or RBF), and letting users choose specific coins to spend. With support for more than 10 languages, Bitcoin Safe can lower the barriers to self-custody.
Solo Satoshi | Introduces Bitaxe Touch
Solo Satoshi, a company advancing home Bitcoin mining, unveiled the Bitaxe Touch, the first Bitcoin home miner with a built-in touchscreen. Scheduled for release in early 2025, the device enables users to monitor key metrics, including Bitcoin’s price, mining performance, power consumption, incoming transactions, and real-time temperature data. It also features a Bitcoin news feed, offering a comprehensive overview of the mining experience. Built using an open-source Bitaxe 601 Gamma, the Bitaxe Touch is designed to simplify Bitcoin mining for individuals. By empowering more people to mine Bitcoin independently, devices like this reduce reliance on large mining pools, strengthening Bitcoin’s decentralization and resistance to censorship.
Mining Pools | Rewarding Miners with Tradeable Ecash Shares
Bitcoin developers are exploring a new way to reward miners using tradeable “ecash shares.” In Bitcoin mining, individuals often join “mining pools” — groups of Bitcoin miners that work together to verify transactions, solve blocks, and share rewards. They do so because pooling resources increases their chances of earning Bitcoin. However, miners in these pools can wait days or weeks for payouts (depending on the pools’ payout structure), and miners often suffer violations of their privacy. With ecash shares, miners could receive their earnings immediately and sell them on an open market (without having to reveal their identity, shielding them from a dictator’s watchful eye). This system could also make it easier for small mining pools to get started and grow. Smaller pools often struggle to attract miners because payouts are uncertain. By using ecash shares, these smaller pools could temporarily operate as clients of larger ones to ensure steady income in the early stages.
F2Pool | Monitoring Global Censorship Risks
Bitcoin developer b10c revealed that F2Pool, one of Bitcoin’s largest mining pools, may be filtering transactions. Over the past weeks, b10c’s miningpool-observer detected 15 transactions from certain addresses that were not mined in the first eligible block. While all transactions were eventually confirmed — proving the Bitcoin network’s overall censorship resistance — F2Pool appears to have excluded some despite negligible fee differences, raising concerns of potential censorship. Notably, no other pools filtered these transactions, revealing the strength of this decentralized software network. However, these observations warrant ongoing monitoring so that the public understands such risks before they metastasize.
Mi Primer Bitcoin | Releases 2025 Bitcoin Diploma
Mi Primer Bitcoin, a nonprofit advancing open-source Bitcoin education, released its updated 2025 Bitcoin Diploma. This 176-page open-source workbook serves as a 10-week educational program and is used by more than 56 projects in 30 countries. The diploma covers topics like the history of money, Bitcoin’s technical and practical applications, and its implication for financial freedom and human rights. The latest edition features enhanced infographics and refined content for improved clarity. Available in multiple languages, the Bitcoin Diploma is a powerful resource for fostering financial literacy and global Bitcoin adoption and is taught by civil society groups even under dictatorships like the one in Cuba.
RECOMMENDED CONTENT
Bitkey Wallet Tutorial by BTC Sessions
In this tutorial, renowned Bitcoin educator Ben Perrin (BTC Sessions) demonstrates how to set up and use the Bitkey hardware wallet on a mobile device. He guides viewers through the process of storing, sending, and receiving Bitcoin, with a focus on user-friendliness and secure practices. He also reveals secret techniques to make the most out of one’s hardware wallet. Don’t miss the full tutorial — watch it here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 5bdb0e24:0ccbebd7
2025-01-23 14:16:24
@ 5bdb0e24:0ccbebd7
2025-01-23 14:16:24Have you ever needed to reference a Linux command line tool's capabilities only to find out there is no manual page and that only the -h (--help) option is available?
Normally, this isn't a problem, but -h doesn't let you search for strings the way man does. That means, if you are trying to use a tool that is quite extensive, scrolling and sifting through the help option's results manually can be quite cumbersome.
The ffuf command is a good example of this, but this can be a problem for many other CLI tools out there.
Thankfully, I found a quick and easy way to search these help messages, and I feel so silly for not thinking of it sooner.
All you need to do is pipe the output of the -h message you are trying to reference into something like less:
ffuf -h | lessNow, after typing a forward slash (/), you can search throughout the -h message without manually scrolling through the whole thing, similarly to how you might search through a manpage.
I'm sure there are other ways to achieve this same result. But this is the one I have found works for me and that I will be using going forward.
If you know an even better way to achieve this, or you have any other underrated Linux command line tips and tricks, feel free to let me know.
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ fd78c37f:a0ec0833
2025-01-23 03:30:28
@ fd78c37f:a0ec0833
2025-01-23 03:30:28In this edition, we invited Nyirenda, a member of the nostr:npub1t4ljwhhg7zlxeahxwgmkwqmn4jjxxq8lzhyuzy0zvy23hq0sacxsdl9fvv community, to share his personal experiences in participating in the Bitcoin community, as well as the challenges the community has faced in its operations and the strategies used to address them.
YakiHonne: Today, we are honored to have a guest from Bitcoin Boma with us. Thank you for joining us. Before we dive in, I'd like to take a moment to introduce YakiHonne and share a bit about what we do. YakiHonne is a decentralized media client built on the Nostr protocol that enables freedom of speech through technology. It empowers creators to create their own voice, assets, and features. It also allows features like smart widgets, verified notes, and focuses on long-form articles. Now today we'll be exploring more about the Bitcoin community. Nyirenda, could you please briefly introduce yourself and tell us a bit about what you do?
Nyirenda:My name is Nyirenda. I'm part of the Bitcoin Boma Education Program and Bitcoin Boma Malawi. Bitcoin Boma Malawi is a coalition of Bitcoin enthusiasts who have come together to raise social, economic, and environmental awareness about Bitcoin in Malawi. Our long-term strategy involves engaging with various stakeholders, including the government, to work towards the legalization of Bitcoin.

YakiHonne: What sparked your interest in Bitcoin, and what motivated you to start a community around it?
Nyirenda: I first came across Bitcoin in 2016 through the news. Back then, its price had already surged to $16,000, which sparked my interest right away. Although the news warned that Bitcoin resembled a Ponzi scheme, I had already built a solid understanding of economic structures, having studied monetary history and the fractional reserve banking system. This gave me the background needed to appreciate Bitcoin. Nyirenda:I began my research journey with Andreas Antonopoulos's lectures and books, which deeply resonated with me. I was quickly drawn to the philosophy behind Bitcoin. Since then, my focus has been on engaging with others and teaching them about Bitcoin, especially within the context of Malawi. Nyirenda:In Malawi, our economic activities face numerous restrictions. The government controls the national fiat currency, limiting what we can do with it. For me, Bitcoin presents a solution to these issues. Today, I remain passionate about educating others about Bitcoin and exploring its potential to transform our economic situation.
YakiHonne: I witnessed the decline of traditional currencies and realized how Bitcoin could play a role in the future. It's truly fascinating to see how it can be implemented. Could you share how the community was formed, how you attracted members in the early stages, and what challenges you faced along the way?
Nyirenda:When I first started diving into Bitcoin, I felt like I needed a teacher. So, I printed a T-shirt that said "Bitcoin accepted here" and wore it whenever I went into town or public places. People would often look at me and ask, "Hey, what's Bitcoin?" I could then briefly explain what Bitcoin is and how it compares to the current fiat system. Nyirenda:Some people were really interested, to the point that we exchanged contacts and started connecting, and it was a great experience. But the turning point came when I saw a tweet from Bitcoin Boma. Someone tweeted about a conference/seminar being organized, in collaboration with Trezor Academy. When I saw this, I knew this was the place to be. So, last July, I met Grant, Ian Foster, and Nick Twyman, who were organizing the event.
 Nyirenda:After we introduced ourselves and started connecting, they said, "Hey, join us as part of our coalition, and let's see what we can do with Bitcoin, especially in education." That’s how things started moving forward. It's been an incredible journey because since then, we've managed to graduate about 12 to 15 students. One of the biggest things we’ve done so far is launching the first Bitcoin education course in Malawi, attracting over 120 people. Of course, only some of them are attending the classes, but so far, the progress has been great.
Nyirenda:After we introduced ourselves and started connecting, they said, "Hey, join us as part of our coalition, and let's see what we can do with Bitcoin, especially in education." That’s how things started moving forward. It's been an incredible journey because since then, we've managed to graduate about 12 to 15 students. One of the biggest things we’ve done so far is launching the first Bitcoin education course in Malawi, attracting over 120 people. Of course, only some of them are attending the classes, but so far, the progress has been great.

YakiHonne: So, what challenges did you face in attracting new members at that stage?
Nyirenda:The first challenge we face is the attitude and perception of Bitcoin. Bitcoin is a new technology and innovation. In a country where people are used to traditional currencies, there are many financial technologies emerging, including centralized coins. This has created challenges. When people hear about Bitcoin, many think of it as a Ponzi scheme. They believe it's a scam or a way to get rich quickly. What I've observed is that most people fail to understand the difference between Bitcoin and centralized currencies. To truly appreciate Bitcoin, they need to experience it. Setting up a custodial wallet and explaining a transaction to them can help. Nyirenda:The second challenge is that people think Bitcoin is too complicated, especially in Africa, and here in Malawi, where the IT and ICT infrastructure is still underdeveloped. I’d say 70% of the population doesn’t have access to the internet. Even in our education system, we don’t learn about computers. It’s mainly by luck if someone has access to a computer and a network, allowing them to appreciate the technology.
YakiHonne: It seems to be common in many countries, where people think Bitcoin is a quick way to get rich. They see it as a scam or a Ponzi scheme. It's a big challenge to get people to believe in Bitcoin as a currency, rather than just their local currency. This is a real barrier in many economies. What principles guide your community, and how do you maintain trust and reliability in discussions? Simply saying, how do you keep the trust of the people?
Nyirenda:I’ll start with Bitcoin BOMA and then extend it to the people we interact with. In Bitcoin BOMA, even though we’re a collaboration, we have clear objectives and a philosophy. Ultimately, we model Bitcoin’s decentralized nature because it allows everyone to participate. In our coalition, we encourage the free flow of ideas and regularly meet to discuss how best to promote Bitcoin education. We focus on its social, economic, and environmental aspects. We assign tasks to each other and work hard to achieve the results. Nyirenda:Malawi has great potential, especially in the energy sector, where we could mine Bitcoin, but we lose a lot of electricity during generation. There were attempts to convince government-run institutions to embrace Bitcoin. However, most of these institutions are controlled by the government, and getting into politics is necessary to convince policymakers. It’s been a challenge because government systems are centralized. There’s a hierarchy to follow, and sometimes, even if a minister understands Bitcoin, it takes a long time to get it approved in parliament and passed into law.This has been one of our ongoing initiatives. Nyirenda:When I go out and interact with people, especially Malawians, I try to explain the transparency of Bitcoin by showing how a decentralized ledger works and how it’s different from traditional systems. I also explain that Bitcoin is reliable and that mismanagement isn’t possible with a decentralized system. Nyirenda:In a country where people are educated in a certain way and believe in competition and power, I often remind them that absolute power corrupts absolutely. I tell them that Bitcoin offers a different space where decentralization allows for a fairer system and benefits everyone. That’s how I try to explain it in simple terms.

YakiHonne: how do you educate your members and keep them updated on Bitcoin development time-to-time?
Nyirenda:For me, learning about Bitcoin is a lifelong process, with always unanswered questions and gaps to fill. I often study, read, and keep an eye on the developments in the Bitcoin community, especially in the African Bitcoin community. My role model is Kenya, particularly how they are enabling people to use Bitcoin through the Tando project. I believe that the value of Bitcoin is not just about holding and waiting for the price to rise, but rather as a tool that can help liberate the world. Nyirenda:Bitcoin is not just about accumulating wealth; I focus more on its role as a tool in the free market. Therefore, I continue to learn, even though I'm not a technical expert and my background is not in this field. I have worked in education, so I apply those skills to better understand Bitcoin and how it works. Nyirenda:I gather information from various sources to understand how Bitcoin works. At the same time, I compare it with the traditional monetary system, as that’s where I began, and it's my foundational layer. As for the Bitcoin BOMA community, I’m happy to say that we have two members with a strong background in economics. We often share interesting content and sometimes engage in debates. We also share many links and videos, learning from each other. Nyirenda:Especially in the Bitcoin Diploma Education Program, I give explanations, and I have peers who help analyze my course content. We remind each other and point out areas that need improvement. We constantly update each other on our progress, ensuring that our activities remain relevant, which helps us continue to improve.

YakiHonne: Does Bitcoin Boomer collaborate with the broader Bitcoin ecosystem, and which partnerships have had the greatest impact so far?
Nyirenda:I'll start with our collaboration with Trezor Academy. Last year, this was one of the most significant partnerships for us in Malawi. Trezor Academy focuses on Bitcoin education, and they provided us with a lot of support. Thanks to this collaboration, we were able to organize a seminar and graduate about 10 to 15 students. It was a major achievement for us. Nyirenda:Additionally, one of our members attended the African Bitcoin Conference held in Kenya, which was a pivotal opportunity. He had the chance to interact with Bitcoiners from across Africa. There were special guests, including nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m and through this exposure, he met the core developers in Kenya and the Tando developers in South Africa. These collaborations have given us insight into what other Bitcoin communities are doing, especially in their projects. Nyirenda:We also had a speaker from Bitcoin Boma who participated in an event in El Salvador. We are working towards making Malawi a Bitcoin node, and he is actively fostering that effort. Big shoutout to Ian Foster for his dedication. He will also be attending a conference in South Africa this January as a guest speaker. These collaborations have been very impactful, and I’m confident that we’ll see the results of these interactions in the future.

YakiHonne: So what challenges has your community faced so far and how have you overcome them while maintaining integrity?
Nyirenda:One of the challenges we face is related to resources, especially when it comes to our learning sessions. We mainly rely on our own resources, and we understand that quality lessons require specific equipment. While we're working toward acquiring these resources, we’re also making the most of what we have. We've agreed to work with what we have, and we believe we can still achieve our objectives. Nyirenda:Another challenge is the attitude towards Bitcoin in Malawi. Most people entering the crypto space have a “get rich quick” mentality. They focus more on the outcomes rather than the learning process. Many crypto traders are primarily interested in exploiting the benefits of Bitcoin. This is a challenge, especially when trying to teach people that Bitcoin is not just about making a profit, but also about liberation. Changing the traditional fiat mindset to embrace this new path is not easy. Nyirenda:Additionally, many people believe that if they invest their time, they must get a return. This is one of the challenges we're currently dealing with. Financial literacy in Malawi still has a long way to go. While people are aware of how economic shocks, especially currency devaluation, affect them, they often act out of desperation. The market is psychologically driven, and people are constantly looking for shortcuts to protect their wealth. When Bitcoin is introduced, it often raises doubts and skepticism. Nyirenda:However, there is no moment of hatred. Instead, we see the growing energy within the community, even if it's just coming from the heart, extending a significant impact on others. There’s a lot of potential and many possibilities ahead. Despite the challenges, we remain hopeful and excited about the future.

YakiHonne: In addition to wearing T-shirts and sparking curiosity, what other methods have you adopted to promote Bitcoin, and what results have you seen?
Nyirenda:First of all, I want to mention the Bitcoin BOMA education diploma program that’s currently running. This is one of the most significant initiatives we have at the moment. We are doing our best to attract people to dive into our education program. So far, the results have been very positive, especially in terms of numbers. People are curious and realize that this is something worth learning. Some have even acknowledged that what they've learned in the traditional education system is very different from the exposure they get from the diploma program. I’d say that’s one of the biggest impacts we've had in promoting Bitcoin. Nyirenda:If we have sufficient resources, we plan to implement further actions such as putting up banners, promoting Bitcoin, and positioning Malawi as a Bitcoin hub. Malawi has great potential, particularly in the tourism sector, with many tourists visiting the country. If we display banners saying “We accept Bitcoin,” it would be appreciated by many people. Personally, I’ve been encouraging businesses to start accepting Bitcoin. Nyirenda:We also have a Bitcoin BOMA Twitter account where we advocate for Bitcoin. We engage in discussions and comment on trends. In the coming months, we plan to host spaces and aim to conduct them in our local language, so more people can appreciate and learn about Bitcoin.
YakiHonne: We’ve reached the end of today’s session, and I must say, you’re doing an incredible job at Bitcoin BOMA. Your personal and collaborative efforts are truly impressive. I’m confident that in the next few years, we’ll be visiting Malawi for a Bitcoin conference. It’s clear that Malawi is heading in the right direction with you leading the way.
-
 @ f7922a0a:82c34788
2025-01-17 23:06:56
@ f7922a0a:82c34788
2025-01-17 23:06:56Now that the 3rd Satellite Skirmish is complete I wanted to highlight some of the cool features on embrace.satskirmish.com
This is what the cutting edge of podcasting 2.0 looks like imo. Live video in an app that allows you to send sats to the artists in real time.
On the left hand side we have a Boost score borad that displays the total amount of sats that have come in during the show, live Boosts/Booastagrams as they come in, total amount of sats from each person Boosting and total amount sent from each app.
The middle is ovisaly the video of the band playing but with some graphics around it and Boost alerts that show up on the screen in the form of snow flakes for this one.
The righthand side is an IRC chat window that connects to an IRC server that the No Agenda community has used for 18+ years thanks to zoidzero++.

The bottom of the page is where things get cool. When you click the Boost the Crew button in the center you can send a Boost that gets split between everyone helping produce the show (hightlighted in yellow).


Each band also has their own Boost button so you can Boost them while they are playing or anytime you visit the page.


-
 @ da18e986:3a0d9851
2025-01-22 23:49:06
@ da18e986:3a0d9851
2025-01-22 23:49:06Since DVMs were introduced to Nostr in July 2023, we've witnessed remarkable growth - over 2.5 million DVM events (Kinds 5000-7000) and counting. Last fall, when Primal added custom feeds (Kind 5300 DVMs), we saw a 10x surge in DVM activity. To handle this growth, I've spent the last few months completely rewriting DVMDash.
The first version of DVMDash, still live at https://dvmdash.live, unfortunately uses full database table scans to compute the metrics. The code was simpler, but the computation ran on the database. This meant the only way to scale the system was to upgrade the database. Using managed databases (like AWS, Azure, Digital Ocean) beyond the lower tiers gets expensive quickly.
The other problem with the first version: it computes metrics globally (well... as global as you can get; there's no true global with Nostr). Global or all-time metrics aren't sustainable with a system that plans to analyze billions of events in the future (a long term goal for DVMDash). Especially metrics like the number of unique DVMs, Kinds, and Users. I spent more time than I care to admit on possible designs, and have settled on these design principles for now:
- Precise accurate metrics will only be computed for the last 30 days of DVM activity.
- At the turn of a new month, we will compute a snapshot of the last month's activity, and a snapshot per DVM and per Kind, and store them in a historical table. This way we can see what any given month in the past looked like from a bird's eye view with metrics like number of job requests, job results, a count of unique DVMs, kinds and users, which DVMs ran jobs on which kinds, etc. The monthly data will all be aggregate.
The goal of the new redesign is to support processing millions of DVM events an hour. Therefore we need to ensure we can horizontally scale the processing as the traffic increases. Horizontal scaling was the primary goal of this new redesign, and early results indicate it's working.
The new architecture for DVMDash uses a redis queue to hold events collected from relays. Then batches of events are pulled off of the queue by dvm event analyzers to compute metrics. Duplicating these analyzers is one way DVMDash can horizontally scale.
To see if increasing the number of dvm event analyzers improves speed, I ran a performance test on Digital Ocean using real DVM events collected from Jan. 1st 2024 to Jan 9th 2025, which includes more than 2.4 million events. The only difference between each run is the number of DVM event analyzers ranging from 1 to 6.

The first graph shows that adding more event analyzers has a significant speed improvement. With only one analyzer it took nearly an hour to process the 2.4 million events. With every added analyzer, there was a noticeable speedup, as can be seen in the graph. With n=6 analyzers, we were able to process all 2.4 million events in about 10 minutes.
When we look at the rate of processing shown in the second graph, we can see that we get up to 300k dvm events processed per minute when n=6, compared to just ~50k events processed when n=1.

While I did test beyond 6 analyzers, I found the sweet spot for the current infrastructure setup to be around 6 analyzers. This provides plenty of headroom above our current processing needs, which typically see less than a million events per month. Even at a million DVM events per day, DVMDash should be able to handle it with n=2 analyzers running. The most important takeaway is that DVMDash can now horizontally scale by adding more analyzers as DVM activity grows in the future.
The code to run these performance tests, either locally or on Digital Ocean (you'd need an API key), is in the dvmdash repo, so anyone can replicate these tests. There's a lot of nuance to scaling that I'm leaving out of this short article, and you can't get away from having to adjust database capacity (especially number of connections). The code for this test can be found in
experiments/test_batch_processing_scaling.pyand the code to produce the graphs is inexperiments/graph_batch_processing_scaling_data.py. For now this is still in thefull-redesignbranch, soon it will be merged intomain.The live version of dvmdash doesn't have these performance updates yet, a complete redesign is coming soon, including a new UI.
I've had my head down working on this rewrite, and couldn't move on to add new features until this was done. Thank you to the folks who made github issues, I'll be getting to those soon.
DVMDash is open source, please drop by and give us a feature request, bug report, pull request or star. Thanks to OpenSats for funding this work.
Github: https://github.com/dtdannen/dvmdash
Shoutout to nostr:npub12xeqxplp5ut4h92s3vxthrdv30j0czxz9a8tef8cfg2cs59r85gqnzrk5w for helping me think through database design choices.
-
 @ 35f3a26c:92ddf231
2025-01-22 20:48:34
@ 35f3a26c:92ddf231
2025-01-22 20:48:34Background
Most people non familiar with Bitcoin thinks that there its has not smart contracts capabilities, and that is incorrect, there are smart contract capabilities, and despite limited in comparison with other blockchain networks, those capabilities are evolving slowly but surely.
The support for smart contracts is done through its scripting language, Script, which allows developers to create complex conditions for transactions.
What can you do with Script? 1. time locks 2. multi-signature requirements 3. other custom logic
opcodes like OP_CHECKLOCKTIMEVERIFY (CLTV) and OP_CHECKSEQUENCEVERIFY (CSV) are used to build more sophisticated smart contracts, these opcodes enable features such as the Lightning Network, a key scaling solution for Bitcoin
back in 2021, the Taproot upgrade introduced Pay-to-Taproot (P2TR), in summary allows for more private and efficient smart contracts, in that soft fork more was added, in addition to Taproot, we got as well Schnorr signatures, which enables multiple signatures to be aggregated into a single signature, improving scalability and privacy and MAST (Merklized Abstract Syntax Trees) which reduces the size of complex smart contracts, making them more efficient, as an added value, this efficiency reduces the cost of transactions.
The Taproot upgrade has laid the foundation for the development of more sophisticated smart contracts on the Bitcoin network, and the use of covenants is an important part of this development.
What is Bitcoin Covenants?
It is a BIP (Bitcoin Improvement Proposal), BIP-347, assigned on April 24, 2024, which marks the first step towards reintroducing functionality removed from Bitcoin by its creator Satoshi Nakamoto in 2010. This proposal aims to bring smart contract functionality to Bitcoin as we see in other EVM networks.
The proposal’s developers authors names are Ethan Heilman and Armin Sabouri, now the community will debate its merits.
Here the link, in case you are curious:
https://github.com/bitcoin/bips/blob/master/bip-0347.mediawiki
It is worth to read the motivation section of the BIP, which reads:
“Bitcoin Tapscript lacks a general purpose way of combining objects on the stack, restricting the expressiveness and power of Tapscript. This prevents, among many other things, the ability to construct and evaluate merkle trees and other hashed data structures in Tapscript. OP_CAT, by adding a general purpose way to concatenate stack values, would overcome this limitation and greatly increase the functionality of Tapscript.
OP_CAT aims to expand the toolbox of the tapscript developer with a simple, modular, and useful opcode in the spirit of Unix. To demonstrate the usefulness of OP_CAT below we provide a non-exhaustive list of some use cases that OP_CAT would enable:
Bitstream, a protocol for the atomic swap (fair exchange) of bitcoins for decryption keys, that enables decentralized file hosting systems paid in Bitcoin. While such swaps are currently possible on Bitcoin without OP_CAT, they require the use of complex and computationally expensive Verifiable Computation cryptographic techniques. OP_CAT would remove this requirement on Verifiable Computation, making such protocols far more practical to build in Bitcoin.
Tree signatures provide a multisignature script whose size can be logarithmic in the number of public keys and can encode spend conditions beyond n-of-m. For instance a transaction less than 1KB in size could support tree signatures with up to 4,294,967,296 public keys. This also enables generalized logical spend conditions.
Post-Quantum Lamport signatures in Bitcoin transactions. Lamport signatures merely require the ability to hash and concatenate values on the stack. [4] It has been proposed that if ECDSA is broken or a powerful computer was on the horizon, there might be an effort to protect ownership of bitcoins by allowing people to mark their taproot outputs as "script-path only" and then move their coins into such outputs with a leaf in the script tree requiring a Lamport signature. It is an open question if a tapscript commitment would preserve the quantum resistance of Lamport signatures. Beyond this question, the use of Lamport Signatures in taproot outputs is unlikely to be quantum resistant even if the script spend-path is made quantum resistant. This is because taproot outputs can also be spent with a key. An attacker with a sufficiently powerful quantum computer could bypass the taproot script spend-path by finding the discrete log of the taproot output and thus spending the output using the key spend-path. The use of "Nothing Up My Sleeve" (NUMS) points as described in BIP-341 to disable the key spend-path does not disable the key spend-path against a quantum attacker as NUMS relies on the hardness of finding discrete logs. We are not aware of any mechanism which could disable the key spend-path in a taproot output without a soft-fork change to taproot.
Non-equivocation contracts in tapscript provide a mechanism to punish equivocation/double spending in Bitcoin payment channels. OP_CAT enables this by enforcing rules on the spending transaction's nonce. The capability is a useful building block for payment channels and other Bitcoin protocols.
Vaults [6] which are a specialized covenant that allows a user to block a malicious party who has compromised the user's secret key from stealing the funds in that output. As shown in OP_CAT is sufficient to build vaults in Bitcoin.
Replicating CheckSigFromStack which would allow the creation of simple covenants and other advanced contracts without having to pre-sign spending transactions, possibly reducing complexity and the amount of data that needs to be stored. Originally shown to work with Schnorr signatures, this result has been extended to ECDSA signatures.
OP_CAT was available in early versions of Bitcoin. In 2010, a single commit disabled OP_CAT, along with another 15 opcodes. Folklore states that OP_CAT was removed in this commit because it enabled the construction of a script whose evaluation could have memory usage exponential in the size of the script. For example, a script that pushed a 1-byte value on the stack and then repeated the opcodes OP_DUP, OP_CAT 40 times would result in a stack element whose size was greater than 1 terabyte assuming no maximum stack element size. As Bitcoin at that time had a maximum stack element size of 5000 bytes, the effect of this expansion was limited to 5000 bytes. This is no longer an issue because tapscript enforces a maximum stack element size of 520 bytes.”
The last update of the BIP was done on Sep. 8 2024 by Ethan Heilman
Controversy
The controversy revolves around two main camps:
- Those who want to preserve Bitcoin’s network for monetary transactions only, arguing that adding smart contract capabilities could introduce risks and complexity.
- Others who advocate for expanding Bitcoin’s capabilities to support a wider range of applications, seeing OP_CAT as a step towards enhancing the network’s utility.
Final Thoughts
Bitcoin have done what no other asset have done in history, neither gold, its success is clear, and now, that BlackRock is involved, “miraculously”, corporations and governments are getting on board and Bitcoin is not anymore only for criminals or “rat poison” or “is going to zero”.
But as all tech, improvements are important, if those improvements are done to secure more the network and to make it more robust, there will be little to none controversy, however, when those changes are aiming at adding new shinning features that would change Bitcoin into a network with similar features as Ethereum in terms of contracts that requires attention and debate, few questions come to mind:
- How will that change affect the security of the network?
- How that change will affect the blockchain usage?
- What is the projected impact over the fees per transaction if this change is approved?
- Will the impact create pressure for the block size increase discussion to come back to the table and with it a second war?
Looking into Ethan Heilman work and contribution to the Bitcoin ecosystem, I am inclined to believe that he has considered most of those questions.
Looking forward to observe the evolution of this proposal.
You liked the article? Make my day brighter!
Like and share!
Last but not least, the following link is an unstoppable domain, it will open a page in which you can perform an anonymous contribution to support my work:
https://rodswallet.unstoppable/
The link didn’t open?
To open the link you need to use a best in class browser that supports web3, two are recommended: Brave Browser and Opera Browser
-
 @ dd664d5e:5633d319
2025-01-09 21:39:15
@ dd664d5e:5633d319
2025-01-09 21:39:15Instructions
- Place 2 medium-sized, boiled potatoes and a handful of sliced leeks in a pot.

- Fill the pot with water or vegetable broth, to cover the potatoes twice over.
- Add a splash of white wine, if you like, and some bouillon powder, if you went with water instead of broth.

- Bring the soup to a boil and then simmer for 15 minutes.
- Puree the soup, in the pot, with a hand mixer. It shouldn't be completely smooth, when you're done, but rather have small bits and pieces of the veggies floating around.

- Bring the soup to a boil, again, and stir in one container (200-250 mL) of heavy cream.
- Thicken the soup, as needed, and then simmer for 5 more minutes.
- Garnish with croutons and veggies (here I used sliced green onions and radishes) and serve.

Guten Appetit!
- Place 2 medium-sized, boiled potatoes and a handful of sliced leeks in a pot.
-
 @ e1d968f7:5d90f764
2025-01-22 17:35:22
@ e1d968f7:5d90f764
2025-01-22 17:35:22When I first started escorting, I didn’t fully grasp the importance of planning for the future. At first, it was all about meeting clients, handling inquiries, and navigating the emotional challenges. But as time passed, I realised this wasn’t just a job—it was a stepping stone for building a secure and fulfilling life.
The Meaning of Investment
Investing in myself doesn’t only mean financial planning (though that’s a big part of it). It also means dedicating time and energy to personal growth, self-care, and education. This job has taught me that my body, mind, and skills are my most valuable assets, and I need to nurture them.
- Financial Security: The unpredictability of this work makes financial planning essential. I’ve set up savings goals, started learning about investments, and ensured I have a safety net. My future self will thank me for every penny I’ve saved.
- Skill Development: Escorting offers a unique skill set—communication, emotional intelligence, and business acumen. I’ve looked into courses and certifications to expand these skills further, knowing they’ll benefit me long after I leave the industry.
Self-Care as an Investment
Taking care of myself is more than a necessity; it’s a form of self-investment. When I prioritise my health, happiness, and well-being, I can show up as my best self for my clients and for my personal goals.
- Health First: Regular check-ups, a healthy diet, and fitness routines are non-negotiable. This isn’t just about looking good but feeling good and staying strong in the long run.
- Mental Wellness: Therapy and mindfulness practices help me process the emotional ups and downs of the job. Protecting my mental health ensures I stay resilient and focused.
The Bigger Picture
I’ve started to think long-term. What do I want my life to look like in five, ten, or even twenty years? Escorting is a chapter, not the whole story. I’m exploring passions, hobbies, and potential career paths that align with who I am and who I want to become.
- Diversifying Income: Beyond savings, I’m exploring other revenue streams, like investments or side projects. It’s empowering to know that my financial stability doesn’t depend on just one source.
- Future Aspirations: Whether it’s furthering my education, starting a business, or simply achieving a sense of independence, having goals keeps me motivated.
Empowerment Through Planning
Investing in myself has transformed how I view my work and my life. This isn’t just about surviving today; it’s about thriving tomorrow. Every hour I put into improving myself, every pound I save, and every skill I hone is a step toward a brighter, more secure future.
Conclusion
The escorting world can be unpredictable, but by investing in myself and my future, I’ve found a sense of stability and purpose. It’s not just about what I do today but about setting myself up for the life I want tomorrow. Each day is an opportunity to grow, build, and prepare for the next chapter.
Rebecca x
-
 @ eee391ee:8d0b97c2
2025-01-22 16:42:17
@ eee391ee:8d0b97c2
2025-01-22 16:42:17Amber 3.1.9
- Add missing logs for relay errors
- Change listen for new connections button text and icons
Download it with zap.store, Obtainium, f-droid or download it directly in the releases page
If you like my work consider making a donation
Verifying the release
In order to verify the release, you'll need to have
gpgorgpg2installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:bash gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6DOnce you have his PGP key you can verify the release (assuming
manifest-v3.1.9.txtandmanifest-v3.1.9.txt.sigare in the current directory) with:bash gpg --verify manifest-v3.1.9.txt.sig manifest-v3.1.9.txtYou should see the following if the verification was successful:
bash gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03 gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>"That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:
bash cat manifest-v3.1.9.txtOne can use the
shasum -a 256 <file name here>tool in order to re-compute thesha256hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly. -
 @ 7ed7d5c3:6927e200
2025-01-08 17:10:00
@ 7ed7d5c3:6927e200
2025-01-08 17:10:00Can't decide if the terrible book you just read is a 1 or 1.5 star book? Look no further than this chart. Was it Shit or just Bad? Was that movie you watched Very Good or just Decent? How many things out there are really Life Changing?
Finally, a rating scale for humans. Use it for anything in your life that needs a rating out of 5 stars.
Rating / Description
0.5 – The worst 1.0 – Shit 1.5 – Bad 2.0 – Eh 2.5 – Entertaining, but not great 3.0 – Neutral 3.5 – Alright 4.0 – Decent 4.5 – Very good 5.0 – Life Changing
P.S. Do not use it to rate your wife's cooking. The author is not liable for any damages.
-
 @ 4506e04e:8c16ba04
2025-01-22 16:37:08
@ 4506e04e:8c16ba04
2025-01-22 16:37:08If you are a researcher in the field of medicine, you are most likely very familiar with PubMed – where you get citations for the articles and studies that drive your work forward. PubMed Central (PMC), the full-text repository of life sciences journal literature managed by the National Library of Medicine (NLM), was established in 2000. Its creation marked a significant milestone in providing open access to biomedical research. Since 2005, PMC has served as the designated repository for papers submitted under the NIH Public Access Policy, reflecting the growing emphasis on transparency and accessibility in scientific research. Over the years, PMC has expanded its scope, becoming a repository for papers aligned with public and open access policies from various research funding organizations, both within and beyond biomedical sciences.
Funding and Partnerships
NLM’s operations, including PubMed and PMC, are supported by a combination of government funding and contributions from influential entities such as The Bill & Melinda Gates Foundation.
The Bill and Melinda Gates Foundation receives significant donations from pharmaceutical companies, as well as other organizations and individuals. The exact amount of money donated by each company can vary from year to year, but here are some examples of the amounts donated by the pharmaceutical companies:
GSK (GlaxoSmithKline):
- In 2020, GSK donated $100 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria, tuberculosis, and HIV/AIDS.
- In 2019, GSK donated $50 million to the Gates Foundation to support the development of a new malaria vaccine.
Pfizer:
- In 2020, Pfizer donated $50 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria, tuberculosis, and HIV/AIDS.
- In 2019, Pfizer donated $25 million to the Gates Foundation to support the development of a new malaria vaccine.
Merck & Co.:
- In 2020, Merck donated $50 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria, tuberculosis, and HIV/AIDS.
- In 2019, Merck donated $25 million to the Gates Foundation to support the development of a new malaria vaccine.
Novartis: - In 2020, Novartis donated $20 million to the Gates Foundation to support the development of new treatments for diseases such as malaria and tuberculosis. - In 2019, Novartis donated $10 million to the Gates Foundation to support the development of a new malaria vaccine.
Johnson & Johnson:
- In 2020, Johnson & Johnson donated $50 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria, tuberculosis, and HIV/AIDS.
- In 2019, Johnson & Johnson donated $25 million to the Gates Foundation to support the development of a new malaria vaccine.
Sanofi:
- In 2020, Sanofi donated $20 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria and tuberculosis.
- In 2019, Sanofi donated $10 million to the Gates Foundation to support the development of a new malaria vaccine.
AstraZeneca:
- In 2020, AstraZeneca donated $20 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria and tuberculosis.
- In 2019, AstraZeneca donated $10 million to the Gates Foundation to support the development of a new malaria vaccine.
Eli Lilly and Company:
- In 2020, Eli Lilly donated $10 million to the Gates Foundation to support the development of new treatments for diseases such as malaria and tuberculosis.
- In 2019, Eli Lilly donated $5 million to the Gates Foundation to support the development of a new malaria vaccine.
Additionally, NLM website [https://cdn.ncbi.nlm.nih.gov/pmc/cms/files/PMCFunderDepositList.xlsx] (list over 200)(!) organisations that are founding it. What could go wrong one might ask?!
The Centralization Challenge
While PubMed and PMC have played a pivotal role in democratizing access to scientific literature, their centralized nature presents vulnerabilities. Over the past century healthcare has grown to become one of the most profitable industries and to believe that the healthcare system we have today is the best we can do is far from understatement.
PubMed's reliance on centralized funding and decision-making processes makes it susceptible to external influences, including lobbying by powerful entities. Moreover, the centralized infrastructure allows for content to be published and removed with relative ease, often without leaving a trace. This raises concerns about the integrity and permanence of the scientific record, particularly in contentious or politically sensitive areas of research.
The ability to alter or erase information from PubMed undermines trust in the system’s objectivity and neutrality. Researchers and the public alike depend on these repositories for reliable and impartial access to scientific knowledge. Any perceived or actual manipulation of content can erode confidence in the platform and compromise its foundational mission.
The Case for Decentralization
To address these challenges, a decentralized alternative built on emerging technologies, such as the Nostr protocol, could offer significant advantages. A decentralized platform would:
-
Enhance Resilience: By distributing data across a network of relays, a decentralized system would eliminate single points of failure, ensuring the scientific record remains intact and always accessible even in the face of technical or political disruptions.
-
Increase Transparency: Decentralized systems inherently log changes, making it nearly impossible to alter or remove content without leaving an auditable trail. This transparency would bolster trust in the integrity of the research.
-
Reduce Susceptibility to Lobbying: Without centralized control, the influence of external entities on the platform’s content would be significantly diminished, preserving the objectivity of the scientific record.
-
Foster Open Collaboration: A decentralized approach aligns with the principles of open science, encouraging global collaboration without the constraints of centralized oversight or bias introduced by big pharma lobby.
Conclusion
While PubMed and PMC have been instrumental in advancing access to scientific literature, their centralized nature leaves them vulnerable to manipulation and external pressures. A shift toward a decentralized, censorship-resistant platform would address these vulnerabilities and provide a more robust and trustless repository for scientific knowledge. Groundbreaking research that dares to challenge the pharmaceutical industry's status quo could be published anonymously, following in the footsteps of the Bitcoin whitepaper's pseudonymous author, Satoshi Nakamoto. Leveraging technologies like the Nostr protocol, the research community can build a system that ensures the permanence, integrity, and impartiality of the scientific record for generations to come.
-
 @ b83e6f82:73c27758
2025-01-22 16:29:15
@ b83e6f82:73c27758
2025-01-22 16:29:15Citrine 0.7.1
- Add the restore follows button back
- Show notification when backing up database
- Listen for pokey broadcasts
Download it with zap.store, Obtainium, f-droid or download it directly in the releases page
If you like my work consider making a donation
Verifying the release
In order to verify the release, you'll need to have
gpgorgpg2installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:bash gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6DOnce you have his PGP key you can verify the release (assuming
manifest-v0.7.1.txtandmanifest-v0.7.1.txt.sigare in the current directory) with:bash gpg --verify manifest-v0.7.1.txt.sig manifest-v0.7.1.txtYou should see the following if the verification was successful:
bash gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03 gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>"That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:
bash cat manifest-v0.7.1.txtOne can use the
shasum -a 256 <file name here>tool in order to re-compute thesha256hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly. -
 @ 5a261a61:2ebd4480
2025-01-30 09:37:26
@ 5a261a61:2ebd4480
2025-01-30 09:37:26The idea of the Bean Bag Game is quite ingenious. I read about it on a BDSM-positive blog. Here’s how it works:
-
Setup:
-
Take a small cloth bag and add 10 white beans (rewards/pleasure) and 10 black beans (punishment/discomfort).
-
When it’s time to play, draw two beans:
-
First bean (the tone): Determines if the activity will be pleasant (white) or uncomfortable (black).
-
Second bean (the task): Decides whether you get a reward (white) or punishment (black).
-
Combination Interpretations:
-
Black + Black\ "No fun, just work."
-
Boring/challenging tasks you’d normally postpone: window cleaning, scrubbing bathroom tiles, polishing shoes.
-
Could also mean no playtime (e.g., "Go straight to bed"). Pure duty – no pleasure, only discipline.
-
White + Black\ "Work with a twist."
-
Punishment or chores, but with a kinky edge:
-
Clean the bathroom wearing a vibrating butt plug.
-
Wash dishes with nipple clamps; add a clothespin to your body for every minute over the time limit.
-
-
Still no orgasms – the black bean ensures denial.
-
Black + White\ "Pleasure with pain (or humiliation)."
-
Mix stimulation and discomfort:
-
Ride a dildo with weighted nipple clamps.
-
Give a "lap dance" to a teddy bear with a strapon.
-
Chat online as a "perfect plaything" for others without touching yourself.
-
-
Again, no orgasms – the black bean overrules the white.
-
White + White\ "Lucky draw… but denial is optional."
-
Freedom to indulge, though I often choose self-denial anyway. Examples:
-
Edge for 30 minutes, then ask permission to climax (50% chance).
-
Use toys freely, but end the session frustrated.
-
The Dynamic Ratio Twist:
-
The starting 10:10 ratio isn’t fixed. Adjust it based on behavior:
-
Good deeds? Swap a black bean for a white one.
-
Mistakes? Replace a white bean with a black one.
-
Single beans can also decide smaller stakes, like:
-
"Should this edge turn into a ruined orgasm?"
-
"Do I deserve dessert tonight?"
Why It Works:
-
Control: The beans dictate your fate, but you tweak the odds through obedience.
-
Flexibility: Use pairs for major tasks, single beans for quick decisions.
-
Psychological tease: Even "white + white" can mean denial – because you choose the rules.
-
-
 @ c3b2802b:4850599c
2025-01-30 09:06:41
@ c3b2802b:4850599c
2025-01-30 09:06:41In Kirpal Sagar ist ein Modell für die Welt entstanden, das soziale mit ökologischen sowie spirituellen Sehnsüchten der Völker unserer Welt verbindet. Knapp 20 Jahre nach der Gründung von Kirpal Sagar wurde mit grossem Brimborium zwar in Rio de Janeiro die Agenda 21 mit ähnlichen Zielen ausgerufen. Doch in den 3 Dekaden danach ist mir kein Projekt begegnet, welches den InitiatorInnen und Aktiven in Kirpal Sagar das Wasser reichen kann.
Konkret: In der Gemeinschaftsküche wird seit Beginn des Projekts, also seit 50 Jahren, für mittellose Menschen kostenloses Essen zubereitet. Die Küche wird vom eigenen Öko – Landwirtschaftsbetrieb beliefert. Um Bedürftigen zu helfen, wurde 1983 das Krankenhaus eingerichtet. Im 1994 eingeweihten Altenheim finden alte Menschen ein Zuhause, die sonst auf sich allein gestellt wären. Bedürftige aus der Umgebung erhalten Unterstützung in Notfällen. Die Kirpal Sagar Academy ist eine Schule, die derzeit 500 Kinder bis zur Hochschulreife führt. Kinder aus mittellosen Familien werden vom Träger unterstützt.
Basis des Zusammenlebens ist ein lebendiger Dialog zwischen den Religionen der beteiligten Menschen. Hier wird keine bestimmte Religion gelehrt, sondern auf die Essenz der Religion, den spirituellen Kern, der allen Religionen gemeinsam ist, verwiesen, wie auch in den weithin sichtbaren Symbolen von Kirpal Sagar (z.B. auf dem Titelbild oben) dargestellt ist.
In einer nach außen offenen Gemeinschaft leben hier ständig mehr als 800 Menschen, viele mit ihren Familien – freiwillige Mitarbeiter, die am Aufbau beteiligt sind, Lehrer, Schüler, Arbeiter, Ärzte, Angestellte usw. Ebenso sind regelmäßig Helfer und Gäste aus dem Ausland vor Ort. So erlebt man ein lebendiges Miteinander verschiedener Kulturen, Religionen und Mentalitäten.
Als ich 2007 erstmals hier war, fand zum Beispiel eine Hochzeitsveranstaltung für Dutzende junge Paare aus ärmsten Verhältnissen statt, welchen ohne Unterstützung keine Trauung möglich war.
Man sieht Menschen ihren alltäglichen Arbeiten nachgehen und kann an Sport- und Schulveranstaltungen teilnehmen. Ebenso sind auch Gäste bei traditionellen Festen oder religiösen Feierlichkeiten und Ritualen willkommen, die jeder seiner Religionszugehörigkeit entsprechend ausüben kann. In diesem Teil des Punjab begegnet man vor allem Hindus und Sikhs, bei größeren Veranstaltungen sind auch Vertreter weiterer Religionen zu Gast. Über Jahre der Zusammenarbeit konnte man praktisch sehen, dass das Ideal „Eine Welt, eine Menschheit“ keine Utopie ist. In Europa gibt es Unterstützer-Initiativen, in denen sich Menschen aus unserem Teil der Erde für Projekte dieser Art engagieren. Details über einzelne Lebensbereiche in der Modellkommune erfahren Sie hier, speziell zu Gesundheitsfragen hier.
Zuerst veröffentlicht auf der Plattform Zukunftskommunen.
-
 @ 2ce0697b:1ee3d3fc
2025-01-22 14:27:35
@ 2ce0697b:1ee3d3fc
2025-01-22 14:27:35Following Trump’s ~~failure to fulfill ~~his promise, much of the Bitcoin community continues to petition for his pardon.(1)
1: Add on: at the end of day one Trump freed Ross. Everything else in this article applies irregardless of that action. Added at 880.358 time chain.
~~Key Fact 1: Trump failed to release Ross Ulbricht on day one.~~
Key Fact 2: Some Bitcoiners fall into the trap of statism by recognizing the legitimacy of the American President.
"The State is the denial of humanity." — Mikhail Bakunin
It seems that in the end, the orange man wasn’t so orange. The orange man was voted for by many of the orange team because they believed he would use the resources at his disposal to create a great stockpile of oranges. But just before taking office, it turned out he started stockpiling manure instead. Bitcoin solves this because, eventually, that manure will fertilize the oranges which, at least for now, will not be produced by the state apparatus controlled by the orange man. Instead, as they always have been, they will continue to be produced by the private sector, contributing much more to decentralization, even at the cost of not achieving at the moment a sharp increase in hashing power.
The orange man was also supported and tolerated by many in the orange team because he promised to release Ross Ulbricht. Ross is someone deprived of liberty for the "crime" of challenging the State by creating Silk Road, a free market. Ross understood that according to natural law, every adult has the right to interact with another by respecting their consent without unwanted third-party interference in the exchange. The orange team shares this vision and understands that imprisoning an innocent person is an injustice that must be corrected. However, not all members of the orange team agree on the reasons or the methods.
There is a portion of the orange team that continuously and respectfully asks the orange man to free Ross. Members of this subcategory of the orange team pray:
"Oh dear Mr. Orange, please grant Ross your mercy! Free him from the clutches of the Federal Government, the same government you’ve always supported, been a part of, and promoted, the same government you administered for four years previously without freeing this innocent man. Oh Mr. Orange, we promise that if you do this, you will have our support to do everything —or almost everything— you want to do. Amen."

What a portion of the orange team fails to see is that Ross is in prison precisely because they accept his imprisonment, despite all the petition campaigns for his release. This sub-category of the orange team is composed by democratic Bitcoiners, Republicans ones, voters in general, and law-abiding Bitcoiners, in other words, statist Bitcoiners. That´s it bitcoiner who support the existence of the State. No matter how much they may dislike it, the reality is that one cannot ask a President for clemency without simultaneously recognizing his legitimate authority to grant that clemency. What some members of this subgroup of the orange team don´t realize is that the orange man is just another person, a human being with the same rights and obligations as anyone else.
The orange man is currently the one holding Ross captive through violence and force. He is the one at fault. It is the orange man who, every minute he remains in power, tolerates the aggression against innocents like Ulbricht. And this is just one example among millions of others who are also victimized by him and his state apparatus, which magnifies aggression. Whoever initiates or perpetuates violence against others is the one who should be punished by society, whether by restricting their actions, excommunicating him, banishing him, depriving him of public resources, or at the very least, ignoring him. By asking the orange man to please cease the violence against Ross while simultaneously tolerating his violence against millions of other innocent people currently coerced by the state apparatus, one unwittingly promotes further injustices.
"Authority is the negation of freedom." — Errico Malatesta
Ross is innocent, but so are all the users of USD who are robbed through inflation. Ulbricht deserves to be free, but so does every human being capable of giving their consent to trade in the manner they choose. The creator of Silk Road deserves to return to his family and enjoy the rest of his life as he sees fit, but so does every prisoner accused of victimless crimes. (For example, in the U.S., one of the most common victimless crimes that feeds the private prison industry is dealing of drugs outside of compliance.) This author cannot help but ask this part of the orange team: If the orange man frees Ross and then Ross reinstates Silk Road, what do you think will happen? Would Ross remain free after committing that act again? And if it’s not Ross but John Doe who does it, wouldn’t John also be persecuted by the same orange man whom you tolerate?
 Wouldn’t it be better for the global human community to ask the orange man, or anyone who occupies his position, to cease violence against all innocents? Or better yet: Wouldn’t it be better to act accordingly by creating peaceful free exchange mechanisms that allow people to escape such violence?
Like it or not, by supporting a potential presidential pardon, one acknowledges state authority. It is an acceptance that there are human beings superior to others, owners of others, whose whims must be tolerated by the rest of society. The difference between the timeline where Ross is a business magnate and the one where he is treated as a criminal lies in the whim of a president and a ruling political caste. But the tolerance of that whim by the rest of society is what is at stake—and, on an individual level, within our control.
Wouldn’t it be better for the global human community to ask the orange man, or anyone who occupies his position, to cease violence against all innocents? Or better yet: Wouldn’t it be better to act accordingly by creating peaceful free exchange mechanisms that allow people to escape such violence?
Like it or not, by supporting a potential presidential pardon, one acknowledges state authority. It is an acceptance that there are human beings superior to others, owners of others, whose whims must be tolerated by the rest of society. The difference between the timeline where Ross is a business magnate and the one where he is treated as a criminal lies in the whim of a president and a ruling political caste. But the tolerance of that whim by the rest of society is what is at stake—and, on an individual level, within our control.Every well-intentioned moral action is correct. Freeing Ross could be a well-intentioned moral action. But it could also simply be a demagogic action intended to perpetuate the inherently immoral state apparatus. The second option is the most likely and logical coming from fiat professional politicians. There is nothing we can do about it since that is beyond our control. But what all members of the orange team can do is deny the authority of the orange man—not only because he is just an ordinary man, equal among humans, but especially to deny the legitimacy of his enterprise. An enterprise based on violence, coercion, monetary inflation, theft, war, and the use of force to benefit his friends at the expense of the rest of humanity.
Camilo JdL at 880,209 timechain. If you find this content helpful, zap it to support more content of the sort and to boost the V4V model.
-
 @ dd664d5e:5633d319
2025-01-07 19:57:14
@ dd664d5e:5633d319
2025-01-07 19:57:14Hodling Bitcoin does not make you a capitalist
I've noticed that Bitcoin-mindedness seems to lead some people to communistic thinking because it's a hard-limited form of capital. Marx, like most Bitcoiners, heavily discounted the possibility of economic growth or transformation changing the economy enough to undermine some minority's control of some form of capital.
What few today understand, is that many of the Dirty Capitalists of Marx's era actually agreed with him; they were just disdainful of labor and worried that the workers finding out that Marxism is correct about the nature of capitalism would cause unrest. They were the original HFSP crowd.
This was the basic idea, that Marx had, and that many Bitcoiners would agree with:
Capital is strictly limited and the people that control it can keep labor from attaining any, except when their labor is necessary.
And, as we know, automation will make human labor increasingly unnecessary.
The math doesn't check out

That underlies all of the calculations of "Well, if I just grab this Bitcoin wallet and hodl for twenty years, then it will grow in value to equal half of everything in existence and then I can just buy up half the planet and rule over everyone like a god."
This is economic nonsense because it assumes that: 1) the value of all things remains static over time, 2) purchasing something with money gives you ownership of it, 3) people will always use that specific money (or any money, at all!) for all transactions, 4) there is no such thing as opportunity cost, 5) people will always value money more than any other thing, and therefore be willing to always trade it for anything else, 6) humans are passive, defenseless, and easy to rule over, 7) someone who is preoccupied with hodling an asset steadily and sharply rising in price would ever be emotionally ready to part with it.
All monies can die.
People use money for everything because it is easy, fast and cheap. If money becomes too precious or scarce, they will simply switch to using other things (as we saw with gold). Humans replace tools that aren't working well, with those that work better, and money is just another tool. Bitcoin is more divisible than gold, but that won't matter, if enough of it is held by too few.
This is why there's a natural cap on the price of a money and why human productivity in the here and now is not irrelevant or in vain.
-
 @ b17fccdf:b7211155
2025-01-22 10:39:19
@ b17fccdf:b7211155
2025-01-22 10:39:19What's changed
- New bonus guide dedicated to install/upgrade/uninstall PostgreSQL
- Modified the LND guide to use PostgreSQL instead of bbolt
- Modified the Nostr relay guide to use PostgreSQL instead of SQLite (experimental)
- Modified the BTCPay Server bonus guide according to these changes
- Used the lndinit MiniBolt organization fork, to add an extra section to migrate an existing LND bbolt database to PostgreSQL (🚨⚠️Experimental - use it behind your responsibility⚠️🚨)
- New Golang bonus guide as a common language for the lndinit compilation
- Updated LND to v0.18
- New Bitcoin Core extra section to renovate Tor & I2P addresses
- New Bitcoin Core extra section to generate a full
bitcoin.conffile - Rebuilt some homepage sections and general structure
- Deleted the
$symbol of the commands to easy copy-paste to the terminal - Deleted the initial incoming and the outgoing rules configuration of UFW, due to it being by default
🪧 PD: If you want to use the old database backend of the LND or Nostr relay, follow the next extra sections:
- Use the default bbolt database backend for the LND
- Use the default SQLite database backend for the Nostr relay
⚠️Attention⚠️: The migration process was tested on testnet mode from an existing bbolt database backend to a new PostgreSQL database using lndinit and the results were successful. However, It wasn't tested on mainnet, according to the developer, it is in experimental status which could damage your existing LND database.🚨 Use it behind your responsibility 🧼
🔧 PR related: https://github.com/minibolt-guide/minibolt/pull/93
♻️ Migrate the PostgreSQL database location
Attention!! These instructions are invalid since the latest changes applied to the PostgreSQL bonus guide. See more information on the recent associated post by clicking ~ > HERE < ~
If you installed NBXplorer + BTCPay Server before 05/06/2024, it is probably you have the database of the PostgreSQL cluster on the default path (
/var/lib/postgresql/16/main/), follow the next instructions to migrate it to the new dedicated location on/data/postgresdbfolder:- With user
admincreate the dedicated PostgreSQL data folder
sudo mkdir /data/postgresdb- Assign as the owner to the
postgresuser
sudo chown postgres:postgres /data/postgresdb- Assign permissions of the data folder only to the
postgresuser
sudo chmod -R 700 /data/postgresdb- Stop NBXplorer and BTCPay Server
sudo systemctl stop nbxplorer && sudo systemctl stop btcpayserver- Stop PostgreSQL
sudo systemctl stop postgresql- Use the rsync command to copy all files from the existing database on (
/var/lib/postgresql/16/main) to the new destination directory (/data/postgresdb)
sudo rsync -av /var/lib/postgresql/16/main/ /data/postgresdb/Expected output:
``` sending incremental file list ./ PG_VERSION postgresql.auto.conf postmaster.opts postmaster.pid base/ base/1/ base/1/112 base/1/113 base/1/1247 base/1/1247_fsm base/1/1247_vm base/1/1249 base/1/1249_fsm base/1/1249_vm [...] pg_wal/000000010000000000000009 pg_wal/archive_status/ pg_xact/ pg_xact/0000
sent 164,483,875 bytes received 42,341 bytes 36,561,381.33 bytes/sec total size is 164,311,368 speedup is 1.00 ```
- Edit the PostgreSQL data directory on configuration, to redirect the store to the new location
sudo nano /etc/postgresql/16/main/postgresql.conf --linenumbers- Replace the line 42 to this. Save and exit
data_directory = '/data/postgresdb'- Start PostgreSQL to apply changes and monitor the correct status of the main instance and sub-instance monitoring sessions before
sudo systemctl start postgresql- You can monitor the PostgreSQL main instance by the systemd journal and check the log output to ensure all is correct. You can exit the monitoring at any time with Ctrl-C
journalctl -fu postgresqlExample of the expected output:
Nov 08 11:51:10 minibolt systemd[1]: Stopped PostgreSQL RDBMS. Nov 08 11:51:10 minibolt systemd[1]: Stopping PostgreSQL RDBMS... Nov 08 11:51:13 minibolt systemd[1]: Starting PostgreSQL RDBMS... Nov 08 11:51:13 minibolt systemd[1]: Finished PostgreSQL RDBMS.- You can monitor the PostgreSQL sub-instance by the systemd journal and check log output to ensure all is correct. You can exit monitoring at any time with Ctrl-C
journalctl -fu postgresql@16-mainExample of the expected output:
Nov 08 11:51:10 minibolt systemd[1]: Stopping PostgreSQL Cluster 16-main... Nov 08 11:51:11 minibolt systemd[1]: postgresql@16-main.service: Succeeded. Nov 08 11:51:11 minibolt systemd[1]: Stopped PostgreSQL Cluster 16-main. Nov 08 11:51:11 minibolt systemd[1]: postgresql@16-main.service: Consumed 1h 10min 8.677s CPU time. Nov 08 11:51:11 minibolt systemd[1]: Starting PostgreSQL Cluster 16-main... Nov 08 11:51:13 minibolt systemd[1]: Started PostgreSQL Cluster 16-main.- Start NBXplorer and BTCPay Server again
sudo systemctl start nbxplorer && sudo systemctl start btcpayserver- Monitor to make sure everything is as you left it. You can exit monitoring at any time by pressing Ctrl+C
journalctl -fu nbxplorer
journalctl -fu btcpayserver
Enjoy it MiniBolter! 💙
-
 @ 3efdaebb:3e0d2681
2025-01-22 01:08:58
@ 3efdaebb:3e0d2681
2025-01-22 01:08:58Hey Nostr! It’s App Store release day for Damus. Thanks again to our loyal Purple subscribers for helping us continue to improve the UX and pointing out important changes and fixes. Highlights of Version 1.12:
Added
- Render Gif and video files while composing posts (Swift Coder)
- Add profile info text in stretchable banner with follow button (Swift Coder)
- Paste Gif image similar to jpeg and png files (Swift Coder)
Changed
- Improved UX around the label for searching words (Daniel D’Aquino)
- Improved accessibility support on some elements (Daniel D’Aquino)
Fixed
- Fixed issue where the "next" button would appear hidden and hard to click on the create account view (Daniel D’Aquino)
- Fix non scrollable wallet screen (Swift Coder)
- Fixed suggested users category titles to be localizable (Terry Yiu)
- Fixed GradientFollowButton to have consistent width and autoscale text limited to 1 line (Terry Yiu)
- Fixed right-to-left localization issues (Terry Yiu)
- Fixed AddMuteItemView to trim leading and trailing whitespaces from mute text and disallow adding text with only whitespaces (Terry Yiu)
- Fixed SideMenuView text to autoscale and limit to 1 line (Terry Yiu)
- Fixed an issue where a profile would need to be input twice in the search to be found (Daniel D’Aquino)
- Fixed non-breaking spaces in localized strings (Terry Yiu)
- Fixed localization issue on Add mute item button (Terry Yiu)
- Replace non-breaking spaces with regular spaces as Apple's NSLocalizedString macro does not seem to work with it (Terry Yiu)
- Fixed localization issues in RelayConfigView (Terry Yiu)
- Fix duplicate uploads (Swift Coder)
- Remove duplicate pubkey from Follow Suggestion list (Swift Coder)
- Fix Page control indicator (Swift Coder)
- Fix damus sharing issues (Swift Coder)
- Fixed issue where banner edit button is unclickable (Daniel D’Aquino)
- Handle empty notification pages by displaying suitable text (Swift Coder)
-
 @ dd664d5e:5633d319
2025-01-06 20:36:17
@ dd664d5e:5633d319
2025-01-06 20:36:17Ingredients
- 1 kg of pork roast with rind, such as shoulder or a lean belly
- 1 bottle of beer, light or dark
- chopped German-style mirepoix (best combination, for this recipe, includes celery root, carrot, red onion, and leeks)
- salt, pepper, nutmeg
- 1 diced garlic clove
Directions
- Spread the vegetables on the bottom of the roasting pan.
- Pour half the beer over the roast. (Drink the other half.)
- Season the meat, to taste.
- Roast the meat at 180 °C, until done (depends upon the weight of the roast).
- Remove the meat from the oven, and wrap in aluminum foil.
- Pour 2-3 cups of water into the roasting pan.
- Pour/scrape everything from the pan into a sieve over a sauce pot.
- Press the vegetables against the sieve, with the back of a spoon, to ensure that you get all that good dripping flavor into the sauce.
- Defat the sauce with a grease separator, then pour it back into the pot.
- Thicken the sauce, slightly (it should remain slightly watery, and not turn into a gravy), according to your usual method.
- Open the foil and slice the roast.
- Serve with the sauce.








-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 812cff5a:5c40aeeb
2025-01-21 21:11:51
@ 812cff5a:5c40aeeb
2025-01-21 21:11:51ما هو أولاس (Olas)
أولاس تطبيق نوستر محاكي للانستغرام

أولاس OLAS هو أول تطبيق نوستر يتم تطويرة بشكل جدي لتقديم تجربة شبيهة بالانستغرام على نوستر. يركز التطبيق على عرض الصور والڤيديو على الصفحة الرئيسية مع قدرة على فلترة الصفحة. التطبيق مصمم أيضا ليعرض الڤيديو بشكل شبيه بالانستغرام رييلز. لكن بسبب بعض الامور التقنية الميزة لا تعمل بشكل جيد الان.
ما الذي يميز تطبيق أولاس
أولاس يتبع نيپ-٨٦ (NIP-68) لعرض الصور والميديا
يتميز تطبيق أولاس بأنه يعتمد على منشورات نوستر من نوع ٢٠ (Kind-20) وهو نوع مخصص للصور والڤيديو يتبع تطوير NIP-68. مما يعني ان المنشورات تظهر فقط على تطبيقات قادرة علة عرض هذه النوع.

وكون هذه هي الطريقة التي تم تصميم فيها التطبيق، أولاس لا يعرض المنشورات المتعارف عليها مثل تويتر أو من نوع ١ (kind-1) ليقدم للمستخدم تجربة جميلة فريدة من نوعها (حتى الأن).
ضرورة تطوير تطبيقات متخصصة
التطبيقات المخصصة هي باب لجذب مستخدمين جدد
من الضروري تطوير تطبيقات شبهة بأولاس من حيث التصميم. أي ان التطبيق موجه لفئة محددة وواضحة. هذا النوع من التطبيقات يجذب مستخدمين غير مهتمين بالاخبار او المنشورات المكتوبة وكل اهتمامهم هو نشر ومشاركة الصور والڤيديو.
كيف يمكنك دعم المشروع؟
شارك في مبادرة السنة #olas365
أولاس حاليا متوفر كتطبيق تجريبي على iOS والويب. يمكنكم الإنضمام وتجربة التطبيق. لكن نود التنبيه ان التطبيق في مراحلة الأولى ويتم تطويره وتحديثه بشكل دوري.
هذا الرابط لتحميل التطبيق: Olas Testflight Link
مطور التطبيق: nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft
-
 @ a42048d7:26886c32
2025-01-04 22:32:52
@ a42048d7:26886c32
2025-01-04 22:32:52OP_CAT, Coffee, and keeping an open mind to Bitcoin soft forks by an 80 IQ BTC Maxi Pleb
TLDR: CAT is both low risk and low appeal to the broader non-dev BTC community. I don’t care and you shouldn’t either. If I am an 80 IQ HODL pleb or a company that caters to that group, can you please give me 2-4 fifth grade level coherent english sentences that explain why I should support CAT? I’m still waiting… CTV or LNHANCE on the other hand have broad appeal.
Five years ago in the office we got a fancy $6,000 coffee maker. It was hooked up to wifi, showed TV on a giant screen, and could make every type of coffee/milkshake you could think of. I was captivated… for about 1 day. After trying a few times I realized almost all the drinks it made were of low quality. The wifi connection actually ended up just being annoying. Half the time I wanted a coffee, only had a 5 minute break, and the machine displayed some inscrutable error. I went back to the proverbial grind un-caffeinated and frustrated wishing we had the old reliable boring coffee maker back. I also found myself only coming back to the 2 drinks I really cared about, espresso and maybe an occasional cappuccino. It was “cool” that new machine could make over 60 different drinks, but when I sat back and thought about it all I really needed or wanted were a few key options that I used constantly. Especially as those extra bells and whistles seemed to be the usual suspect in the coffee machine constantly breaking. I would’ve loved them upgrading from burnt starbucks coffee beans to a local specialty roaster, that would’ve greatly enhanced my daily coffee. Echoing this realization, my coffee setup at home became a simple machine that could only make espresso and a hand crank coffee bean grinder. Still have them years later and they work great. They’re robust and fit exactly what I wanted with no nonsense that created more headache than everyday value. As you probably suspected, this is a loose comparison to OP_CAT. I’ve listened to podcast after podcast, read blog after blog, and sat through every CAT pitch I could find. I genuinely tried to approach with an open mind. However, ultimately what every pro OP_CAT argument boils down to is that there is no simple left curve elevator pitch a pleb will understand or care about. “But we can get this really cool ZK Rollup and have infinite DEFI bridging to altcoin chains! Look we sort of did it on this other altcoin chain.” And they did, they aren’t lying. They have live software on a shitcoin chain like ETH or SOL that does some modest volume. But the story quickly falls apart in the face of a few basic left curve questions: “Why should I, as an 80 IQ left curve BTC maxi give a shit?” “Does this enhance my everyday experience holding and using BTC?” “Why do you have a non-BTC token for your rollup/sidechain/glorified multisig that is totally centralized?” “Why is there only a hard to understand often ill-defined path to de-centralization? Why isn’t it just already decentralized?” “What is a clear use case that the typical non-technical everyday BTC holder can understand and rally behind?” “Why should I care about bridging to ETH, SOL, or whatever shitcoin chain? I only want BTC and don’t want to participate in all that shitcoin bullshit. Bitcoin is a store of value and money to me and it doesn’t help with those use cases in a clear direct way. It sounds like it maybe, kinda, sorta does help with a lot of caveats, ifs, and steps that I struggle to understand.” Sorry yeah I know, that one got a little personal. I’ll try to do better going forward guys.
ZK proofs or other Pro-CAT arguments, are undoubtedly cool and do factually enable potential cool new stuff. It just happens to all be stuff that sounds complex, esoteric, and unappealing to an 80 IQ HODL pleb - let alone a miner, ETF investor, or exchange exec. I don’t mean to say ZK or other tech has no potential and that we won’t eventually move there, but just to say that it’s not in the cards as currently dealt.
I really went out trying to keep an open mind and steelman the case for CAT. I came back firmly believing:
1 Support is deep in the developer community, but nonexistent everywhere else. I have yet to find a single person that supports CAT who is not a dev or working at or sponsored by a company that stands to directly profit from something CAT enables. Which is fine, but I reserve the right to be skeptical of your direct incentive. I acknowledge rough consensus is very hard to judge, and am open to changing my mind on this over time but feel this is a currently accurate assessment.
2 To get a soft fork you need rough consensus. Most people in that potential consensus are not highly technical developers. They care mostly or exclusively about BTC’s store of value use case. No one has yet articulated a clear compelling store of value enhancing use case that they can understand and care about. Without pull demand from potential users and paying customers, CAT will inevitably stall.
3 Lots of factually inaccurate FUD has been thrown at CAT. People saw the Taproot Wizards or shitcoiners pushing CAT, and immediately dismiss CAT as an evil psyop without any real consideration for its technical merits. Frankly most people just hate Udi and say “Fuck CAT” based solely on that. Maybe not fair, but true.
4 CAT is low risk, and it is not a catastrophe waiting to happen. Anything bad it potentially enables is enabled in such an inefficient and/or use hostile way that it is highly unlikely to pose any issues to Bitcoin. CAT’s technical risk is low and this is consistently proven by other chains enabling CAT and having no issues with it, such as Liquid.
5 Lots of people who have no idea wtf they are talking about falsely claim CAT is the apocalypse without any ability whatsoever to explain why. Imho you are no better than Udi and the shitcoiners if you are willing to lie about CAT just because you dislike them. We as the BTC community need the ability to have a rational discussion on technical merits, and not to devolve into a cult of personality based political battle. The question should be, “Is CAT good or bad and why?” and not “I just hate Udi, therefore its a no from me dog.”
Summarizing CAT using TradFi language: those pushing CAT have technology in search of a problem and no clear product market fit. They are pushing their technology to an apathetic audience. Pushers of CAT are not pulled forward by customer demand. In the tech world these are some of the quintessential red flags that every good investor knows mean you need to sit this one out.
CTV or LNHANCE on the other hand are soft fork proposals that have clear use cases you can quickly explain to a broad swathe of the Bitcoin ecosystem: “Hey HOLD pleb, worried about losing your coins? Wouldn’t it be nice to have a simple vault that reduces the chances your coins are lost or stolen? Let’s make self custody and BTC’s store of value use case strictly better, specifically without enabling any shitcoin-ery.” “Hey Blackrock, Van Eck, ARK, Franklin Templeton, and every ETF investor - it would really suck if Coinbase lost all your Bitcoin and that ETF went to zero, right? What it we could create vaults to make that Bitcoin more secure?” “Like Lightning but find it hard to use self-custodially? Let’s make Lightning better, easier, and more scalable with fewer onchain transactions and lower fees.” “Tried or seen the ARK demos yet? They have real working code even without covenants. With covenants we get big ARK volumes and scaling while also making it easier.”
Signing off: See the difference? I, an 80 IQ pleb, can steelman multiple use cases for CTV/LNHANCE that have broad appeal. I have yet to see any such case for CAT, and until then I don’t think it’ll go anywhere.
*Pro-CAT Sources I’ve digested and would encourage others to consider: https://en.bitcoin.it/wiki/Covenants_support https://www.youtube.com/watch?v=no_Nj-MX53w https://www.youtube.com/watch?v=_yp4eYK9S6M
Pro-CTV/LNHANCE sources to consider which have CLEAR use cases with widespead appeal: https://github.com/jamesob/simple-ctv-vault https://github.com/stutxo/op_ctv_payment_pool https://lnhance.org/ https://bitcoinmagazine.com/technical/how-ctv-can-help-scale-bitcoin
-
 @ a4a6b584:1e05b95b
2025-01-02 18:13:31
@ a4a6b584:1e05b95b
2025-01-02 18:13:31The Four-Layer Framework
Layer 1: Zoom Out

Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what."
Example: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems.
- Tip: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage.
Once you have the big picture in mind, it’s time to start breaking it down.
Layer 2: Categorize and Connect

Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas.
Example: Studying biology? Group concepts into categories like cells, genetics, and ecosystems.
- Tip: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track.
With your categories in place, you’re ready to dive into the details that bring them to life.
Layer 3: Master the Details

Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable.
Example: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language.
- Tip: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding.
Now that you’ve mastered the essentials, you can expand your knowledge to include extra material.
Layer 4: Expand Your Horizons

Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams.
Example: Learn about rare programming quirks or historical trivia about a language’s development.
- Tip: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time.
Pro Tips for Better Learning
1. Use Active Recall and Spaced Repetition
Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information.
2. Map It Out
Create visual aids like diagrams or concept maps to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2.
3. Teach What You Learn
Explain the subject to someone else as if they’re hearing it for the first time. Teaching exposes any gaps in your understanding and helps reinforce the material.
4. Engage with LLMs and Discuss Concepts
Take advantage of tools like ChatGPT or similar large language models to explore your topic in greater depth. Use these tools to:
- Ask specific questions to clarify confusing points.
- Engage in discussions to simulate real-world applications of the subject.
- Generate examples or analogies that deepen your understanding.Tip: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective.
Get Started
Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
-
 @ 955e5a04:c03b3cc3
2025-01-30 08:59:36
@ 955e5a04:c03b3cc3
2025-01-30 08:59:36Imagine a world where money moves freely, without borders or middlemen telling you what you can or can’t do. That’s the promise of Bitcoin—a digital currency that isn’t controlled by banks or governments. It’s freedom in your pocket.
But with great power comes great responsibility. In Putin’s People, Catherine Belton reveals how Russia’s elite, including Rosneft, strategic sectors, insiders and KGB-connected figures, used financial systems to move billions and shape global politics. Now, #Bitcoin offers a new tool that could bypass sanctions designed to hold such regimes accountable.
Does this make Bitcoin bad? Not necessarily. It’s a reminder of how innovation can outpace regulation. While some might misuse Bitcoin, it also gives people in oppressed regions a lifeline—a way to protect their savings and avoid corrupt systems.
Can Bitcoin strike a balance between financial freedom and accountability, or is it destined to remain a gray area for both innovation and potential misuse? Let’s talk!
-
 @ cff1720e:15c7e2b2
2025-01-21 19:28:49
@ cff1720e:15c7e2b2
2025-01-21 19:28:49Introduction
The aim of ELI5 (explain me like I'm 5) is to explain difficult things simply. This is urgently needed in our high-tech world, because only by understanding the technologies can we use them properly and develop them further.
I'm starting my series with Nostr, a relatively new internet protocol. What the hell is an Internet protocol? In formal terms, it is an international standard that has ensured that the Internet has been working pretty well for over 30 years. It is the language in which computers communicate with each other and which you also use every day, probably without realizing it. http(s) transports your request to a server (e.g. Amazon), and html ensures that a nice page is created on your screen from the data supplied. A mail is sent to the mail server with smtp and retrieved from it with imap, and since everyone uses the standard, this works with every app on every operating system and with every mail provider.
And with an e-mail address like roland@pareto.space, you can even move at any time, no matter where. Cool, that's state of the art! But why doesn't this work with chat, for example, is there no protocol? Yes, it's called IRC (Internet Relay Chat → remember the name), but it's hardly ever used. The reasons for this are not technical, but rather apps such as Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok and others have deliberately created incompatibilities and user dependencies in order to maximize profits.

Since the standard protocol is not used, each app has its own, and we need a handful of apps to exchange information with everyone we know. A mobile phone number is a prerequisite for every account, allowing app manufacturers to track users comprehensively and earn up to USD 30 per account per month by selling the information. The user is no longer the customer, he is the product! Advertising SPAM is the least of the problems with this business model. Servers with millions of user data are a “honey pot”, so they are often hacked and the access data sold. In 2024, the Twitter account of then President Joe Biden was also hacked and no one knew who had written the messages (nor did they before), meaning that the authenticity of the content is not guaranteed with any of these providers. In the same year, the founder of Telegram was taken into custody in France because he refused to build backdoors into his software. Now, to protect “our democracy”, practically anyone can read what information they exchange with whom, e.g. which shampoo certain politicians use.

Why Nostr?
And anyone who actually believes they can practice freedom of expression on social media will quickly find themselves in the situation of Donald Trump (who was president at the time), whose Twitter account was shut down in 2021 (cancel culture). The user data, i.e. their profile, contacts, documents, images, videos and audio files - no longer belong to them anyway but are the property of the platform operator; read the terms and conditions. But no, not a good idea, there are hundreds of pages and they are constantly being changed. So everyone uses apps whose technology they don't understand, whose rules they don't know, where they have no rights and which steal the results of their actions. What would the five-year-old say if his older sister offered to “manage” all his toys and then hand them over if he was good? “You must be crazy”, and with that the toddler proves he has more sense than the majority of adults.
Conclusion: no standards, no data, no rights = no future!

How does Nostr work?
The developers of Nostr realized that the server-client concept had turned into a master-slave concept. The master is synonymous with centralization and becomes the “single point of failure”, which inevitably makes systems dysfunctional. In a distributed peer2peer system, there are no longer any masters but only equal nodes (relays) on which the information is stored. By storing information redundantly on several relays, the system is more resilient in every respect. It is not only nature that has successfully used this principle for millions of years, the Internet was also designed in this way (the ARPAnet was developed by the US military for use in war situations with massive disruptions). All nostr data is stored on relays and the user can choose between public (usually free) and private relays, e.g. for closed groups or for the purpose of data archiving. As documents are stored on several relays, unique document names (URIs = identifiers) are used instead of URLs (locators), making broken links a thing of the past, as are deletions / losses.
Each document (called an event) is signed by the owner, making it authentic and tamper-proof and can only be deleted by the creator. A key pair consisting of a private (nsec) and public key (npub) is used for this, as known from mail encryption (PGP). This represents a Nostr identity that can be supplemented with a picture, name, bio and a readable Nostr address (e.g. roland@pareto.space ), which is all that is needed to use all the resources of the Nostr ecosystem. And this now consists of over a hundred apps with different focuses, e.g. for personal encrypted messages (DM → OxChat), short messages (Damus, Primal), blog posts (Pareto), meetups (Joinstr), groups (Groups), images (Olas), videos (Amethyst), audio chat (Nostr Nests), audio streams (Tunestr), video streams (Zap.Stream), marketplaces (Shopstr) and much more. Registration is done with a single click (single sign-on) and ALL user data is available to the apps (profile, data, contacts, social graph → followers, bookmarks, comments, etc.), in contrast to the fragmented data silos of the present.
Summary: one open standard, all data, all rights = great future!

Why is Nostr the future of the internet?
“Don't build your house on someone else's property” also applies to the Internet - for all app developers, artists, journalists and users, because their data is also valuable. Nostr guarantees ownership of the data and overcomes its fragmentation. Neither use nor creative freedom is restricted by excessive license and usage conditions. Passive users become active participants through interaction, co-creators in a sharing economy (Value4Value). Open source finally restores trust in software and its providers. Open standards enable developers to cooperate more and develop faster, while guaranteeing freedom of choice for users. Which brings us back to our five-year-old for the last time. Children love Lego more than anything, especially the maxi box “Classic”, because it allows them to live out their imagination to the full in terms of combinations. Adults then give them the far too expensive theme packs, with which you can only build one solution according to the instructions. “What's wrong with my parents, when did they take a wrong turn?” the children rightly ask themselves. But the image can be polished up again if they show their children Nostr, because even five-year-olds understand the advantages.
The new Internet is decentralized. The new Internet is self-determined. Nostr is the new Internet.

\ More infos: https://nostr.net/\ Quick start: https://start.njump.me/
-
 @ da0b9bc3:4e30a4a9
2025-01-30 08:17:19
@ da0b9bc3:4e30a4a9
2025-01-30 08:17:19Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/869648
-
 @ 62a6a41e:b12acb43
2025-01-21 19:19:06
@ 62a6a41e:b12acb43
2025-01-21 19:19:06Bodhidharma, the founder of Zen Buddhism (also known as Zen or Zen meditation), meditated for nine years, simply looking at a wall.
Nine years staring at a wall.
Good things take time. Don’t be afraid to take your time. Forget what Western society has taught us—here, we are slaves to time and productivity.
I believe one of the reasons the Western world is in decline is precisely because we lack the philosophical and religious structures that enable true freedom and focus on understanding.
Christianity is beautiful in its own way, but it simply isn’t as clear or rational as Eastern philosophy. As a result, it hasn’t managed to foster an environment for genuine seekers or free thinkers in the same way.
We need to take the time to think. The West doesn’t understand that.
Take your time. You are free to take your time. It's your time. Take as much time as you want, until you understand what you needed to understand.
-
 @ 79998141:0f8f1901
2025-01-02 05:04:56
@ 79998141:0f8f1901
2025-01-02 05:04:56Happy new year, Anon.
Thanks for tuning in to whatever this long form post will be. I hope to make these more regular, like journal entries as we travel through "real life" and the Nostrverse together. If I'm making time for this reflective writing, then things are going as planned.
2024 was a wildly transformative year for me for many reasons... there's no way I can possibly fit all of them here. They're not all related to Bitcoin and Nostr- I've got a beautiful life outside of all that which has its own independent arc. My wife and I celebrated 7 years of marriage together, stronger than ever (don't believe that "itch" bullshit). We let go of some negative relationships and embraced some positive ones. We cut some bad habits, and we made some good habits. We worked, we traveled, we saw family, and we partied.
But damn, these two technologies have become a huge part of my life. God willing, this trend will continue until they've both eclipsed my professional capacity through our startup, Conduit BTC.
This was the year I was truly orange pilled. Until late 2023, I had traded (quite profitably) Bitcoin, "crypto", stocks, options, prediction markets and whatever else I could get my hands on that felt undervalued. I did this all in my spare time, grinding out a little financial freedom while I hustled at my fiat ventures to support my little family. I wasn't a true believer- just an opportunist with a knack for spotting where and when a crowd might flock to next. That was right up until I ran face first into Lyn Alden's book "Broken Money".
Something about Lyn's engineer/macro-finance inspired prose clicked with me, lock and key. Total one way function. By the end of the book my laser eyes had burned a hole in my bedroom ceiling. I was all in- and acted accordingly both with my capital and my attention. It wasn't long before I discovered Nostr and dove in here too, falling deep into my current orange and purple polyamorous love affair.
"If you know the enemy and know yourself, you need not fear the result of a hundred battles."
Despite the passion, through studying Bitcoin's criticisms (from the likes of Mike Green and Nassim Taleb) I found a hole in the utopian plot: none of this works without Bitcoin actually being used as money. Worldwide transactions must skyrocket demand for blockspace to keep the network secure/stable for the long term. Besides, if everyday folks aren't using Bitcoin as money then we haven't done shit to make the world a better place. In that world, we've only replaced old masters with new ones. Fuck that.
Whatever I did in this space needed to increase the usage of Bitcoin as money. Simple. This was bigger than passion, this was purpose. I knew that come hell or high water I would dedicate myself to this mission.
Lucky for me I found a partner and best friend in @aceaspades to go on this adventure with. I'm infinitely grateful for him. He's an incredible man who also happens to be an insanely creative and talented software developer. We'd tried for years to find the right project to focus on together, experimenting with all kinds of new techy ideas as they came across our field. Nothing had ever captured our attention like this. This was different. By March of 2024 we had formed a company and gotten to work iterating on how we could leverage these beautiful protocols and open-source tech to create something that served our mission. This is @ConduitBTC.
I've done well in my fiat career executing plans downstream of someone else's creative vision. I've learned the ins and outs of an established ecosystem and found ways to profit from it. I take plans developed by others, compete to win contracts to build them, and execute on them in a cashflow-positive way. I'm bringing this no bullshit blue collar skillset with me to the Nostrverse whether they like it or not.
The adventure we're embarking on now is totally different though. We're charting a new course - totally creative, highly intuitive and extremely speculative towards a future that doesn't exist yet. There are few established norms. The potential is vast but unknown. We're diving into a strange quest to sell a map to an imaginary place and to simultaneously architect its creation (alongside all the amazing builders here doing the same thing). This is insanely exciting to me.
We're barely getting started but a lot has been invested under the surface which will show itself in 2025. We'll be sharing updates in a proper post on @ConduitBTC soon.
As for my personal 2025 resolutions, here they are: - zero alcohol for the entire year (did this in 2019 and had a great year, it's time for a rerun) - more focused presence in the moment: especially with my wife - more self care and prioritized mental/physical health - this includes daily: naps, prayer, self hypnosis or meditation, sweat, and stretching/massaging (overworked in 2024 with a fiat 9-5, a board/advisor role in a fiat business I have equity in, and my newfound passion here. Two serious burn out episodes experienced this year - zero is the only acceptable number of burnouts for long term health and success.) - related to the above: get Conduit some mission-aligned funding partners and leave my fiat 9-5. Grow the Conduit team (have put in a serious amount of my personal capital already to get this going, which will show fruit in the new year... but I am not an island) - more authentic and thoughtful posts on Nostr, with a solid amount of shitposting and organic home grown memes to balance it out... more zaps, more geniune connections and interactions with the curious forward thinking people on here - more IRL Nostr/Bitcoin events - more laughter, more jokes
Enough for now. Cheers to you and yours Anon, may 2025 bring you the magic you've been dreaming of.
-
 @ b17fccdf:b7211155
2025-01-21 18:42:14
@ b17fccdf:b7211155
2025-01-21 18:42:14Some guides on MiniBolt / RaMiX have suffered some modifications and need additional instructions to migrate. Here is a summary:
🔘 New installation/update instructions of BTC RPC Explorer to avoid this issue.
🔘 New installation/update method of Node + NPM.
🔘 New installation/update method of PostgreSQL ~ > Attention! If you installed PostgreSQL after 30/09/2024, you do not need to follow these steps related to PostgreSQL.
Update Nodejs + NPM to the latest LTS version (using the new method)
Guide related: Node + NPM
Context: The installation/upgrade section of this guide has suffered some modifications, so to upgrade to the latest LTS released version using the new installation method, you need to follow the next steps:
- Stop the Nodejs + NPM dependencies:
sudo systemctl stop thunderhub btcrpcexplorer- With user admin, update the packages and upgrade to keep up to date with the OS, press "y" and ENTER when needed or ENTER directly:
sudo apt update && sudo apt full-upgrade- Change to a temporary directory which is cleared on reboot:
cd /tmp- Set the environment variable of the version:
VERSION=22- We will use the new NodeSource Node.js Binary Distributions repository instructions. Download the setup script:
curl -fsSL https://deb.nodesource.com/setup_$VERSION.x -o nodesource_setup.sh- Run the setup script:
sudo -E bash nodesource_setup.sh- Update the package manager and update Node.js + NPM to the latest LTS version:
sudo apt update && sudo apt full-upgrade- Check the correct update of NodeJS:
node -vExample of expected output:
v22.12.0- Check the correct installation of NPM:
npm -vExample of expected output:
10.9.0- (Optional) Delete the setup script:
rm nodesource_setup.sh- Start again the Nodejs + NPM dependencies:
sudo systemctl start thunderhub btcrpcexplorer
Update BTC RPC Explorer to the latest version
Guide related: 2.3 Blockchain explorer: BTC RPC Explorer
Context: After this notice, if you deleted the
deprecatedrpc=warningsflag because it is no longer necessary, it is probably that the "Node Details" section of the BTC RPC Explorer got you this error, this is because after the Bitcoin Core v28 update, just like LND, Electrs and other services, they have needed an update to remain compatible. BTC RPC Explorer was updated on this commit, but an official version that includes this correction has not been officially released yet. To fix this, it is necessary to point to the current source code and not the one related to the last released version (3.4.0).~ > Get instructions to get this by following these steps and fix the issue ~ > HERE < ~
Update PostgreSQL (server instance migration & others)
Guide related: PostgreSQL
Attention!! If you installed PostgreSQL after 30/09/2024, you don't need to do anything, and the next steps don't apply to your case.
Context: With each major version jump of PostgreSQL, the update creates a new and dedicated cluster and folder with the number of each version. Also, the changes made between versions cause the need to migrate the database, that is, from one cluster to another, with a specific tool. This was unknown at the beginning, before creating the MiniBolt PostgreSQL installation guide, so a specific folder for the versions was not created. The installation section was changed past 30/09/2024 to use this new method, but people who followed the PostgreSQL installation before that, need to do things to be in line with the MiniBolt guide.
Following the next steps, we are going to do the necessary migrations, the summary is the next:
1. Migrate the PostgreSQL database to a new location (a dedicated folder for each version).
2. Migrate from PostgreSQL server version 16 to 17.
Verification
If you are not sure whether you installed PostgreSQL before or after the mentioned date (30/09/2024), you can check as follows:
- With user
adminlist the existing clusters:
pg_lsclustersExpected output if you installed PostgreSQL after 30/09/2024, (you don't need do anything):
Ver Cluster Port Status Owner Data directory Log file 17 main 5432 online postgres /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.logExpected output if you installed PostgreSQL before 30/09/2024, and performed a full upgrade of the MiniBolt with
sudo apt update && sudo apt full-upgrade, (you need to follow the next steps):Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb /var/log/postgresql/postgresql-16-main.log 17 main 5433 down postgres /var/lib/postgresql/17/main /var/log/postgresql/postgresql-17-main.logExpected output if you have not performed a full upgrade of the MiniBolt with
sudo apt update && sudo apt full-upgradesince 26/09/2024 (the PostgreSQL v17 release) (unlikely case) (you need to follow the next steps):Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb /var/log/postgresql/postgresql-16-main.log
Migrate the PostgreSQL database to the new location
(Only if you installed PostgreSQL following the MiniBolt guide before 30/09/2024)
- Show the existing clusters to show the current path of the database:
pg_lsclusters~ > Expected output if you have not performed a full upgrade of the MiniBolt with
sudo apt update && sudo apt full-upgradesince 26/09/2024 (PostgreSQL v17 release) (unlikely):Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb /var/log/postgresql/postgresql-16-main.log~ > Expected output if you have performed a full upgrade of the MiniBolt with
sudo apt update && sudo apt full-upgradesince 26/09/2024 (PostgreSQL v17 release) (most likely):Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb /var/log/postgresql/postgresql-16-main.log 17 main 5433 down postgres /var/lib/postgresql/17/main /var/log/postgresql/postgresql-17-main.log~ > Check the current "Data directory" column value of the cluster 16 (/data/postgresdb) for the future, we have changed this to a dedicated folder for each version (
/data/postgresdb/16,/data/postgresdb/17,/data/postgresdb/18, etc.)- Stop the PostgreSQL dependencies and the PostgreSQL version 16 cluster:
sudo systemctl stop thunderhub scbackup btcpay lnd nbxplorer nostrelay cloudflared postgresql@16-main~ > Ensure all services are successfully stopped by monitoring the logs of each service, especially lnd ~ >
journalctl -fu lnd.- Monitor the logs of the PostgreSQL version 16 cluster to ensure that it has been stopped gracefully:
journalctl -fu postgresql@16-mainExpected output:
minibolt systemd[1]: Stopping PostgreSQL Cluster 16-main... minibolt systemd[1]: postgresql@16-main.service: Deactivated successfully. minibolt systemd[1]: Stopped PostgreSQL Cluster 16-main.~ > Press
Ctrl + Cto continue.- Create a temporary directory in a place out of the
/data/postgresdbto move the data securely:
sudo mkdir /tmp/postgresdb-temp- Sync the existing data of the current directory
/data/postgresdbto this temporary directory:
sudo rsync -av /data/postgresdb/ /tmp/postgresdb-temp/Example of expected output:
``` [...] pg_xact/ pg_xact/0000 [...]
sent 40,397,103 bytes received 18,619 bytes 80,831,444.00 bytes/sec total size is 40,330,914 speedup is 1.00 ```
~ > Wait until the prompt shows up again.
- Change to the user
roottemporary:
sudo su- Delete the content of the folder that hosted the original database:
sudo rm -rf /data/postgresdb/*- Come back to the
adminuser:
exit- Create a new specific and dedicated folder to the version number and to be in line with the new and current storage method of the current guide:
sudo mkdir /data/postgresdb/16- Assign as the owner to the user
postgres:
sudo chown postgres:postgres /data/postgresdb/16- Assign the correct permissions to the folder:
sudo chmod 700 /data/postgresdb/16- Now you can sync the data from the temporary directory to
/data/postgresdb/16in a secure way since this directory is not inside the source directory:
sudo rsync -av /tmp/postgresdb-temp/ /data/postgresdb/16/Example of expected output:
``` [...] pg_xact/ pg_xact/0000 [...]
sent 40,397,103 bytes received 18,619 bytes 80,831,444.00 bytes/sec total size is 40,330,914 speedup is 1.00 ```
~ > Wait until the prompt shows up again.
- Modify the configuration file (
postgresql.conf) of the PostgreSQL to point to the new directory folder created:
sudo nano +42 /etc/postgresql/16/main/postgresql.conf- Replace the data directory location to match with the new path:
data_directory = '/data/postgresdb/16'- Start again the PostgreSQL service instance:
sudo systemctl start postgresql@16-main- Monitor the logs of the PostgreSQL version 16 cluster to ensure that it works fine:
journalctl -fu postgresql@16-mainExpected output:
minibolt systemd[1]: Starting PostgreSQL Cluster 16-main... minibolt systemd[1]: Started PostgreSQL Cluster 16-main.~ > Press
Ctrl + Cto continue.- Check the new database location with:
pg_lsclusters~ > Expected output if you have not performed a full upgrade of the MiniBolt with
sudo apt update && sudo apt full-upgradesince 26/09/2024 (unlikely):Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log~ > Expected output if you have performed a full upgrade of the MiniBolt with
sudo apt update && sudo apt full-upgradesince 26/09/2024 (most likely):Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log 17 main 5433 down postgres /var/lib/postgresql/17/main /var/log/postgresql/postgresql-17-main.log~ > Check the new path on the "Data directory" column value of the cluster version 16, now (/data/postgresdb/16).
- Start again the PostgreSQL dependencies services:
sudo systemctl start lnd nbxplorer btcpay thunderhub scb-backup nostr-relay cloudflared~ > Check all work fine with the logs of each service, especially lnd ~ >
journalctl -fu lnd.- Stop again the PostgreSQL dependencies services, to continue working:
sudo systemctl stop thunderhub scbackup btcpay lnd nbxplorer nostrelay cloudflared~ > Ensure all services are successfully stopped by monitoring the logs of each service, especially lnd ~ >
journalctl -fu lnd.Migrate from PostgreSQL server version 16 to 17
(Only if you installed PostgreSQL following the MiniBolt guide before 30/09/2024)
Context: If you fully updated your OS after 26/09/2024 (the PostgreSQL v17 launched), using
sudo apt update && sudo apt full-upgrade, and you installed PostgreSQL before that date following the PostgreSQL MiniBolt guide, it is likely that you now are using the old version (v16) of the PostgreSQL server instance.To confirm that, follow the next steps:
Check the PostgreSQL server version in use
- With the user
admin, enter the psql (PostgreSQL CLI):
sudo -u postgres psql- Enter the next command to get the server version:
SELECT version();Expected output:
``` version
PostgreSQL 16.6 (Ubuntu 16.6-1.pgdg22.04+1) on x86_64-pc-linux-gnu, compiled by gcc (Ubuntu 11.4.0-1ubuntu1~22.04) 11.4.0, 64-bit (1 row) ```
~ > Check the previous version is "PostgreSQL 16.6" (an outdated version of the PostgreSQL server), the latest version is PostgreSQL 17.2. 🔧✅ We are going to fix this in the next steps.
- Come back to the
adminuser bash prompt:
\q- List the cluster to show the state of the both PostgreSQL server instances:
pg_lsclusters~ > Expected output if you have not performed a full upgrade of the MiniBolt with
sudo apt update && sudo apt full-upgradesince 26/09/2024 (unlikely):Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log~ > Expected output if you have performed a full upgrade of the MiniBolt with
sudo apt update && sudo apt full-upgradesince 26/09/2024 (most likely):Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log 17 main 5433 down postgres /var/lib/postgresql/17/main /var/log/postgresql/postgresql-17-main.logUpdate PostgreSQL
If you haven't done so before, make sure to update the OS (PostgreSQL included to the latest version 17):
- With user
admin, fully update the OS with the package manager:
sudo apt update && sudo apt full-upgrade~ > Press "y" and enter or directly enter when the prompt asks you.
PostgreSQL server migration
- Stop all existing clusters:
sudo systemctl stop postgresql@16-main postgresql@17-main- Create a new database destination folder for the v17 cluster ready for migration from v16:
sudo mkdir /data/postgresdb/17- Assign the owner as the postgres user:
sudo chown postgres:postgres /data/postgresdb/17- Assign the correct permissions:
sudo chmod 700 /data/postgresdb/17- Delete the cluster created by default for v17:
sudo -u postgres pg_dropcluster 17 main- Update the systemd:
sudo systemctl daemon-reload- Start the migration with the PostgreSQL migration tool:
sudo -u postgres pg_upgradecluster 16 main /data/postgresdb/17~ > ⌛ This may take a lot of time depending on the existing database size (the nostr relay database especially) and your machine's performance; it is recommended to use tmux. Wait until the prompt shows up again.
Example of expected output:
``` Restarting old cluster with restricted connections... Notice: extra pg_ctl/postgres options given, bypassing systemctl for start operation Creating new PostgreSQL cluster 17/main ... /usr/lib/postgresql/17/bin/initdb -D /data/postgresdb/17 --auth-local peer --auth-host scram-sha-256 --no-instructions --encoding UTF8 --lc-collate en_US.UTF-8 --lc-ctype en_US.UTF-8 --locale-provider libc The files belonging to this database system will be owned by user "postgres". This user must also own the server process.
The database cluster will be initialized with locale "en_US.UTF-8". The default text search configuration will be set to "english".
Data page checksums are disabled.
fixing permissions on existing directory /data/postgresdb/17 ... ok creating subdirectories ... ok selecting dynamic shared memory implementation ... posix selecting default "max_connections" ... 100 selecting default "shared_buffers" ... 128MB selecting default time zone ... Etc/UTC creating configuration files ... ok running bootstrap script ... ok performing post-bootstrap initialization ... ok syncing data to disk ... ok Warning: systemd does not know about the new cluster yet. Operations like "service postgresql start" will not handle it. To fix, run: sudo systemctl daemon-reload
Copying old configuration files... Copying old start.conf... Copying old pg_ctl.conf... Starting new cluster... Notice: extra pg_ctl/postgres options given, bypassing systemctl for start operation Running init phase upgrade hook scripts ...
Roles, databases, schemas, ACLs... set_config
(1 row)
set_config
(1 row)
Fixing hardcoded library paths for stored procedures... Upgrading database postgres... Fixing hardcoded library paths for stored procedures... Upgrading database template1... Stopping target cluster... Stopping old cluster... Disabling automatic startup of old cluster... Starting upgraded cluster on port 5432... Warning: the cluster will not be running as a systemd service. Consider using systemctl: sudo systemctl start postgresql@17-main Running finish phase upgrade hook scripts ... vacuumdb: processing database "postgres": Generating minimal optimizer statistics (1 target) vacuumdb: processing database "template1": Generating minimal optimizer statistics (1 target) vacuumdb: processing database "postgres": Generating medium optimizer statistics (10 targets) vacuumdb: processing database "template1": Generating medium optimizer statistics (10 targets) vacuumdb: processing database "postgres": Generating default (full) optimizer statistics vacuumdb: processing database "template1": Generating default (full) optimizer statistics
Success. Please check that the upgraded cluster works. If it does, you can remove the old cluster with pg_dropcluster 16 main
Ver Cluster Port Status Owner Data directory Log file 16 main 5433 down postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log Ver Cluster Port Status Owner Data directory Log file 17 main 5432 online postgres /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log ```
- Reload the systemd again:
sudo systemctl daemon-reload- List the clusters to show the state:
pg_lsclustersExpected output:
Ver Cluster Port Status Owner Data directory Log file 16 main 5433 down <unknown> /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log 17 main 5432 online <unknown> /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log~> Notes: * Don't worry about the
output of the "Owner" column. * Note how the old 16 cluster has automatically gone into status "down" after the migration.
- Stop the version 17 cluster using the
pg_ctlclustertool, to then be able to run it and manage it withsystemd:
sudo pg_ctlcluster 17 main stop- List the clusters again to show the state:
pg_lsclustersExpected output:
Ver Cluster Port Status Owner Data directory Log file 16 main 5433 down <unknown> /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log 17 main 5432 down <unknown> /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log~> Note how the version 17 cluster has gone into status "down".
- Start the version 17 cluster with systemd:
sudo systemctl start postgresql@17-main- Monitor the logs of the PostgreSQL version 17 cluster to ensure that it working fine with
systemd:
journalctl -fu postgresql@17-mainExpected output:
minibolt systemd[1]: Starting PostgreSQL Cluster 17-main... minibolt systemd[1]: Started PostgreSQL Cluster 17-main.~ > Press
Ctrl + Cto continue.- List the clusters again to show the state:
pg_lsclustersExpected output:
Ver Cluster Port Status Owner Data directory Log file 16 main 5433 down <unknown> /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log 17 main 5432 online <unknown> /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log~> Note how the version 17 cluster has come back into the status "online".
- Delete the version 16 (old and disused) cluster:
sudo pg_dropcluster 16 main- List again the clusters to check the correct deletion:
pg_lsclustersExpected output:
Ver Cluster Port Status Owner Data directory Log file 17 main 5432 online <unknown> /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log~> Note how it no longer appears version 16 (old and disused) cluster.
Check the PostgreSQL server version in use
- With the user
admin, enter the psql (PostgreSQL CLI):
sudo -u postgres psql- Enter the next command to get the server version:
SELECT version();Example of expected output:
``` version
PostgreSQL 17.2 (Ubuntu 17.2-1.pgdg22.04+1) on x86_64-pc-linux-gnu, compiled by gcc (Ubuntu 11.4.0-1ubuntu1~22.04) 11.4.0, 64-bit (1 row) ```
~ > Check the previous version in use is now PostgreSQL 17.2 (the latest and current version of the PostgreSQL server at this moment).
- Come back to the
adminuser bash prompt:
\q- Start again the PostgreSQL dependencies services:
sudo systemctl start lnd nbxplorer btcpay thunderhub scb-backup nostr-relay cloudflared~ > Check all works fine with the logs of each service, especially lnd ~ >
journalctl -fu lnd.- (Optional) Once you have verified that everything is working correctly, you can delete the created PostgreSQL backup and temporary directory:
sudo rm -rf /tmp/postgresdb-temp- Delete unnecessary packages:
sudo apt autoremove~ > Press "y" and ENTER when needed or ENTER directly when the prompts ask you.
✅ That's it! If you have any questions or issues, you can go to any RRSS available for the MiniBolt project ~ > HERE < ~
Only for MiniBolters! Enjoy it! 💙
-
 @ b17fccdf:b7211155
2025-01-21 18:39:47
@ b17fccdf:b7211155
2025-01-21 18:39:47~ > Check out the steps to get this ~ > HERE < ~
Note: for different reasons, it is recommended choosing Option 1: DoT & DNSSEC using systemd-resolved, but you could want to use Option 2, choose behind your criteria, both are valid to achieve the same objective.
Some more changes were released recently in other places of the MiniBolt guide, check the full release notes:
Full release notes
~ > Static IP & custom DNS servers bonus guide:
- Adds custom DNS server suggestions.
- Adds different steps to check the changes after configurations.
- Deleted some unnecessary steps.
- Fix some nits.
~ > Modifications on Configuration (
bitcoin.conf) of Bitcoin Core:- Replace proxy value parameter to use UNIX domain socket (
proxy=unix:/run/tor/socks) | (recently enabled on Bitcoin Core v28). - Replace
startupnotify=chmod g+r /home/bitcoin/.bitcoin/.cookietorpccookieperms=groupBitcoin Core PR. - Adds another special bind address to listen to incoming connections from Tor (
bind=127.0.0.1=onion) | (recently changed on Bitcoin Core v28). - Modified systemd service to improve the startup and shutdown process.
Note: remember to restart Bitcoin Core and reload the systemd with
sudo systemctl daemon-reloadto apply changes.
~ > Delete unnecessary parameters of the systemd service of Lightning client.
Note: remember to reload the systemd with
sudo systemctl daemon-reloadto apply changes.
~ > Others:
- New i2pd webconsole section.
- Adds a new "Validation" subsection to the guides to clarify when checks begin.
- New "Use the Tor proxy from another device" section.
- Adds Electrs compatible with Testnet4 on Testnet bonus guide.
- Adds how to build a Guard/Middle relay section on "Tor services: bridges & relays" bonus guide.
- Adds Extras (optional) section to "Tor services: bridges & relays" bonus guide with different utilities like install Nyx, how to "Limit bandwidth" and others.
- Changed Electrs ports to enable simultaneous mode with Fulcrum.
- Updated aliases list to include news additions in line with updates.
- Updated the Networkmap resource to include news additions in line with updates and migrate to a dynamic visual mode.
- Reorganized some menu items and sections to improve the UX and make more sense in the face of the future.
- Restructure and rename the "Tor obfs4 bridge" bonus guide to "Tor services: bridges & relays" and modify it to run the obfs4bridge, relays, and the master, in separate instances.
- Hidden NYM mixnet and Sparrow server bonus guides from the menus due to disuse or poor performance. Note: it will continue to be maintained later if the situation changes due to the development of the associated software.
- Bump version of various services.
~ > Coming soon...
- Enable DNSSEC for your domain using Cloudflare + Namecheap.
- Enable DoH on:
- Desktop/Android browser (Windows/Linux).
- OS: Windows 11 // Linux (Completed ✅)
- Router.
- Enable DoT on:
- Android OS.
- OS: Windows 11 // Linux (Completed ✅) with DNSSEC verification included.
- Router.
Enjoy it MiniBolter!💙
-
 @ db01672e:9f775028
2025-01-30 07:27:15
@ db01672e:9f775028
2025-01-30 07:27:15When looking for the right Alzheimer's care home in Rockwall, choosing a facility that provides specialized care, emotional support, and a comfortable environment is crucial.
Alzheimer's care homes are designed to cater to the unique needs of individuals dealing with Alzheimer's disease or other forms of dementia.
Selecting the right facility can make a significant difference in ensuring a high quality of life for your loved one. Here are eight essential points to consider when choosing an Alzheimer's care home in Rockwall.
Specialized Care for Alzheimer’s and Dementia
Alzheimer’s and dementia patients require tailored care that is different from the general senior living options. https://villagegreenalzheimerscare.com/rockwall/ that provide dedicated Alzheimer’s care should have a trained team familiar with the complexities of memory loss and cognitive decline.
Look for a facility that focuses on the individual needs of each resident, offering personalized care plans that address both physical and emotional well-being.
Safe and Secure Environment
A secure environment is essential for Alzheimer's care homes, as residents may become confused or disoriented and wander. The facility should have secure entrances, exits, and enclosed outdoor areas to keep residents safe.
Additionally, the layout should be easy to navigate, with calming and clear signage to reduce confusion.
Trained and Compassionate Staff
The caregivers at an Alzheimer’s care home in Rockwall should be experienced, patient, and compassionate.
The quality of staff and their training is paramount. Caregivers who understand the behavior and communication challenges of those with Alzheimer’s can help reduce frustration and create a calming atmosphere.
Staff should also have training in first aid, CPR, and handling medical emergencies specific to Alzheimer’s and dementia.
Person-Centered Care Approach
An ideal Alzheimer’s care home will adopt a person-centered approach to care. This method emphasizes respecting the individual’s preferences, life history, and unique needs
A good Alzheimer’s care facility will encourage residents to maintain independence, creating a balance between support and autonomy.
Engaging and Stimulating Activities
Look for a facility that offers a variety of activities designed to engage the mind and body. Alzheimer’s patients benefit from daily activities that promote cognitive stimulation, such as music therapy, art, and memory exercises.
Many assisted living facilities in Rockwall, TX, also offer physical exercises to help mobility and overall health. These tailored activities should reflect residents’ interests and provide comfort and joy.
Comfortable and Homelike Environment
The atmosphere of an Alzheimer’s care home should be warm and inviting, like home. This homelike environment can help residents feel secure and at ease.
The facility should offer comfortable common areas, family-style dining, and private rooms or suites where residents can retreat. Calming colors, familiar furnishings, and soothing lighting can also help reduce anxiety and agitation.
Quality Nutrition and Meal Options
Nutrition plays a vital role in the health of individuals with Alzheimer’s. A memory care facility should provide meals that are not only nutritious but also cater to residents' preferences.
Facilities that offer family-style dining often help create a sense of community and comfort during mealtime. Special diets or modified meals should also be available to accommodate residents' medical or dietary needs.
Physical and Mental Health Services
Assisted living facilities in Rockwall, TX, that offer Alzheimer's care should provide access to various healthcare services, including regular medical checkups and specialized care for related health issues. The facility should partner with doctors, nurses, and therapists who can offer on-site care, ensuring that residents receive the medical attention they need without leaving the facility.
The End Note
Selecting an Alzheimer’s care home in Rockwall involves careful consideration of several factors that will impact the quality of life of your loved one.
From specialized care to a nurturing environment, finding a facility that balances medical needs with emotional support is essential. By focusing on these points, you can make an informed decision to ensure peace of mind for the resident and their family.
-
 @ b17fccdf:b7211155
2025-01-21 18:33:28
@ b17fccdf:b7211155
2025-01-21 18:33:28
CHECK OUT at ~ > ramix.minibolt.info < ~
Main changes:
- Adapted to Raspberry Pi 5, with the possibility of using internal storage: a PCIe to M.2 adapter + SSD NVMe:
Connect directly to the board, remove the instability issues with the USB connection, and unlock the ability to enjoy higher transfer speeds**
- Based on Debian 12 (Raspberry Pi OS Bookworm - 64-bit).
- Updated all services that have been tested until now, to the latest version.
- Same as the MiniBolt guide, changed I2P, Fulcrum, and ThunderHub guides, to be part of the core guide.
- All UI & UX improvements in the MiniBolt guide are included.
- Fix some links and wrong command issues.
- Some existing guides have been improved to clarify the following steps.
Important notes:
- The RRSS will be the same as the MiniBolt original project (for now) | More info -> HERE <-
- The common resources like the Roadmap or Networkmap have been merged and will be used together | Check -> HERE <-
- The attempt to upgrade from Bullseye to Bookworm (RaspiBolt to RaMiX migration) has failed due to several difficult-to-resolve dependency conflicts, so unfortunately, there will be no dedicated migration guide and only the possibility to start from scratch ☹️
⚠️ Attention‼️-> This guide is in the WIP (work in progress) state and hasn't been completely tested yet. Many steps may be incorrect. Pay special attention to the "Status: Not tested on RaMiX" tag at the beginning of the guides. Be careful and act behind your responsibility.
For Raspberry Pi lovers!❤️🍓
Enjoy it RaMiXer!! 💜
By ⚡2FakTor⚡ for the plebs with love ❤️🫂
- Adapted to Raspberry Pi 5, with the possibility of using internal storage: a PCIe to M.2 adapter + SSD NVMe:
-
 @ b17fccdf:b7211155
2025-01-21 18:30:13
@ b17fccdf:b7211155
2025-01-21 18:30:13~ > Available at: https://minibolt.info
~> It builds on a personal computer with x86/amd64 architecture processors.
~> It is based on the popular RaspiBolt v3 guide.
Those are some of the most relevant changes:
- Changed OS from Raspberry Pi OS Lite (64-bits) to Ubuntu Server LTS (Long term support) 64-bit PC (AMD64).
- Changed binaries and signatures of the programs to adapt them to x86/amd64 architecture.
- Deleted unnecessary tools and steps, and added others according to this case of use.
- Some useful authentication logs and monitoring commands were added in the security section.
- Added some interesting parameters in the settings of some services to activate and take advantage of new features.
- Changed I2P, Fulcrum, and ThunderHub guides, to be part of the core guide.
- Added exclusive optimization section of services for slow devices.
~ > Complete release notes of the MiniBolt v1: https://github.com/twofaktor/minibolt/releases/tag/1.0.
~ > Feel free to contribute to the source code on GitHub by opening issues, pull requests or discussions.
Created by ⚡2 FakTor⚡
-
 @ dd664d5e:5633d319
2024-12-29 20:29:03
@ dd664d5e:5633d319
2024-12-29 20:29:03The paparazzi are we

One of the things that bothers me about social media, in general, is that it gives celebrities an air of approachability, that they don't actually offer.
Theoretically, a celebrity could respond to any one of the dozens or even hundreds of people asking them questions or lodging complaints or singing their praises, but they usually only respond very selectively and leave everyone else just sitting there, as a living monument to the ReplyGuy.
And, as a wise man once said, ReplyGuy is a hoe.
Death of a ReplyGuy
This is usually because of time and energy restrictions, but also due to distaste, disdain, or indifference. Regardless of motivation, it is simply the nature of things, when a larger number of people are clamboring for the attention of some particular person.
Ooh, ooh! Can I have the next question?! Would you please address my bug? May I have a microsecond of your time?

Social media (and I include GitHub in this category) ups this game considerably, and potentially turns it all into a dangerous psychological torture, by making us all preoccupied with people who don't interact with us. The most irrational of groupies because we are forever making almost-contact with our stars.
If we can see them talking to one person, we're supposed to feel like they've spoken with all of us. But they haven't. They spoke with someone else, and we were allowed to watch. No different than on television, except that we might be disappointed and eager to return the next day, to renew our futile attempt.
The same intoxicating feeling that playing the lottery elicits. Everyone is a potential winner, but there is only one jackpot. Come back next week. Buy another ticket. This next time, is your time. Promise.
The view from the peanut gallery

It is all an illusion that there is no hierarchy, where there clearly is one. Celebrities of the past had, at least, the decency to remain slightly aloof. But they all want to be one of the Common Folk, now, just as every multi-millionaire aspires to see himself as fundamentally working-class.

All of celebrity social media is a stage, and most of us are merely spectators or commentators, to what is playing on it. This is why, if someone treats me like someone sitting in the peanut gallery, my instinct is to treat them like an actor.
Because, in reality, that is what they are.
-
 @ 89ccea93:df4e00b7
2025-01-30 06:46:51
@ 89ccea93:df4e00b7
2025-01-30 06:46:51Disillusioned with the country you're in? Want to live somewhere else? Can't seem to save at a reasonable rate? In debt due to high cost of living? Ready to retire but worried you don't have enough money?
I would argue that a lot of these problems could be solved by moving to a different country.
Expatriate: one who leaves their country to work abroad. Often called "expats" for short.Consider moving to a country with a lower cost of living. Bring your skills and talents. Earn a wage while working remotely. Or find a job abroad that values your labor more than back home, like being an international school teacher (that's what I do).
Instead of waiting until you're 65 to retire. Earn and save in a stronger currency, making a higher income in NYC, LA, Nashville, etc., then abscond to the beaches of Indonesia, Thailand, or Ecuador where your money stretches way further.
None of this needs to be permanent. Some people work domestically for 6 months and travel for 6 months. Or work for a year and travel for a year.
Speaking from experience as an international school teacher, the math works out pretty well. Competitive salary + lower living costs = serious saving potential, all while living a great life.
There are costs to leaving the country you know. Culture gaps. Language gaps. So you really need to assess your own situation.
I recommend reading the book "Vagabonding" by Rolf Potts. Listen to the "Radical Personal Finance" podcast by Joshua Sheats, who moved his family to Mexico.
Basically, you're not trapped.You're free.Go where you like, do what you like.But please, don't think you need to work til you're 65 at a job you hate just to finally live your dreams sipping martinis on a beach in Thailand or golfing/fishing all day.You can do that right now.The table should help you visualize the cost of living in various countries.
Table 1: Examples of countries relative purchasing power using the US as base 100.
| Rank | Country/Region | Cost index | Monthly income | Purchasing power index | |:----:|---------------|:------------:|:----------------:|:------------------------:| | 1 | Switzerland | 131.4 | 7,958 USD | 94.6 | | 6 | Ireland | 110.6 | 6,644 USD | 93.9 | | 9 | Australia | 107.0 | 5,070 USD | 74.1 | | 15 | United States | 100.0 | 6,398 USD | 100.0 | | 16 |United Kingdom| 98.5| 4,103 USD |65.1| | 18| Sweden |93.9 |5,292 USD| 88.1| | 21 |Japan |84.9 |3,537 USD| 65.1| | 22 |France |83.2 |3,774 USD |70.9| | 24 |Germany |82.3 |4,503 USD |85.6| | 29 |Singapore |72.1 |5,600 USD |121.3| | 31 |Portugal |67.9 |2,163 USD| 49.8| | 32 |United Arab Emirates |67.2 |4,097 USD | 95.3| | 39 |Chile |58.3 |1,280 USD| 34.3| | 40 |China |57.6| 1,071 USD| 29.1| | 44 |Brazil |49.8 |678 USD| 21.3| | 45 |Ecuador |49.7| 525 USD| 16.5| | 48 |El Salvador |48.2 |393 USD| 12.7| | 49 |Honduras |47.5| 229 USD| 7.5| | 63 |Colombia |38.2 |542 USD |22.2| | 67 |Philippines |36.5 |329 USD |14.1| | 75 |Thailand |34.7 |603 USD |27.2| | 77 |Indonesia |33.1 |382 USD |18.0| | 79 |Vietnam |32.4 |334 USD |16.1 |
Source: https://www.worlddata.info/cost-of-living.php
originally posted at https://stacker.news/items/869610
