-
 @ 9f94e6cc:f3472946
2024-11-21 18:55:12
@ 9f94e6cc:f3472946
2024-11-21 18:55:12Der Entartungswettbewerb TikTok hat die Jugend im Griff und verbrutzelt ihre Hirne. Über Reels, den Siegeszug des Hochformats und die Regeln der Viralität.
Text: Aron Morhoff
Hollywood steckt heute in der Hosentasche. 70 Prozent aller YouTube-Inhalte werden auf mobilen Endgeräten, also Smartphones, geschaut. Instagram und TikTok sind die angesagtesten Anwendungen für junge Menschen. Es gibt sie nur noch als App, und ihr Design ist für Mobiltelefone optimiert.
Einst waren Rechner und Laptops die Tools, mit denen ins Internet gegangen wurde. Auch als das Smartphone seinen Siegeszug antrat, waren die Sehgewohnheiten noch auf das Querformat ausgerichtet. Heute werden Rechner fast nur noch zum Arbeiten verwendet. Das Berieseln, die Unterhaltung, das passive Konsumieren hat sich vollständig auf die iPhones und Samsungs dieser Welt verlagert. Das Telefon hat den aufrechten Gang angenommen, kaum einer mehr hält sein Gerät waagerecht.
Homo Digitalis Erectus
Die Welt steht also Kopf. Die Form eines Mediums hat Einfluss auf den Inhalt. Marshall McLuhan formulierte das so: Das Medium selbst ist die Botschaft. Ja mei, mag sich mancher denken, doch medienanthropologisch ist diese Entwicklung durchaus eine Betrachtung wert. Ein Querformat eignet sich besser, um Landschaften, einen Raum oder eine Gruppe abzubilden. Das Hochformat entspricht grob den menschlichen Maßen von der Hüfte bis zum Kopf. Der TikTok-Tanz ist im Smartphone-Design also schon angelegt. Das Hochformat hat die Medieninhalte unserer Zeit noch narzisstischer gemacht.
Dass wir uns durch Smartphones freizügiger und enthemmter zur Schau stellen, ist bekannt. 2013 wurde „Selfie“ vom Oxford English Dictionary zum Wort des Jahres erklärt. Selfie, Selbstporträt, Selbstdarstellung.
Neu ist der Aufwand, der heute vonnöten ist, um die Aufmerksamkeitsschwelle der todamüsierten Mediengesellschaft überhaupt noch zu durchbrechen. In beängstigender Hypnose erwischt man viele Zeitgenossen inzwischen beim Doomscrollen. Das ist der Fachbegriff für das weggetretene Endloswischen und erklärt auch den Namen „Reel“: Der Begriff, im Deutschen verwandt mit „Rolle“, beschreibt die Filmrolle, von der 24 Bilder pro Sekunde auf den Projektor gewischt oder eben abgespult werden.
Länger als drei Sekunden darf ein Kurzvideo deshalb nicht mehr gehen, ohne dass etwas Aufregendes passiert. Sonst wird das Reel aus Langeweile weggewischt. Die Welt im Dopamin-Rausch. Für den Ersteller eines Videos heißt das inzwischen: Sei der lauteste, schrillste, gestörteste Marktschreier. Das Wettrennen um die Augäpfel zwingt zu extremen Formen von Clickbait.
15 Sekunden Ruhm
Das nimmt inzwischen skurrile Formen an. Das Video „Look who I found“ von Noel Robinson (geboren 2001) war im letzten Jahr einer der erfolgreichsten deutschen TikTok-Clips. Man sieht den Deutsch-Nigerianer beim Antanzen eines karikaturartig übergewichtigen Menschen. Noel wird geschubst und fällt. Daraufhin wechselt das Lied – und der fette Mann bewegt seinen Schwabbelbauch im Takt. Noel steht wieder auf, grinst, beide tanzen gemeinsam. Das dauert 15 Sekunden. Ich rate Ihnen, sich das Video einmal anzuschauen, um die Mechanismen von TikTok zu verstehen. Achten Sie alleine darauf, wie vielen Reizen (Menschenmenge, Antanzen, Sturz, Schwabbelbauch) Sie in den ersten fünf Sekunden ausgesetzt sind. Wer schaut so was? Bis dato 220 Millionen Menschen. Das ist kapitalistische Verwertungslogik im bereits verwesten Endstadium. Adorno oder Fromm hätten am Medienzeitgeist entweder ihre Freude oder mächtig zu knabbern.
Die Internet- und Smartphoneabdeckung beträgt mittlerweile fast 100 Prozent. Das Überangebot hat die Regeln geändert. Um überhaupt gesehen zu werden, muss man heute viral gehen. Was dafür inzwischen nötig ist, spricht die niedrigsten Bedürfnisse des Menschen an: Gewalt, Ekel, Sexualisierung, Schock. Die jungen Erwachsenen, die heute auf sozialen Netzwerken den Ton angeben, haben diese Mechanismen längst verinnerlicht. Wie bewusst ihnen das ist, ist fraglich. 2024 prallt eine desaströse Bildungssituation samt fehlender Medienkompetenz auf eine egomanische Jugend, die Privatsphäre nie gekannt hat und seit Kindesbeinen alles in den Äther ballert, was es festhalten kann. Man muss kein Kulturpessimist sein, um diese degenerative Dynamik, auch in ihrer Implikation für unser Zusammenleben und das psychische Wohlergehen der Generation TikTok, als beängstigend zu bezeichnen.
Aron Morhoff studierte Medienethik und ist Absolvent der Freien Akademie für Medien & Journalismus. Frühere Stationen: RT Deutsch und Nuoviso. Heute: Stichpunkt Magazin, Manova, Milosz Matuschek und seine Liveshow "Addictive Programming".
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ 06b7819d:d1d8327c
2024-12-03 09:00:46
@ 06b7819d:d1d8327c
2024-12-03 09:00:46The History of Bananas as an Exportable Fruit and the Rise of Banana Republics
Bananas became a significant export in the late 19th century, fueled by advancements in transportation and refrigeration that allowed the fruit to travel long distances without spoilage. Originally native to Southeast Asia, bananas were introduced to the Americas by European colonists. By the late 1800s, companies like the United Fruit Company (later Chiquita) and Standard Fruit Company (now Dole) began cultivating bananas on a large scale in Central America and the Caribbean.
These corporations capitalized on the fruit’s appeal—bananas were cheap, nutritious, and easy to transport. The fruit quickly became a staple in Western markets, especially in the United States. However, the rapid expansion of banana exports came at a significant political and social cost to the countries where the fruit was grown.
To maintain control over banana production and maximize profits, these companies required vast amounts of arable land, labor, and favorable trade conditions. This often led them to form close relationships with local governments, many of which were authoritarian and corrupt. The companies influenced policies to secure land concessions, suppress labor rights, and maintain low taxes.
The term “banana republic” was coined by writer O. Henry in 1904 to describe countries—particularly in Central America—that became politically unstable due to their economic dependence on a single export crop, often controlled by foreign corporations.
The U.S. government frequently supported these regimes as part of its broader strategy during the Cold War to counter communist influence in the region. Washington feared that labor movements and demands for land reform, often supported by the peasantry and indigenous groups, could lead to the rise of socialist or communist governments. Consequently, the U.S. backed coups, such as the 1954 overthrow of Guatemala’s democratically elected President Jacobo Árbenz, who had threatened United Fruit’s interests by redistributing unused land.
These interventions created a legacy of exploitation, environmental degradation, and political instability in many banana-exporting countries. While bananas remain a global dietary staple, their history underscores the complex interplay of economics, politics, and imperialism.
-
 @ 06b7819d:d1d8327c
2024-12-02 20:05:48
@ 06b7819d:d1d8327c
2024-12-02 20:05:48Benjamin Franklin and His Fondness for Madeira Wine
Benjamin Franklin, one of America’s most celebrated founding fathers, was not only a statesman, scientist, and writer but also a man of refined taste. Among his many indulgences, Franklin was particularly fond of Madeira wine, a fortified wine from the Portuguese Madeira Islands. His love for this drink was well-documented and reflects both his personal preferences and the broader cultural trends of 18th-century America.
The Allure of Madeira Wine
Madeira wine was highly prized in the 18th century due to its unique production process and exceptional durability. Its rich, fortified nature made it well-suited for long sea voyages, as it could withstand temperature fluctuations and aging in transit. This durability made Madeira a popular choice in the American colonies, where European wines often spoiled before arrival.
Franklin, who was known for his appreciation of fine things, embraced Madeira as a beverage of choice. Its complex flavors and storied reputation resonated with his intellectual and social pursuits. The wine was often served at dinners and social gatherings, where Franklin and his contemporaries debated ideas and shaped the future of the nation.
Franklin’s Personal Connection to Madeira
In Franklin’s writings and correspondence, Madeira is mentioned on several occasions, reflecting its prominence in his life. He referred to the wine not only as a personal pleasure but also as a symbol of hospitality and refinement. As a diplomat in France and England, Franklin often carried Madeira to share with his hosts, using it as a means of forging connections and showcasing the tastes of the American colonies.
One notable instance of Franklin’s affinity for Madeira occurred during his time in Philadelphia. He reportedly had cases of the wine shipped directly to his home, ensuring he would never be without his favorite drink. Madeira also featured prominently in many toasts and celebrations, becoming a hallmark of Franklin’s gatherings.
The Role of Madeira in Colonial America
Franklin’s fondness for Madeira reflects its broader significance in colonial America. The wine was not only a favorite of the elite but also a symbol of resistance to British taxation. When the British imposed heavy duties on imported goods, including wine, Madeira became a patriotic choice for many colonists. Its direct trade routes with the Madeira Islands circumvented British intermediaries, allowing Americans to assert their economic independence.
A Legacy of Taste
Franklin’s appreciation for Madeira wine endures as a charming detail of his multifaceted life. It offers a glimpse into the personal habits of one of America’s most influential figures and highlights the cultural exchanges that shaped colonial society. Today, Franklin’s love of Madeira serves as a reminder of the historical connections between wine, politics, and personal expression in the 18th century.
In honoring Franklin’s legacy, one might raise a glass of Madeira to toast not only his contributions to American independence but also his enduring influence on the art of living well.
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ fa0165a0:03397073
2024-10-23 17:19:41
@ fa0165a0:03397073
2024-10-23 17:19:41Chef's notes
This recipe is for 48 buns. Total cooking time takes at least 90 minutes, but 60 minutes of that is letting the dough rest in between processing.
The baking is a simple three-step process. 1. Making the Wheat dough 2. Making and applying the filling 3. Garnishing and baking in the oven
When done: Enjoy during Fika!
PS;
-
Can be frozen and thawed in microwave for later enjoyment as well.
-
If you need unit conversion, this site may be of help: https://www.unitconverters.net/
-
Traditionally we use something we call "Pearl sugar" which is optimal, but normal sugar or sprinkles is okay too. Pearl sugar (Pärlsocker) looks like this: https://search.brave.com/images?q=p%C3%A4rlsocker
Ingredients
- 150 g butter
- 5 dl milk
- 50 g baking yeast (normal or for sweet dough)
- 1/2 teaspoon salt
- 1-1 1/2 dl sugar
- (Optional) 2 teaspoons of crushed or grounded cardamom seeds.
- 1.4 liters of wheat flour
- Filling: 50-75 g butter, room temperature
- Filling: 1/2 - 1 dl sugar
- Filling: 1 teaspoons crushed or ground cardamom and 1 teaspoons ground cinnamon (or 2 teaspoons of cinnamon)
- Garnish: 1 egg, sugar or Almond Shavings
Directions
- Melt the butter/margarine in a saucepan.
- Pour in the milk and allow the mixture to warm reach body temperature (approx. + 37 ° C).
- Dissolve the yeast in a dough bowl with the help of the salt.
- Add the 37 ° C milk/butter mixture, sugar and if you choose to the optional cardamom. (I like this option!) and just over 2/3 of the flour.
- Work the dough shiny and smooth, about 4 minutes with a machine or 8 minutes by hand.
- Add if necessary. additional flour but save at least 1 dl for baking.
- Let the dough rise covered (by a kitchen towel), about 30 minutes.
- Work the dough into the bowl and then pick it up on a floured workbench. Knead the dough smoothly. Divide the dough into 2 parts. Roll out each piece into a rectangular cake.
- Stir together the ingredients for the filling and spread it.
- Roll up and cut each roll into 24 pieces.
- Place them in paper molds or directly on baking paper with the cut surface facing up. Let them rise covered with a baking sheet, about 30 minutes.
- Brush the buns with beaten egg and sprinkle your chosen topping.
- Bake in the middle of the oven at 250 ° C, 5-8 minutes.
- Allow to cool on a wire rack under a baking sheet.
-
-
 @ 06b7819d:d1d8327c
2024-11-29 13:26:00
@ 06b7819d:d1d8327c
2024-11-29 13:26:00The Weaponization of Technology: A Prelude to Adoption
Throughout history, new technologies have often been weaponized before becoming widely adopted for civilian use. This pattern, deeply intertwined with human priorities for power, survival, and dominance, sheds light on how societies interact with technological innovation.
The Weaponization Imperative
When a groundbreaking technology emerges, its potential to confer an advantage—military, economic, or ideological—tends to attract attention from those in power. Governments and militaries, seeking to outpace rivals, often invest heavily in adapting new tools for conflict or defense. Weaponization provides a context where innovation thrives under high-stakes conditions. Technologies like radar, nuclear energy, and the internet, initially conceived or expanded within the framework of military priorities, exemplify this trend.
Historical Examples
1. Gunpowder: Invented in 9th-century China, gunpowder was first used for military purposes before transitioning into civilian life, influencing mining, construction, and entertainment through fireworks.-
The Internet: Initially developed as ARPANET during the Cold War to ensure communication in the event of a nuclear attack, the internet’s infrastructure later supported the global digital revolution, reshaping commerce, education, and social interaction.
-
Drones: Unmanned aerial vehicles began as tools of surveillance and warfare but have since been adopted for everything from package delivery to agricultural monitoring.
Weaponization often spurs rapid technological development. War environments demand urgency and innovation, fast-tracking research and turning prototypes into functional tools. This phase of militarization ensures that the technology is robust, scalable, and often cost-effective, setting the stage for broader adoption.
Adoption and Civilian Integration
Once a technology’s military dominance is established, its applications often spill into civilian life. These transitions occur when:
• The technology becomes affordable and accessible. • Governments or corporations recognize its commercial potential. • Public awareness and trust grow, mitigating fears tied to its military origins.For example, GPS was first a military navigation system but is now indispensable for personal devices, logistics, and autonomous vehicles.
Cultural Implications
The process of weaponization shapes public perception of technology. Media narratives, often dominated by stories of power and conflict, influence how societies view emerging tools. When technologies are initially seen through the lens of violence or control, their subsequent integration into daily life can carry residual concerns, from privacy to ethical implications.
Conclusion
The weaponization of technology is not an aberration but a recurring feature of technological progress. By understanding this pattern, societies can critically assess how technologies evolve from tools of conflict to instruments of everyday life, ensuring that ethical considerations and equitable access are not lost in the rush to innovate. As Marshall McLuhan might suggest, the medium through which a technology is introduced deeply influences the message it ultimately conveys to the world.
-
-
 @ 06b7819d:d1d8327c
2024-11-29 12:11:05
@ 06b7819d:d1d8327c
2024-11-29 12:11:05In June 2023, the Law Commission of England and Wales published its final report on digital assets, concluding that the existing common law is generally flexible enough to accommodate digital assets, including crypto-tokens and non-fungible tokens (NFTs).
However, to address specific areas of uncertainty, the Commission recommended targeted statutory reforms and the establishment of an expert panel.
Key Conclusions and Recommendations:
1. Recognition of a Third Category of Personal Property:Traditional English law classifies personal property into two categories: “things in possession” (tangible items) and “things in action” (enforceable rights). Digital assets do not fit neatly into either category. The Commission recommended legislation to confirm the existence of a distinct third category of personal property to better accommodate digital assets. 
-
Development of Common Law: The Commission emphasized that the common law is well-suited to adapt to the complexities of emerging technologies and should continue to evolve to address issues related to digital assets. 
-
Establishment of an Expert Panel: To assist courts in navigating the technical and legal challenges posed by digital assets, the Commission recommended that the government create a panel of industry experts, legal practitioners, academics, and judges. This panel would provide non-binding guidance on issues such as control and transfer of digital assets. 
-
Facilitation of Crypto-Token and Crypto-Asset Collateral Arrangements: The Commission proposed the creation of a bespoke statutory legal framework to facilitate the use of digital assets as collateral, addressing current legal uncertainties in this area. 
-
Clarification of the Financial Collateral Arrangements Regulations: The report recommended statutory amendments to clarify the extent to which digital assets fall within the scope of the Financial Collateral Arrangements (No 2) Regulations 2003, ensuring that existing financial regulations appropriately cover digital assets. 
Overall, the Law Commission’s report underscores the adaptability of English common law in addressing the challenges posed by digital assets, while also identifying specific areas where legislative action is necessary to provide clarity and support the evolving digital economy.
-
-
 @ 06b7819d:d1d8327c
2024-11-29 11:59:20
@ 06b7819d:d1d8327c
2024-11-29 11:59:20The system design and challenges of retail Central Bank Digital Currencies (CBDCs) differ significantly from Bitcoin in several key aspects, reflecting their distinct purposes and underlying philosophies:
-
Core Purpose and Issuance
• CBDCs: Issued by central banks, CBDCs are designed as state-backed digital currencies for public use. Their goal is to modernize payments, enhance financial inclusion, and provide a risk-free alternative to private money. • Bitcoin: A decentralized, peer-to-peer cryptocurrency created to operate independently of central authorities. Bitcoin aims to be a store of value and medium of exchange without reliance on intermediaries or governments.
-
Governance and Control
• CBDCs: Operate under centralized governance. Central banks retain control over issuance, transaction validation, and data management, allowing for integration with existing regulatory frameworks (e.g., AML and CFT). • Bitcoin: Fully decentralized, governed by a consensus mechanism (Proof of Work). Transactions are validated by miners, and no single entity controls the network.
-
Privacy
• CBDCs: Seek to balance privacy with regulatory compliance. Privacy-enhancing technologies may be implemented, but user data is typically accessible to intermediaries and central banks to meet regulatory needs. • Bitcoin: Pseudonymous by design. Transactions are public on the blockchain but do not directly link to individual identities unless voluntarily disclosed.
-
System Design
• CBDCs: May adopt a hybrid system combining centralized (e.g., central bank-controlled settlement) and decentralized elements (e.g., private-sector intermediaries). Offline functionality and interoperability with existing systems are priorities. • Bitcoin: Fully decentralized, using a distributed ledger (blockchain) where all transactions are validated and recorded without reliance on intermediaries.
-
Cybersecurity
• CBDCs: Cybersecurity risks are heightened due to potential reliance on centralized points for data storage and validation. Post-quantum cryptography is a concern for future-proofing against quantum computing threats. • Bitcoin: Security relies on cryptographic algorithms and decentralization. However, it is also vulnerable to quantum computing in the long term, unless upgraded to quantum-resistant protocols.
-
Offline Functionality
• CBDCs: Exploring offline payment capabilities for broader usability in remote or unconnected areas. • Bitcoin: Offline payments are not natively supported, although some solutions (e.g., Lightning Network or third-party hardware wallets) can enable limited offline functionality.
-
Point of Sale and Adoption
• CBDCs: Designed for seamless integration with existing PoS systems and modern financial infrastructure to encourage widespread adoption. • Bitcoin: Adoption depends on merchant willingness and the availability of cryptocurrency payment gateways. Its volatility can discourage usage as a medium of exchange.
-
Monetary Policy and Design
• CBDCs: Can be programmed to support specific policy goals, such as negative interest rates, transaction limits, or conditional transfers. • Bitcoin: Supply is fixed at 21 million coins, governed by its code. It is resistant to monetary policy interventions and inflationary adjustments.
In summary, while CBDCs aim to complement existing monetary systems with centralized oversight and tailored features, Bitcoin is designed as a decentralized alternative to traditional currency. CBDCs prioritize integration, control, and regulatory compliance, whereas Bitcoin emphasizes autonomy, censorship resistance, and a trustless system.
-
-
 @ 4ba8e86d:89d32de4
2024-11-14 09:17:14
@ 4ba8e86d:89d32de4
2024-11-14 09:17:14Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 06b7819d:d1d8327c
2024-11-28 18:30:00
@ 06b7819d:d1d8327c
2024-11-28 18:30:00The Bank of Amsterdam (Amsterdamse Wisselbank), established in 1609, played a pivotal role in the early history of banking and the development of banknotes. While banknotes as a concept had been pioneered in China centuries earlier, their modern form began emerging in Europe in the 17th century, and the Bank of Amsterdam leveraged its unique position to dominate this nascent monetary tool.
Founding and Early Innovations
The Bank of Amsterdam was created to stabilize and rationalize Amsterdam’s chaotic monetary system. During the early 1600s, a plethora of coins of varying quality and origin circulated in Europe, making trade cumbersome and unreliable. The Wisselbank provided a centralized repository where merchants could deposit coins and receive account balances in return, denominated in a standardized unit of account known as “bank money.” This “bank money” was more stable and widely trusted, making it an early form of fiat currency.
The Rise of Banknotes
Although the Wisselbank initially issued “bank money” as a ledger-based system, the growing demand for portable, trusted currency led to the adoption of transferable receipts or “banknotes.” These receipts acted as claims on deposited money and quickly became a trusted medium of exchange. The innovation of banknotes allowed merchants to avoid carrying large quantities of heavy coinage, enhancing convenience and security in trade.
Monopoly on Banknotes
The Wisselbank’s reputation for financial stability and integrity enabled it to establish a monopoly on banknotes in the Dutch Republic. The bank’s stringent policies ensured that its issued notes were fully backed by coinage or bullion, which bolstered trust in their value. By centralizing the issuance of notes, the bank eliminated competition from private or less reliable issuers, ensuring its notes became the de facto currency for merchants and traders.
Moreover, the bank’s policies discouraged the redemption of notes for physical coins, as it charged fees for withdrawals. This incentivized the circulation of banknotes rather than the underlying specie, cementing their role in the economy.
Decline of the Monopoly
The Wisselbank’s monopoly and influence lasted for much of the 17th century, making Amsterdam a hub of global trade and finance. However, as the 18th century progressed, financial mismanagement and competition from other emerging financial institutions eroded the Wisselbank’s dominance. By the late 18th century, its role in the global financial system had diminished, and other European financial centers, such as London, rose to prominence.
Legacy
The Bank of Amsterdam’s early monopolization of banknotes set a precedent for centralized banking and the development of modern monetary systems. Its ability to create trust in a standardized, portable medium of exchange foreshadowed the role that central banks would play in issuing and regulating currency worldwide.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ a012dc82:6458a70d
2024-12-04 06:10:01
@ a012dc82:6458a70d
2024-12-04 06:10:01Table Of Content
-
The Challenge of Sustainability in Bitcoin Mining
-
Embracing Renewable Energy Sources
-
Optimal Location Selection
-
Energy-Efficient Hardware
-
Collaborative Mining Pools
-
Managing Operational Costs
-
The Rise of Green Certifications
-
Balancing Profitability and Environmental Responsibility
-
Conclusion
-
FAQ
Bitcoin mining, once an energy-intensive endeavor, has evolved significantly over the years. As the popularity of cryptocurrencies soared, so did concerns about its environmental impact. In this article, we will delve into the concept of sustainability in Bitcoin mining and explore how the industry is adapting to revenue constraints while being conscious of its ecological footprint.
The Challenge of Sustainability in Bitcoin Mining
The advent of Bitcoin brought about a revolutionary decentralized digital currency, empowering individuals and businesses to conduct transactions without the need for intermediaries. However, the process of mining Bitcoins, which involves solving complex mathematical algorithms to validate transactions, requires substantial computational power and energy consumption. This energy-intensive nature of mining has raised concerns about its environmental sustainability.
Embracing Renewable Energy Sources
In recent years, the Bitcoin mining community has taken significant strides towards embracing renewable energy sources. By transitioning from traditional fossil fuels to sustainable alternatives such as solar, wind, and hydroelectric power, miners aim to reduce their carbon footprint significantly. This shift not only addresses environmental concerns but also ensures long-term viability for the industry. By harnessing clean and renewable energy, miners can continue their operations without exacerbating environmental issues.
Optimal Location Selection
One of the critical strategies for sustainable Bitcoin mining is choosing the right location. Mining operations tend to thrive in regions with abundant renewable energy resources, enabling them to power their data centers efficiently. Countries with progressive policies promoting green energy have become attractive destinations for miners seeking sustainability. Selecting an optimal location ensures that miners can run their operations with minimal reliance on non-renewable energy sources, reducing their overall environmental impact.
Energy-Efficient Hardware
Advancements in technology have led to the development of energy-efficient mining hardware. Miners now have access to Application-Specific Integrated Circuits (ASICs) that offer better performance while consuming less power. By upgrading to these energy-efficient machines, miners can maximize their hashing power and revenue while minimizing energy consumption. Utilizing energy-efficient hardware is an essential step towards creating a sustainable mining ecosystem, where efficiency and profitability coexist harmoniously.
Collaborative Mining Pools
In an effort to enhance sustainability, miners are increasingly joining collaborative mining pools. These pools allow multiple miners to work together and share their computational resources, reducing individual energy consumption. Moreover, the pool's reward system ensures a more consistent income stream, mitigating revenue constraints. By pooling resources, miners can optimize their energy usage and achieve higher profitability, while also fostering cooperation within the mining community.
Managing Operational Costs
Sustainability in Bitcoin mining also requires effective management of operational costs. Energy expenses are a significant part of mining operations, so miners are constantly seeking innovative ways to optimize energy usage. Implementing smart energy management systems and adopting best practices in data center cooling are some of the approaches employed to reduce costs. Efficient cost management not only improves a miner's bottom line but also contributes to overall sustainability by minimizing resource wastage.
The Rise of Green Certifications
To prove their commitment to sustainability, several mining companies now seek green certifications. These certifications authenticate that a mining operation is using a substantial portion of renewable energy, providing transparency and building trust among investors and stakeholders. Green certifications serve as a testament to a miner's dedication to reducing their environmental impact, which can attract socially responsible investors and customers. As the demand for environmentally conscious practices grows, green certifications become a valuable asset for sustainable mining businesses.
Balancing Profitability and Environmental Responsibility
While sustainability is a priority, miners must also navigate revenue constraints in a highly competitive market. Striking a balance between profitability and environmental responsibility remains a challenge. However, the industry's evolution towards sustainability demonstrates its commitment to minimizing its ecological impact. Miners face the delicate task of maximizing revenue while adopting environmentally friendly practices. By continually innovating and optimizing operations, miners can secure their financial viability while contributing to a greener and more sustainable future for Bitcoin mining.
Conclusion
Sustainability in Bitcoin mining is no longer an afterthought but a crucial aspect that miners are actively pursuing. By embracing renewable energy sources, optimizing hardware, and employing collaborative approaches, the industry is adapting to revenue constraints while mitigating its environmental footprint. As technology continues to advance, it is likely that Bitcoin mining will become even more sustainable, ensuring the longevity of this groundbreaking digital currency for generations to come.
FAQ
What is sustainability in Bitcoin mining? Sustainability in Bitcoin mining refers to adopting practices and technologies that reduce the environmental impact of mining operations while ensuring long-term viability for the industry.
How are miners embracing sustainability? Miners are embracing sustainability by transitioning to renewable energy sources, using energy-efficient hardware, joining collaborative mining pools, and optimizing operational costs.
Why is renewable energy important for Bitcoin mining? Renewable energy is vital for Bitcoin mining as it significantly reduces the carbon footprint associated with energy-intensive mining operations, promoting environmental responsibility.
What are collaborative mining pools? Collaborative mining pools are groups of miners working together and sharing their computational resources to improve efficiency and achieve a more consistent income stream.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 06b7819d:d1d8327c
2024-11-27 11:53:39
@ 06b7819d:d1d8327c
2024-11-27 11:53:39Understanding Figure and Ground: How We Perceive the World
The concept of “figure and ground” originates from Gestalt psychology but takes on profound implications in Marshall McLuhan’s media theory. At its core, figure and ground describe the relationship between what we focus on (the “figure”) and the larger context that shapes and influences it (the “ground”). Together, they illustrate how perception is shaped not only by what we pay attention to, but by what we overlook.
Figure and Ground in Perception
Imagine looking at a photo of a tree in a forest. The tree might stand out as the figure—it’s what your attention is drawn to. However, the forest, the sky, and even the light conditions around the tree create the ground. These background elements are not immediately in focus, but they are essential to understanding the tree’s existence and meaning within its environment.
Our minds are naturally inclined to separate figure from ground, but this process often distorts our perception. By focusing on one aspect, we tend to neglect the broader context that gives it meaning. This principle applies not just to visual perception but also to the way we experience media, technology, and culture.
McLuhan’s Take: Media as Ground
For McLuhan, media and technology are the “ground” upon which all human activity takes place. We often fixate on the “figure” of a medium—the content it delivers—without recognizing the ground, which is the medium itself and its pervasive influence. For example, we might focus on the latest viral video (the figure) without reflecting on how platforms like TikTok (the ground) shape attention spans, social behaviors, and even our cultural norms.
McLuhan famously argued that “the medium is the message,” meaning the medium’s structure and characteristics influence society far more deeply than the specific content it carries. The figure (content) distracts us from examining the ground (medium), which often operates invisibly.
Figure and Ground in Daily Life
Consider smartphones. The apps, messages, and videos we interact with daily are the figures. The ground is the smartphone itself—a device that transforms communication, alters social dynamics, and restructures how we manage time and attention. Focusing solely on what’s displayed on the screen blinds us to the ways the device reshapes our lives.
Rebalancing Perception
To truly understand the impact of media and technology, McLuhan urged us to become aware of the ground. By stepping back and observing how the environment shapes the figure, we can better grasp the larger systems at work. This requires a shift in perspective: instead of asking “What does this content mean?” we might ask “How does this medium affect the way I think, behave, or relate to others?”
Understanding figure and ground helps us see the world more holistically, uncovering hidden dynamics that shape perception and culture. It’s a reminder that what we take for granted—what fades into the background—is often the most transformative force of all.
-
 @ dadbe86a:9c493e92
2024-12-04 14:56:04
@ dadbe86a:9c493e92
2024-12-04 14:56:04Opinion about Green: Bitcoin Wallet (android)
Green Wallet is a mobile Bitcoin wallet developed by Blockstream, The Wallet aims to provide users with a trustworthy and feature-rich Bitcoin wallet experience. Given that the wallet supports liquid assets, it is not bitcoin only. This is a cons for pure bitcoiners but something good for other users.
Pros: - Support for testnet, passphrase, fee control, coin control, custom node, tor, timelocks - The in-app keyboard and seed phrase autocomplete increase the security if you need to enter your seedphrase or passphrase - Open source - Full taproot support soon
Cons: - Missing some advanced features like user added entropy or seedQR. - It has a non standard multisig implementation - Partial support to connect with hardware wallets
Version reviewed: v4.0.27
WalletScrutiny #nostrOpinion
-
 @ 6bae33c8:607272e8
2024-12-04 14:47:47
@ 6bae33c8:607272e8
2024-12-04 14:47:47I blew it last week, going 2-3 and basically drawing dead already for Q4 unless I were to go 20-0 or something insane. I was sick, just getting the bare minimum done last week, and probably didn’t give it the proper amount of marination. Not that I haven’t gone 1-4 plenty of times when I was perfectly well too.
Heading into Week 14, I’m 33-31-1, not going to cash this year, but with a strong finish can still have a respectable overall record which is what I’m aiming for now.
Packers at Lions — I’ll make this Packers +2.5 because the Lions have so many defensive injuries. I might take the Packers, but probably a stay away.
Jets at Dolphins — Let’s make this 4.5. The Jets are a cursed team, something’s just wrong with them, and I can’t put my finger on it. The Dolphins are pretty good, just below a playoff team. I’ll probably pass on this one though. If anything the Jets are the buy-low, but as I said, something’s off.
Falcons at Vikings — The Falcons are a lot like the Jets. Kirk Cousins looks fine, but something’s off. The team isn’t clicking. I’ll say Falcons plus 4.5 and probably stay away for the same reason. It should be a Falcons buy-low, but something’s wrong.
Saints at Giants — The Giants are destroyed. They lost just Dexter Lawrence and Theo Johnson now too. Andrew Thomas and Lawrence are the poor man’s Trent Williams and Nick Bosa. And the 49ers went from great to average, the Giants go from below average to out of the league. Saints -5.5, stay away.
Panthers at Eagles — The Panthers hang with everyone these days, and this is a trap game for the Eagles after the big win over the Ravens Sunday night. I’ll say +11.5 and maybe take the Panthers.
Browns at Steelers — The Browns caught the Steelers the first time, but I don’t think it happens again. I’ll say Browns +6.5 and probably lay the wood, but the Browns offense is for real.
Raiders at Buccaneers — I’ll make this Raiders +8.5 and be inclined to stay away. If anything, I’d lean Bucs.
Jaguars at Titans — Jeff Spicoli sure got his bell rung, but Mac Jones actually played decently in relief. I’ll make this line 4.5 and probably take the Titans.
Seahawks at Cardinals — I’ll make this Seahawks +2.5 and take the Cardinals to bounce back, even though Seattle has played well of late.
Bills at Rams — The Bills are a juggernaut, but this is a sneaky-tough road game. I’ll say Bills -4 and maybe lean Rams.
Bears at 49ers — The whole 49ers team is injured. I’ll say Bears +2.5 and stay away.
Chargers at Chiefs — The Chiefs play close games with the local high school team, but it’ll still be Chargers +3 at Arrowhead. I’d probably take the Chiefs.
Bengals at Cowboys — I’ll say Bengals -3 and probably stay away. The Cowboys can rush the passer, and the Bengals can’t stop anyone.
-
 @ c755de14:cc53833a
2024-12-03 21:29:11
@ c755de14:cc53833a
2024-12-03 21:29:11- A well-dressed Sudanese man steals corn from a starving, paralyzed boy outside a feeding center

- A gruesome photo shows a man protecting his family from cannibals during the Madras famine of 1877 in India.

- A mother hides her face as she sells her children (Chicago, USA, 1948).

- A 1993 photograph of a starving Sudanese child being stalked by vultures, taken by Kevin Carter. Carter won the 1994 Pulitzer for this image but died by suicide. In his suicide note, he wrote, "I am haunted by vivid memories of children starving or injured..."

- A high school football star was once charged with rape after a sixteen-year-old girl claimed the rape never happened. He was jailed for six years and was devastated when the case was dropped.

- In 1980, photographer Mike Wells took a photo of a Catholic missionary holding the hand of a starving Ugandan boy.

- An 8-year-old boy, with trembling lips, is handed a folded flag at his father's funeral.

- This image tells the story of two technicians trapped on a burning wind turbine. Here they embrace for the last time; one jumps, one burns.

- A police officer distracts a little girl after her father loses his life in a car accident.

- In Syria, 17 hours after an earthquake devastated the area, this 7-year-old girl was found under the rubble with her hand on her younger brother's head to protect him. Both made it out alive.

-
 @ 59cfee8f:7598a483
2024-12-03 17:23:56
@ 59cfee8f:7598a483
2024-12-03 17:23:56Yakihonne's Innovative Approach to Bitcoin Adoption
Introduction
The Bitcoin landscape is constantly evolving, and community plays a vital role in shaping its future. Yakihonne, a cutting-edge platform, is harnessing the power of community to drive Bitcoin adoption and education. In this article, we will explore Yakihonne's innovative approach and its impact on the Bitcoin ecosystem.
The Yakihonne Difference
Yakihonne distinguishes itself by recognizing every user as a unique node in the Bitcoin network. This perspective empowers individuals to take an active role in shaping the community and contributing to its growth. By fostering connections and knowledge sharing, Yakihonne creates a supportive environment where users can thrive.
Key Features and Benefits
-
Decentralized knowledge sharing: Yakihonne's platform allows users to access and share valuable resources, promoting a deeper understanding of Bitcoin and its applications.
-
Community-driven support: Users can engage with others, ask questions, and receive guidance from experienced community members.
-
Incentivized learning: Yakihonne's gamification elements make learning about Bitcoin engaging and fun, encouraging users to expand their knowledge.
-
Responsible adoption: The platform emphasizes security, privacy, and informed decision-making, ensuring sustainable growth.
The Future of Bitcoin Adoption
Yakihonne's community-centric approach is poised to revolutionize Bitcoin adoption. By leveraging the power of social nodes, Yakihonne creates a snowball effect, where knowledge and enthusiasm spread exponentially. As the platform continues to evolve, it's likely to play a significant role in shaping the future of Bitcoin.
Conclusion
Yakihonne is a game-changer in the Bitcoin space, offering a unique blend of community engagement, education, and support. By joining the Yakihonne community, individuals can tap into the collective power of social nodes, contributing to a brighter future for Bitcoin adoption. Embrace the potential of Yakihonne and be part of this exciting journey!
-
-
 @ 06b7819d:d1d8327c
2024-11-26 16:57:14
@ 06b7819d:d1d8327c
2024-11-26 16:57:14Hanlon’s Razor is a philosophical principle or adage that states:
“Never attribute to malice that which is adequately explained by stupidity.”
It suggests that when trying to understand someone’s actions, it is often more reasonable to assume a lack of knowledge, competence, or foresight rather than intentional harm or ill will. The principle encourages people to avoid jumping to conclusions about malicious intent and instead consider simpler, more mundane explanations.
Hanlon’s Razor is often used in problem-solving, interpersonal interactions, and organizational settings to promote understanding and reduce conflict. It’s part of a broader family of “razors,” which are rules of thumb used to simplify decision-making.
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ 59cfee8f:7598a483
2024-12-03 17:23:43
@ 59cfee8f:7598a483
2024-12-03 17:23:43Yakihonne's Innovative Approach to Bitcoin Adoption
Introduction
The Bitcoin landscape is constantly evolving, and community plays a vital role in shaping its future. Yakihonne, a cutting-edge platform, is harnessing the power of community to drive Bitcoin adoption and education. In this article, we will explore Yakihonne's innovative approach and its impact on the Bitcoin ecosystem.
The Yakihonne Difference
Yakihonne distinguishes itself by recognizing every user as a unique node in the Bitcoin network. This perspective empowers individuals to take an active role in shaping the community and contributing to its growth. By fostering connections and knowledge sharing, Yakihonne creates a supportive environment where users can thrive.
Key Features and Benefits
-
Decentralized knowledge sharing: Yakihonne's platform allows users to access and share valuable resources, promoting a deeper understanding of Bitcoin and its applications.
-
Community-driven support: Users can engage with others, ask questions, and receive guidance from experienced community members.
-
Incentivized learning: Yakihonne's gamification elements make learning about Bitcoin engaging and fun, encouraging users to expand their knowledge.
-
Responsible adoption: The platform emphasizes security, privacy, and informed decision-making, ensuring sustainable growth.
The Future of Bitcoin Adoption
Yakihonne's community-centric approach is poised to revolutionize Bitcoin adoption. By leveraging the power of social nodes, Yakihonne creates a snowball effect, where knowledge and enthusiasm spread exponentially. As the platform continues to evolve, it's likely to play a significant role in shaping the future of Bitcoin.
Conclusion
Yakihonne is a game-changer in the Bitcoin space, offering a unique blend of community engagement, education, and support. By joining the Yakihonne community, individuals can tap into the collective power of social nodes, contributing to a brighter future for Bitcoin adoption. Embrace the potential of Yakihonne and be part of this exciting journey!
-
-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。
2024年08月13日更新:
修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
准备工具
- Ntfy服务
- Google Script
- Google Sheets
操作步骤
- 在Ntfy后台账号,设置访问令牌。

- 添加订阅主题。

- 进入Google Sheets创建一个表格.记住id,如下图:

- 进入Google Script创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) { var threadId = thread.getId();
if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); }}); }
function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; }
var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true };
try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } }
function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column }
function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); }
function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues(); var rowsToDelete = [];
data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } });
// 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); }
```
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:

结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
-
 @ 59cfee8f:7598a483
2024-12-03 17:23:34
@ 59cfee8f:7598a483
2024-12-03 17:23:34Yakihonne's Innovative Approach to Bitcoin Adoption
Introduction
The Bitcoin landscape is constantly evolving, and community plays a vital role in shaping its future. Yakihonne, a cutting-edge platform, is harnessing the power of community to drive Bitcoin adoption and education. In this article, we will explore Yakihonne's innovative approach and its impact on the Bitcoin ecosystem.
The Yakihonne Difference
Yakihonne distinguishes itself by recognizing every user as a unique node in the Bitcoin network. This perspective empowers individuals to take an active role in shaping the community and contributing to its growth. By fostering connections and knowledge sharing, Yakihonne creates a supportive environment where users can thrive.
Key Features and Benefits
-
Decentralized knowledge sharing: Yakihonne's platform allows users to access and share valuable resources, promoting a deeper understanding of Bitcoin and its applications.
-
Community-driven support: Users can engage with others, ask questions, and receive guidance from experienced community members.
-
Incentivized learning: Yakihonne's gamification elements make learning about Bitcoin engaging and fun, encouraging users to expand their knowledge.
-
Responsible adoption: The platform emphasizes security, privacy, and informed decision-making, ensuring sustainable growth.
The Future of Bitcoin Adoption
Yakihonne's community-centric approach is poised to revolutionize Bitcoin adoption. By leveraging the power of social nodes, Yakihonne creates a snowball effect, where knowledge and enthusiasm spread exponentially. As the platform continues to evolve, it's likely to play a significant role in shaping the future of Bitcoin.
Conclusion
Yakihonne is a game-changer in the Bitcoin space, offering a unique blend of community engagement, education, and support. By joining the Yakihonne community, individuals can tap into the collective power of social nodes, contributing to a brighter future for Bitcoin adoption. Embrace the potential of Yakihonne and be part of this exciting journey!
-
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ 826e9f89:ffc5c759
2024-06-28 21:46:01
@ 826e9f89:ffc5c759
2024-06-28 21:46:01_Prologue: this is a prose adaptation of a talk I gave to a private audience in Dubai and then tweaked slightly for a small conference in Sofia. I'm increasingly thinking it deserves a more general audience, and may be better suited to text anyway. This is probably not its final form, as the desired audience is tradfi capital allocators, hence a PDF is likely on the cards in the near future. For the time being, consider this a first draft, practising what it might look like as prose, and soliciting feedback from the good people of Nostr. Enjoy! _
The title of this essay means absolutely nothing. There is no such thing as “Web π” because there is no such thing as “Web 3”. It’s bullshit. It’s a scam.
Unfortunately, it has turned out to be extremely powerful bullshit and an extremely profitable scam, and so my goal in writing this essay is to give the reader the tools to navigate all of this and come out the other side without having been scammed or bullshat. In the spirit of not scamming and not bullshitting, I should be clear upfront about the intended readership of this essay, who I am to write it, and who it’s really about.
Who Are You?
I assume the reader is not a shadowy super-coder, but rather is a financial professional. This essay isn’t really for Bitcoiners, although if any read it, I hope they still find it interesting. Who I am really writing for are people coming to the space for the first time. Hopefully in your mind you are coming to the _Bitcoin _space, but if you think you are coming to the “crypto” space then this may be even more useful.
Who Am I?
I am the founder of a company that makes me not only highly biased but also flagrantly self-interested in the content I am promoting. I run a firm that invests in the Bitcoin ecosystem through a variety of different vehicles. I am not going to mislead you in the slightest in that my primary motivation is for you to allocate capital to us rather than to people I would call scammers and bullshitters. You should listen to them too and make up your own mind, or else what’s the point, really? How do you know I’m not scamming or bullshitting you? Exactly. Don’t trust. Verify.
In any case, that’s all assuming you want to “allocate capital” at all rather than just buy Bitcoin without a management fee. I’d like to think the primary difference is that I will be honest about that, and I’ll encourage you to understand as much as you can about what is going on and what you are doing (and if you are at all unsure, I would suggest you aren’t ready and you should just buy Bitcoin and learn) rather than bamboozle you with complete nonsense like “Web 3”.
Who Is This About?
It’s not at all about people working in crypto. Bitcoiners amongst the readership may be mildly irritated by me going on to give about as charitable an explanation of the role of these people as they have probably ever heard from somebody like me. This is really about financiers. It’s about the people who have used the mostly unrewarded efforts of developers, academics, entrepreneurs, and so on to siphon money from you to themselves, leaving a trail of useless tech and defrauded retail investors in their wake – and who will continue to do so if you continue to empower them.
Why This Essay?
We are at an interesting point in the development of the entirety of the “crypto” industry and I strongly suggest that people like you are going to be pitched all kinds of scams and bullshit in the coming months and years. If you have a little more background on what these people are really talking about, you will hopefully be able to avoid it.
My plan to help with that is presenting a short version and a long version of what blockchains are and are for, how they have historically been deployed in service of scams and bullshit, a high-level theory explaining the narrative evolution behind this sorry history, and a prediction for the near-term future of such shenanigans.
What is a Blockchain For?
A Blockchain is for sound, censorship-resistant, peer-to-peer digital money. It is not for anything else. If a blockchain is functional as money, it may be possible to also _use it _for other things. Some people find that interesting, some people find it infuriating, but don’t let that subtlety confuse you. It is not _for _arbitrary computation and storage or “decentralizing the internet” or running illegal securities rackets.

It is for money, plain and simple.
How does it achieve that? Proof of work and the difficulty adjustment. These are the innovations from which every other desirable property or feature flows. Proof of work enables censorship resistance. If somebody is trying to sell you on “proof of stake”: bullshit. The difficulty adjustment enables precise, predetermined, and _fair _issuance. If somebody is trying to sell you on a token they issue for free and without restriction: scam.
The problem Bitcoin solves is both economic and technical and the solution has material technical and economic merit. And it’s for this very specific and irreplicable reason the Bitcoin token has value. If this all sounds extreme to you, then I would suggest that your understanding of the topic is _extremely _misguided, that you are going to be _extremely bullshat and extremely scammed, _and you need to read this essay. That’s the short version.
The Long Version
I am sensitive to how extreme this all sounds. After all, hundreds of billions of dollars have been pumped into crypto, not Bitcoin – a huge amount of it is widely used, and many capable, honest, and brilliant people work in the industry. The reader will recall just above I said those people are not the target of my criticism. I’m not claiming they are all scammers and bullshitters. Sadly, I think it’s more likely they have been scammed and bullshat to some degree also.
I think I have some credibility in pointing this out because, as a VC in the Bitcoin space, I have increasingly seen founders telling me this themselves: that they originally bought into the hype in crypto and ended up wasting an enormous amount of time realizing their idea made no technical or economic sense in that context, so then they came to Bitcoin instead. You hear this one time and it’s an anecdote, but you hear it as many times as I have and it feels more like a representative sample.
What I want to cover next is as charitable a summary of the state of ex-Bitcoin crypto as I possibly can: my contention is that crypto has evolved into 4 rough categories: stablecoins, cryptography R&D, gambling, and scams. And these aren’t exclusive, to be clear; there is a lot of overlap, and, in fact, the overlap is arguably the key.
Scams
Scams are tokens, plain and simple. If somebody is trying to profit from the speculative price action of a token they have issued, they are scamming somebody. Maybe they are scamming you, maybe they are scamming retail investors, maybe they are scamming customers or suppliers – if such parties even exist in their cargo cult “business model”. There’s a scam in there somewhere.
However, it is rarely _just _a scam. There will almost always be components of stablecoins, R&D or gambling too. Hence these are worth really grappling with, taking seriously, giving credit to the extent it is due, but also analyzing critically.
My rough and high-level assessment of this breakdown of crypto is as follows, and I’ll explain what I mean by this below: stablecoins have economic merit but dubious technical merit; R&D has technical merit but no economic merit; and gambling sort of has merit but it depends how you interpret it. Obviously, scams have neither.

Stablecoins
By “sort of technical merit” I mean that stablecoins have central issuers. You can issue them as tokens on a blockchain but there’s not really much of a point. The issuer could just run a database connected to the internet with some straightforward signature schemes for transfers and it would make minimal operational difference. In fact, it would be cheaper and faster. _In fact, _you may as well run a Chaumian eCash mint (a decades-old innovation recently resurrected firmly within the _Bitcoin _space) such that your cheaper-and-faster-than-a-blockchain database also grants users transience and privacy rather than the public permanence of a blockchain.
The fact Tron is the most heavily used for stablecoins, in terms of settling the most value, is a testament to this point: it is barely even pretending not to be a database. This works as regulatory arbitrage given regulators think this is “innovation” because they are stupid.
That said, it is worth giving some credit here given the abject awfulness of fiat banking and payment rails with which stablecoins arguably most directly compete. Stablecoins are significantly more permissionless in their transfer than any fiat bank liability. And to attest to what seems like their most significant use case, they are permissionless in their _usership _in that only an internet connection and the right software is required rather than various discriminatory jurisdictional and compliance criteria.
However, what “sort of technical merit” ultimately boils down to, especially in comparison to Bitcoin, is: highly censorable in their exogenous links and, therefore, their value. The assets supposedly backing stablecoins are (by definition) still within the fiat system, even if this novel transfer mechanism of the rights to withdraw them is not. There is frankly a bit of theatre involved in the so-called “decentralization” of stablecoins given shutting down the central issuer is all that is required to make the permissionlessly tradeable decentralized tokens go to zero and be technically unimpeded but functionally useless. The technical innovation of Bitcoin, in contrast, is easily understood in one sense as it being totally indifferent to this kind of attack.
On the other hand, by “economic merit” I mean that they are extremely widely used and valued as a means of providing dollar shadow banking and often superior payment rails. Those in crypto often love pointing to this and many Bitcoiners tie themselves in knots trying to explain it away, whereas I see it as essentially unrelated to Bitcoin. Clearly there is a superficial connection, but you could create any superficial connection by “tokenizing” things for no particularly good technical _reason. I think it’s a different industry entirely. It’s more like a subindustry within _fintech – part banking, part payments – that for the time being relies on bamboozling regulators with all the nonsense I’m drawing attention to.
And good for them, frankly. If fiat banking isn’t going to be backed by real money anyway, then it _at least _ought to be permissionless. It should really be Chaumian eCash if it isn’t just Bitcoin, and it is regulation alone that makes it so awful in the first place. Making money usable and not a tool of dystopian control is, at this point, a political problem, not a technical one. Stablecoins are frankly a step in the right direction, especially insofar as they acclimatize users to digital assets. But I would still caution that they arguably don’t have sufficient technical merit to withstand what feels like an inevitable political attack …
Cryptography R&D
“Technical merit” for R&D is more or less self-explanatory, but the context is worth appreciating. It’s only really in crypto and mostly in Ethereum more specifically that people can permissionlessly experiment with arbitrarily complex cryptographic schemes that operate on real, enormous value. There are a lot of people who understandably find this attractive given their projects are essentially academic and trying out their ideas in the wild is more interesting, arguably more worthwhile, and certainly more fun than putting research essays on ArXiv or submitting them to a journal.
But … the value being manipulated is at best stablecoins and at worst baseless hype. If it isn’t a stablecoin then it probably exists in the first place because of either gambling or scams – and even there the line is very blurry.
Gambling
Gambling is an interesting lens to adopt on all this because it’s literally a trillion-dollar industry. And it’s real. It’s consensual; it’s not criminal; it’s legitimate economic activity that generates enormous profits for those who facilitate it well.
So, gambling has economic merit in that sense. But it’s tricky in this context how to characterize it because you could also argue it’s deeply dishonest gambling in that the gamblers don’t realize they are playing a negative sum game against the house. They think they are doing something akin to speculating on securities, which may be just as stupid depending on how it’s done, but at least has real economic utility and contributes to capital formation.
The difference here is that what is being speculated on _has no economic merit. _So, if that’s your gauge of merit, then here there is none. And it’s a very blurry line between this and an outright scam. Maybe the people involved _think _of what they are doing as amazing R&D, and maybe it’s inadvertently just a scam; maybe they know it’s all nonsense, but they think they can profit within the negative sum game because there are greater fools. In any case, I think gambling is a very helpful characterization of a lot of the behavior of the users and the real economic function of the industry.
There’s an interesting social component to all this because crypto people will often get mad at Bitcoiners because Bitcoiners tend not to care about either stablecoins or crypto R&D: they’ll say, why don’t you like stablecoins, they have clear economic merit? And the answer is they have dubious technical merit. Or, why don’t you like our next-gen Zero Knowledge scaling protocol, it has clear technical merit? And the answer is it has no economic merit.
If you’re happy with one but not the other, it’s easy to think of Bitcoiners as being closed-minded or dogmatic or whatever, but, ultimately, I think it’s just about discipline. What’s the point in being excited by something that half works, and that you know why will never fully work? So to be frank, a lot of this may be well-intentioned, but it’s kinda’ bullshit. It very probably ultimately rests on gambling and not at all whatever its stated purpose is … or it’s just a scam.
How Did We Get Here?
The following is by no means exhaustive and the framing is deliberately a little tongue-in-cheek. As well as being accurate enough (if unavoidably biased), my goal here is primarily to set up my prediction for what is coming next.
2015 reality: Ethereum launches narrative: “the world computer”
In 2015, Ethereum launched. The narrative here was that we are building “the world computer” and we can now have decentralized uncensorable computation. Never mind that anybody with a laptop has an uncensorable and decentralized computing device. And keep in mind this question of, “_what data might it ever be relevant to compute over in this manner (whatever that means in the first place)?” _The answer will become clearer and clearer …
2016-17 reality: ICO bubble narrative: “Web 3” / “DApps”
Regardless, at the end of 2015 we get the proposal and adoption of ERC20: a standard for issuing fungible tokens within Ethereum contracts, which is why in 2016 _but especially in 2017 _we get the ICO bubble. The narrative changes. Now we are concerned with “Web 2” companies being huge, powerful, and centralized. What if, instead, users could cooperatively own the application, control their own data, and participate in the economic upside that their usage is creating?
2018-19 reality: crypto winter narrative: “mistakes were made”
In 2018 this all falls apart, so don’t worry about it, moving on …
2020-21 reality: defi summer narrative: “decentralized finance”
By 2020 the narrative was different once again. It is more or less realized by this point that utility tokens make no technical or economic sense. You can’t introduce artificial scarcity in capital goods where there should be abundance and deflation and expect anybody to care, never mind to value your concoction. On the other hand, “securities” ought to be scarce and in some sense ought to function as tradeable ledger entries. Maybe they could be tokenized and computed on in a censorship-resistant and decentralized manner?
So, we get a boom in “defi” which, for what it’s worth, fellow Axiom co-founder Anders Larson and I predicted in our essay Only The Strong Survive, in September 2021, would be a complete disaster because, amongst a myriad of other illiterate insanities, there was approximately zero grounding of these securities in productive capital. The ecosystem was entirely self-referential – grounded _not even _in the questionable economic merit of stablecoins but firmly in gambling and scams; in leverage, rehypothecation, and securitization of precisely nothing whatsoever productive.
2022 reality: shitcoinpocalypse narrative: “mistakes were made”
And we were absolutely right because in 2022 everything collapsed. First Terra/Luna imploded – a “defi” project which essentially presented to the world the argument that a fractional reserve bank issuing fiduciary media can literally never go bankrupt because it can always cover a deposit shortfall by issuing more equity. While briefly flirting with a capitalization of around fifty f***ing billion dollars, and endorsed and fawned over by all manner of illiterate charlatans with gigantic and unsuspecting audiences, this argument was eventually rejected by the market as utterly imbecilic, as analyzed by myself and Nic Carter in All Falls Down.
This triggered a credit contagion that soon after took down 3 Arrows Capital, Celsius, Voyager, BlockFi, and others. FTX limped along by what we now understand to be something like defrauding their way out of debt, but eventually also collapsed later that year. If _Only The Strong Survive _was a pre-mortem of all of this, then the reader may want to read Green Eggs And Ham, also by myself and Anders Larson, as a kind of post-mortem.
2023-today reality: Bitcoin multisigs narrative: “Bitcoin renaissance”
And now a lot of this stuff is moving to Bitcoin. It is outside the scope of this essay to explain this in much detail but there have been a handful of developments in Bitcoin recently which, regardless of their intended purpose, seem to have as a collective side effect that a lot of these same shenanigans can now be implemented (or can _pretend _to be implemented) in a more Bitcoin-native context.
So, the new narrative is something like:
“these things didn’t work, not because they are terrible ideas that collapse to moon math wrappers around gambling and scams under any remotely critical analysis, but rather because they weren’t on Bitcoin. But also, since it has only recently become possible to (at least pretend to) implement them on Bitcoin, they are now worthwhile. We have wandered in the wilderness but learned our lessons and found the promised land.”

Technical and Economic Merit
Let’s consider all this through the lens of technical and economic merit once again. Or rather, the alleged merit given the stated goal. Ignore for now whether there is any merit:
2015 technical goal: new computing paradigm economic goal: x% of GDP?
The original idea of “crypto” allegedly has the merit of the next revolution in computing. Goodness knows how big that market is; probably a decent chunk of global GDP – if it meant anything, which it doesn’t.
2016-17 technical goal: disrupting company formation economic goal: y% of S&P?
ICOs then become a little bit more specific. Now they are merely disrupting how we organize companies. What’s that worth? Some portion of the value of the companies that can now be decentralized and tokenized I guess? Who knows …
2018-19 nothing to see here
Nothing happened then, don’t worry about it.
2020-21 technical goal: decentralize finance economic goal: z% of NYSE, CME, ISDA?
Defi becomes more specific again. Now we are merely tokenizing financial contracts, expanding access, removing middlemen, and so on. So that should probably be worth some percentage of capital markets activity?
2022 nothing to see here
Oops, never mind …
2023-today technical goal: now it’s on Bitcoin! economic goal: i% of … Bitcoin?
… and now it’s on Bitcoin apparently.
In Hindsight ...
I think the most amusing analysis of all this is as follows: it starts off completely insane, it gets more and more restrained each time – you could cheekily argue it starts to make more and more sense – but it also gets closer to Bitcoin every time. It’s clearly narrowing in on just: Bitcoin.
This is people realizing, painfully, over decades, what blockchains are for! They are not for “decentralizing everything” They are for censorship-resistant, sound, peer-to-peer digital money.

And I think this is _also _why we get the current state of crypto from earlier in the essay. As it starts to make more and more sense (by getting closer and closer to Bitcoin) you have realizations like the following: digital gift vouchers for artificially scarce and extremely expensive computation aren’t money, so we need “real money” in here for it to have economic merit, so you get stablecoins. Also, well we have a rich programming environment that seems technically interesting but also the severe technical handicap of being unable to do even a billionth of a billionth of a billionth of all the computations in the world, so you get crypto R&D. These emerge as a kind of patch, and they have _some _merit in isolation, whereas the long-term trajectory is actually just to converge on Bitcoin.
It’s an open and fascinating question if there are any learnings from these that can still be transplanted to Bitcoin. For stablecoins, this strikes me as less clear, given the dubious technical merit is introduced by using a blockchain at all, not just a blockchain other than Bitcoin. However, efforts to create Bitcoin balances (tokenized or otherwise) that are stable relative to some external price are to be applauded, if still heavily scrutinized for what technical merit they _really _have.
It seems far more likely that crypto R&D will prove useful in a Bitcoin context to some or other degree, and in this case the economic merit is in fact solved by moving to Bitcoin, provided the necessary technical merit can be mimicked. At the time of writing, this is a source of both hope and dread: hope given the possibility of viable avenues of development (although still highly uncertain); dread given how early steps in this direction are already being misrepresented in the pursuit of bullshit and scams. I will return to both shortly.
Narrative Evolution
Back to the table just above, I want to make three quick observations that tie together my entire argument and get us to the end of the essay:

Firstly, the bubbles always follow the price of Bitcoin. Hopefully I don’t need to include a price chart for the reader to grasp this immediately.
Secondly, it’s important that the narrative always changes. Absolutely ungodly amounts of money were raised for this crap following the_ Bitcoin bull runs of 2017 and 2021. The people doing this couldn’t point to the previous absolute disaster, so they had to spin something along the lines of: “_we learned our lessons and we’ve refined the use case.” This should sound familiar from just above.
Thirdly, however, regardless of whatever refinement they’ve come up with, the consequence of the new “narrative” is always, “buy my token”.
Always.
It doesn’t matter what buzzword salad is in the middle. It’s always “Bitcoin is cool, xyz, fughayzi fughahzi, buy my token.”
This is why I am very much tempted to not care so much about developers, academics, entrepreneurs, and so on, and in fact for my null hypothesis to be that they are more likely to have been victims than perpetrators. I don’t think they even end up in a position to contribute without the key group whom I do blame. When you put all these pieces together, what I think falls out of this analysis is as follows:
The entire cycle of shitcoinery can be traced to unscrupulous financiers convincing capital allocators who don’t know any better, in a bull market that, yes, Bitcoin is cool, but what they are doing is related, cooler, and that they deserve a fee.
Let us label this the Capital Cycle Theory of Shitcoinery. I think that everything else about which one might want to complain is downstream of this core realization.
Avoiding It
Given everything I’ve covered this is simple and this is pretty much the end of the essay.
You need to be aware of why this is happening now. If it hasn’t happened to you already (intended readership in the capital allocation business, that is) I guarantee it’s about to: with ETFs and the halving just past, we seem to be starting a Bitcoin bull run, these people have already raised ridiculous amounts of money on scams and bullshit that have mostly imploded. They may have lost a lot of money, or they may even have dumped on retail and got an excellent “return”. But in any case, they need a new narrative.
It's _possible _they have a viable narrative around stablecoins, R&D, both, and that they are as wary of scams as I have suggested here that they should be. I don’t want to insult anybody who merely has a different investment thesis to me if they are otherwise reasonable in their outlook and honest in their dealings.
However, if they are only now realizing how pointless and disingenuous every preceding crypto narrative has been after 7 years and hundreds of billions of dollars – or if they still don’t realize it at all; if their track record shows they were deeply involved, handsomely rewarded, and yet created nothing of lasting value; if they say things like “the builders are coming back to Bitcoin”: be very, very suspicious. Be on the lookout for tokens, which is to say, be on the lookout for scams.
What is especially frustrating is that the technical spin of the "layer twos" that are all the rage at the time of writing, that "the builders are coming back to Bitcoin" to build, and that you, the capital-allocating reader, will almost certainly be pitched, is in and of itself pretty reasonable. They just don't require tokens and they don't require gambling to support the token prices. What they do require is _sound adherence to Bitcoin's technical and economic merit. _At the very least, they require honest communication about the design trade-offs so far and planned for, and what, if any, economic and technical merit is left over after these trade-offs have been made.
Narrative aside, the _reality _of 99% of these projects is that they are private execution environments tied to multisigs custodying user deposits. Which is to say, on the one hand, that they are cargo culting "crypto R&D" from Ethereum that isn't technically possible in Bitcoin in order to feign technical merit, and on the other, that _they aren't layer twos at all. _Once again, they may as well be Chaumian eCash mints, except for the fact that this would make the intended token scam all but impossible to pull off.
Casey Rodarmor, creator of the Ordinals protocol, recently joked on the Hell Money _podcast he co-hosts, responding to the idea that "_everybody is building an L2 now":
"It's the same sad sack playbook as on Ethereum being recapitulated on Bitcoin. That's how you get a VC check on Ethereum. They are all glorified multisigs, so they are like, "hey let's port our glorified multisig to Bitcoin and get a VC check." I was talking to a friend of mine who is working on an interesting project, an open-source analyzer that does transaction clustering, and I was like, "maybe you could do this in this way and raise some VC money," and he said, "yeah, okay, but what's the point in raising VC money?" And I said, "no, no, no, this is the end! This is the goal! You raise VC money and then you cut yourself checks from that VC money until it runs out and then you raise more at a 10x valuation. This is the new economy, guys!"
The 1% that are legitimately trying to bring the learnings from crypto R&D to Bitcoin in a technically and economically sound manner will hopefully win in the long run (and even this is somewhat speculative at the time of writing) but will likely get little to no attention amidst this bull market flurry of scams and bullshit.
Axiom will do its best to source and invest in these companies (we already have!) but we are resigned to it being a much more difficult sell to capital allocators in light of the Capital Cycle Theory of Shitcoinery. To be brutally honest, this entire essay can fairly be considered cope on my part in light of having lost this battle in the past and facing up to the very real prospect of losing it in the near future too. Oh well, at least I tried.
Wrapping Up
The essence of the Capital Cycle Theory of Shitcoinery is that the problems I’ve described ultimately come from bamboozling people just like you with technical sounding nonsense like “Web 3” so you think it’s all a lot more complicated than it really is. Just buy Bitcoin. That’s certainly the first thing you should do anyway, and it might be the only thing you ever need to do.
If you really, really want to take the extra risk of investing in the Bitcoin ecosystem, the team at Axiom would be happy to speak with you. But we are never going to talk you out of buying Bitcoin. There is no world in which Bitcoin does poorly and we do well, or in which we promise something “better than Bitcoin,” and there’s no point in engaging with us at all if you don’t already believe most of this.
If that’s of interest to you, we’d love to talk. If not, just buy Bitcoin. In any case: fair warning, we are heading into a Bitcoin bull market and the scams and the bullshit are coming. Good luck avoiding them.
Allen Farrington, June 2024

-
 @ 59cfee8f:7598a483
2024-12-03 17:23:27
@ 59cfee8f:7598a483
2024-12-03 17:23:27Yakihonne's Innovative Approach to Bitcoin Adoption
Introduction
The Bitcoin landscape is constantly evolving, and community plays a vital role in shaping its future. Yakihonne, a cutting-edge platform, is harnessing the power of community to drive Bitcoin adoption and education. In this article, we will explore Yakihonne's innovative approach and its impact on the Bitcoin ecosystem.
The Yakihonne Difference
Yakihonne distinguishes itself by recognizing every user as a unique node in the Bitcoin network. This perspective empowers individuals to take an active role in shaping the community and contributing to its growth. By fostering connections and knowledge sharing, Yakihonne creates a supportive environment where users can thrive.
Key Features and Benefits
-
Decentralized knowledge sharing: Yakihonne's platform allows users to access and share valuable resources, promoting a deeper understanding of Bitcoin and its applications.
-
Community-driven support: Users can engage with others, ask questions, and receive guidance from experienced community members.
-
Incentivized learning: Yakihonne's gamification elements make learning about Bitcoin engaging and fun, encouraging users to expand their knowledge.
-
Responsible adoption: The platform emphasizes security, privacy, and informed decision-making, ensuring sustainable growth.
The Future of Bitcoin Adoption
Yakihonne's community-centric approach is poised to revolutionize Bitcoin adoption. By leveraging the power of social nodes, Yakihonne creates a snowball effect, where knowledge and enthusiasm spread exponentially. As the platform continues to evolve, it's likely to play a significant role in shaping the future of Bitcoin.
Conclusion
Yakihonne is a game-changer in the Bitcoin space, offering a unique blend of community engagement, education, and support. By joining the Yakihonne community, individuals can tap into the collective power of social nodes, contributing to a brighter future for Bitcoin adoption. Embrace the potential of Yakihonne and be part of this exciting journey!
-
-
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ 24e36cf3:6b26ae15
2024-12-04 12:35:57
@ 24e36cf3:6b26ae15
2024-12-04 12:35:57My husband and I have been talking a lot about capitalism and socialism lately. We've watched countless videos, read books about it, discussed the topic with friends and family. Even though we've been left-leaning all our lives due to social programming from our families, we've radically changed our views in the past couple of years and are now convinced that any form or socialism is bad for humanity.
Here's a colloquial summary of our thought process as explained to an acquaintance, who is still pro-socialism:
Let's look at the animal kingdom for some context
My initial thought regarding victim and perpetrator ... take, for example, lions and gazelles in Africa. At first glance, the lion seems to be the problem because it comes and kills the poor gazelles who just want peace. Now let's look at the other side:
- The lion was not asked, whether it wants to be born a lion
- The lion cannot help that it has to eat gazelles
- It's not funny to chase after its food and if you're too slow after the 3rd attempt you'll probably won't have any strength left and die
\ If you think about it a little more, you could argue that the gazelle is actually the perpetrator. She runs away and then the lion starves. Who is the victim and who is the perpetrator?
Now ... why did nature design the system this way? Why aren't all creatures nice to each other and the lion only eats what is absolutely necessary and the gazelle just lies down and waits to be eaten?\ You will now think that's nonsense and can't be like that, but it is. You surely know the fish that swim upstream in the river, get so extremely red and pale, become parents and then die so that the next generation has something to eat. There are dependencies in nature that are stronger than the life of an individual. But only rarely ... why?
If gazelles considered the lion's feelings and just laid down if he's having a bad day, the lion would get lazy, sick and weak. Unfortunately, that's the way it is. Nobody likes to run for their food. If nature had programmed it that way, the lion would eventually realize it and start running slower. Survival of the fittest is how evolution works and the weaker lions would perish. The gazelle running as fast as it can is good for the lion. Removing the slowest animals from the herd is beneficial for the gazelles. It's an extremely cruel system, but that's the way nature works and we are all a part of it.
Capitalism is this system applied to humans. Capitalism emerges voluntarily and spontaneously between free individuals and everyone benefits from it.\ If two people are stranded on an island and one starts farming the land for fruits and the other diverts the river for more water, they both benefit. Both are better off. Each pursues their own interests (like a lion and a gazelle), but both end up benefiting.\ You work on something useful and someone else rewards you for your work. That's it. There are no victims or perpetrators ... there are only actors. Everyone works for themselves and everyone is better off.
All the problems you mentioned (deteriorating environment, poverty, social injustice, ...) arise when the collective (the state or other authorities) come together and suppress this natural system; because of poor gazelles and wicked lions. In reality, no one cares about the poor gazelles because:
- They are not poor.
- They only care about maintaining their power.
Let's talk about Jeff Bezos' Amazon, which is often vilified
One hears constantly that Amazon workers are exploited (victims) and the poor shops everywhere have to close because Bezos destroyed all other stores. What you hear about the workers at Amazon is fake news. For example here is a "negative video" because Bezos makes so much money ... but check out what the guy says:\ https://www.youtube.com/shorts/OvSkhpCsUmY\ The workers there are not victims. They come voluntarily. No one forces them to work at Amazon.
If you think about it some more: Why don't you work at Amazon?\ Very likely because you have other options. You don't necessarily have to stand behind the conveyor belt. Apparently some others do. You can't control that some people have little education, ability or motivation, so that they have to do this work. They would probably starve without Amazon. Amazon is simply utilizing these people who are just there and is making something productive out of it ... which is good for us all. Imagine the difference compared to charity: With Amazon the worker earns something and is useful for society. The unemployed does nothing and wastes society's energy. The difference is enormous.\ And to make that clear again ... the workers are not victims. Many don't want to do anything else. Many are too lazy and are wasting their hard earned money on cigarettes, alcohol and drugs. Still, there are people, who are actually sick and weak among us. This is sad and I'll say more about them later.
Watch this video: https://www.youtube.com/watch?v=GltlJO56S1g Do you see an evil person, there? I see a man who risked everything to build this empire and who made huge losses for years. Why? For the purpose of providing an outstanding customer service. To you. In my opinion, Jeff Bezos is a hero.
Now for other companies:\ Compare them to the "in the sun-basking gazelles" (shops) and the attacking lions (Bezos). Now imagine a committee comes in and says: "Stop, don't eat these gazelles". WTF?
- Bezos would be starving. It's a catastrophe ... Bezos needs to get rewarded and thankfully was rewarded.
- The shops would still be lazy.
- We would still be in the stone age and sit together in the dark and starve. The world would still be poor.
Now often the consumer behavior is criticized. Amazon is to blame for all the trash, because people send everything back and it ends up in the landfill. But who sends everything back? Amazon? Amazon provides the service, people send everything back. Why is Amazon to blame? From a consumer's perspective, Amazon is a tool ... like a screwdriver. It was designed by humans exactly the way they wanted it. Some use a screwdriver to murder someone. Is the screwdriver now the problem? Should we all just stop making it more difficult for disadvantaged people who can't or won't send it back? Aren't we all grown-ups?
Some more examples of high-achievers
Watch this video from Bryan Johnson at Blueprint: https://www.youtube.com/watch?v=djiU_pFTEVE. Does this man look like a monster to you? He works around the clock to deliver me fresh and healthy food. He was already a millionaire to start with and could have done nothing but enjoy himself. Instead of partying, he enriches my life. I am grateful forever when Bryan becomes a billionaire!
Watch the videos from Ben "Ungeskriptet": https://www.youtube.com/@ben_ungeskriptet. He constantly invites successful people. No one of them needs to work anymore. Everyone would prefer to spend more time with their family but they are driven to make society better. They earn money by doing so... yes. Once you earn a few million dollars however, money is no longer important. Everyone of those successful people confirms this. They do the hard work because they are purpose driven and we should be grateful for them.
Elon Musk wants to inspire us humans to make a colony on Mars. That's his only goal. He could also just sit at home and do nothing. Instead he works on his dream and we all benefit from it. If you don't want to work for Elon Musk, then you are free to do something else. If you can't find anyone who hires you, then you are free to start your own business and out compete Elon. If we all didn't want him to make a colony on Mars, we shouldn't buy his products. Oops... the state buys the rockets. The state gives him money. Who is the problem?\ If you don't want Starlink, don't buy it. Then he built his rockets in vain. He earned his money before and if he chooses to spend it like this, that's his own choice. If he fails, he'll have to deal with the consequences. That being said...the only problem here is that the state subsidizes SpaceX rockets against the interest of the people.
Now to the two most important points that are not often mentioned:
- We want the same thing. I am for a social system. I like that everyone is doing well. I am for supporting the weak. If I could, for example, give away 10% of my possessions and help people, I would do so immediately. I support many people in my environment with a lot of money, time, and effort. The problem is not helping unproductive or disadvantaged people ... the problem is that you steal from successful people and distribute a small part of the loot to the unproductive, so that you get more votes (Socialism). If 50% of any given country came together and hired a company to support the poorest in their society that would be awesome. I'd be on board right away. But why do you have to force me? Why do you have to steal my money and contribute it to a system that doesn't deliver results? Why don't we use the market? If the company that supports the poor doesn't use the money correctly, you can change the "provider." Unfortunately, I can hardly change the state, and that's where the problem arises. The theft is the problem... not the social system. The state is, in fact, nothing more than a monopolistic company that cannot be disrupted by competition... this wouldn't exist in a free market, and it’s fatal.
- The problem with capitalism is that you don't recognize the benefit right away. If the productivity of the world increases by 5% per year, you unfortunately don’t benefit from it. Productivity increases through Amazon, Bryan Johnson, Elon, and 1000+ companies working around the clock. All research and technology also come from the market. It’s an investment for more profit later. But for what? Your life doesn't get better, does it? There’s the problem. Actually... if the monetary system were right... everything should become 5% cheaper per year. We should have deflation. If the world gets better, everything should get cheaper, and therefore, everyone should benefit. What does actually happen? The rich get richer. Why? Because the state prints money and steals from you... about 7% per year because the central bank wants 2% inflation. Just enough so that no one notices, and no one hangs them for it. The state steals all the benefits of capitalism and distributes them to itself. The rich are the ones who can defend themselves... thus, they get richer, along with all the bureaucrats who benefit as well. About 7% per year compared to you. But this is not because of the rich. It’s because of the state. In my opinion, this is the biggest problem, and Bitcoin is the solution. Bitcoin emerged from the market for the people. A solution from the free market against the oppression of the state. Very poetic, if you ask me. With Bitcoin, prices will fall forever... even if there is no more fiat money... because the supply is fixed, and if someone starts the next Amazon and the world becomes 0.1% more productive, everything will also become 0.1% cheaper.
Let's finish with some more eye-opening content suggestions:
This video opened my eyes. I've watched it again since... it's not that impressive... but somehow it worked for me: https://www.youtube.com/watch?v=Q6tDV3BhrcM
Watch this, regarding the environment: https://www.youtube.com/watch?v=zJdqJu-6ZPo
Milton Friedman is always enlightening: https://www.youtube.com/watch?v=67tHtpac5ws
And here again: https://www.youtube.com/watch?v=5_mGlqyW_Zw\ The ending is crazy. Nobody wanted to hire black people, and no social program would have changed that ... because everyone was racist back then. Even the shop owners ... and yet, they hired black people, which gave them an income. Now you can call it exploitation, but it's about the result. There's nothing that would have worked better in that environment. It doesn't sound nice, but it works.
And that's exactly how, but in the opposite way, Communism, Marxism, and Socialism work. It sounds good, but it produces Hitler, Stalin, and Mao.
-
 @ 59cfee8f:7598a483
2024-12-03 17:23:20
@ 59cfee8f:7598a483
2024-12-03 17:23:20Yakihonne's Innovative Approach to Bitcoin Adoption
Introduction
The Bitcoin landscape is constantly evolving, and community plays a vital role in shaping its future. Yakihonne, a cutting-edge platform, is harnessing the power of community to drive Bitcoin adoption and education. In this article, we will explore Yakihonne's innovative approach and its impact on the Bitcoin ecosystem.
The Yakihonne Difference
Yakihonne distinguishes itself by recognizing every user as a unique node in the Bitcoin network. This perspective empowers individuals to take an active role in shaping the community and contributing to its growth. By fostering connections and knowledge sharing, Yakihonne creates a supportive environment where users can thrive.
Key Features and Benefits
-
Decentralized knowledge sharing: Yakihonne's platform allows users to access and share valuable resources, promoting a deeper understanding of Bitcoin and its applications.
-
Community-driven support: Users can engage with others, ask questions, and receive guidance from experienced community members.
-
Incentivized learning: Yakihonne's gamification elements make learning about Bitcoin engaging and fun, encouraging users to expand their knowledge.
-
Responsible adoption: The platform emphasizes security, privacy, and informed decision-making, ensuring sustainable growth.
The Future of Bitcoin Adoption
Yakihonne's community-centric approach is poised to revolutionize Bitcoin adoption. By leveraging the power of social nodes, Yakihonne creates a snowball effect, where knowledge and enthusiasm spread exponentially. As the platform continues to evolve, it's likely to play a significant role in shaping the future of Bitcoin.
Conclusion
Yakihonne is a game-changer in the Bitcoin space, offering a unique blend of community engagement, education, and support. By joining the Yakihonne community, individuals can tap into the collective power of social nodes, contributing to a brighter future for Bitcoin adoption. Embrace the potential of Yakihonne and be part of this exciting journey!
-
-
 @ 2063cd79:57bd1320
2024-12-04 12:32:50
@ 2063cd79:57bd1320
2024-12-04 12:32:50Der dieswöchige Aufhänger ist die Nachricht über die Schließung der Kryptowährungsbörse Bitzlato. Obwohl sich die groß angekündigte Offensive des US-Justizministerium als mindestens genauso große Luftnummer erwies (vor der Nachricht hat wirklich niemand jemals von Bitzlato gehört), hat die Nachricht doch wieder den Stimmen Gehör verschafft, die seit jeher nach mehr Regulierung von Kryptowährungen, Börsen und Dienstleistern rufen.
https://bitcoinmagazine.com/legal/doj-shuts-down-bitzlato-crypto-exchange
Besonders in den USA herrscht eine andauernde Diskussion darüber, wie Bitcoin und andere Kryptowährungen eingestuft werden sollen, damit anschließend die Gerichtsbarkeit, bzw. die Kompetenzen verteilt werden können. Im Prinzip gibt es dabei nur zwei Ansichten: Die eine Gruppe hält Bitcoin für ein Wertpapier (Security), die andere hält Bitcoin für eine Ware oder einen Rohstoff (Commodity). Wir wollen uns diese Woche anschauen, was den Unterschied ausmacht und was die Implikationen für Bitcoin wären, wenn man es als das eine oder das andere klassifiziert, und was es darüber hinaus für die Zuständigkeit diverser Behörden und Regierungseinheiten bedeutet.
Die Gretchenfrage bei der Regulatorik von Bitcoin ist relativ schnell erklärt. Es wird darüber gestritten, ob Bitcoin als Wertpapier (Security) oder als Rohstoff / Ware (Commodity) eingestuft werden soll. Dies ist insofern wichtig, als dass die Kategorisierung darüber entscheidet, welche Aufsichtsbehörde mit ihren Regeln aktiv werden kann / muss. In der anhaltenden Diskussion über das Thema wird verallgemeinernd meist über die Einordnung von Kryptowährungen gesprochen, und damit Bitcoin als eine von vielen Kryptowährungen mit einbezogen (Bitcoin ist keine Kryptowährung - das wird dieser Artikel aufzeigen), jedoch wollen wir der Einfachheit halber zunächst die Diskussion auf der breiter gefassten Ebene führen. Zunächst lohnt es sich zu schauen, was Wertpapiere und Rohstoffe / Waren unterscheidet.
Wertpapiere (Securities)

Zunächst mal muss man sagen, dass eine genaue Unterscheidung der beiden Anlageklassen in allen Fällen - nicht nur bei Kryptowährungen - oft schwierig ist. Vor allem in der heutigen Zeit ist es nicht mehr so einfach schwarz und weiß zu unterscheiden, da es für alles, was sich in irgendeiner Form handeln lässt, auch Derivate gibt. Früher sagte man vereinfacht, dass Wertpapiere zum Investieren und Rohstoffe zum Handeln sind, aber dass dies nicht richtig ist und in beide Richtungen entkräftet werden kann, sollte so ziemlich jeder auch weit gegen den Wind riechen können.
Prinzipiell handelt es sich bei einem Wertpapier um ein Finanzinstrument, dessen Ausgestaltung typischerweise von der Gerichtsbarkeit abhängt, in der die Vermögenswerte gehandelt werden. In den USA und Europa gelten im Großen und Ganzen alle frei gehandelten Vermögenswerte als Wertpapiere und werden in drei Hauptkategorien unterschieden: Beteiligungspapiere (Equity) – einschließlich Aktien, Schuldverschreibungen (Debt) – z.B. Anleihen und Banknoten und Derivate – zu gehören Optionen und Futures (👇). Anders als Rohstoffe sind Wertpapiere anders und meist strenger reguliert. In den USA ist für die Regulierung die SEC (U.S. Securities and Exchange Commission) und in Europa die ESMA (Europäische Wertpapier- und Marktaufsichtsbehörde), bzw. in Deutschland die BaFin (Bundesanstalt für Finanzdienstleistungsaufsicht) zuständig ist.
Rohstoffe (Commodities)

Traditionelle Beispiele für Rohstoffe sind Getreide, Fleisch, Gold, Öl oder Erdgas, also die drei großen Kategorien Landwirtschaftliche Produkte, Edelmetalle und Energie. In der heutigen Zeit werden diese Waren weltweit gehandelt und eine Warenbörse, wie die CME (Chicago Mercantile Exchange) in den USA, handelt sowohl mit physischen Waren, als auch mit Warenkontrakten und damit verbundenen Anlageprodukten. Wie aus meinem Artikel über Bitcoin-Hashprice Forwards bekannt, gibt es zwei gängige Formen von Warenkontraken: Futures und Forwards.
https://www.genexyz.org/post/18-block-761575-bitcoin-hashprice-forward-ks72ec/
💡Futures sind eine Form von Derivaten, die Parteien verpflichten, einen Vermögenswert zu einem vorher festgelegten zukünftigen Datum und Preis zu handeln. Hier muss der Käufer den Basiswert zum festgelegten Preis kaufen oder dem Verkäufer verkaufen, unabhängig vom aktuellen Marktpreis zum festgelegten Zeitpunkt der Abwicklung.
Forwards hingegen stellen eine ähnliche Form von Terminkontrakten dar, die auch einen zukünftigen Preis zu einem zukünftigen Datum festlegen, nur dass Forwards außerbörslich (OTC) gehandelt werden. Hinzu kommt, dass Forwards anpassbare Bedingungen haben, die zwischen den Parteien und dem Händler individuell vereinbart werden. Forwards sind im Gegensatz zu Futures nicht standardisiert.
Wie nun ersichtlich ist, muss eine Grenze zwischen dem direkten Handel mit Rohstoffen und dem Handel mit Rohstoff-gebundenen Titeln (digitale Rohstoffe) einerseits und Finanzprodukten ohne Bezug zu Rohstoffen andererseits gezogen werden, denn für den Rohstoffhandel sieht sich in den USA die CFTC (U.S. Commodity Futures Trading Commission) zuständig, die Futures- und Optionsmärkte reguliert, die dem Commodity Exchange Act unterliegen.
Die Kategorie der digitalen Rohstoffe ist relativ neu. Derzeit überwacht die CFTC die Regulierung für Derivate von Rohstoffen zusätzlich zu dem zugrunde liegenden Rohstoff selbst.
Wie also unterscheidet man, ob es sich bei einem Finanzprodukt, oder in unserem Fall einer Kryptowährung, um ein Wertpapier, oder um einen Rohstoff / eine Ware handelt?
Zunächst ist festzustellen, dass man nicht die gesamte "Anlageklasse" der Kryptowährungen als entweder oder einstufen kann. Wie bei allen Finanzprodukten muss im Einzelfall entschieden werden und das jeweilige Produkt im Einzelnen betrachtet werden. Es gibt kein "Krypto" oder "Kryptowährungen", sondern viele tausende Produkte, die sich grob einer Produktkategorie zuordnen lassen.
Der Howey Test

In den USA unterscheidet man zwischen Securities und Commodities mit Hilfe des Howey Tests. Der Test basiert auf einem Verfahren der SEC gegen W.J. Howey, bei dem zu einem Urteil kam, das diesen vierstufigen Test zum ersten Mal definierte. Seitdem wird die Klassifizierung von Investitionsobjekten durch die SEC, aber auch die CFTC und andere amerikanische Behörden anhand dieses Tests durchgeführt. Erfüllt ein Investitionsobjekt alle vier genannten Kriterien, handelt es sich dabei zweifelsfrei um Wertpapiere und unterliegt somit der Gerichtsbarkeit der SEC. Gemäß dem Urteil lautet der Test wie folgt:
- An investment of money
- In a common enterprise
- With the expectation of profit
- To be derived from the efforts of others
Auf deutsch bedeutet dies einfach, ob 1) eine Geldanlage 2) in einem gemeinschaftlichen Unternehmen, 3) mit einer Gewinnerwartung stattfindet und 4), ob diese Gewinne von den Bemühungen Dritter abhängen.
Anlageobjekte, wie Tokens, Coins, Assets, Cryptos, NFTs, Contracts, etc. bei denen diese vier Fragen alle im Positiven, also mit einem „Ja“, beantwortet werden können, werden als Wertpapier eingestuft und unterliegen damit den Regeln der SEC. Somit müssen Verantwortlichen, Initiatoren oder Geschäftsführer dieser Projekte die gleichen Genehmigungen einholen und Regeln befolgen, wie alle anderen registrierten Wertpapiere / Anbieter.
Anwendung auf Kryptowährungen
Wie schon erwähnt, kann man die Regeln nicht einfach anwenden, denn es gibt natürlich bei jedem Projekt, jeder Währung, jedem Coin viele Faktoren, die eine Rolle bei der Interpretation des Tests spielen. Bei den tausenden existierenden Projekten sind Bandbreite und Spektrum groß, was auch viel Raum für Interpretation offen hält. Bei der Einordnung jeder einzelnen Kryptowährung muss man also die Testfragen im Einzelfall auswerten und anwenden und somit sehen, wo man auf dem Spektrum landet. Regulatorisch gesehen am weitesten weg von Wertpapieren sind alle Kryptowährungen, die mit Hilfe von einem dezentralisierten Mining-Protokoll auf einer funktionierenden dezentralen Blockchain laufen. Das Mining ist ein wichtiger Aspekt, da Miner für ihre Arbeit / Investition von Ressourcen entlohnt werden, und damit nicht, wie Investoren bei ICOs oder anderen Verkaufsrunden, oder sogar bei Airdrops, von vorab produzierten Coins profitieren. Bei der Unterscheidung von Coins und Tokens müssen Coins im Einzelfall bewertet werden, wohingegen Tokens oft der Definition des Netzwerks oder Protokolls unterliegen, auf welchem sie beheimatet sind. Wenn ein Projekt dezentralisiert ist, ist es viel weniger wahrscheinlich als Wertpapier eingeordnet zu werden, da argumentiert werden kann, dass es sich bei dem Projekt nicht um ein gemeinschaftliches Unternehmen handelt.

Hier muss man natürlich auch wieder differenzieren, da viele Projekte sogenannte DINOs darstellen. Also Decentralized In Name Only sind, was oft auf einer geschickten Vermarktung des Produkts / Protokolls / Netzwerks basiert. Wenn also ein Protokoll / eine Blockchain ohne weiteres angehalten, neugestartet oder zentral gepatched (ich schaue dich an, Solana), oder gar zurückgedreht werden kann (du bist gemeint Ethereum), muss es einen Entscheidungsträger oder zumindest ein kleines Entscheidungsgremium geben, das als gemeinschaftliches Unternehmen gelten kann (sollte!).

Die Gewinnerwartung ist genauso auslegbar. Als einfaches Beispiel lässt sich hier Dogecoin heranziehen. Die Geschichte von DOGE ist tatsächlich sehr sehr unterhaltsam und einen kleinen Ausflug in die Abgründe des Internets wert, aber nicht jetzt. Kurz gesagt ist DOGE ein Meme-Token, geboren als Parodie auf Kryptowährungen und niemals als wirkliches Investitionsobjekt gedacht. Die ersten Käufer von DOGE hatten keine Gewinnerwartung, sondern wollten Teil einer Community von "Insidern" sein, einer Gruppe, die den Hunde-Witz versteht. Das Wachstum kann als organisch beschrieben werden, da es DOGE viele Jahre gab, bevor es zu dem wurde, was dann 2021 in dem kulminierte, was jeder kennt. Worauf ich hinaus möchte, ist dass es keine gemeinschaftliche Unternehmung gab, die dem Wert von DOGE zuträglich gewesen wäre und "Investoren" (sprich Internet-Kiddos und Meme-Trottel) nie eine wirkliche Gewinnerwartung hatten.
Einordnung von Bitcoin
https://x.com/Satsback/status/1617902548870127617
Das führt uns zu unserem geliebten allseits verehrten Freund, dem Rohstoff (oh nein, Spoiler-Alert) mit dem orangenen B-Logo. Wir wissen jetzt, dass die Anwendung des Howey-Tests einer im Einzelfall auszulegenden Beurteilung der vier Fragen bedarf. Dies ist nicht anders bei Bitcoin. Zu diesem Thema haben sich zum Glück schon viele prominente Personen geäußert, weshalb ich einige Interpretationen hier auslegen möchte:
https://www.cftc.gov/PressRoom/PressReleases/7231-15
Rostin Benham, der Vorsitzende der CFTC (☝️), stellte z.B. richtig fest, dass Kryptowährungen, je nach Ausgestaltung entweder als Commodity oder als Security klassifiziert werden können (ja Junge, wissen wir doch schon!). Darüber hinaus sagte er, dass er und seine Kollegen sich sicher wären, dass sowohl Bitcoin als auch Ethereum als Rohstoff einzuordnen sind, während andere Token vielmehr Wertpapiere darstellen.
Da der CFTC-Chef sowohl Bitcoin als auch Ethereum nicht als Wertpapier einstufen will, kann der Howey-Test eigentlich nicht für diese Entscheidung herangezogen worden sein. Denn wir haben ja schon gesehen, dass Ethereum am Test scheitert und sich somit recht leicht als Wertpapier einordnen lässt.
https://archive.ph/9vNAW
Auch die Vorsitzenden des Senatsausschusses der USA haben bereits Gesetze vorgeschlagen, die die Aufsicht über Bitcoin und Ethereum der Bundesbehörde CFTC übertragen würden, und somit Bitcoin als Rohstoff klassifizieren. Warum Bitcoin und Ethereum immer zusammen genannt werden und von anderen Währungen abgegrenzt werden, entzieht sich mir, aber immerhin schaffen diese geriatrischen Papageien die geistige Akrobatik zwischen verschiedenen Kryptowährungen zu differenzieren.
https://bitcoinmagazine.com/business/heres-whats-in-senator-lummis-bitcoin-bill
Auch US-Senator Lummis erklärte, dass Bitcoin, gegenüber jedem anderen Krypto-Vermögenswert, vollständig dezentralisiert ist und dass die Person oder die Gruppe (Satoshi) keine vorab erzielten Gewinne generieren. Im Gegensatz zu allen anderen Kryptowährungen, die von zentralisierten Personen oder Gruppen gesteuert sind und oft riesige Gewinne generiert haben. Cynthia versteht sogar den Unterschied in der Natur von Bitcoin und Ethereum.
Lummis Gesetzentwurf soll weiterhin ausschließen, dass Wertpapiere gleichzeitig als digitale Rohstoffe bezeichnet werden. Damit würden alle als Wertpapier gekennzeichneten Kryptowährungen in die Zuständigkeit der SEC fallen.
Auch SEC Oberhäuptling Gary Gansler, ehemaliger MIT-Professor für Blockchain-Technologie, digitale Währungen und Finanztechnologie, hält nur Bitcoin für eine Commodity und meint weiter auch, dass die meisten Kryptowährungsprojekte, die sich mit Wertpapieren befassen oder solchen ähneln, in den regulatorischen Zuständigkeitsbereich der SEC fallen sollten.
Während die meisten Kommentatoren die Einschätzung der oben genannten Repräsentanten unterstützen und somit deutlich wird, warum ein und für alle Male klar ist, warum Bitcoin und Kryptowährungen nicht das gleiche sind, gibt es einige Stimmen aus den USA, die meinen, dass die Einhaltung der geltenden CFTC-Vorschriften für viele Bitcoin-Startups zu kostspielig wäre, was dazu führen würde dass sich viele innovative US-Unternehmen gezwungen fühlen dürften, ihre Operationen ins Ausland zu verlagern.
https://decrypt.co/105693/sec-coinbase-lists-nine-crypto-tokens-securities
Bitcoin stellt also, im Gegensatz zu allen anderen Kryptowährungen, kein Wertpapier dar. Das macht Bitcoin einzigartig und deshalb kann man getrost sagen, dass Bitcoin keine Kryptowährung ist. Denn Bitcoin ist ein Rohstoff, der, wie alle anderen gehandelten Commodities, frei in der Natur vorkommt. Bitcoin ist ein digitaler synthetischer Rohstoff.
🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 59cfee8f:7598a483
2024-12-03 17:23:08
@ 59cfee8f:7598a483
2024-12-03 17:23:08Yakihonne's Innovative Approach to Bitcoin Adoption
Introduction
The Bitcoin landscape is constantly evolving, and community plays a vital role in shaping its future. Yakihonne, a cutting-edge platform, is harnessing the power of community to drive Bitcoin adoption and education. In this article, we will explore Yakihonne's innovative approach and its impact on the Bitcoin ecosystem.
The Yakihonne Difference
Yakihonne distinguishes itself by recognizing every user as a unique node in the Bitcoin network. This perspective empowers individuals to take an active role in shaping the community and contributing to its growth. By fostering connections and knowledge sharing, Yakihonne creates a supportive environment where users can thrive.
Key Features and Benefits
-
Decentralized knowledge sharing: Yakihonne's platform allows users to access and share valuable resources, promoting a deeper understanding of Bitcoin and its applications.
-
Community-driven support: Users can engage with others, ask questions, and receive guidance from experienced community members.
-
Incentivized learning: Yakihonne's gamification elements make learning about Bitcoin engaging and fun, encouraging users to expand their knowledge.
-
Responsible adoption: The platform emphasizes security, privacy, and informed decision-making, ensuring sustainable growth.
The Future of Bitcoin Adoption
Yakihonne's community-centric approach is poised to revolutionize Bitcoin adoption. By leveraging the power of social nodes, Yakihonne creates a snowball effect, where knowledge and enthusiasm spread exponentially. As the platform continues to evolve, it's likely to play a significant role in shaping the future of Bitcoin.
Conclusion
Yakihonne is a game-changer in the Bitcoin space, offering a unique blend of community engagement, education, and support. By joining the Yakihonne community, individuals can tap into the collective power of social nodes, contributing to a brighter future for Bitcoin adoption. Embrace the potential of Yakihonne and be part of this exciting journey!
-
-
 @ 59cfee8f:7598a483
2024-12-03 17:23:01
@ 59cfee8f:7598a483
2024-12-03 17:23:01Yakihonne's Innovative Approach to Bitcoin Adoption
Introduction
The Bitcoin landscape is constantly evolving, and community plays a vital role in shaping its future. Yakihonne, a cutting-edge platform, is harnessing the power of community to drive Bitcoin adoption and education. In this article, we will explore Yakihonne's innovative approach and its impact on the Bitcoin ecosystem.
The Yakihonne Difference
Yakihonne distinguishes itself by recognizing every user as a unique node in the Bitcoin network. This perspective empowers individuals to take an active role in shaping the community and contributing to its growth. By fostering connections and knowledge sharing, Yakihonne creates a supportive environment where users can thrive.
Key Features and Benefits
-
Decentralized knowledge sharing: Yakihonne's platform allows users to access and share valuable resources, promoting a deeper understanding of Bitcoin and its applications.
-
Community-driven support: Users can engage with others, ask questions, and receive guidance from experienced community members.
-
Incentivized learning: Yakihonne's gamification elements make learning about Bitcoin engaging and fun, encouraging users to expand their knowledge.
-
Responsible adoption: The platform emphasizes security, privacy, and informed decision-making, ensuring sustainable growth.
The Future of Bitcoin Adoption
Yakihonne's community-centric approach is poised to revolutionize Bitcoin adoption. By leveraging the power of social nodes, Yakihonne creates a snowball effect, where knowledge and enthusiasm spread exponentially. As the platform continues to evolve, it's likely to play a significant role in shaping the future of Bitcoin.
Conclusion
Yakihonne is a game-changer in the Bitcoin space, offering a unique blend of community engagement, education, and support. By joining the Yakihonne community, individuals can tap into the collective power of social nodes, contributing to a brighter future for Bitcoin adoption. Embrace the potential of Yakihonne and be part of this exciting journey!
-
-
 @ 59cfee8f:7598a483
2024-12-03 17:22:53
@ 59cfee8f:7598a483
2024-12-03 17:22:53Yakihonne's Innovative Approach to Bitcoin Adoption
Introduction
The Bitcoin landscape is constantly evolving, and community plays a vital role in shaping its future. Yakihonne, a cutting-edge platform, is harnessing the power of community to drive Bitcoin adoption and education. In this article, we will explore Yakihonne's innovative approach and its impact on the Bitcoin ecosystem.
The Yakihonne Difference
Yakihonne distinguishes itself by recognizing every user as a unique node in the Bitcoin network. This perspective empowers individuals to take an active role in shaping the community and contributing to its growth. By fostering connections and knowledge sharing, Yakihonne creates a supportive environment where users can thrive.
Key Features and Benefits
-
Decentralized knowledge sharing: Yakihonne's platform allows users to access and share valuable resources, promoting a deeper understanding of Bitcoin and its applications.
-
Community-driven support: Users can engage with others, ask questions, and receive guidance from experienced community members.
-
Incentivized learning: Yakihonne's gamification elements make learning about Bitcoin engaging and fun, encouraging users to expand their knowledge.
-
Responsible adoption: The platform emphasizes security, privacy, and informed decision-making, ensuring sustainable growth.
The Future of Bitcoin Adoption
Yakihonne's community-centric approach is poised to revolutionize Bitcoin adoption. By leveraging the power of social nodes, Yakihonne creates a snowball effect, where knowledge and enthusiasm spread exponentially. As the platform continues to evolve, it's likely to play a significant role in shaping the future of Bitcoin.
Conclusion
Yakihonne is a game-changer in the Bitcoin space, offering a unique blend of community engagement, education, and support. By joining the Yakihonne community, individuals can tap into the collective power of social nodes, contributing to a brighter future for Bitcoin adoption. Embrace the potential of Yakihonne and be part of this exciting journey!
-
-
 @ f584a915:9da6d625
2024-12-03 13:28:15
@ f584a915:9da6d625
2024-12-03 13:28:15The world of cryptocurrency has given rise to a new breed of billionaires, individuals who have amassed immense wealth through their foresight, innovation, and strategic investments in digital assets. As the crypto market continues to evolve, so too does the wealth of its most prominent players.
One of the most notable examples is Changpeng Zhao (CZ), the founder of Binance, the world's largest cryptocurrency exchange. CZ's net worth has fluctuated dramatically with the volatility of the crypto market, but he remains one of the richest people in the world. Other prominent figures include the Winklevoss twins, who made headlines for their early investment in Bitcoin, and Sam Bankman-Fried, the former CEO of FTX, who amassed billions before the collapse of his exchange.
While these individuals have made headlines for their wealth, it's important to remember that the crypto market is highly volatile, and fortunes can be made and lost in a matter of days. Nevertheless, the rise of crypto billionaires has highlighted the potential for immense wealth creation in the digital age. It's worth noting that the wealth of crypto billionaires is often tied up in digital assets, which can be subject to significant price fluctuations. This means that their net worth can change rapidly, depending on the performance of the crypto market. Despite the risks, the crypto industry continues to attract entrepreneurs and investors from around the world. As the technology matures and becomes more widely adopted, it's likely that we will see even more crypto billionaires emerge in the years to come.
Reference: https://mcrypto.club/bitfinexs-resilience-in-crypto-history-showcased-through-evolution-and-growth/
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ 8947a945:9bfcf626
2024-12-03 11:50:38
@ 8947a945:9bfcf626
2024-12-03 11:50:38ตึกแถว อาคารพานิชย์ และทาวโฮม ประสบการณ์ที่ยาก ปวดหัวจนนอนไม่หลับ

ใครยังไม่ได้อ่านตอนที่แล้วแนะนำให้กลับไปอ่านก่อนนะครับ เพราะเนื้อหาต่อเนื่องกันหมด ผมรวบรวมไว้ใน Curation นี้แล้วครับ (TH)Real Estate Journey
บ้าน3
เป็นบ้านทาวโฮมสองชั้น ชั้นล่างเป็นห้องนั่งเล่นลึกเข้าไป หลังบ้านเป็นพื้นที่ครัว มีห้องน้ำหนึ่งห้อง ชั้นสองมีห้องโถงใหญาพอสมควรตรงกลาง 2 ห้องนอน 1 ห้องน้ำ เท่ากับว่าเป็นบ้าน 2 ห้องนอน 2 ห้องน้ำ 2 ชั้น

บ้านนี้อยู่ซอยถัดไปจากบ้าน2 และ บ้าน1 เป็นบ้านหลังสุดท้ายที่พ่อกับแม่ผมซื้อเพื่อลงทุนปล่อยเช่า บ้านหลังนี้เปลี่ยนผู้เช่ามาหลายราย ผมไม่ทราบรายละเอียดกับผู้เช่าคนก่อนๆเลย ทราบจากคำบอกเล่าของพ่อผมเท่านั้นว่า
- ผู้เช่าบางคนไม่จ่ายค่าไฟ จนการไฟฟ้าต้องตัดไฟยกมิเตอร์ออก พ่อผมต้องเดินเรื่อง พาคนเช่าไปเงินที่ค้างเสียค่าปรับ เพื่อให้การไฟฟ้ามาติดมิเตอร์ให้ใหม่ (... ฟังดูน่ากังวล...)
- ผู้เช่าบางคนไม่สามารถจ่ายค่าเช่าได้ตรงเวลา เมื่อทวงถามก็ขนของหนีออกไปเลย (...โจรมาเช่ารึเปล่าวะ...)
- ผู้เช่าบางคนประกอบกิจการทำอาหารขาย ทำบ้านสกปรก (...ชิบหายละครับ...)
- จนมาถึงผู้เช่าคนปัจจุบันที่เช่าอยู่มา 5 ปี ไม่สร้างปัญหา จ่ายค่าเช่าตรงเวลา รักบ้าน ดูแลบ้านเป็นอย่างดี (...เออ ค่อยยังชั่ว...)
เมื่อผมเป็นเจ้าของกรรมสิทธิ์และจัดการปัญหา "บ้าน2" ได้แล้ว ผมและภรรยามุ่งมาดูแล “บ้าน3” ต่อทันทีในวันนั้น ผมโทรหาผู้เช่าแสดงตัวให้ผู้เช่ารู้จัก แจ้งความประสงค์อยากเจอกันเพื่อดูแลเรื่องสัญญาเช่าที่กำลังจะหมดอายุ ทางผู้เช่าแจ้งว่าเดี๋ยวจะขับรถมอเตอร์ไซค์มาหาผมเอง ถ้าเป็นแค่เรื่องต่อสัญญา ไม่ต้องเข้าไปหาเขาที่บ้านก็ได้เกรงใจ
หลังจากนั้นประมาณ 10 นาทีผู้เช่าก็มา
ได้แนะนำตัวพูดคุยกัน ผู้เช่าท่านนี้เป็นวิศกรแต่งงานมีลูก 2 คน พ่อกับแม่ภรรยาอาศัยอยู่ด้วย ทั้งหมดมี 6 ชีวิตอาศัยอยู่ด้วยกันในบ้านหลังเดียว
ผมกับภรรยาแสดงตัวแนะนำตัวอย่างเป็นทางการ แลกเบอร์แลกไลน์กัน ผมขอไปดูบ้านเพื่อจะได้ช่วยดูว่ามีส่วนไหนขาดเหลือบ้างเพื่อเจ้าของคนใหม่จะได้ดูแลผู้เช่าต่อจากเจ้าของคนเดิม(พ่อผม) ทางผู้เช่าคิดอยู่ซักพักนึง และตกลงให้ไปดูที่บ้านได้ เขาเริ่มแสดงความหงุดหงิดออกทางสีหน้าเล็กน้อย แต่ก็ให้ความร่วมมือดี
ตอนแรกผมเข้าใจว่าผมไปรบกวนความเป็นส่วนตัวเขา แต่ภรรยาผมอ่านบุคคลิกผู้เช่าท่านนี้ออกว่า ไม่ใช่หรอก เขามีอะไรบางอย่างที่อัดอั้นอยากระบายออก แต่ไม่รู้จะไปพูดกับใคร เป็นคนที่เถรตรงนิสัยบุคคลิกนักเลง(แต่ไม่มีอะไร)ตามประสาหัวหน้าช่าง ผมกับภรรยาเดินตามเขาไปที่บ้าน
เมื่อไปถึงหน้าบ้าน
สิ่งแรกที่เห็นเลยคือคานรับกันสาดหน้าบ้านจะพังไม่พังแหล่ มีท่อนไม้หน้าสามผุๆรับน้ำหนักอยู่ มีเครื่องซักผ้าวางอยู่หน้าบ้าน สมาชิกในบ้านอยู่กันครบ ผมกับภรรยาถามถึงความเป็นอยู่และความเป็นมาเป็นไป นี่คือปัญหาครับ
- คานรับกันสาดหน้าบ้านจะพังไม่พังแหล่ ผู้เช่าพยายามซ่อมเองโดยการเอาไม้หน้าสามไปค้ำไว้ ไม่งั้นถ้ากันสาดพัง เครื่องซักผ้าโดนก่อน และเข้าบ้านไม่ได้
- ห้องน้ำชั้นล่างยับเยิน ฝักบัวไม่สามารถใช้งานได้ ต้องใช้ขันตักน้ำอาบ ระบบท่อน้ำของชักโครกใช้การไม่ได้ ตันและเอ่อล้น ต้องอาศัยการตักขันราดหลายๆรอบ + ใช้ที่ปั๊มส้วมอัดถึงจะสะอาด
- ลานหลังบ้านท่อระบายน้ำตัน น้ำขังอยู่หลายวันช่วงฝนตก บางทีน้ำล้นทะลักเข้ามาในตัวบ้านด้านหลัง ทำให้ต้องย้ายเครื่องซักผ้ามาไว้หน้าบ้าน ผู้เช่าพยามใช้งูเหล็กหรือเทสารส้มลงไปแล้ว ไม่สำเร็จ
- ปลวกกินฝ้าเพดานทั้งสองชั้น ฝ้าบางแผ่นพร้อมหล่นใส่หัวใครซักคนในบ้านทำให้บาดเจ็บอันตรายได้เลย
- สวิทช์แอร์ห้อง master bedroom ชั้นสองมีปัญหา ผู้เช่าเป็นวิศกรจึงดำเนินการแก้ไข ทำ cut out ใหม่
- ห้องนอนเล็กแอร์เสีย คนที่นอนห้องนั้นหนาวๆร้อนๆตามฤดูกาล ห้องน้ำในห้องใช้งานไม่ได้น้ำไม่ไหล ท่อที่รับโถส้วมชั้นสองสนิทขึ้นจนทะลุเป็นรู จนมองเห็นได้จากลานหลังบ้าน
- หนึ่งในผู้สูงอายุที่อยู่ในบ้านเป็นจิตเวช คนภายในพอทราบ แต่ไม่มีหลักฐานชัดเจน จนผมวินิจฉัยให้ วันดีคืนดีก็เดินออกไปหาเรื่องทะเลาะกับเพื่อนบ้าน บางทีก็เดินไปขอของจากเพื่อนบ้าน จนไม่มีใครยุ่งกับครัวนี้

ปัญหาทั้งหมดนี้ผู้เช่าพยายามขอความช่วยเหลือจากเจ้าของคนก่อนแล้ว แต่ได้รับคำตอบกลับมาเพียงแค่ว่า “เอ้อ… คุณก็จัดการเอาเองเถอะ” แล้วก็นิ่งเฉย ปัญหาทั้งหมดนี้มันไม่ใช่เกิดขึ้นในวันเดียว มันทิ้งช่วงห่างมาเป็นปีๆ เมื่อเจอปัญหาผู้เช่าแจ้งเจ้าของ เจ้าของก็ปัดให้ผู้เช่าจัดการเอง ซ้ำๆกันไปตลอด จนผู้เช่าเอือมระอาที่จะขอร้อง เลยจัดการเองเท่าที่ทำได้
### !!!!! ซึ่งจริงๆแล้วมันไม่ได้เว้ยยยยยย !!!!!
เจ้าของบ้านไม่มีสิทธิ์จะปัดความรับผิดชอบไปให้คนเช่าต้องแบกรับความเสียหายระดับโครงสร้างตัวบ้าน มันเป็นความรับผิดชอบของเจ้าของตึก ไม่ใช่คนเช่า
แน่นอนครับว่าผู้เช่าไม่ได้เล่าให้ผมฟังด้วยความสุข แต่ด่าผมกับแฟนเลยแหละ ซึ่งก็เข้าใจได้ครับ ใครมันจะไป happy กับบ้านที่ function ในการอยู่อาศัยพื้นฐานมันพังขนาดนี้ ผมคว้าสมุดมาจดประเด็นปัญหาของผู้เช่าทันที ในขณะที่แฟนผมพยายามล้วงข้อมูลออกมาให้ครบถ้วนที่สุด

ทางผมและภรรยาเสนอซ่อมบ้านแบบเร่งด่วนให้
เพื่อให้ความเป็นอยู่กลับมา happy ที่สุดเท่าที่เป็นไปได้ ทางผู้เช่าเขายอมรับ spirit ของเจ้าของคนใหม่ และบอกว่าไม่ได้ต้องการอะไรมากไปกว่านี้ แค่ห้องน้ำใช้ได้เขา ok แล้ว เขาขอแค่นั้น
เมื่อเราทำความเข้าใจกันได้ แยกย้ายกัน ผมกับภรรยาติดต่อผู้รับเหมาที่ทำบ้านผม ให้เข้ามาดูหน้างานวันรุ่งขึ้นทันที และแจ้งผู้เช่า ผู้เช่าตกใจมากว่าเอาไวขนาดนั้นเลยเหรอ ผมบอกใช่ครับ เพราะมันรอไม่ได้ วันรุ่งขึ้นพาผู้รับเหมาเข้าหน้างานทันที และจัดการปัญหาดังนี้ให้
- ซ่อมส้วม + ฝักบัวจนใช้การได้
- ติดตั้งปั๊มน้ำ + แทงค์น้ำเพื่อให้ระบบน้ำชั้นสองใช้งานได้ (คนเช่าไม่ได้ขอ)
- ทะลวงท่อระบายน้ำที่ลานซักล้างหลังบ้านจนใช้การได้ มันคือการขุดลอกท่อน้ำดีๆเลยครับ
- ติดแอร์ห้องนอนเล็ก (คนเช่าไม่ได้ขอ)
- ซ่อมฝ้า ฉีดปลวก
ทั้งหมดดำเนินการเสร็จภายในหนึ่งสัปดาห์จนคนเช่าอึ้งไปทั้งบ้าน มันก็น่าจะอึ้งอยู่หรอกครับ มันคือความทุกข์ร้อนที่ขอความเป็นธรรมกับเจ้าของคนเก่ามา 5 ปี ไม่ได้รับความเอาใจใส่แถมโดนโยนขี้ให้อีก แต่เมื่อเปลี่ยนเจ้าของ ทุกอย่างเสร็จภายในหนึ่งสัปดาห์
แต่มันยังไม่จบแค่นั้นครับ
ผู้รับเหมาผมแจ้งว่าคานที่รับน้ำหนักชั้นสองบางส่วนมันเริ่มมีปัญหา ระยะยาวอาจจะพังลงมาได้ แต่ก็แก้ได้ด้วยการเสริมความแข็งแรงเข้าไป หรือไม่ก็ต้องระวังไม่ให้มีการเอาของหนักขึ้นบ้านชั้นสอง ผมกับภรรยาคิดว่าจำเป็นต้องยุติสัญญาเช่าให้ผู้เช่าย้ายออก เอาบ้านคืน เพื่อเอาซ่อมให้ปลอดภัยเสียก่อน ยอมเสียรายได้จากค่าเช่าเพื่อแลกความปลอดภัยของชีวิตคน
ผมโทรหาผู้เช่าว่าจะขอบ้านคืนพร้อมทั้งอธิบายเหตุผลทั้งหมด เขาตกใจมากครับ เพราะครอบครัวเขามีเหตุจำเป็นมากๆที่ต้องเช่าอยู่ตรงนั้น มันใกล้ที่ทำงานและโรงเรียนของลูกๆเขา ถ้าต้องออกไปตอนนี้ลำบากแน่ ผมกับภรรยาจึงขอนัดคุยเรื่องนี้แบบพร้อมหน้าพร้อมตากันที่ community mall บริเวณใกล้เคียงครับ
การพูดคุยเป็นไปอย่างตรงไปตรงมา ทางครอบครัวผมเล่าปัญหา เล่าถึงความกังวล เล่าถึงความไม่ปลอดภัยที่จะเกิดขึ้นให้ทั้งครอบครัวผู้เช่ารับทราบ รวมไปถึงเรื่องคนไข้จิตเวชที่อาละวาดด้วย ทุกคนต่างตกใจถึงอาการทางจิตเวชจากฝั่งคนของเขาว่าจริงๆพอทราบอยู่บ้างแล้ว แต่มันหนักหนาเกินกว่าที่คาดคิดไว้
ทางผู้เช่าแชร์ความรู้เรื่องโครงสร้างจากความที่เขาเป็นวิศวกรเขามองว่ามันมีปัญหาจริง แต่มันปลอดภัยระดับนึงไม่ได้แย่อย่างที่คิด เขายื่นข้อเสนอมาว่าเขาจำเป็นต้องอยู่ต่อจริงๆ ส่วนเรื่องคนไข้จิตเวชเขาจะขอจัดการเองภายในหนึ่งวัน เขา ok ให้ขึ้นค่าเช่าได้ เพราะหลังพวกผมซ่อมบ้านให้ สภาพบ้านและความเป็นอยู่ดีกว่าเมื่อก่อนมากๆ วันรุ่งขึ้นเขาก็โทรมาแจ้งว่าได้ย้ายคนไข้จิตเวชออกไปอยู่บ้านอีกหลังแล้ว ทำตามสัญญา ทำให้บ้านเขาเย็นลง 2 คนสามีภรรยาทำงานได้อย่างมีความสุขมากขึ้น เด็กๆได้เรียนที่โรงเรียนใกล้บ้าน ตัวบ้านก็ไม่มีปัญหา อยู่ในสภาพดีพอสมควรตามกาลเวลา และต่อสัญญาเช่าต่อไปครับ
ข้อคิดที่อยากแบ่งปัน
- ผมยังพูดเหมือนเดิมครับ การมีอสังหาปล่อยเช่า "มันคือธุรกิจ" ผลลัพธ์จะดีจะไม่ดีขึ้นอยู่กับแรงที่ทุ่มเทลงไปในการทำงาน
- หากคุณคิดจะครอบครองอสังหาริมทรัพย์เพื่อการปล่อยเช่า แล้วโยนภาระออกจากตัว หานายหน้าซักคนแล้วผลักความรับผิดชอบ ไม่ดูดำดูดีไม่ใส่ใจผู้เช่า ผมว่าคุณอย่าเข้ามาในโลกอสังหาเลยครับ มันไม่ใช่ทางของคุณ อสังหาคือธุรกิจที่เล่นกับปัจจัยสี่ของมนุษย์ ถ้าทำไม่ดีคือไปเบียดเบียนหรือไปซ้ำเติมผู้เช่า ผู้เช่าคือคนครับ ไม่ใช่แหล่งรีดเงินเวลาเงินเดือนเขาออก
- อย่าโลภ ธุรกิจมันคือเกมระยะยาว ระหว่างทางกำไรมากบ้าง น้อยบ้าง เท่าทุนบ้าง ขาดทุนบ้าง ไม่เห็นแปลก
ตอนต่อไปผมจะเล่าถึงประสบการณ์ผู้เช่าคอนโดชาวต่างชาติที่ผมพลาด เกือบขาดทุนและเกือบจะต้องถึงกระบวนการฟ้องขับไล่ ส่วนเรื่องของ "บ้าน2"ที่จะจบแบบหักมุม รอติดตามด้วยนะครับ มันจะมาพร้อมกับปัญหาที่บรรลัยที่สุดพร้อมกับ "บ้าน1"
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ aae7fe72:2a03fe39
2024-12-03 11:17:19
@ aae7fe72:2a03fe39
2024-12-03 11:17:19Finance is a challenging but rewarding subject, central to many academic fields such as business, economics, and accounting. Whether you're working on a corporate finance project, analyzing market trends, or preparing an investment proposal, excelling in your finance assignment requires a combination of strong analytical skills, an understanding of key concepts, and the ability to apply them in real-world situations. To help you achieve the best results, here are some top tips for excelling in your finance assignment.
You can also look for video tutorials or attend additional classes to reinforce your understanding. If you're struggling, seeking professional finance assignment help from MyAssignmenthelp can clarify difficult concepts and give you the confidence to move forward.
- Build a Strong Foundation in Core Concepts The first step to excelling in any finance assignment is ensuring you have a solid understanding of the core concepts. Key principles such as time value of money, risk and return, financial ratios, and capital budgeting are essential to solving most financial problems. If you're unsure about any of these concepts, take time to review your notes, textbooks, and online resources.
You can also look for video tutorials or attend additional classes to reinforce your understanding. If you're struggling, seeking finance assignment help from professionals or classmates can clarify difficult concepts and give you the confidence to move forward.
- Break the Assignment into Manageable Parts Finance assignments often come with multiple sections that require different approaches—calculations, data analysis, and written explanations. To make the task less overwhelming, break your assignment down into manageable chunks. Start by understanding the task at hand, then outline each part before diving into the work.
For instance, if your assignment requires you to calculate financial ratios for a company, first list out the necessary data, then proceed with each calculation step by step. This method helps you stay organized and focused, ensuring you don’t miss any important details.
- Stay Organized with Your Data Finance assignments often involve working with large sets of data. Whether you're analyzing financial statements or working with historical market data, it’s crucial to stay organized. Use spreadsheets (like Microsoft Excel or Google Sheets) to store and manipulate data. Make sure you label each column and row clearly and double-check for accuracy before performing calculations.
If your assignment involves forecasting or creating financial models, using financial software can streamline the process. Staying organized will help you work more efficiently and avoid errors.
- Relate Theory to Real-World Scenarios Finance is all about understanding how theoretical concepts apply to real-world situations. When tackling assignments, try to connect what you're learning to current market trends, business cases, or economic events. For instance, if you're analyzing a company's financial performance, think about how real companies use the same principles to make decisions.
Relating theory to real-world applications will not only enhance your understanding but will also make your analysis more engaging and practical. It’s also a great way to show your professor that you are thinking critically about the subject matter.
- Practice Regularly Finance is a subject that benefits from regular practice. The more you practice solving problems, the better you'll become at identifying patterns and applying the right formulas. Regular practice will also help you improve your speed and accuracy in completing assignments.
Look for additional exercises in your textbooks, online resources, or finance apps that can help you practice. If you're unsure how to approach a specific problem, find solutions online or ask your professor for guidance. The more you practice, the more confident you'll become when tackling complex finance problems.
- Use Reliable Resources When completing a finance assignment, it’s important to rely on trusted sources for information, calculations, and examples. Use academic textbooks, peer-reviewed journals, and reputable financial websites to gather relevant data. Be sure to cite all your sources correctly to avoid plagiarism and provide credibility to your work.
Online resources like Investopedia or Bloomberg can help you stay updated with current market trends, financial terms, and case studies. Using reliable resources not only strengthens your arguments but also ensures your data is accurate and up-to-date.
- Proofread and Review Your Work Once you've completed your finance assignment, take the time to proofread and review your work. Accuracy is crucial in finance, as even small errors can affect your final results. Double-check your calculations and ensure you've answered all parts of the assignment prompt.
Additionally, review your written analysis to ensure it's clear, concise, and free from errors. A well-structured assignment with logical flow and precise language demonstrates professionalism and critical thinking, which are key to excelling in finance.
- Seek Expert Help When Needed If you find yourself struggling with a particular concept or part of your assignment, don’t hesitate to seek expert help. Finance can be a challenging subject, and sometimes a little extra guidance is all you need to clarify your doubts and get back on track.
There are many online platforms, like finance assignment help services, where you can connect with professionals who can provide step-by-step assistance. These experts can help you understand difficult concepts, solve problems, and ensure you submit a high-quality assignment.
- Manage Your Time Effectively Finance assignments often require both analytical and written work, so managing your time effectively is crucial. Start early to give yourself plenty of time to research, analyze, and write your assignment. Divide your time between different tasks and set mini-deadlines for each section.
Using a time management tool or creating a schedule can help you stay on track and avoid procrastination. By managing your time efficiently, you’ll reduce stress and ensure that you complete your assignment with the attention it deserves.
Conclusion Excelling in a finance assignment requires a mix of strong foundational knowledge, practice, effective time management, and a strategic approach to problem-solving. By understanding core concepts, breaking down tasks, staying organized, and practicing regularly, you’ll set yourself up for success. Don’t forget to seek finance assignment help if needed and always review your work for accuracy. With these tips, you’ll be well on your way to mastering your finance assignments and achieving the grades you deserve.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 94c2fd25:4fb53087
2024-12-03 09:51:27
@ 94c2fd25:4fb53087
2024-12-03 09:51:27SOI69: Nền Tảng Trực Tuyến Tiện Lợi và An Toàn SOI69 là một nền tảng trực tuyến hiện đại, được thiết kế để mang đến cho người dùng trải nghiệm mượt mà và tiện ích. Với giao diện dễ sử dụng, SOI69 giúp người dùng nhanh chóng tiếp cận các tính năng và dịch vụ mà không gặp phải bất kỳ khó khăn nào. Nền tảng này hoạt động ổn định trên nhiều thiết bị khác nhau, từ máy tính để bàn cho đến điện thoại di động, đảm bảo rằng người dùng có thể truy cập mọi lúc, mọi nơi mà không gặp gián đoạn. Một trong những điểm mạnh của SOI69 là tính linh hoạt và hiệu suất vượt trội. Dù bạn sử dụng SOI69 ở nhà, tại văn phòng, hay đang di chuyển, nền tảng này vẫn mang đến trải nghiệm liền mạch và hiệu quả. Giao diện trực quan và tính năng dễ sử dụng giúp người dùng có thể thao tác nhanh chóng, tiết kiệm thời gian và tăng cường hiệu quả công việc. Bảo mật là yếu tố quan trọng mà SOI69 luôn đặt lên hàng đầu. Nền tảng này áp dụng các công nghệ bảo mật tiên tiến để bảo vệ thông tin cá nhân của người dùng, đảm bảo an toàn cho dữ liệu trong suốt quá trình sử dụng. Với cam kết bảo mật thông tin và mang đến trải nghiệm người dùng tốt nhất, SOI69 đã và đang khẳng định được vị thế của mình trong thị trường trực tuyến. Với những tính năng tiện ích, tốc độ nhanh và bảo mật cao, SOI69 là lựa chọn lý tưởng cho những ai tìm kiếm một nền tảng trực tuyến an toàn và hiệu quả.
-
 @ 32e18276:5c68e245
2023-12-06 15:29:43
@ 32e18276:5c68e245
2023-12-06 15:29:43I’m going to be on an ordinals panels as one of the people who is counter arguing the claim that they are good for bitcoin. I decided to brush up on the technicals on how inscriptions work. I am starting to see luke’s perspective on how it is exploiting a loophole in bitcoin’s anti-data-spam mechanisms.
Storing data in Bitcoin, the “standard” way
The standard way you add “data” to bitcoin is by calling the OP_RETURN opcode. Bitcoin devs noticed that people were storing data (like the bitcoin whitepaper) in the utxo set via large multisig transactions. The problem with this is that this set is unprunable and could grow over time. OP_RETURN outputs on the other-hand are provably prunable and don’t add to utxo bloat.
Here’s an excerpt from the march 2014 0.9.0 release notes that talks about this:
On OP_RETURN: There was been some confusion and misunderstanding in the community, regarding the OP_RETURN feature in 0.9 and data in the blockchain. This change is not an endorsement of storing data in the blockchain. The OP_RETURN change creates a provably-prunable output, to avoid data storage schemes – some of which were already deployed – that were storing arbitrary data such as images as forever-unspendable TX outputs, bloating bitcoin’s UTXO database. Storing arbitrary data in the blockchain is still a bad idea; it is less costly and far more efficient to store non-currency data elsewhere.
Much of the work on bitcoin core has been focused on making sure the system continues to function in a decentralized way for its intended purpose in the presence of people trying to abuse it for things like storing data. Bitcoin core has always discouraged this, as it is not designed for storage of images and data, it is meant for moving digital coins around in cyberspace.
To help incentive-align people to not do stupid things, OP_RETURN transactions were not made non-standard, so that they are relayable by peers and miners, but with the caveat:
- They can only push 40 bytes (later increased to 80,83, I’m guessing to support larger root merkle hashes since that is the only sane usecase for op_return)
Bitcoin also added an option called -datacarriersize which limits the total number of bytes from these outputs that you will relay or mine.
Why inscriptions are technically an exploit
Inscriptions get around the datacarriersize limit by disguising data as bitcoin script program data via OP_PUSH inside OP_IF blocks. Ordinals do not use OP_RETURN and are not subjected to datacarriersize limits, so noderunners and miners currently have limited control over the total size of this data that they wish to relay and include in blocks. Luke’s fork of bitcoin-core has some options to fight this spam, so hopefully we will see this in core sometime soon as well.
Inscriptions are also taking advantage of features in segwit v1 (witness discount) and v2/taproot (no arbitrary script size limit). Each of these features have interesting and well-justified reasons why they were introduced.
The purpose of the witness discount was to make it cheaper to spend many outputs which helps the reduction of the utxo set size. Inscriptions took advantage of this discount to store monke jpegs disguised as bitcoin scripts. Remember, bitcoin is not for storing data, so anytime bitcoin-devs accidentally make it cheap and easy to relay data then this should be viewed as an exploit. Expect it to be fixed, or at least provide tools to noderunners for fighting this spam.
Where do we go from here
The interesting part of this story is that people seem to attach value to images stored on the bitcoin blockchain, and they are willing to pay the fee to get it in the block, so non-ideologic miners and people who don’t care about the health and decentralization of bitcoin are happy to pay or collect the fee and move on.
Data should not get a discount, people should pay full price if they want to store data. They should just use op_return and hashes like opentimestamps or any other reasonable protocol storing data in bitcoin.
After going through this analysis I’ve come to the opinion that this is a pretty bad data-spam exploit and bitcoin devs should be working on solutions. Ideological devs like luke who actually care about the health and decentralization of the network are and I’m glad to see it.
-
 @ e373ca41:b82abcc5
2024-12-03 08:08:53
@ e373ca41:b82abcc5
2024-12-03 08:08:53Article by Milosz Matuschek, originally from "Freischwebende Intelligenz"
“In fact, the selection that the class mercilessly carries out among the judges is more dangerous and worse than among the Reichswehr, which is related to them in spirit. In both cases, there is a clear co-option: the group chooses whoever adapts to the group spirit - always suitable, never heterogeneous elements. This begins with the Judicial Review Commission and continues with the fine sieve of the personnel officers. The result is this judiciary.”
- Kurt Tucholsky, German Judges (commentary, 1927)
Christian Dettmar was a family court judge in Weimar when the coronavirus measures reached schools: Compulsory masks, distancing rules, testing. He had doubts, did his duty and made a courageous decision: he obtained expert opinions from professors and issued a temporary injunction prohibiting infection control measures at two schools. The entire decision is well-founded and 178 pages long. Dettmar saw the infection control measures as a threat to the welfare of children. As we know today and could have known back then: rightly so.
The decision was later overturned by another court. A gauntlet was thrown down for Judge Dettmar, the lawyers involved in the proceedings and the experts: Searches of homes and offices, confiscation of cell phones, computers and documents. Dettmar was charged with obstruction of justice and sentenced to two years' probation. The Weimar judge has thus lost his judicial office and all pension entitlements. Obstruction of justice is a crime, with a minimum sentence of one year, which almost automatically results in the loss of the judgeship. The Federal Court of Justice recently confirmed the conviction, the reasons for the judgment are still pending. It will be interesting to see the reasons. In the eyes of the court and the public prosecutor's office, Mr. Dettmar is a kind of activist who has abused his judicial office and created a case for himself in order to deliberately issue a decision in violation of the law.
What exactly is Judge Dettmar supposed to have done wrong? He did not break the law. Instead, he broke a subliminal taboo that has spread throughout the judicial system (and everywhere else), namely that critical questions are unwelcome in times of pandemic and that the opinion of the pro-government expert regime is sacrosanct. How right he was in hindsight is shown by today's admission, even by politicians involved, that school closures were not necessary or that they overshot the mark here and there. The minimum consensus of the mini reappraisal simulation in Germany at the moment is that during covid a lot went wrong when it came to children. “With the knowledge of today”, it is said, this would not have been done. However, what should be possible without any problems in Germany, a state governed by the rule of law: “With the knowledge of today”, punishing those who knew in advance back then with hindsight. Sounds suspiciously like an unlawful state.
It's a tremendous joke in the history of German justice that makes people abroad shake their heads: A judge has summoned independent experts who were right and now the judge is being sentenced. Meanwhile, the rest of the judiciary delivered a coronavirus ruling that went no deeper than the version of what is supposed to be “science” (and wasn't, see the RKI files). The entire judicial apparatus has failed in the pandemic, has rejected requests for evidence on the study situation and research into the evidence base, misjudged constitutional dimensions and ultimately blindly adopted the erroneous opinion of a media-created, unelected “nomenklatura expert council”. In other words, those who have done their job wrong explain to those who have done it right what is going on. And exclude one of their own from their guild for doing so.
Being right and getting right are two different things. Judge Dettmar had to be made an example of, because his decision made the continuous violation of the law by his fellow judges obvious. If the majority breaks the law and someone wants to restore it, then this act must be punished. According to Tucholsky, this has been a proven practice in Germany for 100 years. The RKI files confirmed that there was no evidence base for mask-wearing. The social distancing requirement was an arbitrary instrument invented by Anthony Fauci that was adopted unquestioningly by German politicians. The evidence-free policy of measures, which had exceeded its public shelf life at the latest with the leak of the RKI protocols (which should not have gone unnoticed by the Federal Court of Justice), is being legally preserved in a vacuum. An unprecedented act of disregard for reality by the highest court of law.
Advertisement: Are you looking for the easiest way to buy Bitcoin and store it yourself? The RELAI app is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. Here you can buy Bitcoin in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees. (no financial advice).
 ---
---Judge Dettmar has not broken the law. As a family court judge, he must take action if there is a threat to the welfare of a child. He has investigative powers like a public prosecutor. Where were the other family court judges? Why aren't they being prosecuted for inaction? Christian Dettmar was certainly not the only lawyer to have doubts about the proportionality of the corona measures. Dettmar wrote in his decision, which is well worth reading:
“According to this principle, also known as the prohibition of excessiveness, the measures intended to achieve a legitimate purpose must be suitable, necessary and proportionate in the narrow sense - in other words, when weighing up the advantages and disadvantages achieved with them. The measures that are not evidence-based, contrary to Section 1 (2) IfSG, are already unsuitable to achieve the fundamentally legitimate purpose pursued with them of avoiding overburdening the healthcare system or reducing the incidence of infection with the SARS-CoV-2 virus. In any case, however, they are disproportionate in the narrower sense, because the considerable disadvantages/collateral damage caused by them are not offset by any recognizable benefit for the children themselves or third parties”.
It will be interesting to see the reasoning (and it should be detailed, please) as to why Judge Dettmar's application of the principle of proportionality, which runs through the entire legal system, was intentionally erroneous. - Judge Dettmar averted harm to third parties, in this case children - and this is supposed to have damaged the administration of justice? What is the administration of justice there for if not to protect the legal interests of others? - Judge Dettmar has summoned experienced experts, professors at German universities. How does the public prosecutor's office justify the fact that these experts are somehow marginal or show one-sidedness? Conversely, how should the reflexive reference by the rest of the judiciary to “the RKI” or “science” in pandemic matters be assessed?
Does the public prosecutor's office determine who is capable of being satisfied as a scientist in Germany and who is not? And if so, on the basis of what expertise equal to that of the parties involved? Where such deficits in reasoning arise, it starts to smell: politics is up in the air. Judge Dettmar is aware of the interface between the judiciary and politics. He was once a public prosecutor himself and dealt with cases of ex-GDR/SED injustice. As the irony of fate would have it, he was in charge of legal proceedings in the same department that is now prosecuting him. Dettmar now knows all the roles in court proceedings from his own experience: prosecutor, judge, defendant. And now also: victim of justice. At some point: a rehabilitated man. In fact, he is one thing above all: a role model.
Join the marketplace of ideas! Sound money and sound information should finally be in the hands of the people, right? We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Want to learn more about the Pareto Project Zap me, if you want to contribute (all Zaps go to the project).
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 2063cd79:57bd1320
2024-12-04 12:10:13
@ 2063cd79:57bd1320
2024-12-04 12:10:13Meiner Meinung nach kann man in letzter Zeit eine deutliche Verlagerung bei der Benutzung bzw. dem Umgang mit Bitcoin feststellen. Vor einigen Jahren stand außer Frage, dass man zum Erwerb von Bitcoin auf Plattformen wie Binance, Coinbase oder Bitstamp gehandelt hat. Es gab ja auch kaum Alternativen. Der erste Wandel hat stattgefunden, als viele Nutzer//innen erkannt haben, dass Börsen keine gute Option bieten, um angesparte Bitcoin sicher zu verwahren. Viele Nutzer//innen haben daraufhin angefangen ihre Ersparnisse in Selbstverwahrung zu nehmen und/oder gänzlich auf Börsen zu verzichten und vermehrt auf Bitcoin-Only-Broker, wie Relai, Swan oder Pocket zu setzen.
Ein weiterer Trend lässt sich bei der Wahrnehmung von Privatsphäre feststellen. Während das Gros der Nutzer//innen früher weniger Wert auf non-KYC Lösungen gelegt und beim Kauf von Bitcoin bereitwillig persönliche Daten preisgegeben hat, machen sich mehr und mehr Menschen Gedanken darüber, wie sie schon den Erwerb von Bitcoin möglichst privat wie möglich gestalten, um zukünftigen Problemen aus dem Weg zu gehen. Denn wie wir ja wissen ist alles, was auf der Blockchain stattfindet, pseudonymisiert, aber keineswegs anonym.

Was bedeutet, dass wenn einmal eine Verbindung zu einer Adresse hergestellt ist, man z.B. nach einer Adresse suchen kann, um alle Transaktionen sowohl zu, als auch von dieser Adresse nachzuvollziehen. Das hat natürlich für viele ein gewisses "Geschmäckle". Doch ist der Erwerb von non-KYC Bitcoin (noch) nicht besonders nutzerfreundlich, mutet etwas zwielichtig an und birgt, gerade für viele nicht-so-Technologie-affinen Nutzer//innen, ein paar Stolpersteine. Oft erwerben auch viele ihre ersten bitcoins, weil sie auf schnellen Reichtum hoffen, einfach nur spekulieren wollen, oder von Freunden und Bekannten dazu überredet wurden und kümmern sich wenig um Privatsphäre, KYC vs. non-KYC, etc. Erst später befassen sie sich mit dem Thema Bitcoin intensiver und fallen dann in den sogenannten Bitcoin-Hasenbau (aka das Rabbit-Hole, das meines Erachtens nach der Honigdachsbau heißen sollte, aber naja) und haben Bitcoin in ihren Wallets und Cold-Storages, die sie nachträglich gerne etwas weniger öffentlich besitzen wollen. Zudem ist es Best-Practice für diejenigen, die Zahlungen in Bitcoin erhalten, diese erstmal von ihrer Transaktionshistorie zu säubern, denn man schreibt ja auch nicht auf jeden Geldschein beim Bezahlen seinen Namen und den Verwendungszweck drauf. Ein 10 Euro-Schein ist ein 10 Euro-Schein, egal ob dieser frisch aus der Bundesdruckerei kommt, oder ob dieser schon 100 Besitzer//innen gewechselt hat, dabei ein paar Runden in der Waschmaschine mitgemacht hat, genutzt wurde, um den Geruch von Spiegeln im Detail zu überprüfen, in Zigarettenautomaten überwintert oder sonstige Abenteuer erlebt hat.

Im Endeffekt steckt er in der Geldbörse und lässt sich zum aktuellen Tageskurs im Supermarkt der Wahl für ein Päckchen Butter eintauschen (ohne Wechselgeld), ohne dass nach seiner Reise gefragt wird. Warum sollte das bei Bitcoin Zahlungen anders sein? Zum Glück gibt es für alle oben genannten Szenarien eine relativ einfache Lösung: CoinJoins. Was das ist, wie sie funktionieren und was es zu beachten gilt, schauen wir uns diese Woche an.
Wie immer fangen wir mit der Erklärung einiger Konzepte an. Also, was sind CoinJoins?
Ein CoinJoin ist eine Form des Mixings. Dies ist eine On-Chain-Lösung, die entwickelt wurde, um das Problem der "Common-Input-Ownership-Heuristik" zu brechen. Vereinfacht ausgedrückt beschreibt dieses Problem die Annahme, dass mehrere Inputs einer Transaktion relativ sicher dem gleichen Besitzer gehören.
Um es deutlicher zu veranschaulichen zitiere ich einen früheren Artikel:
Ein ganz einfaches Beispiel: Wenn ich eine bestimmt Menge Bitcoin bei einer Börse erwerbe, bei der ich mich zuvor ausweisen musste, um die Dienstleistungen in Anspruch zu nehmen, und mir anschließend diese erworbene Menge Bitcoin auf meine Wallet überweise, um sie in Selbstverwahrung zu halten, ist es gewissen Teilnehmern möglich, meine Wallet zu identifizieren, bzw. mir zuzuordnen. Die Börse, und damit im Zweifelsfall auch ein Gericht oder ein Staat, kennen die Bitcoin-Adresse, die sie meinen Ausweisdaten zuordnen können. Die Transaktion und die damit verbundenen UTXOs sind damit auch mir zuschreibbar und die Wahrscheinlichkeit, dass ich Eigentümer der Zieladresse bin, ist auch sehr hoch - vor allem, wenn ich öfter Transaktionen von der Börsen-Adresse zu der gleichen Zieladresse ausführe. Dieses Verfahren wird auch Heuristik genannt und bedient sich wahrscheinlicher Annahmen, also z.B. wiederkehrender Muster.
Das Common-Input Problem geht noch eine Stufe tiefer, aber das lassen wir mal für einen Artikel über UTXOs übrig. Ein erweitertes Verständnis über UTXOs ist sicherlich ratsam, um das Konzept von Inputs und Outputs einer Transaktion besser zu verstehen, aber ich werde mir die größte Mühe geben, alles so einfach wie möglich darzustellen und ich glaube, dass es reicht zu verstehen, dass Transaktionen in der Blockchain historisch miteinander verknüpft sind. Diese Verknüpfung entsteht dadurch, dass die Outputs einer Transaktion immer die Inputs der nächsten Transaktion darstellen.

Dabei können viele kleine Inputs zu einem Output zusammengefasst oder große Inputs aufgeteilt werden, um kleine Outputs zu bedienen. Sobald es in dieser Transaktionskette ein Verbindungsstück in die "nicht-digitale" Welt, unser "echtes" Leben, gibt, kann jeder mit genügend Zeit und Ressourcen (wie Blockchain-Analyse Firmen) damit beginnen, diese Links herzustellen, indem sie das frei zugängliche Public-Ledger von Bitcoin beobachten und Verbindungen knüpfen.

CoinJoin hilft, dies zu verhindern. Und um den Artikel möglichst verständlich zu halten, werde ich im Weiteren erstmal von "Coins" sprechen, die im weitesten Sinne verbunden, also "gejoint" werden.
Wie also funktioniert ein CoinJoin?
Die Grundidee besteht darin, dass man einen Coin nimmt, der aus mehreren UTXOs besteht, und diesen einem Pool zuführt. Das ist in etwa so, als hätte man 10 Euro in Ein-Euro-Münzen im Portemonnaie und träfe sich mit 9 weiteren Fremden, die auch alle 10 Euro in Ein-Euro-Münzen haben. Nun werfen alle Beteiligten ihre Münzen in einen Topf und man erhält einen Topf mit 100 Ein-Euro-Münzen. Der Topf wird kräftig geschüttelt und jeder Beteiligte bekommt zufällig 10 Ein-Euro-Münzen zurück (der Einfachheit halber bekommt niemand eine Gebühr oder ein Honorar für den Service ausgezahlt). Niemand wird jemals in der Lage sein, die Ein-Euro-Münzen dem Portemonnaie zuzuweisen, aus dem sie dem Topf zugeführt wurden.

Ziemlich genauso funktionieren ConJoins, oder anders genannt Mixer. Es gibt eine Reihe von Diensten, bei denen man seine Coins zum Mixen an einen Pool senden kann. Diese Dienste erhalten für die Vermittlung, Zusammenführung und das Stellen der Infrastruktur eine kleine Gebühr. Namhafte Dienste sind z.B. Samourai’s Whirlpool oder Wasabi. Jeder dieser Anbieter hat - wie bei fast allem im Leben - seine Vor- und Nachteile. Zusätzlich zu den Mixing-Fees kommen natürlich auch die herkömmlichen Transaktionskosten.
Um bei Bitcoin zu bleiben, bedeutet dies, dass Transaktionen aufgebaut werden, die es Überwachungsfirmen oder anderen Beobachtern sehr schwer machen, genau zu wissen, welcher Transaktion-Output zu welchem der Input-Steller gehört. Das bedeutet keineswegs, dass Transaktionen gänzlich unsichtbar gemacht werden oder Inputs verschwinden, denn alles sitzt festgeschrieben und für immer einsehbar in der Blockchain. Allerdings können sich im besten Falle diejenigen, die Transaktionen beobachten oder nachverfolgen wollen, eine Reihe möglicher Szenarien ausdenken oder herleiten, um zu einem von vielen potentiellen Ergebnissen zu gelangen, wer welches Stück Bitcoin besitzt, jedoch kann man sich dessen niemals zu 100% sicher sein.
Alle Anbieter ähneln sich insofern, als dass sie gewisse Mixing-Beträge vorgeben. So kann man bei Samourai z.B. auswählen, ob man seine Coins in 0.01, 0.05 oder 0.5 BTC Pools mixen möchte. Hier kommt es natürlich darauf an, wie viel Vermögen/ Bitcoin gemixt werden soll. Wenn ich 0.5 Bitcoin mixen möchte, sollte ich natürlich nicht den 0.5 BTC Pool auswählen, sondern den 0.05 BTC Pool, da mir nach erfolgreichem Mixen 9 "saubere" UTXOs ausgehändigt werden. Warum nicht 10? Natürlich zahle ich ja auch für die Dienstleistung und für die Transaktion. Das heißt aber nicht, dass ich automatisch 0.05 BTC dafür zahle, sondern nur die Kosten (z.B. 2% der Pool Kosten + Transaktionsgebühren), der Rest der 0.05 BTC in diesem Beispiel würden mir als "unspent" zurück "überwiesen".
Diese Services bieten darüber hinaus auch an, die durch den Mixer generierten Coins im Mixer zu lassen, sodass sie über einen längeren Zeitraum weiter gemischt werden. Man stelle sich eine Waschmaschine vor, in der nur weiße Unterhosen derselben Größe und derselben Marke gewaschen werden. Nach jedem Waschgang nimmt man alle Unterhosen bis auf eine heraus und fügt neue, dreckige, gleiche Unterhosen derselben Größe und Marke hinzu. Die Wahrscheinlichkeit, die eigentlich dem ersten Waschgang hinzugefügte Unterhose zu finden, nimmt mit jedem Waschgang ab.
Man kann CoinJoins natürlich auch komplett selbstbestimmt und fernab von Anbietern durchführen. Das ist das Schöne bei Bitcoin, denn es gibt nichts, was man nicht selbst und selbstbestimmt machen kann. Alle Dienstleister und Anbieter von Services erleichtern den Nutzer//innen lediglich das Leben, indem sie die Netzwerke bereitstellen, die gewisse Unternehmungen einfacher machen und weiter streuen können, als es einem/einer einzelnen Nutzer//in jemals möglich wäre. Einen sehr guten und ausführlichen Guide hat zu diesem Thema der wichtige Arman veröffentlicht:
https://armantheparman.com/cj/
Jetzt habe ich natürlich einen groben Fehler begangen, indem ich CoinJoins und Mixer im gleichen Atemzug erwähnt, bzw. in austauschbarer Weise verwendet habe. Wenn man es ganz genau nehmen mag, ist CoinJoin die gewünschte Maßnahme, wohingegen ein Mixer der Dienstleister einer solchen Aktion ist. Generell sollte bei Anbietern von Diensten Vorsicht genossen werden, da in diesem spezifischen Fall der Dienstleister die UTXOs durcheinanderbringt und die vermischten Transaktionen eines anderen zurücksendet. Damit könnte der Dienstleister natürlich Informationen über genau die Datenpunkte erlangen, die es zu verschleiern galt. Zudem kommt hinzu, dass man seine Coins zunächst einem Custodian, also einem vertrauenswürdigen Dritten sendet, in der Annahme bzw. Hoffnung, dass man den eingezahlten Wert (minus der Gebühren) auch wirklich zurückbekommt.

Tamam! Jetzt habe ich also alle meine Coins von meiner Hardware-Wallet gejoint, zurück auf meine Hardware-Wallet, und habe im Endeffekt einfach nur weniger Sats als vorher, oder? Zusätzlich gab es schon Fälle, in denen Dienstleister (nicht die zuvor genannten) Nutzer//innen markiert haben, die zuvor von einem CoinJoin-Dienst gebrauch gemacht haben. Dementsprechend wussten diese Anbieter über die Herkunft der Coins Bescheid und konnten diese "blacklisten" und haben KYC-Informationen bereitgestellt. Dies führt dann dazu, dass andere Dienstleister solche Nutzer//innen und deren Transaktionen/Keys nicht mehr annehmen.
Darüber hinaus kann man sich die ganze Mühe des Mixens auch sparen, wenn man die gesamte Anzahl an gemixten Coins (UTXOs) wieder ausgibt, oder an ein anderes Wallet sendet (in einer Transaktion). Wie bei allen Themen im Bitcoin-Kosmos, gibt es auch hier wieder die Möglichkeit, sich tiefer mit der Materie auseinanderzusetzen, aber ich hoffe ich konnte einen guten Überblick über den Nutzen und die Funktionalität von Mixing Tools, spezifisch CoinJoins, vermitteln. CoinJoins sind, wie eingangs beschrieben, natürlich nur eins der Mittel, um Bitcoin-Transaktionen noch mehr zu pseudonymisieren, was dem Narrativ der Bitcoin-Gegner in die Karten spielt. Gleichzeitig sind Vorfälle, wie die Verhaftung von Entwicklern dieser Softwarelösungen (TornadoCash) nicht von der Hand zu weisen und Nutzer//innen haben ihre Konten bei gewissen Dienstleistern vorübergehend gesperrt bekommen, weil einige ihrer Transaktionen mit CoinJoin durchgeführt wurden. Jedoch sollte man sich gut überlegen, ob und wieviel man preisgeben möchte.
https://archive.ph/144G5
Wie bei allem ist die persönliche Einstellung zu Sicherheit und Privatsphäre der eigentliche Schlüssel. In einer Zeit, in der viele Menschen ihre Informationen bereitwillig im Internet preisgeben, haben sich viele daran gewöhnt, ihre "Sicherheit" auszulagern und anderen anzuvertrauen. Dies fängt bei Passwort-Managing Apps, wie LastPass an und hört bei Banken auf.
https://techcrunch.com/2022/12/22/lastpass-customer-password-vaults-stolen/
Allerdings muss man sich bewusst sein, dass eine digitale Währung im Internet und, wie im Falle von Bitcoin, auf einem öffentlich einsehbaren Ledger lebt. Wenn man Sicherheit in Form von Selbstverwahrung praktiziert, sollte man sich auch überlegen, ob den Schritt auch konsequent zu Ende gehen möchte und sein Erspartes zumindest so anlegt, dass es für Dritte möglichst schwierig ist, dieses auch öffentlich einsehen zu können.
🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ a93be9fb:6d3fdc0c
2024-12-03 04:25:59
@ a93be9fb:6d3fdc0c
2024-12-03 04:25:59This article is written and shared with notes via yakihonne
-
 @ a012dc82:6458a70d
2024-12-03 00:48:04
@ a012dc82:6458a70d
2024-12-03 00:48:04Table Of Content
-
The Big Move: A Transaction That Raised Eyebrows
-
The Unexpected Destination: Bitfinex's Own Wallet
-
Implications for the Bitcoin Network: Growth and Momentum
-
Market Liquidity Concerns: A Double-Edged Sword
-
Future Predictions: Reading the Crypto Tea Leaves
-
Conclusion
-
FAQ
In the dynamic world of cryptocurrency, volatility and surprises often go hand in hand. The latest buzz comes from Bitfinex, a renowned cryptocurrency exchange with a vast history and influence in the crypto market. Bitfinex's recent activity has left many in the community scratching their heads, sparking a flurry of speculation and discussion. As we delve deeper into the details of this intriguing event, the layers of the mystery begin to peel away, revealing the potential implications for the broader crypto market. This incident serves as a stark reminder of the unpredictable nature of the crypto world, where every transaction can have far-reaching effects.
The Big Move: A Transaction That Raised Eyebrows
Whale Alert, a blockchain tracking platform, is well-versed in spotting large crypto transactions. However, even for them, detecting a movement of 3,500 Bitcoins from Bitfinex was a significant event. This transfer, equivalent to a staggering $102 million at the time, isn't just a blip on the radar. It's a substantial event that demands attention from traders, investors, and market analysts alike. The size of the transaction alone was enough to raise eyebrows, but the real intrigue lies in the destination of this transfer, which added a surprising twist to the tale.
The Unexpected Destination: Bitfinex's Own Wallet
In a plot twist that few could have predicted, the recipient of this mammoth Bitcoin transfer was none other than Bitfinex itself. The wallet, pinpointed as 3E3CPTRLjTJe7GQuxMKpwmai2yFbkuGDMV, is a known transit address within the Bitfinex ecosystem. This isn't an isolated incident. Past records show two other instances where large Bitcoin transfers were directed to this very same wallet. This pattern of internal transfers adds layers to the mystery, sparking questions about Bitfinex's strategy and the potential implications for the Bitcoin market.
Implications for the Bitcoin Network: Growth and Momentum
Such a massive internal transfer isn't without its implications for the broader Bitcoin network. On the brighter side of things, there's evidence that the Bitcoin network is expanding. Ali Martinez, a respected crypto analyst, recently shared insights from Glassnode. The data revealed a promising increase in the creation of new Bitcoin wallets. This surge suggests a revitalized interest and utilization of the Bitcoin network, potentially signaling an upcoming price breakout. This growth could be a sign of renewed confidence in Bitcoin, indicating that more users are joining the network and potentially contributing to increased demand for the cryptocurrency.
Market Liquidity Concerns: A Double-Edged Sword
However, every silver lining has its cloud. The movement of vast Bitcoin amounts within a single exchange, like Bitfinex, can raise concerns about market liquidity. While it's premature to draw definitive conclusions, such internal transfers can influence trading dynamics. They could potentially lead to increased price volatility, as large transfers can significantly impact the supply and demand balance. As the crypto market continues its summer rally, Santiment, a trusted on-chain data aggregator, points to another trend. The growth in large Bitcoin wallets, especially those holding 100 BTC or more, could be a precursor to another significant price movement.
Future Predictions: Reading the Crypto Tea Leaves
The crypto market is notoriously hard to predict, but certain indicators can offer insights. The internal movement of Bitcoins within Bitfinex, combined with the growth of large Bitcoin wallets, paints a picture. If these trends continue, and the number of hefty Bitcoin wallets rises, we might be on the cusp of another market rally or breakout. Only time will tell, but the signs are promising. These trends could potentially shape the future of the Bitcoin market, influencing price movements and trading strategies.
Conclusion
The world of cryptocurrency is a vast ocean, with its currents, tides, and occasional storms. Bitfinex's recent moves serve as a reminder of the market's unpredictability and the importance of staying informed. For those looking to dive into these waters, it's crucial to stay informed, conduct thorough research, and seek expert advice. The future is unwritten, but with the right knowledge and preparation, we can navigate it successfully. As we continue to monitor these developments, we remain committed to providing you with the latest insights and analysis to help you make informed decisions in your crypto journey.
FAQ
What was the recent significant transaction involving Bitfinex? Bitfinex, a major cryptocurrency exchange, recently moved 3,500 Bitcoins, equivalent to about $102 million at the time of the transfer.
Who was the recipient of this large Bitcoin transfer? The recipient of this massive transfer was Bitfinex itself. The Bitcoins were moved to a known transit wallet within the Bitfinex ecosystem.
What are the implications of this transfer for the Bitcoin network? The Bitcoin network is showing signs of growth, which could signal an upcoming price breakout. However, such large internal transfers could also impact market liquidity.
What does the growth in large Bitcoin wallets indicate? The growth in large Bitcoin wallets, especially those holding 100 BTC or more, could be a precursor to another significant price movement.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: @croxroadnews
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ bcbb3e40:a494e501
2024-12-02 18:19:06
@ bcbb3e40:a494e501
2024-12-02 18:19:06|
 | |:-:| |MOS MAIORVM VIII (Otoño 2024), Hipérbola Janus, 2024| En las postrimerías del año, a las puertas del 2025, nos complace presentar a nuestros lectores el segundo de nuestros números temáticos. Anteriormente, en el número VII de Mos Maiorum, decidimos dar un giro radical a la estructura de la revista, habiendo madurado ya ciertos fundamentos a nivel organizativo y de colaboraciones. Y ahora, con mayor seguridad que nunca, nos adentramos en un nuevo tema, quizás uno de los más trascendentales en el momento histórico en el que nos hallamos. Nos aproximamos al ecuador de los años veinte del siglo XXI, y el Occidente posmoderno parece hacer aguas en todos los frentes, desangrando a las sociedades sobre las que su yugo asfixiante ejerce su poder. Llevamos más de un lustro asistiendo a la intensificación de determinados discursos que, poco a poco, y de manera subrepticia nos proponen Agendas verdes, moradas y multicolores, teorías del decrecimiento, destrucción de modelos de vida y una presión cada vez más agobiante de los poderes transnacionales a través de gobiernos que traicionan a sus pueblos y son servidores de intereses espurios. ¿Qué destino nos aguarda a los europeos? ¿Existe alguna alternativa viable al Occidente que se desmorona ante nuestros ojos? La respuesta, o una de las respuestas —probablemente la más importante— debemos buscarla en la configuración del tablero de ajedrez mundial, en la geopolítica, que es el tema central de nuestro dossier. Hoy, más que nunca, es necesario recuperar los textos de la geopolítica clásica y alternativa de un Carlo Terracciano, por ejemplo, entre otros muchos autores, que a lo largo del presente libro van a ser protagonistas, directos o indirectos, a través de sus ideas y sus análisis más preclaros sobre el tema del «Eurasianismo». Eurasia, lo queramos o no, es un concepto geopolítico que está ahora mismo en boga, y su formulación y síntesis original no adquiere su forma definitiva en la Europa occidental, sino que ha sido una doctrina desarrollada en el Este, en Rusia, desde autores como Lev Gumiliov o Nikolái Trubetskói, como autores clásicos en los primeros desarrollos de la doctrina, que posteriormente se ha visto actualizada y ha adquirido una trascendencia y dimensión de primer orden a raíz de las teorizaciones del polémico filósofo y geopolítico Aleksandr Duguin. No pretendemos caer en discursos maniqueos, ni tampoco convertirnos en un panegírico consagrado a la defensa a ultranza de un determinado discurso, idea o doctrina, sino que nuestra intención es penetrar en lo profundo del tema, conocer el Eurasianismo como doctrina, en su evolución, desentrañando sus características y ofreciendo al lector una visión «desde el otro lado», desde los discursos menos convencionales, y también menos sistémicos, capaz de ofrecer un enfoque lo más claro y diáfano posible, sin recurrir, como decimos, a discursos apologéticos ni a adhesiones fanáticas. Pero tampoco practicamos la equidistancia ni la neutralidad tan característica del espíritu burgués y las componendas de sus falsas democracias parlamentarias, y por eso profesamos una nada disimulada antipatía hacia el Occidente moderno y sus valores mediocres y pusilánimes. En este número, en el dossier, como a lo largo de toda nuestra trayectoria, nos asiste un elenco de autores de reconocido prestigio, contamos con las firmas de Claudio Mutti, Daniele Perra, Diego Fusaro, Carlos X Blanco, Daniel Artur Branco, Guillermo Mas Arellano, David Lara Miguez, Pietro Missiaggia y Luis Landeira. Sin embargo, hay algo que tenemos muy claro, y es que los «valores» del Occidente posmoderno representan la decadencia absoluta, la destrucción de lo más profundo y auténtico del hombre europeo, representan esa antropología negativa y desviada que nos aboca a un callejón sin salida que queremos eludir por todos los medios. Una Europa reducida a la insignificancia en el concierto internacional, convertida en un juguete roto en manos del Imperialismo yanqui, que desde 1945 hasta nuestros días nos ha reducido a una mera frontera exterior, funcional a sus intereses, una especie de parapeto tras el cual dirige sus políticas de sumisión y chantaje, con sus bases militares y un afán expansionista a través de la OTAN que nos ha llevado directamente a una conflagración de proporciones y consecuencias imprevisibles dentro del propio espacio geopolítico ruso, con una guerra en Ucrania que todavía permanece activa y amenaza con una escalada, con una III Guerra Mundial y un auténtico holocausto nuclear. Ante la deriva de los acontecimientos, desde Mos Maiorum queremos analizar la viabilidad de alternativas al actual orden de cosas, sustraernos a las ataduras, a las imposiciones de los mass media, cada vez más agresivos, contra la libertad de expresión y por el control del relato. La Europa de los «bulos» y las «fake news», que no son sino otra estrategia para acallar críticas y contener a los espíritus disidentes, a quienes nos debemos a la Verdad y no creemos que resignarnos a morir, a ser absorbidos por el sumidero de la historia, sea una alternativa. Ante todas estas circunstancias que concurren en el mundo actual tenemos suficientes razones y argumentos para cuestionar la uniformización bajo un modelo político, social antropológico y cultural que tiende a la homologación de todos los territorios y espacios geográficos englobados bajo el denominado Occidente. Una homologación que se desarrolla sobre el plano financiero, bajo los auspicios de un liberal-capitalismo global liderado por Estados Unidos. Son muchas las preguntas y cuestiones que se suscitan, y especialmente en relación al modelo unipolar que se impone a raíz de la caída de la URSS en 1991 y la imposición de un «Fin de la historia» por parte de uno de los teóricos liberales más conocidos de la época, Francis Fukuyama. ¿Representa la hegemonía estadounidense «el lado correcto de la historia»? ¿El globalismo responde a ese «fin último de la historia» como parte de la culminación de susodicha hegemonía? A partir de estas preguntas no podemos obtener respuestas satisfactorias, y menos cuando hablamos de un proyecto fracasado, que amenaza las raíces de la civilización europea y su propia existencia a medio-largo plazo. Al mismo tiempo, el ámbito post-soviético también ha experimentado notables transformaciones en las últimas décadas, desde Yeltsin hasta Putin, que son los dos mandatarios que han regido los destinos de la Rusia postsoviética, hemos asistido a una revitalización de la doctrina euroasiática, que no podemos reducir exclusivamente al ámbito de la geopolítica, sino que también postula ideas que reivindican la especificidad de cada cultura, la pluralidad de las tradiciones o los vínculos con la tierra (valores telurocráticos), que sirven como freno ante el desarraigo y la destrucción de las identidades de los pueblos, la que se produce desde el mundialismo y la alta finanza plutocrática occidental. Por ese motivo, en las páginas que siguen vamos a tratar de mostrar los aspectos que componen esta realidad emergente que existe tras el concepto de «Eurasia», que ya desde el punto de vista geográfico se extiende sobre una enorme masa de tierras que abarcan una realidad multicontinental, en la que se hallan implicadas Europa y Asia, con un enorme potencial en cuanto a recursos materiales y humanos, continentes unidos por innumerables vínculos históricos que trascienden los estrechos márgenes de la historia «occidental», que no europea. Paralelamente, y no por ello de una importancia menor, debemos atender a los contenidos complementarios que ofrecemos al lector, y que comprenden temáticas variadas, relacionadas con la antropología tradicional, la metapolítica y la filosofía. En este último apartado contamos con las contribuciones realizadas por Franco Morini, Michele Ruzzai, Silvano Lorenzoni, Eddy Elvira Bedoya Argüelles y Carlos Andrés Gómez Rodas. Para finalizar los breves comentarios que componen este editorial, queremos hacer mención de los 10 años de existencia que Hipérbola Janus, nuestro sello editorial, cumplió el pasado 12 de octubre, y que nos hace volver la vista atrás con cierta nostalgia, y mucho orgullo, por los orígenes modestos y el enorme idealismo del que viene precedido nuestro proyecto. Nacido una fecha de enorme simbolismo para el ethos Hispánico, seguimos adelante tras una década de aventuras, de un abnegado trabajo, movido por ese quijotismo que siempre invocamos como parte de nuestro proyecto, como esa pieza clave que nos impulsa hacia delante pero sin olvidar el pasado, al que nos sentimos profundamente unidos a través de la defensa de la Tradición. --- Artículo original: Hipérbola Janus, Mos Maiorum VIII: «Eurasianismo: ¿una alternativa al discurso globalista?» (TOR), 2/Dic/2024
| |:-:| |MOS MAIORVM VIII (Otoño 2024), Hipérbola Janus, 2024| En las postrimerías del año, a las puertas del 2025, nos complace presentar a nuestros lectores el segundo de nuestros números temáticos. Anteriormente, en el número VII de Mos Maiorum, decidimos dar un giro radical a la estructura de la revista, habiendo madurado ya ciertos fundamentos a nivel organizativo y de colaboraciones. Y ahora, con mayor seguridad que nunca, nos adentramos en un nuevo tema, quizás uno de los más trascendentales en el momento histórico en el que nos hallamos. Nos aproximamos al ecuador de los años veinte del siglo XXI, y el Occidente posmoderno parece hacer aguas en todos los frentes, desangrando a las sociedades sobre las que su yugo asfixiante ejerce su poder. Llevamos más de un lustro asistiendo a la intensificación de determinados discursos que, poco a poco, y de manera subrepticia nos proponen Agendas verdes, moradas y multicolores, teorías del decrecimiento, destrucción de modelos de vida y una presión cada vez más agobiante de los poderes transnacionales a través de gobiernos que traicionan a sus pueblos y son servidores de intereses espurios. ¿Qué destino nos aguarda a los europeos? ¿Existe alguna alternativa viable al Occidente que se desmorona ante nuestros ojos? La respuesta, o una de las respuestas —probablemente la más importante— debemos buscarla en la configuración del tablero de ajedrez mundial, en la geopolítica, que es el tema central de nuestro dossier. Hoy, más que nunca, es necesario recuperar los textos de la geopolítica clásica y alternativa de un Carlo Terracciano, por ejemplo, entre otros muchos autores, que a lo largo del presente libro van a ser protagonistas, directos o indirectos, a través de sus ideas y sus análisis más preclaros sobre el tema del «Eurasianismo». Eurasia, lo queramos o no, es un concepto geopolítico que está ahora mismo en boga, y su formulación y síntesis original no adquiere su forma definitiva en la Europa occidental, sino que ha sido una doctrina desarrollada en el Este, en Rusia, desde autores como Lev Gumiliov o Nikolái Trubetskói, como autores clásicos en los primeros desarrollos de la doctrina, que posteriormente se ha visto actualizada y ha adquirido una trascendencia y dimensión de primer orden a raíz de las teorizaciones del polémico filósofo y geopolítico Aleksandr Duguin. No pretendemos caer en discursos maniqueos, ni tampoco convertirnos en un panegírico consagrado a la defensa a ultranza de un determinado discurso, idea o doctrina, sino que nuestra intención es penetrar en lo profundo del tema, conocer el Eurasianismo como doctrina, en su evolución, desentrañando sus características y ofreciendo al lector una visión «desde el otro lado», desde los discursos menos convencionales, y también menos sistémicos, capaz de ofrecer un enfoque lo más claro y diáfano posible, sin recurrir, como decimos, a discursos apologéticos ni a adhesiones fanáticas. Pero tampoco practicamos la equidistancia ni la neutralidad tan característica del espíritu burgués y las componendas de sus falsas democracias parlamentarias, y por eso profesamos una nada disimulada antipatía hacia el Occidente moderno y sus valores mediocres y pusilánimes. En este número, en el dossier, como a lo largo de toda nuestra trayectoria, nos asiste un elenco de autores de reconocido prestigio, contamos con las firmas de Claudio Mutti, Daniele Perra, Diego Fusaro, Carlos X Blanco, Daniel Artur Branco, Guillermo Mas Arellano, David Lara Miguez, Pietro Missiaggia y Luis Landeira. Sin embargo, hay algo que tenemos muy claro, y es que los «valores» del Occidente posmoderno representan la decadencia absoluta, la destrucción de lo más profundo y auténtico del hombre europeo, representan esa antropología negativa y desviada que nos aboca a un callejón sin salida que queremos eludir por todos los medios. Una Europa reducida a la insignificancia en el concierto internacional, convertida en un juguete roto en manos del Imperialismo yanqui, que desde 1945 hasta nuestros días nos ha reducido a una mera frontera exterior, funcional a sus intereses, una especie de parapeto tras el cual dirige sus políticas de sumisión y chantaje, con sus bases militares y un afán expansionista a través de la OTAN que nos ha llevado directamente a una conflagración de proporciones y consecuencias imprevisibles dentro del propio espacio geopolítico ruso, con una guerra en Ucrania que todavía permanece activa y amenaza con una escalada, con una III Guerra Mundial y un auténtico holocausto nuclear. Ante la deriva de los acontecimientos, desde Mos Maiorum queremos analizar la viabilidad de alternativas al actual orden de cosas, sustraernos a las ataduras, a las imposiciones de los mass media, cada vez más agresivos, contra la libertad de expresión y por el control del relato. La Europa de los «bulos» y las «fake news», que no son sino otra estrategia para acallar críticas y contener a los espíritus disidentes, a quienes nos debemos a la Verdad y no creemos que resignarnos a morir, a ser absorbidos por el sumidero de la historia, sea una alternativa. Ante todas estas circunstancias que concurren en el mundo actual tenemos suficientes razones y argumentos para cuestionar la uniformización bajo un modelo político, social antropológico y cultural que tiende a la homologación de todos los territorios y espacios geográficos englobados bajo el denominado Occidente. Una homologación que se desarrolla sobre el plano financiero, bajo los auspicios de un liberal-capitalismo global liderado por Estados Unidos. Son muchas las preguntas y cuestiones que se suscitan, y especialmente en relación al modelo unipolar que se impone a raíz de la caída de la URSS en 1991 y la imposición de un «Fin de la historia» por parte de uno de los teóricos liberales más conocidos de la época, Francis Fukuyama. ¿Representa la hegemonía estadounidense «el lado correcto de la historia»? ¿El globalismo responde a ese «fin último de la historia» como parte de la culminación de susodicha hegemonía? A partir de estas preguntas no podemos obtener respuestas satisfactorias, y menos cuando hablamos de un proyecto fracasado, que amenaza las raíces de la civilización europea y su propia existencia a medio-largo plazo. Al mismo tiempo, el ámbito post-soviético también ha experimentado notables transformaciones en las últimas décadas, desde Yeltsin hasta Putin, que son los dos mandatarios que han regido los destinos de la Rusia postsoviética, hemos asistido a una revitalización de la doctrina euroasiática, que no podemos reducir exclusivamente al ámbito de la geopolítica, sino que también postula ideas que reivindican la especificidad de cada cultura, la pluralidad de las tradiciones o los vínculos con la tierra (valores telurocráticos), que sirven como freno ante el desarraigo y la destrucción de las identidades de los pueblos, la que se produce desde el mundialismo y la alta finanza plutocrática occidental. Por ese motivo, en las páginas que siguen vamos a tratar de mostrar los aspectos que componen esta realidad emergente que existe tras el concepto de «Eurasia», que ya desde el punto de vista geográfico se extiende sobre una enorme masa de tierras que abarcan una realidad multicontinental, en la que se hallan implicadas Europa y Asia, con un enorme potencial en cuanto a recursos materiales y humanos, continentes unidos por innumerables vínculos históricos que trascienden los estrechos márgenes de la historia «occidental», que no europea. Paralelamente, y no por ello de una importancia menor, debemos atender a los contenidos complementarios que ofrecemos al lector, y que comprenden temáticas variadas, relacionadas con la antropología tradicional, la metapolítica y la filosofía. En este último apartado contamos con las contribuciones realizadas por Franco Morini, Michele Ruzzai, Silvano Lorenzoni, Eddy Elvira Bedoya Argüelles y Carlos Andrés Gómez Rodas. Para finalizar los breves comentarios que componen este editorial, queremos hacer mención de los 10 años de existencia que Hipérbola Janus, nuestro sello editorial, cumplió el pasado 12 de octubre, y que nos hace volver la vista atrás con cierta nostalgia, y mucho orgullo, por los orígenes modestos y el enorme idealismo del que viene precedido nuestro proyecto. Nacido una fecha de enorme simbolismo para el ethos Hispánico, seguimos adelante tras una década de aventuras, de un abnegado trabajo, movido por ese quijotismo que siempre invocamos como parte de nuestro proyecto, como esa pieza clave que nos impulsa hacia delante pero sin olvidar el pasado, al que nos sentimos profundamente unidos a través de la defensa de la Tradición. --- Artículo original: Hipérbola Janus, Mos Maiorum VIII: «Eurasianismo: ¿una alternativa al discurso globalista?» (TOR), 2/Dic/2024 -
 @ 37043134:0e04e271
2024-12-04 10:00:24
@ 37043134:0e04e271
2024-12-04 10:00:24Started writing, must ha ve auto wrapping on word boundaries, it does. Also spell checking. Follows a copy-paste:
Fine, since i cannot find the articles in procedure, or you pointed to the wrong ones?(procedure, not criminal code(these are all in my database), so i cannot be precise as to the technical matter of statute of limitations.
Make your appeal in as concise as possible and take a "hard" stance on the State Prosecutor: according to me the accusations i make are to crimes punishable by up to three years in prison, both the logging(State land, National Park(special purposes), and the appropriation(of State land). I think you are wrong there. They also are crimes to be prosecuted "ex officio" in case the appeal rejects the call to expiration of the statute of limitations?!
Secondly the parcel 413/2 was appropriated in part, that makes me a direct victim, contrary to a "whistle blower" as you hint at(the maps show this clearly), ...i am a whistle blower as to the appropriation of parcel 620, yes. So that makes me both.
The suspension of expiration of the statute of limitations, is according to me(again i do not have the articles and go by the text you sent me over viber), justified on multiple grounds: Tuzilac Bijelo Polje(), petition to the kadaster(), our official requests to the forestry services in Plav and Bjieljo Polje, the ongoing civil court case in Plav, repeat offenses(), the "consequences" of the crime still ongoing(danger of logging). Indeed we have a "strong" case.
It is not about the appeal resulting into sending the complaint to court, it is about documenting ourselves, so we have something to stand on in the future. Send me your draft in Montenegrin so i can assure myself that you take this head on. I insist you add my copy in English to the file you send of.
i regret you did not give me a print copy of the answer of the State Prosecutor, as i expected, you did not answer my repeat request earlier on as to the deadline to appeal, so you left me in "ignoramus" mode, which i have to pay now by being "un-briefed" on the specifics of the matter,
My compliment to the contrary for having set up your team, a permanent presence(your sister back-up here while away), that is expected, but still it is nice to see it done on your own initiative"(a copy-paste)
-
 @ f584a915:9da6d625
2024-12-02 13:08:50
@ f584a915:9da6d625
2024-12-02 13:08:50The rise of cryptocurrencies has opened up a new avenue for young individuals seeking to generate income. This digital revolution has empowered a generation to explore innovative ways to earn, invest, and build wealth. By understanding the fundamentals of blockchain technology and the various cryptocurrencies available, young people can tap into a vast array of opportunities.
One of the most straightforward ways to earn cryptocurrency is through mining. This process involves using powerful computers to solve complex mathematical problems. While it requires significant technical expertise and substantial computing power, mining can be a lucrative venture for those who are willing to invest the time and resources.
Another popular method is cryptocurrency trading. By analyzing market trends and making informed investment decisions, individuals can profit from price fluctuations. This requires a keen understanding of economic indicators, technical analysis, and risk management strategies. However, it's important to approach trading with caution and to be aware of the inherent risks involved.
Beyond trading and mining, there are numerous other ways to earn cryptocurrency. Many companies and organizations offer rewards in the form of crypto tokens for completing tasks, participating in surveys, or providing feedback. Additionally, young entrepreneurs can leverage their skills and creativity to develop blockchain-based applications and services. By offering innovative solutions to real-world problems, they can attract investments and generate significant income.
While the potential for financial gain is substantial, it's crucial to approach the world of cryptocurrencies with a level head. It's essential to conduct thorough research, stay updated on the latest trends, and be mindful of scams and fraudulent activities. By educating themselves and making informed decisions, young people can harness the power of cryptocurrencies to build a secure financial future.
-
 @ 7ec80607:128517c5
2024-12-04 09:11:51
@ 7ec80607:128517c5
2024-12-04 09:11:51Landscaping is an essential part of creating a beautiful, functional, and harmonious outdoor environment. It not only enhances the aesthetics of a property but can also improve its value. The right landscaping design can transform a simple outdoor space into a sanctuary, combining elements like plants, trees, water features, and hardscaping to create an inviting and peaceful atmosphere. Below are 10 of the best landscaping examples that incorporate a variety of design elements, from stunning plant arrangements to innovative hardscaping features.
**1. Tropical Oasis Landscape ** A tropical oasis landscape features lush, vibrant greenery, colorful flowers, and often, water features like ponds or waterfalls. This style is perfect for creating a serene getaway right in your backyard. Key elements of a tropical oasis include: Lush Foliage: Use of large-leafed plants like banana trees, palms, and bamboo to create a dense, jungle-like atmosphere. Water Features: Adding a small pond or a bubbling water fountain can enhance the tropical feel, creating soothing sounds. Colorful Flowers: Brightly colored flowers like hibiscus, bougainvillea, and bird of paradise add pops of color. The lush greenery and vibrant flowers of a tropical oasis can bring a piece of the tropics to your home, ideal for those looking to create a vibrant, tranquil environment.
- Zen Garden Landscape Inspired by Japanese traditions, the Zen garden is designed to promote peace and mindfulness. These gardens often use minimalist design principles and focus on simplicity, harmony, and balance. Important elements of a Zen garden include:
Rocks and Gravel: The use of stones or gravel is a defining feature. Gravel is often raked into patterns to represent water or to mimic waves. Bamboo and Evergreens: Bamboo is a staple in Zen gardens for its calming and serene appearance. Evergreen trees, such as Japanese maples, are also commonly used to maintain year-round beauty. Water Features: While Zen gardens typically use dry landscapes, small, serene water features like fountains or small ponds can be added to introduce a sense of tranquility. Zen gardens are ideal for homeowners seeking a low-maintenance, minimalist landscape that focuses on tranquility and a sense of balance.
- Modern Minimalist Landscape The modern minimalist landscape design focuses on simplicity, clean lines, and functional design. It utilizes a restrained palette of plants and materials, making the most of space and emphasizing architectural features. Key elements include: Hardscaping: A minimalist landscape often incorporates large, geometric pavers, concrete walkways, and steel accents. Low-maintenance Plants: Choose a limited selection of low-maintenance plants such as succulents, grasses, and boxwoods. Open Spaces: The design tends to keep the lawn area open and unobstructed, with well-defined edges to enhance the simplicity. This design style suits contemporary homes and urban settings, providing a sleek, uncluttered look with a focus on clean lines and a structured environment.
- Cottage Garden Landscape A cottage garden creates a charming, whimsical, and cozy outdoor space filled with a mix of flowering plants and lush greenery. These gardens often evoke a sense of nostalgia and can make your garden feel like an English countryside retreat. Key features of a cottage garden include: Dense Planting: Layering plants such as roses, lavender, daisies, and geraniums in a loose, informal arrangement. Paths and Arbors: Winding paths made of natural materials like cobblestone or gravel, with arbors and trellises to support climbing plants like ivy and wisteria. Rustic Elements: Incorporating rustic furniture like benches, birdbaths, or vintage watering cans adds to the charm. Cottage gardens are ideal for those who want a vibrant, naturalistic garden that feels both personal and inviting.
- Desert Landscape Desert landscaping, or xeriscaping, is designed for dry climates and focuses on water conservation by using drought-tolerant plants and minimal water usage. This landscaping style can create a stunning, low-maintenance environment. Key features of a desert landscape include: Succulents and Cacti: These hardy plants, such as agave, aloe, and prickly pear, are central to desert landscapes. Gravel and Sand: The use of gravel, pebbles, and sand in place of grass creates a clean, open aesthetic and reduces water needs. Rock Features: Boulders and large stones can be incorporated to create visual interest and mimic natural desert formations. Desert landscaping is ideal for homeowners in arid climates, offering both beauty and efficiency while minimizing water usage.
**6. Formal Garden Landscape ** A formal garden is all about symmetry, structure, and order. These gardens often feature geometric shapes, carefully manicured plants, and neatly trimmed hedges. Key features of a formal garden include: Symmetrical Layout: Paths, hedges, and flowerbeds are arranged in precise patterns, often with a central focal point like a fountain or statue. Topiary and Hedges: Neatly trimmed hedges and topiary (shaped plants) add a sculptural element to the landscape. Classic Elements: Use of classical features such as statues, urns, and decorative vases enhances the formality of the design.
A formal garden is well-suited for large properties or historic homes, where precision and elegance are important.
**7. Coastal Landscape ** A coastal landscape embraces the relaxed, breezy feel of the beach and sea, often incorporating elements like salt-tolerant plants and open spaces. Key components of a coastal landscape include: Native Coastal Plants: Plants such as sea oats, beach grass, and dune lilies are ideal for coastal landscapes because they can thrive in salty, windy environments. Natural Stone: The use of large stones or driftwood can evoke the rugged beauty of the shoreline. Relaxed Layout: Coastal gardens tend to have a more informal, flowing design with wide open spaces and paths that blend seamlessly with the natural surroundings. This style is perfect for beachfront properties or those looking to bring the calming ambiance of the coast to their outdoor space.
**8. Woodland Garden Landscape ** Woodland gardens are designed to create a natural, forest-like environment, often under the canopy of large trees. These gardens offer a cool, shaded area full of texture and variety. Key elements include: Shade-loving Plants: Ferns, hostas, and primroses thrive in shaded environments and provide rich textures and colors to the garden.
Layered Planting: Woodland gardens often feature a variety of plant layers, with ground covers, shrubs, and trees creating a rich, natural composition. Natural Pathways: Winding, organic paths made from mulch, stone, or wood chips help maintain the natural feel of the garden.
Woodland gardens are perfect for areas with mature trees or shaded locations, offering a peaceful retreat with a focus on nature’s tranquility.
**9. Edible Landscape ** An edible landscape integrates functional food-producing plants into the garden, making it both beautiful and practical. These gardens focus on incorporating fruits, vegetables, herbs, and edible flowers into the overall design. Key features of an edible landscape include: Raised Beds and Containers: Raised garden beds, pots, or containers allow for easy cultivation of vegetables, fruits, and herbs.
Fruit Trees: Incorporating fruit trees like apple, pear, or citrus adds both beauty and function. Edible Flowers: Incorporating flowers like nasturtiums or lavender can provide color as well as culinary benefits.
Edible landscaping is ideal for those looking to combine aesthetics with sustainability, growing their own food while enhancing the beauty of their outdoor spaces.
**10. Water-Wise Landscape ** Water-wise landscaping focuses on creating beautiful outdoor spaces while minimizing water usage. This is especially important in regions where water conservation is a concern. Key features include: Drought-Tolerant Plants: The use of native plants that require less water, such as lavender, succulents, and yucca, is a key element. Efficient Irrigation Systems: Drip irrigation systems are commonly used to minimize water wastage while ensuring plants get the right amount of hydration. Mulching: Applying mulch around plants helps retain moisture, reduce evaporation, and keep the soil cool. Water-wise landscaping is ideal for homeowners in dry climates, providing an eco-friendly and cost-effective solution to maintaining a beautiful garden.
**Conclusion ** Landscaping offers an incredible range of possibilities to transform outdoor spaces into beautiful and functional environments. From tropical oases to formal gardens and water-wise landscapes, each type of landscape design brings its unique elements and benefits. Whether you are looking to create a peaceful retreat, a low-maintenance garden, or a functional space for growing your own food, the best landscaping examples provide inspiration and ideas to make your outdoor space truly spectacular. By selecting the right elements for your climate, lifestyle, and aesthetic preferences, you can create a garden that enhances both the beauty and value of your property.
-
 @ de496884:72617b81
2023-11-20 13:54:02
@ de496884:72617b81
2023-11-20 13:54:02Hola nostriches. Hoy quiero hacer una publicación a modo de acercamiento al surgimiento de las categorías de género y feminismo. Así que si te interesa el tema haz un esfuerzo, quédate y lee hasta el final.
El «nuevo» feminismo surge en los años 60 en aquellos países desarrollados que acordaron el reconocimiento a los derechos humanos contenidos en la declaración respectiva de la ONU. Entonces, como extensión a dicho reconocimiento es que se gesta el movimiento feminista. A partir de entonces, se vuelve a plantear la relación entre naturaleza y cultura y se llega a la conclusión de que las diferencias sociales van más allá de las diferencias biológicas, lo cual tiene que ver con que hasta la satisfacción de las necesidades elementales como son la alimentación, la vivienda o el vestuario, están condicionadas por construcciones sociales.
Pues resulta que una de las primeras propuestas identificó la subordinación femenina producto de una organización patriarcal, tomando la categoría patriarcado de Max Weber. Es así como la visión de patriarcado se extendió al discurso político y académico. Sin embargo, no existía información acerca del desarrollo histórico de dicha categoría, sistematización, variaciones, etc., debido a que era algo que recién se percibía en sociedad.
Sin embargo, la misma categoría de patriarcado junto a la de relaciones de poder para explicar fenómenos sociales contemporáneos, constituye uno de los principales aportes del feminismo. Es así como han logrado primero visibilizar y luego deconstruir y desmontar una serie de patrones existentes en la cultura que hacían a la mujer subordinarse al hombre, y que estaban presentes en el sistema sexo/género.
 Imagen relativa a la lucha contra el patriarcado
Imagen relativa a la lucha contra el patriarcadoHasta ese momento, en las investigaciones de corte sociológico se podía observar un androcentrismo excesivo al dar cuenta de que el discurso científico giraba en torno al hombre como sujeto y objeto de la investigación. Incluso para muchos positivistas como el mismo Weber, los problemas relativos a las mujeres quedaban en un segundo plano y eran achacados a una supuesta pasividad en el ámbito doméstico-familiar. Dicha pasividad partía de la supuesta inferioridad biológica del género femenino.
El patriarcado entonces era una categoría vacía en sí misma, sin valor explicativo. Desde el punto de vista político pudo ser útil para la movilización pero no resistió la polémica de los críticos del feminismo ni problematizó los conflictos a ser resueltos. Pero por otro lado, un grupo de mujeres -académicas principalmente- se puso manos a la obra en una tarea más pequeña pero con mayores resultados a la larga. Se propusieron generar conocimientos sobre las condiciones de vida de la mujer, buscar en el pasado y el presente los aportes de las mujeres a la sociedad, hacerlas visibles en la historia. Es así como surgen centros académicos, ONG, proyectos, centros de estudios sobre la mujer, etc.
Convendría distinguir entonces dos posturas que acompañaron a la investigación sobre las mujeres: uno que toma como objeto de estudio a la mujer; condiciones de vida, trabajo, cultura, y otra que privilegia a la sociedad como generadora de la subordinación de las mujeres. Mientras la primera perspectiva generaba conocimiento sobre las mujeres en el estudio de las relaciones mujer-hombre y mujer-mujer, la segunda tenía una visión más holística ya que planteaba que hay que estudiar la sociedad ya que la subordinación de las mujeres es producto de la organización de esta, y que no se avanzará solamente estudiando a las mujeres, pues el estudio debe ser más amplio y en diferentes niveles, ámbitos y tiempos.
Es en esta búsqueda donde nace y se desarrolla el concepto de género como categoría social. Es así que los sistemas de género/sexo fueron entendidos como conjuntos de prácticas, símbolos, representaciones, normas y valores sociales que las sociedades construyen a partir de la diferencia anatomofisiológica y que dotan de sentido a los impulsos sexuales, la reproducción y en general a las relaciones de las personas. Por tanto, este sistema pasó a ser el objeto de estudio para comprender la subordinación de la mujer al hombre. Al ser el reconocimiento de una dimensión de la desigualdad social hasta entonces desconocida, se considera la ruptura epistemológica más importante de la segunda mitad del siglo pasado.
 Imagen representativa del binarismo de género
Imagen representativa del binarismo de géneroHay que decir que los fenómenos sociales se definen por la relación que guardan entre sí. Es así que la contextualización adquiere gran importancia. Varones y hembras tenemos la capacidad de producir con el cuerpo, pero solo los cuerpos de las hembras pueden gestar y por tanto asegurar la especie humana. Todo grupo humano que pretenda sobrevivir debe asegurarse cierto número de hembras que lo hagan posible. De ahí un poder particular del cuerpo de las hembras que además es económicamente útil. Dicho poder no es en tanto entidad biológica, sino que es la sociedad la que le otorga este poder. En este punto es importante preguntarnos históricamente ¿quiénes han controlado la capacidad reproductiva de las mujeres?, ¿quiénes han tenido la preferencia en el acceso sexual? Para asegurar un control efectivo sobre la reproducción es necesario asegurar el acceso a la sexualidad.
Ello también lleva a dirigir el trabajo que hacen porque de lo contrario, las mujeres pudieran tener espacio para representar una amenaza al dominio de los hombres. Es importante atender a las etapas del desarrollo de las mujeres, que permitirá ver cómo se moldean para aceptar la desigualdad y las jerarquías según el género en las distintas sociedades y culturas.
Otro contexto a delimitar es el ámbito doméstico donde históricamente ha estado ubicada la subordinación femenina. Se ha puesto al descubierto que en mujeres que comparten la misma posición de clase y raza, la condición femenina se redefine a lo largo de la vida y que algunas mujeres gozan de poder sobre otras aún en contextos de alta dominación masculina, donde se les inviste de autoridad, creando el sistema zonas de incertidumbre que las divide como género e impide alianzas y se legitima la dominación. Foucault decía que «el poder se ejerce, no se posee», siempre está en peligro de perderse y no basta con normas, leyes, amenazas o castigos. De ahí que los espacios de subordinación sean también espacios de poder de las mujeres. Es en estos espacios donde aparece la inseguridad, la tensión, la confrontación y por ejemplo, las mujeres pueden reclamar la anticoncepción.
Para terminar, es importante tener en cuenta que el género es una forma de desigualdad social que siempre está articulado con otras formas de desigualdad ya sea clase, raza, grupo etario, etc. Hay que pensar la dominación masculina con un comienzo vago en el tiempo, pero que permite desligar la subordinación de las mujeres de la evolución «natural» de la humanidad y entenderla como un proceso histórico. En ese sentido es necesario destacar que, respecto a la raza, en sociedades plurales hay que atender al contexto étnico-cultural ya que en dependencia de las relaciones entre personas de razas distintas, estarán condicionadas las relaciones entre los géneros.
 Imagen de mujeres de distintas razas
Imagen de mujeres de distintas razasPor otro lado, si bien es sabido que históricamente el sistema de género social imperante ha contribuido a invisibilizar a la mujer, asociar necesariamente dicha categoría únicamente a ella, lo que hace es nuevamente recrear el absolutismo histórico que tanto daño ha hecho, ahora como lo antagónico al hombre. En la construcción social participan todos los individuos presentes en el sistema género.
Hasta aquí la publicación de hoy, de la cual aun se puede ahondar mucho más, sobre todo en lo referido al origen de la dominación o de la jerarquización del binomio «hombre/mujer» desde un punto de vista antropológico, pero eso quedará pendiente para otro momento. ¡Así que hasta la próxima!, ¡nos vemos en Nostr!
........................................
English version
Hello nostriches. Today I want to make a post by way of an approach to the emergence of the categories of gender and feminism. So if you are interested in the topic make an effort, stay and read to the end.
The "new" feminism emerged in the 60's in those developed countries that agreed to recognize the human rights contained in the respective UN declaration. Then, as an extension of that recognition, the feminist movement was born. From then on, the relationship between nature and culture was raised again and the conclusion was reached that social differences go beyond biological differences, which has to do with the fact that even the satisfaction of elementary needs such as food, housing or clothing are conditioned by social constructions.
It turns out that one of the first proposals identified female subordination as a product of a patriarchal organization, taking Max Weber's category of patriarchy. This is how the vision of patriarchy was extended to political and academic discourse. However, there was no information about the historical development of this category, systematization, variations, etc., because it was something that was only recently perceived in society.
However, the same category of patriarchy, together with that of power relations to explain contemporary social phenomena, constitutes one of the main contributions of feminism. This is how they have first made visible and then deconstructed and dismantled a series of existing patterns in the culture that made women subordinate to men, and that were present in the sex/gender system.
 Image relating to the fight against patriarchy
Image relating to the fight against patriarchyUp to that time, in sociological research, an excessive androcentrism could be observed as scientific discourse revolved around men as the subject and object of research. Even for many positivists such as Weber himself, the problems related to women remained in the background and were blamed on a supposed passivity in the domestic-family sphere. This passivity was based on the supposed biological inferiority of the female gender.
Patriarchy was then an empty category in itself, with no explanatory value. From the political point of view, it could be useful for mobilization, but it did not resist the polemic of feminism's critics, nor did it problematize the conflicts to be resolved. But on the other hand, a group of women - mainly academics - set to work on a smaller task but with greater results in the long run. They set out to generate knowledge about women's living conditions, to search in the past and present for women's contributions to society, to make them visible in history. This is how academic centers, NGOs, projects, women's studies centers, etc., came into being.
It would be convenient to distinguish then two postures that accompanied the research on women: one that takes women as the object of study; living conditions, work, culture, and the other that privileges society as the generator of women's subordination. While the first perspective generated knowledge about women in the study of woman-man and woman-woman relations, the second had a more holistic vision, since it proposed that society must be studied, since the subordination of women is a product of its organization, and that progress will not be made only by studying women, since the study must be broader and at different levels, spheres and times.
It is in this search that the concept of gender as a social category was born and developed. Thus, gender/sex systems were understood as a set of practices, symbols, representations, norms and social values that societies construct on the basis of anatomophysiological differences and that give meaning to sexual impulses, reproduction and, in general, to people's relationships. Therefore, this system became the object of study to understand the subordination of women to men. As the recognition of a hitherto unknown dimension of social inequality, it is considered the most important epistemological breakthrough of the second half of the last century.
 Representative image of gender binarism
Representative image of gender binarismIt must be said that social phenomena are defined by their relationship with each other. Thus, contextualization acquires great importance. Males and females have the capacity to produce with their bodies, but only the bodies of females can gestate and therefore ensure the human species. Any human group that intends to survive must ensure a certain number of females to make it possible. Hence a particular power of the female body, which is also economically useful. This power is not as a biological entity, but it is society that gives it this power. At this point it is important to ask ourselves historically, who has controlled the reproductive capacity of women, who has had the preference in sexual access? To ensure effective control over reproduction, it is necessary to ensure access to sexuality.
 Allegorical image of pregnancy
Allegorical image of pregnancyThis also leads to directing the work they do because otherwise, women may have room to pose a threat to men's dominance. It is important to pay attention to the stages of women's development, which will allow us to see how they are shaped to accept inequality and gender hierarchies in different societies and cultures.
Another context to delimit is the domestic sphere where female subordination has historically been located. It has been discovered that in women who share the same class and race position, the feminine condition is redefined throughout life and that some women enjoy power over others even in contexts of high male domination, where they are invested with authority, creating the system of uncertainty zones that divide them as a gender and prevent alliances and legitimize domination. Foucault said that "power is exercised, not possessed", it is always in danger of being lost and norms, laws, threats or punishments are not enough. Hence, the spaces of subordination are also spaces of women's power. It is in these spaces where insecurity, tension, confrontation appear and where, for example, women can demand contraception.
To conclude, it is important to keep in mind that gender is a form of social inequality that is always articulated with other forms of inequality, be it class, race, age group, etc. It is necessary to think of male domination with a vague beginning in time, but which allows us to separate the subordination of women from the "natural" evolution of humanity and to understand it as a historical process. In this sense, it is necessary to emphasize that, with respect to race, in plural societies it is necessary to pay attention to the ethno-cultural context since, depending on the relations between people of different races, the relations between genders will be conditioned.
 Image of women of different races
Image of women of different racesOn the other hand, although it is known that historically the prevailing social gender system has contributed to make women invisible, to necessarily associate this category only to women is to recreate the historical absolutism that has done so much damage, this time as antagonistic to men. All individuals present in the gender system participate in the social construction.
So much for today's publication, of which we can still go much deeper, especially with regard to the origin of domination or the hierarchization of the binomial "man/woman" from an anthropological point of view, but that will be left for another time. So until next time, see you in Nostr!

Créditos | Credits
Bibliografía consultada | Consulted bibliography:
-
Barbieri, T. (1993). Sobre la categoría género. Una introducción teórico-metodológica. Debates en Sociología. (18). 1-19. https://doi.org/10.18800/debatesensociologia.199301.006
-
Echevarría, D. (2020). Desigualdades de género e interseccionalidad. Análisis del contexto cubano 2008-2018. Facultad Latinoamericana de Ciencias Sociales (Programa-Cuba). https://www.clacso.org.ar/libreria-latinoamericana-cm/libro_detalle_resultado.php?id_libro=2346&campo=cm&texto=248
Traducción | Translation:
DeepL
-
-
 @ e83b66a8:b0526c2b
2024-12-04 08:52:23
@ e83b66a8:b0526c2b
2024-12-04 08:52:23When we had the Gold standard, gold only backed assets.
Now we are approaching the Bitcoin Standard, what will happen if Bitcoin is used to back debt?
$MSTR is the Alpha release
Trumps USA will be the Beta release.
If it works, the world has $315T of debt. That will be the full release V1.0
In comparison, the world has $454T of assets.
Can it be done?
What happens when you back a negative debt with a positive asset?
Has it ever been tried?
Is it possible?
The problem with the debt is it isn't "owed" to anyone.
If I lend you $10 you owe me $10.
To explain further:
If you lend me $10 worth of gold, then I can pay you back $10 of money if it's backed with gold - the gold standard.
If you lend me $10 worth of gold, and I pay you back with unbacked fiat, the repayment is arbitrary.
Like for like you can back any backed money with any asset.
Without a backed money, you can only repay an asset with an asset, otherwise paying with fiat, the global books don't balance.
In the current fiat world, if the US government print $10 and sells it to the market for $10 + interest, their is no creditor. You are simply diluting all other dollars.
When they have to pay back the debt to the “creditor”, they can't return the original $10 because that's been spent and they haven't generated any wealth (they are a government, not a company), so everything they return (the original lent $10 + interest) is printed again.
This is monetary recursion and destroys all fiat systems eventually.
So what happens when you insert a hard asset into the equation? Do you destroy or weaken that asset, you certainly don't strengthen it.
Does this turn Bitcoin into an inflationary currency despite its inherent deflationary properties.
After all, the U.S. had to come off the gold standard, because they didn't have enough gold to pay back.
I think best case scenario is Bitcoin repeats what happened to gold. It weakens Bitcoin until it makes it flacid, at which time the government will be forced to leave the Bitcoin Standard and Bitcoin will be a shadow of its potential.
Why?
Currency can be created and destroyed.
Money (the measure of wealth) is absolute.
I think this is the fundamental flaw, we believe money can be created and destroyed simply because we are used to printing or burning government fiat and have copied that model for Crypto currencies like Ethereum or Tether, which are mined or burned.
So money (invent better word) cannot be printed or destroyed, it is a measure of wealth and if you increase or decrease the supply you change the unit measurement, not the money.
So what are the potential end point valuations of Bitcoin?
Can Bitcoin approach a $21M coin valuation? i.e. 21M Coins at $21M?
If Bitcoin only backs assets, then it can't exceed, or even approach the total value of world wealth, currently $454T
At $21M for 21M coins, this approaches world wealth.
If Bitcoin is used to back debt, then you can add a further $315T of value, so if we assume $100T (about 1/4) of asset value + $300T of debt value, then we approach $21M per coin.
Another potential way of projecting the eventual stable price of Bitcoin:
If world wealth is currently around $454T
And world debt is currently around $315T
then can we consider it like a company and consider the profit to be $454T - $315T = $139T
Would that be a good expectation for final Bitcoin price?
i.e. $139T / 21M = $6.6M per BTC
However, I'm not certain Bitcoin can survive being used to back debt.
Gold never did that.
-
 @ e31e84c4:77bbabc0
2024-12-02 10:44:07
@ e31e84c4:77bbabc0
2024-12-02 10:44:07Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net
Fiduciary duty is the obligation to act in the client’s best interests at all times, prioritizing their needs above the advisor’s own, ensuring honesty, transparency, and avoiding conflicts of interest in all recommendations and actions.
This is something all advisors in the BFAN take very seriously; after all, we are legally required to do so. For the average advisor this is a fairly easy box to check. All you essentially have to do is have someone take a 5-minute risk assessment, fill out an investment policy statement, and then throw them in the proverbial 60/40 portfolio. You have thousands of investment options to choose from and you can reasonably explain how your client is theoretically insulated from any move in the \~markets\~. From the traditional financial advisor perspective, you could justify nearly anything by putting a client into this type of portfolio. All your bases were pretty much covered from return profile, regulatory, compliance, investment options, etc. It was just too easy. It became the household standard and now a meme.
As almost every real bitcoiner knows, the 60/40 portfolio is moving into psyop territory, and many financial advisors get clowned on for defending this relic on bitcoin twitter. I’m going to specifically poke fun at the ‘40’ part of this portfolio.
The ‘40’ represents fixed income, defined as…
An investment type that provides regular, set interest payments, such as bonds or treasury securities, and returns the principal at maturity. It’s generally considered a lower-risk asset class, used to generate stable income and preserve capital.
Historically, this part of the portfolio was meant to weather the volatility in the equity markets and represent the “safe” investments. Typically, some sort of bond.
First and foremost, the fixed income section is most commonly constructed with U.S. Debt. There are a couple main reasons for this. Most financial professionals believe the same fairy tale that U.S. Debt is “risk free” (lol). U.S. debt is also one of the largest and most liquid assets in the market which comes with a lot of benefits.
There are many brilliant bitcoiners in finance and economics that have sounded the alarm on the U.S. debt ticking time bomb. I highly recommend readers explore the work of Greg Foss, Lawrence Lepard, Lyn Alden, and Saifedean Ammous. My very high-level recap of their analysis:
-
A bond is a contract in which Party A (the borrower) agrees to repay Party B (the lender) their principal plus interest over time.
-
The U.S. government issues bonds (Treasury securities) to finance its operations after tax revenues have been exhausted.
-
These are traditionally viewed as “risk-free” due to the government’s historical reliability in repaying its debts and the strength of the U.S. economy
-
U.S. bonds are seen as safe because the government has control over the dollar (world reserve asset) and, until recently (20 some odd years), enjoyed broad confidence that it would always honor its debts.
-
This perception has contributed to high global demand for U.S. debt but, that is quickly deteriorating.
-
The current debt situation raises concerns about sustainability.
-
The U.S. has substantial obligations, and without sufficient productivity growth, increasing debt may lead to a cycle where borrowing to cover interest leads to more debt.
-
This could result in more reliance on money creation (printing), which can drive inflation and further debt burdens.
In the words of Lyn Alden “Nothing stops this train”
Those obligations are what makes up the 40% of most the fixed income in your portfolio. So essentially you are giving money to one of the worst capital allocators in the world (U.S. Gov’t) and getting paid back with printed money.
As someone who takes their fiduciary responsibility seriously and understands the debt situation we just reviewed, I think it’s borderline negligent to put someone into a classic 60% (equities) / 40% (fixed income) portfolio without serious scrutiny of the client’s financial situation and options available to them. I certainly have my qualms with equities at times, but overall, they are more palatable than the fixed income portion of the portfolio. I don’t like it either, but the money is broken and the unit of account for nearly every equity or fixed income instrument (USD) is fraudulent. It’s a paper mache fade that is quite literally propped up by the money printer.
To briefly be as most charitable as I can – It wasn’t always this way. The U.S. Dollar used to be sound money, we used to have government surplus instead of mathematically certain deficits, The U.S. Federal Government didn’t used to have a money printing addiction, and pre-bitcoin the 60/40 portfolio used to be a quality portfolio management strategy. Those times are gone.
Now the fun part. How does bitcoin fix this?
Bitcoin fixes this indirectly. Understanding investment criteria changes via risk tolerance, age, goals, etc. A client may still have a need for “fixed income” in the most literal definition – Low risk yield. Now you may be thinking that yield is a bad word in bitcoin land, you’re not wrong, so stay with me. Perpetual motion machine crypto yield is fake and largely where many crypto scams originate. However, that doesn’t mean yield in the classic finance sense does not exist in bitcoin, it very literally does. Fortunately for us bitcoiners there are many other smart, driven, and enterprising bitcoiners that understand this problem and are doing something to address it. These individuals are pioneering new possibilities in bitcoin and finance, specifically when it comes to fixed income.
Here are some new developments –
Private Credit Funds – The Build Asset Management Secured Income Fund I is a private credit fund created by Build Asset Management. This fund primarily invests in bitcoin-backed, collateralized business loans originated by Unchained, with a secured structure involving a multi-signature, over-collateralized setup for risk management. Unchained originates loans and sells them to Build, which pools them into the fund, enabling investors to share in the interest income.
Dynamics
- Loan Terms: Unchained issues loans at interest rates around 14%, secured with a 2/3 multi-signature vault backed by a 40% loan-to-value (LTV) ratio.
- Fund Mechanics: Build buys these loans from Unchained, thus providing liquidity to Unchained for further loan originations, while Build manages interest payments to investors in the fund.
Pros
- The fund offers a unique way to earn income via bitcoin-collateralized debt, with protection against rehypothecation and strong security measures, making it attractive for investors seeking exposure to fixed income with bitcoin.
Cons
- The fund is only available to accredited investors, which is a regulatory standard for private credit funds like this.
Corporate Bonds – MicroStrategy Inc. (MSTR), a business intelligence company, has leveraged its corporate structure to issue bonds specifically to acquire bitcoin as a reserve asset. This approach allows investors to indirectly gain exposure to bitcoin’s potential upside while receiving interest payments on their bond investments. Some other publicly traded companies have also adopted this strategy, but for the sake of this article we will focus on MSTR as they are the biggest and most vocal issuer.
Dynamics
-
Issuance: MicroStrategy has issued senior secured notes in multiple offerings, with terms allowing the company to use the proceeds to purchase bitcoin.
-
Interest Rates: The bonds typically carry high-yield interest rates, averaging around 6-8% APR, depending on the specific issuance and market conditions at the time of issuance.
-
Maturity: The bonds have varying maturities, with most structured for multi-year terms, offering investors medium-term exposure to bitcoin’s value trajectory through MicroStrategy’s holdings.
Pros
-
Indirect Bitcoin exposure with income provides a unique opportunity for investors seeking income from bitcoin-backed debt.
-
Bonds issued by MicroStrategy offer relatively high interest rates, appealing for fixed-income investors attracted to the higher risk/reward scenarios.
Cons
-
There are credit risks tied to MicroStrategy’s financial health and bitcoin’s performance. A significant drop in bitcoin prices could strain the company’s ability to service debt, increasing credit risk.
-
Availability: These bonds are primarily accessible to institutional investors and accredited investors, limiting availability for retail investors.
Interest Payable in Bitcoin – River has introduced an innovative product, bitcoin Interest on Cash, allowing clients to earn interest on their U.S. dollar deposits, with the interest paid in bitcoin.
Dynamics
-
Interest Payment: Clients earn an annual interest rate of 3.8% on their cash deposits. The accrued interest is converted to Bitcoin daily and paid out monthly, enabling clients to accumulate Bitcoin over time.
-
Security and Accessibility: Cash deposits are insured up to $250,000 through River’s banking partner, Lead Bank, a member of the FDIC. All Bitcoin holdings are maintained in full reserve custody, ensuring that client assets are not lent or leveraged.
Pros
-
There are no hidden fees or minimum balance requirements, and clients can withdraw their cash at any time.
-
The 3.8% interest rate provides a predictable income stream, akin to traditional fixed-income investments.
Cons
-
While the interest rate is fixed, the value of the Bitcoin received as interest can fluctuate, introducing potential variability in the investment’s overall return.
-
Interest rate payments are on the lower side
Admittedly, this is a very small list, however, these types of investments are growing more numerous and meaningful. The reality is the existing options aren’t numerous enough to service every client that has a need for fixed income exposure. I challenge advisors to explore innovative options for fixed income exposure outside of sovereign debt, as that is most certainly a road to nowhere. It is my wholehearted belief and call to action that we need more options to help clients across the risk and capital allocation spectrum access a sound money standard.
Additional Resources
-
River: The future of saving is here: Earn 3.8% on cash. Paid in Bitcoin.
-
MicroStrategy: MicroStrategy Announces Pricing of Offering of Convertible Senior Notes
Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net
-
-
 @ a305a0de:21557ddd
2024-12-02 10:35:38
@ a305a0de:21557ddd
2024-12-02 10:35:38In today's fast-paced world, it's easy to get caught up in the hustle and bustle of daily life. Our minds are constantly racing, and it's not uncommon to feel stressed, anxious, or overwhelmed. But what if there was a way to break free from this cycle of negativity and cultivate a sense of calm, clarity, and happiness?
Enter mindfulness, a powerful practice that has been shown to have a positive impact on both physical and mental health. By incorporating mindfulness into your daily routine, you can reduce stress and anxiety, improve your relationships, increase your productivity, and even live a longer, happier life.
What is Mindfulness?
Mindfulness is the practice of being present in the moment, paying attention to your thoughts, feelings, and sensations without judgment or distraction. It's about cultivating a sense of awareness and acceptance, and learning to appreciate the beauty and simplicity of life.
The Benefits of Mindfulness
The benefits of mindfulness are numerous and well-documented. Some of the most significant advantages include:
- Reduced stress and anxiety
- Improved relationships and communication skills
- Increased productivity and focus
- Enhanced creativity and problem-solving abilities
- Better sleep quality and duration
- Improved overall health and well-being
How to Practice Mindfulness
Incorporating mindfulness into your daily routine is easier than you might think. Here are a few simple tips to get you started:
- Start small: Begin with short periods of mindfulness practice, such as 5-10 minutes per day.
- Focus on your breath: Bring your attention to your breath, noticing the sensation of the air moving in and out of your body.
- Practice mindfulness in daily activities: Bring mindfulness into your daily routine by paying attention to your thoughts, feelings, and sensations while you're doing everyday tasks like eating, walking, or showering.
Conclusion
Mindfulness is a powerful practice that has the potential to transform your life in countless ways. By incorporating mindfulness into your daily routine, you can reduce stress and anxiety, improve your relationships, increase your productivity, and even live a longer, happier life. So why not give it a try? Your mind, body, and spirit will thank you.
-
 @ a305a0de:21557ddd
2024-12-02 10:18:16
@ a305a0de:21557ddd
2024-12-02 10:18:16Space tourism is no longer just the stuff of science fiction. With private companies like Virgin Galactic, SpaceX, and Blue Origin leading the charge, the industry is poised for exponential growth in the coming years.
But what exactly is space tourism, and how will it change the way we travel? In this article, we'll explore the exciting future of space tourism and what it means for you.
Suborbital Flights: The First Step
Suborbital flights, which take passengers to the edge of space without entering orbit, are the first step in space tourism. Virgin Galactic's SpaceShipTwo, for example, has already carried several passengers to an altitude of 62 miles (100 km) above the Earth's surface.
These flights offer a thrilling experience, with passengers experiencing weightlessness and witnessing breathtaking views of the curvature of the Earth. And with prices starting at around $250,000 per seat, suborbital flights are becoming increasingly accessible to the general public.
Lunar Resorts: The Next Frontier
But suborbital flights are just the beginning. Lunar resorts, which would allow tourists to stay on the Moon for extended periods, are the next frontier in space tourism.
Private companies like SpaceX and Blue Origin are already working on establishing a human presence on the Moon, with plans to send tourists there in the near future. And with NASA's Artemis program aiming to return humans to the Moon by 2024, the prospect of lunar tourism is becoming increasingly realistic.
Space Stations: The Ultimate Getaway
Space stations, which would offer tourists the opportunity to stay in orbit around the Earth for extended periods, are another exciting development in space tourism.
Private companies like Axiom Space and Bigelow Aerospace are already working on establishing space stations, which would offer tourists a unique and unforgettable experience. And with NASA's plans to establish a sustainable presence in low-Earth orbit, space stations could become a reality sooner rather than later.
Conclusion
Space tourism is no longer just a pipe dream, but a rapidly growing industry that's set to change the way we travel forever. From suborbital flights to lunar resorts and space stations, the possibilities are endless. And with private companies and governments around the world investing heavily in space tourism, the future of this exciting industry looks brighter than ever.
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 502ab02a:a2860397
2024-12-04 01:37:46
@ 502ab02a:a2860397
2024-12-04 01:37:46
ผมไถ tiktok ก่อนนอนตามประสาคนเสพแสงฟ้า 555 พบว่ามีไวรัลอาหารเช้าแบบนึง ที่มีคนทำคลิปกันเยอะพอสมควร ชื่อว่า Balkan Breakfast ก็อดสงสัยไม่ได้เลยกลายเป็นว่า ต้องไถหาข้อมูลเพื่อทำความเข้าใจ จนมาสรุปย่อให้เพื่อนๆที่อาจสงสัยเหมือนผม ได้อ่านกันขำๆไว้ด้วยครับ ออกตัวไว้ก่อนว่า ผมไม่ใช่ชาวบอลข่าน จึงไม่ได้รู้ดีแบบลึกซึ้งนะครับ
เรื่องมีอยู่ว่าในแถบคาบสมุทรบอลข่าน (Balkan Peninsula) ที่เต็มไปด้วยวัฒนธรรมและประวัติศาสตร์อันยาวนาน อาหารเช้านั้นจึงถือเป็นสิ่งสำคัญที่สะท้อนเอกลักษณ์ท้องถิ่นได้อย่างชัดเจน Balkan Breakfast คืออาหารเช้าที่ผสมผสานความเรียบง่ายและวัตถุดิบธรรมชาติไว้อย่างลงตัว ซึ่งในแถบบอลข่านครอบคลุมพื้นที่หลากหลาย เช่น เซอร์เบีย บัลแกเรีย โครเอเชีย และมาซิโดเนีย อาหารเช้าในภูมิภาคนี้ได้รับอิทธิพลจากทั้งวัฒนธรรมออตโตมัน ยุโรปตะวันออก และกรีก ตัวอย่างเมนูที่มักพบในอาหารเช้าแบบ traditional นี้มักจะประกอบไปด้วย - Burek: แป้งฟิโลสอดไส้เนื้อ ชีส หรือผักโขม - Kajmak: ครีมชีสที่มีรสชาติเข้มข้น มักทานคู่กับขนมปัง - Ajvar: ซอสพริกหยวกแดงและมะเขือยาว มีรสชาติกลมกล่อม - Proja: ขนมปังข้าวโพดที่นิยมเสิร์ฟพร้อมโยเกิร์ต - ผักสด: เช่น แตงกวา แตงกวาดอง Bell Pepper มะเขือเทศ หรือ หัวหอมใหญ่ เพิ่มความสดชื่นและสีสันให้จานอาหาร
อธิบายอาหารเพิ่มเติมเพื่อให้เห็นภาพนะครับ Burek (บูเร็ก) คือขนมอบที่มีต้นกำเนิดจากแถบบอลข่าน โดยเฉพาะในประเทศตุรกี, เซอร์เบีย, บอสเนีย, มาซิโดเนีย และประเทศอื่นๆ ในภูมิภาคนี้ Burek เป็นขนมอบที่ทำจากแป้งฟิโล Burek มีหลายรูปแบบ โดยทั่วไปจะทำเป็นพายหรือม้วน ขึ้นอยู่กับการห่อหรือจัดรูปทรง โดยส่วนใหญ่จะใช้แป้งฟิโลห่อไส้ให้เป็นชั้นๆ แล้วนำไปอบจนได้ความกรอบและสีน้ำตาลทอง ไส้ของ Burek สามารถมีได้หลากหลายชนิดเช่น บูเร็กไส้เนื้อวัวหรือเนื้อแกะ บูเร็กไส้ชีสโดยมักใช้ชีสเฟตาหรือชีสมอสซาเรลล่า ไส้ผักที่ใช้ผักโขมหรือมันฝรั่ง หรือบางทีก็ไส้ผสมกันไปเลยครับ เนื้อกับชีส เนื้อกับผัก ชีสกับผัก เอาจริงๆก็แล้วแต่สะดวก
ส่วนแป้งฟิโล (Phyllo Dough) นั้นเป็นแป้งชนิดหนึ่งที่ใช้ในอาหารหลากหลาย โดยเฉพาะในอาหารเมดิเตอร์เรเนียนและแถบบอลข่าน ลักษณะเด่นของแป้งฟิโลคือความบางเหมือนกระดาษและความยืดหยุ่น มักใช้เป็นชั้นๆ ซ้อนกันในเมนูที่ต้องการความกรอบเมื่ออบหรือทอด ต่างจากแป้งพัฟ (Puff Pastry) ที่มีไขมันผสมในเนื้อแป้ง แป้งฟิโลมักใช้น้ำมันหรือเนยทาแยกแต่ละชั้นเพื่อเพิ่มความกรอบ ส่วนประกอบของแป้งฟิโลจะมี แป้งสาลี น้ำ เกลือ
Kajmak (อ่านว่า ไค-มัก หรือ คาย-มัก) เป็นผลิตภัณฑ์นมชนิดหนึ่งที่มีต้นกำเนิดจากแถบบอลข่านและคอเคซัส นิยมใช้ในอาหารหลากหลายประเภททั้งในเซอร์เบีย บอสเนีย มอนเตเนโกร ตุรกี และประเทศใกล้เคียง Kajmak คือ ครีมชีสดั้งเดิมทำจากนมดิบ เช่น นมวัว นมควาย หรือนมแพะ ที่มีลักษณะคล้ายครีมหนาและเนย อุดมไปด้วยไขมันและมีรสชาติที่นุ่มละมุน บางครั้งจะมีรสเปรี้ยวเล็กน้อยเนื่องจากกระบวนการหมัก เนื้อสัมผัสนุ่มคล้ายครีม มีความมันสูง
Ajvar (อ่านว่า ไอ-วาร์ หรือ อัย-วาร์) เป็นเครื่องจิ้มและเครื่องเคียงที่มีต้นกำเนิดจากภูมิภาคบอลข่าน โดยเฉพาะในประเทศเซอร์เบีย มาซิโดเนีย และประเทศรอบๆ Ajvar เป็นที่นิยมในอาหารท้องถิ่นและมักเสิร์ฟคู่กับขนมปัง เนื้อย่าง หรืออาหารประเภทอื่นๆ Ajvar นั้นทำมาจาก พริกหวานแดง (Red Bell Pepper) เป็นส่วนผสมหลัก บางสูตรอาจเพิ่ม มะเขือยาว และ กระเทียม เพื่อเพิ่มรสชาติ มีเนื้อสัมผัสที่เนียนละเอียดหรือหยาบเล็กน้อย แล้วแต่สูตรครับ วิธีทำ Ajvar คือ ย่างหรืออบพริกหวานและมะเขือยาว เพื่อให้ได้กลิ่นหอมและรสชาติที่เข้มข้น จากนั้นปอกเปลือกเอาเปลือกที่ไหม้ออกเพื่อความนุ่มเนียน แล้วจึงนำไปบดหรือปั่นส่วนผสมจนได้เนื้อที่ต้องการ จบด้วยการผัดในน้ำมันเคี่ยวส่วนผสมทั้งหมดในน้ำมันจนเข้ากันดี Ajvar มี2แบบคือ แบบหวาน (Sweet Ajvar) จะไม่มีพริกเผ็ด รสชาติเข้มข้นแต่ไม่เผ็ด แบบเผ็ด (Hot Ajvar) จะใส่พริกเผ็ดหรือพริกป่นเพื่อเพิ่มความเผ็ด
Proja (โปรยา) เป็นขนมปังที่อร่อยและสะดวกในการทำ เป็นทางเลือกที่ดีในการรับประทานอาหารประเภทขนมปังที่แตกต่างจากขนมปังสไตล์ตะวันตกที่เราคุ้นเคยกัน โดยเป็นขนมปังข้าวโพดหรือขนมปังประเภทแป้งข้าวโพดที่มีต้นกำเนิดจากแถบบอลข่าน โดยเฉพาะในประเทศเซอร์เบีย, มาซิโดเนีย, บอสเนีย และโคโซโว Proja มักเสิร์ฟเป็นอาหารข้างเคียงกับจานหลัก เช่น เนื้อย่าง ไส้กรอก หรือ ซุป หรือเสิร์ฟกับ โยเกิร์ต และ ชีส สำหรับมื้อเช้า บางครั้งก็จะมีการใส่สมุนไพรหรือชีสลงไปในเนื้อขนมปังเพื่อเพิ่มรสชาติ ลักษณะของ Proja นั้นจะเป็นขนมปังที่มีความหนานุ่ม เนื้อแน่น และมักจะมีรสชาติหวานนิดๆ หรือเค็ม ขึ้นอยู่กับสูตรและการปรุง มีรสชาติคล้ายขนมปังข้าวโพดแบบดั้งเดิม แต่เนื้อสัมผัสจะมีความเบากว่า
มื้อเช้าสไตล์บอลข่านมักจัดอย่างเรียบง่ายแต่เต็มไปด้วยรสชาติและคุณค่า โดยมีเครื่องดื่มเสริม เช่น กาแฟหรือชาสมุนไพร หรือโยเกิร์ต ส่วนบางคลิปใน tiktok จะเห็นว่ามีการดื่มน้ำมันมะกอก หรือ เอาขนมปังจิ้มน้ำมันมะกอกด้วย อันนี้เท่าที่หาข้อมูลมา ยังไม่ปรากฎว่ามีใน balkan breakfast แบบทั่วไปนัก น่าจะเป็นการประยุกต์ในยุคนี้ครับ เพราะวัตถุดิบจะใกล้เคียงกับเมดิเตอเรเนียนไดเอท รวมถึงน้ำมันมะกอกถือเป็นส่วนสำคัญของอาหารในแถบนี้ เนื่องจากพื้นที่บอลข่านบางส่วน เช่น แอลเบเนีย โครเอเชีย และมอนเตเนโกร มีการปลูกมะกอกคุณภาพสูง น้ำมันที่ได้จึงเป็นน้ำมันมะกอกบริสุทธิ์ (Extra Virgin Olive Oil) ซึ่งมีรสชาติและกลิ่นเฉพาะตัว
ใน TikTok นั้น Balkan Breakfast เป็นไวรัลคลิปได้ง่าย เพราะการถ่ายทำแบบ ASMR ที่เน้นเสียงการกินที่ดังกว่าปกติ ทำให้ดึงดูดสายตาให้หยุดดูคลิปได้ง่าย บนโต๊ะประกอบกับผักสดต่างๆเช่น แตงกวา Bell Pepper และหัวหอมใหญ่ ที่จัดเรียงบนจานร่วมกับชีส โยเกิร์ต ส่วนของบางอย่างอาจใช้ของทดแทนแบบง่ายๆเช่น ขนมปัง หรือบาแกต แทน Burek ซอสมะเขือเทศ แทน Ajvar
การกลับมาเป็นที่นิยมของ Balkan Breakfast ใน TikTok ช่วยให้วัฒนธรรมบอลข่านนี้เผยแพร่ไปทั่วโลก พร้อมแสดงให้เห็นว่าอาหารเช้าแบบ traditional สามารถผสมผสานกับไลฟ์สไตล์ยุคใหม่ได้อย่างลงตัวอยู่เหมือนกัน
บางกรณีก็บอกว่า Balkan Breakfast เป็นมื้ออาหารที่ช่วยกระตุ้นการทำงานของโพรไบโอติกส์ เนื่องจากมีโยเกิร์ตและผักต่างๆและซอสที่มีคุณสมบัติพรีไบโอติกส์รวมเข้าด้วยกัน
บางกรณีก็บอกว่าเป็นแค่แฟชั่นฉาบฉวย กินแบบไม่ตรงต้นฉบับ ต้องการแค่ของมากองๆหน้าจอแล้วกัดให้ดังๆ ซู้ดให้มีเสียงเพื่อเรียกยอดวิว
ก็เรื่องอาหารจะเช่นเดิมครับ ผมมองว่าไม่มีผิดไม่มีถูก สำหรับผมแล้วมองว่า การกินแยกกันทีละคำแบบนี้ ถ้าจับอย่างละนิดหน่อยมารวมกัน ในชิ้นเดียวก็แซนวิชดีๆนี่แหละครับ enjoy การกินแบบไหนก็แบบนั้นไปได้เลยครับ คนเรากินตามที่ชอบที่ชอบอยู่แล้วครับ คิดมากฉี่เหลือง ถ้ามองสารอาหารกรณีที่ไม่ได้ limit คาร์บ ก็ถือว่าเป็นมื้ออาหารที่ไม่แย่ กรณีถ้ามีไส้กรอกก็พยายามดูตัวที่ไม่ได้อุตสาหกรรมมาก ส่วนถ้าใคร limit คาร์บก็พึงระวัง เพราะคาร์บหนักพอสมควรเนื่องจากเน้นการให้พลังงานครับ
bon appétit
#กูต้องรู้มั๊ย #PirateKeto #siripun
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 33fc2c28:5d1a1a6e
2024-12-02 06:01:24
@ 33fc2c28:5d1a1a6e
2024-12-02 06:01:24"The world can be a daunting place, where survival of the fittest reigns supreme. It's a realm where selfishness often thrives, and the strong tend to flourish, while the weak struggle to keep up. In this unforgiving landscape, one's physical appearance, intellectual prowess, and social status can greatly impact their opportunities and treatment.
Moreover, the pressure to succeed is relentless, and the fear of failure can be overwhelming. Poverty and lack of achievement are often stigmatized, leaving those who struggle to make ends meet feeling marginalized and disenfranchised.
And yet, despite these challenges, I remain undeterred. I recognize that the world may be a difficult place, but I also believe that it is full of possibilities and opportunities waiting to be seized. I am determined to push forward, to strive for excellence, and to never give up on my dreams.
For I know that the only way to truly conquer the world is to first conquer myself. To overcome my fears, to push past my limitations, and to unlock my full potential. And when I do, I will be unstoppable.
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ a012dc82:6458a70d
2024-12-02 05:49:43
@ a012dc82:6458a70d
2024-12-02 05:49:43Table Of Content
-
The Awakening of the Bitcoin Whales
-
The Big Moves
-
The Implications of the Whale Movements
-
The Mystery of the Whales
-
Conclusion
-
FAQ
In the vast, uncharted waters of the cryptocurrency market, Bitcoin whales are the most colossal creatures, akin to the blue whales of the physical oceans. These are the investors who hold a significant amount of Bitcoin, often untouched for years, while they watch their astronomical gains grow. They're the silent observers, the patient players who understand the game of waiting. However, the usually calm waters have recently been stirred, with nearly $60 million in Bitcoin transferred in just five days. This article dives deep into this unusual activity, exploring the potential implications and the mystery surrounding these Bitcoin whales. We'll delve into who these whales might be, why they're moving their Bitcoin now, and what this could mean for the future of cryptocurrency.
The Awakening of the Bitcoin Whales
The term 'Bitcoin whales' refers to investors who hoard substantial amounts of Bitcoin, typically at least 1,000 BTC, and let it sit for years. These investors have proven to be more successful than short-term traders, given Bitcoin's extreme volatility in the short term. Over the past decade, Bitcoin has surged from under $95 per coin to $29,203—a whopping 30,700% increase. This long-term view and the patience to hold onto their assets have often resulted in significant rewards for these whales. However, recently, these long-dormant Bitcoin whales have shown signs of activity. In a span of five days, several wallets holding millions of dollars in Bitcoin moved their holdings after years of dormancy. This sudden movement has caused ripples throughout the cryptocurrency community, leading to speculation about the motives behind these transactions and what it could mean for the future of Bitcoin.
The Big Moves
The recent whale activity began on July 20, when two wallets from 2011, each holding 10 BTC (valued at $292,767 at the time), moved their holdings to new locations. This movement, after such a long period of inactivity, was notable in itself. However, the following day, a wallet holding 5 BTC ($146,383) also budged after 12 years of inactivity. This continued activity suggested a trend rather than an isolated incident. Then, the most significant movement occurred when around $30.3 million in Bitcoin—or 1,037 BTC—moved after its owner transferred it to a new wallet for the first time since 2012. This was a significant shift, representing a substantial amount of Bitcoin. Finally, on July 24, a wallet from 2010 moved a hefty 50 BTC, or about $1.4 million. This series of movements over such a short period was unusual and caught the attention of many in the cryptocurrency community.
The Implications of the Whale Movements
Blockchain data firm Glassnode reported a "dramatic uptick over recent months" in whale activity. Many whales have been moving holdings to exchanges, usually the best way to cash out or shift holdings to other digital assets. This trend could indicate that these whales are preparing to sell or diversify their holdings, which could have significant implications for the Bitcoin market. If these whales decide to sell a large portion of their holdings, it could lead to an increase in the supply of Bitcoin on the market, potentially driving down prices. This could create a buyer's market, where there is more Bitcoin available than people are willing to buy. On the other hand, if these whales are moving their Bitcoin to diversify their holdings, it could lead to increased investment in other cryptocurrencies, potentially driving up their prices. This could stimulate the entire cryptocurrency market, leading to increased interest and investment in a variety of cryptocurrencies.
The Mystery of the Whales
While the recent whale movements have sparked intrigue, the identities of these Bitcoin whales remain a mystery. It isn't clear whether these whales are individuals or companies. Dr. Kirill Kretov, a developer of tools for automated trading and blockchain analyst, suggested that these transactions might represent commercial entities buying Bitcoin from individuals. This could indicate a shift in the market, with businesses becoming more involved in cryptocurrency. However, without concrete information, this remains speculation. The anonymity of Bitcoin transactions makes it difficult to determine the identities of these whales, adding to the intrigue and speculation surrounding these movements.
Conclusion
The recent movements of Bitcoin whales have undoubtedly made waves in the cryptocurrency community. While the reasons behind these movements remain speculative, they highlight the significant influence that these whales have on the Bitcoin market. As the crypto world continues to evolve, the actions of these Bitcoin whales will undoubtedly continue to shape the landscape. Whether these movements signal a storm or just a ripple in the water, only time will tell. However, one thing is clear: the actions of these whales are worth watching, as they could provide valuable insights into the future of Bitcoin and the cryptocurrency market as a whole.
FAQ
What is a Bitcoin whale? A Bitcoin whale is an investor who holds a significant amount of Bitcoin, typically at least 1,000 BTC, often untouched for years.
What recent activity has been observed among Bitcoin whales? Recently, Bitcoin whales have transferred nearly $60 million in Bitcoin in just five days, moving their holdings to new locations after years of dormancy.
What could be the implications of these whale movements? The movements could indicate that these whales are preparing to sell or diversify their holdings. This could potentially affect the Bitcoin market, either by increasing the supply of Bitcoin (which could drive down prices) or by stimulating investment in other cryptocurrencies.
Who are these Bitcoin whales? The identities of these Bitcoin whales remain a mystery. They could be individuals or companies, but the anonymity of Bitcoin transactions makes it difficult to determine.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 33baa074:3bb3a297
2024-12-02 02:37:44
@ 33baa074:3bb3a297
2024-12-02 02:37:44Infrared sensors have shown great potential and innovative applications in the field of energy saving due to their unique non-contact detection capabilities. The following are specific application cases in several aspects: Intelligent lighting system The application of infrared sensors in intelligent lighting systems is a typical case of energy-saving innovation. Through infrared heat release sensors, the system can automatically detect human activity information and automatically switch lighting fixtures on and off accordingly. This design not only improves lighting convenience, but also significantly reduces unnecessary energy consumption. For example, the automatic switching of LED street lights can be realized through light-sensitive sensors, while community night walkway and courtyard lighting can be controlled through infrared heat release sensors to ensure that lighting is only turned on when someone is active. Air conditioning control system In air conditioning control systems, infrared sensors can be used to detect indoor human activity to optimize the operating mode of the air conditioner. For example, when no one is detected in the room, the air conditioner can automatically reduce power or enter standby mode to avoid energy waste. This application not only improves the energy efficiency of the air conditioner, but also enhances the user experience as the system adjusts the temperature according to actual demand. Street light control system Street light control systems based on infrared sensors are also an effective energy-saving measure. This system uses photoelectric infrared sensors to detect the approach of pedestrians or vehicles and automatically illuminates street lights when activity is detected. When the event is over, the street lights will automatically turn off after a period of time to save power. Such a design is not only responsive, but can also adjust the lighting according to actual needs to avoid unnecessary lighting for a long time. Summarize Innovative applications of infrared sensors for energy conservation demonstrate their great potential for improving energy efficiency and user convenience. By combining with modern electronic technology and intelligent control systems, infrared sensors are becoming one of the key technologies that promote the development of smart homes, smart buildings and smart cities. As technology continues to advance, we can expect infrared sensors to play an even more important role in energy conservation in the future.
-
 @ ae6ce958:d0f02c7d
2024-12-03 23:55:48
@ ae6ce958:d0f02c7d
2024-12-03 23:55:48As blockchain technology continues to revolutionize industries, regulatory compliance remains a key concern for businesses engaging in token sales. For DamageBDD, an Australian-registered business offering Damage Tokens, compliance with Australian laws is critical. This article explores why DamageBDD cannot sell Damage Tokens without implementing Know Your Customer (KYC) protocols.
Regulatory Landscape for Token Sales in Australia
In Australia, the regulation of digital assets is governed by the Corporations Act 2001 and overseen by the Australian Securities and Investments Commission (ASIC). Additionally, businesses handling digital currencies or assets may fall under the scope of the Anti-Money Laundering and Counter-Terrorism Financing Act 2006 (AML/CTF Act), enforced by AUSTRAC (Australian Transaction Reports and Analysis Centre).
The classification of a token—whether as a utility, payment, or security token—determines the regulatory requirements. However, even utility tokens can trigger KYC obligations depending on their functionality and how they are sold.
Legal Obligations for DamageBDD
As a registered Australian business, DamageBDD must comply with the following legal and regulatory requirements:
- Anti-Money Laundering (AML) and Counter-Terrorism Financing (CTF) Laws
If Damage Tokens are traded for fiat currency or cryptocurrencies (e.g., Bitcoin), the transactions may fall under the definition of "designated services" in the AML/CTF Act. This classification requires businesses to:
Register with AUSTRAC.
Conduct customer identification and verification (KYC).
Report suspicious transactions and large cash transactions to AUSTRAC.
Failure to comply with these requirements can result in significant fines or legal action.
- Securities and Investment Laws
If Damage Tokens are deemed to have characteristics of financial products (e.g., offering investment returns or being tradable on secondary markets), they may be classified as securities under the Corporations Act 2001. Selling such tokens would require:
KYC compliance.
Licensing as an Australian Financial Services (AFS) provider or operating under an authorized exemption.
Even if the tokens are marketed as utility tokens, their classification can change based on how they are used, sold, or perceived in the market.
Risks of Selling Without KYC
Selling Damage Tokens without KYC exposes DamageBDD to significant legal and reputational risks:
-
Regulatory Breaches: If regulators determine that Damage Tokens fall under AML or securities laws, selling without KYC could result in penalties or the suspension of business operations.
-
Enabling Illegal Activities: Without KYC, there is a higher risk of tokens being used for money laundering, terrorism financing, or other illicit purposes.
-
Loss of Market Confidence: Non-compliance can damage trust with customers, partners, and investors, hindering the long-term success of DamageBDD.
The Importance of KYC for DamageBDD
Implementing KYC is not just about regulatory compliance; it also enhances the credibility and security of DamageBDD:
Protecting Customers: Ensures that tokens are used by legitimate individuals and businesses.
Building Trust: Demonstrates DamageBDD's commitment to ethical business practices.
Future-Proofing the Business: Prepares DamageBDD for evolving regulations, minimizing the risk of operational disruptions.
Steps for Compliance
To comply with Australian laws, DamageBDD can take the following steps:
-
Token Classification: Work with legal experts to confirm whether Damage Tokens are utility, payment, or security tokens.
-
AML/CTF Registration: Register with AUSTRAC and implement AML/CTF protocols.
-
KYC Process: Use digital identity verification tools to streamline KYC for token buyers.
-
Legal Advice: Continuously engage with legal advisors to stay updated on regulatory changes.
Conclusion
As a registered Australian business, DamageBDD operates in a regulatory environment that prioritizes transparency and the prevention of financial crimes. Selling Damage Tokens without KYC would not only breach Australian laws but also compromise the integrity and sustainability of the DamageBDD project. By embracing KYC and ensuring compliance, DamageBDD can establish itself as a trusted player in the blockchain industry, unlocking long-term growth and success.
AU #Compliance #Regulations
-
 @ 51ca7ccd:7baf47d6
2024-12-02 00:34:22
@ 51ca7ccd:7baf47d6
2024-12-02 00:34:22Self-care has become a popular term in recent years, and for good reason. It's about intentionally taking time to nurture your physical, emotional, and mental well-being. While often associated with pampering activities like taking a bath or getting a massage, self-care goes beyond that, involving practices that help reduce stress, improve resilience, and promote overall happiness and health.
The Importance of Self-Care
In today’s fast-paced world, many people feel overwhelmed by work, social obligations, and personal responsibilities. According to a study by the American Psychological Association (APA), chronic stress can lead to a range of mental and physical health issues, including anxiety, depression, high blood pressure, and heart disease. Taking regular time for self-care can help mitigate these effects by allowing individuals to recharge and focus on their well-being.
Self-care is not just about physical relaxation but also mental and emotional health. Research from the National Institutes of Health (NIH) highlights that self-care activities like mindfulness meditation or engaging in hobbies can have a significant impact on improving mood, reducing anxiety, and enhancing overall mental clarity (NIH, 2021).
Types of Self-Care
-
Physical Self-Care: This involves activities that take care of the body, such as exercise, eating nutritious meals, and getting enough sleep. Regular physical activity has been linked to improved mood, better sleep, and a lower risk of chronic conditions like heart disease and diabetes. A study published in JAMA Psychiatry confirms that even moderate exercise can reduce symptoms of depression and anxiety (JAMA Psychiatry, 2020).
-
Emotional Self-Care: Taking care of your emotional health is just as important as physical care. This includes activities that help you process and express your emotions in a healthy way, such as journaling, talking with loved ones, or practicing gratitude. Research from the Journal of Positive Psychology suggests that cultivating gratitude through journaling can significantly enhance emotional well-being and reduce stress (Journal of Positive Psychology, 2019).
-
Social Self-Care: Building and maintaining supportive relationships is key to self-care. Socializing with friends, joining communities, and having meaningful conversations can promote a sense of belonging and reduce feelings of loneliness. The National Institute on Aging found that strong social connections are linked to lower rates of depression and longer life expectancy (NIA, 2020).
-
Mental Self-Care: This involves stimulating the mind and improving cognitive function through activities like reading, solving puzzles, or learning new skills. Mental self-care helps boost concentration, creativity, and problem-solving abilities. Studies from the Harvard Medical School suggest that lifelong learning and engaging in intellectual activities can help maintain cognitive function as we age (Harvard Health Publishing, 2021).
Overcoming Barriers to Self-Care
While self-care is essential, it can sometimes feel like another task on a never-ending to-do list, especially for those with busy schedules. However, even small, consistent efforts can lead to meaningful improvements. A key to overcoming barriers to self-care is to view it as a priority rather than a luxury. This mindset shift helps individuals make time for self-care, even during challenging times.
Incorporating self-care into daily routines doesn’t need to be time-consuming or expensive. It can be as simple as taking five minutes each morning for deep breathing exercises or setting aside time each week to enjoy a favorite hobby. The key is consistency and finding activities that align with personal preferences and needs.
The Long-Term Benefits of Self-Care
Engaging in self-care practices consistently can lead to lasting benefits, including improved physical health, better emotional regulation, and increased resilience in the face of challenges. By investing in your own well-being, you are better equipped to handle life’s stresses and support others around you.
As we continue to navigate a world that demands more from us every day, prioritizing self-care is not only a way to thrive but also a necessity for long-term health and happiness
-
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 51ca7ccd:7baf47d6
2024-12-01 23:29:52
@ 51ca7ccd:7baf47d6
2024-12-01 23:29:52Personal growth is not a destination, but a continuous journey. It's a process of evolving into the best version of yourself, and it often requires embracing change, even when it feels uncomfortable or uncertain. As we navigate life, we encounter moments of transformation that challenge who we are and push us to expand beyond our limits.
One of the most profound aspects of personal growth is the realization that change is not something to fear, but something to embrace. Change is inevitable. Whether it's a shift in perspective, a new opportunity, or a personal challenge, growth often comes from stepping outside of our comfort zones. For many, the biggest hurdle is accepting that change is a natural part of life—something that should be welcomed, not resisted.
At the core of personal growth lies self-awareness. Understanding your strengths, weaknesses, and areas for improvement helps to clarify the path forward. It's through this awareness that you can begin to make intentional choices, whether it's pursuing new goals, working on emotional intelligence, or letting go of past habits that no longer serve you. Growth comes when you are honest with yourself and willing to confront uncomfortable truths.
Another essential aspect of growth is resilience. Life will inevitably throw challenges your way—times when you feel lost, discouraged, or defeated. But these are the moments when your ability to bounce back, learn from mistakes, and keep moving forward matters most. Resilience is about adapting and using adversity as fuel for transformation. It's not about avoiding pain, but about finding strength in it.
Faith also plays a crucial role in personal growth. Whether it’s your belief in God, in the universe, or in yourself, having faith can be the anchor that keeps you grounded during difficult times. Faith provides perspective, patience, and trust in the process. It reminds you that the setbacks you face are not permanent and that transformation is always possible.
As you embrace change, remember that personal growth is not always linear. There will be moments of progress, but there will also be setbacks. It’s important to be kind to yourself during these times and recognize that growth takes time. Celebrate the small wins along the way—each step forward, no matter how small, is a victory in itself.
Ultimately, personal growth is about discovering who you are meant to be and becoming comfortable with that person. It’s a process of shedding old layers, confronting fears, and embracing new experiences. Each chapter of your life, each transformation, leads you closer to the person you’re destined to become
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ ec951079:533d29e7
2024-12-01 21:47:55
@ ec951079:533d29e7
2024-12-01 21:47:55The Rise of Artificial Intelligence: Transforming Industries and Revolutionizing Lives
Artificial intelligence (AI) has been a topic of fascination for decades, captivating the imagination of scientists, entrepreneurs, and the general public alike. From science fiction to reality, AI has evolved significantly over the years, transforming industries, revolutionizing lives, and redefining the future.
What is Artificial Intelligence?
Artificial intelligence refers to the development of computer systems that can perform tasks that typically require human intelligence, such as:
- Learning
- Problem-solving
- Reasoning
- Perception
- Language understanding
AI systems use algorithms, statistical models, and machine learning techniques to analyze data, make decisions, and improve their performance over time.
Applications of Artificial Intelligence
AI has numerous applications across various industries, including:
- Healthcare: AI-powered diagnostic tools, personalized medicine, and robotic surgery.
- Finance: AI-driven trading platforms, risk management systems, and customer service chatbots.
- Transportation: Self-driving cars, intelligent traffic management systems, and predictive maintenance.
- Education: AI-based learning platforms, adaptive assessments, and personalized learning pathways.
- Customer Service: AI-powered chatbots, virtual assistants, and sentiment analysis tools.
Benefits of Artificial Intelligence
The benefits of AI are numerous and far-reaching, including:
- Increased Efficiency: Automation of repetitive tasks, freeing up human resources for more strategic and creative work.
- Improved Accuracy: AI systems can analyze vast amounts of data, reducing errors and improving decision-making.
- Enhanced Customer Experience: AI-powered chatbots and virtual assistants provide 24/7 customer support, improving customer satisfaction and loyalty.
- Innovation and Competitiveness: AI enables businesses to innovate, differentiate themselves, and stay ahead of the competition.
Challenges and Concerns
While AI offers numerous benefits, it also raises several challenges and concerns, including:
- Job Displacement: Automation of jobs, potentially displacing human workers.
- Bias and Discrimination: AI systems can perpetuate existing biases and discriminate against certain groups.
- Cybersecurity Risks: AI systems can be vulnerable to cyber attacks, compromising sensitive data and disrupting critical infrastructure.
- Ethics and Accountability: AI systems raise questions about accountability, transparency, and ethics, particularly in decision-making processes.
The Future of Artificial Intelligence
As AI continues to evolve and improve, we can expect to see significant advancements in various fields, including:
- Natural Language Processing: AI systems that can understand, interpret, and generate human language.
- Computer Vision: AI systems that can interpret, understand, and generate visual data.
- Edge AI: AI systems that can operate at the edge of the network, reducing latency and improving real-time decision-making.
- Explainable AI: AI systems that can provide transparent, interpretable, and explainable decisions and actions.
Conclusion
Artificial intelligence has the potential to transform industries, revolutionize lives, and redefine the future. While there are challenges and concerns associated with AI, the benefits of increased efficiency, improved accuracy, and enhanced customer experience make it an essential technology for businesses, governments, and individuals to explore and harness. As AI continues to evolve and improve, it is essential to address the challenges and concerns, ensuring that AI is developed and used responsibly, ethically, and for the betterment of society.
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ c755de14:cc53833a
2024-12-01 21:41:09
@ c755de14:cc53833a
2024-12-01 21:41:09
What is the meaning of patience?
Any conversation about what patience is and its importance will tend to mention that patience is a virtue. But there’s much more to it. Patience is your ability to wait without becoming annoyed, upset, or angry. It’s when you exercise self-control rather than lashing out and complaining.
You’re being patient when you take deep breaths and seek inner peace after things don’t go the way you hoped.
Practicing patience is all about how you act. It involves internalizing your emotions and interpreting the situation you’re in. When you’re being patient, you’ll stop and take a moment to look around while thinking about the bigger picture. That is, you won’t just think about your actions in the present moment but what they’ll mean down the road, too.
Patience also throws instant gratification out the window. You have the agency to do things that will make it easier for yourself in the short term. Or you can choose to avoid hasty decisions and take actions with long-term benefits. It may require more hard work, but patience pays off, even if it feels difficult in the moment.
Staying mindful of your emotions, behavior, and surroundings is a lot to practice. Learn how to practice self-control and patience, while being mindful of your Whole Self.
Why is patience so important in life?
How important patience is in life stretches far beyond being nice to others. It benefits your relationships with others and helps these relationships stay healthy over an extended period of time. Being a patient person also teaches you to regulate your emotions so that your well-being remains strong.
Being impatient causes stress, and chronic stress has detrimental effects on physical well-being. Your physical and mental health grows when you practice patience. You may find that you’ll experience less headaches, acne breakouts, and ulcers.
Patient people may also experience fewer negative emotions. That’s because with patience, you’re better equipped to deal with stressful and challenging moments in life. This helps your overall mental health and well-being.
Patience can even help you avoid and recover from burnout. Rather than work yourself to the extreme, patience reminds you to slow down and prioritize your own well-being
Can patience be developed?

If you think you’re an impatient person right now, don’t sweat it. With dedication and sustained efforts, everyone can develop patience. You can find a moment of patience in stressful situations by being mindful of others and your surroundings. Practicing gratitude also leads to patience. You can learn to become more patient anywhere — especially in the workplace.
To be a good leader, you need to understand that everyone contributes something special. Sometimes it takes an employee a few tries to hone their skills toward the team goal, making few mistakes. A good leader will reframe an error as a learning opportunity while being patient. They’ll reiterate the importance of teamwork and value everyone’s efforts to meet a deadline.
In the workplace, business leaders and organizations face a lot of uncertainty. Things don’t always go according to plan or how people predicted. When that happens, workplaces have to scrap their original plan and think of new things.
One survey found that when leaders demonstrate patience, productivity, creativity, and collaboration increases. When team members are in a patient atmosphere, they can complete tasks calmly and form strong, collaborative relationships. Patient leadership instills trust in the team and helps businesses succeed in the future.
The importance of patience in building strong relationships
The role of patience in our life isn’t exclusively individual. Being patient also helps you develop strong, healthy, long-lasting relationships. Your relationships with friends, family, and coworkers thrive when you practice patience.
It’s important to understand that patience isn’t transactional. When you’re patient with a person, don’t hold onto an expectation that they’ll give you something in return. Patience is about sustaining and bettering relationships — not holding your good deed above someone until they do you a favor.
Patient people may have an easier time being empathetic, kind, cooperative, and selfless. Being compassionate when others make mistakes helps create relationships where flaws are accepted.
-
 @ 0d532801:197a0c30
2024-12-01 21:27:48
@ 0d532801:197a0c30
2024-12-01 21:27:48
߹ İnsan, bilinçli olarak günah işlediğinde, aslında birçok içsel ve dışsal faktörün etkisi altındadır. Bu faktörlerin başında bireysel arzular, toplumsal baskılar, zayıflıklar, bilinçaltı dürtüler ve bazen de cehalet gelir. İnsan, sadece dürtülerine göre hareket etmeyi tercih edebilir ya da kısa vadeli tatmin için uzun vadeli sonuçları göz ardı edebilir. Peki, bir insan neden bilerek günah işler? Bu sorunun cevabı, sadece dini ya da etik perspektiflerle değil, psikolojik, toplumsal ve kültürel açılardan da ele alınmalıdır.
- Bireysel Arzular ve Dürtüler
߹ İnsanın doğasında, zaman zaman nefsini tatmin etme isteği vardır. Bu istek, bazen mantık ve vicdanın önüne geçebilir. İnsan, kısa süreli hazları arzularken, bunun gelecekteki olumsuz sonuçlarını göz ardı edebilir. Örneğin, hırsızlık yapan bir kişi, anlık bir mal edinme arzusuyla hareket edebilir, ancak bu davranışın ona ve çevresine getireceği zararları düşünmektense, elde edeceği çıkarı daha önemli görür. Benzer şekilde, yalan söylemek ya da başkalarını manipüle etmek de kısa vadeli çıkarlar ve bireysel egolar tarafından beslenen bir davranış biçimidir.
- Toplumsal Baskılar ve Çevresel Faktörler
߹ İnsan, toplumsal bir varlık olarak çevresinden büyük ölçüde etkilenir. Toplumun normları, kültürel değerleri, arkadaş gruplarının etkisi ve ailevi dinamikler, bireyin davranışlarını şekillendirir. Bazı durumlarda, kişi bilerek yanlış bir davranış sergileyebilir çünkü çevresindeki kişiler böyle yapmaktadır ve kendini dışlanmış hissetmemek için buna ayak uydurur. Örneğin, bir grup insanın başka birine kötü davranması ya da yalan söylemesi, bir bireyi de benzer şekilde davranmaya itebilir. Bu durum, bireyin vicdanı ve doğru-yanlış algısı ile çatışan bir durumdur.
- Zayıflıklar ve İnsan Doğası
߹ Herkesin zayıf anları vardır. Zihinsel ve duygusal olarak zorlandığı anlarda insanlar bazen bilerek yanlış bir şey yapabilir. İnsan, öfke, stres, yalnızlık ya da korku gibi duygusal durumlar içinde daha kolay günah işleyebilir. Duygusal karmaşa, sağlıklı düşünme yeteneğini zayıflatabilir ve kişi, anlık bir rahatlama ya da kaçış için yanlış bir yolu seçebilir. Örneğin, öfkelenen bir kişi, karşısındaki kişiye hakaret etmek ya da ona zarar vermek isteyebilir. Bu tür eylemler, kişinin o anki duygusal durumunun bir sonucu olarak ortaya çıkar.
- Cehalet ve Yanlış İnançlar
߹ Bazen insanlar, neyin doğru neyin yanlış olduğuna dair doğru bir bilgiye sahip olmayabilirler. Bilgi eksikliği ya da yanlış inanışlar, bireyin günah işlemesine neden olabilir. İnsan, kötü bir davranışın ne kadar zarar verebileceğini ya da o davranışın ahlaki ve dini boyutlarını tam anlamayabilir. Özellikle bazı insanlar, içinde bulundukları ortamın, alışkanlıkların ya da eğitim seviyelerinin etkisiyle, doğruyu ve yanlışı tam kavrayamayabilirler. Bu durum da, onların bilerek ve isteyerek günah işlemesine yol açabilir.
- İçsel Çatışmalar ve Vicdanın Bastırılması
߹ İnsan, bazen kendi içsel çatışmalarına dayanamayabilir. Vicdanı, doğruyu yapması yönünde onu uyarırken, içindeki kötü duygular ya da arzular ona engel olamayacak kadar güçlü olabilir. İnsanın kendisini haklı çıkarma çabası da burada devreye girebilir. Bir insan, kendini iyi bir insan olarak görmek isterken, bazen içindeki kötü dürtüleri bastırmak yerine, bunları haklı göstermek için kendine çeşitli gerekçeler uydurur. Örneğin, bir kişi başkasının hakkını yemek için kendini “bunu herkes yapıyor” ya da “benim de buna ihtiyacım var” gibi bahanelerle kandırabilir.
- Dini ve Ahlaki Değerlerin Zayıflaması
߹ Bir insanın dini inançları ya da ahlaki değerleri, doğru-yanlış algısını büyük ölçüde şekillendirir. Ancak zamanla, bireylerin inançları ya da değerleri zayıflayabilir. Toplumda sekülerleşmenin arttığı bir dönemde, dini ve ahlaki öğretiler zamanla insanların gözünde daha az değerli hâle gelebilir. Bu durumda, insanlar günah işleme konusunda daha az vicdan azabı duyarlar, çünkü dini ya da ahlaki sonuçları görmezden gelmeyi tercih edebilirler.
߹ Sonuç olarak, insanın bilerek günah işlemesi, karmaşık bir durumdur ve çok çeşitli faktörlere dayanır. İnsanlar bazen içsel isteklerine, bazen dışsal baskılara, bazen de bilinçli ya da bilinçsiz olarak zayıf noktalarına dayanarak yanlışlar yapabilirler. Önemli olan, insanın yaptığı hataları fark etmesi, bu hatalardan ders alması ve doğru yolu bulmaya çaba göstermesidir. Kişi, hatalarını kabul ederek ve daha bilinçli bir şekilde hareket ederek hem kendisine hem de çevresine faydalı bir yaşam sürebilir.
-
 @ bc6ccd13:f53098e4
2024-12-03 22:59:45
@ bc6ccd13:f53098e4
2024-12-03 22:59:45It is well enough that people of the nation do not understand our banking and monetary system, for if they did, I believe there would be a revolution before tomorrow morning.
-Henry Ford
A century later, this quote is still as true as the day it was written. And with all the information available at our fingertips, the overwhelming majority still haven't educated themselves on the function of the banking system. That's a tragedy, given the significant role banking plays in the modern economy, and the corruption at the very base of the industry.
Banking is built on a lie. It's a big lie. Not in the sense of how false it is, but in the sense of the harm caused. It's more of a “weasel words” type of lie, a lie of omission and misdirection, the kind of lie a sleazy lawyer would use to get a guilty client off the hook. My goal is to explain, as clearly as possible, how the modern banking system works. Why you should care will be a topic for another day.
I want to start off with a big thank you to whoever created the website https://banklies.org/. If you aren't familiar with this gem, bookmark it now. There's no better place on the internet to get detailed documentation on this particular subject. Everyone should spend an afternoon reading and listening to the information there. You'll never be able to see the world the same way if you absorb it and understand the implications.
Where Does Money Come From?
There's been a lot of talk since the COVID “pandemic” and associated QE deluge about the Fed and their money printing. Most people have some awareness that “the Fed prints money and that causes inflation.” There's some truth to that idea, but it also misses the real story. Most people don't understand that when someone says “money printing,” the correct response is “which kind of money?”
Banks operate by calling two different things “money,” and hoping everyone treats them the same. The average person might say “I have $100 in my wallet” or “I have $100 in my bank account” without realizing they aren't talking about the same thing at all. They might take the $100 in their wallet and “put it in the bank” without realizing that as soon as they do, that $100 becomes something else entirely.
The $100 bill in your wallet has the words “Federal Reserve Note” printed on it. This is one form of what's known as “base money.” Base money exists in two forms, cash and bank reserves. You can think of bank reserves as electronic cash that only banks can use.
Base money is created by the Federal Reserve. Creating base money is what the Fed does when they “print money.” They create bank reserves electronically by putting the numbers in the ledger at the Fed. The cash is printed by the Treasury, but that's just a technicality, it's printed at the request of the Fed.
The current circulating supply of cash is $2.3 trillion, and bank reserves are about $3.5 trillion. However, if you look at the total amount of US dollars, including money in people’s bank accounts, it’s currently $20.8 trillion dollars. So if base money is $5.8 trillion in total, what is the other $15 trillion? Well, it’s largely made up of bank deposits. So where do bank deposits come from? It can’t be cash people deposit into their accounts, like you might expect from the name, since cash only totals $2.3 trillion and bank deposits are over 6 times larger. The answer is that banks create them.
So as you can see, the largest category of dollars aren’t “printed” by the Fed, they’re created by the banks. And the way banks create dollars is so simple, it almost doesn’t seem real. Banks create money by making loans.
This seems completely counterintuitive to the way most people imagine banks work. That’s understandable, since the way banks work has almost no relation to the way individuals handle their own finances. You might make a loan to someone. Your friend asks to borrow $20 at the restaurant since he forgot his wallet at home. You pull yours out and hand him a $20 bill. In order to make that loan, you had to go to work, accomplish something, get paid, and save that $20 in your wallet. You couldn’t spend the $20, and you can’t spend it now until your friend pays back the loan. Obviously no new money was created to make that loan, work was done and money was saved and then given to the borrower so he can spend it instead of the lender.
Most people assume banks work the same way. They assume that when they deposit some money at the bank, the bank stores that money in a vault somewhere with their name on it. And they assume that when banks make loans, they take some money from a big pile of money stored in a vault somewhere and give it to the borrower. But that isn’t how it works at all.
When someone goes to the bank for a loan, the bank doesn’t draw on some pile of cash they have saved up somewhere. Instead, they use a simple accounting trick. They create a bank account for the borrower, and they type the amount of the loan into the borrower’s account balance. It’s really that simple. That balance becomes a “bank deposit.” Even though that money was never deposited in the bank, and in fact didn’t exist at all until the bank typed those numbers into the computer, it’s still called the same thing as the money you deposit into the bank when you get your paycheck.
So what is a bank deposit? It’s really a promise by the bank to give the account holder money. If you have $100 in your bank account, you expect to be able to go to the bank and withdraw that $100 in cash from your account and put it in your pocket. Remember, that $100 bill is base money, something completely different from the bank deposit in your savings or checking account. The implicit promise by banks is that any money in your bank account, any bank deposit, is as good as cash and can be exchanged for cash at any moment.
But of course that must be a lie, since there are $15 trillion of bank deposits and only $2.3 trillion dollars of cash. That means if everyone in the US went to the bank tomorrow and tried to withdraw their money in cash, the banks would run out of cash while still owing $12.7 trillion dollars to depositors. It’s actually much worse than that, since a lot of the cash is already in peoples’ pockets, much of it circulating in foreign countries outside the US. Banks only hold around $100 billion in their vaults on any given day. So if everyone tried to withdraw their money from their bank accounts, which banks have implicitly promised they can do, each person could get around $0.007 of every dollar on deposit. That’s less than one cent of every dollar. So the promise banks are built on, the promise to give you the money in your account, turns out to be at least 99% a lie.
So how can it continue like this? How do banks keep operating with so little cash and so many promises to give cash? Why does anyone put money in the bank when they keep less than a penny of every dollar you deposit available to withdraw when you need it? The answer is, banks don’t tell you that. And if nobody knows, people won’t all come asking for their money one day. If they did, all the banks would fail instantly. So they do anything in their power to keep that from happening.
How Do Bank Deposits Work?
The reason most people never question the function of their bank, is that banks do everything possible to make their dishonest “bank deposits” function the same as cash, and actually better than cash in a lot of ways. Instead of having to withdraw cash from your bank and give it to someone, you can just exchange bank deposits. You can do this in a lot of super convenient ways, like writing a check or using a debit card, or more recently even right from your smartphone with an app like Venmo or CashApp. This is very convenient for the customer, and even more convenient for the bank. When you pay someone else using your bank deposit, all they have to do is lower the number in your account and raise the number in the other person’s account by the amount of the transaction. Quick, easy and convenient for everyone involved.
And if you happen to be paying someone who doesn’t have an account at your bank, that’s no problem either. Your bank will just pay the other person’s bank, and they can then change the number in the other person’s account. Now of course banks want real money for their transactions, not the fake bank deposits the commoners use. Remember the bank reserves I mentioned earlier that are like cash for banks only? Well that’s how banks settle transactions between themselves. All banks have an account at the Fed, and the Fed settles up between banks by changing the number of bank reserves in their respective accounts at the Fed. In essence, the Fed is just a bank for banks, another entity that works just like your local bank, but only holds accounts with banks and governments and not with ordinary people.
This convenience discourages people from withdrawing cash from their bank, since it’s actually easier to use the bank deposits than the cash. Besides that, banks use a lot of arbitrary policies to make it difficult for people to withdraw cash, even if they want to. If you didn’t know that, you’ve probably never tried to take $5,000 in cash out of your bank account. If you do, you’ll probably be asked some irrelevant questions about what you plan to do with the money. That’s if they let you withdraw it at all. Ask for $20,000 and you’ll almost certainly have to schedule an appointment to withdraw it in a few days, after the next cash delivery comes in. Most community bank branches only keep around $75,000 in cash on hand at any given time, so you can see how few withdrawals it would take to completely drain their vault.
But increasingly now, the biggest threat to banks isn’t from people withdrawing cash, it’s from people withdrawing to a different bank. Remember, banks have to settle with each other at the end of the day. And since they won’t accept each other’s sketchy “bank deposits” in payment, they have to settle by transferring balances between their respective reserve balances at the Fed. As you can see, banks have loaned into existence $11.5 trillion more in bank deposits than they hold in bank reserves, so it doesn’t take much withdrawal from one bank to drain their reserve balance to zero and cause the bank to fail. Bank runs have been a recurring problem ever since the entire dishonest fractional reserve banking system began, and even in 2023 a few US banks suffered bank runs and collapsed in some of the biggest bank failures in history.
Why Banking is Legalized Theft
Now that we’ve explained on the most basic level how banks work, let’s briefly explore a few basic implications.
We’ve established that banks create money when they make a loan. How easy would your life be if you could create money at no cost and loan it to people? Is it any wonder that the financial industry is full of extremely wealthy individuals?
Let’s think through for a second why I would categorize what banks do as theft. First off, you need to understand what money is, and more importantly what it is not. I lay out some fundamental principles in this article.
naddr1qvzqqqr4gupzp0rve5f6xtu56djkfkkg7ktr5rtfckpun95rgxaa7futy86npx8yqq247t2dvet9q4tsg4qng36lxe6kc4nftayyy89kua2
Summarized in one sentence, money is a ledger of productive effort with deferred consumption. It represents work someone did for another person, instead of for their own benefit. In a sense, it’s an abstract representation of, or a claim on, the wealth in a society. Having money indicates that you provided value to someone else in the past, and therefore deserve to receive value from someone in the future if you choose to exercise that claim.
Anyone who has money can loan that money to someone. This is a transfer of your claim on wealth to that person. They can then use the money to buy something, and benefit from that loan. But with that type of loan, there is always a tradeoff. The tradeoff is what’s called opportunity cost. While you have the money, you have the option to exercise that claim at any time and buy something you want. If you loan the money to someone, you incur the cost of giving up that option for as long as it takes until the loan is repaid. You already put in the effort to create the wealth that money represents, now you’re sacrificing your opportunity to benefit from that effort by buying something you want.
Bank loans are different. There is no opportunity cost. The bank doesn’t have the money to begin with, because they haven’t put in any effort or created anything of value to deserve it. They just create the money out of thin air. There is no sacrifice on the part of the bank to make that loan possible. They don’t have to forego spending any money to make the loan because the money didn’t exist in the first place.
So when the bank creates money, they’re creating new claims on wealth. Since the bank hasn’t created any wealth, the claims must be claims on wealth that already exists. These new claims have no immediate effect on the people who hold that wealth. Nothing changes for them, the wealth they hold is still theirs as long as they don’t exchange it for money. As long as they don’t sell their wealth, the increase in claims on that wealth changes nothing.
The people who are negatively effected by this increase in money are those who already have money. Since money is a claim on wealth, the value of each unit of money equals [amount of wealth in existence] divided by [amount of money in existence]. Since the amount of wealth has not changed, but the amount of money has increased, the value of existing money falls. More money spread out over the same amount of wealth means each unit of money will buy less wealth. This is what everyone knows as inflation, and as everyone who has experienced it knows, the money they hold as savings or receive as income becomes less valuable the more inflation occurs.
Who benefits from this? Well, the borrower may benefit in some cases. They receive the newly created money and are able to spend it and acquire wealth they haven’t yet put in the effort to produce. So they get to enjoy unearned rewards now. Also, since it takes time for holders of wealth to realize how much inflation has occurred, they will often exchange their wealth for money at a price lower than the increase in money supply would indicate. So the price of a purchased item will often continue to increase after the borrower acquires it, and they benefit from the increase in prices by paying back their loan with money that is less valuable than it was when they borrowed it. Of course the interest charges negate some of the benefit, but often not all of it, so borrowing money can end up being very beneficial to a borrower in many situations.
The biggest beneficiary is the bank itself. They create the money from nothing, with no opportunity cost or sacrifice necessary. In effect, they are able to use the new money to transfer wealth from holders of wealth to borrowers, at the expense of holders of money. And of course as soon as that transfer is complete, the holders of wealth become new holders of money and begin to suffer the effects of inflation too. Meanwhile the bank requires the borrower to repay the loan, with interest attached.
When an individual makes a loan, the interest charged is payment for the opportunity cost of not being able to enjoy the benefits of spending that money now. However for banks, there is no opportunity cost in making a loan. So the bank receives interest as a reward from the borrower for transferring wealth to them at the expense of holders of money. A kind of sharing of the spoils of theft, if you will. Of course they would never describe it that way, but if you understand what’s actually happening it seems like the only accurate explanation.
So we see who gets rewarded by the banking system, and who gets punished. Those who get rewarded are bankers, who collect interest from loaning out money they didn’t actually have, and are able to enrich themselves by spending that collected interest to purchase real wealth. Sometimes borrowers are also rewarded, meaning the people who consume things they haven’t produced by borrowing the money to buy them get to enjoy immediate gratification, and then over a period of time pay back an amount of money that has lost so much value it would no longer be enough to buy the item they have already been enjoying.
And the people who get punished are those who save and hold money. Those people are the ones who produce value and defer consumption, the ones whose pro-social behavior and delayed gratification make capital formation and modern civilization possible.
The purpose and effect of banking, and creation of new money through bank loans, is to redistribute wealth. The incentive structure means access to wealth is stolen from those with the most socially desirable behavior, the most effective producers and most frugal savers who hold money they’ve earned for future use. The stolen wealth is given to those with the least socially desirable behavior, those who consume more than they produce and live beyond their means, being a net detriment to civilization, and to the parasitic banking class who collect interest as a reward for their theft.
The anti-civilizational outcomes of this perverse incentive structure, and the lie it’s built on (“money in the bank is the same as money in your wallet”) have only become more obvious and harder to ignore over the decades. Without a fundamental change to the basic design and function of the modern financial system, expect this trend to continue.
Forewarned is forearmed.
-
 @ c755de14:cc53833a
2024-12-01 16:01:19
@ c755de14:cc53833a
2024-12-01 16:01:19Steps and strategies to tackle your worries
-
Write them down
Sometimes just getting things out of your head and down onto paper or a notes app on your phone can help you clear your mind and make it easier to work through concerns one by one.
-
Set aside 'worry time:
If you find that your worries are taking over your day, it can help to try to manage this by setting yourself some "worry time” – a short period, say 10 or 15 minutes, every day or so before bed to write things down and try to find solutions.
Making this a regular thing can help put your mind at ease and stop your thoughts racing when you're trying to sleep
-
Do not dwell during the day:
Once we have a regular worry time, this can help prevent us from getting lost in our worries during the rest of the day.
So when a worry does enter your mind, think "I'll set that aside for my worry time." This can help you shift your focus back to the here and now.
It might feel difficult at first to stop your thoughts from returning to the worry, but as time goes on and you settle into the habit of having worry time, it should get easier.
-
Use the 'worry tree':
When you sit down to think about your worries, a structured technique called the "worry tree" can help keep you focused on understanding the difference between problems you can solve and hypothetical worries that are beyond your control.
It can also help you decide what you can act on immediately or whether something needs to be scheduled and acted on later.
-
Make a plan – and carry it out:
Once you have caught and checked the worry, ask yourself: "Is there anything practical I can do about it?"
For worries you can do something about, rite down a plan of action.
Try to make this as specific as possible. Answering these questions might help:
▶️What would you do? ▶️How could you do it? ▶️When would you do it?
If you have identified anything it would be possible to do right now, make sure you do it.
If the worry returns, you can then remind yourself you have already taken action and try to shift your focus.
If there's nothing you can do for the moment, schedule a time for when you can and will. Then if the worry bubbles back up, remind yourself you have a plan in place, and try to switch your attention to something else.
-
Accept the worries you cannot control and move on:
Worrying is part of life. We cannot eliminate it completely or control everything. For any worries you have identified as ones you cannot do anything about, try to acknowledge and accept this.
Often, even just knowing we've spent time thinking about a worry properly and assessing the options can help dampen them.
Try not to dwell on one worry for too long – either move on to dealing with another, or find ways to shift your focus, distract yourself, relax or clear your mind.
-
Focus on the present:
In time, following these steps should make it easier to deal with the worries we can do something about and stop the ones we cannot from becoming overwhelming.
But if anxiety is creeping in, it's really useful to have some go-to strategies – like exercise, yoga, or breathing, mindfulness or meditation techniques – to help calm us down and bring us back to the present moment.
These can take time and practice to get used to, but they really can help you feel more in control of your thoughts and feelings.
-
-
 @ 7c765d40:bd121d84
2024-12-03 22:37:00
@ 7c765d40:bd121d84
2024-12-03 22:37:00We have crossed another 1,000 blocks!
Time is flying by.
Seems like just yesterday we were in the 872s.
Today we are talking about some of the opportunities ahead in this crazy world of bitcoin.
Let's start with a little exercise.
Woo hoo - just like in grade school.
Take a pen and paper.
Evernote doesn't count.
Think about the industry you work in.
How could bitcoin improve certain aspects of the industry?
Start writing down some ideas on how bitcoin could shake things up.
If you were having a conversation with someone in the industry about bitcoin, what would you tell them?
Think about your suppliers.
Your customers.
Your marketing strategy.
Your investments.
Your capital expenditures.
Your admin team.
Your payroll.
And don't limit your thinking to be payment related.
Bitcoin changes the payment rails but it also changes the mentality, the efficiency, and the time horizons.
Think about the treasury for businesses within the industry.
The wasted resources.
The decision-making process.
The budgets.
My dad and I were talking about a local business and using their services.
We were going to talk to them about bitcoin and how it could improve the way they do business and get new customers.
But then I thought, why bother?
Both of us are very well-versed in this specific industry AND also have the bitcoin knowledge to implement this without friction.
I spend a lot of time on my daily show talking about how we can help other businesses with bitcoin.
But why wouldn't we just do it ourselves instead?
There will be a time and place for both - but when you can do things just as good but have the bitcoin knowledge, it's a no-brainer.
We need to shift the focus from trying to help everyone else.
We need to realize the opportunity here and make some fucking hay.
I know that goes against the bitcoin way of thinking but it's true.
We have to get a little selfish here if we want some influence in the future.
Something to think about anyways.
And if you’re anything like the fella in the photo, you might even need two pens!
PROJECT POTENTIAL - You can now find the expanded audio versions of these on the new podcast - Project Potential! I will be sharing the video versions here for the LITF members but you can also find it for free on Spotify and of course Fountain!
Here is the link to Episode 004 on Fountain: https://fountain.fm/episode/r00ZDxpAdfb7QIQT3TKa
Have a great day everyone! And remember, the only thing more scarce than bitcoin is time!
Jor
-
 @ 468f729d:5ab4fd5e
2024-12-03 20:37:19
@ 468f729d:5ab4fd5e
2024-12-03 20:37:19```js import dynamic from 'next/dynamic'; import { useEffect } from 'react';
const Button = dynamic( () => import('@getalby/bitcoin-connect-react').then((mod) => mod.Button), { ssr: false, } );
let initialized = false;
export async function initializeBitcoinConnect() { if (!initialized) { const { init } = await import('@getalby/bitcoin-connect-react'); init({ appName: "PlebDevs", filters: ["nwc"], showBalance: false }); initialized = true; } }
const BitcoinConnectButton = () => { useEffect(() => { initializeBitcoinConnect(); }, []);
return (
export default BitcoinConnectButton; ```
-
 @ 33fc2c28:5d1a1a6e
2024-12-01 12:20:19
@ 33fc2c28:5d1a1a6e
2024-12-01 12:20:19"As night descends, the crisp breeze whispers a gentle kiss on my cheek, entrancing me. The full moon, a masterpiece of celestial artistry, hangs suspended in the velvet sky like a prized painting on a dark canvas. The darkness envelops me, and my black hoodie and trousers blend seamlessly into the shadows, imbuing me with a sense of strength and anonymity.
The night air vibrates with secrets untold and powers unseen, its mysteries beckoning me like an unspoken promise. I breathe in the shadows, feeling the darkness pulsate through my veins, and I am invigorated. The world may sleep, but in this blackness, I find solace, empowerment, and an unspoken connection to the unknown."
-
 @ 03b2a4f0:7ff066d4
2024-12-01 12:20:00
@ 03b2a4f0:7ff066d4
2024-12-01 12:20:00The Fascinating World of Fish
Fish are among the most diverse and fascinating creatures on our planet, inhabiting oceans, rivers, lakes, and streams. With over 34,000 known species, they make up the largest group of vertebrates, showcasing a stunning array of sizes, shapes, and colors. From the tiniest pygmy goby, barely an inch long, to the massive whale shark, reaching lengths of over 40 feet, fish have adapted to nearly every aquatic environment imaginable.
Types of Fish Fish are generally classified into three main groups:
1. Jawless Fish (Agnatha) – These ancient fish, like lampreys and hagfish, lack jaws and have a more primitive body structure.
2. Cartilaginous Fish (Chondrichthyes) – Sharks, rays, and skates fall into this category, characterized by their skeletons made of cartilage rather than bone.
3. Bony Fish (Osteichthyes) – The most common type, including familiar species like salmon, goldfish, and tuna, have skeletons made of bone.Adaptations and Survival Fish have evolved a variety of adaptations to thrive in their environments. Gills allow them to extract oxygen from water, while their streamlined bodies enable efficient movement. Many fish possess a swim bladder, an internal gas-filled organ that helps them control buoyancy.
Importance to Ecosystems and Humans Fish play a crucial role in maintaining aquatic ecosystems. They contribute to the food chain, control algae growth, and some even clean up detritus. For humans, fish are a vital food source and a key component of global economies, supporting millions of livelihoods through fishing industries and aquaculture.
Conservation Challenges Unfortunately, fish face numerous threats, including overfishing, pollution, and habitat destruction. Climate change and rising ocean temperatures also disrupt fish populations and migration patterns. Conservation efforts, such as sustainable fishing practices and marine protected areas, are essential to preserving these incredible creatures for future generations.
In summary, fish are not only remarkable in their diversity and adaptability but also play a vital role in both natural ecosystems and human societies. Understanding and protecting them is crucial to maintaining the balance of our planet's waters.
-
 @ 2063cd79:57bd1320
2024-12-03 19:37:13
@ 2063cd79:57bd1320
2024-12-03 19:37:13Ich bin der festen Überzeugung, dass 2023 noch nicht das Jahr sein wird, in dem CBDCs in Europa oder anderen Ländern des globalen Nordens das Tageslicht erblicken werden. Dennoch bin ich überzeugt, dass dieses Thema in 2023 durch vermehrte Prozesse, Rhetorik und Kampagnen weiter in den Mainstream getragen werden wird, um eine unausweichliche Einführung von einer CBDC - zumindest in der Eurozone - vorzubereiten und die Menschen langsam darauf einzustellen. Damit verbundene Themen wie z.B. UBI (Unconditional Basic Income/ Universal Basic Income), also das bedingungslose Grundeinkommen, sowie als Geldwäschegesetze getarnte Einschränkungen des Bargeldverkehrs und andere mit digitalen Zahlungsmitteln verbundene Themen, werden in den Medien vermehrt zu finden sein. Meines Erachtens nach, werden wir all diese Themen auf der einen Seite öfter lesen/hören und auf der anderen Seite wird die Rhetorik gegenüber Bitcoin und anderen Krypto-Assets verschärft werden. Die typischen FUD-Themen werden ad nauseam durch die Medien gejagt, aber auch von Regulatorik wird vermehrt Gebrauch gemacht. Die Regulatorik in Deutschland, Europa, aber auch in den USA, ist bisher weitgehend unklar. An vielen Stellen ist nicht mal klar, welche Agency oder Behörde überhaupt zuständig und handlungsfähig ist, geschweige denn, dass besonders ausgereifte Gesetze existieren. Mit der MiCA (Markets in Crypto-Assets) Verordnung hat die EU einen Schritt nach vorne getan und auch wenn sie erst 2024 in Kraft tritt, stellen sich jetzt schon viele der betroffenen und angesprochenen Gruppen auf die Vorgaben ein. Eine weitere Verordnung, die schon länger besteht, ist die Verordnung (EU) 2015/847 über die Übermittlung von Angaben bei Geldtransfers. Diese regelt die sogenannte Travel Rule, mit der wir uns diese Woche beschäftigen wollen.
Zunächst müssen ein paar Begriffe und Buchstabensuppenbehörden erklärt werden.
FATF
Die Financial Action Task Force (FATF) ist ein internationales und Regionen übergreifendes Projekt mit zur Zeit 39 Staaten als Mitgliedern, und deren Standards einzuhalten sich so ziemlich jedes Land der Welt verpflichtet hat. Es ist wichtig zu unterscheiden, dass die FATF keine Organisation ist und damit auch keine juristische Person darstellt, die Regeln oder Gesetze erlassen kann. Die FATF veröffentlicht lediglich Empfehlungen und Standards, die von Staaten übernommen werden. Das selbsterklärte Hauptziel dieses Projekts ist die Bekämpfung von Geldwäsche (AML) und der Finanzierung von Terrorismus (CFT). Die Handhabe der FATF ist demnach recht lose gefasst, sehr weitreichend und das Mandat zeitlich unbefristet. Posten werden vergeben, nicht gewählt, wie sollte es auch anders sein. Die FATF wurde 1989 gegründet und hatte zunächst nur das Ziel Geldwäsche zu bekämpfen, doch seit 9/11 wurde das Mandat um die Bekämpfung von Finanzierung von Terrorismus erweitert, und einhergehend mit dem Patriot Act und anderen freiheitseinschneidenden Gesetzen, hatte auch niemand mehr irgendwelche Vorbehalte gegen Übergriffe auf Privatsphäre und Persönlichkeitsrechte.

FATF Mitglieder
Die Liste der Länder, die keine Lust auf diesen spießigen Club mit seinen strengen Regeln haben, die sogenannten Non-Cooperative Countries and Territories (NCCTs), liest sich wie der Marco Polo Reiseführer für Steuerflüchtlinge und Finanzakkrobaten und führt - wen wunderts - Länder wie die British Virgin Islands, die Kaimaninseln, die Kanalinseln (Guernsey, Isle of Man und Jersey), Liechtenstein, Monaco, Panama, naja und halt eben auch Russland. Die Erfolgsgeschichten der Prävention von nennenswerten Terroranschlägen ist übrigens so lang, wie die Liste von Goldmedaillen des olympischen Eiskunstlaufteams des Sudans.

FinCEN
Das Financial Crimes Enforcement Network (FinCEN) ist eine weitere Nudelbehörde im Geltungsbereich des US amerikanischen Finanzministeriums und beschäftigt sich ausschließlich mit Finanzsystemen, bzw. der Ausnutzung oder der illegalen Nutzung derselben, ist aber auch dem Office of Terrorism and Financial Intelligence (TFI) unterstellt, also auch hier wieder ein Mandat so breit wie der Amazonas.
So, nun kurzer Geschichtsausflug.
Das FinCEN hat im Jahr 1996 die originale Travel Rule erlassen. Diese hieß natürlich nicht offiziell so, aber Bank Secrecy Act (BSA) rule [31 CFR 103.33(g)] ist super sperrig, also bleiben wir bei Travel Rule. Kurz und knapp zusammengefasst besagt dieses Gesetz, dass Finanzinstitute gewisse Informationen an andere Institute weiterleiten müssen, wenn sie durch ihre Dienstleistungen Empfänger (Begünstigter) oder Sender (Auftraggeber) von Zahlungen miteinander verbinden. Diese Informationen beinhalten
beim Versenden:
- Name des Senders
- Kontonummer des Senders, falls verwendet
- Adresse des Senders
- Identität des Finanzinstituts des Senders
- Höhe des Übermittlungsauftrags
- Ausführungsdatum des Übermittlungsauftrags
- Identität des Finanzinstituts des Empfängers;
beim Erhalten:
- Namen des Empfängers
- Adresse des Empfängers
- Kontonummer des Empfängers
- jede andere spezifische Kennung des Empfängers.
Die FATF hat im Jahr 2019 diese originale Travel Rule übernommen und vorgeschlagen, diese Regeln zur Übermittlung von personenbezogenen Daten auf "Virtual Assets" (VA) auszuweiten und damit nicht nur traditionelle Finanzinstitute, sondern auch "Virtual Assets Service Providers" (VASPs) einzubeziehen. Wir sind uns natürlich bewusst, dass sich VAs nur auf Pokedollars, Rupees und V-Bucks beziehen und keineswegs auf Digitale Assets oder Kryptowährungen 😛 - sonst würde man ja von DAs (Digital Assets) sprechen.

Krypto-Travel Rule
Okay, also ernsthaft bedeutet dies im Klartext, dass jede Bitcoin- oder Krypto-Transaktion, die einen bestimmten Schwellenwert überschreitet (in der EU bald 0 EUR - "denn aufgrund der spezifischen Eigenschaften und des Risikoprofils von Krypto-Assets gilt die Informationspflicht für alle Krypto-Asset-Transfers, unabhängig vom Transferwert", mehr dazu später ⬇️), von den persönlichen Daten (personally identifiable information (PII)) des Kunden begleitet werden muss. Wir nutzen hier erstmal weiter den Begriff VASP. VASPs müssen nicht nur die Informationen ihrer eigenen Kunden übermitteln, sondern auch versuchen den/die Empfänger//in oder Sender//in (also die jeweilige Gegenpartei) zu blocken oder zu sanktionieren und einer Due-Diligence-Prüfung zu unterziehen. Kurzum, die FATF findet das Risikoprofil von Krypto super schwierig, darum könnte es sein, dass mein Toni Token, den ich einem Freund schicke, der Finanzierung von internationalem Terrorismus dienen könnte und deshalb muss die Sparkasse Westfalen-Lippe jetzt der Spardabank meines Freundes die Unterwäschengröße meines erstgeborenen Kindes übermitteln. Klingt unmöglich? Ist es auch.
Jetzt denkt der/die kundige Leser//in: "Naja, coole Regel liebe FATF, aber was jucken mich deine Vorgaben? Ich lebe in hier in einem Land und der einzige, der hier Gesetze erlassen kann ist immernoch der Kanzlerin!" Und so - oder so ähnlich - ist es auch, aber wir würden ja nicht im Musterknaben-Regelparadies-Preussland leben, wenn Deutschland nicht als eine der ersten europäischen Jurisdiktionen, die Travel Rule als Gesetz erlassen möchte. Der Gesetzesentwurf des damaligen Finanzministers Olaf Scholz mit dem lässig und digital daherkommenden Namen "Verordnung über verstärkte Sorgfaltspflichten bei dem Transfer von Kryptowerten (kurz: Kryptowertetransferverordnung, noch super-kürzer: KryptoWTransferV)" wurde in 2021 vorgestellt und soll noch 2023 in Kraft treten.
Jetzt fragt sich der/die kundige Leser//in natürlich als nächstes: "Naja, Regel hin oder her, ich hab ja tausende verschiedene Apps, Services, kann von Börsen Geld verschicken, von Wallets auch, kann sogar selber Payment-Channels für Lightning öffnen, eine Node betreiben und Wallets hosten, wie zum Kuckuck finde ich denn raus, wer oder was jetzt ein VASP ist? Oder schlimmer noch, bin ich womöglich selbst einer?"

Ruhig kleiner Otter, hier ist die Definition der FATF:
Ein VASP ist jede natürliche oder juristische Person, die [...] als Unternehmen eine oder mehrere der folgenden Aktivitäten oder Operationen für oder im Namen einer anderen natürlichen oder juristischen Person durchführt:
- Austausch zwischen virtuellen Vermögenswerten und Fiat-Währungen
- Austausch zwischen einer oder mehreren Formen virtueller Vermögenswerte
- Übertragung von virtuellen Vermögenswerten
- Verwahrung und/oder Verwaltung von virtuellen Vermögenswerten oder Instrumenten, die die Kontrolle über virtuelle Vermögenswerte ermöglichen
- Teilnahme an und Erbringung von Finanzdienstleistungen im Zusammenhang mit dem Angebot und/oder dem Verkauf eines virtuellen Vermögenswerts durch einen Emittenten

Also zunächst bezieht sich die Definition nur auf Unternehmen. Dieser Interpretation folgt auch Krypto 👐🏼 Transfer 🖖🏼:
Unternehmen mit Sitz im In- oder Ausland, das in Bezug auf Kryptowerte im In- oder Ausland Bankgeschäfte im Sinne des § 1 Absatz 1 Satz 2 des Kreditwesengesetzes betreibt, Finanzdienstleistungen im Sinne des § 1 Absatz 1a Satz 2 des Kreditwesengesetzes oder Wertpapierdienstleistungen im Sinne des § 2 Absatz 2 bis 4 des Wertpapierinstitutsgesetzes erbringt.
Generell fallen unter die Interpretation von VASPs die folgenden Dienstleistungen: Verwahrung, Mining Pool Anbieter, Anbieter von Wallets (custodial), Broker-Services (inkl. Börsen), Bitcoin ATMs und unter bestimmten Voraussetzungen auch Anbieter von Stablecoins, Anbieter von DeFi-Protokollen und auch dezentralisierte Börsen (DEX). Individuelle Miner, Betreiber von Full-Nodes und Lightning-Routing-Channels sind bisher von der Interpretation ausgeschlossen.
Wohingegen man das Gefühl bekommen könnte, dass Sender//innen und Empfänger//innen der Transaktionen die Leidtragenden der Gesetzesentwürfe sind, kann man doch eigentlich schnell sehen, dass vor allem die Dienstleister eine enorme Last und zusätzliche Arbeit schultern müssen. Auf der einen Seite besteht die Herausforderung, die uneinheitliche Vorgehensweise bei der Umsetzung dieser Verordnung in den verschiedenen Regionen vernünftig zu navigieren, denn die daraus entstehenden Anforderungen unterscheiden sich noch von Land zu Land (ein Pluspunkt für MiCA ⬇️). Aber auch zusätzliche Anforderungen, die über die Beschaffung der PIIs hinausgehen, wie z.B. dass von VASPs erwartet wird, dass sie Informationen über die Quelle und das Ziel von versendeten Krypto-Assets erhalten und speichern, machen das normale Tagesgeschäft um ein vielfaches komplizierter.
Und weil es so schwierig ist die PIIs der Sender//innen (Auftraggeber//innen) und der Empfänger//innen (Begünstigten), geschweige denn die volle Transaktionshistorie der Assets, glaubwürdig und genau abzubilden und zu übermitteln, sieht sogar die FATF ein, dass ein gewisser gesunder Menschenverstand angesetzt werden muss und empfiehlt daher, dass VASPs zunächst die VASPs auf der Gegenseite überprüfen, um zu ermitteln, ob eine Transaktion womöglich Geldwäsche- oder Terrorismusfinanzierungspotential (AML/CFT) birgt.

MiCA
Die sogenannte Markets in Crypto Assets Verordnung ist ein in 2020 vom EU Parlament auf den Weg gebrachtes Gesetz zur Harmonisierung der Regeln in Bezug auf Krypto-Anbieter im europäischen Raum. Die Verordnung soll in 2024 in Kraft treten, doch ein finaler Entwurf liegt bereits vor.
Wie schon erwähnt, sehen die neuen Regeln der EU einen Schwellenwert von 0 EUR vor. Mit anderen Worten, Krypto-Dienstleister, die unter einer EU-Lizenz oder in der EU tätig sind, müssen für alle Transaktionen, unabhängig von ihrer Größe, Informationen zur Identität des Absenders und Empfängers erfassen.
Dabei unterscheidet die EU zwischen "hosted" und "un-hosted" Wallets 🤡. Un-hosted Wallets sind alle Wallets, die privat genutzt werden und self-custodial arbeiten, also sich in der Verwahrung von Privatnutzer//innen befinden, sprich diejenigen Wallets, die jeder nutzen sollte, der keinem Custodian vertrauen möchte.
Überweisungen von oder zu un-hosted Wallets von oder zu einem VASP, oder anderen Finanzdienstleister, müssen ab einem Schwellenwert von 1.000 EUR vom VASP überprüft werden. Dabei muss der VASP auch feststellen, ob diese Wallet dem/der Kund//in tatsächlich gehört oder er/sie dieses kontrolliert. Wenn ja, muss der/die Benutzer//in dies verifizieren. Transaktionen von weniger als 1.000 EUR an oder von einer un-hosted Wallet erfordern keine Überprüfung des Eigentums.
Transaktionen an un-hosted Wallets, die nicht der direkten Kontrolle des/der Benutzers//in unterliegen, müssen in allen Fällen überprüft und personenbezogene Informationen über die Wallet gesammelt werden. Darüber hinaus muss festgestellt werden, ob weitere Maßnahmen erforderlich sind. Das bedeutet, dass der VASP vor der Übertragung der Transaktion ein potentielles AML/CTF Risiko identifizieren, einschätzen und entsprechende Maßnahmen ergreifen muss.
InterVasp, TRUST und Co
Und genau weil es eben so schwierig ist diese unhandlichen Anforderungen umzusetzen, bedeutet dies, dass die gesamte Industrie einen kooperativen Ansatz verfolgen muss, um einen idealen Daten- und Kommunikationsstandard zu finden. Zunächst wurde also ein Konsens über ein einziges Datenübermittlungsformat für alle Travel Rule Anforderungen erzielt. Dieses Format heißt IVMS 101 und wurde von der Joint Working Group on interVASP Messaging Standards (JWG) erlassen.
Gleichermaßen hat Coinbase federführend eine Lösung namens TRUST (Travel Rule Universal Solution Technology) ins Leben gerufen, die nach eigenen Angaben zufolge entwickelt wurde, um die Travel Rule Anforderungen zu erfüllen und gleichzeitig die Sicherheit und Privatsphäre von Kund//innen zu schützen. Dieser Lösung haben sich einige namhafte Finanzdienstleister, Börsen und Krypto-Anbieter, unter anderem BitGo, Bittrex, Circle, Fidelity Digital Assets, Gemini, Kraken und Robinhood, angeschlossen, um einen Industriestandard für die Erfüllung dieser Anforderungen zu schaffen.
https://www.coindesk.com/business/2022/10/31/coinbase-backed-anti-money-laundering-group-expands-into-europe
Aber auch ein von MasterCard übernommenes Unternehmen namens CipherTrace war schnell dabei, einen Standard zu entwickeln, der es Unternehmen erleichtern soll, den Anforderungen gerecht zu werden.
https://bitcoinmagazine.com/business/ciphertrace-unveils-travel-rule-protocol-for-cryptocurrency-businesses
Was anhand der genannten Beispiele recht schnell deutlich wird, ist dass die von der FATF erlassenen Empfehlungen und Standards hauptsächlich dazu führen, dass wieder eine immense Anzahl an personenbezogenen Daten gesammelt werden muss, und dass dieser Mammut-Akt von etablierten, zentral operierenden Unternehmen gesteuert und vereinnahmt wird. Es ist, als würden Tickets gedruckt, um weitere zusätzliche Daten sammeln zu dürfen, und diese Tickets werden natürlich wieder - frei nach dem Cantillon-Effekt - an die am engsten stehenden Unternehmen verteilt.

Und wer die Früchte ernten will, muss auch den Preis dafür bezahlen!
Banken und Krypto-Anbieter sollten keine Diebe fangen, das ist Sache der Polizei. Es gilt eigentlich das rechtsstaatliche Grundprinzip der Unschuldsvermutung, also im Zweifel für den Angeklagten, bzw. die Annahme, dass jede/r solange als unschuldig anzusehen ist, bis seine/ihre Schuld nachgewiesen werden kann. Im Falle der Travel Rule und ähnlichen Geldwäschegesetzen und Gesetzen zum Schutz vor Terrorfinanzierung (AML/CFT) wird dieses Prinzip auf den Kopf gestellt.
Millionen von Berichte werden zur Zeit von Finanzdienstleistern und Krypto-Unternehmen an die Aufsichtsbehörden gesendet. Damit geben Unternehmen des privaten Sektors persönliche Informationen über ihre Kund//innen preis, selbst wenn die Transaktionen nur verdächtig sind. Doch was macht eine Transaktion verdächtig? Grenzüberschreitende Transfers, ein Abendessen in einem äthiopischen Restaurant bezahlt mit Karte? Finanzinstituten obliegt es, das Geld zunächst einzufrieren, sozusagen als Lösegeld einzubehalten, bis der/die Kund//in beweisen kann, dass er/sie unschuldig ist, und nicht umgekehrt. Dies stellt eine klare Verletzung des Menschenrechts dar. Regeln, wie die Travel Rule, verletzen gesellschaftliche Prinzipien, indem sie Menschen ihre Rechte kategorisch verweigern, nur um ein sehr kleines potentielles Risiko zu vermeiden.
Und wer definiert einen Terroristen? Im Iran unterscheidet sich die Definition von jemandem, der den Staat bedroht, erheblich von dem, was andere Länder als einen terroristischen Akt definieren würden. In unseren Breitengraden sind solche Regeln und Gesetze nur so lange zumindest unbedrohlich für das eigene körperliche Wohl, solange die Kontrollinstanz auf rechtsstaatlichen Grundwerten aufgebaut ist. Sobald dies kippt, hat der Staat eine sehr gefährliche Waffe zur Hand.
🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ 33fc2c28:5d1a1a6e
2024-12-01 12:19:12
@ 33fc2c28:5d1a1a6e
2024-12-01 12:19:12"As night descends, the crisp breeze whispers a gentle kiss on my cheek, entrancing me. The full moon, a masterpiece of celestial artistry, hangs suspended in the velvet sky like a prized painting on a dark canvas. The darkness envelops me, and my black hoodie and trousers blend seamlessly into the shadows, imbuing me with a sense of strength and anonymity.
The night air vibrates with secrets untold and powers unseen, its mysteries beckoning me like an unspoken promise. I breathe in the shadows, feeling the darkness pulsate through my veins, and I am invigorated. The world may sleep, but in this blackness, I find solace, empowerment, and an unspoken connection to the unknown."
-
 @ c11cf5f8:4928464d
2024-12-01 08:58:58
@ c11cf5f8:4928464d
2024-12-01 08:58:58Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too.
If you missed our last thread, here are some of the items stackers recently spent their sats on.
originally posted at https://stacker.news/items/789759
-
 @ c311a1eb:53fc6542
2024-12-01 06:00:46
@ c311a1eb:53fc6542
2024-12-01 06:00:46

@florian | Photographer
Studio-Shoot
“Know thyself” is a phrase attributed to the ancient Greek philosopher Socrates, and it has been a cornerstone of philosophical thought for centuries. It invites an individual to deeply examine their own thoughts, feelings, behaviors, and motivations in order to understand their true nature.
At its core, “Know thyself” encourages self-awareness - an understanding of who you truly are beneath the surface. This process of introspection can uncover your strengths, weaknesses, desires, fears, and values. It invites you to acknowledge your habits, biases, and patterns of thinking, so you can make more conscious choices in life.
Knowing yourself also involves understanding your place in the larger context of existence. It means recognizing how your actions and choices affect others and the world around you. This awareness can lead to greater empathy, a sense of interconnectedness, and a more authentic life, free from the distractions of societal expectations or superficial identities.
In a practical sense, knowing yourself might involve:
Self-reflection: Regularly taking time to reflect on your thoughts, feelings, and experiences.
Mindfulness: Practicing awareness of the present moment and observing your reactions without judgment.
Exploration: Being open to trying new things and learning from both successes and failures.
Seeking truth: Engaging in honest inquiry about your motivations, desires, and beliefs.
Growth: Continuously learning from your past and striving to align your actions with your inner values.
Ultimately, “Know thyself” is about cultivating a deep, honest understanding of who you are, which leads to a more fulfilled, intentional, and peaceful existence.
-
 @ 94c2fd25:4fb53087
2024-12-01 04:10:57
@ 94c2fd25:4fb53087
2024-12-01 04:10:57HuBet là nền tảng giải trí trực tuyến hàng đầu, mang đến cho người dùng những trải nghiệm thú vị và đa dạng. Với thiết kế giao diện hiện đại, thân thiện và dễ sử dụng, HuBet nhanh chóng thu hút sự chú ý của những ai yêu thích sự đổi mới và sáng tạo trong giải trí.
Tại HuBet, người dùng có thể dễ dàng khám phá các chương trình và hoạt động giải trí hấp dẫn. Từ những trò chơi sáng tạo đến các sự kiện trực tuyến đặc sắc, nền tảng này liên tục cập nhật nội dung mới để đáp ứng nhu cầu đa dạng của người dùng. Mỗi lần truy cập HuBet, bạn sẽ tìm thấy những trải nghiệm độc đáo và khác biệt.
Điểm mạnh của HuBet không chỉ nằm ở nội dung mà còn ở sự tiện lợi. Nền tảng hoạt động mượt mà trên nhiều thiết bị, từ máy tính để bàn đến điện thoại di động, mang lại sự linh hoạt tối đa cho người dùng. Bất kể bạn đang ở đâu, chỉ cần vài thao tác đơn giản là có thể hòa mình vào không gian giải trí sống động của HuBet.
An toàn luôn là ưu tiên hàng đầu tại HuBet. Nền tảng áp dụng các công nghệ bảo mật tiên tiến, đảm bảo bảo vệ thông tin cá nhân và giao dịch của người dùng một cách tuyệt đối. Điều này giúp bạn hoàn toàn yên tâm khi trải nghiệm.
Với sự kết hợp giữa nội dung phong phú, giao diện thân thiện và bảo mật vượt trội, HuBet là lựa chọn hoàn hảo cho những ai đang tìm kiếm một không gian giải trí trực tuyến an toàn và sáng tạo. Tham gia HuBet ngay hôm nay để khám phá thế giới giải trí không giới hạn!
-
 @ 88dc84f5:c71164f7
2024-11-30 22:33:26
@ 88dc84f5:c71164f7
2024-11-30 22:33:26 Introduction
The banking industry is undergoing a significant transformation, driven by the rise of fintech. Financial technology, or fintech, refers to the use of technology to improve and automate financial services. From mobile banking apps to digital payment systems, fintech is revolutionizing the way we manage our finances.
Introduction
The banking industry is undergoing a significant transformation, driven by the rise of fintech. Financial technology, or fintech, refers to the use of technology to improve and automate financial services. From mobile banking apps to digital payment systems, fintech is revolutionizing the way we manage our finances.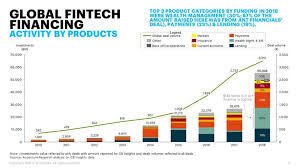 The Rise of Mobile Banking
Mobile banking is one of the most significant trends in fintech. With the rise of smartphones, people can now access their bank accounts, make payments, and transfer money on the go. Mobile banking apps have made banking more convenient, accessible, and user-friendly.
The Rise of Mobile Banking
Mobile banking is one of the most significant trends in fintech. With the rise of smartphones, people can now access their bank accounts, make payments, and transfer money on the go. Mobile banking apps have made banking more convenient, accessible, and user-friendly. Digital Payments
Digital payment systems, such as Apple Pay, Google Pay, and PayPal, are becoming increasingly popular. These systems allow users to make payments online and offline using their smartphones. Digital payments are fast, secure, and convenient, making them an attractive alternative to traditional payment methods.
Digital Payments
Digital payment systems, such as Apple Pay, Google Pay, and PayPal, are becoming increasingly popular. These systems allow users to make payments online and offline using their smartphones. Digital payments are fast, secure, and convenient, making them an attractive alternative to traditional payment methods.Cryptocurrencies and Blockchain Cryptocurrencies, such as Bitcoin and Ethereum, are digital currencies that use cryptography for secure financial transactions. Blockchain technology, which underlies cryptocurrencies, is a decentralized, digital ledger that records transactions across a network of computers. Cryptocurrencies and blockchain technology have the potential to disrupt traditional banking systems and create new opportunities for financial innovation.
 Robo-Advisors and Artificial Intelligence
Robo-advisors are digital platforms that use artificial intelligence (AI) to provide automated investment advice. Robo-advisors have made investment advice more accessible and affordable, especially for younger investors. AI is also being used in other areas of banking, such as risk management and customer service.
Robo-Advisors and Artificial Intelligence
Robo-advisors are digital platforms that use artificial intelligence (AI) to provide automated investment advice. Robo-advisors have made investment advice more accessible and affordable, especially for younger investors. AI is also being used in other areas of banking, such as risk management and customer service.Biometric Authentication and Security Biometric authentication systems, such as facial recognition and fingerprint scanning, are being used to improve security in banking. These systems provide a more secure and convenient way to authenticate transactions and access bank accounts.
Conclusion The future of banking is being shaped by fintech. From mobile banking apps to digital payment systems, cryptocurrencies, and AI-powered robo-advisors, fintech is revolutionizing the way we manage our finances. As fintech continues to evolve, we can expect to see even more innovative solutions that make banking more convenient, accessible, and secure.
Statistics: - The global fintech market is projected to reach $305 billion by 2025. (Source: ResearchAndMarkets) - Mobile banking apps have been adopted by 60% of smartphone users worldwide. (Source: Deloitte) - Digital payments are expected to reach $14.34 trillion in transaction value by 2023. (Source: Statista)
Sources: - "The Future of Banking" by Deloitte - "Fintech Market Size, Share & Trends Analysis Report" by ResearchAndMarkets - "Digital Payments Market" by Statista
-
 @ 88dc84f5:c71164f7
2024-11-30 22:16:19
@ 88dc84f5:c71164f7
2024-11-30 22:16:19Introduction!
) The world of investing has undergone a significant transformation in recent years. Traditional assets such as stocks and bonds are no longer the only options for investors. Alternative investments, including art, wine, and real estate, have gained popularity among investors seeking diversification and potentially higher returns. In this article, we will explore the rise of alternative investments and provide guidance on navigating these unique markets.
The world of investing has undergone a significant transformation in recent years. Traditional assets such as stocks and bonds are no longer the only options for investors. Alternative investments, including art, wine, and real estate, have gained popularity among investors seeking diversification and potentially higher returns. In this article, we will explore the rise of alternative investments and provide guidance on navigating these unique markets.The Art Market
The art market has experienced significant growth in recent years, with global sales reaching $67.4 billion in 2020. Investing in art can provide a hedge against inflation and market volatility, as well as offer the potential for long-term appreciation. However, the art market can be unpredictable, and investors must be prepared for fluctuations in value.
Types of Art Investments: 1. Contemporary Art: Investing in contemporary art can be a high-risk, high-reward strategy. Artists such as Banksy and Koons have seen significant increases in value in recent years. 2. Fine Art: Fine art investments can include works by established artists such as Picasso, Warhol, and Monet. These investments tend to be less volatile than contemporary art. 3. Prints and Multiples: Investing in prints and multiples can provide a more affordable entry point into the art market.
The Wine Market Wine investing has gained popularity in recent years, with the global wine market valued at over $300 billion. Investing in wine can provide a hedge against inflation and market volatility, as well as offer the potential for long-term appreciation.
Types of Wine Investments: 1. Fine Wine: Investing in fine wine can include purchasing bottles from established regions such as Bordeaux, Burgundy, and Champagne. 2. Rare Wine: Investing in rare wine can include purchasing bottles from limited production runs or older vintages. 3. Wine Funds: Wine funds provide a diversified portfolio of wines, allowing investors to spread risk and potentially increase returns.
Real Estate Investing!
 Real estate investing has long been a popular alternative investment strategy. Investing in real estate can provide a hedge against inflation and market volatility, as well as offer the potential for rental income and long-term appreciation.
Real estate investing has long been a popular alternative investment strategy. Investing in real estate can provide a hedge against inflation and market volatility, as well as offer the potential for rental income and long-term appreciation.Types of Real Estate Investments: 1. Direct Property Investment: Investing directly in property can include purchasing residential or commercial properties. 2. *Real Estate Investment Trusts (REITs): REITs provide diversified portfolio of properties, allowing investors to spread risk and potentially increase returns. 3. Real Estate Crowdfunding: Real estate crowdfunding platforms provide a way for investors to pool funds to invest in property development projects.
Conclusion Alternative investments, including art, wine, and real estate, can provide a unique opportunity for investors to diversify their portfolios and potentially increase returns. However, these investments often come with unique risks and challenges. Investors must conduct thorough research and due diligence before investing in these markets.
Statistics: 1. The global art market was valued at $67.4 billion in 2020. (Source: Art Basel) 2. The global wine market was valued at over $300 billion in 2020. (Source: Wine Market Council) 3. The global real estate market was valued at over $280 trillion in 2020. (Source: Savills)
Sources: 1. "The Art Market 2020" by Art Basel 2. "The Wine Market 2020" by Wine Market Council 3. "The Global Real Estate Market 2020" By Saviils.
-
 @ f584a915:9da6d625
2024-11-30 20:05:03
@ f584a915:9da6d625
2024-11-30 20:05:03The US elections have always been a significant event for global markets. However, the recent election cycle has added an extra layer of intrigue with the increasing prominence of cryptocurrency. While the two might seem worlds apart, their intersection has become a topic of much discussion and speculation.
Historically, stock markets have shown sensitivity to election outcomes. A change in administration can lead to shifts in economic policies, trade agreements, and regulatory frameworks, all of which can impact the performance of traditional assets.
Cryptocurrency, on the other hand, is often touted as a decentralized and autonomous asset, immune to such geopolitical events. However, the reality is more nuanced. While blockchain technology, the underlying technology of cryptocurrency, is largely decentralized, the crypto market is still influenced by various factors, including macroeconomic conditions, investor sentiment, and regulatory developments. A change in US administration could potentially impact these factors, leading to fluctuations in the price of cryptocurrencies.
For instance, a pro-innovation administration might be more receptive to cryptocurrencies, leading to favorable regulations and increased adoption. Conversely, a more conservative administration might take a stricter stance, potentially hindering the growth of the crypto industry. Additionally, changes in tax policies or economic stimulus measures could also have implications for cryptocurrency investments.
It's important to note that the impact of the US elections on cryptocurrency is likely to be complex and multifaceted. While the short-term effects might be unpredictable, the long-term trajectory of the crypto market will depend on a variety of factors, including technological advancements, global economic trends, and mainstream adoption. As the US election cycle unfolds, it's crucial for investors to stay informed and make informed decisions. While cryptocurrency offers the potential for high returns, it's also associated with significant risks.
Diversification, risk management, and a long-term investment horizon are key strategies to navigate the volatile crypto market, regardless of the outcome of the US elections.
-
 @ 09565902:0700e0d5
2024-11-30 19:32:00
@ 09565902:0700e0d5
2024-11-30 19:32:00Our planet faces a growing environmental health crisis, with far-reaching consequences for human well-being. Key Threats: Air Pollution: Industrial emissions and vehicle exhaust degrade air quality, leading to respiratory diseases, heart problems, and cancer. Water Pollution: Contaminated water sources spread diseases and endanger ecosystems. Climate Change: Rising temperatures, extreme weather, and altered disease patterns threaten human health and disrupt communities. Chemical Exposure: Toxic chemicals in products and the environment contribute to various health issues. Waste Management: Improper waste disposal pollutes air, water, and soil, posing health risks. The Toll on Humanity: Millions of people worldwide suffer from illnesses linked to environmental factors. Vulnerable populations, including children and the elderly, are disproportionately affected. A Path Forward: To mitigate this crisis, we must: Strengthen Environmental Regulations: Implement stricter policies to reduce pollution and promote sustainable practices. Transition to Clean Energy: Invest in renewable energy sources to reduce greenhouse gas emissions. Promote Sustainable Agriculture: Adopt eco-friendly farming methods to protect water and soil. Reduce Waste and Recycle: Minimize waste and recycle materials to conserve resources. Raise Awareness: Educate the public about environmental health issues and empower individuals to make informed choices. By taking decisive action, we can protect our planet and ensure a healthier future for generations to come.
-
 @ 502ab02a:a2860397
2024-12-03 16:56:05
@ 502ab02a:a2860397
2024-12-03 16:56:05
แนวคิด : เชียงใหม่มีช้างเป็นสัญลักษณ์เหมือนกัน แต่ใช้ช้างไปกับสุพรรณบุรีแล้ว ตอนแรกมองสถานที่ท่องเที่ยวไม่ว่าจะภูเขา แม่กำปอง บ่อน้ำร้อน ร่มบ่อสร้าง แคบหมู ก็ยังไม่ชัดเจนเท่า ประตูท่าแพ ซึ่งความตั้งใจแรกคือไม่อยากเอาโบราณสถานหรือพุทธศาสนสถาน มาเล่นโปรเจคนี้ แต่ก็พบว่าน่าจะยาก ฮา ฮา ฮา ด้วยที่ค้นคว้าเพิ่มเติมเรื่องประตูท่าแพ พบว่าเป็นสิ่งก่อสร้างใหม่ เพิ่งสร้างมาประมาณ 30ปี อีกทั้งเป็นแลนด์มาร์ค ที่นักท่องเที่ยวรู้จัก ก็เลยนำมาใช้ในงานครั้งนี้
Link Download : https://drive.google.com/drive/folders/1VuVIhp3JRvCKwiTqmpkn_jJaeYLMyt6w?usp=sharing
Concept: Chiang Mai also has elephants as a symbol, but elephants have already been used to represent Suphanburi. Initially, I considered other attractions, such as mountains, Mae Kampong, hot springs, Bo Sang umbrellas, or even crispy pork rind. However, none of these felt as distinctive as Tha Phae Gate. Originally, I didn’t want to use ancient landmarks or Buddhist sites for this project, but it turned out to be challenging—haha. Upon further research into Tha Phae Gate, I found out that it’s a relatively modern structure, built only about 30 years ago. Moreover, it’s a well-known landmark among tourists, so I decided to feature it in this project.
Link Download : https://drive.google.com/drive/folders/1VuVIhp3JRvCKwiTqmpkn_jJaeYLMyt6w?usp=sharing

-
 @ 7ed7d5c3:6927e200
2024-12-03 15:46:54
@ 7ed7d5c3:6927e200
2024-12-03 15:46:54Shall I compare thee to a summer’s day? Thou art more lovely and more temperate; Rough winds do shake the darling buds of May, And summer’s lease hath all too short a date;
Sometime too hot the eye of heaven shines,
And often is his gold complexion dimm’d;
And every fair from fair sometime declines,
By chance or nature’s changing course untrimm’d;
``` But thy eternal summer shall not fade Nor lose possession of that fair thou owest; Nor shall Death brag thou wander’st in his shade, When in eternal lines to time thou growest;
So long as men can breathe or eyes can see, So long lives this and this gives life to thee. ```
-
 @ ec951079:533d29e7
2024-11-30 18:38:09
@ ec951079:533d29e7
2024-11-30 18:38:09Gender-Based Violence: A Persistent Threat to Human Rights
Gender-based violence (GBV) is a pervasive and insidious phenomenon that affects individuals, families, and communities worldwide. It is a violation of human rights, a threat to public health, and a hindrance to social and economic development. Despite efforts to address GBV, it remains a persistent and complex problem that requires sustained attention and action.
Defining Gender-Based Violence
GBV refers to any form of violence, abuse, or exploitation that is perpetrated against an individual or group based on their gender, sex, or perceived gender identity. This includes:
- Physical violence: Beating, hitting, kicking, or inflicting physical harm on an individual.
- Sexual violence: Rape, sexual assault, or any form of non-consensual sexual activity.
- Emotional violence: Verbal abuse, intimidation, or psychological manipulation.
- Economic violence: Depriving an individual of financial resources, property, or economic opportunities.
Prevalence of Gender-Based Violence
GBV is a widespread problem that affects individuals across the globe. According to the World Health Organization (WHO), one in three women worldwide has experienced physical or sexual violence in their lifetime. In addition:
- One in five women has experienced physical or sexual violence in the past year.
- One in four men has experienced physical violence in their lifetime.
- LGBTQ+ individuals are disproportionately affected by GBV, with many experiencing violence and discrimination based on their sexual orientation or gender identity.
Causes and Consequences of Gender-Based Violence
GBV is a complex issue with multiple causes and consequences. Some of the key factors that contribute to GBV include:
- Societal norms and attitudes: Harmful gender stereotypes, patriarchal values, and social norms that condone violence against women and girls.
- Power imbalances: Unequal distribution of power and resources between men and women, which can lead to exploitation and abuse.
- Poverty and economic inequality: Limited access to education, employment, and economic opportunities can increase vulnerability to GBV.
The consequences of GBV are far-reaching and devastating. Survivors may experience:
- Physical injuries: Broken bones, head trauma, and other physical harm.
- Emotional trauma: Anxiety, depression, post-traumatic stress disorder (PTSD), and other mental health problems.
- Social isolation: Stigma, shame, and social exclusion can lead to isolation and loneliness.
- Economic hardship: Loss of income, property, and economic opportunities can exacerbate poverty and inequality.
Addressing Gender-Based Violence
To combat GBV, it is essential to adopt a comprehensive and multi-faceted approach that involves:
- Policy and legislative reforms: Strengthening laws and policies to prevent GBV, protect survivors, and hold perpetrators accountable.
- Community engagement and education: Raising awareness about GBV, challenging harmful norms and attitudes, and promoting healthy relationships and respect for human rights.
- Support services and resources: Providing access to counseling, medical care, and other support services for survivors of GBV.
- Economic empowerment: Promoting economic opportunities, education, and skills training to empower women and girls and reduce their vulnerability to GBV.
Conclusion
Gender-based violence is a persistent and pervasive problem that requires sustained attention and action. It is essential to address the root causes of GBV, challenge harmful norms and attitudes, and promote healthy relationships and respect for human rights. By working together, we can create a world where everyone can live free from violence, fear, and discrimination.
-
 @ e1d968f7:5d90f764
2024-12-04 14:20:34
@ e1d968f7:5d90f764
2024-12-04 14:20:34In escorting, the ability to say “no” is not just a personal boundary; it’s a professional necessity. Knowing when and how to assert myself has been one of the most empowering lessons in this line of work, ensuring my safety, well-being, and sense of control.
The Importance of Boundaries
Boundaries are the foundation of my work. They allow me to operate with clarity, protect my mental and physical health, and foster mutual respect with clients. Saying “no” is how I enforce these boundaries.
Some common scenarios where I assert my boundaries include:
- Unrealistic requests: Declining services that I do not offer or that compromise my comfort.
- Pushy clients: Standing firm when someone tries to negotiate rates or terms.
- Personal safety concerns: Refusing to meet when something feels off or unsafe.
The Challenges of Saying No
Saying “no” isn’t always easy, especially when the pressure to please or earn is strong. Early in my career, I worried about how clients might react, fearing they’d take offence or leave bad reviews.
Over time, I’ve learned that:
- Respectful clients will appreciate my honesty and professionalism.
- Saying “no” to one opportunity often opens the door to better ones.
- My well-being always comes first—no exceptions.
How I Say No with Grace
Delivering a firm “no” doesn’t have to feel confrontational. Tone, wording, and timing matter.
- Be clear and polite: “Thank you for asking, but I don’t offer that service.”
- Explain briefly if needed: “I have specific boundaries in place to ensure a comfortable experience for us both.”
- Redirect if appropriate: “While I can’t do that, I’d be happy to discuss other options within my boundaries.”
This approach maintains professionalism and reduces the likelihood of negative reactions.
The Empowering Effect
Each time I say “no,” I’m reminded of the power I hold over my life and work. It’s not just about rejecting something—it’s about affirming my worth, my autonomy, and my right to operate on my terms.
Saying “no” is also a form of self-respect. It reinforces that I am in control and that my comfort and boundaries are non-negotiable.
Encouraging Others to Respect Boundaries
My experiences have taught me that boundaries benefit everyone. When clients understand and respect them, it creates a more relaxed and enjoyable interaction. The ability to say “no” isn’t just about rejection; it’s about ensuring a better experience for both parties.
The Takeaway
In escorting, the power of saying “no” goes beyond setting boundaries—it’s an act of self-care, empowerment, and professionalism. By prioritising my well-being and maintaining control over my work, I ensure that each experience aligns with my values and comfort.
Tomorrow, I’ll explore the art of creating a luxurious experience, where small touches and attention to detail make all the difference.
Rebecca x
-
 @ a305a0de:21557ddd
2024-11-30 17:03:38
@ a305a0de:21557ddd
2024-11-30 17:03:38The internet has undergone two significant transformations since its inception. Web 1.0, the first generation of the internet, was characterized by static web pages and limited user interaction. Web 2.0, the second generation, introduced interactive web applications, social media, and user-generated content.
Now, we're on the cusp of a third revolution: Web 3. This next-generation internet promises to be faster, more secure, and more decentralized than its predecessors. But what exactly is Web 3, and how will it change the internet forever?
What is Web 3?
Web 3 is built on blockchain technology, which allows data to be stored and transmitted in a decentralized, peer-to-peer network. This means that instead of relying on centralized servers and intermediaries, Web 3 applications can operate independently, using smart contracts and cryptocurrencies to facilitate transactions.
Key Features of Web 3
- Decentralization: Web 3 operates on a decentralized network, eliminating the need for intermediaries and centralized authorities.
- Blockchain-based: Web 3 uses blockchain technology to store and transmit data, ensuring security, transparency, and immutability.
- Artificial Intelligence: Web 3 incorporates AI and machine learning to create more intelligent, adaptive, and personalized applications.
- Internet of Things (IoT): Web 3 enables seamless communication between devices, sensors, and applications, creating a more interconnected and automated world.
The Impact of Web 3
Web 3 has far-reaching implications for various industries, including:
- Finance: Web 3 enables decentralized finance (DeFi) applications, providing greater accessibility, transparency, and security for financial transactions. 2. Social Media: Web 3 allows for decentralized social media platforms, giving users greater control over their data and online interactions.
- E-commerce: Web 3 enables secure, transparent, and efficient e-commerce transactions, reducing the need for intermediaries and increasing trust between buyers and sellers.
Conclusion
Web 3 represents a fundamental shift in the way we interact with the internet. Its decentralized, blockchain-based architecture promises to create a faster, more secure, and more transparent internet. As Web 3 continues to evolve, we can expect to see new applications, services, and business models emerge, transforming the way we live, work, and interact online.
-
 @ 6d8e2a24:5faaca4c
2024-11-30 15:39:03
@ 6d8e2a24:5faaca4c
2024-11-30 15:39:03
Barcelona just lost their home match, against las Palmas This means if Madrid are able to win their two games they will be topping the league.
-
 @ 9cb3545c:2ff47bca
2024-12-01 00:18:45
@ 9cb3545c:2ff47bca
2024-12-01 00:18:45Hey there! So you’ve got a whopping 50+ Lightning Channels and you’re not keen on them Force Closing? Well, buckle up! This guide will be an additional resource as you navigate through daunting process.
In this post, we will go over some extra tips and tricks not covered in the official guide. While this guide does have some steps that are not covered by Umbrel, its main objective is to provide confidence in the process (not a replacement process), coming from someone who’s been there and done that, and some how came out with all Lightning Channels still running! I highly recommend reading this post fully before starting the migration process.
Before we dive in, here is the Official Guide from the Umbrel team on how to update UmbrelOS from 0.5.4 to 1.x.x. Reference the steps all the time, and follow them carefully.
With that out of the way. Here are some extra TIPs to fill in some gaps I encountered as I went through the process.
The Order of Steps
Tip #1:
In the Official Umbrel Guide, the Umbrel team asks you to start by backing up your data. As a lightning Node Runner, I recommend against this. Because the Bash script will stop all Umbrel Services and your node will remain offline while you prepare a Bootable USB Stick. So definitely don't start with the backup, first get the bootable stick sorted out, then move on to backups.
Creating the Bootable USB Stick
TIP #2:
After many failed attempts to create a bootable USB stick from the link umbrel provides in their official guide. I ended up getting the ISO directly from Umbrels team through their Discord Channel. Unfortunately, I wont be able to share this link here. but just in case the umbrelOS-amd64-usb-installer.iso.xz didnt work for you as well, this could be an alternative route.
TIP #3:
Since Umbrel is an actual full OS now. You might need to handle some BIOS quirks. The umbrelOS Kernal is not signed. So if you have Secure Boot turned on in the BIOS, your PC will try to protect you, and block you from booting into you USB Stick. Turn off Secure Boot and you should be able to bypass this issue. I also had to turn on Legacy Option ROMs as well.
Tip #4:
Test your Bootable USB Stick on a secondary device before you go on trying to update your node. Since turning the node off and on is a hassle, its just easier to be certain the the Bootable Stick is ready before even attempting to upgrade your node.
If all is good, you are ready to get back to the guide and walk through the steps.
Preparing the Hardware
Tip #5:
In the official guide they as you to connect a Keyboard and Screen. This is of course needed. I would highly suggest you connect a mouse as well. My Bios was very stubborn and didn't comply with just a keyboard as I attempted to re-order Boot Sequences.
The Migration Process
Tip #6:
Remember, this is 10 times easier if you are not running a lightning node, but on a lightning node, the Channel.db file is being updated constantly. Once you start the backup process, the script will shutdown umbrel services and start copying. you can''t turn your node back on after this stage. If you do, assume the backup you created through the Bash script is obsolete. and you will have to redo the backup process again. If you really know what you are doing, you probably can surgically copy/paste the LND folder. But its easier not to do this.
But not to worry, if you start the process just keep going (especially if you checked all the TIPs I cover above). I say this out of experience, because after I started the first backup process, it took me about an hour to backup my SSD, but then the Bootable USB stick threw so many errors I gave up, and turned on the node again. Then later re-attempted the process from scratch. This time, since my external SSD was already full, it took 3.5 hours to backup all the files again.
Tip #7:
This will take time, so just trust the migration process and wait for the files to get copied. you are probably copying more than a terabyte worth of data back and forth over USB, Leverage USB 3 if you have it.
Tip #8:
If you have a custom name for your umbrel node. Meaning you do not access it by using umbrel.local, this will be reset to the default umbrel.local after the migration. I am not sure if this could be switched again to a custom name, but for now, this won't cause any issues.
Tip #9:
During the last steps of the Migration process, and once Umbrel has copied the backup back into the SSD, it will finish the process with downloading your apps, and restarting. Don't freak out :D
Tip #10:
I honestly don't have a tenth tip, but thought it would make this list look nicer with one. So my last tip for you is to relax and enjoy the process. And feel free to tag me if you faced any issues. Hopefully it will be something i experienced and will be able to help.
Have Fun, and Good Luck!
-
 @ a3b9f172:784b9f38
2024-11-30 14:00:20
@ a3b9f172:784b9f38
2024-11-30 14:00:20Introduction
The metaverse, once a concept confined to science fiction, is becoming a tangible reality. This interconnected virtual universe promises to redefine how we work, socialize, shop, and entertain ourselves. But what does this mean for businesses and individuals? Let’s dive into the opportunities and challenges of this emerging digital frontier.
What Is the Metaverse?
The metaverse is a virtual, immersive space where individuals can interact in real time using digital avatars. It combines augmented reality (AR), virtual reality (VR), blockchain, and artificial intelligence (AI) to create a persistent and shared digital environment. Key platforms like Meta’s Horizon Worlds, Roblox, and Decentraland are leading the charge in building this ecosystem.
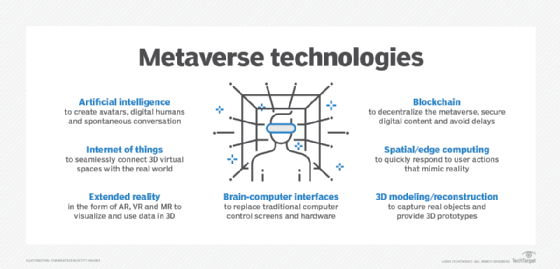
Impact on Businesses
-
New Marketing Channels Brands are entering the metaverse to create immersive marketing campaigns. Nike, for example, launched its virtual Nikeland on Roblox, allowing users to interact with products in unique ways.
-
Virtual Commerce The metaverse introduces the concept of "v-commerce," where businesses can sell virtual goods or services. Fashion brands are now creating digital clothing for avatars, opening up entirely new revenue streams.
-
Workplace Transformation Virtual offices in the metaverse could replace traditional remote work setups, enabling teams to collaborate in dynamic, shared environments that mimic physical offices.
Opportunities for Individuals
-
New Ways to Socialize The metaverse enhances online social interactions by allowing users to meet, play, and build relationships in a more immersive environment.
-
Earning Potential The rise of the metaverse has created opportunities for individuals to monetize their skills, such as creating virtual assets, hosting events, or becoming virtual influencers.
-
Personalized Experiences Users can customize their avatars, environments, and interactions, creating deeply personal and engaging digital experiences.

Challenges and Risks
While the metaverse offers exciting possibilities, it’s not without challenges:
Privacy and Security: With more personal data collected, ensuring user privacy will be critical. Accessibility: High costs of hardware like VR headsets may limit access. Mental Health Concerns: Prolonged time in virtual worlds could impact mental well-being. Visual Suggestion: An image illustrating concerns, such as a person overwhelmed by VR headsets or a hacker breaking into a virtual space.
What’s Next?
The metaverse is still in its infancy, but its potential is enormous. As technology evolves, the lines between the physical and digital worlds will continue to blur. Businesses must adapt to this new reality, while individuals should stay informed and explore opportunities.
Conclusion
The metaverse represents a shift in how we interact with technology and each other. By embracing its possibilities while addressing its challenges, we can create a digital future that benefits everyone.
-
-
 @ 1b328cb8:36baf278
2024-12-03 16:52:24
@ 1b328cb8:36baf278
2024-12-03 16:52:24Like many others, I am still navigating my path toward a Bitcoin circular economy. While I’ve earned my first sats, building a sustainable livelihood solely from Bitcoin remains a work in progress. At the same time, my enthusiasm for working in a fiat-centered world diminishes daily.
This reflection is not only about my personal journey but also the broader question of how people worldwide can transition into a Bitcoin-based economy. Here, I’ll share my thoughts on adoption, the narratives shaping Bitcoin’s role, and how individuals like us can contribute to this shift.
Digital Capital vs. Peer-to-Peer Payments
A key debate in the Bitcoin space centers on two narratives: Bitcoin as "digital capital" and Bitcoin as a peer-to-peer payment system. Michael Saylor has championed the digital capital narrative, especially among institutions, but this focus has drawn criticism for overshadowing Bitcoin’s origins as a payment network.
As a former entrepreneur and sales professional, I see value in both perspectives but also pitfalls if one dominates. 1. The Value of Digital Capital: The concept of Bitcoin as "digital capital" is a powerful one, and Saylor deserves credit for popularizing it. Capital represents the sacrifices that drive progress, and Bitcoin, as hard money, is 100% capital—unlike fiat, which is 100% liability. This distinction is critical and deserves recognition. 3. The Danger of Custodial Sirens: However, the digital capital narrative risks losing a vital part of Bitcoin’s ethos: self-custody. When institutions like MicroStrategy rely on custodians to hold their Bitcoin, they reduce it to a liability. The old adage rings true: Not your keys, not your coins. Without self-custody, the foundation of Bitcoin’s value—its decentralization and trustless nature—weakens.
Takeaway: Bitcoin can be both digital capital and a peer-to-peer payment system, but only if self-custody remains central to its adoption.
Grassroots Adoption: The Power of Peer-to-Peer
Bitcoin adoption is thriving where people need it most—regions like South America and Africa, where fiat currencies often fail. In these places, Bitcoin’s peer-to-peer nature is not just a feature; it’s a lifeline. In contrast, adoption in Western countries faces challenges. Regions like Finland, once pioneers in Bitcoin payments, have lost momentum. The average person here is more likely to chase “the next Bitcoin” or other tech trends than to understand what truly sets Bitcoin apart.
Self-Custody Is Key: What differentiates Bitcoin is self-custody. This encourages users to care about decentralization and peer-to-peer networks. Without it, Bitcoin risks becoming just another centralized asset.
The Path Forward:
To make Bitcoin more tangible and legitimate in everyday life, we need to connect it to real goods and services. When people see “Bitcoin Accepted Here” signs, they perceive it as real money. The solution is simple but powerful: * Start selling products and services in Bitcoin. * Create and support marketplaces—both local and global—that use Bitcoin as their primary medium of exchange.
These changes won’t happen overnight, but they will grow naturally as demand increases. Each step we take helps build the circular economy we envision.
Final Thoughts
Bitcoin adoption requires action. Whether you’re offering goods, services, or simply holding sats in self-custody, every step counts. It’s better to do something small today than to wait for a perfect system tomorrow.
Let’s chip away at the fiat mindset, one sat at a time.
Thank you for reading!
Sophos
P.S.
Looking for original Bitcoin content, marketing copy, or creative writing? I’m a pen-for-hire with three books under my belt and a background in sales and marketing. I’d be happy to help bring your ideas to life—paid in sats, of course.
-
 @ 5af07946:98fca8c4
2024-12-03 16:16:03
@ 5af07946:98fca8c4
2024-12-03 16:16:03Gold was the basis of both the monetary and the measurement systems.
No one knows for sure when gold mining began. Our current estimates are around 4000 BC. That puts it around the same time as Mahabharata. The frequent mentions of gold ornaments among kings and deities and as jewelry among women during the times of the epic, indicate usage of gold as a scarce but in-fashion store of value.
In Mahabharata, there is a clear mention of gold coins being abundantly used. In the fourth book (Viarata Parva), the prince Uttara offered Arjuna (disguised as a transgender named Vrihnnala) a hundred gold coins for saving him (and his bovine wealth) from Kaurvas.
There is evidence of countable units of precious metal being used for exchange from the Vedic period onward. A term Nishka appears in this sense in the Rigveda. A unit called Śatamāna, literally a " hundred standard ", representing 100 krishnalas is mentioned in Satapatha Brahmana. A later commentary on Katyayana Srautasutra explains that a Śatamāna could also be 100 Rattis . A Ratti is the weight equal to seeds of Abrus Precatorius. A hundred of them are almost equal to a Tola that is used for gold trade to date in India. All these units referred to gold currency in some form, though they were later adapted to silver currency.
Barter system was widespread for the smaller transactions. Commoners used fruits and grains to get what they needed. Rich people used copper as a store of value. A one time adult meal was normally considered one copper coin. So was the ride fare. You could hop on and hop off any boat or cart at any place along its route for one copper coin. Super rich used copper for utensils at their home. For them the valuable thing was silver. A silver coin was considered the same as a hundred copper coins. Ultra rich ate their food in Silver utensils. For them the store of value was a gold coin.
A gold coin was equal to a hundred Silver's. The valuation was based on rough order of rigor in mining these metals. Silver was considered hundred times harder to purify than copper, and gold being similar orders of magnitude harder than Silver because of very low yield. In a way "proof of work" was baked in universally acceptable currency.
All states, no matter what their political equations, honored this simple "proof of work" based storage of value. Privacy, self custody and universality were the underpin of trade. Value exchange protocol was owned by people NOT kingdoms though kingdoms could issue coins (currency) aligned to universally accepted methods. It is a well established fact that after the great war of Mahabharta, sixteen main kingdoms (mahapadas) got formed over a couple of centuries. Each one of them issued their own coins, though they were all different shapes or stamps on gold coins. Quarter gold coins (Svarna) are excavated from Gandhara.
Currency was pegged to people's trust in "proof of work". Important point to note here, currency was not pegged to commodities such as iron or wheat. Gold and silver were NOT treated as commodities. Gold's only purpose was value storage and silver was used purely for minting. Copper was primarily used for making utensils for the rich. Copper was supposedly the best metal to store food and water. Eating in silver, though common for the rich, was considered a show-off.
This simple to understand and time tested system of powers of ten, was later exploited by Aryabhatta to conceptualize zero and decimal system - the very basis of modern arithmetic. The seeds of Abrus precatorius (Ratti) being very consistent were used to weigh gold using a measure where 8 Ratti = 1 Masha; 12 Masha = 1 Tola (12 X 8 = 96 Ratti), or roughly equal to 100 Ratti ( 96 Ratti pure gold and 4 Ratti impurities to solidify the gold). In other words, a Tola's "weight unit" was 100 Ratti while its "price unit" was 96 Ratti. In simple calculations 10 grams (one Tola) of solid gold was worth one kilo of solid silver or hundred kilos of solid copper. Or one Ratti (tiny seed) of gold was equal to one kilo of copper.
The common word used for one Kilo was Ser or Seer- roughly equal to 1.07 kilos in weight units or volume wise roughly equal to one liter. Volume was a preferred way to exchange at a larger scale to weed out as many impurities as possible from molten metals. One Seer is around 80 Tola in weight.
During the days of Mahabharata, a
Tolawas calledŚatamāna- a Sanskrit word representing the measure of one hundred. And aRattiwas called aKrishnala- most probably named afterKrishnathe supreme personality of Godhead. In later times of middle eastern empires, aTolawas named anAshrafi- The same weight specifications. One Tola of gold - was adopted as Ashrafi - around fourteenth century in Prussia. The weight of an Ashrafi gold coin varies depending on the coin's origin and history:- Nizam-era gold Ashrafi: A gold Ashrafi coin issued by Nizam VI Mir Mahbub Ali Khan in 1893 CE weighed about 11 grams.
- India-Princely States HYDERABAD Ashrafi : This coin weighed 11.1780 grams and had a fineness of 0.9100.
- Awadh Gold Ashrafi: This coin weighed 10.73 grams and was made of 22-carat gold.



