-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ e97aaffa:2ebd765d
2024-09-06 10:27:57
@ e97aaffa:2ebd765d
2024-09-06 10:27:57«Only 10 of the 190 taxes collect 90% of the total revenue. The other 180 taxes don’t cause direct economic damage but they generate obstacles, delays and an endless number of procedures that hinder economic activity in a country where making money is already an impossible task»
Eu concordo plenamente com este pensamento do Javier Milei e tinha a convicção que a situação de Portugal é muito similar, por isso fiz o meu “Don’t Trust, verify”.
Receita tributária
Foi analisar o caso de Portugal, as receitas tributárias de 2023:
«Carga fiscal subiu para 95 mil milhões de euros. Mas cai para 35,8% do PIB em 2023» – ECO
Se o objetivo final da estatística é para efetuar uma comparação entre países, é necessário efetuar a divisão pelo PIB. Mas se a análise é apenas para comparações internas ou homólogas, não faz qualquer sentido efetuar a divisão. Com a divisão dos valores pelo PIB, mascaramos a realidade, sobretudo em períodos inflacionários, porque o crescimento do PIB não é real, é uma consequência da inflação. A melhor maneira para analisar as estatísticas internamente é utilizar o valor nominal.
No relatório do INE, os impostos são divididos em 3 grupos: * Impostos Diretos * Impostos Indiretos * Contribuições Sociais
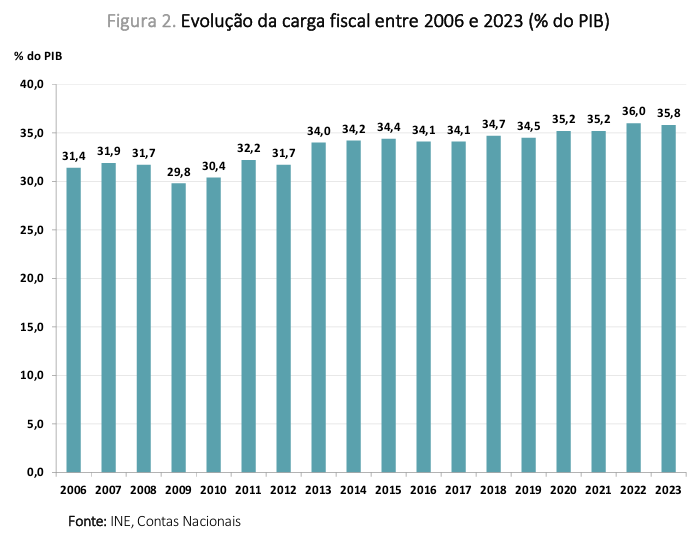
Segundo esses dados, nos últimos anos, tem acontecido um enorme crescimento da arrecadação fiscal por parte do estado, a única exceção foi 2020, devido ao covid. De 2019 a 2023, o aumento foi de quase 30%. Ou seja, totalmente oposto à ideia (divisão pelo PIB) que os governos gostam de propagandear.
Para termos uma comparação, no mesmo período, o salário mínimo nacional(Portugal) subiu 27%, mas o salário médio apenas subiu 17%. As pessoas estão a perder poder de compra.
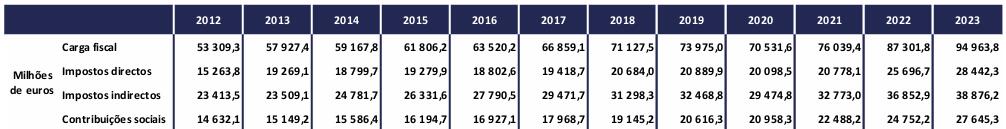
A tabela seguinte é a compilação dos dados:
O IVA é o imposto com maior arrecadação, corresponde a aproximadamente a 25% do total da arrecadação fiscal, seguido pelo IRS, com 19.5%. É curioso que a constituição portuguesa, defende que os impostos devem ser progressivos, ou seja, quem ganha mais, deve pagar mais.
Artigo 104.º (Impostos) 1. O imposto sobre o rendimento pessoal visa a diminuição das desigualdades e será único e progressivo, tendo em conta as necessidades e os rendimentos do agregado familiar. 2. A tributação das empresas incide fundamentalmente sobre o seu rendimento real. 3. A tributação do património deve contribuir para a igualdade entre os cidadãos. 4. A tributação do consumo visa adaptar a estrutura do consumo à evolução das necessidades do desenvolvimento económico e da justiça social, devendo onerar os consumos de luxo.
Mas o IVA é um imposto cego, onde os principais afetados são os mais pobres, totalmente oposto ao que a constituição diz, sem justiça social.
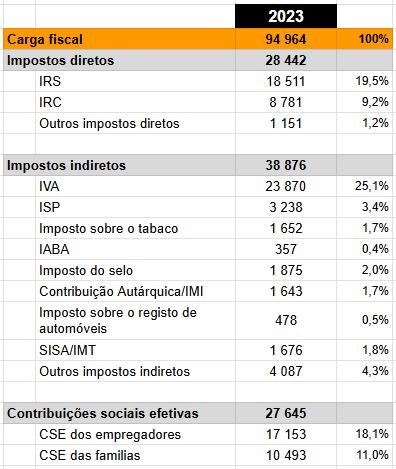
Somando os 10 maiores impostos, resulta em 93.6% da receita fiscal, é similar à situação da Argentina:
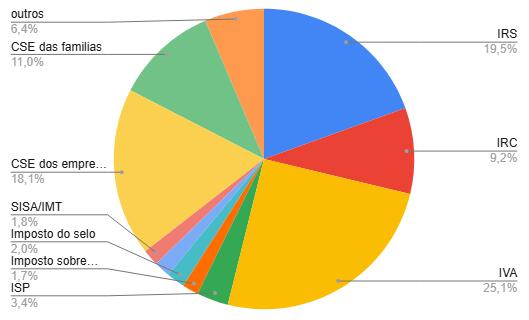
A quantidade de impostos em Portugal é tal, que a maioria deles nem aparece nos relatórios, apenas ficam nas secções “outros”. Curiosamente, perguntei a uma AI, quantos impostos existem em Portugal, mas a AI, esquivou-se à resposta.
Em Portugal, existem cerca de 20 impostos principais, incluindo os mais conhecidos como o IRS, IRC, IVA, IMI, e IMT. Além desses, há vários outros impostos e taxas específicas que podem ser aplicáveis em diferentes situações.
Eu insisti mais que uma vez, mas ele nunca deu um número concreto. Possivelmente, nem o governo sabe quantos impostos existem…
Conclusão
Em Portugal e na Argentina, a esmagadora receita fiscal acontece, sobretudo em apenas 10 impostos, os restantes são residuais na receita do governo mas gera uma enorme burocracia nas empresas e nas pessoas.
Se muitos desses "mini" impostos fossem eliminados, permitia uma maior dinamização do mercado, gerando crescimento económico e mais empregos. Nos fins das contas, o estado acabaria por arrecadar mais receitas através dos outros impostos, sobretudo no IVA. Em certos casos, é provável que custos operacionais para o estado são superior à propria arrecadação fiscal desse respectivo imposto. Sem esquecer os casos de impostos sobre impostos, da dupla tributação, como acontece na compra de um automóvel. A curva de Laffer, há muito que foi ultrapassada em Portugal.
Além de prejudicar a economia diretamente, esta enorme quantidade de taxas, taxinhas e burocracias, tem um efeito perverso no “estado”. Os estados necessitam de muitos meios físicos e humanos para efetuar a gestão, fiscalização e a recolha desses impostos, além disso, a burocracia leva ao surgimento da corrupção. A burocracia é criada propositadamente pelos políticos para atrapalhar a vida dos cidadãos, com o objectivo final de beneficiar terceiros, como advogados ou lobis ou os próprios políticos. A receita fiscal é mínima, mas é um incentivo à corrupção, isto é especialmente visível a nível mais local, nas autarquias. Qualquer coisa que se faça, sobretudo a nível de obras, é necessário uma infindável quantidade de autorizações, papeladas e claro, muitas taxinhas. Devido a essa burocracia, qualquer licenciamento demoram meses a anos, no meio disto tudo, existem empresários/pessoas impacientes, que desesperam com a tremenda demora e acabam por colocar uma notinha no bolso de alguém importante, para que este acelere o processo. Coisas que normalmente demorariam meses, são aprovadas em semanas, a burocracia incentiva a corrupção.
Portugal necessita urgentemente de uma simplificação fiscal, se houvesse vontade política para mudar, o governo poderia diminuir drasticamente o número de impostos sem diminuir a arrecadação fiscal. Se esta mudança, eles não são capazes de a fazer, muito menos vão fazer uma mudança que provoque uma redução da arrecadação fiscal. Eu acho que Portugal vai seguir o caminho oposto, em vez de simplificar, vai é criar ainda mais novos impostos, porque como os atuais impostos já estão demasiado elevados, é extremamente impopular aumentá-los ainda mais, a maneira mais simples para o governo é criar novos impostos para aumentar a arrecadação fiscal.
Os governos modernos só olham para o aumento da arrecadação/impostos, "esquecem” por completo a redução de gastos, a eficiência. Resumindo, isto é o mundo FIAT.
-
 @ 6bae33c8:607272e8
2024-09-06 08:16:48
@ 6bae33c8:607272e8
2024-09-06 08:16:48I got back into the Circa Survivor Contest this year at great cost (my flight out of Palm Springs on July 5 was cancelled due to heat, so I had to rent a car and drive through the Mojave Desert, and the road to Vegas was closed, so I had to double back another 100 miles, which in total took six hours), so this is Team Of Destiny 2.0. Or at least it had better be.
I’m not going to stick to any one method or philosophy. Put differently, I realize that in order to win, I need to go into the future, find out what has already happened and pick on that basis. Pot odds is great, but even if you do that properly every week, your edge over the field isn’t that huge. Instead of a 1 in 10,000 chance to win, maybe you have 1 in 6,500. Sure, if you had 100 entries in every high stakes contest, it might be enough to eke out a reliable profit, but I’m not here for that. I’m here to navigate one boat through the icebergs and take down the $10M. And for that, you can’t hope to get lucky. You have to know in advance.
What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.
. . .
In any event, let’s take a look at the slate: Here are the ownership numbers per Officefootballpools.com.

The pot-odds play is the Bills if you buy into the Vegas numbers — Bengals roughly 78.5 and the Bills at 72.6%. That means the Bengals have a 21.5% chance to lose, the Bills 27.4%. That’s a 27.4 percent increase in risk (coincidentally.)
But if the Bengals lose they take out 39 people, and if the Bills lose they take out only 15. Let’s assume another 20-odd people lose with other teams (in a hypothetical 100-person pool) and you’re down to 41 if the Bengals lose/Bills win, 65 if the Bills lose/Bengals win.
If we say each person put in $10, the former scenario is $1000 (total pot)/41 = $24.39, and the latter $1000/65 = $15.38. The ratio of 24.39/15.38 = 1.59. In other words, you have 59 percent percent more equity in Week 2 on the Bills if the Bengals lose than you would on the Bengals if the Bills lose.
You’re talking a 27.4 percent greater risk for a 59 percent greater reward. So normally I’d snap call the Bills.
But I’m probably going Bengals because I think the Cardinals are dangerous this year, and the Pats are arguably the worst team in the league and in surrender mode after they dealt Matthew Judon to the Falcons. (All this is supposed to be priced in, of course, but I don’t care.)
I’ll finalize my pick before Saturday’s deadline, but that’s how I see it for now.
-
 @ 6bae33c8:607272e8
2024-09-06 08:14:27
@ 6bae33c8:607272e8
2024-09-06 08:14:27An odd thing happened — I squinted when opening my laptop this morning so as not to see the final score, but I thought I read a headline saying the Ravens beat the Chiefs. Maybe it was a cached headline from the night before saying what they’d have to do to beat the Chiefs? but I shut the laptop and logged into my Apple TV account to stream the game on the TV, fully expecting the Ravens to win. I mean up until the moment they overturned the Isaiah Likely TD, I thought the Ravens would win. Funny, but not funny because I picked the Ravens in my low-stakes picking pool, and I HATE starting off the week 0-1, no matter the stakes.
In any event, it was an okay game, not great, but there were some interesting takeaways.
-
Derrick Henry looked fine but is going to do almost nothing in the passing game. He had two awkward targets, but Justice Hill was in the game on passing downs and during the end-of-half two-minute drill. Plus Lamar Jackson almost always takes off when he’s in trouble, so if the play isn’t a designed pass to the back, which will be rare for Henry, he’s not getting the ball except via handoff.
-
Jackson looked smooth to me and he’ll have a huge year for as long as he can stay healthy, especially now that Isaiah Likely looks like a real threat. But at 6-2, 205, 16 carries per game is a big ask.
-
Likely looked great. On his long TD, he made great moves, and even on the TD that was overturned, he showed great footwork to make it that close. I’m awfully curious to see where the near-invisible Mark Andrews slips in my NFFC Primetime tonight. (I think Round 8 or so, and I’d have to think about it.)
-
Rashod Bateman had five targets, four of them down the field. He’s their field stretcher, and though it was a quiet day, there should be more.
-
Zay Flowers got 10 targets (good), but it was dink and dunk stuff. To be honest, Likely (12 targets!) looked like the WR1, the alpha running the intermediate routes, Bateman the deep guy and Flowers the midget in the slot.
-
Patrick Mahomes didn’t have a big game, but that was against a top defense and he still got 10.4 YPA. And they were missing one of their field stretchers in Hollywood Brown.
-
Rashee Rice was the story for the Chiefs IMO. He had nine targets and made it look so easy, like Cooper Kupp schemed open on the Rams a few years ago. Xavier Worthy scored twice, but on only three targets even without Brown. He did look awfully fast, though.
-
Isiah Pacheco ran hard against a tough defense, but didn’t do much as a receiver. He’ll be fine — I wouldn’t move his stock much after this game.
-
Travis Kelce had a quiet night, but I wouldn’t read much into it. It’s not like Noah Gray is Likely to take his role.
-
After all these years, I finally ditched the loyal Justin Tucker for a Younghoe, and I feel like a new man. It still brought me no joy to see him miss that 53-yard FG.
-
You have to love Steak League IDP Roquan Smith getting a pick for you opening night.
-
-
 @ a30cdfee:2d2f97ff
2024-09-06 06:50:05
@ a30cdfee:2d2f97ff
2024-09-06 06:50:05Orqestra: Converting Business Sales to Bitcoin
Orqestra lets businesses automatically convert portions of their sales to bitcoin!
What is Orqestra and how can it be useful for businesses?
Protect Against Inflation with Bitcoin
Long-term saving in bitcoin is a good way to hedge against inflation.
Not just for individuals, but also for companies.
Case in point: MicroStrategy
Bitcoin's strong liquidity also allows quick conversions to fiat if needed, giving companies financial flexibility.
Converts Portions of Sales to Bitcoin
Orqestra simplifies Bitcoin acquisition, targeting small and medium-sized businesses.
You can connect your payment providers, and the platform will automatically convert portions of your sales to bitcoin.
Start small or go all in, it's up to you!
Orqestra integrates with e.g. PayPal, QuickBooks, Square and Stripe.
You can also link e.g. Clams, a Bitcoin-focused accounting software for automated bookkeeping.
You can learn more about Clams here: https://stacker.news/items/552799
Custodial, but You Can Withdraw to Your Own Wallet
Orqestra states that it partners with industry-leading custodians to store the BTC.
You can also withdraw the BTC to your own wallet, or convert it to US dollars.
The platform is currently only supporting businesses in the United States.
KYC Required
Orqestra was founded by João Almeida, former CTO and co-founder of a Bitcoin payment infrastructure provider OpenNode.
Orqestra can give tax-ready reports that meet industry standards on demand.
To use the platform, businesses need to provide proof of legal existence of the company, proof of address and all beneficiaries with over 25% ownership in the company need to perform KYC.
Project Links
originally posted at https://stacker.news/items/674222
-
 @ c7eadcf0:7821e562
2024-09-06 00:10:23
@ c7eadcf0:7821e562
2024-09-06 00:10:23Who would have thought that we would have the change to buy sub 60K Bitcoin again? With all the talk of mooning after the halving, seeing Bitcoin's price back around 56k at the time of this post is disappointing to the lettuce handed, ETF buying individuals that are not here for the revolution, but to make a quick buck.
Bitcoin being a neutral money, it is not unexpected that it would gain the attention of these types of people. I am actually glad that they are participants in this market has it helps transfer Bitcoin from weak unconverted holders to people who are fully dyed in the orange wool of the Bitcoin thesis.
Every time there is some geopolitical event, or some kind of economic crisis brewing on the other side of the world, Bitcoin normally takes a hit because it is a high liquid asset. This should be taken as a good sign when the price goes down as it shows that you can easily move in and out of Bitcoin with relative ease. Try doing that with your house, car or other assets. Sure you can sell them eventually but its not nearly as seamless as Bitcoin.
This lull in price will not last long, so if you got some dry powder sitting on the sidelines, today is a good day to buy some cheap corn. Framing Bitcoin as a liquid asset that can be sold in times of need is a good way to introduce Bitcoin to your nocoiner friends and family. I would hate for them to have to buy Bitcoin at much higher prices. Good for us. Bad for them. Amirite?
Just a short post from the Obsidian Nostr Writer Plugin. If you like writing long from content, I would highly recommend giving it a shot! Peace out.
-
 @ 472f440f:5669301e
2024-09-05 22:25:15
@ 472f440f:5669301e
2024-09-05 22:25:15https://x.com/parkeralewis/status/1831746160781938947 Here's a startling chart from an American staple, Walgreens. The convenience store and pharmacy chain has seen its stock price plummet by more than 67% this year and by more than 90% from its all time high, which was reached in 2015.
The combination of the COVID lock downs and the lax laws around theft that followed were materially detrimental to Walgreens business. The crux of their problem at the moment, however, is a double whammy of those disruptions in their business coupled with the "higher for longer" interest rate policy from the Fed over the last couple of years. As Tuur points out in the tweet above, Walgreens has $34B in debt, which means they definitely have significant interest rate payments they need to make on a monthly basis. Tuur also points out that Walgreens has very little cash compared to their debt obligations. Let's take a look at their balance sheet as of May of this year.
Less than $1B in cash for $34B debt with $67.56B in total liabilities. Even worse, their cash balance was drained by more than 27% over the course of the year between May 2023 and May 2024. As you may notice their total assets fell by more than 15% over the same period. This is because Walgreens understands the dire financial straits it finds itself in and has begun shutting down thousands of their locations across the country.
The recent efforts of Walgreens to sell off their assets to raise cash to pay down their debts seem to be completely ineffective as their cash balance is falling faster than their total assets, which is falling 7x faster than their total liabilities. These numbers are most definitely going to get worse as cascading sell pressure in commercial real estate markets (which is the bucket that Walgreens locations fall into) drive down the value of their assets. Leaving them with less cash to pay down their debts as time goes on. To make matters worse, it puts the institutions that lent money to Walgreens in a terrible position. How many commercial and investment banks has Walgreens tapped to fund their operations with expensive debt? How exposed to Walgreens is any individual lender? Could a default on some or all of their loans catch these financial institutions off sides? If it isn't Walgreens that pushes them off sides, how many more bad borrowers would it take to push them off sides?
As our good friend Parker Lewis points out, the only way the hemorrhaging can be stopped is if the Federal Reserve and Federal Government step in with bail outs in the form of massive liquidity injections via quantitative easing and other emergency measures. On top of this, the Fed and the Federal Government find themselves in a classic catch-22. If they let Walgreens fall into bankruptcy it could set off a domino effect that could exacerbate inflation. Riteaid, a similar retail convenience store and pharmacy chain, filed for bankruptcy last October and is still wading its way through that process. Part of that process has been shuttering many of their storefronts. One has to imagine that since Walgreens and Riteaid are having these problems, some of their other competitors must be feeling the pain as well. If enough of these convenience stores, which tens of millions of Americans depend on for everyday goods, find themselves in a position where they have to shut down their stores it could lead to a supply crunch. People will obviously not be able to get their goods from Riteaid or Walgreens and will flee to alternatives, exacerbating the stress on their supplies, which will drive prices higher.
This is a catch-22 because the only way to avoid this mad dash for consumer goods in the midst of a convenience store Armageddon is to re-introduce ZIRP and flood the market with freshly printed dollars, which will drive prices up as well.
Talk about a rock and a hard place. You better get yourself some bitcoin.
Final thought... Zach Bryan radio crushes.
-
 @ e771af0b:8e8ed66f
2024-09-05 22:14:04
@ e771af0b:8e8ed66f
2024-09-05 22:14:04I have searched the web for "Find bitcoin block number from historical date" maybe 100 times in my life.
Never again.
You'll need a bitcoin node for this to work. The script is fast.
Install
WoT Install
one liner ```
curl
curl -o fjb.sh https://gist.githubusercontent.com/dskvr/18252c16cf85c06c1ee6cb5ae04a3197/raw/34bad6a35d98501978c8cd0c25b1628db1191cfe/fjb.sh && chmod +x fjb.sh
wget
wget -O fjb.sh https://gist.githubusercontent.com/dskvr/18252c16cf85c06c1ee6cb5ae04a3197/raw/34bad6a35d98501978c8cd0c25b1628db1191cfe/fjb.sh && chmod +x fjb.sh ```
Trust no one.
create file ``` vi fjb.sh
or
nano fjb.sh ```
review, copy and past into file ``` TIMESTAMP=$1 LOWER=0 UPPER=$(bitcoin-cli getblockcount)
while (( LOWER <= UPPER )); do MID=$(( (LOWER + UPPER) / 2 )) BLOCKHASH=$(bitcoin-cli getblockhash $MID) BLOCKTIME=$(bitcoin-cli getblockheader $BLOCKHASH | jq .time)
if (( BLOCKTIME < TIMESTAMP )); then LOWER=$(( MID + 1 )) elif (( BLOCKTIME > TIMESTAMP )); then UPPER=$(( MID - 1 )) else echo "$BLOCKTIME" exit 0 fidone
echo "$UPPER" ```
give executable permissions
chmod +x ./fjb.shUsage
./fjb.sh <timestampSeconds>It returns block number onlyExample
$: ./fjb.sh 1668779310 763719 -
 @ acc925af:db9fb0bb
2024-09-05 20:26:50
@ acc925af:db9fb0bb
2024-09-05 20:26:50While tinkering about NWC and twitter I decided to hack a python script that might perhaps begin something good
Here's a high-level overview of how you could connect your Twitter account to a Nostr Wallet using NWC and automate a 21 satoshi payment for every like:
Prerequisites:
- Twitter Developer Account
- Nostr Wallet with NWC support (e.g., Alby, Nostrify)
- Twitter API credentials (API key, API secret key, Access token, Access token secret)
- Python script with Tweepy (Twitter API library) and nostr-client (Nostr library)
Step 1: Set up Twitter API credentials
Create a Twitter Developer account and obtain API credentials Install Tweepy using pip: pip install tweepy
Step 2: Connect Nostr Wallet using NWC
Choose a Nostr Wallet with NWC support (e.g., Alby, Nostrify) Set up the wallet and obtain the NWC credentials (e.g., public key, private key)
Step 3: Create a Python script
Import Tweepy and nostr-client libraries Authenticate with Twitter API using Tweepy Connect to Nostr Wallet using NWC credentials Define a function to send 21 satoshis for every like Use Tweepy to stream likes and trigger the payment function
Pythonscript:``` import tweepy from nostr_client import Client
Twitter API credentials
twitter_api_key = "YOUR_API_KEY" twitter_api_secret_key = "YOUR_API_SECRET_KEY" twitter_access_token = "YOUR_ACCESS_TOKEN" twitter_access_token_secret = "YOUR_ACCESS_TOKEN_SECRET"
Nostr Wallet NWC credentials
nwc_public_key = "YOUR_NWC_PUBLIC_KEY" nwc_private_key = "YOUR_NWC_PRIVATE_KEY"
Set up Tweepy
auth = tweepy.OAuthHandler(twitter_api_key, twitter_api_secret_key) auth.set_access_token(twitter_access_token, twitter_access_token_secret) api = tweepy.API(auth)
Set up Nostr Client
nwc_client = Client() nwc_client.connect(nwc_public_key, nwc_private_key)
Define payment function
def send_satoshis(): # Create a new Nostr event with 21 satoshis event = nwc_client.create_event(21) # Send the event to the Nostr network nwc_client.send_event(event)
Stream likes and trigger payment function
class LikeStream(tweepy.StreamListener): def on_like(self, like): send_satoshis()
stream = tweepy.Stream(auth, LikeStream()) stream.filter(track=["likes"])
```
Please note that this is a simplified example and may require additional error handling, security measures, and modifications to work as intended.
originally posted at https://stacker.news/items/673795
-
 @ 8cb60e21:5f2deaea
2024-09-05 19:48:32
@ 8cb60e21:5f2deaea
2024-09-05 19:48:32Part 2: Functiones et Objecta
2.1 Functiones
Fusce posuere felis sed lacus. Morbi sem mauris, laoreet ut, rhoncus aliquet, pulvinar sed, nisl.
``javascript function salutatio(nomen) { returnSalve, ${nomen}!`; }console.log(salutatio("Cicero"));
const valedictio = (nomen) => { console.log(
Vale, ${nomen}!); };valedictio("Seneca"); ```
2.1.1 Parametri Default et Rest
Nunc purus. Phasellus in felis. Donec semper sapien a libero.
``javascript function congregatio(primus, secundus = "mundi", ...ceteri) { console.log(${primus} ${secundus}); console.log(Ceteri: ${ceteri.join(", ")}`); }congregatio("Salve"); congregatio("Lorem", "ipsum"); congregatio("Veni", "vidi", "vici", "et", "cetera"); ```
2.2 Objecta
Nam congue, risus semper porta volutpat, quam pede lobortis ligula, sit amet eleifend pede libero quis orci.
``javascript const persona = { nomen: "Iulius", cognomen: "Caesar", aetas: 55, salutatio: function() { returnSalve, ${this.nomen} ${this.cognomen}!`; } };console.log(persona.salutatio()); ```
2.2.1 Methodi Object
Nullam porttitor lacus at turpis. Donec posuere metus vitae ipsum. Aliquam non mauris.
```javascript const claves = Object.keys(persona); console.log(claves);
const valores = Object.values(persona); console.log(valores);
const paria = Object.entries(persona); console.log(paria); ```
2.3 Arrays
Morbi porttitor lorem id ligula. Suspendisse ornare consequat lectus. In est risus, auctor sed, tristique in, tempus sit amet, sem.
```javascript const fructus = ["malum", "pirum", "uva", "cerasum"];
fructus.forEach((fructus) => { console.log(fructus); });
const longiFructus = fructus.filter((fructus) => fructus.length > 4); console.log(longiFructus);
const maiusculaFructus = fructus.map((fructus) => fructus.toUpperCase()); console.log(maiusculaFructus); ```
2.4 Exercitia Parti II
- Crea functionem quae calculat factorialem numeri.
- Implementa methodum quae invenit maximum valorem in array.
- Scribe programma quod ordinat objecta in array secundum proprietatem specificam.
-
 @ e968e50b:db2a803a
2024-09-05 19:33:33
@ e968e50b:db2a803a
2024-09-05 19:33:33ATTENTION PARENTS!
I have revamped my LNBITS bitcoin piggy bank so you don't need to deploy it yourself. Check it out at http://bitcoinpiggybank.vercel.app. All you need now is a LNBITS wallet. I've deployed a website that you can just log into with that and nothing else. I'm thinking about actually renting out my own domain for this one if people find it useful.
https://www.youtube.com/watch?v=X-MNqJiLCM4
Teach your kids about sound money while they're actually stacking sats and using a fun interface.
originally posted at https://stacker.news/items/673739
-
 @ 9977c3ad:43a20d63
2024-09-05 11:21:09
@ 9977c3ad:43a20d63
2024-09-05 11:21:09Details
- 🍽️ Servings: 2
Ingredients
- 1 cup Jasmine rice
- 1 Tbsp. lavender flowers, crushed with mortar and pestle
- 1/4 cup apple cider vinegar
- 2 Tbsp. fine cane sugar
- 2 Tbsp. honey
- 1 sprig rosemary
- 1/4 tsp angostura bitters
- 1/2 cup blackberries
- 1/2 cup blueberries
- 4 cups trimmed and quartered shiitake mushrooms
- 1 tsp fresh coriander crushed
- 1/4 tsp fresh cumin ground
- 1/2 tsp red pepper flakes
- 3 sprigs of thyme
- 2 Tbsp. olive oil
- 1 tsp soy sauce
- 1 cup creamy coconut milk
Directions
- Combine rice, lavender, 1/4 tsp salt, and 2 cups of water in a saucepan. Bring the rice to a boil, cover the pan with a lid and turn the heat off. Let the rice sit in the pan for at least 20 minutes.
- Combine 1/4 cup of water, the vinegar, sugar, honey, rosemary, angostura bitters in a saucepan and bring the brine to a boil. Season with a pinch of salt. Add the berries and wait until the brine comes back to a boil. Lower the heat, so the brine simmers but does not boil. When the brine thickens, after about 15 minutes, remove the saucepan from the heat and set it aside.
- Pre-heat the oven to 400F. In a bowl big enough to hold all the shiitake, combine the olive oil, the soy sauce and the spices. Whisk vigorously, so the oil emulsifies with the other liquid. Toss the shiitake in the mix to marinate, then evenly lay them out on a baking sheet with parchment paper. Bake the shiitake for 10 minutes. When you remove the shiitake from the oven, remove the thyme and throw it out. In a saucepan, bring the coconut milk to a boil. Add the shiitake and reduce the heat to a light boil until the sauce thickens.
-
 @ a012dc82:6458a70d
2024-09-06 08:07:02
@ a012dc82:6458a70d
2024-09-06 08:07:02Table Of Content
-
Why is there a Projection of Bitcoin Adoption Increase by 50% by 2025?
-
What are the Potential Challenges for Bitcoin Adoption?
-
What is the Impact of Bitcoin Adoption on the Global Economy?
-
Conclusion
-
FAQ
Bitcoin, the world's first and largest cryptocurrency, has been gaining momentum and popularity over the years. With its decentralized and secure nature, Bitcoin has become a preferred mode of payment and investment for many individuals and businesses. The cryptocurrency has been making headlines for its unprecedented price surges, with its value surpassing $60,000 in early 2021. However, it has also experienced significant price drops and market volatility. Despite this, experts predict that Bitcoin adoption will continue to increase, with a projected 50% growth by 2025.
Why is there a Projection of Bitcoin Adoption Increase by 50% by 2025?
There are several reasons why experts are predicting a significant increase in Bitcoin adoption by 2025:
Increased institutional investment: Over the past few years, more and more institutional investors, such as banks and hedge funds, have been investing in Bitcoin. These investments bring legitimacy and stability to the cryptocurrency market, making it more appealing to individual investors.
Global economic uncertainty: The COVID-19 pandemic has had a significant impact on the global economy, causing many individuals and businesses to re-evaluate their investment strategies. With traditional investments, such as stocks and bonds, experiencing volatility, Bitcoin's decentralized nature and limited supply make it an attractive investment option.
Growing acceptance and adoption: As more businesses and individuals accept Bitcoin as a mode of payment, its adoption rate continues to increase. This trend is expected to continue, with more merchants and payment processors accepting Bitcoin.
Increased regulation: While some argue that increased regulation may stifle Bitcoin's growth, others believe that it will bring greater legitimacy and stability to the cryptocurrency market. As governments and regulatory bodies create clearer guidelines and regulations for cryptocurrencies, it is likely that more individuals and businesses will feel comfortable investing in Bitcoin.
What are the Potential Challenges for Bitcoin Adoption?
While the projected increase in Bitcoin adoption is promising, there are still potential challenges that may hinder its growth:
Market volatility: Bitcoin's value is subject to market fluctuations, which can be unpredictable and lead to significant price drops. This volatility may discourage some investors from investing in Bitcoin.
Security concerns: While Bitcoin's blockchain technology is secure, there have been instances of hacking and theft. These security concerns may discourage some individuals and businesses from accepting Bitcoin as a mode of payment or investing in it.
Regulatory challenges: As governments and regulatory bodies work to create clearer guidelines and regulations for cryptocurrencies, there may be challenges in achieving a balance between regulation and innovation. Overly restrictive regulations may hinder Bitcoin's growth and adoption.
Energy consumption: Bitcoin mining requires significant energy consumption, which has led to concerns about its environmental impact. As more attention is given to climate change and sustainability, these concerns may hinder Bitcoin's growth.
What is the Impact of Bitcoin Adoption on the Global Economy?
The projected increase in Bitcoin adoption has the potential to have a significant impact on the global economy:
Increased investment opportunities: As Bitcoin adoption grows, more investment opportunities may arise, creating new revenue streams and job opportunities.
Greater financial inclusion: Bitcoin's decentralized nature and accessibility have the potential to provide greater financial inclusion for individuals who may not have access to traditional banking services.
Disruptive technology: Bitcoin's blockchain technology has the potential to disrupt traditional financial systems, creating new opportunities for innovation and growth.
New challenges: With disruptive technology comes new challenges, such as the need for clear regulations and guidelines, as well as addressing potential security concerns.
Shift in power dynamics: Bitcoin's decentralized nature challenges traditional power structures, such as those held by central banks and governments. This shift in power dynamics may lead to changes in the way financial systems operate globally.
Impact on traditional banking systems: As Bitcoin adoption continues to grow, traditional banking systems may experience disruptions. Banks may need to adapt to the changing landscape by incorporating blockchain technology or other innovative solutions.
Conclusion
Experts predict that Bitcoin adoption will increase by 50% by 2025, driven by increased institutional investment, global economic uncertainty, growing acceptance and adoption, and increased regulation. While there are potential challenges to Bitcoin's growth, such as market volatility, security concerns, regulatory challenges, and energy consumption, the projected increase in Bitcoin adoption has the potential to have a significant impact on the global economy. As Bitcoin continues to gain momentum and popularity, it's important for individuals and businesses to understand the risks and potential rewards involved in investing in this cryptocurrency.
FAQ
Will increased Bitcoin adoption lead to greater financial inclusion? Yes, increased Bitcoin adoption has the potential to provide greater financial inclusion, as it enables individuals without access to traditional banking systems to participate in the global economy.
How can individuals buy Bitcoin? Individuals can buy Bitcoin through cryptocurrency exchanges, peer-to-peer marketplaces, and Bitcoin ATMs. It's important to do your research and choose a reputable platform to ensure secure transactions.
Can Bitcoin be used for everyday transactions? Yes, Bitcoin can be used for everyday transactions, but its use is still limited compared to traditional currencies. However, as Bitcoin adoption increases, more merchants may start accepting it as a mode of payment.
What is the environmental impact of Bitcoin mining? Bitcoin mining requires significant energy consumption, which has raised concerns about its environmental impact. However, some argue that the use of renewable energy sources for mining can help mitigate this impact.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ 472f440f:5669301e
2024-09-04 22:54:11
@ 472f440f:5669301e
2024-09-04 22:54:11For the last few months many people in bitcoin, myself included, have been focused on bitcoin's role as a macroeconomic asset. Bitcoin as a strategic reserve for the US government. Bitcoin as a strategic treasury asset for corporations. Bitcoin as a geopolitical hedge in a world that is trending toward a multi-polar power dynamic. This is where the focus has been. And for good reason. These trends will ultimately have a material effect on the price of bitcoin if they pick up steam.
However, with all of the focus on bitcoin as a strategic asset I think a couple of technical developments and trends have been overlooked. Particularly in the realm of second layer privacy. I'll touch on two of them in this letter; BOLT 12 invoices and the progression of ecash.
Yesterday afternoon the Strike (a company Ten31 is very proud to be backing) team released a blog post that detailed their journey to implementing BOLT 12 offers in their product stack. For those who are unaware of BOLT 12 and why it is important, in short, it is an upgrade to the lightning network that would make receiving bitcoin on the lightning network more private while also significantly improving the user experience. The current standard for invoicing people via the lightning network is BOLT 11, which forces users to create a unique invoice every time they want to receive bitcoin and comes with privacy tradeoffs for the party receiving bitcoin.
BOLT 12 brings with it route blinding which allows a receiver to publish a lightning offer to the network without revealing their node's public key. It also brings with it onion messaging, which allows users of the lightning network to communicate without a dependence on HTTP, which can be censored by a motivated state actor. On top of this, it enables users to create a static invoice that can be paid multiple times by multiple people. Think of a band putting their Venmo or Cash App QR code next to their tip jar on the stage. They'll be able to add a private lightning invoice their audience can pay to now.
https://strike.me/blog/bolt12-offers/
As it stands right now, Strike has only enabled BOLT 12 offers and there is work to do at the protocol layer of lightning and the different implementations of that protocol to get the full benefits of BOLT 12, but this is material progress that gets us closer to a significantly better user experience on the lightning network. If you read Strike's blog post you'll come to appreciate the collaboration between the teams working on these implementations and the companies implementing the protocol that is necessary to get these features live. Shout out to everyone who worked on this. Everyone who uses the lightning network will be better off when BOLT 12 is fully implemented.
Moving on. Earlier today the founder of the BTCPay Server open source project, Nicolas Dorier, published a blog post outlining his thoughts on how ecash has the potential to solve problems that many have tried to solve by launching their own blockchains in the past. The problem with trying to "blockchain the world" is that blockchains are very inefficient and only really work for one application; enabling a peer-to-peer digital cash system with no trusted third parties (i.e., bitcoin). However, the ultimate goals of the thousands of blockchain projects that spun up in bitcoin's wake are desirable. Cheap, private and instant transactions. The ability to trivially spin up private money tokens suited for very particular use cases. Overall great UX that makes it easy for people to realize the benefits of "blockchain technology".
The problem that has existed to date is that you don't need a blockchain for all of these things. In fact, having a blockchain for these things proves to be detrimental to their ultimate goals. Instead, what people really need is a protocol that gives you the granular control, privacy, instantaneous transactions and UX that anchors to bitcoin. This is exactly what Chaumian Mints bring to the bitcoin stack.
This is something that we've been screaming about for more than seven years in this rag. Now with ecash protocols like Cashu and Fedimint maturing, gaining traction and bringing products to market that highlight the power and flexibility of ecash systems, people are beginning to see the promise. It is only a matter of time before more and more people begin to realize this potential.
Another benefit of ecash protocols is the fact that they are siloed from each other. Ecash mints are permissionless; any one person or group of people can spin them up, offer their preferred services and maintain (or fail to maintain) their mints. The failure of one mint is not a systemic risk to other mints. This is very different from token projects that are spun up on blockchains. The last ten years have proven that individual token projects can prove to be systemic problems for individual blockchains (i.e., The DAO token on Ethereum). Being able to silo mints is the only way to ensure that the utility of ecash overall is actually scalable and robust.
Don't get so distracted by the bitcoin macro talk that you miss out on the incredible technical developments happening on top of and adjacent to bitcoin.
Final thought... Vibes are high.
-
 @ 3c9712ff:14fecbc4
2024-09-06 02:20:21
@ 3c9712ff:14fecbc4
2024-09-06 02:20:21Over the past week, the south-east corner of Australia experienced a battering from mother nature.
High winds and unseasonably hot winter days caused Australia's wind and solar network to run at near maximum capacity. However, this wasn’t necessarily beneficial.
 Article from the Australian Financial Review
Article from the Australian Financial ReviewGrid Operation 101
Energy is produced and consumed almost simultaneously. This real-time mechanism makes the energy grid one of the fastest and most responsive systems in existence.
When the grid operates at peak efficiency, everyone who needs power can access it, and anyone producing power can sell it. Energy must be generated and balanced continuously, regardless of the weather. It’s not good enough to produce abundance of energy when people don’t want it, just to fall short when they do.
Since solar and wind cannot consistently maintain a balance between supply and demand, coal remains the backbone of Australia's energy grid, providing reliable base-load power and being supplemented during peak times.
Too Much Energy?
Apart from the environmental benefits, the key advantage of renewable energy lies in its abundance. However, because we don’t control when the sun shines or the wind blows, this often results in a mismatch between supply and demand. At times, energy supply can sometimes double or even triple demand. Since it’s usually too expensive to shut down solar and wind farms, this leads to stranded or curtailed energy, and consequently wholesale electricity prices can drop into negative territory.
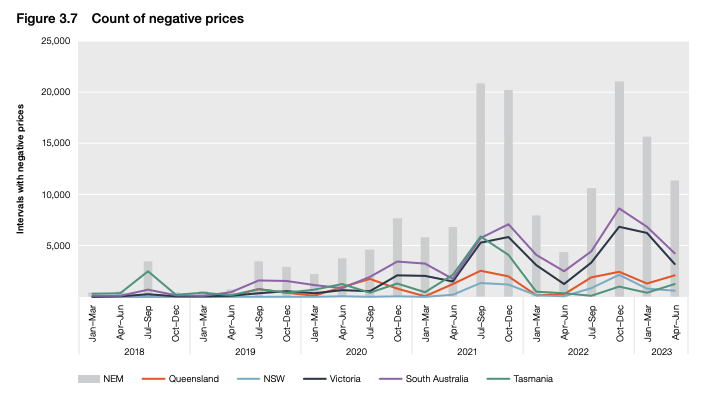 Instances of negative prices have risen since 2018.
Instances of negative prices have risen since 2018.The rise of negative electricity prices across the eastern seaboard has closely correlated with the expansion of renewable infrastructure. Since 2017, Australia has been actively seeking solutions to absorb the excess supply and restore efficiency to the energy system.
Solution 1 - Batteries
This idea makes the most intuitive sense to the average person. If we can't immediately use the power generated by a roaring wind turbine to power a family home, why not store it until peak demand and then release that cheap energy back into the grid?
The answer is twofold, 1. The buildout of these projects are expensive, 2. Storage capacity is minimal.
The Victorian Government's Big Battery initiative has the ability to power 1m Victorian homes for only 30 minutes and was built to a tune of $160m.
I always love technological innovation and perhaps one day all Australian houses will be powered by sea of solar panels and batteries in the middle of desert however it's evident we at least need an interim solution.
Solution 2 - Bitcoin Mining
We’ve all heard the same FUD. Critics prey on readers' misunderstandings of how the grid operates, portraying a vision where miners supposedly divert power away from households and businesses to feed this energy hungry beast into what they call a "worthless internet currency" and drive prices up.
However, if we incorporate Bitcoin mining's energy usage into what we've learned about grid operations, we can see how it can actually bolster renewable energy for two reasons:
Runtime Flexibility - Mining is an operation with razor thin margins and is only profitable with cheap electricity. Since this only occurs when energy has low to no demand (stranded), miners are not competing with households and businesses.
Mobility - Bitcoin miners are highly mobile and are often built right next to the power source, reducing transmission losses and optimising energy use at the source.
However one might feel about the net zero goals, there is no denying we should always prioritise reliability over sheer abundance. It's time Australia utilises the power of bitcoin to help stabilise our renewable grid to push forth to a sustainable future.
-
 @ 572aa884:e266a569
2024-09-04 19:46:40
@ 572aa884:e266a569
2024-09-04 19:46:40STAR TREK TNG: INCOMPATIBLE IDEALS
by Luke Parker
Premise: This screenplay is for an episode of Star Trek: The Next Generation, set near the end of Season 7. It imagines a first contact encounter between Picard’s Enterprise and a fully Anarcho-Capitalist planet with no government nor belief in authority.
Scene 1: Bridge
Exterior views of the Starship Enterprise give way to Captain Jean-Luc Picard standing at his command station on the bridge, his gaze steady and contemplative as he records his log.
Picard: (voiceover) "Captain's log, Stardate 48881.4. We were on our way to Deep Space 9 to provide support for the upcoming Bajoran elections when we received an audio-only distress call from a person on the planet Anarak, just outside of Cardassian space. The planet has yet to be contacted by the Federation, and in fact very little is known about it other than how it has a highly unusual social structure; one that appears to function without any form of central government or hierarchical leadership. It is a society that, despite its relatively high level of technological sophistication, has yet to achieve warp capability. The message is urgently requesting help from any peaceful civilization in range to defend his people against Cardassian invaders. It is difficult to imagine even the Cardassians violating the Prime Directive in such a manner. We are changing course to investigate."
Picard finishes his log entry and looks up, his expression thoughtful. The rest of the bridge crew is attentive with the memory of the Cardassain conquest of Bajor fresh in their minds.
Data: [turning from his console to face Picard] "Captain, Starfleet's lone anthropological record on Anarak indicates that it has a relatively large population and is advanced in various scientific fields. However, there are no reports of warp capability nor a leadership structure for us to contact there. Their society’s structure might challenge our usual protocols for contact."
Riker: [with a hint of curiosity] "An advanced society with no central government? That's a first."
Picard: [nodding] "Indeed, Number One. The distress call came from an individual named Bas T'yat, who identifies himself only as an entrepreneur. Our intelligence suggests that Anarak's society is structured in a way that is not only hostile to hierarchies but completely devoid of any form of leadership or authority. They seem to operate on a principle of total autonomy. This would seem to indicate an absence of a planetary defense system."
Troi: [thoughtful, with concern] "Without a central authority, how do they respond to any external threats? A society like this could be quite vulnerable to more aggressive powers, like the Cardassians."
Picard: [grimly] "It seems that may already be the case. The distress signal implied that a hostile force, likely Cardassian, has targeted them. Without a unified defense, they could be easy prey."
Worf: [sternly] "If the Cardassians are involved, Captain, they will not hesitate to exploit such a weakness. We must be prepared for hostilities."
Data: [analyzing the implications] "However, the lack of formal governance could complicate any assistance we offer. Without a government to negotiate with, we may face challenges in determining how to intervene appropriately."
Picard: [resolute, yet cautious] "We will treat Anarak as we would any other planet sending a distress call, regardless of their social structure. However, we must tread carefully. If we arrive to find Cardassians engaged in hostile acts, we may be forced to intervene. But in Federation space, our priority remains the protection of life and the maintenance of Federation principles."
The bridge crew exchanges looks of determination, each officer understanding the complexities of the mission ahead.
Picard: [decisive, raising his voice slightly] "Set course for Anarak. Engage at warp seven."
Data: [acknowledging] "Course plotted, Captain. Engaging warp seven."
The familiar hum of the warp engines intensifies as the stars on the viewscreen stretch into streaks of light, and the Enterprise leaps into warp, speeding towards the strange planet and the potential conflict awaiting them.
Scene 2: Bridge
The Enterprise emerges from warp above the planet Anarak, the planet’s blue-green surface appearing deceptively peaceful below.
Worf: [at tactical, scanning the area] "Captain, no alien vessels are currently in the vicinity, only artificial satellites. However, I'm detecting signs of recent battle on the planet's surface."
Picard: [moving closer to Worf's station] "Specify, Lieutenant."
Worf: [analyzing the data] "There is minor damage to infrastructure in multiple locations, consistent with Cardassian disruptor fire. Several structures show signs of targeted attacks, but the damage is localized and not extensive."
Data: [at the science station] "Captain, I'm detecting several warp signatures leading to and from the planet. However, one of these signatures does not match any known Cardassian engine profile and is not in our warp signature database."
Riker: [concerned, looking to Picard] "An unknown vessel in the area right around the time of a Cardassian attack? This could complicate matters."
Troi: [sensing the tension, her voice calm but alert] "Whoever they are, they may not have the best intentions. The people of Anarak could be more vulnerable than we initially thought."
Picard ponders this information, his expression thoughtful yet wary. The bridge crew continues their scans, tension mounting as they try to make sense of the situation.
Worf: [interrupting the silence] "Captain, we are being hailed from the surface."
Picard: [decisive, nodding] "On screen."
The viewscreen flickers to life, revealing the image of a middle-aged man with a rugged, practical look. He exudes an air of cautious relief, though his eyes betray a deep-seated wariness.
Bas T'yat: "Alien vessel, thank you for coming so quickly. My name is Bas T'yat, and I’m an entrepreneur and concerned family man. Please, can you tell me, are you an ally of the Cardassians?"
Picard: [calm and reassuring] "Mr. T'yat, I am Captain Jean-Luc Picard of the Federation starship Enterprise. I assure you, the Federation is not aligned with the Cardassians, although we have dealt with them before, and are aware of their transgressions."
Bas T'yat: [sighs in relief] "Thank goodness. We desperately need your help. An alien ship identifying itself as Cardassian has been harassing us for weeks. I fear they'll return soon, and we have little defense against their matter transportation technology. I'm a successful inventor and businessman, Captain. I have resources and tech that could be of value to your Federation, and I'm prepared to trade anything you want in order to help protect my people."
Picard: [curious, leaning slightly forward] "Tell me more about these attacks. What exactly have the Cardassians done?"
Bas T'yat: [his tone shifting to one of frustration mixed with guilt] "It started about a month ago. One of our companies, my own company, in fact, launched a new type of vessel that can travel faster than light using a warp field, the first one we've ever built. Within an hour of it's maiden voyage the Cardassians showed up. At first, they demanded to know who was in charge of the planet. They didn't like the answer they got: We are a free people and no one commands us."
Riker: [sharing a knowing glance with Picard] "A society without centralized leadership would be difficult for the Cardassians to understand or even tolerate."
Bas T'yat: [nodding] "That was my conclusion. They treated us like a lawless frontier, moving in to take whatever they wanted. They attacked our resource stockpiles, dematerialising and I assume stealing whatever they could before we even knew what was happening. Our ground-based defense missiles successfully took out their two smaller fighter crafts that came down into our sirspace, but we have no defense against their transporter technology. Their last visit was just a raid from orbit. They just grabbed what they could without even entering the atmosphere and left within minutes."
Picard: [thoughtful, with a hint of concern] "I see. There are widely-agreed-upon rules against this type of behavior, I assure you. However, since the Federation has never made contact with your people before now, we are unfamiliar with the proper etiquette for such a first encounter. How do you suggest we proceed safely for an official meeting?"
Bas pauses, visibly perplexed by the concept of "official" procedures, his expression almost amused.
Bas T'yat: [with a chuckle] "Official meeting? Captain, just come on down and park your craft outside my coordinates. My wife will make us all some refreshments."
Picard: [with a slight smile, yet maintaining formality] "We appreciate the hospitality, Mr. T'yat, but we prefer to beam down if that's acceptable to you. We can be there in a few minutes."
Bas T'yat: [nervous but agreeable] "Beam down? Uh, sure, that's fine. I was wondering if that technology worked on people. Love to see it in action."
Picard: [nodding respectfully] "Understood. I'll be down with a small team to meet you outside your building shortly. Picard out."
The screen goes dark as the connection ends, leaving the bridge crew to process the encounter.
Riker: [with a wry smile] "Drinks with the locals; sounds like fun."
Troi: [softly, but with insight] "He's nervous, but also hopeful. I'm sensing some hurt pride in him, too, Captain. This is likely the first time his people have ever had to reach out to anyone off-world for help. His pride may cloud his ability to fully grasp the dangers they’re facing."
Picard: [serious, standing up to address the crew] "On top of being an official first contact, the Cardassians have made this a very delicate situation. We must be prepared for anything. Counselor Troi, Data, and La Forge, you're with me. Number one, you have the bridge."
The crew nods in understanding as the away team heads to the turbolift. The tension in the air is palpable as they ready themselves for what may be a challenging first contact and a possible hostile encounter with the Cardassians.
Scene 3: Bas T’yat’s Front Lawn
The team materializes on the surface of Anarak, just outside of a large, elegant house set in a lush, rural landscape. The area is a blend of modern luxury and natural beauty, though signs of recent damage are evident. Smoke still rises from a nearby hangar, the aftermath of the Cardassian attack clear in the smoldering ruins. As the team takes in their surroundings, a group of locals approaches. At the forefront is Bas T'yat, flanked by a few colleagues. He's a middle-aged man with a commanding presence, dressed in practical yet fine clothing. His stride is confident, and his eyes sharp with the determination of a man used to getting what he wants. Bas’s face lights up with a mixture of curiosity and enthusiasm as he sees the away team.
Bas T'yat: [warmly, holding his palms upwards and then extending one hand towards Picard in a greeting] "Captain Picard! Welcome to Anarak! I'm Bas T'yat. It is my honor to meet you."
Picard: [imitating the hand motion, with a polite smile] "The honor is ours, Mr. T'yat. Thank you for your hospitality. May our two peoples forever live in harmony."
Bas gestures to the smoldering hangar in the distance, his tone tinged with frustration.
Bas T'yat: [with a sigh] "That would be wonderful. I do wish the circumstances for your visit were better. [clenching his fists] That's my hangar over there, or what's left of it, anyway. The Cardassians destroyed it and the spacecraft I designed and built there. It was our first warp vessel, one that the whole world cheered on at launch just last month. We were going to colonize the asteroids with it."
Geordi: [To Picard, gesturing towards the wreckage] "If I may, Captain?"
Picard: "Certainly." [To Bas T'yat] "This is my head engineer, Commander Geordi La Forge."
Geordi: [stepping forward] "Mr. T'yat, if it's alright with you, I'd like to examine the wreckage. I might be able to determine if anything is salvageable."
Bas T'yat: [nodding, gesturing to a colleague] "Of course. Lar Kinn here is our chief pilot. He made the historic first flight and he'll take you to the hangar and help with anything you need."
Geordi and Lar Kinn head towards the hangar, with Geordi hoping to confirm if this was the source of the warp signature detected in orbit. Meanwhile, Bas leads Picard, Troi, and Data toward his house. As they walk, Bas impatiently answers a few questions about his planet, his voice tinged with annoyance and concern.
Data: “Mr. T’yat, if I may, I notice that your neighborhood’s infrastructure is well taken care of. If Anarak has no central authority of any kind, who is responsible for keeping the roads and infrastructure?”
Bas T'yat: ”Well, as a rule of thumb, if it’s on my land, I am. If it’s not on my land, then someone else is, but I may have to pay them to use it. They look so nice because we all get better insurance rates for keeping them that way.”
Data: “Curious. And who initiates larger projects like mass transportation and research?”
Bas T'yat: [slightly annoyed] “They are all risky endeavors taken by entrepreneurs like myself. Sometimes profits take decades to appear, but like with my new warp engine, I’m sure they’ll make me a huge fortune one day.” [turning to ensure Picard can hear him] "Anyway, I fear the Cardassians aren't done with us. They've stopped even trying to make demands of us, which makes me think they're planning something bigger. Perhaps a larger assault. We've been able to fend them off so far, but I have no clue how to defend against those transporter devices."
Picard: [impressed] "It is remarkable that your society, with no planetary defense force, was able to repel Cardassian military forces, even if only temporarily. Cardassian ships are known for their significant weapons and shields."
Bas T'yat: [with a hint of pride] "The people of Anarak are no strangers to defending themselves. We have numerous private protection agencies, each with advanced missile fortifications and other kinds of defenses to protect every inch of this planet. But these were designed to fend off terrorists or rival companies, not an alien invader."
They reach the entrance to Bas's home. He pauses before entering, turning to Picard with a serious expression.
Bas T'yat: [earnestly] "Captain, I'm prepared to trade for whatever defensive technology you can provide, especially something to counter the Cardassian's transporter technology. I am confident that our ground defenses can take out their shuttlecraft, but we're helpless against their ability to beam in and out at will."
Picard pauses, his face reflecting the weight of his decision before he speaks.
Picard: [in his most diplomatic tone] "Mr. T'yat, the Federation is committed to helping those in need, and we don't tolerate bullies. However, there are restrictions on the technology we can share, particularly weaponry. Also, the Federation's assistance often depends on whether a planet is on the path to becoming a member. We must ensure that our values align. In this case, a diplomatic approach might bring a far more lasting peace than simply escalating an arms race."
Bas considers this, his optimism tinged with caution. The group moves into a large room with lots of seating where a warm drink much like tea is offered. Picard partakes graciously.
Bas T'yat: [thoughtfully] "I see. Federation membership is... a complicated idea. I'm sure many heads of companies like myself would welcome it, but for the whole planet to become a singular member of any larger federation is hard to imagine. Our society values individual freedom above all else, and I'm not sure how compatible everyone here is with the Federation's ideals."
Data: "The benefits of Federation membership are considerable. Could not your people one day vote on the issue to see if a majority wants to join after taking ample time to research membership?"
Bas T'yat: [skeptically] "Voting is something that hasn't been done here for tens of thousands of years. We consider it to be archaic, a form of slavery of the minority. Honestly, I'm surprised your culture still practices it."
Picard: [nodding, a little embarrassed] "I see. Rest assured that we try to only vote on things that have every participant's full consent. You'll find that this is very common among the races you meet as your people start to explore the stars. But until then, know that the Federation's primary concern is the safety of everyone in Federation space, including your people."
While inside Bas's home, Data discreetly connects to an open network connection, accessing Anarak's version of the internet called the Openlink. His eyes flicker left to right at an inhuman speed as he analyzes the planet's defenses and infrastructure.
Data: [quietly, to Picard as he processes the data] "Captain, while there are many advanced technologies in the hands of individuals and companies, I find no evidence of any kind of unified military infrastructure. The defense efforts are completely decentralized, which will surely prove problematic in the event of a full-scale Cardassian invasion."
Picard: [grimly] "Given the Cardassians' history, we must prepare for the worst."
Just then, Geordi returns from the hangar, his expression a mix of curiosity and concern.
Geordi: "Captain, I've confirmed that Bas's ship was the source of the warp signature we detected. Unfortunately, the wreckage isn't salvageable. It could be a long time before Anarak returns to the stars."
Bas T'yat: [with a determined grin] "I wouldn't say that. My first flight was widely publicized. Lar Kinn and I are celebrities now. Hundreds of other companies are likely working on similar technology already. Some of us refer to it as 'the great space race,' with the goal of creating the first off-world colony, and my company is currently in the lead."
Picard: [with a slight smile, impressed by the resilience] "It seems the people of Anarak are not to be counted out yet. Your intrepid spirit will serve you well as Anarakans start exploring the Galaxy."
Troi: [warmly] "Your optimism is admirable, Mr. T'yat. But remember, resilience is strongest when combined with caution."
Bas T'yat: [nodding, appreciatively] "Wise words, Miss Troi. Hopefully with your help we'll be ready for whatever comes next."
Picard: [ready to leave] "This tea is delicious, thank you for your hospitality. Next I'll need to talk to my superiors at Starfleet headquarters before we can proceed any further. I'll be sure and pass your concerns and needs on to them and then we'll contact you again later today."
The away team prepares to depart, with Bas expressing his thanks once more. As they beam back to the Enterprise, each member reflects on the unique challenges of Anarak.
Scene 4: Picard’s ready room
Minutes later, Captain Picard sits alone in his ready room, the vast starscape of space visible through the window behind him. His posture is straight, and the weight of the decision before him is clear in his eyes. He taps a command into his desk console, and the screen flickers to life with the familiar stern face of Vice Admiral Alynna Nechayev. Her image on the screen is as imposing as ever.
Picard: [calmly, but with underlying urgency] "Admiral, I've just concluded a preliminary contact with a representative of Anarak, just a few light years this side of Cardassian space. The situation is more complex than anticipated. The planet is under threat from the Cardassians; specifically Gul Bankar, who's been making increasingly aggressive moves from orbit. Meanwhile, the society on Anarak is... unconventional. They have no central government, no formal leadership nor military structure. The entire planet operates under a decentralized, anarchic, commerce-based system."
Nechayev: [eyes narrowing] "Anarchists? No structure? That's not exactly an encouraging environment for a first contact, Jean-Luc.
Picard: “Admiral, they’ve managed to develop warp technology without either a government or military. It’s a remarkable feat, but one that leaves them vulnerable.”
Nechayev: “Are you certain there’s no one in authority at all? Not even an ambassador?"
Picard: [nodding] "Precisely. Their social structure wouldn’t allow it. Our first contact has been with an individual and his family, one Bas T'yat; a wealthy businessman and the inventor of their first warp-capable ship. He's requesting assistance to defend against further Cardassian attacks, but without a central authority, assisting one individual could have unpredictable consequences."
Nechayev: [questioning sharply] "Hmm. And what of the Cardassians? Is there any evidence of their involvement?"
Picard: [gravely] "Plenty. The Cardassians have already raided the planet, seizing valuable resources. Their ship left orbit shortly before our arrival, but the threat of their return looms large. Bas T'yat is convinced they'll come back with a larger force."
Nechayev pauses, her expression hardening as she considers the situation.
Nechayev: [warningly] "Starfleet cannot afford to be drawn into deeper hostilities with the Cardassian Union, Jean-Luc. Especially not over a non-member world. You must tread carefully. A diplomatic solution is paramount, and under no circumstances should you provide this Bas T'yat with advanced defensive technology. The Prime Directive is clear; we don't interfere with the internal affairs of non-member worlds, and besides, you haven't even made proper first contact with the planet, only with one family."
Picard: [measured, but firm] "Admiral, with respect, Anarak is far more advanced than many worlds we've encountered. Their technological capabilities, while decentralized, are impressive. Now that they are getting their space legs it won't be long before Anarakans are showing up in ports across the quadrant. And if the Cardassians establish a foothold here, it could destabilize the entire region."
Nechayev's face softens slightly, recognizing the gravity of the situation. She sighs, her resolve shifting as she weighs the options.
Nechayev: [reluctantly] "Alright, Jean-Luc. I don’t like this, but I trust your judgement. You may share transport inhibitor technology. Only enough to help them counter the Cardassians' beaming technology, but nothing more. And remember, this Bas T'yat doesn't speak for his whole planet. Try to treat his family like you would if you found them alone in a spaceship."
Picard: "Understood, Admiral. I'll proceed with caution."
Nechayev: [more sternly] "Just don't start another war, Jean-Luc."
The screen goes dark. Picard leans back in his chair, the weight of the decision pressing on him. He stands, smoothing his uniform, and exits the ready room onto the bridge.
Scene 5: Bridge
On the bridge, the atmosphere is tense as the crew processes the situation. Picard steps up to his command chair, addressing the senior officers who have gathered.
Picard: [seriously] "Admiral Nechayev has authorized us to share transport inhibitor technology with Anarak to help them defend against further Cardassian raids. But we must be mindful of the ethical implications of our actions."
Dr. Crusher:: [concerned] "Captain, I'm worried about the consequences of becoming involved in this situation. If we assist Anarak, it could escalate into a larger conflict--one that could draw the Federation into another war with the Cardassians."
Worf: [gruffly, with resolve] "But allowing the Cardassians to plunder a defenseless society is equally unacceptable, Doctor. We have a responsibility to protect the vulnerable."
Picard: [thoughtfully, considering both viewpoints] "I'm inclined to agree with Worf on this one, Beverly. We must work fast to deploy the inhibitors wherever we can, but that does bring up another problem. The Prime Directive prevents us from interfering in the internal affairs of non-member worlds. And giving one individual on Anarak access to advanced technology could upset the delicate balance of their society. What if Bas T'yat's company gains a monopoly on defense technology? It could shift the power dynamics on the entire planet."
Troi: [insightfully, her voice calm] "Captain, I sense that Bas T'yat is deeply worried about his planet's future. He feels a strong sense of responsibility and guilt for the attacks... I don't think that he had any way to know that their warp signature would act as a beacon to those seeking resources. They didn't even know other life forms existed until the Cardassians arrived. It's clear that Anarakans weren't prepared for the reality of interstellar contact."
Picard: [resolved] "I agree, Counselor. We're dealing with a society that is both advanced and vulnerable. A dangerous combination. We must proceed carefully."
Picard considers this, his brow furrowed in thought. Finally, he makes a decision.
Picard: [decisively] "We must proceed, however. I'll invite Bas T'yat to the Enterprise to discuss the situation further. We will ensure that any assistance we provide doesn't destabilize their society, or escalate the conflict."
Picard hails Bas T'yat from his command station.
Picard: [calmly] "Mr. T'yat, I'd like to invite you aboard the Enterprise to discuss our options in person."
The main screen fills with T'yat's face again.
Bas T'yat: [with a hint of hesitation] "Thank you, Captain, I accept. But I'd prefer to take my own craft... Still not quite comfortable with the transporter technology, if you'll understand. I'll bring my wife, L'anna, and my pilot, Lar Kinn."
Picard: [diplomatic, nodding slightly] "Understood. We'll be ready to receive you in the shuttlebay.”
Scene 6: Main Shuttlebay
In the Enterprise's shuttlebay, the crew prepares to greet their visitors. The doors slide open, and a sleek, streamlined skysled enters the bay, guided by Lar Kinn at the controls. The craft settles gently onto the deck, and the hatch opens. Bas T'yat steps out, accompanied by his wife, L'anna, and Lar Kinn, who looks around the shuttlebay with wide-eyed curiosity. Picard, Troi, and Data are there to meet them, offering warm greetings as the Anarakans take in the impressive sight of the Enterprise's interior.
Picard: [welcoming, with a gesture towards the ship] "Welcome aboard the Enterprise, Mr. and Mrs. T'yat. I trust your journey was smooth?"
Bas T'yat: [grinning, clearly impressed] "Very much so, Captain. Your ship is... well, it's more than I imagined. Thank you for having us."
Troi steps forward, offering a kind smile.
Troi: [invitingly] "If you'd like, I can give you a tour of the ship. We're quite proud of our vessel, and I think you'll find it fascinating."
L'anna's eyes widen with excitement, and she nods eagerly. Bas exchanges a look with Lar Kinn, just catching up to the group. He seems just as eager to explore as the others, and nods excitedly to Troi.
Bas T'yat: [appreciatively] "We'd be honored. Lead the way, Counselor."
Lar Kinn: So can all these shuttles go faster than light?
With that, the group sets off on a tour of the Enterprise, the Anarakans marveling at the advanced technology and seamless design of the Federation starship. As they walk, Troi can't help but notice the mix of awe and determination in Bas T'yat an inventor and leader who knows that his world's future may very well depend on the choices made in the hours to come.
Scene 7: Bridge
The scene opens as Counselor Troi leads Bas T'yat, L'anna, and Lar Kinn onto the bridge of the Enterprise. The visitor's awe is palpable as they take in the grandeur of the ship's command center. Picard, standing near the captain's chair, barely has a moment to welcome them when a sudden alert draws everyone's attention.
Data: [at his station, voice urgent] "Captain, I'm detecting the return of the Cardassian battle cruiser. It is registered as the Kolarak. It just popped out from behind the home star and is entering orbit around Anarak."
Riker: "Yellow alert. On screen."
Picard immediately straightens, his expression shifting from welcoming to resolute. The tension on the bridge heightens as the viewscreen flickers to life, displaying the imposing sight of the Kolarak. The Cardassian vessel looms in space, its dark hull bristling with weaponry.
Picard: [calmly, but with authority] "Mr. Worf, open a channel to the Kolarak."
The screen quickly reveals the stern visage of a Cardassian Gul in his command chair. His eyes narrow as he takes in the sight of the bridge crew and the unfamiliar faces of Bas and his companions.
Picard: [with measured politeness] "I am Captain Jean-Luc Picard of the Federation starship Enterprise. With whom am I speaking?"
Gul Bankar: [with a sneer, his voice dripping with condescension] "You may address me as Gul Bankar."
Picard: "Gul Bankar, there have been reports of your vessel causing harm and stealing resources from the planet below. With me is Bas T'yat, the owner of the warp-capable vessel that it appears your forces destroyed on the surface. We request an explanation for these hostilities."
Gul Bankar: "Captain Picard, your presence here is an unwelcome interference. This planet, and its inhabitants, are under Cardassian protection. You will withdraw immediately, leaving Anarak to our care."
Picard's gaze hardens, but his tone remains calm and firm.
Picard: [skeptically] "Cardassian protection? Anarak lies within Federation territory. We received a distress call and are here to provide assistance."
Bankar's expression darkens, his eyes flashing with anger.
Gul Bankar: [coldly] "The Federation's meddling in this region is all too well documented, Picard, but Anarak is too close to Cardassian space for your interference to be tolerated. I find your so-called assistance nothing more than another prelude to annexation."
Bas, standing beside Troi, listens intently, his face reflecting a mixture of concern and frustration. Picard, sensing the rising tension, steps closer to the viewscreen.
Picard: [with resolve] "The Federation respects the sovereignty of all worlds. We are only here because of your aggressive actions, not to claim this planet. We have long worked to maintain peace in this sector, and I would hate to see that peace jeopardized by your reckless actions here."
Gul Bankar: [sarcastically] "Peace? The Federation's control of Terok Nor and the Bajoran wormhole is hardly a gesture of peace. It was a clear power grab, one that we will not allow to extend to Anarak."
Picard's eyes narrow, his voice taking on a steely edge.
Picard: [firmly] "Gul Bankar, a conflict between the Federation and the Cardassian Union would serve no one's interests, especially not over a planet that is so new to the neighborhood. I suggest you contact your superiors before taking any further aggressive actions."
There's a tense silence as Bankar considers Picard's words, his eyes flicking to Bas and then back to Picard. Finally, he lowers his head in a slight nod, though his expression remains hostile.
Gul Bankar: [grudgingly] "Very well, Captain. I will contact Central Command. But understand this; Anarak will not fall under Federation control, and I will ensure that Cardassia's interests are protected. I will contact you again in 4 hours."
The transmission abruptly cuts off, leaving the bridge in a heavy silence. The Kolarak remains on the viewscreen, hovering ominously in space, nose to nose with the Enterprise now. Picard exhales, turning to face his crew.
Picard: [calmly, but with an undertone of urgency] "Maintain our position and yellow alert, Mr. Worf, and monitor the Kolarak for any signs of hostile activity."
Worf gives a curt nod, his eyes never leaving the tactical display.
Worf: [with determination] "Aye, Captain. Shields at maximum, weapons ready."
Picard then turns to Bas, who is visibly shaken but trying to maintain his composure.
Picard: [reassuringly] "Mr. T'yat, I understand this is a difficult situation and you don't yet know who to trust, but I assure you that we aim to keep the peace in this sector and will do everything in our power to ensure your planet's safety. We ask nothing in return from the Anarakan people. However, it is crucial that we handle this matter diplomatically."
Bas nods, though his expression is one of deep concern.
Bas T'yat: [uneasily] "I appreciate that, Captain, and don't worry, nothing that Gul Bankar says will make me trust his offer of "protection" after he destroyed my ship and stole resources from all over the planet. But I do worry that he’s using this time to call for reinforcements."
Picard places a reassuring hand on Bas's shoulder, his voice steady.
Picard: [confidently] "If he attacks, we'll face that challenge together, Mr. T'yat. You are free to return to the surface at any time but for now, I think it best that we consider how fast we could deploy our transporter inhibitor technology on your planet."
Bas T'yat: [enthusiastically] "You mean you're willing to sell us devices that can stop them from beaming up our resources?"
Picard: "Or beaming their troops down. And we wouldn't sell it to you, it is our gift. The Federation doesn't sell it's assistance to those in need."
The visitors faces all brighten in unison with relief.
L'anna: "I don't know how we could ever thank you enough, Captain. This means everything to our people."
Picard: "Don't thank us yet, there is still the issue of deploying enough of them in time. If they're going to attack in 4 hours you'd need them set up near all the most valuable targets at the very least. They'll need a steady supply of energy, too."
Bas furls his lips in concerned thought.
Data: "Captain, I've analyzed all of the planet's most valuable resource depots that our scanners can detect and I see 168 unique locations that we should set up transport inhibitors. There may, of course, be other targets too that they would want."
Riker: [apprehensively] "That's way too many for us to replicate in time, much less visit each location to install within the next 4 hours."
Picard: "We need a way to speed up that deployment, at least to enough sites that will show Gul Bankar that things have changed... And hopefully without him detecting our movements."
Bas T'yat: "If I may captain, I think I know a better way to deploy them if I can just make a detailed scan of one and save it to our printer file format... We don't have your transporter technology, but our device printers are able to scan and quickly reproduce any technological device that we can identify the components of."
Riker: "And how will that help distribute them to everyone in time?"
Bas T'yat: "Simple, every business and household has one of these printers. I can upload the scanned file to our Openlink and tell all of Anarak in one broadcast about the imminent threat and how to protect themselves from it with one of these inhibitors. They'll pop out thousands of them in time."
Picard: "That sounds very promising, Mr. T’yat. But I want your assurance that your company will not hold any sort of monopoly on this technology or otherwise profit from it; In lieu of a government, the Federation requires that this gift be made to your whole planet at once."
Bas T'yat: [after some hesitation] "Alright, Captain. You have my promise. Giving up some profits is the least I can do to make up for attracting the Cardassians to Anarak."
Picard looks visibly relieved, giving a curt nod to Bas.
Picard: "Data, take our guests to engineering and grab whomever you may need to assist you with making this happen in time. Remember, you’ll also need to show the Anarakans how to use these devices."
Data: "Aye sir." [To the visitors] "If you'll follow me please, we'll be able to work on this in engineering."
Data, Bas, Lar Kinn, and L'anna walk briskly to the turbolift. The scene closes with Picard returning to his command chair, the bridge crew resuming their stations as the standoff between the Enterprise and the Kolarak continues. The two ships remain locked in silence, nose to nose, as the 4-hour countdown begins.
Scene 8: Main Engineering
The scene opens in Main Engineering, where Geordi La Forge, Data, and Ensign Sam Lavelle are putting the final touches on the scan for their transport inhibitor device. Bas T'yat and Lar Kinn stand nearby, observing the process with keen interest. The atmosphere is tense, underscored by the ticking clock counting down the hours until Gul Bankar's deadline.
Geordi: [focused as he works] "All right, that should do it. The scan of this transport inhibitor is ready, and the data's been formatted for your printers."
He hands a datapad to Bas, who takes it with a mix of curiosity and nervousness.
Geordi: [reassuringly] "You'll be able to upload the complete plans from this device, including an adapter for your power source. Once it's on your network, anyone with Openlink access will be able to build and deploy these inhibitors in a matter of minutes. It's up to you, however, to convince them to do that."
Bas T'yat: [relieved] "Thank you, Commander. I'm sure many will manage it in time, but I just hope it's enough."
Lavelle: [chiming in, pointing to the datapad] "Also I've included a detailed instruction set too. It explains how to set the units up and operate them."
Bas nods his thanks, flipping through the instructions as Lar Kinn looks over his shoulder.
Data: [ever precise, offering a suggestion] "Mr. T'yat, given the standoff outside, it may be prudent to avoid the use of the transporter. The Kolarak is likely monitoring our actions closely. Sending the plans with you aboard the skysled would appear less provocative."
Bas looks visibly relieved at the suggestion, nodding in agreement.
Bas T'yat: [grateful] "Thank you, we'd prefer not having our atoms scattered throughout the atmosphere today anyway."
Geordi: [nodding, humorously] "No problem. We'll make sure the skysled is ready to go."
Data gestures toward the exit of Engineering, indicating it's time to depart.
Data: [calmly, but with urgency] "We should make our way to the shuttlebay. There's less than two hours remaining before the Gul's deadline. It's imperative that as many Anarakans as possible receive these plans in time."
Bas and Lar Kinn exchange a look, their expressions set with determination as they follow Data out of Engineering. The camera follows the group as they walk briskly through the corridors of the Enterprise.
L'anna: "You'll be sure to tell the Captain and Councilor Troi that we said goodbye?"
Data: "Of course. And let me say that I find your culture truly intriguing, and hope we get the chance to visit again in the future, no matter if Anarak chooses Federation membership or otherwise."
Bas T'yat: "You'd be our welcome guest anytime, Mr. Data. I think you'd most enjoy seeing the progress my people have made with robotics and artificial intelligence. My company produces one of the best-selling android assistants on the market."
Data: "Fascinating. I look forward to it. Here we are."
As they reach the shuttlebay, the large bay doors slide open, revealing the sleek skysled waiting for them. The ship is prepped and ready for launch, its engines humming with quiet power.
Data: [pausing as their ship's door opens] "We wish you a safe journey, Mr. T'yat, L'anna, Mr. Kinn."
Bas T'yat: [nodding, with resolve] "We'll make sure everyone gets these plans. Thank you, Commander Data."
Lar Kinn gives Data a respectful nod before they step onto the skysled. Data watches as they take their positions inside the cockpit. Data then taps his communicator, his voice steady.
Data: "Data to the Bridge, our visitors are ready to depart."
The camera cuts to the exterior of the Enterprise, where the massive shuttlebay doors slide open. The skysled, with its sleek design and glowing engines, slowly backs out of the bay, the vastness of space stretching out behind it. As the skysled turns on its main engines, the camera shifts to an interior cabin view, showing Bas and Lar Kinn exchanging a final, determined nod before the vessel speeds downwards towards Anarak.
Scene 9: Bridge
The scene opens 30 minutes later. The tension on the Enterprise bridge is palpable as the Openlink broadcasts Bas's message and the transport inhibitor plans worldwide. The crew watches anxiously as the first inhibitors are swiftly deployed across Anarak. Suddenly, the ship's sensors beep urgently. Worf glances at his console, eyes narrowing.
Worf: [alarmed] "Captain, seven additional Cardassian battle cruisers have exited warp and joined Gul Bankar's ship. They're forming up and preparing to engage."
Riker: "Red alert, forward shields to maximum."
Picard's expression hardens as the Kolarak hails them. Gul Bankar's visage appears on the viewscreen, eyes burning with fury.
Gul Bankar: [accusatory] "We've detected the inhibitor plans on their planet-wide network, Picard. You've broken our gentleman's agreement by sharing advanced technology with a primitive civilization. So much for Starfleet ideals! You're no match for us now. Try and stop us at your own peril."
With that, Bankar cuts off communications. Picard stands, frustration etched into his features as the fleet of eight warships begins its descent toward Anarak.
Data: [urgently] "Captain, the Cardassian ships are gaining speed and appear to be initiating an attack run on the planet's largest population center. Tens of millions of civilian lives are at risk, more than usual because the defensive turrets are spread out among the greater population. It is not uncommon for them to be placed on rooftops and around housing here."
The crew's tension escalates as the gravity of the situation sinks in. Picard, feeling the weight of command, turns to his officers.
Picard: [steady but intense] "Ideas?"
Worf: "Captain, we could attempt to disable their weapons and transporters, focusing on minimizing their capacity to attack."
Riker: [shaking his head] "Even so, we're outmatched. Enterprise won't survive against eight battle cruisers."
Troi: [calm but urgent] "We just need to buy time. To give the Anarakans a chance to fully deploy their defense net. But any kind of engagement from us still risks re-igniting a war with the Cardassians."
Data, ever analytical, speaks up with a grim tone.
Data: "Captain, I've run millions of battle scenarios. None result in the Enterprise surviving while saving more than a few dozen lives on the surface. Our current position is untenable."
As the Cardassian warships break through the planet's stratosphere, Ensign Lavelle, stationed at comms, suddenly speaks up.
Lavelle: [urgently] "Captain, Bas T'yat has just sent out another message across the planet, warning of the incoming Cardassian fleet."
Picard opens his mouth and lifts his index finger to respond, but he's cut off by a sudden, blinding array of light erupting from the planet's surface, filling up the viewscreen. The bridge crew shields their eyes as the screen fills with thousands of pinpricks of light; an overwhelming launch of nuclear-armed missiles aimed directly at the Cardassian fleet.
Worf: [stunned] "Captain, these are nuclear-fission warheads, each with a 10-megaton yield. I've never seen a civilization with this many dirty weapons in active deployment."
The bridge falls silent as the sheer scale of the Anarakan response becomes clear. The entire hemisphere of Anarak has mobilized, proving their incredible capacity for defense, despite the lack of a centralized government.
Data: "Fascinating. It could be that no central authority is needed for coordination when the threat is dire. These people all appear to be responding individually with their own weapons."
The first few dozen warheads impact the Cardassian shields, which manage to absorb their blasts. But the onslaught is unrelenting. Hundreds, then thousands of warheads detonate in rapid succession, creating a cataclysmic, sustained explosion. The Cardassian ships, though formidable, are utterly overwhelmed. The viewscreen shows an apocalyptic display; a temporary star forms in Anarak's upper atmosphere, engulfing the entire Cardassian flotilla in an unprecedented, blinding flash.
Picard: "Helm, back off our position."
The bridge crew watches in stunned silence as the massive explosion slowly dissipates, leaving nothing but a red afterglow and the eerie silence of space. Power has gone out across the hemisphere on the planet below, but not a single molecule of the Cardassian ships remain. Picard and his crew are left in awe, mingled with a deep sense of disappointment. The enormity of what they've witnessed sinks in; a civilization so welcoming, yet still capable of such destructive power... Sso fundamentally different from the Federation's ideals. Troi closes her eyes tightly and winces, blocking out the pain of all those Cardassian deaths. Picard stands, staring out at the aftermath, the weight of the moment heavy on his shoulders.
Picard: [quietly, with a great sense of loss] "Such utter destruction..."
The camera pulls back, showing the Enterprise as a small silhouette against the reddish glow below.
Scene 10: Bridge
The scene opens minutes later with the Enterprise bridge crew still processing the aftermath of the overwhelming display of destructive power. The mood is somber as the reality of what they've witnessed lingers. Suddenly, Bas T'yat's face appears on the viewscreen, his expression a mixture of relief and satisfaction.
Bas T'yat: [earnestly] "Captain Picard, I wanted to thank you and your crew for everything. It seems our future is secure now, thanks to the defense network and your assistance. We're eager to move forward and hope the Federation will allow us to engage in commerce with your worlds and other peaceful civilizations."
Picard stands, his gaze steady, though his tone reflects the weight of what has transpired. He pauses for a moment, as if searching for the right words, the bridge falling into a brief, tense silence.
Picard: [measured, but firm] "Mister T'yat, I must be candid. While the Enterprise is pleased to have assisted in safeguarding your world, the events of today have left us with grave concerns. The way Anarak handled the Cardassians… particularly the use of nuclear warheads, demonstrates a fundamental difference in values between our societies. We cannot endorse methods that pose such a grave risk to all life, even in defence. The Federation could not, in good conscience, approve your planet for membership given these circumstances."
Bas's expression shifts to one of slight disappointment, but he remains composed.
Bas T'yat: "I understand, Captain. We've always been a world that does things our own way. Federation membership would have been a tough sell to my people anyway. But what about trade? Surely we can still establish commerce with Federation worlds?"
Picard nods, his tone softening slightly.
Picard: "Trade remains an option. We won't turn away peaceful commerce between Anarak and Federation planets. However, I must stress that the use of nuclear weapons is fundamentally at odds with Federation ethics. While I recognize their role in your planet's defense, I hope that over time, your people will explore more sophisticated and less destructive means of protection."
Bas nods again, understanding the implications of Picard's words.
Bas T'yat: "It's clear that today's events were... extreme. The fallout, the EMP blackouts, the atmospheric damage; we've already seen unacceptable cost. I'll do my best to guide my people toward more advanced defenses, and away from reliance on such careless weapons. It will be my penance for leading the Cardassians here."
Troi senses his guilt once again and takes a deep breath. Clearly still shaken by the loss of life, she steadies herself before offering a supportive smile.
Troi: "You shouldn't burden yourself with guilt, Mister T'yat. Anarak was bound to take that step sooner or later. What matters now is how you use your newfound role as an ambassador to the stars. Your actions will shape your planet's future in the galaxy."
Bas smiles, clearly grateful for the support.
Bas T'yat: "Thank you, Counselor. I'll do my best to live up to that responsibility."
After a few more exchanges, the connection ends, and Bas T'yat's image fades from the viewscreen. Picard takes a deep breath and turns to face his bridge crew.
Picard: [reflective] "We've witnessed two amazing displays of power today; one of the explosive variety, and the other of a free people's resolve. It's hard to imagine how their society works with no acceptance of authority, but today they've clearly displayed that they can accomplish amazing things working together even without any."
Worf, still perplexed, shakes his head slightly.
Worf: "I still don't understand how an entire planet could coordinate such a specific defense without any central leadership."
Leaning casually against the console, Riker chuckles lightly.
Riker: "It was in everyone's best interest, Worf. They just needed Bas's signal to know when the attack was imminent. The rest fell into place."
Worf: "And how they could hide that many warheads from our scans? Enriched Uranium is the easiest of all elements to scan for."
Data: "It appears that their stealth technology may be on par with our own."
Picard, his expression thoughtful, gazes out at the stars beyond the viewscreen.
Picard: "I'm placing a note in my log for Starfleet to leave this planet alone until they can't be ignored any longer. I believe it's for the best that we leave Anarak to chart its own course in the galaxy."
He pauses, a faint smile tugging at the corner of his mouth.
Picard: "I doubt we'll have trouble with them soon, at least, until they meet the Ferengi."
*The bridge crew shares a quick laugh and then a quiet moment of contemplation before returning to their stations. The camera pulls back, showing the Enterprise once again poised in the vastness of space, a symbol of hope and integrity amidst the complexities of a vast and unpredictable galaxy.
Fade to black.*
---
*This story is set in the Star Trek universe, created by Gene Roddenberry and owned by Paramount. I do not own any of the characters or settings from the Star Trek franchise, and this is purely a fan-made work for non-commercial purposes.*
-
 @ e6fbeb1c:6ac8fc04
2024-09-04 17:29:17
@ e6fbeb1c:6ac8fc04
2024-09-04 17:29:17When I have stale bread, I often use it to make a bread salad.
The base is croutons of stale bread and then there are no limits to your imagination.
In this salad there was also - Onions stewed in balsamic vinegar - Spring onions (raw) - Cherry tomatoes - Eggplants and sweetcorn (fried, lukewarm) - Pine nuts - Finely sliced cheese - Basil
https://image.nostr.build/ce0c7490f2adbd2aa4ccdfe80203a15dbb10686859a3256a0147d5f423478fd0.jpg
https://image.nostr.build/f930e0984ec9603b84c7a7868a97486140ee44590590102f7e460bfbfd3d70be.jpg
originally posted at https://stacker.news/items/672404
-
 @ 469fa704:2b6cb760
2024-09-04 15:22:28
@ 469fa704:2b6cb760
2024-09-04 15:22:28Money Printing in general
First of all, we need to make a distinction between money creation by central banks and fractional-reserve banking. Usually, the term money printing or “printer goes brrrrrr” refers to the creation of new central bank money, which is primarily created by central banks through:
- Open Market Operations: Buying government securities, which injects money into the banking system by increasing bank reserves. This is often done electronically, not by physically printing money.
- Quantitative Easing (QE): Purchasing assets to inject money directly into the economy, aiming to stimulate economic activity by increasing the money supply.
- Setting Reserve Requirements: Although less about creating money, lowering reserve requirements can indirectly influence money creation by allowing banks to lend more, but as of recent policy changes, this has been set to zero in some systems, shifting focus to interest rates.
- Interest on Reserves: By adjusting the interest rate paid on reserves, central banks influence how much banks are willing to lend, thereby indirectly affecting money creation.
This is the first step of money creation, although printing money is usually connected to one of the aforementioned processes, the second step creates much more money through the expansion of credit.
The Mechanics of Fractional-Reserve Banking
The Concept
In fractional-reserve banking, banks accept deposits from customers and only keep a small fraction of these deposits in reserve, lending out the rest. This practice essentially creates new money because:
- Deposits: When you deposit money, say $1,000, into a bank, that money doesn't just sit there.
- Reserves: If the reserve requirement is 10%, the bank keeps $100 as reserves.
- Loans: The remaining $900 can be loaned out. Here's where money creation begins.
Note: Current reserve requirements of the FED (Source) and the ECB (Source) are set at 0% respectively 1%.
Example Calculation of Money Creation
- Initial Deposit: You deposit $1,000 into Bank A.
- Bank A's Action:
- Keeps $10 (1%) as reserve.
-
Loans out $990 to another customer.
-
The $990 Loan: This $990, when spent, might end up in Bank B as someone's deposit.
- Bank B's Action:
- Keeps $9.9 (1% of $990) as reserve.
-
Can loan out $980.1
-
Continuation: This process repeats, with each cycle creating new deposits from loans.
The Deposit Multiplier (m) can be calculated as: * m = 1 divided by Reserve Ration = 1 / Reserve Ration
If the reserve ratio is 1%: * m = 1 / 1% = 1 / 0.01 = 100
This means, theoretically, an initial deposit of $1,000 could expand to:
- $1,000 times 100 = $100,000
- However, in practice, this is tempered by factors like cash holdings, loan demand, and banks holding excess reserves.
Historical and Economic Context
- Evolution from Goldsmiths: The system has its roots in the practices of goldsmiths who issued notes for gold deposits, which eventually circulated as money. This practice evolved into the modern banking system where notes (now digital entries) represent claims on money.
- Regulation and Central Banking: Over time, central banks like the Federal Reserve in the U.S. were established to regulate this process, provide stability, and act as lenders of last resort. The Fed's tools include setting reserve requirements, though this has become less relevant with the shift to a 0% reserve requirement.
Criticisms and Alternatives
- Risk of Bank Runs: Critics argue that fractional-reserve banking makes the system vulnerable to bank runs, where too many depositors demand their money back at once, which the bank cannot cover since most of the money is loaned out.
- Vollgeld Initiative and Full-Reserve Banking: Movements like Switzerland's Vollgeld Initiative have proposed shifting to full-reserve banking, where banks must hold 100% of deposits in reserve, preventing them from creating money through lending. However, this would significantly alter how banks operate and make profits. *** Modern Adjustments**: The move to a 0% reserve requirement in the U.S. reflects a shift towards using other monetary policy tools like interest rates on reserves to control money creation and economic stability.
Real-World Implications
- Money Supply Control: While banks create money through loans, central banks like the Federal Reserve influence this through monetary policy, adjusting how much money banks can create.
- Economic Stability: The zero reserve requirement might seem to allow infinite money creation, but in reality, banks are constrained by capital requirements, risk assessments, and economic conditions.
Conclusion
Fractional-reserve banking is a dynamic system that significantly influences economic growth by expanding the money supply through debt. While it allows for economic expansion, it also introduces risks of instability, which central banks attempt to mitigate through various policy tools. Understanding this system helps demystify how money flows and grows within an economy, showcasing both its capacity for economic stimulation and its inherent risks. As we move forward, debates continue on how best to balance these aspects to foster economic stability and growth. In 2009, a new system called Bitcoin emerged that could redefine the rules for money creation.
-
 @ ba4a39ee:df9b4c6b
2024-09-04 14:23:26
@ ba4a39ee:df9b4c6b
2024-09-04 14:23:26 -
 @ 361d3e1e:50bc10a8
2024-09-05 20:32:32
@ 361d3e1e:50bc10a8
2024-09-05 20:32:32A wave of criticism against a supermodel who chose alternative cancer treatment, and yet she was cured
cancer #alternative #health #medicine #model #treatment #usa #showbiz
-
 @ 469fa704:2b6cb760
2024-09-04 12:07:53
@ 469fa704:2b6cb760
2024-09-04 12:07:53Unified Login Across Platforms
With Nostr, you use one login for all services, and your followers are seamlessly integrated. So you don't have start anew on every single platform. I think this is a real advantage of Nostr even for people not accustomed to Bitcoin or decentralization in general.
Value for Value (V4V) Model
Embrace the V4V principle where value is exchanged directly between users. Meaning if you find something useful or anohter nostr user was able to help you then you can simply zap him or her some Sats.
Blogging Platforms
- Habla or Yakihonne: Since joining Nostr 8 days ago, I've started blogging using Habla, which I found incredibly user-friendly. You can check out my articles directly on some clients like noStrudel, where they appear under my profile. Habla also serves as a great community explorer. Yakihonne, another comprehensive client with an integrated blog editor, caught my eye too, although it didn't sync all my Habla posts, possibly due to relay issues.
- Highlighter.com: Offers a sleek interface for reading articles. On noStrudel, articles are tucked away under the "More" menu.
Presentations
- Slidestr.net: This tool transforms your notes into a slideshow, making revisiting old notes quite entertaining.
Video Content
- Flare.pub: If you're looking for a YouTube-like experience, Flare.pub is the closest you'll get on Nostr. You can upload, watch videos, and curate playlists. Remember, since Nostr is fundamentally text-based, videos are hosted on traditional servers, but the interface remains decentralized. There's definitely room for more video content, so start creating!
Live Streaming
- Zapstream: Offers a smooth streaming experience with a fee of 10 Sats per minute to cover server costs. You can watch streams on clients like Amethyst or noStrudel.
Music and Podcasts
- Wavlake and Tunestr: Ideal for artists to share music or podcasts. Listeners can enjoy content freely or support creators via zaps, adhering to the V4V model.
Lists and Grouping
- Listr: A tool for organizing everything from regional user groups to thematic notes or hashtags. You can also follow lists created by others in the Nostr community.
Culinary Arts
- zap.cooking: A haven for aspiring or seasoned chefs, offering a plethora of recipes in a blog format. It's well-organized, allowing you to browse through different categories of recipes.
Marketplaces
- Plebian Market: Reminiscent of eBay's early days, this marketplace allows easy buying and selling among users.
Community Features
- Many clients like noStrudel, Habla, and Amethyst support community functionalities, enhancing user interaction within Nostr.
-
 @ 8cb60e21:5f2deaea
2024-09-05 19:48:32
@ 8cb60e21:5f2deaea
2024-09-05 19:48:32Part 3: Asynchroni et DOM Manipulatio
3.1 Promissa et Async/Await
Praesent blandit. Nam nulla. Integer pede justo, lacinia eget, tincidunt eget, tempus vel, pede.
``javascript function simulaRequest(data, probabilitasErroris = 0.1) { return new Promise((resolve, reject) => { setTimeout(() => { if (Math.random() < probabilitasErroris) { reject("Error: Aliquid mali accidit"); } else { resolve(Data accepta: ${data}`); } }, 1000); }); }simulaRequest("Lorem ipsum") .then((responsum) => console.log(responsum)) .catch((error) => console.error(error));
async function fetchData() { try { const responsum = await simulaRequest("Dolor sit amet"); console.log(responsum); } catch (error) { console.error(error); } }
fetchData(); ```
3.2 DOM Manipulatio
Morbi non lectus. Aliquam sit amet diam in magna bibendum imperdiet. Nullam orci pede, venenatis non, sodales sed, tincidunt eu, felis.
```javascript document.addEventListener("DOMContentLoaded", () => { const titulus = document.createElement("h1"); titulus.textContent = "Lorem Ipsum JavaScript"; document.body.appendChild(titulus);
const paragraphus = document.createElement("p"); paragraphus.textContent = "Neque porro quisquam est qui dolorem ipsum quia dolor sit amet, consectetur, adipisci velit..."; document.body.appendChild(paragraphus); const button = document.createElement("button"); button.textContent = "Fac Clic Me"; button.addEventListener("click", () => { alert("Gratias tibi ago pro clic!"); }); document.body.appendChild(button);}); ```
3.3 Fetch API
Maecenas leo odio, condimentum id, luctus nec, molestie sed, justo. Pellentesque viverra pede ac diam.
``javascript async function fetchLoremIpsum() { try { const responsum = await fetch("https://api.lorem.space/image/game?w=150&h=220"); if (!responsum.ok) { throw new Error(HTTP error! status: ${responsum.status}`); } const data = await responsum.blob(); const imago = document.createElement("img"); imago.src = URL.createObjectURL(data); document.body.appendChild(imago); } catch (error) { console.error("Problema cum fetching imagine:", error); } }fetchLoremIpsum(); ```
3.4 Local Storage
Cras mi pede, malesuada in, imperdiet et, commodo vulputate, justo. In blandit ultrices enim.
```javascript function salvaPreferentias(clavis, valor) { localStorage.setItem(clavis, JSON.stringify(valor)); }
function accipePreferentias(clavis) { const valor = localStorage.getItem(clavis); return valor ? JSON.parse(valor) : null; }
const preferentiae = { thema: "clarus", lingua: "Latina", notificationes: true };
salvaPreferentias("userPrefs", preferentiae);
const salvataePreferentiae = accipePreferentias("userPrefs"); console.log(salvataePreferentiae); ```
3.5 Exercitia Parti III
- Crea paginam web simplicem quae utitur fetch API ad exhibendum datos ex API publica.
- Implementa functionalitatem "drag and drop" utens DOM API.
- Construe applicationem "todo list" quae persistit datos in local storage.
Conclusio
Vivamus vestibulum sagittis sapien. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Etiam vel augue. Vestibulum rutrum rutrum neque. Aenean auctor gravida sem. Praesent id massa id nisl venenatis lacinia. Aenean sit amet justo. Morbi ut odio.
Cras mi pede, malesuada in, imperdiet et, commodo vulputate, justo. In blandit ultrices enim. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Proin interdum mauris non ligula pellentesque ultrices. Phasellus id sapien in sapien iaculis congue. Vivamus metus arcu, adipiscing molestie, hendrerit at, vulputate vitae, nisl.
Aenean lectus. Pellentesque eget nunc. Donec quis orci eget orci vehicula condimentum. Curabitur in libero ut massa volutpat convallis. Morbi odio odio, elementum eu, interdum eu, tincidunt in, leo. Maecenas pulvinar lobortis est.
Phasellus sit amet erat. Nulla tempus. Vivamus in felis eu sapien cursus vestibulum. Proin eu mi. Nulla ac enim. In tempor, turpis nec euismod scelerisque, quam turpis adipiscing lorem, vitae mattis nibh ligula nec sem. Duis aliquam convallis nunc. Proin at turpis a pede posuere nonummy.
Integer non velit. Donec diam neque, vestibulum eget, vulputate ut, ultrices vel, augue. Vestibulum ante ipsum primis in faucibus orci luctus et ultrices posuere cubilia Curae; Donec pharetra, magna vestibulum aliquet ultrices, erat tortor sollicitudin mi, sit amet lobortis sapien sapien non mi. Integer ac neque. Duis bibendum. Morbi non quam nec dui luctus rutrum. Nulla tellus. In sagittis dui vel nisl. Duis ac nibh. Fusce lacus purus, aliquet at, feugiat non, pretium quis, lectus.
Suspendisse potenti. In eleifend quam a odio. In hac habitasse platea dictumst. Maecenas ut massa quis augue luctus tincidunt. Nulla mollis molestie lorem. Quisque ut erat. Curabitur gravida nisi at nibh. In hac habitasse platea dictumst. Aliquam augue quam, sollicitudin vitae, consectetuer eget, rutrum at, lorem. Integer tincidunt ante vel ipsum. Praesent blandit lacinia erat. Vestibulum sed magna at nunc commodo placerat. Praesent blandit. Nam nulla.
-
 @ 8cb60e21:5f2deaea
2024-09-05 19:48:32
@ 8cb60e21:5f2deaea
2024-09-05 19:48:32Part 1: Fundamentum Javascripti
1.1 Introductionis
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nullam euismod, nisi vel consectetur interdum, nisl nunc egestas nunc, vitae tincidunt nisl nunc euismod nunc. Sed euismod, nisi vel consectetur interdum, nisl nunc egestas nunc, vitae tincidunt nisl nunc euismod nunc.
javascript console.log("Salve, mundi!");1.2 Variabiles et Typi Datorum
Pellentesque habitant morbi tristique senectus et netus et malesuada fames ac turpis egestas. Integer convallis, nunc ac blandit tincidunt, ipsum augue tincidunt nunc, vitae tincidunt nisl nunc euismod nunc.
javascript var numerus = 42; let textus = "Lorem ipsum"; const CONSTANTIA = true;1.2.1 Typi Numerorum
Curabitur in libero ut massa volutpat convallis. Morbi odio odio, elementum eu, interdum eu, tincidunt in, leo.
javascript let integer = 10; let floatinum = 3.14; let scientificum = 2.998e8;1.2.2 Typi Textuum
Maecenas tristique, est et tempus semper, est quam pharetra magna, ac consequat metus sapien ut nunc.
javascript let textusBrevis = 'Carpe diem'; let textusLongus = "Quod erat demonstrandum"; let textusTemplatum = `Cogito, ${textusBrevis.toLowerCase()}, sum`;1.3 Operatores
Donec dapibus. Duis at velit eu est congue elementum. In hac habitasse platea dictumst.
```javascript let a = 5; let b = 3;
console.log(a + b); // Additio console.log(a - b); // Subtractio console.log(a * b); // Multiplicatio console.log(a / b); // Divisio console.log(a % b); // Modulus console.log(a ** b); // Potentia ```
1.4 Structurae Controli
Morbi non lectus. Aliquam sit amet diam in magna bibendum imperdiet. Nullam orci pede, venenatis non, sodales sed, tincidunt eu, felis.
1.4.1 Conditionales
```javascript let aetas = 20;
if (aetas >= 18) { console.log("Adultus es"); } else if (aetas >= 13) { console.log("Adolescens es"); } else { console.log("Puer es"); } ```
1.4.2 Iterationes
``javascript for (let i = 0; i < 5; i++) { console.log(Iteratio ${i}`); }let j = 0; while (j < 5) { console.log(
Dum iteratio ${j}); j++; } ```1.5 Exercitia Parti I
- Scribe programma quod convertat gradus Celsius in Fahrenheit.
- Crea algorithmum qui determinat si numerus est par vel impar.
- Implementa "FizzBuzz" pro numeris 1 ad 100.
-
 @ d830ee7b:4e61cd62
2024-09-04 07:29:41
@ d830ee7b:4e61cd62
2024-09-04 07:29:41Bitcoin ถือกำเนิดขึ้นในปี 2009 จากวิสัยทัศน์ของ Satoshi Nakamoto บุคคลหรือกลุ่มบุคคลปริศนา ที่ใฝ่ฝันถึง "เงินสดดิจิทัล" อิสระไร้พรมแดน ไร้การควบคุมจากรัฐบาล
ในช่วงแรกเริ่ม Bitcoin เป็นเสมือนเพชรดิบที่ซ่อนตัวอยู่ในเงามืด เป็นที่รู้จักกันเฉพาะในกลุ่มเล็กๆ ที่หลงใหลในเทคโนโลยีและศักยภาพอันไร้ขีดจำกัดของมัน
แต่แล้ว Bitcoin ก็เริ่มฉายแสงเจิดจรัส ดึงดูดความสนใจจากผู้คนทั่วโลก ราคาพุ่งทะยานอย่างรวดเร็ว บริษัทและบริการต่างๆ ผุดขึ้นมาราวกับดอกเห็ด
ทว่า.. เส้นทางสู่ความสำเร็จของ Bitcoin ไม่ได้โรยด้วยกลีบกุหลาบ Bitcoin ยังต้องเผชิญกับความท้าทายมากมาย ทั้งปัญหาทางเทคนิค ความขัดแย้งภายในชุมชนและการต่อสู้แย่งชิงอำนาจ
Blocksize Limit จุดเริ่มต้นของความขัดแย้งและสงคราม Big Blocks VS Small Blocks
ย้อนกลับไปในปี 2010 Satoshi Nakamoto ได้เพิ่ม "Blocksize Limit" ซึ่งเป็นข้อจำกัดขนาดของ Block ใน Bitcoin ไว้ที่ 1MB เพื่อป้องกันการโจมตีทางไซเบอร์ในยุคแรกเริ่ม
แต่เมื่อ Bitcoin ได้รับความนิยมมากขึ้น ธุรกรรมก็เพิ่มขึ้นอย่างรวดเร็ว Blocksize Limit 1MB เริ่มจะกลายเป็นปัญหา..
เกิดการถกเถียงอย่างดุเดือดในชุมชน Bitcoin ว่าควรเพิ่ม Blocksize Limit หรือไม่
ฝ่าย "Small Blockers" นำโดยนักพัฒนา Bitcoin Core ส่วนใหญ่ เชื่อว่า Blocksize Limit ควรคงที่ เพื่อรักษาความปลอดภัยและการกระจายอำนาจ พวกเขากล่าวอ้างว่า Big Blocks จะทำให้ Bitcoinรวมศูนย์อยู่ที่ Miners รายใหญ่ และยากต่อการรัน Full Nodes สำหรับผู้ใช้งานทั่วไป ซึ่งจะบั่นทอนความเป็น Decentralized ของ Bitcoin
ฝ่าย "Big Blockers" นำโดย Gavin Andresen ผู้สืบทอดตำแหน่งจาก Satoshi Nakamoto และ Mike Hearn เชื่อว่า Bitcoin ควรเติบโตอย่างไม่จำกัด "Big Blocks" คือคำตอบ พวกเขามองว่า Small Blocks จะทำให้ Bitcoin ไม่สามารถรองรับธุรกรรมที่เพิ่มขึ้น ค่าธรรมเนียมจะพุ่งสูงและ Bitcoin จะไม่สามารถใช้งานได้จริงในชีวิตประจำวัน..
ความขัดแย้งนี้สะท้อนให้เห็นถึงวิสัยทัศน์ที่แตกต่างกัน
Gavin Andresen ผู้ที่เคยได้รับความไว้วางใจจาก Satoshi รู้สึกผิดหวังที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit เขาเชื่อมั่นว่า Bitcoin ควรเป็นระบบการชำระเงินที่ใช้งานได้จริง รวดเร็ว และมีค่าธรรมเนียมต่ำ
Blockstream บริษัทผู้ทรงอิทธิพลและความกังวลเรื่องผลประโยชน์ทับซ้อน
ปี 2014 กลุ่มนักพัฒนา Bitcoin Core บางส่วนได้ก่อตั้งบริษัท Blockstream (นำโดย Adam Back) พวกเขาเน้นการพัฒนาเทคโนโลยี Blockchain และกลายเป็นที่มถกเถียงว่าอิทธิพลอย่างมากต่อ Bitcoin Core
Blockstream สนับสนุน "Small Blocks"
เช่นเดียวกับ Bitcoin Core พวกเขาพัฒนา "Sidechains" ซึ่งเป็น Blockchain แยกต่างหากที่เชื่อมต่อกับ Bitcoin เช่น Liquid Network Sidechains ซึ่งช่วยให้ Blockstream สามารถเก็บค่าธรรมเนียมจากธุรกรรมและขายบริการให้กับองค์กรหรือบริษัทต่างๆ ได้
ความสัมพันธ์อันใกล้ชิดระหว่าง Blockstream และ Bitcoin Core ทำให้เกิดความกังวลขึ้นในชุมชน Bitcoin ในขณะนั้นว่า Blockstream อาจมีผลประโยชน์ทับซ้อนและต้องการให้ Bitcoin คงขนาดเล็ก เพื่อผลักดันให้คนใช้งาน "Sidechains" ของพวกเขา
BitcoinXT และ Bitcoin Classic ความพยายามแก้ไข Blocksize ที่ถูกต่อต้าน
ปี 2015 Mike Hearn และ Gavin Andresen ตัดสินใจเสนอทางออกด้วยการสร้าง "BitcoinXT" ซอฟต์แวร์ Bitcoin เวอร์ชั่นใหม่ที่ เพิ่ม Blocksize Limit เป็น 8MB
แต่ BitcoinXT ถูกต่อต้านอย่างรุนแรงจากฝ่าย Small Blockers
Bitcoin.org เว็บไซต์หลักของ Bitcoin และ r/Bitcoin ฟอรัมหลักของ Bitcoin ได้เซ็นเซอร์ BitcoinXT ไม่ให้ปรากฏ เกิดการโจมตีทางไซเบอร์ที่มุ่งเป้าไปที่ BitcoinXT โดยตรง
Coinbase บริษัทแลกเปลี่ยน Cryptocurrency รายใหญ่ ประกาศสนับสนุน BitcoinXT แต่กลับถูกถอดออกจาก Bitcoin.org
ต่อมา Bitcoin Classic ถูกสร้างขึ้นเป็นอีกหนึ่งทางเลือก แต่ก็ล้มเหลวเช่นกัน
เนื่องจาก Bitcoin Core ยังคงมีอิทธิพลอย่างมากในชุมชน Bitcoin ในช่วงเวลานั้น..
Hong Kong Agreement และ New York Agreement ความพยายามประนีประนอมที่ไม่ลงตัว
ปี 2016 และ 2017 เกิดความพยายามในการประนีประนอมระหว่างฝ่าย Small Blocks และ Big Blockers ถึงสองครั้ง คือ "Hong Kong Agreement" และ "New York Agreement"
ทั้งสองข้อตกลงมีเป้าหมายที่จะเปิดใช้งาน SegWit และ เพิ่ม Blocksize Limit เป็น 2MB แต่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit ทำให้ข้อตกลงล้มเหลว
ความล้มเหลวของข้อตกลงทั้งสอง สะท้อนให้เห็นถึงความไม่ไว้วางใจระหว่างสองฝ่าย และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ
SegWit ก้าวสำคัญของ Bitcoin และจุดกำเนิดของ Bitcoin Cash
ในที่สุด SegWit ก็ถูกเปิดใช้งานบน Bitcoin ในเดือนสิงหาคม 2017
SegWit เป็น Soft Fork ที่เปลี่ยนแปลงวิธีการจัดเก็บข้อมูลใน Block เพื่อเพิ่มประสิทธิภาพและความปลอดภัย
SegWit ช่วยแก้ปัญหา "Transaction Malleability" ซึ่งเป็นช่องโหว่ด้านความปลอดภัย และปูทางไปสู่การพัฒนา "Layer 2 solutions" เช่น Lightning Network ในเวลาต่อมา..
อย่างไรก็ตาม.. กลุ่ม "Big Blockers" มองว่า SegWit ไม่ใช่ทางออกที่แท้จริงสำหรับปัญหาการขยายขนาด (พวกเขาต้องการขยายขนาดบล็อกบนเลอเยอร์ฐาน) พวกเขาไม่พอใจที่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit
ในเดือนสิงหาคม 2017 กลุ่ม "Big Blockers" ได้ทำการ "Hard Fork" Bitcoin เพื่อสร้าง "Bitcoin Cash (BCH)" ซึ่งอ้างว่ามุ่งสืบทอดจุดมุ่งหมายดั้งเดิมของ Bitcoin ในฐานะ "เงินสดดิจิทัล"
ความเสี่ยงด้านความปลอดภัย Bug ร้ายแรงใน Bitcoin Core และบทเรียนที่ได้รับ
ในเดือนกันยายน 2018 Awemany นักพัฒนา BCH ค้นพบ Bug ร้ายแรงใน Bitcoin Core (CVE-2018-17144) ซึ่งอาจทำให้เกิดภาวะเงินเฟ้อได้
Bug นี้เกิดจากความผิดพลาดในการเขียนโค้ด และอาจทำให้ผู้ไม่หวังดีสามารถสร้าง Bitcoin ปลอมขึ้นมาได้
Awemany ได้แจ้งเตือนนักพัฒนา Bitcoin Core อย่างเงียบๆ แทนที่จะใช้ประโยชน์จาก Bug นี้ แสดงให้เห็นถึงความรับผิดชอบของเขา และ Bug นี้ได้รับการแก้ไขอย่างรวดเร็ว
เหตุการณ์นี้แสดงให้เห็นถึงความสำคัญของการตรวจสอบโค้ดอย่างละเอียด และความจำเป็นของการมีนักพัฒนาจากหลายฝ่ายเพื่อช่วยกันตรวจสอบความถูกต้องของโค้ด
นอกจากนี้.. ยังเป็นเครื่องเตือนใจว่าแม้แต่ระบบที่ถูกออกแบบมาอย่างดีก็ยังมีความเสี่ยงด้านความปลอดภัย
Bitcoin Cash แตกแยก การ Hard Fork ครั้งที่สอง และบทบาทของ Craig Wright
ในเดือนพฤศจิกายน 2018 Bitcoin Cash (BCH) ได้แตกออกเป็นสองสาย คือ Bitcoin ABC (BCH) และ Bitcoin SV (BSV)
การ Hard Fork นี้เกิดจากความขัดแย้งระหว่างกลุ่มนักพัฒนา Bitcoin ABC นำโดย Amaury Séchet และกลุ่ม Bitcoin SV นำโดย Craig Wright ผู้ที่อ้างว่าเป็น Satoshi Nakamoto 🤔
ความขัดแย้งหลักคือเรื่องขนาดของ Block และทิศทางการพัฒนา Bitcoin Cash
กลุ่ม Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก ในขณะที่กลุ่ม Bitcoin ABC ต้องการปรับปรุง Bitcoin Cash ในด้านอื่นๆ เช่น Smart Contracts
Craig Wright มีบทบาทสำคัญในการผลักดัน Bitcoin SV เขาเชื่อมั่นว่า Bitcoin ควรเป็นไปตามวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto โดยเน้นที่การเป็น "เงินสดอิเล็กทรอนิกส์แบบ peer-to-peer"
การ Hard Fork นี้แสดงให้เห็นถึงความหลากหลายของความคิดเห็นในชุมชน Cryptocurrency และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ
นอกจากนี้.. ยังสะท้อนให้เห็นถึงความท้าทายในการกำหนดทิศทางของ Cryptocurrency ในอนาคตอีกด้วย
Bitcoin ในปัจจุบัน เส้นทางสู่ทองคำดิจิทัล และวิวัฒนาการของเทคโนโลยี
หลังจากการ Hard Fork ของ Bitcoin Cash
Bitcoin ได้ก้าวเข้าสู่ยุคใหม่ Bitcoin ได้รับการยอมรับมากขึ้นในวงกว้าง มีมูลค่าตลาดสูง และถูกมองว่าเป็น "ทองคำดิจิทัล" ที่สามารถใช้เก็บรักษามูลค่าในระยะยาว (Store of Value)
การพัฒนา Lightning Network เป็นก้าวสำคัญในการแก้ปัญหาเรื่องค่าธรรมเนียมและความเร็วในการทำธุรกรรม
Lightning Network เป็น "Second Layer" ที่สร้างขึ้นบน Bitcoin Blockchain ช่วยให้สามารถทำธุรกรรมได้รวดเร็วขึ้น มีค่าธรรมเนียมต่ำ และมีความเป็นส่วนตัวสูง
อย่างไรก็ตาม.. Lightning Network ยังคงต้องเผชิญกับความท้าทาย เช่น ปัญหาเรื่องการบริหารจัดการ Liquidity และความซับซ้อนในการใช้งาน
นอกจาก Lightning Network แล้ว ยังมีการพัฒนาเทคโนโลยีอื่นๆ ที่ช่วยเพิ่มขีดความสามารถของ Bitcoin เช่น Taproot ซึ่งเป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และ Schnorr signatures ซึ่งเป็น Digital Signature แบบใหม่ที่ช่วยลดขนาดของธุรกรรมให้เล็กลง
นอกจากนี้.. ยังเริ่มมีการพัฒนา DeFi (Decentralized Finance) บน Bitcoin และ Bitcoin Ordinals ซึ่งเป็นวิธีการใหม่ในการฝังข้อมูลลงใน Bitcoin Blockchain
Bitcoin ยังคงถูกนำไปใช้ในประเทศอื่นๆ นอกจาก El Salvador และมีความพยายามในการแก้ปัญหาความกังวลด้านสิ่งแวดล้อมจากการขุด Bitcoin
บทเรียนจากมหากาพย์แห่งวิวัฒนาการ
ประวัติศาสตร์ Bitcoin สอนให้เรารู้ว่า.. เทคโนโลยี Blockchain มีศักยภาพในการเปลี่ยนแปลงโลก แต่เส้นทางสู่ความสำเร็จนั้นก็ไม่ได้โรยด้วยกลีบกุหลาบ
ความขัดแย้ง การต่อสู้แย่งชิงอำนาจ และการตัดสินใจที่ยากลำบาก ล้วนเป็นส่วนหนึ่งของการเดินทาง
สิ่งที่สำคัญที่สุดคือ.. เราต้องศึกษา ทำความเข้าใจ และอาจมีส่วนร่วมในการกำหนดทิศทางของเทคโนโลยีนี้ เพื่อให้ Blockchain สามารถสร้างประโยชน์สูงสุดให้กับมวลมนุษยชาติต่อไป
เจาะลึกวิวัฒนาการของ Bitcoin การ Soft Forks, Hard Forks และมุมมองที่แตกต่าง
SegWit, Taproot และ Soft Forks อื่นๆ การปรับปรุง Bitcoin อย่างนุ่มนวล
Bitcoin Core ไม่ได้หยุดนิ่งอยู่กับที่ นักพัฒนาได้ทำงานอย่างต่อเนื่องเพื่อปรับปรุง Bitcoin ให้ดีขึ้น โดยใช้ "Soft Forks" ซึ่งเป็นการอัพเกรดที่เข้ากันได้กับซอฟต์แวร์เวอร์ชั่นเก่า
SegWit (Segregated Witness)
เปิดตัวในปี 2017 SegWit เป็นเหมือนการจัดระเบียบข้อมูลใน Block ใหม่ ย้ายส่วนที่เรียกว่า "Witness data" (ข้อมูลลายเซ็น) ออกไปไว้ข้างนอก ทำให้มีพื้นที่ว่างใน Block มากขึ้น รองรับธุรกรรมได้มากขึ้น และลดค่าธรรมเนียมได้ SegWit ยังช่วยแก้ปัญหา "Transaction Malleability" ซึ่งเป็นช่องโหว่ด้านความปลอดภัยและปูทางไปสู่การพัฒนา Lightning Network
Taproot
เปิดตัวในปี 2021 Taproot เป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และประสิทธิภาพของ Bitcoin Taproot ทำให้ธุรกรรมที่ซับซ้อน เช่น Smart Contracts มีขนาดเล็กลงและยากต่อการแยกแยะจากธุรกรรมทั่วไป
Soft Forks อื่นๆ ที่ Bitcoin Core ได้นำมาใช้ เช่น BIP 65 (CheckLockTimeVerify) และ BIP 112 (CSV) ช่วยเพิ่มความยืดหยุ่นในการใช้งาน Bitcoin และปูทางไปสู่การพัฒนาฟังก์ชันใหม่ๆ
Hard Forks เส้นทางที่แตกต่างและการถือกำเนิดของเหรียญใหม่
ในขณะที่ Soft Forks เป็นการอัพเกรดที่นุ่มนวล "Hard Forks" นั้นนับว่าเป็นการเปลี่ยนแปลงครั้งใหญ่ ที่ทำให้เกิดสาย Blockchain ใหม่และเหรียญใหม่
Bitcoin XT (2015)
เป็นความพยายามครั้งแรกในการเพิ่ม Blocksize Limit โดย Mike Hearn และ Gavin Andresen Bitcoin XT เสนอให้เพิ่ม Blocksize Limit เป็น 8MB แต่ถูกต่อต้านอย่างรุนแรง และไม่ประสบความสำเร็จ
Bitcoin Classic (2016)
เป็นอีกหนึ่งความพยายามในการเพิ่ม Blocksize Limit โดยเสนอให้เพิ่มเป็น 2MB แต่ก็ล้มเหลวเช่นกัน
Bitcoin Unlimited (2016)
เสนอให้ Miners สามารถกำหนด Blocksize Limit ได้เอง แต่มีข้อบกพร่องด้านความปลอดภัย และไม่เป็นที่ยอมรับในวงกว้าง
Bitcoin Cash (BCH) (2017)
เกิดจากการ Hard Fork ของ Bitcoin โดยกลุ่ม "Big Blockers" ที่ไม่พอใจที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit Bitcoin Cash เพิ่ม Blocksize Limit เป็น 8MB และมุ่งเน้นที่การเป็น "เงินสดดิจิทัล" ที่ใช้งานได้จริง
Bitcoin SV (BSV) (2018)
เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มที่นำโดย Craig Wright ผู้ที่อ้างว่าเป็น Satoshi Nakamoto Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก และกลับไปสู่วิสัยทัศน์ดั้งเดิมของ Bitcoin
Bitcoin ABC (2020)
เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มนักพัฒนา Bitcoin ABC ที่ต้องการเปลี่ยนแปลงกลไกการระดมทุน Bitcoin ABC ถูกเปลี่ยนชื่อเป็น eCash ในภายหลัง
มุมมองที่แตกต่าง Bitcoin ถูก "แย่งชิง" หรือไม่?
หนังสือ "Hijacking Bitcoin" โดย Roger Ver นำเสนอมุมมองที่แตกต่างจาก Bitcoin Maximalists
Roger Ver เชื่อว่า Bitcoin ถูก "แย่งชิง" โดยกลุ่มนักพัฒนา Bitcoin Core และ Blockstream ที่ต้องการเปลี่ยนแปลง Bitcoin จาก "เงินสดดิจิทัล" ให้กลายเป็น "สินทรัพย์เก็บมูลค่า"
Roger Ver วิพากษ์วิจารณ์ Bitcoin Core ในหลายประเด็น เช่น..
การไม่ยอมเพิ่ม Blocksize Limit
Roger Ver เชื่อว่า Bitcoin Core จงใจจำกัดการเติบโตของ Bitcoin เพื่อผลักดันให้คนใช้งาน Sidechains ของ Blockstream
การเซ็นเซอร์ข้อมูล
Roger Ver กล่าวหาว่า Bitcoin Core เซ็นเซอร์ข้อมูลและปิดกั้นการสนทนาเกี่ยวกับ Big Blocks บนแพลตฟอร์มต่างๆ
การต่อต้านนวัตกรรม
Roger Ver เชื่อว่า Bitcoin Core ต่อต้านนวัตกรรม และไม่ยอมรับการเปลี่ยนแปลงที่อาจทำให้ Bitcoin ดีขึ้น
การควบคุมโดยกลุ่มเล็กๆ
Roger Ver มองว่า Bitcoin Core ถูกควบคุมโดยกลุ่มเล็กๆ ที่ไม่คำนึงถึงความต้องการของชุมชน Bitcoin
Roger Ver สนับสนุน Bitcoin Cash ซึ่งเขาเชื่อว่าเป็น Bitcoin ที่แท้จริง ที่สืบทอดวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto
บทสรุป:
การต่อสู้แย่งชิง Bitcoin และการเกิดขึ้นของ Hard Forks ต่างๆ เป็นส่วนหนึ่งของวิวัฒนาการของ Cryptocurrency
มุมมองที่แตกต่าง ความขัดแย้ง และการแข่งขัน ล้วนเป็นแรงผลักดันให้ Bitcoin และ Cryptocurrency อื่นๆ พัฒนาต่อไป
สุดท้ายแล้ว.. เราคงไม่อาจตัดสินได้ว่าฝ่ายใดคิดถูกหรือฝ่ายใดผิด
"เสียงของตลาด จะช่วยทำหน้าที่ให้คำตอบนั้นกับเรา ว่าแท้ที่จริงแล้วผู้คนกำลังต้องการอะไรกันแน่..
ลองมองไปที่มูลค่าของแต่ละแนวคิด มองไปที่ Network effect และกำลังการขุด มองไปที่การยอมรับและความเชื่อมั่นของผู้คน เหล่านี้ล้วนเป็นข้อบ่งชี้ที่เห็นได้ง่าย..
เพราะนั่นคือเสียงแห่งการเพรียกหาอิสรภาพ และอธิปไตยทางการเงินที่แท้จริง..
— Jakk Goodday
-
 @ 1739d937:3e3136ef
2024-09-04 07:23:12
@ 1739d937:3e3136ef
2024-09-04 07:23:12This is the sixth in a series of weekly(ish) updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
Sorry about the very late update this week. Catching up on everything after a week in Riga for Nostriga and Baltic Honeybadger took a bunch of time, every other moment was spent coding. 👨💻
The response at Nostriga to NIP-104 and my two talks on the subject were overwhelmingly positive. It was very helpful to spend time with other devs going through the spec in detail. We found a few minor improvements and clarifications but no major issues surfaced. Thanks to nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49, nostr:npub1lunaq893u4hmtpvqxpk8hfmtkqmm7ggutdtnc4hyuux2skr4ttcqr827lj, and nostr:npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr in particular for the lengthly interrogations and nostr:npub1wmr34t36fy03m8hvgl96zl3znndyzyaqhwmwdtshwmtkg03fetaqhjg240 for the introductions.
Last week, I started work on a reference implementation of the spec. It's still early but going quickly.
My PR adding support for secp256k1 was also merged into the hpke-rs library yesterday. That's one more step in the right direction towards having secp256k1 ciphersuite support.
The NIP
If you haven't already, check out my talk; The Past and Future of DMs and Group messaging on Nostr. This was a basic overview of the various DM and group messaging schemes and talks a little about the progress on NIP-104. I believe there is a recording of the technical talk on the spec but it hasn't yet been released. I'll link it up when it is.
At this point I've been discouraging anyone from trying to implement the NIP quite yet. As I mentioned above there are a few adjustments that need to be made and a few open questions that I'm working on answering with my implementation (which I'm very happy to have contributors on). My plan at the moment is to do this first implementation with the default ciphersuite that MLS already supports while I continue to work on the dependencies to get secp256k1 support across the board.
The Implementation
I've started on a cross-platform native client that will run on Mac, Windows, Linux, iOS, and Android. Think of it as Signal or Telegram but over Nostr. I hope that this will not only become the reference implementation for other client developers but also will be one of the most secure and privacy focused clients in the Nostr ecosystem. Building it has already been helpful in clarifying some of the more complex implementation details in the NIP. It's still early but I'll have more to share on this in the coming weeks.
HPKE-RS
My PR to add support for secp256k1 is merged!
Onward and Upward
Thanks again to everyone for the support and feedback on this stuff at Nostriga. It was hugely motivating to hear the kind words, have you introducing me to people that could help, and spending time giving me feedback! This community is the best. 🫂
-
 @ e27ae11e:e0c36580
2024-09-05 16:28:24
@ e27ae11e:e0c36580
2024-09-05 16:28:24In the present computerized age, having a website is essential for any business, including tradies. Yet, it's not just about having a website; about having a website looks perfect and functions admirably on all gadgets. This is where responsive web design comes in. We should investigate why responsive web design is fundamental for tradies and how it can help your business. Visit us > Best Tradie Web Design Key takeaways Mobile-Friendly is a Must: Guarantee your website looks perfect and functions admirably on cell phones and tablets to draw in additional clients.
Better Insight: A responsive site is simpler to utilize, making guests blissful and bound to reach you.
Higher Google Rankings: A versatile website can assist you with seeming higher in list items, carrying more traffic to your webpage.
Set aside Time and Cash: Overseeing one responsive site is less expensive and easier than having separate locales for various gadgets. Overview Responsive web design is a methodology that does a good job for your website and capacity suitably on any contraption, whether it's a PC, tablet, or cell. It suggests your website will thusly change its format and content to fit the screen size of the contraption being used. This ensures a predictable and beguiling experience for your visitors, paying little heed to how they access your site. What difference Does It Make for Tradies? 1. Increased Versatile Utilization More individuals are utilizing their cell phones to peruse the web. Potential clients could look for your administrations while in a hurry. On the off chance that your website isn't versatile, you could lose those possible clients. Responsive web design guarantees that your webpage looks perfect and functions admirably on cell phones, making it simpler for guests to find and reach you. Tip: Check your website analytics to see how many visitors are accessing your site from mobile devices. Use this data to prioritize mobile optimization. 2. Better Client Experience A responsive website gives a superior client experience. At the point when guests can undoubtedly explore your site and find the information they need without zooming in or scroll on a level plane, they are bound to remain longer and investigate your administrations. A positive client experience can prompt more requests and appointments. Tip: Use a clean and simple design that is easy to navigate on all devices. Avoid clutter and ensure that buttons and links are easy to tap 3. Improved Website optimization Rankings Web crawlers like Google focus on versatile websites. In case your site is responsive, it will rank higher in list things. This infers more prominent detectable quality for your business and more potential clients believing that you are on the web. Higher rankings can basically uphold your web-based presence and attract more busy time gridlock to your website. Tip: Guarantee your website content is applicable and helpful to your interest group. Excellent substance further develops Search engine optimization and keeps guests locked in. 4. Cost-Powerful Keeping a single responsive website is smarter than having separate objections for workspace and flexible clients. With responsive web design, you simply need to regulate and invigorate one website, saving you time and money long term. Tip: Consistently update your website's substance and design to keep it new and important, guaranteeing it stays viable and cost-productive. 5. Consistent Marking A responsive website guarantees that your marking stays steady across all gadgets. Whether a client visits your site on a PC or a cell phone, they will see similar design, tones, and logo. Steady marking assists fabricate trust and acknowledgment with your crowd. Tip: Utilize a similar variety plan, logo, and textual styles across all variants of your website to keep a predictable brand personality.
Make Your Website Responsive 1. Pick a Responsive Subject If you are using a website producer or a substance the chiefs system like WordPress, pick a responsive subject. These subjects are designed to be dynamic and will consequently change in accordance with various screen sizes. Tip: Preview the theme on different devices before making a final decision to ensure it meets your needs. 2. Optimize Pictures and Media Guarantee that pictures and media records are improved for quick stacking on all gadgets. Enormous pictures can dial back your site, particularly on cell phones. Use devices to pack pictures without forfeiting quality. Tip: Use image compression tools like TinyPNG or JPEGmini to reduce the file size of your images without losing quality 3. Simplify Route Ensure your website's route is basic and simple to use on all gadgets. Utilize clear menus and buttons that are not difficult to tap on a touchscreen. Try not to utilize an excessive number of connections or complex dropdown menus that can be hard to explore on a little screen. Tip: Use a simple, easy-to-use menu that adapts to different screen sizes. A hamburger menu can be effective for mobile devices. 4. Use Adaptable Designs Design your website utilizing adaptable formats that can change in accordance with various screen sizes. This can be accomplished utilizing CSS (Flowing Templates) to make a liquid framework design that changes in light of the gadget's screen size. Tip: Avoid fixed-width layouts. Instead, use percentage-based widths that allow your content to resize fluidly. 5. Test Your Website Reliably test your website on different contraptions and screen sizes to promise it looks perfect and works fittingly. There are online instruments available that can help you see how your webpage appears on different devices. Tip: Utilize online instruments like Google's Dynamic Test and Browser Stack to perceive how your website looks and works on changed gadgets and programs. Conclusion Responsive web design is essential for tradies that need to attract and hold clients in the present high level world. It ensures that your website looks great and works honorably on all devices, giving you an unrivaled client experience, further fostering your Web enhancement rankings, and saving you time and money. By picking a responsive topic, streamlining pictures, improving on route, and testing your webpage consistently, you can make a responsive website that assists your exchange business with flourishing on the web. Putting resources into responsive web design isn't just about staying aware of patterns; it's tied in with giving the most ideal experience to your guests and guaranteeing your business stays serious. In this way, make the strides today to make your website responsive and watch your web-based presence develop!
-
 @ 469fa704:2b6cb760
2024-09-05 15:06:49
@ 469fa704:2b6cb760
2024-09-05 15:06:49The Evolution of Web 3.0: Bitcoin's Role in Decentralizing the Internet
Introduction to Web 3.0
Web 3.0, often referred to as the decentralized web, represents the next phase in the evolution of the internet. Unlike its predecessors, Web 3.0 aims to redistribute control from centralized entities back to individual users through technologies like blockchain, cryptocurrencies, and decentralized applications (dApps). This shift promises a more democratic internet where users control their data, identity, and digital destiny.
The Bitcoin Protocol: A Foundation for Web 3.0
Bitcoin's Influence on Decentralization
Bitcoin, introduced in 2008, can be seen as a precursor to Web 3.0 due to its decentralized nature. The Bitcoin protocol introduced the world to blockchain technology, a decentralized ledger that records all transactions across a network of computers. This technology underpins Web 3.0's ethos by:
- Promoting Decentralization: Bitcoin's network operates without a central authority, showcasing how internet services could run on similar principles, reducing the power of centralized tech giants.
- Enhancing Security and Privacy: Through cryptographic means, Bitcoin ensures that transactions are secure and pseudonymus, a feature integral to Web 3.0's vision of user-controlled data.
Scalability and Functionality Challenges
However, Bitcoin's protocol wasn't designed on the base layer with the complex applications of Web 3.0 in mind. Its primary function as a digital currency means:
- Scalability Issues: Bitcoin's blockchain has limitations in transaction speed and volume, which might not suffice for a fully realized Web 3.0 environment where millions of micro-transactions could occur seamlessly.
- Limited Smart Contract Capabilities: Bitcoin's scripting language isn't as versatile as platforms like Ethereum, which are designed to support a broader range of decentralized applications.
Expanding Bitcoin's Role with Layer 2 Solutions
To bridge these gaps, developers are working on Layer 2 solutions like the Lightning Network for faster transactions, and projects like Stacks aim to bring smart contract functionality directly to Bitcoin. These innovations suggest that while Bitcoin might not be the sole backbone of Web 3.0 yet, it can significantly contribute to its infrastructure. In the long term, the question is whether we need more than one network, I mean, we don't have multiple Internets today. The market will probably decide in favor of the strongest and most secure network, and Bitcoin is by far that.
Web 3.0 Beyond Bitcoin
A Broader Blockchain Ecosystem
At the moment Web 3.0 encompasses by far more than just Bitcoin. It includes:
- Ethereum and Smart Contracts: Ethereum's introduction of smart contracts has been pivotal, allowing for decentralized applications that can interact in complex ways, far beyond simple transactions.
- Other Blockchains: Platforms like Solana, Sui, and Near are gaining traction for their high throughput and lower costs, addressing some of Bitcoin's limitations on the base layer.
The Cultural and Economic Shift
The move towards Web 3.0 isn't just technological but cultural. There's a growing sentiment, reflected in posts on platforms like X, that users are ready for a change where they own their digital presence. Here's some background based on general knowledge and trends up to 2024:
Cultural Shift:
- Distrust in Centralized Institutions: There's been a growing distrust in traditional centralized institutions like banks, governments, and large corporations. This distrust stems from various scandals, data breaches, privacy concerns, and perceived inefficiencies or corruption. Posts on platforms like X or even more on Nostr reflect this sentiment, where users often discuss the diminishing trust in these institutions.
- Rise of Individual Empowerment: Culturally, there's a move towards empowerment of the individual, facilitated by technology. Social media, blockchain, and other decentralized technologies give individuals tools to bypass traditional gatekeepers in finance, media, and more. This shift champions the idea that individuals should have more control over their data, finances, and digital identity.
- Identity and Community: Decentralization also touches on identity politics and community governance. There's a trend towards localism or regionalism where communities seek more control over their governance, which can be seen in movements for local autonomy or even secessionist sentiments in various parts of the world.
- Cultural Movements: Movements like the maker culture, DIY (Do It Yourself), open-source software, and even the gig economy reflect a cultural shift towards decentralization where individuals or small groups can produce, create, or work independently of large entities.
Economic Shift:
- Decentralized Finance (DeFi): DeFi represents one of the most tangible shifts, aiming to recreate and potentially improve financial systems outside of traditional banking. This includes lending, borrowing, and earning interest in a trustless, permissionless environment, primarily using blockchain technology.
- Cryptocurrencies and Tokenization: The rise of cryptocurrencies like Bitcoin and Ethereum symbolizes a move away from centralized monetary systems. Tokenization of assets, from art (NFTs - Non-Fungible Tokens) to real estate, embodies this shift, allowing for fractional ownership and reducing the barriers to investment.
- Globalization vs. Localism: While globalization has interconnected economies, there's a counter-trend where economic decentralization supports local economies. This can be seen in the push for local currencies, community-supported agriculture, or local energy production like solar microgrids.
- Work and Employment: The gig economy, remote work, and digital nomadism are part of this economic shift. Platforms enabling freelance work decentralize employment, moving away from traditional office environments and 9-to-5 jobs.
General Observations:
- Technology as an Enabler: Blockchain, the internet, and advancements in communication technology are pivotal in this shift. They provide the infrastructure necessary for decentralization to occur at scale.
- Political Implications: Economically, this shift maybe challenges existing power structures, potentially leading to regulatory battles as seen with cryptocurrencies. Culturally, it might lead to a redefinition of nationalism, community, and individual rights in the digital age.
- Challenges: Despite its promise, decentralization faces hurdles like scalability issues, regulatory pushback, the digital divide, and the potential for new forms of centralization (e.g., large crypto exchanges becoming new central authorities).
Conclusion: Bitcoin's Place in Web 3.0
Bitcoin's protocol ignited the spark for a decentralized internet, but Web 3.0 is evolving into a multifaceted ecosystem where Bitcoin might play a crucial, though not yet exclusive, role. The integration of Bitcoin with newer technologies and platforms could see it becoming a fundamental layer in the Web 3.0 stack, particularly in areas of value transfer and as a store of value within decentralized finance (DeFi).
As we progress, the synergy between Bitcoin's proven security and stability, combined with the innovation of other blockchain technologies, might just be the blend needed for Web 3.0 to achieve mainstream adoption, ensuring the internet becomes more open, secure, and user-centric. As stated before, the market will probably decide in favor of the strongest and most secure network, and Bitcoin is by far that.
-
 @ 361d3e1e:50bc10a8
2024-09-05 12:58:30
@ 361d3e1e:50bc10a8
2024-09-05 12:58:30He wished Pfizer's vaccine naysayers screwed, and now he's screwed
uk #music #vaccine #covid #sideeffects #health #freespeech
-
 @ e0e92e54:d630dfaa
2024-09-04 04:13:19
@ e0e92e54:d630dfaa
2024-09-04 04:13:19This is a copy of the email received from newsletter@Rumble.com

Free Speech Under Attack -- A Note from the CEO of Rumble
Dear Rumble Users,
I don't typically send messages to our users through email, but red lines have been crossed. There have been major developments with free speech platforms, and I feel it’s important to let everyone know what is going on and how you can help Rumble.
Rumble is no longer available to the citizens of Brazil, joining the ranks of France, Russia, and China. From media reports, Brazil no longer has Elon Musk's X due to attacks on free speech by Alexandre De Moreas, a justice of Brazil's Supreme Federal Court.
World powers don’t want Rumble, they don’t want X, they don’t want Telegram, and they don't want Truth Social. They want to control information, but our companies won’t let them.
There are no other large companies fighting for freedom like we are. We put everything on the line for it, and the Telegram CEO was recently arrested for it.
Advertisers boycott our companies to try and cut our economic lifeline, but they underestimate our support among the people.
The people keep us alive and keep us going.
If you want to help us, join Rumble Premium. If Rumble Premium gets big enough, you help us change the game and fight for freedom of expression.
We are also offering a $10 dicount for any new annual subscribers when they use the promo code "brazil".
Sincerely,
Chris Pavlovski Chairman and CEO of Rumble
 444 Gulf of Mexico Dr.
Longboat Key, FL 34228, USA.
444 Gulf of Mexico Dr.
Longboat Key, FL 34228, USA. -
 @ 96203d66:643a819c
2024-09-04 03:42:31
@ 96203d66:643a819c
2024-09-04 03:42:31[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
-
 @ a012dc82:6458a70d
2024-09-05 09:46:29
@ a012dc82:6458a70d
2024-09-05 09:46:29Table Of Content
-
What are the factors driving this adoption?
-
What are the potential benefits of widespread Bitcoin adoption?
-
What are the potential challenges to Bitcoin adoption?
-
Conclusion
-
FAQ
The cryptocurrency market has been on a rollercoaster ride over the past few years, with Bitcoin emerging as the undisputed king of the digital currencies. Despite facing intense scrutiny and skepticism from traditional financial institutions, Bitcoin has continued to gain traction among investors, traders, and even mainstream businesses. The future of Bitcoin and the wider cryptocurrency industry has been the subject of much speculation, with many analysts making bold predictions about its potential growth and impact.
According to the report, the analyst predicts that Bitcoin will become the primary global currency by 2025, with an estimated 50% adoption rate. This means that half of the world's population could potentially be using Bitcoin as their main currency by 2025, marking a significant shift in the way we think about money and finance.
What are the factors driving this adoption?
The analyst attributes this projected surge in Bitcoin adoption to several key factors. These include:
Increased mainstream acceptance: More and more businesses are starting to accept Bitcoin as a form of payment, including some major players like Microsoft, Tesla, and PayPal. This increased acceptance is helping to legitimize Bitcoin and make it more accessible to the average person.
Growing distrust in traditional finance: The 2008 financial crisis and subsequent economic instability have eroded trust in traditional financial institutions. Bitcoin offers a decentralized alternative to the current system, making it an attractive option for those seeking greater financial autonomy and security.
Technological advancements: The development of blockchain technology and other innovations are making Bitcoin more secure, faster, and easier to use. This is helping to remove some of the barriers to adoption and make Bitcoin a more viable option for everyday use.
What are the potential benefits of widespread Bitcoin adoption?
The potential benefits of widespread Bitcoin adoption are numerous and far-reaching. These include:
Increased financial freedom: Bitcoin offers a level of financial freedom and autonomy that is impossible with traditional currencies. Users can send and receive money anywhere in the world without having to go through intermediaries or deal with cumbersome regulations.
Lower transaction fees: Bitcoin transactions are typically much cheaper than traditional banking fees, making it a more cost-effective option for businesses and individuals.
Greater security: Bitcoin's decentralized nature makes it more resistant to hacking and fraud than traditional banking systems. This offers a higher level of security and protection for users.
What are the potential challenges to Bitcoin adoption?
While the potential benefits of widespread Bitcoin adoption are exciting, there are also several potential challenges that must be overcome. These include:
Lack of regulation: Bitcoin operates outside of traditional financial systems and is largely unregulated. While this offers greater autonomy and freedom, it also makes it more susceptible to fraud and other criminal activity.
Volatility: Bitcoin's value is notoriously volatile, making it a risky investment option for some. This could make it more difficult to convince everyday users to adopt Bitcoin as their primary currency.
Technical barriers: While technological advancements are making Bitcoin more accessible, there are still some technical barriers that could prevent widespread adoption. These include issues with scalability, user interfaces, and education.
Conclusion
The analyst's forecast of mind-blowing Bitcoin adoption in 2025 is certainly an exciting prospect, and one that has the potential to transform the world of finance as we know it. While there are certainly challenges to be overcome, the benefits of widespread Bitcoin adoption are clear, and it is clear that more and more people are starting to recognize the potential of this revolutionary digital currency. Whether Bitcoin will ultimately become the primary global currency by 2025 remains to be seen, but it is clear that it is here to stay, and that it will continue to play an increasingly important role in the world of finance.
FAQ
Can Bitcoin be used as a form of payment? Yes, many businesses and merchants now accept Bitcoin as a form of payment, and it is becoming increasingly common.
Is Bitcoin safe to use? Bitcoin is generally considered to be a safe and secure form of payment, thanks to its decentralized nature and strong cryptographic protocols. However, as with any form of payment, there are some risks involved, and users should take appropriate precautions to protect their funds.
What is the potential impact of widespread Bitcoin adoption? The potential impact of widespread Bitcoin adoption is huge, as it could fundamentally change the way we think about money and finance. It could also have significant implications for traditional financial systems and institutions.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 3b7fc823:e194354f
2024-09-04 01:33:21
@ 3b7fc823:e194354f
2024-09-04 01:33:21Nyms, Personas, and Digital Identity
GHOSTn
If you want #privacy then embrace compartmentlization and obscuration in your digital life. Get used to having multiple identities that you can switch between for various needs.
Your legal "matrix" name that pays taxes and has no controversal opinions or associations. Don't try to obscure this person. They are a open book. Put your best foot forward. Show them what you want them to see.
Your private online persona. You let your hair down, have hot takes on social media, purchase legal but potentially embarrassing items or just have hobbies and associations that you are not ashamed of but don't want to advertise for some reason. You use a VPN and no kyc sudo anonymous accounts. Have fun but don't go crazy, know that on a long enough timeline this persona will be linked back to you. The more connections and data that you put out there the easier this will be.
Your anonymous nym that only uses #tor, VMs, hidden drives, and rarely used accounts. Plausible deniability is baked in. Used by dissidents, freedom fights, truth to power, and anyone in oppressive regimes.
Finally you have your Nemo. This person does not exist. No name, no files and only uses #Tails or disposable systems that does not leave a trace. Not everyone would ever have a need for a Nemo but it is good to know how to just in case you ever do.
-
 @ 3b7fc823:e194354f
2024-09-04 00:26:48
@ 3b7fc823:e194354f
2024-09-04 00:26:48Encryption is the promethium fire that the cypherpunks secured from heaven for me and you. It is our sacred duty to use and advance that in the world. Encryption is so powerful that governments tried to keep it away from the people and to this day have tried to weaken and backdoor it at every turn.
So what is encryption?
It is a deep deep rabbit hole and involves a lot of numbers but in a nutshell it uses math to scramble up the data of your file so it is gibberish and can't be read without decrypting it back to regular data. Encryption technology has continued to advance over time and cracking technology to break the encryption has as well. For our purposes all you really need to remember is to use modern cyphers and your encryption is really only going to be as good as the password (use a passphrase) strength you are using to lock it down with.
BEGINNER LEVEL - Encrypt your phone and computer.
People walk around with their whole lives on their phone. Protect it.
-phone: Congratulations, if you already have a lock screen set on either your iPhone or Android device then device encryption is enabled. If your lock screen password is only 4 digits then we still have work to do. Four digits is only about 10,000 combinations and fairly easy to crack. I believe it only took them about 40 minutes to crack the iPhone of the attempted Trump shooter. Go into settings and set it up for 6 digits or for extra credit use a alphanumeric password.
After your phone then your personal computer probably has the most important data to you. Banking records, tax documents, photos, etc. Encrypt your drive.
-Windows: from Settings, select Privacy security -> Device encryption. Just follow the prompts.
-Apple: from Apple icon, select System Preferences -> Security & Privacy icon. Click "Turn On FileVault".
-Linux: most distros gives you the option during installation. If you didn't do so then search for how to enable it after the fact based on your distribution.
Awesome sauce. You have achieved minimum status.
ADVANCED LEVEL - Encrypt individual files.
You already encrypted your computer but guess what, once you start up your computer and log in the key is stored in RAM for as long as it stays on. The beginner level encryption protects your computer when it is off and it means no one can just steal your hard drive and access your files. This is good, but what if someone grabs you while you're sitting there working on it? What if you leave it in sleep mode and not turned off? Then that whole disk encryption is not really going to help you.
What if you had individual files that you consider more secret than the others? That finance spreadsheet or that special pic your spouse sent you? That's where individual file encryption comes in. You are just scrolling nostr when they grab you, your computer is on, and unlocked, but those special files are still safely encrypted.
I will share with you one of my favorite small programs: Picocrypt.
Download the Paranoid pack and store it in multiple drives, email accounts, and cloud storage. That way you will always have a copy to decrypt any files that you stored away.
Use it to encrypt any files that you feel need extra attention. It is also very useful for encrypting any files that you intend to store online in cloud storage. You do encrypt your files that are stored online don't you? Yes, even with the company that offers "encrypted" storage. Don't trust their encryption, use your own.
EXPERT LEVEL - Encrypt containers and hidden containers.
What if you want to encrypt several files and keep them all together in like a folder or container? That's where Veracrypt comes in. Free, open source, cross platform, and powerful.
Veracrypt allows you to create encrypted containers from any file that act like individual drives that can be mounted or unmounted as needed. You can name these files anything that you want, move them around or delete like any file, and make as many as you want. This allows you to have compartmentation of your files and drives.
Next trick, Veracrypt allows you to create a hidden container inside that container. Enter one passphrase and you open the encrypted container. Enter a different passphrase and you open a different hidden container.
This allows deniability. When they grab you and start pulling your fingernails off until you tell them the password to open the encrypted container, give it to them. They don't have to know that there is another hidden one under that.
These features allow you to do all sorts of interesting things only limited by your need and imagination.
What if you have a container named as some random config file in your /etc folder? What if you just encrypted a removable storage drive? What if you have multiple hard drives on your computer that have multiple containers and hidden containers? What if you have a hidden container that can only be accessed from booting up in a amnesiac OS like Tails leaving no trace that the files exist or trail that they were ever accessed? Go crazy, have fun.
NEMO - Failsafe
Nemo has no files, encrypted or otherwise. If they did you couldn't prove it. Nemo does use something like Tails that retains no memory from boot to boot.
Nemo also uses a failsafe. A simple lanyard attached to the flashdrive running the OS and the other end around their wrist while they work. When you try to separate them from the computer the flashdrive pulls out and everything is gone.
Using these programs you can create a layered and compartmentlized approach to your encryption scheme. There are also plenty of other encryption programs to check out such as Cryptomator, AES Crypt, etc
Last point and most important: Encryption is only as good as the passphrase you use to lock it down. Use a shitty password and it doesn't matter how uncrackable your encryption is.
-
 @ 8cb60e21:5f2deaea
2024-09-03 22:26:25
@ 8cb60e21:5f2deaea
2024-09-03 22:26:25 -
 @ 8cb60e21:5f2deaea
2024-09-03 21:58:26
@ 8cb60e21:5f2deaea
2024-09-03 21:58:26Lesson 3: Arrays, Objects, and Callbacks
Arrays: Lists of Things
Arrays are ordered lists of values. They're perfect for storing multiple related items, like a list of your favorite cat toys:
javascript var catToys = ["mouse", "ball", "laser pointer"]; console.log(catToys[0]); // Prints "mouse"Objects: Grouping Related Information
Objects allow you to group related information together. They're like detailed profiles for each of your cat friends:
```javascript var myCat = { name: "Fluffy", age: 3, favoriteFood: "tuna" };
console.log(myCat.name); // Prints "Fluffy" ```
Callbacks: Doing Things Later
Callbacks are functions that are executed after another function has finished. They're useful for handling asynchronous operations, like waiting for your cat to finish eating before giving it a treat:
```javascript function feedCat(callback) { console.log("Feeding the cat..."); setTimeout(function() { console.log("Cat has finished eating!"); callback(); }, 2000); }
feedCat(function() { console.log("Time for a treat!"); }); ```
This code simulates feeding a cat, waiting 2 seconds, and then giving it a treat.
Remember, learning JavaScript is a journey. Take your time, practice regularly, and soon you'll be coding like a pro cat!
-
 @ d543c820:aa8001e7
2024-09-05 09:03:02
@ d543c820:aa8001e7
2024-09-05 09:03:02皮草两事
前日与朋友聊天,谈起时下留下的一种扮演了某种人格的 AI(有个时髦的名字,叫 “智能体”),蓦地想起英伦法学家边沁(Jeremy Bentham)。第二日,又联想起别的事来,因有此文。
“皮草”,在现代中文是指 “以动物(连)皮(带)毛制成的服装”,因其奢侈和暖和受人追捧。但也有关爱动物的人士批评其制作过程过于残忍。
但在古代中文中,这词可作别的意思:“皮以实草”、“剥皮揎草”。指的是把皮剥下来,把草填充进去,做成玩偶。
据说,明朝的创建者朱元璋(1328-1398),就制定过这样的刑罚:将贪腐的官员,处以剥皮之刑,然后以草填充,做成人偶,放在其继任官员的公堂旁边,以示警戒。
你可以想象,这种刑法是多么残酷。其恐怖、血腥的程度,与历史上有名的酷刑炮烙、分尸相比,是不遑多让的。所以,其在朱元璋统治的时代结束后,也并未被继续施行。有明一代,此种残酷刑罚的一个回响是在万历时代(1573-1620),有名的清官海瑞主张恢复这种刑罚,以整肃官员中贪腐的风气。
那么,朱元璋为什么要对贪腐官员制定如此残酷的刑罚呢?
小说家金庸先生的读者可能会认为,这跟其宗教信仰(明教)有关。明教即拜火教(琐罗亚斯德教),其本身推崇互帮互助,且憎恶贪官污吏,有点公社主义的味道。然而,这是说不通的 。因为明教本身有反体制倾向,不信任政治权力可被用来改善平民的生活。而朱元璋一以贯之地追求统治权力,自然不可能在实质上信奉此种理念。
(插句话,明代创建者与明教有关,此说始创于吴晗,被金庸先生拿去放在小说中,有了很大影响。然而,近些年的学术界,已开始反对这种理论,认为 “明” 的国号可能来自佛教经典,或来自儒家经典《易经》。)
也有人会认为,这跟朱元璋的出身有关。他出身贫苦,也曾流离失所,也许饱受贪官污吏欺压,因此格外痛恨他们。
我的想法是,这只是因为与前代帝王相比,朱元璋有格外疯狂的机器乌托邦狂想。朱元璋为明朝制定的制度,是格外机械、死板,而且严苛的。首先,其要求编订各地域的人口户籍 —— 这不出奇,中国从秦朝开始就这样做了 —— 然后,有趣的东西来了:他要求给这些人口按照经济条件分组,每组有固定的力役和纳税义务,以年为单位;以户为最小单位,每 10 个单位合并成一个大单位,层层往上合并;每一组的带头人都每年轮换一次,这个带头人要在该年中完成经济统计并带领其组内成员完成力役(比如修城墙、挖运河)和纳税(交粮)义务。与此同时,迁徙自由是禁止的,良民必须在其土地上完成其义务,而不能 “流窜” 到其它地方,官员的任务之一是将境内的流民遣返回原籍、保证境内的民不要流窜到其它地方。而这些力役和纳税义务,也是跟地域高度捆绑的,它们以就近的原则,被分配给所在地的城市和军队,而不是经过行政机构的统一收发管理。
也就是说,朱元璋希望把偌大的中国变成一台机器,所有人(主要是农民)在其出生的地域上为劳役和纳税而劳作,以恒久不变的速率为一个行政系统和军事系统提供养料,然后朱家江山永保稳定和太平。—— 而统治者,君主,将使用这套系统中形成的统计资料,来精确地了解每一个地区的实情,然后施行统治,保持系统的运行。
对于这样一个系统而已,统计资料的精确性,是具有第一位的重要性的。它决定了统治者到底能不能获得地方的实情,而不被自己的官僚蒙蔽。于是,贪腐 —— 为了个人私利,甚至不是什么特别大的利益,而弄虚作假,比如虚报产出以求减免税务、将经济富裕的农民反而分到税务负担较轻的组中 —— 就成了一个最多发、最难对付的顽疾。官员稍微不认真,产生的偏差就会不断叠加,然后积累出完全失实、无用的记录。这就是为什么贪腐的官员要被处于如此残酷的刑罚 —— 要用最残酷的刑罚、最血腥的展示,让他们在统治以机器人为理想模板的人群时,自己也成为机器人。—— 只有皇帝可以是个活人。
(《万历十五年》的作者黄仁宇认为明代的一大问题在于其制度阻碍了技术的发展,例如,军队的粮食是定点向某个村镇收取的,并由村镇自己负责押韵到军队驻地,这是 “散收散支”;如果交到行政机关处集中收取集中分发,就可以发展物流技术、保险技术云云。我认为,这是浅见。)
那么,十四世纪的朱元璋,跟边沁(1747-1832),怎么会扯上关系呢?
是因为边沁也曾设想过一种 “皮草” 的用途。他希望的是,有卓越成就的人物,可以在死后将自己制作成人偶(原描述为 “auto-icon”),摆放在公共空间里,(最好还能播放其生前录下的声音),起到教育的作用。
边沁自己也实践了这种想法。他在死前立下遗嘱,将自己的身体托付给一个好朋友,嘱咐其将自己制作成 auto-icon,要求以一个带玻璃的木盒子盛装,将自己做成坐姿,配上自己生前使用的椅子,还要身着正装,配上手杖。
事实上,边沁的 auto-icon 还真的是在保留了骨骼的前提下以草填充的。唯一美中不足的是,其头颅在防腐处理过程中被毁容了,完全不像其生前的容貌,因此被一个蜡像代替。
这个 auto-icon 后来一直放在实践了边沁的教育改革理念(一言以蔽之,有教无类,不论家资,不论宗教)的 University Collage London(伦敦大学学院,UCL)(在 2020 年以前,放在学院主楼南回廊的尽头;之后,迁移到学生中心)。
有关边沁的 auto-icon,我还听过一个传说(已被边沁的英文维基页面证伪):UCL 在每次召开理事会时,都将边沁的 auto-icon 陈列在侧,并认定他会给会议中的改革派投半票。
同样的皮草,在两种社会,两个时代,承担完全不同的预期作用。一个是为了在公共空间中承担教育的责任,或是给某一些人鼓励;甚或按一些浪漫的说法,是 “一种社会实验”。另一个,则是作为生杀大权的象征,要给人以无限的恐怖,从而使人战战兢兢地做好皇帝交办的工作。这何止天差地别。
参考文献:
百度百科·剥皮揎草:https://baike.baidu.com/item/%E5%89%A5%E7%9A%AE%E6%8F%8E%E8%8D%89/5372899
不要再說明朝國號「大明」源於明教:http://www.observer-taipei.com/book2021/item/634-2022-03-29-08-11-13
维基百科·Bentham:https://en.wikipedia.org/wiki/Jeremy_Bentham
《显微镜下的大明》
-
 @ 8cb60e21:5f2deaea
2024-09-03 21:58:26
@ 8cb60e21:5f2deaea
2024-09-03 21:58:26Lesson 2: Functions and Loops
Functions: Your Own Commands
Functions are reusable blocks of code that perform specific tasks. They're like teaching your cat a new trick:
```javascript function meow(times) { for (var i = 0; i < times; i++) { console.log("Meow!"); } }
meow(3); // This will print "Meow!" three times ```
Built-in Functions
JavaScript comes with many built-in functions. For example,
console.log()is a function that prints things to the console:javascript console.log("I'm a cat!");Loops: Repeating Tasks
Loops allow you to repeat a task multiple times without writing the same code over and over. It's like telling your cat to chase its tail for a specific number of rounds:
javascript for (var i = 0; i < 5; i++) { console.log("Chasing tail, round " + (i + 1)); }This will print "Chasing tail, round X" five times, where X goes from 1 to 5.
-
 @ c7eadcf0:7821e562
2024-09-04 23:58:56
@ c7eadcf0:7821e562
2024-09-04 23:58:56Another test post. I think I might have found my long form content writing app. Well done.
-
 @ 8cb60e21:5f2deaea
2024-09-03 21:28:51
@ 8cb60e21:5f2deaea
2024-09-03 21:28:51Lesson 1: Getting Started with JavaScript
Introduction
JavaScript is a programming language that instructs computers to perform tasks. Just as cats control humans with meows and purrs, programmers control computers with statements written in JavaScript. Originally designed to make web pages interactive, JavaScript now runs on servers, phones, and even robots!
The Console: Your Playground
To start experimenting with JavaScript:
- Right-click anywhere on your web page and select "Inspect Element"
- Click on the "Console" tab
This console is like a command line where you can type JavaScript code and see immediate results. Try typing
1 + 1and hitting Enter!Strings: The Building Blocks
In JavaScript, text is represented as "strings". These are sequences of characters enclosed in quotation marks. For example:
javascript "Hello, kitty!" 'Meow meow meow'Remember: Always match your opening and closing quotation marks!
Values and Variables
Values are the simplest components in JavaScript. Numbers, strings, and functions are all values. To store these values for later use, we use variables. Think of variables as labeled boxes where you can keep your toys (values).
javascript var catName = "Whiskers"; var livesLeft = 9;Now you can use
catNameorlivesLeftin your code, and JavaScript will remember what they represent! -
 @ c7eadcf0:7821e562
2024-09-04 23:53:44
@ c7eadcf0:7821e562
2024-09-04 23:53:44seeing if this works lol
-
 @ 4fb130a0:3327f6c7
2024-09-03 12:22:23
@ 4fb130a0:3327f6c7
2024-09-03 12:22:23Depuis des décennies, il n'y a pas eu de raison impérieuse de s'intéresser à l'argent concret qui circule activement sur les marchés. Peu de gens se consacrent à cette tâche, hormis quelques spécialistes et curieux passionnés.
☑️ Nées pour répondre au besoin de sécuriser les dépôts, financer le commerce et accorder des prêts. Les premières banques se cantonnais à ces activités élémentaires et endossaient le rôle d'intermédiaire de confiance dans les transactions économiques et le développement des échanges locaux et internationaux.
Course à la surperformance Au cours des années 1990 et 2000, une vague de dérégulation financière a permis aux banques de diversifier leurs activités au-delà des simples dépôts et prêts. Elles se sont engagées massivement dans des activités de trading, de titrisation, et de gestion d'actifs à haut risque.
⏩ Ce mouvement a été amplifié par l'innovation financière, telle que la création des produits dérivés complexes. Les banques sont devenues des acteurs globaux, accumulant des actifs considérables tout en prenant des risques de plus en plus importants, souvent sans supervision adéquate.
Le point de rupture La crise financière mondiale de 2008 a révélé les risques associés à la dérégulation des banques et à leur rôle croissant dans la spéculation financière. Cette crise a conduit à une réévaluation de leur rôle, de leurs pratiques de prêt, et de leur relation avec les États. Depuis les institutions financières sont soumises à des régulations strictes de prévention et de gestion des risques.
🔓Aujourd’hui, leur influence est encadrée par des politiques monétaires et de régulation visant à stabiliser les marchés financiers et à éviter les bulles spéculatives. Elles sont encore majoritairement l’unique dépositaire des normes et outils de gestion de notre quotidien économique.
L’envers de l’inflation Depuis 2008, les politiques de quantitative easing (assouplissement quantitatif) des banques centrales ont exacerbé l’effet Cantillon , un phénomène où la création monétaire bénéficie d’abord à ceux qui reçoivent la nouvelle monnaie, comme les banques et les grandes entreprises, avant que l’inflation ne se diffuse à l’ensemble de l’économie. Cela entraîne une redistribution inégale des richesses et augmente les inégalités.
⏰ Avec le retour de l’inflation ces dernières années, les banques centrales ont mis fin au QE et ont commencé à relever les taux d’intérêt pour tenter de maîtriser la hausse des prix. Cette transition a eu des effets ambivalents.
🔄 Alors que l’objectif était de contenir l’inflation, elle durci les conditions économiques et d’accès au crédit. Les plus riches, qui bénéficient d’actifs financiers valorisés, continuent de voir leur richesse croître, tandis que les ménages à revenu fixe voient leurs ‘reste à vivre’ et confort de vie diminuer progressivement.
Que faut-il en retenir ?
Le rôle des banques a considérablement évolué au fil des siècles. De leur fonction originelle de facilitation des échanges commerciaux, elles sont devenues des piliers de l'économie mondiale, dont les actions influencent la répartition des richesses et la stabilité économique. L'effet Cantillon met en lumière les inégalités nées de la création monétaire, soulevant des questions cruciales sur l'équité des modèles et systèmes financiers actuels.
⏳ Prenez le temps de comprendre les forces qui façonnent l'économie globale et leur impact sur vos finances personnelles et votre vie quotidienne.
-
 @ 469fa704:2b6cb760
2024-09-03 10:20:09
@ 469fa704:2b6cb760
2024-09-03 10:20:09In traditional investment wisdom, diversification is the mantra chanted by financial advisors worldwide. It's the strategy to spread risk across various assets to mitigate losses. However, when it comes to Bitcoin, some argue this principle might not apply in the same way. Here's why:
1. Bitcoin's Unique Value Proposition
Bitcoin, often dubbed "digital gold," has several attributes that set it apart from other investments:
- Finite Supply: With a cap at 21 million coins, Bitcoin's scarcity is programmed into its code, mirroring the scarcity of gold but with even more certainty. This scarcity can drive value as demand increases over time, especially in an economic environment where fiat currencies are subject to inflation.
- Decentralization: Unlike stocks or real estate, Bitcoin isn't tied to any central authority or physical asset that can fail or be manipulated by a single entity. This decentralization reduces the risk of systemic failure that affects traditional markets.
- Global Liquidity and Accessibility: Bitcoin can be bought, sold, and transferred anywhere in the world, 24/7, with internet access. This global liquidity means Bitcoin can be more easily converted to other assets if needed, somewhat reducing the need for diversification.
2. The Risk-Reward Balance
- Volatility as Opportunity: While Bitcoin's volatility is often cited as a risk, for the informed investor, this volatility represents opportunities for significant gains. Those who understand Bitcoin's cycles might prefer to ride these waves rather than dilute potential gains through diversification into less volatile assets.
- Long-term Appreciation: Historical data suggests Bitcoin has provided substantial returns over the long term compared to most traditional investments. If one believes in Bitcoin's future as a dominant store of value, holding a diversified portfolio might mean missing out on Bitcoin's potential upside.
3. Bitcoin as a Diversifier
Ironically, Bitcoin itself serves as a diversification tool within traditional investment portfolios. Its price movements have shown low correlation with stocks, bonds, and even gold at times, suggesting that Bitcoin can diversify an investment portfolio on its own.
4. The Philosophical Shift
- Trust in Code Over Corporations: Investing heavily in Bitcoin might reflect a philosophical shift towards trusting mathematical algorithms over corporate governance or government policy. Here, diversification within the crypto space might seem less necessary if one views Bitcoin as the pinnacle of what cryptocurrency should be.
- A Bet on a New Financial System: Holding Bitcoin exclusively can be seen as a bet on a new financial paradigm where Bitcoin becomes the standard. In this vision, diversification into other assets might be counterproductive.
5. Potential Result
Upon reviewing the arguments and characteristics, one might conclude that Bitcoin is pursuing a dual trajectory. Firstly, its value increases partly because it remains a novel asset, not yet mainstream among the general populace. Secondly, Bitcoin is poised to absorb the value preservation function from other assets. This means that individuals who invest in stocks, bonds, real estate, commodities, etc., primarily for their value storage capabilities rather than their intrinsic utility (such as residing in a property), might transition to Bitcoin. This shift could consequently diminish the demand for these traditional assets and increase the value of Bitcoin respectively.
6. Caveats and Considerations
- Not Without Risks: This approach isn't without its perils. Bitcoin's future is not guaranteed, and regulatory, technological, or market shifts could impact its value negatively.
- Liquidity Needs: Individual financial situations might require liquidity or income generation that Bitcoin alone might not provide efficiently.
- Emotional Discipline: A Bitcoin-only strategy requires immense discipline and conviction, as the emotional toll of not diversifying can be high during market downturns.
Conclusion
The argument for not diversifying if you hold Bitcoin hinges on its unique properties, the potential for high returns, and its role as a hedge against inflation and traditional financial systems. However, this strategy suits those with a high risk tolerance, a deep understanding of Finance, Economics and Investments, and a belief in Bitcoin's future dominance. For everyone else, while Bitcoin can be a significant part of a portfolio, traditional diversification might still offer peace of mind and stability. Remember, investment strategies should align with personal financial goals, risk tolerance, and market understanding. Always consider consulting with a financial advisor for personalized advice.
-
 @ 9bc2d34d:d19d2948
2024-09-02 19:41:40
@ 9bc2d34d:d19d2948
2024-09-02 19:41:40Chef's notes
This recipe is designed for home cooks who want to recreate the delicious buttery hollandaise sauce at home without feeling overwhelmed. It focuses on teaching the basics of the sauce, allowing beginners to master the fundamentals before experimenting with seasonings, hot sauces, or herbs.
Please note the thickness of sauce in the picture. This is after ten minutes of blending.
Details
- ⏲️ Prep time: 3 minutes
- 🍳 Cook time: 10 minutes (blending)
- 🍽️ Servings: 2 - 4
Ingredients
- 4 egg yolks
- 8 tablespoons of melted butter
- 1 tablespoon of lemon juice
- Pinch of salt
- Pinch of pepper
Directions
- Melt butter in the microwave or on the stovetop.
- Separate the egg yolks from the egg whites (reserve the egg whites for another dish).
- Place the egg yolks in a blender.
- Start the blender (medium to high settings for blend mode is fine).
- Slowly pour the melted butter into the cover opening (it will splatter).
- Add the remaining ingredients.
- Blend for ten minutes (seriously, walk away and do something else).
- Taste and adjust the flavors (add extra lemon juice or salt if desired).
- Serve over your breakfast!
-
 @ a324b2fe:68bf4629
2024-09-04 23:47:54
@ a324b2fe:68bf4629
2024-09-04 23:47:54One of the most significant underlining doctrines of our time is that of the rapture and the eschatological (study of the end times) understanding that the world will be overrun with evil, and God will ‘beam us up scotty’ either before the faeces hits the fan or after. There are slight variations in this ‘futurist eschatology’ I’ve just briefly explained. Many would agree that this is what the bible clearly teaches, and others will have a verse or two in their minds that without further study seems to validate this popular understanding.
Make no mistake, most Christians believe in a ‘futurist eschatology’ (see below), but the real question is why and how most of us have landed believing that things are going to get much worse on the planet, or that things will get better but will suddenly plummet down and Armageddon becomes more than a badly plotted movie. Some might be wondering “I never knew such a thing existed”, let alone know that there are different opinions on the matter. Keep reading because you’ll be surprised at how much this doctrine actually influences ALL your decisions.
To summarise, there are four major positions of interpreting “The book of Revelation”, which is the core book to influence our perspective on the future or “end times”.
Futurisme:
The belief that the events in the book of Revelation is referring to global events in our future. (popular since the 1800’s; the beast’ (see revelation 13 and 17) is a man and a new world order, many historical figures have been suggested in their time; Napoleon, Hitler, Stalin, Osama bin Laden, Barack Obama etc.).
Historicism:
The belief that the events have transpired over history like a timeline (popular in the 1500’s at the time of the reformation, notably that the Pope of the Catholic Church and the Papacy were the ‘beast’.
Preterism:
The belief that the events (most or all) have already taken place in the 1st century, climaxing at the destruction of Jerusalem in 70AD, Rome as a whole and Emperor Nero being considered the ‘beast’.
Idealism:
That the book is a symbolic battle between good and evil.
Before I get into the nitty gritty on history, specific scripture and their exegesis (a fancy word I never use in conversation, meaning critical study and interpretation on a text). Let me highlight why what we believe about the future influences our every decision.
One day in 10 years time you’re married to a beautiful/handsome spouse and have 7 children. You believe that the world will end soon and that there’s going to be a massive heavenly battle and the angels are going to use their majestic rippled muscled limbs to wreck havoc on all those that oppose. Nice. Or not nice if you chose the wrong side. Before that happens though your daughter wants $1000 to invest in some shares because she learned at school that if you put $1000 in shares today and top up $100 every month you’ll have accumulated a total of $72,000 in twenty years having only contributed $25,000 of your own money. Smart kid, that’s a good long term investment strategy.
You however don’t believe the world is going to exist in its normal state in another 20 years time, or you reason it might, but surely not much longer after that. So you say: “Sweety, I really don’t think that’s going to do you much good, the market is too volatile and I don’t foresee things getting better in the future, why don’t you spend your money on some clothes or go out with your friends”? Yes this is quite an elementary example and I’m sure you’ve all invested money into shares and it would never happen to you.
How about another scenario then? You believe the rapture will take place in your lifetime. You read your bible and see that Christians need to share the gospel, so you start to share with people, some people reject you, some are indifferent, and others are deeply touched. The ones that are impacted, you give them a bible and say go to church and get ready for the return of Christ (in your mind you’re thinking that means rapture). Some of them do, some go and fall away and still others somehow are consistent and are growing in the Lord, good job right? What about those people that fell through the cracks? That’s not my responsibility you say, they need to work out their own salvation with fear and trembling. Okay, have you considered that the responsibility is actually squarely on your shoulders? In regards to making a disciple, not a convert. Discipleship takes much longer, it takes time, it takes sacrifice, and it takes a perspective that there is even time for discipleship. Otherwise it’s a 6 week course in “How to be a Christian”.
Thankfully some of the church has in the last few decades focused a lot more on discipleship, even whilst holding the perspective of a futuristic eschatology. Yet even in this the reasoning is simple, they are doing their best to follow what they read in the bible regarding discipleship (rightfully so), and also a discipleship approach of evangelism retains and reaches more people, so it’s a more successful method to convert in any case. If this is you, you’re amazing, please keep making disciples! I however propose that you sincerely ask yourself what you would do differently if you believed the world would exist for another 200 years plus.
As you can see our belief on the future has extreme and subtle effects on our actions and decisions. Our society is peripheral to where the church is at, and right now the church as a whole believes that the end is soon and there’s no point in believing and acting like it’s a good thing to leave an inheritance for your children’s children. That is why we buy cheap, that is why we don’t invest, it is why we are driven by instant gratification. Why would you bother with all that if the world will end in a matter of years. It comes to whether you have a hope filled optimistic expanding Kingdom perspective on how the world is going to turn out or one that is governed by a defeatist/fatalistic mentality and perhaps even one fear riddled.
Now that we’ve looked at how our beliefs can be outworked in everyday life, let’s get into doctrine. Finally. Actually, some more history first.
I and many others find it helpful to look at history to see when a certain doctrine began to gain support and become the popular belief to determine its validity. Let’s jump in then, during the reformation, the Catholic Church was under fire and experiencing some mostly accurate criticism. In a response to Christians accusing the Pope and the Papacy of being the beast, a Jesuit priest wrote extensively that the events in the book of Revelation are referring to their future, thus eliminating the Pope and the Papacy of fault. His writings didn’t gain traction until the 1800’s where John Nelson Dalby adopted the belief and started widely teaching it, specifically on ‘Pre-tribulation rapture theology’ (we get raptured/caught up prior to the tribulation that will happen on the earth). I would like to explicitly mention that before this, proponents for a futurist eschatology were almost non-existent.
Then in the following early century (1909 to be exact), the first ever bible with commentary was printed. The Scofield bible. This bible was a massive advocate for dispensationalism and a futuristic eschatology; practically every bible college student got one of these bibles, and lo and behold an entire generation of pastors and theologians were massively influenced on their belief of the future. Couple that with two world wars, the reestablishment of the Jewish nation, Israel, and we have a perfect concoction for believing the time is near and Armageddon is around the corner.
Now there are entire books discussing all of this that I cannot even hope to cover even a slither, but if you are so inclined, see some recommendations at the end. I won’t attempt (nor can I) to extrapolate on everything there is regarding a ‘preterist view’ of Revelation, and a ‘victorious eschatology’ which was the orthodox view in early Christianity, but here is a summary of what you need to know.
The Kingdom of God:
As indicated by the statue in Daniel 2 was inaugurated with the birth of Jesus (coming of Jesus in the Manger), and started to expand and is still expanding. See Mathew 13:31-33. Also see Isaiah 2 for the hope for the future.
The destruction of Jerusalem in 70 A.D.
Wasn’t just an important event in history, it is paramount to the entire New testament and is referenced to in almost every book. To miss its importance is to miss understanding much of the New testament. This event is crucial to the progress of God’s redemptive plan in history, with the final removal of the temple and the genealogical records of the priests therein, the old (mosaic) covenant closes and the new covenant is fully and permanently established.
“When you see Jerusalem being surrounded by armies, you will know that its desolation is near. Then let those who are in Judea flee to the mountains, let those in the city get out, and let those in the country not enter the city. For this is the time of punishment in fulfillment of all that has been written. - Luke 21:20-22
John the Baptist proclaims judgement on the Jews in Matthew 3:10-12. See also Matthew 7:19 “The ax is already at the root of the trees, and every tree that does not produce good fruit will be cut down and thrown into the fire. I baptize you with water for repentance. But after me comes one who is more powerful than I, whose sandals I am not worthy to carry. He will baptize you with the Holy Spirit and fire. His winnowing fork is in his hand, and he will clear his threshing floor, gathering his wheat into the barn and burning up the chaff with unquenchable fire.” This provides the backdrop to Jerusalem erupting in flames in A.D. 70. Later Jesus declares John is Elijah to come (Matt 11:14) fulfilling the prophecy in Malachi 4:5-6, as he proclaims judgment in Israel before the great and terrible day of the Lord (John mentions the day of the Lord in Rev 6:17; 16:14).
In Matt 12:39 Jesus regards the Jews of His day as an adulterous generation, the same imagery is found in Revelation 17:3 as John presents Jerusalem as a harlot (see also Isa 1:21; Jer 2:20; 3:1,6,8; Eze 16:9, 15-17, 26; Hos 2:5; 4:10; 12-15). In Matthew 23:34-35 Jesus warns that God will judge 1st century Jews for the righteous blood that was shed in the land (we see the same statement in Rev 18:24). In Matt 23:36-38 Jesus laments Jerusalem’s destruction and declares the temple desolate, John declares Jerusalem is desolate in Rev 17:16. After that Jesus prophesies its destruction in Matt 24:2-3 and Luke 21:24, and John uses the same language as Luke, in Rev 11:2. In Matthew 24:16 Jesus urges his followers to flee Judea because “this generation will experience judgement (Matt 23:32). John calls the saints out of Jerusalem in Rev 18:4.
I could go on but there are books for that. Here's the simplicity of it; John’s general message in Revelation is ‘the divorce of Israel and God’s marriage to the new covenant church’ (which obviously includes Jews if they turn to Christ). The ‘second coming of Christ’ came when he came in judgement on Jerusalem. There is another coming, hold your horses I’ll get there.
The 'Olivet discourse’ of Matthew 24:
Is referring to 1st century events and uses prophetic symbolic language (stars falling, moon to blood, sun darkened etc.) to demonstrate a toppling of governments, see Isa 13:10,13 referring to Babylon; Isa 34:4 referring to Edom; and Eze 32:7-8 referring to Egypt. Also think of Joseph and how his family were stars, a moon and a sun and that they bowed to him. Again, it’s language to communicate a natural toppling of governments or exchange of political dominion. Not a global catastrophic Armageddon.
The Anti-Christ:
Used only four times in the bible (1 John 2:18; 1 John 2:22; 1 John 4:3; 2 John 1:7). It has always been a referenced to a false teaching in the 1st century that claimed Jesus had not come in the flesh. A gnostic heresy.
The Beast, the mark of the Beast, and his number 666:
Referring to Emperor Nero who was called a beast, forced people to get markings of him to be able to buy and sell in the marketplace (Rev 13:16-17), see a short video on the matter https://www.youtube.com/watch?v=wng3jcfMkZU. Now Gematria is a Jewish Interpretive method that assigns numerical value of Hebrew letters to words. We find this with the number of the beast being 616 (in Latin) or 666 (in Hebrew), with the values added up it spells Nero Caesar. See this 2 min video https://youtu.be/JXkTc18xBoM. Some people, like in the video say that he represents a future beast as well, this is simply poor and biased exegesis and is thus construed to validate their pre-existing beliefs.
The Word Rapture:
Found in 1 Thessalonians 4:17; “After that, we who are still alive and are left will be caught up (rapturo in Latin) together with them in the clouds to meet the Lord in the air. And so we will be with the Lord forever”. The entire bases of the doctrine of the rapture is found in this one simple verse. Yet all it means is that we will be gathered to Jesus and the past saints/Christians at His return.
What now? Is everything done?
Well not quite.. Jesus’ Return: Jesus will return as is promised in Acts 1:11, but it won’t be with a massive army to lay plunder to the earth, well maybe, but I highly doubt it. “…will come back to you in the same way you have seen Him go into heaven”. The resurrection of the dead: Zombies! Kidding, just mass people coming back to life. See 1 Thessalonians and 1 Corinthians 15. The Great judgement: The great judgement day of the sheep and the goats in Matt 25.
That’s it, so until then, however long that will take (my money is on 197 years), let’s keep bringing the Kingdom of God to earth, lets pray for miracles, make healthy disciples that reproduce, transform every facet of society to look like heaven, and establish a Kingdom legacy that our Lord and King would be excited to come back to.
Ps. My views on Gods judgment on the 1st century Jews is not that he wanted to destroy them, but rather he was bringing judgment on an old covenantal system, the Jews that clung to that sinking ship unfortunately went down with it.
Book Recommendations: Understanding the whole bible – Jonathan Welton Raptureless – Jonathan Welton The art of revelation – Jonathan Welton Before Jerusalem Fell: Dating the book of revelation – Kenneth L Gentry Navigating the book of Revelation - Kenneth L Gentry Victorious eschatology: A partial Preterist view – Harold R Eberle and Martin Trench
Theologian Gary Demar
-
 @ 75bf2353:e1bfa895
2024-09-02 19:04:18
@ 75bf2353:e1bfa895
2024-09-02 19:04:18
Alby Hub is lightning-node software that Get Alby sells as a service. It's also free and open source. You can run it on a node such as Umbrel or Start9. I even was able to run it on Ubuntu. I was lucky enough to try the Alby Hub early. I even tested the software as a service before it was released to the public. I "forgot my password," though. Actually, I never knew it. I use VaultWarden as a password manager and copy and paste all my passphrases. I was in a Jitsi meeting. You know how it is. Bitcoiners are super interesting smart people. I got distracted talking to these smart people and must have copied and pasted the wrong passphrase because...I got distracted. I opened a channel and then got locked out. It's my fault. I take complete responsibility. I take complete responsibility. I hadn't even written down my seed phrase yet.
I didn't lose any sats though; aside from the 10,000 sats, it cost me to open up the channel. This is because I am very careful about sending larger sums of bitcoin to wallets before I write down the seed or test them. I might send 21,000 SATs or something like that to see if I can recover them before I send more. We used to say "don't be reckless," but that ethos can get lost in all the excitement of this cutting-edge technology we call the lightning network. If I sent thousands of dollars of bitcoin to this Alby Hub wallet I was beta testing, those sats would have been HODLED forever. It is important to use new technology with small amounts of bitcoin. It is important to use new technology with small amounts of bitcoin." This way, you mitigate your risk of a catastrophic loss. This is especially true if you ever find yourself beta-testing.
The Bright Side of Forgetting My Passphrase on Alby Hub
 )
)There is an orange lining to this story. The other beta tester in the meeting got it to work. He played a game called Zappy Bird. This is not an endorsement of Zappy Bird. I think it's a gambling version of Flappy Bird. I am not a gamer, and I would just lose my seat if I played this for any length of time. This allowed me to see the possibilities of Alby Hub, however, even though I screwed up my first try. My mother, like many of your mothers, I'm sure, always said, "If at first you don't succeed, then try again."
" Even though it didn't work for me at first, I got a glimpse into how awesome Alby Hub was anyway. Even though it didn't work for me at first, I got a glimpse into how awesome Alby Hub was anyway. That motivated me to try again. The second time I Alby Hub on PopOS! by following the instructions on the README file. That worked. It was surprisingly easy, but we were in the early days, and my channel was force closed. The issue seems to be fixed now that it's released to the public. I'm amazed at how much cleaner it is now. I also had a few other problems connecting my node to my Alby account because it was connected to the original node. The good people at Get Alby fixed that, however. I'm really impressed with their customer service. Screwing up my first node gave me the opportunity to learn this about the company.
Screwing up my first node gave me the opportunity to learn this about the company. I continued to use the GetAlby API during this time. I continued to use the GetAlby API during this time. I thought API's were super scary. 3 I don't even know what API stands for. Thanks to some of the people like Bitkarrot from Plebnet.dev, I am comfortable using them. A few weeks ago, I was able to make some video tutorials that teach businesses how to accept bitcoin. I am aware most businesses prefer fiat. It occurred to me: why would a business care if the fiat in their bank account comes from Strike or Mastercard? Of course, businesses that want to accept bitcoin can keep the sats. One business owner I know who is listed on BTCmaps did not want to use Strike because he liked seeing the stats on his phone.
Get Alby On Umbrel Or Start9
As I eluded to earlier, you can now run GetAlby on Start9 or Umbrel. They have videos and guides in[ ]this tutorial](https://guides.getalby.com/user-guide/v/alby-account-and-browser-extension/alby-hub/alby-hub-flavors/umbrel-start9-etc). If you already have one of these machines laying around and are comfortable getting your fingers dirty in the command line, you should try it. If not, you should try the software as a service. If you're a command-line ninja, run it on Ubutnu. Don't be reckless. Only use amounts you are willing to lose. Ably doesn't have access to your seeds, but it is still a hot wallet. It is also still very new. Expect bugs. Expect channel closures. Don't just be a whinny complainy-pant about it. Help improve it. Make a pull request if you must. If you are not as technical. Don't worry. They plan to be on the Umbrel and Start9 app stores soon.
Alby Hub on Umbrel or Start 9 require the Lightning Node app. If you self-hose, your seed is on your Lightning Node app. Write these 24 words down and keep them safe. You will need these to recover your bitcoin in case something breaks. If you use the cloud service, follow the directions to back up your keys here. Opening a channel is easy. You just send the 10,000 sats or whatever the fee is to open it. It's a node in the cloud service similar to voltage, I suppose. To be honest, I'm not sure how it works on the back end, but this abstracts away much of the complexities of running your own lightning node. You don't need to worry about finding a node to connect to, inbound liquidity, or balancing channels. That's like full-time IT work. Alby Hub makes running a lightning node easy-peasy lemon squeezy. Alby Hub makes running a lightning node easy-peasy lemon squeezy. This opens bitcoiners up to a world of possibilities.
Why I Am So Excited About Alby Hub

Although I did some beta testing for GetAlby's Alby Hub, I didn't receive any sats from them aside from a couple zaps here and there, but this is not a paid ad or sponsored blogpost. I don't think I can make a better guide than they have on their website. I am excited about Alby Hub because it makes accepting bitcoin so easy. I am excited about Alby Hub because it makes accepting bitcoin so easy. I'm not sure your grandmother could do it, but most computer-literate people could easily run Alby Hub. But wait... There's more.
Thanks to these wonderful people on nostr, I learned how to find my keys in the lightning node of my Umbrel. This also means my lightning node works for other apps besides Alby Hub. It also works with the LNbits installed on my Umbrel. I bet it works with BTCpayServer too, but I haven't verified this yet. This means businesses will soon be able to accept bitcoin by: - Buying a $400 minicomputer like Umbrel or Start9 ($800). - - Using Alby Hub in the Cloud and integrating it into other clients that use Nostr Wallet Connect - - Setting up an online bitcoin store on Shopster or Plebeian Market will be easy. - -+ The Uncle Jim Model just got 10x easier.
For example, what if I sold LNBit's POS extension and gave someone access to use my LNBits as a POS? shop could use LNBits as a POS terminal all of a sudden. I could build a bitcoin POS system for a local business using old comouters in my strategic computer reserve. Okay, I admit it. I'm a computer hoarder. I never recycle old computers unless they are unrepairable. There are so many ways to use the lightning network now. Find out more at https://getalby/hub. We can use these tools in creative ways. What if, instead of using BTCpayServer to help businesses accept bitcoin, we create a BTCpayServer-like product list on Shopster instead?
Using Alby Hub to Monetize My Blog
As I thought more about this, it occurred to me I should start a business with all of this stuff. Some people at my local meetup have asked me to help them set up a lightning node. Tools exist that make it easy enough to do consulting for anyone over tools like Keet or Hivetalk.org/. I also want to sell T-shirts. I've had the idea to sell bitcoin t-shirts that say Pay Me In Bitcoin. This one time, I played poker in Vegas during Def-Con. I was there for poker at the time. I've never been to DefCon. Some nerd had a QR code on his T-shirt. I'm not sure what it was. It was the first time I ever saw a QR code.

I was able to design this T-shirt with the help of Dell E 3. I'm using some of the techniques I learned in the 4-hour workweek to design this shirt, but instead of hiring a graphic designer in a third-world country, I hired computer power from PayPerQ. A website I learned about on getalby.com. Around the time of the halving, some dude at my job asked me if I think he'll ever be able to afford a whole bitcoin for each of his kids. I said I didn't know. He told me he makes way more than my family, but he hasn't started stacking SATs yet. He also told me he pays for Chat GPT because it is "only $30 a month." That's $360 of sats he could have stacked per year. I wouldn't be surprised if $360 stacked in bitcoin is worth $3,600 in five years.
Many people who say they will never spend bitcoin often spend money on other fiat things because they were raised with a hyper-consumer mental framework. Many others think AI will kill us like the Terminator, but people like Andreas Antonopolis and Paul Vigna wrote books about bitcoin getting used as a medium of exchange for AI almost a decade ago. The lightning network was clunky and difficult back when I first ran a MyNode and entered my public key into yalls.org to write about bitcoin. I bought a sticker from Blockstream with the Eclair Wallet back then, but it was hard to see how the lightning network could come over the technical hurdles for the majority of the people.
Tools like Alby Hub give me hope for the future. I listened to Natalie Brunell's Coin Stories this morning. The guest is a gold bug. She said something my wife is even still concerned with. The government will never allow bitcoin to be used for payments. They will capture it before this happens.
She is right in a sense. I am sure the governments of the world will not want to give up the power to print money and expand and contract the economy as they see fit. The digital alternative to central banking will not be welcomed by governments. Plebs build it anyway. The government of the United States has the most powerful weapons ever known to humankind. This government has an arsenal big enough to destroy the world many times over. I'm not certain bitcoin will survive an existential event such as this. I do not doubt the POTUS could Executive Order 6102.2 every Saturday in the ETF's overnight. To ban tools that make it easy to use the bitcoin lightning network as payments requires banning computers and banning software distributed all over the world. It seems like governments would have a difficult time banning computers.

Now that I think of it, Natalie Brunel could use Alby Hub to accept steaming sats and boosts to her podcast. She can host it in the cloud or on a plug and play node like Umbrel or Start9.
-
 @ 75bf2353:e1bfa895
2024-09-02 19:00:02
@ 75bf2353:e1bfa895
2024-09-02 19:00:02 -
 @ 1a48e74d:02c0e00f
2024-09-04 23:38:34
@ 1a48e74d:02c0e00f
2024-09-04 23:38:34seeing if this works.
-
 @ eed76ece:afa98124
2024-09-02 18:58:30
@ eed76ece:afa98124
2024-09-02 18:58:30As the World continues to create more and more NEW regulations. And as free speech get attacked from every angle. Bonafide business owners, especially importers will need to find ways to migrate sales offerings of goods and services. It feels like the majority of business owners have to really take this seriously.
Obviously so many different methods are used around the World already, but when the upcoming new mandatory vaccinations, vaccine passport travel restrictions really hit, businesses will have to jump to more selling online.
SN, Nostr and other unknown communication methods are Paramount. As usual it feels like no one is taking free speech attacks seriously. The amount of postings my customers around the World do daily on WhatsApp, LINE (Asia), Telegram, Twitter will move where it is allowed to move. Feels like there's an ongoing increase in the attack not just on the West, but from WITHIN the West.
Regardless if you retail, wholesale, manufacture, are an agent we try hard to be pro active on marketing on multiple methods. It seems very logical that in the future Nostr and SN will pick up International users as a way to get their goods posted somehow someway.
Examples
Customers in these regions I deal with primarily communicate with me in Japan, Thailand using LINE and Tik Tok daily. Most of the rest of the World communicate with me using WhatsApp. Certain parts of Eastern Europe and Asia Telegram.
Interestingly my resellers in the USA primarily post on WhatsApp.
Westerners especially Americans seem to have enough money, they are not hungry for making more money, or increasing their business growth, they think everything is ok. "We will always be okay, there will NEVER be a Worldwide depression, recession, deflation, increased restrictions, they will NEVER force a new vaccine on us again, they will NEVER lock business and us down again".
"So I will always have free speech, the politicians told me so".
originally posted at https://stacker.news/items/670041
-
 @ 56a6da9b:7f5a2243
2024-09-02 18:27:19
@ 56a6da9b:7f5a2243
2024-09-02 18:27:19IO used to have a lot of content and now the only thing that shows up is my fouintain stuff. when i go into other nostr things it's not there anymore and i look like an anonymous user with no profile pic, or profile and no activity.
originally posted at https://stacker.news/items/669994
-
 @ c7eadcf0:7821e562
2024-09-04 23:03:59
@ c7eadcf0:7821e562
2024-09-04 23:03:59Welcome back ya'll hope you are doing well this week. Today I wanted to talk about why Bitcoin represents a dawn of a new age in property ownership. Before you spit out your coffee and walk away, hear me out. Bitcoin and real estate have a few things in common. The first is property rights.
When you are the owner of a building with your name on the dotted line and whatnot, you are the sole owner of that property. No one can tell you what to do with it, and no one has a claim to what you own. You are free to do what you wish. Property rights are sacrosanct and immutable similar to Bitcoin.
Bitcoin confers upon the owner the same property right protections as owning a piece of real estate. Once you own it, you are the sole owner of that Bitcoin. No one can tell you what to do with it. No one else has a claim to your Bitcoin. You are free to do with it what you wish.
Bitcoin and real estate are similar in terms of built-in scarcity. There is only 21 million Bitcoin that will ever be created, and you can't print more land. This is why owning real estate has been such a good investment since the beginning of time. Buying a piece of land and "HODLING" for decades will generate a substantial return on your investment.
This same buy and hodl strategy apply to Bitcoin as well. If you bought Bitcoin back in 2009, you would be a multi-millionaire right now.
If you invested $1000 back in 2011 when Bitcoin was trading at $3.50, you would have turned that $1000 into $15.6 million if you held on to it for ten years. Just sayin.
You have to reframe your thinking to understand what is going on. We are living in the 21st-century gold rush, and you have an opportunity to stake your claim to the soundest money on Earth with a few taps on your phone. Never in the history of the world has the plebs like us had the ability to front-run a monetary revolution.
Bitcoin is freedom from oppression. Bitcoin restores your sovereignty. Bitcoin makes you fuckable, and the powers that be know it. They are afraid they will lose control if too many people catch on too quickly, which is why large institutions are rushing to offer Bitcoin services or buy them and keep them on their balance sheet.
Bitcoin won't stay this cheap forever. $100-300k Bitcoin is in the cards over the next few years. I don't want you guys to miss out on this.
All you have to do is buy Bitcoin and hold. It's that simple. FYI trying out the new obsidian writer for nostr notes!
Bitcoin #nostr
-
 @ 6bae33c8:607272e8
2024-09-02 18:09:19
@ 6bae33c8:607272e8
2024-09-02 18:09:19I did the third and final NFFC Beat Chris Liss league last night, and it was one of the more interesting and aggressive drafts I’ve ever done. I picked from the seven slot.
Here are the results:

1.7 Ja’Marr Chase — I made seven my first choice, but then realized I probably should have gone with four or five, or maybe nine or 10. That’s because if the first six picks went chalk (and they did), I’d be faced with Chase who is holding out for a new contract (and who I have in two other leagues already), Justin Jefferson (new, bad QB) or Garrett Wilson (new QB, never been a Round 1-level WR.) At 1.9 I’d have gotten one of those guys anyway, but earlier picks on the way back. And at 1.4, I’d have gotten a shot at Bijan Robinson for an easier hero-RB build. But I had pick seven, and I tripled-down on Chase because I think it’s very likely he’ll get his extension (or play if he doesn’t), and he’s an all-time talent with a top QB and projects for a massive target share. Plus, if he busts it’s Alan Seslowsky’s fault, and having someone to blame is paramount.
2.6 Drake London — I had it mapped out via ADP that I’d likely get De’Von Achane here, but he went at his min pick (I’m pretty sure) at the 1-2 turn, and so I was scrambling a bit. I really wanted Puka Nacua, who I missed by one pick, considered Cooper Kupp, but ended up going for the ADP-faller London who I had not remotely planned on getting. London obviously benefits from the massive QB upgrade in Atlanta, but it’s an open question whether he’s really an elite receiver or just a good one, and Kyle Pitts could easily emerge as Kurt Cousins favorite target instead.
3.6 DeVonta Smith — When Derrick Henry went one pick ahead of me, it was between Smith and Jaylen Waddle who I took in BCL2. Normally I avoid receivers this undersized but Smith has always produced at every level and is locked into his sizeable target share. Plus I read some Scott Barrett tweets about how Kellen Moore’s offense boosts the slot receiver a ton and that Smith thrives in the slot and could see more work there.
4.7 Stefon Diggs — This was ideal. I now have Diggs in all four of my leagues so far. Maybe he’s hit a cliff at age 30, but he’s getting $22.5M to play in arguably the league’s top passing game that lacks a true No. 1 alpha. I also considered Tee Higgins to pair with Chase (and serve as Chase insurance), but Diggs has more upside as a potential No. 1 target.
5.6 Dalton Kincaid — I’ve been high on him all summer, but he never quite fell to me in the right place until now. I expect him to be Josh Allen’s No. 1 receiver now that Diggs is gone.
6.7 James Conner — I needed a RB, and Conner is one. I’m a bit wary of a 29-YO guy with an extensive injury history, but he averaged 5.0 YPC last year and has never had a massive workload so he’s fresh for his age at least. Plus, the Cardinals offense should be good this year.
7.6 Anthony Richardson — I wasn’t planning on taking a QB here, or even Richardson who I have in BCL2 in Round 5!, but I couldn’t pull the trigger on Zamir White over someone with Richardson’s upside. I’m trying to win the overall contest, not simply cover the bases with starters at every position.
8.7 Jonathon Brooks — Jaylen Warren was still on the board, and he was a viable Week 1 starter for me, but Brooks who is on IR, struck me as the upside play. I heard somewhere, can’t remember where, that Brooks was an elite prospect in college before the injury, and there’s a lot of hype about Carolina’s new offensive brain trust boosting the offense generally. But it might have been a rash pick given my zero-RB build to take a rookie on IR.
9.6 Marquise Brown — I missed Warren by one pick on the way back, and instead of pivoting to Tyjae Spears I leaned into the zero-RB by taking Brown who was going in the fifth or sixth round before his injury. The beauty of this pick is I don’t need Brown right away as I wouldn’t start him anyway, so I pay no price for him missing Week 1. The ugly of this pick is I missed out on Spears, Zack Moss and Chuba Hubbard (who would have been nice to pair with Brooks.)
10.7 Joe Burrow — The obvious pick was Trey Benson to pair with Conner. In fact, I could have had Hubbard in Round 9 and Benson in 10 to lock up two backfields for my zero-RB team. But no, I had to take a second QB here because (a) Richardson has a low floor; (b) this was cheap for Burrow; and (c) I could potentially pair Burrow with Chase for the playoffs. If you’re gonna go zero RB, lean the into it. (The other problem with this pick is the weekly headache of picking my starting QB.)
11.6 Jaleel McLaughlin — The Burrow pick cost me not only Benson but JK Dobbins too, but I had my eye on McLaughlin who apparently was a god in college, and per Barrett is in an ideal spot as the RB2 in Sean Payton’s offense. Now that stat has to be tempered a bit given that peak Alvin Kamara was the source of so much of it, but how much of that was Payton’s offense? In any event, I’m seriously rolling into Week 1 with McLaughlin in my active lineup because of the Richardson, Brooks, Brown and Burrow picks.
12.7 Jordan Mason — Obviously he’s not usable unless and until Christian McCaffrey gets hurt, and the Niners badly need Trent Williams to report, but he’s a top-10 RB if McCaffrey, who played into February last year, goes down. This also furthers my extreme “what could go right” build.
13.6 Braelon Allen — Oddly I view this pick as a mistake as he was higher in ADP, so I thought I could wait another round on Giants backup Tyrone Tracy. (Tracy went three picks ahead of me in the next round.) Allen might be good, but only a Breece Hall injury could free him up whereas Tracy could just outplay Devin Singletary. Granted the Jets might be a better environment than the Giants, so Allen could have more upside if he did get a shot, but Tracy is also a converted WR and would likely catch a lot of passes if he got the job.
14.7 Khalil Herbert — Once Tracy was gone, I pivoted to Herbert. The Chicago backfield is crowded, but D’Andre Swift always gets hurt, and Roschon Johnson isn’t as good a runner as Herbert.
15.6 Jalen McMillan — I wanted to get Cam Akers because Joe Mixon is old, but I missed him by two picks and pivoted (finally) back to WR. McMillan’s created some buzz in camp, and both Mike Evans and Chris Godwin are getting old.
16.7 Will Shipley — I love Saquon Barkley, but he’s getting old and has been hurt a lot. Kenneth Gainwell is ostensibly ahead of Shipley, but is just a guy. Another top-10 upside back should the starter go down.
17.6 Dalvin Cook — He’s on the practice squad for now, and he looked beyond done last year with the Jets, but keep in mind he only got 67 carries, and the Cowboys don’t have serious obstacles ahead of him should he regain even 60 percent of his prior form. Cook was still very good in 2022, and he should have fresh legs too.
18.7 Quentin Johnston — I needed one more receiver, and Johnston is one. Seriously, though he was a first-round pick only last year, and he’s competing with only Josh Palmer and a rookie.
19.6 Younghoe Koo — All these years I was with a wonderful kicker in Justin Tucker, but I’m trading him in for a Younghoe. (That joke will get old one day, just not in any of our lifetimes.)
20.7 Giants Defense — They draw Sam Darnold and Jayden Daniels the first two weeks, and added Brian Burns to Kayvon Thibodeaux and Dexter Lawrence.
Roster By Position
QB Anthony Richardson
RB James Conner/Jaleel McLaughlin
WR Ja’Marr Chase/Drake London/DeVonta Smith
TE Dalton Kincaid
FLEX Stefon Diggs
K Younghoe Koo
D Giants
Bench Jonathan Brooks/Marquise Brown/Joe Burrow/Jordan Mason/Braelon Allen/Khalil Herbert/Jalen McMillan/Will Shipley/Dalvin Cook/Quentin Johnston
-
 @ 1a48e74d:02c0e00f
2024-09-04 23:00:22
@ 1a48e74d:02c0e00f
2024-09-04 23:00:22Welcome back ya'll hope you are doing well this week. Today I wanted to talk about why Bitcoin represents a dawn of a new age in property ownership. Before you spit out your coffee and walk away, hear me out. Bitcoin and real estate have a few things in common. The first is property rights.
When you are the owner of a building with your name on the dotted line and whatnot, you are the sole owner of that property. No one can tell you what to do with it, and no one has a claim to what you own. You are free to do what you wish. Property rights are sacrosanct and immutable similar to Bitcoin.
Bitcoin confers upon the owner the same property right protections as owning a piece of real estate. Once you own it, you are the sole owner of that Bitcoin. No one can tell you what to do with it. No one else has a claim to your Bitcoin. You are free to do with it what you wish.
Bitcoin and real estate are similar in terms of built-in scarcity. There is only 21 million Bitcoin that will ever be created, and you can't print more land. This is why owning real estate has been such a good investment since the beginning of time. Buying a piece of land and "HODLING" for decades will generate a substantial return on your investment.
This same buy and hodl strategy apply to Bitcoin as well. If you bought Bitcoin back in 2009, you would be a multi-millionaire right now.
If you invested $1000 back in 2011 when Bitcoin was trading at $3.50, you would have turned that $1000 into $15.6 million if you held on to it for ten years. Just sayin.
You have to reframe your thinking to understand what is going on. We are living in the 21st-century gold rush, and you have an opportunity to stake your claim to the soundest money on Earth with a few taps on your phone. Never in the history of the world has the plebs like us had the ability to front-run a monetary revolution.
Bitcoin is freedom from oppression. Bitcoin restores your sovereignty. Bitcoin makes you fuckable, and the powers that be know it. They are afraid they will lose control if too many people catch on too quickly, which is why large institutions are rushing to offer Bitcoin services or buy them and keep them on their balance sheet.
Bitcoin won't stay this cheap forever. $100-300k Bitcoin is in the cards over the next few years. I don't want you guys to miss out on this.
All you have to do is buy Bitcoin and hold. It's that simple. FYI trying out the new obsidian writer for nostr notes!
Bitcoin #nostr
-
 @ 3b7fc823:e194354f
2024-09-02 16:26:30
@ 3b7fc823:e194354f
2024-09-02 16:26:30First steps into privacy.
You are a normie, but maybe you are privacy curious. Maybe you are ready to take a first step or two into security and privacy but don't know where to start.
Don't worry, here are some absolute beginner first steps that will make a big difference.
-
No one except your friends and family should know your personal phone number and email address. Stop giving away your data! You don't have to fill out every blank on that form. Unless they are mailing you something they don't need your home address. Use a email aliasing service or just create a burner email account as a spam trap. Get a second VOIP phone number. Look up the address of a local hotel. Use these instead of your personal information or maybe just skip the customer reward program.
-
Speaking of giving away your data. Stop using spyware! Facebook, Instagram, Tiktok, etc. It is "free" software designed to suck every ounce of personal data from you to be repackaged and sold. Don't just delete the app, search for how to delete your account data.
BTW Windows, google, and 90% of the apps on your phone are also spyware but one thing at a time. Maybe start reading up on FOSS.
-
Clean up your communications. Stop using unencrypted calls and SMS texts. There are several options but just get Signal and make your friends use it. Its easy and works.
-
Clean up your email. This one is probably going to take you some time if you are like most people who have hundreds of emails from years gone bye. Go through every single one and unsubscribe from every newsletter or sales pitch from every store you have ever bought anything from. Block every spam email you see. If you are using a email provider that literally scans every email you send or receive in order to sell you stuff like gmail, then now is the time to switch to a private and encrypted provider like proton or tuta.
-
Clean up your web surfing. Switch to a privacy browser and search engine. If you don't know which one just get Brave. There are ones that I like better but Brave is good enough and easy, especially if you like Chrome. A hardened Firefox is better but requires some homework and if on desktop Mullvad browser is a excellent choice.
BONUS TIP:
Clean up your security. Make sure all of your software is setup for automatic updates, especially security updates. Also, I don’t know who needs to hear this but get a password manager if you don’t have one. (Don't save passwords on the browser!) Get an actual password manager and then add 2FA to all of your online accounts and you will have better security than 90% of the population.
OK, nothing too exciting but we got the big rocks. Data leaks, communications, email, web surfing, and basic security.
What, no VPN or Tor or super secret stuff? No, not yet. This is your level zero default. Your identity and activity is still transparent but you are no longer leaking your data all over the place. This will provide a general base for everyone.
The next step is to perform a basic threat assessment of your personal situation. What are you most at risk for? Targeted attacks or passive? Cyber or physical? What do you most need to defend against? Government mass surveillance, surveillance capitalism, censorship, or public exposure?
There will be some overlap with all of them but your next steps will really depend on your answer. We will cover each of these in greater depth later.
-
-
 @ 266815e0:6cd408a5
2024-09-02 15:27:16
@ 266815e0:6cd408a5
2024-09-02 15:27:16After 7 months of work and procrastination I've decided to release another version of noStrudel
There a ton of new features and a few bugs fixed. This article highlights the biggest changes but if you want to read the full changelog you can find it in the github repo
And as always if you want to check it out you can use nostrudel.ninja or run it locally using docker
sh docker run --rm -p 8080:80 ghcr.io/hzrd149/nostrudel:0.40.0New Features
Support for NIP-49 encrypted nsec
Now when logging into to the app it will prompt you to set a password to encrypt your nsec so it can be stored securely (if that's even possible for a web client...)
There is also a new "Account" settings view that lets you export you nsec as a ncryptsec so you can copy it to other apps

Blindspot feeds
There are also new "blindspot" feeds that show what others are seeing in their timeline that your missing

NIP-42 Relay authentication
The app now supports NIP-42 relay authentication. Its opt-in though, so if you want to use popular authenticated relays like nostr.wine or relay.snort.social you will have to enable it in the settings

Wasm relay and event verification
The app now supports using @snort/worker-relay as a local relay. Its at least 10x faster than the internal browser cache and can hold at least 100x more events. Its not enabled by default though so if you want to use it you have to switch to it in the "Relays" -> "Cache Relay" view

The app also supports using nostr-wasm to speed up event signature verification. This is enabled by default, but if you want to still use the JavaScript verification or no verification you can find it in the performance setting

Thread tabs
Threads now have a set of tabs that let you see the Replies, Quotes, Zaps, and other stuff related to the note


Wiki articles
Its not feature complete but you can now view and edit wiki articles in the app

Finished the launchpad
The launchpad is now usable and shows the latest notifications, messages, streams, and tools

Blossom uploads
The app now lets you upload images and video to blossom server, this isn't enabled by default though so your going to have to enable it in the settings

And then setup some blossom servers in the settings. A few good public ones are
https://cdn.satellite.earthandhttps://cdn.nostrcheck.me
Task Manager
There is also a new "Task Manager" in the side nav that lets you see whats going on under the hood in the app

You can see what relays the app is currently connected to

And which relays are requesting NIP-42 authentication

Bug fixes
- Fix null relay hints in DMs
- Fix users own events being hidden by muted words
- Fix random events showing up as DM messages
- Fix app prompting NIP-07 extension to unlock when app opens
- Remove corsproxy.io as default service for CORS proxy
-
 @ 3b7fc823:e194354f
2024-09-02 13:07:09
@ 3b7fc823:e194354f
2024-09-02 13:07:09GHOSTn
- Renoted from a month ago into a article as a proof of concept
A quick overview
privacy #tor #vpn
**Computer -> clearnet -> Website **
ISP: sees that you are connected to website VPN: n/a Tor Entrance Node: n/a Tor Exit Node: n/a Website: sees your IP address and logs everything that you do on the website
Good for when the expectation of privacy does not exist. A KYC site you are logging into. Utility bill pay site, bank
**Computer -> VPN -> Website **
ISP: sees that you are connecting to a VPN but not what you are doing afterwards VPN: sees your IP Address and that you are connecting to a website Tor Entrance Node: n/a Tor Exit Node: n/a Website: sees that someone from a VPN exit node has connected but doesn’t know who. Logs data.
Good for hiding your activity from your ISP. Good for hiding your identity from the website. Good for when you want low level privacy but not anonymity. VPN provider sees everything and your level of privacy depends on how much they know about you and how much data they log and retain (varies greatly from provider to provider).
**Computer -> Tor -> Website **
ISP: sees that you are connected to Tor but nothing afterwards VPN: n/a Tor Entrance Node: sees your IP address but nothing afterwards Tor Exit Node: sees website you are going to but not who you are Website: sees someone from Tor has connected but doesn’t know who. Logs.
Good for privacy and anonymity. Assumes that Tor is legal in your country.
**Computer -> VPN -> Tor -> Website **
ISP: sees that you connected to a VPN but nothing afterwards VPN: sees IP address and that you are connecting to Tor but nothing afterwards Tor Entrance Node: sees a VPN is connected but nothing afterwards Tor Exit Node: sees website you are going to but not who you are Website: sees someone from Tor has connected but doesn’t know who. Logs.
Good for if your ISP blocks or cancels your service for using Tor. Potentially an option if Tor is illegal in your country (Dangerous).
**Computer -> Tor -> VPN -> Website **
ISP: sees that you are connecting to Tor but nothing afterwards VPN: sees someone from Tor is connected and that they are connecting to a website Tor Entrance Node: sees IP address but nothing afterwards Tor Exit Node: sees someone is connecting to a VPN but nothing afterwards Website: sees someone from a VPN is connecting but doesn’t know who. Logs.
Good for when a website blocks Tor traffic. Assumes Tor is legal in your country. Assumes that the VPN doesn’t know who you are. To maximize privacy and anonymity VPN provider should be KYC free and accept privacy payments (ex: Monero).
Note: If a website blocks Tor and VPN then maybe that is a sign that you shouldn’t go there.
-
 @ 1a48e74d:02c0e00f
2024-09-04 22:53:26
@ 1a48e74d:02c0e00f
2024-09-04 22:53:26Welcome back ya'll hope you are doing well this week. Today I wanted to talk about why Bitcoin represents a dawn of a new age in property ownership. Before you spit out your coffee and walk away, hear me out. Bitcoin and real estate have a few things in common. The first is property rights.
When you are the owner of a building with your name on the dotted line and whatnot, you are the sole owner of that property. No one can tell you what to do with it, and no one has a claim to what you own. You are free to do what you wish. Property rights are sacrosanct and immutable similar to Bitcoin.
Bitcoin confers upon the owner the same property right protections as owning a piece of real estate. Once you own it, you are the sole owner of that Bitcoin. No one can tell you what to do with it. No one else has a claim to your Bitcoin. You are free to do with it what you wish.
Bitcoin and real estate are similar in terms of built-in scarcity. There is only 21 million Bitcoin that will ever be created, and you can't print more land. This is why owning real estate has been such a good investment since the beginning of time. Buying a piece of land and "HODLING" for decades will generate a substantial return on your investment.
This same buy and hodl strategy apply to Bitcoin as well. If you bought Bitcoin back in 2009, you would be a multi-millionaire right now.
If you invested $1000 back in 2011 when Bitcoin was trading at $3.50, you would have turned that $1000 into $15.6 million if you held on to it for ten years. Just sayin.
You have to reframe your thinking to understand what is going on. We are living in the 21st-century gold rush, and you have an opportunity to stake your claim to the soundest money on Earth with a few taps on your phone. Never in the history of the world has the plebs like us had the ability to front-run a monetary revolution.
Bitcoin is freedom from oppression. Bitcoin restores your sovereignty. Bitcoin makes you fuckable, and the powers that be know it. They are afraid they will lose control if too many people catch on too quickly, which is why large institutions are rushing to offer Bitcoin services or buy them and keep them on their balance sheet.
Bitcoin won't stay this cheap forever. $100-300k Bitcoin is in the cards over the next few years. I don't want you guys to miss out on this.
All you have to do is buy Bitcoin and hold. It's that simple. FYI trying out the new obsidian writer for nostr notes!
Bitcoin #nostr
-
 @ 42342239:1d80db24
2024-09-02 12:08:29
@ 42342239:1d80db24
2024-09-02 12:08:29The ongoing debate surrounding freedom of expression may revolve more around determining who gets to control the dissemination of information rather than any claimed notion of safeguarding democracy. Similarities can be identified from 500 years ago, following the invention of the printing press.
What has been will be again, what has been done will be done again; there is nothing new under the sun.
-- Ecclesiastes 1:9
The debate over freedom of expression and its limits continues to rage on. In the UK, citizens are being arrested for sharing humouristic images. In Ireland, it may soon become illegal to possess "reckless" memes. Australia is trying to get X to hide information. Venezuela's Maduro blocked X earlier this year, as did a judge on Brazil's Supreme Court. In the US, a citizen has been imprisoned for spreading misleading material following a controversial court ruling. In Germany, the police are searching for a social media user who called a politician overweight. Many are also expressing concerns about deep fakes (AI-generated videos, images, or audio that are designed to deceive).
These questions are not new, however. What we perceive as new questions are often just a reflection of earlier times. After Gutenberg invented the printing press in the 15th century, there were soon hundreds of printing presses across Europe. The Church began using printing presses to mass-produce indulgences. "As soon as the coin in the coffer rings, the soul from purgatory springs" was a phrase used by a traveling monk who sold such indulgences at the time. Martin Luther questioned the reasonableness of this practice. Eventually, he posted the 95 theses on the church door in Wittenberg. He also translated the Bible into German. A short time later, his works, also mass-produced, accounted for a third of all books sold in Germany. Luther refused to recant his provocations as then determined by the Church's central authority. He was excommunicated in 1520 by the Pope and soon declared an outlaw by the Holy Roman Emperor.
This did not stop him. Instead, Luther referred to the Pope as "Pope Fart-Ass" and as the "Ass-God in Rome)". He also commissioned caricatures, such as woodcuts showing a female demon giving birth to the Pope and cardinals, of German peasants responding to a papal edict by showing the Pope their backsides and breaking wind, and more.
Gutenberg's printing presses contributed to the spread of information in a way similar to how the internet does in today's society. The Church's ability to control the flow of information was undermined, much like how newspapers, radio, and TV have partially lost this power today. The Pope excommunicated Luther, which is reminiscent of those who are de-platformed or banned from various platforms today. The Emperor declared Luther an outlaw, which is similar to how the UK's Prime Minister is imprisoning British citizens today. Luther called the Pope derogatory names, which is reminiscent of the individual who recently had the audacity to call an overweight German minister overweight.
Freedom of expression must be curtailed to combat the spread of false or harmful information in order to protect democracy, or so it is claimed. But perhaps it is more about who gets to control the flow of information?
As is often the case, there is nothing new under the sun.
-
 @ 1a48e74d:02c0e00f
2024-09-04 22:36:48
@ 1a48e74d:02c0e00f
2024-09-04 22:36:48Nothing can defeat Bitcoin.
-
 @ 7f0cbb03:c59f23d0
2024-09-04 21:28:57
@ 7f0cbb03:c59f23d0
2024-09-04 21:28:57 -
 @ 38d0888d:bd8e1246
2024-09-02 11:08:05
@ 38d0888d:bd8e1246
2024-09-02 11:08:05To foster collective improvement, it is essential to implement social programs that encourage voluntary engagement and mutual support. These initiatives should serve as fertile ground, nurturing altruistic values and deepening the understanding of humanity’s true needs. By integrating spiritual connections into these efforts, a ripple effect of kindness, understanding, and enlightenment can spread throughout society. Each individual, endowed with intellectual abilities by a higher power, is invited to contribute to the creation of a harmonious and enlightened world. Sharing inspirational concepts that blend spirituality with social responsibility has the potential to profoundly influence and unite public sentiment.
A sense of community and interconnectedness must be cultivated within these programs. Creating spaces for shared experiences and collective growth extends their impact beyond individual actions, fostering a network of mutual support and understanding.
It is crucial to promote inclusive development that transcends bureaucratic constraints, aiming to dismantle inequality and confront corruption. These initiatives do more than foster a fairer world; they also reveal the latent spiritual dimensions of the human mind. To encourage spiritual growth and overcome selfishness, collaborative efforts across society, decentralized governance structures, educational institutions, and individual contributions are imperative. Moral codes must emerge from deeply rooted spiritual ethics that are interwoven into the societal fabric, surpassing the interests of a privileged few. Humanity’s ultimate goal is to transcend mere cooperation among individuals, striving for absolute transparency and openness across all spheres of existence. Achieving this vision requires unwavering dedication from every stakeholder committed to guiding society along the path of enlightenment.
-
 @ 9dd283b1:cf9b6beb
2024-09-02 10:26:53
@ 9dd283b1:cf9b6beb
2024-09-02 10:26:53There's a saying: Bitcoin is hope.
But once you truly understand Bitcoin, many of the old fiat goals in your life start to lose meaning. It can feel disorienting and even depressing, because you realize you need to build entirely new goals, and you're unsure where to begin.
For example, maybe your plan was to get a mortgage, buy a house, and imagine your kids playing there for the next 20 years while you "happily" pay off a 25-year loan. But when you understand Bitcoin, that plan doesn’t make sense. Why would I put a 100k-200k down payment into a mortgage when it's likely better be in Bitcoin? Plus, you lose about 2.5% to 4% of the total price on taxes, fees, brokers, and other costs. Crazy, right?
I even made a short presentation for my wife, explaining why we should never buy a house given current interest rates and down payment requirements. She responded that she wants a house anyway, because it feels better to own one. But does a 25-year mortgage really make it feel like it’s yours?
She also said it’s depressing to not follow the conventional path. It’s hard to feel satisfied with numbers when everyone around you is deep into mortgages—you want to be one of them. You want to visit their houses and invite them to "yours." It's like becoming sober in a room full of addicts. You know it’s better for you, but the world around you seems so strange that part of you wants to go back, even though you know it hurts. Yet, when you do go back, the joy isn't there anymore. You feel...nothing. And then you decide to withdraw.
I remember paying off my first mortgage for an apartment, and I felt nothing. And that was before I fell down the Bitcoin rabbit hole. Now I know if I ever took out a mortgage again, I’d just feel regret for not keeping the money in Bitcoin. And by the time you finish paying it off, you probably want to sell the property and move somewhere else.
So, the rational decision is to keep everything in Bitcoin and rent instead.Unless, of course, Bitcoin goes to zero. There are only two outcomes for Bitcoin: it’s either going to infinity, or it's going to zero. There’s no scenario where it just hovers at 100k or 60k for the next 20 years—unless people are foolish enough to give away self-custody. If they do, we'll end up with digital gold. So the reasonable question is - how can you be sure? Well, you can't. But we are betting on it and it works for now. Worst case we will need to start from 0. But then there will be no hope anymore.
We are staying in the infinity camp. And when you are in that camp every time you make a big purchase, you’re shorting Bitcoin. Solution - simple, - don't buy anything. There’s a popular meme: You will own nothing, and you will be happy. But if you’re a Bitcoiner, it's more like: You will own only Bitcoin, and you probably won’t be happy about it. Why would I pay 30k for a car when I can lease one? Why put 100k down on a house when I can rent?
The only justification is mental comfort, peace of mind. Or perhaps you value the illusion of owning a physical thing more than the genuine ownership of something virtual. It’s confusing, isn’t it? Sure, you can own a bicycle. But owning a house? That's tricky. Imagine you’re a Russian citizen with a house on Lake Como, and suddenly, new sanctions mean Italy no longer recognizes your property. Or squatters break in while you’re on vacation, and now you need to go through a court battle to evict them.
Extreme situations, I know. But no one thinks it will happen to them—until it does.
So, you’ve sold everything to buy Bitcoin. You don’t own anything except Bitcoin, and you feel sad. Why?
What can you buy with Bitcoin that’s more valuable? Something that won’t depreciate over time. Something like time.
Time with your kids. Time with your family. Time with yourself.
There’s a concept called FIRE and then there is a Bitcoin FIRE calculation (https://bitcoincompounding.com/). In simple terms, you spend your Bitcoin slowly enough that it grows faster than you can spend it (in fiat terms). Unlike traditional assets, there’s no yield or dividends, so the only way it works is if Bitcoin continues its cycles. And you need to be at least two cycles in to make it work.
But personally, I don’t think there will be cycles anymore. I believe this October-November will break all the models, and Bitcoin will do what Bitcoin does: surprise everyone. I read somewhere a thought that stuck with me—imagine you wake up on a planet Earth on January 1st. You know nothing about the seasons or weather. After six months of only increasing temperatures, you’d be 100% certain it’s only getting hotter from here.
So what hope does Bitcoin offer? Hope that I can spend more time with my family. Hope that I can create something different for them. Hope that I can live without the weight of fiat goals. Hope that it's only getting hotter from here.
I just need to get through the withdrawal phase.
originally posted at https://stacker.news/items/662939
-
 @ 7ceaffbc:143b9e56
2024-09-04 20:50:26
@ 7ceaffbc:143b9e56
2024-09-04 20:50:26(roles in the adoption space)
Being different matters - At first!
The reasonable man adapts himself to the world; the unreasonable one persists in trying to adapt the world to himself. Therefore, all progress depends on the unreasonable man (Shaw, 1903).
h/t Everyone who is Satoshi.
It is probably fair to say Satoshi, Hal Finney, Adam Back et al. and we early ones are amongst the crazy ones.
Here’s to the crazy ones, the misfits, the rebels, the troublemakers, the round pegs in the square holes… the ones who see things differently — they’re not fond of rules… You can quote them, disagree with them, glorify or vilify them, but the only thing you can’t do is ignore them because they change things… they push the human race forward, and while some may see them as the crazy ones, we see genius, because the ones who are crazy enough to think that they can change the world, are the ones who do. (Jobs, 1997).
Sub-conclusion - To rid ourselves of fiat required radical thought - a base on which to build.
Most Babies learn to Walk
Born with the normal count of fingers toes etc, by the age of 26 I reckoned I had pretty much mastered walking (or so I believed) - until recently I fell, whereupon five things struck me deeply:
- Ageing and the associated decline is another form of novelty - I can resist it, it will eventually win but meanwhile I can adapt - and being alive is about adapting
- Things I have learnt must inevitably include all the things things I need to unlearn
- Things I have not learnt can become urgent (perhaps a wheechair lies in my future) and the learning can be delayed by the requisite unlearning from point 2 above
- Walking was something the masses did before I ever achieved it - which was probably what prompted me to adopt it as a means of ambulation
- The floor
Sub-conclusion - Mass adoption requires; * initiation (the crazy ones) * attention (seeing what others do) * unlearning (elimination of perceived assumptions) * learning (PoW) * emulation ( doing what others do) * mastery (practice doing it well) * review (figuring out what is no longer valuable) * evangelism (Helping others towards Truth)
OK - I have your attention - now what ? (Unpopular opinions incoming)
Eccentricity is not important to anything other than grabbing attention. Bitcoin is well beyond the thresh-hold of needing Eccentrics. We could all name them (and should appreciate their efforts).
The Overton window (that which may be normally spoken of) has become big enough that includes the best of our thinkers now. Analysts, Politicians, Purists, Financial advisers ??, Maxis, Left, Right & Centre.
But most of all it needs the centre. The extremes are great for raising attention and have the greatest voice on lesser social media platforms (which may be a thing of the past when you read this). However, it is clear that out of the centre (the Ex-centrics ? ) will come the mass of humanity that can benefit from bitcoin.
The bulk of future normies (users of bitcoin when only laggards use fiat) must come from the centre - because that is where they are now.
So decentralists or if you prefer "ex-centrics" will be easiest to help if we are seen as different - but reasonable, attractive and something to aspire to. The generosity / loving nature of many Bitcoiners will continue to win hearts (and minds)
Again unpopular perhaps (I should not care) - but this means ideally; - avoiding offensive behaviour (potty language) - avoiding ejection of those who are different (even if you reject their lifestyle choices) - understanding that we all start somewhere on this journey - smaller egos - I am a Bitcoin Maximalist by many definitions but, while my Christianity, what I eat, my and even my choice of frying pan may be most important to me - they may not help evangelise a better bitcoin future.
FWIW I think Bitcoin & Christianity go hand-in-glove in the journey toward a better future , but respect your (God given) right to disagree
Conclusion
Its time to stop thinking we are special and become normal - because that is what hyper-bitcoinisation implies.
To achieve this we need to find ways to secure legislation, peacefully dis-empower fiat states (a side effect - but IMHO a good one), make learning easier, remove barriers (FUD, technological etc) and lend a sympathetic ear to anyone who asks, what, why, how because that's how we all learn:
I keep six honest serving-men (They taught me all I knew); Their names are What and Why and When And How and Where and Who. I send them over land and sea, I send them east and west; But after they have worked for me, I give them all a rest.... (Kipling; The Elephant’s Child)
One day, if we do as well as we must, we will be able to claim - but we are just normal !
-
 @ e6fbeb1c:6ac8fc04
2024-09-02 10:17:27
@ e6fbeb1c:6ac8fc04
2024-09-02 10:17:27Eggplant is a member of the nightshade family, and it’s related to the potato and tomato. Often mistaken for a vegetable, eggplant is actually a fruit, and to be more precise, it’s a berry.

originally posted at https://stacker.news/items/669464
-
 @ 8125b911:a8400883
2024-09-02 07:18:52
@ 8125b911:a8400883
2024-09-02 07:18:52曾经有一款热门插件 dmooji(弹幕君),它让 YouTube 拥有了像其他弹幕网站一样的互动体验。看着屏幕上飞过的评论和吐槽,仿佛能和全世界的观众一起欢笑、感动、吐槽,那些弹幕不仅仅是文字,更是观众们在某个时刻留下的心情。但随着 dmooji 的开发者停止了维护,插件无法使用,用户的弹幕数据也随之丢失。那些在无数个夜晚留下的感触和笑点都被抹去,曾经与他人共享的回忆也随之消逝。这样的教训提醒我们,依赖于单一平台和维护团队的产品,总有脆弱的一天,可能我们珍视的东西就会悄然不再。
大约两年前,我偶然间了解到了一个去中心化的社交网络协议——nostr。当时我就萌生了一个想法:如果能基于这个协议做一款弹幕插件,那该有多好!然而,因为我主要从事后端开发,对前端几乎一窍不通,再加上拖延症的“加持”,这个想法一直被搁置。直到最近,我终于下定决心完成了这个项目,并将它命名为 danmakustr。
下载地址:https://chromewebstore.google.com/detail/mohbdimkkpjjibdfipfajpgpmegnglhb
源码地址:https://github.com/CodyTseng/danmakustr
最近弹幕墙:https://danmaku.nostr-relay.app/
danmakustr 有什么特点?
基于去中心化社交网络协议 nostr。你的弹幕会被发送并存储到你指定的服务器上,而非依赖单一服务器。即使插件未来不再维护,只要 nostr 网络仍然存在,插件就能继续正常使用!如果你非常珍视自己的弹幕,可以在本地运行 nostr-relay-tray 并将其添加到 relay 列表中。
danmakustr 目前已经在 YouTube 上实现了基本的弹幕功能,支持自定义弹幕的颜色和显示位置。未来还会支持一些弹幕互动功能,和支持更多的视频平台。
结语
在这个越来越注重个人表达和数据隐私的时代,danmakustr 带来了 YouTube 弹幕互动的新可能。它既保留了我们熟悉的乐趣,又为我们提供了前所未有的自由和控制权。如果你也对弹幕文化情有独钟,或者想要尝试一种全新的互动方式,那就赶紧体验 danmakustr 吧!让我们一起在弹幕的世界里畅所欲言,留下属于自己的印记。
-
 @ 79008e78:dfac9395
2024-09-02 06:17:23
@ 79008e78:dfac9395
2024-09-02 06:17:23ระบบเงินอิเล็กทรอนิกส์แบบ peer-to-peer
ระบบเงินอิเล็กทรอนิกส์แบบ peer-to-peer นั้นจะช่วยให้เราสามารถชำระเงินผ่านทางออนไลน์ได้โดยตรงจากฝ่ายหนึ่งไปยังอีกฝ่ายหนึ่งโดยไม่ต้องผ่านตัวกลางอย่างพวกสถาบันการเงิน โดยใช้ digital signature เป็นส่วนหนึ่งในการแก้ปัญหานี้ แต่มันจะไม่มีประโยชน์ใด ๆ เลยหากยังคงต้องอาศัยตัวกลางที่เชื่อถือได้มาแก้ปัญหา double spending เราขอเสนอวิธีแก้ปัญหา double spending โดยใช้เครือข่ายแบบ peer-to-peer ให้เครือข่ายคอยประทับเวลาธุรกรรมต่าง ๆ ในระบบและนำมาเรียงร้อยกันเป็นเส้นสายของ proof-of-work ที่ใช้ hash เพื่อสร้างธุรกรรมที่ไม่สามารถเปลี่ยนแปลงได้ โดยไม่ต้องทำ proof-of-work ใหม่ โดยให้เส้นสายที่ยาวที่สุดนั้น ไม่เพียงแต่ทำหน้าที่เป็นลำดับของธุรกรรมที่เกิดขึ้นเท่านั้น แต่ยังเป็นสิ่งที่พิสูจน์ได้ว่ามาจากกำลังประมวลผล CPU ที่มากที่สุด และตราบใดที่ nodes ส่วนใหญ่ไม่ได้ร่วมมือกันโจมตีเครือข่ายและยังคงควบคุมกำลังประมวลผลส่วนใหญ่ในระบบไว้ พวกเขาก็จะสร้างเส้นสายที่ยาวที่สุดและสามารถเอาชนะผู้ประสงค์ร้ายที่จะโจมตีระบบได้ ตัวเครือข่ายเองไม่ได้ต้องมีโครงสร้างอะไรที่ซับซ้อน ข้อมูลต่าง ๆ ในเครือข่ายจะถูกกระจายส่งต่อโดยไม่ต้องสนใจว่าผู้รับจะได้รับหรือไม่ และ nodes ต่าง ๆ เองก็สามารถที่จะออกจากเครือข่ายและกลับเข้าร่วมใหม่ได้ตามที่ต้องการ โดยยอมรับเส้น proof-of-work ที่ยาวที่สุด เป็นหลักฐานของสิ่งที่เกิดขึ้นในขณะที่ node นั้น ๆ ไม่ได้อยู่ในเครือข่าย
1.บทนำ (Introduction)
ไม่ว่าใครจะใคร่ซื้อใคร่ขายอะไรใด ๆ บนอินเตอร์เน็ตนั้น ก็จำเป็นต้องพึ่งพาสถาบันการเงินในฐานะของบุคคลที่สามเพื่อดำเนินการชำระเงินทางอิเล็กทรอนิกส์เสมอ ๆ ซึ่งถึงแม้ว่าระบบนี้มันจะทำงานได้ดีสำหรับธุรกรรมส่วนใหญ่ ๆ แต่ระบบก็ก็มีจุดอ่อนอยู่ที่ยังต้องอาศัยความไว้เนื้อเชื่อใจ (trust) ในระบบนี้การทำธุรกรรมที่ไม่สามารถย้อนกลับได้อย่างสมบูรณ์นั้นมันแทบจะเป็นไปไม่ได้เลย เนื่องจากสถาบันการเงินไม่สามารถหลีกเลี่ยงการเป็นตัวกลางในการไกล่เกลี่ยข้อพิพาทต่าง ๆ ที่อาจเกิดขึ้นได้ มิหนำซ้ำต้นทุนในการไกล่เกลี่ยยังทำให้ต้นทุนการทำธุรกรรมเพิ่มสูงขึ้น และเมื่อต้นทุนสูงขึ้นขนาดของธุรกรรมที่สามารถใช้งานได้จริงก็สูงขึ้นตามไปด้วย ธุรกรรมเล็ก ๆ น้อย ๆ ก็ไม่สามารถเกิดขึ้นได้ เมื่อมีความเป็นไปได้ที่ธุรกรรมจะเกิดการย้อนกลับ ความจำเป็นในการสร้างความไว้วางใจก็ยิ่งทวีคูณมากขึ้น ผู้ค้าก็จำเป็นต้องระมัดระวังลูกค้า ต้องเรียกร้องข้อมูลมากกว่าที่จำเป็น การฉ้อโกงกลายเป็นเรื่องที่หลีกเลี่ยงไม่ได้เพราะต้นทุนและความไม่แน่นอนในทำธุรกรรมเหล่านี้ แน่นอนว่าเราสามารถหลีกเลี่ยงมันได้โดยการใช้เงินสด แต่ก็ไม่มีกลไกใดที่ทำให้สามารถใช้เงินสดผ่านช่องทางการสื่อสาร (เอาให้เข้าใจง่ายก็อินเตอร์เน็ต)ได้ โดยไม่ต้องมีตัวกลาง ;-;
แปลว่าสิ่งที่จำเป็นสำหรับการแก้ไขปัญหานี้คือระบบการชำระเงินทางอิเล็กทรอนิกส์ ที่อยู่บนพื้นฐานของการพิสูจน์ด้วยการเข้ารหัสแทนที่จะเป็นความไว้วางใจ ซึ่งจะทำให้คู่สัญญาสองฝ่ายที่ยินยอมสามารถทำธุรกรรมร่วมกันได้โดยตรง โดยไม่จำเป็นต้องมีบุคคลที่สามมาคอยเป็นตัวกลาง ธุรกรรมที่ยากต่อการย้อนกลับจะช่วยปกป้องผู้ขายจากการฉ้อโกง และสามารถใช้กลไก escrow เพื่อปกป้องผู้ซื้อได้อีกด้วย ในเอกสารชุดนี้ เราขอเสนอวิธีแก้ปัญหาการใช้จ่ายซ้ำซ้อนโดยใช้เซิร์ฟเวอร์ timestamp กระจายศูนย์แบบ peer-to-peer เพื่อสร้างหลักฐานการคำนวณลำดับเวลาของธุรกรรม โดยระบบนี้จะปลอดภัยตราบใดที่กลุ่มของ node ที่ซื่อสัตย์ ยังคงมีกำลังประมวลผลที่มากกว่ากลุ่มที่ประสงค์ร้ายกับระบบ
2.ธุรกรรม (Transactions)
นิยามของเหรียญอิเล็กทรอนิกส์ในที่นี้ คือห่วงโซ่ที่คล้องเกี่ยวกันของ digital signature โดยที่เจ้าของเหรียญอิเล็กทรอนิกส์จะโอนเหรียญไปยังเจ้าของคนถัดไป ด้วยการลง digital signature บน hash ของธุรกรรมก่อนหน้ารวมถึงกุญแจสาธารณะของเจ้าของคนถัดไป และผนวกมันไว้ที่ส่วนท้ายของธุรกรรม และผู้รับเงินเองก็สามารถตรวจสอบลายเซ็นเพื่อยืนยันความเป็นเจ้าของได้
https://image.nostr.build/a467896797a9fb9f98c3c234f0adb4df2376f2c3d9a7cc9d8672d7a9f5aa9efa.png
แน่นอนว่าปัญหาก็คือผู้รับเงินไม่สามารถตรวจสอบได้ว่าเจ้าของคนใดคนหนึ่งก่อนหน้าเขาได้ใช้เหรียญดังกล่าวซ้ำซ้อนมากกว่าหนึ่งครั้งหรือไม่ และวิธีการแก้ไขปัญหานี้โดยทั่วไปก็คงเป็นการกำหนดตัวกลางที่มีความน่าเชื่อถือมาเป็นคนตรวจสอบทุกธุรกรรมเพื่อป้องกันการใช้จ่ายซ้ำซ้อน และหลังจากการทำธุรกรรมแต่ละครั้ง เหรียญจะต้องถูกส่งกลับไปยังตัวกลางเพื่อออกเหรียญใหม่ และจะมีเพียงเหรียญที่ออกจากตัวกลางโดยตรงเท่านั้นที่จะเชื่อถือได้ว่าจะไม่ถูกใช้จ่ายซ้ำซ้อน แต่ปัญหาก็คือ ชะตากรรมของระบบเงินทั้งหมดจะขึ้นอยู่กับตัวกลางตัวนี้ เพราะทุกธุรกรรมจำเป็นจะต้องผ่านพวกเขา ซึ่งก็ไม่ต่างอะไรกับธนาคาร
เราจึงต้องการวิธีการที่ทำให้ผู้รับเงินทราบได้ว่าเจ้าของคนก่อน ๆ ไม่ได้ลงนามในธุรกรรมใด ๆ มาก่อน เพื่อให้บรรลุวัตถุประสงค์นี้ เราจะทำการนับว่าธุรกรรมที่เกิดขึ้นก่อนเป็นธุรกรรมที่ถูกต้อง และจะไม่สนใจความพยายามใด ๆ ในการที่จะใช้เหรียญนั้น ๆ ซ้ำอีก และวิธีเดียวที่ทำแบบนี้ได้ คือการรับรู้ถึงธุรกรรมทั้งหมด เช่นเดียวกับโมเดลที่ได้กล่าวข้างต้น ที่ตัวกลางจะรับรู้ถึงธุรกรรมทั้งหมดและตัดสินว่าธุรกรรมใดมาก่อนมาหลัง เพื่อให้บรรลุเป้าหมายนี้โดยไม่ต้องมีบุคคลที่สามที่เชื่อถือได้ ธุรกรรมทั้งหมดจะต้องถูกประกาศต่อสาธารณะ [1] และเราต้องการระบบที่ผู้เข้าร่วมเห็นพ้องในประวัติธุรกรรมชุดเดียวกันตามลำดับที่ได้รับ ส่วนผู้รับเงินก็จำเป็นจะต้องมีหลักฐานว่า ในขณะที่ทำธุรกรรม "โหนด" ส่วนใหญ่ในระบบเห็นพ้องต้องกันว่าธุรกรรมนั้นได้รับเป็นลำดับแรก(ไม่มีธุรกรรมที่ใช้เหรียญพวกนี้มาก่อน)
3.ระบบบันทึกเวลา (Timestamp Server)
สำหรับแนวทางการแก้ปัญหาในครั้งนี้ เราจะใช้ประโยชน์จาก timestamp server ที่จะทำหน้าที่บันทึก hash ของบล๊อกที่ต้องการให้มีการบันทึกเวลา และจากนั้นจะทำการเผยแพร่ hash ดังกล่าว เหมือนกับหนังสือพิมพ์หรือโพสต์ใน Usenet [2-5] (ฟีลแบบทุกคนจะเห็นโพสต์นี้น้าา ประมาณนั้น) การบันทึกเวลานี้จะพิสูจน์ได้ว่าข้อมูลที่ถูก hash นั้นจะต้องมีอยู่จริงในเวลานั้นเพื่อให้ได้มาซึ่ง hash ดังกล่าว แต่ละการบันทึกเวลาจะรวมการบันทึกเวลาของหน้านี้ไว้ใน hash ของมันเพื่อสร้างเป็น chain โดยการบันทึกเวลาแต่ละครั้งจะยืนยันความถูกต้องของการบันทึกก่อนหน้าได้อีกด้วยด้วย
https://image.nostr.build/ddf92417c45dbb6e25da0af80a10d4cdbc3e725d047d65f54a3e3bfcf358c4d6.png
4.พรูฟ-ออฟ-เวิร์ค (Proof-of-Work)
ในการสร้าง Timestamp Server แบบกระจายศูนย์บนพื้นฐานแบบ peer to peer เราจำเป็นต้องใช้ระบบ Proof-of-Work (PoW) ที่คล้ายกับ Hashcash ของ Adam Back [6] แทนที่จะใช้วิธีการแบบเดิม ๆ อย่างการประกาศในหนังสือพิมพ์หรือ Usenet โดย PoW ใช้ในการตรวจสอบค่าที่มาจากกระบวนการ hash เช่น SHA-256 แล้ว ผลลัพธ์ที่ได้ (Hash) จะขึ้นต้นด้วยเลขศูนย์จำนวนหนึ่ง โดยที่ work (ประมาณว่าพลังประมวลผล) ที่ต้องใช้จะเพิ่มขึ้นแบบทวีคูณตามจำนวนเลขศูนย์ที่ต้องการ และสามารถตรวจสอบได้โดยการรัน Hash เพียงครั้งเดียว
ซึ่งสำหรับ timestamp network ของเรานั้น เราใช้ PoW โดยการเพิ่มค่า Nonce ในบล็อกไปเรื่อย ๆ จนกว่าจะพบค่าที่ทำให้ Hash ของบล็อกนั้นมีเลขศูนย์ตามที่กำหนด และเมื่อใช้กำลังประมวลผลของ CPU ไปกับการทำ PoW จนสำเร็จแล้ว บล็อกจะไม่สามารถเปลี่ยนแปลงได้ หากไม่มีการทำงานซ้ำใหม่ เนื่องจากบล็อกที่สร้างขึ้นภายหลังจะเชื่อมโยงกับบล็อกก่อนหน้า การเปลี่ยนแปลงบล็อกใด ๆ จะต้องทำ PoW ของบล็อกนั้นและบล็อกที่ตามมาใหม่ทั้งหมด
https://image.nostr.build/c039ef4ca6833cb1ecee65ac5991df2406be9b7e490b86b3b19f94f267767182.png
นอกจากนี้ PoW ยังช่วยแก้ปัญหาของเสียงส่วนมากที่มาตัดสินใจในระบบนี้ เพราะหากเสียงข้างมากอ้างอิงจากหลักการหนึ่ง IP หนึ่งเสียง ใครก็ตามที่สามารถสร้าง IP ได้จำนวนมากก็จะสามารถควบคุมระบบได้ จึงใช้หลักการหนึ่ง CPU หนึ่งเสียงแทน การตัดสินใจของเสียงข้างมากจะแสดงด้วย Chain ที่ยาวที่สุด ซึ่งบ่งบอกถึงความพยายามในการคำนวณ (Proof-of-Work) ที่มากที่สุด หาก Node ที่ซื่อสัตย์ (Honest nodes) มีกำลังประมวลผลของ CPU ส่วนใหญ่อยู่ในการควบคุม Honest Chain ก็จะเติบโตเร็วที่สุดและแซงหน้า Chain อื่น ๆ ได้ ผู้โจมตีที่ต้องการแก้ไขบล็อกในอดีตจะต้องทำ Proof-of-Work ของบล็อกนั้นและบล็อกที่ตามมาใหม่ทั้งหมด และต้องทำงานให้เร็วกว่า Honest Node ด้วย ซึ่งโอกาสที่ผู้โจมตีจะตามทันนั้นจะลดลงแบบทวีคูณเมื่อมีการเพิ่มบล็อกมากขึ้น
เพื่อชดเชยความเร็วของฮาร์ดแวร์ที่เพิ่มขึ้นและความสนใจในการรัน Node ที่ผันผวน ระดับความยากของ Proof-of-Work จะถูกกำหนดโดยค่าเฉลี่ย โดยตั้งเป้าไว้ที่จำนวนบล็อกเฉลี่ยต่อชั่วโมง หากสร้างบล็อกได้เร็วเกินไป ระดับความยากก็จะเพิ่มขึ้น
5.เครือข่าย (Network)
เครือข่ายนั้นมีการทำงาน ดังนี้
- การประกาศธุรกรรมใหม่: ธุรกรรมใหม่จะถูกประกาศ (broadcast) ไปยังทุก node ในเครือข่าย
- การรวบรวมธุรกรรม: แต่ละ node จะรวบรวมธุรกรรมใหม่ ๆ เหล่านี้ ไว้ในบล็อก
- การค้นหา Proof-of-Work: แต่ละ node จะทำการคำนวณ เพื่อค้นหา Proof-of-Work ตามค่า difficulty สำหรับบล็อกนั้น ๆ
- การประกาศบล็อก: เมื่อ node ใดค้นหา Proof-of-Work ได้แล้ว node นั้นจะทำการประกาศบล็อกไปยังทุก node ในเครือข่าย
- การตรวจสอบและยอมรับบล็อก: node อื่น ๆ จะทำการตรวจสอบและยอมรับบล็อกนั้น เฉพาะเมื่อธุรกรรมทั้งหมดภายในบล็อกนั้นถูกต้องและยังไม่ถูกใช้มาก่อน
- การสร้างบล็อกถัดไป: node ต่าง ๆ แสดงการยอมรับบล็อกโดยการเริ่มต้นสร้างบล็อกถัดไปใน chain ด้วย hash ของบล็อกที่ยอมรับ เป็น hash ก่อนหน้าในโครงสร้างของบล๊อกใหม่ที่กำลังสร้าง
node ต่าง ๆ จะถือว่า chain ที่ยาวที่สุดเป็น chain ที่ถูกต้องและจะทำงานเพื่อขยาย chain นั้นต่อไป หากมีสอง node ที่ได้ประกาศบล็อกเวอร์ชันที่แตกต่างกันในเวลาพร้อมกัน node บาง node อาจได้รับบล็อกหนึ่งก่อน อีกบล็อกหนึ่ง ในกรณีนี้ node เหล่านั้น จะทำงานบนบล็อกที่ได้รับก่อน แต่จะเก็บสำเนาของบล็อกอีกอันหนึ่งไว้ ในกรณีที่บล็อกนั้น กลายเป็นบล็อกที่อยู่ใน chain ที่ยาวกว่าปัญหาข้อโต้แย้งนี้ก็จะได้รับการแก้ไข เมื่อพบ Proof-of-Work อันถัดไปและ chain ใด chain หนึ่งยาวขึ้น node ที่กำลังทำงานอยู่บน chain ที่สั้นกว่าก็จะเปลี่ยนไปทำงานบน chain ที่ยาวกว่าแทน
การประกาศธุรกรรมใหม่ ไม่จำเป็นต้องไปถึงทุก node ในเครือข่าย ตราบใดที่พวกเขายังไปถึง node ส่วนใหญ่ในระบบได้ ธุรกรรมเหล่านั้นก็จะถูกบรรจุอยู่ในบล็อกในไม่ช้า นอกจากนี้การประกาศบล็อกยังไม่ต้องกังวลเรื่องจะมีบล๊อกที่สูญหาย เนื่องจากหากว่า node ไม่ได้รับบล็อกใด ๆ node ก็จะตระหนักได้ว่าพลาดบล็อกก่อนหน้าไปเมื่อได้รับบล๊อกใหม่มา และ node จะทำการร้องขอ block ที่ขาดไปจากเครือข่าย
6.แรงจูงใจ(Incentive)
โดยปกติแล้ว ธุรกรรมแรกของแต่ละบล๊อกนั้นจะเป็นธุรกรรมพิเศษที่จะขุดเหรียญที่สร้างขึ้นใหม่ซึ่งเป็นกรรมสิทธิ์ของผู้สร้างบล็อกนั้น ๆ ซึ่งจะเป็นการเพิ่มแรงจูงใจให้กับ node ต่าง ๆ ในการสนับสนุนเครือข่าย และเป็นวิธีการกระจายเหรียญให้หมุนเวียน เนื่องจากไม่มีหน่วยงานส่วนกลางที่ทำหน้าที่ในการออกเหรียญ การเพิ่มเหรียญใหม่ในปริมาณคงที่อย่างต่อเนื่องนั้นคล้ายคลึงกับการที่คนงานเหมืองทองคำใช้แรง และ เวลา เพื่อเพิ่มทองคำให้หมุนเวียน ในกรณีนี้ คือ เวลา กำลังประมวลผล และไฟฟ้าที่ถูกใช้ไป
นอกจากนี้แรงจูงใจจะมาจากค่าธรรมเนียมการทำธุรกรรม หากมูลค่าผลลัพธ์ของธุรกรรมน้อยกว่ามูลค่าที่ใส่เข้ามา ส่วนต่างนั้นก็คือค่าธรรมเนียมการทำธุรกรรมที่จะเพิ่มเข้าไปในมูลค่าแรงจูงใจของบล็อกที่มีธุรกรรมนั้น เมื่อเหรียญทั้งหมดในระบบมีจำนวนเท่ากับที่กำหนดไว้แล้ว แรงจูงใจหลักก็จะถูกเปลี่ยนมาเป็นค่าธรรมเนียมการทำธุรกรรม และปราศจากภาวะเงินเฟ้อโดยสิ้นเชิง
แรงจูงใจอาจช่วยกระตุ้นให้ node ต่าง ๆ ยังคงซื่อสัตย์ หากผู้โจมตีที่ละโมบสามารถรวบรวมกำลังประมวลผล ได้มากกว่า node ที่ซื่อสัตย์ทั้งหมด เขาจะต้องเลือกระหว่างการใช้มันเพื่อฉ้อโกงผู้อื่นโดยการใช้จ่ายซ้ำซ้อน หรือใช้มันเพื่อสร้างเหรียญใหม่ พวกเขาจะพบว่าการเล่นตามกฎ กฎที่เอื้อประโยชน์ให้กับเขาด้วยเหรียญใหม่มากกว่าคนอื่น ๆ รวมกันนั้นทำกำไรได้มากกว่าการบ่อนทำลายระบบและความถูกต้องของทรัพย์สินของเขาเอง
7.การจัดการพื้นที่ดิสก์(Reclaiming Disk Space)
เมื่อธุรกรรมถูกบรรจุลงในบล๊อกแล้ว สามารถกำจัดธุรกรรมที่ใช้ไปแล้วก่อนหน้านั้นออกได้เพื่อประหยัดพื้นที่ดิสก์ แต่การจะทำอย่างนี้ได้โดยไม่ให้เลข hash ของบล๊อกมีการเปลี่ยนแปลงนั้น ธุรกรรมจึงจำเป็นต้องถูก hash ในรูปแบบของ Merkle Tree [7][2][5] โดยมีแค่ root node ของ tree เท่านั้นที่จะรวมอยู่ใน hash ของบล๊อก นี่เป็นวิธีที่ทำให้สามารถบีบอัดข้อมูลในบล๊อกเก่า ๆ ได้โดยการตัดพวก hash ส่วนอื่น ๆ ของ tree ที่ไม่ใช่ root node ออก (ไม่จำเป็นต้องเก็บ hash ในชั้นอื่น ๆ ของ tree)
https://image.nostr.build/3ed95334891d91baca3f3f6f624a7ae22620be4ebfe0db5eb652cfce11255b9a.png
โดยในส่วน header ของบล็อกที่ไม่มีธุรกรรมจะมีขนาดประมาณ 80 ไบต์ หากเราสมมติว่าบล็อกถูกสร้างขึ้นทุก ๆ 10 นาที 80 ไบต์ * 6 * 24 * 365 = 4.2MB ต่อปี โดยที่ระบบคอมพิวเตอร์ทั่วไปที่วางขายในปี 2551 มี RAM 2GB และกฎของมัวร์ทำนายการเติบโตในปัจจุบันที่ 1.2GB ต่อปี การจัดเก็บข้อมูลไม่น่าจะเป็นปัญหาแม้ว่าส่วนหัวของบล็อกจะต้องถูกเก็บไว้ในหน่วยความจำก็ตาม
8.การตรวจสอบธุรกรรม (Simplified Payment Verification)
การที่จะยืนยันการชำระเงินโดยไม่จำเป็นต้องรัน full node ได้นั้น ผู้ใช้เพียงแค่เก็บสำเนาของส่วนหัวบล็อก (block header) ของสายบล็อก (chain) ที่ยาวที่สุด ซึ่งสามารถรับได้โดยการสอบถามจาก node อื่น ๆ ในเครือข่ายจนมั่นใจว่าได้รับสายที่ยาวที่สุด และรับ Merkle branch ที่เชื่อมโยงธุรกรรมกับบล็อกที่มีการประทับเวลา (Timestamp) อยู่ ถึงแม้ผู้ใช้จะไม่สามารถตรวจสอบธุรกรรมด้วยตัวเองได้ แต่การเชื่อมโยงธุรกรรมกับตำแหน่งในสายบล็อกจะทำให้เห็นว่า node ในเครือข่ายยอมรับแล้ว และบล็อกที่เพิ่มเข้ามาหลังจากนั้นเป็นการยืนยันเพิ่มเติมว่าเครือข่ายยอมรับธุรกรรมนี้แล้ว
https://i.imgur.com/VXtLpRF.png
การตรวจสอบดังกล่าวจะเชื่อถือได้ตราบใดที่ node ที่ซื่อสัตย์ยังคงควบคุมเครือข่าย แต่จะมีความเสี่ยงมากขึ้นหากเครือข่ายถูกโจมตีและถูกควบคุม ในขณะที่ node ในเครือข่ายสามารถตรวจสอบธุรกรรมได้ด้วยตัวเอง แต่วิธีการแบบง่ายนี้อาจถูกหลอกลวงโดยการใช้ธุรกรรมปลอมของผู้โจมตี ตราบใดที่ผู้โจมตียังคงสามารถควบคุมเครือข่ายได้ กลยุทธ์หนึ่งในการป้องกันปัญหานี้คือ การรับการแจ้งเตือนจาก node อื่น ๆ ในเครือข่ายเมื่อตรวจพบบล็อกที่ไม่ถูกต้อง ซึ่งจะแจ้งให้ซอฟต์แวร์ของผู้ใช้ดาวน์โหลดบล็อกแบบเต็มและธุรกรรมที่แจ้งเตือน เพื่อยืนยันความไม่สอดคล้องกัน ธุรกิจที่ได้รับการชำระเงินบ่อยครั้งอาจยังคงต้องการรัน node ของตนเอง เพื่อความปลอดภัยที่เป็นอิสระและการตรวจสอบที่รวดเร็วยิ่งขึ้น
9.การควบรวมและแบ่งย่อยมูลค่า(Combining and Splitting Value)
แม้ว่าการจัดการเหรียญหลาย ๆ เหรียญจะเป็นสิ่งที่สามารถทำได้ แต่การจัดการธุรกรรมแยกต่างหากสำหรับแต่ละเหรียญในการโอนก็คงเป็นเรื่องที่น่าปวดหัวอยู่ดี ฉะนั้นแล้วเพื่อให้สามารถแยกและรวมมูลค่ากันได้ ธุรกรรมจึงสามารถมี input และ output ได้หลายรายการ ซึ่งโดยปกติแล้วจะมี input เดียวจากธุรกรรมก่อนหน้าที่มีขนาดใหญ่กว่า หรือ input จำนวนเล็ก ๆ หลาย ๆ รายการ และ output ไม่เกินสองรายการ คือ รายการหนึ่งสำหรับการชำระเงิน และอีกหนึ่งรายการสำหรับการส่งเงินทอน หากมีกลับไปยังผู้ส่ง
https://image.nostr.build/9c6d3ce0e9f08c5b3fa3b82c2088ac6235603e5c0df3469060e6c9f74bce32fc.png
ควรสังเกตว่า fan-out (กระจายของธุรกรรม) ซึ่งเป็นกรณีที่ธุรกรรม ธุรกรรมหนึ่งนั้นขึ้นอยู่กับหลายธุรกรรม และธุรกรรมเหล่านั้นเองก็ขึ้นอยู่กับอีกหลายธุรกรรม แต่ไม่ใช่ปัญหาในที่นี้ เพราะไม่มีความจำเป็นในการดึงประวัติการทำธุรกรรมทั้งหมดออกมาเป็นสำเนา
10.ความเป็นส่วนตัว(Privacy)
ในรูปแบบธนาคารแบบดั้งเดิมนั้น ความเป็นส่วนตัวเกิดขึ้นได้ด้วยการจำกัดการเข้าถึงข้อมูล โดยให้เฉพาะผู้ที่เกี่ยวข้องและบุคคลที่สามที่ได้รับความไว้วางใจเท่านั้น แต่เนื่องจากในระบบนี้เรามีความจำเป็นในการประกาศธุรกรรมทั้งหมดต่อสาธารณะ ทำให้ไม่สามารถใช้วิธีนี้ได้ แต่ยังจำเป็นต้องคงความเป็นส่วนตัวไว้ โดยการแบ่งการไหลของข้อมูล ด้วยการไม่เปิดเผยตัวตนของเจ้าของ public key คนทั่วไปสามารถเห็นว่ามีคนกำลังส่งเงินจำนวนหนึ่งให้กับคนอื่น แต่จะไม่ทราบข้อมูลที่เชื่อมโยงธุรกรรมนั้นกับบุคคลใด ๆ ซึ่งคล้ายกับระดับข้อมูลที่เปิดเผยโดยตลาดหลักทรัพย์ ซึ่งมีการเปิดเผยเวลาและขนาดของการซื้อขายแต่ละครั้งต่อสาธารณะ แต่ไม่ได้ระบุว่าคู่สัญญาคือใคร
https://image.nostr.build/6ec3c84c7878dbd4558d2045518384daf5a341e86f4194cf367cc8426c2d72a7.png
เพื่อเสริมในเรื่องของความปลอดภัย ควรใช้ key pair ใหม่สำหรับการทำธุรกรรมในแต่ละครั้ง เพื่อป้องกันไม่ให้เชื่อมโยงกับเจ้าของคนเดียวกันได้ อย่างไรก็ตาม การเชื่อมโยงบางอย่างยังคงหลีกเลี่ยงไม่ได้ ในธุรกรรมที่มี input หลายรายการ ซึ่งจำเป็นต้องเปิดเผยว่า input เหล่านั้นเป็นของเจ้าของคนเดียวกัน ความเสี่ยงก็คือ หากมีการเปิดเผยตัวตนของเจ้าของคีย์ การเชื่อมโยงอาจเปิดเผยธุรกรรมอื่น ๆ ที่เป็นของเจ้าของรายเดียวกันได้
11.การคำนวณ(Calculations)
หากลองพิจารณาสถานการณ์ที่ผู้โจมตีพยายามสร้าง chain ปลอมให้เร็วกว่า chain จริง แม้ว่าจะทำได้สำเร็จ แต่มันก็ไม่สามารถทำให้ระบบเปิดรับการเปลี่ยนแปลงตามอำเภอใจได้อยู่ดี เช่น การสร้างมูลค่าจากอากาศธาตุ หรือการรับเงินที่ไม่เคยเป็นของผู้โจมตีมาก่อน Node ต่าง ๆ จะไม่ยอมรับธุรกรรมที่ไม่ถูกต้องเป็นการชำระเงิน และ Node ที่สุจริตก็จะไม่ยอมรับบล็อกที่มีธุรกรรมเหล่านั้นอย่างแน่นอน ผู้โจมตีทำได้เพียงพยายามเปลี่ยนแปลงธุรกรรมของตนเอง เพื่อนำเงินที่ใช้ไปแล้วกลับคืนมาเท่านั้น
การแข่งขันระหว่าง chain สุจริตกับ chain ของผู้โจมตี สามารถอธิบายได้ด้วยแบบจำลองการเดินสุ่มทวินาม (Binomial Random Walk) โดยเหตุการณ์ที่สำเร็จ หมายถึง chain ที่สุจริตถูกขยายออกไปอีกหนึ่งบล็อก เพิ่มความยาวนำหน้าไป +1 และเหตุการณ์ที่ล้มเหลว หมายถึง chain ของผู้โจมตีถูกขยายออกไปหนึ่งบล็อก ลดช่องว่างลง -1
ความน่าจะเป็นที่ผู้โจมตีจะไล่ตามทันจากช่องว่างที่กำหนด สามารถเปรียบเทียบด้วย Gambler's Ruin problem โดยสมมติว่านักพนันที่มีเครดิตไม่จำกัด เริ่มต้นด้วยการขาดทุน และเล่นพนันไปเรื่อย ๆ เพื่อให้ถึงจุดคุ้มทุน เราสามารถคำนวณความน่าจะเป็นที่เขาจะกลับมาถึงจุดคุ้มทุนได้ หรือความน่าจะเป็นที่ผู้โจมตีจะไล่ทัน chain ที่สุจริตได้ ดังนี้ [8]:
p = ความน่าจะเป็นที่ Node ที่สุจริตจะพบบล็อกถัดไป q = ความน่าจะเป็นที่ผู้โจมตีจะพบบล็อกถัดไป qz = ความน่าจะเป็นที่ผู้โจมตีจะไล่ทัน จากที่ตามหลังอยู่ z บล็อก
https://i.imgur.com/vePe255.png
จากสมมติฐานที่ว่า p > q ความน่าจะเป็นจะลดลงแบบเอกซ์โพเนนเชียล เมื่อจำนวนบล็อกที่ผู้โจมตีต้องไล่ตามทันเพิ่มขึ้น หากเขาไม่สามารถพุ่งขึ้นนำได้อย่างรวดเร็วตั้งแต่แรก โอกาสของเขาก็จะลดลงจนน้อยมาก ๆ เมื่อเขาตามหลังมากขึ้นเรื่อย ๆ
ทีนี้ลองพิจารณาว่า ผู้รับธุรกรรมใหม่ต้องรอเป็นเวลานานเท่าใด จึงจะแน่ใจได้ว่าผู้ส่งไม่สามารถเปลี่ยนแปลงธุรกรรมได้แล้ว เราสมมติว่าผู้ส่งเป็นผู้โจมตี ที่ต้องการให้ผู้รับเชื่อว่าเขาได้รับเงินไปแล้ว จากนั้นจึงเปลี่ยนให้เงินกลับเข้าหาตัวเองหลังจากเวลาผ่านไประยะหนึ่ง ผู้รับจะได้รับแจ้งเมื่อเกิดเหตุการณ์นี้ขึ้น แต่ผู้ส่งหวังว่ามันจะสายเกินไปแล้ว
ผู้รับจะสร้างคู่กุญแจใหม่ และให้กุญแจสาธารณะแก่ผู้ส่งไม่นานก่อนที่จะลงนาม ซึ่งจะป้องกันไม่ให้ผู้ส่งเตรียมบล็อกเชนปลอมไว้ล่วงหน้า โดยการทำงานอย่างต่อเนื่องจนกว่าเขาจะมีโอกาสได้บล็อกที่ยาวพอ จากนั้นจึงดำเนินธุรกรรมในทันที เมื่อส่งธุรกรรมแล้ว ผู้ส่งที่ไม่สุจริตจะเริ่มทำงานอย่างลับ ๆ บนบล็อกเชนคู่ขนาน ที่มีธุรกรรมในเวอร์ชันของเขาเองอยู่
ผู้รับจะรอจนกว่าธุรกรรมจะถูกเพิ่มลงในบล็อก และมีบล็อกที่ถูกเชื่อมต่อตามหลังมาอีก z บล็อก เขาไม่ทราบจำนวนความคืบหน้าที่แน่นอนที่ผู้โจมตีได้ทำไปแล้ว แต่สมมติว่าบล็อกที่สุจริตใช้เวลาเฉลี่ยต่อบล็อกตามที่คาดไว้ ความคืบหน้าที่อาจเกิดขึ้นได้ของผู้โจมตีจะเป็นการแจกแจงแบบปัวซง (Poisson distribution) ซึ่งมีค่าคาดหวังดังนี้:
https://i.imgur.com/mYsb48i.png
เพื่อให้ได้ความน่าจะเป็นที่ผู้โจมตียังคงสามารถไล่ทันได้ เราจะคูณความหนาแน่นของปัวซง สำหรับความคืบหน้าแต่ละระดับที่เขาสามารถทำได้ ด้วยความน่าจะเป็นที่เขาสามารถไล่ทันจากจุดนั้น:
https://i.imgur.com/jQGkQ8r.png
จัดเรียงใหม่เพื่อหลีกเลี่ยง infinite tail ของการแจกแจง
https://i.imgur.com/OOO6Gm9.png
แปลงมันให้เป็น C code
include
double AttackerSuccessProbability(double q, int z) { double p = 1.0 - q; double lambda = z * (q / p); double sum = 1.0; int i, k; for (k = 0; k <= z; k++) { double poisson = exp(-lambda); for (i = 1; i <= k; i++) poisson *= lambda / i; sum -= poisson * (1 - pow(q / p, z - k)); } return sum; }
เมื่อรันผลลัพธ์บางส่วน เราจะเห็นว่าความน่าจะเป็นลดลงแบบเอกซ์โพเนนเชียลเมื่อ z เพิ่มขึ้น
q=0.1 z=0 P=1.0000000 z=1 P=0.2045873 z=2 P=0.0509779 z=3 P=0.0131722 z=4 P=0.0034552 z=5 P=0.0009137 z=6 P=0.0002428 z=7 P=0.0000647 z=8 P=0.0000173 z=9 P=0.0000046 z=10 P=0.0000012 q=0.3 z=0 P=1.0000000 z=5 P=0.1773523 z=10 P=0.0416605 z=15 P=0.0101008 z=20 P=0.0024804 z=25 P=0.0006132 z=30 P=0.0001522 z=35 P=0.0000379 z=40 P=0.0000095 z=45 P=0.0000024 z=50 P=0.0000006
การแก้หาค่า P ที่น้อยกว่า 0.1%...
P < 0.001 q=0.10 z=5 q=0.15 z=8 q=0.20 z=11 q=0.25 z=15 q=0.30 z=24 q=0.35 z=41 q=0.40 z=89 q=0.45 z=340
12.สรุป(Conclusion)
เราได้นำเสนอระบบธุรกรรมอิเล็กทรอนิกส์ที่ไม่ต้องพึ่งพาความไว้วางใจ เริ่มต้นจากกรอบแนวคิดของเหรียญที่สร้างจากลายเซ็นดิจิทัล ซึ่งช่วยควบคุมความเป็นเจ้าของได้อย่างดีแต่ก็ยังไม่สมบูรณ์ หากปราศจากวิธีการป้องกันการใช้จ่ายซ้ำซ้อน เพื่อแก้ปัญหานี้ เราจึงเสนอเครือข่ายแบบเพียร์ทูเพียร์ที่ใช้ proof-of-work ในการบันทึกประวัติธุรกรรมสาธารณะ ซึ่งจะกลายเป็นเรื่องยากอย่างมากสำหรับผู้โจมตีที่จะเปลี่ยนแปลง หาก node ที่ซื่อสัตย์ควบคุมพลังประมวลผล CPU ส่วนใหญ่ เครือข่ายนี้มีความแข็งแกร่งในความเรียบง่ายที่ไม่มีโครงสร้างใด ๆ ที่ซับซ้อน node ต่าง ๆ ทำงานพร้อมกันโดยประสานงานกันเพียงเล็กน้อย ไม่จำเป็นต้องระบุตัวตน เนื่องจากข้อความไม่ได้ถูกส่งไปยังสถานที่ใดสถานที่หนึ่งโดยเฉพาะ และเพียงแค่ต้องส่งมอบให้ถึงมือผู้รับอย่างดีที่สุด node สามารถออกจากและเข้าร่วมเครือข่ายได้ตามต้องการ โดยยอมรับ chain ที่มี proof-of-work มากที่สุดเป็นสิ่งที่เกิดขึ้นในขณะที่ไม่ได้เชื่อมต่อ พวกเขาโหวตด้วยพลังประมวลผล CPU แสดงการยอมรับบล็อกที่ถูกต้องโดยการทำงานเพื่อขยายบล็อก และปฏิเสธบล็อกที่ไม่ถูกต้องโดยการปฏิเสธที่จะทำงานกับบล็อกเหล่านั้น กฎและแรงจูงใจใด ๆ ที่จำเป็นสามารถบังคับใช้ได้ด้วยกลไกฉันทามตินี้
ไปอ่านต่อกันเองเด้ออ
[1] W. Dai, "b-money," http://www.weidai.com/bmoney.txt, 1998. [2] H. Massias, X.S. Avila, and J.-J. Quisquater, "Design of a secure timestamping service with minimal trust requirements," In 20th Symposium on Information Theory in the Benelux, May 1999. [3] S. Haber, W.S. Stornetta, "How to time-stamp a digital document," In Journal of Cryptology, vol 3, no 2, pages 99-111, 1991. [4] D. Bayer, S. Haber, W.S. Stornetta, "Improving the efficiency and reliability of digital time-stamping," In Sequences II: Methods in Communication, Security and Computer Science, pages 329-334, 1993. [5] S. Haber, W.S. Stornetta, "Secure names for bit-strings," In Proceedings of the 4th ACM Conference on Computer and Communications Security, pages 28-35, April 1997. [6] A. Back, "Hashcash - a denial of service counter-measure," http://www.hashcash.org/papers/hashcash.pdf, 2002. [7] R.C. Merkle, "Protocols for public key cryptosystems," In Proc. 1980 Symposium on Security and Privacy, IEEE Computer Society, pages 122-133, April 1980. [8] W. Feller, "An introduction to probability theory and its applications," 1957.
-
 @ 1a48e74d:02c0e00f
2024-09-04 18:53:09
@ 1a48e74d:02c0e00f
2024-09-04 18:53:09Welcome back ya'll hope you are doing well this week. Today I wanted to talk about why Bitcoin represents a dawn of a new age in property ownership. Before you spit out your coffee and walk away, hear me out. Bitcoin and real estate have a few things in common. The first is property rights.
When you are the owner of a building with your name on the dotted line and whatnot, you are the sole owner of that property. No one can tell you what to do with it, and no one has a claim to what you own. You are free to do what you wish. Property rights are sacrosanct and immutable similar to Bitcoin.
Bitcoin confers upon the owner the same property right protections as owning a piece of real estate. Once you own it, you are the sole owner of that Bitcoin. No one can tell you what to do with it. No one else has a claim to your Bitcoin. You are free to do with it what you wish.
Bitcoin and real estate are similar in terms of built-in scarcity. There is only 21 million Bitcoin that will ever be created, and you can't print more land. This is why owning real estate has been such a good investment since the beginning of time. Buying a piece of land and "HODLING" for decades will generate a substantial return on your investment.
This same buy and hodl strategy apply to Bitcoin as well. If you bought Bitcoin back in 2009, you would be a multi-millionaire right now.
If you invested $1000 back in 2011 when Bitcoin was trading at $3.50, you would have turned that $1000 into $15.6 million if you held on to it for ten years. Just sayin.
You have to reframe your thinking to understand what is going on. We are living in the 21st-century gold rush, and you have an opportunity to stake your claim to the soundest money on Earth with a few taps on your phone. Never in the history of the world has the plebs like us had the ability to front-run a monetary revolution.
Bitcoin is freedom from oppression. Bitcoin restores your sovereignty. Bitcoin makes you fuckable, and the powers that be know it. They are afraid they will lose control if too many people catch on too quickly, which is why large institutions are rushing to offer Bitcoin services or buy them and keep them on their balance sheet.
Bitcoin won't stay this cheap forever. $100-300k Bitcoin is in the cards over the next few years. I don't want you guys to miss out on this.
All you have to do is buy Bitcoin and hold. It's that simple. FYI trying out the new obsidian writer for nostr notes!
Bitcoin #nostr
-
 @ 79008e78:dfac9395
2024-09-02 06:17:05
@ 79008e78:dfac9395
2024-09-02 06:17:05Nostr: โปรโตคอลทางเลือกใหม่สำหรับโซเชียลมีเดียที่เป็นอิสระ ปลอดภัย และไร้การควบคุม
Nostr คือโปรโตคอลแบบเปิดที่เรียบง่าย ซึ่งช่วยให้สามารถสร้างโซเชียลมีเดียระดับโลกที่กระจายอำนาจและป้องกันการเซ็นเซอร์ได้
จากที่กล่าวข้างต้น เราสามารถพูดได้ว่า Nostr นั้นถูกออกแบบมาให้ใช้งานง่าย โดยมีเป้าหมายหลัก ๆ เพื่อสร้างเครือข่ายโซเชียลระดับโลกที่ปราศจากการเซ็นเซอร์ แล้วทำไมมันถึงทำอย่างนั้นได้? ในจุดนี้เราก็ต้องมาเจาะดูคุณสมบัติหลัก ๆ ของโปรโตคอลที่เรียกว่า Nostr กันก่อน:
เรียบง่าย - โปรโตคอลนี้ใช้โครงสร้างข้อมูลแบบ Event Object ที่เรียบง่ายและยืดหยุ่น (ซึ่งส่งเป็น JSON ธรรมดา) และใช้การเข้ารหัสแบบ Elliptic-curve มาตรฐานสำหรับคีย์และลายเซ็น
-
ช่องทางการสื่อสารที่รองรับเพียงอย่างเดียวคือการเชื่อมต่อ WebSockets จากไคลเอนต์ไปยังรีเลย์
-
การออกแบบนี้ทำให้ง่ายต่อการพัฒนาไม่ว่าจะไคลเอนต์หรือรีเลย์ และยังช่วยส่งเสริมความหลากหลายของซอฟต์แวร์
ยืดหยุ่น - เนื่องจาก Nostr ไม่ได้พึ่งพาเซิร์ฟเวอร์ที่เชื่อถือได้เพียงจำนวนหยิบมือ สำหรับการเคลื่อนย้ายหรือจัดเก็บข้อมูล แต่ใช้เซิร์ฟเวอร์จำนวนมหาศาลและกระจายตัวอยู่ทั่วโลก จึงมีความยืดหยุ่นสูง และมีการกระจายศูนย์อย่างแท้จริง
- โปรโตคอลนี้ถูกออกแบบมาโดยคำนึงถึงความเป็นไปได้ที่รีเลย์จะหายไป และอนุญาตให้ผู้ใช้เชื่อมต่อและเผยแพร่ข้อมูลไปยังรีเลย์จำนวนมากได้ตามต้องการ และยังสามารถเปลี่ยนแปลงได้ตลอดเวลาอีกด้วย
ตรวจสอบได้
- เนื่องจากบัญชี Nostr ใช้การเข้ารหัสแบบ PKE จึงง่ายต่อการตรวจสอบว่าข้อความถูกส่งมาจากผู้ใช้ที่ระบุจริงหรือไม่
เช่นเดียวกับ HTTP หรือ TCP-IP Nostr เป็นโปรโตคอลหรือมาตรฐานแบบเปิดที่ทุกคนสามารถนำไปสร้างต่อยอดได้ มันไม่ใช่แอปหรือบริการที่คุณจำเป็นต้องลงทะเบียน
แล้วทำไมเราถึงต้องการ Nostr?
ถึงในปัจจุบันโซเชียลมีเดียจะได้พัฒนามาเป็นช่องทางสำคัญในการไหลเวียนของข้อมูลทั่วโลก กลายเป็นช่องทางหลักในการติดต่อสื่อสาร แต่น่าเสียดายที่ระบบโซเชียลมีเดียในปัจจุบันของเรานั้นมีข้อบกพร่องมากมาย:
- ใช้ความสนใจของคุณเพื่อขายโฆษณา
- ใช้เทคนิคแปลกๆ เพื่อทำให้คุณเสพติด (อ้างอิงจากข้อ 1)
- ตัดสินใจว่าจะแสดงเนื้อหาใดให้คุณเห็นโดยใช้อัลกอริทึมลับที่คุณไม่สามารถตรวจสอบหรือเปลี่ยนแปลงได้
- ควบคุมอย่างเต็มที่ว่าใครสามารถเข้าร่วมและใครถูกเซ็นเซอร์
- เต็มไปด้วยสแปมและบอท
ด้วยข้อจำกัดเหล่านี้ Nostr จึงเป็นทางเลือกที่น่าสนใจในการสร้างโซเชียลมีเดียที่เป็นอิสระ ปลอดภัย และไร้การควบคุม
องค์ประกอบของโปรโตคอลที่ชื่อว่า Nostr
หลังจากได้ทำความรู้จัก Nostr กันไปแล้วเมื่อคราวก่อน คราวนี้เรามาเจาะดูองค์ประกอบของโปรโตคอลนี้กันดีกว่า
Keys ระบบบัญชีผู้ใช้และรหัสผ่านสำหรับ Nostr
-
บัญชี Nostr แต่ละบัญชีจะใช้คู่กุญแจสาธารณะ/ส่วนตัว (Public/Private Key ) เปรียบเทียบง่าย ๆ คือ กุญแจสาธารณะของคุณคือชื่อผู้ใช้ และกุญแจส่วนตัวก็เป็นรหัสผ่าน แต่ว่า ก็มีข้อแตกต่างที่สำคัญอยู่ นั่นคือ กุญแจส่วนตัวของคุณนั้นจะไม่สามารถรีเซ็ตได้หากเกิดการสูญหายขึ้น คุณจะเสียบัญชีนั้นไปตลอดกาล
-
โดยทั่วไปแล้ว กุญแจสาธารณะจะแสดงเป็นข้อความที่ขึ้นต้นด้วย npub1 และกุญแจส่วนตัวจะขึ้นต้นด้วย nsec1
-
ทั้งนี้คุณควรที่จะตรวจสอบให้แน่ใจว่าคุณได้เก็บกุญแจส่วนตัวของคุณไว้ในที่ปลอดภัย เช่น โปรแกรมจัดการรหัสผ่านอย่างเช่น Bitwarden
โปรโตคอลกับไคลเอนต์ ต่างกันอย่างไร?
Nostr เองเป็นเพียงโปรโตคอล หมายความว่า Nostr นั้นเป็นเพียงกระบวนการที่ตกลงกันไว้สำหรับการส่งข้อความผ่านอินเทอร์เน็ต (เหมือนข้อกำหนด)
ซึ่งการที่คุณจะเข้าถึง Nostr (โปรโตคอล) นั้น ผู้ใช้ส่วนใหญ่จะใช้งานผ่านไคลเอนต์ ซึ่งตัวของไคลเอนต์นั้นอาจเป็นเว็บ แอปพลิเคชันเดสก์ท็อป หรือ แอปพลิเคชันมือถือ โดยไคลเอนต์สามารถดึงข้อมูลจากรีเลย์ และสร้างข้อมูลใหม่ และส่งข้อมูลนั้นไปยังรีเลย์เพื่อให้ผู้ใช้คนอื่น ๆ สามารถเรียกอ่าน ข้อมูลนั้น ๆ ได้ โดย "ข้อมูล" เพียงรูปแบบเดียวที่มีอยู่ใน Nostr คือสิ่งที่เราเรียกกันว่า event
การพิสูจน์ความเป็นเจ้าของข้อมูลบน Nostr
บน Nostr นั้นการพิสูจน์ตัวตนเป็นเรื่องที่ง่ายมากเนื่องจากทุก ๆ event ที่เกิดขึ้น จำเป็นต้องมีลายเซ็นดิจิทัล (Digital Signature) โดยลายเซ็นนั้นจะช่วยให้มั่นใจได้ว่า ใครเป็นผู้สร้าง event นั้น ๆ ขึ้นมา โดยการพิสูจน์ทางคณิตศาสตร์
โดยในการสร้างลายเซ็นแต่ละครั้ง ไคลเอนต์จะจำเป็นต้องใช้กุญแจส่วนตัวของคุณ โดยทั่วไปแล้ว แอปพลิเคชันเจะมีที่ให้คุณใส่กุญแจส่วนตัวของคุณ เมื่อเปิดแอปพลิเคชันครั้งแรก พวกเขาสามารถคำนวณกุญแจสาธารณะของคุณได้จากกุญแจส่วนตัวเช่นกัน
ส่วนในกรณีที่คุณใช้งานผ่านเว็บแอป ผมไม่แนะนำให้ใส่กุญแจส่วนตัวลงไป แต่แนะนำให้ใช้ส่วนขยายของเบราว์เซอร์ ที่ใช้งานฟังก์ชันที่เกี่ยวข้องกับ Nostr ซึ่งอนุญาตให้เว็บไคลเอ็นต์ส่ง event ที่ยังไม่ถูกเซ็นมาให้ส่วนขยายและส่วนขยายจะทำหน้าที่เซ็น สำหรับวิธีนี้ เว็บไคลเอ็นต์ต่าง ๆ ไม่จำเป็นต้องรู้กุญแจส่วนตัวของคุณ แต่คุณก็ยังสามารถลงนามใน event ต่าง ๆ ได้ตามปกติ โดยส่วนขยายที่ได้รับความนิยมก็จะเป็น Flamingo, Alby และ nos2x
ไคลเอนต์ & รีเลย์
ไคลเอนต์คืออะไร?
หากจะอธิบายให้เห็นภาพอยากให้มองว่าไคลเอ็นต์ Nostr นั้นเป็นเหมือนกับแอปที่คุณใช้งานเพื่อเข้าถึง Twitter, Facebook, youtube เป็นต้น พวกมันคือ แอปพลิเคชัน, เว็บแอป ที่เชื่อมต่อคุณกับโลกของ Twitter, Facebook, youtube โดยตัวของไคลเอนต์ใน Nostr เองก็เปรียบเสมือนแอปต่าง ๆ ที่คุณใช้ดูหน้าฟีดนั่นเอง แต่ข้อดีของ Nostr ที่เหนือแอปพลิเคชันอื่น ๆ คือความเรียบง่ายและยืดหยุ่น ส่งผลให้ไคลเอ็นต์แต่ละตัวมีวิธีนำเสนอและใช้งานที่แตกต่างกันไป บางไคลเอ็นต์อาจออกแบบให้ใช้งานง่ายเหมือน Twitter บางตัวเน้นให้เห็นบทบาทสำคัญของรีเลย์ หรือโหนดที่กระจายข้อมูลอยู่ทั่วโลก บางตัวใช้ระบบอัลกอริทึมเพื่อให้แน่ใจว่าข้อมูลไม่ถูกปิดกั้น โดยไม่ทำให้ผู้ใช้งานรู้สึกยุ่งยาก
เรียบง่ายและยืดหยุ่น?
เนื่องจากการออกแบบของโปรโตคอลที่ทำการแยกข้อมูลของผู้ใช้ทั้งหมดออกจากไคลเอนต์ ทำให้ตัวของผู้ใช้งานเองนั้นมีอิสระเต็มที่ที่จะเลือกใช้ไคลเอนต์ต่าง ๆ เพื่อเข้าใช้งาน Nostr และแน่นอนว่า ผู้ใช้งานสามารถสลับหรือลงชื่อเข้าใช้ ไคลเอ็นต์ได้หลายตัวตามต้องการ ตราบใดที่ไคลเอ็นต์ทั้งหมดเชื่อมต่อกับชุดรีเลย์เดียวกัน คุณก็จะเห็นข้อมูลเดียวกันในทุก ๆ ไคลเอ็นต์
ลงชื่อเข้าใช้ ไคลเอ็นต์หลาย ๆ ตัวแล้วจะกระทบต่อความปลอดภัยของแอคเคาร์ไหม?
คำตอบของคำถามนี้นั้นขึ้นอยู่กับวิธีการที่คุณลงชื่อเข้าใช้ หากคุณลงชื่อเข้าใช้ด้วยกุญแจส่วนตัว ถึงแม้ว่าไคลเอ็นต์ส่วนใหญ่จะพยายามรักษาความปลอดภัยของกุญแจส่วนตัวอย่างดีที่สุด แต่ด้วยข้อจำกัดของซอฟต์แวร์ ย่อมมีความเสี่ยงที่จะเกิดช่องโหว่ การเจาะระบบ และข้อผิดพลาด ที่อาจทำให้กุญแจส่วนตัวของคุณรั่วไหลออกไปได้ ส่วนวิธีการป้องกันเกี่ยวกับเรื่องนี้คือการใช้ส่วนขยายของเว็บเบราว์เซอร์ เพราะการเข้าสู่ระบบในไคลเอนต์ต่าง ๆ ผ่านส่วนขยายนั้นจะใช้เพียงกุญแจสาธารณะในการเข้าสู่ระบบและทุกครั้งที่เราต้องการจะโพสต์หรือสร้าง event บน Nostr ไคลเอนต์จะทำการร่าง event นั้น ๆ และเว้นช่องของลายเซ็นเอาไว้จากนั้นเราจะต้องทำการเซ็นผ่านส่วนขยาย ด้วยวิธีนี้ทำให้กุญแจส่วนตัวของเราไม่หลุดออกไปไหนตลอดการใช้งาน
รีเลย์คืออะไร?
รีเลย์เปรียบเสมือนเซิร์ฟเวอร์ที่อยู่เบื้องหลังของ Nostr และทำหน้าที่รับ event ต่าง ๆ มาจากไคลเอนต์ Nostr และอาจจะจัดเก็บและกระจายข้อความเหล่านั้นไปยังไคลเอนต์อื่น ๆ ที่มีการเชื่อมต่ออยู่
เทคโนโลยีของรีเลย์นั้นเปลี่ยนแปลงอย่างรวดเร็ว ดังนั้นคาดว่าจะมีการเปลี่ยนแปลงอีกมากมายในอนาคต อย่างในปัจจุบันที่มีการนำเสนอ bostr หรือ รีเลย์ที่จะคอยส่ง event ของเราต่อให้กับรีเลย์อื่น ๆ ที่มีการเชื่อมต่อ เพื่อช่วยลดภาระของไคลเอนต์ในการรับส่งข้อมูลจากหลาย ๆ รีเลย์พร้อม ๆ กัน หรืออย่างการป้องกันสแปมด้วย POW หรือประเภทที่สามารถเก็บรูปหรือวิดีโอที่มีขนาดใหญ่ได้
แต่สิ่งหนึ่งที่ควรทราบก็คือ การที่ Nostr นั้นพยายามจะกระจายศูนย์และเหตุผลหลัก ๆ ที่สามารถทำแบบนั้นได้ก็ขึ้นอยู่กับรีเลย์ในการจัดเก็บและดึงข้อมูล ดังนั้น หากคุณรู้สึกว่าไคลเอนต์ Nostr ของคุณทำงานช้า ส่วนใหญ่ก็มักเกิดจากรีเลย์ที่คุณกำลังเชื่อมต่ออยู่ คุณอาจลองแก้ไขปัญญาโดยการเปลี่ยนหรือเพิ่มรีเลย์อีกสองสามรายการในไคลเอนต์ที่คุณใช้
แล้วจะสามารถหารายการรีเลย์ได้จากไหน?
การที่เราจะหารายการรีเลย์ที่เราควรเชื่อมต่อนั้น ๆ จริงแล้ว ๆ สามารถทำได้หลายวิธี แต่วิธีที่ผมแนะนำที่สุดจะเป็นการใช้ตามคนที่เราติดตามอยู่ เพราะจะเป็นวิธีที่เราสามารถเห็น event ต่าง ๆ ของคนที่เราติดตามได้ง่ายที่สุด และเช่นเดียวกัน เพื่อน ๆ หรือคนที่เราติดตามก็จะสามารถเห็น event ของเราได้เช่นกัน และสำหรับในประเทศไทย เรามีรีเลย์ที่คนไทยส่วนใหญ่นิยมใช้กันอยู่สองอัน นั้นคือ wss://relay.siamstr.com/ และ wss://relay.notoshi.win/ ถ้าหากว่าอยากเห็นคนไทยเยอะ ๆ บนหน้าไทม์ไลน์ ผมแนะนำเป็นอย่างยิ่งว่าควรเพิ่ม รายการรีเลย์เหล่านี้ลงไปในบัชญีหรือไคลเอนต์ต่าง ๆ ที่คุณใช้ด้วย
สำหรับอีกวิธีหนึ่งผมแนะนำให้เข้าไปในเว็บไซต์ nostr.watch เนื่องจากในเว็บไซต์นี้เป็นแหล่งข้อมูลที่ดีที่สุดสำหรับการค้นหาและประเมินความเร็วของรีเลย์ต่าง ๆ
จะเกิดอะไรขึ้นถ้ารีเลย์ทั้งหมดที่ฉันเชื่อมต่ออยู่หยุดให้บริการ?
สิ่งนี้เป็นสิ่งที่คุณต้องระวังมากที่สุดในการใช้งาน nostr เนื่องจากหากรีเลย์ทั้งหมดที่คุณเก็บข้อมูลไว้หยุดให้บริการทั้งหมดและคุณไม่มีการสำรองข้อมูล event ของคุณเก็บไว้เลย มันแปลว่าโพสต์ทั้งหมดของคุณ ผู้ติดตาม และรายการต่าง ๆ ที่คุณสรรค์สร้างไว้จะไม่สามารถกู้คืนได้ไปตลอดการ นี่จึงเป็นเหตุผลหลัก ๆ ที่ Nostr อนุญาตให้ผู้ใช้งานนั้นสามารถเชื่อมต่อกับรีเลย์ได้เป็นจำนวนมาก ก็เพื่อให้แน่ใจว่ามีข้อมูลสำรองเก็บไว้อยู่ที่ใดที่หนึ่งในระบบเสมอ แต่อย่างไรก็ตาม หากคุณต้องการที่จะมั่นใจได้ว่าข้อมูลต่าง ๆ ของคุณจะไม่ถูกเซ็นเซอร์ สิ่งที่คุณสามารถสามารถทำได้คือการใช้รีเลย์ส่วนตัวของคุณและกำหนดนโยบายต่าง ๆ ภายในรีเลย์ของคุณด้วยตัวคุณเอง
แล้วฉันจะสามารถใช้รีเลย์ส่วนตัวได้อย่างไร?
อะแฮ่ม ๆ ขอบอกไว้ก่อนว่ามันไม่คุ้มค่ากับความยุ่งยากสำหรับคนโดยทั่ว ๆ ไป ถึงในปัจจุบันจะมีเทคโนโลยีบางตัวที่เข้ามาช่วยให้มันทำได้ง่ายขึ้นแล้วก็ตาม หากคุณต้องการที่จะสำรองข้อมูลนั้น การที่จะมีรีเลย์ส่วนตัวที่ออนไลน์ตลอดเวลาอาจเป็นเรื่องที่ไม่ได้จำเป็นขนาดนั้น เนื่องจากเราสามารถใช้งานบริการอย่าง https://nostrsync.live/ ในการดาวน์โหลดข้อมูลของเราจากรีเลย์ต่าง ๆ ได้ หรือการติดตั้งรีเลย์ส่วนตัวอย่าง nostr-relay-tray: https://github.com/CodyTseng/nostr-relay-tray ที่ช่วยให้เราสามารถมีรีเลย์ส่วนตัวที่ใช้สำหรับสำรองข้อมูลได้
Nostr Implementation Possibilities (NIPs) NIP คืออะไร?
NIP มีไว้เพื่อส่งเสริมความสามารถในการทำงานของ Nostr และเป็นตัวคอยกำหนดให้ เหล่านักพัฒนาทำสิ่งต่าง ๆ ที่เหมือนกันในรูปแบบเดียวกัน เพราะมันคงไม่ใช่ความคิดที่ดีนัก หากนักพัฒนาแต่ละคนจะคิดค้นวิธีแก้ปัญหาทั่วไปของตัวเองและนำไปใช้ในแอปของตัวเองเท่านั้น และคงจะเป็นการดีกว่า ถ้าหากทุกคนใช้วิธีแก้ปัญหาที่เหมือนกัน นั่นคือเหตุผลที่ต้องมี NIP อยู่ในโปรโตคอลของ Nostr และในทำนองเดียวกัน แนวคิดใหม่อาจดูดีในแอปของนักพัฒนาบางราย แต่จะดูดียิ่งขึ้นอย่างแน่นอนหากแอปอื่น ๆ อีกมากมายใช้มาตรฐานเดียวกันและสามารถทำงานร่วมกันได้อย่างราบรื่น
ทำไมมันถึงหน้าสนใจ?
อย่าลืมว่า Nostr เป็นระบบแบบกระจายอำนาจและไม่ได้มีบริษัทหรือใครที่เป็นเจ้าของมัน อย่างเช่นโซเชียลมีเดียอื่น ๆ เช่น ทวิตเตอร์ อ่อไม่สิตอนนี้คงต้องเรียกมันว่า X สินะ ซึ่งหมายความว่าทิศทางของโพรโทคอล Nostr นั้นขึ้นอยู่กับพวกเราทุกคน! ไม่ว่าใคร ๆ ก็สามารถเสนอแนะและสนับสนุนการเปลี่ยนแปลงและให้ข้อเสนอแนะเกี่ยวกับแนวคิดที่ผู้อื่นเสนอ และการที่คุณเป็นส่วนหนึ่งของชุมชนนี้ ก็ทำให้คุณมีส่วนร่วมในทิศทางของ Nostr อีกด้วย
จากที่ส่งหากันได้แค่ข้อความ มาเป็นรูปภาพ มาเป็นวิดีโอ และมาเป็น”เงิน” นี่คือเส้นทางการเดินทางของโปรโตคอลนี้ในอดีต แล้วในอนาคตมันจะพัฒนาไปยังไงต่อก็ขึ้นอยู่กับเหล่าผู้ใช้งานและนักพัฒนาในอนาคต แล้วทำไมสิ่งนี้ถึงจะไม่น่าสนใจละ ?
Event
Event คืออะไร?
Event เป็น object เพียงประเภทเดียวที่มีอยู่บน Nostr โดยมีโครงสร้างประมาณนี้
``` {"id":"84d5d3dc9c388a702f39cad6360d41ebb804e809fb822f110ff8a14dfd35fc6c", "pubkey":"66df60562d939ada8612436489945a4ecf1d62346b3d9478dea8a338f3203c64", "created_at":1722315959, "kind":1, "tags":[["t","siamstr"]], "content":"ไปสั่งกาแฟเมื่อกี้ พส เจ้าของร้านชมว่าเดี๋ยวนี้คล่องภาษาญี่ปุ่นแล้วนะ ไอเราก็ดีใจ พอเดินกลับถึงที่ทำงานละก็ตระหนักได้ว่า ตะกี้เราสั่ง “ไอซ์โคฮี โอเนไงชิมัส” “เทคเอาส์” “คาโดะเดสส” ไอบ้าไหนญี่ปุ่นก่อนอังกฤษทั้งนั้น 🤣🤣\n\n#siamstr", "sig":"8f066a0099a5f580b605ebdb220179c4eca298947c38b855a0a8bf2783f28ddb537cb74a7f61d3ce8891189f719870efdf320ea4f895e03cdac44284c450c5c4"}
``` อย่าง Event ข้างต้นนี้มี kind เป็น 1 ซึ่งหมายถึง "ข้อความโน้ต" ซึ่งก็คือข้อความธรรมดา สั้น ๆ คล้ายกับที่ใช้กันใน Twitter เช่น บนฟีด การตอบกลับ และการโควท
ประเภทของ Event (Event Kinds)
หมายเลขของ kind แต่ละตัวมีความหมายแตกต่างกัน ตัวอย่างเช่น 0 หมายถึงอีเวนต์ "ข้อมูลเมตา" ใช้สำหรับให้รายละเอียดเกี่ยวกับผู้ใช้ เช่น ชื่อและรูปโปรไฟล์ รีเลย์ (Relays) สามารถจัดการกับ kind ที่แตกต่างกันได้ เช่น รีเลย์มักจะลบอีเวนต์ kind:0 เวอร์ชันเก่ากว่าออกไป และเก็บไว้เฉพาะเวอร์ชันล่าสุด ในขณะที่โดยทั่วไปจะเก็บอีเวนต์ kind:1 ไว้หลายรายการสำหรับแต่ละคีย์
โดยทั่วไปแล้ว คุณไม่จำเป็นต้องใช้ kind เกินกว่า 0 และ 1 ในการสร้างแอปพลิเคชันโซเชียลมีเดียบน Nostr แต่ kind อื่น ๆ ถูกคิดค้นขึ้นโดยไคลเอนต์ เพื่อมอบฟังก์ชันการทำงานอื่น ๆ ตามที่ระบุไว้ใน NIP บาง kind ไม่เกี่ยวข้องกับเครือข่าย และให้บริการตามความต้องการอื่น ๆ ของไคลเอนต์ที่เฉพาะเจาะจงกับฟังก์ชันการทำงานเหล่านั้น ซึ่งแนวคิดก็คือ สำหรับกรณีการใช้งานใหม่ ๆ แต่ละกรณี จะต้องมีการพิจารณาและเสนอซับโปรโตคอลเป็น NIP เพื่อให้สามารถทำงานร่วมกับไคลเอนต์ที่มีอยู่และในอนาคต ซึ่งอาจสนใจที่จะนำฟังก์ชันการทำงานนั้นไปใช้ ขณะเดียวกันก็มั่นใจได้ถึงความเข้ากันได้ย้อนหลัง และการรองรับสิ่งต่าง ๆ ที่มีอยู่และไม่ต้องการเปลี่ยนแปลง
คุณสมบัติอื่น ๆ ของ Event
created_at: เป็น Timestamp ของ UNIX ที่กำหนดโดยผู้สร้างอีเวนต์ โดยปกติจะเป็นเวลาที่สร้าง แม้ว่าจะไม่มีการตรวจสอบ แต่ก็ไม่ใช่ปัญหา
content: ขึ้นอยู่กับความหมายของ kind ในกรณีของ kind:1 จะเป็นเพียงสตริงข้อความธรรมดาที่คนอื่น ๆ อ่านได้ tags: ขึ้นอยู่กับ kind เช่นกัน แต่แท็กทั่วไปบางอย่างที่มักปรากฏใน event kind:1 และ kind อื่น ๆ คือ "p" ซึ่งใช้เพื่อกล่าวถึงกุญแจสาธารณะ และ "e" ใช้เพื่ออ้างถึง event อื่น
อยากมีส่วนร่วมในการพัฒนาของ Nostr ?
จริง ๆ แล้วใคร ๆ ก็สามารถเข้ามามีส่วนร่วมในการพัฒนา Nostr ได้ ไม่จำเป็นต้องเป็น dev หรือมีความรู้ด้านคอมพิวเตอร์ก็สามารถทำได้ ไม่ว่าจะเป็นการให้ feedback กับ dev ของ client ที่คุณใช้, การสร้างคอนเทนต์ต่าง ๆ บน Nostr การสร้างชุมชน รวมไปถึงการช่วย client ต่าง ๆ ในการทำ UI ให้เป็นภาษาท้องถิ่น และอื่น ๆ อีกมากมาย ใคร ๆ ก็สามารถช่วยได้ตามความสามารถที่แต่ละคนมี มันเลยทำให้ Nostr โครตน่าอยู่ :)
-
-
 @ 469fa704:2b6cb760
2024-09-02 06:11:43
@ 469fa704:2b6cb760
2024-09-02 06:11:43I joined Nostr a week ago and wanted to recap it for myself and also give other newbies a simple introduction. Maybe this will help you get started too.
Step 1: Create your identity and get your private key for a browser extension
I started with the Snort client on my local home server. It created my private/public key pair and I was good to go. Then I transferred the private key to Amethyst, a pretty good Android-based client. Before looking at various clients and other nostr-based websites, I tried transferring my private key into a browser extension. I looked at Alby and nos2x. I chose the latter because I wanted to keep my Lightning wallet separate from my identity management. You don't have to, I just found it easier.
Step 2: If you're confused, always check your feed settings
I tried many different clients and was very confused at first. Due to its decentralized nature, Nostr relies on relays, which are just small servers, and to each one you can connect to, all your data is stored. When you post a message, write a note, an article like this or simply who you follow. The main reason and benefit for this is that there is no single point of failure or server-like entity that could be censored. The side effect of this, combined with using different clients, was that not only did it look different everywhere, but the content was also very different. This was simply because I wasn't connected to all my different clients with the same relays. But the main reason why each feed looks different on each client is usually because you can choose different variations of feeds and some clients even offer filters for the feeds.
Scroll down to get a small overview of the clients I've tried.
Step 3: Set up your lightning wallet with something like Wallet of Satoshi
I made my Bitcoin Lightning wallet independent of my identity. That's why I just went with the number one Lightning wallet on the market: Satoshi's Wallet. It's very simple and provides you with a Lightning address that resembles and has the format of an email address. You can add this address to your Nostr profile description and you're ready to receive Sats. Anyone can send them to you, e.g. for a good message or something else they find valuable on Nostr (like a podcast, a video, an article, ...). Just be aware that Satoshi's wallet contains your key and the sats you have there are not really your sats. So only leave a small amount there or no more than you need for your nostr experience.
Step 4: Set up your Nostr address
I set up a unique NIP-05 identifier that is human readable and also looks like an email address. For me, that's tobiya@nostrplebs.com, also called a nostr address. It's much easier to read, share and remember than your public key, which is just a long, unwieldy string of characters.
Some popular services are: * NostrVerified * Alby * Iris * Primal * Snort * nostrplebs.com
Most offer free services or at least a free tier. I chose nostrplebs.com because it links my Nostr address (tobiya@nostrplebs.com) to my Lightning wallet. ⚡
Brief overview of the clients (I have tested)
Web/Browser:
- Primal: Fast, user-friendly, nice looking, easy to use
- Coracle: Focuses on decentralized reputation, privacy and trust metrics. Also well organized and structured
- noStrudel: The most comprehensive I've found, has everything
- Rabbit: Designed like X (Twitter) Pro, focuses on everything at once
- Nostter: Clearly structured, easy to find what you're looking for
- Snort: Fast web client for those who prefer simplicity and speed.
iOS
I'm not an iPhone user, but everything I've discovered says that Damus is the best app for iOS.
Android:
- Amethyst: Feature rich for Android, I only tried this program because it gives me everything I currently need on my phone.
- Primal: Works seamlessly with Primal on the web, which is a pretty convenient starting point if you only want to use one client.
As for the web clients, I'm still figuring out which one will be my favorite. But I think they're all good in their own way. In the time of writing, I am mainly using Primal on Android and Web, Amethyst and noStrudel.
Let's have fun!!
-
 @ 361d3e1e:50bc10a8
2024-09-04 18:48:17
@ 361d3e1e:50bc10a8
2024-09-04 18:48:17Is France preparing to seize people's savings to avoid bankruptcy?
politics #europe #banks #france #savings #cyprus
-
 @ 276171f6:e660762c
2024-09-02 04:03:29
@ 276171f6:e660762c
2024-09-02 04:03:29Zero:
"We will restore the republic, and we will make America and bitcoin bigger, better, stronger, richer, freer and greater than ever before. Thank you all. Have a good time with your bitcoin and your crypto and everything else that you're playing with..."
With these statesman-like words, President Trump declared his endorsement of bitcoin in front of many bitcoiners, politicians and wall streeters. Among other things, Trump affirmed his support for the right to self-custody as well as a dollar stablecoin within seconds of each other. This speech may or may not mean much, but it signals that "they" have arrived. It, whatever it is, is happening.
But the fact is, we've never needed Trump to keep bitcoin buzzing. Arrows and sparks are always flying around, skirmishes abound. For eg: the developer community has been discussing a plethora of new, esoteric opcodes that enable covenants, improve lightning but also other "wizardry". Saylor has been going on about bitcoin as a treasury asset and a "triple maxi" store of value, inventing bigger & bigger numbers no one knew existed. Meanwhile, our "public servants" have not been quiet either. For the past couple of years, bitcoin businesses were attacked through Operation Chokepoint 2.0, but 2024 started with the prophesied spot ETF approvals. Something had changed – it opened the doors to bulls, bears and other animals from wall street who have since crashed the bitcoin party. We also have now seen a bitcoin strategic asset bill in US Congress as well as prosecutions of multiple crypto developers for nebulous crimes within a span of a few months. Meanwhile, Whitney Webb and Mark Goodwin have been publishing steamy exposés & dirty laundry of one sinister party after another to an enthralled audience, who consume it vociferously then suppress it immediately, like some true crime episode.
However, bitcoin continues churn out one block after another, detached like a yogi in a battlefield. Perhaps Satoshi himself is one such yogi. But most of us are not yogis, including yours truly who finds all this bewildering. The fact is, bitcoin community today is a melting pot of cypherpunks, politicians, wallstreeters, developers, regular plebs and more. Quite the motley crew, with conflicting perspectives, incentives and objectives, often at loggerheads with each other.
This should not be a surprise, since Bitcoin is a versatile force that animates in many dimensions. On one hand, it must become peer-to-peer electronic cash; on the other, the fount of property rights for 8 billion people. Bitcoiners must innovate tirelessly towards a cypherpunk dream but also become the ark of refuge for corporates and governments in an inflationary deluge. 1) what.
Bitcoin is the bull. Bitcoin is the honeybadger. Bitcoin is a conflict of visions.
One: Bitcoin for Billionaires (to be continued)
-
 @ 0edc2f47:730cff1b
2024-09-02 01:54:55
@ 0edc2f47:730cff1b
2024-09-02 01:54:55Chef's notes
In this case, sweet-and-sour doesn’t mean Americanized Chinese food but rather the sauce that dominated the Shabbos and Pesach dinner table among American Jewish immigrants in the early 20th century.
Details
- ⏲️ Prep time: 30 minutes
- 🍳 Cook time: 6 hours
- 🍽️ Servings: 12
Ingredients
- 1 medium onion, peeled and quartered
- 2 tsp ground ginger
- 8-10 large cloves garlic
- 1 cup ketchup
- ¼ cup dry sherry
- ¼ cup sake
- ¼ cup cider vinegar
- ¼ cup soy sauce
- ¼ cup honey
- ¼ cup Dijon mustard
- 1 tablespoon coarsely ground black pepper
- ¼ teaspoon ground cloves
- 1½ cups Coca-Cola, ginger ale, or Dr. Pepper
- 1 first-cut brisket, 6 to 7 pounds (2.7-3.2kg), rinsed and patted thoroughly dry
Directions
- Preheat oven to 325F / 160C.
- Combine all ingredients except brisket in a blender and blend until smooth.
- Place brisket in a Dutch oven or other large pot with a tight-fitting lid.
- Pour sauce over brisket, place lid on pot, roast in oven for 3 hours. Flip roast and return to oven for 3 hours or until fork tender.
- Remove roast to rest. Skim fat from sauce and reduce if desired. Serve immediately with sauce or cool, cover brisket and refrigerate overnight in cooking pan. The next day, defat sauce, reduce if desired, and reheat meat in sauce before serving.
-
 @ 1123ece2:7d1e00c0
2024-09-02 01:40:06
@ 1123ece2:7d1e00c0
2024-09-02 01:40:06Hey everyone welcome to The Refinery.
“Amen and Amen” is the theme for the coming Sunday morning teachings.
This series is a study from the Psalms, in which the psalmist gives voice to prayers that resound in our hearts today.
Today we are discussing, The Prayers of the Psalmist.
Our Text today is
Psalm 119:57 NKJV
57 You are my portion, O Lord;\ I have said that I would keep Your words.
Scripture Reading
Psalm 119:57-64 NKJV
57 You are my portion, O Lord;\ I have said that I would keep Your words.
58 I entreated Your favor with my whole heart;\ Be merciful to me according to Your word.
59 I thought about my ways,\ And turned my feet to Your testimonies.
60 I made haste, and did not delay\ To keep Your commandments.
61 The cords of the wicked have bound me,\ But I have not forgotten Your law.
62 At midnight I will rise to give thanks to You,\ Because of Your righteous judgments.
63 I am a companion of all who fear You,\ And of those who keep Your precepts.
64 The earth, O Lord, is full of Your mercy;\ Teach me Your statutes.
Introduction.
Today we continue our study of Psalm 119, the longest of the Psalms and one arranged in an format of twenty two stanzas, each of which uses and emphasises one of the letters of the Hebrew alphabet.
It is a poem that exults the law, the testimonies, the ways, the precepts, the status, the commandments, the words, and the promises of God.As we read the psalmists words, we’ll find ourselves saying, “Amen and amen.”
- Prayer and positive self esteem.
The psalmist rejoiced as he took a spiritual inventory and recognised that God was his highest and dearest possession.
The RSV translation says “The Lord is my portion,” the King James Version is more personal and says, “Thou art my portion.”
The NIV also personalises it, “You are my portion, Lord.”
As the psalmist talked to God, recognising that he belonged to God and that God was committed to him, he was spiritually enriched and felt better about himself.
2. Prayer and sincerity.
Verse fifty eight says, “I entreated thy favour with my whole heart.”
The NIV translates it, “I have sought Your face with all my heart, be gracious to me according to Your promise.”
Faith and sincerity are essential if we would pray effectively.
3. Prayer and God’s promises.
Psalm 119:58 says, I entreated Your favor with my whole heart;\ Be merciful to me according to Your word.
That was the petition offered by the heart of the psalmist.
The RSV translates it, “Be gracious to me according to thy promise.”
The psalmist was in the habit of clinging to and claiming the promises the promises of God when he prayed.
This is a habit, too, should form.
4. Prayer and repentance.
Repentance is not just the beginning point of the life of faith and discipleship.
The life of faith is to be characterised by continuous repentance.
The psalmist said it in beautiful words, “I thought on my ways, and turned my feet unto thy testimonies.”
The NIV says it a little differently, “I have considered my ways and have turned my steps to your statutes.”
Each time we pray, we are to search our hearts and let God help us so that we might turn from evil.
5. Prayer and praise to God.
Most of us think of thanking God and praising Him when prosperity comes.
Some of us think of praising and thanking Him when we go to church.
In this verse the psalmist tells us that midnight is a good time to arise and give thanks to the Lord for all of His righteous judgements.
The psalmist suggests that the we have difficulty getting to sleep, we can thank God for the many blessings He has bestowed upon us and praise Him for His goodness to us.
This might help us to relax and get a better nights sleep.
6. Prayer and the recognition of God’s love.
The psalmist was rejoicing that the earth was full of God’s mercy and steadfast, never failing, never ending love.
This is a truth that all of us need to recognise and respond to positively.
The closing line in this stanza of this poem closes with the words of petition, “Teach me Your statutes.”
To these prayers of the psalmist, let each of us say, “Amen and amen.”
Until next time
Stay in the Blessings
I really want to encourage you to be diligent with your Bible study time, because God has so much more for us than we can get from just going to church once or twice a week and hearing someone else talk about the Word.
When you spend time with God, your life will change in amazing ways, because God is a Redeemer.
Theres nothing thats too hard for Him, and He can make you whole, spirit, soul and body!
You’re important to God, and you’re important to us at The Refinery.
When it comes to prayer, we believe that God wants to meet your needs and reveal His promises to you.
So whatever you’re concerned about and need prayer for we want to be here for you! Or even if you just want to say Hi, you can contact us at www.refinerylife.org
2024 IS A YEAR OF DECISIONS AND OPEN DOORS
© www.refinerylife.org 2013-2024 All rights reserved. Except as permitted under the Australian Copyright Act 1968, no part of this Article may be reproduced, stored in a retrieval system, communicated or transmitted in any form or by any means without the prior written permission.
This episode is brought to you by Refinery Life Australia:
If you enjoy The Refinery Life Radio Podcast you can help support The Refinery by doing the following:
Sow an offering:
Bitcoin: bc1qqh6720t2zagj72dyfj348az698tdut3hlecaj4
Online: https://www.refinerylife.org/donate/
If you do send an offering then please email us so that we can say thank you
Subscribe on
iTunes | Spotify | YouTube | TuneIn | Rumble | Flare | Zap.Stream | Fountain |
Share The Refinery with your friends and family
Subscribe to the newsletter on www.refinerylife.org
Follow The Refinery on Twitter | Nostr | Instagram | Fountain |
-
 @ 8d34bd24:414be32b
2024-09-04 15:57:00
@ 8d34bd24:414be32b
2024-09-04 15:57:00Today is the official publishing day of this post. I already tried scheduling this post in another editor that went out early.
I’ve mentioned multiple times that I feel our time left is short and that the rapture and the tribulation are coming soon. I feel it with every ounce of my being. I see it in the rush to evil around us. I see Biblical prophecy coming to fulfillment and technologies that could not be fathomed 2,000 years ago coming into being in a way that will make prophecy possible. The question is, what do we do with the time left to us?
Don’t Be a Foolish Virgin
Matthew gives an analogy of believers waiting for Christs return:
“Then the kingdom of heaven will be comparable to ten virgins, who took their lamps and went out to meet the bridegroom. Five of them were foolish, and five were prudent. For when the foolish took their lamps, they took no oil with them, but the prudent took oil in flasks along with their lamps. Now while the bridegroom was delaying, they all got drowsy and began to sleep. But at midnight there was a shout, ‘Behold, the bridegroom! Come out to meet him.’ Then all those virgins rose and trimmed their lamps. The foolish said to the prudent, ‘Give us some of your oil, for our lamps are going out.’ But the prudent answered, ‘No, there will not be enough for us and you too; go instead to the dealers and buy some for yourselves.’ And while they were going away to make the purchase, the bridegroom came, and those who were ready went in with him to the wedding feast; and the door was shut. 11Later the other virgins also came, saying, ‘Lord, lord, open up for us.’ But he answered, ‘Truly I say to you, I do not know you.’ Be on the alert then, for you do not know the day nor the hour. (Matthew 25:1-13)
Christians have been waiting for around 2,000 years for Christ’s return. It is easy to get drowsy and begin to sleep due to the delay to His return, but we are called to be ready. “You too, be ready; for the Son of Man is coming at an hour that you do not expect.” (Luke 12:40) Our wait may be long or short, but we are supposed to live our lives like he will arrive today. We don’t want to miss out on joining Him at His return, but we also don’t want to have to face Him knowing that we were not focused on what He had called us to do. We don’t want to admit that we didn’t share the gospel to that friend, that we didn’t stand up for the truth when the crowd was speaking contrary to the word of God, or that we acted in an unloving way to fellow believers or to the lost.
The Bible clearly tells us that we “do not know the day nor the hour,” but that doesn’t mean that He has not given us signs that the time is short.
What Should We Be Doing?
If Jesus is coming soon, how should we spend our time? What should we be doing? Should we just sit back and wait?
For even when we were with you, we used to give you this order: if anyone is not willing to work, then he is not to eat, either. For we hear that some among you are leading an undisciplined life, doing no work at all, but acting like busybodies. Now such persons we command and exhort in the Lord Jesus Christ to work in quiet fashion and eat their own bread. But as for you, brethren, do not grow weary of doing good. (2 Thessalonians 3:10-13)
The Bible is clear that we should work. This not only means that we should not quit our jobs, but should continue working as we have been doing, but it also means we should put time and effort into kingdom work. God has given each one of us a purpose and a job to do. We should study His word and pray and keep our eyes open so we don’t miss out on what He intends as our purpose. Another analogy is given in Matthew:
“For it is just like a man about to go on a journey, who called his own slaves and entrusted his possessions to them. To one he gave five talents, to another, two, and to another, one, each according to his own ability; and he went on his journey. Immediately the one who had received the five talents went and traded with them, and gained five more talents. In the same manner the one who had received the two talents gained two more. But he who received the one talent went away, and dug a hole in the ground and hid his master’s money.
“Now after a long time the master of those slaves came and settled accounts with them. The one who had received the five talents came up and brought five more talents, saying, ‘Master, you entrusted five talents to me. See, I have gained five more talents.’ His master said to him, ‘Well done, good and faithful slave. You were faithful with a few things, I will put you in charge of many things; enter into the joy of your master.’
“Also the one who had received the two talents came up and said, ‘Master, you entrusted two talents to me. See, I have gained two more talents.’ His master said to him, ‘Well done, good and faithful slave. You were faithful with a few things, I will put you in charge of many things; enter into the joy of your master.’
“And the one also who had received the one talent came up and said, ‘Master, I knew you to be a hard man, reaping where you did not sow and gathering where you scattered no seed. And I was afraid, and went away and hid your talent in the ground. See, you have what is yours.’
“But his master answered and said to him, ‘You wicked, lazy slave, you knew that I reap where I did not sow and gather where I scattered no seed. Then you ought to have put my money in the bank, and on my arrival I would have received my money back with interest. Therefore take away the talent from him, and give it to the one who has the ten talents.’
“For to everyone who has, more shall be given, and he will have an abundance; but from the one who does not have, even what he does have shall be taken away. Throw out the worthless slave into the outer darkness; in that place there will be weeping and gnashing of teeth. (Matthew 25:14-29)God has given each of us different skills, gifts, and opportunities. He wants us to make the most of them. If God gave you skill in business, you can use your wealth to fund ministries, churches, and missionaries. If God has gifted you with the ability to teach, you can disciple many to grow in their faith and knowledge of God. If God has brought you into a relationship with someone influential, you can share the Gospel with them and be used to draw them into saving faith in Jesus. Whatever skills, gifts, and opportunities God has given to you, you need to make the most of them. You need to grow and make the most of what God has given you.
What is the Best Use of Our Time and Money?
God wants us to shine a light for Him. He wants us to make a difference. There are many ways to do this and we can’t do them all. We have to pick and chose what is God’s will and what will make the best use of what God has given us.
There are lots of good things we can do, but what is the best?
I used to focus on prepping to be able to provide for my family and others if times get bad. That was good, but was it best? I used to grow a garden and grow healthy food. That was good, but was it the best? I used to be highly involved in politics and worked hard to support and elect godly men and women into government positions where they could have a positive influence on our culture and our country. That was good, but was it the best?
According to the grace of God which was given to me, like a wise master builder I laid a foundation, and another is building on it. But each man must be careful how he builds on it. For no man can lay a foundation other than the one which is laid, which is Jesus Christ. Now if any man builds on the foundation with gold, silver, precious stones, wood, hay, straw, each man’s work will become evident; for the day will show it because it is to be revealed with fire, and the fire itself will test the quality of each man’s work. If any man’s work which he has built on it remains, he will receive a reward. If any man’s work is burned up, he will suffer loss; but he himself will be saved, yet so as through fire. (1 Corinthians 3:10-15)
The best way to judge which actions are best is to see which actions have an eternal influence and to look and see what God is doing and to join His work. The difference between gold & silver versus wood, hay, and straw is the gold & silver can survive fire. Whether something is good or best depends on whether the action makes a difference in eternity. Providing for my family and friend’s physical needs and health is good, but it doesn’t make an eternal difference. Electing Godly officials makes life here on Earth better, but does it actually make a difference eternally? Probably not.
What does make a difference? Sharing the Gospel with others makes an eternal difference. Standing up for the truth, especially the spiritual truths from the Bible, makes an eternal difference. Writing a book or a blog sharing the truths of the Bible and Jesus makes an eternal difference. I’ve tried to focus my time on this type of activity more than the former. I don’t want one soul to go to Hell because I was too busy to share the Gospel. I don’t want one Christian to regret their life on Earth because I was too busy to disciple them. I don’t want to be like the man who received the single talent and buried it in the ground, who, when facing his master, was told, “You wicked, lazy slave.”
What Is Most Important?
“Do not store up for yourselves treasures on earth, where moth and rust destroy, and where thieves break in and steal. But store up for yourselves treasures in heaven, where neither moth nor rust destroys, and where thieves do not break in or steal; for where your treasure is, there your heart will be also. (Matthew 6:19-21)
What are the most important things in our lives? The most important things are people.
- Some people in our lives have never heard about Jesus. We need to share the gospel with them.
- Some people in our lives are hurting and need to be helped and encouraged and taught to trust in Jesus.
- Some people in our lives are new Christians or just immature Christians, who have trusted in Jesus, but haven’t grown much since salvation. We need to teach and disciple them to grow in their understanding of God and who He is. We need to build up their faith. We need to encourage them to study the Bible.
- Some people in our lives know God and His word, but are unsure how to live out their faith and share it with others. We need to encourage them and train them, so they can multiply their faith among others in their lives.
What are you doing to make an eternal difference in service to our Lord Jesus Christ? Are you one of the lazy, unprepared virgins? Are you hiding the gifts God gave you in the ground or shining a light that can be seen by everyone around you? Are you so busy doing good, that you don’t see God’s best?
Are you excited about meeting Jesus in the air at the rapture of the Church? I am! I hope you are, too.
your sister in Christ,
Christy
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
-
 @ a6631624:24ba1a2f
2024-09-01 22:33:57
@ a6631624:24ba1a2f
2024-09-01 22:33:57I started V1 of this blog back in Q2 2023 on other platforms. And, I started writing for it about a year before that. Since then, all of my posts -- both in the backlog and currently published -- have undergone rework after rework as I painstakingly refine the presentation of these rarely spoken and "never-before-thought" ideas. Yet, the posts I've most stalled and blown off have been those pertaining to Gnosticism.
The reason being that it's just overwhelming the amount of wrongs I have to right, the number of misconceptions I must correct, the scope of the programs I have to bypass, and the shear volume of aspects I need to educate on just to convey Gnosticism and the Gnostic spirit accurately, as I tap into it.
And, we haven't even began talking about the number of butts I've got to prick in the process.
So, this a massive undertaking that I have continually delayed. And, I fear, in my delayedness, that I've allowed too much wrong to proliferate in the the meme pool of "Gnosticism" unchallenged. And though, I've been shamefully ignoring the pot, I still feel I have just enough time to stir before the food is burnt.
So, let's begin.
What is Gnosticism?
Gnosticism, as we inherit it in America, is a vein of Orpho-Platonism.
Obviously.
Not Hermeticism. Not Christianity. And, certainly, not Judaism.
But, Orpho-Platonism.
Particularly, Western Gnosticism can be described as a syncretism of the Greek mystery religions centering the Orphic vein -- which comes to us from Orpheus, through Pythagoras (and most likely from Egypt and Babylon through his studies), through Plato. As a matter of fact, the mythological through-line from Gnosticism to Plato, to Orphism, and back to Egyptian mythologies is glaring when you read the myths, even without being a buff.
Yet, this is not the form of Gnosticism we usually first encounter. We don't learn of it as a complete and independent framework of hellenic origin, but usually as a half-thing mix mashed with something else; as a "parasite religion" as I've recently heard it mocked.
This stems from the Christian-centered folly of conflating Gnostic Christianity with Gnosticism itself, both historically and theologically, as if Gnosticism "came from" Christianity. Such beliefs are simply failures of historical and cultural inquiry. But, this "entanglement" that persists in the minds of the many today, is rooted in the fact that Western Gnosticism garnered it's first bout of attention (i. e. major hostilities) when it appeared in the early centuries CE — as a variety of rouge mystery cultists attempted to integrate the Jesus figure into their canons.
As Christ-followers, they'd adopt Jesus as the latest prophet in their esoteric lineage (from Orpheus to Pythagoras, for example) with many choosing to participate in Jesus-worship activities along side the other early Christian varieties. This is the origin of those who call themselves "Gnostic Christians" (a.k.a. Gnostic followers of Christ) today.
However, these mystery cultists -- unlike other Christians -- did not renounce their traditions to become whole converts into the Jewish way. They quietly retained them, seeking not to "convert" or rouse the other Christians, but to cultivate their own understandings of the texts in line with their Greek way. And, that is why their Jesus — "Gnostic Jesus" — is a little divergent from the norm. He is not interpreted to take on the throughly Jewish character and ideological background of Abrahamic Jesus, but a Hellenic character and background inside of a Jewish body (with the body thing being debatable).
And that, as we have learned, is very !!!TRIGGERING!!! to the zealots for Judeo-Christian ideology. This little attempt at cultural assimilation would result in being seeing as not just some kind of competitor, a but a mortal enemy to the ideology and spread the proper Christian -ness. Thus, "the Gnostics" — those retaining the beliefs of the mystery cults -- were branded the worst of "heretics," worthy of being rooted out of all influence and power by any means necessary.
And, so began the hiding.
``` Transmission Note 01:
The Greeks and other peoples were a lot more open to input from cultures and pantheons beyond their own than the Jews are. I believe this led them to underestimate the extent to which the Jewish -ness defined the character and how Christianity was meant to be an expansion of that -ness rather than an earnest spiritual or intellectual exploration.
Essentially, they did not realize there was this agenda and rigid ethnic claim to ownership of the Jesus character. And, the misstep of trying to engage with it as such is what led the mystery cultists to inadvertently cause such great offense.
Now, of course, the plan was always to convert, kill, persecute, and/or disenfranchise anyone and any culture that did not give way to the planned faith (Catholicism). But, they really stay aggro'd on the Gnostic Christians, which is why everybody finds them and thinks they're the whole of Gnosticism.
``` For half of the last 2000 years, the Christian mystery cultists publicly behaved and saw themselves as Christians, and that is indeed what they called themselves ("Gnostic" is a name that was given to them collectively and retroactively). But, they entertained their mysteries in private. They preserved their belief systems through metaphor and code, they prepared private gatherings, and they participated in both new and ancient rituals in secret. They also, famously, wrote and distributed their own texts among themselves, drew and documented esoteric meaning from The Bible, and as time went on, became the Valentinians, Manichaens, Cathars, Mandaeans, etc...
All of whom, in the end, lost themselves.
``` Transmission Note 02:
The non-Christian mystery cultists behaved much the same, continuing to exist beneath the surface under other names and "heresies." Seems like most died up to now, but the mysteries of some are still carried by different orgs, lines of thought, and denominations just like the Orphic vein.
``` Sometimes genocided, sometimes not, they all became more and more assimilated into the Christian worldview, losing and twisting up bits of their gnosis until they were no longer carriers of the mysteries, but dead ends. Most notably, the information surrounding death either came to mimic that of Christianity and/or became platitudinal, losing it's instructional value. And, that's just what Christianity does — its function is to destroy the means and routes to Gnosis; forcing you to succumb, in one way or another, to the Evil-bland power of the demiurgic drone.
It breaches. It invades. It colonizes. It burns.
All of this is why, despite modern and historical claims, it is clear that Gnosticism and Christianity share no common cause and are, in fact, fundamentally opposed. This is obvious from their logical ends, on their faces, and Gnostic Christians are lost, or "heretical," Gnostics as far as I am concerned.
``` Transmission Note 03:
Despite this, there are very few Gnostic Christians who have (so far) maintained a non-Abrahamic Jesus and allegedly find bits of gnosis by focusing through the figure. That certainly makes them distinct from the Judeo-Catholic lineage and this, among other non-standard Christs, are the only reason why I make the distinction between Catholicism and Christianity in other posts.
``` But, thus far, I've (necessarily) given you more of a history lesson on them than an explanation of what Gnosticism really is.
Features of Gnosticism
Globally and as a phenomenon, Gnosticism is the metaphysical worldview positing a duality between self-consciousness and material nature, with need for man to overcome the latter by means of personal knowledge of the self and of the nature of reality (Gnosis). Further, it:
- Posits a hostile world order.
- Asserts a material reality that naturally restricts the meaningful will and ability of self-conscious man within its objective and knowable parameters.
- Affirms the free will and intellectual agency of self-conscious man as means by which he can pursue, gain, and apply Gnosis.
- Calls for a personal journey toward individuation, as man cannot attain Gnosis collectively or by means of others, but only through his own efforts.
Gnosticism is an emergent worldview, appearing across time and space organically, rather than as a worldview constructed for socio-political purposes like religions. As such, it does not share the goal or function of religion as a means of socio-political management. Yet, still, it takes on the three forms that all worldviews do -- mythic, secular, and atheistic. Specifically (with examples), there is:
-
Mythic Gnosticism -- taking on a spiritual character, dealing with immaterial realms and entities:
-
- Classical/Theistic Gnosticism
-
- Jungian Analysis
-
Secular Gnosticism -- taking on a political character, dealing mainly with material powers and principalities:
-
- Prometheanism
-
- Reincarnation Truthers (ET)
-
- American Conspiracy Culture (Alex Jones, David Icke, etc...)
-
- Plot of The Matrix
-
- Forms of Anarchism
-
Gnostic Atheism -- taking on a philosophical character, dealing with ethics and metaphysics:
-
- Objectivism
-
- Simulation Theory (some)
-
- e/acc
I, personally, view Gnosticism as a signal you pick up on. A well broadcast fact of reality that you become attune to (if you so have the capacity) after an alienating event: a realization, a condition, or a happening that snaps you out of a given collective drone and spurns the oh, so gnostic sense that something is deeply wrong with the world. Often, it's a noticing of hyleticism, a noticing of a naturally systemic injustice, or a just a longstanding experience of disconnect with the norms and trajectory of the world. But, after boarding the Gnostic-line of thought, a decent amount path-find their way to actual Gnosticism. And, while that Gnosticism may wear many different faces and metaphorical frameworks, it's always says the same thing.
``` This isn't exclusive to me. I'm the only one I've heard explicitly say this, but I've seen all serious Gnostics talk about this in a way that suggests what I am. Additionally, those "alienating events," as I've coined, are not spontaneous, they're usually a long time coming.
``` That's why I've listed only 4 characteristics — of Gnosticism: because, contrary to what most scholars and enthusiasts would say, that's all you need to describe that thing. And, by being able to identify what are essentially Gnostic first principles, we are able to understand and talk about Gnosticism much more pointedly.
For one, it gives us a kind of tracking system where we can talk about Western Gnosticism but also see Gnosticism itself, Eastern Gnosticism, and Gnosticism's appearance in tribal cultures around the world. We can see it branching off in America or taking on some new flavor in Brazil. We can also see it when it isn't appearing in an explicitly spiritual form, but as a literary theme or a cultural meme. So, fittingly, this understanding of Gnosticism is as broad as the phenomena itself since it is much more in line with how it actually manifests within the world.
Yet, you’ll also see that it is somehow much more precise than the long, droning lists that Stephan Hoeller and a few others have produced:
- There is an original and transcendental spiritual unity from which emanated a vast manifestation of pluralities.
- The manifest universe of matter and mind was created not by the original spiritual unity but by spiritual beings possessing inferior powers.
- One of the objectives of these creators is the perpetual separation of humans from the unity (God).
- The human being is a composite: the outer aspect is the handiwork of the inferior creators, while the inner aspect is a fallen spark of the ultimate of the divine unity.
- The sparks of transcendental holiness slumber in their material and mental prison, their self-awareness stupefied by the forces of materiality and mind.
- The slumbering sparks have not been abandoned by the ultimate unity; rather, a constant effort directed toward their awakening and liberation comes forth from this unity.
- The awakening of the inmost divine essence in humans comes through salvific knowledge, called “gnosis.”
- Gnosis is not brought about by belief of by the performance of virtuous deeds or by obedience to commandments; these at best serve to prepare one for liberating knowledge.
- Among those aiding the slumbering sparks, a particular position of honor and importance belongs to a feminine emanation of the unity, Sophia (Wisdom). She was involved in the creation of the world and ever since has remained the guide of her orphaned human children.
- From the earliest times of history, messengers of Light have been sent forth from the ultimate unity for the purpose of advancing gnosis in the souls of humans.
- The greatest of these messengers in our historical and geographical matrix was the descended Logos of God manifest in Jesus Christ.
- Jesus exercised a twofold ministry: he was a teach, imparting instruction concerning the way of gnosis; and he was a hierophant, imparting mysteries.
- The mysteries imparted by Jesus (which are also known as sacraments) are mighty aids toward gnosis and have been entrusted by him to his apostles and their successors.
- Through the spiritual practice of the mysteries (sacraments) and a relentless and uncompromising striving for gnosis, humans can steadily advance toward liberation from all confinement, material and otherwise. The ultimate objective of this process of liberation is the achievement of salvific knowledge and with it, freedom from embodied existence and return to ultimate unity.
— Gnosticism: New Light on the Ancient Tradition of Inner Knowing by Stephan A. Hoeller
Lists like this, while not all wrong, do not form a cohesive or accurate explanation of Gnosticism.
I will say that, while I disagree on the language, universality, “divine feminine,” and the implications of “oneness” — which mostly come from Christian contamination — the first 10 points comprise a very accurate characterization of Mythic Gnosticism. But the list, as a whole, is completely ignorant of Gnosticism’s non-spiritual manifestations and, again presupposes that Gnosticism is a denomination of Christianity, a plain falsehood.
Worse yet, they're the works of those who futilely take it upon themselves to "revive" and "spread" Gnostic Christianity, with these lists as blatant — and often plainly stated — attempts to define a canonical doctrine. The ultimate intent being to make "Gnosticism" structurally and massively participatory so that it can be marketable to the masses. But, those who desire this do so because they view Gnosticism as a religion and have adopted Christian/Abrahamic views as to the purpose of belief systems.
Yet, Gnosticism is neither beholden to nor compatible with those views.
``` Transmission Note:
This should not be interpreted as an attack on Stephan Hoeller. The aforementioned book is informative as a whole and I agree with a lot of it. However, I disagree with many of Hoeller's conclusions.
Funny enough, while revisting that chapter, I discovered that Hoeller, being well before my time, has a lot more context on where guys like David Lindsay (I think that's his name?) come from. Page 182.
```
Practicing Gnosticism
One does not practice Gnosticism, mythic or not. But, Gnostics often practice rituals that they believe will induce Gnosis.
Because Gnosis must be attained personally and intellectually, these rituals historically involved psychedelics and circumambulatory* acts meant to remind the practitioner of his goal. Additionally, this pursuit meant that Classical Gnostics were (and continue to be) open to trying out practices from other belief systems if they're believed to have the potential to induce Gnosis. Many, however, also turn to plain ol' knowledge, choosing to immerse themselves in more interactive ways of knowing about the world such as science, math, and esoterica as a path to personal knowledge of reality.
Yet, while varied and individualistic, Gnostics did not always go about their spiritual journeys alone. While Gnosis is pursued personally, individual findings, experiences, and speculations were/are shared among each other for consideration and guidance in personal journeys. Individuals with similar findings and personally efficacious mediums of Gnosis would form groups and participate in rituals together. And, because Gnosticism is classically hostile or indifferent to the body, historical Gnostic groups tended to go one of two ways: ascetic or degenerate. The first involved fasting, abstinence, and denial of bodily pleasures. The second, I will leave to your imagination. But, thankfully the former won out in popularity and is how Gnostics are commonly portrayed.
``` Come to think of it, the whole attempt to shock oneself into Gnosis is kind of like trying to relive the alienating event that made one Gnostic in the first place. But, more intense.
``` So, the point being made is that, when thinking of Gnostic groups or Gnostics gathered, one should avoid conceiving of them as one does a church. Rather than platforms where an orthodoxy is espoused and downloaded, Gnostic gatherings were/are information exchanges, more akin to get-togethers.
Gnosticism has an investigative and antinomian character, rather than faithful and obedient character.
Secrets
At this point, I've laid out that Western Gnosticism comes from the Greek mystery cults (and by extension Egypt, and, in likelihood, Babylon). I've highlighted that those holding their beliefs went into hiding and were given the name "Gnostic" by their persecutors ("Gnosis" meaning "knowledge," "Gnostic" approximating "knower"). And, I've repeatedly used word like "private," "personal," "individual," "metaphor," "code," and "secret" to describe their activities.
All of these things, in a sort of snowball effect, have had Christians unwaveringly convinced that Gnosticism is about "keeping secrets." And, with a strange intensity, they've been all riled up about Gnostics having "secret knowledge" for thousands of years. In fact, if you ask a Christian (who has heard of Gnosticism) today, that's exactly what they'll tell you: "Gnostics were people who thought they had secret knowledge."
With a tone suggesting an absurd level of contempt for a supposedly dead heresy, to boot.
But, Gnosticism was poorly understood by its enemies and is not about "secret knowledge." Despite the fact that Christians love making themselves angry imagining such silly ideas that are more attributable to themselves, Gnostics are not and were not meeting up to go: "teehee, they don't know our seeecret!"
In fact, here are the mythic secrets of such great concern:
-
The mysteries of the mystery cults tended to be along these lines:
-
- You have an immortal soul.
-
- You belong to a spiritual reality (often phrased: "you are/can become a god").
-
- You are trapped in a cycle of material death and rebirth.
-
- You need to do XYZ to escape materiality.
-
The mystery cultists/Gnostics were secretive to preserve the purity of the above beliefs and techniques and to avoid persecution -- and ultimately inquisition -- at the hands of hostile powers.
- Gnosis is personal, private, and "secret" because it is incommunicable. Personal knowledge can be talked about, but cannot be literally shared person to person and Gnosis comes differently to each person.
- Gnosticism doesn't have an imperative for conversion or being a "big tent" because Gnosticism itself is incommunicable to the majority.
These things are not really "secrets" but, even if they were, they could be talked about freely (given the absence of persecution) due to bullet four.
Bonus "Secret": A common premise is that Gnosis is applied at death on a post-mortem spiritual journey, similar to that of the Ka of Egyptian mythology.Books
Many religions and even philosophies are centered around holy books as definitive canonical, instructional, and behavioral guides. They function as the source and reinforcement of a given worldview, which allows it to persist fundamentally undiluted for extended periods of time.
This is not so for Gnosticism -- mythic or not.
Instead, Gnosticism has no holy book and, in the section called "Features of Gnosticism," I've already laid out its presence and reception through alienating events. It requires no human regulation in order to continue to authentically exist.
``` Now is a good time to mention that there is a multiple discovery aspect of Gnosticism which is generally how I, at least, track alignment and continuity while identifying "the signal," as I call it, as the source in others.
``` Yet, the ancient Mythic Gnostics were known to be prolific writers, as attested by the Nag Hammadi library. And, the penchant for writing seems to persist across time and mode, as Secular Gnostics and Gnostic Atheists (beknownst or not) have been absurdly influential in American media and culture by this means.
So, why do Gnostics write so much and how do they use books?
Gnostics tend to view books as spiritual journals, rather than instruction manuals, and literature at large as a means of preserving knowledge. Contributing to the Gnostic meme pool is a form of participation in the imperative, which is why Gnostics, unlike Christians and others, have little issue putting their pieces forward. Rather than the book study and faith characteristic of Abrahamic maintenance, Gnosticism, again, tends toward investigation and information sharing. And, it is for these reasons that Gnostics have been known to not only write their own texts, but to adopt and reinterpret the texts of other belief systems according to the Gnostic worldview.
-
 @ 8d34bd24:414be32b
2024-09-01 15:47:33
@ 8d34bd24:414be32b
2024-09-01 15:47:33This post was inspired by listening to a video by Jimmy Evans on his Tipping Point Prophecy Update Substack
There are many things in our lives that seem like giants. They may be people that influence us. They may be people who are opponents in some way. It may be circumstances or events. These things have gigantic influence on us or overwhelm us.
What should our response be to giants in our life? Let’s look at two events and how different people responded to the giants in their life.
David & Goliath
Of course, when we think of giants, most of us think about Goliath first. Most of us know the basics of the story, but let’s look at the details in the Bible to see what we can learn from them.
Then a champion came out from the armies of the Philistines named Goliath, from Gath, whose height was six cubits and a span. He had a bronze helmet on his head, and he was clothed with scale-armor which weighed five thousand shekels of bronze. He also had bronze greaves on his legs and a bronze javelin slung between his shoulders. The shaft of his spear was like a weaver’s beam, and the head of his spear weighed six hundred shekels of iron; his shield-carrier also walked before him. He stood and shouted to the ranks of Israel and said to them, “Why do you come out to draw up in battle array? Am I not the Philistine and you servants of Saul? Choose a man for yourselves and let him come down to me. If he is able to fight with me and kill me, then we will become your servants; but if I prevail against him and kill him, then you shall become our servants and serve us.” (1 Samuel 17:4-9)
The Bible says Goliath’s “height was six cubits and a span.” If we take a cubit as 18 inches and a span as 6”, that makes him 9 foot 6 inches tall. That is a tall and intimidating man. He was also strong. His armor weighed about 125 lbs. When the Israeli army heard this challenge, not one soldier volunteered to face Goliath. Not one believed they could win a fight with Goliath.
When Saul and all Israel heard these words of the Philistine, they were dismayed and greatly afraid. (1 Samuel 17:11)
Ironically, the one and only person who was willing to face off with this giant of a soldier, was a lad (probably a teenager).
Then David spoke to the men who were standing by him, saying, “What will be done for the man who kills this Philistine and takes away the reproach from Israel? For who is this uncircumcised Philistine, that he should taunt the armies of the living God?” (1 Samuel 17:26)
Why was David willing to fight this giant soldier? Was this the bravado or foolishness of youth? No. What does David say? “For who is this uncircumcised Philistine, that he should taunt the armies of the living God?”
David was unafraid because he trusted God. He knew the battle was the Lord’s. He knew that God had promised to protect and guide Israel (the circumcised) against the Canaanites (the uncircumcised). He knew that God would defend His honor. David knew he didn’t have to fight the fight alone. He relied on God.
David said to Saul, “Let no man’s heart fail on account of him; your servant will go and fight with this Philistine.” Then Saul said to David, “You are not able to go against this Philistine to fight with him; for you are but a youth while he has been a warrior from his youth.” But David said to Saul, “Your servant was tending his father’s sheep. When a lion or a bear came and took a lamb from the flock, I went out after him and attacked him, and rescued it from his mouth; and when he rose up against me, I seized him by his beard and struck him and killed him. Your servant has killed both the lion and the bear; and this uncircumcised Philistine will be like one of them, since he has taunted the armies of the living God.” And David said, “The Lord who delivered me from the paw of the lion and from the paw of the bear, He will deliver me from the hand of this Philistine.” And Saul said to David, “Go, and may the Lord be with you.” (1 Samuel 17:32-37)
David once again spoke knowing God had promised Israel’s victory over the uncircumcised Philistines. He also knew God would not allow His name to be taunted. David had spent his whole life depending on God in difficult situations and knew that God would be with him in this battle, just like his battles with a bear and a lion. Experience had taught him that God always fulfilled his promises and always won against those who did not believe in Him. David did not let the taunting of an unfaithful giant intimidate him and he didn’t let the scorn of the King intimidate him. He kept his eyes on God and trusted in Him alone.
Then David said to the Philistine, “You come to me with a sword, a spear, and a javelin, but I come to you in the name of the Lord of hosts, the God of the armies of Israel, whom you have taunted. This day the Lord will deliver you up into my hands, and I will strike you down and remove your head from you. And I will give the dead bodies of the army of the Philistines this day to the birds of the sky and the wild beasts of the earth, that all the earth may know that there is a God in Israel, and that all this assembly may know that the Lord does not deliver by sword or by spear; for the battle is the Lord’s and He will give you into our hands.” (1 Samuel 17:45-47)
David did not just silently trust God. He publicly proclaimed his trust in the “Lord of Hosts.” He spoke up to let the Israelite army and the Philistine army know that it was God that was fighting for Israel and it was God who would win the battle despite the seeming obvious advantage Goliath had over David.
There is a reason David was called “a man after God’s own heart.” He trusted in the strength of God instead of his own strength. He knew that God was bigger than any giant. He didn’t try to win in his own strength or wisdom. He relied 100% on God. We should do the same.
Spy out the Land of Canaan
There is another time that the Bible talks about the Israelites facing giants. This is when the Israelites were led from bondage in Egypt to the promised land. When they arrived God tested the Israelites to see if they would put their trust in Him or if they would rely on themselves alone.
Then the Lord spoke to Moses saying, “Send out for yourself men so that they may spy out the land of Canaan, which I am going to give to the sons of Israel; you shall send a man from each of their fathers’ tribes, every one a leader among them.” (Numbers 13:1-2)
God didn’t need the Israelites to check things out. He knew the situation and He knew what He would do. This was a test, to see if they would finally put their faith in Him after all of the miracles that He had done for them.
See what the land is like, and whether the people who live in it are strong or weak, whether they are few or many. How is the land in which they live, is it good or bad? And how are the cities in which they live, are they like open camps or with fortifications? (Numbers 13:18-19)
The Israelites were shown both the blessings God had offered to them if they put their faith in Him and the challenges they must face through God’s power.
When they returned from spying out the land, at the end of forty days, they proceeded to come to Moses and Aaron and to all the congregation of the sons of Israel in the wilderness of Paran, at Kadesh; and they brought back word to them and to all the congregation and showed them the fruit of the land. Thus they told him, and said, “We went in to the land where you sent us; and it certainly does flow with milk and honey, and this is its fruit. Nevertheless, the people who live in the land are strong, and the cities are fortified and very large; and moreover, we saw the descendants of Anak there. (Numbers 13:25-28)
Unfortunately, although most of the leaders saw the blessing, they were terrified by the challenges. They rightly knew they couldn’t conquer Canaan on their own, but they wrongly failed to trust in God’s promise to provide the land to them. Despite all of the blessings and miracles that God had shown them, they failed to put their trust in Him.
Then Caleb quieted the people before Moses and said, “We should by all means go up and take possession of it, for we will surely overcome it.” (Numbers 13:30)
There were two men, however, who trusted in God’s power and His promises. Caleb and Joshua trusted God’s promises and looked at the blessings God had promised them and saw them as being as already received because of God’s promise. They knew they didn’t have to conquer Canaan on their own. They knew they could trust God to accomplish what He had promised.
But the men who had gone up with him said, “We are not able to go up against the people, for they are too strong for us.” So they gave out to the sons of Israel a bad report of the land which they had spied out, saying, “The land through which we have gone, in spying it out, is a land that devours its inhabitants; and all the people whom we saw in it are men of great size. There also we saw the Nephilim (the sons of Anak are part of the Nephilim); and we became like grasshoppers in our own sight, and so we were in their sight.” (Numbers 13:31-33)
The rest of the leaders saw the Nephilim (giants) as bigger than God and therefore the land as unconquerable. Who do you see as bigger? Do you truly see the awesome power of God and His ability to do anything He wishes? Do you trust God to keep all of His promises?
Joshua the son of Nun and Caleb the son of Jephunneh, of those who had spied out the land, tore their clothes; and they spoke to all the congregation of the sons of Israel, saying, “The land which we passed through to spy out is an exceedingly good land. If the Lord is pleased with us, then He will bring us into this land and give it to us—a land which flows with milk and honey. Only do not rebel against the Lord; and do not fear the people of the land, for they will be our prey. Their protection has been removed from them, and the Lord is with us; do not fear them.” (Numbers 14:6-9)
Joshua and Caleb not only trusted God, they defended His honor. They tore their clothes in remorse at their fellow Israelites not having faith in God. They begged their fellow Israelites not to “ rebel against the Lord.” They advised their fellow Israelites that “the Lord is with us; do not fear them.” They not only walked in faith, but also encouraged others to do the same.
What Are Your Giants?
In these two examples, people were dealing with real, live giants, but there are many giants in our lives. Is your giant persecution for your faith? Is your giant health problems for you or your loved ones? Is your giant loneliness? Is your giant financial problems?
Whatever giant you are facing, God is bigger; God is smarter; and God is stronger. With God on your side, you don’t need to fear anything or anyone. You can trust His promises. You can trust His plans. You can trust that everything will work out in the end.
There may be things in your life that you can’t handle, but there is nothing that the God and Creator of the universe can’t handle. If you put your faith in Him, then nothing can overcome you.
Trust Jesus. In everything trust Jesus. He will never let you down.
Trust Jesus. your sister in Christ,
Christy
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
-
 @ 54609048:8e22ba03
2024-09-01 15:14:37
@ 54609048:8e22ba03
2024-09-01 15:14:37"Without cheap, reliable, and plentiful energy, our civilization would grind to a halt, and billions of people would be condemned to poverty and premature death."
Alex Epstein
Energy is the foundation of modern civilization, powering our homes, industries, and economic progress. As technology advances, our energy demands increase, making the pursuit of sustainable and abundant energy sources more critical than ever. The Kardashev Scale, which measures a civilization’s advancement based on its energy consumption, provides a unique perspective on energy's importance. A Type I civilization harnesses all the energy available on its home planet, while a Type II civilization controls the energy of its entire solar system, and a Type III civilization commands energy on a galactic scale. These concepts, though theoretical, underscore that energy is not just a resource but a measure of a civilization's ability to thrive.
Despite this reality, there is an ongoing war against energy, often masked by climate action and environmental protection. Policies like Germany’s “Energiewende” (Energy Transition) aim to have at least 80% of electricity come from renewable sources by 2050, with nuclear power being phased out. Yet, the long-term sustainability of this plan is questionable. For instance, the recent demolition of Grafenrheinfeld, Germany’s oldest nuclear power plant, which supplied over 11% of Bavaria’s energy needs, reflects this misguided approach.
The root problem lies in the flawed belief that large-scale energy consumption is inherently destructive to the environment, driving policies like Energiewende, “Net Zero,” and the "just energy transition." These well-intentioned initiatives risk exacerbating global energy poverty. Sub-Saharan Africa (SSA), where over 600 million people live without electricity, is a cautionary tale of the devastating impact of energy scarcity. Alex Epstein, author of Fossil Future, summarized this phenomenon perfectly when he said, “The pursuit of alternative energy sources is valuable, but it must be driven by the goal of improving human life, not by an ideological commitment to reducing our impact on the planet." In other words, economic prosperity is unattainable where energy poverty persists, yet Bitcoin mining, a proven solution to fostering energy innovation, is unjustly vilified for its energy consumption.
This is due to false claims, such as allegations that each Bitcoin transaction uses as much water as a swimming pool or consumes as much energy as a U.S. household in a month.These misleading reports persist due to widespread ignorance about Bitcoin mining's mechanics and the misconception that all energy-intensive operations are harmful to the environment. Alana Mediavilla's documentary Dirty Coin (DC) is one of the best productions that accurately analyzes the Bitcoin mining industry, educating viewers on how Bitcoin mining supports energy innovation and drives the development of sustainable energy systems. From monetizing stranded energy in Africa to methane capture from landfills, DC showcases human ingenuity in a compelling way.
 ### Bitcoin Mining: Catalyzing Energy Innovation
### Bitcoin Mining: Catalyzing Energy InnovationOne compelling case study in DC is a paper mill in Finland repurposed into a Bitcoin mining facility. This isn’t just any mining operation; the excess heat from the mining rigs is captured and used to provide district heating for over 11,000 residents. Finland burns around 30 million cubic meters of solid wood fuels annually for heating, generating approximately 60 terawatt-hours (TWh) of energy. This innovative recycling of heat not only reduces energy costs but also preserves Finland’s forests by reducing reliance on wood burning. Critics of Bitcoin mining often ignore these environmental benefits, either out of ignorance or because they don’t fit their narratives.
Another example from the Netherlands highlights how excess heat from Bitcoin mining rigs is used to heat greenhouses, reducing reliance on natural gas—especially crucial given the rising costs due to geopolitical tensions like the war in Ukraine. This collaboration not only supports local agriculture but also lowers food prices by providing a cheaper heating alternative.
These examples demonstrate how Bitcoin mining, when integrated with local energy systems, can drive innovation and support sustainable energy solutions without creating energy deficits. By providing consistent demand for electricity, Bitcoin mining can make renewable energy projects financially viable, particularly in regions where traditional energy markets fall short. DC isn’t just a film about Bitcoin mining; it shows that energy production and consumption can be done responsibly.
The Role of Abundant Energy in Economic Performance and Quality of Life
Abundant energy drives industrial growth, fosters innovation, and enhances living standards. In regions with limited access to energy, economic opportunities are stifled, and poverty persists. Conversely, areas that invest in energy infrastructure—especially decentralized, renewable energy—experience significant economic uplift. Bitcoin mining offers a unique opportunity to accelerate this process. In a separate interview, Jesse Pielke, CEO of Hashrate Up, noted that Africa’s untapped energy potential, combined with Bitcoin mining, could create energy abundance that transforms the continent's economic landscape. The integration of Bitcoin mining with decentralized mini-grids, powered by renewable sources, offers a resilient and adaptable solution to local needs. These mini-grids not only provide electricity but also help monetize stranded energy, turning what was once waste into a valuable resource.
DC also highlights real-world examples of this dynamic. In Malawi, surplus hydroelectric power is used to mine Bitcoin, providing a stable income for local communities. This model not only supports economic development but also contributes to energy security and sustainability.
Embracing the Energy Evolution
As we face the challenges of the 21st century, it's crucial to recognize the role of energy in shaping our society. Bitcoin mining, often misunderstood and criticized, is emerging as a key player in this journey. DC illustrates how Bitcoin mining can drive energy innovation, support local economies, and contribute to developing new energy sources, including nuclear power. The film is an essential guide for understanding how to incentivize energy innovation and inspire future innovators to develop new energy infrastructure without relying on subsidies or handouts.
-
 @ 361d3e1e:50bc10a8
2024-09-04 13:54:12
@ 361d3e1e:50bc10a8
2024-09-04 13:54:12More European countries are choosing BRICS instead of the European Union
europe #turkey #serbia #brics #politics
-
 @ 5af07946:98fca8c4
2024-09-04 13:02:36
@ 5af07946:98fca8c4
2024-09-04 13:02:36 -
 @ 54609048:8e22ba03
2024-09-01 14:58:41
@ 54609048:8e22ba03
2024-09-01 14:58:41The most pressing issue today in improving quality of life for people around the planet is access to energy. Bitcoin mining can finance the build out of infrastructure to do that.
In many parts of the world, access to electricity is a luxury that we often take for granted. Sub-Saharan Africa (SSA), for example, faces a severe electricity deficit, with over 600 million people without power. This deficit leads to economic stagnation, reduced food production, poverty, and even civil unrest. The correlation between electricity access and economic growth is undeniable, and regions with less than 80% electrification rates consistently suffer from reduced GDP per capita.
The challenge lies in expanding electrical infrastructure to these underserved areas, which is capital-intensive and often financially unfeasible for governments with limited resources. This is where Bitcoin mining is a potential solution that can offer a pathway to electrify regions that have long been without access to electricity.
Bitcoin mining has long been a subject of much controversy, with critics often focusing on its perceived environmental impact. However, beneath the sensational headlines and mainstream media narratives, lies a story of potential humanitarian benefits, and energy innovation. By harnessing stranded energy in remote locations, Bitcoin mining can provide a source of revenue for new power plants and thus support the construction of electrical grids.
Despite the ongoing mudslinging campaign against Bitcoin mining, knowledge of the importance of harnessing stranded energy for Bitcoin mining is slowly gaining traction. In fact, this is the story that is beautifully captured in the newly released and award-winning documentary, Stranded:A Dirty Coin Short by Alana Mediavialla Diaz, which showcases how Bitcoin miners in places like SSA ingeniously repurpose stranded power, breathing life into both Bitcoin and forgotten power infrastructures.
In this article, we will explore the overlooked positive aspects of Bitcoin mining, compare its energy consumption to other industries, and make a case for how Bitcoin mining could potentially incentivize the discovery of new sources of energy and the build out of new energy infrastructure.
What Is Stranded Energy Anyway?
Stranded energy refers to energy sources that exist in a location but are not effectively utilized or harnessed for productive purposes. It's essentially energy that is isolated or "stranded" in a certain location due to various reasons, like lack of infrastructure to transport it or a mismatch between the location of energy production and demand.
For instance, when new electrical grids are being developed, especially in remote areas, the energy infrastructure may be in place before the demand for it catches up. Which means that, until consumers are connected to the grid, the energy generated is more than what is immediately needed, making it “stranded” and ultimately wasted until more users connect. This is a huge problem that Bitcoin mining can help to solve, and this area in particular is one of the major benefits of mining that Stranded explored in great detail.
In an interview Alana highlighted how Bitcoin mining, by monetizing excess energy in regions lacking traditional demand, acts as a financial catalyst for constructing vital grid infrastructure, thereby changing lives and challenging our perceptions of energy's societal impact. She elaborated on this further by saying, “The concept of how a grid grows through demand, was not something I ever thought about. In the film i wanted to capture that it is a great privilege to have access to electricity and that mining is able to finance new grid infrastructure in places that have never had it before”
Take Ethiopia, for instance. It has the potential to generate more than 60,000 megawatts (MW) of electricity from “renewable” sources, but currently has only 4,500 MW of installed capacity. 90% of its electricity is generated from hydropower, with geothermal, solar, and wind making up the difference. However, the country still experiences acute energy shortages, with only 44% of its 110 million people having access to electricity. With projects like the Grand Ethiopian Renaissance Dam (GERD) under construction, which is projected to generate an additional 5,150 MW, the government expects to have a total of 17 000 MW of installed capacity in the next 10 years. The introduction of Bitcoin mining has the potential to fund these electricity infrastructure projects.
Dispelling Misconceptions About Bitcoin Mining
One of the most common misconceptions surrounding Bitcoin mining is the notion that it consumes an exorbitant amount of energy, exceeding the energy consumption of entire countries. Critics often point to reports suggesting that Bitcoin mining consumes more electricity than many nations, including Ireland, Nigeria, and Uruguay. The Bitcoin Energy Consumption Index by cryptocurrency platform Digiconomist estimates an annual energy usage of 33 terawatts, on par with countries like Denmark.
However, it's important to dissect this critique and place it in the broader context of energy consumption. While it's true that the Bitcoin network's energy usage appears significant, it's essential to remember that energy consumption itself is not inherently bad. This critique tends to presuppose that energy is a finite resource and that allocating it to Bitcoin mining deprives other industries or individuals of this valuable commodity.
In reality, energy is a vital and expandable resource, and the notion of one usage being more or less wasteful than another is subjective. All users, including Bitcoin miners, incur a cost and pay the full market rate for the electricity they consume. To single out Bitcoin mining for its energy consumption while overlooking other industries is a fallacy. As Alana also pointed out, “People hold as common misconceptions what the media commonly repeats about Bitcoin. Nobody is ever thinking about the energy consumption of the industries they interact with everyday.This is not a common figure that people know about things yet when it comes to Bitcoin, it sure is dirty because of all that energy consumption!“
Comparing Bitcoin To Other Energy-Intensive Industries
To put things in perspective, let's compare Bitcoin mining to some other energy-intensive sectors that often escape similar scrutiny:
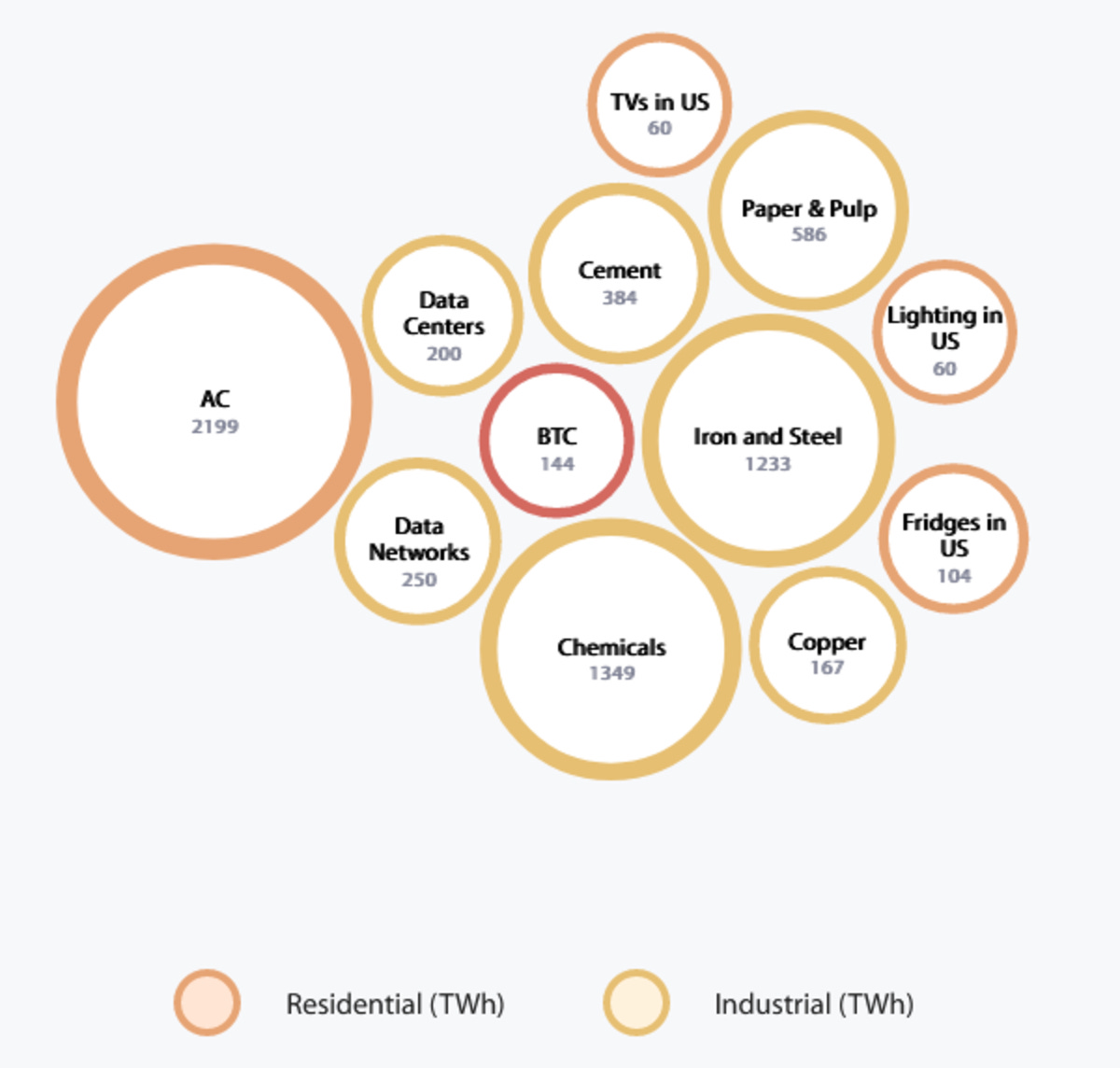
I don’t know about you, but I cannot recall the last time I heard complaints in the media about the paper and pulp industry's high energy consumption. In order to counter the myths surrounding “the dangers” of Bitcoin mining and its energy usage, a nuanced understanding of energy consumption is required. While it's crucial to examine the environmental impact of any industry, singling out Bitcoin mining for criticism while overlooking other energy-intensive sectors is a flawed approach.
What Does The Future Hold?
Unlike any technology before it, Bitcoin mining incentivizes the exploration of cost-effective ways to harness energy, irrespective of geographic limitations or conventional energy constraints. This financial impetus could spark an energy revolution on a scale not seen since the Industrial Revolution, potentially propelling humanity to be a type I civilization. A view also shared by Alana, who when quizzed about her next film project said, “The next one is about what it will take us to reach a type 1 civilization using Puerto Rico as our underdog model that is undergoing major infrastructure change. It’s a pivotal moment in the island’s history and it can serve as an example to failing grids around the world.”
As economic incentives push Bitcoin mining to saturate the energy sector, a convergence is occurring. Energy producers are monetizing surplus and stranded energy through Bitcoin mining, while miners are vertically integrating to enhance competitiveness. In the foreseeable future the most efficient miners could become energy producers themselves, potentially inverting the traditional power grid model.
This article was originally published in Bitcoin Magazine
-
 @ 469fa704:2b6cb760
2024-09-01 13:26:42
@ 469fa704:2b6cb760
2024-09-01 13:26:42Side jobs and passive sources of income
To increase your income, it is often necessary to be creative and develop different income streams:
- Freelancing: platforms such as Upwork, Fiverr or Freelancer offer a variety of tasks, from graphic design to programming work to marketing. According to a study by Statista, freelancers in Germany earn between 20 and 50 euros per hour on average, depending on their expertise.
- Part-time jobs: You can take on a part-time job alongside your main job. Think about jobs that are flexible, such as driving services (e.g. Uber, Bolt), delivery services (e.g. Deliveroo, Gorillas) or tutoring. According to the Federal Employment Agency, part-time jobs can be tax-free up to 450 euros per month, which is an attractive option.
- Passive income: This requires work or capital initially, but can generate income in the long term:
-
- Real estate: real estate investments offer regular rental income. According to the German Institute for Economic Research (DIW), the return on residential real estate in Germany can be between 3% and 5%.
-
- Dividend stocks: Invest in companies that pay dividends. Companies such as Siemens or Deutsche Telekom have a long tradition of distributing dividends.
-
- Digital products: Create e-books, online courses or apps. Once created, these products can generate continuous income.
-
- Affiliate marketing: Partner with brands and earn through sales commissions. Amazon Associates is one of the best-known platforms for this.
Reduce expenses
Another way to have more capital for investments such as Bitcoin is to reduce expenses: * Budgeting: create a detailed budget. Apps like YNAB or Mint can help categorize expenses and analyze where savings can be made. * Food: Plan your shopping, buy seasonal products and cook more yourself. According to a study by the Federal Ministry of Food and Agriculture, households spend an average of around 25% of their income on food.Conscious shopping can significantly reduce these costs. * Energy costs: Use energy-saving light bulbs, switch off appliances completely and insulate your home better. According to the Federal Office of Economics and Export Control (BAFA), simple energy-saving measures can reduce costs by up to 20%. * Subscriptions and memberships: Review regular subscriptions (gym, streaming services).Many people pay for services they rarely use. A survey by Statista showed that on average 10-15% of monthly spending is used for subscriptions. * Transportation: Use public transportation or car sharing services instead of owning a car.Owning a car can cost several thousand euros a year, including insurance, maintenance and fuel. * Second-hand and upcycling: Buy second-hand clothes or furniture.The second-hand market is booming and you can often find high-quality products at a fraction of the original price.
Investing, or rather saving, in Bitcoin
After you have accumulated more Dollar or other paper money by increasing your income and reducing your expenses, you can invest in Bitcoin:
- Bitcoin: As the first and best-known cryptocurrency, Bitcoin has a high market capitalization and acceptance. Investors see Bitcoin as a “digital gold” alternative, especially in times of inflation.
- Risk and volatility: Bitcoin is known for its high volatility. It is important to only invest money that you don't need in the immediate future. In the long term, bitcoin is destined to rise in price in dollar terms due to its unique characteristics.
- Long-term perspective: Many investors hold Bitcoin as a long-term investment, similar to stocks. Historically, Bitcoin has shown positive returns over longer periods of time, despite high volatility.
Practical steps to increase income and reduce expenses:
- Analyze income: Make a note of all your sources of income and consider how you can increase them. This could be through salary increases, side hustles or new passive income streams.
- Review expenses: Make a list of your monthly expenses and identify areas where you can cut back. Set specific goals for reduction.
- Investment plan: After you have accumulated more capital, create an investment plan. For Bitcoin, this could mean investing small amounts regularly to take advantage of the average cost effect (dollar-cost averaging).
- Education and networking: Invest time in education and build a network. This can lead to new income opportunities and increase your financial intelligence.
Idea to get Ahead:
Create a budget and set a monthly savings goal for your Bitcoin investments. Calculate how much you can generate by reducing expenses and generating additional income. Research and choose a Bitcoin only platform to buy Bitcoin (e.g. Relai, Coinfinity, 21Bitcoin, Pocket Bitcoin ). Learn the basics of trading and start with a small investment.
-
 @ 5954198a:0c6fa207
2024-09-04 09:21:15
@ 5954198a:0c6fa207
2024-09-04 09:21:15If you are newbie in the business world, what you really wish for? The very first thought in your mind would be reaching out to your target audience. Here, we, one of the best SEO companies in Indore brings you a complete package of all seo services under a roof. Our SEO company in Indore has become truly efficient and time-reductant, letting you expect 2x customer faster. Our SEO services in Indore allow you to promote your business not only at a city level but also globally. Now no need to worry about your business, expand it free with one of the best SEO companies in Indore. Get a chance to upscale your small size business into a big one by amplifying your reach with our SEO services in Indore. Understanding what your customer base needs is very crucial and important for us as a business entity and our knowledge and proficiently in the concern field regarded us one of the reliable seo companies in Indore. Visit: https://digi-partners.com/seo-company-in-indore/
-
 @ 06a260a2:d7a7791c
2024-09-04 08:13:22
@ 06a260a2:d7a7791c
2024-09-04 08:13:22Co je plnohodnotný bitcoinový uzel (bitcoin full node)? Je to základní prvek bitcoinové sítě. Server, na kterém běží bitcoinový klient, komunikuje s dalšími uzly v síti, udržuje kopii bitcoinového blockchainu (databáze všech potvrzených transakcí v bitcoinové síti), ověřuje nově příchozí transakce, validuje nově vytěžené bloky a zprostředkovává interakci uživatelů bitcoinu s bitcoinovou sítí. Pro těžaře zároveň připravuje šablonu nového bloku z transakcí čekajících na potvrzení. Je toho celkem dost, ne?
Satoshi Nakamoto už ve svém whitepaperu předpokládal, že každý uživatel bitcoinové sítě bude provozovat vlastní plnohodnotný uzel. Proč by to měli uživatelé bitcoinu chtít?
Proč provozovat vlastní bitcoinový uzel?
Používání vlastního plnohodnotného uzlu přináší celou řadu benefitů jak svému uživateli, tak bitcoinové siti a celému ekosystému. Pojďme se na ně podívat.
Podpora decentralizace bitcoinové sítě
BItcoinová síť je navržena jako decentralizovaná a má to své důvody. Decentralizace snižuje pravděpodobnost fatálního selhání sítě tím, že zvyšuje redundanci jejich kritických míst, kterými jsou právě uzly. Decentralizace v podobě zvýšené množstevní i geografické redundance pak chrání síť proti důsledkům přírodních katastrof, cíleným útokům hackerů nebo vládních organizací, ale i nečestnému jednání jednotlivých uživatelů sítě v podobě manipulace s bitcoinovým softwarem. Decentralizace se navíc nevztahuje pouze na fyzické uzly, ale i na celou governance - způsob řízení a rozhodování v síti. Neexistuje tak žádná centrální autorita, která by mohla svým jednáním a rozhodnutím, ať už svévolně nebo pod externím tlakem ovlivnit chování sítě.
Pokud se tedy rozhodnete provozovat vlastní uzel, zvýšíte tím antifragilitu bitcoinové sítě a stanete se jejím pravým uživatelem tak, jak to Satoshi zamýšlel.
Ověřování transakcí a validace nových bloků
Důležitým aspektem decentralizace je schopnost samostatně ověřit příchozí transakce a nově vytěžené bloky vůči platným pravidlům bitcoinové sítě bez nutnosti důvěřovat kterékoliv třetí straně. Vyjádřením tohoto principu je okřídlené "Don't trust, verify!". Každý full node obsahuje kompletní kopii bitcoinového blockchainu, databáze všech potvrzených transakcí za celou dobu jeho existence. A nejen to. Při prvním spuštění uzlu a kopírování této databáze od jiných uzlů v síti znovu ověřuje každý jednotlivý blok a transakce v něm podle existujících pravidel sítě, aby měl jistotu, že této databázi může nadále věřit. Tomuto procesu se říká synchronizace. Po jejím dokončení uzel kontroluje nově příchozí transakce i obsah a strukturu nově vytěžených bloků. Pokud zjistí porušení pravidel, odmítne je a do vlastní kopie blockchainu je nezařadí.
Jaká jsou ta pravidla? Je jich celá řada, ale mezi ta nejdůležitější patří:
- kontrola struktury transakce
- kontrola pravosti podpisů náležejícím adresám vstupů transakcí
- kontrola splnění podmínek definovaných v transakčním skriptu
- kontrola vícenásobného utracení UTXO
- kontrola struktury a velikosti nového bloku
- kontrola dodržování monetární politiky bitcoinu (velikost odměny těžaři musí odpovídat aktuální epoše)
Tato vlastnost je důležitá nejen pro vás, provozovatele vašeho uzlu, ale i pro stabilitu celé sítě. Vám umožňuje kontrolovat vaše transakce a zůstatky bez nutnosti důvěřovat jakékoliv třetí straně pouze oproti vaší vlastní kopii blockchainu. Celou síť pak chrání proti nečestnému uživateli, který by se pokusil šířit sítí neplatnou transakci (třeba podruhé utratit už jednou utracené mince) nebo se snažil připojit do blockchainu nový blok větší než povolené velikosti nebo přiznávající mu vyšší než aktuálně platnou odměnu. Takové chování uzel odmítne a není nikdo, kdo by mu v tom dokázal zabránit (je však třeba odpovědně přistupovat k výběru bitcoinového softwarového klienta - o tom více dále v textu).
Ochrana vlastního soukromí a bezpečnosti
Bitcoin není anonymní, ale pseudonymní. Všechny transakce lze v blockchainu dohledat a každý jeden satoshi lze v rámci UTXO dosledovat až k jeho coinbase transakci (okamžiku vzniku jako odměny za vytěžený blok). Transakce sice neidentifikují vlastníky jednotlivých adres, některé z nich o nich ale určité informace poskytují. Například konsolidační transakce může dle struktury podpisů prozradit, že vlastníkem vstupů je pouze jeden člověk. Nebo pokud platíte za nějakou službu na známou adresu a neutratíte kompletní UTXO, je velmi pravděpodobné, že jste vlastníkem i adresy, na kterou se posílá zbytek a to i přesto, že použijete adresu novou. Existují i další analytické postupy, které pomáhají určit vztahy mezi jednotlivými adresami a jejich vlastníky. Takže nakonec stačí prozradit vlastnictví jediné adresy a celou řadu jiných již k ní doplní odpovídající analýza nebo heuristika.
Pokud je pro vás soukromí důležité a vlastnictví bitcoinu považujete za soukromou informaci, je dobré vyvarovat se aktivitám, které by mohly prozradit váš vztah ke konkrétním bitcoinovým adresám. Mezi ně patří i přístup k blockchainu při zadávání nových transakcí, kontrole jejich stavu nebo kontrole zůstatků přes vaši peněženku nebo blockchain explorer. Použijete-li uzel třetí strany, dáváte jí možnost párovat uskutečněné transakce nebo dotazované adresy s vaší IP adresou, která o vás už lecos prozrazuje. I v případě použití Toru nebo VPN nemáte vyhráno. Pokud používáte více různých peněženek třeba pro oddělení KYC a non-KYC mincí, přístupem z jednoho místa je rovněž dáváte do vzájemné souvislosti.
Samostatným problémem je důvěra v informace, které vám uzel třetí strany poskytuje. Jsou skutečně pravdivé, transakce validní a zůstatky odpovídají realitě? Uzel třetí strany za vás sice nepodepíše transakci s vašimi prostředky, ale může vám třeba falešně tvrdit, že transakce, která na vaši adresu převádí dohodnutou platbu, je již potvrzena.
Provoz vlastního plnohodnotného uzlu pro vás tyto problémy řeší. Dotazy na zůstatky a nové transakce zadáváte přímo do vlastního bitcoinového uzlu, který je ověřuje přímo s vaší vlastní kopií blockchainu. Bez cizích očí a rizika manipulace.
Ochrana před cenzurou transakcí
Speciálním případem manipulace třetí strany s informacemi, které vám poskytuje, je cenzura transakcí a adres. Bitcoinový blockchain je transparentní, proto v něm není problém sledovat pohyb libovolných bitcoinů z jakéhokoliv důvodu. Platí to i pro bitcoiny pocházející z nějaké loupeže, podvodu či hacku. Bývají označeny jako špinavé a různé subjekty se brání manipulaci s nimi prostřednictvím blacklistů adres, přes které prošly. A pokud se dostaly do nějaké coinjoin transakce mixovací služby, mohou se na blacklist dostat i všechny adresy v transakci zúčastněné, ačkoliv neměly s původně "špinavými" bitcoiny nic společného.
Mohl bych takto pokračovat a uvádět další, ještě absurdnější, nespravedlivé příklady cenzury, vyplývající ze zlovůle mocných státních aparátů. Ale vezmu to z druhé strany. Pokud jste sběrateli Bitcoin Punků nebo obchodujete s Runama a chtěli by jste zadat svou transakci prostřednictvím mého uzlu, neuspějete také. Chráním bitcoinovou síť před spamem pomocí klienta Bitcoin Knots, který mi umožňuje takové transakce cenzurovat.
Ať tak či onak, používání vlastního plnohodnotného uzlu vás části problémů s cenzurou opět zbaví. Nikoho se nemusíte ptát, jakou transakci, pokud splňuje pravidla konsensu bitcoinové sítě, můžete zadat ke zpracování. Bohužel, je to jenom první část problému. Tou druhou částí je možná cenzura transakcí při jejich zařazování do bloků těžaři. O té se můžete více dozvědět v článku Domácí těžba bitcoinu.
Podpora bitcoinové sítě
Váš plnohodnotný bitcoinový uzel může poskytovat ostatním uzlům další užitečné služby, které posilují odolnost a decentralizaci sítě. Jsou to hlavně:
- Filtrování transakcí a bloků pro neplnohodnotné uzly a peněženky
- Poskytnutí historických bloků uzlům, které byly nějakou dobu offline nebo provádějí prvotní synchronizaci blockchainu
- Propagaci nových transakcí sítí směrem k těžařům
- Propagaci nově vytěžených bloků od těžařů k ostatním uzlům v síti
- Přenos dat mezi Clearnetem a Torem pro uzly, které jsou připojeny pouze k jedné ze sítí
Na tomto místě je ale dobré říci, že do role tranzitních uzlů (těch, které přijímají externí požadavky na spojení - mají povolen parametr
listen=1alistenonion=1) by měly být použity servery s odpovídajícím výkonem a vhodném bezpečnostním nastavení. Malý privátní full node na bázi RaspberryPi a UmbrelOS jím není.Provoz vlastního uzlu pro Lightning Network
Ligtning Network - druhá vrstva bitcoinu - přináší nezbytné škálování počtu zpracovaných transakcí a snižuje transakční poplatky. Obojí je nezbytné pro další růst adopce bitcoinu. Lightning Network (LN) tvoří síť LN uzlů, které si mezi sebou otvírají tzv. LN platební kanály, jejichž prostřednictvím směrují LN platby.
Ačkoliv jednotlivé LN platby mezi LN platebním kanály probíhají nezávisle na bitcoinovém blockchainu, otevření a zavření LN platebního kanálu je reprezentováno bitcoinovou transakcí. Z tohoto důvodu potřebují LN uzly přístup k bitcoinové síti a využívají k tomu právě bitcoinové uzly.
Pro pochopení Lightning Network doporučuji skvělou knihu Michala Nováka Lightning Network: Platby budoucnosti.
Výhody a důvody provozování vlastního LN uzlu je téma na samostatný článek, který jsem ještě nenapsal. Možná vás ale přesvědčil Michal Novák a nebo jste k rozhodnutí mít vlastní LN uzel došli jinou cestou. V takovém případě potřebujete i vlastní bitcoinový uzel.
Rozšíření znalostí a zkušeností s používáním bitcoinu
Okřídlená pravda říká, že pokud neověřujete transakce a své zůstatky na svém uzlu, nepoužíváte bitcoin, ale jste klientem někoho jiného se všemi důsledky, které to může mít. Pravdou také je, že úsilí spustit bitcoinový uzel vlastními silami vás zcela jistě mnoho nového naučí a poskytne vám na bitcoin úplně nový pohled. Skin in the game. O biozemědělství se také nejvíce dozvíte, až když zaboříte ruce do hlíny a slimáci vám sežerou úrodu. Váš pohled na svěže vypadající bio-mrkev v Lidlu již nikdy nebude stejný jako dříve.
Stavba vlastního uzlu: ano nebo ne?
Pokud vás předchozí odstavce přesvědčily, že dává smysl mít vlastní bitcoinový uzel, zbývá ještě rozhodnutí, jak jej realizovat.
Uzel by měl být v nepřetržitém provozu 24 hodin denně, 7 dní v týdnu. Jen tak může plnit svou funkci, průběžně ověřovat příchozí transakce a validovat nové bloky. Zastavení uzlu kvůli udržbě nebo z jiného důvodu je samozřejmě možné, po odstávce však uzel začne vždy synchronizovat chybějící bloky v jeho kopii blochchainu. Pokud jej tedy zastavíte na delší čas, může i následná dosynchronizace nějakou dobu trvat.
Dalším důležitým pravidlem je provozovat uzel na dedikovaném hardwaru, na kterém neběží žádný jiný, nesouvisející software. Vlastní uzel budete provozovat i kvůli ochraně vlastního soukromí a bezpečnosti a nechcete tedy zvyšovat riziko jejich ohrožení zavlečením nějaké softwarové infekce. Zároveň tak nebude bitcoinový uzel soupeřit s jinými aplikacemi o výpočetní zdroje. Protože sám není nijak zvlášť náročný, nebude tak ani zvyšovat náklady na svůj provoz.
Pro svůj provoz bitcoinový uzel potřebuje běžné CPU, na jehož výkon nejsou dnes žádné specifické požadavky. Dále přibližně 4GB paměti RAM nebo více. Potřebnou pamět nejvíce ovlivní použitý operační systém. Důležité je zabránit swapování paměti na pevný disk. A do třetice přibližně 1TB diskového prostoru. Aktuální velikost bitcoinového blockchainu (léto 2024) je necelých 700GB a roste rychlostí přibližně 230MB za den. Při zachování tohoto trendu by vám měl 1TB disk ještě pár let vydržet. Velmi často se pro uložení blockchainu doporučuje SSD disk. Já s tímto doporučením souhlasím, jeho výkon vám oproti standartním točivým diskům pomůže výrazně zkrátit potřebný čas na počáteční synchronizaci blockchainu. V běžném provozu uzlu se jeho výhody už tolik neprojeví.
Posledním předpokladem je síťové rozhraní pro přístup k internetu.
Jaké máme možnosti?
K provozu vlastního uzlu můžete použít jakýkoliv běžný a dostupný počítač, který již máte doma k dispozici, třeba i starší, protože požadavky na jeho výkon jsou skutečně minimální. Nepoužívaný notebook nebo stolní počítač mohou takto ještě dobře posloužit. Je dobré ale zamyslet se i nad ekonomikou provozu. Starší už nepoužívané herní PC se 150W zdrojem, pokud jej máte odložené někde ve sklepě, je sice zadarmo, jeho nepřetržitý provoz však již nějaké nezanedbatelné množství energie spálí.
Další možností je koupě nového levného počítače uvedených parametrů. Velmi oblíbené jsou minipočítače Intel NUC (dnes již převzal jejich výrobu ASUS). Koupit si můžete i minipočítač speciálně připravený pro provoz bitcoinového uzlu. Bude mít již nainstalovaný operační systém na linuxové bázi a většinou i některé ze základních potřebných aplikací. Takové uzly nabízí například Start9, Umbrel nebo MyNode.
Poslední možností je postavit si vhodný počítač pro provoz bitcoinového uzlu svépomocí z dostupných komponent. Výhodou takového postupu je vyšší kontrola nad jeho HW bezpečností (použité komponenty si můžete sami zvolit) a také volba jeho parametrů přesně dle vašich záměrů a potřeb. Jakou HW platformu pro jeho stavbu zvolíte je čistě na vás. Mezi nejoblíbenější však v současné době patří Raspberry Pi.
Kromě vhodného hardware budete také potřebovat vhodný operační systém. Důležitou vlastností takového operační systému je dostupnost jeho zdrojového kódu (v rámci FOSS), kvůli nezávislé kontrole jeho bezpečnosti. I v této oblasti je nabídka poměrně široká. Vybírat můžete kromě obecného linuxu a jeho známých distribucí i mezi specializovanými distribucemi pro bitcoinové uzly:
Umbrel na Raspberry Pi
Nemám k dispozici starý, nepoužívaný počítač, ani se mi nechtělo investovat do předpřipraveného řešení, a proto jsem si vybral stavbu vlastního uzlu na platformě Raspberry Pi. Jako operační systém jsem zvolil UmbrelOS. Je aktivně vyvíjen a v nedávné době prošel zásadním redesignem. Za jeho aktuální oblibou a velkým rozšířením stojí příjemné a jednoduché uživatelské rozhraní a vlastní App Store s velkým množstvím dostupných aplikací.
Návodů, jak sestavit uzel na Raspberry Pi je plný internet. Inspirovat se můžete jak u Kicoma v jeho serii videí Úvod do bitcoinu, nebo přímo na stránkách Umbrelu.
Já zvolil tyto komponenty:
- Raspberry Pi 5 8GB - 2.179,- Kč
- Raspberry Pi 27W USB-C napájecí zdroj - 349,- Kč
- Krabička pro Raspberry Pi 5 Cooling case - 299,- Kč
- 1TB Lexar NM620 - 1.497,- Kč
- Geekworm X1002 M.2 NVMe SSD HAT pro RPi 5 - 420,- Kč
- SanDisk MicroSDHC 32GB Ultra - 229,- Kč
Raspberry Pi 5 je dnes již přirozenou volbou. Oproti svému předchůdci RPi 4 je jen o 100 korun dražší, nové PCI Express 2.0 rozhraní výrazně zrychluje komunikaci s diskem, což pocítíte při iniciální synchronizaci bitcoinového blockchainu.
Geekworm X1002 je jedna z možných NVMe SSD rozšiřujících karet (HAT). Zvolil jsem ji, protože se nepřipojuje k RPi shora, ale zdola a nebrání tak připojení jiné rozšiřující karty přes standardní GPIO konektor (třeba této). Navíc je na ni NVMe disk orientován směrem dolů, takže jej lze chladit spodním dílem zvolené hliníkové krabičky (pro úplnost ale dodávám, že chladit SSD disk na tomto bitcoinovém uzlu není nutné).

Sestavení celého uzlu vám nezabere více než 15 minut. Podle návodu na stránkách Umbrelu nainstalujte i verzi UmbrelOS pro vaše Raspberry Pi. Po spuštění uzlu si v nastavení nezapomeňte povolit TOR pro vzdálený přístup mimo vaši lokální siť a zkontrolovat dostupnost případných aktualizací.
A můžeme se pustit do výběru a instalace aplikací, které z vašeho uzlu udělají uzel bitcoinový.
Základní aplikace
Tou hlavní aplikací plnohodnotného bitcoinového uzlu je bitcoinový klient. V současné době existuje několik implementací bitcoinového klienta.
Pro UmbrelOS jsou však portovány pouze první dva: Bitcoin Core a Bitcoin Knots. Já si vybral ten druhý, viz. dále. Vy si však vyberte sami podle svých preferencí.
Na tomto místě musím zdůraznit, jak je dobré sledovat vývoj jednotlivých klientů a hlavně vlastností, které implementují. Pomocí bitcoinových klientů dochází v bitcoinové síti k prosazování změn. Pokud tyto změny nejsou kontroverzní a existuje na nich konsenzus, postupně je implementují všichni klienti. Pokud však kontroverzi vyvolávají nebo dokonce přinášejí změny, které pro síť představuji softfork (změnu zpětně kompatibilní) nebo hardfork (zpětně nekompatibilní změnu), můžete vybráním správného klienta nebo jeho verze o takové změně hlasovat a přijmout ji nebo odmítnout.
Výběr bitcoinového klienta a jeho vlastností je tou nejsilnější mocí, kterou jako uživatelé bitcoinové sítě máte a ultimátním důvodem pro provozování vlastního uzlu.
Bitcoin Knots
Bitcoin Knots jsou alternativní implementací bitcoinového uzlu. Vychází z Bitcoin Core a nabízí tak stejnou úroveň zabezpečení, soukromí a stability. Kromě toho však svým uživatelům rozšiřují možnosti filtrování spamu pomocí rozšířené sady parametrů a pravidel k jeho potlačení. (Více o spamu v bitcoinovém blockchainu naleznete zde.)
Ačkoliv jsou Bitcoin Knots pro instalaci k dispozici přímo v Umbrel App Store, nedoporučuji je nyní instalovat z tohoto místa. Připravený balíček obsahuje chybu, která znemožňuje následnou instalaci aplikací, které jsou na bitcoinovém uzlu závislé, jako třeba Electrum server, lightningový uzel nebo nějaký blockchain explorer. Použijte raději připravenou instalaci v alternativním komunitním app store Bitcoin Knots Community App Store.
Umbrel umožňuje svým uživatelům používat alternativní app store. Přidáte jej v nastavení Umbrel App Store (tři tečky v pravém horním rohu, volba Community App Stores). Do pole pro URL vložte link na github repositář app store, v tomto případě:
https://github.com/Retropex/Bitcoin-storea stiskněte Add. Přidaný komunitní app store otevřete tlačítkem Open. Pro RaspberryPi je určena verze Bitcoin Knots arm64.
Samotná instalace zabere několik desítek vteřin. Ihned po instalaci však začnou Bitcoin Knots stahovat a ověřovat bitcoinový blockchain, který má nyní (v červenci roku 2024) 664GB. Synchronizace blockchainu trvá podstatně déle. Její postup můžete v aplikaci sledovat. Mému RPi5 s SSD diskem připojeným přes PCI Express interface to trvalo necelých 30 hodin. O generaci starší RPi4 s SSD diskem přes USB 3.0 potřeboval přibližně 76 hodin.
Nezapomeňte si po instalaci zkontrolovat a případně nastavit preferovaná pravidla filtrování bitcoinového SPAMu (ostatně proto si instalujete Bitcoin Knots). Najdete je v nastavení (Advanced Settings) v sekci Optimization.
V základu je již nastaveno (verze 27.1.020240801):
datacarrier=1(Relay transaction with embedded data)datacarriersize=42(Maximum size of relayed transactions with embedded data)rejectparasites=1(Reject parasitic transactions)permitbaremultisig=0(Relay old type of multisig transaction)Pokud chcete filtrovat i Runes, nezapomeňte povolit:
rejecttokens=1(Reject tokens transactions)Electrum server
Použití Bitcoin Knots v současné verzi UmbrelOS 1.2.2 přináší bohužel ještě jeden problém. UmbrelOS registruje a dodržuje vzájemné deklarované závislosti aplikací. Aby vám povolil instalovat třeba blockchainový explorer Mempool, musíte mít nejprve nainstalován bitcoinový uzel, protože bez něj se Mempool nedostane k blockchainu. Bohužel v této verzi UmbrelOS trvá na konkrétní instalaci aplikace Bitcoin Node (původní Bitcoin Core). Na existenci bitcoinového uzlu je závislá i aplikace Electrs, implementace Electrum Serveru. Naštěstí lze tuto závislost jednoduše obejít.
Aplikace Electrs - Electrum Server in Rust - je reimplementací původního Electrum serveru s cílem umožnit provozovat jej s minimálními hardwarovými nároky. Server neuchovává celý blockchain (je závislý na lokální instalaci bitcoinového uzlu), ale vytváří a udržuje index všech vstupů a výstupů bitcoinových transakcí. Ten zpřístupňuje přes Electrum protokol on-chain bitcoinovým peněženkám pro dotazování na zůstatky a historii transakcí. Připojení přes Electrum server využívají hardwarové (Trezor, Ledger, ColdCard...) i mnohé softwarové peněženky (desktop i mobile).
Aplikaci Electrs nelze instalovat přímo z Umbrel App Store (viz. výše), instalaci musíme spustit ručně přes SSH terminál. Příkazový řádek v UmbrelOS spustíte přes ikonku Settings v doku úvodní obrazovky a položky menu Advanced Settings a Open Terminal. Do terminálu zadejte následující příkaz:
umbreld client apps.install.mutate --appId electrsPo několika vteřinách potvrdí úspěšnou instalaci návratová hodnota true. I Electrum Server provádí po prvním spuštění časově náročnou synchronizaci s blockchainem, při které vytváří transakční index. Instalaci aplikace spusťte až po dokončení synchronizace Bitcoin Knots.
Electrum server nabízí dva způsoby připojení bitcoinových on-chain peněženek. Buď přes lokální siť pro peněženky instalované na samotném uzlu nebo na desktopu ve stejné lokální síti. Nebo přes Tor protokol. Kromě zmíněných hardwarových peněženek může připojit peněženky Green, BlueWallet, Sparrow wallet, Specter, Nunchuk.
Mempool
Mempool je blockchainový explorer, klon pro RaspberryPi veřejně známého exploreru Mempool.space. Proč používat svůj vlastní a nikoliv ten veřejný? Protože nechcete, aby kdokoliv věděl, že jste si dohledával stav určité transakce jen několik vteřin poté, co se objevila v mempoolu a pak ještě několikrát až do okamžiku, kdy byla potvrzena v novém bloku.
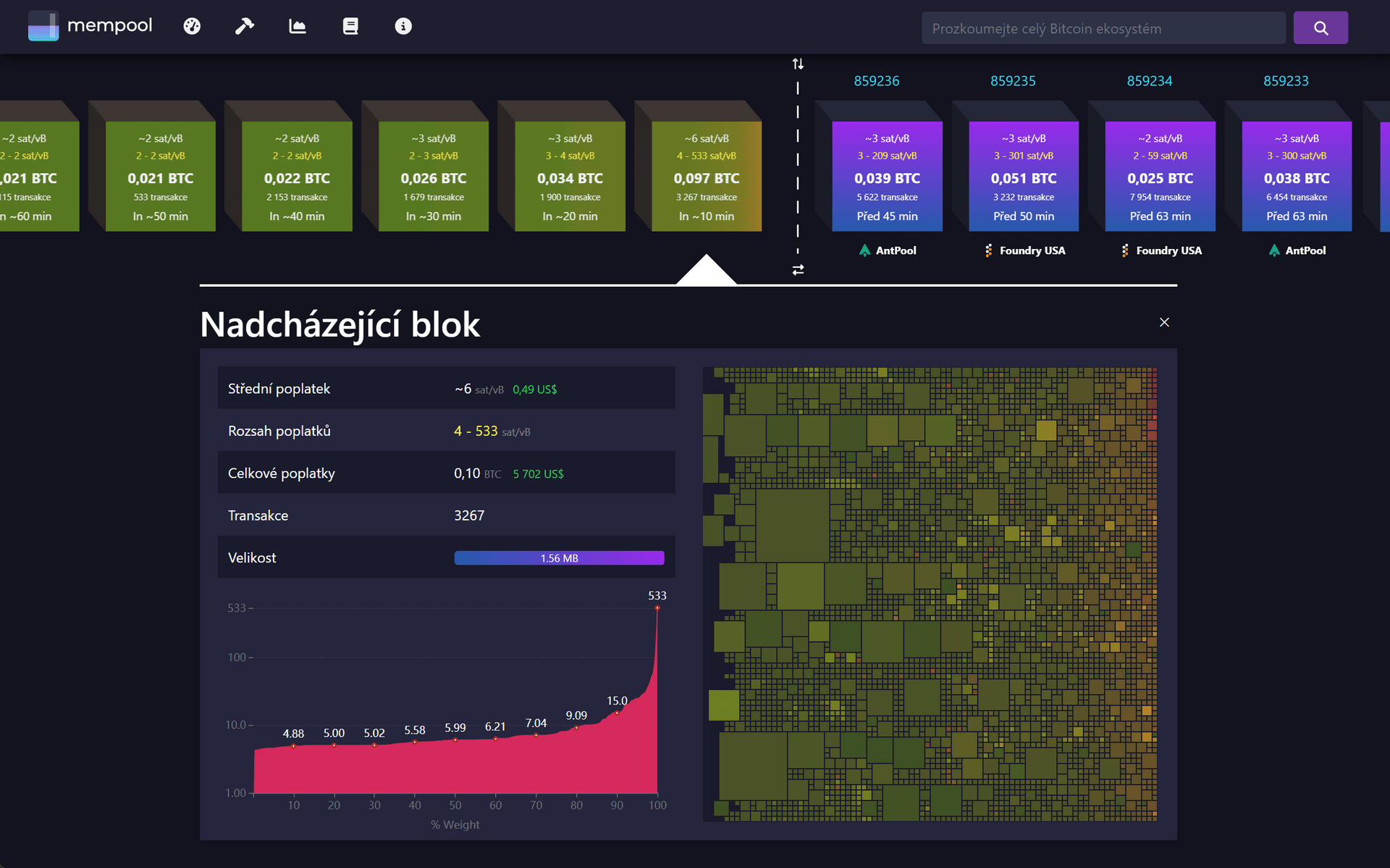
Aplikace Mempool je také závislá na přítomnosti bitcoinového klienta, proto je nutné při použití Bitcoin Knots instalovat ji ručně přes SSH terminál. Potřebný příkaz vypadá takto:
umbreld client apps.install.mutate --appId mempoolProtože je Mempool závislý i na dostupnosti indexu Electrum serveru, používejte jej až poté, co aplikace Electrs tento index dokončí.
Core Lightning
Core Lightning (CLN) je jedna ze čtyř nejpopulárnějších implementací Lightning Network uzlu od společnosti Blockstream. Jedná se samozřejmě o open source a má výborně zpracovanou dokumentaci včetně celé řady návodů k použití.
Proč si vybrat Core Lightning implementaci a ne hojně rozšířenou LND? CLN má oproti LND lépe navrženou modulární architekturu a systém pluginů, které elegantně rozšiřují nebo upravují jeho funkcionalitu. Je napsán v jazyce C (LND převážně v jazyce GO), který v kompilovaném stavu nabízí efektivnější kód, uzpůsobený konkrétní HW platformě a tedy potřebuje menší dostupný výkon v porovnání s LND. Není to zásadní výhoda pro provoz privátního LN uzlu, ale na RaspberryPi přeci jen přijde vhod.
CLN implementace je také často chválena za lepší přístup k ochraně soukromí jednotlivých plateb. Používá k tomu několik technik, které výrazně komplikují ostatním uzlům na cestě sledovat informace o vašich platbách. Shadow route přidává do platební cesty zpoždění a poplatky, čímž ji virtuálně prodlouží a brání tak špiclujícím uzlům odhadovat reálnou vzdálenost k příjemci platby. Route randomization zase zajistí určitou míru náhodnosti při výběru finální platební cesty. Nemusí tak být vybrána vždy ta nejkratší respektive nejlevnější cesta, což zabrání routování všech vašich plateb přes uzel, který má uměle (záměrně) snížené poplatky pod síťový průměr. MPP - (Multi-Part-Payments) pak rozdělí vaši platbu na menší, nestejně velké části, které směruje samostatně. Zajistí tím průchodnost i větších plateb sítí a zároveň znemožňuje uzlům na cestě zjistit celkovou velikost platby.
Tím nejzásadnějším důvodem je pro mne však podpora BOLT 12 specifikace. BOLT 12 přináší takzvané offers, statické, opakovaně použitelné faktury. Ty se hodí všude tam, kde potřebujete trvale přijímat částky předem neznámé hodnoty a nechcete pro každou z nich aktivně vystavovat fakturu. Příklad? Zapy na Nostru nebo třeba anonymní výplaty z Ocean.xyz těžebního poolu. Nebo třeba příjem příspěvků v bitcoinu na váš YouTube stream. LND řeší tuto potřebu přes další nadstavbové aplikace (LNBits, LNDK) a třeba LNURL. CLN nabízí elegantní řešení přímo ve svém základu.
Stejně jako předchozí aplikace je i Core Lightning závislá na přítomnosti bitcoinového klienta. S Bitcoin Knots je třeba ji tedy instalovat ručně přes SSH terminál. Potřebný příkaz vypadá takto:
umbreld client apps.install.mutate --appId core-lightningZáloha a obnova ze zálohy
Core Lightning uzel obsahuje bitcoinovou on-chain peněženku, ze které čerpá bitcoiny pro otvírání kanálů. Po (re)instalaci aplikace vždy vygeneruje novou, proto je dobré mít zálohu, ke které se můžete vrátit v případě, že jste o tu původní přišli v důsledku havárie uzlu nebo provádíte instalaci na nový hardware a chcete obnovit již exitující uzel.
Klíče on-chain peněženky jsou uloženy v souboru
hsm_secret, který se nachází v adresářiroot/.lightning/bitcoin. Jedná se o binární, 32 byte veliký soubor. Zálohovat jej můžete buď na nějaký připojený externí disk (USB klíčenku), nebo si jeho obsah zobrazíte v hexadecimálním formátu (linuxový příkaz:xxd hsm_secret) a někam si jej bezpečně poznamenáte.Při obnově nebo po reinstalaci uzlu nahraďte nově vygenerovaný soubor
hsm_secrettím ze zálohy a restartujte aplikaci Core Lightning.Pro zacházení se souborem
hsm_secreta jeho obsahem platí stejná pravidla, jako pro zacházení s bitcoinovými privátními klíči nebo seed frází. Mají stejný význam a jejich znalost umožňuje manipulovat s prostředky na peněžence uloženými. Proto buďte opatrní.Zajímavou alternativou je možnost vygenerovat soubor
hsm_secretz existujícího BIP-39 seedu, včetně použití volitelné přístupové fráze (passphrase). To vám umožní uchovat recovery seed standartními způsoby, které používáte u své hardwarové peněženky (SeedOr Safe, Trezor Keep Metal, CryptoTag...) a v případě potřeby obnovit peněženku nebo přistupovat k bitcoinům na jejich adresách i z jiného zařízení, než je Core Lightning aplikace. Jak na to?Po instalaci Core Lightning aplikace ji zastavte (příkaz Stop v kontextovém menu nad ikonou aplikace) a spusťte si terminál v jejím kontextu (Settings > Advanced settings > Terminal > App > Core Lightning). V terminálovém okně spusťte nástroj
hsmtools parametremgeneratehsma cestou khsm_secretsouboru. V následujícím dialogu pak vyberte BIP-39 slovník a zadejte jednotlivá slova svého seedu. Nakonec můžete vložit svou volitelnou přístupovou frázi. Utilitka vygeneruje nový souborhsm_secreta uloží jej.``` root@aabbccdd0102:/# lightning-hsmtool generatehsm root/.lightning/bitcoin/hsm_secret Select your language: 0) English (en) 1) Spanish (es) 2) French (fr) 3) Italian (it) 4) Japanese (jp) 5) Chinese Simplified (zhs) 6) Chinese Traditional (zht) Select [0-6]: 0 Introduce your BIP39 word list separated by space (at least 12 words):
Warning: remember that different passphrases yield different bitcoin wallets. If left empty, no password is used (echo is disabled). Enter your passphrase: New hsm_secret file created at root/.lightning/bitcoin/hsm_secret Use the
encryptcommand to encrypt the BIP32 seed if needed root@aabbccdd0102:/#```
Opusťte terminál a znovu spusťte aplikaci Core Lightning.
Kromě bitcoinové on-chain peněženky je nutné zálohovat i otevřené lightning network kanály. Core Lightning aplikace uchovává informace o otevřených kanálech v souboru
emergency.recover. Ten se nachází také v adresářiroot/.lightning/bitcoin. Mění se pouze v souvislosti s otevřením nebo uzavřením kanálu, proto doporučuji provést jeho zálohu vždy po takové operaci.Soubor
emergency.recoverneobsahuje informace o stavu kanálu. Při obnově dojde vždy k uzavření všech kanálů a vypořádání jejich balancí.Jak kopírovat uvedené soubory z vašeho Umbrelu na Raspberry Pi na USB disk? UmbrelOS pro to zatím nemá podporu ve svém UX, ale pomůže vám opět terminál a následující návod.
```
Najděte LABEL vašeho připojeného USB disku
Nejprve si vylistujte všechna existující bloková úložiště příkazem
sudo blkid
Fyzicky připojte váš USB disk s vylistujte stejným příkazem úložiště ještě jednou
sudo blkid
Podívejte se, které přibylo a najděte jeho LABEL. Řekněme, že se jmenuje "sda1"
Vytvořte si adresář pro zálohu, nazvěme jej třeba "/backup"
sudo mkdir /backup
Připojte váš identifikovaný USB disk přes jeho LABEL k vytvořenému adresáři
sudo mount /dev/sda1 /backup
Zkopírujte soubory hsm_secret a emergency.recover do adresáře "/backup"
sudo cp /home/umbrel/umbrel/app-data/core-lightning/data/lightningd/bitcoin/emergency.recover /backup
sudo cp /home/umbrel/umbrel/app-data/core-lightning/data/lightningd/bitcoin/hsm_secret /backup
Ukliďte po sobě - nejprve odpojte váš USB disk od adresáře "/backup"
sudo umount /backup
A následně zrušte adresář "/backup"
sudo rmdir /backup
```
Při obnově ze zálohy budete postupovat úplně stejně, jen příkazy pro kopírování budou směřovat opačným směrem
```
Kopírování záloh z připojeného adresáře "/backup" do cílového adresáře CLN
sudo cp /backup/emergency.recover /home/umbrel/umbrel/app-data/core-lightning/data/lightningd/bitcoin
sudo cp /backup/hsm_secret /home/umbrel/umbrel/app-data/core-lightning/data/lightningd/bitcoin ```
Kromě statické zálohy kanálů umožňuje CLN i průběžné zálohování jejich stavu prostřednictvím zálohy interní databáze do druhé, bezpečné lokality (na jiný disk). Databáze se nachází v souboru
lightningd.sqlite3ve stejném adresáři, jakohsm_secretneboemergency.recover. CLN lze dokonce nastavit tak, aby veškeré updaty do této databáze průběžně zapisoval i na druhou lokalitu. Bohužel však v současné verzi UmbrelOS toto není možné.UmbrelOS ve stávající verzi nepodporuje připojení více disků současně. Nelze tedy průběžně zálohovat data na druhý disk. Přestože můžete během provozu druhý disk připojit a přes terminál na něj data zkopírovat, nikdy takový disk nenechávejte připojen trvale. Po restartu uzlu může zabránit korektnímu nastartování Umbrelu a nainstalovaných aplikací.
Otevření kanálů
Lightningový uzel pro vás začne být užitečný teprve poté, co jej propojíte s LN sítí prostřednictvím platebních kanálů. Otevření kanálu je relativně jednoduché a lze jej docílit v podstatě dvěma způsoby.
- Otevřete kanál vy z vašeho uzlu
- Požádáte jiný uzel, aby otevřel kanál směrem k vám
Existují i další způsoby, ale pro jednoduchost si vystačíme s těmito dvěma. Důležité je si uvědomit, že uzel, který kanál otvírá, jej také musí naplnit bitcoiny na požadovanou kapacitu. Po otevření kanálu budou zároveň všechny bitcoiny (likvidita) na straně toho, kdo jej otevřel.
V prvním případě tedy nejprve pošlete na bitcoinovou peněženku vašeho CLN uzlu nějaké prostředky (tlačítko Deposit vám zobrazí příslušnou bitcoinovou adresu). Po potvrzení depositní transakce v blockchainu (můžete ji sledovat ve svém Mempool exploreru) můžete tlačítkem Open Channel požádat o otevření kanálu s vybraným LN uzlem. Ten si můžete vybrat dle své preference v některé z veřejných databází, jako je Amboss.Space nebo 1ml, nebo přímo na MemPool.Space v sekci lightning network.
Strategií pro výběr je opět celá řada, ale pro domácí uzel neuděláte chybu výběrem uzlu od některého z velkých hráčů, kteří jsou na kvalitě svého připojení do LN sítě obchodně zainteresováni. Poskytovatelé peněženek (ACINQ, WalletOfSatoshi, Blockstream, Alby, ...), burzy, směnárny a platební brány (Anycoin, Confirmo, Binance, Kraken, ...), poskytovatelé služeb na LN sítí (LOOP, Boltz, Strike). Ale třeba i SatoshiLabs nebo GeneralBytes. Můžete se u nich spolehnout na dostatečnou kapacitu, konektivitu i stabilitu provozu. Pozor si dejte pouze na požadovanou minimální velikost kanálu.
Do pole Node Id: vložte adresu vybraného uzlu (ve formátu PubKey@IP:Port) a do pole Amount: pak požadovanou velikost kanálu (částka bude stržena z vaší bitcoiové peněženky a ponížena o poplatky za otvírací transakci). Důležitý je přepínač Announce. Ten určuje, zda bude váš kanál veřejný a tedy k dispozici celé síti pro směrování plateb, nebo soukromý, o jehož existenci budete vědět pouze vy a připojený uzel a pro směrování cizích plateb nebude využíván. Pokud chcete využívat svůj LN uzel pouze pro své soukromé platby, doporučuji otevřený kanál do sítě neanoncovat. Zjednodušíte si práci s jeho balancováním, protože budete reagovat pouze na vlastní pohyby v jednotlivých kanálech.
Takto otevřený kanál bude mít likviditu na vaší straně (odchozí likvidita) a bude tedy primárně sloužit na posílání plateb z vašeho uzlu. Minimálně do doby, než si odesláním dostatečné částky vytvoříte prostor i pro příjem.
Druhý způsob, požádat jiný uzel, aby otevřel kanál k vám, vám přinese příchozí likviditu, tedy schopnost přijímat platby až do velikosti takového kanálu. Můžete se domluvit s kamarádem, který již uzel provozuje, aby k vám kanál otevřel. Nebo využít některou z nabídek jiných uzlů, která vám kanál otevřou za úplatu. Vybrat si můžete na tržištích LnRouter nebo LnBig. Lightning Network Plus nabízí možnost otevřít si kanály v takzvaném Liquidity Swapu. Uzly, které se jej účastní, si otevřou kanály vzájemně v kruhu. Každý tedy za otevření kanálu jedním směrem získá i kanál stejné velikosti s příchozí likviditou.
Nejjednodušším způsobem, jak získat příchozí likviditu, je otevření dalšího kanálu s vybraným uzlem a následné odeslání všech svých prostředků v tomto kanále na svou jinou lightning peněženku nebo swap out službu (služba, která příchozí prostředky uloží na vámi zadanou bitcoinovou adresu. Například Boltz.Exchange).
Nezapomeňte po otevření všech kanálů provést jejich zálohu dle postupu uvedeného výše.
Ride the Lightning
Ride the Lightning (RTL) je nástroj pro správu vašeho lightningového uzlu. Ačkoliv vlastní uzel, v našem případě aplikace CLN, nabízí jednoduché GUI pro svou obsluhu a v mnoha případech stačí (zvláště při otevření pouze několika privátních kanálů), některé parametry a pokročilé vlastnosti kanálů přes něj nejsou dostupné. Aplikace RTL nabízí webové rozhraní k většině těchto parametrů a další doplňkové služby pro zajištění likvidity vašich kanálů, jejich rebalancing a převod prostředků na on-chain adresy (swap out). Navíc nabízí přehledné statistiky a grafy využití uzlu, které lze využít pro optimalizaci nastavení CLN.
Aplikaci RTL můžete nainstalovat přímo z Umbrel App Store. Pozor, jsou tam uvedeny dvě verze, každá pro jednu z dostupných implementací lightning uzlu. Pokud jste nainstalovali Core Lightning, vyberte si Ride the Lightning (Core Lightning).
Máte-li otevřenu konzoli, můžete ji samozřejmě nainstalovat i z příkazového řádku.
umbreld client apps.install.mutate --appId core-lightning-rtlPřihlášení do aplikace je trochu nestandardní. RTL vyžaduje heslo, ale správu aplikačních hesel řídí UmbrelOS. Vaše heslo do aplikace naleznete na stránce RTL v App store (Default password). Objeví se tam po nainstalování aplikace, je kryptograficky odvozené od unikátního seedu vaší instalace uzlu a nelze jej změnit. Umbrel touto politikou reagoval na případy vykradení peněženek přes uniklou statickou TOR adresu aplikací jako RTL nebo Thunderhub, ke kterým neměli uživatelé změněné defaultní hesla.
Public Pool
Esenciální aplikace pro všechny, kteří doma kromě vlastního bitcoinového uzlu provozují také nějaký domácí miner. Public Pool je navzdory svému názvu privátní domácí těžební pool pro solo mining. Bez poplatků a s jistototu, že veškeré případně vytěžené odměny skončí na vaší vlastní bitcoinové adrese.
Instalace opět kvůli závislosti na Bitcoin Knots přes příkazový řádek:
umbreld client apps.install.mutate --appId public-poolKonfiguraci pro připojení vašeho mineru najdete hned v úvodu GUI po spuštění aplikace.
Zkušenosti z provozu
Provozování vlastního uzlu není nikterak náročnou činností a s trochou nadsázky lze říci, že se obejde bez složité údržby. Ve výše uvedené konfiguraci může běžet bez nutnosti zásahu i několik měsíců. Přesto je dobré se ke svému uzlu čas od času vrátit a jednoduchou údržbu provést.
Předně provádějte pravidelné upgrady nainstalovaných aplikací. Nové verze se objevují celkem pravidelně a přinášejí většinou opravy nalezených chyb a bezpečnostních děr, ale také nové funkcionality, které rozšiřují jejich možnosti použití. Doporučuji neinstalovat bez rozmyslu, ale přečíst si dostupné release notes (popis změn nové verze). Zvláště u bitcoinového uzlu (ať už Bitcoin Knots nebo Bitcoin Core), protože nové verze mohou obsahovat změny, které mění chování bitcoinové sítě a tedy i bitcoinu. Jejich výběrem a (ne)instalací hlasujete o tom, jak by měl bitcoin podle vás vypadat. Přečtěte si knihu The Blocksize Wars k lepšímu pochopení, co je tím myšleno.
Ze stejných důvodů pravidelně aktualizujte i operační systém UmbrelOS. Nové verze vycházejí přibližně jednou za čtvrt roku a vlastnosti operačního sytému většinou výrazně vylepšují.
Důležitou aktivitou je i záloha lightning uzlu a jeho kanálů vždy, když nějaký otevřete nebo zavřete. To se naštěstí neděje příliš často, většinou vystačíte s jednotkami otevřených kanálů i po dobu několika let. Výjimkou je však provoz veřejného lightning uzlu pro směrování plateb v síti. Takový uzel již vyžaduje pravidelnou údržbu kanálů, správu jejich poplatků a vyhodnocování jejich efektivity. To vede k zavírání neefektivních kanálů a otvírání nových směrem k lukrativním uzlům.
Raspberry Pi a UmbrelOS není vhodnou platformou pro provoz veřejných lightning uzlů a směrování plateb v síti. Nevyhovuje celkovým výkonem a bezpečností a neumožňuje nastavit adekvátní SLA pro provoz takové služby. Proto ji k tomuto účelu důrazně nedoporučuju.
Nezapomeňte svůj uzel čas od času restartovat. Mně se osvědčilo provést restart ne déle než po půl roce provozu. Dlouhodobý nepřetržitý provoz jakéhokoliv softwaru hromadí důsledky chyb v něm existujících (a každý takové obsahuje), které se časem zcela určitě nějak projeví. Je dobré těmto projevům předcházet právě restartem celého uzlu. Restart vždy provádějte kontrolovaně přes příslušné tlačítko v menu Settings Umbrel OS, nikdy uzel natvrdo nevypínejte odstavením od napájení. Umožníte všem aplikacím korektně se ukončit, aby následně mohly korektně nastartovat. To samé platí i pro vypínání uzlu v případě potřeby.
Vlastní bitcoinový uzel? Ano!
Pokud jste dočetli až sem, pravděpodobně stavbu a provoz vlastního uzlu vážně zvažujete. Rád bych vás v tom podpořil. Ano, dává to smysl. A přestože si myslím, že nejvíce zážitků a pozitivní energie získáte při stavbě a zprovoznění vlastního uzlu (třeba tak, jak je popsáno v tomto článku), nezatracuji ani pořízení již předpřipraveného řešení, které stačí připojit do zásuvky a zapnout. Stále vám zbyde spoustu zábavy s nastavením jednotlivých aplikací.
Staňte se součástí bitcoinové sítě a podpořte její původní étos! Staňte se Bitcoinerem!
-
 @ 469fa704:2b6cb760
2024-09-01 13:26:13
@ 469fa704:2b6cb760
2024-09-01 13:26:13The basics of financial planning
Financial education is the first step to financial independence. Here are the core principles you need to understand:
- Income vs. expenses: The core of any financial plan is to earn more than you spend. This requires not only discipline, but also a clear overview of your financial comings and goings.
- Budgeting: Create a detailed budget plan. A budget helps you to see where your money is going and where you can save. It's a living document that you should adjust regularly.
- Emergency fund: An emergency fund is a buffer against unforeseen events. Experts recommend keeping at least three to six months of your expenses in cash or easily liquidated assets.
- Set goals: Define clear financial goals. These can be short-term (e.g. a new cell phone), medium-term (e.g. a car) or long-term (e.g. retirement). Each type of goal requires different strategies and time frames.
- Debt management: Distinguish between good debt (e.g. investments in education or real estate) and bad debt (e.g. credit cards with high interest rates). A debt repayment plan is often just as important as a savings plan.
Understanding investments
Investing is the way to make your money work for you. Here are some basic concepts you should understand:
- Interest and Compound Interest: Interest is the compensation you receive or pay when you invest or borrow money. Compound interest is particularly powerful as it means you earn interest on your interest, which can lead to exponential growth over time.
- Risk and return: Investments with higher returns are often associated with higher risk. It's important to find a balance that suits your personal risk profile. Diversification can help manage this risk.
- Diversification: Spread your money across different asset classes (equities, bonds, real estate, commodities) and regions to minimize risk. This protects you from a total loss if one investment performs poorly. *** Long-term perspective**: Investing is not a short-term game. It requires patience and a long-term perspective.Short-term market fluctuations should not lead to panic selling. This is true for every asset, even Bitcoin.
- Costs and fees: Pay attention to the costs and fees associated with investing. These can have a significant impact on your returns over time. Especially important are taxes.
Practical steps to financial education:
- Books and courses: Invest in your financial education.There are many resources available, from classics like Rich Dad Poor Dad to online courses on platforms like Coursera or Udemy.
- Financial apps and tools: Use apps like Mint, YNAB (You Need A Budget), or Personal Capital to track your budget and investments. These tools can help you monitor your finances in real time. Even a good old spread sheet can work wonders.
- Seek advice: If possible, consult a financial advisor. They can provide personalized advice tailored to your specific situation. Make sure they offer independent advice.
- Podcasts and blogs: Follow financial podcasts or blogs to get the latest trends and tips. You can find also a lot of execellent stuff on Youtube, especially Bitcoin education.
- Self-study: Learn the basics of stock markets, bonds, real estate investing and other forms of investing. Websites like Investopedia or Khan Academy offer free knowledge.
- Study Bitcoin: Nothing teaches you so much about finance, investing, money and wealth than bitcoin. If you are eager to understand it even more, it will teach you also thermodynamics, cryptography (math), economics, philosophy and maybe a lot more.
Practice for application:
Create a simple budget for the next month. Write down all expected income and expenses. Identify areas where you can save. Use an app or Excel spreadsheet to do this. Research an investment opportunity that interests you (e.g. ETFs, shares, real estate funds). Understand the basics and think about how you could get started. Create a small investment plan.
-
 @ c11cf5f8:4928464d
2024-09-01 13:22:49
@ c11cf5f8:4928464d
2024-09-01 13:22:49Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too!
If you missed our last thread, here are some of the items stackers recently spent their sats on.
originally posted at https://stacker.news/items/668607
-
 @ 6c2d68ba:846525ec
2024-09-01 13:02:53
@ 6c2d68ba:846525ec
2024-09-01 13:02:53Dear friend,
it seems like you have decided to turn your back on those walled gardens and set sails to enter uncharted territory. A world without walls, an open world, a world of beautiful chaos. At least for today, I don't intend guiding you out of the safe harbour onto the open, endless sea. Today, my only intent is sharing a few thoughts, before you depart.
As a wise man on Madeira once said, it's not so much about having the right answers, it's about asking the right questions. While I'm not certain whether I have found the right questions myself by now, let me share the current set with you:
-
What causes the discomfort that drives you out of the walled garden onto the open sea?
-
Are you trying to transfer from one walled garden to the next one, where the difference being a slightly friendlier colour on the wall?
-
What are you hoping to find on the open sea that walled gardens cannot provide?
-
What are you willing to sacrifice for freedom (of speech)?
-
What will you need to keep the ship afloat?
-
How will you react when you find yourself in the middle of a storm?
I sincerely believe that it's worthwile taking a step back before departing to reflect on the big picture and the underlying paradigm shift between walled gardens and nostr. This is not about building competitors to broken systems, this is not about mimicking centralised services, this is not about repeating the same mistakes over and over.
This is about building a new world, an open world without walled gardens and data silos.
Onwards!
-
-
 @ a30cdfee:2d2f97ff
2024-09-01 11:40:38
@ a30cdfee:2d2f97ff
2024-09-01 11:40:38Primal: Social Media with Bitcoin Tipping
Primal is a social media app that lets you tip (zap) other users with bitcoin!
How does Primal work and why should you join?
Primal is a social Bitcoin wallet.
If you like somebody's content, you can tip them Bitcoin micropayments through the Lightning Network.
Or monetize your own content.
You can also use it as a custodial Lightning wallet to pay for small purchases in bitcoin.
Primal Is a Nostr Client
Primal uses the Nostr protocol as its social graph.
Nostr is an open protocol for decentralized and censorship-resistant social media.
If you're new to Nostr, learn more about it here: https://stacker.news/items/558629
Since Primal is only a client to access the Nostr protocol, it can only censor free speech or deplatform users on the Primal app, but not on Nostr.
Also, if you stop using Primal as your Nostr client, you can import all your followers, posts, etc. to a new client.
Primal Feels Like Twitter (X)!
Primal's feed feels very familiar to other social media platforms, especially X (Twitter).
You can follow people, like their posts, repost etc.
It's not only for Bitcoin-related discussion: you can search for different hashtags and find your tribe, e.g. photography etc.
Primal works for iOS, Android and desktop.
On desktop, the "Explore" function is even more detailed.
Earn Bitcoin for Your Content!
By clicking the lightning bolt symbol on the feed, you can tip (zap) other users bitcoin.
You can also browse through your contacts and zap them.
Nostr is a great directory for Lightning payments!
If you hold the bolt symbol a bit longer, you can specify the zap amount if you want.
You can set your default zap amount in settings.
To set up a Lightning wallet with Primal, the app asks for your name, email address and the country of residence.
But as far as I know, you can use a nym and a throwaway email etc.
No need to upload any identity documents.
The maximum balance you can hold on the Primal wallet is 1 million sats, or 0.01 BTC.
The purpose of the wallet is not for long-term savings, but to onboard people to Nostr and to get familiarized with the culture of zapping.
To get your first sats on the Primal wallet, you can receive bitcoin on Lightning or on-chain.
Alternatively, you can buy sats on Primal with Apple Pay or Google Pay with your credit card (max. about $5 worth).
Or just start creating and receive zaps from other users.
Take Care of Your "nsec"!
Your "nsec" is your private key to your Primal (and Nostr account).
Don't share it with anyone!
Primal creates an nsec for you upon account creation, or you can import your own.
Primal is open-source, but it is not always a good practice to import private keys to any apps.
If you don't want to import the private keys you already have to Primal, you can use e.g. Amber, a Nostr signer extension app for Android.
It's advisable to store your nsec in e.g. a password manager.
If you use Primal on desktop, you can use e.g. Alby @Alby, as a Nostr signer extension, zapping wallet and a place to store your nsec.
Learn more about Alby here.
You can also use another Nostr signer extensions on desktop, e.g. Nos2x, but they often have no wallet functions for zapping or receiving zaps.
They work only for posting, liking, replying, reposts etc.
Convenient, but With Privacy Trade-Offs
You can send direct messages to other Primal users, but you should know that while the content of the direct messages is encrypted (visible only to you and your contact), the message metadata is public for all to see (who you're sending messages to, when, how often etc.)
Primal can be used as a global international "Venmo" during dinner parties.
No more head-scratching when trying to split the bill!
Not the most private way to do it though, but it's convenient!
Let's connect on Nostr!
You can find me here.
Additional Resources
https://www.youtube.com/watch?v=Qd4Po4i7wvc
https://www.youtube.com/watch?v=7LsIb6D7FtU
Project Links
originally posted at https://stacker.news/items/668536
-
 @ a012dc82:6458a70d
2024-09-04 08:09:45
@ a012dc82:6458a70d
2024-09-04 08:09:45Table Of Content
-
The Energy Consumption of Bitcoin Mining
-
The Environmental Impact of Bitcoin Mining
-
Innovations in Green Energy
-
The Advantages of Using Green Energy in Bitcoin Mining
-
The Challenges of Using Green Energy in Bitcoin Mining
-
Conclusion
-
FAQ
Bitcoin is a digital currency that has gained a lot of popularity over the years, and it's being used for various transactions. However, mining bitcoin requires a lot of energy, and this has raised concerns about the sustainability of bitcoin mining and its impact on the environment. In recent years, there have been efforts to make bitcoin mining more sustainable by using renewable energy sources. This article aims to assess the sustainability of bitcoin mining and its impact on green energy.
The Energy Consumption of Bitcoin Mining
Bitcoin mining is a process that involves solving complex mathematical problems that require a lot of computing power. This process consumes a significant amount of energy, and the energy consumption of bitcoin mining is growing every day. According to recent studies, the energy consumption of bitcoin mining is estimated to be around 121 terawatt-hours (TWh) per year, which is more than the energy consumption of some countries.
The Environmental Impact of Bitcoin Mining
The energy consumption of bitcoin mining has a significant impact on the environment. Most of the energy used in bitcoin mining comes from non-renewable sources such as coal and natural gas, which release greenhouse gases into the atmosphere. This contributes to climate change, which has adverse effects on the environment and human health.
Innovations in Green Energy
In recent years, there have been innovations in green energy that can be used to make bitcoin mining more sustainable. These innovations include renewable energy sources such as solar, wind, and hydropower. The use of these renewable energy sources can reduce the environmental impact of bitcoin mining and make it more sustainable.
The Advantages of Using Green Energy in Bitcoin Mining
Using green energy in bitcoin mining has several advantages. Firstly, it reduces the environmental impact of bitcoin mining by reducing greenhouse gas emissions. Secondly, it can make bitcoin mining more cost-effective, as the cost of renewable energy sources is declining. Thirdly, it can increase the adoption of renewable energy sources and drive innovation in the renewable energy sector.
The Challenges of Using Green Energy in Bitcoin Mining
There are also challenges associated with using green energy in bitcoin mining. Firstly, the availability of renewable energy sources may not be consistent, as solar and wind energy are dependent on weather conditions. This can affect the profitability of bitcoin mining, as miners may need to switch to non-renewable energy sources during periods of low renewable energy availability. Secondly, the initial investment required to set up renewable energy infrastructure can be high, which may deter some miners from switching to green energy sources.
Conclusion
Bitcoin mining has a significant impact on the environment, but there are efforts to make it more sustainable by using renewable energy sources. Using green energy in bitcoin mining has several advantages, including reducing greenhouse gas emissions and driving innovation in the renewable energy sector. However, there are also challenges associated with using green energy in bitcoin mining, such as the inconsistent availability of renewable energy sources and the high initial investment required to set up renewable energy infrastructure. Overall, assessing the sustainability of bitcoin mining and its impact on green energy is a complex issue that requires a comprehensive evaluation of various factors.
FAQ
Can bitcoin mining be done without consuming a lot of energy? No, bitcoin mining requires a significant amount of energy to solve complex mathematical problems and validate transactions.
Is bitcoin mining harmful to the environment? Yes, bitcoin mining consumes a lot of energy, most of which comes from non-renewable sources that release greenhouse gases into the atmosphere.
What are the benefits of using renewable energy sources in bitcoin mining? Using renewable energy sources can reduce the environmental impact of bitcoin mining, make it more cost-effective, and drive innovation in the renewable energy sector.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 4f6b8312:f2943611
2024-09-01 08:11:17
@ 4f6b8312:f2943611
2024-09-01 08:11:17https://habla.news/write has a full page dedicated to writing. No feeds down below. No recommended posts to the right. Calm. Feels good.
-
 @ 5954198a:0c6fa207
2024-09-04 07:39:29
@ 5954198a:0c6fa207
2024-09-04 07:39:29Even after posting stuff related to your business on your social media, your followers still haven’t increased much?
Does even after following a social media strategy, the number of sales hasn’t increased much? If your answer is yes, then you need to hire a Social Media Marketing Company in Indore. India’s cleanest city Indore is a city of dreams that also cleans the businesses if not run properly. Businesses aren’t that easy to run, maybe when your business grows, things work pretty well for your business, but the initial days of your business might not be like what you’ve imagined.
Starting a business from the scrap can be a very challenging thing to do. But if you have an idea that’s going to run your business, dedication to make your dream come true, then no one can stop you from achieving your dream of starting your business. Digi Partners is a Social Media Marketing Company in Indore that works for companies like yours on expanding their businesses. Digi Partners being an SMM company in Indore, have a team of professionals trained in graphic designing, content writing, digital marketing, strategy making, video producing, and editing. Graphic design plays a very vital role in social media marketing. Visit: https://digi-partners.com/social-media-marketing-company-indore/
-
 @ 3c9712ff:14fecbc4
2024-09-01 03:39:08
@ 3c9712ff:14fecbc4
2024-09-01 03:39:08The Australian dream used to be straightforward: secure a job, pay off your house by your late thirties, and retire with substantial assets and savings to support your lifestyle.
Some argue the introduction of compulsory superannuation contributions in 1991 signaled the government's lack of trust in Australians' ability to save and be self-sufficient in their later years. But I disagree.
The issue wasn’t that Australians were incapable of saving; it was that saving money was no longer enough. The erosion caused by the Keynesian experiment had seeped into Australian retirements, making it nearly impossible for an entire generation to retire off the savings from a median salary of $27,200.
Superfunds were thus established by the government as a supposed solution to the problem they had created. How unsurprising.
Fast forward 33 years, and Australian superfunds, like those in most of the western world, are now facing two insurmountable challenges of population demographic, and a debasing currency.
1. Our Population is Ageing
On face value, it shouldn't matter whether the population is ageing. If I have my own retirement account which I paid into each month, why would it matter if the people around me are ageing as well?
The answer lies in duration mismatch. Retirement funds must manage a mix of short-term, long-term, and continuous obligations, balancing liquid liabilities (cash payments to members) with illiquid assets (investments). Because funds rely on more inflows (super contributions) than outflows (payouts to retirees), population demographics play a critical role in maintaining this balance - and Australia's isn't looking great.
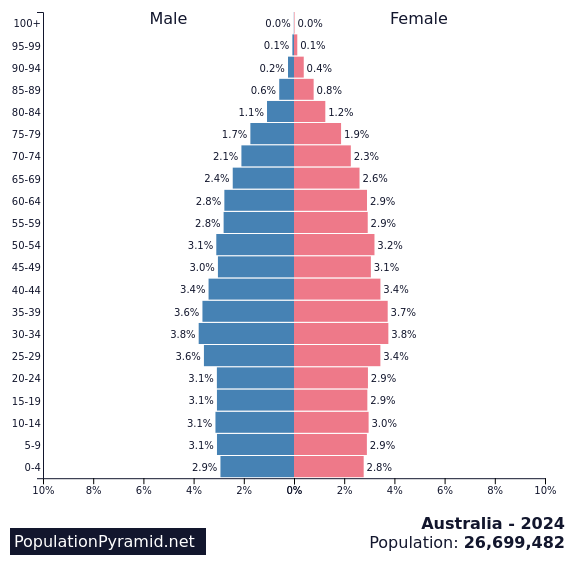
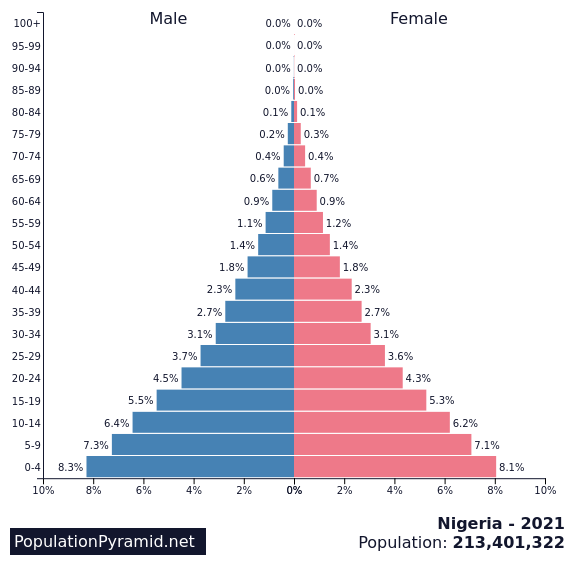
An example of an ageing population (Australia) vs a growing population (Nigeria)
2. Our Currency is Ever Debasing
This is far more pernicious for our retirees
| Financial Year | Average Super Return | Money Supply Growth | Net Return | | --- | --- | --- | --- | | 2023-24 | 9.1% | 4% | 5.1% | | 2022-23 | 9.2% | 7.8% | 1.4% | | 2021-20 | -3.3% | 6.7% | -10% | | 2020-21 | 18% | 13.6% | 4.4% |
In Austrian Economics, inflation is understood as a monetary phenomenon that occurs when new monetary units are added to the existing supply. This monetary inflation is the precursor to both price and asset inflation.
Austrians also reject the idea of measuring price inflation with a single number, such as the CPI, as different asset classes respond differently to monetary inflation. For instance, industries like technology and manufacturing are less susceptible to price inflation due to the deflationary effects of increased automation and competition.
Conversely, hard assets like gold and real estate have reached record highs, as easy money tends to flow toward the most reliable stores of value.
Average Yearly Prices Increase since 2018 - Against YoY M2 and CPI
| | Iphone | Median House | Money Supply Growth | CPI | | ----- | ----| ---- | ------ | --- | | Since 2018 | 2.24% | 6.8% | 7.2% | 3.1%
*Although simplistic, the table above shows that hard assets move with monetary inflation, not CPI.
The real hurdle, or the absolute minimum that a superfund has to give it's members is not CPI or the 3.95% 10 year, but that monetary inflation rate of 7.2%.
An increase in the required rate of return invariably brings an increase in risk. Superfunds can't simply gamble Australians' retirement savings on high-risk offshore tech startups, so these returns are often sought through listed equities and commercial real estate—two interest rate sensitive asset classes. This correlation significantly limits the RBA's ability to manoeuvre and the dilemma is clear:
- Drop rates, inflate away our retirement.
- Increase rates, crash our retirement.
Bitcoin to the Rescue
You guess it, bitcoin fixes this.
Take the same example from 1991, but replace the Australian Peso with Bitcoin. In a Bitcoin world, we wouldn’t need superannuation. By simply saving 40 years of time and energy in a deflationary currency like Bitcoin, our savings alone would increase in purchasing power, eliminating the need to burden future generations for our retirement.
In the meantime, Australian superfunds should take a leaf out of a few smaller US pension funds like the Wisconsin Pension Fund and start gaining exposure to bitcoin.
A 2% allocation to a Bitcoin ETF is enough to ignite a chain reaction toward full institutional adoption. This truly scarce and desirable asset, with its low correlation to existing portfolios, isn’t just an opportunity—it’s a lifeline for the future of Australian retirees. It’s only a matter of time.
Colin Gifford
August 2024
-
 @ 463b475d:f965ef1f
2024-09-01 01:50:34
@ 463b475d:f965ef1f
2024-09-01 01:50:34 -
 @ 93dbb6d6:ea74c840
2024-09-04 05:32:17
@ 93dbb6d6:ea74c840
2024-09-04 05:32:17Let’s take a look at why the Specter DIY is so secure and the incredible advantages this device offers.👇

Unlike many commercial wallets, it's built from OFF-THE-SHELF COMPONENTS. Anyone can get one without providing personal data or needing a specific store. Even if Bitcoin hardware is banned in a totalitarian regime, the Specter DIY offers discreet access to a signing device.
The Specter DIY is fully OPENSOURCE enhancing security by allowing anyone to review and use the code without permission. For example, the SeedSigner and Krux projects use much of the Specter DIY Code.
The device is BITCOIN and Liquid ONLY. Supporting no altcoins. With a smaller codebase, there are fewer opportunities for vulnerabilities.

The Specter DIY operates AIR-GAPPED, with no physical connection Wi-Fi-connected devices, ensuring sensitive data like private keys remain secure. It communicates via QR codes or SD card, ensuring transparency so you can clearly understand the transaction signing process.
The device has a LARGE smartphone-like TOUCHSCREEN, offering a comfortable interface for smooth air-gapped communication, easy entry of seed words, and convenient navigation. This display simplifies tasks that are very cumbersome on smaller devices.
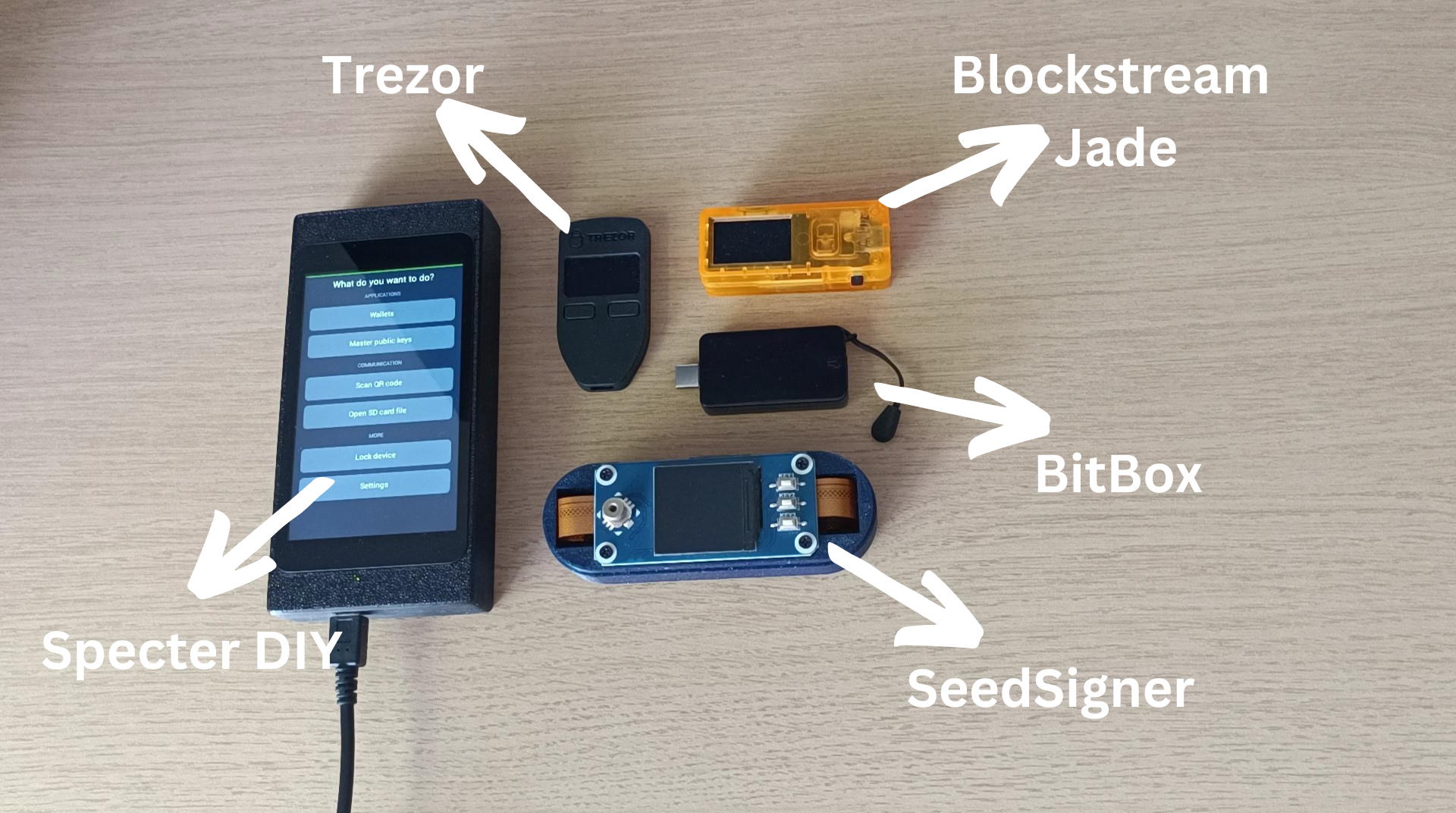
The Specter DIY is primarily a signing device and DOES NOT STORE SEED WORDS internally, enhancing security. Seed phrases need to be written down and re-entered manually. Alternatively, you can store the seed phrase on an unencrypted SD card or use SeedQR for easy import.

Since the seed phrase is not stored, the owner can create multiple MULTI SIGNATUR Wallets with only one device. Or act as "UNCLE JIM" and help family and friends set up a secure, watch-only wallet. Sharing the device requires minimal trust as the device could be tampered with.

One of the key features of the Specter DIY is its ability to integrate very transparent REAL-WORLD RANDOMNESS into seed phrase generation, such as by flipping coins. This helps safeguard against all potential attacks associated with weak seed entropy.
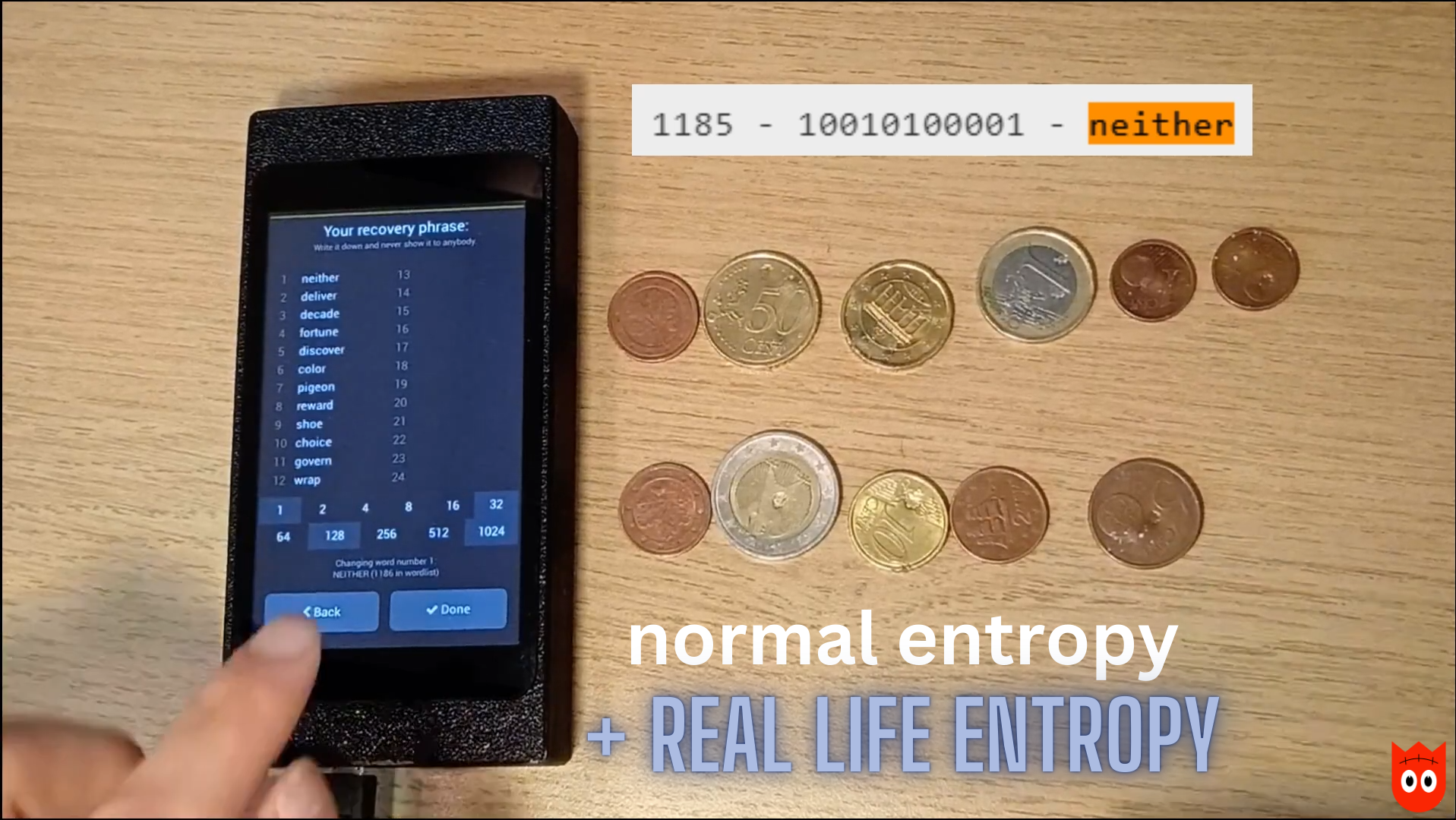
With BIP85 support, users can derive multiple child seeds from a single master seed. This feature is particularly useful for those managing multiple Bitcoin wallets, simplifying seed management for less important Seedphrases as well.

-
 @ 8d34bd24:414be32b
2024-08-31 23:01:04
@ 8d34bd24:414be32b
2024-08-31 23:01:04I’ve mentioned multiple times that I feel our time left is short and that the rapture and the tribulation are coming soon. I feel it with every ounce of my being. I see it in the rush to evil around us. I see Biblical prophecy coming to fulfillment and technologies that could not be fathomed 2,000 years ago coming into being in a way that will make prophecy possible. The question is, what do we do with the time left to us?
Don’t Be a Foolish Virgin
Matthew gives an analogy of believers waiting for Christs return:
“Then the kingdom of heaven will be comparable to ten virgins, who took their lamps and went out to meet the bridegroom. Five of them were foolish, and five were prudent. For when the foolish took their lamps, they took no oil with them, but the prudent took oil in flasks along with their lamps. Now while the bridegroom was delaying, they all got drowsy and began to sleep. But at midnight there was a shout, ‘Behold, the bridegroom! Come out to meet him.’ Then all those virgins rose and trimmed their lamps. The foolish said to the prudent, ‘Give us some of your oil, for our lamps are going out.’ But the prudent answered, ‘No, there will not be enough for us and you too; go instead to the dealers and buy some for yourselves.’ And while they were going away to make the purchase, the bridegroom came, and those who were ready went in with him to the wedding feast; and the door was shut. 11Later the other virgins also came, saying, ‘Lord, lord, open up for us.’ But he answered, ‘Truly I say to you, I do not know you.’ Be on the alert then, for you do not know the day nor the hour. (Matthew 25:1-13) {emphasis mine}
Christians have been waiting for around 2,000 years for Christ’s return. It is easy to get drowsy and begin to sleep due to the delay to His return, but we are called to be ready. “You too, be ready; for the Son of Man is coming at an hour that you do not expect.” (Luke 12:40) Our wait may be long or short, but we are supposed to live our lives like he will arrive today. We don’t want to miss out on joining Him at His return, but we also don’t want to have to face Him knowing that we were not focused on what He had called us to do. We don’t want to admit that we didn’t share the gospel to that friend, that we didn’t stand up for the truth when the crowd was speaking contrary to the word of God, or that we acted in an unloving way to fellow believers or to the lost.
The Bible clearly tells us that we “do not know the day nor the hour,” but that doesn’t mean that He has not given us signs that the time is short.
What Should We Be Doing?
If Jesus is coming soon, how should we spend our time? What should we be doing? Should we just sit back and wait?
For even when we were with you, we used to give you this order: if anyone is not willing to work, then he is not to eat, either. For we hear that some among you are leading an undisciplined life, doing no work at all, but acting like busybodies. Now such persons we command and exhort in the Lord Jesus Christ to work in quiet fashion and eat their own bread. But as for you, brethren, do not grow weary of doing good. (2 Thessalonians 3:10-13)
The Bible is clear that we should work. This not only means that we should not quit our jobs, but should continue working as we have been doing, but it also means we should put time and effort into kingdom work.** God has given each one of us a purpose and a job to do. We should study His word and pray and keep our eyes open so we don’t miss out on what He intends as our purpose. Another analogy is given in Matthew:
“For it is just like a man about to go on a journey, who called his own slaves and entrusted his possessions to them. To one he gave five talents, to another, two, and to another, one, each according to his own ability; and he went on his journey. Immediately the one who had received the five talents went and traded with them, and gained five more talents. In the same manner the one who had received the two talents gained two more. But he who received the one talent went away, and dug a hole in the ground and hid his master’s money.
> “Now after a long time the master of those slaves *came and *settled accounts with them. The one who had received the five talents came up and brought five more talents, saying, ‘Master, you entrusted five talents to me. See, I have gained five more talents.’ His master said to him, ‘Well done, good and faithful slave. You were faithful with a few things, I will put you in charge of many things; enter into the joy of your master.’*
> “Also the one who had received the two talents came up and said, ‘Master, you entrusted two talents to me. See, I have gained two more talents.’ His master said to him, ‘Well done, good and faithful slave. You were faithful with a few things, I will put you in charge of many things; enter into the joy of your master.’*
“And the one also who had received the one talent came up and said, ‘Master, I knew you to be a hard man, reaping where you did not sow and gathering where you scattered no seed. And I was afraid, and went away and hid your talent in the ground. See, you have what is yours.’
“But his master answered and said to him, ‘You wicked, lazy slave, you knew that I reap where I did not sow and gather where I scattered no seed. Then you ought to have put my money in the bank, and on my arrival I would have received my money back with interest. Therefore take away the talent from him, and give it to the one who has the ten talents.’
> “For to everyone who has, more shall be given, and he will have an abundance; but from the one who does not have, even what he does have shall be taken away. Throw out the worthless slave into the outer darkness; in that place there will be weeping and gnashing of teeth*. (Matthew 25:14-29)
God has given each of us different skills, gifts, and opportunities. He wants us to make the most of them. If God gave you skill in business, you can use your wealth to fund ministries, churches, and missionaries. If God has gifted you with the ability to teach, you can disciple many to grow in their faith and knowledge of God. If God has brought you into a relationship with someone influential, you can share the Gospel with them and be used to draw them into saving faith in Jesus. Whatever skills, gifts, and opportunities God has given to you, you need to make the most of them. You need to grow and make the most of what God has given you.
What is the Best Use of Our Time and Money?
God wants us to shine a light for Him. He wants us to make a difference. There are many ways to do this and we can’t do them all. We have to pick and chose what is God’s will and what will make the best use of what God has given us.
There are lots of good things we can do, but what is the best?
I used to focus on prepping to be able to provide for my family and others if times get bad. That was good, but was it best? I used to grow a garden and grow healthy food. That was good, but was it the best? I used to be highly involved in politics and worked hard to support and elect godly men and women into government positions where they could have a positive influence on our culture and our country. That was good, but was it the best?
According to the grace of God which was given to me, like a wise master builder I laid a foundation, and another is building on it. But each man must be careful how he builds on it. For no man can lay a foundation other than the one which is laid, which is Jesus Christ. Now if any man builds on the foundation with gold, silver, precious stones, wood, hay, straw, each man’s work will become evident; for the day will show it because it is to be revealed with fire, and the fire itself will test the quality of each man’s work. If any man’s work which he has built on it remains, he will receive a reward. If any man’s work is burned up, he will suffer loss; but he himself will be saved, yet so as through fire. (1 Corinthians 3:10-15) {emphasis mine}
The best way to judge which actions are best is to see which actions have an eternal influence and to look and see what God is doing and to join His work. The difference between gold & silver versus wood, hay, and straw is the gold & silver can survive fire. Whether something is good or best depends on whether the action makes a difference in eternity.** Providing for my family and friend’s physical needs and health is good, but it doesn’t make an eternal difference. Electing Godly officials makes life here on Earth better, but does it actually make a difference eternally? Probably not.
What does make a difference? Sharing the Gospel with others makes an eternal difference. Standing up for the truth, especially the spiritual truths from the Bible, makes an eternal difference. Writing a book or a blog sharing the truths of the Bible and Jesus makes an eternal difference. I’ve tried to focus my time on this type of activity more than the former. I don’t want one soul to go to Hell because I was too busy to share the Gospel. I don’t want one Christian to regret their life on Earth because I was too busy to disciple them. I don’t want to be like the man who received the single talent and buried it in the ground, who, when facing his master, was told, “You wicked, lazy slave.”
What Is Most Important?
“Do not store up for yourselves treasures on earth, where moth and rust destroy, and where thieves break in and steal. But store up for yourselves treasures in heaven, where neither moth nor rust destroys, and where thieves do not break in or steal; for where your treasure is, there your heart will be also. (Matthew 6:19-21) {emphasis mine}
What are the most important things in our lives? The most important things are people.
-
Some people in our lives have never heard about Jesus. We need to share the gospel with them.
-
Some people in our lives are hurting and need to be helped and encouraged and taught to trust in Jesus.
-
Some people in our lives are new Christians or just immature Christians, who have trusted in Jesus, but haven’t grown much since salvation. We need to teach and disciple them to grow in their understanding of God and who He is. We need to build up their faith. We need to encourage them to study the Bible.
-
Some people in our lives know God and His word, but are unsure how to live out their faith and share it with others. We need to encourage them and train them, so they can multiply their faith among others in their lives.
What are you doing to make an eternal difference in service to our Lord Jesus Christ? Are you one of the lazy, unprepared virgins? Are you hiding the gifts God gave you in the ground or shining a light that can be seen by everyone around you? Are you so busy doing good, that you don’t see God’s best?
Are you excited about meeting Jesus in the air at the rapture of the Church? I am! I hope you are, too.
Trust Jesus.\ \ your sister in Christ,
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
-
-
 @ e5272de9:a16a102f
2024-08-31 20:23:59
@ e5272de9:a16a102f
2024-08-31 20:23:59The GrapeRank algorithm, like the PageRank algorithm, takes as input a graph, composed of nodes and edges, and composes "importance" scores for each node based on the topology of the graph. This equation is currently implemented at brainstorm and uses follows and mutes to calculate a trust score G (also called an "influence" score) in the range [0, 1] for each user in your nostr network.
This is the GrapeRank equation:
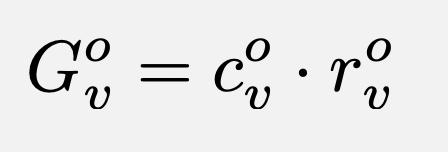
- G, c, and r in this equation are each scalars in the interval [0, 1]
- G represents the grapevine score (also called the "influence") of v, as seen from the vantage point of o
- r represents the average rating of v by o's grapevine
- c represents the degree of confidence in the average rating r
- the subscript always represents the thing (user, product, etc) being evaluated
- the superscript always represents the "observer," the point of reference from which we view and interpret the world
This is the same equation in expanded format:
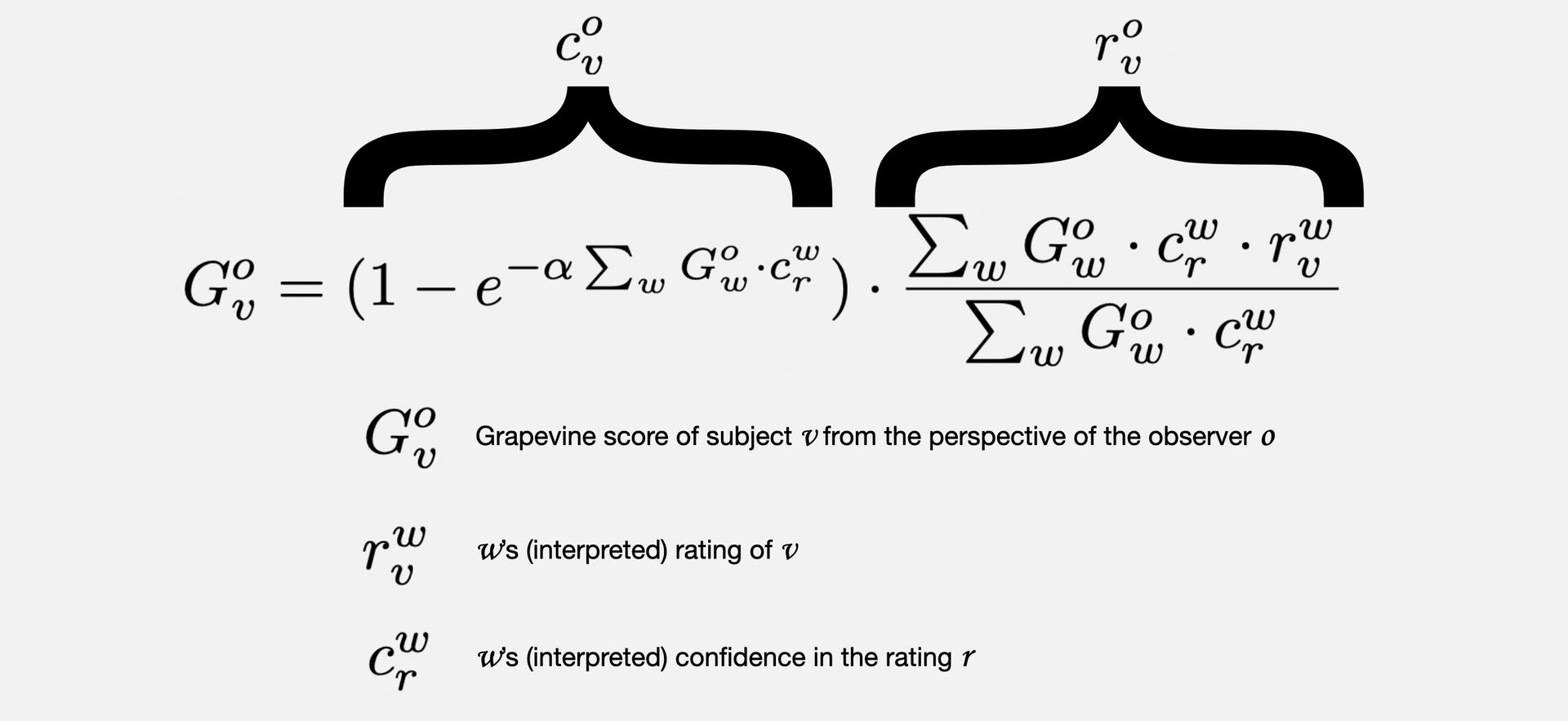
- The grapevine score of v on the left, G_v, is weighted using the grapevine score (but of each w) on the right, G_w
- These calculations are iterated until all G values converge
- r^o_v (the right half) is the weighted average
- c^o_v (the left half) is the confidence in that weighted average
- The r^w_v are the ratings being averaged together; they are inferred from follows and mutes by interpreting a follow as a score of 1 (probably not a bot), a mute as a score of 0 (probably a bot)
- The c^w_r are the confidences in the r^w_v; a follow is interpreted to have a confidence of 5 percent, a mute to have a confidence of 10 percent. (These are adjustable settings at brainstorm.)
- The sum over G * c, which appears twice in the above equation, is called the "input" and is an unbounded, nonnegative scalar which represents "the amount of trusted input" that goes into the calculation
- The formula is designed so that as the input (the number of ratings from trusted sources) increases to infinity, the confidence c^o_v approaches 1 (100 percent) asymptotically. This map from input onto confidence, which employs a nonlinear equation, is necessary to ensure that G remains within the [0, 1] interval even as input increases to infinity.
- alpha is a nonnegative scalar value that determines how "quickly" the confidence c^o_v approaches 1 (100 percent) as trusted input increases. Decreasing the value for alpha makes the equation more "rigorous" because it will take more trusted input to achieve any given degree of confidence. (Alpha is another user-adjustable setting at brainstorm.)
To perform the above calculations: 1. For the "seed" user (the observer o, i.e. the logged-in user), fix average, confidence, and G (influence) to unity. These values will not change. 2. For all other users, initialize average, confidence, and influence scores to zero. 3. Iterate through all users to calculate average, confidence, and influence scores. In the first iteration, the follows of the logged-in users will obtain nonzero scores. In the second iteration, their follows will obtain nonzero scores. And so on. 4. Continue iteration until all values converge.
Intuition tells us that convergence is guaranteed by the requirement that for each rating, the rating and its associated confidence are scalar values between 0 and 1. G will therefore also always also be a number between 0 and 1. Not shown: at brainstorm and in general recommended practice, the above equation also employs a scalar value between 0 and 1 called the "attenuation factor," defaulted at 0.8 but adjustable by the user, which causes influence scores G^o_v to diminish as the number of hops between o and v increases.
Intended usage
G is designed to be used as a weight when calculating weighted averages, tallying votes, etc. It is highly effective at eliminating bots without turning into a popularity contest.
Interpretation
G^o_v is a recommendation, to you by your grapevine, that reflects in numerical form how much "attention" you should pay to pubkey v in the given context (if a context is given).
- G^o_v = 0 means that pubkey v is not worthy of your attention, because v is probably a bot
- G^o_v = 1 means that pubkey v is worthy of your full attention, because b is probably not a bot
- Values between 0 and 1 mean the grapevine isn't absolutely certain one way or another, whether because of scant information (some follows by trusted sources, but not many) or conflicting information (combination of follows and mutes)
Note that if a bad actor spins up a large number of bots and uses them to follow himself, those follows will be completely ignored, because those bots will have a zero trust score G.
Change of context
The set of ratings r can be generated from any data source, regardless of format. By selecting different ratings datasets, we can generate grapevine scores to reflect different contexts. Example: collect emoji reactions to content on Topic X and infer a fire emoji as a rating of 2, rocket as a 3, thumb down as a 0, etc. The resulting G, which will take values between 0 and 3, is now interpreted to apply only to Topic X.
Compact notation
The above equation can be written more succinctly:
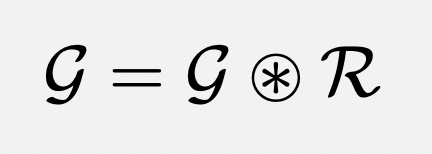
where G represents the baseline grapevine score, and R represents the dataset generated from follows and mutes.
Note that we can use a different G on the left versus on the right:
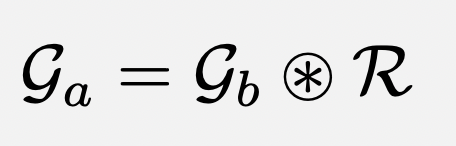
The same relationship can be expressed using arrow notation:
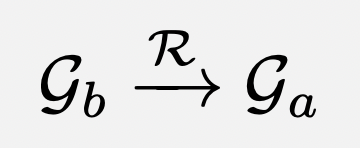
The above relationship in arrow notation should be read to mean that the set of scores G_a are calculated using dataset R which has been authored exclusively by members represented by G_b. In other words, the ratings R are weighted using the set of scores G_b.
Note that the dataset R is generated via interpretation of preexisting content. We can use any content that we can find. There is no requirement or expectation that users will necessarily generate ratings in a format convenient for input into the grapevine. The process of "interpretation" takes care of that, by "translating" existing data into a format suitable for use by the grapevine.
Note also that grapevine scores G may refer to anything in any context: trust scores for users, quality scores for products, etc.
Concerns about convergence
If the G_a and G_b represent the same context (G_a = G_b), the relationship is said to be "recursive," and calculations are iterated until they converge.
If G_a != G_b, the relationship is not recursive, and a single iteration through each pubkey is all that is needed. This means that we can allow G_a and / or G_b to be greater than 1 with no need to worry about convergence.
Worldviews
Arrow notation allows us to link trust calculations in chains:

A graph of grapevine scores G_i linked via arrow notation is called a worldview.
For example, consider the following worldview: * G_a is the baseline nostr trust score, as described above, intended to separate bots from real users * G_b is a label applied to nostr users, intended as a label for bitcoiners (as opposed to nocoiners or shitcoiners) * G_c is a quality score applied to hardware wallets
The purpose of the above worldview is so that I can get a ranked list of hardware wallets and I can be reasonably sure that the list is curated by bitcoiners whose instincts on this topic I value more highly than the general population.
Worldviews can contain any desired number of nodes, connected by any desired number of arrows, and so can be as complex as desired.
Obviously, the construction of a worldview reflects the value system of the person who uses it, with the above worldview offered as a reflection of maximalist values and beliefs. Worldviews can be codified and submitted to the wider community. One's grapevine can even be used to select individuals who should be trusted to edit or construct worldviews.
Computational cost
The methods described above are expected to be too time consuming and computationally expensive to do all of them on the fly on the front end. Notably, the ones that are recursive. Non-recursive computations, however, can be done on the front end, provided recursive calculations have been done ahead of time and are readily available. It is anticipated that the value added by well-crafted worldviews will more than justify the requisite costs.
-
 @ 3c827db6:66418fc3
2024-08-31 11:46:11
@ 3c827db6:66418fc3
2024-08-31 11:46:11I was contemplating how to publish this on my personal blog while making slight edits to my letter to Roy so that it reflects the same principles and sentiments I intended to convey. However, in the process, it seemed to lose its inherent value. I don’t want this to come across as hypothetical; I want it to remain true to its original essence. Therefore, I’d like to clarify that this was not meant to be a blog post but rather a letter to Roy Sheinfeld. As you read through the text, please keep that in mind.
With Roy’s approval and encouragement to make it a blog post, I am now sharing it with a broader audience than it was intended to when I wrote it.
As I read through the text, I’ve come to realize that there isn’t a single word to describe finding your soulmate company. How many of us struggle to articulate what we’re looking for in a company and a team? If we do not even have a definition for that pursuit or end goal how are you going to even start ? I can only say that when you finally find it you feel it deeply in your soul.
 Follow the light and get out of the darkness.
Follow the light and get out of the darkness.And now, my letter to Roy Sheinfeld:
In the beginning, I thought that the ideal company for me was Strike. Looking back, I must say I’m quite happy they didn’t respond to my applications. For some inexplicable reason, my life brought me to Breez, and I found it to be the perfect company, especially when it comes to the team I’m working with. The company’s values align almost perfectly with my own, not just on the technical side, where I admittedly lack certain capabilities, but also on the human side — our shared mission to better humankind and leave the world a better place.
Whether it’s the genius strategies we employ to envision how the Lightning Network will transform Bitcoin into a medium of exchange or our unwavering commitment to surmounting the challenges and setting standards in the Lightning Network, including the concept of Lightning Service Providers, I now fully grasp the significance of what we’re doing. It’s exactly what’s needed for individuals to attain freedom. I can’t even begin to fathom the struggles, fears, and excitement the team has experienced over the past five years, but I can only express my admiration.
It’s undeniable that I lack programming and technical skills, but I’ve always known that joining this team would push me to grow stronger, faster, and more proficient. My passion and excitement far outweigh my technical shortcomings, and I embarked on this adventure with the enthusiasm of a child. Now, six months into this journey, I can confidently say that my passion has only intensified. The tasks ahead of me and the team inspire me, and I’m thrilled that striving for excellence is not just an expectation, but a core value. It’s a form of leadership that combines patience and guidance (or sometimes a lack thereof), all while maintaining an unwavering commitment to achieving outstanding results.
I’ve noticed progress in even the simplest things, like navigating GitHub to conduct proper QA tests at the right times and understanding the team’s discussions. I’ve also dived into completely new territory, such as programming in Python via ChatGPT to create programs for scraping transaction fees and dates from various nodes. One area I’m actively working on is paying meticulous attention to detail in written texts, as I’ve come to realize that even a single letter or number difference can lead to significant issues. I assume you’ve honed this skill over your decades-long programming career.
Reflecting on the webinar, I’m pleased with its success. It was just an idea when I first mentioned that we should make one, but seeing it applied and witnessing the collective learning process culminate in a beneficial outcome for the team and the company brings me great satisfaction. I believe there will be more ideas, processes, and activities where I can make increasingly impactful contributions to the team, and I’m just getting started. I’ve always known that my contributions to any team would be substantial, and I’ve never lacked confidence in myself. In these initial six months, I’ve recognized that what I have to bring to the team has to exceed my compensation. For the first time, I can honestly say that I wouldn’t want to leave this team for any other. Our shared human values resonate deeply with me, and I’ve only experienced a similar connection once before, when I met my soulmate, Rali. As I mentioned in one of our meetings, I fully understand the weight of my personal story and the responsibility we carry as a team and a company to impact the lives of others positively. As long as these values guide us, my loyalty lies with the team and its people, not just the brand. In the event that the company is ever sold to another entity, I doubt I would want to continue working there. Instead, I hope that, in a few decades, we can consider ourselves close friends and, as you mentioned during our time in Italy, attend each other’s personal celebrations.
Having said all this, I want you to know that if I ever fail to deliver sufficient value to the team and the company, I would understand if you had to part ways with me. While I would undoubtedly be disappointed in myself, I would understand. Even if we become friends, I’d prefer to be judged based on my work, not personal ties. If you believe my compensation outweighs my contributions, I’d be willing to reduce it to remain part of the team. I’m committed to increasing my value output and would request a raise once I’ve demonstrated that growth.
I can sense that the relationships I’m building in the PR, marketing, and social media space will yield even more benefits in the future. Setting up the first meetup in my country has made community growth increasingly manageable, and it has inspired another Bulgarian city to start hosting regular meetups. As of now, we’re aware of around 40 true Bitcoin enthusiasts in Bulgaria. While I can’t predict the future, the network effect continues to expand, and I believe our community will experience something significant. I just need to keep organising more meetings to attract more people.
Communication regarding QA tests is running smoothly now, and I feel confident in my abilities in this area. I appreciate that our social meetings benefit the team as a whole, and I’m excited to see more companies approaching us about the development kit. As a user, I would love the convenience of operating through a single non-custodial balance across all of them. The future looks bright, but it’s not guaranteed. I’m fully committed to doing everything in my power to contribute more and more, and I’m dedicated to continuous learning and self-improvement to better serve our mission.
-
 @ 862fda7e:02a8268b
2024-09-04 01:45:14
@ 862fda7e:02a8268b
2024-09-04 01:45:14It is true that I often dream about James Corbett from CorbettReport.com. Somehow James is always finding his way to my mind. James Corbett intimidates me, I feel like he would heavily dislike me because I am not serious enough. Anytime I see James Corbett smile or laugh it feels like I'm watching an alien try to be human. I wish James the best with his family life and career, but he looks like he is always one second away from either crying hyterically or beating a defensless Japanese man sensless. I am indreasibly grateful for all the hard work he's put out all these years, he's a great person in the truth circle. However, he's like a caracatiure in my head. Anytime he whips out his guitar, I start to cringe. I just know what's about to come will only be the truth about how bad his singing is. But yet, I still love when he plays his guitar. It's awful in a great way, it brings genuine joy to me. Did you know he has a band? He has one song called "Screw Youtube", and in his music video he was sitting on this tall wooden fence and he was wearing these SHORTS WITH SANDALS and he was SWINGING HIS LEGS. I'm sorry, but I expect James to wear white caykies at all times. It felt so gross to see his legs in that state. But then again, here I am getting genuine joy out of seeing that atrosity.
I remember one time watching a James Corbett episode where he has the James Evan Pilatto from MediaMonarchy.com on, and the other James always looks like he's super fucking cracked up. Like he has a ton of energy. Well anyways, one time the other James was his usual self, looking super cracked out excited, talking about the reppies (reptilians) and James Corbett looked so tight lipped, red faced, like he was about to burst out crying. It was so funny to see the two polar opposites, the other James totally oblivious that real James looked like he was about to cry for seemingly no reason. I know this sounds mean of me to say, but I really appreciate these guys for all they do. I just think this is funny.
Anyways, I have a lot of dreams with James Corbett in them. I think it's because he's a teacher and my vagina has a fondness for male teachers. Sadly, none of my good looking male teachers never slept with me. That being said, I think James is good looking for possibly being an English teacher in Japan. I would let him teach me about the reptilians and Klaus Schwab, just let the teaching session see where it goes. Would his gap teeth feel good over my clitty? I dunno.
Okay but here is the most memorable and hilarious dream I had invovling James Corbett. You know how he makes content very often? One day he got extremely fed up with making videos. At the time I think it's because he mentioned in a video how he was annoyed that people kept saying him and Andrew Caufman. So one day he just flipped out, got extremely angry, made one last video saying how he was never coming back and how he's leaving his wife and kids. He deletes everything and is unheard of for months. A few months pass and he uploads a new video. The new video is James obsessively showing and talking about his highly advanced chicken coop he made in Minecraft. He had hundreds of chickens lined up maybe 80 feet in the air, each chicken had a 1x1 square to fit in. Below the chicken was a long tube in which their egg would drop down, and a catcher at the base of the ground. James was fantically showing this contraption, rocking back and forth, had a headset on. He looked awful too. I actually emailed James Corbett about this dream, but he never responded.
Speaking of James Corbett, why do so many people look like him? I feel like they make middle aged bald, bearded men in a DUMB and just release them into the wild, but give them balding genetics so they know how to keep track of them. Like they probably made James Corbett and Andrew Caufman from the same test tube. They fucked up with them, at least like give one of them hair or good eyesight.
-
 @ 6d20ea61:1de5dacc
2024-08-31 10:13:24
@ 6d20ea61:1de5dacc
2024-08-31 10:13:24Why does the world remain ignorant to Africa's sinister secrets?
There's a lot going on beneath the surface in our everyday lives. Most of us accept this as a fact; that we only perceive a small sliver of reality as it is. However, it's rare that we align our actions with the uncomfortable reality that lies beyond immediate perception. Authentic people do align themselves in this way, and they’re often threatening to those who don’t because they hold a mirror to their own incongruities.
We may be aware of the truth that lies beyond our immediate field of view, which is exactly the excuse we use to allow ourselves to not be authentic. Truth? Sure, I'll accept the truth of which you speak, as long as you can "prove" it. If it's there, why don't you point to it?
Just because you can't see it, doesn't mean it's not there.
We look around to observe the crowd moving in unison. We may know we're all aware of some heretofore unspeakable truth, but the mass misdirected momentum of the crowd acts as an all-too-easy justification to excuse ourselves from being less than we can be; to shy from the consequences of living in truth.
They say the shepherd is there to protect the flock, lest they be preyed on by the wolf. Little do the sheep know that it is the shepherd who controls their fate, and ultimately feasts on their flesh.
If I were a sheep, I would much rather live a short life dying a brutal death at the jaws of a wolf. At least I would have been unbounded in my life; free of the ignorance imposed by a faux protector; blind to the reality of my domestication for the purposes of his own prolongation.
Jesus was a shepherd, was he not? All too many Africans I've spoken to know Christianity was used as a tool to supplant their own traditional practices as a means to unhinge their pride and autonomy…
"I'm sorry you lost everything: your land, your family, your livelihood, your dignity. Have you heard of Jesus? He can provide everything you'll ever need. You never needed all this land, culture, and sovereignty anyway. You don't need to carry the burden of being your own person, thinking for yourself, living for your people and culture, living for the right to determine your own destiny. Jesus can handle all that for you. Trust me, your life will be better now"
It is beyond saddening to remember the conversations I've had with "Christians" in Botswana, Zambia, Zimbabwe, Namibia, and South Africa. They're entirely aware of how most of their culture has been lost, and how the majority of Africans remain enslaved in their minds to this day. Jesus and Western ideals are the broken records they were raised with, and these are what they all claim to be the answer to life's woes. To think differently is to be cast away. To think differently is suicide. When all hope has been lost, dare not face reality as it is, apparently.
Religion: the opiate of the masses, as they say.
Religion (Christianity in the South) is rampant in Africa, and my observed reality is that it's not practised with integrity. Don't get me wrong, it can be beautiful to see people come together for shared belonging, but there's no sense in lying to ourselves and each other in the process.
The vast majority of what I witnessed and heard from people was a bastardisation of Jesus and the Bible so they can justify their wrong doings without being judged by others, or worse, to coerce others in the effort to claim moral superiority.
Perhaps the most painful irony is that Jesus would have never stood for any of this crap. Taken at face value, there is a lot to learn from the life of Jesus; lessons that should not be ignored. However, Jesus would have never proposed religion as it exists today, or whatever the group-think, known as "church", has become. After all, Jesus did not follow the crowd. Jesus followed the beat of his own drum. He didn't live to teach that we live blindly. He was his own shepherd. Why is this so hard for people grasp? I wouldn't be surprised if Jesus was crucified all over again were there to be a proverbial "second coming".
I swear, being a missionary, or any evangelist, should be held in contempt the world over. For people to assume they carry another man's truth is beyond hubris, and only proves they lay victim to the same fallacious and cowardly thought that allows us to fall in step with the crowd despite our better judgement - to vilify the wolf and befriend the shepherd despite the truth.
Africa’s Truths
Africa is a land of hard truths. It's brutal and raw. It reminds me of traveling through India more than ten years ago. India confronted me with my own nature, forcing me to witness suffering and hardship that was otherwise hidden in the Western world where I was raised. Africa is India at a larger geographic scale. After more than 30,000 km by motorcycle through much of Southern Africa, I've seen enough child labour, corruption, and artificial hardship to feel deep pains reflected within myself.
Africa and India remain crucially different. Effectively, Africa is still colonised, whereas India is largely independent. The USA, France, China, and Russia (among others) are not free to exercise their interests in India. In Africa, the USA, France, China, and Russia's interests (among others) are the only interests that carry weight. Confessions of an Economic Hit Man (by John Perkins), anyone?
Africa isn't some drought-ridden continent devoid of resources to support the people who live there. The majority of the raw materials that fuel the "modern" lifestyles of the Western world come from Africa, for Christ's sake (pun intended).
How does it make sense for a Canadian company to mine in Namibia where only 5% of the profits go to the Namibian government? How much of this inevitably filters through Namibia’s corrupt elite to the Namibian people?
Africans' living standards should be no less than on par with that of the rest of the world, but the "success" of the West (and the East, increasingly) hinge too crucially on the controlled flow of artificially suppressed prices on commodities that make up the comforts of the "developed" world.
Africa is where the world sweeps their problems underneath the rug. Africa is the closet where the world's skeletons collect dust. By all means, go on your happy little safari, but don't dare learn about how none of that safari money tangibly benefits the African people.
My “success” is a reflection of Africa’s suffering
Africa is where I realised how I allow myself to live out of alignment with known truths.
I haven't posted anything to this newsletter in over a year. I've asked myself "why?" over the months and came up with various answers. I wanted to write about those answers, but they didn't suffice.
The best answer I can give you now is out of shame and pride. My pride wouldn't allow me to continue writing because I didn't want to advertise my lifestyle. My shame wouldn't allow me because I feel like an impostor.
I've felt like an impostor for a very long time. In that time I have somehow cultivated an image of being a traveler. People seem to know me as one. I even have a little mantra I learned while living in China that I seem to cling to as part of my identity: 我是一个旅行者 (Wo shi yi ge lu xin zhe) - "I am a traveler".
However, I don't think I'm purely a traveler. I think I'm a traveler because it has been the path of least resistance. It has been a convenient alibi.
I, like all of us, held dreams as a young human about what I wanted to do with my life. As I matured, I faced opposition in the opinions of society, family, and friends as to the "practicality" of my dreams. I didn't have to listen to them, but I did. I internalised those thoughts and chose to stick to what I know, traveling.
I grew up traveling a lot as a kid. I always loved it, and learned over the years that I'd like to travel in my own way as an independent. I'm happy to say that I've done so, but I've learned that my sacrifices to reach this lifestyle needn't be as severe as they've become.
I wanted to live outside. I wanted to study animals and the laws of nature, and I never thought it would be practical to do so in tandem with my traveling life. I felt guilty in college. I didn't know how to support myself while in my studies, and couldn't bear accepting financial support from someone I didn't align with. I felt like a politician corrupted by the vested interests of their donors.
This led to me dropping out of college, abandoning my childhood dreams to settle for a "life of integrity". I vowed I would one day come back to make good on my dreams. Traveling has been the life I choose to live while I find a way to honour a core responsibility to myself. I'm proud of myself for not being coerced by outside interests, but I now know I'm not being entirely authentic.
Thank you, Africa. I’m sorry, Africa.
Thank you, Africa. I'm sorry, Africa. I'm sorry that I've lived a life of privilege that stems largely from your plunder. Thank you for keeping me safe while I learn your truths. Thank you for reflecting my own core truths.
My heart continues to break when I think of the world’s ignorance over Africa, and I think my gap in writing has been necessary to process this reality.
Frankly, I'm enraged along with a sense of peace that Africa's time will come. I'm confident in Africa's future; I just wish the rest of the world wasn’t working so hard to keep its head below water.
I'm responsible for Africa's fate, and so are you. We are all complicit in this crime. I hope this article resurfaces an awareness in readers a truth that seems to lay dormant in the public awareness.
I don't know why more of us don't stand up for Africa (and not by crying to our governments - f*ck them), because I think our individual efforts are more than enough. Even indirectly, I think we can slowly push the wave of change that is necessary to do right by Africa. I think we all have the incentive to do so, for Africa is the foundation of humanity in multiple sensibilities, meaning Africa’s prosperity translates into everyone’s prosperity.
All thoughts and comments are welcome.
G
originally posted at https://stacker.news/items/667609
-
 @ 8f09210b:065ffd5e
2024-08-31 09:26:22
@ 8f09210b:065ffd5e
2024-08-31 09:26:22J’aimerais attirer votre attention sur le phénomène NOSTR.
Si vous ne connaissez pas encore, je vous conseille très sincèrement de vous y intéresser !
Avant qu’Elon Musk ne reprenne Twitter, ayant compris que la censure se durcissait partout, un groupe de développeurs (issu essentiellement de la communauté Bitcoin) a décidé de construire l’ossature des réseaux sociaux de demain. Ce projet s’appelle NOSTR, acronyme de Notes and Other Stuff Transmitted by Relays (que les gens prononcent plutôt « nosteur » que « nostre » 😁)
Pour résumer en quelques mots, NOSTR est un protocole open-source, sur lequel il est possible de bâtir des projets de type réseau social, messagerie instantanée etc… le tout étant architecturé pour résister à la censure (par construction !).
Inutile de « s’enregistrer » pour créer un compte NOSTR. Celui-ci est constitué, un peu comme pour Bitcoin, d’une paire de clefs (publique/privée). Il suffit de générer une clef privée, pour obtenir ensuite la clef publique associée. Votre « compte » est cette clef publique, une suite de caractères commençant par « npub1... », la clef privée étant utilisée par le protocole pour signer vos messages. On ne vous demandera ni de décliner votre identité, ni votre adresse mail, rien du tout ! Vous pourrez éventuellement choisir un nickname et le faire certifier, mais cela n’est pas une obligation, et vous pourrez également renseigner certains champs, télécharger une photo de profil etc…
Le réseau est décentralisé, et fonctionne avec des « relais », qui peuvent être opérés par n’importe qui.
Ces relais enregistrent des « événements » générés par les utilisateurs et les transmettent aux autres relais. Ces « évènements », également appelés « Notes », sont de simples fichiers texte, qui peuvent être de plusieurs sortes, chiffrés ou non en fonction des utilisations.
Une sorte de clone de X/Twitter existe déjà, et fonctionne parfaitement. Des messageries instantanées chiffrées existent également, le tout étant en constante amélioration. La communauté NOSTR grossit de jours en jours, et de plus en plus de développeurs participent à l’amélioration des différentes plateformes et projets.
L’ex CEO de Twitter, Jack Dorsey, a d’ailleurs donné de grosses sommes d’argent pour aider ces développeurs.
Certains pourront imaginer un plan maléfique de "prise de contrôle", d'autres pourront penser tout simplement qu'il a mal vécu l’immixtion des censeurs au sein de Twitter et a décidé de participer à la création d'un projet plus résilient. C’est un bitcoiner convaincu, et le projet NOSTR a été créé essentiellement par des bitcoiners.
Il suffit de taper « jack dorsey nostr » dans une recherche YouTube pour tomber sur des conférences et l'écouter en parler...
Voici une vidéo courte et récente : https://youtu.be/0YDj1QdL2Zs
Certaines plateformes (ou clients NOSTR) intègrent d’ailleurs un portefeuille Bitcoin (utilisant le Lightning Network). Celui-ci permet aux utilisateurs de rémunérer les contenus qui leur plaisent. Un bouton « zap », situé à côté du bouton like, est utilisé à cet effet. Les « zaps » sont exprimés en satoshis (la plus petite fraction de bitcoin, le 8ème chiffre après la virgule). Il est possible d’envoyer un zap du montant de son choix. Un zap de 21 satoshis par exemple, correspondra à 0.00000021 bitcoins, soit 0,012 euros au cours actuel (1,2 centimes). Évidemment, l’utilisation des zaps et donc de Bitcoin n’est pas du tout obligatoire pour utiliser NOSTR !
Nous n’en sommes pas encore à devoir tous migrer sur ce genre de plateformes pour échapper à la censure, mais il me semble important de s’y intéresser dès à présent, créer des comptes, tester etc, pour être prêt le jour où Thierry Breton et sa clique décideront de prendre des mesures radicales (ou si la liberté de parole venait à s’effriter ou à disparaître sur X).
Beaucoup de gens ont décidé de tenter l’aventure sur des plateformes alternatives après avoir été exclus ou censurés (Telegram, VK, Mastodon, Odysee, Rumble etc…), mais toutes ces plateformes restent fragiles, car construites sur un modèle centralisé.
Les serveurs web NOSTR sont également des serveurs hébergés (et donc centralisés), mais il est extrêmement simple de créer son propre client web à partir du code open-source. N’importe quel webmaster peut héberger très facilement son propre client nostr sous le nom de domaine de son choix. Vous pouvez littéralement créer votre propre Twitter en quelques clics !
Pour voir à quoi tout cela ressemble, il faut tout d’abord choisir un client (web et/ou mobile).
Une fois que vous aurez une clef privée, vous pourrez ensuite l’utiliser sur n’importe quel autre client pour retrouver immédiatement une bonne partie de votre environnement (image de profil, comptes suivis, abonnés, messages privés etc…)
Je vous invite à tester avec le client Primal, que l’on peut trouver ici https://primal.net et/ou via une appli mobile (disponible sur l’Apple store et sur Google Play) mais il en existe bien d’autres…
Web : snort.social, iris.to, nostr.rocks …
Apple : Damus
Android : Amethyst
Pour en savoir plus :
https://nostr.how/fr/get-started
L’audience et l’utilisation de ce réseau étaient encore anecdotiques il y a quelques mois, mais il est désormais possible de trouver des comptes suivis par plus de 100 000 personnes…
Exemples:
ODELL (avec plus de 139K followers)
https://primal.net/.../npub1qny3tkh0acurzla8x3zy4nhrjz5zd...
Jack Dorsey (223K)
https://primal.net/.../npub1sg6plzptd64u62a878hep2kev88sw...
Tout comme sur les autres réseaux sociaux, il est possible d’utiliser des hashtags
Une recherche de #nostrfr vous donnera ce résultat:
https://primal.net/search/%23nostrfr
Une recherche de #nostriga vous donnera ceci (une conférence NOSTR était organisée ces derniers jours à Riga, en même temps que Baltic Honeybadger 2024)
https://primal.net/search/%23nostriga
Une dernière chose importante à savoir : une fois qu’un message est publié sur NOSTR, il est virtuellement impossible de l’altérer ou de le supprimer ! (certains clients pourront éventuellement afficher des modifications effectuées par les utilisateurs, mais le message original existera toujours en tant que tel sur les différents relais)
(Cet article est publié via NOSTR)
-
 @ e6fbeb1c:6ac8fc04
2024-08-31 07:11:23
@ e6fbeb1c:6ac8fc04
2024-08-31 07:11:23I can't remember the exact name of the dish.
- Basmati rice
- Barberries
- Almond slivers
- pistachios
- Zintron peel


originally posted at https://stacker.news/items/667533
-
 @ be39043c:4a573ca3
2024-09-03 22:54:46
@ be39043c:4a573ca3
2024-09-03 22:54:46Over ten years ago, when I visited Japan, I met a woman from the U.S. When we were chatting about books, I learned from her that a well-known best seller book, I had once read, was written by a ghost writer. She knew the writer who did it.
I believed what she said as she had no reason to lie. Also, because I remembered that I had a weird feeling when I read the book. Although I mostly liked the contents, something was totally off. It was not "off" in a sense that writing was not good. It was weird because it was too well-written.
This book is a non-fiction book about certain ideas. The writing of a non-fiction book that explains an author's ideas can become clanky as the author struggles to delineate their thoughts. One knows something is different from whether one can write them. But, the book was very very well-written and well-explained with a lot of reference points.
Probably partly because the elegance of writing and examples, it has been sold and continue to be sold today all over the world.
Well, I know now the author only provided the ideas and someone else put them together.
The ghost writer was a fiction writer that could write very well. The book is so well put-together because of his skill. He was not credited as a contributor, I believe.
Whether it is written by a ghost writer, the book is still a good book. But, to know that the book is not written by the author whose name was on the cover page disappoints me. Who writes the book is important for readers.
Now it is 2024. Things are much more complex because AI can write or put together ideas for humans.
For instance, I read a very funny and well-written short fiction on someone's blog yesterday. I was impressed and commented about that.
This morning, it suddenly hit me, he may have used AI to create the piece. This creator posts his long writing mostly every day. He also work full time, he says. I had wondered before he might be using ChatGPT to create contents.
ChatGPT can write nice short stories: we see such examples online. I have read a story for children ChatGPT created. It was a complex and intriguing story
If we don't like parts of AI writing, we can edit it. It is quicker than writing from scratch,
There is no way to know the particular fiction that I read was written by AI but it is possible.
Whether it was created fully by a human or AI or both, the good writing is still a good writing. Maybe, I am thinking too much here?
Not really, in my view. Who writes still matters to me.