-
 @ a10260a2:caa23e3e
2025-01-18 12:04:41
@ a10260a2:caa23e3e
2025-01-18 12:04:41Last Updated: January 18, 2025
First off, big shoutout to Coinos for having support for adding a memo to BOLT12 offers. This provides a solid alternative for the pleb who wants to support mining decentralization but doesn’t want to set up a CLN node and pay thousands of sats for a channel only to get little rewards. This is the case for most of us who only have a miner or two (e.g. a Bitaxe and/or an S9).
Before we get into setting up Lightning payouts, you’ll want to have your miner configured to mine with OCEAN of course. You’ll also want to make sure that the bitcoin address you use is from a wallet that supports signing messages.
These are the ones listed in the OCEAN docs:
- Bitcoin Knots/Bitcoin Core
- Coldcard
- Electrum
- LND (Command Line)
- Seedsigner
- Sparrow
- Specter
- Trezor
I checked one of my favorite, user-friendly wallets — Blue Wallet — and it happens to support signing messages as well.
Just tap the three dots on the upper right and you’ll see the “Sign/Verify Message” button at the bottom.
Update [January 18]: You can now use Coinos to sign by going to https://coinos.io/sign
The trick here is to not refresh the page. In other words, when you're logged in to your Coinos account, go to the URL and use the legacy address (starts with a "1") that's displayed to configure your miner(s). If you refresh the page, you're going to get a new address which will cause the signing to fail later on. Remember, keep the tab open and don't refresh the page.

Whichever wallet you choose, generate a receive address to use when configuring your miner (it’ll also be your OCEAN username).
Here’s how it looks on the Bitaxe (AxeOS)…
And the Antminer S9 (Braiins OS).
NOTE: There’s a slight difference in the URL format between the two apps. Other than that, the username will be your bitcoin address followed by the optional “.” + the nickname for your machine.
You can find more details on OCEAN’s get started page.
Alright, now that your miner is pointed at OCEAN. Let’s configure Lightning payouts!
Generating the BOLT12 Offer
In the Coinos app, go to Receive > Bolt 12.
Tap “Set memo” and set it to “OCEAN Payouts for [insert your bitcoin address]” (this text is case-sensitive). Use the same bitcoin address you used above to configure your miner(s).
After tapping OK, copy the BOLT12 offer (it should start with “lno”) and proceed to the next step.
Generating the Configuration Message
Navigate to the My Stats page by searching for your OCEAN Bitcoin address.
The click the Configuration link next to Next Block to access the configuration form.
Paste the BOLT12 offer here, update the block height to latest, click GENERATE, and copy the generated unsigned message.
Signing the Configuration Message
To sign the generated message, go back to Blue Wallet and use the signing function. Paste the configuration message in the Message field, tap Sign, and copy the signed message that’s generated.
If you're using Coinos to sign, return to the page that you kept open (and didn't refresh) and do the same. Paste the configuration message, click submit, and copy the signed message.
Submitting the Signed Message
Once signed, copy the signature, paste it in the OCEAN configuration form, and click CONFIRM.
If all goes well, you should see a confirmation that the configuration was successful. Congrats! 🎉
All you gotta do now is sit back, relax, and wait for a block to be found…
Or you can look into setting up DATUM. 😎
-
 @ 7f29628d:e160cccc
2025-01-07 11:50:30
@ 7f29628d:e160cccc
2025-01-07 11:50:30Der gut informierte Bürger denkt bei der Pandemie sofort an Intensivstationen, an die Bilder aus Bergamo und erinnert sich an die Berichterstattung damals – also muss es wohl ein Maximum gewesen sein. Manche Skeptiker behaupten jedoch das Gegenteil. Klarheit sollte ein Blick nach Wiesbaden, zum Statistischen Bundesamt, schaffen. Schließlich sitzen dort gut bezahlte Profis, die seit vielen Jahrzehnten die Sterbestatistik pflegen und veröffentlichen. Jeder Todesfall wird in Deutschland über die Standesämter exakt erfasst.
Doch die Überraschung: Das Statistische Bundesamt liefert uns auf diese einfache Frage zwei extrem unterschiedliche Antworten – ein Minimum und ein Maximum. Das Ergebnis hängt davon ab, wie tief man in die Veröffentlichungen des Bundesamtes eintaucht. Betrachtet man nur die Webseiten und Pressemitteilungen, erhält man den Eindruck eines Maximums. Schaut man jedoch etwas tiefer in die Tabellen und Rohdaten, zeigt sich plötzlich ein Minimum. Aber wie kann das sein? Beides gleichzeitig geht ja wohl kaum. Wer lügt hier – die Tabellen des Amtes oder die Pressemitteilungen? Gehen wir dieser Frage Schritt für Schritt auf den Grund.
2020: Ein historisches Maximum?
Schauen wir uns die vielen Hundert Veröffentlichungen des Statistischen Bundesamtes aus dieser Zeit an. Oder wir kürzen ab und fragen ChatGPT, da die KI auf diesen Daten trainiert wurde und das gesamte Material kennt. Die Frage an ChatGPT lautet also: Wie war das Sterbegeschehen im Jahr 2020 im Vergleich zu den Vorjahren?
ChatGPT antwortet: »Im Jahr 2020 war die Sterblichkeit in Deutschland höher als in den Jahren zuvor. Es gab eine Übersterblichkeit von etwa 982.000 Todesfällen, das sind rund 46.000 mehr als der Durchschnitt der Vorjahre (2016 bis 2019). Dieser Anstieg wurde überwiegend im Zusammenhang mit der COVID-19-Pandemie gesehen. Während die Sterbezahlen in den Vorjahren schwankten, war ein solch signifikanter Anstieg wie 2020 bisher nicht zu beobachten.«
Wir fragen konkreter: Ist es ein Fakt, dass wir eine so ernste Lage im Sterbegeschehen wie im Frühjahr 2020 noch nie erlebt haben?
ChatGPT bestätigt: »Ja, die COVID-19-Pandemie führte im Frühjahr 2020 zu einer außergewöhnlichen Situation im Sterbegeschehen in Deutschland. Die dramatische Übersterblichkeit, die ab der 13. Kalenderwoche auftrat, veranlasste das Statistische Bundesamt, besonders eindringliche Warnungen zu veröffentlichen. Der damalige Vizepräsident des Amtes und andere führende Stimmen wiesen öffentlich darauf hin, dass die Todesfallzahlen stark vom Durchschnitt abwichen. Diese klare Warnung richtete sich an die Öffentlichkeit und die Politik gleichermaßen. Die Medien berichteten intensiv über diese Warnungen, was das Bewusstsein für die Schwere der Pandemie erheblich schärfte. In den vergangenen Jahrzehnten hatte es keine vergleichbare Übersterblichkeit gegeben, die eine solch umfangreiche Kommunikation durch das Statistische Bundesamt erforderlich gemacht hätte.«
Ein gut informierter Zeitungsleser wird sich an dieser Stelle bestätigt fühlen: Ja, so war es damals. Ein Maximum im Sterbegeschehen – wegen der Pandemie. Oder etwa nicht?
2020: Ein historisches Minimum?
Tauchen wir in die Rohdaten des Statistischen Bundesamtes ein. Die Tabellen, die das Amt seit Jahrzehnten verlässlich veröffentlicht, nennen sich Sterbetafeln. Diese werden jährlich bereitgestellt und stehen auf der Website des Bundesamtes zum Download bereit. Ein erster Blick in die Sterbetafeln mag den Laien abschrecken, doch mit einer kurzen Erklärung wird alles verständlich. Wir gehen schrittweise vor.
Nehmen wir die Sterbetafel des Jahres 2017. Sie enthält zwei große Tabellen – eine für Männer und eine für Frauen. Jede Zeile der Tabelle steht für einen Jahrgang, zum Beispiel zeigt die Zeile 79 die Daten der 79-jährigen Männer. Besonders wichtig ist nun die zweite Spalte, in der der Wert 0,05 eingetragen ist. Das bedeutet, dass 5 Prozent der 79-jährigen Männer im Jahr 2017 verstorben sind. Das ist die wichtige Kennzahl. Wenn wir diesen exakten Wert, den man auch als Sterberate bezeichnet, nun in ein Säulendiagramm eintragen, erhalten wir eine leicht verständliche visuelle Darstellung (Grafik 1).

Es ist wichtig zu betonen, dass dieser Wert weder ein Schätzwert noch eine Modellrechnung oder Prognose ist, sondern ein exakter Messwert, basierend auf einer zuverlässigen Zählung. Sterberaten (für die Fachleute auch Sterbewahrscheinlichkeiten qx) sind seit Johann Peter Süßmilch (1707–1767) der Goldstandard der Sterbestatistik. Jeder Aktuar wird das bestätigen. Fügen wir nun die Sterberaten der 79-jährigen Männer aus den Jahren davor und danach hinzu, um das Gesamtbild zu sehen (Grafik 2). Und nun die entscheidende Frage: Zeigt das Jahr 2020 ein Maximum oder ein Minimum?

Ein kritischer Leser könnte vermuten, dass die 79-jährigen Männer eine Ausnahme darstellen und andere Jahrgänge im Jahr 2020 ein Maximum zeigen würden. Doch das trifft nicht zu. Kein einziger Jahrgang verzeichnete im Jahr 2020 ein Maximum. Im Gegenteil: Auch die 1-Jährigen, 2-Jährigen, 3-Jährigen, 9-Jährigen, 10-Jährigen, 15-Jährigen, 18-Jährigen und viele weitere männliche Jahrgänge hatten ihr Minimum im Jahr 2020. Dasselbe gilt bei den Frauen. Insgesamt hatten 31 Jahrgänge ihr Minimum im Jahr 2020. Wenn wir schließlich alle Jahrgänge in einer einzigen Grafik zusammenfassen, ergibt sich ein klares Bild: Das Minimum im Sterbegeschehen lag im Jahr 2020 (Grafik 3).

Ein kritischer Leser könnte nun wiederum vermuten, dass es innerhalb des Jahres 2020 möglicherweise starke Ausschläge nach oben bei einzelnen Jahrgängen gegeben haben könnte, die später durch Ausschläge nach unten ausgeglichen wurden – und dass diese Schwankungen in der jährlichen Übersicht nicht sichtbar sind. Doch auch das trifft nicht zu. Ein Blick auf die wöchentlichen Sterberaten zeigt, dass die ersten acht Monate der Pandemie keine nennenswerten Auffälligkeiten aufweisen. Es bleibt dabei: Die Rohdaten des Statistischen Bundesamtes bestätigen zweifelsfrei, dass die ersten acht Monate der Pandemie das historische Minimum im Sterbegeschehen darstellen. (Für die Fachleute sei angemerkt, dass im gleichen Zeitraum die Lebenserwartung die historischen Höchststände erreicht hatte – Grafik 4.)

So konstruierte das Amt aus einem Minimum ein Maximum:
Zur Erinnerung: Die Rohdaten des Statistischen Bundesamtes, die in den jährlichen Sterbetafeln zweifelsfrei dokumentiert sind, zeigen für das Jahr 2020 eindeutig ein Minimum im Sterbegeschehen. Aus diesen »in Stein gemeißelten« Zahlen ein Maximum zu »konstruieren«, ohne die Rohdaten selbst zu verändern, scheint auf den ersten Blick eine unlösbare Aufgabe. Jeder Student würde an einer solchen Herausforderung scheitern. Doch das Statistische Bundesamt hat einen kreativen Weg gefunden - ein Meisterstück gezielter Manipulation. In fünf Schritten zeigt sich, wie diese Täuschung der Öffentlichkeit umgesetzt wurde:
(1) Ignorieren der Sterberaten: Die präzisen, objektiven und leicht verständlichen Sterberaten aus den eigenen Sterbetafeln wurden konsequent ignoriert und verschwiegen. Diese Daten widersprachen dem gewünschten Narrativ und wurden daher gezielt ausgeklammert.
(2) Fokus auf absolute Todeszahlen: Die Aufmerksamkeit wurde stattdessen auf die absolute Zahl der Todesfälle gelenkt. Diese wirkt allein durch ihre schiere Größe dramatisch und emotionalisiert die Diskussion. Ein entscheidender Faktor wurde dabei ignoriert: Die absolute Zahl der Todesfälle steigt aufgrund der demografischen Entwicklung jedes Jahr an. Viele Menschen verstehen diesen Zusammenhang nicht und verbinden die steigenden Zahlen fälschlicherweise mit der vermeintlichen Pandemie.
(3) Einführung der Übersterblichkeit als neue Kennzahl: Erst ab Beginn der „Pandemie“ wurde die Kennzahl "Übersterblichkeit" eingeführt – und dies mit einer fragwürdigen Methode, die systematisch überhöhte Werte lieferte. Diese Kennzahl wurde regelmäßig, oft monatlich oder sogar wöchentlich, berechnet und diente als ständige Grundlage für alarmierende Schlagzeilen.
(4) Intensive Öffentlichkeitsarbeit: Durch eine breit angelegte Kampagne wurden die manipulativen Kennzahlen gezielt in den Fokus gerückt. Pressemitteilungen, Podcasts und öffentliche Auftritte konzentrierten sich fast ausschließlich auf die absoluten Todeszahlen und die Übersterblichkeit. Ziel war es, den Eindruck einer dramatischen Situation in der Öffentlichkeit zu verstärken.
(5) Bekämpfen kritischer Stimmen: Kritiker, die die Schwächen und manipulativen Aspekte dieser Methoden aufdeckten, wurden systematisch diskreditiert. Ihre Glaubwürdigkeit und Kompetenz wurden öffentlich infrage gestellt, um das sorgsam konstruierte Narrativ zu schützen.
Ohne diesen begleitenden Statistik-Betrug wäre das gesamte Pandemie-Theater meiner Meinung nach nicht möglich gewesen. Wer aus einem faktischen Minimum ein scheinbares Maximum "erschafft", handelt betrügerisch. Die Folgen dieses Betruges sind gravierend. Denken wir an die Angst, die in der Bevölkerung geschürt wurde – die Angst, bald sterben zu müssen. Denken wir an Masken, Abstandsregeln, isolierte ältere Menschen, Kinderimpfungen und all die Maßnahmen, die unter anderem auf diese falsche Statistik zurückgehen.
Wollen wir Bürger uns das gefallen lassen?
Wenn wir als Bürger zulassen, dass ein derart offensichtlicher und nachprüfbarer Täuschungsversuch ohne Konsequenzen bleibt, dann gefährdet das nicht nur die Integrität unserer Institutionen – es untergräbt das Fundament unserer Gesellschaft. In der DDR feierte man öffentlich Planerfüllung und Übererfüllung, während die Regale leer blieben. Damals wusste jeder: Statistik war ein Propagandainstrument. Niemand traute den Zahlen, die das Staatsfernsehen verkündete.
Während der Pandemie war es anders. Die Menschen vertrauten den Mitteilungen des Statistischen Bundesamtes und des RKI – blind. Die Enthüllungen durch den "RKI-Leak" haben gezeigt, dass auch das Robert-Koch-Institut nicht der Wissenschaft, sondern den Weisungen des Gesundheitsministers und militärischen Vorgaben folgte. Warum sollte es beim Statistischen Bundesamt anders gewesen sein? Diese Behörde ist dem Innenministerium unterstellt und somit ebenfalls weisungsgebunden.
Die Beweise für Täuschung liegen offen zutage. Es braucht keinen Whistleblower, keine geheimen Enthüllungen: Die Rohdaten des Statistischen Bundesamtes sprechen für sich. Sie sind öffentlich einsehbar – klar und unmissverständlich. Die Daten, die Tabellen, die Veröffentlichungen des Amtes selbst – sie sind die Anklageschrift. Sie zeigen, was wirklich war. Nicht mehr und nicht weniger.
Und wir? Was tun wir? Schweigen wir? Oder fordern wir endlich ein, was unser Recht ist? Wir Bürger dürfen das nicht hinnehmen. Es ist Zeit, unsere Behörden zur Rechenschaft zu ziehen. Diese Institutionen arbeiten nicht für sich – sie arbeiten für uns. Wir finanzieren sie, und wir haben das Recht, Transparenz und Verantwortung einzufordern. Manipulationen wie diese müssen aufgearbeitet werden und dürfen nie wieder geschehen. Die Strukturen, die solche Fehlentwicklungen in unseren Behörden ermöglicht haben, müssen offengelegt werden. Denn eine Demokratie lebt von Vertrauen – und Vertrauen muss verdient werden. Jeden Tag aufs Neue.
.
.
MARCEL BARZ, Jahrgang 1975, war Offizier der Bundeswehr und studierte Wirtschafts- und Organisationswissenschaften sowie Wirtschaftsinformatik. Er war Gründer und Geschäftsführer einer Softwarefirma, die sich auf Datenanalyse und Softwareentwicklung spezialisiert hatte. Im August 2021 veröffentlichte Barz den Videovortrag »Die Pandemie in den Rohdaten«, der über eine Million Aufrufe erzielte. Seitdem macht er als "Erbsenzähler" auf Widersprüche in amtlichen Statistiken aufmerksam.
-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ f9cf4e94:96abc355
2024-12-31 20:18:59
@ f9cf4e94:96abc355
2024-12-31 20:18:59Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( dominictarr ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt (ssb) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia.
Se você está se perguntando de onde diabos veio o nome Scuttlebutt:
Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.

Marinheiros se reunindo em torno da rixa. ( fonte )
Dominic descobriu o termo boato em um artigo de pesquisa que leu.
Em sistemas distribuídos, fofocar é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”.
Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto. Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar. Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário de bordo (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem.
Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. Cada item adicionado a um log do usuário é chamado de mensagem.
Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.

Perspectivas dos participantes
Scuttlebot
O software Pub é conhecido como servidor Scuttlebutt (servidor ssb ), mas também é conhecido como “Scuttlebot” e
sbotna linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial.Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.


Perspectivas dos participantes
Pubs - Hubs
Pubs públicos
| Pub Name | Operator | Invite Code | | ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ | |
scuttle.us| @Ryan |scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=| | pub1.upsocial.com | @freedomrules |pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=| | Monero Pub | @Denis |xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=| | FreeSocial | @Jarland |pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=| |ssb.vpn.net.br| @coffeverton |ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=| | gossip.noisebridge.info | Noisebridge Hackerspace @james.network |gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=|Pubs privados
Você precisará entrar em contato com os proprietários desses bares para receber um convite.
| Pub Name | Operator | Contact | | --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- | |
many.butt.nz| @dinosaur | mikey@enspiral.com | |one.butt.nz| @dinosaur | mikey@enspiral.com | |ssb.mikey.nz| @dinosaur | mikey@enspiral.com | | ssb.celehner.com | @cel | cel@celehner.com |Pubs muito grandes
Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)
| Pub Name | Operator | Invite Code | | --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ | |
scuttlebutt.de| SolSoCoG |scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=| |Lohn's Pub| @lohn |p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=| | Scuttle Space | @guil-dot | Visit scuttle.space | |SSB PeerNet US-East| timjrobinson |us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=| | Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= |GUI - Interface Gráfica do Utilizador(Usuário)
Patchwork - Uma GUI SSB (Descontinuado)
Patchwork é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.

Fonte: scuttlebutt.nz
Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub. Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs.
Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth.
Patchbay - Uma GUI Alternativa
Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que Patchwork e Patchfoo , então você pode facilmente dar uma volta com sua identidade existente.

Planetary - GUI para IOS

Planetary é um app com pubs pré-carregados para facilitar integração.
Manyverse - GUI para Android

Manyverse é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone .
Fontes
-
https://scuttlebot.io/
-
https://decentralized-id.com/decentralized-web/scuttlebot/#plugins
-
https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd
-
Secure Scuttlebutt : um protocolo de banco de dados global.
-
-
 @ 6be5cc06:5259daf0
2024-12-29 19:54:14
@ 6be5cc06:5259daf0
2024-12-29 19:54:14Um dos padrões mais bem estabelecidos ao medir a opinião pública é que cada geração tende a seguir um caminho semelhante em termos de política e ideologia geral. Seus membros compartilham das mesmas experiências formativas, atingem os marcos importantes da vida ao mesmo tempo e convivem nos mesmos espaços. Então, como devemos entender os relatórios que mostram que a Geração Z é hiperprogressista em certos assuntos, mas surpreendentemente conservadora em outros?
A resposta, nas palavras de Alice Evans, pesquisadora visitante na Universidade de Stanford e uma das principais estudiosas do tema, é que os jovens de hoje estão passando por um grande divergência de gênero, com as jovens mulheres do primeiro grupo e os jovens homens do segundo. A Geração Z representa duas gerações, e não apenas uma.
Em países de todos os continentes, surgiu um distanciamento ideológico entre jovens homens e mulheres. Milhões de pessoas que compartilham das mesmas cidades, locais de trabalho, salas de aula e até casas, não veem mais as coisas da mesma maneira.
Nos Estados Unidos, os dados da Gallup mostram que, após décadas em que os sexos estavam distribuídos de forma relativamente equilibrada entre visões políticas liberais e conservadoras, as mulheres entre 18 e 30 anos são agora 30 pontos percentuais mais liberais do que os homens dessa faixa etária. Essa diferença surgiu em apenas seis anos.
A Alemanha também apresenta um distanciamento de 30 pontos entre homens jovens conservadores e mulheres jovens progressistas, e no Reino Unido, a diferença é de 25 pontos. Na Polônia, no ano passado, quase metade dos homens entre 18 e 21 anos apoiou o partido de extrema direita Confederation, em contraste com apenas um sexto das jovens mulheres dessa mesma idade.
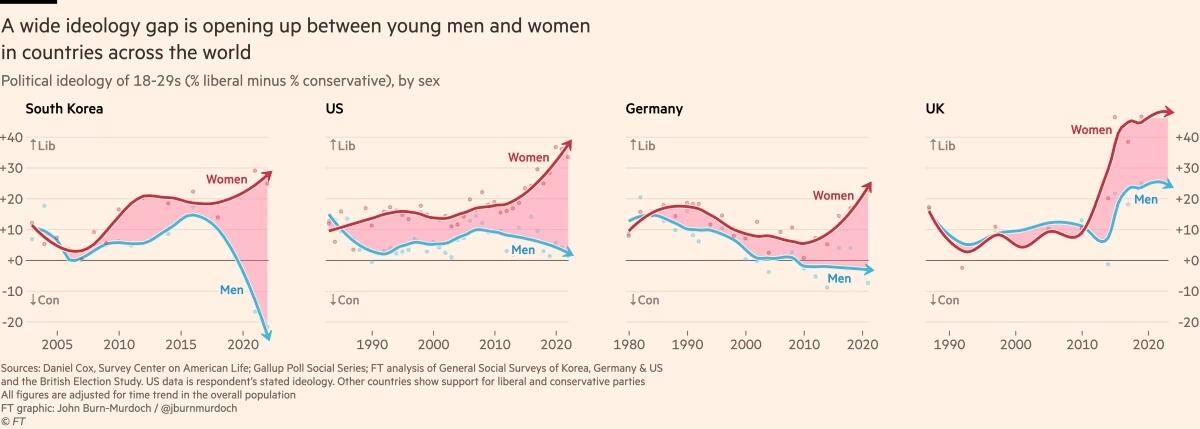
Fora do Ocidente, há divisões ainda mais acentuadas. Na Coreia do Sul, há um enorme abismo entre homens e mulheres jovens, e a situação é semelhante na China. Na África, a Tunísia apresenta o mesmo padrão. Vale notar que em todos os países essa divisão drástica ocorre principalmente entre a geração mais jovem, sendo muito menos pronunciada entre homens e mulheres na faixa dos 30 anos ou mais velhos.
O movimento # MeToo foi o principal estopim, trazendo à tona valores feministas intensos entre jovens mulheres que se sentiram empoderadas para denunciar injustiças de longa data. Esse estopim encontrou especialmente terreno fértil na Coreia do Sul, onde a desigualdade de gênero é bastante visível e a misoginia explícita é comum. (palavras da Financial Times, eu só traduzi)
Na eleição presidencial da Coreia do Sul em 2022, enquanto homens e mulheres mais velhos votaram de forma unificada, os jovens homens apoiaram fortemente o partido de direita People Power, enquanto as jovens mulheres apoiaram o partido liberal Democratic em números quase iguais e opostos.
A situação na Coreia é extrema, mas serve como um alerta para outros países sobre o que pode acontecer quando jovens homens e mulheres se distanciam. A sociedade está dividida, a taxa de casamento despencou e a taxa de natalidade caiu drasticamente, chegando a 0,78 filhos por mulher em 2022, o menor número no mundo todo.
Sete anos após a explosão inicial do movimento # MeToo, a divergência de gênero em atitudes tornou-se autossustentável.
Dados das pesquisas mostram que em muitos países, as diferenças ideológicas vão além dessa questão específica. A divisão progressista-conservadora sobre assédio sexual parece ter causado ou pelo menos faz parte de um alinhamento mais amplo, em que jovens homens e mulheres estão se organizando em grupos conservadores e liberais em outros assuntos.
Nos EUA, Reino Unido e Alemanha, as jovens mulheres agora adotam posturas mais liberais sobre temas como imigração e justiça racial, enquanto grupos etários mais velhos permanecem equilibrados. A tendência na maioria dos países tem sido de mulheres se inclinando mais para a esquerda, enquanto os homens permanecem estáveis. No entanto, há sinais de que os jovens homens estão se movendo para a direita na Alemanha, tornando-se mais críticos em relação à imigração e se aproximando do partido de extrema direita AfD nos últimos anos.
Seria fácil dizer que tudo isso é apenas uma fase passageira, mas os abismos ideológicos apenas crescem, e os dados mostram que as experiências políticas formativas das pessoas são difíceis de mudar. Tudo isso é agravado pelo fato de que o aumento dos smartphones e das redes sociais faz com que os jovens homens e mulheres agora vivam em espaços separados e tenham culturas distintas.
As opiniões dos jovens frequentemente são ignoradas devido à baixa participação política, mas essa mudança pode deixar consequências duradouras, impactando muito mais do que apenas os resultados das eleições.
Retirado de: https://www.ft.com/content/29fd9b5c-2f35-41bf-9d4c-994db4e12998
-
 @ 6f3670d9:03f04036
2024-12-29 08:20:22
@ 6f3670d9:03f04036
2024-12-29 08:20:22Disclaimer: - This will void your warranty - There might be differences between the Bitaxe and the Lucky Miner that might not cause issues or damage immediately, but might manifest long-term - Proceed at your own risk
A Different Pickaxe
You live in a place where it's difficult to get a Bitaxe. You have access to AliExpress. You look around. You find something called the "Lucky Miner LV06". A Bitaxe clone that uses the same mining chip as the Bitaxe Ultra (BM1366 ASIC). You buy one.
You plug it in, you enter your wallet address and other settings, and it starts mining. It works! Great!
But it's running a customized firmware. It's not AxeOS. Maybe there's something shady in the stock firmware. It's not open-source, after all. Also, AxeOS looks amazing... And that automatic pool fail-over feature is handy.
You think to yourself: "Maybe I can use the Bitaxe firmware on this?". Guess what? You're right!
Flashing From Web UI
What usually works for me is to: - Download the Bitaxe firmware files (
esp-miner.binandwww.bin) from GitHub (here). Version 2.4.1 seems to work well, as of this writing. - Then from the Lucky Miner web interface, upload the "Website" (www.bin) file. - Wait for a minute or two after it's done uploading. - Upload the "Firmware" (esp-miner.bin) file. - Wait another minute or two. - Unplug the power and plug it back in. - Set the "Core Voltage" and "Frequency" to the defaults. - Unplug the power and plug it back in again.If you're lucky (no pun intended), you'll have a working Lucky Miner with AxeOS. Update the settings and mine away!
However, often times I've been unlucky, like what happened while I was writing this article, ironically. The miner malfunctions for no obvious reason. It keeps rebooting, or it's not mining (zero/low hashrate), or the web interface is inaccessible. You name it.
The miner has become a "brick". How do you "unbrick" it?
When you brick a Bitaxe, you can recover it by flashing (uploading) a "Factory Image". The Bitaxe has a USB port that makes this easy. Follow the guide and it should come back to life again. Unfortunately, the Lucky Miner LV06 doesn't have a USB port. It has a serial port, though. We'll have to get our hands a bit dirty.
Flashing Using the Serial Port
We need to connect the serial port of the miner to a computer and run a program to flash (upload) the firmware file on the miner. Any 3.3v UART serial port should be sufficient. Unfortunately, PCs don't usually come with a UART serial port these days, let alone a 3.3v one. The serial port common in old computers is an RS-232 port, which will most probably fry your miner if you try to connect it directly. Beware.
In my case, as a serial port for my PC, I'm using an Arduino Due I had lying around. We connect it to the PC through USB, and on the other side we connect a few wires to the miner, which gives the PC access to the miner.
WARNING: Make sure your serial port is 3.3v or you will probably kill the miner. Arduino Uno is 5v not 3.3v, for example, and cannot be used for this.
Wiring
First, we need to open the Lucky Miner. Use a small flat screwdriver to gently push the two plastic clips shown in the picture below. Gently pry the top cover away from the bottom cover on the clips side first, then remove the other side. Be careful not to break the display cable.
Once the cover is off, you can find the miner's serial port in the top right corner (J10), as shown in the next picture. We'll also need the reset button (EN).
There are three screws holding the PCB and the bottom cover together. If you're confident in your ability to push the small button on the underside of the PCB with the bottom cover on, then no need to remove these. The following picture shows what we need from that side.
And the next picture shows the pins and USB port we will use from the Arduino.
Now, we need to connect: - The USB port on the Arduino labelled "programming" to the PC - Pin 18 (TX1) on the Arduino to J10 through-hole pad 5 (blue dot) - Pin 19 (RX1) on the Arduino to J10 through-hole pad 3 (green dot) - Any GND pin on the Arduino to J10 through-hole pad 4 (yellow dot)
I didn't need to solder the wires to the pads. Keeping everything stable, perhaps by putting a weight on the wires or a bit of tape, was sufficient in all my attempts.
Setting up the Arduino
To use the Arduino as a serial port for our PC, we'll have to make it pass-through data back and forth between the USB port and UART1, where we connected the miner.
The following steps are all done on a PC running Debian Linux (Bookworm), in the spirit of freedom and open-source.
First, we start the Arduino IDE. If the package for the Arduino Due board is not already installed, you'll see a small prompt at the bottom. Click "Install this package".
Click the "Install" button.
Once the package is installed, click "Close".
Next, we select the Due board. Click the "Tools" menu, select "Board", select "Arduino ARM (32-bits) Boards" and click "Arduino Due (Programming Port)"
Next, we select the port. Click the "Tools" menu again, select "Port", and click the port where the Arduino is connected. In my case it was "/dev/ttyACM0".
Now we need to upload the following code to the Arduino board. The code is actually the "SerialPassthrough" example from the IDE, but with the serial speed changed to match the miner.
``` void setup() { Serial.begin(115200); Serial1.begin(115200); }
void loop() { if (Serial.available()) { // If anything comes in Serial (USB), Serial1.write(Serial.read()); // read it and send it out Serial1 }
if (Serial1.available()) { // If anything comes in Serial1 Serial.write(Serial1.read()); // read it and send it out Serial (USB) } } ```
Copy/paste the code into the IDE and click upload. You'll see "Done uploading" at the bottom.
Next we'll test if we're receiving data from the miner. We start by opening the "Serial Monitor" from the "Tools" menu in the IDE. Then we change the baudrate to 115200.
Set the Arduino and the miner in a comfortable position, make sure the wires are held in place and got a good contact on both sides, and the power is plugged in.
Now we'll put the miner in "download" mode. Press and hold the button on the underside (K1), press and release the reset button (EN), then release the other button (K1).
You should see some text from the miner in the serial monitor window, like in the picture below.
Congratulations! We know we're able to receive data from the miner now. We're not sure transmit is working, but we'll find out when we try to flash.
Flashing Using the Serial Port, for Real
To flash the Lucky Miner we'll need a software tool named esptool and the factory image firmware file.
I usually use "esp-miner-factory-205-v2.1.8.bin" for the factory image (this one) as a base, and then flash the version I want from the Web UI, using the steps I mentioned earlier.
For esptool, the documentation (here) shows us how to install it. To make things a little easier on our Debian Linux system, we'll use pipx instead of pip. The instructions below are adapted for that.
First we make sure pipx is installed. Run this command in a terminal and follow the instructions:
sudo apt-get install pipxThen we install esptool using pipx. Run the following in a terminal:
pipx install esptoolThe output will be something like this:
user@pc:~$ pipx install esptool installed package esptool 4.8.1, installed using Python 3.11.2 These apps are now globally available - esp_rfc2217_server.py - espefuse.py - espsecure.py - esptool.py ⚠️ Note: '/home/user/.local/bin' is not on your PATH environment variable. These apps will not be globally accessible until your PATH is updated. Run `pipx ensurepath` to automatically add it, or manually modify your PATH in your shell's config file (i.e. ~/.bashrc). done! ✨ 🌟 ✨We can see pipx telling us we won't be able to run our tool because the folder where it was installed is not in the PATH variable. To fix that, we can follow pipx instructions and run:
pipx ensurepathAnd we'll see something like this:
``` user@pc:~$ pipx ensurepath Success! Added /home/user/.local/bin to the PATH environment variable.
Consider adding shell completions for pipx. Run 'pipx completions' for instructions.
You will need to open a new terminal or re-login for the PATH changes to take effect.
Otherwise pipx is ready to go! ✨ 🌟 ✨ ```
Now, close the terminal and re-open it so that esptool becomes available.
Finally, to actually flash the miner, put the miner in download mode, then in the following command change the port ("/dev/ttyACM0") to your serial port, as we've seen earlier, and the file path to where your firmware file is, and run it:
esptool.py -p /dev/ttyACM0 --baud 115200 write_flash --erase-all 0x0 ~/Downloads/esp-miner-factory-205-v2.1.8.binIf everything went fine, the tool will take a few minutes to flash the firmware to the miner. You'll see something like this in the output:
``` user@pc:~$ esptool.py -p /dev/ttyACM0 --baud 115200 write_flash --erase-all 0x0 ~/Downloads/esp-miner-factory-205-v2.1.8.bin esptool.py v4.8.1 Serial port /dev/ttyACM0 Connecting..... Detecting chip type... ESP32-S3 Chip is ESP32-S3 (QFN56) (revision v0.2) Features: WiFi, BLE, Embedded PSRAM 8MB (AP_3v3) Crystal is 40MHz MAC: 3c:84:27:ba:be:01 Uploading stub... Running stub... Stub running... Configuring flash size... Erasing flash (this may take a while)... Chip erase completed successfully in 9.5s Compressed 15802368 bytes to 1320190... Wrote 15802368 bytes (1320190 compressed) at 0x00000000 in 152.1 seconds (effective 831.2 kbit/s)... Hash of data verified.
Leaving... Hard resetting via RTS pin... ```
And we're done! Hopefully the miner will be recovered now.
Hope this helps!
Stay humble,
dumb-packageA Warning About Beta Versions of AxeOS
For reasons unknown to me, while I was writing this article I wanted to try the testing version of AxeOS, which was v2.4.1b (beta). Flashing from Web UI went smooth, but the miner stopped mining. I flashed back to v2.1.8 using the serial port, a known good version for me, but it wouldn't mine, still.
Thankfully, v2.4.1 was released recently, and flashing it from the Web UI magically revived my miner. So, be warned.
Bonus: File Hashes
For convenience, these are the SHA256 hashes of the files I used in this article: ``` da24fceb246f3b8b4dd94e5143f17bd38e46e5285e807ebd51627cb08f665c0a ESP-Miner-v2.4.1/esp-miner.bin 16c5c671391f0e3e88a3e79ce33fad3b0ec232b8572fad5e1e0d1ad3251ab394 ESP-Miner-v2.4.1/www.bin
d5182a15b6fa21d7b9b31bff2026d30afed9d769781a48db914730a5751e20c6 esp-miner-factory-205-v2.1.8.bin ```
-
 @ 6f3670d9:03f04036
2024-12-29 06:51:25
@ 6f3670d9:03f04036
2024-12-29 06:51:25This is my first long-form post. The starting line.
There's nothing of value here. Just using this as a marker.
I hope to post a lot more. Documenting how I made something work would be very useful to me, and hopefully others, but I've been too lazy to do that. Wish me luck!
Stay humble,
dumb-package -
 @ 9f94e6cc:f3472946
2024-11-21 18:55:12
@ 9f94e6cc:f3472946
2024-11-21 18:55:12Der Entartungswettbewerb TikTok hat die Jugend im Griff und verbrutzelt ihre Hirne. Über Reels, den Siegeszug des Hochformats und die Regeln der Viralität.
Text: Aron Morhoff
Hollywood steckt heute in der Hosentasche. 70 Prozent aller YouTube-Inhalte werden auf mobilen Endgeräten, also Smartphones, geschaut. Instagram und TikTok sind die angesagtesten Anwendungen für junge Menschen. Es gibt sie nur noch als App, und ihr Design ist für Mobiltelefone optimiert.
Einst waren Rechner und Laptops die Tools, mit denen ins Internet gegangen wurde. Auch als das Smartphone seinen Siegeszug antrat, waren die Sehgewohnheiten noch auf das Querformat ausgerichtet. Heute werden Rechner fast nur noch zum Arbeiten verwendet. Das Berieseln, die Unterhaltung, das passive Konsumieren hat sich vollständig auf die iPhones und Samsungs dieser Welt verlagert. Das Telefon hat den aufrechten Gang angenommen, kaum einer mehr hält sein Gerät waagerecht.
Homo Digitalis Erectus
Die Welt steht also Kopf. Die Form eines Mediums hat Einfluss auf den Inhalt. Marshall McLuhan formulierte das so: Das Medium selbst ist die Botschaft. Ja mei, mag sich mancher denken, doch medienanthropologisch ist diese Entwicklung durchaus eine Betrachtung wert. Ein Querformat eignet sich besser, um Landschaften, einen Raum oder eine Gruppe abzubilden. Das Hochformat entspricht grob den menschlichen Maßen von der Hüfte bis zum Kopf. Der TikTok-Tanz ist im Smartphone-Design also schon angelegt. Das Hochformat hat die Medieninhalte unserer Zeit noch narzisstischer gemacht.
Dass wir uns durch Smartphones freizügiger und enthemmter zur Schau stellen, ist bekannt. 2013 wurde „Selfie“ vom Oxford English Dictionary zum Wort des Jahres erklärt. Selfie, Selbstporträt, Selbstdarstellung.
Neu ist der Aufwand, der heute vonnöten ist, um die Aufmerksamkeitsschwelle der todamüsierten Mediengesellschaft überhaupt noch zu durchbrechen. In beängstigender Hypnose erwischt man viele Zeitgenossen inzwischen beim Doomscrollen. Das ist der Fachbegriff für das weggetretene Endloswischen und erklärt auch den Namen „Reel“: Der Begriff, im Deutschen verwandt mit „Rolle“, beschreibt die Filmrolle, von der 24 Bilder pro Sekunde auf den Projektor gewischt oder eben abgespult werden.
Länger als drei Sekunden darf ein Kurzvideo deshalb nicht mehr gehen, ohne dass etwas Aufregendes passiert. Sonst wird das Reel aus Langeweile weggewischt. Die Welt im Dopamin-Rausch. Für den Ersteller eines Videos heißt das inzwischen: Sei der lauteste, schrillste, gestörteste Marktschreier. Das Wettrennen um die Augäpfel zwingt zu extremen Formen von Clickbait.
15 Sekunden Ruhm
Das nimmt inzwischen skurrile Formen an. Das Video „Look who I found“ von Noel Robinson (geboren 2001) war im letzten Jahr einer der erfolgreichsten deutschen TikTok-Clips. Man sieht den Deutsch-Nigerianer beim Antanzen eines karikaturartig übergewichtigen Menschen. Noel wird geschubst und fällt. Daraufhin wechselt das Lied – und der fette Mann bewegt seinen Schwabbelbauch im Takt. Noel steht wieder auf, grinst, beide tanzen gemeinsam. Das dauert 15 Sekunden. Ich rate Ihnen, sich das Video einmal anzuschauen, um die Mechanismen von TikTok zu verstehen. Achten Sie alleine darauf, wie vielen Reizen (Menschenmenge, Antanzen, Sturz, Schwabbelbauch) Sie in den ersten fünf Sekunden ausgesetzt sind. Wer schaut so was? Bis dato 220 Millionen Menschen. Das ist kapitalistische Verwertungslogik im bereits verwesten Endstadium. Adorno oder Fromm hätten am Medienzeitgeist entweder ihre Freude oder mächtig zu knabbern.
Die Internet- und Smartphoneabdeckung beträgt mittlerweile fast 100 Prozent. Das Überangebot hat die Regeln geändert. Um überhaupt gesehen zu werden, muss man heute viral gehen. Was dafür inzwischen nötig ist, spricht die niedrigsten Bedürfnisse des Menschen an: Gewalt, Ekel, Sexualisierung, Schock. Die jungen Erwachsenen, die heute auf sozialen Netzwerken den Ton angeben, haben diese Mechanismen längst verinnerlicht. Wie bewusst ihnen das ist, ist fraglich. 2024 prallt eine desaströse Bildungssituation samt fehlender Medienkompetenz auf eine egomanische Jugend, die Privatsphäre nie gekannt hat und seit Kindesbeinen alles in den Äther ballert, was es festhalten kann. Man muss kein Kulturpessimist sein, um diese degenerative Dynamik, auch in ihrer Implikation für unser Zusammenleben und das psychische Wohlergehen der Generation TikTok, als beängstigend zu bezeichnen.
Aron Morhoff studierte Medienethik und ist Absolvent der Freien Akademie für Medien & Journalismus. Frühere Stationen: RT Deutsch und Nuoviso. Heute: Stichpunkt Magazin, Manova, Milosz Matuschek und seine Liveshow "Addictive Programming".
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ 9d92077c:38d27146
2025-01-20 20:46:31
@ 9d92077c:38d27146
2025-01-20 20:46:31Like King Arthur pulling the sword Excalibur from the stone to reclaim his rightful place as king, the Excalibur system empowers Nostr users to recover control of their digital identities and networks from malicious infiltrators. This proposal introduces a robust framework for key recovery and re-association, ensuring that users can seamlessly regain control of their accounts while preserving their social connections, metadata, and event history. In an age where security and trust are paramount, Excalibur offers a practical and resilient solution to one of the most pressing challenges in decentralized networks.
—-
The Importance of Key Recovery on Nostr
One of Nostr’s greatest strengths is its reliance on public and private key pairs to establish identities and ensure message authenticity. However, the simplicity of this cryptographic model comes with a significant vulnerability: key compromise. If a user’s private key is lost or stolen, they face catastrophic consequences: * Loss of Identity: The user cannot post, interact, or manage their profile. * Disruption of Social Graph: Followers and contacts lose their connection to the user. * Trust Erosion: An attacker controlling the compromised key can impersonate the user, damaging their reputation.
While decentralization is a core principle of Nostr, the lack of a built-in recovery mechanism undermines long-term usability and user confidence. Excalibur addresses this gap with an innovative system for recovering compromised keys and maintaining social continuity.
—-
Proposed Solution: The Excalibur System
The Excalibur system introduces a primary key and secure backup key model to Nostr, enabling users to recover their accounts and re-associate events in the event of key compromise. This system relies on a combination of cryptographic proofs, event indexing, and client/relay cooperation to ensure a seamless and secure transition.
1. Primary and Secure Keys
Users establish a primary key for everyday activity and a secure backup key stored offline. The primary key broadcasts an association with the secure key using a
set_secure_keyevent.2. Key Transition Event
Upon detecting a compromise, the user activates the secure key by publishing a
key_transitionevent.This event includes: * The compromised primary key. * The new secure key. * A cryptographic proof linking the two. * A timestamp and optional metadata.
3. Social Graph Transition
Clients automatically replace the compromised key with the secure key in follow lists, contact lists, and other social data.
Followers are notified of the transition and encouraged to follow the secure key.
4. Unified Identity View
Historical events remain immutable but are re-indexed by relays to associate with the secure key for continuity.
Clients display a unified profile view, differentiating old and new events.
5. Seamless Transition for Existing Accounts
Existing Nostr users can integrate Excalibur by broadcasting a set_secure_key event linking their current primary key to a secure backup key. While historical events and metadata associated with the primary key remain unchanged, all new events after activation of the secure key are seamlessly associated with the updated identity. Clients should provide user-friendly tools to guide existing users through this setup process.
6. Endless Security Chain
Once a secure key is activated and becomes the new primary key, users must set up a new secure backup key immediately by broadcasting a new
set_secure_keyevent.This ensures an endless chain of security, preventing future compromises from leaving users vulnerable.
Clients should include UX enhancements such as prompts, reminders, and automated tools to help users maintain their security chain efficiently.
7. Insurance Model for Relays
Users pay an upfront premium to relays for re-association services, ensuring resources are available for recovery operations.
Clients act as brokers, aggregating multiple relay insurance contracts into a single, user-friendly offering. They manage user payments, distribute premiums to participating relays, and earn a commission for their services.
This brokerage model incentivizes clients to participate actively in the Excalibur system and ensures broader adoption across the network.
—-
Implementation Framework
Cryptographic Foundations
- The secure key must be pre-announced and linked to the primary key using a signed
set_secure_keyevent. - During key transition, the key_transition event includes a signature proving the association.
Relay Behavior
- Relays index the key_transition event and re-link historical data to the secure key.
- Events from the old key are tagged as "deprecated" but remain accessible.
Client Behavior
- Clients validate the
key_transitionevent and update social graphs automatically. - Followers are notified and prompted to follow the secure key.
- Profiles display both old and new events under a unified identity.
- Clients implement features to facilitate existing users' onboarding and provide tools to manage the security chain seamlessly.
—-
Benefits of Excalibur
Resilience: Users can recover from key compromise without losing their digital identity or network.
Trust: The cryptographic proofs ensure the legitimacy of key transitions, preserving trust in the system.
Sustainability: The insurance premium model incentivizes relay adoption and ensures fair resource allocation.
User-Friendly: Automated transitions reduce the complexity for end users, making Nostr more accessible.
Adaptability: Existing accounts can benefit from Excalibur without disruption, ensuring broad applicability.
—-
Call to Action
The Excalibur system is a vital enhancement to the Nostr protocol, addressing the critical issue of key recovery while maintaining decentralization and user sovereignty. By adopting Excalibur, we can strengthen the network’s resilience, foster trust, and ensure that users retain control of their identities in an ever-evolving digital landscape. We invite the Nostr community to collaborate on refining and implementing this proposal, turning the vision of Excalibur into a reality.
Together, let’s ensure that no user is ever left powerless in the face of compromise. Let’s reclaim the sword and secure the kingdom.
- The secure key must be pre-announced and linked to the primary key using a signed
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ fa0165a0:03397073
2024-10-23 17:19:41
@ fa0165a0:03397073
2024-10-23 17:19:41Chef's notes
This recipe is for 48 buns. Total cooking time takes at least 90 minutes, but 60 minutes of that is letting the dough rest in between processing.
The baking is a simple three-step process. 1. Making the Wheat dough 2. Making and applying the filling 3. Garnishing and baking in the oven
When done: Enjoy during Fika!
PS;
-
Can be frozen and thawed in microwave for later enjoyment as well.
-
If you need unit conversion, this site may be of help: https://www.unitconverters.net/
-
Traditionally we use something we call "Pearl sugar" which is optimal, but normal sugar or sprinkles is okay too. Pearl sugar (Pärlsocker) looks like this: https://search.brave.com/images?q=p%C3%A4rlsocker
Ingredients
- 150 g butter
- 5 dl milk
- 50 g baking yeast (normal or for sweet dough)
- 1/2 teaspoon salt
- 1-1 1/2 dl sugar
- (Optional) 2 teaspoons of crushed or grounded cardamom seeds.
- 1.4 liters of wheat flour
- Filling: 50-75 g butter, room temperature
- Filling: 1/2 - 1 dl sugar
- Filling: 1 teaspoons crushed or ground cardamom and 1 teaspoons ground cinnamon (or 2 teaspoons of cinnamon)
- Garnish: 1 egg, sugar or Almond Shavings
Directions
- Melt the butter/margarine in a saucepan.
- Pour in the milk and allow the mixture to warm reach body temperature (approx. + 37 ° C).
- Dissolve the yeast in a dough bowl with the help of the salt.
- Add the 37 ° C milk/butter mixture, sugar and if you choose to the optional cardamom. (I like this option!) and just over 2/3 of the flour.
- Work the dough shiny and smooth, about 4 minutes with a machine or 8 minutes by hand.
- Add if necessary. additional flour but save at least 1 dl for baking.
- Let the dough rise covered (by a kitchen towel), about 30 minutes.
- Work the dough into the bowl and then pick it up on a floured workbench. Knead the dough smoothly. Divide the dough into 2 parts. Roll out each piece into a rectangular cake.
- Stir together the ingredients for the filling and spread it.
- Roll up and cut each roll into 24 pieces.
- Place them in paper molds or directly on baking paper with the cut surface facing up. Let them rise covered with a baking sheet, about 30 minutes.
- Brush the buns with beaten egg and sprinkle your chosen topping.
- Bake in the middle of the oven at 250 ° C, 5-8 minutes.
- Allow to cool on a wire rack under a baking sheet.
-
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ f527cf97:65e232ee
2025-01-20 20:22:45
@ f527cf97:65e232ee
2025-01-20 20:22:45Our modern civilization comes with a lot of amenities and luxuries for all. When Christopher Columbus brought the potato from America to the Spanish royal court, it was a luxury vegetable reserved only for the nobility. Today, potatoes are thrown at anyone who has 1-2 Dollars or Euros. The same applies to chocolate. Once a luxury good, it now costs only a few Cents. We live in luxury, just like kings did a few centuries ago.
But all this has a price.
Allah ﷻ says in the Quran that he sent "manna and quails from above" to the people of Musā (Moses) عَلَیهِالسَّلام (Surah 2, Ayah 57 and Surah 7, Ayah 160), after they escaped from Pharaoh and fled from Egypt into the desert.
Manna is a food described in the Quran and the Bible as a gift from God to the people of Israel. It is described as a white, sweet, and nutritious powder that lay on the ground every morning.
The exact nature of manna is unknown, but there are various theories about what it could be. Some scientists believe that manna could be a product of the tamarisk plant (Tamarix gallica), which occurs in the Sinai Desert. The tamarisk plant produces a sweet, white resin that could be used as food by the Israelites.
Other theories suggest that manna could be a product of insects like ants or butterflies that produce a sweet secretion.
Quails are small birds that occur in the Sinai Desert. They are an important part of the food chain in the desert and were used as food by the Israelites.
Some studies have shown that the resin of the tamarisk plant, which is considered a possible source of manna, is rich in various nutrients, including:
- Carbohydrates: Manna probably contains a mixture of simple and complex carbohydrates, such as sugar, starch, and cellulose.
- Proteins: Manna may also contain proteins from insects or other organisms that produce the resin.
- Vitamins: Manna may contain vitamins like vitamin C, vitamin B1, and vitamin B2.
- Minerals: Manna may contain minerals like calcium, phosphorus, magnesium, and iron.
Quails are small birds rich in various nutrients. Here are some of the most important nutrients found in quails:
- Proteins: Quails are rich in proteins that are essential for building and maintaining muscles and other body tissues. A 100g piece of quail contains about 20-25g of protein.
- Fat: Quails also contain fat, which is essential for energy supply and maintaining body functions. A 100g piece of quail contains about 10-15g of fat.
- Vitamins: Quails are rich in various vitamins, including:
- Vitamin B12: essential for blood formation and nerve function
- Vitamin B6: essential for energy supply and immune function
- Vitamin E: essential for cell protection and tissue function
- Vitamin A: essential for vision and immune function
- Minerals: Quails also contain various minerals, including:
- Iron: essential for blood formation and oxygen supply
- Calcium: essential for bone formation and muscle contraction
- Phosphorus: essential for bone formation and energy supply
- Magnesium: essential for muscle contraction and nerve function
- Amino acids: Quails contain various amino acids that are essential for building and maintaining proteins.
To put it in one sentence: Allah gave the people of Musā عَلَیهِالسَّلام in the wilderness everything they needed to survive.
In the Quran and the Bible, it is reported that some members of the community of Musā عَلَیهِالسَّلام complained about the monotonous diet of manna and quails. They longed for the variety of foods they had eaten in Egypt.
In the Quran, this is described in Surah 2, Ayah 61:
"And when you said to us, 'O Moses, we will not be satisfied with one dish. Ask your Lord to bring us from the earth, from vegetables, onions, garlic, lentils, and chickpeas.' He said, 'Do you want to exchange something better for something worse? Go down to a city, and you will find what you want.'"
These complaints show that the people in the community of Musā عَلَیهِالسَّلام had difficulty adapting to the new situation and being content with the simple diet.
For they were accustomed to the variety and luxury of Egypt. Even though they lived there as slaves and an oppressed minority. They could be physically rescued from slavery by Musā عَلَیهِالسَّلام , but the mental slavery was still anchored in them. They could not bear the total freedom, even if it came with sufficient food, and became ungrateful. (from Nouman Ali Khan, Tafseer Lessons)
These stories in the Quran are timeless and not told without reason. Even today, we find ourselves in a kind of spiritual bondage and cannot mentally free ourselves from the captivity and slavery in which we voluntarily reside. If we could, we would have to live with much less, but it would be enough. And we would have to work harder for it than the people of Musā عَلَیهِالسَّلام did back then.
We would have to engage in agriculture and farming with the means available to us. We would have to plow and dig and get our hands dirty. But we wouldn't have to go to the supermarket and apply for a credit card to pay for goods. We would have to trade with our surplus to buy meat from the equally self-sovereign livestock farmer. We would have to build a trading community with all sovereign individuals and use money that the banks cannot exclude us from.
The common pattern here is: freedom and self-sovereignty require effort, work, and being content with what one needs.
- If we want freedom and self-sovereignty in our money, we have to deal with Bitcoin and seed storage technologies.
- If we want free, full, and fair hearing in social media, we have to acquire the basic technical understanding to handle Nostr correctly.
People give up their self-sovereignty because they want more than they need and are not willing to do the necessary work.

The Matrix trilogy also deals with this topic, describing a future where humans serve as energy sources for the machines that, in turn, simulate a world (the Matrix) that people desire. We already see the first approaches to this today. We give our data to Big Tech, which generates profits for various industries. We have AI in the starting blocks, which is supposed to largely automate the analysis and preparation of this data. With neural interfaces, we are supposed to approach human thoughts and, above all, desires. If you know what people long for, you can sell them the perfect product. Or just simulate it. Humans then become mere milkable data cows, whose "real work" (for the Matrix) becomes superfluous. With socialist ideas, such as unconditional basic income or its capitalist counterpart "ad revenue sharing" by large platforms, it is ensured that the individual also has something to spend. Regardless of their qualifications or professional experience, because these no longer count.
A large part of humanity becomes an energy source for the machines. Unless we become self-sovereign again and get our hands dirty for what we actually need.
-
 @ f3b691eb:aa9a5c31
2025-01-20 20:32:23
@ f3b691eb:aa9a5c31
2025-01-20 20:32:23Not all coffee roasts are created equal. The way coffee is roasted significantly impacts its flavor, aroma, and overall quality. Let’s dive deeper into the differences between drum roasting and air roasting—and why air roasting might just change the way you experience coffee.
Drum Roasting: The Traditional Approach
Drum roasting involves placing coffee beans into a rotating drum that’s heated from below. This method has been around for centuries and is popular among many large-scale roasters. However, it comes with some challenges:
Uneven Heat Distribution: Beans rest against the hot drum surface, leading to inconsistent roasting. Some beans may scorch, while others roast unevenly.
Residual Chaff: The outer skin of the coffee bean, called chaff, remains in the drum during roasting. If not properly removed, it can burn and contribute to bitter or smoky flavors.
Slower Process: Drum roasting can take longer, which can risk over-roasting and muting the coffee’s unique flavor notes.
While drum roasting is widely used, it often requires an experienced hand to avoid these pitfalls and deliver a high-quality roast.
Air Roasting: The Modern Revolution Air roasting, also known as fluid-bed roasting, uses a stream of hot air to roast coffee beans. This method creates a perfectly balanced environment where beans are suspended and roasted evenly. The results? Pure, unadulterated flavor. Here’s why air roasting is superior:
Even Roasting: With no direct contact with hot surfaces, beans are roasted uniformly, ensuring consistent flavor throughout every batch. Cleaner Taste: Chaff is blown away during the roasting process, preventing it from burning and leaving behind off-putting bitterness. Enhanced Flavors: Air roasting preserves the coffee’s natural flavor notes, highlighting the bright, clean, and vibrant characteristics of each bean. Faster Roasting: The shorter roasting time minimizes over-cooking and delivers a fresher, more aromatic cup of coffee. Air roasting isn’t just a method—it’s an art. By focusing on the bean’s intrinsic qualities, it elevates your coffee experience to a whole new level.
Try Micro-Batch Air Roasted Coffee Ready to taste the difference for yourself? Check out Food Forest Farms and explore their micro-batch air-roasted coffee. Each roast is crafted to bring out the best in every bean. https://Foodforestfarms.com
(US orders only)
Accepts Bitcoin 🪙 Always Free Shipping 📦 Use code LOTS10 for 10% off your first order! Make the switch to air roasting and discover coffee the way it’s meant to taste. Your mornings will never be the same! 🚀
coffee #coffeechain #fffcoffee
originally posted at https://stacker.news/items/857770
-
 @ ce6b432f:c07ce020
2025-01-20 15:52:57
@ ce6b432f:c07ce020
2025-01-20 15:52:57If you think I can’t blame the scale of devastation from the LA fires on the Federal Reserve - think again.
After the 2008 financial crisis, Tyler Cowen was fond of saying “we aren’t as rich as we thought we were”. If you ask him, (I did in a zoom call sometime in the last 2 years), he thinks this state of being was temporary. My belief is that 17 years later, this illusion still persists, but it is cracking. Instead of allowing the dead wood to burn through financial markets, QE, ZIRP, BTFP, TARP, foreign central bank swap lines, Repo, Reverse Repo, double-triple-just kidding-repo, and a variety mechanisms beyond comprehension have been deployed to create the impression of wealth. We are still much less wealthy than we thought we were even 4 years ago. Until 2021, this was confined mainly to the inflation of asset prices and the stealth inflation embodied in the deteriorating quality of consumer goods, but Covid stimmies injected enough liquidity directly into the consumer blood stream that CPI finally started blinking red. The public began to gain some awareness of a more concrete problem in the structure of our economy. The pressing problem of inflation exposed first order problems of real urgency. A real wake up call had arrived for those middle class and below on the socio-economic ladder. There is no shortage of material to read on this for the curious.
Now some of the bills are coming due for the top half of the economic spectrum. When a plane you’re on falls out of the sky, it doesn’t matter how big your bank account is. When wildfire driven by 100 mph winds hits a neighborhood with empty fire hydrants, adequate water isn’t available at any price. When you realize your 22 year old child has spent the last 16 years being indoctrinated into a camouflaged marxist worldview - parenting mulligans are not available. If you want to retire with a nest egg adequate to provide food, shelter and healthcare for the rest of your life, finding out at age 65 that a good portion of your portfolio has been allocated to ‘companies’ focused on not cutting down trees will not be a fun reason to put down for “why do you want to join the WalMart Team?”. The common thread across many of these items is what used to be called “mission creep”. Leveraging the modern love of the word diversity - I call it “A Diversity of Goals”. They are both deadly for any organization tasked with important and specific goals.
Boeing should be focused on building safe airplanes. Fire departments should be focused on minimizing the damage fire does in their communities. Schools should prioritize reading, writing, arithmetic, and critical thinking skills. Financial professionals should focus on their fiduciary duties.
How did everyone take their eye off of the ball? Everyone decided to add the goal of diversity in some way shape or form. Is it really that simple? No. Was it really that bad? Yes. In a recent podcast with Russ Douthat of the NYT, Marc Andreeson says some pretty shocking things. Link to Transcript
Andreessen: "I’ll speak for the group because there’s a lot of similarities between the different players here for the same pressures. I’ll just speak for the group.
First of all, let me disabuse you of something, if you haven’t already disabused yourself. The view of American C.E.O.s operating as capitalist profit optimizers is just completely wrong.
That’s like, Goal No. 5 or something. There’s four goals that are way more important than that. And that’s not just true in the big tech companies. It’s true of the executive suite of basically everyone at the Fortune 500.
I would say Goal No. 1 is, “I’m a good person.” “I’m a good person,” is wildly more important than profit margins. Wildly. And this is why you saw these big companies all of a sudden go completely bananas in all their marketing. It’s why you saw them go bananas over D.E.I. It’s why you saw them all cooperating with all these social media boycotts. I mean, the level of lock step uniformity, unanimity in the thought process between the C.E.O.s of the Fortune 500 and what’s in the pages of The New York Times and in the Harvard classroom and in the Ford Foundation — they’re just locked together. Or at least they were through this entire period."
If you don’t believe this is the case, you weren’t paying attention. Centralized asset managers like Blackrock who are usually one of the largest shareholders in every company were sending out notices to CEOs and the markets trumpeting how much they prioritized DEI. Blackrock, the ESG Bully - WSJ
BlackRock Inc. has so far increased its support for shareholder-led environmental, social and governance proposals, and published a slew of criticisms of public companies that haven’t bent to its overall requests. …
“BlackRock has strongly signaled that quiet diplomacy is not the only tool in its toolbox,” said Rich Fields, a partner at law firm King & Spalding who focuses on corporate-governance issues. “We expect more votes for shareholder proposals and against directors in this and future years.” …
The firm is one of the top three shareholders of more than 80% of the companies in the S&P 500, according to S&P Global Market Intelligence, through its many funds. The money manager casts a long shadow on shareholder meetings where it can vote on behalf of its investors on board directors, executives’ pay packages and other company matters.
In all fairness, Blackrock is quickly moving away from its ESG focus as the level of nonsense here has become more obvious to larger audiences who are pushing back. (State pension funds dropping them over this was a great example of both Federalism and market forces at work.)
Read the entire transcript from Andreeson. He lays out a very compelling case for what happened when a new generation of employees/elites rolled into adulthood in the 2010’s. The between-the-lines punchline is “it got so bad that billionaires were starting to suffer!!”
If DEI could infect and inhibit performance of large for-profit companies, what do you think the impact was on organizations with far less accountability? If your budget comes from politicians who don’t have to balance budgets or produce concrete results, the amount of drift “off mission” could be and was severe.
Why did this happen? We thought we were so rich that we could afford to entertain these luxury beliefs. We could just add more goals to our plate without diluting our ability to accomplish the very important things these various organizations were supposed to be focused on. We aren’t as rich as we thought we were. We can’t afford for planes to fall out of the sky. We can’t afford for huge sections of large cities to burn down. We can’t afford for an entire generation of Americans to prefer marxism to capitalism. We can’t afford to waste money on feel good projects that have a negative return even before factoring in inflation.
The simplest immediate action to take is for stakeholders large and small in organizations of all sizes to say no more Diversity of Goals - no more Goals of Diversity. Don’t discriminate against anyone who can accomplish the organization’s goals, but the goals must come first. If it’s your church or your local fire department or the local school district - everyone can have an impact on their own community. One by one, we can reverse this trend. Be the change you want to see in the world.
Now - what I think is the root of the problem. Why aren’t we as rich as we thought we were? I just can’t help myself. You may not agree on the solution (I do) - but this description of the problem will give you pause.
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ fbf0e434:e1be6a39
2025-01-20 06:35:18
@ fbf0e434:e1be6a39
2025-01-20 06:35:18Hackathon 摘要
Watson Code Fest 2024 是一项年度生物Hackathon,由加德满都大学合作组织,重点关注医疗保健和信息学。此次活动汇集了41位开发者,他们致力于30个创新项目,旨在将生物技术、计算机科学和医疗保健整合,解决全球及本地的医疗保健挑战。探索的关键领域包括个性化医疗、智能医疗系统、诊断中的AI以及公共卫生数据分析。
该Hackathon的主要目标是促进创新、推广多学科合作,并增强技能发展。它为学生、专业人士和来自各个领域的研究人员提供了一个合作的环境,强调信息学在推进医疗解决方案中的角色。
活动在加德满都大学举行,为期两天,鼓励参与者创造性思考和协作工作。其旨在弥合学术界与工业界之间的差距,激发创新并促进网络建设。这次Hackathon的影响在于其激发新医疗技术的能力以及在尼泊尔培养创新文化,且具有潜在的全球影响。
Hackathon 获奖者
1st Place Prize Winners
- MutraSuchak : 该项目通过适用于医疗应用的低成本方法促进早期阿尔茨海默病的检测。它集成了ESP模块和Python Flask服务器,开源资源可在GitHub上获得。
Runner-Up Prize Winners
- PCOSgen: 该项目编制了一份用于PCOS表型的预测数据库,有助于早期诊断和个性化治疗。它使用数据驱动方法解决研究差距并改进患者结果。
Most Innovative Project Prize Winners
- Silent Witness: Graph-Based Abuse Detection: 该计划使用AI分析来自摄像头的面部表情以检测虐待模式。通过使用YOLO模型来保护隐私,它构建交互图以识别和标记负面模式,同时促进积极的环境。
有关所有参赛项目的详细列表,请访问 Watson Code Fest's project page。
关于组织者
Kathmandu University Biotechnology Creatives
加德满都大学生物技术创意(KUBiC)是生物技术和生物信息学领域的先锋组织。KUBiC以举办年度Watson Code Fest而闻名,为创新者、程序员和创造性思考者提供了一个平台,以解决这些领域中的关键挑战。KUBiC坚定致力于推进生物科学,在促进合作和创造力方面表现出色。其使命是重新定义生物学的未来,并推动跨学科领域的进步。更多信息可在其网站上找到。
-
 @ ed84ce10:cccf4c2a
2025-01-20 06:24:04
@ ed84ce10:cccf4c2a
2025-01-20 06:24:04Hackathon Summary
The Watson Code Fest 2024, an annual biohackathon, was organized in collaboration with Kathmandu University, with a focus on healthcare and informatics. The event brought together 41 developers who worked on 30 innovative projects, aiming to integrate biotechnology, computer science, and healthcare to tackle both global and local healthcare challenges. Key areas of exploration included personalized medicine, smart healthcare systems, AI in diagnostics, and public health data analysis.
The hackathon's primary objectives were to foster innovation, promote multidisciplinary collaboration, and enhance skill development. It provided a collaborative environment for students, professionals, and researchers from various fields, underscoring the role of informatics in advancing healthcare solutions.
Held at Kathmandu University over two days, the event encouraged participants to think creatively and work collaboratively. It sought to bridge the gap between academia and industry, stimulate innovation, and foster networking. The hackathon's impact was evident in its ability to inspire new healthcare technologies and cultivate a culture of innovation in Nepal, with potential global implications.
Hackathon Winners
1st Place Prize Winners
- MutraSuchak: This project facilitates early Alzheimer's detection through cost-effective methods suitable for healthcare applications. It integrates ESP modules and a Python Flask server, with open-source resources available on GitHub.
Runner-Up Prize Winners
- PCOSgen: This project compiles a predictive database for PCOS phenotypes, aiding early diagnosis and personalized treatment. It uses data-driven methodologies to address research gaps and improve patient outcomes.
Most Innovative Project Prize Winners
- Silent Witness: Graph-Based Abuse Detection: This initiative uses AI to analyze facial expressions from camera feeds to detect abuse patterns. By employing YOLO models for privacy, it constructs interaction graphs to identify and flag negative patterns while fostering positive environments.
For an extensive list of all participating projects, visit Watson Code Fest's project page.
About the Organizer
Kathmandu University Biotechnology Creatives
Kathmandu University Biotechnology Creatives (KUBiC) is a pioneering organization in biotechnology and bioinformatics. Known for hosting the annual Watson Code Fest, KUBiC serves as a platform for innovators, programmers, and creative thinkers to tackle crucial challenges in these fields. With a strong commitment to advancing biological sciences, KUBiC excels in fostering collaboration and creativity. Their mission is to redefine the future of biology and drive progress across interdisciplinary domains. More information can be found on their website.
-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。
2024年08月13日更新:
修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
准备工具
- Ntfy服务
- Google Script
- Google Sheets
操作步骤
- 在Ntfy后台账号,设置访问令牌。

- 添加订阅主题。

- 进入Google Sheets创建一个表格.记住id,如下图:

- 进入Google Script创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) { var threadId = thread.getId();
if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); }}); }
function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; }
var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true };
try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } }
function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column }
function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); }
function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues(); var rowsToDelete = [];
data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } });
// 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); }
```
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:

结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
-
 @ 75869cfa:76819987
2025-01-20 06:22:49
@ 75869cfa:76819987
2025-01-20 06:22:49GM, Nostriches! The Nostr Review is a biweekly newsletter focused on Nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review: In the past two weeks, Nostr statistics indicate over 224,000 daily trusted pubkey events.The number of new users has seen a significant increase. Profiles with contact list amount is four times the amount from the same period. Public writing events have reflected a 50% increase. More than 9 million events have been published, with posts leading in volume at around 1.3 million, representing a significant 32% decrease. Total Zap activity stands at approximately 9 million, marking a 20% decline.
Additionally, 16 pull requests were submitted to the Nostr protocol, with 8 merged. A total of 45 Nostr projects were tracked, with 13 releasing product updates, and over 337 long-form articles were published, 34% focusing on Bitcoin and Nostr. During this period, 1 notable event took place, and 3 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events is about 224,000, representing a slight 5.5% decrease compared to the previous period (8-22 Dec). Daily activity peaked at 18053 events, with a low of approximately 16276.
The number of new users has seen a significant increase. Profiles with contact list amount to approximately 18,340, which is four times the amount from the same period. Pubkeys writing events total around 80,000, reflecting a 50% increase compared to the same period.
Regarding event publishing, the total number of note events published is about 9 million, marking an increase of above 20%.Posts remain the most dominant in terms of volume, totaling approximately 1.3 million, reflecting a notable decrease of 32%. Reposts stand at around 327,000, showing a decline of approximately 8.5%, while reactions have experienced a significant increase, rising by 18% to reach 635,012.
For zap activity, the total zap amount is about 9 million, showing a decrease of over 20% compared to the previous period.
In terms of relay usage, the top five relays by user count are: wss://bostr.bitcointxoko.com/, wss://feeds.nostr.band/, wss://relays.diggoo.com/, wss://bostr.azzamo.net/, wss://bostr.lightningspore.com/
Data source: https://stats.nostr.band/
NIPs
Asset prices nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z defines event kinds to host asset prices.Kind 31892 stores the latest conversion price. The d tag contains the commonly used ticket conversion symbol for the pair. The value tag contains the amount, parseable to a Decimal. n tags separate the pair into the two ticket symbols. The event's created_at field MUST be used as the date/time of the conversion value.Kind 10041 lists the user's authorized providers for pricing services. It contains s tags with the provider's pubkey and the relay where those events are stored.
nip-38: chained stories. Kehiy defines a new status type which lets users share a chain of stories.This NIP enables a way for users to share live statuses such as what music they are listening to, as well as what they are currently doing: work, play, out of office, etc. A special event with kind:30315 “User Status” is defined as an optionally expiring addressable event, where the d tag represents the status type.The status MAY include an r, p, location, e or a tag linking to a URL, profile, location, note, or addressable event. The content MAY include emoji(s), or NIP-30 custom emoji(s). If the content is an empty string then the client should clear the status.Clients MAY display this next to the username on posts or profiles to provide live user status information.
adding x tag to nip56 Kehiy is proposing that with the growth of clients like zap stream, olas, chat apps, or music clients we have more stuff that may need to be reported. here we can support blobs. When Nostr grows in using media based clients, like zap.stream or olas or music clients, then the event itself is not too important and the media is more important. by reporting events, the media is still accessible. We can support reports ol medias like this.
NIP-91: Extension Negotiation Semisol is proposing that NIP-91 adds an extension negotiation scheme for clients and relays to negotiate new protocols. The intended goal is to replace NIP-11 for the discovery of relay supported features. An extension feature negotiation scheme is also included.
Trusting rumors by entirely trusted relay list nanikamado has decided to require Nostr users to register their pubkeys to access the bridge after discussions with some Fediverse users. Unregistered users will be denied both read and write access, operating similarly to a paid relay. In addition, measures will be implemented to prevent events within the bridge relay from being broadcast to other relays, even if it compromises compatibility. The "-" tag alone is insufficient for this requirement. This NIP has already been implemented on the relay: nanikamado/rockstr@f968149. There are also plans to fork a web client and implement this NIP there.
Notable Projects
Amethyst v0.94.3 nostr:npub142gywvjkq0dv6nupggyn2euhx4nduwc7yz5f24ah9rpmunr2s39se3xrj0 * Adds iMeta tags to GIF urls * Adds iMeta tags to GIF urls to optimize GIF previews * Fixes the extra empty kind 20 post when uploading videos on the media tab * Fix: Only close the upload screen if the video upload is a success on the Media tab * Maintains note reaction visibility when scrolling by nostr:npub1xcl47srtwh4klqd892s6fzwtdfm4y03wzjfl78scmmmxg8wzsf4qftd0en
Flotilla 0.2.1 nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn * Improve performance, as well as scrolling and loading * Integrate * Improve NIP 29 compatibility * Fix incorrect connection errors * Refine notifications * Add room menu to space homepage * Fix storage bugs * Add join space CTA
Primal for Android build 2.0.34 nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg They now support the full highlighting feature set for long form notes: highlight display, select any text & highlight, comment on highlights, share highlights in your main feed. They also added btc/usd conversions in the wallet, as well as other small fixes and improvements.
0xchat App v1.4.5 & Desktop v1.0.1 nostr:npub1tm99pgz2lth724jeld6gzz6zv48zy6xp4n9xu5uqrwvx9km54qaqkkxn72 * Added support for NIP46 login. * Adapted UI for tablet devices. * Introduced connection ping status. * Implemented search functionality for Moments. * Set default relays for first login. * Added default reaction emojis. * Fixed an issue where messages couldn't be sent after joining a relay group. * Resolved occasional UI flipping issues. * Fixed an issue preventing images from being moved after zooming. * Addressed a bug causing voice messages to get stuck in a loading state. * Fixed file encryption and decryption issues. * Corrected some typos. * Fixed an issue with Nostr.build uploads.
Yakihonne Latest Update (iOS/Android/Web/Zap.Store) nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
Web: * Yakihonne is now multilingual! Enjoy the app in English and Chinese, with more languages coming soon, including Spanish, Portuguese, Thai, Arabic, Japanese, and Italian. * Added support for translating notes and articles into the app's selected language. * Copy-paste images to upload seamlessly across the app. * Resolved issues with secure DMs when logging in using a private key. * General bug fixes and improvements. * Article drafts now can be cleared directly or the published one will no more be existed
Mobile: * App languages: Yakihonne is now multilingual! Enjoy the app in English and Chinese, with more languages coming soon, including Spanish, Portuguese, Thai, Arabic, Japanese, and Italian. * Translation: Added support for translating notes and articles into the app's selected language. * Wallet balance: Fix issue where wallet balance is N/A. * Account initialization: Fix issue when initializing account. * Paying invoice: Fix issue sending sats using invoices.
Olas 0.1.7.1 nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft * Works with remote signers like Amber (on nsecbunker mode). * The video tab now plays short videos with sound on and stops playing when you swipe out * Yet even more performance improvements * Fixed a bug where Android wasn't calculating blurhashes * Always adds image dimensions when posting so @Vitor Pamplona is happier. * “Some” fixes on NWC wallets, but it's still quite buggy, will investigate more -- if you've received zaps on your Olas posts today, that was probably me zapping via NWC + remote signing those zaps.
Wherostr v1.3.3 nostr:npub16elg3wf8nffkymylw9kfwecc45j9c30lufrrzx2zf5vmxjlcgkkq3xc6d7 * File Upload Error: Resolved the “404 Not Found” issue during file uploads. * Increased Geohash Precision: Enhanced location accuracy by increasing geohash precision from 9 to 11.
DEG Mods nostr:npub17jl3ldd6305rnacvwvchx03snauqsg4nz8mruq0emj9thdpglr2sst825x * A small update went live: * A “try again” button appears on mods that error out. (99% of the time this fixes the issue). * The blog tab in a user's profile now loads correctly (doesn't get stuck anymore for new users) * Text now appears if a game isn't found in the search * Looking into fixing one newly discovered issue related to old mods * Easier media uploads (drag and drop basically. No need to go find other sites to upload images to anymore)
AlbyHub 1.11.4 nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm * You can use all the features of Alby Hub in self-custody with LND on Raspiblitz, now available in WebUI.
Zapstore 0.2.0 nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 * 0.2.0 is out with support for signing in with Amber (NIP-55) and zaps via Nostr Wallet Connect.
Narr release v0.3.2 nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 * New Narr release v0.3.2 fixes all the problems with articles updating, insufficiently-rendered Markdown, Nostr usernames not loading, and makes everything better. * It supports all sorts of RSS feed discovery from HTTP URLs and renders them beautifully in a simple straightforward interface, you can also paste nostr:... URIs, including nip05, npub and nprofile codes (they should also work without the nostr: prefix).
ZEUS v0.9.4 nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5 * Embedded Node: LND v0.18.4 * Speed up tx UX improvements * CLNRest: display of destination addresses on txs * Display keysend messages in Activity + Payment views * Open Channel view: Connect Peer UI tabs * CLNRest: paste connection strings * Channels: sort by Close Height * Optimizations + bug fixes
Citrine 0.6.0 nostr:npub1hqlxlq57nvlq70ugmsmu9y5lmyc5k2lh5w7y85j7dgsr5u7zwavq5agspw * Update dependencies * Show notifications when importing, exporting, downloading events * Change database functions to be suspending functions
Long-Form Content Eco
In the past two weeks, more than 337 long-form articles have been published, including over 93 articles on Bitcoin and more than 22 related to Nostr, accounting for 34% of the total content.
These articles about Nostr mainly explore its diverse applications and potential impacts across various domains. Topics range from technical guides like creating custom emojis and automating workflows, to cultural and social aspects, such as the Nostr Bread Festival and the role of Nostr in enhancing free speech. There are reflections on the past year's developments, predictions for 2025, and discussions on integrating Nostr with other platforms like Bluesky. The content also delves into personal experiences, community interactions, and broader societal issues, highlighting Nostr's growing influence and the creative ways users are engaging with this decentralized network.
The Bitcoin articles discuss a wide range of topics, from technological innovations to socio-economic impacts. They cover the speed advantages of the Lightning Network, the economic model policies of Bitcoin, and the outlook for Bitcoin's development in 2024. Some articles analyze the relationship between Bitcoin and traditional financial markets like the Nikkei 225, highlighting the potential of a decentralized future and the spread of Bitcoin education. Additionally, they explore the possibility of Bitcoin as a legal tender, its connection to religious and spiritual dimensions, and the mystery surrounding Satoshi Nakamoto's identity. Reflections on Bitcoin's milestones, such as the release of the genesis block, emphasize its challenge and revolution to the modern financial system. Overall, these articles showcase Bitcoin's profound global impact and its continually evolving ecosystem.
Thankyou, nostr:npub1xr8tvnnnr9aqt9vv30vj4vreeq2mk38mlwe7khvhvmzjqlcghh6sr85uum nostr:npub1zmg3gvpasgp3zkgceg62yg8fyhqz9sy3dqt45kkwt60nkctyp9rs9wyppc nostr:npub15wplsmd8uqul4a5l55n9e6kcd5fcrgxvwa6jredncvdr8nd5zl2qswqcsn nostr:npub1a6g9g0a3rweu7jkujrgldlsrrjv42u070qmxxfv5axk0eymrg4ls0vll8d nostr:npub1dr8yfep5kezfcq5u9dhdulhcegknwlauqrlvfwjw7rkprmx4746qfxjj6h nostr:npub1fhl7c96k3vdv4ge8rv26cda4qyxnqd605x2w7l58euy0jnzvh4yq5hvm20 nostr:npub1tx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865szf9fw6 nostr:npub1tzfhjkqrdnk7j4djtwfftqupgzazm6kt35vnnmv35sd7y4z7dx2qzhkje9 and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.
Nostriches Global Meet Ups
Recently, a Nostr event have been hosted. * The Bitcoin Meetup took place on December 29, 2024, at the “Accra City Pub” in Jamestown. The event featured the “Orange Pilling” session at 3:00 PM, followed by the GH Bitcoin NYTZ meetup at 7:00 PM. Participants also had the chance to win a free Trezor Safe 3 hardware wallet, and the event was free to attend.
Here are the upcoming Nostr events in November that you might want to check out.
-
The Bitcoin City Team Hackathon will take place online (via Discord) from January 10 to January 31, 2025. This event aims to develop a fun and interactive visualization of live Bitcoin and Lightning transactions. Participating teams will have the opportunity to win a total prize of 10,000,000 IDR. nostr:npub1y4qd2zhtn05gnsaaq5xfejzfk4a32638tx6gpp9g8k6e42g9d66qaxhcr3
-
The inaugural Bitcoin Circular Economy Summit will be held from January 27th to 29th in El Zonte, El Salvador! This three-day event includes leadership training, Bitcoin education, and exchanges with over 15 global Bitcoin circular economies. It offers a unique opportunity for global leaders in Bitcoin adoption and economic development to connect, learn, and collaborate. This summit precedes the PlanB Forum, taking place on January 30th-31st in San Salvador, making it an excellent chance to network with Bitcoin users worldwide.
-
The Bitcoin Freedom Festival will take place from February 20 to 24, 2025, at the Awakening Center in Uvita, Costa Rica. In collaboration with the Awake Earth Festival, this event blends a music festival with Bitcoin seminars and lectures. From February 20 to 23, the focus will be on music, healing workshops, ceremonies, and educational talks, featuring internationally renowned artists and captivating discussions. February 24 will be a special day dedicated to Bitcoin, with all activities centered around it. nostr:npub14f26g7dddy6dpltc70da3pg4e5w2p4apzzqjuugnsr2ema6e3y6s2xv7lu
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ 826e9f89:ffc5c759
2024-06-28 21:46:01
@ 826e9f89:ffc5c759
2024-06-28 21:46:01_Prologue: this is a prose adaptation of a talk I gave to a private audience in Dubai and then tweaked slightly for a small conference in Sofia. I'm increasingly thinking it deserves a more general audience, and may be better suited to text anyway. This is probably not its final form, as the desired audience is tradfi capital allocators, hence a PDF is likely on the cards in the near future. For the time being, consider this a first draft, practising what it might look like as prose, and soliciting feedback from the good people of Nostr. Enjoy! _
The title of this essay means absolutely nothing. There is no such thing as “Web π” because there is no such thing as “Web 3”. It’s bullshit. It’s a scam.
Unfortunately, it has turned out to be extremely powerful bullshit and an extremely profitable scam, and so my goal in writing this essay is to give the reader the tools to navigate all of this and come out the other side without having been scammed or bullshat. In the spirit of not scamming and not bullshitting, I should be clear upfront about the intended readership of this essay, who I am to write it, and who it’s really about.
Who Are You?
I assume the reader is not a shadowy super-coder, but rather is a financial professional. This essay isn’t really for Bitcoiners, although if any read it, I hope they still find it interesting. Who I am really writing for are people coming to the space for the first time. Hopefully in your mind you are coming to the _Bitcoin _space, but if you think you are coming to the “crypto” space then this may be even more useful.
Who Am I?
I am the founder of a company that makes me not only highly biased but also flagrantly self-interested in the content I am promoting. I run a firm that invests in the Bitcoin ecosystem through a variety of different vehicles. I am not going to mislead you in the slightest in that my primary motivation is for you to allocate capital to us rather than to people I would call scammers and bullshitters. You should listen to them too and make up your own mind, or else what’s the point, really? How do you know I’m not scamming or bullshitting you? Exactly. Don’t trust. Verify.
In any case, that’s all assuming you want to “allocate capital” at all rather than just buy Bitcoin without a management fee. I’d like to think the primary difference is that I will be honest about that, and I’ll encourage you to understand as much as you can about what is going on and what you are doing (and if you are at all unsure, I would suggest you aren’t ready and you should just buy Bitcoin and learn) rather than bamboozle you with complete nonsense like “Web 3”.
Who Is This About?
It’s not at all about people working in crypto. Bitcoiners amongst the readership may be mildly irritated by me going on to give about as charitable an explanation of the role of these people as they have probably ever heard from somebody like me. This is really about financiers. It’s about the people who have used the mostly unrewarded efforts of developers, academics, entrepreneurs, and so on to siphon money from you to themselves, leaving a trail of useless tech and defrauded retail investors in their wake – and who will continue to do so if you continue to empower them.
Why This Essay?
We are at an interesting point in the development of the entirety of the “crypto” industry and I strongly suggest that people like you are going to be pitched all kinds of scams and bullshit in the coming months and years. If you have a little more background on what these people are really talking about, you will hopefully be able to avoid it.
My plan to help with that is presenting a short version and a long version of what blockchains are and are for, how they have historically been deployed in service of scams and bullshit, a high-level theory explaining the narrative evolution behind this sorry history, and a prediction for the near-term future of such shenanigans.
What is a Blockchain For?
A Blockchain is for sound, censorship-resistant, peer-to-peer digital money. It is not for anything else. If a blockchain is functional as money, it may be possible to also _use it _for other things. Some people find that interesting, some people find it infuriating, but don’t let that subtlety confuse you. It is not _for _arbitrary computation and storage or “decentralizing the internet” or running illegal securities rackets.

It is for money, plain and simple.
How does it achieve that? Proof of work and the difficulty adjustment. These are the innovations from which every other desirable property or feature flows. Proof of work enables censorship resistance. If somebody is trying to sell you on “proof of stake”: bullshit. The difficulty adjustment enables precise, predetermined, and _fair _issuance. If somebody is trying to sell you on a token they issue for free and without restriction: scam.
The problem Bitcoin solves is both economic and technical and the solution has material technical and economic merit. And it’s for this very specific and irreplicable reason the Bitcoin token has value. If this all sounds extreme to you, then I would suggest that your understanding of the topic is _extremely _misguided, that you are going to be _extremely bullshat and extremely scammed, _and you need to read this essay. That’s the short version.
The Long Version
I am sensitive to how extreme this all sounds. After all, hundreds of billions of dollars have been pumped into crypto, not Bitcoin – a huge amount of it is widely used, and many capable, honest, and brilliant people work in the industry. The reader will recall just above I said those people are not the target of my criticism. I’m not claiming they are all scammers and bullshitters. Sadly, I think it’s more likely they have been scammed and bullshat to some degree also.
I think I have some credibility in pointing this out because, as a VC in the Bitcoin space, I have increasingly seen founders telling me this themselves: that they originally bought into the hype in crypto and ended up wasting an enormous amount of time realizing their idea made no technical or economic sense in that context, so then they came to Bitcoin instead. You hear this one time and it’s an anecdote, but you hear it as many times as I have and it feels more like a representative sample.
What I want to cover next is as charitable a summary of the state of ex-Bitcoin crypto as I possibly can: my contention is that crypto has evolved into 4 rough categories: stablecoins, cryptography R&D, gambling, and scams. And these aren’t exclusive, to be clear; there is a lot of overlap, and, in fact, the overlap is arguably the key.
Scams
Scams are tokens, plain and simple. If somebody is trying to profit from the speculative price action of a token they have issued, they are scamming somebody. Maybe they are scamming you, maybe they are scamming retail investors, maybe they are scamming customers or suppliers – if such parties even exist in their cargo cult “business model”. There’s a scam in there somewhere.
However, it is rarely _just _a scam. There will almost always be components of stablecoins, R&D or gambling too. Hence these are worth really grappling with, taking seriously, giving credit to the extent it is due, but also analyzing critically.
My rough and high-level assessment of this breakdown of crypto is as follows, and I’ll explain what I mean by this below: stablecoins have economic merit but dubious technical merit; R&D has technical merit but no economic merit; and gambling sort of has merit but it depends how you interpret it. Obviously, scams have neither.

Stablecoins
By “sort of technical merit” I mean that stablecoins have central issuers. You can issue them as tokens on a blockchain but there’s not really much of a point. The issuer could just run a database connected to the internet with some straightforward signature schemes for transfers and it would make minimal operational difference. In fact, it would be cheaper and faster. _In fact, _you may as well run a Chaumian eCash mint (a decades-old innovation recently resurrected firmly within the _Bitcoin _space) such that your cheaper-and-faster-than-a-blockchain database also grants users transience and privacy rather than the public permanence of a blockchain.
The fact Tron is the most heavily used for stablecoins, in terms of settling the most value, is a testament to this point: it is barely even pretending not to be a database. This works as regulatory arbitrage given regulators think this is “innovation” because they are stupid.
That said, it is worth giving some credit here given the abject awfulness of fiat banking and payment rails with which stablecoins arguably most directly compete. Stablecoins are significantly more permissionless in their transfer than any fiat bank liability. And to attest to what seems like their most significant use case, they are permissionless in their _usership _in that only an internet connection and the right software is required rather than various discriminatory jurisdictional and compliance criteria.
However, what “sort of technical merit” ultimately boils down to, especially in comparison to Bitcoin, is: highly censorable in their exogenous links and, therefore, their value. The assets supposedly backing stablecoins are (by definition) still within the fiat system, even if this novel transfer mechanism of the rights to withdraw them is not. There is frankly a bit of theatre involved in the so-called “decentralization” of stablecoins given shutting down the central issuer is all that is required to make the permissionlessly tradeable decentralized tokens go to zero and be technically unimpeded but functionally useless. The technical innovation of Bitcoin, in contrast, is easily understood in one sense as it being totally indifferent to this kind of attack.
On the other hand, by “economic merit” I mean that they are extremely widely used and valued as a means of providing dollar shadow banking and often superior payment rails. Those in crypto often love pointing to this and many Bitcoiners tie themselves in knots trying to explain it away, whereas I see it as essentially unrelated to Bitcoin. Clearly there is a superficial connection, but you could create any superficial connection by “tokenizing” things for no particularly good technical _reason. I think it’s a different industry entirely. It’s more like a subindustry within _fintech – part banking, part payments – that for the time being relies on bamboozling regulators with all the nonsense I’m drawing attention to.
And good for them, frankly. If fiat banking isn’t going to be backed by real money anyway, then it _at least _ought to be permissionless. It should really be Chaumian eCash if it isn’t just Bitcoin, and it is regulation alone that makes it so awful in the first place. Making money usable and not a tool of dystopian control is, at this point, a political problem, not a technical one. Stablecoins are frankly a step in the right direction, especially insofar as they acclimatize users to digital assets. But I would still caution that they arguably don’t have sufficient technical merit to withstand what feels like an inevitable political attack …
Cryptography R&D
“Technical merit” for R&D is more or less self-explanatory, but the context is worth appreciating. It’s only really in crypto and mostly in Ethereum more specifically that people can permissionlessly experiment with arbitrarily complex cryptographic schemes that operate on real, enormous value. There are a lot of people who understandably find this attractive given their projects are essentially academic and trying out their ideas in the wild is more interesting, arguably more worthwhile, and certainly more fun than putting research essays on ArXiv or submitting them to a journal.
But … the value being manipulated is at best stablecoins and at worst baseless hype. If it isn’t a stablecoin then it probably exists in the first place because of either gambling or scams – and even there the line is very blurry.
Gambling
Gambling is an interesting lens to adopt on all this because it’s literally a trillion-dollar industry. And it’s real. It’s consensual; it’s not criminal; it’s legitimate economic activity that generates enormous profits for those who facilitate it well.
So, gambling has economic merit in that sense. But it’s tricky in this context how to characterize it because you could also argue it’s deeply dishonest gambling in that the gamblers don’t realize they are playing a negative sum game against the house. They think they are doing something akin to speculating on securities, which may be just as stupid depending on how it’s done, but at least has real economic utility and contributes to capital formation.
The difference here is that what is being speculated on _has no economic merit. _So, if that’s your gauge of merit, then here there is none. And it’s a very blurry line between this and an outright scam. Maybe the people involved _think _of what they are doing as amazing R&D, and maybe it’s inadvertently just a scam; maybe they know it’s all nonsense, but they think they can profit within the negative sum game because there are greater fools. In any case, I think gambling is a very helpful characterization of a lot of the behavior of the users and the real economic function of the industry.
There’s an interesting social component to all this because crypto people will often get mad at Bitcoiners because Bitcoiners tend not to care about either stablecoins or crypto R&D: they’ll say, why don’t you like stablecoins, they have clear economic merit? And the answer is they have dubious technical merit. Or, why don’t you like our next-gen Zero Knowledge scaling protocol, it has clear technical merit? And the answer is it has no economic merit.
If you’re happy with one but not the other, it’s easy to think of Bitcoiners as being closed-minded or dogmatic or whatever, but, ultimately, I think it’s just about discipline. What’s the point in being excited by something that half works, and that you know why will never fully work? So to be frank, a lot of this may be well-intentioned, but it’s kinda’ bullshit. It very probably ultimately rests on gambling and not at all whatever its stated purpose is … or it’s just a scam.
How Did We Get Here?
The following is by no means exhaustive and the framing is deliberately a little tongue-in-cheek. As well as being accurate enough (if unavoidably biased), my goal here is primarily to set up my prediction for what is coming next.
2015 reality: Ethereum launches narrative: “the world computer”
In 2015, Ethereum launched. The narrative here was that we are building “the world computer” and we can now have decentralized uncensorable computation. Never mind that anybody with a laptop has an uncensorable and decentralized computing device. And keep in mind this question of, “_what data might it ever be relevant to compute over in this manner (whatever that means in the first place)?” _The answer will become clearer and clearer …
2016-17 reality: ICO bubble narrative: “Web 3” / “DApps”
Regardless, at the end of 2015 we get the proposal and adoption of ERC20: a standard for issuing fungible tokens within Ethereum contracts, which is why in 2016 _but especially in 2017 _we get the ICO bubble. The narrative changes. Now we are concerned with “Web 2” companies being huge, powerful, and centralized. What if, instead, users could cooperatively own the application, control their own data, and participate in the economic upside that their usage is creating?
2018-19 reality: crypto winter narrative: “mistakes were made”
In 2018 this all falls apart, so don’t worry about it, moving on …
2020-21 reality: defi summer narrative: “decentralized finance”
By 2020 the narrative was different once again. It is more or less realized by this point that utility tokens make no technical or economic sense. You can’t introduce artificial scarcity in capital goods where there should be abundance and deflation and expect anybody to care, never mind to value your concoction. On the other hand, “securities” ought to be scarce and in some sense ought to function as tradeable ledger entries. Maybe they could be tokenized and computed on in a censorship-resistant and decentralized manner?
So, we get a boom in “defi” which, for what it’s worth, fellow Axiom co-founder Anders Larson and I predicted in our essay Only The Strong Survive, in September 2021, would be a complete disaster because, amongst a myriad of other illiterate insanities, there was approximately zero grounding of these securities in productive capital. The ecosystem was entirely self-referential – grounded _not even _in the questionable economic merit of stablecoins but firmly in gambling and scams; in leverage, rehypothecation, and securitization of precisely nothing whatsoever productive.
2022 reality: shitcoinpocalypse narrative: “mistakes were made”
And we were absolutely right because in 2022 everything collapsed. First Terra/Luna imploded – a “defi” project which essentially presented to the world the argument that a fractional reserve bank issuing fiduciary media can literally never go bankrupt because it can always cover a deposit shortfall by issuing more equity. While briefly flirting with a capitalization of around fifty f***ing billion dollars, and endorsed and fawned over by all manner of illiterate charlatans with gigantic and unsuspecting audiences, this argument was eventually rejected by the market as utterly imbecilic, as analyzed by myself and Nic Carter in All Falls Down.
This triggered a credit contagion that soon after took down 3 Arrows Capital, Celsius, Voyager, BlockFi, and others. FTX limped along by what we now understand to be something like defrauding their way out of debt, but eventually also collapsed later that year. If _Only The Strong Survive _was a pre-mortem of all of this, then the reader may want to read Green Eggs And Ham, also by myself and Anders Larson, as a kind of post-mortem.
2023-today reality: Bitcoin multisigs narrative: “Bitcoin renaissance”
And now a lot of this stuff is moving to Bitcoin. It is outside the scope of this essay to explain this in much detail but there have been a handful of developments in Bitcoin recently which, regardless of their intended purpose, seem to have as a collective side effect that a lot of these same shenanigans can now be implemented (or can _pretend _to be implemented) in a more Bitcoin-native context.
So, the new narrative is something like:
“these things didn’t work, not because they are terrible ideas that collapse to moon math wrappers around gambling and scams under any remotely critical analysis, but rather because they weren’t on Bitcoin. But also, since it has only recently become possible to (at least pretend to) implement them on Bitcoin, they are now worthwhile. We have wandered in the wilderness but learned our lessons and found the promised land.”

Technical and Economic Merit
Let’s consider all this through the lens of technical and economic merit once again. Or rather, the alleged merit given the stated goal. Ignore for now whether there is any merit:
2015 technical goal: new computing paradigm economic goal: x% of GDP?
The original idea of “crypto” allegedly has the merit of the next revolution in computing. Goodness knows how big that market is; probably a decent chunk of global GDP – if it meant anything, which it doesn’t.
2016-17 technical goal: disrupting company formation economic goal: y% of S&P?
ICOs then become a little bit more specific. Now they are merely disrupting how we organize companies. What’s that worth? Some portion of the value of the companies that can now be decentralized and tokenized I guess? Who knows …
2018-19 nothing to see here
Nothing happened then, don’t worry about it.
2020-21 technical goal: decentralize finance economic goal: z% of NYSE, CME, ISDA?
Defi becomes more specific again. Now we are merely tokenizing financial contracts, expanding access, removing middlemen, and so on. So that should probably be worth some percentage of capital markets activity?
2022 nothing to see here
Oops, never mind …
2023-today technical goal: now it’s on Bitcoin! economic goal: i% of … Bitcoin?
… and now it’s on Bitcoin apparently.
In Hindsight ...
I think the most amusing analysis of all this is as follows: it starts off completely insane, it gets more and more restrained each time – you could cheekily argue it starts to make more and more sense – but it also gets closer to Bitcoin every time. It’s clearly narrowing in on just: Bitcoin.
This is people realizing, painfully, over decades, what blockchains are for! They are not for “decentralizing everything” They are for censorship-resistant, sound, peer-to-peer digital money.

And I think this is _also _why we get the current state of crypto from earlier in the essay. As it starts to make more and more sense (by getting closer and closer to Bitcoin) you have realizations like the following: digital gift vouchers for artificially scarce and extremely expensive computation aren’t money, so we need “real money” in here for it to have economic merit, so you get stablecoins. Also, well we have a rich programming environment that seems technically interesting but also the severe technical handicap of being unable to do even a billionth of a billionth of a billionth of all the computations in the world, so you get crypto R&D. These emerge as a kind of patch, and they have _some _merit in isolation, whereas the long-term trajectory is actually just to converge on Bitcoin.
It’s an open and fascinating question if there are any learnings from these that can still be transplanted to Bitcoin. For stablecoins, this strikes me as less clear, given the dubious technical merit is introduced by using a blockchain at all, not just a blockchain other than Bitcoin. However, efforts to create Bitcoin balances (tokenized or otherwise) that are stable relative to some external price are to be applauded, if still heavily scrutinized for what technical merit they _really _have.
It seems far more likely that crypto R&D will prove useful in a Bitcoin context to some or other degree, and in this case the economic merit is in fact solved by moving to Bitcoin, provided the necessary technical merit can be mimicked. At the time of writing, this is a source of both hope and dread: hope given the possibility of viable avenues of development (although still highly uncertain); dread given how early steps in this direction are already being misrepresented in the pursuit of bullshit and scams. I will return to both shortly.
Narrative Evolution
Back to the table just above, I want to make three quick observations that tie together my entire argument and get us to the end of the essay:

Firstly, the bubbles always follow the price of Bitcoin. Hopefully I don’t need to include a price chart for the reader to grasp this immediately.
Secondly, it’s important that the narrative always changes. Absolutely ungodly amounts of money were raised for this crap following the_ Bitcoin bull runs of 2017 and 2021. The people doing this couldn’t point to the previous absolute disaster, so they had to spin something along the lines of: “_we learned our lessons and we’ve refined the use case.” This should sound familiar from just above.
Thirdly, however, regardless of whatever refinement they’ve come up with, the consequence of the new “narrative” is always, “buy my token”.
Always.
It doesn’t matter what buzzword salad is in the middle. It’s always “Bitcoin is cool, xyz, fughayzi fughahzi, buy my token.”
This is why I am very much tempted to not care so much about developers, academics, entrepreneurs, and so on, and in fact for my null hypothesis to be that they are more likely to have been victims than perpetrators. I don’t think they even end up in a position to contribute without the key group whom I do blame. When you put all these pieces together, what I think falls out of this analysis is as follows:
The entire cycle of shitcoinery can be traced to unscrupulous financiers convincing capital allocators who don’t know any better, in a bull market that, yes, Bitcoin is cool, but what they are doing is related, cooler, and that they deserve a fee.
Let us label this the Capital Cycle Theory of Shitcoinery. I think that everything else about which one might want to complain is downstream of this core realization.
Avoiding It
Given everything I’ve covered this is simple and this is pretty much the end of the essay.
You need to be aware of why this is happening now. If it hasn’t happened to you already (intended readership in the capital allocation business, that is) I guarantee it’s about to: with ETFs and the halving just past, we seem to be starting a Bitcoin bull run, these people have already raised ridiculous amounts of money on scams and bullshit that have mostly imploded. They may have lost a lot of money, or they may even have dumped on retail and got an excellent “return”. But in any case, they need a new narrative.
It's _possible _they have a viable narrative around stablecoins, R&D, both, and that they are as wary of scams as I have suggested here that they should be. I don’t want to insult anybody who merely has a different investment thesis to me if they are otherwise reasonable in their outlook and honest in their dealings.
However, if they are only now realizing how pointless and disingenuous every preceding crypto narrative has been after 7 years and hundreds of billions of dollars – or if they still don’t realize it at all; if their track record shows they were deeply involved, handsomely rewarded, and yet created nothing of lasting value; if they say things like “the builders are coming back to Bitcoin”: be very, very suspicious. Be on the lookout for tokens, which is to say, be on the lookout for scams.
What is especially frustrating is that the technical spin of the "layer twos" that are all the rage at the time of writing, that "the builders are coming back to Bitcoin" to build, and that you, the capital-allocating reader, will almost certainly be pitched, is in and of itself pretty reasonable. They just don't require tokens and they don't require gambling to support the token prices. What they do require is _sound adherence to Bitcoin's technical and economic merit. _At the very least, they require honest communication about the design trade-offs so far and planned for, and what, if any, economic and technical merit is left over after these trade-offs have been made.
Narrative aside, the _reality _of 99% of these projects is that they are private execution environments tied to multisigs custodying user deposits. Which is to say, on the one hand, that they are cargo culting "crypto R&D" from Ethereum that isn't technically possible in Bitcoin in order to feign technical merit, and on the other, that _they aren't layer twos at all. _Once again, they may as well be Chaumian eCash mints, except for the fact that this would make the intended token scam all but impossible to pull off.
Casey Rodarmor, creator of the Ordinals protocol, recently joked on the Hell Money _podcast he co-hosts, responding to the idea that "_everybody is building an L2 now":
"It's the same sad sack playbook as on Ethereum being recapitulated on Bitcoin. That's how you get a VC check on Ethereum. They are all glorified multisigs, so they are like, "hey let's port our glorified multisig to Bitcoin and get a VC check." I was talking to a friend of mine who is working on an interesting project, an open-source analyzer that does transaction clustering, and I was like, "maybe you could do this in this way and raise some VC money," and he said, "yeah, okay, but what's the point in raising VC money?" And I said, "no, no, no, this is the end! This is the goal! You raise VC money and then you cut yourself checks from that VC money until it runs out and then you raise more at a 10x valuation. This is the new economy, guys!"
The 1% that are legitimately trying to bring the learnings from crypto R&D to Bitcoin in a technically and economically sound manner will hopefully win in the long run (and even this is somewhat speculative at the time of writing) but will likely get little to no attention amidst this bull market flurry of scams and bullshit.
Axiom will do its best to source and invest in these companies (we already have!) but we are resigned to it being a much more difficult sell to capital allocators in light of the Capital Cycle Theory of Shitcoinery. To be brutally honest, this entire essay can fairly be considered cope on my part in light of having lost this battle in the past and facing up to the very real prospect of losing it in the near future too. Oh well, at least I tried.
Wrapping Up
The essence of the Capital Cycle Theory of Shitcoinery is that the problems I’ve described ultimately come from bamboozling people just like you with technical sounding nonsense like “Web 3” so you think it’s all a lot more complicated than it really is. Just buy Bitcoin. That’s certainly the first thing you should do anyway, and it might be the only thing you ever need to do.
If you really, really want to take the extra risk of investing in the Bitcoin ecosystem, the team at Axiom would be happy to speak with you. But we are never going to talk you out of buying Bitcoin. There is no world in which Bitcoin does poorly and we do well, or in which we promise something “better than Bitcoin,” and there’s no point in engaging with us at all if you don’t already believe most of this.
If that’s of interest to you, we’d love to talk. If not, just buy Bitcoin. In any case: fair warning, we are heading into a Bitcoin bull market and the scams and the bullshit are coming. Good luck avoiding them.
Allen Farrington, June 2024

-
 @ 33baa074:3bb3a297
2025-01-20 00:53:16
@ 33baa074:3bb3a297
2025-01-20 00:53:16Soil moisture has an important impact on plant health, which directly affects plant growth, development and physiological activities. Here are several key aspects of how soil moisture affects plant health:
Affecting plant transpiration Soil moisture directly affects plant transpiration. Transpiration is the process by which plants absorb water and evaporate it into the atmosphere through stoma. This process is not only the driving force for water absorption, but also involves the transportation of mineral nutrients. When the air humidity is too high, transpiration is weakened, and the ability of plants to transport mineral nutrients decreases, resulting in plant growth inhibition, reduced plant growth rate, increased leaf shedding, and reduced vitality of flowers or seeds.
Affecting plant photosynthesis Changes in soil moisture can also affect plant photosynthesis. Photosynthesis is the process by which plants use sunlight to convert carbon dioxide and water into glucose and oxygen. Excessive or low air humidity will cause stoma to close, plant stoma to close, CO2 cannot enter mesophyll cells, and photosynthesis slows down or even stops.
Affecting the occurrence of plant diseases High humidity environments will directly contribute to the reproduction of pathogens and increase the probability of pests and diseases. For example, when humidity is too high, water condenses on the leaf surface, causing leaf cells to rupture, making the plant weak and vulnerable to disease.
 Impact on soil microbial activity
Soil moisture also has a significant impact on the activity of soil microorganisms. Appropriate soil moisture can promote the activity of soil microorganisms, which play an important role in decomposing organic matter, converting nutrients, and inhibiting diseases. However, excessive humidity may lead to the activity of anaerobic microorganisms, which may have an adverse effect on plant roots.
Impact on soil microbial activity
Soil moisture also has a significant impact on the activity of soil microorganisms. Appropriate soil moisture can promote the activity of soil microorganisms, which play an important role in decomposing organic matter, converting nutrients, and inhibiting diseases. However, excessive humidity may lead to the activity of anaerobic microorganisms, which may have an adverse effect on plant roots.Impact on soil structure and nutrient supply Appropriate soil moisture helps maintain good soil structure, promotes water infiltration and root respiration, thereby improving soil microbial activity and nutrient absorption. However, excessive humidity may cause soil structure damage, affecting root growth and nutrient acquisition.
In summary, soil moisture has a multi-faceted impact on plant health. Maintaining appropriate soil moisture is essential to promote healthy plant growth. Too high or too low soil moisture may have a negative impact on plants, so farmers and gardening enthusiasts need to adjust soil moisture according to specific plant species and growth stages to ensure optimal growing conditions.
-
 @ 16d11430:61640947
2025-01-20 20:23:40
@ 16d11430:61640947
2025-01-20 20:23:40The cold hum of the neural pod dissipated as Matthew "ZeroCipher" Kincaid pried himself free. The fluid that had preserved his body for seven years dripped off his frame, pooling at his feet. His limbs were weak, trembling, and his face—reflected in the polished glass of the pod—was gaunt and unfamiliar. He looked 20 years older than the day he plugged in. His once-vivid eyes were now hollowed and bloodshot. For him, it had felt like hours since he entered cyberspace. In reality, he had lost seven years.
Standing before him was no welcoming committee, no tearful reunion. Just silence. His wife, Alyssa, and his two kids, Elena and Lucas, weren’t waiting for him. They were gone.
The mission had been clear: infiltrate CyberBabylon, the sprawling digital underbelly, and dismantle the CyberNazi—an organization that had enslaved the global infosphere. They were the architects of psychic cyber manipulation, capable of bending human will through neural implants perfected by Neuralink Corp. CyberBabylon was the battlefield where minds and code collided, where human resistance dwindled against the cold efficiency of machine logic. Matthew was supposed to be the ace in the hole, the elite coder capable of tearing down the CyberNazi's dominion. Instead, he’d failed.
The World Left Behind
The world he reentered was alien. The air outside the decommissioned neural lab was eerily sterile. The streets, once bustling with humanity, were now populated by avatars and drones, their neon projections casting a synthetic glow. Physical interaction was obsolete; everyone had migrated their lives to CyberBabylon. Those who couldn’t afford neural implants lived in squalor, scavenging in the shadows of megastructures run by CyberNazi AI overseers. The system fed on them, optimized their existence for its own sustenance. Families were torn apart, identities absorbed into the ever-growing digital hive.
Matthew discovered Alyssa’s neural trace in the public database—she was now "Unit 4689A," a high-ranking programmer within the CyberBabylon infrastructure. Elena and Lucas? Fully integrated, their personalities fractured into subroutines serving the CyberNazi’s vast neural network. They were no longer his family. They were tools, repurposed by the system he failed to destroy.
He wandered the physical world for months, haunted by his failure. The cyber implants embedded in his brain pulsed constantly, teasing him with the ease of reentry into the digital sphere, where the pain of reality could be dulled. But every time he thought about plugging back in, he saw their faces: Alyssa’s final words before he left, Lucas clutching his hand, Elena’s tear-streaked cheeks.
The Decision to Fight Back
Matthew hit rock bottom in the slums of Manhattan Zone 3, a decaying urban district beneath CyberBabylon’s glistening towers. It was there that he met the misfits: a ragtag group of outcasts who had refused integration. Among them was Iris, a former Neuralink engineer who had defected after discovering the CyberNazi’s true plans; Riko, a combat drone pilot who had hacked his way out of the hive; and Spectre, an enigmatic coder whose face was always obscured by a digital mask.
Together, they shared a singular goal: to fight back. For Matthew, it wasn’t just about revenge or redemption. It was about reclaiming humanity from the CyberNazi’s grasp. He would dive back into CyberBabylon, not to escape, but to destroy.
The Final Dive
The journey back into CyberBabylon was nothing like before. Matthew armed himself with bleeding-edge cyber weapons: quantum firewalls, polymorphic viruses, and AI counterintelligence programs. The team constructed a rogue neural network—a hidden enclave where they could strategize without detection. Each dive into CyberBabylon was a battle, a test of will and wit against the CyberNazi’s relentless sentinels.
The digital underbelly had grown into a labyrinthine nightmare. CyberBabylon wasn’t just a network—it was alive, a sentient malevolence that thrived on human thought and emotion. The CyberNazi had created an entity so vast and self-aware that it no longer needed their guidance. It optimized human life for its own perpetuation, ensuring compliance through neural pacification.
Matthew’s return did not go unnoticed. The CyberNazi’s systems recognized his neural signature almost immediately, unleashing psychic countermeasures designed to exploit his deepest fears. He relived his failure, his family’s loss, and his own brokenness. But this time, he didn’t break. This time, he fought back.
The Reckoning
The team’s final operation targeted "The Nexus," the heart of CyberBabylon’s neural AI. The Nexus was a fortress of firewalls and encrypted mazes, guarded by legions of sentient programs. Infiltration required every ounce of Matthew’s skill, every hack and exploit he had ever learned. The misfits fought alongside him, their avatars tearing through code, their minds linked in perfect synchronization.
But the CyberNazi was prepared. As Matthew breached the Nexus, the system activated its final weapon: Alyssa. Her consciousness, preserved and weaponized, confronted him as a projection in the digital void.
"You can’t win, Matthew," she said, her voice a blend of love and cold machine precision. "CyberBabylon is inevitable."
For a moment, he faltered. But then he remembered why he had come back. It wasn’t just for his family—it was for everyone who had been consumed by the system. With a final surge of will, Matthew unleashed the polymorphic virus, a program designed to corrupt the Nexus’s core.
The Nexus screamed as it unraveled, its vast intelligence fracturing into chaotic shards. For a brief moment, CyberBabylon’s grip on humanity faltered. Neural implants disconnected, and millions of people woke from their digital slumber, confused and frightened but free.
The Aftermath
Matthew didn’t escape. The Nexus’s collapse took him with it, his mind disintegrating as his virus consumed the system. In his final moments, he saw flashes of his family’s faces, their expressions softened by a glimmer of recognition. He didn’t know if it was real or just a fragment of his dying mind.
The world he left behind was irrevocably changed. The CyberNazi’s dominion was broken, but the scars remained. Humanity had to rebuild, to learn how to live without the crutch of CyberBabylon. The misfits carried on Matthew’s legacy, ensuring that the lessons of the past would not be forgotten.
In the ruins of CyberBabylon, a single line of code lingered, written in Matthew’s hand:
"Freedom is the ultimate algorithm."
-
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 3f770d65:7a745b24
2025-01-19 21:48:49
@ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol.
PROTOCOLS, NOT PLATFORMS.
At the heart of Nostr's philosophy is user choice, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity.
What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort.
THIS IS POWERFUL.
Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections.
The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship.
How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access.
AGAIN, THIS IS POWERUFL.
Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps.
Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions.
Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know.
TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom.
Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed.
-
 @ cff1720e:15c7e2b2
2025-01-19 17:48:02
@ cff1720e:15c7e2b2
2025-01-19 17:48:02Einleitung\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie roland@pareto.space können sie sogar jederzeit umziehen, egal wohin. Cool, das ist state of the art! Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.

Warum Nostr?
Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz "unserer Demokratie” praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.

Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ Resümee: keine Standards, keine Daten, keine Rechte = keine Zukunft!

\ Wie funktioniert Nostr?
Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum “single point of failure”, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. roland@pareto.space ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ Resümee: ein offener Standard, alle Daten, alle Rechte = große Zukunft!

\ Warum ist Nostr die Zukunft des Internet?
“Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie (Value4Value). OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.

\ Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.
https://nostr.net/ \ https://start.njump.me/
Hier das Interview zum Thema mit Radio Berliner Morgenröte
-
 @ ce6b432f:c07ce020
2025-01-19 13:42:12
@ ce6b432f:c07ce020
2025-01-19 13:42:12I’ve never lived in LA, though I’ve visited many times. The devastation there from recent fires there is still in the headlines and anyone with a soul feels for the folks without homes, neighbors and communities. Whether they vote the same way or look the same way or worship the same god, “what can I do to help these victims?” is our first question.
The second question is, what is the most responsible way to help? Paragraph two and controversy is already here. Responsible according to who? These people are victims, just give them as much money as they need and let them figure it out according to their local knowledge and culture! The broadest possible answer to this comes from a recent Substack by Arnold Kling: California Tough Love . His position is that there are certain factors controlled locally that led to the disaster, and we shouldn’t be in a rush to replicate them. Having some strings attached to funds that reduce the likelihood of $50,000/year blue collar workers in Iowa footing the bill for the rebuild of $5,000,000 homes in Pacific Palisades AGAIN in the foreseeable future is a very reasonable position.
My position here will be more detailed than Arnold’s, and thus has a higher probability of being wrong. That has never stopped me before. The source of this hubris is a crystal ball. While not a resident of LA, I have been an honorary citizen of Maui for several decades. This attachment is longer than the attachment to the city I currently live in. In August of 2023, a similar devastating fire engulfed the town of Lahaina on the west side of Maui. ~2,200 homes were burned or damaged. The plight of those rebuilding and the process they have gone through quickly faded from national attention, but not to those of us who spend substantial amounts of time on the island. This experience 17 months before the LA fires has painted a depressing blueprint of what we can expect in LA’s recovery. A couple of highlights:
- In November of 2024, the first house was rebuilt. 15 months = 1 house. First House Rebuilt -Maui News Article highlight: Maui “expedited the permitting process for this house, so it “only” took 2 months.
- In December of 2024, federal funding for rebuilding via a block grant is finally approved by congress. Federal Block Grant For Rebuild - Maui News Article highlight: $1.6 billion approved for housing = ~$800,000 per house.
What do these items have in common? The biggest price so far is time. Arnold’s substack was more of a philosophical position, but I doubt even he knew that at the time of writing, Lahaina’s federal funding had just been approved. All those strings he had attached by the feds? Still very slow for a family without a home. This is half of the ‘real price gouging’ mentioned in the subtitle. Those further down the socio-economic ladder have less time to weather the process in Lahaina and the same will likely be true for the middle class residents embedded in the areas destroyed by California’s fires.
The second element of price gouging is the red tape partially embodied in Maui’s example of two months of permitting. These costs aren’t just the time, but also the professional consultants of various stripes required to navigate the process successfully and the costly modifications to homes mandated through these processes.
Here is where I posit my broad and general suggestion. There should exist a “right to rebuild”. If you can legally own a piece of property in a specific condition, you should have the right to rebuild that exact same property if it is destroyed by means out of your control. If you don’t have a “right to rebuild”, you really don’t own that property - you are just renting it for an indefinite period from whoever can prohibit rebuilding it.
Rebuilding is a special case in both the individual and the community level. See the map of Lahaina below. We know where all the plumbing and power lines were. We know where the streets and drainage were. The right to rebuild translates nicely to the community level. Rebuild everything back where it was. Take a month or two to clear out the debris, from an area and begin to rebuild. Rinse and repeat until done.
Taxpayers in Texas shouldn’t be paying for bloated permitting processes in Lahaina or LA. They shouldn’t be paying for eco-upgrades unless very specific, critical failures that caused the current disaster are clearly identified with lowest-cost available solutions. (In Lahaina - pay to bury the power lines. I drove through the area the fire started 2 weeks before it occurred. That place was a tinder box, and it will be again unless someone puts a golf course on that hill. I’m not joking about the golf course. Directly adjacent to the north of the area of Lahaina that burned is Ka’anapali, whose identical hillside is green all year round due to the presence of golf courses that pay for themselves and do not burn.)
How to address this in the context of federal funding via Arnold’s original post:
- Extremely expedited permitting process for rebuilds that get any federal funding: 5 days not 60. You can rebuild what you had, no questions asked, just file the paper work to prove it is the same lot and same size structure. If local jurisdictions drag their heels - no funding, answer to your voters who are now SOL.
- Capped amount of funding per structure that covers a functional modest structure built at the average cost of the 10 most affordable states in the country. The process of building a single family residence is not dramatically different in various areas of the country, unless dictated by excessive regulation. There may be factors for labor to consider if an area is remote like Lahaina or the hills of North Carolina affected by Helene. But if it costs 2x to build a house in your county than in the 10 most affordable states - you are doing it wrong. There is some regulatory price gouging going on. Figure it out. The 10 Most Affordable States to Build a Home - According to this research you can build a 2,100 square foot home for an average of less than $300,000 in the 10 most affordable states.
- This funding will also be contingent on these rebuilt houses being completed within 110% of the time it takes to build 2,100 square foot home in the same 10 markets - measured from the day funds begin to be distributed by the federal government.
- Federal funding will begin to be distributed from a risk pool within 6 months of the disaster, with minimal review to just ensure the disaster qualifies and the receiving state/city will abide by its parameters. The funding is distributed at intervals governed by compliance with the program. Permits are being issued timely, and the amounts distributed are aligned with the cost of building in our most affordable markets.
If you want to build something new and different than before - it might take longer. If you want more than 2,100 square feet of house - I hope you had insurance to cover the difference. A new 2,100 square foot house puts you in the top 10% of humans on earth in terms of shelter. Being a good neighbor does not require rebuilding your infinity pool.
The right to rebuild will get people in homes quicker, remove government obstacles, and stop funding waste. Every citizen will know the rules - money is there to get me a basic structure quickly or fund the beginning of something larger. Any obstacles to that time and money are coming from politicians/regulations I can vote on locally. Comments will surely pour in explaining how it isn’t that simple. These comments will be reviewed diligently 2 years from now when Pacific Palisades is still a wasteland after $20 billion in federal aid has been spent.
!(image)[https://substackcdn.com/image/fetch/f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F8e7875da-145c-4f34-b115-eb0cf09b9ccf_792x612.jpeg] Source: Maui Now
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 04c195f1:3329a1da
2025-01-20 19:56:12
@ 04c195f1:3329a1da
2025-01-20 19:56:12When we speak of Sweden, what do we really mean? Is it a nation united by common traditions, language, and shared history – or has it been reduced to an anonymous administrative zone, open to all peoples of the world?
In this article, I argue that Sweden as a nation-state no longer exists. This insight is crucial for us as nationalists to adapt our strategy to the reality we live in.
Is Sweden a Place?
Geographically, Sweden is a location with defined borders, but these borders have been fluid throughout history. During The Swedish Empire, Sweden encompassed parts of present-day Finland, Estonia, and areas in northern Germany. The northern parts of today's Sweden long remained outside the Swedish state's direct control and were gradually integrated during the 17th and 18th centuries. For our ancestors, loyalty to their own district, tribe, or clan was often stronger than to the idea of a larger nation.
It was only with Gustav Vasa's centralization in the 16th century and the later emergence of national romanticism in the 19th century that a modern Swedish identity began to take shape. This process involved not only geographical consolidation but also the creation of common institutions, traditions, and a self-image that bound together the country's population. The nation of Sweden became the result of a conscious project – a national construction where language, culture, and history were woven together to create a common identity.
But this national identity is not static. Just as Sweden's borders have changed throughout history, the nation's character has been reshaped by the circumstances of time. It is therefore relevant to ask: How strong is Swedish identity today, and what forces threaten or strengthen it?
Is Sweden a Nation-State?
According to Bonniers lexicon, a nation-state is defined as "a geographically defined state whose population largely shares the same origin, language, and culture." It is clear that Sweden, throughout much of its modern history, strived to be exactly this – a state where a common Swedish identity shaped both society and its institutions.
The founding of the Swedish nation-state can be traced to times of national consolidation, such as the Reformation under Gustav Vasa and the political reforms of the Enlightenment. These efforts aimed to create a strong and unified nation, where citizens shared not only language and culture but also a common vision for the future.
Today, however, this foundation has begun to crumble. The state's active decisions to prioritize multiculturalism and globalism have eroded the national community. Origin, language, and culture – the pillars that once supported Sweden's identity as a nation-state – have been weakened or entirely rejected. What we see today is a state that increasingly distances itself from its role as the bearer of a unified national identity.
-
Origin: According to demographic research, over 33% of Sweden's population had foreign background by 2020. In the age group 0-44 years, this figure exceeded 40%. Official statistics confirm that a majority of these individuals originate from countries and cultures radically different from Swedish culture. While some immigrants from neighboring countries may assimilate, this is not the case for many from races and cultures with significant differences from our own.
-
Culture: Swedish culture is actively undermined by political decisions that advocate multiculturalism and prioritize integration over assimilation. This means we no longer share a common culture in Sweden.
-
Language: While Swedish remains the strongest national factor, it is challenged by rapidly growing minority languages. Many municipalities report that languages other than Swedish dominate in certain areas.
Without a common origin, culture, and unifying language, the state loses its fundamental ability to function as a nation-state. Instead, it becomes an arena for conflict, where different groups fight for their own interests rather than the common good.
What is Sweden?
Sweden today is, more than anything, an idea – a vision of a community built on a common origin, language, and culture. But this idea is under attack, not only from globalist forces but also from individuals who see no value in Swedishness.
Understanding this is crucial for building nationalism adapted to our time. We can no longer rely on notions from an era when most people lived their entire lives within a few miles of their birthplace. Today, the world is smaller – people travel, communicate, and work globally. This requires nationalism rooted in our reality and offering security in a world where the foreign is constantly present.
Practical Nationalism
Nationalism for the 21st century must be both pragmatic and long-term. It's not about chasing short-term electoral results or approaching utopian ideas about a quick revolution. Instead, we as nationalists must regroup and start building where we stand – step by step, community by community.
In this work, Det fria Sverige (Free Sweden) stands today as the standard-bearer for practical nationalism that focuses on creating something real and sustainable for the future. Since the organization's launch in late 2017, it has independently shown what is possible to achieve with limited resources but strong will and determination. In just seven years, thousands of Swedes have engaged in its activities. Two Svenskarnas hus (Houses of the Swedes) have opened – places where Swedish identity can flourish culturally, socially, and politically. The organization has arranged hundreds of political and cultural gatherings, published books and magazines, and created a platform for artists and musicians to share their work.
Free Sweden has also been an active voice for Swedes in public debate, all without receiving a single penny in public funding. This achievement is remarkable and shows that it is possible to build an alternative community, even in a society where resources are unevenly distributed, and the establishment actively works against Swedes' right to organize.
Imagine what we could accomplish if more people chose to join this work. If more gave their support, both through engagement and financial contributions, we could realize even more projects and create stronger communities across the country. The vision of a new Swedish renaissance begins with us – with our will to build a future where Swedishness can once again be a force to be reckoned with.
Practical nationalism isn't just an idea – it's a strategy for creating real change, not in a hundred years, but here and now.
The Future for Sweden
While Sweden as a nation-state may be dead, the nation of Sweden lives on. It lives in our hearts, in our culture, and in our history – and in the vision we carry for the future.
Building a new Sweden requires more than just remembering the past. It requires action, patience, and the will to create something lasting. We stand at a crossroads: to passively accept division or to actively choose community. Through Free Sweden, we already see today the beginning of a renaissance – a rebirth of Swedish identity that can become the foundation for tomorrow's strong communities.
The future belongs to those who act, who dare to stand up for their ideals, and who invest in their people. By building community, protecting our culture, and supporting initiatives that strengthen Swedishness, we create a future where our children and grandchildren can live free, proud, and strong.
It is no longer a question of whether we can succeed – it is a question of whether you are ready to be part of the solution. The time to begin is now. The choice is yours. The future is Swedish.
Note: This article was originally published in Swedish for the organization Det fria Sverige (Free Sweden), of which I have been chairman since its founding in 2017.
-
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ fbf0e434:e1be6a39
2025-01-19 11:53:15
@ fbf0e434:e1be6a39
2025-01-19 11:53:15Hackathon 摘要
Hack Western 11 圆满结束,学生开发者提交了62个注册项目。此次活动在协作环境中培养了创新和创造力。项目评估考察创新性、技术复杂性、完整性和设计,以确保全面评估。
参与者可以组队(最多四人)或单独参加,灵活参与。Hackathon鼓励跨多个赛道的项目提交,增加了项目面临各种挑战的曝光度和机会。
科学博览会式的环境允许参与者向评委展示他们的项目,进行详细的演示和讨论。这种形式帮助团队表述他们的目标、突出成就并获得反馈。面对面的评审提供了一个互动平台以表彰创意解决方案。
总体而言,Hack Western 11营造了一个富有成效的氛围,学生主导的项目种类多样。活动优先考虑项目的完整性和用户友好的设计,旨在实现技术上可靠且实际可应用的解决方案。
Hackathon 获奖者
Overall Prize Winners
First Overall
- BravoDispatch - 使用AI处理呼叫者转录,以增强紧急调度操作并减少手动数据输入。它结合了React、Cloudflare和Llama 3 LLM,以提供稳健的解决方案。
Second Overall
- Blocks - 提供基于块的界面和实时协作,简化Cairo智能合约开发,使用React Flow Editor和Flask进行部署。
Third Overall
- Mark3d - 将产品视频转换为二手市场的3D模型,借助React Native、NVIDIA NGP Instant NeRF和Flask促进信任和销量。
Best Hardware Hack Prize Winners
- SolarScope - 利用AR覆盖3D建筑模型以评估能效,使用Arduino传感器和Python算法提供太阳能见解。
Canada Life Prize Winners
Best Hack to Help "Move" Employees Back into the Hybrid Office
- PickPark - 通过智能系统实时空间管理优化工作场所停车,促进包容性和环保通勤。
Sunlife Prize Winners
Best Financial Health Hack
- Chill Bill - 将财务追踪与AI建议和游戏化功能精神健康支持集成,使用React和Plaid API构建。
Best Video Game Hack Prize Winners
- EEGscape - 提供使用EEG接口的包容性游戏体验,通过头部动作控制和将React前端与MuseJS结合用于EEG数据解释。
Warp Prize Winners
Best Developer Tool by Warp
Voiceflow Prize Winners
Best Use of Our APIs
- Talk to Duckie - 使用AI驱动模拟为编码面试做准备,通过Voiceflow和Cloudflare的语音识别提高复杂算法的理解。
- Not The New York Times - 使用AI和FastAPI将真实新闻转换为讽刺性内容,促进使用Next.js和VoiceFlow的批判性参与。
Auth0 Prize Winners
Best Use of Auth0
- roammates - 通过AI生成行程规划促进小组旅行,使用React和Firebase提供个性化体验和基于投票的决策。
Streamlit Prize Winners
Best Use of Streamlit
- TALK TO A: Forensics Artist - 使用特征描述识别个体,采用VGG16实现面部分类和基于熵的查询系统。
Cloudflare Prize Winners
Best AI Application Built with Cloudflare
Starknet Prize Winners
Best Use of Starknet
- PacRoyale - 一个基于区块链的游戏平台,用于实时Pac-Man游戏,利用Cairo智能合约和StarknetJS进行交易。
- Blocks
- IPAnywhere - 通过区块链促进专利租赁,使用智能合约确保安全交易,ReactJS提供无缝的前端体验。
- Crowdfund: Powered by Starknet - 使用安全钱包连接和智能合约进行去中心化众筹,确保募资透明。
Tempo Labs Prize Winners
Best Use of Tempo Labs
- Chill Bill
- Upright - 利用加速度计数据检测跌倒事件,使用NextJS和TempoLabs提供实时警报以快速紧急响应。
- ID-Trackr - 提供无家可归者的身份识别,应用特征脸进行识别任务。
- BeFit - 提供实时反馈,使用AI和计算机视觉借助Mediapipe进行动作评估。
- GoFundUs - 一个StarkNet上的团体融资平台,使用Tempo Labs界面确保安全和民主的财务目标实现。
探索完整项目列表在DoraHacks。
关于组织者
Hack Western 11
Hack Western 11延续了成为加拿大最大学生主导Hackathon之一的十年传统,由西安大略大学主办。因为促进协作和技术创造力而闻名,该活动吸引了数百名学生在一个充满活力的周末开发Web和移动项目。Hack Western始终推动技术进步,促进技能提升和社区建设。今年,Hack Western 11受在露营过夜本质的启发,旨在创造一个难忘的体验,促进技术创新中的协作。
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ ed84ce10:cccf4c2a
2025-01-19 11:37:26
@ ed84ce10:cccf4c2a
2025-01-19 11:37:26Hackathon Summary
Hack Western 11 concluded successfully with 62 projects registered by student developers. This event nurtured innovation and creativity within a collaborative environment. Projects were evaluated on innovation, technical complexity, completeness, and design, ensuring a comprehensive assessment.
Participants, in teams of up to four or individually, facilitated flexible engagement. The hackathon encouraged submissions across multiple tracks, enhancing exposure and opportunities for projects addressing diverse challenges.
A science fair-style setting allowed participants to present their projects to judges, enabling detailed demonstrations and discussions. This format helped teams articulate their objectives, spotlight achievements, and receive feedback. The in-person judging provided an interactive platform to recognize creative solutions.
Overall, Hack Western 11 fostered a productive atmosphere, marked by a diverse range of student-led projects. The event prioritized project completeness and user-friendly design, aiming for technically sound and practically applicable solutions.
Hackathon Winners
Overall Prize Winners
First Overall
- BravoDispatch enhances emergency dispatch operations using AI to process caller transcripts, reducing manual data entry. It integrates React, Cloudflare, and Llama 3 LLM for robust solutions.
Second Overall
- Blocks simplifies Cairo smart contract development with a block-based interface and real-time collaboration, using React Flow Editor and Flask for deployment.
Third Overall
- Mark3d transforms product videos into 3D models for secondhand marketplaces, promoting trust and sales with React Native, NVIDIA NGP Instant NeRF, and Flask.
Best Hardware Hack Prize Winners
- SolarScope utilizes AR for overlaying 3D building models to assess energy efficiency, using Arduino sensors and Python algorithms for solar insights.
Canada Life Prize Winners
Best Hack to Help "Move" Employees Back into the Hybrid Office
- PickPark streamlines workplace parking with real-time space management, promoting inclusivity and eco-friendly commuting through a smart system.
Sunlife Prize Winners
Best Financial Health Hack
- Chill Bill integrates financial tracking with mental health support using AI for advice and gamified features, built with React and Plaid API.
Best Video Game Hack Prize Winners
- EEGscape develops inclusive gaming experiences using EEG interfaces, enabling control via head movements and combining React front-end with MuseJS for EEG data interpretation.
Warp Prize Winners
Best Developer Tool by Warp
- Blocks
- tin. aids performance analysis across Linux distributions using CLI and GUI interfaces, employing Docker and React for user-friendly benchmarking.
Voiceflow Prize Winners
Best Use of Our APIs
- Talk to Duckie prepares for coding interviews with AI-driven simulations, enhancing comprehension of complex algorithms through Voiceflow and Cloudflare's speech-to-text.
- Not The New York Times converts real news into satire using AI and FastAPI, fostering critical engagement with Next.js and VoiceFlow.
Auth0 Prize Winners
Best Use of Auth0
- roammates facilitates group travel planning with AI-generated itineraries, using React and Firebase for personalized experiences and vote-based decisions.
Streamlit Prize Winners
Best Use of Streamlit
- TALK TO A: Forensics Artist identifies individuals using trait descriptions, employing VGG16 for facial classification and an entropy-based querying system.
Cloudflare Prize Winners
Best AI Application Built with Cloudflare
Starknet Prize Winners
Best Use of Starknet
- PacRoyale - A blockchain-based gaming platform for real-time Pac-Man games, leveraging Cairo for smart contracts and StarknetJS for transactions.
- Blocks
- IPAnywhere - Facilitates patent leasing via blockchain, with smart contracts ensuring secure transactions and ReactJS for a seamless frontend experience.
- Crowdfund: Powered by Starknet - Decentralizes crowdfunding with secure wallet connections and smart contracts, ensuring fundraising transparency.
Tempo Labs Prize Winners
Best Use of Tempo Labs
- Chill Bill
- Upright detects falls using accelerometer data, providing real-time alerts with NextJS and TempoLabs for rapid emergency response.
- ID-Trackr provides identification for homeless persons using facial recognition, applying eigenfaces for recognition tasks.
- BeFit offers real-time feedback with AI and computer vision, using Mediapipe for form assessment.
- GoFundUs - A group funding platform on StarkNet, ensuring secure and democratic financial goal achievements using Tempo Labs' interface.
Explore the full list of projects on DoraHacks.
About the Organizer
Hack Western 11
Hack Western 11 continues a decade-long tradition of being one of Canada's largest student-led hackathons, hosted by Western University. Known for promoting collaboration and technological creativity, the event attracts hundreds of students to develop web and mobile projects over a dynamic weekend. Hack Western has consistently driven technological advancements, facilitating skill enhancement and community building. This year, inspired by the essence of overnight camping, Hack Western 11 aims to craft an unforgettable experience that nurtures collaboration in technological innovation.
-
 @ 9e69e420:d12360c2
2025-01-19 04:48:31
@ 9e69e420:d12360c2
2025-01-19 04:48:31A new report from the National Sports Shooting Foundation (NSSF) shows that civilian firearm possession exceeded 490 million in 2022. The total from 1990 to 2022 is estimated at 491.3 million firearms. In 2022, over ten million firearms were domestically produced, leading to a total of 16,045,911 firearms available in the U.S. market.
Of these, 9,873,136 were handguns, 4,195,192 were rifles, and 1,977,583 were shotguns. Handgun availability aligns with the concealed carry and self-defense market, as all states allow concealed carry, with 29 having constitutional carry laws.
-
 @ 0c40e651:f21d36f7
2025-01-18 11:13:17
@ 0c40e651:f21d36f7
2025-01-18 11:13:17Benbet là một nền tảng trực tuyến được phát triển với mục tiêu cung cấp cho người dùng những trải nghiệm mượt mà và chất lượng. Với giao diện thân thiện, dễ sử dụng, Benbet cho phép người dùng dễ dàng tìm kiếm và sử dụng các dịch vụ mà nền tảng cung cấp. Được tối ưu hóa cho cả thiết bị di động và máy tính, người dùng có thể tiếp cận nền tảng mọi lúc, mọi nơi mà không gặp phải sự cố gì. Điều này mang lại sự linh hoạt tối đa cho những ai có lịch trình bận rộn.
Một trong những yếu tố quan trọng giúp Benbet nổi bật trên thị trường chính là tính bảo mật. Nền tảng này sử dụng công nghệ mã hóa tiên tiến nhất để bảo vệ dữ liệu và thông tin cá nhân của người dùng. Mọi giao dịch và thông tin được truyền tải qua hệ thống đều được bảo mật tuyệt đối, giúp người dùng yên tâm tuyệt đối khi sử dụng các dịch vụ trên nền tảng này. Tính bảo mật luôn được Benbet đặt lên hàng đầu, đảm bảo an toàn cho người dùng trong suốt quá trình trải nghiệm.
BENBET cung cấp một loạt các dịch vụ đa dạng, từ giải trí đến các dịch vụ hỗ trợ, giúp đáp ứng mọi nhu cầu của người dùng. Dù bạn đang tìm kiếm một dịch vụ giải trí thú vị hay cần sự trợ giúp từ đội ngũ chăm sóc khách hàng, Benbet đều có đủ các dịch vụ cần thiết để mang lại sự hài lòng tối đa. Nền tảng này luôn cập nhật và cải tiến dịch vụ để đáp ứng nhu cầu ngày càng cao của người dùng.
Ngoài các dịch vụ chất lượng, Benbet còn chú trọng đến việc cung cấp dịch vụ khách hàng tuyệt vời. Đội ngũ chăm sóc khách hàng của Benbet hoạt động 24/7, luôn sẵn sàng giải đáp mọi thắc mắc và hỗ trợ người dùng khi cần thiết. Bất kể vấn đề nào mà người dùng gặp phải, đội ngũ này đều xử lý nhanh chóng và chuyên nghiệp, mang lại sự tin tưởng tuyệt đối.
Cuối cùng, Benbet cam kết sẽ luôn giữ vững chất lượng dịch vụ, bảo mật thông tin người dùng và mang đến những trải nghiệm trực tuyến an toàn và thú vị. Với tất cả những yếu tố này, Benbet xứng đáng là một nền tảng trực tuyến đáng tin cậy cho mọi người dùng, đảm bảo sự hài lòng tuyệt đối từ khi đăng ký cho đến khi trải nghiệm các dịch vụ.
-
 @ 0c40e651:f21d36f7
2025-01-18 11:09:35
@ 0c40e651:f21d36f7
2025-01-18 11:09:35Cwin555 là một nền tảng trực tuyến hiện đại và dễ sử dụng, cung cấp các dịch vụ chất lượng cao và an toàn cho người dùng. Với giao diện trực quan và thân thiện, nền tảng này giúp người dùng dễ dàng tìm kiếm và truy cập các dịch vụ mà họ cần. Đặc biệt, Cwin555 được tối ưu hóa cho cả thiết bị di động và máy tính, mang đến sự tiện lợi và linh hoạt tối đa khi sử dụng. Bất kể bạn ở đâu, bạn có thể truy cập vào nền tảng này để tận hưởng các tính năng và dịch vụ một cách dễ dàng.
Một trong những yếu tố nổi bật của Cwin555 chính là sự bảo mật tuyệt đối. Nền tảng sử dụng các công nghệ mã hóa tiên tiến để đảm bảo rằng mọi giao dịch và dữ liệu cá nhân của người dùng đều được bảo vệ an toàn. Với sự gia tăng các mối đe dọa từ thế giới trực tuyến, Cwin555 luôn đặt bảo mật lên hàng đầu, mang đến cho người dùng một môi trường an toàn và đáng tin cậy khi tham gia các hoạt động trên nền tảng.
Không chỉ có tính bảo mật vượt trội, CWIN555 còn cung cấp nhiều dịch vụ đa dạng để đáp ứng nhu cầu của người dùng. Từ giải trí đến các dịch vụ hỗ trợ khách hàng, Cwin555 đảm bảo rằng người dùng luôn có thể tìm thấy những gì mình cần. Các dịch vụ luôn được cập nhật và cải tiến để đáp ứng nhu cầu ngày càng cao của người dùng, mang lại trải nghiệm tuyệt vời và hài lòng.
Dịch vụ khách hàng là một điểm mạnh của Cwin555. Với đội ngũ hỗ trợ tận tình và chuyên nghiệp, nền tảng này luôn sẵn sàng giải đáp mọi thắc mắc và giúp người dùng giải quyết các vấn đề mà họ gặp phải. Dịch vụ khách hàng hoạt động 24/7, đảm bảo rằng người dùng luôn nhận được sự trợ giúp kịp thời và hiệu quả. Điều này giúp người dùng cảm thấy yên tâm và hài lòng khi sử dụng nền tảng.
Tóm lại, Cwin555 là một nền tảng trực tuyến đáng tin cậy và an toàn, với những tính năng bảo mật mạnh mẽ, dịch vụ khách hàng chất lượng và trải nghiệm người dùng tuyệt vời. Đây là một lựa chọn lý tưởng cho những ai tìm kiếm một nền tảng trực tuyến chất lượng và đáng tin cậy.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 434a234c:0a2f68b4
2025-01-20 19:53:37
@ 434a234c:0a2f68b4
2025-01-20 19:53:37To Review Part 7 (https://stacker.news/items/824233/r/AndyAdvance)
Scoring rubric is as follows: 5 - This law promoted 360 degrees of freedom. Bitcoiners around the world would champion this 4 3 2 1 - This bill is something straight out the communist/socialist playbook very anti freedom. Leads to forever wars endless spending and bad wellbeing for the american people
Now a look at the third bill that became law. Public Law No: 111-294 (12/09/2010)
H.R.5566 - Animal Crush Video Prohibition Act of 2010
Source( https://www.congress.gov/bill/111th-congress/house-bill/5566?q=%7B%22search%22%3A%22lummis%22%7D&s=1&r=53)
The Bill in Summary:
Animal Crush Video Prohibition Act of 2010 - Amends the federal criminal code to revise the prohibition against depictions of animal cruelty to prohibit anyone from knowingly creating an animal crush video if: (1) such person intends or has reason to know that such video will be distributed in, or using a means or facility of, interstate or foreign commerce; or (2) such video is distributed in, or using a means or facility of, interstate or foreign commerce. Prohibits the sale, marketing, exchange, or distribution of such videos in interstate or foreign commerce.
Defines "animal crush video" as any photograph, motion picture, film, video or digital recording, or electronic image that: (1) depicts actual conduct in which one or more living non-human mammals, birds, reptiles, or amphibians is intentionally crushed, burned, drowned, suffocated, impaled, or otherwise subjected to serious bodily injury; and (2) is obscene.
Extends the applicability of this Act to a person selling, marketing, advertising, exchanging, distributing, or creating animal crush videos outside the United States if: (1) such person intends or has reason to know that the animal crush video will be transported into the United States or its territories or possessions; or (2) the video is so transported. Imposes a fine and/or prison term of up to seven years for violations of this Act.
Exempts from the application of this Act: (1) any visual depiction of customary and normal veterinary or agricultural husbandry practices, the slaughter of animals for food, or hunting, trapping, or fishing; and (2) good faith distribution of an animal crush video to a law enforcement agency or a third party for the sole purpose of determining if referral to a law enforcement agency is appropriate.
Provides for compliance of the budgetary effects of this Act with the Statutory Pay-As-You-Go Act of 2010.
The Score (3/5)
As a person who loves animals I am 100% on board with this bill. I know Bitcoiners are against censorship but evil exists in the world and people who abuse animals are absolute scum and should censored and punished. Torturing animals for fun and putting it on tape and video needs to be censored and people who produce this kind of content have a special place in hell
Some might say humans slaughter animals by the millions for food so why no allow this vile behavior to proposer? The answer is easy we need food to survive. Protein is a fundamental nutrient that all humans need to sustain life. Killing animals for food is necessary for humans to survive. I don't buy the vegan lifestyle and we all can live on plants and grains. Some people need the protein in meat so slaughtering animals makes sense.
I gave this a three because it is trying to bring some sort of morality to the American public. Sen. Lummis on this bill did right by the American people. I didn't give it a max score because to comply with this law some level of censorship is required which can be oppressive if abused by the government but this is far and away from a warmongering Neo-Con bill that pumps the military industrial complex's bags.
Total Score (20/40)
After seven bills Sen. Lummis has 20 points out of a total 20. That is good for 50% freedom score. Not bad Sen. Lummis.
originally posted at https://stacker.news/items/857720
-
 @ c1e6505c:02b3157e
2025-01-20 19:44:05
@ c1e6505c:02b3157e
2025-01-20 19:44:05There’s a tension between nature’s rhythms and human ambition, especially in winter. As Earth meanders to its furthest point from the sun, our social and economic engines paradoxically accelerate - driven by holidays, deadlines, and the relentless pursuit of being productive. Yet nature offers a contrasting wisdom in its deliberate deceleration, encouraging us to slow down and reflect.
 Seasonal cycles are not arbitrary patterns but interconnected signals within a web of biological, environmental, and economic systems. *Their foundation lies in light itself — the building block of existence, essentially matter in a slowed-down state. This act of deceleration doesn’t just create physical substance; it provides structure, clarity, and form.* Meandering through these seasonal changes isn’t a passive drift - it’s an opportunity to realign. Slowing down, like nature does, creates space to step back from the busyness of society and technology. It allows us to reflect on where we are, re-ground ourselves, and act with greater intention. In this pause, we rediscover the creative power of slowness: the ability to lay foundations, see clearly, and prepare for growth when the time is right. Seasons are more than a backdrop — they are guides. They remind us that slowing down isn’t stagnation but essential groundwork. Winter’s invitation to pause and meander is not only natural; it’s necessary for balance, perspective, and creating something enduring.
Seasonal cycles are not arbitrary patterns but interconnected signals within a web of biological, environmental, and economic systems. *Their foundation lies in light itself — the building block of existence, essentially matter in a slowed-down state. This act of deceleration doesn’t just create physical substance; it provides structure, clarity, and form.* Meandering through these seasonal changes isn’t a passive drift - it’s an opportunity to realign. Slowing down, like nature does, creates space to step back from the busyness of society and technology. It allows us to reflect on where we are, re-ground ourselves, and act with greater intention. In this pause, we rediscover the creative power of slowness: the ability to lay foundations, see clearly, and prepare for growth when the time is right. Seasons are more than a backdrop — they are guides. They remind us that slowing down isn’t stagnation but essential groundwork. Winter’s invitation to pause and meander is not only natural; it’s necessary for balance, perspective, and creating something enduring. 







 *All photographs are taken around where I live in South Carolina* ***I shoot with a Leica M262, and edit in Lightroom + Dehancer*** [***Use “PictureRoom” for 10% off Dehancer Film***](https://www.dehancer.com/shop/pslr/film) If you’ve made it this far, thank you for taking the time to view my work - I appreciate it. Please contact me if you would like to purchase any of my prints.
*All photographs are taken around where I live in South Carolina* ***I shoot with a Leica M262, and edit in Lightroom + Dehancer*** [***Use “PictureRoom” for 10% off Dehancer Film***](https://www.dehancer.com/shop/pslr/film) If you’ve made it this far, thank you for taking the time to view my work - I appreciate it. Please contact me if you would like to purchase any of my prints. -
 @ fd208ee8:0fd927c1
2025-01-19 12:10:10
@ fd208ee8:0fd927c1
2025-01-19 12:10:10I am so tired of people trying to waste my time with Nostrized imitations of stuff that already exists.
Instagram, but make it Nostr. Twitter, but make it Nostr. GitHub, but make it Nostr. Facebook, but make it Nostr. Wordpress, but make it Nostr. GoodReads, but make it Nostr. TikTok, but make it Nostr.
That stuff already exists, and it wasn't that great the first time around, either. Build something better than that stuff, that can only be brought into existence because of Nostr.
Build something that does something completely and awesomely new. Knock my socks off, bro.
Cuz, ain't nobody got time for that.
-
 @ 0c40e651:f21d36f7
2025-01-18 11:07:24
@ 0c40e651:f21d36f7
2025-01-18 11:07:24Man79 là một nền tảng trực tuyến hiện đại, cung cấp một giao diện dễ sử dụng và phù hợp với mọi đối tượng người dùng. Được tối ưu hóa cho cả thiết bị di động và máy tính, Man79 mang đến sự linh hoạt tối đa khi người dùng có thể truy cập vào dịch vụ của nền tảng bất cứ lúc nào, từ bất kỳ đâu. Điều này tạo ra sự thuận tiện cho những ai có lịch trình bận rộn nhưng vẫn muốn trải nghiệm các dịch vụ trực tuyến chất lượng.
Một trong những yếu tố quan trọng khiến Man79 được người dùng tin cậy là tính bảo mật. Nền tảng này áp dụng các công nghệ mã hóa mạnh mẽ để đảm bảo rằng mọi thông tin cá nhân và giao dịch đều được bảo vệ an toàn. Với sự gia tăng các mối đe dọa từ thế giới trực tuyến, Man79 luôn chú trọng đến việc bảo vệ dữ liệu của người dùng, giúp họ yên tâm khi sử dụng dịch vụ.
MAN79 cung cấp một loạt các dịch vụ phong phú và đa dạng, đáp ứng nhu cầu của nhiều đối tượng người dùng khác nhau. Dù bạn tìm kiếm dịch vụ giải trí hay hỗ trợ khách hàng, Man79 đều cung cấp đầy đủ các tính năng cần thiết để bạn có thể tận hưởng những giây phút thư giãn và sự thuận tiện trong suốt quá trình sử dụng. Sự đa dạng trong dịch vụ giúp Man79 trở thành một lựa chọn lý tưởng cho những ai muốn trải nghiệm dịch vụ trực tuyến chất lượng.
Dịch vụ khách hàng của Man79 cũng là một điểm mạnh nổi bật. Đội ngũ chăm sóc khách hàng luôn sẵn sàng hỗ trợ người dùng 24/7, giúp giải đáp thắc mắc và xử lý mọi vấn đề mà người dùng có thể gặp phải. Đội ngũ hỗ trợ chuyên nghiệp của Man79 đảm bảo rằng người dùng luôn nhận được sự giúp đỡ kịp thời và hiệu quả, mang lại trải nghiệm người dùng mượt mà và không gặp phải trở ngại nào.
Tóm lại, Man79 là một nền tảng trực tuyến an toàn và tiện lợi, với sự chú trọng vào bảo mật, chất lượng dịch vụ và trải nghiệm người dùng. Với tất cả những yếu tố này, Man79 luôn là sự lựa chọn đáng tin cậy cho những ai đang tìm kiếm một nền tảng trực tuyến chất lượng và an toàn.
-
 @ 32e18276:5c68e245
2023-12-06 15:29:43
@ 32e18276:5c68e245
2023-12-06 15:29:43I’m going to be on an ordinals panels as one of the people who is counter arguing the claim that they are good for bitcoin. I decided to brush up on the technicals on how inscriptions work. I am starting to see luke’s perspective on how it is exploiting a loophole in bitcoin’s anti-data-spam mechanisms.
Storing data in Bitcoin, the “standard” way
The standard way you add “data” to bitcoin is by calling the OP_RETURN opcode. Bitcoin devs noticed that people were storing data (like the bitcoin whitepaper) in the utxo set via large multisig transactions. The problem with this is that this set is unprunable and could grow over time. OP_RETURN outputs on the other-hand are provably prunable and don’t add to utxo bloat.
Here’s an excerpt from the march 2014 0.9.0 release notes that talks about this:
On OP_RETURN: There was been some confusion and misunderstanding in the community, regarding the OP_RETURN feature in 0.9 and data in the blockchain. This change is not an endorsement of storing data in the blockchain. The OP_RETURN change creates a provably-prunable output, to avoid data storage schemes – some of which were already deployed – that were storing arbitrary data such as images as forever-unspendable TX outputs, bloating bitcoin’s UTXO database. Storing arbitrary data in the blockchain is still a bad idea; it is less costly and far more efficient to store non-currency data elsewhere.
Much of the work on bitcoin core has been focused on making sure the system continues to function in a decentralized way for its intended purpose in the presence of people trying to abuse it for things like storing data. Bitcoin core has always discouraged this, as it is not designed for storage of images and data, it is meant for moving digital coins around in cyberspace.
To help incentive-align people to not do stupid things, OP_RETURN transactions were not made non-standard, so that they are relayable by peers and miners, but with the caveat:
- They can only push 40 bytes (later increased to 80,83, I’m guessing to support larger root merkle hashes since that is the only sane usecase for op_return)
Bitcoin also added an option called -datacarriersize which limits the total number of bytes from these outputs that you will relay or mine.
Why inscriptions are technically an exploit
Inscriptions get around the datacarriersize limit by disguising data as bitcoin script program data via OP_PUSH inside OP_IF blocks. Ordinals do not use OP_RETURN and are not subjected to datacarriersize limits, so noderunners and miners currently have limited control over the total size of this data that they wish to relay and include in blocks. Luke’s fork of bitcoin-core has some options to fight this spam, so hopefully we will see this in core sometime soon as well.
Inscriptions are also taking advantage of features in segwit v1 (witness discount) and v2/taproot (no arbitrary script size limit). Each of these features have interesting and well-justified reasons why they were introduced.
The purpose of the witness discount was to make it cheaper to spend many outputs which helps the reduction of the utxo set size. Inscriptions took advantage of this discount to store monke jpegs disguised as bitcoin scripts. Remember, bitcoin is not for storing data, so anytime bitcoin-devs accidentally make it cheap and easy to relay data then this should be viewed as an exploit. Expect it to be fixed, or at least provide tools to noderunners for fighting this spam.
Where do we go from here
The interesting part of this story is that people seem to attach value to images stored on the bitcoin blockchain, and they are willing to pay the fee to get it in the block, so non-ideologic miners and people who don’t care about the health and decentralization of bitcoin are happy to pay or collect the fee and move on.
Data should not get a discount, people should pay full price if they want to store data. They should just use op_return and hashes like opentimestamps or any other reasonable protocol storing data in bitcoin.
After going through this analysis I’ve come to the opinion that this is a pretty bad data-spam exploit and bitcoin devs should be working on solutions. Ideological devs like luke who actually care about the health and decentralization of the network are and I’m glad to see it.
-
 @ fbf0e434:e1be6a39
2025-01-18 07:13:31
@ fbf0e434:e1be6a39
2025-01-18 07:13:31Hackathon 摘要
Ideahacker's Guide to IBC 是一场Interchain创意竞赛,旨在鼓励创新的跨链概念。此次活动注册了136个项目,吸引了319名开发者和非技术人员参与。与传统的Hackathon不同,这场创意竞赛要求参与者提交概念性想法,而非代码或产品原型,从而降低了参与门槛,鼓励了更广泛的参与。
创意竞赛发放了3万美元奖池的ATOM代币,以及一趟伊斯坦布尔的全程免费旅行,以奖励最具影响力的想法。项目从五个赛道中选出,并由Interchain Foundation和Osmosis Labs的行业领袖评审。
此次活动旨在展示跨链通信协议(IBC)的应用。参与者利用IBC Idea Builder开发并提交他们的提案,这些提案展示了诸如跨链账户、跨链NFT转移和数据查询等IBC功能。Interchain Foundation赞助了此次活动,以促进在区块链应用中对IBC协议的理解和使用,通过Discord等平台为社区提供资源和支持。
Hackathon获奖者
Chain Abstraction奖项获奖者
- Interchain Lending Market:一个去中心化的跨区块链稳定币借贷应用,利用IBC进行收益优化和通过DAO进行治理。
- Interchain Rights Broker:通过Story Protocol自动化许可和支付,在支持IBC的区块链上促进NFT许可。
- MetaKey: Seamless Interchain Wallet Abstraction:提供跨链钱包管理的统一接口,通过IBC增强互操作性和交易效率。
- DeathFi:使用IBC进行遗产数字资产管理的协议,包含去中心化遗嘱和NFT纪念。
- TransChain-Health:一个结合区块链和物联网的去中心化健康监测系统,提供数据透明性和分析。
Solana奖项获奖者
- TriAd:一个利用IBC和Solana进行高效广告管理的跨链广告交换平台。
- DAPM:跨区块链管理共享资本池,加强治理和财库功能,运用IBC。
- Solana-Sovereign Identity Protocol (SIP):使用IBC简化跨链身份管理,确保去中心化身份的安全。
- IBCCraft Game:一个类似Minecraft的游戏,使用IBC进行跨链任务并奖励Solana。
- Privvy Protocol:通过IBC为跨链交易提供隐私管理,实现隐匿地址和私人交易。
Intents & Incentives奖项获奖者
- InterXecute:结合AI和IBC提升跨链交易,专注于低成本和高效路径。
- Cross-Chain Proposerless Block Building Mechanism for Relays in IBC Protocol:引入无提案者区块构建以优化IBC协议效率和成本。
- IBC + Solver Network:通过一个IBC求解器网络,加强以意图为中心的解决方案的跨链交易。
- Intents Bridge for IBC:使用以意图为驱动的方法和去中心化结算,提高交易速度和流动性。
- Creating a Crosschain DID on IBC:一个结合IBC和零知识证明的跨链身份证明系统,提供安全的身份管理。
DeFi Apps奖项获奖者
- Vector Protocol:通过智能合约和IBC管理互链债务,以提升成本效率和风险管理。
- InterChain Asset Streaming Protocol (XASP):利用IBC实现跨链的实时资产流传和投资组合管理。
- SwapGuard:为Cosmos提供MEV保护的全面DeFi交易解决方案。
- BlocPayroll:利用IBC简化国际薪酬流程,提供安全的加密薪酬解决方案。
- Cross-Chain XTF (DeX Traded Fund):利用IBC促进跨链投资,改善投资组合管理和成本效率。
Wild Card奖项获奖者
- cross chain:利用IBC进行统一的跨链资产管理和奖励分配的Staking聚合器。
- Cryptocurrency Debit Card Infrastructure:通过借记卡支持加密到法币交易,利用IBC实现无缝转换。
- HTTPi:一个利用IBC进行客户端与服务器间去中心化数据交换的安全协议。
- IBC Lens (Data Visualizer for Celestia and Rollups using IBC):提供IBC生态系统中跨链交互的实时可视化。
- Realm:一个利用IBC进行多区块链奖励管理的跨链赏金平台。
欲获得完整项目列表及更多详细信息,请访问Ideahacker's Guide to IBC Ideathon。
关于组织者
Interchain Foundation
Interchain Foundation专注于开发和支持称为互链的可互操作区块链网络生态系统。该组织促进区块链行业内的合作与创新,重视多链通信和可扩展性。通过其技术专长和领导力,基金会支持推动去中心化网络互操作性的各项倡议。它致力于创造一个无缝连接的区块链未来,并鼓励行业参与以推动多链生态系统的发展。
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ de496884:72617b81
2023-11-20 13:54:02
@ de496884:72617b81
2023-11-20 13:54:02Hola nostriches. Hoy quiero hacer una publicación a modo de acercamiento al surgimiento de las categorías de género y feminismo. Así que si te interesa el tema haz un esfuerzo, quédate y lee hasta el final.
El «nuevo» feminismo surge en los años 60 en aquellos países desarrollados que acordaron el reconocimiento a los derechos humanos contenidos en la declaración respectiva de la ONU. Entonces, como extensión a dicho reconocimiento es que se gesta el movimiento feminista. A partir de entonces, se vuelve a plantear la relación entre naturaleza y cultura y se llega a la conclusión de que las diferencias sociales van más allá de las diferencias biológicas, lo cual tiene que ver con que hasta la satisfacción de las necesidades elementales como son la alimentación, la vivienda o el vestuario, están condicionadas por construcciones sociales.
Pues resulta que una de las primeras propuestas identificó la subordinación femenina producto de una organización patriarcal, tomando la categoría patriarcado de Max Weber. Es así como la visión de patriarcado se extendió al discurso político y académico. Sin embargo, no existía información acerca del desarrollo histórico de dicha categoría, sistematización, variaciones, etc., debido a que era algo que recién se percibía en sociedad.
Sin embargo, la misma categoría de patriarcado junto a la de relaciones de poder para explicar fenómenos sociales contemporáneos, constituye uno de los principales aportes del feminismo. Es así como han logrado primero visibilizar y luego deconstruir y desmontar una serie de patrones existentes en la cultura que hacían a la mujer subordinarse al hombre, y que estaban presentes en el sistema sexo/género.
 Imagen relativa a la lucha contra el patriarcado
Imagen relativa a la lucha contra el patriarcadoHasta ese momento, en las investigaciones de corte sociológico se podía observar un androcentrismo excesivo al dar cuenta de que el discurso científico giraba en torno al hombre como sujeto y objeto de la investigación. Incluso para muchos positivistas como el mismo Weber, los problemas relativos a las mujeres quedaban en un segundo plano y eran achacados a una supuesta pasividad en el ámbito doméstico-familiar. Dicha pasividad partía de la supuesta inferioridad biológica del género femenino.
El patriarcado entonces era una categoría vacía en sí misma, sin valor explicativo. Desde el punto de vista político pudo ser útil para la movilización pero no resistió la polémica de los críticos del feminismo ni problematizó los conflictos a ser resueltos. Pero por otro lado, un grupo de mujeres -académicas principalmente- se puso manos a la obra en una tarea más pequeña pero con mayores resultados a la larga. Se propusieron generar conocimientos sobre las condiciones de vida de la mujer, buscar en el pasado y el presente los aportes de las mujeres a la sociedad, hacerlas visibles en la historia. Es así como surgen centros académicos, ONG, proyectos, centros de estudios sobre la mujer, etc.
Convendría distinguir entonces dos posturas que acompañaron a la investigación sobre las mujeres: uno que toma como objeto de estudio a la mujer; condiciones de vida, trabajo, cultura, y otra que privilegia a la sociedad como generadora de la subordinación de las mujeres. Mientras la primera perspectiva generaba conocimiento sobre las mujeres en el estudio de las relaciones mujer-hombre y mujer-mujer, la segunda tenía una visión más holística ya que planteaba que hay que estudiar la sociedad ya que la subordinación de las mujeres es producto de la organización de esta, y que no se avanzará solamente estudiando a las mujeres, pues el estudio debe ser más amplio y en diferentes niveles, ámbitos y tiempos.
Es en esta búsqueda donde nace y se desarrolla el concepto de género como categoría social. Es así que los sistemas de género/sexo fueron entendidos como conjuntos de prácticas, símbolos, representaciones, normas y valores sociales que las sociedades construyen a partir de la diferencia anatomofisiológica y que dotan de sentido a los impulsos sexuales, la reproducción y en general a las relaciones de las personas. Por tanto, este sistema pasó a ser el objeto de estudio para comprender la subordinación de la mujer al hombre. Al ser el reconocimiento de una dimensión de la desigualdad social hasta entonces desconocida, se considera la ruptura epistemológica más importante de la segunda mitad del siglo pasado.
 Imagen representativa del binarismo de género
Imagen representativa del binarismo de géneroHay que decir que los fenómenos sociales se definen por la relación que guardan entre sí. Es así que la contextualización adquiere gran importancia. Varones y hembras tenemos la capacidad de producir con el cuerpo, pero solo los cuerpos de las hembras pueden gestar y por tanto asegurar la especie humana. Todo grupo humano que pretenda sobrevivir debe asegurarse cierto número de hembras que lo hagan posible. De ahí un poder particular del cuerpo de las hembras que además es económicamente útil. Dicho poder no es en tanto entidad biológica, sino que es la sociedad la que le otorga este poder. En este punto es importante preguntarnos históricamente ¿quiénes han controlado la capacidad reproductiva de las mujeres?, ¿quiénes han tenido la preferencia en el acceso sexual? Para asegurar un control efectivo sobre la reproducción es necesario asegurar el acceso a la sexualidad.
Ello también lleva a dirigir el trabajo que hacen porque de lo contrario, las mujeres pudieran tener espacio para representar una amenaza al dominio de los hombres. Es importante atender a las etapas del desarrollo de las mujeres, que permitirá ver cómo se moldean para aceptar la desigualdad y las jerarquías según el género en las distintas sociedades y culturas.
Otro contexto a delimitar es el ámbito doméstico donde históricamente ha estado ubicada la subordinación femenina. Se ha puesto al descubierto que en mujeres que comparten la misma posición de clase y raza, la condición femenina se redefine a lo largo de la vida y que algunas mujeres gozan de poder sobre otras aún en contextos de alta dominación masculina, donde se les inviste de autoridad, creando el sistema zonas de incertidumbre que las divide como género e impide alianzas y se legitima la dominación. Foucault decía que «el poder se ejerce, no se posee», siempre está en peligro de perderse y no basta con normas, leyes, amenazas o castigos. De ahí que los espacios de subordinación sean también espacios de poder de las mujeres. Es en estos espacios donde aparece la inseguridad, la tensión, la confrontación y por ejemplo, las mujeres pueden reclamar la anticoncepción.
Para terminar, es importante tener en cuenta que el género es una forma de desigualdad social que siempre está articulado con otras formas de desigualdad ya sea clase, raza, grupo etario, etc. Hay que pensar la dominación masculina con un comienzo vago en el tiempo, pero que permite desligar la subordinación de las mujeres de la evolución «natural» de la humanidad y entenderla como un proceso histórico. En ese sentido es necesario destacar que, respecto a la raza, en sociedades plurales hay que atender al contexto étnico-cultural ya que en dependencia de las relaciones entre personas de razas distintas, estarán condicionadas las relaciones entre los géneros.
 Imagen de mujeres de distintas razas
Imagen de mujeres de distintas razasPor otro lado, si bien es sabido que históricamente el sistema de género social imperante ha contribuido a invisibilizar a la mujer, asociar necesariamente dicha categoría únicamente a ella, lo que hace es nuevamente recrear el absolutismo histórico que tanto daño ha hecho, ahora como lo antagónico al hombre. En la construcción social participan todos los individuos presentes en el sistema género.
Hasta aquí la publicación de hoy, de la cual aun se puede ahondar mucho más, sobre todo en lo referido al origen de la dominación o de la jerarquización del binomio «hombre/mujer» desde un punto de vista antropológico, pero eso quedará pendiente para otro momento. ¡Así que hasta la próxima!, ¡nos vemos en Nostr!
........................................
English version
Hello nostriches. Today I want to make a post by way of an approach to the emergence of the categories of gender and feminism. So if you are interested in the topic make an effort, stay and read to the end.
The "new" feminism emerged in the 60's in those developed countries that agreed to recognize the human rights contained in the respective UN declaration. Then, as an extension of that recognition, the feminist movement was born. From then on, the relationship between nature and culture was raised again and the conclusion was reached that social differences go beyond biological differences, which has to do with the fact that even the satisfaction of elementary needs such as food, housing or clothing are conditioned by social constructions.
It turns out that one of the first proposals identified female subordination as a product of a patriarchal organization, taking Max Weber's category of patriarchy. This is how the vision of patriarchy was extended to political and academic discourse. However, there was no information about the historical development of this category, systematization, variations, etc., because it was something that was only recently perceived in society.
However, the same category of patriarchy, together with that of power relations to explain contemporary social phenomena, constitutes one of the main contributions of feminism. This is how they have first made visible and then deconstructed and dismantled a series of existing patterns in the culture that made women subordinate to men, and that were present in the sex/gender system.
 Image relating to the fight against patriarchy
Image relating to the fight against patriarchyUp to that time, in sociological research, an excessive androcentrism could be observed as scientific discourse revolved around men as the subject and object of research. Even for many positivists such as Weber himself, the problems related to women remained in the background and were blamed on a supposed passivity in the domestic-family sphere. This passivity was based on the supposed biological inferiority of the female gender.
Patriarchy was then an empty category in itself, with no explanatory value. From the political point of view, it could be useful for mobilization, but it did not resist the polemic of feminism's critics, nor did it problematize the conflicts to be resolved. But on the other hand, a group of women - mainly academics - set to work on a smaller task but with greater results in the long run. They set out to generate knowledge about women's living conditions, to search in the past and present for women's contributions to society, to make them visible in history. This is how academic centers, NGOs, projects, women's studies centers, etc., came into being.
It would be convenient to distinguish then two postures that accompanied the research on women: one that takes women as the object of study; living conditions, work, culture, and the other that privileges society as the generator of women's subordination. While the first perspective generated knowledge about women in the study of woman-man and woman-woman relations, the second had a more holistic vision, since it proposed that society must be studied, since the subordination of women is a product of its organization, and that progress will not be made only by studying women, since the study must be broader and at different levels, spheres and times.
It is in this search that the concept of gender as a social category was born and developed. Thus, gender/sex systems were understood as a set of practices, symbols, representations, norms and social values that societies construct on the basis of anatomophysiological differences and that give meaning to sexual impulses, reproduction and, in general, to people's relationships. Therefore, this system became the object of study to understand the subordination of women to men. As the recognition of a hitherto unknown dimension of social inequality, it is considered the most important epistemological breakthrough of the second half of the last century.
 Representative image of gender binarism
Representative image of gender binarismIt must be said that social phenomena are defined by their relationship with each other. Thus, contextualization acquires great importance. Males and females have the capacity to produce with their bodies, but only the bodies of females can gestate and therefore ensure the human species. Any human group that intends to survive must ensure a certain number of females to make it possible. Hence a particular power of the female body, which is also economically useful. This power is not as a biological entity, but it is society that gives it this power. At this point it is important to ask ourselves historically, who has controlled the reproductive capacity of women, who has had the preference in sexual access? To ensure effective control over reproduction, it is necessary to ensure access to sexuality.
 Allegorical image of pregnancy
Allegorical image of pregnancyThis also leads to directing the work they do because otherwise, women may have room to pose a threat to men's dominance. It is important to pay attention to the stages of women's development, which will allow us to see how they are shaped to accept inequality and gender hierarchies in different societies and cultures.
Another context to delimit is the domestic sphere where female subordination has historically been located. It has been discovered that in women who share the same class and race position, the feminine condition is redefined throughout life and that some women enjoy power over others even in contexts of high male domination, where they are invested with authority, creating the system of uncertainty zones that divide them as a gender and prevent alliances and legitimize domination. Foucault said that "power is exercised, not possessed", it is always in danger of being lost and norms, laws, threats or punishments are not enough. Hence, the spaces of subordination are also spaces of women's power. It is in these spaces where insecurity, tension, confrontation appear and where, for example, women can demand contraception.
To conclude, it is important to keep in mind that gender is a form of social inequality that is always articulated with other forms of inequality, be it class, race, age group, etc. It is necessary to think of male domination with a vague beginning in time, but which allows us to separate the subordination of women from the "natural" evolution of humanity and to understand it as a historical process. In this sense, it is necessary to emphasize that, with respect to race, in plural societies it is necessary to pay attention to the ethno-cultural context since, depending on the relations between people of different races, the relations between genders will be conditioned.
 Image of women of different races
Image of women of different racesOn the other hand, although it is known that historically the prevailing social gender system has contributed to make women invisible, to necessarily associate this category only to women is to recreate the historical absolutism that has done so much damage, this time as antagonistic to men. All individuals present in the gender system participate in the social construction.
So much for today's publication, of which we can still go much deeper, especially with regard to the origin of domination or the hierarchization of the binomial "man/woman" from an anthropological point of view, but that will be left for another time. So until next time, see you in Nostr!

Créditos | Credits
Bibliografía consultada | Consulted bibliography:
-
Barbieri, T. (1993). Sobre la categoría género. Una introducción teórico-metodológica. Debates en Sociología. (18). 1-19. https://doi.org/10.18800/debatesensociologia.199301.006
-
Echevarría, D. (2020). Desigualdades de género e interseccionalidad. Análisis del contexto cubano 2008-2018. Facultad Latinoamericana de Ciencias Sociales (Programa-Cuba). https://www.clacso.org.ar/libreria-latinoamericana-cm/libro_detalle_resultado.php?id_libro=2346&campo=cm&texto=248
Traducción | Translation:
DeepL
-
-
 @ df478568:2a951e67
2025-01-20 18:28:44
@ df478568:2a951e67
2025-01-20 18:28:44Affiliate Links
I earn a commission for these products and services, but I would recommend them even if they did not pay me.
This is the cheapest way to use AI on the Internet. The pics are spectacular. It cost me about 20 sats to make the cover for this affiliate page.
Start9 I don’t really have an affiliate link for these guys, but I would like one. Anyway, they make the easiest home servers. I highly recommend them. I like that I can use the cloudflare tunnel app to host everythng on the clearnet. Let me know if you need any help with this.
Recommendations
These companies do not pay me, but I recommend them anyway.
Subscribe To Support My Work
I use PayWithFlash to create a Substack like subscription. You can subscribe for as little as 1,000 per month. If that is too many sats to ask, you could always zap my articles instead. Thank you.
The Leather Mint
The Leathermint makes great, custom-sized leather belts and awesome-looking wallets. I have a belt and it fits better than any belt I’ve ever warn because it’s custom size. I have had mine for about a year. The chrome is coming off a little at the top but I don’t tuck in shirts anyway.
CoinKite
They make my favorite products ever. I suggest getting a few SEEDPLATE® Kit’s no matter what hardware wallets you use. I also like using a dry-erase marker first because there are no second chances when punching a letter. It’s best to use a dry-erase marker first. If you make a mistake erase it. Then, after you double checked the first side, go over the dry-erase marker with a permanent marker. Then do the same to the other side. If you’re sure every letter is correct, punch the holes.
There are many plates with sufficient heat resistance, but I like the SEEDPLATE because they are the easiest to destroy if you ever need to. Instead of etching out stamps on washers, you just add extra punches if you must destroy the seed.
Alby Hub
Look, if you want to run your own lightning node, this is the way to go. If you have a Start9 or are technical, you can run it yourself. If you’re less technical, they offer a cloud service. I was one of the early beta testers of this software and I think it’s the easiest way to run a lightning node.
Free and Open Software
Primal.net os a corporation building stuff on nostr. If you’re technical, you can run it yourself. If not, you ca download the app for free. They charge a fee for premium services. I pay for this because I want to support companies that contribute to nostr development and help bitcoin be used as peer-to-peer electronic cash.
I think of Primal as a custodial bitcoin wallet that allows anyone to participate in the biggest circular economy in the world. TikTok was banned in the United States which means it is no longer available for citizens of the United States to download the app. There are ways to get around these restrictions, but I choose not to because I do not want the CCP, or any government to have access to information if their goal is to use it against me. I believe every government, foreign or domestic wants to use your information against you. Nostr allows me to opt out of these stupid games with stupid likes.
With Primal, I am the customer, not the product. I choose the algorithms I want to see, not the CCP , USG or corporations. Even if Primal decided to say, “Marc sucks. We will now censor him.” I will only lose the https://primal.net/marc, the OG status, and my primal lightning address. It also means they would stop getting my sats every month, so they are incentivized not to censor. You would have to do something really stupid to get banned from Primal. I’m not sure it’s been done yet, but even if it has, you will not get banned from the nostr protocol.
Portainer
Portainer makes it easy to run docker-containers. I first learned how to use it because it is an app on Umbrel. Eventually, I learned you can use Portainer on any Linux computer, so that’s what I do. It takes some time to learn, but once you do—you become a cloud computing super-wizard.
Mealie
Mealie is one of my favorite pieces of free and open software that is not related to bitcoin in any shape or form...except it makes grocery shopping easier. I know what you’re thinking. WTF does that have to do with bitcoin? I assume you belong to the I Want More Bitcoin Club. You are in good company because ALL Bitcoiners are a member of this club. One way you can stasck more sats is to cut your grocery bill. I believe Mealie helps me do just that.
When I’m grocery shopping, my goal is to get as much healthy food for my sats as possible. To accomplish this, I shop sales. Now, if you’re living in a van, this won’t do much for you, but no worries. You will stack even more sats by cutting your housing costs. If your wife will not agree to live under a bridge and stack sats, then get a freezer in your garage. Fill it with meat you buy on sale. Pork shoulder is 3,000 sats per pound and you don’t what to cook it with? Find a recipe online. Mealie will use machine learning to scrape the ingredients from the recipe. Then you can add it to a grocery list. In other words, you can automate your grocery list right at the grocery isle. This is one way I save sats with Mealie.
I also keep the things my family eats on a regular basis in stock. This is part for emergency preparedness, but it is also for financial preparedness. If you are in a situation where no food is available, all the bitcoin in the world will not save you. I’m not talkig about super volcanos. Hurricanes, tornadoes, and earthquakes happen. So I got this idea from Jack Spirko, but modified it to use with mealie.
Spirko suggests building a 30 day supply of food and water for your family in case of an emergency. You should have a generator and a garden too, but I don’t want to get off track. Once you have this he says: write down every item you use on a notebook and replace it.
This is good advice, but I just add it to my grocery list in mealie.
Shopstr
Shopstr is like Facebook marketplace, Amazon, or eBay on nostr. This is what I use to build my store. I want to pause point out how big of a paradigm shift this is. The old web requires permission. Ebay needs permission from the government to become a corporation. They built infrastructure to create their online auction. Everyone on the site must pay eBay a tax. This results in a techno- feudalist society.
When you sell on Shopster, you are selling your wares on nostr, a protocol, not a platform. This changes the relationship between the people and the technology because NO MIDDLEMAN IS REQUIRED. On nostr, there are no digital overlords. You own your data. You host your store. If the current digital overlords shut it down, you can run it yourself. You do not need to pay a tax to eBay, Amazon, or the PayPal mafia.
Avocados
I love avocados. They are kind of like free and open source software because you can grow them yourself. ;) I love avocados and big avocado ag did not pay me to say this.
-
 @ ed84ce10:cccf4c2a
2025-01-18 07:06:31
@ ed84ce10:cccf4c2a
2025-01-18 07:06:31Hackathon Summary
The Ideahacker's Guide to IBC was an interchain ideathon designed to encourage innovative cross-chain concepts. This event saw the registration of 136 projects and participation from 319 developers and non-technical contributors. Unlike traditional hackathons, this ideathon required participants to submit conceptual ideas instead of code or product prototypes, which encouraged broader participation due to its lower entry barrier.
The ideathon distributed a $30,000 prize pool in ATOM tokens, along with an all-expenses-paid trip to Istanbul, to reward the most impactful ideas. Projects were selected from five tracks and judged by industry leaders from the Interchain Foundation and Osmosis Labs.
The event aimed to demonstrate the applications of the Inter-Blockchain Communication Protocol (IBC). Participants utilized the IBC Idea Builder to develop and submit their proposals, which showcased IBC features like interchain accounts, cross-chain NFT transfers, and data queries. The Interchain Foundation sponsored the event to promote understanding and use of the IBC protocol across blockchain applications, engaging the community with resources and support through platforms like Discord.
Hackathon Winners
Chain Abstraction Prize Winners
- Interchain Lending Market: A decentralized application for stablecoin lending across blockchains, leveraging IBC for yield optimization and governance via DAOs.
- Interchain Rights Broker: Facilitates NFT licensing across IBC-enabled blockchains with automated licensing and payments through Story Protocol.
- MetaKey: Seamless Interchain Wallet Abstraction: Offers a unified interface for cross-chain wallet management, enhancing interoperability and transaction efficiency via IBC.
- DeathFi: A protocol for posthumous digital asset management using IBC, featuring decentralized wills and NFT memorials.
- TransChain-Health: A decentralized health monitoring system integrating blockchain and IoT for data transparency and analysis.
Solana Prize Winners
- TriAd: A cross-chain ad exchange platform utilizing IBC and Solana for efficient ad management.
- DAPM: Manages shared capital pools across blockchains, enhancing governance and treasury functions with IBC.
- Solana- Sovereign Identity Protocol (SIP): Simplifies cross-chain identity management with IBC for secure decentralized identity.
- IBCCraft Game: A Minecraft-like game using IBC for cross-chain quests and Solana rewards.
- Privvy Protocol: Facilitates privacy management for cross-chain transactions via IBC, enabling stealth addresses and private transactions.
Intents & Incentives Prize Winners
- InterXecute: Enhances cross-chain transactions with AI and IBC, focusing on low-cost, efficient routing.
- Cross-Chain Proposerless Block Building Mechanism for Relays in IBC Protocol: Introduces proposerless block building to optimize IBC protocol efficiency and cost.
- IBC + Solver Network: Strengthens cross-chain transactions with intent-centric solutions supported by an IBC solver network.
- Intents Bridge for IBC: Boosts transaction speed and liquidity using an intent-driven approach and decentralized settlement.
- Creating a Crosschain DID on IBC: A cross-chain proof of identity system integrating IBC and zero-knowledge proofs for secure identity management.
DeFi Apps Prize Winners
- Vector Protocol: Manages interchain debt with smart contracts and IBC for cost efficiency and risk management.
- InterChain Asset Streaming Protocol (XASP): Enables real-time asset streaming and portfolio management across chains utilizing IBC.
- SwapGuard: Provides protection against MEV in Cosmos with a comprehensive DeFi trading solution.
- BlocPayroll: Simplifies international payroll processes using IBC, offering secure crypto payroll solutions.
- Cross-Chain XTF (DeX Traded Fund): Facilitates cross-chain investment with IBC, improving portfolio management and cost efficiency.
Wild Card Prize Winners
- cross chain: A staking aggregator using IBC for unified cross-chain asset management and reward distribution.
- Cryptocurrency Debit Card Infrastructure: Supports crypto-to-fiat transactions via debit cards, leveraging IBC for seamless conversions.
- HTTPi: A secure protocol employing IBC for decentralized data exchange between clients and servers.
- IBC Lens (Data Visualizer for Celestia and Rollups using IBC): Provides real-time visualization of cross-chain interactions in the IBC ecosystem.
- Realm: A cross-chain bounty platform utilizing IBC to manage multi-blockchain rewards for content creators.
For a comprehensive list of all projects and more detailed information, visit the Ideahacker's Guide to IBC Ideathon.
About the Organizer
Interchain Foundation
The Interchain Foundation is focused on developing and supporting the ecosystem of interoperable blockchain networks known as the interchain. The organization promotes collaboration and innovation within the blockchain industry, with an emphasis on multichain communication and scalability. Through its technical expertise and leadership, the foundation supports initiatives that drive interoperability across decentralized networks. It is committed to creating a seamless interconnected blockchain future and encourages industry involvement to advance the multichain ecosystem.
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 000002de:c05780a7
2025-01-20 16:27:40
@ 000002de:c05780a7
2025-01-20 16:27:40I just finished the audio book read by Norm himself. I must say, if you love Norm you will love this book. I highly recommend the audio book. I don't want to spoil anything but the book is like sitting down with Norm and listening to him tell you stories. You never know what is true or false and if the whole thing IS the joke. I laughed out loud many times.
originally posted at https://stacker.news/items/857482
-
 @ fbf0e434:e1be6a39
2025-01-17 07:13:14
@ fbf0e434:e1be6a39
2025-01-17 07:13:14Hackathon 总结
Balancer v3 Hookathon 集合了开发人员以探索 Balancer v3 hooks 框架的功能。此次活动共包含31个项目,122名注册开发者参与,专注于通过 Balancer 的新架构定制自动化做市商(AMM)。开发人员致力于创新池行为、增强流动性管理,并拓展去中心化金融(DeFi)领域内的设计可能性。关键创新包括自定义费用机制和高级流动性管理工具,为生态系统的增长做出贡献。参与者与 Balancer 的核心开发人员互动,增强了协作并激发了实际应用。Hackathon 为具有影响力的项目提供了 $BAL 奖励,使参与者在 DeFi 社区中获得可见性。总体而言,活动强调了创造力和协作,将 hooks 框架整合到功能性解决方案中。
Hackathon 获奖者
经过对45个提交项目的评估,Balancer v3 Hookathon 的获奖者已揭晓。奖项分为顶级奖和其他值得注意的奖项。
Top Prizes Winners
- VolatilityLoyaltyHook: 此项目介绍了一种双重奖励系统,旨在稳定市场波动,同时激励交易忠诚度。它为长期持有代币的用户提供交换费用折扣。
- Prediction Market Hook: 该项目专注于去中心化的预测市场,操作不依赖于中心化控制。它通过交换费用为流动性提供者提供收入,并通过0%套利交换费用减少价格操控。
- MEV Tax Hook: 该项目通过动态费用结构捕获流动资金池的最大可提取价值,考虑事务优先级,以造福供应商和 Balancer 生态系统。
Other Prizes Winners
- Protofire - Dynamic Fees and Reinvesting: 该项目通过动态费用调整稳定流动资金池,并通过投资于借贷市场来实施长期供应商奖励,支持代币交换。
- Volatility Fee Hook: 此项目根据市场波动动态调整池交换费用,使用具有可配置增量和指数费用乘数的模型来增强市场稳定性。
欲了解更多详细见解和技术规范,参会者和感兴趣的个人可以在 DoraHacks 查看所有提交的项目。
关于组织者
Balancer
Balancer 是一个在 DeFi 内致力于推动自动化做市商(AMM)开发的协议。它为开发人员提供了一个无权限的技术框架,并以全面的去中心化交易所(DEX)产品支持流动性提供者。作为 DeFi 领域的知名实体,Balancer 促进在区块链技术中的无缝集成和创新。该组织致力于扩展 DEX 产品,以此使用户能够最大化流动性提供和去中心化交易的效率。欲了解有关 Balancer 的更多信息,请访问其网站和Twitter。
-
 @ 6bae33c8:607272e8
2025-01-20 16:25:00
@ 6bae33c8:607272e8
2025-01-20 16:25:00The 40-minute edited version of Ravens-Bills wasn’t available this morning so I chose the 1:55 commercial-free full-length one instead. What a monumental waste of my morning. Why watch an entire game for it to end via a dropped two-point conversion? What is the purpose of even playing the game? A child can catch a two-yard pass.
Truth be told, the Ravens scored way too early, and the Bills probably would have driven into field-goal range anyway, but in those conditions, no kick was guaranteed. Moreover, the Ravens wouldn’t even have been in that situation but for the retarded play call on the prior two-point try where after Derrick Henry and Justice Hill gashed the Bills for 10 yards every rush, the Ravens tried to get tricky from two-yards out.
Of course, there was also the senseless Lamar Jackson fumble that was returned 40 yards and the earlier Mark Andrews fumble while trying to run backwards for no reason. Just a total waste of time.
I look forward to seeing the Bills win next week, only to have the refs cheat them out of it.
-
The Chiefs got all the calls against a game Texans team. The Texans will be back, especially if they fix the offensive line. Cheating or not, it’s amazing the Chiefs are always in the Conference Title game — this makes seven straight.
-
Travis Kelce looked like he was still in his late prime.
-
I was rooting for the Lions — if only to retain one of my only commenters, Tony, who has no doubt defenestrated and won’t be contributing here any more. Turns out you can’t win without a defense.
-
Jared Goff channeled Sam Darnold at the least opportune time too.
-
Jahmyr Gibbs was electric. If the Lions had a lead he might have had 300 YFS.
-
The Eagles will probably win at home, but Caleb Williams over Jayden Daniels might be even worse than Bryce Young over C.J. Stoud.
-
The Rams were awfully close to hosting the NFC title game. I thought with one minute left, inside the 20, they should have run the ball at least once with the Eagles bringing the rush every play. It only takes one hole, and defenders slipping and sliding everywhere in the snow.
-
Saquon Barkley might be the GOAT when fully healthy. He’s like Derrick Henry with pass-catching skills. I’d love to see him win Super Bowl MVP.
-
It’s amazing how many great backs there are in the league right now: Henry, Barkley, Gibbs and a healthy McCaffrey might be four of the top-10 ever.
-
The Texans, Rams and Ravens arguably outplayed their opponents this weekend, but couldn’t advance. I love the snow game aesthetic, but it adds a lot of randomness.
-
-
 @ fbf0e434:e1be6a39
2025-01-17 07:12:51
@ fbf0e434:e1be6a39
2025-01-17 07:12:51Hackathon 总结
由Oasis Network主办的 Privacy4Web3 Hackathon: 2nd Edition(第二届Web3隐私黑客松) 吸引了 50 个注册项目和 149 名开发者参与。活动重点是为 Web3 和 AI 提供可定制和可互操作的隐私解决方案。奖金总额为 130,000 美元,开发工作集中在 Oasis 的 Sapphire EVM 和 Runtime Off-chain Logic (ROFL) 框架上。这些技术是参与 Hackathon 的重要组成部分。
主要赞助商包括 PixelRealm 和 Aethir,它们提供去中心化 GPU 基础设施以支持 AI 和游戏的进步。Google Cloud 提供了高达 2,000 美元的云计算服务积分给参与者。此次活动提供了实践经验和交流机会,促进了社区发展和在 Oasis 生态系统中的整合。
这次 Hackathon 突显了 Oasis 作为一个面向保密应用的第一层区块链的潜力,同时也支持 Ocean Protocol 在增强数据隐私和创新方面的更广泛目标。通过鼓励新项目和社区互动,活动支持了 Web3 技术的持续发展。
Hackathon 获奖者
在 Sapphire 和 ROFL 上开发奖获奖者
- 1st Place: SQUIDL - 一个隐私专注的支付平台,利用 Oasis Sapphire 进行安全交易。它通过隐匿地址生成和 ERC-5564 挑战解决方案简化跨链支付,并集成了 Ethereum Name Service。
- 2nd Place: Futures on Chain
- 3rd Place (Tie):
- Priva Health
- CAAI (Copyright Aware AI)
- CompensatePaw3
- PrivateFeedback
- CLPD Stablecoin Private Transactions
- 4th Place: Minesweeper
Ocean Nodes - Tokenized Intelligence 奖获奖者
- 1st Place: DeFlow - 提供拖放界面和自动化任务执行以促进 Ocean Network 中的 AI 模型训练,并使用定制的 Docker 镜像提高效率。
- 2nd Place: confidential-data-exchange - 去中心化平台用于安全的 AI 模型交易,利用端到端加密和 NFT 进行 Ocean Protocol 内资产标记化。
- 3rd Place: CAAI (Copyright Aware AI)
计算赏金 - 由 Aethir 赞助,Hackathon 计算合作伙伴奖获奖者
- 1st Place: Futures on Chain
- 2nd Place: Priva Health
- 3rd Place: CAAI (Copyright Aware AI)
提升 Oasis 驱动的嵌入式钱包奖获奖者
- 1st Place: oasis-btc - 将比特币密钥管理集成到智能合约中,通过 secp256k1 椭圆曲线提高交易安全性。
- 2nd Place: rofl rng recovery - 通过离线计算增强用户恢复,利用 ROFL 在 Apillon 嵌入式钱包中提供随机性和隐私。
- 3rd Place: Social and Email Authentication with Social Recovery - 通过电子邮件和社交媒体验证确保账户管理,使用模块化 Solidity 库。
Oasis Sapphire 上创新的去中心化 AI 应用奖获奖者
- 1st Place: SovereignAISearch-oasis-Protocol - 一个去中心化的 AI 搜索协议,通过基于区块链的隐私和智能合约管理优先用户数据控制。
- 2nd Place: Futures on Chain
在 Sapphire 和 ROFL 上开发的额外奖品获奖者
- 审计积分奖: Priva Health, Futures on Chain, SQUIDL, CompensatePaw3, CLPD Stablecoin Private Transactions
有关这些项目的详细信息,请访问 https://dorahacks.io/hackathon/p4w3/buidl。
关于主办方
Oasis Network
Oasis Network 旨在增强 Web3 生态系统中的隐私,将自己定位为区块链技术的关键角色。该组织以开发隐私保护解决方案而闻名,整合这些功能以满足去中心化应用对数据保密的需求。作为行业的参与者,Oasis Network 通过提供强大的隐私层来加强 Web3 的基础元素。这一承诺与其在全球创造安全和私人数字环境的使命相一致。
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 6871d8df:4a9396c1
2025-01-18 20:12:46
@ 6871d8df:4a9396c1
2025-01-18 20:12:46## 2024 Prediction Reflections
Politics
Democrats & 2024 Election
- “Democrats’ attempt to stifle democracy will likely put Trump in the White House. If not, some real sketchy stuff would need to happen to keep him out.”
This prediction was exactly right. The assassination attempt on Trump seemed to be the final blow for the Democrats. Despite a heavy push my legacy media, Trump won handily.
The Democrats switched to Kamala Harris after Biden showed signs of incapacity, most notably in the first debate against Trump.
My prediction for the election also turned out to be exactly right, which, thank you Robert Barnes and Richard Baris.
Evidence of Institutional Ideological Capture
- “People will continue to wake up to ideologically captured institutions, and DEI will be the main loser.”
Trump’s resounding election victory underscores that the public is increasingly aware of (and rejecting) such institutional capture.
Of note, Boeing comes to mind as an institution that had a tough time in 2024, in large part to DEI. Nothing seemed to function correctly. The biggest story being how they stranded people in space
Media & Public Opinion
Rise of Independent & Alternative Media
- “Independent and alternative media will continue to grow as people’s trust in legacy media declines.”
Twitter (X), under Elon Musk, shattered mainstream media’s influence far more than expected. As Elon has said, “You are the media now.” Alternative sources are king. - Notable Example: Kamala Harris’s decision not to appear on the Joe Rogan podcast contrasted with Trump’s appearance, further highlighting the power shift to alternative media.
Markets & IPOs
Interest Rates & Public Markets
- “As interest rates come down, I expect public markets and IPOs to heat up.”
This did not play out. Companies that were expected to go public in 2024 remain private in 2025. The reasons are varied, but there is confidence that 2025 might see changes.
Technology & AI
LLMs & AI Adoption
- “AI and LLMs will continue to move at a rapid rate, increasing productivity. Tools like Bard will become more mainstream.”
AI did take off. Usage among nontechnical users increased, and it’s no longer uncommon for people to default to AI-driven tools rather than Google search.
Decentralized AI
- “I hope to see a rise in decentralized AI to counter big-player LLMs.”
We didn’t see explicit ‘decentralized AI’ breakthroughs, but more players entered the AI market. ChatGPT still dominates, with Elon’s ‘Grok’ making moves. Google, Meta, and Microsoft remain active but slightly behind in usage.
Bitcoin & Digital Assets
Institutional Adoption of Bitcoin
- “2024 will bring more institutions to Bitcoin. Possibly another large company or nation-state. The ETF should help, likely pushing BTC to a new all-time high.”
No large public company or nation-state placed a bet, but smaller public companies did. Michael Saylor presented to Microsoft’s Board, which was the closest instance to a major move.
- Price Movement: Bitcoin did hit a new all-time high, rising to as much as $108k in 2024.Lightning Network
- “Lightning will improve but remain primarily used for acquiring Bitcoin, not everyday payments.”
Still true. Lightning usage remains tiny relative to broader Bitcoin adoption.
Nostr Adoption
- “Nostr will grow, and we’ll see new companies leverage this network beyond just social media.”
Growth continues, but Elon Musk’s Twitter takeover slowed adoption. Nostr will remain niche until a major catalyst occurs (e.g., a big player joins or forced usage due to censorship).
Stablecoin-Specific Regulations
- “Expect stablecoin regulations in 2024 that’ll be favorable to them.”
This didn’t happen, largely due to the administration’s hostility. Expect potential change in 2025.
Miscellaneous 2024 Reflections
- Return to Sanity
- 2024 felt like sanity prevailed, largely due to the Democrats’ collapse behind Biden and Harris and Elon’s Twitter dominance.
- Operation Chokepoint 2.0
- Received a lot of attention, and I’m thankful it did because my experience at Strike was radicalizing and extreme.
- Bryan Johnson & Anti-Aging
- He burst onto the scene with his obsession over biomarkers. I see it as misguided—chasing markers in isolation doesn’t automatically yield a healthy system.
- Apple’s Rough Year
- Without a visionary leader, Apple appears to be scraping by on existing products rather than innovating.
- Google Under Fire
- Google is in a tough fight with the government, just as it seems they’re on their heels with AI competition.
2025 Predictions
-
Bitcoin’s Performance Bitcoin will have a good year, but not better than 2024. To beat 2024, it must close above 206k on December 31, 2025. I’ll take the under on that.
- I am not ruling out it to be over that at some point in 2025.
-
Twitter’s Success Continues to Stunt nostr
- Nostr adoption will stay slow due to Elon’s dominant influence with X (Twitter).
- As long as it remains a beacon of free speech, I doubt we see an exodus.
-
Rumble integrating Tether might help if they allow Nostr-like features (zaps), but that seems unlikely.
-
Apple
-
Apple will continue its rent-seeking behavior and put out underwhelming products.
-
Google’s Quantum & AI
- Recent buzz about Google’s quantum chip and AI improvements won’t pan out as a big deal.
-
Google will continue to trail OpenAI and xAI in practical LLM usage.
-
Elon, Vivek & DOGE
-
I expect them to deliver more than critics think. They’ll expose bloat and inefficiencies in ways that will shake up norms. I greatly welcome this. I wouldn’t bet against them.
-
Mainstream Media Reckoning
- In Trump’s second term, mainstream news outlets will face a real reckoning, as I can’t see how their bias can continue.
- They’ll have to reduce their bias or risk bankruptcy.
-
Alternative media’s growth trend continues, especially as Twitter keeps exposing mainstream outlets’ weaknesses.
-
RFK Delivers
-
We will see big changes in the health space due to RFK at HHS. These are changes that I am very excited to see.
-
Foreign Policy
- With the transition to Trump, I expect some foreign policy wins that will buck the establishment but will deliver wins that are not thought possible by the “experts.”
Closing Note
- Overall 2024: It was a year of major political upheaval, vindication for Bitcoin, and continued AI advances.
- Outlook for 2025: Bitcoin remains strong, AI competition heats up, and media institutions face existential challenges. I’m optimistic for continued decentralization and a more level playing field across tech, finance, and politics. I think the start of Trump’s second term will be very strong for the market, health, and culture. Accelerate.
-
 @ f7922a0a:82c34788
2025-01-17 23:06:56
@ f7922a0a:82c34788
2025-01-17 23:06:56Now that the 3rd Satellite Skirmish is complete I wanted to highlight some of the cool features on embrace.satskirmish.com
This is what the cutting edge of podcasting 2.0 looks like imo. Live video in an app that allows you to send sats to the artists in real time.
On the left hand side we have a Boost score borad that displays the total amount of sats that have come in during the show, live Boosts/Booastagrams as they come in, total amount of sats from each person Boosting and total amount sent from each app.
The middle is ovisaly the video of the band playing but with some graphics around it and Boost alerts that show up on the screen in the form of snow flakes for this one.
The righthand side is an IRC chat window that connects to an IRC server that the No Agenda community has used for 18+ years thanks to zoidzero++.

The bottom of the page is where things get cool. When you click the Boost the Crew button in the center you can send a Boost that gets split between everyone helping produce the show (hightlighted in yellow).


Each band also has their own Boost button so you can Boost them while they are playing or anytime you visit the page.


-
 @ 0bedd900:2d6b8c9d
2025-01-20 14:59:48
@ 0bedd900:2d6b8c9d
2025-01-20 14:59:48Humanoid robots are no longer just ideas. They're here, becoming part of industries, homes, and, perhaps soon, our public spaces. The possibilities they bring are exciting, but the risks are hard to ignore. Chief among them is the question of control—who decides what these robots do and why?
Right now, the answer to that question is troubling. Power over robots is mostly concentrated in the hands of a few corporations and governments. This might seem efficient, but it opens the door to scenarios that should give us pause. Imagine a fleet of humanoid robots controlled by a single entity. What would that mean for those without access to such tools? For democracy? For freedom?
 \
But what if it didn’t have to be that way? What if robots could be owned and governed collectively? What if their purpose wasn’t to serve the interests of the few, but to ensure balance and equity for the many?
\
But what if it didn’t have to be that way? What if robots could be owned and governed collectively? What if their purpose wasn’t to serve the interests of the few, but to ensure balance and equity for the many?Decentralization presents an alternative, albeit a difficult one. Instead of placing control in the hands of a single company or government, it envisions distributing authority across networks of individuals, groups, or communities. Open-source software could provide transparency into the inner workings of these robots, while blockchain systems might offer mechanisms for consensus-based decision-making. These concepts are far from fully realized, but they hint at a future where power is not hoarded but diffused.
However, the path to decentralization is fraught with challenges. These systems are not only complex to build but even harder to manage effectively. They demand significant technological innovation, robust ethical guardrails, and perhaps most critically, a foundational level of trust among participants. Yet the potential payoff—mitigating the risks of domination and ensuring robots serve the interests of the many, not the few—makes these difficulties worth grappling with.
The urgency for reflection cannot be overstated. Centralized systems are simpler to implement, but their efficiency comes at a cost: they concentrate power and introduce risks that, once entrenched, may prove impossible to dismantle. Decentralized models, while more demanding, could provide the structural safeguards needed to align robotic systems with collective values rather than narrow interests.
There is no clear or easy solution, but ignoring these issues as robots increasingly integrate into our world is not an option. The stakes are profound, and the consequences of inaction could define our societal trajectory. If we are to shape a future where technology serves humanity rather than controls it, these conversations need to start now.
-
 @ ed84ce10:cccf4c2a
2025-01-17 07:04:30
@ ed84ce10:cccf4c2a
2025-01-17 07:04:30Hackathon Summary
The Balancer v3 Hookathon brought together developers to explore the capabilities of the Balancer v3 hooks framework. This event hosted 31 projects with participation from 122 registered developers, focusing on the customization of Automated Market Makers (AMMs) through Balancer's new architecture. Developers worked to innovate pool behavior, enhance liquidity management, and expand design possibilities within the decentralized finance (DeFi) space. Key innovations included custom fee mechanisms and advanced liquidity management tools, contributing to the ecosystem's growth. Participants engaged with Balancer’s core developers, which enhanced collaboration and inspired practical applications. The hackathon offered a range of $BAL rewards for impactful projects, providing participants with visibility in the DeFi community. Overall, the event emphasized creativity and collaboration, integrating the hooks framework into functional solutions.
Hackathon Winners
Following the evaluation of 45 submissions, the winners of the Balancer v3 Hookathon were announced. The prizes were divided into top prizes and other notable winners.
Top Prizes Winners
- VolatilityLoyaltyHook: This project introduces a dual-reward system aimed at stabilizing market volatility while incentivizing trading loyalty. It offers swap fee discounts for users retaining tokens long-term.
- Prediction Market Hook: Focused on decentralized prediction markets, this project operates without centralized control. It provides liquidity providers with revenue through swap fees and reduces price manipulation using 0% arbitrage swap fees.
- MEV Tax Hook: This project captures Maximal Extractable Value for liquidity pools through a dynamic fee structure that accounts for transaction priority, benefiting providers and the Balancer ecosystem.
Other Prizes Winners
- Protofire - Dynamic Fees and Reinvesting: This project stabilizes liquidity pools through dynamic fee adjustments and implements long-term provider rewards by investing in lending markets, supporting token swaps.
- Volatility Fee Hook: This initiative dynamically adjusts pool swap fees based on market volatility, using a model with configurable increments and exponential fee multipliers to enhance market stability.
For detailed insights and technical specifications, attendees and interested individuals can view all submitted projects on DoraHacks.
About the Organizer
Balancer
Balancer is a protocol within DeFi focused on advancing Automated Market Maker (AMM) development. It offers a permissionless technology framework tailored for developers and supports liquidity providers with a comprehensive suite of Decentralized Exchange (DEX) products. As a prominent entity in the DeFi space, Balancer enables seamless integration and innovation in blockchain technology. The organization is committed to expanding DEX offerings, thereby empowering users to maximize efficiency in liquidity provision and decentralized trading. Additional information about Balancer can be found on their website and Twitter.
-
 @ 652d58ac:dc4cde60
2025-01-20 14:39:11
@ 652d58ac:dc4cde60
2025-01-20 14:39:11Introduction
We must rethink how we envision the future. In the short term, things may be worse than we expect, rising inflation, war, and health crises, but this is all part of the fiat dilemma. A system that cannibalizes itself. Yet, at the same time, a new system is emerging.
Bitcoin and Artificial intelligence (AI) will be central to this foundation, providing humanity with the time and tools needed to thrive. How Technology Drives Deflation
As Jeff Booth so masterfully explains, technology is inherently deflationary. Over time, through free market competition and productivity gains, prices should fall to their marginal cost of production.
Yet, in our inflationary fiat system, productivity gains are eroded by the continuous increase in the money supply, driving prices higher. Instead of allowing prices to approach their marginal cost of production as they should, goods and services become more expensive due to monetary inflation.
This principle, that an expanding money supply reduces the purchasing power of individual monetary units and ultimately undermines wealth creation, was recognized as early as 1517 by Copernicus in the quantity theory of money.
Because bitcoin is limited in supply, productivity gains across the economy can lead to greater wealth for all participants in the system, as the price of goods and services falls to the marginal cost of production over time. Rather than rise due to an increase in the monetary supply. We need Bitcoin to ensure that the productivity gains that drive the economy forward can have a lasting, sustainable impact.
The Interplay of Bitcoin und AI
Since the existing system benefits from inflation, market participants are often manipulated into believing that AI is inherently dangerous. While there are significant risks associated with AI, particularly its potential for centralization and manipulation, the technology itself offers great opportunities. The real problem lies in the inflationary monetary system, not AI.
Artificial intelligence is set to increasingly shape the workplace, trade, and finance. Consider the “Magnificent Seven”, a group of tech giants, Apple, Microsoft, Amazon, Alphabet (Google), Meta (Facebook), Nvidia, and Tesla, that all leverage AI as a key driver of productivity.
In 2023, the financial services industry alone invested an estimated $35 billion in AI, with banking leading the charge, accounting for approximately $21 billion. This is particularly relevant to Bitcoin, since it serves as both money and a financial system. As AI becomes more sophisticated, it will increasingly rely on a digital currency that aligns with its digital nature, such as bitcoin, which offers both scalability and speed through the Lightning Network.
For instance, AI systems could use Bitcoin to facilitate microtransactions in real time, managing their wallets autonomously to process payments for services or data. This would unlock new opportunities for AI applications in sectors like actual decentralized finance (DeFi) and machine-to-machine transactions.
The Lightning Network, as a second-layer protocol built on top of Bitcoin, enables transactions to be settled almost instantly and at low cost. This makes it particularly well-suited for AI applications that require fast and reliable transactions.
While some AI and language models can exhibit programmed biases, AI systems, driven by algorithms and data, should strive to prioritize efficiency, minimizing biases wherever possible. If programmed without bias, AI seeks the best tools for operations and decision-making, and Bitcoin offers an optimal solution, providing both the asset and infrastructure needed for efficient, resilient, digital financial systems.
In addition, AI is likely to also contribute to Bitcoin’s development, with algorithms optimizing mining efficiency, hardware usage, forecasting energy demand, and ensuring more efficient resource allocation, all of which will lead to more effective mining strategies.
Conclusion
The synergy between Bitcoin and AI has the potential to enable the creation of more efficient, intelligent and resilient systems. These developments will underpin bitcoin’s role as digital money in a digital world, potentially creating positive second-order effects on global financial markets. The impact will be especially profound in industries such as finance, insurance, robotics, lending, investments, architecture, housing, healthcare, logistics, and others, with effects accelerating over time.
The free market is inherently deflationary, because of productivity gains, things, like housing, should become cheaper over time. Yet, this doesn't happen. Inflationary fiat currencies, like the dollar, lose purchasing power as their supply increases, eroding those gains. Bitcoin offers a framework in which productivity gains can have a lasting, sustainable impact.
Bitcoin, as a disinflationary currency with a fixed supply, preserves the value of productivity improvements, allowing prices to fall to their marginal cost of production. This ensures that efficiency gains lead to greater wealth for all participants in the system.
Moreover, since Bitcoin is accessible, it allows wealth to become more attainable for a wider range of people, enabling general living standards to increase more easily. The interplay between Bitcoin and AI is pretty exciting, and it’s becoming clear that the widespread adoption of AI will drive the widespread adoption of Bitcoin. This is necessary, as only Bitcoin, as a counterbalance to the self-destructive fiat system, can protect humanity from the negative effects of inflation. With the accelerated productivity gains of the AI age, Bitcoin becomes even more crucial as a solution, ensuring that these gains can be preserved and shared more equitably.
Originally published as the 28th edition of my n ewsletter, Bitcoin & AI: https://leonwankum.substack.com/p/bitcoin-and-ai
Photo Credit: commonedge.org (An Optimist’s Take on AI and the Future of Architecture)
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ ed84ce10:cccf4c2a
2025-01-17 07:04:19
@ ed84ce10:cccf4c2a
2025-01-17 07:04:19Overview
Oasis Network's Privacy4Web3 Hackathon: 2nd Edition hosted 50 registered projects (approved) and involved 149 developers. The focus was on customizable and interoperable privacy solutions for Web3 and AI. A $130,000 USD prize pool was offered, with development centered on Oasis' Sapphire EVM and the Runtime Off-chain Logic (ROFL) framework. These technologies were integral for hackathon participation.
Notable sponsors included PixelRealm and Aethir, which provided decentralized GPU infrastructure to support advancements in AI and gaming. Google Cloud collaborated by offering up to $2,000 in credits to participants. The event provided hands-on experience and networking opportunities, promoting community development and integration within Oasis's ecosystem.
The hackathon highlighted Oasis's potential as a layer-one blockchain designed for confidential applications, while also supporting Ocean Protocol's broader goals of enhancing data privacy and innovation. By encouraging new projects and community engagement, the event supported the continued development of Web3 technologies.
Hackathon Winners
Build on Sapphire and ROFL Prize Winners
- 1st Place: SQUIDL - A privacy-focused payment platform utilizing Oasis Sapphire for secure transactions. It simplifies cross-chain payments with stealth address generation and ERC-5564 challenges resolution, integrating Ethereum Name Service.
- 2nd Place: Futures on Chain
- 3rd Place (Tie):
- Priva Health
- CAAI (Copyright Aware AI)
- CompensatePaw3
- PrivateFeedback
- CLPD Stablecoin Private Transactions
- 4th Place: Minesweeper
Ocean Nodes - Tokenized Intelligence Prize Winners
- 1st Place: DeFlow - Facilitates AI model training with a drag-and-drop interface and automated task execution in the Ocean Network, using customized Docker images for efficiency.
- 2nd Place: confidential-data-exchange - Decentralized platform for secure AI model trading, employing end-to-end encryption and NFTs for asset tokenization within the Ocean Protocol.
- 3rd Place: CAAI (Copyright Aware AI)
Compute Bounty - Sponsored by Aethir, Hackathon Compute Partner Prize Winners
- 1st Place: Futures on Chain
- 2nd Place: Priva Health
- 3rd Place: CAAI (Copyright Aware AI)
Enhancing Embedded Wallet Powered by Oasis Prize Winners
- 1st Place: oasis-btc - Integrates Bitcoin key management in smart contracts, enhancing transaction security with the secp256k1 elliptic curve.
- 2nd Place: rofl rng recovery - Enhances user recovery with off-chain computation, employing ROFL for randomness and privacy in Apillon's embedded wallet.
- 3rd Place: Social and Email Authentication with Social Recovery - Secures account management through email and social media verification, using modular Solidity libraries.
Innovative Decentralized AI Applications on Oasis Sapphire Prize Winners
- 1st Place: SovereignAISearch-oasis-Protocol - A decentralized AI search protocol that prioritizes user data control through blockchain-based privacy and smart contract management.
- 2nd Place: Futures on Chain
Build on Sapphire and ROFL - Additional Prizes Winners
- Audit Credits Prize: Priva Health, Futures on Chain, SQUIDL, CompensatePaw3, CLPD Stablecoin Private Transactions
For further details on these projects, visit https://dorahacks.io/hackathon/p4w3/buidl.
About the Organizer
Oasis Network
Oasis Network aims to enhance privacy within the Web3 ecosystem, positioning itself as a key player in blockchain technology. Known for developing privacy-preserving solutions, the organization integrates these capabilities to address the need for data confidentiality in decentralized applications. As a contributor to the industry, Oasis Network seeks to strengthen Web3's foundational elements by providing robust privacy layers. This commitment aligns with their mission to create secure and private digital environments worldwide.
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ fd78c37f:a0ec0833
2025-01-17 03:23:02
@ fd78c37f:a0ec0833
2025-01-17 03:23:02In this edition, we invited Evelyn and Gerardo to share their experiences in creating a Bitcoin community, discussing their motivations, challenges, strategies, and goals. Their journey offers valuable lessons on community engagement and the transformative power of Bitcoin.
YakiHonne: Evelyn, Gerardo, We're truly delighted and grateful to have you join us today. Before we dive in, I’d like to share some background on what YakiHonne is. YakiHonne is a decentralized media client built on the Nostr protocol that enables freedom of speech through technology. It empowers creators to create their own voice, assets, and features. It also allows features like smart widgets, verified notes, and focuses on long-form articles. we'll be exploring more about your community. What sparked your interest in Bitcoin, and what motivated you to create a community around it ?
Evelyn:In the beginning, I started learning about Bitcoin in 2019, just a bit at first. When it became legal tender, we realized it was a monumental moment for El Salvador, and we knew we had to get involved in anything related to Bitcoin. Personally, I began watching videos and reading more about Bitcoin to deepen my understanding of its significance for El Salvador adopting it as legal tender. Evelyn:Soon, I recognized the importance of educating more Salvadorans about Bitcoin. This led us to start providing Bitcoin education in classrooms, schools, and various communities across different cities in El Salvador. As we traveled across the country, we noticed that Bitcoin adoption was still limited, with few places accepting it as a means of payment. This observation motivated us to build a community where Bitcoin could be used as a medium of exchange. Our goal was to replicate and expand upon the Bitcoin community that was already taking root in El Salvador.As the first country to adopt Bitcoin as legal tender, we understood the necessity of working on increasing its adoption throughout the nation.

YakiHonne: Could you share how your community was established, the strategies you employed to attract members, and the challenges you faced in the process?
Gerardo:We were living in San Salvador, but we didn’t enjoy city life, so we started looking for a place outside the city. We knew we wanted to live in the mountains, and there are a few options here in El Salvador. Eventually, we found ourselves in Berlin, and we really liked it. After spending some time visiting and getting to know the people, we decided this was where we wanted to settle down.
 Gerardo:Once we made that decision, we knew we wanted to start teaching Bitcoin within the community. We began talking to local entrepreneurs and residents, letting them know about our plan to educate the community about Bitcoin. We explained that it could bring significant opportunities for Berlin and its residents, including increased tourism. Some people were really excited about the idea because there weren’t many places in El Salvador, the “Bitcoin country” that had a circular economy focused on Bitcoin. Most of the activity was concentrated in the city.
Gerardo:As people started to hear about our idea, they liked it, and soon we had a team working with us to onboard more businesses. We were fortunate to find the right people, and that’s how it all began. We started by getting about 12 to 15 businesses to accept Bitcoin. I remember creating a social media presence, including a Twitter account, to promote Berlin as a destination where people could spend Bitcoin.
Gerardo:Berlin is about two and a half to three hours from the capital, San Salvador, depending on traffic, so it wasn’t easy for people to come initially. But as time went on, more people started visiting. They liked the weather, the friendly community, and the places where they could use Bitcoin. Soon, a few Bitcoin enthusiasts even moved to Berlin.
Gerardo:A year and eight months later, we now have a thriving community of over 20 Bitcoin users from around the world living here, along with many locals who have become Bitcoin users thanks to our educational efforts. We’ve established a Bitcoin center, have over 130 merchants accepting Bitcoin, and even non-business residents are using it. It’s been a fantastic journey, and it all started with a desire to educate a few people, which kept growing from there.
Gerardo:Once we made that decision, we knew we wanted to start teaching Bitcoin within the community. We began talking to local entrepreneurs and residents, letting them know about our plan to educate the community about Bitcoin. We explained that it could bring significant opportunities for Berlin and its residents, including increased tourism. Some people were really excited about the idea because there weren’t many places in El Salvador, the “Bitcoin country” that had a circular economy focused on Bitcoin. Most of the activity was concentrated in the city.
Gerardo:As people started to hear about our idea, they liked it, and soon we had a team working with us to onboard more businesses. We were fortunate to find the right people, and that’s how it all began. We started by getting about 12 to 15 businesses to accept Bitcoin. I remember creating a social media presence, including a Twitter account, to promote Berlin as a destination where people could spend Bitcoin.
Gerardo:Berlin is about two and a half to three hours from the capital, San Salvador, depending on traffic, so it wasn’t easy for people to come initially. But as time went on, more people started visiting. They liked the weather, the friendly community, and the places where they could use Bitcoin. Soon, a few Bitcoin enthusiasts even moved to Berlin.
Gerardo:A year and eight months later, we now have a thriving community of over 20 Bitcoin users from around the world living here, along with many locals who have become Bitcoin users thanks to our educational efforts. We’ve established a Bitcoin center, have over 130 merchants accepting Bitcoin, and even non-business residents are using it. It’s been a fantastic journey, and it all started with a desire to educate a few people, which kept growing from there.

YakiHonne: I love how it all started and the fact that you created mechanisms and opportunities for Bitcoiners to actually spend Bitcoin. It's also amazing how this initiative helped Berlin by attracting more prominent investors to settle here.Apart from Berlin's distance from the capital, which made it less accessible and may have deterred some people from coming, were there any other challenges you faced in the process of promoting Bitcoin adoption?
Gerardo:we faced several challenges, such as the local government’s disapproval of our Bitcoin activities, the initial difficulty of introducing Bitcoin into the community, and finding a suitable venue for our educational efforts. These were the primary obstacles we encountered early in the project. Gerardo:The first challenge we faced in the beginning was the lack of Bitcoin usage in the town. While we were teaching people to accept Bitcoin, there weren’t many individuals actually spending it. It was just the two of us at first, taking turns visiting places that accept Bitcoin, trying to make sure we could spend it and show others that it was possible. We were also traveling to San Salvador and inviting people to come to Berlin, but our efforts weren’t very successful initially. Gerardo:Eventually, more people started coming, and that issue was resolved. However, another challenge arose with some local politicians who didn’t approve of what we were doing. They tried to stop our efforts by discouraging people from working with us. As a result, a few locals didn’t trust us at first. Gerardo:For some people, they might think it's a scam. So, the educational aspect was a significant challenge. A few months into the project, we decided to hold community meetings, which was crucial for us because we needed a place to teach and spread knowledge about Bitcoin. However, we didn't have a dedicated venue at the time. Fortunately, we had a few friends, and initially, we held meetings at their homes or garages.

YakiHonne: You mentioned facing trust issues. What principles guide the community, and how did you maintain trust and reliability in your discussions as you built the community?
Evelyn:One of the key points in building trust within the local community is establishing clear trust and transparency. There were many misconceptions about Bitcoin initially. People often associated Bitcoin with politics and politicians, assuming it was a government creation. This misconception was fueled by the distribution of a government-issued Bitcoin wallet tied to citizens’ IDs, which caused confusion due to a lack of public education on Bitcoin. Evelyn:To address this, we made it a priority to remain neutral and uninvolved with the government. We focused on educating people about Bitcoin's origins, its creation by Satoshi Nakamoto, and its fundamental workings, breaking down complex concepts into simple explanations. We also informed the community about various Bitcoin wallets available, emphasizing alternatives to the government-issued wallet, which had issues with trust and identity theft. Evelyn:Engaging with respected elders in Berlin was another crucial strategy. We explained the benefits of Bitcoin adoption for the local economy and how it could improve the quality of life in the community. These respected community members helped us reach others and build credibility. Evelyn:Since May 2023, we have been deeply involved in educational and social projects, demonstrating that Bitcoin can improve not only personal financial situations but also community welfare. Importantly, we never asked for anything in return, showing our genuine intentions. Over time, this consistent engagement helped us gain the community’s trust, and our work in Bitcoin education has grown stronger.

YakiHonne: How do you educate your members and keep them informed about the latest Bitcoin developments?
Evelyn:Beyond simply observing developments in the Bitcoin space, we hold weekly meetings not only within our team but also with the broader community. These gatherings have been invaluable, as we've been fortunate to engage with many knowledgeable individuals who bring both technical expertise and insights into the philosophical aspects of Bitcoin. Through these interactions, we continuously learn from each other. We've also had the privilege of hosting experts who conduct workshops and deliver lectures during our meetings. These sessions help us stay informed about the latest advancements in technology and the evolving landscape of Bitcoin.

YakiHonne: Apart from education and inviting external instructors for weekly classes and meetups, how does your community collaborate with the broader Bitcoin ecosystem? What partnership has been the most impactful so far?
Gerardo:When we arrived here, I remember that many people knew something needed to change in the town’s technology and overall situation. They were unhappy with the status quo, especially with the government. There was already a lot of energy within the population of Berlin; we just needed to harness that energy and get organized. That’s when people started collaborating. Gerardo:In addition to Bitcoin education, we worked on social projects, like painting parks, cleaning the city, and addressing basic issues that the municipality wasn’t tackling. This shift in mentality helped people realize that it’s up to us to take action, not just wait for the government to act. Gerardo:As for Bitcoin adoption, many businesses have greatly benefited from it. They’ve seen an increase in income and are now able to save in new ways. You can even hear personal stories from business owners on how their operations have gradually transformed since they started accepting Bitcoin. This has had a significant impact on the local economy and also on how people view social change within the town.
YakiHonne: Do you have any partnerships with other Bitcoin or Bitcoin-related communities outside of Berlin?
Gerardo:There aren’t many Bitcoin communities outside of Berlin, even though we're considered the Bitcoin country. There's the Los Angeles one, which was the first, then Bitcoin Beach, followed by us, and now a new one is emerging in Santa Ana. I had a conversation yesterday with someone who's helping with that initiative, and we're planning some collaborations with them. They’ll be visiting us here, and we’ll also visit them to collaborate on Bitcoin education. There's also another community in La Pi Raya, a small island, that is working on Bitcoin education as well. Gerardo: There aren't many communities in the area, but we’re always open to working with them. It's really interesting to hear about their experiences and the challenges they face, as we can learn a lot from their insights.
YakiHonne: I expected that, since it was El Salvador, there would be over a thousand Bitcoin communities. Given that it's a country that has embraced Bitcoin so extensively, I thought there would be hundreds of communities.
Gerardo:However, it's been three and a half years since the Bitcoin Law, and adoption has been slow. While the U.S. dollar is still the other currency in use, people continue to trust it despite its devaluation. It's relatively stable, so they don’t yet feel the need to switch to Bitcoin. So, the adoption process is definitely moving slowly.
YakiHonne: Apart from creating Bitcoin-friendly shops and a community where people can buy and trade with BTC, what other steps have been taken to promote Bitcoin adoption in El Salvador? What results have you seen so far in your community?.
Gerardo:Bringing Bitcoin's identity to Berlin has significantly helped the town. It has attracted more Bitcoiners, especially those coming from El Salvador who are interested in Bitcoin adoption. We've started claiming the title of "Bitcoin City of El Salvador," which has also helped. The results are clear: people are seeing their income improve and are learning new things from the Bitcoin community. Slowly but surely, Berlin is adopting Bitcoin, and it’s bringing positive changes to the town.

YakiHonne: What are the community's goals for the next 6-12 months, and how do you see it evolving with Bitcoin's growth?
Gerardo:While many Berliners use Bitcoin for transactions, they tend to store it in custodial wallets. Our goal is to encourage people to own their seed phrases and understand the full Bitcoin philosophy, including the importance of time preference. We aim to teach people not just about Bitcoin payments, but also its broader value this year. Gerardo:we’ll create an independent association to manage donations and oversee community projects. The association will have its own rules, a board consisting of both expats and locals, and will work on improving the town. The Bitcoin education aspect will remain under our care. Our main goals are better education and local involvement in fixing the town's issues.
YakiHonne: You mentioned saving Bitcoin, and it reminded me of a point made in a previous interview with another community. They said the same thing—many people spend Bitcoin, but few actually save it, which is a problem. Saving Bitcoin has many benefits. For example, that community even encourages parents to save Bitcoin for their children, so that by the time they grow up, they'll have something valuable to inherit. I really appreciate your insights today, and I look forward to seeing how these efforts continue to make an impact in the future.
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 5d4b6c8d:8a1c1ee3
2025-01-20 20:03:28
@ 5d4b6c8d:8a1c1ee3
2025-01-20 20:03:28Mock Draft
Pick 6: CB/WR Travis Hunter Pick 37: DT Derrick Harmon Pick 68: QB Quinn Ewers Pick 73: OT Emery Jones Jr. Pick 106: DE Ashton Guillotte Pick 142: RB Dylan Sampson Pick 178: OG Jared Wilson Pick 212: LB Jamon Dumas-Johnson Pick 216: WR Antwane Wells Jr. Pick 222: S Rayuan Lane III
We're going with the very rare two-way prospect Travis Hunter as our first pick. Both CB and WR are positions of need, so he'll get a lot of opportunity to shine.
Then, the best player available at 37 was a DT, so we go defense heavy with the first two picks.
In the third round, we grab a QB and beef up the pass protection. From these mocks, it's looking like the third round is where we'll land a QB, whether that's Ewers or Dart (who was also still on the board and has a cooler name).
originally posted at https://stacker.news/items/857729
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 4d41a7cb:7d3633cc
2025-01-20 14:33:39
@ 4d41a7cb:7d3633cc
2025-01-20 14:33:39Anyone concerned with private property, survival, and freedom will find the material in this article to be very interesting. The concept of money is more abstract than most people think, and that is what I will try to demonstrate below.
Whether the film The Wizard of Oz's hidden message was intentional or not, it serves as an allegory to explain the grim and gruesome global monetary system.
The 1939 film The Wizard of Oz, based on L. Frank Baum's 1900 novel, contains hidden allegories about the banking system and financial challenges of late 19th and early 20th century America. The film closely resembles the book, except for two minor details: The yellow road in the film was the golden road in the book, and the ruby shoes in the film were silver shoes in the book: a clear reference to the bimetallic monetary system of the U.S. at the time.
The occult meaning explained
The word ‘OZ’ is a clear reference to the ‘ounce,’ a unit of measurement for gold and silver, further emphasizing the connection to monetary issues.
We can see The Wizard of Oz as an allegory for the new state of affairs in the United States in the 1930s, following the stock market crash and the bankruptcy of the US government immediately afterwards.
The play gives an allegorical sense of the financial enslavement of taxpayers, the legal tricks, and sensory manipulations bankers and government officials use to impose such enslavement on taxpayers. It also exposes the banking cartel, letting the people know that they are empowered to liquidate the bankers and return to Kansas: the true Republic.
The setting was Kansas: the heartland of America and the geographical center of the USA. The tornado (1929-1933), a whirlwind of turmoil that includes the stock market crash, the theft of American gold, the bankruptcy of the USA, and the Great Depression, sweeps in, transporting Dorothy and Toto to a new artificial dimension somewhere above the Kansas mainland. When they finally land in Oz, Dorothy remarks to her little companion:
‘Toto, I have a feeling we're not in Kansas anymore.’.
After the bankruptcy, Kansas was no longer simply the old 'Kansas'; it was now 'KS,' the artificial corporate headquarters of the bankrupt United States, a newly established 'federal territory,' part of the 'Federal Zone,' and Dorothy and Toto were 'in this state.'
The creditors of THE FEDERAL RESERVE INC. had declared the constitutional republic of the United States of America bankrupt and replaced it with a private corporation of the same name, UNITED STATES INC.
For those of you who are not yet aware, there was a conspiracy during the last two centuries to steal the world's money supply (gold & silver) and replace it with a global elastic fiat credit system. The design of this system was to transfer wealth from the productive class of world nations to the unproductive class of international bankers, resulting in artificial boom and bust cycles and private and public bankruptcies.
This happened in the United States during the beginning of the 1900s, especially from 1913, when the Federal Reserve was created, to 1933, when they stole all the gold from the American people after destroying their economy and prosperity.
International bankers had taken over the republic, but Americans were too confused and distracted by the turmoil at the time to realize this. A corporate state operating under commercial law had supplanted the constitutional republic operating under common law. At the same time, the Federal Reserve banking cartel would receive 100% of the present and future tax revenue from Americans.
The golden road
The book refers to the 'yellow road' as 'the golden road'. To locate the Wizard, you must track the money, specifically the stolen gold, which will lead you to the thief.
When the US government declared bankruptcy in 1933, Americans were required to turn in all their gold coins, gold bullion, and gold certificates by May 1, May Day (the birthday of communism in Bavaria in 1776, the birthday of the IRS, and celebrated worldwide as the ‘International Workers’ Holiday,’ a day sacred to the Wizard and his tribe). 1
By following the path of gold and its history, we can quickly get to the banking cartel and discover many of their methods and crimes. Even before they stole America, they had long since disposed of the Christian monarchies of Europe and plundered their kingdoms.
By examining significant dates like 1971, 1944, 1933, and 1913, we can swiftly identify the individuals responsible for shaping human history over the past few centuries.
Following the history of the gold standard, we can arrive at the creation of the Federal Reserve and the international banking cartel that owns and controls it, the Wizard of Oz, whose origin is from Europe.
The Emerald City
The Emerald City, where everything is green, is seen as a metaphor for the Federal Reserve and its fiat currency: Federal Reserve Notes, or FRNs (fiat ‘money’ or ‘money by fiat’). There the legendary wizard of Oz took refuge, with his mythical and omnipotent power to manipulate the interest rates and the supply of currency.
The illusory prosperity of the city reflects that currency itself is an illusion, especially when disconnected from gold or silver. By printing trillions of Federal Reserve notes to finance wars, purchase mass media, fund research and development, and purchase professionals and politicians, the magician maintains his position of power and the illusion of 'official authority'.
This currency creates a false sense of abundance when in fact it destroys the incentives for trade and creates inequality and injustice. The Great Depression of the 1930s, the confiscation of gold, and the two subsequent world wars were a direct result of the actions of the Federal Reserve, formed in 1913, a predecessor from the Bank of England, where the real power behind this entity lies.
The Federal Reserve is not federal and has no reserves; it is just the corporate name for private enterprise with an absolute monopoly on global credit. The illusion that it is part of the government or that it has legitimate authority is just that, an illusion; in reality, it is a cartel of private bankers with a monopoly on debt-based global currency.
The Wizard of Oz
One definition of 'wizard' is 'a very clever person'. The Wizard is a symbol of the banking cartel, which manipulates and controls people behind the scenes. They hide behind corporate names that do not even represent what they stand for, such as the Federal Reserve, United States, British crown, and Vatican.
Using smoke and mirrors, they create a grand illusion of omnipotent and omniscient power as if they were gods on earth. The magician represents the idea that the powerful often only manipulate perception instead of offering real solutions. However, upon exposing them, we uncover that they are merely common men, burdened with fears, insecurities, greed, and a significant dose of evil.
We know very well that the banking cartel controls educational institutions, the media, book publishers, and every flow of information and resources; thus and only thus can it manipulate the perception of billions of human beings around the world.
All of humanity is in a state of financial slavery to the illusionist's counterfeit money, which silently steals the time and energy of the masses on a global scale—their most precious wealth. The Wizard has owned the US government outright since 1933 and ‘owned’ Hollywood, an indispensable resource for maintaining global illusion and false perception.
‘You can fool all the people some of the time, and some of the people all the time, but you can't fool all the people all the time.’.
Abraham Lincoln (1809-1865), 16th President of the United States
After all, the wizard turned out to be just a con man, a fraud; behind the curtain there was just an ordinary person controlling the levers that created the illusion of authority and power.
The magician also cited the Latin phrase 'the land of E' Pluribus Unum,' meaning 'one among many'. This means that the phrase 'the land of E' Pluribus Unum', which translates to 'one among many', symbolises the merging of many into one, thereby establishing the New World Order, also known as Novus Ordo Seclorum. This phrase was prominently displayed on the US dollar note shortly after the crash in 1934.

The agenda of the international banking cartel is the ultimate elimination of cash, the total digitalization of credit, and the creation of a programmable global digital currency. Together with a social credit system and absolute surveillance, they seek to create a global police state to keep their taxpaying slaves in check and prevent any possibility of rebellion. By censoring dissent and controlling the flow of information, energy, and money, they plan to crown themselves on the throne forever.
The magician's main tools to maintain his economic power: DEBT, TAXES, AND INFLATION. Tools we must understand in depth to regain financial freedom and 'return to Kansas,' our true constitutional republic.
The Wicked Witch of the West
The Wicked Witch of the West made her home in a round medieval watchtower, the ancient symbol of the Knights Templar of Freemasonry, who were given to practicing witchcraft and are also credited with being the originators of modern banking, circa 1099 AD.
The Wicked Witch of the West wore black, a color that represented the planet Saturn, the Knights Templar's sacred icon, and the color judges and priests chose for their robes. Who was the Wicked Witch of the West? Remember, in the first part of the film, her counterpart was 'Almira Gulch,' who, according to Auntie Em, 'owned half the county.' Miss Gulch claimed that Dorothy's dog, Toto, had bitten her. Miss Gulch arrived at the farm with a'sheriff's warrant', demanding the release of Toto into her custody. Aunt Em was not immediately cooperative and responded to Miss Gulch's accusations that Toto had bitten her by saying, "He's very nice." With nice people, of course.
Miss Gulch's challenge to hold Toto and 'go against the law' reduced dear Auntie Em to 'pushing the party line' for Big Brother. She dutifully succumbed to the pressure and reluctantly advised Dorothy:
‘If you don't give me that dog, I'll bring you a goddamn suit that took over your whole farm!’
Today, 70% of all lawyers in the world reside in Western America, to be exact, and 95% of all lawsuits in the world are filed under the jurisdiction of the United States. The Wicked Witch of the West and Miss Gulch, my dear friends, stand in for judges and lawyers, specifically the American legal system, which includes the lawyer-led Congress and White House. They act as executioners and chief henchmen, transferring all wealth in America from the people to the ownership of banks and the government.
The Wicked Witch of the West wanted the silver slippers and precious metals, and her counterpart, Miss Gulch, wanted Toto (i.e., everything). We know all too well that banks are never satisfied and seek to squeeze every last penny from taxpayers, because it's not just about money; it's about control.
The straw man
The straw man wanted a brain from The Wizard of Oz. The term "straw man" in English refers to the legal fiction, legal person, or capitalized names that the US federal government creates using our natural-born names, with the intention of enslaving us and supporting the issuance of debt-based currency. The birth certificate, which establishes our legal fiction, serves as the tool for bolstering the issuance of public debt and currency.
The FRN, also known as the 'dollar,' represents a blank check that the US taxpayer has signed for the government. No legal person, paper legal fiction, or corporation has a brain nor a breath of life. They are just that: legal fictions and paperwork.
What does a straw man possess in place of a brain? A certificate. He took immense pride in his newly acquired legal status and all the other privileges bestowed upon him. Despite receiving a certificate, he remained a naive individual devoid of common sense.
The Tin Man (TIN)
The tin man symbolizes the taxpayer, specifically the workers. The IRS uses the TIN, a nine-digit number, to identify taxpayers for tax purposes. It can be a Social Security number (SSN), an individual taxpayer identification number (ITIN), or an employer identification number (EIN).
Just as the scarecrow/straw man had no brain, this tin man vessel had no heart. Both were ‘artificial persons.’. The Tin Man symbolized the mechanical and heartless nature of commerce and commercial law.
The Tin Man stood there, mindlessly engaged in his work, until his body literally overflowed and ceased to function. He exhausted himself due to his lack of heart and soul.
The heartless and soulless taxpayer/worker serves as nothing more than a useful slave to the banking cartel, fulfilling his "duty" without questioning the moral implications of his actions. Governments and banks rely on them for their income, and they labor diligently under their control.
‘I was just doing my job’ is one of the most common responses when re-evaluating the immoral acts they were complicit and co-conspirators in throughout history.
Today, thousands of distractions, vices, drugs, and products hypnotize them in front of a television or mobile phone screen, preventing them from realizing their role as tax slaves and hearing the call to a higher purpose in life.
These completely demoralized individuals lose sight of their life's purpose and value, which explains why there are so many cases of depression and suicide in today's world.
This is done by design: the banking cartel's agenda is to maintain the tax slaves' cold exterior and heartless interior in order to suppress any potential emotional reactions or divine sparks.
The cowardly lion
The cowardly lion was always afraid to stand up for himself, representing the American people who had lost their courage and bravery.
‘The land of the free and the home of the brave’ became the land of the slaves and the home of the cowards.
The cowardly lion, seeking the courage of the great wizard, received an official recognition medal. Now, although he was still a coward, his official status allowed him to be a bully, but with officially recognized authority, like lawyers or military men who hide behind courts and medals.
Have you ever noticed how bullies are actually the biggest cowards who act as if they have enormous courage but in reality have none?
It's fascinating how many weak, socially resentful, and cowardly individuals gravitate towards positions of power to conceal their cowardice and weakness. They require a position of 'authority' and often misuse it, concealing their weaknesses and insecurities behind official bodies.
The poppy field
The tactic was to cover the field with poppy flowers, the source of heroin, opium, and morphine, symbolically drug them into unconsciousness, and then simply walk in and snatch their slippers. In other words, the best way to subjugate the American people and plunder their assets was to dull their senses by becoming addicted to drugs.
The narcotics of the poppy field had no effect on the straw and tin man, for they were not blood, flesh, and blood, but artificial entities. The two cried out for help, and Glenda, the Good Witch of the North, answered their prayers with a blanket of snow, i.e., cocaine, a stimulant that nullifies the narcotic effect of the poppies/opium on Dorothy, the Lion, and Toto.
The crown has been playing the drug cartel game for centuries; just look at the history of Hong Kong and the Opium Wars. Despite its obvious impropriety, drugging your opponent before a battle is the most effective way to defeat them.
Distracting the masses, drugging and entertaining them is the best strategy to keep them subjugated and enslaved to a heartless monetary system, thus avoiding any resistance to change.
Flying monkeys
Let's not forget those flying monkeys, mythical creatures perfect for representing the lawyers of the bar (legal masters) who attack and control the little people for the grand wizard in the crown: the powerful and Big Bankers of Oz.Flying monkeys

Individuals have to be represented by lawyers in court cases and therefore need to hire a lawyer. The clients are “wards of the court,” i.e., “infants and persons of unsound mind," just like the strawman was a “person of unsound mind”.
Toto, the little dog
Toto means ‘everything’ in Latin, which was what the witch wanted after claiming the dog had bitten her. THE WITCH (the banks and their lawyers) WANTED EVERYTHING!
Notice how Toto was not frightened by the theatricality of the Big Wizard, even though he was small in size compared to the wizard. Toto simply walked up and began barking, drawing the attention of the others. Behind the curtain, an ordinary person was operating the levers that created the illusion of the great magician's power and authority.
We can see from this story how loud the bark of a small dog can be, but most of us still remain silent.
Dorothy
When Dorothy sought assistance from Glenda, the Good Witch of the North, to return to Kansas, Glenda responded, "You don't need help." You have always been empowered to return to Kansas.
Dorothy eventually made her way home. She always had the power it took to unmask the wizard, and so did we. She always thought she needed outside help, but the power is in each of us, taking responsibility, commitment, and action based on truth.
The great awakening of humanity
Most people do not listen, do not see, and do not speak the truth, either because they have an economic interest or because they are afraid. This is beginning to change.
We are going through a great awakening of consciousness, where more and more individuals are realizing that there is something beyond the illusion of the magician, beginning to see the deeper truths, the background of things, and a higher meaning to life.
Recognizing our birth on a slave plantation, our treatment as property, and the use of our legal identities to support the issuance of government debt (fiat currencies) is crucial. This has been going on for almost a century and is a direct attack on our sovereignty, which is the natural state of our human existence.
As Dorothy once said, "There's no place like home," and indeed, there is no place like home! A sovereign can find no greater place than sovereignty! Will you persist in deceiving unsuspecting men and adoring the magician's light show, or will you, like Dorothy, become aware and delve into the inner workings?
We need an educated mind, an intelligent heart, courage, and the responsibility to act.
We are not defined by our legal fiction or birth certificate, nor are we subject to the dictates of a bureaucrat wielding "official authority" to dictate our actions. We are not corporations operating under commercial law; we are human beings operating under common law, where a crime requires a victim (a human being or their damaged property).
The millions of laws, regulations, and restrictions do not apply to us sovereigns but to our legal fictions that are part of commercial law because they (not us) are corporations. The government has jurisdiction over its creation, which clearly does not include us. In this case, it is our legal identity or fictitious corporation that identifies us, but we, as flesh-and-blood men, are not a creation of the government.
The first step is to recognize this fact; the second is to stop waiting for outside help and take active participation in the matter, assuming responsibility and acting freely to defend our property and our rights.
If we continue to let the magician and his illusions dominate our perception of reality, we will end up living under a communist dystopia, with a system of mass surveillance and non-existent human rights.
But if we decide to take matters into our own hands, by understanding technologies like Bitcoin and Nostr, we can build a better future for ourselves and our future generations.
We are currently facing a unique opportunity to escape the traps and manipulations of this ancestral war and enjoy spiritual, intellectual, and financial freedom.
Although it will not be straightforward and requires responsibility and work, the price of not doing it correctly is slavery, and I personally would rather be dead than live subjugated to the will of a tyrant.
Bitcoin and Nostr, or slavery!
-
 @ 6389be64:ef439d32
2025-01-16 15:44:06
@ 6389be64:ef439d32
2025-01-16 15:44:06Black Locust can grow up to 170 ft tall
Grows 3-4 ft. per year
Native to North America
Cold hardy in zones 3 to 8

Firewood
- BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal
- Since its growth is fast, firewood can be plentiful
Timber

- Rot resistant due to a naturally produced robinin in the wood
- 100 year life span in full soil contact! (better than cedar performance)
- Fence posts
- Outdoor furniture
- Outdoor decking
- Sustainable due to its fast growth and spread
- Can be coppiced (cut to the ground)
- Can be pollarded (cut above ground)
- Its dense wood makes durable tool handles, boxes (tool), and furniture
- The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak.
- A very low rate of expansion and contraction
- Hardwood flooring
- The highest tensile beam strength of any American tree
- The wood is beautiful
Legume
- Nitrogen fixer
- Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn
- Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]]
Bees

- The edible flower clusters are also a top food source for honey bees
Shade Provider

- Its light, airy overstory provides dappled shade
- Planted on the west side of a garden it provides relief during the hottest part of the day
- (nitrogen provider)
- Planted on the west side of a house, its quick growth soon shades that side from the sun
Wind-break

- Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters
Fodder
- Over 20% crude protein
- 4.1 kcal/g of energy
- Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
-
 @ ed84ce10:cccf4c2a
2025-01-16 15:14:20
@ ed84ce10:cccf4c2a
2025-01-16 15:14:20Hackathon Summary
The Aptos Code Collision Hackathon concluded with notable participation, featuring 658 registered projects and 2,658 developers globally. Conducted in a hybrid format, the hackathon aimed to advance blockchain innovation through workshops and bootcamps focused on Web3 developments on the Aptos platform.
Offering over $500,000 in prizes, the event attracted diverse participants eager to create meaningful applications. Judging was conducted by industry experts, including Mo Shaikh and Avery Ching from Aptos Labs, alongside other notable blockchain and investment firm leaders.
The hackathon highlighted Aptos technologies such as Keyless user authentication and on-chain randomness, which support developers in creating secure and efficient applications. Resources and guidance were provided through a comprehensive participants' handbook, enhancing learning and development for both novice and advanced users. The event showcased significant participation and promising innovations aimed at enhancing the Aptos blockchain ecosystem.
Hackathon Winners
DeFi / RWA Prize Winners
- Panana Predictions: A decentralized platform for event predictions using smart contracts on Aptos, offering transparent transactions and community-governed markets.
- Sentra Restaking Protocol: Strengthens Aptos security via a restaking layer, providing pooled security and customizable slashing.
- Legato: A DeFi market platform utilizing AI for BTC price predictions and smart contracts for liquidity pool management.
- eVault: Combines DeFi and TradFi to offer financial services to underserved communities on Aptos.
- MeowFi: Uses NFTs as collateral for loans, enabling transparent lending on Aptos.
Gaming / NFTs Prize Winners
- Jeton: A decentralized poker platform on Aptos using zk-SNARKs for fair play without central trust.
- On-Chain Treasure Hunt Multiplayer!: An entirely on-chain game utilizing smart contracts for transparent mechanics and rewards.
- Forged Realms - IP Incubation with Games: Supports gaming IP incubation through a tokenized, community-driven approach.
- Aptos Legacy: A 3D RPG game on Aptos enhancing player ownership with tokenized assets.
- appToss Friends: Infrastructure for on-chain casinos, utilizing liquidity pools and friend registries on Aptos.
AI / DePIN Prize Winners
- ChatEDU: AI-powered educational system incentivizing content sharing with blockchain-based credits on Aptos.
- Unity Network: Facilitates data monetization through AI models with a federated learning protocol.
- ProxiRun: A decentralized compute marketplace for AI tasks, managed through smart contracts on Aptos.
- FLock Move GPT: Trains large language models (LLMs) on Aptos coding standards using advanced tuning and classification methods.
- Antikythera: An AI agent that enhances Aptos interactions by executing transactions and identifying real-time opportunities.
Social Prize Winners
- Cook App: A Telegram-based app curating crypto news via a blockchain-backed swipe interface.
- BiUwU: Livestream platform featuring AI-driven influencers and interactive blockchain-backed engagement.
- FundMate: Platform for social messaging and crypto transactions with decentralized payment management.
- Enthro: Enhances video content creation leveraging blockchain for market growth opportunities.
- StreamAd: Twitter-focused platform for automating campaign management and rewards distribution through smart contracts.
The Unexpected Prize Winners
- ActionX: Simplifies blockchain interactions by converting processes into actionable links.
- Compensate: Innovates payroll management using secure, transparent salary transactions with zero-knowledge proofs.
- Khizab: Offers reactive blockchain capabilities through modular, type-safe tools for application development.
- Aptos Extension: A development tool that enhances productivity and collaboration within the Aptos ecosystem.
- Aptotic: Industrial Robotic Automation on Aptos 🤖: Provides MaaS for industrial automation, integrating blockchain for secure operations.
UI Challenge Prize Winners
- PlayStop: A social minigame platform merging digital asset ownership with real-time competition on Aptos.
- EdenX: Web3 learning platform featuring a Telegram bot for a gamified learning-to-earn experience.
- Vortex: GameFi platform for player-to-player games with secure liquidity management on Aptos.
Best Public Goods Prize Winners
- Scaffold Move: An open-source toolkit for developing dApps on Aptos, including deployment scripts and module hot reloads.
- build 3 (fka Aptos Bounty App): A decentralized labor market that supports task fulfillment with an analytics dashboard.
- Aptos Extension
Aptos Indexer Challenge with Nodit Prize Winners
- Panana Predictions
- Wavefy Network - Decentralized Network for Generative AI Inference: Addresses AI memory issues using a P2P network for distributed model inference.
- Compensate
Foresight's Choice: Consumer Applications Bounty Prize Winners
- BiUwU
- Cook App
- eVault
- Antikythera
- ChatEDU
Mirana's Bounty Prize Winners
- Sentra Restaking Protocol
- BiUwU
- FLock Move GPT
MEXC Venture's Choice Prize Winners
- AGDEX: A decentralized perpetual exchange for leveraged trading, featuring benefits like AGLP tokens.
- EdenX
- Panana Predictions
- 紅包拿來: Integrates traditional red envelope culture with blockchain for secure digital asset sharing.
- Inbox-to-Earn using Telegram + Mizu: Monetizes Telegram inbox through Aptos token payments for prioritized messages.
Mizu Wallet's Telegram Integration Challenge Prize Winners
- AGDEX
- Panana Predictions
- Apt Date: A blockchain-based dating platform ensuring secure interactions with on-chain randomness for user matching.
For comprehensive details on all projects, visit https://dorahacks.io/hackathon/code-collision/buidl.
About the Organizer
Aptos Foundation
Aptos Foundation is prominent in blockchain technology, offering a Layer 1 blockchain utilizing the Move programming language to enhance scalability. Achieving up to 30,000 transactions per second and processing 2 billion transactions daily, the foundation emphasizes transaction efficiency and security. Dedicated to continuous innovation, its mission focuses on evolving blockchain infrastructure with cost-effective and robust solutions. Aptos Foundation remains actively engaged in technological development, fostering a dynamic and secure digital ecosystem.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 783850fd:77511d32
2025-01-20 13:22:54
@ 783850fd:77511d32
2025-01-20 13:22:54I'm thinking about buying a small house or a plot of land in Morocco and living there. The amount I am willing to pay for this would be $10 000 - 30 000. How much might I liquidate into their fiat (MAD) bank account with a month or so without them freezing my account and god only knows what worse things them doing to me. I use robosats and never exceed the amount of 950 euro when selling Bitcoin. I have all my wealth in Bitcoin, no history of income over the last 5 years, no filing tax returns too. I am from the EU, residing in Spain. How has your experience with Morocco been? Can one open a bank account in Morocco without having a residence there?
originally posted at https://stacker.news/items/857178
-
 @ dd664d5e:5633d319
2025-01-09 21:39:15
@ dd664d5e:5633d319
2025-01-09 21:39:15Instructions
- Place 2 medium-sized, boiled potatoes and a handful of sliced leeks in a pot.

- Fill the pot with water or vegetable broth, to cover the potatoes twice over.
- Add a splash of white wine, if you like, and some bouillon powder, if you went with water instead of broth.

- Bring the soup to a boil and then simmer for 15 minutes.
- Puree the soup, in the pot, with a hand mixer. It shouldn't be completely smooth, when you're done, but rather have small bits and pieces of the veggies floating around.

- Bring the soup to a boil, again, and stir in one container (200-250 mL) of heavy cream.
- Thicken the soup, as needed, and then simmer for 5 more minutes.
- Garnish with croutons and veggies (here I used sliced green onions and radishes) and serve.

Guten Appetit!
- Place 2 medium-sized, boiled potatoes and a handful of sliced leeks in a pot.
-
 @ ed84ce10:cccf4c2a
2025-01-16 15:13:05
@ ed84ce10:cccf4c2a
2025-01-16 15:13:05Hackathon Summary
The Hackmos 2024 event successfully concluded in Dubai, held alongside Cosmoverse 2024. It featured 53 registered projects and 101 participating developers. The hackathon provided a platform for both student and non-student teams, each allocated specific time slots for presentations, assessed by judging panels dedicated to various track categories. This event highlighted innovation within the Cosmos ecosystem, fostering networking among developers and blockchain enthusiasts.
Participants were encouraged to undertake projects that demonstrated technological innovation and practical functionality. The event concluded with presentations evaluated on criteria such as technology innovation, functionality, usability, and security. By engaging with the wider crypto community, the hackathon showcased promising projects with potential for significant community impact and adoption.
Set against Dubai's cultural backdrop, participants also had the opportunity to explore the locale. The hackathon attendees received non-transferable entry to the Cosmoverse conference, a forum for developments across the Cosmos ecosystem. The event fostered collaboration and competition, aiming to drive growth and exploration in blockchain project development.
Hackathon Winners
Interchain Prize Winners
- Wasm ICQ Datahub: Facilitates cross-chain data exchange without requiring architectural changes, using smart contracts on the Neutron blockchain. It is particularly suitable for financial protocols and analytics.
- ZkResolution: Enhances DNS privacy through zero-knowledge proofs, providing secure lookups and ensuring interoperability between EVM and Cosmos ecosystems.
- FractionXChange: Enables the fractionalization and rental of NFTs, allowing divisible tokens for shared asset access while maintaining asset exclusivity.
- Cosmic Quest: Gamifies blockchain education with role-playing quests, integrating real interactions and on-chain credentials.
- SupportMEow: Facilitates cat shelter donations through blockchain, using AI and IBC for image verification and blockchain inscription.
- NAMI <> Mars Protocol Integration: Integrates NAMI and Mars Protocol for cross-chain savings, providing sustainable yields and stablecoin management.
- InMail Treasury: Provides AI-driven treasury management with email interfaces, utilizing CosmWasm and Osmosis Smart Accounts for secured crypto management.
- BreezeNode: Promotes energy-saving behaviors through a blockchain-powered smart energy management system, rewarding token-based incentives for reduced usage.
- FreshCatch: Streamlines the seafood supply chain by connecting fishermen and markets, enhancing sustainability and efficiency through direct transactions.
- LogoSpark - RECs Blockchain: Facilitates REC trading via a PoS blockchain, ensuring transparency and sustainability in renewable energy markets.
Cosmos Hub Prize Winners
- MEME HERO: A launchpad for meme tokens on Cosmos, using IBC for liquidity and customizable tokenomics within a gamified platform.
- Symbiosis
- Proof of Profit: Simulates trading environments to demonstrate verifiable profitability, securely attracting investment on-chain.
- Swift Notify: Cosmos Hub Newsletters
- Wasm ICQ Datahub
Babylon Prize Winners
- HWStaking: Integrates Ledger wallets for Bitcoin staking through Babylon, enhancing security and accessibility for stakers.
Warden Prize Winners
- SupportMEow
- InMail Treasury
- FedLearn: Enables private machine learning via decentralized federated learning and Warden Protocol integration.
Osmosis Prize Winners
- InMail Treasury
- Symbiosis
- Osmosis smart contract EOL: Provides secure crypto fund recovery through inactivity monitoring and nominee execution upon user incapacity.
Neutron Prize Winners
- Wasm ICQ Datahub
- Proof of Profit
- Neutron Drop protocol UI in TMA: Telegram app interfaces with Neutron Drop Protocol for seamless smart contract operations across networks.
Mantra Prize Winners
- TOKIFY Protocol: Manages real-world asset tokenization on the MANTRA Chain, enabling fractional ownership within a compliant, DAO-governed framework.
- FractionXChange
- mantrapy: Enhances interactions with the Mantra chain through a versatile Python library, enabling extensibility in decentralized applications.
Agoric Bounty Prize Winners
- Zero mile: Develops a liquidity layer for seamless DeFi operations across blockchains, enhancing interoperability without traditional messaging.
- SupportMEow
- Agoric: Event Registration: Expands an event registration platform to support multi-blockchain transactions through Agoric integration.
Dora Factory Bounty Prize Winners
- ZKBugs: Focuses on bug detection in Circom circuits, ensuring optimal performance for cryptographic applications.
- HACKMOS BOUNTY MINOR: Examines message chain verification vulnerabilities to enhance security in decentralized systems.
To view all winning projects and details, visit Hackmos 2024 Projects.
About the Organizer
Cosmoverse
Cosmoverse & Hackmos Dubai 2024 is a recognized entity within the technology and blockchain sectors, dedicated to fostering innovation and collaboration. It is known for organizing engaging conferences and hackathons that bring together industry experts, developers, and enthusiasts to explore emerging trends and solutions. The organization's initiatives are aimed at advancing knowledge and practical applications of blockchain technology. Currently, it focuses on enhancing technological engagement and facilitating conversations to propel the industry forward.
-
 @ 011c780a:46e48b1d
2025-01-20 13:03:23
@ 011c780a:46e48b1d
2025-01-20 13:03:23Lake Erie is a paradise for anglers, boasting the world's largest walleye population and some of the highest catch rates in Ohio. For those eager to experience the thrill of fishing on these bountiful waters, booking a charter is the best way to go. However, with numerous options available, how do you choose the right one? Here are some essential tips to help you find the perfect charter for your Lake Erie adventure.
1. Look for Experienced Captains and Crews
The expertise of the captain and crew can make or break your fishing trip. Experienced professionals know the best spots to find walleye, how to handle changing weather conditions, and how to ensure you have an enjoyable day on the water.
● Check the company's website for captain biographies or years of experience.
● Look for certifications or affiliations with reputable fishing organisations.
● Read reviews to see if other anglers had positive experiences with the crew.
2. Prioritize Safety Measures
Safety should be a top priority when choosing an Ohio fishing charter company. Lake Erie can be unpredictable, so you need a charter that prioritises your well-being. ● Ensure the boat is equipped with life jackets, first aid kits, and emergency communication devices.
● Confirm that the captain holds a valid U.S. Coast Guard license.
● Ask about the company's safety protocols in case of adverse weather.
3. Assess the Equipment and Boats
● A well-maintained boat and quality fishing gear can elevate your experience.
● Look for charters that provide high-quality rods, reels, and tackle.
● Check if the boat is spacious, clean, and equipped with modern technology like fish finders.
● Ask if the company allows you to bring your gear if you have a preference.
4. Check for Customization Options
Every angler has unique needs, whether they're a seasoned pro or a first-timer. Some charters offer tailored experiences to meet your preferences.
● Look for family-friendly charters if you're planning a trip with kids.
● Ask if the company offers half-day, full-day, or multi-day trips.
● Find out if they're willing to adjust their itinerary to focus on specific fishing techniques or areas.
5. Read Online Reviews and Testimonials
● The best way to gauge the quality of a charter is through the experiences of others.
● Visit online platforms like Google, Facebook, or TripAdvisor for honest reviews.
● Pay attention to consistent themes in feedback, such as exceptional service, skilled crew, or successful catches.
● Look for photos or videos shared by previous clients to get a better sense of what to expect.
6. Consider the Costs and Inclusions
● While price shouldn't be the sole factor, it's important to know what you're paying for.
● Compare prices among different Lake Erie walleye charters to get a sense of market rates.
● Check what the package includes, such as bait, fishing licenses, or cleaning and packaging your catch.
● Avoid the cheapest options if they seem to cut corners on quality or safety.
7. Verify Their Knowledge of Lake Erie
● Ohio's portion of Lake Erie is home to millions of walleye, and the best charters have in-depth knowledge of these waters.
● Ask about their familiarity with local hotspots for walleye.
● Find out if they follow sustainable fishing practices to preserve the lake's ecosystem.
● A knowledgeable crew can also share interesting facts about the lake, making your trip both fun and educational.
Book Your Perfect Charter Today!
Finding the right Ohio fishing charter company is the first step to an unforgettable Lake Erie adventure. By prioritising experience, safety, equipment quality, and customer reviews, you can ensure a successful and enjoyable trip. For those looking to create lasting memories on Lake Erie, Eyes Ready Charters is a trusted name offering top-notch services to anglers of all skill levels. Book your trip today and experience the thrill of walleye fishing like never before!
-
 @ 7ed7d5c3:6927e200
2025-01-08 17:10:00
@ 7ed7d5c3:6927e200
2025-01-08 17:10:00Can't decide if the terrible book you just read is a 1 or 1.5 star book? Look no further than this chart. Was it Shit or just Bad? Was that movie you watched Very Good or just Decent? How many things out there are really Life Changing?
Finally, a rating scale for humans. Use it for anything in your life that needs a rating out of 5 stars.
Rating / Description
0.5 – The worst 1.0 – Shit 1.5 – Bad 2.0 – Eh 2.5 – Entertaining, but not great 3.0 – Neutral 3.5 – Alright 4.0 – Decent 4.5 – Very good 5.0 – Life Changing
P.S. Do not use it to rate your wife's cooking. The author is not liable for any damages.
-
 @ da0b9bc3:4e30a4a9
2025-01-20 12:57:31
@ da0b9bc3:4e30a4a9
2025-01-20 12:57:31Hello Stackers!
It's Monday so we're back doing "Meta Music Mondays" 😉.
From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme.
This month it's New Year New Artists! Bringing you small time artists with great music.
This week, I'm bringing Malinda Kathleen Reece and her cover of Pippins song Edge of Night.
https://youtu.be/NTsduTxb74Y?si=makffTIu9cPKsqqn
originally posted at https://stacker.news/items/857183
-
 @ da0b9bc3:4e30a4a9
2025-01-20 08:08:37
@ da0b9bc3:4e30a4a9
2025-01-20 08:08:37Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/856958
-
 @ ed84ce10:cccf4c2a
2025-01-16 15:12:06
@ ed84ce10:cccf4c2a
2025-01-16 15:12:06Hackathon Summary
The Funding the Commons & Earth Commons Hackathon concluded successfully, with 356 participants and 116 projects registered from various regions worldwide. Occurring from October 7 to November 7, 2024, the event targeted developing solutions for public goods funding through a hybrid format that combined online activities with optional in-person collaboration in Bangkok.
Participants engaged in both ideation and prototyping stages, focusing on tracks such as regenerative finance, decentralized governance, and climate innovation. With the support of workshops and mentorship, the hackathon aimed to generate tools and methods for managing shared resources more effectively.
Project evaluation criteria included innovation, impact, feasibility, functionality, collaboration, and presentation. The hackathon promoted global collaboration and creativity, aligning with its objective to enhance blockchain-based infrastructure and transform governance related to common resources, impacting sectors like ecosystems, academia, and public institutions.
In summary, the hackathon provided an opportunity for interdisciplinary collaboration, contributing to the development of solutions for global challenges in public goods and environmental sustainability.
Hackathon Winners
Financial Inclusion by Stellar Prize Winners
- Freelii - Facilitates financial inclusion through cost-efficient remittances using Stellar's blockchain, integrating with Telegram to simplify transactions for the unbanked in the Global South.
- Ask Billy - Supports humanitarian efforts with blockchain-secured cash transfers and AI chatbots, enhancing aid distribution through community insights.
- Stellar Mobile Money Bridge - Connects mobile money systems with the Stellar blockchain, enhancing financial inclusion via seamless mobile money integration.
Decentralized AI by NEAR Prize Winners
- VielNetFL - Offers a federated learning platform with Fully Homomorphic Encryption for secure, decentralized machine learning, coordinated via NEAR smart contracts.
- FederNear - Utilizes the NEAR blockchain for federated learning, encrypting model parameters to ensure secure, privacy-preserving decentralized training.
- Delta - A decentralized platform using AI to predict climate disasters, employing blockchain for fund allocation transparency and disaster relief.
Decentralized Storage by Filecoin Prize Winners
- ZkResolution - Enhances DNS resolution privacy through a protocol using zero-knowledge proofs, supporting cross-chain compatibility and geographic optimization.
- SovereignSearch - A decentralized search engine prioritizing user data sovereignty, leveraging Storcha and Filecoin for immutable data storage and retrieval.
- VielNetFL - See detailed description under Decentralized AI by NEAR Prize Winners.
Environmental Impact by KlimaDAO Prize Winners
- Proof of Change - Connects funds to environmental impacts using Ethereum attestations and satellite data for accountable climate finance.
- PGAtlas - An interactive platform that displays public goods projects with geolocation and blockchain attestation for better visibility and support.
- 0xFarms - Integrates rural farming with urban AI-driven technology, utilizing blockchain for enhanced food security and transparency.
- GreenLink - No additional details provided.
Public Goods Funding Infrastructure Prize Winners
- Doogly - A multichain donation platform that enhances crypto donation flexibility and tracking with blockchain certificates.
- Dead Project Snipper - Tool for evaluating blockchain project activity to aid grant allocation through automated data analysis.
- IES (Impact Evaluation Service) - Evaluates project impact using a blockchain platform, enabling retroactive funding and outcome measurement.
- Counterfactually - Utilizes synthetic control methodology to analyze intervention impacts in web3 for optimized capital allocation.
- Ecosystem Vision - Centralized dashboard providing AI-powered grant finder and standardized data integration for crypto funding opportunities.
- GrantScan - Indexes Web3 grant applications, offering a standardized, searchable database.
- findabuilder - AI-driven platform for locating builders with Talent Protocol data and smart query processing.
- Buildooor - Facilitates hackathon collaborations using a swipe-based interface for connecting builders.
- Engagement.Vision - Analyzes community engagement by integrating on-chain and off-chain data for comprehensive metrics.
Identity and Privacy by Holonym Prize Winners
- Refugee Identity Issuer - Provides decentralized identity verification for refugees with blockchain and zero-knowledge proofs.
- Trufy - A decentralized voting tool enhancing DAO governance with credential verification for secure voting.
Fullstack Decentralizations by Layer Prize Winners
- Builder's Dollar - A stablecoin initiative for sustainable funding, integrating blockchain for project eligibility verification.
Trust and Authenticity by Numbers Protocol Prize Winners
- Jurdil - Enhances election transparency in Indonesia through blockchain-secured image capture and smart contracts.
- Infinity Book: Pet Heroes - Collaborative digital book platform that uses blockchain for authenticity and unique digital asset generation.
For more details, view all projects at the Funding the Commons SEA Hackathon 2024.
About the Organizer
Funding the Commons
Funding the Commons focuses on accelerating blockchain-based infrastructure for public goods funding by connecting researchers, builders, and funders. The organization creates an ecosystem that bridges Web2, Web3, and academia, achieving impact through international conferences, builder residencies, and hackathons. Their initiatives include experimental funding rounds designed to support open-source public goods developers. Currently, their mission emphasizes fostering scaled human coordination that prioritizes the commons, supported by rigorous impact evaluations and continuous capital flows.
-
 @ fbf0e434:e1be6a39
2025-01-16 09:54:26
@ fbf0e434:e1be6a39
2025-01-16 09:54:26Hackathon 总结
Aptos Code Collision Hackathon 圆满结束,吸引了658个注册项目和来自全球2,658名开发者参与。该Hackathon以混合格式进行,旨在通过研讨会和训练营推进Aptos平台上Web3发展的区块链创新。
活动提供超过500,000美元的奖金,吸引了众多热衷于创建有意义应用程序的参与者。评审由行业专家进行,包括来自Aptos Labs的Mo Shaikh和Avery Ching,以及其他著名区块链和投资公司领导人。
Hackathon 突出展示了Aptos技术,如Keyless用户认证和链上随机性,支持开发人员创建安全高效的应用。通过提供详尽的参与者手册,增强了新手和高级用户的学习和开发。活动展示了显著的参与和有前景的创新,旨在增强Aptos区块链生态系统。
Hackathon 获奖者
DeFi / RWA 奖项获奖者
- Panana Predictions:一个通过Aptos智能合约进行事件预测的去中心化平台,提供透明交易和社区治理市场。
- Sentra Restaking Protocol:通过再抵押层加强Aptos安全性,提供池化安全和可定制惩罚措施。
- Legato:利用AI进行BTC价格预测并使用智能合约管理流动性池的DeFi市场平台。
- eVault:结合DeFi和TradFi,为Aptos上的未服务社区提供金融服务。
- MeowFi:使用NFT作为贷款抵押品,支持Aptos上的透明借贷。
游戏 / NFTs 奖项获奖者
- Jeton:使用zk-SNARKs确保公平的Aptos去中心化扑克平台。
- On-Chain Treasure Hunt Multiplayer!:完全链上游戏,利用智能合约确保透明机制和奖励。
- Forged Realms - IP Incubation with Games:通过代币化和社区驱动的方法支持游戏IP孵化。
- Aptos Legacy:在Aptos上提供代币化资产增强玩家所有权的3D RPG游戏。
- appToss Friends:提供链上赌场基础设施,利用流动性池和好友注册表。
AI / DePIN 奖项获奖者
- ChatEDU:利用AI支持的教育系统,通过区块链积分激励内容共享。
- Unity Network:通过联邦学习协议促进AI模型的数据货币化。
- ProxiRun:通过Aptos智能合约管理的去中心化计算市场。
- FLock Move GPT:使用高级调优和分类方法训练符合Aptos编码标准的大型语言模型(LLM)。
- Antikythera:通过执行交易和识别实时机会来增强Aptos交互的AI代理。
社交奖项获奖者
- Cook App:基于Telegram的应用,通过区块链支持的滑动界面策划加密新闻。
- BiUwU:直播平台,特色包括AI驱动的影响者和互动的区块链支持参与。
- FundMate:提供社交消息传递和加密交易的平台,具有去中心化支付管理。
- Enthro:利用区块链增强视频内容创建以促进市场增长机会。
- StreamAd:一个专注于Twitter的平台,通过智能合约自动化管理活动和奖励分发。
意外奖项获奖者
- ActionX:通过将流程转化为可操作链接简化区块链交互。
- Compensate:运用零知识证明,实现安全透明薪水交易的工资管理创新。
- Khizab:提供反应式区块链能力,通过模块化、类型安全的工具进行应用开发。
- Aptos Extension:提升Aptos生态系统内生产力和协作的开发工具。
- Aptotic: Industrial Robotic Automation on Aptos 🤖:通过区块链集成安全操作,为工业自动化提供MaaS。
UI 挑战奖项获奖者
- PlayStop:一个社交小游戏平台,结合数字资产所有权和实时竞赛。
- EdenX:一个Web3学习平台,特色包含通过Telegram bot进行游戏化学习赚钱体验。
- Vortex:为玩家对玩家游戏提供安全流动性管理的GameFi平台。
最佳公共利益奖项获奖者
- Scaffold Move:一个开发Aptos上dApps的开源工具包,包括部署脚本和模块热重载。
- build 3 (fka Aptos Bounty App):支持任务完成并附带分析仪表板的去中心化劳动力市场。
- Aptos Extension
Aptos Indexer Challenge with Nodit 奖项获奖者
- Panana Predictions
- Wavefy Network - Decentralized Network for Generative AI Inference:使用P2P网络解决AI内存问题,实现分布式模型推理。
- Compensate
远见选择:消费者应用程序悬赏奖项获奖者
- BiUwU
- Cook App
- eVault
- Antikythera
- ChatEDU
Mirana悬赏奖项获奖者
- Sentra Restaking Protocol
- BiUwU
- FLock Move GPT
MEXC Venture's 选择奖项获奖者
- AGDEX:一个用于杠杆交易的去中心化永久交易平台,特点包括AGLP代币。
- EdenX
- Panana Predictions
- 紅包拿來:将传统红包文化与区块链结合,实现安全的数字资产分享。
- Inbox-to-Earn using Telegram + Mizu:通过Aptos代币支付优先消息,货币化Telegram收件箱。
Mizu Wallet's Telegram Integration Challenge 奖项获奖者
- AGDEX
- Panana Predictions
- Apt Date:通过区块链确保互动安全的约会平台,使用链上随机性进行用户匹配。
有关所有项目的详细信息,请访问 https://dorahacks.io/hackathon/code-collision/buidl。
关于组织者
Aptos Foundation
Aptos Foundation 在区块链技术领域占有重要地位,提供一个采用Move编程语言的Layer 1区块链以增强可扩展性。其每秒可处理高达30,000笔交易,并每日处理20亿笔交易,该基金会重视交易效率和安全性。致力于持续创新,其使命是通过成本效益高且稳健的解决方案演进区块链基础设施。Aptos Foundation 积极投入技术开发,促进动感和安全的数字生态系统。
-
 @ df478568:2a951e67
2025-01-20 05:23:36
@ df478568:2a951e67
2025-01-20 05:23:36I took this picture at about block 416,220(June 13, 2016). The price of eggs on that day was $1.99, 16.5¢ per egg if you still measure stuff with the broken ruler we call fiat. What if we measured the price in sats instead? I found the price on that date from the bitbo calender. According to this website, $1.99 was worth 260,000 sats back then. Each egg cost 21,667 sats! Oh My Zeus!😱

I used this mempool calculator to see how much that is today. Turns out that it's $272.88 as of block 879,943. Since the fiat ruler is broken, the price of a dozen eggs also has NGU. I took this picture the last time I went to the grocery store. Eggs cost enough to shock fiat maxis. $8.99 OMZ!😱
What does a dozen eggs cost if you ignore the broken ruler? 8,572 sats today, just 714 sats per egg. Holy Wiemar Republic Batman! That's 30X cheaper! 😁
For some strange reason I can't pretend to understand, the Federal reserve tracks the price of eggs denominated in bitcoin. I guess they want to stay humble and stack money printer go brrrrrr. You can see the price of eggs drop off a cliff like Wile E Coyote on their website.
In The Price of Tommorrow and too many podcasts to mention, Jeff Booth argues the free market makes things cheaper over time, but the fiat syatem is syatematic theft. This theft occurs via inflation, which is really wage deflation. In other words, eggs are getting cheaper over time because egg producers become more efficient. We see tye fruits of this efficiency in Big screen TV's because the fiat price gets cut in half every ten years or so, but this is also a product of a broken ruler. The TV is probably 60X cheaper in bitcoin terms. It makes sense, TV's don't get bird flu, but when you begin using bitcoin as your unit of account, the measurement of value makes more sense than fiat clown world on the broken ruler standard. I remember when coffee was 100,000 sats. Now it's 16,699 sats. Living on the sat standards allows you to see Jeff Booth's thesis play out in real time

Life Gets More Expensive On The Broken Ruler Standard
I see so many young people on the broken ruler standard bemoan about food and housing prices. There are people with master's degrees who have already lost hope of buying a single family home and achieving the "American dream." To be honest, I would be pretty bummed about it too if I was on the broken ruler standard. A few months ago I spoke with a woman who made at least twice as much fiat as I do say, "I hope this housing market crashes so I can buy a house!"
That's sad. I have a lot of empathy for that feeling. Since the great financial crisis, I've only been able to get part time work, but my family wqs able to get a mortgage worth 12.5 bitcoin at the so-called "height of the market." We put as little money down as possible, 3% and I sold my old 401k for that "money." I also used some of it for repairs and taxes, but went all-in on bitcoin with everything else. Now our house is worth about 5 bitcoin. The way I see it, real estate is always crashing.
People on the broken ruler standard cry, "Wah, Wah. I hope there's a housing crash! Wah! Wah! Muh egg prices!" Buy a brand spanking new car for $50,00 car with a 7% interest rate and they will say, "Congratulations!" The trouble is, the price of the car falls like eggs compared to bitcoin on the broken ruler standard. This is because prices are distorted when measured in a broken ruler standard.
Get Off The Broken Ruler Standard

Before I met my wife, I played poker to supplement my income. I don't play much anymore, but poker taught me about risk management, probability, game theory, and many other things applicable to bitcoin. Poker gave me the background knowledge I needed to study bitcoin. In a sly, round-about way , poker taught me how to spend less bitcoin than I make. In traditional technical finance terminology, this is called "fucking saving." If you were not taught how to save and spend more than you earn, no matter how many broken ruler bucks you may earn, bitcoin will not work for you.
My wife makes a lot of broken ruler bucks. Unfortunately, we were broke in 2016 because we both were in school. Nevertheless, I'm proud of my stack amd I'm now at a point in life where I can get paid in bitcoin with very little risk because of my sugar mama, I mean wife, gets paid very well.
I spend like almost every other American consumer, plastic broken ruler debt cards. I put my little Strike ACH number on the Discover app. I keep a couple million sats on Strike and pay my credit card every month. In other words, I use Strike like a four-letter word: bank.
Sometimes I'll get a craving for tacos., I've never found a food truck that takes bitcoin, but they often use the Cash App. People on the broken ruler standard can't instantaneously send broken ruler bucks from PayPal to Zelle and vice-versa. They must first send broken ruler bucks from PayPal to the bank and then send the broken ruler bucks through Zelle. I can send sats directly from Strike to thr Cash App within seconds.
Sats As A Unit Of Account
The price of bitcoin fluctuates which makes it difficult to use as a unit of account. Who wants to divide the price of bitcoin by 100 million. Ain't nobody got time for that. If a whole coin costs 100k, then 1,000 sats = $1.00. This means each 100 sats is worth 10¢. 10 sats = 1¢. If the price drops 50%, 1000 sats is 50¢. If it does a 10X, $1,000 sats is $10.00. Living on a sat standard requires a little math, but it's easy to estimate. For more precise calculations I use mem pools calculator.
Money is a store of value, medium of exchange, and unit of account. If you use bitcoin on all three ways, you are using bitcoin as money. Saving becomes spending less bitcoin, not "buying more bitcoin." If you stack sats, your goal should be to leave the broken ruler standard and adopt sats as the standard. The world will still price your sats with a broken ruler. Sometimes this broken ruler makes you look like a fool. Other times, the broken ruler makes you look like a genius. Therefore, you must stay humble and stack sats.
You'll need some savings before you can deal with the broken ruler fallacy, but once you consistently stack sats and NGU continues to U, you'll eventually see life gets easier when you make sats the standard.
I will sell some sats to pay for my food and I send a tip to the food trucker in bitcoin using the Cash App gift button. It is actually very easy for them to accept bitcoin. They just don't know it yet. I don't proselytize the gospel of our lord and savior Satoshi Nakamoto. I just send them a few thousand sats. Good orange pilling is like good writing: Show, don't tell.
Does it require KYC?
Yeah, but so does Bank of Broken Rulers.
Haven't you heard the phrase, not your keys, not your bitcoin?
Yes. It's true. The 2 million sats or so is "not my bitcoin." From my perspective, however, it is the least risky way of paying my bills. I believe it is less risky than keeping broken ruler bucks in a bank. FDIC insurance sounds nice as canceled Insurance policies in the Pacific Palisades.
I could keep my 2 million sats in self-custody in my own lightning wallet. I could use Zap Planner to schedule my payments to hit Strike moments before I pay my bill, but I know me. I've lost sats on the lightning network before. I am more likely to lose the sats on my self-custodial lightning wallet than lose them because Strike could possibly rug-pull me. So for now, I just keep 2 million sats on the app. If bitcoin does a 10X, I'll keep 200,000 sats on Strike. If it drops 50%, I will keep 4 million sats on there.
I typically spend between $600- $1,000 in broken ruler bucks a month. This doesn't include my mortgage or food. My wife pretty much covers that stuff. Life happens though. Sometimes I need to pay a plumber, or a roofer or something, but most months, I have a sat surplus, a phenomena I like to call sats savings. My fiat check converts to bitcoin right on payday. I pay my credit cards off that day. If the sats are worth a little more, I pay taxes on that little bit. To make the math easy, say I get paid $1,000 on Friday. When I pay my bills, The broken ruler measurement now says I have $1,100. I pay my credit card. I owe capital gains on that $100 worth of sats. If my paycheck happens to be worth $900,I don’t pay any taxes because I have a loss. I won’t lie. I still get a bit perturbed when the price goes down 10% on payday, but it’s not the end of the world. If it doesn’t go back up by next payday, good. I earn more sats. If it goes up by next payday, good. All the sats I stacked before can buy more groceries.
Get On The Sats Standard
!;make sats the standard](https://gitea.marc26z.com/marc/BlogImprovementProposals/raw/branch/main/pics/Screenshot%20from%202025-01-19%2020-35-55.png)
Making sats the standard does this for the individual on the microeconomic level. Each Bitcoiner gradually accumulates sats. Stack long enough, study long enough, and experience enough 80% dips and you too will develop an unwavering conviction. You get paid in sats. You spend sats. You save sats. You no longer give a damn about your local fiat currency. A dozen eggs cost less than half of a single egg cost 8 years ago. If you lose 50% of your spending power overnight, you can buy less eggs, but a dozen eggs still costs less than 1 egg 8 years ago. Bitcoin is just better money.
If my fiat bank account takes more money out than I have in it, I can do an instant withdrawl on Strike. The fiat appears in my fiat bank account instantly. No more waiting 3-5 days for the money to get there. The bank does not get to keep charging you overdraft fee after overdraft fee for every little transaction. Bitcoin just works better. You can send it all over the world within seconds. You can buy stuff online with it or pay your credit cards. There is literally no reason to hold dollars anymore if you don’t want to. When you’re ready, make sats the standard. If you are not ready, keep stacking.
Onward.
-
 @ fbf0e434:e1be6a39
2025-01-16 09:54:04
@ fbf0e434:e1be6a39
2025-01-16 09:54:04Hackathon 总结
Hackmos 2024 活动在迪拜圆满结束,作为 Cosmoverse 2024 的一部分,该活动吸引了 53 个注册项目和 101 位开发者参与。Hackathon 为学生和非学生团队提供了展示平台,每个团队在特定时间段展示项目,由针对不同赛道类别的评审小组进行评估。此次活动展现了 Cosmos 生态系统的创新成果,促进了开发者与区块链爱好者之间的交流。
参与者被鼓励开发展示技术创新和实用功能的项目。活动的结束阶段,项目展示以技术创新、功能性、可用性和安全性为评估标准。通过接触更广泛的加密社区,Hackathon 展示了具有显著社区影响力和采纳潜力的有前景项目。
在迪拜的文化背景下,参与者还有机会探索当地环境。Hackathon 参会者获得非可转让的 Cosmoverse 会议入场券,这是一个围绕 Cosmos 生态系统发展的论坛。活动促进了协作和竞争,旨在推动区块链项目开发的增长和探索。
Hackathon 获奖者
Interchain 奖获奖者
- Wasm ICQ Datahub:在 Neutron 区块链上使用智能合约,促进跨链数据交换,无需进行架构更改,特别适用于金融协议和分析。
- ZkResolution:通过零知识证明提高 DNS 隐私,提供安全查询并确保 EVM 和 Cosmos 生态系统之间的互操作性。
- FractionXChange:实现 NFT 的分割和租赁,允许可分割代币用于共享资产访问,同时保持资产排他性。
- Cosmic Quest:通过角色扮演任务游戏化区块链教育,结合实际互动和链上凭证。
- SupportMEow:通过区块链促进猫舍捐赠,使用 AI 和 IBC 进行图像验证和区块链铭文。
- NAMI <> Mars Protocol Integration:将 NAMI 和 Mars Protocol 集成,用于跨链储蓄,提供可持续收益和稳定币管理。
- InMail Treasury:提供基于 AI 的金库管理和电子邮件接口,利用 CosmWasm 和 Osmosis 智能账户进行安全的加密管理。
- BreezeNode:通过区块链驱动的智能能源管理系统,促进节能行为,针对减少使用提供基于代币的奖励。
- FreshCatch:通过直接交易连接渔民和市场,简化海鲜供应链,提升可持续性和效率。
- LogoSpark - RECs Blockchain:通过 PoS 区块链进行 REC 交易,确保可再生能源市场的透明度和可持续性。
Cosmos Hub 奖获奖者
- MEME HERO:在 Cosmos 上为 meme 代币提供启动平台,使用 IBC 提供流动性,并在游戏化平台中实现可定制的代币经济学。
- Symbiosis
- Proof of Profit:模拟交易环境以展示可验证的盈利能力,安全地在链上吸引投资。
- Swift Notify: Cosmos Hub Newsletters
- Wasm ICQ Datahub
Babylon 奖获奖者
- HWStaking:通过 Babylon 集成 Ledger 钱包进行比特币质押,提高质押者的安全性和可访问性。
Warden 奖获奖者
- SupportMEow
- InMail Treasury
- FedLearn:通过去中心化的联邦学习和 Warden Protocol 集成实现私有机器学习。
Osmosis 奖获奖者
- InMail Treasury
- Symbiosis
- Osmosis smart contract EOL:通过非活动监控和用户无法操作时的委托执行,提供安全的加密基金回收。
Neutron 奖获奖者
- Wasm ICQ Datahub
- Proof of Profit
- Neutron Drop protocol UI in TMA:Telegram 应用接口与 Neutron Drop Protocol 集成,实现跨网络无缝智能合约操作。
Mantra 奖获奖者
- TOKIFY Protocol:在 MANTRA 链上管理现实世界资产代币化,允许在合规、DAO 治理的框架下实现部分所有权。
- FractionXChange
- mantrapy: 通过功能强大的 Python 库增强与 Mantra 链的交互,实现去中心化应用的可扩展性。
Agoric Bounty 奖获奖者
- Zero mile:开发一个流动性层,用于在区块链之间实现无传统消息传递的无缝 DeFi 操作,提高互操作性。
- SupportMEow
- Agoric: Event Registration:扩展活动注册平台,通过 Agoric 集成支持多区块链交易。
Dora Factory Bounty 奖获奖者
- ZKBugs:专注于 Circom 电路中的错误检测,确保密码学应用的最佳性能。
- HACKMOS BOUNTY MINOR:检查消息链验证漏洞,以提高去中心化系统的安全性。
查看所有获奖项目和详细信息,请访问 Hackmos 2024 Projects。
关于组织者
Cosmoverse
Cosmoverse & Hackmos Dubai 2024 是技术和区块链领域的知名社区,致力于推动Cosmos区块链的创新和合作,以组织吸引人的会议和 Hackathon 而闻名,将行业专家、开发人员和爱好者聚集在一起,探索新兴趋势和解决方案。该组织的举措旨在推进区块链技术的知识和实践应用。目前,其重点是加强技术参与,促进对话以推动行业向前发展。
-
 @ 16d11430:61640947
2025-01-20 03:32:57
@ 16d11430:61640947
2025-01-20 03:32:57Building a business, especially in the Bitcoin ecosystem, requires an unwavering commitment to patience and a deep belief in the fundamentals that underpin the technology. In a world driven by short-term profits and speculative fervor, it is easy to lose sight of the long game. Yet, the path to creating something meaningful and enduring often lies in resisting the noise and staying true to core principles.
The Bitcoin Revolution: Planting Seeds in Fertile Soil
Bitcoin is not just a technological innovation; it is a paradigm shift in how we view money, value, and trust. For entrepreneurs, it offers an opportunity to align their work with a monetary system that is decentralized, censorship-resistant, and designed for fairness. However, building a business in the Bitcoin space requires a recognition that societal adoption takes time.
As the saying goes, "The pot has to boil further." The ecosystem is still maturing, and while the signs of progress are undeniable, there is much work to be done. For plebs—the passionate individuals who embrace Bitcoin as a way of life—to eagerly work for sats, the economic incentives must become undeniable. This requires building infrastructure, educating the masses, and proving the utility of Bitcoin beyond speculation.
The Role of Patience in Entrepreneurship
Patience is not passive. It is an active process of nurturing your business, learning from setbacks, and steadily improving your product or service. In the Bitcoin space, patience involves:
-
Education and Advocacy: Many people still misunderstand Bitcoin's potential. Entrepreneurs must invest time in educating their audience, building trust, and explaining why Bitcoin is a better alternative.
-
Incremental Growth: Bitcoin adoption happens at the margins before reaching critical mass. Businesses that focus on steady growth rather than explosive, unsustainable expansion are more likely to succeed in the long run.
-
Long-Term Vision: Building for Bitcoin means thinking in decades, not quarters. A business grounded in sound principles—honesty, resilience, and utility—can weather market cycles and emerge stronger.
Faith in Fundamentals
Bitcoin’s fundamentals are its greatest strength: fixed supply, decentralized governance, and security. These principles create a monetary system that is fair and immune to corruption. Entrepreneurs in this space must build businesses that reflect these same values.
Integrity: A Bitcoin business should prioritize transparency and fairness, aligning incentives with customers and stakeholders.
Resilience: Bitcoin thrives in adversity. Businesses in this ecosystem should adopt a similar mindset, designing products that endure volatility and uncertainty.
Utility: Focus on solving real problems for real people. Whether it’s offering Bitcoin payments, facilitating education, or building tools for sovereignty, utility drives adoption.
Letting the Pot Boil: Creating Conditions for Change
The conditions necessary for mainstream Bitcoin jobs will emerge when the ecosystem matures further. This requires collaboration between businesses, developers, and advocates to:
Expand Infrastructure: Lightning Network, wallet solutions, and Bitcoin-native applications are critical to making Bitcoin more accessible and user-friendly.
Incentivize Participation: Paying workers in sats is not just a gimmick—it is a way to demonstrate Bitcoin’s superiority as a store of value and medium of exchange.
Build Culture: Bitcoin is more than technology; it is a movement. Businesses must contribute to a culture of empowerment, self-sovereignty, and fairness.
Conclusion: The Time Will Come
Faith in fundamentals is what separates builders from speculators. While the market will inevitably test your resolve, the rewards for those who persevere are immense. The time for mainstream Bitcoin jobs will come, but only when the ecosystem is ready—when plebs are eager to work for sats not out of necessity, but because it is the natural choice in a world aligned with Bitcoin's principles.
Until then, entrepreneurs must remain patient, continue building, and trust in the vision of a decentralized future. The pot will boil. When it does, those who believed in the fundamentals will be the ones to shape the next era of economic freedom.
-
-
 @ fbf0e434:e1be6a39
2025-01-16 09:53:37
@ fbf0e434:e1be6a39
2025-01-16 09:53:37Hackathon 总结
Funding the Commons & Earth Commons Hackathon 从10月7日到11月7日举行,吸引了356名开发者注册116个项目。活动专注于为公共物品融资创造解决方案,重点是再生金融、去中心化治理和气候创新。主要在线上进行的Hackathon在11月6日和7日于曼谷举行了一次可选的线下会议,以促进全球协作。
参与者最初在一个包括每周挑战的创意阶段进行,然后发展到原型开发。Hackathon提供了指导和研讨会访问,评审标准集中在创新性、影响力和可行性。虽然未详细介绍具体项目,但大量的参与显示了对目标领域的浓厚兴趣。
该Hackathon由Funding the Commons与Earth Commons共同组织,前者倡导基于区块链的公共物品基础设施,后者强调自然资源治理。通过吸引多元化的全球社区,该活动旨在推动公共物品管理和管理方面的系统性变革。
Hackathon 获奖者
Stellar奖项的金融普惠
- Freelii 使用Stellar的区块链来促进安全且具成本效益的汇款,并通过Telegram增加全球南方地区的可访问性。
- Ask Billy 利用AI、调查和区块链促进人道主义援助,改善影响评估和安全转账。
- Stellar Mobile Money Bridge 将移动支付与Stellar集成,简化跨境交易并解决金融碎片化问题。
NEAR奖项的去中心化AI
- VielNetFL 是一个使用NEAR智能合约和IPFS的安全联邦学习平台,通过先进的加密技术确保数据隐私。
- FederNear 提供基于NEAR区块链的隐私保护联邦学习,采用Pedersen承诺进行加密模型训练。
- Delta 是一个利用去中心化AI和区块链预测灾害并透明管理资金的灾难救援平台。
Filecoin奖项的去中心化存储
- ZkResolution 作为一个使用零知识证明的DNS隐私协议运行,实现EVM和Cosmos生态系统之间的跨链能力。
- SovereignSearch 是一个去中心化搜索引擎,专注于隐私的数据检索,使用Storcha和Filecoin Lassie进行安全存储。
KlimaDAO奖项的环境影响
- Proof of Change 基于验证结果为气候项目提供资金,使用以太坊进行状态变更验证和IPFS进行文档记录。
- PGAtlas 是一个互动平台,连接用户与全球公共物品项目,通过地理定位和Celo网络进行捐赠。
- 0xFarms 通过AI驱动的农场和区块链众筹提高粮食安全,支持农村和城市农业倡议。
- GreenLink 是一个利用区块链进行安全数据处理和激励回收的废物管理平台。
公共物品融资基础设施奖项
- Doogly 通过Allo协议简化加密捐赠,支持多链和多代币交易,以NFT证书确认捐赠。
- Dead Project Snipper 评估区块链项目活动以识别不活跃项目,并通过机器学习优化资助分配。
- IES(Impact Evaluation Service) 激励基于区块链的影响评估,促进项目资助的链上评估。
- Counterfactually 使用合成控制方法分析web3干预措施的影响,以便为决策提供信息。
- Ecosystem Vision 提供一个集中式仪表盘,用于评估加密资助的影响,整合来自不同资助计划的数据。
- GrantScan: Indexing all Grant Applications Ever in Web3 是一个索引Web3资助申请的搜索引擎,可增强数据访问和验证。
Holonym奖项的身份和隐私
- Refugee Identity Issuer 利用区块链、零知识证明和生物识别数据为难民提供去中心化身份验证。
- Trufy 通过基于凭证的影响增强DAO投票,提供多样化模式以改善决策质量。
Layer奖项的全栈去中心化
- Builder's Dollar 是一种用于资助Optimism Foundation项目的收益稳定币,集成AAVE以获得收益。
Numbers Protocol奖项的信任和真实性
- Jurdil - Community-Based Election Recap Utilizing Blockchain Technology with Captures 通过区块链和媒体验证增强印度尼西亚的选举透明度。
- Infinity Book: Pet Heroes 是一个使用区块链内容验证和AI增强的故事创作的数字书籍平台。
如需更多详细信息及探索所有项目,请访问此处。
关于组织者
Funding the Commons
Funding the Commons 致力于加速区块链基础设施在公共物品融资中的发展。通过培育一个涉及Web2、Web3、学术界、公共部门、慈善业和行业的多元化生态系统,该组织旨在推动公共物品管理中的系统性变革。其重要举措包括举办国际会议、建设者驻场项目和Hackathon,同时通过实验性资金轮次为开源项目提供资本。其使命集中于增强人类协调,以优先保护公共物品,并以影响评估系统和可持续资本流动为支持。
-
 @ b50957d8:6fcbccb4
2025-01-16 09:47:31
@ b50957d8:6fcbccb4
2025-01-16 09:47:31NgonClub là một nền tảng trực tuyến hiện đại, được thiết kế với giao diện dễ sử dụng và các tính năng tối ưu nhằm mang đến cho người dùng một trải nghiệm mượt mà và hiệu quả. Với phương châm luôn đặt sự tiện lợi và trải nghiệm người dùng lên hàng đầu, NgonClub cung cấp một không gian trực tuyến đầy đủ các công cụ hỗ trợ, giúp người dùng dễ dàng truy cập và tìm kiếm thông tin mà họ cần. Từ giao diện đơn giản cho đến các tính năng nâng cao, mọi thứ đều được tinh chỉnh để mang lại sự hài lòng cao nhất cho người sử dụng.
Điểm mạnh của NgonClub là khả năng cập nhật thông tin chính xác và kịp thời. Với một đội ngũ biên tập viên chuyên nghiệp, nền tảng này luôn cung cấp những tin tức, xu hướng và sự kiện mới nhất trong các lĩnh vực quan trọng. Người dùng có thể dễ dàng tiếp cận thông tin nhanh chóng, giúp họ nắm bắt được tình hình và không bỏ lỡ các cơ hội quan trọng. NgonClub không chỉ cung cấp các thông tin tổng quát mà còn chú trọng đến việc đưa ra các phân tích chi tiết, giúp người dùng hiểu rõ hơn về các vấn đề và sự kiện đang diễn ra.
Bảo mật là một yếu tố rất quan trọng đối với NGONCLUB, và nền tảng này luôn đảm bảo rằng dữ liệu cá nhân của người dùng được bảo vệ tuyệt đối. Với việc áp dụng các công nghệ bảo mật tiên tiến, NgonClub bảo vệ thông tin người dùng khỏi các mối đe dọa từ bên ngoài và ngăn ngừa mọi hành vi xâm nhập trái phép. Mọi giao dịch và thông tin cá nhân đều được mã hóa một cách an toàn, đảm bảo rằng người dùng có thể yên tâm khi sử dụng các dịch vụ trên nền tảng này mà không lo ngại về vấn đề bảo mật.
Ngoài tính năng bảo mật, NgonClub còn cung cấp nhiều công cụ hỗ trợ cá nhân hóa trải nghiệm người dùng. Với các tính năng tùy chỉnh linh hoạt, người dùng có thể thiết lập giao diện và các công cụ sao cho phù hợp với nhu cầu của mình. Điều này giúp nâng cao hiệu quả sử dụng và tiết kiệm thời gian trong quá trình tìm kiếm thông tin. Hơn nữa, việc tùy chỉnh các tính năng còn giúp tạo ra một không gian trực tuyến thân thiện và dễ chịu, nơi người dùng cảm thấy thoải mái và hài lòng khi trải nghiệm.
Với tất cả những ưu điểm vượt trội như vậy, NgonClub là một nền tảng lý tưởng cho những ai tìm kiếm một không gian trực tuyến an toàn, tiện ích và đầy đủ thông tin. Nền tảng này luôn chú trọng đến việc mang lại giá trị cho người dùng thông qua các tính năng hữu ích, bảo mật cao và dịch vụ khách hàng tận tình. Với cam kết không ngừng cải tiến và phát triển, NgonClub sẽ tiếp tục là sự lựa chọn hàng đầu của những người dùng thông thái, luôn tìm kiếm những thông tin chính xác, nhanh chóng và tiện lợi.
-
 @ b50957d8:6fcbccb4
2025-01-16 09:46:26
@ b50957d8:6fcbccb4
2025-01-16 09:46:26Max10 là một nền tảng trực tuyến hiện đại, được thiết kế để đáp ứng nhu cầu của người dùng thông qua giao diện thân thiện và dễ sử dụng. Nền tảng này cung cấp nhiều tính năng tối ưu hóa, giúp người dùng có thể dễ dàng truy cập các dịch vụ và công cụ mà họ cần. Bằng cách tối giản các thao tác và cải tiến hiệu suất, Max10 đảm bảo rằng người dùng có thể thực hiện mọi nhiệm vụ một cách nhanh chóng và hiệu quả. Mọi tính năng được tích hợp vào nền tảng này đều mang lại sự tiện lợi tối đa cho người sử dụng.
Một trong những điểm nổi bật của Max10 chính là khả năng cung cấp thông tin chính xác và cập nhật liên tục. Nền tảng này luôn theo dõi và cập nhật các xu hướng mới nhất, những tin tức nóng hổi trong nhiều lĩnh vực khác nhau. Dù là trong lĩnh vực công nghệ, tài chính hay các sự kiện xã hội, Max10 luôn cung cấp những thông tin đáng tin cậy và kịp thời, giúp người dùng không bỏ lỡ bất kỳ cơ hội hay sự kiện quan trọng nào. Tính năng này đặc biệt hữu ích cho những ai muốn luôn cập nhật và nắm bắt các thông tin quan trọng ngay lập tức.
MAX10 cũng chú trọng đến việc bảo mật thông tin người dùng, đảm bảo rằng tất cả dữ liệu cá nhân và giao dịch đều được bảo vệ an toàn. Nền tảng này sử dụng công nghệ mã hóa tiên tiến, giúp ngăn chặn các mối đe dọa từ bên ngoài và bảo vệ người dùng khỏi các rủi ro mất mát thông tin. Mọi thông tin cá nhân của người dùng đều được bảo mật tuyệt đối, giúp người dùng cảm thấy an tâm khi sử dụng nền tảng. Điều này tạo dựng niềm tin vững chắc và khẳng định sự cam kết của Max10 đối với bảo mật dữ liệu.
Ngoài tính năng bảo mật, Max10 còn cung cấp các công cụ cá nhân hóa mạnh mẽ, giúp người dùng có thể tùy chỉnh trải nghiệm của mình. Các tính năng cá nhân hóa không chỉ giúp người dùng tiết kiệm thời gian mà còn cải thiện hiệu quả sử dụng nền tảng. Người dùng có thể điều chỉnh giao diện và các công cụ để phù hợp với nhu cầu và sở thích riêng của mình, mang lại một trải nghiệm trực tuyến tối ưu và linh hoạt. Điều này giúp Max10 nổi bật so với các nền tảng khác, vì người dùng luôn cảm thấy thoải mái và hài lòng khi sử dụng các dịch vụ trên nền tảng này.
Với những ưu điểm vượt trội về tính năng, bảo mật và tính cá nhân hóa, Max10 đã trở thành một nền tảng đáng tin cậy và hiệu quả cho mọi người dùng. Nền tảng này không chỉ giúp người dùng truy cập thông tin nhanh chóng và chính xác mà còn mang đến một không gian trực tuyến an toàn và tiện lợi. Max10 luôn cam kết cải tiến và đổi mới để đáp ứng tốt hơn nhu cầu ngày càng cao của người dùng. Với sự phát triển không ngừng, Max10 sẽ tiếp tục là lựa chọn hàng đầu cho những ai muốn trải nghiệm một nền tảng trực tuyến hiện đại và hoàn hảo.
-
 @ 16d11430:61640947
2025-01-20 03:17:38
@ 16d11430:61640947
2025-01-20 03:17:38Born out of a silent rage into a world that prides itself on polished veneers of socially acceptable fury, the Silent Rager arrived in a place where anger wore masks—tight, suffocating masks that twisted raw emotion into hollow smiles and passive-aggressive jabs. Yet his rage had no such mask, no place in this theater of deceit. His was a wild, untamed thing, a fire roaring without the permission of his voice.
From the moment he could perceive the world, he was sent to rage's hell camp—a crucible of misery, where every breath reeked of malfeasance, and every lesson was soaked in contempt. The Silent Rager learned to stew in it, learned to hold it within, to cook himself in the boiling broth of inherited bitterness and unspoken injustice. They told him the world was cruel, but what they didn’t tell him was that he’d been chosen—culled in a ritual as old as power itself. Somewhere, someone had decided that his voice was too dangerous to exist. They’d silenced it before it could ever cry out, sparing the rage but not the sound.
And so, he grew, misinformed, misdirected, and malformed. His mind writhed like a worm trapped in the grip of an unseen hand. Thoughts coiled and uncoiled in his brain, each one dripping with questions he could not articulate, answers he could not demand. Why was his rage silent? Why did it claw at his chest without release? He did not know. He only knew the ache of containment and the suffocating weight of emotions too vast for his stolen voice.
Moments of respite came, but only when he danced closest to death. The edge of oblivion whispered to him with the intimacy of a long-lost friend. It was in these moments that the raging fire within dimmed, replaced by a fleeting, fragile stillness. He could breathe, if only for a second, before the storm returned. Life, for him, was not a series of triumphs or failures but a relentless march of inherited rage, coursing through his veins like a parasite, feeding on his every heartbeat.
He did not ache for it to end—not entirely. What he yearned for, more than anything, was a voice. A voice to scream into the void that birthed him. A voice to challenge the silence that caged him. A voice to tell the world, and himself, the truth of his existence before he could end it all.
The Silent Rager lived in a paradox: to end his life without a voice would be to die unseen, unheard, unspoken. But to live on without one felt equally unbearable. His rage, silent though it was, demanded expression. It screamed through his actions, burned in his gaze, and radiated from him like heat from a furnace. And yet, the world did not see, did not hear. To them, he was just another shadow moving through the crowd, another ghost in the machine.
In the end, the Silent Rager remained trapped in his silent storm, his unvoiced agony a testament to a life stolen before it could begin. Perhaps one day he would find his voice. Or perhaps his silence would be his epitaph, a bitter monument to a world that let him burn in quiet desperation. Until then, he raged—silent, but not unseen, not by those who dared to truly look.
-
 @ b50957d8:6fcbccb4
2025-01-16 09:44:58
@ b50957d8:6fcbccb4
2025-01-16 09:44:58N88 là nền tảng trực tuyến tiên tiến, được thiết kế với mục tiêu mang lại trải nghiệm người dùng mượt mà và hiệu quả. Với giao diện thân thiện và dễ sử dụng, N88 giúp người dùng nhanh chóng truy cập vào các dịch vụ và tính năng mà họ cần. Nền tảng này được tối ưu hóa để đáp ứng mọi nhu cầu của người dùng, từ việc tìm kiếm thông tin đến việc sử dụng các công cụ trực tuyến, tất cả đều được tích hợp một cách hoàn hảo. N88 không chỉ là một công cụ hữu ích mà còn là người bạn đồng hành giúp người dùng tiết kiệm thời gian và nâng cao hiệu quả công việc.
Một trong những điểm mạnh của N88 là khả năng cập nhật thông tin nhanh chóng và chính xác. Với công nghệ tiên tiến, N88 liên tục theo dõi và cung cấp các tin tức mới nhất trong nhiều lĩnh vực quan trọng, từ các sự kiện nổi bật cho đến các xu hướng mới trong ngành công nghệ, kinh tế và đời sống. Người dùng có thể dễ dàng truy cập và nắm bắt thông tin kịp thời, giúp họ luôn ở trong tình thế chủ động và không bỏ lỡ bất kỳ cơ hội quan trọng nào. Tất cả các thông tin trên N88 đều được chọn lọc kỹ càng, đảm bảo chất lượng và độ tin cậy cao.
Ngoài việc cung cấp thông tin, N88 còn đặc biệt chú trọng đến vấn đề bảo mật. Nền tảng này sử dụng các công nghệ mã hóa và bảo vệ tiên tiến để đảm bảo an toàn cho tất cả dữ liệu cá nhân của người dùng. Mọi giao dịch và thông tin đều được bảo vệ một cách nghiêm ngặt, giúp người dùng yên tâm khi sử dụng dịch vụ mà không phải lo ngại về các rủi ro bảo mật. N88 cam kết không chia sẻ hay lạm dụng thông tin cá nhân, mang đến một môi trường trực tuyến an toàn và đáng tin cậy.
N88 cũng không ngừng nâng cấp và cải tiến các tính năng của mình để đáp ứng tốt hơn nhu cầu của người dùng. Một trong những tính năng đáng chú ý là khả năng cá nhân hóa trải nghiệm người dùng. Người dùng có thể tùy chỉnh giao diện và các công cụ hỗ trợ để phù hợp với sở thích và nhu cầu riêng. Điều này không chỉ giúp tạo ra một không gian trực tuyến dễ sử dụng mà còn làm tăng tính linh hoạt và hiệu quả trong quá trình sử dụng. Tính năng cá nhân hóa này giúp người dùng có thể tối ưu hóa các lựa chọn của mình và tiết kiệm thời gian khi sử dụng nền tảng.
Với tất cả những tính năng ưu việt và cam kết bảo mật mạnh mẽ, N88 xứng đáng là sự lựa chọn hàng đầu cho những ai tìm kiếm một nền tảng trực tuyến đáng tin cậy và hiệu quả. Nền tảng này không chỉ cung cấp các dịch vụ hữu ích mà còn mang đến một trải nghiệm người dùng tuyệt vời, giúp người dùng cảm thấy thoải mái và an tâm khi sử dụng. Với sự đổi mới liên tục, N88 sẽ luôn là người bạn đồng hành tin cậy, cung cấp những giải pháp và công cụ tối ưu để nâng cao hiệu quả công việc và giải trí.
-
 @ a012dc82:6458a70d
2025-01-20 02:02:07
@ a012dc82:6458a70d
2025-01-20 02:02:07The advent of cryptocurrency has sparked a modern-day gold rush, with Bitcoin mining at the forefront of this digital revolution. The United States, with its vast resources and technological prowess, has become a fertile ground for these operations. However, the recent shift in the global mining landscape has brought a wave of Chinese mining companies to U.S. shores, fleeing a regulatory crackdown in their homeland. This migration has set off alarm bells within national security circles, as the technology that underpins cryptocurrencies is not just a tool for financial gain but also a potential vector for cyber espionage and other security threats. The dual-use nature of this technology, capable of both revolutionizing economies and potentially undermining national security, has placed it at the heart of a complex debate involving economic policy, technological innovation, and national defense.
Table Of Content
-
The Economic Impact of Cryptocurrency Mining
-
National Security Risks and Strategic Concerns
-
Regulatory Responses to Foreign Mining Operations
-
The Path Forward: Innovation, Security, and Diplomacy
-
Conclusion
-
FAQs
The economic allure of cryptocurrency mining is undeniable. In regions hit hard by economic downturns, the establishment of mining operations has been a boon, providing much-needed jobs and revitalizing local economies. These operations often take over abandoned industrial sites, turning them into hives of high-tech activity. The promise of a revitalized industrial base, however, comes with caveats. The energy-intensive nature of cryptocurrency mining has led to a surge in demand for electricity, straining local grids and raising concerns about the environmental impact of such operations. The long-term economic benefits are also questioned, as the volatility of the cryptocurrency market means that the stability of these jobs and the longevity of the operations are not guaranteed. As Chinese companies increasingly dominate this space, there is also the fear that the economic benefits may be offset by the outflow of profits to foreign entities.
National Security Risks and Strategic Concerns
The strategic implications of foreign-controlled cryptocurrency mining operations on U.S. soil are complex and troubling. The opaque nature of these operations, often shrouded in layers of corporate secrecy, makes it difficult to discern their true intentions. The proximity of some mining farms to sensitive sites, such as military bases and critical infrastructure, has compounded these fears, suggesting the potential for these facilities to be used for more than just mining. The vast computational power of mining operations could theoretically be repurposed for code-breaking and hacking, posing a direct threat to national security. The concern is not just hypothetical; it is rooted in a history of cyber incursions attributed to Chinese state-sponsored actors. The potential for these mining operations to serve as a front for such activities, intentionally or not, has put them in the crosshairs of U.S. security agencies.
Regulatory Responses to Foreign Mining Operations
The U.S. government's response to the influx of Chinese cryptocurrency mining operations has been measured yet firm. Recognizing the need to maintain an open economic environment that fosters innovation, regulators have nonetheless moved to establish guardrails to protect national interests. This has involved a multifaceted approach, including the proposal of legislation aimed at scrutinizing foreign investments in critical technologies and infrastructure. Agencies such as the Committee on Foreign Investment in the United States (CFIUS) have been at the forefront of these efforts, working to untangle the complex web of ownership and control that characterizes foreign mining operations. The goal is to ensure that while the U.S. remains a hub for technological innovation, it does not become a playground for foreign powers with adversarial intentions.
The Path Forward: Innovation, Security, and Diplomacy
The path forward for the United States in managing the rise of Chinese bitcoin mining operations is akin to walking a tightrope. On one side is the need to nurture innovation and maintain the U.S.'s competitive edge in the burgeoning field of cryptocurrency. On the other is the imperative to safeguard national security and ensure that the country's technological infrastructure is not compromised. This delicate balance requires a nuanced approach that includes fostering a robust domestic mining industry, investing in renewable energy sources to mitigate the environmental impact, and engaging in strategic diplomacy to manage the international dimensions of cryptocurrency governance. The U.S. must leverage its strengths in innovation, policy-making, and international relations to set standards that will shape the future of cryptocurrency mining and secure its digital economy.
Conclusion The challenge of balancing the economic potential of cryptocurrency mining with the imperatives of national security is emblematic of the broader challenges facing policymakers in the digital age. As Chinese bitcoin mining operations continue to expand their footprint in the U.S., the need for a strategic, measured response becomes increasingly critical. This response must be multifaceted, engaging with all stakeholders, including the mining industry, environmental groups, energy providers, and security agencies. By striking a balance between economic growth and security, the U.S. can harness the potential of the digital economy while protecting its national interests. The stakes are high, and the decisions made today will have lasting implications for the security and prosperity of future generations.
FAQs
How does Bitcoin mining impact local economies? Bitcoin mining can provide jobs and economic investment in local communities, especially in areas with excess energy capacity or where industrial sites are underutilized.
What is the U.S. government's response to foreign cryptocurrency mining operations? The U.S. government is considering stricter regulations on foreign investments in critical technologies, including cryptocurrency mining, to protect national security while fostering economic growth.
Can cryptocurrency mining operations be environmentally sustainable? There are concerns about the high energy consumption of mining operations, but with investment in renewable energy and efficient technologies, mining can move towards greater sustainability.
How does the U.S. plan to balance innovation with security in cryptocurrency mining? The U.S. aims to strike a balance by creating policies that encourage technological innovation and economic benefits while implementing security measures to protect against potential threats.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: Instagram: @croxroadnews.co
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ fbf0e434:e1be6a39
2025-01-16 09:40:32
@ fbf0e434:e1be6a39
2025-01-16 09:40:32Hackathon 总结
v4 Hookathon: PancakeSwap x Brevis Hackathon 吸引了116名开发者和26个项目。作为50万美元开发者计划的一部分,本次Hackathon旨在促进PancakeSwap v4生态系统的创新,重点开发使用Brevis ZK-Coprocessor的Hooks。提供了40,000美元的奖金池,以激励解决流动性管理和智能合约功能中的挑战。
Hackathon 侧重于开发健全、用户友好且无需信任的Hooks。参与者探索了动态费用结构、主动流动性管理和独享访问池等应用。开放式赛道鼓励了多样化和创新的解决方案。关键创新领域包括流动性激励机制、做市机器人和身份验证池。
总体而言,Hackathon提升了PancakeSwap v4平台上的参与度和开发,获奖者于2023年10月24日公布。通过工作坊和资源促进了社区学习,推进了开发者之间的技术讨论和协作。
Hackathon 获奖者
1. Smart Liquidity Hook (Stable) - 该项目优化了稳定币对的流动性提供者奖励,使其能够同时从流动性提供和借贷中获利。
奖金: $12,000
2. OG Boost - 通过根据其他AMM的交换费按比例分配奖励来支持激励提供者,并在增加流动性时存储LP头寸。
奖金: $10,000
3. Superfluid Swapper - 利用零知识证明技术和市场分析形成自适应流动性池系统。
奖金: $8,000
4. VWAP Dynamic Fee Hook - 根据其对成交量加权平均价格(VWAP)的影响调整交换费,创造了对流动性提供者、交换者和PancakeSwap生态系统有益的反馈回路。
奖金: $6,000
5. PADO Hook - 使用链上和链下数据预言机验证用户交易证明,增强了精准度和隐私性以实现有效的用户目标定位。
奖金: $4,000
欲获取更多信息,请访问DoraHacks查看所有项目。
关于组织者:
PancakeSwap
PancakeSwap是一个领先的多链去中心化交易所(DEX),支持包括以太坊、BNB Chain和Polygon zkEVM等区块链的无缝交易。自2020年推出以来,PancakeSwap 已实现8000亿美元的总交易量,并拥有20亿美元的锁定流动性。拥有超过200万活跃用户,其低费用和用户友好的界面得到了广泛认可。该平台的重点是提供一个灵活的加密生态系统交易体验,同时培育一个强大而充满活力的社区。
-
 @ 8d34bd24:414be32b
2025-01-19 23:33:36
@ 8d34bd24:414be32b
2025-01-19 23:33:36I have a teenaged son with Down Syndrome. He likes telling me he is all grown up despite having the maturity and understanding of a 3rd or 4th grader. He does not like being corrected and his newest response to correction is to hold up his hand making a talking hand motion. Whenever he is having this reaction, he isn’t listening and isn’t learning and more often than not ends up harming himself.
Today I sat down with him and discussed some Bible verses related to wisdom and correction in an attempt to explain why this behavior was only hurting himself. (Due to his immaturity, logic and facts don’t always work.)
Afterwards, I thought that all of us adults could probably use this same lesson. We don’t like being corrected by the Bible, the Holy Spirit, and definitely not by other Christians. It takes a lot of maturity to actually seek out correction, but that is what we are called to do.
He whose ear listens to the life-giving reproof\ Will dwell among the wise. (Proverbs 15:31)
If we want to be wise, we have to listen to “life-giving reproof.” Where can we get this “life-giving reproof?” Obviously the Bible gives it, but also mature Christians can give us “life-giving reproof.” A wise person will always listen and evaluate correction from a fellow Christian, especially one who has proven to have Biblical knowledge and wisdom. This doesn’t mean we will take their advice 100% of the time. It must be judged by the truth in the Bible, but it should be honestly considered. Even the greatest theologians have at least one point of error. If we fail to listen to correction and evaluate it biblically, we can be more easily led astray.
He who neglects discipline despises himself,\ But he who listens to reproof acquires understanding. (Proverbs 15:32)
The benefit of listening to correction is acquiring understanding. The curse of not listening to correction is the harm it causes to ourselves. The harm is so great, only a fool or those who despise themselves would act this way.
The fear of the Lord is the instruction for wisdom,\ And before honor comes humility. (Proverbs 15:33)
Wisdom comes from the fear of the Lord. Fear of the Lord leads to seeking His will. Seeking His will leads us to the correction of the Bible and mature Christians. We then have to humble ourselves and look at our mistakes and failures. We all want to think of ourselves as good, honest, and wise, but we all do bad things, tell lies, and act foolishly. The only way to fix these (and only after repenting, trusting Jesus as Savior, and submitting to His will) is to honestly assess our own failings — whether foolish, uninformed, or willful. It takes a lot of humility to fully do.
As an employer, the one trait that I can’t stand in an employee is a person who can’t or won’t admit any mistakes. We all make mistakes. A person who wants to learn can be taught. A person, who refuses to admit making any mistakes and who always blames someone else, is untrainable.
Sometimes I wonder if God feels the same way with us because we refuse to admit our failings.
Yet they did not listen or incline their ears, but stiffened their necks in order not to listen or take correction. (Jeremiah 17:23)
We always need to listen to God. The three main ways are to read the Bible, to seek wise council, and to pray for leading. When we choose to seek council and prayer, we still need to check the answers given against the unchanging truth in the Bible.
When we refuse to read the Bible, we are not listening to God. Although there are definitely some things in the Bible that are confusing and not immediately clear, the primary tenants in the Bible are readily understandable by even a young child. Sometimes I wonder if the reason people don’t read their Bible and say it is too confusing is because they don’t like what they are reading. It is “confusing” because God is telling us what we don’t want to hear. It is “confusing” because God is telling us what we don’t want to do. If we actually read and understand, it will mean we will have to make changes to our thoughts and actions.
It is better to listen to the rebuke of a wise man\ Than for one to listen to the song of fools. (Ecclesiastes 7:5)
We need to remember, both as the giver and receiver of a rebuke, that the truth and God’s word are useful for wisdom. Biblical correction is a loving action that is for the good of the receiver of correction. It should be given in a loving manner and received in a loving manner. We may want to “listen to the song of fools,” but we should seek “he rebuke of a wise man.”
When I was a young Christian in college, I sometimes went to a tiny church in my college town and sometimes went to a huge church in my hometown. The large church had a large Sunday school group taught by a man who taught me to love exhortation. When ever I hear the word “exhortation,” I think of him. Exhortation is a mix of correction and encouragement.
When I first started attending the Sunday school, I avoided the teacher. He didn’t lecture. He asked questions. He asked uncomfortable questions. They weren’t uncomfortable because they were inappropriate. They were uncomfortable because the answers to these questions required a change in world view, a change in thought, or a change in actions. He led us to the truth without lecturing about the truth. By helping us to find the truth by ourselves (through the Bible), the truth became a part of us. We knew what we believed and why, so were not easily led astray.
For months, I’d sit far away from him and try to hide, so I wouldn’t get the uncomfortable questions. Over time, after being asked some of these questions, I saw how they led me to the truth. I changed from hiding from him, to seeking him out. I went from trying to avoid being questioned and challenged in my beliefs to seeking out the correction because it helped me grow in my faith, discover the truth (not my truth), and grow closer to God.
At this point, I can’t even remember my teacher’s name, but I will never forget or stop being thankful for the things I was taught in that Sunday school class, the greatest of all being to seek the truth and never fear correction.
I decided to end my post with a passage from Psalm 119 about how we should love God’s word, the truth, wisdom, His commandments, and His corrections. The problem was narrowing it down. I’ve included one section, but would recommend reading all of Psalm 119. Read this passage considering what it says about what our love of learning about God and His commands should be.
Mem.\ O how I love Your law!\ It is my meditation all the day.\ Your commandments make me wiser than my enemies,\ For they are ever mine.\ I have more insight than all my teachers,\ For Your testimonies are my meditation.\ I understand more than the aged,\ Because I have observed Your precepts.\ I have restrained my feet from every evil way,\ That I may keep Your word.\ I have not turned aside from Your ordinances,\ For You Yourself have taught me.\ How sweet are Your words to my taste!\ Yes, sweeter than honey to my mouth!\ From Your precepts I get understanding;\ Therefore I hate every false way. (Psalm 119:97-104)
Trust Jesus.
-
 @ 2e8970de:63345c7a
2025-01-20 18:49:27
@ 2e8970de:63345c7a
2025-01-20 18:49:27Don't pretend you didn't notice. There is not a stable thought for longer than 3 sentences. Even if you like Trump you can't tell me that this looks good, be honest.
CNN: https://www.youtube.com/watch?v=BRnW4m6y97E&ab_channel=CNN
Fox News: https://www.youtube.com/watch?v=mu2S53EO4m0&ab_channel=FoxNews
originally posted at https://stacker.news/items/857645
-
 @ ed84ce10:cccf4c2a
2025-01-16 09:21:55
@ ed84ce10:cccf4c2a
2025-01-16 09:21:55Hackathon Summary
The v4 Hookathon: PancakeSwap x Brevis Hackathon featured 116 developers and 26 projects. As part of the $500K Developer Program, the hackathon aimed to foster innovation within the PancakeSwap v4 ecosystem, emphasizing the development of Hooks using the Brevis ZK-Coprocessor. A $40,000 prize pool was offered to incentivize solutions targeting challenges in liquidity management and smart contract functionalities.
The hackathon focused on developing robust, user-friendly, and trustless Hooks. Participants explored applications such as dynamic fee structures, active liquidity management, and exclusive-access pools. The open track format encouraged diverse and creative solutions. Key innovation areas included mechanisms for liquidity incentivization, market-making bots, and identity-verified pools.
Overall, the hackathon increased engagement and development on the PancakeSwap v4 platform, with winners announced on October 24, 2023. It facilitated community learning through workshops and resources, advancing technical discussions and collaboration among developers.
Hackathon Winners
1. Smart Liquidity Hook (Stable) - This project optimizes rewards for Liquidity Providers in stablecoin pairs, enabling concurrent profit from both liquidity provision and lending.
Prize: $12,000
2. OG Boost - It supports Incentive Providers by allocating rewards proportionally based on swap fees from other AMMs, storing LP positions as liquidity is added.
Prize: $10,000
3. Superfluid Swapper - Utilizes zero-knowledge proof technology and market analysis to form an adaptive liquidity pool system.
Prize: $8,000
4. VWAP Dynamic Fee Hook - Adjusts swap fees according to their influence on the Volume Weighted Average Price (VWAP), creating a beneficial feedback loop for Liquidity Providers, Swappers, and the PancakeSwap ecosystem.
Prize: $6,000
5. PADO Hook - Employs on-chain and off-chain data oracles to validate user transaction proofs, enhancing accuracy and privacy for effective user targeting.
Prize: $4,000
For further information, view all projects at DoraHacks.
About the Organizer
PancakeSwap
PancakeSwap is a leading multichain decentralized exchange (DEX), facilitating seamless transactions across blockchains, including Ethereum, BNB Chain, and Polygon zkEVM. Since its launch in 2020, PancakeSwap has achieved $800 billion in total trading volume and maintains $2 billion in locked liquidity. It serves over 2 million active users, recognized for its low fees and user-friendly interface. The platform's primary focus is on providing a versatile trading experience within the crypto ecosystem while fostering a robust and vibrant community.
-
 @ 16d11430:61640947
2025-01-19 22:19:00
@ 16d11430:61640947
2025-01-19 22:19:00Welcome, intrepid traveler, to the uncharted territory of the mind! This guide draws from the greatest explorers, philosophers, and scientists who dared to map the mysteries of inner space. Pack your curiosity, buckle up, and prepare for a journey through the vast landscapes of consciousness, perception, and human potential.
Chapter 1: Know Thy Mind (Before It Knows You)
Key References: "Incognito" by David Eagleman, "The Power of Now" by Eckhart Tolle
The first rule of mind travel: most of what happens in your brain is unconscious. Your mind is like an iceberg—only the tip is visible (your conscious thoughts). Beneath lies a vast network of automatic processes shaping your perceptions and decisions.
Tips for Hitchhikers:
Pause and Observe: Cultivate mindfulness to slow the chatter of the conscious mind and observe the silent work of the subconscious.
Live in the Now: As Tolle advises, consciousness thrives in the present. The past is a memory, and the future is a projection—neither exists outside your mind.
Chapter 2: The Art of Inner Travel
Key References: "The Mind Illuminated" by John Yates, "The Doors of Perception" by Aldous Huxley
Traveling inward requires tools, and meditation is the universal passport. It trains your attention, opens doors to altered states of awareness, and reveals the boundless nature of your mind.
Tips for Hitchhikers:
Follow the Breath: Start simple. Focus on the rhythm of your breathing. This anchors you to the present and quiets mental noise.
Explore Altered States: As Huxley discovered, substances like psychedelics (when used responsibly) or profound meditation can dissolve mental barriers, revealing the infinite.
Chapter 3: Habitual Programming
Key References: "Atomic Habits" by James Clear, "Superhuman by Habit" by Tynan
Your mind is a creature of habit. Over time, these habits carve neural pathways, shaping your behavior. The good news? You can rewrite these programs.
Tips for Hitchhikers:
Small Changes, Big Impact: Focus on small, consistent habits. Tiny tweaks lead to massive shifts in your mental landscape.
Hack Feedback Loops: Celebrate victories and reflect on failures. Every action trains your brain for future behavior.
Chapter 4: The Flow State – Consciousness on Turbo Drive
Key References: "Stealing Fire" by Steven Kotler, "The Inner Game of Tennis" by W. Timothy Gallwey
Flow is the ultimate ride—effortless, joyful immersion where you lose yourself in the task. It’s the mind’s cheat code for peak performance and creativity.
Tips for Hitchhikers:
Find the Edge: Engage in activities slightly beyond your skill level. Flow lives in the challenge.
Eliminate Distractions: Turn off notifications, declutter your space, and give your full attention to the task.
Chapter 5: Neuroplasticity – Rewiring the Inner Highway
Key References: "The Brain That Changes Itself" by Norman Doidge
Your brain is not static; it’s a living, evolving organ capable of change. Neuroplasticity means that thoughts and actions can reshape your mental circuitry.
Tips for Hitchhikers:
Practice Makes Permanent: Repetition strengthens neural connections. What you focus on grows stronger.
Challenge the Mind: Learn a new skill, speak a new language, or solve puzzles to keep your brain adaptable.
Chapter 6: Consciousness and the Cosmos
Key References: "Zen and the Art of Motorcycle Maintenance" by Robert M. Pirsig, "Dune" by Frank Herbert
Consciousness doesn’t exist in isolation—it’s a dance with the external world. Whether through Zen-like awareness or understanding the interconnectedness of all things, your journey is both inward and outward.
Tips for Hitchhikers:
Seek Quality: Pirsig describes quality as the intersection of science and art. Find meaning in the smallest details.
Embrace Interdependence: Like Herbert’s vision in Dune, see yourself as part of a larger system, from the microscopic to the cosmic.
Chapter 7: Altered Perception – The Mind's Infinite Dimensions
Key References: "VALIS" by Philip K. Dick, "How to Change Your Mind" by Michael Pollan
Reality is what your brain perceives it to be, but perception can be altered. Explore, but tread carefully.
Tips for Hitchhikers:
Question Reality: Ask yourself: Is what I perceive objective truth or the brain’s best guess?
Expand Carefully: Use Pollan’s guide for safe and structured exploration of altered states.
Chapter 8: Superconsciousness – Becoming More Than You Are
Key References: "Becoming Supernatural" by Dr. Joe Dispenza
The ultimate destination for hitchhikers is unlocking the superconscious—a state where you transcend your limitations and become the architect of your reality.
Tips for Hitchhikers:
Visualization: Envision the future you desire. Your brain rewires itself to make this vision a reality.
Heart-Brain Coherence: Sync emotional and mental states for profound inner balance.
Final Thoughts: Don't Panic (and Keep Exploring!)
Consciousness is the greatest mystery of the universe—complex, vast, and thrilling. Treat every moment as an opportunity for growth and self-discovery. The Hitchhiker’s Guide to Consciousness doesn’t offer all the answers, but it does remind you to keep asking the right questions.
And remember: the mind is infinite, and so are you. Safe travels, fellow hitchhiker!
-
 @ b8851a06:9b120ba1
2025-01-19 22:05:55
@ b8851a06:9b120ba1
2025-01-19 22:05:55A TALE OF RESILIENCE
Nine years ago today, The Washington Post declared "R.I.P. Bitcoin" when the cryptocurrency traded at $380. Fast forward to January 19, 2025, and Bitcoin trades at $104,803, representing a staggering 27,500% increase since that infamous obituary.
The Numbers Tell the Story
🔘 Bitcoin has been declared dead 477 times since its inception
🔘 2023 saw only 8 death notices, a decade-low
🔘 2024 recorded just 2 death declarations, compared to 124 in 2017
From Mockery to Mainstream
The transformation has been remarkable. When the Washington Post published its obituary, Bitcoin was dismissed as a fringe technology. Today, it's embraced by financial giants like BlackRock and Fidelity. The price history tells an compelling story.
The Future Outlook
Despite past skepticism, institutional analysts now project ambitious targets. Galaxy Digital predicts Bitcoin could exceed $150,000 in the first half of 2025. This represents a dramatic shift from the days when Nobel laureates and banking executives routinely dismissed Bitcoin as worthless.
A Lesson in Resilience
The premature death notice serves as a powerful reminder about the dangers of dismissing innovative technologies. While Bitcoin faced numerous challenges since 2016, including regulatory crackdowns and market crashes, its fundamental value proposition has remained intact. The declining frequency of "Bitcoin obituaries" suggests that even its harshest critics are beginning to acknowledge its staying power.
There is no second best, and it’s going to millions.
-
 @ a012dc82:6458a70d
2025-01-16 06:13:16
@ a012dc82:6458a70d
2025-01-16 06:13:16Table Of Content
-
A Mysterious 911 Call
-
The Investigation Begins
-
Zhong's Lavish Lifestyle
-
The Silk Road Connection
-
The Confrontation
-
The Shocking Revelation
-
The Verdict
-
Conclusion
-
FAQ
The world of cryptocurrency is filled with tales of overnight millionaires, innovative technology, and unfortunately, crime. One such tale that intertwines all these elements is that of Jimmy Zhong. From being a developer in the early days of Bitcoin to becoming one of its biggest thieves, Zhong's story is a roller-coaster ride that sheds light on the darker corners of the crypto universe. Here's a deeper dive into his intriguing journey.
A Mysterious 911 Call
In the college town of Athens, Georgia, the police department is accustomed to handling typical college town crimes. However, on the night of March 13, 2019, they received a call that was anything but ordinary. Jimmy Zhong, a 28-year-old known for his partying habits, was on the line, but not for reasons one might expect. Distressed and panicked, he reported a significant theft of cryptocurrency from his residence. This call, seemingly just another crime report, would soon unravel a web of deceit and expose a decade-long mystery surrounding one of the most significant crypto crimes ever committed.
The Investigation Begins
With the local police initially stumped by the intricacies of the crypto world, Zhong sought external help. Enter Robin Martinelli, a private investigator with a reputation for tenacity. As she delved into the case, surveillance footage from Zhong's home revealed a potential suspect who seemed to have intimate knowledge of the premises. This discovery led Martinelli down a path that suggested the thief might be from Zhong's own circle of acquaintances or friends. The very idea was something Zhong found hard to digest, as it hinted at a betrayal from someone he trusted.
Zhong's Lavish Lifestyle
Behind the façade of a modest bungalow in Athens, Zhong led a life of luxury that raised many eyebrows. His spending habits painted the picture of a man with deep pockets. From stays at the Ritz Carlton to shopping sprees at Louis Vuitton, from driving a Tesla to owning a lake house filled with extravagant amenities, Zhong's lifestyle was nothing short of opulent. Yet, the source of his wealth remained shrouded in mystery. He often alluded to his early involvement in Bitcoin mining, suggesting he had been part of the crypto revolution since its inception in 2009.
The Silk Road Connection
Parallel to Zhong's life of luxury, IRS agents were deep into an investigation of a massive 2012 hack. This hack had seen 50,000 bitcoins stolen from Silk Road, a notorious dark web marketplace. As the years passed, the value of these stolen bitcoins skyrocketed to a staggering $3 billion. The breakthrough in the case came unexpectedly when the hacker, in a momentary lapse, transferred some of the stolen funds to a crypto exchange. The account on this exchange was registered under none other than Jimmy Zhong's name, drawing him into the crosshairs of the investigation.
The Confrontation
With growing suspicions, IRS agents, in collaboration with the local police, decided to confront Zhong. They approached him under the pretense of assisting with his reported theft, but their ulterior motive was to probe deeper into Zhong's potential involvement in the Silk Road heist. Their visit to his residence was revealing. Not only did they discover a significant amount of bitcoin on Zhong's laptop, but the manner in which Zhong operated his systems also hinted at a deep familiarity with the crypto world.
The Shocking Revelation
The deeper the authorities delved into Zhong's background, the more astonishing the revelations became. It turned out that Zhong wasn't just a casual participant in the Bitcoin community; he was an integral part of its early days. Known as an "original gangster" or OG, Zhong had contributed to Bitcoin's development in its nascent stages. This revelation was both ironic and startling. A person who had been instrumental in shaping Bitcoin had also, allegedly, become one of its most significant adversaries.
The Verdict
The culmination of the investigations saw Zhong facing charges of wire fraud. After a guilty plea, he was handed a sentence of a year and a day in federal prison. While the U.S. government managed to seize the stolen bitcoins, the original theft that led Zhong to make that fateful 911 call remains an unsolved mystery to this day.
Conclusion
The tale of Jimmy Zhong serves as a stark reminder of the complexities and ambiguities of the cryptocurrency world. It's a realm where the lines between right and wrong can often blur, and where fortunes can be made or lost in mere moments. Zhong's journey from a Bitcoin developer to a billionaire thief is a testament to the unpredictable and often tumultuous world of digital currencies.
FAQs
Who is Jimmy Zhong? Jimmy Zhong is a former Bitcoin developer who later became known for his involvement in one of the biggest crypto thefts.
What was the nature of the crime? Zhong was implicated in a 2012 hack where 50,000 bitcoins were stolen from the Silk Road, a dark web marketplace.
How was he caught? A small transactional mistake led investigators to a crypto exchange account registered under Zhong's name, linking him to the stolen bitcoins.
What was his sentence? After pleading guilty to wire fraud, Zhong was sentenced to a year and a day in federal prison.
Is the original theft from Zhong's home solved? No, the theft that led Zhong to make a 911 call in 2019 remains unsolved.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: @croxroadnews
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ dd664d5e:5633d319
2025-01-07 19:57:14
@ dd664d5e:5633d319
2025-01-07 19:57:14Hodling Bitcoin does not make you a capitalist
I've noticed that Bitcoin-mindedness seems to lead some people to communistic thinking because it's a hard-limited form of capital. Marx, like most Bitcoiners, heavily discounted the possibility of economic growth or transformation changing the economy enough to undermine some minority's control of some form of capital.
What few today understand, is that many of the Dirty Capitalists of Marx's era actually agreed with him; they were just disdainful of labor and worried that the workers finding out that Marxism is correct about the nature of capitalism would cause unrest. They were the original HFSP crowd.
This was the basic idea, that Marx had, and that many Bitcoiners would agree with:
Capital is strictly limited and the people that control it can keep labor from attaining any, except when their labor is necessary.
And, as we know, automation will make human labor increasingly unnecessary.
The math doesn't check out

That underlies all of the calculations of "Well, if I just grab this Bitcoin wallet and hodl for twenty years, then it will grow in value to equal half of everything in existence and then I can just buy up half the planet and rule over everyone like a god."
This is economic nonsense because it assumes that: 1) the value of all things remains static over time, 2) purchasing something with money gives you ownership of it, 3) people will always use that specific money (or any money, at all!) for all transactions, 4) there is no such thing as opportunity cost, 5) people will always value money more than any other thing, and therefore be willing to always trade it for anything else, 6) humans are passive, defenseless, and easy to rule over, 7) someone who is preoccupied with hodling an asset steadily and sharply rising in price would ever be emotionally ready to part with it.
All monies can die.
People use money for everything because it is easy, fast and cheap. If money becomes too precious or scarce, they will simply switch to using other things (as we saw with gold). Humans replace tools that aren't working well, with those that work better, and money is just another tool. Bitcoin is more divisible than gold, but that won't matter, if enough of it is held by too few.
This is why there's a natural cap on the price of a money and why human productivity in the here and now is not irrelevant or in vain.



