-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ 8cb60e21:5f2deaea
2024-08-18 21:01:07
@ 8cb60e21:5f2deaea
2024-08-18 21:01:07 -
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8cb60e21:5f2deaea
2024-08-18 20:57:03
@ 8cb60e21:5f2deaea
2024-08-18 20:57:03 -
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 3bf0c63f:aefa459d
2024-03-23 08:57:08
@ 3bf0c63f:aefa459d
2024-03-23 08:57:08Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 8cb60e21:5f2deaea
2024-08-18 20:50:48
@ 8cb60e21:5f2deaea
2024-08-18 20:50:48 -
 @ 8cb60e21:5f2deaea
2024-08-18 20:46:51
@ 8cb60e21:5f2deaea
2024-08-18 20:46:51 -
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8cb60e21:5f2deaea
2024-08-18 20:46:46
@ 8cb60e21:5f2deaea
2024-08-18 20:46:46```js import { getCourseById, updateCourse, deleteCourse } from "@/db/models/courseModels";
export default async function handler(req, res) { const { slug } = req.query;
if (req.method === 'GET') { try { const course = await getCourseById(slug); if (course) { res.status(200).json(course); } else { res.status(404).json({ error: 'Course not found' }); } } catch (error) { res.status(500).json({ error: error.message }); } } else if (req.method === 'PUT') { try { const course = await updateCourse(slug, req.body); res.status(200).json(course); } catch (error) { res.status(400).json({ error: error.message }); } } else if (req.method === 'DELETE') { try { await deleteCourse(slug); res.status(204).end(); } catch (error) { res.status(500).json({ error: error.message }); } } else { // Handle any other HTTP method res.setHeader('Allow', ['GET', 'PUT', 'DELETE']); res.status(405).end(
Method ${req.method} Not Allowed); } } ``` -
 @ 5e5fc143:393d5a2c
2024-01-04 12:44:26
@ 5e5fc143:393d5a2c
2024-01-04 12:44:26We are now given a choice of digital freedom #nostr .
Creativity for every nostrich is now unleashed from the cage of bigtech censorship , rules and algo. But freedom comes with responsibility so pick right one(s). I will try share here some learning experience both technical and also from fundamental point of view. Just wanted kick start this article n fill as we go like living reference document.
Nostr itself is an application layer protocol that can used beyond just social media mirco or long blogging. Each nostr client heavily dependent on back-end servers call nostr "Relay servers" or in short "rs" or "relays" Relays can hosted anywhere in clearnet internet, onion net , vpn , i2p , nym Relays are controlled by their respective admins based NIP specs that they select to implement according to own decisions. Relays can have certain ToS (Terms of Service) Rules to adhered too.
New users can choose and pick client or app (ios / android/ windows) with preset of relays in the simplest form , but other advanced users need to do a regular manual relay management.
Relay management is an active regular task based on where when n how you are using.
Relay list are saved within you npub profile backup file which can edited and broadcast anytime.
Relay management is an active regular task based on where when and how you are using.
Relay list always need to be updated time to time as and when needed.
2 Users MUST a common RELAY between them even if one only need to follow another. Occasionally you may notice certain npub accounts you are following already but cannot see frequent notes publish by them – one of cause maybe you not sharing a common relay
Most nostr client applications has SETTINGS where user choose add/remove relays Also user choose which function to enable - READ or WRITE
Relay list for your account is always saved within you npub profile backup file which can edited and broadcast anytime. Hence any app or browser when u login with you npub the same relay list will be enforced. There could valid reasons why u need have list for if you trying to save bandwidth and traveling.
Functions in app.getcurrent.io and primal.net app for mobile apple or android are ideal for user traveling abroad and wanted to save bandwidth since relay management is done the providers in backend and saves hassle for basic usage.
Remember if someone is selecting relay on your behalf then you may not be necessarily able to pull and get some specific and special content that you may need. Such providers like coracle and nostrid also give option to override the default relays they selected.
Relay types: They can be categorized by various features or policy or technologies.
FREE PUBLIC Relays vs PAID PUBLIC Relays
PAID relays provide unrestricted access / write / filtering options than FREE relays but both are public clearnet relays. Just subscribing to PAID relays will not solve all problems unless you choose the relays properly and enable settings correctly.
Private Replay or Tor Relays – normally not easily visible until unless someone tell you. You can also host own private relay not opened to internet of archive and back of your own notes.
The technical landscape in nostr can be fast changing as more NIPs get proposed or updated. Relays admin can choose implement certain NIPs or not based on policy or technical limitations.
Example NIP33 defines “long notes” aka blogs as you now reading this in habla site which #1 UI and site for "Editable" long notes – some relays donot implement or allow this. NIP07 is used for client authentication like nos2x and is implemented by all relays in fact.
To be continued again ... reference pics will added later also Hope this help you understand "why when what" to tune and maintain active set of proper relays. Relay Proxy, Relay aggregator or Relay multiplexer – Paid, Public, Free, Private, Event, Relays That’s all for now n more later ... Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️ PV 💜 🤙
References: https://habla.news/relays https://relay.exchange/ https://relays.vercel.app/ https://nostr.info/relays/ https://nostrudel.ninja/#/relays
Related Articles: https://thebitcoinmanual.com/articles/types-nostr-relays/ nostr:naddr1qqd5c6t8dp6xu6twvukkvctnwss92jfqvehhygzwdaehguszyrtp7w79k045gq80mtnpdxjuzl9t7vjxk52rv80f888y5xsd5mh55qcyqqq823cf39s98 https://habla.news/u/current@getcurrent.io/1694434022411
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 8d34bd24:414be32b
2024-08-18 20:43:03
@ 8d34bd24:414be32b
2024-08-18 20:43:03I’ve been reading The Unchanging Word of God by David Jeremiah. This book has chapters from multiple books he wrote previously. I was particularly inspired by some of what I read in his chapter entitled “When You are at Your Wits’ End.” The title of this article was inspired by something he said as well.
What Prayer Says About Our Faith
To start us off, I’m going share the quote that led to this post. It is found on page 145.
A devoted believer will pray for God’s deliverance from problems, but a wiser one will pray for God’s use of them.
I would expand upon this quote and say, “In times of trouble, a foolish believer will try to fix things himself; a generally faithful believer will pray for God to deliver him from hardship; but a wise believer, who knows what an awesome, holy, good God we have, will pray for God to use the problem/hard times for good according to His will.”
Truly understanding who God is (His holiness, goodness, omniscience, omnipotence etc.) and truly understanding our own weakness and lack of understanding enables us to honestly pray “thy will be done on Earth as it is in Heaven.” When we think too highly of ourselves and to lowly of God, then we want to fix things ourselves or we just ask for deliverance. Nothing that happens to us is an accident or God being unfair.
And we know that God causes all things to work together for good to those who love God, to those who are called according to His purpose. (Romans 8:28)
The Good Father
God is like a parent. He wants the best for His children, knows what is best better than His children, and gives His children what is best for their long-term good rather than their short-term happiness.
As a parent, I make my kids eat healthy food rather than the junk food they may want (especially my youngest). As a parent, I tell my kids not to do certain things that I know will cause them harm. Sometimes they don’t understand the why and try to do otherwise. When my kids were very little and just learning to crawl, I found a few spots with 1-3 steps and allowed them to fall off the steps scaring them and maybe even allowing minor pain. I did this so they would learn about the dangers of heights. If they fell off 1-3 steps, the worst thing they could get was a minor bruise and a scare. On the other hand, if they fell off a great height, they could break a bone, become paralyzed, or even die. By allowing them to have a small, short-term pain, they learned an important lesson that would prevent greater harm.
God does the same for us. He seeks our long-term good rather than our short-term comfort. He intentionally puts us through temporary hardship so we can grow in strength, wisdom, and faith to prepare us for eternity. We look at the here and now and wonder why God would allow such awful things to happen to us, but He looks at what will help us grow in faith and likeness to Himself. God is not limited by time, so He does not look at things in the same way we do. He always controls things with an eternal perspective and with complete knowledge of all things throughout eternity. He knows how each and every event or action affects every other. He works out everything according to His very good plan. We just have to reach the point of knowing that everything will work out according to God’s plan and that everything will work out for good. Sometimes God allows us to see the good in this life and other times not till we reach heaven. When we trust Jesus, we don’t have to worry.
Secure in the Storm
On page 150 of Dr. David Jeremiah’s The Unchanging Word of God, he writes:
We are far more secure in the storm with Jesus in our boat than we will ever be on the shore without Him.
Let’s start with this narrative from Luke 8:
Now on one of those days Jesus and His disciples got into a boat, and He said to them, “Let us go over to the other side of the lake.” So they launched out. But as they were sailing along He fell asleep; and a fierce gale of wind descended on the lake, and they began to be swamped and to be in danger. They came to Jesus and woke Him up, saying, “Master, Master, we are perishing!” And He got up and rebuked the wind and the surging waves, and they stopped, and it became calm. And He said to them, “Where is your faith?” They were fearful and amazed, saying to one another, “Who then is this, that He commands even the winds and the water, and they obey Him?” (Luke 8:22-25)
In this event, The disciples are crossing a lake with Jesus in the boat. They have the creator God with them in the boat when a terrible storm rolls in while they are far from shore. Instead of trusting in their friend and God, they cry out in terror. “Master, Master, we are perishing!” Instead of looking for God’s miracles (of which they had seen many), they instantly assumed they were about to die. Did they really need to worry? Of course not. Did they need to be afraid? Not at all. God was in control. Should they have been looking for another miracle? Absolutely Yes.
How often do we fear a financial calamity, lament an illness, mourn a loss, or otherwise have the wrong attitude about things happening around us or to us? For most (all?) of us, I’d guess the answer is “way too often.” If we know how wise, loving, and powerful our God is, we shouldn’t fear, lament, or mourn. We should just trust Him. We should lay our needs before Him and trust His goodness and power will take care of things. We should be actively looking for how God is going to use these hardships.
God is good all of the time. He isn’t being unfair. He isn’t making a mistake. He isn’t being mean. He is working for our good and the good of others. Nothing can happen outside His will.
I know that living out this belief can be difficult when you are in the storm, but trust me. Hard times with Jesus are always better than easy times without Him. Yes, we really can have joy and happiness even in the worst situation when we trust Jesus and join Him in having an eternal perspective.
Trust Jesus.your
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
Find more articles at my Trust Jesus Substack
-
 @ bcbb3e40:a494e501
2024-08-16 18:00:07
@ bcbb3e40:a494e501
2024-08-16 18:00:07El hombre y el contexto
El pensamiento tradicionalista español cuenta con una amplia trayectoria en la que concurren personajes, situaciones e ideas gestadas en el transcurso de dos siglos, en los que debemos distinguir el conflicto dinástico y el papel del legitimismo de la propia doctrina, que es algo que se construirá en el tiempo, con la contribución de figuras como el protagonista de este escrito, Don Juan Vázquez de Mella, así como por la confluencia de fuerzas de diferente signo que tiene lugar a lo largo del siglo XIX y la consolidación del Estado liberal, que lo hará siempre en lucha abierta contra las peculiaridades y el carácter genuino del pueblo español. Vázquez de Mella, nuestro autor, quizás represente la consolidación y madurez doctrinal del movimiento tradicionalista español, uno de sus primeros y más brillantes sistematizadores. No se destacó por una obra extensa ni especialmente difundida más allá de sus discursos, de sus artículos en periódicos y sus escritos dispersos, los cuales fue capaz de dotar de una especial significación y dignidad fruto de su enorme carisma y especial clarividencia para dar una forma definida y meridianamente clara a las ideas y doctrinas que nutrieron el tradicionalismo español madurado al calor de las armas, de las tres guerras que el carlismo libró contra el liberalismo español.
|
 |
|:-:|
|Juan Vázquez de Mella|
|
|:-:|
|Juan Vázquez de Mella|Nuestro autor, de origen asturiano, y nacido en Cangas de Onís un 8 de junio de 1861, ha mantenido vivo su prestigio y el valor de sus aportaciones teórico-doctrinales, ampliamente reconocidos por sus sucesores, por Rafael Gambra Ciudad (1920-2004) y Francisco Elías de Tejada y Espinola (1918-1978), así como de otros autores como Álvaro D'Ors (1915-2004) y otros muchos, que han reivindicado su figura en el tiempo y se han nutrido de sus fecundas enseñanzas. Se ha destacado la rectitud de su pensamiento, su inquebrantable voluntad y su impagable contribución en la creación de un marco teórico y conceptual para dar un sentido y una forma a las ideas del tradicionalismo español. Hijo de un militar de origen gallego, muerto prematuramente, quedó huérfano de padre durante su niñez, por lo cual pasó al cuidado de unos parientes de origen modesto. Estudió en la Universidad de Santiago de Compostela, donde mostró tempranamente su temperamento y habilidades oratorias, que explotó convenientemente a través de diarios como La Restauración o El pensamiento galaico, donde también mostró sus filiaciones militantes con el catolicismo tradicional. Sus habilidades y la brillantez de sus escritos pronto llegaron a Madrid, a las más altas instancias del Carlismo, lo que le permitió dar continuidad a sus actividades desde un medio más amplio, a través de El correo español.
En su militancia política llegó a las más altas cotas de su trayectoria con la elección en 1893 como representante de las Cortes por el distrito de Estella, Navarra, que ya con sus primeros discursos obtuvo un notable éxito, incluso entre los propios liberales, hasta 1900, fecha en la que se vio obligado a marcharse a Portugal, acusado de participar en una conspiración para derrocar el régimen de la Restauración. No regresó a España hasta 1905, manteniendo su estatus como diputado hasta 1919. De todos modos, no queremos dar más protagonismo a la biografía en detrimento de la doctrina, que es lo que nos interesa en este artículo, de ahí que obviemos otros datos biográficos trascendentes, polémicas con otras facciones del carlismo o sus posturas respecto a la dictadura del general Miguel Primo de Rivera, que nos harían desviar la atención del propósito principal que acabamos de enunciar.
La gran paradoja del Carlismo fue que a pesar de su derrota en la Tercera Guerra Carlista (1872-1876), y pese a la posterior escisión integrista en 1888, el partido carlista continuó manteniendo una fuerza y preponderancia significativa en la sociedad española del régimen de la Restauración durante el último cuarto de siglo. El Carlismo se vio inmerso en un buen número de paradojas, de situaciones encontradas, especialmente en relación al Desastre del 98 y la pérdida de los últimos territorios ultramarinos. Mientras que la gran esperanza del tradicionalismo español estaba depositada en el desmoronamiento y caída final de la restauración alfonsina, por otro lado este mismo régimen trataba de defender, al menos en teoría, los últimos restos del imperio español y, de algún modo, a la España católica frente a una nación protestante, como era la anglosajona estadounidense. Al mismo tiempo, durante esta época el tradicionalismo español se enfrentó a los grandes retos que presentaba una sociedad en cambio, con transformaciones políticas y sociales de gran calado como la emergencia del sufragio universal o el nacimiento de los separatismos periféricos (propiciados por la burguesía liberal), las cuales requerían de nuevas estrategias y reestructuraciones internas capaces de enfrentar la envergadura de todos estos cambios. Fue en este contexto donde se significó la figura de Juan Vázquez de Mella, quien merced a la obra de sistematización a la que ya hemos hecho alusión, y de sus concurridas conferencias, dio lugar a la denominada Acta Loredán, redactada por el tradicionalista asturiano y publicado en El correo español. Este escrito tenía como ejes fundamentales la defensa de la nación política española fundamentada en la monarquía, el catolicismo y el régimen foral. Al mismo tiempo, también recogía la reivindicación de un programa corporativista y gremial al abrigo de la doctrina social de la Iglesia defendido en la encíclica Rerum Novarum (1891), y es lo que se conoce como el «sociedalismo», cuyos antecedentes encontramos ya en autores como Donoso Cortés o Antonio Aparisi Guijarro. Son precisamente los atributos de esta doctrina, que contribuyó a la revitalización del pensamiento carlista, los que nos disponemos a desarrollar a continuación.
La figura del tradicionalista asturiano, de Don Juan Vázquez de Mella, aparece como necesaria ante una serie sucesiva de destrucciones que el régimen liberal ha producido sobre los fundamentos tradicionales de España, pero su papel no fue, como ya venimos apuntando, el de un gran intelectual erudito, y de hecho, como apunta Rafael Gambra, las mayores debilidades de su pensamiento se encuentran en los principios filosóficos, y destacando, en cambio, su papel de «revulsivo espiritual» podemos ubicarlo mejor en el ámbito de lo político y lo espiritual. Para ello debió tomar en cuenta las fuentes de sus predecesores, entre los cuales podemos ubicar perfectamente al ya mencionado Donoso Cortés y Jaime Balmes, así como también a otro contemporáneo suyo, Menéndez Pelayo. De los dos primeros tomó su capacidad de síntesis y la sencillez expositiva, mientras que de Menéndez Pelayo tomó, al menos en parte, el sentido de la crítica histórica en aras de la restauración de una Tradición nacional. Pero más allá de los sistemas de pensamiento y elementos retóricos, vemos a Vázquez de Mella profundamente interesado por la vida política de los pueblos medievales de Las Españas, lo cual fue, en definitiva, el marco de referencia para una síntesis política de conjunto más allá de los posicionamientos teóricos, como algo que puede ser llevado a la práctica en sus aspectos concretos y que es perfectamente viable. Todo un sistema edificado sobre el pensamiento tomista y una una profunda religiosidad, En este contexto, y más allá de las ideas formuladas por realistas y carlistas en la primera mitad del siglo XIX, Mella teoriza junto a la concepción del espíritu medieval, la idea de la coexistencia de dos soberanías, una política y otra social, una teoría de la soberanía tradicional inspirada por un principio dinámico y que se cimenta en las propias experiencias humanas en el devenir de la historia.
|
 |
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad, Hipérbola Janus, 2023|
|
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad, Hipérbola Janus, 2023|El concepto de lo social
Lo social para Mella no tiene absolutamente nada que ver con las denominadas «políticas sociales», tan comunes en el lenguaje político de las democracias liberales, en las que se contempla lo social como un elemento externo a la propia estructura política, donde prevalece el individualismo a todos los niveles, y la sociedad aparece como un mero agregado de individuos. Muy al contrario, lo social, en el tradicionalismo de nuestro autor, implica la afirmación de un principio intrínseco tanto al modelo social como al tipo humano, así como a la naturaleza de las cosas en las que la persona desarrolla su existencia en común con los demás. Nos referimos a las instituciones, a los elementos jurídicos y otros órganos gestados en el tiempo por la experiencia histórica, que regulan la vida común.
En el ámbito de la sociedad cristiana medieval, en plena Reconquista, cuando todavía no existía un Estado unitario como tal, cada municipio tenía sus propias leyes y sus normas, adaptadas a su modelo de vida y costumbres, Las comunidades se concebían como agrupaciones de familias con un sistema de propiedad comunal y privado en las que el patrimonio y el estatus de cada uno de sus miembros venía garantizado por el ejercicio activo de una serie de derechos en defensa de las libertades concretas, cuya fuente última era el derecho natural. Los señores feudales y los reyes se limitaban a reclamar tributos para la guerra, pero sin interferir en la defensa de estas libertades concretas ni vulnerar el sistema que las sustentaba.
Eran gobiernos autárquicos, muy estables e inspirados por un principio democrático, el cual nada tenía que ver con las democracias liberales plutocráticas de la actualidad, cuya idea del derecho y la justicia está pervertida por el formalismo jurídico vacío e inane de sus constituciones, abstractas y plenamente funcionales a las oligarquías, al servicio de intereses espurios. En este caso, el hombre alcanzaba una plena dignidad y desarrollo en el contexto de una comunidad donde prevalecía el vínculo comunitario, al amparo de un modelo tradicional, de normas consuetudinarias y concretas que permitían la defensa efectiva del propio derecho. Ni siquiera con el advenimiento de los Estados modernos, y la centralización de algunos elementos de poder, como la Hacienda o el Ejército, se vieron alterados significativamente estos elementos, que representaban a los denominados «cuerpos intermedios» de la sociedad, y que adquirieron su propia expresión particular bajo el nombre de «Fueros», los que los propios reyes juraron respetar a lo largo de toda la Edad Moderna y hasta el advenimiento del régimen borbónico.
La antropología tradicional vincula al hombre a un medio social, a una familia, a una estirpe o a un pueblo, que reproducen esa misma estructura familiar, aunque a mayor escala. En nuestro caso particular lo vemos a través de la convivencia de pequeños grupos humanos, de ahí la importancia de los municipios o de los concejos en un marco de vida comunitaria fuertemente institucionalizada. Al mismo tiempo este modelo y estructura también se replicaba en otros ámbitos, como en la vida económica y profesional, impregnando todas las esferas de la vida del hombre. Instituciones naturales, amparadas en el derecho natural, y orientadas a la protección y garantía de prosperidad de los hombres, y esto por encima de cualquier interés particular y mercantil de negocio. Para Mella, la ruptura con este mundo, y en general con las experiencias del pasado, es la que nos lleva, merced a la acción del liberalismo, a los tiempos actuales, y lo hace recorriendo un itinerario que todos conocemos, y que tienen su punto de partida en la Ilustración y la posterior Revolución Francesa, la irrupción del elemento racional y abstracto y la destrucción de la religión, considerada como fruto de la superstición. La destrucción del orden feudal, que todavía pervivía como marco de convivencia en el mundo rural, como una suerte de prolongación de ese espíritu medieval, hizo desaparecer de un plumazo ese entorno de relaciones concretas y personales para sustituirlas por lo «público» entendido como la centralización estatal uniforme, ignorando las realidades particulares subyacentes en el cuerpo social, los denominados «cuerpos intermedios», que fueron despojados de su autonomía, corporaciones y patrimonios. De modo que la destrucción de estas «sociedades intermedias» que mediaban entre el Estado y la sociedad desenraizó y destruyó la propia sociedad, al mismo tiempo que los fundamentos cristianos del derecho natural sobre la cual se hallaba asentada, para hacer prevalecer esos principios racionales y abstractos traídos por la revolución.
Al mismo tiempo, y anejo a este desarraigo, del individuo se encuentra sometido a poderes arbitrarios del propio Estado liberal, sin un conglomerado institucional propio que lo proteja de estos atropellos, sumido en el individualismo ajeno a toda institución y destino colectivo, se limita al voto cada cuatro años de los partidos al servicio de oligarquías e intereses espurios, contrarios al Bien común. En este sentido, y advirtiendo las posibles acusaciones de «absolutismo» que en ocasiones se han lanzado contra el tradicionalismo, hay que señalar que Mella las rechaza por completo, dado que viola la idea de contrapoderes frente a la autoridad del rey que éste formula, ya que el absolutismo creía en la existencia de un poder ilimitado y tiránico del rey, transmitido por Dios y ajeno a la participación de la sociedad y sus estamentos. Como bien señaló Julius Evola, el absolutismo es un fenómeno antitradicional, vinculado a la descomposición y desacralización de las estructuras tradicionales. De hecho, el absolutismo, como los regímenes liberales de hoy, dejan al individuo totalmente desprotegido, sin un asidero sobre el que apoyarse en la defensa de sus libertades concretas. El propio Mella, como bien saben todos los que se adentren en su obra, fue partidario de contrarrestar el creciente poder del aparato estatal, tal y como hemos visto y seguiremos viendo en lo sucesivo, a lo largo del presente artículo.
|
 |
|:-:|
|EVOLA, Julis; Metapolítica, Tradición y Modernidad: Antología de artículos evolianos, Hipérbola Janus, 2020|
|
|:-:|
|EVOLA, Julis; Metapolítica, Tradición y Modernidad: Antología de artículos evolianos, Hipérbola Janus, 2020|En nuestro caso particular, la desaparición de la organización gremial y corporativa tuvo unas consecuencias especialmente nefastas, y en especial después de las dos desamortizaciones liberales (Mendizabal y Madoz) al despojar a los grupos sociales populares de su natural organización sociohistórica. Asimismo, desvincularon la propiedad en las relaciones comunitarias y su uso patrimonial para vincularla al uso privado y anónimo, para fines puramente especulativos, los que caracterizan al liberal-capitalismo. De ahí nace la figura del asalariado, del contratado como mera mercancía, en un proceso de alienación del trabajo característico en el desarrollo del capitalismo burgués. De aquí parte lo que algunos tradicionalistas, como Gambra, denominan el «problema social», frente al cual, y al margen de las recetas ideológicas de la modernidad, Mella reivindica la restauración de los antiguos vínculos corporativos y orgánicos de inspiración medieval.
La idea de soberanía social
Todos los procesos disolutivos que conducen a la Modernidad liberal tienen su punto de inicio con el Renacimiento, con la afirmación del individualismo y la ruptura definitiva del ecumene cristiano medieval, algo que aparece indefectiblemente unido a la Reforma luterana, así como la «valorización» del mundo clásico, con la reemergencia de teorías de tipo hedonista, como las de Epicuro, por ejemplo, generando una disolución de los vínculos con el medio concreto. Esto supone la aparición de un nuevo tipo, que es el hombre abstracto que escapa cada vez más al entorno inmediato y vital, esto al tiempo que el poder del Estado se robustece y se vuelve omnipotente. Es por ese motivo que en lo sucesivo se ha impuesto en nuestras sociedades la falta de concreción, tanto en lo teórico como en lo político, lo cual ha propiciado el triunfo del contrato social roussoniano y la justificación del orden social en virtud de componendas voluntarias y totalmente artificiales. Estas construcciones político-ideológicas son las que contribuyen a la construcción de la sociedad liberal, asentada sobre patrones puramente racionales, individualistas y mercantilistas.
De hecho, la mayor preocupación de Mella es la destrucción de las instituciones locales y ese vínculo afectivo del hombre con su realidad inmediata, algo que impregnaba su relación con el trabajo, con su obra, con su impronta vocacional y devota, imprimiéndole, como en el caso del artesano, un sello propio y particular a su trabajo.
Y en este sentido, Mella afirma que la sociedad moderna ha perdido su sentido institucional como base estable de la sociabilidad. A través del elemento jurídico y la participación en las instituciones es el medio a partir del cual la comunidad se cohesiona y construye sus vínculos y su particular autonomía, que le hace tener una vida propia e interna, y con la institución nos podemos referir desde una asociación profesional, a la universidad o una cofradía etc. El individualismo ha representado el factor disolutivo y corrosivo que ha destruido este vínculo social fundado en múltiples solidaridades que han enfrentado y polarizado al cuerpo social, con el enfrentamiento entre «clases sociales» y la negación de las jerarquías naturales.
Ante todo lo relatado, y como consecuencia de las destrucciones provocadas por la revolución, Mella plantea su teoría de la soberanía social. Esta teoría consiste básicamente en encuadrar de nuevo a la sociedad en sus raíces naturales, concebida en todos sus órdenes como portadora de un dinamismo propio en una suerte de organización geométrica en la que conviven objetivos y finalidades variadas y concretas con su propia legitimidad y autonomía. Estas finalidades, amparadas en el derecho natural, son junto al poder del propio Estado las únicas formas de limitación del poder. La particularidad de esta idea de soberanía social está en el hecho de que la formación de la jerarquía social tiene una dirección ascendente, que tiene como punto de partida a las personas colectivas y concretas, pasando por una serie de instituciones, hasta llegar al Estado central, de forma escalonada y plenamente conscientes de sus funciones. Así lo expresa Mella en su propio lenguaje: «la jerarquía de personas colectivas, de poderes organizados, de clases, que suben desde la familia hasta la soberanía que llamo política concretada en el Estado, que deben auxiliar, pero también contener». Es lo que Mella concibe como el sociedalismo, que supone la reintegración de la sociedad en la vida concreta de los hombres, con el desarrollo de una vida política común y estable en el marco de instituciones naturales que potencien las relaciones humanas y sociales, estimulando la sociabilidad. Y hablamos, desde la perspectiva de la integración de distintas sociedades, fuertemente institucionalizadas con funciones y finalidades concretas, más allá del sentido democrático y pactista que pueda entenderse en términos modernos o de cualquier asociación u organización relacionada con el «problema social».
¿Qué es la Tradición?
De este modo quedan formuladas las dos soberanías, la política y la social, que coexisten en un mismo espacio limitándose y apoyándose recíprocamente en lo que es uno de los fundamentos del sociedalismo de Mella. No obstante, esta doble soberanía no explica todavía la concreción política de cada pueblo y el vínculo superior que lo lleva a federarse con las diferentes sociedades y a mantenerse unido en una historia y espíritu comunes. Los vínculos que las mantienen unidas en el tiempo tienen que ver con un orden histórico concreto, con un vínculo espiritual que las entrelaza interiormente de una generación a otra, y en última instancia de ese orden tradicional que lo engloba todo, y que al mismo tiempo se asienta en la monarquía y la religión católica. La lealtad a Dios y a un solo rey en torno a los cuales se aglutina la fe, viene a coronar todas estas estructuras y lazos forjados en el fermento de la historia.
No se trata de la Tradición en términos de un «ultraconservadurismo», que ya sabemos que el prefijo «ultra» (lo que sea) es muy recurrente en nuestros días, con la idea de un medio social y político petrificado e invariable, sino que es el producto de un proceso de maduración y evolución histórica, de carácter dinámico y nutrido de experiencias humanas. Nada que ver con las monstruosas ideologías progresistas y modernas, nacidas de lo abstracto e impulsadas por un desbocado «ir hacia delante», desarraigado y que tiende siempre hacia la deshumanización y la destrucción de toda creación humana natural forjada en el devenir de los siglos. Este mismo dinamismo, planteado por Mella, en torno al concepto e idea de Tradición tiene continuidad y adquiere fuerza en sus sucesores y depositarios. Y al fin y al cabo, Mella no hace más que partir de la propia etimología del término, que viene del latín tradere, entregar, de la generación que entrega los frutos de su experiencia a la siguiente, perfeccionándola, haciéndola más estable y segura.
Podríamos seguir extrayendo más conclusiones del pensamiento tradicional de Vázquez de Mella, pero probablemente excedería, y por mucho, el modesto propósito de este escrito, de modo que nos quedaremos aquí, no sin advertir a nuestros lectores de la posibilidad de que en un futuro volvamos a retomar nuevamente el tema.
Antes de acabar queremos llamar la atención sobre una polémica acontecida hace unos años en torno a una Plaza en Madrid que llevaba el nombre de nuestro autor y que se cambio para dedicársela a un sujeto cuyos méritos eran, por decirlo suavemente, más que discutibles, concretamente a Pedro Zerolo, miembro del PSOE y activista al servicio del lobby homosexualista. Durante aquella época, en 2019, muchos miembros de la izquierda globalista trataron de identificar a Vázquez de Mella como un «pensador franquista», cuando en realidad ni cronológica ni ideológicamente tuvo nunca nada que ver con el franquismo. Recordemos que murió en 1928, y la impronta de su pensamiento ha tenido como continuadores a sus propios correligionarios dentro del ámbito tradicional, aunque en su tiempo llegó a ser muy respetado también por sus adversarios, los liberales. Aunque la retirada del nombre de una calle pueda resultar algo banal, o carente de una importancia excesiva, también contribuye, a su modo, a una forma de damnatio memoriae que condena al olvido y al ostracismo a grandes autores de la Tradición, portadores de un Patriotismo sano y capaz de entender las peculiaridades y el Dasein profundo de España, que si bien no nació invertebrada, como pretendían los Orteguianos, su esencia y naturaleza es mucho más compleja que cualquiera de las grandes naciones de Europa.
Artículo original: Hipérbola Janus, Juan Vázquez de Mella y el tradicionalismo español, 16/Ago/2024
-
 @ 8cb60e21:5f2deaea
2024-08-18 20:42:25
@ 8cb60e21:5f2deaea
2024-08-18 20:42:25```js import { getCourseById, updateCourse, deleteCourse } from "@/db/models/courseModels";
export default async function handler(req, res) { const { slug } = req.query;
if (req.method === 'GET') { try { const course = await getCourseById(slug); if (course) { res.status(200).json(course); } else { res.status(404).json({ error: 'Course not found' }); } } catch (error) { res.status(500).json({ error: error.message }); } } else if (req.method === 'PUT') { try { const course = await updateCourse(slug, req.body); res.status(200).json(course); } catch (error) { res.status(400).json({ error: error.message }); } } else if (req.method === 'DELETE') { try { await deleteCourse(slug); res.status(204).end(); } catch (error) { res.status(500).json({ error: error.message }); } } else { // Handle any other HTTP method res.setHeader('Allow', ['GET', 'PUT', 'DELETE']); res.status(405).end(
Method ${req.method} Not Allowed); } } ``` -
 @ 5afdec5b:2d631be1
2024-08-14 09:42:29
@ 5afdec5b:2d631be1
2024-08-14 09:42:29Introducing Our New Whitepaper on Escrow-Less Bitcoin-Collateralized Lending
We are thrilled to release our latest whitepaper, elaborating on our innovative Escrow-Less Bitcoin-Collateralized Lending protocol. This pioneering system leverages the power of Discreet Log Contracts (DLCs) and Hash Time Lock Contracts (HTLCs) to create a trustless, peer-to-peer lending environment that aligns with the ethos of decentralization and user empowerment.
Empowering Users with Our Architecture
Our protocol is meticulously designed to empower users by allowing them to borrow against their Bitcoin while retaining full control over it. We believe that this is not just a technological advancement, but a crucial step towards crafting a more decentralized, trust-minimized, and secure financial ecosystem. By eliminating the need for intermediaries, we aim to give users greater autonomy and flexibility, freeing them from traditional constraints.
Addressing Market Needs for Peer-to-Peer, Trustless Lending
Extensive market research highlights a significant, growing demand for peer-to-peer, trustless lending solutions. Users consistently expressed a desire for more control over their assets and greater flexibility in their lending options. Our Escrow-Less Lending protocol directly addresses these needs, providing a robust framework that enhances user control while maintaining the integrity and security of the lending process.
Exploring the Potential of Ark for Microloan Liquidity Management
Initially, our focus was predominantly on micro-loans. However, user interviews revealed a relatively limited demand for such products at this time. Nonetheless, we identified Ark as good solution in the context of Bitcoin microloans. Ark's capabilities could unlock new possibilities and efficiencies, making microloans more viable and attractive.
Remaining Flexible and Adaptable
Even as our primary focus shifts, the potential of Ark continues to intrigue us. Our protocol's design is inherently flexible and adaptable, allowing for continuous refinement and adjustments based on user interest and feedback. Should there be sufficient interest in the future, we are open and ready to explore Ark's integration once again to better serve our users’ needs.
Revolutionizing Bitcoin Borrowing and Lending
We firmly believe that our Escrow-Less Bitcoin-Collateralized Lending protocol has the potential to revolutionize the borrowing and lending landscape within the Bitcoin ecosystem. Our commitment is steadfast; we aim to make this innovative protocol a reality and will diligently work to iterate and improve based on user feedback. Together, let’s shape the future of decentralized lending.
Your Feedback Matters
We invite you to delve into our whitepaper and share your thoughts and feedback on this groundbreaking approach. Your insights are invaluable as we strive to create a more user-centric, flexible, and secure lending protocol. Read the full whitepaper here
Feel free to reach out with your thoughts, questions, or suggestions. We’re eager to engage with you and iterate based on your valuable input.
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 8cb60e21:5f2deaea
2024-08-18 19:04:49
@ 8cb60e21:5f2deaea
2024-08-18 19:04:49 -
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 06830f6c:34da40c5
2024-08-11 20:13:46
@ 06830f6c:34da40c5
2024-08-11 20:13:46On August 10, 2024, the vibrant Sarit Expo was alive with energy as Bitcoin Dada celebrated the graduation of its seventh cohort. This momentous event, dedicated to advancing the understanding and application of cryptocurrency, showcased the dynamism and innovation of the Bitcoin Dada community.
 The evening began with the MC engaging the audience in a series of lively questions. “What is Bitcoin? Explain it to me like I’m five,” was one such question that underscored the diverse range of understanding in the room. While some answers were complex, others offered simpler explanations, highlighting the challenge of conveying intricate concepts.
The evening began with the MC engaging the audience in a series of lively questions. “What is Bitcoin? Explain it to me like I’m five,” was one such question that underscored the diverse range of understanding in the room. While some answers were complex, others offered simpler explanations, highlighting the challenge of conveying intricate concepts.

As the MC continued, participants were asked for their impressions of the event space and suggestions for improvement. Comments ranged from critiques of overly bright lighting to discussions about the relevance of Bitcoin. One participant proposed an intriguing app idea that combined Eventbrite and WhatsApp, reflecting the innovative spirit of the audience.
The highlight of the evening was the inspiring opening speech by the CEO of Bitcoin Dada.
 She addressed the marginalization of women in tech, celebrating Bitcoin Dada’s commitment to inclusivity and support. She introduced her team
She addressed the marginalization of women in tech, celebrating Bitcoin Dada’s commitment to inclusivity and support. She introduced her team 
each member contributing uniquely: Edith, the community lead from Uganda; Sabina, the recruiter who found a sense of belonging; and Memelord, the project manager with a flair for comedy.

The ideathon segment was particularly thrilling. Debra’s third-place pitch proposed a Bitcoin-powered marketplace aimed at reducing youth unemployment by showcasing skills. Shantelle’s second-place idea focused on using Bitcoin to address global issues, such as helping refugees find safe zones with GPS technology. The top prize went to Meg, with her solution promising a significant impact—though the specifics were left as a tantalizing cliffhanger. 🌟🏆
PS : Sabina also gave a preview of the #tando app tha you can check out here on my youtube channel Link HERE
Meeting Inspiring Figures and Making Connections 📸
Throughout the event, I had the pleasure of meeting some remarkable individuals who are deeply involved in the Bitcoin community.
First, I met Felix from TheCore, a key panelist in the discussion on the financial revolution amidst economic unrest. We took a photo together, capturing a moment of shared enthusiasm for the potential of Bitcoin.

Later, I connected with a Bitcoin Dada and gamer who is actively involved with Thndr Games, Mary Imasuen. We took a photo showcasing our shared passion for Bitcoin and gaming.

I also had the chance to meet a Bitcoin enthusiast named Hope and she was adorned in Bitcoin-themed merchandise. We snapped a photo together, celebrating our mutual enthusiasm for Bitcoin and its future.

Panel Discussions: Insightful Exchanges and Thoughtful Dialogues
The panel discussion titled “Financial Revolution Amidst Economic Unrest” featured Felix from TheCore, Jason, a Bitcoin Dada supporter, and Bill, a lawyer with expertise in Bitcoin. They delved into the major challenges Kenyans face in adopting Bitcoin, emphasizing the importance of education and community support. They discussed the solid foundation of Bitcoin’s base layer and the need for further development in subsequent layers to enhance its functionality.

The discussion also touched on Kenya’s future in the Bitcoin space. Bill suggested integrating Bitcoin with fiat transactions and stock exchanges, while Jason highlighted the government's welcoming stance and the need for energy to support Bitcoin. Felix proposed making Bitcoin legal tender and finding sustainable energy sources to bolster its use. ⚖️🌍

Audience questions added further depth to the conversation. One attendee asked about using Bitcoin to offset government debt, while another inquired about measures for improving public education on Bitcoin. The responses stressed the need for comprehensive educational initiatives. When asked about alternative cryptocurrencies, the panel firmly rejected the idea of “shitcoins,” focusing instead on the value of Bitcoin. 🚫💸
The second panel discussion, moderated by Sharon from ₿-Trust, explored personal experiences with Bitcoin Dada. Panelists Anon, Vera, and Caroline shared how the program impacted their perspectives.

- Anon discovered a niche and a supportive community, emphasizing Bitcoin’s role as “lightning-fast internet money,” especially with Layer 2 advancements. 🌐⚡
- Vera found Bitcoin to be a valuable medium of exchange, advocated against other cryptocurrencies as “shitcoins,” and highlighted opportunities for women. 💪💰
- Caroline expanded her knowledge and aimed to educate others, describing Bitcoin as a store of value and emphasizing the importance of combating inflation through education. 📚🔍

The panelists also discussed opportunities for Bitcoin in their communities: - Anon saw potential for learning and growth through knowledge-sharing. - Vera mentioned BitSacco, a solution for saving in Bitcoin, and other upcoming projects like Sabina’s Tando app. - Caroline stressed the importance of education to counteract misconceptions about Bitcoin and its benefits. 🏡📈
In their closing remarks, the panelists shared their future aspirations: - Anon aimed to become a developer impacted by Bitcoin. - Vera planned to engage with the community and learn from others. - Caroline focused on educating the community to dispel myths about Bitcoin. 🌟👩💻
The event concluded with a warm dinner where attendees mingled, exchanged ideas, and enjoyed a meal together. WATCH https://video.nostr.build/4d0fbc2dd6ae0c20e0d45aa071a9e88000a9544f4289414900c91134d13960da.mp4
The Bitcoin Dada Cohort 7 graduation was more than just a celebration of individual achievements; it was a testament to the collective potential of the Bitcoin community.
As the event wrapped up, the atmosphere was charged with optimism and a shared commitment to advancing bitcoin technology. The graduating cohort left with new skills, fresh ideas, and a network of like-minded individuals, ready to make a significant impact on the future of Bitcoin. 🌍💡 #kenya #bitbiashara #kenya
-
 @ 8cb60e21:5f2deaea
2024-08-18 19:04:33
@ 8cb60e21:5f2deaea
2024-08-18 19:04:33```js import { createCourseDraft } from '@/db/models/courseDraftModels';
export default async function handler(req, res) { if (req.method === 'POST') { try { const { userId, title, summary, image, price, topics, resources, drafts } = req.body;
const courseDraft = await createCourseDraft({ userId, title, summary, image, price, topics, resources: { connect: resources.map(id => ({ id })) }, drafts: { connect: drafts.map(id => ({ id })) } }); res.status(201).json(courseDraft); } catch (error) { res.status(500).json({ error: 'Failed to create course draft' }); } } else { res.setHeader('Allow', ['POST']); res.status(405).end(`Method ${req.method} Not Allowed`); }} ```
-
 @ 41fa852b:af7b7706
2024-08-18 18:25:54
@ 41fa852b:af7b7706
2024-08-18 18:25:54“Bitcoin is the train that is coming. You can either be on the train or on the tracks. —Andreas M. Antonopoulos
Welcome aboard, folks! Please take your seats as we embark on our tour of the UK Bitcoin scene. 🚂
This scenic journey will take us through nine meetups, from Glasgow all the way down to Penzance. Along the way, we’ll stop at six new Bitcoin-accepting merchants, offering everything from fish and chips to music lessons.
Tickets are free as always—just make sure to share the newsletter with your fellow Bitcoiners.
All aboard! Mind the gap, and let’s roll…
Upcoming Bitcoin Meetups
Happening this week...
- Newcastle upon Tyne Bitcoin Meetup: The next Newcastle meetup is on Tuesday 20th August at The Ware Rooms Bar. 6:30 PM. This month is a Seedsigner special, learn how to build your very own low-cost hardware wallet/signing device. ✍🏼
- Cyphermunk House: Join the London Cyphermunk House group for a session on 'Sovereign Computing', on Tuesday at 6:30 PM. They have a live demonstration of how to use Start9 Labs software and a discussion about the future of the internet. 👨🏻💻
- Canterbury Bitcoin: Meeting this month at The Parrot, 1-9 Church Lane, Canterbury, CT1 2AG at 7 PM on Tuesday the 20th. An informal meetup to discuss Bitcoin and chat. 🦜
- Bitcoin Glasgow: Bitcoin Glasgow meet every 3rd Wednesday of the month and this month will be at The Maltman, 59-61 Renfield Street at 6 PM to 8 PM. 🏴
- Bitcoin Bristol: August's Bitcoin Bristol Social is at Canteen, Hamilton House, Stokes Croft from 6.15pm on Weds 21st. Support local & enjoy a balmy summer evening with some Bristol Bitcoiners. ☀️
- Shropshire Bitcoin**: On the 21st, the Shropshire crew will meet at the Admiral Benbow in Shrewsbury. You'll find them at 7 PM, all welcome. 🍻
- Penzance Bitcoin: Will be at The Dolphin Tavern on Quay Street on Thursday 22nd at 8 PM. They'll be meeting in the 'little room' at table 21. Everyone is welcome from beginners to OG's. 🍻
- Bitcoin Walk - Edinburgh**: Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🏻🚶🏻♀️🚶♂️
- Real Bedford - Home Game: Peter MacCormack's boys are at home this Saturday, the 24th playing North Leigh. Join them for a 3 pm kickoff. ⚽️
New Businesses Accepting Bitcoin
It’s a huge week for merchant onboarding, with 6 new businesses to report across the country.
- The Mining Shop: The Mining Shop UK began with a passion for Bitcoin and has grown into a community of Bitcoin enthusiasts, IT professionals, and traders. They aim to make mining accessible to all, led by passionate Bitcoiners. A great selection of mining equipment can be purchased with bitcoin. Great work by the Newcastle meetup for spotting this one. ⛏️🖥️
- Nemo Cafe: Nemo Cafe at Hampton railway station serves great coffee, ice creams and a range of refreshing drinks, plus a small selection of edible treats; and they now accept bitcoin and Lightning Network payments! Well done to Rob for onboarding these guys.⚡️☕️🥐🍦
- The Lone Fisherman The Lone Fisherman in Tooting Market serves authentic fresh Caribbean dishes, salt fish fritters, jerk chicken and more. They now accept bitcoin and Lightning Network payments!⚡️🇯🇲
- Gav's Fish & Chips: The UK’s most southwesterly business that accepts bitcoin and Lightning Network payments! Gav’s on the Isles of Scilly for fresh-caught fish, lobster scampi and more! Shout-out to OPD for another business onboarded.🐟
- Lynsey Clarke Music: Looking for piano or singing lesson in Scotland? Thanks to Zaprite, Lynsey Clarke now accepts bitcoin & Lightning Network payments! 🎹🎤
- Blue Fox Homes: Looking for an AirBnB in Worcestershire? Check out Blue Fox Homes in Pershore, a modern, spacious 3 bedroom house that sleeps 5; they now accept bitcoin and Lightning payments with a 10% DISCOUNT!!⚡️
Upcoming Special Events
These events aren’t happening next week, but they’re important to add to your calendar now as tickets are selling fast.
- Bitcoin - The change you've been waiting for: Mark your calendars for August 31 at 10:30 am for "The Change You’ve Been Waiting For" at Glasgow University Union. This seminar, costing £10, focuses on Bitcoin's transformative potential. With Bitcoin impacting individuals and businesses globally, understanding it is crucial. Guest speaker Allen Farrington will share his expertise, making this event perfect for both seasoned investors and the Bitcoin-curious. Don't miss this opportunity to explore how Bitcoin can shape your financial future.
- Bitcoin Whitepaper Party: Celebrate Bitcoin’s 16th birthday on Bitcoin Whitepaper Day at the Dockside Vaults this Halloween. Currently, you can buy two tickets for £25 as an early bird deal, the regular price is £21.40 for a single ticket. Enjoy a performance by Roger9000 and DJ sets from MadMunky, itsTOMEKK, and ZAZAWOWOW. The party kicks off at 19:30. Bitcoin is accepted at the venue, and you can also pay for tickets with Bitcoin here.
Get Involved
- Volunteer Opportunities: Bridge2Bitcoin is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on Twitter or through our website.
- Start Your Own Meetup: Interested in launching a Bitcoin meetup? We’re here to support you every step of the way. We’ve assisted numerous UK Bitcoin meetups in getting started. Get in touch via Twitter.
- Telegram users: You might find our Telegram Channel another useful way to keep up-to-date with UK meetups.
- Feedback and Suggestions: We value your input! Share your ideas on how we can enhance this newsletter.
Products I Endorse
Laser Eyes Cards: Bolt Cards with laser eyes. Worldwide shipping. Visit lasereyes.cards/buy-now.
Get out and support the meetups where you can, visit Bitcoin Events UK for more info on each meetup and to find your closest on the interactive map.
Stay tuned for more updates next week!
Simon.
-
 @ 9d51218e:a0c80d65
2024-08-18 18:13:42
@ 9d51218e:a0c80d65
2024-08-18 18:13:42Full story Covid and Monkeypox - What an amazing coincidence in Germany It turns out that the new pandemic (Monkeypox) begins in an absolutely identical way, just like the old one pandemic - the covid.
-
 @ e6ce6154:275e3444
2023-07-27 14:12:49
@ e6ce6154:275e3444
2023-07-27 14:12:49Este artigo foi censurado pelo estado e fomos obrigados a deletá-lo após ameaça de homens armados virem nos visitar e agredir nossa vida e propriedade.
Isto é mais uma prova que os autoproclamados antirracistas são piores que os racistas.
https://rothbardbrasil.com/pelo-direito-de-ser-racista-fascista-machista-e-homofobico
Segue artigo na íntegra. 👇
Sem dúvida, a escalada autoritária do totalitarismo cultural progressista nos últimos anos tem sido sumariamente deletéria e prejudicial para a liberdade de expressão. Como seria de se esperar, a cada dia que passa o autoritarismo progressista continua a se expandir de maneira irrefreável, prejudicando a liberdade dos indivíduos de formas cada vez mais deploráveis e contundentes.
Com a ascensão da tirania politicamente correta e sua invasão a todos os terrenos culturais, o autoritarismo progressista foi se alastrando e consolidando sua hegemonia em determinados segmentos. Com a eventual eclosão e a expansão da opressiva e despótica cultura do cancelamento — uma progênie inevitável do totalitarismo progressista —, todas as pessoas que manifestam opiniões, crenças ou posicionamentos que não estão alinhados com as pautas universitárias da moda tornam-se um alvo.
Há algumas semanas, vimos a enorme repercussão causada pelo caso envolvendo o jogador profissional de vôlei Maurício Sousa, que foi cancelado pelo simples fato de ter emitido sua opinião pessoal sobre um personagem de história em quadrinhos, Jon Kent, o novo Superman, que é bissexual. Maurício Sousa reprovou a conduta sexual do personagem, o que é um direito pessoal inalienável que ele tem. Ele não é obrigado a gostar ou aprovar a bissexualidade. Como qualquer pessoa, ele tem o direito pleno de criticar tudo aquilo que ele não gosta. No entanto, pelo simples fato de emitir a sua opinião pessoal, Maurício Sousa foi acusado de homofobia e teve seu contrato rescindido, sendo desligado do Minas Tênis Clube.
Lamentavelmente, Maurício Sousa não foi o primeiro e nem será o último indivíduo a sofrer com a opressiva e autoritária cultura do cancelamento. Como uma tirania cultural que está em plena ascensão e usufrui de um amplo apoio do establishment, essa nova forma de totalitarismo cultural colorido e festivo está se impondo de formas e maneiras bastante contundentes em praticamente todas as esferas da sociedade contemporânea. Sua intenção é relegar ao ostracismo todos aqueles que não se curvam ao totalitarismo progressista, criminalizando opiniões e crenças que divergem do culto à libertinagem hedonista pós-moderna. Oculto por trás de todo esse ativismo autoritário, o que temos de fato é uma profunda hostilidade por padrões morais tradicionalistas, cristãos e conservadores.
No entanto, é fundamental entendermos uma questão imperativa, que explica em partes o conflito aqui criado — todos os progressistas contemporâneos são crias oriundas do direito positivo. Por essa razão, eles jamais entenderão de forma pragmática e objetiva conceitos como criminalidade, direitos de propriedade, agressão e liberdade de expressão pela perspectiva do jusnaturalismo, que é manifestamente o direito em seu estado mais puro, correto, ético e equilibrado.
Pela ótica jusnaturalista, uma opinião é uma opinião. Ponto final. E absolutamente ninguém deve ser preso, cancelado, sabotado ou boicotado por expressar uma opinião particular sobre qualquer assunto. Palavras não agridem ninguém, portanto jamais poderiam ser consideradas um crime em si. Apenas deveriam ser tipificados como crimes agressões de caráter objetivo, como roubo, sequestro, fraude, extorsão, estupro e infrações similares, que representam uma ameaça direta à integridade física da vítima, ou que busquem subtrair alguma posse empregando a violência.
Infelizmente, a geração floquinho de neve — terrivelmente histérica, egocêntrica e sensível — fica profundamente ofendida e consternada sempre que alguém defende posicionamentos contrários à religião progressista. Por essa razão, os guerreiros da justiça social sinceramente acreditam que o papai-estado deve censurar todas as opiniões que eles não gostam de ouvir, assim como deve também criar leis para encarcerar todos aqueles que falam ou escrevem coisas que desagradam a militância.
Como a geração floquinho de neve foi criada para acreditar que todas as suas vontades pessoais e disposições ideológicas devem ser sumariamente atendidas pelo papai-estado, eles embarcaram em uma cruzada moral que pretende erradicar todas as coisas que são ofensivas à ideologia progressista; só assim eles poderão deflagrar na Terra o seu tão sonhado paraíso hedonista e igualitário, de inimaginável esplendor e felicidade.
Em virtude do seu comportamento intrinsecamente despótico, autoritário e egocêntrico, acaba sendo inevitável que militantes progressistas problematizem tudo aquilo que os desagrada.
Como são criaturas inúteis destituídas de ocupação real e verdadeiro sentido na vida, sendo oprimidas unicamente na sua própria imaginação, militantes progressistas precisam constantemente inventar novos vilões para serem combatidos.
Partindo dessa perspectiva, é natural para a militância que absolutamente tudo que exista no mundo e que não se enquadra com as regras autoritárias e restritivas da religião progressista seja encarado como um problema. Para a geração floquinho de neve, o capitalismo é um problema. O fascismo é um problema. A iniciativa privada é um problema. O homem branco, tradicionalista, conservador e heterossexual é um problema. A desigualdade é um problema. A liberdade é um problema. Monteiro Lobato é um problema (sim, até mesmo o renomado ícone da literatura brasileira, autor — entre outros títulos — de Urupês, foi vítima da cultura do cancelamento, acusado de ser racista e eugenista).
Para a esquerda, praticamente tudo é um problema. Na mentalidade da militância progressista, tudo é motivo para reclamação. Foi em função desse comportamento histérico, histriônico e infantil que o famoso pensador conservador-libertário americano P. J. O’Rourke afirmou que “o esquerdismo é uma filosofia de pirralhos chorões”. O que é uma verdade absoluta e irrefutável em todos os sentidos.
De fato, todas as filosofias de esquerda de forma geral são idealizações utópicas e infantis de um mundo perfeito. Enquanto o mundo não se transformar naquela colorida e vibrante utopia que é apresentada pela cartilha socialista padrão, militantes continuarão a reclamar contra tudo o que existe no mundo de forma agressiva, visceral e beligerante. Evidentemente, eles não vão fazer absolutamente nada de positivo ou construtivo para que o mundo se transforme no gracioso paraíso que eles tanto desejam ver consolidado, mas eles continuarão a berrar e vociferar muito em sua busca incessante pela utopia, marcando presença em passeatas inúteis ou combatendo o fascismo imaginário nas redes sociais.
Sem dúvida, estamos muito perto de ver leis absurdas e estúpidas sendo implementadas, para agradar a militância da terra colorida do assistencialismo eterno onde nada é escasso e tudo cai do céu. Em breve, você não poderá usar calças pretas, pois elas serão consideradas peças de vestuário excessivamente heterossexuais. Apenas calças amarelas ou coloridas serão permitidas. Você também terá que tingir de cor-de-rosa uma mecha do seu cabelo; pois preservar o seu cabelo na sua cor natural é heteronormativo demais da sua parte, sendo portanto um componente demasiadamente opressor da sociedade.
Você também não poderá ver filmes de guerra ou de ação, apenas comédias românticas, pois certos gêneros de filmes exaltam a violência do patriarcado e isso impede o mundo de se tornar uma graciosa festa colorida de fraternidades universitárias ungidas por pôneis resplandecentes, hedonismo infinito, vadiagem universitária e autogratificação psicodélica, que certamente são elementos indispensáveis para se produzir o paraíso na Terra.
Sabemos perfeitamente, no entanto, que dentre as atitudes “opressivas” que a militância progressista mais se empenha em combater, estão o racismo, o fascismo, o machismo e a homofobia. No entanto, é fundamental entender que ser racista, fascista, machista ou homofóbico não são crimes em si. Na prática, todos esses elementos são apenas traços de personalidade; e eles não podem ser pura e simplesmente criminalizados porque ideólogos e militantes progressistas iluminados não gostam deles.
Tanto pela ética quanto pela ótica jusnaturalista, é facilmente compreensível entender que esses traços de personalidade não podem ser criminalizados ou proibidos simplesmente porque integrantes de uma ideologia não tem nenhuma apreciação ou simpatia por eles. Da mesma forma, nenhum desses traços de personalidade representa em si um perigo para a sociedade, pelo simples fato de existir. Por incrível que pareça, até mesmo o machismo, o racismo, o fascismo e a homofobia merecem a devida apologia.
Mas vamos analisar cada um desses tópicos separadamente para entender isso melhor.
Racismo
Quando falamos no Japão, normalmente não fazemos nenhuma associação da sociedade japonesa com o racismo. No entanto, é incontestável o fato de que a sociedade japonesa pode ser considerada uma das sociedades mais racistas do mundo. E a verdade é que não há absolutamente nada de errado com isso.
Aproximadamente 97% da população do Japão é nativa; apenas 3% do componente populacional é constituído por estrangeiros (a população do Japão é estimada em aproximadamente 126 milhões de habitantes). Isso faz a sociedade japonesa ser uma das mais homogêneas do mundo. As autoridades japonesas reconhecidamente dificultam processos de seleção e aplicação a estrangeiros que desejam se tornar residentes. E a maioria dos japoneses aprova essa decisão.
Diversos estabelecimentos comerciais como hotéis, bares e restaurantes por todo o país tem placas na entrada que dizem “somente para japoneses” e a maioria destes estabelecimentos se recusa ostensivamente a atender ou aceitar clientes estrangeiros, não importa quão ricos ou abastados sejam.
Na Terra do Sol Nascente, a hostilidade e a desconfiança natural para com estrangeiros é tão grande que até mesmo indivíduos que nascem em algum outro país, mas são filhos de pais japoneses, não são considerados cidadãos plenamente japoneses.
Se estes indivíduos decidem sair do seu país de origem para se estabelecer no Japão — mesmo tendo descendência nipônica legítima e inquestionável —, eles enfrentarão uma discriminação social considerável, especialmente se não dominarem o idioma japonês de forma impecável. Esse fato mostra que a discriminação é uma parte tão indissociável quanto elementar da sociedade japonesa, e ela está tão profundamente arraigada à cultura nipônica que é praticamente impossível alterá-la ou atenuá-la por qualquer motivo.
A verdade é que — quando falamos de um país como o Japão — nem todos os discursos politicamente corretos do mundo, nem a histeria progressista ocidental mais inflamada poderão algum dia modificar, extirpar ou sequer atenuar o componente racista da cultura nipônica. E isso é consequência de uma questão tão simples quanto primordial: discriminar faz parte da natureza humana, sendo tanto um direito individual quanto um elemento cultural inerente à muitas nações do mundo. Os japoneses não tem problema algum em admitir ou institucionalizar o seu preconceito, justamente pelo fato de que a ideologia politicamente correta não tem no oriente a força e a presença que tem no ocidente.
E é fundamental enfatizar que, sendo de natureza pacífica — ou seja, não violando nem agredindo terceiros —, a discriminação é um recurso natural dos seres humanos, que está diretamente associada a questões como familiaridade e segurança.
Absolutamente ninguém deve ser forçado a apreciar ou integrar-se a raças, etnias, pessoas ou tribos que não lhe transmitem sentimentos de segurança ou familiaridade. Integração forçada é o verdadeiro crime, e isso diversos países europeus — principalmente os escandinavos (países que lideram o ranking de submissão à ideologia politicamente correta) — aprenderam da pior forma possível.
A integração forçada com imigrantes islâmicos resultou em ondas de assassinato, estupro e violência inimagináveis para diversos países europeus, até então civilizados, que a imprensa ocidental politicamente correta e a militância progressista estão permanentemente tentando esconder, porque não desejam que o ocidente descubra como a agenda “humanitária” de integração forçada dos povos muçulmanos em países do Velho Mundo resultou em algumas das piores chacinas e tragédias na história recente da Europa.
Ou seja, ao discriminarem estrangeiros, os japoneses estão apenas se protegendo e lutando para preservar sua nação como um ambiente cultural, étnico e social que lhe é seguro e familiar, assim se opondo a mudanças bruscas, indesejadas e antinaturais, que poderiam comprometer a estabilidade social do país.
A discriminação — sendo de natureza pacífica —, é benévola, salutar e indubitavelmente ajuda a manter a estabilidade social da comunidade. Toda e qualquer forma de integração forçada deve ser repudiada com veemência, pois, mais cedo ou mais tarde, ela irá subverter a ordem social vigente, e sempre será acompanhada de deploráveis e dramáticos resultados.
Para citar novamente os países escandinavos, a Suécia é um excelente exemplo do que não fazer. Tendo seguido o caminho contrário ao da discriminação racional praticada pela sociedade japonesa, atualmente a sociedade sueca — além de afundar de forma consistente na lama da libertinagem, da decadência e da deterioração progressista — sofre em demasia com os imigrantes muçulmanos, que foram deixados praticamente livres para matar, saquear, esquartejar e estuprar quem eles quiserem. Hoje, eles são praticamente intocáveis, visto que denunciá-los, desmoralizá-los ou acusá-los de qualquer crime é uma atitude politicamente incorreta e altamente reprovada pelo establishment progressista. A elite socialista sueca jamais se atreve a acusá-los de qualquer crime, pois temem ser classificados como xenófobos e intolerantes. Ou seja, a desgraça da Europa, sobretudo dos países escandinavos, foi não ter oferecido nenhuma resistência à ideologia progressista politicamente correta. Hoje, eles são totalmente submissos a ela.
O exemplo do Japão mostra, portanto — para além de qualquer dúvida —, a importância ética e prática da discriminação, que é perfeitamente aceitável e natural, sendo uma tendência inerente aos seres humanos, e portanto intrínseca a determinados comportamentos, sociedades e culturas.
Indo ainda mais longe nessa questão, devemos entender que na verdade todos nós discriminamos, e não existe absolutamente nada de errado nisso. Discriminar pessoas faz parte da natureza humana e quem se recusa a admitir esse fato é um hipócrita. Mulheres discriminam homens na hora de selecionar um parceiro; elas avaliam diversos quesitos, como altura, aparência, status social, condição financeira e carisma. E dentre suas opções, elas sempre escolherão o homem mais atraente, másculo e viril, em detrimento de todos os baixinhos, calvos, carentes, frágeis e inibidos que possam estar disponíveis. Da mesma forma, homens sempre terão preferência por mulheres jovens, atraentes e delicadas, em detrimento de todas as feministas de meia-idade, acima do peso, de cabelo pintado, que são mães solteiras e militantes socialistas. A própria militância progressista discrimina pessoas de forma virulenta e intransigente, como fica evidente no tratamento que dispensam a mulheres bolsonaristas e a negros de direita.
A verdade é que — não importa o nível de histeria da militância progressista — a discriminação é inerente à condição humana e um direito natural inalienável de todos. É parte indissociável da natureza humana e qualquer pessoa pode e deve exercer esse direito sempre que desejar. Não existe absolutamente nada de errado em discriminar pessoas. O problema real é a ideologia progressista e o autoritarismo politicamente correto, movimentos tirânicos que não respeitam o direito das pessoas de discriminar.
Fascismo
Quando falamos de fascismo, precisamos entender que, para a esquerda política, o fascismo é compreendido como um conceito completamente divorciado do seu significado original. Para um militante de esquerda, fascista é todo aquele que defende posicionamentos contrários ao progressismo, não se referindo necessariamente a um fascista clássico.
Mas, seja como for, é necessário entender que — como qualquer ideologia política — até mesmo o fascismo clássico tem o direito de existir e ocupar o seu devido lugar; portanto, fascistas não devem ser arbitrariamente censurados, apesar de defenderem conceitos que representam uma completa antítese de tudo aquilo que é valioso para os entusiastas da liberdade.
Em um país como o Brasil, onde socialistas e comunistas tem total liberdade para se expressar, defender suas ideologias e até mesmo formar partidos políticos, não faz absolutamente o menor sentido que fascistas — e até mesmo nazistas assumidos — sofram qualquer tipo de discriminação. Embora socialistas e comunistas se sintam moralmente superiores aos fascistas (ou a qualquer outra filosofia política ou escola de pensamento), sabemos perfeitamente que o seu senso de superioridade é fruto de uma pueril romantização universitária da sua própria ideologia. A história mostra efetivamente que o socialismo clássico e o comunismo causaram muito mais destruição do que o fascismo.
Portanto, se socialistas e comunistas tem total liberdade para se expressar, não existe a menor razão para que fascistas não usufruam dessa mesma liberdade.
É claro, nesse ponto, seremos invariavelmente confrontados por um oportuno dilema — o famoso paradoxo da intolerância, de Karl Popper. Até que ponto uma sociedade livre e tolerante deve tolerar a intolerância (inerente a ideologias totalitárias)?
As leis de propriedade privada resolveriam isso em uma sociedade livre. O mais importante a levarmos em consideração no atual contexto, no entanto — ao defender ou criticar uma determinada ideologia, filosofia ou escola de pensamento —, é entender que, seja ela qual for, ela tem o direito de existir. E todas as pessoas que a defendem tem o direito de defendê-la, da mesma maneira que todos os seus detratores tem o direito de criticá-la.
Essa é uma forte razão para jamais apoiarmos a censura. Muito pelo contrário, devemos repudiar com veemência e intransigência toda e qualquer forma de censura, especialmente a estatal.
Existem duas fortes razões para isso:
A primeira delas é a volatilidade da censura (especialmente a estatal). A censura oficial do governo, depois que é implementada, torna-se absolutamente incontrolável. Hoje, ela pode estar apontada para um grupo de pessoas cujas ideias divergem das suas. Mas amanhã, ela pode estar apontada justamente para as ideias que você defende. É fundamental, portanto, compreendermos que a censura estatal é incontrolável. Sob qualquer ponto de vista, é muito mais vantajoso que exista uma vasta pluralidade de ideias conflitantes na sociedade competindo entre si, do que o estado decidir que ideias podem ser difundidas ou não.
Além do mais, libertários e anarcocapitalistas não podem nunca esperar qualquer tipo de simpatia por parte das autoridades governamentais. Para o estado, seria infinitamente mais prático e vantajoso criminalizar o libertarianismo e o anarcocapitalismo — sob a alegação de que são filosofias perigosas difundidas por extremistas radicais que ameaçam o estado democrático de direito — do que o fascismo ou qualquer outra ideologia centralizada em governos burocráticos e onipotentes. Portanto, defender a censura, especialmente a estatal, representa sempre um perigo para o próprio indivíduo, que mais cedo ou mais tarde poderá ver a censura oficial do sistema se voltar contra ele.
Outra razão pela qual libertários jamais devem defender a censura, é porque — ao contrário dos estatistas — não é coerente que defensores da liberdade se comportem como se o estado fosse o seu papai e o governo fosse a sua mamãe. Não devemos terceirizar nossas próprias responsabilidades, tampouco devemos nos comportar como adultos infantilizados. Assumimos a responsabilidade de combater todas as ideologias e filosofias que agridem a liberdade e os seres humanos. Não procuramos políticos ou burocratas para executar essa tarefa por nós.
Portanto, se você ver um fascista sendo censurado nas redes sociais ou em qualquer outro lugar, assuma suas dores. Sinta-se compelido a defendê-lo, mostre aos seus detratores que ele tem todo direito de se expressar, como qualquer pessoa. Você não tem obrigação de concordar com ele ou apreciar as ideias que ele defende. Mas silenciar arbitrariamente qualquer pessoa não é uma pauta que honra a liberdade.
Se você não gosta de estado, planejamento central, burocracia, impostos, tarifas, políticas coletivistas, nacionalistas e desenvolvimentistas, mostre com argumentos coesos e convincentes porque a liberdade e o livre mercado são superiores a todos esses conceitos. Mas repudie a censura com intransigência e mordacidade.
Em primeiro lugar, porque você aprecia e defende a liberdade de expressão para todas as pessoas. E em segundo lugar, por entender perfeitamente que — se a censura eventualmente se tornar uma política de estado vigente entre a sociedade — é mais provável que ela atinja primeiro os defensores da liberdade do que os defensores do estado.
Machismo
Muitos elementos do comportamento masculino que hoje são atacados com virulência e considerados machistas pelo movimento progressista são na verdade manifestações naturais intrínsecas ao homem, que nossos avôs cultivaram ao longo de suas vidas sem serem recriminados por isso. Com a ascensão do feminismo, do progressismo e a eventual problematização do sexo masculino, o antagonismo militante dos principais líderes da revolução sexual da contracultura passou a naturalmente condenar todos os atributos genuinamente masculinos, por considerá-los símbolos de opressão e dominação social.
Apesar do Brasil ser uma sociedade liberal ultra-progressista, onde o estado protege mais as mulheres do que as crianças — afinal, a cada semana novas leis são implementadas concedendo inúmeros privilégios e benefícios às mulheres, aos quais elas jamais teriam direito em uma sociedade genuinamente machista e patriarcal —, a esquerda política persiste em tentar difundir a fantasia da opressão masculina e o mito de que vivemos em uma sociedade machista e patriarcal.
Como sempre, a realidade mostra um cenário muito diferente daquilo que é pregado pela militância da terra da fantasia. O Brasil atual não tem absolutamente nada de machista ou patriarcal. No Brasil, mulheres podem votar, podem ocupar posições de poder e autoridade tanto na esfera pública quanto em companhias privadas, podem se candidatar a cargos políticos, podem ser vereadoras, deputadas, governadoras, podem ser proprietárias do próprio negócio, podem se divorciar, podem dirigir, podem comprar armas, podem andar de biquíni nas praias, podem usar saias extremamente curtas, podem ver programas de televisão sobre sexo voltados única e exclusivamente para o público feminino, podem se casar com outras mulheres, podem ser promíscuas, podem consumir bebidas alcoólicas ao ponto da embriaguez, e podem fazer praticamente tudo aquilo que elas desejarem. No Brasil do século XXI, as mulheres são genuinamente livres para fazer as próprias escolhas em praticamente todos os aspectos de suas vidas. O que mostra efetivamente que a tal opressão do patriarcado não existe.
O liberalismo social extremo do qual as mulheres usufruem no Brasil atual — e que poderíamos estender a toda a sociedade contemporânea ocidental — é suficiente para desmantelar completamente a fábula feminista da sociedade patriarcal machista e opressora, que existe única e exclusivamente no mundinho de fantasias ideológicas da esquerda progressista.
Tão importante quanto, é fundamental compreender que nenhum homem é obrigado a levar o feminismo a sério ou considerá-lo um movimento social e político legítimo. Para um homem, ser considerado machista ou até mesmo assumir-se como um não deveria ser um problema. O progressismo e o feminismo — com o seu nefasto hábito de demonizar os homens, bem como todos os elementos inerentes ao comportamento e a cultura masculina — é que são o verdadeiro problema, conforme tentam modificar o homem para transformá-lo em algo que ele não é nem deveria ser: uma criatura dócil, passiva e submissa, que é comandada por ideologias hostis e antinaturais, que não respeitam a hierarquia de uma ordem social milenar e condições inerentes à própria natureza humana. Com o seu hábito de tentar modificar tudo através de leis e decretos, o feminismo e o progressismo mostram efetivamente que o seu real objetivo é criminalizar a masculinidade.
A verdade é que — usufruindo de um nível elevado de liberdades — não existe praticamente nada que a mulher brasileira do século XXI não possa fazer. Adicionalmente, o governo dá as mulheres uma quantidade tão avassaladora de vantagens, privilégios e benefícios, que está ficando cada vez mais difícil para elas encontrarem razões válidas para reclamarem da vida. Se o projeto de lei que pretende fornecer um auxílio mensal de mil e duzentos reais para mães solteiras for aprovado pelo senado, muitas mulheres que tem filhos não precisarão nem mesmo trabalhar para ter sustento. E tantas outras procurarão engravidar, para ter direito a receber uma mesada mensal do governo até o seu filho completar a maioridade.
O que a militância colorida da terra da fantasia convenientemente ignora — pois a realidade nunca corresponde ao seu conto de fadas ideológico — é que o mundo de uma forma geral continua sendo muito mais implacável com os homens do que é com as mulheres. No Brasil, a esmagadora maioria dos suicídios é praticada por homens, a maioria das vítimas de homicídio são homens e de cada quatro moradores de rua, três são homens. Mas é evidente que uma sociedade liberal ultra-progressista não se importa com os homens, pois ela não é influenciada por fatos concretos ou pela realidade. Seu objetivo é simplesmente atender as disposições de uma agenda ideológica, não importa quão divorciadas da realidade elas são.
O nível exacerbado de liberdades sociais e privilégios governamentais dos quais as mulheres brasileiras usufruem é suficiente para destruir a fantasiosa fábula da sociedade machista, opressora e patriarcal. Se as mulheres brasileiras não estão felizes, a culpa definitivamente não é dos homens. Se a vasta profusão de liberdades, privilégios e benefícios da sociedade ocidental não as deixa plenamente saciadas e satisfeitas, elas podem sempre mudar de ares e tentar uma vida mais abnegada e espartana em países como Irã, Paquistão ou Afeganistão. Quem sabe assim elas não se sentirão melhores e mais realizadas?
Homofobia
Quando falamos em homofobia, entramos em uma categoria muito parecida com a do racismo: o direito de discriminação é totalmente válido. Absolutamente ninguém deve ser obrigado a aceitar homossexuais ou considerar o homossexualismo como algo normal. Sendo cristão, não existe nem sequer a mais vaga possibilidade de que algum dia eu venha a aceitar o homossexualismo como algo natural. O homossexualismo se qualifica como um grave desvio de conduta e um pecado contra o Criador.
A Bíblia proíbe terminantemente conduta sexual imoral, o que — além do homossexualismo — inclui adultério, fornicação, incesto e bestialidade, entre outras formas igualmente pérfidas de degradação.
Segue abaixo três passagens bíblicas que proíbem terminantemente a conduta homossexual:
“Não te deitarás com um homem como se deita com uma mulher. Isso é abominável!” (Levítico 18:22 — King James Atualizada)
“Se um homem se deitar com outro homem, como se deita com mulher, ambos terão praticado abominação; certamente serão mortos; o seu sangue estará sobre eles.” (Levítico 20:13 — João Ferreira de Almeida Atualizada)
“O quê! Não sabeis que os injustos não herdarão o reino de Deus? Não sejais desencaminhados. Nem fornicadores, nem idólatras, nem adúlteros, nem homens mantidos para propósitos desnaturais, nem homens que se deitam com homens, nem ladrões, nem gananciosos, nem beberrões, nem injuriadores, nem extorsores herdarão o reino de Deus.” (1 Coríntios 6:9,10 —Tradução do Novo Mundo das Escrituras Sagradas com Referências)
Se você não é religioso, pode simplesmente levar em consideração o argumento do respeito pela ordem natural. A ordem natural é incondicional e incisiva com relação a uma questão: o complemento de tudo o que existe é o seu oposto, não o seu igual. O complemento do dia é a noite, o complemento da luz é a escuridão, o complemento da água, que é líquida, é a terra, que é sólida. E como sabemos o complemento do macho — de sua respectiva espécie — é a fêmea.
Portanto, o complemento do homem, o macho da espécie humana, é naturalmente a mulher, a fêmea da espécie humana. Um homem e uma mulher podem naturalmente se reproduzir, porque são um complemento biológico natural. Por outro lado, um homem e outro homem são incapazes de se reproduzir, assim como uma mulher e outra mulher.
Infelizmente, o mundo atual está longe de aceitar como plenamente estabelecida a ordem natural pelo simples fato dela existir, visto que tentam subvertê-la a qualquer custo, não importa o malabarismo intelectual que tenham que fazer para justificar os seus pontos de vista distorcidos e antinaturais. A libertinagem irrefreável e a imoralidade bestial do mundo contemporâneo pós-moderno não reconhecem nenhum tipo de limite. Quem tenta restabelecer princípios morais salutares é imediatamente considerado um vilão retrógrado e repressivo, sendo ativamente demonizado pela militância do hedonismo, da luxúria e da licenciosidade desenfreada e sem limites.
Definitivamente, fazer a apologia da moralidade, do autocontrole e do autodomínio não faz nenhum sucesso na Sodoma e Gomorra global dos dias atuais. O que faz sucesso é lacração, devassidão, promiscuidade e prazeres carnais vazios. O famoso escritor e filósofo francês Albert Camus expressou uma verdade contundente quando disse: “Uma só frase lhe bastará para definir o homem moderno — fornicava e lia jornais”.
Qualquer indivíduo tem o direito inalienável de discriminar ativamente homossexuais, pelo direito que ele julgar mais pertinente no seu caso. A objeção de consciência para qualquer situação é um direito natural dos indivíduos. Há alguns anos, um caso que aconteceu nos Estados Unidos ganhou enorme repercussão internacional, quando o confeiteiro Jack Phillips se recusou a fazer um bolo de casamento para o “casal” homossexual Dave Mullins e Charlie Craig.
Uma representação dos direitos civis do estado do Colorado abriu um inquérito contra o confeiteiro, alegando que ele deveria ser obrigado a atender todos os clientes, independente da orientação sexual, raça ou crença. Preste atenção nas palavras usadas — ele deveria ser obrigado a atender.
Como se recusou bravamente a ceder, o caso foi parar invariavelmente na Suprema Corte, que decidiu por sete a dois em favor de Jack Phillips, sob a alegação de que obrigar o confeiteiro a atender o “casal” homossexual era uma violação nefasta dos seus princípios religiosos. Felizmente, esse foi um caso em que a liberdade prevaleceu sobre a tirania progressista.
Evidentemente, homossexuais não devem ser agredidos, ofendidos, internados em clínicas contra a sua vontade, nem devem ser constrangidos em suas liberdades pelo fato de serem homossexuais. O que eles precisam entender é que a liberdade é uma via de mão dupla. Eles podem ter liberdade para adotar a conduta que desejarem e fazer o que quiserem (contanto que não agridam ninguém), mas da mesma forma, é fundamental respeitar e preservar a liberdade de terceiros que desejam rejeitá-los pacificamente, pelo motivo que for.
Afinal, ninguém tem a menor obrigação de aceitá-los, atendê-los ou sequer pensar que uma união estável entre duas pessoas do mesmo sexo — incapaz de gerar descendentes, e, portanto, antinatural — deva ser considerado um matrimônio de verdade. Absolutamente nenhuma pessoa, ideia, movimento, crença ou ideologia usufrui de plena unanimidade no mundo. Por que o homossexualismo deveria ter tal privilégio?
Homossexuais não são portadores de uma verdade definitiva, absoluta e indiscutível, que está acima da humanidade. São seres humanos comuns que — na melhor das hipóteses —, levam um estilo de vida que pode ser considerado “alternativo”, e absolutamente ninguém tem a obrigação de considerar esse estilo de vida normal ou aceitável. A única obrigação das pessoas é não interferir, e isso não implica uma obrigação em aceitar.
Discriminar homossexuais (assim como pessoas de qualquer outro grupo, raça, religião, nacionalidade ou etnia) é um direito natural por parte de todos aqueles que desejam exercer esse direito. E isso nem o direito positivo nem a militância progressista poderão algum dia alterar ou subverter. O direito natural e a inclinação inerente dos seres humanos em atender às suas próprias disposições é simplesmente imutável e faz parte do seu conjunto de necessidades.
Conclusão
A militância progressista é absurdamente autoritária, e todas as suas estratégias e disposições ideológicas mostram que ela está em uma guerra permanente contra a ordem natural, contra a liberdade e principalmente contra o homem branco, cristão, conservador e tradicionalista — possivelmente, aquilo que ela mais odeia e despreza.
Nós não podemos, no entanto, ceder ou dar espaço para a agenda progressista, tampouco pensar em considerar como sendo normais todas as pautas abusivas e tirânicas que a militância pretende estabelecer como sendo perfeitamente razoáveis e aceitáveis, quer a sociedade aceite isso ou não. Afinal, conforme formos cedendo, o progressismo tirânico e totalitário tende a ganhar cada vez mais espaço.
Quanto mais espaço o progressismo conquistar, mais corroída será a liberdade e mais impulso ganhará o totalitarismo. Com isso, a cultura do cancelamento vai acabar com carreiras, profissões e com o sustento de muitas pessoas, pelo simples fato de que elas discordam das pautas universitárias da moda.
A história mostra perfeitamente que quanto mais liberdade uma sociedade tem, mais progresso ela atinge. Por outro lado, quanto mais autoritária ela for, mais retrocessos ela sofrerá. O autoritarismo se combate com liberdade, desafiando as pautas de todos aqueles que persistem em implementar a tirania na sociedade. O politicamente correto é o nazismo dos costumes, que pretende subverter a moral através de uma cultura de vigilância policial despótica e autoritária, para que toda a sociedade seja subjugada pela agenda totalitária progressista.
Pois quanto a nós, precisamos continuar travando o bom combate em nome da liberdade. E isso inclui reconhecer que ideologias, hábitos e costumes de que não gostamos tem o direito de existir e até mesmo de serem defendidos.
-
 @ cc05487a:8eddd6a8
2024-07-22 17:51:32
@ cc05487a:8eddd6a8
2024-07-22 17:51:32I've shared this story a couple of times and often I have second thoughts about sharing the story again. But if my sharing it here can save ONE life, it's worth it., this issue is too important to stay silent about, so I want to raise awareness.
In November 2018, I was diagnosed with stage T2b intermediate prostate cancer. To make matters worse, it was an aggressive form genetically meaning there was a high likelihood of metastasis if I didn't take action.
Hearing the doctor deliver this news was devastating. I was stunned, caught off guard, and I broke down. Given the context of the preceding 18 months, it felt like a knockout blow:
- My mother passed away in June 2017.
- My father passed away in April 2018.
- My uncle (my mom's older brother) passed away in August 2018.
With all the grief I'd been dealing with, my first thought upon receiving the diagnosis was, "Am I next?"
Reflecting on it, I realized I experienced a microcosm of the stages of grief. I initially tried to deny the diagnosis, but there it was, staring me in the face. I got angry and sought a second opinion, hoping the first doctor was wrong. But the facts were undeniable. Facts don't care about your fears. As anyone close to me can tell you, I became deeply depressed. I was no fun to be around during the holidays. But then I realized that wallowing in fear and sadness was hurting me and those around me. I was still scared, but I knew I had to take action.
My wife was instrumental in helping me through this difficult time. I couldn’t have done it without her.
In the weeks following my diagnosis, I consulted with my urologist to devise a plan of action. He strongly recommended surgery over radiation. After doing some research, I understood why: given the aggressive nature of my cancer, radiation would leave a lingering uncertainty about recurrence. And if the cancer returned, I would have no options left. Despite the fear, surgery was the best option. I had to keep reminding myself of one thing:
I was going to have the final word on this cancer. I was determined to remove it by any means necessary and move on with my life. Was I still scared? Absolutely. But the sooner I got treatment, the better.
My urologist referred me to Swedish Urology for treatment, saying, "I'm good, but they're better, and I think you need to see them for treatment." More blood tests and planning ensued throughout December. In January, I met with my surgeon and got on the schedule.
A few months later, I underwent surgery to remove the cancer. If you're curious about the procedure, look up "da Vinci robotic surgery" online. My wife and I had to drive through the final (and worst) snow of the year on the day of the surgery, but everything went as planned. My wife stayed with me during pre-op, chatting with the anesthesiologist and nurses while they completed the final checklists. I wasn't too nervous at first, but seeing her walk away to the waiting area made everything suddenly real. In hindsight, I probably should have taken the valium they offered.
The surgery went well overall, despite a few hiccups that extended my hospital stay by a night. The pain was intense; Oxycodone helped, but I didn't enjoy the hallucinations it caused (like letters on the dry erase board melting down the board), so I minimized its use.
My wife never left my side, sleeping on an uncomfortable cot next to me. She's incredibly strong and courageous. Maybe I should get her something special for her birthday... perhaps those diamonds she was eyeing the other day.
A week later I had my first follow-up and reviewed the final pathology report. The results were good: no metastasis. I was still sore and recovering, but getting better every day. Was I out of the woods yet? Mostly, yes. There's some concern that some cancer cells might have been left behind. The cancer had advanced between my initial biopsy and final pathology report, from a Gleason score of 4+3=7 to 4+5=9. Opting for surgery was the right call. If follow-up radiation is ever needed, it will be minimal and focused.
So why am I sharing all of this? It's not about seeking attention. I'm sharing this to shake a few people out of complacency. If you're reading this and have concerns, don't ignore them. Looking back, I realize there were warning signs I dismissed as mere aging. Those ads on TV promising miracle supplements? Ignore them. They should be against the law...! They almost cost me dearly. Ask yourself:
- Are you over 40?
- Do you have a family history of reproductive or pancreatic cancers?
- Have you noticed any changes or discomfort when sitting, using the restroom, or riding a bicycle?
- Any unusual discharge in your underwear?
If you answered 'yes' to any of these, see a doctor. Go now. Get a PSA test. If your doctor dismisses the need for it, find another doctor. PSA tests do work. My PSA was only 7 (normal is 1 to 4), and my first urologist didn't think they would find anything. But here I am, post-prostatectomy. PSA tests are easy: a simple blood draw, and the results come back in a few days. If it's below 4, check it again in six months to ensure it hasn't risen. And if you're over 50, definitely get a direct exam.
Did you know the percentage of males with prostate cancer increases linearly with age? It does: 30% of males in their 30s have prostate cancer, 40% in their 40s, and so on. Recent studies have found this, and urologists are taking these findings seriously. Ignoring early warning signs is not worth your life.
Ignore those TV ads for miracle supplements. They’re a dangerous distraction. Many contain Saw Palmetto, which can suppress PSA levels and create a false sense of security. Instead of relying on these supplements, see a doctor.
Go get checked. Talk to a doctor. Do it now.
Finally, I want to thank my wife. I know this has been tough, but I'm glad you're here. I couldn't have done this without you. I love you.
-
 @ 361d3e1e:50bc10a8
2024-08-18 18:13:10
@ 361d3e1e:50bc10a8
2024-08-18 18:13:10Full story Covid and Monkeypox - What an amazing coincidence in Germany It turns out that the new pandemic (Monkeypox) begins in an absolutely identical way, just like the old one pandemic - the covid.
germany #covid #monkeypox #pandemic #health #medicine
-
 @ 1739d937:3e3136ef
2024-07-19 20:16:01
@ 1739d937:3e3136ef
2024-07-19 20:16:01This is the fourth in a series of weekly updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
The dependency train continues to roll. This week I was in touch with the maintainers of both OpenMLS and the hkpe-rs library and have pushed my changes forward in both areas. I've also gotten closer to understanding the wire format and relay requirements for the NIP I'm working on.
To be honest, the progress feels pretty slow at the moment but I've seen this story often enough to know that I'm on the right track. To be clear, my goal here is do this right and make it as easy as possible for Nostr devs to implement MLS based messaging across all of Nostr. That necessarily requires ensuring that all the implementation libraries support the right pieces and that our NIP is clean and well thought through (no one likes a shed full of bikes).
HPKE-RS
My PR to add support for secp256k1 is moving. I've been adding tests this week and fixing a few issues. Once this is merged, I'll update my
secp256k1-based library as well. One unfortunate roadblock has been a lack of solid test vectors - this has eaten some time.OpenMLS Nostr Crypto
I had a short call with the OpenMLS maintainer team this week and was able to clarify what I'm trying to do and how they see it fitting in best. I was also able to get a better idea about how clients will need to process incoming messages. One interesting highlight: Messages have to be processed in the right order. Otherwise it's impossible to keep the ratchet tree in the correct state. My left-curve solution to this for now is to use both created at (as a dumb first pass at sorting) + a hash of the previous message content. This will give Nostr clients a simple way to double check that they have the messages in the correct order before they attempt to process them. Unfortunatley, this doesn't do a good job accounting for messages that are missing. My guess is that this isn't going to be a major issue, but I won't have a clear idea until there is a working Nostr relay based demo.
The next steps in my code for OpenMLS is to refactor the ciphersuites trait to make it easier to use custom ciphersuites. My initial PR hardcoded our secp256k1 based suite into the library but the clearly better solution is to refactor a few things to make sure that there isn't any hardcoding in the main OpenMLS library, the ciphersuite, or the credentials (which hold your identity information and make prekey bundles possible). The library's maintainers are open to this, so I've started on that this week.
Request for feedback
I'd love to hear from devs on one point. The OpenMLS library currently makes it very easy to serialize messages (both group control messages and actual messages between users). These messages have a lot of data in them about the current structure of the ratchet tree and whatever message or control event they're trying to communicate. My current plan is to simply NIP-44 encrypt those serialized messages into the content field of a new event kind. The messages themselves are deserialized and processed in two simple calls by the OpenMLS library so I don't see any reason to keep destructured or deserialized data in the nostr events that are heading over the wire. This also makes it easier to keep metadata about messages hidden to observers.
Goals Recap
It's been a few weeks since I've talked about why this is important so, it's time to recap what we're aiming for:
- Private and Confidential DMs and Group messages
- Private means that an observer cannot tell that Alice and Bob are talking to one another, or that Alice is part of a specific group. This necessarily requires protecting metadata.
- Confidential means that the contents of conversations can only be viewed by the intended recipients.
- Forward secrecy and Post-compromise security (PCS) in the case of any key material being leaked, whether that's your main Nostr identity key (your nsec) or any of the keys used in the MLS ratchet trees.
- Forward secrecy means that encrypted content in the past remains encrypted even if key material is leaked.
- Post compromise security means that leaking key material doesn't allow an attacker to continue to read messages indefinitely into the future.
- Scales well for large groups. MLS provides this from a computational standpoint, but we need to make sure this works in a scalable way when multiple relays are involved.
- Allows for the use of multiple device/clients in a single conversation/group. Importantly, we're not aiming to enable a device/client to be able to reconstruct the full history of a conversation at any point.
Onward and Upward
Grind, grind, grind. Touch grass & hug family. I'm visiting family starting next week for a few weeks. I'm going to be taking some time off in there so expect a few light updates in the coming weeks.
-
 @ 5e5fc143:393d5a2c
2023-04-15 17:18:11
@ 5e5fc143:393d5a2c
2023-04-15 17:18:11Just revisiting some quick tips for #newbies #pow #public #blockchain users only.
if you just getting started with bitcoin or any pow crypto coins or been using or storing them for a while, you not must forget the roots and fundamentals.
Hot Wallet — It gets connected to live internet at some point in time essentially to sign / send a tx i.e. spending transaction — exposes the private key of the address from in the process
Cold Wallet — It never ever gets connected or online and can always keep receiving inbound amounts Paper wallets are best n cheapest form of cold wallet that can used once n thrown away.
Cold wallets need to either “import”ed or “sweep”ed in order to used or spend — https://coinsutra.com/private-key-import-vs-sweep-difference/

Any thin #wallet is always dependent on connectivity to live up2date node server where-as self-sufficient qt / cli wallet takes a while to sync up to latest block height in order to be usable.
Beginners should always resist the attraction of quick and fast — thin n 3rd party wallets and always start a long learning journey of core wallets of any coin — either “qt” GUI wallet or command line “coin-cli” wallet
Almost all #proofofwork #blockchains i.e. #POW has #node #wallet - everyone who use support he #public #blockchain secures own you coin value
You can run fullnode either on clearnet or over onion 🧅 #BTC has >55% of nodes running in onion out of total 15000+ live fullnodes and 50000+ bitcoincore wallets around blockheight 777000 . Other notable pow chains are #LTC #RVN and rest are babychains for now !
Always delete hot wallet to test practice restoration before sending any large refunds to it to be safe.
Large funds are always best to keep in self custody node wallets rare n occasional use
Final word — Cannot see private key 🔑 or seed 🌱 in any wallet means not your coin. 😲
That’s all for now n Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️
Some Cold wallet nostr posts nostr:note1p6ke5wqshgxtfzj5de3u04hejl2c5ygj8xk8ex6fqdsg29jmt33qnx57y2 nostr:note1rse0l220quur6vfx0htje94ezecjj03y6j7lguwl09fmvmpt6g3q0cg7yw nostr:note1q5w8dyjuqc7sz7ygl97y0ztv6sal2hm4yrf5nmur2tkz9lq2wx9qcjw90q
some nostr specific lightning ⚡️ Layer2 wallets with blockchain mainnet option nostr:naddr1qqsky6t5vdhkjm3qd35kw6r5de5kueeqf38zqampd3kx2apqdehhxarjqyv8wue69uhkummnw3e8qun00puju6t08genxven9uqkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgchgefsw4a8xdnkdgerjatddfshsmr3w93hgwpjdgu8zdnswpuk2enj0pcnqdnydpersepkwpm8wenpw3nkkut2d44xwams8a38ymmpv33kzum58468yat9qyt8wumn8ghj7un9d3shjtngv9kkuet59e5k7tczyqvq5m2zcltylrpetrvazrw45sgha24va288lxq8s8562vfkeatfxqcyqqq823ckqlhc8 related blog post nostr:naddr1qqxnzd3cxyenjv3c8qmr2v34qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qydhwumn8ghj7mn0wd68ytn4wdjkcetnwdeks6t59e3k7tczyp6x5fz66g2wd9ffu4zwlzjzwek9t7mqk7w0qzksvsys2qm63k9ngqcyqqq823cpdfq87
-
 @ 6bae33c8:607272e8
2024-07-18 19:19:16
@ 6bae33c8:607272e8
2024-07-18 19:19:16These are my very preliminary RB rankings, my only research being the RotoWire depth charts and player notes.
**Tier 1
Christian McCaffrey**
He’s 28 years old, has 1,402 career carries including the postseason and weighs only 205 pounds at 5-11. But McCaffrey is arguably the greatest running back all time, when you include the pass catching, and he’s in the league’s best system for backs. Health is really the only variable, and anyone can get hurt.
**Tier 2
Breece Hall, Bijan Robinson, Saquon Barkley, Jonathan Taylor**
These are the three-down backs with elite skill sets. Hall should be better another year removed from the ACL tear and playing with a better QB, Robinson should get the heavy usage he merits with Arthur Smith gone, Barkley finally gets a quality offensive line and QB and Taylor plays next to a running QB and has little competition for carries.
**Tier 3
Jahmyr Gibbs, De’Von Achane, Kyren Williams, Travis Etienne**
These are the little guys, all of whom can run and catch passes, plus Etienne. Williams is the biggest risk as an early-down high-workload guy, but he was also insanely productive when he played in Sean McVay’s lead-back-friendly system. Gibbs seems like peak Alvin Kamara, only faster and Achane in the Miami offense was the most efficient back in league history by a mile. I originally had Etienne in Tier 4, but he doesn’t have much competition for the job and should be a three-down back.
**Tier 4
Isaiah Pacheco, Josh Jacobs, Joe Mixon, James Cook, David Montgomery, Derrick Henry, Kenneth Walker, Racchad White, James Conner, Rhamondre Stevenson, Zack Moss, Javonte Williams, Devin Singletary **
This is a big tier, but these are all the incomplete players guaranteed reps if healthy. Pacheco could be moved to Tier 3, but Patrick Mahomes doesn’t check down to the back all that often, and Pacheco rarely gets to 20 carries in a game. Jacobs is a beast but has a ton of mileage in a short span and fell off last year. Mixon is another old warhorse with a lot of mileage, albeit also in a good situation. Cook suffers due to Josh Allen’s goal-line prowess and tendency to take off rather than check down. Montomgery will cede the third-down work, Henry is old and doesn’t catch many passes, Walker splits carries, gets hurt often, White is a ham and egger who happened to see a huge workload, Conner is 29 and always misses time, Stevenson is a workhorse on a bad team, Moss is an average back in a good spot, Williams is another year off the injury, but on a bad team and Singletary is the clear lead back on a poor offense.
**Tier 5
Tony Pollard, D’Andre Swift, Jonathan Brooks, Alvin Kamara, Brian Robinson, Jaylen Warren, Austin Ekeler, Chuba Hubbard, Zamir White, Raheem Mostert, Aaron Jones, Najee Harris, Nick Chubb, Tyjae Spears, Trey Benson, Zach Charbonnet ** These are mostly timeshare backs, with the exception of Kamara whose efficiency fell through the floor and White who I’m not convinced will lock down the job all year.
**Tier 6
Kenneth Gainwell, Rico Dowdle, Gus Edwards, Jerome Ford, Zeke Elliott, Roschon Johnson, Jaylen Wright, Bucky Irving, JK Dobbins, Antonio Gibson, Chase Brown, Elijah Mitchell, Jaleel McLaughlin, Tyler Algeier, MarShawn Lloyd**
This is the backup tier, all of whom probably need an injury ahead of them to break out.
These rankings will change, but I like to get my preliminary ones down on paper before I get influenced by ADP and training camp hype.
-
 @ 361d3e1e:50bc10a8
2024-08-18 18:13:10
@ 361d3e1e:50bc10a8
2024-08-18 18:13:10Full story Covid and Monkeypox - What an amazing coincidence in Germany It turns out that the new pandemic (Monkeypox) begins in an absolutely i... This is a preview of my post. Join my community and get access to this and more of my work.
https://highlighter.com/npub1xcwnu8sx6vs5ae478lzzahpmg46428nkewa46prev4jhz59uzz5qqhm0u6
-
 @ dd664d5e:5633d319
2024-07-10 14:45:43
@ dd664d5e:5633d319
2024-07-10 14:45:43The Law Giver
In my previous article, I briefly went into the topic of how contract law is holy law.
The Father of the Christians, you see, is a God of Covenants, and He sent His Son to Earth to fulfill the Law and pay a Price for our salvation. The Father also created the Natural Order to confirm His Laws through our observation of that Law in action.
That is why Christians have a deep respect for honest contracts, true prices, fair measures, natural systems, and good laws. Not merely for their own sake, but also because understanding them helps us to understand and emulate the Law Giver.
The tired What would Jesus do? meme is actually an attempt to capture this emulation of the Highest Judge. Jesus knows the Law, since His Father defined it and He is One with the Father, so how would He apply the Law best, in this situation?
The Last Things
Working together with him, then, we entreat you not to accept the grace of God in vain. For he says, “At the acceptable time I have listened to you, and helped you on the day of salvation.”
Behold, now is the acceptable time; behold, now is the day of salvation.
-- 2 Corinthians 6:1-2 New Testament, RSV Bible
One of the things most devout Christians frequently ruminate over, is when Christ will return.
Every day, we ponder. We go for a walk, and ponder. We cook dinner, and ponder.
At the same time, we are called upon to live each day in a productive manner, and to not simply lie around, vegetating, and staring at the heavens. Not only for our own sake, but also because to do so would be to limit our ability to inform others about the Good News, so that they can take to pondering with us. We are called to ponder with as many people as we can produce, adopt, convert, or simply collect through our daily interactions.
This means that we are not of the world (as our eyes are watching God and baptism has made us Immortals), but we are definitely in the world (involved in, and effected by, the everyday dealings around us.) It is a very difficult balancing act to know when we are paying too much attention to the one or the other, or to know where to store up our treasures, if we can't put them all immediately into the Final Treasury.
So, we worked today and earned a bit of fiat cash and we have no immediate usage for it. What to do with it?
Well, some of it should go to charity or be invested in a business that provides important goods, services, and employment. Some of it will be needed to simply cover the day-to-day costs of our own life, or that of those dependent upon us. But it might be prudent to store up some of it, for the mysterious length of time between receipt of the monies and our own ascent into Heaven.
Typically, that store was the local currency, but that's being inflated away at an alarming rate. Then we all began to move to precious metals, and many of us still do, but they are so difficult to spend and can't be broken into small bits or transported over wide distances at low cost.
Enter Bitcoin.
The Great Ledger
In our frustration, more and more Christians are turning to a new technology, to save up some treasure in a liquid asset, for the mid-term. And, once we begin using it, and begin to understand how it works, we quickly grow fond of it.
Bitcoin is a beautiful money because it is a money based upon keeping precise accounts, using a fair measure, and obeying the Laws of Nature.
In essence, Bitcoin is a debt note emitted by a universal debtor (the network) in exchange for some good or service. This frees the individual people using it from ever needing to carry debt, as the debt stays in the network, the value and enforceability of that debt note is protected by the effort used to create and maintain the network, and the eagerness with which other people wish to store their efforts up in that same network. The debt still exists, but it can be so thinly and widely spread that it no longer rests as a burden upon one particular person.
The debt, in other words, has been disassociated from humans and the management has been distributed to machines. This is the precise opposite process of a "fiat" (by decree) currency, which only has value so long as it is associated with some particularly solvent group of humans (who personally vouch for repayment of any debts denominated in the currency), and where management is centralized to some other group of humans.
Have you accepted Bitcoin as your personal money and store of value?
You have invested $10 to buy the electricity to mine Bitcoin? Then you receive $10 of Bitcoin in return. The Bitcoin network now owes you the $10 purchasing power equivalent of that electricity.
If someone then gives you $5 worth of pizza, then you can then give them a $5 portion of your $10 worth of Bitcoin. You have taken a part of your Bitcoin debt note and shared it with them.
They now hold $5 worth of Bitcoin invested in the network and can spend it on some other good or service. Or they can simply hold it and wait for it to rise in value, as more people "mine" more of it (and produce more notes, paradoxically making the existing notes more useful and therefore valuable) and more people try to gain the notes in order to manage their own finances by storing their energy in the network or transporting their energy using the network.
Bitcoin, in other words, is an accounting book that needs no accountant because it stores, tracks, and controls the ledger on its own. It is a Natural Ledger that runs according to the the Laws.
It is the only human-made ledger that allows for true and immediate Final Settlement. This Final Settlement is what allows people to trade using the convenience of digital debt notes, with neither person occurring or even risking any personal debt. We Christians know that all debt is a burden, including monetary debts, which is why we are called to forgive each other's debt and to hope that our own debts are forgiven. Better still, is to avoid the accumulation of debts, altogether.
So, Final Settlement? Final Settlement is what Jesus would do.
-
 @ 2c7cc62a:622a5cdc
2024-07-08 10:24:56
@ 2c7cc62a:622a5cdc
2024-07-08 10:24:56Nostr で見掛けた焼肉店情報。いつか見返す。
ちょうしゅう
石垣島
http://yugafu-llc.com/
nostr:note1tgnt39hgyvn4lskp5s684czgsce9y55xm8ysfrfdj4mp3gguhhvsu6jtjw
とらじ
http://www.toraji.net/
大阪上新庄
nostr:note1x3fhl9w0wf5r7e75aem3n4ffcqcuqggp3uda6cj8p3ewg4hgrrjqwye9lc
瑞園
https://tabelog.com/osaka/A2701/A270307/27001977/
大阪上新庄
nostr:note1whjkp27hztcy5yey5r7nvc23yjcavpu322q5xyp8grua98rshz7stz9grh
たん清
https://www.tankiyo.com/
東京秋葉原
nostr:note1ke9ekpe3h92nq7qgjg4w4nmz4u7s4wyn753gagsf49pam4h6aefsddwr0k
-
 @ 9171b08a:8395fd65
2024-07-06 00:48:33
@ 9171b08a:8395fd65
2024-07-06 00:48:33The rhythmic thump thump of the wipers’ frantic attempt to rid the windshield of raindrops glimmering in the passing streetlights came and went in Jonah’s sight. A thin layer of water about the lonely street glistened in the headlights. His breaths were heavy between the squeal and thump, thump.
“Your mom was right, you know?” were the words Julia, his wife had said. The street lights stretched across the darkness then vanished over her reflection in the rearview mirror revealing only a split second of the shimmer in her eyes.
Their boy cooed in the car seat behind Jonah as Julia fed him with her left hand. Their girl slept, head bobbing gently in the seat to Julia’s right.
“Julia, c’mon. You can’t be serious.”
“You haven’t been there for us. You haven’t been there for me and it's embarrassing that your mom had to call you out on it. You think you're a man?”
Jonah’s breaths were heavy between the thump thump and squeal of the windshield wipers. The lights were stagnant then, when the engine ticked strangely and he had the taste of iron in his mouth.
The words he had said a few moments before echoed in his head, “Julia, I was doing it for you and the kids.”
“The kids needed you home. I nee—” Julia’s voice cracked, “I needed you.” Her voice slipped into a soft whine of desperation, “We can get by with your parents' help. It’s ok to ask for help.”
“Why do we need their help? We can do this on our own. I can do this for us,” growled Jonah. His rage was building but he didn’t dare raise his voice and wake the children. “I can do this,” he repeated, staring at Julia.
Julia couldn’t fight the frown. She wiped away a tear and said, “Maybe you can. But I can’t. Not anymore, I already told your mother I’ll be comi—”
Thump.
Thump.
The street lights and water filled the splintered windshield glass like streams of gold. The Red and blue lights flashing wildly against the concrete median came and went in Jonah’s sight. Julia hung limp in her seat. Her body was tethered down by the seatbelt; her hands suspended above her head. It was dark even with all the lights and it wasn’t until there came the glare of a flashlight and Jonah noticed the blood streaming from the gash in Julia’s face that he really noticed the taste of iron in his mouth.
All sounds were muffled. When he looked at the glaring light the moment just vanished.
Beep. Beep. Beep.
Jonah shivered. The pain was unbearable but the cold still racked his body. He shook awake and was blinded by the overhead light.
“Easy. Easy,” came a familiar voice.
His mother’s voice brought tears to Jonah’s eyes. Eyes still sensitive to the light. His mother’s silhouette shifted beside him. Then, he felt her touch and though there was warmth against the chill, he shook. Jonah realized he was in the hospital and now it was the pain that racked his body.
Jonah wheezed, “Julia? Julia? Mom.” His voice cracked. “Grayson? Tory? What happened?”
Jonah’s mother hugged him, “You were in an accident son.”
“Mom,” Jonah wheezed again as he spoke and struggled to free himself from her embrace. “What room are they in? Are they ok?”
His mother spoke softly as she separated from him and said, “Jonah, you need to rest.”
“I need to see my wife and kids! Tell them to come in.” Jonah searched the bedside table for his phone. Then he searched the bed. His arms were riddled with sutures and streaks of black coagulated blood. “I’ll call Julia. Pass me my phone,” he said wanting to raise his hand in his inquiry but the pain was unbearable.
His mother covered her mouth and shook her head as she cried.
“Mom?” Her silence bothered Jonah. The wounds of his ego after the way his family turned on him that weekend were still fresh. At that moment, it was fresher still than the wounds of the accident. The idea that his mother was still treating him like he wasn’t man enough to care for his family enraged him. “Will you stop treating me like a boy? I’m thirty years old. I have a family. I don’t need to be coddled.”
His mother gasped and reached out a hand that Jonah swatted away. “Oh, no son. You don’t understand.”
Jonah winced at his mother’s reaction. It wasn’t uncommon for his mother to turn the tables on him and make him feel like the scum of the earth for having any sort of feelings whatsoever. For the first time however, that wouldn’t come. She was speechless and remorse blanketed her face. Jonah finally came to the realization that something was very wrong. He fought the frown that his lips wanted to take. “What’s wrong? What happened?”
His mother inhaled slowly and struggled to answer, “The paramedics tried their best, but you were the only one who made it to the hospital alive.”
Jonah stared at his mother in disbelief. The weight of the news made him sink further into the bed sheets. “No, no no no.” He struggled to conjure the sound of Julia’s voice from his memories of her.
“Your mom was right, you know?” Julie had said. “I already told your mother I’ll be comi—” were her last words. The streetlights expanding across her face in the rearview mirror and the glimmer of her tears was the last image he held of her. His daughter’s bobbing head and his son’s coo were the last memories he had of his children.
Everyone was right. His mother was right. Why had he insisted on spending so much time away from home in search of money. In search of greatness. Little did he know that the seconds were ticking away and every moment he spent away from his family was one less minute he would have memories of.
-
 @ 3c7d12a6:9532013e
2024-06-20 14:47:12
@ 3c7d12a6:9532013e
2024-06-20 14:47:12NUD: Pubkey to colors
This NUD defines how to convert pubkey to colors.
Why?
npubis nonsense to display.- too long.
npub1bla...blais nonsense to display.npub1takes too much space....means nothing.
Specs
- Uses hex pubkey.
- Converts 64 characters to 8 colors.
- Splits 64 with 8 length chunks.
- Converts each 2 in 8 into
- Alpha (0-255 -> 0.0-1.0)
- Hue (0-255 -> 0.0-360.0)
- Saturation (0-255 -> 0.0-1.0)
- Light (0-255 -> 0.0-1.0)
- Supports dark and light theme.
- When Light is 1.0, flip the Light for light theme (0.0).
-
 @ 1bc70a01:24f6a411
2024-06-16 23:02:59
@ 1bc70a01:24f6a411
2024-06-16 23:02:59We’re all daily users of Nostr, so it can be easy to see things through an advanced user lens while forgetting what it felt like to be a newbie. I thought I would take some time to go over major client from the start in hopes of evaluating what it might feel like for a new user.
The other reason for running this review is to hopefully improve the overall nostr retention rate across clients. As it stands, according to nostr.band, retention of trusted users 30 days after signups trends to 0 for recent cohorts. This seems to be supported by the lack of growth in daily active users, with the average remaining in the 10,000-12,000 range for “trusted” pub keys.
The following report consists of several criteria which I felt were essential to basic first-time social media experience:
- Ease of signup
- Ease of logging in
- Ability to understand what you are looking at (sufficient explanations)
- Seeing a good initial feed
- Ability to follow something of interest
- Minimizing technical /dev lingo
- A fast scrolling experience
- Ability to easily upload media
- A good search experience overall
- Good keyword searching
- Hashtag searching
- Ability to follow hashtags
- Easily accessing followed hashtags
- Good experience reacting to notes
In total there are 140 points, 10 for each category. This is by far not the most comprehensive score card, but I felt it did a decent job covering most things you’d want to do in a social client.
Some notes of caution:
- This report and score card are meant to be a general quick glance at where your client may stand in overall UX. It does not differentiate between the intended target audiences.
- The criteria that I deem important may not be important to you as the founder / developer, so take it for what it’s worth. Adding your desired criteria may increase your score significantly. For example, I did not evaluate the zap experience, or thoroughly test nested replies.
- This report is not a substitute for proper user testing. It’s just one person’s observations. While we have done some user testing in the past, I highly recommend doing your own. You can do so by approaching and interviewing new users (if you are able to distinguish if they came from your client), or via other user testing software. Talk to me (@karnage) if you need some help getting set up.
- People’s reported experience regarding usability may vary greatly depending on their familiarity with cryptographic concepts, their background, and technical experience. What I may deem as a great score of 10, may not be a 10 for others. I have seen user tests where “obvious” things were not obvious to testers.
- This report only looks at the English language version of the client. The actual user experience for someone on a different language version of the app could be totally different from what is graded here. It’s worth considering geographies of where users are coming from and how they experience your client.
- I did not test re-activation of new users. Meaning, once they close the app, I did not test if they are pulled back by some notification or other means. This is a crucial aspect of any new app usage that should be considered carefully.
Tested Clients: Damus, Amethyst, Primal iOS, Snort (web), Iris (sort of), Coracle, Nostur.
I also tested Instagram and X/Twitter for comparison.
Results, highest points to lowest: Primal iOS: 136 Twitter: 125 Instagram: 109 Nostur: 108 Coracle: 99 Amethyst: 93 Snort: 90 Damus: 87 Iris: N/A Facebook: could not test.
My main takeaway was that among all apps (including Twitter and Instagram), the traditional apps win simply by having much better content selection. You get to see a variety of interesting things that Nostr simply can’t match. Going forward, this is an area I would probably recommend focusing on - how to engage people to post more interesting content, onboard creators etc… Nostr is lacking in content and I believe this could be the primary reason people are not sticking around after trying it.
Other Nostr Notes:
There seemed to be little of interesting topics to follow or stick around for. The experience of joining nostr doesn't feel special or different in any way opposed to X for example. Twitter has interesting accounts, TikTok has interesting videos, what does Nostr have? The lack of "popular" conent due to the generally low number of users is probably to blame. In a way we suffer from the chicken / egg problem where new users are needed to generate more content, and more content is needed to retain new users. Going forward, I think clients should think about ways to encourage users to share content (whether that be their own, or posted from other platforms). Nostr also does not seem to have any external growth loops. For example, there is no way to invite people to the platform by email with a single click (by accessing the address book). Even if a friend does manage to join and you can find them, they are in no way notified when tagged (as far as I know). People have to have a habit of opening the app to know if something is happening. The habit formation of using a new app is important in the early usage phase and nostr seems to have a weak spot here.
You can find all of the detailed scoring, notes for each client and other thoughts in this spreadsheet: https://docs.google.com/spreadsheets/d/14w8-aQ1sHfGBSuNpqvOA9i7PHNSfhn6lUOV6H293caw/edit?usp=sharing
-
 @ 3c984938:2ec11289
2024-06-09 14:40:55
@ 3c984938:2ec11289
2024-06-09 14:40:55I'm having some pain in my heart about the U.S. elections.
Ever since Obama campaigned for office, an increase of young voters have come out of the woodwork. Things have not improved. They've actively told you that "your vote matters." I believe this to be a lie unless any citizen can demand at the gate, at the White House to be allowed to hold and point a gun to the president's head. (Relax, this is a hyperbole)
Why so dramatic? Well, what does the president do? Sign bills, commands the military, nominates new Fed chairman, ambassadors, supreme judges and senior officials all while traveling in luxury planes and living in a white palace for four years.
They promised Every TIME to protect citizen rights when they take the oath and office.
...They've broken this several times, with so-called "emergency-crisis"
The purpose of a president, today, it seems is to basically hire armed thugs to keep the citizens in check and make sure you "voluntarily continue to be a slave," to the system, hence the IRS. The corruption extends from the cop to the judge and even to politicians. The politicians get paid from lobbyists to create bills in congress for the president to sign. There's no right answer when money is involved with politicians. It is the same if you vote Obama, Biden, Trump, or Haley. They will wield the pen to serve themselves to say it will benefit the country.
In the first 100 years of presidency, the government wasn't even a big deal. They didn't even interfere with your life as much as they do today.
^^ You hold the power in your hands, don't let them take it. Don't believe me? Try to get a loan from a bank without a signature. Your signature is as good as gold (if not better) and is an original trademark.
Just Don't Vote. End the Fed. Opt out.
^^ I choose to form my own path, even if it means leaving everything I knew prior. It doesn't have to be a spiritual thing. Some, have called me religious because of this. We're all capable of greatness and having humanity.
✨Don't have a machine heart with a machine mind. Instead, choose to have a heart like the cowardly lion from the "Wizard Of Oz."
There's no such thing as a good president or politicians.
If there was, they would have issued non-interest Federal Reserve Notes. Lincoln and Kennedy tried to do this, they got shot.
There's still a banner of America there, but it's so far gone that I cannot even recognize it. However, I only see a bunch of 🏳🌈 pride flags.
✨Patrick Henry got it wrong, when he delivered his speech, "Give me liberty or give me death." Liberty and freedom are two completely different things.
Straightforward from Merriam-Webster Choose Right or left?
No control, to be 100% without restrictions- free.
✨I disagree with the example sentence given. Because you cannot advocate for human freedom and own slaves, it's contradicting it. Which was common in the founding days.
I can understand many may disagree with me, and you might be thinking, "This time will be different." I, respectfully, disagree, and the proxy wars are proof. Learn the importance of Bitcoin, every Satoshi is a step away from corruption.
✨What does it look like to pull the curtains from the "Wizard of Oz?"
Have you watched the video below, what 30 Trillion dollars in debt looks like visually? Even I was blown away. https://video.nostr.build/d58c5e1afba6d7a905a39407f5e695a4eb4a88ae692817a36ecfa6ca1b62ea15.mp4
I say this with love. Hear my plea?
Normally, I don't write about anything political. It just feels like a losing game. My energy feels it's in better use to learn new things, write and to create. Even a simple blog post as simple as this. Stack SATs, and stay humble.
<3 Onigirl
-
 @ d830ee7b:4e61cd62
2024-06-02 05:44:01
@ d830ee7b:4e61cd62
2024-06-02 05:44:01This article is a translation of my original Thai-language article, which will be published as a long-form piece in the coming days.
.........................
After listening to these two masters go back and forth, circling each other like intellectual gladiators, I gotta say… the lines between the "real world" and the "virtual world" are getting seriously blurry.
Watch more > Alt+Tab Season 2 EP4 : "พี่ชิต" ดร.วิชิต ซ้ายเกล้า
The battle for power is changing, man.
Forget tanks and explosions, the most powerful weapon now is invisible, hiding in plain sight. It's woven into the fabric of society. We call it "Soft Power", the unseen influence that slowly consumes us, manipulates us... without us even realizing it.
"The wars we see today..." Wichit says with a voice that sends shivers down your spine, "It's just throwing percentages at each other in the air."
Piriya nods in agreement. "Like you said, humans are getting smarter, more cunning. Those old-school, head-on confrontations? They just lead to destruction. Waste of resources, waste of life..."
They're right, you know... Back in the day, if you wanted something, you just sent an army to take it. Conquered land, plundered resources. It was all about "Hard Power."
Direct, brutal, effective... but the scars ran deep.
The world today is way more complex. Humans have learned to use "influence" to infiltrate every aspect of life.. individuals, societies, even international relations. No bloodshed, but the results are even more potent...
That's why "Soft Power" has become the most powerful weapon in this new age.
Imagine...
A world where information is the new crude oil... Where attention is the currency... And beliefs are weapons... Used cunningly in this invisible battlefield...
"Influence" is the real victory. Not about conquering land anymore. It's about controlling minds, hearts, and actions...

Here are some prime examples of "Soft Power" playing out in our everyday lives.
Online Warfare - Fake news, twisted facts, everyone's sharing it like crazy on social media. A few taps on a screen can destroy reputations, incite hatred, and control people's thoughts without breaking a sweat. (Wichit calls it "promiscuous bits" in his lectures.)
Have you ever... almost made a bad decision because you believed a rumor or fake news? Have you ever... fallen prey to manipulation, been tricked into hating or opposing someone without even knowing why?
That, my friend, is Soft Power working its magic... behind the scenes...
Economic Control - Think about those skyrocketing interest rates, inflation… everything's getting more expensive by the day while our wallets get thinner.
That's the consequence of Soft Power wielded by a handful of people who control the global economy.
Ever wonder... why your money seems to be worth less and less each day? Why you work harder, but life doesn't get any better?
The "money" system, controlled by the few… that's the culprit...
Cultural Domination - Movies, TV shows, music, fashion… We consume it all every day, and it slowly seeps in, shaping our thoughts, values, and behavior without us even realizing it. It's a tool used by certain groups to manipulate and steer society...
Have you ever… wanted to be, have, or act like what you see in the media? Ever gone along with trends or fads, even if they didn't really reflect who you are?
That's the power of "Cultural Domination"...
"The scary part is… most people don't even realize they're being manipulated." Piriya shakes his head.
"It's like a frog being boiled alive. By the time they realize it, it's too late..."
Wichit sighs...
"The system is broken, slowly eroding us from the inside... God knows where it'll all end, but it's not gonna be pretty."
...

Wait, what about "Money"? Isn't that Soft Power too?
Money used to be a mirror, reflecting the "value" of work, of resources. It was a tool for exchanging, saving, building wealth...
But today... the "money" system is designed to be conjured up out of thin air. No real cost, no sweat. Just print more bills, and suddenly its value is distorted. Leading to "bubbles of inequality" and a crisis of faith in money itself...
It's like sand… the tighter you grip it, the more it slips away…
"Like when America ditched the Bretton Woods system and embraced Fiat currency, which they can print endlessly… It's how they became the world's financial superpower." Wichit explains.
"Countries that used to hoard gold, like Europe, China, Russia… they lost power because the money they held wasn't worth as much anymore."
"So what about Thailand? We're just a small country. How can we survive?" Piriya asks, worried.
"We can't just print our own money. We have no control over the global economy..."
"That's the million-dollar question…" Wichit says with a serious tone.
"If we don't wake up, if we're not prepared, Thailand could become a victim in this power struggle."
"We need to build up our "immunity," man..."
...
Bitcoin.. Hope or Menace?
In the midst of this Soft Power battleground, filled with deception and distorted truths, Bitcoin emerges… like a beacon of light piercing through the darkness. A glimmer of hope for a fairer world, a chance to reshape the global economy...
"Weapons should be used for self-defense, not to attack others." Wichit says, implying that Bitcoin is no different.
"It's a tool that can be used for good or for evil. It all depends on who's wielding it."
Bitcoin is presented as a symbol of "Truth" in the digital realm.
No one can counterfeit it or control it. It's finite, requiring energy to "mine." It's like applying the laws of physics to the financial system, creating honesty and transparency that traditional money can't achieve.
Imagine… a public ledger that everyone can see, transparent, unchangeable... That's Bitcoin.
"It's like a monetary revolution, creating a new system that's fair, transparent, and accessible to everyone." Piriya says excitedly.
"No one can print more Bitcoin on a whim. No one controls it."
"Exactly." Wichit adds.
"If people understand and accept it, Bitcoin can change the world. Bring balance, reduce inequality, and return power to the people."
"Imagine… a world where money belongs to the people, not the government or banks..."
But Bitcoin is a double-edged sword... In the hands of the righteous, it's a beacon of hope. A chance to create a fairer world.
*But in the wrong hands? *
It could become a menace, a tool for money laundering, crime, even a "weapon" for cyber warfare…
...

Where Does Thailand Stand?
"The question is… with Bitcoin challenging the old powers, how should Thailand respond?" Piriya asks seriously.
"Do we embrace it? Resist it? Or just ignore it?"
"Doing nothing is not an option, just like when we missed the boat on the gold standard." Wichit emphasizes.
"Back then, England pushed for the gold standard, but Thailand clung to the old way. We ended up losing out, trade deficits, economic downturn... We can't let history repeat itself."
"I agree." Piriya nods.
"We need to learn from the past and prepare for the future."
"The government and the people need to wake up, study, and truly understand Bitcoin." Wichit continues.
"Not just knowing what it is… but understanding its mechanisms, its potential, its risks."
"You mean… we should push for Bitcoin to be the main currency of Thailand?" Piriya asks.
"Whoa, hold your horses, Professor." Wichit smiles.
"No need to rush things. I think we should start by creating a space for people to learn and experiment with Bitcoin. Promote innovation and businesses related to blockchain. Maybe the government could set up a "regulatory sandbox" to control and mitigate risks along the way."
"But will the government be willing to relinquish control over money and embrace Bitcoin?" Piriya asks skeptically.
"It won't be easy." Wichit sighs…
"Power is seductive. Everyone wants to hold on to it. But if we see Bitcoin as an opportunity for Thailand to develop, to create stability and prosperity for the people, I believe the government will see the benefits and eventually embrace it."
"So what can we, the people, do?" Piriya asks.
"We need to be aware of Soft Power." Wichit answers.
"Question the information we receive, be savvy about media tactics, don't fall prey to anyone's agenda. And most importantly, use Soft Power constructively, for the betterment of society."
"Absolutely." Piriya agrees wholeheartedly.
"We need to be informed citizens, not manipulated victims."
"And remember… Bitcoin is not some far-off concept anymore. We need to learn, stay informed, and be prepared because the future is in our hands." Wichit concludes. "The future of money, the future of our country, the future of the world…"
The conversation ends… but the crucial question lingers.
Will Thailand keep up and be ready for the world's seismic shift?
The answer… lies with each and every one of us...
...

This conversation between Wichit and Piriya is like a doorway to another dimension.
A dimension we're familiar with, but never truly see clearly. A world teeming with games, power struggles, and manipulations happening all around us… often without us even realizing it.
They're trying to show us the "Soft Power," the formless force that lurks in every corner of our lives. From the news we consume, the economic systems we rely on, to the culture and values that shape our thoughts and actions.
They're not trying to scare us, but to "wake us up," make us aware, so we don't become victims in this game.
The things they emphasize most is the "importance of education." We need to understand Bitcoin, blockchain, and all these new technologies transforming our world. Not just "knowing" what they are, but "understanding" their mechanisms, their potential, their risks.
So we can decide how to use them, "for what," and "how."
Where does Thailand stand in this world where "Soft Power" is thriving?
Wichit and Piriya don't offer a clear-cut answer. Instead, they "invite" us to "ask questions," "think critically," and find our own answers.
We… as "citizens" of this new world… must be aware, learn, and adapt wisely to the changes. "Soft Power" isn't scary if we understand it and use it constructively.
We can turn "threats" into "opportunities."
The lessons from this conversation aren't just about "Soft Power" or "Bitcoin." They're about "awareness," "questioning," "critical thinking," and "taking responsibility" for the future of ourselves, our society, and our nation.
It's a wake-up call, revealing the "truth" of the world hidden beneath the "illusion" of "Soft Power." And it reminds us of the true "power" that lies in our hands…
the power to "choose," "decide," and "create" the future we want...

Decoding Wichit's Thoughts. "Soft Power" vs. "Hard Power" - The Game of Power in the Modern World
From the conversation, we see that Wichit views "power" beyond just weapons and military force. He defines it as the "ability to influence, persuade, control, or direct the behavior, thoughts, and decisions of others" without resorting to physical force or coercion.
Wichit sees a fascinating connection between Soft Power, Bitcoin, and national security in the digital age. Imagine a "power triangle" where each side influences and is intertwined with the others.
He divides "power" into two main forms..
First, there's "Hard Power," the traditional approach focused on using force, coercion, and direct control. It relies on tangible resources like military might, weapons, economic clout, or sanctions.
Think of examples like waging war, military occupation, controlling trade routes, or imposing economic sanctions.
Then there's "Soft Power." This new form of power emphasizes influence, persuasion, and attraction, making others "want" to follow without force or coercion.
Examples include using information to shape narratives and guide thinking, employing culture and entertainment to create values and trends that influence behavior, or using economic systems to incentivize desired actions.
Wichit believes that in today's world, Soft Power is gaining more influence and impact than Hard Power.
Why?
Because beliefs, values, and information can spread and penetrate people's minds easier and faster than brute force or coercion.
He compares modern warfare to "throwing percentages at each other in the air." Meaning that the fight for dominance in this era is no longer about physical destruction like in the past. It's a battle on an invisible battlefield, where the stakes are "information," "beliefs," and "influence."
In Wichit's view, Bitcoin can be both a "tool" and a "weapon" in the game of Soft Power.
And ultimately, "power," in any form, has both light and dark sides. It depends on the user, whether they choose to use it for creation or destruction...
When "Influence" Becomes a "Chain" on Thai Society
Yes, Soft Power has a glamorous, alluring side, evident in movies, music, TV shows, food, fashion, and tourism, all of which contribute to Thailand's income and image.
But there's a dark side... one that slowly erodes our thoughts, values, and identity... without us even noticing.
Look around… Is our younger generation today more obsessed with Korean dramas, Western series, K-pop, and designer brands than Thai movies, music, fabrics, or cuisine?
Do they dream of living like idols, celebrities, rather than ordinary Thais?
This is the consequence of Soft Power, influencing us to want to "be" and "have" like others, forgetting our roots, our identity, and our own values.
The Government Uses Soft Power to Control the People Too!
Ever wonder… why people believe government pronouncements more than news from fellow citizens? Why we accept unfair policies without much resistance?
Is Soft Power in the hands of the government used to craft an image, hide the truth, distract, and control people's thoughts?
I don't know... We need to observe and find the answers.
Are Today's Youth "Victims" or "Awakened"?
The younger generation, raised with the internet, social media, and global entertainment, is more susceptible to Soft Power's influence. But... they also have the potential to be aware, to question, to analyze, and to break free from the chains of manipulation.
Don't let influence become your prison…
Be "aware," "question everything," and "be yourself"
This is just a taste of what's discussed in the full video. To truly savor the "flavor" of "Soft Power" and "Bitcoin," you gotta watch the whole thing.
Watch more > Alt+Tab Season 2 EP4 : "พี่ชิต" ดร.วิชิต ซ้ายเกล้า
Trust me... you'll be blown away by the depth and intensity of the conversation.
"One listen is not enough."
Let me tell you… This video is "heavy," "dense," and "intense." Even me had to rewind several times to let it all sink in.
But it's "worth it," I promise. You'll "decode" the world today, understand the mechanics of "power" and "money" in a way no one's ever explained before.
So why share it?
Because "truths" like these shouldn't be hidden. "Knowledge" like this should be "spread" to "everyone."
But… to be honest, this video is "deep," "complex," and "hard to grasp" for the average person. So we have to transform ourselves into "interpreters," "translating" the "divine language" into "human language." Explain it simply, clearly, and visually.
Remember… sharing is not just "talking," it's about communication that's easy to understand, relatable, and resonates with the listener.
Because knowledge is precious… if it's "shared."
PS. Wichit's ideas and concepts regarding Soft War are heavily influenced and inspired by the book "Softwar: A Novel Theory on Power Projection and the National Strategic Significance of Bitcoin" by Major Jason P. Lowery. (2023)
-
 @ 1ad8f5d3:bb624486
2024-05-31 03:54:02
@ 1ad8f5d3:bb624486
2024-05-31 03:54:02Likes and views are great, but how about earning some money?
If you're someone who values your time and effort, you might be curious about the buzz surrounding the new NOSTR web and how everyone is getting paid on it. So, what exactly is NOSTR?
What is NOSTR?
NOSTR is revolutionizing the way we interact online. It offers content creators, curators, and even commenters with an easy way to earn real bitcoin for their contributions, while simplifying the content-sharing process. NOSTR is a communication protocol that enables modern social media apps to provide users with a seamless multi-app experience, where content only needs to be posted once to be viewed anywhere.
Say goodbye to the hassle of updating profiles and reposting content across multiple accounts, managing various comment sections, and juggling multiple inboxes. NOSTR unifies everything, allowing you to switch between different apps without losing followers or posts. The best part? The bitcoin rewards incentivize higher quality content, transforming social media into an unparalleled experience where a casual poster can evolve into an article author or a meme maker into a marketing guru.
How do I connect to NOSTR?
For a quick start with NOSTR try Alby. 1) Open the Firefox browser. 2) Add-on the Alby browser extension. 3) Set a passcode for unlocking.
4) Connect your Alby account or connect your own wallet.You're ready to start! Alby has generated a NOSTR identity for you. If you've used NOSTR before, you might already have an identity. To continue using it, simply import the identity's private key (npriv) into the browser extension.
Here's how:
- Go to wallet settings -> key management -> NOSTR settings.
- Choose to delete, keep, or import your npriv.
You can install the extension on multiple devices, such as your desktop, laptop, and mobile. After installing, check the NOSTR settings to ensure you're using the same identity across all devices. You could also install mobile nostr apps like Amethyst, Primal & Damus.
Where do I begin with NOSTR?
1. Set Up Your NOSTR Profile.
- Open a NOSTR Client: Start by opening a NOSTR client in your browser, such as noStrudel, and log in using your browser extension.
- Edit Your Profile: Navigate to your profile and find the edit button. Here, you can input your Display Name, Profile Picture, Bio, and add your lightning address.
- Lightning Address: If you're using an Alby account, your lightning address can be found in the browser extension (e.g. orangemart@getalby.com). Alternative lightning address providers include Blink, Coinos, WoS, ZBD and more. If you run your own node then your address could be yourname@yourdomain.
2. Make Your First Post.
In this step, we'll use a different NOSTR web client, such as Snort.
- Sign In: Sign in with your browser extension.
- Profile Information: You'll notice that all the profile information you updated in the previous step with the other client is already set up here. This seamless transfer of information is one of the advantages of using NOSTR.
- Make Your First Post: Let's make our first post using Snort.
- Switch Clients: After posting, switch to another NOSTR client to view your post. This exercise will help you understand how to navigate and interact with the new web.
Why Post to NOSTR?
Posting your content to NOSTR is worth your time for many reasons:
- Uncensorable: NOSTR supports an unlimited number of clients and servers (including self-hosted), ensuring your content is always accessible to your followers.
- Innovative: NOSTR's open and competitive environment constantly brings new and innovative ways for your audience to discover and enjoy your content.
- Monetizable: From the first view, you can earn bitcoin for your content without any gatekeeping or advertisers.
What can I do on NOSTR?
- Broadcast a livestream with zap.stream.
- Author an article with habla.news.
- Discover and share insights with highlighter.com.
- Host images, gifs, music and videos with nostr.build.
- Start a discussion forum with satellite.earth and host files with Satellite's media CDN.
- Socialise with coracle.social and snort.social.
- Share a video with flare.pub.
- Host a voice chat room with nostrnests.com.
- Curate lists with pinstr.app.
- Sell stuff with shopstr.store and plebeian.market.
- Collaborate and produce music with Stemstr.app.
- Contribute cooking recipes to zap.cooking.
- Create emoji sets with emojito.meme.
- Share files with dtan.xyz
- View and manage all your nostr activity and discover new tools with nostrudel.ninja.
- and so much more for you to discover!
Conclusion
NOSTR is a protocol for communicating across the web. NOSTR features native "zapping", which enables little bits of Bitcoin to flow between users. Your identity is controlled by you, not any one platform. With one identity, you can connect to an ever-growing number of apps.
Get started on NOSTR today with Alby and if you appreciate this post then consider zapping some sats our way.
-
 @ 6ad3e2a3:c90b7740
2024-08-18 16:49:15
@ 6ad3e2a3:c90b7740
2024-08-18 16:49:15I do a lot of Sudoku. They’re logic puzzles, using the numbers one through nine in a nine-by-nine grid. The goal is to use all nine numbers once and only once in every nine-field row, column and box. If you find yourself with two sixes in the same row, for example, you’ve blown it.
It’s pure deductive reasoning, no probability, no induction (if it happened this way in nine of the last 10 puzzles, it’s probably the case here!), no guessing. You do not want to fill in a number unless you are absolutely sure it’s the only place it could go. As in bet-your-life-on-it sure. If there’s more than one place for it, you do not guess. It’s like Highlander: “There can only be one!”
I find it relaxing — there is no ambiguity, no argument. You either know for sure and know why you know, or you don’t know.
What a contrast to the information environment the last few years, where there are so many people, wittingly or not, feigning certainty while espousing bullshit. Compromised fact-checkers relying on captured science and medicine, misleading the demoralized and credulous, desperate for a narrative to hold off the tidal wave of fear and doubt. A giant chorus of the obedient protecting themselves from dangerous dissent with their various incantations: “Conspiracy Theory!’ “You Are Not An Epidemiologist!” “Trust the Science!”
But if the 6 can’t be here and here, and the 5 must be there, then there’s nowhere else for the 7 except there. And once we know the 7 is there, the 7 in the bottom left box must be there. That means the 8 is in the lower row, so we can eliminate the eights from the upper and middle rows of that box…
Even when you can’t immediately solve a Sudoku, when the lightning bolt of insight that opens up the whole puzzle hasn’t yet struck, at least you know for sure what you don’t know. No matter how difficult the puzzle, there is such simplicity, order and peace in the realm of pure deductive logic.
. . .
The harder puzzles require you to make assumptions. That is, you might have a box with two possible candidates, and you assume one is correct conditionally and go through the implications of it.
For example, if a box can contain only a 1 or a 3, you might assume it’s a 1, see what happens to the boxes around it, and then alternatively assume it’s a 3, and see the effects of that. If some other box has three candidates, say 3, 4 and 7, and the 1-assumption, makes it a 3, and the 3 makes it a 7, you can be sure it’s not a 4.
Eliminating the 4 doesn’t tell you what the answer is, either for it or the initial box, but it narrows down the possibilities and enables you to play out further conditional scenarios more easily. In other words, by running scenarios for both, “if x is true” and “if x is false” you can find out that “z must be false” even though you still don’t know the truth with respect to x.
It’s important though not to treat your conditional findings as true. In the example above, assuming a 1 in the first box yielded a 3 in the second. If you fill in the 3, though, you just making a 50/50 gamble that might screw up the entire puzzle.
That sounds obvious, but that’s only because my example contains two boxes. Imagine you’re five or six boxes down the cascading chain, making assumptions (and then assumptions within assumptions — like the dreams within dreams of Inception — and you can see how easily you could get it confused.
There is a big difference between “this is the case if x is true”, and “this is case, period.” But sometimes when you’re deep down the assumption rabbit hole, you forget that the entire edifice is based on a conditional. That’s how you wind up with two 6s in the same box and realize the entire 40 minutes you’ve spent wrestling with this puzzle were wasted. You thought you were making breakthroughs, but it turns out you were living a lie the entire time!
. . .
The real world is infinitely more complex than even the hardest Sudoku. It requires us to make conditional assumptions within conditional assumptions all the time. Assuming, the data from this study in the Lancet is correct, assuming that its design is not flawed, assuming it hasn’t been influenced by its funding sources, assuming the subjects in the study don’t differ in some material respect from me (lifestyle, genetics, etc.), you should consider it’s findings.
But if you forget the assumptions involved and simply fill in the box based on the conclusions therein, you run the risk of making a serious error. Many people adopted low-fat, high sugar diets to defeat cholesterol, got on statins, avoided the sun, became vegan for health. It’s pretty obvious where I stand on those practices, but irrespective of whether they’re in fact beneficial, the decision to adopt them is based on many (dubious) assumptions being true.
. . .
The beauty of Sudoku is not only do you know — or find out soon at minimal cost — what you don’t know, but also your assumptions (at least initially) are explicit. You say to yourself, “assume this is a 1, and let’s see what it does, and assume it’s instead a 3, and let’s see what that does.” You are therefore capable of untangling the results of your conditional experiments and drawing sound conclusions from them.
Often when I talk with people about health, civil liberties, medicine or other matters of import, the conversation gets derailed due to conflicting assumptions. Can we examine a question and in so doing untangle the conditional beliefs informing it? Can we agree that what one is saying is only true if one buys into particular premises, and that those premises themselves cannot be taken as a given, but also should be examined?
If you support giving endless weapons to Ukraine no matter the cost, is that because you believe it is an innocent being attacked without provocation by the evil Vladimir Putin? Is that assumption beyond scrutiny? It doesn’t matter where you come out on that question so much as recognizing you are filling in a box based on that assumption, and should that assumption be false, your entire policy prescription is bankrupted.
Let’s say you do believe Putin invaded Ukraine because he is evil and will move onto the rest if Europe next, i.e., he’s basically Hitler. Why do you believe that? Do you have first-hand knowledge of him, or is it something you read in the New York Times? If the latter, then your belief about Putin being true depends on the Times being reliable with respect to geopolitics.
If you follow this sort of reasoning to its logical conclusion, you end up looking for first principles. What can I trust? How can I be sure to fill in the boxes accurately so as not to find out later I was living a lie?
It’s difficult in the real world to find certainty. Even René Descartes, who settled on “I think, therefore I am” didn’t get far*. The best we can do, in my opinion, is via the scientific method, offering a hypothesis that purports to fit the facts, and scrapping it as new facts and better-fitting (more explanatory) hypotheses come along.
The allegory of a perfectly deductive realm like Sudoku then isn’t in completing the puzzle. It’s in not filling in the boxes inappropriately. Forget about believing what’s true, but take great pains to avoid the lie.
*And at best Descartes found an Oscillating Truth, if you think, then you must exist, but you could be deluded, so maybe not, but if you can be deluded then you must exist, but you could be deluded about that, so maybe not, but if you can be deluded about that, then you exist… ad infinitum.
-
 @ 56a6da9b:7f5a2243
2024-08-18 15:08:04
@ 56a6da9b:7f5a2243
2024-08-18 15:08:04From The Precipice Lectures Archive
DAY 17, IN THIS DIMENSION, OF FLASH AUGUST FICTION. I woke up giggling yesterday morning. That's pretty much all I have to say about this one, except here is some background info on the 4th dimension from an earlier episode: How's the Fourth Dimension? _
I am on the web3 apps. The podcast is called “Smell the Inside of Your Nose. Do it Right Now”. _
Here's the Substack podcast. Here is Spotify. RSS here. I think listening is better, that's just me. _ _
Dr. Freebius Lipsmaciladapus: The Absence of Pathology in the 4th Dimension
From The Precipice Lectures Archive 1019 WORDS WRITTEN IN ABOUT 45 MINUTES _
[ Clears throat ] Gentlemen,
To discuss the 4th dimension, we must discuss some of the laws that govern the 3rd-dimensional existence we are currently experiencing.
It is not necessary to understand how electricity works in order to use it. When one walks into a room, one uses a light switch, and the light fills the room. This is functional knowledge. We need not comprehend the details and intricacies of electronics in order to use electronics. In our experience in these three dimensions, there are many activities that are possible. It is possible to do unnecessary and even undesirable things. It is not wise or necessary to do a thing, simply because it is possible. Doing such things, however, does not alter or disrupt the nature of this three-dimensional realm.
The use of devastating weapons, for instance, is utilized by those with devious and avaricious intent and who do not possess the capacity for the creation and exchange of values. This is possible and, in fact, common in our plane of existence in this realm. There is no law of nature or physics in this dimension that prevents this.
These activities are not possible in the 4th dimension, to which some will become a part. There are laws of nature and physics in the fourth dimension that prevent such puerility. Actors will be bound to this dimensional realm that we are experiencing until better thinking and practices happen as a matter of course along their lifetimes.
First, we must describe how the fourth dimension is structured and what material it comprises. Our imaginations are the best example for describing the material; the matter that the fourth dimension comprises.
It does not function in the same way that our imaginations do, but it is comprised of the same matter. That is not to say that the fourth dimension allows you to create ex-nihilo. That is to say one cannot simply create something from nothing in the fourth dimension, as we can in our imaginations.
In this three-dimensional existence, we watch skilled magicians create flowers out of thin air and pull rabbits out of hats. These are illusions. To actually do that is not possible in the fourth dimension. However, existing matter can easily be manipulated physically using only one's hands and bodies. For instance, one might have a bowl of soup but no spoon, only a butter knife. In the 4th dimension, one can shape the knife easily with one's fingers to fashion a spoon for eating the soup.
Suppose there is a large basket on the dinner table, but only two tomatoes are in the basket, and the basket is taking up too much room on the table. One simply takes the basket and, using one's hands, and understanding the lattice of the basket, simply compresses the basket with one's hands. One can reshape the basket so that it fits the two tomatoes. Now there is more room on the table. This sort of thing is common practice in the fourth dimension. These are elementary examples.
You have a small box, but you need a large box for a large item. One simply changes the size of the box for your large item, and so on. One cannot pull things out of thin air, as you can with your imagination, but you can manipulate already existing material physically in a way that is not physically possible in our current realm.
There are certain conceptions about value and function that are simply a part of a person's nature there. The very nature of the fourth dimension is integrated with all the natures associated in it. Therefore, pathology cannot be part of that dimension. Pathological people and such behaviors would be prohibitive to the very matter that existence is comprised of in the fourth dimension, and it is necessary for the fourth dimension to exist. All dimensions must exist. They coincide, and are related.
If pathologies that are possible in the current dimension that we are experiencing in this moment were to breach the fourth dimension, it would be a prohibitive disruption effecting all of existence in all dimensions. The sort of piracy and mendaciousness that can exist in this dimension simply cannot, by nature and the laws of physics, be a part of the fourth dimension. There are no violations of laws in physics, in any dimension.
One might consider the reports of military personnel, where crafts appear above nuclear silos. These may be concerned beings from other dimensions, understanding how such operations could affect them in their dimension. They perhaps feel a need to intervene in this dimension in order to preserve their own.
Why? Some ask. Why is it not possible for such mendacity to exist in the fourth dimension? Is it perfect there? Of course, it is not perfect; it is more advanced, so to speak, but not perfect. There are imperfect events and, of course, imperfect people who make mistakes and take liberties that are possible, though perhaps not wise. To understand the reason, it's an imperative to remember that the material; the very matter of the 4th dimension consists of the same matter that our imaginations are comprised of.
Here is the illustration to use. You may think of the imaginations of individuals as fields of energy, or waves, or particles. It should be easy then to understand how affecting the fields, or waves; or particles of the fourth dimension as a whole, in the behaviors that we have become accustomed to in this dimension, would be disruptive and, in fact, destructive to existence itself.
For this simple reason, those who rule the three-dimensional realm that we experience simply could not be a part of the fourth dimension. Again, only those who would by their matter of course master the practice of value creation and production be a part of that dimension. While there are blunders and varying degrees of judgement there, no pathological behavior is possible, as it is antithetical to the very existence of the matter; the field; the waves; the particles of which the fourth dimension is comprised. These are simply the natural and physical laws of the fourth dimension.
The End
That was a wild dream, and that’s what I got out of it. I was glad I was able to get a story out of it. Here is another link to a different episode where I get into coinciding planes and why other beings can’t always interact with us. It is called Alien Avoidance On Our Coinciding Plane. I hope you might get a paid subscription, or buy me a coffee, or donate some bitcoin.
I wish you the best in these messed up times. My target audience are the people doing the very difficult and risky anti-corporate, anti-war, independent, honest journalism. I want to be a brief respite from the craziness for them. If you know any of them and want to point out my 10-20 minute, daily storytelling podcast, that would be the best. I’m Herschel Sterling, and I’m here to help.
originally posted at https://stacker.news/items/653477
-
 @ b12b632c:d9e1ff79
2024-05-29 12:10:18
@ b12b632c:d9e1ff79
2024-05-29 12:10:18One other day on Nostr, one other app!
Today I'll present you a new self-hosted Nostr blog web application recently released on github by dtonon, Oracolo:
https://github.com/dtonon/oracolo
Oracolo is a minimalist blog powered by Nostr, that consists of a single html file, weighing only ~140Kb. You can use whatever Nostr client that supports long format (habla.news, yakihonne, highlighter.com, etc ) to write your posts, and your personal blog is automatically updated.
It works also without a web server; for example you can send it via email as a business card.Oracolo fetches Nostr data, builds the page, execute the JavaScript code and displays article on clean and sobr blog (a Dark theme would be awesome 👀).
Blog articles are nostr events you published or will publish on Nostr relays through long notes applications like the ones quoted above.
Don't forget to use a NIP07 web browser extensions to login on those websites. Old time where we were forced to fill our nsec key is nearly over!
For the hurry ones of you, you can find here the Oracolo demo with my Nostr long notes article. It will include this one when I'll publish it on Nostr!
https://oracolo.fractalized.net/
How to self-host Oracolo?
You can build the application locally or use a docker compose stack to run it (or any other method). I just build a docker compose stack with Traefik and an Oracolo docker image to let you quickly run it.
The oracolo-docker github repo is available here:
https://github.com/PastaGringo/oracolo-docker
PS: don't freak out about the commits number, oracolo has been the lucky one to let me practrice docker image CI/CD build/push with Forgejo, that went well but it took me a while before finding how to make Forgejo runner dood work 😆). Please ping me on Nostr if you are interested by an article on this topic!
This repo is a mirror from my new Forgejo git instance where the code has been originaly published and will be updated if needed (I think it will):
https://git.fractalized.net/PastaGringo/oracolo-docker
Here is how to do it.
1) First, you need to create an A DNS record into your domain.tld zone. You can create a A with "oracolo" .domain.tld or "*" .domain.tld. The second one will allow traefik to generate all the future subdomain.domain.tld without having to create them in advance. You can verify DNS records with the website https://dnschecker.org.
2) Clone the oracolo-docker repository:
bash git clone https://git.fractalized.net/PastaGringo/oracolo-docker.git cd oracolo-docker3) Rename the .env.example file:
bash mv .env.example .env4) Modify and update your .env file with your own infos:
```bash
Let's Encrypt email used to generate the SSL certificate
LETSENCRYPT_EMAIL=
domain for oracolo. Ex: oracolo.fractalized.net
ORACOLO_DOMAIN=
Npub author at "npub" format, not HEX.
NPUB=
Relays where Oracolo will retrieve the Nostr events.
Ex: "wss://nostr.fractalized.net, wss://rnostr.fractalized.net"
RELAYS=
Number of blog article with an thumbnail. Ex: 4
TOP_NOTES_NB= ```
5) Compose Oracolo:
bash docker compose up -d && docker compose logs -f oracolo traefikbash [+] Running 2/0 ✔ Container traefik Running 0.0s ✔ Container oracolo Running 0.0s WARN[0000] /home/pastadmin/DEV/FORGEJO/PLAY/oracolo-docker/docker-compose.yml: `version` is obsolete traefik | 2024-05-28T19:24:18Z INF Traefik version 3.0.0 built on 2024-04-29T14:25:59Z version=3.0.0 oracolo | oracolo | ___ ____ ____ __ ___ _ ___ oracolo | / \ | \ / | / ] / \ | | / \ oracolo | | || D )| o | / / | || | | | oracolo | | O || / | |/ / | O || |___ | O | oracolo | | || \ | _ / \_ | || || | oracolo | | || . \| | \ || || || | oracolo | \___/ |__|\_||__|__|\____| \___/ |_____| \___/ oracolo | oracolo | Oracolo dtonon's repo: https://github.com/dtonon/oracolo oracolo | oracolo | ╭────────────────────────────╮ oracolo | │ Docker Compose Env Vars ⤵️ │ oracolo | ╰────────────────────────────╯ oracolo | oracolo | NPUB : npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2 oracolo | RELAYS : wss://nostr.fractalized.net, wss://rnostr.fractalized.net oracolo | TOP_NOTES_NB : 4 oracolo | oracolo | ╭───────────────────────────╮ oracolo | │ Configuring Oracolo... ⤵️ │ oracolo | ╰───────────────────────────╯ oracolo | oracolo | > Updating npub key with npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2... ✅ oracolo | > Updating nostr relays with wss://nostr.fractalized.net, wss://rnostr.fractalized.net... ✅ oracolo | > Updating TOP_NOTE with value 4... ✅ oracolo | oracolo | ╭───────────────────────╮ oracolo | │ Installing Oracolo ⤵️ │ oracolo | ╰───────────────────────╯ oracolo | oracolo | added 122 packages, and audited 123 packages in 8s oracolo | oracolo | 20 packages are looking for funding oracolo | run `npm fund` for details oracolo | oracolo | found 0 vulnerabilities oracolo | npm notice oracolo | npm notice New minor version of npm available! 10.7.0 -> 10.8.0 oracolo | npm notice Changelog: https://github.com/npm/cli/releases/tag/v10.8.0 oracolo | npm notice To update run: npm install -g npm@10.8.0 oracolo | npm notice oracolo | oracolo | >>> done ✅ oracolo | oracolo | ╭─────────────────────╮ oracolo | │ Building Oracolo ⤵️ │ oracolo | ╰─────────────────────╯ oracolo | oracolo | > oracolo@0.0.0 build oracolo | > vite build oracolo | oracolo | 7:32:49 PM [vite-plugin-svelte] WARNING: The following packages have a svelte field in their package.json but no exports condition for svelte. oracolo | oracolo | @splidejs/svelte-splide@0.2.9 oracolo | @splidejs/splide@4.1.4 oracolo | oracolo | Please see https://github.com/sveltejs/vite-plugin-svelte/blob/main/docs/faq.md#missing-exports-condition for details. oracolo | vite v5.2.11 building for production... oracolo | transforming... oracolo | ✓ 84 modules transformed. oracolo | rendering chunks... oracolo | oracolo | oracolo | Inlining: index-C6McxHm7.js oracolo | Inlining: style-DubfL5gy.css oracolo | computing gzip size... oracolo | dist/index.html 233.15 kB │ gzip: 82.41 kB oracolo | ✓ built in 7.08s oracolo | oracolo | >>> done ✅ oracolo | oracolo | > Copying Oracolo built index.html to nginx usr/share/nginx/html... ✅ oracolo | oracolo | ╭────────────────────────╮ oracolo | │ Configuring Nginx... ⤵️ │ oracolo | ╰────────────────────────╯ oracolo | oracolo | > Copying default nginx.conf file... ✅ oracolo | oracolo | ╭──────────────────────╮ oracolo | │ Starting Nginx... 🚀 │ oracolo | ╰──────────────────────╯ oracolo |If you don't have any issue with the Traefik container, Oracolo should be live! 🔥
You can now access it by going to the ORACOLO_DOMAIN URL configured into the .env file.
Have a good day!
Don't hesisate to follow dtonon on Nostr to follow-up the future updates ⚡🔥
See you soon in another Fractalized story!
PastaGringo 🤖⚡ -
 @ 3bf0c63f:aefa459d
2024-05-24 12:31:40
@ 3bf0c63f:aefa459d
2024-05-24 12:31:40About Nostr, email and subscriptions
I check my emails like once or twice a week, always when I am looking for something specific in there.
Then I go there and I see a bunch of other stuff I had no idea I was missing. Even many things I wish I had seen before actually. And sometimes people just expect and assume I would have checked emails instantly as they arrived.
It's so weird because I'm not making a point, I just don't remember to open the damn "gmail.com" URL.
I remember some people were making some a Nostr service a while ago that sent a DM to people with Nostr articles inside -- or some other forms of "subscription services on Nostr". It makes no sense at all.
Pulling in DMs from relays is exactly the same process (actually slightly more convoluted) than pulling normal public events, so why would a service assume that "sending a DM" was more likely to reach the target subscriber when the target had explicitly subscribed to that topic or writer?
Maybe due to how some specific clients work that is true, but fundamentally it is a very broken assumption that comes from some fantastic past era in which emails were 100% always seen and there was no way for anyone to subscribe to someone else's posts.
Building around such broken assumptions is the wrong approach. Instead we should be building new flows for subscribing to specific content from specific Nostr-native sources (creators directly or manual or automated curation providers, communities, relays etc), which is essentially what most clients are already doing anyway, but specifically Coracle's new custom feeds come to mind now.
This also reminds me of the interviewer asking the Farcaster creator if Farcaster made "email addresses available to content creators" completely ignoring all the cryptography and nature of the protocol (Farcaster is shit, but at least they tried, and in this example you could imagine the interviewer asking the same thing about Nostr).
I imagine that if the interviewer had asked these people who were working (or suggesting) the Nostr DM subscription flow they would have answered: "no, you don't get their email addresses, but you can send them uncensorable DMs!" -- and that, again, is getting everything backwards.
-
 @ 7308f407:94057dcf
2024-05-22 18:12:02
@ 7308f407:94057dcf
2024-05-22 18:12:02Details
- ⏲️ Prep time: Prep Time for Birria Beans
- 🍳 Cook time: Initial Boiling: 10 minutes Simmering: 2 to 3 hours (depending on the desired softness of the beans) In total, the estimated cooking time is approximately 2 hours and 10 minutes to 3 hours and 10 minutes.
- 🍽️ Servings: The serving size for the Birria Beans recipe depends on the quantity of beans and broth used. Given the ingredients listed, this recipe typically serves approximately 8-10 people+.
Ingredients
- 12 cups broth from birria (previous recipe)
- 1/2 onion
- 4 jalapeños or serrano peppers
- Water
- Salt to taste
- Beef from birria (optional)
Directions
- Wash the beans and let them soak for 30 minutes.
- In a large pot, add all the ingredients above.
- Set the heat to high and allow the mixture to come to a boil. Let it boil for 10 minutes.
- Reduce the heat to medium-low and cook for about 2 to 3 hours until the beans become soft.
- -To check the consistency of the beans, remove one from the pot to a plate. Using a fork, poke through to cut it in half. This method will help you easily tell if they are soft. You can also taste the beans.
- -If they are not soft yet, continue to cook for another 30 minutes.
- Every 30 minutes to 1 hour, check the beans to ensure they have enough water to cover them. They will dry out if the water level drops below the beans.
- You can also add beef from birria into the beans for added flavor.
- Enjoy the savory and slightly spicy flavor of the pinto beans cooked in red birria broth, topped off with cilantro, onion, and lime.
-
 @ 126a29e8:d1341981
2024-05-22 06:47:20
@ 126a29e8:d1341981
2024-05-22 06:47:20Esta es la traducción de una carta de Ross Ulbricht que se publicó en su blog en Septiembre de 2019. Podéis leer el artículo original aquí: https://rossulbricht.medium.com/bitcoin-equals-freedom-6c33986b4852
Algo especial sucedió en el primer año después de que Satoshi nos regalara Bitcoin. Algo que nadie esperaba y que muchos pensaban que era imposible. Intenta imaginar Bitcoin en aquel entonces, antes de que pudieras comprar cosas con él, antes de que hubiera un tipo de cambio, antes de que nadie supiera realmente qué pasaría con él, si es que pasaba algo. Bitcoin no empezó como dinero. Se convirtió en dinero, pero lo hizo de forma distinta a cualquier dinero anterior. A pesar de todas las cosas que Bitcoin ha hecho posibles, a pesar de todas las formas en que está cambiando nuestro mundo, no apreciamos plenamente o ni siquiera entendemos lo que sucedió en aquellos primeros días, cuando era sólo un juguete para geeks.
Cualquier otro dinero anterior al Bitcoin -en la larga historia de la civilización humana- se valoraba por razones distintas a su uso como dinero. El ganado en África, los sellos de correos en las prisiones, las conchas marinas y los metales preciosos se han utilizado como dinero y encajan en este patrón. La única excepción es el dinero fiduciario -algo declarado como dinero por una autoridad-, pero incluso las monedas fiduciarias nacionales estuvieron en su día respaldadas por algo con valor previo, como el oro.
Bitcoin cambió todo eso. Bitcoin no tenía ningún valor previo y nadie estaba obligado a utilizarlo, pero de alguna manera se convirtió en un medio de intercambio. Las personas que no entienden y se preocupan poco por Bitcoin pueden, sin embargo, aceptarlo como pago porque saben que puede ser utilizado para pagar por otra cosa o ser intercambiado por dinero convencional.
La gente suele mencionar las pizzas que se compraron por diez mil bitcoins y, en retrospectiva, se burlan del tipo que se comió lo que se convertiría en un almuerzo multimillonario. A mí me interesa más la persona que renunció a dos pizzas en perfecto estado por meros bitcoins. ¿Qué vio en esos bits y bytes, en esa firma digital de algo que la gente llamaba cadena de bloques? Lo que motivó al vendedor de pizzas pudo haber llamado también la atención de los primeros mineros, que no podían vender pero acumulaban alegremente. Quizá inspiró a los que simplemente regalaban bitcoins por miles. Fuera lo que fuese, era algo nuevo.
La teoría económica clásica dice que un intercambio no se produce a menos que ambas partes valoren más lo que reciben que lo que entregan. Entonces, ¿de dónde viene el valor? Bitcoin nunca debería haber despegado, pero lo hizo. Incluso un producto nuevo tiene algún tipo de valor, y los primeros en adoptarlo corren el riesgo de no obtener el valor de su dinero, pero aún así esperan ganar con el intercambio.
En cambio, los primeros usuarios de Bitcoin no tenían ni idea de lo que sabemos ahora. Todo lo que tenían era un sueño, una convicción y el entusiasmo suficiente para convertir un artilugio digital en un fenómeno multimillonario del que sólo estamos empezando a ver los efectos.
Te diré lo que creo que pasó, aunque lo cierto es que nadie lo sabe. Es casi magia que Bitcoin pudiera surgir de la nada y, sin valor previo ni decreto de autoridad, convertirse en dinero. Pero Bitcoin no se originó en el vacío. Fue la solución a un problema con el que los criptógrafos llevaban lidiando muchos años: Cómo crear dinero digital sin autoridad central que no pudiera falsificarse y en el que se pudiera confiar.
Este problema persistió durante tanto tiempo que algunos dejaron la solución a otros y soñaron en cambio con cómo sería nuestro futuro si el dinero digital descentralizado llegara a existir de alguna manera. Soñaban con un futuro en el que el poder económico del mundo estuviera al alcance de todos, en el que el valor pudiera transferirse a cualquier lugar con sólo pulsar una tecla. Soñaban con que la prosperidad y libertad dependieran únicamente de las matemáticas de una encriptación robusta.
Bitcoin nacía pues en terreno fértil y era reconocido por quienes lo habían estado esperando. Fue un momento histórico para ellos, mucho más importante que las pizzas o las facturas de la electricidad generadas por la minería. La promesa de libertad y el encanto del destino dieron energía a la comunidad inicial. Bitcoin se adoptó consciente y espontáneamente como dinero mientras nadie lo veía, y nuestro mundo nunca volverá a ser el mismo.
https://freeross.org
-
 @ 6ad3e2a3:c90b7740
2024-05-21 16:36:06
@ 6ad3e2a3:c90b7740
2024-05-21 16:36:06I heard it somewhere, I think it was from Preston Pysh, who suggested the bitcoin ETFs might be a trap of sorts, wherein once a sufficient number of coins were in their custody*, the government would “6102” them for national security.
* I think Coinbase might actually hold the keys to the ETF coins, so “custody” probably isn’t the right word to describe the arrangement between the ETFs and those buying price exposure to, but not actual, bitcoin via those instruments.
The number “6102” refers to the Emergency Banking Relief Act of 1933 and Executive Order 6102 that authorized President Roosevelt to force American citizens to turn in their gold. (He did this to issue more gold-backed money during The Great Depression.)
Because bitcoin private keys are merely information and therefore difficult to seize from individuals en masse (you’d have to make people cough up information they could claim to have lost or forgotten), the ETFs could be a roundabout way to create a concentrated and easy-to-seize hard money to which to peg the dollar.
As it stands, the US-based ETFs collectively have amassed nearly a million coins, roughly five percent of the total 21 million supply, (a few million of which are likely lost forever.) Let’s fast forward a few years and assume the following (all of which seem plausible to me, though the exact numbers are not important):
The national debt, presently at $35 trillion, balloons to $50 trillion. The interest expense alone on the debt at five percent rates is 2.5 trillion per year, roughly three times the size of the entire (on the books) defense budget. Official inflation numbers are running north of five percent, even though people know real inflation is upwards of 10. Bitcoin is trading at $1 million per coin (roughly 14x where it is now.) If you think that’s crazy, consider $70K is 14x $5K where it was in the spring of 2020. Let’s also assume the ETFs collectively have two million coins (more than 10 percent) at that point.
Essentially, the dollar is on the brink of hyper-inflating, the US at risk of going full Weimar. Gold is at $10K per ounce, but it’s just a rock and can’t underpin a global system where money moves at the speed of light, and there’s no way for people to audit its supply in an environment of increasing global distrust.
The US government policy makers put on poker faces for the public to buy time, but are well aware of the precarity. They are faced with two terrible choices: raise rates to try and tame inflation the way Paul Volcker did in the 1970s, thereby skyrocketing the interest expense on our much larger debt and crippling the economy, or cut rates, make already severely debased money even cheaper and usher in almost certain hyperinflation.
Under these circumstances, where both choices portend a high likelihood of government collapse, it’s not only conceivable, but I’d argue, probable they avail themselves of a third option: 6102 the ETF coins.
I imagine it might go down like this: The administration, whoever it is, meets with Brian Armstrong of Coinbase and the CEOs of the ETF issuers, gives them a very brief heads up: “We’re taking the coins for national security and compensating all your clients at the face value at which they’re trading,” i.e., they would just give them today’s market value if they were to sell, i.e., $1M per coin. So if there were two million coins in ETF custody, that would be $2T distributed pro rata among the investors.
Most of the investors would realize a significant (nominal) profit from where they bought. Moreover, the CEOs would be considered patriots (by the government) if they complied and criminals if they refused. They would probably be allowed/encouraged to buy underlying coins for themselves that day, knowing what was about to happen too. In short, it’s almost inconceivable to me they wouldn’t go along, and in fact, might have an inkling of this end game already.
After the government surreptitiously gained control of the keys to the ETF coins, they would make an announcement: the US dollar is now fully backed by the hardest money in human history and fully redeemable at $30M USD per coin. In other words, their two million coins would now be worth $60 trillion, more than enough to pay off the debt in its entirety and restore confidence in the dollar.
The dollar would inflate immediately now that it was debased 30:1 vs its prior bitcoin price. But that ratio would apply only to bitcoin. Real estate prices might go up 5x, food 2x, it’s impossible to say. The dollar would have real redeemable value for something of finite supply and would no longer be printable via fiat so long as that tether remained in place. In fact, and this is beyond my tech knowledge, the announcement could be tied to some kind of cryptographically unforgeable and legally binding arrangement wherein the dollar must always be pegged at that 30:1 rate. If it could be arbitrarily debased further, there might be no point.
Of course, this would handicap the government significantly — no longer could it print money to fund proxy wars in Ukraine, invade Iraq or shell out off-the-books blank checks for CIA operations in Central America. It would lose much of its power as the expenses of empire would have to be justified or greatly curtailed. And while those that wield this excessive and dangerous power would never go along with it voluntarily, under the circumstances above — facing chaotic collapse — they would have little choice.
There would be significant pain — even my arbitrary estimates of real estate and food inflation would be catastrophic for many, and it could easily be much worse than that. But compared to the alternative it would be like an airplane touching down on the runway during a storm with but a mild bump.
-
 @ 75da9402:77a65b5c
2024-05-19 00:07:36
@ 75da9402:77a65b5c
2024-05-19 00:07:36Empezare este articulo indicando que iba hacer publicado como un hilo en Twitter o X o como diablos se llame ahora por que mi intencion era trasmitir a otros que existe algo mucho mejor donde pueden empezar nuevamente a disfrutar de otra forma de comunicarse, pero mi sorpresa fue grande al momento de enviar el hilo de tweets, me salio el mensaje "no se puede enviar" usted debe UPDATE TO PREMIUM para atreverse hacer un post en esta empresa que protege la libertad de expresion...lol...(:-O). Como yo casi ya no escribo nada en X y lo uso solo para informarme de lo que pasa en mi pais, no sabia esta nueva limitacion. Ahora volvi a recordar por que deje de usarlo. Pero bueno, aqui voy a desahogar mi hilo para luego compartirlo en X, por que me van a leer quieran o no, jajaja.
Te cuento una pequeňa historia.
Alguna vez me preguntaron por qué me gustaba Twitter (hoy X) más que otras redes sociales ya que yo era un joven audaz que siempre interactuaba ahi jaja. Y mi respuesta fue simple en esos aňos: Twitter es una selva digital donde se genera el debate público e informativo a nivel mundial y aqui puedo decir lo que yo quiera (pobre iluso). Pero luego las cosas fueron cambiando en mi RRSS favorita, en algun momento se convirtio en un hueco lleno de toda clase de basura digital de la cual habia huido siempre, hasta que llego un familiar mio a comprar la empresa y pense: AL FINNN... volveran los dias de gloria, y efectivamente algo parecio mejorar y con eso me conforme, pero aclaro que no me gusto al final el rumbo que tomo la empresa familiar después que mi tío Elon la compró pero es lo que habia en ese entonces y aguante. HASTA AHORA..
Te gusta twitter pero a la vez estás arto de lo mismo?
Hace meses hice 1 post de por qué me gustaba X, pero también explicaba el rumbo que está tomando el mundo de la tecnología con respecto a las redes sociales. Y ahora te explicaré de qué se trata.
Todo ha evolucionado en el mundo de la tecnologia a velocidad vertiginosa, por ejemplo tu tia antes enviaba un Piolin de BUENOS DIAS todas las mañanas en su muro de Facebook a sus amigos y familiares que la seguian, ahora hace lo mismo por el WAZA (grupo familiar que pasa silenciado por siempre) y si ya no lo hace es por que TU eres la TIA del Piolin ahora jajaja, pero volviendo al tema las RRSS no han evolucionado desde hace 20 años, ojo me refiero a la forma de generar contenido, monetizar y consumir, todo es lo mismo que cuando abrí mi cuenta de Twitter hacer 15 años. Han aparecido muchas otras RRSS si es cierto, #tiktok la última. Pero todas hacen lo mismo darte a ti el usuario: entretenimiento, distracción ludica y tal vez “informar”; y esto entre comillas por qué lo que lees, escuchas y te informas es lo que los dueños de estas RRSS, las marcas auspiciantes y quienes pagan su verificación quieren, NO lo que TÚ quieres. Ellos dictan y te “Sugieren el contenido que puedes ver” pero tu no te das cuenta y crees que lo que estas viendo es por que tu asi lo decidiste. Lo cual es una triste y deprimente mentira....
Y no es invento mío, te adjunto una entrevista a Jack Dorsey fundador de Twitter, donde él explica detalladamente por qué sucede esto que afirmó anteriormente. Léelo en tu tiempo libre, no tiene desperdicio. Usa traductor si no le haces mucho al inglés:
https://www.piratewires.com/p/interview-with-jack-dorsey-mike-solana
Y si te preguntas, Alguien está haciendo algo para mejorar esto? SI, un montón de gente (Jack incluido) y otros mas que aportan con muchos recursos: técnicos, económicos, tenologicos y sobre todo tiempo y amor a su profesion. Esta gente está trabajando en cambiar todo esto que esta mal y de ese esfuerzo en conjunto nacieron soluciones como Mastodon, Bluesky y Nostr.
Pero que son Mastodon, Bluesky y Nostr?
Mastodon y Bluesky son básicamente lo mismo, nuevas RRSS donde encuentras de todo. Nacieron con la idea de enfrentar a Twitter la primera, y mejorarlo la segunda como lo explica Jack en su entrevista. Pero al final terminaron teniendo lo mismo, es decir marcas asupiciantes, moderadores verificados y dueños o juntas directivas. Mas de lo mismo....
Nostr en cambio es el giro de tuerca que las RRSS y las comunicaciones humanas necesitan para el futuro, y de hecho Instagram (Threads) y otros ya lo están probando en sus plataformas lanzando puentes desde sus empresas para que sus usuarios tengan interoperatibilidad entre diferentes rrsss del fediverse.
-Y por qué sucede esto con Nostr?
Por qué Nostr no es una RRSS ni una empresa, ni tampoco tiene dueños o moderadores de contenido que dictaminan lo que puedes o no ver, leer, escuchar y consumir en tu feed, ya que es un protocolo de comunicación como los que usas para el correo, para navegar en internet, etc.
-Y que ganamos los usuarios?
Ganamos un largo etc. de beneficios para consumo de contenido REAL, mas humano y mas limpio, pero lo que si diré que NO encontraras es nada de lo que te tiene hastiado de las otras RRSS. Aquí un video que te gustaría ver para entender de lo que escribo:
https://youtu.be/aA-jiiepOrE?si=iaMu5K3qKqh_JxsR
Te interesa usar y aprender que puedes hacer con Nostr?
Te dejo unos link 🔗 para que empieces a explorar una nueva forma de comunicarse entre seres humanos. Usa alguno de estos servicios, pruebalos.
- Lives: https://zap.stream/
- Música: https://wavlake.com/
- Blogs: https://yakihonne.com/
- Podcast: https://www.fountain.fm/
Y muchas más aplicaciones y sevicios en: https://www.nostrapps.com/
Si lo tuyo es consumir contenido en algo como Twitter/X estás apps son para ti:
En iOS: - Primal: https://primal.net/ - Damus: https://damus.io/ - Nostur: http://nostur.com/ - NosSocial: https://nos.social/
En ANDROID: - Primal: https://primal.net/ - Amethys: https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst&hl=en
En WEB: - Primal: https://primal.net/ - Nostrudel: https://nostrudel.ninja/ - Snortsocial: https://snort.social/ - Coracle: https://coracle.social/
Debes saber que puedes con el mismo usuario y contraseña (en #Nostr se dicen llaves) puedes ingresar a TODAS las aplicaciones mencionadas en este articulo, y esto puede lograrse por que el protocolo es el mismo, es NOSTR.
Ya vas en tendiendo? no hay empresas, no hay dueños..😏, TU eres el dueño del contenido que produces y del contenido que consumes.
Quieres saber mas informacion sobre Nostr, visita estas web. Resolveran muchas de tus dudas.
https://nostr.com/ https://nostr.how/
Para terminar con este pequeño hilo... (te odio Elon) jajaja
Nostr esta empezando y tiene mucho por mejorar pero al dia de HOY ya existen cosas increibles que puedes hacer y son mejores que en otras RRSS y te aseguro algo, TODOS nosotros terminaremos tarde o temprano usandolo en el futuro, es inevitable si queremos evolucionar nuestra forma de comunicarnos.
Si tu quieres ser uno de los primeros en experimentar una nueva era de las RRSS. Anímate y empieza a usar NOSTR como TU quieras. Solo haz lo siguiente:
- Descarga cualquier aplicacion en tu movil tipo Twitter detallada en este articulo.
- Crea el Usuario (npub....) llave 1
- Crea la contraseña (nsec....) llave 2
- Guarda tus llaves, que no se te olviden. (anótalas)
- Envia tu primer post colocando al final el hashtag #introductions
- Y a disfrutar de #nostr
Si te gustó este hilo (Elon de >:{ #$%&) dale RT o cómo diablos se diga ahora 😂 o postealo y compartelo donde quieras para que mas gente lea sobre Nostr. Tal vez a alguien le interese.
Si deseas seguirme en #Nostr •𓅦
primal.net/p/npub1whdfgqn66sytcta0l6c7vlt3h2lg67xcnsmzpk3pyvpmsaaxtdwqr8vs60
Alla nos vemos...escríbeme y pregunta lo que quieras.
Saludos, johnny
-
 @ ec965405:63996966
2024-05-18 18:02:00
@ ec965405:63996966
2024-05-18 18:02:00Re #introductions
For the next couple of months, the team at nos.social, led by @Rabble@nos.social, is supporting me in building engaging social media for my community with their new Nostr client. I'm an activist who is dedicating this season of my life to learning how computers and the Internet work. After stumbling across Nostr last year in search of better social media experiences, I entered a blogging contest with https://nostr.build and won a creator account. My interest and enthusiasm for this protocol has only grown.
RE #introducciones
Durante los próximos meses, el equipo de nos.social, liderado por Rabble@nos.social, me ayudará a crear una experiencia atractiva para mi comunidad con su nuevo cliente de Nostr. Soy un activisa dedicado a aprender cómo funcionan las computadoras y el Internet. Despues de encontrar a Nostr el año pasado en la busqueda de mejores experiencias en las redes sociales, participé en un concurso de blogs con [[nostr.build]] y gané una cuenta de creador. Mi interés y entusiasmo por este protocolo no ha hecho más que aumentar.
Liberation Tech
The world is having a moment right now. Social media is evolving into a tool for collective liberation. It couldn't have come at a better time. We have an opportunity to reconstruct a digital public commons. Tools like Nostr are blueprints for building resilient social media and represent a rejection of the factory of manufactured consent that defines our current political realities. A liberated fifth estate built on open protocols could channel people power into material improvements within our lifetimes. We are not going back to the way things used to be.
Tecnología de Liberación
Actualmente estamos viviendo un momento critical. Las redes sociales se estan evolucionando hacia una herramienta para nuestra liberación colectiva. No podría haber llegado en mejor momento. Tenemos una oportunidad de reconstruir la plaza digital del pueblo. Herramientas como Nostr son modelos para construir redes sociales resistentes y representan un rechazo a la fábrica de consentimiento manufacturado que define nuestras realidades políticas actuales. Un quinto estado liberado, basado en protocolos abiertas podría canalizar el poder del pueblo hacia un cambio material en el transcurso de nuestras vidas.
Explore my Asteroid
I host my main web page from an asteroid with Uberspace, a small team of supportive technologists who provide an affordable Linux server that runs on renewable energy. On it I run a personal relay for on-boarding my community to Nostr as well as learning to code. Find resources and more about what I'm working on at https://miguelalmodo.com.
Explora mi asteroide.
Mi pagina web principal se encuentra en un asteroide con Uberspace, un equipo chiquito de tecnólogos solidarios que ofrecen un servidor Linux barata que funciona con energía renovable. En él, gestiono un relevo personal para incorporar a mi comunidad a Nostr, además de aprender a programar. Encuentra rescursos y mas sobre lo que estoy creando en https://miguelalmodo.com
-
 @ df67f9a7:2d4fc200
2024-05-13 21:43:50
@ df67f9a7:2d4fc200
2024-05-13 21:43:50What I’m Building
Meet Me On Nostr is an app for sharing Nostr with friends. More than ‘just’ an onboarding client, this project will bring the power of “Social Onboarding” to Nostr. The project’s measurable objectives are to grow the number of new users, to increase the retention of active users, and to strengthen the interconnected webs of trusted users. All this can be accomplished “simply” by supporting Nostr advocates in sharing Nostr with their friends.
This project can be broken into two distinct efforts.
-
Web Client for “socially onboarding” new accounts (with customizable invite QR codes for advocates, low friction profile creation for friends, built in direct messaging with advocates, and WoT powered discovery of new friends, clients, relays, and other stuff recommended by the advocate and their web of trusted friends)
-
Advocate Support & Metrics to build community and incentivize users around onboarding and retaining their trusted friends on Nostr.
Why Social Onboarding?
Social Onboarding is Nostr’s superpower. Friends sharing Nostr with friends is not only easy and natural, but also happens to be a great way to strengthen Nostr’s webs of trusted users. While it’s not a given that Nostr’s growth will be sustainable, developing tools to support “networks of trusted friends” can only help.
Because Nostr is owned by nobody, anybody is able to benefit (monetarily or socially) from its success. Everybody wins when Nostr grows, but also, everybody wants something different. With Nostr, the superpower comes when everybody gets what they want. Harnessing #grownostr to support “networks of trusted friends” may be as simple as giving advocates the tools and incentives to “curate” their own corner of the broader social network.
Invite your trusted friends, and help them to stay a while.
Because there is no “sherif of Nostr”, traditional approaches to content moderation have no power. To overcome the growing influence of bots and bad actors, Webs of Trust is still the best (and only?) form of decentralized moderation. The challenge for onboarding, in this context, is to “rapidly on-ramp” new users into trusted networks, BEFORE the spambots ruin their vibe. Social Onboarding by Nostr advocates solves this problem, while being “relatively” straightforward to tool up and incentivize.
Development Timeline & Milestones
As of this writing, I have an “almost MVP complete” web client (alpha-0.4) running live at nostrmeet.me. MVP could be completed by the time of BTC Prague (3 weeks). Target Release may have an early release as soon as Nostriga, but will likely be feature complete by mid autumn (6 months)
Minimum Viable Product
When complete, the Minimum Viable Product will allow advocates to invite their friends to a direct message chat on Nostr with minimal “onboarding” friction. What’s live today, is the invite and profile creation, but lacking DM integration.
[+] Invite QR codes [+] Invite accept screen with “low friction” profile creation. [+] Automatic Nip05 addresses for new profiles. [+] Private “cloud encrypted” key storage using NIP46 (password not stored) providing key management for new profiles. [+] Receipt logging of accepted invites (allows tracking of account creation by web client through encrypted receipts) [+] Optional “do not store” encrypted key and “keep me anonymous” receipt logging. [+] Login to web client with “cloud encrypted” key using only username and password. Retrieve nsec (unencrypted key) anytime. [ ] Direct message integration for new accounts and their advocates.
Target Release
The Target Release (maybe as soon as Nostriga), will push forward on both efforts of this project (web client and advocate support) to solidify a “baseline” toolset to measure and implement Social Onboarding for Nostr.
[ ] Customizable Invites for Advocates (allowing for private invites, limited use invites, private group invites, follow a list from invite, join relays from invite, zap to ecash after invite, and other extendable options) [ ] WoT Network Explorer for new users to find new follows and trusted friends (and view their timelines) directly from the web client. [ ] WoT Recomendations for new users to discover (and launch or subscribe to) clients and relays (and other stuff?) right from the web client. [ ] Metrics and data collection to quantify the success of “social onboarding”, and what accounts are involved. [ ] Top Advocates Awards (using these data) to incentivize onboarding of new, active, and trusted users. [ ] Advocate Training and support (in the form of chat groups, hangouts, meetups, wikis, etc) to share best practices and tips for growing one’s own web of trusted friends.
Funding and Moving Forward …
So far, this is a passion project. Born from many hours conversation with and observation of Nostr advocates and new users.
In January 2024, I managed to secure a $10k seed sponsorship for MVP development from Blockhenge. I hope to continue funding this project through sponsorships from Nostr adjacent businesses.
Everybody wins when more trusted friends join Nostr.
I am currently looking for a dev assistant and funding to last us both through fall 2024. Please contact me directly if your business might be interested.
-
-
 @ 3c984938:2ec11289
2024-05-11 12:21:43
@ 3c984938:2ec11289
2024-05-11 12:21:43👉play the audio to listen to the article. https://media.nostr.build/av/749a03816c328c599054f31113588f9f5a47b5e67681e3a1eb9ee97c8f2e0dd3.mp3
Welcome to Nostr!
Introduction. Is this your first time here in Nostr? Welcome! Nostr has a oddball acronym for "Notes and Other Stuff Transmitted by Relays" with a simple goal, to be censorship-resistance. An alternative to traditional social media, communications, blogging, streaming, podcasting and eventually email (in development) with decentralization that empowers you, dear user. No more will you have to be plagued by ads, held by centralized entities and data hungry algorithms that monetizes you.
Allow me to be your host! I'm Onigirl! I'm on a quest to explore the world of Nostr, a decentralized communication protocol. I write about the tools, and the awesome developers within Nostr that bring this realm roaring with life.

Welcome to Nostr Wonderland
You're about to step into another world that will explode your mind from all the decentralized apps, clients, web3 enabled sites that you can use. You're never going to look at communications, logging in, 2FA, and social media the same way ever again. All thanks to Nostr's cryptographic nature inspired by Bitcoin blockchain technology. Each user, when they create a Nostr account, they get two keys, a private and a public key. These are your keys to your very own kingdom. Whatever you write, sing, podcast, stream, anything you create --all of it belongs to you. The sky is literally the limit!

A Gold and Silver Key
A friend of mine and I, call this "Identity by Encryption" because your Identity is encrypted. You can share your silver key, "npub" to other users to connect and follow. Use your gold key, "nsec" to unlock your account to plugin into a plethora of applications. Keep this key safe at all times. There is no reason to be caged ever again by social platforms TOS henceforth!
👉Give it a whirl, you can follow me by copying and pasting my public key into your search bar on any client that you decide to use.
Onigirl
npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3Don't have a client yet? Select the best option
Find the right App for you! This is where you can use your gold key, "nsec" to login into these wonderful tools. You can also visit Nostr's app page here. Before you start pasting your gold key everywhere on apps, consider using a signers (for web3 enabled sites) please look at the next image for details, also refer to the legend.

Get a Signer extension via chrome webstore
A signer is an extension in the chrome webstore on Google. Nos2x and NostrConnect are widely accepted extension for logins. This simplifies the process of logging into web3 sites instead of copying and pasting your gold key, "nsec" each and every time, you keep it within the extension and give it permission(s) to sign you in.

👉⚡⚡Get a Bitcoin lightning wallet to send/receive Zaps⚡⚡ (This is optional)

Here on Nostr, we use the Bitcoin Lightning network (L2). You will need to get a lightning wallet in order to send/receive Satoshi. These are the smallest denominations of a Bitcoin. It is a one hundred millionth of a single bitcoin (0.00000001 BTC). Zaps are a form of "micropayment with sats" here on Nostr. If you enjoy a user content, it is the norm to "⚡zap⚡" a.k.a "tip" for their content. For example, If you like my content, you can zap me with SATs to reward my work. But you just arrived, you don't have a wallet yet. No worries! I got you covered!
"Stacker.News" is a platform where users can earn SATs by writing articles and engaging with other users. You.

👉Stacker.News is also the easiest place to get a Bitcoin Lighting wallet address.
- Log in with your "Signer" extension either "Nos2x or NostrConnect" click your profile which will be random letters and numbers in the upper right corner.
You will see something like this:

- Click "edit"
and choose a name that you like, and if you don't like it. You can change again later.

- Click "save"
- Create a bio and the SN community are very welcoming and will zap you some sats to welcome you.
- You new Bitcoin Lightning Wallet address will appear like this:
 #### ^^Do not zap this address; this is purely for educational purposes!
#### ^^Do not zap this address; this is purely for educational purposes! - With your New Bitcoin Lightning wallet address you can put this into any client or app of your choice. To do this, go to your profile page and under your wallet address under "LN Address," enter your new address and hit "save" and there ya go. Congratulations!
👉✨Eventually, you may want to move to self custodial options and maybe consider to even self-host your own LN node for better privacy. Good news is stacker.news is also moving away from being a custodian wallet.
Nostr, the maverick of Servers
 Instead of using a single instance or a centralized server Nostr is built to have several databases to exchange messages using "relays." Relays, which are neutral and nondiscriminatory, store and broadcast public messages in the Nostr network. They transmit messages to all other clients connected to them, securing communications in the decentralized network.
Instead of using a single instance or a centralized server Nostr is built to have several databases to exchange messages using "relays." Relays, which are neutral and nondiscriminatory, store and broadcast public messages in the Nostr network. They transmit messages to all other clients connected to them, securing communications in the decentralized network.My friends in Nostr welcome you!
Welcome to the tea Party, would you like a spot of tea?🍵

There's so much more!
This is just the tip of the iceberg. Follow me as I continue to explore new lands and the developers, called "knights" behind this ever-growing ecosystem. Meet me here for more content like this and share this with future nostr users. Learn about the knights fighting for freedomTech within Nostr and the projects that are contributing to make it happen. Make your life more decentralized with Nostr. 💋
Onigirl @npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3
- Log in with your "Signer" extension either "Nos2x or NostrConnect" click your profile which will be random letters and numbers in the upper right corner.
You will see something like this:
-
 @ 56a6da9b:7f5a2243
2024-08-18 14:41:44
@ 56a6da9b:7f5a2243
2024-08-18 14:41:44_
LISTEN HERE (The podcasts are more complete and nuanced, imo)
DAY 13 OF FLASH AUGUST FICTION. Not a lot to say about this one. A skill I have is building. I was a bricklayer and a stonemason, and I know fire tech. What that means is that I can build fireplaces, masonry heaters, flue systems, and chimneys. I think a lot about how the buildings around us affect us. I hate gargoyles. I love angels. I’m Commercial Herschel, and I’m here to help.
Purge the Gargoyles
The People Agreed
614 WORDS WRITTEN IN A HALF HOUR
Mayor Jackson won the election in surprising fashion. No one expected her to win. She had no real money, she didn't have any high-profile support, and the other two candidates were as shocked as she was that she won. Her campaign was simple. “Our City for Us”.
The dominant Party was on the outs with the people. They usually controlled the big cities, and the people finally stopped falling for them. They had lost favor, and there was no politics, or even violence, that would bring the people back to them. The other Party was more of a rural and suburban party, but the idea that they could get this city was like a conquest. They courted Mrs. Jackson, but they could not win her. They offered her money, and all sorts of corporations made all sorts of promises, but he just wanted her city to be for her people.
Her campaign was so unfamiliar. All of these corporations were making all of these promises to her. Her response was, “We'll see.” She didn't present herself as a candidate with all sorts of business and influence as leverage behind her. Instead, she presented herself as someone with the support of the people as the leverage behind her, so she could get the best deal for the people that she could. Her attitude toward the corporations was, “Look, do you see all these people I have behind me? If you want their business, I'm here to be sure you make a really good deal for my people.”
Once she took office, there were so many questions. The media and her critics were all over her, looking for answers to all the tough policy questions. She knew these were pressing concerns, but she wanted to truly ground herself. She had to establish some things in some kind of permanent way.
Her first press conference after the election was the time that she could establish her intent.
“Ma'am, no one expected you to win this election. What was the first thought you had when you saw the results?” One of the media people asked.
“My first thought was that the establishment didn't expect that they would have to cheat on me, so they didn't try very hard.”
Another reporter shouts out the next question. “Mrs. Jackson, what's the first thing you want to do with your new position?”
“Well, the Library really bothers me,” she says.
People are perplexed, it doesn't make sense. What could be the problem with a library?
“You don't like libraries, ma'am?” One of the reporters asks.
“Of course, I like libraries. Who does not like libraries? What I don't understand is why the library has gargoyles all over the roof-line. I want to replace those demonic gargoyles with angels.”
DAY 13 OF FLASH AUGUST FICTION
There are a lot of raised eyebrows among the press crew, it's not what they were expecting.
“I'm not going to use the city budget to do this,” the new mayor says. “I'm going to ask people to make donations at the library.”
Within a matter of days, the library had enough donations to replace the gargoyles with angels. There was a contest for some different angel designs. Some weird, wealthy people offered money for the old gargoyles, but the mayor crushed them into dust and dumped them into the nearby lake.
People felt better, something was right about this. It set the new administration on a good path, and the mayor was able to cut a lot of good deals that benefited the people of the city. She won several elections and served for three terms until she retired at an age that would allow her to enjoy her grandchildren.
The End.
I hope you might get a paid subscription, or buy me a coffee, or donate some bitcoin. I wish you the best. I’m Commercial Herschel, and I’m here to help.
originally posted at https://stacker.news/items/653465
-
 @ c69b71dc:426ba763
2024-08-18 14:35:51
@ c69b71dc:426ba763
2024-08-18 14:35:51Chef's notes
You will need a blender! 🌱 This breakfast is nutritious, healthy, easy, and quick to make. 🌱 It's gluten free and vegan.
Details
- ⏲️ Prep time: 10 min.
- 🍳 Cook time: 0
- 🍽️ Servings: 2
Ingredients
- 1 Apple 🍏
- 2 Ripe Peaches 🍑
- 1 Banana 🍌
- 1/2 cup (Wild) Blueberries 🫐 (frozen or fresh)
- 1/2 cup pine nuts (or optional ground almonds)
- 4 tbsp Almond Butter (or optional cashew butter)
- 2 Pitted Dates
- 1 tbsp Vegan Protein Vanilla Powder (optional)
Directions
- Peach, apple, pine nuts, pitted dates, and vanilla protein powder: Blend until smooth.
- Peel and slice the banana into rounds.
- Blueberries (thaw in a water bath if frozen) and just mix and stir with a spoon in a little bowl with almond butter. (no need to blend with a blender)
- Alternate layers of peach-apple mixture, banana and blueberry-almond butter mix in a glass.
- Garnish with grapes, pine nuts, cacao nibs, and a drizzle of almond butter
- Enjoy and tag me, when you try the recipe 💜🙏🏽💚
-
 @ 9d51218e:a0c80d65
2024-08-18 14:17:04
@ 9d51218e:a0c80d65
2024-08-18 14:17:04The huge share of ultra-processed foods, especially in the United States, is due to the fact that the food industry is in the hands of several global corporations. They have literally occupied all the supermarkets with their products. Full story
-
 @ 361d3e1e:50bc10a8
2024-08-18 14:16:17
@ 361d3e1e:50bc10a8
2024-08-18 14:16:17The huge share of ultra-processed foods, especially in the United States, is due to the fact that the food industry is in the hands of several global corporations. They have literally occupied all the supermarkets with their products. Full story
-
 @ 361d3e1e:50bc10a8
2024-08-18 14:16:17
@ 361d3e1e:50bc10a8
2024-08-18 14:16:17The huge share of ultra-processed foods, especially in the United States, is due to the fact that the food industry is in the hands of several global... This is a preview of my post. Join my community and get access to this and more of my work.
https://highlighter.com/npub1xcwnu8sx6vs5ae478lzzahpmg46428nkewa46prev4jhz59uzz5qqhm0u6
-
 @ d830ee7b:4e61cd62
2024-05-10 14:03:50
@ d830ee7b:4e61cd62
2024-05-10 14:03:50จุดเริ่มต้นของตำนาน
ท่ามกลางแสงแดดเจิดจ้าและลมทะเลเย็นสบายของหาดเมืองแกลง ชายหนุ่มรูปร่างกระทัดรัดนามว่า "ซุป" กำลังนั่งจดจ่ออยู่หน้าจอคอมพิวเตอร์ ดวงตาเป็นประกายฉายแววความสนใจขณะไล่อ่านบทความวิชาการทางด้านเศรษฐศาสตร์ ความรู้ไม่ได้เป็นเพียงแค่ตัวอักษรบนหน้าจอ แต่มันคือแรงบันดาลใจ เปรียบเสมือนขุมทรัพย์ที่รอการขุดค้นสำหรับเขา
ซุป ไม่ใช่หนุ่มนักเรียนหัวกะทิหรือบัณฑิตจบใหม่จากรั้วมหาวิทยาลัยดัง แต่เป็นชายหนุ่มธรรมดาที่หลงใหลในศาสตร์แห่งการจัดสรรทรัพยากรอันหายาก เศรษฐศาสตร์ ไม่ว่าจะเป็นสำนักคลาสสิคหรือออสเตรียน ล้วนดึงดูดความสนใจของเขาให้เข้าไปสำรวจอย่างลึกซึ้ง ยิ่งเรียนรู้ ซุปยิ่งค้นพบความมหัศจรรย์ของศาสตร์นี้ มันไม่ใช่แค่ทฤษฎีบนหน้ากระดาษ แต่สะท้อนอยู่ในทุกๆ การกระทำของมนุษย์
มันเหมือนเวลาที่เราไปเที่ยวทะเล.. เราไม่ได้แค่เห็นน้ำทะเลสีฟ้าสวยงาม แต่เราสัมผัสได้ถึงไอเย็นของลมทะเล ได้ยินเสียงคลื่นซัดสาด ได้กลิ่นอายของเกลือ ความรู้ด้านเศรษฐศาสตร์เองก็เช่นกัน เราจะมองเห็นมันได้ในทุกๆ การตัดสินใจ ทุกๆ การกระทำ ตั้งแต่การซื้อของในร้านสะดวกซื้อ ไปจนถึงการเลือกอาชีพ
หนึ่งในขุมทรัพย์ความรู้ที่ซุปหลงใหลมากที่สุด คือ เศรษฐศาสตร์สำนักออสเตรียน โดยเฉพาะแนวคิดเรื่อง "มูลค่าอัตวิสัย" (Subjective Value) ทฤษฎีนี้สอนให้เขาเข้าใจว่ามูลค่าของสิ่งต่างๆ ไม่ได้ขึ้นอยู่กับต้นทุนการผลิต หรือแรงงานที่ใส่ลงไป แต่มันขึ้นอยู่กับการประเมินของแต่ละบุคคล สิ่งที่สำคัญสำหรับคนหนึ่ง อาจดูไร้ค่าสำหรับอีกคน และมูลค่าของสิ่งเดียวกันก็อาจเปลี่ยนแปลงไปตามกาลเวลาและสถานการณ์
ซึ่งก็เหมือนกับตอนเรายังเด็กๆ ของเล่นชิ้นโปรดอาจเป็นตุ๊กตากันหมีตัวเก่าๆ แต่วันนี้ ตุ๊กตาตัวนั้นอาจถูกเก็บไว้ในกล่องใต้เตียงไปแล้ว เพราะความต้องการของเราเปลี่ยนไป เราให้คุณค่ากับสิ่งอื่นๆ มากกว่าเมื่อเวลาผ่านไป
ความหลงใหลในเศรษฐศาสตร์สำนักออสเตรียนนำพาซุปไปรู้จักกับ อ.พิริยะ และทีมงาน Right Shift กลุ่มคนรุ่นใหม่ที่มุ่งมั่นเผยแพร่ความรู้ทางเศรษฐศาสตร์อย่างเข้าใจง่าย ซุปกลายเป็นแฟนตัวยง ติดตามผลงานแทบทุกชิ้น และใฝ่ฝันว่าสักวันหนึ่งจะได้มีโอกาสร่วมงานกับทีม แต่ด้วยความขี้อายและอ่อนน้อมถ่อมตน ซุปจึงไม่เคยกล้าเอ่ยปาก เขาเลือกที่จะเป็นผู้สนับสนุนอยู่ห่างๆ อย่างเงียบๆ
บางครั้ง.. ความฝันก็เหมือนเมล็ดพันธุ์ เราต้องหมั่นรดน้ำ พรวนดิน และดูแลมันอย่างดี ถึงแม้จะไม่รู้ว่ามันจะเติบโตงอกงามเมื่อไร แต่ถ้าเรายังคงดูแลมันต่อไป สักวันหนึ่งมันจะผลิดอกออกผลให้เราได้ชื่นชม

จุดเปลี่ยนแห่งโชคชะตา
ชีวิตของซุป.. เหมือนเรือเล็กที่ล่องลอยไปตามกระแสน้ำ มีความสุขกับการเรียนรู้ เสพย์ติดความรู้ด้านเศรษฐศาสตร์และมีความฝันเล็กๆ ที่อยากร่วมงานกับทีม Right Shift
วันหนึ่ง.. โชคชะตาก็เล่นตลก เหมือนส่งคลื่นลูกใหญ่ซัดเข้ามาหาเรือลำน้อยของซุป
Right Shift กำลังประสบปัญหาขาดแคลนนักตัดต่อวิดีโอคลิป จนกระทั่ง Jakk Goodday หนึ่งในผู้ก่อตั้ง ต้องลงมาทำเองแก้ขัดไปก่อน ข่าวนี้แพร่สะพัดไปถึงหูของซุป เขาถึงกับอุทานออกมาเบาๆ
"เอ๊ะ.. นี่มันโอกาสของเราหรือเปล่านะ?"
สถานการณ์แบบนี้มันเหมือนตอนเราเดินเล่นอยู่ริมชายหาด แล้วเจอขวดแก้วที่ถูกคลื่นซัดมาเกยตื้น ข้างในมีกระดาษเขียนข้อความลอยอยู่ เราจะเก็บมันขึ้นมาอ่านไหมหรือจะปล่อยให้คลื่นซัดมันกลับลงทะเลไป?
ความคิดมากมายวนเวียนอยู่ในหัวของซุป เขาไม่ใช่มืออาชีพ แต่ก็พอมีฝีมือด้านการตัดต่ออยู่บ้าง จะลองเสี่ยงดูดีไหมนะ? ถ้าไม่ลอง.. ก็คงไม่มีโอกาส แต่ถ้าลองแล้วไม่สำเร็จล่ะ? จะกลายเป็นตัวตลกหรือเปล่านะ?
ในที่สุด.. ซุปก็ตัดสินใจ "เอาวะ! ลองดูสักตั้ง อย่างน้อยก็ได้พิสูจน์ตัวเอง"
เขาส่งข้อความไปหา Jakk บอกเล่าความสามารถและความตั้งใจ พร้อมกับยื่นมือเข้าช่วยเหลือ
บางครั้ง.. โอกาสก็มาในรูปแบบของปัญหา คนที่มองเห็นโอกาสและกล้าที่จะคว้ามันไว้ ก็จะประสบความสำเร็จ
สิ่งที่เกิดขึ้นหลังจากนั้นมันราวกับความฝัน Jakk ตอบรับและให้โอกาสซุปเข้ามาทดลองงาน ความกดดันถาโถมเข้ามาอย่างหนัก แต่ซุปก็พยายามอย่างเต็มที่ เขาใช้ความรู้ด้านเศรษฐศาสตร์สำนักออสเตรียนในการประเมินคุณค่าของโอกาสนี้ มันมีค่ามากกว่าความสบายใจในฐานะแฟนคลับ มากกว่าความกลัวที่จะล้มเหลว
"ความกลัว คือ กำแพงที่กั้นระหว่าง ตัวเรา กับ ความฝัน"
ซุปทุ่มเททุกอย่างให้กับงาน ไม่เคยเกี่ยงงอนหรือบ่นว่าเหนื่อย เพราะสำหรับเขา.. นี่คือโอกาสทอง มันคือการได้ทำงานที่รักร่วมกับทีมที่เขาชื่นชม
ทฤษฎีมูลค่าอัตวิสัยสอนให้เรารู้ว่า มูลค่าของสิ่งต่างๆ ไม่ได้ขึ้นอยู่กับปัจจัยภายนอก เช่น ราคา หรือ ต้นทุนการผลิต แต่มันขึ้นอยู่กับ การประเมินของแต่ละบุคคล
การตัดสินใจครั้งสำคัญของซุป นำพาเขาไปสู่เส้นทางใหม่ เส้นทางที่เต็มไปด้วยความท้าทาย แต่ก็เต็มไปด้วยโอกาสเช่นกัน เส้นทางที่เขาจะได้เรียนรู้ เติบโต และสร้างคุณค่าให้กับตัวเองและสังคม การตัดสินใจของซุปนั้นมันช่างสอดคล้องกับหลักการของเศรษฐศาสตร์สำนักออสเตรียนที่เน้นการกระทำของมนุษย์ การประเมินมูลค่า และการตัดสินใจ

วันเวลาแห่งการสร้างคุณค่า
แสงไฟจากจอคอมพิวเตอร์ยังคงสาดส่องใบหน้าของซุป.. ดวงตาของเขาจดจ้องอยู่กับเส้นเวลา ตัดต่อ เรียบเรียง ประกอบร่าง วิดีโอคลิปแต่ละชิ้นให้สมบูรณ์ งานที่ได้รับมอบหมายไม่ใช่งานง่าย แต่ซุปไม่เคยปริปากบ่น เขาก้มหน้าก้มตาทำงานของตัวเองไปอย่างเต็มที่
"นี่มันคือความฝันของเราเลยนะ จะมัวบ่นทำไมกัน" ซุปพึมพำกับตัวเอง
ซุปในตอนนี้ก็เหมือนนักปีนเขาที่กำลังไต่ขึ้นสู่ยอดเขา เส้นทางอาจจะลำบาก ขรุขระ และเต็มไปด้วยอุปสรรค แต่ทุกย่างก้าวก็คือ ความท้าทาย และความภาคภูมิใจ
แม้จะไม่ได้รับผลตอบแทนมากมาย แต่สำหรับซุป ความสุขที่ได้รับจากการทำงานมันมีค่ามากกว่าเงินทอง เขาได้เรียนรู้อะไรใหม่ๆ มากมาย ได้ฝึกฝนทักษะ ได้สร้างสรรค์ผลงาน และที่สำคัญที่สุด คือ ได้เป็นส่วนหนึ่งของทีมที่เขารัก
ในทางเศรษฐศาสตร์สำนักออสเตรียน เราเรียกสิ่งนี้ว่า "การประเมินมูลค่าโดยการใช้ประโยชน์ที่มีค่าน้อยที่สุด" (Valuation by the Least Valuable Use) หมายความว่า.. เมื่อคนเราต้องตัดสินใจ เราจะประเมินมูลค่าของสิ่งต่างๆ โดยพิจารณาจากประโยชน์ที่เราจะได้รับจากการใช้งานนั้นๆ
ในกรณีของซุป.. การทำงานกับ Right Shift อาจไม่ได้ทำให้เขาร่ำรวย แต่เขาได้รับประสบการณ์ ความรู้ และความสุข ซึ่งสิ่งเหล่านี้มีมูลค่าสำหรับซุปมากกว่าเงินทอง
บางครั้ง.. คุณค่าของสิ่งต่างๆ ก็ไม่สามารถวัดได้ด้วยเงิน
นอกจากนี้.. การทำงานกับ Right Shift ยังเปิดโอกาสให้ซุปได้พบปะผู้คนมากมาย ทั้งคนดัง ผู้เชี่ยวชาญ และบุคคลที่น่าสนใจ ซึ่งเป็นเหมือน "อรรถประโยชน์ส่วนเพิ่ม" (Marginal Utility) ที่เติมเต็มความสุขในการทำงานของเขา
เหมือนเวลาเรากินข้าวจานแรกอาจจะอร่อยมากเพราะเราหิว แต่พอจานที่สอง จานที่สาม ความอร่อยก็เริ่มลดลง จนกระทั่งเราอิ่ม จนไม่อยากกินอีกแล้ว
ประสบการณ์ใหม่ๆ ก็เช่นกัน ครั้งแรกที่ได้เจออาจจะตื่นเต้น ประทับใจ แต่พอเจอบ่อยๆ ความตื่นเต้นก็จะลดลง แต่ความทรงจำและความรู้สึกดีๆ ยังคงอยู่
แนวคิดเรื่อง "อรรถประโยชน์ส่วนเพิ่ม" ช่วยอธิบายว่า ทำไมคนเราถึงแสวงหาประสบการณ์ใหม่ๆ แม้ว่าความตื่นเต้นจะลดลงตามกาลเวลา
ซุป ยังคงทำงานอย่างหนัก พัฒนาตัวเองและสร้างสรรค์ผลงาน เขาไม่รู้ว่าอนาคตจะเป็นอย่างไร แต่เขารู้ว่า.. เขาได้เลือกเส้นทางที่ถูกต้องแล้ว เส้นทางที่เขาได้สร้างคุณค่าให้กับตัวเองและสังคม
"ความสุข ไม่ได้อยู่ที่ปลายทาง แต่อยู่ในระหว่างทาง"

บทเพลงแห่งการแบ่งปัน
เวลาผ่านไป.. ซุปสั่งสมประสบการณ์และความรู้มากขึ้น จากชายหนุ่มขี้อาย เขากลายเป็นนักตัดต่อมือฉมัง และที่สำคัญคือความรู้ด้านเศรษฐศาสตร์สำนักออสเตรียนที่สั่งสมมาตลอดมันเริ่มผลิดอกออกผล
ซุป อยากแบ่งปันความรู้ อยากให้คนอื่นๆ ได้สัมผัสความมหัศจรรย์ของศาสตร์นี้เหมือนที่เขาเคยสัมผัส เขาปรึกษากับ Jakk และ อิสระ (น้องเล็กในทีม) ซึ่งมีความสนใจในเรื่องเดียวกันและต่างก็มีแรงปรารถนาที่จะจะเผยแพร่มันเช่นกัน
ซุป: "พี่ Jakk, อิส ผมอยากทำรายการเกี่ยวกับเศรษฐศาสตร์สำนักออสเตรียน พี่คิดว่าไงครับ"
Jakk: "ไอเดียดีนะซุป แต่จะทำยังไงให้มันเข้าใจง่าย ไม่น่าเบื่อ ไม่เอาศัพท์แสงบ้าบอคอแตกนะ"
อิสระ: "พี่ซุปเล่าเรื่องเก่ง เราทำเป็นนิทานก็ได้นี่ครับ"
ซุป: "นิทานอิสซุป เหมือนที่ อ.พิริยะ ตั้งให้อะหรอ เออ.. ชื่อนี้ เข้าท่าดีนะ"
และแล้ว "นิทานอิสซุป" ก็ถือกำเนิดขึ้น รายการที่นำเสนอความรู้ด้านเศรษฐศาสตร์สำนักออสเตรียนในรูปแบบง่ายๆ สบายๆ เข้าใจง่าย เสียงนุ่มๆ ของซุป บวกกับลีลาการเล่าเรื่องที่เป็นเอกลักษณ์ของอิสระ ดึงดูดผู้ชมได้อย่างมากมาย
เหมือนแม่น้ำที่ไหลรินลงจากยอดเขา นำพาธาตุอาหารไปหล่อเลี้ยง ต้นไม้ พืชพันธุ์และสัตว์น้อยใหญ่ ความรู้ก็เช่นกัน เมื่อถูกแบ่งปันมันจะสร้างคุณค่าให้กับผู้รับและผู้ให้ ซุปมีความสุขที่ได้แบ่งปันความรู้ และยิ่งแบ่งปันเขาก็ยิ่งได้รับความสุขและคุณค่ามากขึ้น
นี่อาจคล้าย "กฎของอรรถประโยชน์ส่วนเพิ่มที่ลดลง" (Law of Diminishing Marginal Utility) เมื่อเรามีบางสิ่งบางอย่างมากขึ้น ความพึงพอใจที่ได้รับจากหน่วย (Unit) ที่เพิ่มขึ้นจะค่อยๆ ลดลง
แต่.. กฎนี้ใช้ไม่ได้กับ “ความรู้” และ “การแบ่งปัน” ยิ่งเรามีความรู้มากขึ้น ยิ่งเราแบ่งปันมากขึ้น ความสุขและ คุณค่าที่ได้รับก็จะยิ่งเพิ่มขึ้น ซึ่ง ซุป ก็เข้าใจหลักการนี้จึงเลือกที่จะแบ่งปันความรู้เพื่อสร้างคุณค่าให้กับสังคม และเติมเต็มความสุขให้กับตัวเอง
"นิทานอิสซุป" ไม่ได้เป็นเพียงแค่รายการ แต่เป็นพื้นที่ ที่ซุปได้แสดงออกถึงความรักและความหลงใหลในเศรษฐศาสตร์สำนักออสเตรียน เขาไม่ได้ทำเพื่อชื่อเสียงหรือเงินทอง แต่ทำเพื่อแบ่งปันและสร้างคุณค่าให้กับสังคม
การให้ คือ การได้รับ ที่ยิ่งใหญ่ที่สุด
"นิทานอิสซุป" จึงเป็นมากกว่านิทานวิชาการ มันคือบทเพลงแห่งการแบ่งปัน บทเพลงที่ ซุป บรรจงแต่ง เพื่อส่งต่อความรู้และแรงบันดาลใจให้กับผู้คน
"เพราะ.. ความรู้ คือ แสงสว่าง ที่ช่วยขับไล่ความมืดมน"

ก้าวสู่แสงไฟ
นิทานอิสซุป กลายเป็นจุดเริ่มต้นของเส้นทางใหม่ เส้นทางที่นำพา ซุป ก้าวออกจากเงามืดไปสู่แสงไฟ เหมือนดอกไม้ที่เบ่งบานท่ามกลางแสงแดด อวดสีสันและกลิ่นหอม ดึงดูดผึ้งและผีเสื้อให้เข้ามาดอมดม
ซุป ไม่ใช่แค่นักเล่านิทาน แต่เขาได้ค่อยๆ กลายเป็นหนึ่งในอินฟลูเอนเซอร์ในวงการบิตคอยน์ไทยอย่างช้าๆ ภายใต้ฉายา "ประธานซุป" เขาได้รับเชิญไปบรรยาย ออกรายการ และร่วมงานกับบุคคลที่มีชื่อเสียงมากมาย
ความสำเร็จ มันก็มักจะมาพร้อมกับความรับผิดชอบและความคาดหวัง เส้นทางของ ซุป ไม่ได้ถูกโรยด้วยกลีบกุหลาบ เขาต้องตัดสินใจครั้งสำคัญหลายครั้ง เช่น การทิ้งรายได้จากงานฟรีแลนซ์, การสละโอกาสทางการเมือง เพื่อทุ่มเทให้กับ Right Shift
“การตัดสินใจ” คือ กระบวนการเลือกทางเลือกหนึ่ง เหนือทางเลือกอื่นๆ โดยพิจารณาจาก การประเมินมูลค่าอัตวิสัย
ซุป เลือกที่จะเสียสละสิ่งที่คนอื่นมองว่ามีค่า เพื่อสิ่งที่เขามองว่ามีค่ามากกว่า นั่นคือ.. ความฝัน ความสุข และ การสร้างคุณค่าให้กับสังคม
"การเสียสละ คือ บทพิสูจน์ ของความมุ่งมั่น"
ตลอดเส้นทาง ซุป ได้รับการสนับสนุนและคำแนะนำ จาก Jakk Goodday ผู้ที่เชื่อมั่นในศักยภาพของเขา ตั้งแต่วันแรก ความสัมพันธ์ระหว่าง ซุป และ Jakk สะท้อนให้เห็นถึงความสำคัญของ "การแลกเปลี่ยนที่เป็นประโยชน์ร่วมกัน" (Mutually Beneficial Exchange) ซึ่งเป็นหัวใจสำคัญของ เศรษฐศาสตร์สำนักออสเตรียน
Jakk เห็นคุณค่าในตัว ซุป จึงให้โอกาสและสนับสนุนเขา ในขณะที่ ซุป ก็ตอบแทนด้วยการทำงานอย่างเต็มที่ และ สร้างคุณค่าให้กับทีม Right Shift
การให้ และ การรับ นั้นเป็นวัฏจักรที่สร้างสรรค์ และ ยั่งยืน
เส้นทางของ "ซุป" จากแฟนคลับสู่ประธานซุป เป็นบทเรียนชีวิตที่สอนให้เรารู้ว่า.. ความฝัน ความมุ่งมั่น การเสียสละ และการสร้างคุณค่า คือ สิ่งสำคัญที่นำพาเราไปสู่ความสำเร็จ
และทุกคน ก็มีศักยภาพที่จะสร้างคุณค่า และประสบความสำเร็จ ในแบบของตัวเอง
คุณค่าที่แท้จริง
เรื่องราวของ "ซุป" ไม่ได้เป็นเพียงแค่เรื่องราวของความสำเร็จ แต่เป็นบทเรียนชีวิตที่สอนให้เราเข้าใจถึงคุณค่าที่แท้จริง
เหมือนต้นไม้ใหญ่ที่เติบโตแผ่กิ่งก้านสาขา ให้ร่มเงาและผลิดอกออกผล ซุป เปรียบเสมือนต้นไม้ต้นนั้น เขาเติบโต จากเมล็ดพันธุ์เล็กๆ ที่หลงใหลในความรู้ ด้วยการหมั่นรดน้ำ พรวนดิน ใส่ปุ๋ย คือความมุ่งมั่น ความอดทน และ การเสียสละ จนกระทั่งเติบใหญ่ แผ่กิ่งก้านสาขาให้ร่มเงา คือการแบ่งปันความรู้และผลิดอกออกผล คือความสำเร็จและการเป็นแรงบันดาลใจให้กับผู้อื่น
หลักการของ ทฤษฎีมูลค่าอัตวิสัย (Subjective value) สะท้อนให้เห็นในทุกๆ การตัดสินใจของ ซุป
การประเมินมูลค่า >> ซุป ประเมินคุณค่าของโอกาส ประสบการณ์ และความสุข มากกว่าเงินทองและชื่อเสียง การเสียสละ >> ซุป ยอมสละรายได้และโอกาสทางการเมือง เพื่อหันมาทำในสิ่งที่เขารักและเชื่อมั่น ความอดทน >> ซุป ทำงานหนัก พัฒนาตัวเองและอดทนรอคอย จนกระทั่งประสบความสำเร็จ การสร้างคุณค่า >> ซุป แบ่งปันความรู้และสร้างแรงบันดาลใจ ให้กับผู้อื่น
เรื่องราวของ ซุป สะท้อนให้เห็นถึง "ปฏิทรรศน์น้ำ-เพชร" (Water-Diamond Paradox) ซึ่งเป็นแนวคิดใน เศรษฐศาสตร์สำนักออสเตรียน ที่อธิบายว่า.. ทำไมสิ่งที่จำเป็นอย่าง น้ำ ถึงมีราคาถูก ในขณะที่สิ่งฟุ่มเฟือยอย่าง เพชร ถึงมีราคาแพง
ในชีวิตจริง.. สิ่งที่สำคัญสำหรับคนหนึ่ง อาจไม่ได้สลักสำคัญสำหรับอีกคน และมูลค่าของสิ่งต่างๆ ก็ขึ้นอยู่กับ บริบทและความต้องการของแต่ละบุคคล
ความสุข และ ความสำเร็จ ไม่ได้มีสูตรสำเร็จตายตัว แต่ละคนต้องค้นหาและสร้างมันขึ้นมาเอง
ซุป ค้นพบ “คุณค่าที่แท้จริง” ของชีวิต เขาไม่จำเป็นต้องมีเงินทองมากมาย หรือมีชื่อเสียงโด่งดัง แต่เขามีความสุขกับการได้ทำในสิ่งที่รักและสร้างคุณค่าให้กับสังคม
“จงค้นหาคุณค่าที่แท้จริงของชีวิต และ ใช้ชีวิตให้มีความหมาย”
"คุณค่าของคน อยู่ที่ผลของงาน"

11 พฤษภาคม เป็นวันคล้ายวันเกิดของ ซุป บทความนี้ผมจึงอุทิศน์ให้กับเขา และขอให้เจ้าตัวมีความสุขในการมุ่งมั่นสร้างคุณค่าในแบบของตัวเองสืบต่อไป ขอให้ทุกคนได้ร่วมอวยพรและให้กำลังใจเพื่อนคนเก่งของเราคนนี้กันด้วยครับ
ภาคผนวก
Subjective Value มองคุณค่าผ่านเลนส์ของตัวเอง
ทฤษฎีมูลค่าอัตวิสัย (Subjective Value) เปรียบเสมือนแว่นตาพิเศษที่ช่วยให้เราเข้าใจว่าทำไมคนเราถึงมองเห็น "คุณค่า" ของสิ่งต่างๆ แตกต่างกัน
ลองนึกภาพว่าเรากำลังดูภาพวาด abstract บางคนอาจมองว่ามันสวยงาม มีเอกลักษณ์ ในขณะที่บางคนอาจมองว่ามันดูยุ่งเหยิง ไม่มีความหมาย
ทฤษฎีนี้บอกเราว่า "คุณค่า" ไม่ได้ติดมากับสิ่งของ หรือถูกกำหนดโดยปัจจัยภายนอก เช่น ต้นทุนการผลิตหรือแรงงานที่ใช้ แต่ "คุณค่า" เกิดขึ้นจากการประเมินของแต่ละบุคคล ขึ้นอยู่กับความต้องการ ความชอบ ประสบการณ์ และสถานการณ์ของแต่ละคน
นักเศรษฐศาสตร์สำนักออสเตรียนเชื่อว่า "มนุษย์" เป็นศูนย์กลางของกิจกรรมทางเศรษฐกิจ และการตัดสินใจของมนุษย์นั้นขับเคลื่อนด้วย "มูลค่าอัตวิสัย" ที่พวกเขามีต่อสิ่งต่างๆ
ยกตัวอย่างง่ายๆ
คนที่กำลังหิวโหย อาจมองว่า "ข้าวเปล่า 1 จาน" มีค่ามาก แต่สำหรับคนที่เพิ่งกินอิ่มมา ข้าวเปล่าจานนั้นอาจไม่มีค่าเลย
นักสะสมงานศิลปะ อาจยอมจ่ายเงินมหาศาลเพื่อซื้อภาพวาด แต่สำหรับคนที่ไม่เข้าใจศิลปะ ภาพวาดนั้นอาจดูไร้ค่า
นักเรียนที่กำลังเตรียมสอบ อาจมองว่า "เวลา 1 ชั่วโมง" มีค่ามาก แต่สำหรับคนที่กำลังว่าง เวลา 1 ชั่วโมงอาจไม่มีค่าอะไรเลย
การเข้าใจ "ทฤษฎีมูลค่าอัตวิสัย" ช่วยให้เรายอมรับความแตกต่างและเคารพการตัดสินใจของผู้อื่น เพราะสิ่งที่สำคัญสำหรับเราอาจไม่สำคัญสำหรับคนอื่น และที่สำคัญ "มูลค่า" ยังสามารถเปลี่ยนแปลงไปตามกาลเวลาและสถานการณ์
โทรศัพท์มือถือรุ่นเก่า ที่เมื่อก่อนอาจมีมูลค่ามาก แต่ตอนนี้อาจกลายเป็นของสะสมหรือ ขยะอิเล็กทรอนิกส์
บ้านหลังเก่า เมื่อก่อนอาจเคยเป็นบ้านในฝัน แต่ตอนนี้อาจทรุดโทรม จนต้องซ่อมแซม
เรื่องราวของ "ซุป" สะท้อนให้เห็นถึงการเปลี่ยนแปลงของ "มูลค่า" เขาเคยให้คุณค่ากับความสบายใจในฐานะแฟนคลับ แต่เมื่อมีโอกาสเขาก็เปลี่ยนมาให้คุณค่ากับการทำงาน การสร้างคุณค่า และการแบ่งปันความรู้
"ทฤษฎีมูลค่าอัตวิสัย" จึงเป็นเครื่องมือสำคัญที่ช่วยให้เราเข้าใจการตัดสินใจ พฤติกรรม และการกระทำของมนุษย์ ทั้งในชีวิตประจำวันและในระบบเศรษฐกิจ
เลือกสิ่งที่ดีที่สุด ณ เวลานั้น
"การประเมินมูลค่าโดยการใช้ประโยชน์ที่มีค่าน้อยที่สุด" (Valuation by the Least Valuable Use) ฟังดูอาจจะซับซ้อนทำความเข้าใจได้ยาก แต่จริงๆแล้วมันคือหลักการง่ายๆ ที่เราใช้ในการตัดสินใจในชีวิตประจำวัน
เวลาเราเข้าไปในร้านขายเสื้อผ้าที่มีเสื้อผ้ามากมายหลากหลายแบบ เราจะเลือกซื้อ เสื้อผ้าตัวไหน?
เราคงไม่เลือกซื้อเสื้อผ้าทุกตัวในร้าน แต่จะเลือกเสื้อผ้าที่ตอบโจทย์ความต้องการของเรามากที่สุด ณ เวลานั้น เช่น เสื้อผ้าที่ใส่ไปทำงาน เสื้อผ้าที่ใส่ไปเที่ยว หรือเสื้อผ้าที่ใส่ไปออกกำลังกาย
ทฤษฎีนี้อธิบายว่า.. เมื่อคนเรามีสินค้าหรือบริการหลายอย่าง เราจะเลือกใช้สินค้าหรือ บริการที่ตอบสนองต่อความต้องการที่เร่งด่วนที่สุดก่อน
ยกตัวอย่างเช่น..
เราอาจจะมีการแบ่งเงินเป็นหลายก้อน แต่ก้อนที่เราจะใช้ก่อน คือก้อนที่เราต้องการใช้ มากที่สุด ณ เวลานั้น เช่น ค่าอาหาร ค่าเดินทางหรือค่าเช่าบ้าน การตัดสินใจของคนเรา จึงขึ้นอยู่กับความต้องการและสถานการณ์ ณ เวลานั้น
ดังนั้น "การประเมินมูลค่าโดยการใช้ประโยชน์ที่มีค่าน้อยที่สุด" จึงเป็นหลักการที่ช่วยให้เราจัดลำดับความสำคัญ และเลือกสิ่งที่ดีที่สุดสำหรับตัวเรา ณ เวลานั้น
ซุป ก็ใช้หลักการนี้ในการตัดสินใจ เช่น การเลือกทำงานกับ Right Shift แม้ว่า จะไม่ได้รับ ผลตอบแทนมากมายนัก แต่เขาได้รับความสุขและประสบการณ์ ซึ่งมีค่ามากกว่าสำหรับเขา
อิ่มเอม...แต่ไม่เท่าเดิม
"กฎของอรรถประโยชน์ส่วนเพิ่มที่ลดลง" (Law of Diminishing Marginal Utility) เป็นกฎพื้นฐานทางเศรษฐศาสตร์ที่อธิบายถึงความรู้สึก "อิ่มเอม" ที่ลดลง เมื่อเราบริโภคสินค้าหรือบริการมากขึ้น
ลองนึกภาพว่าเรากำลังกินพิซซ่า ชิ้นแรกอร่อยมาก ชิ้นที่สองก็ยังอร่อยอยู่ แต่พอชิ้นที่สาม ชิ้นที่สี่ ความอร่อยก็เริ่มลดลง จนกระทั่งเราอิ่ม และไม่อยากกินอีกแล้ว
นั่นเป็นเพราะ "อรรถประโยชน์ส่วนเพิ่ม" (Marginal Utility) หรือความพึงพอใจที่ได้รับ จากการบริโภค สินค้าหรือบริการ จากหน่วย (Unit) เพิ่มเติมนั้นลดลง
กฎนี้อธิบายว่า ยิ่งเราบริโภคสินค้าหรือบริการมากขึ้น ความพึงพอใจที่ได้รับจากหน่วย เพิ่มเติมจะลดลง
ยกตัวอย่างเช่น..
เสื้อผ้าตัวใหม่อาจจะทำให้เรารู้สึกดี ตื่นเต้น แต่พอมีเสื้อผ้าเยอะๆ ความตื่นเต้นก็จะ ลดลง
เงินก้อนแรกที่เราหามาได้ อาจจะมีค่ามาก แต่พอมั่งคั่งเงินก้อนต่อๆ ไปก็จะมีค่าน้อยลง
กฎนี้สอนให้เรารู้จักพอเพียง และเห็นคุณค่าของสิ่งที่เรามี
อย่างไรก็ตาม "กฎของอรรถประโยชน์ส่วนเพิ่มที่ลดลง" มีข้อยกเว้น เช่น ความรู้ และ การแบ่งปัน ตามที่ได้กล่าวถึงในบทความ
win-win situation
"การแลกเปลี่ยนที่เป็นประโยชน์ร่วมกัน" (Mutually Beneficial Exchange) เป็นหัวใจสำคัญของระบบเศรษฐกิจ และเป็นเหตุผลที่ทำให้คนเรา "ค้าขาย" กัน
เวลาเราไปตลาด เราเอาเงินไปแลกกับอาหาร แม่ค้าได้เงิน เราก็ได้อาหาร ต่างคนต่างได้ประโยชน์ การแลกเปลี่ยนจะเกิดขึ้นก็ต่อเมื่อ ทั้งสองฝ่าย เชื่อว่า พวกเขาจะ "ได้" มากกว่า "เสีย"
นักเศรษฐศาสตร์สำนักออสเตรียน เชื่อว่า การแลกเปลี่ยนที่เป็นประโยชน์ร่วมกันเกิดขึ้นได้ เพราะคนเรามี "มูลค่าอัตวิสัย" ที่แตกต่างกัน
ยกตัวอย่างเช่น..
ชาวนามีข้าวแต่ไม่มีปลา ชาวประมงมีปลาแต่ไม่มีข้าว ทั้งสองจึงแลกเปลี่ยนสินค้ากัน เพื่อ เพื่อตอบสนองความต้องการของตัวเอง
นายจ้างต้องการคนทำงาน ลูกจ้างต้องการรายได้ ทั้งสองจึงทำสัญญาจ้าง เพื่อแลกเปลี่ยน แรงงานกับเงินเดือน
การแลกเปลี่ยนช่วยให้คนเราได้สินค้าและบริการที่หลากหลาย มากกว่าที่จะผลิตเอง ทั้งหมด นอกจากนี้ การแลกเปลี่ยนยังกระตุ้นให้เกิดการพัฒนาและนวัตกรรม เพราะผู้ผลิตต้องแข่งขันกัน เพื่อตอบสนองความต้องการของผู้บริโภค
"การค้า คือ การสร้างสรรค์ ความมั่งคั่ง ร่วมกัน"
แกะปริศนา "ปฏิทรรศน์น้ำ-เพชร"
มาถึงตรงนี้.. หลายคนอาจจะสงสัยว่าทำไม "น้ำ" ซึ่งเป็นสิ่งที่จำเป็นต่อการดำรงชีวิต ถึงมีราคาถูกหรือบางที่ก็ฟรี ในขณะที่ "เพชร" ซึ่งเป็นแค่เครื่องประดับกลับมีราคาแพงหูฉี่
เหมือนเวลาเราไปร้านอาหาร เราสั่ง "ข้าวผัด" จานใหญ่ราคา 50 บาท แต่ "ไข่ดาว" ฟองเล็กๆ ราคา 10 บาท ทำไมข้าวผัดถึงถูกกว่า ไข่ดาว ทั้งที่ ข้าวผัดมี ข้าว ผัก เนื้อสัตว์ เครื่องปรุง ตั้งหลายอย่าง
คำตอบอยู่ที่ "ความขาดแคลน" (Scarcity) และ "อรรถประโยชน์ส่วนเพิ่ม" (Marginal Utility) ซึ่งเป็นแนวคิดสำคัญในเศรษฐศาสตร์สำนักออสเตรียน
น้ำ มีอยู่มากมาย ในขณะที่ เพชร นั้นหายาก น้ำ แก้วแรกอาจจะช่วยชีวิตเราได้ แต่ น้ำ แก้วที่ 10 อาจจะทำให้เราจุก
"อรรถประโยชน์ส่วนเพิ่ม" หมายถึง ความพึงพอใจที่ได้รับจากการบริโภคสินค้าหรือ บริการในหน่วย (Unit) เพิ่มเติม (ในจำนวนมากขึ้น)
เมื่อน้ำมีอยู่มาก เราจึงประเมินมูลค่าของน้ำแก้วที่ 10 ต่ำ เพราะมันไม่ได้ตอบสนองความต้องการที่เร่งด่วน แต่เพชรที่หายาก ทำให้แม้แต่เพชรเม็ดเล็กๆ ก็ยังมีมูลค่าสูง
คุณค่า ไม่ได้ขึ้นอยู่กับความจำเป็นหรือความฟุ่มเฟือย แต่ขึ้นอยู่กับความขาดแคลนและ การประเมินมูลค่าของแต่ละบุคคล
ดังนั้น ปฏิทรรศน์น้ำ-เพชร (Water-Diamond Paradox) จึงไม่ใช่ความขัดแย้ง แต่เป็น การสะท้อนให้เห็นถึงหลักการพื้นฐานของเศรษฐศาสตร์ นั่นคือ มูลค่า เป็นเรื่องส่วนบุคคล และขึ้นอยู่กับบริบท
เรื่องราวของ "ซุป" ก็เช่นกัน.. เขาประเมินมูลค่าของ ความรู้ ความสุข และการสร้างคุณค่า สูงกว่าเงินทองและชื่อเสียง
เขาเลือกที่จะเดินบนเส้นทางที่คนอื่นอาจมองว่า "ขาดแคลน" คือ เส้นทางที่ไม่ได้เต็มไปด้วยเงินทองหรือชื่อเสียง แต่เป็นเส้นทางที่เต็มไปด้วย ความสุข ความหมาย และคุณค่า
"ความสุข ที่แท้จริง หาซื้อไม่ได้ ด้วยเงิน"
-
 @ c11cf5f8:4928464d
2024-08-18 10:05:33
@ c11cf5f8:4928464d
2024-08-18 10:05:33Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too. If you missed our last thread, here are some of the items stackers recently spent their sats on.
originally posted at https://stacker.news/items/653241
-
 @ 8f69ac99:4f92f5fd
2024-04-30 15:38:38
@ 8f69ac99:4f92f5fd
2024-04-30 15:38:38Recently the UFC star Renato Moicano urged fans to read Mises 6 Lessons, and praised private property and the Austrian economist teachings. What are exactly the 6 Lessons?
"Economic Policy: Thoughts for Today and Tomorrow" consists of a series of six lectures delivered by Ludwig von Mises in Buenos Aires, Argentina, in 1959. The lectures were given over a series of nights to audiences comprising businessmen, students, and other professionals interested in economic theories and policies. These lectures encapsulate Mises’s robust defense of free-market economics and critique of interventionist and socialist policies, distilled into accessible and persuasive discourses aimed at a general audience, not just academics.
The lectures were later compiled and published into a book by Mises’s wife, Margit von Mises. Margit played a pivotal role in preserving and promoting her husband's legacy, particularly after his death. She not only managed his papers but also ensured that his lectures and unpublished works were accessible to the public. Her efforts were instrumental in compiling these lectures into the book format, making Mises's ideas available to a broader audience beyond those who were able to attend the lectures in person.
Margit von Mises’s contribution to the preservation and dissemination of Ludwig’s work was crucial, especially considering the contextual and historical importance of these lectures. The book not only serves as a record of Mises's thought processes at that time but also provides insights into the practical applications of his economic philosophies against the backdrop of the global economic conditions of the mid-20th century.
Significance and Impact
The publication of these lectures in book form has significantly impacted the field of economics, particularly among proponents of the Austrian School of economic thought, of which Mises was a leading figure. By addressing complex economic issues in a straightforward manner, Mises made the principles of the Austrian School accessible to a wider audience, enhancing the understanding and appreciation of market mechanisms and individual-based economics.
Contemporary Relevance
Today, "Economic Policy: Thoughts for Today and Tomorrow" remains a relevant and influential work. It is often cited in discussions around economic policies, especially in debates concerning the merits and drawbacks of capitalism versus more controlled economic systems. The book serves as both a historical document and a continuing source of economic philosophy that champions individual liberty and free-market principles.
Lecture 1: Capitalism
This lecture articulates a compelling defense of capitalism, which Mises defines as a system characterized by private ownership of the means of production, voluntary exchange, and competition. This perspective builds on his foundational work in "Human Action," where he conducts a thorough analysis of human action and its pivotal role in shaping economic systems. Mises champions capitalism as the optimal framework for individuals to freely pursue their personal and economic interests, unimpeded by government intervention or coercion.
Mises argues that capitalism's foremost advantage is its propensity to drive economic growth. By nurturing an environment ripe for voluntary exchange and competition, capitalism serves as a catalyst for innovation and entrepreneurship. This, in turn, leads to heightened productivity and economic expansion. Moreover, capitalism bolsters individual freedom and autonomy, empowering people to chase their aspirations without state interference.
Nevertheless, Mises acknowledges and addresses several criticisms of capitalism. For instance, in response to claims that capitalism engenders inequality, he argues that differences in intelligence, talent, and effort are inherent to humanity. He contends that efforts to equalize outcomes are misguided and instead advocates for policies that foster economic growth and mobility, enabling individuals to advance through their own endeavors.
Mises also rebuts the notion that capitalism perpetuates exploitation, where the wealthy allegedly exploit the poor. He maintains that voluntary exchange is mutually consensual and that market prices genuinely reflect the value consumers place on goods and services. This viewpoint fundamentally contradicts the idea that capitalists exploit workers, instead underscoring the reciprocal benefits of exchange.
Furthermore, Mises addresses concerns that capitalism inherently leads to monopolies, which could stymie competition and innovation. He argues that fostering competition through deregulation and the protection of property rights can enable new entrants to challenge established firms and spur innovation.
In conclusion, Mises's work robustly defends capitalism, highlighting its capacity to stimulate economic growth and promote individual liberty. As we delve deeper into the Austrian School's principles, we'll further explore human action, economics, and government's role in economic outcomes. By examining Mises's responses to criticisms of capitalism, we gain a deeper appreciation for this economic system's advantages and the critical need to curtail government intervention in the economy.
Lecture 2: Socialism
In this lecture, Ludwig von Mises offers a rigorous critique of socialism, an economic system where private ownership of the means of production is replaced by state or collective ownership. Mises argues that socialism, despite its goal of achieving social equality through wealth redistribution, invariably leads to numerous inefficiencies and issues.
Key Failures of Socialist Systems:
- Lack of Incentives: Mises points out that without the motivations provided by private ownership and profit potential, individuals have little impetus to innovate or improve efficiency. This lack of personal stake in the outcomes can lead to stagnation and a decline in productivity.
- Problems with Central Planning: Central planning, a common feature of socialist economies, often results in resource misallocation. Planners lack the localized knowledge that market signals provide, leading to inefficient production processes and general productivity declines.
- Suppression of Freedom: Socialism’s elimination of private property and market mechanisms not only undermines individual autonomy but also limits personal freedom, as economic choices become heavily regulated by the state.
Historical Evidence
Mises utilizes historical examples to substantiate his critique. He references the economic hardships faced by the Soviet Union under socialist governance, which were characterized by widespread inefficiencies and shortages. He also critiques the nationalization efforts in European countries during World War II, which he argues led to economic stagnation and reduced growth.
Bureaucratic Inefficiencies
According to Mises, socialism’s focus on collective ownership and central planning results in excessive bureaucracy, which can hinder decision-making and innovation. The focus on meeting arbitrary production targets, rather than responding to market demands, often results in outdated or inefficient production processes.
Through his critique of socialism, Mises underscores the critical importance of private property, individual freedom, and market mechanisms in fostering economic prosperity and human development. By examining the theoretical underpinnings, criticisms, and empirical failures of socialism, we gain a clearer understanding of the potential pitfalls of collectivist economic systems and the benefits of limiting governmental control over the economy.
Contrasting Capitalism:
Mises contrasts these issues with the benefits of capitalism, as outlined in his previous lecture, emphasizing that the freedoms and efficiencies inherent in a market economy lead to better outcomes for individual and societal wealth and well-being. As we continue to explore the Austrian School's ideas, the principles of human action, economics, and the minimal role of government in economic affairs become increasingly evident, highlighting the advantages of individual freedom and market-based mechanisms in promoting economic prosperity and human flourishing.
Lecture 3: Interventionism
In this lecture, Mises explains interventionism as an economic system where the government oversteps its essential roles—protecting property and preventing fraud—to meddle in market operations like prices, wages, interest rates, and profits. According to Mises, this approach is deeply flawed, forcing entrepreneurs to make decisions that deviate from those they would choose in a market governed solely by consumer preferences.
Consequences of Interventionism:
Mises outlines several detrimental effects of interventionism on the economy:
- Economic Instability: Government manipulation of the money supply and credit can lead to inflation, which undermines the value of money and creates economic cycles of booms and busts. These cycles disrupt business planning and investment, as companies cannot predict future economic conditions reliably.
- Stifled Innovation: By restricting market forces, interventionism curtails individual creativity and innovation. When the government dictates economic actions, it reduces the incentive for businesses to innovate and respond agilely to market demands.
- Inefficiency and Waste: Interventionist policies often lead to misallocated resources and inefficiencies in production. Government planners lack the localized knowledge that entrepreneurs and markets naturally use to allocate resources most effectively.
Historical Examples:
Mises uses specific historical instances to illustrate his points:
- He cites the interventionist policies of the 1920s and 1930s, such as the Federal Reserve’s monetary policies and the Smoot-Hawley Tariff Act, as exacerbating the Great Depression.
- He references Germany's hyperinflation after World War I, triggered by excessive government spending and money creation, as a stark warning of interventionism's risks.
Through this critique, Mises underscores the necessity of limiting government intervention and allowing free-market mechanisms to operate. He posits that the health of an economy and the prosperity of its society hinge on the extent to which free markets are permitted to function without government interference.
Mises's insights into the dangers of interventionism are profoundly relevant today. By understanding these pitfalls, we can appreciate the virtues of a market economy and recognize the importance of restraining governmental overreach in economic affairs.
Lecture 4: Inflation
In this lecture, Mises offers a comprehensive exploration of inflation, identifying it as a primarily monetary phenomenon with profound economic and societal impacts. He asserts that the central cause of inflation is the excessive expansion of the money supply by central banks, which introduces new purchasing power into the economy that is not matched by an increase in production. This discrepancy leads to price increases as consumers rush to spend their new wealth.
Mises also points out additional contributors to inflation, such as excessive government spending, borrowing, and expansionary fiscal policies like tax cuts or increased government expenditures. These actions can further stimulate demand and exacerbate price rises, leading to inflation.
The ramifications of inflation, according to Mises, are severe and far-reaching. It undermines the value of savings, complicating individuals’ financial planning and goal achievement. Inflation also injects uncertainty into economic planning, making it challenging for businesses to make informed investment decisions as future prices become unpredictable. Additionally, inflation can distort resource allocation, prompting individuals and businesses to prioritize short-term gains over long-term productivity.
To combat inflation, Mises recommends several measures:
- Monetary Discipline: Central banks should exercise restraint and avoid excessive expansion of the money supply.
- Gold Standard: Adopting a gold standard could restrict central banks' ability to print money indiscriminately, thus controlling inflation.
- Fiscal Responsibility: Governments need to curtail their spending to prevent fueling inflation further.
- Indexation of Wages and Contracts: Implementing mechanisms that adjust wages and contracts to reflect inflation can help mitigate its impacts.
In conclusion, Mises's discussion on inflation underscores the necessity of maintaining monetary discipline and embracing sound fiscal policies to ensure economic stability. His recommendations aim to shield economies from the disruptive effects of inflation and emphasize the importance of a stable currency in fostering economic prosperity.
Lecture 5: Foreign Investment
In this lecture, Ludwig von Mises emphasizes the crucial role of foreign investment in stimulating economic growth and development. He views foreign investment as an essential means of bringing in new technologies, management expertise, and capital, which collectively can enhance local industries and propel economic expansion.
Mises argues that host countries reap significant benefits from foreign investment. These include access to cutting-edge technologies and management practices that can boost productivity and competitiveness. Additionally, the influx of capital from foreign investors helps to create jobs, stimulate local industries, and accelerate economic growth.
To maximize the benefits of foreign investment, Mises advocates for a set of policies centered on economic liberalization and minimal governmental interference. He champions free trade as a mechanism for allowing goods and services to move across borders unimpeded, which fosters specialization and increases efficiency. Capital freedom is also critical, according to Mises, as it permits investors to pursue the most profitable opportunities, thus optimizing resource allocation. Moreover, he stresses the importance of robust property rights to ensure that foreign investors are neither expropriated nor burdened by arbitrary regulations.
Mises's analysis also touches on the potential drawbacks of poorly managed foreign investment, such as overdependence on external capital and the possible erosion of local industries. However, he maintains that these risks can be mitigated through wise policy choices that prioritize economic freedom and a welcoming business environment.
In conclusion, Mises's lecture on foreign investment underscores its importance as a driver of economic growth and an enhancer of competitiveness in the global market. By adopting policies that encourage free trade, capital mobility, and strong property rights, countries can effectively harness the potential of foreign investment to improve their economic standing and the quality of life for their citizens. As we continue exploring the Austrian School's ideas, we appreciate more deeply the profound impact of liberal economic policies on fostering prosperity and development.
Lecture 6: Policies and Ideas
In this concluding lecture, Ludwig von Mises synthesizes the core principles of his economic philosophy, consistently advocating for a laissez-faire approach. He emphasizes the primacy of individual freedom and market mechanisms in guiding efficient resource allocation and economic stability.
Mises firmly opposes interventionism, which he views as a precursor to economic instability and inefficiency. Instead, he champions monetary discipline and a gold standard to prevent inflation and promote stability. His advocacy extends to free trade and the staunch protection of property rights, which he argues are indispensable for fostering economic growth and development.
Central to Mises's discourse is the impact of ideas and ideology on economic policy. He warns that economic policies are often shaped more by ideological predispositions than by empirical evidence. He posits that the propagation of flawed ideas can lead to dire economic outcomes, whereas sound ideas can significantly enhance economic prosperity.
Looking ahead, Mises envisions a global economy liberated from excessive government intervention, where free markets are the primary drivers of resource allocation. He calls for the reinstatement of the gold standard to curtail monetary manipulation and advocates for unfettered international trade. Above all, Mises underscores the importance of upholding individual freedoms and minimal governmental interference in economic activities.
Through this lecture, Mises articulates a clear vision for future economic policies rooted in classical liberal principles. His teachings emphasize the enduring importance of individual liberty, market efficiency, and minimal state intervention, providing a cogent blueprint for economic liberalization and the safeguarding of personal and economic freedoms.
Conclusion
Through his influential lectures compiled in "Economic Policy: Thoughts for Today and Tomorrow," Ludwig von Mises provides a rigorous exploration of economic principles, offering a profound case for the importance of individual freedom, market dynamics, and minimal government intervention. His insights continue to resonate, shaping modern economic policy and classical liberal thought.
Economic Methodology: In his first lecture, Mises stresses the importance of logical reasoning and real-world evidence over abstract mathematical models, which he believes often fail to capture the nuances of economic behavior. His emphasis on theoretical frameworks and conceptual analysis seeks to ground economic thinking in reality rather than in idealized equations.
Human Action: The concept of human action, introduced in the second lecture, forms the cornerstone of Austrian economics. Mises argues that economics is fundamentally about individuals acting out of self-interest, making decisions independently of government or collective market forces. This perspective underscores the significance of personal autonomy and voluntary exchanges in a healthy economy.
Market Process: In discussing the market process, Mises highlights how entrepreneurial spirit and competition are critical for innovation and economic development. The dynamic adjustment of prices in response to supply and demand signals facilitates this process, driving societal advancements and increased welfare.
Inflation: The fourth lecture deals with inflation, which Mises identifies as a destructive outcome of central banks' interference in the money supply. He vividly illustrates how inflation undermines savings, fosters uncertainty, and results in the poor allocation of resources, contributing to broader economic malaise.
Foreign Investment: Mises champions foreign investment as a catalyst for economic progress in his fifth lecture. By advocating for open trade and minimal regulatory barriers, he underscores how international capital flows can bring about technological advancement, management expertise, and overall economic growth.
Policies and Ideas: Finally, Mises delves into the profound impact of ideological underpinnings on economic policy. He promotes a laissez-faire economic policy, arguing vigorously against interventionism and in favor of policies that protect individual liberties and foster market-led resource allocation.
In summary, Mises's lectures articulate a compelling vision for economic policy that privileges individual agency, market processes, and a restrained role for government. His work not only critiques prevalent economic systems like socialism and interventionism but also lays a robust intellectual foundation for advocating free markets and individual rights. As we continue to face economic and political challenges today, the timeless relevance of Mises's ideas offers valuable insights into fostering environments that encourage economic stability, growth, and human flourishing.
-
 @ 3c827db6:66418fc3
2024-08-18 06:57:22
@ 3c827db6:66418fc3
2024-08-18 06:57:22The challenges associated with physical work and delayed payments, as discussed in the construction and logistics industries articles, might not be as directly applicable to industries with less physical movement. However, the principles of instant settlement and the removal of intermediaries can still bring efficiency and innovation to various sectors. The advantages of instant settlement, such as reduced transaction fees, faster payment processing, and increased transparency, can positively impact industries beyond the physical realm. Whether it's in the realm of digital services, intellectual property, or other sectors that are already dematerialized, the application of instant settlement principles can streamline transactions and enhance overall efficiency.
Navigating The Written Odyssey
Entering the realm of book publishing, especially for a debut author, is a journey filled with challenges. The primary hurdle involves persuading a publishing house to forge a deal, a daunting task for those yet to establish their reputation in the market. The negotiation landscape is complicated by endless uncertainties, making it difficult to strike a mutually beneficial deal. Even if you try to be fair for both sides it is hard. Most people will prioritize themselves and what they get in an uncertain environment - like figuring out how many books will be sold for a first time author. The dynamics intensify when publishing houses provide editors to authors--an arrangement that frequently sparks friction. Authors, protective of their creative work, may resist alterations, but editors, with seasoned expertise, have to navigate the delicate balance between preserving the author's vision and refining the content.
The complexities extend to the business side, with potential pitfalls surrounding signing bonuses. Questions linger: What if the bonus overshoots and the book underperforms? What if the book succeeds, but the bonus proves inadequate, leading the author to seek alternatives for subsequent works? Marketing poses another challenge, raising dilemmas about investments, audiobook adaptations, navigating royalty payments, and banking fees for small markets and international payments.
Just like in the logistics industry here with royalties, we have the same problem of counterparty risk. In addition to stopping the payments to the authors completely, do you trust the publishers that they are giving the correct sales numbers? Translation decisions add another layer, raising queries about language choices, and fair compensation for translators. What about the illustrators? Each party involved creates more and more friction in the system just because everyone is seeking fair compensation. The payment system does not allow them to focus on what they provide in terms of value, but focuses everyone on mitigating the shortcomings of it. Addressing these multifaceted challenges requires not only innovation but also transparent and adaptive contractual frameworks to foster a more equitable and efficient publishing ecosystem.
The challenges for authors extend beyond the realm of creative content, and the intricacies of the publishing and marketing landscape. While the invention of ebooks has somewhat dismantled barriers, enabling easier self-publishing, the journey is not without hurdles. Authors opting for self-publishing must navigate the complexities of setting up accounts and managing distribution before reaching the point of uploading their work. Once published, the dual role of author and marketer emerges, demanding not only literary prowess but also strategic promotional efforts to capture the audience's attention and drive sales. The demanding nature of marketing leaves authors with limited time for their core competency - writing - which hinders the development of subsequent books that they would like to write.
Lighting Up Publishing: From Solo Authors to Collaborative Ventures, Unleashing the Potential of Instant Split Payments
Now that this is the third industry that we are looking into, we know that delayed payments are the problem and that they are tied to time and not actual work - “You have to write the book till this date or else…” “We will gather all payments and royalties will be paid later”. Since we know now that the Lightning Network can fix this let’s dig into the solution and what it may look like.
If you're a first-time author and choose to publish your book on your self-made app, you can instantly receive 100% of the income for each purchase. By utilizing a non-custodial solution like Breez, where no one holds money for others, you avoid the complexities associated with traditional payment methods. This setup eliminates the need for currency exchanges, providing a seamless global payment network directly connected to your app. The benefits go beyond mere currency considerations, freeing buyers from the hassle of exchange rate fees and relieving them of the complexities associated with navigating diverse regulations and processes across various countries. Who knows what regulations you have to deal with to be able to operate with the Iranian Rial just to sell a simple book? With a non-custodial solution on the Lightning Network, you get to avoid all that.
That is a big benefit for one-man shows in the book industry, but let’s take it a step further. In this scenario, where the relationship involves only the author and a publisher, the process becomes streamlined without the need for intricate negotiations, personal data sharing, or complex contracts with various clauses. With the instant settlement, there's no need for advance payments, both the author and publisher receive a percentage from each sale instantly when the purchase is made. The publisher, responsible for uploading and promoting the book on their website, and the author are now aligned in the common goal of selling more books. The only task left is to determine the fair percentage splits between the author and the publisher, fostering a collaborative and efficient partnership. Now the word royalties will have a completely new meaning.
Okay, that is between two entities, but we are not going to stop there. Now that the book is published the book can be translated to other languages. In that case, the complexity does not increase a lot. They just have to determine the percentage share split between the publisher, author, and translator for each sale of the translated version. Upon purchase of the translated book, each payment will be split three ways. Meanwhile, the original language version undergoes a two-way split, with the translator excluded from this split since they didn't contribute to that version. This ensures that the relevant individuals receive sats exclusively for their specific contributions. There might be a need for a separate publisher for the translated language, leading to a split between the author, translator, and second publisher. For the original language, the split occurs between the author and the first publisher. Theoretically, the current system goes through a similar structure for the payments, but I am reminding you here that only the instant split settlement makes that plan match the reality in practice. The moment that any entity starts holding funds for someone else even for a little, then the problems go up exponentially. This is why Breez is committed to preserving the peer-to-peer nature of Bitcoin in lightning payments.
Instant Splits For Narrators, Producers, And All Contributors - A Symphony Of Fair Compensation
We are not done yet with the benefits. Now that we have a path for each language, what will it look like for audiobooks? In that case, you just add one more split based on the agreement between the parties. If you create an audiobook in the original language then the split will be between Author, Publisher, and Audiobook creator. The creation of an audiobook is a project on its own of casting, recording, post-production, and distribution. That has multiple people involved so the split for the audiobook payment in reality may look like this:
Author, Publisher, Producer, Recording engineer, Narrator, Editing/mastering engineer.
In this dynamic model, contributors may wear multiple "hats" within a project, allowing them to assume various roles and, consequently, earn a share for each responsibility they undertake. For instance, an Author might take on the roles of both Producer and Narrator, performing additional work beyond their original scope. In such cases, the Author receives a percentage for each distinct role. However, should the Author choose not to take on these additional roles, someone else can assume those responsibilities and reap the corresponding benefits. This structure ensures alignment, with compensation tied directly to individual contributions at the time of each book sale, eliminating compensation for time or speculation based on future sales.
Unlike the other two industries we explored in construction here and logistics here, the timing of payment in the publishing industry differs. In the preceding sectors, individuals receive compensation instantly upon completing their respective tasks. However, in the realm of authors, payment is not immediate for the act of writing; it occurs when someone is willing to pay the price for the published work. This distinction highlights a fundamental principle: everyone is remunerated when they deliver value to someone else who is willing to pay. Whether delivering a package to the correct address or constructing a house for someone else to inhabit, optimizing the process with the client in mind becomes paramount. Therefore, receiving sats is contingent on providing intrinsic value to others, aligning the industry with similar principles observed in construction and logistics. If you build or deliver something that people do not want, that means you did not provide value.
Instant Influence: From Metrics To Value - A Paradigm Shift In Compensation For Promotions
Now let’s take it even a step further. This will not be the only industry where the influencers can change their business model, but I will use it as an example to explain the change that they will experience in their service. Currently, the influencers get paid for views or mentions depending on whether the medium is audio or video. Their value, as perceived by those paying them, hinges on metrics such as subscriber counts, views, and downloads. But for the person that is paying, is it going to matter if the influencer talks about a book but then it does not result in sales of the book? Or again what happens if someone mentions it but the sales are extraordinary, then the influencer has to receive a more fair compensation. Connecting payments directly to actual value, rather than relying on derivative indicators, ensures influencers receive fair compensation in line with their impact on sales.
Well, the instant settlement fixes that. Authors can now decide on a fixed percentage for influencers per sale, allowing anyone to become an influencer without the need for a massive following. Even a small blog with a modest readership of less than fifty people can result in direct, instant compensation for sales generated. This eliminates barriers to entry for the influencers to have a following and aligns incentives for authors seeking broader promotion. There is a massive friction in the influencer market currently because with poor measuring tools you do not want the money to be wasted on promotion that does not work. This future system is not going to waste a single sat for promotion because it is not paying for a promotion. You are negotiating a commission on every sale which the actual buyer pays - increasing sales is the intent of the authors reaching out to influencers anyway.
Now that we have an influencer promoting a book the UX (user experience) is going to be completely different. Right now to promote anything as an influencer you receive a code that you have to ask for, from the publisher in this case. Then your viewers/listeners have to go to the website and fill in all the information about themselves. Then they have to enter their card information which has to be secured from the website somehow. Then they enter the promo code and receive the ebook that they wanted. On the other side, the publisher has to hope he does not get a chargeback for whatever reason in the next 30 days. The instant settlement UX will be:
-
Influencers enter a lightning address where they want to receive their commissions from for every sale.
-
Then they display a link or a QR code that will be a lightning invoice for the specific book.
-
The buyer enters an email where they want the ebook to be sent.
The instant split payment is sent and everyone including the influencer receives their share of it. This way even influencers might realize that the likes, views and comments are not the most important thing and focus on providing real value for their viewers. This not only streamlines the process but may also alleviate the impact of negative comments and dislikes for influencers. Because their income is not tied to the likes that means it will no longer be the most important thing. They will focus on promoting quality products that sell a lot so they get a piece of those sales and the likes will be secondary.
The transformation in influencer behavior triggered by instant settlement not only disrupts their traditional approaches but sparks competition among publishers and influencers alike. Authors may opt for a model where they focus solely on writing, leveraging influencers to handle promotion without dealing with traditional editors. This introduces a more diverse competitive landscape, where publishing houses will compete with content creators from different industries who passionately recommend authors they love. While these changes benefit readers, authors, and participants, those resistant to competition may be the only ones disliking this evolving landscape. image1
Indeed, envisioning the transformative power of instant payments, there's an opportunity for an innovator to replicate what Amazon did to bookstores. By adopting a model built on advanced technology and leveraging the advantages of instant settlements, this individual can start with books and subsequently explore avenues for expansion. The potential for such a disruptive force lies not only in reshaping the publishing landscape but also in inspiring new possibilities across diverse industries.
Now let’s go and publish that app.
-
-
 @ 6b9da920:7841cc6e
2024-04-25 06:43:22
@ 6b9da920:7841cc6e
2024-04-25 06:43:22When I was a corporate programmer, I never had the chance to directly work with designers because I was a backend developer and more importantly, individual contributors usually have no sayings on what designers should be. Usually, the project manager discusses with designers and decides what should be done and we as programmers just receive the decisions.
In this context, programmers are not treated as engineers because real engineers have to influence the design.
I have the chance to work on designs and with designers for the first time in my life since I started Nostr last year. It has been a huge learning journey for me.
At first, I simply saw UI designers as some kind of painter that drew the shapes I want as the product creator. I have worked with several different designers to come up with UIs or graphics in a side gig, ad-hoc way, either paid or as a community effort.
I need to thank @Karnage and nostr:npub10000003zmk89narqpczy4ff6rnuht2wu05na7kpnh3mak7z2tqzsv8vwqk who have volunteered to help me a bit.
However, the problem unveiled itself shortly. I never finished their design! Roughly 12 months ago, I asked @Karnage to do a redesign of Blowater. He finished it in like a week. But I still have not implemented 30% of what he designed!
Why?
The surface reason is that there are designs that I don't like or visuals that simply goes against the functionality intention. I, as the product creator, did not communicate clearly with the designer what functionalities I want. Therefore, many changes, iterations are needed.
The root reason is, in an exploratory project, designers can't be treated as ad-hoc helpers or outsourced laborers. They have to participate in the core process to shape the product. They can't just do the UIs, they have to actively get involved into the design of the whole product, from functionalities to UIs. This is what I did not understand back then and it took me 12 months to realize. While a designer does not need to spend 40 hours working on a single project. They still need to be considered as a full-time team member instead of an occasional helper.
To address the title, moving forward, I either have to become a UI designer myself, or I have to work with a designer who shares similar visions and is willing to work with me as a long term collaborator. I will never outsource ad-hoc design works again.
-
 @ 6b9da920:7841cc6e
2024-04-24 12:36:55
@ 6b9da920:7841cc6e
2024-04-24 12:36:55I am the author of Blowater, a Discord style nostr client.
Here is a list of my learnings after 15 months of DM focusing development.
I have used Blowater for more than 10,000 DMs so there is some credibility of my findings.
1. 100% Delivery is the most important problem
For example, if user1 wants to send messages to user2, they have to connect to at least 1 common relay. For whatever reasons, if they are not on the same relay, even just for several minutes, some messages will be missing.
It is fine for a user to not see all kind-1s, aka social media. Partial discovery/delivery is how Nostr is designed originally.
But for kind-4s, aka directed messages, this problem is a deal breaker. It's more critical than meta data leak and other privacy/security problems. If you can't deliver your message, it's useless to have a secure message.
Therefore, I believe that while problems like meta data leaks and authentications are important, it's less prioritized than the delivery problem.
Ideas such as Inbox Model are more urgent at this moment.
But, before we step into these discussions, we need to clearly define our design/architecture boundary.
We can at least divide solutions to 4 categories:
| Head | Single Client | Cross Client | | --- | --- | --- | | Single Relay | Centralized | Semi-centralized | | Cross Relay | Slack style | Decentralized |
Now, the problem is, can we achieve 100% delivery +
cross client+cross relayat the same time?Because 100% delivery is not compromisable, if we have to sacrifice, should we give up
cross clientorcross relay?In my opinion, we should sacrifice
cross clientand keepcross relaybecause the client is the most influential place to ensure a good user experience.Blowater used to work
cross client+cross relaywith the original NIP-4. For rational described above, Blowater changed tosingle client+single relaywith the adoption of NIP-44. Yes, the DM of Blowater is pretty much centralized at this moment because we have not figured out a reliable way of delivering messages cross relays.That's why I look forward to inbox-mode.
2. Offline mode and working with bad relays are necessary
If you are on a bad network condition, you still want to browse messages and potentially search them on your device. People usually message themselves as a clever way to take notes and reminders. In fact, it is 10X more useful and convenient than specialized note taking & reminder apps.
Because of this design & engineering goal, Blowater stores all events locally and never deletes. Searching through half a millions notes (including kind-1) only takes a few milliseconds.
As a side effect, Blowater does not need NIP-50 to have a proper search. NIP-50 is nice to have but not a necessity.
The same design & engineering choice also applies to working with bad relays that either do not implement all the NIPs this client needs or return data in an incorrect or inconvenient way.
Relying on the authority of servers is the mental model of a centralized world. Because nostr events are immutable, data stored in clients are not cache. They are the source of truth as well. Therefore, storing as many events locally as possible is a good thing that makes the client both faster and independent from network conditions.
Clients can be seen as relays with UIs and only stores events relevant to the logged in npub. Relays can be seen as clients that have no UIs and stores events of many npubs.
WebSocket-only is a horrible design choice
There are 2 aspects of this statement.
The first being that WebSocket is a streaming API and streaming API for everything is a bad choice. Mainly for 2 use cases:
- get event by ID
Nostr events are immutable, if I have the ID of an event, it does not change. It makes no sense to have a stream of only 1 thing. A relay either has this event or it does not. A HTTP GET of 200 / 404 is much better.
Supporting HTTP API does not make client nor relay implementations harder. WebSocket relies on HTTP/1.1. If you support WebSocket, you have to support HTTP in the first place.
- post events to relays
A simple HTTP POST is a much better way to send data to relays. It makes ad-hoc writing much simpler. The client does not need to establish a WebSocket connection. It's more performant.
To summarize, streaming API is for working with unknown size, possibly infinite data (either in size or in time). If the data size is known & finite, request/response API is much better.
The second aspect is that WebSocket is not a good streaming protocol, at least for the web browsers. There is no way to force close/kill a WebSocket connection on the client side if the server is offline.
For example, client A connects to relay B at time X. At time X + 1, A sends a disconnection message to relay B which was down for whatever reason. Client A will wait there forever and the WebSocket connection, at least from client's perspective, will never be closed.
The WebSocket specification requires the client to wait for the server acknowledgement of closing the connection which prevents client from force closing.
Therefore, it's pretty much impossible to have a reliable browser client that connects to many relays and works reliably for long days. People tend to close their browser tabs so it's not likely to happen but it's still a fundamental flaw.
Additionally, because WebSocket is HTTP/1.1, it does not have all the goodies that HTTP/3 might give us. This is not a problem at the moment. But if we want to have a future proof system, we need future proof design.
WebSocket & many Web clients might serve as a nice starting point to bootstrap the ecosystem. But we can't stay here forever. We have to grow out.
Here you go, 3 main takes away I have about Nostr development. It's not all the learning that I have but I believe they are the most relevant for many developers.
-
 @ fcc4252f:e9ec0d5d
2024-04-17 22:52:57
@ fcc4252f:e9ec0d5d
2024-04-17 22:52:57Check out the latest auctions and products below 👀
Plebeian Market sees growth every week, with new merchants setting up stalls and showcasing their products and services. We are grateful to each and every one of you for your ongoing support! Thank you!
Latest Auctions on the Marketplace
MaxisClub - The Halving
Celebrate the next bitcoin epoch with another classic MaxisClub meme!
Isabel Sydow Greeting Cards

Newest Merchants
Depbit - QR Code Kits
Depbit offers an alternative to metal plated backup QR seed. The problem is that metal ones are very expensive and very difficult to make. Generally people don't buy more than one metal backup plate and then it is the only one they keep which isn’t best practices for backing up your seed. With Depbit you can buy 15 plastics QR kits to use and discard them as needed.
Watch Video Here
In principle, everyone prefers the metal option. But after fighting with the hammer and seeing how easy the plastic one is. Everyone who has tried it has loved it, so try it for yourself!
Order Here

Join Us!
Plebeian Market is a commerce platform that supports open trade and communications while helping individuals and merchants transition onto a bitcoin standard.
Let's Build Together
Bekka
-
 @ 38f9a05c:6999fc04
2024-04-07 12:08:30
@ 38f9a05c:6999fc04
2024-04-07 12:08:30
In today's world, where self-promotion appears to be the standard, there exists a subtle charm in modesty. As a child, I frequently encountered the expression, "Only a donkey praises their tail." its significance has remained with me throughout my life. It serves as a reminder that authentic excellence does not require shouting from the rooftops; instead, it manifests itself in actions, not words.
Allow me to now introduce Alfred Adler, a pioneer in the field of psychology. Born in Vienna in 1870, Adler's theories challenged the prevailing views of his time, particularly Sigmund Freud's emphasis on the unconscious mind. Adler proposed individual psychology, focusing on the unique experiences and perceptions that shape each person's worldview. Central to his theories was the concept of the "inferiority complex" and its counterpart, the "superiority complex," shedding light on how individuals grapple with feelings of inadequacy and superiority.
Inferiority complex
The "inferiority complex" describes persistent feelings of inadequacy and self-doubt, stemming from early experiences. Individuals afflicted with this complex often seek validation and may engage in compensatory behaviors. Therapy and self-reflection are key to addressing and overcoming these feelings, fostering healthier self-esteem and confidence.
An example of an inferiority complex might be a person who, from a young age, consistently felt overshadowed by their siblings' achievements and talents. Despite their own unique abilities and successes, they internalize a belief that they are inherently inferior to others. This belief could manifest in various ways throughout their life, such as constantly seeking approval from others, feeling anxious or inadequate in social situations, or striving excessively for success in an attempt to prove their worth.
Superiority Complex
Conversely, the "superiority complex" manifests as an exaggerated sense of self-importance and entitlement. Individuals with this complex may exhibit arrogance and lack empathy towards others, struggling with meaningful relationships and criticism.
An example of a superiority complex could be seen in a person who consistently belittles others and insists on being the center of attention in social settings. They might boast about their achievements, talents, or possessions in an attempt to assert their superiority over those around them.
Back to the childhood phrase "Only a donkey brags praises their tail." Returning to the childhood adage "Only a donkey brags praises their tail,” modesty and humility are often misconstrued as weakness or a lack of self-confidence. Nevertheless, it is far from that. It entails possessing a realistic view of oneself and comprehending that one's value should not rely solely on external validation or praise. Instead, it's found in the genuine connections we make with others and the positive impact we have on the world around us.
By abstaining from boasting about ourselves, we provide room for others to shine. It is not about denigrating our accomplishments or pretending to be less than we are. On the contrary, it involves acknowledging our abilities without feeling compelled to advertise them to the public continually. Therein lies the elegance of allowing our actions to speak louder than our words.
Moreover, humility allows for personal growth and learning. When we're humble, we're open to feedback and constructive criticism. Instead of becoming defensive or dismissive, we approach each opportunity for improvement with an open mind and a willingness to learn. This mindset not only helps us develop professionally but also fosters a sense of humility and gratitude for the knowledge and experiences that others bring to the table.
Humility enables personal development and learning. When we're not constantly focused on ourselves, we become more attuned to the needs and experiences of those around us. We listen more intently, offer support more readily, and celebrate the successes of others with genuine enthusiasm. In doing so, we cultivate deeper connections and create a more inclusive and supportive community.
In a society that often glorifies self-promotion and individualism, it can be challenging to embrace humility fully. However, it's a quality worth cultivating, both personally and professionally. By focusing on what we can contribute rather than what we can gain, we create a more harmonious and compassionate world. Hence, should you ever find the urge to trumpet your achievements or magnify your ego, pause to reflect on the timeless wisdom encapsulated in the age-old adage: "Only a donkey praises their tail," alongside the profound insights of the Austrian psychiatrist's psychological framework. Instead of trying to prove yourself with words, show who you are through your actions. Embrace humility, which means being modest and not bragging. True greatness isn't about loudly boasting about your good qualities. It's about having inner strength and making a positive impact on the people around you.
Lastly as the Great Roman emperor Marcus Aurelius said, "Waste no more time arguing about what a good man should be. Be one."
-
 @ 3c827db6:66418fc3
2024-08-18 06:55:26
@ 3c827db6:66418fc3
2024-08-18 06:55:26The spread of the Lightning Network may change the incentives behind human interactions, thus also affecting the world of jobs. In the first episode: the construction industry.
When talking about the social implications of Bitcoin, reference is often made to the potential effects of Bitcoin's spread that are not immediately evident: these are second, third, and fourth-degree effects that could change the way people behave in everyday life. Even if the thought might sound hyperbolic, the fact of the matter is that technology has already changed the features of our everyday life, more than once.
Raise your hand if, in the 1980s, you would not have found crazy the idea that one-day people would choose which restaurant to go to based on star ratings and reviews on a digital screen. Who would have thought that one day it would no longer be necessary to pay attention to the route to take by car to reach one's destination and, possibly, learn it by heart, because software would calculate the best route for them based on traffic? How would you have reacted if, back in the 1970s, a friend had told you that in the future he might fall in love with a girl he had never seen who lived on the other side of the world, thanks to text messages processed by software that allows you to meet like-minded people?
Innovation changes social interactions: it always has and will continue to do so, especially if technology is particularly disruptive.
The effects of the large-scale diffusion of the Lightning Network - a technology that allows instant payments from one part of the world to another at almost non-existent costs - can be extremely profound, and can act to change entire sectors. In the first example, in this article, we will discuss how instant settlement could revolutionize the construction industry.
The construction industry is a complex ecosystem involving a myriad of stakeholders, each with its own set of incentives. These often conflicting interests lead to inefficiencies, delays, and increased costs.
The Lightning Network offers a solution to align these disparate interests.
The problems
Misaligned Incentives
In the traditional construction setup, each stakeholder operates with a different set of incentives. More specifically: Buyers aim for high-quality construction within a stipulated time and budget. Planners, including architects, designers, and engineers, are primarily concerned with their designs and less about the actual construction. Construction companies are focused on maximizing profits, realizing the building as quickly as possible and with the lowest possible quality at the agreed price. Supervisors' incentives are tied to bonuses, which may or may not align with the project's overall goals. Construction workers are paid for their time, not the quality or efficiency of their work.
Let's step outside the imagery of the construction site for a moment and think about football. Can you imagine if defenders had a bonus for putting the ball out of bounds? And midfielders had one for the most passes? And strikers for the most goals? Imagine the chaos on the pitch if the different skills of all the players were not employed for only two goals: to score goals and to avoid conceding them. Such a team would hardly be efficient or successful.
The construction industry, with its varied incentives, faces a similar problem, leading to delays, increased costs, and compromised quality.
The underlying issues
Several other issues exacerbate the inefficiencies in the construction industry. Machinery and tools, often owned by the construction company, are not well-maintained by the workers. This leads to faster wear and tear, increasing costs for the company. Small changes in the project requested by the buyer are not usually compensated, adding to the company's costs. Planners are not held accountable for design flaws that manifest during construction, leading to additional costs and delays.
The solution: instant task-based payments
Construction workers
In a hyperbitcoinized world, the Lightning Network's instant settlement feature can be a game-changer.
Workers would be paid for tasks completed rather than time spent. For instance, upon successful construction of a wall or installation of windows, payments could be made instantly. This aligns the workers' incentives with quality and efficiency, as they would aim to complete as many tasks as possible to earn more.
Because workers are paid per task there will be no need for a company to hire workers on a payroll. The company just needs to post the tasks, for example on its app, and anyone can apply for them, do their tasks, and get paid for each execution. The more tasks a worker does, the more bitcoin he earns, the better his skills become, the better his reputation will be in the app. Isn't that what already happens with Uber drivers - except for the Bitcoin part, for now?
Supervisors
This system would also eliminate the need for supervisors to focus on time management, allowing them to concentrate solely on quality assurance. If a task meets the quality standards, the worker gets paid instantly. This would eliminate the need for time-based bonuses or penalties.
Supervisors would be incentivized to focus even more on quality alone by the split payments feature made possible by the Lightning Network. When a specific task is up for grabs, multiple workers can apply for it via a specialized app. The workers then negotiate among themselves to determine the division of payment - be it an even 50/50 split or a more nuanced arrangement like 60/40. This self-organization extends to scenarios involving more than two workers, where payment divisions could be negotiated as 33.3% for each in a three-way split, or perhaps a 40/40/20 arrangement.
The self-organizing mechanism alleviates the supervisory burden. Instead of mediating disputes or assigning tasks, the supervisor's role becomes even more focused on quality control. Once a task is completed to satisfaction, the supervisor approves it in the app, triggering the release of funds. The app itself is programmed to automatically split the payments among the workers based on their pre-negotiated terms, streamlining the entire process and eliminating the need for manual intervention.
Tools ownership
Since workers are compensated for completed tasks rather than time spent, there's a heightened incentive to complete tasks as efficiently as possible. More tasks, more money. The quickest route to efficiency? Utilizing high-quality, well-maintained tools.
When multiple workers vie for the same task, the one equipped with the best tools gains a distinct advantage, capable of completing the task more swiftly and effectively. This system has a ripple effect on tool ownership. Over time, workers might prefer using their own tools over company-provided ones, ensuring better maintenance and ultimately contributing to a more efficient and effective construction process.
In short, the instant payment system would also encourage workers to invest in and maintain their own high-quality tools, further improving efficiency and competition in the construction workers market. This would also reduce the company's costs related to tool maintenance and replacement.
Planners and buyers
Planners would be more involved in the construction process, ensuring that their designs are being followed accurately. They would be paid partially upfront for their blueprints, with the rest being released upon successful completion of tasks. This system would make planners more accountable and invested in the successful execution of their plans.
The task-based payment system also benefits the buyer and the construction company by reducing financial risks. Payments would be made for completed tasks, ensuring that neither party is financially exposed. This would also make the negotiation process smoother, as both parties would know exactly what is included in the price for each task.
Construction companies
While the Lightning Network's instant settlement feature promises to decentralize many aspects of the construction industry, the need for centralized oversight cannot be entirely eliminated. A single entity must be accountable for the holistic execution of the project, meticulously tracking resources required for each construction phase and ensuring the right personnel are deployed at the appropriate times.
Technological advancements have made it possible for specialized apps to manage these complex tasks. Such apps could, in theory, allow the buyer of the finished building to oversee the entire project. However, this assumes that the buyer possesses the requisite expertise in construction management, which is often not the case. As a result, most buyers prefer to employ specialized companies to manage the project until its completion.
This scenario closely mirrors the current state of Lightning Network nodes. While anyone can set up a node, doing so effectively requires a certain level of expertise. Some individuals may choose to manage their own nodes to earn revenue, but the majority are willing to pay fees for expert management, opting for non-custodial apps to simplify the process. Similarly, some buyers may use construction management apps to avoid paying a construction company, but they must then assume full responsibility for the project's outcome.
Now go and build
The next logical step is clear: it's time to build that pay-per-task app and usher in a new era of decentralized construction. By leveraging the capabilities of the Lightning Network and Bitcoin, we can shift the balance of power towards those who are at the heart of every construction project—the workers. These are the individuals who bring blueprints to life, who lay each brick and install each window. By empowering them with instant, task-based payments, we not only align incentives across the board but also elevate the entire industry to new heights of efficiency and quality.
-
 @ 3c984938:2ec11289
2024-04-01 09:36:34
@ 3c984938:2ec11289
2024-04-01 09:36:34A long time ago, a girl resided on a tropical island. The girl's name is Sirena. She resided with her mother in close proximity to the Hagåtña River. Sirena's mother was a bit strict and tried to teach her to follow her in footsteps to be a lady, but Sirena only dreamed of swimming all day.\
 \
Sirena's only outlet was when her Godmother would come visit. She always brought surprises, such as new trinkets, stories, and secretly gave her coconut candy.
\
Sirena's only outlet was when her Godmother would come visit. She always brought surprises, such as new trinkets, stories, and secretly gave her coconut candy.
Sirena's mother was preparing for a special event and needed her to acquire special ingredients from the nearby village. She had a significant amount of preparations to complete, therefore she requested that Sirena procure the necessary ingredients and return promptly. Sirena made a promised to her mother that she would hurry back.\

She was on the village path. She kept her eyes on the trail, trying her best to be a good daughter and hurry back. But she took one glance briefly at the river.
 \
She is mesmerized by the water and jumps in before she realizes it. She swims down the river to the ocean, completely forgetting her mother's errand and promise. Sirena does not returned home even after the sun has set and was still swimming. Her mother, frustrated and angry, unleashes a powerful curse. The godmother begged her daughter to calm down. She shouted, "She's swimming again! Look at how late it is! "If you have such a profound love for the ocean, then become a fish," she exclaims to the ocean. Knowing the extent of her daughter's curse. She tries to counteract her daughter's curse. She pleads to the ocean, "Please, let me keep my Goddaughter's heart, please let that much remain."\
\
She is mesmerized by the water and jumps in before she realizes it. She swims down the river to the ocean, completely forgetting her mother's errand and promise. Sirena does not returned home even after the sun has set and was still swimming. Her mother, frustrated and angry, unleashes a powerful curse. The godmother begged her daughter to calm down. She shouted, "She's swimming again! Look at how late it is! "If you have such a profound love for the ocean, then become a fish," she exclaims to the ocean. Knowing the extent of her daughter's curse. She tries to counteract her daughter's curse. She pleads to the ocean, "Please, let me keep my Goddaughter's heart, please let that much remain."\
 \
In the eerie glow of the moonlight, upon realizing her mother's task, she swims back to where the ocean meets the river. But she experiences a strange sensation in her lower half. The water swirls around her. She looks down to see that she has now fins instead of feet. With the new transformation, she regrets not finishing her mother's errand.
\
In the eerie glow of the moonlight, upon realizing her mother's task, she swims back to where the ocean meets the river. But she experiences a strange sensation in her lower half. The water swirls around her. She looks down to see that she has now fins instead of feet. With the new transformation, she regrets not finishing her mother's errand.
Sirena was happy because now she can be in the water all day long. However, Sirena also wished she did what her mother asked and found another way to punish her. A part of her will forever be saddened by the loss of her Mother and Godmother.
It said that sailors have spotted mermaids on their voyage across the sea. Just that their too crafty & swift to be caught.
Historical Notes/context
 The story originates from the indigenous island of Guam and has been shared for generations. There are multiple versions of the story. The term Sirena is not present in the Chamorro language; however, in Spanish, it refers to the mythological creature known as the mermaid. The capital of the Island is Hagåtña. The Hagåtña river flows beneath the Spanish Bridge, where it is possible to observe her monument. Many believe Sirena resided here. There is speculation that this story was crafted to frighten children into listening to their parents and not playing in the river's water, as it was a vital water source. This was more prevalent when the Spanish established Guam as a port for whaling, pirates, and trade during the Spanish Galleon trade era(16th century). It should be noted that the women's role in the Chamorro version reflects a matrilineal society, which can be seen with Grandma/Godmother.
The story originates from the indigenous island of Guam and has been shared for generations. There are multiple versions of the story. The term Sirena is not present in the Chamorro language; however, in Spanish, it refers to the mythological creature known as the mermaid. The capital of the Island is Hagåtña. The Hagåtña river flows beneath the Spanish Bridge, where it is possible to observe her monument. Many believe Sirena resided here. There is speculation that this story was crafted to frighten children into listening to their parents and not playing in the river's water, as it was a vital water source. This was more prevalent when the Spanish established Guam as a port for whaling, pirates, and trade during the Spanish Galleon trade era(16th century). It should be noted that the women's role in the Chamorro version reflects a matrilineal society, which can be seen with Grandma/Godmother. 
👉I like to point out in this, Thomas Edison patented the light bulb in 1879. So visually the lights outside and inside the huts as flames. As Ai(text to image) does not account for these type of items.
👉This also goes back to be careful what you wish for because you may actual get your wish.
👉Chamorro people are Pacific Islanders, similar to Hawaiians, and have a brown/tan skin complexion.\

👉My mermaid looks strikingly similar to the Disney's recent version of Ariel. I Thought that was interesting because I put just "mermaid" into the text prompt. Its worth pointing out ai limitations as it's not advanced as I originally thought, likely due to its limited data. In this case only disney as a reference for mermaid.
based on ordinary prompts\

 Prompt used:\
Prompt used:\
 That's all-Thank you until next time (N)osyters!
That's all-Thank you until next time (N)osyters!If you like it, send me some ❤❤hearts❤ and if you didn't like it-⚡⚡🍑🍑zap⚡⚡🍑🍑 me!🍑🍑 me!
For email updates you can subscribe to my paragraph.xyz/\@onigirl or below if using the Yakihonne App
-
 @ 41d0a715:9733c512
2024-08-17 22:55:02
@ 41d0a715:9733c512
2024-08-17 22:55:02Fits snugly behind the ear, just slap with your hand ... most realistic bloody ear ever! 6 pieces $12.95.
originally posted at https://stacker.news/items/652908
-
 @ 41d0a715:9733c512
2024-08-17 22:29:22
@ 41d0a715:9733c512
2024-08-17 22:29:22Fits snugly behind the ear, just slap with your hand ... most realistic bloody ear ever! 6 pieces $12.95.
originally posted at https://stacker.news/items/652889
-
 @ 6389be64:ef439d32
2024-08-17 18:00:03
@ 6389be64:ef439d32
2024-08-17 18:00:03From creating connections to taming #LLM-generated chaos, we dive into how embeddings can turn digital noise into meaningful insights. Join Liminal from Project Alexandria and me as we explore the fun side of navigating the wild web of ideas and relational knowledge in Episode 937 of Bitcoin And.
Liminal is sharing 50% of this episode's revenue so use a modern podcasting app to generously BOOST, STREAM, and ZAP Sats.
-
Project Alexandria
-
nostr's Ecosystem
-
Zettlekasten Note Taking
-
LLM's Role in Deleting Relational Noise
-
The Future
Listen to the interview on @fountain --> https://fountain.fm/episode/vvZkH5FKqYVuyFAP312V <--
originally posted at https://stacker.news/items/652671
-
-
 @ 5d4b6c8d:8a1c1ee3
2024-08-17 17:36:38
@ 5d4b6c8d:8a1c1ee3
2024-08-17 17:36:38I wanted to share the crazy odds I managed to get at Nitrobetting, when they rolled out their new site overhaul. I blew pretty much the remainder of my sats on NFL Futures, which they didn't used to offer.
- Raiders to win the AFC West (+900)
- Lions make the Super Bowl (+550)
- Chiefs make the Super Bowl (+375)
- Bills make the Super Bowl (+700)
- 49'ers win the Super Bowl (+10000)
This is the 49'ers year!
originally posted at https://stacker.news/items/652649
-
 @ 97c70a44:ad98e322
2024-03-23 04:34:58
@ 97c70a44:ad98e322
2024-03-23 04:34:58The last few days on developer nostr have involved quite a kerfluffle over the gossip model, blastr, banning jack, and many related misunderstandings. This post is an attempt to lay out my thoughts on the matter in an organized and hopefully helpful way.
What's wrong with gossip?
It all started with a post from jack asking why more devs haven't implemented the gossip model. There are many answers to this question, not least having to do with there being two standards for user relay selections, and ongoing changes to NIP 65. But I don't want to talk about compatibility here.
nevent1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszymhwden5te0wfjkccte9enrw73wd9hj7qpq2uf488j3uy084kpsn594xcef9g9x3lplx4xnglf0xwghyw2n3tfqqnrm02
Mazin responded with some numbers which estimate how many connections the gossip model requires. Too many connections can become expensive for low-power clients like mobile phones, not to mention some privacy issues stemming from nosy relays.
nevent1qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qgewaehxw309amk2mrrdakk2tnwdaehgu3wwa5kuef0qyghwumn8ghj7mn0wd68ytnhd9hx2tcqyp2xzsjktypudzmygplljkupmuyadzzr6rkgnvx9e0fx3zwhdm0vkz4ceg7
I have some minor disagreements with Mazin's numbers, but I basically agree with his point — a purist gossip model, where a large proportion of nostr users run their own relays results in a high number of connections to different relays. I brought this question up late last year in my interview with Mike Dilger and in a conversation with fiatjaf, who convinced me that in practice, this doesn't matter — enough people will use a handful of larger hubs that there will be a good amount of overlap in relay selections between most pubkeys.
To articulate this more clearly: the goal is not "personal web nodes", which is a pipe dream the Farcasters and BlueSkys (BlueSkies?) of the world aim at, but a more pragmatic mix between large hubs and smaller purpose-built relays. These small relays might be outlets for large publishers, small groups, or nerds who also run their own SMTP servers and lightning nodes.
The point of the gossip model is that these small nodes be possible to run, and discoverable from the rest of the network so that we can preserve the censorship-resistant qualities of nostr that brought us here in the first place.
Blast It!
It's no secret that I've long been a critic of Mutiny's blastr relay implementation. My main objection is that the blastr approach doesn't account for the hard limits involved in scaling smaller relays. If the goal is to cross-pollinate notes across all relays in the network, all relays will require the same size database, and contain all notes in the network. This works right now (sort of), but as the network grows, the relays running on a $5 VPS are going to have their disks fill up and will inevitably fall over.
nevent1qyvhwumn8ghj76r0v3kxymmy9ehx7um5wgcjucm0d5hszxnhwden5te0wpuhyctdd9jzuenfv96x5ctx9e3k7mf0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qqs07jr9qx49h53nhw76u7c3up2s72k7le2zj94h5fugmcgtyde4j9qfrnwxj
Not only that, but the content breakdown on any given relay by default becomes an undifferentiated soup of "GM", chinese notes, bots, bitcoin memes, and porn. Blastr makes it impossible to run an interesting relay without implementing write policies.
Which is actually fine! Because that's always been true — servers that allow anonymous uploads always get abused. Tony is just helpfully pointing out to us that this is no less true of nostr relays. I only wish he could have waited a little longer before mounting his attack on the network, because lots of hobbyists are interested in running interesting relays, but the tools don't yet exist to protect those servers from unsolicited notes.
One other note on blastr — Tony at one point described blastr as a relay proxy. This is an interesting perspective, which puts things in a different light. More on proxies later.
Ban Jack?
Here's a thought experiment: how might we actually "ban blastr"? @Pablof7z suggested to me in a conversation that you could configure your relay to check every note that gets published to your relay against the big nostr hubs, and if it exists on any of them to simply delete it. Of course, that would result in your relay being basically empty, and the hubs having all of your content. That's game theory for you I guess.
Another approach that was floated was to encourage users to only publish to small relays. In theory, this would force clients to implement gossip so users could still see the content they were subscribed to. Fiatjaf even posted two identical notes, one to his personal relay, and one to a hub to see which would get more engagement. The note posted to the mainstream relay got 10x more replies and likes than the more obscure note.
nostr:nevent1qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qgmwaehxw309aex2mrp0yh8wetnw3jhymnzw33jucm0d5hszymhwden5te0wp6hyurvv4cxzeewv4ej7qpqdc2drrmdmlkcyna5kkcv8yls4f8zaj82jjl00xrh2tmmhw3ejsmsmp945r
Of course, this is thwarted by blastr, since blastr not only replicates notes posted to it, it also actively crawls the network as well. So the next logical step in this train of thought would be for hubs to encourage people to use small relays by actively blocking high-profile accounts.
nostr:nevent1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpzdmhxue69uhhyetvv9ujue3h0ghxjme0qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qpqpjhnn69lej55kde9l64jgmdkx2ngy2yk87trgjuzdte2skkwwnhqv5esfq
This would of course never happen (Damus is one client that hasn't implemented NIP 65, and they also run the biggest relay), but it was a fun thought experiment. At any rate, the silliness of the suggestion didn't stop certain people from getting offended that we would "disrupt the free market" by "forcing" our opinions on everyone else. Oh well.
Death to Blastr
In reality, even though blastr makes it a little harder to adopt gossip in the short term, its days are numbered. Eventually, relay operators will start to feel the pain of unsolicted notes, and will either shut their relays down or look for tools that will help them curate the content they host.
From my perspective, these tools take two forms — read protection and write protection. This is something I alluded to in my talk at Nostrasia last November.
Write protection is straightforward — already many relays have access control lists based on active subscriptions, invite codes, or just static whitelists that determine who is allowed to post to a given relay, or what event authors are represented there. This approach effectively prevents blastr from using relays as free storage, which is a huge improvement.
Read protection is more tricky, because anything publicly readable will be scraped by blastr and replicated to unauthenticated-write relays across the network. In most cases, this is ok, but there are use cases for relays to exist that host a unique collection of notes oriented around some organizing principle. Unfortunately, with blastr in action (or any scraper that might exist), the only way to do this is to actively protect proprietary content. There are a few approaches that can work to make this happen:
- IP-based access control lists
- AUTH-based access control lists
- Stripping signatures when serving events
- Storing and serving encrypted content
Each of these approaches has its own set of trade-offs. But depending on use case, any of them or a combination of them could work to allow relay operators to carve out their own piece of the nostr-verse. In fact, this is a big part of what Coracle is about — the white-labeled version of the product confines certain notes to proprietary relays, with optional encrypted group support.
Enough of my polemic against blastr. Let's talk about how to make the gossip model actually work.
Hints are pointless
Right now, clients that implement the gossip model rely pretty heavily on relay hints to find related notes — whether user profiles, reply parents, or community definitions. The problem with hints is that they are prone to link rot. Many of the relays that were set up a year ago when nostr took off are no longer online, and yet they persist in user relay lists, and in relay hints. These hints can't be updated — they are set in stone. What this means is that a different mechanism has to be used to find the notes the hints were supposed to help locate.
Because of this, I've come around to the position that hints are basically pointless. They are fine as a stopgap, and might be appropriate for certain obscure and ill-defined use cases where relay urls are the most durable address type available. But they provide basically no value in supporting the long-term robustness of the network.
What are durable, however, are pubkeys. Pubkeys are available pretty much everywhere, except in event id hints — and there is a proposal in the works to add a pubkey to those too. The cool thing about pubkeys as hints is that once you have a pubkey, all you need to do is find that person's kind 10002 inbox/outbox selections, and you should be able to find any note they have published.
This goes with the caveat that when users change their relay selections, or rotate their key, they (or their relays) should be sure to copy their notes to the new relay/pubkey.
The question then is: how do I find a given pubkey's relay selections?
There are already several mechanisms that make this reasonably easy. First of all, NIP 65 explicitly recommends publishing relay selections to a wide range of relays. This is a place where the blastr approach is appropriate. As a result, relay selections are usually available on the most popular public relays. Then there are special purpose relays like purplepag.es, which actively seek out these notes and index them.
These indexes are not confined to relays either. It would be trivial to create a DVM that you could ask for a pubkey's relay selections, optionally for a fee. Alex Gleason's proxy tag could also be used to indicate indexes that exist outside the nostr network — whether that be torrents, DHT keys, or what have you.
The best part is that this doesn't negatively impact the decentralization of the network because in principle these indexes are stateless — in other words, they're easily derived from the state of the public part of the nostr network.
Just do it for me
Looping back to where we started — the complexity and technical challenges of implementing the gossip model — there is a simple solution that many people have experimented with in different ways that could solve both issues at once: proxies.
As I mentioned above, Tony thinks of blastr as a proxy, and he's right. More specifically, it's a write-proxy. This is only part of its functionality (it also acts as an independent agent which crawls the network. EDIT: apparently this is not true!), but it is an essential part of how people use it.
Another kind of proxy is a read proxy. There are several implementations of these, including my own multiplextr proxy, which is gossip-compatible (although it requires a wrapper protocol for use). The advantage of a proxy like this is that it can reduce the number of connections a client has to open, and the number of duplicate events it has to download.
Proxies can do all kinds of fancy things in the background too, like managing the gossip model on behalf of the client, building an index of everything the user would be likely to ask for in advance to speed up response times, and more.
One interesting possibility is that a NIP 46 signer could double as a proxy, reducing the number of round trips needed. And since a signer already has access to your private key, this kind of proxy would not result in an escalation in permissions necessary for the proxy to work.
It's simple
The number of cool and creative solutions to the content replication and indexing problem is huge, and certainly doesn't end with blastr. Just to summarize the next steps I'm excited to see (to be honest, I want to build them myself, but we all know how that goes):
- More clients supporting gossip
- Gossip implementations maturing (Coracle's still has some issues that need to be worked out)
- A shift from relying on relay hints to relying on pubkey hints + relay selection indexes of some kind
- Proxy/signer combos which can take on some of the heavy lifting for clients of delivering events to the right inboxes, and pulling events from the right outboxes
Let's get building!
-
 @ 42342239:1d80db24
2024-03-21 09:49:01
@ 42342239:1d80db24
2024-03-21 09:49:01It has become increasingly evident that our financial system has started undermine our constitutionally guaranteed freedoms and rights. Payment giants like PayPal, Mastercard, and Visa sometimes block the ability to donate money. Individuals, companies, and associations lose bank accounts — or struggle to open new ones. In bank offices, people nowadays risk undergoing something resembling being cross-examined. The regulations are becoming so cumbersome that their mere presence risks tarnishing the banks' reputation.
The rules are so complex that even within the same bank, different compliance officers can provide different answers to the same question! There are even departments where some of the compliance officers are reluctant to provide written responses and prefer to answer questions over an unrecorded phone call. Last year's corporate lawyer in Sweden recently complained about troublesome bureaucracy, and that's from a the perspective of a very large corporation. We may not even fathom how smaller businesses — the keys to a nation's prosperity — experience it.
Where do all these rules come?
Where do all these rules come from, and how well do they work? Today's regulations on money laundering (AML) and customer due diligence (KYC - know your customer) primarily originate from a G7 meeting in the summer of 1989. (The G7 comprises the seven advanced economies: the USA, Canada, the UK, Germany, France, Italy, and Japan, along with the EU.) During that meeting, the intergovernmental organization FATF (Financial Action Task Force) was established with the aim of combating organized crime, especially drug trafficking. Since then, its mandate has expanded to include fighting money laundering, terrorist financing, and the financing of the proliferation of weapons of mass destruction(!). One might envisage the rules soon being aimed against proliferation of GPUs (Graphics Processing Units used for AI/ML). FATF, dominated by the USA, provides frameworks and recommendations for countries to follow. Despite its influence, the organization often goes unnoticed. Had you heard of it?
FATF offered countries "a deal they couldn't refuse"
On the advice of the USA and G7 countries, the organization decided to begin grading countries in "blacklists" and "grey lists" in 2000, naming countries that did not comply with its recommendations. The purpose was to apply "pressure" to these countries if they wanted to "retain their position in the global economy." The countries were offered a deal they couldn't refuse, and the number of member countries rapidly increased. Threatening with financial sanctions in this manner has even been referred to as "extraterritorial bullying." Some at the time even argued that the process violated international law.
If your local Financial Supervisory Authority (FSA) were to fail in enforcing compliance with FATF's many checklists among financial institutions, the risk of your country and its banks being barred from the US-dominated financial markets would loom large. This could have disastrous consequences.
A cost-benefit analysis of AML and KYC regulations
Economists use cost-benefit analysis to determine whether an action or a policy is successful. Let's see what such an analysis reveals.
What are the benefits (or revenues) after almost 35 years of more and more rules and regulations? The United Nations Office on Drugs and Crime estimated that only 0.2% of criminal proceeds are confiscated. Other estimates suggest a success rate from such anti-money laundering rules of 0.07% — a rounding error for organized crime. Europol expects to recover 1.2 billion euros annually, equivalent to about 1% of the revenue generated in the European drug market (110 billion euros). However, the percentage may be considerably lower, as the size of the drug market is likely underestimated. Moreover, there are many more "criminal industries" than just the drug trade; human trafficking is one example - there are many more. In other words, criminal organizations retain at least 99%, perhaps even 99.93%, of their profits, despite all cumbersome rules regarding money laundering and customer due diligence.
What constitutes the total cost of this bureaurcratic activity, costs that eventually burden taxpayers and households via higher fees? Within Europe, private financial firms are estimated to spend approximately 144 billion euros on compliance. According to some estimates, the global cost is twice as high, perhaps even eight times as much.
For Europe, the cost may thus be about 120 times (144/1.2) higher than the revenues from these measures. These "compliance costs" bizarrely exceed the total profits from the drug market, as one researcher put it. Even though the calculations are uncertain, it is challenging — perhaps impossible — to legitimize these regulations from a cost-benefit perspective.
But it doesn't end there, unfortunately. The cost of maintaining this compliance circus, with around 80 international organizations, thousands of authorities, far more employees, and all this across hundreds of countries, remains a mystery. But it's unlikely to be cheap.
The purpose of a system is what it does
In Economic Possibilities for our Grandchildren (1930), John Maynard Keynes foresaw that thanks to technological development, we could have had a 15-hour workweek by now. This has clearly not happened. Perhaps jobs have been created that are entirely meaningless? Anthropologist David Graeber argued precisely this in Bullshit Jobs in 2018. In that case, a significant number of people spend their entire working lives performing tasks they suspect deep down don't need to be done.
"The purpose of a system is what it does" is a heuristic coined by Stafford Beer. He observed there is "no point in claiming that the purpose of a system is to do what it constantly fails to do. What the current regulatory regime fails to do is combat criminal organizations. Nor does it seem to prevent banks from laundering money as never before, or from providing banking services to sex-offending traffickers
What the current regulatory regime does do, is: i) create armies of meaningless jobs, ii) thereby undermining mental health as well as economic prosperity, while iii) undermining our freedom and rights.
What does this say about the purpose of the system?
-
 @ 20d29810:6fe4ad2f
2024-03-15 20:51:56
@ 20d29810:6fe4ad2f
2024-03-15 20:51:56













































-
 @ d8a2c33f:76611e0c
2024-02-26 03:10:36
@ d8a2c33f:76611e0c
2024-02-26 03:10:36Let's start with definitions:
Cashu - Cashu is a free and open-source Chaumian ecash system built for Bitcoin. Cashu offers near-perfect privacy for users of custodial Bitcoin applications. Nobody needs to know who you are, how much funds you have, and who you transact with. - more info here https://cashu.space/
Cashu-adress - it is a protocol that runs on top of cashu mints. More info here: https://docs.cashu-address.com/
Npub.cash - service that runs on top of cashu-address protocol. Let's you use your npub@npub.cash as a lightning address to receive zaps or incoming sats. More info here https://npub.cash/
Pay to public key - Like bitcoin you can cashu tokens are bearer assets and can be locked to a public key. This means only the person who has the private key can use that token.
What do you use it for? - Use your npub cash as your lightning address replacement.
Why? I believe everyone knows what a lightning address is. Lightning address is usually provided by your wallet provider who also runs their lightning node. E.g. if you have @alby.com lightning address then you already have an account setup with alby and using their lightning node to get your sats. With npub.cash you can simply put your npubaddress@npub.cash without registering first or signing up. And you can keep this forever even while changing your lightning wallet from alby to any other provider or running your own lightning node.
Npub.cash locks the received tokens into your nostr public key (Still work in progress) so that only the owner of Nostr public key who has the private key can claim the token and push it to their wallet of choice.
Benefits Over Traditional Custodial Lightning Addresses:
Privacy: With Cashu-Address, your financial activities are not visible to your custodian. This added layer of privacy ensures that your transactions remain your own.
Flexibility in Custodian Selection: Unlike traditional Lightning Addresses, Cashu-Address allows you to choose your custodian freely. If your needs change, you can switch your custodian anytime without hassle.
No User Exclusion: Custodians cannot exclude individual users. Because mints do know know which user eCash belongs to, they can not censor certain users. How to claim your username@npub.cash - This is what makes it so cool. You can actually get a vanity username for your profile name. E.g. I got mine as starbuilder@npub.cash. Simply visit npub.cash website and click the get username button. Put in your vanity username and pay 5k sats to get your profile@npub.cash
How to claim your username@npub.cash- This is what makes it so cool. You can actually get a vanity username for your profile name. E.g. I got mine as starbuilder@npub.cash. Simply visit npub.cash website and click the get username button. Put in your vanity username and pay 5k sats to get your profile@npub.cash . This is onetime and you can use this address forever..!
Frequently asked Questions:
-
What connect string to use to login with NIP-46 on iOS. - try setting up an account at https://use.nsec.app/home . This is still WIP. If it does not work, just try the Nostr extension using laptop browser
-
Is there a notification when I receive sats/zaps? Not yet. We are working on it. However, just go to npub.cash every couple of days to sweep your collected sats to your wallet
-
Which cashu wallet to use? Use enuts (android & ios) https://www.enuts.cash/ or minibits.cash for android https://www.minibits.cash/
-
Will anyone be able to claim my sats? NO. When you start the claim process you need to sign with your Nostr extenstion signer to claim sats. So only the person controlling the private key to the npub can claim sats.
-
I really struggle to understand the flow of what happened concretely. - Don't break your head. the devs got you covered. Also, this is super new and everyone is trying to get their heads around. Just follow instructions, play with it and ask for help.
- Is it non-custodial? - When we lock your sats to your pubkey we cannot spend it. However locking to pubkey is not enabled until wallets can start supporting them.
- How do I ask for help? - just post #asknpub.cash and post your questions. We will get to you.
- Who are the devs behind this? @calle (Master of Cashu) @egge (Core dev) @starbuilder (dev support)
Here's what everyone is talking about #npub.cash on Nostr
nostr:nevent1qvzqqqqqqypzqx78pgq53vlnzmdr8l3u38eru0n3438lnxqz0mr39wg9e5j0dfq3qythwumn8ghj7um9v9exx6pwdehhxtn5dajxz7f0qqsxcwntv9d342ashe5yvyv0fg40wm873jaszt6d2u0209vqz5gkcdq6avwyr
nostr:nevent1qvzqqqqqqypzq5qzedy85msr57qayz6dz9dlcr5k40mcqtvm5nhyn466qgc6p4kcqythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qythwumn8ghj7um9v9exx6pwdehhxtn5dajxz7f0qqsvek7d8v4lddrmj2mynegsnrc4r4gnmswkddm02qzenwuc7x9perctaedre
nostr:nevent1qvzqqqqqqypzpfpqfrt75fhfcd4x0d0lyek9pzyz4zwmudh0vq7vn3njvvngsmpjqyghwumn8ghj7mn0wd68ytnhd9hx2tcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsqgyjwfsgr80xmha8x2wwd4klzsxcagmlpk3wsfyyvqnlvzn2rcvnhu534kj5
nostr:nevent1qvzqqqqqqypzp3yw98cykjpvcqw2r7003jrwlqcccpv7p6f4xg63vtcgpunwznq3qyfhwumn8ghj7mmxve3ksctfdch8qatz9uq36amnwvaz7tmwdaehgu3wvf5hgcm0d9hx2u3wwdhkx6tpdshsqg8v5hfgmwangecpejcw22fm4uk2s438p8ahpu5l985wserctr0h6gysle9m
nostr:nevent1qvzqqqqqqypzp6y2dy0f3kvc0jty2gwl7cqztas8qqmc5jrerqxuhw622qnc2pq3qy88wumn8ghj7mn0wvhxcmmv9uq3xamnwvaz7tm0venxx6rpd9hzuur4vghsqgx68ujht0r9qqqp4l27u0x27sg4p5l2ks0xd9kxm9w2vkjhppttlur0et6k
-
-
 @ 6871d8df:4a9396c1
2024-02-24 22:42:16
@ 6871d8df:4a9396c1
2024-02-24 22:42:16In an era where data seems to be as valuable as currency, the prevailing trend in AI starkly contrasts with the concept of personal data ownership. The explosion of AI and the ensuing race have made it easy to overlook where the data is coming from. The current model, dominated by big tech players, involves collecting vast amounts of user data and selling it to AI companies for training LLMs. Reddit recently penned a 60 million dollar deal, Google guards and mines Youtube, and more are going this direction. But is that their data to sell? Yes, it's on their platforms, but without the users to generate it, what would they monetize? To me, this practice raises significant ethical questions, as it assumes that user data is a commodity that companies can exploit at will.
The heart of the issue lies in the ownership of data. Why, in today's digital age, do we not retain ownership of our data? Why can't our data follow us, under our control, to wherever we want to go? These questions echo the broader sentiment that while some in the tech industry — such as the blockchain-first crypto bros — recognize the importance of data ownership, their "blockchain for everything solutions," to me, fall significantly short in execution.
Reddit further complicates this with its current move to IPO, which, on the heels of the large data deal, might reinforce the mistaken belief that user-generated data is a corporate asset. Others, no doubt, will follow suit. This underscores the urgent need for a paradigm shift towards recognizing and respecting user data as personal property.
In my perfect world, the digital landscape would undergo a revolutionary transformation centered around the empowerment and sovereignty of individual data ownership. Platforms like Twitter, Reddit, Yelp, YouTube, and Stack Overflow, integral to our digital lives, would operate on a fundamentally different premise: user-owned data.
In this envisioned future, data ownership would not just be a concept but a practice, with public and private keys ensuring the authenticity and privacy of individual identities. This model would eliminate the private data silos that currently dominate, where companies profit from selling user data without consent. Instead, data would traverse a decentralized protocol akin to the internet, prioritizing user control and transparency.
The cornerstone of this world would be a meritocratic digital ecosystem. Success for companies would hinge on their ability to leverage user-owned data to deliver unparalleled value rather than their capacity to gatekeep and monetize information. If a company breaks my trust, I can move to a competitor, and my data, connections, and followers will come with me. This shift would herald an era where consent, privacy, and utility define the digital experience, ensuring that the benefits of technology are equitably distributed and aligned with the users' interests and rights.
The conversation needs to shift fundamentally. We must challenge this trajectory and advocate for a future where data ownership and privacy are not just ideals but realities. If we continue on our current path without prioritizing individual data rights, the future of digital privacy and autonomy is bleak. Big tech's dominance allows them to treat user data as a commodity, potentially selling and exploiting it without consent. This imbalance has already led to users being cut off from their digital identities and connections when platforms terminate accounts, underscoring the need for a digital ecosystem that empowers user control over data. Without changing direction, we risk a future where our content — and our freedoms by consequence — are controlled by a few powerful entities, threatening our rights and the democratic essence of the digital realm. We must advocate for a shift towards data ownership by individuals to preserve our digital freedoms and democracy.
-
 @ 0461fcbe:35a474dd
2024-08-17 16:59:15
@ 0461fcbe:35a474dd
2024-08-17 16:59:15Cloudflare is controversial among FOSS/decentralization enthusiasts due to its reliance on a centralized third-party. But if you're going to use it, you should at least use it right.
By default, Cloudflare intercepts DNS traffic, but does not protect your webserver at all. This means anyone with your server's direct IP address can still attack it. Attackers might be crawling all IPs, or they might be able to figure out your server's IP if it makes outgoing requests.
When you use Cloudflare, requests should only be coming from Cloudflare's upstream IPs: https://www.cloudflare.com/ips/
Therefore, you should block traffic from all IPs by default, and whitelist only Cloudflare's IPs for the best protection. UFW is a firewall that comes installed by default on most Linux distros, so you only need to configure it.
Default rules
First configure ufw defaults, so that outgoing requests are allowed and incoming requests are denied by default.
sh ufw default deny incoming ufw default allow outgoingAllow ssh
Next enable ssh so you can still shell in from anywhere.
sh ufw allow sshFor extra security, you should also edit
/etc/ssh/sshd_configand setPasswordAuthentication noso only login by key is supported.You can also whitelist certain IPs for SSH, but you can accidentally lock yourself out this way. For most sites I run, I find this is good enough security (as long as something like Heartbleed doesn't happen again).
Enable UFW
Now you're ready to enable UFW. Your SSH connection should stay intact since you allowed ssh, but this will block all incoming web requests. If you're doing this on an existing production webserver, delay this step until the very end.
sh ufw enableWhitelist Cloudflare IPs
Next we allow traffic from Cloudflare's upstream webservers. This will allow our website to work normally as long as requests go through Cloudflare first, essentially blocking any sort of direct attack on the webserver.
Cloudflare IPs are taken from: https://www.cloudflare.com/ips/
```sh
ipv4
ufw allow from 173.245.48.0/20 to any port 80 ufw allow from 103.21.244.0/22 to any port 80 ufw allow from 103.22.200.0/22 to any port 80 ufw allow from 103.31.4.0/22 to any port 80 ufw allow from 141.101.64.0/18 to any port 80 ufw allow from 108.162.192.0/18 to any port 80 ufw allow from 190.93.240.0/20 to any port 80 ufw allow from 188.114.96.0/20 to any port 80 ufw allow from 197.234.240.0/22 to any port 80 ufw allow from 198.41.128.0/17 to any port 80 ufw allow from 162.158.0.0/15 to any port 80 ufw allow from 172.64.0.0/13 to any port 80 ufw allow from 131.0.72.0/22 to any port 80 ufw allow from 104.16.0.0/13 to any port 80 ufw allow from 104.24.0.0/14 to any port 80 ufw allow from 2400:cb00::/32 to any port 80 ufw allow from 2606:4700::/32 to any port 80 ufw allow from 2803:f800::/32 to any port 80 ufw allow from 2405:b500::/32 to any port 80 ufw allow from 2405:8100::/32 to any port 80 ufw allow from 2a06:98c0::/29 to any port 80 ufw allow from 2c0f:f248::/32 to any port 80
ipv6
ufw allow from 173.245.48.0/20 to any port 443 ufw allow from 103.21.244.0/22 to any port 443 ufw allow from 103.22.200.0/22 to any port 443 ufw allow from 103.31.4.0/22 to any port 443 ufw allow from 141.101.64.0/18 to any port 443 ufw allow from 108.162.192.0/18 to any port 443 ufw allow from 190.93.240.0/20 to any port 443 ufw allow from 188.114.96.0/20 to any port 443 ufw allow from 197.234.240.0/22 to any port 443 ufw allow from 198.41.128.0/17 to any port 443 ufw allow from 162.158.0.0/15 to any port 443 ufw allow from 172.64.0.0/13 to any port 443 ufw allow from 131.0.72.0/22 to any port 443 ufw allow from 104.16.0.0/13 to any port 443 ufw allow from 104.24.0.0/14 to any port 443 ufw allow from 2400:cb00::/32 to any port 443 ufw allow from 2606:4700::/32 to any port 443 ufw allow from 2803:f800::/32 to any port 443 ufw allow from 2405:b500::/32 to any port 443 ufw allow from 2405:8100::/32 to any port 443 ufw allow from 2a06:98c0::/29 to any port 443 ufw allow from 2c0f:f248::/32 to any port 443 ```
That's it!
Now your server is protected from direct IP traffic, and requests must go through Cloudflare.
-
 @ ec965405:63996966
2024-02-15 01:06:05
@ ec965405:63996966
2024-02-15 01:06:05I am beginning to see the clarity that my mentors promised I would as I progressed through my late 20s into my 30s, and it's getting clearer every day. I am inspired to change the world and bring my community with me. I know God has my back. A better world is within our grasp! I'm going to do my part in bringing my community with me by blogging about my upcoming trip to Cuba with Solidarity Collective via Nostr.
In February I'll be back in the skies headed to Havana, where I will participate in a delegation with Solidarity Collective to learn about Pan Africanism in the Cuban context. Some questions we will be exploring during this delegation are:
How do Cubans, in a Black-majority country, approach environmental protection, religion, housing rights, and healthcare?
What is the role of historic and contemporary abolitionist practices in their quest to eradicate racism?
What challenges remain to build an equitable society, especially under the yoke of 60 years of the u.s. Blockade?
What do these lessons mean for the struggle for black liberation in the u.s.?

I've dreamed about the next time I would visit Cuba and how I would track down the friends I made there in 2017. At that time, the government controlled access to internet via these cards that you would purchase then redeem on your device for timed access. The idea was that you would take your Wi-Fi card and head to a communal place like La Plaza with your device to access the Internet with others.
While some north americans might find that kind of Internet access draconian, surfing the web in public like that made me value my time on the Internet more. Has this changed since I was last there? I am personally interested in how groups are leveraging tech and the Internet for education and organizing. I now have a solid couple of years of IT/programming education to reference while I meet with teachers and journalists at the Martin Luther King Jr. Center and hear about the right to free education from daycare through university and literacy campaigns. I wonder if they've heard about decentralized social media protocols like Nostr or Activitypub or if they ever experienced censorship from the authorities on the Internet.
I recently experienced censorship in the YouTube comments as I explained to fellow web surfers why we must include Vieques and the other islands in the archipelago when talking about Puerto Rico politically. My ability to comment was restricted as I tried to convince others who talked down on Haiti and Cuba as failed states to instead take my Pan Caribbean perspective. I really enjoyed Dread's talk at Nostrasia 2023 about how he is using Bitcoin and Nostr to bring the islands together as the US Dollar and financial institutions like Western Union and the IMF keep us divided and oppressed.
The more I learn about Bitcoin as a tool for global wealth distribution, the more I understand how these institutions rob youth and families of basic necessities and facilitate the rise of authoritarian regimes and systems that punish journalists and activists through political repression. The corporate ownership of our means of internet communication by the likes of technocrats like Musk and Zuckerberg won't let authentic conversation between Caribbean-based diaspora happen on their platforms while they get to destroy countries like Myanmar and shape public discourse to their whim. That's why I'm glad I found Nostr.
My personal blog currently lives on my Uberspace asteroid in a Bludit instance that lacks much functionality outside of themes and data analytics, so it's just sits there as a personal repo for my thoughts. Nostr provides all of this with a direct link to my Bitcoin wallet address and comment functionality. If people value my content, I can get "zapped" and earn money for my content. I can now engage with my audience directly without a middle man. No Substack, no moderators censoring my messages, just community. The job now is to bridge my community and this new way of socializing on the Internet.
To help make this as educational of an experience as possible, I ask my audience: What questions or feedback do you have about my trip and the types of questions I want to explore? Is there anything you've ever wondered about Cuba? What suggestions do you have in terms of how I can better present information; written word, audio interviews, video, or photo essays?
Leave me some love in the comments and stay tuned!

-
 @ 99fdaa11:3157ec8e
2024-08-17 14:29:51
@ 99fdaa11:3157ec8e
2024-08-17 14:29:51 -
 @ 6871d8df:4a9396c1
2024-02-05 23:29:22
@ 6871d8df:4a9396c1
2024-02-05 23:29:22The Apple Vision Pro was released, and it is the talk of the town right now. To be frank, I think it's a stupid product. It's not useful or particularly enticing to me in its current form factor. It's a toy, not a tool. All the features seem gimmicky as opposed to generally helpful. I'm not saying it may never be worthwhile, but as of this first release, it is only a party trick.
Coincidently, this is the first product that does not have any of Steve Jobs' influence. To me, it shows. I don't think Jobs would have ever let this product see the light of day.
Jobs understood product. He didn't make things for the sake of progress or to make sci-fi reality; he made things because he 'wanted to make a dent in the world.' He wanted to solve problems for everyday people by innovating with cutting-edge technology. He aspired to make people's lives better. Steve Jobs' genius was the way he married cutting-edge technologies with valuable tools that made those cutting-edge technologies simple and elegant.
The Vision Pro may be technically innovative, but it is not a tool, at least in its current form. It may be one day, but that is precisely my point; Jobs would have never released a product where the form factor would hold it back from becoming a tool. At best, it is an intriguing toy that is additive to some content at the behest of being very awkward to wear or be seen in. In my view, mainstream adoption can happen only in a world where we can use the Vision Pro as a contact lens or very small, discreet, minimalist glasses, but certainly not this iteration where it covers more than half your face.
Seeing people's eyes makes us human. So much emotion, understanding, and communication happens with just a look. It is a window into the soul. I don't want to live in a world where we are actively bringing all the negatives about communicating in the digital world to the physical one.
https://image.nostr.build/2365609411f144f5d789ffd684ffce9b4d867626a7bfe11bb311cb0f61057199.jpg
I can't help but wonder or hypothesize what Steve Jobs would focus on if he were still alive today. I think Apple's priorities would be completely different. My gut tells me he would not have let Siri get as bad as it is. Siri is a horrible product; I never use it, and everyone I know who tries to use it does so unsuccessfully, at least most of the time. I personally always default to ChatGPT or Bard. These AI systems make my life dramatically more productive. They are tools in the purest sense.
In my opinion, Steve would not have missed this train. Sure, Apple could wake up and integrate these systems into Siri — if they were smart, they would — but in its current form, it is so far behind that it almost astounds me. My intuition leads me to believe he would be closer to what [Rabbit] is doing.
Who knows? Maybe I am entirely wrong, and Apple just kickstarted VR's mass adoption phase. Unfortunately, I think this will likely be the biggest failure of a physical product that Apple will have seen since Jobs returned ages ago. The Vision Pro is only slightly better than the Oculus, and Facebook has already deprioritized VR for AI. Apple is further behind, and I don't see a world where they do not make the same pivot. There is a skill to creating successful, innovative products, and it makes me sad to see the torch that Jobs passed lose its flame. As someone who respected how Apple used to innovate, watching this decay in real-time is jarring as this is just the latest in a string of disappointing decisions that exemplify that 'peak Apple' is behind us.
-
 @ 0d6c8388:46488a33
2024-02-02 01:15:40
@ 0d6c8388:46488a33
2024-02-02 01:15:40I'm just a normal guy that likes Jesus and bitcoin!
Here are some things you should know about me:
Well that's all for now hope you have a good day!
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28How IPFS is broken
I once fell for this talk about "content-addressing". It sounds very nice. You know a certain file exists, you know there are probably people who have it, but you don't know where or if it is hosted on a domain somewhere. With content-addressing you can just say "start" and the download will start. You don't have to care.
Other magic properties that address common frustrations: webpages don't go offline, links don't break, valuable content always finds its way, other people will distribute your website for you, any content can be transmitted easily to people near you without anyone having to rely on third-party centralized servers.
But you know what? Saying a thing is good doesn't automatically make it possible and working. For example: saying stuff is addressed by their content doesn't change the fact that the internet is "location-addressed" and you still have to know where peers that have the data you want are and connect to them.
And what is the solution for that? A DHT!
DHT?
Turns out DHTs have terrible incentive structure (as you would expect, no one wants to hold and serve data they don't care about to others for free) and the IPFS experience proves it doesn't work even in a small network like the IPFS of today.
If you have run an IPFS client you'll notice how much it clogs your computer. Or maybe you don't, if you are very rich and have a really powerful computer, but still, it's not something suitable to be run on the entire world, and on web pages, and servers, and mobile devices. I imagine there may be a lot of unoptimized code and technical debt responsible for these and other problems, but the DHT is certainly the biggest part of it. IPFS can open up to 1000 connections by default and suck up all your bandwidth -- and that's just for exchanging keys with other DHT peers.
Even if you're in the "client" mode and limit your connections you'll still get overwhelmed by connections that do stuff I don't understand -- and it makes no sense to run an IPFS node as a client, that defeats the entire purpose of making every person host files they have and content-addressability in general, centralizes the network and brings back the dichotomy client/server that IPFS was created to replace.
Connections?
So, DHTs are a fatal flaw for a network that plans to be big and interplanetary. But that's not the only problem.
Finding content on IPFS is the most slow experience ever and for some reason I don't understand downloading is even slower. Even if you are in the same LAN of another machine that has the content you need it will still take hours to download some small file you would do in seconds with
scp-- that's considering that IPFS managed to find the other machine, otherwise your command will just be stuck for days.Now even if you ignore that IPFS objects should be content-addressable and not location-addressable and, knowing which peer has the content you want, you go there and explicitly tell IPFS to connect to the peer directly, maybe you can get some seconds of (slow) download, but then IPFS will drop the connection and the download will stop. Sometimes -- but not always -- it helps to add the peer address to your bootstrap nodes list (but notice this isn't something you should be doing at all).
IPFS Apps?
Now consider the kind of marketing IPFS does: it tells people to build "apps" on IPFS. It sponsors "databases" on top of IPFS. It basically advertises itself as a place where developers can just connect their apps to and all users will automatically be connected to each other, data will be saved somewhere between them all and immediately available, everything will work in a peer-to-peer manner.
Except it doesn't work that way at all. "libp2p", the IPFS library for connecting people, is broken and is rewritten every 6 months, but they keep their beautiful landing pages that say everything works magically and you can just plug it in. I'm not saying they should have everything perfect, but at least they should be honest about what they truly have in place.
It's impossible to connect to other people, after years there's no js-ipfs and go-ipfs interoperability (and yet they advertise there will be python-ipfs, haskell-ipfs, whoknowswhat-ipfs), connections get dropped and many other problems.
So basically all IPFS "apps" out there are just apps that want to connect two peers but can't do it manually because browsers and the IPv4/NAT network don't provide easy ways to do it and WebRTC is hard and requires servers. They have nothing to do with "content-addressing" anything, they are not trying to build "a forest of merkle trees" nor to distribute or archive content so it can be accessed by all. I don't understand why IPFS has changed its core message to this "full-stack p2p network" thing instead of the basic content-addressable idea.
IPNS?
And what about the database stuff? How can you "content-address" a database with values that are supposed to change? Their approach is to just save all values, past and present, and then use new DHT entries to communicate what are the newest value. This is the IPNS thing.
Apparently just after coming up with the idea of content-addressability IPFS folks realized this would never be able to replace the normal internet as no one would even know what kinds of content existed or when some content was updated -- and they didn't want to coexist with the normal internet, they wanted to replace it all because this message is more bold and gets more funding, maybe?
So they invented IPNS, the name system that introduces location-addressability back into the system that was supposed to be only content-addressable.
And how do they manage to do it? Again, DHTs. And does it work? Not really. It's limited, slow, much slower than normal content-addressing fetches, most of the times it doesn't even work after hours. But still although developers will tell it is not working yet the IPFS marketing will talk about it as if it was a thing.
Archiving content?
The main use case I had for IPFS was to store content that I personally cared about and that other people might care too, like old articles from dead websites, and videos, sometimes entire websites before they're taken down.
So I did that. Over many months I've archived stuff on IPFS. The IPFS API and CLI don't make it easy to track where stuff are. The
pincommand doesn't help as it just throws your pinned hash in a sea of hashes and subhashes and you're never able to find again what you have pinned.The IPFS daemon has a fake filesystem that is half-baked in functionality but allows you to locally address things by names in a tree structure. Very hard to update or add new things to it, but still doable. It allows you to give names to hashes, basically. I even began to write a wrapper for it, but suddenly after many weeks of careful content curation and distribution all my entries in the fake filesystem were gone.
Despite not having lost any of the files I did lose everything, as I couldn't find them in the sea of hashes I had in my own computer. After some digging and help from IPFS developers I managed to recover a part of it, but it involved hacks. My things vanished because of a bug at the fake filesystem. The bug was fixed, but soon after I experienced a similar (new) bug. After that I even tried to build a service for hash archival and discovery, but as all the problems listed above began to pile up I eventually gave up. There were also problems of content canonicalization, the code the IPFS daemon use to serve default HTML content over HTTP, problems with the IPFS browser extension and others.
Future-proof?
One of the core advertised features of IPFS was that it made content future-proof. I'm not sure they used this expression, but basically you have content, you hash that, you get an address that never expires for that content, now everybody can refer to the same thing by the same name. Actually, it's better: content is split and hashed in a merkle-tree, so there's fine-grained deduplication, people can store only chunks of files and when a file is to be downloaded lots of people can serve it at the same time, like torrents.
But then come the protocol upgrades. IPFS has used different kinds of hashing algorithms, different ways to format the hashes, and will change the default algorithm for building the merkle-trees, so basically the same content now has a gigantic number of possible names/addresses, which defeats the entire purpose, and yes, files hashed using different strategies aren't automagically compatible.
Actually, the merkle algorithm could have been changed by each person on a file-by-file basis since the beginning (you could for example split a book file by chapter or page instead of by chunks of bytes) -- although probably no one ever did that. I know it's not easy to come up with the perfect hashing strategy in the first go, but the way these matters are being approached make me wonder that IPFS promoters aren't really worried about future-proof, or maybe we're just in Beta phase forever.
Ethereum?
This is also a big problem. IPFS is built by Ethereum enthusiasts. I can't read the mind of people behind IPFS, but I would imagine they have a poor understanding of incentives like the Ethereum people, and they tend towards scammer-like behavior like getting a ton of funds for investors in exchange for promises they don't know they can fulfill (like Filecoin and IPFS itself) based on half-truths, changing stuff in the middle of the road because some top-managers decided they wanted to change (move fast and break things) and squatting fancy names like "distributed web".
The way they market IPFS (which is not the main thing IPFS was initially designed to do) as a "peer-to-peer cloud" is very seductive for Ethereum developers just like Ethereum itself is: as a place somewhere that will run your code for you so you don't have to host a server or have any responsibility, and then Infura will serve the content to everybody. In the same vein, Infura is also hosting and serving IPFS content for Ethereum developers these days for free. Ironically, just like the Ethereum hoax peer-to-peer money, IPFS peer-to-peer network may begin to work better for end users as things get more and more centralized.
More about IPFS problems:
- IPFS problems: Too much immutability
- IPFS problems: General confusion
- IPFS problems: Shitcoinery
- IPFS problems: Community
- IPFS problems: Pinning
- IPFS problems: Conceit
- IPFS problems: Inefficiency
- IPFS problems: Dynamic links
See also
- A crappy course on torrents, on the protocol that has done most things right
- The Tragedy of IPFS in a series of links, an ongoing Twitter thread.
-
 @ 47e48df6:0a966eb3
2024-08-17 14:25:36
@ 47e48df6:0a966eb3
2024-08-17 14:25:36Teste 01 do Workshop Nostr
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A vision for content discovery and relay usage for basic social-networking in Nostr
Or how to make a basic "social-networking" application using the Nostr protocol that is safe and promotes decentralization.
The basic app views
Suppose a basic "social-networking" app is like Twitter. In that, one has basically 3 views:
- A home feed that shows all notes from everybody you follow;
- A profile view from a specific user that shows all notes from that user;
- A replies view that shows all replies to one specific note.
Some Nostr clients may want to also provide another view, the global feed which shows posts from everybody.
A simple classification of relays
And suppose that all existing relays can be classified in 3 groups (according to one's subjective evaluation):
- spammy relays, in which people of any kind can post whatever they want with no filters at all;
- safe relays, in which there are some barriers to entry, like requiring a fee, or requiring some cumbersome user registration process, and spammers or people who post bad things are banned -- but this is still a relay fundamentally open to anyone (although this is also subjective depending on the kind of restrictions);
- closed relays, in which only certain kinds of people enter, for example, members of a group of friends or a closed online community.
How to follow and find posts from a given profile
To follow someone on Nostr, it is necessary to know one or more relays in which that person is publishing their notes, otherwise it is impossible to fetch anything from them.
When a user starts to follow someone, that may be done through 4 different ways:
- from seeing that person in the app
- using an
nprofileURI - using a NIP-05 address
- using a bare pubkey ('npub`)
Situation 1 may happen when that person is seen in the replies of yours or someone else's post, on a global feed post, or from a note referenced or republished from them by someone else. When that happens, it is expected that the references (in
eandptags) contain relay URLs. We must them inject that information to tentatively associate that person with a relay URL at that first contact.In situations 2 and 3 both the
nprofileand the NIP-05 addresses should contain a list of preferred relays for that person, so we can bootstrap the relay list for that person based on that.In situation 4 there is no relay list, so we must either prompt the user through an annoying popup or something -- or it can try searching for that pubkey in one of their known relays. This remains an option for the other methods too.
Once we have relay URLs for a given profile we can use these relays to query notes from that pubkey. As time passes that user may migrate to other relays, or it may become known that the user is also posting to other relays. To make sure these things are discovered, we must pay attention to hints sent in tags of all events seen everywhere -- from anyone --, and also events of kind 2 and 3, and upgrade our local database that has the knowledge of relationship between profiles and relays accordingly.
Rendering the app views
From what we've gathered until now, we can easily render the home feed and the profile view. To do that it just uses local information about relationships between profiles and relays and fetch notes:
- for the home feed, from all people we're following;
- for the profile view, from just that specific profile.
Since we'll be asking for very specific data from these relays, we do not care about where they're safe or not. They will never send us spam (and if they do that will just be filtered out since it wouldn't match our strict filter).
Now whenever the user clicks on a note we will want to display the replies view. In this case we will just query only the safe and the closed relays, since otherwise spam might be injected into the application. The same principle applies to the global feed view.
Other heuristics and corner cases
There are probably many corner cases not covered in this document. This was meant to just describe one way that seems to me to be sufficiently robust for a decentralized Nostr.
For example, how to display a note that was referenced by someone? If it has a relay hint we query that relay. If it doesn't we can try the relays associated with the person who have just mentioned it, or the same relay we've just seen the note that mentioned it -- as, when mentioning it, one might have published it directly to their own relays -- and so on. But all this may fail and then it is probably not a big deal.
Final thoughts
More important than all, is that we must keep in mind that Nostr is just a very loose set of servers with basically no connection between them, there are no guarantees of anything, and the process of keeping connected to others and finding content must be addressed through many different hackish attempts. To write Nostr applications and to use Nostr one must embrace the inherent chaos.
-
 @ 4657dfe8:47934b3e
2024-01-08 19:37:37
@ 4657dfe8:47934b3e
2024-01-08 19:37:37Hey,
We're trying to maintain the most up-to-date and interesting list of various "LN apps" (Lightning and Nostr web apps) that can be used with Alby, calling it our Discover Page
However, for the past few weeks... we couldn't encounter anyting fresh and working. And it is very possible we overlooked some must-visit website.
What should we add to the Discover Page? Asking for nice recommendations.
We'll pay 2,100 sats per each! 😊 Cheers 🚀🚀
-
 @ e1ff3bfd:341be1af
2024-01-06 19:41:35
@ e1ff3bfd:341be1af
2024-01-06 19:41:35Over the last few months it feels the bitcoin community has gotten more and more jaded on lightning. To be honest, this is for good reason, back in 2017 we were promised a decentralized payment network that would always have cheap payments and everyone would be able to run their own node. Nowadays, the average lightning user actually isn't using lightning, they are just using a custodial wallet and the few of that do run lightning nodes often find it a burdensome task. For us at Mutiny Wallet, we are trying to make this better by creating a lightweight self-custodial wallet and in my opinion we have been executing on that dream fairly well. In this post, I'll analyze these issues and present a new way to view lightning and what that means for bitcoin going forward.
First and foremost one of the hardest UX challenges of lightning is channel liquidity. No other payment system has these problems today besides lightning so this often confuses lots of users. To make matters worse, there aren't any practical hacks that we can do to get around this. Muun Wallet used an on-chain wallet + submarine swaps to get around the channel liquidity problem, this worked very well until fees went up and everyone realized it wasn't actually a lightning wallet. The better solution is JIT liquidity like we do in Mutiny or splicing like that is done in Phoenix. These solutions abstract some of it away but not enough, we often get support questions confused on why some payments have fees and others do not. The fact is channel liquidity is not a usable UX for most end users.
The other major pain point of lightning is the offline receive problem. Inherently, you must be online with your private keys to sign and claim a payment. There is technically an ongoing spec proposal to be able to work around this (essentially creating a notification system of when people are online to receive payments), but it doesn't solve the fundamental problem and still has limitations. There has been a few attempts to get around this, most notably was Zeus Pay lightning addresses. These essentially worked by just creating stuck payments and waited for the user to come online to claim, this caused a ton of problems for people and even forced us at Mutiny to block users from paying them because it caused so many force closures. This is a hard problem because the entire rest of the bitcoin/crypto ecosystem works by just copy-paste an address and you can send to it whenever, there isn't caveats around asking your friend to open their wallet. This is further exacerbated by things like lightning address that requires a webserver to even get an invoice in the first place.
Channel liquidity and offline receives in my opinion are the two most obvious reasons why self-custodial lightning is not popular. When most users hear about any of these, they just think screw that and move to a custodial wallet because it is so much easier. If these were our only two problems, I think self-custodial lightning would be fine, it may never be the predominant way people use lightning, but we could get the UX good enough that we have a significant portion of people using lightning in a sovereign way. However, there are more problems under the surface.
Channel liquidity is a problem, but it is also deceptive. When you have 100k sats of inbound liquidity you would think you could receive up to 100k sats, but this isn't the case, often you can't actually receive any. This is because of on-chain fees, when a payment is being made in lightning you are creating pre-signed transactions that have outputs for every in-flight payment, these outputs cost potential on-chain fees and the high on-chain fees go the more it eats into your liquidity. After we've solved most of our force close issues Mutiny this has been number one support request. Even if you do everything right, understand liquidity and have enough for your payment, sometimes it still won't work because on-chain fees are too high. This is always really discouraging because isn't the whole point of lightning to not have to pay on-chain fees? Fundamentally, all current lightning channels could become entirely useless if on-chain fees went high enough because a single payment would require too many reserves. Obviously this is hyperbolic, but I hope I am getting the point across that on-chain fees don't just effect the opening and closing costs of channels, even if you are a diligent node runner that only opens channels when fees are low, that is not enough, your channels need to be large enough to pay for the on-chain fees of each HTLC at any future on-chain fee rate. As on-chain fees go up and up this problem will only get worse.
The proposed solution to these reserve issues are things like anchor channels, package relay, ephemeral anchors, etc. These are all well and good but kind of just mask the problem. They do solve it so the fee reserve can be much lower and possibly zero, however with the tradeoff that you need on-chain funds available to fee-bump your force closes so they can actually get into a block. This again breaks the UX for self-custodial users because they have hold on-chain funds alongside their lightning funds so they can do those on-chain fee bumps. The size requirements for their on-chain funds is still dynamically based on how high on-chain fees can spike. Solutions for this can include having someone else bump your transaction fees but this brings basically a trusted 3rd party into the mix and isn't ideal.
When you lay out all the different tradeoffs a lightning node needs to make, especially in a high fee environment, it makes me think, what are we doing here, are we going down the wrong path? Lightning is still fundamentally a fantastic payment protocol but its limitation is that it requires scale. Basically every problem I've outlined goes away when you have a large lightning node with lots of liquidity and high uptime so many we should optimize for that. The market has been telling us this for years already, +90% of lightning users are using custodial wallets because it works so much better at scale. So how can we use large scale lightning nodes without custodial wallets?
Combining existing large scale lightning infrastructure with self-custodial solutions sadly, isn't totally possible. The only real way to do that as of now is Muun Wallet which as we talked about earlier, doesn't really solve the problem because everything is just an on-chain transaction. However, Muun was onto something. The architecture of having a simpler protocol interface with lightning is genius and gives us the best of both worlds. We can make fast cheap payments and let the big boys collect fees for running the lightning node. Aqua Wallet just launched which is essentially a Muun Wallet but on top of Liquid, this is a good bandaid fix but doesn't get to the root of the problem.
Before we go further we should take a step back and break down what problems we are trying to solve. Bitcoin has a fundamental scaling limitation through the block size, if we could make infinite, then we wouldn't necessarily need any layer 2s because we could just make on-chain payments. However, we live in the real world and have a 1mb block size limit, and this limits the number of transactions we can make on-chain. Lightning is a huge improvement to bitcoin because we don't need to put every transaction on-chain, we just need to open a channel and can make seemingly countless payments. So why isn't lightning the silver bullet? Lightning lets us move payments off-chain but what it doesn't do is let us move ownership off-chain. Fundamentally lightning still relies on that, at the end of the day, a utxo goes to single user. So even if every on-chain transaction was a lightning channel, we still run into the limit of how many people can actually own those channels. What we need is another layer 2 that can scale utxo ownership and caninterop with lightning, that way we have a way to scale ownership combined with scaling payments.
So how do we scale ownership? Simply put, the answer today is custody, whether that is pure custodial like a Wallet of Satoshi or in the grey area like fedimints and liquid, the only way to do it today is through custody or federated bridges. In bitcoin, the only way to delegate ownership of a utxo to multiple parties is through multisig, however, that requires every user to be online when anyone wants to transact, and when you take go down this path far enough you end up just reinventing lightning.
Are we doomed then? Is there no way to scale bitcoin in a self-sovereign way? Luckily, the answer is no, but we need some soft-forks. Covenants are the way to scale bitcoin ownership. There are a bunch of covenant proposals but at their core what they propose to do is to add a way, so you can have a bitcoin address that limits where and how the coins in it can be spent. This can seem scary, but we already have these in bitcoin today, OP_CTLV (Check LockTime Verify), which was soft forked in 2016, only allows you to spend from a bitcoin address if the transaction has a given locktime, this lets you gate when a utxo can be spent. What the current covenant proposals do is let you gate where a utxo can be spent. With that simple primitive many different protocols can be built that allow for scaling ownership.
There are a lot of current covenant proposals, the main ones being: OP_CTV, OP_VAULT, OP_CSFS, OP_TXHASH, OP_CAT, and APO. They all have different functionality and tradeoffs but in my opinion we should be looking towards activating a form of covenants because otherwise we will likely be moving towards a future of less sovereign bitcoin users.
The future is not bleak however, even without covenants we can still scale bitcoin for the world, just not in the ideal way. At Mutiny, we are full steam ahead on implementing fedimint into the wallet, in my opinion (and the rest of the team's) it looks like the best current scaling solution for bitcoin. Fedimints give us the ability to dynamically share ownership over a group of utxos and is able to interop with lightning through gateways. It is the pinnacle of the scaling dream for bitcoin with current technology and I can't wait to help make it reality while we can.
-
 @ 97c70a44:ad98e322
2024-01-05 22:03:37
@ 97c70a44:ad98e322
2024-01-05 22:03:37Today marks the biggest release so far in Coracle's history. There have been many good days, like when I introduced Coracle to the nostr telegram group, or when I got my fellowship with FUTO, or when I got my grant from OpenSats, or when I got to speak at Nostrasia. But in terms of realizing the vision I've had for the software - for over two years - today is the day.
Coracle now has private groups.
This means you can now send almost any nostr event over an encrypted channel to the rest of the group's members. This is substantially different from group chats, in that it uses rotating shared keys to provide weak forward secrecy, better scaling, and dynamic member access. This more closely approximates one of the most popular social media products in existence - The Nostr is now a direct competitor of The Facebook.
I built this for my community. I wanted something "good enough" to entice people to leave the advertising-fueled surveillance honeypot that is Facebook. In order to work, it needed to at least support notes, events, and marketplace listings. Although support is still quite basic, Coracle has checked all three of these boxes.
Before I get into the details though, it's important to mention that these groups should not be considered "private" any more than Facebook groups or Mastodon servers are (although privacy is substantially better). A better analog might be WeChat, which uses encryption with the same set of trade-offs. So don't post anything to private groups that might get you in trouble!
With that said, it's possible to run a highly private group. The backbone of this spec is e2e encryption, but relay selection can play an important part in hiding metadata from the rest of the network. If you have a relay you trust to protect notes and not share metadata, your security is significantly increased.
Prior art
Nostr-compatible group products aren't a totally novel thing, as it turns out. In fact draft NIP 112 has been around since June, and is already implemented in ArcadeCity. So why am I creating a new standard? I'l get into the positive benefits of my approach more below, but the quick answers are:
- The new encryption standard is going to break compatibility anyway. If we can end up with a better spec, now is the time.
- ArcadeCity development seems to have stalled.
- NIP-72 communities already have a ton of traction, and match what I'm trying to achieve with encrypted channels.
Of course I'm highly indebted to the project, the design of which is still visible in my final design.
Another product that exists to do something similar in a nostr-compatible way is Soapbox by Alex Gleason. This is a great project, particularly since his Mostr project bridges the ActivityPub world and Nostr. ActivityPub works well for highly centralized communities, but the architecture suffers from this centralization too. In particular, not even DMs are e2e encrypted, and just like regular notes are protected only by authentication enforced by servers.
Finally, there's NIP 29, which is fiatjaf's competing groups project. This has some interesting properties, for example the ability to "fork" a group by linking events together. However, similar to ActivityPub it relies exclusively on relays to protect user privacy, and in a fairly non-standard way. You do get to take advantage of nostr's multi-master architecture though, and signatures are also stripped from events in order to discourage propagation through the network.
None of these solutions quite satisfied me, so I built my own.
How it works
One of the coolest things about a NIP 72 community-based group spec is that is supports a spectrum of privacy requirements. A group admin might choose to publish group metadata privately so that it's only visible to the group, publicly so that other people can find the group and ask to join, or leave off a private component entirely.
Likewise, since private groups are backwards-compatible with public communities, it's easy to add a private component to existing groups. This can be useful especially for groups run by a business or content publisher, since public exposure is a good thing but certain group members might have more or less access. This could be used to support a patreon-type model, automating group membership based on subscription tier, for example.
An important aspect of the design that makes automation possible is the concept of a dedicated administration key. By decoupling this key from the original creator of the group, ownership can be shared as simply as sharing the key. This allows multiple admins to manage the group simultaneously either manually or using automations built into the group relays or special purpose bot-clients.
This of course raises the issue of admin access revocation, which isn't possible - that is, until we have a solution for key rotation for normal accounts. Once that's in place, the same process can be used to rotate group admin keys.
In the meantime, it's also trivial to reduce the exposure an admin key gets. You wouldn't generally want to simply paste the key wherever it's needed, but luckily that problem has already been solved as well. Instead of giving every admin or admin bot the key, it's trivial to set up an nsecbunker that authorizes each admin client - and can revoke access as needed.
This level of administration is of course fairly complex, but I think it's important to think through the requirements businesses and other advanced users will eventually impose and anticipate them as we're able, not through over-engineering, but through simple concepts that can be reused.
One other neat feature of this NIP is the definition of invite codes, which are essential for running a private group at any kind of scale. When requesting access to a group, a user can send along a "claim", which can be anything - for example a static invite code, a payment receipt, or an explanation of why they want to join. This claim can be validated by hand by a human, or processed by a bot to instantly admit the new member to the group.
When a new member is admitted to the group, the admin can either share an existing access key with them, or they can rotate the key for the entire group. If relays expire access keys after a certain amount of time, this can create a weak form of forward secrecy, where attackers won't be able to access old content, even if they gain access to the admin key.
Limitations and Future Work
The bar for new nostr clients has risen significantly since I first put Coracle out there. The new groups component is far more mature than Coracle was for much of its early life, but it has its rough edges. Many of these just need to be smoothed out through further UX work, but some are more technical in nature.
- The groups spec relies on NIP 44, which isn't yet available in most signer extensions. That means that unless you log in with your private key (please don't), you won't be able to create or gain access to any private groups.
- Hybrid groups (public groups with a private area) aren't really tested yet, or fully supported in Coracle's UI. It's an open question whether this is even a good idea, since it becomes pretty hard for users to know if they're posting publicly or privately in every context.
- Moderation is not implemented, so if you're creating a public group there is currently no way in Coracle to approve posts. Also, groups created in Coracle don't show up in Satellite for some reason — this is something I'll be working on improving.
- Whether this approach actually scales is another question. It's very hard to build member lists of hundreds of thousands of people, and without a relay helping to filter events, it might become prohibitively expensive to download and analyze all the events posted to a group. We'll see what develops as the design matures and the implementation undergoes stress testing.
Conclusion
Something I like about both nostr and bitcoin is that it empowers the users of the software. The corollary of this of course is that it's important to exercise this power with care - real damage can be done with this group spec, just as real damage can be done to bitcoin holders through low entropy key generation or poor key handling practices. So please, if you're going to implement this spec, communicate clearly with your users its limitations, and encourage them to run their own relays.
Nevertheless, I am stoked to be another 1% closer to my goal of helping my community - and anyone else who uses nostr - to exercise individual sovereignty and protect their freedom and privacy. Let's keep at it.
-
 @ bcbb3e40:a494e501
2024-08-17 10:52:50
@ bcbb3e40:a494e501
2024-08-17 10:52:50|
 |
|:---:|
| Weltanschauung Italia, Breviarios contra la posmodernidad: Bosquejo de ideas para una era en disolución, Hipérbola Janus, 2023 |
|
|:---:|
| Weltanschauung Italia, Breviarios contra la posmodernidad: Bosquejo de ideas para una era en disolución, Hipérbola Janus, 2023 |En el actual orden de cosas, con la vorágine de cambios en los que nos encontramos inmersos, al ritmo y velocidad con que se van sucediendo, con el bombardeo «informativo» indiscriminado, los propios de una sociedad hipertecnológica y consagrada a la virtualidad permanente, a la confusión y el caos que parece reinar por doquier, el hombre está en la obligación (ética, moral y casi existencial) de exigir un punto de equilibrio o un lugar donde asirse y poder digerir el valor y alcance de todos ellos. Breviarios contra la posmodernidad: Bosquejo de ideas para una era en disolución aparece ante nosotros como un apoyo necesario, tanto para adquirir algo de conciencia del mundo en el que vivimos, así como para mantenernos «vivos» en un contexto histórico y unas coyunturas en las que todo parece languidecer y aproximarse hacia un irreversible ocaso.
Ciertamente, el espíritu crítico, y la capacidad para analizar de la manera más objetiva posible la realidad que nos rodea es una tarea complicada y puede llegar a adquirir proporciones titánicas debido a los condicionamientos y prejuicios a los que nos vemos expuestos tanto por el entorno social como por los mass media. Una presión que directa o indirectamente, consciente o inconscientemente, busca una permanente adhesión a una narrativa, a un discurso construido ex profeso por terceros y que es obvio que no busca el beneficio de la sociedad ni de los pueblos, ni mucho menos nos conduce hacia el tan cacareado «progreso» que se nos ha vendido durante décadas y que para nada representa mejora alguna en las condiciones de existencia de nuestros pueblos, sino más bien lo contrario. De modo que el individuo, o más bien la persona, queda desprotegida, a merced del gregarismo de la masa y los mercenarios de la «información», reducidos a meros transmisores y ejecutores de los planes y designios de los poderes fácticos, de las élites, de quienes deciden impunemente el destino de millones de personas. ¿Y cuáles son los recursos y medios con los que cuenta esta persona frente a unas formas de poder cada vez más opresivas, arbitrarias e incluso invasivas en los aspectos más íntimos y particulares de la vida del hombre? Pues bien, el principal recurso, el más elemental, y que parece venir a menos, en continua devaluación, es el razonamiento crítico, la capacidad para establecer un análisis objetivo de la realidad, cultivar el espíritu inconformista, hacerse preguntas, no aceptar acríticamente cualquier imposición, e incluso hacerse fuerte en aquello que revela la experiencia de quienes nos precedieron, y cuyo valor acumulativo ha servido para pertrechar las sociedades del pasado, las de nuestros abuelos, y que no es otra cosa que la Tradición; cúmulo de conocimientos y experiencias que hunden sus raíces en el pasado más remoto, que nos aportaron una cosmovisión, una Weltanschauung que al mismo tiempo que nos da seguridad, es expresión de una forma de ser y estar en el mundo, que nos fortalece en las raíces, para no desviarnos del camino ni zozobrar en los tiempos de cambio e incertidumbre.
Estos son los parámetros en los que podemos enmarcar la obra de Weltanschauung Italia, articulado como un think tank que, haciendo honor a su nombre, se convierte en vector de una cosmovisión del mundo, ofreciendo un cuadro interpretativo de gran valor para el lector que se cuestiona el actual orden de cosas y quiere mantenerse activo, que no quiere claudicar frente al mundo que viene y se está conformando. De alguna forma, Breviarios contra la posmodernidad encierra en sí mismo un principio de rebelión, aunque solo sea a través del pensamiento, pero como los propios autores se encargan de recordarnos, no hay acción que no se nutra de los pensamientos, que no sea diseccionada y previamente diseñada por el acto del pensar, si no quiere ser un hacer frenético y desbocado, algo que, por otro lado, viene siendo habitual en el mundo moderno.
Pero el espíritu crítico y un sistema de representaciones de la realidad que nos proporcione un cuadro claro y nítido del mundo que nos rodea no solo es una necesidad individual, no sólo sirve al propio conocimiento, sino que nos implica a todos y cada uno de nosotros, y de ahí el valor ético-moral que se deriva y le es inherente, en la medida que busca despertar el mismo ánimo en los demás, y es portador de una visión del mundo, de una idea de bien y justicia, o de una concepción del hombre, de una forma de vivir y organizarse en el mundo. Por ese motivo al ejercer una visión crítica y fruto de ella articular una visión del mundo, también adquirimos un compromiso. Lo contrario implicaría una existencia pasiva, reducida a lo puramente instintivo y animal, a los «automatismos de la especie», igualados a cualquier otro ser del mundo animal y negando lo más propio y genuino del ser humano.
Al fin y al cabo, como se demuestra en cada uno de los artículos que componen la obra, lo que está en juego en nuestros días es seguir siendo humanos, afirmarnos como tales en un mundo en el que la técnica, mediante el uso de la tecnología, nos ha hecho pasar de ser sujetos a objetos, totalmente instrumentalizables e intercambiables y al servicio de poderes e intereses espurios, que como en 1984 van mucho más allá de la elaboración de sistemas de control social, que siempre han existido, para poner cerco a la propia condición humana a través de la construcción de una nueva antropología que niega la civilización del Ser de la que nos hablaba Curzio Nitoglia, y desfigura la esencia de lo humano hasta el punto de realizar una obra de inversión de naturaleza satánica. No les basta con poseer el control sobre las personas y sobre los cuerpos, también quieren penetrar en las almas y corromperlas, crear esclavos que amen sus cadenas y que defiendan activamente a sus opresores y verdugos, en la línea del «no tendrás nada y serás feliz» que tan recurrente se ha vuelto en nuestros días. No en vano, en varios de los artículos se nos recuerda los famosos «dos minutos del odio» que en 1984 servía para aglutinar a los esclavos en torno al poder, para moldearlos y fidelizarlos en torno a un enemigo común, totalmente imaginario e irreal.
|
 |
|:---:|
| NITOGLIA, Curzio, En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad, Hipérbola Janus, 2023 |
|
|:---:|
| NITOGLIA, Curzio, En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad, Hipérbola Janus, 2023 |Del mismo modo, hemos vivido durante los últimos años, especialmente con la llamada «pandemia», un proceso similar en muchos aspectos a lo que la famosa novela distópica nos venía describiendo. La instrumentalización y manipulación sistemática a través de poderosas herramientas de propaganda, conciencias y mentes reducidas a la mínima expresión, destruídas por el miedo y entregadas a cualquier discurso, por absurdo y grotesco que éste fuera, hundidas en un episodio de psicosis y alucinación colectiva que parecía más el producto de un encantamiento o de un embrujo de magia negra. Un episodio de guerra psicológica lanzada contra los pueblos del llamado Occidente posmoderno, que en realidad fue su principal objetivo, con el fin de conseguir un cambio de paradigma, al tiempo que saltaban por los aires los valores, principios y concepciones ético-morales que se suponía que existían hasta febrero del año 2020. Obviamente, todo ello es una demostración de que la humanidad del Occidente posmoderno estaba ya madura para convertirse en objeto de la aplicación de la Agenda poshumanista del 2030, diseñada por los grandes jerifaltes del poder globalista, auténticos psicópatas liberticidas en un proyecto de deshumanización nunca visto.
La obra se estructura a través de tres partes diferenciadas:
-
La primera de ellas nos introduce a los autores, reunidos en torno a Weltanschauung Italia, organizados como un think tank, en una declaración de intenciones que nos da respuesta al motivo del anonimato que impera entre sus miembros, los fundamentos generales que animan su actividad y una serie de ideas generales que nos van a permitir entender el enfoque general de la obra.
-
La segunda parte, bajo el título «Más allá del pensamiento único» nos ofrece un abundante compendio de artículos sobre diferentes aspectos de la realidad presente, cuestiones que forman parte del espectro político y social, analizando las paradojas insolubles de nuestro tiempo, manifestadas a través de una democracia liberal cada vez más cínica, hipócrita y desnaturalizada bajo las nuevas formas de gobernanza mundial en gestación, las falsas prédicas de tolerancia, el culto al cientifismo o la permanente erosión de la identidad individual y colectiva a través de procesos de disgregación deliberados y en absoluto fruto del azar.
-
Una tercera parte, «Pandemia y nuevo orden post-democrático» nos introduce de lleno en un análisis de la denominada «pandemia del covid-19», cuyas prolongaciones y consecuencias se extienden hasta nuestros días. Los autores se adentran en las entrañas de este proceso análogo y concurrente con la Agenda 2030 y el cambio de paradigma al que venimos asistiendo. Haciendo uso de una lucidez y gran ingenio, Weltanschauung Italia, nos muestra una serie de lugares comunes dentro del fenómeno pandémico, y los desmenuza críticamente haciendo uso de una lógica implacable, poniendo al desnudo las contradicciones, absurdos e iniquidades que han caracterizado a lo que se llega a calificar, con mucha razón, como un «proceso de psicosis colectiva», en la que todos los valores precedentes, las ideas, razonamientos y visiones que imperaban, sufren una inversión dramática que nos recuerdan a aquella afirmación, casi profética, que Chesterton lanzó en su día: «Llegará un día en el que haya que desenvainar la espada para defender que el pasto es verde». Ese día ya ha llegado, y se puede decir, como es habitual en estos casos, que la realidad supera a la ficción. El texto viene enriquecido por citas de autores de gran relevancia para el pensamiento disidente, tales como Friedrich Nietzsche, Ernst Jünger, Julius Evola o J.R. Tolkien, que sirven para introducir ideas y principios considerados como irrenunciables.
|
 |
|:---:|
| CHESTERTON, G.K., Antología de ensayos políticos, Hipérbola Janus, 2018 |
|
|:---:|
| CHESTERTON, G.K., Antología de ensayos políticos, Hipérbola Janus, 2018 |Al final, el sentido común y la lógica más elemental es la que sirve de guía en un mundo en penumbra, y como apoyo permanente la Tradición, ese punto de referencia que jamás deberíamos perder de vista, que por siempre debe vivir en nuestro horizonte más inmediato, pertrecharse en sagrados principios y convertirnos en ejemplo a través de nuestras acciones, servir de referente moral y existencial para aquellos que nos rodean, e incluso «convertirlos» en la medida de lo posible en nuevos Despiertos, dispuestos a defender la integridad y la dignidad de lo humano frente a las fuerzas subversivas del mal, frente al posthumanismo tecnocrático que trata de engatusarnos con eufemismos y abstractas promesas de felicidad, que al final solo tienen como conclusión autodestrucción, degradación y esclavitud.
Artículo original: Hipérbola Janus, Presentación de «Breviarios contra la posmodernidad: Bosquejo de ideas para una era en disolución», 6/Jun/2023
-
-
 @ e1ff3bfd:341be1af
2023-12-17 18:49:31
@ e1ff3bfd:341be1af
2023-12-17 18:49:31A bunch of people have been shilling Liquid has a scaling solution with on-chain fees on the rise. I wanted to take the time to breakdown why this is a fool's errand and there are better ways to go about this.
Liquid is based on Elements which as they claim in their README is
a collection of feature experiments and extensions to the Bitcoin protocol. Liquid is just another blockchain. It is a fork of bitcoin with a few fancy things added (Tokens, CT, covenants) and bundled together with a 1 minute block time, federated custody, and some blockstream branding.Blockchains do not scale. As we are seeing today, the bitcoin blockchain does not have enough throughput for everyone's transactions. This is for good reason, keeping the cost of running a full node low is a priority, this was one of the main reasons the blocksize wars were fought.
So why does Liquid exist? People lately have been touting it as a way to ease fee pressure but in my opinion this is a fool's errand, no different than people back in 2017 saying to use litecoin because fees on bitcoin were too high. Liquid is just a fork of bitcoin, it has the exact same scaling problems and the only reason it has smaller fees is because it is never really been used. For now, it can work as a temporary stop-gap (essentially finding arbitrage for fees), but building actual infrastructure on top of liquid will run into the exact same problems as on-chain bitcoin.
The problem is that Liquid is trying to use trust as a scaling solution but did it in a completely inefficient way. When you are trusting the 11-of-15 multisig, you don't need all the benefits that a blockchain gives you, everything is dictated by the functionaries anyways. The problem is if liquid gets any meaningful amount of users it will also end up with huge fees and we'll be back to square one because Liquid's architecture didn't actually leverage any of the trust tradeoffs it took and just inherited all the same problems of on-chain bitcoin.
There are real solutions available. Lightning is the obvious alternative but it does have it's own problems, I think a lot of people have been seeing the problems with small scale self-custodial lightning, it is extremely hard to scale. This is why I am extremely excited about fedimint. Fedimint has almost the exact same trust model of Liquid (a federated multisig) but is built on a much better architecture that actually allows for scaling. Fedimints don't have a blockchain but instead operate as a chaumian ecash mint. This allows for them to do actually innovative things instead of just being bitcoin plus a couple features. There isn't a block size, instead the transaction throughput is just gated by the processing power of the guardians. Smart contracts are limited by having to do everything on-chain with bitcoin script, they are pure rust code and allows for all sorts of crazy things. And it all still interoperates with Lightning, essentially giving a Wallet of Satoshi with way less rug-pull risk, tons of new features, and is extremely private.
All this said, it is sad we aren't talking about self-custodial scaling solutions. Today the only real one is Lightning and with current fees, it isn't reasonable unless you have a few million sats. The problem is that this is just inherently a limitation with Lightning. Lightning is excellent when you have high value channels and can make payments across the network, but it does excel at "pleb nodes" where one guy puts 100k sats to try it out, this comes with too many limitations with paying on-chain fees and needing to have reserves to pay future on-chain fees. However, this is potentially solvable. Lightning has solved the problem of scaling payments, where if you have channels, one on-chain transaction can represent many actual payments. What lightning did not solve is that one utxo still represents one user, and this is the limitation we are running into today. Currently the only way we solve this is using a multisig sig (Liquid and Fedimint), but we can solve this in a self-custodial way if we activated covenants. Covenants essentially let us give fine grained control of what is going to be spent from a UTXO before the UTXO even exists. Currently, there are a few proposals (CTV, APO, TXHASH) all with varying ways to do it and different tradeoffs, but imo something like this is desperately needed if we want any chance to scale bitcoin in a self-custodial way.
-
 @ 2edbcea6:40558884
2023-12-10 16:57:25
@ 2edbcea6:40558884
2023-12-10 16:57:25Happy Sunday #Nostr !
Here’s your #NostrTechWeekly newsletter brought to you by nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk written by nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2
The #NostrTechWeekly is a weekly newsletter focused on the more technical happenings in the Nostr-verse.
Let’s dive in!
Recent Upgrades to Nostr (AKA NIPs)
1) (Proposed) NIP 71: Video Events
If Nostr wants to disrupt Netflix or Youtube, we’ll need support for video content.
So far Nostr devs have mostly shied away from storing full files (videos, PDFs, images, etc) on relays in favor of storing files on dedicated file storage/CDN solutions (e.g. nostr.build). That has meant that to bring file-based content into the nostr-verse it has to be referenced within a note or (via NIP 94 ) just publish a Nostr event that is just a reference to a file.
NIP 94 is powerful because we can wrap something that’s not on Nostr in a Nostr event which makes it referenceable and make that reference shareable natively via relays.
This proposal is to create a wapper around NIP 94 to help facilitate more than just hosting the video content. This proposal helps allow video-based clients to do two things: 1) create a replaceable nostr event for the video (so if the creator uploads a new version or switches hosts, people can still reference the same Nostr event). 2) Track video view counts.
It’s still under development but could be helpful as we try to bring more content creators over to Nostr 💪
Author: zmeyer44
2) (Proposed) NIP 44: Places 🌏
Much physical commerce is discovered by consumers via map apps. You go on Google or Apple Maps to find an art supply store near your apartment, or coffee shops that are open right now when you’re in a new city. These centralized solutions have dominated, but Yondar seeks to change that.
Yondar is a Nostr client that allows users to publish places on a map. This could be places of business or events, really anything that has a location. It could unlock crowdsourcing the place-based apps we’re used to using, so we can wrest control back from the tech giants.
This NIP is a proposal to make “place” events a protocol that’s available to any Nostr client. So that the idea can spread beyond just Yondar. Can’t wait!
Author: arkin0x
Notable Projects
Updates to negentroopy and strfry 🛜
nostr:npub1yxprsscnjw2e6myxz73mmzvnqw5kvzd5ffjya9ecjypc5l0gvgksh8qud4 is the primary author of the StrFry relay. It’s one of the most popular relay implementations used by relay operators because it’s performant and extensible.
Doug announced a slew of improvements this week to a library underpinning strfy, called negentropy. Negentropy (from my limited understanding) is a protocol for set-reconciliation, which I would summarize as optimizing the process of syncing two sets of data quickly and with minimal compute resources and data transfer.
I don’t know the innards of strfry but I do know that when scaling systems like relays much of the difficulty comes from distributing data onto many servers so that the relay can hold increasing amounts of data but still serve users requests quickly. You usually can’t have your cake and eat it too.
Improvements to projects like negentropy allow us have relays which are both larger and more performant. They’re not the sexiest advances and usually go un-celebrated, but Nostr will be faster for users and relay operation should get cheaper because of this project.
Thanks Doug!
StrFrui ✔️
Relays are inundated with new events constantly and sometimes relay operators want to “sift” through new Nostr events pushed to the relay to ensure that unwanted content can be rejected. This has been done for rate-limiting, spam filtering, and sometimes outright npub censorship. Which as a relay operator is their right.
Problem is, as Nostr usage scales, relay operators will need more sophisticated tools to manage content on their relays. nostr:npub168ghgug469n4r2tuyw05dmqhqv5jcwm7nxytn67afmz8qkc4a4zqsu2dlc built StrFrui which is a framework for building sifters for relays running strfry (common, performant relay). Thanks for helping Nostr scale 🫡.
Latest conversations: nsecBunker
The landscape for security of Nostr keys is rapidly evolving. Here are the current options:
- Paste your nsec into the client - yikes, but sometimes there’s no alternative, like on iOS Nostr Browser Extension (nos2x, Nostr Connect, etc) - good if you’re on a browser, not encrypted at rest.
- Android Signing App - great if you’re on Android and the client supports it.
- nsecBunker - great security if you want to be hands on managing a bunker
We’re early so we’re still learning the architectures that work the best and those that will be compatible with future, more user-friendly experiences. I’m starting to think nsecBunker has the most potential, because it’s cross platform, encrypted at rest, and can be built so that users never have to manage Nostr keys if they don’t want to.

How does nsecBunker work?
Short answer: it’s complicated. Slightly longer answer: 1. Give the bunker your nsec (or let it generate one). 1. You authorize a client with certain permissions (can publish kind 1 notes for 10 hours, etc). 1. That generates and npub+token that you can use to log in to clients that support nsecbunker. 1. While that authorization lasts, that client can take authorized actions on behalf of the user who’s key is in the bunker.
There’s also a flow in reverse (starts with the client wanting to take an action), but I’m not going to get into it right now. It’s much harder to explain.
How is this better?
NsecBunker has a few advantages over other solutions:
1. Users never need to copy/paste the nsec 1. Nsec is encrypted in the bunker with a passphrase so even if bunker is hacked you’re ok.
1. Bunkers can work in any Nostr context (browser, mobile app, hardware device, whatever).The biggest downside to nsecBunker is that you need a Nostr account to be the admin of the keys stored in the bunker. Whereas the Nostr Browser Extensions you can have one account and self-manage it.
The pot of gold at the end of the rainbow
There are always going to be people that want to custody their own Nostr keys, but most humans likely won’t have the knowledge nor inclination to do so. What they want is something that’s more like the “Login with Twitter” button.
In this future, a user would sign up with a Bunker provider (these could be paid services). The user would use a email/password to manage their account with the provider. The user could generate as many Nostr accounts as they like, but the Bunker custodies the keys.
Clients would then have a “Login with Bunker” button that allows the user to put in their Nostr address (NIP 05) and that will be de-referenced to a bunker and a few relays to help the client and the bunker do all the coordination to get the user logged in and ready to use the client. It will basically be OAuth but using Nostr events as the transfer protocol instead of just HTTP requests.
This architecture allows the least technical users to have a familiar experience while benefiting from all the security and control tools that sophisticated companies still struggle with.
Best of all, if users can export their keys in the future, then they can always migrate out of a custodial solution and self-custody once they learn the advantages. More freedom for users and freedom tech still gets more accessible to everyday folks. nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft created a proof of concept of just such an onboarding flow, check it out here.
What needs to be built
While bunker providers would need to build some management software around nsecBunker (user/subscription management, passing along permission requests to users, etc) most of the work to make this possible is client-side.
More clients will need to support the authorization scheme that nsecbunker requires. This would require new login capabilities, as well as supporting nsecBunker style remote signing capabilities (to delegate authorization to the nsecbunker instead of relying on the user’s nsec being on the same device as the client).
It’s not insurmountable, but it is not trivial; and if history is any guide, client adoption will take time. We’ve seen that Nostr browser extensions still haven’t become universal, even though most developers will tell you they should be mandatory at this point.
My prediction is that iOS clients will lead the charge because iOS doesn’t have the same ability as android for apps to interact with each other (via Android Signing Apps) so nsecBunker may be their only way for iOS clients to stop requiring users to paste in their nsec directly into the client 😬.
I think we’re well on our way to this future, and it’s one that will be much easier for normies to utilize while still allowing for people to opt-out and self custody if they wish.
Until next time 🫡
If you want to see something highlighted, if we missed anything, or if you’re building something we didn’t post about, let us know. DMs welcome at nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk
Stay Classy, Nostr.
-
 @ 21b41910:91f41a5e
2023-12-03 19:36:27
@ 21b41910:91f41a5e
2023-12-03 19:36:27Summary
A user lost 180,000 sats due to a series of unfortunate events involving nostr clients, user error, lack of validation checks, lack of key rotation or mitigation approaches.
What happened
On Saturday 2023 December 2, a user had their profile set to a zeuspay address. Zeuspay addresses are not readily zappable as the receiver needs to acknowledge each zap sent to them. A request was made that they change their lightning address.
The user chose to change to the getalby address that they had previously setup. After entering an older incorrect value, they went to update their profile, but then managed to accidentally post their LND Wallet connection string instead.
A fellow nostrich realized their mistake and informed them. The user began setting up a stacker.news account, while helper connected via bluewallet using the connection string and moved funds out. Helper noted to user that the alby account can't create a separate wallet per account or rotate to new wallet and in order to continue using getalby, they would need to establish an entirely new alby account with a different email. The funds were sent from helper to user's new stacker.news account.
After this, the user linked their stacker.news account with the alby account having the compromised wallet. The user moved some funds to a different account. Later, after going to sleep, the user found remaining funds were pulled from their stacker.news account. It's believed that Zeus wallet or Bluewallet was used with the wallet connection information to LNURL-Auth login to stacker.news
User believes their NSEC was compromised as well and has setup new Nostr account, marked old as compromised and establishing new wallets for zaps.
Realizations
Not only do Nostr keys have no key rotation, LNURL-Auth suffers from this as well. While implementation approaches can be done, we need to get more work in this area to establish common, consistent patterns for how to rotate to new keys, wallets, etc.
In the case of a lightning wallet being compromised its quite severe as different services have no way to know the wallet is compromised as there is by design no central server to query against.
Recomendations
Users
-
Take extra caution when setting up wallet connect information and lightning address in your preferred clients.
-
Make note of where your lightning address and wallet connection information is being used. E.g., track in a password manager.
-
Be prepared to immediately take steps to update if ever compromised.
-
Where possible, use a dedicated lightning wallet (without funds) for LNURL Auth logins, separate from your extensions for logging in and signing events for Nostr.
General Nostr Clients
-
Where user profiles can be edited, add appropriate validation checks on the LUD06 and LUD16 fields. There are plenty of profiles with junk data that dont make sense.
-
LUD06 should be deprecated, but should be a LNURL string if provided.
-
LUD16 should be preferred, and only allow for values in username@domain format. Here's a sample regex:
[a-z0-9-_]*@(([a-zA-Z]{1})|([a-zA-Z]{1}[a-zA-Z]{1})|([a-zA-Z]{1}[0-9]{1})|([0-9]{1}[a-zA-Z]{1})|([a-zA-Z0-9][a-zA-Z0-9-_]{1,61}[a-zA-Z0-9]))\.([a-zA-Z]{2,6}|[a-zA-Z0-9-]{2,30}\.[a-zA-Z]{2,3})LNDHub, LNBits, Accounts type systems
- Add support for rotating from a compromised wallet account to a new one.
- Users and Admins should be able to mark a wallet as compromised.
- No spends should be able to performed from the account.
- Received funds should instead be diverted to replacement wallet.
- Can continue allowing LNURL-Auth to function
- Enhance API calls to ascertain if a wallet is marked as compromised
Blue Wallet, Zeus, any using LNDHub like accounts
- Add support for any new API calls that can indicate a wallet as compromised
- Recommend separation of wallets used for receiving value vs for LNURL-Auth
Alby Recommendations
-
Where Wallet Connection warning is, make it more prominent. Use bold red colors. Inform the user that this gives full access to the wallet and is non-revocable.
-
Add support for multiple wallets on an alby account. Preferably one per subaccount.
-
See notes for LNDHub about handling compromised wallets.
-
-
 @ d8a2c33f:76611e0c
2023-11-27 16:52:20
@ d8a2c33f:76611e0c
2023-11-27 16:52:20This is part of a series of articles that I am writing to better understand and explain how AI agents will transform how we create and consume content in the near future. If you want to start from the first article, please start here.
In the previous article, 2: What makes an AI agent unique?, I discussed how AI agents become unique through their specific instructions, domain knowledge, and actions.
Let's delve into the concept of knowledge. Simply put, you visit a dentist for teeth cleaning, an accountant for financial management, and a primary care physician for health check-ups. In each scenario, you seek their services because they possess the domain expertise that you require.
Consider another instance. Suppose you use a Software as a Service (SaaS) platform for payments and encounter a question. Your first instinct might be to initiate a Google search, which often results in a barrage of ads and irrelevant site links. After some scrolling, you find the correct website, click on it, and are presented with FAQs and support articles. Now, you must sift through this information to determine if it answers your question.
Imagine, however, if there was an AI agent equipped with FAQs, blogs, articles, and other useful information. All you would need to do is pose your question to this AI agent, and it would provide the appropriate information. This approach not only saves time and effort for the user but also enhances the overall user experience.
The importance of domain-specific knowledge in AI agents cannot be overstated. These agents, armed with specialized knowledge, can offer more accurate and insightful responses, thereby revolutionizing the way users seek information and interact with platforms. This is the future of AI - niche applications that are tailored, efficient, and truly transformative.
To see how this works, we created this functionality on PlebAI, where anyone can create AI agents. When creating them, you can add knowledge by attaching a PDF document, text file, or even a URL from a website. Behind the scenes, these data are retrieved, transformed into vectors, and stored in a vector store. This data can be both public and private as it is stored securely and only shared with LLM (Large Language Model) in the form of embeddings.
With this knowledge, the LLM can easily answer the user's questions correctly.
Here's how to add knowledge:
- Go to PlebAI
- Click 'Create Text AI agents'
- Fill in all the necessary information
- Add knowledge in the form of documents or website URLs
- Start using them either privately or publicly

Once you add all the necessary information, the AI agent is now equipped to answer any user question related to the stored knowledge. You can also enable user web browsing so that it can retrieve any additional knowledge available on their website. Here's the response from the Zaprite Help AI agent answering a question from its FAQ.

Marc Andreessen, a renowned entrepreneur and investor, has been quoted as saying, "The content of each new medium is the old medium." This quote encapsulates the idea that each new form of media tends to repurpose the content of its predecessor.
With this view, we can start to push website and app content into AI agents and make them available inside any chat interface.
Let me know what you think and if you have any feedback or comments.
-
 @ d1e60465:c5dee193
2023-11-24 14:01:31
@ d1e60465:c5dee193
2023-11-24 14:01:31Todos los que hemos utilizado Bitcoin alguna vez sabemos lo básico sobre una wallet y de la importancia de la frase de recupero (las 12 o 24 palabras). Esa frase de recupero es única para toda la wallet. También somos conscientes de que las direcciones no deben ser reutilizadas para proteger nuestra privacidad, entonces nuestra wallet genera virtualmente infinitas direcciones. Ahora bien, ¿cómo es eso posible teniendo sólo una única frase de recupero? ¿Acaso hay algo más, además de dicha frase, que determina dónde están nuestros bitcoins?
Aquí es donde entran las wallets HD (hierarchical deterministic = jerárquicas determinísticas) y los “derivation paths” (caminos de derivación). Dicho esto, no hay mejor momento que este para tomar nuestra pala e irnos a enterrar riquezas.
Enterrando nuestra riqueza
Supongamos que tenés un tesoro que querés resguardar y se te ocurre la genial idea de enterrarlo (lo hacían los piratas, por qué vos no?). Lo primero que hacés es buscar un terreno muy MUY grande, elegís una ubicación lo más aleatoria posible, tomás la pala, cavás el pozo, y enterrás el tesoro. Por último, y muy importante, te anotás las coordenadas de dicha ubicación (llave privada) para volver luego por tu riqueza cuando la necesites.
Supongamos ahora que pasa el tiempo y seguís generando riquezas que querés proteger. Siguiendo tu idea original volvés al mismo terreno a cavar mas pozos, enterrar más tesoros y anotar más coordenadas. Si esto se repite varias veces más llegará un momento en el que guardar tantas coordenadas resultará incómodo para llevar un correcto registro, y riesgoso ya que si perdés una de ellas perdés un tesoro.
Con la pala en mano, sentado sobre un pozo, y mirando el horizonte se te ocurre una genial idea. Podrías sólo anotar la coordenada de un único punto arbitrario y diferente a los demás dentro de ese terreno (llave privada maestra), en donde no vas a enterrar nada. Pero hacés que todos los pozos, donde sí enterrarás tesoros, se ubiquen de forma relativa al punto inicial de una manera específica (camino de derivación). De esta forma llegarías a cualquier pozo partiendo de esa ubicación original. Por ejemplo: “los tesoros estarán ubicados en intervalos de 10 pasos hacia el norte desde el punto origen”. Incluso podrías definir ciertos recorridos fijos y complejos dependiendo el tesoro. Por ejemplo: “caminando hacia el norte, cada 10 pasos, pozos con oro; caminando hacia el este, cada 5 pasos, joyas; y para regalos misceláneos irás con intervalos de 4 pasos al oeste, pero cada vez que caves caminarás 2 más al sur (es decir, como si formases una letra L)”.
Todo este mecanismo parece complejo a primera vista, pero tiene una ventaja fundamental y es que los recorridos no tienen que guardarse de manera secreta ya que sin la coordenada origen nadie podrá encontrar el tesoro. Gracias a esta particularidad podríamos definir patrones de recorrido que sean públicos y todos compartamos, e incluso convertirlos en un estándar global (BIP44 o BIP86). En otras palabras, los caminos para llegar a cada pozo serán de público conocimiento y podrán estar anotados en múltiples lugares, mientras que las coordenadas de partida serán secretas de cada individuo.
Para repasar, tenemos presente que para encontrar el tesoro necesitamos la coordenada original y el recorrido de pasos. Física y visualmente podríamos pensarlo como una hoja transparente donde están dibujados los recorridos, y otra hoja con un mapa (secreto) que marque el punto origen. Ambos superpuestos darán la información necesaria (wallet HD) para encontrar todos los tesoros enterrados. Ambos son necesarios, pero sólo uno de ellos necesita ser secreto.
Cambiando la pala por criptografía
En Bitcoin, esta idea de tener una llave privada maestra (el punto de origen) y luego diferentes caminos de derivación fue introducida en el BIP 32. Explicado en términos (muy) simples podemos partir de que nuestra llave privada maestra no es más que un número, y lo que hace este mecanismo es realizar operaciones matemáticas sobre ese número para obtener nuevos números: las llaves hijas.
En la práctica, una situación habitual que genera pánico en aquellas personas que comienzan en Bitcoin se da cuando restauran una wallet utilizando la frase de recupero y la wallet no muestra su balance. El terror de ver “0 BTC” en lugar de sus ahorros detiene el tiempo durante unos segundos. Sin embargo, un poco más de atención sobre la situación revelaría que no sólo se muestra un balance en 0, sino que tampoco se muestra ninguna de las transacciones realizadas previamente. Es decir, es como si estuviésemos mirando otra wallet. Lo que sucede en estos casos es que, si bien la frase de recupero y por ende la llave privada maestra (coordenada original) se restauró correctamente, la wallet en cuestión utiliza otro derivation path, otro camino. Entonces, por más que partimos desde el mismo punto a caminar, estamos caminando para el lugar equivocado para encontrar el tesoro. Esto se debe a que, si bien existen estándares de derivation paths, no todas las wallets los respetan al 100%. Esta web detalla los diferentes caminos utilizadas por cada una de las diferentes wallets conocidas que existen en el mercado, y así evitar situaciones desagradables: https://walletsrecovery.org
Existen más particularidades no cubiertas por la analogía, como que en este esquema también se hace presente una llave pública maestra que puede tener derivaciones y así generar múltiples direcciones (y monitorearlas) pero sin tener acceso a las llaves privadas de cada una para mover los fondos asociados. Aparece también el concepto de “hardened” (fortalecido o endurecido), que hace referencia a sub-llaves derivadas de las principales ajustando el algoritmo para evitar filtración de datos sensibles y que un atacante pueda reconstruir nuestra llave privada maestra. Todos estos detalles están explicados en el BIP para quien le interese.
Epílogo
En Bitcoin, una llave privada maestra sería el equivalente a elegir una coordenada origen cualquiera en todo el planeta (incluyendo agua)… de entre más de 900000000000000000000000000000000000000000000000000000000000000 planetas Tierra. Podemos estar tranquilos que la coordenada que elijamos seguramente no sea elegida por otra persona.
Links útiles
- https://walletsrecovery.org Wallets Recovery — Derivation paths por wallet
- https://github.com/bitcoin/bips/blob/master/bip-0032.mediawiki BIP32 — “Hierarchical Deterministic Wallets”
- https://github.com/bitcoin/bips/blob/master/bip-0044.mediawiki BIP44 — “Multi-Account Hierarchy for Deterministic Wallets”
- https://github.com/bitcoin/bips/blob/master/bip-0086.mediawiki BIP86 — “Key Derivation for Single Key P2TR Outputs”
Este artículo está inspirado en un hilo de Twitter que hice en 2021: https://twitter.com/diegogurpegui/status/1408931266616041475
-
 @ 52b4a076:e7fad8bd
2023-11-10 23:08:02
@ 52b4a076:e7fad8bd
2023-11-10 23:08:02Nostr has a funding problem. Developers and infrastructure is severely underfunded and reliant on flawed economic models, and this could pose a risk to the future of Nostr as a protocol.
To understand it, we need to understand what resources are needed to make Nostr work, how they aren't funded properly and what could happen next.
The costs of what makes Nostr work
Nostr works because: 1. Developers build clients on it 2. There is infrastructure to support clients
If there are no developers, there are no clients. If there is no infrastructure, clients have no purpose.
The costs of developing a client, and the reliance on developers
Clients require time to develop the client, and money to run infrastructure for it.
Without developers, there would be no clients, and no Nostr.
Developers have lives and need to make money somehow in exchange for the time they spend. Developing a client is a significant cost, even for small ones (assuming 1 hr/day, no infrastructure costs and the average salary of a software developer, $1500) and needs to be covered somehow.
We have multiple models, all of which have large downsides: 1. Donations/V4V/Bounties:
This model suffers from the problem that a minority pays for the majority, which will lead to the majority demanding exclusive benefits for their money or otherwise cutting off funding since they have no reason to pay.
This also suffers from the fact that donations are unreliable. 2. Grants from OpenSats and similar non-profits:
These suffer from the same problems as the donations model, but also suffer from the following problems: - the managers of these non-profits may have views not aligned with their donors, leading to misfunding. - that such projects are mostly stopgaps that add additional complexity to a direct donation model. 3. Paywalled features:
It is very hard to find the balance between paywalling enough features to make money, and discouraging too many users from using the client. There may not even be such a sweet spot. 4. Cuts: It is extremely hard to balance these so that people don't complain, and it is likely that there will be forks of FOSS clients that remove these features by some users.
5. Paid clients:
People do not want to spend a lot on services that they expect to be free or cheap, and spending $5/month on this client, $10/month on that client, so on won't scale, even though that is way less than the actual value they are getting. 6. Ads:
Ads are usually underpaying and mostly make money for the ad companies instead of the client developers. Ads are also an invasion of privacy and may not be well received by some users. 7. VC funding:
VCs put profit above protocol health, which may accelerate some issues that I will discuss later. They also may disincentivize the development of some apps (uncensored social media for example) for pushing their own agenda.Even if we find some good way to fund clients, it doesn't end there...
The cost of infrastructure
There are multiple types of infrastructure for Nostr, such as relays, services like Noswhere's search relay, push notifications, etc. All of these cost money to operate, and are the other half of what make Nostr work.
These have even more limited funding options, which have even bigger downsides: 1. Client funding:
Clients already struggle on funding as I discussed in the previous section. This would mean infrastructure is even more underfunded. 2. User payments:
Users do not understand the details and importance of infrastructure, and have no reason to fund it. Making this problem worse, infrastructure providers can falsely advertise their services, diverting money away from infrastructure that is higher quality and should be funded. This is already happening. 3. Grants from OpenSats and similar non-profits (relays only):
Again, these suffer from problems specified in the last section about grants. These entities will likely want the highest value from their donations, therefore leading them to encouraging a few big relays than many medium sized ones. Since relays are more important infrastructure, and they could have more control, these entities can also exert more control over the network. 4. Data harvesting and selling:
This would discourage people from using their providers, but this is likely going to happen to some extent. The issue is that it would not generate sufficient revenue for the amount of users it will drive away.Both infrastructure and developers being underfunded can lead to issues that may kill the protocol, which I'll discuss in the next section.
The risks of improper funding
1. The protocol fizzles out and dies without reaching critical mass
This is one of the less likely options since there will probably be people developing for the sake of it, but is likely. With client developers being underfunded and infrastructure shutting down, Nostr would become smaller and worse to use until it completely fizzled out except maybe a few people.
2. The enshittification of Nostr
This is the most likely outcome, and the worst one. As Nostr continues developing, developers and infrastructure developers will want to maximize revenue, so they will begin by making good products to attract users at a loss.
After they have a sufficiently large user base, they would slowly erode bridges to their competitors, only leaving what is required so that their users won't complain.
After this stage, it is likely that clients will start merging with other ones to make larger "everything" apps and kill the last bridges, turning them into proprietary walled gardens, returning us to where we are today.
How do we fix this?
I have no idea. Please share your opinions if you do :)
-
 @ 3bf0c63f:aefa459d
2023-11-08 15:06:55
@ 3bf0c63f:aefa459d
2023-11-08 15:06:55I think it's undeniable at this point that the creation of Lightning Address has made the usage of custodial Lightning solutions increase -- or at least be more prominent. We see these stats everywhere of how many of Nostr Lightning Addresses are custodial, and how services like Nodeless and Geyser only work if you give them a Lightning Address, and that probably sounds like a lament to many people who thought Lightning would be this amazing network of self-hosted nodes that everybody runs, and is indeed sad.
Well, on the other hand the Lightning Address flow is clearly an improvement -- to most people -- over the cumbersome invoice flow. Since the early days of Lightning people had been complaining about the fact that there is no way to "just send money to an address". Even though I personally liked the invoice flow much more (especially if they had structured, signatures, clear descriptions and amounts, payment proofs and so on) the fact is that most people didn't and slowly invoices were losing their meaning entirely anyway.
This improvement in the payment flow, along with the open, easy and interoperable way that Lightning Addresses work, has opened space for new use cases that maybe wouldn't have existed otherwise -- like the services mentioned above, and others. So we can't really say this was all a bad thing.
We also shouldn't say it was a bad thing to have Lightning Addresses being invented at all, because if they hadn't been invented like they were, there is a high probably they would have been invented in other forms, probably much worse, that would involve private deals and proprietary integrations with ad-hoc APIs, SDKs and JavaScript widget buttons with iframes. I even remember some of these things starting to happen at the time Lightning Address was created, and we have more evidence of these things even after Lightning Address, like some "partnerships" here and there and the "UMA" protocol. So maybe Lightning Address was just the best possible protocol at the best time, and all its problems are not really its problems, but symptons of the problems of the Lightning Network (or maybe you wouldn't call these "problems", just natural properties, but doesn't matter).
The saddest realization of all this process, for me, was that Lightning payments are mostly used for tipping and not for commerce as I thought they would in the beginning (hence my love for the invoice flow). Specifically, LNURL-pay and its cool hidden features that went mostly unsupported, were all designed with the goal of enabling new use cases for commerce in the real life, outside the web, and Lightning Addresses would have tied nicely into that vision too -- but that was all definitely an irredeemable failure.
I thought I had more things to say about this, but either I didn't or I forgot. The end.
-
 @ 2edbcea6:40558884
2023-11-05 18:23:21
@ 2edbcea6:40558884
2023-11-05 18:23:21Happy Sunday #Nostr !
Here’s your #NostrTechWeekly newsletter brought to you by nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk written by nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2
The #NostrTechWeekly is a weekly newsletter focused on the more technical happenings in the nostr-verse.
Before we dive in I want to congratulate the winners of the NostrAsia hackathon: eNuts, Shopstr, Zappdit, and the runner up Nosskey. Thanks for hacking away and building for the community. 😊
Let’s dive in!
Recent Upgrades to Nostr (AKA NIPs)
1) (Proposed) Updates to NIP 72: Moderated Communities
As mentioned in previous weeks, moderated communities as currently outlined in NIP 72 publish kind 1 events (tweet-like text notes), and they show up without context in clients like Damus, Amethyst, Snort, etc.
One solution to the lack of context is to make activities in moderated communities use event kinds other than 1 so that you have to be in a client specialized for moderated communities to see those activities.
There have been a few attempts to update NIP 72 to accomplish that goal, and this is the latest iteration. Unique to this proposal is the idea of community scoped user data, not just posts. For example you could follow people within the community within the scope of the community but not add them to your general following list for your whole Nostr account. They’d show up in your feed in the moderated community but not in your general feed.
There’s a lot of potential in moderated communities to become a core pillar of Nostr usage as the network scales, especially since the censorship and API management regimes of Reddit have gotten more restrictive. People want better and Nostr can be that solution.
Author: nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6
2) (Proposed) NIP 49: Nostr Wallet Auth
Having a Lightning Wallet connected to Nostr is a powerful tool for content monetization and nostr-based marketplaces. There’s a lot of great work done on Nostr Wallet Connect, but it all “hinges on having the user copy-paste a wallet connection URI into the app they wish to connect with. This can be a UX hurdle and often has the user handling sensitive information that they may not understand.”
“This NIP proposes a new protocol that solves these problems by having the wallet and app generate a NWC connection URI together. This URI is then used to connect the wallet and app.”
Making it easier for new users (especially those that are less technical) to participate in the new economy is fundamental to making Nostr the best place for content creators to make a living without middlemen and heavy handed platforms. 💪
Author: nostr:npub1u8lnhlw5usp3t9vmpz60ejpyt649z33hu82wc2hpv6m5xdqmuxhs46turz
3) (Proposed) Updates to NIP 15: Nostr-based Marketplaces
This proposal expands the capabilities of Nostr-based Marketplaces to support auctions. Think about a Nostr-based eBay where users can post an item for sale by auction using a marketplace Nostr client.
The auction going live is a Nostr event, and users can publish bids as Nostr events, and when the auction is closed it’ll be determined by the bid event with the highest offering. Which anyone can verify. This is a very interesting way to make marketplaces more censorship resistant.
Author: ibz
Notable Projects
Yondar (social maps) 🌐
Much physical commerce is discovered by consumers via map apps. You go on Google or Apple Maps to find an art supply store near you, or coffee shops that are open at 2pm when you’re in a new city. These centralized solutions have dominated, but no more! Enter Yondar.
Yondar is a Nostr client that allows users to publish places on a map. This could be places of business or events, really anything that has a location.
True to Nostr form, people can also socially interact with these places: do a kind 1 comment in response to an upcoming event published on Yondar. Or someone could create a Nostr client for restaurant reviews and publish one of those in response to a place published via Yondar. The possibilities are endless 🤯.
Author(s): npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w
WavLake 🎵
WavLake is a music player for web and mobile. It’s part Spotify music player and music discovery tool, part music monetization platform. They host the actual music files in their own cloud hosted system, but they publish Nostr events to represent the content that’s stored by WavLake, so other clients could help people discover music hosted and published via WavLake.
If musicians can get paid more for their music via solutions like WavLake, they will start using Nostr purely for selfish monetary reasons. This could be the start of purple-pilling that particular artistic community.
P.S. I listened to WavLake Radio while writing this, it was nice writing music.
Authors: based on the linked Github repo it’s nostr:npub1j0shgumvguvlsp38s49v4zm8algtt92cerkwyeagan9m6tnu256s2eg9a7 and blastshielddown
Opt-in content moderation on nos.social 👍👎
nostr:npub1wmr34t36fy03m8hvgl96zl3znndyzyaqhwmwdtshwmtkg03fetaqhjg240 gave a presentation at NostrAsia about making Nostr more accessible for normies. One of the items that was announced was the implementation of opt-in content moderation in his Nostr client nos.social.
They now support content warnings set by users publishing content, reporting content with various tags, as well as the ability for users to opt-in to moderation that changes their feed based on what they want to filter out.
People that don’t want moderation don’t need to use it, but I applaud nos.social’s work to develop these tools and patterns so that people have the choice to moderate their own feed.
Latest conversations: Interoperability
NostrAsia really highlighted the superpowers of Nostr and one of the foremost is interoperability. nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft gave a great talk about this topic and explained NIP 31 and NIP 89.
In summary, imagine there’s a Nostr client for movie reviews and they publish the review in a specific structure with Kind 12345678. Most Nostr clients will see that event but won’t know how to display that content or help users interact with it.
If clients adopt NIPs 31 and 89 then Nostr events will have an “alt” tag and a way to find a suggested app to handle that type of Nostr content. The alt tag helps clients display something to the user and the suggested app handler helps the client indicate to the user how to interact with that content more natively.
Maximum interoperability is useful in allowing Nostr to grow without centralizing. We can all experiment and build and all efforts still support the usage of the Nostr ecosystem in general.
Kind 1 clients as gateways to the Nostr app ecosystem
This interoperable future points to a framework where Kind 1 clients (Damus, Amethyst, Snort, Primal, etc) are the entrypoint or gateway to the Nostr ecosystem. Kind 1 clients are the core social use case and the foundation of most social interaction and could be amazing standalone apps and businesses, but Nostr makes them something more.
People will post Kind 1 notes referencing all kinds of Nostr events: music published via WavLake or Stemstr, places shared via Yondar, recipes created on Nostr.Cooking, etc. Clients will display some context on what the comment is on (music, place, video, recipe, etc) and then help the user find the right plugin/app/website to use to interact with that content natively.
This makes the Kind 1 clients the purple pill. This is only possible because of the unique interoperability capabilities of Nostr.
Interoperability with non-Nostr services
Even more amazing about Nostr is that it’s fairly easy to make the network interoperable with services outside the Nostr-verse. We already have pretty good bridges to ActivityPub-based systems like Mastadon as well as Twitter (with Exit). That reduces the switching cost for people that want to explore Nostr and eventually make the switch.
Even within Nostr-verse we have services like nostr.build that provide services in a way that doesn’t lock users in. Nostr.build provides file hosting services and because they follow NIP 96, there’s a standard way for clients to interact with nostr.build as a user’s preferred file storage provider for pictures and videos. It is easy for users to switch providers and clients can easily pick up the change. Efforts like NIP 96 makes file storage much more interoperable across the Nostr-verse without centralization.
Continuing to build solutions that allow users to have freedom AND a great experience will make Nostr the best game in town.
Don’t reinvent the wheel: use ISO when possible
I’m not sure if every developer knows this, but there’s an International Standards Organization (ISO) that has done a ton of work to promote standards of all kinds. The most common one developers have all used is the ISO datetime format. No matter what language or database you’re using, you’re likely representing timezone aware datetimes in the ISO format so that you can pass that data around safely.
ISO has codified standards for everything : how to store medical history, how to interact with USB, even stuff as obscure as how to represent data around holograms
Nostr is doing a lot of work to define structure to data that will be stored as Nostr events. We’re essentially inventing standards for social-related data of all kinds.
There are some things we’re building support for in Nostr, and I will encourage folks to see if there’s an ISO standard to follow first. It may save you a ton of time and brain power. On top of that, adopting ISO standards makes Nostr more compatible with future development that we can’t even imagine yet.
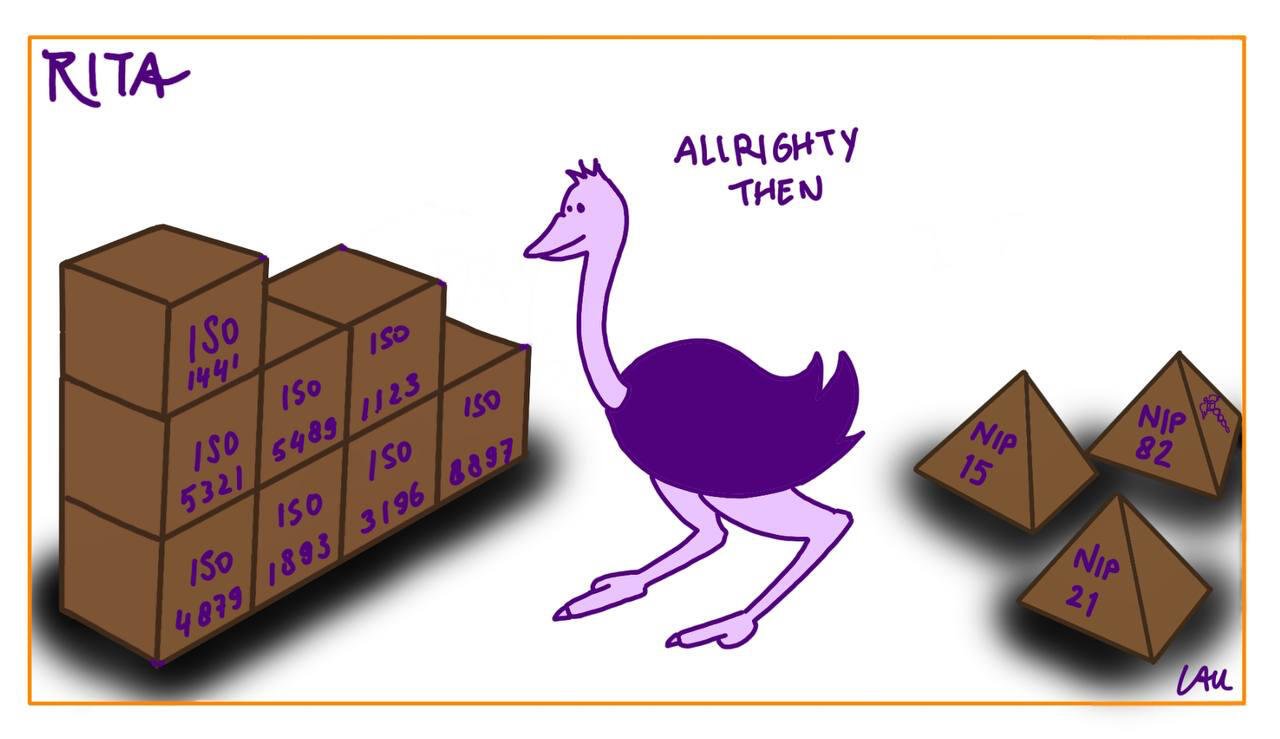
Invest in interoperability to support the cause
The Nostr-verse is under construction and the best time to plan for interoperability is before the building is done. Devs have done a great job retaining interoperability as a cambrian explosion of Nostr development has taken place. I hope we can continue to invest in interoperability because it may just be the thing that makes Nostr able to take on the giants of Big Tech when the time is right.
Until next time 🫡
If you want to see something highlighted, if we missed anything, or if you’re building something we didn’t post about, let us know. DMs welcome at nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk
Stay Classy, Nostr.
