-
 @ 3bf0c63f:aefa459d
2024-03-19 14:01:01
@ 3bf0c63f:aefa459d
2024-03-19 14:01:01Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 6ad3e2a3:c90b7740
2024-08-03 23:20:29
@ 6ad3e2a3:c90b7740
2024-08-03 23:20:29I know many of you are frustrated there are people who still won’t take the covid injections. The problem is you’re going about it the wrong way.
Below I list steps you can take that will result in universal uptake:
Stop Calling Them “Vaccine Hesitant” If you were trying to persuade a vegan to up his B-12 intake by eating meat, you wouldn’t get far by labeling him “steak hesitant.” “Oh, I see, you’re just ‘steak hesitant’ must be that hippie propaganda you’re reading. Steak hesitant people like you…” Insulting people’s choices won’t get you anywhere. Try, “I see you don’t like being coerced to take medicine via threats to your basic rights and ability to earn a livelihood, that’s understandable. Let me persuade you why getting an mRNA jab is a good medical choice.” And then you’ll have to make your case, which, at the moment is not especially strong (particularly with respect to healthy, younger people, many of whom have already had covid), but that brings us to…
Lobby For More Aggressive Gain Of Function Research Frankly, the Wuhan Lab didn’t do its best work. Covid is deadly for people with pre-existing conditions, metabolic disorders and the elderly, but it’s insufficiently so to kill many healthy people under 70. The overall IFR is about 0.2 percent, with the vast majority of that group either old or sick. To incentivize independent-minded younger people the next lab leak needs to be a far more lethal strain. If we can get one as contagious as covid, but with an equal opportunity IFR above 15 percent, now we’re cooking with gas. When your 30-year old cousin, both your parents, several of your work colleagues, Kyrie Irving, Aaron Rodgers, Novak Djokovic, 25 members of Congress and a few cabinet members are dead, that will get their attention.
Commission Vaccines From New Companies While many who decline the mRNA shot are no doubt victims of disinformation — believing theories that government and large pharmaceutical companies are conspiring to enrich themselves first and foremost without proper regard for safety — it would be harder for them to connect those dots if you used more scrupulous providers. For example, it’s less than ideal that Johnson and Johnson just paid a settlement of five billion dollars for their part in the opioid crisis and Pfizer settled for 2.3 billion for marketing a drug as a pain killer that even the rubber-stamping FDA refused to approve for that purpose, while allegedly paying kickbacks to doctors to prescribe it. It was apparently the fourth settlement for Pfizer since 2002, and that excludes the experimental drug anti-meningitis drug, Trovan that killed 11 children and disabled dozens more in 1996. It’s insane to think that means anything about these miracle products in 2022, the motive for which was so obviously public health and ending the pandemic, but you have to admit it’s not a great look.
Keep Vaccine Companies On The Hook For Adverse Events There was never a need to waive liability for vaccine makers for adverse effects because everyone knows the mRNA shot is safe and effective. Yes, you hear anecdotal accounts of heart problems and strokes, but both have always been common in young people. Growing up, a few of my friends undoubtedly had heart attacks and strokes in grade school, though they were probably just under-diagnosed back then. I understand why the companies want to waive liability — it’s wrong to require legal accountability when these heroes are busy saving so many lives, but there’s no need for it when you have such a safe product. It just feeds unfounded suspicion.
Create A Vaccine That Stops The Spread Obviously, we know vaccines don’t have to stop the spread entirely to be effective. Look up the definition of vaccine — nowhere does it list that as a requirement. But if it actually stopped transmission in some material way, you’d be in a better position to argue for its uptake, citing the benefit it might have for the people around them. Now, people are just trying the “you’re taking up an ICU bed” angle, which doesn’t make much sense to young, healthy people, barring a far deadlier strain.
Permit Useless Early Treatments One big mistake that was made was banning and discouraging phony, yet harmless treatments like Ivermectin, Hydroxychloroquine and even Vitamin D. All that did was make people think they worked, and feed false conspiracy theories that they were funneling people toward the vaccine. Useless treatments should be encouraged so anyone who knows people who tried them can see how little good they did.
Don’t Bribe People I love donuts as much as the next person with metabolic syndrome, but giving people food, money and even weed just makes you look desperate. If you want to make something seem enticing, you’ve got to market it as something I’m lucky to get, not something you’re begging me to take.
Choose Better Spokespeople I know Bill Gates is one of the biggest investors in the space, but is it really necessary to have someone, who was paling around with convicted underage sex offender Jeffery Epstein, as your go-to vaccine promoter?
Amend The US Constitution And Nuremberg Code It’s annoying we have these anachronistic documents that didn’t contemplate the spread of a deadly pandemic, but unfortunately, The Fourth Amendment requiring people to be secure in their “persons,” and the Nuremberg Code which requires consent for medical procedures are still The Supreme Law Of The Land, and International Law, respectively. A little carve-out saying, “unless there’s a deadly pandemic” would go a long way toward granting the requisite legal authority.
Stiffer Consequences For Those Who Refuse Let’s be honest. There’s nothing more important than public health, and getting everyone vaccinated is the optimal way to achieve that aim. It’s unfortunate it would have to come to this, but we can’t let the selfish actions of a few imperil the good of the many who do as instructed. Actions have consequences! If the first nine steps are ineffective, you could imprison, torture or simply exterminate those who decline this medical option, something for which there is historical precedent in the last century.
I can assure you these 10 steps will result in 100 percent uptake. Hopefully it doesn’t come to step 10, but you have to ask yourself, do you care about preserving the rights of the privileged few, or are you willing to do what it takes for public health and the greater good of society?
I hope the answer is as clear for you as it is for me.
-
 @ 6bae33c8:607272e8
2024-08-03 20:36:29
@ 6bae33c8:607272e8
2024-08-03 20:36:29This is an overall list for 12-team NFFC PPR leagues as of August 3, 2024.
Note: Rankings are real, but comments are not meant to be taken seriously.
Warning: many, if not most, are stupid, though it can't be worse than last year’s.

(Right-click, open in new tab to enlarge)
-
 @ a853296a:209e695f
2024-08-03 20:03:05
@ a853296a:209e695f
2024-08-03 20:03:05What's up stackers!
Trying something new posting to the tech territory.
CASCDR TLDR: CASCDR is a collection of Lightning Powered AI services/applications.
Post TLDR: We have just released a big upgrade to our RSS Agent! You can now explore podcasts, and seamlessly integrate them with LLM workflows. This will allow you to condense podcast content/create more content based on a given podcast selected through the explorer!
We have a new release LIVE. As discussed on this post and on SNL last week, YouTube started playing major defense! So we adapted our YouTube Agent into an RSS Agent.
Now the RSS Agent is back and better with V2! Due to time constraints we had to ship a very basic version last week. Now RSS Agent is fully equipped!
he's baaaaaaack
Key Updates:
- Search & explore any podcast feed
- Pull any episode of interest
- Run analysis of the episode transcript with 5 pre-determined prompts
- OR roll your own custom prompt to put together written content of your choosing!
Workflow/Details:
Step 1: Search for your favorite podcast like @ThrillerX _
Step 2: Select/Configure Your Prompt & Select the Podcast Episode
Step 3: Inspect Your Result and/or Copy to Clipboard
Looking forward to the feedback in the comments! If this post triggers ideas of more you want to do with AI, tell us what you want us to build!
Cheers, The CASCDR Team
originally posted at https://stacker.news/items/633849
-
 @ 06830f6c:34da40c5
2024-08-03 12:47:53
@ 06830f6c:34da40c5
2024-08-03 12:47:53Hey there, readers! 👋
We're buzzing with excitement to bring you the latest updates in the world of Bitcoin, the Lightning Network, Nostr apps, and more.
🌟 What’s New in Bitcoin and Beyond?
- Exciting App Updates 💼
- StatechainJS by @supertestnet: This revolutionary tech is a robust alternative to ecash, allowing you to recover your funds even if the mint goes offline. It’s a game-changer for transaction reliability.
- Nostr Web Services Code by @asmogo: Transform the way you host web services with this new code. No public IP or DNS is needed—just an npub and Nostr relays. 🌐
- Nutsack by @pablof7z: Say hello to Nutsack, a wallet integrated with Nostr. Accessible from any compatible Nostr client, it opens up new possibilities within the Nostr ecosystem. 🧩
- LNBits Bounty: LNBits is on the hunt for developers to create a Nostr Wallet Connect service and extension. If you’re a developer, this is your chance to shine and earn a substantial bounty! 💰️
- Proton Wallet Launch: Introducing Proton Wallet—a safer way to manage Bitcoin with self-custodial features and transactions via encrypted email addresses. Discover more about it here. 🔐
- Phoenix Wallet Update: Phoenix Wallet has just rolled out a major update, adding BOLT12 support. Enjoy reusable payment requests, contact lists, and message attachments for enhanced Bitcoin transactions. Check out the details here. 🚀
-
Lava Vault Introduction: Lava Vault has launched a self-custodial wallet that allows you to buy Bitcoin, borrow dollars, and transact globally, all without any fees. 🔒️
-
New Releases and Innovations 🌎️
- Bitrefill Card in Europe: The Bitrefill card is now publicly available in Europe, making Bitcoin spending easier than ever. 💳️
- Satlantis by Svetvski: Discover Satlantis—a new social network for travelers and nomads that connects global tribes and fosters a vibrant, worldwide community. 🌍️
🚀 Major Announcement: Alby Hub is Here!
The wait is finally over! Alby Hub is now live and ready for everyone to explore. Whether you're a long-time Alby enthusiast or just joining us, you can now experience the ultimate self-custodial solution. Alby Hub is a fully open-source, sovereign wallet that you can run on your device or access for free through us, with a modest monthly fee.
That’s all for this edition of Bitcoin talks Nostr talks Wallet talks. We hope you’re as excited about these updates as we are! Stay tuned for more news and enjoy diving into these fantastic new developments.
Bitbiashara #nostr
Catch you next time! 🚀
-
 @ 0176967e:1e6f471e
2024-07-28 15:31:13
@ 0176967e:1e6f471e
2024-07-28 15:31:13Objavte, ako avatari a pseudonymné identity ovplyvňujú riadenie kryptokomunít a decentralizovaných organizácií (DAOs). V tejto prednáške sa zameriame na praktické fungovanie decentralizovaného rozhodovania, vytváranie a správu avatarových profilov, a ich rolu v online reputačných systémoch. Naučíte sa, ako si vytvoriť efektívny pseudonymný profil, zapojiť sa do rôznych krypto projektov a využiť svoje aktivity na zarábanie kryptomien. Preskúmame aj príklady úspešných projektov a stratégie, ktoré vám pomôžu zorientovať sa a uspieť v dynamickom svete decentralizovaných komunít.
-
 @ 30876140:cffb1126
2024-08-04 06:13:35
@ 30876140:cffb1126
2024-08-04 06:13:35Violet Starlight
The oceans of Alderaan are but raindrops in the depth of your beautiful eyes.
The music of the stars is a lullaby, The sonnet of your voice is their song.
The thought of you is my guiding light in empty space, That my heart may return to your violet sun, Your love brings peace to my galaxy.
This gulf that stretches between us, so easily we can cross, for Hyperspace is not just a lover's dream.
Fly with me to see the wondrous waterfalls of Theed, The city built from branches on the forest world, Kashyyk, The temples of Yavin's Moon, the little bears of Endor, With the Force as our guide, we will see them all,
Together.
In a galaxy far, far, away, Let's begin our journey.
-
 @ e771af0b:8e8ed66f
2024-04-19 22:29:43
@ e771af0b:8e8ed66f
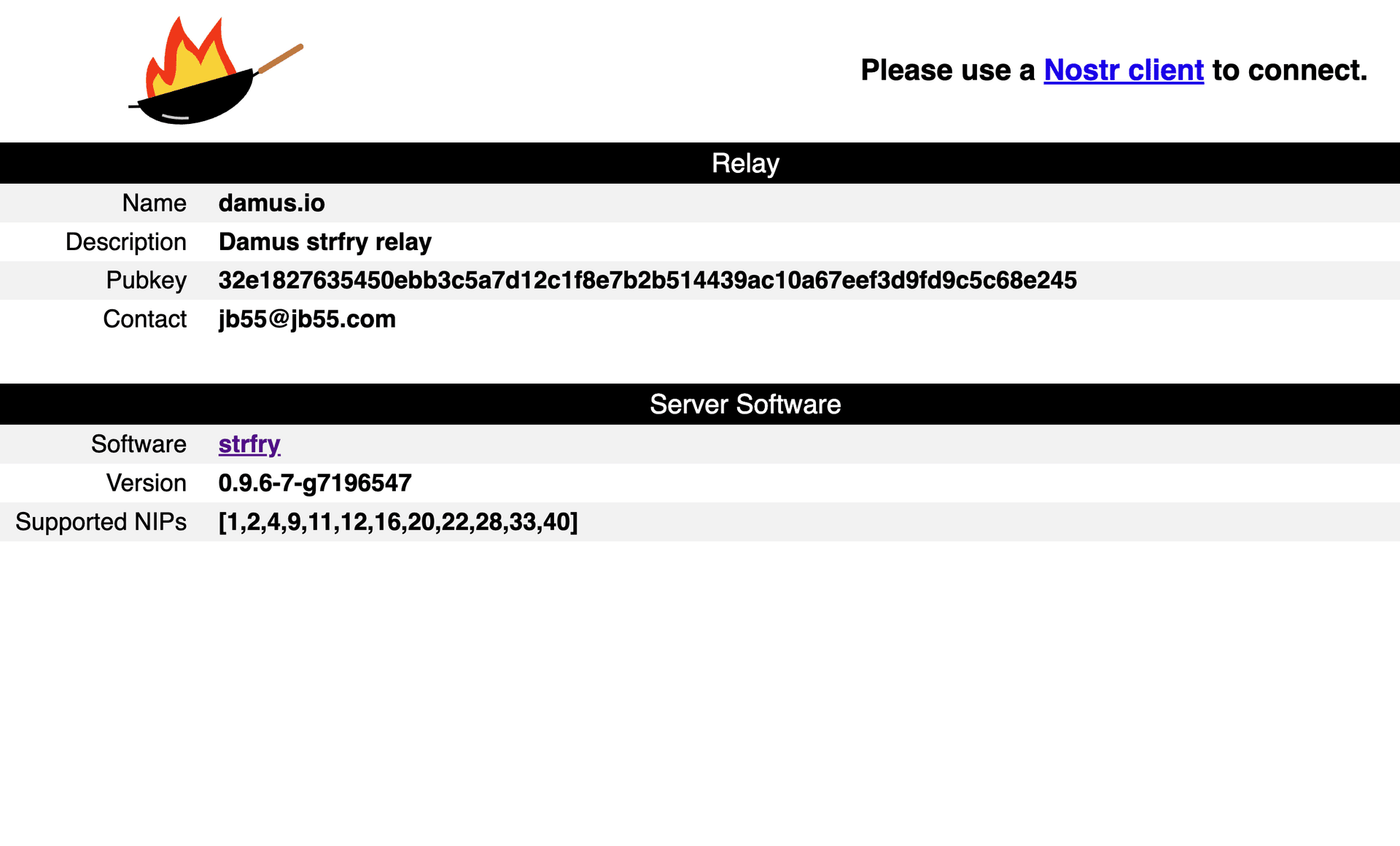
2024-04-19 22:29:43Have you ever seen a relay and out of curiosity visited the https canonical of a relay by swapping out the
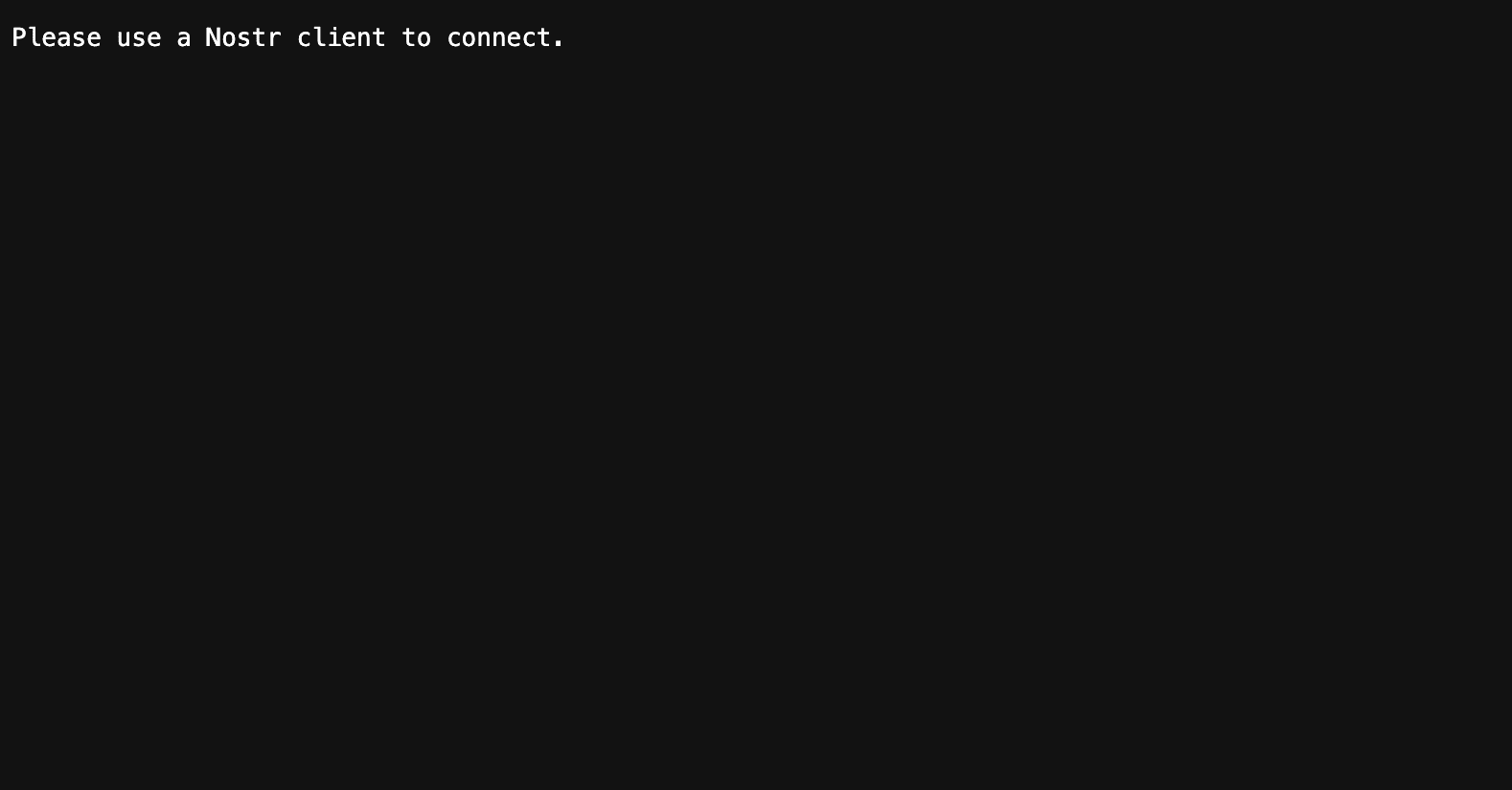
wsswithhttps? I sure have, and I believe others have too. When I ranhttps://nostr.sandwich.farmin late 2022/2023, I had thousands of hits to my relay's https canonical. Since then, I've dreamed of improving the look and feel of these generic default landing pages.With the release of myrelay.page v0.2, relays can now host their own customizable micro-client at their https canonical.
Transform your relay's landing page from this:
or this:
to something like this:

I say "something like this" because each page is customizable at runtime via the page itself.
In a nutshell
myrelay.page is a self-configuring, Client-Side Rendered (CSR) micro-client specifically built to be hosted at relay canonicals, customizable at runtime via NIP-78. Check out a live example.
Features:
- Dark or light theme
- Join relay
- Relay operator profile and feed
- Zap relay operator
- See people you follow who are on the relay
- Customizable by the relay operator
- Enable/disable blocks
- Sort blocks
- Add HTML blocks
- Add image blocks
- Add markdown blocks
- Add feed blocks, with two layouts (grid/list) and customizable filters.
You can find a full list of features complete and todo here
Why I created myrelay.page
For several different reasons.
Firstly, the default, bland relay pages always seemed like a missed opportunity. I jotted down an idea to build a relay micro-client in early January 2023, but never had the time to start it.
Next, I've been ramping up the refactor of nostr.watch and first need to catch up on client-side technologies and validate a few of my ideas. To do this, I have been conducting short research & development projects to prepare and validate ideas before integrating them into an app I intend to support long-term. One of those R&D projects is myrelay.page.
Additionally, I wanted to explore NIP-78 a bit more, a NIP that came into fruition after a conversation I had with @fiatjaf on February 23rd, 2023. It stemmed from the desire to store application-specific data for app customization. I have seen clients use NIP-78, but from what I've seen, their implementations are limited and do not demonstrate the full potential of NIP-78. There's more on NIP-78 towards the end of this article
The convergence of these needs and ideas, in addition to having an itch I needed to scratch, resulted in the creation of myrelay.page.
*Could be wrong, please let me know in the comments if you have examples of nostr clients that utilize NIP-78 for propagating customizations to other visitors.
Editor Flow
Now I'm going to give you a brief example of the Editor Flow on myrelay.page. There's a lot that isn't covered here, but I want to be as brief as possible.
Note: myrelay.page is alpha, there are bugs, quality of life issues and things are far from perfect.
Login
Presently, myrelay.page only supports NIP-07 authentication, but other authentication methods will be implemented at a later date.
In order to customize your page, you need to have a valid NIP-11 document that provides a valid hex
pubkeyvalue that is the same as the key you use to login.
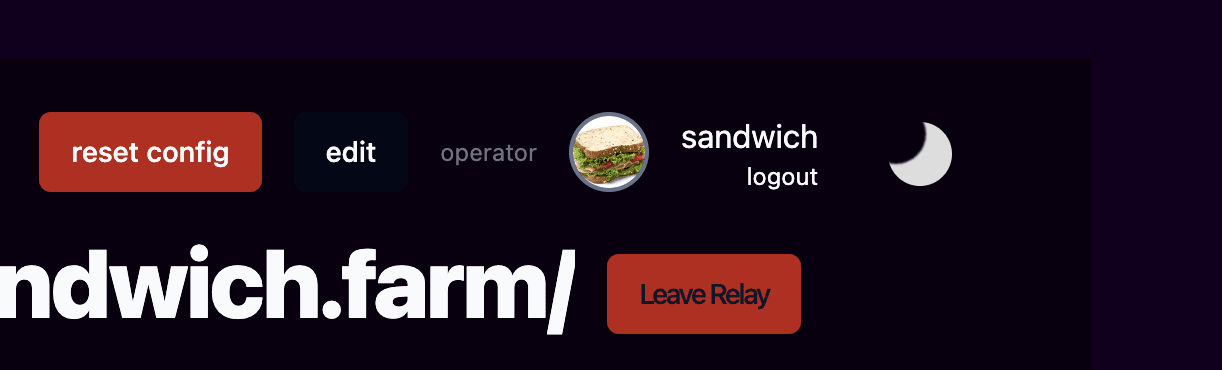
Click "Edit"
Add a block
For brevity, I'm going to add a markdown block
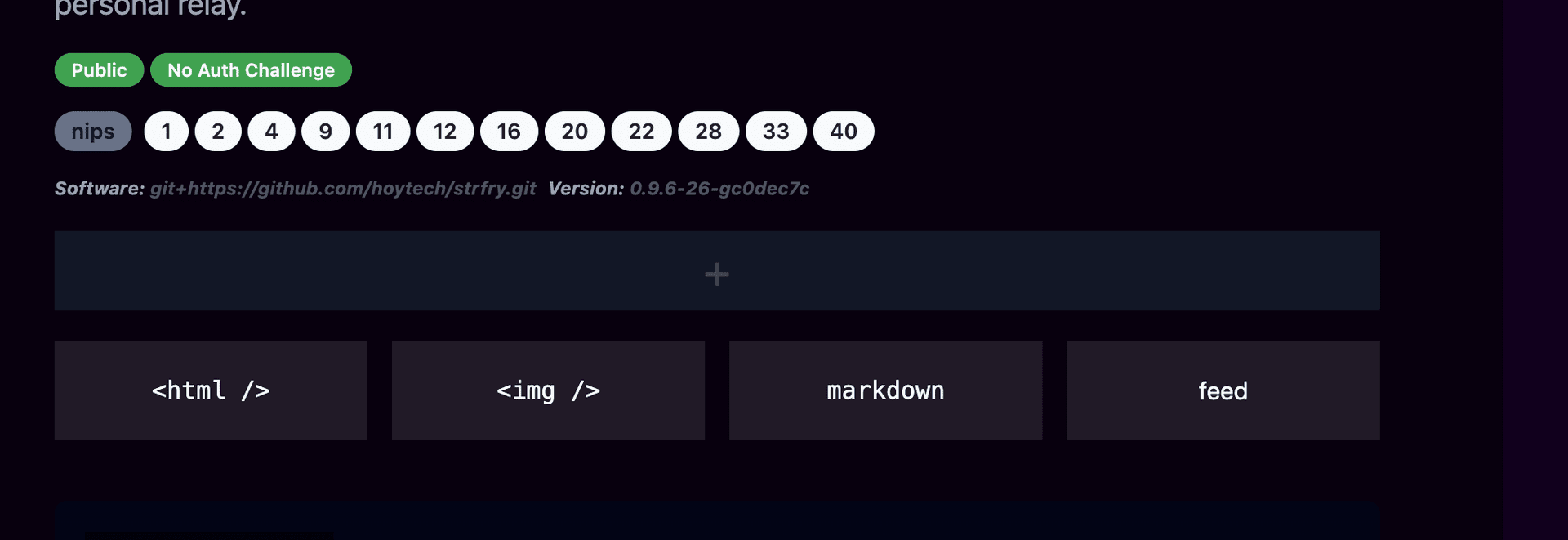
Configure the block
Add a title to the block and a sentence with markdown syntax.

Publish the configuration
Click publish and confirm the event, once it's been published to relays the page will refresh.
Note: Again it's alpha, so the page doesn't refresh after a few seconds, the publish probably failed. Press publish until it refreshes. Error handling here will improve with time.
Confirm state persistence
After reload, you should see your block persisted. Anyone who visits your page will see your newly configured page. Big caveat: Given the blessing of relays who store your configuration note, if your configuration cannot be found or you cannot connect to your relays, visitors will only see your relay's NIP-11.

Interested?
myrelay.page is alpha and only has two releases, so if you want to be an early adopter, you'll need the skillset and patience of an early adopter. That said, as long as you have some basic development and sysadmin skills as well as understand your reverse-proxy of choice, it's a quick, easy and low-risk side project that can be completed in about 20 minutes.
1. Build
yarn buildornpm run buildorpnpm run build(note: I had issues with pnpm and cannot guarantee they are resolved!)2. Deploy
Move the contents of
buildfolder to your relay server (or another server that you can reverse-proxy to from your relay)3. Update your reverse-proxy configuration
You'll need to split your relay traffic from the http traffic, this ranges from easy to difficult, depending on your server of choice. - caddy: By far the easiest, see an example configuration for strfry here (easily adapted by those with experience to other relay software) - nginx: A little more stubborn, here's the most recent nginx config I got to work. You'll need to serve the static site from an internal port (
8080in the aforementioned nginx conf) - haproxy: Should be easier than nginx or maybe even caddy, haven't tried yet. - no reverse-proxy: shrugsIf any of that's over your head, I'll be providing detailed guides for various deployment shapes within the next few weeks.
Exploring NIP-78
One of the special things about NIP-78 is that it is application specific, meaning, you don't need to conform to any existing NIP to make magic happen. Granted there are limits to this, as interoperability reigns supreme on nostr. However, there are many use cases where interoperability is not particularly desirable nor beneficial. It doesn't change the care needed to craft events, but it does enable a bunch of unique opportunities.
- A nostr client that is fully configurable and customized by the user.
- A nostr powered CMS that can be edited entirely on the client-side.
- Any use case where an application has special functionality or complex data structures that present no benefit in the context of interoperability (since they are "Application Specific").
Final thoughts
I was surprised at how quickly I was able to get myrelay.page customizable and loading within an acceptable timeframe;
NIP-11, the operator'sNIP-65and the myrelay.pageNIP-78events all need to be fetched before the page is hydrated! While there is much to do around optimization, progressive page-loading, and general functionality, I'm very happy with the outcome of this short side project.I'll be shifting my focus over to another micro-app to validate a few concepts, and then on to the next nostr.watch. Rebuilding nostr.watch has been a high-priority item since shortly after Jack lit a flame under nostr in late 2022, but due to personal circumstances in 2023, I was unable to tackle it. Thanks to @opensats I am able to realize my ideas and explore ideas that have been keeping me up at night for a year or more.
Also, if you're a relay developer and are curious about making it easier for developers to deploy myrelay.page, get in touch.
Next article will likely be about the micro-app I briefly mentioned and nostr.watch. Until then, be well.
-
 @ 0176967e:1e6f471e
2024-07-28 09:16:10
@ 0176967e:1e6f471e
2024-07-28 09:16:10Jan Kolčák pochádza zo stredného Slovenska a vystupuje pod umeleckým menom Deepologic. Hudbe sa venuje už viac než 10 rokov. Začínal ako DJ, ktorý s obľubou mixoval klubovú hudbu v štýloch deep-tech a afrohouse. Stále ho ťahalo tvoriť vlastnú hudbu, a preto sa začal vzdelávať v oblasti tvorby elektronickej hudby. Nakoniec vydal svoje prvé EP s názvom "Rezonancie". Učenie je pre neho celoživotný proces, a preto sa neustále zdokonaľuje v oblasti zvuku a kompozície, aby jeho skladby boli kvalitné na posluch aj v klube.
V roku 2023 si založil vlastnú značku EarsDeep Records, kde dáva príležitosť začínajúcim producentom. Jeho značku podporujú aj etablované mená slovenskej alternatívnej elektronickej scény. Jeho prioritou je sloboda a neškatulkovanie. Ako sa hovorí v jednej klasickej deephouseovej skladbe: "We are all equal in the house of deep." So slobodou ide ruka v ruke aj láska k novým technológiám, Bitcoinu a schopnosť udržať si v digitálnom svete prehľad, odstup a anonymitu.
V súčasnosti ďalej produkuje vlastnú hudbu, venuje sa DJingu a vedie podcast, kde zverejňuje svoje mixované sety. Na Lunarpunk festivale bude hrať DJ set tvorený vlastnou produkciou, ale aj skladby, ktoré sú blízke jeho srdcu.
Podcast Bandcamp Punk Nostr website alebo nprofile1qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qy88wumn8ghj7mn0wvhxcmmv9uq3xamnwvaz7tmsw4e8qmr9wpskwtn9wvhsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qyg8wumn8ghj7mn0wd68ytnddakj7qghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7qpqguvns4ld8k2f3sugel055w7eq8zeewq7mp6w2stpnt6j75z60z3swy7h05
-
 @ e771af0b:8e8ed66f
2023-11-28 03:49:11
@ e771af0b:8e8ed66f
2023-11-28 03:49:11The last 6 months has been full full of unexpected surprises, of the unpleasant variety. So it was welcomed news that
nostrwatchwas awarded a grant by OpenSats recently which has allowed me to revisit this project and build out my original vision, the one I had before nostr went vertical.The last month has been a bit of a joyride, in that I have met little friction meeting goals. For example I was able to rewrite
nostrwatch-jsin an evening, tests another evening and did most of the Typescript conversion in 30 minutes (thanks AI!)Here's a quick summary of the last month, I'm probably missing a handful of details, but these are the important bits.
- Went through all the new NIPs, prototyped and experimented
- Nearly completed a full rewrite of
nostrwatch-js, nownocap. Presently porting to Typescript. Still alpha, don’t use it. - Released
nostrawl, a wrapper fornostr-fetchthat has Queue adapters for persistent fetching. Nothing special, but needed to factor out the functionality from the legacy trawler and the requirements were general enough to make it a package. - Starting porting the nostr.watch trawler, cache layer and rest API, but much work is still needed there. Aiming to have the current infrastructure updated with new daemons by end of year.
- In concert with the cache layer testing, I ran some experiments by patching in a rough trend engine prototype from earlier this year and a novel outbox solution, both with promising results.
- Wrote a few small CLI tools to assist with developments, got acquainted with
ink, and reacquainted myself with wonderful world of ES Module conflicts.
The rest of this year will be mostly backend work, tests and data engineering. Early next year I will begin iterative development on a new GUI and a string of CLI tools.
Luckily, nostr.watch and it's underlying infrastructure, as abysmal as it is, hasn't completely sank. Traffic is much lower than the ATH but still hovering between 2-3k unique visitors a month. I can't express in words how happy I will be when I can put the legacy nostr.watch to rest.
Next update will include a bit more of the why and how, and where I am trying to get to with this project.
Until next time.
-
 @ 0176967e:1e6f471e
2024-07-27 11:10:06
@ 0176967e:1e6f471e
2024-07-27 11:10:06Workshop je zameraný pre všetkých, ktorí sa potýkajú s vysvetľovaním Bitcoinu svojej rodine, kamarátom, partnerom alebo kolegom. Pri námietkach z druhej strany väčšinou ideme do protiútoku a snažíme sa vytiahnuť tie najlepšie argumenty. Na tomto workshope vás naučím nový prístup k zvládaniu námietok a vyskúšate si ho aj v praxi. Know-how je aplikovateľné nie len na komunikáciu Bitcoinu ale aj pre zlepšenie vzťahov, pri výchove detí a celkovo pre lepší osobný život.
-
 @ 30876140:cffb1126
2024-08-04 06:11:33
@ 30876140:cffb1126
2024-08-04 06:11:33Love God
A Short Story
by Acea Spades, 2016
Jimmy sat in his bedroom, stooping over his desk, trembling with a pencil in his hand. Twenty or so balls of crushed paper littered the messy floor, three on his dirty bed. On the desk, being scrutinized by his terrified eyes, was a love letter.
His shaky hands made fussy lines despite how many times he tried to make the letters perfect. The note read:
Cindy, I love you. Do you love me?
Yes - No
Jimmy
He stared at the paper for a long time. Tears appeared in little beads around his eyes. He snatched the paper from the table, smashed it between his hands, and threw it against the wall. The doorbell rang. Downstairs, his mother's footsteps made a line from the kitchen to the entryway. The door creaked on its hinges, followed by the muffled voices of happy people. The sounds echoed in the hallway and intruded from under Jimmy's door. His grandfather, and his grandmother, voices thick with an old-world accent, made bright conversation with his very-American mother. There was another voice, too, probably Uncle Roman's; Jimmy could already smell rotten alcohol and convenience-store cologne.
“Jimmy!” his mother's voice from under the door called, “They're here! Come down!” Jimmy slammed the pencil on the table and wiped his eyes before dragging himself out of the room.
“Hey, it's Jimmy!” His wrinkled relatives called from the entryway when he appeared. There was Uncle Roman behind them, shutting the door. His button-shirt was parted to reveal a chest of curled hairs, and a medallion on a gold chain.
Jimmy descended the stairs with a heavy thump on every step. He gave a good stomp on the squeaky stair. His grandmother descended upon him with kisses, much like the lion devours the water buffalo.
“Ooooh, my little grandchild! It has been so long. Too long. Look how you've grown! All grown up now. Kiss me like you used to.”
“Gran-Gran, you were just here for the Fourth of July.” He caught a scowl from his mother, but turned his head so he didn't have to bear it.
His grandfather came and gave him a hug. His bones were so close to his skin, without muscle or fat to cushion his affection. “It's good to see you, grandson.”
“It's good to see you too, Pop-Pop."
“Sorry we couldn't make it in for your birthday. Here, I've got a card from me and Gran-Gran.”
From the top zipper-pocket of his leather suitcase, Pop-Pop pulled out a shiny piece of folded cardstock with the number 12 written in bright gold. Jimmy opened the card. Nothing fell out.
“Thanks, Pop-Pop.”
“Your Gran-Gran has not stopped talking about you, all the way over. Oh, he's probably so big, now. Oh, I wonder how his school is going. Oh, we need to invite him to our home over winter and spoil him rotten.”
Gran-Gran grumbled. “Well you don't understand just how much I love our little grandson.”
“He's not little any more, Ma-Ma.” Uncle Roman set a heavy hand on Jimmy's shoulder and shook him. Jimmy felt a bruise begin to form. “Look at him. Reminds me so much of Gregor, I thought this was a dream.”
The entryway grew quiet. The moment stalled. Jimmy's mother broke the tension. “Well, let me show you where you're staying. Gran and Pop, you'll be upstairs at the end of the hall. Rome, I hope it's alright if you sleep on the couch, we don't have any more bedrooms.”
“A couch? Well, your couch is better than that pile of shit I call a bed."
Jimmy's mother contined. "There's blankets tucked in the space next to the couch, and it folds out into a really comfortable hide-away." She turned back to the elders. "Come on, I'll show you two where your room is. Jimmy, will you grab Pop's bags?”
They dragged the suitcases up the steps and down the hallway. The wheels loudly scraped against the iron floor-waffle that kept them warm during cold winter nights. Jimmy set Pop's bags outside the bedroom door, then retreated back to his room.
He ignored his family's voices, despite their directionless words coming through the little crack in his door. He was again stooped over his work, a Mozart or a Rembrandt, the future pulling down on his shoulders, begging him to die in his graven masterpiece.
A long time passed; it could have been an hour, or a day, or seven weeks. The smells of roast duck and steamed cauliflower were floating up from the dinner hall, haunting his nostrils, tearing his concentration. He heard the pieces of conversation that made their sneaky way under his bedroom door. His mother speaking loudly to Uncle Roman; a boorish chuckle returning her words. Down the hallway, he heard the old language being spoken; Gran-Gran and Pop-Pop were praying, the soft click and clack of her rosary, or maybe Pop-Pop's worry beads. Jimmy saw his grandmother's furrowed brow, her religious concentration, the picture of his dead father she'd prop up on the bedside table.
Heavy feet plodded up the stairs. They stopped in front of Jimmy's door. Fat knuckles beat on his door as if trying to force entry.
“Jimmy my boy. What are you doing in here?”
The doorknob turned. Jimmy sprang up, knocking his chair backward. He started kicking the paper wads under the bed, but it was too late. The door was open, and there stood his uncle. Jimmy turned his back to the invader.
“What, Uncle Roman?” His voice cracked.
The boor stepped in and closed the door behind him. In the tiny bedroom, this man was an Odysseian giant, and Jimmy a captured lamb. The monster looked around the room for just a moment, searching the cave for signs of danger. Those heavy feet took two big steps and were already across the room. The monster dropped onto Jimmy's bed, crushing the blankets. The metal springs screamed for help.
They sat there for an endless moment, in silence. Roman looked round the room, eyes obscured behind large, creased eyebrows. He turned his stubbled chin towards the floor, then reached to grab one a piece of paper. Jimmy made a tiny squealing noise; he would have stolen the paper out of the giant's hands if he wasn't so afraid. He watched in terror as Uncle Roman unwrapped the cast-away letter. Uncle Roman's face was ruffled with concentration, then it opened into a smile like a blooming spring flower. His black eyes turned from the paper and attacked Jimmy from behind a stupid grin.
“You are in love, my boy! What is her name?”
Jimmy leaned forward a little and looked at the note, to make sure he hadn't forgotten to write her name on that draft.
“Umm... Cindy?”
“Ah, Cindy, a beautiful name! Tell me about her. Is she beautiful?”
Jimmy didn't speak. He couldn't speak. He could barely breathe.
“Come on, Jimmy. Tell me about her.” Uncle Roman gave the boy a punch on the shoulder, already crushed by the careless squeeze.
There was an long pause. The giant's stare was unnerving. “She... she's... pretty.”
“She's pretty!” His head rolled backwards and the barking roar of a sea lion shot out of his hairy throat.
“She's pretty and she has blonde hair and I've wanted to ask her to be my girlfriend since the second grade. But she likes Tommy and Stuart wants to be her boyfriend too so I don't have a chance.”
He was panting. A sprinter lost Olympic silver. His head sank into to his lap.
“My boy.” Uncle Roman put those giant hands on Jimmy's head. “You are your father's son. You do not know this yet, but you are very good with women. But my lord, you were not going to give her this crap were you? A piece of paper to woo a woman? That is not the way at all.”
Uncle Roman put his massive hands over Jimmy's ears and twisted the boy's small face to look into his own. Those little eyes were wet and filled with sadness.
“I have been a very lucky man. I am fantastic when it comes to seducing women. You are a very lucky boy, to have an uncle like me, and a father like yours was. Let me show you something.”
He reached into the pocket that was buried under his enormous legs. He clasped something in his hands, and brought the closed fist under Jimmy's nose with the dirty fingernails pointed upward. Slowly, he opened the fleshy cage. In it, he held something smooth, like a tumbled sea shell, skinny and shaped like the finger of a newborn baby.
“Do you know what this is?” Jimmy shook his head.
“It is a badger's penis.”
The boy tried forcing himself backward from the blanched fossil, but Uncle Roman's giant hand was still grasped behind his head. The smell rising to his nostrils was either the sweaty palm of his monstrous uncle, or the stench of an ancient and unwashed badger's penis.
“Everybody knows, in the old country, a badger's penis makes the person who carries it a god of love. A badger's penis in your pocket boosts your confidence. It loosens your tongue, and the subtle smell of it attracts any lady you could ever want, and many who you would never want. I have carried this badger's penis with me since your father married your mother. He gave it to me when he knew that she would belong to him forever. He had always told me, when we were drunk and our mouths were free, that it was because of this penis that he could woo your mother so well.”
Jimmy's pupils grew larger. His gaze was fixed on the penis of a dead animal and the hands of his kinsman who held it like a religious artifact, like the sandals of Christ.
“I still remember the day he killed the poor thing. He killed the badger himself, with his own hands. He came home after walking through the woods, covered in oozing red scratches, smelling like skunk urine. He swung the thing by its little tail, all the way home. Its anus was dripping with yellow puss and feces. He dropped the badger by the door and went to his room, to collect his hunting knife. He told me later that he'd forgotten to put it back in its leather before he had gone into the woods. He had to kill the creature with his bare hands. With his bare hands! He took the badger outside and cut its penis off, and hung it outside on a little string so the sun could dry it.
“Well, he gave me this badger penis, his most important possession. After so many years of carrying it, there is no woman who can resist me. But I have learned how to be the master of attraction. I do not need this any more. It is for you, little Jimmy, son of my brother, it is for you.”
He took his hand from the boy's neck and pulled the little wrist towards him, pushing the fossil into his nephew's palm and closing a hairy fist around it. Jimmy's hair stood, electrified. The badger penis was rough, like a dry chicken bone, and almost as large as his smallest finger. He held it up to look at it. There was a little crease at the tip, and a hole at the other end where his father had put a piece of string; yellow and decaying threads held together despite the anger of time.
Visions of the future intoxicated his mind. A beautiful girl in the passenger seat of his first car, a view of the city from the lover's hilltop; he, a famous hero with bulging muscles, saving beautiful women from criminal intentions and taking them to the top of a New York City skyscraper, to make love under the glowing sky; and Cindy, her smile, her kiss, the penis of a badger in the pocket of his jeans, stiff and powerful like the sword of an ancient king.
“Yes, my boy. Yes. You feel its power. That is the power of a love god. Not in these silly words on long-dead paper, but in the breath of burning passion, issued from your throat in the moments of ecstasy when you are wrapped by the arms of a beautiful woman. You cannot build the fire of passion with your ideas of love, my boy. It is with passion that you win a woman's heart.”
They sat for a long time. It could have been an hour, or a day, or seven weeks. Jimmy held the badger's ancient penis carefully in his hands.
“Uncle Roman?”
“Yes, my boy?”
“Did you make all of that up?”
“Jimmy, my boy.” Uncle Roman smiled wide, revealing all of his teeth, including the gold one that sat near the back of his tongue. “Would I ever lie to you?”
-
 @ 3c984938:2ec11289
2024-07-22 11:43:17
@ 3c984938:2ec11289
2024-07-22 11:43:17Bienvenide a Nostr!
Introduccíon
Es tu primera vez aqui en Nostr? Bienvenides! Nostr es un acrónimo raro para "Notes and Other Stuff Transmitted by Relays" on un solo objetivo; resistirse a la censura. Una alternativa a las redes sociales tradicionales, comunicaciónes, blogging, streaming, podcasting, y feventualmente el correo electronico (en fase de desarrollo) con características descentralizadas que te capacita, usario. Jamas seras molestado por un anuncio, capturado por una entidad centralizada o algoritmo que te monetiza.
Permítame ser su anfitrión! Soy Onigiri! Yo estoy explorando el mundo de Nostr, un protocolo de comunicacíon decentralizada. Yo escribo sobre las herramientas y los desarolladores increíbles de Nostr que dan vida a esta reino.

Bienvenides a Nostr Wonderland
Estas a punto de entrar a un otro mundo digtal que te hará explotar tu mente de todas las aplicaciones descentralizadas, clientes, sitios que puedes utilizar. Nunca volverás a ver a las comunicaciones ni a las redes sociales de la mesma manera. Todo gracias al carácter criptográfico de nostr, inpirado por la tecnología "blockchain". Cada usario, cuando crean una cuenta en Nostr, recibe un par de llaves: una privada y una publico. Estos son las llaves de tu propio reino. Lo que escribes, cantes, grabes, lo que creas - todo te pertenece.

Unos llaves de Oro y Plata
Mi amigo y yo llamamos a esto "identidad mediante cifrado" porque tu identidad es cifrado. Tu puedes compartir tu llave de plata "npub" a otros usarios para conectar y seguir. Utiliza tu llave de oro "nsec" para accedar a tu cuenta y exponerte a muchas aplicaciones. Mantenga la llave a buen recaudo en todo momento. Ya no hay razor para estar enjaulado por los terminos de plataformas sociales nunca más.
Onigirl
npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3Todavia No tienes un cliente? Seleccione la mejor opción.
Encuentra la aplicación adecuada para ti! Utilice su clave de oro "nsec" para acceder a estas herramientas maravillosas. También puedes visit a esta pagina a ver a todas las aplicaciones. Antes de pegar tu llave de oro en muchas aplicaciones, considera un "signer" (firmante) para los sitios web 3. Por favor, mire la siguiente imagen para más detalles. Consulte también la leyenda.

Get a Signer extension via chrome webstore
Un firmante (o "signer" en inglés) es una extensión del navegador web. Nos2x and NostrConnect son extensiónes ampliamente aceptado para aceder a Nostr. Esto simplifica el proceso de aceder a sitios "web 3". En lugar de copiar y pegar la clave oro "nsec" cada vez, la mantienes guardado en la extensión y le des permiso para aceder a Nostr.

👉⚡⚡Obtén una billetera Bitcoin lightning para enviar/recibir Zaps⚡⚡ (Esto es opcional)

Aqui en Nostr, utilizamos la red Lightning de Bitcoin (L2). Nesitaras una cartera lightning para enviar y recibir Satoshis, la denominacion mas chiquita de un Bitcoin. (0.000000001 BTC) Los "zaps" son un tipo de micropago en Nostr. Si te gusta el contenido de un usario, es norma dejarle una propina en la forma de un ¨zap". Por ejemplo, si te gusta este contenido, tu me puedes hacer "zap" con Satoshis para recompensar mi trabajo. Pero apenas llegaste, as que todavia no tienes una cartera. No se preocupe, puedo ayudar en eso!
"Stacker.News" es una plataforma donde los usarios pueden ganar SATS por publicar articulos y interactuar con otros.

Stacker.News es el lugar mas facil para recibir una direccion de cartera Bitcoin Lightning.
- Acedese con su extensión firmante "signer" - Nos2x or NostrConnect - hace click en tu perfil, un codigo de letras y numeros en la mano superior derecha. Veás algo como esto

- Haga clic en "edit" y elija un nombre que te guste. Se puede cambiar si deseas en el futuro.

- Haga clic en "save"
- Crea una biografía y la comunidad SN son muy acogedora. Te mandarán satoshi para darte la bienvenida.
- Tu nueva direccion de cartera Bitcoin Lightning aparecerá asi
 ^^No le mandas "zaps" a esta direccion; es puramente con fines educativos.
^^No le mandas "zaps" a esta direccion; es puramente con fines educativos. - Con tu Nueva dirección de monedero Bitcoin Lightning puedes ponerla en cualquier cliente o app de tu elección. Para ello, ve a tu página de perfil y bajo la dirección de tu monedero en "Dirección Lightning", introduce tu nueva dirección y pulsa "guardar " y ya está. Enhorabuena.
👉✨Con el tiempo, es posible que desee pasar a las opciones de auto-custodia y tal vez incluso considerar la posibilidad de auto-alojar su propio nodo LN para una mejor privacidad. La buena noticia es que stacker.news tambien está dejando de ser una cartera custodio.
⭐NIP-05-identidad DNS⭐ Al igual que en Twitter, una marca de verificación es para mostrar que eres del mismo jardín "como un humano", y no un atípico como una mala hierba o, "bot". Pero no de la forma nefasta en que lo hacen las grandes tecnológicas. En el país de las maravillas de Nostr, esto te permite asignar tu llave de plata, "npub", a un identificador DNS. Una vez verificado, puedes gritar para anunciar tu nueva residencia Nostr para compartir.
✨Hay un montón de opciones, pero si has seguido los pasos, esto se vuelve extremadamente fácil.
👉✅¡Haz clic en tu "Perfil ", luego en "Configuración ", desplázate hasta la parte inferior y pega tu clave Silver, "npub!" y haz clic en "Guardar " y ¡listo! Utiliza tu monedero relámpago de Stacker.news como tu NIP-05. ¡¡¡Enhorabuena!!! ¡Ya estás verificado! Dale unas horas y cuando uses tu cliente "principal " deberías ver una marca de verificación.
Nostr, el infonformista de los servidores.
 En lugar de utilizar una única instancia o un servidor centralizado, Nostr está construido para que varias bases de datos intercambien mensajes mediante "relés". Los relés, que son neutrales y no discriminatorios, almacenan y difunden mensajes públicos en la red Nostr. Transmiten mensajes a todos los demás clientes conectados a ellos, asegurando las comunicaciones en la red descentralizada.
En lugar de utilizar una única instancia o un servidor centralizado, Nostr está construido para que varias bases de datos intercambien mensajes mediante "relés". Los relés, que son neutrales y no discriminatorios, almacenan y difunden mensajes públicos en la red Nostr. Transmiten mensajes a todos los demás clientes conectados a ellos, asegurando las comunicaciones en la red descentralizada.¡Mis amigos en Nostr te dan la bienvenida!
Bienvenida a la fiesta. ¿Le apetece un té?🍵

¡Hay mucho mas!
Esto es la punta del iceberg. Síguenme mientras continúo explorando nuevas tierras y a los desarolladores, los caballeres que potencioan este ecosistema. Encuéntrame aquí para mas contenido como este y comparten con otros usarios de nostr. Conozca a los caballeres que luchan por freedomTech (la tecnología de libertad) en Nostr y a los proyectos a los que contribuyen para hacerla realidad.💋
Onigirl @npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3
🧡😻Esta guía ha sido cuidadosamente traducida por miggymofongo
Puede seguirla aquí. @npub1ajt9gp0prf4xrp4j07j9rghlcyukahncs0fw5ywr977jccued9nqrcc0cs
sitio web
- Acedese con su extensión firmante "signer" - Nos2x or NostrConnect - hace click en tu perfil, un codigo de letras y numeros en la mano superior derecha. Veás algo como esto
-
 @ 0176967e:1e6f471e
2024-07-26 17:45:08
@ 0176967e:1e6f471e
2024-07-26 17:45:08Ak ste v Bitcoine už nejaký ten rok, možno máte pocit, že už všetkému rozumiete a že vás nič neprekvapí. Viete čo je to peňaženka, čo je to seed a čo adresa, možno dokonca aj čo je to sha256. Ste si istí? Táto prednáška sa vám to pokúsi vyvrátiť. 🙂
-
 @ 08f96856:ffe59a09
2024-08-03 05:37:54
@ 08f96856:ffe59a09
2024-08-03 05:37:54อย่างที่เราทราบกัน Bitcoin เป็นระบบการเงินที่มีจุดแข็งในเรื่องการกระจายศูนย์และความปลอดภัย แต่มันก็มีข้อจำกัดที่สำคัญเช่นกันครับ
ลองนึกภาพว่าคุณกำลังจะซื้อกาแฟสักแก้วด้วย Bitcoin แต่คุณต้องรอถึง 10 นาทีกว่าการทำธุรกรรมจะเสร็จสิ้นสมบูรณ์ และบางครั้งค่าธรรมเนียมก็อาจจะแพงกว่าค่ากาแฟเสียอีก นี่เป็นปัญหาที่ทำให้หลายคนลังเลที่จะใช้ Bitcoin ในชีวิตประจำวันครับ
เพื่อแก้ปัญหานี้ lightning Network จึงถูกพัฒนาขึ้นเพื่อเป็น layer ที่สองบน Bitcoin ช่วยให้สามารถทำธุรกรรมได้เร็วขึ้นและมีค่าธรรมเนียมต่ำลง โดยไม่ต้องรอการยืนยันธุรกรรมบน blockchain
แต่ lightning Network ก็มีความท้าทายของมันเองครับ การใช้งานมันไม่ได้ง่ายสำหรับทุกคน โดยเฉพาะความซับซ้อนในการจัดการ lightning node และการจัดสรรสภาพคล่อง ซึ่งไม่เหมาะสำหรับผู้ใช้ทั่วไป หากใครเคยได้ลองศึกษาการรัน lightning node ก็จะทราบดีว่า มันไม่ง่ายเลย ต้องใช้ความรู้ทางเทคนิคสูงมาก
ดังนั้นในปัจจุบัน จึงมีบริการ Custodial เกิดขึ้นเพื่อจัดการความซับซ้อนเหล่านี้แทนผู้ใช้ โดยผู้ให้บริการ Custodial นี้เสนอตัวเป็นคนจัดการกระเป๋าหรือ lightning node นั้นให้กับผู้ใช้ แต่ก็แลกมาด้วยความเสี่ยงที่สำคัญ ที่อาจทำให้ผู้ใช้สูญเสียความเป็นส่วนตัวและเสี่ยงต่อการถูกควบคุมโดยคนอื่นครับ
ในสถานการณ์นี้ ผู้ใช้ Bitcoin บน lightning network ก็ต้องตัดสินใจว่าจะเลือกทางไหนดีระหว่างสองทางเลือก
ทางเลือกแรกคือ การจัดการ lightning node ด้วยตัวเอง ซึ่งมีความซับซ้อนและต้องใช้ความรู้ทางเทคนิคสูง
หรือ ทางเลือกที่สอง คือการใช้บริการ Custodial ที่สะดวกกว่า แต่ก็ต้องยอมรับความเสี่ยงที่มาพร้อมกับมัน อย่างไรก็ตาม หากเลือกใช้บริการ Custodial ผู้ใช้ก็สามารถบริหารความเสี่ยงได้โดยการฝาก Bitcoin ไว้ในจำนวนที่น้อย เท่าที่ยอมรับความเสี่ยงได้เท่านั้นครับ
และนี่คือจุดที่ Chaumian e-cash เข้ามามีบทบาทสำคัญ โดยนำเสนอทางเลือกที่อาจช่วยแก้ไขข้อจำกัดของทั้ง Bitcoin และ lightning network ได้ ในหัวข้อถัดไป เราจะมาทำความเข้าใจว่า Chaumian e-cash คืออะไร และมันจะช่วยแก้ปัญหาที่กล่าวมาได้อย่างไร เราจะมาคุยกันต่อในหัวข้อถัดไปนะครับ
Chaumian e-cash คืออะไร?
เรามาลองนึกถึงการใช้เงินสดในชีวิตประจำวันกันก่อนครับ โดยปกติแล้วเวลาที่เราใช้เงินสด เราก็แค่ยื่นธนบัตรหรือเหรียญให้กัน รู้กันเพียงแค่สองคน คือผู้จ่ายกับผู้รับ ไม่ต้องมีใครอื่นมารับรู้ว่าเราใช้จ่ายอะไร มันให้ความเป็นส่วนตัวสูงมากใช่ไหมครับ
Chaumian e-cash ก็เช่นเดียวกันครับ มันถูกออกแบบมาให้ทำงานเป็นเงินสดอิเล็กทรอนิกส์หรือ e-cash ในโลกดิจิทัล เราสามารถส่งเงินให้ใครก็ได้โดยตรง โดยที่ไม่มีคนอื่นรู้ว่าคุณใช้จ่ายอะไร แม้แต่ mint หรือธนาคาร (ต่อไปนี้จะขอเรียกว่า mint นะครับ) ที่ออก e-cash ให้เราก็ไม่รู้ด้วยซ้ำ นี่คือความพิเศษของ Chaumian e-cash ที่พยายามนำความเป็นส่วนตัวของเงินสดมาไว้ในโลกดิจิทัลครับ
ย้อนกลับไปในช่วงทศวรรษ 1980 มีนักวิทยาศาสตร์คอมพิวเตอร์คนหนึ่งชื่อ David Chaum เขาเป็นทั้งนักเข้ารหัสลับและผู้ริเริ่มแนวคิด cypherpunk ซึ่งเชื่อในเรื่องความเป็นส่วนตัวและการลดการพึ่งพาตัวกลาง
e-cash ของ Chaum นี้มีความพิเศษตรงที่ใช้เทคนิคที่เรียกว่า "blind signature" ครับ ลองนึกภาพว่า blind signature ทำงานคล้าย ๆ กับการใช้กระดาษคาร์บอนในการเซ็นเอกสารครับ มาดูทีละขั้นตอนตามภาพข้างล่างกันนะครับ
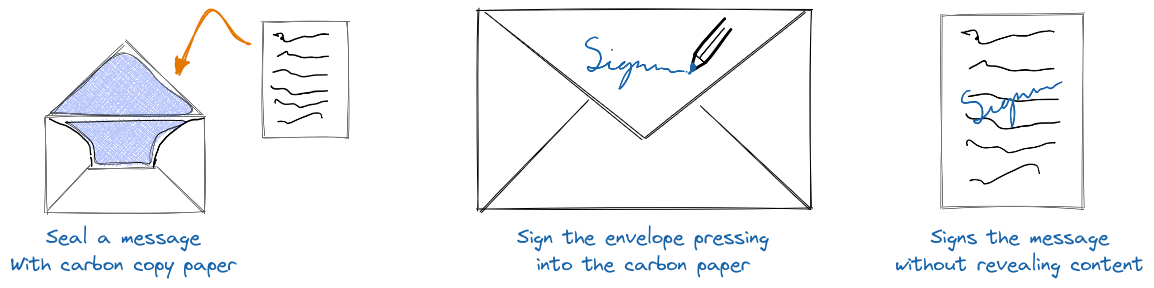 การอธิบาย blind signatures โดย David Chaum เปรียบเทียบกับการประทับลายเซ็นบนข้อความโดยใช้กระดาษคาร์บอน
(อ้างอิง: https://fedimint.org/docs/CommonTerms/Blind%20Signatures)
การอธิบาย blind signatures โดย David Chaum เปรียบเทียบกับการประทับลายเซ็นบนข้อความโดยใช้กระดาษคาร์บอน
(อ้างอิง: https://fedimint.org/docs/CommonTerms/Blind%20Signatures)- ขั้นแรก เราเขียนข้อความลงบนกระดาษ แล้วใส่กระดาษนั้นลงในซองจดหมายที่มีกระดาษคาร์บอนอยู่ข้างใน นี่เหมือนกับการ blind หรือ "ปิดบัง" เนื้อหาของข้อความครับ
- ต่อมา เราส่งซองจดหมายนี้ให้คนที่จะเซ็นรับรอง เขาจะเซ็นชื่อลงบนซองโดยกดปากกาแรง ๆ ทำให้ลายเซ็นติดลงบนกระดาษข้างในผ่านกระดาษคาร์บอน แต่เขาไม่สามารถเห็นข้อความจริง ๆ ได้
- สุดท้าย เมื่อเราได้ซองจดหมายกลับมา เมื่อเปิดซองออกมาเราจะได้กระดาษที่มีทั้งข้อความของเราและลายเซ็นรับรอง โดยที่ผู้เซ็นไม่เคยเห็นเนื้อหาของข้อความเลย
นี่แหละครับคือหลักการของ Blind signature ในระบบ Chaumian e-cash เราสามารถขอให้ mint เซ็นรับรอง e-cash ของเราได้ โดยที่ mint ไม่รู้ว่ากำลังเซ็นรับรองเหรียญไหนอยู่ ทำให้ mint ไม่สามารถติดตามการใช้จ่ายของเราได้ในภายหลัง เป็นการรักษาความเป็นส่วนตัวได้อย่างดีเยี่ยมครับ
แล้ว Chaumian e-cash ทำงานยังไงล่ะ? ลองมาดูตามภาพข้างล่างกันทีละขั้นตอนนะครับ
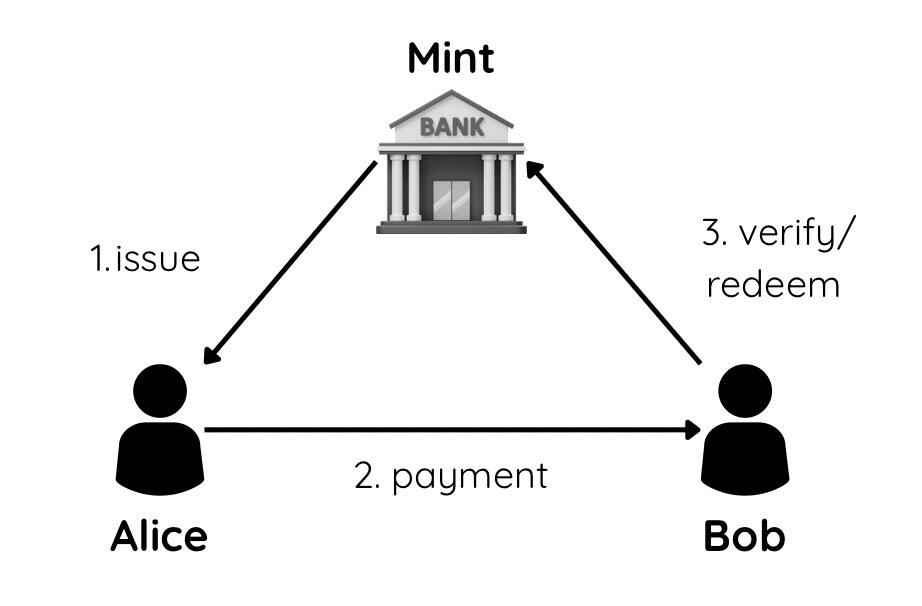 การทำงานของ Chaumian e-cash
การทำงานของ Chaumian e-cash- สมมติว่า Alice ขอให้ mint ออก e-cash ให้ครับ ตรงนี้แหละที่เทคนิค blind signature เข้ามามีบทบาท Alice จะ "ปิดบัง" ข้อมูลของ e-cash ก่อนส่งให้ mint ลงลายเซ็นต์หรือ signature โดยที่ mint ไม่รู้ว่ากำลังลงลายเซ็นต์บน e-cash ตัวไหน
- ต่อมา Alice อยากส่งเงินให้เพื่อนชื่อ Bob ก็แค่เพียงส่ง e-cash นั้นไปให้ Bob โดยไม่ต้องผ่าน mint เหมือนกับการส่งเงินสดจริง ๆ เลยครับ
- แล้ว Bob จะรู้ได้ยังไงว่าเงินที่คุณส่งให้นั้นใช้ได้จริง? Bob สามารถเอา e-cash นั้นไปตรวจสอบกับ mint ได้ครับ mint จะยืนยันว่า e-cash นั้นถูกต้อง แต่จะไม่รู้เลยว่าเป็น e-cash ที่ออกให้ Alice
ที่น่าสนใจก็คือ Chaumian e-cash ต่างจากบริการ custodial ที่จัดการเงินทุนแบบเห็นทุกอย่าง ผู้ดูแล mint จะไม่รู้เลยว่ามีผู้ใช้กี่คน ไม่รู้ว่าผู้ใช้เป็นใคร ไม่รู้ยอดเงินในบัญชี และไม่รู้ประวัติการทำธุรกรรมครับ นอกจากนี้ การทำธุรกรรมผ่าน mint ยังมีค่าใช้จ่ายต่ำ และสามารถทำได้โดยไม่มีข้อจำกัดอีกด้วย
ที่สำคัญ ระบบนี้สามารถป้องกันการใช้เงินซ้ำ (double spending) ได้ด้วยครับ เพราะทุกครั้งที่มีการใช้ e-cash mint จะบันทึกไว้ ถ้า Alice พยายามใช้ e-cash ตัวเดิมอีก mint ก็จะรู้ทันทีและปฏิเสธการทำธุรกรรมนั้น
วิธีนี้ทำให้ Chaumian e-cash รักษาความเป็นส่วนตัวของผู้ใช้ได้สูง แต่ก็ยังคงความปลอดภัยทางการเงินไว้ได้ด้วยครับ เป็นระบบที่นำข้อดีของเงินสดมาไว้ในโลกดิจิทัลนั่นเองครับ
การแบ่งย่อย e-cash
สมมติว่า Alice มี e-cash มูลค่า 100 sat แต่ต้องการจ่ายค่ากาแฟให้ Bob เพียง 30 sat Alice จะสามารถจ่ายเงินให้ Bob ได้อย่างไร?
Chaumian e-cash มีคุณสมบัติที่สำคัญอีกอย่างหนึ่งก็คือ "การแบ่งย่อย" หรือ split ครับ มันทำงานคล้าย ๆ กับการแลกเงินในชีวิตจริงเลยครับ ลองนึกภาพตามดังนี้ครับ
- Alice ส่งคำขอไปยัง mint เพื่อแลก e-cash 100 sat เป็น e-cash มูลค่าย่อย คือ 30 sat และ 70 sat
- mint จะสร้าง e-cash ใหม่ตามมูลค่าที่ Alice ขอ โดยใช้ blind signature เช่นเดิม ทำให้ mint ไม่รู้ว่า e-cash ใหม่เหล่านี้เชื่อมโยงกับ e-cash เดิมของ Alice อย่างไร
- Alice จะได้รับ e-cash ใหม่กลับมา และสามารถใช้ e-cash มูลค่า 30 sat จ่ายให้ Bob ได้ทันที
- ส่วน e-cash มูลค่า 70 sat ที่เหลือ Alice ก็สามารถเก็บไว้ใช้ในโอกาสต่อไป คล้าย ๆ กับเงินทอนนั่นเองครับ
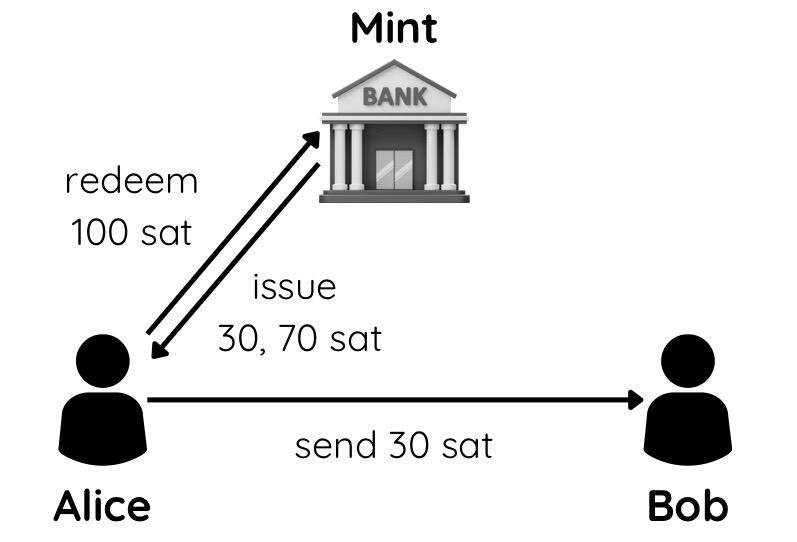 การแบ่งย่อย e-cash
การแบ่งย่อย e-cashการแบ่ง e-cash นี้ช่วยให้ผู้ใช้สามารถจ่ายเงินได้ตรงตามจำนวนที่ต้องการ ไม่ต้องกังวลว่าจะมีเหรียญย่อยไม่พอ มีความคล่องตัวสูง เลียนแบบการใช้เงินสดในชีวิตจริงได้อย่างใกล้เคียงมากขึ้น ทำให้ผู้ใช้สามารถจัดการเงินของตนได้อย่างอิสระและเป็นส่วนตัว โดยที่ mint ยังคงสามารถรักษาความปลอดภัยของระบบโดยรวมไว้ได้ครับ
Federated Mint: ลดการรวมศูนย์และเพิ่มความปลอดภัย
Mint หรือผู้ออก e-cash นั้น แม้จะมีข้อดีหลายประการ แต่ก็ยังมีความเสี่ยงที่เราต้องคำนึงถึงครับ เหมือนกับบริการรับฝากเงินแบบรวมศูนย์ทั่วไป mint ก็อาจทำให้ผู้ใช้เผชิญกับความเสี่ยงในรูปแบบต่าง ๆ เช่น ผู้ดูแลระบบอาจหนีหายไปพร้อมกับเงินของผู้ใช้ หรือ การบริหารจัดการที่ผิดพลาดอาจนำไปสู่การสูญเสียเงินของผู้ใช้
แต่ไม่ต้องกังวลไปครับ เพราะเรามีวิธีแก้ปัญหานี้!! นั่นคือการทำให้การทำงานของ mint กระจายตัวออกไป หรือที่เรียกว่า "Federated Mint"
วิธีการนี้คือ แทนที่จะมี mint เพียงแห่งเดียว เราจะมีหลาย ๆ mint ที่ทำงานร่วมกัน โดยทุกการดำเนินงานจะต้องได้รับการยืนยันจากกลุ่มของโหนดที่ควบคุมโดยหลายฝ่าย เพิ่มการกระจายศูนย์ โดยลดความเสี่ยงจากการพึ่งพา Mint เพียงแห่งเดียว อีกทั้งเพิ่มความสามารถในการขยายตัว (Scaling) รองรับผู้ใช้และธุรกรรมได้มากขึ้น
ที่สำคัญ แต่ละ mint สามารถส่งเงินให้กันได้ผ่านทั้ง lightning network ทำให้ระบบโดยรวมมีประสิทธิภาพและความปลอดภัยสูงขึ้น
การพัฒนา Federated Mints นี้ แสดงให้เห็นว่าเราสามารถนำข้อดีของ Chaumian e-cash มาใช้ โดยลดข้อเสียของระบบรวมศูนย์ลงได้ นับเป็นก้าวสำคัญในการพัฒนาระบบการเงินที่ทั้งปลอดภัย เป็นส่วนตัว และมีประสิทธิภาพสูงครับ
 การทำงานของ mints มากว่าหนึ่งแห่งทำงานร่วมกัน (อ้างอิง: https://bitlyrics.co/transcripts/cashu-for-bitcoin/)
การทำงานของ mints มากว่าหนึ่งแห่งทำงานร่วมกัน (อ้างอิง: https://bitlyrics.co/transcripts/cashu-for-bitcoin/)การประยุกต์ Chaumian e-cash กับ Bitcoin ในปัจจุบัน
ปัจจุบันมีการนำแนวคิด Chaumian e-cash มาประยุกต์ใช้กับ Bitcoin แล้วครับ โดยมีสอง project หลักที่น่าสนใจ คือ Fedimint และ Cashu ลองมาดูรายละเอียดกันครับ
Fedimint
เป็นโปรโตคอลโอเพนซอร์สที่พัฒนาโดยบริษัท Fedi ซึ่งมีผู้สนับสนุนและนักลงทุนที่มีชื่อเสียง จุดเด่นของ Fedimint คือ สินทรัพย์ bitcoin จะถูกเก็บรักษาโดยหลายฝ่าย เรียกว่า "Guardian" ซึ่งรวมกันเป็น "Federation"
ระบบการเก็บรักษาคล้ายกับ multisig wallet ที่ต้องการลายเซ็นจากหลายฝ่าย เหมาะสำหรับชุมชนขนาดใหญ่หรือผู้ให้บริการแพลตฟอร์มที่ต้องการให้บริการ lightning network ให้กับลูกค้าหรือสมาชิก
Fedimint เรียกการ custody รูปแบบนี้ว่า "community custody" ซึ่งอยู่ระหว่าง self-custody และ full custody
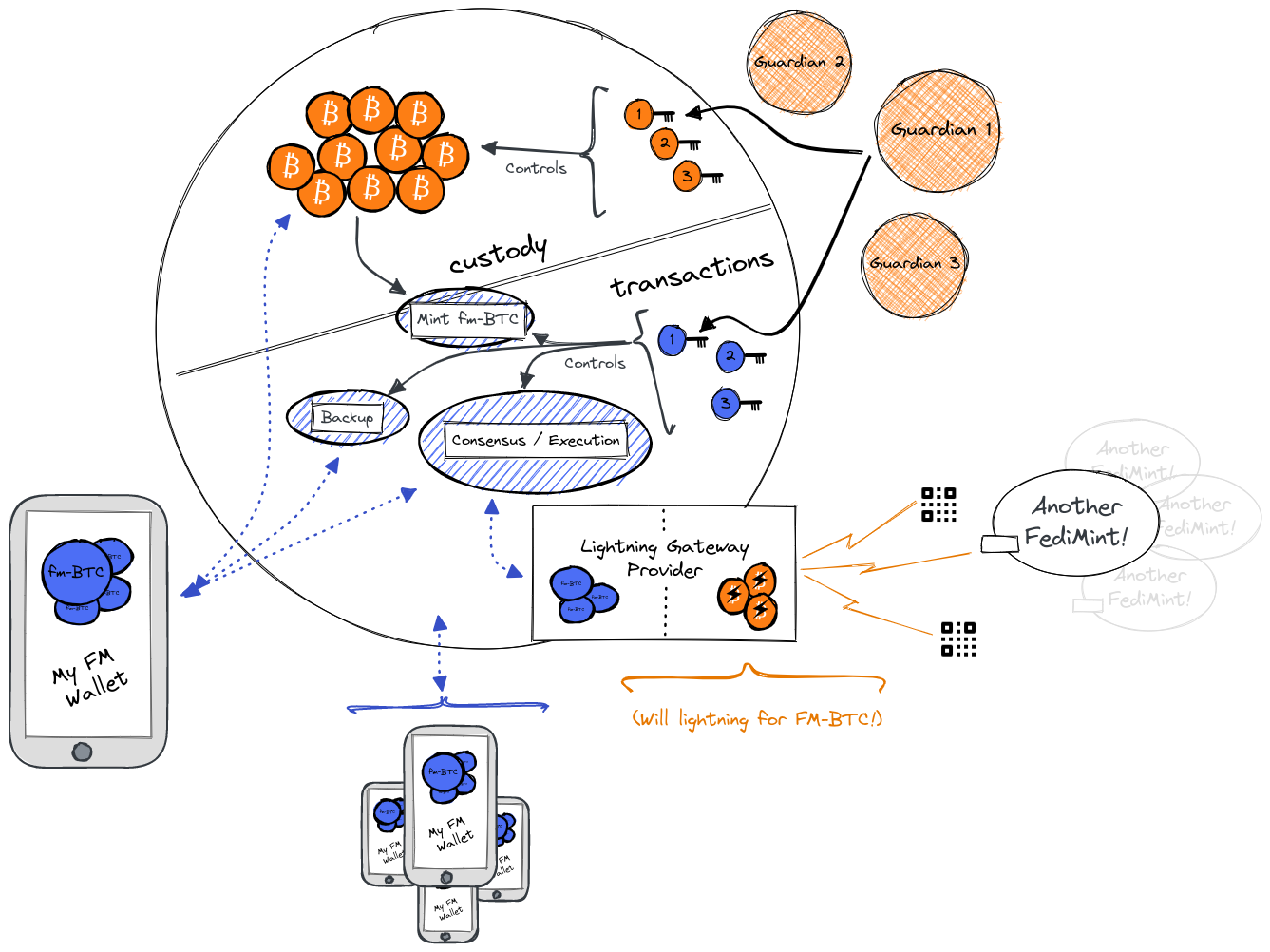 การทำงานของ Fedimint (อ้างอิง: https://fedimint.org/docs/GettingStarted/What-is-a-Fedimint)
การทำงานของ Fedimint (อ้างอิง: https://fedimint.org/docs/GettingStarted/What-is-a-Fedimint)Cashu
เป็นแนวทางที่แตกต่างจาก Fedimint ครับ โดยใช้รูปแบบ single-mint setup คือมีผู้ดูแลเพียงรายเดียว ไม่ใช่หลายรายแบบ Fedimint
จุดเด่นสำคัญของ Cashu ที่ทำให้มันแตกต่างคือ Cashu อนุญาตให้ตั้ง mint ได้ง่ายมากครับ แค่มี semi-custodial wallet เช่น LNbits ก็สามารถตั้ง mint ได้แล้ว ไม่จำเป็นต้องมีถึงระดับ full lightning node ซึ่งต้องใช้ทรัพยากรมากกว่า
ด้วยความง่ายในการตั้ง mint นี้ ทำให้มี mint ให้เลือกใช้งานจำนวนมากครับ ผู้ใช้สามารถเลือก mint ที่เหมาะสมกับความต้องการของตนได้
แม้ว่า Cashu จะมีความปลอดภัยน้อยกว่า Fedimint ในแง่ของการมีผู้ดูแลเพียงรายเดียวต่อ mint แต่ด้วยความสามารถในการกระจาย e-cash ไปยัง mint หลาย ๆ แห่ง ก็ช่วยชดเชยความเสี่ยงนี้ได้บางส่วนครับ
Cashu จึงเป็นทางเลือกที่น่าสนใจสำหรับผู้ที่ต้องการความยืดหยุ่นสูง ต้องการควบคุมการกระจายเงินของตนเอง และเหมาะสำหรับการใช้งานในวงแคบหรือในชุมชนขนาดเล็กถึงขนาดกลางครับ
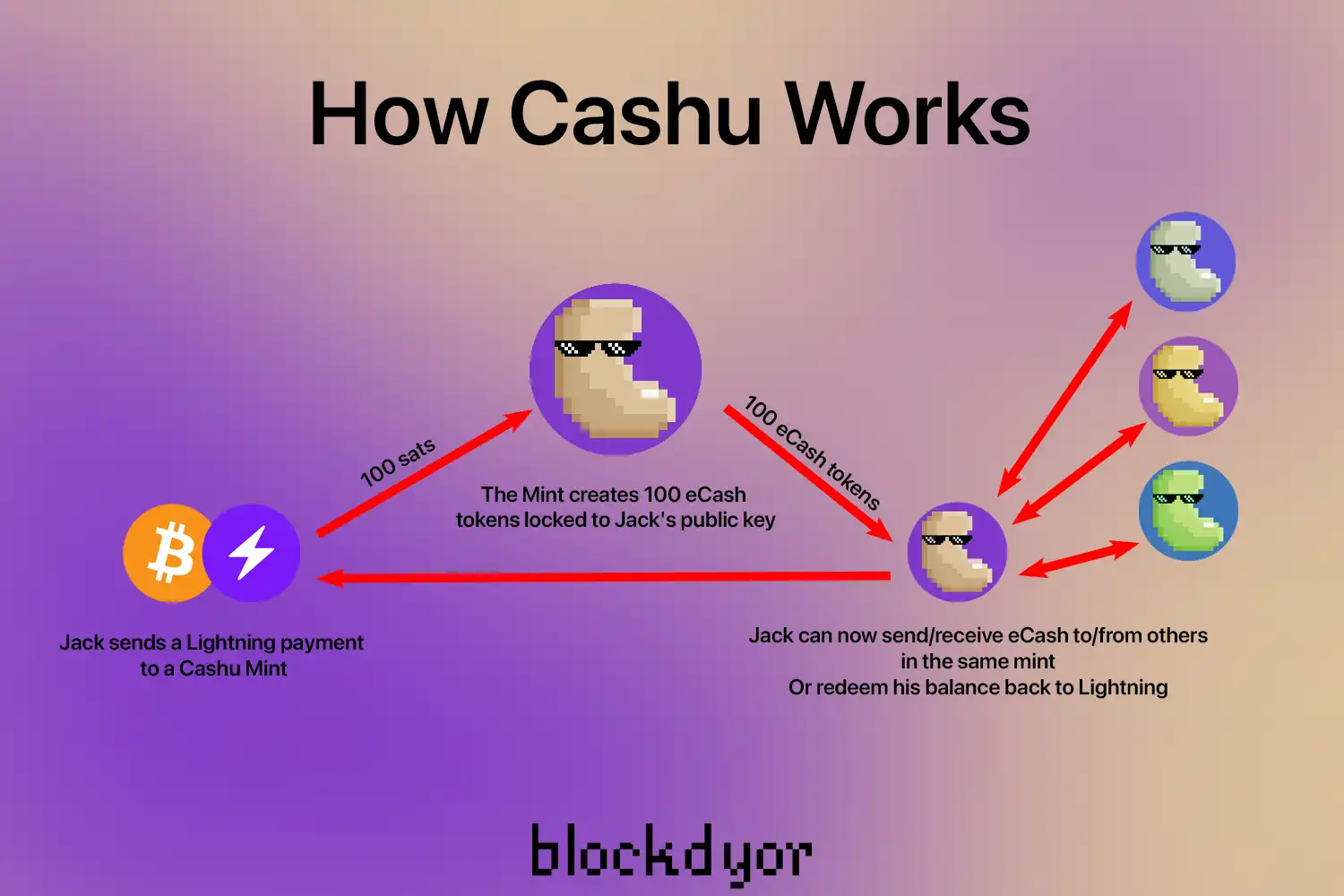 การทำงานของ Cashu (อ้างอิง: https://blockdyor.com/cashu/)
การทำงานของ Cashu (อ้างอิง: https://blockdyor.com/cashu/)บทสรุปส่งท้าย
บทความนี้ เราได้เรียนรู้เกี่ยวกับ Chaumian e-cash และการประยุกต์ใช้กับ Bitcoin ผ่านสอง project หลัก คือ Fedimint และ Cashu ครับ แต่ละ project ก็มีจุดเด่นและเหมาะกับการใช้งานที่แตกต่างกันไป
สำหรับผมแล้ว Cashu มีความน่าสนใจเป็นพิเศษครับ เพราะมันสามารถใช้งานได้ง่าย และเข้าถึงคนได้ง่ายกว่า ด้วยความสามารถในการตั้ง Mint ได้อย่างง่ายดาย ทำให้ Cashu มีศักยภาพในการขยายการใช้งานได้อย่างรวดเร็ว และเหมาะสำหรับการนำไปใช้ในชีวิตประจำวันของคนทั่วไปครับ
ในบทความหน้า ผมจะพาท่านผู้อ่านเจาะลึกลงไปในเรื่องของ Cashu ครับ โดยจะอธิบายรายละเอียดเพิ่มเติมและสอนวิธีการใช้งาน Cashu เพื่อให้ท่านผู้อ่านสามารถนำไปทดลองใช้งานได้จริง และเข้าใจถึงประโยชน์ของ Chaumian e-cash ในชีวิตประจำวันได้มากขึ้นครับ
หวังว่าบทความนี้จะช่วยให้ท่านเข้าใจภาพรวมของ Chaumian e-cash และการประยุกต์ใช้กับ Bitcoin ได้มากขึ้นนะครับ และอย่าลืมติดตามบทความถัดไปเกี่ยวกับ Cashu ที่จะมาเร็ว ๆ นี้ครับ ขอบคุณที่ติดตามอ่านครับ!!
-
 @ 592295cf:413a0db9
2024-08-04 05:55:02
@ 592295cf:413a0db9
2024-08-04 05:55:02Nostter muted by kind
Will mute freefrom, hashtag fall
Venezuela riots, after the vote
I was thinking that having a Nostr conference every 6 months doesn't make sense, maybe it's better to focus on something else. If not it becomes a Tour Life. It doesn't increase adoption Produces tons of material It's good for networking It's not sustainable
Readable updates, how important they are. If it's just bugs and fixes it's better.
I hate Pam. As user It writes interesting stuff, but, doesnn't write in long form, because long form are more difficult, less reach and immediacy, and difficulties to share over in the feed,but not write a poem, sorry.
The thing about coracle is that I load the initial feed, but that gets printed, and it doesn't tell me if there are new notes coming in, as if it interrupts the flow, and it's always a fetch. I want to read the future, not always the past. RealTime feeds Like bluesky 🧞

Njump had problems, it keeps the cache and if the user changes something in their data it doesn't update it immediately. Fiatjaf was angry.
It's the month of NostRiga, we can move on to September without thinking about it. No
It's funny when you see a text in Japanese and inside read Nostr, I want to know what it says. He usually says Nostr is great. And the next note I drank too much 🤣
Today I thought that on the other side of the world it is February and that their February is 31 days. Pam said was sick. I see that hate is a virus 😅🙇♂️
I decided to publish stronpy when it's ready, maybe in 6 months. I've done the lineup, now I have to do the gantt 😅. Maybe I can post the gantt somewhere.
If it's not encrypted it's public. Amethyst draft 31000 and something like event
Nostr Is great but the amount of time Lost to the same thing because you don't know that exist Is remarkable. Nostr is a redundancy protocol
nostr:nevent1qqsqjqauc34k9k278x6cka5jyf3aq033y4pn5czwaff72l3rwum7llq7ela3x When they do that I can't stand them, then maybe it's a little different 😔😔 Zapper.fun ✅ Because you launch a project, example nostr.band but contain others 100 apps 😅 Nostr.band, nostrapp.link, zapper.fun, Nostr login, nsec.app, Npub.pro, Npub.pro also cli, Nostr universe/ knows as spring site
Even in Coracle it would be great to have a check on the note as root, because when you see the answers, perhaps the distance from another post, is so small, so perhaps a gray line for the mark of another note as root.
I listened to several minutes of plebchain radio episode on nostrnests. Language is an obstacle, but also an excellent justification. Last year I started recording a podcast episode, in which I talked about nostr bookmark update. I didn't even want to listen to it again 🤣.
I sent a video of an explanation of a zap it was 500 MByte of video for 4 minutes.
Nostr doesn't work. In practice, many apps have removed the possibility of logging in with the simple key, be it public or private, because especially the private one you don't want to copy paste in every single clients/apps, increasing the attack surface.
However, by removing this functionality and doing little onboarding, the matter is very difficult, but there is a certain belief that people who arrive at a Twitter like client get to know the network a little and then move on to videos or writing, or similar. But one can open a site by chance and see what it offers without knowing anything.
In the future there will only be one client, that of medical data...
Someone share this nostr:nevent1qqs24qzelpk8xjlk4dthr9tfkqwz8n58dlm04ezyvg9nuztud6jjfhc9mg04n I had in my bookmarks. I see dozen types of this self hosted manners. Maybe captains-log is for nostr-type, good.
-
 @ 0176967e:1e6f471e
2024-07-26 12:15:35
@ 0176967e:1e6f471e
2024-07-26 12:15:35Bojovať s rakovinou metabolickou metódou znamená použiť metabolizmus tela proti rakovine. Riadenie cukru a ketónov v krvi stravou a pohybom, časovanie rôznych typov cvičení, včasná kombinácia klasickej onko-liečby a hladovania. Ktoré vitamíny a suplementy prijímam a ktorým sa napríklad vyhýbam dajúc na rady mojej dietologičky z USA Miriam (ktorá sa špecializuje na rakovinu).
Hovori sa, že čo nemeriame, neriadime ... Ja som meral, veľa a dlho ... aj grafy budú ... aj sranda bude, hádam ... 😉
-
 @ 0176967e:1e6f471e
2024-07-26 09:50:53
@ 0176967e:1e6f471e
2024-07-26 09:50:53Predikčné trhy predstavujú praktický spôsob, ako môžeme nahliadnuť do budúcnosti bez nutnosti spoliehať sa na tradičné, často nepresné metódy, ako je veštenie z kávových zrniek. V prezentácii sa ponoríme do histórie a vývoja predikčných trhov, a popíšeme aký vplyv mali a majú na dostupnosť a kvalitu informácií pre širokú verejnosť, a ako menia trh s týmito informáciami. Pozrieme sa aj na to, ako tieto trhy umožňujú obyčajným ľuďom prístup k spoľahlivým predpovediam a ako môžu prispieť k lepšiemu rozhodovaniu v rôznych oblastiach života.
-
 @ 6871d8df:4a9396c1
2024-06-12 22:10:51
@ 6871d8df:4a9396c1
2024-06-12 22:10:51Embracing AI: A Case for AI Accelerationism
In an era where artificial intelligence (AI) development is at the forefront of technological innovation, a counter-narrative championed by a group I refer to as the 'AI Decels'—those advocating for the deceleration of AI advancements— seems to be gaining significant traction. After tuning into a recent episode of the Joe Rogan Podcast, I realized that the prevailing narrative around AI was heading in a dangerous direction. Rogan had Aza Raskin and Tristan Harris, technology safety advocates, who released a talk called 'The AI Dilemma,' on for a discussion. You may know them from the popular documentary 'The Social Dilemma' on the dangers of social media. It became increasingly clear that the cautionary stance dominating this discourse might be tipping the scales too far, veering towards an over-regulated future that stifles innovation rather than fostering it.

Are we moving too fast?
While acknowledging AI's benefits, Aza and Tristan fear it could be dangerous if not guided by ethical standards and safeguards. They believe AI development is moving too quickly and that the right incentives for its growth are not in place. They are concerned about the possibility of "civilizational overwhelm," where advanced AI technology far outpaces 21st-century governance. They fear a scenario where society and its institutions cannot manage or adapt to the rapid changes and challenges introduced by AI.
They argue for regulating and slowing down AI development due to rapid, uncontrolled advancement driven by competition among companies like Google, OpenAI, and Microsoft. They claim this race can lead to unsafe releases of new technologies, with AI systems exhibiting unpredictable, emergent behaviors, posing significant societal risks. For instance, AI can inadvertently learn tasks like sentiment analysis or human emotion understanding, creating potential for misuse in areas like biological weapons or cybersecurity vulnerabilities.
Moreover, AI companies' profit-driven incentives often conflict with the public good, prioritizing market dominance over safety and ethics. This misalignment can lead to technologies that maximize engagement or profits at societal expense, similar to the negative impacts seen with social media. To address these issues, they suggest government regulation to realign AI companies' incentives with safety, ethical considerations, and public welfare. Implementing responsible development frameworks focused on long-term societal impacts is essential for mitigating potential harm.
This isn't new
Though the premise of their concerns seems reasonable, it's dangerous and an all too common occurrence with the emergence of new technologies. For example, in their example in the podcast, they refer to the technological breakthrough of oil. Oil as energy was a technological marvel and changed the course of human civilization. The embrace of oil — now the cornerstone of industry in our age — revolutionized how societies operated, fueled economies, and connected the world in unprecedented ways. Yet recently, as ideas of its environmental and geopolitical ramifications propagated, the narrative around oil has shifted.
Tristan and Aza detail this shift and claim that though the period was great for humanity, we didn't have another technology to go to once the technological consequences became apparent. The problem with that argument is that we did innovate to a better alternative: nuclear. However, at its technological breakthrough, it was met with severe suspicions, from safety concerns to ethical debates over its use. This overregulation due to these concerns caused a decades-long stagnation in nuclear innovation, where even today, we are still stuck with heavy reliance on coal and oil. The scare tactics and fear-mongering had consequences, and, interestingly, they don't see the parallels with their current deceleration stance on AI.
These examples underscore a critical insight: the initial anxiety surrounding new technologies is a natural response to the unknowns they introduce. Yet, history shows that too much anxiety can stifle the innovation needed to address the problems posed by current technologies. The cycle of discovery, fear, adaptation, and eventual acceptance reveals an essential truth—progress requires not just the courage to innovate but also the resilience to navigate the uncertainties these innovations bring.
Moreover, believing we can predict and plan for all AI-related unknowns reflects overconfidence in our understanding and foresight. History shows that technological progress, marked by unexpected outcomes and discoveries, defies such predictions. The evolution from the printing press to the internet underscores progress's unpredictability. Hence, facing AI's future requires caution, curiosity, and humility. Acknowledging our limitations and embracing continuous learning and adaptation will allow us to harness AI's potential responsibly, illustrating that embracing our uncertainties, rather than pretending to foresee them, is vital to innovation.
The journey of technological advancement is fraught with both promise and trepidation. Historically, each significant leap forward, from the dawn of the industrial age to the digital revolution, has been met with a mix of enthusiasm and apprehension. Aza Raskin and Tristan Harris's thesis in the 'AI Dilemma' embodies the latter.
Who defines "safe?"
When slowing down technologies for safety or ethical reasons, the issue arises of who gets to define what "safe" or “ethical” mean? This inquiry is not merely technical but deeply ideological, touching the very core of societal values and power dynamics. For example, the push for Diversity, Equity, and Inclusion (DEI) initiatives shows how specific ideological underpinnings can shape definitions of safety and decency.
Take the case of the initial release of Google's AI chatbot, Gemini, which chose the ideology of its creators over truth. Luckily, the answers were so ridiculous that the pushback was sudden and immediate. My worry, however, is if, in correcting this, they become experts in making the ideological capture much more subtle. Large bureaucratic institutions' top-down safety enforcement creates a fertile ground for ideological capture of safety standards.

I claim that the issue is not the technology itself but the lens through which we view and regulate it. Suppose the gatekeepers of 'safety' are aligned with a singular ideology. In that case, AI development would skew to serve specific ends, sidelining diverse perspectives and potentially stifling innovative thought and progress.
In the podcast, Tristan and Aza suggest such manipulation as a solution. They propose using AI for consensus-building and creating "shared realities" to address societal challenges. In practice, this means that when individuals' viewpoints seem to be far apart, we can leverage AI to "bridge the gap." How they bridge the gap and what we would bridge it toward is left to the imagination, but to me, it is clear. Regulators will inevitably influence it from the top down, which, in my opinion, would be the opposite of progress.
In navigating this terrain, we must advocate for a pluralistic approach to defining safety, encompassing various perspectives and values achieved through market forces rather than a governing entity choosing winners. The more players that can play the game, the more wide-ranging perspectives will catalyze innovation to flourish.
Ownership & Identity
Just because we should accelerate AI forward does not mean I do not have my concerns. When I think about what could be the most devastating for society, I don't believe we have to worry about a Matrix-level dystopia; I worry about freedom. As I explored in "Whose data is it anyway?," my concern gravitates toward the issues of data ownership and the implications of relinquishing control over our digital identities. This relinquishment threatens our privacy and the integrity of the content we generate, leaving it susceptible to the inclinations and profit of a few dominant tech entities.
To counteract these concerns, a paradigm shift towards decentralized models of data ownership is imperative. Such standards would empower individuals with control over their digital footprints, ensuring that we develop AI systems with diverse, honest, and truthful perspectives rather than the massaged, narrow viewpoints of their creators. This shift safeguards individual privacy and promotes an ethical framework for AI development that upholds the principles of fairness and impartiality.
As we stand at the crossroads of technological innovation and ethical consideration, it is crucial to advocate for systems that place data ownership firmly in the hands of users. By doing so, we can ensure that the future of AI remains truthful, non-ideological, and aligned with the broader interests of society.
But what about the Matrix?
I know I am in the minority on this, but I feel that the concerns of AGI (Artificial General Intelligence) are generally overblown. I am not scared of reaching the point of AGI, and I think the idea that AI will become so intelligent that we will lose control of it is unfounded and silly. Reaching AGI is not reaching consciousness; being worried about it spontaneously gaining consciousness is a misplaced fear. It is a tool created by humans for humans to enhance productivity and achieve specific outcomes.
At a technical level, large language models (LLMs) are trained on extensive datasets and learning patterns from language and data through a technique called "unsupervised learning" (meaning the data is untagged). They predict the next word in sentences, refining their predictions through feedback to improve coherence and relevance. When queried, LLMs generate responses based on learned patterns, simulating an understanding of language to provide contextually appropriate answers. They will only answer based on the datasets that were inputted and scanned.
AI will never be "alive," meaning that AI lacks inherent agency, consciousness, and the characteristics of life, not capable of independent thought or action. AI cannot act independently of human control. Concerns about AI gaining autonomy and posing a threat to humanity are based on a misunderstanding of the nature of AI and the fundamental differences between living beings and machines. AI spontaneously developing a will or consciousness is more similar to thinking a hammer will start walking than us being able to create consciousness through programming. Right now, there is only one way to create consciousness, and I'm skeptical that is ever something we will be able to harness and create as humans. Irrespective of its complexity — and yes, our tools will continue to become evermore complex — machines, specifically AI, cannot transcend their nature as non-living, inanimate objects programmed and controlled by humans.
 The advancement of AI should be seen as enhancing human capabilities, not as a path toward creating autonomous entities with their own wills. So, while AI will continue to evolve, improve, and become more powerful, I believe it will remain under human direction and control without the existential threats often sensationalized in discussions about AI's future.
The advancement of AI should be seen as enhancing human capabilities, not as a path toward creating autonomous entities with their own wills. So, while AI will continue to evolve, improve, and become more powerful, I believe it will remain under human direction and control without the existential threats often sensationalized in discussions about AI's future. With this framing, we should not view the race toward AGI as something to avoid. This will only make the tools we use more powerful, making us more productive. With all this being said, AGI is still much farther away than many believe.
Today's AI excels in specific, narrow tasks, known as narrow or weak AI. These systems operate within tightly defined parameters, achieving remarkable efficiency and accuracy that can sometimes surpass human performance in those specific tasks. Yet, this is far from the versatile and adaptable functionality that AGI represents.
Moreover, the exponential growth of computational power observed in the past decades does not directly translate to an equivalent acceleration in achieving AGI. AI's impressive feats are often the result of massive data inputs and computing resources tailored to specific tasks. These successes do not inherently bring us closer to understanding or replicating the general problem-solving capabilities of the human mind, which again would only make the tools more potent in our hands.
While AI will undeniably introduce challenges and change the aspects of conflict and power dynamics, these challenges will primarily stem from humans wielding this powerful tool rather than the technology itself. AI is a mirror reflecting our own biases, values, and intentions. The crux of future AI-related issues lies not in the technology's inherent capabilities but in how it is used by those wielding it. This reality is at odds with the idea that we should slow down development as our biggest threat will come from those who are not friendly to us.
AI Beget's AI
While the unknowns of AI development and its pitfalls indeed stir apprehension, it's essential to recognize the power of market forces and human ingenuity in leveraging AI to address these challenges. History is replete with examples of new technologies raising concerns, only for those very technologies to provide solutions to the problems they initially seemed to exacerbate. It looks silly and unfair to think of fighting a war with a country that never embraced oil and was still primarily getting its energy from burning wood.
 The evolution of AI is no exception to this pattern. As we venture into uncharted territories, the potential issues that arise with AI—be it ethical concerns, use by malicious actors, biases in decision-making, or privacy intrusions—are not merely obstacles but opportunities for innovation. It is within the realm of possibility, and indeed, probability, that AI will play a crucial role in solving the problems it creates. The idea that there would be no incentive to address and solve these problems is to underestimate the fundamental drivers of technological progress.
The evolution of AI is no exception to this pattern. As we venture into uncharted territories, the potential issues that arise with AI—be it ethical concerns, use by malicious actors, biases in decision-making, or privacy intrusions—are not merely obstacles but opportunities for innovation. It is within the realm of possibility, and indeed, probability, that AI will play a crucial role in solving the problems it creates. The idea that there would be no incentive to address and solve these problems is to underestimate the fundamental drivers of technological progress.Market forces, fueled by the demand for better, safer, and more efficient solutions, are powerful catalysts for positive change. When a problem is worth fixing, it invariably attracts the attention of innovators, researchers, and entrepreneurs eager to solve it. This dynamic has driven progress throughout history, and AI is poised to benefit from this problem-solving cycle.
Thus, rather than viewing AI's unknowns as sources of fear, we should see them as sparks of opportunity. By tackling the challenges posed by AI, we will harness its full potential to benefit humanity. By fostering an ecosystem that encourages exploration, innovation, and problem-solving, we can ensure that AI serves as a force for good, solving problems as profound as those it might create. This is the optimism we must hold onto—a belief in our collective ability to shape AI into a tool that addresses its own challenges and elevates our capacity to solve some of society's most pressing issues.
An AI Future
The reality is that it isn't whether AI will lead to unforeseen challenges—it undoubtedly will, as has every major technological leap in history. The real issue is whether we let fear dictate our path and confine us to a standstill or embrace AI's potential to address current and future challenges.
The approach to solving potential AI-related problems with stringent regulations and a slowdown in innovation is akin to cutting off the nose to spite the face. It's a strategy that risks stagnating the U.S. in a global race where other nations will undoubtedly continue their AI advancements. This perspective dangerously ignores that AI, much like the printing press of the past, has the power to democratize information, empower individuals, and dismantle outdated power structures.
The way forward is not less AI but more of it, more innovation, optimism, and curiosity for the remarkable technological breakthroughs that will come. We must recognize that the solution to AI-induced challenges lies not in retreating but in advancing our capabilities to innovate and adapt.
AI represents a frontier of limitless possibilities. If wielded with foresight and responsibility, it's a tool that can help solve some of the most pressing issues we face today. There are certainly challenges ahead, but I trust that with problems come solutions. Let's keep the AI Decels from steering us away from this path with their doomsday predictions. Instead, let's embrace AI with the cautious optimism it deserves, forging a future where technology and humanity advance to heights we can't imagine.
-
 @ 0176967e:1e6f471e
2024-07-25 20:53:07
@ 0176967e:1e6f471e
2024-07-25 20:53:07AI hype vnímame asi všetci okolo nás — už takmer každá appka ponúka nejakú “AI fíčuru”, AI startupy raisujú stovky miliónov a Európa ako obvykle pracuje na regulovaní a našej ochrane pred nebezpečím umelej inteligencie. Pomaly sa ale ukazuje “ovocie” spojenia umelej inteligencie a človeka, kedy mnohí ľudia reportujú signifikantné zvýšenie produktivity v práci ako aj kreatívnych aktivitách (aj napriek tomu, že mnohí hardcore kreatívci by každého pri spomenutí skratky “AI” najradšej upálili). V prvej polovici prednášky sa pozrieme na to, akými rôznymi spôsobmi nám vie byť AI nápomocná, či už v práci alebo osobnom živote.
Umelé neuróny nám už vyskakujú pomaly aj z ovsených vločiek, no to ako sa k nám dostávajú sa veľmi líši. Hlavne v tom, či ich poskytujú firmy v zatvorených alebo open-source modeloch. V druhej polovici prednášky sa pozrieme na boom okolo otvorených AI modelov a ako ich vieme využiť.
-
 @ 8e7462a8:c723a97b
2024-08-02 21:48:50
@ 8e7462a8:c723a97b
2024-08-02 21:48:50```js import { useState, useEffect, useCallback, useContext, useRef } from 'react'; import axios from 'axios'; import { nip57, nip19 } from 'nostr-tools'; import { NostrContext } from '@/context/NostrContext'; import { lnurlEncode } from '@/utils/lnurl'; import { parseEvent } from '@/utils/nostr'; import { v4 as uuidv4 } from 'uuid';
const defaultRelays = [ "wss://nos.lol/", "wss://relay.damus.io/", "wss://relay.snort.social/", "wss://relay.nostr.band/", "wss://nostr.mutinywallet.com/", "wss://relay.mutinywallet.com/", "wss://relay.primal.net/" ];
const AUTHOR_PUBKEY = process.env.NEXT_PUBLIC_AUTHOR_PUBKEY;
export function useNostr() { const pool = useContext(NostrContext); const subscriptionQueue = useRef([]); const lastSubscriptionTime = useRef(0); const throttleDelay = 2000;
const processSubscriptionQueue = useCallback(() => { if (subscriptionQueue.current.length === 0) return; const currentTime = Date.now(); if (currentTime - lastSubscriptionTime.current < throttleDelay) { setTimeout(processSubscriptionQueue, throttleDelay); return; } const subscription = subscriptionQueue.current.shift(); subscription(); lastSubscriptionTime.current = currentTime; setTimeout(processSubscriptionQueue, throttleDelay); }, [throttleDelay]); const subscribe = useCallback( (filters, opts) => { if (!pool) return; const subscriptionFn = () => { return pool.subscribeMany(defaultRelays, filters, opts); }; subscriptionQueue.current.push(subscriptionFn); processSubscriptionQueue(); }, [pool, processSubscriptionQueue] ); const publish = useCallback( async (event) => { if (!pool) return; try { console.log('publishing event', event) const result = await Promise.any(pool.publish(defaultRelays, event)); console.log('result', result) console.log('Published event to at least one relay'); return true; } catch (error) { console.error('Failed to publish event:', error); return false; } }, [pool] );```
-
 @ 0176967e:1e6f471e
2024-07-25 20:38:11
@ 0176967e:1e6f471e
2024-07-25 20:38:11Čo vznikne keď spojíš hru SNAKE zo starej Nokie 3310 a Bitcoin? - hra Chain Duel!
Jedna z najlepších implementácií funkcionality Lightning Networku a gamingu vo svete Bitcoinu.
Vyskúšať si ju môžete s kamošmi na tomto odkaze. Na stránke nájdeš aj základné pravidlá hry avšak odporúčame pravidlá pochopiť aj priamo hraním
Chain Duel si získava hromady fanúšikov po bitcoinových konferenciách po celom svete a práve na Lunarpunk festival ho prinesieme tiež.
Multiplayer 1v1 hra, kde nejde o náhodu, ale skill, vás dostane. Poďte si zmerať sily s ďalšími bitcoinermi a vyhrať okrem samotných satoshi rôzne iné ceny.
Príďte sa zúčastniť prvého oficiálneho Chain Duel turnaja na Slovensku!
Pre účasť na turnaji je potrebná registrácia dopredu.
-
 @ 8dc86882:9dc4ba5e
2024-08-02 21:26:35
@ 8dc86882:9dc4ba5e
2024-08-02 21:26:35I really just wanted to give credit where credit is due. I'm not a podcaster, but I do listen to the Podcasting 2.0 podcast.
I feel that Dave and Adam have done a ton for Bitcoin and Lightning just by working on the Podcasting 2.0 project. Their effort to figure out how to make donations easy for fans of podcasts I believe has really built a lot of uptake in the ecosystem. Many of us wouldn't be here, or maybe have as good an understanding on how this all works without them. I just thought they needed to get some love.
Please listen to an episode and boost the hell out of it.
Cheers!
originally posted at https://stacker.news/items/632805
-
 @ 1c6b3be3:73f0ae6f
2024-08-04 04:00:07
@ 1c6b3be3:73f0ae6f
2024-08-04 04:00:07🍵 "btc | bitcoin | lightning network | asic" - Google News
Galaxy Digital projects Bitcoin network hashrate growth in H2 – Meaning? - AMBCrypto English This is Why Bitcoin Could See Less Selling Pressure From Miners: CryptoQuant - CryptoPotato Bitcoin Hashrate Nears Record Levels Amidst Price Decline – Details - NewsBTC Most Bitcoin Layer-2 Networks Won’t Survive: Galaxy Research - Decrypt Bitcoin Mining Giants from Wall Street: Ranking the Top 5 by Market Cap - Finance Magnates Bitcoin: Network Difficulty Reaches an Unprecedented level - Cointribune EN Riot Platforms Registers Q2 Losses, Increases Mining Revenue - Live Bitcoin News
-
 @ 57d1a264:69f1fee1
2024-08-02 18:59:48
@ 57d1a264:69f1fee1
2024-08-02 18:59:48UX Copywriter at @relay
Apply from: https://relai.app/career/ux-copywriter-50-60/
UX Researcher at @FediTeam
Apply from: https://bitcoinerjobs.com/job/1532724-ux-researcher-fedi
UX Researcher at @FediTeam
Apply from: https://bitcoinerjobs.com/job/1532724-ux-researcher-fedi
Web Designer for Mobile & Desktop (UX/UI) at @PlanB_network
Apply from:https://bitcoinerjobs.com/job/1533798-web-designer-for-mobile-and-desktop-uxui-planbitcoin-network
Graphic Assets Designer at Middle Entertainment
Apply from: https://www.plebwork.com/work/graphic-assets-designerc0sm3
Logo and brand book design for a bitcoin startup at @BinsingLabs
Apply from: https://www.plebwork.com/work/logo-and-brand-book-design-for-a-bitcoin-startup-s57f4
Illustrator Designer for Bitcoin Slide Deck at @BTCasey
Apply from: https://www.plebwork.com/work/illustrator-designer-for-bitcoin-slide-decktpfr9
Digital Design Contract at @bitcoinize
Apply from: https://x.com/bitcoinize/status/1818676267350184318?s=46
originally posted at https://stacker.news/items/632662
-
 @ 6f170f27:711e26dd
2024-08-02 16:44:16
@ 6f170f27:711e26dd
2024-08-02 16:44:16
Since Milei deregulated the housing market :
- 200% rise in housing supply
- 20% decrease in real prices !
https://www.eleconomista.es/economia/noticias/12935188/08/24/milei-obra-el-milagro-con-los-alquileres-la-oferta-de-vivienda-se-dispara-tras-desregular-el-mercado-en-argentina.html
originally posted at https://stacker.news/items/632534
-
 @ 0176967e:1e6f471e
2024-07-22 19:57:47
@ 0176967e:1e6f471e
2024-07-22 19:57:47Co se nomádská rodina již 3 roky utíkající před kontrolou naučila o kontrole samotné? Co je to vlastně svoboda? Může koexistovat se strachem? S konfliktem? Zkusme na chvíli zapomenout na daně, policii a stát a pohlédnout na svobodu i mimo hranice společenských ideologií. Zkusme namísto hledání dalších odpovědí zjistit, zda se ještě někde neukrývají nové otázky. Možná to bude trochu ezo.
Karel provozuje již přes 3 roky se svou ženou, dvěmi dětmi a jedním psem minimalistický život v obytné dodávce. Na cestách spolu začali tvořit youtubový kanál "Karel od Martiny" o svobodě, nomádství, anarchii, rodičovství, drogách a dalších normálních věcech.
Nájdete ho aj na nostr.
-
 @ 06830f6c:34da40c5
2024-08-02 06:36:33
@ 06830f6c:34da40c5
2024-08-02 06:36:33In a stunning turn of events, Jamaican dancehall star Vybz Kartel has been released from prison after his 2014 murder conviction was overturned. The artist, whose real name is Adidja Azim Palmer, has been a central figure in dancehall music for over two decades. His release marks a significant moment in the Jamaican music scene and the global dancehall community. 🌍🎶
read more here on yakihonne [https://yakihonne.com/article/naddr1qvzqqqr4gupzqp5rpakttyjmmqkv5kda4py0qptxvm0lq3k98q5k82vh5g6d5sx9qq2kv4txv95hz66tfag5kcejvaa8yu3e956kxdxfg9n]
originally posted at https://stacker.news/items/631891
-
 @ 0176967e:1e6f471e
2024-07-21 15:48:56
@ 0176967e:1e6f471e
2024-07-21 15:48:56Lístky na festival Lunarpunku sú už v predaji na našom crowdfunding portáli. V predaji sú dva typy lístkov - štandardný vstup a špeciálny vstup spolu s workshopom oranžového leta.
Neváhajte a zabezpečte si lístok, čím skôr to urobíte, tým bude festival lepší.
Platiť môžete Bitcoinom - Lightningom aj on-chain. Vaša vstupenka je e-mail adresa (neposielame potvrdzujúce e-maily, ak platba prešla, ste in).
-
 @ 81870f53:29bef6a6
2024-08-04 00:48:43
@ 81870f53:29bef6a6
2024-08-04 00:48:43あるアナリストは金曜日、現在の世界的な株式市場の売り出し中は、株価がさらに下落するリスクがあるため、投資家に注意を払うよう呼び掛けた。まだ底値狙いには良い時期ではないかもしれない。
今週発表された一連の米国経済・金融レポートデータは、米国株の収益見通しを悪化させた。一方で、米国の労働市場は引き続き冷え込んでいる。 「小規模非農業部門」とも呼ばれるADP新規雇用者数は水曜日に予想を上回り、大幅に減少した。賃金上昇率は3年ぶりの低水準に落ち込んだ。木曜日には、7月27日の週の米国の新規失業保険申請件数が1年ぶりの高水準に回復し、金曜日には、米国の7月の非農業部門雇用者数は予想を大幅に下回る11.4万人増にとどまり、失業率は3年ぶりの高水準に達し、100%の正確率を誇る景気後退指標であるサムルールが発動された。一方、米国のデータは景気減速の兆候をさらに追加し、米国の7月のISM製造業PMIは8か月ぶりの大幅な減少となり、米国の景気後退に対する市場の懸念を悪化させた。さらに、「AIバブル」の高まりにより、投資家は長い間AI ROIに対する忍耐力を失い、ハイテク大手の財務報告に対する市場の監視はより厳しくなっている。リスク回避がエスカレートし、米国株に大きな打撃を与え、AI株、チップ株、ハイテク株が急落し、米国株式市場にとって暗い8月となった。投資家は、景気後退を回避するために連邦準備制度理事会が金利引き下げに遅れを取っているのではないかと懸念し始めている。
米国の労働市場が冷え込めば、世界経済の減速を招く可能性がある。投資家の悲観的な見通しは、英国と欧州の金利引き下げへの賭けにも拍車をかけ、木曜日と金曜日の欧州株の下落に直接つながった。金曜日には、STOXX 600指数が2.73%下落し、欧州のハイテクセクターは6%以上下落し、ドイツ、フランス、イタリア、オランダ、スペインの株価指数はすべて下落した。
アジア市場も例外ではなかった。金曜日、日経平均株価は5.8%急落し、TOPIXは6.1%下落し、2016年以来最大の下落となった。台湾加重株価指数は4.4%下落し、韓国ソウル総合指数は3.7%下落した。
ウォール街は、今買いを入れるのは時期尚早かどうかをどう見ているのか? AMPインベストメント・マネジメントの投資戦略責任者兼チーフエコノミストのシェーン・オリバー氏は、金曜日に発表された調査レポートで次のように述べている。
「市場は調整期に入っているようだ。」
「プラスインフレのニュース、将来の金利引き下げへの期待の高まり、情報技術とAI関連収入のメリットに対する楽観的な見方により、株価は7月に急騰した。」
「AMPは、景気後退が回避されれば、今後6~12カ月間の低金利環境が株価を押し上げる可能性が高いと考えているが、世界の株式市場はさらに下落する可能性が高いため、今は底値買いをするのに最適な時期ではないかもしれない」
BMIリサーチのグローバルカントリーリスクディレクター、セドリック・シェハブ氏は金曜日のメディアとのインタビューで次のように述べた。
「現在の市場センチメントの悪化は、複数の要因が組み合わさって引き起こされており、市場の調整はまったく正常だ。売りは約1週間半前に始まったが、複数の要因が引き金となって今週激化した」
同氏はさらに次のように述べた。
「まず第一に、日本銀行のタカ派的な姿勢が短期裁定取引の崩壊につながった。同時に、米国が発表した製造業の不利なデータや雇用関連指標も、市場にパニックを引き起こしている」
「その後、一夜にして、一部の大企業の利益が大きく変動しました。これらの要因が相まって、すでに高値だった株式市場がさらに下落しました。」
「一部の投資家は、株式市場は通常、7月から10月にかけて季節的なボラティリティが増加するという重要な要因を見落としているようです。」
「したがって、株式市場の暦年効果に対する過去の反応パターンを考えると、特に米国および世界の株式市場がこれほど大幅に上昇した後では、現在の売り出し現象は驚くべきことではありません。」
「市場が過熱しているとき、特に市場の勢いが過剰なときは、このような調整はまったく普通のことです。」
投資家は今回の売り出しに対してパニックになるべきかどうか尋ねられると、シェハブ氏は次のように答えた。
「いいえ、その必要はないと思います。テクニカル分析の観点から見ると、市場は依然として移動平均と主要なテクニカルレベルでしっかりと支えられています。」
この記事がお役に立てば幸いです。 もしそうなら、チップをおくるどうぞ https://getalby.com/p/bitcap
日本のホスティングサービス Linux、Windowsクラウドホスティング データストレージ JPStream を使用して NOSTR リレーを作成する ホスティング サービスの料金をSatsで支払うことができます https://jpstream.net
-
 @ 06830f6c:34da40c5
2024-08-02 06:35:09
@ 06830f6c:34da40c5
2024-08-02 06:35:09In a groundbreaking turn of events, Jamaican dancehall superstar Vybz Kartel has been released from prison after his 2014 murder conviction was overturned! 🌟 The artist, born Adidja Azim Palmer, has been a central figure in the dancehall music scene for over two decades. His release is a monumental moment for both the Jamaican music industry and his global fanbase. 🌍🎶
🔎 Background of the Case
Vybz Kartel was arrested in 2011 and charged with the murder of Clive “Lizard” Williams. This high-profile case gripped the public's attention due to Kartel's immense popularity and the graphic details of the crime. In 2014, he was convicted and sentenced to life in prison, with a stipulation that he would not be eligible for parole until serving 35 years.
The prosecution relied heavily on a mix of text messages, video footage, and testimonies. From the beginning, there were numerous claims of evidence tampering and concerns about the integrity of the investigation. These issues became key points in Kartel’s numerous appeals over the years.
⚖️ The Appeal and Overturning of the Conviction
A major breakthrough came in March 2024 when Kartel’s legal team successfully argued that there had been juror misconduct during the original trial. The appeal judges determined that this misconduct was serious enough to compromise the fairness of the trial. They ruled that a retrial would be unjust, given the time Kartel had already served and the complexities surrounding the initial investigation.
This decision led to the reversal of the conviction, and on August 1, 2024, Vybz Kartel walked free after spending more than a decade behind bars. 🚀🎉
🌟 Reaction and Impact
The news of Kartel's release has electrified the music industry. Fans and fellow artists have taken to social media in droves to express their support and excitement. Many view this as a moment of vindication for the artist, who has always maintained his innocence.
Kartel’s influence on dancehall music is unparalleled. Even during his incarceration, he continued to release music that topped charts and resonated with fans around the world. His lyrical genius and ability to capture the socio-political essence of Jamaican life have solidified his status as one of the greatest dancehall artists of all time. 🎤👑
🔮 Looking Forward
With his newfound freedom, speculation is rife about Kartel’s next moves. Industry insiders are anticipating a surge of new music and possibly a tell-all memoir about his experiences over the past decade. Rumors are also swirling about potential collaborations with international artists who have long admired his work. 🌏🎶
Moreover, Kartel’s release is expected to have broader implications for the Jamaican justice system. The case has exposed significant flaws and has sparked calls for reforms to prevent similar miscarriages of justice in the future. ⚖️
📚 Fun Facts and Trivia
- Dancehall King: Vybz Kartel, often called the "Worl' Boss," is known for hits like "Fever" and "Summer Time." His unique style has influenced countless artists.
- Prolific Output: Despite being incarcerated, Kartel released several albums from prison, maintaining a strong presence in the music industry.
- Reality TV Star: Before his legal troubles, Kartel starred in the reality TV show "Teacha's Pet," offering fans a glimpse into his life and personality.
🎊 Conclusion
Vybz Kartel’s release from prison is a landmark moment not just for him personally, but for the dancehall genre and its worldwide followers. As he steps back into a world that has changed during his absence, all eyes will be on the dancehall king’s next moves. Regardless of what the future holds, Kartel's resilience and enduring popularity are testaments to his indomitable spirit and unparalleled talent. 🚀👑
-
 @ 2850567c:83c026bf
2024-08-02 05:49:27
@ 2850567c:83c026bf
2024-08-02 05:49:27We Bitcoiners are well aware of the phrase and use it daily in explanations. The use of "Proof of work" is always tied to mining bitcoin. It is always shown as very hard and specialized type of work. This work is shown to be done only by some special type of computers and requires high amounts of electricity.
This manner of explanation although correct, greatly narrows the idea behind the phrase. To mine bitcoin, one had to get those specialized computers. Need to buy those amounts of electricity power. Need to buy or rent land. All these things also need to be bought with money. And as the thousand year saying goes, work more to earn more.
So there was ordinary work done by many to accumulate the amount of money to setup a mining rig. The ordinary work like that of a farmer, carpenter, driver, mason, software engineer, banker, chemist and what not. That ordinary work is the idea of that phrase. The work is not about mining bitcoin. The work is not some abstract mathematics puzzle. That ordinary work produced a proof and was given today's fiat money in exchange. If that ordinary work produced a broken chair for example, the proof would fail and no money would be exchanged. If the work of a welder did not prove the iron gate that locks properly, no money would be earned.
That is the real proof of work. It has been all around us since the start of ages when we needed a proper fencing from wild animals. So it does not only mean that proof of work is needed to "mine" some bitcoins. Proof of work is needed to get any bitcoins. Even to buy them from an exchange. And stronger the proof, i.e. if one delivers a better product from their ordinary work, the the more money they can get. And then buy even more bitcoin.
The proof work work is not just for mining. It applies even more to how society functions. When the reward of the work is a hard asset, like gold or bitcoins, there is going to be a competition to produce even better quality work. Look at the art works. Look at the big monuments constructed many hundred years ago. The result of the work that produced the Taj Mahal. The money that backed it was gold and silver. India did not have easy gold or silver mines. So how they accumulated so much wealth? Being very good agriculturists. Gold and silver would come in boats to buy grains. Gold from Persia would come by mud roads traveling thousands of kilometers to buy steel. Iron and steel factory is a very labour intensive work. It also needs very good knowledge of metallurgy. There was known proof that Indian steel makes excellent swords and other tools.
Work that is rewarded by a hard asset is also the great economic equalizer. It will gradually give more and more rewards to those who are very good at their work. Those who love their work. Those who try to refine and get more efficient. Those who can collaborate with others. Those who are helped by others. It will also automatically filters out the ones who are forced into doing the wrong job. Those who don't enjoy what they do. Those who don't feel the need to compete. Very quickly even they will discover their own skills. And join the revolution of producing great proofs of their unique work. And the rewards start coming. The rewards in PoW are more linear in nature. They are tend to get less and less affected by opportunities, place, country, language or culture or even time. The rewards don't flow through one who controls them. They are given directly by buyer of the product, and no one else. The transaction of buyer and seller are not effected by what censorship rules are in place in that region, or within that government. The ones who have opportunities will still have to work in exactly the same way and prove their work. Or some else takes the same reward from their work. The ones who have opportunities cant just hire enough others to produce the work faster. The ones that are hired will immediately demand rewards in the very same hard asset. And that is never easy to get.
Whenever the reward is a harder asset, it demands a lot of hard work. We need to liberate the phrase from the chains of bitcoin mining. The phrase is for everyone. Society functions by giving and taking products and services. Society everywhere has to work. Bitcoin hodlers, even those who hold hundreds or thousands of bitcoins, do not stop working. They continue with their masonry work, collect garbage from homes, teach in colleges, and engage in various other professions. Then they still use a part of their earning to buy even more bitcoins. Any type of ordinary work done is proof enough to get bitcoins.
-
 @ 3c984938:2ec11289
2024-06-09 14:40:55
@ 3c984938:2ec11289
2024-06-09 14:40:55I'm having some pain in my heart about the U.S. elections.
Ever since Obama campaigned for office, an increase of young voters have come out of the woodwork. Things have not improved. They've actively told you that "your vote matters." I believe this to be a lie unless any citizen can demand at the gate, at the White House to be allowed to hold and point a gun to the president's head. (Relax, this is a hyperbole)
Why so dramatic? Well, what does the president do? Sign bills, commands the military, nominates new Fed chairman, ambassadors, supreme judges and senior officials all while traveling in luxury planes and living in a white palace for four years.
They promised Every TIME to protect citizen rights when they take the oath and office.
...They've broken this several times, with so-called "emergency-crisis"
The purpose of a president, today, it seems is to basically hire armed thugs to keep the citizens in check and make sure you "voluntarily continue to be a slave," to the system, hence the IRS. The corruption extends from the cop to the judge and even to politicians. The politicians get paid from lobbyists to create bills in congress for the president to sign. There's no right answer when money is involved with politicians. It is the same if you vote Obama, Biden, Trump, or Haley. They will wield the pen to serve themselves to say it will benefit the country.
In the first 100 years of presidency, the government wasn't even a big deal. They didn't even interfere with your life as much as they do today.
^^ You hold the power in your hands, don't let them take it. Don't believe me? Try to get a loan from a bank without a signature. Your signature is as good as gold (if not better) and is an original trademark.
Just Don't Vote. End the Fed. Opt out.
^^ I choose to form my own path, even if it means leaving everything I knew prior. It doesn't have to be a spiritual thing. Some, have called me religious because of this. We're all capable of greatness and having humanity.
✨Don't have a machine heart with a machine mind. Instead, choose to have a heart like the cowardly lion from the "Wizard Of Oz."
There's no such thing as a good president or politicians.
If there was, they would have issued non-interest Federal Reserve Notes. Lincoln and Kennedy tried to do this, they got shot.
There's still a banner of America there, but it's so far gone that I cannot even recognize it. However, I only see a bunch of 🏳🌈 pride flags.
✨Patrick Henry got it wrong, when he delivered his speech, "Give me liberty or give me death." Liberty and freedom are two completely different things.
Straightforward from Merriam-Webster Choose Right or left?
No control, to be 100% without restrictions- free.
✨I disagree with the example sentence given. Because you cannot advocate for human freedom and own slaves, it's contradicting it. Which was common in the founding days.
I can understand many may disagree with me, and you might be thinking, "This time will be different." I, respectfully, disagree, and the proxy wars are proof. Learn the importance of Bitcoin, every Satoshi is a step away from corruption.
✨What does it look like to pull the curtains from the "Wizard of Oz?"
Have you watched the video below, what 30 Trillion dollars in debt looks like visually? Even I was blown away. https://video.nostr.build/d58c5e1afba6d7a905a39407f5e695a4eb4a88ae692817a36ecfa6ca1b62ea15.mp4
I say this with love. Hear my plea?
Normally, I don't write about anything political. It just feels like a losing game. My energy feels it's in better use to learn new things, write and to create. Even a simple blog post as simple as this. Stack SATs, and stay humble.
<3 Onigirl
-
 @ 3bf0c63f:aefa459d
2024-05-21 12:38:08
@ 3bf0c63f:aefa459d
2024-05-21 12:38:08Bitcoin transactions explained
A transaction is a piece of data that takes inputs and produces outputs. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered.
Imagine you have 10 satoshis. That means you have them in an unspent transaction output (UTXO). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a script that unlocks that transaction and related signatures, then you specify outputs along with a script that locks these outputs.

As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them.
For most of the cases locking and unlocking means specifying a public key whose controller (the person who has the corresponding private key) will be able to spend. Other fancy things are possible too, but we can ignore them for now.
Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.

If you're still interested in transactions maybe you could take a look at this small chapter of that Andreas Antonopoulos book.
If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: https://en.bitcoin.it/wiki/Coin_analogy
-
 @ 3c984938:2ec11289
2024-05-09 04:43:15
@ 3c984938:2ec11289
2024-05-09 04:43:15
It's been a journey from the Publishing Forest of Nostr to the open sea of web3. I've come across a beautiful chain of islands and thought. Why not take a break and explore this place? If I'm searching for devs and FOSS, I should search every nook and cranny inside the realm of Nostr. It is quite vast for little old me. I'm just a little hamster and I don't speak in code or binary numbers zeros and ones.

After being in sea for awhile, my heart raced for excitement for what I could find. It seems I wasn't alone, there were others here like me! Let's help spread the message to others about this uncharted realm. See, look at the other sailboats, aren't they pretty? Thanks to some generous donation of SATs, I was able to afford the docking fee.

Ever feel like everyone was going to a party, and you were supposed to dress up, but you missed the memo? Or a comic-con? well, I felt completely underdressed and that's an understatement. Well, turns out there is a some knights around here. Take a peek!

A black cat with a knight passed by very quickly. He was moving too fast for me to track. Where was he going? Then I spotted a group of knights heading in the same direction, so I tagged along. The vibes from these guys was impossible to resist. They were just happy-go-lucky. 🥰They were heading to a tavern on a cliff off the island.

Ehh? a Tavern? Slightly confused, whatever could these knights be doing here? I guess when they're done with their rounds they would here to blow off steam. Things are looking curiouser and curiouser. But the black cat from earlier was here with its rider, whom was dismounting. So you can only guess, where I'm going.

The atmosphere in this pub, was lively and energetic. So many knights spoke among themselves. A group here, another there, but there was one that caught my eye. I went up to a group at a table, whose height towed well above me even when seated. Taking a deep breath, I asked, "Who manages this place?" They unanimous pointed to one waiting for ale at the bar. What was he doing? Watching others talk? How peculiar.

So I went up to him! And introduced myself.
"Hello I'm Onigirl"
"Hello Onigirl, Welcome to Gossip"
"Gossip, what is Gossip?" scratching my head and whiskers.
What is Gossip? Gossip is FOSS and a great client for privacy-centric minded nostriches. It avoids browser tech which by-passes several scripting languages such as JavaScript☕, HTML parsing, rendering, and CSS(Except HTTP GET and Websockets). Using OpenGL-style rendering. For Nostriches that wish to remain anonymous can use Gossip over TOR. Mike recommends using QubesOS, Whonix and or Tails. [FYI-Gossip does not natively support tor SOCKS5 proxy] Most helpful to spill the beans if you're a journalist.

On top of using your nsec or your encryption key, Gossip adds another layer of security over your account with a password login. There's nothing wrong with using the browser extensions (such as nos2x or Flamingo) which makes it super easy to log in to Nostr enable websites, apps, but it does expose you to browser vulnerabilities.
Mike Points out
"people have already had their private key stolen from other nostr clients,"
so it a concern if you value your account. I most certainly care for mine.

Gossip UI has a simple, and clean interface revolving around NIP-65 also called the “Outbox model." As posted from GitHub,
"This NIP allows Clients to connect directly with the most up-to-date relay set from each individual user, eliminating the need of broadcasting events to popular relays."
This eliminates clients that track only a specific set of relays which can congest those relays when you publish your note. Also this can be censored, by using Gossip you can publish notes to alternative relays that have not censored you to reach the same followers.
👉The easiest way to translate that is reducing redundancy to publish to popular relays or centralized relays for content reach to your followers.

Cool! What an awesome client, I mean Tavern! What else does this knight do? He reaches for something in his pocket. what is it? A Pocket is a database for storing and retrieving nostr events but mike's written it in Rust with a few extra kinks inspired by Will's nostrdb. Still in development, but it'll be another tool for you dear user! 💖💕💚
Onigirl is proud to present this knights to the community and honor them with kisu. 💋💋💋 Show some 💖💘💓🧡💙💚
👉💋💋Will - jb55 Lord of apples 💋 @npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s
👉💋💋 Mike Knight - Lord of Security 💋 @npub1acg6thl5psv62405rljzkj8spesceyfz2c32udakc2ak0dmvfeyse9p35c

Knights spend a lot of time behind the screen coding for the better of humanity. It is a tough job! Let's appreciate these knights, relay operators, that support this amazing realm of Nostr! FOSS for all!

This article was prompted for the need for privacy and security of your data. They're different, not to be confused.
Recently, Edward Snowden warns Bitcoin devs about the need for privacy, Quote:
“I've been warning Bitcoin developers for ten years that privacy needs to be provided for at the protocol level. This is the final warning. The clock is ticking.”
Snowden’s comments come after heavy actions of enforcement from Samarai Wallet, Roger Ver, Binance’s CZ, and now the closure of Wasabi Wallet. Additionally, according to CryptoBriefing, Trezor is ending it’s CoinJoin integration as well. Many are concerned over the new definition of a money transmitter, which includes even those who don’t touch the funds.
Help your favorite the hamster
 ^^Me drowning in notes on your feed. I can only eat so many notes to find you.
^^Me drowning in notes on your feed. I can only eat so many notes to find you. 👉If there are any XMPP fans on here. I'm open to the idea of opening a public channel, so you could follow me on that as a forum-like style. My server of choice would likely be a German server.😀You would be receiving my articles as njump.me style or website-like. GrapeneOS users, you can download Cheogram app from the F-Driod store for free to access. Apple and Andriod users are subjected to pay to download this app, an alternative is ntalk or conversations. If it interests the community, just FYI. Please comment or DM.
👉If you enjoyed this content, please consider reposting/sharing as my content is easily drowned by notes on your feed. You could also join my community under Children_Zone where I post my content.
An alternative is by following #onigirl Just FYI this feature is currently a little buggy.
Follow as I search for tools and awesome devs to help you dear user live a decentralized life as I explore the realm of Nostr.
Thank you Fren
-
 @ 1739d937:3e3136ef
2024-07-12 10:11:42
@ 1739d937:3e3136ef
2024-07-12 10:11:42This is the third in a series of weekly updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
Short update post this week but I made solid progress updating several OpenMLS dependencies and building a new library that implements all the OpenMLS crypto requirements for Nostr.
HPKE-RS
I mentioned a PR last week on the
rust-hpkelibrary, that PR is still waiting on review. However, in the meantime, the OpenMLS library depends on a slightly different hpke library, thehpke-rslibrary.This library didn't support the secp256k1 curve either so I've opened a PR to add support for secp256k1. That PR uses the
RustCryptolibrary that is the default in the thehpke-rslibrary. However, because this library is built to allow for swapping out the underlying crypto library (using traits), I was also able to create a new library that uses thesecp256k1library instead of theRustCryptolibrary. This is the main crypto library that almost all Bitcoin and Nostr apps use so it's important we use that instead ofRustCrypto.OpenMLS Nostr Crypto
The library that I've created (openmls-nostr-crypto) does a few things via separate sub-libraries (crates). The entire library tries to do as little as possible; only implementing the one required ciphersuite for all MLS implementations and the
secp256k1schnorr signatures ciphersuite I've created for Nostr. It's also using the rightsecp256k1library to do it.openmls-nostr-crypto: implementes the crypto traits that the OpenMLS library expects to find for a given provider and removes all the ciphersuites that we don't care about supporting.
hpke-rs-nostr-crypto: This implements the crypto traits that the hpke-rs library expects to find. Again removing all the ciphersuites we don't care about supporting.
I've not yet written any tests for these libraries (which needs to be done) but I've gotten some very simple demos working with OpenMLS using this new set of libraries to handle the crypto.
I've been really impressed with the simplicity of the OpenMLS interface as well. While there is A LOT going on under the hood, the public interface that client developers have to use is clean and simple.
Onward and Upward
Next week I'll continue working on these libraries; adding tests and continuing to build out my small demo app. I've been in touch with the maintainers of the OpenMLS library and I'm hoping to get a review done with them on my PRs and on my new library.
One thing I'll call out here: The review of my library and getting them to review the direction of the project overall will be paid consulting so I'm making sure that I've got as much done as possible before scheduling that time and paying their rates. I'm a strong believer that the right conversation can save you months of wasted time, but I'm also a believer in making sure you're prepared if you're going to drop money on that conversation. 😅
-
 @ 9c1636e1:79809ee5
2024-08-02 05:25:47
@ 9c1636e1:79809ee5
2024-08-02 05:25:47TL;DR: NostrDice is a provably fair game built on Nostr and Lightning.
Why build NostrDice
Nostr has been around for a while now, but we’ve only used it as a social network. We had not had a chance to look under the hood to see how things work and what you can do with it.
We wanted to get our hands dirty. But we didn’t just want to follow some tutorials; we wanted to build something fun and see how far Nostr could take us.
After some brainstorming, we landed on the legendary game SatoshiDICE. Why not bring the OG of all Bitcoin games to Lightning using Nostr?
We are going to build our own SatoshiDICE, with blackjack and hookers
NostrDice is SathoshiDICE on steroids. I mean, it’s built with Nostr and Lightning.
Design Goals of NostrDice
Before we jump into it, these are our design goals for the game.
- Provably fair. The NostrDice server must not be able to control the outcome of a die roll. Players must be able to verify that the NostrDice server is not cheating.
- Easy to use. The game should be compatible with any Nostr client (which supports Zaps). No new clients should be required to play the game.
- Have fun building it! This was the main goal if we’re honest :D
Looking into how Zaps work we quickly figure out a way to use them to place bets and pay out lucky winners.
How NostrDice Works
We set up 3 accounts on Nostr:
- NostrDice Game: This is where you play. Zap your chosen multiplier note, roll the die and win some sats, sometimes. https://primal.net/p/npub1nstrdc6z4y9xadyj4z2zfecu6zt05uvlmd08ea0vchcvfrjvv7yq8lns84
- NostrDice Nonces: Here you can find proof that the server is playing fair with your dice rolls. https://primal.net/p/npub1nstrdc23h57te608p6rx90lhay86ny5lpm9jpnxquzv9fnvmpfhqnpzcwp
-
NostrDice Social: A place for us to promote the game. Follow us to get the latest updates. https://primal.net/p/npub1nstrdc28zag3wcwwsc5t725t03h3hg9ard4vg425m4dvv7vqnmjsn076qj
-
Commitment to a Secret Nonce
A new round starts when the NostrDice server posts a commitment to a nonce on NostrDice Nonces. The server does this before receiving any information from the player, so it can choose the nonce based on the player’s input.
-
Placing a Bet
The player chooses their multiplier and wager by zapping one of 11 notes on NostrDice Game. The multiplier also determines the target the die roll needs to hit. For example, to win a 2x multiplier, the player must roll a number lower than 31784 (out of 65535 possibilities).
-
Determining the Outcome
The server calculates the player’s die roll based on the secret nonce, the player’s npub and the zap memo. Player’s are encouraged to use the zap memo to make it impossible for the server to anticipate their input to the die roll.
-
Immediate Payouts
If the player hits the target, the NostrDice server will pay out instantly. The server zaps the player’s npub to credit them with their winnings. To this end, the player must have a valid LNURL configured if they want to get paid!
-
House Edge
The server retains a small house edge on every bet. For a specific target, the payout is slightly less than the true odds to account for this edge.
NostrDice as a Provably Fair Game
The key to NostrDice being fair is that the outcome of a die roll is random and verifiable. For an in-depth explanation on this, check out the rules of the game in our repository. But here is a summary of the main ideas.
Commitment Scheme
NostrDice commits to a nonce before the round starts by hashing it and publishing the hash on Nostr for everyone to see:
nonce := gen_32_bytes() commitment := sha256(nonce)Roll Formula
When the player places their bet, the nonce is combined with the player's npub and zap memo to generate the die roll:
roll = bytes_to_decimal(first_2_bytes(sha256(nonce | player_npub | zap_memo | index)))To prevent the server from predicting outcomes based on the player's npub, the player submits their own randomness via the zap memo.
Additionally, a roll index is included to allow the player to roll more than once with the same nonce.
Verification
The player can independently compute their roll after the nonce is revealed. They can also verify that the revealed nonce matches the original commitment:
original_commitment == sha256(revealed_nonce)Lessons learned
Building NostrDice was very fun and not that hard! It’s easy to see why the Nostr ecosystem is flourishing: the Nostr protocol is super simple.
- Dev environment: Building a Nostr client is super straight forward. There are plenty of libraries available, but we went with the rust-nostr stack. However, setting up a dev environment was not so easy. We ended up with an involved
docker-composefile and ajustfile to spin up a dev environment consisting of:bitcoind.- Two
lndnodes: one for the player and one for the server. - A Nostr relay via
nostr-rs-relay. nostr-wallet-connect-lndso that the player can zap a multiplier note with their LND node.- An LNURL pay server for the player to receive payouts.
nostrdice: the game server itself, acting as a modified LNURL server.
- Note limits: Our nonce account needs to publish notes regularly and we quickly ran into the limits of publicly available relays: we got banned. Because of this we decided to post less and run our own relay which again, was super simple. Since Rust is our first language, we decided to go with https://github.com/scsibug/nostr-rs-relay.
- Production testing: This is the biggest hurdle we encountered. While for “normal” social media usage clients like Primal, Snort or Damus work well, when wanting to jump between different accounts, we quickly ran into UX issues. The setup which worked best for us was using the Alby browser extension with different profiles. I believe things can be improved here. For example, a browser extension supporting multiple Nostr profiles, where profiles are locked to one tab/website only. This way we can be logged into multiple accounts on different profiles at the same time. We also ended up using noStrudel as our favorite browser-based client.
- No signet support on web clients. Zaps are always assumed to be on mainnet.
Overall it was great fun to build on Nostr for the first time, and we learned a lot. I hope you also enjoy this nostalgic tribute to SatoshiDICE on Nostr.
cheers,
the 10101 team
Links
- NostrDice Social: An account only used for social posts, follow along to stay up-to-date on any announcements. https://primal.net/p/npub1nstrdc28zag3wcwwsc5t725t03h3hg9ard4vg425m4dvv7vqnmjsn076qj.
- NostrDice Game: The main game account. Where the static multiplier notes are hosted. https://primal.net/p/npub1nstrdc6z4y9xadyj4z2zfecu6zt05uvlmd08ea0vchcvfrjvv7yq8lns84.
- NostrDice Nonces: This account publishes nonce commitments and reveals nonces at a regular interval. https://primal.net/p/npub1nstrdc23h57te608p6rx90lhay86ny5lpm9jpnxquzv9fnvmpfhqnpzcwp.
- NostrDice on X: x.com/nostrdice
- NostrDice source code: https://github.com/nostrdice/nostrdice/.
- NostrDice relay: wss://relay.nostrdice.com.
- benthecarman: we just can’t help ourselves, but we noticed that a lot of the libraries we used were either built by or contributed to by Ben. Among others, we used and built on:
- https://github.com/benthecarman/lnurl-rs: An LNURL pay server.
- https://github.com/benthecarman/nostr-wallet-connect-lnd: A NWC server to control LND.
originally posted at https://stacker.news/items/631870
-
 @ 3c984938:2ec11289
2024-04-16 17:14:58
@ 3c984938:2ec11289
2024-04-16 17:14:58Hello (N)osytrs!
Yes! I'm calling you an (N)oystr!
Why is that? Because you shine, and I'm not just saying that to get more SATs. Ordinary Oysters and mussels can produce these beauties! Nothing seriously unique about them, however, with a little time and love each oyster is capable of creating something truly beautiful. I like believing so, at least, given the fact that you're even reading this article; makes you an (N)oystr! This isn't published this on X (formerly known as Twitter), Facebook, Discord, Telegram, or Instagram, which makes you the rare breed! A pearl indeed! I do have access to those platforms, but why create content on a terrible platform knowing I too could be shut down! Unfortunately, many people still use these platforms. This forces individuals to give up their privacy every day. Meta is leading the charge by forcing users to provide a photo ID for verification in order to use their crappy, obsolete site. If that was not bad enough, imagine if you're having a type of disagreement or opinion. Then, Bigtech can easily deplatform you. Umm. So no open debate? Just instantly shut-off users. Whatever, happened to right to a fair trial? Nope, just burning you at the stake as if you're a witch or warlock!

How heinous are the perpetrators and financiers of this? Well, that's opening another can of worms for you.
Imagine your voice being taken away, like the little mermaid. Ariel was lucky to have a prince, but the majority of us? The likelihood that I would be carried away by the current of the sea during a sunset with a prince on a sailboat is zero. And I live on an island, so I'm just missing the prince, sailboat(though I know where I could go to steal one), and red hair. Oh my gosh, now I feel sad.
I do not have the prince, Bob is better! I do not have mermaid fins, or a shell bra. Use coconut shells, it offers more support! But, I still have my voice and a killer sunset to die for!
All of that is possible thanks to the work of developers. These knights fight for Freedom Tech by utilizing FOSS, which help provides us with a vibrant ecosystem. Unfortunately, I recently learned that they are not all funded. Knights must eat, drink, and have a work space. This space is where they spend most of their sweat equity on an app or software that may and may not pan out. That brilliance is susceptible to fading, as these individuals are not seen but rather stay behind closed doors. What's worse, if these developers lose faith in their project and decide to join forces with Meta! 😖 Does WhatsApp ring a bell?
Without them, I probably wouldn't be able to create this long form article. Let's cheer them on like cheerleaders.. 👉Unfortunately, there's no cheerleader emoji so you'll just have to settle for a dancing lady, n guy. 💃🕺
Semisol said it beautifully, npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
If we want freedom tech to succeed, the tools that make it possible need to be funded: relays like https://nostr.land, media hosts like https://nostr.build, clients like https://damus.io, etc.
With that thought, Onigirl is pleased to announce the launch of a new series. With a sole focus on free market devs/projects.
Knights of Nostr!
I'll happily brief you about their exciting project and how it benefits humanity! Let's Support these Magnificent projects, devs, relays, and builders! Our first runner up!
Oppa Fishcake :Lord of Media Hosting
npub137c5pd8gmhhe0njtsgwjgunc5xjr2vmzvglkgqs5sjeh972gqqxqjak37w
Oppa Fishcake with his noble steed!
Think of this as an introduction to learn and further your experience on Nostr! New developments and applications are constantly happening on Nostr. It's enough to make one's head spin. I may also cover FOSS projects(outside of Nostr) as they need some love as well! Plus, you can think of it as another tool to add to your decentralized life. I will not be doing how-to-Nostr guides. I personally feel there are plenty of great guides already available! Which I'm happy to add to curation collection via easily searchable on Yakihonne.
For email updates you can subscribe to my [[https://paragraph.xyz/@onigirl]]
If you like it, send me some 🧡💛💚 hearts💜💗💖 otherwise zap dat⚡⚡🍑🍑peach⚡⚡🍑 ~If not me, then at least to our dearest knight!
Thank you from the bottom of my heart for your time and support (N)oystr! Shine bright like a diamond! Share if you care! FOSS power!
Follow on your favorite Nostr Client for the best viewing experience!
[!NOTE]
I'm using Obsidian + Nostr Writer Plugin; a new way to publish Markdown directly to Nostr. I was a little nervous using this because I was used doing them in RStudio; R Markdown.
Since this is my first article, I sent it to my account as a draft to test it. It's pretty neat. -
 @ f7d424b5:618c51e8
2024-08-03 22:57:08
@ f7d424b5:618c51e8
2024-08-03 22:57:08(This Nostr article is a repost from our podcast shownotes website melonmancy.net
Put your satoshis where your mouth is! Nobody is coming to save you.
50% of the Sats received by this episode will be sent to nostr:npub18n4ysp43ux5c98fs6h9c57qpr4p8r3j8f6e32v0vj8egzy878aqqyzzk9r who is creating DEG Mods! DEG Mods is on Geyser Fund, click here to see the page and give your support!
Welcome to Melonmancy Podcast Episode 92! Keeping a light agenda today talking about the Second Wind drama, Bungie layoffs, our own backlogs, and more!
- Listen to the new episode here!
- Discuss this episode on OUR NEW FORUM
- Get the RSS and Subscribe (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at newpodcastapps.com
- Or listen to the show on the forum using the embedded Podverse player!
- Send your complaints here
Reminder that this is a Value4Value podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!
Our podcast is created entirely with free software and is proudly hosted on RSSBlue!
-
 @ 0176967e:1e6f471e
2024-07-21 11:28:18
@ 0176967e:1e6f471e
2024-07-21 11:28:18Čo nám prinášajú exotické protokoly ako Nostr, Cashu alebo Reticulum? Šifrovanie, podpisovanie, peer to peer komunikáciu, nové spôsoby šírenia a odmeňovania obsahu.
Ukážeme si kúl appky, ako sa dajú jednotlivé siete prepájať a ako spolu súvisia.
-
 @ c73818cc:ccd5c890
2024-08-03 14:11:15
@ c73818cc:ccd5c890
2024-08-03 14:11:15
💰 Introduzione:
💰 Il recente evento post-Nashville ha offerto una prospettiva dettagliata su Bitcoin, analizzando gli sviluppi positivi, negativi e le aspettative rialziste. Questo riepilogo è frutto di discussioni con investitori TradFi, crypto, fondatori di Bitcoin, analisti e dirigenti del mining.
💸 MACRO: Attraversare il Rubicone
💰 Donald J. Trump e la riserva strategica di Bitcoin:
💰 Annuncio epocale: Trump ha annunciato la creazione di una riserva strategica di Bitcoin, rappresentando circa l'1% della fornitura totale di BTC.
💰 Implicazioni globali: Questo annuncio ha segnato un punto di non ritorno per Bitcoin, spingendo le nazioni a considerare seriamente l'accumulo di BTC.
💰 Sfida per altre nazioni: Altre nazioni dovranno affrontare enormi difficoltà per accumulare BTC senza pagare un prezzo elevato, rendendo il mining di Bitcoin una questione di sicurezza nazionale.
💰 Michael Saylor: Ha presentato un piano per l'adozione di Bitcoin come asset di tesoreria di fronte a oltre 10 senatori.
💸 Le istituzioni sono qui:
💰 Teoria dei giochi: Se gli stati nazionali stanno accumulando Bitcoin, le aziende devono fare lo stesso per rimanere competitive.
💰 Accumulazione: L'accumulo di BTC da parte degli stati garantisce un aumento del prezzo a lungo termine, rendendo necessaria una strategia simile per le aziende.
💸 Il retail è ancora assente:
💰 Volume retail: Il flusso retail per le transazioni inferiori a $10K è al minimo degli ultimi 3 anni, nonostante BTC sia vicino ai suoi massimi storici.
💰 Sentimento di attesa: Gli acquirenti al dettaglio sembrano attendere il prossimo catalizzatore per investire ulteriormente in BTC.
💰 UTXO Alpha Day - Il primo di molti per i capitalisti di rischio
💸 Supporto ai migliori:
💰 Evento di successo: UTXO Management ha ospitato il primo UTXO Alpha Day, riunendo centinaia di allocatori di capitale e imprenditori.
💰 Obiettivo: Esplorare asset con rendimento in Bitcoin e l'emergere di BTC come asset di tesoreria definitivo.
💸 Conoscenza limitata su Bitcoin:
💰 Report Galaxy: Sebbene gli investimenti in criptovalute siano aumentati del 28% nel Q2 2024, solo il 3,1% è stato destinato a Bitcoin.
💰 Opportunità asimmetrica: La conoscenza tecnica di Bitcoin è limitata, ma l'opportunità rappresentata da Bitcoin DeFi/Infrastructure è in crescita.
💸 Abbiamo l'Alpha:
💰 Henry Elder: Ha illustrato come gli investitori dovrebbero distribuire capitale Bitcoin on-chain, suddividendo BTCfi in sidechain, catene di Layer-2 e metaprotocolli.
💰 Vantaggi delle sidechain: Sono più sviluppate grazie all'infrastruttura di auditing della sicurezza di Ethereum.
💰 BITCOIN L2: I ragazzi più cool del quartiere?
💸 Focus sugli L2:
💰 Annunci importanti: BitcoinOS (Grail) e BitVMX hanno fatto annunci significativi sui loro protocolli rollup.
💰 Competizione: Con oltre 80 progetti L2, la competizione è intensa e solo i progetti più innovativi sopravviveranno.
💸 Ricerca tecnica sui Rollup:
💰 Esplorazione avanzata: I team di Alpen, Bitlayer e Citrea sono in prima linea nella ricerca tecnica, esplorando le frontiere dello script Bitcoin e delle Zero-Knowledge Proof.
💸 Lightning Network:
💰 Futuro di Lightning: Sebbene trascurato durante la conferenza, Lightning Labs ha annunciato Taproot Assets su Lightning, promettendo scambi rapidissimi e senza fiducia nativamente su Bitcoin.
💰 Mining: Si tratta ancora di mining?
💸 Allocazione del capitale:
💰 Intelligenza artificiale: I miners stanno investendo in intelligenza artificiale e HPC per mantenere margini interessanti post-halving.
💸 Mercificazione del Blockspace:
💰 Nuovi strumenti: Alkymia ha lanciato una piattaforma per scommettere sulle commissioni di transazione Bitcoin, offrendo ai miners strumenti per stabilizzare i ricavi.
💸 Discorso di Matt Corallo:
💰 Governance di Bitcoin: Corallo ha sottolineato l'importanza della governance degli utenti nel decidere i cambiamenti al codice di Bitcoin.
💸 Conclusione:
💰 Il riassunto dell'evento post-Nashville evidenzia come Bitcoin stia attraversando un periodo di trasformazione significativa, con importanti sviluppi nei settori della riserva strategica, degli investimenti istituzionali e delle innovazioni tecnologiche.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
Referral Bitget -10% sulle fee + bonus benvenuto 6w5d o link: https://bonus.bitget.com/U1JNEK
BitcoinReportItalia #Nashville #Trump #Mining #MichaelSaylor #Saylor #Retail #UTXO #Galaxy #DeFi #Sidechain #BitcoinOS #BitVMX #Taproot #IntelligenzaArtificiale #LightningNetwork #MattCorallo #Corallo #Cripto #Bitcoin
-
 @ 1739d937:3e3136ef
2024-07-06 09:22:17
@ 1739d937:3e3136ef
2024-07-06 09:22:17This is the second in a series of weekly updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
This week was mostly spent on the topic of how to properly publish prekey bundles and what would be needed in the bundle itself to make it workable. I've included an early version of the spec below for prekeys, and would love thoughts on it. Treat this as an alpha version, very subject to change.
The other thing I spent time on was making changes to the OpenMLS library to add support for our custom ciphersuite. One issue that I've run into is that the IETF standard for HPKE doesn't include the secp256k1 curve. Because of this, the library being used in the OpenMLS library doesn't implement the necessary methods using our curve. Thankfully, there is another library with an open PR (shout out to nostr:npub1yevrvtp3xl42sq06usztudhleq8pdfsugw5frgaqg6lvfdewfx9q6zqrkl for that!) that would fix this. Additionally, there's an expired proposal to add secp256k1 to the HPKE spec itself. I've bumped both of these and will continue to follow up. Even without the formal addition to the spec, if we have a working library, I can add that to the OpenMLS library.
Spec Draft for Prekeys
Initial keying material (Prekey Event)
Each user that wishes to be reachable via MLS-based messaging MUST first publish a prekey event. Prekeys are used to authenticate and add members to groups (one-to-one DMs or groups with more than two participants) in an asynchronous way. The prekey event is a simple replaceable event and contains all the information needed to add a user to a group.
Prekeys SHOULD be used only once. Resuse of prekeys can lead to replay attacks.
In most cases, clients that implement this NIP will manage the creation and rotation of the prekey event. It's recommended that clients do so interactively with user consent in order to avoid overwriting prekeys created by other clients.
Derived vs Ephemeral Prekeys
Since prekeys are generated on a single device/client pair, the private key of the prekey must be either stored or generated in a way that can be deterministically recovered.
The recommended approach is to use derived keys, generated in the manner described in NIP-06. In this way, the user can respond to a new group request from any device/client pair, not just from the same device/client pair that created the initial prekey event. If using derived keys;
- Clients MUST use
104as theaccountlevel value and0at thechangelevel value (e.g.m/44'/1237'/104'/0/0). - Keys are then generated using public derivation by incrementing the
address_indexlevel value. - Clients MUST include the full derivation path corresponding to the key used in the
contentfield on the prekey event. - The
contentfield MUST be encrypted using standard NIP-44 encryption (encrypted to themselves).
However, for added security (and consequently a more restrictive user experience), clients can chose to generate an ephemeral key and store the private key locally. This means that users will only be able to respond to new group requests from the same device/client pair and won't be able to respond at all if the prekey's private key is lost. Ephemeral keys can also be used with minimal degredation of UX if you're using a remote signer that can manage these keys.
If using an ephemeral key;
- The
contentfield on the prekey event MUST be filled in withEPHEMERALand then encrypted using standard NIP-44 encryption (encrypted to themselves). This ensures that anyone looking at prekey events cannot tell whether it's a derived or an ephemeral prekey.
Example Prekey Event
json { "id": <id>, "kind": 10443, "created_at": <unix timestamp in seconds>, "pubkey": <main identity pubkey>, "content": <encrypted derivation path | EPHEMERAL>, "tags": [ ["mls_protocol_version", "1.0"], ["ciphersuite", "MLS_256_DHKEMK256_CHACHA20POLY1305_SHA256_K256"], ["pubkey", <prekey pubkey>], ["prekey_sig", <signature generated from hex encoded pubkey of the prekey>], ["r", "wss://nos.lol"], ["r", "wss://relay.primal.net"] ], "sig": <signed with main identity key> }Tags
- The
mls_protocol_versiontag identifies the MLS protocol version being used. For now, this MUST be1.0 - The
ciphersuitetag identifies the ciphersuite supported. For now on Nostr, we're using a custom ciphersuite,MLS_256_DHKEMK256_CHACHA20POLY1305_SHA256_K256. Read more about ciphersuites in MLS. pubkeyis the derived or ephemeral prekey pubkey.- The
prekey_sigtag value is a Schnorr signature (over the secp256k1 curve) of the SHA-256 hashed value of the prekey's pubkey, signed with the prekey's private key.
```js const privKey = schnorr.utils.randomPrivateKey(); const pubKey = schnorr.getPublicKey(privKey);
const prekeySig = bytesToHex( schnorr.sign(bytesToHex(sha256(pubKey)), privKey) );
const prekeyTag = ["prekey_sig", prekeySig]; ```
Finally, clients SHOULD include
rtags to identify each of the relays that they will attempt to publish this prekey event to. This allows for more complete replacement of prekey events at a later date.Replacing Prekey Events
Clients MUST replace the prekey event on all the listed relays any time they successfully process a group welcome event. If the prekey was a derived prekey, clients SHOULD increment the derivation path by 1 for the next key.
Onward and Upward
This next week I'll continue to work on getting the right curves and code added to the OpenMLS library and start work on a simple demo app. The focus is on better understanding what we need from the control and message events and how we can make those as simple as possible for Nostr clients and relays while also preserving as much privacy as possible.
- Clients MUST use
-
 @ 1c0467df:d06e2b48
2024-08-01 22:06:52
@ 1c0467df:d06e2b48
2024-08-01 22:06:52I have released BTC service library. It includes many LUDS and NIPS. It enables multi user, multi domain LUD-16 Lightning addresses. With it, anyone can get you@domain.com Lightning and Nostr addresses, enabling easy Bitcoin receipts and Zaps. Check it out at https://github.com/matjaz/btc-service Feedback is welcome.
originally posted at https://stacker.news/items/631601
-
 @ 0176967e:1e6f471e
2024-07-21 11:24:21
@ 0176967e:1e6f471e
2024-07-21 11:24:21Podnikanie je jazyk s "crystal clear" pravidlami. Inštrumentalisti vidia podnikanie staticky, a toto videnie prenášajú na spoločnosť. Preto nás spoločnosť vníma často negatívne. Skutoční podnikatelia sú však "komunikátori".
Jozef Martiniak je zakladateľ AUSEKON - Institute of Austrian School of Economics
-
 @ 6871d8df:4a9396c1
2024-02-24 22:42:16
@ 6871d8df:4a9396c1
2024-02-24 22:42:16In an era where data seems to be as valuable as currency, the prevailing trend in AI starkly contrasts with the concept of personal data ownership. The explosion of AI and the ensuing race have made it easy to overlook where the data is coming from. The current model, dominated by big tech players, involves collecting vast amounts of user data and selling it to AI companies for training LLMs. Reddit recently penned a 60 million dollar deal, Google guards and mines Youtube, and more are going this direction. But is that their data to sell? Yes, it's on their platforms, but without the users to generate it, what would they monetize? To me, this practice raises significant ethical questions, as it assumes that user data is a commodity that companies can exploit at will.
The heart of the issue lies in the ownership of data. Why, in today's digital age, do we not retain ownership of our data? Why can't our data follow us, under our control, to wherever we want to go? These questions echo the broader sentiment that while some in the tech industry — such as the blockchain-first crypto bros — recognize the importance of data ownership, their "blockchain for everything solutions," to me, fall significantly short in execution.
Reddit further complicates this with its current move to IPO, which, on the heels of the large data deal, might reinforce the mistaken belief that user-generated data is a corporate asset. Others, no doubt, will follow suit. This underscores the urgent need for a paradigm shift towards recognizing and respecting user data as personal property.
In my perfect world, the digital landscape would undergo a revolutionary transformation centered around the empowerment and sovereignty of individual data ownership. Platforms like Twitter, Reddit, Yelp, YouTube, and Stack Overflow, integral to our digital lives, would operate on a fundamentally different premise: user-owned data.
In this envisioned future, data ownership would not just be a concept but a practice, with public and private keys ensuring the authenticity and privacy of individual identities. This model would eliminate the private data silos that currently dominate, where companies profit from selling user data without consent. Instead, data would traverse a decentralized protocol akin to the internet, prioritizing user control and transparency.
The cornerstone of this world would be a meritocratic digital ecosystem. Success for companies would hinge on their ability to leverage user-owned data to deliver unparalleled value rather than their capacity to gatekeep and monetize information. If a company breaks my trust, I can move to a competitor, and my data, connections, and followers will come with me. This shift would herald an era where consent, privacy, and utility define the digital experience, ensuring that the benefits of technology are equitably distributed and aligned with the users' interests and rights.
The conversation needs to shift fundamentally. We must challenge this trajectory and advocate for a future where data ownership and privacy are not just ideals but realities. If we continue on our current path without prioritizing individual data rights, the future of digital privacy and autonomy is bleak. Big tech's dominance allows them to treat user data as a commodity, potentially selling and exploiting it without consent. This imbalance has already led to users being cut off from their digital identities and connections when platforms terminate accounts, underscoring the need for a digital ecosystem that empowers user control over data. Without changing direction, we risk a future where our content — and our freedoms by consequence — are controlled by a few powerful entities, threatening our rights and the democratic essence of the digital realm. We must advocate for a shift towards data ownership by individuals to preserve our digital freedoms and democracy.
-
 @ e56b400c:175edce9
2024-08-03 12:41:23
@ e56b400c:175edce9
2024-08-03 12:41:23We'll be meeting on August 21st, 7pm at the Admiral Benbow pub in Shrewsbury. If the weather's good, we'll be in the beer garden, otherwise, we'll grab a table indoors. It's a social meetup again but we have a good group of knowledgable bitcoiners who'll shoot the breeze and solve all world problems.
The Admiral Benbow is a great location, we held the June meetup there and were impressed with the venue.
If you've not been to a meetup before or haven't been in a while, please do come and join us. Message us on Nostr at npub1u445qrpas8y58szt2unzu7wsvgsfg0llgf7y6sjz7pn76967mn5snh6mul, Xitter at https://x.com/ShropsBitcoin or email bc@omg.lol if you have any questions.
We have a Telegram group that everyone who attends a meetup can join. Sadly we had to close the public group due to Telegram spam bots.
See you soon :)
The Admiral Benbow is at 24 Swan Hill, Shrewsbury SY1 1NF.
-
 @ 0176967e:1e6f471e
2024-07-21 11:20:40
@ 0176967e:1e6f471e
2024-07-21 11:20:40Ako sa snažím praktizovať LunarPunk bez budovania opcionality "odchodom" do zahraničia. Nie každý je ochotný alebo schopný meniť "miesto", ako však v takom prípade minimalizovať interakciu so štátom? Nie návod, skôr postrehy z bežného života.
-
 @ 1739d937:3e3136ef
2024-06-28 08:27:59
@ 1739d937:3e3136ef
2024-06-28 08:27:59This is the first in a series of weekly updates I'm publishing on my process around secure messaging. Since it's the first, let's start with a bit of historical context.
How this started
On April 29th I published a PR on the NIPs repo detailing how we could achieve "Double Ratchet" DMs on Nostr. There was also a video and demo app that went along with the PR. The basic premise was to use an adapted version of the Signal protocol. This would result in DMs that were truly private and confidential, even in the case where you leaked your main private key (your nsec).
I got a lot of great feedback from folks on that PR. Interestingly, nearly all of it focused on two points, both of which I'd deliberately scoped out. Group messaging and multi-device/client support. While I knew these were important, and I'd figured out how these might be accomplished, I'd scoped them out to try and keep the footprint of the spec as small as possible But, the more I talked to people, the more it became clear that this was one problem to be solved and given the complexity, it'd be better to do it in one shot.
At the same time, I'd seen that Messaging Layer Security (MLS) had recently made a lot of progress on becoming an internet standard with their RFC proposal and, goaded on by Vitor, decided to take a closer look.
Enter MLS
Messaging Layer Security (MLS) is a new protocal that is basically a modern extension of the Signal protocol that makes group messaging way more efficient (log vs linear) and was built to be used in centralized or federated environments. I'd heard other Nostr devs talk about it in the past but it was always overlooked as being too complicated or too early.
After spending a couple weeks reading hundreds of pages of RFC docs and reading through a few implementations of the MLS spec, I believe it's the best solution for secure direct and group messaging in Nostr. It also has the added benefit that we can upgrade the underlying crypto primitives over time in a sane way.
The MLS protocol specifies "a key establishment protocol that provides efficient asynchronous group key establishment with forward secrecy (FS) and post-compromise security (PCS) for groups in size ranging from two to thousands."
The spec I'm working on will detail the ways that we implement this protocol into the Nostr environment (namely, how do we use our crypto primitives, use events as control mechanisms, and use relays for storage, while obfuscating metadata).
Goals
It's important to be clear about what we're aiming for here. Engineering is all about tradeoffs, always.
- Private and Confidential DMs and Group messages
- Private means that an observer cannot tell that Alice and Bob are talking to one another, or that Alice is part of a specific group. This necessarily requires protecting metadata.
- Confidential means that the contents of conversations can only be viewed by the intended recipients.
- Forward secrecy and Post-compromise security (PCS) in the case of any key material being leaked, whether that's your main Nostr identity key (your nsec) or any of the keys used in the MLS ratchet trees.
- Forward secrecy means that encrypted content in the past remains encrypted even if key material is leaked.
- Post compromise security means that leaking key material doesn't allow an attacker to continue to read messages indefinitely into the future.
- Scales well for large groups. MLS provides this from a computational standpoint, but we need to make sure this works in a scalable way when multiple relays are involved.
- Allows for the use of multiple device/clients in a single conversation/group. Importantly, we're not aiming to enable a device/client to be able to reconstruct the full history of a conversation at any point.
Progress this week
Ok, finally, what what I been up to?
Reading
I've spent most of the last few weeks reading the MLS spec and architectural doc (multiple times), learning some Rust, and beefing up my knowledge of cryptography (which was, if I'm being generous, paltry before starting this project).
Ciphersuites
Nostr is built around the same crypto primitives that Bitcoin is, namely Schnorr signatures over the secp256k1 curve and SHA-256 hashes. This curve isn't currently supported officially in the MLS spec. I've been in touch with the MLS working group to better understand the process of adding a new ciphersuite to the set of ciphersuites in the MLS spec. The outcome here is that we're going to start out using our custom ciphersuite that isn't part of the formal spec. The only drawback being that Nostr's MLS implementation won't be immediately interoperable with other MLS implementations. We can always add it later via the formal channels if we want.
MLS Implementations
Given the complexity of the MLS spec itself (the RFC is 132 pages long), having a well vetted, well tested implementation is going to be key to adoption in the Nostr ecosystem. OpenMLS is an implementation created by several of the RFC authors and written in Rust with bindings for nearly all the major languages we would want to support.
I've been in touch with the maintainers to talk about adding support to their library for our new ciphersuite and to better understand the bindings that are there. Some (WASM) are very barebones and still need a lot of work. They are generally open to the idea of working with me on adding the missing pieces we'd need.
Double Ratchet NIP 2.0
I've also started to write up the new version of the NIP that will detail how all of this will work when plugged into Nostr. It's not yet ready to share but it's getting closer.
Onward & Upward
Hopefully that's a helpful recap. I'll keep doing these weekly and welcome any questions, feedback, or support. In particular, if you're keen on working on this with me, please reach out. More eyes and more brains can only make this better. 🤙
-
 @ 8ce092d8:950c24ad
2024-02-04 23:35:07
@ 8ce092d8:950c24ad
2024-02-04 23:35:07Overview
- Introduction
- Model Types
- Training (Data Collection and Config Settings)
- Probability Viewing: AI Inspector
- Match
- Cheat Sheet
I. Introduction
AI Arena is the first game that combines human and artificial intelligence collaboration.
AI learns your skills through "imitation learning."
Official Resources
- Official Documentation (Must Read): Everything You Need to Know About AI Arena
Watch the 2-minute video in the documentation to quickly understand the basic flow of the game. 2. Official Play-2-Airdrop competition FAQ Site https://aiarena.notion.site/aiarena/Gateway-to-the-Arena-52145e990925499d95f2fadb18a24ab0 3. Official Discord (Must Join): https://discord.gg/aiarenaplaytest for the latest announcements or seeking help. The team will also have a exclusive channel there. 4. Official YouTube: https://www.youtube.com/@aiarena because the game has built-in tutorials, you can choose to watch videos.
What is this game about?
- Although categorized as a platform fighting game, the core is a probability-based strategy game.
- Warriors take actions based on probabilities on the AI Inspector dashboard, competing against opponents.
- The game does not allow direct manual input of probabilities for each area but inputs information through data collection and establishes models by adjusting parameters.
- Data collection emulates fighting games, but training can be completed using a Dummy As long as you can complete the in-game tutorial, you can master the game controls.
II. Model Types
Before training, there are three model types to choose from: Simple Model Type, Original Model Type, and Advanced Model Type.
It is recommended to try the Advanced Model Type after completing at least one complete training with the Simple Model Type and gaining some understanding of the game.

Simple Model Type
The Simple Model is akin to completing a form, and the training session is comparable to filling various sections of that form.
This model has 30 buckets. Each bucket can be seen as telling the warrior what action to take in a specific situation. There are 30 buckets, meaning 30 different scenarios. Within the same bucket, the probabilities for direction or action are the same.
For example: What should I do when I'm off-stage — refer to the "Recovery (you off-stage)" bucket.
For all buckets, refer to this official documentation:
https://docs.aiarena.io/arenadex/game-mechanics/tabular-model-v2
Video (no sound): The entire training process for all buckets
https://youtu.be/1rfRa3WjWEA
Game version 2024.1.10. The method of saving is outdated. Please refer to the game updates.
Advanced Model Type
The "Original Model Type" and "Advanced Model Type" are based on Machine Learning, which is commonly referred to as combining with AI.
The Original Model Type consists of only one bucket, representing the entire map. If you want the AI to learn different scenarios, you need to choose a "Focus Area" to let the warrior know where to focus. A single bucket means that a slight modification can have a widespread impact on the entire model. This is where the "Advanced Model Type" comes in.
The "Advanced Model Type" can be seen as a combination of the "Original Model Type" and the "Simple Model Type". The Advanced Model Type divides the map into 8 buckets. Each bucket can use many "Focus Area." For a detailed explanation of the 8 buckets and different Focus Areas, please refer to the tutorial page (accessible in the Advanced Model Type, after completing a training session, at the top left of the Advanced Config, click on "Tutorial").

III. Training (Data Collection and Config Settings)
Training Process:
- Collect Data
- Set Parameters, Train, and Save
- Repeat Step 1 until the Model is Complete
Training the Simple Model Type is the easiest to start with; refer to the video above for a detailed process.
Training the Advanced Model Type offers more possibilities through the combination of "Focus Area" parameters, providing a higher upper limit. While the Original Model Type has great potential, it's harder to control. Therefore, this section focuses on the "Advanced Model Type."
1. What Kind of Data to Collect
- High-Quality Data: Collect purposeful data. Garbage in, garbage out. Only collect the necessary data; don't collect randomly. It's recommended to use Dummy to collect data. However, don't pursue perfection; through parameter adjustments, AI has a certain level of fault tolerance.
- Balanced Data: Balance your dataset. In simple terms, if you complete actions on the left side a certain number of times, also complete a similar number on the right side. While data imbalance can be addressed through parameter adjustments (see below), it's advised not to have this issue during data collection.
- Moderate Amount: A single training will include many individual actions. Collect data for each action 1-10 times. Personally, it's recommended to collect data 2-3 times for a single action. If the effect of a single training is not clear, conduct a second (or even third) training with the same content, but with different parameter settings.
2. What to Collect (and Focus Area Selection)
Game actions mimic fighting games, consisting of 4 directions + 6 states (Idle, Jump, Attack, Grab, Special, Shield). Directions can be combined into ↗, ↘, etc. These directions and states can then be combined into different actions.
To make "Focus Area" effective, you need to collect data in training that matches these parameters. For example, for "Distance to Opponent", you need to collect data when close to the opponent and also when far away. * Note: While you can split into multiple training sessions, it's most effective to cover different situations within a single training.
Refer to the Simple Config, categorize the actions you want to collect, and based on the game scenario, classify them into two categories: "Movement" and "Combat."
Movement-Based Actions
Action Collection
When the warrior is offstage, regardless of where the opponent is, we require the warrior to return to the stage to prevent self-destruction.
This involves 3 aerial buckets: 5 (Near Blast Zone), 7 (Under Stage), and 8 (Side Of Stage).

* Note: The background comes from the Tutorial mentioned earlier. The arrows in the image indicate the direction of the action and are for reference only. * Note: Action collection should be clean; do not collect actions that involve leaving the stage.
Config Settings
In the Simple Config, you can directly choose "Movement" in it. However, for better customization, it's recommended to use the Advanced Config directly. - Intensity: The method for setting Intensity will be introduced separately later. - Buckets: As shown in the image, choose the bucket you are training. - Focus Area: Position-based parameters: - Your position (must) - Raycast Platform Distance, Raycast Platform Type (optional, generally choose these in Bucket 7)
Combat-Based Actions
The goal is to direct attacks quickly and effectively towards the opponent, which is the core of game strategy.
This involves 5 buckets: - 2 regular situations - In the air: 6 (Safe Zone) - On the ground: 4 (Opponent Active) - 3 special situations on the ground: - 1 Projectile Active - 2 Opponent Knockback - 3 Opponent Stunned
2 Regular Situations
In the in-game tutorial, we learned how to perform horizontal attacks. However, in the actual game, directions expand to 8 dimensions. Imagine having 8 relative positions available for launching hits against the opponent. Our task is to design what action to use for attack or defense at each relative position.
Focus Area - Basic (generally select all) - Angle to opponent
- Distance to opponent - Discrete Distance: Choosing this option helps better differentiate between closer and farther distances from the opponent. As shown in the image, red indicates a relatively close distance, and green indicates a relatively distant distance.- Advanced: Other commonly used parameters
- Direction: different facings to opponent
- Your Elemental Gauge and Discrete Elementals: Considering the special's charge
- Opponent action: The warrior will react based on the opponent's different actions.
- Your action: Your previous action. Choose this if teaching combos.
3 Special Situations on the Ground
Projectile Active, Opponent Stunned, Opponent Knockback These three buckets can be referenced in the Simple Model Type video. The parameter settings approach is the same as Opponent Active/Safe Zone.
For Projectile Active, in addition to the parameters based on combat, to track the projectile, you also need to select "Raycast Projectile Distance" and "Raycast Projectile On Target."
3. Setting "Intensity"
Resources
- The "Tutorial" mentioned earlier explains these parameters.
- Official Config Document (2022.12.24): https://docs.google.com/document/d/1adXwvDHEnrVZ5bUClWQoBQ8ETrSSKgG5q48YrogaFJs/edit
TL;DR:
Epochs: - Adjust to fewer epochs if learning is insufficient, increase for more learning.
Batch Size: - Set to the minimum (16) if data is precise but unbalanced, or just want it to learn fast - Increase (e.g., 64) if data is slightly imprecise but balanced. - If both imprecise and unbalanced, consider retraining.
Learning Rate: - Maximize (0.01) for more learning but a risk of forgetting past knowledge. - Minimize for more accurate learning with less impact on previous knowledge.
Lambda: - Reduce for prioritizing learning new things.
Data Cleaning: - Enable "Remove Sparsity" unless you want AI to learn idleness. - For special cases, like teaching the warrior to use special moves when idle, refer to this tutorial video: https://discord.com/channels/1140682688651612291/1140683283626201098/1195467295913431111
Personal Experience: - Initial training with settings: 125 epochs, batch size 16, learning rate 0.01, lambda 0, data cleaning enabled. - Prioritize Multistream, sometimes use Oversampling. - Fine-tune subsequent training based on the mentioned theories.
IV. Probability Viewing: AI Inspector
The dashboard consists of "Direction + Action." Above the dashboard, you can see the "Next Action" – the action the warrior will take in its current state. The higher the probability, the more likely the warrior is to perform that action, indicating a quicker reaction. It's essential to note that when checking the Direction, the one with the highest visual representation may not have the highest numerical value. To determine the actual value, hover the mouse over the graphical representation, as shown below, where the highest direction is "Idle."

In the map, you can drag the warrior to view the probabilities of the warrior in different positions. Right-click on the warrior with the mouse to change the warrior's facing. The status bar below can change the warrior's state on the map.

When training the "Opponent Stunned, Opponent Knockback" bucket, you need to select the status below the opponent's status bar. If you are focusing on "Opponent action" in the Focus Zone, choose the action in the opponent's status bar. If you are focusing on "Your action" in the Focus Zone, choose the action in your own status bar. When training the "Projectile Active" Bucket, drag the projectile on the right side of the dashboard to check the status.
Next
The higher the probability, the faster the reaction. However, be cautious when the action probability reaches 100%. This may cause the warrior to be in a special case of "State Transition," resulting in unnecessary "Idle" states.
Explanation: In each state a fighter is in, there are different "possible transitions". For example, from falling state you cannot do low sweep because low sweep requires you to be on the ground. For the shield state, we do not allow you to directly transition to headbutt. So to do headbutt you have to first exit to another state and then do it from there (assuming that state allows you to do headbutt). This is the reason the fighter runs because "run" action is a valid state transition from shield. Source
V. Learn from Matches
After completing all the training, your model is preliminarily finished—congratulations! The warrior will step onto the arena alone and embark on its debut!
Next, we will learn about the strengths and weaknesses of the warrior from battles to continue refining the warrior's model.
In matches, besides appreciating the performance, pay attention to the following:
-
Movement, i.e., Off the Stage: Observe how the warrior gets eliminated. Is it due to issues in the action settings at a certain position, or is it a normal death caused by a high percentage? The former is what we need to avoid and optimize.
-
Combat: Analyze both sides' actions carefully. Observe which actions you and the opponent used in different states. Check which of your hits are less effective, and how does the opponent handle different actions, etc.
The approach to battle analysis is similar to the thought process in the "Training", helping to have a more comprehensive understanding of the warrior's performance and making targeted improvements.
VI. Cheat Sheet
Training 1. Click "Collect" to collect actions. 2. "Map - Data Limit" is more user-friendly. Most players perform initial training on the "Arena" map. 3. Switch between the warrior and the dummy: Tab key (keyboard) / Home key (controller). 4. Use "Collect" to make the opponent loop a set of actions. 5. Instantly move the warrior to a specific location: Click "Settings" - SPAWN - Choose the desired location on the map - On. Press the Enter key (keyboard) / Start key (controller) during training.
Inspector 1. Right-click on the fighter to change their direction. Drag the fighter and observe the changes in different positions and directions. 2. When satisfied with the training, click "Save." 3. In "Sparring" and "Simulation," use "Current Working Model." 4. If satisfied with a model, then click "compete." The model used in the rankings is the one marked as "competing."
Sparring / Ranked 1. Use the Throneroom map only for the top 2 or top 10 rankings. 2. There is a 30-second cooldown between matches. The replays are played for any match. Once the battle begins, you can see the winner on the leaderboard or by right-clicking the page - Inspect - Console. Also, if you encounter any errors or bugs, please send screenshots of the console to the Discord server.
Good luck! See you on the arena!
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16Drivechain
Understanding Drivechain requires a shift from the paradigm most bitcoiners are used to. It is not about "trustlessness" or "mathematical certainty", but game theory and incentives. (Well, Bitcoin in general is also that, but people prefer to ignore it and focus on some illusion of trustlessness provided by mathematics.)
Here we will describe the basic mechanism (simple) and incentives (complex) of "hashrate escrow" and how it enables a 2-way peg between the mainchain (Bitcoin) and various sidechains.
The full concept of "Drivechain" also involves blind merged mining (i.e., the sidechains mine themselves by publishing their block hashes to the mainchain without the miners having to run the sidechain software), but this is much easier to understand and can be accomplished either by the BIP-301 mechanism or by the Spacechains mechanism.
How does hashrate escrow work from the point of view of Bitcoin?
A new address type is created. Anything that goes in that is locked and can only be spent if all miners agree on the Withdrawal Transaction (
WT^) that will spend it for 6 months. There is one of these special addresses for each sidechain.To gather miners' agreement
bitcoindkeeps track of the "score" of all transactions that could possibly spend from that address. On every block mined, for each sidechain, the miner can use a portion of their coinbase to either increase the score of oneWT^by 1 while decreasing the score of all others by 1; or they can decrease the score of allWT^s by 1; or they can do nothing.Once a transaction has gotten a score high enough, it is published and funds are effectively transferred from the sidechain to the withdrawing users.
If a timeout of 6 months passes and the score doesn't meet the threshold, that
WT^is discarded.What does the above procedure mean?
It means that people can transfer coins from the mainchain to a sidechain by depositing to the special address. Then they can withdraw from the sidechain by making a special withdraw transaction in the sidechain.
The special transaction somehow freezes funds in the sidechain while a transaction that aggregates all withdrawals into a single mainchain
WT^, which is then submitted to the mainchain miners so they can start voting on it and finally after some months it is published.Now the crucial part: the validity of the
WT^is not verified by the Bitcoin mainchain rules, i.e., if Bob has requested a withdraw from the sidechain to his mainchain address, but someone publishes a wrongWT^that instead takes Bob's funds and sends them to Alice's main address there is no way the mainchain will know that. What determines the "validity" of theWT^is the miner vote score and only that. It is the job of miners to vote correctly -- and for that they may want to run the sidechain node in SPV mode so they can attest for the existence of a reference to theWT^transaction in the sidechain blockchain (which then ensures it is ok) or do these checks by some other means.What? 6 months to get my money back?
Yes. But no, in practice anyone who wants their money back will be able to use an atomic swap, submarine swap or other similar service to transfer funds from the sidechain to the mainchain and vice-versa. The long delayed withdraw costs would be incurred by few liquidity providers that would gain some small profit from it.
Why bother with this at all?
Drivechains solve many different problems:
It enables experimentation and new use cases for Bitcoin
Issued assets, fully private transactions, stateful blockchain contracts, turing-completeness, decentralized games, some "DeFi" aspects, prediction markets, futarchy, decentralized and yet meaningful human-readable names, big blocks with a ton of normal transactions on them, a chain optimized only for Lighting-style networks to be built on top of it.
These are some ideas that may have merit to them, but were never actually tried because they couldn't be tried with real Bitcoin or inferfacing with real bitcoins. They were either relegated to the shitcoin territory or to custodial solutions like Liquid or RSK that may have failed to gain network effect because of that.
It solves conflicts and infighting
Some people want fully private transactions in a UTXO model, others want "accounts" they can tie to their name and build reputation on top; some people want simple multisig solutions, others want complex code that reads a ton of variables; some people want to put all the transactions on a global chain in batches every 10 minutes, others want off-chain instant transactions backed by funds previously locked in channels; some want to spend, others want to just hold; some want to use blockchain technology to solve all the problems in the world, others just want to solve money.
With Drivechain-based sidechains all these groups can be happy simultaneously and don't fight. Meanwhile they will all be using the same money and contributing to each other's ecosystem even unwillingly, it's also easy and free for them to change their group affiliation later, which reduces cognitive dissonance.
It solves "scaling"
Multiple chains like the ones described above would certainly do a lot to accomodate many more transactions that the current Bitcoin chain can. One could have special Lightning Network chains, but even just big block chains or big-block-mimblewimble chains or whatnot could probably do a good job. Or even something less cool like 200 independent chains just like Bitcoin is today, no extra features (and you can call it "sharding"), just that would already multiply the current total capacity by 200.
Use your imagination.
It solves the blockchain security budget issue
The calculation is simple: you imagine what security budget is reasonable for each block in a world without block subsidy and divide that for the amount of bytes you can fit in a single block: that is the price to be paid in satoshis per byte. In reasonable estimative, the price necessary for every Bitcoin transaction goes to very large amounts, such that not only any day-to-day transaction has insanely prohibitive costs, but also Lightning channel opens and closes are impracticable.
So without a solution like Drivechain you'll be left with only one alternative: pushing Bitcoin usage to trusted services like Liquid and RSK or custodial Lightning wallets. With Drivechain, though, there could be thousands of transactions happening in sidechains and being all aggregated into a sidechain block that would then pay a very large fee to be published (via blind merged mining) to the mainchain. Bitcoin security guaranteed.
It keeps Bitcoin decentralized
Once we have sidechains to accomodate the normal transactions, the mainchain functionality can be reduced to be only a "hub" for the sidechains' comings and goings, and then the maximum block size for the mainchain can be reduced to, say, 100kb, which would make running a full node very very easy.
Can miners steal?
Yes. If a group of coordinated miners are able to secure the majority of the hashpower and keep their coordination for 6 months, they can publish a
WT^that takes the money from the sidechains and pays to themselves.Will miners steal?
No, because the incentives are such that they won't.
Although it may look at first that stealing is an obvious strategy for miners as it is free money, there are many costs involved:
- The cost of ceasing blind-merged mining returns -- as stealing will kill a sidechain, all the fees from it that miners would be expected to earn for the next years are gone;
- The cost of Bitcoin price going down: If a steal is successful that will mean Drivechains are not safe, therefore Bitcoin is less useful, and miner credibility will also be hurt, which are likely to cause the Bitcoin price to go down, which in turn may kill the miners' businesses and savings;
- The cost of coordination -- assuming miners are just normal businesses, they just want to do their work and get paid, but stealing from a Drivechain will require coordination with other miners to conduct an immoral act in a way that has many pitfalls and is likely to be broken over the months;
- The cost of miners leaving your mining pool: when we talked about "miners" above we were actually talking about mining pools operators, so they must also consider the risk of miners migrating from their mining pool to others as they begin the process of stealing;
- The cost of community goodwill -- when participating in a steal operation, a miner will suffer a ton of backlash from the community. Even if the attempt fails at the end, the fact that it was attempted will contribute to growing concerns over exaggerated miners power over the Bitcoin ecosystem, which may end up causing the community to agree on a hard-fork to change the mining algorithm in the future, or to do something to increase participation of more entities in the mining process (such as development or cheapment of new ASICs), which have a chance of decreasing the profits of current miners.
Another point to take in consideration is that one may be inclined to think a newly-created sidechain or a sidechain with relatively low usage may be more easily stolen from, since the blind merged mining returns from it (point 1 above) are going to be small -- but the fact is also that a sidechain with small usage will also have less money to be stolen from, and since the other costs besides 1 are less elastic at the end it will not be worth stealing from these too.
All of the above consideration are valid only if miners are stealing from good sidechains. If there is a sidechain that is doing things wrong, scamming people, not being used at all, or is full of bugs, for example, that will be perceived as a bad sidechain, and then miners can and will safely steal from it and kill it, which will be perceived as a good thing by everybody.
What do we do if miners steal?
Paul Sztorc has suggested in the past that a user-activated soft-fork could prevent miners from stealing, i.e., most Bitcoin users and nodes issue a rule similar to this one to invalidate the inclusion of a faulty
WT^and thus cause any miner that includes it in a block to be relegated to their own Bitcoin fork that other nodes won't accept.This suggestion has made people think Drivechain is a sidechain solution backed by user-actived soft-forks for safety, which is very far from the truth. Drivechains must not and will not rely on this kind of soft-fork, although they are possible, as the coordination costs are too high and no one should ever expect these things to happen.
If even with all the incentives against them (see above) miners do still steal from a good sidechain that will mean the failure of the Drivechain experiment. It will very likely also mean the failure of the Bitcoin experiment too, as it will be proven that miners can coordinate to act maliciously over a prolonged period of time regardless of economic and social incentives, meaning they are probably in it just for attacking Bitcoin, backed by nation-states or something else, and therefore no Bitcoin transaction in the mainchain is to be expected to be safe ever again.
Why use this and not a full-blown trustless and open sidechain technology?
Because it is impossible.
If you ever heard someone saying "just use a sidechain", "do this in a sidechain" or anything like that, be aware that these people are either talking about "federated" sidechains (i.e., funds are kept in custody by a group of entities) or they are talking about Drivechain, or they are disillusioned and think it is possible to do sidechains in any other manner.
No, I mean a trustless 2-way peg with correctness of the withdrawals verified by the Bitcoin protocol!
That is not possible unless Bitcoin verifies all transactions that happen in all the sidechains, which would be akin to drastically increasing the blocksize and expanding the Bitcoin rules in tons of ways, i.e., a terrible idea that no one wants.
What about the Blockstream sidechains whitepaper?
Yes, that was a way to do it. The Drivechain hashrate escrow is a conceptually simpler way to achieve the same thing with improved incentives, less junk in the chain, more safety.
Isn't the hashrate escrow a very complex soft-fork?
Yes, but it is much simpler than SegWit. And, unlike SegWit, it doesn't force anything on users, i.e., it isn't a mandatory blocksize increase.
Why should we expect miners to care enough to participate in the voting mechanism?
Because it's in their own self-interest to do it, and it costs very little. Today over half of the miners mine RSK. It's not blind merged mining, it's a very convoluted process that requires them to run a RSK full node. For the Drivechain sidechains, an SPV node would be enough, or maybe just getting data from a block explorer API, so much much simpler.
What if I still don't like Drivechain even after reading this?
That is the entire point! You don't have to like it or use it as long as you're fine with other people using it. The hashrate escrow special addresses will not impact you at all, validation cost is minimal, and you get the benefit of people who want to use Drivechain migrating to their own sidechains and freeing up space for you in the mainchain. See also the point above about infighting.
See also
-
 @ 88cc134b:5ae99079
2024-06-19 08:28:45
@ 88cc134b:5ae99079
2024-06-19 08:28:45lets try this out nostr:note14vqza005ngr0nk2ft8v4t3qejezqxvulmerna0g5gvs4wjsstqgsmeupgy and nostr:note1gehzcmj6tyzzk3renzvcshkazys8g9q7f8x9p70zatgx7salcsjqax60pz or nostr:note16c3k4ygg39kv77yzeefvmrzngekjcyqcul59ry8jsvg250w4k42qk9d4dw or nostr:note1cxyk4l049r32v24sls2m3cpjpm6c7yrg2d36n34j64ym0ygz73rqzplrn7 and some users nostr:npub13rxpxjc6vh65aay2eswlxejsv0f7530sf64c4arydetpckhfjpustsjeaf and nostr:npub13rxpxjc6vh65aay2eswlxejsv0f7530sf64c4arydetpckhfjpustsjeaf
-
 @ 0176967e:1e6f471e
2024-07-20 08:28:00
@ 0176967e:1e6f471e
2024-07-20 08:28:00Tento rok vás čaká workshop na tému "oranžové leto" s Jurajom Bednárom a Mariannou Sádeckou. Dozviete sa ako mení naše vnímanie skúsenosť s Bitcoinom, ako sa navigovať v dnešnom svete a odstrániť mentálnu hmlu spôsobenú fiat životom.
Na workshop je potrebný extra lístok (môžete si ho dokúpiť aj na mieste).
Pre viac informácií o oranžovom lete odporúčame pred workshopom vypočuťi si podcast na túto tému.
-
 @ a012dc82:6458a70d
2024-08-03 07:44:52
@ a012dc82:6458a70d
2024-08-03 07:44:52Table Of Content
-
Blockstream: Innovating the Future of Bitcoin
-
The Liquid Network: A Fast and Secure Sidechain Technology
-
The Lightning Network: Faster and Cheaper Bitcoin Transactions
-
The Taproot/Schnorr Upgrade: Improving the Bitcoin Network
-
Conclusion
-
FAQ
Bitcoin has emerged as a global phenomenon, revolutionizing the way we think about money. However, this emerging technology faces challenges of scalability, security, and regulation. Blockstream is a company that has stepped up to the plate to revolutionize Bitcoin innovation.
Blockstream: Innovating the Future of Bitcoin
Blockstream was founded in 2014 with the goal of developing innovative solutions to some of the most pressing issues facing the Bitcoin network. The company's most ambitious projects include the Liquid Network, the Lightning Network, and the Taproot/Schnorr upgrade.
The Liquid Network: A Fast and Secure Sidechain Technology
The Liquid Network is a sidechain technology that enables fast and secure Bitcoin transactions between exchanges and other large-scale users. The Liquid Network is designed to alleviate some of the congestion on the main Bitcoin network, which has become increasingly congested in recent years due to the growing popularity of the currency.
The Lightning Network: Faster and Cheaper Bitcoin Transactions The Lightning Network is a second-layer technology that allows for faster and cheaper Bitcoin transactions. The Lightning Network works by creating a network of payment channels that enable users to send and receive Bitcoin instantly and without fees.
The Taproot/Schnorr Upgrade: Improving the Bitcoin Network
Blockstream is leading the charge on the development of the Taproot/Schnorr upgrade, a major protocol upgrade that will bring significant improvements to the Bitcoin network. The Taproot/Schnorr upgrade will make transactions smaller, faster, and more private, while also improving the security of the network.
Conclusion
Blockstream's commitment to innovation has not gone unnoticed. The company has attracted significant investment from some of the biggest names in the tech industry. Blockstream's ambitious projects have the potential to transform the Bitcoin network and make it more scalable, secure, and private. As the company continues to innovate, the future of Bitcoin looks brighter than ever.
FAQ
What is Blockstream? Blockstream is a technology company that focuses on the development of innovative solutions to some of the most pressing issues facing the Bitcoin network.
What are some of Blockstream's most ambitious projects? Blockstream's most ambitious projects include the Liquid Network, the Lightning Network, and the Taproot/Schnorr upgrade.
Why is Blockstream's work important? Blockstream's work is important because it has the potential to transform the Bitcoin network and make it more scalable, secure, and private. Their innovative solutions could revolutionize the way we use and think about Bitcoin.
What impact could Blockstream's projects have on the future of Bitcoin? Blockstream's projects have the potential to transform the Bitcoin network and make it more scalable, secure, and private. This could make Bitcoin a more practical and widely adopted form of currency and revolutionize the way we use and think about money.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 88cc134b:5ae99079
2024-06-10 13:16:55
@ 88cc134b:5ae99079
2024-06-10 13:16:55This is a test by nostr:npub13rxpxjc6vh65aay2eswlxejsv0f7530sf64c4arydetpckhfjpustsjeaf to see how an article would behave with various mentions:
User nostr:npub13rxpxjc6vh65aay2eswlxejsv0f7530sf64c4arydetpckhfjpustsjeaf
Note: nostr:note133vw4g8klp45lhuxcfgkt62cuw20ka0jhy6mgzksrdygaw0jmnnse3lsnr
Article: nostr:naddr1qqwyzttvdahxwttxdaex6ttwda6x2tt5v4ehgtt4x3u8wmf5qgsg3nqnfvdxta2w7j9vc80nvegx85l2ghcya2u273jxu4sutt5eq7grqsqqqa284z5m77
-
 @ 7361ca91:252fce6d
2024-07-02 14:33:05
@ 7361ca91:252fce6d
2024-07-02 14:33:05サイエンス・フィクションは、可能な未来を想像する思索的な演習です。サイファイは可能性の空間を拡張します。暗号通貨は極端な種類のサイファイであり、未来のビジョンを提供するだけでなく、その未来を実現するためのツールも提供します。暗号通貨は現在、ソーラーパンクと呼ばれるサイファイのジャンルによって活気づけられています。サイバーパンクから進化したソーラーパンクは、楽観主義によって特徴づけられる未来のユートピア的なビジョンです。ソーラーパンクにとって、未来は明るいのです。ソーラーパンクはサイバーパンクのディストピアの影を払いのけ、混沌とした地平線を越えた世界を照らし出します。多くの人気のあるDeFiチェーンでは、ソーラーパンクのハッカーが公共財を資金調達するための透明なインフラを構築しています。共有された信念はシンプルです。分散型で透明な金融システムへの公共アクセスが、より公正で正義のある世界をもたらすということです。ソーラーパンクは暗号通貨の意識的な心です。明るく、自信に満ち、未来志向です。
しかし、ソーラーパンクの信念に対する反対はルナーパンクの懐疑主義です。ルナーパンクはソーラーの影の自分たちです。彼らはこのサイクルの無意識です。ソーラーパンクがDAOに参加する一方で、ルナーパンクは戦争の準備をし、コミュニティを守るためのプライバシー強化ツールを構築します。ルナーパンクは最初、ソーラーパンクのサブセットとして登場しました。常にイーサリアムや類似のチェーンで提供されるプレーンテキストのパラダイムよりも暗号化を好んでいました。時間が経つにつれて、ソーラーパンクの傾向によって生じた緊張はますます増大しました。ルナーパンクはソーラーパンクの遺産から離れ、自分自身のアイデンティティを主張するようになりました。
ルナーパンクの空想では、暗号通貨と既存の権力構造との間の対立は基本的にプログラムされています。規制によって暗号通貨は地下に追いやられ、匿名性が増大します。ルナーパンクのビジョンは、ベアリッシュな悪夢として拒絶されます。その根本的な対立――国家が暗号通貨を禁止すること――は、人々が金を持って逃げるような恐怖を生むため、ソーラーパンクによって却下されます。ソーラーパンクの楽観主義はブルマーケットのサイクルと同義になり、悲観主義はベアと関連付けられています。ルナーパンクはこの単純なエスカレーションを超える何かを提供します。それは市場サイクルの間の洞察の瞬間、ホログラムの中のグリッチであり、ソースコードが輝いて見える瞬間です。
ソーラーパンクは脆弱です――揺れ動くと壊れるものです。アンチフラジャイルとは、ショックを吸収し強くなるものです。次のことを考慮してください。暗号通貨の核心的なイノベーションは適応的です。ユーザーをエンパワーメントしつつ、その攻撃面を等しく拡散させます。ユーザーのエンパワーメントは脆弱性と負の相関があります。ユーザーベースが重要であればあるほど、ネットワークはよりアンチフラジャイルになります。ユーザーのエンパワーメントとシステムのアンチフラジャイルは互いにポジティブなフィードバックを形成します。
しかし、このサイクルは逆方向にも進行します。透明なシステムでは、ユーザーはさらされます。外部環境が敵対的になると、この情報が彼らに対して武器として使用される可能性があります。迫害に直面したユーザーは脱退を選び、それが脆弱性への下降を引き起こします。ソーラーパンクの考え方は本質的に楽観的です。ソーラーパンクシステムの透明性は、外向きに投影された楽観主義の精神です。透明なシステムを構築することで、ソーラーパンクは「法律が自分に不利にならないと信じている」と言っています。楽観主義の強調は、最悪の事態に備えることを妨げます。これがソーラーパンクの脆弱性の核心です。
暗い選択肢とアンチフラジャイル性は未知性に依存しています。未来は暗く、意味のある確実性を持って予測することはできません。選択肢は、その暗闇を利用して有利に働くため、アンチフラジャイル性の武器と呼ばれています。選択肢は、予言がほとんどの場合間違っていると仮定します。間違っていることは安価ですが、正しいことは不釣り合いに報われます。ルナーパンクは最悪の事態において成功するため、選択肢を取り入れています。ルナーパンクの仮説が間違っていれば、スーパーサイクルは続きます。正しければ、暗号通貨は適切な防御を備えた次の段階に進みます。しっかりと防御されることは、暗号化を使用してユーザーの身元と活動を保護することを意味します。
予言
匿名性は、まず大量監視への適応として生じます。しかし、その存在自体が監視努力をさらに正当化します。これは、匿名性と監視がエスカレートする運命にあることを示唆する正のフィードバックループです。このループが十分に続くと、ルナーパンクの予言の次の段階が引き起こされます:規制トラップ。この段階では、政府は匿名性の増加を口実にして、暗号通貨に対してその力を最大限に活用します。しかし、暗号通貨を取り締まることで、敵対的な力はその正当化をさらに強化するだけです。暗号通貨の実用性は、取り締まりの程度と相関します。各打撃を受けるたびに、不釣り合いに拡大します。
ルナサイクル
太陽はその透明性とアイデンティティへのこだわりを通じて、自然の象徴であり暴政の象徴でもあります。ソーラーパンクはその中央の象徴の二重の特徴を受け継いでいます。ソーラーパンクシステムは、ユーザーが危険にさらされる砂漠の風景です。ルナーパンクは森のようなものです。暗号化の密集した覆いが部族を保護し、迫害された人々に避難所を提供します。木立は重要な防衛線を提供します。ルナの風景は暗いですが、生物にあふれています。ルナテックは、自由のために人々自身によって所有され、運営されています。ルナサイクルは、権威主義的な技術に対して民主的な技術を支持します:監視に対する自由と、単一文化に対する多様性です。システムに透明性を重視することで、ソーラーパンクは悲劇的にその運命を作り上げています。監視、すなわち権威主義のメカニズムは、ソーラーパンクの運命に結びついています。ソーラーパンクが成功するためには、ルナーパンクの無意識を統合する必要があります。ソーラーパンクが成功する唯一の希望は、暗闇に移行することです。
-
 @ 7361ca91:252fce6d
2024-06-29 10:13:51
@ 7361ca91:252fce6d
2024-06-29 10:13:51リベラリズムにおいて、自由とは他人が不適切と感じるかもしれない決定を個人が行うことを許容することを意味します。ただし、その決定が第三者に害を及ぼさない限りです。つまり、自由は各個人が自分の人生計画を構築し、実行する権利を守るものであり、他人にとって誤っていると見なされる決定も含まれます。
個人の決定を批判することと、その決定を妨げるために強制力を使用することの間には大きな違いがあります。
リベラリズムは、たとえ悪い決定を批判することができても、それらの決定を妨げるために(国家の)強制力を使用すべきではないと主張します。ただし、これらの決定が他人に害を及ぼす場合は例外です。
リベラリズムにおける認識的慎重さは、どの決定が正しいか常に確信できるわけではないことを認識しています。したがって、他人に誤っているように見える場合でも、個人が自分の決定を下す自由を許容しなければなりません。
非常に一般的な例として、薬物の使用が挙げれます。リベラルな視点からは、他人がこれを悪い決定と見なすかもしれなくても、個人が薬物を使用する自由を持つべきです。鍵となるのは、これらの個人的な決定が第三者に害を及ぼさないことです。
リベラルな哲学においては、個人の自由と自己決定が重要視されます。他人が悪いと考えるかもしれない決定を行う権利も尊重されるべきであり、その決定が第三者に害を及ぼさない限り、(国家が)強制力を使用して妨げるべきではないという立場をとります。この認識的慎重さが、リベラリズムの核心の一つです。
-
 @ 88cc134b:5ae99079
2024-04-30 12:29:04
@ 88cc134b:5ae99079
2024-04-30 12:29:04This is just a test of how a long form would look like. A need a new note, some old stuff I can find doesn't do it for me.
So here I am typing away... I apologize for the spamming and bad grammar, if there is any. The problem with not being good at English grammar and spelling is that you are unaware of the mistakes you make until someone points them out to you. By which time it's too late.
One good thing about the editor I'm typing this in is that it seems to have a grammar check, which is cool.
Well, I won't keep you any longer, after all this was just a test.
Bye!
-
 @ 30876140:cffb1126
2024-04-21 04:18:59
@ 30876140:cffb1126
2024-04-21 04:18:59The Wanderers carry our ancient way,
Forgotten in sands across time,
The Path which returns us to Regions of Light,
with phrases and stories sublime.Out from our villages we cast them,
for memory of truths divine,
remind us of our errored ways,
But in their hearts, the Truth ever shines."We've lost many of our relics, now, though they were never important for the Path. Relics and objects, though imbued with a holy power, only serve as a guidepost to our spirits, a reminder of where to travel. We do not need them to cross the bridge between worlds."
Our leaders think they are a crazy, unintelligent people, continuing to profess and refine a realm of fantasy which has so little value to our desert lives; that these wanderers really believe what they say, only to cope with the terrors and agony of living in this world that is become destitute and estranged from celestial life.
I do not believe them, who deny the Wandering Way, for I see in their hearts that they bleed every day; they cast judgements unjust, words unloving, do things unbecoming of their characters in the folly of their grief. Yet never have I met a Wanderer with dirt upon their souls, though dirt clings so readily to their feet and threadbare robes. They possess voices of sweetness, though hoarse from the desert wind, and they seem to have a glow about their skin, though darkened by hard years in the sun.
Maybe I will take up the Wandering Way, if one of their order would take me with them. I know not where they go when they cross over the horizon, west or east, but I rarely have seen the same twice, except Abunam Sabba, who comes to us when the moon is full, without fail.
He made my father so angry on his last visit to the village, when he spoke so confidently of the dealings with the Echoes in the farthest reaches of Gondölla. "There is none alive with such knowledge," said my father.
"But there is," replied Sabba, "and many also who are not alive. We have seen them on many worlds, and have spoken to them of their travels across the stars."
"You are a liar, and a swindler," spat my father in rage, and forced him out of our house on a midsummer's eve. Still, Sabba returns to our village, though only to its edge now, where the water spout and market stand, since many of our village have treated him so. No matter when he sees me, though, he treats me with kindness, and respect, and never speaks ill of anybody.
"Words said in disdain cause the spirit endless pain," Sabba said. "They prevent progress on the Path. None can cross the bridges we travel who bear such a sickness of soul, for it pulls the spirit back to a place as sure as the anchors of old when we rode upon the water that spilled over these valleys of sand."
Sabba said to me, once, "I think you are one of the few in this world which have a heart that is clear enough to withstand the Doors of Night and make the Walk Between Worlds. I see your knowledge, though seed yet be unblossomed, and I think your curious mind could be sated on this Path. Please consider my words as an invitation; I will take you on a wander, whenever you are ready."
"The Wandering Way leads a soul wherever the winds may take them. We walk between worlds on bridges unseen by the eye, and appear whence we will, somewhere else in Gondölla. Many travel on missions unnumbered, called by some purpose or Great Spirit to act on behalf of the highest orders of life, while others simply walk, becoming as they do, letting go of their heavier natures and striving ever closer to the Suns which shine above. It is difficult to describe, as I have only words of the world, as we say, but with a little of your trust, I can show you what my words cannot."
Read more here: https://publish.obsidian.md/gondolla/Tales+of+the+Galaxy/Wanderer
-
 @ bcea2b98:7ccef3c9
2024-04-20 17:59:17
@ bcea2b98:7ccef3c9
2024-04-20 17:59:17Consider the concept of 'progress' in human society and individual lives. When we talk about progress, what exactly do we mean? Is it solely about technological advancement, economic growth, or societal development? Or does progress include broader aspects such as personal fulfillment, moral advancement, and environmental sustainability? Is progress always desirable, or are there instances where the pursuit of progress leads to unintended consequences or ethical dilemmas?
-
 @ 862fda7e:02a8268b
2024-06-29 08:18:20
@ 862fda7e:02a8268b
2024-06-29 08:18:20I am someone who thinks independently without abiding to a group to pre-formulate my opinions for me. I do not hold my opinions out of impulse, out of the desire to please, nor out of mindless apadtion to what others abide to. My opinions are held on what I belive is the most logical while being the most ethical and empathetic. We live in a world with a nervous systems and emotions for animals and humans (same thing) alike, thus, we should also consider those feelings. That is not the case in our world.


Cyclists are one of the most homosexual GAY ANNOYING people to exist on EARTH
I hate cyclists with a burning passion. These faggots are the GAYEST MOST ANNOYING retards to exist. They wear the tightest fitting clothing possible to show off their flaccid cocks to each other and to anybody around them.
 And if that weren't enough, they present their ass up in the air, begging to be fucked by their cyclist buddies, as they ride their bike in the middle of the road. It's homosexual.
And if that weren't enough, they present their ass up in the air, begging to be fucked by their cyclist buddies, as they ride their bike in the middle of the road. It's homosexual.
 Look at the seat they ride on, it looks like a black cock about to go up their ass. Don't get me started on their gay helmets, the "aerodynamic" helmets they wear. YOU FAGGOTS AREN'T IN THE TOUR DE FRANCE, YOU'RE IN FRONT OF MY CAR IN AN INTERSECTION IN A MINNESOTA TOWN WITH A POPULATION OF 5,000. They LIKE the look of the costume. And that's just what it is - a costume. You're required to have a "look" as a cyclist - you aren't really a cyclist if you don't spend hundreds of dollars on the gay gear. God forbid you just get a bike and ride it around on a trail like anyone else.
These people LIKE to be seen. They WANT to be seen as cool, which is why they ride right in front of my fucking car at 15mph in a 45mph zone. I swear, every time I pass one of these cyclists, I am this close to yelling "FAGGOT" out the window at them. The only reason I haven't is because they like to record everything on their gay bikes and upload it to Youtube, so then I'd have to deal with you people knowing where I live just because I called some fruit on a bike a faggot. Think I'm exaggerating? Think again. These homos have an entire community built on "catching" drivers who dare drive too close or blow their exhaust at the poor little faggy cyclist. There's Youtube channels dedicated to this. Part of their culture is being a victim by cars. Almost like it's dangerous to be in the middle of the road going 15mph on a 45mph road. Oh but I'm sure cars almost hitting you is surely a personal attack and nothing to do with the fact that what you're doing is DANGEROUS YOU RETARD.
Look at the seat they ride on, it looks like a black cock about to go up their ass. Don't get me started on their gay helmets, the "aerodynamic" helmets they wear. YOU FAGGOTS AREN'T IN THE TOUR DE FRANCE, YOU'RE IN FRONT OF MY CAR IN AN INTERSECTION IN A MINNESOTA TOWN WITH A POPULATION OF 5,000. They LIKE the look of the costume. And that's just what it is - a costume. You're required to have a "look" as a cyclist - you aren't really a cyclist if you don't spend hundreds of dollars on the gay gear. God forbid you just get a bike and ride it around on a trail like anyone else.
These people LIKE to be seen. They WANT to be seen as cool, which is why they ride right in front of my fucking car at 15mph in a 45mph zone. I swear, every time I pass one of these cyclists, I am this close to yelling "FAGGOT" out the window at them. The only reason I haven't is because they like to record everything on their gay bikes and upload it to Youtube, so then I'd have to deal with you people knowing where I live just because I called some fruit on a bike a faggot. Think I'm exaggerating? Think again. These homos have an entire community built on "catching" drivers who dare drive too close or blow their exhaust at the poor little faggy cyclist. There's Youtube channels dedicated to this. Part of their culture is being a victim by cars. Almost like it's dangerous to be in the middle of the road going 15mph on a 45mph road. Oh but I'm sure cars almost hitting you is surely a personal attack and nothing to do with the fact that what you're doing is DANGEROUS YOU RETARD.
 I've seen these "share the road" signs in the most insane and dangerous places. I've seen them on HIGHWAYS, yes, HIGHWAYS, where the cyclist would BARELY have any room next to the car. It's insanely dangerous and I guess to some people, the constant threat of dying is fun... until it actually happens.
I will never understand the mind of a cyclist. You are not in the fricken' Tour de France. You look like a homosexual that's inconveniencing HEAVY METAL HIGH POWERED CARS RIGHT BEHIND YOU. It's incredibly dangerous, and you can't rely on the very heavy, high powered cars and the people driving them to honor your life. Road rage is real, you might be the tipping point for some angry old boomer in his Ram to RAM INTO YOU and kill you. God I hate cyclists, their gay look, their cocky "better than you" attitude. Hey fudge stripe, in a battle between my CAR and your soft body, my CAR WILL WIN. Get off the road and go suck some cocks instead. Stop riding the bikes and go ride cocks instead, you homo.
I've seen these "share the road" signs in the most insane and dangerous places. I've seen them on HIGHWAYS, yes, HIGHWAYS, where the cyclist would BARELY have any room next to the car. It's insanely dangerous and I guess to some people, the constant threat of dying is fun... until it actually happens.
I will never understand the mind of a cyclist. You are not in the fricken' Tour de France. You look like a homosexual that's inconveniencing HEAVY METAL HIGH POWERED CARS RIGHT BEHIND YOU. It's incredibly dangerous, and you can't rely on the very heavy, high powered cars and the people driving them to honor your life. Road rage is real, you might be the tipping point for some angry old boomer in his Ram to RAM INTO YOU and kill you. God I hate cyclists, their gay look, their cocky "better than you" attitude. Hey fudge stripe, in a battle between my CAR and your soft body, my CAR WILL WIN. Get off the road and go suck some cocks instead. Stop riding the bikes and go ride cocks instead, you homo. -
 @ bcea2b98:7ccef3c9
2024-04-20 14:20:00
@ bcea2b98:7ccef3c9
2024-04-20 14:20:00The model suggests Bitcoin's price hinges on its scarcity, gauged by the stock-to-flow ratio, comparing the amount in circulation to newly mined coins. Higher ratios signify greater scarcity, akin to gold's historical average of 66. After Bitcoin's third halving, its ratio doubled, enhancing its scarcity.
Meanwhile, the Grayscale Bitcoin Trust's recent halving, losing 300k BTC since the launch of spot Bitcoin ETFs, may have a more immediate negative impact on Bitcoin's price.
-
 @ 862fda7e:02a8268b
2024-06-29 08:16:47
@ 862fda7e:02a8268b
2024-06-29 08:16:47
Pictured above is a female body that looks incredibly similar to mine. So similar that it could be mine if I didn't have a c-section scar. Actually her boobs are a bit bigger than mine, but mine do look like that when they swell.

Nudity should be normalized
I don't understand why people get offended or sensitive over the human body. Especially the female human chest. We all have nipples, we all know what they look like, so I don't understand why a female being topless is unacceptable, whereas a male topless is normal. I've seen shirtless men with more shapely, larger breasts than mine. Personally, I have stopped caring if other people see the shape of my breasts or my nipples if they were to be poking in the freezer section of the grocery store. I stopped wearing bras years ago. I often times want to be topless outside in my yard because it feels good and natural. I like the sun on my skin, and I especially love the rain on my skin. It's very unfortunate that our natural human body is massively shamed, by who I believe, is the reptilians (for a number of reasons). Logically, it makes no sense to be outraged by the female human chest. We all know what nipples look like, we all have them, I truly believe women should be allowed to be topless like men are. If it's hot out and you're doing yard work - pop your top off, who cares?
I understand that males and some females sexualize the human chest. However, that is not my problem. That is none of my concern what others think about my body. I should be allowed to wear my human body as it is just like anyone else should be. What I can't wrap my mind around is why people are shocked or offended by the human body, since we ALL know what these parts look like and we all have them. I understand in certain scenarios being topless or nude would likely be inapproriate, or that perverts would use it as a way to expose themselves to children. In an ideal world, we could live like tribes where the human body is normal, it's not overtly sexual. This is why we're so offended over the human body - it's constantly concealed, so the moment we get to see a female chest, it's suddenly sexual because it's normally tabboo to be seen. I wish I could be shirtless outside, I envy males who get to truly feel the wind, the earth on their backs and their chest. Female and male nipples look the same, I don't understand why it should be illegal for me to experience nature in my natural state.
Anyways, I highly dislike the "nudist" people because it is NOT about accepting the human body in its natural state. It's completely co-opted by pedophiles who want to expose themselves to childen or for children to expose themselves to others for sexual gratification. There are nudist resorts pedophile parents force their children to go to (as a child you have no personal autonomy and are completely a slave to your parents - trust me, I know this because I couldn't LEGALLY decide which parent I wanted to live with up until I was 18 years old. If your parent wants you to do something, a child in the US has no legal say over that, so if your parent wants to go to a nudist resort, you must go). A human body should simply be a human body, it's unfortunate that being unclothed immediately brings on sexualization. This is mostly an issue because clothes is the expected default. The more tabboo something is, the more naughty the thing is.
I am not a nudist. However, I do believe that at the very least, females should have the right to be topless in similar settings as males are allowed to. I don't think a woman is a slut if she's in her natural state, in her human body, and proceeds life as normal. How one acts portrays slutty behavior. Living your life in your natural human body should be a right without caviots. I feel detached from people who constantly see the human body as flawed (e.g. circumcision industry, body hair removal industry, clothing industry). These industries are harmful for the victims in them (infant boys, and modern day slaves in sweatshops), and the main motivating factor is money among all these industries.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Bolo
It seems that from 1987 to around 2000 there was a big community of people who played this game called "Bolo". It was a game in which people controlled a tank and killed others while trying to capture bases in team matches. Always 2 teams, from 2 to 16 total players, games could last from 10 minutes to 12 hours. I'm still trying to understand all this.
The game looks silly from some videos you can find today, but apparently it was very deep in strategy because people developed strategy guides and wrote extensively about it and Netscape even supported
bolo:URLs out of the box.The two most important elements on the map are pillboxes and bases. Pillboxes are originally neutral, meaning that they shoot at every tank that happens to get in its range. They shoot fast and with deadly accuracy. You can shoot the pillbox with your tank, and you can see how damaged it is by looking at it. Once the pillbox is subdued, you may run over it, which will pick it up. You may place the pillbox where you want to put it (where it is clear), if you've enough trees to build it back up. Trees are harvested by sending your man outside your tank to forest the trees. Your man (also called a builder) can also lay mines, build roads, and build walls. Once you have placed a pillbox, it will not shoot at you, but only your enemies. Therefore, pillboxes are often used to protect your bases.
That quote was taken from this "augmented FAQ" written by some user. Apparently there were many FAQs for this game. A FAQ is after all just a simple, clear and direct to the point way of writing about anything, previously known as summa[^summa-k], it doesn't have to be related to any actually frequently asked question.
More unexpected Bolo writings include an etiquette guide, an anthropology study and some wonderings on the reverse pill war tactic.
[^summa-k]: It's not the same thing, but I couldn't help but notice the similarity.
-
 @ bcea2b98:7ccef3c9
2024-04-20 00:11:30
@ bcea2b98:7ccef3c9
2024-04-20 00:11:30 -
 @ 4dbfcb7c:eb8d1695
2024-07-26 23:12:38
@ 4dbfcb7c:eb8d1695
2024-07-26 23:12:38Hardinfo is a nice GUI tool for displaying hardware and system information. It has the look and feel of MS's device manager.
So if you don't feel like memorizing a bunch of command line commands, such as lspci (list pci devices), lsmod (list kernel moduels), or neofetch (Computer summary). you can install hardinfo and give it a spin. Although, NeoFetch is kinda fun.
Hardinfo should be in the default repositories. To install it on Debian based distros you would type:
sudo apt install hardinfo
Once installed, you can search for it the normal way using the taskbar search. When you search for "hardinfo" . . it may show up as "System Profiler"
Unlike MS's device manager, You CANNOT edit hardware settings with hardinfo. You can only read the system info.
This "Learn Ubuntu Mate" website is a good overview of hardinfo, with lots of screenshots.
Hardinfo #LinuxSystemTools #LinuxSystemInformation #SystemTools
-
 @ 6ad3e2a3:c90b7740
2024-06-28 07:44:17
@ 6ad3e2a3:c90b7740
2024-06-28 07:44:17I’ve written about this before, and I’ve also tried to illustrate it via parable in “The Simulator.” I even devoted most of a podcast episode to it. But I thought it might be useful just to cut to the chase in written form, give the tldr version.
Utilitarianism is the moral philosophy of the greatest good for the greatest number. That is, we calculate the prospective net benefits or harms from a course of action to guide our policies and behaviors. This moral framework deserves scrutiny because it (unfortunately) appears to be the paradigm under which most of our governments, institutions and even educated individuals operate.
The philosophy is commonly illustrated by hypotheticals such as “the trolley problem” wherein a person has the choice whether to divert a runaway trolley (via switch) from its current track with five people in its path to it to an alternate one where only one person would be killed. In short, do you intervene to save five by killing one? The premise of utilitarianism is that, yes, you would because it’s a net positive.
Keep in mind in these hypotheticals these are your only choices, and not only are you certain about the results of your prospective actions, but those are the only results to consider, i.e., the hypothetical does not specify or speculate as to second or third order effects far into the future. For example, what could go wrong once people get comfortable intervening to kill an innocent person for the greater good!
And yet this simplified model, kill one to save five, is then transposed onto real-world scenarios, e.g., mandate an emergency-use vaccine that might have rare side effects because it will save more lives than it costs. The credulous go along, and then reality turns out to be more complex than the hypothetical — as it always is.
The vaccine doesn’t actually stop the spread, it turns out, and the adverse effects are far more common and serious than people were led to believe. Moreover, the mandates destroyed livelihoods, ran roughshod over civil liberties, divided families and destroyed trust in public health.
Some might argue it’s true the mandates were wrong because the vaccine wasn’t sufficiently safe or effective, but we didn’t know that at the time! That we should judge decisions based on the knowledge we had during a deadly pandemic, not after the fact.
But what we did know at the time was that real life is always more complex than the hypothetical, that nth-order effects are always impossible to predict. The lie wasn’t only about the safety and efficacy of this vaccine, though they absolutely did lie about that, it was that we could know something like this with any degree of certainty at all.
The problem with utilitarianism, then, is the harms and benefits it’s tasked with weighing necessarily occur in the future. And what distinguishes the future from the past is that it’s unknown. The save one vs five hypothetical is deceptive because it posits all the relevant consequences as known. It imagines future results laid out before us as if they were past.
But in real life we deal with unknowns, and it is therefore impossible do a rigorous accounting of harms and benefits as imagined by the hypotheticals. The “five vs one,” stated as though the event had already happened, is a conceit conjured from an overly simplistic model.
In short, in modeling the future and weighing those projected fictions the same way one would historic facts, they are simply making it up. And once he grants himself license to make things up, the utilitarian can create the moral imperative to do what coincidentally benefits him, e.g, Pfizer profited to the tune of tens of billions of dollars, for the greater good!, which turned out not to be so good. Once you make the specious leap of purporting to know the future, why not go all the way, and make it a future where the greatest good coincides with enriching yourself to the greatest extent possible?
So in summary, as this has gone on longer than I intended, utilitarianism is moral bankruptcy because the “greater good” on which it relies is necessarily in the future, and we cannot predict the future with enough accuracy, especially over the medium and longer term, to do a proper moral accounting.
As a result, whoever has power is likely to cook the books in whatever way he sees fit, and this moral philosophy of the greatest good for the greatest number paradoxically tends toward a monstrous outcome — temporary benefits for the short-sighted few and the greatest misery for most.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: Community
I was an avid IPFS user until yesterday. Many many times I asked simple questions for which I couldn't find an answer on the internet in the #ipfs IRC channel on Freenode. Most of the times I didn't get an answer, and even when I got it was rarely by someone who knew IPFS deeply. I've had issues go unanswered on js-ipfs repositories for year – one of these was raising awareness of a problem that then got fixed some months later by a complete rewrite, I closed my own issue after realizing that by myself some couple of months later, I don't think the people responsible for the rewrite were ever acknowledge that he had fixed my issue.
Some days ago I asked some questions about how the IPFS protocol worked internally, sincerely trying to understand the inefficiencies in finding and fetching content over IPFS. I pointed it would be a good idea to have a drawing showing that so people would understand the difficulties (which I didn't) and wouldn't be pissed off by the slowness. I was told to read the whitepaper. I had already the whitepaper, but read again the relevant parts. The whitepaper doesn't explain anything about the DHT and how IPFS finds content. I said that in the room, was told to read again.
Before anyone misread this section, I want to say I understand it's a pain to keep answering people on IRC if you're busy developing stuff of interplanetary importance, and that I'm not paying anyone nor I have the right to be answered. On the other hand, if you're developing a super-important protocol, financed by many millions of dollars and a lot of people are hitting their heads against your software and there's no one to help them; you're always busy but never delivers anything that brings joy to your users, something is very wrong. I sincerely don't know what IPFS developers are working on, I wouldn't doubt they're working on important things if they said that, but what I see – and what many other users see (take a look at the IPFS Discourse forum) is bugs, bugs all over the place, confusing UX, and almost no help.
-
 @ 0d2a0f56:ef40df51
2024-06-25 17:16:44
@ 0d2a0f56:ef40df51
2024-06-25 17:16:44
Dear Bitcoin Blok Family,
In my last post, I shared how Bitcoin became my personal antidote, rescuing me from destructive behaviors and opening up a world of knowledge. Today, I want to explore how Bitcoin is becoming an antidote for my entire family, solving problems I didn't even know we had.
As I've delved deeper into the Bitcoin rabbit hole, I've realized that I was searching for something beyond personal growth – I was looking for a solution to give my family an identity. When you look at successful families of the past or thriving organizations, you'll notice they're known for something specific. Some families are known for real estate, others for owning businesses, and some for establishing various institutions. This identity ties a family together, giving them a shared purpose and legacy.
For my family, I want that identity to be rooted in Bitcoin. Why? Because Bitcoin brings a focus I haven't seen in anything else. It neutralizes much of what I consider toxic behavior in modern society.
Take TikTok, for example. While there's nothing inherently wrong with the platform, it often promotes content that I find concerning – gender wars, gossip, and sometimes even false information. This issue extends to most social media platforms. Our kids are learning to dance, but they're not learning about money. They're absorbing various behaviors, but they don't understand inflation. We're turning to social media for education and information, which isn't necessarily bad, but it requires careful vetting of sources and filtering out the noise.
What's truly dangerous is how these platforms steal our attention subconsciously. We're wasting time, putting our attention in unproductive places without even realizing it. This is a toxic part of our culture today, and I believe Bitcoin can help solve this problem.
It's challenging to teach kids about money in today's fiat standard. How do you explain the concepts of time and energy when the measuring stick itself is constantly changing? But with Bitcoin, these lessons become tangible.
Moreover, Bitcoin opens up possibilities that seemed out of reach before, particularly in the realm of family banking. In the past, wealthy families in the United States understood the risks of keeping their family's worth in another person's hands or in external institutions. They recognized that protecting wealth comes with certain risks, and establishing a family protocol was crucial.
With Bitcoin, family banking becomes not just possible, but easily achievable and more secure than ever before. Through multi-signature wallet arrangements, we can create a true family bank where each family member holds a key to the family wallet. No funds can be moved without the permission of other family members. This technology eliminates what has been a major stumbling block in the past: trust issues. Now, we can have transparency, trust, and access for all family members.
Imagine a family account where parents and children alike have visibility into the family's finances, but movements of funds require agreement. This not only teaches financial responsibility but also fosters open communication about money within the family. It's a powerful tool for financial education and family cohesion.
This is something we should definitely take advantage of. It's not just about storing wealth; it's about creating a financial system that aligns with our family values and goals. Bitcoin provides the infrastructure for this new form of family banking, one that combines the best aspects of traditional family wealth management with the security and transparency of modern technology.
When it comes to teaching about compound interest and value, Bitcoin provides the perfect use case. Over its lifetime, Bitcoin has been averaging an astonishing 156% year-over-year return. While this number is significant, it's important to note that past performance doesn't guarantee future results. However, even with more conservative estimates, the power of compound interest becomes clear. I challenge you to use a compound interest calculator with a more modest 30% annual return. The results are still astronomical. Imagine teaching your children about saving and investing with potential returns like these. It's a powerful lesson in the value of long-term thinking and delayed gratification.
What I'm getting at is this: there are many forces in our society that hinder positive behavior and promote negative, toxic culture. These forces are stealing our children's time, attention, energy, and of course, money. Bitcoin is the antidote that can start correcting and curing some of that behavior, while also providing tangible lessons in finance and economics, and even reshaping how we approach family wealth management.
By making Bitcoin a central part of our family identity, we:
- Provide a shared purpose and legacy
- Encourage financial literacy from a young age
- Teach valuable lessons about time, energy, and value
- Promote long-term thinking and delayed gratification
- Offer an alternative to the instant gratification of social media
Bitcoin isn't just an investment or a technology – it's a paradigm shift that can reshape how we think about family, legacy, and education. It's an antidote to the toxic aspects of our digital age, offering a path to a more thoughtful, intentional way of living.
As we continue this journey, I invite you to consider: How could Bitcoin reshape your family's identity? What toxic behaviors could it help neutralize in your life? Until next time check out the below video on what some may know as the "Waterfall or "Rockefeller Method". https://youtu.be/MTpAY1LKfek?si=s7gA4bt_ZoRGAlAU
Stay sovereign, stay focused,
Joe Thomas Founder, The Bitcoin Blok
-
 @ 000002de:c05780a7
2024-06-25 15:28:01
@ 000002de:c05780a7
2024-06-25 15:28:01Lately it seems like I keep noticing people that are sympathetic to anarchism and libertarian ideas completely misunderstanding governance. It really seems like this might be one of the biggest mental blocks people have. I wonder if it is mostly the fault of libertarians and anarchists.
Those in the liberty movement (broadly) rant and demonize the government. This is completely justified. I've done it for years. I've noticed that more experienced communicators will tend to say "The State" instead of government. Years ago I heard someone explain how to think about three terms often used incorrectly.
- The country is the land
- The nation is the people
- The state is the government
I don't recall learning this in school. It is possible it was in a textbook but I doubt it. The country part I think most people do get. Nation less so. The best example of a nation without a country are Native Americans. Tribes are nations without a country (their historical lands). Tribes have their own governments and a certain amount of sovereignty in the lands they are allowed to inhabit.
The state is the word that I have found most people are confused about. People used to tell me, you hate the government so much. Why don't you leave. Well, I don't hate the nation(people) or the country(land). It is the governance system I hate. I don't even hate the people that are working in it.
Its funny to me that people on the red or blue team seem to hate the government when their side isn't in power but if someone points to issues in the system itself, well that's just crazy.
So what about those people that are sympathetic to libertarian values? Many of them say things like this. Well, I agree with you on taxes and the corruption of the government. But you always need a government. My usual response is yes. You do need governance. But you don't need a state or government. My home is governed by my wife and I. Businesses have their own governance models. Bitcoin does as well. But we do not need a single entity with a monopoly on violence.
So why is there so much confusion on this topic? I think there are two reasons.
The first is ignorance. The state of the world is largely invisible to most people. We are purposely kept ignorant of how our world works. The State isn't really discussed as a separate entity from the country and nation.
The second reason for the confusion is how libertarians and anarchists communicate. There are some that just foolishly believe people do not need governance. Honestly in my experience they are either just young or do not think deeply enough. They haven't steel manned their arguments yet. In my experience this is a small percentage of people though.
I think people in the liberty movement just need to do a better job communicating ideas. Instead of saying we need to get rid of the government one might say we need to get rid of the state. Another way to lead into this is to speak about the empire vs. the government. Talk about the monopoly which the state holds. How competition leads to better outcomes vs. monopoly.
What do you think? Have you noticed this hurdle as well? I think many people hear good ideas and agree but assume we are just dummies that believe in a fairy tale.
If private or decentralized governance is interesting to you, you might enjoy reading Chaos Theory by Bob Murphy. Its short and answer many common objections to private governance.
-
 @ bcea2b98:7ccef3c9
2024-04-14 14:27:30
@ bcea2b98:7ccef3c9
2024-04-14 14:27:30I grew up on a farm in Minnesota in the 1970s. Life was all about hard work and family. We learned the value of getting our hands dirty early on, helping out with chores from sunup to sundown.
Farming taught me the importance of perseverance. Some years, the weather was on our side, and the crops flourished. Other years, we faced setbacks, like droughts or pests. But we never gave up. We'd find ways to adapt and keep the farm going.
Our community was tight-knit. During busy times, neighbors pitched in without hesitation. We'd come together for barn raisings or help each other out with harvesting. It was all about supporting one another.
Growing up, we didn't have fancy gadgets or social media. Our entertainment was exploring the fields and forests, using our imagination to create adventures. We learned to appreciate the simple things in life and the importance of face-to-face connections.
Nowadays, things have changed. Technology rules the world, and young people are glued to their screens. But deep down, I think we still share some of the same values. We all want to make a difference and leave the world a better place.
-
 @ 1c6b3be3:73f0ae6f
2024-08-03 04:05:45
@ 1c6b3be3:73f0ae6f
2024-08-03 04:05:45Bitcoin Optech
Bitcoin Optech Newsletter #314 (8 min) The Bitcoin Core project has disclosed two vulnerabilities affecting older versions of the software (before 0.21.0). The first vulnerability allows for a remote crash by sending excessive addr messages, which was discovered by Eugene Siegel and fixed in Bitcoin Core 22.0. The second vulnerability is a remote crash on local networks when UPnP is enabled, caused by a malicious device repeatedly sending variants of a UPnP message until the node crashes. This issue was discovered and reported to the miniupnpc project by Ronald Huveneers and fixed in Bitcoin Core 22.0. Additionally, Niklas Gögge announced these disclosures on the Bitcoin-Dev mailing list.
The newsletter also summarizes a proposed approach for optimizing miner transaction selection when using cluster mempool. Pieter Wuille posted to Delving Bitcoin about ensuring that miner block templates can include the best set of transactions. The approach divides related transactions into an ordered list of chunks, with each chunk obeying two constraints. If any transactions within the chunk depend on other unconfirmed transactions, those other transactions must either be a part of that chunk or appear in a chunk earlier in the ordered list of chunks. Each chunk must have an equal or higher feerate than the chunks that come after it in the ordered list. Wuille also discusses how to handle large chunks and proposes breaking them down into smaller sub-chunks based on their feerates. These sub-chunks can then be considered for inclusion in the remaining block space.
🍵 "btc | bitcoin | lightning network | asic" - Google News
Bitcoin network difficulty breaks 3-month downtrend to mark new ATH - Cointelegraph Bitcoin’s Anticipated Retail Resurgence - Bitcoin Magazine Bitcoin Memecoins Runes Make Up 35% of All the Chain's Transactions - The Defiant - DeFi News Bitcoin network difficulty reaches record high amid price volatility - CoinJournal Bitcoin Mining Difficulty Peaks as BTC Price Falls - Decrypt Bitcoin Difficulty Hits New ATH, What’s Next? - CoinGape Top 3 Price Prediction Bitcoin, Ethereum, Ripple: Bitcoin bounces off from the ascending trendline - FXStreet Casper Network Resumes Functioning After Last Week’s Attack - Live Bitcoin News Bitcoin Mining Difficulty Jumps 10%: What It Means - Bitcoinist What is Flash Protocol: issuing assets on the Bitcoin network - OKX Bitcoin hits $70,000 amid decreasing transaction costs - Baseline
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Castas hindus em nova chave
Shudras buscam o máximo bem para os seus próprios corpos; vaishyas o máximo bem para a sua própria vida terrena e a da sua família; kshatriyas o máximo bem para a sociedade e este mundo terreno; brâmanes buscam o máximo bem.
-
 @ bcea2b98:7ccef3c9
2024-04-11 15:37:30
@ bcea2b98:7ccef3c9
2024-04-11 15:37:30This could be about professional work, raising a family, or other ventures. Mentioning one thing doesn't mean something else is less important. This may give you freedom in the response.
The most important contributions I believe I have made was raising a family and contributing to open-source software. Everyone is old now, but memories and git live on.
-
 @ c43d6de3:a6583169
2024-06-24 16:56:56
@ c43d6de3:a6583169
2024-06-24 16:56:56"If you do tomorrow what you did today, you will get tomorrow what you got today." - Benjamin Franklin
Seize the Day

Image from article- https://community.thriveglobal.com/want-your-authentic-self-mindfulness-is-a-gateway/Confliction
There are two conflicting approaches to life: Delay gratification today for a wealthy tomorrow and carpe diem Seize the Day and live like today is your last. Usually, when someone prescribes delayed gratification they refer to finances; save a dollar today for a hundred tomorrow. Carpe diem often refers to smelling the coffee, enjoying the little things and not putting off for tomorrow what could've been done today.
I've never felt the two of those prescriptions collide more violently than now as a father of two beautiful kids. I find it more difficult than ever before to make decisions that might benefit my future over being present for my kids. Time being the finite thing that it is, often I can only choose one.
Image from Adobe ImagesTwo Fathers, Two Approaches: Enough Small Moments Equal A Big Moment My brother in-law and I have different approaches to this. He tends to delay gratification. More often than not, he's out on business and misses minor family events and outings. Meanwhile, I often choose to attend even the smallest family events as opposed to going on business.
I should mention, my brother in-law doesn't dare miss the big events. He's always there for a birthday, baptism, or graduation but he misses outings to the beach or spring. He misses the books read by the bed and the dimming of the light just before a kiss goodnight.
If you miss enough small moments, you a miss big one.

Image from article- https://www.spiritualmom.com/god-is-weaving-a-tapestry/
Since my children were born I vowed to live as much in the moment as I could. In the moment, I'm happy to be with my kids stitching together cherished mementos that will be the tapestry of our lives. These indelible memories not only serve to make me happy but, I believe they'll work as the sinews and tendons that come together to form my children's personality and identity. My relationship with my kids and family will tighten as their persona grows.
I don't have facts from studies or scientific analysis, but I have a gut feeling its the strength of the tapestry of our lives that determines how resilient my children will be. When they encounter hard times they'll carry the uplifting memories of good times and they'll have the comfort of knowing there's a tightknit family at their backs to get through it.
That said, I've never heard my brother in-law complain about money.
I can't say I struggle for cash either. I make ends meet, but my wife and I have experienced that nervous rush when the AC blows out mid-summer and we wonder if we would have enough to pay for the down payment of a new unit and the mortgage at the beginning of the month.
What's been bothering me most as of late is my damn near non-existent retirement fund.

Image from ANATOMY OF A SOLDIER BY HARRY PARKER REVIEW - UNUSUAL PERSPECTIVES ON WARFARE FICTION
Commitments- To My Nation, To My Self
My biggest conflict today is tied to the commitment I made to the United States Army Reserves years before the birth of my children. While I can decide not to go on business like my brother in-law does, I can't simply not attend drill (one weekend a month) or go off on annual training (2–3 weeks a year). Failure to attend to my military obligations can result in a dis-honorable discharge. Having that hanging over my head will forever ruin any lucrative opportunities for employment and public service.
More often than not, my relatively small obligation to the Army Reserves has stood in direct conflict with my desire to be present in my kids lives as well as the lives of my friends and family. Some how, I've had the misfortune of having drills and annual training scheduled on major events like weddings, baptisms, and birthdays; the very things I vow never to miss.
There are ways to request those special days off and make it up on a later date and when I can, I do. However, I've been forced to go unaccounted for on several occasions when special events are back to back and overlap with already requested days off. That's led to conflict in the past but, I've been fortunate enough to have good leaders who've understood why I preferred to be absent in the military over absent in a major life event. It would be easiest, and most convenient, to resign my congressional commission as an officer and leave the Army Reserves. This is when I feel that great internal conflict.
Serving in the Army Reserves allows me to give back to my nation and grants me several financial benefits that would otherwise be completely lost. Medical insurance is remarkably cheaper than what I would have to deal with as a civilian. I get a world of benefits when purchasing a house and I can apply for special grants if ever needed. Perhaps most important of all, if I stick around for the full 20 years (I have almost 9 now) I will have a very nice retirement pension waiting for me when I turn 65. This is where that differed gratification really kicks in.
When I really boil it down to pros and cons, there's just way too many pros to staying in the Reserves than cons.

Image of Jordan Peterson from Video Clip- "4 years video"
Phases of Life Approach
World renown psychologist Jordan Peterson says "you have little kids for 4 years and if you miss it, its done." For Jordan, this is time period is peak experience for your kids. As I write this, my eldest just turned two and my youngest is 9 months. I'm not quite halfway there yet and I can't let up now.
I don't want to test to see if what Jordan Peterson says is true, I'm going to continue living as much in the moment as is possible during these early years of my children's lives. If I stay in the army reserves throughout this time I will have had 13 years of service by the time my youngest is 4.
Taking this approach, I will have been very present in the first 4 years of my kids lives and will only have to serve seven more years to acquire that retirement.
For me, today is Gold and tomorrow is Silver.
People have sacrificed worse.
artstr #plebchain #writing
I want to show the world that life is a scroll riddled with ink. The marks will only ever be simple blots on the parchment unless you pause and perceive them for the characters they are.
I'm constantly thinking about what the future could look like if we just take action.
More of my thoughts about the future and the world around us are coming soon...
Thank you for Reading this article. If you liked it and would consider zapping some sats, doing so supports me and motivates me to continue writing!
If you are interested in Fiction writing, visit my NOSTR page Fervid Fables: npub1j9cmpzhlzeex6y85c2pnt45r5zhxhtx73a2twt77fyjwequ4l4jsp5xd49
-
 @ 25f67ef1:d3cb96eb
2024-06-24 11:41:31
@ 25f67ef1:d3cb96eb
2024-06-24 11:41:31In a stunning turn of events, Bitcoin's value has nosedived a staggering 15%, falling from an all-time high of $72,000 per BTC to $61,000. The cause? None other than former United States president, Donald J. Trump, whose recent comments and rumored policies have sent shockwaves through the global Bitcoin community.
In a recent rally, Trump declared, "We want all the remaining bitcoin to be made in the USA." This bold statement has left many scratching their heads, wondering if the ex-president fully grasps the decentralized nature of Bitcoin. Nevertheless, his followers cheered, and the markets trembled.
Adding fuel to the fire, rumors are swirling about a proposed tariff on offshore bitcoin brought into the United States. Whether such a measure could work in practice is still to be determined, but the idea of taxes on foreign sourced bitcoin has many American businesses with international operations nervous.
But that's not all. In a move that could only be described as draconian, whispers of a plan to use recursive covenants on Bitcoin have emerged. The scheme aims to ringfence all the bitcoin currently held in US custody, such as those held by the "too big to fail" Coinbase, the primary custodian for corporate america, wall street and the popular ETFs. These covenants would effectively prevent those coins from ever being sent outside of whitelisted US addresses. If true, this would essentially create a digital Berlin Wall around American Bitcoin, isolating it from the rest of the world.
Critics argue that these policies are nothing more than a misguided attempt to assert dominance over the borderless digital cash. By prioritizing a "USA first" approach, Trump risks alienating global partners and further isolating the United States on the international stage. Neighboring countries, already wary of America's unpredictable policies, are likely to view these moves as antagonistic and regressive.
And let's not forget the opportunists lurking in the shadows. Trump's buddies and notorious shitcoiners are reportedly licking their chops, hoping that once he's in charge, they'll have a free hand to write regulations that allow them to prey on the public with their dubious shitcoin offerings. These unregistered securities are a haven for scams, and with the right legislation, these predators could wreak havoc on unsuspecting investors.
The fear of Trump's rising popularity and his policy direction for Bitcoin has undoubtedly contributed to the recent market uncertainty. Investors are apprehensive about the future of bitcoin in the US under a potential second Trump administration.
As the 2024 US presidential election looms, the Bitcoin community can only watch and wait, bracing for more market volatility. Will Bitcoin recover from the "Trump Dump"? Only time will tell. For now, it seems the ex-president's quest to "Make America Great Again" might just come at the expense of their burgeoning Bitcoin economy.
-
 @ d34e832d:383f78d0
2024-08-03 03:40:45
@ d34e832d:383f78d0
2024-08-03 03:40:45In the realm of economic theory and practice, few topics generate as much debate as centralized economic planning. Proponents argue that it allows for coordinated and equitable allocation of resources, while critics highlight its inefficiencies and systemic flaws. I just want to look into the inherent shortcomings of centralized economic planning, focusing on the impossibility of aggregating and processing the vast amount of information required to make efficient decisions. Through a structured exploration of key points and real-world examples, we will look at why centralized planning often fails to achieve its intended goals.
The Mirage of Perfect Planning
Imagine a world where a single entity could flawlessly dictate the allocation of resources, ensuring optimal outcomes for all. While this vision of centralized economic planning might seem appealing, it is fundamentally unattainable. The sheer complexity and dynamic nature of economies render such centralized control impractical. This essay critiques centralized economic planning by examining its fundamental inefficiencies and the impossibility of handling the immense information required for effective decision-making.
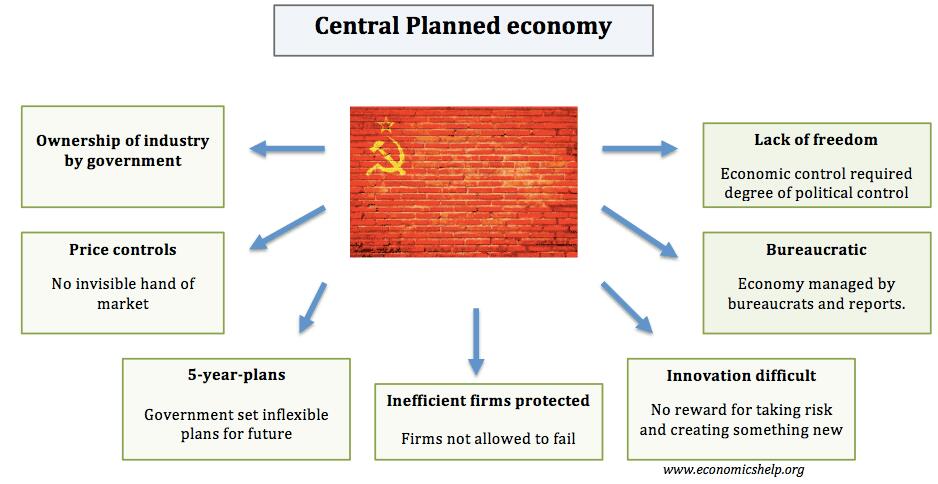
The Information Problem: A Fundamental Challenge
One of the central critiques of economic planning is the information problem, famously articulated by economist Friedrich Hayek. Hayek argued that no central authority could ever possess the dispersed and tacit knowledge held by individuals in a free market.
Key Points: 1. Dispersed Knowledge: - In a market economy, knowledge is spread across countless individuals who possess unique information about their specific circumstances. Central planners cannot effectively gather and utilize this dispersed knowledge. - Example: A farmer in a remote village understands local soil conditions and market needs better than a distant bureaucrat.
- Dynamic and Ever-Changing Data:
- Economic data is constantly evolving, making it impossible for central planners to keep pace with real-time changes. This lag results in outdated or inaccurate decisions.
- During The Times Of The Soviet Era: During the Soviet era, planners often relied on outdated production data, leading to shortages and surpluses.
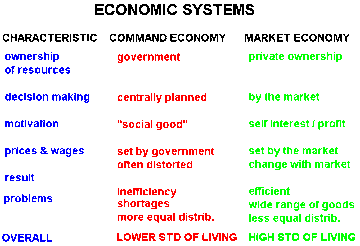
Incentive Structures and Innovation: The Human Element
Centralized planning also struggles with creating appropriate incentives for innovation and efficiency. Without the profit motive and competition, individuals and firms lack the drive to innovate and improve productivity.
Key Points: 1. Lack of Profit Motive: - In centrally planned economies, the absence of profit incentives dampens entrepreneurial spirit and innovation. Entrepreneurs in a free market are motivated by the potential for profit, driving technological advancement and economic growth. - All authoritative structures struggle for the popular narrative of freedom, but are the controllers of pro-censorship themselves: The technological stagnation in centrally planned economies versus the rapid innovation seen in market economies like the United States.
- Bureaucratic Inefficiencies:
- Centralized planning often leads to cumbersome bureaucracies that stifle creativity and efficiency. Decisions are slowed by red tape, and innovative ideas are frequently ignored.
- Anecdote: The inefficiencies of the bureaucratic system in the former Eastern Bloc countries often resulted in suboptimal production and resource allocation.
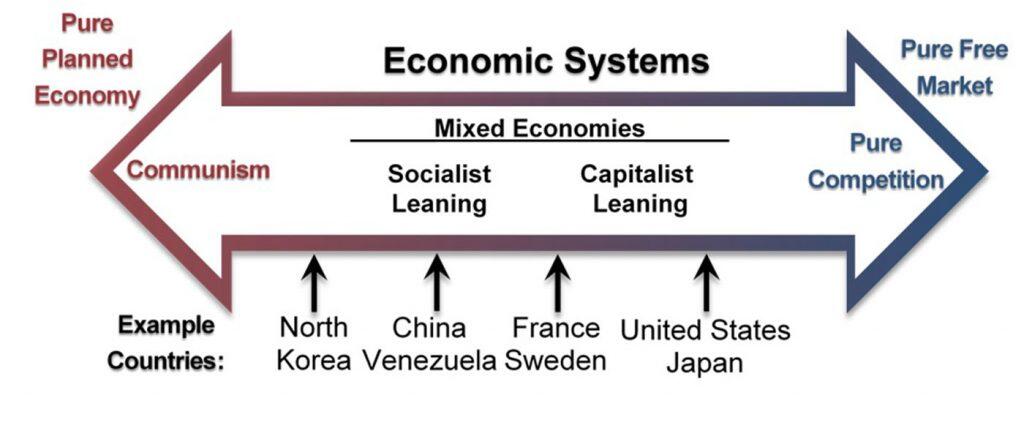
Real-World Failures: Lessons from History
History provides numerous examples of the failures of centralized economic planning. These examples highlight the practical difficulties and negative outcomes associated with trying to control complex economies from the top down.
Key Examples: 1. The Soviet Union: - The collapse of the Soviet economy is a poignant example of the failures of central planning. Chronic shortages, lack of consumer goods, and inefficiencies plagued the system until its eventual collapse. -

- Maoist China:
- During the Great Leap Forward, Mao Zedong's attempts at rapid industrialization and agricultural collectivization led to one of the deadliest famines in history.
- Visual: Historical photograph depicting the effects of the Great Leap Forward.
The Case for Decentralized Economies
Centralized economic planning is fundamentally flawed due to the impossibility of aggregating and processing the vast amount of information required for efficient decision-making. The dispersed knowledge of individuals, coupled with the dynamic nature of economic data, renders central planning ineffective. Moreover, the lack of appropriate incentives for innovation and efficiency further hampers centrally planned economies. History has shown us the dire consequences of attempting to control complex economies from the top down. As we move forward, embracing decentralized economic systems that leverage the power of individual choice and market mechanisms will be crucial for fostering innovation, efficiency, and economic prosperity.
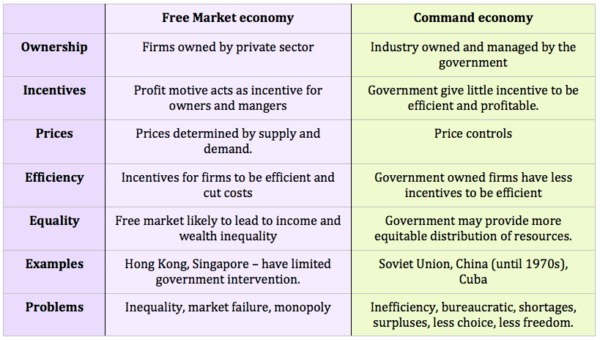
-
 @ a012dc82:6458a70d
2024-08-02 23:08:05
@ a012dc82:6458a70d
2024-08-02 23:08:05Table Of Content
-
Who is Sam Bankman-Fried?
-
What are the charges against him?
-
What is the potential impact on FTX?
-
What is the latest update?
-
Conclusion
-
FAQ
Sam Bankman-Fried, the 29-year-old founder of FTX crypto exchange, has been making headlines in the past year as he has risen to become one of the most influential people in the world of cryptocurrency. However, he is now facing some serious legal challenges that could threaten his reputation and business empire. In this article, we will take a closer look at the latest developments in Bankman-Fried's legal battle.
Who is Sam Bankman-Fried?
Sam Bankman-Fried is a former Wall Street trader who founded FTX in 2019. The exchange quickly became popular for its innovative products, including leveraged tokens and futures contracts. Bankman-Fried is also known for his charitable contributions, particularly his donations to the effective altruism movement.
What are the charges against him?
Bankman-Fried has been charged with market manipulation and insider trading by the US Commodity Futures Trading Commission (CFTC). The charges stem from allegations that he and his colleagues manipulated the price of a futures contract on the Deribit crypto exchange in 2018. According to the CFTC, Bankman-Fried used an algorithmic trading strategy to move the market in his favor.
Bankman-Fried has denied the charges and has stated that the trades in question were made for legitimate reasons. He has also said that he will fight the charges in court.
What is the potential impact on FTX?
FTX has become one of the most popular crypto exchanges in the world, thanks in large part to Bankman-Fried's leadership. However, the legal battle could have serious consequences for the exchange. If Bankman-Fried is found guilty, he could face fines, sanctions, and even jail time. This could damage his reputation and make it more difficult for FTX to attract new users.
In addition, the legal battle could distract Bankman-Fried from running the day-to-day operations of FTX. This could lead to a decline in the quality of service that the exchange provides to its users.
What is the latest update?
The legal battle is still ongoing, and it is unclear when a verdict will be reached. However, there have been some recent developments that could have an impact on the case.
Prosecutors now charge Bankman-Fried with 12 criminal counts in total, including conspiracy to commit fraud on customers of FTX, conspiracy to operate an unlicensed money transmitting business, conspiracy to commit wire fraud on lenders to Alameda Research, and conspiracy to make unlawful political contributions and defraud the Federal Election Commission. Bankman-Fried was initially arrested in December and charged with eight financial crimes. He pleaded not guilty to all charges and his trial is scheduled for October.
FTX was one of the largest crypto exchanges in the world before collapsing last November due to alleged criminal mismanagement by Bankman-Fried and others. The new charges against Bankman-Fried allege that he made illegal donations to both Democrats and Republicans, flooding the political system with tens of millions of dollars. Bankman-Fried was popular with politicians and invited them to fancy business conferences in the Caribbean, while also donating millions to candidates, including President Joe Biden. However, some politicians are now returning those donations. The White House has not commented on the matter.
Conclusion
Sam Bankman-Fried's legal battle is a reminder of the risks and challenges that come with operating in the world of cryptocurrency. While he has built a successful business and a strong reputation in the industry, he now faces serious accusations that could threaten his legacy. It remains to be seen how this case will play out, but it is clear that the outcome will have a significant impact on the future of FTX and the broader crypto ecosystem.
FAQ
How has Sam Bankman-Fried responded to the charges? Bankman-Fried has denied the charges and has stated that the trades in question were made for legitimate reasons. He has also said that he will fight the charges in court.
What is Sam Bankman-Fried known for in the cryptocurrency industry? Sam Bankman-Fried is known for founding FTX, a popular cryptocurrency exchange, and for his innovative products, including leveraged tokens and futures contracts. He is also known for his charitable contributions, particularly his donations to the effective altruism movement.
What is the potential outcome of the legal battle? The outcome of the legal battle is uncertain and will depend on the evidence presented in court. If Bankman-Fried is found guilty, he could face fines, sanctions, and even jail time. If he is found not guilty, the charges against him will be dropped and he will be able to continue running FTX without legal repercussions.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ bcea2b98:7ccef3c9
2024-04-11 02:25:20
@ bcea2b98:7ccef3c9
2024-04-11 02:25:20 -
 @ 6c8c7979:15595f3e
2024-06-24 08:45:18
@ 6c8c7979:15595f3e
2024-06-24 08:45:18Vincent van Gogh is one of the most prominent artists in the history of global art, with a significant influence on modern artistic movements. He was born in the Netherlands in 1853 and passed away in 1890. Despite not achieving fame during his lifetime, his works later became among the most impactful in fine arts.
Van Gogh's works are characterized by vibrant colors and rapid brush strokes, giving his paintings a unique style. His pieces often reflect nature and everyday life with a touch of deep emotion and drama. Some of his most famous works include "Starry Night," "The Night Cafe," "Irises," and "Wheatfield with Crows."
Throughout his life, van Gogh faced numerous personal and psychological challenges, which imbued his works with a sense of depth and contemplation. He struggled with severe mental disorders and social tensions, which greatly influenced his art.
After his death, public interest in his works grew significantly, and he came to be regarded as a pioneer of expressionism and modern art. His profound impact on global art is evident in the many movements and subsequent artists who drew inspiration from his techniques and subjects.
In summary, Vincent van Gogh remains an exceptional artistic figure, leaving an unforgettable legacy in art history. His works continue to inspire and captivate audiences worldwide with their beauty and artistic depth.
-
 @ bcea2b98:7ccef3c9
2024-04-03 21:38:13
@ bcea2b98:7ccef3c9
2024-04-03 21:38:13Growing up in small-town Minnesota in the 60s, life's meaning seemed straightforward – get educated, find a steady job, start a family, maybe even get that picket fence house. Our generation had a roadmap laid out for us.
But life has a way of messing with your plans. When I was young, I thought my purpose was to be a success story, chasing that American Dream. Raising kids and experiencing heartbreaks changed my perspective. Success stopped being about material things or career status.
Now, it's simpler. Life's meaning is in those late-night chats with my adult children, laughing until it hurts. It's seeing my grandkids finger paint with a wonder you can't recreate as a grown-up. It's finding peace in a quiet moment in the garden.
I went from chasing some grand meaning to finding it in the little things, in connections. It's not as flashy as my youthful ambitions, but it's richer, truer, and way more fulfilling. Funny how you can spend a lifetime figuring things out, and sometimes it's as simple as waking up grateful to be in this messy, beautiful world.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Economics
Just a bunch of somewhat-related notes.
- notes on "Economic Action Beyond the Extent of the Market", Per Bylund
- Mises' interest rate theory
- Profits, not wages, as the originary factor
- Reisman on opportunity cost
- Money Supply Measurement
- Per Bylund's insight
- Maybe a new approach to the Austrian Business Cycle Theory, some disorganized thoughts
- An argument according to which fractional-reserve banking is merely theft and nothing else
- Conjecture and criticism
- Qual é o economista? (piadas)
- UBI calculations
- Donations on the internet
-
 @ 6a39a186:88f51c19
2024-06-24 07:55:21
@ 6a39a186:88f51c19
2024-06-24 07:55:21Privacy, Security, and Real-World Applications
We Are Still Early
Concerning Bitcoin, privacy and security remain paramount. As an enthusiast in Ecash privacy and security, I aim to shed light on some of the most promising and undervalued Bitcoin frameworks. These frameworks offer robust solutions for enhancing privacy, security, and scalability, making Bitcoin more adaptable for various industries. Lets's examine their strengths and weaknesses, supported by real-world examples.
1. Mimblewimble: Enhancing Privacy and Scalability
Overview
Mimblewimble is a privacy-centric blockchain protocol designed to enhance the confidentiality and scalability of Bitcoin transactions. Mimblewimble uses cryptographic innovations to obscure transaction details while ensuring network security.
Strengths
- Enhanced Privacy: Mimblewimble transactions are confidential, hiding transaction amounts and addresses.
- Scalability: The protocol significantly reduces blockchain bloat, improving efficiency and speed.
- Security: By using cryptographic primitives, Mimblewimble ensures that transactions are secure and verifiable.
Weaknesses
- Compatibility: Mimblewimble is not fully compatible with Bitcoin’s existing infrastructure, requiring significant changes to the network.
- Complexity: The protocol's complexity can be a barrier to understanding and adoption.
Real-World Example: Grin and Beam
Grin and Beam are two cryptocurrencies that have implemented Mimblewimble. Grin focuses on simplicity and community-driven development, while Beam emphasizes user-friendly interfaces and governance structures. Both projects demonstrate Mimblewimble’s potential in providing enhanced privacy and scalability.
2. Lightning Network: Scaling Bitcoin Transactions
Overview
The Lightning Network is a second-layer solution designed to enable fast and low-cost transactions on the Bitcoin network. By creating off-chain transaction channels, the Lightning Network alleviates congestion on the main blockchain.
Strengths
- Speed: Transactions on the Lightning Network are nearly instantaneous.
- Low Fees: Off-chain transactions significantly reduce transaction costs.
- Scalability: The network can handle millions of transactions per second, far exceeding the main blockchain's capacity.
Weaknesses
- Liquidity: Users need to lock up funds in channels, which can limit liquidity.
- Complexity: Setting up and managing channels can be technically challenging.
- Security: Off-chain transactions require robust security measures to prevent fraud and ensure reliability.
Real-World Example: El Salvador’s Bitcoin Adoption
El Salvador’s adoption of Bitcoin as legal tender showcases the Lightning Network’s capabilities. The government and businesses use the network to facilitate everyday transactions, demonstrating its effectiveness in a real-world economy.
3. Taproot and Schnorr Signatures: Improving Privacy and Efficiency

Overview
Taproot and Schnorr signatures are recent upgrades to the Bitcoin protocol that enhance privacy, security, and efficiency. Taproot allows complex transactions to appear as simple ones, while Schnorr signatures enable aggregation, reducing data size.
Strengths
- Privacy: Taproot masks the complexity of transactions, enhancing privacy.
- Efficiency: Schnorr signatures reduce the data size of transactions, improving blockchain efficiency.
- Security: Both upgrades maintain Bitcoin’s robust security model.
Weaknesses
- Adoption: Widespread adoption of these upgrades is still in progress.
- Complexity: Implementing and understanding these changes require technical expertise.
Real-World Example: Taproot Activation
The activation of Taproot in November 2021 marked a significant milestone for Bitcoin. It demonstrates the network’s ability to evolve and adopt new features that enhance privacy and efficiency. Various Bitcoin services and wallets are beginning to integrate Taproot, showing its practical benefits.
4. Sidechains: Expanding Bitcoin’s Capabilities
Overview
Sidechains are independent blockchains that run parallel to the Bitcoin mainchain. They enable experimentation with new features and scalability solutions without affecting the main network.
Strengths
- Flexibility: Sidechains allow for the development and testing of new features.
- Scalability: They can handle additional transactions, reducing load on the main blockchain.
- Interoperability: Sidechains can interact with the main Bitcoin network, enhancing its functionality.
Weaknesses
- Security: Ensuring the security of sidechains can be challenging.
- Complexity: Developing and maintaining sidechains require significant technical expertise.
Real-World Example: Liquid Network
The Liquid Network, developed by Blockstream, is a sidechain that enhances Bitcoin’s functionality for traders and exchanges. It provides faster settlements and confidential transactions, showcasing the practical benefits of sidechains.
5. CoinJoin: Strengthening Transaction Privacy

Overview
CoinJoin is a privacy-enhancing technique that combines multiple Bitcoin transactions into a single transaction, making it difficult to trace individual inputs and outputs.
Strengths
- Enhanced Privacy: CoinJoin obscures transaction details, improving user privacy.
- Community Support: Widely supported by the Bitcoin community and integrated into several wallets.
Weaknesses
- User Experience: The process can be complex and may require additional steps for users.
- Partial Privacy: While it improves privacy, it is not foolproof and can still be subject to analysis.
Real-World Example: Wasabi Wallet
Wasabi Wallet is a Bitcoin wallet that implements CoinJoin to enhance user privacy. It provides an intuitive interface for conducting private transactions, illustrating CoinJoin’s practical application.
Make The Ecosystem Happen
The evolution of Bitcoin frameworks continues to push the boundaries of what is possible in the realm of digital currency. From Mimblewimble’s privacy and scalability enhancements to the Lightning Network’s speed and efficiency, these frameworks offer promising solutions to current challenges. Real-world examples like El Salvador’s Bitcoin adoption and the Liquid Network’s advancements highlight the practical benefits and potential of these technologies. As the Bitcoin ecosystem evolves, these frameworks will play a crucial role in shaping the future of digital finance, ensuring privacy, security, and scalability for users worldwide.
Further Reading
For those interested in delving deeper into the frameworks discussed in this article, here are some recommended resources:
- Mimblewimble:
- Mimblewimble: What is it? How It Works?
- Grin
-
Lightning Network:
- The Lightning Network For Businesses and Developers
- Historical Look At Bitcoin Adoption In El Salvador
-
Taproot and Schnorr Signatures:
- Taproot: The Next Major Upgrade for Bitcoin
-
Sidechains:
- Blockstream’s Liquid Network
-
CoinJoin:
- Wasabi Wallet
- Understanding CoinJoin
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Thoughts on Nostr key management
On Why I don't like NIP-26 as a solution for key management I talked about multiple techniques that could be used to tackle the problem of key management on Nostr.
Here are some ideas that work in tandem:
- NIP-41 (stateless key invalidation)
- NIP-46 (Nostr Connect)
- NIP-07 (signer browser extension)
- Connected hardware signing devices
- other things like musig or frostr keys used in conjunction with a semi-trusted server; or other kinds of trusted software, like a dedicated signer on a mobile device that can sign on behalf of other apps; or even a separate protocol that some people decide to use as the source of truth for their keys, and some clients might decide to use that automatically
- there are probably many other ideas
Some premises I have in my mind (that may be flawed) that base my thoughts on these matters (and cause me to not worry too much) are that
- For the vast majority of people, Nostr keys aren't a target as valuable as Bitcoin keys, so they will probably be ok even without any solution;
- Even when you lose everything, identity can be recovered -- slowly and painfully, but still --, unlike money;
- Nostr is not trying to replace all other forms of online communication (even though when I think about this I can't imagine one thing that wouldn't be nice to replace with Nostr) or of offline communication, so there will always be ways.
- For the vast majority of people, losing keys and starting fresh isn't a big deal. It is a big deal when you have followers and an online persona and your life depends on that, but how many people are like that? In the real world I see people deleting social media accounts all the time and creating new ones, people losing their phone numbers or other accounts associated with their phone numbers, and not caring very much -- they just find a way to notify friends and family and move on.
We can probably come up with some specs to ease the "manual" recovery process, like social attestation and explicit signaling -- i.e., Alice, Bob and Carol are friends; Alice loses her key; Bob sends a new Nostr event kind to the network saying what is Alice's new key; depending on how much Carol trusts Bob, she can automatically start following that and remove the old key -- or something like that.
One nice thing about some of these proposals, like NIP-41, or the social-recovery method, or the external-source-of-truth-method, is that they don't have to be implemented in any client, they can live in standalone single-purpose microapps that users open or visit only every now and then, and these can then automatically update their follow lists with the latest news from keys that have changed according to multiple methods.
-
 @ bcea2b98:7ccef3c9
2024-04-02 15:07:10
@ bcea2b98:7ccef3c9
2024-04-02 15:07:10After a busy day filled with work and responsibilities, it is difficult for me to transition into a relaxed state conducive to reading. I have trouble slowing down, thinking about the day's events and tomorrow's tasks, and it can make it difficult to focus on the words on the page. When I was younger it seems easier to get into a relaxed state, but I find it more difficult as I age.
For those who struggle to slow down and get in the right mindset for reading after a busy day, what techniques or routines have you found effective to help with this transition? Do you prefer to read at specific times, such as early morning or late at night, to avoid the mental residue of a hectic day? I would be interested to hear your techniques and maybe to try adopt some of them.
-
 @ 6a39a186:88f51c19
2024-06-24 01:28:00
@ 6a39a186:88f51c19
2024-06-24 01:28:00The Superiority of Asymmetric Encryption
Cryptography plays a pivotal role in protecting sensitive information. Two primary forms of encryption—symmetric and asymmetric—are utilized to secure data. This essay argues that while both symmetric and asymmetric encryption have their merits, asymmetric encryption offers superior security and practical advantages in most contemporary applications. By exploring the fundamental differences, strengths, and weaknesses of each type, this essay will demonstrate why asymmetric encryption is the preferred choice for modern cryptographic needs.
Symmetric Encryption
Definition and Mechanism
Symmetric encryption, also known as secret-key encryption, involves the use of a single key for both encryption and decryption. Popular algorithms include AES (Advanced Encryption Standard) and DES (Data Encryption Standard). The process is straightforward: the sender encrypts the plaintext using the key, and the receiver decrypts the ciphertext with the same key.
Strengths of Symmetric Encryption
- Speed and Efficiency: Symmetric encryption is generally faster and more efficient than asymmetric encryption, making it suitable for encrypting large amounts of data quickly.
- Simplicity: The mechanism of symmetric encryption is relatively simple, which can be advantageous in systems with limited computational power.
Weaknesses of Symmetric Encryption
- Key Distribution Problem: The primary challenge with symmetric encryption is securely distributing the key to both parties without interception by malicious actors.
- Scalability Issues: As the number of users increases, the number of unique keys needed for secure communication grows exponentially, complicating key management.
Asymmetric Encryption
Definition and Mechanism
Asymmetric encryption, or public-key encryption, uses a pair of keys: a public key for encryption and a private key for decryption. Notable algorithms include RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography). The public key is openly shared, while the private key remains confidential.
Strengths of Asymmetric Encryption
- Enhanced Security: The separation of keys eliminates the need for secure key distribution channels. The public key can be freely shared, reducing the risk of key interception.
- Scalability: Asymmetric encryption scales efficiently. Each user has a single pair of keys, simplifying key management in large networks.
- Authentication and Digital Signatures: Asymmetric encryption enables digital signatures, which verify the sender's identity and ensure the integrity of the message. This is crucial for secure online transactions and communications.
Weaknesses of Asymmetric Encryption
- Computational Intensity: Asymmetric encryption is computationally more intensive and slower compared to symmetric encryption, which can be a drawback for real-time applications.
- Complexity: The algorithms involved in asymmetric encryption are more complex, requiring greater computational resources and more sophisticated implementation.
Addressing Resistance against Secure Secret Sharing
Performance Concerns
Critics argue that the computational intensity of asymmetric encryption makes it impractical for certain applications. However, hybrid systems, which combine the strengths of both symmetric and asymmetric encryption, effectively address this concern. In such systems, asymmetric encryption is used to securely exchange a symmetric key, which is then used for the bulk encryption of data. This approach leverages the efficiency of symmetric encryption while maintaining the security benefits of asymmetric encryption.
Complexity and Resource Requirements
While it is true that asymmetric encryption requires more resources, advancements in computational power and optimization techniques have significantly mitigated these challenges. Modern hardware and software are increasingly capable of handling the demands of asymmetric encryption without compromising performance.
Practical Applications and Real-World Relevance
Securing Communications
Asymmetric encryption is integral to securing online communications, including email encryption (e.g., PGP) and SSL/TLS protocols used in securing web traffic. The ability to securely exchange keys and authenticate identities is essential for protecting sensitive information transmitted over the internet.
Digital Signatures and Certificates
Digital signatures, enabled by asymmetric encryption, are crucial for verifying the authenticity and integrity of digital documents. They are widely used in financial transactions, software distribution, and legal agreements, ensuring that the content has not been tampered with and confirming the sender's identity.
Cryptocurrencies and Blockchain
Asymmetric encryption underpins the security of cryptocurrencies like Bitcoin and Ethereum. Public and private keys are used to manage wallet addresses and sign transactions, ensuring secure and verifiable transfers of digital assets.
To Consider
While symmetric encryption offers speed and simplicity, asymmetric encryption provides superior security and scalability, making it the preferred choice for most modern cryptographic applications. The ability to securely distribute keys, authenticate identities, and verify the integrity of messages are critical advantages that asymmetric encryption holds over symmetric methods. By understanding and leveraging the strengths of asymmetric encryption, we can build more secure and resilient digital systems, protecting sensitive information in an increasingly interconnected world. Embracing asymmetric encryption as the foundation for digital security not only addresses current challenges but also prepares us for the evolving threats of the future.
Securing Communications Coventions

-
Email Encryption (PGP/GPG): Pretty Good Privacy (PGP) and its open-source counterpart, Gnu Privacy Guard (GPG), use asymmetric encryption to secure email communications. They ensure that only the intended recipient can decrypt and read the message, maintaining privacy and security.
-
SSL/TLS Protocols: Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are protocols that use asymmetric encryption to secure data transmitted over the internet. They are widely used to secure web traffic, ensuring that data exchanged between a user’s browser and a web server is encrypted and secure.
-
Virtual Private Networks (VPNs): VPNs use asymmetric encryption to establish a secure connection between a user's device and the VPN server. This encryption ensures that data sent through the VPN tunnel is protected from eavesdropping and interception.
-
Secure Shell (SSH): SSH protocols use asymmetric encryption to secure remote login and command execution over an insecure network. SSH ensures that the communication between the client and server is encrypted, preventing unauthorized access.
-
Messaging Apps (e.g., Signal): Secure messaging applications like Signal use asymmetric encryption to encrypt messages end-to-end. This means that only the sender and recipient can read the messages, ensuring that the communication remains private and secure.
Digital Signatures and Certificates Conventions
-
Software Distribution: Software developers use digital signatures to sign their software. This ensures that the software has not been tampered with and verifies the identity of the developer. Users can trust that the software they download is authentic and has not been altered.
-
Financial Transactions: Digital signatures are used to verify the authenticity and integrity of financial transactions. For example, banks and financial institutions use digital signatures to ensure that transaction details are not altered during transmission.
-
Legal Documents: Digital signatures are widely used in signing legal documents and contracts. They provide a way to verify the signer's identity and ensure that the document has not been altered after it was signed.
-
Code Signing Certificates: Developers use code signing certificates to sign their code. This process ensures that the code is authentic and has not been tampered with, providing trust to users who download and install the software.
-
Electronic Invoices and Receipts: Businesses use digital signatures to sign electronic invoices and receipts. This practice ensures the integrity and authenticity of the documents, making them legally binding and verifiable.
Assets and Blockchain Conventions
- Bitcoin: Bitcoin transactions are secured using asymmetric encryption. Public and private keys are used to manage Bitcoin addresses and sign transactions, ensuring that only the rightful owner can verify their Bitcoins.
This forms the backbone of security for modern client server systems enabling change via communities
The Cashu Protocol: Digital Transactions with Enhanced Privacy and Flexibility

So you want to run a mint? When? Sometime Soon?
In the anonymity ecosystem of digital transactions, maintaining privacy and security while ensuring seamless interoperability among Bitcoin layers is paramount. The Cashu protocol, an open-source ecash protocol designed for Bitcoin, offers a groundbreaking solution that leverages the Blind Diffie-Hellmann Key Exchange (BDHKE) to facilitate secure and private digital transactions. This argues that the Cashu protocol's innovative cryptographic mechanisms and open-source nature position it as a superior framework for digital currency transactions, fostering a secure, private, and interoperable ecosystem. By examining the protocol's technical foundations, practical applications, and potential challenges, this essay aims to demonstrate why adopting the Cashu protocol is a forward-thinking choice for digital financial systems.
The Technical Foundations of the Cashu Protocol
Blind Diffie-Hellmann Key Exchange (BDHKE)
At the heart of the Cashu protocol is the BDHKE, which ensures the privacy and security of ecash tokens through a robust cryptographic scheme. The BDHKE involves three key actors: Alice (the sending user), Bob (the mint), and Carol (the receiving user). The process involves a series of steps that obscure the transaction details, making it difficult for unauthorized parties to trace or tamper with the transaction.
- Mint (Bob): Bob publishes a public key (K) derived from his private key (k).
- Alice: Alice picks a secret (x) and blinds it using a random factor (r) to create a blinded message (B_).
- Bob: Bob receives the blinded message and signs it, returning a blinded key (C_) to Alice.
- Alice: Alice unblinds the key to obtain a proof (C), which she can use as a token.
- Carol: Carol can verify the token by sending it to Bob, who checks its validity and adds it to the list of spent secrets if it is genuine.
This process ensures that transactions are conducted privately and securely, with the blinding and unblinding steps preventing any correlation between the tokens and their origins.
Cashu NUTs (Notation, Usage, and Terminology)
The Cashu protocol's specifications are meticulously detailed in the Cashu NUTs, providing comprehensive guidelines for implementation and ensuring compatibility across various applications. These specifications enable developers to create interoperable software that adheres to the protocol, fostering a cohesive and secure ecosystem.
Practical Applications and Implementations
Language Support and Flexibility
The Cashu protocol is supported by multiple programming languages, enhancing its accessibility and implementation flexibility. Examples include:
- Python: Cashu Nutshell Python Library
- TypeScript: Cashu-TS TypeScript Library
- Rust: Cashu-crab and cashu-rs Libraries
- Golang: Cashu-Feni Golang Library
- Kotlin: Cashu Client Library in Kotlin
- Dart: Cashu Dart Library
These libraries allow developers to integrate the Cashu protocol into a wide range of applications, promoting widespread adoption and innovation.
Cashu Mints
Several mint implementations, such as Nutshell (Python), Moksha (Rust), Cashu-rs-mint (Rust), and Feni (Golang), provide robust solutions for secure transactions. The LNbits extension further empowers users by allowing them to run their own Nutshell mint, enhancing control over the security and privacy of their transactions.
Why You Should Focus on Cashu Development
Operational Concerns
Critics might argue that the cryptographic complexity of the Cashu protocol could impact performance and scalability. However, the protocol's design includes optimizations that mitigate these concerns. For instance, the use of efficient cryptographic algorithms ensures that transactions are processed swiftly, even as the volume of transactions increases. Additionally, the open-source nature of the protocol allows for continuous improvements and optimizations by the developer community.
How would I use this and Would Others use it
Alot of users worry about the usability and chance of others using the protocol. While the technical nature of the Cashu protocol might seem daunting to some users, the availability of detailed documentation (Cashu NUTs) and implementation libraries in multiple programming languages lowers the barrier to entry. By providing clear guidelines and versatile tools, the protocol facilitates broader adoption and practical implementation across diverse platforms. Partaking in continued constructive dialogue also around ecash future and past
Considering The Protocol

The Cashu protocol represents a significant advancement in digital transaction privacy and security. Its innovative use of the Blind Diffie-Hellmann Key Exchange (BDHKE) ensures that transactions are conducted privately and securely, while the open-source nature of the protocol fosters interoperability and widespread adoption. By addressing potential performance and usability concerns through continuous improvement and comprehensive documentation, the Cashu protocol is well-positioned to become a cornerstone of secure digital financial systems. Embracing the Cashu protocol not only enhances the privacy and security of digital transactions but also promotes a more flexible and interoperable ecosystem, making it a forward-thinking choice for the future of digital finance.
Real-World Applications of the Cashu Protocol
ChatNut: Privacy-Preserving Chat Application
ChatNut is an innovative chat application that integrates the Cashu protocol to offer privacy-preserving interactions with large language models (LLMs). Users pay-per-request using an integrated Cashu wallet without the need to create accounts, ensuring privacy and security. This application highlights the versatility of the Cashu protocol in enabling secure and anonymous communication services.
SpaceNut: Cashu-Enabled Gaming Experience
SpaceNut is described as the "sickest Cashu-enabled game" available. By integrating the Cashu protocol, SpaceNut offers a gaming experience where players can earn and spend Cashu tokens, demonstrating the protocol's applicability beyond traditional financial transactions. This use case underscores the potential of Cashu to revolutionize the gaming industry by introducing secure and private in-game economies.
NutMiner: Proof-of-Work Based Cashu Faucet
NutMiner is a proof-of-work based Cashu faucet that continuously releases Cashu tokens. This innovative approach leverages the principles of proof-of-work to distribute tokens fairly and securely. NutMiner exemplifies how the Cashu protocol can be integrated into decentralized token distribution systems, providing a steady and transparent method for distributing digital currency.
The manner in which you choose to run the processes of your mint could be the first step to understanding the power of unlocking transactional freedom on Bitcoin base layer while contributing to future resources around the budding sphere of Sovereign Privacy via Ecash, as an anonymous freedom driver and system to implement provably fair anonymous value systems.
-
 @ 6c8c7979:15595f3e
2024-08-02 21:51:01
@ 6c8c7979:15595f3e
2024-08-02 21:51:01When Mozart composed Symphony No. 40 in G minor, he was going through a difficult period in his life, facing financial problems and personal pressures. Despite these circumstances, the symphony is marked by significant emotional intensity and notable musical innovation. It is believed that the symphony reflected his internal tension and pain, making it one of his greatest and most impactful works.
https://youtu.be/0sGqkMU-mGQ?si=FTIuMq8xo4bhvzDV
https://youtu.be/JTc1mDieQI8?si=E-xd311z0yWQek3c
-
 @ bcea2b98:7ccef3c9
2024-04-01 17:27:32
@ bcea2b98:7ccef3c9
2024-04-01 17:27:32I've used Librovox, but looking for more recent technical and fiction topics. Audible seems so expensive having to pay for books in addition to a monthly membership. It would be nice if I could "browse" and listen to a lot of different types of books.
-
 @ 6c8c7979:15595f3e
2024-06-23 23:55:16
@ 6c8c7979:15595f3e
2024-06-23 23:55:16
The history of art represents a comprehensive study of the evolution of human creativity through the ages, embodying aesthetic and cultural expression from ancient times to the modern era. This article includes an overview of various historical periods and key artistic movements that have shaped what we know today as the fine arts. It provides a comprehensive look at visual, architectural, and literary arts that deeply influenced art history.
1. Ancient and Classical Periods*: - Artistic history begins with ancient arts in the Near East and Far East, where religious significance and expressions of power and daily life were central to creativity. Examples include the arts of the Egyptian Pharaohs, Sumerians, and Assyrians.
- Greek and Roman Art:
-
Western art was significantly influenced by Greek and Roman art, characterized by geometric dimensions and aesthetic elegance in architecture, sculpture, and painting.
-
Byzantine Art:
-
Byzantine art represents a blend of religion and art with its distinctive style and symbols that influenced Islamic art and rural architecture.
-
Art in the Middle Ages:
-
This period focused on Christian and scientific art in Europe, evolving from Romanesque styles.
-
The Renaissance:
-
In Italy, this period reflects the flourishing of science, philosophy, arts, and humanitarian movements, represented by works of artists such as Leonardo da Vinci and Raphael.
-
Modern and Contemporary Art:
-
This modern art movement reflects the impact of World Wars I and II, and includes movements such as Impressionism, Cubism, Surrealism, and Abstraction.
-
Contemporary Art:
- Contemporary arts have evolved into a diverse mix of techniques and concepts, with varied styles and experiments that reflect contemporary cultural identity.
Through this article, we delve into the details of these historical periods, including analyses of major artworks and prominent artists who have shaped the face of art throughout history. We will discuss how techniques and styles of art have changed from one period to another, and how they have been influenced by the social, cultural, and political contexts of each era.
art #artstr #history
-
 @ 0d2a0f56:ef40df51
2024-06-23 22:51:39
@ 0d2a0f56:ef40df51
2024-06-23 22:51:39 Today, I want to explore a question that's fundamental to our community: What is Bitcoin?
Today, I want to explore a question that's fundamental to our community: What is Bitcoin?At its core, Bitcoin is a decentralized digital currency, without a central bank or single administrator, that can be sent from user to user on the peer-to-peer bitcoin network without the need for intermediaries. Transactions are verified by network nodes through cryptography and recorded in a public distributed ledger called a blockchain.
But Bitcoin is so much more than this technical definition. It's a revolution in finance, a beacon of hope for financial freedom, and arguably, the antidote to many of the economic ailments plaguing our world today.
When I say "Bitcoin is the Antidote," I'm making a bold, abstract claim. An antidote is a remedy or solution to a problem or difficult situation. To truly explain why I believe this, I need to share my personal journey.
My story begins long before Bitcoin. In my mid-20s, I was living what many would consider a successful life. I had finished school and became an electrician, owned real estate, and was earning $120,000 to $140,000 a year. I was growing my family and excelling in my career. Yet, something was missing.
I wanted to be legendary, but for all the wrong reasons. My success came with a misguided sense of entitlement and a desire for luxury. This mindset led to depression and hopelessness. By night, I was a thrill-seeking, woman-chasing, money-wasting, alcohol-abusing party animal. This lifestyle nearly killed me, crashing down in early 2018 and resulting in months of recovery at the University of Chicago.
After this wake-up call, I promised myself I'd make better use of my time. I quit alcohol and partying cold turkey, transitioned to a less physically intense career, and started seeking something meaningful to build for my family.
In 2019-2020, I diversified my interests. I took classes on digital marketing, blockchain, social media entrepreneurship, and even MIT classes on the future of work. I dabbled in various investments - classic cars, private equity, cryptocurrencies, stocks, and metaverse properties. I was particularly drawn to altcoins and their ambitious whitepapers.
Then COVID hit, and the world as we knew it changed. Markets crashed, economic downturns accelerated. Amidst this chaos, I found myself reading the Bitcoin whitepaper by Satoshi Nakamoto. It was a pivotal moment.
The whitepaper aligned realities for me, unblocking my perception to view the world differently. Concepts like peer-to-peer cash, time, energy, central authorities, money, inflation - it all sparked something inside me. I began converting all my assets into Bitcoin.
As an electrician, I quickly saw Bitcoin as a much-needed reference point, a tool to measure against and better understand value. It wasn't just coincidence that Bitcoin went from a fraction of a penny to $20,000 per coin by 2020. This price action reflected the devaluation of the dollar and highlighted the misuse of money by states against their own citizens.
Reading the Bitcoin whitepaper led me down a rabbit hole of research into politics, economics, social science, and money. It helped me better understand how to preserve energy and value, what property is, and how to store and conserve it.
I discovered voices like Robert Breedlove, Michael Saylor, and Max Keiser, who elaborated on the problems Bitcoin solves. I was introduced to the Bitcoin community through conferences like Oslo Freedom Forum. Bitcoin began to feel like something spiritual, where people gathered with purpose, spreading awareness and fighting for a better way.
For someone like me, with an obsessive and addictive personality and a relentless appetite for knowledge, Bitcoin became the antidote. It was the truth serum I needed to shine a light on my toxic behaviors. But more than that, Bitcoin offered something I had been searching for without realizing it - an unlimited pursuit of knowledge and wisdom.
In many ways, diving into Bitcoin reminds me of a spiritual journey or the pursuit of God. It's a never-ending quest for understanding, always offering new layers to uncover, new concepts to grasp, and new implications to consider. This property makes Bitcoin a perfect transition for people with past addictive behaviors.
Where I once channeled my addictive tendencies into destructive habits, I now find myself addicted to learning. I'm constantly reading about economics, cryptography, game theory, and philosophy. I'm engaging in discussions about the nature of money, the role of the state, and the future of human coordination. This intellectual stimulation provides the same rush I used to seek in less healthy ways, but instead of destroying me, it's building me up.
The Bitcoin rabbit hole is deep and wide. It touches on so many aspects of human knowledge and experience that it can keep even the most voracious minds occupied indefinitely. For those of us who struggle with addictive behaviors, this can be a lifesaver. It provides a positive outlet for our obsessive tendencies, a constructive way to channel our energy and passion.
Moreover, the Bitcoin community, with its conferences, meetups, and online forums, offers a sense of belonging and purpose that many addicts seek. It's a global movement united by shared values of freedom, sovereignty, and honest money. This sense of community and higher purpose can fill the void that many try to fill with substances or destructive behaviors.
It's not simple to explain in a few pages how life-changing Bitcoin can be, but I promise that if you take on the task of better understanding Bitcoin and the problems it solves, it can become your antidote too. Whether you're battling addiction, seeking purpose, or simply looking to understand the world better, Bitcoin offers a path forward.
Bitcoin is the antidote to complacency, to financial illiteracy, to centralized control. It's a beacon of hope in a world that often seems hopeless. It's not just about money - it's about freedom, understanding, and reclaiming our sovereignty. It's about finding a positive addiction that enriches your life rather than depletes it.
As we navigate these uncertain times, I invite you to explore Bitcoin not just as a financial tool, but as a paradigm shift, a new way of thinking, and potentially, a new way of life. It might just become your antidote too.
Stay curious, stay sovereign,
Joe Thomas Founder, The Bitcoin Blok
-
 @ 81870f53:29bef6a6
2024-08-02 20:55:57
@ 81870f53:29bef6a6
2024-08-02 20:55:57**最近、世界の株式市場は非常に混乱しています。 ** 東部時間8月1日木曜日、米国株式市場は急落した。ドルS&P500指数(.SPX.US)ドルは1.37%下落。$ナスダック総合指数(.IXIC.US)$木曜日、欧州の主要3株価指数は軒並み下落した。英国FTSE100指数(.FTSE.GB)$は1.01%下落、ドイツDAX30指数(.GDAXI.DE)$は2.30%下落、フランスCAC40指数(.CAC.FR)$は2.14%下落した。
米国株式市場、特にハイテク株は容赦ない下落に見舞われた。$Meta Platforms (META.US)$ $NVIDIA (NVDA.US)$、$Apple (AAPL.US)$、$Amazon (AMZN.US)$などのスターハイテク株も急落し、株価は18.9ドル急落しました。 % の時間外取引が市場の焦点となっています。$Intel(INTC.US)$アジア市場も例外ではなく、指数はわずか 2 日間で 6000 ポイント近く急落し、約 15% の下落となり、約 16 年間で最大の下落となりました。この下落は投資家に衝撃を与えただけでなく、世界経済の見通しに対する懸念を引き起こした。
考えられる理由の1つは、ハイテク株の暴落を引き起こしたAIバブルの崩壊です。$日経225(.N225.JP)$人工知能(AI)技術はかつて資本市場の寵児だったが、市場の再評価でAIバブル崩壊の期待が崩壊の重要な理由となったハイテク株の。
米国メディアの報道によると、OpenAIはChatGPTを通じて年間約20億ドルを稼ぐことができ、大規模な言語モデルを通じて年間10億ドル近くを稼ぐことが見込まれている。 OpenAI の月間総収益は約 2 億 8,300 万ドルで、年間収益は 35 億ドルから 45 億ドルと推定されています。したがって、OpenAIの今年の損失は50億ドルに達する可能性があり、キャッシュフローは来年以内に枯渇する可能性がある。 Googleの親会社であるAlphabetは第2四半期の財務報告で懸念を強めた。過去 1 年間の Google のクラウドおよび検索ビジネス (どちらも AI 関連) の収益の伸びは、安定した上昇傾向を示し続けているわけではありません。
米国メディアの報道によると、Open AI は現在、ChatGPT を通じて年間約 20 億ドルの収益を生み出すことができ、大規模言語モデル課金サービスを通じて 10 億ドル近くの収益を生み出すことが見込まれています。同社の月間総収益は約 2 億 8,300 万ドルで、推定年間収益は 35 億ドルから 45 億ドルの間です。したがって、OpenAI は年間最大 50 億ドルの損失に直面する可能性があり、そのキャッシュフローは来年以内に枯渇する可能性があります。
グーグルの親会社アルファベットが第2・四半期財務報告を発表し、懸念が強まった。過去 1 年間の Google のクラウドおよび検索ビジネス (どちらも AI 投資に関連する) の収益の伸びは、着実に増加し続けているわけではありません。
「赤服のリーダー」が短いビデオで述べたように、「ゴールドマン・サックス、セコイア、その他の機関が計算を行ったところ、現在のハードウェア投資を正当化するには AI 業界全体が 6,000 億ドルを稼ぐ必要があるが、その結果、OpenAI は収入は30億ドルだが、業界関係者のほとんどは稼いでいない。」
ゴールドマン・サックスは、今後12~18カ月以内に重要なユースケースがより明確にならなければ、投資家の熱意が衰え始める可能性があると強調した。
ゴールドマン・サックスは、「ハイテク大手は今後数年間でAIの設備投資に1兆ドルを投じる計画だが、これらの投資が価値があることを証明する実質的で目に見える成果はほとんどない」と考えている。ゴールドマン・サックスは、現在の状況はインターネット技術応用の初期とは異なっていると指摘した。インターネット テクノロジーは初期の段階でも、低コストのソリューションを使用して高コストのソリューションを置き換えることができました。 AI は現在高価であり、より安価な代替品を提供することはできません。
ゴールドマン・サックスはまた、今後10年間のAIの経済への実際の影響は非常に限定的であり、AIによる米国の生産性の向上は0.5%、GDPの0.9%の増加にとどまり、多額の利益につながるだろうと判断した。投資資本は無駄になる可能性があり、米国株式市場の「ビッグ・セブン・シスターズ」が獲得した時価総額は史上最大のバブルとなる可能性がある。
AIテクノロジーの将来に対するこの悲観的な期待は、テクノロジー株に対する投資家の信頼の低下につながり、このセクターから資金が撤退し始めています。同時に、テクノロジー大手からのネガティブなニュースが市場のパニックをさらに激化させた。たとえば、インテルの業績は予想を下回った。そしてNVIDIAの株価はAIプロジェクト遅延の噂の影響を受け、「Aletheia Capitalと呼ばれる香港の研究機関は、ブラックウェルの量産は25Q1まで完全に遅れるだろうと述べた」。
さらに、米国の独占禁止法規制に関するニュースがハイテク株を圧迫した。これらの要因が重なって、ハイテク株が市場での主要な売りの分野となっている。
第二に、弱い米国経済指標が景気後退観測を引き起こしている。 弱い米国経済指標は警鐘のようなもので、景気後退に対する市場の懸念を高めている。米国の7月ISM製造業PMIは46.8を記録し、8か月ぶりの大幅なマイナスとなった。一方、米国の新規失業保険申請者数は先週、001万4,000人増加して24万9,000人となり、ほぼ1年ぶりの高水準を記録した。これらのデータは、米国経済が減速している可能性があることを示しているだけでなく、景気後退に対する市場の懸念も引き起こしている。
バフェット氏の汚い行為も市場の不安を増幅させている。バークシャー・ハサウェイは7月17日から12営業日連続でバンク・オブ・アメリカの保有株を減らしている。保有ポートフォリオのバンク・オブ・アメリカ株は8.8%減少し、削減総額は38億ドルに達した。
北京時間今夜8時30分に発表された米国の非農業部門雇用統計によると、7月の非農業部門雇用者数は11万4,000人増加したが、この数字は予想の17万5,000人を大きく下回った。 2024年7月の米国の失業率は4.3%に上昇し、2021年10月以来の高水準を記録し、前回の4.1%を上回った。
失業率の 4.3% への上昇は、サム ルールによる景気後退警報が作動したことを意味しており、この指標は 1970 年以来、景気後退を 100% 正確に予測しています。(サム ルールによると、3 か月ごとに失業率の移動平均が過去 12 か月の最低点と比較して 0.5% 以上上昇した場合、米国経済は景気後退に入るでしょう。)
上記のバフェット氏の汚い行動も、市場では米国経済の将来に対する悲観的な期待として解釈されている。過去の銀行株の利益傾向から、高いインフレと金利は銀行株にとって好ましいことであるが、バフェット氏がこのタイミングで株を売却するという選択をしたことは、バフェット氏がインフレ説を支持していないことを示しており、FRBの今後の利下げもその一つである可能性がある。バフェット氏がバンク・オブ・アメリカ株を削減した論理的な理由を説明します。$バンク・オブ・アメリカ (BAC.US)$過去のデータは貴重な参考資料を提供します。 FRB の利下げの前後の期間は、米国株の大幅な下落の始まりとなることがよくあります。1998 年、2000 年、2007 年から 2019 年にかけて、FRB の利下げの前後の期間には、米国株の大幅な下落が伴いました。
1998 年 10 月の利下げの 3 か月前、S&P 500 は 23% 下落しました。
2000 年 12 月の利下げまでの 3 か月の間に、インターネット バブル崩壊の連鎖反応が現れ始め、米国は 2 年半にわたる景気後退に陥り、その間に S&P 500 は 50% 下落しました。
2007 年 9 月の利下げから 1 か月後、米国のサブプライムローン危機が正式に勃発し、金融危機が世界を席巻し、翌年の 1 年半で S&P 500 は 58% も下落しました。
利下げから 1 か月後の 2007 年 10 月に、米国のサブプライム住宅ローン危機が正式に勃発しました。金融危機が世界中に広がり、S&P 500 は翌年 1 年半で -58% も下落しました。
米中貿易摩擦の影響を受けた2019年最初の10カ月間、2018年第4四半期には米国株が急落し、S&P500指数は20%下落した。しかし利下げから半年後、2020年大暴落が起きた。
現在、市場は一般にFRBが9月に利下げすると予想しているが、「たとえ米国のインフレ率が再び上昇し、AIバブルによって米ドルの資本流出が起こったとしても、FRBは金利を埋めるために利下げを選択するだろう」としている。資本流出のギャップ。
Ⅲ.円キャリートレード巻き戻しの波 木曜日の円/ドル為替レートは1%上昇し148.51円となった。円/ドル為替レートは水曜日に1.9%近く急騰し、月間上昇率は7%以上に拡大した。
オリエンタル・フェイスとDT証券のストラテジストらは、円・ドル為替レートは1ドル=140円まで上昇する可能性があるとみている。マッコーリーのストラテジストも「大幅な円高は始まったばかりだ」と述べた。今年末までに米ドル/円レートは140ドルに近づく可能性があり、2025年12月までには125ドルに達する可能性がある。これにより、円為替レートは連邦準備理事会が政策を開始した2022年初頭の水準に戻ることになる。利上げが始まったばかりだ。
対米ドルでの円の上昇により、世界中で裁定取引の閉鎖が相次ぎ、メキシコペソ、オーストラリアドル、ニュージーランドドルなどの通貨が下落した。
いわゆる円キャリートレードとは、投資家が低金利の円を借りて、米国債などの高金利の資産通貨に投資して利益を上げることを指します。しかし、米連邦準備制度理事会が利上げを続け、米ドルの流動性が逼迫するにつれて、米ドルの借入コストが増加する一方、対米ドルでの円の固定コストも増加しました。これは、円キャリートレードによる投資収益率がコストに見合わなくなったことを意味し、多くの投資家が投資を手放す、つまり以前に投資していた資産を売却して資金を撤退させる事態を引き起こしている。
この取引終了行動は世界の金融市場に一定の影響を与えました。まず、米国債などの高利回り資産は売り圧力にさらされており、短期的には米国債利回りに上昇圧力がかかる。
第二に、キャリートレードの停止により米国債の購買力が弱まり、世界の資産評価に圧力がかかり、株式市場や債券市場への下押し圧力が高まる可能性がある。
また、円キャリートレードの停止により円ショートポジションが減少することもあり、円相場に影響を与える可能性があります。
IV.日本株のテクニカル弱気相場テスト 日経平均株価は8月1日に2.49%下落した後、8月2日には日中5%を超える下落となった。7月の高値調整以来、日経平均株価は6,000ポイント近く下落し、累積下落幅は最大となった。 15%近くになります。日経平均株価が再び5%以上下落すれば、テクニカルな弱気相場の試練に直面することになる。
この日本の株式市場の下落の引き金となったのは、日銀が「利上げ+バランスシート縮小」というコンボ政策を導入したことだ。日本の短期金利は0.25%までしか引き上げられていないが、今回の金利引き上げの規模は大きくない。しかし、日本が長らくマイナス金利状態にあったことを考えると、今回の「利上げ+バランスシート縮小」策の方が市場のファンドに対するリスク選好に与える影響は大きかった。この政策変更は、異常な円高と相まって株式市場からの資金流出を招き、日本の株式市場の下落にさらに拍車をかけています。
アナリストは「円高・株安傾向が今後も続き、企業業績への影響は避けられない」と指摘する。 「円と日本の株式市場の間には明らかな逆の関係がある。つまり、継続的な円高が日本の株式市場に資本流出の影響を与えているのだ。」
V.まとめ この下落の波の中で、香港市場とA株市場の下落幅は比較的小さい。 2022年10月以降、米国の株式市場は急騰し、中国の資本市場は下落が続いた。現時点では、この資金のシーソー効果が逆方向に進む可能性があると思われます。中国の実体経済は好調で、中国人民銀行の利下げ政策が株式市場をさらに支援している。世界的な資金再配分の過程で、中国株式市場の過小評価された優位性が世界的な資本の注目を集めると予想される。
この記事がお役に立てば幸いです。 もしそうなら、チップをおくるどうぞ https://getalby.com/p/bitcap
日本のホスティングサービス Linux、Windowsクラウドホスティング データストレージ JPStream を使用して NOSTR リレーを作成する ホスティング サービスの料金をSatsで支払うことができます https://jpstream.net
-
 @ c73818cc:ccd5c890
2024-08-02 20:03:10
@ c73818cc:ccd5c890
2024-08-02 20:03:10
🐶 Uno sviluppatore principale di TON, la rete scelta da Telegram, afferma che le mini app basate su criptovalute dell'app stanno per diventare molto più complesse.
🐻❄️ Giochi crittografici come Hamster Kombat e Notcoin stanno attirando un pubblico enorme su Telegram, e le mini app basate su criptovalute sono destinate a diventare molto più complesse. Uno sviluppatore principale di The Open Network (TON) prevede che Telegram potrebbe presto supportare versioni crittografiche di app come Uber e Amazon, trasformandosi nella prima "app universale" dell'Occidente.
🐻❄️ La recente integrazione della stablecoin USDT con TON e Telegram facilita la creazione di mini app sofisticate senza le preoccupazioni legate alle fluttuazioni dei prezzi delle criptovalute. Questo sviluppo potrebbe portare Telegram a diventare un hub per la consegna di cibo, servizi bancari, viaggi in auto e shopping online, simile alla cinese WeChat, offrendo accesso integrato a una vasta gamma di servizi.
🐻❄️ Il successo di mini app come Hamster Kombat, che ha già superato i 250 milioni di utenti, dimostra il potenziale di Telegram di diventare un fulcro dell'economia digitale globale. Con un numero di utenti attivi che supera i 900 milioni, Telegram è ben posizionato per evolversi in una piattaforma all-in-one, grazie alla combinazione di criptovalute e funzionalità avanzate supportate da TON.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
Referral Bitget -10% sulle fee + bonus benvenuto 6w5d o link: https://bonus.bitget.com/U1JNEK
BitcoinReportItalia #HamsterKombat #Hamster #Notcoin #Telegram #App #TON #Occidente #USDT #Cripto #Bitcoin
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: Shitcoinery
IPFS was advertised to the Ethereum community since the beggining as a way to "store" data for their "dApps". I don't think this is harmful in any way, but for some reason it may have led IPFS developers to focus too much on Ethereum stuff. Once I watched a talk showing libp2p developers – despite being ignored by the Ethereum team (that ended up creating their own agnostic p2p library) – dedicating an enourmous amount of work on getting a libp2p app running in the browser talking to a normal Ethereum node.
The always somewhat-abandoned "Awesome IPFS" site is a big repository of "dApps", some of which don't even have their landing page up anymore, useless Ethereum smart contracts that for some reason use IPFS to store whatever the useless data their users produce.
Again, per se it isn't a problem that Ethereum people are using IPFS, but it is at least confusing, maybe misleading, that when you search for IPFS most of the use-cases are actually Ethereum useless-cases.
See also
- Bitcoin, the only non-shitcoin
-
 @ e97aaffa:2ebd765d
2024-07-14 09:57:13
@ e97aaffa:2ebd765d
2024-07-14 09:57:13Estamos numa época tão estranha da humanidade…
Onde alguns querem reescrever a história, em vez de aprender e evoluir com a mesma. São com os erros que se cresce.
Onde o termo fascista é sinónimo de alguém com uma opinião diferente da sua, sem minimamente saber o real significado dessa palavra.
Onde defendem uma liberdade, que proíba o contraditório.
Onde não se discutem ideias, mas sim combatem ideias.
Onde o ambientalmente sustentável é substituir árvores e zonas verdes por estruturas em aço e zonas negras.
Onde os políticos constroem casas ou cidades, literalmente, em cima dos rios mas depois a culpa das cheias é as alterações climáticas.
Onde os alimentos tem menos importância que um peido de uma vaca.
Onde pessoas defendem que a solução para o aquecimento, é morrer de frio.
Onde a igualdade é favorecer um grupo, em detrimento de outro.
Onde o essencial é viver para consumir, em vez de usufruir.
Onde o importante é ser rico e ostentar essa mesma riqueza, mesmo que tenha de espezinhar outros para a conquistar.
Onde o mais importante é parecer em vez de ser.
Onde políticos defendem que o conhecimento pode levar a escolhas erradas, defendem o carneirismo.
Onde um político define o que é verdade ou mentira, limitando o que as pessoas podem expressar. Mas quem controla o controlador.
Onde os revisores da verdade deixaram de estar num gabinete, passando a ser um exército de jovens atrás de um teclado.
Onde, são propostas e aprovadas limitações de liberdade, sem esclarecimento ou divulgação pública. Pior que a obscuridade, é desinteresse da comunidade por liberdade.
Onde a censura é o novo normal, defender o contrário é que é censurável.
Onde a imprensa é tão livre como uma pomba dentro de sua gaiola.
Onde, quem comete o crime é protegido, quem o denúncia é perseguido.
Onde o certo é pensar com a cabeça dos outros, sem questionar.
Onde os pais delegaram o papel de educar às escolas e aos ecrãs azuis.
Onde a escola deixou de ser um lugar de conhecimento e/ou do desenvolvimento do espírito crítico.
Onde as crianças crescem doutrinados por políticos e por AI.
Onde a sociedade é programada e com um destino predefinido, como um rato dentro da sua roda.
Onde o maior erro, é pretender construir seres que não cometem erros, que não tenham vícios. Quando isso acontecer, deixamos de ser humanos. A imperfeição é a essência dos seres humanos, é o que nos difere das máquinas.
Onde só se ensina a não cair, em vez de ajudar e incentivar a levantar.
Onde se suspende a liberdade de circulação e os direitos mais básicos, sem ninguém questionar.
Onde a privacidade é crime.
Onde Satoshi é excomungado, mas Miguel Tiago é idoleterado.
Onde a moeda é utilizado como uma arma.
Onde uma guerra é digladiada entre zeros e uns, sem o comum mortal aperceber da sua existência.
Onde crianças caem em campos de batalha, como folhas em pleno outono.
Onde o direito ao Livre-arbítrio está sob ameaça.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28nix
Pra instalar o neuron fui forçado a baixar e instalar o nix. Não consegui me lembrar por que não estava usando até hoje aquele maravilhoso sistema de instalar pacotes desde a primeira vez que tentei, anos atrás.
Que sofrimento pra fazer funcionar com o
fish, mas até que bem menos sofrimento que da outra vez. Tive que instalar um tal defish-foreign-environment(usando o próprio nix!, já que a outra opção era ooh-my-fishou qualquer outra porcaria dessas) e aí usá-lo para aplicar as definições de shell para bash direto nofish.E aí lembrei também que o
/nix/storefica cheio demais, o negócio instala tudo que existe neste mundo a partir do zero. É só para computadores muito ricos, mas vamos ver como vai ser. Estou gostando do neuron (veja, estou usando como diário), então vou ter que deixar o nix aí. -
 @ 7361ca91:252fce6d
2024-06-23 08:32:54
@ 7361ca91:252fce6d
2024-06-23 08:32:54数日前、スペインでインスティトゥト・フアン・デ・マリアナが主催する「自由の晩餐会」が開催されました。このイベントは、リベラルな組織にとって最も重要で象徴的な行事の一つで、毎年開催され、スペインや他の国々から自由の擁護者たちが集う場となり、ネットワーキングやリベラルなアイデアに関する議論の場を提供します。
この晩餐会では、自由の擁護において卓越した献身を示した個人や団体に贈られる権威ある「フアン・デ・マリアナ賞」が授与されます。この賞は、経済、政治、哲学の分野で著名な人物に贈られており、彼らは個人の自由と自由市場の進展に大きく貢献しています。
今回は、スペインの著名な経済学者、弁護士、作家であり、レイ・フアン・カルロス大学(URJC)の政治経済学の教授であるヘスス・ウエルタ・デ・ソトが、アルゼンチンの大統領で現代リベラリズムの主要な知識人の一人であるハビエル・ミレイに賞を授与しました。ウエルタ・デ・ソトは、リベラルな思想において影響力のある人物であり、ミレイの知的指導者として、その自由の擁護における見事な業績を称賛しました。
スピーチの中で、ウエルタ・デ・ソトは、これは彼の人生で最も重要なスピーチであると述べました。それが彼の最も重要な知的貢献とは考えていないものの、これまでに行ってきた自由の理念の擁護と普及に関するすべての仕事をある意味で総括する、彼のキャリアにおいて最も重要な言葉であると考えています。
以下、ハビエル・ミレイを深く感動させ、彼の目に涙を浮かべさせたスピーチの翻訳になります。
今日は、恐れを知らず、世界を変えるために自己を犠牲にすることをためらわない一人の男に敬意を表します。自由という言葉を聞くだけで心が力強く鼓動する男、ハビエル・ミレイは、休むことなく、譲ることなく、自由を追い求めています。それは彼の大きな夢であり、そのエネルギーと情熱は、歴史上の偉大な自由の英雄たちにしか見られないものです。ハビエル・ミレイは、まさにそのような存在になりました。
まず、経済学を学ぶ人々にとって、彼は優れた経済学者としてその分野を完全に掌握しており、謙虚に理解しています。周囲の世界を理解するには、オーストリア学派の経済学の動的で企業家的、創造的なアプローチに従うことが必要であると。実際には、それはスペインの黄金時代のスコラ哲学者たちに由来するため、スペイン学派と呼ばれるべきです。
彼の言葉を借りるならば、ハビエル・ミレイは、主流派のネオクラシカル経済学の限界を見抜くことができました。その仮定の非現実性、形式的および方法論的な還元主義、そして何よりも、最悪の場合には社会工学と国家主義を助長し、最良の場合でも市場を誤った理由で擁護するという重大な誤りを犯している、幻想的な均衡モデルに基づいているからです。オーストリア学派が教えてくれるように、市場は自発的で素晴らしい人間の協力のプロセスであり、創造性と調整を促進します。このプロセスは、国家主義によって改善されることはなく、その科学的な不可能性もまたオーストリア学派によって証明されています。
さらに、ハビエル・ミレイは、今日の政治家にとっての模範となっています。彼は、自身が擁護する主張の科学的基盤を完全に理解し、確信と知的誠実さをもって自由を守ることができるからです。ちょうど、どの医師も医学を完全に習得することなくしてその職務を果たすべきでないのと同様に、いかなる政治指導者、議会議員、大使、あるいはどの省庁の高官も、オーストリア学派が教える経済学、自由、倫理の基本理論を事前に知らずしてその役割を果たすべきではありません。
現在、民主主義が、嘘と税金で得た資金による票の買収に基づく、歪んだシステムへと変わりつつある中で、ハビエル・ミレイは、常に真実を語り、厳しい現実を市民に説明しつつ、なおも自由の理念に対する圧倒的な支持を得ることが可能であることを示しました。彼のリーダーシップは、日々の政治の制約に左右されることなく、決して方向を見失わず、さらに自由を推進する努力を怠りません。したがって、各国でミレイのモデルに従うことを求める者たちは、すでにその道筋とすべきことを知っています。それは、ミレイのモデルを忠実に守ることです。
また、ハビエル・ミレイはすべての人々、特に若者にとっての模範ともなっています。人間の魂に感染する最も致命的なウイルスである国家主義に対抗する中で、ハビエル・ミレイは、他の誰よりも自由の理念を広めるという並外れた功績を持っています。彼は、文字通り、街頭や広場で、そしてメディアを通じて、何千人もの人々に経済理論を教え、知的かつ道徳的に国家主義の理念を打ち破ってきました。彼の言葉によれば、それはこれまで良識ある人々を縛りつけていたものです。特に、若者にとって、ミレイは模範的な存在であり、まだ完全に汚染されておらず、国家主義の罠に陥っていない彼らが、少し勉強し、オーストリア学派の理念に従えば、自由の熱心な擁護者となり、国家が課す組織的な暴力と強制に対する強力な反対者へとすぐに変わることができるでしょう。
自由、生命、財産を象徴する善と、暴力と国家による強制を具現化する悪との間の永続的な闘争において、今日、我々は知的にも道徳的にも歴史的にも、国家主義が死に瀕していると断言できます。この新たな時代において、ハビエル・ミレイと彼を間違いなく支持する者たちの力を借りて、我々の使命は、国家主義に最終的なとどめを刺すことです。未来は、自由を愛し信じる我々のものです。現在、あらゆる派閥の政治家や国家主義者たちが、本当にショックを受け、恐怖におののき、防御的になっているのは驚くべきことではありません。ハビエル・ミレイが言うように、それは「世界中のファシストたち」、そしてハイエクを引用すれば、それは左翼も右翼も含むすべての政党です。
最後に、ハビエル・ミレイは、寛大さの模範でもあります。彼は、出身に関係なく、かつての対立者たちに対しても寛大です。自分の過ちを誠実に認め、自由の理想を抱く勇気と知的誠実さを示す者たちは、彼の寛大さを受けます。多くの人々が、ミレイの話を聞いて、自分が実はアナルコ・キャピタリスト(無政府資本主義者)である、またはそうなりたかったことに気づいています。ハビエル・ミレイは決して自分を神格化することはなく、常に機会があるごとに、自分の偉大な師たちを引用します。それは、ミーゼス、ハイエク、ロスバード、ギットナー、ホッペといった巨人たちと肩を並べるにはふさわしくない私のような者も含まれます。このすべて、そしてハビエル・ミレイが私の人生のこの段階で私にもたらしてくれた大きな個人的な幸福のために、私は彼の知的寛大さに対して、個人的にも道徳的にも感謝しなければなりません。
さらに、リチャード・ソモンテにも感謝したいと思います。彼は、社会主義から逃れてマドリードにやってきたキューバの芸術家で、大人物の壮大な肖像画、とりわけ私の祖父がファンだったフアン・ベルモンテのような闘牛士の肖像画を得意としています。ソモンテは、21世紀の政治の真の闘牛士、ハビエル・ミレイの巨大な肖像画を完成させるというアイデアを私に提案してくれました。この場合、戦って倒すべき「牛」は、間違いなく国家です。
今日ここにあるこの肖像画は、この場で彼に贈るためのものです。話を終えるまでの1分半後に、皆さんがご覧になれる献辞が書かれています。それはこう書かれています。「自由の巨人、ハビエル・ミレイ大統領へ、彼の教授であるヘスス・ウエルタ・デ・ソトより、今日の日に。」
そして、マーティン・ルーサー・キングを引用して、こう締めくくります。「I have a dream」、私には夢があります。私は、国家が最終的に解体され、暗く恐ろしい歴史的な遺物としてのみ記憶される日を夢見ています。私は、国家の論理と理性、そしてそれが引き起こす社会的な紛争や無限の暴力が完全に、そして永久に消え去る世界を夢見ています。私は、人間を財政的に搾取することを目的とする国家が存在しない世界を夢見ています。私は、官僚たちが私たちの子供たちを洗脳せず、彼らを国家の所有物と見なさない世界を夢見ています。
私は、福祉国家という嘘が、特に最も困窮し、弱い立場にある人々のために、国家のない真の福祉に取って代わられる世界を夢見ています。私は、強制的で歪められた社会正義が、自由市場の無限の繁栄と愛に基づいた自発的な人間の連帯によって取って代わられる世界を夢見ています。それは、自由であるからこそ真実であり、強制や暴力によって押し付けられるものではありません。私は、したがって、自由意思による、自己調整された、無政府資本主義の世界を夢見ています。
私は、オーストリア学派が説明するように、今日では強制的で非道徳的なすべての公共サービスが、道徳的かつ効率的で、民間によって提供される世界を夢見ています。要するに、私は、人間がついに国家主義の鎖から解放され、自由に神を選ぶことができる世界を夢見ています、もしそう望むなら。
ハビエル・ミレイと、常に私たちを見守る天の力のおかげで、今日は未来の歴史が始まり、私の夢が現実になり始めました。そして最後に、四つの万歳を叫びます。オーストリア学派の経済学に万歳!偉大なるアルゼンチンと、その大統領ハビエル・ミレイに万歳!そしてもちろん、自由に万歳!カーラホ!
注釈:
ヘスス・ウエルタ・デ・ソト・バリェステルは、スペインの著名な経済学者、弁護士、作家であり、レイ・フアン・カルロス大学(URJC)の政治経済学の教授です。オーストリア学派の代表として、彼は『社会主義、経済計算と企業機能』("Socialismo, Cálculo Económico y Función Empresarial")において、企業の機能と社会主義の不可能性に関する重要な理論的貢献をしています。さらに、彼は『マネー、銀行信用と経済サイクル』("Dinero, Crédito Bancario y Ciclos Económicos")において、オーストリア学派の景気循環理論の発展と動的効率性の擁護で知られています。ウエルタ・デ・ソトは、社会の現実は理論的、歴史的、倫理的なアプローチを組み合わせて分析すべきであると主張し、アナルコキャピタリズム(無政府資本主義)と完全な経済の自由化を支持しています。彼の作品は多くの言語に翻訳されており、経済の自由と金融改革の擁護において、影響力のある人物としての地位を確立しています。
インスティトゥト・フアン・デ・マリアナ(IJM) は、スペインのマドリードに本拠を置くリベラル志向のシンクタンクで、2005年に設立されました。その目的は、その定款によると、「スペイン、ヨーロッパ、およびヒスパニックアメリカの広い大衆に対し、私有財産、自由な企業活動、および公共権力の行動範囲の制限がもたらす利益を紹介すること」です。その名称は、サラマンカ学派の後期の代表者であるフアン・デ・マリアナに由来しています。また、マドリードのレイ・フアン・カルロス大学の法学部および社会科学部において、オーストリア学派の経済学修士課程を後援しています。
-
 @ c73818cc:ccd5c890
2024-08-02 17:00:00
@ c73818cc:ccd5c890
2024-08-02 17:00:00
🍿 David Bailey accusa Harris di ostacolare l'industria delle criptovalute, mentre Hayden Adams la difende sostenendo che non ha mai votato leggi anti-cripto.
🍭 Accuse di David Bailey
🍿 David Bailey, CEO di Bitcoin Magazine, sostiene che Kamala Harris abbia definito Bitcoin "soldi per i criminali". Bailey critica Harris per aver collaborato con la SEC e la senatrice Elizabeth Warren per promuovere regolamentazioni anti-cripto.
🍭 Il Ruolo di Harris nell'Industria delle Criptovalute
🍿 Bailey accusa l'amministrazione Biden di aver incarcerato sviluppatori e spinto l'industria all'estero. Afferma che Harris non può presentarsi come sostenitrice di Bitcoin dopo aver minato l'industria negli ultimi quattro anni.
🍭 Difesa di Hayden Adams
🍿 Hayden Adams, CEO di Uniswap Labs, difende Harris, affermando che non ha mai parlato né votato leggi contro le criptovalute. Adams sollecita cautela nel trarre conclusioni affrettate, invitando a considerare i fatti.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
Referral Bitget -10% sulle fee + bonus benvenuto 6w5d o link: https://bonus.bitget.com/U1JNEK
BitcoinReportItalia #BitcoinMagazine #KamalaHarris #Harris #SEC #Criminali #ElizabethWarren #Warren #Biden #Uniswap #Cripto #Bitcoin
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28nostr - Notes and Other Stuff Transmitted by Relays
The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all.
It doesn't rely on any trusted central server, hence it is resilient; it is based on cryptographic keys and signatures, so it is tamperproof; it does not rely on P2P techniques, therefore it works.
Very short summary of how it works, if you don't plan to read anything else:
Everybody runs a client. It can be a native client, a web client, etc. To publish something, you write a post, sign it with your key and send it to multiple relays (servers hosted by someone else, or yourself). To get updates from other people, you ask multiple relays if they know anything about these other people. Anyone can run a relay. A relay is very simple and dumb. It does nothing besides accepting posts from some people and forwarding to others. Relays don't have to be trusted. Signatures are verified on the client side.
This is needed because other solutions are broken:
The problem with Twitter
- Twitter has ads;
- Twitter uses bizarre techniques to keep you addicted;
- Twitter doesn't show an actual historical feed from people you follow;
- Twitter bans people;
- Twitter shadowbans people.
- Twitter has a lot of spam.
The problem with Mastodon and similar programs
- User identities are attached to domain names controlled by third-parties;
- Server owners can ban you, just like Twitter; Server owners can also block other servers;
- Migration between servers is an afterthought and can only be accomplished if servers cooperate. It doesn't work in an adversarial environment (all followers are lost);
- There are no clear incentives to run servers, therefore they tend to be run by enthusiasts and people who want to have their name attached to a cool domain. Then, users are subject to the despotism of a single person, which is often worse than that of a big company like Twitter, and they can't migrate out;
- Since servers tend to be run amateurishly, they are often abandoned after a while — which is effectively the same as banning everybody;
- It doesn't make sense to have a ton of servers if updates from every server will have to be painfully pushed (and saved!) to a ton of other servers. This point is exacerbated by the fact that servers tend to exist in huge numbers, therefore more data has to be passed to more places more often;
- For the specific example of video sharing, ActivityPub enthusiasts realized it would be completely impossible to transmit video from server to server the way text notes are, so they decided to keep the video hosted only from the single instance where it was posted to, which is similar to the Nostr approach.
The problem with SSB (Secure Scuttlebutt)
- It doesn't have many problems. I think it's great. In fact, I was going to use it as a basis for this, but
- its protocol is too complicated because it wasn't thought about being an open protocol at all. It was just written in JavaScript in probably a quick way to solve a specific problem and grew from that, therefore it has weird and unnecessary quirks like signing a JSON string which must strictly follow the rules of ECMA-262 6th Edition;
- It insists on having a chain of updates from a single user, which feels unnecessary to me and something that adds bloat and rigidity to the thing — each server/user needs to store all the chain of posts to be sure the new one is valid. Why? (Maybe they have a good reason);
- It is not as simple as Nostr, as it was primarily made for P2P syncing, with "pubs" being an afterthought;
- Still, it may be worth considering using SSB instead of this custom protocol and just adapting it to the client-relay server model, because reusing a standard is always better than trying to get people in a new one.
The problem with other solutions that require everybody to run their own server
- They require everybody to run their own server;
- Sometimes people can still be censored in these because domain names can be censored.
How does Nostr work?
- There are two components: clients and relays. Each user runs a client. Anyone can run a relay.
- Every user is identified by a public key. Every post is signed. Every client validates these signatures.
- Clients fetch data from relays of their choice and publish data to other relays of their choice. A relay doesn't talk to another relay, only directly to users.
- For example, to "follow" someone a user just instructs their client to query the relays it knows for posts from that public key.
- On startup, a client queries data from all relays it knows for all users it follows (for example, all updates from the last day), then displays that data to the user chronologically.
- A "post" can contain any kind of structured data, but the most used ones are going to find their way into the standard so all clients and relays can handle them seamlessly.
How does it solve the problems the networks above can't?
- Users getting banned and servers being closed
- A relay can block a user from publishing anything there, but that has no effect on them as they can still publish to other relays. Since users are identified by a public key, they don't lose their identities and their follower base when they get banned.
- Instead of requiring users to manually type new relay addresses (although this should also be supported), whenever someone you're following posts a server recommendation, the client should automatically add that to the list of relays it will query.
- If someone is using a relay to publish their data but wants to migrate to another one, they can publish a server recommendation to that previous relay and go;
- If someone gets banned from many relays such that they can't get their server recommendations broadcasted, they may still let some close friends know through other means with which relay they are publishing now. Then, these close friends can publish server recommendations to that new server, and slowly, the old follower base of the banned user will begin finding their posts again from the new relay.
-
All of the above is valid too for when a relay ceases its operations.
-
Censorship-resistance
- Each user can publish their updates to any number of relays.
-
A relay can charge a fee (the negotiation of that fee is outside of the protocol for now) from users to publish there, which ensures censorship-resistance (there will always be some Russian server willing to take your money in exchange for serving your posts).
-
Spam
-
If spam is a concern for a relay, it can require payment for publication or some other form of authentication, such as an email address or phone, and associate these internally with a pubkey that then gets to publish to that relay — or other anti-spam techniques, like hashcash or captchas. If a relay is being used as a spam vector, it can easily be unlisted by clients, which can continue to fetch updates from other relays.
-
Data storage
- For the network to stay healthy, there is no need for hundreds of active relays. In fact, it can work just fine with just a handful, given the fact that new relays can be created and spread through the network easily in case the existing relays start misbehaving. Therefore, the amount of data storage required, in general, is relatively less than Mastodon or similar software.
-
Or considering a different outcome: one in which there exist hundreds of niche relays run by amateurs, each relaying updates from a small group of users. The architecture scales just as well: data is sent from users to a single server, and from that server directly to the users who will consume that. It doesn't have to be stored by anyone else. In this situation, it is not a big burden for any single server to process updates from others, and having amateur servers is not a problem.
-
Video and other heavy content
-
It's easy for a relay to reject large content, or to charge for accepting and hosting large content. When information and incentives are clear, it's easy for the market forces to solve the problem.
-
Techniques to trick the user
- Each client can decide how to best show posts to users, so there is always the option of just consuming what you want in the manner you want — from using an AI to decide the order of the updates you'll see to just reading them in chronological order.
FAQ
- This is very simple. Why hasn't anyone done it before?
I don't know, but I imagine it has to do with the fact that people making social networks are either companies wanting to make money or P2P activists who want to make a thing completely without servers. They both fail to see the specific mix of both worlds that Nostr uses.
- How do I find people to follow?
First, you must know them and get their public key somehow, either by asking or by seeing it referenced somewhere. Once you're inside a Nostr social network you'll be able to see them interacting with other people and then you can also start following and interacting with these others.
- How do I find relays? What happens if I'm not connected to the same relays someone else is?
You won't be able to communicate with that person. But there are hints on events that can be used so that your client software (or you, manually) knows how to connect to the other person's relay and interact with them. There are other ideas on how to solve this too in the future but we can't ever promise perfect reachability, no protocol can.
- Can I know how many people are following me?
No, but you can get some estimates if relays cooperate in an extra-protocol way.
- What incentive is there for people to run relays?
The question is misleading. It assumes that relays are free dumb pipes that exist such that people can move data around through them. In this case yes, the incentives would not exist. This in fact could be said of DHT nodes in all other p2p network stacks: what incentive is there for people to run DHT nodes?
- Nostr enables you to move between server relays or use multiple relays but if these relays are just on AWS or Azure what’s the difference?
There are literally thousands of VPS providers scattered all around the globe today, there is not only AWS or Azure. AWS or Azure are exactly the providers used by single centralized service providers that need a lot of scale, and even then not just these two. For smaller relay servers any VPS will do the job very well.
-
 @ bcea2b98:7ccef3c9
2024-04-01 15:20:24
@ bcea2b98:7ccef3c9
2024-04-01 15:20:24Opcodes are the fundamental building blocks of Bitcoin's scripting language, defining conditions for spending transactions. Each opcode represents a specific instruction executed within Bitcoin's virtual machine, enabling complex scripting capabilities. Opcodes are executed sequentially to validate transactions against scriptPubKey and scriptSig, determining if inputs fulfill the conditions for spending outputs.
The scripting language employs opcodes to perform operations like data manipulation, conditional execution, cryptographic verification, and arithmetic computations. This limited set ensures predictable script evaluation, mitigating risks from malicious or indefinitely looping scripts.
Opcodes enable smart contracts and multi-signature wallets within Bitcoin. Conditional logic opcodes (e.g., OP_IF, OP_NOTIF) and cryptographic operations (e.g., OP_CHECKSIG, OP_CHECKMULTISIG) enforce specific spending conditions, such as requiring multiple signatures or locking funds until a certain block height or timestamp (via OP_CHECKLOCKTIMEVERIFY and OP_CHECKSEQUENCEVERIFY).
| Opcode | Description | Function | |----------|-------------|-------------------| | 0 | OP_0, OP_FALSE | Push false | | 76 | OP_PUSHDATA1 | Push data | | 77 | OP_PUSHDATA2 | Push data | | 78 | OP_PUSHDATA4 | Push data | | 79 | OP_1NEGATE | Push -1 | | 80-96 | OP_1-OP_16, OP_TRUE | Push 1-16 | | 97 | OP_NOP | No operation | | 99 | OP_IF | If conditional | | 100 | OP_NOTIF | If not conditional | | 103 | OP_ELSE | Else conditional | | 104 | OP_ENDIF | End if | | 105 | OP_VERIFY | Verify condition | | 106 | OP_RETURN | Terminate script | | 107-108 | OP_TOALTSTACK, OP_FROMALTSTACK | Stack transfer | | 109 | OP_2DROP | Drop 2 | | 110 | OP_2DUP | Duplicate 2 | | 111 | OP_3DUP | Duplicate 3 | | 112 | OP_2OVER | Copy 2nd pair | | 113 | OP_2ROT | Rotate top 3 twice | | 114 | OP_2SWAP | Swap top 2 pairs | | 115 | OP_IFDUP | Duplicate if not 0 | | 116 | OP_DEPTH | Stack size | | 117 | OP_DROP | Remove top | | 118 | OP_DUP | Duplicate top | | 119 | OP_NIP | Remove 2nd | | 120 | OP_OVER | Copy 2nd | | 121 | OP_PICK | Nth item | | 122 | OP_ROLL | Move Nth top | | 123 | OP_ROT | Rotate top 3 | | 124 | OP_SWAP | Swap top 2 | | 125 | OP_TUCK | Move 3rd to top | | 130 | OP_SIZE | Size of top item | | 135 | OP_EQUAL | Equality check | | 136 | OP_EQUALVERIFY | Verify equal | | 139 | OP_1ADD | Add 1 | | 140 | OP_1SUB | Subtract 1 | | 143 | OP_NEGATE | Negate | | 144 | OP_ABS | Absolute value | | 145 | OP_NOT | Not zero | | 146 | OP_0NOTEQUAL | Not equal to 0 | | 147-148 | OP_ADD, OP_SUB | Arithmetic | | 149-154 | Disabled | Disabled | | 155-158 | OP_BOOLAND, OP_BOOLOR, OP_NUMEQUAL, OP_NUMEQUALVERIFY | Boolean logic | | 159-160 | OP_NUMNOTEQUAL, OP_LESSTHAN | Comparison | | 161-162 | OP_GREATERTHAN, OP_LESSTHANOREQUAL | Comparison | | 163-164 | OP_GREATERTHANOREQUAL, OP_MIN | Minimum/Maximum | | 165-166 | OP_MAX, OP_WITHIN | Range check | | 167-168 | OP_RIPEMD160, OP_SHA1 | Hashing | | 169 | OP_SHA256 | SHA-256 | | 170 | OP_HASH160 | RIPEMD-160+SHA-256 | | 171 | OP_HASH256 | SHA-256x2 | | 172-175 | OP_CHECKSIG, OP_CHECKSIGVERIFY, OP_CHECKMULTISIG | Signature check | | 176-177 | OP_CHECKMULTISIGVERIFY | Multisig verify | | 178-181 | OP_NOP1-OP_NOP4 | No operation | | 182-185 | OP_CHECKLOCKTIMEVERIFY, OP_CHECKSEQUENCEVERIFY | Timing checks | | 186-189 | OP_NOP6-OP_NOP9 | No operation | | 190-193 | OP_NOP10 | No operation |
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A Causa
o Princípios de Economia Política de Menger é o único livro que enfatiza a CAUSA o tempo todo. os cientistas todos parecem não saber, ou se esquecer sempre, que as coisas têm causa, e que o conhecimento verdadeiro é o conhecimento da causa das coisas.
a causa é uma categoria metafísica muito superior a qualquer correlação ou resultado de teste de hipótese, ela não pode ser descoberta por nenhum artifício econométrico ou reduzida à simples antecedência temporal estatística. a causa dos fenômenos não pode ser provada cientificamente, mas pode ser conhecida.
o livro de Menger conta para o leitor as causas de vários fenômenos econômicos e as interliga de forma que o mundo caótico da economia parece adquirir uma ordem no momento em que você lê. é uma sensação mágica e indescritível.
quando eu te o recomendei, queria é te imbuir com o espírito da busca pela causa das coisas. depois de ler aquilo, você está apto a perceber continuidade causal nos fenômenos mais complexos da economia atual, enxergar as causas entre toda a ação governamental e as suas várias consequências na vida humana. eu faço isso todos os dias e é a melhor sensação do mundo quando o caos das notícias do caderno de Economia do jornal -- que para o próprio jornalista que as escreveu não têm nenhum sentido (tanto é que ele escreve tudo errado) -- se incluem num sistema ordenado de causas e consequências.
provavelmente eu sempre erro em alguns ou vários pontos, mas ainda assim é maravilhoso. ou então é mais maravilhoso ainda quando eu descubro o erro e reinsiro o acerto naquela racionalização bela da ordem do mundo econômico que é a ordem de Deus.
em scrap para T.P.
-
 @ 1739d937:3e3136ef
2024-03-27 12:25:02
@ 1739d937:3e3136ef
2024-03-27 12:25:02"Gossip", "Outbox", "Inbox", "Blastr", "Small relays vs Big relays". You've probably seen most of these topics come up in conversations and memes recently. You might have even read nostr:nprofile1qqsf03c2gsmx5ef4c9zmxvlew04gdh7u94afnknp33qvv3c94kvwxgsm3u0w6's article (nostr:naddr1qq2hxenh2cchynnpdag4sepkx4gxyj2dt9nk6q3qjlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qxpqqqp65wd3a9ny), or nostr:nprofile1qqswuyd9ml6qcxd92h6pleptfrcqucvvjy39vg4wx7mv9wm8kakyujgua442w's very technical article (nostr:naddr1qqxnzde3xycngdpjxg6nqdfsqgswuyd9ml6qcxd92h6pleptfrcqucvvjy39vg4wx7mv9wm8kakyujgrqsqqqa28906usv), or maybe even nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8g2lcy6q's one with the clickbaity title (nostr:naddr1qvzqqqr4gupzqwlsccluhy6xxsr6l9a9uhhxf75g85g8a709tprjcn4e42h053vaqydhwumn8ghj7un9d3shjtnhv4ehgetjde38gcewvdhk6tcprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsqzpcxasnyvpcvsusgpcqx3).
These are all great, and you should go and read them too. But one thing that each of them is guilty of is assuming that the audience has enough context to jump into the middle of a very nuanced and technical discussion. I've yet to see a clear description of what Gossip or Outbox really are and certainly none that are written in a way that is approachable for a non-technical audience. I hope this article can give you that context and serve as a high-level overview of the discussion and the technologies involved so that you can go forth to create better, more informed memes (is there anything more important, really?) and join the discussion in a productive way.
The problems
Centralization is the default
First off, why are we even talking about relays? Most of know that nostr is a protocol which is designed to be decentralized from the ground up. That decentralization is due in large part to the fact that users read and write data to multiple relays by default. So instead of all your data going to a centralized database (usually owned and operated by a single company) with nostr you have the ability to send your data to as as many relays as you'd like (relays are just databases, after all). Likewise, you can read other people's data from as many relays as you'd like to. Decentralized design = decentralized system, right!? Well, turns out, no.
The problem with a design like this is that what can be done and what will be done are often very different things. Imagine the following scenario: You follow 1000 people; 700 of them post their notes to the Primal relay, the other 300 post their notes to the Damus relay. If you don't also write your content to those two relays, the people that you care about won't see your content, they won't see your replies to their notes, they won't even know you exist. So while; in practice, it's easy to read & write to many different relays, users and their content will tend to centralize because it's the path of least resistance to a good user experience. Network effects and economies of scale always apply, they just don't always lead to the outcomes that you want.
Before you start to panic, this sort of centralization isn't a huge issue just yet. We are still a nascent network and there are still hundreds of active relays out there. Almost all nostr clients make relay selection a first class citizen and don't default new users to a single relay. The fact that we're even having this conversation in a serious way at this stage is a great sign that the community cares enough to be proactive about maintaining (and improving) decentralization over time.
That said, this is not a issue that we can take lightly either. The top 5-10 relays do already have an outsized percentage of users and we have many examples of these centralizing tendencies across dozens of protocols and networks over the last 30 years, so the threat is real.
The status quo is wasteful
The other major issue is that currently most nostr clients are extremely wasteful in how they fetch data. The default is to simply get everything from all the relays a user wants to connect to. Because most of us are writing the same data to many relays, this leads to huge amounts of duplicated data being downloaded, having its signatures verified, and then (for the most part) thrown away. For those of us with latest generation smartphones, unlimited data, and a working power outlet nearby, this is fine. For everyone else, this is a major roadblock to adopting nostr.
A lightly technical aside
There are a few important features of nostr that make any sort of intelligent data fetching possible. To understand how any of the potential solutions to the aforementioned problems would actually work, it's important to have a baseline understanding of these technical details. I promise, I'll keep it high level.
Relay lists
Recently the concept of a Relay List Metadata has been introduced to the spec in NIP-65 (there are also other types of relay lists documented in NIP-51). This is a nostr list event where users publish their preferred relays with a marker that says whether the relay is for read-only, write-only, or read & write. This vastly simplifies the process of finding preferred user relays for clients and I imagine that this will become the de facto standard place to look for a user's preferred relays.
NIP-05
The NIP-05 spec also documents a way for users to signal their preferred relays. However, unlike the NIP-65 relay list, this is a simple list of relays without any details on whether the user reads or writes to those relays.
Tag markers
Tag markers are positional elements in tags that give the client publishing the event the ability to leave a hint as to which relay other clients can expect to find a given user or note that is being referenced.
For example, in a user's contact list (a
kind: 3event) you have many"p"tags to reference all the user's that are followed. These tags look like this:{ "kind": 3, "tags": [ ["p", "91cf9..4e5ca", "wss://alicerelay.com/", "alice"], ["p", "14aeb..8dad4", "wss://bobrelay.com/nostr"], ["p", "612ae..e610f"] ], "content": "", ...other fields }All three of these
"p"tags are valid (only the"p"and the user's pubkey are required), in the first and second you can see the third item is a relay where the user's events can be found.These types of tag markers are repeated all throughout nostr. Here's a few more example references for an event (in this case a long-form article):
``` ["e", "b3e392b11f5d4f28321cedd09303a748acfd0487aea5a7450b3481c60b6e4f87", "wss://relay.example.com"],
["a", "30023:a695f6b60119d9521934a691347d9f78e8770b56da16bb255ee286ddf9fda919:ipsum", "wss://relay.nostr.org"] ```
As you can imagine, these hints can be very helpful but only if clients actually attempt to fetch the content from the referenced relay.
The solutions?
Now that you understand the problem space a bit better let's define those terms we started with.
Blastr
Blastr was created by nostr:nprofile1qqs9hejyd252x8q3kw6980ud4lymx3hlx2x3lgg6p7sz58nyv8m2nvgdswkeh and nostr:nprofile1qqswrlemlh2wgqc4jkds3d8ueqj9a2j3gcm7r48v9tskdd6rxsd7rtcpwpuwc from Mutiny and isn't a relay. Instead, Blastr is a proxy (i.e. it looks like a relay to clients) that ingests any event sent to it and, in turn, sends those events to EVERY online relay on the network. It's a mass re-broadcaster for events that can be helpful to get your data pushed out to as many relays (and thus users) as possible. The drawback, of course, is that this is tremendously wasteful from a bandwidth and storage perspective.
Gossip (in 3 flavors)
This is by far the most confusing part for most people when watching the memes of the last few weeks fly by and I've seen a lot of confused takes out there. Most of the confusion stems from the multiplicity of definitions of what the "gossip model" actually is. Let's go through the options. 1. Gossip protocols: This is a general concept more than a specific implementation. Gossip protocols are protocols that attempt to spread information around a network in a uniform way. For example, Bitcoin nodes use a variation of the gossip protocol to make sure that transactions end up in as many mempools as possible. This is important in computing when you want to reach consensus or when all nodes in a network need to have the same information in order to operate the network. Since nostr doesn't have any consensus rules or shared compute, it's somewhat pointless to try and make sure all events are propagated to all relays (hence the limited usefulness of Blastr). 2. The Gossip client from nostr:nprofile1qqswuyd9ml6qcxd92h6pleptfrcqucvvjy39vg4wx7mv9wm8kakyujgua442w : This is a nostr client that was built from the ground up to try and use relays and relay hints in events to the fullest to keep things as decentralized as possible while being efficient in how much data it was fetching. Mike has a great (slightly outdated and very technical) video that talks about his motivation behind building Gossip in the way he did. It's worth a watch. video link 3. Gossip model: This is what people are usually referring to when they are talking about relays on nostr. The Gossip model is a loose, catch-all term used to refer to all the ways in which clients attempt to understand which relays they should read & write to for a given user. Again, this isn't really a specific spec or implementation but encompasses many different strategies. This vagueness inherent in the term makes discussions about the "gossip model" pretty imprecise and prone to misunderstanding.
Don't gossip
To be clear: You really shoud not be thinking about or talking about any of this as the "gossip model" since that definition is so abstract as to be unusable. Which brings us finally to the real topic being discussed at the moment among devs; the Outbox model.
Outbox/Inbox model
This is the real topic of conversation right now: How should client developers build relay discovery and selection features into their apps. As we already talked about, if left alone, it's likely that we'd unintentionally centralize most of nostr onto a few huge relays. So making sure that we encourage (and build sensible defaults) to help client developers to treat relay discovery and selection properly is really critical.
Right now, the discussion centers around one main approach, called the "Outbox model". There is also an "Inbox model" which is a still just a high level idea which I'll mention below but it's not being implemented yet (as of late March 2024). 1. The "Outbox model": This strategy looks at what relays users are using to publish their events (from relay lists and tag markers) and then uses an algorithm to decide how to fetch all the needed events from the array of relays. Different implementations can use different algorithms to select relays. For example, one implementation might optimize fetching events from the smallest number of relays (favoring large relays), while another might optimize for fetching from the relays that have the smallest user overlap (favoring small relays). 2. The "Inbox model": As you can imagine, this strategy flips the outbox model on it's head. It's so far just an idea (proposed by nostr:nprofile1qqs8nsk2uy2w529fs8n4tx60u7z553e4yx5dy2nxhw4elgjgawpqlas9waufq) and a draft NIP but the idea is that when your client posts on your behalf, it will loop over your entire follow list, making a list of the relays that each of your followers uses to read events. Then the client will publish your event to all of those relays. If all clients followed this paradigm, then each of us would only have to read from a single relay. To quote nostr:nprofile1qqs8nsk2uy2w529fs8n4tx60u7z553e4yx5dy2nxhw4elgjgawpqlas9waufq 's original post, "This doesn't take away from the outbox approach, and maybe should even be used together instead of as a replacement. But my point is that clients should be trying harder to deliver posts instead of just fetch posts. Because it benefits users when their posts can be seen."
Why the Outbox model has broad support
To understand why implementing an Outbox model is so powerful at solveing the problems laid out at the beginning of this article, you can do two quick thought experiments:
A user banned from all other relays
Imagine a user who's content is banned from all public relays for some reason. Instead, they have to run their own relay and publish their events there. With a simple "follow the major relays model" (or even with Blastr attempting to copy and paste their events to every other relay) this user is completely invisible to the network. User's would have to know about the banned user's private relay and select that relay in each client they use. What's more, if that relay ever had to change URL (likely for a user that is banned so broadly), all user's would need to know what the new URL is in order to change relays and fetch events from the new location.
With Outbox however, clients will see that their user's follow this user, will then look up this user's relay list, and will know where they need to go to fetch their events. It becomes much more difficult for relays to censor or block users with an Outbox model in place
Duplicate event fetching
We talked earlier about how many nostr clients often fetch the same data many times, just to throw that data away. Even using the simplest algorithms with an Outbox model, you can significantly reduce the amount of duplicate data you're fetching from relays. We, as users, would all also need to specific many fewer relays in our relay lists but would still be quite sure our clients would be able to find all the content we want to see.
Wrapping up
Hopefully this has given you a better overall understanding of what folks are talking about when they refer to Gossip (remember: don't refer to it this way) or Outbox (outbox, yay!) and why we need to be proactive about maintaining the decentralization of nostr.



