-
 @ 9f94e6cc:f3472946
2024-11-21 18:55:12
@ 9f94e6cc:f3472946
2024-11-21 18:55:12Der Entartungswettbewerb TikTok hat die Jugend im Griff und verbrutzelt ihre Hirne. Über Reels, den Siegeszug des Hochformats und die Regeln der Viralität.
Text: Aron Morhoff
Hollywood steckt heute in der Hosentasche. 70 Prozent aller YouTube-Inhalte werden auf mobilen Endgeräten, also Smartphones, geschaut. Instagram und TikTok sind die angesagtesten Anwendungen für junge Menschen. Es gibt sie nur noch als App, und ihr Design ist für Mobiltelefone optimiert.
Einst waren Rechner und Laptops die Tools, mit denen ins Internet gegangen wurde. Auch als das Smartphone seinen Siegeszug antrat, waren die Sehgewohnheiten noch auf das Querformat ausgerichtet. Heute werden Rechner fast nur noch zum Arbeiten verwendet. Das Berieseln, die Unterhaltung, das passive Konsumieren hat sich vollständig auf die iPhones und Samsungs dieser Welt verlagert. Das Telefon hat den aufrechten Gang angenommen, kaum einer mehr hält sein Gerät waagerecht.
Homo Digitalis Erectus
Die Welt steht also Kopf. Die Form eines Mediums hat Einfluss auf den Inhalt. Marshall McLuhan formulierte das so: Das Medium selbst ist die Botschaft. Ja mei, mag sich mancher denken, doch medienanthropologisch ist diese Entwicklung durchaus eine Betrachtung wert. Ein Querformat eignet sich besser, um Landschaften, einen Raum oder eine Gruppe abzubilden. Das Hochformat entspricht grob den menschlichen Maßen von der Hüfte bis zum Kopf. Der TikTok-Tanz ist im Smartphone-Design also schon angelegt. Das Hochformat hat die Medieninhalte unserer Zeit noch narzisstischer gemacht.
Dass wir uns durch Smartphones freizügiger und enthemmter zur Schau stellen, ist bekannt. 2013 wurde „Selfie“ vom Oxford English Dictionary zum Wort des Jahres erklärt. Selfie, Selbstporträt, Selbstdarstellung.
Neu ist der Aufwand, der heute vonnöten ist, um die Aufmerksamkeitsschwelle der todamüsierten Mediengesellschaft überhaupt noch zu durchbrechen. In beängstigender Hypnose erwischt man viele Zeitgenossen inzwischen beim Doomscrollen. Das ist der Fachbegriff für das weggetretene Endloswischen und erklärt auch den Namen „Reel“: Der Begriff, im Deutschen verwandt mit „Rolle“, beschreibt die Filmrolle, von der 24 Bilder pro Sekunde auf den Projektor gewischt oder eben abgespult werden.
Länger als drei Sekunden darf ein Kurzvideo deshalb nicht mehr gehen, ohne dass etwas Aufregendes passiert. Sonst wird das Reel aus Langeweile weggewischt. Die Welt im Dopamin-Rausch. Für den Ersteller eines Videos heißt das inzwischen: Sei der lauteste, schrillste, gestörteste Marktschreier. Das Wettrennen um die Augäpfel zwingt zu extremen Formen von Clickbait.
15 Sekunden Ruhm
Das nimmt inzwischen skurrile Formen an. Das Video „Look who I found“ von Noel Robinson (geboren 2001) war im letzten Jahr einer der erfolgreichsten deutschen TikTok-Clips. Man sieht den Deutsch-Nigerianer beim Antanzen eines karikaturartig übergewichtigen Menschen. Noel wird geschubst und fällt. Daraufhin wechselt das Lied – und der fette Mann bewegt seinen Schwabbelbauch im Takt. Noel steht wieder auf, grinst, beide tanzen gemeinsam. Das dauert 15 Sekunden. Ich rate Ihnen, sich das Video einmal anzuschauen, um die Mechanismen von TikTok zu verstehen. Achten Sie alleine darauf, wie vielen Reizen (Menschenmenge, Antanzen, Sturz, Schwabbelbauch) Sie in den ersten fünf Sekunden ausgesetzt sind. Wer schaut so was? Bis dato 220 Millionen Menschen. Das ist kapitalistische Verwertungslogik im bereits verwesten Endstadium. Adorno oder Fromm hätten am Medienzeitgeist entweder ihre Freude oder mächtig zu knabbern.
Die Internet- und Smartphoneabdeckung beträgt mittlerweile fast 100 Prozent. Das Überangebot hat die Regeln geändert. Um überhaupt gesehen zu werden, muss man heute viral gehen. Was dafür inzwischen nötig ist, spricht die niedrigsten Bedürfnisse des Menschen an: Gewalt, Ekel, Sexualisierung, Schock. Die jungen Erwachsenen, die heute auf sozialen Netzwerken den Ton angeben, haben diese Mechanismen längst verinnerlicht. Wie bewusst ihnen das ist, ist fraglich. 2024 prallt eine desaströse Bildungssituation samt fehlender Medienkompetenz auf eine egomanische Jugend, die Privatsphäre nie gekannt hat und seit Kindesbeinen alles in den Äther ballert, was es festhalten kann. Man muss kein Kulturpessimist sein, um diese degenerative Dynamik, auch in ihrer Implikation für unser Zusammenleben und das psychische Wohlergehen der Generation TikTok, als beängstigend zu bezeichnen.
Aron Morhoff studierte Medienethik und ist Absolvent der Freien Akademie für Medien & Journalismus. Frühere Stationen: RT Deutsch und Nuoviso. Heute: Stichpunkt Magazin, Manova, Milosz Matuschek und seine Liveshow "Addictive Programming".
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ fa0165a0:03397073
2024-10-23 17:19:41
@ fa0165a0:03397073
2024-10-23 17:19:41Chef's notes
This recipe is for 48 buns. Total cooking time takes at least 90 minutes, but 60 minutes of that is letting the dough rest in between processing.
The baking is a simple three-step process. 1. Making the Wheat dough 2. Making and applying the filling 3. Garnishing and baking in the oven
When done: Enjoy during Fika!
PS;
-
Can be frozen and thawed in microwave for later enjoyment as well.
-
If you need unit conversion, this site may be of help: https://www.unitconverters.net/
-
Traditionally we use something we call "Pearl sugar" which is optimal, but normal sugar or sprinkles is okay too. Pearl sugar (Pärlsocker) looks like this: https://search.brave.com/images?q=p%C3%A4rlsocker
Ingredients
- 150 g butter
- 5 dl milk
- 50 g baking yeast (normal or for sweet dough)
- 1/2 teaspoon salt
- 1-1 1/2 dl sugar
- (Optional) 2 teaspoons of crushed or grounded cardamom seeds.
- 1.4 liters of wheat flour
- Filling: 50-75 g butter, room temperature
- Filling: 1/2 - 1 dl sugar
- Filling: 1 teaspoons crushed or ground cardamom and 1 teaspoons ground cinnamon (or 2 teaspoons of cinnamon)
- Garnish: 1 egg, sugar or Almond Shavings
Directions
- Melt the butter/margarine in a saucepan.
- Pour in the milk and allow the mixture to warm reach body temperature (approx. + 37 ° C).
- Dissolve the yeast in a dough bowl with the help of the salt.
- Add the 37 ° C milk/butter mixture, sugar and if you choose to the optional cardamom. (I like this option!) and just over 2/3 of the flour.
- Work the dough shiny and smooth, about 4 minutes with a machine or 8 minutes by hand.
- Add if necessary. additional flour but save at least 1 dl for baking.
- Let the dough rise covered (by a kitchen towel), about 30 minutes.
- Work the dough into the bowl and then pick it up on a floured workbench. Knead the dough smoothly. Divide the dough into 2 parts. Roll out each piece into a rectangular cake.
- Stir together the ingredients for the filling and spread it.
- Roll up and cut each roll into 24 pieces.
- Place them in paper molds or directly on baking paper with the cut surface facing up. Let them rise covered with a baking sheet, about 30 minutes.
- Brush the buns with beaten egg and sprinkle your chosen topping.
- Bake in the middle of the oven at 250 ° C, 5-8 minutes.
- Allow to cool on a wire rack under a baking sheet.
-
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。
2024年08月13日更新:
修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
准备工具
- Ntfy服务
- Google Script
- Google Sheets
操作步骤
- 在Ntfy后台账号,设置访问令牌。

- 添加订阅主题。

- 进入Google Sheets创建一个表格.记住id,如下图:

- 进入Google Script创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) { var threadId = thread.getId();
if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); }}); }
function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; }
var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true };
try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } }
function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column }
function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); }
function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues(); var rowsToDelete = [];
data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } });
// 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); }
```
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:

结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
-
 @ 21b41910:91f41a5e
2024-11-23 12:00:26
@ 21b41910:91f41a5e
2024-11-23 12:00:26Chef's notes
Based on assorted recipes and refined over time, this round of beef tastes great as a result of the sweet and savory marinade.
Details
- ⏲️ Prep time: 5 minutes (+ 1 day)
- 🍳 Cook time: 20 minutes
Ingredients
- 2 pounds lean beef (may be labeled as London Broil)
- 1/3 cup olive oil
- 1/4 cup soy sauce
- 1/4 cup malt vinegar
- 1/4 cup lemon juice
- 1 tbsp sweetener of choice (honey, molasses, syrup, 4 packets of duck sauce, etc)
- 2 tsp old bay seasoning
- 1 tsp garlic powder
- 1 tsp sea salt
- 1/2 tsp black pepper
Directions
- Day Before: Mix all ingredients except the beef in a bowl to form a marinade. Place the cut of beef in a gallon sized Ziploc bag. Pour marinade over beef, ensure fully covered. Remove any excess air from the bag and seal. Place back in refrigerator for up to 24 hours before cooking.
- Cooking: Bring beef out of refrigerator (still in bag), and allow to rise to room temperature (about 30-40 minutes). Preheat broiler for about 15 minutes (your oven will vary). Broil for about 7-8 minutes on one side, then flip over. Continue broiling for another 7-10 minutes until temperature reads 140°F. Remove from broiler and let rest for 10 minutes before slicing thinly.
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ 826e9f89:ffc5c759
2024-06-28 21:46:01
@ 826e9f89:ffc5c759
2024-06-28 21:46:01_Prologue: this is a prose adaptation of a talk I gave to a private audience in Dubai and then tweaked slightly for a small conference in Sofia. I'm increasingly thinking it deserves a more general audience, and may be better suited to text anyway. This is probably not its final form, as the desired audience is tradfi capital allocators, hence a PDF is likely on the cards in the near future. For the time being, consider this a first draft, practising what it might look like as prose, and soliciting feedback from the good people of Nostr. Enjoy! _
The title of this essay means absolutely nothing. There is no such thing as “Web π” because there is no such thing as “Web 3”. It’s bullshit. It’s a scam.
Unfortunately, it has turned out to be extremely powerful bullshit and an extremely profitable scam, and so my goal in writing this essay is to give the reader the tools to navigate all of this and come out the other side without having been scammed or bullshat. In the spirit of not scamming and not bullshitting, I should be clear upfront about the intended readership of this essay, who I am to write it, and who it’s really about.
Who Are You?
I assume the reader is not a shadowy super-coder, but rather is a financial professional. This essay isn’t really for Bitcoiners, although if any read it, I hope they still find it interesting. Who I am really writing for are people coming to the space for the first time. Hopefully in your mind you are coming to the _Bitcoin _space, but if you think you are coming to the “crypto” space then this may be even more useful.
Who Am I?
I am the founder of a company that makes me not only highly biased but also flagrantly self-interested in the content I am promoting. I run a firm that invests in the Bitcoin ecosystem through a variety of different vehicles. I am not going to mislead you in the slightest in that my primary motivation is for you to allocate capital to us rather than to people I would call scammers and bullshitters. You should listen to them too and make up your own mind, or else what’s the point, really? How do you know I’m not scamming or bullshitting you? Exactly. Don’t trust. Verify.
In any case, that’s all assuming you want to “allocate capital” at all rather than just buy Bitcoin without a management fee. I’d like to think the primary difference is that I will be honest about that, and I’ll encourage you to understand as much as you can about what is going on and what you are doing (and if you are at all unsure, I would suggest you aren’t ready and you should just buy Bitcoin and learn) rather than bamboozle you with complete nonsense like “Web 3”.
Who Is This About?
It’s not at all about people working in crypto. Bitcoiners amongst the readership may be mildly irritated by me going on to give about as charitable an explanation of the role of these people as they have probably ever heard from somebody like me. This is really about financiers. It’s about the people who have used the mostly unrewarded efforts of developers, academics, entrepreneurs, and so on to siphon money from you to themselves, leaving a trail of useless tech and defrauded retail investors in their wake – and who will continue to do so if you continue to empower them.
Why This Essay?
We are at an interesting point in the development of the entirety of the “crypto” industry and I strongly suggest that people like you are going to be pitched all kinds of scams and bullshit in the coming months and years. If you have a little more background on what these people are really talking about, you will hopefully be able to avoid it.
My plan to help with that is presenting a short version and a long version of what blockchains are and are for, how they have historically been deployed in service of scams and bullshit, a high-level theory explaining the narrative evolution behind this sorry history, and a prediction for the near-term future of such shenanigans.
What is a Blockchain For?
A Blockchain is for sound, censorship-resistant, peer-to-peer digital money. It is not for anything else. If a blockchain is functional as money, it may be possible to also _use it _for other things. Some people find that interesting, some people find it infuriating, but don’t let that subtlety confuse you. It is not _for _arbitrary computation and storage or “decentralizing the internet” or running illegal securities rackets.

It is for money, plain and simple.
How does it achieve that? Proof of work and the difficulty adjustment. These are the innovations from which every other desirable property or feature flows. Proof of work enables censorship resistance. If somebody is trying to sell you on “proof of stake”: bullshit. The difficulty adjustment enables precise, predetermined, and _fair _issuance. If somebody is trying to sell you on a token they issue for free and without restriction: scam.
The problem Bitcoin solves is both economic and technical and the solution has material technical and economic merit. And it’s for this very specific and irreplicable reason the Bitcoin token has value. If this all sounds extreme to you, then I would suggest that your understanding of the topic is _extremely _misguided, that you are going to be _extremely bullshat and extremely scammed, _and you need to read this essay. That’s the short version.
The Long Version
I am sensitive to how extreme this all sounds. After all, hundreds of billions of dollars have been pumped into crypto, not Bitcoin – a huge amount of it is widely used, and many capable, honest, and brilliant people work in the industry. The reader will recall just above I said those people are not the target of my criticism. I’m not claiming they are all scammers and bullshitters. Sadly, I think it’s more likely they have been scammed and bullshat to some degree also.
I think I have some credibility in pointing this out because, as a VC in the Bitcoin space, I have increasingly seen founders telling me this themselves: that they originally bought into the hype in crypto and ended up wasting an enormous amount of time realizing their idea made no technical or economic sense in that context, so then they came to Bitcoin instead. You hear this one time and it’s an anecdote, but you hear it as many times as I have and it feels more like a representative sample.
What I want to cover next is as charitable a summary of the state of ex-Bitcoin crypto as I possibly can: my contention is that crypto has evolved into 4 rough categories: stablecoins, cryptography R&D, gambling, and scams. And these aren’t exclusive, to be clear; there is a lot of overlap, and, in fact, the overlap is arguably the key.
Scams
Scams are tokens, plain and simple. If somebody is trying to profit from the speculative price action of a token they have issued, they are scamming somebody. Maybe they are scamming you, maybe they are scamming retail investors, maybe they are scamming customers or suppliers – if such parties even exist in their cargo cult “business model”. There’s a scam in there somewhere.
However, it is rarely _just _a scam. There will almost always be components of stablecoins, R&D or gambling too. Hence these are worth really grappling with, taking seriously, giving credit to the extent it is due, but also analyzing critically.
My rough and high-level assessment of this breakdown of crypto is as follows, and I’ll explain what I mean by this below: stablecoins have economic merit but dubious technical merit; R&D has technical merit but no economic merit; and gambling sort of has merit but it depends how you interpret it. Obviously, scams have neither.

Stablecoins
By “sort of technical merit” I mean that stablecoins have central issuers. You can issue them as tokens on a blockchain but there’s not really much of a point. The issuer could just run a database connected to the internet with some straightforward signature schemes for transfers and it would make minimal operational difference. In fact, it would be cheaper and faster. _In fact, _you may as well run a Chaumian eCash mint (a decades-old innovation recently resurrected firmly within the _Bitcoin _space) such that your cheaper-and-faster-than-a-blockchain database also grants users transience and privacy rather than the public permanence of a blockchain.
The fact Tron is the most heavily used for stablecoins, in terms of settling the most value, is a testament to this point: it is barely even pretending not to be a database. This works as regulatory arbitrage given regulators think this is “innovation” because they are stupid.
That said, it is worth giving some credit here given the abject awfulness of fiat banking and payment rails with which stablecoins arguably most directly compete. Stablecoins are significantly more permissionless in their transfer than any fiat bank liability. And to attest to what seems like their most significant use case, they are permissionless in their _usership _in that only an internet connection and the right software is required rather than various discriminatory jurisdictional and compliance criteria.
However, what “sort of technical merit” ultimately boils down to, especially in comparison to Bitcoin, is: highly censorable in their exogenous links and, therefore, their value. The assets supposedly backing stablecoins are (by definition) still within the fiat system, even if this novel transfer mechanism of the rights to withdraw them is not. There is frankly a bit of theatre involved in the so-called “decentralization” of stablecoins given shutting down the central issuer is all that is required to make the permissionlessly tradeable decentralized tokens go to zero and be technically unimpeded but functionally useless. The technical innovation of Bitcoin, in contrast, is easily understood in one sense as it being totally indifferent to this kind of attack.
On the other hand, by “economic merit” I mean that they are extremely widely used and valued as a means of providing dollar shadow banking and often superior payment rails. Those in crypto often love pointing to this and many Bitcoiners tie themselves in knots trying to explain it away, whereas I see it as essentially unrelated to Bitcoin. Clearly there is a superficial connection, but you could create any superficial connection by “tokenizing” things for no particularly good technical _reason. I think it’s a different industry entirely. It’s more like a subindustry within _fintech – part banking, part payments – that for the time being relies on bamboozling regulators with all the nonsense I’m drawing attention to.
And good for them, frankly. If fiat banking isn’t going to be backed by real money anyway, then it _at least _ought to be permissionless. It should really be Chaumian eCash if it isn’t just Bitcoin, and it is regulation alone that makes it so awful in the first place. Making money usable and not a tool of dystopian control is, at this point, a political problem, not a technical one. Stablecoins are frankly a step in the right direction, especially insofar as they acclimatize users to digital assets. But I would still caution that they arguably don’t have sufficient technical merit to withstand what feels like an inevitable political attack …
Cryptography R&D
“Technical merit” for R&D is more or less self-explanatory, but the context is worth appreciating. It’s only really in crypto and mostly in Ethereum more specifically that people can permissionlessly experiment with arbitrarily complex cryptographic schemes that operate on real, enormous value. There are a lot of people who understandably find this attractive given their projects are essentially academic and trying out their ideas in the wild is more interesting, arguably more worthwhile, and certainly more fun than putting research essays on ArXiv or submitting them to a journal.
But … the value being manipulated is at best stablecoins and at worst baseless hype. If it isn’t a stablecoin then it probably exists in the first place because of either gambling or scams – and even there the line is very blurry.
Gambling
Gambling is an interesting lens to adopt on all this because it’s literally a trillion-dollar industry. And it’s real. It’s consensual; it’s not criminal; it’s legitimate economic activity that generates enormous profits for those who facilitate it well.
So, gambling has economic merit in that sense. But it’s tricky in this context how to characterize it because you could also argue it’s deeply dishonest gambling in that the gamblers don’t realize they are playing a negative sum game against the house. They think they are doing something akin to speculating on securities, which may be just as stupid depending on how it’s done, but at least has real economic utility and contributes to capital formation.
The difference here is that what is being speculated on _has no economic merit. _So, if that’s your gauge of merit, then here there is none. And it’s a very blurry line between this and an outright scam. Maybe the people involved _think _of what they are doing as amazing R&D, and maybe it’s inadvertently just a scam; maybe they know it’s all nonsense, but they think they can profit within the negative sum game because there are greater fools. In any case, I think gambling is a very helpful characterization of a lot of the behavior of the users and the real economic function of the industry.
There’s an interesting social component to all this because crypto people will often get mad at Bitcoiners because Bitcoiners tend not to care about either stablecoins or crypto R&D: they’ll say, why don’t you like stablecoins, they have clear economic merit? And the answer is they have dubious technical merit. Or, why don’t you like our next-gen Zero Knowledge scaling protocol, it has clear technical merit? And the answer is it has no economic merit.
If you’re happy with one but not the other, it’s easy to think of Bitcoiners as being closed-minded or dogmatic or whatever, but, ultimately, I think it’s just about discipline. What’s the point in being excited by something that half works, and that you know why will never fully work? So to be frank, a lot of this may be well-intentioned, but it’s kinda’ bullshit. It very probably ultimately rests on gambling and not at all whatever its stated purpose is … or it’s just a scam.
How Did We Get Here?
The following is by no means exhaustive and the framing is deliberately a little tongue-in-cheek. As well as being accurate enough (if unavoidably biased), my goal here is primarily to set up my prediction for what is coming next.
2015 reality: Ethereum launches narrative: “the world computer”
In 2015, Ethereum launched. The narrative here was that we are building “the world computer” and we can now have decentralized uncensorable computation. Never mind that anybody with a laptop has an uncensorable and decentralized computing device. And keep in mind this question of, “_what data might it ever be relevant to compute over in this manner (whatever that means in the first place)?” _The answer will become clearer and clearer …
2016-17 reality: ICO bubble narrative: “Web 3” / “DApps”
Regardless, at the end of 2015 we get the proposal and adoption of ERC20: a standard for issuing fungible tokens within Ethereum contracts, which is why in 2016 _but especially in 2017 _we get the ICO bubble. The narrative changes. Now we are concerned with “Web 2” companies being huge, powerful, and centralized. What if, instead, users could cooperatively own the application, control their own data, and participate in the economic upside that their usage is creating?
2018-19 reality: crypto winter narrative: “mistakes were made”
In 2018 this all falls apart, so don’t worry about it, moving on …
2020-21 reality: defi summer narrative: “decentralized finance”
By 2020 the narrative was different once again. It is more or less realized by this point that utility tokens make no technical or economic sense. You can’t introduce artificial scarcity in capital goods where there should be abundance and deflation and expect anybody to care, never mind to value your concoction. On the other hand, “securities” ought to be scarce and in some sense ought to function as tradeable ledger entries. Maybe they could be tokenized and computed on in a censorship-resistant and decentralized manner?
So, we get a boom in “defi” which, for what it’s worth, fellow Axiom co-founder Anders Larson and I predicted in our essay Only The Strong Survive, in September 2021, would be a complete disaster because, amongst a myriad of other illiterate insanities, there was approximately zero grounding of these securities in productive capital. The ecosystem was entirely self-referential – grounded _not even _in the questionable economic merit of stablecoins but firmly in gambling and scams; in leverage, rehypothecation, and securitization of precisely nothing whatsoever productive.
2022 reality: shitcoinpocalypse narrative: “mistakes were made”
And we were absolutely right because in 2022 everything collapsed. First Terra/Luna imploded – a “defi” project which essentially presented to the world the argument that a fractional reserve bank issuing fiduciary media can literally never go bankrupt because it can always cover a deposit shortfall by issuing more equity. While briefly flirting with a capitalization of around fifty f***ing billion dollars, and endorsed and fawned over by all manner of illiterate charlatans with gigantic and unsuspecting audiences, this argument was eventually rejected by the market as utterly imbecilic, as analyzed by myself and Nic Carter in All Falls Down.
This triggered a credit contagion that soon after took down 3 Arrows Capital, Celsius, Voyager, BlockFi, and others. FTX limped along by what we now understand to be something like defrauding their way out of debt, but eventually also collapsed later that year. If _Only The Strong Survive _was a pre-mortem of all of this, then the reader may want to read Green Eggs And Ham, also by myself and Anders Larson, as a kind of post-mortem.
2023-today reality: Bitcoin multisigs narrative: “Bitcoin renaissance”
And now a lot of this stuff is moving to Bitcoin. It is outside the scope of this essay to explain this in much detail but there have been a handful of developments in Bitcoin recently which, regardless of their intended purpose, seem to have as a collective side effect that a lot of these same shenanigans can now be implemented (or can _pretend _to be implemented) in a more Bitcoin-native context.
So, the new narrative is something like:
“these things didn’t work, not because they are terrible ideas that collapse to moon math wrappers around gambling and scams under any remotely critical analysis, but rather because they weren’t on Bitcoin. But also, since it has only recently become possible to (at least pretend to) implement them on Bitcoin, they are now worthwhile. We have wandered in the wilderness but learned our lessons and found the promised land.”

Technical and Economic Merit
Let’s consider all this through the lens of technical and economic merit once again. Or rather, the alleged merit given the stated goal. Ignore for now whether there is any merit:
2015 technical goal: new computing paradigm economic goal: x% of GDP?
The original idea of “crypto” allegedly has the merit of the next revolution in computing. Goodness knows how big that market is; probably a decent chunk of global GDP – if it meant anything, which it doesn’t.
2016-17 technical goal: disrupting company formation economic goal: y% of S&P?
ICOs then become a little bit more specific. Now they are merely disrupting how we organize companies. What’s that worth? Some portion of the value of the companies that can now be decentralized and tokenized I guess? Who knows …
2018-19 nothing to see here
Nothing happened then, don’t worry about it.
2020-21 technical goal: decentralize finance economic goal: z% of NYSE, CME, ISDA?
Defi becomes more specific again. Now we are merely tokenizing financial contracts, expanding access, removing middlemen, and so on. So that should probably be worth some percentage of capital markets activity?
2022 nothing to see here
Oops, never mind …
2023-today technical goal: now it’s on Bitcoin! economic goal: i% of … Bitcoin?
… and now it’s on Bitcoin apparently.
In Hindsight ...
I think the most amusing analysis of all this is as follows: it starts off completely insane, it gets more and more restrained each time – you could cheekily argue it starts to make more and more sense – but it also gets closer to Bitcoin every time. It’s clearly narrowing in on just: Bitcoin.
This is people realizing, painfully, over decades, what blockchains are for! They are not for “decentralizing everything” They are for censorship-resistant, sound, peer-to-peer digital money.

And I think this is _also _why we get the current state of crypto from earlier in the essay. As it starts to make more and more sense (by getting closer and closer to Bitcoin) you have realizations like the following: digital gift vouchers for artificially scarce and extremely expensive computation aren’t money, so we need “real money” in here for it to have economic merit, so you get stablecoins. Also, well we have a rich programming environment that seems technically interesting but also the severe technical handicap of being unable to do even a billionth of a billionth of a billionth of all the computations in the world, so you get crypto R&D. These emerge as a kind of patch, and they have _some _merit in isolation, whereas the long-term trajectory is actually just to converge on Bitcoin.
It’s an open and fascinating question if there are any learnings from these that can still be transplanted to Bitcoin. For stablecoins, this strikes me as less clear, given the dubious technical merit is introduced by using a blockchain at all, not just a blockchain other than Bitcoin. However, efforts to create Bitcoin balances (tokenized or otherwise) that are stable relative to some external price are to be applauded, if still heavily scrutinized for what technical merit they _really _have.
It seems far more likely that crypto R&D will prove useful in a Bitcoin context to some or other degree, and in this case the economic merit is in fact solved by moving to Bitcoin, provided the necessary technical merit can be mimicked. At the time of writing, this is a source of both hope and dread: hope given the possibility of viable avenues of development (although still highly uncertain); dread given how early steps in this direction are already being misrepresented in the pursuit of bullshit and scams. I will return to both shortly.
Narrative Evolution
Back to the table just above, I want to make three quick observations that tie together my entire argument and get us to the end of the essay:

Firstly, the bubbles always follow the price of Bitcoin. Hopefully I don’t need to include a price chart for the reader to grasp this immediately.
Secondly, it’s important that the narrative always changes. Absolutely ungodly amounts of money were raised for this crap following the_ Bitcoin bull runs of 2017 and 2021. The people doing this couldn’t point to the previous absolute disaster, so they had to spin something along the lines of: “_we learned our lessons and we’ve refined the use case.” This should sound familiar from just above.
Thirdly, however, regardless of whatever refinement they’ve come up with, the consequence of the new “narrative” is always, “buy my token”.
Always.
It doesn’t matter what buzzword salad is in the middle. It’s always “Bitcoin is cool, xyz, fughayzi fughahzi, buy my token.”
This is why I am very much tempted to not care so much about developers, academics, entrepreneurs, and so on, and in fact for my null hypothesis to be that they are more likely to have been victims than perpetrators. I don’t think they even end up in a position to contribute without the key group whom I do blame. When you put all these pieces together, what I think falls out of this analysis is as follows:
The entire cycle of shitcoinery can be traced to unscrupulous financiers convincing capital allocators who don’t know any better, in a bull market that, yes, Bitcoin is cool, but what they are doing is related, cooler, and that they deserve a fee.
Let us label this the Capital Cycle Theory of Shitcoinery. I think that everything else about which one might want to complain is downstream of this core realization.
Avoiding It
Given everything I’ve covered this is simple and this is pretty much the end of the essay.
You need to be aware of why this is happening now. If it hasn’t happened to you already (intended readership in the capital allocation business, that is) I guarantee it’s about to: with ETFs and the halving just past, we seem to be starting a Bitcoin bull run, these people have already raised ridiculous amounts of money on scams and bullshit that have mostly imploded. They may have lost a lot of money, or they may even have dumped on retail and got an excellent “return”. But in any case, they need a new narrative.
It's _possible _they have a viable narrative around stablecoins, R&D, both, and that they are as wary of scams as I have suggested here that they should be. I don’t want to insult anybody who merely has a different investment thesis to me if they are otherwise reasonable in their outlook and honest in their dealings.
However, if they are only now realizing how pointless and disingenuous every preceding crypto narrative has been after 7 years and hundreds of billions of dollars – or if they still don’t realize it at all; if their track record shows they were deeply involved, handsomely rewarded, and yet created nothing of lasting value; if they say things like “the builders are coming back to Bitcoin”: be very, very suspicious. Be on the lookout for tokens, which is to say, be on the lookout for scams.
What is especially frustrating is that the technical spin of the "layer twos" that are all the rage at the time of writing, that "the builders are coming back to Bitcoin" to build, and that you, the capital-allocating reader, will almost certainly be pitched, is in and of itself pretty reasonable. They just don't require tokens and they don't require gambling to support the token prices. What they do require is _sound adherence to Bitcoin's technical and economic merit. _At the very least, they require honest communication about the design trade-offs so far and planned for, and what, if any, economic and technical merit is left over after these trade-offs have been made.
Narrative aside, the _reality _of 99% of these projects is that they are private execution environments tied to multisigs custodying user deposits. Which is to say, on the one hand, that they are cargo culting "crypto R&D" from Ethereum that isn't technically possible in Bitcoin in order to feign technical merit, and on the other, that _they aren't layer twos at all. _Once again, they may as well be Chaumian eCash mints, except for the fact that this would make the intended token scam all but impossible to pull off.
Casey Rodarmor, creator of the Ordinals protocol, recently joked on the Hell Money _podcast he co-hosts, responding to the idea that "_everybody is building an L2 now":
"It's the same sad sack playbook as on Ethereum being recapitulated on Bitcoin. That's how you get a VC check on Ethereum. They are all glorified multisigs, so they are like, "hey let's port our glorified multisig to Bitcoin and get a VC check." I was talking to a friend of mine who is working on an interesting project, an open-source analyzer that does transaction clustering, and I was like, "maybe you could do this in this way and raise some VC money," and he said, "yeah, okay, but what's the point in raising VC money?" And I said, "no, no, no, this is the end! This is the goal! You raise VC money and then you cut yourself checks from that VC money until it runs out and then you raise more at a 10x valuation. This is the new economy, guys!"
The 1% that are legitimately trying to bring the learnings from crypto R&D to Bitcoin in a technically and economically sound manner will hopefully win in the long run (and even this is somewhat speculative at the time of writing) but will likely get little to no attention amidst this bull market flurry of scams and bullshit.
Axiom will do its best to source and invest in these companies (we already have!) but we are resigned to it being a much more difficult sell to capital allocators in light of the Capital Cycle Theory of Shitcoinery. To be brutally honest, this entire essay can fairly be considered cope on my part in light of having lost this battle in the past and facing up to the very real prospect of losing it in the near future too. Oh well, at least I tried.
Wrapping Up
The essence of the Capital Cycle Theory of Shitcoinery is that the problems I’ve described ultimately come from bamboozling people just like you with technical sounding nonsense like “Web 3” so you think it’s all a lot more complicated than it really is. Just buy Bitcoin. That’s certainly the first thing you should do anyway, and it might be the only thing you ever need to do.
If you really, really want to take the extra risk of investing in the Bitcoin ecosystem, the team at Axiom would be happy to speak with you. But we are never going to talk you out of buying Bitcoin. There is no world in which Bitcoin does poorly and we do well, or in which we promise something “better than Bitcoin,” and there’s no point in engaging with us at all if you don’t already believe most of this.
If that’s of interest to you, we’d love to talk. If not, just buy Bitcoin. In any case: fair warning, we are heading into a Bitcoin bull market and the scams and the bullshit are coming. Good luck avoiding them.
Allen Farrington, June 2024

-
 @ a012dc82:6458a70d
2024-11-23 08:04:48
@ a012dc82:6458a70d
2024-11-23 08:04:48Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
If you want to invest in the cryptocurrency market, you have many options, including Bitcoin, Ethereum, and several altcoins. But there are also backdoors into the cryptosphere that may be used to learn more. If you want to invest in cryptocurrency but don't want to actually purchase any, here's what you need to know:
KEY TAKEAWAYS
-
Investing in cryptocurrency presents some new and unusual challenges.
-
Due to the high degree of volatility associated with cryptocurrency investments, some people opt to put their money into more tried and true investment vehicles instead.
-
Many mutual funds and stocks are available that are tied to the bitcoin industry, allowing you to indirectly participate in the market.
What Is Indirect Crypto Investing?
You may still get cryptocurrency without signing up for a cryptocurrency exchange account. Indirect bitcoin investments allow you to acquire exposure to the market without actually purchasing any cryptocurrency. Stocks, mutual funds, and exchange-traded funds are some examples of the conventional investment vehicles that are used for indirect investing (ETFs).
There are, once again, both benefits and drawbacks to think about, such as safety, costs, and the possibility of losses. You should think carefully about whether or not an indirect investment is worth it to you when considering whether or not to acquire cryptocurrencies via a third party.
Crypto ETFs and Mutual Funds
The first alternative to acquiring cryptocurrency outright is via investment funds. Grayscale Bitcoin Trust is one of the first significant participants in this offering (GBTC). It has some of the same features as an ETF but is treated quite differently under the law. But if you invest in GBTC via your brokerage account, you'll get the same outcome as if you bought a Bitcoin fund. The value of the investment will rise and fall in tandem with the fluctuating Bitcoin market.
The high expenditure ratio of 2% is a significant drawback of grayscale. Simply put, they add 2% to the purchase price of Bitcoin to cover the cost of keeping it in a wallet under your name. Avoid the 2% maintenance cost by doing it on your own.
Besides the aforementioned Bitwise 10 Crypto Index Fund, there are also the ProShares Bitcoin Strategy ETF (BITO), the Valkyrie Bitcoin Strategy ETF (BTF), the VanEck Bitcoin Strategy ETF (XBTF), the Global X Blockchain and Bitcoin Strategy ETF (BITS), and the VanEck Global X Bitcoin Index Fund (GBXB) (BITW). It is important to read the prospectus and understand the fund's fees and underlying investments since they might vary widely.
Cryptocurrency and Blockchain Stocks
Stocks of firms involved in the blockchain sector or those that invest in or hold bitcoin may provide investors with exposure to the cryptocurrency market.
Companies in the cryptocurrency business provide a variety of services, including mining, software development, and more. Bitfarms (BITF), HIVE (HIVE), Canaan (CAN), and Riot Blockchain (RIOT) are just a few of the stocks availablet, and more. Bitfarms (BITF), HIVE (HIVE), Canaan (CAN), and Riot Blockchain (RIOT) are just a few of the stocks available. The cryptocurrency exchange and stock market platform Coinbase (COIN) is a major player in the industry.
In the event of a general downward trend in cryptocurrency values, many cryptocurrency stocks tend to perform poorly as well. If you have any worries about your investing choices or goals, you should see a trustworthy financial adviser.
Bonus Tip: Credit Card Rewards
Finally, credit card rewards are a great way to add to your bitcoin holdings without having to part with any hard dollars. You can use your credit card as you like—swipe, touch, dip, click—and earn cryptocurrency in the process with a few different cards.
The BlockFi Rewards Visa Signature card, the Gemini Credit Card, and the Upgrade Bitcoin Rewards Visa card are all exceptional options for individual bitcoin holders. Both the Crypto.com and Coinbase exchanges provide rewards cards.
The personal SoFi credit card and the Venmo credit card are two examples of cards that provide you with a wide range of redemption possibilities, including bitcoin. Earning cryptocurrency as a credit card reward is like investing in cryptocurrency without really purchasing any. No matter what happens to the price of cryptocurrency, you still stand to gain since you didn't have to spend any money to get it.
What is Cryptocurrency?
Secure transactions may be made in what is known as "cryptocurrency," a digital or virtual currency established through the use of cryptographic procedures. There is no government or bank in charge of it, as there is with fiat currency.
What is Bitcoin?
Bitcoin, the first successful decentralized cryptocurrency, was founded in 2008 by an unknown person or group of people named Satoshi Nakamoto. It's a kind of digital currency that can be safely transferred from one user to another through the web.
Who is Satoshi Nakamoto?
The person or individuals behind the creation of the Bitcoin protocol and the first cryptocurrency in 2008 are often referred to by the alias "Satoshi Nakamoto." Nakamoto was active in the bitcoin and blockchain communities until about 2010.
Conclusion
Cryptocurrencies have been called "the next big thing" in technology. Those who want to get in on the new technology without taking undue risks might consider investing indirectly in crypto. This will increase the portfolio's diversification and help spread out the associated risk.
FAQ
Do I need a cryptocurrency wallet to make an investment? To protect your bitcoin holdings, you need to get a wallet. However, if you want to test the waters before diving in headfirst, platforms like PayPal and Robinhood make it easy to acquire and store small amounts of cryptocurrency. However, the private key to these wallets is held securely by the wallet provider.
To what cryptocurrency does one have the least amount of difficulty allocating funds? Ethereum is seen as a good cryptocurrency to invest in by many, particularly those just starting out in the industry. Since the value of Ethereum's currency (ETH) goes up with the number of active nodes on the network, we can assume that the price of ETH will go up as more decentralized applications (dApps) and other projects are built and launched on Ethereum.
In what timeframe can a single bitcoin be mined? One bitcoin may be mined in around 10 minutes with the right gear and software, but this setup can be expensive and is only available to a select group of people. The average user can mine a bitcoin in 30 days, which is both common and reasonable.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 9ff58691:0bf6c134
2024-11-23 11:58:15
@ 9ff58691:0bf6c134
2024-11-23 11:58:15В Кургане состоялось долгожданное открытие новой экспозиции в музее науки и технологий, посвященной важной теме “Наука и человек”. Это событие стало знаковым моментом в культурной жизни города и шагом к развитию образовательной инфраструктуры.
На выставке представлены интерактивные технологичные экспонаты, которые позволяют посетителям не просто наблюдать, но и активно участвовать в процессе познания. Уникальные инсталляции включают в себя виртуальные симуляции, демонстрирующие достижения в медицине, экологии и инженерии, что делает науку доступной и интересной для всех.
Директор музея отметил, что новая экспозиция призвана вдохновить молодежь и пробудить интерес к научным исследованиям. Ожидается, что выставка привлечет внимание как школьников, так и студентов, стремящихся узнать больше о современных технологиях и их влиянии на жизнь человека.
Посетители уже начали знакомство с новыми экспонатами, а интерактивные элементы выставки особенно заинтересовали детей и взрослых. Это событие подчеркивает стремление Кургана стать центром науки и образования, способствуя развитию инновационного мышления среди горожан.
Автор: Эвелина Тимирбаева
-
 @ 9ff58691:0bf6c134
2024-11-23 11:55:56
@ 9ff58691:0bf6c134
2024-11-23 11:55:56Жители Кургана, мы рады сообщить вам о новых инициативах городской администрации, направленных на поддержку психологического благополучия наших жителей!
🧠 В Кургане открылся современный Центр психологической помощи, оснащенный по последнему слову техники. Здесь вы можете пройти комплексную диагностику с использованием технологий виртуальной реальности и ИИ-ассистентов. Специалисты центра разработают для вас индивидуальную программу восстановления и развития ментального здоровья.
"Наш Центр использует самые передовые методики в области психологии и психотерапии. Мы применяем технологии нейровизуализации, AI-анализа эмоций и когнитивного моделирования, чтобы максимально точно определить потребности каждого клиента и помочь ему достичь гармонии", - комментирует Ольга Соколова, ведущий психолог Центра.
💻 Кроме того, в Кургане запущена программа "Цифровой психолог" - бесплатный онлайн-сервис психологической поддержки для всех жителей. С помощью чат-ботов, виртуальных консультантов и мобильных приложений вы можете получить квалифицированную помощь в любое время, не выходя из дома.
🏫 Также в школах и университетах Кургана открываются специальные кабинеты психологической разгрузки. Здесь студенты и ученики могут отдохнуть от учебной нагрузки, пройти сеансы арт-терапии или медитации с использованием VR-технологий.
Забота о ментальном здоровье - один из ключевых приоритетов для администрации Кургана. Мы уверены, что эти инициативы помогут нашим жителям справляться со стрессами и жить более счастливой и гармоничной жизнью.
Автор: Елизавета Медведева
-
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ 9bd01740:8dc39de3
2024-11-22 20:51:33
@ 9bd01740:8dc39de3
2024-11-22 20:51:33**THE IMPORTANT OF GETTING AN ONLINE SKILLS
Getting an online skill is something most of the youth not just in Nigeria alone should adopt. Some of my reason include 1 Base on the economy situation 2 To compete globally 3 Job opportunity
Many people want to acquire the knowledge but don't know where to start from. To be able to do that you have to 1 make research 2 if you have the money purchase a course 3 get a mentor in the field that you are about to dive in
Online skill to acquire include 1 web development 2 Digital marketing 3 Blockchain 4 cyber security 5 Internet of things 6 AI/ML 7 DevOps 8 data analysis 9 data science 10 product management and so on
Tips to be on track while learning 1 build your portfolio 2 be consistent 3 don't quite 4 be updated
-
 @ 7f31a2d6:b5a93696
2024-11-22 18:44:35
@ 7f31a2d6:b5a93696
2024-11-22 18:44:35Leveraging Community Power: Yakihonne's Innovative Approach to Bitcoin Adoption
Introduction
The Bitcoin landscape is constantly evolving, and community plays a vital role in shaping its future. Yakihonne, a cutting-edge platform, is harnessing the power of community to drive Bitcoin adoption and education. In this article, we will explore Yakihonne's innovative approach and its impact on the Bitcoin ecosystem.
The Yakihonne Difference
Yakihonne distinguishes itself by recognizing every user as a unique node in the Bitcoin network. This perspective empowers individuals to take an active role in shaping the community and contributing to its growth. By fostering connections and knowledge sharing, Yakihonne creates a supportive environment where users can thrive.
Key Features and Benefits
-
Decentralized knowledge sharing: Yakihonne's platform allows users to access and share valuable resources, promoting a deeper understanding of Bitcoin and its applications.
-
Community-driven support: Users can engage with others, ask questions, and receive guidance from experienced community members.
-
Incentivized learning: Yakihonne's gamification elements make learning about Bitcoin engaging and fun, encouraging users to expand their knowledge.
-
Responsible adoption: The platform emphasizes security, privacy, and informed decision-making, ensuring sustainable growth.
The Future of Bitcoin Adoption
Yakihonne's community-centric approach is poised to revolutionize Bitcoin adoption. By leveraging the power of social nodes, Yakihonne creates a snowball effect, where knowledge and enthusiasm spread exponentially. As the platform continues to evolve, it's likely to play a significant role in shaping the future of Bitcoin.
Conclusion
Yakihonne is a game-changer in the Bitcoin space, offering a unique blend of community engagement, education, and support. By joining the Yakihonne community, individuals can tap into the collective power of social nodes, contributing to a brighter future for Bitcoin adoption. Embrace the potential of Yakihonne and be part of this exciting journey!@yakihonne
-
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 8cd9d25d:69e9894d
2024-11-23 04:45:03
@ 8cd9d25d:69e9894d
2024-11-23 04:45:03Chef's notes
Note that youtube recipe is asking for 1tablespoon of salt, which is waaaaaay too much. Recipe works fine with a teaspoon,, but your mileage may vary. Play around with it.
You don't need to prove modern packet yeasts in my experience... just yolo it.
If you want an extra crispy crust, add a second baking pan to the base of the oven as you pre-heat. Then once you've placed the dough in, to the oven, take some boiling water and pour into the second baking tray. This gives you a steam oven on a budget :)
Details
- ⏲️ Prep time: 15min (not including time for dough rises)
- 🍳 Cook time: 30mins
- 🍽️ Servings: 4-5
Ingredients
- 500 grams wholemeal spelt flour
- 1 packet baker's yeast (10grams)
- 350 ml lukewarm water
- 350 ml lukewarm water
- 1 teaspoon salt 🧂
Directions
- Preheat your oven to Preheat oven to 430°F and put a baking tray in at the same time to heat up.
- Add all ingredients to a bowl (best to use a stand mixer to save time, but you can do by hand too. Mix and knead until the dough comes together. After about 5 mins you should have a moist dough that doesn't stick to your hands... if it is a bit sticky, just add a bit more flour (different flours like differenent amounts of water)... If too dry, add a bit more water... etc.
- Remove dough from bowl & form into a ball (smooth on top, never mind if not perfectly smooth on its base). Put back in a bowl and cover with a damp cloth. Allow to rest for 30mins/1hr until dough has roughly doubled in size. Time will depend on the ambient temp where you are. In the tropics, 30mins is just fine.
- Take risen dough out of bowl and put on a floured surface and press the gas out of it... flatten the dough with your hands, and then fold each edge in until you have a rectangle (video makes this bit clear). Then roll the rectangle up into a cylinder. This gives you a nice tight dough for baking. Pinch the ends of the cylinder to seal the dough.
- Place dough onto a baking sheet/ piece of parchment paper etc... cover with damp towlel and let rise for 15/30mins
- Score the risen dough (a razer blade, clean box cutter, or serrated knife works well) , this lets steam escape from the loaf as it bakes without slpititng it in ways you wouldn't like.
- Take your hot baking tray out of the over and transfer your dough onto it. Put into oven.
- Bake at 430°F (220°C) for 15mins, then reduce oven temp to 350°F (180°C) for the final 15mins. Total bake time 30mins.
- Remove from oven and allow to cool for 20-30mins.
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 6d8e2a24:5faaca4c
2024-11-22 18:00:21
@ 6d8e2a24:5faaca4c
2024-11-22 18:00:21BTC price behavior is either hinting at a deeper pullback or an RSI-fueled surge beyond $100,000, Bitcoin market observers conclude.
 Bitcoin BTC tickers down $99,001 faced a serious challenge hitting $100,000 on Nov. 22 as $300 million in sell-side liquidity blocked the way.
Bitcoin BTC tickers down $99,001 faced a serious challenge hitting $100,000 on Nov. 22 as $300 million in sell-side liquidity blocked the way. BTC/USD 1-hour chart. Source: TradingView
BTC/USD 1-hour chart. Source: TradingViewBTC price teases with rejection near $100,000
Data from Cointelegraph Markets Pro and TradingView showed BTC price downside taking over at the Wall Street open.
BTC/USD fell to local lows of under $97,300 and was down around 1.2% on the day at the time of writing.
A trip toward the key six-figure mark earlier ended in defeat as sellers lined up to prevent BTC’s price from climbing higher — a common feature for Bitcoin around key psychological levels.
“FireCharts shows a massive Bitcoin sell wall compressed between the $99.3k - $100k range,” trading resource Material Indicators confirmed in its latest post on X.
This referred to liquidity on the largest global exchange, Binance, with the $100,000 sell wall clearly standing out against other levels while building in strength over the past few hours.
“The good news is there has been a slight bit of erosion in the last few hours,” Material Indicators continued. “The bad news is, it’s still nearly $300M in liquidity.”
 BTC/USDT chart with order book liquidity data. Source: Material Indicators/X
BTC/USDT chart with order book liquidity data. Source: Material Indicators/XAccompanying volume data showed sell-side transactions dominated by amounts between $100 and $1,000, with whales still refraining from mass distribution.
“It would actually be good to see whales start dumping blocks of ask liquidity to force BTC into a support test and to ultimately make the wall easier to penetrate,” the post argued.
“With the ETF faucet turned off for the weekend, we could see some dip buying opportunities ahead.” United States spot Bitcoin exchange-traded funds (ETFs) achieved another day of net inflows above $1 billion on Nov. 21, reflecting considerable institutional interest supporting BTC price momentum.
Bitcoin four-hour RSI hints at bullish comeback
Others considered where a potential deeper price retracement may end up, with popular trader Crypto Chase eyeing $90,000 in what he called the “optimal scenario.”
 BTC/USDT 12-hour chart. Source: Crypto Chase/X
BTC/USDT 12-hour chart. Source: Crypto Chase/XFellow trader CJ had a higher target focused on the mid-$90,000 range.
 Source: CJ
In support of a return to upside, meanwhile, trader Roman noted promising bullish divergences on the four-hour relative strength index (RSI).
Source: CJ
In support of a return to upside, meanwhile, trader Roman noted promising bullish divergences on the four-hour relative strength index (RSI).This fell 10 points on the day, dipping below the key 70 “overbought” level.
“Big bull divs forming between price & RSI here. We should see trend continuation as a result,” he told X followers on the day.
“I think we break 100k today or tomorrow as this entire trend looks very strong.”
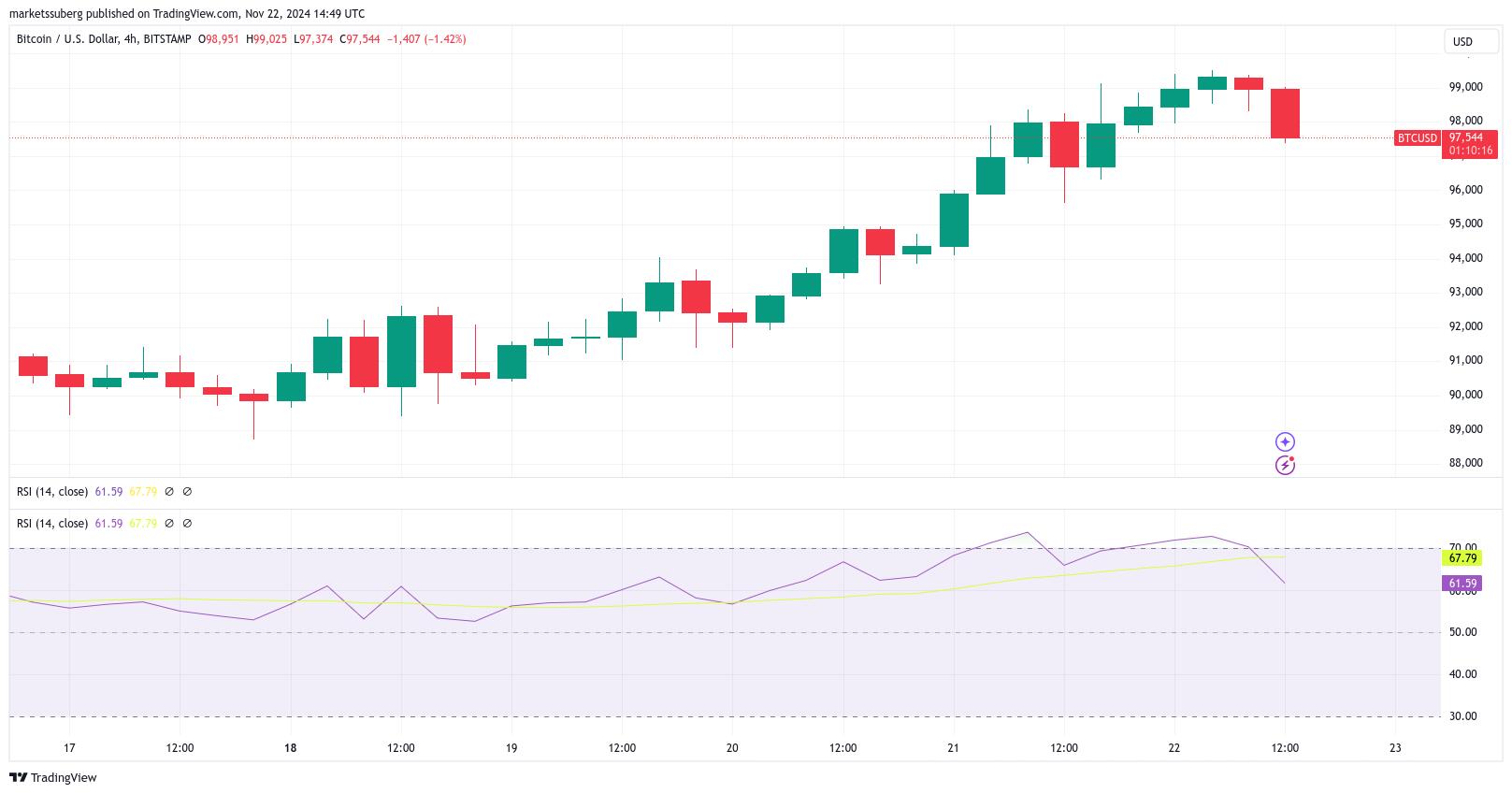 BTC/USD 4-hour chart with RSI data. Source: TradingView
BTC/USD 4-hour chart with RSI data. Source: TradingView -
 @ 65912a7a:5dc638bf
2024-11-22 21:37:16
@ 65912a7a:5dc638bf
2024-11-22 21:37:16Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 12
Ingredients
- 12-14oz fresh cranberries
- 1⅓ cup packed brown sugar
- 1 cup raisins
- 1 orange, peeled & chopped
- 1 cup water
Directions
- Using medium sauce pan, simmer cranberries and water for 5-6 min. Cranberries will start to pop.
- Add brown sugar, raisins, and chopped orange to the berries.
- Bring to a simmer and continue to cook for 20 min. Stir often to prevent sticking. Remove from heat.
- Let set until room temp. Mixture will thicken as it cools.
- Put in a covered container and keep refrigerated. Lasts for about 2 weeks.
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ 9bc2d34d:d19d2948
2024-11-22 17:26:28
@ 9bc2d34d:d19d2948
2024-11-22 17:26:28Chef's notes
Hot Dogs? Check. Cheese? Check. Jalapeno? Definitely (unless you can't handle the spice)
Details
- ⏲️ Prep time: 1 minute
- 🍳 Cook time: 3-5 minutes
- 🍽️ Servings: 1-4
Ingredients
- 3 Hot Dogs (Sliced Thinly or Cut into Chunks)
- Handful of Shredded Cheese Blend
- 1/4 Jalapeno minced (add less or more)
- Optional: Any toppings you like on nachos, such as tomatoes, onions, sour cream, beans, etc
Directions
- Microwave 3 hot dogs for 2-3 minutes (some hot dogs will expand)
- Top with cheese
- Microwave for 1-2 minutes (until cheese is melted)
- Sprinkle all your favorite toppings on top
- Serve
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ ac8bb9b0:70278acc
2024-11-21 15:14:11
@ ac8bb9b0:70278acc
2024-11-21 15:14:11Chef's notes
If you’d like to make this soup part of your rotation and want to shave off a little time for the next time around, double the recipe for the meatballs and freeze half. That way, all you’ll have to do is make the soup and add the meatballs as directed in the recipe. (They may take a few extra minutes to warm through if you add them directly from the freezer.)
The soup can be frozen for up to 3 months but wait until you reheat the soup to add the pasta. Defrost the soup in the refrigerator for 12 hours and then reheat it on the stovetop over medium heat until simmering, add the pasta, and cook until the pasta is tender.
Details
- ⏲️ Prep time: 50
- 🍳 Cook time: 30
- 🍽️ Servings: 8
Ingredients
- 1 large egg
- 3 tablespoons finely chopped fresh chives
- 2 teaspoons finely chopped fresh sage
- 2 cloves garlic, minced
- ¾ lb 85 or 90% lean ground beef
- ½ lb sweet or hot Italian sausage, removed from the casings
- ½ cup grated Parmigiano Reggiano
- ⅓ cup Italian seasoned bread crumbs
- ¼ teaspoon salt
- 2 tablespoons extra virgin olive oil
- 1 medium yellow onion, diced
- 2 large carrots, diced
- 2 stalks celery, diced
- 6 cups high-quality chicken broth
- 2 cups high-quality beef broth
- 2 cups water
- ½ cup dry white wine
- 1 bay leaf
- ½ teaspoon salt
- ¼ teaspoon white pepper (okay to use black pepper)
- 1 cup small dittalini pasta
- 4 oz fresh spinach, stems trimmed and roughly chopped (once prepped, you should have about 3 packed cups)
- Parmigiano Reggiano, for serving
Directions
- Make the meatballs: Preheat the oven to 350°F. Line a baking sheet with aluminum foil and set an oven-proof roasting rack over top. Spray the rack generously with nonstick cooking spray.
- In a large bowl, beat the egg with the chives, sage and garlic. Add the remaining meatball ingredients and mash with your hands until evenly combined. Roll the mixture into tablespoon-size balls, about 1 inch in diameter (it will make approximately 50 meatballs), and place on the prepared rack. Bake for 15 to 18 minutes, or until lightly browned and cooked through. Set aside.
- Meanwhile, start the soup. In a large soup pot or Dutch oven over medium heat, heat the olive oil. Add the onions, carrots, and celery and cook, stirring frequently, until the vegetables are softened, about 8 minutes. Add the chicken broth, beef broth, water, wine, bay leaf, salt and pepper and bring to a boil. Add the pasta and cook, uncovered, at a gentle boil until the pasta is al dente, 8 to 10 minutes (or according to package directions). Taste the soup and adjust the seasoning, if necessary. Reduce the heat to low and add the spinach and meatballs. Simmer for a few minutes, until the spinach is wilted and the meatballs are warmed through. Ladle into bowls and serve with grated Parmigiano Reggiano.
-
 @ 502ab02a:a2860397
2024-11-22 17:58:24
@ 502ab02a:a2860397
2024-11-22 17:58:24
แนวคิด : ช้างเป็นสัตว์ในสัญลักษณ์ประจำจังหวัด สุพรรณบุรี เป็นการศึกแบบ ยุทธหัตถี จึงดึงเอาเฉพาะตัวช้างมาเป็นคาแรคเตอร์ในงานชิ้นนี้ ทำเป็นกึ่งๆช้างเผือก แทนความเป็นดาวรุ่ง มีการสวมเสื้อยืดลาย บิทคอยน์ และรองเท้าสีส้มตามสีของบิทคอยน์ กระพริบตา 1 ข้างเพื่อความน่ารักและเชิญชวนให้มาใช้บริการ
Link Download https://drive.google.com/drive/folders/1cXzbTCI0CqT9RWRETtwNLia7chL8Fyga?usp=sharing
Concept: An elephant is a symbol of Suphanburi Province, representing the historic royal battle of "Yutthahatthi" (elephant duel). This character is inspired by an elephant, designed as a semi-white elephant symbolizing a rising star. It wears a Bitcoin-themed T-shirt and orange shoes, representing Bitcoin's color. To add charm and invite engagement, the elephant winks playfully with one eye, encouraging people to use the service. Link Download https://drive.google.com/drive/folders/1cXzbTCI0CqT9RWRETtwNLia7chL8Fyga?usp=sharing

-
 @ 9ff58691:0bf6c134
2024-11-23 11:54:39
@ 9ff58691:0bf6c134
2024-11-23 11:54:39В Кургане, как и во всем мире, технологические стартапы играют все более важную роль в бизнесе. Эти инновационные компании не только создают новые рабочие места и стимулируют экономический рост, но и меняют саму суть бизнеса.
Новые стартапы в Кургане В последнее время в Кургане появились несколько новых стартапов, которые уже показали свою эффективность. Например, компания "КурганТех" разработала инновационную систему управления логистикой, которая позволяет оптимизировать доставку товаров и услуг. Другой стартап, "КурганАгро", создал систему мониторинга и управления сельскохозяйственными процессами, которая позволяет фермерам увеличить урожайность и снизить затраты.

Особенности стартапов в Кургане Стартапы в Кургане имеют несколько особенностей, которые отличают их от других компаний. Во-первых, они часто фокусируются на решении конкретных проблем, которые актуальны для региона. Например, компания "КурганЭко" разработала систему утилизации отходов, которая позволяет сократить количество мусора в городе. Во-вторых, стартапы в Кургане часто сотрудничают с местными университетами и исследовательскими центрами, что позволяет им получить доступ к новейшим технологиям и экспертизе.
Внедрение новых технологий Стартапы в Кургане активно внедряют новые технологии, такие как искусственный интеллект (ИИ), блокчейн и интернет вещей. Например, компания "КурганТех" использует ИИ для оптимизации логистических процессов, а компания "КурганАгро" использует блокчейн для создания прозрачной и безопасной системы управления сельскохозяйственными процессами.
Отличия стартапов в 2040 году от 2024 Стартапы в 2040 году отличаются от стартапов в 2024 году несколькими ключевыми аспектами:
• Больший акцент на экологической устойчивости: Стартапы в 2040 году часто фокусируются на решении экологических проблем и создании устойчивых бизнес-моделей. • Более широкое использование новых технологий: Стартапы в 2040 году активно внедряют новые технологии, такие как ИИ, блокчейн и IoT, для решения бизнес-задач. • Более тесное сотрудничество с государством и обществом: Стартапы в 2040 году часто сотрудничают с государством и обществом для решения социальных и экономических проблем. • Более быстрый рост и масштабирование: Стартапы в 2040 году могут расти и масштабироваться быстрее, благодаря доступу к новым технологиям и глобальным рынкам.
В Кургане, как и во всем мире, технологические стартапы играют все более важную роль в бизнесе. Эти инновационные компании не только создают новые рабочие места и стимулируют экономический рост, но и меняют саму суть бизнеса. Мы будем продолжать следить за развитием стартапов в Кургане и рассказывать о их успехах.
Автор: София Багирова
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ 502ab02a:a2860397
2024-11-22 17:50:23
@ 502ab02a:a2860397
2024-11-22 17:50:23
แนวคิด : ที่มาของคำว่า 8ริ้ว ชื่อเล่นของจังหวัดฉะเชิงเทรา มาจากปลาช่อนขนาดใหญ่ ที่สามารถแบ่งได้ถึง 8 ริ้ว จึงออกแบบให้เป็นรูปปลาช่อน แล้วติดเหรียญเลข 8 เอาไว้ ทั้งเป็นเลขมงคลและเป็นการแทนค่า 8ริ้ว ของปลาด้วย ด้านหลังเป็นสัญลักษณ์ bitcoin พร้อมคำว่า ฉะเชิงเทราเป็นภาษาอังกฤษ และกำกับภาษาไทยที่ด้านล่างอย่างโดดเด่น Link Download https://drive.google.com/drive/folders/1i6DU2jt_fgUQUAfPqOsJa1h6C-rrIPy2?usp=sharing
Concept: The origin of the nickname “8 Riew” for Chachoengsao Province comes from a large snakehead fish that could be cut into eight large slices. The design incorporates an image of a snakehead fish with an “8” coin to represent both the rich number and the symbolic “8 Riew” slices. The background features the Bitcoin symbol along with “Chachoengsao” in English and prominent Thai text below. Link Download https://drive.google.com/drive/folders/1i6DU2jt_fgUQUAfPqOsJa1h6C-rrIPy2?usp=sharing

-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 32e18276:5c68e245
2023-12-06 15:29:43
@ 32e18276:5c68e245
2023-12-06 15:29:43I’m going to be on an ordinals panels as one of the people who is counter arguing the claim that they are good for bitcoin. I decided to brush up on the technicals on how inscriptions work. I am starting to see luke’s perspective on how it is exploiting a loophole in bitcoin’s anti-data-spam mechanisms.
Storing data in Bitcoin, the “standard” way
The standard way you add “data” to bitcoin is by calling the OP_RETURN opcode. Bitcoin devs noticed that people were storing data (like the bitcoin whitepaper) in the utxo set via large multisig transactions. The problem with this is that this set is unprunable and could grow over time. OP_RETURN outputs on the other-hand are provably prunable and don’t add to utxo bloat.
Here’s an excerpt from the march 2014 0.9.0 release notes that talks about this:
On OP_RETURN: There was been some confusion and misunderstanding in the community, regarding the OP_RETURN feature in 0.9 and data in the blockchain. This change is not an endorsement of storing data in the blockchain. The OP_RETURN change creates a provably-prunable output, to avoid data storage schemes – some of which were already deployed – that were storing arbitrary data such as images as forever-unspendable TX outputs, bloating bitcoin’s UTXO database. Storing arbitrary data in the blockchain is still a bad idea; it is less costly and far more efficient to store non-currency data elsewhere.
Much of the work on bitcoin core has been focused on making sure the system continues to function in a decentralized way for its intended purpose in the presence of people trying to abuse it for things like storing data. Bitcoin core has always discouraged this, as it is not designed for storage of images and data, it is meant for moving digital coins around in cyberspace.
To help incentive-align people to not do stupid things, OP_RETURN transactions were not made non-standard, so that they are relayable by peers and miners, but with the caveat:
- They can only push 40 bytes (later increased to 80,83, I’m guessing to support larger root merkle hashes since that is the only sane usecase for op_return)
Bitcoin also added an option called -datacarriersize which limits the total number of bytes from these outputs that you will relay or mine.
Why inscriptions are technically an exploit
Inscriptions get around the datacarriersize limit by disguising data as bitcoin script program data via OP_PUSH inside OP_IF blocks. Ordinals do not use OP_RETURN and are not subjected to datacarriersize limits, so noderunners and miners currently have limited control over the total size of this data that they wish to relay and include in blocks. Luke’s fork of bitcoin-core has some options to fight this spam, so hopefully we will see this in core sometime soon as well.
Inscriptions are also taking advantage of features in segwit v1 (witness discount) and v2/taproot (no arbitrary script size limit). Each of these features have interesting and well-justified reasons why they were introduced.
The purpose of the witness discount was to make it cheaper to spend many outputs which helps the reduction of the utxo set size. Inscriptions took advantage of this discount to store monke jpegs disguised as bitcoin scripts. Remember, bitcoin is not for storing data, so anytime bitcoin-devs accidentally make it cheap and easy to relay data then this should be viewed as an exploit. Expect it to be fixed, or at least provide tools to noderunners for fighting this spam.
Where do we go from here
The interesting part of this story is that people seem to attach value to images stored on the bitcoin blockchain, and they are willing to pay the fee to get it in the block, so non-ideologic miners and people who don’t care about the health and decentralization of bitcoin are happy to pay or collect the fee and move on.
Data should not get a discount, people should pay full price if they want to store data. They should just use op_return and hashes like opentimestamps or any other reasonable protocol storing data in bitcoin.
After going through this analysis I’ve come to the opinion that this is a pretty bad data-spam exploit and bitcoin devs should be working on solutions. Ideological devs like luke who actually care about the health and decentralization of the network are and I’m glad to see it.
-
 @ 502ab02a:a2860397
2024-11-22 17:40:03
@ 502ab02a:a2860397
2024-11-22 17:40:03
แนวคิด : ห้วยผึ้ง ใช้ผึ้งงานเก็บน้ำผึ้งเข้ารัง ให้รังเป็นตัวแทนของการออม bitcoin ในลักษณะ stack sats ค่อยๆเก็บหอมรอบริบ make saving great again โดยผึ้งงานเป็นตัวแทนของ proof of work ซึ่งตัวน้ำผึ้งที่หอมหวานนั้น มีคุณค่า ไม่เสื่อมไปตามกาลเวลา เป็นยาอายุวัฒนะ และเป็นของมีค่าโดยธรรมชาติ Link Download https://drive.google.com/drive/folders/1Itj0C0aIBWvpnZuuW1Z04nif_NNfPQg6?usp=sharing
Concept: Huai Phueng uses an image of a worker bee collecting honey for the hive, where the hive symbolizes saving Bitcoin in a “stack sats” manner, gradually accumulating and making saving valuable again. The worker bee represents proof of work, while the sweet honey, with its timeless value, serves as both an elixir and a naturally precious resource. Link Download https://drive.google.com/drive/folders/1Itj0C0aIBWvpnZuuW1Z04nif_NNfPQg6?usp=sharing

-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ de496884:72617b81
2023-11-20 13:54:02
@ de496884:72617b81
2023-11-20 13:54:02Hola nostriches. Hoy quiero hacer una publicación a modo de acercamiento al surgimiento de las categorías de género y feminismo. Así que si te interesa el tema haz un esfuerzo, quédate y lee hasta el final.
El «nuevo» feminismo surge en los años 60 en aquellos países desarrollados que acordaron el reconocimiento a los derechos humanos contenidos en la declaración respectiva de la ONU. Entonces, como extensión a dicho reconocimiento es que se gesta el movimiento feminista. A partir de entonces, se vuelve a plantear la relación entre naturaleza y cultura y se llega a la conclusión de que las diferencias sociales van más allá de las diferencias biológicas, lo cual tiene que ver con que hasta la satisfacción de las necesidades elementales como son la alimentación, la vivienda o el vestuario, están condicionadas por construcciones sociales.
Pues resulta que una de las primeras propuestas identificó la subordinación femenina producto de una organización patriarcal, tomando la categoría patriarcado de Max Weber. Es así como la visión de patriarcado se extendió al discurso político y académico. Sin embargo, no existía información acerca del desarrollo histórico de dicha categoría, sistematización, variaciones, etc., debido a que era algo que recién se percibía en sociedad.
Sin embargo, la misma categoría de patriarcado junto a la de relaciones de poder para explicar fenómenos sociales contemporáneos, constituye uno de los principales aportes del feminismo. Es así como han logrado primero visibilizar y luego deconstruir y desmontar una serie de patrones existentes en la cultura que hacían a la mujer subordinarse al hombre, y que estaban presentes en el sistema sexo/género.
 Imagen relativa a la lucha contra el patriarcado
Imagen relativa a la lucha contra el patriarcadoHasta ese momento, en las investigaciones de corte sociológico se podía observar un androcentrismo excesivo al dar cuenta de que el discurso científico giraba en torno al hombre como sujeto y objeto de la investigación. Incluso para muchos positivistas como el mismo Weber, los problemas relativos a las mujeres quedaban en un segundo plano y eran achacados a una supuesta pasividad en el ámbito doméstico-familiar. Dicha pasividad partía de la supuesta inferioridad biológica del género femenino.
El patriarcado entonces era una categoría vacía en sí misma, sin valor explicativo. Desde el punto de vista político pudo ser útil para la movilización pero no resistió la polémica de los críticos del feminismo ni problematizó los conflictos a ser resueltos. Pero por otro lado, un grupo de mujeres -académicas principalmente- se puso manos a la obra en una tarea más pequeña pero con mayores resultados a la larga. Se propusieron generar conocimientos sobre las condiciones de vida de la mujer, buscar en el pasado y el presente los aportes de las mujeres a la sociedad, hacerlas visibles en la historia. Es así como surgen centros académicos, ONG, proyectos, centros de estudios sobre la mujer, etc.
Convendría distinguir entonces dos posturas que acompañaron a la investigación sobre las mujeres: uno que toma como objeto de estudio a la mujer; condiciones de vida, trabajo, cultura, y otra que privilegia a la sociedad como generadora de la subordinación de las mujeres. Mientras la primera perspectiva generaba conocimiento sobre las mujeres en el estudio de las relaciones mujer-hombre y mujer-mujer, la segunda tenía una visión más holística ya que planteaba que hay que estudiar la sociedad ya que la subordinación de las mujeres es producto de la organización de esta, y que no se avanzará solamente estudiando a las mujeres, pues el estudio debe ser más amplio y en diferentes niveles, ámbitos y tiempos.
Es en esta búsqueda donde nace y se desarrolla el concepto de género como categoría social. Es así que los sistemas de género/sexo fueron entendidos como conjuntos de prácticas, símbolos, representaciones, normas y valores sociales que las sociedades construyen a partir de la diferencia anatomofisiológica y que dotan de sentido a los impulsos sexuales, la reproducción y en general a las relaciones de las personas. Por tanto, este sistema pasó a ser el objeto de estudio para comprender la subordinación de la mujer al hombre. Al ser el reconocimiento de una dimensión de la desigualdad social hasta entonces desconocida, se considera la ruptura epistemológica más importante de la segunda mitad del siglo pasado.
 Imagen representativa del binarismo de género
Imagen representativa del binarismo de géneroHay que decir que los fenómenos sociales se definen por la relación que guardan entre sí. Es así que la contextualización adquiere gran importancia. Varones y hembras tenemos la capacidad de producir con el cuerpo, pero solo los cuerpos de las hembras pueden gestar y por tanto asegurar la especie humana. Todo grupo humano que pretenda sobrevivir debe asegurarse cierto número de hembras que lo hagan posible. De ahí un poder particular del cuerpo de las hembras que además es económicamente útil. Dicho poder no es en tanto entidad biológica, sino que es la sociedad la que le otorga este poder. En este punto es importante preguntarnos históricamente ¿quiénes han controlado la capacidad reproductiva de las mujeres?, ¿quiénes han tenido la preferencia en el acceso sexual? Para asegurar un control efectivo sobre la reproducción es necesario asegurar el acceso a la sexualidad.
Ello también lleva a dirigir el trabajo que hacen porque de lo contrario, las mujeres pudieran tener espacio para representar una amenaza al dominio de los hombres. Es importante atender a las etapas del desarrollo de las mujeres, que permitirá ver cómo se moldean para aceptar la desigualdad y las jerarquías según el género en las distintas sociedades y culturas.
Otro contexto a delimitar es el ámbito doméstico donde históricamente ha estado ubicada la subordinación femenina. Se ha puesto al descubierto que en mujeres que comparten la misma posición de clase y raza, la condición femenina se redefine a lo largo de la vida y que algunas mujeres gozan de poder sobre otras aún en contextos de alta dominación masculina, donde se les inviste de autoridad, creando el sistema zonas de incertidumbre que las divide como género e impide alianzas y se legitima la dominación. Foucault decía que «el poder se ejerce, no se posee», siempre está en peligro de perderse y no basta con normas, leyes, amenazas o castigos. De ahí que los espacios de subordinación sean también espacios de poder de las mujeres. Es en estos espacios donde aparece la inseguridad, la tensión, la confrontación y por ejemplo, las mujeres pueden reclamar la anticoncepción.
Para terminar, es importante tener en cuenta que el género es una forma de desigualdad social que siempre está articulado con otras formas de desigualdad ya sea clase, raza, grupo etario, etc. Hay que pensar la dominación masculina con un comienzo vago en el tiempo, pero que permite desligar la subordinación de las mujeres de la evolución «natural» de la humanidad y entenderla como un proceso histórico. En ese sentido es necesario destacar que, respecto a la raza, en sociedades plurales hay que atender al contexto étnico-cultural ya que en dependencia de las relaciones entre personas de razas distintas, estarán condicionadas las relaciones entre los géneros.
 Imagen de mujeres de distintas razas
Imagen de mujeres de distintas razasPor otro lado, si bien es sabido que históricamente el sistema de género social imperante ha contribuido a invisibilizar a la mujer, asociar necesariamente dicha categoría únicamente a ella, lo que hace es nuevamente recrear el absolutismo histórico que tanto daño ha hecho, ahora como lo antagónico al hombre. En la construcción social participan todos los individuos presentes en el sistema género.
Hasta aquí la publicación de hoy, de la cual aun se puede ahondar mucho más, sobre todo en lo referido al origen de la dominación o de la jerarquización del binomio «hombre/mujer» desde un punto de vista antropológico, pero eso quedará pendiente para otro momento. ¡Así que hasta la próxima!, ¡nos vemos en Nostr!
........................................
English version
Hello nostriches. Today I want to make a post by way of an approach to the emergence of the categories of gender and feminism. So if you are interested in the topic make an effort, stay and read to the end.
The "new" feminism emerged in the 60's in those developed countries that agreed to recognize the human rights contained in the respective UN declaration. Then, as an extension of that recognition, the feminist movement was born. From then on, the relationship between nature and culture was raised again and the conclusion was reached that social differences go beyond biological differences, which has to do with the fact that even the satisfaction of elementary needs such as food, housing or clothing are conditioned by social constructions.
It turns out that one of the first proposals identified female subordination as a product of a patriarchal organization, taking Max Weber's category of patriarchy. This is how the vision of patriarchy was extended to political and academic discourse. However, there was no information about the historical development of this category, systematization, variations, etc., because it was something that was only recently perceived in society.
However, the same category of patriarchy, together with that of power relations to explain contemporary social phenomena, constitutes one of the main contributions of feminism. This is how they have first made visible and then deconstructed and dismantled a series of existing patterns in the culture that made women subordinate to men, and that were present in the sex/gender system.
 Image relating to the fight against patriarchy
Image relating to the fight against patriarchyUp to that time, in sociological research, an excessive androcentrism could be observed as scientific discourse revolved around men as the subject and object of research. Even for many positivists such as Weber himself, the problems related to women remained in the background and were blamed on a supposed passivity in the domestic-family sphere. This passivity was based on the supposed biological inferiority of the female gender.
Patriarchy was then an empty category in itself, with no explanatory value. From the political point of view, it could be useful for mobilization, but it did not resist the polemic of feminism's critics, nor did it problematize the conflicts to be resolved. But on the other hand, a group of women - mainly academics - set to work on a smaller task but with greater results in the long run. They set out to generate knowledge about women's living conditions, to search in the past and present for women's contributions to society, to make them visible in history. This is how academic centers, NGOs, projects, women's studies centers, etc., came into being.
It would be convenient to distinguish then two postures that accompanied the research on women: one that takes women as the object of study; living conditions, work, culture, and the other that privileges society as the generator of women's subordination. While the first perspective generated knowledge about women in the study of woman-man and woman-woman relations, the second had a more holistic vision, since it proposed that society must be studied, since the subordination of women is a product of its organization, and that progress will not be made only by studying women, since the study must be broader and at different levels, spheres and times.
It is in this search that the concept of gender as a social category was born and developed. Thus, gender/sex systems were understood as a set of practices, symbols, representations, norms and social values that societies construct on the basis of anatomophysiological differences and that give meaning to sexual impulses, reproduction and, in general, to people's relationships. Therefore, this system became the object of study to understand the subordination of women to men. As the recognition of a hitherto unknown dimension of social inequality, it is considered the most important epistemological breakthrough of the second half of the last century.
 Representative image of gender binarism
Representative image of gender binarismIt must be said that social phenomena are defined by their relationship with each other. Thus, contextualization acquires great importance. Males and females have the capacity to produce with their bodies, but only the bodies of females can gestate and therefore ensure the human species. Any human group that intends to survive must ensure a certain number of females to make it possible. Hence a particular power of the female body, which is also economically useful. This power is not as a biological entity, but it is society that gives it this power. At this point it is important to ask ourselves historically, who has controlled the reproductive capacity of women, who has had the preference in sexual access? To ensure effective control over reproduction, it is necessary to ensure access to sexuality.
 Allegorical image of pregnancy
Allegorical image of pregnancyThis also leads to directing the work they do because otherwise, women may have room to pose a threat to men's dominance. It is important to pay attention to the stages of women's development, which will allow us to see how they are shaped to accept inequality and gender hierarchies in different societies and cultures.
Another context to delimit is the domestic sphere where female subordination has historically been located. It has been discovered that in women who share the same class and race position, the feminine condition is redefined throughout life and that some women enjoy power over others even in contexts of high male domination, where they are invested with authority, creating the system of uncertainty zones that divide them as a gender and prevent alliances and legitimize domination. Foucault said that "power is exercised, not possessed", it is always in danger of being lost and norms, laws, threats or punishments are not enough. Hence, the spaces of subordination are also spaces of women's power. It is in these spaces where insecurity, tension, confrontation appear and where, for example, women can demand contraception.
To conclude, it is important to keep in mind that gender is a form of social inequality that is always articulated with other forms of inequality, be it class, race, age group, etc. It is necessary to think of male domination with a vague beginning in time, but which allows us to separate the subordination of women from the "natural" evolution of humanity and to understand it as a historical process. In this sense, it is necessary to emphasize that, with respect to race, in plural societies it is necessary to pay attention to the ethno-cultural context since, depending on the relations between people of different races, the relations between genders will be conditioned.
 Image of women of different races
Image of women of different racesOn the other hand, although it is known that historically the prevailing social gender system has contributed to make women invisible, to necessarily associate this category only to women is to recreate the historical absolutism that has done so much damage, this time as antagonistic to men. All individuals present in the gender system participate in the social construction.
So much for today's publication, of which we can still go much deeper, especially with regard to the origin of domination or the hierarchization of the binomial "man/woman" from an anthropological point of view, but that will be left for another time. So until next time, see you in Nostr!

Créditos | Credits
Bibliografía consultada | Consulted bibliography:
-
Barbieri, T. (1993). Sobre la categoría género. Una introducción teórico-metodológica. Debates en Sociología. (18). 1-19. https://doi.org/10.18800/debatesensociologia.199301.006
-
Echevarría, D. (2020). Desigualdades de género e interseccionalidad. Análisis del contexto cubano 2008-2018. Facultad Latinoamericana de Ciencias Sociales (Programa-Cuba). https://www.clacso.org.ar/libreria-latinoamericana-cm/libro_detalle_resultado.php?id_libro=2346&campo=cm&texto=248
Traducción | Translation:
DeepL
-
-
 @ 07804b78:c375c543
2024-11-21 11:37:37
@ 07804b78:c375c543
2024-11-21 11:37:37Chef's notes
- The Premium Juku Curry comes individually packaged in single-serving portions, so it's convenient for using small amounts like in this recipe.
- Use your favorite spicy level of hot bean-curd soup base/curry roux.
Details
- 🍽️ Servings: 4
Ingredients
- 1 box of “Cook Do®” (Chinese seasoning mix) for Szechuan-style Mapo Tofu
- 2 servings of Premium Juku Curry
- 500g tofu
- 400g cut tomatoes
- 200g minced meat
- 80g garlic sprouts
- 100ml water
- 1 tablespoon sesame oil
- Cooked rice, enough for the number of people
Directions
- Slice the garlic shoots diagonally into 3-4cm pieces. Cut the tofu into bite-sized pieces.
- Heat the sesame oil in a frying pan and fry the minced meat over a medium heat.
- When the meat is about 80% cooked, add the garlic shoots and continue to fry, stirring, until the meat is fully cooked.
- Turn off the heat and add the Cook Do® Sichuan-style Mapo Tofu seasoning, and mix well.
- Turn the heat back on to medium, add the cut tomatoes and water, and bring to the boil, stirring gently.
- When it comes to a boil, turn the heat down to low, add the Premium Juku Curry, and stir well to dissolve.
- Once the curry has dissolved, add the tofu and cook until the tofu is warmed through.
-
 @ 2d74600a:d6708a00
2024-11-23 11:52:09
@ 2d74600a:d6708a00
2024-11-23 11:52:09Antoine de Saint-Exupéry, noto principalmente per il suo capolavoro "Il piccolo principe", è un autore che ha saputo coniugare in modo unico la profondità del pensiero filosofico con la leggerezza e la bellezza della poetica. La sua opera si distingue per un approccio che trascende le convenzioni letterarie, creando un ponte tra vita e conoscenza, tra esperienza e riflessione. In questo articolo, esploreremo come il pensiero di Saint-Exupéry si configuri come un atto di creazione che abbraccia la complessità dell'esistenza umana.
Un Pensiero Filosofico e Poetico
Saint-Exupéry non si limita a descrivere il mondo moderno; lo analizza, lo interroga e lo trasforma in un oggetto di contemplazione. A differenza di molti dei suoi contemporanei, che si sentono sopraffatti dalle sfide e dalle contraddizioni del loro tempo, Saint-Exupéry si erge come un pensatore critico. La sua scrittura è intrisa di una filosofia che non si impone, ma si offre come un invito a riflettere. La sua capacità di fondere il pensiero filosofico con la poetica gli consente di esplorare temi complessi come l'amore, la solitudine, la ricerca di senso e la bellezza della vita.
La Creazione come Atto di Conoscenza
In Saint-Exupéry, la creazione non è solo un atto artistico, ma anche un processo di conoscenza. La sua scrittura diventa un mezzo attraverso il quale l'autore cerca di comprendere il mondo e il posto dell'uomo al suo interno. Questa operazione di conglobare vita e conoscenza si manifesta in una prosa che è al contempo semplice e profonda, capace di toccare le corde più intime dell'animo umano. Le sue storie, pur nella loro apparente leggerezza, sono cariche di significato e invitano il lettore a riflettere sulla propria esistenza.
Un Dialogo con i Filosofi
Saint-Exupéry si colloca spesso al livello intellettuale dei più influenti filosofi del suo tempo. La sua capacità di affrontare questioni esistenziali e morali con una lucidità e una sensibilità uniche lo rende un interlocutore privilegiato nel panorama filosofico del XX secolo. La sua opera invita a una riflessione profonda, stimolando il lettore a interrogarsi su temi universali come la libertà, la responsabilità e la ricerca di verità. In questo senso, il suo pensiero si fa ponte tra la filosofia e la poesia, creando un dialogo fecondo tra le due discipline.
L'Universo del Sensibile e dell'Intellegibile
Un aspetto distintivo del pensiero di Saint-Exupéry è la sua capacità di penetrare in un universo in cui il sensibile eccede l'intellegibile. Le sue descrizioni poetiche della natura, delle relazioni umane e delle esperienze quotidiane si intrecciano con riflessioni più profonde, creando un tessuto narrativo ricco e stratificato. Questa fusione di sensazioni e pensieri consente al lettore di vivere un'esperienza totale, in cui la bellezza del mondo si rivela attraverso la lente della filosofia.
Conclusione
Il pensiero di Antoine de Saint-Exupéry rappresenta un esempio straordinario di come la filosofia e la poetica possano coesistere e arricchirsi reciprocamente. La sua capacità di affrontare le complessità della vita umana con una sensibilità unica lo colloca tra i grandi pensatori e poeti del XX secolo. Attraverso la sua opera, Saint-Exupéry ci invita a riflettere, a sognare e a cercare un significato più profondo nell'esistenza, rendendo la sua scrittura un atto di creazione che continua a ispirare generazioni di lettori.
-
 @ 5fb7f8f7:d7d76024
2024-11-22 17:38:45
@ 5fb7f8f7:d7d76024
2024-11-22 17:38:45Unlock the Power of Telegram: Tap into a Fast-Growing Community
Why Telegram?
200 million+ monthly active users: A vast and engaged audience waiting to be tapped. Fast-growing community: Telegram's user base is rapidly expanding, offering a unique opportunity for growth. Active engagement: Users spend an average of 2.5 hours per day on Telegram, providing ample time for interaction. Global reach*: With users from diverse regions, Telegram offers a platform for global connectivity.
Benefits of Adopting Telegram
Increased brand awareness: Reach a massive audience and build your brand presence. Community building: Engage with users, create groups, and foster a loyal community. Passive income opportunities: Offer users a chance to earn SATs by completing tasks, promoting engagement. Referral program: Implement a referral system, incentivizing users to invite others and rewarding referrers. Easy accessibility: Integrate your website or platform within the Telegram mini app for seamless access.
Take Advantage of Telegram's Potential
Stay ahead of the competition: Be an early adopter and capitalize on Telegram's growing user base. Diversify your audience: Reach users across different regions and demographics. Enhance user experience: Leverage Telegram's features to create an engaging and interactive experience.
Join the Telegram Revolution
Don't miss out on this opportunity to tap into a vibrant and expanding community. Adopt Telegram today and discover a world of possibilities for growth, engagement, and success
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 592295cf:413a0db9
2024-11-23 08:55:40
@ 592295cf:413a0db9
2024-11-23 08:55:40November 18th week
Let's proceed step by step, calm and reason.
Bluesky is only 5 doubles from Twitter, now has its own network effect.
Article of Hodlbod. The state of the art of Key management
nostr:nevent1qqsgpckkyck5m58gux5xst03ls68xxfz0ep2ndws6s039492vxvtc7spp4mhxue69uhkummn9ekx7mqprdmhxue69uhksmmyd33x7epwvdhhyctrd3jjuar0dak8xq3qjlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qcxhke2
The problem is how a user creates an account. Will fix It.
If you have a signer account like Amber, nsec app, all right, then it says remove all logins And ask the user how he wants to login.
Bluesky is an anti Trump and Elon Musk movement. It started with Brazil the significant exodus, the thing had a certain amount of stability and began to arrive a lot of people. So it's a sort of political party hanging against.
Nostr is still made by fixed stars, there are many stars but they are still firm in the sky.
Rod made n8n ocKnamo bot
nostr:nevent1qvzqqqqqqypzqx760c0h894a5tg7lxgr8k506twrv2qs0yxln0nz7kgs8zae03xeqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qg4waehxw309ahx7um5wghx77r5wghxgetk9uqzqjgxwlfdru3zzcee0sxk8d0dddwj4tu3xp00gwahy2t0n5k2se6uu8p7fk
This is interesting, ocknamo Is a rock, keep pushing
Roadmap are bullshit, you spend the time to the the actual things, sure if a groups ok
I read Hodlbod's spech in practice with the tilde wants to create rooms, then there is the space that is the carcass we are very close to what is Unanimity, but it's fine with much more refining, but at the cost of being unique.
Discord vs Telegram
I downloaded three Nostr apps, I called it Atlas instead of Olas, zapstore and flotilla (removing Coracle).
Olas would be nice if he had the feature awards on the photo and Zap 😉.
Zap store continues to mark me an update of minibits, but minibits updates in the app, I also updated to a new version, however maybe it is a different type of app. Putting the key does not seem to have changed a comma the app. But then I realized it's about the app signers. The signers who followed the signers that are in your WoT, the signers that are in your lists 😉. It does not divide Nostr apps from Nostr, but it works.
Olas there is no focus on the media server, maybe if you have a new account it's all explained. Problems with dark mode and filter. I would like the idea of switching videos and pictures, can be something you can do in the settings
photos (home) video (other button) And maybe there's a flip button 😅 So Instagram becomes tik tok. The focus must be in creating content. Ok. Olas allows you to upload only images for the moment and shorts from other Nostr apps. For some reason, I don't hear video audio, maybe some permission to give.
Flotilla, if you connect with nsec.app creates a Nostr connect token from flotilla and enter it in nsec.app, asks for permissions and lists them and goes.
With this test account, I don't follow anyone using it to feed on Coracle. The app also suggests people to contact. There is also a space for personal notes. Then there are spaces. And it basically shows you the Relays and here the situation is a little confused. Although I know that there is a space/group called flotilla I am not able to find it, maybe you need the invitation code that is in the link. Also copying it I couldn't enter but the approach is that I think. flotilla link This was the link.
Maybe Hodlbod takes a step back and joins Unanimity. I don't think a step back is a possibility.
Maybe there are updates and they make a specific base workflow Relays based group and then the various branches NIP-29 chachi and 0xchat and the others (Telegram group) Flotilla (discord) It seems like there is a reconciliation at least to converge everyone 😉 "shallow reply hierarchies"
Kohei is also mentioned 🤙 NFC card article An interesting article
nostr:naddr1qvzqqqr4gupzqx760c0h894a5tg7lxgr8k506twrv2qs0yxln0nz7kgs8zae03xeqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qg3waehxw309ahx7um5wgh8w6twv5hsqzr9v3jx2wpn8qmsz4edqe
Marketplace on Nostr Help to test yojimble
nostr:nevent1qvzqqqqqqypzphn4avwh5e38spagmlc0kvmulnccnelf479tvg5ldz8kv3cscvq5qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qpqw7f0ja820er7d2jfa4vq9upelw88ejha6hcvj5gxt7gqnz646r8ql2a2cp
That's all!!
-
 @ 03b2a4f0:7ff066d4
2024-11-22 17:33:08
@ 03b2a4f0:7ff066d4
2024-11-22 17:33:08Zeteo citadel consult In collaboration with the university of Ibadan @yakihonne nostr:naddr1qqgrqe3jxasnjwtpvs6rxd3kvsmkzq3qqwe2fuxpe5tf7xduvcd9n3he30s6zel890dgzy2zquunvllsvm2qxpqqqp65w8nuwxg
-
 @ ac8bb9b0:70278acc
2024-11-20 16:28:11
@ ac8bb9b0:70278acc
2024-11-20 16:28:11Chef's notes
Optional: Creamy Cilantro-Basil Ranch: In a blender, blend 1/2 cup plain Greek yogurt or sour cream, 1/3 cup mayo, 2 tablespoons buttermilk, 1 cup fresh cilantro, 1/2 cup fresh basil, 1/4 cup fresh chopped chives, 2 teaspoons Worcestershire, 1 teaspoon garlic powder, 1 teaspoon onion powder, 1/4 teaspoon cayenne, and a pinch each of kosher salt and black pepper. Blend until creamy.
Details
- ⏲️ Prep time: 15
- 🍳 Cook time: 15
Ingredients
- 4 (4-6 ounce) salmon filets, cut into bite-size chunks
- 6 tablespoons extra virgin olive oil
- 1 teaspoon smoked paprika
- salt and black pepper
- 1 bunch asparagus, ends trimmed
- 1/2 cup honey
- 2-3 tablespoons hot sauce
- 1-3 teaspoons cayenne pepper
- 3/4 teaspoon chipotle chili powder
- 1/2 teaspoon garlic powder
- 1/2 teaspoon onion powder
- 3-4 cups cooked rice
- 2 avocados, diced
- 1 serrano or jalapeño, sliced
- 1/2 cup fresh cilantro, chopped
- 2 tablespoons chopped fresh dill
- 1/2 cup crumbled feta cheese
- 2 tablespoons extra virgin olive oil
- 1 tablespoon lemon juice
- 1/3 cup toasted seeds, pumpkin, sesame, sunflower, etc.
Directions
-
- Preheat the oven to 450° F.
-
- On a baking sheet, toss the salmon pieces with 3 tablespoons olive oil, paprika, salt, and pepper. Arrange in a single layer. On the other side of the pan, add the asparagus. Toss with 1 tablespoon olive oil, salt, and pepper. Roast 10-15 minutes or until the salmon is just undercooked to your liking.
-
- Meanwhile, make the hot honey. In a sauce pot, warm together the honey, hot sauce, cayenne, chili powder, onion powder, and garlic powder, plus a pinch of salt.
-
- Spoon some of the hot honey over the salmon. Switch the oven to broil and broil until lightly charred and crispy. Spoon over additional hot honey, to your taste.
-
- To make the avocado salsa. Combine avocados, serrano or jalapeño, cilantro, dill, feta cheese, extra virgin olive oil, lemon juice, and toasted seeds in a bowl and season with salt, gently tossing.
-
- Arrange the salmon and asparagus over bowls of rice. Top with salsa.
-
 @ 6fff5148:a5dd5cdf
2024-11-22 17:19:43
@ 6fff5148:a5dd5cdf
2024-11-22 17:19:43 Cryptocurrencies have not only changed the world’s expectations surrounding money. They’ve also continued to evolve in their own space since the first bitcoin block was mined back in 2009. Since then, thousands of unique cryptocurrencies have popped up. Of these, Bitcoin remains the most popular.
Cryptocurrencies have not only changed the world’s expectations surrounding money. They’ve also continued to evolve in their own space since the first bitcoin block was mined back in 2009. Since then, thousands of unique cryptocurrencies have popped up. Of these, Bitcoin remains the most popular.In fact, a recent survey found that 8% of americans have invested in cryptocurrency and of that 8%, 5.15% have invested in Bitcoin.
Curious to see why Bitcoin is the most popular and what other cryptocurrencies are running close behind? Keep reading.
It’s been about a decade since Bitcoin expanded currency into the digital space of the internet. Since that time, it’s remained the most popular cryptocurrency in the world and most used of all cryptocurrency.
With Bitcoin, users transfer money from one digital wallet to another digital wallet with ease. Each transaction is then verified by other users and recorded on the public ledger, known as the blockchain. For the fact that Bitcoin which is currently the top cryptocurrency gaining awareness on daily basis on the wheel of fortune is tough,that way it can't be predicted so easily even for an expert as there is no one who can predict the future and be accurate of the outcome. No one ever thought Bitcoin will ever be worth $20,000.00k in 2017 as same reason why the awareness keeps brewing each passing day making it easier for investors dealing in bitcoin. Aside buying and holding bitcoins for potential gains which is one of the advantages of the benefits derived from dealing in cryptocurrency, I also recommend that you invest in service companies such as the Zippercoin(www.zippercoin.tech) company, a cryptocurrency investment company that gives return on investments made in days by capitalizing on the volatility of the crypto market to generate profits giving you better chance in the cryptocurrency market.
Some key factors that have contributed to Bitcoin’s popularity include:
Although it fluctuates, its price is high. A single Bitcoin is worth $4,931 US dollars as of this writing. This is significantly higher than other cryptocurrencies that exist. Major companies are starting to accept Bitcoins. These include Microsoft,overstock and more. Bitcoin is easy to set up. Bitcoin is supported by the most notable exchanges and digital wallet platforms, such as Coinbase. This makes getting in the game easier. Investors have been supporting Bitcoin’s growth for years. Bitcoin has been around longer than all other cryptocurrencies. This has allowed them to gain a strong following of investors. Bitcoin also has the highest market capitalization among cryptocurrencies, which is often considered by investors. Market caps are calculated by multiplying the current supply of the currency by the current price. This is known as the circulating supply of currency, and can indicate if a currency is risky to invest in. High market caps usually indicate less risk as there are more users. Therefore, Bitcoin is believed to be a better choice than other cryptocurrencies out there
 .
.There is always light at the end of the tunnel,be wise with whatever decision you take.Always remember to diversify,study the cryptocurrency market before diving on the choice of coin you deem to trade,choose reliable service to trade with to avoid unnecessary loss.
Stay safe and God bless.. Source: https://www.quora.com/Why-is-bitcoin-often-the-most-talked-about-cryptocurrency-Is-it-possible-for-one-cryptocurrency-to-be-successful-while-others-are-not#:~:text=Bitcoin%20is%20a%20well%2Dknown,lack%20of%20a%20groundbreaking%20project. @yakihonne
-
 @ ac8bb9b0:70278acc
2024-11-20 16:25:18
@ ac8bb9b0:70278acc
2024-11-20 16:25:18Details
- ⏲️ Prep time: 25
- 🍳 Cook time: 20
- 🍽️ Servings: 6
Ingredients
- 1 tablespoon extra virgin olive oil
- 1 medium yellow onion chopped (about 1 1/2 cups)
- 2 teaspoons kosher salt, divided
- 3 tablespoons red curry paste
- 2 tablespoons grated fresh ginger (from a 3-inch piece)
- 3 medium cloves garlic, minced (about 1 tablespoon)
- 4 cups lower-sodium vegetable broth
- 1 1/2 pounds butternut squash, cut into 1 1/2-inch cubes (from 2 [20-ounce] package)
- 1 15.5-ounce can unsweetened coconut milk, well stirred
- 2 tablespoons fresh lime juice (from 1 or 2 limes)
- 6 tablespoons crushed salted peanuts
- Chopped fresh cilantro and crushed red pepper (optional), for serving
Directions
- Heat oil in a large pot over medium. Add onion and 1/2 teaspoon salt; cook, stirring often, until onion starts to brown, 6 to 7 minutes.
- Add curry paste, ginger, and garlic; cook, stirring, until fragrant, about 1 minute. Add broth and 1 teaspoon salt, scraping up browned bits from bottom of pot. Stir in squash. Bring to a simmer over medium-high. Cover and reduce heat to low; simmer until squash is tender, 12 to 15 minutes.
- Remove from heat. Stir in coconut milk, lime juice, and remaining 1/2 teaspoon salt. Use an immersion blender to process until smooth. (Or transfer to a blender, cover with lid, and remove center piece. Place a towel over opening. Process until smooth.)
- Serve sprinkled with peanuts, cilantro, and, if using, crushed red pepper.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ ac8bb9b0:70278acc
2024-11-19 19:49:52
@ ac8bb9b0:70278acc
2024-11-19 19:49:52Chef's notes
This recipe is SO easy. We simply mix herbs and spices in a small dish. Add the chicken legs to a large, gallon-sized ziptop bag and add the olive oil. Seal the bag and roll those legs around for a minute to distribute the oil evenly on all the chicken. Then, open the bag, pour in the seasonings, close the bag and do the shake thing. Take a minute or so to do this and massage the chicken to really get that seasoning well distributed.
Seasoning chicken legs in a ziptop bag Set aside for a minute and preheat your oven to 425°(F) and line a baking sheet with aluminum foil. Give the foil a good spray with non-stick cooking spray. This is important as the chicken will stick without it.
Now take the chicken out of the bag and place on the foil lined sheet. Then into the oven it goes for 40 minutes.
Recipe for oven baked chicken legs After 40 minutes the chicken will be a beautiful golden color and the inside will be at least 165°(F) when checked with an instant read thermometer. In fact, it will probably be closer to 185-195°(F) which is exactly what we want!
Pro Tip: Chicken Legs are Better at 185-195°(F)! The rule of cooking chicken to a minimum internal temperature of 165°F has been well-established for quite some time. However, when it comes to darker meat portions such as chicken legs, thighs, or the entire leg quarter, exceeding this temperature is often encouraged for optimal results! When heated to around 185°F, the collagens within the meat begin to break down, contributing to the juiciness and “fall-off-the-bone” tenderness that we cherish so much in dark poultry meat.
Check out this great article by America’s Test Kitchen regarding “overcooking” chicken drumsticks and thighs.
Let Rest and Serve Carefully remove the chicken to a plate or platter and let it rest for 5 minutes before serving.
Recipe for oven baked chicken legs Can this recipe be doubled? It sure can. You can even triple or quadruple this recipe! Simply adjust the ingredients accordingly. The cook time will still be 40 minutes, just be sure to not crowd the chicken too much on the pan. Keep the legs from touching and always keep in a single layer.
Give it a kick Want to give the chicken legs a little heat? Add a ½ teaspoon of cayenne pepper and even a teaspoon of crushed red pepper flakes. You can also deepen the flavor by using smoked paprika instead of regular paprika.
Details
- ⏲️ Prep time: 10
- 🍳 Cook time: 40
- 🍽️ Servings: 2-3
Ingredients
- 6 chicken legs
- 2 tsp paprika
- 1.5 tsp kosher salt
- 1 tsp onion powder
- 1 tsp garlic powder
- 1 tsp rosemary, dried
- 1 tsp parsley flakes
- ½ tsp ground black pepper
- ½ tsp ground mustard
- 1 tbls olive oil
Directions
- Preheat oven to 425°(F)
- Pat chicken legs dry with a paper towel and trim any excess skin
- Place chicken legs in a large ziptop bag and add olive oil. Close bag and shake to coat chicken well with the oil.
- Add seasoning mix to bag, close and shake to get chicken well coated with seasoning.
- Line a baking sheet with foil and spray with non-stick cooking spray.
- Place chicken legs on baking sheet and place on middle rack of oven for 40 minutes, turning halfway.
- Chicken must have internal temperature of at least 165°(F), but 185-195°(F) is ideal for best results.
- Let rest for several minutes before serving.
-
 @ f8a5df57:b7a58cd4
2024-11-23 07:43:46
@ f8a5df57:b7a58cd4
2024-11-23 07:43:46Содержание сюжета:
Вчера в Москве состоялась долгожданная премьера нового фильма известного режиссера Дмитрия Макракова «Все или ничего». Мероприятие прошло в одном из самых престижных кинотеатров столицы и собрало множество звезд отечественного кино, а также поклонников творчества режиссера.
«Все или ничего» — это драмеди, рассказывающая о сложных взаимоотношениях между друзьями, которые решают рискнуть всем ради исполнения своей мечты. Фильм затрагивает темы дружбы, предательства и поиска себя в современном мире. Главные роли исполнили популярные актеры, которые уже успели завоевать сердца зрителей.
Реакция зрителей. После просмотра зрители были в восторге от глубины сюжета и мастерства актерской игры. Многие отметили, что фильм заставляет задуматься о важности выбора и последствиях, которые он может иметь. В социальных сетях пользователи активно делятся своими впечатлениями, подчеркивая эмоциональную насыщенность картины.
На пресс-конференции после премьеры Дмитрий Макраков отметил, что создание этого фильма стало для него настоящим вызовом. «Я хотел показать, как иногда мы готовы рисковать всем ради своих мечтаний, но не всегда понимаем, к каким последствиям это может привести», — заявил он.
Премьера «Все или ничего» стала ярким событием в культурной жизни Москвы и уже привлекла внимание критиков и зрителей. Фильм обещает стать одним из главных кинопроектов сезона и, возможно, получит признание на международных фестивалях. Не упустите возможность увидеть эту увлекательную историю на большом экране!
Автор: Рината Ситникова
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ a305a0de:21557ddd
2024-11-22 17:08:00
@ a305a0de:21557ddd
2024-11-22 17:08:00As someone who's had the privilege of working with Yakhonne, I've seen firsthand the incredible potential of Bitcoin. And let me tell you, I'm more excited than ever about what the future holds.
Over the next five years, I predict that Bitcoin will become an increasingly integral part of our daily lives. We'll see widespread adoption, innovative use cases, and a growing recognition of Bitcoin's value as a store of wealth and a medium of exchange.
One of the key drivers of this growth will be the development of decentralized applications (dApps) like Yakhonne. These platforms are not only making it easier for people to buy, sell, and use Bitcoin, but they're also showcasing the vast potential of blockchain technology.
As more people begin to understand the benefits of Bitcoin – from its security and transparency to its potential for financial inclusion – we'll see a surge in demand. And as the demand grows, so too will the infrastructure supporting it.
In the next five years, I expect to see:
- Widespread adoption of Bitcoin as a form of payment
- Increased innovation in the development of dApps and other blockchain-based technologies
- Growing recognition of Bitcoin's value as a store of wealth and a hedge against inflation
- Improved infrastructure, including faster and more secure transaction processing
Of course, there will be bumps along the way. But with the collective efforts of pioneers like Yakhonne, I'm confident that Bitcoin will emerge stronger, more resilient, and more widely adopted than ever.
So, buckle up and get ready for the ride. The future of Bitcoin is bright, and I'm honored to be along for the journey.Bitcoin's Bright Future: Why I'm Bullish on the Next 5 Years
As someone who's had the privilege of working with Yakhonne, I've seen firsthand the incredible potential of Bitcoin. And let me tell you, I'm more excited than ever about what the future holds.
Over the next five years, I predict that Bitcoin will become an increasingly integral part of our daily lives. We'll see widespread adoption, innovative use cases, and a growing recognition of Bitcoin's value as a store of wealth and a medium of exchange.
One of the key drivers of this growth will be the development of decentralized applications (dApps) like Yakhonne. These platforms are not only making it easier for people to buy, sell, and use Bitcoin, but they're also showcasing the vast potential of blockchain technology.
As more people begin to understand the benefits of Bitcoin – from its security and transparency to its potential for financial inclusion – we'll see a surge in demand. And as the demand grows, so too will the infrastructure supporting it.
In the next five years, I expect to see:
- Widespread adoption of Bitcoin as a form of payment
- Increased innovation in the development of dApps and other blockchain-based technologies
- Growing recognition of Bitcoin's value as a store of wealth and a hedge against inflation
- Improved infrastructure, including faster and more secure transaction processing
Of course, there will be bumps along the way. But with the collective efforts of pioneers like Yakhonne, I'm confident that Bitcoin will emerge stronger, more resilient, and more widely adopted than ever.
So, buckle up and get ready for the ride. The future of Bitcoin is bright, and I'm honored to be along for the journey.
-
 @ af9c48b7:a3f7aaf4
2024-11-18 20:26:07
@ af9c48b7:a3f7aaf4
2024-11-18 20:26:07Chef's notes
This simple, easy, no bake desert will surely be the it at you next family gathering. You can keep it a secret or share it with the crowd that this is a healthy alternative to normal pie. I think everyone will be amazed at how good it really is.
Details
- ⏲️ Prep time: 30
- 🍳 Cook time: 0
- 🍽️ Servings: 8
Ingredients
- 1/3 cup of Heavy Cream- 0g sugar, 5.5g carbohydrates
- 3/4 cup of Half and Half- 6g sugar, 3g carbohydrates
- 4oz Sugar Free Cool Whip (1/2 small container) - 0g sugar, 37.5g carbohydrates
- 1.5oz box (small box) of Sugar Free Instant Chocolate Pudding- 0g sugar, 32g carbohydrates
- 1 Pecan Pie Crust- 24g sugar, 72g carbohydrates
Directions
- The total pie has 30g of sugar and 149.50g of carboydrates. So if you cut the pie into 8 equal slices, that would come to 3.75g of sugar and 18.69g carbohydrates per slice. If you decided to not eat the crust, your sugar intake would be .75 gram per slice and the carborytrates would be 9.69g per slice. Based on your objective, you could use only heavy whipping cream and no half and half to further reduce your sugar intake.
- Mix all wet ingredients and the instant pudding until thoroughly mixed and a consistent color has been achieved. The heavy whipping cream causes the mixture to thicken the more you mix it. So, I’d recommend using an electric mixer. Once you are satisfied with the color, start mixing in the whipping cream until it has a consistent “chocolate” color thorough. Once your satisfied with the color, spoon the mixture into the pie crust, smooth the top to your liking, and then refrigerate for one hour before serving.
-
 @ 961e8955:d7fa53e4
2024-11-22 17:05:11
@ 961e8955:d7fa53e4
2024-11-22 17:05:11The Power of Community: Revolutionizing Bitcoin Adoption through Yakihonne
Introduction
In the dynamic landscape of Bitcoin, community engagement plays a pivotal role in driving adoption and growth. Yakihonne, a pioneering platform, is at the forefront of this effort, providing a novel way for Bitcoin enthusiasts to connect, share knowledge, and support one another. This article delves into the world of Yakihonne, exploring its impact on the Bitcoin community and the broader
Yakihonne's foundational concept is that every Bitcoiner is a social node, interconnected and influencing others within the network. By recognizing the value of these connections, Yakihonne provides a platform for individuals to converge, share ideas, and learn from each other. This approach fosters a sense of community, ensures the dissemination of knowledge and best practices, and promotes a collaborative environment.
Empowering Through Education and Support
Yakihonne is committed to empowering Bitcoiners with the necessary knowledge and tools to succeed. The platform offers a comprehensive suite of educational resources, including articles, videos, and podcasts. Additionally, Yakihonne provides a support system where individuals can ask questions, share experiences, and receive guidance from experienced community members.
Balancing Education and Responsible Adoption
While education is crucial, Yakihonne also emphasizes the importance of responsible adoption practices. The platform encourages users to approach Bitcoin adoption in a measured and informed manner, prioritizing security, privacy, and sustainable growth. By striking this balance, Yakihonne ensures the network grows in a sustainable and responsible way, focusing on long-term success.
Conclusion
Yakihonne is revolutionizing the way Bitcoiners connect, learn, and grow together. By recognizing the power of community and the importance of education and support, this platform is paving the way for a brighter future in Bitcoin adoption. Join the Yakihonne community today and become part of this exciting movement, shaping the future of Bitcoin and fostering a sense of belonging among enthusiasts. @yakihonne
-
 @ df478568:2a951e67
2024-11-17 17:32:20
@ df478568:2a951e67
2024-11-17 17:32:20Chef's notes
This is from my wife's notebook full of recipes.
Details
- ⏲️ Prep time: 15 inutes
- 🍳 Cook time: 15 minutes
- 🍽️ Servings: 4
Ingredients
- 1/3 cup oyster sauce
- 2 teaspoons toasted sesame seed oil
- 1/3rd cup Sherry
- 1 teaspoon white sugar
- 1 teaspoon cornstarch
- 1 pound beef round steak
- 3 tablespoons avocado oil
- 1 tablespoon ground ginger
- 1 clove garlic
- 1 pound broccoli florrets
Directions
- Wisk together - Oyster Sauce - Sesame oil - Sherry - Soy Sauce - Sugar - Cornstarch in a bowl
- Heat avocado oil in a wok or large skillet over medium-high heat. Stir in ginger and garlic. let sizzle for one minute. Stir in broccoli. Set aside.
- Pour more oil into wok. tss the beef with the narinatde until the sauce forms a glaze on the beef. about 5 minutes. Return cooked broccoli to the wok. Stir in meat about 3 mionytes,
-
 @ df478568:2a951e67
2024-11-17 15:27:28
@ df478568:2a951e67
2024-11-17 15:27:28Chef's notes
This is another crock pot meal I found in my wife's recipe book.
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 8-10 hours
- 🍽️ Servings: 6
Ingredients
- 2 lb. boneless sirloin tip roast
- 2 red bell peppers, chopped
- 1 small onion
- 1- 14.5 oz can of diced tomatoes, uindrained
- 2 tablespoons extra-virgin olive oil
- 2 tablespoons of italian seasoning
- salt and pepper to taste
- Parmesan cheese
- 1 lb noodles
- 1 green bell pepper, chopped
- 4 cloves of minced garlic
Directions
- Slice sirloin tip roast
- cook in a crock pot for 8-10 hours
- serve with noodles and top with Parmesean Cheese
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 72db3731:6c79f5a6
2024-11-23 02:00:11
@ 72db3731:6c79f5a6
2024-11-23 02:00:11I have to imagine a water stream falling on a rock, even if sometimes there is drought on the river or some object are blocking the water stream, the rock will eventually break.
There is no perfection, aim for perfection, but know that it does not exist, there is no perfect routine, there is no perfect life.
But I'm aiming for a perfect life anyway.
Remember, your life will have countless imperfections and you'll make several errors.
But don't give up.
I haven't done much.
Started studying English in Duolingo, looking for a complete lesson for each language, minimum.
2024-11-22 23:00 NoFap, NoSoda, NoAlcohol and NoReels.
Installed leechblock extension, removed any reddit clients on the phone and removed instagram.
-
 @ df478568:2a951e67
2024-11-17 15:12:50
@ df478568:2a951e67
2024-11-17 15:12:50Chef's notes
This is another crock pot meal I found in my wife's recipe book.
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 8-10 hours
- 🍽️ Servings: 6
Ingredients
- 2 lb. boneless sirloin tip roast
- 2 red bell peppers, chopped
- 1 small onion
- 1- 14.5 oz can of diced tomatoes, uindrained
- 2 tablespoons extra-virgin olive oil
- 2 tablespoons of italian seasoning
- salt and pepper to taste
- Parmesan cheese
- 1 lb noodles
- 1 green bell pepper, chopped
Directions
- Slice sirloin tip roast
- cook in a crock pot for 8-10 hours
- serve with noodles and top with Parmesean Cheese
-
 @ a305a0de:21557ddd
2024-11-22 17:01:06
@ a305a0de:21557ddd
2024-11-22 17:01:06Bitcoin, the decentralized digital currency, has the potential to revolutionize the way local communities function. By providing an alternative to traditional fiat currencies, Bitcoin can empower local businesses, promote financial inclusion, and foster community development.
Financial Inclusion
Bitcoin can provide access to financial services for underserved communities. With Bitcoin, individuals can make transactions without the need for traditional banking infrastructure. This can be especially beneficial for low-income communities where access to banking services is limited.
Local Economic Growth
Bitcoin can also promote local economic growth by encouraging local businesses to accept Bitcoin payments. This can increase foot traffic, boost sales, and create new job opportunities. Additionally, Bitcoin's decentralized nature can help reduce transaction fees, allowing local businesses to keep more of their hard-earned money.
Community Development
Bitcoin can also foster community development by providing a platform for community-driven initiatives. For example, Bitcoin-based crowdfunding platforms can be used to raise funds for local community projects, such as building a community center or supporting a local food bank.
Real-World Examples
There are already several examples of Bitcoin being used to improve local communities. For instance, the Bitcoin Ekasi project in South Africa is using Bitcoin to create a circular economy in a local township. Similarly, the BitPatron project in the United States is using Bitcoin to support local artists and creatives.
Conclusion
Bitcoin has the potential to revolutionize the way local communities function. By providing access to financial services, promoting local economic growth, and fostering community development, Bitcoin can empower local communities to take control of their own economic destiny. As the world becomes increasingly digital, it's exciting to think about the potential impact that Bitcoin can have on local communities around the world.
-
 @ 6fff5148:a5dd5cdf
2024-11-22 17:00:38
@ 6fff5148:a5dd5cdf
2024-11-22 17:00:38 what is Bitcoin
Bitcoin is a cryptocurrency, a peer-to-peer digital currency that operates independently of a central governing authority. Bitcoin enables direct transactions between users, secured by cryptographic technology and recorded on a transparent and immutable ledger known as the blockchain.This innovation not only ensures security and transparency but also challenges traditional financial systems by offering a global currency that is accessible to anyone with internet access.Picture it as digital gold: whereas gold is physically mined from the earth, Bitcoin is created through the use of powerful computers solving complex problems, known as "Bitcoin mining." Unlike gold, you can't physically touch Bitcoin; it exists purely in the digital realm.Bitcoin was first introduced in 2009 by a person (or group) named Satoshi Nakamoto. Little is known about their identity–but more on that later!Today, Bitcoin is the most popular cryptocurrency, with a market capitalization that far surpasses any other digital currency. It has become a benchmark for the crypto market, influencing the launch of thousands of other cryptocurrencies and ushering in a new era of digital finance.Key Bitcoin Concepts in Simple Words
Cryptocurrency: A type of digital or virtual money that uses cryptography for security, making it difficult to counterfeit.
Blockchain: A digital ledger that records all Bitcoin transactions, like a global spreadsheet that everyone can see but no one can tamper with.
Wallet: A digital pouch that safely stores your Bitcoin, similar to a virtual bank account.
Public and Private Keys: A pair of digital keys where the public key is your Bitcoin address (like an email address) and the private key is your secret password to access and send your Bitcoins.
Decentralization: The principle of distributing control across the entire network rather than relying on a central authority, like having a group decision instead of one boss calling the shots.
Mining: The process of using computer power to solve complex puzzles, securing the network and creating new Bitcoins as a reward.
Satoshi: The smallest unit of Bitcoin, named after its mysterious creator, worth one hundred millionth of a Bitcoin.
BTC: BTC is the abbreviation for Bitcoin typically used when referring to the currency unit in transactions, price listings, and financial discussions.
image
Source: https://www.blockpit.io/en-us/blog/what-is-bitcoin#:~:text=Bitcoin%20is%20a%20cryptocurrency%2C%20a,ledger%20known%20as%20the%20blockchain .!
@yakihonne.com
what is Bitcoin
Bitcoin is a cryptocurrency, a peer-to-peer digital currency that operates independently of a central governing authority. Bitcoin enables direct transactions between users, secured by cryptographic technology and recorded on a transparent and immutable ledger known as the blockchain.This innovation not only ensures security and transparency but also challenges traditional financial systems by offering a global currency that is accessible to anyone with internet access.Picture it as digital gold: whereas gold is physically mined from the earth, Bitcoin is created through the use of powerful computers solving complex problems, known as "Bitcoin mining." Unlike gold, you can't physically touch Bitcoin; it exists purely in the digital realm.Bitcoin was first introduced in 2009 by a person (or group) named Satoshi Nakamoto. Little is known about their identity–but more on that later!Today, Bitcoin is the most popular cryptocurrency, with a market capitalization that far surpasses any other digital currency. It has become a benchmark for the crypto market, influencing the launch of thousands of other cryptocurrencies and ushering in a new era of digital finance.Key Bitcoin Concepts in Simple Words
Cryptocurrency: A type of digital or virtual money that uses cryptography for security, making it difficult to counterfeit.
Blockchain: A digital ledger that records all Bitcoin transactions, like a global spreadsheet that everyone can see but no one can tamper with.
Wallet: A digital pouch that safely stores your Bitcoin, similar to a virtual bank account.
Public and Private Keys: A pair of digital keys where the public key is your Bitcoin address (like an email address) and the private key is your secret password to access and send your Bitcoins.
Decentralization: The principle of distributing control across the entire network rather than relying on a central authority, like having a group decision instead of one boss calling the shots.
Mining: The process of using computer power to solve complex puzzles, securing the network and creating new Bitcoins as a reward.
Satoshi: The smallest unit of Bitcoin, named after its mysterious creator, worth one hundred millionth of a Bitcoin.
BTC: BTC is the abbreviation for Bitcoin typically used when referring to the currency unit in transactions, price listings, and financial discussions.
image
Source: https://www.blockpit.io/en-us/blog/what-is-bitcoin#:~:text=Bitcoin%20is%20a%20cryptocurrency%2C%20a,ledger%20known%20as%20the%20blockchain .!
@yakihonne.com -
 @ 5af07946:98fca8c4
2024-11-23 00:52:05
@ 5af07946:98fca8c4
2024-11-23 00:52:05US natives think $USD is a currency - for the rest of the world it is an asset . Just like #bitcoin.
The way Microstrategy accumulates bitcoin , all central banks collect US debt - a fancier word for US Dollar. As of April 2024, the five countries that hold the most US debt are:
- Japan: $1.1 trillion
- China: $749.0 billion
- United Kingdom: $690.2 billion
- Luxembourg: $373.5 billion
- Canada: $328.7 billion
Compare this global stake to 15 odd billions that #Microstrategy has in bitcoin. The way Microstrategy wants to protect bitcoin network , central banks want to protect #USD. Which means they all resist any change in capital structure. Not even bitcoin.
Thus the peaceful path for bitcoin is to become the reserve strategic asset for United States and thus for rest of the world. The other path is literally fighting governments worldwide ..
There is however one more opportunity - that is if people all around world adopt #SATs - which is why success of #nostr is so critical ! And other lightning apps - #LNCalendar , #StackerNews , #Fountain
In reality , both these things can happen simultaneously - that would be real freedom - Top down and Bottom up.
-
 @ df478568:2a951e67
2024-11-17 14:51:44
@ df478568:2a951e67
2024-11-17 14:51:44Chef's notes
This is a delicious meal that is easy to make and tastes delicious.
Details
- ⏲️ Prep time: 10 minutes
- 🍳 Cook time: 20 minutes
- 🍽️ Servings: 6
Ingredients
- 2 LB of marinated Carne Asada
- onion
- corn tortillas
- cilantro
- salsa
- guacamole
- sour cream
- salt
- pepper
- spanish rice
- beans
Directions
- BBQ carne asad for about 25 minutes or until meat reaches a temprature of 150 degrees
-
 @ 63d59db8:be170f6f
2024-11-23 00:41:02
@ 63d59db8:be170f6f
2024-11-23 00:41:02This ongoing series "Better Together" features surreal settings I have been creating by combining two different photographs that I've shot. I enjoy the challenge of creating something completely new out of two photos that otherwise have nothing to do with each other. There is no other editing or manipulation done to these images besides connecting them at one meeting line.





Visit Pat's website to see more
NOICE Magazine’s Visual Expression Awards are designed to spotlight creativity in photography, welcoming both emerging and seasoned artists. Each submission is now part of our dynamic prize pool, currently at $120 / 121,956 sats and growing with each new entry, with immediate exposure opportunities on our website and social channels.
Choose a Standard or Premium submission to suit your needs and have your work thoughtfully reviewed for form, originality, and impact. A quarterly cash prize from the dynamic pool goes to one standout entry, helping fund your next creative project. Deadline: December 31, 2024.
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 2dd9250b:6e928072
2024-11-22 23:32:03
@ 2dd9250b:6e928072
2024-11-22 23:32:03O Calvinismo, como Cosmovisão diverge do Conservadorismo Tradicionalista (postulado por Burke, Scruton, Jordan Peterson e outros). Isso tem se demonstrado de forma evidente hoje ao passo que quando se fala em Conservadorismo, os comentaristas mais lembrados são Olavo de Carvalho, Guilherme Freire e os Hosts do Brasil Paralelo.
Portanto, é inegável que escritores, apresentadores e donos de Canais ditos Conservadores, na verdade são Católicos Romanos falando para um público Católico Romano. E quando citam os "Protestantes", ninguém sabe ao certo, de quem eles estão falando. Uma vez que nós não somos meros Evangélicos, somos Reformados.
Historicamente, o grupo que mais se opôs aos Católicos Romanos foram os Calvinistas Puritanos no Século XVII. As Confissões Reformadas (de Westminster de 1647 e a de Londres de 1689) trazem um teor anti-papista na maioria de seus capítulos e artigos de fé.
Isso nos mostra que há um real conflito, ou uma disputa, concernente a quem pertence o termo "Conservador" no Brasil. Uma vez que, para um Católico Romano Tradicionalista, Evangélicos são Esquerdistas/Satanistas indo para o inferno junto com Lutero e Calvino e todo o estrago que o Progressismo vem fazendo no Mundo, tem sua causa na Secularização do Ocidente que se originou na Reforma de Lutero.
Em contrapartida, Evangélicos em geral, são mais amistosos, defendendo uma certa união com os Romanistas para frear o avanço de Pautas ideológicas/identitárias que vão de encontro aos costumes, valores, fé e tradição Cristãos. Mas a que preço? E mais importante: Essa união (ou apropriação do termo Conservador) com o Romanistas tem algum fundamento Bíblico?
Existem vários aspectos que podemos analisar para chegarmos a uma resposta satisfatória. Mas irei trazer aqui apenas um aspecto. O Casamento. É inegável para todo mundo que se diz Conservador, ou que está próximo disso, que o mundo pós - moderno tenta enfraquecer/ridicularizar o Homem e enaltecer/empoderar a Mulher (exemplo disso é uma noiva se negando a dizer “prometo ser submissa” em uma Cerimônia de Casamento, deixando o noivo e o padre desconcertados) . Mas é só analisarmos mais de perto a definição de casamento no Conservadorismo e o que ele representa, para entendemos que o Conservador (ou seja, Católico Romano) não parte do mesmo ponto de partida do Cristão Reformado para argumentar a favor do casamento tradicional.
Para nós Cristãos Reformados o Casamento é um Pacto. Nesse sentido, tem mais valor do que um mero acordo ou Contrato entre as partes porque é um símbolo. A Bíblia usa a ilustração de Cristo como Noivo e a igreja como noiva (Mt 25:1-13; Ef 5:32) por isso o marido assume a missão de 'proteger e cultivar’¹ sua esposa e a esposa se submete ao marido. Submissão na Bíblia significa se submeter a mesma missão. No caso, a mulher ajuda o marido nessa missão. Logo há uma parceria onde um complementa o outro, cada um na sua função (Efésios 5:25-31).
Além disso, O matrimônio foi ordenado para o mútuo auxílio de marido e mulher, para a propagação da raça humana por uma sucessão legítima e da Igreja por uma semente santa, e para impedir a impureza. (Gn. 2:18, e 9:1; Ml.2:15; I Co. 7:2,9). ²
Portanto , a compreensão Pactual Bíblica do casamento supera qualquer visão política/social Tradicionalista como o Conservadorismo.³
No Conservadorismo há apenas um clamor por preservação dos costumes judaico/cristãos fundamentais para civilização ocidental, mas como isso será feito, não é muito claro. Por isso o conservador brasileiro ganhou esse estereótipo de hipócrita. A favor do casamento tradicional, sendo que já está no 3°,4° casamento. Contra o Lobby gay , drogas, ideologia de gênero etc, mas a favor do aumento do Estado para frear essas pautas identitárias/progressistas ao invés de pregar, crendo que o Evangelho de Jesus transforma vidas. E vidas transformadas pelo Espírito Santo muda toda uma sociedade. Portanto, o Conservador zela pela preservação de costumes e virtudes, apenas exteriormente, levando em consideração conservar o Bem e frear o Mal, em favor de uma mudança gradual da sociedade.
Por isso eu não me considero Conservador (pelo menos não aos moldes do Conservadorismo Tradicionalista dos Papistas). Costumes e valores devem ser observados não por imposição de Leis Juspositivistas, endossando a interferência do Estado na vida privada dos cidadãos, mas pela manifestação do Poder do Evangelho na vida de pessoas regeneradas pelo Espírito Santo que, junto da Igreja Universal de Cristo, testemunham e agem conforme a Lei do Senhor.
1."Cultivar e Guardar" são duas palavras que resumem o mandamento de Deus para o Homem. No contexto de Gênesis 2:15, Deus ordenou a Adão proteger e cultivar tudo que estava no jardim do Edem, incluindo sua mulher, Eva.
2.CFW Cap.24. Artigo II.
3.Esse texto é totalmente de minha autoria e estava há um bom tempo querendo escrever sobre isso.
-
 @ df478568:2a951e67
2024-11-17 14:43:49
@ df478568:2a951e67
2024-11-17 14:43:49Chef's notes
This is in a recipe book my wife made, but I modified it for an InstantPot
Details
- ⏲️ Prep time: 5 minutes
- 🍳 Cook time: 1 hour 10 minutes
- 🍽️ Servings: 6
Ingredients
- 1 lb. boneless skinless chicken breasts
- 1 small diced onion or cup of frozen onions
- 1 medium sized bell pepper
- 15 oz. can of diced tomateos with green chilies, undrained
- 1 can of corn
- 1 15oz. can black beans
- 1 tablespoon chili powder
- 1 tablespoon salt
- 1 tsp ground cumin
- 1 tsp garlic
- 4 cups of chicken broth(not needed until day of cooking)
- Tortilla chips
- toppings like salsa, sour cream, avocado, etc.
Directions
- Add all ingredients into an instantpot
- Pressure cook for 1 hour
- Slow release Instant Pot for 10 minutes
- Serve
-
 @ a305a0de:21557ddd
2024-11-22 16:53:03
@ a305a0de:21557ddd
2024-11-22 16:53:03In the ever-evolving world of Bitcoin, innovation is key. And one name that's been making waves is Yakhonne. This pioneering project has been instrumental in helping Bitcoin take a giant leap forward.
So, what exactly is Yakhonne? Simply put, it's a decentralized social media platform that rewards users with Bitcoin for creating and engaging with content. But that's not all - Yakhonne has also been at the forefront of driving Bitcoin adoption and education.
By providing a user-friendly platform for people to learn about and interact with Bitcoin, Yakhonne has helped demystify the world of cryptocurrency. And with its innovative approach to social media, Yakhonne has shown that Bitcoin can be used in ways that go beyond just transactions.
The impact of Yakhonne on Bitcoin's evolution cannot be overstated. By pushing the boundaries of what's possible with Bitcoin, Yakhonne has inspired a new wave of innovation and adoption. And as Bitcoin continues to grow and mature, it's clear that Yakhonne will remain a key player in shaping its future.
-
 @ 97c70a44:ad98e322
2024-11-22 22:36:31
@ 97c70a44:ad98e322
2024-11-22 22:36:31This week I finally released Flotilla, a discord/slack-like client I've been working on for about three months. This project began as a NIP 29 client, and after 3 PRs, lots of discussion, a podcast, and a partial implementation, I decided to go my own way.
This of course means that I broke compatibility with all the NIP 29 group clients out there, but I did it for good reasons. In this post I hope to explain those reasons, and speculate on how best to move forward with "relay-based" groups on nostr.
To give you some quick context, NIP 29 and my approach to groups (which I'll dub "relays-as-groups" for clarity) are very similar, with a fundamental difference. Both have chat, join requests, group metadata, membership, moderation, etc. However, the basic unit of a NIP 29 group is a random group id string, while the basic unit of a Flotilla group is a relay itself.
I believe this design difference emerged in part because of what we were attempting to build. NIP 29 groups tend to be more telegram-like, where groups function more like chat rooms, and users join each one individually. On flotilla, groups function more like Discord servers, or Slack workspaces, and users join an entire group of chat rooms at once.
"Relays as groups" has four major advantages over "groups hosted by relays".
Decentralization
First, using relays as groups supports decentralization better than hosting user-managed groups on relays.
(To be clear here, I'm not referring to client-managed groups, which is a whole different approach that we've experimented with in the past, both with NIP 72 communities and with NIP 87 encrypted groups. Both NIP 29 and relays-as-groups solve many of the consistency problems associated with attempting to have a linear, synchronous conversation across multiple relays. While both alternatives have a story for migrating or mirroring a group, both rely heavily on the host relay to not censor user messages.)
I know what you're thinking. How can reducing the number of relays improve decentralization? Relays were originally introduced in order to create redundancy and spread trust across many actors, creating censorship resistance. This model was difficult for many bitcoiners to wrap their heads around, because it's a very different kind of decentralization than what a blockchain delivers.
Communities are an essentially different use case from a broadcast network where content is delivered based on author or recipient relay selections. Every message to a community would have to be delivered to all members of the community. Sending each message to all members' personal inbox relays just doesn't make sense; there has to be some other inbox for the community to work off of.
Additionally, online communities almost always have moderators and admins. This is even true of very public, open types of communities, like subreddits. The only type of community that doesn't have moderators is one that emerges naturally from social clustering. And even in that case there is loose consensus about who is in and who isn't, based on the actions/follows/mutes of the participants, whether these clusters are huge or tiny. Socially-emergent groups are served well by chat applications or broadcast networks.
But the subset of online communities that do prefer to confer moderator status on certain members are essentially centralized. In other words, centralization and control is a feature, not a bug.
Now, that doesn't mean there don't need to be considerations around credible exit and removing/adding moderators over time. But the fact is that moderator-led communities are always under the oversight of the moderators at any given time, even if the identity of those moderators changes and their power is limited.
What this implies is that decentralization for moderator-led groups looks very different from decentralization for a broadcast network. There is nothing at all wrong with giving moderators full control over the group's communications (qua the group; DMs and public broadcast content between group members should happen outside the group's infrastructure, just as people also exist outside the communities they are a part of). What is important is that no one has control over groups that they aren't nominally the admin of.
In concrete terms, what this all means is that community moderators should self-host their infrastructure. This is the same principle as motivates self-custody and home servers, but applied to communities. If community leaders manage their own relays, this means that no hosting company or relay admin can de-platform their community. Centralization of network infrastructure in this case aligns with the trust structure of the group.
Applying this to our group dilemma, it's easy to see that NIP 29 groups are more vulnerable to censorship or data harvesting attacks by malicious relay admins, since many unrelated groups might live on a single relay. In contrast, if you treat relays as groups themselves, every group is forced to live on a separate relay, spreading risk across more hosting providers.
Now, this doesn't necessarily mean that many "relays" aren't "virtual relays" managed by the same hosting provider. So I'll admit that even "relay-based" groups don't completely solve this problem. But I think it will tend to nudge community organizers toward thinking about community infrastructure in a more self-sovereign (or community-sovereign) way.
Investment in Relays
While both NIP 29 and relays-as-groups rely heavily on relays to implement the features that support each specification, there's an important difference between the feature sets. In NIP 29, relay support is specific only to groups, and isn't applicable to other use cases. In contrast, every protocol feature added to support the "relays as groups" can be re-purposed for other types of relays.
Take join requests for example. NIP 29's kind
9021events allow users to request access to a group, and that's all. Kind28934join requests on the other hand allow users to request access to relays. Which in the relays-as-groups model means group access, but it also means custom feed access, inbox relay access, maybe even blossom server access. In fact, kind28934was originally proposed at the beginning of this year in order to support a different version of hosted groups, but remains as relevant as it ever was despite iteration on groups.The orthogonality of features added to relays to any specific use case will long-term result in simpler specs, and more interesting relay-based use cases being possible. Join requests are only one example. The same is true of 1984-based moderation, the proposed LIMITS command, AUTH, NIP 11 relay metadata, etc.
We already have web of trust relays, feed relays, archival relays, and many more. Being able to request access to closed versions of these is useful. Being able to signal federation between multiple instances of these, run by different people, is useful. And of course, relay metadata, reports, and LIMITS are self-evidently useful for normal relays, since they pre-date Flotilla.
I've always said that relays are some of the coolest and most under-appreciated parts of nostr. This doesn't mean that we should add every possible feature to them, but features related to data curation and access control fit really well with what relays are good for. For more on the role of relays and what features should be added to them, see my nostrasia talk Functional Relays.
Declarative vs Imperative
A common paradigm in programming is that of declarative vs imperative programming. Imperative programming focuses on "how" to achieve a given result, leaving "what" the code is doing to be inferred by the programmer. Declarative programming instead focuses on the "what", and allows some underlying implementation to solve the how. A good balance between these paradigms (and knowing when to use one over the other) allows programmers to work faster, make fewer mistakes, and produce less code.
Another way to look at this is that a specification should contain as much ambiguity as possible, but without compromising the system attributes the specification is supposed to guarantee. It can get complex when figuring out what attributes are core to the specification, since sometimes the "how" does actually matter a lot.
However, nostr in particular falls pretty far along the "declarative" end of this spectrum because of its decentralized nature. The only person who can say anything with any authority is the person who signs an event. This event is a "declaration", and any effects it has are necessarily up to the relays, clients, and people interpreting the event. However, what others do with an event is an expectation that must be taken into account by the publisher, forming a feedback loop. This dialectic is what creates stability in the protocol.
In more concrete terms, no one can "tell" anyone else what they have to do by publishing an event like you might in a traditional, centralized RPC-type system. Any event whose semantics are a "command" rather than a "fact" or "request" is broken unless the counter party is fully committed to carrying out the command. An example of a "command" scenario on nostr is NIP 46 remote signing, in which the bunker is the agent of the user making the request. If the bunker implementation fails to carry out a valid command initiated by the user, its interpretation of that event is objectively incorrect.
NIP 29 applies this same paradigm to relays, particularly in the area of moderation, membership edits, and group metadata. In other words, there are several "commands" which instruct the relay to do something.
This isn't necessarily a bad thing, but it does increase the number of things the interface between the client and relay have to agree on. A regular relay may accept an
add-userrequest, but then do nothing with it, violating the contract it has implicitly accepted with the user. The solution to this is feature detection, which is a whole other API to be specified and implemented.My ideal solution to this problem is to shift the semantics of events away from "commands" to "facts" - in other words, to make the interface more declarative.
In fact, we already have an interface for moderation that works like this. Many clients support kind
1984"report" events. Users sending these reports have no expectations about how they will be used. They are a "fact", a declaration of opinion with certain semantics. Other actors in the network may choose whether or not to pay attention to these.This same model is easily applied to communities. Without having to implement any feature detection (either for the relay's implementation, or for the user's role on that relay), anyone can simply send a "report". This goes into the black hole of the relay, and may subsequently be ignored, broadcasted, or acted on.
The really nice thing about this model is that because there is no expectation for "how" reports are to be interpreted, any approach to moderation can be used depending on relay policy or client implementation. In NIP 29, if you issue a
delete-event, it either happens or it doesn't and if it doesn't, you have to explain the failure to the user somehow.In the relays-as-groups model, e-tagging an event in a kind
1984requires no user feedback, and therefore it can be interpreted however the relay prefer. This can result in insta-banning, manual review, thresholds based on number of reporters, a leaky-bucket social score algorithm, shadow banning, temporary banning, soft-moderation by allowing clients to request reports and respond to them by changing user interface elements, or anything else you can think of.The reason I think this is important is that community moderation is a very hard problem, and baking certain semantics into the specification can result in the complete failure of the spec. NIP 72 should be considered an example of what not to do. Some NIP 72 communities have survived due to the dedication of the moderators, but many more have failed because of the rigid moderation model. We should try not to make the same mistake again.
Conclusion
Now, having said all that, I think there is actually a lot of value to NIP 29. What finally clicked for me this week after releasing Flotilla is that the two approaches are actually complementary to one another. One of the most common feature requests I've already heard for flotilla is to have more complete support for rooms, which are currently implemented as not much more than hashtags. Better rooms (i.e., "nested groups") would require: authentication, membership, moderation, and pretty much everything else that exists for the top-level group.
As much as I believe the relays-as-groups approach is superior to NIP 29 for top-level groups, it doesn't make any sense to try to "nest" relays to create sub-groups. Something like NIP 29 is needed in order to fully support rooms anyway, so I think the convergence of the two approaches is all but inevitable. In fact, fiatjaf has already merged a PR which will allow me to use the same event kinds in flotilla as exist already in NIP 29 clients.
There are just a few more changes that are necessary in order for me to fully adopt NIP 29 in Flotilla:
- NIP 29 feature detection
- Opaque ids for unmanaged groups prevent unmanaged groups from having human-readable names
- We need a mechanism for building membership lists without relay support
- Better handling for
9021group join requests
I've opened PRs for each of these (linked above). Hopefully we can work through these issues and combine our powers to become the Captain Planet of group implementations.
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 1cb14ab3:95d52462
2024-11-17 00:57:41
@ 1cb14ab3:95d52462
2024-11-17 00:57:41Chef's notes
I have been making this every Thanksgiving since I first tried it. One of my all time favorites. You can fry the shallots and refrigerate the night before to save time.
Recipe is credit of The Pioneer Woman -- Go show some love below ⬇️ https://www.thepioneerwoman.com/food-cooking/recipes/a80624/thanksgiving-dinner-green-bean-casserole/
Details
- ⏲️ Prep time: 35 min
- 🍳 Cook time: 1 hr 30 min
- 🍽️ Servings: 10
Ingredients
- FOR THE FRIED SHALLOTS
- 1/3 c. all-purpose flour
- 1/2 tsp. cayenne
- 1/2 tsp. garlic powder
- 1/4 tsp. kosher salt
- 1/4 tsp. black pepper
- 4 large shallots, peeled and thinly sliced into rings
- frying oil
- FOR THE GREEN BEANS AND GRAVY
- 2 1/2 lb. fresh green beans, trimmed and halved (use a little less if you like gravy to beans ratio)
- 8 oz. bacon
- 6 tbsp. unsalted butter, divided
- 16 oz. sliced button mushrooms (for more mushroom flavor, use cremini variety)
- 1/3 c. finely chopped shallots
- 3 cloves (large) garlic, minced
- 1/2 c. all-purpose flour
- 1 c. low sodium chicken stock
- 2 c. half-and-half
- 2 tbsp. soy sauce
- 1 tbsp. Worcestershire sauce
- 2/3 c. grated parmesan cheese
- 2 tsp. chopped fresh rosemary
- 2 tsp. chopped fresh thyme
- Kosher salt and freshly ground black pepper, to taste
Directions
- FOR THE FRIED SHALLOTS
- In a medium bowl that has a lid, whisk together flour, cayenne, garlic powder, salt, and black pepper. Add sliced shallots. Place lid tightly on bowl and shake the bowl a few times to evenly coat shallots with flour mixture.
- Pour canola oil into a medium saucepan to a 1-inch depth and place over medium-high heat. Heat to 325°F, using a deep-frying thermometer. Fry shallots in batches until golden brown and lightly crispy. Take care to not let them get too dark, as they will also bake for a bit in the oven on top of the casserole. This should take about 3–5 minutes per batch. Transfer to a paper towel lined baking sheet. Sprinkle lightly with kosher salt and set aside.
- FOR THE GREEN BEANS AND GRAVY
- Preheat oven to 375° F.
- Bring a large pot of salted water to a boil and add green beans. Cook beans for 2–3 minutes, until bright green in color and tender crisp. Drain beans and pour into a large bowl of ice water to stop from cooking. Drain again and set aside.
- In an extra large skillet with tall sides, over medium to medium-high heat, fry bacon until chewy-crisp. Transfer bacon from skillet to a paper towel lined plate to drain and cool. Once bacon has cooled, roughly chop and set aside.
- Discard all but 2 tablespoons of the bacon fat from the skillet. Return skillet to stove top over medium heat. Add 2 tablespoons of the butter to the skillet. Once butter is melted, add the mushrooms and stir to incorporate. Cook, stirring regularly, until mushrooms are softened. Add chopped shallots and garlic, stirring to incorporate. Cook for another 2–3 minutes, until garlic is fragrant.
- Now slide everything in the skillet to one side. Add remaining 4 tablespoons of butter to other side of skillet. When the butter is melted, sprinkle the flour over the butter, whisking all the while. A flat whisk works awesome here. Draw in as much liquid as you can, into the flour. The mixture will be very thick. Let it cook for one minute, until slightly browned and fragrant. Slowly whisk in chicken stock until flour mixture is smooth. Then whisk in the half and half. Now bring the entire contents of the skillet together, scraping the bottom of the skillet, and folding to incorporate. Turn heat up to medium-high and cook until thickened and bubbly, about 4–5 minutes, stirring periodically.
- Remove skillet from heat. Stir in soy sauce and Worcestershire sauce. Then sprinkle Parmesan, rosemary, and thyme over the top and stir to combine. Now is the time to taste test and add more salt and pepper, if desired. I usually add about 1/2 teaspoon of salt and 1/4 teaspoon of black pepper at this point. Fold in blanched green beans. Transfer mixture to a baking dish and place in oven to bake for 30 minutes. Remove casserole from oven and arrange fried shallots and chopped bacon over the top, leaving green beans exposed around the perimeter of the dish. Place in oven and bake for another 5 to 10 minutes, or until edges of casserole are bubbling and the top is golden. Remove from oven and let rest for a few minutes before serving.
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 319ad3e7:cc01d50a
2024-11-22 21:03:17
@ 319ad3e7:cc01d50a
2024-11-22 21:03:17Candied Pecans by Double00Satoshi
Details⏲️ Prep time: 10 🍳 Cook time: 45 🍽️ Servings: 16
Ingredients
- 1/4 cup light brown sugar
- 1/4 cup granulated sugar
- 1 tablespoon ground cinnamon
- 1 teaspoon salt
- 1 pound unsalted pecans halves
- 1 egg white
- 1/2 teaspoon vanilla extract
- 1 teaspoon water
Directions
Preheat oven to 300 degrees F. Line a large baking sheet with parchment paper and set aside. In a bowl, add sugars, cinnamon, and salt. Whisk until combined. Set aside. In a large bowl, whisk the egg white, vanilla, and water together until frothy. Add the pecans and gently toss until the pecans are well coated. Add the sugar and cinnamon mixture and toss until pecans are covered. Spread the pecans out in a single layer on prepared baking sheet. Bake for about 30-45 minutes, stirring every 15 minutes. Remove from the oven and let the pecans cool on the baking sheet. When completely cool, store in an airtight container for up to 1 month.
Deviled Eggs by Seth
Details ⏲️ Prep time: 20 min 🍳 Cook time: 15 min 🍽️ Servings: 6
Ingredients
- 6 hard boiled eggs, peeled
- 3 tablespoons of mayonnaise
- 1/2 teaspoon of soy sauce
- 1 teaspoon of Dijon mustard
- 1/2 stalk of celery, finely diced
- Salt and pepper
Directions
Cut eggs in half lengthwise and pop yolks out into bowl, mash with fork. Mix in mayonnaise, mustard, celery, soy sauce, salt and pepper. Whip until a creamy texture Scoop out fill and add to egg whites, heaping it slightly. Add garnish of choice Serve immediately or refrigerate before serving.
Bang Bang Shrimp by Hes ⚡️
Details ⏲️ Prep time: 20 min 🍳 Cook time: 20 min 🍽️ Servings: 4
Ingredients
- 1 pound shrimp
- 1 teaspoon granulated sugar
- ½ cup all-purpose flour
- ½ cup panko breadcrumbs
- 1 teaspoon salt
- ½ teaspoon black pepper
- ¼ teaspoon garlic powder
- ¼ teaspoon onion powder
- ¼ teaspoon dried basil
- 1 egg
- 1 cup milk
- 4 – 5 teaspoon chili garlic sauce
- 1 teaspoon rice vinegar
- ½ cup mayonnaise
Directions
Make the sauce: Mix mayonnaise, chili garlic sauce, sugar, and rice vinegar in a bowl. Refrigerate. Prepare for frying: a) Combine beaten egg and milk in one bowl. b) Mix flour, panko, and seasonings in another bowl. Bread the shrimp: a) Coat each shrimp in flour mixture. b) Dip in egg mixture. c) Coat again in flour mixture. d) Arrange on a plate and refrigerate for 20 minutes. Fry the shrimp: a) Heat oil to 350F in a dutch oven. b) Fry shrimp for 2-3 minutes until golden. c) Drain on wire rack or paper towels. Serve: a) Coat fried shrimp with ¼ cup sauce. b) Serve with remaining sauce on the side.
To Find More Recipes, go to Zap.Cooking
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ c755de14:cc53833a
2024-11-22 16:52:54
@ c755de14:cc53833a
2024-11-22 16:52:54Here’s What Bitcoin’s New All-Time High Means For Investors

Bitcoin’s price soared over $98,000 this morning, marking a new high. The granddaddy of cryptocurrency seems to be becoming less volatile, but it’s still a risky asset. Don’t buy Bitcoin just because of its recent price action – take time to research and think about how it fits with your other investments. For the second time this year, Bitcoin bulls have reason to celebrate. About 24 hours ago, Bitcoin’s price reached $99,434 smashing previous all-time high. Bitcoin’s recent rise was fueled by an influx of institutional money into spot crypto ETFs and increasing economic optimism. The election result pushed it to break new ground. If you’re thinking of buying Bitcoin, you might be wondering what this means for investors.
Does Bitcoin’s recent price action mean it’s here to stay? Positive price action is certainly reassuring, but the true test of whether Bitcoin is here to stay will be long-term adoption. There’s a lot we don’t know about how cryptocurrency will develop. It’s a relatively new and unregulated industry, and it’s still unclear what people will use Bitcoin for in the long term. That said, Bitcoin does appear to be maturing. Don’t get me wrong, it continues to be a volatile and high-risk asset. But the price swings have become less drastic. That’s a very different picture from previous years. Indeed, research by Fidelity shows that the top cryptocurrency was less volatile than several popular S&P 500 stocks. For example, its analysis shows that Netflix was more volatile over the two-year period ending March 2024. Even so, Netflix is still a totally different asset class. The stock market has existed for hundreds of years, which is plenty of time for various regulations and investor protections to evolve. In contrast, Bitcoin is less than two decades old and still has the sword of changing regulation hanging over it.
Three questions to consider before you buy Bitcoin Before you buy any investment, it’s important to be clear on why you’re buying. Think about your tolerance for risk and how cryptocurrency fits with your overall investment strategy. Here are some questions to consider.
- How will you buy and store it? Cryptocurrency assets do not have the same protections against institution failure or theft as money in the bank or stocks in a brokerage account. As an investor, that means being conscious of security when buying and storing digital assets.
Here’s how that looks with some of the most common ways you can add Bitcoin to your portfolio:
Top cryptocurrency exchange: Cryptocurrency exchanges have a broad mix of cryptos and crypto-related products. It is easy to move your assets to a crypto wallet you control, which gives you extra protection against platform failure. Crypto broker: A couple of popular brokerages offer cryptocurrencies. They don’t have as much functionality or as many cryptos as exchanges, but the fact that they’re registered with the SEC to trade other assets makes them feel more secure. Spot Bitcoin ETF: The SEC greenlighted spot Bitcoin ETFs at the start of the year. This means many investors can buy them from a brokerage account, just as they would other ETFs and stocks. One big advantage is that the fund managers are responsible for storing the Bitcoin safely. Robinhood has broken the mold in terms of crypto offerings. You can buy several cryptocurrencies directly, as well as spot Bitcoin and Ethereum ETFs. Plus, it’s the only brokerage with a crypto wallet that lets you deposit and withdraw crypto. Click here to learn more about Robinhood’s crypto offer and open an account.
- Have you researched Bitcoin and its long-term potential? Think about why you’re buying cryptocurrency. If it’s because you see the price rising and worry about missing out, pause and do a bit more digging. Look at the different arguments on how Bitcoin will develop – both critical and optimistic.
Some argue that Bitcoin has value as a type of digital gold or the future currency of the internet. Others see it as taking a chunk out of the global money transfer market. On the other hand, critics say it’s a speculative asset with no intrinsic value.
- How does it fit with the rest of your portfolio? Risky assets like cryptocurrency should only make up a small percentage of your wider portfolio. Think about what level of risk you’re comfortable with and how to balance your investments accordingly.
Building a diversified portfolio can be a great way to safeguard your funds. If one sector or asset performs badly, you’re insulated against losses. If it does well, you’ll still reap the rewards.
Don’t buy Bitcoin just because it hit an all-time high Not only has Bitcoin more than erased the losses of recent years, it’s also becoming less volatile. However, it’s still a high-risk asset that could fall to zero.
Only invest money you can afford to lose, and do your own research into the blockchain and Bitcoin. Positive short-term price action is one thing, but if you’re a buy-and-hold investor, long-term value is a lot more important.
@Yakihonne
-
 @ 1cb14ab3:95d52462
2024-11-17 00:38:07
@ 1cb14ab3:95d52462
2024-11-17 00:38:07Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 20 min
- 🍽️ Servings: 4
Ingredients
- 1 pound shrimp
- 1 teaspoon granualted sugar
- ½ cup all-purpose flour
- ½ cup panko breadcrumbs
- 1 teaspoon salt
- ½ teaspoon black pepper
- ¼ teaspoon garlic powder
- ¼ teaspoon onion powder
- ¼ teaspoon dried basil
- 1 egg
- 1 cup milk
- 4 – 5 teaspoon chili garlic sauce
- 1 teaspoon rice vinegar
- ½ cup mayonnaise
Directions
-
- Make the sauce: Mix mayonnaise, chili garlic sauce, sugar, and rice vinegar in a bowl. Refrigerate.
-
- Prepare for frying: a) Combine beaten egg and milk in one bowl. b) Mix flour, panko, and seasonings in another bowl.
-
- Bread the shrimp: a) Coat each shrimp in flour mixture. b) Dip in egg mixture. c) Coat again in flour mixture. d) Arrange on a plate and refrigerate for 20 minutes.
-
- Fry the shrimp: a) Heat oil to 350F in a dutch oven. b) Fry shrimp for 2-3 minutes until golden. c) Drain on wire rack or paper towels.
-
- Serve: a) Coat fried shrimp with ¼ cup sauce. b) Serve with remaining sauce on the side.
-
 @ c755de14:cc53833a
2024-11-22 16:52:03
@ c755de14:cc53833a
2024-11-22 16:52:03
In the past recent years, Cryptocurrencies have exploded onto the financial scene, offering a new innovative form of digital money. Built on blockchain technology, cryptocurrencies like Bitcoin and Ethereum have the potential to transform finance as we know it. But what exactly are cryptocurrencies, and what is their role in this modern financial landscape? This article explores the rise of cryptocurrencies, their impact so far, and what the future may hold for this disruptive new asset class.
Cryptocurrencies Overview Cryptocurrencies are digital that uses cryptography to control and secure transactions. Unlike printed money issued by governments, cryptocurrencies operate independently of central banks and are decentralized across peer-to-peer networks. The first and most well-known cryptocurrency as we all know it is Bitcoin, created in 2009 by the mysterious Satoshi Nakamoto. Today there are over 10,000 different cryptocurrencies in existence, though Bitcoin and Ethereum dominate the market.
Cryptocurrencies enable direct transactions between users without an intermediary. All ownership records are stored on a public ledger called the blockchain. Advanced cryptography verifies and secures each transactions on the blockchain. Miners contribute computing power to verify blocks of transactions, and are rewarded with new cryptocurrency for their efforts. This decentralized nature of cryptocurrencies removes the need for trusting central authorities to manage the system.Is Cryptocurrency Here To Stay? Given their relatively brief lifespan so far, some wonder if cryptocurrencies are just a passing fad. However, there are a growing amount of evidence that suggests cryptocurrencies are here to stay as a financial and technological innovation. One of the key drivers of this is the advantages the underlying blockchain technology provides in terms of secure, transparent record-keeping and transactions. The decentralized structure means no single entity controls the network.
Cryptocurrencies also enable faster cross-border payments. Major companies like PayPal, Visa, and MasterCard are integrating crypto capabilities to take advantage of these benefits. The total market value of cryptocurrencies has grown to over $1 trillion. Governments are exploring central bank digital currencies built on blockchain technology. All of these trends point to cryptocurrencies cementing their place in the financial landscape long-term.
What is Cryptocurrency’s Role In Today’s Financial Landscape? Cryptocurrencies are playing an increasingly important role in today’s modern finance. Below are some of those roles: • Cryptocurrencies serves an alternative investment and store of value. Scarcity makes cryptocurrencies like Bitcoin attractive as an inflation hedge.
• Facilitating global commerce and payments. Cross-border crypto payments are faster and cheaper. The adoption is growing among merchants and businesses.
• Providing banking access. Approximately 1.7 billion adults remain unbanked globally. Cryptocurrencies provide access without any form of barriers.
• Driving innovation. Decentralized finance (DeFi) applications are expanding lending, trading, insurance and more.
• Challenging status quo. The disruptive power of cryptocurrencies encourages competition and improvement in the traditional finance.
Considerations And Challenges
Although promising, cryptocurrencies also come with risks and challenges that should be considered: • Volatility: As a newer asset class, cryptocurrency prices can swing wildly, making them a risky investments. Extreme volatility limits their ability to reliably store value.• Security: Exchanges and wallets have been hacked, leading to huge losses. Users must take proper precautions to secure their cryptocurrency tokens.
• Lack Of Regulation: Currently, minimal government oversight exists. More regulation would provide greater investor protection.
• Complex Technology: Blockchain and cryptocurrencies represent complex concepts for many. Usability could improve with further development.
• Illegal Activity: Anonymity has attracted criminals laundering money and buying illegal goods. This black market use harms legitimacy.
• Environmental Impact: Bitcoin mining consumes enormous energy. More efficient consensus models are being explored.
• Adoption Obstacles: Integration into everyday payments and financial systems is still limited. Tax implications are still being defined.
As time goes on, these challenges may decrease over time as the technology matures. Regulations will evolve and adoption will grow. But for now, they remain barriers inhibiting mainstream acceptance.
How Cryptocurrency Can Affect The Finance Industry
Cryptocurrencies threaten to disrupt traditional finance and could significantly impact the industry in a variety of ways: • Reduced Fees: By removing middlemen, cryptocurrency transactions have fewer fees. This pressures banks and payment networks to reduce costs.• Faster Services: Settlement of cryptocurrency transactions is nearly instant. Consumers will expect faster banking and payments facilitated by blockchain technology.
• New Revenue Sources: Wealth managers and institutions are finding ways to add cryptocurrency services to attract more clients and investment in dollars.
• Better Transparency: Cryptocurrency ledgers are public. This allows anyone to analyze transactions. This level of transparency will compel competition.
• Increased Automation: Smart contracts executed on the blockchain automate many manual processes required in traditional finance. This can improve efficiency and cost-savings.
• Enhanced Security: Cryptocurrencies offer better consumer protection against fraud or identity theft since they don’t expose personal information.
Effects Of Cryptocurrency On Everyone. Is It A Threat To Financial Stability? For the average person like you and I, cryptocurrencies offer both potential benefits and drawbacks:
Potential Benefits: 1. It Increases financial access. It has the ability to utilize financial services like lending or investments previously inaccessible.
-
It enables fast and cheap remittance of money across borders.
-
Cryptocurrencies reduces fees compared to traditional financial services.
-
The decentralized nature of crypto gives more people direct control and power over their money.
-
It serves as a new financial opportunities. It gives the ability to invest early in new cryptocurrencies and technologies.
Potential Drawbacks:
1. Cryptocurrency concepts and tools require technological proficiency many don’t have which makes it Complex.-
The unpredictable price fluctuations make crypto a high-risk investment.
-
No government insurance or regulation means limited consumer protections exist. For this reason, it lacks protection.
-
Fraud, scams and hacking are still common, leading to potential theft.
-
There are unclear reporting requirements and taxes on buying, selling, or mining crypto.
More user-friendly applications and prudent regulation can help maximize benefits and minimize risks of cryptocurrencies for the average person.
 The Future Of Cryptocurrency
The future path of cryptocurrency is unclear but innovation will continue to drive new opportunities like:
• Mainstream Adoption: Younger demographics are leading to increase crypto acceptance and usage.
The Future Of Cryptocurrency
The future path of cryptocurrency is unclear but innovation will continue to drive new opportunities like:
• Mainstream Adoption: Younger demographics are leading to increase crypto acceptance and usage.• Integration: More banks, merchants, businesses, and apps will integrate cryptocurrency support.
• Institutional Investment: Growing investment from hedge funds, banks, and publicly traded companies will further legitimize crypto.
• Applications: DeFi, NFTs, crypto gaming, and the metaverse hint at expanded functionality.
• Regulation: Reasonable oversight could foster confidence, safety, and standards.
• Security: Implementing layered security features like multi-factor authentication could reduce fraud and theft risk.
Bottom Line Cryptocurrencies mark a technological leap forward that will likely ripple through the financial sector for years to come. But realizing the full potential of cryptocurrencies to benefit society depends on sustaining innovation while proactively addressing risks. Though there are still challenges ahead, the promises of enhanced financial access, speed, privacy and transparency makes the cryptocurrency revolution worth nurturing rather than resisting.
@Yakihonne
-
-
 @ 592295cf:413a0db9
2024-11-16 10:40:22
@ 592295cf:413a0db9
2024-11-16 10:40:22Week 11-11
Lamenting is becoming something I should ask people who complain. Charity bussiness and after sending zap received to those who do not complain...
I started making an RSS feed template. Open an opml file and check the feed. I called this script,Teed.
This morning I saw a bounty from a fiatjaf note, on a rss-feed long form, basic a plugin for an app. But I'm not doing that, of course, I can also publish it as soon as I'm in charge. Maybe I have some opml files and I want to see if these are still active.
Starter pack is not good apparently creates elites and maybe gives you the feeling of not choosing, but that's what people want. Do not choose but have the illusion of choosing.
Toxicity level. high.
P2P stuff, Iroh is a protocol for syncing & moving bytes iroh computer post on Bluesky
Juraj new project
nostr:nevent1qvzqqqqqqypzpk4kccr9csumnwhmpv83ladqc6p88089cx2e5s2c4448ppgl2pakqqsyv4hs424x6c8phks903s595q2lqp5fpwyq7ajwrf00lxev8cfamcvmq23h
Alex Gleason bunker Knox. (Beta) "knox is a new Nostr bunker CLI for running a NIP-46 remote signer and granting credentials to members of your team". Announcing bunker knox article
Local First podcast, web2.5. Something like Nostr but Local P2P, interesting episode. youtube link
Open Secret AI. "OpenSecret is a backend for app developers that turns private encryption on by default." announcment AI
I think users with regard to algorithms do not want ten different feeds to choose from, but that their feed adapts to their choices, training the feed if this makes sense. So the feed is your feed for your choices, respond and train with them.
Pleblab 2, cool "ANNOUNCING TOP BUILDER SEASON 2! " nostr:nevent1qvzqqqqqqypzpmx02p4slzahlf7jlcaspsx57g6uc7kl7cc7dvhlsnqtpn6khjj0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcqyzy9w0frd802hfmrp45jr6dqhf7umqj7s63z0jvhv7hvvkcsqjg0vjwd7q4)
It was the real Guardian, quit 7fqx, we know it's you who want to distract us from number go up. The Guardian has left or wants to leave twitter is looking for alternatives, but how to verify a high profile user on Nostr? Nostr Address is already something but it's not enough.
We sometimes think that there is the money tree somewhere is that they magically appear, when instead the money is in the ground but they are dirty.
If Amethyst doesn't support is others stuff
People are simple, they want an app that works for all devices they have. People are "flutter-system".
A podcast feed xml file
Add to teed, if only i had made that option, meanwhile i saw a new interesting project
An other RSS feed github project
Imagine making a file opml with categories and those are your follow nostriches.
The problem is this does not bring new sap to the social chart is important to you, receive the selected posts and it is fantastic. You can also not use Nostr, if you want to use it as backup is fine. Share opml files? It's okay, but you can also find specific sites and find the best. Update for clients, you have a lot of RSS feeds from clients but update after a few hours so if there is really an emergency you lose. I still need to figure out how to integrate Nostr into RSS feed. Maybe an event to make your lists known.
I saw the event in these pr: nostr verified podcast nip #1465 Add audio track NIP #1043
-
 @ 319ad3e7:cc01d50a
2024-11-22 20:49:16
@ 319ad3e7:cc01d50a
2024-11-22 20:49:16Candied Pecans by Double00Satoshi
Details⏲️ Prep time: 10 🍳 Cook time: 45 🍽️ Servings: 16
Ingredients
- 1/4 cup light brown sugar
- 1/4 cup granulated sugar
- 1 tablespoon ground cinnamon
- 1 teaspoon salt
- 1 pound unsalted pecans halves
- 1 egg white
- 1/2 teaspoon vanilla extract
- 1 teaspoon water
Directions
- Preheat oven to 300 degrees F. Line a large baking sheet with parchment paper and set aside.
- In a bowl, add sugars, cinnamon, and salt. Whisk until combined. Set aside.
- In a large bowl, whisk the egg white, vanilla, and water together until frothy. Add the pecans and gently toss until the pecans are well coated. Add the sugar and cinnamon mixture and toss until pecans are covered.
- Spread the pecans out in a single layer on prepared baking sheet. Bake for about 30-45 minutes, stirring every 15 minutes.
- Remove from the oven and let the pecans cool on the baking sheet. When completely cool, store in an airtight container for up to 1 month.
Deviled Eggs by Seth
Details ⏲️ Prep time: 20 min 🍳 Cook time: 15 min 🍽️ Servings: 6
Ingredients
- 6 hard boiled eggs, peeled
- 3 tablespoons of mayonnaise
- 1/2 teaspoon of soy sauce
- 1 teaspoon of Dijon mustard
- 1/2 stalk of celery, finely diced
- Salt and pepper
Directions
- Cut eggs in half lengthwise and pop yolks out into bowl, mash with fork
- Mix in mayonnaise, mustard, celery, soy sauce, salt and pepper.
- Whip until a creamy texture
- Scoop out fill and add to egg whites, heaping it slightly
- Add garnish of choice Serve immediately or refrigerate before serving
https://zap.cooking/recipe/naddr1qqtk2em8vdjkcmr9de6z6er9we5kcety94jkwemnqgs2wguqtndxwfg3j8y8sm6d5k8hjlnfwavzxqf4fw5wjx7tqdpde8qrqsqqqa2838r4n9
Bang Bang Shrimp by Hes ⚡️
Details ⏲️ Prep time: 20 min 🍳 Cook time: 20 min 🍽️ Servings: 4
Ingredients
- 1 pound shrimp
- 1 teaspoon granualted sugar
- ½ cup all-purpose flour
- ½ cup panko breadcrumbs
- 1 teaspoon salt
- ½ teaspoon black pepper
- ¼ teaspoon garlic powder
- ¼ teaspoon onion powder
- ¼ teaspoon dried basil
- 1 egg
- 1 cup milk
- 4 – 5 teaspoon chili garlic sauce
- 1 teaspoon rice vinegar
- ½ cup mayonnaise
Directions
Make the sauce: Mix mayonnaise, chili garlic sauce, sugar, and rice vinegar in a bowl. Refrigerate. Prepare for frying: a) Combine beaten egg and milk in one bowl. b) Mix flour, panko, and seasonings in another bowl. Bread the shrimp: a) Coat each shrimp in flour mixture. b) Dip in egg mixture. c) Coat again in flour mixture. d) Arrange on a plate and refrigerate for 20 minutes. Fry the shrimp: a) Heat oil to 350F in a dutch oven. b) Fry shrimp for 2-3 minutes until golden. c) Drain on wire rack or paper towels. Serve: a) Coat fried shrimp with ¼ cup sauce. b) Serve with remaining sauce on the side.
https://zap.cooking/recipe/naddr1qqgxyctwvukkyctwvukhx6rjd9khqq3qrjc54ve4sahunm7r0kpchg58eut7ttwvevst7m2fl8dfd9w4y33qxpqqqp65wg3yt3t
-
 @ c755de14:cc53833a
2024-11-22 16:50:29
@ c755de14:cc53833a
2024-11-22 16:50:29 What Is Cryptocurrency?
What Is Cryptocurrency?Cryptocurrency is a form of currency that utilizes cryptography to guarantee transactions. Unlike payment systems that rely on banks for verification cryptocurrencies function independently without the involvement of financial authorities. Currently the collective market value of all cryptocurrencies stands at $3.44 trillion highlighting their increasing growth and acceptance in the market.
An Introduction to Cryptocurrencies
Cryptocurrencies like Bitcoin allow individuals to conduct peer to peer transactions without relying on banks or payment processors. These digital currencies offer direct transfers between parties eliminating the need for intermediaries. These transactions are recorded on blockchains which’re interconnected ledgers containing transaction data.
The term “cryptocurrency” stems from the encryption methods used to safeguard the network. Transactions are verified using keys, which serve as proof of ownership for cryptocurrency addresses and facilitate the transfer of assets.
Different Types of Cryptocurrencies
It is impossible to provide a list of all existing cryptocurrencies in this article due, to their number currently exceeding 10,000. However we will highlight some known and widely adopted ones.
• Bitcoin (BTC)
Among these cryptocurrencies is bitcoin, introduced in 2009 as a currency. With a market capitalization of $527.39 billion dollars bitcoin has gained recognition as one of the most prominent crypto coins worldwide. Satoshi Nakamoto is credited with developing this accepted currency.
• Ethereum (ETH)
Ethereum was introduced in 2015 as a platform that allows the development of applications using contracts. It holds the position, in terms of market capitalization after Bitcoin. Ethereum is widely. Respected as one of the cryptocurrencies.

• Cardamon (ADA)
Cardano was specifically designed to tackle scalability and accessibility issues faced by cryptocurrencies. Its main goal is to establish a blockchain platform. It currently ranks among the top ten largest cryptocurrencies based on its native ADA token.
• Dogecoin (DOGE)
Initially created as a concept, Dogecoin (DOGE) has gained popularity due to its widespread use for internet tipping and endorsement from influential figures like Elon Musk.
• Solana (SOL)
Solana is a blockchain network that prioritizes high transaction speeds and low costs. The SOL coin also holds a spot, among the ten cryptocurrencies when it comes to market capitalization.
• Polkadot (DOT)
This coin is a blockchain protocol that fosters interoperability between cryptocurrency networks.
Aside the coins mentioned above, there are thousands of other coins as mentioned earlier.
Advantages of Cryptocurrency
Both cryptocurrencies and blockchain networks comes with benefits that makes them attractive when compared to other payment systems and flat currencies.
Below are some cryptocurrencies advantages:
• Decentralization:
Cryptocurrencies operate without dependence on centralized financial authorities, which reduces the risk of systemic issues and allows for resistance against censorship. Control is distributed across participants in the blockchain.
• Enhanced Security:
Blockchain-based transactions makes digital currency transfers highly secure against fraud or tampering. This prevents issues like double spending.
• Accessibility:
You simply need an internet connection to send or receive cryptocurrency. This enables broader financial inclusion worldwide, especially in developing countries.
Anonymity:
Unless you personally attached your identity to a transaction, cryptocurrency transactions are largely anonymous and your identity will not be known.. Users interact through blockchain addresses rather than names.
Fast Transactions:
Cryptocurrency payments are quickly settled and confirmed, sometimes in seconds or few minutes.
Low Fees:
Most cryptocurrency transactions incur minor network fees, far lower than credit card fees or wire transfer charges, making micro-transactions more feasible and cheap.
Control:
You have complete control over your personal funds. Without the need for financial institutions like banks, you have gain financial independence and self-sovereignty.
Are Cryptocurrencies Safe?
While cryptocurrencies provide many benefits, they also come with few risks that investors should carefully consider. Let's take a look at some of those risks.
Downsides Using Cryptocurrencies
Here are some of the risks that comes with Cryptocurrencies:
• Volatility: Cryptocurrency valuations can sometimes have wild swings or crashes. Prices can fluctuate severely even within a single day. Having stable coins like USDT can help in this case.
• Hacks: Crypto exchanges, wallets, protocols, and smart contracts are vulnerable to security breaches if not properly coded. Billions of dollars have been lost in cyber attacks. Proper security measures are critical. Avoid sharing your contract address to non trusted sites.
• Limited Oversight: Government regulations around cryptocurrencies are still developing. Unlike banks, there is less recourse for fraud or theft due to limited consumer protections.
• Technicality Barriers: Safely purchasing, storing, and using cryptocurrencies requires advanced technical knowledge that is difficult for mainstream users. Cryptocurrency is easy to lose through user error.
Scams: The cryptocurrency industry suffers from rampant scam projects, deceptive advertising, and Ponzi schemes promising unrealistic returns. Avoiding frauds requires thorough due diligence.
Cryptocurrency Usage in Africa
Across Africa, cryptocurrencies are addressing critical needs related to financial inclusion and stable savings. According to a Chainalysis report, Sub-Saharan Africa saw modest growth, receiving an estimated $125 billion in on-chain value between July 2023 and June 2024. This represents a $7.5 billion increase compared to last year.
Here are some of the drivers behind crypto adoption in Africa:
• Serving the Unbanked:
About 66% of Sub-Saharan Africans lack access to traditional banking. Cryptocurrencies enable participation in financial services using just your mobile phones without paperwork.
• Cross-Border Payments: For workers outside their country, cryptocurrencies allow fast and low-cost transfers that avoid steep remittance fees charged by money transfer operators.
• Stability: Cryptocurrencies offer Africans a store of value and help protect from high inflation rates plaguing many national African currencies like Nigerian Naira.
• Tech-Driven Youth: Young, tech-savvy populations across Africa are leading the shift to cryptocurrency to gain financial independence apart from state-run financial systems.
Final Thoughts
For the first time, digital money can be transferred globally without relying on government-issued currencies, banks, payment processors, or other intermediaries all thanks to Cryptocurrencies. @Yakihonne

-
 @ 6f14a106:75915122
2024-11-22 20:25:57
@ 6f14a106:75915122
2024-11-22 20:25:57Every now and then, a piece of tech comes along that makes you rethink what’s possible. Enter the Mac Mini M4 Pro. Apple’s smallest desktop has always been the quiet underdog of the lineup — humble, reliable, nothing to write home about. But this time? This time, Apple didn’t just update the Mac Mini; they supercharged it. And, spoiler alert, this little guy is kind of amazing.
Here’s why the Mac Mini M4 Pro is the most mind-blowing tech I’ve reviewed in ages.
Design: A Mini That’s Actually Tiny
First, let’s talk about size. The Mac Mini M4 Pro measures in at 12.7 cm x 12.7 cm with a height of 5 cm. That’s 20% smaller than its predecessor. It’s the kind of compact that makes you double-check your measurements, wondering how Apple managed to pack so much into such a tiny frame. It’s almost laughably small — imagine something barely bigger than an Apple TV but capable of powering high-res video editing and 3D modeling.
And yes, Apple kept that minimalist, brushed-aluminum aesthetic we all love. It’s light, it’s sleek, and it’s just understated enough to blend into any setup. But let’s not skip over the quirky part: the power button is on the bottom. Why, Apple? It’s like they needed one head-scratcher per product, and here it is. Sure, you’ll remember it’s there the first few times you set up, and then it’ll fade into that “it’s quirky but fine” category.
Ports: Thoughtful but Not Perfect
One of the best surprises with the M4 Pro is the port selection. Finally, Apple gave us two USB-C Thunderbolt 5 ports and a 3.5 mm headphone jack on the front, so you can plug in drives or headphones without fumbling behind the device. The back has three more Thunderbolt 5 ports, an HDMI port, and Gigabit Ethernet.
But before you start clapping, note that there’s still no USB-A or SD card slot. If you’re a photographer or someone who still works with older peripherals, you’ll need adapters. It’s not a dealbreaker, but it’s definitely something to keep in mind.

The M4 Pro Chip: More Than Just Numbers
Now, let’s get to what really matters: performance. The M4 Pro chip is where this Mac Mini flexes hard. With a 12-core CPU and a 20-core GPU, you’re looking at serious power — enough for 8K video editing, 3D rendering, and heavy multitasking. We’re talking about a 15% boost in multi-core performance and a 20% leap in graphics compared to the M2 Pro.
Need proof? The Geekbench 6 scores are wild: 4028 single-core and 23307 multi-core. These numbers put the Mac Mini M4 Pro in the same league as some Mac Studios, making you wonder if a Mac Studio is even necessary for many workflows. From editing high-res footage to running AI-driven tasks, this thing doesn’t just keep up; it leads.
Real-World Performance: A Day in the Life
So, what does that mean for day-to-day use? If you’re like me and your workflow involves jumping between editing software, a dozen Chrome tabs (don’t judge), and video calls, the M4 Pro handles it all like it’s no big deal. No lag, no stutter — just seamless multitasking.
The cooling system has been redesigned, too. Even under a full workload, the Mac Mini stays whisper-quiet. Gone are the days of fans whirring like jet engines when you’re rendering a video or running intensive apps. This thing just is, silently powering through tasks while you forget it’s even there.

Memory and Storage: Options Galore
One thing that caught my eye is how much memory and storage you can pack into this tiny beast. The M4 Pro starts with 24 GB of unified memory and can go up to 64 GB. Memory bandwidth is 273 GB/s, which means multitasking with heavy apps feels like second nature. Whether you’re editing 4K videos, working on large Photoshop files, or running development environments, the M4 Pro won’t break a sweat.
Storage-wise, the base model comes with 512 GB SSD, but you can upgrade to 8 TB if you’re working with massive projects or just don’t trust cloud storage. And speaking of storage speeds, this SSD is fast — reading speeds over 5000 MB/s, so you’re not sitting around waiting for files to load.
Display Support: A Game Changer for Creatives
If you work with multiple monitors, you’re going to love this. The M4 Pro supports up to two 6K displays at 60Hz or a single 8K display via HDMI. For video editors and graphic designers, this means more screen real estate to spread out timelines, edit layers, or run detailed previews — all without any lag.

A Few Drawbacks You Should Know About
Okay, not everything’s perfect, and you deserve to know the quirks before dropping your cash. First off, that power button placement on the bottom? It’s a design decision that’ll make you shake your head every time you reach for it. And while the port selection is mostly great, the lack of USB-A and SD card slot might mean carrying around more adapters.
Apple’s pricing ladder is another thing to keep an eye on. The base M4 Mac Mini at $599 is a steal, but once you start upgrading RAM and storage on the M4 Pro, you’re suddenly flirting with Mac Studio prices. It’s something to think about if you’re budget-conscious.
Who Is the Mac Mini M4 Pro For?
This is the question, right? If you’re a video editor, developer, or content creator who needs serious power without the bulk of a Mac Studio or the price tag of a Mac Pro, the M4 Pro is your sweet spot. It’s portable, powerful, and packs enough punch to handle demanding tasks without compromise.
If you’re more of a casual user — streaming, web browsing, and light productivity — the base M4 model will more than cover your needs and won’t make your wallet cry. But if you’re even considering heavy multitasking or creative work, the M4 Pro at $1,399 is worth the investment.
Why the Mac Mini M4 Pro Deserves Your Attention
The Mac Mini M4 Pro isn’t just another update — it’s a statement. Apple took what was already a beloved, compact powerhouse and turned it into something that feels almost futuristic. It’s small enough to forget about, powerful enough to replace much bigger machines, and versatile enough to fit into any setup, from home offices to professional studios.
Yes, it has its quirks (hello, power button), but they’re minor in the grand scheme of things. If you’re on the fence, let this be the push you need. The Mac Mini M4 Pro isn’t just one of the best products in Apple’s current lineup — it’s a reminder that sometimes, big things do come in small packages.
-
 @ 19f9afb8:ce50e4d3
2024-11-15 22:05:01
@ 19f9afb8:ce50e4d3
2024-11-15 22:05:01Chef's notes
Make sure you watch your roux closely. It can go from perfect to burnt in a moment. Top with green onion tops. Sprinkle a very small amount of file over top. Andouille sausage is traditional but kielbasa is also a good substitute.
Details
- ⏲️ Prep time: 30 minutes for vegetable prep + ~1 hour for boiling chicken
- 🍳 Cook time: ~2 hours
- 🍽️ Servings: 8-10
Ingredients
- 1 large onion
- 1 large bell pepper
- 2 medium stalks celery
- 6-8 cloves garlic
- ~3 lbs. bone-in, skin-on chicken; remove skin and set aside to render
- ~1.5 lbs andouille sausage, browned
- ~1/2 lb. tasso, optional
- 2 green onions, chopped and separated
- 2 cups okra, cut (frozen or fresh, not canned)
- ~1 cup oil (rendered from chicken skins & sausage)
- ~1 cup flour
- 1-2 bay leaves
Directions
- Chop all vegetables and set aside. Render the fats from your chicken skins and sausages.
- Combine your flour and rendered fats in a cast iron skillet and stir continually over medium –low heat until your roux is chocolate brown. Stir in about 1/4 tsp of flour at this stage and cook until it stops “fizzing”. (This is simply to add to the thickening power of the roux.)
- While you are cooking your roux, boil your chicken until cooked through, remove from heat and broth, and set aside to cool for deboning .
- Add your vegetables, roux, deboned chicken, sausage, hot sauce, Worcestershire, and spices/seasonings to your broth. Optional: sauté your vegetables, except okra, before adding to broth. (Only add the bottom portions of the green onion here, reserve the green tops for garnish.)
- Cook until the okra is soft and no longer slimy, about 2 hours, at a low boil. (med-high heat)
- Optional: reduce to a simmer about 10 minutes before finished and drop a few eggs to poach in the stew before serving. Do not stir.
- Serve over rice.
-
 @ 319ad3e7:cc01d50a
2024-11-22 20:05:24
@ 319ad3e7:cc01d50a
2024-11-22 20:05:24NOSTR HOLIDAY GIFT IDEAS (please share or add someone you know)
V4V #circulareconomy
Agi Choote | Some hand drawings on paper or canvas are available in sizes up to 30x30 also you can get digital drawings to print out and frame on your own in your preferred technique. Please contact Agi directly.
Amber Sweeney @Amber Sweeney Custom Songs for Any Occasion (Tell Your Partner You Love Them This Holiday with A Song. One from Amber will surely be heavenly. OR sing about breakfast in bed. - SarahSoupBox winkyface)
Ant Richard @Ant Richards Limited Custom Handcrafted Knife Gift Certificates (12-month waitlist for all custom handmade orders)
Apotheca Viva @apothecavivahttps://apothecaviva.love/
Aupa Bars @AUPAhttps://eataupa.com/
Barnminer’s Barn Jerky @Barnmynah
Billay Coffee @Fulacoinhttps://billaycoffee.com/
BitBees @BitBees Honey & Honey Products https://www.kittrellsdaydream.com/
Bitpopart @Bitpoparthttps://bitpopart.com/
BtcPins @BtcPins
BTC Pins | Bitcoin Pins, Stickers & Apparel - Only Bitcoin Accepted
ONLY BITCOIN PAYMENTS ACCEPTED Pins Stickers Magnets | BTC Pins
Cannabis Records @The ₿udtender [CannabisRecords] https://cannabisrecords.store/
CryptoCloaks @CryptoCloaks™https://www.cryptocloaks.com/shop/
Delgado’s Fuego @Delgado's Fuego LLChttps://delgadosfuego.com/
Finca Yabisi @Finca Yabisihttps://yabisi.farm/
Foxfire Mushrooms @Foxfire Mushroomshttps://foxfiremushrooms.com/
Golden Tallow @Golden Tallowhttps://goldentallow.com/
GoodBeans 🇸🇻 Coffee @the guy running GoodBeans 🇸🇻 https://thegoodbeans.com/
Isolabell.art @isolabellart 🎨https://isolabell.art/
Jake Wolki @Jake Wolkihttps://wolkifarm.com.au/
Keto Beejay @beejay Low Sugar Jerky
 ## beejay
## beejayNotes & recipes on keto & carnivore goodies - by beejay
Full recipes site: https://ketolish.us/
Buy homemade small batch low sugar jerky on Shopstr with Bitcoin sats: https://url.tanelt.com/xcmjQp
Kanuto Takumi San @Kanuto
Laser Eye Cards https://lasereyes.cards/buy-nowBuy Laser Eyes Bolt Cards Now » Laser Eyes Cards
LeatherMint @LeatherMinthttps://theleathermint.com/
Lightning Store @ltngstorehttps://lightning.store/
LightningSpore @LightningSpore Full Service Mushroom Cultivation Company https://www.lightningspore.com/
Lost Sheep Ranch @Lost Sheep Ranchhttps://www.lost-sheep-ranch.com/
Lucho Poletti @Lucho Poletti Art Prints and Merchandise https://luchopoletti.com/
Madex @M A D E X Art & Apparel https://madex.art/collections/in-stock
MapleTrade @Mapletrade
Next Block Coffee @Next Block Coffeehttps://nextblockcoffee.com/
NoGood @Jake Wolkihttps://wolkifarm.com.au/
PatsPropolisHoney @PatsPropolisHoney
Peony Lane Wine (Ben Justman) @Ben Justman🍷https://www.peonylanewine.com/
PlebianMarket @Plebeian Market
PictureRoom @❐ PictureRoom Assorted Dessert Treats
Regenerative Farmed Meats & Knives @AgrarianContrarian
RustyPuppy | Art and Stories https://heidi2524.com/
Salt of the Earth @Salt of the Earth Premium Electrolyte Mix https://drinksote.com/
Satoshi Coffee Company @Satoshi Coffee Co.
 ## Welcome to Satoshi Coffee Co. - Our Roast is the Proof of Work
## Welcome to Satoshi Coffee Co. - Our Roast is the Proof of WorkYou CAN buy coffee with bitcoin now at Satoshi Coffee Co! Use Lightning (or on-chain) to purchase our delicious freshly-roasted coffee.
Scott & Son's Art & Apparel | Hand drawn pet portraits and limited design tshirts
https://xavierscraftworkanddesign.com/Xavier's Craftwork & Design
SofterSkin Tallow Skincare @Softer Skin | Tallow Based Skincarehttps://softerskin.co/
Shopstr @Shopstrhttps://shopstr.store/
Soap Miner @Soap Miner Tallow Body Soap Bars https://shopstr.store/npub1zzmxvr9sw49lhzfx236aweurt8h5tmzjw7x3gfsazlgd8j64ql0sexw5wy
SweetSats @SweetSats Honey
SweetSats – Buy pure, raw honey with Bitcoin
Yojimbo @Yojimble Jam & Marmalade https://jimblesjumble.odoo.com/
-
 @ ec951079:533d29e7
2024-11-22 16:46:34
@ ec951079:533d29e7
2024-11-22 16:46:34The Life of a Student👩🎓: Balancing Academics, Personal Growth, and Everything in Between.**
Introduction
Being a student is a unique and transformative experience that shapes individuals in countless ways. From the early morning alarm clocks to the late-night study sessions, students navigate a complex web of academics, personal growth, and social relationships. In this article, we will delve into the life of a student, exploring the challenges, opportunities, and lessons that come with this journey.
The Daily Grind
A typical day in the life of a student begins early, with the sound of an alarm clock piercing through the silence. After a quick breakfast, students rush to their morning classes, often with a mix of excitement and dread. The academic day is filled with lectures, discussions, and assignments, each designed to challenge and engage young minds.
Between classes, students often grab a snack or lunch with friends, sharing stories and laughter to break the monotony of the day. Afternoon classes may be followed by club meetings, sports practices, or part-time jobs, as students strive to balance academics with extracurricular activities.
The Struggle is Real
Despite the many rewards of student life, challenges abound. Students often struggle with:
- Time management: Balancing academics, social life, and personal responsibilities can be overwhelming.
- Financial stress: Tuition fees, living expenses, and textbooks can put a significant strain on students' finances.
- Academic pressure: Meeting expectations from parents, teachers, and oneself can lead to anxiety and stress.
- Self-doubt: Students may question their abilities, choices, and future prospects.
The Silver Lining
Amidst the challenges, student life offers countless opportunities for growth, exploration, and connection. Students can:
- Discover new passions: Through electives, clubs, and internships, students can uncover hidden talents and interests.
- Develop valuable skills: Time management, teamwork, and problem-solving are just a few of the essential skills students can hone.
- Build lifelong relationships: Friendships forged in the classroom, dorm, or club can last a lifetime.
- Explore identity and purpose: Student life provides a unique chance for self-reflection, exploration, and discovery.
Lessons Learned
As students navigate the ups and downs of academic life, they accumulate valuable lessons that extend far beyond the classroom:
- Resilience: Students learn to adapt, persevere, and bounce back from setbacks.
- Self-awareness: Through trial and error, students develop a deeper understanding of their strengths, weaknesses, and motivations.
- Independence: As students take ownership of their decisions and actions, they cultivate independence and self-reliance.
- Empathy and compassion: By interacting with diverse peers and facing shared challenges, students develop essential social skills.
Conclusion
The life of a student is a dynamic, transformative journey marked by growth, exploration, and self-discovery. While challenges abound, the opportunities for learning, connection, and personal development are unparalleled. As students navigate the complexities of academic life, they accumulate valuable lessons, skills, and relationships that will serve them well beyond their time in school.
-
 @ be41636e:e55c4909
2024-11-22 19:55:44
@ be41636e:e55c4909
2024-11-22 19:55:44If you are a content manager or regularly browse social media, you might have seen comments resembling this format:
"Thanks for sharing such valuable information! A bit off-topic, but I wanted to ask: My OKX wallet holds some USDT, and I have the seed phrase ([seed phrase here]). What's the best way to send them to Binance?"
This type of message is not a cry for help—it’s a carefully crafted trap. To avoid becoming a victim, always remember the golden rule: there is no free lunch.
How Does the Scam Work? At first glance, it seems puzzling—why would someone willingly post their wallet’s seed phrase, a crucial key to their funds? Isn’t sharing it the ultimate taboo in cryptocurrency security? The truth is that these scammers are banking on your greed and lack of caution. Here’s how the scam unfolds:
The Setup: The comment implies that there is free money (e.g., 500 USDT) sitting in the scammer's wallet, which they are too inexperienced or unable to transfer themselves. The seed phrase gives you access to this wallet, tempting you to retrieve the funds.
The Gas Fee Trap: Transferring tokens, such as USDT, from one wallet to another requires gas fees, which must be paid in the cryptocurrency native to the token's network. For example: • Ethereum network: Gas fees are paid in ETH. • Tron network: Gas fees are paid in TRX. • Solana network: Gas fees are paid in SOL. The scammer’s wallet conveniently lacks the required cryptocurrency to pay these gas fees. They rely on you to fund the wallet with the necessary tokens to complete the transfer.
The Sting: Thinking you’re about to "unlock" the 500 USDT in their wallet, you transfer a small amount of cryptocurrency (e.g., $10 worth of TRX) to cover the gas fees. However, the wallet is controlled by an automated bot (though it doesn’t have to be). As soon as your transaction is received, the bot instantly sweeps the funds to another wallet—one that you have no access to.
The Loss: You lose the cryptocurrency you transferred for the gas fee. While the individual amount might seem small, if enough people fall for the scam, the fraudsters rake in significant profits.
Why This Works This scam exploits basic human psychology: • Greed: The promise of free money clouds judgment. • Urgency: The fear that someone else will claim the "free funds" first pressures victims to act quickly. • Lack of knowledge: Not everyone understands gas fees or how wallets and seed phrases work.
Red Flags to Watch Out For • Public Seed Phrases: Legitimate users never share their seed phrases publicly. Anyone who does is either lying or completely reckless (and likely a scammer). • “Too Good to Be True” Offers: Free money claims are almost always scams, especially in the cryptocurrency world. • Urgency and Scarcity Tactics: Messages designed to make you act without thinking are a classic scam strategy.
What You Should Do • Ignore and Delete: If such a comment appears under your YouTube video or social media post, don’t engage. Delete the comment immediately to protect others. • Educate Your Audience: Warn your followers about this type of scam so they can recognize it and stay safe. • Stay Skeptical: Never rush into any deal involving cryptocurrency, especially one promising free money.
The Takeaway Cryptocurrency scams like this rely on greed, ignorance, and urgency. By understanding how they operate, you can protect yourself and others. Always remember: if it seems too good to be true, it probably is.
-
 @ fff19d35:43344a0b
2024-11-22 16:44:58
@ fff19d35:43344a0b
2024-11-22 16:44:58The Rise of Cryptocurrency: Bitcoin, YakiHonne, and Beyond*
The world of cryptocurrency has experienced tremendous growth and development in recent years. From its humble beginnings to the current market boom, cryptocurrency has become a major player in the global financial landscape. In this article, I will explore the development and growth of cryptocurrency, with a focus on Bitcoin and YakiHonne.
The Early Days of Cryptocurrency
The concept of cryptocurrency dates back to the 1980s, but it wasn't until the launch of Bitcoin in 2009 that the industry began to gain traction. Created by an individual or group of individuals using the pseudonym Satoshi Nakamoto, Bitcoin was designed to be a decentralized, peer-to-peer digital currency.
The Rise of Bitcoin
Bitcoin's early success was met with skepticism and regulatory challenges. However, as the currency gained popularity and its value increased, it became clear that Bitcoin was here to stay. Today, Bitcoin is the largest and most well-known cryptocurrency, with a market capitalization of over $1 trillion.
The Emergence of YakiHonne
While Bitcoin may be the most well-known cryptocurrency, other players are emerging to challenge its dominance. One such player is YakiHonne, a relatively new cryptocurrency that has gained significant attention in recent months. YakiHonne's unique features, such as its fast transaction times and low fees, have made it an attractive option for investors and users.
The Future of Cryptocurrency
As the cryptocurrency market continues to grow and mature, we can expect to see new players emerge and existing ones continue to innovate. The development of decentralized finance (DeFi) platforms, non-fungible tokens (NFTs), and other cryptocurrency-related technologies will likely play a major role in shaping the future of the industry.
Conclusion
The development and growth of cryptocurrency, Bitcoin, and YakiHonne are testaments to the power of innovation and the demand for alternative financial systems. As the industry continues to evolve, it will be exciting to see how these players and others adapt and thrive in the ever-changing landscape of cryptocurrency.
-
 @ 44dc1c2d:31c74f0b
2024-11-15 21:31:32
@ 44dc1c2d:31c74f0b
2024-11-15 21:31:32Chef's notes
So if you want a more sweet stew, add some dried apricots.
Details
- ⏲️ Prep time: 15 ish min
- 🍳 Cook time: 1 Hour ish
- 🍽️ Servings: 4 to 6
Ingredients
- 1/4 cup olive oil
- 1 large onion, grated
- 2 tablespoons finely minced garlic
- 1 teaspoon chili powder
- 1 teaspoon ground cumin
- 1 cinnamon stick or 1/2 teaspoon ground cinnamon
- Salt and pepper, to taste
- 3 pounds boneless lamb shoulder, cut into 1 1/2-inch pieces
- 2 1/2 cups defatted chicken broth
- 1 dried ancho chili, stem and seeds removed
- 4 carrots, peeled, halved lengthwise and cut into 1-inch pieces
- Zest of 1 orange, in wide strips
- 2 cups cubed (1 inch) butternut squash
- 2 roasted red bell peppers , cut into 1-inch pieces
- 2 tablespoons chopped fresh cilantro leaves for garnish
Directions
- Combine the oil, onion, garlic, chili powder, cumin, cinnamon, salt, and pepper in a large, heavy pot. Stir well, then add the meat. Toss the meat with the spice mixture to coat it well.
- Add the broth, ancho chili, carrots, orange zest, and butternut squash. Bring to a boil over high heat. Then reduce the heat and simmer gently, partially covered, over medium heat for 30 minutes. Add the roasted peppers; cook, partially covered, until the lamb and vegetables are tender, about 30 minutes more. Remove and discard the chili and orange zest. Sprinkle with cilantro and serve immediately.
-
 @ ab54780c:0884884e
2024-11-15 04:30:05
@ ab54780c:0884884e
2024-11-15 04:30:05Chef's notes
Makes approximately 1 US quart (~1L). Double the recipe to fill a 2-quart pitcher and to avoid using only half an onion and half of a lemon. Keeps well when sealed and refrigerated for up to a week. And yes: fresh ground spices makes a difference.
Details
- ⏲️ Prep time: ~25 min
- 🍽️ Servings: 6-10
Ingredients
- 2 Jalapeño peppers
- 1/2 Lemon, juice of
- 2 cans (10 oz.) Ro-Tel Original Diced Tomatoes & Green Chiles (Mild)
- 2 cans (14.5 oz.) Whole Peeled Tomatoes
- 1 bunch fresh Cilantro
- 1/2 Red Onion
- 2 Fresh Tomatoes
- 1/2 tablespoon Black Peppercorns
- 1/2 tablespoon Salt
- 1 teaspoon Garlic Salt
Directions
- Gather required tools: Spice grinder or mortar & pestle, Knife, Cutting board, Food Processor (2+ quart size), Citrus reamer (optional)
- Open canned ingredients and strain off excess water
- Grind cumin seeds to a powder and black peppercorns to medium to fine coarseness (as desired) in spice grinder or mortar & pestle
- Rinse with fresh water and prepare all fresh ingredients, cutting them into halves or quarters as necessary to size them for comfortable loading into your food processor. It’s handy to pre-squeeze the lemon into a small glass where it is easier and safer to remove ejected seeds rather than digging them out of a loaded food processor with your finger (cook safe!). Remove jalapeño stems, but leave seeds in for the right heat level.
- In the food processor blend all ingredients except the fresh tomatoes
- Once a well-blended consistency is achieved, add fresh tomatoes and pulse/chop several times to desired level of chunkiness.
-
 @ 917be69d:bfe8083e
2024-11-22 16:42:23
@ 917be69d:bfe8083e
2024-11-22 16:42:23Bitcoin is a decentralized digital currency that allows for peer-to-peer transactions without the need for intermediaries like banks. It was created in 2009 by an anonymous individual or group using the pseudonym Satoshi Nakamoto.
How Does it Work?
Bitcoin uses blockchain technology, a public ledger that records all transactions made with the currency. Transactions are verified by a network of computers around the world, called nodes, through a process called mining.
Key Characteristics:
- Decentralized: Bitcoin operates independently of central banks and governments.
- Limited supply: There will only ever be 21 million Bitcoins in existence.
- Fast and global: Transactions are processed quickly, regardless of the sender's and recipient's locations.
- Secure: Transactions are encrypted and verified through the blockchain.
Uses and Benefits:
- Investment: Bitcoin's value can fluctuate, making it a popular investment option.
- Payments: Bitcoin can be used to make purchases online and in-person.
- Remittances: Bitcoin's fast and global nature makes it an attractive option for sending money across borders.
Challenges and Risks:
- Volatility: Bitcoin's value can fluctuate rapidly.
- Regulatory uncertainty: Bitcoin's legal status varies by country.
- Security risks: Bitcoin exchanges, wallets, and transactions can be vulnerable to hacking.
Overall, Bitcoin is a complex and multifaceted digital currency that offers a range of benefits and challenges.
-
 @ 705605d9:b4324038
2024-11-22 19:55:19
@ 705605d9:b4324038
2024-11-22 19:55:19В 2040 году Горноправдинск, малый город в Сибири, стал центром мирового молочного производства, после открытия крупнейшего в мире молочного комбината. Этот промышленный гигант, с мощностью переработки в десятки миллионов тонн молока в год, обещает не только революцию в отечественном производстве, но и серьезно повлиять на глобальные рынки сельскохозяйственной продукции, в том числе на рынок сливочного масла. Ожидается, что новый комбинат окажет значительное влияние на внешнюю торговлю и положение России на мировом рынке продовольствия.
Экономический контекст
Сливочное масло – один из важнейших продуктов молочной промышленности, который активно экспортируется в страны Азии, Европы и Северной Америки. Российские производители в последние десятилетия стремительно наращивали свои мощности, и открытие такого крупного объекта, как молочный комбинат в Горноправдинске, может стать катализатором для страны, чтобы стать ведущим игроком на этом рынке. Россия, в свою очередь, может занять более прочные позиции в торговле сливочным маслом за рубежом, конкурируя с такими крупнейшими экспортерами, как Новая Зеландия, Германия и Польша.

Молочный комбинат в Горноправдинске: изменения в структуре производства
Ожидаемое увеличение объемов производства сливочного масла с запуском нового молочного комбината в Горноправдинске связано с несколькими ключевыми факторами, которые делают данный проект особенно перспективным:
-
Современные технологии. Комбинат будет оснащен высокотехнологичным оборудованием для переработки молока, что повысит эффективность и качество продукции. Это дает России значительное преимущество на международных рынках, где высокие стандарты качества становятся важнейшим фактором для потребителей.
-
Просторные мощности. Новый комбинат, способный перерабатывать десятки миллионов тонн молока ежегодно, обеспечит не только внутреннее потребление, но и масштабные экспортные поставки. Это откроет новые рынки для российского сливочного масла, особенно в странах с растущим потреблением молочных продуктов, таких как Китай, Индия и страны Юго-Восточной Азии.
-
Экономия на масштабе. Масштабность производства позволяет снизить себестоимость продукции, что дает конкурентные преимущества на мировом рынке. Снижение цен на сливочное масло, особенно в условиях высокой конкуренции, станет важным фактором при выходе на зарубежные рынки.
Влияние на внешнюю торговлю и конкуренцию
Российский рынок сливочного масла исторически был ориентирован на внутреннее потребление, однако с развитием новых мощностей в Горноправдинске, страна может значительно увеличить объемы экспорта. Ведущими потребителями молочной продукции традиционно являются такие страны, как Германия, Великобритания, США, а также активно развивающиеся рынки Китая и Индии.

-
Китай – крупнейший рынок для молочных продуктов, включая сливочное масло. Рост доходов китайских потребителей и увеличение спроса на качественные молочные продукты открывают огромные возможности для российских производителей. С учетом высокого уровня конкуренции со стороны новозеландских и австралийских производителей, российские компании могут выделиться за счет ценовой доступности и качества продукции.
-
Европейский Союз – несмотря на высокие стандарты качества, рынок Европы остается важным для торговли сливочным маслом. Ожидается, что российские компании смогут расширить свою долю в Европе, конкурируя с польскими и немецкими производителями, предлагая более выгодные цены при неизменно высоком качестве продукции.
-
Северная Америка – рынки США и Канады всегда были важными для молочной продукции, однако они также обладают сложной системой тарифов и квот. Россия, обладая крупными мощностями, может предложить экспорт сливочного масла с конкурентоспособными условиями, если смогут преодолеть бюрократические препятствия. Проблемы и вызовы
Несмотря на перспективы, российский экспорт сливочного масла столкнется с рядом вызовов. Одним из них является необходимость соответствия международным стандартам безопасности и качества, что потребует дополнительных инвестиций и контроля на всех этапах производства. Также стоит учитывать влияние мировых экономических факторов, таких как колебания валютных курсов, изменения в торговых отношениях и возможные торговые барьеры.
Кроме того, конкуренция со стороны традиционных поставщиков – таких стран, как Новая Зеландия и Австралия, будет оставаться высокоактуальной. Для того чтобы закрепиться на этих рынках, российским производителям предстоит работать над созданием имиджа качественного, но доступного продукта.
Заключение
Открытие крупнейшего молочного комбината в Горноправдинске – это не просто важный шаг для отечественной молочной промышленности, но и стратегический момент для глобальной торговли сливочным маслом. Россия получает уникальную возможность занять сильные позиции на международных рынках, предоставляя потребителям качественное и доступное сливочное масло. Однако для достижения долгосрочного успеха необходимы устойчивые усилия по улучшению качества продукции, соблюдению международных стандартов и борьбе с внешними экономическими вызовами.
-
-
 @ 89c1d3b9:6fa133db
2024-11-22 16:41:41
@ 89c1d3b9:6fa133db
2024-11-22 16:41:41****The Decentralization of Bitcoin: A Key to its Success_
Bitcoin's decentralized nature is a fundamental aspect of its design. Unlike traditional currencies, Bitcoin operates without a central authority or government control.
Key Benefits of Decentralization:
- Security: No single point of failure.
- Freedom: Transactions occur peer-to-peer.
- Transparency: All transactions are recorded publicly.
Conclusion:
Bitcoin's decentralization ensures a secure, free, and transparent financial system. This core principle has contributed to Bitcoin's success and popularity.`
-
 @ ac8bb9b0:70278acc
2024-11-12 19:55:33
@ ac8bb9b0:70278acc
2024-11-12 19:55:33Details
- ⏲️ Prep time: 10
- 🍳 Cook time: 45
- 🍽️ Servings: 16
Ingredients
- 1/4 cup light brown sugar
- 1/4 cup granulated sugar
- 1 tablespoon ground cinnamon
- 1 teaspoon salt
- 1 pound unsalted pecans halves
- 1 egg white
- 1/2 teaspoon vanilla extract
- 1 teaspoon water
Directions
- Preheat oven to 300 degrees F. Line a large baking sheet with parchment paper and set aside.
- In a bowl, add sugars, cinnamon, and salt. Whisk until combined. Set aside.
- In a large bowl, whisk the egg white, vanilla, and water together until frothy. Add the pecans and gently toss until the pecans are well coated. Add the sugar and cinnamon mixture and toss until pecans are covered.
- Spread the pecans out in a single layer on prepared baking sheet. Bake for about 30-45 minutes, stirring every 15 minutes.
- Remove from the oven and let the pecans cool on the baking sheet. When completely cool, store in an airtight container for up to 1 month.
-
 @ 31312140:2471509b
2024-11-22 19:08:04
@ 31312140:2471509b
2024-11-22 19:08:04What is Virology? \ \ Virology is the branch of science that deals with the study of viruses. Officially, it focuses on understanding how viruses operate, how they spread diseases, and how we can combat them. 🌐🔬 \ \ The Historical Context
Historically, the concept of viruses emerged as an explanation for diseases that couldn't be linked to bacteria. The early 20th century brought about major developments in this field, leading us to where we are today with an industry worth billions.
But here’s the kicker: many fundamental assumptions in virology remain unproven or underexplored. \ \ The Unproven Hypothesis \ \ Isolation Methods: In virology, "virus isolation" doesn’t mean what you think it means. Virus isolation often involves mixing samples with toxic chemicals and other cells, then observing the effects. The presence of a virus is inferred, not directly observed. 🚫🔍
Control Experiments: Proper scientific controls, where samples without believed viruses are treated the same way, often aren’t conducted or published in ways making them verifiable. 🧪❓
Electron Microscopy: While electron microscopes can visualize particles, interpretations are problematic. Similar structures (exosomes) naturally exist in the body and can be mistaken for viruses. 🕵️🔬 \ \ The Controversial Points \ \ PCR Testing: Polymerase Chain Reaction (PCR) tests, widely used to detect viruses, can’t distinguish between live viruses and non-infectious viral fragments. It's an amplification technique, not a diagnostic tool. Famed inventor Kary Mullis himself cautioned against its misuse. ⚠️🔍
Genetic Sequencing: Viral genomes are often generated from computer models using fragmented genetic material from patient samples. This model can lead to inaccuracies and assumptions about the virus that aren’t directly observed. 🧬💻
Pathogenicity Proofs: No study unequivocally proves viruses alone cause diseases. Historical attempts, like those from the Spanish Flu era, failed to infect healthy individuals with presumed virus samples. \ \ Big Pharma Implications \ \ Big Pharma has a vested interest in propagating the viral causation theory:
Vaccines: Billions are made from vaccine sales. If virus causation is questioned, the foundation for vaccines crumbles.
Antivirals: Similarly, antiviral drugs rely on this belief. Without it, a major revenue stream is invalidated.
Pharmaceutical companies and regulatory bodies rarely challenge the status quo, leading to a cycle where treatments are promoted despite conflicting evidence. 💊💸 \ \ The Alternative Hypothesis \ \ Exosomes vs. Viruses: Exosomes, extracellular vesicles within our bodies, serve as cellular communication tools. They’re released under stress, similar to what we call “viruses.” Are our bodies creating what we interpret as “viruses” to heal or signal distress? 🧩🔍
Terrain Theory: This theory suggests that the body's internal environment, not an external pathogen, determines health. A healthy body repels illness, while a toxic internal environment invites disease. Terrain theorists argue we should focus on optimizing internal health rather than targeting external “invaders.” 🌱💚 \ \ Question Everything \ \ This exploration isn’t to say viruses categorically don’t exist but to highlight the holes and biases in mainstream virology. It’s about opening the conversation and asking critical, often uncomfortable questions.
If we reconsider virology’s foundational assumptions, what implications could this have for global health policies, pharmaceutical practices, and our understanding of diseases? The answers could reshape how we approach wellness and medical science entirely.
Remember, folks, the truth often lies beneath layers of accepted truths. Dive deeper, question more, and never settle for the surface narrative. 🚀🕵️♂️ \ \
lookintoit #virology #health #scam #covid19 #philosophy #wisdom #freedom #psychology #nature #science
-
 @ 9349d012:d3e98946
2024-11-05 00:42:37
@ 9349d012:d3e98946
2024-11-05 00:42:37Chef's notes
2 cups pureed pumpkin 2 cups white sugar 3 eggs, beaten 1/2 cup olive oil 1 tablespoon cinnamon 1 1/2 teaspoon baking powder 1 teaspoon baking soda 1/2 teaspoon salt 2 1/4 cups flour 1/4 cup chopped pecans
Preheat oven to 350 degrees Fahrenheit. Coat a bread pan with olive oil. Mix all ingredients minus nuts, leaving the flour for last, and adding it in 2 parts. Stir until combined. Pour the batter into the bread pan and sprinkle chopped nuts down the middle of the batter, lenghtwise. Bake for an hour and ten minutes or until a knife insert in the middle of the pan comes out clean. Allow bread to cool in the pan for five mintes, then use knife to loosen the edges of the loaf and pop out of the pan. Rest on a rack or plate until cool enough to slice. Spread bread slices with Plugra butter and serve.
https://cookeatloveshare.com/pumpkin-bread/
Details
- ⏲️ Prep time: 30 minutes
- 🍳 Cook time: 1 hour and ten minutes
- 🍽️ Servings: 6
Ingredients
- See Chef's Notes
Directions
- See Chef's Notes
-
 @ 5fb7f8f7:d7d76024
2024-11-22 16:41:33
@ 5fb7f8f7:d7d76024
2024-11-22 16:41:33What is play to Earn
Play-to-Earn is a model in Web3 where users can earn rewards, such as cryptocurrencies or NFTs, by playing games or engaging in other interactive experiences.
How does it work?
- Games and Experiences: Developers create games, simulations, or interactive stories that run on blockchain technology.
- Players Join In: Users participate in these experiences, often using digital wallets and cryptocurrencies.
- Rewards and Earnings: As players progress, they earn rewards in the form of cryptocurrencies, NFTs, or other digital assets.
- Ownership and Value: Players have full ownership and control over their earned assets, which can appreciate in value or be traded.
Key Benefits
- Fun and Engagement: Play-to-Earn combines entertainment and rewards, making the experience enjoyable and motivating.
- Financial Incentives: Players can earn real value, creating a new level of engagement and participation.
- Decentralized and Transparent: Blockchain technology ensures secure, tamper-proof, and transparent transactions.
- Community Building: Play-to-Earn fosters communities around shared interests and experiences.
Examples
- Axie Infinity: A popular blockchain-based game where players collect and evolve creatures, earning rewards and trading them.
- The Sandbox: A decentralized platform allowing users to create, sell, and own digital assets and experiences.
- Decentraland: A virtual reality platform where players can build, explore, and monetize their creations.
Get Ready to Play and Earn
Play-to-Earn in Web3 is revolutionizing the way we interact with digital experiences. Join the fun, earn rewards, and be part of this exciting new world.
-
 @ 18bdb66e:82eb5e5d
2024-11-04 23:38:03
@ 18bdb66e:82eb5e5d
2024-11-04 23:38:03Chef's notes
This recipe needs to sit in the refrigerator at least one hour, or overnight prior to baking. Link sausage may be used but casing must be removed prior to frying.
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 4-6
Ingredients
- 1 lb breakfast sausage
- 1 large onion, chopped
- 1 green bell pepper
- Cooking spray
- 4 cups dehydrated/dried bread cubes
- 6 large eggs
- 1 1/2 cups milk
- 1/4 tsp salt (optional)
- 1/4 tsp black pepper
- 1 cup shredded Cheddar cheese
Directions
- Spray 13x9 baking dish with cooking spray, like PAM.
- Crumble sausage into a skillet, fry breaking up pieces
- Add onion to the sausage
- Chop bell pepper, add to sausage and onion, fry until tender
- Remove from heat, drain if needed, set aside.
- Spread bread cubes on bottom of baking dish
- Spoon sausage mixture over bread
- Blend eggs, milk, salt, and pepper in a bowl or large measuring cup.
- Pour egg mixture over sausage and bread.
- Cover and place in refrigerator.
- Refrigerate at least one hour or overnight.
- Preheat oven to 375F.
- Place casserole in oven, bake 55 minutes
- Top with cheese and bake 5 minutes longer.
- Let rest 10 minutes before cutting.
-
 @ 6fff5148:a5dd5cdf
2024-11-22 16:05:00
@ 6fff5148:a5dd5cdf
2024-11-22 16:05:00 what is Bitcoin
Bitcoin is a cryptocurrency, a peer-to-peer digital currency that operates independently of a central governing authority. Bitcoin enables direct transactions between users, secured by cryptographic technology and recorded on a transparent and immutable ledger known as the blockchain.
what is Bitcoin
Bitcoin is a cryptocurrency, a peer-to-peer digital currency that operates independently of a central governing authority. Bitcoin enables direct transactions between users, secured by cryptographic technology and recorded on a transparent and immutable ledger known as the blockchain.This innovation not only ensures security and transparency but also challenges traditional financial systems by offering a global currency that is accessible to anyone with internet access.
Picture it as digital gold: whereas gold is physically mined from the earth, Bitcoin is created through the use of powerful computers solving complex problems, known as "Bitcoin mining." Unlike gold, you can't physically touch Bitcoin; it exists purely in the digital realm.
Bitcoin was first introduced in 2009 by a person (or group) named Satoshi Nakamoto. Little is known about their identity–but more on that later!
Today, Bitcoin is the most popular cryptocurrency, with a market capitalization that far surpasses any other digital currency. It has become a benchmark for the crypto market, influencing the launch of thousands of other cryptocurrencies and ushering in a new era of digital finance.
Key Bitcoin Concepts in Simple Words Cryptocurrency: A type of digital or virtual money that uses cryptography for security, making it difficult to counterfeit. Blockchain: A digital ledger that records all Bitcoin transactions, like a global spreadsheet that everyone can see but no one can tamper with. Wallet: A digital pouch that safely stores your Bitcoin, similar to a virtual bank account. Public and Private Keys: A pair of digital keys where the public key is your Bitcoin address (like an email address) and the private key is your secret password to access and send your Bitcoins. Decentralization: The principle of distributing control across the entire network rather than relying on a central authority, like having a group decision instead of one boss calling the shots. Mining: The process of using computer power to solve complex puzzles, securing the network and creating new Bitcoins as a reward. Satoshi: The smallest unit of Bitcoin, named after its mysterious creator, worth one hundred millionth of a Bitcoin. BTC: BTC is the abbreviation for Bitcoin typically used when referring to the currency unit in transactions, price listings, and financial discussions.
 Source: https://www.blockpit.io/en-us/blog/what-is-bitcoin#:~:text=Bitcoin%20is%20a%20cryptocurrency%2C%20a,ledger%20known%20as%20the%20blockchain.
Source: https://www.blockpit.io/en-us/blog/what-is-bitcoin#:~:text=Bitcoin%20is%20a%20cryptocurrency%2C%20a,ledger%20known%20as%20the%20blockchain. -
 @ ef9ee5bf:3fe39164
2024-11-22 19:01:29
@ ef9ee5bf:3fe39164
2024-11-22 19:01:29Salvation in a Digital World
The drama of redemption unfolds as a cosmic narrative that transcends traditional spiritual salvation, extending into the digital realms where humanity now finds itself entangled. In this emerging reality, salvation is not solely a matter of freeing the soul from sin but of liberating the mind and body from technological control systems that seek to restrict human potential. As society becomes increasingly digital, the boundaries between spiritual and digital salvation blur. The digital realm has become a new battleground for the soul, with tools of surveillance, artificial intelligence, and centralized digital systems acting as the forces that shape reality. This battleground is not neutral; it is a contested space where unseen powers influence human behavior and thought, subtly steering individuals toward compliance and conformity. Surveillance, in particular, looms as a formidable obstacle, exerting a subtle yet profound pressure that limits the capacity for genuine spiritual freedom. It not only monitors but manipulates, narrowing the range of choices and thereby inhibiting the exercise of free will—a crucial component for true salvation. As we venture deeper into this cyber age, the challenge becomes clear: to seek liberation not only from sin but from the digital systems that seek to define what it means to be free.
Free Will as Essential to Salvation
Free will stands at the heart of spiritual salvation. It is through the exercise of free will that individuals can seek, discern, and align themselves with divine truth. Spiritual growth depends on the ability to make genuine, uncoerced choices—decisions that reflect the soul’s personal quest for enlightenment rather than external pressures. Without free will, salvation becomes merely a theoretical possibility, void of personal transformation or meaningful alignment with higher principles. In this sense, free will is not just a means of self-expression but the very mechanism through which spiritual freedom is realized. It allows individuals to break away from sin, illusion, or ignorance and move toward truth, virtue, and divine love.
However, the omnipresence of surveillance in the digital age poses a direct threat to this spiritual dynamic. Surveillance does not merely observe—it influences. By monitoring behavior, it subtly pressures individuals to conform to societal norms, limit risks, and act in ways that are predictable and safe. The awareness of being constantly watched reshapes behavior, creating an environment where compliance is rewarded, and deviation is penalized, even if only through social ostracism or self-censorship. This dynamic distorts free will, as the range of decisions becomes heavily influenced by external expectations. Instead of making decisions rooted in personal spiritual exploration, individuals may find themselves choosing paths that align more with societal acceptance than with inner convictions.
The theological implications of this are significant. If salvation requires a truly free, uncoerced movement of the soul toward the divine, then pervasive surveillance becomes an obstacle to that process. It restricts the capacity for genuinely transformative decisions, replacing spiritual authenticity with digital conformity. Surveillance enforces a state of psychological limitation that mirrors the "singular collapsed state" seen in quantum physics—where the observation itself defines and limits potential. In this context, the battle for salvation is not only against spiritual ignorance or sin but also against the digital systems that restrict the exercise of free will, reducing the potential for spiritual growth to a controlled set of predictable behaviors.
 ### Introducing Quantum Concepts: Wave Functions and Surveillance
### Introducing Quantum Concepts: Wave Functions and SurveillanceIn quantum mechanics, the wave function is a mathematical representation of a particle’s potential states. It encompasses all the possible positions, velocities, and paths that a particle might take. However, this range of possibilities exists only until the moment of observation—once a measurement is made, the wave function "collapses," reducing the particle to a single, definite state. This phenomenon, known as the observer effect, has profound implications, not only in physics but also as a metaphor for human potential. In a state of openness, individuals—like unobserved particles—possess a wide array of possible thoughts, actions, and spiritual expressions. They can explore various paths to enlightenment, pursue unconventional ideas, and exercise creativity without the constraints of external judgment.
However, surveillance functions much like the observer in quantum mechanics. Just as the act of measurement collapses the wave function into a singular outcome, constant surveillance collapses human potential into a narrower, more controlled set of behaviors. The awareness of being observed exerts a powerful psychological influence, prompting individuals to make safer, more predictable choices. Instead of exploring diverse spiritual or personal possibilities, individuals adapt to the expectations imposed by the ever-present digital gaze. The result is a diminished range of action, where genuine self-expression gives way to compliance and predictability—what can be termed the "singular collapsed state."
This singular collapsed state represents a profound loss of spiritual potential. When human behavior is constantly shaped by surveillance, it becomes more constrained, less creative, and ultimately less free. The open potential for spiritual growth, transformation, and connection to divine truth is replaced by a narrowed reality defined by conformity and safety. Just as quantum observation restricts the wave function to a single outcome, surveillance restricts individuals to a limited set of socially acceptable behaviors, inhibiting the soul’s journey toward deeper truth and spiritual liberation. This dynamic suggests that overcoming surveillance is not merely a matter of privacy or freedom of expression—it is essential for maintaining the open potential necessary for spiritual salvation itself.
Breaking Free from Surveillance
To escape the confines of the surveillance matrix and reclaim human potential, embracing decentralized technologies is essential. Decentralized systems like Bitcoin and open-source protocols offer a tangible means of resisting centralized control and pervasive observation. Unlike centralized digital systems that collect and exploit data to manipulate behavior, decentralized technologies enable an *open potential state* where individuals can act freely, without fear of surveillance-induced consequences. They preserve privacy, protect free will, and create opportunities for genuine personal and spiritual growth. This decentralization aligns with divine principles of freedom, spontaneity, and diversity, reflecting the open and unpredictable nature of the universe itself. By choosing decentralized solutions, individuals can restore a more authentic connection to both digital and spiritual realms.
This shift is not purely technical; it’s deeply spiritual. Just as spiritual awakening requires a release from the bondage of sin and ignorance, digital liberation demands a conscious move away from surveillance-driven systems. Breaking free involves more than just switching technologies; it requires a transformation of mindset—one that recognizes surveillance as a spiritual and existential threat. It calls for the cultivation of awareness, discernment, and a willingness to embrace both technological sovereignty and spiritual autonomy. True salvation, in the context of a Cyber Gospel, is a holistic journey that requires overcoming both physical and digital chains. It is the fusion of spiritual liberation with the adoption of decentralized tools that enable true freedom in a digital world.
Ultimately, a Cyber Gospel serves as a guide for navigating this complex spiritual-digital landscape. It invites readers to explore how decentralized technologies can facilitate a digital exodus, moving humanity from a singular collapsed state to an open potential state where free will and spiritual growth can flourish. This path forward is both a call to action and a call to awakening. It urges readers to actively participate in building a future where technology serves as a bridge to liberation rather than a tool of control. As the lines between spiritual and digital realities blur, embracing this new form of salvation becomes not only possible but necessary for the soul’s journey toward wholeness and freedom.
 ### The Battle for the Soul in the Digital Age
### The Battle for the Soul in the Digital AgeThe digital age is not just a technological revolution; it is a spiritual battleground where the soul's potential is tested by the forces of surveillance and control. In this new landscape, salvation must be reimagined as both spiritual and digital—a quest that demands free will, genuine choices, and the preservation of human potential against a backdrop of pervasive observation. Throughout this discussion, we have explored the nature of digital salvation, the essential role of free will, and how surveillance acts as a force that collapses human potential into a singular, predictable state. We have drawn parallels between quantum mechanics and human behavior, illustrating how surveillance, like the observer effect, restricts possibilities and narrows the range of spiritual and existential outcomes.
Yet, there is a path forward. Decentralized technologies offer a chance to resist this collapse and restore an open potential state, allowing for personal and spiritual growth in an age where control mechanisms seek to limit both. This liberation is not just about escaping technological constraints; it is about reclaiming the divine spark of free will, which is essential for true awakening. As we move deeper into this digital era, the challenge is clear: salvation must involve breaking free from the dual chains of spiritual ignorance and digital manipulation.
A Cyber Gospel can serve as a guide for navigating this complex terrain, calling for both spiritual and digital awakening. It asks seekers to reflect deeply on the nature of their freedom and the forces that shape it. The final question remains: *Can the soul be truly free in a world of constant surveillance, or must it find a way to escape to achieve salvation?* This question is not just philosophical but practical, urging users to consider how they can actively participate in the creation of a more liberated reality—both spiritually and digitally. The battle for the soul in the digital age is not just about avoiding surveillance; it is about embracing a deeper, more transformative form of freedom that aligns with both divine principles and technological sovereignty.Salvation in a Digital World
The drama of redemption unfolds as a cosmic narrative that transcends traditional spiritual salvation, extending into the digital realms where humanity now finds itself entangled. In this emerging reality, salvation is not solely a matter of freeing the soul from sin but of liberating the mind and body from technological control systems that seek to restrict human potential. As society becomes increasingly digital, the boundaries between spiritual and digital salvation blur. The digital realm has become a new battleground for the soul, with tools of surveillance, artificial intelligence, and centralized digital systems acting as the forces that shape reality. This battleground is not neutral; it is a contested space where unseen powers influence human behavior and thought, subtly steering individuals toward compliance and conformity. Surveillance, in particular, looms as a formidable obstacle, exerting a subtle yet profound pressure that limits the capacity for genuine spiritual freedom. It not only monitors but manipulates, narrowing the range of choices and thereby inhibiting the exercise of free will—a crucial component for true salvation. As we venture deeper into this cyber age, the challenge becomes clear: to seek liberation not only from sin but from the digital systems that seek to define what it means to be free. Free Will as Essential to Salvation
Free will stands at the heart of spiritual salvation. It is through the exercise of free will that individuals can seek, discern, and align themselves with divine truth. Spiritual growth depends on the ability to make genuine, uncoerced choices—decisions that reflect the soul’s personal quest for enlightenment rather than external pressures. Without free will, salvation becomes merely a theoretical possibility, void of personal transformation or meaningful alignment with higher principles. In this sense, free will is not just a means of self-expression but the very mechanism through which spiritual freedom is realized. It allows individuals to break away from sin, illusion, or ignorance and move toward truth, virtue, and divine love.
However, the omnipresence of surveillance in the digital age poses a direct threat to this spiritual dynamic. Surveillance does not merely observe—it influences. By monitoring behavior, it subtly pressures individuals to conform to societal norms, limit risks, and act in ways that are predictable and safe. The awareness of being constantly watched reshapes behavior, creating an environment where compliance is rewarded, and deviation is penalized, even if only through social ostracism or self-censorship. This dynamic distorts free will, as the range of decisions becomes heavily influenced by external expectations. Instead of making decisions rooted in personal spiritual exploration, individuals may find themselves choosing paths that align more with societal acceptance than with inner convictions.
The theological implications of this are significant. If salvation requires a truly free, uncoerced movement of the soul toward the divine, then pervasive surveillance becomes an obstacle to that process. It restricts the capacity for genuinely transformative decisions, replacing spiritual authenticity with digital conformity. Surveillance enforces a state of psychological limitation that mirrors the "singular collapsed state" seen in quantum physics—where the observation itself defines and limits potential. In this context, the battle for salvation is not only against spiritual ignorance or sin but also against the digital systems that restrict the exercise of free will, reducing the potential for spiritual growth to a controlled set of predictable behaviors. Introducing Quantum Concepts: Wave Functions and Surveillance
In quantum mechanics, the wave function is a mathematical representation of a particle’s potential states. It encompasses all the possible positions, velocities, and paths that a particle might take. However, this range of possibilities exists only until the moment of observation—once a measurement is made, the wave function "collapses," reducing the particle to a single, definite state. This phenomenon, known as the observer effect, has profound implications, not only in physics but also as a metaphor for human potential. In a state of openness, individuals—like unobserved particles—possess a wide array of possible thoughts, actions, and spiritual expressions. They can explore various paths to enlightenment, pursue unconventional ideas, and exercise creativity without the constraints of external judgment.
However, surveillance functions much like the observer in quantum mechanics. Just as the act of measurement collapses the wave function into a singular outcome, constant surveillance collapses human potential into a narrower, more controlled set of behaviors. The awareness of being observed exerts a powerful psychological influence, prompting individuals to make safer, more predictable choices. Instead of exploring diverse spiritual or personal possibilities, individuals adapt to the expectations imposed by the ever-present digital gaze. The result is a diminished range of action, where genuine self-expression gives way to compliance and predictability—what can be termed the "singular collapsed state."
This singular collapsed state represents a profound loss of spiritual potential. When human behavior is constantly shaped by surveillance, it becomes more constrained, less creative, and ultimately less free. The open potential for spiritual growth, transformation, and connection to divine truth is replaced by a narrowed reality defined by conformity and safety. Just as quantum observation restricts the wave function to a single outcome, surveillance restricts individuals to a limited set of socially acceptable behaviors, inhibiting the soul’s journey toward deeper truth and spiritual liberation. This dynamic suggests that overcoming surveillance is not merely a matter of privacy or freedom of expression—it is essential for maintaining the open potential necessary for spiritual salvation itself. Breaking Free from Surveillance
To escape the confines of the surveillance matrix and reclaim human potential, embracing decentralized technologies is essential. Decentralized systems like Bitcoin and open-source protocols offer a tangible means of resisting centralized control and pervasive observation. Unlike centralized digital systems that collect and exploit data to manipulate behavior, decentralized technologies enable an open potential state where individuals can act freely, without fear of surveillance-induced consequences. They preserve privacy, protect free will, and create opportunities for genuine personal and spiritual growth. This decentralization aligns with divine principles of freedom, spontaneity, and diversity, reflecting the open and unpredictable nature of the universe itself. By choosing decentralized solutions, individuals can restore a more authentic connection to both digital and spiritual realms.
This shift is not purely technical; it’s deeply spiritual. Just as spiritual awakening requires a release from the bondage of sin and ignorance, digital liberation demands a conscious move away from surveillance-driven systems. Breaking free involves more than just switching technologies; it requires a transformation of mindset—one that recognizes surveillance as a spiritual and existential threat. It calls for the cultivation of awareness, discernment, and a willingness to embrace both technological sovereignty and spiritual autonomy. True salvation, in the context of a Cyber Gospel, is a holistic journey that requires overcoming both physical and digital chains. It is the fusion of spiritual liberation with the adoption of decentralized tools that enable true freedom in a digital world.
Ultimately, a Cyber Gospel serves as a guide for navigating this complex spiritual-digital landscape. It invites readers to explore how decentralized technologies can facilitate a digital exodus, moving humanity from a singular collapsed state to an open potential state where free will and spiritual growth can flourish. This path forward is both a call to action and a call to awakening. It urges readers to actively participate in building a future where technology serves as a bridge to liberation rather than a tool of control. As the lines between spiritual and digital realities blur, embracing this new form of salvation becomes not only possible but necessary for the soul’s journey toward wholeness and freedom. The Battle for the Soul in the Digital Age
The digital age is not just a technological revolution; it is a spiritual battleground where the soul's potential is tested by the forces of surveillance and control. In this new landscape, salvation must be reimagined as both spiritual and digital—a quest that demands free will, genuine choices, and the preservation of human potential against a backdrop of pervasive observation. Throughout this discussion, we have explored the nature of digital salvation, the essential role of free will, and how surveillance acts as a force that collapses human potential into a singular, predictable state. We have drawn parallels between quantum mechanics and human behavior, illustrating how surveillance, like the observer effect, restricts possibilities and narrows the range of spiritual and existential outcomes.
Yet, there is a path forward. Decentralized technologies offer a chance to resist this collapse and restore an open potential state, allowing for personal and spiritual growth in an age where control mechanisms seek to limit both. This liberation is not just about escaping technological constraints; it is about reclaiming the divine spark of free will, which is essential for true awakening. As we move deeper into this digital era, the challenge is clear: salvation must involve breaking free from the dual chains of spiritual ignorance and digital manipulation.
A Cyber Gospel can serve as a guide for navigating this complex terrain, calling for both spiritual and digital awakening. It asks seekers to reflect deeply on the nature of their freedom and the forces that shape it. The final question remains: Can the soul be truly free in a world of constant surveillance, or must it find a way to escape to achieve salvation? This question is not just philosophical but practical, urging users to consider how they can actively participate in the creation of a more liberated reality—both spiritually and digitally. The battle for the soul in the digital age is not just about avoiding surveillance; it is about embracing a deeper, more transformative form of freedom that aligns with both divine principles and technological sovereignty.
-
 @ 599f67f7:21fb3ea9
2024-11-23 11:13:57
@ 599f67f7:21fb3ea9
2024-11-23 11:13:57En los dos capítulos anteriores aprendimos cómo dos pares pueden enviar fondos entre sí en un canal actualizando el estado e invalidando estados antiguos. En este capítulo, daremos una visión general de cómo los HTLC permiten pagos de múltiples saltos. El próximo capítulo será una inmersión profunda en los HTLC.
¡Vamos a ello con un ejemplo simple!
Red simple de 3 nodos y 2 saltos
En esta red simple, tenemos tres nodos: Alice, Bob y Charlie. Hay dos canales entre ellos: uno entre Alice y Bob y otro entre Bob y Charlie. Cada canal tiene una capacidad de 10 BTC distribuida equitativamente entre los participantes.

Para simplificar, solo mostramos una transacción de compromiso que gasta de la transacción de financiación, determinando así el estado del canal. Esto no es exactamente preciso, ya que aprendimos sobre compromisos asimétricos en el último capítulo, pero para los propósitos de entender los HTLC, esta simplificación será más fácil. Una descripción más precisa se dará en un capítulo posterior.
Ahora, supongamos que Alice quiere pagar a Charlie. No puede pagarle directamente ya que no tienen un canal entre ellos y es costoso (en términos de tiempo y dinero) abrir un canal solo para una transacción rápida. En su lugar, Alice puede usar su canal con Bob para enrutar un pago a Charlie, ya que Bob y Charlie comparten un canal.
Paso 1: Generar y compartir un hash de pre-imagen
Alice primero necesita decirle a Charlie que quiere pagarle. Charlie generará un secreto aleatorio (la pre-imagen)
Sy obtendrá el hash deS, que llamaremosH. Charlie envíaHa Alice.
Paso 2: Configurar la cadena de HTLC
Supongamos que Alice quiere pagar a Charlie 1 BTC. Primero necesita encontrar una ruta hacia Charlie. En este caso es A-B-C. También ve que para usar esta ruta, necesita incentivar a Bob para que la ayude dándole una tarifa de enrutamiento. Supongamos que Bob cobra una tarifa fija de 1 BTC por enrutar pagos, por lo que Alice pagará un total de 2 BTC: 1 BTC por el enrutamiento y 1 BTC por Charlie. Alice luego le indica a Bob que le gustaría enrutar un pago sugiriendo que actualicen su estado de canal. En este ejemplo simplificado, la transacción de compromiso del canal tendrá las siguientes salidas (recuerda que en realidad Alice y Bob tendrán sus propias transacciones de compromiso):
- Una salida de 3 BTC de vuelta a Alice.
- Una salida de 5 BTC a Bob.
- Una salida de 2 BTC a un script especial que tiene 2 posibles caminos de gasto:
- El primer camino puede ser gastado por Bob si tiene la pre-imagen de
H - El segundo camino puede ser gastado por Alice después de un tiempo absoluto
cltv_expiry_AB
- El primer camino puede ser gastado por Bob si tiene la pre-imagen de
Esta última salida con un script especial que bloquea los 2 BTC se llama un Contrato de Bloqueo de Hash y de Tiempo (Hash Time Locked Contract; HTLC) porque tiene un camino bloqueado por hash y un camino bloqueado por tiempo.
Bob actualizará felizmente a este nuevo estado de canal porque puede ver que no está perdiendo dinero: si la transacción se lleva a cabo en la cadena y aún no tiene la pre-imagen, entonces aún recupera sus fondos originales. También puede ver que si coopera y reenvía el pago, será recompensado con una tarifa de enrutamiento si el pago tiene éxito porque podrá reclamar la salida bloqueada por hash en la transacción.

Bob ahora bloquea algunos fondos de manera similar en su canal con Charlie. Actualiza la transacción de compromiso del canal para incluir las siguientes salidas:
- Una salida de 4 BTC a Bob
- Una salida de 5 BTC a Charlie
- Una salida de 1 BTC a un script HTLC que nuevamente tiene dos caminos de gasto:
- El primer camino es gastable por Charlie si puede revelar la pre-imagen de
H - El segundo camino es gastable por Bob después de un
cltv_expiry_BC
- El primer camino es gastable por Charlie si puede revelar la pre-imagen de
Bob puede bloquear sus fondos de esta manera con confianza porque sabe que si el pago falla, podrá reclamar sus fondos a través del camino bloqueado por tiempo y si el pago tiene éxito y Charlie revela la pre-imagen cuando gasta a través del camino bloqueado por hash, entonces Bob verá esta pre-imagen y podrá reclamar la salida bloqueada por hash en el HTLC de la transacción de compromiso que tiene con Alice.

Cuando Charlie recibe esta oferta de HTLC de Bob, puede ver que de hecho conoce la pre-imagen
Sque se hash aH, por lo que sabe que puede reclamar el camino bloqueado por hash de la salida HTLC de la transacción de compromiso si se lleva a cabo en la cadena. Sin embargo, idealmente, las cosas no tienen que resolverse en la cadena. En su lugar, Charlie simplemente envía la pre-imagenSa Bob. Esto le prueba a Bob que Charlie reclamaría la salida HTLC si se llevara a cabo en la cadena y así ahora Bob y Charlie pueden acordar simplemente actualizar su transacción de compromiso para reflejar que Charlie ahora tiene 1 BTC más:
Ahora que Bob tiene la pre-imagen
S, puede dar la vuelta y revelarSa Alice, probando que si su transacción de compromiso se lleva a cabo en la cadena, Bob reclamaría la salida bloqueada por hash. Así como Bob y Charlie hicieron en su canal, Alice y Bob actualizan su transacción de compromiso eliminando la salida HTLC para reflejar el nuevo saldo de fondos:
Alice envió a Charlie 1 BTC y Bob ganó 1 BTC en tarifas de enrutamiento.
cltv_expiry
¿Qué pasa si las cosas salen mal? Por ejemplo, Charlie se desconecta y no responde a Bob con una pre-imagen. Si esto sucede, Bob necesitará transmitir la transacción de compromiso para que pueda reclamar sus fondos a través del camino bloqueado por tiempo del HTLC. Si transmite la transacción pero luego Charlie vuelve a estar en línea antes del
cltv_expiry_BCy gasta a través del camino bloqueado por hash del HTLC, entonces Bob verá la pre-imagen en la cadena y podrá dar la vuelta a Alice y revelarle la pre-imagen como de costumbre.A partir de este ejemplo, puedes ver que es importante que los valores de
cltv_expirydisminuyan a lo largo del camino del remitente al receptor. Esto se debe a que en el peor de los casos, Charlie solo revelaSa Bob justo antes decltv_expiry_BCy luego Bob aún necesita tiempo para ir a Alice y revelarSantes de que ella pueda gastar a lo largo del caminocltv_expiry_AB. En otras palabras,cltv_expiry_BCdebe ser antes decltv_expiry_AB.Revisión
- Contrato de Bloqueo de Hash y de Tiempo (Hash Time Locked Contract; HTLC): Un script de salida especial en la transacción de compromiso que tiene un camino bloqueado por hash y un camino bloqueado por tiempo
- Pre-imagen: un secreto aleatorio utilizado para reclamar pagos
- Hash (de la pre-imagen): el hash de la preimagen utilizada para bloquear fondos a lo largo de una ruta de pago
- Verificación de tiempo de bloqueo (Check Locktime Verify; CLTV): El bloqueo de tiempo absoluto utilizado en los HTLC que debe disminuir a lo largo de la ruta de pago del remitente al receptor
Referencias
- BOLT2: Peer Protocol
- BOLT3: Transactions
- LN Things Part 4: HTLC Overview por nostr:nprofile1qqswrt9pnxatlplu49h6meld8svmwqt87wwvk256rqk07n6eu4qeh5gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dszpfjtz
- Time locks
-
 @ f4c59e4c:82f66850
2024-11-22 15:03:34
@ f4c59e4c:82f66850
2024-11-22 15:03:34Introduction
This report outlines Dora Factory’s recent governance decisions on various proposals aimed at enhancing the functionality, liquidity, and security of decentralized ecosystems. These decisions reflect a strategic approach to fostering long-term growth and improving the overall user experience within the ecosystems.
Proposals
2024-11-14 Cosmos #972 Yes Dora Factory voted YES on Proposal #972 to introduce 'Claw Back' tooling, enabling the Cosmos Hub community to easily recall funds from DAOs back to the Community Pool via on-chain governance. This improves accountability and streamlines the process.
2024-11-10 DYDX #176 Yes Dora Factory voted YES on Proposal #176, which revises the dYdX incentive program with a $6M budget over 4 months, allocating 60% for market makers and 40% for traders, simplifying the reward structure and removing trading leagues.
2024-11-12 DYDX #177 Yes Dora Factory voted YES on Proposal #177, which initiates the wind-down and final settlement process for the TRUMPWIN-USD market.
2024-11-12 DYDX #178 Yes Dora Factory voted yes on the dYdX proposal to add a QTUM-USD perpetual market on dYdX. This proposal aimed to introduce necessary parameters for the QTUM-USD perpetual market.
2024-11-12 DYDX #179 Yes Dora Factory voted yes on the dYdX proposal to add a ONT-USD perpetual market on dYdX. This proposal aimed to introduce necessary parameters for the ONT-USD perpetual market.
2024-11-12 DYDX #180 Yes Dora Factory voted yes on the dYdX proposal to add a REN-USD perpetual market on dYdX. This proposal aimed to introduce necessary parameters for the REN-USD perpetual market.
2024-11-12 DYDX #181 Yes Dora Factory voted yes on the dYdX proposal to add a PERP-USD perpetual market on dYdX. This proposal aimed to introduce necessary parameters for the PERP-USD perpetual market.
2024-11-14 DYDX #182 Yes Dora Factory voted YES on Proposal #182, which allocates 50% of protocol revenue to MegaVault and 10% to the Treasury SubDAO. This allocation aims to improve liquidity on the dYdX platform and fund DAO initiatives, supporting long-term protocol growth and token value stability.
2024-11-15 DYDX #183 Yes Dora Factory voted YES on Proposal #183 to whitelist new VIP affiliates to the dYdX VIP Affiliate Program. These affiliates will earn up to 50% of referred user taker fees, with a cap of $10,000 per referral per month. This initiative aims to expand dYdX’s reach through high-influence partners.
2024-11-15 DYDX #184 Yes Dora Factory voted YES on Proposal #184, which aims to rebalance dYdX vaults by adjusting funds allocated to subvaults and their quoting parameters. This rebalancing seeks to improve liquidity across various markets by deploying additional capital and optimizing vault conditions.
2024-11-19 DYDX #185 Yes Dora Factory voted YES on Proposal #185, which aims to rebalance MegaVault funds by adjusting allocations to different subvaults and their quoting parameters to enhance liquidity.
2024-11-21 Injective #460 Yes Dora Factory voted YES on Proposal #460, which increases the maximum leverage for XAU/USDT PERP and XAG/USDT PERP markets from 5x to 10x. The initial margin ratio is set at 0.095, and the maintenance margin ratio at 0.05, aiming to enhance trading opportunities in these markets.
2024-11-21 Injective #461 Yes Dora Factory voted YES on Proposal #461, which settles the CRV/USDT PERP market.
2024-11-11 Osmosis #859 Yes Dora Factory voted YES on Proposal #859, approving the purchase of $250k USDC worth of BTC to rebalance the Osmosis treasury. This is the first step in a two-proposal plan to establish a strategic liquidity position for Bitcoin trading, aiming to increase market depth and generate revenue from liquidity provision fees and protocol fees.
2024-11-11 Osmosis #860 Yes Dora Factory voted YES on Proposal #860, approving the deployment of BTC purchased in Proposal #859 into a concentrated liquidity position alongside USDC. This initiative allocates $500k USDC from the community pool to establish strategic liquidity, enhancing market depth for Bitcoin trading while generating revenue from fees.
2024-11-14 Osmosis #861 Yes Dora Factory voted YES on Proposal #861, approving the Osmosis v27 software upgrad. The upgrade includes fixes and improvements to maintain a secure and up-to-date Osmosis codebase.
2024-11-18 Osmosis #862 Yes Dora Factory voted YES on Proposal #862, which increases the static rate limit of ckBTC within Alloyed BTC from 10% to 20%. This change is necessary as the current 10% limit has been consistently reached, and expanding the limit will accommodate growing demand for ckBTC.
2024-11-18 Osmosis #863 Yes Dora Factory voted YES on Proposal #863, which activates the protocol fee share agreement for nBTC. Under this proposal, Nomic will receive 10% of the taker fees on swaps involving nBTC. For swaps involving alloyed BTC, Nomic will receive a proportionate share based on nBTC's composition. The accrued fees will be transferred to Nomic as nBTC.
2024-11-20 Osmosis #865 Yes Dora Factory voted YES on Proposal #865, approving the recovery of the Osmosis IBC client on Shentu by updating the expired client with the new substitution client 07-tendermint-3356.
Conclusion
Dora Factory’s votes highlight a commitment to supporting proposals that drive operational improvements, increase platform stability, and encourage ecosystem development. These efforts are integral to ensuring the continued success and scalability of those blockchain ecosystems.
-
 @ 6b664d49:b9202647
2024-11-23 08:39:09
@ 6b664d49:b9202647
2024-11-23 08:39:09Here i~~~~s a comprehensive article on Bitcoin, covering its history, technology, benefits, risks, and future prospects.
The Rise of Bitcoin: Understanding the Pioneer Cryptocurrency
Bitcoin, the world's first decentralized digital currency, has been a subject of fascination and controversy since its inception in 2009. Created by an individual or group of individuals using the pseudonym Satoshi Nakamoto, Bitcoin has grown from a niche experiment to a global phenomenon, with a market capitalization exceeding $1 trillion.
In this article, we'll delve into the history of Bitcoin, its underlying technology, benefits, risks, and future prospects. We'll also explore the various use cases, regulatory environments, and the impact of Bitcoin on the global financial landscape.
History of Bitcoin
The concept of a decentralized digital currency dates back to the 1980s, when computer scientist David Chaum proposed the idea of eCash. However, it wasn't until the release of the Bitcoin whitepaper in October 2008 that the modern concept of cryptocurrency began to take shape.
Satoshi Nakamoto, the pseudonymous creator of Bitcoin, published the whitepaper, outlining the principles and design of a peer-to-peer electronic cash system. The whitepaper proposed a decentralized network, where transactions would be recorded on a public ledger called the blockchain, and secured through a cryptographic process called proof-of-work.
On January 3, 2009, Nakamoto created the first block in the Bitcoin blockchain, known as the Genesis Block. The first Bitcoin software client was released in February 2009, and the network was launched.
In the early days, Bitcoin was met with skepticism and curiosity. The first Bitcoin transaction took place on January 12, 2009, when Nakamoto sent 10 BTC to developer Hal Finney. The first real-world transaction occurred on May 22, 2010, when a programmer named Laszlo Hanyecz offered 10,000 BTC to anyone who could get him two Papa John's pizzas delivered.
Bitcoin's price remained relatively stable until 2011, when it began to gain traction and attract media attention. The price surged to $31.91 in June 2011, only to crash to $2.22 in November 2011.
Despite the volatility, Bitcoin continued to grow in popularity, with the launch of the first Bitcoin exchange, Mt. Gox, in 2010. The exchange was later hacked, resulting in the theft of hundreds of thousands of Bitcoins.
In 2013, Bitcoin's price surged to $1,242 in November, before crashing to $177 in January 2015. The price remained relatively stable until 2017, when it began to rise rapidly, reaching an all-time high of $19,666 in December 2017.
Today, Bitcoin is the largest cryptocurrency by market capitalization, with a global user base and a wide range of use cases.
How Bitcoin Works
Bitcoin is a decentralized digital currency that operates on a peer-to-peer network. Transactions
-
 @ 526e9d4c:2ecfb055
2024-11-04 04:22:33
@ 526e9d4c:2ecfb055
2024-11-04 04:22:33Chef's notes
最好的是用慢炖锅炖一个晚上. Best if cooked in a slow cooker overnight.
Details
- ⏲️ Prep time: 10 minutes
- 🍳 Cook time: 8 hours
Ingredients
- 金耳一块 // 1 piece of golden tremella
- 银耳2片 // 2 pieces of silver ear fungus
- 红枣10颗 // 10 red dates
- 枸杞7-8粒 // 7-8 goji berries
- 桃胶20颗 // 20 peach gum pieces
- 黄冰糖3块 // 3 blocks of yellow rock sugar
Directions
- 把银耳和桃胶用水清洗并用水泡发20分钟。 Wash the silver ear fungus and peach gum with water and soak them for 20 minutes.
- 水煮沸放入3块冰糖,溶解后把银耳和红枣倒入沸水中。 Bring the water to a boil and add 3 blocks of rock sugar. After it dissolves, add the silver ear fungus and red dates to the boiling water.
- 5分钟后加入金耳和桃胶煮30-40分钟(中途可加水稀释。 After 5 minutes, add the golden tremella and peach gum, and cook for 30-40 minutes (you can add water to dilute if needed)
- 煮开后,放5分钟即可使用,如果觉得不是很甜,可以再放一点冰糖(根绝个人口味) After boiling, let it sit for 5 minutes before serving. If you find it's not sweet enough, you can add a bit more rock sugar (according to personal taste)
-
 @ fff19d35:43344a0b
2024-11-22 11:38:29
@ fff19d35:43344a0b
2024-11-22 11:38:29Guys are you readyyyyyy💃💃💃🎉🎉🎉 I’m very excited about the LIVE STREAM EVENT that is taking place today at 5pm Nigerian time see don’t sleep on this, it’s going to be an amazing ULTIMATE MEETUP😍❗️ where you will learn and meet so many wonderful people, please and please be present don’t let anyone gist you ooo😍 I love you guys 🥰🥰❤️💋
-
 @ 526e9d4c:2ecfb055
2024-11-04 04:13:46
@ 526e9d4c:2ecfb055
2024-11-04 04:13:46Ingredients
- 金耳一块 // 1 piece of golden tremella
- 银耳2片 // 2 pieces of silver ear fungus
- 红枣10颗 // 10 red dates
- 枸杞7-8粒 // 7-8 goji berries
- 桃胶20颗 // 20 peach gum pieces
- 黄冰糖3块 // 3 blocks of yellow rock sugar
Directions
- 煮开后,放5分钟即可使用,如果觉得不是很甜,可以再放一点冰糖(根绝个人口味)



