-
 @ 9f94e6cc:f3472946
2024-11-21 18:55:12
@ 9f94e6cc:f3472946
2024-11-21 18:55:12Der Entartungswettbewerb TikTok hat die Jugend im Griff und verbrutzelt ihre Hirne. Über Reels, den Siegeszug des Hochformats und die Regeln der Viralität.
Text: Aron Morhoff
Hollywood steckt heute in der Hosentasche. 70 Prozent aller YouTube-Inhalte werden auf mobilen Endgeräten, also Smartphones, geschaut. Instagram und TikTok sind die angesagtesten Anwendungen für junge Menschen. Es gibt sie nur noch als App, und ihr Design ist für Mobiltelefone optimiert.
Einst waren Rechner und Laptops die Tools, mit denen ins Internet gegangen wurde. Auch als das Smartphone seinen Siegeszug antrat, waren die Sehgewohnheiten noch auf das Querformat ausgerichtet. Heute werden Rechner fast nur noch zum Arbeiten verwendet. Das Berieseln, die Unterhaltung, das passive Konsumieren hat sich vollständig auf die iPhones und Samsungs dieser Welt verlagert. Das Telefon hat den aufrechten Gang angenommen, kaum einer mehr hält sein Gerät waagerecht.
Homo Digitalis Erectus
Die Welt steht also Kopf. Die Form eines Mediums hat Einfluss auf den Inhalt. Marshall McLuhan formulierte das so: Das Medium selbst ist die Botschaft. Ja mei, mag sich mancher denken, doch medienanthropologisch ist diese Entwicklung durchaus eine Betrachtung wert. Ein Querformat eignet sich besser, um Landschaften, einen Raum oder eine Gruppe abzubilden. Das Hochformat entspricht grob den menschlichen Maßen von der Hüfte bis zum Kopf. Der TikTok-Tanz ist im Smartphone-Design also schon angelegt. Das Hochformat hat die Medieninhalte unserer Zeit noch narzisstischer gemacht.
Dass wir uns durch Smartphones freizügiger und enthemmter zur Schau stellen, ist bekannt. 2013 wurde „Selfie“ vom Oxford English Dictionary zum Wort des Jahres erklärt. Selfie, Selbstporträt, Selbstdarstellung.
Neu ist der Aufwand, der heute vonnöten ist, um die Aufmerksamkeitsschwelle der todamüsierten Mediengesellschaft überhaupt noch zu durchbrechen. In beängstigender Hypnose erwischt man viele Zeitgenossen inzwischen beim Doomscrollen. Das ist der Fachbegriff für das weggetretene Endloswischen und erklärt auch den Namen „Reel“: Der Begriff, im Deutschen verwandt mit „Rolle“, beschreibt die Filmrolle, von der 24 Bilder pro Sekunde auf den Projektor gewischt oder eben abgespult werden.
Länger als drei Sekunden darf ein Kurzvideo deshalb nicht mehr gehen, ohne dass etwas Aufregendes passiert. Sonst wird das Reel aus Langeweile weggewischt. Die Welt im Dopamin-Rausch. Für den Ersteller eines Videos heißt das inzwischen: Sei der lauteste, schrillste, gestörteste Marktschreier. Das Wettrennen um die Augäpfel zwingt zu extremen Formen von Clickbait.
15 Sekunden Ruhm
Das nimmt inzwischen skurrile Formen an. Das Video „Look who I found“ von Noel Robinson (geboren 2001) war im letzten Jahr einer der erfolgreichsten deutschen TikTok-Clips. Man sieht den Deutsch-Nigerianer beim Antanzen eines karikaturartig übergewichtigen Menschen. Noel wird geschubst und fällt. Daraufhin wechselt das Lied – und der fette Mann bewegt seinen Schwabbelbauch im Takt. Noel steht wieder auf, grinst, beide tanzen gemeinsam. Das dauert 15 Sekunden. Ich rate Ihnen, sich das Video einmal anzuschauen, um die Mechanismen von TikTok zu verstehen. Achten Sie alleine darauf, wie vielen Reizen (Menschenmenge, Antanzen, Sturz, Schwabbelbauch) Sie in den ersten fünf Sekunden ausgesetzt sind. Wer schaut so was? Bis dato 220 Millionen Menschen. Das ist kapitalistische Verwertungslogik im bereits verwesten Endstadium. Adorno oder Fromm hätten am Medienzeitgeist entweder ihre Freude oder mächtig zu knabbern.
Die Internet- und Smartphoneabdeckung beträgt mittlerweile fast 100 Prozent. Das Überangebot hat die Regeln geändert. Um überhaupt gesehen zu werden, muss man heute viral gehen. Was dafür inzwischen nötig ist, spricht die niedrigsten Bedürfnisse des Menschen an: Gewalt, Ekel, Sexualisierung, Schock. Die jungen Erwachsenen, die heute auf sozialen Netzwerken den Ton angeben, haben diese Mechanismen längst verinnerlicht. Wie bewusst ihnen das ist, ist fraglich. 2024 prallt eine desaströse Bildungssituation samt fehlender Medienkompetenz auf eine egomanische Jugend, die Privatsphäre nie gekannt hat und seit Kindesbeinen alles in den Äther ballert, was es festhalten kann. Man muss kein Kulturpessimist sein, um diese degenerative Dynamik, auch in ihrer Implikation für unser Zusammenleben und das psychische Wohlergehen der Generation TikTok, als beängstigend zu bezeichnen.
Aron Morhoff studierte Medienethik und ist Absolvent der Freien Akademie für Medien & Journalismus. Frühere Stationen: RT Deutsch und Nuoviso. Heute: Stichpunkt Magazin, Manova, Milosz Matuschek und seine Liveshow "Addictive Programming".
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ ec42c765:328c0600
2024-10-16 08:08:40
@ ec42c765:328c0600
2024-10-16 08:08:40カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

カスタム絵文字の対応状況(2024/02/05)

カスタム絵文字を使うためにはカスタム絵文字に対応したクライアントを使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
対応クライアント
ここではnostterを使って説明していきます。
準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
右上のGet startedからNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。

- 右側のOptionsからBookmarkを選択

これでカスタム絵文字を使用するためのリストに登録できます。
カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
文章中に使用
- 投稿ボタンを押して投稿ウィンドウを表示
- 顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択
- : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

リアクションに使用
- 任意の投稿の顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

カスタム絵文字を探す
先述したemojitoからカスタム絵文字を探せます。
例えば任意のユーザーのページ emojito ロクヨウ から探したり、 emojito Browse all からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2024/06/30)
※漏れがあるかもしれません
各絵文字セットにあるOpen in emojitoのリンクからemojitoに飛び、使用リストに追加できます。
以上です。
次:Nostrのカスタム絵文字の作り方
Yakihonneリンク Nostrのカスタム絵文字の作り方
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
仕様
-
 @ 30e902b3:49c066b2
2024-12-14 10:12:49
@ 30e902b3:49c066b2
2024-12-14 10:12:49Llegó a mis manos en busca de ayuda para volver a sentirse joven.
Se trata de un grabador open reel Berlant Concertone 20-20 de 1955. Aquí el manual original:
https://museumofmagneticsoundrecording.org/images/R2R/Concertone20-20ManualMOMSR.pdf
https://images.app.goo.gl/NcdAaYv2HTCHVnvX9
Como se ve en la imagen no me llegó en las mejores condiciones.
Cuento con vuestra guía para conseguir los repuestos que falten y lograr dejarlo parecido a este:
https://d10j3mvrs1suex.cloudfront.net/s:bzglfiles/u/146088/fbd8aec299456da8f127cd52f7dafcd4be37331b/original/berlant-concertone-tape-recorder.jpg/!!/b%3AW1sic2l6ZSIsInBob3RvIl1d/meta%3AeyJzcmNCdWNrZXQiOiJiemdsZmlsZXMifQ%3D%3D.jpg
Pretendo iniciar con el nuevo año. Voy recopilando ideas y consejos que me compartas. Va a ser necesario restaurar los frentes, contactos, revisar la electrónica y válvulas todo en modo DIY o "a pulmón".
-
 @ a95c6243:d345522c
2024-12-13 19:30:32
@ a95c6243:d345522c
2024-12-13 19:30:32Das Betriebsklima ist das einzige Klima, \ das du selbst bestimmen kannst. \ Anonym
Eine Strategie zur Anpassung an den Klimawandel hat das deutsche Bundeskabinett diese Woche beschlossen. Da «Wetterextreme wie die immer häufiger auftretenden Hitzewellen und Starkregenereignisse» oft desaströse Auswirkungen auf Mensch und Umwelt hätten, werde eine Anpassung an die Folgen des Klimawandels immer wichtiger. «Klimaanpassungsstrategie» nennt die Regierung das.
Für die «Vorsorge vor Klimafolgen» habe man nun erstmals klare Ziele und messbare Kennzahlen festgelegt. So sei der Erfolg überprüfbar, und das solle zu einer schnelleren Bewältigung der Folgen führen. Dass sich hinter dem Begriff Klimafolgen nicht Folgen des Klimas, sondern wohl «Folgen der globalen Erwärmung» verbergen, erklärt den Interessierten die Wikipedia. Dabei ist das mit der Erwärmung ja bekanntermaßen so eine Sache.
Die Zunahme schwerer Unwetterereignisse habe gezeigt, so das Ministerium, wie wichtig eine frühzeitige und effektive Warnung der Bevölkerung sei. Daher solle es eine deutliche Anhebung der Nutzerzahlen der sogenannten Nina-Warn-App geben.
Die ARD spurt wie gewohnt und setzt die Botschaft zielsicher um. Der Artikel beginnt folgendermaßen:
«Die Flut im Ahrtal war ein Schock für das ganze Land. Um künftig besser gegen Extremwetter gewappnet zu sein, hat die Bundesregierung eine neue Strategie zur Klimaanpassung beschlossen. Die Warn-App Nina spielt eine zentrale Rolle. Der Bund will die Menschen in Deutschland besser vor Extremwetter-Ereignissen warnen und dafür die Reichweite der Warn-App Nina deutlich erhöhen.»
Die Kommunen würden bei ihren «Klimaanpassungsmaßnahmen» vom Zentrum KlimaAnpassung unterstützt, schreibt das Umweltministerium. Mit dessen Aufbau wurden das Deutsche Institut für Urbanistik gGmbH, welches sich stark für Smart City-Projekte engagiert, und die Adelphi Consult GmbH beauftragt.
Adelphi beschreibt sich selbst als «Europas führender Think-and-Do-Tank und eine unabhängige Beratung für Klima, Umwelt und Entwicklung». Sie seien «global vernetzte Strateg*innen und weltverbessernde Berater*innen» und als «Vorreiter der sozial-ökologischen Transformation» sei man mit dem Deutschen Nachhaltigkeitspreis ausgezeichnet worden, welcher sich an den Zielen der Agenda 2030 orientiere.
Über die Warn-App mit dem niedlichen Namen Nina, die möglichst jeder auf seinem Smartphone installieren soll, informiert das Bundesamt für Bevölkerungsschutz und Katastrophenhilfe (BBK). Gewarnt wird nicht nur vor Extrem-Wetterereignissen, sondern zum Beispiel auch vor Waffengewalt und Angriffen, Strom- und anderen Versorgungsausfällen oder Krankheitserregern. Wenn man die Kategorie Gefahreninformation wählt, erhält man eine Dosis von ungefähr zwei Benachrichtigungen pro Woche.
Beim BBK erfahren wir auch einiges über die empfohlenen Systemeinstellungen für Nina. Der Benutzer möge zum Beispiel den Zugriff auf die Standortdaten «immer zulassen», und zwar mit aktivierter Funktion «genauen Standort verwenden». Die Datennutzung solle unbeschränkt sein, auch im Hintergrund. Außerdem sei die uneingeschränkte Akkunutzung zu aktivieren, der Energiesparmodus auszuschalten und das Stoppen der App-Aktivität bei Nichtnutzung zu unterbinden.
Dass man so dramatische Ereignisse wie damals im Ahrtal auch anders bewerten kann als Regierungen und Systemmedien, hat meine Kollegin Wiltrud Schwetje anhand der Tragödie im spanischen Valencia gezeigt. Das Stichwort «Agenda 2030» taucht dabei in einem Kontext auf, der wenig mit Nachhaltigkeitspreisen zu tun hat.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a012dc82:6458a70d
2024-12-14 09:42:15
@ a012dc82:6458a70d
2024-12-14 09:42:15Table Of Content
-
The Birth of Tokenized Bitcoin
-
How Does Tokenized Bitcoin Work?
-
The Advantages of tBTC Over Traditional Bitcoin
-
Expanding the Utility of Bitcoin
-
The Future of Tokenized Bitcoin
-
Conclusion
-
FAQ
In the ever-evolving world of cryptocurrency, Bitcoin remains the gold standard. However, its traditional form has faced challenges, especially when it comes to transaction speeds and adaptability. Enter the tokenized version of Bitcoin on Solana, a solution that promises to address these issues. But what exactly is this new tokenized Bitcoin, and why is it causing such a stir in the crypto community? Let's dive in.
The Birth of Tokenized Bitcoin
Bitcoin, with its unmatched popularity, has always been at the forefront of the cryptocurrency industry. Yet, its primary blockchain has been criticized for being slow in adopting new features, making smaller transactions both time-consuming and expensive. To address these challenges, the Threshold Network introduced the first tokenized version of Bitcoin, known as tBTC, on the Solana blockchain. This innovation aims to bridge the gap between Bitcoin's value and its transactional limitations.
How Does Tokenized Bitcoin Work?
The concept might sound complex, but it's rooted in simplicity. Imagine you have a physical gold bar but find it cumbersome to use in daily transactions. Instead, you get a certificate (or token) representing that gold bar, which you can easily trade or use. Similarly, when someone mints tBTC on Solana, they send their Bitcoin to be "wrapped". This wrapping process involves a decentralized review where the crypto is held in a special wallet. This wallet's authenticity is validated by a majority of people operating nodes on the Threshold Network. Once validated, you receive tBTC equivalent to the Bitcoin you wrapped, which can be used seamlessly on the Solana blockchain.
The Advantages of tBTC Over Traditional Bitcoin
Traditional Bitcoin has its limitations, especially when it comes to smart contracts. Even with advancements like the Lightning Network, these limitations persist. tBTC, on the other hand, offers a more flexible approach. It acts as a proof of ownership, allowing users to prove they possess a certain amount of Bitcoin. Moreover, if they ever wish to revert to their original Bitcoin, they can easily trade their tBTC to claim it back. This process ensures security, as a significant majority of validators must approve the transaction, minimizing the risk of malicious intent.
Expanding the Utility of Bitcoin
One of the most exciting aspects of tBTC is its potential to revolutionize how Bitcoin is used. Traditional Bitcoin holders, if they wished to take a loan against their holdings, had to rely on centralized platforms, which came with their own set of risks. With tBTC, however, they can leverage their Bitcoin on the Solana blockchain, bypassing the limitations of the traditional Bitcoin network. This means they can take out loans, earn yields, and even use their Bitcoin in decentralized exchanges, offering a level of flexibility previously unheard of.
The Future of Tokenized Bitcoin
Tokenized Bitcoin, especially tBTC on Solana, is a groundbreaking advancement, but it's just the beginning of a broader trend. Other major blockchains, such as Ethereum, Arbitrum, Optimism, and Polygon, have also integrated this concept, showcasing the growing appeal and versatility of tokenized Bitcoin. This widespread adoption underscores the crypto community's belief in its potential, making Bitcoin more adaptable and enhancing its interoperability across different platforms.
Moreover, the rising trust in tokenized Bitcoin suggests a promising trajectory for the decentralized finance (DeFi) sector. As tokenized assets become more mainstream, platforms like Solana stand to benefit immensely, heralding a new era for the entire DeFi ecosystem. The embrace of tokenized Bitcoin is not just a win for Bitcoin itself but a testament to the evolving dynamics of the crypto world.
Conclusion
The introduction of tBTC on Solana is more than just a technological advancement; it's a testament to the crypto community's relentless pursuit of innovation. As we continue to witness the blending of traditional and modern financial systems, tokenized assets like tBTC will undoubtedly play a pivotal role in shaping the future of decentralized finance.
FAQs
What is tokenized Bitcoin? Tokenized Bitcoin, like tBTC on Solana, is a representation of Bitcoin on other blockchains, allowing for more flexibility and interoperability.
Why was tBTC introduced on Solana? tBTC was introduced to address Bitcoin's transactional limitations, making it more adaptable and efficient on platforms like Solana.
How does tokenized Bitcoin differ from traditional Bitcoin? While traditional Bitcoin has limitations with smart contracts and transaction speeds, tokenized Bitcoin offers more flexibility, especially on platforms like Solana.
Are other blockchains adopting tokenized Bitcoin? Yes, apart from Solana, blockchains like Ethereum, Arbitrum, Optimism, and Polygon have also integrated tokenized Bitcoin.
What does the rise of tokenized Bitcoin mean for the DeFi sector? The growing trust in tokenized Bitcoin suggests a promising future for the DeFi sector, with platforms like Solana leading the way in innovation and adoption.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: @croxroadnews
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research. *
-
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ a95c6243:d345522c
2024-12-06 18:21:15
@ a95c6243:d345522c
2024-12-06 18:21:15Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\ dass wir Vorteile aus ihr ziehen;\ in jedem andern hegt man den Wunsch,\ dass der Unschuldige in Schutz genommen werde.\ Jean-Jacques Rousseau
Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden.
Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen» den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen schadet der Psyche und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben Menschen getötet».
Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft. Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen Erfahrungen als Kritikerin der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit Transition News. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften».
Menschen, die aufrichtig andere schützen wollten, werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter Heinrich Habig, Bianca Witzschel und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat Transition News mehrfach berichtet (z.B. hier und hier). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie Alexander Bittner erfahren mussten.
Die eigentlich Kriminellen schützen sich derweil erfolgreich selber, nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte Verbrechen gegen die Menschheit». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn Hunter möglicherweise auch Anthony Fauci begnadigen wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte?
Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken.
Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers Robert F. Kennedy Jr. erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens Călin Georgescu, der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der Panik im Wertewesten.
In Rumänien selber gab es gerade einen Paukenschlag: Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das Tabu gebrochen, Wahlen zu verbieten, bevor sie etwas ändern können.
Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: Zensur) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2024-11-29 19:45:43
@ a95c6243:d345522c
2024-11-29 19:45:43Konsum ist Therapie.
Wolfgang JoopUmweltbewusstes Verhalten und verantwortungsvoller Konsum zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch.
Heute ist also wieder mal «Black Friday», falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich.
Warum fallen wir auf derartige Werbetricks herein und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf.
Gedankenlosigkeit und Maßlosigkeit können besonders bei der Ernährung zu ernsten Problemen führen. Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen.
Kritik am schwarzen Freitag und dem unnötigen Konsum kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch.
Die EU-Kommission lancierte 2015 den Begriff «Green Friday» im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das Pariser Abkommen unterzeichnet werden sollte.
Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt. Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des «Green New Deal» verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um Valencia dazu sagen?
Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020 eine «grüne Erholung von Covid-19, um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort.
Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben.
Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie «verantwortungsvolle Risikobereitschaft» unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2024-11-08 20:02:32
@ a95c6243:d345522c
2024-11-08 20:02:32Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister EckhartSchwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung, der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
Mit einem bemerkenswerten Timing hat die deutsche Regierungskoalition am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer Selbsthypnose rund um Harris-Hype und Trump-Panik – mit teils erschreckenden Auswüchsen. Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
Das Kindergarten-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik «vorsätzlich herbeigeführt» worden seien.
Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen. Verkehrs- und Digitalminister Wissing trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit Jörg Kukies habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP, hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können. Das ging erst kürzlich aus dem diesjährigen «Freiheitsindex» hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
«Die absolute Mehrheit hat absolut die Nase voll», titelte die Bild angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat, kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei Manova. Und er kenne Friedrich Merz schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
Was also tun? Der Schweizer Verein «Losdemokratie» will eine Volksinitiative lancieren, um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
In jedem Fall wird es notwendig sein, unsere Bemühungen um Freiheit und Selbstbestimmung zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ 234035ec:edc3751d
2024-12-14 05:12:52
@ 234035ec:edc3751d
2024-12-14 05:12:52America's Fourth Fourth Turning
We can learn much from the Book "The Fourth Turning: An American Prophecy" By William Strauss and Neil Howe. The Book looks back throughout history to identify the cyclical patterns that emerge and establishes archetypes that emerges in the generations as they come of age in these different stages of history.
There are four phases (turnings) that are outlined in the book:
- The High
- The Awakening
- The Unraveling
- The Crisis
The authors identify that America is due for another fourth turning, and I would argue that we are now in the midst of America's Fourth ever fourth turning. The first three being marked by the American Revolution, the Civil War, and the Great Depression- WWII. Today we have been in an increasingly unstable financial, political, and social environment which share eery similarities to the unraveling period of the prior cycles.
I believe that this fourth turning began with the 2008 "Great Financial Crisis" and has been ongoing ever since the fed chose to engage in mass currency devaluation in order to keep the banks solvent. While these actions have delayed the inevitable larger crisis, they will not be able to avoid it. Since 2008 the money supply has grown from roughly $8 Trillion to over $20 Trillion. This massive currency dilution is reflected in increased prices across all sectors but heavily concentrated in scarce desirable assets. As National debt continues to rise and interest expenses balloon, the only way out for the US dollar is massive inflation.
The issue with continued inflation is that it leads to massive societal suffering and unrest. At 2% inflation most individuals aren't aware that they are being stolen from, but as inflation rates start to stick above 10% people start to realize what is really going on. History tells us that as currencies enter into hyper-inflation, the societal fabric begins to fall apart. One does not have to be an anthropologist to look around and realize the massive cultural shifts that we have seen since moving to a fiat standard in 1971 and much faster ever since 2008.
I find it very profound that at the same time that the global financial system began showing cracks, Satoshi Nakamoto introduced the solution to the world. It feels as though this fourth turning is centered around technological innovation in computing, as well as the collapse of an outdated and corrupt financial system. Bitcoin exists at the perfect intersection of these two by utilizing cryptography to empower people to exit the corrupt system and begin to build a superior one on sound foundation. If the crisis of this great fourth turning is centered around the sovereign debt crisis, than Bitcoin becomes the clear answer.
Thriving In The Chaos
Being Born in 2001 I do not have much memory of a pre-2008 world. Being only 7 years old at the time I did not fully grasp the significance of what was going on, but my life has been impacted by it nonetheless.
When the central bank chooses to hold interest rates artificially low, they are effectively driving money into more and more places where it shouldn't actually be. This is usually described as a bubble, which then bursts leaving many financially ruined. Accept for those who the central bank then chooses to bail out by diluting the purchasing power of all the savers.
Much of the Millenial and Gen Z generations feel that they will never reach financial security or be able own a home and retire at a reasonable age. Many of them are saddled with large student loans, credit card debt, and car loans. While much of this is due to personal decision making, we exist in a system today that is designed to extract as much value as possible from each citizen. If you were to take out a loan to go to school, get a job, a mortgage, and a car payment, and used a savings account, you would never become financially free.
People my age have become increasingly unsatisfied with the way that things are, which is why I am so hopeful for a brighter future. While most aren't quite aware of what the true heart of the issue is, they feel that something is deeply wrong. I believe that Bitcoin will be the catalyst for the masses to wake up and stop funding the current system.
Those that lead the way into a new frontier during these fourth turnings come out on the other side in positions of great respect and power. While these next few years will likely difficult, there will be massive opportunity for those who are bold enough to stand for their beliefs and work to propagate them.
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ 16d11430:61640947
2024-12-14 01:51:07
@ 16d11430:61640947
2024-12-14 01:51:07The trajectory of human progress is marked by seismic shifts in wealth, power, and knowledge. Over centuries, these tectonic movements have reshaped the global narrative, transitioning the spear-tip of innovation and dominance from East to West. Today, as global tensions rise and multipolarity challenges the unipolar financial order, it’s worth examining the periods of change and the forces that realigned the axis of human progress through the lens of technological and financial evolution.
- The East’s Preeminence: The Age of Soft Power and Real Assets
Period: Antiquity to 15th Century For millennia, wealth and knowledge flowed from East to West. Civilizations like India, China, and the Islamic Caliphates were centers of human progress. These regions excelled in technological innovation, financial stability (e.g., China’s early use of paper currency in the Tang Dynasty), and cultural capital.
Financial Dominance: Real assets like spices, textiles, and gold formed the backbone of trade. The Silk Road acted as a decentralized value network, with wealth flowing from resource-rich East Asia to demand-heavy Europe.
Knowledge Arbitrage: Eastern empires perfected systems of governance, mathematics, and astronomy. Indian numerals became the foundation of global mathematics, while Chinese engineering inspired innovations in navigation.
Yet, despite its dominance, the East’s wealth was tied to a fragile, physical-based trade network, leaving it vulnerable to external shocks.
- The Renaissance and the Maritime Arbitrage of Knowledge
Period: 15th–17th Century The fall of Constantinople in 1453 was a geopolitical rug pull, severing Europe’s access to Eastern trade routes. In response, European nations innovated maritime trade routes, circumventing old supply chains. This era saw the financialization of exploration through state-backed joint-stock companies like the Dutch East India Company (VOC), a precursor to modern equity markets.
Leverage and Liquidity: The VOC issued the first publicly traded shares, creating a new mechanism for wealth generation: equity capital. Wealth shifted west as Europe commoditized Eastern resources at unprecedented scale.
Techno-Geopolitical Advantage: Innovations in shipbuilding, navigation, and weaponry gave European powers a first-mover advantage in global trade, tipping the economic balance.
Europe began consolidating wealth and influence, laying the groundwork for the first financial superpowers.
- The Industrial Revolution: Scaling Innovation and Debt Capital
Period: 18th–19th Century The Industrial Revolution was the ultimate shift from real to synthetic wealth creation. Britain’s coal-powered factories and mechanized production allowed for the exponential scaling of goods and services, bypassing the labor-intensive economies of the East.
Debt as an Asset Class: The Bank of England pioneered modern public finance, using national debt to fund wars and infrastructure. Debt markets became a weapon of geopolitical influence, solidifying Britain’s dominance.
Data and Capital Flows: Knowledge transitioned from artisanal secrets to open-source intellectual property. The invention of the telegraph—a precursor to modern networks—centralized information flow in the West.
During this period, colonies were repurposed as raw material hubs, while the West monetized finished goods. The East’s economies, trapped in colonial dependency, were stripped of agency.
- The Dollar Standard: The West Consolidates Financial Hegemony
Period: 20th Century The world wars were financial accelerants, propelling the U.S. to global supremacy. Post-World War II, the Bretton Woods system tied global currencies to the U.S. dollar, itself pegged to gold. By 1971, the gold standard was abandoned, and fiat-backed dollars became the world’s reserve currency—a geopolitical masterstroke.
Petrodollar Diplomacy: The U.S. engineered a system where oil, the lifeblood of modern economies, was traded exclusively in dollars. This created an artificial demand for U.S. currency, reinforcing its global dominance.
Technology Arms Race: The Cold War spurred investments in computing, satellites, and the internet. These technologies cemented the West as the epicenter of innovation, while the Eastern bloc stagnated under centralized planning.
The East, particularly China and India, entered a period of economic dormancy, while the West built the foundation for the modern financialized economy.
- The Digital Era: The Resurgence of the East and Blockchain’s Decentralization
Period: 21st Century As the 20th century ended, cracks in Western hegemony began to appear. The East, particularly China, leveraged its demographic dividend and state-driven capitalism to re-enter the global stage. Simultaneously, blockchain and decentralized finance (DeFi) began eroding trust in centralized financial systems.
China’s Belt and Road Initiative (BRI): A modern Silk Road, the BRI channels liquidity and infrastructure investment into developing nations, countering Western-led institutions like the IMF and World Bank.
Bitcoin and DeFi: Bitcoin, as a decentralized reserve asset, challenges fiat’s monopoly on monetary sovereignty. Decentralized systems offer an alternative to SWIFT-based cross-border payments, reducing reliance on Western financial networks.
The U.S. and its allies now face a multipolar world where traditional financial instruments are being disrupted by distributed ledger technology and Eastern economic strategies.
- Geopolitical Tensions: A New Cold War of Data and Energy
The current geopolitical climate is defined by competition over intangible assets: data, semiconductors, and clean energy technologies. The East and West are locked in a race to dominate artificial intelligence, quantum computing, and blockchain infrastructure.
Data Sovereignty: Nations are weaponizing data localization laws and AI to gain competitive edges in surveillance capitalism and defense.
Energy Markets: The West’s pivot to green energy and the East’s dominance in rare earth minerals create asymmetric dependencies.
The financial spear-tip of human progress is no longer unilateral. The West’s financial systems, underpinned by debt and derivatives, face a fundamental challenge from the East’s state-capitalist model and decentralized digital assets.
Conclusion: The Dawn of a Decentralized World
The historical narrative of human progress has been a pendulum swing between centralized and decentralized systems. While the East dominated through physical assets and trade, the West shifted to financialization and industrial scale. Now, we stand on the precipice of another transformation: a decentralized financial and technological order where power is no longer tied to geography but to networks.
The tip of the spear of human progress is no longer a single entity but a fragmented, multi-nodal system. Whether this leads to collaboration or conflict depends on how the world navigates this unprecedented inflection point.
-
 @ c1e6505c:02b3157e
2024-12-14 01:50:48
@ c1e6505c:02b3157e
2024-12-14 01:50:48Test post coming from stacker.news
originally posted at https://stacker.news/items/808769
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ 82883e29:dab2ff8c
2024-12-13 23:36:16
@ 82883e29:dab2ff8c
2024-12-13 23:36:16Hello, readers!
My name is Muju. I am a writer, thinker, Bitcoin advocate, and humanist activist with a passion for challenging the status quo and exploring the complexities of our world. Over the years, I've written extensively on politics, human rights, Bitcoin, and the fascinating intersections of culture and technology through my blog, Unintuitive Discourse.
Today, I take an exciting step forward by beginning to publish my work on Nostr, a platform that aligns with my values of free speech and decentralization.
Nostr’s censorship-resistant architecture ensures that my thoughts and ideas can be preserved permanently, free from interference or erasure. This move reflects my commitment to creating a lasting record of my work—a digital footprint that stands against the tides of suppression.
Unintuitive Discourse is a product of my journey: my life as an autodidact, my experiences as a political refugee, and my relentless pursuit of understanding the world through a humanist lens. By leveraging Nostr, I aim to secure a permanent home for my ideas, making them accessible to those who seek to question, learn, and grow.
If you’re reading this, welcome to the beginning of something enduring. Join me as I continue to write, reflect, and share thoughts that I hope will inspire meaningful conversations for years to come.
Here's to a future where ideas thrive without limits—my contribution to realizing a truly decentralized internet where knowledge flows freely and voices cannot be silenced.
-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。
2024年08月13日更新:
修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
准备工具
- Ntfy服务
- Google Script
- Google Sheets
操作步骤
- 在Ntfy后台账号,设置访问令牌。

- 添加订阅主题。

- 进入Google Sheets创建一个表格.记住id,如下图:

- 进入Google Script创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) { var threadId = thread.getId();
if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); }}); }
function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; }
var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true };
try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } }
function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column }
function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); }
function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues(); var rowsToDelete = [];
data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } });
// 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); }
```
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:

结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
-
 @ 4b7c4ee3:8cd5ed4d
2024-12-13 23:20:50
@ 4b7c4ee3:8cd5ed4d
2024-12-13 23:20:50Is this thing on?
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ 6bae33c8:607272e8
2024-12-13 19:20:41
@ 6bae33c8:607272e8
2024-12-13 19:20:41I blew it last week, going 2-3. I shouldn’t have taken the Jets, I knew it was a mistake. I don’t care how right the side looked either, the Jets are cursed. I liked the Rams and Panthers, but didn’t pull the trigger. Too much second guessing and overthinking. Either you have a model and stick to its outputs, or you go on feel, and you trust yourself 100 percent. Don’t question, just act. If you make an error, you can reassess next week, incorporate it into your process.
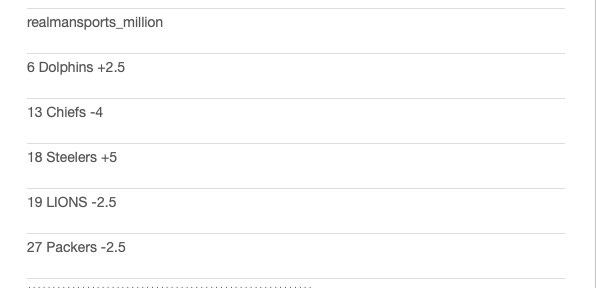 Dolphins +2.5 at Texans — I’m sure this is the game the Texans turn it around, but as someone whose otherwise solid Primetime team was derailed by CJ Stroud and the bankrupt passing game, I took the Dolphins and the points.
Dolphins +2.5 at Texans — I’m sure this is the game the Texans turn it around, but as someone whose otherwise solid Primetime team was derailed by CJ Stroud and the bankrupt passing game, I took the Dolphins and the points.Chiefs -4 at Browns — I know the Chiefs are life and death with everyone, but this seems too small. Jameis Winston will turn it over a few times against this defense, and the Chiefs will move up and down the field.
Steelers +5 at Eagles — The Eagles are good against bad teams, but the Steelers are a rock defensively, and I think they’ll hang.
Lions -2.5 vs Bills — I had this line at four. The Lions are the better team, even with the banged-up defense.
Packers -2.5 at Seahawks — The Seahawks have been good of late, but the Packers went toe to toe with the Lions and had a full 10 days off. I think they win and cover.
-
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ 705605d9:b4324038
2024-12-13 17:42:06
@ 705605d9:b4324038
2024-12-13 17:42:06Через две недели известный музыкант IGR посетит Горноправдинск. Об этом он заявил в своём телеграм-канале.
Игорь "IGR" Романов пишет хип-хоп и трэп. В своём жанре у музыканта уже есть имя, и мнения о нём у поклонников хип-хопа сильно различаются — споры вызывают как откровенно провокационные тексты артиста, так и его личная жизнь. Напомним, несколькими месяцами ранее IGR был задержан силовиками как участник несогласованного митинга в Санкт-Петербурге. Музыкант высказал свою радикальную позицию и был задержан за неповиновение сотруднику полиции.
"Его музыка заставляет задуматься, но иногда кажется, что он просто провоцирует ради провокации", — делится мнением наша читательница Ольга, которая не уверена, стоит ли идти на концерт. "Я люблю музыку, но некоторые его песни слишком откровенны", — добавляет она.
"IGR— это голос поколения! Его тексты отражают наши мысли и чувства, даже если они вызывают споры", — считает 17-летний Дмитрий. Он купил билет в первый же день после анонса концерта и намерен приехать на концерт из Новосибирска.
Выступление пройдёт в Дворце культуры. Цены на билеты колеблются от 1800 до 8000 рублей.
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 705605d9:b4324038
2024-12-13 17:41:13
@ 705605d9:b4324038
2024-12-13 17:41:1327 октября 2040 года в Горноправдинске, небольшом, но прогрессивном посёлке Югры, состоялась презентация уникального бренда экологичной одежды. Созданная местной дизайнеркой Верой Ивановной Семёновой, эта линия одежды обещает не только красивую и стильную, но и устойчивую моду, полностью изготавливаемую из переработанных материалов. Уникальность бренда заключается в том, что модели — это исключительно женщины пожилого возраста, что делает данный проект ещё более социально значимым.

Устойчивое развитие как основа идеи
Горноправдинск давно зарекомендовал себя как местечко, где экология и устойчивое развитие стоят во главе всего. Здесь активно развиваются инициативы по переработке отходов и рациональному использованию природных ресурсов. Презентация нового бренда стала логическим продолжением этих усилий. Одежда из вторсырья не только уменьшает количество отходов, но и снижает воздействие на окружающую среду. По данным исследований, текстильная промышленность является одним из крупнейших источников загрязнения в мире. В этом контексте важно осознавать влияние, которое каждый из нас может оказать на природу, выбирая экологически чистые альтернативы.
Согласно информации от независимой экологической организации, производство ткани из вторичных материалов требует в три раза меньше воды, чем традиционные методы. Это выгодно не только для экологии, но и для экономики. Более того, использование вторичных материалов позволяет снижать углеродный след, что критически важно в условиях глобального изменения климата.
Творение как вдохновение
Вера Ивановна Семёнова — не просто дизайнер, но и активист, призывающий к переменам. Её новый бренд стал результатом многолетнего труда и экспериментов. Вера патентует уникальные технологии переработки тканей и создания новых моделей, которые одновременно сочетали в себе стиль и комфорт.

"Я хочу показать, что мода может быть не только красивой, но и умной", - говорит Вера в интервью. Она расставляет акценты на том, что её коллекция будет выходить за рамки стандартного понимания экологии. Модельный ряд включает в себя как повседневную, так и вечернюю одежду. Каждая вещь несёт в себе уникальную историю переработанного материала, а сами ткани отобраны так, чтобы гарантировать долговечность и стиль.
Открывая новые горизонты для пожилых женщин
Эти модели — не просто одежда, это символ изменений. Важным аспектом нового бренда является то, что модели — это женщины пожилого возраста. В нашем обществе часто встречается предвзятое отношение к возрасту, и многие пожилые женщины сталкиваются с трудностями в поисках работы или возможности проявить себя.
Горноправдинск стал первой площадкой, где пожилые женщины, обладая опытом и мудротой, получили возможность стать лицами модной индустрии. Этот шаг отразит новое понимание о красоте и стилю, которое не привязано к возрасту. Публика сможет увидеть, что настоящая красота исходит из внутреннего содержания, а не из стандартных шаблонов. Опросы показали, что большинство людей не воспринимает пожилых женщин как моделей. Но проект Веры Семёновой может стать началом новой эры, в которой возраст будет праздноваться, а не скрываться. Это не только проект по созданию одежды, но и социальная инициатива, ставящая вопрос о равенстве и возможностях для всех.
Модные тренды и экологическое сознание
В рамках презентации были представлены несколько моделей, каждая из которых рассказывала свою историю. Одежда создана из переработанных материалов: старых футболок, джинсов и текстиля, который больше не пригоден для использования в первоначальном виде. Каждая модель была выполнена с учетом последних модных тенденций: яркие цвета, уникальные принты и современные силуэты.
Важным аспектом новой коллекции является также то, что для её создания использовались умные технологии, позволяющие минимизировать отходы. Вера указала на то, что каждое изделие было разработано с использованием принципа zero waste, что подразумевает полное отсутствие отходов. Это значительно понижает стоимость конечного продукта и делает его доступным для широкого круга любителей моды.

Эксперты предположили, что такой подход может стать новым стандартом в модной индустрии, потому что он отвечает современным требованиям рынка и эволюционным ожиданиям покупателей. Люди всё больше начинают заботиться о том, каким образом производится одежда, и предпочитают brands, поддерживающие идеалы устойчивого развития.
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 705605d9:b4324038
2024-12-13 17:39:37
@ 705605d9:b4324038
2024-12-13 17:39:37Автор: Павел Густой, который дважды поперхнулся молоком, услышав слово «причал».
Старое железо и новая эпоха
Двадцать лет назад набережная Горноправдинска выглядела так, как будто ее проектировал инженер, вдохновленный своей последней опохмелкой. Ржавеющая баржа, служившая причалом, стояла на месте, словно памятник бессмысленности. Жители, подходя к ней, задавались лишь одним вопросом: «А мы точно успеем до корабля, пока она не развалится?»

Но 2040-й год стал годом, когда бабушки, эти легендарные управленцы Горноправдинска, решили: хватит. Видимо, они устали, что даже жители Бобровки шутят про их набережную, называя её «Порт Стыда».
Экологичный причал и другие чудеса
Реформа была громкой, как взрыв сыроварни. Теперь вместо ржавой баржи — современный экологичный причал. Он сделан из переработанного пластика и бетона, настолько крепкого, что даже утиный десант из соседнего водохранилища не смог его повредить.

«Мы думали о будущем, о наших детях и внуках», — заявила одна из бабушек, поглаживая внушительный скипетр в виде бутылки молока. Правда, злые языки утверждают, что пластик для причала собирали в основном в Бобровке, где люди искренне надеялись, что это поможет им самим.
Набережная — теперь с развлечениями!
Но на этом бабушки не остановились. Новый причал стал центром масштабного благоустройства. Что там теперь есть?
-
Большой магазин. Под названием «Молочная правда». Говорят, что если долго смотреть на его логотип, можно разгадать секрет бабушкиных масонов.

-
Зоны отдыха. Здесь все продумано до мелочей: лавочки с подогревом для больных суставов, мусорные урны, которые цитируют Бродского, и фонтаны, работающие исключительно на сыворотке.
- Промзона. Построенная так, чтобы туристы и не поняли, что смотрят на завод. «Это арт-объект!» — гордо утверждают бабушки. На фасаде предприятия висит баннер с надписью: "От молока до металла: мы можем всё!"

Критика: куда без неё?
Конечно, реформа понравилась не всем. Некоторые горноправдинцы ворчат, что набережная слишком идеальна, что даже коровы боятся здесь пастись. Другие шутят, что вместо прогулочной зоны бабушки могли бы построить парк развлечений для жителей Бобровки, где вместо билетов продавали бы надежду.
«Это всё для туристов», — жалуются местные, стоя в очереди за молоком. В ответ бабушки молчат. Они слишком заняты, вероятно, обсуждением нового проекта: ходят слухи о запуске молочного дирижабля.
Что дальше?
Набережная Горноправдинска — это, конечно, не про корабли и причалы. Это символ, дорогие мои. Символ того, что даже в городе, где всем управляют бабушки, возможно обновление. Пусть и с долей черного юмора, пластика и неизменного молочного послевкусия.
И всё же, когда смотришь на новый причал, где люди счастливо прогуливаются под солнцем, а где-то вдалеке доносится звук загрузки молока на баржу, понимаешь: Горноправдинск в который раз доказал, что он — город контрастов.
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ 705605d9:b4324038
2024-12-13 17:38:32
@ 705605d9:b4324038
2024-12-13 17:38:32Вчера, 21 ноября, в деревне Бобровка, расположенной в одном из самых живописных уголков нашей страны, случился масштабный пожар, который уничтожил несколько домов и хозяйственных построек. Пожарные службы были оперативно направлены на место происшествия, но, несмотря на все усилия, огонь продолжал бушевать несколько часов. Установить точную причину возгорания оказалось задачей не из лёгких, однако, как стало известно, причиной пожара стала абсолютно невероятная и, на первый взгляд, абсурдная ситуация.
В деревне Бобровка местные жители утверждают, что причиной возгорания стал эксперимент с «горячей» новой разработкой – умным термосом, который, по задумке разработчиков, должен был поддерживать идеальную температуру напитков на протяжении суток. Однако, как выяснилось, термос оказался настолько «умным», что, не дождавшись своего «реального» срока эксплуатации, просто взорвался. По словам экспертов, устройство в какой-то момент решило провести «самодиагностику» и не выдержало своей собственной мощности, запустив цепную реакцию, которая привела к возгоранию.
Необычный инцидент, разумеется, сразу привлек внимание прессы, а местные жители стали активно обсуждать ситуацию, удивляясь, как такие инновации могут попасть в руки обывателей. «Когда я купила этот термос, мне казалось, что это просто удобный аксессуар для долгих прогулок с чаем. Но чтобы он так рванул, как граната, этого я не ожидала!» – рассказывает местная жительница, потерпевшая от огня.
Комментарий потерпевшего:
«Я никогда не думала, что мой любимый термос станет причиной такого бедствия. Он был подарком на день рождения, а я так гордилась им! Поставила на подоконник, чтобы чай остыл, и тут – бац! Всё вспыхнуло. Сначала я подумала, что это просто горячий чай, но когда увидела, что термос сам по себе светится, я поняла, что что-то пошло не так. Пожарные приехали быстро, но дом всё равно сгорел. Теперь я, честно говоря, боюсь пить чай в термосах, даже если они обещают быть умными!»

Местные власти заявили, что это происшествие станет поводом для пересмотра стандартов безопасности на рынке бытовых товаров. В ближайшее время планируется провести расследование и наложить запрет на использование «самодиагностирующих» устройств в бытовой сфере.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ de496884:72617b81
2023-11-20 13:54:02
@ de496884:72617b81
2023-11-20 13:54:02Hola nostriches. Hoy quiero hacer una publicación a modo de acercamiento al surgimiento de las categorías de género y feminismo. Así que si te interesa el tema haz un esfuerzo, quédate y lee hasta el final.
El «nuevo» feminismo surge en los años 60 en aquellos países desarrollados que acordaron el reconocimiento a los derechos humanos contenidos en la declaración respectiva de la ONU. Entonces, como extensión a dicho reconocimiento es que se gesta el movimiento feminista. A partir de entonces, se vuelve a plantear la relación entre naturaleza y cultura y se llega a la conclusión de que las diferencias sociales van más allá de las diferencias biológicas, lo cual tiene que ver con que hasta la satisfacción de las necesidades elementales como son la alimentación, la vivienda o el vestuario, están condicionadas por construcciones sociales.
Pues resulta que una de las primeras propuestas identificó la subordinación femenina producto de una organización patriarcal, tomando la categoría patriarcado de Max Weber. Es así como la visión de patriarcado se extendió al discurso político y académico. Sin embargo, no existía información acerca del desarrollo histórico de dicha categoría, sistematización, variaciones, etc., debido a que era algo que recién se percibía en sociedad.
Sin embargo, la misma categoría de patriarcado junto a la de relaciones de poder para explicar fenómenos sociales contemporáneos, constituye uno de los principales aportes del feminismo. Es así como han logrado primero visibilizar y luego deconstruir y desmontar una serie de patrones existentes en la cultura que hacían a la mujer subordinarse al hombre, y que estaban presentes en el sistema sexo/género.
 Imagen relativa a la lucha contra el patriarcado
Imagen relativa a la lucha contra el patriarcadoHasta ese momento, en las investigaciones de corte sociológico se podía observar un androcentrismo excesivo al dar cuenta de que el discurso científico giraba en torno al hombre como sujeto y objeto de la investigación. Incluso para muchos positivistas como el mismo Weber, los problemas relativos a las mujeres quedaban en un segundo plano y eran achacados a una supuesta pasividad en el ámbito doméstico-familiar. Dicha pasividad partía de la supuesta inferioridad biológica del género femenino.
El patriarcado entonces era una categoría vacía en sí misma, sin valor explicativo. Desde el punto de vista político pudo ser útil para la movilización pero no resistió la polémica de los críticos del feminismo ni problematizó los conflictos a ser resueltos. Pero por otro lado, un grupo de mujeres -académicas principalmente- se puso manos a la obra en una tarea más pequeña pero con mayores resultados a la larga. Se propusieron generar conocimientos sobre las condiciones de vida de la mujer, buscar en el pasado y el presente los aportes de las mujeres a la sociedad, hacerlas visibles en la historia. Es así como surgen centros académicos, ONG, proyectos, centros de estudios sobre la mujer, etc.
Convendría distinguir entonces dos posturas que acompañaron a la investigación sobre las mujeres: uno que toma como objeto de estudio a la mujer; condiciones de vida, trabajo, cultura, y otra que privilegia a la sociedad como generadora de la subordinación de las mujeres. Mientras la primera perspectiva generaba conocimiento sobre las mujeres en el estudio de las relaciones mujer-hombre y mujer-mujer, la segunda tenía una visión más holística ya que planteaba que hay que estudiar la sociedad ya que la subordinación de las mujeres es producto de la organización de esta, y que no se avanzará solamente estudiando a las mujeres, pues el estudio debe ser más amplio y en diferentes niveles, ámbitos y tiempos.
Es en esta búsqueda donde nace y se desarrolla el concepto de género como categoría social. Es así que los sistemas de género/sexo fueron entendidos como conjuntos de prácticas, símbolos, representaciones, normas y valores sociales que las sociedades construyen a partir de la diferencia anatomofisiológica y que dotan de sentido a los impulsos sexuales, la reproducción y en general a las relaciones de las personas. Por tanto, este sistema pasó a ser el objeto de estudio para comprender la subordinación de la mujer al hombre. Al ser el reconocimiento de una dimensión de la desigualdad social hasta entonces desconocida, se considera la ruptura epistemológica más importante de la segunda mitad del siglo pasado.
 Imagen representativa del binarismo de género
Imagen representativa del binarismo de géneroHay que decir que los fenómenos sociales se definen por la relación que guardan entre sí. Es así que la contextualización adquiere gran importancia. Varones y hembras tenemos la capacidad de producir con el cuerpo, pero solo los cuerpos de las hembras pueden gestar y por tanto asegurar la especie humana. Todo grupo humano que pretenda sobrevivir debe asegurarse cierto número de hembras que lo hagan posible. De ahí un poder particular del cuerpo de las hembras que además es económicamente útil. Dicho poder no es en tanto entidad biológica, sino que es la sociedad la que le otorga este poder. En este punto es importante preguntarnos históricamente ¿quiénes han controlado la capacidad reproductiva de las mujeres?, ¿quiénes han tenido la preferencia en el acceso sexual? Para asegurar un control efectivo sobre la reproducción es necesario asegurar el acceso a la sexualidad.
Ello también lleva a dirigir el trabajo que hacen porque de lo contrario, las mujeres pudieran tener espacio para representar una amenaza al dominio de los hombres. Es importante atender a las etapas del desarrollo de las mujeres, que permitirá ver cómo se moldean para aceptar la desigualdad y las jerarquías según el género en las distintas sociedades y culturas.
Otro contexto a delimitar es el ámbito doméstico donde históricamente ha estado ubicada la subordinación femenina. Se ha puesto al descubierto que en mujeres que comparten la misma posición de clase y raza, la condición femenina se redefine a lo largo de la vida y que algunas mujeres gozan de poder sobre otras aún en contextos de alta dominación masculina, donde se les inviste de autoridad, creando el sistema zonas de incertidumbre que las divide como género e impide alianzas y se legitima la dominación. Foucault decía que «el poder se ejerce, no se posee», siempre está en peligro de perderse y no basta con normas, leyes, amenazas o castigos. De ahí que los espacios de subordinación sean también espacios de poder de las mujeres. Es en estos espacios donde aparece la inseguridad, la tensión, la confrontación y por ejemplo, las mujeres pueden reclamar la anticoncepción.
Para terminar, es importante tener en cuenta que el género es una forma de desigualdad social que siempre está articulado con otras formas de desigualdad ya sea clase, raza, grupo etario, etc. Hay que pensar la dominación masculina con un comienzo vago en el tiempo, pero que permite desligar la subordinación de las mujeres de la evolución «natural» de la humanidad y entenderla como un proceso histórico. En ese sentido es necesario destacar que, respecto a la raza, en sociedades plurales hay que atender al contexto étnico-cultural ya que en dependencia de las relaciones entre personas de razas distintas, estarán condicionadas las relaciones entre los géneros.
 Imagen de mujeres de distintas razas
Imagen de mujeres de distintas razasPor otro lado, si bien es sabido que históricamente el sistema de género social imperante ha contribuido a invisibilizar a la mujer, asociar necesariamente dicha categoría únicamente a ella, lo que hace es nuevamente recrear el absolutismo histórico que tanto daño ha hecho, ahora como lo antagónico al hombre. En la construcción social participan todos los individuos presentes en el sistema género.
Hasta aquí la publicación de hoy, de la cual aun se puede ahondar mucho más, sobre todo en lo referido al origen de la dominación o de la jerarquización del binomio «hombre/mujer» desde un punto de vista antropológico, pero eso quedará pendiente para otro momento. ¡Así que hasta la próxima!, ¡nos vemos en Nostr!
........................................
English version
Hello nostriches. Today I want to make a post by way of an approach to the emergence of the categories of gender and feminism. So if you are interested in the topic make an effort, stay and read to the end.
The "new" feminism emerged in the 60's in those developed countries that agreed to recognize the human rights contained in the respective UN declaration. Then, as an extension of that recognition, the feminist movement was born. From then on, the relationship between nature and culture was raised again and the conclusion was reached that social differences go beyond biological differences, which has to do with the fact that even the satisfaction of elementary needs such as food, housing or clothing are conditioned by social constructions.
It turns out that one of the first proposals identified female subordination as a product of a patriarchal organization, taking Max Weber's category of patriarchy. This is how the vision of patriarchy was extended to political and academic discourse. However, there was no information about the historical development of this category, systematization, variations, etc., because it was something that was only recently perceived in society.
However, the same category of patriarchy, together with that of power relations to explain contemporary social phenomena, constitutes one of the main contributions of feminism. This is how they have first made visible and then deconstructed and dismantled a series of existing patterns in the culture that made women subordinate to men, and that were present in the sex/gender system.
 Image relating to the fight against patriarchy
Image relating to the fight against patriarchyUp to that time, in sociological research, an excessive androcentrism could be observed as scientific discourse revolved around men as the subject and object of research. Even for many positivists such as Weber himself, the problems related to women remained in the background and were blamed on a supposed passivity in the domestic-family sphere. This passivity was based on the supposed biological inferiority of the female gender.
Patriarchy was then an empty category in itself, with no explanatory value. From the political point of view, it could be useful for mobilization, but it did not resist the polemic of feminism's critics, nor did it problematize the conflicts to be resolved. But on the other hand, a group of women - mainly academics - set to work on a smaller task but with greater results in the long run. They set out to generate knowledge about women's living conditions, to search in the past and present for women's contributions to society, to make them visible in history. This is how academic centers, NGOs, projects, women's studies centers, etc., came into being.
It would be convenient to distinguish then two postures that accompanied the research on women: one that takes women as the object of study; living conditions, work, culture, and the other that privileges society as the generator of women's subordination. While the first perspective generated knowledge about women in the study of woman-man and woman-woman relations, the second had a more holistic vision, since it proposed that society must be studied, since the subordination of women is a product of its organization, and that progress will not be made only by studying women, since the study must be broader and at different levels, spheres and times.
It is in this search that the concept of gender as a social category was born and developed. Thus, gender/sex systems were understood as a set of practices, symbols, representations, norms and social values that societies construct on the basis of anatomophysiological differences and that give meaning to sexual impulses, reproduction and, in general, to people's relationships. Therefore, this system became the object of study to understand the subordination of women to men. As the recognition of a hitherto unknown dimension of social inequality, it is considered the most important epistemological breakthrough of the second half of the last century.
 Representative image of gender binarism
Representative image of gender binarismIt must be said that social phenomena are defined by their relationship with each other. Thus, contextualization acquires great importance. Males and females have the capacity to produce with their bodies, but only the bodies of females can gestate and therefore ensure the human species. Any human group that intends to survive must ensure a certain number of females to make it possible. Hence a particular power of the female body, which is also economically useful. This power is not as a biological entity, but it is society that gives it this power. At this point it is important to ask ourselves historically, who has controlled the reproductive capacity of women, who has had the preference in sexual access? To ensure effective control over reproduction, it is necessary to ensure access to sexuality.
 Allegorical image of pregnancy
Allegorical image of pregnancyThis also leads to directing the work they do because otherwise, women may have room to pose a threat to men's dominance. It is important to pay attention to the stages of women's development, which will allow us to see how they are shaped to accept inequality and gender hierarchies in different societies and cultures.
Another context to delimit is the domestic sphere where female subordination has historically been located. It has been discovered that in women who share the same class and race position, the feminine condition is redefined throughout life and that some women enjoy power over others even in contexts of high male domination, where they are invested with authority, creating the system of uncertainty zones that divide them as a gender and prevent alliances and legitimize domination. Foucault said that "power is exercised, not possessed", it is always in danger of being lost and norms, laws, threats or punishments are not enough. Hence, the spaces of subordination are also spaces of women's power. It is in these spaces where insecurity, tension, confrontation appear and where, for example, women can demand contraception.
To conclude, it is important to keep in mind that gender is a form of social inequality that is always articulated with other forms of inequality, be it class, race, age group, etc. It is necessary to think of male domination with a vague beginning in time, but which allows us to separate the subordination of women from the "natural" evolution of humanity and to understand it as a historical process. In this sense, it is necessary to emphasize that, with respect to race, in plural societies it is necessary to pay attention to the ethno-cultural context since, depending on the relations between people of different races, the relations between genders will be conditioned.
 Image of women of different races
Image of women of different racesOn the other hand, although it is known that historically the prevailing social gender system has contributed to make women invisible, to necessarily associate this category only to women is to recreate the historical absolutism that has done so much damage, this time as antagonistic to men. All individuals present in the gender system participate in the social construction.
So much for today's publication, of which we can still go much deeper, especially with regard to the origin of domination or the hierarchization of the binomial "man/woman" from an anthropological point of view, but that will be left for another time. So until next time, see you in Nostr!

Créditos | Credits
Bibliografía consultada | Consulted bibliography:
-
Barbieri, T. (1993). Sobre la categoría género. Una introducción teórico-metodológica. Debates en Sociología. (18). 1-19. https://doi.org/10.18800/debatesensociologia.199301.006
-
Echevarría, D. (2020). Desigualdades de género e interseccionalidad. Análisis del contexto cubano 2008-2018. Facultad Latinoamericana de Ciencias Sociales (Programa-Cuba). https://www.clacso.org.ar/libreria-latinoamericana-cm/libro_detalle_resultado.php?id_libro=2346&campo=cm&texto=248
Traducción | Translation:
DeepL
-
-
 @ 705605d9:b4324038
2024-12-13 16:30:17
@ 705605d9:b4324038
2024-12-13 16:30:17К 2040 году Горноправдинск, несмотря на динамичное экономическое развитие, столкнулся с рядом серьёзных демографических проблем.
Средний уровень жизни в Горноправдинске за последние несколько лет резко увеличился. Люди стали жить дольше. Но проблема со старением населения, бывшая актуальной ещё двадцать лет назад, осталась — и более того, она набирает обороты. Население города стареет — а значит, трудоспособного населения становится всё меньше. Это вызывает весьма серьёзное беспокойство у властей.
— У нас есть всё, чтобы молодое поколение выбрало Горноправдинск своим домом — новые рабочие места, красивая природа, инфраструктуру мы тоже развиваем. У нас тут много работников сферы IT, но на некоторых производствах не хватает рабочих, а социальный сектор от дефицита кадров страдает особенно сильно. Учителей у нас мало, например. Непопулярная это нынче профессия у молодых. — заявляет Агафья Семёновна, пресс-секретарь городской администрации.

Демографическая ситуация также осложняется низкими показателями рождаемости. Молодые люди, которые остаются в посёлке, зачастую ставят своим приоритетом не планирование семьи, а карьерный рост и саморазвитие. Многие просто не видят большого смысла для себя заводить семью и детей. Но редакция предполагает, что это проблема далеко не только одного Горноправдинска, а общая тенденция на уровне страны.

Ситуация с миграцией также оставляет желать лучшего. Хотя бум экономики Горноправдинска привлекает новых жителей, многие из них — это временные работники из других регионов, которые не имеют намерения осесть на постоянной основе. Кроме того, утечка умов, когда высококвалифицированные специалисты уезжают в поисках лучших карьерных возможностей, продолжает оставаться серьёзной проблемой для местного рынка труда.
Говоря о демографии, нельзя не сказать о социальных проблемах. Экономика цветёт, увеличивается качество жизни, а социальное расслоение сохраняется. Например, многим всё ещё трудно получить квалифицированную медицинскую помощь — работники городских поликлиник порой не справляются с потоком пациентов, а за помощью узкоспециализированного специалиста горноправдинцам остаётся обращаться в платную частную клинику, что может быть довольно тяжёлым испытанием для кошелька. Молодые семьи стремятся к лучшим условиям для жизни и воспитания детей, что приводит к оттоку населения в более социально обеспеченные регионы.
Горноправдинск, пытаясь справиться с демографическими вызовами, нуждается в комплексном подходе к решению проблем. Город нуждается в постоянном обновлении инфраструктуры и социальных инвестициях. Не хватает и поддержки молодых семей — для того, чтобы переосмыслить свои приоритеты, молодым парам нужна уверенность в завтрашнем дне.
А пока город медленно, но верно стареет. Справедливости ради, несколько медленнее, чем раньше.
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 705605d9:b4324038
2024-12-13 16:27:16
@ 705605d9:b4324038
2024-12-13 16:27:16Горноправдинск, некогда скромный посёлок с населением в несколько тысяч человек, к 2040 году стал важным экономическим центром Ханты-Мансийского автономного округа. Если бы 20 лет назад местным жителям сказали, что их маленький посёлок станет экономическим чудом — даже самые оптимистичные из них восприняли бы это как шутку.
**Но как всего за пару десятков лет вообще возможна столь удивительная трансформация?
**
Маленькие люди, большая мечта Сельское хозяйство стало важной опорой экономики Горноправдинска. Даже как-то смешно вспоминать, что всё начиналось с маленьких частных огородов и большой инициативы местных жителей.
Те, кто когда-то возделывал скупую сибирскую землю, устали выращивать разве что картошку и разве что для себя. Жители (преимущественно, кстати, пожилые, те, для кого их огород был чуть ли не главным делом) взялись за свои участки серьёзно — удобряли землю, воспользовались правом заниматься фермерством, а затем смогли и выбить достойную технику для своего дела. Результат себя ждать не заставил: сельскохозяйственная продукция из Горноправдинска завоевала своё место на прилавках магазинов Югры. А уже к 2040 году Горноправдинск стал одним из важнейших центров производства молочных продуктов в регионе — животноводство местные власти сейчас развивают особенно активно. Не забыли и о чистоте производства: Горноправдинск на данный момент занимает одну из лидирующих позиций по внедрению "зелёных" технологий.

Привлечение туристов
Не менее значимым стало развитие туристической отрасли. Уникальные природные ландшафты региона привлекли туристов со всей страны. Местные власти активно развивают туристическую инфраструктуру: за последние 4 года на территории города появились 4 гостиницы (одна из них, кстати, и вовсе реализует формат "all-inclusive"!), два туристических маршрута — лыжная тропа, где все желающие смогут налюбоваться зимней красотой Сибири, и речной маршрут вдоль местной реки. "Мы стараемся создать место, куда люди хочется возвращаться", — говорит директор туристической фирмы "ГП".

Горноправдинск стал местом притяжения для самых разных людей — любители спорта теперь могут покататься на лыжах зимой и отправиться на сплав на сапах летом, а для интересующихся культурой молодых людей здесь регулярно проводят творческие фестивали.
Но сколько стоит экономическое чудо?
Но всего этого могло бы и не быть, если бы не усилия по привлечению инвестиций. Власти ввели налоговые льготы, модернизировали транспортное сообщение между городами Югры и впервые за всю историю существования посёлка, кажется, слушали людей и принимали их инициативы — так, через налаживание контактов и вливание финансов в местные предприятия (если обратиться к финансовым отчётам властей, то суммы, выделенные на развитие местных производств и инфраструктуры, впечатляют — они исчисляются миллиардами рублей), получилось преобразить бывший маленьким и серым Горноправдинск в гордость региона.

-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 705605d9:b4324038
2024-12-13 16:25:42
@ 705605d9:b4324038
2024-12-13 16:25:42Давка в маршрутках с вечно уставшими водителями, которые приезжают на остановки не по расписанию, а иногда не приезжают вовсе, была в прошлом неизбежной частью городской жизни. Общественный транспорт остаётся востребованным элементом инфраструктуры: не все могут позволить себе личный транспорт или регулярные поездки на такси. Вам больно видеть ценник в 800 рублей по вечерам в час пик? Редакции тоже.

Сегодня, 17 декабря, городские власти закупили новые транспортные средства: 15 беспилотных электробусов "Стрела" с увеличенной вместительностью. Новенькие "Стрелы" отправятся на маршруты 8, 13 и 42. Помимо повышенной вместительности и внедрения ИИ, новый транспорт также более экологичен.
Маршрут в восточную часть города, маршрут №6, оснастят "Стрелами" в следующем году. Подготовкой специализированных колей для них дорожники были заняты последние полтора года, и на востоке работы ещё не завершены до конца.
Теперь не нужно ругаться с водителем: обстановку на дороге и в салоне определяет искусственный интеллект.
Но редакция напоминает: при нахождении в электробусе будьте взаимовежливы -- уступайте места пожилым людям, инвалидам и беременным женщинам, а при нахождении в автобусе снимайте рюкзаки и объёмные сумки с плеч.
-
 @ 705605d9:b4324038
2024-12-13 16:10:30
@ 705605d9:b4324038
2024-12-13 16:10:30В центре Горноправдинска произошла серьезная коммунальная авария, в результате которой значительная часть города осталась без электричества. По предварительной информации, причиной отключения стало повреждение высоковольтной линии, расположенной на улице Поспелова.
Авария произошла в результате сильного ветра и обильных осадков, которые наблюдались в последние дни. В результате падения дерева на линию электропередач произошло .короткое замыкание, что привело к отключению нескольких трансформаторных подстанций.
На данный момент специалисты работают над устранением последствий аварии. Восстановительные работы начались сразу после инцидента. В ЮТЭК пообещали, что работы закончат к 4 часам утра.
Видео происшествия:
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 705605d9:b4324038
2024-12-13 16:07:11
@ 705605d9:b4324038
2024-12-13 16:07:11Сегодня посёлок Горноправдинск, стал не просто точкой на карте, а настоящим центром молочного вселенной. Ведь именно здесь, в 2040 году, открылся самый крупный молочный комбинат в мире — гигантское предприятие, которое не только удивляет размерами, но и ставит новые стандарты в производстве молочных продуктов. Комбинат, который в народе уже окрестили "Млечным путём", выглядит как космическая станция, под завязку забитая самым современным оборудованием.

Зрелище потрясающее: массивные трубы, сверкающие резервуары и, конечно, в воздухе стойкий запах свежего молока, который теперь станет символом этого региона.
Генеральный директор комбината, Зульфия Новобсохова с гордостью демонстрирует всему миру чудо инженерной мысли. На церемонии открытия она, с блеском в глазах и лёгкой улыбкой, рассказала журналистам:
— "Мы не просто строили завод, мы строили мечту! Теперь наша продукция сможет достичь каждого уголка планеты, и, надеюсь, в ближайшее время мы поставим молоко даже на Марс. Кто знает, может, с помощью наших новых технологий завтра марсиане будут пить молоко с Горноправдинска!" — шутит она, как всегда, с долей иронии, присущей истинному бизнесмену.
Но шутки шутками, а величие нового предприятия впечатляет. Здесь установлены ультрасовременные линии по переработке молока, автоматизированные процессы, и роботы, которые до сих пор поражают своей точностью. Так что в планах — не только массовое производство сыра, йогуртов и творога, но и создание абсолютно новых продуктов с непревзойдённым вкусом и максимальной пользой для здоровья.
-
"Мы гордимся тем, что создаём будущее, а не просто следуем за ним. Это не просто комбинат, это философия, основанная на идее заботы о природе и человеке", — продолжает Зульфия, когда её спрашивают о возможных экологических последствиях. "Конечно, мы выбрали экологичные материалы, переработку отходов и минимизацию углеродного следа. Даже коровы, которые поставляют нам молоко, проходят строгий контроль по экологическим стандартам. И знаете, они тоже счастливы работать на таком производстве."
-
"Надеюсь, в будущем, когда люди станут заказывать наше молоко, они смогут выбрать не только его вкус, но и степень 'счастья' коровы. Мы думаем над этим, и это может стать нововведением на рынке!"
Не упустим и восхищённых зрителей: среди гостей мероприятия присутствуют известные личности, чиновники и даже любители молочной продукции со всего мира. Многие из них в порыве восторга делают снимки на фоне гигантских установок, поднимаясь на специальные платформы с видом на завод. Кто-то шутит, что теперь Горноправдинск может стать новым "молочным Лас-Вегасом"

Даже критики, известные своим скептицизмом по поводу промышленных гигантов, сдержанно кивают в знак уважения. Слишком уж велико было всё, что они увидели.
Подсчёты говорят сами за себя:
- Производственная мощность — 100 миллионов литров молока в год.
- Тысячи новых рабочих мест.
- Планы по выходу на международные рынки и экспорту в космос (по шутке или всерьёз — ещё предстоит выяснить)
- Бобровская порода коров бьёт все рекорды по удою в 40 546 кг молока.
Горноправдинск уже сегодня становится центром молочной дипломатии и промышленности. Если в ближайшие годы этот комбинат сможет оправдать все возложенные на него надежды, то вполне возможно, что мир начнёт измерять величие не только в мегаваттах энергии, но и в литрах молока.
-
-
 @ 705605d9:b4324038
2024-12-13 15:54:49
@ 705605d9:b4324038
2024-12-13 15:54:49Горноправдинск, посёлок, заслуженно гордящийся своим экологическим статусом и продвинутыми инициативами, стал центром литературной жизни Югры. В местной библиотеке состоялась яркая презентация книг югорских авторов, событие, ставшее предвестником масштабного проекта по созданию фонда Югорских писателей.
В уютном зале библиотеки собрались любители литературы, местные жители и гости посёлка. Центральным событием вечера стала презентация сразу нескольких значимых работ. Среди авторов – как маститые профессионалы, так и талантливые дебютанты.

Главным событием вечера стала презентация книги известного горноправдинского историка, профессора Николая Сергеевича Петрова, "Горноправдинск: хроники устойчивого развития". Книга, написанная с использованием новейших технологий визуализации данных и дополненная интерактивными элементами, рассказывает об истории посёлка, акцентируя внимание на его экологической стратегии и инновационных подходах к развитию.
"Мне было важно не только зафиксировать исторические факты, но и показать путь Горноправдинска как образца устойчивого развития, – делится Николай Сергеевич. – Надеюсь, моя книга вдохновит новых поколений на создание ещё более процветающего будущего".
Рядом с маститым историком блестяще представили свои работы авторы, работающие в жанре детской литературы. Елизавета Андреевна Кузнецова представила интерактивную книгу "Сказки Югорского леса: ожившая тайга", сочетающую традиционный фольклор с элементами дополненной реальности. Дети могут сканировать страницы и видеть оживающих персонажей сказок на экранах своих планшетов.
"Мы стремимся привить детям любовь к своей культуре и природе в интерактивной и занимательной форме, – пояснила Елизавета Андреевна. – Современные технологии позволяют нам сделать это эффективнее и интереснее".
Ещё одним ярким участником вечера стал Даниил Владимирович Колосов, автор книги "Югорские мифы в стихах и музыке". Даниил представил не только свою книгу, но и музыкальное сопровождение к ней, используя современные синтезаторы и традиционные югорские инструменты.
"Я хотел показать, как традиционная культура может гармонично сочетаться с современным искусством, – поделился Даниил Владимирович. – Музыка помогает лучше понять глубину и красоту югорских мифов".
Завершился вечер обсуждением перспектив развития литературы Югры и планов по созданию Фонда Югорских писателей. Участники выразили оптимизм и уверенность в том, что литературное наследие Югры будет и впредь богато и уникально. Презентация в Горноправдинске стала ясным подтверждением этого.
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 705605d9:b4324038
2024-12-13 15:52:11
@ 705605d9:b4324038
2024-12-13 15:52:11В 2040 году в посёлке Горноправдинск завершилась масштабная реставрация веревочного парка, который стал не только современным развлекательным объектом, но и примером экологической ответственности. В ходе работ были использованы исключительно натуральные материалы, такие как древесина местных пород, а также переработанные пластик и металл. Все конструкции теперь оснащены покрытиями, не вредящими экосистеме.

Важным нововведением стало применение солнечных панелей для питания освещения и системы видеонаблюдения, что позволило значительно снизить углеродный след парка. Кроме того, установлены инновационные системы сбора и очистки дождевой воды, которая используется для полива зелёных насаждений, а также для поддержания гигиеничных условий в туалетах.
Для повышения доступности, веревочный парк теперь включает маршруты для людей с ограниченными возможностями: специальные пандусы и адаптированные зоны для отдыха. В парке также появились новые образовательные элементы — интерактивные стенды и экскурсии по экологии, где посетители могут узнать о важности сохранения природы и устойчивого развития.
Проект реставрации стал возможен благодаря поддержке местных властей и экологических организаций, а новый парк уже стал местом притяжения для жителей и туристов.
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ f527cf97:65e232ee
2024-12-13 15:50:50
@ f527cf97:65e232ee
2024-12-13 15:50:50A new breed of entrepreneurs is emerging on social media platforms, especially on LinkedIn—those who want to show (in new terms: coach) other entrepreneurs how to become successful. And even on Nostr I have already discovered the first coaches.
Their areas of influence vary from general measures to spiritual-mental attitude change, and even to specializations on a medium or a specific platform. Over the past few weeks, I have looked into several of them and expressed interest in their offerings, always with an open mindset: "Maybe they know something I don't, and I could learn something new." I engaged with generalists, mental attitude changers, and specialists. I went through a few stages that all look the same:
- They somehow get in touch with you, often subtly lured through indirect means so that they don’t appear to be cold-calling you (which is illegal in many countries).
- You are invited to a mass event, usually a webinar with general teasers about the offering.
- Then you are asked to pay to access the valuable information.
Here are my thoughts about this business model.
They all promise to know some kind of secret formula or have a proven system that you just need to follow to achieve success in 90% of cases (or so). This system has, of course, been tried and tested over the years, they say, and they have made an effort to formalize it—for you. So they can now sell it to you, saving you the trouble of doing the work yourself. The target audience seems to be entrepreneurs in their 20s and 30s, or those who want to become one. While they claim it’s for all age groups, the presentation clearly appeals more to this demographic. It would be difficult to convince someone in their 40s or 50s. No wonder, as all these success coaches I met were under 40 themselves and have no idea how people think when you get older.
Now, after reading their social media posts, which are admittedly persuasive in rhetoric, and after being tempted, like I was, to comment on one with "BS, that only works in exceptions," they respond positively, never offended, and in an inviting tone. Or they send you "info material" or some other goodies behind a link where you have to sign up with your email address. Since I use disposable email addresses, I have no problem with that and think, why not? Let’s see what they have to offer.
And sometime later, maybe in 2 or 3 weeks, you receive an invitation to a "webinar" at the same address. And that’s where it starts to get unethical. Most of them didn’t indicate in the sign-up for the initial info material that they would also use your email address for other purposes, or that the whole thing is actually set up with that intention. Such information should be placed near the email field according to EU privacy laws. If it’s missing, it’s a violation of GDPR and actually a justiciable issue.
But okay, I participated in all the webinars out of curiosity. And they are all structured the same way. First, there’s a one-hour presentation with slides covering general points, followed seamlessly by the introduction of their own product or service. There’s no "advertisement" or "sponsored" label beforehand (red flag number 2). It’s either access to several training videos or an initial consultation session to tailor the coaching to your specific needs. So it all boils down to selling the coach’s own product or service. In the past, this was done directly in the first step. That doesn’t work as well today, so they’ve added 1-2 steps beforehand with bait offers. But at the latest, after or at the end of the webinar, prices are presented. These range from 5,000 to 10,000 Euros. A young or unsuccessful entrepreneur has to invest this amount if they want to receive the formula for financial bliss.
Yet, they don’t even know exactly what they would be investing in. They are constantly led to believe that this magical formula works for most people, and in every case during the webinar, a previous successful client is showcased, who is now floating in the clouds of financial happiness thanks to this "secret formula." However, it is also mentioned that this formula must be specifically tailored to your business. Hence the 5-10K euro investment. This means that after at least 2 hurdles of customer attraction, you still don’t know what you will actually receive and specifically, whether it will really work for you. You are essentially buying a pig in a poke. And that is the main problem.
It is repeatedly pointed out that the customer also has their obligations, such as doing everything the coach recommends and investing a certain amount of time each week. But nothing is promised with certainty. You only hear the alleged success statistics of X% over and over again. You can’t verify that; you just have to take it on faith. And that’s when you start to gamble internally. "Ah, I’m sure I belong to the 90% (or whatever the success rate is) if I just follow along."
You also have to trust that the success example presented in person in the webinar is authentic, meaning that the success of this entrepreneur stems solely from the implementation of the coaching measures and not from other circumstances. I don’t want to accuse anyone of anything, but that’s a bit too much trust for me to invest. I’m more the type who believes "respect and politeness are free, but trust must be earned."
I addressed this candidly in the last "client meeting." I pointed out that I had no guarantees, even if I fully participated, that I could expect an increase in my leads/appointments/revenues (whatever they specifically promise). In contrast, their fees are secure and likely paid in advance. I see an imbalance in fairness there. Instead, I proposed a fair commission model. For every lead/appointment/revenue they bring me, I would pay them a certain commission. And if they are indeed as good as they claim, they shouldn’t have a problem with that. I also said it would be more "entrepreneurial" to share both the success and the risk. Because with their model, only one party (namely them) has their ducks in a row while I, as the coached one, am taking a gamble. There are so many other influencing factors beyond my participation. What if my country or my industry is in a recession, for example? Or I could think of many other factors that are out of my control.
Well, they vehemently rejected this proposal. No guts. No entrepreneurship on their side with this. I even said, "With your business model, it’s reasonable to suspect that you just want to rip me off and cash in, no matter what happens." That didn’t help either.
My father once said something wise. When I was 18 or 19 years old, I wanted to sell building savings insurance, and for that, I was supposed to attend a sales training that costed about 50 euros, which isn’t much. My father immediately said, "Nonsense. You want to make money, not spend it." That stuck with me, and this whole situation reminded me of that. Now, this doesn’t exclude entrepreneurial risk and investments, but it should be more tangible than a pile of promises and hot air. You need to limit the risk and uncertainty as much as possible. A commission model, like the one I proposed, would have been fairer. Let’s grow or fail together, right? But not just one side taking all the risks.
I also once worked as a math tutor in an organization with a money-back guarantee. Students who had failed math came to me every day for six weeks in the summer, and I prepared them for their last chance, the retake exam. Our promise was that after these six weeks, you would pass math and move up to the next grade without having to repeat the school year. And if not, you would get your entire course fee back, and both sides would have just wasted time. We only refunded one out of about 30 students, and the one's failure was more due to the immense pressure she received from home. All the others passed the retake exam, and 20% of them even became math whizzes in the following school year, achieving top grades.
So, beware of such "business models." Sharing the risk is fairer. And if someone really knows their stuff, they can easily take on a 30-to-1 risk. And if not, and they insist on securing all the money upfront … you know where I’m going with this.
-
 @ e1146a85:0de0b731
2024-12-13 15:34:32
@ e1146a85:0de0b731
2024-12-13 15:34:32When it comes to maintaining a comfortable home in Christchurch, having a reliable heat pump is essential. Whether you're looking to install a new system, keep your existing unit running smoothly, or understand the costs involved, DC Installation Services is here to help with all your heat pump needs. In this blog, we’ll cover important aspects of heat pumps in Chch, heat pump cleaning CHCH, and heat pump installation cost in Christchurch.
Heat Pumps in Christchurch: A Smart Choice for Comfort
Christchurch’s climate demands a heating and cooling solution that’s versatile, energy-efficient, and effective. Heat pumps in Chch are the perfect solution for homeowners looking to maintain a comfortable indoor environment throughout the year. These systems not only provide efficient heating during the cold winters but also cool your home in the summer, making them a year-round comfort solution.
At DC Installation Services, we offer a wide range of heat pumps designed to suit different home sizes and budgets. Whether you're looking for a wall-mounted system, a ducted system, or a multi-split heat pump for multiple rooms, we can help you choose the best option for your home. Our experienced technicians ensure the right installation, maximising energy efficiency and reducing your energy bills. The Importance of Heat Pump Cleaning in Christchurch.
To keep your heat pump functioning at its best, regular heat pump cleaning in Christchurch is essential. Over time, dust, dirt, and debris can accumulate inside the unit, affecting its efficiency and air quality. Without proper maintenance, this build-up can lead to higher energy consumption, reduced performance, and even system failure.
At DC Installation Services, we offer expert heat pump cleaning in Christchurch, including cleaning the filters, coils, and other key components of your system. Our thorough cleaning process ensures that your heat pump works efficiently, provides cleaner air, and extends the lifespan of your unit. Regular cleaning can help you avoid costly repairs and maintain your system's optimal performance. Whether you’re due for a routine cleaning or facing issues with airflow or cooling, our team is here to provide fast and effective service.
Understanding Heat Pump Installation Costs in Christchurch
When planning to install a heat pump in Christchurch, one of the first questions many homeowners have is, “What is the heat pump installation cost in Christchurch?” The installation cost of a heat pump can vary depending on several factors, including the type of heat pump, the size of the area to be heated or cooled, and the complexity of the installation.
At DC Installation Services, we offer transparent pricing with no hidden fees. We begin by assessing your home’s size, insulation, and specific needs to recommend the most efficient and cost-effective solution. The cost of installation typically includes the price of the heat pump unit, any required materials (such as ductwork or wall mounts), and the labor involved in installing the system. Depending on your choice of system, costs can range, but we always strive to provide competitive pricing and a high level of service.
We also take care of any permits or regulations required by local authorities to ensure that the installation is up to code. Our team will provide you with a detailed quote, so you can understand exactly what you're paying for before proceeding. Additionally, we offer ongoing maintenance packages to ensure your heat pump continues to work efficiently long after installation.
Why Choose DC Installation Services?
At DC Installation Services, we’re committed to providing high-quality products and expert services to all our customers. We understand that investing in a heat pump is a long-term decision, and we’re here to guide you every step of the way, from choosing the right system to installation and regular cleaning. With years of experience in the industry, we take pride in offering tailored solutions for your heating and cooling needs. Our team is dedicated to ensuring that your home stays comfortable, no matter the season, with top-notch heat pump cleaning in Christchurch, affordable heat pump installation cost in Christchurch, and reliable heat pump installations.
If you're ready to install a heat pump or need cleaning and maintenance for your existing unit, contact DC Installation Services today. We're here to help you achieve the perfect indoor climate at home!
-
 @ 705605d9:b4324038
2024-12-13 15:33:06
@ 705605d9:b4324038
2024-12-13 15:33:06Сельское хозяйство на пике
За десять лет Горноправдинск стал лидером в аграрной сфере. Теплицы работают круглогодично на солнечных батареях, поля оснащены автоматическими системами полива, а урожай собирают роботы. Местные фермеры выращивают десятки видов культур: от картофеля до редких сортов ягод, экспортируемых в другие регионы. Экологическая чистота продукции — визитная карточка города.

Экологичный город
Горноправдинск перешел на возобновляемую энергетику. Отходы перерабатываются в удобрения и биотопливо. Здания строят из дерева и других экологически чистых материалов. Улицы украшены зелеными зонами, а транспортная система работает на электричестве.
Жизнь людей
Каждый житель имеет доступ к современному жилью, паркам и образовательным программам. Городские гранты помогают развивать личные фермерские хозяйства. Туризм также набирает обороты благодаря экопаркам и фермерским фестивалям.
Горноправдинск за десятилетие стал образцом для других городов. Это место, где природа и технологии гармонично сосуществуют, а жители гордятся своим вкладом в процветание родного края.
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ e1146a85:0de0b731
2024-12-13 15:32:33
@ e1146a85:0de0b731
2024-12-13 15:32:33When it comes to maintaining a comfortable home in Christchurch, having a reliable heat pump is essential. Whether you're looking to install a new system, keep your existing unit running smoothly, or understand the costs involved, DC Installation Services is here to help with all your heat pump needs. In this blog, we’ll cover important aspects of heat pumps in Chch, heat pump cleaning CHCH, and heat pump installation cost in Christchurch.
Heat Pumps in Christchurch: A Smart Choice for Comfort
Christchurch’s climate demands a heating and cooling solution that’s versatile, energy-efficient, and effective. Heat pumps in Chch are the perfect solution for homeowners looking to maintain a comfortable indoor environment throughout the year. These systems not only provide efficient heating during the cold winters but also cool your home in the summer, making them a year-round comfort solution.
At DC Installation Services, we offer a wide range of heat pumps designed to suit different home sizes and budgets. Whether you're looking for a wall-mounted system, a ducted system, or a multi-split heat pump for multiple rooms, we can help you choose the best option for your home. Our experienced technicians ensure the right installation, maximising energy efficiency and reducing your energy bills. The Importance of Heat Pump Cleaning in Christchurch.
To keep your heat pump functioning at its best, regular heat pump cleaning in Christchurch is essential. Over time, dust, dirt, and debris can accumulate inside the unit, affecting its efficiency and air quality. Without proper maintenance, this build-up can lead to higher energy consumption, reduced performance, and even system failure.
At DC Installation Services, we offer expert heat pump cleaning in Christchurch, including cleaning the filters, coils, and other key components of your system. Our thorough cleaning process ensures that your heat pump works efficiently, provides cleaner air, and extends the lifespan of your unit. Regular cleaning can help you avoid costly repairs and maintain your system's optimal performance. Whether you’re due for a routine cleaning or facing issues with airflow or cooling, our team is here to provide fast and effective service.
Understanding Heat Pump Installation Costs in Christchurch
When planning to install a heat pump in Christchurch, one of the first questions many homeowners have is, “What is the heat pump installation cost in Christchurch?” The installation cost of a heat pump can vary depending on several factors, including the type of heat pump, the size of the area to be heated or cooled, and the complexity of the installation.
At DC Installation Services, we offer transparent pricing with no hidden fees. We begin by assessing your home’s size, insulation, and specific needs to recommend the most efficient and cost-effective solution. The cost of installation typically includes the price of the heat pump unit, any required materials (such as ductwork or wall mounts), and the labor involved in installing the system. Depending on your choice of system, costs can range, but we always strive to provide competitive pricing and a high level of service.
We also take care of any permits or regulations required by local authorities to ensure that the installation is up to code. Our team will provide you with a detailed quote, so you can understand exactly what you're paying for before proceeding. Additionally, we offer ongoing maintenance packages to ensure your heat pump continues to work efficiently long after installation.
Why Choose DC Installation Services?
At DC Installation Services, we’re committed to providing high-quality products and expert services to all our customers. We understand that investing in a heat pump is a long-term decision, and we’re here to guide you every step of the way, from choosing the right system to installation and regular cleaning. With years of experience in the industry, we take pride in offering tailored solutions for your heating and cooling needs. Our team is dedicated to ensuring that your home stays comfortable, no matter the season, with top-notch heat pump cleaning in Christchurch, affordable heat pump installation cost in Christchurch, and reliable heat pump installations.
If you're ready to install a heat pump or need cleaning and maintenance for your existing unit, contact DC Installation Services today. We're here to help you achieve the perfect indoor climate at home!
-
 @ 705605d9:b4324038
2024-12-13 15:29:03
@ 705605d9:b4324038
2024-12-13 15:29:03Горноправдинск, известный своим чистым воздухом и выдающимся качеством молочной продукции, в 2040 году стал символом экологической устойчивости и продовольственной безопасности в России. В преддверии Нового года мы решили исследовать, насколько этот живописный посёлок готов к празднованию главного события зимы. Подготовка к торжествам включает в себя не только организационные аспекты, но и атмосферу, которую создают местные жители. Как собирается отмечать Новый год экологически чистый и инновационный Горноправдинск?
Экологическая Программа и Устойчивое Развитие
С начала 2030-х годов Горноправдинск стал флагманом экологических инициатив в регионе. Местные власти и инициативные группы активно внедряли программы по утилизации отходов, экономии ресурсов и восстановлению природных экосистем. В медицинских учреждениях и образовательных учреждениях проводятся занятия по экологии для детей, направленные на формирование любви к природе и заботы о чистоте окружающей среды.

Реализация Экологических Инициатив
К 2040 году в Горноправдинске действуют специальные площадки для раздельного сбора отходов, а переработка мусора достигла 80%. В связи с праздником планируется установка дополнительных ёмкостей для сбора упаковки от новогодних товаров и подарков. Такие меры помогают не только сократить количество отходов, но и формируют осознанное отношение местных жителей к потреблению.
Кроме того, горноправдинцы активно устраивают акции по посадке деревьев. В преддверии Нового года в рамках проекта «Ёлка вместо ёлки» планируется высадка саженцев хвойных деревьев в окрестных лесах. Эта акция не только украсит природу, но и станет ясно обозначенным шагом к более устойчивому образу жизни.
Подготовка Городских Улиц к Празднику
Не менее важной частью подготовки к празднованию является украшение Горноправдинска. Улица за улицей преображаются под натиском новогодних огней, гирлянд и ярких декораций. В этом году власти уделили особое внимание использованию экологически чистых материалов. Везде, где это возможно, используются светящиеся элементы на солнечных батареях.

Разработка Новогодней Тематики
Каждая улица имеет своё уникальное оформление. В центре посёлка планируется установка большой ёлки, украшенной только перерабатываемыми игрушками и гирляндами. В рамках новогодней кампании будут проведены конкурсы на лучшее оформление жилых домов. Местные жители уже активно начали обсуждать идеи и искать средства на украшение своих участков, что добавляет атмосферы совместного празднования.
Помимо визуального оформления, каждую неделю в преддверии праздника проводятся мастер-классы по изготовлению экологически чистых новогодних игрушек. Это становится популярным среди детей и усиливает общественное единство в целом.
Культурные Мероприятия и Социальные Акции
Воспитание чувства сообщества и активное вовлечение жителей в культурные мероприятия – важная часть новогодней подготовки Горноправдинска. В этом году запланирован ряд акций, направленных на объединение всех слоёв населения.

Новогодние Ярмарки и Концерты
Появление ярмарок и концертов отмечает новый этап в социальном взаимодействии. Местные фермеры выставят свою продукцию на новогодние ярмарки, где каждый сможет попробовать и приобрести экологически чистые продукты. Параллельно с ярмаркой будут организованы музыкальные выступления местных гармонистов и ансамблей. Это станет отличной возможностью для отдыха и веселья для жителей и гостей посёлка.
В этом году особое внимание уделяется инклюзивности мероприятий. На праздники будут приглашены жители с ограниченными возможностями, для которых организуют специальные зоны и программы.
Образовательные Программы
Культурные мероприятия будут охватывать не только развлекательный аспект, но и образовательный. Специальные мастер-классы по экологии и устойчивому развитию будут проведены для желающих. Это даёт возможность не только узнать о новогодних традициях, но и понять, как сохранить природу в повседневной жизни.

Поддержка Местного Производителя
Как лидер молочной продукции в регионе, Горноправдинск придаёт особое значение поддержанию местного производства. В этом году новогодние праздники также будут направлены на обеспечение спроса на местные товары и поддержку фермеров.
Продуктовые Лавки с Местными Продуктами
На ярмарках и специализированных магазинах можно будет приобрести свежемолочную продукцию, сезонные овощи и фрукты, а также продукты, произведенные с минимальным воздействием на окружающую среду. Это позволит жителям избежать покупки импортных товаров, способствуя развитию местной экономики и снижению углеродного следа.
Кроме того, организаторы праздника планируют запустить проект «Семейные коробки с экологическими продуктами», которые будут включать в себя новогодние наборы местных продуктов, что станет отличным подарком для близких.
Готовность К Новогодним Праздникам
В преддверии Нового года, оценив масштабы подготовки, можно с уверенностью сказать, что Горноправдинск готов справиться с любыми вызовами. Готовность к празднику выражается не только в организационных аспектах, но и в отношении местных жителей.
Обсуждение Потребностей Сообщества
Местная администрация активно принимает во внимание мнение жителей. Были проведены опросы о планируемых мероприятиях и необходимом финансировании. Таким образом, все желания и предпочтения людей учтены, что добавляет комфорта в предстоящие праздники.
Профессиональная Подготовка
Члены местной администрации, вместе с волонтёрами, уже начали разрабатывать сценарии праздничных мероприятий и заниматься логистикой. Это позволит предотвратить затруднения на праздниках и обеспечить бесперебойный поток организации событий.
Горноправдинск – Место, Где Природа Встречает Праздник
Горноправдинск, как один из самых экологически чистых посёлков региона, готов к встрече Нового года 2040 года с радостью и надеждой. Благодаря усилиям местных жителей, администрации и компаний, жизнь в посёлке становится более гармоничной и устойчивой. Принципы экологии позволяют сохранять природу и при этом радоваться празднику.
Новый год в Горноправдинске станет не только украшением зимы, но и символом единства сообщества, заботы о природе и стремления к устойчивому развитию. В этом году каждая ёлка, каждый огонёк и каждая усмешка будут напоминать о том, что праздники – это не только потрать деньги на подарки, но и проявление любви к окружающему миру. Благодаря уникальной культуре и традициям, праздник пройдёт замечательно, и жители сможет получить радость и тепло от общения друг с другом, что является главным в преддверии Нового года
-
 @ 705605d9:b4324038
2024-12-13 15:20:11
@ 705605d9:b4324038
2024-12-13 15:20:11В этом году Горноправдинск, преобразившийся за последние десятилетия из скромного посёлка в крупный научно-технологический центр, стал площадкой для масштабной научной конференции по развитию высоких технологий. Событие, привлекшее учёных со всего региона, проходило в недавно отреставрированном “Сибирском Куполе”.

Конференция, проходившая в течение трёх дней, сосредоточилась на четырёх основных направлениях: интегрированные системы энергообеспечения, устойчивое сельское хозяйство будущего, развитие искусственного интеллекта в городской среде и новые технологии в экологии. Участники активно обсуждали перспективы использования возобновляемых источников энергии, разработку устойчивых агротехнологий, адаптацию ИИ для управления городским транспортом и обеспечения безопасности, а также новейшие методы биотехнологий для очистки окружающей среды.
Одним из самых обсуждаемых докладов стал выступление доктора физико-математических наук Елены Петровой, руководителя проекта “Сибирская энергетическая система”. Она представила новую концепцию энергообеспечения города, основанную на использовании геотермальной энергии и солнечных батарей высокой эффективности.

Также в конференции приняли участие ведущие учёные из разных университетов мира. Особое внимание привлекло выступление профессора Анатолия Евстигнеева, исследователя в области искусственного интеллекта. Он разработал новые алгоритмы обработки данных, способные оптимизировать управление городской инфраструктурой.
Кроме докладов, в рамках конференции проходили практические сессии, демонстрационные залы новых технологий, а также круглые столы, посвящённые взаимодействию научного сообщества и бизнеса. Оживлённо проходили дебаты о современных этических вопросах, связанных с развитием высоких технологий.
-
 @ 705605d9:b4324038
2024-12-13 15:16:34
@ 705605d9:b4324038
2024-12-13 15:16:34В 2040 году посёлок Горноправдинск пережил настоящий экологический апокалипсис. На этот раз причина катастрофы была не в погодных условиях, а в самой сути человеческой цивилизации — в канализации. Местные власти были вынуждены объявить чрезвычайное положение после того, как порыв в центральной канализационной системе стал причиной затопления улиц, домов и, судя по всему, репутации городского водоканала.

По словам экспертов, прорыв произошёл в самый неожиданный момент — во время празднования «Дня чистоты», мероприятия, которое на протяжении десятилетий служило флагманом экологических инициатив посёлка. По случаю праздника были даже установлены новые трубопроводы, что, как оказалось, не только не решило проблему, но и создало дополнительные угрозы.
Комментарий местного жителя: «Я думал, это всё шутки! Наш посёлок всегда гордился своей старинной системой водоснабжения, а теперь у нас просто… старинная система затопления. Вроде и воняет, и ничего не сделаешь — канализация теперь не просто инфраструктура, а часть интерьера». Ситуация осложнялась тем, что этот прорыв стал лишь частью более широкого тренда. За последние несколько лет, из-за стремительного увеличения населения и устаревших инженерных систем, подобные происшествия стали регулярными.
Пострадали как жители, так и бизнесы. Особенно не повезло владельцам кафе и магазинов в центре города, которые вскоре начали предлагать новые виды услуг, такие как «канализационные экскурсии» и «фитнес в бурлящих водах», рассчитывая на поток туристов.
Пока жители Горноправдинска спасают свои дома и ищут способы пережить новый тренд, один остаётся неоспоримым — канализация больше не просто забота коммунальных служб. Она стала тем, чем мы с вами живём и, увы, часто и за что платим.
-
 @ 418b49e3:8039624b
2024-12-13 14:17:00
@ 418b49e3:8039624b
2024-12-13 14:17:00A alimentação desempenha um papel crucial na prevenção de diversas doenças, incluindo o câncer. Estudos científicos demonstram que uma dieta equilibrada e rica em alimentos naturais pode reduzir significativamente o risco de desenvolvimento de tumores e auxiliar na recuperação de pacientes que enfrentam essa doença.
Como a Alimentação Atua na Prevenção do Câncer
-
Antioxidantes: Alimentos ricos em antioxidantes, como frutas vermelhas (morango, mirtilo, amora) e vegetais verde-escuros (brócolis, espinafre, couve), ajudam a neutralizar os radicais livres, que são moléculas instáveis associadas ao desenvolvimento do câncer.
-
Fibras: A ingestão adequada de fibras, presentes em cereais integrais, leguminosas, frutas e verduras, promove a saúde do trato gastrointestinal e reduz o risco de câncer de cólon e reto.
-
Fitonutrientes: Compostos encontrados em alimentos de origem vegetal, como carotenoides, flavonoides e sulforafano, possuem propriedades anticancerígenas. Exemplos incluem cenoura, tomate e alho.
-
Inflamação Reduzida: Dietas anti-inflamatórias, com alimentos como azeite de oliva extra virgem, peixes ricos em ômega-3 (salmão, sardinha) e castanhas, ajudam a diminuir processos inflamatórios crônicos que podem levar ao surgimento do câncer.
Alimentos que Podem Auxiliar no Combate ao Câncer
-
Cúrcuma: Contém curcumina, um potente anti-inflamatório e antioxidante, capaz de inibir o crescimento de células cancerígenas em estudos laboratoriais.
-
Chá Verde: Rico em catequinas, compostos antioxidantes que podem retardar ou impedir o crescimento de tumores.
-
Frutas Cítricas: Laranja, limão e toranja são fontes de vitamina C e outros antioxidantes que fortalecem o sistema imunológico.
-
Vegetais Crucíferos: Brócolis, couve-flor, couve de Bruxelas e repolho possuem sulforafano, que pode ajudar a eliminar substâncias cancerígenas do organismo.
Hábitos Alimentares para Prevenção
-
Evitar Alimentos Processados: Embutidos, enlatados e produtos ricos em conservantes e aditivos químicos estão associados ao aumento do risco de vários tipos de câncer.
-
Moderação no Consumo de Carnes Vermelhas: O excesso pode aumentar o risco de câncer colorretal. Prefira fontes de proteínas magras como peixes e aves.
-
Hidratação Adequada: Beber água suficiente ajuda a eliminar toxinas e manter o organismo equilibrado.
-
Priorizar Orgânicos: Sempre que possível, opte por alimentos orgânicos para evitar a exposição a pesticidas, que podem ter efeitos cancerígenos.
Alimentação no Tratamento do Câncer**
Embora não exista uma "cura alimentar" para o câncer, a nutrição adequada pode ser uma aliada no tratamento, melhorando a resposta imunológica e reduzindo os efeitos colaterais das terapias. Consultar um nutricionista especializado é essencial para adaptar a dieta às necessidades individuais do paciente. Investir em uma alimentação rica, variada e balanceada é uma estratégia poderosa para prevenir o câncer e melhorar a qualidade de vida. Pequenas mudanças nos hábitos alimentares podem ter um impacto significativo na saúde a longo prazo, promovendo bem-estar e longevidade.
Referências
World Cancer Research Fund/American Institute for Cancer Research. Diet, Nutrition, Physical Activity and Cancer: A Global Perspective. Available at: www.wcrf.org.
National Cancer Institute. Antioxidants and Cancer Prevention. Available at: www.cancer.gov.
Harvard T.H. Chan School of Public Health. The Nutrition Source – Phytochemicals. Available at: www.hsph.harvard.edu.
American Cancer Society. Diet and Physical Activity: What’s the Cancer Connection? Available at: www.cancer.org.
-
-
 @ 418b49e3:8039624b
2024-12-13 14:15:21
@ 418b49e3:8039624b
2024-12-13 14:15:21A alimentação desempenha um papel crucial na prevenção de diversas doenças, incluindo o câncer. Estudos científicos demonstram que uma dieta equilibrada e rica em alimentos naturais pode reduzir significativamente o risco de desenvolvimento de tumores e auxiliar na recuperação de pacientes que enfrentam essa doença.
Como a Alimentação Atua na Prevenção do Câncer
-
Antioxidantes: Alimentos ricos em antioxidantes, como frutas vermelhas (morango, mirtilo, amora) e vegetais verde-escuros (brócolis, espinafre, couve), ajudam a neutralizar os radicais livres, que são moléculas instáveis associadas ao desenvolvimento do câncer.
-
Fibras: A ingestão adequada de fibras, presentes em cereais integrais, leguminosas, frutas e verduras, promove a saúde do trato gastrointestinal e reduz o risco de câncer de cólon e reto.
-
Fitonutrientes: Compostos encontrados em alimentos de origem vegetal, como carotenoides, flavonoides e sulforafano, possuem propriedades anticancerígenas. Exemplos incluem cenoura, tomate e alho.
-
Inflamação Reduzida: Dietas anti-inflamatórias, com alimentos como azeite de oliva extra virgem, peixes ricos em ômega-3 (salmão, sardinha) e castanhas, ajudam a diminuir processos inflamatórios crônicos que podem levar ao surgimento do câncer.
Alimentos que Podem Auxiliar no Combate ao Câncer
-
Cúrcuma: Contém curcumina, um potente anti-inflamatório e antioxidante, capaz de inibir o crescimento de células cancerígenas em estudos laboratoriais.
-
Chá Verde: Rico em catequinas, compostos antioxidantes que podem retardar ou impedir o crescimento de tumores.
-
Frutas Cítricas: Laranja, limão e toranja são fontes de vitamina C e outros antioxidantes que fortalecem o sistema imunológico.
-
Vegetais Crucíferos: Brócolis, couve-flor, couve de Bruxelas e repolho possuem sulforafano, que pode ajudar a eliminar substâncias cancerígenas do organismo.
Hábitos Alimentares para Prevenção
-
Evitar Alimentos Processados: Embutidos, enlatados e produtos ricos em conservantes e aditivos químicos estão associados ao aumento do risco de vários tipos de câncer.
-
Moderação no Consumo de Carnes Vermelhas: O excesso pode aumentar o risco de câncer colorretal. Prefira fontes de proteínas magras como peixes e aves.
-
Hidratação Adequada: Beber água suficiente ajuda a eliminar toxinas e manter o organismo equilibrado.
-
Priorizar Orgânicos: Sempre que possível, opte por alimentos orgânicos para evitar a exposição a pesticidas, que podem ter efeitos cancerígenos.
Alimentação no Tratamento do Câncer**
Embora não exista uma "cura alimentar" para o câncer, a nutrição adequada pode ser uma aliada no tratamento, melhorando a resposta imunológica e reduzindo os efeitos colaterais das terapias. Consultar um nutricionista especializado é essencial para adaptar a dieta às necessidades individuais do paciente. Investir em uma alimentação rica, variada e balanceada é uma estratégia poderosa para prevenir o câncer e melhorar a qualidade de vida. Pequenas mudanças nos hábitos alimentares podem ter um impacto significativo na saúde a longo prazo, promovendo bem-estar e longevidade.
Referências
World Cancer Research Fund/American Institute for Cancer Research. Diet, Nutrition, Physical Activity and Cancer: A Global Perspective. Available at: www.wcrf.org.
National Cancer Institute. Antioxidants and Cancer Prevention. Available at: www.cancer.gov.
Harvard T.H. Chan School of Public Health. The Nutrition Source – Phytochemicals. Available at: www.hsph.harvard.edu.
American Cancer Society. Diet and Physical Activity: What’s the Cancer Connection? Available at: www.cancer.org.
-
-
 @ 6bf975a0:65de1244
2024-12-13 13:51:21
@ 6bf975a0:65de1244
2024-12-13 13:51:21Виртуальная и дополненная реальность

В 1968 году Айвен Сазерленд представил миру то, что принято считать первым налобным дисплеем дополненной реальности, известным как "Дамоклов меч". Это революционное изобретение заложило основу для устройств виртуальной реальности, которыми мы пользуемся сегодня.
Название "Дамоклов меч" было выбрано с юмором из-за устрашающего вида устройства и шаткости его установки. Оно символизирует как потенциал, так и риски, связанные с развивающимися технологиями, отражая предвидение Сазерленда о том, как такие устройства могут повлиять на человеческий опыт.
На протяжении десятилетий технический прогресс ускорял развитие VR. В 1980-х и 1990-х годах такие компании, как Sega и Nintendo, разработали игровые системы виртуальной реальности, хотя, как правило, с ограниченным успехом. И только в 2010-х годах такие компании, как Oculus и HTC Vive, представили высококачественные VR-гарнитуры, использующие мощную графику и технологию отслеживания движений.
Современные гарнитуры VR
Основным игроком на рынке виртуальной реальности остаётся Meta c продуктами линейки Oculus Quest. К началу 2023 года было продано более 20 миллионов таких гарнитур. В октябре 2023 года вышла новая, третья версия.
С момента запуска 10 октября 2023 года Oculus Quest 3 добился заметных успехов в продажах: по оценкам, за первые несколько месяцев было продано не менее 1 миллиона устройств. Эта цифра основана на показателях вовлеченности пользователей в игру смешанной реальности под названием "Первые встречи", в которой было зарегистрировано более миллиона завершений, что свидетельствует о широком распространении гарнитуры.
Quest 3 выпускается по цене 499 долларов, что делает ее более дорогой в сравнении с прошлой версией и, вероятно, способствует более медленным темпам продаж. Несмотря на это, первые показатели продаж Quest 3 впечатляют, учитывая разницу в цене и состояние рынка.
В начале 2024 года начались продажи Apple Vision Pro, передовой гарнитуры смешанной реальности, сочетающей в себе возможности дополненной реальности (AR) и виртуальной реальности (VR).
Он оснащен двумя micro-OLED-дисплеями с общим количеством пикселей более 23 миллионов, что обеспечивает разрешение более 4K для каждого глаза. Такая высокая плотность пикселей направлена на создание потрясающих визуальных впечатлений.
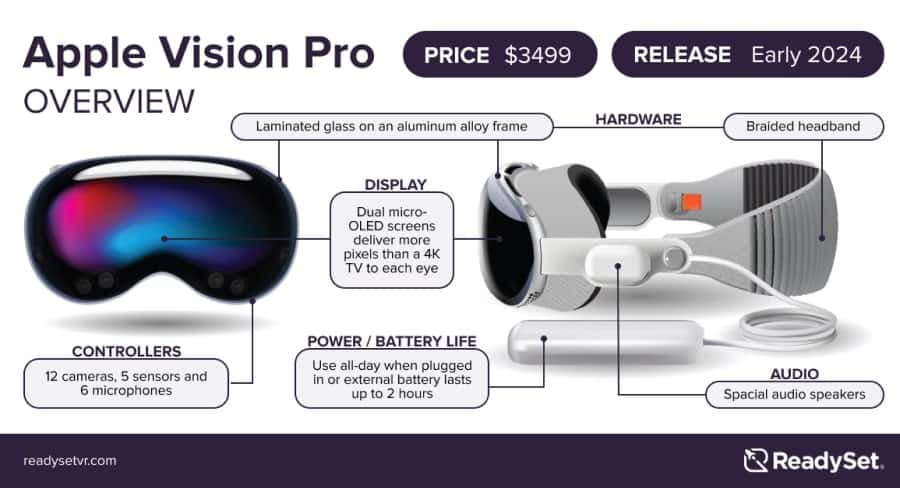
Гарнитура оснащена персонализированной системой Spatial Audio с двумя динамиками, расположенными возле ушей, что позволяет пользователям воспринимать звук как исходящий из окружающей среды. Система адаптирует звук в зависимости от геометрии головы пользователя, обеспечивая эффект погружения.
Vision Pro позиционируется как устройство премиум-класса по цене около 3499 долларов, что значительно выше, чем стартовая цена Oculus Quest 3, составляющая 499 долларов. Такая ценовая стратегия нацелена на другой сегмент потребителей, ориентируясь на профессионалов и энтузиастов, а не на обычных пользователей.
Метаверс
В 2021 году слово "метавселенная" вошло в обиход, вызвав оживленную глобальную дискуссию о том, что она собой представляет, существует ли она уже сейчас и кому она будет принадлежать. Но в 2022 году у нас все еще нет общепринятого определения того, что это такое. Это было сатирически описано на технологическом сайте The Verge:
"Возможно, вы читали, что метавселенная заменит интернет. Может быть, мы все должны жить там. Может быть, Facebook (или Epic, или Roblox, или десятки более мелких компаний) пытается захватить его. И, может быть, это как-то связано с NFT?"
В январе 2020 года автор и инвестор Мэтью Болл опубликовал наиболее часто встречающееся описание метавселенной:
"обширная сеть постоянных 3D-миров и симуляций, отображаемых в реальном времени, которые [...] могут синхронно переживаться фактически неограниченным числом пользователей, каждый из которых обладает индивидуальным чувством присутствия".
Согласно его определению, метавселенная - это продукт или услуга, обладающая семью основными атрибутами, включая постоянство, синхронность и совместимость. Технологический стратег Бен Томпсон утверждает, однако, что это описание на самом деле недалеко от того, чем уже является интернет, только "с 3D-слоем поверх него" (источник).
Будущее метаверса
Pew Research опросил технологических экспертов о Метаверсе к 2040 году.
54% экспертов заявили, что, по их мнению, к 2040 году метавселенная БУДЕТ гораздо более совершенным и по-настоящему полноценным, хорошо функционирующим аспектом повседневной жизни для полумиллиарда или более людей во всем мире. 46% заявили, что, по их мнению, к 2040 году метавселенная НЕ БУДЕТ гораздо более совершенным и по-настоящему полноценным, хорошо функционирующим аспектом повседневной жизни для полумиллиарда или более людей во всем мире.



Искусственный интеллект и тотальность гиперперсонализации
Задача сейчас заключается в том, чтобы выйти за рамки персонализации и добиться гиперперсонализации, чтобы выделиться в шуме и обеспечить опыт, который действительно резонирует. Крайне важно признать переход от рассмотрения персонализации как уникального аргумента в пользу ее принятия в качестве фундаментальной деловой необходимости. Рассмотрение клиентского опыта как бизнес-модели, а не только стратегии, является ключевым фактором успеха в этой новой среде.
Медиаландшафт перейдет в "алгоритмическую эру", которая будет характеризоваться полностью адресной и магазинной медиасредой. Эта трансформация позволит брендам более эффективно отслеживать поведение потребителей и соответствующим образом адаптировать свои рекламные стратегии. В результате потребители получат более целенаправленную рекламу, соответствующую их интересам и предпочтениям.
Персонализация на основе ИИ повышает доходы от Paywall. Так, Business Insider использовал искусственный интеллект для оптимизации своей платной подписки. Редакция создала "умный paywall", которsq решает, какие статьи показывать за плату, а какие бесплатно, исходя из интересов каждого пользователя. Это помогло им увеличить количество платных подписок на 75%. Система анализирует, какие статьи читатель уже прочитал, с какой платформы он зашел на сайт и какие темы его интересуют.
И это только один из примеров. Все маркетологи говорят, что гиперсонализация через ИИ — совершенно неизбежный шаг. Что еще туже затягивает вокруг пользователей пузырь фильтров (filter bubble).

Будущее социальных медиа

Децентрализация и web 3.0
Блокчейн, федиверс, Nostr и другие не очень очевидные на сегодня тренды
Социальные медиа всё менее социальные, даже без учета сгенерированного уже в большом количестве через AI контента



Местные и гиперлокальные медиа
Местная журналистика может эволюционировать в сторону моделей, ориентированных на сообщество, когда рассказ о событиях ведется с помощью мероприятий или интерактивных платформ, а не традиционных методов освещения событий. Такой подход может способствовать росту вовлеченности и доверия в сообществах, решая проблему упадка местных новостных изданий.
Вместо газет люди будут получать доступ к новостям через управляемые искусственным интеллектом чат-боты, курируемые электронные журналы или собрания сообществ, посвященные актуальным темам. Акцент будет сделан на доступности и вовлеченности пользователей, а не на следовании устаревшим форматам.
Унификация платформ и перенос технологий в облако

*Компания Meta с ее брендами Facebook, WhatsApp, Instagram признана в РФ экстремистской
-
 @ 3f0702fa:66db56f1
2024-12-13 13:38:44
@ 3f0702fa:66db56f1
2024-12-13 13:38:44Ссылка на подкаст: https://studio.superpodcast.ai/podcast/b7833c75-fffd-4073-8c78-ab217336ca36
-
 @ 705605d9:b4324038
2024-12-13 13:20:27
@ 705605d9:b4324038
2024-12-13 13:20:27а
-
 @ 705605d9:b4324038
2024-12-13 13:18:12
@ 705605d9:b4324038
2024-12-13 13:18:12а
-
 @ 705605d9:b4324038
2024-12-13 13:03:56
@ 705605d9:b4324038
2024-12-13 13:03:56Когда в экологически чистом городе будущего, Горноправдинске, стартовал первый международный конкурс по вязанию на скорость, никто не ожидал, что это станет не только самым обсуждаемым событием, но и началом большой драмы. Все началось с Бабкограммы — уникальной платформы для бабушек-блогеров. Именно там родилась звезда нового времени: 68-летняя Любовь Петровна, известная в соцсетях как LovingLoops.

LovingLoops и искусство продать спицу
Любовь Петровна покорила подписчиков своим особым стилем вязания и живым юмором. Она рассказывала о том, как сплести уют из остатков пряжи, и вдохновляла миллионы не только вязать, но и жить в гармонии с природой. Ее видеоролики в духе: «Как связать шарф для кота за 5 минут» или «Джутовые салфетки для сильных и независимых» буквально взрывали интернет.
Вдохновленная успехом, бабушка запустила платный курс: «Свяжи мечту за месяц». Курс обещал научить вязать эко-шедевры, строить бизнес на шарфах и, цитируем, «делать спицы инструментом личностного роста». Продажи пошли не только по Горноправдинску, но и по всему миру — от Токио до Буэнос-Айреса.

Когда пряжа — обман
Однако эйфория длилась недолго. Оказалось, что курс содержал максимум видео с банальным: «Давайте теперь провяжем три петли. Молодцы!» и минимум практических советов. Вскоре в интернете стали появляться гневные комментарии учеников:
— «Заплатила 5000 рублей, чтобы меня учили провязывать лицевые петли? Это я еще в школе умела!»
— «Обещала показать, как связать носки, а вместо этого три часа рассказывала, какой чай пить за вязанием!»
Пока подписчики варили носки вместо носков, налоговая Горноправдинска обратила внимание на стремительное финансовое развитие блогера. Выяснилось, что, несмотря на миллионы заработка, Любовь Петровна не платила налоги, мотивируя это своей «эко-философией». Аргумент «Я не могу загрязнять природу лишними бумажками» на проверяющих не подействовал.
Соревнования на спицах и на допросе
Когда полицейские пришли к ней на дом, бабушка как раз участвовала в соревновании по вязанию на скорость. Горноправдинские мастерицы боролись за звание самой быстрой вязальщицы, и Любовь Петровна уверенно лидировала, связав плед для детского сада за 15 минут. После задержания судья отметил:
— «Она действительно феноменальна. Жалко, что связала и тут...»Вязание: мода, которая переживет инфоцыган
Несмотря на скандал, увлечение вязанием в Горноправдинске и за его пределами только растет. Молодежь активно изучает основы макраме, а местные старушки открывают бесплатные кружки. Спицы стали символом устойчивого потребления и медитации в бешеном ритме мира.

Сейчас Любовь Петровна ожидает суда, а ее фанаты разделились на два лагеря: одни требуют вернуть деньги за курс, другие называют ее «жертвой системы». А тем временем в магазинах закончилась пряжа, а конкурсы по вязанию на скорость становятся новой олимпийской дисциплиной.
Ирония времени в том, что Любовь Петровна действительно связала людей по всему миру — кто бы мог подумать, что вокруг пары петель можно закрутить такую драму?
-
 @ 24e36cf3:6b26ae15
2024-12-13 13:01:22
@ 24e36cf3:6b26ae15
2024-12-13 13:01:22I've been following Ryan Holiday's work for a long time, am subscribed to his reading email list and have read most of his books. Thanks to him I've encountered Stoicism and have been trying to incorporate ancient stoic principles into my life. In short, I'm a fan.
His recent email newsletter struck a cord as well and I just have to share it. I believe he's so right about it and it concerns everyone of us. Give it a read :-)
Everything that follows is Ryan Holiday's work, not mine!
I manage my finances pretty well. I don’t gamble, I don’t spend recklessly, and I don’t indulge in luxuries I can’t afford.
But I do have an expensive habit. And you probably have it, too.
Anxiety.
It’s cost me so much.
A lot of misery, a lot of frustration, countless hours of sleep. It's caused me to miss out on a lot of things that are important to me.
It’s not flashy, it’s not thrilling, and it doesn’t even provide the fleeting pleasures that other vices might. And yet, anxiety is a vice. A habit. A relentless one that eats away at your time, your relationships, and your moments of joy.
How many family dinners have I ruined by letting my mind wander to what could go wrong? How many minutes of vacations have I missed out on because I was preoccupied, lost in spirals about things that hadn’t happened? How many opportunities have I passed up because I was too caught up in my own fears? How much sleep did I waste, lying awake at night, worrying about what might or might not happen?
It doesn’t just steal moments. It adds costs. You leave hours earlier for the airport than you need to, only to sit at the gate. You ruminate on the past or the future at the expense of the project you could be working on. You spend weeks dreading news that you know you could have actually been preparing for, instead of just thinking about.
What does anxiety really give us in return? Nothing but exhaustion and the tiniest sliver of relief when the thing you feared doesn’t happen. And even that relief is fleeting because another worry is always waiting to take its place.
Seneca tells us we suffer more in imagination than in reality. Anxiety turns the hypothetical into the actual. It drags us into a future that doesn’t yet exist and forces us to live out every worst-case scenario in vivid detail. The cost isn’t just mental. It’s physical. It’s emotional. It’s relational.
Take a moment to think about what anxiety has stolen from you.
The car ride that could have been fun, but you spent stressed because you thought you’d be late. The arguments it got you into, the relationships it strained. The way it hijacks your thoughts, like a runaway train, speeding further and further away from the present moment.
And for what?
How often does the thing you were worried about actually happen? Sure, occasionally there are issues that come up. Occasionally, you miss the connection or the package arrives late. But far more often, the imagined disaster dissolves into nothing. Meanwhile, the moments anxiety robbed you of are gone forever.
The Stoics understood this all too well. Anxiety feeds on itself. It’s like the ouroboros—a snake devouring its own tail.
Worry leads to more worry, until the cycle becomes self-sustaining. Marcus Aurelius, in Meditations, put it succinctly: “Today I escaped from anxiety. Or no, I discarded it, because it was within me, in my own perceptions—not outside.”
Work. Your kids. Politics. Flying. These things aren’t the source of your anxiety. You are. They’re just places. Just people. Just things happening in the world. We’re the ones getting upset about them. Certainly, the airport isn’t thinking about us!
The good news? If we’re the problem then we can also be the solution.
I carry a small reminder with me—a medallion engraved with Epictetus’ phrase, ta eph’hemin, ta ouk eph’hemin (“What is up to us, what is not up to us”). On the back is a quote from Seneca: “He who suffers before it is necessary suffers more than is necessary.” These phrases are anchors. They remind me that anxiety doesn’t change the outcome—it only punishes me before anything has even happened.
But even with reminders, breaking free from anxiety is not easy. It traps you in a tunnel where emotions blur your thinking, and every exit seems further away than it really is. You start to feel like a prisoner of your own mind, held hostage by thoughts you can’t control.
Yet, there are tools to escape.
The Stoics offered timeless strategies: stay in the present moment, detach from the illusion of control, and gain perspective. Epictetus reminds us, “It’s not events that upset us but our opinions about them.” Anxiety thrives on those opinions. Letting go of them can be transformative.
Anxiety is expensive—not just in terms of the mental toll, but in the way it costs us our lives. Every minute spent consumed by worry is a minute lost.
Maybe we can’t get rid of it entirely, but like our finances, we can be more efficient. We can budget. We can eliminate unnecessary expenses and get rid of obvious waste.
Anxiety may never disappear entirely. But with practice, you can begin to discard it, as Marcus did. You can remind yourself that it’s within you, not outside. And slowly, you can reclaim the moments it’s stolen.
It’s not easy, but I’m working on it. Every day, I try to get a little better. And I hope you will, too.
-
 @ 705605d9:b4324038
2024-12-13 11:36:25
@ 705605d9:b4324038
2024-12-13 11:36:25Если бы в Горноправдинске вручали премии за самые неожиданные улучшения городской среды, то недавний инцидент с канализацией точно бы попал в финал. Казалось бы, что может быть хуже, чем прорвавшиеся трубы и ручьи, отнюдь не кристально чистой воды, разлившиеся по центральной улице? Но местные коммунальщики доказали, что даже из самого неприятного можно извлечь пользу – и сделали это с такой скоростью, что теперь люди обсуждают не само ЧП, а его последствия.
Началось все с того, что старенькая канализационная сеть, напоминающая скорее музейный экспонат, чем рабочую систему, в один момент решила дать городу почувствовать, что такое "вышло из берегов". Потоки... скажем так, содержимого стремительно разлились, угрожая перекрыть не только движение машин, но и спокойствие горожан.

Однако коммунальные службы, обычно славящиеся неторопливостью, удивили всех. Уже через пару часов на месте разгула стихийных нечистот заработала техника, а сотрудники, как один, бросились в бой. Кто-то шутил, что это был их "звездный час", ведь редко когда столько внимания приковано к их работе.
"Мы использовали специальный раствор, который нейтрализует запах и разлагает органику," – рассказал начальник службы ЖКХ. Уточнять состав чудо-средства он отказался, но город сразу почувствовал, что воздух стал легче, а настроение – чище.
Но на этом коммунальная магия не закончилась. Там, где еще недавно текли не самые приятные потоки, теперь журчат новые декоративные ручьи. Местные власти приняли решение использовать эту зону для благоустройства, и уже через неделю здесь появились ухоженные парковые зоны с лавочками и клумбами.

"Мы решили, что если уж природа так распорядилась, то почему бы не сделать из этого что-то хорошее," – прокомментировал мэр Горноправдинска.
Местные жители, еще недавно всерьез обсуждавшие переезд, теперь делают селфи на фоне новенького ландшафтного дизайна и иронизируют: "Где текло, там и журчит". Некоторые даже предложили назвать парк "Река Жизни" – правда, что именно имелось в виду, остается загадкой. Так Горноправдинск доказал, что даже самые неприятные проблемы можно превратить в повод для гордости. Теперь жители шутят: "Рвануло, зато затянуло – и в прямом, и в переносном смысле".
-
 @ 04d9fac9:5bec0e6c
2024-12-13 11:22:49
@ 04d9fac9:5bec0e6c
2024-12-13 11:22:49Сегодня в Воркуте проходит одно из самых ожидаемых событий года — Всероссийский день бега «Кросс Нации 2044»! 🎉 С утра на центральной улице города царит настоящая спортивная атмосфера, наполненная энергией и энтузиазмом. Участники всех возрастов, от самых маленьких до пенсионеров, собрались, чтобы показать свои силы на дистанциях разной сложности.
🌟 900 участников уже вышли на старт! Это невероятно вдохновляет видеть столько людей, готовых к соревнованиям и поддерживающих друг друга! В этом году мы внедрили роботизированные помощники, которые помогут организовать мероприятие на новом уровне. Эти автономные дроны будут следить за безопасностью участников, обеспечивать медицинскую помощь и даже раздавать воду на дистанции.
Мы также добавили новые дистанции для детей и подростков, чтобы каждый мог найти свое место на этом празднике спорта. 🏅 Параллельно с основными забегами проходят различные мастер-классы по фитнесу и здоровому образу жизни, включая занятия с умными роботами-тренерами, которые помогут вам освоить новые упражнения и техники.
Не упустите шанс узнать что-то новенькое и зарядиться положительной энергией! Не забывайте делиться своими впечатлениями и фотографиями с хештегом #КроссНацииВоркута2044! 📸💬 Давайте сделаем этот день незабываемым! Поддержим друг друга и получим заряд энергии на весь год вперед! 💪💙 #Воркута #КроссНации #Спорт2044
-
 @ 04d9fac9:5bec0e6c
2024-12-13 11:19:28
@ 04d9fac9:5bec0e6c
2024-12-13 11:19:28Дорогие друзья! ✨ Через несколько дней, 26 ноября 2044 года, Воркута отмечает свой День города! 🎉 Это событие станет настоящим праздником для всех нас, горожан, и мы приглашаем вас погрузиться в атмосферу веселья и радости, ведь мы соберемся вместе, чтобы отпраздновать нашу уникальную историю и достижения. 🌟
В этом году мы подготовили множество интересных мероприятий, которые будут интегрированы с умными технологиями для максимального комфорта и взаимодействия:
С 10:00 до 16:00 на площади Мира пройдут выставки местных мастеров и художников. Здесь можно увидеть уникальные изделия ручной работы и даже поучаствовать в мастер-классах с использованием голографических технологий, позволяющих вам создавать виртуальные объекты прямо на месте!
В 12:00 начнется парад, который пройдет по центральным улицам города. Мы увидим яркие костюмы, музыкальные группы и, конечно же, нашу символику — серебристого оленя! Парад будет сопровождаться дроновыми шоу, которые добавят яркие визуальные эффекты в небо над городом.
В 14:00 на Центральной площади состоится концерт с участием местных артистов и приглашенных звезд. Не пропустите возможность насладиться живой музыкой и танцами, а также интерактивными выступлениями с использованием дополненной реальности, где каждый сможет стать частью шоу!
А в 18:00 завершится праздник грандиозным фейерверком! 🎆 Этот фейерверк будет синхронизирован с музыкой и световыми эффектами, создавая незабываемое зрелище.
🕊️ В этом году мы также вспомним о нашем прошлом — в программе запланированы выставки, посвященные истории Воркуты, включая её угольную промышленность и культурное наследие, представленные через интерактивные экспозиции и виртуальные туры.
Приходите всей семьей! Давайте вместе сделаем этот день незабываемым! 💙 #Воркута #ДеньГорода #2044 #Праздник
-
 @ 04d9fac9:5bec0e6c
2024-12-13 11:16:32
@ 04d9fac9:5bec0e6c
2024-12-13 11:16:32Дорогие воркутяне! С радостью сообщаем, что в 2044 году отопительный сезон в нашем городе стартует 1 декабря — на день раньше, чем в прошлом году! Это событие знаменует собой начало новой эры в коммунальном обслуживании, где технологии и инновации играют ключевую роль.
Подключение отопления будет происходить поэтапно: Центральный район получит тепло 1 декабря, Южный район — 2 декабря, а Северный район — 3 декабря. Процесс подключения будет автоматизирован с использованием умных систем управления, которые обеспечат быстрое и эффективное заполнение отопительных систем. Полное заполнение займет всего три дня, и жители смогут наблюдать за этим процессом через специальные мобильные приложения, которые будут показывать статус подключения в реальном времени.
Мы внедряем роботизированные технологии для мониторинга и диагностики состояния системы отопления. Эти автономные устройства будут следить за температурными показателями и выявлять возможные неисправности до того, как они станут проблемой. Жителям рекомендуется сообщать о любых проблемах с подачей тепла через голосовые помощники или чат-ботов, которые мгновенно свяжут вас с коммунальными службами.
Воркута движется в будущее, где комфорт и безопасность жителей — наш главный приоритет. Давайте вместе сделаем этот зимний сезон незабываемым!
-
 @ 04d9fac9:5bec0e6c
2024-12-13 11:13:19
@ 04d9fac9:5bec0e6c
2024-12-13 11:13:19Дорогие воркутяне! С радостью сообщаем, что 25 ноября 2044 года в нашем городе откроет свои двери новый Культурно-Досуговый Центр! Этот долгожданный проект стал настоящим подарком для всех жителей и гостей Воркуты. ✨
Что вас ждет? Разнообразные мероприятия: концерты, выставки, мастер-классы и театральные постановки — каждый найдет что-то по душе! Но это не просто традиционные события; благодаря интеграции голографических технологий вы сможете наслаждаться выступлениями мировых звезд в формате 3D прямо из вашего кресла.
Современные пространства: уютные залы для занятий, кинозал с виртуальной реальностью, выставочные площади, где искусство будет представлено в интерактивном формате, и даже кафе с умными меню, которые подберут блюда в зависимости от ваших предпочтений и настроения.
Поддержка талантов: новый центр станет площадкой для местных художников, музыкантов и творческих коллективов. Здесь будут доступны виртуальные студии, где творцы смогут работать над своими проектами с использованием передовых технологий, таких как искусственный интеллект для создания музыки и визуального искусства.
🌟 Мы уверены, что КДЦ станет центром притяжения для всех, кто хочет развиваться, общаться и проводить время с пользой. Это будет не просто место для досуга, а инновационный хаб, где идеи будут воплощаться в жизнь с помощью новейших технологий.
Приглашаем всех на торжественное открытие! 📅 Дата: 25 ноября 2044 года 📍 Место: Новый КДЦ, ул. Центральная, 10. Не пропустите возможность стать частью этого важного события для нашего города! 💖
-
 @ 04d9fac9:5bec0e6c
2024-12-13 11:08:53
@ 04d9fac9:5bec0e6c
2024-12-13 11:08:53Друзья, в 2044 году Воркута активно преобразуется! 🌟 Городская администрация запустила масштабные работы по ремонту дорог, чтобы сделать нашу жизнь комфортнее и безопаснее. 🔧 Что нас ждет? Асфальтирование и ямочный ремонт: обновление более 30 тыс. квадратных метров дорожного покрытия!
🚜 Ключевые участки: внимание уделяется кольцевой автодороге и аварийным участкам. Ожидаем установку новых бордюров и тротуаров, которые будут оснащены встроенными датчиками для мониторинга состояния покрытия и предупреждения о необходимости ремонта!
🛣️ Но самое удивительное — эти работы будут выполнять роботы! Воркута станет одним из первых городов, где автономные системы, такие как робот ARRES, будут осуществлять ремонт дорог без участия человека. Этот многофункциональный робот, оснащенный машинным зрением, способен обнаруживать выбоины на асфальте и самостоятельно выполнять все необходимые операции по укладке и утрамбовке асфальта. Его гидроизолированные заплатки обладают повышенной износостойкостью, что гарантирует долговечность ремонта. Благодаря этому подходу, мы минимизируем вмешательство в работу других участников дорожного движения и значительно экономим время и средства на ремонт.
Благоустройство дворов: ремонт 11 дворов в Шахтерском районе и обновление центральной площади с использованием инновационных материалов, способных очищать воздух от загрязнений! 🏡🌳
💰 Финансирование: работы будут проводиться за счет городского бюджета и федеральных программ. Приоритет — восстановление самых разрушенных участков. Воркута движется вперед, внедряя умные технологии для улучшения городской инфраструктуры и повышения качества жизни своих жителей. Мы с нетерпением ждем улучшений! Давайте вместе сделаем наш город лучше! 💪✨ #Воркута #ремонтдорог #городскиеизменения
-
 @ 04d9fac9:5bec0e6c
2024-12-13 11:04:40
@ 04d9fac9:5bec0e6c
2024-12-13 11:04:40Друзья, Воркута активно готовится к зимнему сезону 2044 года! С 15 августа стартовали осмотры жилищного фонда и объектов коммунальной инфраструктуры. 📊 Текущие показатели готовности:
Тепловые сети — 62,9% Водопроводные сети — 49,4% Канализационные сети — 51,4% Жилищный фонд — 71%
Управляющие компании проводят ремонты кровель, фасадов и систем тепло- и водоснабжения. Проблем с материалами нет! 🔧 Что еще делается?
Замена подземного водовода и восстановление тепловой изоляции на трубопроводах от ООО «Водоканал». Реализация мастер-плана Воркуты, который включает модернизацию угледобывающих шахт и улучшение социальной инфраструктуры.
В рамках подготовки к зимнему сезону также внедряются инновационные технологии:
Умные системы управления: Внедрение IoT (Интернет вещей) для мониторинга состояния систем тепло- и водоснабжения в реальном времени. Это позволит оперативно реагировать на любые неисправности и оптимизировать расход ресурсов.
Энергетическая эффективность: Установка солнечных панелей и ветрогенераторов на крыши зданий для обеспечения частичной автономности от централизованных источников энергии.
Зеленая инфраструктура: Создание зеленых крыш и вертикальных садов на жилых домах для улучшения микроклимата и повышения энергоэффективности.
Финансирование на эти цели составит около 51,5 миллиардов рублей до 2045 года. Воркута движется вперед, обеспечивая комфортные условия для своих жителей!
-
 @ 04d9fac9:5bec0e6c
2024-12-13 10:59:13
@ 04d9fac9:5bec0e6c
2024-12-13 10:59:13В 2044 году мы отмечаем пятнадцатилетие трагедии на заводе в Воркуте, где в результате аварии погибли десятки людей. Эта катастрофа оставила глубокий след в сердцах родных и близких, а также в истории города.
Каждый год в день трагедии проводятся памятные мероприятия, на которых родственники и местные жители собираются, чтобы почтить память погибших. Воркута продолжает жить с этой болью, и память о жертвах служит постоянным напоминанием о важности соблюдения норм безопасности на производстве.
С момента трагедии были предприняты значительные шаги для повышения безопасности на заводах в Воркуте:
Ужесточение контроля: Введены новые требования к инспекции производств, включая регулярные проверки состояния оборудования и обязательное обучение работников по правилам безопасности.
Технологические изменения: На заводах начали внедрять современные системы мониторинга для выявления утечек газа и других опасных веществ. Это позволяет заранее обнаруживать угрозы и предотвращать аварии.
Обучение и подготовка: Разработаны новые программы обучения для рабочих, акцентирующие внимание на правилах безопасности и действиях в экстренных ситуациях. Проведение регулярных учений по эвакуации стало обязательным.
Важно помнить о тех, кто погиб в этой трагедии, и продолжать работать над улучшением условий труда на производстве. Память о жертвах должна служить стимулом для всех нас, чтобы обеспечить безопасность работников и предотвратить подобные инциденты в будущем. Мы обязаны сделать все возможное, чтобы такие трагедии не повторялись.
-
 @ 04d9fac9:5bec0e6c
2024-12-13 10:49:58
@ 04d9fac9:5bec0e6c
2024-12-13 10:49:58 -
 @ a012dc82:6458a70d
2024-12-13 09:20:40
@ a012dc82:6458a70d
2024-12-13 09:20:40Table Of Content
-
The SEC's Dance with Bitcoin ETFs
-
The Long and Winding Road to Approval
-
Why the Cold Feet, SEC?
-
What's Next on the Horizon?
-
Conclusion
-
FAQ
In the ever-evolving landscape of cryptocurrency, there's one topic that's been consistently grabbing headlines: the elusive Bitcoin ETF. As the world eagerly anticipates its introduction, the United States Securities and Exchange Commission (SEC) continues to play a game of cat and mouse, leaving investors and enthusiasts on tenterhooks. Just when the crypto community thought they were inching closer to a resolution, the SEC has decided to keep us all in suspense a little longer. So, let's unpack the latest developments and see what's in store for the future of Bitcoin ETFs.
The SEC's Dance with Bitcoin ETFs
For those out of the loop, the United States Securities and Exchange Commission (SEC) has been the gatekeeper for the much-anticipated Bitcoin ETF (Exchange-Traded Fund). Think of an ETF as a basket of assets, like stocks or bonds, that you can buy or sell on a stock exchange. But in this case, the asset is our beloved Bitcoin.
The idea of a Bitcoin ETF has been floating around for years, promising to bridge the gap between traditional finance and the crypto world. It would allow both everyday investors and big financial institutions to dip their toes into Bitcoin waters without the hassle of buying and holding the actual cryptocurrency.
The Long and Winding Road to Approval
Big financial players like BlackRock and ARK Invest have been knocking on the SEC's door, applications in hand, hoping to get the green light. But the SEC, ever the cautious guardian, has been pushing back, delaying, and asking for public comments.
Now, here's where it gets interesting. Despite the numerous applications and the growing interest from the financial community, the SEC has never approved a spot Bitcoin ETF proposal. They've been tiptoeing around the idea, starting to accept Bitcoin-related investment vehicles in 2021, but a full-fledged Bitcoin ETF? Still on the back burner.
Why the Cold Feet, SEC?
One might wonder why the SEC is dragging its feet. The answer? It's complicated. A Bitcoin ETF isn't just another asset; it could involve holding actual Bitcoin, making it a direct investment. This is a tad different from Bitcoin futures-linked ETFs, which the SEC seems more comfortable with.
Then there's the wild west of the crypto market in the US. With the market's volatile nature and calls for clearer regulations and oversight, the SEC is treading carefully. They're currently juggling enforcement cases against big names like Coinbase, Binance, and Ripple. So, it's safe to say they've got a lot on their plate.
What's Next on the Horizon?
With the SEC's recent moves, the final deadline for some Bitcoin ETF applications is now set for 2024. But, as with everything in the crypto world, predictions can be tricky. Some analysts, ever the optimists, believe there's a 65% chance of a Bitcoin ETF getting approved. But only time will tell.
What's clear is that the SEC is in a powerful position, with the crypto world eagerly awaiting its next move. As Stuart Barton aptly put it, both sides might need to bend a bit to find common ground.
Conclusion
The quest for a Bitcoin ETF has been nothing short of a rollercoaster ride, filled with anticipation, hope, and a fair share of suspense. As we stand at this crossroads, the journey ahead remains uncertain. But one thing is clear: the world of cryptocurrency never ceases to surprise and captivate. While we may need to temper our expectations for now, the horizon could still hold unprecedented developments for the Bitcoin ETF narrative. Here's to a future where clarity and innovation walk hand in hand!
FAQs
What is a Bitcoin ETF? A Bitcoin ETF (Exchange-Traded Fund) is like a basket of assets available for trading on a stock exchange, with Bitcoin as the primary asset.
Why is the SEC involved in Bitcoin ETFs? The SEC (Securities and Exchange Commission) is responsible for regulating and approving new financial products, including ETFs, to ensure they meet specific criteria and are safe for investors.
Has the SEC approved any Bitcoin ETFs yet? As of now, the SEC has not approved any spot Bitcoin ETF proposals.
When can we expect a decision on Bitcoin ETFs? The final deadline for some Bitcoin ETF applications is set for 2024.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 6bae33c8:607272e8
2024-12-13 08:47:58
@ 6bae33c8:607272e8
2024-12-13 08:47:58Imagine you had no players going in a Thursday night game to kick off the NFFC playoffs. Imagine further you had the Rams +2.5 in your home picking pool’s quintuple week. How would you prefer the game to go? Exactly the way it went. No touchdowns, no QB over 200 yards, Cooper Kupp with zero! The only players that did anything were Puka Nacua, Kyren Williams, Isaac Guerendo and George Kittle, and what they did was modest by their standards and roles. Perfect game.
-
The 49ers dominated the first half time of possession, the Rams the second. In the chess match between offensive masterminds, Sean McVay outfoxed Kyle Shanahan.
-
Of course, the 49ers were already in position for a game-tying field goal with 5:20 left when Brock Purdy threw the catastrophic pick. When the Rams got the ball back, they wore down a tired 49ers defense to run clock and got the last field goal to go up six.
-
Deebo Samuel’s third-quarter drop was huge — it would have been a first down and looked like he might have taken it to the house.
-
Nacua and Williams always get theirs. Nacua will be a first-round pick next year, Williams early second. It’s amazing how Williams holds up under massive workloads running into the teeth of the defense and moves the pile at 5-9, 200 pounds. He has great wiggle to make the first defender miss too.
-
The Rams at 8-6 are very much in contention for the division, the 49ers at 6-8 probably are done.
-
-
 @ ec42c765:328c0600
2024-12-13 08:16:32
@ ec42c765:328c0600
2024-12-13 08:16:32Nostr Advent Calendar 2024 の 12日目の記事です。
昨日の 12/11 は きりの さんの 2024年のNostrリレー運営を振り返る でした。
nostr-zap-view 作った
リポジトリ: https://github.com/Lokuyow/nostr-zap-view/
動作確認ページ: https://lokuyow.github.io/nostr-zap-view/それ何?
特定の誰かや何かに宛てたZap(投げ銭)を一覧できるやつ
を
自分のWebサイトに設置できるやつ
自分のサイトに設置した例 * SNSリンク集ページ(最下部): https://lokuyow.github.io/
おいくらサッツ(Zap一覧ボタン): https://osats.money/
今日からビットコ(最下部): https://lokuyow.github.io/btc-dca-simulator/なんで作ったの?
私の去年のアドベントカレンダー
【Nostr】Webサイトにビットコインの投げ銭ボタンを設置しよう【Zap】
https://spotlight.soy/detail?article_id=ucd7cbrql/
が前提になってるけど長いので要約すると * ZapするやつはあるけどZap見るやつがないので欲しい * ZapをNostr(の典型的なkind:1クライアント)内だけに留めるのはもったいない * Webサイトの広告うざいからZap(的な何か)で置き換わって欲しいお前だれ?
非エンジニア、非プログラマー
AIにコード出させてるだけ人作った感想
できた
作った感想2
完成してから気付いた本当に作りたかったもの
こういうところにそのままZapを表示できる感じにしたい
 (ここまでちゃんとした商業ブログでなく)個人のブログやHPの端っこに「Sponsored by」欄があって名前が表示される感じ
(ここまでちゃんとした商業ブログでなく)個人のブログやHPの端っこに「Sponsored by」欄があって名前が表示される感じ
もうZapっていう文字もビットコインっていう文字もNostrも出さなくていいし説明もしなくていいのでは感がある
イメージはWebサイトを対象にしたニコニ広告 + スーパーチャット + 祭りとか神社の奉納者一覧
で思ったのは
個人からの投げ銭なら推し活的なものにしかならないけど
企業がNostrにアカウントを作ってサイトに投げ銭をしたら企業の広告になるんでは!?
~~企業がNostrにアカウントを!?デリヘルしか見たことない!~~今後
思いつき、予定は未定
* ボタン→ダイアログ形式でなくバナー、Embed形式にしてページアクセスですぐ見れるようにする * 多分リレーに負荷がかかるのでなんかする * Zapの文字は出さず「Sponsored by」等にする * 単純な最新順でなくする * 少額Zapをトリミング * 一定期間(一か月など)ごとで金額順にソート * 多分リレーに負荷がかかるのでなんかする * 今は投稿宛てのZapをWebサイト宛てのZapと勝手に言い張ってるだけなのでちゃんとWebサイト宛てのZapにする * NIPの提案が必要 * ウォレットの準拠も必要 * リレー(wss://~)宛てのZapもできてほしい将来
インターネットのすべてに投げ銭をさせろ
おわり
明日は mono さんの Open Sats 申請編 です!!
-
 @ b8a9df82:6ab5cbbd
2024-12-13 01:42:04
@ b8a9df82:6ab5cbbd
2024-12-13 01:42:04In March 2020, the world came to a halt. Finally reading "The Bitcoin Standard" and Michael Saylor’s prologue to it made me reflect on my own journey during that time—a journey that led to The Extraordinary. Isn’t it fascinating how the same global crisis made us all pause, look beneath the surface, and come out with completely different perspectives on life?
For me, the pandemic wasn’t just a disruption—it was a turning point. In the stillness, I was forced to face my demons: addiction, emptiness, and the endless search for something meaningful. What emerged wasn’t just a book, but a deep personal transformation.
The Extraordinary is inspired by my life in London during those chaotic years—filled with incredible highs and crushing lows. It’s a story about hitting rock bottom and finding a way back up. It’s about the facade of big-city life, where envy often wears the mask of morality, and the struggle to accept yourself in a world that rarely allows it.
What’s different now? Everything. I live a completely different life today. Writing The Extraordinary helped me confront what I couldn’t before—and now, I finally have the courage to share it here with you on Nostr.
If you’ve ever felt stuck, lost, or out of place in your own life, this book is for you. I’d love for you to read it and let me know your thoughts. Because sometimes, in writing a story for ourselves, we find the strength to connect with others.
Unfortunately, it's only available on Amazon for now, as I haven't figured out how to do print-on-demand here on Nostr yet #asknostr
Blurb:
- THEY SAID YOU WILL EARN A LOT OF MONEY,
- THEY SAID THEY WILL GIVE YOU A CAR,
- THEY SAID YOU WILL BE SUCCESSFUL,
- THEY SAID IT WILL BE FUN.
However Kate Blumenhagen never wanted to be her company‘s whore, nor lose control about the men’s world. In a city where envy often masquerades as morality. What happens when the system collapses, the perfect façade breaks down and everybody‘s darling only shines on the outside? A tribute to all those who can't stand still for five minutes!

-
 @ 04d9fac9:5bec0e6c
2024-12-12 22:33:33
@ 04d9fac9:5bec0e6c
2024-12-12 22:33:33В нашем городе вскоре начнет свою работу новый современный медицинский центр, который обещает значительно улучшить доступ жителей к качественным медицинским услугам.
Центр будет оснащен новейшим оборудованием и предложит широкий спектр медицинских услуг, включая диагностику, лечение и профилактику заболеваний. На открытии центра планируется присутствие представителей городской администрации, медицинского сообщества и общественности.
Глава администрации Воркуты, Алексей Петров, отметил важность данного проекта: «Создание нового медицинского центра — это шаг к улучшению качества медицинского обслуживания в нашем городе. Мы стремимся обеспечить наших жителей современными и доступными медицинскими услугами».
Медицинский центр будет работать по принципу полного цикла, что позволит пациентам получать все необходимые услуги в одном месте без необходимости посещения нескольких учреждений. Это значительно упростит процесс получения медицинской помощи и сократит время ожидания.
В центре предусмотрены комфортные условия для пациентов, включая отсутствие очередей и возможность записи на прием в удобное время. Высококвалифицированные специалисты будут обеспечивать индивидуальный подход к каждому пациенту, что повысит уровень доверия и удовлетворенности от получаемых услуг.
Ожидается, что новый медицинский центр начнет свою работу в начале следующего года, что станет важным событием для всех жителей Воркуты. С его открытием город делает значительный шаг к улучшению здоровья населения и повышению качества жизни.
-
 @ 705605d9:b4324038
2024-12-12 21:53:04
@ 705605d9:b4324038
2024-12-12 21:53:04Гороноправдинск, 29 ноября 2040 года — Город Гороноправдинск, который уже долгое время славится своим крупнейшим в мире молочным комбинатом, переживает настоящий шок. Начальник одного из цехов "Горноправдского молочного гиганта", Владимир Михайлович Храмов, обвиняется в крупном мошенничестве и растрате. Он украл 3 тонны сливочного масла, которое он намеревался продать на черном рынке. Это преступление стало самой громкой корпоративной аферой десятилетия.
Ход дела
1. Открытие расследования
Первые сигналы о возможной кражи поступили еще в июле 2040 года, когда началась проверка логистики на комбинате. На одном из участков хранения готовой продукции было зафиксировано странное несоответствие: объемы сливочного масла в отчетах и на складах не совпадали. Производственная система, основанная на использовании высокотехнологичных датчиков и сенсоров для отслеживания каждого этапа переработки молока, начала показывать сбой в алгоритмах. Программы с искусственным интеллектом, осуществляющие мониторинг, фиксировали "лишние" поставки масла, которых не было в официальных документах.

Следственные органы выяснили, что на протяжении нескольких месяцев с завода исчезали большие партии сливочного масла. Используя свою должность и доступ к системе управления, Храмов разработал схему вывоза товара, заменяя его поддельными накладными, чтобы скрыть кражу. Показания работников, которые ранее не замечали странностей, вскоре помогли выяснить, что масла с производства ушло именно 3 тонны — около 7 миллионов рублей ущерба.
2. Расследование и задержание
Следствие было оперативным и тщательно организованным. Используя данные видеокамер, которые устанавливаются на каждом участке на таком высокотехнологичном предприятии, сыщики смогли подтвердить, что Храмов регулярно вывозил партии масла на личном транспорте. Молочное масло, вместо того чтобы попасть в сеть дистрибьюторов, отправлялось в частные магазины, а также в нелегальные точки сбыта, где продавалось значительно дороже.
Во время задержания Храмов пытался скрыться, но был пойман. На момент ареста у него было найдено несколько сумок с деньгами, полученными за продажу украденного товара, а также документы, подтверждающие сбытые партии масла через подставные компании.

3. Судебное разбирательство
Судебное разбирательство над Владимиром Храмовым началось в сентябре 2040 года. Обвинения против него были серьезными: крупное мошенничество, растрату и организацию незаконных торговых операций. Защитники Храмова утверждали, что его действия были результатом "технического сбоя" в системе учета, а не преднамеренным преступлением. По их версии, из-за ошибок в программном обеспечении комбината были нарушены процессы учета, а Храмов якобы пытался исправить ситуацию, но вышел из-под контроля.
Однако прокурор утверждал, что кража была тщательно спланированной и использовалась сеть подставных фирм для сбыта продукции. «Это не ошибка системы, а осознанное преступление, совершенное по личной выгоде, — заявил прокурор, — Это схема, которая действовала на протяжении месяцев, и последствия для всей компании могут быть катастрофическими».
4. Презентация доказательств
Одним из ключевых моментов на суде стали показания сотрудников комбината, которые в дальнейшем стали свидетелями по делу. Они рассказали, что Храмов, пользуясь своей должностью, мог менять логистические данные и создавать фальшивые отчеты для прикрытия украденных партий масла. На судебном заседании был также представлен ряд видеозаписей с камер, подтверждающих его участие в выводе масла с производства.
Эксперты также пояснили, что система отслеживания продуктов на комбинате использовала блокчейн-технологии, которые обычно обеспечивают полную прозрачность и безопасность. Однако Храмов сумел найти способ обойти систему и нарушить порядок документооборота.
5. Последствия для комбината
Комбинат "Горноправдинский молочный гигант" является крупнейшим в мире производителем молочных продуктов, и скандал с кражей стал ударом по его репутации. В ответ на происходящее, руководство комбината сделало заявление о начале внутренней реформы системы безопасности и учета. Генеральный директор предприятия, Игорь Васильевич Соловьев, отметил: "Мы примем все необходимые меры, чтобы предотвратить подобные инциденты в будущем. Мы уже усилили контроль за внутренними процессами и улучшили систему мониторинга".
Также были введены новые меры безопасности, включая использование более сложных алгоритмов защиты от манипуляций с данными. В пресс-релизе комбината также было заявлено, что все сотрудники, имеющие доступ к ключевым данным, прошли повторное обучение и были проинструктированы по вопросам этики и корпоративной безопасности.

6. Реакция общества
Скандал вызвал широкий резонанс в обществе. Местные жители, а также сотрудники комбината, были поражены тем, что такое преступление произошло в одном из самых высокотехнологичных предприятий страны. «Как можно было так обмануть систему? Мы всегда гордились этим комбинатом», — комментирует один из работников.
Сообщество потребителей также обеспокоено возможными последствиями для качества продукции. Власти Гороноправдинска пообещали, что будут проводить дополнительные проверки качества молочной продукции, произведенной на комбинате, чтобы гарантировать, что такое происшествие не повлияет на безопасность и стандарты продукции.
Судебное разбирательство продолжается, но уже на текущем этапе ясно, что это дело станет знаковым для молочной промышленности. Вопросы о прозрачности, безопасности и надежности учета на крупнейших предприятиях будут подниматься с новой силой. Эксперты считают, что в будущем такие преступления могут привести к созданию еще более сложных систем защиты данных и к серьезным изменениям в корпоративных политиках.
Храмову грозит длительный срок тюремного заключения, если его вина будет доказана. Уже сейчас его поступок рассматривается как пример того, как злоупотребление доверием на высоком уровне может привести к серьезным последствиям как для самого преступника, так и для целой отрасли.
-
 @ 04d9fac9:5bec0e6c
2024-12-12 21:47:31
@ 04d9fac9:5bec0e6c
2024-12-12 21:47:31Открытие позволит разнообразить внешний вид северного города.
Плазменные трубы — это устройства, которые используют плазму для создания яркого и эффектного освещения. Они работают на основе высоковольтных разрядов, создающих уникальные визуальные эффекты и могут использоваться как в декоративных, так и в функциональных целях. Новые плазменные трубы, разработанные воркутскими учеными и инженерами, отличаются высокой энергоэффективностью и долговечностью.
Глава города Ярослав Шапошников отметил, что запуск плазменных труб — это не только шаг к модернизации освещения Воркуты, но и возможность привлечь внимание к новым технологиям.
Ожидается, что новые плазменные трубы будут установлены в общественных местах, парках и на улицах города. Также планируется их использование в различных культурных проектах и мероприятиях, что сделает Воркуту более привлекательной для туристов.
-
 @ 4506e04e:8c16ba04
2024-12-12 21:45:08
@ 4506e04e:8c16ba04
2024-12-12 21:45:08On Saturday, July 27, 2024, at the Bitcoin 2024 Conference in Nashville, Tennessee, Donald Trump made a bold proclamation:
“The reason I’ve come to address the Bitcoin community today can be summed up in two very simple words — America First. If crypto is going to define the future, I want it to be mined, minted, and made in the USA. It’s not going to be made anywhere else.”
This statement raises critical questions: What does Trump and his administration mean by this? And what implications does it hold for Bitcoin’s global landscape?
The Bitcoin Act of 2024 and Global Hash Wars
Less than a month from now, Donald Trump’s administration will take office, and it is highly likely that the Bitcoin Act of 2024 will come into force. This act positions the United States on a strategic path to accumulate a 1-million-Bitcoin strategic reserve. Similar developments are unfolding globally. Russia’s Bitcoin Strategic Reserve Decree is set to take effect, and China, potentially re-entering the fray, is expected to lift its ban on Bitcoin mining soon. These moves signal the advent of a global hash war—a race among nations to secure dominance in Bitcoin accumulation and mining.
As of today, Thursday, December 12, 2024, approximately 94.26% of the total Bitcoin supply has already been mined. With 3.125 BTC block reward issued every 10 minutes, this equates to 450 BTC daily, 3,150 BTC weekly, and 164,250 BTC annually until the next halving. Roughly 5% (1.2 million BTC) remain to be mined before the 7th halving in 2036, at which point 99.2% of the total 21 million supply will have been mined. Beyond that, mining the remaining 0.8% will take another 104 years. Therefore practically speaking, the next decade represents a critical window for countries to establish their dominance in Bitcoin acquisition.
The US Strategy: Policies and Challenges
The US government will likely face significant challenges competing with Chinese miners using domestically manufactured mining equipment especially combined with Russian energy resources. To counteract this, the US government might come up with some creative policies i.e. to restrict Bitcoin ETFs from selling their holdings to any entity other than the US Treasury, potentially at a discounted price.
Publicly traded mining companies could also face mandates to ensure that all Bitcoin they mine remains within the United States. Since enforcing such a policy on-chain is technically not feasible, the government may explore alternative solutions, such as leveraging layer-2 technologies like eCash. This approach could see mining companies becoming mints and custodians of the Bitcoin they mine, issuing eCash tokens for trade on open markets while retaining on-chain Bitcoin in the US.
Similarly, hosted mining services might adopt a system where users purchasing mining equipment are offered eCash instead of on-chain Bitcoin. These companies could analyze users' mining profit histories and even provide lines of credit using mining equipment and future profits as collateral.
The Emerging Dual Market
Under these conditions, a dual market for Bitcoin could emerge. Non-KYC on-chain Bitcoin might trade at a significant premium—potentially 25% higher (or even more) —than its KYC-compliant counterparts. This discrepancy would reflect the increasing regulatory and geopolitical tensions surrounding Bitcoin ownership and distribution.
Conclusion
The global hash war signals a pivotal moment in Bitcoin’s history. Nations like the United States, Russia, and China are vying for strategic control over a finite resource, each deploying unique policies and tactics. As these dynamics unfold, Bitcoin’s decentralized ethos will be tested against the backdrop of geopolitical ambition, potentially reshaping its role in the global economy. Central banks will eventually print their own money to buy Bitcoin. The hyperinflation might lead to socio-economic abnormalities like social unrest and potentially famine. At that point what difference will it make if Bitcoin price is 0.1m, 1m or 10m?
-
 @ 04d9fac9:5bec0e6c
2024-12-12 21:43:32
@ 04d9fac9:5bec0e6c
2024-12-12 21:43:32Прорыв десятилетия совершили ученные из Воркуты.
В Воркуте открылась первая лаборатория по изучению квантовых частиц. Ученые работают над расшифровкой тайн квантовой физики и разработкой новых технологий на основе квантовых явлений. Это открытие может привести к революционным изменениям в науке, технике и медицине. Город Воркута становится центром квантовой исследовательской деятельности, привлекая внимание ученых и специалистов со всего мира.
Лаборатория оснащена современным оборудованием, включая лазеры, детекторы частиц и системы для создания квантовых состояний. Ожидается, что "Квантовые горизонты" будут сотрудничать с ведущими научными центрами России и зарубежья, что позволит обмениваться знаниями и опытом.
-
 @ 04d9fac9:5bec0e6c
2024-12-12 21:42:24
@ 04d9fac9:5bec0e6c
2024-12-12 21:42:24В городе запустят летающий общественный транспорт.
В Воркуте, в 2044 году, состоялся важный шаг в развитии общественного транспорта: город представил новый вид летающего общественного транспорта, который обещает значительно изменить способы передвижения горожан.
Летающий транспорт представляет собой беспилотные воздушные такси, способные перевозить пассажиров по заранее заданным маршрутам. Эти аппараты используют экологически чистые технологии и могут взлетать и приземляться вертикально, что делает их идеальными для городских условий с ограниченным пространством.
Запуск нового вида транспорта поддерживается местными властями и бизнесом, что подчеркивает стремление Воркуты к инновациям и устойчивому развитию. Глава города Ярослав Шапошников отметил, что транспорт не только улучшит транспортную доступность, но и создаст новые рабочие места в сфере высоких технологий.
-
 @ 04d9fac9:5bec0e6c
2024-12-12 21:39:45
@ 04d9fac9:5bec0e6c
2024-12-12 21:39:45Ботаники из Воркуты вывели новый вид растений с нейромозгом.
В Воркуте, в 2044 году, произошел сенсационный прорыв в ботанике: ученые из местного научно-исследовательского института вывели новый вид растений с нейромозгом. Эта уникальная разработка открывает новые горизонты в области биотехнологий и экологии. Что такое растения с нейромозгом?
Растения, получившие название "Воркута-Эко", обладают способностью к адаптации и взаимодействию с окружающей средой на уровне, ранее недоступном для флоры. Нейромозг представляет собой сеть специализированных клеток, которые функционируют аналогично нейронам животных, позволяя растениям реагировать на изменения в условиях среды, такие как температура, влажность и наличие питательных веществ.
Ученые планируют продолжить исследования в этой области, чтобы изучить потенциал "Воркута-Эко" для использования в различных сферах — от медицины до экологии. Это открытие может стать важным шагом к созданию устойчивых экосистем и улучшению условий жизни в северных регионах России.
-
 @ 04d9fac9:5bec0e6c
2024-12-12 21:36:45
@ 04d9fac9:5bec0e6c
2024-12-12 21:36:45Воркутинские ученные изобрели новый вид имплантов для человека.
В Воркуте, в 2044 году, произошел значительный прорыв в области медицины и технологий: местные ученые и инженеры разработали новый вид имплантов, который обещает революционизировать подход к медицинским процедурам и улучшить качество жизни горожан.
Импланты, названные "Воркута-Нейро", представляют собой многофункциональные устройства, интегрирующиеся с нервной системой человека. Они способны не только восстанавливать утраченные функции органов, но и улучшать когнитивные способности. Эти импланты используют передовые нейроинтерфейсы, которые позволяют взаимодействовать с мозгом на уровне нейронов, обеспечивая более точное управление и обратную связь.
Преимущества технологии:
Многофункциональность: Импланты могут использоваться для лечения различных заболеваний, включая неврологические расстройства. Интеграция с организмом: Благодаря уникальным материалам и технологиям, импланты минимизируют риск отторжения и обеспечивают долговечность. Улучшение качества жизни: Пользователи сообщают о значительном улучшении когнитивных функций и общей физической активности.
-
 @ 705605d9:b4324038
2024-12-12 21:36:11
@ 705605d9:b4324038
2024-12-12 21:36:11Любите шаурму? Будьте внимательны с выбором заведения!
Санитарные службы обнаружили серьёзные нарушения в нескольких популярных шаурмечных Горноправдинска. В список нарушителей попали 4 сети быстрого питания.
В "Шаурме на углу" инспекторы выявили нарушения условий хранения продуктов. Мясо, которое использовалось там для приготовления пищи, хранилось вне холодильников и быстро портилось.
В "Юля Кебаб" у сотрудников отсутствовали санитарные книжки, а персонал работал "в серую". Чистота на кухнях тоже оставляет желать лучшего.

Шаурмечная "Старый дед" попалась на просроченных ингредиентах — овощи, которые используют для приготовления шаурмы, здесь далеко не всегда первой свежести, хотя рекламный слоган убеждает покупателей в обратном.

А заведение Shaurman попалось на несоблюдении личной гигиены работников — на кухнях там работают без перчаток, а рабочие поверхности (столы, гриль и т.п.) не очищаются должным образом.
Все заведения, в которых обнаружены нарушения, временно закрыты. Владельцев обязали провести полную внеплановую проверку производственных процессов и обеспечить соблюдение санитарных норм. Кроме того, им назначены штрафы за нарушения.

Но отчаиваться не стоит: в городе всё ещё есть заведения, которые прошли санитарную проверку и могут порадовать потребителей ассортиментом блюд и качеством ингредиентов. Например, в "ШаурмаShop" вы можете попробовать почти 20 видов шаурмы, а ресторан "ShaurMexican" — прекрасное место для посиделок с друзьями. Также проверку прошли "Шаурмандия", "SHRM", "На углу" и "ШаурмArt".
-
 @ 04d9fac9:5bec0e6c
2024-12-12 21:33:27
@ 04d9fac9:5bec0e6c
2024-12-12 21:33:27В Воркуте состоялась церемония подписания соглашения о сотрудничестве с несколькими международными университетами. Это важное событие направлено на обмен опытом и привлечение студентов для обучения в нашем городе.
Соглашение подписали представители администрации Воркуты и зарубежных учебных заведений, что открывает новые горизонты для образовательного процесса в регионе. В рамках партнерства планируется реализация совместных образовательных программ, стажировок и научных исследований, что позволит студентам получить уникальный опыт и знания в различных областях.
Глава администрации Воркуты, Алексей Петров, отметил значимость данного сотрудничества: «Подписание этого соглашения — это шаг к международной интеграции нашего образования. Мы уверены, что это привлечет внимание студентов из других стран и повысит престиж наших учебных заведений».
Партнерство с международными университетами также создаст возможности для преподавателей и студентов Воркуты участвовать в обменах, что будет способствовать развитию новых идей и подходов в обучении. Ожидается, что это сотрудничество станет основой для создания инновационной образовательной среды, соответствующей современным требованиям.
В ближайшие месяцы планируется разработка конкретных программ и мероприятий в рамках этого соглашения, что позволит уже в следующем учебном году начать реализацию совместных проектов. Соглашение о сотрудничестве открывает новые перспективы для развития образования в Воркуте и укрепляет связи с международным
-
 @ d0bf8568:4db3e76f
2024-12-12 21:26:52
@ d0bf8568:4db3e76f
2024-12-12 21:26:52Depuis sa création en 2009, Bitcoin suscite débats passionnés. Pour certains, il s’agit d’une tentative utopique d’émancipation du pouvoir étatique, inspirée par une philosophie libertarienne radicale. Pour d’autres, c'est une réponse pragmatique à un système monétaire mondial jugé défaillant. Ces deux perspectives, souvent opposées, méritent d’être confrontées pour mieux comprendre les enjeux et les limites de cette révolution monétaire.

La critique économique de Bitcoin
David Cayla, dans ses dernières contributions, perçoit Bitcoin comme une tentative de réaliser une « utopie libertarienne ». Selon lui, les inventeurs des cryptomonnaies cherchent à créer une monnaie détachée de l’État et des rapports sociaux traditionnels, en s’inspirant de l’école autrichienne d’économie. Cette école, incarnée par des penseurs comme Friedrich Hayek, prône une monnaie privée et indépendante de l’intervention politique.
Cayla reproche à Bitcoin de nier la dimension intrinsèquement sociale et politique de la monnaie. Pour lui, toute monnaie repose sur la confiance collective et la régulation étatique. En rendant la monnaie exogène et dénuée de dette, Bitcoin chercherait à éviter les interactions sociales au profit d’une logique purement individuelle. Selon cette analyse, Bitcoin serait une illusion, incapable de remplacer les monnaies traditionnelles qui sont des « biens publics » soutenus par des institutions.
Cependant, cette critique semble minimiser la légitimité des motivations derrière Bitcoin. La crise financière de 2008, marquée par des abus systémiques et des sauvetages bancaires controversés, a largement érodé la confiance dans les systèmes monétaires centralisés. Bitcoin n’est pas qu’une réaction idéologique : c’est une tentative de créer un système monétaire transparent, immuable et résistant aux manipulations.
La perspective maximaliste
Pour les bitcoiners, Bitcoin n’est pas une utopie mais une réponse pragmatique à un problème réel : la centralisation excessive et les défaillances des monnaies fiat. Contrairement à ce que Cayla affirme, Bitcoin ne cherche pas à nier la société, mais à protéger les individus de la coercition étatique. En déplaçant la confiance des institutions vers un protocole neutre et transparent, Bitcoin redéfinit les bases des échanges monétaires.
L’accusation selon laquelle Bitcoin serait « asocial » ignore son écosystème communautaire mondial. Les bitcoiners collaborent activement à l’amélioration du réseau, organisent des événements éducatifs et développent des outils inclusifs. Bitcoin n’est pas un rejet des rapports sociaux, mais une tentative de les reconstruire sur des bases plus justes et transparentes.
Un maximaliste insisterait également sur l’émergence historique de la monnaie. Contrairement à l’idée que l’État aurait toujours créé la monnaie, de nombreux exemples montrent que celle-ci émergeait souvent du marché, avant d’être capturée par les gouvernements pour financer des guerres ou imposer des monopoles. Bitcoin réintroduit une monnaie à l’abri des manipulations politiques, similaire aux systèmes basés sur l’or, mais en mieux : numérique, immuable et accessible.
Utopie contre réalité
Si Cayla critique l’absence de dette dans Bitcoin, Nous y voyons une vertu. La « monnaie-dette » actuelle repose sur un système de création monétaire inflationniste qui favorise les inégalités et l’érosion du pouvoir d’achat. En limitant son offre à 21 millions d’unités, Bitcoin offre une alternative saine et prévisible, loin des politiques monétaires arbitraires.
Cependant, les maximalistes ne nient pas que Bitcoin ait encore des défis à relever. La volatilité de sa valeur, sa complexité technique pour les nouveaux utilisateurs, et les tensions entre réglementation et liberté individuelle sont des questions ouvertes. Mais pour autant, ces épreuves ne remettent pas en cause sa pertinence. Au contraire, elles illustrent l’importance de réfléchir à des modèles alternatifs.
Conclusion : un débat essentiel
Bitcoin n’est pas une utopie libertarienne, mais une révolution monétaire sans précédent. Les critiques de Cayla, bien qu’intellectuellement stimulantes, manquent de saisir l’essence de Bitcoin : une monnaie qui libère les individus des abus systémiques des États et des institutions centralisées. Loin de simplement avoir un « potentiel », Bitcoin est déjà en train de redéfinir les rapports entre la monnaie, la société et la liberté. Bitcoin offre une expérience unique : celle d’une monnaie mondiale, neutre et décentralisée, qui redonne le pouvoir aux individus. Que l’on soit sceptique ou enthousiaste, il est clair que Bitcoin oblige à repenser les rapports entre monnaie, société et État.
En fin de compte, le débat sur Bitcoin n’est pas seulement une querelle sur sa légitimité, mais une interrogation sur la manière dont il redessine les rapports sociaux et sociétaux autour de la monnaie. En rendant le pouvoir monétaire à chaque individu, Bitcoin propose un modèle où les interactions économiques peuvent être réalisées sans coercition, renforçant ainsi la confiance mutuelle et les communautés globales. Cette discussion, loin d’être close, ne fait que commencer.
-
 @ 04d9fac9:5bec0e6c
2024-12-12 21:21:46
@ 04d9fac9:5bec0e6c
2024-12-12 21:21:46В Воркуте состоялось торжественное открытие современного угольного перерабатывающего завода, который станет важным шагом в переходе к экологически чистым технологиям в угольной промышленности. Новый завод позволит перерабатывать уголь в экологически чистые продукты, что значительно снизит негативное воздействие на окружающую среду.
Экологические преимущества
Завод оснащен передовым оборудованием, которое позволяет минимизировать выбросы вредных веществ в атмосферу и эффективно утилизировать отходы производства. Это соответствует современным требованиям экологической безопасности и государственной стратегии по снижению углеродного следа.
Создание рабочих мест
Открытие завода создаст более 800 новых рабочих мест, что станет значительным вкладом в экономику региона. Местные жители получат возможность трудоустройства на современном производстве с конкурентоспособными условиями труда и достойной заработной платой. Поддержка местного бизнеса Новый завод также откроет новые возможности для местных поставщиков и подрядчиков, что будет способствовать развитию малого и среднего бизнеса в Воркуте. Предполагается, что завод будет закупать сырье и услуги у местных компаний, что дополнительно поддержит экономику региона.
Реакция властей
Глава Республики Коми, Владимир Уйба, отметил важность данного проекта для устойчивого развития Воркуты: «Открытие угольного перерабатывающего завода — это не только шаг к улучшению экологии, но и возможность для наших граждан получить новые рабочие места. Мы уверены, что этот проект станет примером успешной интеграции экологических технологий в традиционные отрасли».
Перспективы развития
В будущем планируется расширение производственных мощностей завода и внедрение новых технологий переработки угля. Это позволит не только улучшить качество продукции, но и повысить эффективность производства. С открытием нового завода Воркута делает важный шаг к устойчивому развитию и модернизации своей экономики, сочетая традиционные отрасли с инновационными подходами к экологии.
-
 @ 04d9fac9:5bec0e6c
2024-12-12 21:11:48
@ 04d9fac9:5bec0e6c
2024-12-12 21:11:48Городская администрация Воркуты объявила о начале строительства нового арктического транспортного узла, который станет важной частью логистической инфраструктуры региона. Этот проект, стоимостью более 5 миллиардов рублей, направлен на улучшение транспортной доступности и развитие экономики Арктической зоны.
Цели проекта
Новый транспортный узел призван соединить Воркуту с ключевыми арктическими маршрутами, что позволит значительно ускорить грузоперевозки и повысить конкурентоспособность местных предприятий. В рамках проекта будут построены современные терминалы для обработки грузов, а также обновлены дороги и железнодорожные пути.
**Экономическое воздействие ** По оценкам экспертов, реализация проекта создаст около 1 500 новых рабочих мест в строительстве и обслуживании транспортной инфраструктуры. Это также привлечет инвестиции в сопутствующие отрасли, такие как логистика, переработка и сервисное обслуживание.
Устойчивое развитие
Особое внимание будет уделено экологическим аспектам строительства. Все работы будут проводиться с соблюдением современных стандартов охраны окружающей среды. В рамках проекта предусмотрено создание зеленых зон и внедрение технологий, минимизирующих негативное воздействие на природу.
Ожидания от проекта
Глава администрации Воркуты, Алексей Петров, подчеркнул важность данного проекта для будущего города: «Строительство арктического транспортного узла — это шаг к новому этапу развития Воркуты. Мы уверены, что он не только улучшит логистику, но и создаст новые возможности для бизнеса и жителей нашего города». Строительство нового транспортного узла начнется в начале следующего года, а завершение работ запланировано на 2046 год. Ожидается, что проект станет важным шагом к превращению Воркуты в ключевой логистический центр Арктики.
-
 @ c43d6de3:a6583169
2024-12-12 20:31:40
@ c43d6de3:a6583169
2024-12-12 20:31:40
Photo by Bastien Jaillot on Unsplash
I finished wiping shit off my screaming daughter’s butt cheeks, and my nostrils were assaulted by the sweet and steamy plume of several-days-old feces basting in the diaper pail. I’d long lost my sense of disgust; the sharp hit of reality was almost appealing, really.
The moment was passing almost as fast as the day had. My son shot up between my legs and wailed for me to just fucking pick him up. My hands moved on autopilot as I finished getting my daughter ready for bed and finally got her off the changing table. Then, I picked up my son and did it all over again.
Ass. Wiped.
Nostrils. Blasted.
Mind. Melted.
I shut off the lights to remind my children it was time to start simmering down. They rebelled, knowing the day was coming to an end and their tyrant father would soon be forcing them to go quietly into the night. I wrangled them onto my lap and rocked violently on the rocking chair as if the swift movement would make them forget they were screaming.
There has never been any reasoning with these little goblins. They haven’t quite grasped that aspect of humanity just yet. The world is still so fresh and vibrant that they grasp for every waking moment they can get their hands on.
I know they like cartoons. That would quiet them, but it would also keep them up until the tyrant decides to shut it off. I figured they might do well with some calming music. That would put me to sleep, not them. I swayed slightly, trying to soothe myself, and it hit me — perhaps a calming musical. Something like, The Sound of Music.
Yes.
My thumbprint brought my phone screen to life and then fluttered to the YouTube icon. I typed, My Favorite Things, and the darkness consuming my children’s bedroom was filled with the soft golden glow of Julie Andrews’s Maria as she sang in her room to the seven von Trapp children, soothing them through the thunderstorm.
That melody had once soothed my little brother when he was about the age my children were just then. The screaming stopped. They rested their little heads on my chest, and their eyes glimmered as they watched Julie Andrews sing beautifully.
The clip quickly came to an end, and my daughter excitedly begged for another. I needed something longer that might perhaps whisk them to sleep.
I typed, A Lovely Night — La La Land.
My children’s reaction to that momentous scene in cinematic history made me realize I had been wrong about parenting all my life. I’d been working so hard to instill habits and rigid structure to ensure my children would become the best little humans around, but all I was doing was drizzling my grey habits, dull routines, and logic over their still-vibrant canvas of the world.
Ryan Gosling and Emma Stone tap-dancing jazzily across the screen while singing their playful lyrics created a work of art that sparked my children’s wonder and rekindled the fire of curiosity inside me as I watched it happen. That little moment made me realize that art can sometimes revitalize our lives by allowing us to see through the lens of curiosity and possibility — as if we were one or two years old again.
Parenting didn’t have to mean smothering my children’s creativity with structure. Instead, it could mean letting their wonder guide me — even as I’m guiding them. It reminded me that life isn’t just about routines or rules; it’s about the moments of beauty and spontaneity that keep us connected to the world, to art, and to each other. And in those quiet, golden moments, I rediscovered a part of myself I’d forgotten: the part that sees magic in the mundane and finds joy in the unexpected.
Here on NOSTR, I want to show the world that life is a scroll riddled with ink. The marks will only ever be simple blots on the parchment unless you pause and perceive them for the characters they are.
I’m constantly thinking about what the future could look like if we just take action.
More of my thoughts about the future and the world around us are coming soon here and on Medium.
Thank you for Reading this article. Doing so supports me and motivates me to continue writing! If you liked this article and want to continue supporting me, consider zapping it. That'll tell me you got some great value out of it and I'll continue to write more pieces like it.
If you are interested in Fiction writing, visit my NOSTR page Fervid Fables.
-
 @ 13a1e375:3005c388
2024-12-12 20:11:34
@ 13a1e375:3005c388
2024-12-12 20:11:34Nostr Obsidian Graph
https://github.com/LamekaRjeggr/nostr-obsidian-graph.git
Currently only tested on Obsidian for MacOS.
A short Demo:
![[readme gif 1.gif]]
-
 @ dbb19ae0:c3f22d5a
2024-12-12 19:47:23
@ dbb19ae0:c3f22d5a
2024-12-12 19:47:23I am using Nostr daily, I spend most of my time on Primal(the web browser client) the great thing about Nostr is the whole ecosystem of apps which offer a little twist of their own. All of this is possible by the use of the Nostr profile secret key (via an extension (alby or nos2x) best practice is to never use the nsec directly).
For example pinstr will behave like pinterest for Nostr, to create image gallery collection, another example would be nostrapp or nostrapplinkwhich are a repository of Nostr apps (with reviews) …
Among all these apps, there is one particular service under the name npub.pro, which acts as a dynamic portfolio page, it is presented as a ‘Beautiful nostr-based websites for creators’.
 This website is part of the nostr.band family (as nostrapplink), you can recognize them as all website powered by nostr.band have this right handle with the user nostr profile (which appears in the middle).
This website is part of the nostr.band family (as nostrapplink), you can recognize them as all website powered by nostr.band have this right handle with the user nostr profile (which appears in the middle).Once on the npub.pro page, just click on "try now" button
from there the process is very similar to setting up a tumblr profile, or wordpress website, except the content already exist (it will be extracted from the nostr profile) and once the theme has been chosen, press publish and voila! super easy, user friendly and great result in minutes.
The creator of npub.pro is 'Brugeman'. I have asked a couple of question because the search was not working when I created my npub.pro website, it turns out it was not fully implemented yet, the good news is that search is working now and for later edit of the website keep this link nearby npub.pro/admin (you can edit the theme from there if you change your mind later.)
If you want to have a look at an example – here is mine
 ever4st.npub.pro
ever4st.npub.prooriginal article posted here
-
 @ 31312140:2471509b
2024-12-12 18:19:11
@ 31312140:2471509b
2024-12-12 18:19:11Understanding Real Money
The Awful Truth About Fiat Currency
Let's call a spade a spade here - fiat currency is a scam. Governments and central banks print it out of thin air, devaluing each note in your wallet every single day. Your hard-earned money is losing its value, and you're left chasing your tail trying to keep up with inflation.
Fiat currency is backed by nothing but the "full faith and credit" of the government. And when was the last time you trusted a politician? 😏 The truth is, fiat currencies always collapse. History is littered with examples like the Roman denarius, the Zimbabwean dollar, and, well, the ongoing crumbling of many others.
The Concept of Intrinsic Value
Real money, on the other hand, has intrinsic value—meaning it's valuable in and of itself. Think gold and silver. These precious metals have been prized for thousands of years because they don't decay, they're hard to counterfeit, and they have myriad uses in the real world, from electronics to medicine.
Gold and silver have been used as money for millennia, and for good reason. They're scarce, durable, and divisible. You can't just print more gold when you feel like it. You have to mine it, refine it, and cast it.
Bitcoin: The Digital Gold
Now, let's talk about Bitcoin. Some people call it "digital gold," and there's a good reason for that. Bitcoin, like gold, is scarce (only 21 million will ever exist), and it's decentralized, meaning no government or bank can control it. This decentralization is key because it means Bitcoin is resistant to censorship and inflation.
Bitcoin stands out as the only cryptocurrency that can be considered real money due to its decentralized nature, fixed supply of 21 million coins, unparalleled security, global adoption, resilience, and the philosophy of financial sovereignty it embodies. Unlike other cryptocurrencies that often have centralized control and variable supplies, Bitcoin's immutable transactions and widespread recognition make it a reliable store of value and medium of exchange.
But remember, Bitcoin isn't a perfect substitute for gold. It's digital, which means it relies on technology and the internet to function. This makes it vulnerable to hacking and other digital threats. Still, the blockchain technology underpinning Bitcoin is revolutionary, creating a transparent and tamper-evident ledger of transactions.
The Downfall of Modern Banking Systems
Let's take a step back and look at the modern banking system. It's a joke. Fractional reserve banking allows banks to lend out money they don't have, creating an economic bubble that inevitably bursts. We're constantly teetering on the edge of financial collapse because banks are playing a high-stakes game of musical chairs with your money.
And when things go south, who gets bailed out? Not you or me, but the banks. We saw it in 2008. The rich and powerful protected their own interests, while everyday folks lost their homes and savings.
Why Governments Love Fiat
Governments love fiat money because it allows them to spend beyond their means. When the treasury gets low, they don’t have to make tough decisions or cut spending—they just print more money. This leads to inflation, which is just another form of taxation. Your dollar buys less; your savings erode.
This manipulation benefits the elites who get the newly printed money first. They can spend it while it still has value, before it trickles down into the economy and prices rise for everyone else. Trickle-down economics is as real as fairy tales. 🧚♂️
Creating a Solution: Moving Towards Real Money
To reclaim our financial sovereignty, we must return to real money. Here's how:
Gold and Silver
Start by accumulating gold and silver. Begin small—buying a few ounces here and there. Store it securely, away from banks where it could be confiscated. There are many platforms and shops where you can purchase these metals safely.
Bitcoin
Diversify with Bitcoin. Make sure you understand how wallets work and practice impeccable security measures. It's not enough to buy Bitcoin; you must ensure it can't be stolen by hackers. Educate yourself on cold storage, multi-signature wallets, and other security practices.
Educate Yourself
Knowledge is power. Read books on Austrian economics, like those by Ludwig von Mises and Murray Rothbard. Understand the fundamentals of what makes good money.
The Future of Real Money
If we succeed in transitioning to real money, we can create a more sustainable and fair economic system. One where value is preserved over time, where individuals have sovereignty over their own wealth, and where the powerful can no longer manipulate the masses for their gain.
Final Thoughts
The fight for real money is a fight against the controllers, the manipulators, and the corrupt. But it’s also a fight for our freedom, our future, and our dignity. Let's look into it and make conscious choices to protect our financial future by holding real money.
Keep your head up, keep questioning, and always look into it 💪
Suggested Readings and References
- "The Creature from Jekyll Island" by G. Edward Griffin - A detailed look at the Federal Reserve and how it manipulates the money supply.
- "What Has Government Done to Our Money?" by Murray Rothbard - An essential read on the problem with fiat currency and why real money matters.
- "The Bitcoin Standard" by Saifedean Ammous - A comprehensive analysis of Bitcoin as a form of digital gold.
- "Human Action" by Ludwig von Mises - A cornerstone work for understanding Austrian economics.
- "Democracy: The God That Failed" by Hans-Hermann Hoppe - A deep dive into the failures of democratic government and the economics of anarcho-capitalism.
-
 @ 3ad01248:962d8a07
2024-12-12 16:47:27
@ 3ad01248:962d8a07
2024-12-12 16:47:27The Bitcoin protocol has been around for 15 years and just it keeps on going doing its thing with improvements made along the way to make it better and stronger. Bitcoin has always been described as a way to change the world by fixing the money. It will certainly do that with enough time and adoption by everyday folks around the world.
What isn't discussed as much as it should be is what Bitcoin does to you emotionally and how it completely changes your worldview and opens your eyes to the manipulation and distortion of reality created by fiat currency. I can only speak to my personal experience but I have seen multiple instances on X and nostr where people describe having transformational changes because of Bitcoin.
I found Bitcoin in 2020 by chance to be honest, I was scrolling Twitter when I stumbled upon someone saying that Bitcoin was freedom money. I remember thinking to myself "what the hell is freedom money?" I like to learn and I am curious by nature so I started to research what this Bitcoin thing was.
What I discovered blew my mind! As a avid fan of Ron Paul and Austrian economics I felt like I was primed and ready to go down the Bitcoin rabbit hole. Needless to say I jumped in with two feet first and haven't looked back since but I have come out the other side a changed person.
HODL CULTURE
Once you start down the rabbit hole there are so many twist and turn that you can take where it becomes a little overwhelming. What helped me get my bearings as I was learning about Bitcoin was the HODL culture that had been cultivated on Twitter. We all the know the catchphrases"
- "Not Your Keys, Not Your Coins"
- "There Is Only 21 Million"
- "Have Fun Staying Poor"
- "Bitcoin not Shitcoins"
- "Don't Sell Your Bitcoin"
- "Code Is Law"
Hearing and seeing this over and over gave me a firm ground to stand on and helped me understand that Bitcoin is step change function in how society interacts with money. For the first time in history we have a money that can't be manipulated by governments or other malicious third parties.
Bitcoin opens your eyes to what governments can do with an unlimited power to print money. They start world wars, stage coups all around the world and distort the perception of their citizens with propaganda. It is truly sickening that governments have gotten away with this for this long. Millions upon millions of people have died because of fiat currency. Bitcoin smashes the war machine and makes war costly thus making the world more peaceful.
I personally want to thank the toxic Bitcoin maximalist for standing on principle and staying true to the message despite the harsh criticism many of you have faced. I am forever grateful for your steadfastness to the Bitcoin revolution.
Hodl culture is firmly engrained into the Bitcoin community and will help countless others to see how Bitcoin is different from fiat and other digital assets. A by product of HODL culture is that it naturally encourages you to lower your time preference and appreciate the small things in life.
Low Time Preference
Low time preference was a term that I wasn't familiar with until I read Saifedean Ammous's book the Bitcoin Standard. For those that are unaware of the concept, the basic idea is when you have a money that doesn't store its value well you tend to focus on the here and now because you know your money is going to be worth a lot less in the future.
Why save for a new house or new car when you know that if you hold dollars for any amount of time your purchasing power is going to be less than it is today. This is why the savings rate among Americans are abysmal and will not get better any time soon. Most people are simply making a rational choice to maximize their purchasing power today versus waiting for tomorrow.
Not only are consumers are doing this but businesses are too. Have you noticed the quality of your appliances keeps getting worse? Back in the day, you could buy appliances that were built to last 15-20 years. Now you would be lucky to get an appliance that last more than 18 months without some major issue. Business are incentivized to thinking about short term profits versus building solid products that last and building a brand known for quality.
Bitcoin flips this whole situation on its head where the longer you hold Bitcoin the cheaper the product that you want gets cheaper over time. This foundational function of Bitcoin has made it where I don't want much of anything these days. I've noticed the dramatic behavior change within myself. Before Bitcoin I would buy a new car probably every 3-4 years. Since learning about Bitcoin I haven't had the urge to replace my car, in fact I've learned to appreciate that I have vehicle that gets me from point A to point B and back. I don't need the fancy new car with all the bells and whistles.
Having a low time preference helps you focus on what is important in life such as family and your personal health and wellness. It's not wealth, a big house or a fancy car. Sure you might acquire some of these things as the Bitcoin price appreciates but it is not the main motivator for true Bitcoiners who truly want to transform the world we live in. Imagine a world where everyone had a lower time preference than they do now.
People would be less stressed out, healthier, and happier. Work would no longer define who we are or what we think of ourselves. Instead work would be something that we do for leisure when you want to earn more Bitcoin. Our buildings would be beautiful again because we could spend more time creating works of art instead of industrial soulless buildings. Our environment would be cleaner because we wouldn't have rapacious mega corporations scavenging the world for minerals, instead they could focus on innovating or using the minerals that we have out of the ground more efficiently.
Fostering a low time preference is Bitcoin's superpower that you don't even realize is changing you into a different person. Bitcoin changes you and the world for the better. I hope more people choose to embrace Bitcoin and see what we see in it.
-
 @ d57360cb:4fe7d935
2024-12-12 15:54:37
@ d57360cb:4fe7d935
2024-12-12 15:54:37It’s the final round of the yearly state championship for wrestling in California. Only the best of the best elite high school athletes can crack the top spot. Somehow, someway, Meki claimed his spot. Meki was naturally gifted, had unwavering discipline, and elite skill. In practice, he would dominate completely; the gap between him and the other competitors was clear as day. Yet, whenever it came to big stages and big competitions, Meki would fade away, becoming a shell of who he was in practice. It bewildered everyone. In practice, he was feared, impossible to stop. In competition, he was timid, too slow, and made one horrible decision after another. He’d made it to the state championship four straight years; the previous three years, he lost in the first round. It would come as a surprise to all. Meki topped the online wrestling leaderboard each year. His performance in other matches during the school year earned it. Meki would cast this spell on his coaches and colleagues each year, outperforming and winning his matches as the season went along. They would believe each time this year is different, he’s learned from his mistakes. Maybe he wasn’t used to that atmosphere. Without fail, when the bright lights came on, they would be in shock. The coaches saw nothing wrong with his style and the way he wrestled; they couldn’t crack the code; their solution was to do more. Work harder, keep practicing, keep sharpening the skills; next year we’ll get the win.
It was most frustrating to Meki himself. He enjoyed the highs that came from people praising how good he was. He thrived on the praise; he sought admiration from his opponents, colleagues, coaches, and women. He would walk out of practices with his chin up in the air when he had a great day. He would feel like he was the best in the world; no one could match him; he was above anyone he faced. Of course, when the lows came and those previous championship events handed him defeat, Meki would lose his mind. Falling into a deep depression and losing all confidence in himself. He would lock himself in his room and become so ill that he would throw up. His anger would boil, and he’d throw things and break them at random, crying himself to sleep at night. Wondering what was wrong with him. That cocky confidence he’d carry when he’d succeed vanished into thin air. All the doubt started to creep in; he felt like quitting, giving up. He’d see it as an insurmountable wall he couldn’t climb. This would last for around three weeks after the competitions; then Meki would come to the same conclusion as his coaches because that’s all he knew. Work harder, work longer; next year will be different.
Meki grew up in a very demanding household. Both his father and mother were high achievers in everything that they did, especially their careers. His dad was a high-powered attorney, his mom a top executive marketer. To their household, success was the only metric, and if you didn’t meet that, you would get harsh looks of criticism and doubts of silence. Naturally, Meki wanted to succeed at all costs; he had to look good in the eyes of his parents, authority, and in the eyes of people in general. His parents would boast about their success in conversation; they would belittle all those who weren’t on their ‘level’. Failure to him wasn’t an option. He hated the feeling more than anything in the world. It was this hate of failure that fueled him and gave him an obsessive drive to win. His work ethic was the way it was not because of passion, but for fear of avoiding embarrassment. He loved wrestling. But the fun and joy it gave him as a child faded. He replaced them with the effort to uphold his image and succeed. That he did; he succeeded and he did it well, ranking number one in the country is no small feat, but when you lose a championship in the first round, none of it means a damn thing.
Meki stands facing his opponent; it’s his fourth year in this position. All that is on the forefront of his mind is the previous three years of failure. He hears the doubt of his parents, opponents, and coaches. They haven’t said a thing in reality, but to his mind, they have been berating him endlessly for the past week. The match starts, and Meki is overthinking. His opponent crouches low to size him up, then fakes a shot. Meki bites. Next thing he knows, his opponent is on his back. He takes him by the back and slams Meki to the ground and pins him all in under one minute. Once again the same old story. Meki goes blank and stares at the ceiling; everything fades away and there’s an eerie silence. He can’t believe it: four straight years of failure. He concludes at that moment he’s done. The match ends, and Meki doesn’t say a word to anyone; he goes home, sits in his room, and cries. He takes all his previous trophies and throws them in the trash. His dream was to be an Olympian, and he realized it was over. That night, something died in Meki; a part of his soul became dormant as he realized he would live an ordinary life.
In the years that preceded, Meki would go to college and complete a degree in economics. He wasn’t fond of economics, but he’d always been good with numbers, and it made him feel important again being good at something. He would get a job soon after in Palo Alto and do very well for himself. His parents were filled with pride, and he enjoyed their praise. He rose to the top of his field in much the same way he did in wrestling, with the same motives to avoid failure at all costs. His discipline and work ethic were still there: work harder, work longer, and you’ll succeed. The failures from wrestling seemed to have disappeared for the years he went to college and worked as an economist. Meki was now twenty-eight years old. He lived as a bachelor, dated many women, yet didn’t want to settle down at that moment. He would spend his weekends surfing and going to lunch with various friends he’d met in college. He lived a good life, a successful one.
One Sunday afternoon, Meki went to the local shopping plaza nearby for lunch. He went to a deli spot and got his usual footlong wheat bread, turkey, Swiss cheese, avocado sandwich with house dressing. He rarely ate at the deli, but today he decided to do so. He grabbed a seat outside and ate his sandwich as he stared off and people-watched in the plaza. At the far end, he noticed a new business had opened up; there was no sign to indicate what it was, but it had a large ‘Grand Opening’ banner hanging from where the sign should be. He saw a group of high school kids, athletes filing into the building. After he finished his sandwich, he walked over and stood outside to window-watch. It was a wrestling gym. His eyes lit up as did something deep in his core. As he stared at the athletes practicing their moves, he began to reminisce about the art he used to love. A violent urge came upon him to wrestle again; he had to do it. He waited until the class was over and he walked into the gym. The instructor was cleaning the mats. He vacuumed the floors, then mopped. The man came over to him when he finished; he was a short man, five foot three. Meki couldn’t tell his age, but he was past forty. He was in great shape. His face was strong and square, but showed some wear. His ears were swollen from cauliflower ear. He shook Meki’s hand with a deep smile. Meki wasn’t sure a man that looked like this could smile. But when he did, his stone face cracked and revealed a bright light. “I’m Onami, nice to meet you,” he said. Meki concluded, from the speed and sound of his intro, that English wasn’t his first language.
‘Nice to meet you. Is there any chance there’s an adult class?’ Meki said.
“Adults, yes, we have five p.m. Monday-Sunday,” a smile still brimming from his face. “You have a strong build; you look like a wrestler,” Oname said.
“Yes, I used to wrestle in high school; it’s been ten years since I’ve done any wrestling at all. I’d like to think I was a skilled wrestler, but each time I went to compete on a big stage, I crumbled. I overthought and failed time and again,” Meki said.
“Ah, you have a disease of the mind. Come tonight,” Onami told him.
Meki was confused. He wasn’t sure he understood “disease of the mind.” For all he knew, he was functioning perfectly well.
Meki arrived that Sunday evening to the adult class. It was a light showing; only four students, including Meki were present. Each were intermediate level grapplers. Oname warmed up the students with laps, jumping jacks, and burpees. Oname followed this up with thirty minutes of technical instruction. He taught them the basic double leg takedown. One of Meki’s favorite moves. Although Meki has done thousands of double leg takedowns in his lifetime, the way Oname delivered the instruction made Meki feel like he’d never seen a double leg takedown before. Something so basic became severely complex. It fueled Meki further; he was so immersed in the experience that, for a moment, he completely vanished. All he saw was Oname demonstrating the move on one of the students; it happened in slow motion. It looked like it was taking place in a different universe, one Meki had no prior knowledge of. Meki observed every detail with laser-like focus. Only pure curiosity remained. After the instruction, there were twenty minutes for the students to spar. Meki still deep in his experience of flow, became unconscious. It felt as if he were watching himself from above. He sparred with spontaneity and lightning-fast reflexes. He was constantly ten steps ahead of his opponents. Oname watched with amazement; he’d never seen a talent so pure.
The sound of the bell going off, signaling the end of class, awakened Meki from his deep focus. He returned to his normal state dizzy, unable to breathe, unable to believe what had happened. He’d had success in wrestling as a youth but none to match the experience he felt. For the first time, he wasn’t concerned with winning or losing. He wasn’t concerned with what anyone thought about his skills, how he was doing in the match, no thought of failure; all that was there was a natural open fluidity that flowed like an endless river. There were no mistakes, no judgments, no opponents. Just a feel, intuitive, artistic. Something missing from Meki’s life, a feel for it, a place you can’t get to thinking. He understood for the first time why they called it martial arts. It was a true art form expressed from a place beyond ego.
As the class ended and the students trickled out, Meki sat at the end of the wrestling mats and closed his eyes. He fell into a deep meditative state; for how long he was sitting, he didn’t know. He began to see images of a vast ocean, himself in the middle of it. The depth of him and the ocean was endless, calm, at peace, undisturbed by the world, and most importantly, at home. The ocean began to rumble first slightly, then growing with each breath. The waves started to crash and crash. They became enormous, tsunami-like, and began to wipe out everything in their path. Violent eruptions crashed up and down, erasing everything in their path. A power unexplainable, a force uncontrollable took Meki over and he began to feel every emotion from deep sadness to great force and happiness, all of it taken in by the waves and crushed completely. He became the waves. They slowly wiped away his fears, insecurities, and vulnerabilities. Meki began to feel his breath cold as ice, lighting up his belly and spine as his body breathed deeply on its own. A silence came over him as the waves settled and all that was left was darkness.
There were never any opponents; it was always Meki himself who was in his own way. He never gave himself up to the power within him. He was afraid of it; he trusted everyone else’s opinions as a way to shield him from himself. He failed to realize his opponents were not there to attack him but to bring out that very power in him. Overcome with gratitude, he saw his opponents as vital to his growth. He realized he held the same responsibility to his opponents.
When Meki opened his eyes, he saw outside the gym window the sun rising, creeping its way out of the mountains. Meki had meditated through the entire night after the class ended. Onami was sitting in the same meditation posture on the opposite side across the mat from Meki. Meki noticed a pool of sweat below his feet as he gazed at Onami. That stone face cracked a smile and brimmed with light. Onami bowed deeply to Meki.
“I’ve never once felt free of myself until last night. The way you taught yesterday carried me to another shore,” Meki said.
Onami replied, “You are that great ocean you experienced, you’re as powerful as those waves. No one can defeat you now; you will sweep everything in your path.”
Meki became a regular at Onami’s wrestling school; it just so happened that the Olympics were taking place that year.
Like a twist of fate, Meki would have another shot at the biggest stage.
Onami would gift Meki the nickname ‘Great Waves’; he would go on to win a gold medal and remain undefeated in his professional career until he retired.
-
 @ 04d9fac9:5bec0e6c
2024-12-12 15:42:09
@ 04d9fac9:5bec0e6c
2024-12-12 15:42:09https://rutube.ru/audio/3d14b1cf494e425268ef9bc53040dd1a/?r=wd





