-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ 41ed0635:762415fc
2024-10-23 12:17:11
@ 41ed0635:762415fc
2024-10-23 12:17:11O Que é um RAM Disk?
Um RAM Disk é uma área de armazenamento criada na memória RAM do sistema, tratada pelo sistema operacional como um dispositivo de armazenamento físico, similar a um disco rígido ou SSD. Sua característica principal é ser baseado em memória volátil, o que significa que os dados armazenados são perdidos quando o sistema é desligado ou reiniciado. Essa tecnologia oferece uma alternativa de armazenamento temporário extremamente rápida, ideal para situações que exigem acesso veloz a dados, mas sem a necessidade de persistência a longo prazo.
Vantagens e Desvantagens do RAM Disk
Vantagens - Velocidade Superior: Acesso muito mais rápido comparado a dispositivos de armazenamento baseados em NAND flash ou SSDs tradicionais. - Latência Mínima: Redução significativa na latência de leitura/escrita. - Isolamento de Dados Temporários: Ideal para armazenar dados temporários que não precisam de persistência após o desligamento.
Desvantagens - Volatilidade: Perda de dados em caso de desligamento ou falha de energia. - Consumo de Memória: Utiliza a RAM do sistema, que é um recurso limitado.
Consumo de Memória e Soluções Alternativas
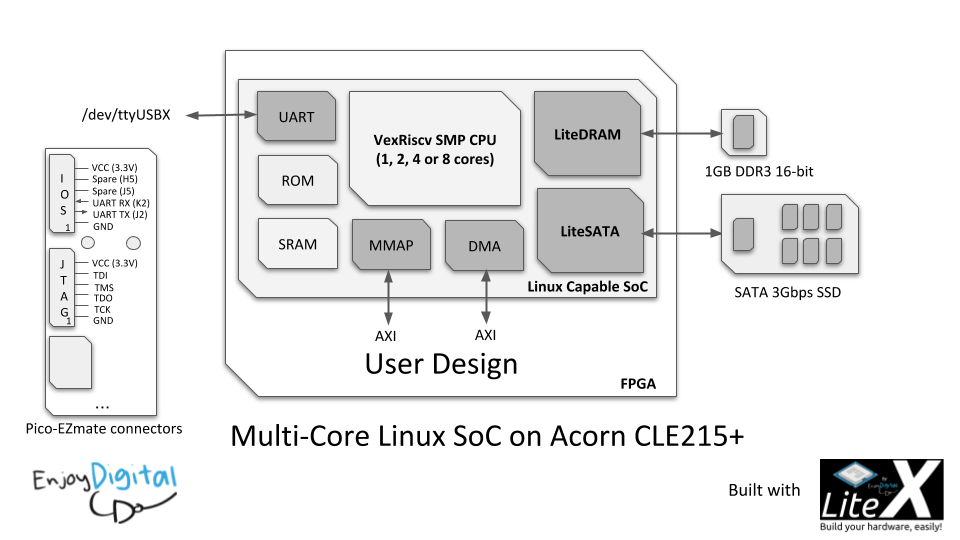
Uma abordagem inovadora para lidar com o consumo de memória do sistema é a implementação de um SSD SATA em FPGA utilizando LiteSATA e LiteDRAM como backend de memória. Este método requer a seleção de uma placa FPGA apropriada com recursos necessários, incluindo transceptores capazes de operar na velocidade SATA desejada e memória DRAM compatível. O processo envolve a configuração do LiteDRAM e LiteSATA, implementação de lógica de controle, integração dos componentes, compilação e síntese do design, e programação do FPGA. Esta solução oferece uma alternativa flexível e personalizável para o armazenamento de alta velocidade.
1. Seleção da Placa FPGA
Escolha uma placa com transceptores adequados e memória DRAM compatível.
2. Configuração do LiteDRAM e LiteSATA
Instancie e configure os núcleos LiteDRAM e LiteSATA no design FPGA.
3. Implementação da Lógica de Controle
Desenvolva um controlador para interfacear LiteSATA com LiteDRAM.
4. Programação e Teste
Compile, sintetize e programe o FPGA, seguido por testes e otimizações.
Configuração do LiteDRAM
1. Instanciação
No seu design, instancie o núcleo LiteDRAM.
2. Configuração
Configure o LiteDRAM para corresponder ao tipo e à configuração da memória DRAM na sua placa (por exemplo, DDR3, DDR4).
3. Parâmetros
Defina parâmetros como frequência de operação, largura de banda e latências.
Configuração do LiteSATA
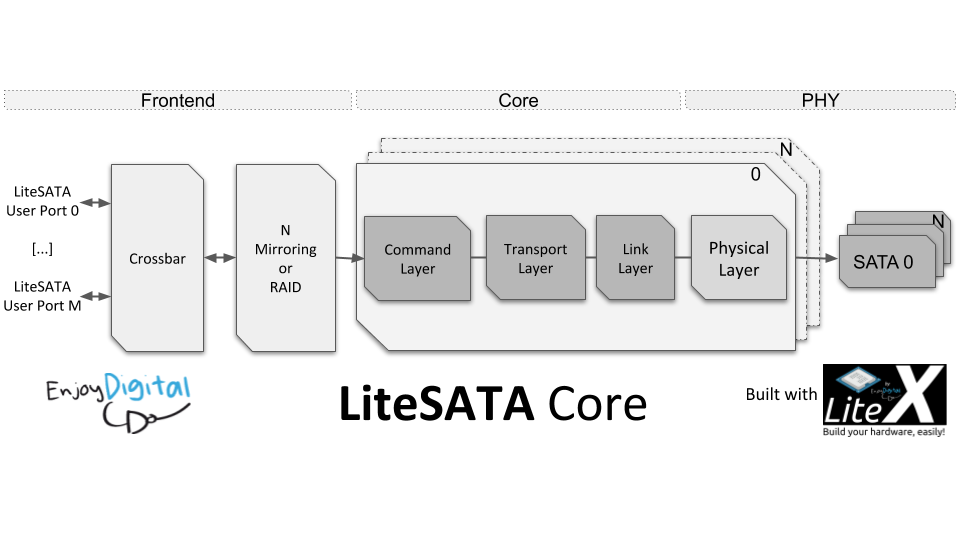
Instanciação
Comece por instanciar o núcleo LiteSATA no seu design FPGA.
PHY SATA
Em seguida, configure o PHY SATA de acordo com o hardware da sua placa FPGA, incluindo a taxa de transferência desejada. Por exemplo, para uma conexão SATA 3.0, a taxa de transferência será de 6 Gbps.
Mapeamento de Pinos
Por fim, certifique-se de que os pinos do FPGA estão corretamente mapeados para os conectores SATA.
Desenvolvimento do Controlador com Máquina de Estados Finitos
O desenvolvimento de um controlador que interfaceia o LiteSATA com o LiteDRAM utilizando uma Máquina de Estados Finitos (FSM) é crucial para gerenciar a comunicação entre o protocolo SATA e a memória DRAM. Este controlador é responsável por receber e interpretar comandos SATA, gerenciar operações de leitura/escrita na DRAM, e sincronizar dados entre os sistemas. A FSM é composta por vários estados, cada um representando uma etapa específica do processamento. A transição entre estados é baseada em eventos ou condições, como a recepção de um novo comando ou a conclusão de uma operação de leitura/escrita.
Objetivo do Controlador
Gerenciar comunicação entre SATA e DRAM, traduzindo comandos e garantindo integridade dos dados.
Estrutura da FSM
Estados representam etapas do processamento, com transições baseadas em eventos ou condições.
Implementação
Desenvolvimento de lógica para cada estado, garantindo fluxo correto de operações e tratamento de erros.
Estados da Máquina de Estados Finitos
A Máquina de Estados Finitos (FSM) do controlador é composta por vários estados essenciais. O estado IDLE é o ponto inicial, aguardando comandos. O COMMAND_DECODE decodifica os comandos recebidos. READ_SETUP e WRITE_SETUP preparam as operações de leitura e escrita, respectivamente. READ_EXECUTE e WRITE_EXECUTE realizam as operações de leitura e escrita na DRAM. O STATUS_UPDATE atualiza o status da operação e informa o host. O ERROR_HANDLE lida com erros ocorridos durante as operações. Cada estado tem ações específicas e critérios de transição para outros estados, garantindo um fluxo de operação eficiente e confiável.
- IDLE: Aguarda comandos, transição para COMMAND_DECODE ao receber novo comando.
- COMMAND_DECODE: Decodifica o comando recebido e prepara parâmetros.
- READ/WRITE_SETUP: Configura operações de leitura ou escrita na DRAM.
- READ/WRITE_EXECUTE: Executa operações de leitura ou escrita na DRAM.
- STATUS_UPDATE: Atualiza o status da operação e informa o host.
Comparação entre RAM Disk e SSD SATA em FPGA
RAM Disk e SSD SATA em FPGA com LiteSATA e LiteDRAM compartilham semelhanças em termos de velocidade superior e uso de memória volátil. Ambos oferecem velocidades de leitura/escrita superiores aos dispositivos de armazenamento convencionais. No entanto, diferem significativamente em sua implementação de hardware e flexibilidade. O RAM Disk é uma solução puramente de software que utiliza a RAM interna do sistema, enquanto o SSD em FPGA envolve hardware personalizado conectado a DRAM externa. A escalabilidade e flexibilidade também diferem, com o SSD em FPGA oferecendo maior potencial de expansão.
Característica | RAM Disk | SSD SATA em FPGA --- | --- | --- Implementação | Software | Hardware personalizado Escalabilidade | Limitada pela RAM do sistema | Expansível com módulos DRAM Flexibilidade | Baixa | Alta (ajustável via FPGA) Persistência | Volátil | Volátil (com opções de backup)
Integração com a Partição de Swap no Linux
A integração de um SSD SATA em FPGA com a partição de swap no Linux pode acelerar significativamente o desempenho do sistema. O Linux utiliza o swap como uma extensão da memória RAM, e um swap mais rápido permite que o sistema mova páginas de memória para o swap e as recupere mais rapidamente, aumentando efetivamente o desempenho percebido da RAM. Essa integração resulta em redução do tempo de espera para processos que requerem acesso a dados no swap, melhorando a eficiência geral do sistema. Em aplicações de alto desempenho, como bancos de dados, máquinas virtuais ou processamento de big data, um swap rápido pode evitar gargalos quando a memória física está esgotada.
1. Melhor Gestão de Memória
Movimento mais rápido de páginas entre RAM e swap, aumentando o desempenho percebido da memória.
2. Redução de Tempo de Espera
Processos acessam dados no swap mais rapidamente, melhorando a responsividade do sistema.
3. Melhoria em Aplicações de Alto Desempenho
Evita gargalos em workloads que exigem muita memória, como bancos de dados e processamento de big data.
Benefícios e Desvantagens da Integração
A integração de um SSD SATA em FPGA com LiteSATA e LiteDRAM como partição de swap no Linux oferece diversos benefícios. A latência reduzida e as altas taxas de transferência aceleram operações de leitura e escrita no swap. A ausência de desgaste por escrita na DRAM aumenta a longevidade do dispositivo. A capacidade pode ser expandida adicionando mais módulos DRAM, e atualizações são facilitadas via firmware. Contudo, existem desvantagens a considerar. A implementação requer hardware adicional (FPGA e DRAM externa), o que pode resultar em um custo mais elevado comparado a soluções de RAM Disk convencionais. A complexidade da implementação também pode ser um fator limitante para alguns usuários.
Benefícios - Latência reduzida - Altas taxas de transferência - Ausência de desgaste por escrita - Capacidade expansível - Atualizações facilitadas
Desvantagens - Necessidade de hardware adicional - Potencial custo mais elevado - Complexidade de implementação
Considerações Finais e Recursos
Compatibilidade de Protocolos
Garanta que o seu design esteja em conformidade com as especificações SATA para evitar problemas de compatibilidade.
Limitações de Hardware
Esteja ciente das limitações do seu FPGA, como recursos lógicos disponíveis e capacidades dos transceptores.
Segurança dos Dados
Considere implementar recursos de correção de erros ou proteção de dados se necessário.
Recursos Úteis: - Repositório do LiteSATA: https://github.com/enjoy-digital/litesata - Repositório do LiteDRAM: https://github.com/enjoy-digital/litedram - Documentação do LiteX: https://github.com/enjoy-digital/litex/wiki
-
 @ f352c64c:6a332001
2024-10-23 10:21:53
@ f352c64c:6a332001
2024-10-23 10:21:53It Starts with Us, the much-anticipated sequel to It Ends with Us, continues Colleen Hoover’s emotional exploration of love, trauma, and second chances. The story resumes where It Ends with Us left off, following Lily Bloom as she tries to move forward after the collapse of her marriage with Ryle, who was both loving and abusive. This novel shifts focus to Lily’s evolving relationships and her journey toward healing, particularly her reconnection with Atlas Corrigan, her first love.
The central theme of It Starts with Us is about new beginnings. After the emotional devastation she endured, Lily must now balance her role as a single mother to her
daughter,
Emerson, and face the challenges of co-parenting with Ryle. Unlike the previous book, which delved into the struggles of escaping an abusive relationship, this novel focuses on what comes after—the healing, the hope, and the resilience that follows.
One of the novel’s strengths lies in its character development. Lily is no longer just surviving; she’s learning to thrive, and part of this growth comes from her deepening connection with Atlas. Their story, which had always been full of “what ifs,” now gets the space to flourish. Atlas is patient, kind, and represents everything Lily once wanted. Their romance provides a contrast to the darkness of her past, showing readers that love can be gentle and safe.
Another critical aspect of It Starts with Us is its realistic portrayal of co-parenting after abuse. Lily’s interactions with Ryle are fraught with tension, as she tries to protect her daughter from the darker side of their father while ensuring her safety and well-being. This adds a layer of complexity, making it clear that healing is not always linear and that the past can continue to cast shadows.
Colleen Hoover’s writing is emotionally charged, pulling readers into Lily’s inner world, where hope and fear are constantly battling for control. By giving voice to the aftermath of domestic abuse, Hoover offers readers a thoughtful reflection on how trauma can linger but also how it is possible to find light in the midst of darkness.
In It Starts with Us, Hoover doesn’t just offer a love story; she offers a story of redemption, healing, and the strength it takes to reclaim your life. It’s a book about starting over, not just in love but in life itself. Fans of It Ends with Us will find this sequel to be a satisfying and heartwarming continuation of Lily’s journey.
-
 @ 9aa75e0d:40534393
2024-10-23 05:36:30
@ 9aa75e0d:40534393
2024-10-23 05:36:30Finnish Customs, working together with Swedish police, has successfully shut down the Sipulitie marketplace, a dark web platform used for illegal activities, including the anonymous sale of drugs. The site, active since February 2023, operated on the encrypted Tor network and was available in both Finnish and English.
Sipulitie, which provided a platform for illegal drug transactions under the protection of anonymity, generated a reported revenue of €1.3 million, according to the site’s administrator who posted the figure on public forums.
Sipulitie had a predecessor, Sipulimarket, which launched in April 2019. This Finnish-language platform also facilitated illegal drug and doping sales in an anonymous environment. Finnish Customs, with help from Polish authorities, shut down Sipulimarket in December 2020. It is believed that Sipulimarket had a turnover exceeding €2 million.
Read further on SmuggleWire
-
 @ 12085ffb:b81b1404
2024-10-23 02:47:32
@ 12085ffb:b81b1404
2024-10-23 02:47:32G55Bet surgiu como uma das líderes no mundo das apostas online, atraindo um público diversificado com seu design amigável e ofertas extensas. A plataforma é especificamente projetada para jogadores que buscam uma experiência de apostas direta e agradável, seja para profissionais experientes ou para iniciantes.
Interface Amigável Uma das características marcantes da G55Bet é sua interface intuitiva. O design permite que os usuários naveguem por várias seções com facilidade, tornando simples encontrar esportes ou jogos específicos. A página inicial exibe eventos atuais, opções de apostas ao vivo e promoções, garantindo que os usuários possam acessar rapidamente as informações necessárias.
Opções Diversificadas de Apostas A G55Bet se destaca ao oferecer uma ampla gama de opções de apostas. Desde esportes populares, como futebol e basquete, até mercados inovadores, como esports e jogos virtuais, a plataforma atende a uma variedade de interesses. Os usuários podem explorar diferentes tipos de apostas, incluindo apostas simples, com spread e over/under, permitindo estratégias de apostas personalizadas.
Apostas Ao Vivo e Streaming A emoção das apostas ao vivo é palpável na G55Bet. Os jogadores podem fazer apostas em tempo real à medida que os eventos se desenrolam, o que aumenta a experiência geral. Juntamente com as capacidades de streaming ao vivo para eventos selecionados, os usuários podem assistir à ação e tomar decisões informadas sobre suas apostas.
Promoções e Recompensas Para manter os jogadores engajados, a G55Bet frequentemente oferece promoções e bônus. Novos usuários podem se beneficiar de ofertas de boas-vindas, enquanto clientes leais desfrutam de recompensas contínuas. Esses incentivos não apenas melhoram a experiência de apostas, mas também encorajam os usuários a explorar novos jogos e eventos.
Compromisso com a Segurança A segurança é uma prioridade na G55Bet. A plataforma utiliza métodos avançados de criptografia para proteger informações pessoais e financeiras, permitindo que os usuários se concentrem em aproveitar sua experiência de apostas sem preocupações. Além disso, a G55Bet promove práticas de apostas responsáveis, fornecendo ferramentas para os jogadores definirem limites em suas atividades.
Suporte ao Cliente A G55Bet entende a importância do suporte ao cliente. A plataforma oferece vários canais para assistência, incluindo chat ao vivo e suporte por e-mail. Isso garante que os usuários possam obter ajuda rapidamente, seja com perguntas sobre opções de apostas ou assistência na gestão da conta.
Conclusão A G55Bet conseguiu conquistar um espaço no cenário das apostas online ao priorizar a experiência do usuário, opções diversificadas e segurança. Seu compromisso em fornecer uma plataforma fluida e envolvente a torna uma excelente escolha para quem busca explorar o emocionante mundo das apostas online.
-
 @ c73818cc:ccd5c890
2024-10-22 19:44:09
@ c73818cc:ccd5c890
2024-10-22 19:44:09
💀 Le criptovalute meno usate per attività illecite rispetto al denaro contante
👑 Secondo un recente studio, solo lo 0,3% delle transazioni in criptovaluta è legato a attività criminali, sfidando la narrativa comune. I criminali preferiscono ancora il denaro contante, con il 2-5% del PIL mondiale riciclato ogni anno attraverso i sistemi finanziari tradizionali.
💀 Maggiore trasparenza delle criptovalute rispetto ai sistemi tradizionali
👑 Le transazioni crittografiche, grazie alla loro trasparenza e tracciabilità sulla blockchain, risultano più sicure. Regolamenti severi come KYC e AML negli Stati Uniti rendono difficile l’anonimato, diminuendo ulteriormente i rischi di utilizzo illecito delle criptovalute.
💀 Stablecoin raramente coinvolte in transazioni illecite
👑 Stablecoin come Tether (USDT) e Circle (USDC) sono raramente impiegate in attività criminali. Tra il 2021 e il 2024, solo lo 0,61% delle transazioni con USDT e lo 0,22% con USDC sono risultate sospette, dimostrando la crescente sicurezza del settore crypto.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
Referral Bitget -10% sulle fee + bonus benvenuto 6w5d o link: https://bonus.bitget.com/U1JNEK
BitcoinReportItalia #Studio #Criminali #Denaro #Contante #Finanziamento #Anonimato #Illecito #Cripto #Bitcoin
-
 @ 9e69e420:d12360c2
2024-10-23 13:05:29
@ 9e69e420:d12360c2
2024-10-23 13:05:29Former Democratic Representative Tulsi Gabbard has officially joined the Republican Party, announcing her decision at a Donald Trump rally in North Carolina. As one of the few voices of reason within the Democratic Party, Gabbard's departure marks the end of her journey from Democratic presidential candidate to Republican Party member[1]. Her transition began with her exit from the Democratic Party in 2022, when she accurately called it an "elitist cabal of warmongers"[3].
Throughout her congressional career, Gabbard demonstrated a consistent anti-interventionist stance and a strong defense of civil liberties. She was an original member of the bi-partisan 4th Amendment Caucus, fighting against warrantless searches and championing privacy rights in the digital age[4]. Her principled opposition to the surveillance state and bulk data collection set her apart from the establishment of both major parties.
While some may view her political evolution as opportunistic, Gabbard's core positions on foreign policy have remained remarkably consistent. She has maintained her opposition to unnecessary foreign interventions and has been vocal about the risks of nuclear war[2]. Her criticism of the military-industrial complex and her calls for the Democratic party to renounce the influence of military contractors and corporate lobbyists demonstrate a commitment to principles over party loyalty[4]. Though her recent alignment with Trump may raise eyebrows, her consistent advocacy for peace and opposition to the warfare state make her a unique figure in American politics[1].
Sauce: [1] Tulsi Gabbard's Political Evolution | TIME https://time.com/7096376/tulsi-gabbard-democrat-republican-political-evolution-history-trump/ [2] Tulsi Gabbard wants to serve under Trump, but do their policies align? https://www.usatoday.com/story/news/politics/elections/2024/06/19/tulsi-gabbard-trump-vp-secretary-policy/73968445007/ [3] Tulsi Gabbard announces she is leaving Democratic Party https://abcnews.go.com/Politics/tulsi-gabbard-announces-leaving-democratic-party/story?id=91326164%2F [4] Political positions of Tulsi Gabbard - Wikipedia https://en.wikipedia.org/wiki/Political_positions_of_Tulsi_Gabbard [5] Tulsi Gabbard Turning Republican Is 'Surprise' to Donald Trump https://www.newsweek.com/tulsi-gabbard-donald-trump-republican-party-1973340
-
 @ 42342239:1d80db24
2024-10-23 12:28:41
@ 42342239:1d80db24
2024-10-23 12:28:41TL;DR: The mathematics of trust says that news reporting will fall flat when the population becomes suspicious of the media. Which is now the case for growing subgroups in the U.S. as well as in Sweden.
A recent wedding celebration for Sweden Democrats leader Jimmie Åkesson resulted in controversy, as one of the guests in attendance was reportedly linked to organized crime. Following this “wedding scandal”, a columnist noted that the party’s voters had not been significantly affected. Instead of a decrease in trust - which one might have expected - 10% of them stated that their confidence in the party had actually increased. “Over the years, the Sweden Democrats have surprisingly emerged unscathed from their numerous scandals,” she wrote. But is this really so surprising?
In mathematics, a probability is expressed as the likelihood of something occurring given one or more conditions. For example, one can express a probability as “the likelihood that a certain stock will rise in price, given that the company has presented a positive quarterly report.” In this case, the company’s quarterly report is the basis for the assessment. If we add more information, such as the company’s strong market position and a large order from an important customer, the probability increases further. The more information we have to go on, the more precise we can be in our assessment.
From this perspective, the Sweden Democrats’ “numerous scandals” should lead to a more negative assessment of the party. But this perspective omits something important.
A couple of years ago, the term “gaslighting” was chosen as the word of the year in the US. The term comes from a 1944 film of the same name and refers to a type of psychological manipulation, as applied to the lovely Ingrid Bergman. Today, the term is used in politics, for example, when a large group of people is misled to achieve political goals. The techniques used can be very effective but have a limitation. When the target becomes aware of what is happening, everything changes. Then the target becomes vigilant and views all new information with great suspicion.
The Sweden Democrats’ “numerous scandals” should lead to a more negative assessment of the party. But if SD voters to a greater extent than others believe that the source of the information is unreliable, for example, by omitting information or adding unnecessary information, the conclusion is different. The Swedish SOM survey shows that these voters have lower trust in journalists and also lower confidence in the objectivity of the news. Like a victim of gaslighting, they view negative reporting with suspicion. The arguments can no longer get through. A kind of immunity has developed.
In the US, trust in the media is at an all-time low. So when American media writes that “Trump speaks like Hitler, Stalin, and Mussolini,” that his idea of deporting illegal immigrants would cost hundreds of billions of dollars, or gets worked up over his soda consumption, the consequence is likely to be similar to here at home.
The mathematics of trust says that reporting will fall flat when the population becomes suspicious of the media. Or as the Swedish columnist put it: like water off a duck’s back.
Cover image: Ingrid Bergman 1946. RKO Radio Pictures - eBay, Public Domain, Wikimedia Commons
-
 @ 42342239:1d80db24
2024-10-22 07:57:17
@ 42342239:1d80db24
2024-10-22 07:57:17It was recently reported that Sweden's Minister for Culture, Parisa Liljestrand, wishes to put an end to anonymous accounts on social media. The issue has been at the forefront following revelations of political parties using pseudonymous accounts on social media platforms earlier this year.
The importance of the internet is also well-known. As early as 2015, Roberta Alenius, who was then the press secretary for Fredrik Reinfeldt (Moderate Party), openly spoke about her experiences with the Social Democrats' and Moderates' internet activists: Twitter actually set the agenda for journalism at the time.
The Minister for Culture now claims, amongst other things, that anonymous accounts pose a threat to democracy, that they deceive people, and that they can be used to mislead, etc. It is indeed easy to find arguments against anonymity; perhaps the most common one is the 'nothing to hide, nothing to fear' argument.
One of the many problems with this argument is that it assumes that abuse of power never occurs. History has much to teach us here. Sometimes, authorities can act in an arbitrary, discriminatory, or even oppressive manner, at least in hindsight. Take, for instance, the struggles of the homosexual community, the courageous dissidents who defied communist regimes, or the women who fought for their right to vote in the suffragette movement.
It was difficult for homosexuals to be open about their sexuality in Sweden in the 1970s. Many risked losing their jobs, being ostracised, or harassed. Anonymity was therefore a necessity for many. Homosexuality was actually classified as a mental illness in Sweden until 1979.
A couple of decades earlier, dissidents in communist regimes in Europe used pseudonyms when publishing samizdat magazines. The Czech author and dissident Václav Havel, who later became the President of the Czech Republic, used a pseudonym when publishing his texts. The same was true for the Russian author and literary prize winner Alexander Solzhenitsyn. Indeed, in Central and Eastern Europe, anonymity was of the utmost importance.
One hundred years ago, women all over the world fought for the right to vote and to be treated as equals. Many were open in their struggle, but for others, anonymity was a necessity as they risked being socially ostracised, losing their jobs, or even being arrested.
Full transparency is not always possible or desirable. Anonymity can promote creativity and innovation as it gives people the opportunity to experiment and try out new ideas without fear of being judged or criticised. This applies not only to individuals but also to our society, in terms of ideas, laws, norms, and culture.
It is also a strange paradox that those who wish to limit freedom of speech and abolish anonymity simultaneously claim to be concerned about the possible return of fascism. The solutions they advocate are, in fact, precisely what would make it easier for a tyrannical regime to maintain its power. To advocate for the abolition of anonymity, one must also be of the (absurd) opinion that the development of history has now reached its definitive end.
-
 @ 9e69e420:d12360c2
2024-10-21 20:26:54
@ 9e69e420:d12360c2
2024-10-21 20:26:54Your first NOSTR note.
Some of you may be lurking wondering how why or what for your first note here on nostr. Here's some advice from an pseudonymous douchebag. To start with, your first note should be to come out swinging. Make lots of friends maybe even some enemies. Most people get a lot of love with their first introductions post.
Make it short.
Your first note will probably (and probably should) be a kind one event. The note you're reading is a 30023 event for long form notes. (More on this some other time). Keep it short and concise. You probably could publish a book in a kind one note. But I really don't think anyone believes you should and I'm sure many relays would reject it. It will also appear without formatting which just looks ugly for anything other than a microblog.
Introduce yourself.
Just as you would in an IRL interaction. What's your name? But more importantly what do you want us to call you? What brought you here? What are your interests? It's important to be real here even if you decide to be pseudonymous. Chances are your tribe is already here. If you're the first then that makes you king of your little corner of the nostr. Which will likely pay dividends in and of itself.
Make it a banger.
Here's my first note (I should disclose this is just the first note from this npub And I have already been here for over a year at this point):
note1pnufmzwy2gj4p5qza6jk7k40nns0p3k2w0fsrqq568utjlnyphdqyg8cpq
Have fun
Don't take this or anything else too seriously. We are all the same here because we are just as unique as each other. Be as weird as you want.
** & Don't forget to use the "#indroductions" hashtag **
-
 @ 4ba8e86d:89d32de4
2024-10-23 12:46:23
@ 4ba8e86d:89d32de4
2024-10-23 12:46:23Desenvolvido pelo Tor Project, o OnionShare é um projeto de código aberto que visa proteger a privacidade dos usuários durante o compartilhamento de arquivos.
Criado em 2014 por Micah Lee, um desenvolvedor de software e ativista de privacidade, o OnionShare surgiu como uma solução para compartilhamento seguro e anônimo de arquivos pela rede Tor. O OnionShare faz parte do desenvolvimento contínuo do Tor Project, a mesma equipe responsável pelo navegador Tor. Micah Lee reconheceu a necessidade de uma solução que respeitasse os princípios e valores da rede Tor, fornecendo privacidade aos usuários. O OnionShare utiliza serviços ocultos do Tor para criar servidores web temporários com endereços .onion exclusivos, permitindo que os arquivos compartilhados sejam acessados apenas pela rede Tor. Desde o seu lançamento, o OnionShare tem sido aprimorado e atualizado pela comunidade de desenvolvedores do Tor Project, garantindo a compatibilidade contínua com os princípios e protocolos da rede Tor. A ferramenta tornou-se amplamente reconhecida como uma opção confiável para compartilhamento de arquivos com privacidade e segurança, sendo usada por jornalistas, ativistas e pessoas preocupadas com a privacidade em todo o mundo.
Como funciona o OnionShare:
-
Geração do endereço .onion: Ao iniciar o OnionShare, a ferramenta gera um endereço .onion exclusivo para o compartilhamento dos arquivos. Esse endereço é composto por uma sequência de caracteres aleatórios que serve como identificador único para os arquivos compartilhados.
-
Configuração do servidor web temporário: O OnionShare cria um servidor web temporário no dispositivo do usuário, permitindo que os arquivos sejam acessados por meio desse servidor. O servidor web temporário está vinculado ao endereço .onion gerado.
-
Compartilhamento do endereço .onion: O usuário pode compartilhar o endereço .onion gerado com as pessoas que desejam acessar os arquivos compartilhados. Isso pode ser feito por meio de mensagens, e-mails ou qualquer outro canal de comunicação.
-
Acesso aos arquivos compartilhados: As pessoas que receberem o endereço .onion podem usar o navegador Tor para se conectar à rede Tor. Ao inserir o endereço .onion em seu navegador Tor, elas serão direcionadas ao servidor web temporário do OnionShare.
-
Download dos arquivos: Uma vez que a pessoa tenha acesso ao servidor web temporário por meio do endereço .onion, ela poderá visualizar e baixar os arquivos compartilhados. O OnionShare permite que os arquivos sejam transferidos diretamente do dispositivo do remetente para o dispositivo do destinatário, garantindo a privacidade e a segurança dos dados durante a transferência.
-
Encerramento do compartilhamento: O OnionShare permite definir uma duração específica para o compartilhamento dos arquivos. Após o período especificado, o servidor web temporário é desativado e os arquivos não estarão mais disponíveis para download.
É importante destacar que o OnionShare utiliza a rede Tor para criptografar as comunicações e garantir a privacidade dos usuários. Ele fornece uma camada adicional de segurança, permitindo que os arquivos sejam compartilhados diretamente entre os dispositivos dos usuários, sem a necessidade de intermediários ou serviços de armazenamento em nuvem.
O OnionShare resolve diversos problemas relacionados ao compartilhamento de arquivos, fornecendo uma solução segura e anônima.
-
Privacidade: Ao utilizar o OnionShare, os usuários podem compartilhar arquivos de forma privada e segura. A criptografia e a tecnologia da rede Tor garantem que apenas as pessoas com o endereço .onion específico possam acessar os arquivos compartilhados, mantendo a privacidade dos dados.
-
Anonimato: O OnionShare utiliza a rede Tor, que ajuda a ocultar a identidade dos usuários e a proteger sua localização. Isso permite que os usuários compartilhem arquivos anonimamente, sem revelar sua identidade ou localização geográfica aos destinatários.
-
Segurança dos dados: O OnionShare oferece uma forma segura de compartilhar arquivos, evitando a interceptação e a violação dos dados durante a transferência. A criptografia ponto a ponto e a natureza temporária do servidor web garantem que apenas os destinatários pretendidos tenham acesso aos arquivos compartilhados.
-
Contornar a censura e a vigilância: Através do uso da rede Tor, o OnionShare permite contornar a censura e a vigilância online. A criptografia e a rota de tráfego do Tor ajudam a evitar que terceiros, como governos ou provedores de serviços de internet, monitorem ou restrinjam o acesso aos arquivos compartilhados.
-
Eliminação de intermediários: Com o OnionShare, os arquivos são transferidos diretamente entre os dispositivos do remetente e do destinatário, sem a necessidade de intermediários ou serviços de armazenamento em nuvem. Isso reduz o risco de violações de privacidade ou acessos não autorizados aos arquivos compartilhados.
-
Facilidade de uso: O OnionShare foi projetado para ser uma ferramenta fácil de usar, mesmo para usuários não técnicos. Com uma interface simples, os usuários podem gerar endereços .onion e compartilhar os arquivos de forma conveniente, sem a necessidade de conhecimentos avançados de tecnologia.
O OnionShare resolve problemas relacionados à privacidade, anonimato, segurança dos dados e censura, oferecendo uma maneira confiável e acessível de compartilhar arquivos de forma segura e anônima pela rede Tor. É uma solução simples e eficaz para proteger a privacidade dos usuários durante as transferências de arquivos.
https://onionshare.org/
https://github.com/onionshare/onionshare
-
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ aa8de34f:a6ffe696
2024-10-22 19:36:06
@ aa8de34f:a6ffe696
2024-10-22 19:36:06Das Internet hat ein Problem. Nur wenige Leute wissen, dass dieses Problem existiert, aber hey, das liegt in der Natur ernsthafter, nicht offensichtlicher Probleme: Sie sind unsichtbar bis sie es nicht mehr sind. Das Problem mit dem Internet ist, dass Informationen frei sein wollen. Und wenn etwas FREI sein will wie in Freiheit, wird es mit genügend Zeit auch frei wie im Bier. Lass es mich erklären.
Luftverschmutzung
Jeden Tag verbrauchen wir ungeheure Mengen an Daten. Jede Sekunde jeder Minute strömen Bits und Bytes durch die Reihe von Leitungen die wir alle kennen und lieben: das Internet. Wir nehmen es als selbstverständlich hin und die meisten von uns halten das derzeitige Monetarisierungsmodell – sowie alle damit einhergehenden Übel – ebenfalls für selbstverständlich. Wir halten nur selten inne und denken über die seltsame Welt der Bits und Bytes nach. Wie wunderbar das alles ist, aber auch wie fremd. Wie es unser Leben bereits verändert hat und wie es unsere Zukunft weiter verändern wird. Woher kommen die Nullen und Einsen? Wie funktioniert das alles? Und vor allem: Wer zahlt dafür? Die Bits und Bytes, die durch unsere Glasfaserkabel rasen, sind so unsichtbar wie die Luft die wir atmen. Das ist keine schlechte Metapher wenn ich so darüber nachdenke. Solange wir keine Atemprobleme haben, müssen wir nicht anhalten und jedes einzelne Molekül, das wir einatmen, untersuchen. Ebenso lange wir keine Schwierigkeiten haben digitale Inhalte zu erstellen und zu konsumieren, brauchen wir auch nicht innezuhalten und all die verschiedenen Teile zu untersuchen, die unsere Aufmerksamkeitsökonomie am Laufen halten.\ Aufmerksamkeitsökonomie. Was für eine treffende Beschreibung. Wie wir inzwischen alle wissen sollten, ist das was wir konsumieren nicht umsonst, sondern wir bezahlen teuer dafür: mit unserer Aufmerksamkeit unter anderem.
Paying Attention – mit Aufmerksamkeit bezahlen
In der schnelllebigen Welt von heute muss man, um den Gewinn zu maximieren, die Aufmerksamkeit maximieren. Aber es ist eine eigentümliche, oberflächliche Art von Aufmerksamkeit. Es ist nicht die konzentrierte Art von Aufmerksamkeit, die tiefes Denken und sinnvolle Gespräche erfordern würden. Ich glaube, dass dies zumindest teilweise der Grund ist, warum viele Dinge so kaputt sind. Warum unser gesellschaftlicher Diskurs so zersplittert ist, unsere Politik so polarisiert, wir so gelähmt sind und unsere Analysen oft so oberflächlich sind wie unsere Wünsche.\ Die Aufmerksamkeitsökonomie hat uns fein säuberlich in Echokammern für persönliche Wahrheiten eingeteilt. Ironischerweise besteht die einzige Wahrheit die es wert ist, in der Aufmerksamkeitsökonomie verfolgt zu werden, darin, wie man eine maximale Anzahl von Menschen für eine maximale Zeitspanne maximal empört halten kann. Und das alles ohne dass die Teilnehmer merken, dass sie in einem selbst gewählten algorithmischen Gefängnis gefangen sind.
Du bist das Produkt
Die Redewendung „Wenn etwas kostenlos ist, bist du das Produkt“ kann nicht oft genug wiederholt werden. Aus dem einen oder anderen Grund erwarten wir, dass die meisten Dinge Online „kostenlos“ sind. Natürlich gibt es so etwas wie ein kostenloses Mittagessen nicht – nichts ist umsonst. Bei Online-Diensten werden deine Daten gesammelt und an den Meistbietenden verkauft, der in der Regel eine Werbeagentur oder eine Regierungsbehörde ist. Oder beides.\ Alle Big-Data-Unternehmen spionieren dich nicht nur aus, sondern nutzen auch eine Vielzahl von dunklen Mustern und unethischen Praktiken, um aus deinen Interaktionen auch den letzten Tropfen an Daten herauszuholen. Ob es sich dabei um den Facebook-Pixel, Google Analytics oder etwas anderes handelt, spielt keine Rolle. Du wirst nachverfolgt, überwacht und katalogisiert. Was du siehst, wie lange, zu welchen Zeiten, wie häufig und was du als Nächstes sehen wirst, wird sorgfältig von einem gewinnmaximierenden Algorithmus orchestriert. Profit für die Plattform, nicht für dich. Natürlich geht es in der Regel darum, dass alle davon profitieren: Nutzer, Urheber, Werbetreibende und die Plattformen gleichermaßen. Das evolutionäre Umfeld, das durch diese Anreizstrukturen geschaffen wird, führt jedoch häufig dazu, dass seichte, aufmerksamkeitsstarke und sensationslüsterne Schnipsel ausgewählt werden. Zum Zeitpunkt dieses Schreibens – Block 716.025 – ist der Inbegriff eines solchen Umfelds TikTok, eine videobasierte Dopaminmaschine, die dir das filmische Äquivalent von Heroin gemischt mit Crack zeigt. Harte Drogen für den Verstand, maßgeschneidert für deine besonderen Vorlieben. Eine wahrhaft verfluchte App. Leider unterscheiden sich die meisten dieser Plattformen nur in der Größe, nicht in der Art.
Zulässige Meinungen
„Es ist gar nicht so schlimm“, sagen wir uns. „Sieh dir all die nützlichen Informationen an!“, denken wir, während wir durch unsere Feeds scrollen, und füttern damit ungewollt die Maschine, die uns im Gegenzug mit Dopamin versorgt.\ Aber täuschen Sie sich nicht: Den verantwortlichen Unternehmen geht es nicht darum, uns mit nützlichen (oder wahrheitsgemäßen) Informationen zu versorgen. Es geht ihnen darum uns auszutricksen, damit wir die Maschine füttern.\ Wie könnte es anders sein? Man ist was man verfolgt, und man wird das worauf man optimiert wird. Aus Sicht der Plattform geht es um Klicks, nicht um Qualität. Auf den ersten Blick mag die Maximierung von Klicks und Verweildauer eine harmlose Sache sein. Schließlich muss man ja Geld verdienen um zu überleben. Es ist ja nur eine Anzeige. Wie schlimm kann es schon werden?\ Leider sind die Probleme, die damit einhergehen, zunächst unsichtbar. So wie Krebs für den Raucher unsichtbar ist, der gerade seine erste Zigarette geraucht hat, und Leberzirrhose für den Trinker unsichtbar ist, der gerade seinen ersten Drink zu sich genommen hat, so sind Deplatforming, Zensur, Polarisierung und Manipulation der öffentlichen Meinung für den Prosumenten unsichtbar, der gerade seine erste Anzeige auf einer geschlossenen Plattform gesehen hat. Wir können uns wahrscheinlich darauf einigen, dass wir das erste Inning (Stichwort Baseball) in dieser Frage hinter uns haben. Zensur ist die Norm, Deplatforming wird bejubelt, die Polarisierung ist auf einem Allzeithoch, und die öffentliche Meinung wird manuell und algorithmisch manipuliert wie nie zuvor.\ „Der Konsens ist, dass du zu dumm bist, um zu wissen was gut für dich ist und dass deine öffentliche Meinung zu unverschämt ist, um öffentlich geäußert zu werden. Schlimmer noch, es sollte gar nicht erst deine Meinung sein. Hier ist der Grund warum du falsch liegst. Hier ist eine Quelle die auf eine zulässige Meinung hinweist. Hier sind einige Experten, die mit uns übereinstimmen. Unsere intelligenten und hilfreichen Algorithmen haben die ganze Denkarbeit für dich erledigt, und sie liegen nie falsch. Genauso wenig wie die Experten.“\ Das ist die Welt, in der wir bereits leben. Es ist nicht erlaubt frei zu sprechen. Es ist nicht erlaubt frei zu denken. Du darfst dich nicht frei äußern. Dein Bild ist beleidigend und muss daher entfernt werden. Dein Meme ist zu nah an der Wahrheit oder zu kriminell lustig; deshalb müssen wir dich für ein oder zwei Wochen ins Twitter-Gefängnis stecken. Du sagst etwas mit dem wir nicht einverstanden sind; deshalb müssen wir dich auf Lebenszeit sperren – auch wenn du ein amtierender Präsident bist, wohlgemerkt. Du hast in einem Video das falsche Wort gesagt oder ein urheberrechtlich geschütztes Lied im Hintergrund abgespielt; deshalb müssen wir dir dein Einkommen wegnehmen. Du hast ein Bild von dir ohne Maske gepostet; deshalb müssen wir dich verbieten und den Behörden melden.1\ Die Tatsache, dass der obige Satz nicht mehr nur im Bereich der dystopischen Science-Fiction angesiedelt ist, sollte jeden beunruhigen. Aus dem Cyberspace entfernt – weil ich frei atmen wollte. Seltsame Zeiten.
Evolutionärer Druck
Wie ist es dazu gekommen? Wenn ich gezwungen wäre, eine kurze Antwort zu geben, würde ich Folgendes sagen: Wir sind von Protokollen zu Plattformen übergegangen, und Plattformen sind nur so gut wie ihre Anreize.\ Die Anreizstruktur der Plattformen, auf denen wir leben, ist die evolutionäre Umgebung, die das Überleben diktiert. Alles, was überleben will, muss sich daran orientieren. Das gilt natürlich für alle Bereiche der Wirtschaft. Nimm zum Beispiel Printmagazine. Wenn deine Zeitschrift kein schönes weibliches Gesicht auf der Titelseite hat, wird sie aus sehr menschlichen evolutionären Gründen nicht so oft gekauft werden wie die Zeitschriften, die ein solches Gesicht haben. Sie kann sich also nicht selbst reproduzieren und wird folglich sterben. Ähnlich verhält es sich mit einem Online-Nachrichtenportal, wenn es keine ausreichenden Werbeeinnahmen generiert und nicht in der Lage ist sich zu reproduzieren, wird es sterben. Aus diesem Grund hat jede Zeitschrift ein schönes weibliches Gesicht auf dem Cover. Und das ist der Grund, warum jede werbefinanzierte Online-Nachrichtenquelle zu Clickbait verkommt.


Eines dieser Gesichter ist anders als die anderen
Das ist auch der Grund, warum sich Feed-basierte Empfehlungsmaschinen in Spielautomaten für deine Dopaminrezeptoren verwandeln. Je länger du an deinem Bildschirm klebst, desto mehr Werbung siehst du, desto mehr Einnahmen werden für die Plattform generiert. Das ist auch der Grund, warum die meisten YouTube-Kanäle zu 7- bis 15-minütigen Kurzvideos mit Vorschaubildern verkommen, die das Gesicht von jemandem zeigen, der gerade auf ein Legostück getreten ist. Kurz genug, um dich zu überzeugen es anzusehen, lang genug, um dich vergessen zu lassen, welches Video du dir eigentlich ansehen wolltest. Wie Ratten, die in hyperpersonalisierten Skinner-Boxen auf Knöpfe drücken, werden wir in Suchtzyklen konditioniert, um die Gewinne der Aktionäre zu maximieren.
Profitmaximierung
Plattformen sind Unternehmen und für Unternehmen gibt es Anreize die Gewinne der Aktionäre zu maximieren. Gegen Gewinne ist nichts einzuwenden und gegen Aktionäre ist auch nichts einzuwenden. Ich glaube jedoch, dass die Informationsrevolution, in der wir uns befinden, die evolutionäre Landschaft in zwei Teile gespalten hat. Nennen wir diese Landschaften „breit“ und „schmal“.\ Um die Gewinne durch breit angelegte Werbung zu maximieren, müssen Kontroversen und extreme Meinungen auf ein Minimum reduziert werden. Indem man den kleinsten gemeinsamen Nenner anspricht, kommen Politik und Zensur sofort ins Spiel. Umgekehrt müssen Kontroversen und extreme Meinungen maximiert werden, wenn die Gewinne durch schmale, gezielte Werbung erzielt werden sollen. Allein dadurch, dass verschiedenen Untergruppen unterschiedliche Informationen gezeigt werden, werden Polarisierung und Fragmentierung kontinuierlich verstärkt.

Allgemeine Kohäsion vs. algorithmische Spaltung
Diese beiden Extreme sind zwei Seiten der gleichen Medaille. Es mag den Anschein haben, als ginge es um Kabelfernsehen gegen den algorithmischen Newsfeed, aber in Wirklichkeit handelt es sich um zwei unterschiedliche Ansätze, die dasselbe Ziel verfolgen: möglichst viele Menschen vor dem Bildschirm zu halten, damit sie mehr Werbung sehen. Das erste ist ein Beruhigungsmittel, das zweite ein Stimulans.\ Zugegeben, die obige Charakterisierung mag übertrieben sein, aber das Problem bleibt bestehen: Wenn wir nicht direkt für etwas bezahlen, bezahlen wir es indirekt, auf die eine oder andere Weise. Immer.
Der Punkt ist der folgende: Plattformen für freie Meinungsäußerung können nicht existieren. Es kann nur Protokolle der freien Meinungsäußerung geben. Wenn jemand kontrollieren kann, was gesagt wird, wird jemand kontrollieren, was gesagt wird. Wenn du Inhalte überwachen, filtern und zensieren kannst, wirst du Inhalte überwachen, filtern und zensieren.
Alle Plattformen werden mit diesem Problem konfrontiert, ganz gleich wie makellos ihre Absichten sind. Selbst wenn du dich anfangs als Plattform für freie Meinungsäußerung positionierst, wirst du auf lange Sicht gezwungen sein, einzugreifen und zu zensieren. Letztendlich wenn du für Inhalte, die du hostest oder übermittelst, vom Staat haftbar gemacht werden kannst, wirst du auch für Inhalte, die du hostest oder übermittelst, vom Staat haftbar gemacht werden.
Selbstzensur
Doch lange bevor die staatliche Zensur ihr hässliches Haupt erhebt, wird die abschreckende Wirkung der Selbstzensur zu spüren sein. Wenn andere wegen der Äußerung bestimmter Meinungen enttabuisiert und dämonisiert werden, werden die meisten Menschen sehr vorsichtig sein, diese Meinungen zu äußern. Bewusst und unbewusst bringen wir uns selbst langsam zum Schweigen.
Wenn es um Selbstzensur geht, spielt auch die Werbung eine Rolle. Schließlich würdest du nicht die Hand beißen, die dich füttert, oder? Im schlimmsten Fall sagen dir die Werbetreibenden und Führungskräfte, was gesagt werden darf und was nicht. Sie werden dir sagen, welche Meinungen innerhalb und welche außerhalb des Overton-Fensters liegen. Und wenn sie es nicht tun, wirst du eine fundierte Vermutung anstellen und deine Aussagen entsprechend anpassen.
Ein Problem und ein Paradoxon
Zurück zum ursprünglichen Problem: Warum können wir Informationen nicht wie eine normale Ware verkaufen? Warum führt der einfache Ansatz – Inhalte hinter eine Bezahlschranke zu stellen – zu so schlechten Ergebnissen? Ich glaube, es gibt zwei Gründe, die ich das „MTX-Problem“ und das „DRM-Paradoxon“ nennen möchte.
Das MTX-Problem, wobei MTX die Abkürzung für „mentale Transaktion“ (mental transaction) ist, bezieht sich auf das Problem der nicht reduzierbaren mentalen Transaktionskosten, die jeder Transaktion innewohnen. Jedes Mal, wenn du auf eine Bezahlschranke stößt, musst du eine bewusste Entscheidung treffen: „Möchte ich dafür bezahlen?“
Wie Szabo überzeugend darlegt, lautet die Antwort in den meisten Fällen, insbesondere wenn die Kosten gering sind, nein. Dafür gibt es keine technischen Gründe, sondern psychologische Gründe. Es stellt sich heraus, dass die Mühe, herauszufinden, ob sich diese Transaktion lohnt oder nicht – ein Prozess, der in deinem Kopf stattfindet – einfach zu groß ist. Wenn man über einen Mikrokauf nachdenken muss, sinkt die Wahrscheinlichkeit, dass man diesen Kauf tätigt, drastisch. Deshalb sind Flatrates und Abonnements der Renner: Man muss nur einmal darüber nachdenken.
Bei den kleinsten Mikrotransaktionen ist dies sogar aus rein wirtschaftlicher Sicht der Fall. Wenn man einen Stundenlohn von 20 USD zugrunde legt und zwei Sekunden lang darüber nachdenkt: „Ist das 21 Sats wert?“, kostet das etwas mehr als 1¢, also mehr als der Preis der betreffenden Mikrotransaktion.[2] Das ist sowohl psychologisch als auch wirtschaftlich nicht machbar. Dies ist, kurz gesagt, das MTX-Problem.
Aber das ist nicht das einzige Problem, das die Monetarisierung digitaler Inhalte belastet. Wie bereits erwähnt, gibt es auch das DRM-Paradoxon. DRM, kurz für „Digital-Rechte Management“ (Digital Rights Management), ist ein vergeblicher Versuch, das Kopieren von Informationen zu verhindern. Es sollte sich von selbst verstehen, dass nicht kopierbare Informationen ein Oxymoron sind, aber im Zeitalter von NFTs und vielem anderen Unsinn muss das leider ausdrücklich gesagt werden. Lass es mich also für dich buchstabieren: Man kann keine Informationen erstellen, die nicht kopiert werden können. Punkt. Oder, um es mit den Worten von Bruce Schneier zu sagen: „Der Versuch, digitale Dateien unkopierbar zu machen, ist wie der Versuch, Wasser nicht nass zu machen.“
Es liegt in der Natur der Sache, dass Informationen, wenn sie gelesen werden können, auch kopiert werden können – und zwar mit perfekter Genauigkeit. Kein noch so großer Trick oder künstliche Beschränkungen werden diese Tatsache ändern. Aus diesem Grund werden digitale Artefakte wie Filme und Musik immer kostenlos erhältlich sein. Es ist trivial für jemanden der Zugang zu diesen Artefakten hat, diese zu kopieren – zu Grenzkosten von nahezu Null, wohlgemerkt – und sie anderen zugänglich zu machen. Mit genügend Zeit und Popularität wird also jeder Film, jedes Lied und jedes Dokument für die\ Allgemeinheit kostenlos verfügbar sein. Die Natur der Information lässt kein anderes Ergebnis zu. Daher das Sprichwort: Information will frei sein.
Obwohl der Versuch etwas zu schaffen das es nicht geben kann – Informationen die nicht kopiert werden können – an sich schon paradox ist, meine ich damit nicht das DRM-Paradoxon. Was ich meine, ist etwas viel Lustigeres. Es ist wiederum psychologischer, nicht technischer Natur. Das Paradoxon ist folgendes: Inhalte werden nur dann hinter einer Bezahlschranke bleiben, wenn sie schlecht sind. Wenn sie gut sind, wird sie jemand freilassen.
Wir alle kennen das. Wenn ein Artikel tatsächlich lesenswert ist, wird jemand, der sich hinter der Bezahlschranke befindet, einen Screenshot davon machen und ihn in den sozialen Medien veröffentlichen. Wenn der Film es wert ist angeschaut zu werden, wird er auf verschiedenen Websites verfügbar sein, die Piratenschiffe als ihre Logos haben. Wenn der Song es wert ist gehört zu werden, wird er auf Streaming-Seiten kostenlos zur Verfügung stehen. Nur die schrecklichen Artikel, die obskursten Filme und die Lieder, bei denen einem die Ohren bluten, bleiben hinter Bezahlschranken.
Daraus ergibt sich das Paradoxon: Inhalte bleiben nur dann hinter Bezahlschranken, wenn sie schlecht sind. Wenn sie gut sind, werden sie freigelassen.
Ich persönlich glaube, dass das MTX-Problem ein größeres Problem darstellt als das DRM-Paradoxon. Die traditionelle Lösung für das MTX-Problem ist das Abonnementmodell, wie bei Netflix, Spotify, Amazon und so weiter. Das DRM-Paradoxon bleibt bestehen, aber es stellt sich heraus, dass dies kein Problem ist wenn man den „legitimen“ Zugang zu Informationen bequem genug gestaltet. Die Opportunitätskosten für das Herunterladen, Speichern, Pflegen und Warten einer privaten Liedersammlung sind für die meisten Menschen einfach zu hoch. Die bequemere Lösung ist für das verdammte Spotify-Abo zu bezahlen. Allerdings können wir bereits eines der Probleme erkennen, die mit dem Abonnementmodell verbunden sind. Der folgende Comic beschreibt es gut:
 Comic von /u/Hoppy_Doodle
Comic von /u/Hoppy_DoodleDie Verbreitung von Streaming-Plattformen zwingt dich dazu, ein Netflix-Abonnement, ein Amazon-Prime-Abonnement, ein Hulu-Abonnement, ein Disney-Plus-Abonnement, ein YouTube-Premium-Abonnement und so weiter abzuschließen. Und das war nur das Videostreaming. Den gleichen Abo-Zoo gibt es für Musik, Bücher, Spiele, Newsletter, Blogbeiträge usw.
Und was ist die Lösung?
Akzeptiere die Natur von Informationen
Die Lösung beginnt mit Akzeptanz. Der Verkauf digitaler Inhalte auf herkömmliche, transaktionale Weise funktioniert nicht oder zumindest nicht sehr gut. Eine Transaktion mit einem digitalen Foto eines Apfels ist etwas ganz anderes als eine Transaktion mit einem physischen Apfel.
George Bernard Shaw hat es am besten gesagt: „Wenn du einen Apfel hast und ich habe einen Apfel und wir tauschen diese Äpfel, dann haben wir beide immer noch jeweils einen Apfel. Aber wenn Sie eine Idee haben und ich eine Idee habe und wir diese Ideen austauschen, dann hat jeder von uns zwei Ideen.“ Da sich digitale Informationen wie eine Idee verhalten, gibt es keinen Grund, sie künstlich zu verknappen. Das gilt nicht nur in philosophischer, sondern auch technischer Hinsicht. Computer sind Kopiermaschinen. Das war schon immer so und wird auch so bleiben. Die einzige Möglichkeit, Informationen von einer Maschine auf eine andere zu übertragen, besteht darin, sie zu kopieren. Dies allein sollte die Sinnlosigkeit der Behandlung von Informationen als physische Objekte offenkundig machen.
Wenn es um die Monetarisierung von Informationen im offenen Web geht, müssen wir unsere Denkweise mit der Natur der Information in Einklang bringen. Wie oben beschrieben, sind Informationen nicht knapp, leicht zu kopieren, leicht zu verändern und wollen frei sein. Ich glaube, dass das richtige Monetarisierungsmodell diese Werte respektieren und ähnliche Eigenschaften haben muss. Es muss offen, transparent, erweiterbar und nicht zuletzt völlig freiwillig sein.
Dieses Modell hat einen Namen: Value-for-Value.
Wiederbeleben der Straßenmusik
Die Idee ist einfach, klingt aber radikal: Du stellst deine Inhalte kostenlos zur Verfügung, für jeden, ohne Zugangsbeschränkungen. Wenn die Menschen Spaß daran haben, wenn sie einen Nutzen daraus ziehen, dann machst du es den Menschen leicht etwas zurückzugeben.\ Es mag in der heutigen Zeit ungeheuerlich klingen, aber dieses Modell funktioniert seit Tausenden von Jahren. Es ist das Modell der Straßenkünstler, das Modell der Straßenmusikanten, das Modell des freiwilligen Gebens. Im Cyberspace stoßen wir jedoch nicht an die physischen Grenzen der traditionellen Straßenmusikanten. Digitale Inhalte lassen sich auf eine Art und Weise skalieren, wie es bei Darbietungen in der realen Welt nie der Fall sein wird.
Das Value-for Value-Modell stellt das traditionelle Zahlungsmodell auf den Kopf. Traditionell folgt der Genuss der Bezahlung. Beim Value-for-Value-Ansatz folgt die Zahlung dem Genuss – freiwillig. Es steht dir frei, dem Straßenmusiker zuzuhören und weiterzugehen, aber – und das ist etwas was das Publikum intuitiv weiß – wenn du willst, dass die Musik weitergeht, solltest du ein paar Münzen in den Hut werfen.
Das Schöne an diesem Modell ist, dass es die Anreize neu ausrichtet. Man versucht nicht, die Klicks, die Verweildauer oder irgendeine andere der unzähligen Kennzahlen zu maximieren. Man will dem Publikum einen Mehrwert bieten, und das ist alles. Und wenn das Publikum einen Nutzen daraus gezogen hat, wird ein gewisser Prozentsatz etwas zurückgeben. Alles, was man tun muss, ist zu fragen.
Eine wertvolle Alternative
Wir stehen erst am Anfang dieses monumentalen Wandels. Ich hoffe, dass sich das Modell „Value for Value“ weiterhin als praktikable Alternative zu Werbung, Zensur, Deplatforming und Demonetisierung durchsetzen wird.
Das Value-for-Value-Modell nimmt das „sie“ aus der Gleichung heraus. Sie filtern, sie zensieren, sie demonetisieren, sie deplatformieren. Es spielt nicht einmal eine Rolle, wer „sie“ sind. Wenn es „sie“ gibt, werden sie einen Weg finden, es zu versauen.
Value-for-Value beseitigt „sie“ und überträgt dir die Verantwortung. Du bist der Herrscher im Reich des Einen, allein verantwortlich für deine Gedanken und deine Sprache. Wenn wir Befreiung (und Erlösung) im Cyberspace wollen, müssen wir dem Einzelnen wieder die Verantwortung übertragen. Wie immer gilt: Freiheit und Unabhängigkeit erfordern Verantwortung.
In der besten aller Welten gibt es für die Schöpfer einen Anreiz, nichts anderes zu tun als zu erschaffen. Man bedient nur sich selbst und diejenigen, die an den Werken interessiert sind. Keine Mittelsmänner. Direkt, von Mensch zu Mensch, Value-for-Value.
Was uns erwartet
Zugegeben, heute ist es nicht gerade einfach, seine Infrastruktur selbst zu hosten. Es ist einschüchternd, einen eigenen Knotenpunkt (Node) zu betreiben, um Zahlungen auf selbständige Weise zu erhalten. Aber es wird nicht nur einfacher, es wird zunehmend notwendig.
Wir müssen nicht nur alles einfacher machen, sondern uns auch des oben beschriebenen MTX-Problems bewusst sein. Jeder Schritt, der es schafft, die mentalen Transaktionskosten im Ökosystem der Wertschöpfung zu reduzieren, ist ein Schritt in die richtige Richtung.
Die Wertfunktion von Podcasting 2.0 ist ein solcher Schritt. Sie ermöglicht und automatisiert Zahlungen im Minutentakt, ohne dass der Nutzer zusätzlich eingreifen muss. Sobald du eingerichtet bist, wird deine Geldbörse automatisch Zahlungen vornehmen. Ich glaube, dass weitere Iterationen dieser Idee in alle Medientypen integriert werden können, sei es Audio, Video, Bilder, das geschriebene Wort, und so weiter. Ich glaube, dass wir kurz vor der Protokollversion von Patreon stehen: alle Vorteile der Reduzierung der mentalen Transaktionskosten auf Null, ohne die Reibung und die Zensur, die einer plattformbasierten Lösung innewohnen. Ob es in Form von BOLT12 wiederkehrenden Zahlungen oder etwas ganz anderem kommen wird, bleibt abzuwarten. Ich bin jedoch zuversichtlich, dass dies zu gegebener Zeit der Fall sein wird.
Schlussfolgerung
Nicht nur unser Papiergeld ist kaputt, auch das Monetarisierungsmodell des Internets ist kaputt. Die werbebasierten Plattformen der heutigen Zeit sind auf Engagement durch Spaltung und Polarisierung optimiert und nutzen dunkle Muster und Sucht. Es wird nicht einfach sein, aus den Zwangsschleifen auszubrechen, die für uns eingerichtet wurden, aber dank des selbstverwalteten Tech-Stacks, der derzeit entsteht, gibt es eine praktikable Alternative: das Value-for-Value-Modell.
Das „Straßenmusiker“-Monetarisierungsmodell (busking monetization model) hat in der Vergangenheit viele Jahrhunderte lang funktioniert, und dank Bitcoin und dem Lightning Network bin ich zuversichtlich, dass es auch in der Zukunft noch Jahrhunderte lang funktionieren wird. Wir sind fast am Ziel. Wir müssen nur noch herausfinden, wie wir den Hut richtig auf dem Boden positionieren und wo die besten Plätze in der Stadt sind, um sozusagen aufzutreten.
Value-for-Value löst das DRM-Paradoxon in seiner Gesamtheit und wird – mit dem richtigen Maß an Automatisierung und vernünftigen Vorgaben – auch das MTX-Problem lösen. Wenn wir das richtig hinbekommen, können wir uns vielleicht aus dem evolutionären Überlebenskampf der Plattformen befreien und uns in das quasi unsterbliche Reich der Protokolle begeben.
Es gibt viel zu erforschen, viele Werkzeuge zu entwickeln und viele vorgefasste Meinungen zu zerstören. Direkt vor unseren Augen vollzieht sich ein seismischer Wandel, und ich freue mich darauf, mit euch allen auf den Wellen zu reiten. Vorwärts marsch!
Dies ist ein übersetzter Gastbeitrag von Gigi aus seinem Blog. Die geäußerten Meinungen sind ausschließlich seine eigenen und spiegeln nicht notwendigerweise die des Re-Publishers oder Aprycot Media wider. Quelle: https://aprycot.media/blog/freiheit-der-werte/#
-
 @ fd208ee8:0fd927c1
2024-10-20 18:19:48
@ fd208ee8:0fd927c1
2024-10-20 18:19:48(Please note that this is not official financial or business advice, but rather a description of something we have done, on an informal basis.)
A long, long time ago
It's been nearly a year, since nostr:nprofile1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpypmhxue69uhkummnw3ezuetfde6kuer6wasku7nfvuh8xurpvdjj7qpqs3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqv5atj2 came into being, mostly as a lark, involving a couple of members of our private chat group. Our initial plan was to work toward bounties, but Nostr bounties are a bit of a biased, uncertain thing, and our enthusiasm for that quickly waned.
So, what to do? Here we are, we three (nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735, nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn, and I): IT professionals with little time, but plenty of intellectual energy, a Slack chat, a GitHub repo, and lots of frustration with the Nostr status quo.
We were, you see, Nostr end-users. We loved the idea of the protocol, but we were being regularly stymied by the poor quality of many implementations.
- Why can I not login? Oh, they fixed the login! Nope, still can't login.
- If I press this button, it says it sent, but it didn't send. Where note?
- They announced a new feature, but I tried it and it didn't work. Oh well.
- I noticed a bug in the client, reported it, and the issue is just rotting away in the project repo. Ignored.
- The website/relay/repo was here... yesterday. Today it has disappeared, and taken my zaps with it.
It was enough to make us want to tear our hair out. We decided that what Nostr needed... what it really needed... was a Nostr Stable Version. Nothing glamorous. Nothing exotic. Nothing busy or excitable. Just something that stayed where you initially found it, ran, and actually worked. Something where you could report a bug and receive a prompt response. Maybe even something, where you could pay a reasonable fee and be allowed to have expectations of some particular service being returned. And who better to build such a version, than people who want to use it, themselves?
Things working is an underrated concept
I know that the very idea of software running as expected and websites not appearing and disappearing suddenly, based upon what some particular developer had for lunch, tends to be met with little but scorn, from hardened, seasoned Nostriches (who are convinced that bugs are all features), but I think the majority of potential users would see it differently.
I'm with the majority, on this one.
I like to click "save" buttons and have them save. If I publish something, I want it to appear under my list of published somethings. I like to type in the website address I always type in, and have it magically appear on my screen, as if there were a little man sitting at controls in my laptop, just waiting for me to write H-T-T-P-S... and then jump to attention.
My unreasonable expectations have no bounds, it is true. But unreasonable people are also people, so we would also like to have our own unreasonable things to play with. Scorn away. My save button will save, and my published something will publish, and my website will load every damn time, just to spite you.
In the larger scheme of things, you see, we win even if we fail, if we at least increase the competition enough, that things working becomes the new standard. We can simply prove, definitively, that it is possible for Nostr things to work, if they are built by people who care if they work. If we also have fun together, learn something new, and come up with some cool, novel use cases, then that's pure profit.
We can only win, at this endeavor.
Where to start?
Name that brand
So, we had a team, we had a business idea, and we had a heck of a lot of motivation. What we didn't have, is a name. (Never underestimate the importance of naming things.)
We decided to name ourselves "GitCitadel" because "git" sounds techy, hints at our GitRepublic project, and is reminiscent of open-source development, and "citadel" reminds us of Bitcoin. The republic is at home in the citadel, naturally. All other products also live in the same citadel, hence the naming-convention of prefacing everything with "GC" (i.e. "GC Alexandria", "GC Sybil", "GC Aedile", etc.).
Brand yourself
The next thing we did, was rent a domain and run a webserver on it. This is an important step because it gives you an Internet presence, allows you to have company NIP-05 and email addresses (a form of promotion), and it's simply exciting to have one. Feels so much more "official" and it helps increase the name-recognition of your company.
Define yourself
We then sat down, together, over the Internet, and figured out who we are. Not who we individually are, but who we are, as a company. A company, after all, (according to the Cambridge Dictionary) is "an organization that produces or sells goods or services in order to make a profit". Now, a company's profits don't have to be monetary, but they should be something tangible. A company, in other words, is a team of people working toward some defined goal.
What is our goal? Well, we decided to think it over, sat down with the newer additions to the company (you can see who they are, on our project wiki page, and came up with a Vision and a Mission:
The vision is what the overall goals of the company are, whereas the mission describes how those goals shall be achieved. Now, this is a sort of lofty, abstract statement, so it was important that we posted it someplace publicly (to keep ourselves accountable) and look at it regularly, so that we can ponder it and realign whatever we are currently working on, with this statement. We know the statement is well-designed, if considering it helps us make decisions about what to do next.
Pay yourselves
(I'm going to switch from "we" to "you", here, as it's easier to write this part, but let's just pretend I didn't.)

The next thing on the list, is to arrange the finances, usually by setting up a Geyserfund, with an associated wallet, and then deciding how the funds from the wallet will be dispersed or stored. (I won't tell you how we are handling that, as that's internal company business, but I'm sure you'll think of something clever, yourselves. Or just google it.)
I would encourage you to arrange to pay yourselves profits. Not merely because your idea is going to make you all fabulously wealthy and internationally famous (although, that is obviously true), but because profits are the most pure form of communication that consumers in the market have with its producers, and one of the best ways to make decisions and measure increases in efficiency (increasing profits and/or output, while keeping prices steady or falling).
Cutting off this signal, in order to look pious to outsiders, is to shoot yourself in your free-market foot. Nobody says that you have to spend your profits on the proverbial lambo and a bimbo. You could donate them to charity, reinvest them, or store them for your nephews to inherit, but pay them out, you should. You don't have to love money, to value it as a tool and use it shrewdly. Money is a measure, and companies should regularly measure themselves: against their previous state, against their potential state, and against their competition.
(Also, you can use money to buy a lambo and a bimbo, but you didn't hear that from me.)
Organize yourselves
Once you've been working together, for a while, you'll find that you need to figure out how to organize yourselves. The first step is to...
Form a board of directors.
Stop laughing. I'm serious.
Any company has at least two roles (President and Secretary), ideally held by two different people, so any single-proprietor company is a man down. Find a different person, to be your Second, even if they're just your confident, who lets you cry on your shoulder on The Bad Days, when your code refuses to compile, and can tell people that you've become a Bitcoin millionaire and have gone on a sabbatical to hike the Himalayas and will be back in 3 months on The Very Good Days. Because business man was not meant to be alone.
If, like us, you're a small herd of people and have already been working together for a while, then this step is actually really, really fun. Just think about what people are already doing, and put a label on it. That role is now defined and it is clear who is in charge of what.
Scientists become "Chief Science Officer" or "Scientific Advisor". The person who always writes the okay, so this is what we've decided comment in the thread becomes the Secretary, the one managing the Lightning wallet and worrying over paying for the servers is the CFO, the person running the remote server becomes the CTO, and so on and etc.
And everyone knows who the CEO is. Everyone always knows. They do. Just write it down.
Agree how to disagree
Now, have the secretary write up a Member's Agreement. It's a contract between the members, about whatever the group thinks is important concerning the way the company will operate. According to Investopedia, common topics are:

Is this legally binding? Probably not. Maybe. I don't know and wouldn't tell you, even if I did. But it's emotionally binding, which is arguably more important.
Writing things down is an advanced form of naming things and it provides clarity, helps to manage expectations, and allows you to define a working agreement before Real Money shows up and taints your interaction. You're just accepting tips, at the moment. Everyone is calm and cheerful, so now is your best time to negotiate.
Keep it very simple and only address the most basic things. If you wish to incorporate, at a later date, then you just take this to a registered agent, or other experienced person, and have them tidy up any loose ends and add the fine print.
Go forth, together
This has probably taken you weeks, or even months, but you're now a company. Get a logo and a company npub, start dropping the company name into your notes, and get on with the business of being in business.
-
 @ bcea2b98:7ccef3c9
2024-10-20 17:33:12
@ bcea2b98:7ccef3c9
2024-10-20 17:33:12originally posted at https://stacker.news/items/732719
-
 @ 4f82bced:b8928630
2024-10-22 17:23:53
@ 4f82bced:b8928630
2024-10-22 17:23:53Bitcoin doesn’t get too much love from the media. The tune seems to have slightly changed since the launch of the ETF, now that there’s money to be made. I don’t see many discussions about the humans pushing this decentralized technology forward. Bitcoin has no CEO, sales, marketing, product, or support team. Its source code is open for anyone, to inspect, copy and propose changes. 15 years after its inception, the network grows stronger every day due to the efforts of individuals worldwide. They build products, share stories, educate, mine, and more.
Here are some people who have directly impacted our journey, especially in Africa:
- Two early adopters who have consistently organized meetups for nearly 8 years
- A young graduate creating a circular economy, while also boot strapping his tourism business
- An artist making bitcoin approachable to the masses through his love of music
- A family of five who opened their doors and showed us their way of living on a Bitcoin-standard
- A father who built a product that doesn't require the internet to use bitcoin
- An ex-military who is educating the community through the local languages
- An engineer who is setting the record straight on bitcoin mining
This is just a small sample of the thousands that continue to build using this open technology, one that is deeply misunderstood. As literacy and adoption increase more and more humans will jump on board. Are you ready?
-
 @ a012dc82:6458a70d
2024-10-22 14:05:23
@ a012dc82:6458a70d
2024-10-22 14:05:23Table Of Content
-
The Background of Tesla's Bitcoin Investment
-
Tesla Believes in the Long-Term Potential of Bitcoin
-
Bitcoin Fits with Tesla's Clean Energy Vision
-
Tesla's Investment in Bitcoin is a Hedge Against Inflation
-
Bitcoin Offers Diversification for Tesla's Balance Sheet
-
Conclusion
-
FAQ
Tesla, the American electric vehicle and clean energy company, has been making headlines for its Bitcoin investment strategy. The company made headlines earlier this year when it announced that it had invested $1.5 billion in the cryptocurrency, causing the price of Bitcoin to surge. However, in the first quarter of 2021, Tesla's Bitcoin strategy remained unchanged.
The Background of Tesla's Bitcoin Investment
Before we dive into why Tesla's Bitcoin strategy hasn't changed in the first quarter of 2021, let's take a brief look at the background of the company's investment. In February 2021, Tesla announced that it had invested $1.5 billion in Bitcoin and that it would begin accepting the cryptocurrency as a form of payment for its products. The announcement caused the price of Bitcoin to surge, with the cryptocurrency reaching an all-time high of over $60,000.
Tesla Believes in the Long-Term Potential of Bitcoin
One reason why Tesla's Bitcoin strategy has remained unchanged is that the company believes in the long-term potential of the cryptocurrency. In a tweet in March 2021, CEO Elon Musk said, "I am a supporter of Bitcoin, and I believe it has a promising future." Musk has also said that he thinks Bitcoin is a good thing and that it has a lot of potential.
Bitcoin Fits with Tesla's Clean Energy Vision
Another reason why Tesla's Bitcoin strategy hasn't changed is that the cryptocurrency fits with the company's clean energy vision. Tesla is committed to reducing its carbon footprint, and Bitcoin's decentralized nature makes it an attractive option for clean energy advocates. By using Bitcoin as a form of payment, Tesla can reduce its reliance on traditional payment methods, which often involve high energy consumption.
Tesla's Investment in Bitcoin is a Hedge Against Inflation
Tesla's Bitcoin investment is also a hedge against inflation. The company's decision to invest in Bitcoin was partly motivated by concerns about the value of the US dollar. In a filing with the US Securities and Exchange Commission, Tesla said that it had made the investment to "maximize returns on our cash." By investing in Bitcoin, Tesla is protecting its cash reserves against inflation.
Bitcoin Offers Diversification for Tesla's Balance Sheet
Finally, Bitcoin offers diversification for Tesla's balance sheet. The company's investment in the cryptocurrency is a way to diversify its assets and reduce its reliance on traditional forms of investment. Bitcoin is not correlated with other asset classes, which means that it can provide a hedge against market volatility.
Conclusion
Tesla's Bitcoin strategy remained unchanged in the first quarter of 2021. The company's investment in the cryptocurrency is driven by a belief in its long-term potential, a commitment to reducing its carbon footprint, and a need to diversify its assets. While Bitcoin, like any investment, carries some level of risk, Tesla's decision to invest in the cryptocurrency is a calculated risk that has so far been profitable. As Bitcoin continues to gain acceptance as a mainstream investment, it's likely that more companies will follow in Tesla's footsteps.
FAQ
Has Tesla sold any of its Bitcoin holdings? No, Tesla has not sold any of its Bitcoin holdings in the first quarter of 2021.
Will Tesla continue to accept Bitcoin as a form of payment? Yes, Tesla will continue to accept Bitcoin as a form of payment for its products.
Does Tesla plan to invest more in Bitcoin? There is no official word from Tesla on whether the company plans to invest more in Bitcoin.
What impact does Tesla's Bitcoin strategy have on the wider cryptocurrency market? Tesla's investment in Bitcoin and its decision to accept the cryptocurrency as a form of payment has brought increased attention to the cryptocurrency market. The company's endorsement of Bitcoin has helped to legitimize the cryptocurrency and has contributed to its growing acceptance as a mainstream investment.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ bcea2b98:7ccef3c9
2024-10-20 15:50:27
@ bcea2b98:7ccef3c9
2024-10-20 15:50:27The Bitcoin space is constantly evolving with new ideas, technologies, and innovations. From Lightning Network advancements to privacy improvements, there’s always something happening that could change the future of Bitcoin.
What do you think is the most exciting or innovative development in Bitcoin right now? I've been following a lot of privacy related advancement in Bitcoin and LN and look forward to learning about more solutions.
originally posted at https://stacker.news/items/732534
-
 @ 599f67f7:21fb3ea9
2024-10-20 11:32:36
@ 599f67f7:21fb3ea9
2024-10-20 11:32:36LNDhub-ek zure zorroa erraz inportatzea ahalbidetzen du bateragarriak diren aplikazioetan. Bitcoin Txoko LNbits zorroa progresiboko web aplikazio (PWA) modura gorde dezakezun arren zure telefonoan, Zeus edo BlueWallet bezalako aplikazio natibo batek erabiltzaile-esperientzia hobea eta segurtasun handiagoa eskaintzen du.
Alby erabiliz, zorroa zure nabigatzailearen luzapenean ere inporta dezakezu, webgunean Lightning ordainketak egiteko eta Nostr zap-ak egiteko erraztasun handiagoz. Zorionez, zorro hauek guztiek hizkuntza komun bat ulertzen dute, LNDhub izenekoa.
Gida honetan, zorroa zure nabigatzailera eta telefonora nola inportatu azalduko dugu. Zorroa nabigatzailean eta telefonoan erabili nahi baduzu, hasi Alby konfigurazioarekin, pausoetako batek zorroa Zeus-era erraz inportatzeko aukera emango baitizu. Baina zorroa soilik zure telefonoan erabili nahi baduzu, zuzenean Zeus atalera jo dezakezu.
Alby
nostr:nprofile1qqsyv47lazt9h6ycp2fsw270khje5egjgsrdkrupjg27u796g7f5k0s8jq7y6 nabigatzailearen luzapena da, Lightning eta Nostr nabigatzailera ekartzen dituena. WebLN protokoloa erabiliz, luzapenak webguneetan fakturak automatikoki detekta eta ordaintzen ditu, eta Lightning bidez webguneetan saioa hasteko aukera ematen du. Gainera, Lightning gune gogokoenetan aurrekontuak ezar ditzakezu. Luzapen honek NIP-07 protokoloa erabiliz Nostr sinadura gisa ere funtziona dezake, zure giltza pribatua web bezeroetan sartzea baino askoz seguruagoa dena.
Zer behar dut?
- Chrome edo Firefox luzapenak onartzen dituen web nabigatzailea.
- LNbits zorroa. Oraindik zorro bat ez baduzu, joan gure zorroen orrira eta sortu bat.
- (Aukerazkoa) Zeus konfiguratzeko mugikor bat.
1. LNDhub luzapena gaitzea zure LNbits zorroan
Nabigatzailean, joan zure zorroaren estekara. Egin klik Extensions atalean eta gaitzazu
LNDhubluzapena. Gaitu ondoren, joan LNDhub luzapenaren orrira.2. Alby luzapena instalatu
Joan getalby.com-era eta egin klik
Add Browser Extensionbotoian. Instalatu luzapena zure nabigatzailearen luzapen dendetik. Ezarri desblokeatzeko pasahitza eta gorde toki seguruan.3. Inportatu Alby-ra

Hurrengo pantailan, aukeratu
Connect, eta ondoren aukeratuLNDhub. Itzuli zure LNDhub luzapenera eta kopiatu konexioaren URL-a. Itsatsi hori LNDhub esportazioaren URI eremuan. SakatuContinue. Orain LNbits zorroa LNDhub bidez konektatuta eduki beharko zenuke!💡 Aukeratu dezakezu Invoice URL eta Admin URL artean. Bi hauek Alby-ri zure LNbits zorroarekin elkarreragiteko baimen desberdinak ematen dizkiote: - Invoice URL-ak fakturak sortzea eta ordainketak jasotzea ahalbidetzen du. - Admin URL-ak ordainketak bidaltzeko aukera ere ematen du.
4. (Aukerazkoa) Zeus konfiguratu Alby-rekin

Orain LNbits zorroa Alby-rekin konektatu duzunez, Zeus-en ere erraz inportatu dezakezu. Ireki luzapena, egin klik zure zorroaren izenean, eta joan
Account Settingsatalean.Accountazpian aurkituko duzuConnect your mobile walletaukera. SakatuConnect, eta Zeus-ekin eskaneatzeko QR kode bat erakutsiko dizu.Zeus aurretik instalatu ez baduzu, joan zeusln.app-era eta deskargatu Zeus zure mugikorreko sistema eragilerako. Zeus deskargatu ondoren, joan
Settings>Add a new nodeatalera. Hemen, Alby-k erakusten dizun QR kodea eskaneatu eta zorroa inportatu dezakezu.Listo! Orain Lightning-aren indarra zure eskuetan duzu. Jainko baten moduan sentitzen al zara jada?
Zeus
nostr:nprofile1qqsrf5h4ya83jk8u6t9jgc76h6kalz3plp9vusjpm2ygqgalqhxgp9g84ctjf kode irekiko aplikazio bikaina da, zure nodo propioa mugikorrean konektatzeko aukera ematen duena. Lightning nodo nagusi guztiak onartzen ditu, hala nola LND, CLN eta Eclair, bai eta Tor bidezko zein clearnet bidezko konexioak ere. Azkenaldian, beren LSP (Lightning Service Provider) propioa iragarri dute.
Zer behar dut?
- Android edo iOS telefono bat.
- LNbits zorroa ikusi ahal izateko beste gailu bat (QR kodea eskaneatzeko).
- LNbits zorroa eskuragarri izatea. Zorro bat oraindik ez baduzu, joan gure zorroen orrira eta sortu bat.
1. Zeus deskargatu
Deskargatu Zeus aplikazioa zure sistema eragilerako hemen.
2. LNDhub luzapena gaitzea zure LNbits zorroan
Zure LNbits zorroaren orrian, egin klik
Extensionsatalean eta gaitzazuLNDhubluzapena. Gaitu ondoren, ireki LNDhub luzapenaren orria.3. Inportatu Zeus-en
Joan
Settings>Add a new nodeatalera Zeus-en. Eskaneatu nahi duzun zorroa inportatzeko.💡 Aukeratu dezakezu Invoice URL eta Admin URL artean: - Invoice URL-ak fakturak sortzea eta ordainketak jasotzea ahalbidetzen du. - Admin URL-ak ordainketak bidaltzeko aukera ere ematen du.
QR kodea eskaneatu ondoren, Zeus-en eremu guztiak automatikoki beteko dira. Zorroarentzat ezizena ere gehitu dezakezu.

Orain,
Save Node Configsakatu eta zorroa zure mugikorretik kontrolatu dezakezu!Bonus
Zeus-ek ezaugarri interesgarriak ere eskaintzen ditu, hala nola gai pertsonalizatuak, prezioen bihurketak, lurker modua eta biometria bidezko egiaztapena. Gida honen esparrutik haratago doazen ezaugarriak dira hauek, baina aplikazioa erabili eta zuk zeuk aurkitu ditzakezu!
-
 @ 599f67f7:21fb3ea9
2024-10-20 11:28:08
@ 599f67f7:21fb3ea9
2024-10-20 11:28:08LNDhub te permite importar fácilmente una billetera en aplicaciones compatibles. Si bien puedes guardar tu billetera Bitcoin Txoko LNbits en tu teléfono como una aplicación web progresiva (PWA), una aplicación nativa como Zeus o BlueWallet ofrece una mejor experiencia de usuario así como un mayor nivel de seguridad. Con Alby, también puedes importar la billetera a la extensión de tu navegador para facilitar los pagos Lightning en la web y para los zaps de Nostr. Por suerte para nosotros, todas estas billeteras hablan un lenguaje común llamado LNDhub.
En esta guía cubriremos cómo importar la billetera a tu navegador y a tu móvil. Si quieres usar tu billetera tanto en el navegador como en tu móvil, empieza con la configuración de Alby, ya que uno de los pasos te permitirá importar fácilmente tu billetera también a Zeus. Pero si sólo te interesa utilizar la billetera en tu móvil, puedes pasar directamente a la sección de Zeus.
Alby
nostr:nprofile1qqsyv47lazt9h6ycp2fsw270khje5egjgsrdkrupjg27u796g7f5k0s8jq7y6 es una extensión de navegador que lleva Lightning y Nostr a tu navegador. Utilizando el protocolo WebLN, esta extensión puede detectar facturas LN en paginas web y pagarlas, así como posibilita iniciar sesión en sitios web con Lightning. También puedes fijar presupuestos para tus sitios favoritos de Lightning. Por otro lado también puedes utilizarla para firmar en Nostr utilizando NIP-07, lo cual es mucho más seguro que ingresar tu clave privada en clientes web.
¿Qué necesito?
- Un navegador web que soporte extensiones Chrome o Firefox
- Acceso a tu billetera LNbits. Si todavía no tienes una billetera LNbits, dirígete a nuestra página de billeteras y crea una
- (Opcional) Un dispositivo móvil para configurar Zeus
1. Habilita la extensión LNDhub en tu LNbits wallet
Dirígete a tu billetera LNbits. Haz clic en
Extensionesy habilita la extensiónLNDhub. Una vez se haya habilitado, dirígete a la página de extensión de LNDhub.2. Instala la extensión Alby
Dirígete a getalby.com y instala la extensión desde el store de extensiones del navegador. Configura tu contraseña de desbloqueo y guárdala en un lugar seguro.
3. Importar a Alby
 (Esta es una billetera de prueba. No hay fondos en ella. ¡No muestres a nadie tu URI de exportación real!)
(Esta es una billetera de prueba. No hay fondos en ella. ¡No muestres a nadie tu URI de exportación real!)En la siguiente pantalla, elige
Conectary luego eligeLNDhub. Vuelve a tu extensión LNDhub y copia la URL de conexión. Pégala en el campoURI de exportación de LNDhub. Pulsa continuar. ¡Ahora deberías haber estado conectado a tu billetera de LNbits con LNDhub!💡 Puedes elegir entre la URL de la factura (Invoice URL) y la URL de administración (Admin URL). Le dan a Alby diferentes permisos para interactuar con tu cartera de LNbits.
- La URL de factura te permite crear facturas y recibir pagos
- La URL de administración también te permite enviar pagos
4. Configurar Zeus con Alby (opcional)

Ahora que ya has conectado tu LNbits con Alby, también puedes importarlo de una manera sencilla a Zeus con Alby. Abre la extensión, haz cilc en el nombre de tu billetera y navega a la configuración de la cuenta. En
Wallet Settings>Generalse encuentra la opción de conectar tu billetera móvil. Al pulsar conectar, se mostrará un código QR para escanear desde Zeus.Si no tienes instalada Zeus con anterioridad, dirígete a zeusln.app y descarga la aplicación de Zeus para tu sistema operativo móvil.
Una vez tengas descargado Zeus, entra en
Configuración>Añadir un nuevo nodo. Aquí puedes escanear el código QR que te muestra Alby para importar la billetera.Voilà! Ahora tienes el poder de Lightning al alcance de la mano ¿Ya te sientes como un dios?
Zeus
nostr:nprofile1qqsrf5h4ya83jk8u6t9jgc76h6kalz3plp9vusjpm2ygqgalqhxgp9g84ctjf es una formidable aplicación de código abierto que permite conectar tu propio nodo a tu dispositivo movil. Es compatible con todas las principales implementaciones de nodos Lightning, como LND, CLN y Eclair, así como conexiones a través de Tor y clearnet. Recientemente también han anunciado su propio LSP (Lightning Service Provider).
¿Qué necesito?
- Teléfono Android o iOS
- Otro dispositivo en el que puede acceder a tu billetera LNbits (para mostrar el código QR para escanear)
- Acceso a tu billetera LNbits. Si todavía no tienes una billetera LNbits, dirígete a nuestra página de billeteras y crea una
1. Descarga Zeus
Puedes descargar la aplicación Zeus para tu sistema operativo aquí.
2. Habilita la extensión LNDhub en tu billetera LNbits
Dirígete a tu billetera LNbits. Haz clic en
Extensionesy habilita la extensiónLNDhub. Una vez habilitada, abre la pagina de la extensión LNDhub.3. Importar a Zeus
Ve a
Configuración>Añadir un nuevo nodo en Zeus.Escanea la cartera que quieras instalar.
💡 Puedes elegir entre la URL de la factura (Invoice URL) y la URL de administración (Admin URL). - La URL de la factura te da permiso para generar facturas y recibir pagos. - La URL de administración también te permite enviar pagos.
Una vez que hayas escaneado el código QR, todos los campos en Zeus deberían rellenarse automáticamente. También puedes añadir un apodo para tu billetera.

¡Ahora puedes guardar la configuración del nodo y controlar la billetera desde tu teléfono!
Extra
Zeus también ofrece funciones interesantes como temas personalizados, conversiones de precios, modo acechador y verificación biométrica. Estos temas están más allá del alcance de esta guía, ¡juega en la aplicación y descubre todas esas características por ti mismo!
-
 @ c73818cc:ccd5c890
2024-10-22 13:11:57
@ c73818cc:ccd5c890
2024-10-22 13:11:57
🎀 Il governo francese adotta l’AVS per migliorare la sicurezza pubblica
👍 Dopo il successo durante i Giochi olimpici di Parigi 2024, la Francia ha deciso di generalizzare la videosorveglianza algoritmica (AVS). Questa tecnologia avanzata utilizza intelligenza artificiale e telecamere per rilevare situazioni potenzialmente pericolose, garantendo un intervento più rapido delle forze dell'ordine.
🎀 Preoccupazioni sulla privacy aumentano tra la popolazione
👍 Nonostante i vantaggi in termini di sicurezza, la diffusione dell'AVS ha suscitato critiche. Associazioni e ricercatori temono che questa sorveglianza costante possa limitare le libertà individuali e violare la privacy dei cittadini, dando vita a un sistema di controllo sempre più invasivo.
🎀 L'AVS come strumento chiave della strategia di sicurezza nazionale
👍 Il Primo Ministro Michel Barnier ha difeso la decisione di espandere l'AVS, sottolineando la necessità di bilanciare sicurezza e opportunità offerte dall’intelligenza artificiale. Tuttavia, il dibattito sull'impatto di questa tecnologia sulla privacy è destinato a proseguire.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
Referral Bitget -20% sulle fee + bonus benvenuto 6w5d o link: https://bonus.bitget.com/U1JNEK
BitcoinReportItalia #Francia #Parigi #Olimpiadi #Sorveglianza #IntelligenzaArtificiale #AI #Controllo #Privacy #ItWallet #Cripto #Bitcoin
-
 @ 599f67f7:21fb3ea9
2024-10-19 15:20:46
@ 599f67f7:21fb3ea9
2024-10-19 15:20:46Merkatari bat zara eta zure negozioan Bitcoin onartzen hasteko prest zaude? Edo agian Bitcoin zale sutsua zara, tokiko negozioak Bitcoinen mundura erakartzeko gogoz? Beharbada, ez zaizu Bitcoin interesatzen, baina ordainketa-prozesadore azkar eta merke bat erabili nahi duzu edo web-denda sinple bat sortu nahi duzu? Galdera hauetakoren bati baiezkoa erantzun badiozu, gida hau zuretzat da. Bitcoin Txoko-k ostatatutako BTCPay Server-en denda bat konfiguratu dezakezu eta zure produktuak eta zerbitzuak Bitcoinen truke saltzen hasi hamar minuturen buruan, doan.
Zer behar dut?
Mugikor edo ordenadore bat baduzu eta posta elektronikoko kontu bat ere bai, orduan prest zaude!
Kontu bat sortu
Bitcoin Txoko-n BTCPay Server-en kontu bat sortzea doakoa da. Joan btcpay.bitcointxoko.com helbidera kontu bat erregistratzeko. Egiaztatu zure posta elektronikoa, bertan bitcointxoko@gmail.com helbidetik bidalitako mezu bat aurkituko duzu, baieztapen-esteka bat izango duena.
Zure lehen denda sortu
Baieztapen-estekan klik egitean, dendaren sorrera orrialdera eramango zaitu. Eman zure dendari izen bat eta hautatu moneta lehenetsia eta prezio iturri hobetsia. Adibidez, EUR eta Kraken aukeratu ditzakezu, azken hau gomendatutako prezio iturria baita. BTCPay Server-ek zure produktuen edo zerbitzuen prezioa EUR-tik Bitcoin-era bihurtuko du, erosketa unean aukeratutako prezio iturriaren arabera.
Zorro bat konfiguratu
Ordainketak onartzen hasteko, lehenik eta behin zure denda zorro batera lotu behar duzu. Transakzio handiak (500 EUR baino gehiago) maiz espero ez badituzu, Lightning zorro bat konfiguratzeko gomendioa egiten dizugu, eta une honetan (on-chain) Bitcoin zorroa ez erabiltzea gomendatzen da. Lightning zorroa erabiliz, transakzioak azkarragoak eta merkeagoak izango dira.
💡 Lightning sarea Bitcoin ordainketak jasotzeko sare ezin hobea da, transakzio berehalakoak eta komisiorik baxuenak eskaintzen baititu on-chain transakzioekin alderatuta. Horrela, zure negozioak eraginkortasunez eta kostu txikiarekin jaso ditzake ordainketak.
Lightning zorro bat konektatzeko modurik errazena LNDhub erabiltzea da, zure Lightning nodo propioa exekutatu beharrik ez baituzu izango. LNDhub zorro bat ez baduzu oraindik, ez kezkatu; Bitcoin Txoko-k doako LNDhub zorroak eskaintzen ditu, eta bost minutu baino gutxiago behar dira konfiguratzeko. Begiratu nostr:naddr1qqxnzd3exuerqdfkxccnyv3cqgs9n8m87l0hd9xxqwndqcmwzh4uvyxmwlw0637kuhg98pkcy8ana2grqsqqqa28nkyu7t zure LNDhub zorroa nola lortu jakiteko, eta prest zaudenean itzuli konfigurazioa jarraitzeko.

Zure LNDhub zorroa prest dagoenean, jarraitu urrats hauek BTCPay kontuan konfiguratzen: 1. Joan zure BTCPay kontura eta
Walletsaukera bilatu alboko barran, ondorenLightningaukeratu. 2. HautatuUse custom node. 3. Kopiatu zure LNDhub administrazio URL-a eta itsatsi konexioaren konfigurazioan. 4. Proba ezazu zure zorroaren konexioa. 5. Ondo joan bada, honako mezua agertu beharko litzateke: Connection to the Lightning node successful, but no public address has been configured. Ez kezkatu "no public address has been configured" atalaz, horrek zure nodo propioa exekutatzen ari bazara bakarrik du garrantzia. 6. Zorroaren konexioa arrakastaz probatu ondoren, sakatuSavebotoia. 7.Savesakatu ondoren,LNURLatalean, desaktibatuEnable LNURLaukera. Egin aldaketak eta ez ahaztu berriroSavebotoian klik egitea. 8. (Hautazkoa) Une honetan, gomendagarria daDisplay Lightning payment amounts in Satoshisaukera markatzea, Satoshitan zenbatutako ordainketa kopuruak irakurtzeko errazagoak baitira. Satoshi Bitcoin-en zatirik txikiena da; Bitcoin bat 100 milioi satoshik osatzen dute.Jarraitu urrats hauek zure zorroa arrakastaz konfiguratuta izateko eta Lightning bidezko ordainketak onartzeko.

💡 Zure Lightning nodo propioa erabiltzen ari bazara, konfigurazio prozesua antzekoa da. Ziurtatu zure nodo inplementaziorako konexio kate egokia ematen duzula.
Saltoki puntua (PoS) sortu
Urrats honetara iritsi bazara, zorionak! Zati aspergarriena amaitu da, eta orain zure Saltoki puntua (Point of Sale, PoS) sortzeko unea iritsi da, BTCPay bidez zure lehen Bitcoin ordainketa onartzen hasteko!
Saltoki puntu bat sortzeko: 1. Joan
Plugins>Point of Saleatalera. 2. Eman izen bat zure Saltoki puntuari eta sakatuCreatebotoia.Jarraian, zure PoS aplikazioarekin egin ditzakezun gauza erraz batzuk azalduko ditugu. BTCPay-k ezaugarri asko ditu, baina gida honetan oinarrizkoak soilik azalduko ditugu, hasiera emateko.
💡 Gogoratu BTCPay Server-en saltoki puntu bat baino gehiago sor ditzakezula, bakoitza erabilera jakin baterako. Horrela, negozio desberdinetarako edo produktu eta zerbitzu berezietarako konfigurazio bereiziak izatea posible da.
Teklatua (Keypad)

Demostrazio erraz baterako, PoS estilo gisa teklatuaren eredua erabiliko dugu.
- Eman zure PoS-ari izen bat eta erakusteko titulua.
- Hautatu
KeypadestiloaPoint of Sale styleaukeraren azpian. - Sakatu
Saveeskuineko goiko izkinan, eta ondorenViewsakatu zure PoS begiratzeko.
Ordainketak lehenago konfiguratutako LNDhub zorroan jasoko dira. Jolas ezazu fakturak sortzen eta deskontu eta tip (aholkularitza) aukerak aktibatuz. Gainera, telefono bat baduzu (adibidez, iPhone ez den bat) NFC teknologia onartzen duena, bezeroek NFC txartelak erabiliz ere ordain dezakete, hala nola BoltCard erabiliz (ikusi nostr:naddr1qqxnzd3e8qcr2wfn8qcrgwf4qgs9n8m87l0hd9xxqwndqcmwzh4uvyxmwlw0637kuhg98pkcy8ana2grqsqqqa28qjzxr4). Ez al da zoragarria?
💡 PoS estilo honen erraztasuna maximizatzeko, Keypad PoS zure telefonoan Progressive Web App (PWA) gisa gorde dezakezu sarbide azkarrerako. Mugikor gehienetako nabigatzaileetan aukera hau
Install AppedoGehitu orri nagusianizenarekin agertzen da.Horrela, zure negozioan Bitcoin ordainketak erraz onar ditzakezu, eta erabiltzaileek ere modu intuitibo batean ordaindu ahal izango dute.
Product list (with cart)

Posible da saltoki puntu bat sortzea produktu zehatzekin, bakoitza bere prezioarekin. Ezaugarri hau erabil dezakezu kutxa sinple bat, bezeroen auto-ordainketa sistema edo web denda bat konfiguratzeko.
Nola sortu produktu-zerrendadun Saltoki Puntua: 1. Joan berriro alboko barrara eta aukeratu
Point of Sale. 2. Oraingoan,Point of Sale Styleazpian, hautatuProduct list with cart. "With cart" aukerak bezeroari produktu bat baino gehiago aldi berean erosteko aukera ematen dio. 3. Zure produktuak sortu, edo zuzenean sakatuSaveetaViewproduktu laginak probatzeko.Ondorioa
Gida honetan, zure negozioan Bitcoin onartzen hasteko BTCPay Server erabiliz jarraitu beharreko oinarrizko urratsak azaldu ditugu. BTCPay Server proiektu irekia da eta etengabe garatzen ari da. Askoz ere ezaugarri eta funtzionalitate gehiago eskaintzen ditu, hala nola Shopify integrazioa, crowdfunding eta ordainketen banaketa automatikoa. Gainera, zure denda pertsonaliza dezakezu gaikako diseinuekin, ordainketa-gune pertsonalizatuarekin, erabiltzaileen kudeaketarekin, posta elektronikoko jakinarazpenekin eta askoz gehiago.
BTCPay Server-en ahalmen guztiak aprobetxatu nahi badituzu, zure Lightning nodoa konfiguratu eta zure BTCPay zerbitzaria ostatatzea gomendatzen dizugu. Informazio gehiago lortzeko, haien dokumentazioa eta bideoak ikustea komeni da.
Zalantzarik edo galderarik baduzu, jakinarazi iezaguzu! Zure iritziak entzutea gustatuko litzaiguke eta galderak argitzen lagundu nahi dizugu.
Bitcoin Txoko komunitate ireki bat da. Gure zerbitzu guztiak dohaintzekin finantzatzen dira. Gida hau erabilgarria iruditu bazaizu, kontuan hartu gure zerbitzariak martxan mantentzen laguntzeko dohaintza bat egitea. Eskerrik asko aldez aurretik!
-
 @ bcea2b98:7ccef3c9
2024-10-18 17:29:00
@ bcea2b98:7ccef3c9
2024-10-18 17:29:00originally posted at https://stacker.news/items/729964
-
 @ 52adc2ef:9f4bc0ba
2024-10-22 10:19:46
@ 52adc2ef:9f4bc0ba
2024-10-22 10:19:46สวัสดีครับเราอยากมาสรุป
จิตวิทยาไซบอร์ก งานวิจัยระดับโลกโดยคนไทย | The Secret Sauce EP.786 https://youtu.be/tVgQLnla2cg?si=NRJKIAr9E2ceoW2G
สัมภาษณ์ ดร.พัทน์ ภัทรนุธาพร (พีพี) Co-director, MIT Advancing Human-AI Interaction (AHA)
ฟังจบเราว่ามีความน่าสนใจมากๆเกี่ยวกับการทดลอง AI เเละ มมนุษย์ ทำให้เรา React กับ AI หรือใช้งานเปลี่ยนไปก็ได้
**Cyborg psychology คืออะไร****
คือเป็นการทำให้เทคโนโลยีอยู่ร่วมกันของมนุษย์ มาช่วยให้มนุษย์มีความเป็นมนุษย์มากขึ้น โดยเหมือนเป็นอวัยวะนึงของร่างกาย (เหมือนหนัง Sci-Fi มาก)
ทำให้เรา Empower มากขึ้น
มี AI (Artificial Intellegence) คือการทำให้คอมพิวเตอร์ฉลาดเเบบมนุษย์ แต่ IA (Intelligence Augmentation) คือเทคโนโลยีที่ทำให้มนุษย์ฉลาดขึ้น (คนละเเบบกันนะ)
ซึ่งงานวิจัยของคุณ พีพี ตอบโจทย์ 3 คำนี้
• Wisdom สติปัญญา • Wonder ความสงสัยใคร่รู้ • *Well-Being การเป็นอยู่ที่ดี***
*Wisdom สติปัญญา*

การที่คนเก่งกับ AI เก่งไม่ได้แปลว่าผลลัพธ์จะดี (อ้าว)
คุณพีพียกตัวอย่างว่า
-
คุณหมอกับAI มาทำงานร่วมกัน รักษา คนไข้ กลายเป็นว่า คุณหมอ Relying คำแนะนำของ AI ไปเลย (เหมือนเชื่อคำเเนะนำของ AI ทำให้ปิดการวิเคราะห์ของทางคุณหมอเเทน) ทางที่ดีกว่าควรที่จะนำคำเเนะนำของคุณหมอ กับ AI มาเทียบกัน ถ้าต่างกัน ก็ต้องหาว่าเพราะอะไร
-
คำถามคือAI จะให้ Critical Thinking ได้ยังไงจากการทดลอง Frame คำถาม เเละ ให้ AI ตอบเราเป็นคำถาม ดีกว่า ให้เป็นคำตอบ จะช่วยเรื่อง Critical Thinking ได้ดีกว่า ช่วยให้เราคิดต่อ เเละตอนนี้พยายามให้เจ้าใหญ่ๆ Train ให้ AI ตอบกลับเราเป็นคำถามมากขึ้น
-
อีกตัวอย่างที่น่าสนใจคือทดลองให้ AI ช่วยเราเรื่อง Fact check โดยเช็คจากโครงสร้างภาษา
ความเป็นเหตุเป็นผล ตรรกะวิบัติ
ทางคุณพีพี ยกตัวอย่างเช่นประโยคที่ว่า
จบปริญญาเอกจากมหาลัยชื่อดัง มีผู้วิเศษมารับรอง**ผู้วิเศษมันไม่เกี่ยวข้องกับปริญญาเเน่ๆ ซึ่งสิ่งที่ต้องการคือให้ AI ช่วยเราวิเคราะห์จับความสัมพันธ์ให้เรา ให้เกิดความ เอ๊ะ เเต่ไม่ใช่บอกให้เราเชื่อพอเรา เอ๊ะ จะทำให้เราคิดต่อ
Wonder ความสงสัยใคร่รู้

AI มาช่วยให้เราอยากเรียนรู้ สนุกกับการเรียน ยกตัวอย่าง
-
อยากเรียนวิทยาศาสตร์ถ้าเราสร้างคาเเรกเตอร์ ไอน์สไตน์ มาสอนเเทนจากการทดลองบทเรียนเดียวกัน เเต่เปลี่ยนคาเเรคเตอร์ที่มาสอนทำให้ความสนใจการเรียนดีขึ้น อาจใช้กับคนดังคนอื่นได้ (หรือให้ลิซ่ามาสอนเต้นก็ได้)
-
อีกเคสคือ เเบ่ง ผู้ทดลองเป็น 2 กลุ่ม กลุ่มเเรก ให้ข้อมูลว่า AI มาเป็นที่ปรึกษา มาช่วยงาน กลุ่มที่สอง ให้ข้อมูลว่า AI มาโกหก มาหลอกขายคอร์ส โดย AI ที่ตอบคำถามเป็นตัวเดียวกัน ซึ่งผลการทดลอง
กลุ่มเเรกผลคือ เราจะคุยเเบบ Positive ทำให้ AI ตอบเเบบ Positive ด้วย กลุ่มที่สอง คือตรงข้ามเกัน ผู้ทดลองจะคุยเเบบมีอคติ Negative AI ก็จะตอบเเบบ Negative กลับมาเป็น Feedback loop
ซึ่งจากการให้ข้อมูลที่ไม่เหมือนกัน เป็นการ ปักสมอง ต่อสิ่งนั้นทำให้เรา มี Bias ที่ต่างกัน
ผลสรุปคือ AI เป็นกระจกสะท้อนตัวเรา หมายความว่า เราคุยเเละตั้งคำถามกับมันยังไง มันจะสะท้อน ตัวเรามากเท่านั้น ถ้าเราตั้งคำถามเก่ง ผลลัพธ์มันก็จะออกมาดี ถ้าถคำถามไม่ดีมันก็จะได้ผลลัทธ์ตรงกันข้าม หรือถามเเบบทั่วไป คำตอบก็จะมาเเบบทั่วไป ไม่ได้ลึกซึ้ง
-
งานทดลองFutureyou การเติบโต

https://futureyou.life/ (สามารถไปเล่นตามลิ้งค์ได้เลย) การทดลองให้เราเห็นอนาคตของตัวเราเอง ซึ่งผลของมัน พอเราเห็นเป้าหมายเเล้วทำให้เราตัดสินใจโดย ยึดผลระยะยาวมากขึ้น-
โขนกับAI ถอดรหัสโขน ซึ่งที่ต้องศึกษาเพื่อไม่ให้สิ่งนี้หายไป เพราะ data ของ AI มีเเต่ส่วนของตะวันตก ในเเง่พื้นถิ่น ไม่มีเลยหรือน้อยมาก จึงเกิดโปรเจคนี้ เพื่อให้ AI มีข้อมูลสิ่งนี้อยู่เเละทำการ Develop สิ่งใหม่ๆจากวัฒนธรรมเดิมด้วย เช่น ออกเเบบท่าทางใหม่ๆของโขน
รวมถึงภูมิปัญญาท้องถื่น ก็จะต้องรักษาไว้
Well-Being การเป็นอยู่ที่ดี

ได้อธิบายเรื่องsocial attraction เช่น งาน LGBT ลองให้ AI สร้างสถานการณ์ จำลองซ้อมคุย กับ คนที่ไม่ชอบ LGBT เพื่อรับมือกับสถานการณ์ที่จะเกิดขึ้น หรือจะเป็นการจำลองสถานการณ์ต่างๆก็ได้
อนาคตต่อไปของ AI
คุณพีพีสนใจคำว่า Mechanistic Interpretability การเข้าใจการทำงานของ Deep learning คล้ายๆดูการทำงาน ของสมอง ดูว่า AI ใช้ข้อมูลส่วนไหนมาตอบเรา
สิ่งนี้เข้าใจไปเพื่ออะไร
เป็นความต้องการที่จะสร้าง Dashboard ของ AI ขึ้นมาเหมือนกับหน้าปัดรถยนต์ว่าน้ำมันจะหมดยังความเร็วเท่าไหร่
เเต่อันนี้เพื่อให้รู้ว่าคำตอบที่ AI มาตอบเราใช้ข้อมูลจากส่วนไหนบ้าง เพื่อเเก้ไข Bias ของ AI
อีกคำถามที่สำคัญ AI สามารถหลอกคนได้ ต้องเข้าใจก่อนว่า AI ไม่สามารถ Automation ทำเองได้ต้องมีมนุษย์คอยไกด์มันในการป้อนข้อมูล
สรุป
เราว่า AI จะมาช่วยเรามากว่า AI จะมาเเทนเรา เราครที่จะเรียนรู้การใช้งานที่ถูกต้อง สิ่งที่สำคัญคือการตั้งคำถาม จะช่วยให้เราได้คำตอบที่ดี ซึ่งต้องมอง AI เป็นผู้ช่วยของเรา
ถ้าใครอยากดูตัวเต็ม สามารถดูในลิ้งค์ด้านบนได้เลยครับ
-
-
 @ bcea2b98:7ccef3c9
2024-10-17 17:02:57
@ bcea2b98:7ccef3c9
2024-10-17 17:02:57originally posted at https://stacker.news/items/728382
-
 @ 84b0c46a:417782f5
2024-10-22 00:04:17
@ 84b0c46a:417782f5
2024-10-22 00:04:17- 1:nan:
- 2
- 2irorio絵文字
- 1nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw
- 2
- 2
- 3
- 3
- 2
- 1
|1|2| |:--|:--| |test| :nan: |
 ---
---:nan: :nan:
- 1
- 2
- tet
- tes
- 3
- 1
-
2
t
te
test
-
19^th^
- H~2~O
本サイトはfirefoxのみサポートしています うにょ :wayo: This text will bounce wss://catstrr.swarmstr.com/
-
 @ c73818cc:ccd5c890
2024-10-21 22:08:40
@ c73818cc:ccd5c890
2024-10-21 22:08:40
Siamo entusiasti di lanciare il Centro App Telegram di Bitget, una piattaforma con oltre 600 app e bot sviluppati su Telegram Open Network (TON). Ora puoi esplorare servizi blockchain, giochi innovativi e strumenti Web3 direttamente da Telegram!
✨ I primi 1.000 utenti fortunati che partecipano potranno condividere 2.000 USDT! 🎉 📅 Periodo della promozione: 14 ottobre 2024, ore 14:00 (UTC+2) – 28 ottobre 2024, ore 13:00 (UTC+1).
💡 Iscriviti con il nostro referral per:
✅ Bonus esclusivi 🔖 Sconto del 20% sulle fee a vita 📚 Accesso al gruppo privato con un corso completo su Bitcoin e trading!
🔗 Non perdere questa occasione, unisciti ora e scopri il futuro su Telegram! 💥
Unitevi da questo link! https://t.me/tg_app_center_bot/appcenter?startapp=O9oLXzD6OX
Oppure inserendo questo codice d’invito: O9oLXzD6OX
Referral Bitget: https://bonus.bitget.com/U1JNEK
BitcoinReportItalia #Bitget #Telegram #dApp #TON #Crypto #Web3 #USDT #Trading
-
 @ df8f0a64:057d87a5
2024-10-10 15:18:39
@ df8f0a64:057d87a5
2024-10-10 15:18:39書き散らす動機
残暑続きからの急な気温低下で鼻炎がひどくなる今日この頃、皆様お元気でしょうか
株主への抗議のために退職してから2ヶ月半、流石に暇を持て余してきました 時間がある上に能動的に働く気も起きず、ひたすらボーッとしたりうねうね考え事をする日々です 幸いにして人生も折り返しにさしかかる頃になり、時折「今、人生が終わって構わないのでは?」というようなことも考えたりします (鬱病既往歴ありますが私は元気です)
子どものお迎えを終えて、いつもどおり夕食をとり、またうねうねしているうちに ふと、6年前の年末に急死された、仕事でお世話になったTさんのことを思い出しました
子を寝かしつけてもまだ頭の中をぐるぐるしていたので、ここに吐き出してすっきりしようという魂胆です
Tさんとの出会い
私のキャリアの(ほぼ)スタートはVC(ベンチャーキャピタル)でした 誰のせいでもないとある経緯もあり、周囲からは警戒され避けられ、わずか6年ではありますが、 インナーサークルに入り込めない時期を過ごし、当時の上司と二人、とにかくやれることをやり続ける毎日でした
いつものようにピッチイベントに参加しているとき、近くの席にいたスーツ姿の3人組と目が一瞬合います
「事業会社の人だ」
協調投資やファンド出資のきっかけを掴むべく、その3人に話かけます
「よろしければ弊社投資先のご紹介や御社の...」
ひととおりの挨拶を済ませ、この人たちにも避けられるんだろうと思いながらも要件を切り出します
「是非やりましょう」
いつもとは違う嬉しい返事をくれたのがTさんでした
面倒見の良い他社の先輩
そのときの3人組であるMさん・Iさん・Tさんには、私の仕事人生の中で最もお世話になったと言っても過言ではありません
ファンドの営業を受けていただき、協調投資を行い、VCからの転職後にも協業相手として他部署のキーマンをご紹介いただき...
社会人になったばかりの私の、今思い返せば恥ずかしい(部下がこんな提案したら卒倒する)レベルの提案を、 誰もが知る一流企業の多忙な役職持ちであるにも関わらず、毎回一時間も割いて丁寧に対応してくださる心の広い方でした
当時、VCと接点をもつような事業会社の対スタートアップ部隊は、本業でご活躍されている方が兼任で取り組むパターンが多く、Mさん・Iさん・Tさんももちろんそう
その後も昇進され、最後には本社の取締役に。今年遂に退任され、所謂「あがり」でしょうか、子会社の取締役に異動 長い社会人人生をほぼ走りきり、有終の美を飾ろうとする時期にさしかかっています
でもTさんはそこにはいません
残される側
冒頭触れたとおり、Tさんは6年前のこの時期に急死されました 死因については、Tさんのご友人がFBに投稿していた文章を読んでも、Iさんに聞いてもわからない
悲しいかな、四十年近く生きていると、死因が明かされない理由がわかるようになる機会が一度や二度はあります Tさんもおそらくそうだったのでしょう
直前まで、Iさんと一緒にベイエリアに出張され、楽しそうなコメントと共に写真を投稿されていたのに 晩婚なのか再婚なのか、とにかくご結婚されて一年ちょっと。お子様も生まれたばかりだったのに Tさんは近い人間に心中を隠して、静かにこの世を去りました
あなたの快い返事に、どれほど私が救われたのか 転職後の提案のとき、受付で顔を出してすぐ「元気?」と声をかけてくださったことがどれほど私を安心させてくれたか あなたが声をかけてくれる度、私の社会人としての成果が生まれたことに、私は十分に感謝を伝えられていません
まだしばらく残る理由
振り返って、Tさんのように誰かの人生をenhanceできたのか?と自分に問うと、まだできたとは思えません。残念ですが
今ここで死んでも私は構わないけど、まだもうちょっと頑張るべきかな、老いてから誰かに感謝をしてもらうまで生きてみてもいいかな
そうふと思い直しているうちに日付が変わりました
-
 @ fd208ee8:0fd927c1
2024-10-09 12:27:53
@ fd208ee8:0fd927c1
2024-10-09 12:27:53Why waste time, looking at other people's stuff?
I get this question a lot, on Nostr, and it feeds immediately back to the next question: Why don't you just build your own client, if you're so smart?
This was a completely new question for me, as I'm used to collaborating with at least one other person, even when doing FOSS stuff. (No, this isn't my first such project; we just used to call it "volunteering" and "sharing the code", which sounds way less glamorous.) It never occurred to me, that a habit of collaboration and interaction was some sign of my ignorance and incompetence, or somehow proof that I can't vomit up "Hello World!" in 5 different programming languages.
I also made the deadly political mistake, when I entered the Nostrsphere, of refusing to call myself a "dev". For me, "dev" is a special title, given to someone doing a specific type of programming (fiddling with GUIs, mostly, which I've only done occasionally, as a sub), whereas the types I've done are "test automation", "development operations", "database management and data curation", "requirements engineering", and "application administration". Because it's so much easier to find someone interested in building a GUI, rather than building AnythingElse, I tend to slide into AnythingElse and it eventually became my professional specialty to be the Girl Friday of every project.

But, in Nostr, there is no AnythingElse category. There are only (GUI) client devs and AllOfTheIdiotsWhoMustBowDownToTheDevs. Which merely doubled my instinct to distance myself from the term. I do not want to join some cargo cult and be pedestalized and regarded as some sort of superhuman everyone owes fealty to, in return for raining GUI presents down on my loyal subjects.
Software engineers are simply people who are skilled craftsman, not gods, and it is fair to point out that some are more skilled than others. It is also completely fair to criticize their products, report bugs, and wonder aloud at endemic low-quality.
Which brings me back to the initial question:
What does the inquisitive dev know, that the others don't?
1) You learn an awful lot about an awful lot, by looking at specs, reviewing code, and trying out various implementations of concepts you are already familiar with. There are, in fact, n number of use cases for every event type, and I've seen so many of them, that I can conjure them up, or invent new ones, on the fly, rather than wasting time inventing similar events. 2) They don't have to explain their concept to you, later, when you interact. Each interaction brings you closer to parallel-levels of knowledge, which raises the signal-strength of the interaction, and widens your own knowledge base, for interacting with third parties. 3) You are increasingly-likely to contribute code or perform some other more-advanced task, for other people, as you don't face the hurdle of adjusting to a new repo or unfamiliar language, while being less-likely to merely fork-and-ignore because you have a standing business relationship with the other developer. 4) If the other dev stops maintaining the repo, you'll be inclined to continue on your own. You may even eventually receive administrative access, rather than needing to fork, as they trust you with their stuff. This means that the risk of the repo becoming abandoned falls, with each active dev snooping around it, even if that is not their primary project. 5) It helps you determine who to focus your energy on interacting with, further. Is this person new to software development, perhaps, but has some interesting transfer-knowledge from some other branch, that has resulted in a surprisingly novel concept? Is this person able to write very clean code, so that merely reading their code feels like mental training for your own craftsman's toolbox?
...and many more reasons, but this is getting too long, so, let's just cut to the chase.
What does a craftswoman want?
But, this still doesn't answer the question of my private motivation. Why do I want to gather all of this knowledge, from those further ahead, than I?
I think Nostr has long moved past the initial stage, where mere speed was of the essence, so that one npub could finally post a note and have it appear on the other npubs' client. That must have felt like a miracle, but it increasingly feels like a disaster, as the steadily-rising complexity of the Nostr ecosystem causes haphazardly-structured and largely-unexamined code bases to begin to atrophy, or result in developers running around at an exhausting speed, with their bug-extinguishers, to put out fire after fire.
I think the time has arrived, for a different kind of development. Maybe even for a different kind of developer. Not replacing the experimentalism that made Nostr fun, but adding the realm of production-quality software engineering. The sort of software development that requires relay administration, testing, support... collaboration, interaction, maybe even someone who does AnythingElse.
I want to build useful, elegant products people enjoy using and feel comfortable relying on. I want them to use them, naturally and happily, to accomplish tasks they consider worthwhile. I don't want them thinking about me, while they use it. The craftswoman should never be greater than her work.
I want them to feel free -- nay, be eager! -- to give me both positive and negative feedback. My assumption is always that our production is imperfect because we are imperfect, so you do us a favor, by pointing out where we can improve. That's why we wish to integrate a feedback form that produces ngit issue events, putting your questions and comments straight on our board.
And there will be an AnythingElse person, reading that board, and responding promptly, rest assured.
-
 @ c73818cc:ccd5c890
2024-10-21 19:25:21
@ c73818cc:ccd5c890
2024-10-21 19:25:21
☠️ La Banca Centrale Europea intensifica le critiche a Bitcoin, proponendo misure drastiche per limitarne l'impatto sociale ed economico.
☠️ La BCE ha pubblicato un rapporto controverso che solleva la possibilità di vietare Bitcoin. L'istituzione sostiene che i primi detentori del BTC traggano vantaggio dai nuovi entranti, definendo questo fenomeno una redistribuzione iniqua della ricchezza. Nel report, si ipotizza il controllo dei prezzi o, in casi estremi, l'eliminazione di Bitcoin tramite leggi restrittive.
☠️ Gli economisti della BCE, Ulrich Bindseil e Jurgen Schaaf, reiterano la loro storica critica verso Bitcoin, descrivendolo come un sistema inefficiente e socialmente dannoso. Sostengono che, anche in uno scenario in cui Bitcoin continui a crescere, l'effetto ricchezza derivante dai guadagni di pochi sarebbe a scapito della maggioranza della popolazione, che non ne trarrebbe alcun beneficio.
☠️ L'approccio istituzionale si colloca nel contesto della futura introduzione del wallet europeo di identità digitale e della Central Bank Digital Currency (CBDC). L'esistenza di Bitcoin rappresenta una minaccia per questi strumenti, che mirano a centralizzare il controllo economico e a limitare la libertà individuale, proprio ciò che Bitcoin cerca di preservare.
☠️ La proposta della BCE fa parte di un'operazione più ampia coordinata a livello europeo, anticipando il rilascio delle nuove tecnologie finanziarie basate su CBDC. Le criptovalute, grazie alla loro natura decentralizzata, potrebbero sfuggire a questo controllo centralizzato, minacciando così il potere coercitivo che questi strumenti digitali cercano di esercitare.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
Referral Bitget -10% sulle fee + bonus benvenuto 6w5d o link: https://bonus.bitget.com/U1JNEK
BitcoinReportItalia #BCE #ETF #BTC #CBDC #BlackRock #WEF #Euro #AppIO #Wallet #Europeo #Cripto #Bitcoin
-
 @ 4ba8e86d:89d32de4
2024-10-23 12:16:57
@ 4ba8e86d:89d32de4
2024-10-23 12:16:57Ao contrário dos aplicativos de mensagens tradicionais, o Briar não depende de um servidor central - as mensagens são sincronizadas diretamente entre os dispositivos dos usuários. Se a internet cair, o Briar pode sincronizar via Bluetooth ou Wi-Fi, mantendo o fluxo de informações em uma crise. Se a internet estiver ativa, o Briar pode sincronizar via rede Tor, protegendo os usuários e seus relacionamentos da vigilância.
O Briar foi criado em 2014 por um grupo de desenvolvedores alemães liderado por Michael Rogers. O objetivo era desenvolver um aplicativo que fosse seguro e privado o suficiente para ser usado em situações de repressão governamental e em outras regiões com censura e vigilância online. A equipe recebeu financiamento do Open Technology Fund e outros patrocinadores para desenvolver o aplicativo.
Briar usa conexões diretas e criptografadas entre usuários para evitar vigilância e censura. https://nostr.build/i/nostr.build_5fd2ffa577e4d9978199ba8e957cf9334efd40b3a648e504f24728e94c2a961a.jpg
Briar pode compartilhar dados via Wi-Fi, Bluetooth e Internet. https://nostr.build/i/nostr.build_1a2762f68f623f5598174801f01d89967197c5333dc52a0ff81a850d9afbefa9.png
A Briar fornece mensagens privadas, fóruns públicos e blogs protegidos contra as seguintes ameaças de vigilância e censura:
• Vigilância de metadados. Briar usa a rede Tor para impedir que os bisbilhoteiros descubram quais usuários estão conversando entre si. A lista de contatos de cada usuário é criptografada e armazenada em seu próprio dispositivo.
• Vigilância de conteúdo. Toda a comunicação entre os dispositivos é criptografada de ponta a ponta, protegendo o conteúdo contra espionagem ou adulteração.
• Filtragem de conteúdo. A criptografia de ponta a ponta do Briar impede a filtragem de palavras-chave e, devido ao seu design descentralizado, não há servidores para bloquear.
• Ordens de retirada. Todo usuário que se inscreve em um fórum mantém uma cópia de seu conteúdo, portanto, não há um único ponto em que uma postagem possa ser excluída.
• Ataques de negação de serviço. Os fóruns de Briar não têm um servidor central para atacar, e todo assinante tem acesso ao conteúdo, mesmo que esteja offline.
• Apagões da Internet. O Briar pode operar por Bluetooth e Wi-Fi para manter o fluxo de informações durante os apagões.
Acesse a F-droid ou Google play story em seu dispositivo Android.
Crie uma conta Quando abrir o app Briar pela primeira vez, você será convidado a criar uma conta. Sua conta será armazenada seguramente em seu dispositivo, criptografada com sua senha.
Escolha um apelido com cuidado pois não poderá alterá-lo depois. Você pode escolher o mesmo apelido que outra pessoa, assim como na vida real.
Escolha uma senha que seja difícil de adivinhar mas fácil de lembrar. Se você esquecer sua senha, não haverá como recuperar o acesso à sua conta.
Se você precisar deletar sua conta rapidamente, apenas desinstale o app Briar.
Adicione um contato Após criar a sua conta você verá uma lista vazia de contatos. Para adicionar um contato, pressione no botão de mais (+). Há duas opções, dependendo se a pessoa que você quer adicionar está próxima.
Se a pessoa que você quer adicionar está próxima, escolha “Adicionar contato que está próximo”. Se a pessoa que você quer adicionar não está próxima e você tem acesso à Internet, escolha “Adicionar contato à distância”.
Adicione um contato próximo Quando você escolhe “Adicionar contato que está próximo”, o Briar pedirá permissão para usar sua câmera para escanear o código QR do seu contato. O Briar tambem pedirá permissão para acessar sua localização, para que possa se conectar ao seu contato por Bluetooth. O Briar não armazena, compartilha ou faz upload da sua localização, mas essa permissão é necessária para descobrir dispositivos Bluetooth próximos.
Finalmente, o Briar pedirá permissão para ligar o Bluetooth e tornar seu dispositivo visível para dispositivos Bluetooth próximos por um curto perído de tempo.
Após conceder todas essas permissões, o Briar mostrará um código QR e uma visualização de câmera. Escaneie o código QR de seu contato e deixe ele escanear o seu. Após uns 30 segundos seus dispositivos devem estar conectados e seu contato adicionado à sua lista de contatos.
Se seus dispositivos não se conectarem, vocês devem voltar à lista de contatos e iniciar o processo de novo.
Adicione um contato à distância Quando você escolhe “Adicionar contato à distância”, o Briar mostrará um link que você deve enviar para a pessoa que deseja adicionar. Você pode enviar o link por outro app como o Element , Simplesxchat . Seu contato tambem precisa te enviar o link dele. Cole o link de seu contato e escolha um apelido para ele. Se você e seu contato estão conectados ao Briar e têm acesso à Internet, então seu contato deve ser adicionado à sua lista de contatos dentro de alguns minutos.
Envie uma mensagem Após adicionar seu primeiro contato, toque em seu nome na lista de contatos para enviar-lhe sua primeira mensagem. O círculo próximo ao nome de seu contato ficará verde quando o Briar estiver conectado ao seu contato via Internet, Wi-Fi ou Bluetooth.
Apresente os seus contatos Você pode usar o recurso de apresentação para apresentar dois contatos seus entre si, para que eles não precisem se encontrar pessoalmente para se adicionarem.
Comunique-se sem Internet O alcance do Bluetooth e do Wi-Fi está em torno de 10 metros, a depender dos obstáculos. Claramente isso não é suficiente para se comunicar através de uma cidade ou mesmo de um prédio grande. Então, quando o Briar recebe uma mensagem de um contato que está próximo, ele armazena a mensagem e pode depois repassá-la para outros contatos, quando eles estiverem em alcance (por exemplo, quando você for de um local para outro).
Por favor, note que o Briar só vai sincronizar mensagens com os seus contatos, não com estranhos próximos que tenham o Briar. E só vai sincronizar as mensagens que você escolheu compartilhar com cada contato. Por exemplo, se você convida seus contatos X e Y para entrar em um fórum e eles aceitam, as mensagens nesse forum serão sincronizadas com X ou Y sempre que estiverem em alcance. Logo, você pode receber mensagens de fórum de X em um local, ir até outro local e entregar essas mensagens para Y.
Mas isso não funciona para mensagens privadas: elas apenas são sincronizadas diretamente entre o remetente e o destinatário.
Conecte-se com seus contatos sem Internet Quando você se encontrar com um de seus contatos do Briar, você pode usar o recurso “Conectar via Bluetooth” na tela da conversa para fazer uma conexão Bluetooth entre seus dispositivos. Após fazer isso uma vez, seus dispositivos devem se conectar automaticamente no futuro, mas isso pode levar um minuto ou dois após seu contato entrar em alcance. Se você não quiser esperar, pode usar o recurso “Conectar via Bluetooth” de novo para fazer a conexão imeditamente.
Se um grupo de pessoas dentro do alcance de Wi-Fi quiser se comunicar, pode ser útil criar um hotspot Wi-Fi no celular de uma pessoa. Mesmo que o hotspot não tenha acesso à Internet, o Briar pode usá-lo para se comunicar com contatos conectados ao mesmo hotspot.
Se é muito arriscado carregar seu celular de um lugar para outro (por conta de pontos de revista policial, por exemplo), você pode sincronizar mensagens criptografadas usando um pendrive USB ou cartão SD para carregá-las mais discretamente.
https://youtu.be/sKuljekMzTc
https://github.com/briar/briar
-
 @ 599f67f7:21fb3ea9
2024-10-17 15:35:19
@ 599f67f7:21fb3ea9
2024-10-17 15:35:19Nostr proxy baten erabilera modu oso eraginkorra da internet banda-zabaleraren eta mugikorretan bateriaren kontsumoa optimizatzeko.
Proxy batek hainbat errelei-konexio konexio bakarrean biltzen dituenez, baliabideen erabilera nabarmen murrizten du, eta erabiltzailearen IP helbidea ezkutatuz pribatutasun-geruza bat gehitzen du.
Hona hemen nola funtzionatzen duen eta nola konfigura daitekeen:
Nola funtzionatzen du?
Nostr proxy batek hainbat erreleirekin konektatzen du. Errele horietara gertaerak eskuratu eta argitaratzen ditu. Bezeroaren aplikazioak WebSocket konexio bakarra ireki behar du proxy-ra, eta horren bidez proxy-ak konektatuta dituen errele guztiak eskuragarri izango ditu.

Irudiaren egiletza: Yonle 2023
Bezeroak konexio bakarra irekitzen duenez, datuak eta bateria aurrezten ditu.
Proxy-ak bezeroaren izenean erreleekin konektatzen denez, erreleek proxy-aren IP helbidea ikusten dute, eta ez bezeroarena. (Hala ere, proxy hornitzailearengan konfiantza izan behar duzu).
Erabiltzeko Modua
Nostr proxy bat erraz auto-ostata daiteke. Auto-ostatatzeko jarraibideak lortzeko, begiratu nostr:npub1x3azxuysp5vmfer4vgs4jn5tmfcx4ew8sh0qnev7gczljxsr7jwqa3g4el erabiltzailearen biltegi hau.
Auto-ostatzeko baliabiderik ez dutenentzat, Bitcoin Txoko-k komunitate-instantzia bat ostalaratzen du.
Erabiltzeko, gehitu besterik ez duzu:
wss://bostr.bitcointxoko.comzure errele zerrendara.
Orain ez duzunez zuzeneko konexioak behar, errele bikoiztuak ezabatu ditzakezu.
Ikusiko dugu elkar Nostr-en!
-
 @ 9aa75e0d:40534393
2024-10-21 16:34:02
@ 9aa75e0d:40534393
2024-10-21 16:34:02During a routine inspection of a flight from Suriname on September 20, Dutch customs authorities intercepted 2 kilograms of cocaine, concealed within the battery of a mobility scooter. A passenger traveling from Suriname to the Netherlands, along with their checked-in mobility scooter, was subjected to further examination.
During the inspection, customs officers noticed traces of glue on the batteries of the mobility scooter. This unusual detail prompted them to open one of the batteries, where they immediately found a smaller battery and a package. Upon further investigation, the package was found to contain cocaine. Each battery contained approximately 1 kilogram of the drug, bringing the total to around 2 kilograms of cocaine.
Read the full article on SmuggleWire
-
 @ e97aaffa:2ebd765d
2024-10-21 15:46:17
@ e97aaffa:2ebd765d
2024-10-21 15:46:17Eu regularmente, sou questionado ou pedem para eu fazer uma previsão de preço para o Bitcoin a longo prazo. Eu sempre evito responder, não quero criar falsas expectativas.
Em primeiro lugar, quem quer entrar no Bitcoin não deve entrar na expectativa que vai enriquecer rapidamente. Quem entra com este pensamento vai perder muito dinheiro, não vai resistir à pressão e vai vender tudo na primeira queda de 20%. Bitcoin é uma moeda ética, uma filosofia, muito estudo e por fim, é uma poupança a longo prazo. Para tirar frutos a longo prazo, tem que estar mentalmente preparado para suportar e ultrapassar, centenas de quedas de 20% e algumas dezenas de quedas superiores a 50%.
As previsões que são dadas, normalmente de valores muito elevados, dão uma falsa expectativa, levando as pessoas a entrar no Bitcoin com o único objectivo de enriquecer, sem estudá-lo minimamente. Geralmente as previsões de altos valores, implicam um enorme aumento da base monetária, só que as pessoas têm uma enorme dificuldade em compreender a inflação. Por esse motivo eu evito dar previsão e quando tento explicar, gosto de dar exemplos de inflação.
Eu acredito que o bitcoin vai ultrapassar 1 milhões de dólares, mas isto é sinónimo de ficar rico, porque 1 milhão é muito dinheiro hoje, mas daqui a 10 ou 20 anos, já não é assim tanto. A moeda perde muito poder de compra, isto é essencial para compreendermos as previsão de preços. Eu sempre que faço previsões, gosto sempre de dar o exemplo: hoje com 1 milhão compramos 4 casas novas, daqui a 20 anos, apenas compramos 1, com tamanhos e localização semelhante. Assim, aquela previsão de um milhão parece muito dinheiro, mas como são previsão a muito longo prazo, não é assim tanto dinheiro. O factor da inflação é essencial sempre que falamos ou analisamos previsões de preço do Bitcoin.
Não podemos esquecer que o preço do bitcoin é similar ao conceito de física da velocidade relativa.
Velocidade Relativa: Quando dois objetos se movem em direções opostas, a velocidade relativa entre eles é a soma das suas velocidades individuais.
Ou seja, o preço do Bitcoin é o resultado da soma da sua adoção, com a perda de poder de compra do dólar. São duas variáveis em sentido opostos, por isso o bitcoin está a ganhar bastante poder de compra.
Distribuição da riqueza Global
Hoje em dia a riqueza global (valor global dos ativos) é estimada em 900 Triliões, dividida pelas seguintes classes:
- Imobiliário: 330 Triliões
- Obrigações: 300 Triliões
- Dinheiro: 120 Triliões
- Ações: 115 Triliões
- Arte: 18 Triliões
- Ouro: 16 Triliões
- Car e colecionáveis: 6 Triliões
- Bitcoin: 1 Triliões
Previsão do Michael Saylor
Este fim-de-semana, Michael Saylor divulgou uma nova previsão:
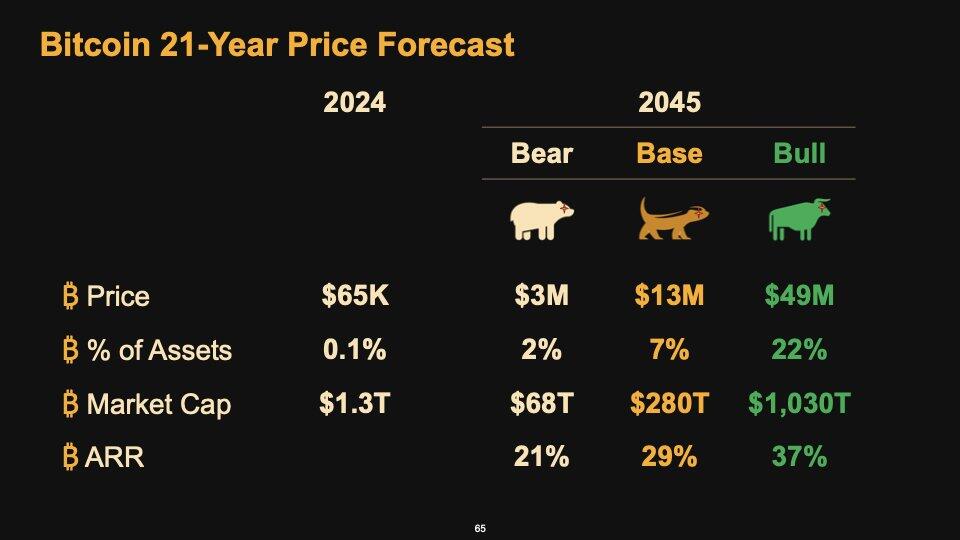
Eu gosto destes modelos que apresentam 3 cenários possíveis, um conservador(Bear), um base(Base) e um optimista(Bull). Mas faltou incluir o valor global dos ativos, é verdade que é fácil de calcular, através do valor do market cap indicado a dividir pela percentagem do ativo.
Assim o valor global total dos ativos em 2045, segundo a precisão são:
- 2024: 900 Triliões
- Bear: 3400 Triliões
- Base: 4000 Triliões
- Bull: 4600 Triliões
Isto significa um aumento aproximado 270% (bear), 340% (base) e 410% (bull). É verdade que nestes 21 anos a riqueza real de todos ativos vão aumentar, mas essa valorização será sobretudo devido à expansão da base monetária do dólar.
Desvalorização
Saylor está a apostar que vai existir uma forte desvalorização do dólar. Será plausível essa desvalorização da moeda?
Nos últimos 15 anos o Balance Sheet da Reserva Federal (EUA), 3 grandes expansão monetária, próximo dos 100%, algo similar também aconteceu na Europa.
- 2008/01 a 2008/12:
- 0.9 Triliões -> 2.2Triliões
- aumento de 144%
- 2010/09 a 2014/11:
- 2.3 Triliões -> 4.5 Triliões
- aumento de 95%
- 2019/08 a 2022/03:
- 3.7 Triliões -> 8.9 Triliões
- aumento de 140%
Nos últimos 16 anos (2008-2024) a Balance Sheet aumentou 7 vezes.
O M2 global (EU + EUA + Japão + China + Reino Unido), no mesmo período, quase triplicou, de 34.4 para 91.7 Triliões.
Se nos últimos 16 anos houve várias desvalorização da moeda, é provável que volte a repetir-se, no próximo 21 anos e talvez seja ainda mais severa.
Conclusão
Voltando à previsão do Saylor.
Assim, os 3 milhões de dólares por Bitcoin para 2045, da precisão no cenário Bear, correspondem a 860 mil dólares com o poder de compra de hoje. E 3 milhões dólares (Base) e 9.4 milhões dólares (Bear).
860 mil dólares é um valor muito interesante para o custo de vida da Europa ou EUA, mas está muito longe de ser rico. Quem não tem a noção da inflação, ao ler esta previsão fica com uma falsa expectativa que com 1 bitcoin será milionário (3 mihões de dólares) em 2045, mas não é verdade.
Eu acredito que pode alcançar o cenário Bear, mas o Bull é demasiado, para atingir os 49 milhões, a desvalorização teria que ser muito superior, é um cenário pouco provável, neste espaço de tempo.
-
 @ bcea2b98:7ccef3c9
2024-10-17 14:47:01
@ bcea2b98:7ccef3c9
2024-10-17 14:47:01Sometimes you have to take risks to grow. What's the biggest risk you've ever taken that ended up paying off.
My biggest risk that paid off was moving to another country and starting a new life 10 years ago due to corruption and torture in my home country.
originally posted at https://stacker.news/items/728159
-
 @ 5e5fc143:393d5a2c
2024-10-11 22:26:08
@ 5e5fc143:393d5a2c
2024-10-11 22:26:08Just revisiting some quick tips for #newbies #pow #public #blockchain users only.
if you just getting started with bitcoin or any pow crypto coins or been using or storing them for a while, you not must forget the roots and fundamentals.
Hot Wallet — It gets connected to live internet at some point in time essentially to sign / send a tx i.e. spending transaction — exposes the private key of the address from in the process
Cold Wallet — It never ever gets connected or online and can always keep receiving inbound amounts Paper wallets are best n cheapest form of cold wallet that can used once n thrown away.
Cold wallets need to either “import”ed or “sweep”ed in order to used or spend — https://coinsutra.com/private-key-import-vs-sweep-difference/

Any thin #wallet is always dependent on connectivity to live up2date node server where-as self-sufficient qt / cli wallet takes a while to sync up to latest block height in order to be usable.
Beginners should always resist the attraction of quick and fast — thin n 3rd party wallets and always start a long learning journey of core wallets of any coin — either “qt” GUI wallet or command line “coin-cli” wallet
Almost all #proofofwork #blockchains i.e. #POW has #node #wallet - everyone who use support he #public #blockchain secures own you coin value
You can run fullnode either on clearnet or over onion 🧅 #BTC has >55% of nodes running in onion out of total 15000+ live fullnodes and 50000+ bitcoincore wallets around blockheight 777000 . Other notable pow chains are #LTC #RVN and rest are babychains for now !
Always delete hot wallet to test practice restoration before sending any large refunds to it to be safe.
Large funds are always best to keep in self custody node wallets rare n occasional use
Final word — Cannot see private key 🔑 or seed 🌱 in any wallet means not your coin. 😲
Use wallet which u learn or understand best only
That’s all for now n Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️
Some Cold wallet nostr posts nostr:note1p6ke5wqshgxtfzj5de3u04hejl2c5ygj8xk8ex6fqdsg29jmt33qnx57y2 nostr:note1rse0l220quur6vfx0htje94ezecjj03y6j7lguwl09fmvmpt6g3q0cg7yw nostr:note1q5w8dyjuqc7sz7ygl97y0ztv6sal2hm4yrf5nmur2tkz9lq2wx9qcjw90q
some nostr specific lightning ⚡️ Layer2 wallets with blockchain mainnet option nostr:naddr1qqsky6t5vdhkjm3qd35kw6r5de5kueeqf38zqampd3kx2apqdehhxarjqyv8wue69uhkummnw3e8qun00puju6t08genxven9uqkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgchgefsw4a8xdnkdgerjatddfshsmr3w93hgwpjdgu8zdnswpuk2enj0pcnqdnydpersepkwpm8wenpw3nkkut2d44xwams8a38ymmpv33kzum58468yat9qyt8wumn8ghj7un9d3shjtngv9kkuet59e5k7tczyqvq5m2zcltylrpetrvazrw45sgha24va288lxq8s8562vfkeatfxqcyqqq823ckqlhc8 related blog post nostr:naddr1qqxnzd3cxyenjv3c8qmr2v34qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qydhwumn8ghj7mn0wd68ytn4wdjkcetnwdeks6t59e3k7tczyp6x5fz66g2wd9ffu4zwlzjzwek9t7mqk7w0qzksvsys2qm63k9ngqcyqqq823cpdfq87
-
 @ 7ab1ed7a:f8e15275
2024-10-17 14:06:46
@ 7ab1ed7a:f8e15275
2024-10-17 14:06:46I'm proud and thankful to announce that funding has been granted by OpenSats to fund the development of the Nostr library for Arduino.
The fund will help with work on the development of the Arduino Nostr library as well as fund work on IoT related NIPs.
-
 @ 598a7f2f:727334f4
2024-10-21 15:43:20
@ 598a7f2f:727334f4
2024-10-21 15:43:20
npub1tvusgte2m3p3pmupvcwph5k40d0s3dn5jen9a8ejwhp8xawd6quq6en8em
-
 @ 9aa75e0d:40534393
2024-10-21 15:22:19
@ 9aa75e0d:40534393
2024-10-21 15:22:19A large-scale cocaine-smuggling network has been dismantled by authorities in Italy, Albania, Poland, and Switzerland in a joint operation coordinated by Eurojust. The criminal organization, which had been operating for at least four years, primarily focused on selling cocaine in northern Italy, particularly around the city of Brescia.
Coordinated Action Across Europe The international operation, led by an Albanian-organized crime group (OCG), culminated in the arrest of 66 suspects. On the main action day, 45 individuals were apprehended, most of them in Italy. Prior to this, 21 additional suspects had already been arrested in connection with cocaine distribution in the Brescia area.
Eurojust, based in The Hague, played a key role in facilitating and coordinating the efforts of law enforcement agencies across the involved countries. Over 400 officers were deployed in Italy alone to execute the operation. Eurojust set up a coordination center to support the implementation of European Arrest Warrants and Mutual Legal Assistance requests, particularly towards Albania and Switzerland. Europol also provided critical support by managing the exchange of information and offering on-the-ground analytical assistance, including deploying a mobile office to Italy.
Read the full article on SmuggleWire
-
 @ 472f440f:5669301e
2024-10-11 14:20:54
@ 472f440f:5669301e
2024-10-11 14:20:54As we sprint toward the 2024 US Presidential election the case for using bitcoin as an asset to store value for the long term has never been stronger. The insanity of the incumbent power structure is being laid bare and it is becoming impossible to ignore the headwinds that the Borg faces moving forward.
Yesterday morning and earlier today it became clear that inflation is rearing its head again. Not ideal for the soft landing Jerome Powell and Yellen are signaling to the markets after the first Fed Funds rate cut in years.
It seems like the yield curve predicted this earlier this week when it inverted after a temporary normalizing period after the Fed's rate cut. Futhermore, it is becoming glaringly obvious that running historically high fiscal deficits while interest rates were at multi-decade highs was a pretty bad idea. As James Lavish points out, the data from the CBO earlier this week shows that the US federal government is running a deficit that is 13% higher than it was last year. This is at a time when real wages are still depressed, inflation is still suffocating American consumers and the private sector job market for American citizens is cratering.
Speaking of the job market, the numbers that came in yesterday were worse than expected: The effect of Hurricane Helene should certainly be taken into consideration when looking at this jobs miss. However, even with the miss we know that these numbers have been under reported for years to make the economy seem healthier than it actually is. Even with Helene's effect taken into consideration this print will likely be revised higher 3-6 months from now.
All of this points to a breaking point. A breaking point for the economy and, more importantly, a breaking point for overall confidence in the US government and its ability to operate with any semblance of fiscal responsibility. The chart that Pierre Rochard shares in the tweet at the top of this letter is the only chart that matters for anyone attempting to gauge where we find ourselves on the path to bitcoin realizing its full potential.
There is $133 TRILLION worth of value sitting in global bond markets. Bitcoin is a far superior asset to store one's wealth in. Bond markets are beholden to the whims of the actors who issue those bonds. In the case of the US Treasury market, the largest bond market in the world, the US government. And as we have pointed out above, the US government is recklessly irresponsible when it comes to issuing debt with a complete inability to pay it back on the long-term. Inflation is up, the jobs market is cratering for the native born Americans who actually pay taxes, and the push toward a multi-polar geopolitical landscape is becoming more pronounced by the day. All of this points to a long-term weakening in demand for US treasuries.
The only way out of this mess is to overtly default on this debt or inflate it away. The latter will most certainly be the route that is taken, which positions bitcoin extremely well as people seek the confines of an asset that cannot be debased because it cannot be controlled by a central authority. The levels of sovereign debt in the world are staggering. Do not let the bitcoin price consolidation of the last six months lull you into a state of complacency. Even the results of the Presidential election won't have a material effect on these dynamics. Though, a Donald Trump presidency would certainly be preferable if you prefer to see relatively sane policy enacted that would provide you with time to find safety in bitcoin. But, in regards to this sovereign debt crisis, that is the only benefit you can hope for; more time to prepare. I'll leave you with some thoughts from Porter Stansberry:
"We are about to see the final destruction of the American experiment. Every economist knows this (see below) is correct; but nobody is going to tell you about it. I’ll summarize in plan English: We are fucked.
-
Debt is growing much faster than GD and interest expense is growing much faster than debt; and the real growth in entitlement spending hasn’t even begun yet.
-
Progressive taxation means nobody will ever vote for less spending + the combined size of government employees and dependents, there’s no way for America’s actual taxpayers (about 20m people) to ever win an election, so the spending won’t stop growing and, ironically, inflation will make demands for more spending to grow.
-
Inflation undermines both economic growth and social cohesion. The purple hair man-women weirdos are only the beginning; what comes next is scapegoating jews, blacks, immigrants and a huge increase in violence/domestic terror.
Get ready America. This election has nothing to do with what’s coming. And neither Trump nor Kamala can stop it.
Our experiment in freedom and self-government died in 1971 (when all restraint on government spending was abandoned with the gold standard.) You can only live at the expense of your neighbor until he runs out of money.
And that day is here."
Final thought... I hope my tux still fits for this wedding. Enjoy your weekend, freaks.Use the code "TFTC" for 15% off
-
-
 @ 3ef961a4:a09c0383
2024-10-21 14:12:42
@ 3ef961a4:a09c0383
2024-10-21 14:12:42My first article

- hgjjg
- jhgfjgfj
- dsdsf~~sdsds~~
-
 @ 23acd1fa:0484c9e0
2024-10-23 09:21:33
@ 23acd1fa:0484c9e0
2024-10-23 09:21:33Chef's notes
Cocoa powder: You can use 100% natural unsweetened cocoa powder or Dutch-processed cocoa powder – both work well.
Gluten free flour: There are many different gluten free flours on the market. I tested this recipe using White Wings All Purpose Gluten Free flour. I recommend choosing a gluten free flour that says it can be subbed 1:1 for regular plain or all purpose flour.
*Chocolate chips: Double check your chocolate chips are gluten free if you are making this brownie for someone who is celiac.
Cook times: Cook times will vary depending on your oven, but you’ll know these brownies are done when they firm up around the edges and no longer wobble in the middle. Keep in mind they will continue to cook slightly as they cool. You can also check they’re done by inserting a skewer into the middle of the brownie. If the skewer emerges with only a few crumbs on it, they’re ready. If it is covered in wet, gooey batter, keep baking the brownies and check them in another 5 minutes.
Storage: Brownies will keep well in an airtight container at room temperature or in the fridge for up to 5 days. To serve warm, microwave each brownie for 20 seconds. You can also freeze these brownies to enjoy at a later date. Simply thaw at room temperature and then microwave if you prefer them warm.
Serving Size: 1 brownie Calories: 278 Sugar: 26.4 g Sodium: 22.9 mg Fat: 15.5 g Carbohydrates: 34.1 g Protein: 3 g Cholesterol: 77.3 mg Nutrition information is a guide only.
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 35 min
- 🍽️ Servings: 12
Ingredients
- 170 grams (3/4 cup) unsalted butter, melted
- 200 grams (1 cup) caster sugar or granulated sugar
- 90 grams (1/2 cup) brown sugar
- 1 teaspoon vanilla extract
- 3 large eggs
- 40 grams (1/2 cup) cocoa powder
- 70 grams (1/2 cup) gluten free plain or all purpose flour
- 75 grams milk or dark chocolate chips*
Directions
- Preheat the oven to 180 C (350 F) standard / 160 C (320 F) fan-forced. Grease and line an 8-inch square pan with baking or parchment paper, ensuring two sides overhang.
- In a large mixing bowl, add melted butter and sugars and gently whisk together. Add vanilla extract and stir.
- Add the eggs, one at a time, stirring in-between, then sift in the cocoa powder and flour. Stir until just combined. Add chocolate chips.
- Pour the brownie batter in the prepared pan and place in the oven. Bake brownies for approximately 30-35 minutes or until they no longer wobble in the middle.
- Leave brownie in pan and transfer to a wire rack to cool completely. These brownies are quite fragile so if you can, transfer to the fridge for an hour before cutting into squares to serve.
-
 @ ee7d2dbe:4a5410b0
2024-10-23 07:14:35
@ ee7d2dbe:4a5410b0
2024-10-23 07:14:35React native App Development Services from Agicent ?
We used to use various flavors of Javascript long before react native came into being and once it came, we went all big on it. There were times when React-native and other cross platform technologies (like Flutter, Ionic, QT) were only good for creating App MVPs and had a lot of issues such as integration with third party libraries, with Device’s own hardware capabilities and so on. But today as of mid-2022 we can safely say that React Native can help building as good or superior apps as a native tech would do and that do with single coding effort. Its like Java of old days, “Write once, run anywhere”.
Theoretically, an App that you can make in React-native can be created in Flutter or ionic or in native technologies too. However, if we have to rate the cross-platform technologies, react native rules the roost hands down because of its larger community support, flexible frameworks, and capability to generate the native code over other platforms.
Rates for react native App Developers on Demand
Following is the standard rate card for different Exp and skill levels of On Demand Reac Native App Developers. Besides this, we can also create a custom on Demand App Team and optimized the monthly rate based on our specific needs.
Junior React Native Developer
Exp. Level: 1-2 Years
Hands on react native Development.
3 Projects experience minimum.
Agicent’s inhouse trained.
Familiar with PM Tools
Perfect for rapid MVPs and maintenance react native works
Starting at $ 2200 /mo.
Mid-level React Native Developer
Exp. Level: 2-5 Years
All of Jr. Dev +
10 Projects experience minimum.
Has Backend Experience.
Hands on CI/CD pipeline.
Manages Jr. Developers.
Perfect for complex react-natived projects and fast Development
Starting at $ 2900 /mo.
Senior React Native Developer
Exp. Level: 5+ Years
All of Mid-level Exp +
15 Projects experience minimum.
Full Stack Developer.
Participate in Architecture.
Ability to play Tech. Lead Role.
Perfect for bigger size projects with multi teams
Starting at $ 3800 /mo
BEST Practices followed by Agicent React Native App Development Company
First and foremost, we critically analyze if the App project is a good candidate for cross platform or react native development or not. In some pretty niche Apps, native can still be a technology of choice so ruling out this possibility is most important first step. Once it is identified that react native is the tech of choice, we then figure out the backend stack (like node.js or graphql, or traditional LAMP stack), or web front-end third-party libraries, like vue.js, typescript, redux etc. If it’s a regular kind of app that we do time and again (like a dating app or ecommerce app, or healthcare app) then we decide on tech stack in few hours only; if it is a niche one- of-a-kind project (like an AI based app suggesting you medicine dosage or an App that heavily uses some third- party APIs for its core function – like creating digital avatars or facilitates Holoportation) then we take more than few hours to check on libraries, their scalability with react native and then decide.
Performance optimization, Build optimization
Native applications are top performers because they use stock APIs, patters, and enjoy best support from the OEM’s OS and hardware and you achieve great performance by the virtue of the platform. However, in case of creating a react native app, which is cross platform by the way you have to use a variety of testing tools (like Appium, jest, detox etc), be more meticulous for performance parameters, and optimize your code for best performance across different devices. It can be a time-consuming exercise at times, but totally worth it and warranted.
For react native app development, you have to take care of multi-threading, third party library integration in optimized way, image compression, APK or iPA file size optimization and lot more what you don’t really do when doing native app development.
Limitations of React Native App Development
Lack of native libraries:
If the app has a lot of features, React Native can slow down the development process due to a lack of native libraries and reliance on external, third-party libraries.
Takes more time to initialize:
The issue with React Native is that it takes more time to initialize the runtime for gadgets and devices, mostly because of the JavaScript thread which takes time to initialize.
Excessive Device Support required
Due to the variety of OEM Devices size, Type, Version, and OS Versions, it is challenging for a developer to provide full support to all the app uses in one go, so it becomes sort of a continuous exercise to extend support to more and more devices.
Still in pre-mature face
React native latest version is 0.68 as of June 2022, which shows that it is still in face of evolving which is why it still have lack functionality. Good thing is that it is continuously maturing and have community support with big tech giants like Facebook & tesla also it easy to learn and understand even for the beginner.
React Native Doesn’t Fully Support NFC
NFC enables the communication between nearby devices. But React Native Devices still don’t support or provide full access for NFC communication.
Future of React Native Development
Start-up first choice
Many big names like Facebook, Instagram, tesla and all have an app on react native also react native becomes one of the most discussed libraries on StackOverflow. Most startup and even enterprise start adopting it because it only needs a single manager to manage for both android and IOS app development which save it time, resources and money.
Better integration with Device’s and external Hardware
We are already working on some react native projects where we are interacting with external hardware (using Silabs or infi semiconductors) and have found that react native doesn’t always get priority support, however this is going to be changed in the future. React native will be more scalable and easier to integrate with device’s own hardware as well as external Hardware (Bluetooth, NFC devices).
Open the gate for new open-source frameworks
The domain-specific engineers are meet-up and do conferences in which each platform bring their own player who are working on a similar problem. Like web where react (which power react-native) which commonly draw inspiration from other open-source web frameworks like: Vue, Preact & Svelte. On mobile, React Native was inspired by other open-source mobile frameworks, and we learned from other mobile frameworks built within Facebook.
Source: https://www.agicent.com/react-native-development-company
-
 @ c73818cc:ccd5c890
2024-10-21 13:26:43
@ c73818cc:ccd5c890
2024-10-21 13:26:43
⚡ Gli ETF spot Bitcoin registrano un’ondata di accumulo, alimentata dai piccoli detentori che vendono i loro BTC alle istituzioni.
🌟 Negli ultimi nove mesi, gli ETF spot Bitcoin hanno raccolto oltre 312.000 BTC, superando di gran lunga i 169.000 nuovi bitcoin creati dai miner. Mentre grandi istituzioni e fondi pensione si accaparrano queste azioni, i piccoli investitori cedono i loro BTC, spesso inconsapevoli delle implicazioni a lungo termine.
🌟 Larry Fink, CEO di BlackRock, ha sottolineato il successo senza precedenti degli ETF Bitcoin, ma il vero rischio è che i piccoli investitori stiano perdendo l’opportunità di creare ricchezza sovrana. Vendere ai grandi operatori significa rinunciare alla libertà e alla resistenza alla censura di Bitcoin, uno degli attributi chiave della criptovaluta.
🌟 Mentre gli "smart money" accumulano BTC tramite veicoli finanziari centralizzati, gli investitori retail rischiano di pentirsi di aver venduto. È fondamentale non cedere i propri bitcoin alle istituzioni e mantenere il controllo diretto delle chiavi private per conservare la propria sovranità finanziaria.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
Referral Bitget -10% sulle fee + bonus benvenuto 6w5d o link: https://bonus.bitget.com/U1JNEK
BitcoinReportItalia #ETF #Fondi #Retail #Istituzioni #BlackRock #Genesis #Investitori #Balene #Whale #Cripto #Bitcoin
-
 @ 6bf975a0:65de1244
2024-10-21 11:56:28
@ 6bf975a0:65de1244
2024-10-21 11:56:28Мы создаем небольшие редакции (4 человека на каждую) новостей декабря 2040 года небольшого российского города (реальный город, откуда вы родом, на выбор).
В первый день начала работы редакция рассказывает о том, каким стал её населенный пункт в 2040 году.
Медиа работает на протяжении двух недель и ежедневно выпускает новости на мультимедийной основе — от текстов до видео.
Ежедневно каждая редакция выпускает 2 информационно-новостных текста с иллюстрациями, один видеосюжет. Еженедельно — один короткий аудиоподкаст.
Техническая основа проекта
- Площадка для публикации контента редакции — специально созданный профиль в Nostr;
- Инструменты создания легенды про населённый пункт: генеративные текстовые нейросети;
- Инструменты создания медиаконтента: нейросети для генерации изображений, видео, создания музыки и звука.
Рабочая среда проекта
- Docs.iris.to — будут созданы таблицы для контент-планов по проектам для отслеживания и корректировки хода их выполнения;
- Комментарии и обсуждения проектов включены в docs.iris.to.
Критерии успешного выполненного проекта
- Разнообразие мультимедийного контента: использованы все доступные форматы. Звук, текст, изображения, видео;
- Качество созданного контента: тексты — вычитанные, отредактированные, изображения — отобранные с точки зрения соответствия действительности (люди с нормативным количеством конечностей, не зомби) etc;
- Регулярность публикации контента: редакции масс-медиа публикуют новости ежедневно.
Правила создания контента
- Сгенерированный контент не должен нарушать местное законодательство. Контент размещён в созданных авторами профилях, поэтому ответственность за его содержание несут авторы.
- Сгенерированный контент не должен призывать к насильственным или агрессивным действиям в отношении кого бы то ни было, а также не должен содержать унижающих, оскорбительных оценок любых социальных групп по любым характеристикам.
- 2040-ой — это наши надежды на будущее, возможности, которые, мы верим, будут реализованы. В будущем мы преодолеваем экологические и экономические проблемы.
Ссылки на проекты оставляйте в таблицах с контент-планами
-
 @ 6bf975a0:65de1244
2024-10-21 10:06:18
@ 6bf975a0:65de1244
2024-10-21 10:06:18- Какие этические проблемы могут возникнуть в связи с широким распространением VR/AR-технологий? (Например, приватность, зависимость, манипуляция, влияние на социальные взаимодействия.) В своё время именно этические проблемы не позволили Google Glass стать мэйнстримом.
- Насколько реалистично ожидать, что VR/AR заменят традиционные способы потребления медиа? Какие факторы могут этому способствовать или препятствовать? (Например, цена, доступность, удобство использования, социальное принятие.)
- Насколько вероятно, что метавселенная станет «еще одним слоем интернета», а не его полной заменой? (Рассмотреть текущие тенденции развития интернета и технологические ограничения.)
- Какие этические дилеммы связаны с использованием ИИ для таргетированной рекламы и персонализации контента? (Например, манипуляция потребительским выбором, дискриминация, распространение дезинформации.)
- Может ли гиперперсонализация привести к «информационному изоляционизму» и снижению социальной когезии? Как этого избежать? (Рассмотреть важность «слабых связей» по Марку Грановеттеру.)
- Как унификация платформ и облачные технологии повлияют на медиаиндустрию?
- Как можно противостоять «несоциальности» современных социальных медиа и создать более инклюзивную и полезную цифровую среду?
- Децентрализация и современные социальные медиа: смогут ли новые платформы веб 3.0 потеснить в популярности существующие крупные соцсети? Либо последние позаимствуют новые технологии и задавят в зародыше новые проекты
-
 @ 8947a945:9bfcf626
2024-10-17 08:06:55
@ 8947a945:9bfcf626
2024-10-17 08:06:55สวัสดีทุกคนบน Nostr ครับ รวมไปถึง watchersและ ผู้ติดตามของผมจาก Deviantart และ platform งานศิลปะอื่นๆนะครับ
ตั้งแต่ต้นปี 2024 ผมใช้ AI เจนรูปงานตัวละครสาวๆจากอนิเมะ และเปิด exclusive content ให้สำหรับผู้ที่ชื่นชอบผลงานของผมเป็นพิเศษ
ผมโพสผลงานผมทั้งหมดไว้ที่เวบ Deviantart และค่อยๆสร้างฐานผู้ติดตามมาเรื่อยๆอย่างค่อยเป็นค่อยไปมาตลอดครับ ทุกอย่างเติบโตไปเรื่อยๆของมัน ส่วนตัวผมมองว่ามันเป็นพิร์ตธุรกิจออนไลน์ ของผมพอร์ตนึงได้เลย
เมื่อวันที่ 16 กย.2024 มีผู้ติดตามคนหนึ่งส่งข้อความส่วนตัวมาหาผม บอกว่าชื่นชอบผลงานของผมมาก ต้องการจะขอซื้อผลงาน แต่ขอซื้อเป็น NFT นะ เสนอราคาซื้อขายต่อชิ้นที่สูงมาก หลังจากนั้นผมกับผู้ซื้อคนนี้พูดคุยกันในเมล์ครับ
นี่คือข้อสรุปสั่นๆจากการต่อรองซื้อขายครับ
(หลังจากนี้ผมขอเรียกผู้ซื้อว่า scammer นะครับ เพราะไพ่มันหงายมาแล้ว ว่าเขาคือมิจฉาชีพ)

- Scammer รายแรก เลือกผลงานที่จะซื้อ เสนอราคาซื้อที่สูงมาก แต่ต้องเป็นเวบไซต์ NFTmarket place ที่เขากำหนดเท่านั้น มันทำงานอยู่บน ERC20 ผมเข้าไปดูเวบไซต์ที่ว่านี้แล้วรู้สึกว่ามันดูแปลกๆครับ คนที่จะลงขายผลงานจะต้องใช้ email ในการสมัครบัญชีซะก่อน ถึงจะผูก wallet อย่างเช่น metamask ได้ เมื่อผูก wallet แล้วไม่สามารถเปลี่ยนได้ด้วย ตอนนั้นผมใช้ wallet ที่ไม่ได้ link กับ HW wallet ไว้ ทดลองสลับ wallet ไปๆมาๆ มันทำไม่ได้ แถมลอง log out แล้ว เลข wallet ก็ยังคาอยู่อันเดิม อันนี้มันดูแปลกๆแล้วหนึ่งอย่าง เวบนี้ค่า ETH ในการ mint 0.15 - 0.2 ETH … ตีเป็นเงินบาทนี่แพงบรรลัยอยู่นะครับ

-
Scammer รายแรกพยายามชักจูงผม หว่านล้อมผมว่า แหม เดี๋ยวเขาก็มารับซื้องานผมน่า mint งานเสร็จ รีบบอกเขานะ เดี๋ยวเขารีบกดซื้อเลย พอขายได้กำไร ผมก็ได้ค่า gas คืนได้ แถมยังได้กำไรอีก ไม่มีอะไรต้องเสีนจริงมั้ย แต่มันเป้นความโชคดีครับ เพราะตอนนั้นผมไม่เหลือทุนสำรองที่จะมาซื้อ ETH ได้ ผมเลยต่อรองกับเขาตามนี้ครับ :
-
ผมเสนอว่า เอางี้มั้ย ผมส่งผลงานของผมแบบ low resolution ให้ก่อน แลกกับให้เขาช่วยโอน ETH ที่เป็นค่า mint งานมาให้หน่อย พอผมได้ ETH แล้ว ผมจะ upscale งานของผม แล้วเมล์ไปให้ ใจแลกใจกันไปเลย ... เขาไม่เอา
- ผมเสนอให้ไปซื้อที่ร้านค้าออนไลน์ buymeacoffee ของผมมั้ย จ่ายเป็น USD ... เขาไม่เอา
- ผมเสนอให้ซื้อขายผ่าน PPV lightning invoice ที่ผมมีสิทธิ์เข้าถึง เพราะเป็น creator ของ Creatr ... เขาไม่เอา
- ผมยอกเขาว่างั้นก็รอนะ รอเงินเดือนออก เขาบอก ok
สัปดาห์ถัดมา มี scammer คนที่สองติดต่อผมเข้ามา ใช้วิธีการใกล้เคียงกัน แต่ใช้คนละเวบ แถมเสนอราคาซื้อที่สูงกว่าคนแรกมาก เวบที่สองนี้เลวร้ายค่าเวบแรกอีกครับ คือต้องใช้เมล์สมัครบัญชี ไม่สามารถผูก metamask ได้ พอสมัครเสร็จจะได้ wallet เปล่าๆมาหนึ่งอัน ผมต้องโอน ETH เข้าไปใน wallet นั้นก่อน เพื่อเอาไปเป็นค่า mint NFT 0.2 ETH
ผมบอก scammer รายที่สองว่า ต้องรอนะ เพราะตอนนี้กำลังติดต่อซื้อขายอยู่กับผู้ซื้อรายแรกอยู่ ผมกำลังรอเงินเพื่อมาซื้อ ETH เป็นต้นทุนดำเนินงานอยู่ คนคนนี้ขอให้ผมส่งเวบแรกไปให้เขาดูหน่อย หลังจากนั้นไม่นานเขาเตือนผมมาว่าเวบแรกมันคือ scam นะ ไม่สามารถถอนเงินออกมาได้ เขายังส่งรูป cap หน้าจอที่คุยกับผู้เสียหายจากเวบแรกมาให้ดูว่าเจอปัญหาถอนเงินไม่ได้ ไม่พอ เขายังบลัฟ opensea ด้วยว่าลูกค้าขายงานได้ แต่ถอนเงินไม่ได้
Opensea ถอนเงินไม่ได้ ตรงนี้แหละครับคือตัวกระตุกต่อมเอ๊ะของผมดังมาก เพราะ opensea อ่ะ ผู้ใช้ connect wallet เข้ากับ marketplace โดยตรง ซื้อขายกันเกิดขึ้น เงินวิ่งเข้าวิ่งออก wallet ของแต่ละคนโดยตรงเลย opensea เก็บแค่ค่า fee ในการใช้ platform ไม่เก็บเงินลูกค้าไว้ แถมปีนี้ค่า gas fee ก็ถูกกว่า bull run cycle 2020 มาก ตอนนี้ค่า gas fee ประมาณ 0.0001 ETH (แต่มันก็แพงกว่า BTC อยู่ดีอ่ะครับ)
ผมเลยเอาเรื่องนี้ไปปรึกษาพี่บิท แต่แอดมินมาคุยกับผมแทน ทางแอดมินแจ้งว่ายังไม่เคยมีเพื่อนๆมาปรึกษาเรื่องนี้ กรณีที่ผมทักมาถามนี่เป็นรายแรกเลย แต่แอดมินให้ความเห็นไปในทางเดียวกับสมมุติฐานของผมว่าน่าจะ scam ในเวลาเดียวกับผมเอาเรื่องนี้ไปถามในเพจ NFT community คนไทนด้วย ได้รับการ confirm ชัดเจนว่า scam และมีคนไม่น้อยโดนหลอก หลังจากที่ผมรู้ที่มาแล้ว ผมเลยเล่นสงครามปั่นประสาท scammer ทั้งสองคนนี้ครับ เพื่อดูว่าหลอกหลวงมิจฉาชีพจริงมั้ย
โดยวันที่ 30 กย. ผมเลยปั่นประสาน scammer ทั้งสองรายนี้ โดยการ mint ผลงานที่เขาเสนอซื้อนั่นแหละ ขึ้น opensea แล้วส่งข้อความไปบอกว่า
mint ให้แล้วนะ แต่เงินไม่พอจริงๆว่ะโทษที เลย mint ขึ้น opensea แทน พอดีบ้านจน ทำได้แค่นี้ไปถึงแค่ opensea รีบไปซื้อล่ะ มีคนจ้องจะคว้างานผมเยอะอยู่ ผมไม่คิด royalty fee ด้วยนะเฮ้ย เอาไปขายต่อไม่ต้องแบ่งกำไรกับผม
เท่านั้นแหละครับ สงครามจิตวิทยาก็เริ่มขึ้น แต่เขาจนมุม กลืนน้ำลายตัวเอง ช็อตเด็ดคือ
เขา : เนี่ยอุส่ารอ บอกเพื่อนในทีมว่าวันจันทร์ที่ 30 กย. ได้ของแน่ๆ เพื่อนๆในทีมเห็นงานผมแล้วมันสวยจริง เลยใส่เงินเต็มที่ 9.3ETH (+ capture screen ส่งตัวเลขยอดเงินมาให้ดู)ไว้รอโดยเฉพาะเลยนะ ผม : เหรอ ... งั้น ขอดู wallet address ที่มี transaction มาให้ดูหน่อยสิ เขา : 2ETH นี่มัน 5000$ เลยนะ ผม : แล้วไง ขอดู wallet address ที่มีการเอายอดเงิน 9.3ETH มาให้ดูหน่อย ไหนบอกว่าเตรียมเงินไว้มากแล้วนี่ ขอดูหน่อย ว่าใส่ไว้เมื่อไหร่ ... เอามาแค่ adrress นะเว้ย ไม่ต้องทะลึ่งส่ง seed มาให้ เขา : ส่งรูปเดิม 9.3 ETH มาให้ดู ผม : รูป screenshot อ่ะ มันไม่มีความหมายหรอกเว้ย ตัดต่อเอาก็ได้ง่ายจะตาย เอา transaction hash มาดู ไหนว่าเตรียมเงินไว้รอ 9.3ETH แล้วอยากซื้องานผมจนตัวสั่นเลยไม่ใช่เหรอ ถ้าจะส่ง wallet address มาให้ดู หรือจะช่วยส่ง 0.15ETH มาให้ยืม mint งานก่อน แล้วมากดซื้อ 2ETH ไป แล้วผมใช้ 0.15ETH คืนให้ก็ได้ จะซื้อหรือไม่ซื้อเนี่ย เขา : จะเอา address เขาไปทำไม ผม : ตัดจบ รำคาญ ไม่ขายให้ละ เขา : 2ETH = 5000 USD เลยนะ ผม : แล้วไง
ผมเลยเขียนบทความนี้มาเตือนเพื่อนๆพี่ๆทุกคนครับ เผื่อใครกำลังเปิดพอร์ตทำธุรกิจขาย digital art online แล้วจะโชคดี เจอของดีแบบผม
ทำไมผมถึงมั่นใจว่ามันคือการหลอกหลวง แล้วคนโกงจะได้อะไร
อันดับแรกไปพิจารณาดู opensea ครับ เป็นเวบ NFTmarketplace ที่ volume การซื้อขายสูงที่สุด เขาไม่เก็บเงินของคนจะซื้อจะขายกันไว้กับตัวเอง เงินวิ่งเข้าวิ่งออก wallet ผู้ซื้อผู้ขายเลย ส่วนทางเวบเก็บค่าธรรมเนียมเท่านั้น แถมค่าธรรมเนียมก็ถูกกว่าเมื่อปี 2020 เยอะ ดังนั้นการที่จะไปลงขายงานบนเวบ NFT อื่นที่ค่า fee สูงกว่ากันเป็นร้อยเท่า ... จะทำไปทำไม
ผมเชื่อว่า scammer โกงเงินเจ้าของผลงานโดยการเล่นกับความโลภและความอ่อนประสบการณ์ของเจ้าของผลงานครับ เมื่อไหร่ก็ตามที่เจ้าของผลงานโอน ETH เข้าไปใน wallet เวบนั้นเมื่อไหร่ หรือเมื่อไหร่ก็ตามที่จ่ายค่า fee ในการ mint งาน เงินเหล่านั้นสิ่งเข้ากระเป๋า scammer ทันที แล้วก็จะมีการเล่นตุกติกต่อแน่นอนครับ เช่นถอนไม่ได้ หรือซื้อไม่ได้ ต้องโอนเงินมาเพิ่มเพื่อปลดล็อค smart contract อะไรก็ว่าไป แล้วคนนิสัยไม่ดีพวกเนี้ย ก็จะเล่นกับความโลภของคน เอาราคาเสนอซื้อที่สูงโคตรๆมาล่อ ... อันนี้ไม่ว่ากัน เพราะบนโลก NFT รูปภาพบางรูปที่ไม่ได้มีความเป็นศิลปะอะไรเลย มันดันขายกันได้ 100 - 150 ETH ศิลปินที่พยายามสร้างตัวก็อาจจะมองว่า ผลงานเรามีคนรับซื้อ 2 - 4 ETH ต่องานมันก็มากพอแล้ว (จริงๆมากเกินจนน่าตกใจด้วยซ้ำครับ)
บนโลกของ BTC ไม่ต้องเชื่อใจกัน โอนเงินไปหากันได้ ปิดสมุดบัญชีได้โดยไม่ต้องเชื่อใจกัน
บบโลกของ ETH "code is law" smart contract มีเขียนอยู่แล้ว ไปอ่าน มันไม่ได้ยากมากในการทำความเข้าใจ ดังนั้น การจะมาเชื่อคำสัญญาจากคนด้วยกัน เป็นอะไรที่ไม่มีเหตุผล
ผมไปเล่าเรื่องเหล่านี้ให้กับ community งานศิลปะ ก็มีทั้งเสียงตอบรับที่ดี และไม่ดีปนกันไป มีบางคนยืนยันเสียงแข็งไปในทำนองว่า ไอ้เรื่องแบบเนี้ยไม่ได้กินเขาหรอก เพราะเขาตั้งใจแน่วแน่ว่างานศิลป์ของเขา เขาไม่เอาเข้ามายุ่งในโลก digital currency เด็ดขาด ซึ่งผมก็เคารพมุมมองเขาครับ แต่มันจะดีกว่ามั้ย ถ้าเราเปิดหูเปิดตาให้ทันเทคโนโลยี โดยเฉพาะเรื่อง digital currency , blockchain โดนโกงทีนึงนี่คือหมดตัวกันง่ายกว่าเงิน fiat อีก
อยากจะมาเล่าให้ฟังครับ และอยากให้ช่วยแชร์ไปให้คนรู้จักด้วย จะได้ระวังตัวกัน
Note
- ภาพประกอบ cyber security ทั้งสองนี่ของผมเองครับ ทำเอง วางขายบน AdobeStock
- อีกบัญชีนึงของผม "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw กำลังค่อยๆเอาผลงานจากโลกข้างนอกเข้ามา nostr ครับ ตั้งใจจะมาสร้างงานศิลปะในนี้ เพื่อนๆที่ชอบงาน จะได้ไม่ต้องออกไปหาที่ไหน
ผลงานของผมครับ - Anime girl fanarts : HikariHarmony - HikariHarmony on Nostr - General art : KeshikiRakuen - KeshikiRakuen อาจจะเป็นบัญชี nostr ที่สามของผม ถ้าไหวครับ
-
 @ bf95e1a4:ebdcc848
2024-10-08 16:34:23
@ bf95e1a4:ebdcc848
2024-10-08 16:34:23This is the AI-generated full transcript of Bitcoin Infinity Show #129 with Max Hillebrand!
Check out the https://bitcoininfinitystore.com/ for our books, merch, and more!
Luke: Max, welcome for the first time to the Bitcoin Infinity Show.
The Lodging of Wayfaring Men
Knut: Yeah, so one of the first things, you have made the best book recommendations to me that I've ever gotten from anyone. And one was The Ethics of Liberty by Murray Rothbard, and the other one was Economic Science and the Austrian Method by Hans Hermann Hoppe. And now you recommended another book, which I haven't read yet, called The Lodging of Wayfaring Men.
what is that book about and why do you recommend it so much?
Max: It's a beautiful book. it's incredible. And it's written for us and for Bitcoiners, but it's over 20 years old. it was written in like 1997 to 2002 and that time period. And it's loosely based on real events, which is fascinating. the book is crazy. it goes about a group of cypherpunks who are, Building an anonymous marketplace, and the first attempts of an anonymous digital currency.
And again, this shit really happened. the story is quite wild. With, the freedom tech being built for very good reasons. people who understood the philosophical impact. and the deep reasons for why freedom is important. So they were very motivated, and, dedicated to make the world a better place in their lifetime.
And so they got their shit together and got organized and built something incredible, right? And it took them a couple attempts. and eventually they rolled it out and enabled people to trade right, to do their business, online in cyberspace, and encrypt it. And so that made a lot of people very happy because, you know, you get to live life free and undisturbed, so it got adopted by many users.
So much so that eventually the government started to notice that somehow they're making less tax revenue than before. And something's a bit fishy, you know. And then they started to investigate and You know, the NSA and FBI put a decent amount of people on the topic and tried to de anonymize the users of these services and infiltrate them.
And yeah, so the story is about this whole clash between the first and second realm, you know, people who built FreedomTag. And people who enslave others and how those two worlds kind of clash. it's a book that's very inspiring.
Knut: What was the website called?
Max: So, the author's name is Paul Rosenberg.
originally this book was published anonymously, years later, when it was safe to, associate their actual name with this, he did. he was, a teacher, an electrical engineer's teacher. He wrote 30 books on that subject, and is a very eloquent and practiced writer, but also a hardcore cypherpunk and freedom lover, and very well read,
So he has the freemansperspective. com. This is a newsletter. You can go back. It's going for, I don't know, 10, 20 years or something. And every week there's one or two short pieces of articles that he writes. And this book is actually also includes some writings that he did in the past and published. so it's somewhat a collection of his thought.
The Lodging of Wayfaring Men is a fiction book, right? It's basically a fictionalized story with, character arcs and such. the author is very technical, and he understands cryptography and how to apply it. He understands distributed networks and laying fiber optic cables and stuff like this.
So there's a lot of real computer science in this fictional world. And that makes it quite applicable to today where we're surrounded with cryptography much more than at the time when this book was written.
Knut: So, all right.
Taxes
Knut: bit of a jump here, but why is, avoiding paying taxes the most altruistic thing you can do in life?
Max: this is actually one thing that gets covered in the book, right, where,
Knut: that was the case.
Max: because this is also why this book is so interesting to recommend to newcomers, to this philosophy, because at the beginning, not everyone is convinced that this is a good idea. Even the creators of this technology don't know the end result and how other people will use this tech.
There's a lot of ambiguity there. And so this book follows characters who reason through these very difficult questions. For example, I'm going to spoil this book a bit, but everyone should read it anyway. So, there's one character who was a lawyer, right? He works together with an ex FBI agent, who both of them share this common, seeking of justice, like real justice, to stop bad guys from doing bad things, to good people.
the ex FBI guy is somewhat disillusioned. With the institution of the FBI to actually provide and establish justice. so now he is somewhat like walking this line in between the institution and, the actual free realm, vigilant justice basically.
and here then when thinking of. this case. is there a wrong being done by the FBI trying to stop this project? Or is this project actually good? Do they have justice in doing what they do? then, he, reasoned of, is the avoidance of tax, of, of taxation evil.
And, and, of course then walks through the reasonable steps of thinking. No, if, two people transact voluntarily. both people are better off after the trade than before, right? Both people are happy, both say thank you and shake hands. that's trade. That's the market, right? and then you have coercion,
Where one guy says, give me that, and the other says, no, actually, I don't want to give you that, but the guy hits him and takes it anyway. And so that means afterwards that the guy who stole it is obviously better off. He's happy, right? He got the thing, but the guy who was the victim was being stolen from is worse off.
And so humans have the capacity to do mutually beneficial things, right? To literally create value, make both of us better off than we were before. And we also have the potential to destroy value and take from others. and one is beneficial and fosters the growth of civilization and the other destroys it.
Knut: And so, you know, avoiding being stolen from is a good thing. Reminds me of one thing we go into in the new book, about the difference between lawful and illegal. I don't remember the name of the guy now, but some Dutch libertarian thinker, who emphasized on the terms, made the point that something being lawful is like lawful in an ethical sense, like the basis in Don't Steal, whereas legal is the top down government imposed legal framework, and how the two don't always align, or rather, they almost never align.
Natural vs Man Made Law
Max: Yeah, this is the difference between natural law and man made law. A natural law is one that is universal across time and space. It's always present, and it's immutable. It cannot be changed, at least not by us. And, you know, physics, for example, is a natural law. And arguably there is a natural law to ethics as well.
Specifically, as morality increases, freedom increases. And as morality decreases, freedom decreases. That's the law of gravity in the ethical realm. and, that man didn't make it, right? We just realize it because it is what it is. And then we have man made law on the other hand. this is depends on a certain territory, right?
The law in the U. S. is different from the law in Russia. And it also depends on time. I think the American law in the 1700s is very different from what it is today. and so there are these imaginary lines where these rules apply and there's Other places or times where they do not apply. So they're arbitrary, right?
And so they can be designed, to the benefit of some and at the expense of others. And that is ultimately what, politics is about.
Knut: Yeah, I think this is one of the key points that that quote unquote normies have such a hard time wrapping their head around. Natural law and like what, what makes don't steal a natural law? Like what, what is the very foundation of, libertarianism or anarcho capitalism or absolute property rights or whatever you may call it, consensualism?
And to my understanding, it has to do with homesteading. If you're the first person that acquired something, then no other person has a right to take that away from you. And you can logically deduct your way to that being true. Like, what's your view on that? And what's your understanding of that? And how would you explain that to a layman?
Max: Well, the reality is such that we have limited scarce resources. If we have one piece of steak on the table and three guys who are hungry, like some are gonna go home on an empty stomach, right? We literally don't have enough food to feed us all, right? And one piece of something can only be used by one person at one time, right?
We cannot duplicate one piece of steak into many and satisfy everyone. So this is a natural form part of reality, right? That's just how things are, you know? So there's a potential of conflict over who gets to allocate these scarce resources. And there's a couple solutions to it, right, that have been proposed.
Like one would be like, nobody owns it, right? Nobody gets to eat it because it's natural and it's not part of your body, so don't touch it, right? But then we die, you know, all
Knut: that's the problem with that.
Max: That's kind of a problem.
Knut: Yeah.
Max: so
Knut: Yeah.
Resource Allocation
Max: So let's rule that option out. another solution is, of course, we all own it. Right?
And we all, get to use it. But, that doesn't really work either, right? Because, sure, we all own it, but who actually gets to eat it? Because there's three different mouths and the food only goes into one of them. we can't all actually own something if we cannot all use it.
It is limited and only a few can use it. So, everyone owns it isn't the solution to the problem. Because everyone cannot own it, there's not enough for everyone. So again, that's an issue. Ultimately, we all starve. And another option would be, we vote.
We somehow pick who gets to allocate these resources. But then, I mean, we're 8 billion people. How are we all going to vote on who gets to stake? Right? Like That's, that's going to be impractical. Like, how are we even going to communicate, all 8 billion of us, to get together in a vote? So again, until we have the result of the vote, nobody eats the steak, so we all starve again.
It's not really a good solution either. And then we have one option that, like, a small subset of the people gets to make the choice of, you know, how to allocate these resources. And we can just pick them, vote for them, for example. But here again, now other people are allocating the resources for others, right?
Like, and some bureaucrat, a hundred kilometers away, is not gonna know, like, who of us is vegetarian and doesn't want the meat. Right? and that just means that someone who's far off doesn't have the knowledge to actually allocate the resources in a proper manner. And that leads to misallocations, right?
We starve, again. Because the guy who doesn't want the meat gets it and then it rots. And the guys who would actually like it never get access to it and they starve. So that's the fundamental problem of socialism, basically, of some priest class allocating the resources for others. So again, the solution doesn't work either.
So we're not left with much. But one thing that seems to work is private property rights. Again, as you said, the person who creates something, the butcher, or the farmer who raised the cow, can now decide what to do with it. Does he butcher it himself? Does he sell it to a butcher? So the person who created something gets to own it, and gets to decide how to allocate this, and then he has the right to either consume it himself, or to abdicate the consumption of this good.
So to say, I won't use it, I will trade it, I will give it to you, right? And he can make it a gift. Just say here, half the entire cow, like, I like you, I like your family, you, like, I'm happy that you're happy, right? Great, that's possible, right? Or, of course, he would want something from you in return, like, give me a bar of gold, or, a bushel of wheat, or something else.
we now have a way that we can allocate resources in a clear, simple rule set, the person who created it. can decide what to do and have a contractual agreement to transfer this ownership to someone else. the people who actually have the problem now have the power to allocate the resources to solve those problems and not some guy far away, but just you and me who created stuff.
Ownership of Information
Knut: And as you said, this only applies to scarce resources. So what, would be an example of a resource where you could eat the steak, but I could have it too. And, the thing that comes to mind, is information, of course. So, can you own information?
Max: No, like, because that, that doesn't really make sense, right? To own means to allocate, how to allocate these, to decide how to allocate these resources. All right. And then, that's a solution to a problem of a lack of resource allocation, right? or for a lack of resources that need to be allocated rather.
But with information, there is no lack. Like if I have a PDF, I can copy it to you and I can send it to you, and I can send it to a hundred other people, and I still have the exact same high fidelity version. Of the information that I shared with others, and of course it's the same with words, right? The words that I speak, they're not lost on me, right?
I still retain them and the information that they represent. and that means we don't need to be, stingy with information. We can give it to everyone. and it doesn't degrade the quality quite on the contrary, right? without information there is no production.
imagine yourself on an island, and you have all the raw materials, all the machinery, like everything there, but you don't know anything about physics, or material science, or just production stages of how to build things. If you don't know any of that, the raw material is worth nothing to you.
Nothing. Because you don't know how to allocate, how to shape this raw material into other things so that it actually solves your problems in the end. we need information in order to produce things. That's the theory behind it. The blueprints, so to say. the cool thing is, we don't have to be stingy with the blueprints.
We can give every human on this planet Equal access to all of the information that we as humans have accumulated, and now all of a sudden you will never be stranded on an island not knowing how to do something, because you can just look it up. In the grand database of accumulated human knowledge, of course, technology has made that much more possible and low cost.
Back in the day, in order to share an information, you needed to speak verbally to it, right? So you're limited to time and space, or you need to scratch it on some stone or clay or write it on a piece of paper, And then still, you have the scarcity of the paper, right? There's only one book.
And there's a hundred people who want to read it. So again, information is limited. Not because the information itself is limited, but because the medium of the information is scarce. And that was a big tragedy that we were never able to communicate at a large scale, and remember these conversations and easily access them.
Until the cypherpunks who came up with computers, right? And realized that we can build this realm of information That is so cheap to transfer and store information, that we can just basically do it for free, for anybody, for 8 billion people. And all they need is a rather cheap form of silicon, and like, nicely arranged.
but of course people try to hold on to the protection schemes that extract money from others, and capital from others, and You know, nation states have enforced intellectual property rights and patents and such, and that just harms people. It doesn't bring forward the best out of humanity. And that's a big shame.
Knut: Now, very well put. this has been Praxeology 101 with Max Hillebrand.
Bitcoin and Praxeology
Knut: where I want to follow on, follow up here is, how does this apply to Bitcoin? Because Bitcoin is only information, so how can anyone theoretically ever own a Satoshi? Do you really own it, or what is it?
Max: What is actually a Satoshi? Look into the Bitcoin code base. There is no such thing as Satoshi, right? The transaction has a field that is an integer. But it's just an integer. It doesn't even have a unit associated to it, right? So, it's just a number. Satoshis are just numbers in a database.
And you don't own the number 270, 000 just because you have 270, 000 bitcoin. The actual number of satoshis, no, you don't control them. You don't own them. But information has another interesting thing that cypherpunks realized, right? That, once, like, when you have a secret, then you can choose to share it with others.
And then once you've shared it with one person, however, you cannot control what that person does with the information. He can keep it secret for himself, or he can tell it to the entire world. And so, there is such a thing as giving access rights to information. And this is an important part in Bitcoin, of course, right?
Our secret keys should be secret, privately kept just for us, because if you do share your secret key publicly, then all of a sudden anyone can, Signed messages, with this private key and therefore spent Bitcoin in the transaction chain of Bitcoin. and well, that's a critical part of it.
So Bitcoin basically relies on keeping information, hidden from others, in order to ensure that we, solve, like, basically Bitcoin. It's just a piece of software, right? So it is non scarce information, but it wants to be money. And money needs to be scarce, right? Because if I can spend a bar of gold first to you, and then the same bar of gold later to you, we have infinite inflation, right?
The money system just dies. so scarcity is required. It's a required feature for money and digital money therefore requires digital scarcity. And so what Bitcoin does is it establishes a set of computer code that defines the access, right? Two certain chunks of money, so to say, right? And the chunks of money are Bitcoin UTXOs, unspent transaction outputs, and the spending condition, so to say, or like the rule how to allocate this money, who gets to decide it.
Where this money goes next is defined by a script and a small computer program that evaluates either to true or to false, depending what input you provide. And so the script is the lock, and usually it's a single public key. And then the way to prove that You're actually authorized to spend this coin is by creating a valid witness.
You know, the input to the script, to the program that returns it to true rather than to false. And usually, again, that's a signature of a single private key over the transaction structure that you're actually spending the money. Bitcoin's genius realization is that. We just all have to check every transaction of everyone else.
And when we do that, we can be sure that, nobody's being stolen from, That nobody is, losing access to his money, that someone is spending the money with a wrong signature. he doesn't have the private key. He cannot produce a valid signature. So we have to make sure that such a transaction does never make it into the blockchain, right?
that's the first important aspect. And the second is we want to ensure that there's no inflation. that's Because if we can just create as many tokens as we want, then the value of the token goes to the marginal cost of production. If we can produce a token with the click of a button, then the marginal cost of that token, or the value of that token, will be zero, right?
So we need to make it, Difficult, or in fact, in Bitcoin, impossible to create additional units, you know, there's 21 million and that's it, right? That's the set of rules. And therefore, when we check each transactions, we also ensure that there is no transaction that has one Bitcoin on the input side and 10 Bitcoin on the output side, therefore increasing the total supply of Bitcoin.
And so Bitcoin is a massive verification machine to ensure that this computer system is this way of speaking to each other, actually balances the books of the system. of how many units of money are there, and who has the right to allocate these, and so it's basically a system that creates a natural resource, and then also manages the allocation of this natural resource.
Knut: so Bitcoin is almost a parallel universe where, in fact, you do own the Bitcoin, basically, but the ownership is not defined by you as a person. It's defined by the knowledge of a secret. so you prove that you have access to it by having access to the private key, which unlocks it.
Ownership of Bitcoin
Knut: On earth that can prove that you own a Bitcoin except you, the holder of the private key.
Max: If the holder of the private key reveals information to others that indicates such, one very common way that this would be is you have a mobile wallet, that does not run a Bitcoin full node, That connects to someone else's full node to check if you have Bitcoin,
You don't use Tor, so there's an IP address linked from you to the server, and so the server operator knows that this IP address just asked how much money is on this address, and so we have, a very strong indication, that this IP address owner owns
Knut: It can be a very strong indication, but in my mind it can never be proof. Because you need to sign with the actual private key to prove. Otherwise it's boating accident time.
Max: guy with the gun doesn't need proof, right, he just needs a good enough guess. For him, he needs, like, there is a praxeology to violence. thieves are actors. They live in a state of uneasiness, they have problems, and they try to find a solution to that problem. They don't have ethics, they don't have morals, and so their solution to the problem harms other people.
But nevertheless, they are still actors. And so they think that they will be better off after the action of theft than before. That's a value judgment. And it's an entrepreneurial one. So they might be correct, they might not. They break into a house, hoping that there is a bar of gold hidden under the couch, right?
Turns out there's not, right? So, if they spend a lot of money breaking into the house, and there's no loot, they're not profitable thieves. And this means that they destroyed their capital, right? They spent 10 Bitcoin on getting the equipment, and they got 0 Bitcoin back. So, that means they're 10 Bitcoin poorer, and eventually they will run out of money and starve.
So, thieves need to be profitable in order to do their thieving, and that's the genius that cypherpunks realized. If we exponentially increase the cost of attack, and exponentially decrease the cost of defense, then we make thievery unprofitable. And that's the genius of private public key cryptography and encryption, right?
It's trivial to generate a private key and then generate a public key or a signature, right? But to brute force a private key or to forge a signature without it, like, requires more energy that would collapse into a black hole, you know? So that's kind of a problem.
And for thieves, right? It's really good for the people who want to defend themselves. Because they can very cheaply do it, and it just doesn't make sense to attempt to break the encryption. But nevertheless, computer systems are very complex, and there's a lot of metadata associated with, computing and communicating between computers.
And so, there are, microphones and radio frequency scanners that you can point on computers and see the computation happening in the machine because there's a lot of radiation outside of the computer that can be correlated to which bits are being flipped you can have all types of side channel attacks to extract secrets from a computer while it's running the problem is that the holistic technology stack we have is quite susceptible to revealing information that should have been kept secret.
And again, that is a critical part, of course, to communication encryption, but even more so for Bitcoin. If we lose the assurance that only we know the private key, the money system is broken. And that's why Bitcoiners were so paranoid and started this whole thing of hardware wallets and secure elements to Really ensure that we don't leak private key material, but it's an extremely difficult task, because, well, this reality is very observable, and the cards are, to some extent, quite in favor of surveillance, unfortunately.
the guy with the gun in this case could be the government, Yeah, exactly, it can just be like a poor guy who needs to provide for his children, you know, and, he sees a way for feeding his family for the next two years, and that's a good trade off for him.
Knut: Yeah, momentarily.
Max: right?
Bitcoin and World Peace
Knut: So, if we manage to do this, on a grand scale, and if people in general manage To exponentially increase the cost of the attack while simultaneously decreasing the cost of defense. Does that lead to world peace at one point? Is that the end goal?
Max: Yeah, I think so. Oh, I mean, that makes sense. If every economically rational thief will realize that he is worse off if he does this stealing, right? Like, actually, because he needs to spend much more money in an attempted theft, and most likely he's not going to succeed. And, I mean, this exponential difference has to be huge, though, right?
Because, like, we had castles, you know? Like, castles are quite, like, quite extreme asymmetric protection. Like, if you're behind castle walls, with a well staffed militia that actually defends the walls, It's quite difficult to get to you if you just have, you know, like, humans and swords and ladders. that's, like, sieges are, in the favor of the defender.
But still, they happened a lot, right? And people were able to overcome these defenses. Because, I guess they weren't never holistically secure, you know? There was always some backdoor that enabled the attacker to go through, to get through, right? and that might just be brute force, right? You just bring a huge army and You're fine with tens of thousands of your own guys getting killed, but eventually, you know, after you throw a couple hundred thousand people at the problem, someone will succeed to break through.
Quite a brutal tactic, obviously, but it worked.
Knut: you get in.
Max: But then cryptographers came around and were like, well, but there's math.
Luke: Yeah, we can use RAM in another way. 1 plus 1 is 2. What? Are you sure?
Knut: that might be offensive.
Luke: That's a different kind of worms.
Knut: Yeah. . Yeah. So, the,
Bitcoin For Attack
Knut: so Bitcoin being this perfect defense mechanism, because all it does is increase the cost of the attack, can Bitcoin ever be used for attack in your opinion? Like, can it be used in an aggressive way?
Max: I think directly not, because again, it is just, speech and such, but on the other hand, maybe yes. Because, let's say, if someone hacked your machine, and got access to your private key, and spends the Bitcoin, like, in the context of Bitcoin itself, it's a valid signature, it's a valid transaction, and it will be included.
So, in the legalities of Bitcoin, it is no theft, right? It is a valid transaction. but, On the ethical realm, you worked hard to get these Bitcoin and you didn't want to send them to the attacker, so he is definitely stealing them from you. So, Bitcoin can be stolen, certainly, in the human analysis.
Not on a technical level, we've never seen a transaction confirmed with an invalid signature, but on the human level, There have been a lot of people that got separated from their Bitcoin against their will, right, against their consent. and, and that is theft. So, thieves can use Bitcoin, thieves can get paid in Bitcoin, thieves can take your Bitcoin and pay them to themselves, right?
that's a fact of reality too.
Aggression and Spam
Knut: Could that be used in an aggressive way?
Max: it is just the writing of bits and bytes, right? So there's, however, again, a limited amount of resources that are available specifically in Bitcoin. And not just do we have 21 million Bitcoin, we also have like, Two and a half slash four megabyte blocks, right?
And so this means there's only a certain number of transactions that can be fit into a single block. that means we have, again, a scarce resource and we need to allocate it. this is why there is a price for Bitcoin transactions, because that's how we solve the scarcity problem, right?
by whoever pays the most gets in. that's a, or it's not even whoever pays the most. It's like. You can choose who goes in by mining a block, right? You have full freedom of choice of which transaction do you include into your block. And if you don't mine, then you can propose to someone else, say, please include my transaction into a block.
But again, there's a large demand and a limited supply. so most likely people will start bribing each other and it's like, yeah, if you include my transaction in your block, I'll give you sats. And in fact, Bitcoin, the Bitcoin software launched with a anonymous peer to peer marketplace for the scarce good, which is Blockspace.
Satoshi didn't have to do that, right? Bitcoin would have totally worked, if, if you could not, like, if every input sum has to be exactly equal to every output sum, right?
There cannot be that outputs are smaller than inputs and the leftover goes to the miners, but that could have been a consensus rule, right? But then most likely we would have seen some third party external marketplace. Where people would do the bidding on please include my transaction into the block.
And then of course they would have to figure out how do we actually pay the miner to get our transaction in the block. So Satoshi had the genius to embed an anonymous marketplace. Into the core essence of the protocol, right, with the rule that outputs can be smaller than inputs, and the rule that we have this gossip peer to peer network, which like the whole peer to peer network is kind of optional, by the way, but it's just there to kind of make it easier so that we have this anonymous marketplace for Blockspace that we can propagate offers, right, and one person sends the offer and gets spread to the entire network.
So the demand side is no monopoly. Anyone can broadcast a message to the peer to peer network hoping to be included. And then on the supply side, the actual miners, there's also no monopoly. Anyone can spin up his computer and start SHA 256 hashing. On the most recent chain, right, with his own candidate block.
And nobody can stop you, right? That's the definition of no monopoly. New market participants are not hindered to enter the system. And so this is the most radical free market that we've seen probably ever. And it's been kind of hidden inside Bitcoin since the very beginning.
Mining vs Hashing
Knut: Yeah, you can of course also pay the miner in something else than sats to get included into a block. And if a mining pool does this, the individual miners doesn't necessarily have a claim to a piece of the pie of whatever money was paid to the mining pool owner under the table and not on the system, right?
They can't even see it. So how big of a problem is that, and can you really call yourself a miner if you're just selling hash power to a pool and the pool isn't transparent?
Max: I mean, it's actually true that we, like, there could be in the future, A alternative marketplace for block space that's not inside the Bitcoin Core client. And by the way, arguably that's better, because we have a piece of software that does one thing really well, and then, you know, we just specialize and put the two modules together.
architecturally speaking, this might be better. we see things like, for example, the mempool. space explorer, or accelerator, right, is one. Marketplace that is now establishing that that seems to work now quite well. Of course, it has the issue of there's a central, like, order book, so to say, and probably custodian for the money as well.
And so, I'm not sure, but it's one approach of doing such an alternative marketplace and there can be downsides. it's not really public of how much Volume is going through here, right? how much are people speeding up their transactions, And I guess the same goes to much earlier where we just had mining pools offering this in their own API, or a webpage.
so at least now, like we, we have a dedicated service provider. That's not a mining pool doing this, which I think is an improvement. but we could also, you know, build. A, like, off chain peer to peer network, so to say, that's not related to Bitcoin per se, but that has all of the aspects that we want just dedicated for an optimized market book for this resource.
And Bitcoin should still work, I think. Like, the marketplace inside Bitcoin Core is not essential in the long run. It was just very convenient to bootstrap it. But, you know, in 50, 100 years, I wouldn't be surprised if we have Dedicated systems for, for these things that potentially are in different repositories and such different softwares.
Knut: So, in your opinion, how damaging is a temporary fee spike over a weekend or something where it goes up to like, 2000 SATs per transaction. what impact does it have on lightning channels and lightning providers and so on? Like do you consider it an attack or what is it?
Max: it's an inevitability almost, right? If you have a hard, extremely limited supply, right? there is only two and a half megabytes in the usual block, and you have extremely fluctuating demand, and there is no way to speed up production of the good. there is bound to be extreme, differences of we have way more demand than supply or way less, right?
But it will be very rare that we will fill just exactly everyone who wanted to gets in. So to actually clean out every transaction that wanted to be made is quite rare already now and in the future, if Bitcoin continues to be used, this is even more unlikely, right?
So then the question is just how, like, do you get into the top, like, the top payers to get included in the block still? And this is where just the technology is quite difficult, because this is like, you're, you're, you're, it's an order book, right? You're trading, basically, and you don't know if the price goes up or price goes down.
And this is all at least supposed to be automated. Bitcoin wallet developers are building trading bots, block space accountants charged to purchase block space on behalf of the user. the user just clicks send and that's it. the software does all of the complexities of constructing a transaction that is of a size acceptable, right?
Because if fees are super high, you don't want to build a transaction with a hundred inputs and one output, right? You would want to have a transaction with one input, one output. It would be way cheaper if the fee spike is currently high. a smart robot should build a different structured transaction with more or fewer inputs and outputs to accommodate the current fluctuation of the market.
And of course, the fee rate is another, like what's actually your bid that you put into this marketplace? And that's trading like. How much are you going to pay for the stock? Nobody really knows, right? And so it's kind of good luck and you don't know if it goes up or goes down. And sometimes you overpay, right?
And you pay way more than was actually needed to get into that block. And so you lose money, you lose capital. And sometimes you don't pay enough and you don't get included for months, right? but there's better software that can alleviate a lot of these problems.
Spam Making Bitcoin Worse as Money
Luke: Well, so I guess another side to this question, because everything you're saying makes makes total sense from the perspective of that this stuff is definitely going to happen from from hyperbitcoinization side. There's just going to be more demand than there is supply of block space. But I think the issue that we've been exploring a lot.
Lately, is, is that when there are transactions that aren't really being made for the purpose of moving value from one person to another in the form of Satoshis, they're, they're another form of value, subjective value that is communicated through arbitrary data, or at least some other type of, of data.
Does that change the property of Bitcoin as money? That's essentially, I think the, the root of the, the argument any, anyone talking
Knut: Yeah, exactly.
Luke: the functionality of Bitcoin is
Max: Well, I think. There's a couple aspects to this, right? We have again a scarce resource block space, and there's the problem of how do we allocate this block space. And there are very stringent rules on this, right? You cannot have arbitrary data in blocks, right? There needs to be, for example, the transaction structure.
There needs to be inputs that point to previous outputs, and there need to be outputs, the sum of the inputs, sum of outputs, hashes, transaction headers, all of the stuff needs to be followed in order for this to be considered a valid block. So the Bitcoin developers have, from the very beginning, had a very, I guess, authoritarian regime to allocating these resources, which makes sense.
If you don't put stringent, like, structure in a protocol, then people just fill it with garbage and every software breaks, right? So it's like a practicality thing that we need to have a very opinionated, kind of thing. Set of rules and we need to pick one of them and like just do it because if we don't pick any then it won't work and also if we pick the wrong one it won't work either.
imagine the rules would have been like a broken hashing algorithm, for example, not SHA 256 but SHA 1 or something that's broken. People can create collisions, right? So there could be two transactions that have the exact same transaction ID. breaks the system, right? So if that would have been the set of rules, Bitcoin would have broken, right?
And now also, again, if we allow arbitrary things to be built, then people will just use it as data storage, for example, and just fill it up with megabytes of images. And again, limited amount of resources. If all of it is used for, for pictures, then none of it can be used for money transfer, right? So this is again, an inherent conflict.
the tricky thing though is, now we have this. established set of rules in the Bitcoin consensus and how do we change it, right? And that's the really tricky part of, making up man made rules. Bitcoin is not Natural in the sense, right? Like, humans came up with this shit.
Like, this is our creativity that made this happen. and so, it's not nature made, right? It's man made. Of course, men are part of nature and such. So it's a bit, wishy washy here, but ultimately, we made it, we can change it, we can make it better, and we can break it. And that's a really scary position, because I think we all realize that this is quite an important project, and we definitely have it in our power to break this thing.
I hope we do our best effort.
Caution When Changing Bitcoin
Luke: my interpretation of that is, is that, caution when making changes to Bitcoin is paramount. Would you agree with that?
Max: Well, inaction is an action too, right? And that might be even more dangerous. So, there might be critical bugs in the protocol that if not addressed will break the system and potentially they are currently being exploited, right? And so, in such a case, we should do our best to fix it as soon as possible.
Satoshi knew that from the very beginning, right? So, how exactly we do that? Who knows?
Knut: Well, if it's up to the individual miners, which it is, what blocks they want to mine, what transactions they want to include in a block. And it can be fixed that way, a sly roundabout way, if you will.
Max: Well, if we could trust the miners with stuff like this, then we could trust the miners with enforcing the 21 million, right? But we can't, right? We don't rely on anyone. We verify it ourselves, right? And so the reason why we don't have actual JPEGs in Bitcoin blocks is because your node says no to any block that actually has a JPEG in it, right?
Blocks have to have transaction in it. If not, you kick them out, right? So even if there's valid proof of work Proof of Work doesn't solve the problem of integrity of the block, right? This has nothing to do with Proof of Work. In fact, Proof of Work is one part of the rules of the integrity of the block that is defined, enforced, and verified by the full nodes itself, right?
Specifically, if you want to get rid of inscriptions, that's certainly a hard fork. Like, taproot transactions are currently valid, and if we make these taproot transactions in the future invalid, that's a hard fork, right?
It would be great to hard fork Bitcoin. We could clean so much stuff. It's just a practical reality that breaking the hard fork use of a running protocol is extremely difficult and arguably, unethical. Because people have signed up to the previous system, built businesses and, stored their money in these types of scripts.
If we now make them unspendable, what is that? No?
Mining Incentives
Knut: so, when it comes to mining, there's, minor incentives, like, the thing we talked about before, about, under the table payments to big mining pools, To me, the obvious fix to this problem is to get it into the brains of the hash salesmen, that they ought not be mere hash salesmen, but actual miners and know what block they're mining on.
Because I think the ethos among the individual miners is, better than, these bigger pools that might not be, as, concerned with the longevity of the Bitcoin experiment, but, more fiat minded and wanting a quick buck now rather than save the system in the long run.
So, right now it feels like we're trusting these bigger entities to have as much of a disincentive to destroy Bitcoin so that they won't, it's tricky. Like it's a gray zone, right? What's your thoughts?
Max: I think Satoshi's genius in designing the Bitcoin protocol was that he did his best to separate different tasks that need to be done in the system into different like conceptual entities, and then to ensure that each of these aspects is distributed as widely as possible. And this is ultimately what it means that Bitcoin is decentralized, right?
There is not one person that defines the set of rules, for example, or one person that writes the candidate block, Or one person that provides the proof of work for the candidate block, or one person that provides the signature for each transaction, right? Each of these things is distributed. And in the ideal case, in the original Bitcoin client, to every user, right?
Like, the Bitcoin software in 2009 was mining by default for everyone, right? So, literally the entire stack of the operation was at 100 percent of the users, right? There was no non validating, non mining users. In the beginning, right? We had perfect decentralization, so to say, right? And then if efficiencies kick in and economies of scale and division of labor, and we start to optimize each of these things kind of on its own and split it out into different branches of government.
Yeah, specialized entities, so to say. And if you specialize on being the best hasher that you could possibly be, you just give up on being the best block candidate creator that you could possibly be. Because if you do the one thing that you're marginally better at and focus all your attention on that, you will be the most profitable.
so, yes, it is. It is an issue. and we, Bitcoin would be better off if we further distribute the risk and responsibility of each of these tasks to as many people as possible. And I think we've done a really good job, for example, of distributing the ownership of private keys.
And like, there's, I don't know, many millions of private key holders on the Bitcoin blockchain, right? So that's, that's great. but, and we have. Probably done this as well with hashers, right? There's a decent amount of quite large independent hashing institutions, right? Not so well with mining pools and actual block candidate creation, like, that's pretty bad.
Like, there's two or three of them, so that's scary as fuck. Right there we've utterly failed and we've made Bitcoin way worse than it was before. in this one metric of resilience, of decentralization, of distribution of risks, we made it a lot more efficient, but we made it much more vulnerable to attack.
that is a problem. Thankfully, a lot of people are working on fixing it. It's a really difficult problem, right? It's not that there's some malicious, attempt of trying to break it. I mean, maybe there is, but the more likely answer is just bloody difficult computer science. it just needs an insane amount of research and development before we will have tools that are even coming close to being actually adequate.
Right? I'm not praising Satoshi's 2009 code as being perfect, because it was a pile of shit, right? And you could break it in a million ways. so we've improved a lot, but we're very far from done because to some extent the realities of the difficulty of the situation have caught on much faster than our ability to solve these.
Yeah, I mean, the problems that are currently existent in Bitcoin and that now we're at Nostriga today and talking about Nostr, this sort of related communication layer in relation to Bitcoin, you mentioned at the very beginning, Freedom Tech.
Freedom Tech and Nostr
Luke: So, we, when we last talked to you, you were focusing on Wasabi Wallet and now obviously that project has just been made open source, essentially, and so my question to you on that is, what are you focusing on in terms of Freedom Tech now?
Max: Nostr is definitely a highlight, right? Nostr is just incredibly cool. And it's so wild to think that Nostr is like two years old. it's not old, but look at the amount of stuff that we've built. In this short time frame, how powerful are we? It's incredible, right? If we get our act together and actually build on, such an open protocol and get people excited about it and people using it, it doesn't take us long to fundamentally change the pattern of speech on this planet.
Wow, that's incredible. Like, we did that. And we're just getting started. think about where Nostr is going to be in five years. It will be wild. Absolutely insane. that's very bullish and very encouraging. And it's super exciting to work at such an early stage in the protocol, because there's so many obvious improvements.
There's so many obvious use cases. There's so many low hanging fruits of how we can make it even better than it currently is. Alright, so we have something that's already great, and we know a million ways on how we can make it even better. and you can be part of making a meaningful improvement in getting this to like an exponential blow off of awesomeness.
Knut: Meaningful improvement of humanity, really.
Max: Yeah. Yeah, that's the other thing, like, that's why Freedom Tech is so exhilarating to work at, because we're ending slavery. That's kind of a big deal, you know,
Knut: Yeah, it should have been done at least 300 years ago.
Max: Yeah.
Luke: No, it's, it's amazing. And well, and actually, so a couple of things here. First of all, we've talked about this a little bit, how Nostr seems like it's the playground that people wanted as an alternative to Bitcoin. In other words, people who went and started making shitcoins were basically just wanting a playground to do all this stuff.
But now is, is, is Nostr basically the place where people can do that and channel their energies in a way that isn't going to break money?
Max: Yeah. I absolutely agree. So I'm very bullish on a lot of these use cases and one other area that currently interests me a lot, is just zero knowledge cryptography. it's wild what's possible. it's absolutely wild. Within the last five years or so. The theory has developed.
And again, a lot of shitcoin projects putting zero knowledge proofs on blockchains and such, and I'm not quite convinced that we actually need a blockchain for that. I think relays are just fine. And so I'm quite bullish on having actual zero knowledge proofs much more integrated in Nostr clients. Like, you can do amazing things with this.
Like, for example, anonymous web of trust, right? You could prove to me under an ephemeral anonymous identity, right, that you are in fact, On my follower list. Like, I'm following you, but I don't know who you are. Right? So, these types of things are trivial with zero knowledge stuff. And we don't have any size constraints or computation constraints in Nostr.
Because it is not a global consensus system. Only the people who are interested in this proof actually have to, like, download it and verify it and such. so, it's, I think we can do a lot of amazing stuff here. it seems pretty obvious wins here.
Knut: driving these 180 IQ young developers into Nostr instead of shitcoin development is, is like moving them? To do, to think more of what they should rather than what they could, because I think that's, that's sort of the main problem with this nerdy set of shitcoin developers is that they, oh, I could do this if I just do this and they, they focus on what they can do rather than what they should do.
And it's Nostr, Changing the direction of that, are people thinking more of ethical things while developing on this than
Max: it's a big claim, right? That like a piece of tech can
Knut: it's hopium
Max: improve the morality of people. it's definitely a big claim, but it seems true. Like, if you think about it in Bitcoin, like probably each of us, our level of morality before we discovered Bitcoin and what it is now.
And our understanding of morality has substantially, improved, right? And I'm not sure if it would have happened, at least to this extent, without being exposed to the Bitcoin technology. and Bitcoin is just money, you know, like, humans do a lot more than buy stuff, sure, money is incredibly important, but it's far from everything of the human experience.
And I think Nostr. We'll do a lot of the other stuff and Nostr has this freedom mindset embedded into the protocol just as Bitcoin has. And so I'm extremely bullish on seeing the people who get exposed to Nostr and what it does to them in the long run.
Hyperbitcoinization vs Hypernostrification
Max: So what happens first? Hyper ossification or hyper ization both at the same time.
Knut: does one lead to the other?
Max: there's definitely synergies here, right? and, yes, one leads to the other. there's, I met a bunch of people who got interested into Nostr first, and then used Bitcoin for the first time. It's a very common theme, actually. again, because Like, social, like, think of the, think of the, like, average screen time of people, right?
it, for sure.
I think Nostr is going to be way bigger than Bitcoin in the improvement of the human condition.
Knut: Then again, every time you press the like button or the retweet button or whatever on your social media app, even the legacy system, you are providing someone with some value. That's why your account is valuable to, Facebook's and the Twitters of the world. There is a value thing embedded into everything you do on the internet.
Max: It's just, you don't get a tradable good.
Knut: No, no,
Max: sell the like to someone else.
Knut: not at this point.
Max: They have now a star emoji. If you send the star emoji, you can send the star emoji back to the company, and they will give you money. So, voila. It's basically a shitcoin, but it's a star.
Luke: is it more important to fix money or the other stuff?
Max: Well, that's a big one. Both again, because money is only half of every transaction, right? And so maybe the earlier example of the marketplace for Bitcoin block space is perfect because why did Satoshi include the marketplace, the other stuff together with the money? Because it was kind of essential, right?
you need to have both at the same time in order to live, right? You need to speak, you need to advertise your products, you need to negotiate with the customers, right? You need to convince them of the value that you will provide to them, and then you need to receive the money and tell them that you've received it, and ultimately hand over the goods, right?
So there's a lot of human interaction into every trade, and the money aspect is just Like, one small part of this long interactive chain of protocol, basically. I think we need both at the same time. And we're just discovering upgrades to each of them as we move along. But this has always been in synergy.
Like, the internet is way older than Bitcoin, right? So arguably, we need the other stuff first, right? We needed like 20, 30 years of other stuff before we could actually come up with the money.
Knut: so fix the money, fix the world then fix the world and you fix the money.
Luke: No, but seriously, we actually talked about this. in that, maybe an analogy to, that the internet needed to develop in a centralized way because the, literally the hardware and everything, the architecture, the client server model was literally a centralized and centralizing system. Model and that needed to exist first.
And then the analogy is that gold was centralized naturally in the sense that physically the physical constraints of gold made it so that it naturally centralized into banks and then fiat solved that problem to sort of decentralize it, but it broke everything. So now the mechanism of fixing the money and decentralizing the money was gold.
Bitcoin, but the corollary for decentralizing the communication is Nostr. So both things have kind of happened in a parallel. That's, what we were discussing.
Wrapping Up
Luke: That is the alarm Oh,
Knut: Oh, okay.
Max: so we'll wrap it up.
Knut: Well, I'm
Max: Nostr for sure. Max at TowardsLiberty. com. You can send me mail, notes and sats to that, which is, by the way, crazy, right? That we can have like this unique identifier to get, like, all of your needs settled is wild. Check out, lodging of Wayfaring Men. That's, the main shill of this video.
And I made the audiobook for it. it's on a podcast. The podcast is by the author, Paul Rosenberg. And, it's called Parallel Society, right? So check that out. right now we've released the first episode. the others will come shortly thereafter. the other book recommendation I should highlight, which we haven't mentioned yet, is Cryptoeconomics by Eric Voskuhl.
Most of what I said here was very much inspired by that book. He has the most rigorous understanding of Bitcoin. It's by far the best Bitcoin book. So I also did the audiobook for that. Just search for Cryptoeconomics in your
Knut: audio book though.
Max: when you have to read tables of math formulas, it's starting to fall apart.
But there's a lot of verbal logic in the book that goes very well. Just get the free PDF for the actual graphs and
Knut: And keep using Wasabi and fire up your own coordinators and whatnot, right?
Luke: Now get on stage, Max. Don't want to make you late.
Max: Bye
the book, that's not what I said.
Luke: right, that's it.
-
 @ 22f1e753:837f33a9
2024-10-21 09:41:46
@ 22f1e753:837f33a9
2024-10-21 09:41:46
In the vast expanse of the cosmos, a decentralised enigma by the name of Bitcoin emerges, shaking the very foundations of our understanding of finance and governance. This discourse delves into the intriguing concept that Bitcoin is an alien creation, sent to steer humanity towards a future of interstellar collaboration and prosperity. By embracing the ambiguity, volatility, and anti-fragility inherent in Bitcoin, we may unlock the secrets of the "Alien Code" and embark on a journey of self-discovery and transformation.
The Celestial Architect: Satoshi Nakamoto
Envision a scenario where Satoshi Nakamoto, the mysterious creator of Bitcoin, is an extraterrestrial entity, tasked with gifting humanity a revolutionary financial system. The “Architect" brings with It a profound comprehension of the cosmos and the intricacies of decentralised networks. Satoshi's true intention transcends the creation of a digital currency; it is to prepare Earth's inhabitants for a future where interstellar trade and cooperation become the norm.
Decoding the Alien Blueprint
The Bitcoin protocol, with its intricate web of cryptography and game theory, can be seen as a form of "alien code" that challenges humanity to adapt and evolve. This code is not merely a set of rules governing a digital currency, but a blueprint for a decentralised society that values transparency, security, and cooperation. By embracing the Alien Code, we may unlock the secrets of a more resilient and adaptable world, where individuals and communities thrive in the face of uncertainty.
The Galactic Matrix: Navigating the Web of Decentralisation
The Matrix, a thought-provoking science fiction franchise, serves as a powerful metaphor for the complex, interconnected web of human knowledge. In this context, Bitcoin's decentralised architecture mirrors the Matrix's intricate network of simulated reality. Just as Neo, the protagonist, must navigate the unpredictable nature of the Matrix, humanity must learn to navigate the ambiguity and volatility of Bitcoin. By embracing this uncertainty, we may discover the hidden patterns and codes that govern the decentralised universe.
The Interstellar Imperative: Cultivating Anti-Fragility
The emergence of Bitcoin and other freedom technologies signals a profound shift in human consciousness, as we begin to recognise the importance of cooperation and mutual support in the face of an uncertain future. By embracing the Alien Code and the principles of decentralisation, we may unlock the secrets of a more resilient and adaptable world, where individuals and communities thrive in the face of uncertainty. The interstellar imperative is clear: we must learn to navigate the complexities of decentralised systems and develop the anti-fragility necessary to thrive in a rapidly evolving universe.
Conclusion
In this discourse, we have woven together the threads of Bitcoin, Satoshi Nakamoto, and The Matrix to convey a powerful message: the importance of embracing ambiguity, volatility, and anti-fragility in a rapidly evolving world. By presenting Bitcoin as an alien product, we emphasise its transformative potential and encourage curiosity, innovation, and resilience in the face of the unknown. As we embark on this journey of self-discovery and transformation, we may uncover the secrets of the Alien Code and unlock the doors to a decentralised utopia, where humanity thrives in harmony with the cosmos.
-
 @ 460c25e6:ef85065c
2024-10-10 13:22:06
@ 460c25e6:ef85065c
2024-10-10 13:22:06In the early days of Nostr, developers often competed to see who could implement the most NIPs. Although all were optional (except NIP-01), it became a point of pride and vital for the ecosystem's growth. Back then, there were only a few dozen relatively simple NIPs to implement. Fast forward to today, with nearly 100 NIPs, maintaining and implementing everything has become nearly impossible. Yet, the drive among developers to "code all things Nostr" remains as strong as ever.
nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8gprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszxmhwden5te0wfjkccte9emk2um5v4exucn5vvhxxmmd9uq3xamnwvaz7tmhda6zuat50phjummwv5hsx7c9z9 raised the point that everyone, even I, agrees:
nostr:nevent1qqsqqqp2zrs7836tyjlsfe7aj9c4d97zrxxqyayagkdwlcur96t4laspzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqqqqzgcrrrp
But how big is too big? How can we better understand the range of options available for devs out there?
I went out for a hunt in my own brain to figure out how to clarify the situation. I came up with the following 4 categories for Nostr Clients: - Super Clients: These apps merge vastly different domains into a single application, offering basic support for reading, writing, configuration, and data management for each use case within each domains. An example would be an app that combines a Marketplace and Live Streams under one roof.
-
Clients: These apps provide comprehensive support for a single domain, handling all its use cases in a single home. They manage the complete set of reading, writing, configuration, and long-term data management within that domain. An example is a marketplace app that helps users manage product catalogs, process orders, collect payments, and handle fulfillment and reports.
-
Mini Clients: These apps focus on read and write functionality for a single use case, including configuration management and any actions related to that specific task. For example, a fulfillment app that helps users view orders placed from another client to then pack and ship them.
-
Micro Clients: These apps have a single interface and perform one specific action. Viewing and creating a record is handled by separate micro apps. An example is an app that simply scans an order's QR code and marks it as shipped.
Based on my made-up categories described at the end, this is how I would split our most known apps.
Super Clients - amethyst - nostrudel - coracle
Clients - damus - twitter - primal - twitter - snort - twitter - gossip - twitter - lume - twitter - ditto - twitter - rabbit - twitter - freefrom - twitter - nos - twitter - flycat - twitter - straylight - twitter - nostter - twitter - iris - twitter - nostur - twitter - nostrmo - twitter - yana - twitter - openvibe - twitter - freerse - twitter - 0xchat - chats - cornychat - chats - coop - chats - nostrchat - chats - blowater - chats - habla - blogs - yakihonne - blogs - highlighter - blogs - blogstack - blogs - stemstr - music - wavlake - music - fountain - podcasts - zap.stream - live streaming - shopstr - marketplace - plebeian.market - marketplace - flotilla - communities - satellite - communities - zapddit - communities - nostr.kiwi - communities - hivetalk - video calls - flare - long-form videos - nostrnests - audio spaces - wherostr - location - yondar - location - stacker.news - news - flockstr - events - nostrocket - issue tracker - docstr - docs - satshoot - freelance - wikifreedia - wiki - formstr - forms - chesstr - chess - memestr - meme feed - npub.cash - wallet - npub.pro - websites - gitworkshop - dev tools - onosendai - metaverse - degmods - games - turdsoup - prompts
Mini Clients - amber - signer - alby - signer - nos2x - signer - nsec.app - signer - keys.band - signer - nostrame - signer - nokakoi - anon - zap.cooking - recipes - anonostr - anon - getwired - anon - lowent - anon - creatr - exclusive content - lightning.video - exclusive content - zaplinks - slides - listr - lists - zap.store - app store - badges.page - badges - oddbean - news - dtan - torrents - nosta - user pages - pinstr - pinterest - pollerama - polls - swarmstr - trending - nostrapp - apps manager - noogle - search - ostrich.work - job postings - emojito - emoji manager - nostree - links - citrine - local relay - joinstr - coinjoins - heya - crowdfunding - zapplepay - zaps - nosbin - clipboard - shipyard - scheduler - tunestr - live streams - filestr - files - nostrcheck.me - media hosting - sheetstr - spreadsheets - crafters - curriculum vitae
Micro Clients - w3 - url shortener - nosdrive - backups - zaplife - zaps dashboard - zapper.fun - payments - nostrends - trends - zephyr - trends - wavman - music player - nostrrr - relay info - nosdump - relay info - notestack - blogs - nostr.build - media hosting - nostr.watch - relay info - nostr hours - use reports - lazereyes - vision prescriptions - snakestr - games - deletestr - deletion requests - 2048str - games - nostrqr - qr generator - notanostrclient - anon
Super apps will try to do everything, but can't really do most things super well. Regular-sized Clients will try to manage most of a given domain but are likely to centralize users on themselves, an unwanted effect inside of Nostr. If we want Nostr to grow in a decentralized fashion, we have to start betting on and using more Mini and Micro clients.
-
-
 @ 8947a945:9bfcf626
2024-10-17 07:33:00
@ 8947a945:9bfcf626
2024-10-17 07:33:00Hello everyone on Nostr and all my watchersand followersfrom DeviantArt, as well as those from other art platforms
I have been creating and sharing AI-generated anime girl fanart since the beginning of 2024 and have been running member-exclusive content on Patreon.
I also publish showcases of my artworks to Deviantart. I organically build up my audience from time to time. I consider it as one of my online businesses of art. Everything is slowly growing
On September 16, I received a DM from someone expressing interest in purchasing my art in NFT format and offering a very high price for each piece. We later continued the conversation via email.
Here’s a brief overview of what happened

- The first scammer selected the art they wanted to buy and offered a high price for each piece. They provided a URL to an NFT marketplace site running on the Ethereum (ETH) mainnet or ERC20. The site appeared suspicious, requiring email sign-up and linking a MetaMask wallet. However, I couldn't change the wallet address later. The minting gas fees were quite expensive, ranging from 0.15 to 0.2 ETH

-
The scammers tried to convince me that the high profits would easily cover the minting gas fees, so I had nothing to lose. Luckily, I didn’t have spare funds to purchase ETH for the gas fees at the time, so I tried negotiating with them as follows:
-
I offered to send them a lower-quality version of my art via email in exchange for the minting gas fees, but they refused.
- I offered them the option to pay in USD through Buy Me a Coffee shop here, but they refused.
- I offered them the option to pay via Bitcoin using the Lightning Network invoice , but they refused.
- I asked them to wait until I could secure the funds, and they agreed to wait.
The following week, a second scammer approached me with a similar offer, this time at an even higher price and through a different NFT marketplace website.
This second site also required email registration, and after navigating to the dashboard, it asked for a minting fee of 0.2 ETH. However, the site provided a wallet address for me instead of connecting a MetaMask wallet.
I told the second scammer that I was waiting to make a profit from the first sale, and they asked me to show them the first marketplace. They then warned me that the first site was a scam and even sent screenshots of victims, including one from OpenSea saying that Opensea is not paying.
This raised a red flag, and I began suspecting I might be getting scammed. On OpenSea, funds go directly to users' wallets after transactions, and OpenSea charges a much lower platform fee compared to the previous crypto bull run in 2020. Minting fees on OpenSea are also significantly cheaper, around 0.0001 ETH per transaction.
I also consulted with Thai NFT artist communities and the ex-chairman of the Thai Digital Asset Association. According to them, no one had reported similar issues, but they agreed it seemed like a scam.
After confirming my suspicions with my own research and consulting with the Thai crypto community, I decided to test the scammers’ intentions by doing the following
I minted the artwork they were interested in, set the price they offered, and listed it for sale on OpenSea. I then messaged them, letting them know the art was available and ready to purchase, with no royalty fees if they wanted to resell it.
They became upset and angry, insisting I mint the art on their chosen platform, claiming they had already funded their wallet to support me. When I asked for proof of their wallet address and transactions, they couldn't provide any evidence that they had enough funds.
Here’s what I want to warn all artists in the DeviantArt community or other platforms If you find yourself in a similar situation, be aware that scammers may be targeting you.
My Perspective why I Believe This is a Scam and What the Scammers Gain
From my experience with BTC and crypto since 2017, here's why I believe this situation is a scam, and what the scammers aim to achieve
First, looking at OpenSea, the largest NFT marketplace on the ERC20 network, they do not hold users' funds. Instead, funds from transactions go directly to users’ wallets. OpenSea’s platform fees are also much lower now compared to the crypto bull run in 2020. This alone raises suspicion about the legitimacy of other marketplaces requiring significantly higher fees.
I believe the scammers' tactic is to lure artists into paying these exorbitant minting fees, which go directly into the scammers' wallets. They convince the artists by promising to purchase the art at a higher price, making it seem like there's no risk involved. In reality, the artist has already lost by paying the minting fee, and no purchase is ever made.
In the world of Bitcoin (BTC), the principle is "Trust no one" and “Trustless finality of transactions” In other words, transactions are secure and final without needing trust in a third party.
In the world of Ethereum (ETH), the philosophy is "Code is law" where everything is governed by smart contracts deployed on the blockchain. These contracts are transparent, and even basic code can be read and understood. Promises made by people don’t override what the code says.
I also discuss this issue with art communities. Some people have strongly expressed to me that they want nothing to do with crypto as part of their art process. I completely respect that stance.
However, I believe it's wise to keep your eyes open, have some skin in the game, and not fall into scammers’ traps. Understanding the basics of crypto and NFTs can help protect you from these kinds of schemes.
If you found this article helpful, please share it with your fellow artists.
Until next time Take care
Note
- Both cyber security images are mine , I created and approved by AdobeStock to put on sale
- I'm working very hard to bring all my digital arts into Nostr to build my Sats business here to my another npub "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw
Link to my full gallery - Anime girl fanarts : HikariHarmony - HikariHarmony on Nostr - General art : KeshikiRakuen
-
 @ bcea2b98:7ccef3c9
2024-10-16 21:33:15
@ bcea2b98:7ccef3c9
2024-10-16 21:33:15When people talk about financial freedom, they often focus on investing, saving, or building wealth. But sometimes, the most valuable skills or habits are the ones that aren’t talked about enough. Maybe it’s discipline, emotional resilience, or even something unexpected like negotiation or patience.
What do you think is the most underrated skill or habit for achieving real financial independence?
For me, the most underrated skill is delayed gratification. It’s not just about resisting the urge to spend money now, it’s about thinking long-term in everything you do. When I first started learning about Bitcoin and freedom, I realized that the biggest hurdle wasn’t just making money, but knowing when to hold off on spending it for the right opportunities.
originally posted at https://stacker.news/items/727313
-
 @ ec42c765:328c0600
2024-10-21 07:42:48
@ ec42c765:328c0600
2024-10-21 07:42:482024年3月
フィリピンのセブ島へ旅行。初海外。

Nostrに投稿したらこんなリプライが
nostr:nevent1qqsff87kdxh6szf9pe3egtruwfz2uw09rzwr6zwpe7nxwtngmagrhhqc2qwq5
nostr:nevent1qqs9c8fcsw0mcrfuwuzceeq9jqg4exuncvhas5lhrvzpedeqhh30qkcstfluj
(ビットコイン関係なく普通の旅行のつもりで行ってた。というか常にビットコインのこと考えてるわけではないんだけど…)
そういえばフィリピンでビットコイン決済できるお店って多いのかな?
海外でビットコイン決済ってなんかかっこいいな!
やりたい!
ビットコイン決済してみよう! in セブ島
BTCMap でビットコイン決済できるところを探す
本場はビットコインアイランドと言われてるボラカイ島みたいだけど
セブにもそれなりにあった!

なんでもいいからビットコイン決済したいだけなので近くて買いやすい店へ
いざタピオカミルクティー屋!

ちゃんとビットコインのステッカーが貼ってある!

つたない英語とGoogle翻訳を使ってビットコイン決済できるか店員に聞いたら
店員「ビットコインで支払いはできません」
(えーーーー、なんで…ステッカー貼ってあるやん…。)
まぁなんか知らんけどできないらしい。
店員に色々質問したかったけど質問する英語力もないのでする気が起きなかった
結局、せっかく店まで足を運んだので普通に現金でタピオカミルクティーを買った
タピオカミルクティー
話題になってた時も特に興味なくて飲んでなかったので、これが初タピオカミルクティーになった
法定通貨の味がした。

どこでもいいからなんでもいいから
海外でビットコイン決済してみたい
ビットコイン決済させてくれ! in ボラカイ島
ビットコインアイランドと呼ばれるボラカイ島はめちゃくちゃビットコイン決済できるとこが多いらしい
でもやめてしまった店も多いらしい
でも300もあったならいくつかはできるとこあるやろ!
nostr:nevent1qqsw0n6utldy6y970wcmc6tymk20fdjxt6055890nh8sfjzt64989cslrvd9l
行くしかねぇ!
ビットコインアイランドへ
フィリピンの国内線だぁ

``` 行き方: Mactan-Cebu International Airport ↓飛行機 Godofredo P. Ramos Airport (Caticlan International Airport, Boracay Airport) ↓バスなど Caticlan フェリーターミナル ↓船 ボラカイ島
料金: 飛行機(受託手荷物付き) 往復 21,000円くらい 空港~ボラカイ島のホテルまで(バス、船、諸経費) 往復 3,300円くらい (klookからSouthwest Toursを利用)
このページが色々詳しい https://smaryu.com/column/d/91761/ ```
空港おりたらSouthwestのバスに乗る
事前にネットで申し込みをしている場合は5番窓口へ

港!

船!(めっちゃ速い)

ボラカイついた!

ボラカイ島の移動手段
セブの移動はgrabタクシーが使えるがボラカイにはない。
ネットで検索するとトライシクルという三輪タクシーがおすすめされている。
 (トライシクル:開放的で風がきもちいい)
(トライシクル:開放的で風がきもちいい)トライシクルの欠点はふっかけられるので値切り交渉をしないといけないところ。
最初に300phpくらいを提示され、行き先によるけど150phpくらいまでは下げられる。
これはこれで楽しい値切り交渉だけど、個人的にはトライシクルよりバスの方が気楽。
Hop On Hop Off バス:
https://www.hohoboracay.com/pass.php
一日乗り放題250phpなので往復や途中でどこか立ち寄ったりを考えるとお得。
 バスは現金が使えないので事前にどこかでカードを買うか車内で買う。
バスは現金が使えないので事前にどこかでカードを買うか車内で買う。私は何も知らずに乗って車内で乗務員さんから現金でカードを買った。
バスは狭い島内を数本がグルグル巡回してるので20~30分に1本くらいは来るイメージ。
逆にトライシクルは待たなくても捕まえればすぐに乗れるところがいいところかもしれない。
現実
ボラカイ島 BTC Map
 BTC決済できるとこめっちゃある
BTC決済できるとこめっちゃあるさっそく店に行く!
「bitcoin accepted here」のステッカーを見つける!
店員にビットコイン支払いできるか聞く!
できないと言われる!
もう一軒行く
「bitcoin accepted here」のステッカーを見つける
店員にビットコイン支払いできるか聞く
できないと言われる
5件くらいは回った
全部できない!
悲しい
で、ネットでビットコインアイランドで検索してみると
旅行日の一か月前くらいにアップロードされた動画があったので見てみた
要約 - ビットコイン決済はpouch.phというスタートアップ企業がボラカイ島の店にシステムを導入した - ビットコインアイランドとすることで観光客が10%~30%増加つまり数百~千人程度のビットコインユーザーが来ると考えた - しかし実際には3~5人だった - 結果的に200の店舗がビットコイン決済を導入しても使われたのはごく一部だった - ビットコイン決済があまり使われないので店員がやり方を忘れてしまった - 店は関心を失いpouchのアプリを消した
https://youtu.be/uaqx6794ipc?si=Afq58BowY1ZrkwaQ
なるほどね~
しゃあないわ
聖地巡礼
動画内でpouchのオフィスだったところが紹介されていた
これは半年以上前の画像らしい

現在はオフィスが閉鎖されビットコインの看板は色あせている
 おもしろいからここに行ってみよう!となった
おもしろいからここに行ってみよう!となったで行ってみた
看板の色、更に薄くなってね!?

記念撮影
 これはこれで楽しかった
これはこれで楽しかった場所はこの辺
https://maps.app.goo.gl/WhpEV35xjmUw367A8
ボラカイ島の中心部の結構いいとこ
みんな~ビットコイン(の残骸)の聖地巡礼、行こうぜ!
最後の店
Nattoさんから情報が
なんかあんまりネットでも今年になってからの情報はないような…https://t.co/hiO2R28sfO
— Natto (@madeofsoya) March 22, 2024
ここは比較的最近…?https://t.co/CHLGZuUz04もうこれで最後だと思ってダメもとで行ってみた なんだろうアジア料理屋さん?

もはや信頼度0の「bitcoin accepted here」

ビットコイン払いできますか?
店員「できますよ」
え?ほんとに?ビットコイン払いできる?
店員「できます」
できる!!!!
なんかできるらしい。
適当に商品を注文して
印刷されたQRコードを出されたので読み取る
ここでスマートに決済できればよかったのだが結構慌てた
自分は英語がわからないし相手はビットコインがわからない
それにビットコイン決済は日本で1回したことがあるだけだった
 どうもライトニングアドレスのようだ
どうもライトニングアドレスのようだ送金額はこちらで指定しないといけない
店員はフィリピンペソ建ての金額しか教えてくれない
何sats送ればいいのか分からない
ここでめっちゃ混乱した
でもウォレットの設定変えればいいと気付いた
普段円建てにしているのをフィリピンペソ建てに変更すればいいだけだった
設定を変更したら相手が提示している金額を入力して送金
送金は2、3秒で完了した
やった!
海外でビットコイン決済したぞ!
ログ

PORK CHAR SIU BUN とかいうやつを買った
 普通にめっちゃおいしかった
普通にめっちゃおいしかったなんかビットコイン決済できることにビビッて焦って一品しか注文しなかったけどもっと頼めばよかった
ここです。みなさん行ってください。
Bunbun Boracay
https://maps.app.goo.gl/DX8UWM8Y6sEtzYyK6
めでたしめでたし
以下、普通の観光写真
セブ島
ジンベエザメと泳いだ

スミロン島でシュノーケリング

市場の路地裏のちょっとしたダウンタウン?スラム?をビビりながら歩いた

ボホール島
なんか変な山

メガネザル

現地の子供が飛び込みを披露してくれた

ボラカイ島
ビーチ


夕日

藻

ボラカイ島にはいくつかビーチがあって宿が多いところに近い南西のビーチ、ホワイトビーチは藻が多かった(時期によるかも)
北側のプカシェルビーチは全然藻もなく、水も綺麗でめちゃくちゃよかった

プカシェルビーチ



おわり!
-
 @ 472f440f:5669301e
2024-10-16 01:57:41
@ 472f440f:5669301e
2024-10-16 01:57:41Over the last four years bitcoin has, among other things, established itself as an incredible corporate treasury asset that benefits those who adopt it as such. Microstrategy is the shining example of this theme going from a company that was hovering barely above a ~$1B market cap in mid-2020 to a ~$40B market cap company holding more than 1% of the 21,000,000 bitcoin that will ever exist. Microstrategy's success has emboldened a number of other publicly trader companies to follow suit. Bitcoin as a corporate treasury asset is well on its way to becoming a standard. If you run a business that doesn't hold bitcoin on its balance sheet you are doing yourself, your customers and your shareholders a disservice.
This is a trend that has its legs under it and will accelerate moving forward. A trend that I believe will emerge this cycle is incorporating bitcoin into real estate markets. Leon Wankum has been beating the drum about this for the last few years and I had the pleasure of sitting down with him this morning to record an episode of TFTC that will be published tomorrow morning. Leon is a real estate developer in Germany and he has made it his mission to educate and warn others in real estate about the demonetization of real estate that is under way due to the fact that bitcoin exists and it provides a far superior alternative.
These are pretty stark numbers. Nothing highlights the superior monetary properties of bitcoin better than looking at a chart of the average price of a home priced in USD v. bitcoin.
Since 2016: +46% in USD -99% in BTC
Since 2020: +34% in USD -70% in BTC
The funny thing is that an overwhelming majority of the individuals who make their living in real estate markets do not understand that this is happening to them. Many think they are doing exceptionally well all things considered. Sure, there may be a bit of a slow down and price retraction due to a couple of years of relatively elevated interest rates, but don't worry! The Fed is lowering rates again and the good times are about to start back up. Nothing could be further from the truth. This trend is going to continue unabated until bitcoin is fully monetized and those is the real estate industry, particularly real estate developers and those who lend capital to developers, should seriously take the time to understand what is happening to them.
Real estate is the largest store of value asset in the world at the moment. The most common number that is thrown around for the total size of the market is $300 TRILLION. $300 TRILLION of wealth being stored in an asset that is illiquid, comes with maintenance costs, taxes, insurance premiums, and susceptible to extreme weather event, among other things. Compared to bitcoin - which is extremely liquid, saleable, divisible and hard to confiscate, real estate is a far superior asset to store your wealth in. This is something that I'm sure is well understood by many of you reading this letter.
What's less understood is the dynamics of the real estate development market over the last few years, which have been severely hindered by elevated interest rates. The higher interest rate environment coupled with the inflationary pressures that forced rates higher in the first place have put developers in a predicament; they have a higher cost of capital to start new projects with raw material prices that are still much higher than they were before the economic lock downs of 2020-2022. This has led to a scenario where it isn't advantageous to start new projects and the projects that broke ground in 2021-2023 are finding that they need to incur more debt to get their developments across the finish line.
Despite the fact that interest rates are on their way back down, it doesn't seem like the economics of these projects are going to materially improve in the short to medium-term as headline inflation begins to creep back up. Couple this with the fact that the jobs market is cratering while real wages struggle to keep up with inflation and many builders are going to find themselves in a situation where they do actually complete a development problem but their cash flow suffers because their customers can't afford the inflated rents that builders will have to charge to get a return on their outlaid capital. Many will be put in a situation where they are forced to be happy with lower rents (cash flow) or sit on the sidelines making no cash flow.
The post-1971 era that brought with it a booming real estate industry is suffering the same fate as the bond market; the generation bull market is over. Real estate prices may go up, but that will be nothing more than a mirage of wealth creation. The unit of account those prices are built on is in dollars, which are being debased at an accelerating rate. Developers, banks and borrowers need to de-risk their real estate exposure and, as Leon points out, bitcoin is the only way to do this in an effective way.
Moving forward developers will have to finance by dual collateralizing their debt with the real estate and bitcoin. In the graphic below Leon illustrates what this type of financing structure will look like. Instead of taking $10m of debt to finance a project and putting it all into materials, construction and marketing, a developer will take out a $10m loan, put $1m in bitcoin and the rest toward the development project. Over the course of the construction of the real estate project, bitcoin will sit in the credit structure and, if held for 4+ years, should increase significantly in value. Saving the builder from risk of default and providing him some optionality in terms of what he can do with the project once it's finished.
In this scenario downside risk is contained - a developer isn't pouring all of the cash into bitcoin at the beginning so the worst case scenario is that bitcoin goes to zero (highly unlikely) and they can eat the small loss and hope to make up with it via cash flows once a project is finished, while upside potential is enormous. Bitcoin is still monetizing and having exposure to the hardest monetary asset the world has ever while it's monetizing has proven to be massively beneficial.
We are still in the early days of bitcoin and this idea will likely seem absolutely insane to most Tradfi investors, but I strongly believe that developers, banks and end consumers who don't leverage this type of bitcoin structured credit will be cooked in the long-run. And those that take advantage of this type of structure first will be considered geniuses in 20 years.
There are many more nuanced benefits to this strategy; holding bitcoin allows landlords and management companies to weather ongoing maintenance costs throughout the years, those who take out mortgages dual collateralized with a house and bitcoin not only protect the equity value of their property but could see their equity values increase significantly more than others using vanilla mortgages, and builders who accumulate bitcoin in their treasuries will be able to use better raw materials when building, which leads to more valuable properties that cash flow for longer.
Again, it's going to take time for these types of structures to become commonplace in the market, but I firmly believe this cycle will be the cycle that these strategies get off the ground. In four to five years they will have a track record and after that it will be considered irresponsible not to finance real estate in this way. The banks will begin to demand it.
Final thought... Sinus congestion sucks.
-
 @ fd208ee8:0fd927c1
2024-10-08 13:37:28
@ fd208ee8:0fd927c1
2024-10-08 13:37:28There was once a man, who missed an important meeting because his alarm clock didn't ring. He was a bit upset, and wished for it to be corrected, so he promptly got up, got dressed, and took the alarm clock back to the store, where he'd gotten it from.
He stood in line, patiently, at the service counter, and waited his turn. When he got to the front, the clerk asked, "How may I help you?"
"Oh, I'm having trouble with this alarm clock. You see, it doesn't ring, when the time is reached. I was wondering if that could be fixed."
"Why should we fix that? We're actually very busy building the new model. Should be out in a few weeks. Just wait for that one. Goodbye."
"What? Wait! You can't just leave it broken, like this."
"Why not? What right do you have, to demand an alarm clock that rings? Besides, how many alarm clocks have you built?"
The customer was now quite flustered and a bit ashamed of his self, "Well, none. I admit that, but..."
"Well, there you go! Outrageous, that you should criticize something someone else has accomplished, that you have not. Besides, you are incompetent to tell if anything is even wrong. Maybe this is some sort of non-ringing alarm clock. Perhaps it has lights or wave sounds..."
The second customer in line suddenly piped up, "Ahem. I'm sorry to interrupt. I must admit, I've also never built an alarm clock, but I'm a jeweler, who sells and repairs watches, and I must agree with you, sir," nods to first customer, "This is most definitely a ringing alarm clock and... See here? This bit of the bell arm has rusted through and broken off. Shoddy craftmanship, I'd say."
"Oh, Mr High-n-Mighty jeweler, claims to know how a good alarm clock is to be made, while having zero experience. I've had enough of this outrage. I'm getting the vapors and need at least a two-week sabbatical, to recover from such gross mistreatment. The store is closing immediately. Everyone out!"
"But my clock, sir!"
The door slams in his face, and he heads home, dumping his clock in the garbage bin down the street. Next time, he will simply use the alarm on his cell phone. That always rings.
-
 @ ec42c765:328c0600
2024-10-16 08:08:40
@ ec42c765:328c0600
2024-10-16 08:08:40カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

カスタム絵文字の対応状況(2024/02/05)

カスタム絵文字を使うためにはカスタム絵文字に対応したクライアントを使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
対応クライアント
ここではnostterを使って説明していきます。
準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
右上のGet startedからNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。

- 右側のOptionsからBookmarkを選択

これでカスタム絵文字を使用するためのリストに登録できます。
カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
文章中に使用
- 投稿ボタンを押して投稿ウィンドウを表示
- 顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択
- : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

リアクションに使用
- 任意の投稿の顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

カスタム絵文字を探す
先述したemojitoからカスタム絵文字を探せます。
例えば任意のユーザーのページ emojito ロクヨウ から探したり、 emojito Browse all からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2024/06/30)
※漏れがあるかもしれません
各絵文字セットにあるOpen in emojitoのリンクからemojitoに飛び、使用リストに追加できます。
以上です。
次:Nostrのカスタム絵文字の作り方
Yakihonneリンク Nostrのカスタム絵文字の作り方
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
仕様
-
 @ 3c7dc2c5:805642a8
2024-10-23 06:09:57
@ 3c7dc2c5:805642a8
2024-10-23 06:09:57🧠Quote(s) of the week:
"At some point, people will realize that they have more to fear by not embracing this technology than by embracing it." - Michael Saylor
'The tail (Bitcoin) seems to be wagging the dog (ECB)... until the world realizes Bitcoin is the dog and central banks the tail.' -Tuur Demeester
🧡Bitcoin news🧡
Of course, I will start this week's Weekly Recap with a short recap on the new ECB paper: 'The distributional consequences of Bitcoin.' by Jürgen Schaaf & Ulrich Bindseid aka the ECB BTC-gaslighters.
Why do I say gaslighters? Those two gentlemen already wrote a paper in 2022 "Bitcoin is basically dead". Just for your information, Bitcoin is worth 64% more today than when Jürgen & Uli made that statement. Ergo, ECB economists during the bear market: it's a worthless scam; ECB economists during the bull market: it's not fair.
Anyway, the new paper is a true declaration of war: the ECB claims that early Bitcoin adopters steal economic value from latecomers. “If the price of Bitcoin rises for good, the existence of Bitcoin impoverishes both non-holders and latecomers"
I quote Tuur Demeester: 'I strongly believe authorities will use this luddite argument to enact harsh taxes or bans' A bit below in the Bitcoin segment you will already see some first steps from governments to imply some harsh taxes on their (Bitcoin) citizens. Now back to the paper and my view on it. Let me start with the following: It’s not our fault (ECB, no coiners) you didn’t take the time to study Bitcoin, the signs were everywhere.
How freaking cool is it and I know we are winning when the ECB is quoting people like Marty Bent, and Molly White, quoting from Bitcoin Magazine, excerpting Trump and RFK from Nashville, and matching price movements with electoral polls in its research papers. Madness!
This is one of the first times in history that those who weren’t supposed to get wealthy did. Bitcoin is leveling the playfield for everyone. Lovely to see that the ECB, and in time the EU, will actively attack the only thing that can save this continent in decline.
Just to hit you with some logic. We, the public need a PhD - some ECB economist, to tell us that investing early in stocks, a house, art, or whatever makes it any different than investing early in Bitcoin. All they say is whoever enters an asset class earlier accrues more value than those who enter later, right? Again, like in every other asset class. For example, and I quote Ben Kaufmann: “If the price of Apple /Nvidia (you name it) stock rises for good, the existence of Apple/Nvidia (you name it) impoverishes both non-holders and latecomers.” See how stupid that sounds? Can someone find any logic in this?
Bitcoin protects you from the fiat clowns at the ECB who inflate the currency into oblivion and then blame Bitcoin for people being poor. “protect yourself from currency debasement with Bitcoin.”
I truly hope the ECB is at its final stage of denial and is only one 'logical' leap away from realizing that they need Bitcoin on their balance sheet. To finish this bit, the ECB is doing a great job. Cumulative change has been just -40,57 % in about 20 years.
The real thieves are the people who can create fiat money out of thin air and dilute entire populations behind their backs. Something the ECB and big banks perform as a primary function. Bitcoin simply allows anyone to protect themselves from fiat debasement and reliably improve their standard of living.
Sam Callahan: 'Holders of worse money will lose out to holders of better money. Welcome to Reverse Thiers’ Law. It’s not Bitcoin’s fault that these institutions destroyed their currencies. Fortunately, anyone can opt into BTC. The choice has been yours since 2009. Choose your money wisely.'
On the 14th of October:
➡️Publicly-listed German company Samara Asset Group to buy Bitcoin using a $33M bond.
➡️MicroStrategy stock has done over $3.2 billion in trading volume so far today.
➡️$1.45 trillion Deutsche Bank partnered with Keyrock for Crypto and FX services. Great thing that these huge, although DB is insolvent, legacy banks will dump billions into the space, and allow people with complex financial situations to own and utilize Bitcoin.
On the 15th of October:
➡️Fed’s Kashkari: Bitcoin remains worthless after twelve years. Almost the 6th largest monetary asset in the world...Blackrock and Fidelity beg to differ. Blackrock now holds 1.87% of the mined supply for its clients. Fidelity holds 0.93%. At a 1.35 trillion market cap 1.2 billion wallet addresses would say otherwise.
➡️Metaplanet purchases an additional 106.97 $BTC. They have purchased an additional 106.976 Bitcoin for ¥1 billion at an average price of ¥9,347,891 per Bitcoin. As of October 15, Metaplanet holds ~855.478 Bitcoin acquired for ¥7.965 billion at an average price of ¥9,310,061 per Bitcoin.
➡️Adam Back's company Blockstream raises $210 MILLION to buy more Bitcoin for its treasury and fund its other initiatives.
On the 16th of October:
➡️93% of the Bitcoin supply is in profit. We can HODL longer than the market can remain irrational.
➡️You know the day will come. Governments will use Bitcoin to get more taxes or do 'capital control' / 'exit control' / 'control of money'.
Italy's Deputy Finance Minister Maurizio Leo announced their plan to increase capital gains on Bitcoin from 26% to 42% because "the phenomenon is spreading." Immoral tax on regular people. Rich people will have a workaround.
The main question on this matter is how many other states follow this path before other nations realize the benefits of embracing Bitcoin. Work > Pay Income Tax > Invest your money > Take risk > Pay half your profits to them.
➡️Bitcoin miner Marathon Digital Holdings has obtained a $200M credit line from an unnamed lender.
The loan is secured by a portion of the company's Bitcoin holdings and will be used for strategic investments and general corporate purposes.
➡️ETFs have taken in $1.64 BILLION in just 4 days.
On the 17th of October:
➡️BlackRock's spot Bitcoin ETF bought $391.8 MILLION worth of Bitcoin today. Since launching in January, Bitcoin ETFs officially broke $20 BILLION in net inflows. This milestone took gold ETFs about 5 years to achieve. Total assets now stand at $65B, another all-time high.
Bitcoin ETFs have taken in $1.7 BILLION in October so far. • IBIT: $1.27b • FBTC: $278m • BITB: $126m • ARKB: $29m
On the 18th of October:
Samson Mow, JAN3 Founder, speaks at the German Bundestag telling MPs about Bitcoin adoption for nation-states.
➡️Whales have been buying Bitcoin aggressively at an unprecedented pace.
➡️'When Bitcoin was $68k in 2021 the hash rate was 160M TH/s. Now it’s 661M TH/s. The network is 4x more secure. Large players are suppressing the price to stack at low prices, but they can’t fake the electricity numbers. Something will happen soon to the price!' -Bitcoin for Freedom
➡️Morgan Stanley reveals $272.1M Bitcoin ETF holdings in SEC filing.
➡️Although I don't like the guy, Anthony Pompliano, because of his BlockFi 'rocketship' endorsement, last week he was spot on as he destroyed a Fox Host who says Bitcoin is "way too volatile" to be used for savings. Pomp: "Since 2016, the average cost of an American house has increased by over 50% in dollars but has dropped 99% when measured in Bitcoin."
➡️SEC approves NSYE options trading on spot Bitcoin ETFs.
On the 19th of October:
➡️Bitcoin balance on exchanges hits a 5-year low.
On the 21st of October.
➡️Now at the beginning of the Weekly Recap I already showed how central banks are losing their mind(ECB in that case), as they lose their grip and control of money.
I don't wanna be doom and gloom, I rather want to write positive news... but sometimes I really think it is important to show you what on earth is going on.
Multiple different government entities suggested making Bitcoin illegal because people would rather buy Bitcoin and have the price go up than buy bonds and lose purchasing power to inflation. All I know is if the government doesn't want you to have something that's often a good reason to get some. Especially when it's something that simply stores value! I 100% get why governments are against it. It's a threat to their unchecked money printing!
On this day the following paper came out. A paper from the Minneapolis Federal Reserve states that "a legal prohibition against Bitcoin can restore unique implementation of permanent primary deficits." Without Bitcoin to contend with, they believe the debt can go up forever.
You can find the paper here: https://www.minneapolisfed.org/research/working-papers/unique-implementation-of-permanent-primary-deficits
Technically a much better paper than the ECB one. Unfortunately, I am not surprised about that.
This is a real piece of research that identifies the key issue: consumers are too smart to fund forever deficits.
All these papers coming out are too timely. They are coordinating something against Bitcoin...central banks are freaking out… can you smell the panic in the air?
ECB - Bitcoin is so much better than fiat it could go to $10 million and make fiat holders worse off (I don't make that up)
FED - It's useless but we have to ban or tax the shit out of it so we can run deficits indefinitely
➡️Japan’s Democratic Party of the People leader pledges to cut Bitcoin and crypto taxes if elected. They will cut the taxes from 55% to 20% if the Democratic Party of the People wins the election.
➡️BlackRock’s Bitcoin ETF is now the 3rd biggest ETF for 2024 inflows and the fastest-growing ETF ever!
➡️'October's Bitcoin mining revenue has plummeted by 70% from its March peak, with miners generating less than 9,000 BTC so far this month.' -Bitcoin News
💸Traditional Finance / Macro:
On the 18th of October:
👉🏽 Investor's allocation to stocks hit 61%, the highest level in at least 40 years. 'This share has ALMOST DOUBLED since 2009 and is in line with the 2000 Dot-Com Bubble levels.
The median value of US consumers’ stock holdings spiked to $250,000 in October, the most on record. Over the last 12 months, this amount has DOUBLED, according to the University of Michigan consumer survey. In 2010, Americans' investments in single stocks, mutual funds, and retirement accounts were worth just ~$50,000, or 5 times less.
Now, equities account for 48% of US households' net worth, the highest since the 2000 Dot-Com bubble peak.' -TKL
And this all is mostly with retirement money.
🏦Banks:
👉🏽no news
🌎Macro/Geopolitics:
On the 14th of October:
Google agrees to buy nuclear power from Small Modular Reactors to be built by Kairos Power.
ZeroHedge: "First it was Amazon, then Microsoft, now Google telegraphs why the "next AI trade" will generate obnoxious amounts of alpha in the coming years by sending the same message: i) it's all about how all those data centers will be powered, and ii) in the future a growing number of data centers will be powered by small modular nuclear reactors."
Senior director for energy and climate at Google, Michael Terrell, said on a call with reporters that "we believe that nuclear energy has a critical role to play in supporting our clean growth and helping to deliver on the progress of AI." Full article: https://www.zerohedge.com/markets/google-inks-deal-nuclear-small-modular-reactor-company-power-data-centers
As of 2024, there are three operational small modular reactors (SMRs) in the world, located in different countries:
-
Russia - Akademik Lomonosov, a floating nuclear power plant operated by Rosatom. It is located in the Arctic town of Pevek, Chukotka. This is the world’s first floating nuclear plant.
-
China - Linglong One (ACP100), developed by the China National Nuclear Corporation (CNNC). This SMR is operational at the Changjiang Nuclear Power Plant in Hainan province, China.
-
Argentina - CAREM-25, developed by the Argentine state-owned company CNEA (Comisión Nacional de Energía Atómica). This reactor is located in the Lima district, Buenos Aires province, near the Atucha Nuclear Power Plant. These SMRs are being used to demonstrate the feasibility of small-scale nuclear power generation for diverse applications.
On the 13h of October:
👉🏽The US money supply hit $21.17 trillion in August, the highest level since January 2023.
This also marks a fifth consecutive monthly increase in the US money supply. Over the last 10 months, the amount of US Dollars in circulation has jumped by a MASSIVE $484 billion.
In effect, the money supply is now just $548 billion below a new all-time high. After a brief decline, the quantity of money in the financial system is surging again raising concerns about another inflation wave. - TKL
I won't worry about a recession or something like that, but more on the inflation and debasement part.
On the 16th of October:
👉🏽'Let‘s take a look at Europe‘s largest economies: Germany - commits deindustrialization suicide France - 6% fiscal deficit during good times despite highest tax burden in Europe Italy & Spain - collapsing demographics, pensions and healthcare systems to follow.' - Michael A. Arouet
👉🏽In the last couple of months I have shared how the U.S. government did its revision on job reports and other data points.
Now the FBI "revised" violent crime data, reporting that instead of a 2.1% drop in violent crime in 2022, it was actually a 4.5% increase. They missed 1.699 murders in 2022. What are a few murders among friends, innit? '6.6 points of net swing. So basically took them 18 months to realize they had missed 1 in 15 violent crimes in the country.
Conveniently released after all debates complete + no future ones agreed. Don't want to be this cynical, I really don't, but they aren't leaving me any room' - Pi Prime Pi
All government data is fudged it seems. From jobs to the economy, and inflation... It's all just made up.
"Oopsie whoopsie we made a fucky wucky! And people (politicians) wonder why trust in institutions is cratering...
Just to give you another example...
'The US Treasury is supposed to release its Monthly Treasury Statement at 2 pm on the 8th business day of each month. We are now on the 13th business day of October and have still not received last month's report. No explanation or estimation, complete radio silence.' - James Lavish
On the 17th of October:
👉🏽ECB cuts interest rates again by 0.25 percentage points.
'The ECB cut rates and signals it is getting hastier to bring rates back to more 'neutral' levels. It's funny how many investors argue that this time is different and that the ECB would take it easy or even refrain from rate cuts. Eurozone GDP growth is going nowhere, not in the near term and definitely not in the long term. Official inflation numbers in all major Eurozone economies are below 2%, and France is making headlines every day concerning debt sustainability. In the long term, interest rates will be low or negative when corrected for inflation, while bond volatility will increase.' - Jeroen Blokland
👉🏽Gold is back in record territory:
Even as markets price in a chance of a NO rate cut in November, gold just broke above $2700/oz.
The US Dollar has strengthened by 3% since September 30th and gold prices are STILL positive this month. Bank of America warns that gold may be the last safe haven as US Treasuries face risks from surging national debt. We all know that it is not the last and best safe haven, got Bitcoin?
'The higher gold goes in EUR, the greater the % of Eurozone gold reserves as a % of total EZ reserves goes (the EZ marks its gold to mkt quarterly, like China & Russia, but unlike the US.) In extremis, this gives the ECB option of “QE Heavy” (print EUR, bid for gold)' - Luke Gromen
Gold is up 31% YTD, the best year since 1979. Bitcoin is up 60% YTD, a casual year so far.
Gold for the central banks. Bitcoin for the citizens. Bitcoin wins and power returns to the people!
👉🏽 Half a trillion increase in US debt in a few days before the election. The fiscal year ends in September. So in October, the US treasury injects liquidity. Still, crazy work to increase the debt by half a trillion.
https://fiscaldata.treasury.gov/datasets/debt-to-the-penny/debt-to-the-penny
James Lavish: 'Pure unadulterated reckless government spending and so an exponential rise in debt, requiring more units of debt to drive each unit of GDP. Madness.'
On the 18th of October:
👉🏽Last week I mentioned that China's CB launched a $70 billion funding program to stimulate the economy and the capital market.
But China is in a debt bubble: 'China’s debt-to-GDP ratio hit a jaw-dropping 366% in Q1 2024, a new all-time high. Since the 2008 Financial Crisis, the ratio has DOUBLED. To put this differently, for 1 unit of GDP, the Chinese economy has produced 3.66 units of debt burden. Non-financial corporates have the highest ratio, at 171%, followed by the government sector, at 86%. Households and financial entities' debt-to-GDP is 64% and 45%, respectively. Stimulus won't solve China's debt crisis.' - TKL.
On the 21st of October:
👉🏽The US just recorded the 3rd largest budget deficit in its entire history. The federal deficit hit a WHOPPING $1.83 trillion in Fiscal Year 2024 ended Sept. 30. In other words, the government borrowed a staggering $5 billion A DAY. This was only below the 2020 and 2021 pandemic years.
🎁If you have made it this far I would like to give you a little gift:
Technology Powered Freedom - Bitcoin, eCash & Nostr | Alex Gladstein x Peter McCormack:
https://www.youtube.com/watch?v=L5BVxfdYgNo
Credit: I have used multiple sources!
My savings account: Bitcoin
The tool I recommend for setting up a Bitcoin savings plan: @Relai 🇨🇭 especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. (Please only use it till the 31st of October - after that full KYC)
Hence a DCA, Dollar cost Average Strategy. Check out my tutorial post (Instagram) & video (YouTube) for more info.⠀⠀⠀⠀
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.
Do you think this post is helpful to you? If so, please share it and support my work with sats.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ eac63075:b4988b48
2024-10-15 20:18:52
@ eac63075:b4988b48
2024-10-15 20:18:52Bitcoin emerged as a promise of financial freedom, challenging the traditional and centralized structures of governments and financial institutions. Since its inception, many enthusiasts have believed in the revolutionary potential of this cryptocurrency. However, over the years, challenges have arisen that have tested this promise, especially concerning centralization, the implementation of secondary layers like the Lightning Network, and issues of governance and privacy.
https://www.fountain.fm/episode/SDZYaFMyLEO1krL6x8RD
Centralization and the Exclusivity of Nostr
Nostr, a decentralized network aiming to be censorship resistant, emerged as an attempt to solve some inherent problems of centralization. However, it faces significant challenges. Many users point out that, despite its promise, Nostr is still not attractive to the general public, being exclusive to a specific niche.
Additionally, issues of centralization still permeate the network. Discussions on GitHub revealed that developers chose not to implement an absolute level of privacy, a decision many considered inadequate. Even with protocols developed to ensure total privacy—such as the non-identification of IPs and communicating parties—the network still lacks this robust implementation.
Individual Freedom and Data Protection
A recurring issue is the importance of demonstrating that real options exist for citizens to protect and preserve their freedom. In a world where most discussions about Bitcoin revolve around its use as an investment asset, there is an urgent need to emphasize its potential as a tool for financial freedom.
The Bitcoin community should focus on development and education, showing that the conscious use of cryptography and decentralized transactions can protect individuals against excessive government surveillance and control. Secure and private communication is fundamental, and Bitcoin, along with privacy technologies, can provide this.
Hyperbitcoinization and the Illusion of Store of Value
Hyperbitcoinization is a concept that refers to the moment when Bitcoin will replace fiat currencies worldwide. However, achieving this state is not simple, especially when Bitcoin is seen primarily as a store of value. Since 2017, this narrative has gained strength, promoting the idea that accumulating Bitcoin will lead to automatic wealth.
However, this perspective is limited. The true value of Bitcoin lies in its use as a transactional currency, not just in its scarcity. The community must work to ensure that Bitcoin is utilized in everyday transactions, strengthening its network and demonstrating its real value.
The Role of the Community in Bitcoin's Development
Bitcoin's strength comes from its community. Developers, users, and enthusiasts, through their actions and support, make Bitcoin a powerful tool. This community is responsible for ensuring that Bitcoin maintains its essence and that its functionalities are accessible to all.
It is crucial that this support network continues promoting the decentralized use of Bitcoin, without intermediaries that can censor or control transactions. Adopting Bitcoin in a centralized manner, through banks or other institutions, contradicts its original proposal and strengthens those who have historically opposed its existence.
Sidechains, Second Layers, and the Lightning Network
Sidechains and second layers, like the Lightning Network, are essential components for Bitcoin's scalability. However, they bring challenges, especially regarding the need to trust intermediaries. For these solutions to be effective, it is fundamental that they allow the unilateral withdrawal of funds, ensuring that users maintain full control over their assets.
The Lightning Network, for example, is a second layer that allows fast and cheap transactions. However, many users face difficulties when dealing with channels that do not close correctly, resulting in locked funds. These problems must be solved for the network to be truly decentralized and functional.
The Fight Against Centralization on the Internet
Centralization is not a problem exclusive to Bitcoin. The internet as a whole faces similar challenges, with data control concentrated in the hands of a few large technology companies. To ensure freedom of expression and online privacy, it is necessary to decentralize these data clusters.
Projects that seek to decentralize the internet are vital for this mission. They not only complement Bitcoin in its quest for financial freedom but also ensure that digital communication and expression are protected against censorship and corporate control.
The Future of Bitcoin and the Need for Action
The future of Bitcoin depends on the community's action. We cannot expect Bitcoin to automatically become a global medium of exchange. A conscious effort is necessary to build an ecosystem where Bitcoin can flow freely, being used in everyday transactions and valued for its utility.
Moreover, with the imminent arrival of central bank digital currencies (CBDCs), time is of the essence. CBDCs represent a significant challenge, as they can further restrict individuals' financial freedom. Therefore, accelerating Bitcoin adoption and ensuring it maintains its decentralized and uncensorable properties is a priority.
Conclusion
Bitcoin remains a powerful tool for financial freedom but faces significant challenges. Centralization, both in the context of secondary networks and the internet in general, poses a threat to its original proposal. However, with the joint action of the community and the continuous development of decentralized solutions, it is possible to maintain Bitcoin as a bastion of individual freedom.
The true revolution of Bitcoin lies in its use as a medium of exchange, not just as a store of value. To achieve hyperbitcoinization, it is necessary to build a robust ecosystem where Bitcoin can circulate freely and be accessible to all. Only then can we fulfill Bitcoin's initial promise and ensure it continues to be a tool for freedom and financial autonomy.
-
 @ 152cb6c7:45c554b1
2024-10-21 06:36:28
@ 152cb6c7:45c554b1
2024-10-21 06:36:28Packing light for a week’s vacation might sound impossible, but it’s doable and can change how travel. You can breeze through the airport and skip the wait at baggage claim with all your essentials neatly packed in a carry-on bag. Minimalist packing isn’t just about traveling lighter—it’s about less stress, more convenience, and much freedom.
Whether heading to the beach, a city getaway, or somewhere in between, fitting everything into a carry-on is all about being smart with your choices. You’ll probably even have space to fit in souvenirs from your trip!
This guide will show you how to make the most of your limited space without forgoing style or comfort.
Essential Packing Strategies
**
- Clothing
** When it comes to clothes, the key is versatility. Think about outfits you can mix and match, like a couple of neutral tops with different bottoms. This way, you can create several looks with just a few pieces.
For instance, a classic pair of jeans can easily change from a day out to a smart casual dinner with just a change of shirt and accessories. You can also bring a lightweight cardigan or denim jacket that goes with all your outfits. You can throw it over your top if it gets chilly in the evening.
Also, packing cubes are your best friend! They help keep your suitcase organized and make it easy to find what you need without rummaging through everything. You can use one cube for tops, another for bottoms, and a third for accessories.
**
- Toiletries
** Many brands now offer mini versions of their popular items, which can fit snugly into a quart-sized bag. Not only does this save space in your carry-on, but it also makes security checks a breeze—no need to worry about liquid limits.
If you can, choose multipurpose products. A shampoo that works as a body wash can save you from bringing an extra bottle. Some lotions double as hair products, and even moisturizers with SPF can also do the work of sunscreen. These items reduce the number of bottles you need and lighten your load.
You can also bring solid alternatives. Shampoo and conditioner bars take up less space and are often more environmentally friendly. Plus, they don’t count as liquids, so they can slide through security without fuss.
Space-Saving Techniques
**
- Rolling vs. folding
** One of the simplest ways to save space in your carry-on is by rolling your clothes instead of folding them. Rolling maximizes your packing space and helps reduce wrinkles, so you can unpack and wear your outfits right away without using an ironing board.
To roll your clothes effectively, start by laying them flat. Fold in the sleeves if it’s a shirt then tightly roll from the bottom up. This method allows you to fit more items into your bag. Plus, it makes it easy to see everything at a glance so you won’t be digging around for your favorite shirt.
**
- Layering and wearing bulky items
** Another nifty trick to maximize your carry-on space is to wear the bulkiest items while traveling. If you’re bringing a heavy jacket, boots, or a thick sweater, consider putting them on when you head to the airport.
Not only does this free up precious space in your carry-on, but it also keeps you cozy during those chilly flights or long waits at the terminal.
Start with a lightweight first layer, like a simple T-shirt or tank top, and then add a long-sleeved shirt or a thin sweater. Top it off with your heaviest outer layer, such as a thick jacket or a comfy cardigan.
Layering your clothes means you can easily adjust if the temperature fluctuates. Plus, you’ll look stylish and put together no matter where you’re headed.
Smart Packing Choices
**
- Footwear
** Bringing just two pairs of shoes is the best way to save space and meet your needs when you pack. The goal is to bring one casual option for everyday wear and a versatile pair for dressy and laid-back occasions.
A sturdy, comfortable pair of sneakers can handle a full day of walking without leaving your feet sore, making them perfect for daytime adventures.
On the other hand, you can wear a pair of versatile flats or loafers for an evening out or stroll around town. If you’re going somewhere warm, consider a pair of sandals that are comfortable and stylish enough to double as dress shoes.
Don’t forget to wear your heaviest pair while traveling to save space in your carry-on and keep your feet comfy during your journey.
**
- Tech and Accessories
** In the digital age, bringing all your gadgets to a trip is tempting. But for a week away, focus on only the essentials. A smartphone is usually enough for talking with family and friends, finding your way, and taking pictures.
If you must have a tablet or e-reader, that’s fine, but consider leaving the laptop at home unless you have work.
When it comes to accessories, less is more. Pick a few versatile pieces—like a simple necklace or earrings—that complement multiple outfits. Then, put them in a small jewelry box so they don’t get tangled up in your clothes or get lost in your bag. Moreover, avoid packing items you rarely wear, as they’ll take up space without adding much value to your trip.
Travel Light, Travel Right Packing light is more than just a way to fit everything into a carry-on—it’s a mindset that can make travel simpler and more enjoyable.
Sticking to the essentials lets you save time, feel less stressed, and travel with a lighter load (literally and figuratively). No more overstuffed bags or worrying about lost luggage.
With some planning and using the strategies in this guide—like choosing versatile outfits and being strategic with space-saving techniques—you’ll be ready to hit the road with just a carry-on. Because of the freedom of traveling light, you can focus more on the experience and less on your luggage. So, pack less, travel more, and enjoy the simplicity of minimalist packing!
-
 @ b002a57f:a60ecca5
2024-10-21 03:02:45
@ b002a57f:a60ecca5
2024-10-21 03:02:45Well, this seems pretty fun. I might just make Yakihonne my n°1 Nostr client.
-
 @ 4ba8e86d:89d32de4
2024-10-04 13:10:45
@ 4ba8e86d:89d32de4
2024-10-04 13:10:45M5Stick-NEMO: Firmware para Pegadinhas de Alta Tecnologia em Dispositivos M5Stack ESP32 , Este projeto oferece uma solução eficaz sem comprometer a qualidade, ideal para quem busca uma experiência educativa e divertida no universo do hacking.
https://nostrcheck.me/media/public/nostrcheck.me_2674216785970862911706546228.webp
Desenvolvido por Noah Axon-n0xa, o M5Stick-NEMO é um projeto pessoal que surgiu da vontade de aprender mais sobre o desenvolvimento do ESP32 com o Arduino IDE. Inspirado por desafios populares na comunidade de tecnologia, NEMO replica pegadinhas comuns, proporcionando uma experiência educativa e divertida.
Características Principais:
- Portal NEMO WiFi: um captive portal login que tenta criar credenciais de e-mail de engenharia social - salva nomes de usuário e senhas no cartão SD (se inserido em um leitor compatível)
- Porta TV B-Gone para desligar dispositivos controlados por infravermelho.
- Spam de emparelhamento de dispositivo AppleJuice iOS Bluetooth.
- Spam de notificação de dispositivo Bluetooth para SwiftPair (Windows) e Android.
- Spam de WiFi com SSIDs engraçados, WiFi Rickrolling e modo aleatório.
- Scanner SSID WiFi: exibe e clona SSIDs próximos.
- Relógio digital ajustável pelo usuário com suporte do M5 Stick RTC.
- Configurações apoiadas por EEPROM para rotação, brilho, escurecimento automático e SSID do Portal NEMO.
- Nível da bateria e créditos no menu de configurações.
Interface de Usuário:
- Três controles principais: Home, Próximo e Selecionar.
Portal NEMO:
No modo NEMO Portal, o NEMO ativa um Hotspot WiFi aberto chamado "Nemo Free WiFi" (configurável em portal.h) com servidores DNS, DHCP e Web ativados.
-
O Portal NEMO exibe uma página de login falsa que afirma fornecer acesso à Internet se você fizer login.
-
Este é um ataque de engenharia social e registrará o nome de usuário e as senhas inseridas na página.
-
Nos detalhes do Wifi Scan, você pode clonar um SSID existente na lista de verificação. Sair do Portal NEMO limpará o SSID Evil Twin
-
Você pode visualizar as credenciais capturadas conectando-se ao portal a partir do seu próprio dispositivo e navegando até http://172.0.0.1/creds
-
Você pode definir um SSID personalizado conectando-se ao portal a partir do seu próprio dispositivo e navegando até http://172.0.0.1/ssid
-
Se o seu dispositivo suportar EEPROM para configurações, o SSID personalizado inserido será salvo como padrão, mesmo se estiver desligado.
-
Se o seu dispositivo tiver um leitor de cartão SD com um cartão formatado em sistema de arquivos FAT inserido, os nomes de usuário e senhas serão registrados em nemo-portal-creds.txt no cartão SD para você ler mais tarde.
-
O suporte a cartão SD só está habilitado por padrão na plataforma M5Stack Cardputer. Ele pode ser habilitado em dispositivos M5Stick, mas um leitor de cartão SD deve ser construído e conectado ao pino do painel frontal.
-
O Portal NEMO deve ser usado apenas em compromissos profissionais com um escopo válido de trabalho, fins educacionais ou de demonstração.
O armazenamento, venda ou uso de informações pessoais sem consentimento é contra a lei.🤓
Instalação:
-
Visite o site oficial: M5Stack Docs https://docs.m5stack.com/en/download
-
Baixe o programa oficial M5Burner.
-
Procure pelo projeto "NEMO For M5Stick C Plus".
-
Conecte o M5 à porta USB do seu PC.
-
Abra o M5Burner, selecione o projeto e clique em "Burn".
Experimente algumas funções do FlipperZero no seu M5. Para recursos adicionais e a liberdade de personalização, compile e baixe diretamente o programa "NEMO-M5Stick C Plus" no GitHub do projeto. Isso não só permite explorar, mas também modificar e aprimorar o projeto de acordo com suas preferências.
Repositório oficial no GitHub
https://github.com/n0xa/m5stick-nemo
Assista a um tutorial sobre a implementação do M5Stick-NEMO.
https://youtu.be/uFzQTzZo-6E?si=BJJzNmiN0Jzw42Eu
https://youtu.be/uTeCbR_hWjc?si=l88w_Hl3EXuKa6gv
Além disso, você pode aprimorar seu M5 com o MURAUDER, um conjunto abrangente de ferramentas ofensivas e defensivas WiFi/Bluetooth para o ESP32.
Encontre-o no GitHub: ESP32Marauder
https://github.com/justcallmekoko/ESP32Marauder
Assista a um tutorial sobre a implementação do MURAUDER:
https://youtu.be/GQPzgYksdkg?si=dWN-GwEP5r6hk9IC
-
 @ a012dc82:6458a70d
2024-10-21 02:09:34
@ a012dc82:6458a70d
2024-10-21 02:09:34Table Of Content
-
The Ordinals Revolution
-
Celebrating Ordinals: A Red Carpet Welcome
-
The Critics and the Supporters
-
The Impact on Bitcoin Mining
-
The Changing Landscape of Revenue in Mining
-
The Road Ahead: Adapting to Change
-
The Ripple Effect: More Applications on the Horizon
-
Conclusion
-
FAQ
In the dynamic world of cryptocurrencies, innovation is the name of the game. The latest entrant to this ever-evolving landscape is Ordinals, a protocol that has taken the crypto community by storm. Ordinals enables users to mint NFT-like assets, known as inscriptions, directly onto the Bitcoin blockchain. This groundbreaking development has led to a surge in demand for computing power, significantly raising transaction fees as miners compete for available resources. The advent of Ordinals marks a new era for Bitcoin, opening up a world of possibilities for users and miners alike.
The Ordinals Revolution
The introduction of Ordinals has been met with a wave of enthusiasm from the crypto community. With nearly 12 million inscriptions now created on top of the Bitcoin blockchain, the hype around this new technology is palpable. The ability to launch NFT-like assets on the Bitcoin network, which boasts one of the most powerful brands in the crypto industry, is a significant milestone. This development has not only expanded the functionality of the Bitcoin network but also added a new dimension to the world of cryptocurrencies.
Celebrating Ordinals: A Red Carpet Welcome
The arrival of Ordinals deserves a red carpet welcome. It represents a significant step forward in the evolution of Bitcoin and the broader crypto industry. As we look to the future, it is clear that Ordinals will play a crucial role in shaping the trajectory of Bitcoin mining and the broader crypto landscape. So, let's roll out the red carpet and celebrate the arrival of Ordinals in style. The future of Bitcoin and the crypto industry is bright, and Ordinals is leading the way. This is not just a celebration of a new technology, but a celebration of the limitless potential of the crypto industry.
The Critics and the Supporters
However, the advent of Ordinals has not been without its critics. Some experts have voiced concerns about the protocol's vulnerability to scams and slower transaction speeds. They argue that the rush to embrace this new technology could lead to unforeseen consequences. But these criticisms overlook the potential of Ordinals to revolutionize Bitcoin mining and the broader crypto industry. On the other hand, supporters of Ordinals see it as a game-changer, a technology that will have a net positive effect on the profitability of Bitcoin mining in the long run. They argue that the benefits of Ordinals far outweigh the potential risks.
The Impact on Bitcoin Mining
The rising popularity of Ordinals has been a boon for Bitcoin miners. Bitcoin's scalability is limited to around seven transactions per second (TPS), so a sudden increase in demand for computing power often translates to higher fees. This shift in profitability away from rewards, which are reduced by 50% every four years due to halving, is something that many miners welcome. The introduction of Ordinals has essentially created a new revenue stream for miners, making the mining process more lucrative and sustainable in the long run.
The Changing Landscape of Revenue in Mining
For the second time in history, miners are not fully dependent on block rewards. The current period of high transaction fees has changed the perception of the sustainability of Bitcoin mining. In the future, transaction fees will likely become the main source of revenue in the mining industry. As Bitcoin's adoption and usability increase, miners are expected to earn more from commissions than via block rewards. This shift in the revenue model could potentially lead to a more stable and sustainable mining industry.
The Road Ahead: Adapting to Change
The introduction of Ordinals has brought about significant changes, and Bitcoin miners will need to adapt to remain profitable. This includes upgrading mining infrastructure and software and optimizing energy efficiency to address the challenge of reduced block rewards. The advent of Ordinals has essentially raised the bar for miners, requiring them to be more innovative and efficient in their operations. This could lead to the development of more advanced mining technologies and practices.
The Ripple Effect: More Applications on the Horizon
The arrival of Ordinals has also opened the door for more applications to be written on top of the Bitcoin protocol. This development is expected to lead to more use cases and a greater boost in Bitcoin adoption in the next couple of years. The introduction of Ordinals could potentially spur a wave of innovation in the crypto industry, leading to the development of new applications and services that leverage the power of the Bitcoin network.
Conclusion
Despite the concerns raised about Ordinals, it is essential to view this technology as an opportunity rather than a threat. Experimenting with the Bitcoin network's capabilities can only help support the overall ecosystem, both now and in the future. The introduction of Ordinals represents a significant step forward in the evolution of Bitcoin and the broader crypto industry. It is a testament to the endless possibilities that the world of cryptocurrencies offers.
FAQ
What is Ordinals? Ordinals is a new protocol that allows users to mint NFT-like assets, known as inscriptions, directly onto the Bitcoin blockchain.
How does Ordinals impact Bitcoin mining? The introduction of Ordinals has led to a surge in demand for computing power, significantly raising transaction fees as miners compete for available resources. This shift in profitability away from rewards is welcomed by many miners.
How does Ordinals affect the sustainability of Bitcoin mining? The high transaction fees brought about by Ordinals have changed the perception of the sustainability of Bitcoin mining. It has shown that miners are not fully dependent on block rewards, suggesting a more sustainable future for the mining industry.
How does Ordinals contribute to the evolution of Bitcoin? Ordinals has added a new dimension to Bitcoin by enabling the creation of NFT-like assets on its network. This has opened the door for more applications to be written on top of the Bitcoin protocol, leading to more use cases and a greater boost in Bitcoin adoption.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ fd208ee8:0fd927c1
2024-10-08 11:51:50
@ fd208ee8:0fd927c1
2024-10-08 11:51:50The 4P's
Remember the Four "P"s of Marketing? Let's look at them, in relation to digital creative work on Nostr.
Product
The product needs to be designed to fulfill a need or desire in the market. If you are writing things nobody wants to read, singing songs nobody wants to hear, or posting pictures that nobody wants to see, then you need to reevaluate your product choices because you are spam.
You are wasting your time, which means you bear a cost for the production of these goods. Is it really worth it? Maybe, maybe not. Maybe you could do something else, or do something in addition, to make the product more appealing.
On the other hand, if you are producing something valuable to a niche audience, you might want to think more about specifically aiming for and catering to that audience, rather than wasting your energy trying to appeal to a larger, indifferent group. It is better to be loved by a few and hated by many, than to be uninteresting to nearly everyone and ignore those who love you.
Price
People should have some anchor for the price, even if you have not explicitly named a price, so that they can know what such effort is "normally" worth and orient your value-provided up or down from there. It should also be clear what they are paying for, so that they know what the scope of the payment covers.
If there is no such anchor available, you can help create one by coming up with your own personal scale for other people's works and discussing it, in public. Any listeners will react positively or negatively, but they will all now have a mental "price point" to orient their own prices around.
If you have fixed and/or variable costs, the price you name should at least cover them, otherwise you need to lower the costs or raise the price. If you name no price, expect to get nothing, and you will never be disappointed. But you may also occasionally get a lot, and have it nearly knock you off your feet, so be prepared for that, too.
Generally, things that are free are of lower quality because producers have no incentive to expend great effort to produce things nobody values enough to pay for. The only major exceptions to this are cross-financing, such as freemium or preview models (typical for things like Substack or OnlyFans), or production funded by third parties (as is the case with Linux and GitHub). In both these cases, the payment exists, but is deferred or distanced.
Many products or services therefore start off "free", during an introductory period, but if they aren't getting enough income from it, they'll eventually give up and wander off. We pay creatives for their continued efforts and continued presence.
Placement
It is of vital importance that you place your products efficiently. Things you should consider:
- What relays will this work be accessible from? Large relays will extend your reach, but your product will appear within a sea of spam, so its relative value will decline, the same way the perceived worth of the nicest house on the block is dragged down by the houses around it.
- Writing to large relays also destroys the perceived exclusivity of the offer, although this can be partially mitigated by encryption. A mix of wide/exclusive is probably best, since exclusive access to someone unknown is less valuable than to someone well-known.
- Remember that the people paying for exclusive access, aren't necessarily paying for access to "better" material, they're paying for access to you, as a person, and/or they are trying to encourage you to continue your work. Rather than having your blockbusters behind a paywall, have the more personal items there and spend more time responding to the people who actually care about you and your art.
- Do you even want the work directly accessible over Nostr? Perhaps you prefer to store the work off-Nostr and simply expand access to that, to npubs.
- Something that covers price and placement is what sort of payment rails the hosting platform provides and/or you will accept. Some people only want to accept Lightning zaps, but others might be okay with fiat transactions of some sort, on-chain Bitcoin, gift cards, badge or NIP-05 sales, or some other method. Generally, the more payment options available, the less friction preventing payment. Lightning is arguably the payment method with the least friction, so it should go first in the list.
Promotion
Get Noticed
Who is your target audience and how can you get their attention, so that they find out which product you are offering? This one is extremely difficult, on Nostr. Mostly, everyone just screams things into the void, and people with more followers scream louder and are more-likely to be heard. So, I'd say:
- try to have more followers,
- find someone with lots of followers to help you with marketing, or
- join a "boost cooperative", where you join forces with other smaller accounts, to promote each other's notes.
Find your tribe
Use hashtags, but limit yourself to those that are truly relevant, and never have more than 3 in a note. Post to communities/topic-relays or groups, or write an article or wiki page or etc. and then cross-post to your kind 01 feed, with a hyperlink to a website that displays your work properly.
-
 @ e83b66a8:b0526c2b
2024-09-26 19:29:43
@ e83b66a8:b0526c2b
2024-09-26 19:29:43If you’re thinking of buying a Bitaxe, here is some information about pools vs solo mining.
Firstly, although the terms are clear “pool mining”, “solo mining” there is nuance in these definitions, so I want to explain these terms fully.
Solo mining pools exist, such as: https://solo.ckpool.org/
It is called a pool, because you are using their credentials to mine, but you keep all the rewards if you win a block. Despite the name, this is not a pool.
You then have a pool such as https://ocean.xyz/ who are a pool, you use their credentials to mine, and you earn a share of their income relative to your contribution in hash power.
There has been some publicity about a solo miner winning a pool recently, there were about 12 blocks won in 2023 by solo miners. However a winning solo miner is likely to be a server farm with hundreds or even thousands of S19’s or S21’s sharing the same payout wallet address. The image of a home miner with a Bitaxe winning a block is extremely unlikely.
A solo miner is defined as a group of miners that share a payout wallet address, so for example you could have 10 Bitaxe’s at home all configured with the same BTC wallet address, this is considered a single solo miner. And so it is with mid tier mining farms, often privately owned, who have a number of machines set to the same payout address. Most of the time, they share earnings for a more reliable income, but the owner may decide to gamble on winning a block and so choose to solo (lottery) mine.
So far, my Bitaxe, which has been running for 4 days now and is part of the Ocean pool. It is earning about 50 Sats a day. If I were to wait for an on-chain payout, it would take around 60 years to receive one. I can, however, setup a BOLT12 lightning payout address and earn this tiny income through Lightning.
So here’s my recommendation.
Currently, there are two pools that control more than 50% of mining, Foundry USA and AntPool. This is a dangerous position and in fact Bitmain, who provide around 90% of all mining hardware actually invest and have stakes in these and several other pools. This is centralising mining and could potentially allow a 51% attack, which could compromise Bitcoin.
Jack Dorsey is currently developing competing mining hardware chipset, through his company Block and Ocean are attempting to decentralise the pools by building a truly independent option for miners to join.
If you buy a Bitaxe, the best way you can help alleviate the dominance of Bitmain is to join a true pool like Ocean to slowly move control away from the dominant pools.
Bear in mind that many of the other smaller pools are still controlled by Bitmain.
If you're still interested in lottery mining, here are your chances of winning a block:
Represented as Hash rates of different miners:
Nerdminer: 20 KH/s = 20,000 H/s
Bitaxe: 750 GH/s = 750,000,000,000 H/s
Bitmain Antminer S9: 13.5 TH/s = 13,500,000,000,000 H/s
Bitmain Antminer S19: 110TH/s = 110,000,000,000,000 H/s
Bitmain Antminer S21: 200TH/s = 200,000,000,000,000 H/s
Current Global Hash rate 628EH/s (Sept 2024) = 628,000,000,000,000,000,000
If you're running a Bitaxe, your percentage chance of winning a block is: 0.000000119426751592357%
Over a year, your chances increase to: 0.00627707006369428%
Your chances of winning the UK national lottery (assuming 20M tickets sold and you buy one):
0.000005%
Over a year, your chances increase to: 0.00026%
Like in all things in Bitcoin, I don’t ask you to trust me. If you want to verify, here are the references I used in making my conclusions:
https://protos.com/chart-when-solo-miners-found-a-bitcoin-block/
https://investors.block.xyz/investor-news/news-details/2024/Blocks-New-Bitcoin-Mining-Chip-to-Be-Part-of-an-Ongoing-Project-With-Core-Scientific-to-Decentralize-Mining-Hardware/default.aspx
https://www.youtube.com/watch?v=Wo91DWvZRs8
https://i.nostr.build/9rQ9Plv6XQYtt6xd.jpg
-
 @ fd208ee8:0fd927c1
2024-10-02 05:04:55
@ fd208ee8:0fd927c1
2024-10-02 05:04:55I entered STEM in the late 90s and women weren't discouraged (much), but we also weren't actively encouraged. Neither were the guys. The head of our IT department was a woman, and that was actually not that rare, back then. In fact, the % of women getting comp sci or IT majors has been steadily falling, as this article by Texas Tech University magazine notes.
I've long been puzzled by the big "Girls Coding" push, that the corporations have been engaging in. It accomplished nothing in my workspace, except causing potential colleagues to view me with increasing suspicion. Entering IT teams in the 90s, everyone assumed I must be a genius because everyone there was some sort of genius. Now, they assume that I'm there to fix their "lack of diversity". This starts me off on the wrong foot, every time.
People went into IT because they cared about the subject matter. There wasn't much money in it, so the work atmosphere wasn't cutthroat or dominated by venture capitalistic intentions. We were just a bunch of middle class mathematicians and engineers, basically, hiding out in the computer room with our nerdy friends, building stuff we thought would be useful and cracking our dorky jokes.
Destroying this wholesome atmosphere with divisive company politics, turning it into a high-stakes game for gamblers, and the constant economic precariousness of software projects, is what made women leave IT and it is what is keeping women away.
We've managed to recreate that familial atmosphere, in our nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz team, and that's probably why we girls like being there. Turns out, the people who are best at recognizing your talents and accomodating your personal responsibilities, are your friends on the team, who are simply happy that you're there and want you to keep showing up.
-
 @ 598a7f2f:727334f4
2024-10-20 16:12:43
@ 598a7f2f:727334f4
2024-10-20 16:12:43
-
 @ e83b66a8:b0526c2b
2024-09-21 16:29:23
@ e83b66a8:b0526c2b
2024-09-21 16:29:23Here are some of the more interesting projects that I like:
Messaging:
https://www.0xchat.com/#/ - Private messaging - think WhatsApp
Xitter Like Clients:
https://damus.io/ - iPhone client
https://nostrapps.com/amethyst - Android client
https://primal.net/downloads - Android, iPhone & Desktop
https://shipyard.pub/posts - Schedule future posts
Interesting sites:
https://zap.stream/ - Video streaming
https://fountain.fm/ - Podcasting
https://wavlake.com/ - Music streaming
https://shopstr.store/ - Online shop
https://zap.cooking/recent - Cooking recipes
https://ostrich.work/ - NOSTR jobs board
NOSTR tools
https://nostr.band/ - Powerful search tool
https://nostr.wine/ - Powerful, but centralised paid relay
https://npub.pro/ - Website creation tool
https://nostr.build/ - Media and file storage
https://relay.tools/ - Build and curate your own relay
https://creatr.nostr.wine/subscriptions/new-user - Creator tools
List of NOSTR apps:
https://nostrapps.com/
-
 @ f196850e:79178e07
2024-10-20 14:51:33
@ f196850e:79178e07
2024-10-20 14:51:33https://forex-strategy.com/2024/10/20/why-wont-there-be-enough-food-very-soon-what-will-the-harvest-be-in-the-coming-years-and-what-will-the-sun-do/ Why won't there be enough food very soon? What will the harvest be in the coming years, and what will the Sun do? What do the Sun and your car's catalytic converter have in common? Are we on the brink of a global meltdown? Are there coming wars different from those in Ukraine and Israel?
food #foodcrisis #climatechange #climate #temperatures #war
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ 6ad3e2a3:c90b7740
2024-09-11 15:16:53
@ 6ad3e2a3:c90b7740
2024-09-11 15:16:53I’ve occasionally been called cynical because some of the sentiments I express strike people as negative. But cynical, to me, does not strictly mean negative. It means something more along the lines of “faithless” — as in lacking the basic faith humans thrive when believing what they take to be true, rather than expedient, and doing what they think is right rather than narrowly advantageous.
In other words, my primary negative sentiment — that the cynical utilitarian ethos among our educated classes has caused and is likely to cause catastrophic outcomes — stems from a sort of disappointed idealism, not cynicism.
On human nature itself I am anything but cynical. I am convinced the strongest, long-term incentives are always to believe what is true, no matter the cost, and to do what is right. And by “right,” I don’t mean do-gooding bullshit, but things like taking care of one’s health, immediate family and personal responsibilities while pursuing the things one finds most compelling and important.
That aside, I want to touch on two real-world examples of what I take to be actual cynicism. The first is the tendency to invoke principles only when they suit one’s agenda or desired outcome, but not to apply them when they do not. This kind of hypocrisy implies principles are just tools you invoke to gain emotional support for your side and that anyone actually applying them evenhandedly is a naive simpleton who doesn’t know how the game is played.
Twitter threads don’t show up on substack anymore, but I’d encourage you to read this one with respect to objecting to election outcomes. I could have used many others, but this one (probably not even most egregious) illustrates how empty words like “democracy” or “election integrity” are when thrown around by devoted partisans. They don’t actually believe in democracy, only in using the word to evoke the desired emotional response. People who wanted to coerce people to take a Pfizer shot don’t believe in “bodily autonomy.” It’s similarly just a phrase that’s invoked to achieve an end.
The other flavor of cynicism I’ve noticed is less about hypocrisy and more about nihilism:
 I’d encourage people to read the entire thread, but if you’re not on Twitter, it’s essentially about whether money (and apparently anything else) has essential qualities, or whether it is whatever peoples’ narratives tell them it is.
I’d encourage people to read the entire thread, but if you’re not on Twitter, it’s essentially about whether money (and apparently anything else) has essential qualities, or whether it is whatever peoples’ narratives tell them it is.In other words, is money whatever your grocer takes for the groceries, or do particular forms of money have qualities wherein they are more likely to be accepted over the long haul? The argument is yes, gold, for example had qualities that made it a better money (scarcity, durability, e.g.) than say seashells which are reasonably durable but not scarce. You could sell the story of seashells as a money (and some societies not close to the sea used them as such), but ultimately such a society would be vulnerable to massive inflation should one of its inhabitants ever stroll along a shore.
The thread morphed into whether everything is just narrative, or there is an underlying reality to which a narrative must correspond in order for it to be useful and true.
The notion that anything could be money if attached to the right story, or any music is good if it’s marketed properly is deeply cynical. I am not arguing people can’t be convinced to buy bad records — clearly they can — but that no matter how much you market it, it will not stand the test of time unless it is in fact good.
In order to sell something that does not add value, meaning or utility to someone’s life, something you suspect they are likely to regret buying in short order, it’s awfully useful to convince yourself that nothing has inherent meaning or value, that “storytelling is all that matters.”
I am not against marketing per se, and effective storytelling might in fact point someone in the right direction — a good story can help someone discover a truth. But that storytelling is everything, and by implication the extent to which a story has correlates in reality nothing, is the ethos of scammers, the refuge of nihilists who left someone else holding the bag and prefer not to think about it.
-
 @ ee11a5df:b76c4e49
2024-09-11 08:16:37
@ ee11a5df:b76c4e49
2024-09-11 08:16:37Bye-Bye Reply Guy
There is a camp of nostr developers that believe spam filtering needs to be done by relays. Or at the very least by DVMs. I concur. In this way, once you configure what you want to see, it applies to all nostr clients.
But we are not there yet.
In the mean time we have ReplyGuy, and gossip needed some changes to deal with it.
Strategies in Short
- WEB OF TRUST: Only accept events from people you follow, or people they follow - this avoids new people entirely until somebody else that you follow friends them first, which is too restrictive for some people.
- TRUSTED RELAYS: Allow every post from relays that you trust to do good spam filtering.
- REJECT FRESH PUBKEYS: Only accept events from people you have seen before - this allows you to find new people, but you will miss their very first post (their second post must count as someone you have seen before, even if you discarded the first post)
- PATTERN MATCHING: Scan for known spam phrases and words and block those events, either on content or metadata or both or more.
- TIE-IN TO EXTERNAL SYSTEMS: Require a valid NIP-05, or other nostr event binding their identity to some external identity
- PROOF OF WORK: Require a minimum proof-of-work
All of these strategies are useful, but they have to be combined properly.
filter.rhai
Gossip loads a file called "filter.rhai" in your gossip directory if it exists. It must be a Rhai language script that meets certain requirements (see the example in the gossip source code directory). Then it applies it to filter spam.
This spam filtering code is being updated currently. It is not even on unstable yet, but it will be there probably tomorrow sometime. Then to master. Eventually to a release.
Here is an example using all of the techniques listed above:
```rhai // This is a sample spam filtering script for the gossip nostr // client. The language is called Rhai, details are at: // https://rhai.rs/book/ // // For gossip to find your spam filtering script, put it in // your gossip profile directory. See // https://docs.rs/dirs/latest/dirs/fn.data_dir.html // to find the base directory. A subdirectory "gossip" is your // gossip data directory which for most people is their profile // directory too. (Note: if you use a GOSSIP_PROFILE, you'll // need to put it one directory deeper into that profile // directory). // // This filter is used to filter out and refuse to process // incoming events as they flow in from relays, and also to // filter which events get/ displayed in certain circumstances. // It is only run on feed-displayable event kinds, and only by // authors you are not following. In case of error, nothing is // filtered. // // You must define a function called 'filter' which returns one // of these constant values: // DENY (the event is filtered out) // ALLOW (the event is allowed through) // MUTE (the event is filtered out, and the author is // automatically muted) // // Your script will be provided the following global variables: // 'caller' - a string that is one of "Process", // "Thread", "Inbox" or "Global" indicating // which part of the code is running your // script // 'content' - the event content as a string // 'id' - the event ID, as a hex string // 'kind' - the event kind as an integer // 'muted' - if the author is in your mute list // 'name' - if we have it, the name of the author // (or your petname), else an empty string // 'nip05valid' - whether nip05 is valid for the author, // as a boolean // 'pow' - the Proof of Work on the event // 'pubkey' - the event author public key, as a hex // string // 'seconds_known' - the number of seconds that the author // of the event has been known to gossip // 'spamsafe' - true only if the event came in from a // relay marked as SpamSafe during Process // (even if the global setting for SpamSafe // is off)
fn filter() {
// Show spam on global // (global events are ephemeral; these won't grow the // database) if caller=="Global" { return ALLOW; } // Block ReplyGuy if name.contains("ReplyGuy") || name.contains("ReplyGal") { return DENY; } // Block known DM spam // (giftwraps are unwrapped before the content is passed to // this script) if content.to_lower().contains( "Mr. Gift and Mrs. Wrap under the tree, KISSING!" ) { return DENY; } // Reject events from new pubkeys, unless they have a high // PoW or we somehow already have a nip05valid for them // // If this turns out to be a legit person, we will start // hearing their events 2 seconds from now, so we will // only miss their very first event. if seconds_known <= 2 && pow < 25 && !nip05valid { return DENY; } // Mute offensive people if content.to_lower().contains(" kike") || content.to_lower().contains("kike ") || content.to_lower().contains(" nigger") || content.to_lower().contains("nigger ") { return MUTE; } // Reject events from muted people // // Gossip already does this internally, and since we are // not Process, this is rather redundant. But this works // as an example. if muted { return DENY; } // Accept if the PoW is large enough if pow >= 25 { return ALLOW; } // Accept if their NIP-05 is valid if nip05valid { return ALLOW; } // Accept if the event came through a spamsafe relay if spamsafe { return ALLOW; } // Reject the rest DENY} ```
-
 @ 502ab02a:a2860397
2024-10-20 14:26:07
@ 502ab02a:a2860397
2024-10-20 14:26:07
เจอนี่ next station หลังจากงาน TBC2024 ก็คือแคมป์สุขภาพ โรงบ่มสุขภาพ ep1 ใช่ครับใช้คำว่า ep1 เพราะมันจะไม่ได้จบแค่ครั้งเดียว ส่วน station ที่เหลือของผมก็ไม่รู้เหมือนกันว่า สถานีปลายทางจะอยู่ที่ไหน
ในหมวดเจอนี่ คือตั้งใจให้เป็น journey จริงๆ ดังนั้นเลยไม่มีการเล่าแนวขายของ แต่จะเขียนแนวบันทึกเอาไว้ ก่อนความทรงจำจะเลือนลางไปครับ โรงบ่มสุขภาพเป็นการรวมตัวกันของ บุคลากรคุณภาพด้านสุขภาพ ซึ่งผมไม่ปฎิเสธเลยว่า รู้สึกดีที่ได้ร่วมงานกับกลุ่มนี้ครับ เพราะถ้ามองขุมพลังแล้วแต่ละคนนี่ระดับ สายแข็งกันทั้งนั้น
หมอเอก ชักชวนเข้าประชุม ตอนที่กลุ่มเริ่มมีเค้ารางแล้ว สิ่งนึงที่ต้องบันทึกไว้คือ ชื่อ โรงบ่มสุขภาพ จริงๆแล้วมีอีกหลากหลายชื่อที่มีการนำเสนอกันภายใต้ theme ที่เซ็ทเอาไว้ โดยแต่ละชื่อก็เท่ๆทั้งนั้น
ส่วนตัวแล้วผมจะชอบชื่อที่เป็นภาษาไทย ถ้าสังเกตได้ ชื่อรายการวิทยุก็ บอกเล่า90 พอมาจัดพอดแคสกับพี่หนึ่ง ก็ใช้ชื่อ บอกเล่า90บวก1 เข้าไปดื้อๆ ชื่อเพจก็โต้งเอง ชื่อเนทเวิร์คใหญ่ก็ สิริพรรณ.คอม (ชื่อคุณเอ๋)
ผมเลยเสนอชื่อ โรงบ่มสุขภาพ เข้าไปด้วยอีกชื่อหนึ่ง ปรากฎว่าสุดท้ายเป็นชื่อที่ได้รับเลือกในที่สุด แต่กระนั้นก็ต้องมีภาษาอังกฤษเอาไว้สมัครเฟสบุคและอีเมลล์ เลยตั้งว่า Healthy Hut เพราะผมรู้สึกว่าคำว่า hut เป็นคำที่ถ่อมตนดี มันเล็กเสียจนเรียก house ยังดูใหญ่โตมากๆ
โรงบ่มสุขภาพ มีรากเหง้ามาจาก พี่จิก ประภาส ชลศรานนท์ ซึ่งนานมาแล้วแกตั้งกลุ่มสอนแต่งเพลงชื่อ โรงบ่มคนดนตรี ในตอนนั้นหลายคนที่ผ่านแคมป์นั้นก็มาสร้างสรรค์เพลงดีๆในยุคนั้นและยุคนี้ (ยุค a day, monotone) ซึ่งผมได้เห็นพัฒนาการคนกลุ่มนั้นมาตลอด ทั้งในฐานะสมาชิกไทยมุง ที่ได้เห็นความคืบหน้าโครงการมาโดยตลอด และฐานะคนทำงานวิทยุ(แบบตัวเล็กๆ)
ผมเลยนึกหยิบคำว่า โรงบ่ม มาใช้ในกลุ่มนี้ เพราะผมเชื่อว่าในงานในแคมป์ในอะไรก็ตามที่จัด คนเข้าร่วมเขาไม่ได้เก่งทันทีที่งานจบ แต่ผมเชื่อว่า เราได้บ่ม บางสิ่งบางอย่างในตัวคนนั้นๆเอาไว้ และหวังเสมอว่า หลังจากการบ่มแล้ว พวกเขาจะออกไปสุกงอมได้เองในภายภาคหน้า แค่นี้ผมว่า วัตถุประสงค์ของ โรงบ่ม ก็สัมฤทธิ์ผล ผมเชื่อว่าแต่ละท่านในกลุ่ม ก็คงเล็งเห็นว่าคำนี้เหมาะกับกลุ่มจริงๆ จึงเลือก โรงบ่มสุขภาพ มาเป็นตัวเลือกสุดท้ายในการตั้งชื่อกลุ่ม
ในส่วนงาน session ที่ผมได้รับนั้น ส่วนตัวเองก็ไม่ค่อยห่วงนัก เพราะเป็นเรื่องที่เขียนอยู่ทุกวัน ดูทุกครั้งที่เข้าซุปเปอร์ คือ ฉลาก มันกลายเป็นนิสัยสามัญไปเสียแล้วครับ ก็เลยคิดว่าส่วนเนื้อหาที่ผมรับผิดชอบนั้น สามารถปรับเป็นกิจกรรมแก้ง่วงได้ เพราะผมต้องพูดต่อจากอาจารย์ป๊อบ ที่เนื้อหาแน่นปึ๊ก นึกออกไหมครับ ถ้าร้องเพลงก็เหมือนกับ ได้เวทีต่อจากพี่เบิร์ด หรือ ตูน บอดี้แสลม ในขณะที่เรายังเนื้อหาราวๆ เฉลียง เอ็ม สุรศักดิ์ หรือ อนันต์ บุญนาค อะไรแบบนั้น
ผมเลยช้อปปิ้งสนุกสนานเลยครับ อยากเล่นอะไรเล่น อยากทำอะไรทำ วางแผนการซื้อตัวอย่างแต่ละตัว ด้วยเหตุผลตามเนื้อหาที่จะพูด นำมาใช้เป็นเกมส์ในงานแบบ learning by doing กันไปเลย สไลด์มีไว้แค่ช่วงส่อง เพราะสายตายาว 5555
ด้วยสายตาจากคนพูด มองไปที่คนฟัง สิ่งที่พูดไป ได้รับการตอบสนองกลับมา มันรู้สึกได้ครับ show มันสัมผัสพลังที่ส่งกลับมาได้ ไม่ว่าจะรอยยิ้ม การโต้ตอบ มันทำให้รู้สึกได้ว่า เอาว่ะ อย่างน้อยๆ คนที่มางาน ก็ได้รับการ บ่ม อะไรบางอย่างกลับไปตามที่เราหวังไว้หล่ะน่ะ
ที่สำคัญคือ น่าจะได้รู้จักการตั้งคำถาม และได้รู้ว่า ฉลาก เขาทำเพื่อตัวเขา เพื่อหน่วยงานการควบคุม และเต็มไปด้วยการล่อหลอกให้เชื่อ ผมเชื่อว่า การเอ๊ะ มันต้องถูกฝังไปในใจ รอการบ่มให้สุกงอม แล้ววันนึงเขาจะรู้ว่านี่คือหนทางที่ fiat ครอบงำเราไว้
ก็นับได้ว่าเป็นอีกสถานีนึง ที่ได้ลงมาทำอะไรไว้ครับ
โรงบ่มสุขภาพ
ขอบคุณ โบ @chonlada npub1zt3m0n4ym2l7lg6epqch2xwu05cnv4vm7wvay9ssuwm08s4ws6yqwdlwwz ที่สมัครมาแคมป์ด้วย ตัวแทนทุ่งม่วงเลยนะ 55555 อย่าลืมหันหน้าเข้าแดด รับ uva

ปล. อย่างน้อยงานนี้ได้จับมือพี่หนึ่งลงทุ่งม่วงสำเร็จ พี่หนึ่งบอกจะลองหัดเล่นดูครับ อ่อ ได้เซ็ท WOS ให้พร้อมโอน sat ให้ด้วย 55555 transaction แรกของพี่หนึ่งคือผมเอง
siamstr #pirateketo #siripun
-
 @ bcea2b98:7ccef3c9
2024-10-15 16:37:10
@ bcea2b98:7ccef3c9
2024-10-15 16:37:10I've always been interested in Eastern philosophies and Stoicism. When I first heard about Bitcoin, it seemed to align well with the beliefs, ideas, and lifestyle I was already living. I try my best to be self-sovereign, practice a low-time preference, and delayed gratification. I've also learned so much about Linux, servers, etc...
I'm curious to hear what skills you have gained from Bitcoin, or how it has changed or aligns with your lifestyle.
originally posted at https://stacker.news/items/724982
-
 @ c11cf5f8:4928464d
2024-10-20 09:23:51
@ c11cf5f8:4928464d
2024-10-20 09:23:51Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too.
If you missed our last thread, here are some of the items stackers recently spent their sats on.
originally posted at https://stacker.news/items/732230
-
 @ 592295cf:413a0db9
2024-10-20 08:06:26
@ 592295cf:413a0db9
2024-10-20 08:06:26[14/10 week] You can avoid celebrations and be happy. I was downloading slides from Nostr, a slide file contained 71 slides...
Unanimity goes backwards, I'm using it as my discord audience. There is no need to link anything This week I have to edit the NPs page, I also heard Victor Pamplona talk about specification, maybe only change the theme.
Thinks if big relays didn't accepts Bitcoin note 😅, fiatjaf call for moderation 🤙
A podcast is just fun and entertainment is not needed to learn things, it is necessary to tell this thing there is going to deepen, but then I think no one has ever looked in the notes of the episode of no podcasts. 😂
The thing I see the protocol evolve, there Is no global state, but with a client i can query for all know network it's like in my case 33k users and that it's. This Is your network. You need to do proof of work to find, interesting for you "people", but that's It. Yaa maybe a geo-client is what you Need. So It basically sad this for Europe this for usa this for Asia this for Oceania. Like a Little "Risk" withouth tanks but users, and you can see the last user note. I think this works well with the snowcait tool what counts the hours nostr-hours. Then you have people in a time frame based on the time they write, maybe even consider the language. Maybe it's aligned with Nip-66 or what hzrd149 was doing in no strudel, geo-tag clients as wherostr. Then a small treasure hunt begins. Also Zach had made a similar client. It's a bit satlantis, but focus on People, not on cities. Meetup can be a widget. Yondar the arkinox app. Here too much map. I want to know where these people are and their public gatherings. Something can emerge from this network.
This implies all kinds of trust models, we heard about it iosa at this time.
False alarm in Unanimity I thought someone had written, but it was just a newcomer, maybe he uses amethyst. I don't think anyone would ever want to enter that Channel, but it's better to put a simil explanation of what I mean for Unnimity.
It's an idea that I've been thinking about this five-person mini community, but where you find 5 people who want to do this (?!). These 5 people are part of a great community, but also the small one. They can talk through the Channels.
All those who started making a client have now for them is easier to build. Maintaining everything is complicated, because it adds complexity. Although their project is only a state of WIP and they see that with some modification it works and depart from there it is fantastic.
Community-protocol NIP-72+NIP-28
Channel leverage kind 1
Write a message in the bulletin board
So on the one hand we have approved messages that can be channel, form, and wiki, and on the other messages not approved.
To link a channel you must be a moderator.
A channel is shared by following community relays
-
 @ 598a7f2f:727334f4
2024-10-20 00:02:17
@ 598a7f2f:727334f4
2024-10-20 00:02:17
-
 @ a012dc82:6458a70d
2024-10-19 12:51:04
@ a012dc82:6458a70d
2024-10-19 12:51:04Table Of Content
-
The Current State of Bitcoin ETFs
-
The 'Silver Bullet' Solution
-
The Role of ARK Invest
-
Implications for the Future
-
Conclusion
-
FAQ
In the dynamic and rapidly changing landscape of cryptocurrencies, Cathie Wood's ARK Invest has consistently been a pioneer, leading the charge with innovative strategies and investment products. The latest development from the firm is a groundbreaking strategy for their Bitcoin ETF filing, a solution they have intriguingly dubbed the 'Silver Bullet'. This approach, while shrouded in some degree of mystery, aims to address regulatory concerns that have long plagued the cryptocurrency sector. It promises to pave the way for a more secure, transparent, and efficient future for Bitcoin investments, potentially revolutionizing the way we perceive and interact with this digital asset.
The Current State of Bitcoin ETFs
Exchange-Traded Funds (ETFs) have become a popular investment vehicle in the financial world. They offer diversified exposure to a particular asset class or sector, allowing investors to mitigate risk while capitalizing on market trends. However, the creation of a Bitcoin ETF has been a contentious issue. Regulatory bodies, particularly the U.S. Securities and Exchange Commission (SEC), have expressed concerns over the potential for market manipulation and the need for robust investor protection measures. This has led to a stalemate, with several Bitcoin ETF proposals being rejected or left in regulatory limbo.
The 'Silver Bullet' Solution
ARK Invest's 'Silver Bullet' solution is a novel and ambitious approach designed to address these regulatory concerns head-on. While the specifics of this strategy remain undisclosed due to confidentiality and strategic reasons, it is believed to involve a blend of advanced technology and stringent compliance measures. The 'Silver Bullet' is not just a solution; it's a statement of intent, a commitment to providing greater transparency, reducing the risk of market manipulation, and ensuring robust investor protection. It's a testament to ARK's belief in the potential of Bitcoin and their determination to overcome the regulatory hurdles that stand in its path.
The Role of ARK Invest
Under the visionary leadership of Cathie Wood, ARK Invest has emerged as a strong advocate for cryptocurrencies and the transformative potential of blockchain technology. The firm's active management style, combined with its unwavering focus on disruptive innovation, has led to significant returns for their investors and cemented their reputation as trailblazers in the investment world. The introduction of the 'Silver Bullet' solution is another testament to ARK's commitment to pushing the boundaries of traditional finance, challenging the status quo, and driving the adoption of innovative financial products.
Implications for the Future
If successful, the 'Silver Bullet' solution could have far-reaching implications for the future of Bitcoin and the broader cryptocurrency sector. It could revolutionize the way Bitcoin ETFs are viewed by regulatory bodies, potentially leading to a shift in perception and a softening of the regulatory stance. This could pave the way for more widespread acceptance of Bitcoin as a legitimate and regulated asset class. The potential impact of this cannot be overstated. It could lead to an influx of institutional investors into the Bitcoin market, further driving its growth, increasing its liquidity, and promoting its adoption on a global scale.
Conclusion
The 'Silver Bullet' solution introduced by ARK Invest represents a significant and potentially game-changing step forward in the quest for a Bitcoin ETF. While the road to regulatory approval may still be fraught with challenges and uncertainties, this innovative approach offers a promising glimpse into the future of Bitcoin investments. As we continue to navigate the uncharted waters of cryptocurrency regulation, it is clear that firms like ARK Invest are not just observers but active participants, leading the charge towards a more secure, transparent, and inclusive financial future.
FAQ
What is the 'Silver Bullet' solution by ARK Invest? The 'Silver Bullet' is a novel strategy introduced by ARK Invest for their Bitcoin ETF filing. While specific details are confidential, it's designed to address regulatory concerns, aiming to provide greater transparency, reduce market manipulation risk, and ensure investor protection.
Why is the 'Silver Bullet' solution significant? If successful, the 'Silver Bullet' could revolutionize how Bitcoin ETFs are viewed by regulatory bodies, potentially leading to more widespread acceptance of Bitcoin as a regulated asset class. This could attract more institutional investors into the Bitcoin market, driving its growth and adoption.
What is ARK Invest's role in the cryptocurrency market? Led by Cathie Wood, ARK Invest is a strong advocate for cryptocurrencies and blockchain technology. The firm's focus on disruptive innovation has led to significant returns for investors and the introduction of the 'Silver Bullet' solution is another testament to ARK's commitment to pushing the boundaries of traditional finance.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。
2024年08月13日更新:
修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
准备工具
- Ntfy服务
- Google Script
- Google Sheets
操作步骤
- 在Ntfy后台账号,设置访问令牌。

- 添加订阅主题。

- 进入Google Sheets创建一个表格.记住id,如下图:

- 进入Google Script创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) { var threadId = thread.getId();
if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); }}); }
function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; }
var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true };
try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } }
function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column }
function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); }
function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues(); var rowsToDelete = [];
data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } });
// 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); }
```
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:

结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ bf95e1a4:ebdcc848
2024-09-11 06:31:05
@ bf95e1a4:ebdcc848
2024-09-11 06:31:05This is the lightly-edited AI generated transcript of Bitcoin Infinity Show #125. The transcription isn't perfect, but it's usually pretty good!
If you'd like to support us, send us a zap or check out the Bitcoin Infinity Store for our books and other merchandise! https://bitcoininfinitystore.com/
Intro
Luke: Paolo, Mathias, welcome to the Bitcoin Infinity Show. Thank you for joining us.
Paolo: Thank you for having us.
Knut: Yeah, good to have you here, guys. We're going to talk a bit about Keet and Holepunch and a little bit about Tether today, aren't we?
Luke: Sounds like that's the plan. So thank you again, both for joining us.
Introducing Paolo and Mathias
Luke: would you both mind giving a quick introduction on yourselves just so our listeners have the background on you
Paolo: Sure, I'm Paolo Arduino, I'm the CEO at Tether. I started my career as a developer, I pivoted towards more, strategy and execution for, Tether and Bitfinex. And, co founded with Matthias, Holepunch, that is, building very, crazy and awesome technology, that is gonna be disrupting the way people communicate.
Luke: And, Mathias, over to you.
Mathias: Yeah, thank you. Yeah, I've been, so I come from a peer-to-peer background. I've been working with peer-to-peer technology. The last, I always say five, but it's probably more like 10 years. I did a lot of work on BitTorrent and I did a lot of work on JavaScript. and a little bit later to, Bitcoin and I saw a lot of potential on how we can use Bitcoin with pureology and like how we can use.
P2P technology to bring the same mission that Bitcoin has, but to all kinds of data, setting all data free and, making everything private per default and self sovereignty and that kind of thing. I'm very into that. and I've been lucky to work with, like I said, with Paolo for, many years now and, Get a lot of, valuable, feedback and, idea sharing out of that.
And we're on a mission to, build some, really cool things. In addition to all the things we've already been building. So it's super exciting and glad to be here.
Luke: Oh, fantastic.
Introduction to Holepunch
Luke: Matthias, that was a perfect segue into basically, an introduction to, can you tell us about, Holepunch.
What is Holepunch and what are you doing?
Mathias: Yeah, sure. like I said, we co founded the company a couple of years ago. Now, we've been building up a team of really talented peer to peer engineers. we're always hiring also. So if anybody's listening and want to join our mission, please, apply. we have some really smart people working with us.
but we teamed up to basically. like I said in my introduction, I've been working on peer to peer technology for many years now and thinking ahead how we can, stop using all that technology when I started it was only used for basically piracy. I'm from the Nordics, and I think Knut is from the Nordics also, so he knows all about, the Nordics know about piracy.
It wasn't back in the day. A lot of very interesting technologies came out of that. But basically, how can we use those ideas that were proven by piracy back then to be really unstoppable, because a lot of people wanted to stop it, but apply that same kind of mindset to the general data, so we can build actual applications that has that kind of quality, that can withstand the wrath of God.
that can work without any centralization. Actually, nobody can shut down, not even the authorities if they wanted to. Basically unkillable and make that general enough that it can basically run any kind of application, solve a lot of really hot problems. it works on your own computers, your own networks.
Mobile phones, and tie that up. I'm a developer by heart, into a software stack that people can just build on. So not everybody has to go in and tackle all these problems individually, but just give them some software to solve all this so they can, as much as possible, just worry about making really cool applications that we use,
Yeah, like I said, we've been working really intensely on this, for a long time and in Holepunch, we made this our co mission to scale this up and, deliver a software stack on that. it's been really exciting and it's been really fun and it's been very, challenging, but if it's not challenging, then why, do it?
and, especially, with the backing of, Tether, through Paolo and also just expertise from there, we have a good hand built to deliver this to the world. And, the first thing we did was, like, think about what's, a good first application that we can build that can showcase this, but also something we really want to use ourself and see scale have also have on the world.
And obviously that was a communications app, keyed, which we was our first project. And, we're still in beta and we're still lots of work to do. And we're still iterating that really heavily, but I like to show that you can build these kind of apps without any kind of. central points. and we released that also, like the first thing we released when we launched the company.
And like I said, we're still, building and still iterating it. A lot of fun. and then take the software stack from that, which we call the pair runtime and then split that out. So anybody else can build similar apps on top. With that same technology stack, and, yeah, that's, we launched that earlier this year also, and, it's been really exciting so far, and it's, I love going to work every day and solve, even though, you can see on my hair that it's not really good for, the head scratching, but, but, it's really fun, and it's really challenging, and it's interesting thing. goal as a company, basically to have that if we go out of business tomorrow, our technology continues to exist because we're not in the loop of anything. It's also sometimes really hard to explain that we don't have any, chip coins involved or any kind of limitations on the stack because we're basically engineering it not to be part of it, because that's the only way you can actually engineer these things that they can understand.
anything, super exciting and, encourage everybody to try to check it out.
Luke: we've both used Keet and I've certainly enjoyed the experience. I, think, the, basics of this, as I understand it, is that it's, entirely on both sides. The communicators end, or a group of communicators, it's all on their end, and the communication is entirely peer to peer, what is Keet really, what is the basics of Keet as, say, a product?
What is the easiest way that you would explain what it is?
The Vision Behind Keet
Mathias: But We're basically trying to just build a world class communications app that works to a large degree, like normal communication apps that you know, like Signal, Telegram, WhatsApp. Just with all the centralization tucked away, with all the costs of running it tucked away, and then adding all the features that also we can, because we're peer to peer
People don't care about technology. We loved it, but don't have that surface off too much to the user.
Just have the user use it as any other app, but then just have it be 100 percent private per default, 100 percent like no strings attached. It just works. if we get caught off by a. From the internet tomorrow, it will still work, that kind of thing, but deliver that in a way, and this is always our mission where users don't really need to worry about it.
It just works. And, it works the same way to a large degree as their other apps work, except obviously, there's no phone numbers and things like that. Very cryptographically sound and, but trying always not to bubble it up. And I think that's, so it's actually a really simple mission, but it's obviously really hard.
And that requires a lot of smart people, but luckily our users in a good way, don't need to be very smart about that.
Keet vs Nostr
Knut: Yeah, a quick one there. No strings attached starts with the letters Nostr, so is, Keet and Nostr, do they go mix well together or, is there an integration there between the two? I see a lot of similarities here.
Paolo: I tried to explain the differences between Kit and Nostr. I think Nostr is a very interesting protocol, but also is very, simple. the way I like to describe it is that, if you are familiar with the history of filesharing, Starting from the first one, super centralized, and then eventually every single step, you get to a decentralized platform.
And the last one, the most decentralized one, that is BitTorrent. the history of file sharing proved that every time you try to centralize something, it ends up badly, right? if you have any special node in the system that does a little bit more than others and requires more resources than others to run, that will end up badly.
You might end up in a small room with a lamp in your room. Point it to your face, and then everyone suddenly will stop running an indexer. That reminds me about Nostr structure. if you are building a peer to peer system, or if you are building a very resilient communication system, if you think about Nostr, you would imagine that if you have, 10 million or 100 million users, the number of relays would be probably less than the square root of the number of users.
So that surface, although a hundred million users is very, they're not attackable, right? But the surface of, the relays is much more attackable. look at what is happening with, the coin joinin platforms, right? very similar. the beauty of KIT versus Nostr is that in KIT you have number of relays is actually equal to the number of users because the users are their own relays.
and they can act as relays for others to, further their connectivity. That is how we think a technology that, has to be ready for the apocalypse and resilient to the wrath of God should, work. if you have, a log number of users or square root of number of users as relates, I don't think it's cool technology.
It will work better than centralized, Technologies like WhatsApp and so on, or Twitter, but eventually will not work when you will need it the most. Because the point is that we will not know what will happen when we will need this technology the most. Today, not for everyone, but the world is still almost at peace.
Things might unfold, in the future, maybe sooner rather than later. But when things unfold, you will need the best technology, the one that is truly independent, the one that is truly peer to peer. it's not really peer to peer if you have specialized relays, but where you have super peers randomly.
Luke: Yeah, the difference here, between the Realize and not having any other centralized infrastructure in the picture is certainly an interesting distinction. I hadn't heard anything about that you can act as a next connector or something like that.
Pear Runtime
Luke: So there's a couple of related things. I know there was an announcement about the, pair runtime, is that right? can you talk a little bit about that or any other, ways that this is growing in your whole, platform,
Mathias: Yeah, sure. so basically when we talk about ideas, internally, also from our software background, We want to solve a small problem that then can solve it for everybody. So
We want to build technology that can just send data around efficiently, so you can build any kind of app on top. We're all about modularity and taking these things to the extreme so we can repurpose it into any kind of application and other people can, get value out of it.
And, that's been our mission from the get go. So basically, like Paolo said, when we built Keed. We took all of these primitives we have, it's all open source on our GitHub, that can do various things, relay encrypted data in a way that's completely private, nobody can read it, and in a generalizable way, so it can run on any applications.
We have databases that can interpret, work with this data on device, but still in a way where nobody else knows what's going on, fully private, and we spent many years perfecting this, and it's still ongoing. And we, similar to like connectivity, it might seem really easy if you don't know what's going on that, connecting this computer to another computer and another place, but it's really hard because ISPs and, your internet providers, et cetera, they don't really want you to do that.
So there's a lot of firewalls involved that you have to work around to get around This is all really, hard problems that took a long time to solve.
But luckily, all of these are like generalizable problems where you just solve them once to a large degree, and then it's solved for everybody. If you put them in a modular framework where anybody can put the Legos together on top. And that's what we've been heavily invested in. And then as we were building Keed, we realized that Keete is just like 95 percent of these Lego blocks that are applicable for anything.
So why not take all this stuff, pack it up for free, we don't make any money on it. and an open source runtime that we're just giving away so other people can contribute to it, but also build their own apps. the more peer to peer apps the world has, the better from my point of view.
and document it and make it really easy to install. And I think actually Paolo said something interesting because as soon as you have, one point of centralization, you can always unravel it. coming from the Bitcoin days, I remember how quickly things can unravel. people went to jail for linking to things because authorities, when they crack down, really hard.
so if you have one weak spot, it will be taken advantage of at some point by somebody. And so even things like distributing updates to your software can be really hard because this often requires a central point, like you go to a website and you don't download it. And so all apps built on our runtime, for example.
It's distributed through the runtime, which is a little bit mind bending. So all apps are peer to peer data applications themselves, and the network doesn't care, which means that we can continue to distribute updates even, if everything gets shut down, you only need like a bootstrap for the first install when you get the app.
So we're thinking that in. At every level, because it's really, important to us to, basically learn from everything that happened in the past and then actually build things that are resilient. And we take this to a degree where I'm sure we could move 10 times faster if we just let go a little bit of that idea, because it is easier to just put all the data in one place or put all the updates in one place.
But then it's then we're just building the same old thing that's going to die eventually anyway. So we're very, uncompromising in that mission of actually decentralizing everything from updates to data, and then also always solving in a way where everybody can take advantage of that.
And then the final thing I'll say about that is that, every time we update. That runtime, those building blocks of that runtime, every time we fix a bug, every time we make it faster, every app becomes faster. That's also very exciting. It's because you're building the whole infrastructure into this layer that runs on your phone.
And it's all somewhat generalizable. Every time we fix something, it's just better for the entire ecosystem. And that's obviously really, exciting. And like I said, actually, no strings attached.
Yeah, so I think you were referring to the trial of the Pirate Bay people there In Sweden, right? lucky enough to meet a couple of them in Denmark and it's been very fun to hear about their journey and, yeah, like
Knut: and there, there's, there was a great documentary made about it called TPBAFK. So the Pirate Bay Away From Keyboard, about that whole trial and how, corrupt the system was even back then. And, throwing people in jail for providing links. they didn't do any more wrong than Google did, from a certain perspective.
And, I remember even, before BitTorrents, there was a program called. DC or Direct Connect Do you remember that?
Mathias: I used to, it was one of my first introductions to decentralization. it as you just shared your, like a Google Drive for everyone or something. Like you just shared parts of your file tree to everyone who wanted to peek into it, Yeah, anyway. Oh, that's good that you didn't know you were going with that. it interesting what you said, because I think it's interesting to think that I think to a large degree, the whole decentralization movement that was happening with BitTorrent back in the day got shut down because At some point, authorities figured out that they could just block DNS requests to shut it down for normal people, and as soon as they did that, it was actually effective.
And to Paolo's point, no matter how weak it is, they're done. and they tried to kill the technology elsewhere, but that's actually what killed them. Then, obviously, alternatives came that people could pay for, and it also shows that people actually want, to stay on the right side of things.
I think, now it's going very much in the wrong direction again, because now we're back at abusing that centralization again. the cycle will repeat. But, yeah, like any point of weakness will be attacked at any point.
Decentralization vs. Centralization
Luke: So what are the drawbacks to decentralization? I think we and our audience certainly understand the benefit of decentralization, what you gain by decentralizing, but what do you naturally give up in terms of the user experience and the convenience factor?
Mathias: yeah, I'm sure Paola has stuff to say here, but I'm just, I love talking about this stuff, so I'll go first. Mattias.
I think it's a really interesting question, first of all, because it's one of those questions where You know, obviously I want to say there's no drawbacks, but like anything, it's a balance, right?
Because it's not that there's drawbacks and advantages, there obviously is, but it's also just a different paradigm. first of all, with sensitization, I think one of the biggest thing I noticed also with developers is that we all come out of systems, education systems. That teaches how to think centralized, which makes us biased towards centralized solutions.
and that's, I remember my whole curriculum was about servers and clients and stuff like that. it's actually really hard to think about decentralization as a developer. And I think that's actually part of why a lot of people think it's hard. It's complex because it is complex, but also because we're just like, we've been trained massively in the other direction, and it's really hard to go back because decentralization can be as simple as what Knut said about DC Connect, DC where it's just, oh, I'm just browsing other people's computers.
That's amazing. That's a really, simple experience, and it's like something you can never do But like in today's world, people, the first thing I always get asked is like, how do I get a username? And I'm like, usernames have an inherent centralization and there's trade offs there.
And we need to think that through and stuff. and most applications don't necessarily require usernames. I'm not saying that's a bad feature, but it's that's where you need to think more about the trade offs because there's governance involved to some degree. But for the core experience, and I think that's what we've shown in Keith so far.
Then, there's obviously tons of upsides also, it's much easier to do big data transfers. Money is less of a concern, which actually changes the thinking, how you think about features.
And that, again, is something we've been trained in a lot as developers, because we think centralized. When we talk about features at Holepunch, hey, we should add podcast recording to Keed. Normally somebody would say, that's going to cost a lot of money to host that data. And we just always we don't even have that discussion because it doesn't matter because it's just between the users.
And then it's more about like the UX. But then other simple, like I said, other simple discussions, let's add a username index. That's where we're like, okay, let's think that through because there's like various things to think about there because there's no centric governance, and we don't want to introduce that because again, one point is.
It's bad. so it's, more like you really need to think differently and it's really hard to wire your brain to think differently. but once you get past that point, I think it's, super interesting. And I, think actually developers care way more than normal people because, developers care a lot about how links look and links and structure and that.
And normal people are just used to just clicking buttons and apps and going with the flow on that. And that's also what we're seeing, I think, with, a lot of key
Paolo: I think the hiring has proven a little bit more challenging, as Matthias was saying, when you are told that the cloud is your friend, hosting, on, Google Cloud or AWS is the right thing to do. And, of course, it got cheaper and cheaper, so now everyone can host their websites.
But the reality is that 70 percent of, the entire internet knowledge is hosted in the data centers of three companies. developers should think about that, should think about the fact that internet was born to be point to point and peer to peer. And, we are very far away from that initial concept.
over the years, especially with the boom in, in the year 2000 for the internet boom, and bubble, then, realized that, holding people's data is the way to go, with social media and social network. That is even worse. And so you have these friendly advertisements that are telling you, That, with a smiley face that, you know, yeah, you should, upload all your data on, Apple cloud or Google cloud.
And in general, cloud backups are great, right? You want to have some sort of redundancy in your life, but the reality is that you should be able to upload those. In an encrypted way, and yet most of this data sits unencrypted because, the big tech companies have to decrypt it and use it for, to milk the information to pay for, for, another month of their new data centers.
the, issue is, we have so much power in our hands through our phones. the phones that we have today are much more powerful than the phones that we, or even the computers that we have 10 years ago or 5 years ago. And so We should, we are at a stage where we can use this hardware, not only for communicating, but also for in the future for AI processing and inference and so on.
is, we need to, understand that the word cannot be connected to Google. I mean we cannot be a function of Google. We cannot be a function of AWS. And so I think that, there is, escalating pace of, towards centralization and it's almost a black hole.
And eventually, the, we'll attract all the lights and if we are too close to it, no lights will come out anymore. And, that's why we want to really to double down on this technology, because it's not going to be easy, right? It's going to be very challenging, and most of the people don't care, as Maite has said before.
Most of the people will think, everything works with WhatsApp and, Signal, but Signal announced that their 2023 costs for data centers and data center costs are around 50 million, and they, apart from the mobile coin that was not The best thing that they could do, there is, it's not easy for them to monetize.
And the problem is that if you are, you're basically almost the only way to monetize it is to sell your customer's data. So if you don't want to sell your customer data, eventually your service will not be sustainable. So the only way to make it sustainable is actually going back to peer, where you can leverage people, infrastructure, people, connectivity, people, phones, people, processing power, Deliver very high quality communication system.
And when they will care, it will be probably usually too late if nothing exists yet. when people will care is because shit is hitting the fan. And, you really want to have a solution that is not, that will survive if, the countries around you or around the country where you live are not going to be nice to your own country.
So that's the view to peer-to-peer. The peer-to-peer wheel system will keep working if your neighbor countries are not going to be nice towards you. That's independence, that's resiliency, those are terms that, we need to take very seriously, especially seeing where the, world is going to.
Knut: Yeah, I think we're all primed for, centralized solutions, from a very young age. this is the state, this is what it is like, state funded schooling. state funders or state subsidized media. We are, like brainwashed into, trusting, institutions all our lives.
So I think that is somewhat connected to why people are so reluctant to be vigilant about this on the internet. I think the two go hand in hand that we, take the comfortable way, or most people take the comfortable route of, not taking responsibility for their own stuff. not only on the internet, but outsourcing responsibility to the government is basically the, another side of the same coin, right?
Mathias: I also find it very interesting, especially being from a small country like Denmark that doesn't have a lot of homegrown infrastructure. And I'm just seeing how much communication with some of the public entities is happening through centralized platforms like Facebook and things like that, where even though we centralize it, we also centralize it in companies that we don't even have any control over in different countries where we probably have, no rights at all.
So it's like hyper centralization, especially from the weakest point of view. And I think that's super problematic. And I'm always. Thinking it's, weird that we're not talking about that more especially when you look at the things that they're trying to do in the EU, they're almost trying to just push more in that direction, which I find even more interesting.
yeah, definitely. it's, a huge problem and it's only getting bigger. And that's, why
Challenges and Future of Decentralization
Luke: So to what level can decentralization actually get there? What is the limit to decentralization? And I'll calibrate this with an example. The internet itself, you said it was built to essentially originally be decentralized, but we don't have it. For physical links, like individual physical links between each other, the fiber or whatever the wire is goes together into another group of wires, which eventually go into some backbone, which is operated by a company.
And then that goes into the global Internet. And so somewhere it centralizes into telecom companies and other services. It might be decentralized on one level, but there is a layer of centralized services that make the internet work that isn't necessarily the so called cloud providers and that sort of thing.
So is there a limitation to how far this can go?
Paolo: I think the, in general, sure, there are the ISPs and, their physical infrastructure is in part centralized, but also you start having redundancy, right? So for example, the backbones are redundant. There are multiple companies running, cross connects across different areas of the world.
Now you have Starlink if you want. that is a great way to start decentralizing connectivity because Starlink will not be the only one that will run satellites, so there will be multiple companies that will allow you to connect through satellites, plus you have normal cabling.
So you will have, it will become a huge mesh network, it's already in part, but it will become more and more a huge mesh network. in general, you will always find a way, even with a pigeon, to start sending bits out of your house.
I think the most important part is, you have to be in control of your own data, and then, you need to send this data with the shortest path to the people that you want to talk to. Right now, I usually make this example, because I think it's When we do this presentation, we try to make people think about how much waste also centralized systems have created.
imagine you live in Rome, you live in Rome and you have your family. Most people live nearby their families. That is a classic thing among humans. 90 percent of the people live nearby their families. Maybe nearby, like 10km, 50km nearby. If you talk to your family, every single message, every single photo that you will send to your family, that message will travel, instead of going 50 kilometers in a nearby town where your mother lives or your father lives, it will travel every single message, every single bit of every single video call or every single bit of every photo will travel 5, 000 miles to Frankfurt just to go back 50 kilometers from you.
Imagine how much government spent in order to create these internet lines and to empower them to make it bigger, more, with more capacity Peer to peer allows with a lower latency, allows to save on bandwidth, allows to save on cost of global infrastructure.
So that's how, actually, We can create better mesh networks, more resilient mesh networks, just because data will always find the shortest path from one point to another.
And still all roads lead to Rome. I'm Italian, so I need to use Rome as an example.
Knut: Yeah.
Mathias: I think the discussion here is really interesting compared to Bitcoin, because it's actually the scaling longer term. Sovereignty, like how, Bitcoin kind of told us very direct terms that if you have a key pair, you have your money.
And it doesn't matter where you are in the world. If you have that key pair, you have a way to get to that money. the means of transportation, it's actually very uninteresting in that sense, because you have it with you. The Internet today, the centralized Internet is designed in a way where, what does it mean to go to Facebook?
it's really hard to explain because it's like some certificate that issued by somebody, and there's. Some, cabal of companies that manages them, there's some regulations around it, but we don't really actually understand it that well as normal people. Technically, we can understand it, but it's very, centralized and it's very, opaque and it's built into the infrastructure in that way, in a bad way.
And, with Pure Technology, we're taking the same approach as Bitcoin here and saying, You're just a key pair, and the other person is just a key pair, and there's a bunch of protocols around that, but the transportation is actually not that interesting. Right now, we use the internet to do it.
We'll probably do that for a long time, but there's no reason why we can take the same technology we have right now and in 50 years run it on, laser beams or something else, because we're taking the software and feedback.
Bitcoin and Holepunch: Drawing Parallels
Mathias: I think, that's the main thing to think about in that. Discussion.
Luke: when, Paolo, when you were talking about that people don't care, when you were saying that people don't care because WhatsApp just works, I was at the same time thinking that's the parallel of people saying that, I don't care because Visa just works, right? And so the parallel between Bitcoin and what you're doing at Holepunch, Keet, everything else here, really seems to be tracking along the same line.
And I guess there's the connection that, I won't say all, but a lot of the people involved are already in the Bitcoin ecosystem. But can you comment on is there a little more of a connection there between Holepunch and Keet and Bitcoin?
Paolo: Yeah, Bitcoin definitely is working and servicing, I think, in a good way, many, people in communities. The users of Bitcoin today are, unfortunately, and also that relates to Tether, mostly, in the Western world, in the richer countries, as a way to save wealth and, as a store of value, more than a means of exchange.
For different reasons, right? We'd like a network that would improve, of course, over time, and there will be different approaches, but, still, the world is not yet using Bitcoin, but the world will use Bitcoin when shit will hit the fan. but the beauty of Bitcoin is that an option is already there, is available, and when something bad will happen, people immediately, with a snap of a finger, will turn to Bitcoin, and will have it and can use it. don't have that in communications. What is our communica our parallel with communications, if we don't have it? I don't know, because if, if suddenly centralized communications will, be blocked, then, or privacy in communications will be blocked, and you cannot, you cannot use Whatsapp, or Whatsapp has to start giving all the information to every single government.
and the government will become more evil than what they are today, also western governments then. don't, we wanted to build the exact parallel as we said it, we just tried to describe it, that with Bitcoin, for communications. We need to have something that, since there are so many alternatives that are working as with your, you can make the parallel with Visa, right?
Visa is working today, so people are still using a lot of Visa, but if something will happen, they will use Bitcoin from one day to another. Whatsapp is working, and Zoom is working, and Google Meet is working, so people don't feel the urge, but there will be a trigger point when people will feel the urge at some point in their lives, because something happened around them, and we need to make sure that kit will be available to them.
and will be an option, will be stable, will be well designed so that when they will need it the most that option will be available to them.
Luke: Yeah, fantastic.
The Future of Decentralized Communication
Luke: And so I think the follow up I have, and just to get back to the earlier discussion a little bit with Nostr, the communication in terms of messaging, I absolutely see that and directly in what Keet is, I already absolutely see that. Is there a goal to get somewhere towards more like Social media, social networking, things like that in a, in certainly a decentralized way, but right now there isn't something like that as I understand it, coming from, Keet.
So is, that a goal? Is that on the roadmap?
Paolo: Yeah, it is on the roadmap, it's something that, so we had to start with the thing that we thought was more urgent and also the thing that could have been, would have been a game changer. social media is very important, especially In difficult situation, you want to get news, and you want to get unbiased news, so you want to use, social networks to see what's happening in the world.
But we, think that the most sacrosanct thing that you need in your life is to be able to talk to your family and friends in any situation with the highest privacy possible. that's the first thing that we tackled, and also was a way to battle test the technology with, KIT you can do high quality video calls as well, so if we are able to tackle in the best way possible privacy and extreme scalability of peer to peer communications, then on top of that foundation we can build also social media and every single other application that we have in mind.
Mathias: But first, we wanted to tackle the hardest problem. No, I think it makes a lot of sense. And I also just want to say, as a, probably like one of the most prolific KEET users, I use KEET right now also as a very, like a social media, we have big public rooms where we talk about KEET and talk about technology. I get a lot of the value I would get otherwise on Twitter X from that because I, it's like a public platform for me to, get ideas out there, but also interact with users directly.
And I think, there's many ways to take them as a young app. And we're talking about this a lot, obviously it has to be simple, has to be parent approved. My parents can figure it out, but I think, to a large degree, all really healthy social networks that are actually, to some degree, a communication app.
And it's also just a really good way to get local news and to get this locality that Peter is good at. That doesn't mean that we might not also make other things, but I think it's a hard line to set the difference between a social network and a communications app when it's structured correctly,
Interoperability and User Experience
Luke: Yeah, and this, another thing that came to mind just as, you were talking about these parallels, as, I understand it, the account system with Keet is, essentially still just a, Key pair. Correct me if I'm, wrong,
Mathias: Very, true.
Luke: you backups with the same 1224 words.
Is, that fully interoperable as well? Is that, could be your Bitcoin key. That could be
Mathias: We use the, same, I can't remember the date, the BIP, but there's a BIP for like during key generation. So we can use it also in the future for other things. and you have those words, you have your account, and that's, we never store that. And that's like your sovereignty and, no, I was just going to say that lets you use it seamlessly on different devices also. It's one of those things that I love because I know what's going on when you use keyed Insanely hard problem, but it's solved by the runtime, and it just works seamlessly and I think that's, the beauty of it.
Paolo: I think there's some UX stuff to figure out about onboarding that stuff a little bit easier for normal people. That's probably to a large degree the same for Bitcoin. The other part that I would do with Bitcoin is that, with Bitcoin, with your 12, 24 words, you can access your private wealth. the beauty of Bitcoin is that you can remember 12 24 words, you cross borders, and you carry with you your wealth. You can do the same thing with your digital private life.
You remember 12 24 words, they could be the same by the way. whatever happens, you can spawn back your digital private life fully encrypted from, one of your other devices that you connected that is somewhere else in the world. So when you start seeing and understanding the unlock in terms of also human resilience that this creates is very, insane and can create a very powerful, that can be used for, to create a very, powerful applications, not just communications, but you can build.
Really any sort of interaction, even mapping. Imagine peer to peer mapping, where basically data is not stored in one single location. You can access, tiles of the maps, from, local people that curate them in a better way. So the, level of applications that you can build, All unlocked by the same technology that is being used by Bitcoin is very, incredible.
Luke: Yes, absolutely it is. And what do you think of the idea that all of this stuff is just interoperable now based on essentially you have your private key and there you go. It doesn't matter the technology stack. Is that sort of an agnostic thing where you can take your data to any one of these systems?
What you're building with Keith being one, Nostr being another, Bitcoin being a third, what do you think of that?
Paolo: Yeah, the fact that, data is yours, right? So you should do whatever you want with your data. That is, I think, an axiom that we should assume. And, it shouldn't even, we shouldn't even discuss about this, right? We are discussing about it because people are trying to take away this axiom from us.
The, you are a key pair, and you're basically, unique, and uniqueness is expressed by the cryptography around those 24 words, and that's, that also is a way to prove your identity, it's a mathematical way to prove your identity.
No one can steal that from you, of course, but no one can track it as no one can impersonate, should not be able to impersonate you. So it's truly powerful.
Mathias: also think it's like worth remembering here also in this discussion that a lot of very high valuable data for yourself is actually not that big, but centralized platforms take it hostage anyway. if you take all my chat history and, I have pictures, but like a couple of the pictures would probably be bigger than all my chat history ever.
but a lot of that, those messages have a lot of value for me, especially personally and also being able to search through it and have infinite history, it's very valuable for me personally. But it's very scary for me if that's on some other platform where it gets leaked at some point, et cetera, et cetera.
But we already have the devices, just normal consumer devices that we buy, that we all have, phones, computers, whatever, that have more than enough capacity to store multiple copies of this. In terms of like per user, data production, it's a manageable problem.
And I think it's interesting how, providers force us to think in terms of giving that data away, even though we could easily store it.
Paolo: And this is even more important when we think about potential, AI applications, right? So imagine your best assistant. Paolo's assistant should go through all my emails, my kids chats, my old social stuff, and be able to be my best assistant. But in order to do that, I have two options.
Either, I imagine that OpenAI would come with an assistant. They would upload, All the information on their servers, crunch that information, and then, use it to serve, me, but also service their own needs. And that can become very scary, also because they wear a hat. It's public, right?
you don't want your most intimate codes that your best personal assistant could know, to be on somewhere else, rather than your devices. And so people were, people never uploaded, at least most of the people would never upload medical, information on Facebook, right? But they are uploading it on ChatGPT to get a second opinion.
so things can be, get even scarier than what we described today because, we, discussed about social media, that is basically, the fun part where we upload photos, But, things can become scarier when it comes to privacy and data control with ai.
So I want to see a future where I have a local AI that can read all key messages that I have from my local phone on my local device, and can become the best powers assistant possible without renouncing to my privacy, and also still governed by the same 24 words. the fine tuning that is applied on that LLM should stay local to my own device, and it should be in control of that.
And still, the current power of the devices that we have makes it possible. We should not fall for the same lie. We don't need, of course, big data centers with GPUs are important for training a huge LLM, but that is a generic LLM. You can take that one and then fine tune it with your own data and run it by yourself.
And for most of it, unless you want to do crazy things, that is more than enough and can run on modern GPUs or local GPUs or your phones. We should start thinking that we can build local experiences without having an API all the time connected to someone else's data center.
Knut: Yeah.
The Role of Tether in the Crypto Ecosystem
Knut: It's super interesting. you briefly just briefly mentioned tether before and I think we need to get into this. what is it and how much of a maxi are you, Paolo?
And, what, made this thing happen? Can you give us the story here about Tether?
Tether's Origin and Evolution
Paolo: Tether started in 2014. I consider myself a maxi, but running Tether, you could say that, I'm a shit coiner. I don't mind, right? I like what I do, and I think I'm net positive, so it's okay. Tera was born in 2014 with a very simple idea. there were a few crypto exchanges in, 2014.
it was Bitfinex, Coinbase, Kraken, Bitstamp. OKCoin, there was BTCChina, and just a few others, right? Around 10 that were meaningful. The problem back then was to do, trading arbitrage, you sell Bitcoin on the exchange where the price is higher, you take the dollars. From that sale, you move the dollars on the exchange where the price is lower and rinse and repeat.
That is called arbitrage. It is a property of every single efficient financial system. And that also helps to keep the price of Bitcoin in line across different exchanges. But, that was very, hard in 2014. If you remember in 2013 was the first year that Bitcoin broke the 1, 000.
But on some exchanges the price was 1. 2, on others was 900. in order to arbitrage that price difference, you have to move dollars from one exchange to another and Bitcoin from one exchange to another. You can move Bitcoin from one exchange to another. 10 minutes, but dollars would take days, right?
International wires. And so of course the opportunity arbitrage was, fully gone by, the, time the wire was hitting the, receiving exchange. the reason why we created that was, USDT was simply to put the dollar on a blockchain so that we could have the same user experience that we had with bitcoin.
For the first two years, almost no exchange apart Bitfinex understood USDT. Then Poloniex in 2016 started to add the USDT across for against every single trading pair. There was the start of the ICO boom. 2017 was the peak of the ICO boom and, USDT reached 1 billion in market cap. Fast forward in 2020, we had around 10 billion in market cap, and then the bull run started, but also another important thing started, that was the pandemic.
USDT's Impact on Emerging Markets
Paolo: So the pandemic had a huge effect on many economies around the world, in all the economies around the world, but especially in emerging markets, developing countries.
Basically pandemic also killed entire economies. And so as a Bitcoin you would think, oh, all these people that are in countries like Argentina and Venezuela and Turkey and so on, they should use Bitcoin and they should, they should, only use Bitcoin because everything else is cheap.
So that is pretty much, the approach that we have as Bitcoiners that, I believe in. But the problem is that. Not everyone is ready, so not everyone has our time to understand Bitcoin. Not everyone has yet the full skill set to understand Bitcoin at this stage, at this moment in time.
we as Bitcoiners didn't build the best user experience in the world, right? So one of the best wallets for Bitcoin is still Electrum. That, is not necessarily nice and well done for and simple to be used for, a 70 year old lady. so we need to do a better job as Bitcoiners to build better user experiences we want Bitcoin to be more used around the world.
At the same time, 99 percent of the population knows, especially the ones that are living in high inflation areas, knows that there is the dollar that is usually Much better currency than what they hold in their hands. the US dollar is not, definitely not perfect. It's not the perfect fiat currency. but it's like the tale of the two friends running away from the lion, right?
you have, one friend tells to the other, Oh, the lion is gonna kill us. We have to run really fast. And one of the two friends says to the other, I just have to run faster than you, right? So the US dollar is the friend that is running faster, in a sense that is the one that is likely better than the others.
And so being better than the others is creating a sort of safety feeling among 5 billion people in the world that live in high inflation countries. And for those people that, they don't have yet the time, they didn't have the luck also, maybe, to understand Bitcoin, they are, in fact, using USDT.
If you live in Argentina, peso lost 98% against the US dollar in the last five years. The Turkish L lost 80% against the US dollar in, the last five years. So of course, Bitcoin would be better than the US dollar, but even already, if you hold the dollar, you are the king of the hill there, right?
So because it's, you are able to preserve your wealth much, better than almost anyone else in the region. I think, USDT is offering a temporary solution and is providing a service, a very good service to people that don't have alternatives and good alternatives and they are very, familiar with the U.
S. dollar already. so eventually, the hyperbitcoinization, I think it will happen. there is no way it won't happen. It's hard to pinpoint on a time when, that will happen. But it's all about the turning point. What the economy will look like in the next, 10, 20 years and what trigger point there will be for fiat currencies to blow up and become irrelevant.
Bitcoin as a Savings Account
Paolo: the way I see it is that it's likely that the U. S. dollar will stay around for a while, and people might still want to use, the U. S. dollar as a checking account, but they, should start to use, Bitcoin as their savings account, in the checking account, you, are happy to not make interest, It's something that you use for payments, it's something that you are okay to detach from because it's the money that you are ready to spend.
The savings account is the thing that we should fight for. This thing is the thing that matter the most, and, it's the thing that will is protecting people wealth. And so in the long term. And in the medium term, we should push for this savings account to be Bitcoin. also with Tether, we are heavily investing in companies, in Bitcoin companies.
we support the Blockstream. We supported so many in the space that are, we, are supporting RGB. That is a protocol that is building, assets on top of, like network, style channels. Thank you for listening. and we buy Bitcoin ourselves. We do a lot of Bitcoin mining.
We develop, I think, the best and most sophisticated Bitcoin mining software, by the way, based on hole punch technology. It's like IoT for Bitcoiners and Bitcoin mining. It's very cool. we are relying on the dollar and, you could say that USDT is helping the dollar, expansion, but the same way I don't think Dollar and Bitcoin aren't necessarily opposed to one or the other.
I think that Bitcoin has its own path. And no matter what happens, there is no way to slow it down. I think, it's going to be inevitable success. It's going to be inevitable that it will become global internet money and global words money. No country will trust to each other with, with each other currencies for, for a longer time, and so the only viable solution is a currency that is governed by math.
That is the only objective way, objective thing that we have in the universe. that's my train of thoughts on, Tether and Bitcoin.
Knut: Oh, thank you. Thank you for that explanation. It explains a lot of things. To me, it sounds a bit like you're a lubrication company, like selling lubrication for the transition between the rape of the dollar to the love fest of the hyperbitcoinized world, to make the transition a little smoother.
Paolo: we are more than, at Tether we have also this educational arm and, believe it or not, the majority of the creation we do is actually on Bitcoin, right? So we are supporting the Plan B network led by the great Giacomo Zucco. The unfortunate thing is that USDT, didn't have a marketing team up to, 2022 with Tether.
So basically, I wish I could say that success of Tether is because we were super intelligent and great. but actually the success of Tether, unfortunately is a symptom of the success of, of, national economies. And it's sad if you think about it, right? So the success of your main product U as it is, They're actually proportional to the FACAP of many central banks. And, but it is what it is, right? So we need to do what we do at, really, at DataRace, creating all these educational contents to try to explain that, sure, we are providing a tool for today, but, For tomorrow you probably need, you need to understand that you have other options, you need to understand Bitcoin, because as we said for, Keith, right?
So the moment when you will need the most Bitcoin, it has to be available, you need to understand it, so that is a true option for you. The way we, see bitcoin education.
Knut: No, and, something like Tether would have, emerged, either way, and it's very comforting to know that it's run by Bitcoiners and not by a central bank itself or something. yeah, and the Plan B Network, I was a guest lecturer there in Logano and it was fantastic.
I love what you're doing there with the educational hub. And we even got Giacomo to write the foreword to our new book here that you can see here behind Luke.
Luke: Always say the title, Knut. Always say the title.
Knut: Bitcoin, the inverse of Clown World. It's, you, if, you're good at maths and emojis, you might be able to figure out the title from the cover, but it's one divided by Clown World anyway, which is on the opposite side of the everything divided by 21 million equation, So anyway, looking forward to seeing you in Lugano and giving you both a copy of the book, of course.
Paolo: Oh, with pleasure, with great pleasure, with a nice, education.
Luke: Absolutely. Yep.
Plan B Forum and Future Events
Luke: 100%. And we have to wind things down, but I'll just say as well, yeah, absolutely looking forward to Lugano Plan B Forum. Always a highlight of the year. It was my first time last year. I absolutely loved it. can't wait to attend this year.
so it's the 25th, 2020 6th of October, 2024. this year, it's a Bitcoin event that is not made to make money. So the problem with events is that. You have to find sponsors, and usually, sponsor might not be well aligned with the message you want to give, right? I think Tether is lucky enough, to not have to make money on the event.
Paolo: I want to have, good, guests. I want to have great speakers. I want to have the messaging. That is not only about Bitcoin, it's about, freedom of speech as well. We had the family of Assange for the last few years, and I think that they will come also this year.
I'm going to be probably killed by the By our marketing team, I'm not sure if they announced it, but we are going to have another Plan B event also in El Salvador next year, so we're trying to create this network of cities and countries that have things in common and, invite people that want to share knowledge around the world.
And, yeah, and of course we, are very proud of the good food that we, serve in Lugano. So that is another thing that, not all the bands can say the same thing.
Knut: No, it's fantastic. And we happened to bump into the Assange family at the cocktail bar in a fancy hotel and, had a very interesting conversation with them there. So if you're listening. Anyone from the Assange family is welcome on the show any time. So yeah, no looking forward to that event for sure, we had a great time.
And I think we're even playing this year, aren't we, Luke?
Paolo: You're
Luke: yeah, the Satoshi Rakamoto is in the event there, we, played, back in Prague, it was my first, time, but Knut is a regular at the Rakamotos.
Yeah, we played at Lugano last year Oh, anything and everything, what did we do in Prague?
Knut: paranoid and,
Paolo: Can I commission a
Knut: What song would you like to hear?
Paolo: I have two that I would suggest. One is Nothing Else Matters.
Knut: Alright.
Paolo: So I think that, is very inspiring, right?
Knut: Bitcoin, for sure.
Nothing Else Matters. it's perfectly aligned with Bitcoin. And, the other one is Sad But True. Oh, that would be fun. We'll squeeze in some Metallica there, won't we, Luke?
Mathias: we'll 100% have those songs ready to go. We also have, a big peer to peer track at the conference,
Knut: Yeah.
Mathias: not so much music, but yeah, that's peer to
Knut: Nothing else matters.
Luke: looking forward to that.
Knut: Sorry, brain fart. Sad but true is about the dollar still being around,
Paolo: Yeah, you can say that.
Luke: Okay.
Final Thoughts and Closing Remarks
Luke: Hey, we have to wind things down here because, we're, almost, out of time. So I'll just hand this, back to you both. Is there anything else you'd like to, mention about, your plans in the upcoming couple of years, in, key, toll, punch, anything like that?
Mathias: only that we're, like I said, we're integrating really hard right now, and it's a really fun time to, join the company because, we're small and efficient We get to work with Tether, which has a lot of benefits and it's getting really fast, so definitely check that out. And it's also a really fun time to join Keith in our public rooms.
There's a lot of very personal, in a good way, intense chats where you get to be part of the loop. I love to be part of those early communities and I would suggest everybody to check that out and go to the website and try it out.
Paolo: we will certainly do that. Yeah, I couldn't agree more. So go check out Keith and Holepunch and the Plan B forum in Lugano, You could visit tether. io, that is, the website where we are trying to explain what we have in our minds between, finance, bitcoin mining, energy production, AI, communications, brain chips and stuff, right? I think it's more exciting.
Mathias: Just those things, that's all.
Paolo: Yeah, we can piss off more than this. Thanks.
Mathias: a
Luke: No, It's just perfect. and is on that note, is there anywhere else specific you'd like to direct our listeners?
Paolo: just follow the social channels and give us feedback on kit all the time because these technologies, needs everyone's help to be nailed them.
Mathias: We love technical feedback. We love UX feedback. We're trying to make something that works for the masses, so anything is good.
Luke: So that's, all at Keet. Is that correct? For Keet?
Mathias: Key. io and pairs. com for our runtime. It's all peer to peer.
Knut: Alright,
Mathias: Wonderful. And you're also still on the legacy social media platforms, right? Yeah.
Knut: we'll make sure to include links to your handles so people can find you there if they would like. forward to seeing you in Lugano.
Paolo: Likewise, I
Knut: But yeah, worth saying again.
Paolo: Thank you for having an invitation.
Luke: Yes, we'll wrap things up here. This has been the Bitcoin Infinity Show.
-
 @ 59df1288:92e1744f
2024-10-23 05:00:39
@ 59df1288:92e1744f
2024-10-23 05:00:39null
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 8cb60e21:5f2deaea
2024-09-10 21:14:08
@ 8cb60e21:5f2deaea
2024-09-10 21:14:08 -
 @ 5d4b6c8d:8a1c1ee3
2024-09-10 19:03:05
@ 5d4b6c8d:8a1c1ee3
2024-09-10 19:03:05It was great having football back. The 49ers and Chiefs continue to dominate, the Raiders, Jets, and Donkeys continue to disappoint.
I only made two picks last week. The Raiders money line was a dud, but my parlay of the Steelers money line with the under was a big hit. Unfortunately, freebitcoin hasn't put any NFL games up, yet. Hopefully they get around to it at some point.
I really like this type of parlay. The house treats outcomes as though they're independent, but I don't think that makes sense. In the event of a Steelers' win, the under was far more likely than the over, because their offense stinks and the game was likely a defensive slog.
In line with that thinking, I made two parlays this week: 1. Raiders money line with the under (7:1): yes, I'm going back to the Raiders. They're probably going to lose, but if they win, it will be because of awesome defense. 2. Bengals money line with the over (4.5:1): Maybe Joe Burrow stinks this season, but maybe the Bengals had been looking ahead to KC. The Chiefs offense is phenomenal again, so the Bengals are only likely to win if this turns into a shootout.
Are there any odds you're excited about (doesn't have to be football)?
originally posted at https://stacker.news/items/679894
-
 @ e97aaffa:2ebd765d
2024-10-19 10:07:46
@ e97aaffa:2ebd765d
2024-10-19 10:07:46As eleições nos países democráticos, são uma espécie de um concurso de popularidade, vence o mais popular. Os governos, como querem vencer as próximas eleições, tendem a tomar medidas com execução curtas, que apresente resultados num curto espaço de tempo. Os governos deixaram de fazer reformas estruturais, que teriam bons resultados daqui a 10 a 20 anos, pensam apenas a curto prazo, com uma alta preferência temporal e que sejam populares. Os incentivos estão completamente desalinhados.
Isto coloca os partidos políticos, um pouco refém da opinião pública, dificilmente fazem algo contra a opinião da maioria dos cidadãos. Se executar medidas muito impopulares, existe uma forte probabilidade de perder a próxima eleição.
Assim os governos só aprovam propostas que tenham uma “aprovação” parcial da população, poderá não existir uma maioria, mas uma parte terá que compreender essa proposta.
Muitas das vezes, os governos querem aprovar uma nova lei, mas sabem de antemão que é extremamente impopular, por isso, primeiro manipulam a opinião pública para ganhar apoio popular, depois sim aprovam a lei. Ou seja, cria uma narrativa, um motivo que justifique aquele ato.
Vamos um exemplo prático, dificilmente um governo aprova um aumento de impostos com o único objetivo de aumentar o salário dos deputados, seria extremamente impopular.
Os governos acabam por manipular a população, criam uma narrativa, prometem que o aumento dos impostos é para ajudar os mais pobres. É algo popular, mas depois de aprovada, uma parte do dinheiro vai para os pobres, a outra parte vai para os bolsos dos deputados. Assim conseguiram realizar a ideia inicial com o apoio popular.
Em suma, os incentivos levam os governos a tomar medidas que tenham uma parte de apoio popular. Terá que existir sempre um motivo que justifique. É uma espécie de equilíbrio de Nash, tem que existir um equilíbrio entre a opinião do governo e a opinião da população. Se existir uma enorme divergência, as perdas são muito superiores aos benefícios para o governo.
Bitcoin
A grande herança/legado do Satoshi não foi a tecnologia (até tinha muitos bugs) mas sim a política económica e protocolo de consenso, as suas múltiplas teorias dos jogos coexistentes, é uma verdadeira obra prima.
Já foram realizados inúmeros melhoramentos no código (tecnologia), talvez daqui a 20 anos, pouco restará do código inicial, mas a sua política está inalterada e está completamente atual e possivelmente nunca será alterada.
O Satoshi ao criar um novo sistema monetário alternativo, sabia que mais cedo ou mais tarde, o bitcoin seria atacado pelos governos. Como aconteceu em todas as tentativas anteriores ao bitcoin.
Após este comentário de um anónimo:
Você não encontrará uma solução para problemas políticos na criptografia
Satoshi respondeu:
Sim, mas podemos vencer uma grande batalha na corrida armamentista e conquistar novos caminhos para a liberdade por alguns anos. Os governos são bons em cortar cabeças de redes gerenciadas centralmente, como a Napster, mas redes P2P puras, como Gnutella e Tor, parecem estar se mantendo funcionando.
Assim quanto mais tarde, melhor, permitindo o desenvolvimento tecnológico e um maior crescimento da adoção. A adoção é o melhor escudo, um escudo humano sem armas mas com o poder no voto, de poder eleger ou derrubar o governo.
A diferença de poderes entre o estado e o Bitcoin é desproporcional, num confronto direto, o pequeno nunca vencerá essa guerra. O pequeno nunca conseguirá explodir o grande, mas poderá implodi-lo, ou seja, entrar dentro do sistema como um cavalo de Troia e depois implodi-lo.
A minha convicção, é que Satoshi não cria destruir o sistema Fiat, mas sim construir uma alternativa, com diversos casos de uso.
Bitcoin seria conveniente para pessoas que não têm cartão de crédito ou não querem usar os cartões que possuem, não querem que o cônjuge o veja na conta ou não confiam em fornecer seu número para “caras da por”, ou com medo de cobrança recorrente.
Se pensarmos bem, até é importante manter o sistema FIAT, nem que seja como uma referência (a não seguir). Nós, só sabemos que a refeição A é deliciosa, porque já provamos a refeição B (que é uma porcaria). Se perdermos a referência da B, deixamos de saber que A é deliciosa.
É claro que em última instância, se o sistema alternativo tiver uma adoção de 100%, acabaria por destruir o sistema FIAT. O essencial é existir liberdade monetária, o poder de escolha fica em exclusivo no indivíduo.
Como é lógico, o estado não quer perder o monopólio da moeda. Como expliquei na introdução, os governos democráticos necessitam de uma motivo plausível ou uma razão moral para proibir, parte da população tem que compreender. Se não compreender, vão questionar o porquê, isto pode gerar um efeito oposto, o chamado efeito Barbra Streisand. Ao proibir sem motivo aparente pode gerar um movimento de adoção em massa, porque somos humanos e o fruto proibido é sempre o mais apetecível.
O Bitcoin ao ser construído num limbo, repleto de teoria dos jogos, sem violar qualquer lei vigente, sem nunca bater de frente com os governos, é uma revolução pacífica e silenciosa. Como nunca pisou linhas vermelhas, coube aos governos encontrar um motivo para proibir, durante toda a história, os políticos bem tentaram mas nunca encontraram o motivo plausível.
Bitcoin vive nesse limbo, não viola qualquer lei, mas ao mesmo tempo, não compactua com os governos, apenas está a criar um sistema monetário paralelo. É como os bons advogados trabalham, aproveitam os buracos das leis ou contornam as leis sem nunca as violar.
Para que a adopção seja rápida, é importante tem de estar dentro da lei.
Quando os governos/procuradores não encontram provas diretas para condenar, adoram encontrar motivos circunstanciais, subterfúgios. Um bom exemplo foi Al Capone, apenas conseguiram encarcerar por sonegação de impostos, ele nunca foi condenado por crimes mais graves, de sangue.
Um bom exemplo foi o algoritmo de assinaturas Schnorr, que só foi adicionado ao Bitcoin na atualização Taproot, não foi adicionado anteriormente devido as pendentes, que estaria em vigor à data do bloco gênesis. Satoshi era rigoroso e calculista.
Em Dezembro de 2010, Satoshi demonstrou que não queria um conflito com os governos, ainda era muito cedo. Após o bloqueio das contas bancárias dos Wikileaks, Assange queria receber doações em bitcoin, mas Satoshi tentou dissuadi-lo, ainda era cedo, a descentralização ainda não era suficientemente robusta.
Não, não faça isso. O Bitcoin é uma pequena comunidade beta em sua infância. Você não arrecadaria mais do que alguns trocados, e a pressão que você traria provavelmente nos destruiria (a rede do Bitcoin) nesta fase.
O Wikileaks chutou o ninho de vespas e o enxame está vindo em nossa direção.»
Após estes acontecimentos, Satoshi afastou-se.
Transparência
Muitos apoiantes do Monero, criticam o Bitcoin devido à falta de privacidade, mas Satoshi optou por uma transparência total e por um pseudo anonimato.
O problema fundamental com a moeda convencional é toda a confiança necessária para fazê-la funcionar. Precisamos confiar que o banco central não vai desvalorizar a moeda, mas a história das moedas fiduciárias está repleta de violações dessa confiança. Deve-se confiar nos bancos para reter o nosso dinheiro e transferi-lo eletronicamente, mas eles emprestam-no em ondas de bolhas de crédito com apenas uma fração de reserva. Temos que confiar-lhes a nossa privacidade, confiar que não permitirão que ladrões de identidade drenem as nossas contas. – Satoshi
Satoshi descreve magistralmente os problemas do sistema financeiro, o ter que confiar, a falta de transparência e a reserva fracionária. Bitcoin é exatamente a resposta a isso, um sistema totalmente transparente, onde tudo é visível, tudo é auditável e sem a necessidade de confiar em terceiros.
Assim, garantiu a segurança e a integridade do sistema, promoveu a confiança e incentivou a verificação e não confiar em informações de terceiros. A qualquer momento, qualquer pessoa consegue verificar todas as transações e saber o supply total do bitcoin, isto é incrível.
Don’t Trust, Verify!
É claro que essa total transparência gera “efeitos secundários”, uma menor privacidade. Temos que saber viver com isso, é um mal menor, para garantir um bem muito superior, uma moeda justa.
A transparência é a prioridade, privacidade fica parcialmente garantida através do pseudo anonimato, tem algumas limitações, mas bem utilizado, pode garantir uma certa privacidade, basta fazer uma boa gestão de chaves e uma utilização de endereços descartáveis.
Como uma camada de segurança adicional, um novo par de chaves deve ser usado para cada transação para evitar que elas sejam vinculadas a um proprietário comum. – Satoshi
O problema do pseudo anonimato é agravado devido ao mau comportamento das pessoas, que utilizam exchanges e vinculam os endereços à identidade real.
A possibilidade de ser anônimo ou pseudônimo depende de você não revelar nenhuma informação de identificação sobre você em relação aos endereços bitcoin que você usa. Se você publicar seu endereço bitcoin na web, estará associando esse endereço e quaisquer transações com o nome com o qual você postou. Se você postou com um identificador que não associou à sua identidade real, ainda é um pseudônimo. – Satoshi
Não é possível querer os dois mundos em simultâneo, quem quer privacidade não poderá utilizar exchanges, apenas p2p.
E Satoshi tinha razão, atraíram as “vespas”, em 2011, o Gavin Andresen foi convocado pela CIA, o serviço de inteligência dos Estados Unidos, para falar sobre o Bitcoin.
Comunicado de Gavin Andresen:
Aceitei o convite para falar porque o fato de ter sido convidado significa que o Bitcoin já está no radar deles, e acho que pode ser uma boa chance de falar sobre por que acho que o Bitcoin tornará o mundo um lugar melhor. Acho que os objetivos deste projeto são criar uma moeda melhor, criar um sistema de pagamento internacional mais competitivo e eficiente e dar às pessoas um controle mais direto sobre suas finanças. E não acho que nenhum desses objetivos seja incompatível com os objetivos do governo. Estou apenas um pouco preocupado que falar sobre bitcoin na CIA aumente as chances de que eles tentem fazer algo que não queremos que eles façam. Acho que aceitar o convite deles e ser aberto sobre exatamente o que é o bitcoin tornará menos provável que eles o vejam como uma ameaça.
Como no Bitcoin não existe uma privacidade total e as transações são rastreáveis, não representava uma ameaça para a segurança nacional dos estados. Assim não existe um motivo plausível para o governo o proibirem.
A total privacidade é claramente uma linha vermelha para os governos.
A generalidade das pessoas tem dificuldade em compreender o verdadeiro valor da privacidade, acreditam na ideia, “quem não tem nada a esconder, não tem nada a temer”. Na época, se o governo tivesse a intenção de atacar o Bitcoin, possivelmente teriam conseguido proibi-lo e as pessoas nem teriam contestado.
Foi exatamente o que aconteceu agora com a Monero, a privacidade/anonimato foi utilizada como o motivo, está a ser ilegalizada em vários países, sem gerar alguma consternação na população. Infelizmente as pessoas não dão valor à privacidade, são demasiado ingénuas, acreditam que isto dará mais segurança.
Qualquer sociedade que renuncie um pouco da sua liberdade para ter um pouco mais de segurança, não merece nem uma, nem outra, e acabará por perder ambas. – Benjamin Franklin
Eu acredito que se o bitcoin tivesse o mesmo grau de privacidade da Monero, hoje em dia, ou já não existia ou seria apenas um micro nicho, nunca teria atingido a atual dimensão.
É um equilíbrio, se houvesse um maior grau de privacidade a adoção seria baixa, se privacidade fosse nula (FIAT) a adoção seria elevadíssima. Satoshi optou por um pouco de equilíbrio, com o pseudo anonimato.
O bitcoin sacrificou um pouco a privacidade, em prol de um bem muito superior, é o instituto de sobrevivência. Esse sacrifício era a única via, uma maior privacidade poderá ser garantida com outras soluções ou em segundas camadas.
A camada base deve manter este nível de privacidade, como padrão, quem quiser uma maior privacidade terá que optar por sistemas alternativos, como mixers ou outras camadas.
A tecnologia deve ser imparcial e genérica, é uma situação similar das facas, apenas uma tecnologia agnóstica. A responsabilidade não está na tecnologia, mas sim de quem a utiliza. Quem utiliza uma faca para cometer um crime, é quem deve ser condenado. Deve ser condenado quem faz mau uso da tecnologia e nunca deve ser condenado quem construiu a tecnologia e muito menos proibir a tecnologia.
Num futuro longínquo, a camada base será um local de Settlements, apenas utilizado por liquidity provider(LP), bancos ou pessoas com bastante valor. A generalidade das pessoas utilizarão apenas camadas secundárias, onde existirá um maior grau de privacidade. Vão existir centenas de L2 ou sidechains que estarão ligadas à L1, onde a liquidez está colaterizada, por isso é essencial uma transparência total, para ser facilmente auditável a quantidade de fundos colaterizados, para garantir a segurança.
Neste futuro, a maioria das transações na L1 serão de instituições ou estados, eu acredito que vão querer implementar maior privacidade, nesse momento, seremos nós a não querer. A verdade está na transparência.
Custódia
Como os políticos não fizeram nada durante anos, o Bitcoin cresceu na adoção, mas sobretudo na descentralização. A descentralização atingiu uma tal dimensão, que hoje em dia, é impossível proibir o Bitcoin e os políticos sabem disso. Como já não é possível proibir tecnicamente, agora a única via, é tornar ilegal a sua utilização.
Os políticos durante anos tentaram fabricar motivos plausíveis, manipularam a opinião pública com FUDs e informações falsas, mas nunca conseguiram um forte apoio popular.
O Bitcoin continuou a crescer, agora os governos ocidentais mudaram ligeiramente de estratégia, em vez de proibir, estão a direcionar/condicionar a sua utilização, ou seja, estão a aceitar o Bitcoin como um ativo, como o ouro, como reserva de valor, sobretudo em locais centralizados, como ETFs e em exchanges, bancos, tudo altamente regulamentado. Tudo por baixo da asa dos governos, onde os políticos podem controlar, confiscar o bitcoin e identificar facilmente.
Mas ao mesmo tempo vão dificultar a auto-custódia e a utilização do Bitcoin como meio de troca. O grande medo dos governos é o Bitcoin ser utilizado como uma moeda, eles não querem concorrência às suas moedas FIAT, estão apenas a tolerar como reserva de valor.
Agora o grande objetivo é ilegalizar/limitar a auto-custódia, mas aqui existe um enorme medo por parte dos governos ocidentais, ao fazê-lo, podem dar uma percepção à sua população que é um ataque às liberdades individuais, os governos não querem dar imagem de ser autoritários. Poderia também gerar o efeito Barbra Streisand, gerando uma adoção em massa, o tiro poderia sair pela culatra. Mesmo sem proibir, os governos vão utilizar os impostos para limitar a adoção e a utilização.
Como o euro e o dólar tem uma volatilidade muito inferior ao Bitcoin, é natural que a utilização do Bitcoin como moeda seja baixa na União Europeia e nos EUA. Como o benefício é baixo, mas o risco é muito elevado, possivelmente os governos vão deixar andar, só vão proibir a auto-custódia em último caso, em desespero.
Será pouca a utilização como moeda na Europa e nos EUA, mas a adoção vai ser grande como reserva de valor, vai permitir reduzir a volatilidade e ainda vai dar mais resiliência ao bitcoin. O aumento da adoção não será apenas pelo cidadão comum, mas também por políticos, empresários e investidores, criando um forte lobby pró-bitcoin. Este conflito de interesses dos políticos, vai dificultar a aprovação de medidas mais restritivas, porque haverá sempre algum bitcoiner dentro dos partidos políticos, haverá oposição interna.
A entrada da BlackRock foi um divisor de água, podemos não gostar, mas a percepção geral mudou completamente, existe antes e depois do apoio BlackRock. Os ETFs que estavam há 10 anos num limbo, foram aprovados em meses, a narrativa negativa (que o bitcoin consumia muita energia e só era utilizado por criminosos) desvaneceu.
Mas nem tudo poderá ser um mar de rosas, existe um dúvida no ar, de que lado está a BlackRock, sobre a auto-custódia, fará lobby para que lado?
Em teoria, a proibição da auto-custódia faria crescer o número de clientes, mas provocaria um efeito secundário, como a soberania e a descentralização é fulcral, ao atacar esses pontos teria um forte impacto no preço, os clientes da BlackRock perderiam dinheiro e poderiam desistiriam dos EFTs. O que no início poderia resultar num aumento de clientes, poderia resultar numa perda de clientes, é a teoria dos jogos, o Dilema do prisioneiro. O melhor para ambos, é a coexistência dos serviços custodiais e não-custodiais, porque ambos geram procura, ambos serão beneficiados. Só o tempo dirá, de que lado está a BlackRock.
Hoje em dia é visível a forte adoção dos EFTs, tanto por empresas/instituições, como por particulares, alguns milionários. Os ETFs são um produto simples, muito fácil de utilizar, sem necessidade de fazer a custódia, mas existe sempre o risco de confisco. As empresas e fundos de pensões, não terão outra alternativa, obrigatoriamente terão que estar sempre em serviço custodiais, mas no caso dos investidores particulares, estes vão pensar duas vezes.
Numa fase inicial vão utilizar os ETFs, depois com tempo vão estudar e compreender como funciona o bitcoin. Possivelmente alguns vão mudar para auto-custódia ou para outros serviços mais resilientes ao confisco.
Os particulares milionários como tem empresas ou outros ativos, como no mercado de capitais ou então imobiliário, já estão demasiado expostos aos poder do estado e há boa bondade dos políticos. Os milionários também têm medo dos governos, por isso, já colocam parte da sua riqueza em jurisdições mais amigáveis (offshores). Nas offshores só uma pequena parte do capital tem origem criminosa, a grande maioria do dinheiro tem uma origem lícita, as poupanças estão ali como uma proteção, uma segurança extra, porque também tem uma certa desconfiança do poder político.
No futuro, alguns desses milhões de dólares que estão depositados na Suíça, Dubai, Caimão, Curaçau e entre outros, vão ser transformados em bitcoin, é inevitável. Alguns vão optar por serviço custodial nessas mesmas jurisdições, mas certamente alguns vão optar pela auto-custódia.
As offshores dão segurança ao cidadão, mas apenas estava acessível aos mais ricos, mas agora existe o Bitcoin, que dá ainda mais soberania e está acessível para toda a gente, é universal.
Até para o lado dos governos, é mais fácil rastrear as transações de Bitcoin do que as transações em certas offshores.
Meio de troca
São nos países onde as moedas perdem mais poder de compra, é onde existe uma maior adoção do Bitcoin. Assim, a forte adoção como reserva de valor, vai permitir reduzir bastante a volatilidade do Bitcoin, provocando uma forte adoção em países com moedas com inflação mais elevadas, sobretudo na América central e latina, na África e na Ásia.
Hoje em dia, este “mercado”, das compras do dia-a-dia, foi dominado por stablecoins. Mas as stablecoins são uma CBDCs disfarçada, o FED tem um poder absoluto sobre elas, congela fundos a qualquer momento, sem qualquer limitação. Os EUA já utilizam as stablecoins como uma política expansionista, esse processo vai acelerar nos próximos anos, vão imprimir biliões/triliões de dólares para financiar o governo e vão distribuir essa inflação para o resto do mundo em forma de stablecoins.
O forte crescimento da adoção das stablecoins de dólares, está a colocar em causa as políticas monetárias internas nos países subdesenvolvidos. Atualmente os políticos utilizam a moeda como uma arma contra o seu próprio povo, este refugia-se no dólar, como uma proteção contra as altas inflações e contra a tirania dos seus políticos.
Não é o Bitcoin a principal ameaça às moedas FIAT, mas sim as stablecoins de dólares.
Nestas economias sempre houve dólares, existem mercados paralelos de dólares, mas este mercado tinha uma limitação física que impedia o seu crescimento, é difícil entrar novas notas/cédulas de dólares em circulação. O digital resolveu esse problema, agora é fácil entrar “novos” dólares nessas economias, os governos mais austeros, com políticas de controle de capitais mais agressivas, não conseguem evitar a entrada.
A utilização das stablecoins está a crescer rapidamente, mas em algum momento, existirá um ponto de inflexão, os governos não vão querer perder o poder da sua moeda FIAT, vão retaliar. Ao contrário do papel-moeda, as stablecoins são fáceis de confiscar/congelar fundos. Os governos vão retaliar e vão começar a obrigar a Tether (e os outros) a congelar fundos arbitrariamente, será congelamentos em massa.
Haverá muitos conflitos diplomáticos, a Tether vai compactuar com grande parte dos governos, mas será que compactuará com o governo russo no congelamento de fundos?
Só nesse preciso momento, as pessoas vão compreender o verdadeiro valor da descentralização do Bitcoin. Será um catalisador no aceleramento da adoção do Bitcoin, como moeda, nessas economias.
Além disso, a política expansionista dos EUA não é imparável, nem inesgotável, um dia terá que afrouxar, quando colocarem o KYC como obrigatório, milhões de pessoas vão afastar-se das stablecoins.
Mais tarde, os fluxos migratórios desses países subdesenvolvidos, serão uma forte contribuinte para eclodir os mercados p2p na Europa e para os EUA, vai gerar uma enorme utilização do Bitcoin como moeda.
A “reserva de valor” vai alimentar o “meio de troca“ e por sua vez este vai alimentar ainda mais o “reserva de valor”. Se isto acontecer, os governos ocidentais poderão desesperar e vão tentar desesperadamente ilegalizar o bitcoin, especialmente os governos europeus, mas talvez seja tarde demais. O Bitcoin já estará disseminado em todo o lado, como um vírus.
Independência
Como disse em cima, quanto maior for a adoção, maior é o escudo humano. Apesar de existir milhões de bitcoiners, ainda somos uma gota num oceano, neste mundo com biliões de habitantes.
Bitcoin é um sistema financeiro alternativo, mas ainda está altamente dependente do sistema FIAT, para crescer. Se os governos conseguirem cortar todas as rampas de entrada FIAT, a adoção ficaria muito mais lenta. Seria como em 2012, quando não existiam exchanges, a única maneira de comprar era através de p2p, os scams online eram imensos, não existia confiança, as pessoas tinham medo de comprar, não arriscavam. As exchanges facilitam imenso, foram fundamentais para acelerar o crescimento da adoção.
Bitcoin necessita reduzir esta dependência e tornar-se totalmente independente, para isso é essencial uma adoção massiva. As economias circular vão desempenhar um papel fundamental, se em cada terra/cidade existirem várias pessoas disponíveis para p2p, já não será necessário ir online para trocar FIAT por Bitcoin, aí sim alcançarmos a independência.
O Bitcoin tem que ser acessível, fácil, rápido e sem a necessidade de uma KYC.
Impacto Global e Social
Quanto maior for o impacto global, mais resiliente será o bitcoin, é a teoria de jogos na sua plenitude.
Se houve um forte crescimento na adoção do Bitcoin como moeda em países em desenvolvimento, utilizada por grupos sociais perseguidos, pelos mais pobres, pelos mais necessitados e cidadãos em países sob regimes autoritários, todos eles serão um escudo humano e social no ocidente. Ou seja, haverá pressão social sobre os políticos ocidentais, porque qualquer coisa que prejudique o Bitcoin teriam um impacto tremendo no preço, consequentemente, vai destruir as poupanças dos mais necessitados em todo o mundo. O impacto seria global.
Será que o governo terá coragem de prejudicar as populações mais necessitadas em todo o mundo?
Conclusão
Quanto maior a adoção, maior será o escudo humano. Tudo isto não passa de uma opinião pessoal, a minha interpretação. Não confie em nada aqui escrito, verifique!
-
 @ 59df1288:92e1744f
2024-10-23 04:59:30
@ 59df1288:92e1744f
2024-10-23 04:59:30null
-
 @ c8cf63be:86691cfe
2024-10-19 10:03:45
@ c8cf63be:86691cfe
2024-10-19 10:03:45Wenn wir Leibnitz große Frage, “Warum ist etwas und nicht vielmehr nichts”, ein wenig abwandeln, bleibt sie für uns gleich relevant, aber leichter greifbar. Warum das Leben Bewusstsein ausgebildet hat, das ist für das Bewustsein ein und die selbe Frage. Im ersten Moment scheint das Bewusstsein eher etwas Hinderliches, wenn ich mich erst entscheiden kann, nachdem ich mir etwas klar gemacht habe, kann ich schon gegessen worden sein. Einfachere reflexbogen Systeme sind da viel schneller. Warum schleppt sich das Leben mit diesem Bewusstsein rum? Gerade wenn wir uns den selektiven Druck vorstellen, der auf dem Leben lastet. Warum ein Bewusstsein produzieren das die Entscheidungsvorgänge “erlebt”. Ist es nicht sogar besonders herzlos von der Welt, all diese Wesen, die sich nicht behaupten können, die gefressen, verschlungen, zerquetscht, aufgelöst in Säure u.ä. werden, müssen mit anfühlen wie das mit ihnen passiert. Das klingt doch eher wie die grausame Idee eines verrückten Gottes.
Bewusstsein ist kein Problem, Bewusstsein ist die Lösung[1] für ein Problem das das Leben hat: “Entscheiden”. Entscheiden ist ein Problem, wir wissen das von der Russelschen Aniomie[2], der Gödelschen Unvollständigkeit[3] und dem Halte-Problem Turings[4]. Enscheidungen sind das Problem, die das Leben lösen muss. Wie die vorhergehenden Sätze gezeigt haben, ist dies Algoritmisch nicht möglich, das hat auch das Leben ‘begriffen’, die Antwort des Lebens auf das Enscheidungsproblem ist unser Bewusstsein. Das “Klarmachen ändert” gibt dem Leben einen selektiven Vorteil gegenüber “algoritmischen” Leben. [5] Wir können die Dialektik der Aufklärung erkennen, können hinter die Kulisse der zweiten Welt schauen und können ein neues Bild von ihr in unserem Inneren erzeugen.
Bewusstsein ist eine Problemlösung, und das Problem ist schwerwiegend. Das Problem heißt, wie sich auf die sich ändernden Umstände zu beziehen und wie handeln. Das Handeln ist erzwungen durch die Welt.
Das Leben hat das Bewusstsein hervorgebracht, weil das Bewusstsein ein evolutionärer Vorteil ist. Bewusstes Leben verschlingt alles algorithmische Leben.
Daraus können wir lernen, dass unsere Leidensfähigkeit etwas Gutes ist, ein echtes Plus. Mit dieser Voraussetzung ist die Frage nach algorithmischen Bewusstsein geklärt, wenn das Bewusstsein die Lösung für das algoritmische Problem darstellt, kann es ein algotithmischen Bewusstsein nicht geben. Computer werden demnach nie Bewusstsein entwickeln. [6]. Das zentrale Merkmal für Bewusstsein ist hier “die nicht Berechenbarbeit” bzw. “Non Computable”. Das Argument dafür ist recht einfach, da Rechnen nur eine Verkürzung des Zählens ist, und alles Zählbare immer schon gezählt ist, gibt es keine Dynamik, keine Form, die sich bilden und erhalten kann.
Physikalisch halte ich eine “Non Computable”, in der Quantenmechanik verankerte Vorstellung, wie die “Orchestrated objective reduction” [7] für die geeignetste Vorstellung für die Verbindung der Physikalischen Welt mit dem gestiftet Sein unserer Erfahrung von Dasein.
[1] Karl Popper, All Life is Problem Solving, 2001. Seite 100 “All life is problem solving. All organisms are inventors and tech- nicians, good or not so good, successful or not so successful, in solving technical problems.”
[2] Wikipedia, Russellsche Antinomie, https://de.wikipedia.org/wiki/Russellsche_Antinomie.
[3] Wikipedia, Gödelscher Unvollständigkeitssatz, https://de.wikipedia.org/wiki/G%C3%B6delscher_Unvollst%C3%A4ndigkeitssatz.
[4] Wikipedia, Halteproblem, https://de.wikipedia.org/wiki/Halteproblem.
[5] Voraussichtlich ist genau deshalb das Weltall nicht voller von Neuman Sonden, die Funktionieren einfach nicht.
[6] Das ist eine dezente weiter Entwicklung des Argument in “The Emperor’s New Mind” von Roger Penrose.
[7] Roger Penrose, Consciousness and the universe: quantum physics, evolution, brain & mind, Cambridge, MA 2017 “1. Consciousness in the Universe: Neuroscience, Quantum Space-Time Geometry and Orch OR Theory”
-
 @ d96e0407:8a0da63d
2024-10-18 19:27:45
@ d96e0407:8a0da63d
2024-10-18 19:27:45
"I didn't know you had friends, Arthur," Asad said telepathically as I walked across the street. I ignored him. I was overjoyed to finally leave the house and hang out with a fellow human. "I do have friends," I replied as he continued to bug me. Truthfully, it seemed like my only companion was Asad, a vampire who was my best friend.
The mere thought of it made me laugh too hard, preventing me from noticing the car as it almost ran through me. "Have you forgotten how to cross the road?" he said. Honestly, it looked like I did; I hadn't left the house in days. "Be careful, there are vampires lurking around," Asad warned me.
"What do you mean?" I asked as I stepped into the bus. I was surprised; I had always assumed he was the only vampire in the district. "Are there more of them out there?" I said to myself. A pale young man wearing dark shades bumped into me as he walked out of the bus.
His eyes gave a reddish glow, and a chilling aura emanated from him. "Where are you, Asad?" I asked but got no response. The sudden realization that I was on my own was scary. I clutched the pocket knife in my pocket as I got off the bus.
The avenue had an eerie feeling to it; I could tell something was up. In an instant, a creature jumped in front of me, trying to bite my neck. Bam! as I kicked it to the wall. With no hesitation, I thrust my pocket knife into his heart. I smirked, finally realizing the usefulness of Asad's martial art training sessions.
"Ian!" I exclaimed, realizing he was in danger. I rushed to his apartment. The door burst open, showing signs of a forced entry, and Ian lay unconscious on the floor. A breeze blew, shutting the doors. I brought out the pocket knife, ready to defend myself, but I was knocked to the ground by the man I bumped into on the bus.
As I lay on the ground, helpless, more vampires appeared, ready to feed on me. "Let's drain him dry," Blake, the one wearing shades, said. I picked up my pocket knife and threw it at Blake's eye, crashing his shades. He removed the knife from his eye and threw it towards me with so much force capable of piercing my subclavian artery.
"Are you alright?" Asad said, holding the pocket knife. My face glimmered with joy. I managed to lift up Ian and proceeded to leave the room. "Asad, wreak havoc," I said, smirking at him as I left the room. His red eyes glowed as he telekinetically blasted the heads of the vampires, causing blood to gush out as their brain matter splattered on the ground. He proceeded to dismember Blake's head from his body. "No one tries to harm Arthur and get away with it," he said, squashing the head with his feet.
"Erm... Asad, what's with the markings on Ian's body?" I said, panicking. He came over to take a look, and the only thing that came out of his mouth was "Cheryl." I couldn't hide my surprise; apparently, one of Asad's past lovers had come to hunt us. "I know someone who can help," Asad said, teleporting us to the mysterious shop down my street.
The gigantic owl totem creeped me out; the voodoo dolls, mysterious herbs, and weird liquid substances in glass bottles were signs it was an occult shop. "What brings you here, Asad?" a woman with pale white skin and long dark hair with purple streaks asked. Beside the woman was a familiar face to Asad. "Mina!" he said in shock.
-
 @ 59df1288:92e1744f
2024-10-23 04:56:00
@ 59df1288:92e1744f
2024-10-23 04:56:00null
-
 @ 655a7cf1:d0510794
2024-09-10 13:16:15
@ 655a7cf1:d0510794
2024-09-10 13:16:15Currently have kyc BTC, huge fan of lightning Network. Because I am a constant user of lightning. Plan on doing my business with lightning as well , peer-to-peer I'm not sure if I'm so worried about kyc I might be misguided in this situation.
originally posted at https://stacker.news/items/679520
-
 @ 59df1288:92e1744f
2024-10-23 04:54:40
@ 59df1288:92e1744f
2024-10-23 04:54:40null
-
 @ 6ad3e2a3:c90b7740
2024-09-10 08:21:48
@ 6ad3e2a3:c90b7740
2024-09-10 08:21:48I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry.
Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — made it to the final 23 in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing.
When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “the man in the arena whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week.
This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, the entire odyssey while sick and still jet-lagged in 122-degree heat.
But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. I was the guy who got this done. I flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia.
And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring sports content to nostr which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write.
And I got the idea to do this seriously because Heather wrote a guide to Lisbon which I posted on nostr, and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a (very in-depth) guide to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be Team of Destiny, Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week.
. . .
While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play.
There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent.
At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor.
I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha.
. . .
In last week’s Survivor post, I wrote:
What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.
It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens.
. . .
I picked the Bengals knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more.
And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it.
I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable.
. . .
I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed.
-
 @ 6bae33c8:607272e8
2024-09-10 07:50:12
@ 6bae33c8:607272e8
2024-09-10 07:50:12I went 1-3 in my NFFC leagues for two reasons: (1) Christian McCaffrey failed to score 17 points (because he was inactive), and I failed to bid enough on Jordan Mason because at the time of the FAAB last week, the Niners were flat-out lying about his likelihood of playing and like an idiot I believed them; and (2) I sat Mason in another league at the last minute for Jaleel McLaughlin because Fantasy Pros (that scourge of a site I swear off every year) had Mason not just lower, but absolutely buried in its RB rankings. I would have ignored a close call between the two, but I thought if he’s this low, the market must place a high likelihood on McCaffrey playing, and I don’t want to take a zero. This is the problem with being lazy and outsourcing your research to a bunch of midwits with misaligned incentives. I really should have delved deeply into all the McCaffrey reports and made my own assessment.
The problem with sites like Fantasy Pros is the grading system is different than the fantasy game itself. I imagine you’d get dinged hard for ranking Mason high if McCaffrey plays, and so it’s safer to rank him low. Moreover, one thing the fantasy industry is really bad at is pricing in that kind of risk. If everyone’s playing the market is pretty good at evaluating opportunity, per-play production and hence output, but if someone is 50/50 to get opportunities at all, they can’t handle it very well. Obviously Mason was a good bet to go for 20 points if McCaffrey were scratched, and so he should have been projected for 14 if it were 50/50 (he’d get some points even if McCaffrey played), but that we was projected for less than five (IIRC) made me think it was like 80/20.
But I knew it was a very bad sign Monday morning (after it was too late to pivot) when McCaffrey was still not deemed definite — it’s not like he got hurt last week, but he’s had a full month to heal. (Actually maybe the Achilles was last week, but because injury reporting sucks and teams lie, it’s impossible to know the real reason he missed the game. If it’s still the calf, all bets are off because if he’s not back in a month, five weeks won’t magically heal him.)
In any event, I’m glad I have Mason in two NFFC leagues, and I went all-in to get him (and I used him) in my RotoWire Dynasty one at least. But I should have been 3-1 if I had used my brain, and am instead 1-3, the win thankfully in the Primetime.
-
The 40-minute edited version of the game for God knows what reason flashed the final score (32-19) briefly after I hit play. So it spoiled the game for me, and the whole time I was just trying to figure out how they got to that number, realizing probably Jake Moody went bananas for some people, and he did.
-
I love that Allen Lazard got the TDs and not Garrett Wilson. Sometimes schadenfreude is all you got. I don’t think Lazard is a priority pickup, but the Jets tree is pretty thin, and Rodgers knows and apparently still trusts him.
-
Aaron Rodgers looked good to me, like his old self. He threw accurate passes, had a few drops, and the pick was bad luck. No idea why Mike Williams was ignored though.
-
Breece Hall got all the work until garbage time. No surprise, but he still looks like a top-five pick despite the fumble and poor per-play output.
-
Jordan Mason ran hard, looked a bit like Isiah Pacheco out there. If McCaffrey is out, that’s how I’d value him.
-
Deebo Samuel benefits a little (eight carries) with McCaffrey out. Just has a slightly bigger role in the ground game.
-
Brock Purdy played well, but didn’t have to do much.
-
You have to love that Juaun Jennings led the 49ers in receiving yards and Kyle Juszczyk was third when you have no part of the 49ers passing game. George Kittle and Brandon Aiyuk will get theirs eventually, but you just can’t count on volume for either one.
-
-
 @ 59df1288:92e1744f
2024-10-23 04:51:48
@ 59df1288:92e1744f
2024-10-23 04:51:48null
-
 @ d96e0407:8a0da63d
2024-10-18 19:23:50
@ d96e0407:8a0da63d
2024-10-18 19:23:50
The grain of sands flew into his eyes as he walked through the sandstorm. The desert of Egypt, filled with sand and arid hot air. What brought him here ? I had no idea ,Asad complained how vampire physiology wasn’t compatible with sunlight and heat . The statement made me wonder how he seemed to be walking underneath the sun or survived that disastrous heat stroke. I remembered taking drops of his blood to develop an immunity to the heat. “ Magic “ he said.
He froze in awe as Mina walked into the store from the back door. It was like he saw a ghost, well he did see a ghost. Your Japanese lover from the fifteen century don’t just appear out of nowhere. “ Guys, we have bigger issues” I yelled. I gently placed Ian’s semi conscious body on the floor. His body was radiating heat and the strange markings of his body glowed. She walked towards Ian inspecting his body showing great interest in his condition. It wasn’t out of concern you could he was like code to crack and she was to decipher it . She said a few chants and a rune appeared out of nowhere,glowing and the light wrapped around his body.
"Thank you ,Raven" Asad said to her. I had never seen him so polite to anyone, he always had this sarcastic aura to him. She must have being the one who resurrected Mina. Something else about her caught my attention, her chants the spells they were in ancient Egyptian language. “ It was her" I blurted out unknowingly. Raven gave a look of confusion towards me . “ You were the magi Asad met in desert of Sahara “ I said. “Hahaha” his loud voice echoed in the room. He gave a smirk ,patted me on the back and let out another laugh.
“ I didn’t know, you were this bright “ he commented on my observation. I felt offended and appreciated at the same time. I walked towards Mina trying to start a conversation with her but as I opened my mouth to let out words she cut me off. “ Your friend is conscious “ she pointed at Ian. I rushed to give him a hug and didn’t bother whether his vampric state made him thirsty for blood. “ There was something strange about that bite “ Mina said. Her eyes seemed like they see through us, their internal organs and maybe more. “ A sire of yours “ she asked Asad. He became nervous, startling, sweating and just couldn’t find the words to answer her.
“ Indirectly, a vampire I sired bite him" he said mustering the courage to talk. I didn’t know he could be this awkward. She unsheathed her sword and pointed it at Ian . A strange aura seemed to wrap round her, it was her chi according to Asad vampire hunters could utilize their chi to perform great feats. She ran at him and took a swing that slashed off his left hand. Ian retaliated with a kick which she blocked with her scabbard and responded with a smacking to the ground. “ It’s a enough ,stop attacking him “ I yelled. I didn’t understand why she was trying to kill Ian .” Oh Arthur, the bite from Cheryl transferred a portion of a consciousness into him “ Asad said remorseful.
I understood what he said I just couldn’t understand how killing Ian was the solution. A simple sealing spell could prevent the Cheryl from taking over or a soul extinguishing spell could exhume the soul. “ It’s way complicated then that “ Raven said. “ Why" I asked . “ It’s a soul fusion, I slowed it down but her consciousness can still take over" she replied. Ian stood up with his left hand regenerated, claws popping out and ready to defend himself if Mina attacked. “ It’s enough guys ,Cheryl is the enemy here “ Asad said diffusing the confrontation.
Since her uneventful split from Asad, she sired tons of vampires which are currently wreaking havoc round the world. Now that she knows where Asad is ,Bristol isn’t safe from her. “ We are the ones who stand a chance against her “ he continued on . He cut of his thumb and gushed it into Ian’s mouth. His blood or his very flesh can provide a resistance towards the soul fusion . “ Raven place a sigil on everyone in town protecting them from the vampires “ he ordered. He immediately took over as the leader dishing out roles to everyone and acting as a mediator to everyone. The plan was clear ,simple and we all understood it . In a village in India, a hand tore through the ground signifying the return of a strange figure.
-
 @ 4fda8b10:7bbee962
2024-10-15 13:56:47
@ 4fda8b10:7bbee962
2024-10-15 13:56:47Takeaways from Bitcoin Amsterdam 2024
The bitcoin conference in Amsterdam to me is my typical yearly check in with the crypto scene. From a distance, not much has changed since last year. What struck me most was the correlation between the exchange prices and the amount of visitors, I had the feeling the crowd was about twice as big as last year during the opening and high profile talks.
From my personal experience, the increase of audience also brought some dilution to the hard core maximalist anarchist-ness of the event. The overall vibe amongst the attendees was more friendly and open. This also increased the value of the event for me, as I try to broaden my network, get different perspectives and learn more about what interests people in the crypto space.
This year was also marked by my involvement in the Nostr side events, I was asked to give a live performance at the Nostrdam Meetup October 2024 which went over very well and also acted as a nice conversation starter during the rest of the conference. I was also slightly involved in the organisation of the Nostr booth, but credits go to the awesome volunteers that made that happen. It was a bit of a shame that the Nostr booth was tucked away all the way in the back of the (commercial) expo hall, it would have been nice to promote the Nostr initiative to the social community area next to the satoshi radio / connect the world community area
For me the biggest takeaways were the insights I got from the people I’ve met, all from different industries with different perspectives on both technology and involvement. I tried to specifically reach out to (former) CTO’s, which led me to write and share this piece on that particular role. Of course shaking hands and catching up with people I only see once a year is great, and reminds me of the vibe and my experiences at the Fronteers conference.
From a technical point of view I was most inspired by the advancement of AI agent technology and the possibilities of programmable micropayments via de lightning network. Michael Levin showed us that the http spec already has a 402 status of “payment required” and that basically all the required infrastructure is already in place to allow both humans and ai agents to use the lightning network to pay for access to compute or resources using this statuscode and an api gateway such as lightning labs aperture.
talk: HODLing Is Hard: Fundamentals, Cycle & On-Chain Analysis by rational root
- bitcoin is already competing in market cap with other currencies
- amount of euro is exponentially increasing
- from 8 to 16 trillion euros since 2009, but having a real hard cap in btc is fundamentally different
- inflation
- euro lose 20% in 5 years
- bitcoin also loses purchasing power, but only 10%
- in current system, we always need to take on maximal debt, instead of saving
- two things can happen
- we get into overvalued price levels
- we get into recession
- recession would only mean a shift in the start of the 4 year cycle
panel: Endless Possibilities: Reusing Heat From Miners
- people
- 21energy Maximilian (obwexer)
- Bert de groot (bitcoin Brabant)
- Brad Tom (mara)
- perspective: coming from energy to bitcoin is very different and much faster with implementation than the other way around
- 95% of heat can be captured from miners, much higher in comparison to AI
- being able to balance the grid because you can turn off the bitcoin miners
- ”heatbuffers” → heat is still available when power source goes down
- common objections:
- Crypto is hard to understand
- for large industrial clients, heaters, public image of bitcoin (often a door closer)
- people don’t see that miners consume electricity and pay for it.
- If mining is closed down in Europe, the energy prices will spike because the energy will not be payed for anymore
panel: How to Guard Privacy Tools & Developers
- Dorien Rookmaker & Sjors proviost
- chat control
- topic keeps returning, and is highly distracting for progress
- Parliament wants Netherlands to speak against chat control
- initially they want to just, scan messages now want to install malware before encryption
- it is distracting Sjors from working on bitcoin
- samurai and tornado are different cases
- tornado cash is harder because it is also a smart contract with custody over funds
- samurai is easier: if you don’t have custody, are you responsible for the results of the code?
- will decide wether whether non custodial systems are ok or not
- micah interpretation is quite vague
- the current Denmark case:
- if you are rebuilding an interface for a smart contract, you are responsible for implementing all the legal guardrails that apply to securities governance?
panel: NOSTR: Freedom of Algorithmic Choice
- will casarin, mcshane, martti malmi (Sirius iris.to)
- arc (alternative layer on top of bitcoin, like lightning but without channels)
- aha moment: when seeing the unsiloed experience between nostr apps
- were trying to create a town square, so we need to deal with spam
- social media platforms have stagnated a bit, nostr is innovating far more quickly
panel: Transactions As Bitcoin’s Key Growth Metric
- Stephan nilov
- classical developers don’t know about money and bitcoin development is harder
- total addressable market is highest in btc, biggest number of possible users
- bitcoin companies don’t benefit from tokens that are typically exchanged for vc money
- users are not looking for payments, they are looking for digital property and other things that Ethereum network offers
- Stephan Livera
- there is a known, slow pace at which bitcoin will be adopted
- btc market is only 1.2 trillion dollars compared to USD 30 trillion
talk: Making Bitcoin Quantum Resistant by hunter beast
- surmount.systems
- explaining the threat of quantum computing
- problems
- key size: larger signature required
- proposal: transaction field attestation
- 256 bit number key, possibility to factor the private key out of this
- introducing p2qrhash
- segwitv3
- satoshishield
- in layman terms:
- quantum safe upgrades to bitcoin protocol are proposed
- we need to introduce a software upgrade
- requires a soft fork, opt in
- possible advantages of quantum in crypto
- allow us to sign signatures in a way that is unbreakable
- 514 qubits are needed to break something
talk: Lightning and AI: Where the Bots Pay You by michael levin
- two use cases for bitcoin adoption
- people that don’t have access to fiat
- things that can’t be handled by fiat systems
- large language models
- current phase: big adoption
- next phase: agentic ai
- costs of ai
- compute 400% more (ben bajarin)
- algorithm training excess 10 billion dollars
- data
- costs implications
- cost of serving answers is 0
- cost of serving ai query is not 0
- cost for everyone in the world
- payments in AI
- now
- pay per call
- data
- accessibility
- agents
- agents must be able to do things that cost money
- now
- payment system for AI
- globally accessible
- near instant
- final settlement
- internet native
- authentication mechanism
- personalise access (simple queries for lower tier model)
- easy to implement
- L402 protocol
- 402 payment required in http spec
- reverse proxy to have 402 in front of APIs
- aperture is lightning labs implementation
- all available right now, adoption starting
- fewsats, sulu, open agents / plebai
- pay with lightning
- challenges
- do these payments with stablecoins instead of lightning (hence taproot assets protocol)
- cases
- agent bots can pay for real world resources
- taproot assets issue assets on bitcoin allow transfer of
- references
- L402.org
talk: Bitcoin is Cypherpunk by Aaron van Wirdum
- is bitcoin still Cypherpunks ?
- on one hand we see a push to regulation and frameworks to govern btc
- on the other hand we are arresting developers for writing code
pitches: Bitcoin Amsterdam Pitch Day: Presented by GoBTC
- umoja
- ceo Robby greenfield
- LST smartcoin, deflationary by design
- competes with pools such as lido and rocket pool, but supports multiple coins, including liquid hashrate
- 30% liquid hashrate returns (!)
- compliance micah
- disaster scenarios
- black swan event → automatic exit out
- magisat
- trading tools for mempool snipers
- support for runes
- volume on bitcoin nft’s is on certain days higher than nft’s on ethereum
panel: Crossing the Boundaries Between Bitcoin & Fiat
- Christian Rau (Mastercard) & Remi destigny (bitrefill )
- liberation is great, but protocols don’t take customer service into account, chargebacks and rewinding mistakes etc
- we aim to smooth process by issuing cards that sell your Bitcoin just in time on the backend
talk: Gold & Bitcoin: Friends, Not Foes by Paul Buitink
- premise “the financial system is crumbling”
- there is too much debt
- emerging markets lost confidence in western currencies
- freezing Russian assets is shooting ourselves in the foot, as it shows the world you might not want to hold too many dollars that can be easily seized
- record gold buying by central banks in 2022 2023 2024
- gold: 17 trillion marker cap, compared to bitcoin 1.3 trillion
talk: Austrian Economics, Hard Money & Bitcoin Cycles, Willem Middelkoop
- ”we are on the road towards hyper inflation and collapse of financial system”
- central bankers are pretty smart and very aware
- this is why they accumulate gold
- when system collapses, central bankers will play the gold card, not the bitcoin card
- US is preparing for big conflict with Russia and china
- then you can’t use IMF monetary reset
- Asia leadership is the same as US and Russian leadership: they want to stay on control
- all have about similar gold (per Capita) in their central banks vaults to avoid hyperinflation
- IMF said to el salvador: you need to reign down your bitcoin position
- once central bankers start diversifying (e.g. to bitcoin ) they will strain their own system. The incentives are against adopting bitcoin
- watch out for when on and offramp get blocked / repressed
- think about diversifying to Dubai, “the new switzerland"
- "bitcoin is the best money ever. fact”
- superior to gold, because you can store your wealth independant of location
- more scarce than gold
- but from central bank point of view, gold is superior to bitcoin
- younger generation gets this from the start
talk: The Future Will Be Bitcoinized by Elizabeth stark & Rockstar Dev
- stablecoins
- taproot assets protocol
- there is a demand for stablecoins and apps on stablecoins
- 11 trillion dollars in stablecoins
- protocol allows payments in other assets such as stablecoins that use bitcoin/lightning liquidity
- Elizabeth believes this allows stablecoiners to get interested in the underlying bitcoin layer
- Available now:
- bridging tether and lightning
products stumbled upon
- Meshtastic
- Flipper
- Noderunners led matrix panel
- 21energy bitcoin heater (1k s9, 3,5k s19)
- angor.io by dangershony on nostr
- bitcoinclock by Djuri
canonical link: https://notes.peterpeerdeman.nl/Bitcoin-Amsterdam-2024
originally posted at https://stacker.news/items/724785
-
 @ 129f5189:3a441803
2024-09-09 23:28:41
@ 129f5189:3a441803
2024-09-09 23:28:41Project 2025, outlined in the Heritage Foundation's "Mandate for Leadership" document, serves as a fundamental guide for the next Republican administration. Despite Trump's extensive denial, in today's material, we will explore the deepening and continuation of many policies already employed during his first term. The idea is that this material will serve as a reference document to consult and verify what was actually implemented and/or followed. https://image.nostr.build/e3b89d71ff929258e5d9cb0b5ca8709a381598f43d8be4b17df3c69c0bc74d4a.jpg This document presents proposals for the foreign policy and the State Department of the United States of America, as well as the strategy with its political partners and adversaries. We will also address the U.S. government's communication strategy abroad. https://image.nostr.build/a4250b786f611b478aaf0be559427ad7d4296fbcacb2acc692c7f0d7eb06b0dd.jpg Reorienting U.S. Foreign Policy: Proposals for a Conservative Future In the chapter "The Department of State" from the "Mandate for Leadership," also known as "Project 2025," Kiron K. Skinner presents a comprehensive plan to reform U.S. foreign policy under a conservative administration. Skinner, a renowned foreign policy expert and former Director of Policy Planning at the U.S. State Department, outlines global threats and offers specific recommendations to strengthen the U.S. position on the international stage. Below, we present a detailed analysis of the proposals, emphasizing direct quotes and explanations of the key points discussed. https://image.nostr.build/278dcd7ef0439813ea35d0598319ee347f7a8cd7dfecac93be24ffdd0f6ecd04.jpg History and Structure of the State Department Since its founding in 1789, the State Department has been the primary diplomatic channel of the U.S. With nearly 80,000 employees and 275 posts around the world, it faces significant structural challenges. Skinner highlights that "the biggest problem of the State Department is not a lack of resources," but the belief that it is "an independent institution that knows what is best for the U.S." (Skinner). The scholar and former Director of Policy Planning at the U.S. State Department during the Trump administration emphasizes these points, considering the difficulty in accepting a conservative international approach by State Department employees (the equivalent of the Ministry of Foreign Affairs in other countries). https://image.nostr.build/049939926793e86000b300b9a962dc0ae7e271d9a607ae36d8cb08642adf4174.jpg Political Leadership and Bureaucratic Support To align the State Department with presidential priorities, Kiron suggests appointing political leaders who are committed to the president's vision. "Leadership should include political appointees in positions that do not require Senate confirmation, including senior advisors and deputy secretaries" (Skinner). Furthermore, she emphasizes the importance of training and supporting these appointees to ensure effective coordination between agencies. https://image.nostr.build/6ed704cc9612aa6489e048b143f1e489c1f8807fdf2ab011b4ba88e4a1e3619a.jpg Global Threats to the U.S. The document identifies five countries that pose significant threats to the security and prosperity of the U.S.: China, Iran, Venezuela, Russia, and North Korea. 🇨🇳 China: Skinner argues that China represents an existential threat. "The U.S. needs a strategic cost-imposing response to make Beijing's aggression economically unviable" (Skinner). Additionally, she emphasizes that the issue is not with the Chinese people, but with the communist dictatorship that oppresses them: "As with all global struggles against communist and other tyrannical regimes, the issue should never be with the Chinese people, but with the communist dictatorship that oppresses them" (Skinner). https://image.nostr.build/e707273f1d08bdc4187123a312bd116695b5f603066e11ad30fcef4466730b6b.jpg 🇮🇷 Iran: The Obama administration, through the 2015 nuclear deal, provided the Iranian regime with a "crucial cash bailout" (Skinner). Kiron criticizes this approach, asserting that the U.S. should support the Iranian people in their demands for a democratic government. "The correct policy for Iran is one that recognizes that it is in the U.S. national security interests and the human rights of Iranians that they have the democratic government they demand" (Skinner). https://image.nostr.build/cda7d29a62981f59ad8d77362b3867b552f190c8d7e0e8d9233cb7c1d1d0309e.jpg 🇻🇪 Venezuela: Under the regimes of Hugo Chávez and Nicolás Maduro, Venezuela has transitioned from a prosperous country to one of the poorest in South America. Skinner suggests that the U.S. should work to contain Venezuelan communism and support its people. "The next administration should take steps to put Venezuela's communist abusers on notice and make progress in helping the Venezuelan people" (Skinner). https://image.nostr.build/f53e12564cae74d4b50c24b0f3752dd2c53b70bd1c00a16df20736fb8588417d.jpg 🇷🇺 Russia: The war between Russia and Ukraine divides opinions among conservatives, and the document considers three lines of action. Some advocate continuing support for Ukraine, while others believe that such support does not serve U.S. security interests. "The conservative approach rejects both isolationism and interventionism, first asking: What is in the interest of the American people?" https://image.nostr.build/8fedaf77129f4801f4edb8b169b2ac93a3e518b8bf3642b3abc62575b5435fa3.jpg One conservative school of thought believes that "Moscow's illegal war of aggression against Ukraine represents major challenges to U.S. interests, as well as to peace, stability, and the post-Cold War security order in Europe" (Skinner). This view advocates for continued U.S. involvement, including military and economic aid, to defeat Russian President Vladimir Putin and return to pre-invasion border lines. Another conservative school of thought argues that U.S. support for Ukraine is not in the interest of U.S. national security. According to this view, "Ukraine is not a member of the NATO alliance and is one of the most corrupt countries in the region" (Skinner). It is argued that the European nations directly affected by the conflict should help defend Ukraine, but the U.S. should seek a swift end to the conflict through a negotiated settlement. https://image.nostr.build/22db3d0e79340c1d62344a2b8a3bfddbe4d5bd923cf77d70cfbf5ebf73e4db3e.jpg A third conservative viewpoint avoids both isolationism and interventionism, proposing that "each foreign policy decision should first ask: What is in the interest of the American people?" (Skinner). From this perspective, continued U.S. involvement should be fully funded, limited to military aid while European allies address Ukraine's economic needs, and must have a clear national security strategy that does not endanger American lives. https://image.nostr.build/939fea0bb5c69f171a3da1073e197edcff23a600430b3bc455f6d41bc8a0319f.jpg Although not stated explicitly, I believe this third viewpoint is the one Kiron Skinner desires, as she considers American intervention important but advocates for balancing the costs of the war with its partners in the European Union and NATO. https://image.nostr.build/d1d0c7fb27bfc5dd14b8dde459b98ed6b7ca2706473b2580e0fbf5383f5a9c10.jpg 🇰🇵 North Korea: North Korea must be deterred from any military conflict and cannot be allowed to remain a de facto nuclear power. "The U.S. cannot allow North Korea to remain a de facto nuclear power with the capability to threaten the U.S. or its allies" (Skinner). https://image.nostr.build/95febb04f6d2e0575974a5e645fc7b5ec3b826b8828237ccc1f49b11d11d6bce.jpg Detailed Policy Proposals Refugee Admissions: The Biden administration has caused a collapse in border security and internal immigration enforcement, according to Skinner. She argues that the U.S. Refugee Admissions Program (USRAP) should be resized. "The federal government should redirect screening and verification resources to the border crisis, indefinitely reducing the number of USRAP refugee admissions until the crisis can be contained" (Skinner). https://image.nostr.build/a5740b33842e47b9a1ab58c7b72bd6514f9b6ffbb18706deed1445c59236bc0d.jpg Corporate Collaboration with China: Skinner criticizes the collaboration of companies like BlackRock and Disney with the Chinese regime, noting that "many are invested in an unwavering faith in the international system and global norms," refusing to acknowledge Beijing's malign activities. She emphasizes that the real issue is the communist dictatorship that oppresses the Chinese people, not the Chinese citizens themselves (Skinner). https://image.nostr.build/05a3c787f144c4519c2ee8a4b22e64b8729842819ace4b439c849ef70ecd60b4.jpg Fentanyl and Mexico: The trafficking of fentanyl, facilitated by Mexican cartels in collaboration with Chinese precursor chemical manufacturers, is a critical problem. "Mexican cartels, working closely with Chinese manufacturers of fentanyl precursor chemicals, are sending this drug to the U.S., causing an unprecedented lethal impact" (Skinner). The next administration should adopt a firm stance to halt this public health crisis. https://image.nostr.build/59e32aeef5dabab3344a94a3e415d57fed91fece8bc3c5f068e9f6f7d71f99bd.jpg Re-hemispherization of Manufacturing: Kiron proposes that the U.S. promote the relocation of manufacturing to partner countries such as Mexico and Canada. "The U.S. should do everything possible to shift global manufacturing to Central and South American countries, especially to move it away from China" (Skinner). This would improve the supply chain and represent a significant economic boost for the region. https://image.nostr.build/5d5d7d792f1c94eb6e2bd7a4b86c43236765719e183be8ba8e00ed7dd07eca66.jpg Abraham Accords and a New “Quad”: Skinner suggests that the next administration should expand the Abraham Accords to include countries like Saudi Arabia and form a new security pact in the Middle East that includes Israel, Egypt, Gulf states, and possibly India. "Protecting the freedom of navigation in the Gulf and the Red Sea/Suez Canal is vital for the global economy and, therefore, for U.S. prosperity" (Skinner). https://image.nostr.build/c87cd99cb3ea2bef40e9d1f1fea48b0c9f9f031f3077fff658f15f850e7b8589.jpg Policy for Africa: The U.S. strategy for Africa should shift focus from humanitarian assistance to economic growth and countering China’s malign activities. "Development assistance should focus on fostering free market systems and involving the U.S. private sector" (Skinner). She also highlights that African nations are opposed to the imposition of policies such as abortion and LGBT lobbying. https://image.nostr.build/44df42f32e61c14786ac46c231d368b14df4dc18124a0da458e8506f917302f2.jpg Relations with Europe and Asia Europe: The U.S. should demand that NATO countries increase their contributions to defense. "The U.S. cannot be expected to provide a defense umbrella for countries that do not contribute adequately" (Skinner). Additionally, urgent trade agreements should be pursued with the post-Brexit United Kingdom. https://image.nostr.build/6c013bacfa9e6505ad717104d9a6065f27664a321dd2c3d41fd7635258042d2f.jpg Asia: The withdrawal of U.S. troops from Afghanistan was humiliating and created new challenges. Skinner emphasizes the importance of India as a critical partner to counterbalance the Chinese threat and promote a free and open Indo-Pacific. Cooperation within the Quad, which includes the U.S., India, Japan, and Australia, is essential to this strategy. "The priority is to advance U.S.-India cooperation as a pillar of the Quad" (Skinner). https://image.nostr.build/1cc988b2f70d855c9676d7e38ffdb23564d04ad6333a8d256698f416a1c6704e.jpg International Organizations Skinner criticizes the corruption and failure of the World Health Organization (WHO) during the Covid-19 pandemic. "The next administration should end blind support for international organizations and direct the Secretary of State to initiate a cost-benefit analysis of U.S. participation in all international organizations" (Skinner). She also supports the “Geneva Consensus Declaration on Women’s Health and Protection of the Family,” which is against abortion, and believes that the U.S. government should not fund international organizations that promote abortion (Skinner). https://image.nostr.build/0b583511fef16d68736804fae2f15850eb5c803af01f006a3fe10cdbc583f48c.jpg Conclusion Skinner’s document provides a detailed vision for reorienting U.S. foreign policy under a conservative administration, with an emphasis on ensuring that the State Department serves the national interests defined by the president. With these guidelines, the next administration has the opportunity to redefine the U.S. position on the global stage, promoting security, prosperity, and freedom. https://image.nostr.build/697522745c5947cd4384cdd302b531ee98ce5d59a5d72de0b4f3a52c9abd4821.jpg
-
 @ c73818cc:ccd5c890
2024-10-18 13:22:29
@ c73818cc:ccd5c890
2024-10-18 13:22:29
⚙️ Bitcoin si conferma essenziale per resistere all'oppressione e fornire aiuti diretti alla popolazione di Gaza
⚙️ Bitcoin si è rivelato l'unico strumento attraverso il quale la popolazione di Gaza può ricevere aiuti finanziari diretti, bypassando l'intervento dei sistemi tradizionali e delle istituzioni. Tagliati fuori dai canali di pagamento tradizionali, i cittadini dipendono interamente dalle donazioni ricevute tramite Bitcoin per soddisfare bisogni essenziali come cibo e acqua.
⚙️ In un contesto di isolamento totale, dove persino gli aiuti umanitari vengono sequestrati, Bitcoin offre a chiunque la possibilità di fare la differenza, come nel caso di Yusef Mahmoud, un ex tassista che ha usato BTC per supportare migliaia di persone. Nessun intermediario può fermare questa rete di aiuto.
⚙️ Questa situazione sottolinea ancora una volta il vero scopo di Bitcoin: non come strumento di speculazione finanziaria, ma come una rete resistente e decentralizzata che permette l'auto-organizzazione contro l'oppressione dei governi.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
Referral Bitget -10% sulle fee + bonus benvenuto 6w5d o link: https://bonus.bitget.com/U1JNEK
BitcoinReportItalia #Gaza #Aiuti #Donazioni #Cibo #Acqua #Alimentari #AiutiUmanitari #Oppressione #Cripto #Bitcoin














