-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 3bf0c63f:aefa459d
2024-03-19 14:01:01
@ 3bf0c63f:aefa459d
2024-03-19 14:01:01Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ ee11a5df:b76c4e49
2024-07-11 23:57:53
@ ee11a5df:b76c4e49
2024-07-11 23:57:53What Can We Get by Breaking NOSTR?
"What if we just started over? What if we took everything we have learned while building nostr and did it all again, but did it right this time?"
That is a question I've heard quite a number of times, and it is a question I have pondered quite a lot myself.
My conclusion (so far) is that I believe that we can fix all the important things without starting over. There are different levels of breakage, starting over is the most extreme of them. In this post I will describe these levels of breakage and what each one could buy us.
Cryptography
Your key-pair is the most fundamental part of nostr. That is your portable identity.
If the cryptography changed from secp256k1 to ed25519, all current nostr identities would not be usable.
This would be a complete start over.
Every other break listed in this post could be done as well to no additional detriment (save for reuse of some existing code) because we would be starting over.
Why would anyone suggest making such a break? What does this buy us?
- Curve25519 is a safe curve meaning a bunch of specific cryptography things that us mortals do not understand but we are assured that it is somehow better.
- Ed25519 is more modern, said to be faster, and has more widespread code/library support than secp256k1.
- Nostr keys could be used as TLS server certificates. TLS 1.3 using RFC 7250 Raw Public Keys allows raw public keys as certificates. No DNS or certification authorities required, removing several points of failure. These ed25519 keys could be used in TLS, whereas secp256k1 keys cannot as no TLS algorithm utilizes them AFAIK. Since relays currently don't have assigned nostr identities but are instead referenced by a websocket URL, this doesn't buy us much, but it is interesting. This idea is explored further below (keep reading) under a lesser level of breakage.
Besides breaking everything, another downside is that people would not be able to manage nostr keys with bitcoin hardware.
I am fairly strongly against breaking things this far. I don't think it is worth it.
Signature Scheme and Event Structure
Event structure is the next most fundamental part of nostr. Although events can be represented in many ways (clients and relays usually parse the JSON into data structures and/or database columns), the nature of the content of an event is well defined as seven particular fields. If we changed those, that would be a hard fork.
This break is quite severe. All current nostr events wouldn't work in this hard fork. We would be preserving identities, but all content would be starting over.
It would be difficult to bridge between this fork and current nostr because the bridge couldn't create the different signature required (not having anybody's private key) and current nostr wouldn't be generating the new kind of signature. Therefore any bridge would have to do identity mapping just like bridges to entirely different protocols do (e.g. mostr to mastodon).
What could we gain by breaking things this far?
- We could have a faster event hash and id verification: the current signature scheme of nostr requires lining up 5 JSON fields into a JSON array and using that as hash input. There is a performance cost to copying this data in order to hash it.
- We could introduce a subkey field, and sign events via that subkey, while preserving the pubkey as the author everybody knows and searches by. Note however that we can already get a remarkably similar thing using something like NIP-26 where the actual author is in a tag, and the pubkey field is the signing subkey.
- We could refactor the kind integer into composable bitflags (that could apply to any application) and an application kind (that specifies the application).
- Surely there are other things I haven't thought of.
I am currently against this kind of break. I don't think the benefits even come close to outweighing the cost. But if I learned about other things that we could "fix" by restructuring the events, I could possibly change my mind.
Replacing Relay URLs
Nostr is defined by relays that are addressed by websocket URLs. If that changed, that would be a significant break. Many (maybe even most) current event kinds would need superseding.
The most reasonable change is to define relays with nostr identities, specifying their pubkey instead of their URL.
What could we gain by this?
- We could ditch reliance on DNS. Relays could publish events under their nostr identity that advertise their current IP address(es).
- We could ditch certificates because relays could generate ed25519 keypairs for themselves (or indeed just self-signed certificates which might be much more broadly supported) and publish their public ed25519 key in the same replaceable event where they advertise their current IP address(es).
This is a gigantic break. Almost all event kinds need redefining and pretty much all nostr software will need fairly major upgrades. But it also gives us a kind of Internet liberty that many of us have dreamt of our entire lives.
I am ambivalent about this idea.
Protocol Messaging and Transport
The protocol messages of nostr are the next level of breakage. We could preserve keypair identities, all current events, and current relay URL references, but just break the protocol of how clients and relay communicate this data.
This would not necessarily break relay and client implementations at all, so long as the new protocol were opt-in.
What could we get?
- The new protocol could transmit events in binary form for increased performance (no more JSON parsing with it's typical many small memory allocations and string escaping nightmares). I think event throughput could double (wild guess).
- It could have clear expectations of who talks first, and when and how AUTH happens, avoiding a lot of current miscommunication between clients and relays.
- We could introduce bitflags for feature support so that new features could be added later and clients would not bother trying them (and getting an error or timing out) on relays that didn't signal support. This could replace much of NIP-11.
- We could then introduce something like negentropy or negative filters (but not that... probably something else solving that same problem) without it being a breaking change.
- The new protocol could just be a few websocket-binary messages enhancing the current protocol, continuing to leverage the existing websocket-text messages we currently have, meaning newer relays would still support all the older stuff.
The downsides are just that if you want this new stuff you have to build it. It makes the protocol less simple, having now multiple protocols, multiple ways of doing the same thing.
Nonetheless, this I am in favor of. I think the trade-offs are worth it. I will be pushing a draft PR for this soon.
The path forward
I propose then the following path forward:
- A new nostr protocol over websockets binary (draft PR to be shared soon)
- Subkeys brought into nostr via NIP-26 (but let's use a single letter tag instead, OK?) via a big push to get all the clients to support it (the transition will be painful - most major clients will need to support this before anybody can start using it).
- Some kind of solution to the negative-filter-negentropy need added to the new protocol as its first optional feature.
- We seriously consider replacing Relay URLs with nostr pubkeys assigned to the relay, and then have relays publish their IP address and TLS key or certificate.
We sacrifice these:
- Faster event hash/verification
- Composable event bitflags
- Safer faster more well-supported crypto curve
- Nostr keys themselves as TLS 1.3 RawPublicKey certificates
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 2c7cc62a:622a5cdc
2024-07-09 14:49:44
@ 2c7cc62a:622a5cdc
2024-07-09 14:49:44todo-mattn #todo
Nostr 上で todo 管理する仕組み
bot と対話する?
vim-jp radio のイベント自動投稿
今欲しい要件としては、vim-jp radio のオフィシャルアカウントを作る事なのだけど、秘密鍵は別の方(Nostr にはいない)の管理としたい。代理で投稿する人間には秘密鍵は持たせたくない。 ここでは手動投稿に加え自動投稿が必要になるので、代理署名機能が必要になる。
代理署名としては NIP-46 が考えられる。NIP-46 は 3way handshake の様に機能する。
まず投稿者は bunker:
という認証情報を使ってリレーに代理投稿依頼を投げる。kind は 24133 の短命イベント。 このイベントを署名者が監視(代理署名サーバ)していて同じ bunker に書かれているパスワードを使って解読、署名を行って返信する。キーはオリジナルのイベントのIDを使うので、同じ時刻の同じコンテンツでさえなければバッティングする事はない。 投稿者はその返信をリレー経由で受け取って署名済み投稿をリレーに投げるという事になる。 今回の要件を満たすかを考えた場合、Nostr にいない vim-jp radio の発案者に秘密鍵のみを渡す事を考えた場合、この代理署名サーバを常時稼働させておく必要があるという事。しかも現状は pubkey 1つに対して1つ起動する必要がある。ちょっとリソース食い。
また代理署名サーバを起動する際に秘密鍵が必要になる。この時点で初めの要件である「代理で投稿する人間には秘密鍵は持たせたくない」を満たせなくなる。特にイベント発案者が Nostr にいないならなおさらである。
という事で本件で NIP-46 を使うアイデアについては一旦保留。
-
 @ 2c7cc62a:622a5cdc
2024-07-08 10:24:56
@ 2c7cc62a:622a5cdc
2024-07-08 10:24:56Nostr で見掛けた焼肉店情報。いつか見返す。
ちょうしゅう
石垣島
http://yugafu-llc.com/
nostr:note1tgnt39hgyvn4lskp5s684czgsce9y55xm8ysfrfdj4mp3gguhhvsu6jtjw
とらじ
http://www.toraji.net/
大阪上新庄
nostr:note1x3fhl9w0wf5r7e75aem3n4ffcqcuqggp3uda6cj8p3ewg4hgrrjqwye9lc
瑞園
https://tabelog.com/osaka/A2701/A270307/27001977/
大阪上新庄
nostr:note1whjkp27hztcy5yey5r7nvc23yjcavpu322q5xyp8grua98rshz7stz9grh
たん清
https://www.tankiyo.com/
東京秋葉原
nostr:note1ke9ekpe3h92nq7qgjg4w4nmz4u7s4wyn753gagsf49pam4h6aefsddwr0k
-
 @ 700c6cbf:a92816fd
2024-07-14 00:51:44
@ 700c6cbf:a92816fd
2024-07-14 00:51:44... something else
This is the final image. Or is it? Likely, it is not. I have already started on a perfect version of my Mother Earth painting.
Of course, there is no such thing as a perfect painting. What I mean is that I already started on a vector version of Mother Earth. You're familiar with vector vs. pixel, right?
But let's start at the beginning, not the end.
This here is a pic from the sketching phase. I am not one who can just magically and with a few strokes produce an amazing sketch of something that resembles a human. There are artists out there that do this wonderfully. It's amazing but it is not me (unfortunately).

Here I am starting to color in the sketch with a watercolor brush. This is all done in Procreate App on an iPad Pro. The coloring is on a separate layer with the pencil sketch set to multiply to shine through the colors. That's why the pencil strokes now are black. I like that look.

And here, I am almost done. Just need to decide on the background color. And as you can see from the gif and video I didn't really decide. Though at the moment I am favoring that muted pinkish red - LOL

Which color is your favorite?


Here you can see the whole process in a timelapse. Above pictures were grabbed from it to detail the process a little.
https://cdn.satellite.earth/05774dcaaf4679c34cbeb46cb43b4c4f85553a3d2b4850a7256d26a871b0c4f3.mp4
And that's it my Nostr friends for my first longform post in this community.
I hope you enjoyed this post. Comments are encouraged an appreciated. Thank you.
Cheers, OceanBee
-
 @ a8d1560d:3fec7a08
2024-07-14 00:17:38
@ a8d1560d:3fec7a08
2024-07-14 00:17:38I have made an event viewer and an event crafter for #Nostr using https://websim.ai. The event crafter works flawlessly, but sadly without NIP-07. It can be used to craft events of any kind, with any tags you want. You can find it here:
https://websim.ai/c/tZxeQ9DWZf9bCkTd1
As for the event viewer, making it brought several difficulties, and I'm not really happy with it in its current state. But it does show any event of any kind. If you enter your own pubkey, you can choose to only show events from pubkeys you follow. And you can always choose to either show all events or use a pubkey filter.
https://websim.ai/c/KI87SEQljLys4nVIX
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 21ac2956:09d1e2df
2024-07-06 06:37:06
@ 21ac2956:09d1e2df
2024-07-06 06:37:06簡単にブログが作れそうだし実際開設は簡単すぎたけど、設定がようわからん。
Long-form Contentも初めてなのでとりあえず habla でポストしてみる。
どうやらマークダウンも覚えなきゃならないようだ。
追記:編集もできるのか!
-
 @ 7361ca91:252fce6d
2024-07-02 14:33:05
@ 7361ca91:252fce6d
2024-07-02 14:33:05サイエンス・フィクションは、可能な未来を想像する思索的な演習です。サイファイは可能性の空間を拡張します。暗号通貨は極端な種類のサイファイであり、未来のビジョンを提供するだけでなく、その未来を実現するためのツールも提供します。暗号通貨は現在、ソーラーパンクと呼ばれるサイファイのジャンルによって活気づけられています。サイバーパンクから進化したソーラーパンクは、楽観主義によって特徴づけられる未来のユートピア的なビジョンです。ソーラーパンクにとって、未来は明るいのです。ソーラーパンクはサイバーパンクのディストピアの影を払いのけ、混沌とした地平線を越えた世界を照らし出します。多くの人気のあるDeFiチェーンでは、ソーラーパンクのハッカーが公共財を資金調達するための透明なインフラを構築しています。共有された信念はシンプルです。分散型で透明な金融システムへの公共アクセスが、より公正で正義のある世界をもたらすということです。ソーラーパンクは暗号通貨の意識的な心です。明るく、自信に満ち、未来志向です。
しかし、ソーラーパンクの信念に対する反対はルナーパンクの懐疑主義です。ルナーパンクはソーラーの影の自分たちです。彼らはこのサイクルの無意識です。ソーラーパンクがDAOに参加する一方で、ルナーパンクは戦争の準備をし、コミュニティを守るためのプライバシー強化ツールを構築します。ルナーパンクは最初、ソーラーパンクのサブセットとして登場しました。常にイーサリアムや類似のチェーンで提供されるプレーンテキストのパラダイムよりも暗号化を好んでいました。時間が経つにつれて、ソーラーパンクの傾向によって生じた緊張はますます増大しました。ルナーパンクはソーラーパンクの遺産から離れ、自分自身のアイデンティティを主張するようになりました。
ルナーパンクの空想では、暗号通貨と既存の権力構造との間の対立は基本的にプログラムされています。規制によって暗号通貨は地下に追いやられ、匿名性が増大します。ルナーパンクのビジョンは、ベアリッシュな悪夢として拒絶されます。その根本的な対立――国家が暗号通貨を禁止すること――は、人々が金を持って逃げるような恐怖を生むため、ソーラーパンクによって却下されます。ソーラーパンクの楽観主義はブルマーケットのサイクルと同義になり、悲観主義はベアと関連付けられています。ルナーパンクはこの単純なエスカレーションを超える何かを提供します。それは市場サイクルの間の洞察の瞬間、ホログラムの中のグリッチであり、ソースコードが輝いて見える瞬間です。
ソーラーパンクは脆弱です――揺れ動くと壊れるものです。アンチフラジャイルとは、ショックを吸収し強くなるものです。次のことを考慮してください。暗号通貨の核心的なイノベーションは適応的です。ユーザーをエンパワーメントしつつ、その攻撃面を等しく拡散させます。ユーザーのエンパワーメントは脆弱性と負の相関があります。ユーザーベースが重要であればあるほど、ネットワークはよりアンチフラジャイルになります。ユーザーのエンパワーメントとシステムのアンチフラジャイルは互いにポジティブなフィードバックを形成します。
しかし、このサイクルは逆方向にも進行します。透明なシステムでは、ユーザーはさらされます。外部環境が敵対的になると、この情報が彼らに対して武器として使用される可能性があります。迫害に直面したユーザーは脱退を選び、それが脆弱性への下降を引き起こします。ソーラーパンクの考え方は本質的に楽観的です。ソーラーパンクシステムの透明性は、外向きに投影された楽観主義の精神です。透明なシステムを構築することで、ソーラーパンクは「法律が自分に不利にならないと信じている」と言っています。楽観主義の強調は、最悪の事態に備えることを妨げます。これがソーラーパンクの脆弱性の核心です。
暗い選択肢とアンチフラジャイル性は未知性に依存しています。未来は暗く、意味のある確実性を持って予測することはできません。選択肢は、その暗闇を利用して有利に働くため、アンチフラジャイル性の武器と呼ばれています。選択肢は、予言がほとんどの場合間違っていると仮定します。間違っていることは安価ですが、正しいことは不釣り合いに報われます。ルナーパンクは最悪の事態において成功するため、選択肢を取り入れています。ルナーパンクの仮説が間違っていれば、スーパーサイクルは続きます。正しければ、暗号通貨は適切な防御を備えた次の段階に進みます。しっかりと防御されることは、暗号化を使用してユーザーの身元と活動を保護することを意味します。
予言
匿名性は、まず大量監視への適応として生じます。しかし、その存在自体が監視努力をさらに正当化します。これは、匿名性と監視がエスカレートする運命にあることを示唆する正のフィードバックループです。このループが十分に続くと、ルナーパンクの予言の次の段階が引き起こされます:規制トラップ。この段階では、政府は匿名性の増加を口実にして、暗号通貨に対してその力を最大限に活用します。しかし、暗号通貨を取り締まることで、敵対的な力はその正当化をさらに強化するだけです。暗号通貨の実用性は、取り締まりの程度と相関します。各打撃を受けるたびに、不釣り合いに拡大します。
ルナサイクル
太陽はその透明性とアイデンティティへのこだわりを通じて、自然の象徴であり暴政の象徴でもあります。ソーラーパンクはその中央の象徴の二重の特徴を受け継いでいます。ソーラーパンクシステムは、ユーザーが危険にさらされる砂漠の風景です。ルナーパンクは森のようなものです。暗号化の密集した覆いが部族を保護し、迫害された人々に避難所を提供します。木立は重要な防衛線を提供します。ルナの風景は暗いですが、生物にあふれています。ルナテックは、自由のために人々自身によって所有され、運営されています。ルナサイクルは、権威主義的な技術に対して民主的な技術を支持します:監視に対する自由と、単一文化に対する多様性です。システムに透明性を重視することで、ソーラーパンクは悲劇的にその運命を作り上げています。監視、すなわち権威主義のメカニズムは、ソーラーパンクの運命に結びついています。ソーラーパンクが成功するためには、ルナーパンクの無意識を統合する必要があります。ソーラーパンクが成功する唯一の希望は、暗闇に移行することです。
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 9edd72eb:cb697b0a
2024-07-13 22:16:45
@ 9edd72eb:cb697b0a
2024-07-13 22:16:45If one knows exactly what to do to alleviate one's pain, comfort oneself, and emerge more or less unscathed from Adversity, I think it can be said that one has reached a fairly high level of Wisdom in Life.
originally posted at https://stacker.news/items/607422
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ e6ce6154:275e3444
2023-07-27 14:12:49
@ e6ce6154:275e3444
2023-07-27 14:12:49Este artigo foi censurado pelo estado e fomos obrigados a deletá-lo após ameaça de homens armados virem nos visitar e agredir nossa vida e propriedade.
Isto é mais uma prova que os autoproclamados antirracistas são piores que os racistas.
https://rothbardbrasil.com/pelo-direito-de-ser-racista-fascista-machista-e-homofobico
Segue artigo na íntegra. 👇
Sem dúvida, a escalada autoritária do totalitarismo cultural progressista nos últimos anos tem sido sumariamente deletéria e prejudicial para a liberdade de expressão. Como seria de se esperar, a cada dia que passa o autoritarismo progressista continua a se expandir de maneira irrefreável, prejudicando a liberdade dos indivíduos de formas cada vez mais deploráveis e contundentes.
Com a ascensão da tirania politicamente correta e sua invasão a todos os terrenos culturais, o autoritarismo progressista foi se alastrando e consolidando sua hegemonia em determinados segmentos. Com a eventual eclosão e a expansão da opressiva e despótica cultura do cancelamento — uma progênie inevitável do totalitarismo progressista —, todas as pessoas que manifestam opiniões, crenças ou posicionamentos que não estão alinhados com as pautas universitárias da moda tornam-se um alvo.
Há algumas semanas, vimos a enorme repercussão causada pelo caso envolvendo o jogador profissional de vôlei Maurício Sousa, que foi cancelado pelo simples fato de ter emitido sua opinião pessoal sobre um personagem de história em quadrinhos, Jon Kent, o novo Superman, que é bissexual. Maurício Sousa reprovou a conduta sexual do personagem, o que é um direito pessoal inalienável que ele tem. Ele não é obrigado a gostar ou aprovar a bissexualidade. Como qualquer pessoa, ele tem o direito pleno de criticar tudo aquilo que ele não gosta. No entanto, pelo simples fato de emitir a sua opinião pessoal, Maurício Sousa foi acusado de homofobia e teve seu contrato rescindido, sendo desligado do Minas Tênis Clube.
Lamentavelmente, Maurício Sousa não foi o primeiro e nem será o último indivíduo a sofrer com a opressiva e autoritária cultura do cancelamento. Como uma tirania cultural que está em plena ascensão e usufrui de um amplo apoio do establishment, essa nova forma de totalitarismo cultural colorido e festivo está se impondo de formas e maneiras bastante contundentes em praticamente todas as esferas da sociedade contemporânea. Sua intenção é relegar ao ostracismo todos aqueles que não se curvam ao totalitarismo progressista, criminalizando opiniões e crenças que divergem do culto à libertinagem hedonista pós-moderna. Oculto por trás de todo esse ativismo autoritário, o que temos de fato é uma profunda hostilidade por padrões morais tradicionalistas, cristãos e conservadores.
No entanto, é fundamental entendermos uma questão imperativa, que explica em partes o conflito aqui criado — todos os progressistas contemporâneos são crias oriundas do direito positivo. Por essa razão, eles jamais entenderão de forma pragmática e objetiva conceitos como criminalidade, direitos de propriedade, agressão e liberdade de expressão pela perspectiva do jusnaturalismo, que é manifestamente o direito em seu estado mais puro, correto, ético e equilibrado.
Pela ótica jusnaturalista, uma opinião é uma opinião. Ponto final. E absolutamente ninguém deve ser preso, cancelado, sabotado ou boicotado por expressar uma opinião particular sobre qualquer assunto. Palavras não agridem ninguém, portanto jamais poderiam ser consideradas um crime em si. Apenas deveriam ser tipificados como crimes agressões de caráter objetivo, como roubo, sequestro, fraude, extorsão, estupro e infrações similares, que representam uma ameaça direta à integridade física da vítima, ou que busquem subtrair alguma posse empregando a violência.
Infelizmente, a geração floquinho de neve — terrivelmente histérica, egocêntrica e sensível — fica profundamente ofendida e consternada sempre que alguém defende posicionamentos contrários à religião progressista. Por essa razão, os guerreiros da justiça social sinceramente acreditam que o papai-estado deve censurar todas as opiniões que eles não gostam de ouvir, assim como deve também criar leis para encarcerar todos aqueles que falam ou escrevem coisas que desagradam a militância.
Como a geração floquinho de neve foi criada para acreditar que todas as suas vontades pessoais e disposições ideológicas devem ser sumariamente atendidas pelo papai-estado, eles embarcaram em uma cruzada moral que pretende erradicar todas as coisas que são ofensivas à ideologia progressista; só assim eles poderão deflagrar na Terra o seu tão sonhado paraíso hedonista e igualitário, de inimaginável esplendor e felicidade.
Em virtude do seu comportamento intrinsecamente despótico, autoritário e egocêntrico, acaba sendo inevitável que militantes progressistas problematizem tudo aquilo que os desagrada.
Como são criaturas inúteis destituídas de ocupação real e verdadeiro sentido na vida, sendo oprimidas unicamente na sua própria imaginação, militantes progressistas precisam constantemente inventar novos vilões para serem combatidos.
Partindo dessa perspectiva, é natural para a militância que absolutamente tudo que exista no mundo e que não se enquadra com as regras autoritárias e restritivas da religião progressista seja encarado como um problema. Para a geração floquinho de neve, o capitalismo é um problema. O fascismo é um problema. A iniciativa privada é um problema. O homem branco, tradicionalista, conservador e heterossexual é um problema. A desigualdade é um problema. A liberdade é um problema. Monteiro Lobato é um problema (sim, até mesmo o renomado ícone da literatura brasileira, autor — entre outros títulos — de Urupês, foi vítima da cultura do cancelamento, acusado de ser racista e eugenista).
Para a esquerda, praticamente tudo é um problema. Na mentalidade da militância progressista, tudo é motivo para reclamação. Foi em função desse comportamento histérico, histriônico e infantil que o famoso pensador conservador-libertário americano P. J. O’Rourke afirmou que “o esquerdismo é uma filosofia de pirralhos chorões”. O que é uma verdade absoluta e irrefutável em todos os sentidos.
De fato, todas as filosofias de esquerda de forma geral são idealizações utópicas e infantis de um mundo perfeito. Enquanto o mundo não se transformar naquela colorida e vibrante utopia que é apresentada pela cartilha socialista padrão, militantes continuarão a reclamar contra tudo o que existe no mundo de forma agressiva, visceral e beligerante. Evidentemente, eles não vão fazer absolutamente nada de positivo ou construtivo para que o mundo se transforme no gracioso paraíso que eles tanto desejam ver consolidado, mas eles continuarão a berrar e vociferar muito em sua busca incessante pela utopia, marcando presença em passeatas inúteis ou combatendo o fascismo imaginário nas redes sociais.
Sem dúvida, estamos muito perto de ver leis absurdas e estúpidas sendo implementadas, para agradar a militância da terra colorida do assistencialismo eterno onde nada é escasso e tudo cai do céu. Em breve, você não poderá usar calças pretas, pois elas serão consideradas peças de vestuário excessivamente heterossexuais. Apenas calças amarelas ou coloridas serão permitidas. Você também terá que tingir de cor-de-rosa uma mecha do seu cabelo; pois preservar o seu cabelo na sua cor natural é heteronormativo demais da sua parte, sendo portanto um componente demasiadamente opressor da sociedade.
Você também não poderá ver filmes de guerra ou de ação, apenas comédias românticas, pois certos gêneros de filmes exaltam a violência do patriarcado e isso impede o mundo de se tornar uma graciosa festa colorida de fraternidades universitárias ungidas por pôneis resplandecentes, hedonismo infinito, vadiagem universitária e autogratificação psicodélica, que certamente são elementos indispensáveis para se produzir o paraíso na Terra.
Sabemos perfeitamente, no entanto, que dentre as atitudes “opressivas” que a militância progressista mais se empenha em combater, estão o racismo, o fascismo, o machismo e a homofobia. No entanto, é fundamental entender que ser racista, fascista, machista ou homofóbico não são crimes em si. Na prática, todos esses elementos são apenas traços de personalidade; e eles não podem ser pura e simplesmente criminalizados porque ideólogos e militantes progressistas iluminados não gostam deles.
Tanto pela ética quanto pela ótica jusnaturalista, é facilmente compreensível entender que esses traços de personalidade não podem ser criminalizados ou proibidos simplesmente porque integrantes de uma ideologia não tem nenhuma apreciação ou simpatia por eles. Da mesma forma, nenhum desses traços de personalidade representa em si um perigo para a sociedade, pelo simples fato de existir. Por incrível que pareça, até mesmo o machismo, o racismo, o fascismo e a homofobia merecem a devida apologia.
Mas vamos analisar cada um desses tópicos separadamente para entender isso melhor.
Racismo
Quando falamos no Japão, normalmente não fazemos nenhuma associação da sociedade japonesa com o racismo. No entanto, é incontestável o fato de que a sociedade japonesa pode ser considerada uma das sociedades mais racistas do mundo. E a verdade é que não há absolutamente nada de errado com isso.
Aproximadamente 97% da população do Japão é nativa; apenas 3% do componente populacional é constituído por estrangeiros (a população do Japão é estimada em aproximadamente 126 milhões de habitantes). Isso faz a sociedade japonesa ser uma das mais homogêneas do mundo. As autoridades japonesas reconhecidamente dificultam processos de seleção e aplicação a estrangeiros que desejam se tornar residentes. E a maioria dos japoneses aprova essa decisão.
Diversos estabelecimentos comerciais como hotéis, bares e restaurantes por todo o país tem placas na entrada que dizem “somente para japoneses” e a maioria destes estabelecimentos se recusa ostensivamente a atender ou aceitar clientes estrangeiros, não importa quão ricos ou abastados sejam.
Na Terra do Sol Nascente, a hostilidade e a desconfiança natural para com estrangeiros é tão grande que até mesmo indivíduos que nascem em algum outro país, mas são filhos de pais japoneses, não são considerados cidadãos plenamente japoneses.
Se estes indivíduos decidem sair do seu país de origem para se estabelecer no Japão — mesmo tendo descendência nipônica legítima e inquestionável —, eles enfrentarão uma discriminação social considerável, especialmente se não dominarem o idioma japonês de forma impecável. Esse fato mostra que a discriminação é uma parte tão indissociável quanto elementar da sociedade japonesa, e ela está tão profundamente arraigada à cultura nipônica que é praticamente impossível alterá-la ou atenuá-la por qualquer motivo.
A verdade é que — quando falamos de um país como o Japão — nem todos os discursos politicamente corretos do mundo, nem a histeria progressista ocidental mais inflamada poderão algum dia modificar, extirpar ou sequer atenuar o componente racista da cultura nipônica. E isso é consequência de uma questão tão simples quanto primordial: discriminar faz parte da natureza humana, sendo tanto um direito individual quanto um elemento cultural inerente à muitas nações do mundo. Os japoneses não tem problema algum em admitir ou institucionalizar o seu preconceito, justamente pelo fato de que a ideologia politicamente correta não tem no oriente a força e a presença que tem no ocidente.
E é fundamental enfatizar que, sendo de natureza pacífica — ou seja, não violando nem agredindo terceiros —, a discriminação é um recurso natural dos seres humanos, que está diretamente associada a questões como familiaridade e segurança.
Absolutamente ninguém deve ser forçado a apreciar ou integrar-se a raças, etnias, pessoas ou tribos que não lhe transmitem sentimentos de segurança ou familiaridade. Integração forçada é o verdadeiro crime, e isso diversos países europeus — principalmente os escandinavos (países que lideram o ranking de submissão à ideologia politicamente correta) — aprenderam da pior forma possível.
A integração forçada com imigrantes islâmicos resultou em ondas de assassinato, estupro e violência inimagináveis para diversos países europeus, até então civilizados, que a imprensa ocidental politicamente correta e a militância progressista estão permanentemente tentando esconder, porque não desejam que o ocidente descubra como a agenda “humanitária” de integração forçada dos povos muçulmanos em países do Velho Mundo resultou em algumas das piores chacinas e tragédias na história recente da Europa.
Ou seja, ao discriminarem estrangeiros, os japoneses estão apenas se protegendo e lutando para preservar sua nação como um ambiente cultural, étnico e social que lhe é seguro e familiar, assim se opondo a mudanças bruscas, indesejadas e antinaturais, que poderiam comprometer a estabilidade social do país.
A discriminação — sendo de natureza pacífica —, é benévola, salutar e indubitavelmente ajuda a manter a estabilidade social da comunidade. Toda e qualquer forma de integração forçada deve ser repudiada com veemência, pois, mais cedo ou mais tarde, ela irá subverter a ordem social vigente, e sempre será acompanhada de deploráveis e dramáticos resultados.
Para citar novamente os países escandinavos, a Suécia é um excelente exemplo do que não fazer. Tendo seguido o caminho contrário ao da discriminação racional praticada pela sociedade japonesa, atualmente a sociedade sueca — além de afundar de forma consistente na lama da libertinagem, da decadência e da deterioração progressista — sofre em demasia com os imigrantes muçulmanos, que foram deixados praticamente livres para matar, saquear, esquartejar e estuprar quem eles quiserem. Hoje, eles são praticamente intocáveis, visto que denunciá-los, desmoralizá-los ou acusá-los de qualquer crime é uma atitude politicamente incorreta e altamente reprovada pelo establishment progressista. A elite socialista sueca jamais se atreve a acusá-los de qualquer crime, pois temem ser classificados como xenófobos e intolerantes. Ou seja, a desgraça da Europa, sobretudo dos países escandinavos, foi não ter oferecido nenhuma resistência à ideologia progressista politicamente correta. Hoje, eles são totalmente submissos a ela.
O exemplo do Japão mostra, portanto — para além de qualquer dúvida —, a importância ética e prática da discriminação, que é perfeitamente aceitável e natural, sendo uma tendência inerente aos seres humanos, e portanto intrínseca a determinados comportamentos, sociedades e culturas.
Indo ainda mais longe nessa questão, devemos entender que na verdade todos nós discriminamos, e não existe absolutamente nada de errado nisso. Discriminar pessoas faz parte da natureza humana e quem se recusa a admitir esse fato é um hipócrita. Mulheres discriminam homens na hora de selecionar um parceiro; elas avaliam diversos quesitos, como altura, aparência, status social, condição financeira e carisma. E dentre suas opções, elas sempre escolherão o homem mais atraente, másculo e viril, em detrimento de todos os baixinhos, calvos, carentes, frágeis e inibidos que possam estar disponíveis. Da mesma forma, homens sempre terão preferência por mulheres jovens, atraentes e delicadas, em detrimento de todas as feministas de meia-idade, acima do peso, de cabelo pintado, que são mães solteiras e militantes socialistas. A própria militância progressista discrimina pessoas de forma virulenta e intransigente, como fica evidente no tratamento que dispensam a mulheres bolsonaristas e a negros de direita.
A verdade é que — não importa o nível de histeria da militância progressista — a discriminação é inerente à condição humana e um direito natural inalienável de todos. É parte indissociável da natureza humana e qualquer pessoa pode e deve exercer esse direito sempre que desejar. Não existe absolutamente nada de errado em discriminar pessoas. O problema real é a ideologia progressista e o autoritarismo politicamente correto, movimentos tirânicos que não respeitam o direito das pessoas de discriminar.
Fascismo
Quando falamos de fascismo, precisamos entender que, para a esquerda política, o fascismo é compreendido como um conceito completamente divorciado do seu significado original. Para um militante de esquerda, fascista é todo aquele que defende posicionamentos contrários ao progressismo, não se referindo necessariamente a um fascista clássico.
Mas, seja como for, é necessário entender que — como qualquer ideologia política — até mesmo o fascismo clássico tem o direito de existir e ocupar o seu devido lugar; portanto, fascistas não devem ser arbitrariamente censurados, apesar de defenderem conceitos que representam uma completa antítese de tudo aquilo que é valioso para os entusiastas da liberdade.
Em um país como o Brasil, onde socialistas e comunistas tem total liberdade para se expressar, defender suas ideologias e até mesmo formar partidos políticos, não faz absolutamente o menor sentido que fascistas — e até mesmo nazistas assumidos — sofram qualquer tipo de discriminação. Embora socialistas e comunistas se sintam moralmente superiores aos fascistas (ou a qualquer outra filosofia política ou escola de pensamento), sabemos perfeitamente que o seu senso de superioridade é fruto de uma pueril romantização universitária da sua própria ideologia. A história mostra efetivamente que o socialismo clássico e o comunismo causaram muito mais destruição do que o fascismo.
Portanto, se socialistas e comunistas tem total liberdade para se expressar, não existe a menor razão para que fascistas não usufruam dessa mesma liberdade.
É claro, nesse ponto, seremos invariavelmente confrontados por um oportuno dilema — o famoso paradoxo da intolerância, de Karl Popper. Até que ponto uma sociedade livre e tolerante deve tolerar a intolerância (inerente a ideologias totalitárias)?
As leis de propriedade privada resolveriam isso em uma sociedade livre. O mais importante a levarmos em consideração no atual contexto, no entanto — ao defender ou criticar uma determinada ideologia, filosofia ou escola de pensamento —, é entender que, seja ela qual for, ela tem o direito de existir. E todas as pessoas que a defendem tem o direito de defendê-la, da mesma maneira que todos os seus detratores tem o direito de criticá-la.
Essa é uma forte razão para jamais apoiarmos a censura. Muito pelo contrário, devemos repudiar com veemência e intransigência toda e qualquer forma de censura, especialmente a estatal.
Existem duas fortes razões para isso:
A primeira delas é a volatilidade da censura (especialmente a estatal). A censura oficial do governo, depois que é implementada, torna-se absolutamente incontrolável. Hoje, ela pode estar apontada para um grupo de pessoas cujas ideias divergem das suas. Mas amanhã, ela pode estar apontada justamente para as ideias que você defende. É fundamental, portanto, compreendermos que a censura estatal é incontrolável. Sob qualquer ponto de vista, é muito mais vantajoso que exista uma vasta pluralidade de ideias conflitantes na sociedade competindo entre si, do que o estado decidir que ideias podem ser difundidas ou não.
Além do mais, libertários e anarcocapitalistas não podem nunca esperar qualquer tipo de simpatia por parte das autoridades governamentais. Para o estado, seria infinitamente mais prático e vantajoso criminalizar o libertarianismo e o anarcocapitalismo — sob a alegação de que são filosofias perigosas difundidas por extremistas radicais que ameaçam o estado democrático de direito — do que o fascismo ou qualquer outra ideologia centralizada em governos burocráticos e onipotentes. Portanto, defender a censura, especialmente a estatal, representa sempre um perigo para o próprio indivíduo, que mais cedo ou mais tarde poderá ver a censura oficial do sistema se voltar contra ele.
Outra razão pela qual libertários jamais devem defender a censura, é porque — ao contrário dos estatistas — não é coerente que defensores da liberdade se comportem como se o estado fosse o seu papai e o governo fosse a sua mamãe. Não devemos terceirizar nossas próprias responsabilidades, tampouco devemos nos comportar como adultos infantilizados. Assumimos a responsabilidade de combater todas as ideologias e filosofias que agridem a liberdade e os seres humanos. Não procuramos políticos ou burocratas para executar essa tarefa por nós.
Portanto, se você ver um fascista sendo censurado nas redes sociais ou em qualquer outro lugar, assuma suas dores. Sinta-se compelido a defendê-lo, mostre aos seus detratores que ele tem todo direito de se expressar, como qualquer pessoa. Você não tem obrigação de concordar com ele ou apreciar as ideias que ele defende. Mas silenciar arbitrariamente qualquer pessoa não é uma pauta que honra a liberdade.
Se você não gosta de estado, planejamento central, burocracia, impostos, tarifas, políticas coletivistas, nacionalistas e desenvolvimentistas, mostre com argumentos coesos e convincentes porque a liberdade e o livre mercado são superiores a todos esses conceitos. Mas repudie a censura com intransigência e mordacidade.
Em primeiro lugar, porque você aprecia e defende a liberdade de expressão para todas as pessoas. E em segundo lugar, por entender perfeitamente que — se a censura eventualmente se tornar uma política de estado vigente entre a sociedade — é mais provável que ela atinja primeiro os defensores da liberdade do que os defensores do estado.
Machismo
Muitos elementos do comportamento masculino que hoje são atacados com virulência e considerados machistas pelo movimento progressista são na verdade manifestações naturais intrínsecas ao homem, que nossos avôs cultivaram ao longo de suas vidas sem serem recriminados por isso. Com a ascensão do feminismo, do progressismo e a eventual problematização do sexo masculino, o antagonismo militante dos principais líderes da revolução sexual da contracultura passou a naturalmente condenar todos os atributos genuinamente masculinos, por considerá-los símbolos de opressão e dominação social.
Apesar do Brasil ser uma sociedade liberal ultra-progressista, onde o estado protege mais as mulheres do que as crianças — afinal, a cada semana novas leis são implementadas concedendo inúmeros privilégios e benefícios às mulheres, aos quais elas jamais teriam direito em uma sociedade genuinamente machista e patriarcal —, a esquerda política persiste em tentar difundir a fantasia da opressão masculina e o mito de que vivemos em uma sociedade machista e patriarcal.
Como sempre, a realidade mostra um cenário muito diferente daquilo que é pregado pela militância da terra da fantasia. O Brasil atual não tem absolutamente nada de machista ou patriarcal. No Brasil, mulheres podem votar, podem ocupar posições de poder e autoridade tanto na esfera pública quanto em companhias privadas, podem se candidatar a cargos políticos, podem ser vereadoras, deputadas, governadoras, podem ser proprietárias do próprio negócio, podem se divorciar, podem dirigir, podem comprar armas, podem andar de biquíni nas praias, podem usar saias extremamente curtas, podem ver programas de televisão sobre sexo voltados única e exclusivamente para o público feminino, podem se casar com outras mulheres, podem ser promíscuas, podem consumir bebidas alcoólicas ao ponto da embriaguez, e podem fazer praticamente tudo aquilo que elas desejarem. No Brasil do século XXI, as mulheres são genuinamente livres para fazer as próprias escolhas em praticamente todos os aspectos de suas vidas. O que mostra efetivamente que a tal opressão do patriarcado não existe.
O liberalismo social extremo do qual as mulheres usufruem no Brasil atual — e que poderíamos estender a toda a sociedade contemporânea ocidental — é suficiente para desmantelar completamente a fábula feminista da sociedade patriarcal machista e opressora, que existe única e exclusivamente no mundinho de fantasias ideológicas da esquerda progressista.
Tão importante quanto, é fundamental compreender que nenhum homem é obrigado a levar o feminismo a sério ou considerá-lo um movimento social e político legítimo. Para um homem, ser considerado machista ou até mesmo assumir-se como um não deveria ser um problema. O progressismo e o feminismo — com o seu nefasto hábito de demonizar os homens, bem como todos os elementos inerentes ao comportamento e a cultura masculina — é que são o verdadeiro problema, conforme tentam modificar o homem para transformá-lo em algo que ele não é nem deveria ser: uma criatura dócil, passiva e submissa, que é comandada por ideologias hostis e antinaturais, que não respeitam a hierarquia de uma ordem social milenar e condições inerentes à própria natureza humana. Com o seu hábito de tentar modificar tudo através de leis e decretos, o feminismo e o progressismo mostram efetivamente que o seu real objetivo é criminalizar a masculinidade.
A verdade é que — usufruindo de um nível elevado de liberdades — não existe praticamente nada que a mulher brasileira do século XXI não possa fazer. Adicionalmente, o governo dá as mulheres uma quantidade tão avassaladora de vantagens, privilégios e benefícios, que está ficando cada vez mais difícil para elas encontrarem razões válidas para reclamarem da vida. Se o projeto de lei que pretende fornecer um auxílio mensal de mil e duzentos reais para mães solteiras for aprovado pelo senado, muitas mulheres que tem filhos não precisarão nem mesmo trabalhar para ter sustento. E tantas outras procurarão engravidar, para ter direito a receber uma mesada mensal do governo até o seu filho completar a maioridade.
O que a militância colorida da terra da fantasia convenientemente ignora — pois a realidade nunca corresponde ao seu conto de fadas ideológico — é que o mundo de uma forma geral continua sendo muito mais implacável com os homens do que é com as mulheres. No Brasil, a esmagadora maioria dos suicídios é praticada por homens, a maioria das vítimas de homicídio são homens e de cada quatro moradores de rua, três são homens. Mas é evidente que uma sociedade liberal ultra-progressista não se importa com os homens, pois ela não é influenciada por fatos concretos ou pela realidade. Seu objetivo é simplesmente atender as disposições de uma agenda ideológica, não importa quão divorciadas da realidade elas são.
O nível exacerbado de liberdades sociais e privilégios governamentais dos quais as mulheres brasileiras usufruem é suficiente para destruir a fantasiosa fábula da sociedade machista, opressora e patriarcal. Se as mulheres brasileiras não estão felizes, a culpa definitivamente não é dos homens. Se a vasta profusão de liberdades, privilégios e benefícios da sociedade ocidental não as deixa plenamente saciadas e satisfeitas, elas podem sempre mudar de ares e tentar uma vida mais abnegada e espartana em países como Irã, Paquistão ou Afeganistão. Quem sabe assim elas não se sentirão melhores e mais realizadas?
Homofobia
Quando falamos em homofobia, entramos em uma categoria muito parecida com a do racismo: o direito de discriminação é totalmente válido. Absolutamente ninguém deve ser obrigado a aceitar homossexuais ou considerar o homossexualismo como algo normal. Sendo cristão, não existe nem sequer a mais vaga possibilidade de que algum dia eu venha a aceitar o homossexualismo como algo natural. O homossexualismo se qualifica como um grave desvio de conduta e um pecado contra o Criador.
A Bíblia proíbe terminantemente conduta sexual imoral, o que — além do homossexualismo — inclui adultério, fornicação, incesto e bestialidade, entre outras formas igualmente pérfidas de degradação.
Segue abaixo três passagens bíblicas que proíbem terminantemente a conduta homossexual:
“Não te deitarás com um homem como se deita com uma mulher. Isso é abominável!” (Levítico 18:22 — King James Atualizada)
“Se um homem se deitar com outro homem, como se deita com mulher, ambos terão praticado abominação; certamente serão mortos; o seu sangue estará sobre eles.” (Levítico 20:13 — João Ferreira de Almeida Atualizada)
“O quê! Não sabeis que os injustos não herdarão o reino de Deus? Não sejais desencaminhados. Nem fornicadores, nem idólatras, nem adúlteros, nem homens mantidos para propósitos desnaturais, nem homens que se deitam com homens, nem ladrões, nem gananciosos, nem beberrões, nem injuriadores, nem extorsores herdarão o reino de Deus.” (1 Coríntios 6:9,10 —Tradução do Novo Mundo das Escrituras Sagradas com Referências)
Se você não é religioso, pode simplesmente levar em consideração o argumento do respeito pela ordem natural. A ordem natural é incondicional e incisiva com relação a uma questão: o complemento de tudo o que existe é o seu oposto, não o seu igual. O complemento do dia é a noite, o complemento da luz é a escuridão, o complemento da água, que é líquida, é a terra, que é sólida. E como sabemos o complemento do macho — de sua respectiva espécie — é a fêmea.
Portanto, o complemento do homem, o macho da espécie humana, é naturalmente a mulher, a fêmea da espécie humana. Um homem e uma mulher podem naturalmente se reproduzir, porque são um complemento biológico natural. Por outro lado, um homem e outro homem são incapazes de se reproduzir, assim como uma mulher e outra mulher.
Infelizmente, o mundo atual está longe de aceitar como plenamente estabelecida a ordem natural pelo simples fato dela existir, visto que tentam subvertê-la a qualquer custo, não importa o malabarismo intelectual que tenham que fazer para justificar os seus pontos de vista distorcidos e antinaturais. A libertinagem irrefreável e a imoralidade bestial do mundo contemporâneo pós-moderno não reconhecem nenhum tipo de limite. Quem tenta restabelecer princípios morais salutares é imediatamente considerado um vilão retrógrado e repressivo, sendo ativamente demonizado pela militância do hedonismo, da luxúria e da licenciosidade desenfreada e sem limites.
Definitivamente, fazer a apologia da moralidade, do autocontrole e do autodomínio não faz nenhum sucesso na Sodoma e Gomorra global dos dias atuais. O que faz sucesso é lacração, devassidão, promiscuidade e prazeres carnais vazios. O famoso escritor e filósofo francês Albert Camus expressou uma verdade contundente quando disse: “Uma só frase lhe bastará para definir o homem moderno — fornicava e lia jornais”.
Qualquer indivíduo tem o direito inalienável de discriminar ativamente homossexuais, pelo direito que ele julgar mais pertinente no seu caso. A objeção de consciência para qualquer situação é um direito natural dos indivíduos. Há alguns anos, um caso que aconteceu nos Estados Unidos ganhou enorme repercussão internacional, quando o confeiteiro Jack Phillips se recusou a fazer um bolo de casamento para o “casal” homossexual Dave Mullins e Charlie Craig.
Uma representação dos direitos civis do estado do Colorado abriu um inquérito contra o confeiteiro, alegando que ele deveria ser obrigado a atender todos os clientes, independente da orientação sexual, raça ou crença. Preste atenção nas palavras usadas — ele deveria ser obrigado a atender.
Como se recusou bravamente a ceder, o caso foi parar invariavelmente na Suprema Corte, que decidiu por sete a dois em favor de Jack Phillips, sob a alegação de que obrigar o confeiteiro a atender o “casal” homossexual era uma violação nefasta dos seus princípios religiosos. Felizmente, esse foi um caso em que a liberdade prevaleceu sobre a tirania progressista.
Evidentemente, homossexuais não devem ser agredidos, ofendidos, internados em clínicas contra a sua vontade, nem devem ser constrangidos em suas liberdades pelo fato de serem homossexuais. O que eles precisam entender é que a liberdade é uma via de mão dupla. Eles podem ter liberdade para adotar a conduta que desejarem e fazer o que quiserem (contanto que não agridam ninguém), mas da mesma forma, é fundamental respeitar e preservar a liberdade de terceiros que desejam rejeitá-los pacificamente, pelo motivo que for.
Afinal, ninguém tem a menor obrigação de aceitá-los, atendê-los ou sequer pensar que uma união estável entre duas pessoas do mesmo sexo — incapaz de gerar descendentes, e, portanto, antinatural — deva ser considerado um matrimônio de verdade. Absolutamente nenhuma pessoa, ideia, movimento, crença ou ideologia usufrui de plena unanimidade no mundo. Por que o homossexualismo deveria ter tal privilégio?
Homossexuais não são portadores de uma verdade definitiva, absoluta e indiscutível, que está acima da humanidade. São seres humanos comuns que — na melhor das hipóteses —, levam um estilo de vida que pode ser considerado “alternativo”, e absolutamente ninguém tem a obrigação de considerar esse estilo de vida normal ou aceitável. A única obrigação das pessoas é não interferir, e isso não implica uma obrigação em aceitar.
Discriminar homossexuais (assim como pessoas de qualquer outro grupo, raça, religião, nacionalidade ou etnia) é um direito natural por parte de todos aqueles que desejam exercer esse direito. E isso nem o direito positivo nem a militância progressista poderão algum dia alterar ou subverter. O direito natural e a inclinação inerente dos seres humanos em atender às suas próprias disposições é simplesmente imutável e faz parte do seu conjunto de necessidades.
Conclusão
A militância progressista é absurdamente autoritária, e todas as suas estratégias e disposições ideológicas mostram que ela está em uma guerra permanente contra a ordem natural, contra a liberdade e principalmente contra o homem branco, cristão, conservador e tradicionalista — possivelmente, aquilo que ela mais odeia e despreza.
Nós não podemos, no entanto, ceder ou dar espaço para a agenda progressista, tampouco pensar em considerar como sendo normais todas as pautas abusivas e tirânicas que a militância pretende estabelecer como sendo perfeitamente razoáveis e aceitáveis, quer a sociedade aceite isso ou não. Afinal, conforme formos cedendo, o progressismo tirânico e totalitário tende a ganhar cada vez mais espaço.
Quanto mais espaço o progressismo conquistar, mais corroída será a liberdade e mais impulso ganhará o totalitarismo. Com isso, a cultura do cancelamento vai acabar com carreiras, profissões e com o sustento de muitas pessoas, pelo simples fato de que elas discordam das pautas universitárias da moda.
A história mostra perfeitamente que quanto mais liberdade uma sociedade tem, mais progresso ela atinge. Por outro lado, quanto mais autoritária ela for, mais retrocessos ela sofrerá. O autoritarismo se combate com liberdade, desafiando as pautas de todos aqueles que persistem em implementar a tirania na sociedade. O politicamente correto é o nazismo dos costumes, que pretende subverter a moral através de uma cultura de vigilância policial despótica e autoritária, para que toda a sociedade seja subjugada pela agenda totalitária progressista.
Pois quanto a nós, precisamos continuar travando o bom combate em nome da liberdade. E isso inclui reconhecer que ideologias, hábitos e costumes de que não gostamos tem o direito de existir e até mesmo de serem defendidos.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 7361ca91:252fce6d
2024-06-29 10:13:51
@ 7361ca91:252fce6d
2024-06-29 10:13:51リベラリズムにおいて、自由とは他人が不適切と感じるかもしれない決定を個人が行うことを許容することを意味します。ただし、その決定が第三者に害を及ぼさない限りです。つまり、自由は各個人が自分の人生計画を構築し、実行する権利を守るものであり、他人にとって誤っていると見なされる決定も含まれます。
個人の決定を批判することと、その決定を妨げるために強制力を使用することの間には大きな違いがあります。
リベラリズムは、たとえ悪い決定を批判することができても、それらの決定を妨げるために(国家の)強制力を使用すべきではないと主張します。ただし、これらの決定が他人に害を及ぼす場合は例外です。
リベラリズムにおける認識的慎重さは、どの決定が正しいか常に確信できるわけではないことを認識しています。したがって、他人に誤っているように見える場合でも、個人が自分の決定を下す自由を許容しなければなりません。
非常に一般的な例として、薬物の使用が挙げれます。リベラルな視点からは、他人がこれを悪い決定と見なすかもしれなくても、個人が薬物を使用する自由を持つべきです。鍵となるのは、これらの個人的な決定が第三者に害を及ぼさないことです。
リベラルな哲学においては、個人の自由と自己決定が重要視されます。他人が悪いと考えるかもしれない決定を行う権利も尊重されるべきであり、その決定が第三者に害を及ぼさない限り、(国家が)強制力を使用して妨げるべきではないという立場をとります。この認識的慎重さが、リベラリズムの核心の一つです。
-
 @ 862fda7e:02a8268b
2024-06-29 08:18:20
@ 862fda7e:02a8268b
2024-06-29 08:18:20I am someone who thinks independently without abiding to a group to pre-formulate my opinions for me. I do not hold my opinions out of impulse, out of the desire to please, nor out of mindless apadtion to what others abide to. My opinions are held on what I belive is the most logical while being the most ethical and empathetic. We live in a world with a nervous systems and emotions for animals and humans (same thing) alike, thus, we should also consider those feelings. That is not the case in our world.


Cyclists are one of the most homosexual GAY ANNOYING people to exist on EARTH
I hate cyclists with a burning passion. These faggots are the GAYEST MOST ANNOYING retards to exist. They wear the tightest fitting clothing possible to show off their flaccid cocks to each other and to anybody around them.
 And if that weren't enough, they present their ass up in the air, begging to be fucked by their cyclist buddies, as they ride their bike in the middle of the road. It's homosexual.
And if that weren't enough, they present their ass up in the air, begging to be fucked by their cyclist buddies, as they ride their bike in the middle of the road. It's homosexual.
 Look at the seat they ride on, it looks like a black cock about to go up their ass. Don't get me started on their gay helmets, the "aerodynamic" helmets they wear. YOU FAGGOTS AREN'T IN THE TOUR DE FRANCE, YOU'RE IN FRONT OF MY CAR IN AN INTERSECTION IN A MINNESOTA TOWN WITH A POPULATION OF 5,000. They LIKE the look of the costume. And that's just what it is - a costume. You're required to have a "look" as a cyclist - you aren't really a cyclist if you don't spend hundreds of dollars on the gay gear. God forbid you just get a bike and ride it around on a trail like anyone else.
These people LIKE to be seen. They WANT to be seen as cool, which is why they ride right in front of my fucking car at 15mph in a 45mph zone. I swear, every time I pass one of these cyclists, I am this close to yelling "FAGGOT" out the window at them. The only reason I haven't is because they like to record everything on their gay bikes and upload it to Youtube, so then I'd have to deal with you people knowing where I live just because I called some fruit on a bike a faggot. Think I'm exaggerating? Think again. These homos have an entire community built on "catching" drivers who dare drive too close or blow their exhaust at the poor little faggy cyclist. There's Youtube channels dedicated to this. Part of their culture is being a victim by cars. Almost like it's dangerous to be in the middle of the road going 15mph on a 45mph road. Oh but I'm sure cars almost hitting you is surely a personal attack and nothing to do with the fact that what you're doing is DANGEROUS YOU RETARD.
Look at the seat they ride on, it looks like a black cock about to go up their ass. Don't get me started on their gay helmets, the "aerodynamic" helmets they wear. YOU FAGGOTS AREN'T IN THE TOUR DE FRANCE, YOU'RE IN FRONT OF MY CAR IN AN INTERSECTION IN A MINNESOTA TOWN WITH A POPULATION OF 5,000. They LIKE the look of the costume. And that's just what it is - a costume. You're required to have a "look" as a cyclist - you aren't really a cyclist if you don't spend hundreds of dollars on the gay gear. God forbid you just get a bike and ride it around on a trail like anyone else.
These people LIKE to be seen. They WANT to be seen as cool, which is why they ride right in front of my fucking car at 15mph in a 45mph zone. I swear, every time I pass one of these cyclists, I am this close to yelling "FAGGOT" out the window at them. The only reason I haven't is because they like to record everything on their gay bikes and upload it to Youtube, so then I'd have to deal with you people knowing where I live just because I called some fruit on a bike a faggot. Think I'm exaggerating? Think again. These homos have an entire community built on "catching" drivers who dare drive too close or blow their exhaust at the poor little faggy cyclist. There's Youtube channels dedicated to this. Part of their culture is being a victim by cars. Almost like it's dangerous to be in the middle of the road going 15mph on a 45mph road. Oh but I'm sure cars almost hitting you is surely a personal attack and nothing to do with the fact that what you're doing is DANGEROUS YOU RETARD.
 I've seen these "share the road" signs in the most insane and dangerous places. I've seen them on HIGHWAYS, yes, HIGHWAYS, where the cyclist would BARELY have any room next to the car. It's insanely dangerous and I guess to some people, the constant threat of dying is fun... until it actually happens.
I will never understand the mind of a cyclist. You are not in the fricken' Tour de France. You look like a homosexual that's inconveniencing HEAVY METAL HIGH POWERED CARS RIGHT BEHIND YOU. It's incredibly dangerous, and you can't rely on the very heavy, high powered cars and the people driving them to honor your life. Road rage is real, you might be the tipping point for some angry old boomer in his Ram to RAM INTO YOU and kill you. God I hate cyclists, their gay look, their cocky "better than you" attitude. Hey fudge stripe, in a battle between my CAR and your soft body, my CAR WILL WIN. Get off the road and go suck some cocks instead. Stop riding the bikes and go ride cocks instead, you homo.
I've seen these "share the road" signs in the most insane and dangerous places. I've seen them on HIGHWAYS, yes, HIGHWAYS, where the cyclist would BARELY have any room next to the car. It's insanely dangerous and I guess to some people, the constant threat of dying is fun... until it actually happens.
I will never understand the mind of a cyclist. You are not in the fricken' Tour de France. You look like a homosexual that's inconveniencing HEAVY METAL HIGH POWERED CARS RIGHT BEHIND YOU. It's incredibly dangerous, and you can't rely on the very heavy, high powered cars and the people driving them to honor your life. Road rage is real, you might be the tipping point for some angry old boomer in his Ram to RAM INTO YOU and kill you. God I hate cyclists, their gay look, their cocky "better than you" attitude. Hey fudge stripe, in a battle between my CAR and your soft body, my CAR WILL WIN. Get off the road and go suck some cocks instead. Stop riding the bikes and go ride cocks instead, you homo. -
 @ 862fda7e:02a8268b
2024-06-29 08:16:47
@ 862fda7e:02a8268b
2024-06-29 08:16:47
Pictured above is a female body that looks incredibly similar to mine. So similar that it could be mine if I didn't have a c-section scar. Actually her boobs are a bit bigger than mine, but mine do look like that when they swell.

Nudity should be normalized
I don't understand why people get offended or sensitive over the human body. Especially the female human chest. We all have nipples, we all know what they look like, so I don't understand why a female being topless is unacceptable, whereas a male topless is normal. I've seen shirtless men with more shapely, larger breasts than mine. Personally, I have stopped caring if other people see the shape of my breasts or my nipples if they were to be poking in the freezer section of the grocery store. I stopped wearing bras years ago. I often times want to be topless outside in my yard because it feels good and natural. I like the sun on my skin, and I especially love the rain on my skin. It's very unfortunate that our natural human body is massively shamed, by who I believe, is the reptilians (for a number of reasons). Logically, it makes no sense to be outraged by the female human chest. We all know what nipples look like, we all have them, I truly believe women should be allowed to be topless like men are. If it's hot out and you're doing yard work - pop your top off, who cares?
I understand that males and some females sexualize the human chest. However, that is not my problem. That is none of my concern what others think about my body. I should be allowed to wear my human body as it is just like anyone else should be. What I can't wrap my mind around is why people are shocked or offended by the human body, since we ALL know what these parts look like and we all have them. I understand in certain scenarios being topless or nude would likely be inapproriate, or that perverts would use it as a way to expose themselves to children. In an ideal world, we could live like tribes where the human body is normal, it's not overtly sexual. This is why we're so offended over the human body - it's constantly concealed, so the moment we get to see a female chest, it's suddenly sexual because it's normally tabboo to be seen. I wish I could be shirtless outside, I envy males who get to truly feel the wind, the earth on their backs and their chest. Female and male nipples look the same, I don't understand why it should be illegal for me to experience nature in my natural state.
Anyways, I highly dislike the "nudist" people because it is NOT about accepting the human body in its natural state. It's completely co-opted by pedophiles who want to expose themselves to childen or for children to expose themselves to others for sexual gratification. There are nudist resorts pedophile parents force their children to go to (as a child you have no personal autonomy and are completely a slave to your parents - trust me, I know this because I couldn't LEGALLY decide which parent I wanted to live with up until I was 18 years old. If your parent wants you to do something, a child in the US has no legal say over that, so if your parent wants to go to a nudist resort, you must go). A human body should simply be a human body, it's unfortunate that being unclothed immediately brings on sexualization. This is mostly an issue because clothes is the expected default. The more tabboo something is, the more naughty the thing is.
I am not a nudist. However, I do believe that at the very least, females should have the right to be topless in similar settings as males are allowed to. I don't think a woman is a slut if she's in her natural state, in her human body, and proceeds life as normal. How one acts portrays slutty behavior. Living your life in your natural human body should be a right without caviots. I feel detached from people who constantly see the human body as flawed (e.g. circumcision industry, body hair removal industry, clothing industry). These industries are harmful for the victims in them (infant boys, and modern day slaves in sweatshops), and the main motivating factor is money among all these industries.
-
 @ 6ad3e2a3:c90b7740
2024-06-28 07:44:17
@ 6ad3e2a3:c90b7740
2024-06-28 07:44:17I’ve written about this before, and I’ve also tried to illustrate it via parable in “The Simulator.” I even devoted most of a podcast episode to it. But I thought it might be useful just to cut to the chase in written form, give the tldr version.
Utilitarianism is the moral philosophy of the greatest good for the greatest number. That is, we calculate the prospective net benefits or harms from a course of action to guide our policies and behaviors. This moral framework deserves scrutiny because it (unfortunately) appears to be the paradigm under which most of our governments, institutions and even educated individuals operate.
The philosophy is commonly illustrated by hypotheticals such as “the trolley problem” wherein a person has the choice whether to divert a runaway trolley (via switch) from its current track with five people in its path to it to an alternate one where only one person would be killed. In short, do you intervene to save five by killing one? The premise of utilitarianism is that, yes, you would because it’s a net positive.
Keep in mind in these hypotheticals these are your only choices, and not only are you certain about the results of your prospective actions, but those are the only results to consider, i.e., the hypothetical does not specify or speculate as to second or third order effects far into the future. For example, what could go wrong once people get comfortable intervening to kill an innocent person for the greater good!
And yet this simplified model, kill one to save five, is then transposed onto real-world scenarios, e.g., mandate an emergency-use vaccine that might have rare side effects because it will save more lives than it costs. The credulous go along, and then reality turns out to be more complex than the hypothetical — as it always is.
The vaccine doesn’t actually stop the spread, it turns out, and the adverse effects are far more common and serious than people were led to believe. Moreover, the mandates destroyed livelihoods, ran roughshod over civil liberties, divided families and destroyed trust in public health.
Some might argue it’s true the mandates were wrong because the vaccine wasn’t sufficiently safe or effective, but we didn’t know that at the time! That we should judge decisions based on the knowledge we had during a deadly pandemic, not after the fact.
But what we did know at the time was that real life is always more complex than the hypothetical, that nth-order effects are always impossible to predict. The lie wasn’t only about the safety and efficacy of this vaccine, though they absolutely did lie about that, it was that we could know something like this with any degree of certainty at all.
The problem with utilitarianism, then, is the harms and benefits it’s tasked with weighing necessarily occur in the future. And what distinguishes the future from the past is that it’s unknown. The save one vs five hypothetical is deceptive because it posits all the relevant consequences as known. It imagines future results laid out before us as if they were past.
But in real life we deal with unknowns, and it is therefore impossible do a rigorous accounting of harms and benefits as imagined by the hypotheticals. The “five vs one,” stated as though the event had already happened, is a conceit conjured from an overly simplistic model.
In short, in modeling the future and weighing those projected fictions the same way one would historic facts, they are simply making it up. And once he grants himself license to make things up, the utilitarian can create the moral imperative to do what coincidentally benefits him, e.g, Pfizer profited to the tune of tens of billions of dollars, for the greater good!, which turned out not to be so good. Once you make the specious leap of purporting to know the future, why not go all the way, and make it a future where the greatest good coincides with enriching yourself to the greatest extent possible?
So in summary, as this has gone on longer than I intended, utilitarianism is moral bankruptcy because the “greater good” on which it relies is necessarily in the future, and we cannot predict the future with enough accuracy, especially over the medium and longer term, to do a proper moral accounting.
As a result, whoever has power is likely to cook the books in whatever way he sees fit, and this moral philosophy of the greatest good for the greatest number paradoxically tends toward a monstrous outcome — temporary benefits for the short-sighted few and the greatest misery for most.
-
 @ 0d2a0f56:ef40df51
2024-06-25 17:16:44
@ 0d2a0f56:ef40df51
2024-06-25 17:16:44
Dear Bitcoin Blok Family,
In my last post, I shared how Bitcoin became my personal antidote, rescuing me from destructive behaviors and opening up a world of knowledge. Today, I want to explore how Bitcoin is becoming an antidote for my entire family, solving problems I didn't even know we had.
As I've delved deeper into the Bitcoin rabbit hole, I've realized that I was searching for something beyond personal growth – I was looking for a solution to give my family an identity. When you look at successful families of the past or thriving organizations, you'll notice they're known for something specific. Some families are known for real estate, others for owning businesses, and some for establishing various institutions. This identity ties a family together, giving them a shared purpose and legacy.
For my family, I want that identity to be rooted in Bitcoin. Why? Because Bitcoin brings a focus I haven't seen in anything else. It neutralizes much of what I consider toxic behavior in modern society.
Take TikTok, for example. While there's nothing inherently wrong with the platform, it often promotes content that I find concerning – gender wars, gossip, and sometimes even false information. This issue extends to most social media platforms. Our kids are learning to dance, but they're not learning about money. They're absorbing various behaviors, but they don't understand inflation. We're turning to social media for education and information, which isn't necessarily bad, but it requires careful vetting of sources and filtering out the noise.
What's truly dangerous is how these platforms steal our attention subconsciously. We're wasting time, putting our attention in unproductive places without even realizing it. This is a toxic part of our culture today, and I believe Bitcoin can help solve this problem.
It's challenging to teach kids about money in today's fiat standard. How do you explain the concepts of time and energy when the measuring stick itself is constantly changing? But with Bitcoin, these lessons become tangible.
Moreover, Bitcoin opens up possibilities that seemed out of reach before, particularly in the realm of family banking. In the past, wealthy families in the United States understood the risks of keeping their family's worth in another person's hands or in external institutions. They recognized that protecting wealth comes with certain risks, and establishing a family protocol was crucial.
With Bitcoin, family banking becomes not just possible, but easily achievable and more secure than ever before. Through multi-signature wallet arrangements, we can create a true family bank where each family member holds a key to the family wallet. No funds can be moved without the permission of other family members. This technology eliminates what has been a major stumbling block in the past: trust issues. Now, we can have transparency, trust, and access for all family members.
Imagine a family account where parents and children alike have visibility into the family's finances, but movements of funds require agreement. This not only teaches financial responsibility but also fosters open communication about money within the family. It's a powerful tool for financial education and family cohesion.
This is something we should definitely take advantage of. It's not just about storing wealth; it's about creating a financial system that aligns with our family values and goals. Bitcoin provides the infrastructure for this new form of family banking, one that combines the best aspects of traditional family wealth management with the security and transparency of modern technology.
When it comes to teaching about compound interest and value, Bitcoin provides the perfect use case. Over its lifetime, Bitcoin has been averaging an astonishing 156% year-over-year return. While this number is significant, it's important to note that past performance doesn't guarantee future results. However, even with more conservative estimates, the power of compound interest becomes clear. I challenge you to use a compound interest calculator with a more modest 30% annual return. The results are still astronomical. Imagine teaching your children about saving and investing with potential returns like these. It's a powerful lesson in the value of long-term thinking and delayed gratification.
What I'm getting at is this: there are many forces in our society that hinder positive behavior and promote negative, toxic culture. These forces are stealing our children's time, attention, energy, and of course, money. Bitcoin is the antidote that can start correcting and curing some of that behavior, while also providing tangible lessons in finance and economics, and even reshaping how we approach family wealth management.
By making Bitcoin a central part of our family identity, we:
- Provide a shared purpose and legacy
- Encourage financial literacy from a young age
- Teach valuable lessons about time, energy, and value
- Promote long-term thinking and delayed gratification
- Offer an alternative to the instant gratification of social media
Bitcoin isn't just an investment or a technology – it's a paradigm shift that can reshape how we think about family, legacy, and education. It's an antidote to the toxic aspects of our digital age, offering a path to a more thoughtful, intentional way of living.
As we continue this journey, I invite you to consider: How could Bitcoin reshape your family's identity? What toxic behaviors could it help neutralize in your life? Until next time check out the below video on what some may know as the "Waterfall or "Rockefeller Method". https://youtu.be/MTpAY1LKfek?si=s7gA4bt_ZoRGAlAU
Stay sovereign, stay focused,
Joe Thomas Founder, The Bitcoin Blok
-
 @ 000002de:c05780a7
2024-06-25 15:28:01
@ 000002de:c05780a7
2024-06-25 15:28:01Lately it seems like I keep noticing people that are sympathetic to anarchism and libertarian ideas completely misunderstanding governance. It really seems like this might be one of the biggest mental blocks people have. I wonder if it is mostly the fault of libertarians and anarchists.
Those in the liberty movement (broadly) rant and demonize the government. This is completely justified. I've done it for years. I've noticed that more experienced communicators will tend to say "The State" instead of government. Years ago I heard someone explain how to think about three terms often used incorrectly.
- The country is the land
- The nation is the people
- The state is the government
I don't recall learning this in school. It is possible it was in a textbook but I doubt it. The country part I think most people do get. Nation less so. The best example of a nation without a country are Native Americans. Tribes are nations without a country (their historical lands). Tribes have their own governments and a certain amount of sovereignty in the lands they are allowed to inhabit.
The state is the word that I have found most people are confused about. People used to tell me, you hate the government so much. Why don't you leave. Well, I don't hate the nation(people) or the country(land). It is the governance system I hate. I don't even hate the people that are working in it.
Its funny to me that people on the red or blue team seem to hate the government when their side isn't in power but if someone points to issues in the system itself, well that's just crazy.
So what about those people that are sympathetic to libertarian values? Many of them say things like this. Well, I agree with you on taxes and the corruption of the government. But you always need a government. My usual response is yes. You do need governance. But you don't need a state or government. My home is governed by my wife and I. Businesses have their own governance models. Bitcoin does as well. But we do not need a single entity with a monopoly on violence.
So why is there so much confusion on this topic? I think there are two reasons.
The first is ignorance. The state of the world is largely invisible to most people. We are purposely kept ignorant of how our world works. The State isn't really discussed as a separate entity from the country and nation.
The second reason for the confusion is how libertarians and anarchists communicate. There are some that just foolishly believe people do not need governance. Honestly in my experience they are either just young or do not think deeply enough. They haven't steel manned their arguments yet. In my experience this is a small percentage of people though.
I think people in the liberty movement just need to do a better job communicating ideas. Instead of saying we need to get rid of the government one might say we need to get rid of the state. Another way to lead into this is to speak about the empire vs. the government. Talk about the monopoly which the state holds. How competition leads to better outcomes vs. monopoly.
What do you think? Have you noticed this hurdle as well? I think many people hear good ideas and agree but assume we are just dummies that believe in a fairy tale.
If private or decentralized governance is interesting to you, you might enjoy reading Chaos Theory by Bob Murphy. Its short and answer many common objections to private governance.
-
 @ c43d6de3:a6583169
2024-06-24 16:56:56
@ c43d6de3:a6583169
2024-06-24 16:56:56"If you do tomorrow what you did today, you will get tomorrow what you got today." - Benjamin Franklin
Seize the Day

Image from article- https://community.thriveglobal.com/want-your-authentic-self-mindfulness-is-a-gateway/Confliction
There are two conflicting approaches to life: Delay gratification today for a wealthy tomorrow and carpe diem Seize the Day and live like today is your last. Usually, when someone prescribes delayed gratification they refer to finances; save a dollar today for a hundred tomorrow. Carpe diem often refers to smelling the coffee, enjoying the little things and not putting off for tomorrow what could've been done today.
I've never felt the two of those prescriptions collide more violently than now as a father of two beautiful kids. I find it more difficult than ever before to make decisions that might benefit my future over being present for my kids. Time being the finite thing that it is, often I can only choose one.
Image from Adobe ImagesTwo Fathers, Two Approaches: Enough Small Moments Equal A Big Moment My brother in-law and I have different approaches to this. He tends to delay gratification. More often than not, he's out on business and misses minor family events and outings. Meanwhile, I often choose to attend even the smallest family events as opposed to going on business.
I should mention, my brother in-law doesn't dare miss the big events. He's always there for a birthday, baptism, or graduation but he misses outings to the beach or spring. He misses the books read by the bed and the dimming of the light just before a kiss goodnight.
If you miss enough small moments, you a miss big one.

Image from article- https://www.spiritualmom.com/god-is-weaving-a-tapestry/
Since my children were born I vowed to live as much in the moment as I could. In the moment, I'm happy to be with my kids stitching together cherished mementos that will be the tapestry of our lives. These indelible memories not only serve to make me happy but, I believe they'll work as the sinews and tendons that come together to form my children's personality and identity. My relationship with my kids and family will tighten as their persona grows.
I don't have facts from studies or scientific analysis, but I have a gut feeling its the strength of the tapestry of our lives that determines how resilient my children will be. When they encounter hard times they'll carry the uplifting memories of good times and they'll have the comfort of knowing there's a tightknit family at their backs to get through it.
That said, I've never heard my brother in-law complain about money.
I can't say I struggle for cash either. I make ends meet, but my wife and I have experienced that nervous rush when the AC blows out mid-summer and we wonder if we would have enough to pay for the down payment of a new unit and the mortgage at the beginning of the month.
What's been bothering me most as of late is my damn near non-existent retirement fund.

Image from ANATOMY OF A SOLDIER BY HARRY PARKER REVIEW - UNUSUAL PERSPECTIVES ON WARFARE FICTION
Commitments- To My Nation, To My Self
My biggest conflict today is tied to the commitment I made to the United States Army Reserves years before the birth of my children. While I can decide not to go on business like my brother in-law does, I can't simply not attend drill (one weekend a month) or go off on annual training (2–3 weeks a year). Failure to attend to my military obligations can result in a dis-honorable discharge. Having that hanging over my head will forever ruin any lucrative opportunities for employment and public service.
More often than not, my relatively small obligation to the Army Reserves has stood in direct conflict with my desire to be present in my kids lives as well as the lives of my friends and family. Some how, I've had the misfortune of having drills and annual training scheduled on major events like weddings, baptisms, and birthdays; the very things I vow never to miss.
There are ways to request those special days off and make it up on a later date and when I can, I do. However, I've been forced to go unaccounted for on several occasions when special events are back to back and overlap with already requested days off. That's led to conflict in the past but, I've been fortunate enough to have good leaders who've understood why I preferred to be absent in the military over absent in a major life event. It would be easiest, and most convenient, to resign my congressional commission as an officer and leave the Army Reserves. This is when I feel that great internal conflict.
Serving in the Army Reserves allows me to give back to my nation and grants me several financial benefits that would otherwise be completely lost. Medical insurance is remarkably cheaper than what I would have to deal with as a civilian. I get a world of benefits when purchasing a house and I can apply for special grants if ever needed. Perhaps most important of all, if I stick around for the full 20 years (I have almost 9 now) I will have a very nice retirement pension waiting for me when I turn 65. This is where that differed gratification really kicks in.
When I really boil it down to pros and cons, there's just way too many pros to staying in the Reserves than cons.

Image of Jordan Peterson from Video Clip- "4 years video"
Phases of Life Approach
World renown psychologist Jordan Peterson says "you have little kids for 4 years and if you miss it, its done." For Jordan, this is time period is peak experience for your kids. As I write this, my eldest just turned two and my youngest is 9 months. I'm not quite halfway there yet and I can't let up now.
I don't want to test to see if what Jordan Peterson says is true, I'm going to continue living as much in the moment as is possible during these early years of my children's lives. If I stay in the army reserves throughout this time I will have had 13 years of service by the time my youngest is 4.
Taking this approach, I will have been very present in the first 4 years of my kids lives and will only have to serve seven more years to acquire that retirement.
For me, today is Gold and tomorrow is Silver.
People have sacrificed worse.
artstr #plebchain #writing
I want to show the world that life is a scroll riddled with ink. The marks will only ever be simple blots on the parchment unless you pause and perceive them for the characters they are.
I'm constantly thinking about what the future could look like if we just take action.
More of my thoughts about the future and the world around us are coming soon...
Thank you for Reading this article. If you liked it and would consider zapping some sats, doing so supports me and motivates me to continue writing!
If you are interested in Fiction writing, visit my NOSTR page Fervid Fables: npub1j9cmpzhlzeex6y85c2pnt45r5zhxhtx73a2twt77fyjwequ4l4jsp5xd49
-
 @ 25f67ef1:d3cb96eb
2024-06-24 11:41:31
@ 25f67ef1:d3cb96eb
2024-06-24 11:41:31In a stunning turn of events, Bitcoin's value has nosedived a staggering 15%, falling from an all-time high of $72,000 per BTC to $61,000. The cause? None other than former United States president, Donald J. Trump, whose recent comments and rumored policies have sent shockwaves through the global Bitcoin community.
In a recent rally, Trump declared, "We want all the remaining bitcoin to be made in the USA." This bold statement has left many scratching their heads, wondering if the ex-president fully grasps the decentralized nature of Bitcoin. Nevertheless, his followers cheered, and the markets trembled.
Adding fuel to the fire, rumors are swirling about a proposed tariff on offshore bitcoin brought into the United States. Whether such a measure could work in practice is still to be determined, but the idea of taxes on foreign sourced bitcoin has many American businesses with international operations nervous.
But that's not all. In a move that could only be described as draconian, whispers of a plan to use recursive covenants on Bitcoin have emerged. The scheme aims to ringfence all the bitcoin currently held in US custody, such as those held by the "too big to fail" Coinbase, the primary custodian for corporate america, wall street and the popular ETFs. These covenants would effectively prevent those coins from ever being sent outside of whitelisted US addresses. If true, this would essentially create a digital Berlin Wall around American Bitcoin, isolating it from the rest of the world.
Critics argue that these policies are nothing more than a misguided attempt to assert dominance over the borderless digital cash. By prioritizing a "USA first" approach, Trump risks alienating global partners and further isolating the United States on the international stage. Neighboring countries, already wary of America's unpredictable policies, are likely to view these moves as antagonistic and regressive.
And let's not forget the opportunists lurking in the shadows. Trump's buddies and notorious shitcoiners are reportedly licking their chops, hoping that once he's in charge, they'll have a free hand to write regulations that allow them to prey on the public with their dubious shitcoin offerings. These unregistered securities are a haven for scams, and with the right legislation, these predators could wreak havoc on unsuspecting investors.
The fear of Trump's rising popularity and his policy direction for Bitcoin has undoubtedly contributed to the recent market uncertainty. Investors are apprehensive about the future of bitcoin in the US under a potential second Trump administration.
As the 2024 US presidential election looms, the Bitcoin community can only watch and wait, bracing for more market volatility. Will Bitcoin recover from the "Trump Dump"? Only time will tell. For now, it seems the ex-president's quest to "Make America Great Again" might just come at the expense of their burgeoning Bitcoin economy.
-
 @ 6c8c7979:15595f3e
2024-06-24 08:45:18
@ 6c8c7979:15595f3e
2024-06-24 08:45:18Vincent van Gogh is one of the most prominent artists in the history of global art, with a significant influence on modern artistic movements. He was born in the Netherlands in 1853 and passed away in 1890. Despite not achieving fame during his lifetime, his works later became among the most impactful in fine arts.
Van Gogh's works are characterized by vibrant colors and rapid brush strokes, giving his paintings a unique style. His pieces often reflect nature and everyday life with a touch of deep emotion and drama. Some of his most famous works include "Starry Night," "The Night Cafe," "Irises," and "Wheatfield with Crows."
Throughout his life, van Gogh faced numerous personal and psychological challenges, which imbued his works with a sense of depth and contemplation. He struggled with severe mental disorders and social tensions, which greatly influenced his art.
After his death, public interest in his works grew significantly, and he came to be regarded as a pioneer of expressionism and modern art. His profound impact on global art is evident in the many movements and subsequent artists who drew inspiration from his techniques and subjects.
In summary, Vincent van Gogh remains an exceptional artistic figure, leaving an unforgettable legacy in art history. His works continue to inspire and captivate audiences worldwide with their beauty and artistic depth.
-
 @ 6a39a186:88f51c19
2024-06-24 07:55:21
@ 6a39a186:88f51c19
2024-06-24 07:55:21Privacy, Security, and Real-World Applications
We Are Still Early
Concerning Bitcoin, privacy and security remain paramount. As an enthusiast in Ecash privacy and security, I aim to shed light on some of the most promising and undervalued Bitcoin frameworks. These frameworks offer robust solutions for enhancing privacy, security, and scalability, making Bitcoin more adaptable for various industries. Lets's examine their strengths and weaknesses, supported by real-world examples.
1. Mimblewimble: Enhancing Privacy and Scalability
Overview
Mimblewimble is a privacy-centric blockchain protocol designed to enhance the confidentiality and scalability of Bitcoin transactions. Mimblewimble uses cryptographic innovations to obscure transaction details while ensuring network security.
Strengths
- Enhanced Privacy: Mimblewimble transactions are confidential, hiding transaction amounts and addresses.
- Scalability: The protocol significantly reduces blockchain bloat, improving efficiency and speed.
- Security: By using cryptographic primitives, Mimblewimble ensures that transactions are secure and verifiable.
Weaknesses
- Compatibility: Mimblewimble is not fully compatible with Bitcoin’s existing infrastructure, requiring significant changes to the network.
- Complexity: The protocol's complexity can be a barrier to understanding and adoption.
Real-World Example: Grin and Beam
Grin and Beam are two cryptocurrencies that have implemented Mimblewimble. Grin focuses on simplicity and community-driven development, while Beam emphasizes user-friendly interfaces and governance structures. Both projects demonstrate Mimblewimble’s potential in providing enhanced privacy and scalability.
2. Lightning Network: Scaling Bitcoin Transactions
Overview
The Lightning Network is a second-layer solution designed to enable fast and low-cost transactions on the Bitcoin network. By creating off-chain transaction channels, the Lightning Network alleviates congestion on the main blockchain.
Strengths
- Speed: Transactions on the Lightning Network are nearly instantaneous.
- Low Fees: Off-chain transactions significantly reduce transaction costs.
- Scalability: The network can handle millions of transactions per second, far exceeding the main blockchain's capacity.
Weaknesses
- Liquidity: Users need to lock up funds in channels, which can limit liquidity.
- Complexity: Setting up and managing channels can be technically challenging.
- Security: Off-chain transactions require robust security measures to prevent fraud and ensure reliability.
Real-World Example: El Salvador’s Bitcoin Adoption
El Salvador’s adoption of Bitcoin as legal tender showcases the Lightning Network’s capabilities. The government and businesses use the network to facilitate everyday transactions, demonstrating its effectiveness in a real-world economy.
3. Taproot and Schnorr Signatures: Improving Privacy and Efficiency

Overview
Taproot and Schnorr signatures are recent upgrades to the Bitcoin protocol that enhance privacy, security, and efficiency. Taproot allows complex transactions to appear as simple ones, while Schnorr signatures enable aggregation, reducing data size.
Strengths
- Privacy: Taproot masks the complexity of transactions, enhancing privacy.
- Efficiency: Schnorr signatures reduce the data size of transactions, improving blockchain efficiency.
- Security: Both upgrades maintain Bitcoin’s robust security model.
Weaknesses
- Adoption: Widespread adoption of these upgrades is still in progress.
- Complexity: Implementing and understanding these changes require technical expertise.
Real-World Example: Taproot Activation
The activation of Taproot in November 2021 marked a significant milestone for Bitcoin. It demonstrates the network’s ability to evolve and adopt new features that enhance privacy and efficiency. Various Bitcoin services and wallets are beginning to integrate Taproot, showing its practical benefits.
4. Sidechains: Expanding Bitcoin’s Capabilities
Overview
Sidechains are independent blockchains that run parallel to the Bitcoin mainchain. They enable experimentation with new features and scalability solutions without affecting the main network.
Strengths
- Flexibility: Sidechains allow for the development and testing of new features.
- Scalability: They can handle additional transactions, reducing load on the main blockchain.
- Interoperability: Sidechains can interact with the main Bitcoin network, enhancing its functionality.
Weaknesses
- Security: Ensuring the security of sidechains can be challenging.
- Complexity: Developing and maintaining sidechains require significant technical expertise.
Real-World Example: Liquid Network
The Liquid Network, developed by Blockstream, is a sidechain that enhances Bitcoin’s functionality for traders and exchanges. It provides faster settlements and confidential transactions, showcasing the practical benefits of sidechains.
5. CoinJoin: Strengthening Transaction Privacy

Overview
CoinJoin is a privacy-enhancing technique that combines multiple Bitcoin transactions into a single transaction, making it difficult to trace individual inputs and outputs.
Strengths
- Enhanced Privacy: CoinJoin obscures transaction details, improving user privacy.
- Community Support: Widely supported by the Bitcoin community and integrated into several wallets.
Weaknesses
- User Experience: The process can be complex and may require additional steps for users.
- Partial Privacy: While it improves privacy, it is not foolproof and can still be subject to analysis.
Real-World Example: Wasabi Wallet
Wasabi Wallet is a Bitcoin wallet that implements CoinJoin to enhance user privacy. It provides an intuitive interface for conducting private transactions, illustrating CoinJoin’s practical application.
Make The Ecosystem Happen
The evolution of Bitcoin frameworks continues to push the boundaries of what is possible in the realm of digital currency. From Mimblewimble’s privacy and scalability enhancements to the Lightning Network’s speed and efficiency, these frameworks offer promising solutions to current challenges. Real-world examples like El Salvador’s Bitcoin adoption and the Liquid Network’s advancements highlight the practical benefits and potential of these technologies. As the Bitcoin ecosystem evolves, these frameworks will play a crucial role in shaping the future of digital finance, ensuring privacy, security, and scalability for users worldwide.
Further Reading
For those interested in delving deeper into the frameworks discussed in this article, here are some recommended resources:
- Mimblewimble:
- Mimblewimble: What is it? How It Works?
- Grin
-
Lightning Network:
- The Lightning Network For Businesses and Developers
- Historical Look At Bitcoin Adoption In El Salvador
-
Taproot and Schnorr Signatures:
- Taproot: The Next Major Upgrade for Bitcoin
-
Sidechains:
- Blockstream’s Liquid Network
-
CoinJoin:
- Wasabi Wallet
- Understanding CoinJoin
-
 @ 6a39a186:88f51c19
2024-06-24 01:28:00
@ 6a39a186:88f51c19
2024-06-24 01:28:00The Superiority of Asymmetric Encryption
Cryptography plays a pivotal role in protecting sensitive information. Two primary forms of encryption—symmetric and asymmetric—are utilized to secure data. This essay argues that while both symmetric and asymmetric encryption have their merits, asymmetric encryption offers superior security and practical advantages in most contemporary applications. By exploring the fundamental differences, strengths, and weaknesses of each type, this essay will demonstrate why asymmetric encryption is the preferred choice for modern cryptographic needs.
Symmetric Encryption
Definition and Mechanism
Symmetric encryption, also known as secret-key encryption, involves the use of a single key for both encryption and decryption. Popular algorithms include AES (Advanced Encryption Standard) and DES (Data Encryption Standard). The process is straightforward: the sender encrypts the plaintext using the key, and the receiver decrypts the ciphertext with the same key.
Strengths of Symmetric Encryption
- Speed and Efficiency: Symmetric encryption is generally faster and more efficient than asymmetric encryption, making it suitable for encrypting large amounts of data quickly.
- Simplicity: The mechanism of symmetric encryption is relatively simple, which can be advantageous in systems with limited computational power.
Weaknesses of Symmetric Encryption
- Key Distribution Problem: The primary challenge with symmetric encryption is securely distributing the key to both parties without interception by malicious actors.
- Scalability Issues: As the number of users increases, the number of unique keys needed for secure communication grows exponentially, complicating key management.
Asymmetric Encryption
Definition and Mechanism
Asymmetric encryption, or public-key encryption, uses a pair of keys: a public key for encryption and a private key for decryption. Notable algorithms include RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography). The public key is openly shared, while the private key remains confidential.
Strengths of Asymmetric Encryption
- Enhanced Security: The separation of keys eliminates the need for secure key distribution channels. The public key can be freely shared, reducing the risk of key interception.
- Scalability: Asymmetric encryption scales efficiently. Each user has a single pair of keys, simplifying key management in large networks.
- Authentication and Digital Signatures: Asymmetric encryption enables digital signatures, which verify the sender's identity and ensure the integrity of the message. This is crucial for secure online transactions and communications.
Weaknesses of Asymmetric Encryption
- Computational Intensity: Asymmetric encryption is computationally more intensive and slower compared to symmetric encryption, which can be a drawback for real-time applications.
- Complexity: The algorithms involved in asymmetric encryption are more complex, requiring greater computational resources and more sophisticated implementation.
Addressing Resistance against Secure Secret Sharing
Performance Concerns
Critics argue that the computational intensity of asymmetric encryption makes it impractical for certain applications. However, hybrid systems, which combine the strengths of both symmetric and asymmetric encryption, effectively address this concern. In such systems, asymmetric encryption is used to securely exchange a symmetric key, which is then used for the bulk encryption of data. This approach leverages the efficiency of symmetric encryption while maintaining the security benefits of asymmetric encryption.
Complexity and Resource Requirements
While it is true that asymmetric encryption requires more resources, advancements in computational power and optimization techniques have significantly mitigated these challenges. Modern hardware and software are increasingly capable of handling the demands of asymmetric encryption without compromising performance.
Practical Applications and Real-World Relevance
Securing Communications
Asymmetric encryption is integral to securing online communications, including email encryption (e.g., PGP) and SSL/TLS protocols used in securing web traffic. The ability to securely exchange keys and authenticate identities is essential for protecting sensitive information transmitted over the internet.
Digital Signatures and Certificates
Digital signatures, enabled by asymmetric encryption, are crucial for verifying the authenticity and integrity of digital documents. They are widely used in financial transactions, software distribution, and legal agreements, ensuring that the content has not been tampered with and confirming the sender's identity.
Cryptocurrencies and Blockchain
Asymmetric encryption underpins the security of cryptocurrencies like Bitcoin and Ethereum. Public and private keys are used to manage wallet addresses and sign transactions, ensuring secure and verifiable transfers of digital assets.
To Consider
While symmetric encryption offers speed and simplicity, asymmetric encryption provides superior security and scalability, making it the preferred choice for most modern cryptographic applications. The ability to securely distribute keys, authenticate identities, and verify the integrity of messages are critical advantages that asymmetric encryption holds over symmetric methods. By understanding and leveraging the strengths of asymmetric encryption, we can build more secure and resilient digital systems, protecting sensitive information in an increasingly interconnected world. Embracing asymmetric encryption as the foundation for digital security not only addresses current challenges but also prepares us for the evolving threats of the future.
Securing Communications Coventions

-
Email Encryption (PGP/GPG): Pretty Good Privacy (PGP) and its open-source counterpart, Gnu Privacy Guard (GPG), use asymmetric encryption to secure email communications. They ensure that only the intended recipient can decrypt and read the message, maintaining privacy and security.
-
SSL/TLS Protocols: Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are protocols that use asymmetric encryption to secure data transmitted over the internet. They are widely used to secure web traffic, ensuring that data exchanged between a user’s browser and a web server is encrypted and secure.
-
Virtual Private Networks (VPNs): VPNs use asymmetric encryption to establish a secure connection between a user's device and the VPN server. This encryption ensures that data sent through the VPN tunnel is protected from eavesdropping and interception.
-
Secure Shell (SSH): SSH protocols use asymmetric encryption to secure remote login and command execution over an insecure network. SSH ensures that the communication between the client and server is encrypted, preventing unauthorized access.
-
Messaging Apps (e.g., Signal): Secure messaging applications like Signal use asymmetric encryption to encrypt messages end-to-end. This means that only the sender and recipient can read the messages, ensuring that the communication remains private and secure.
Digital Signatures and Certificates Conventions
-
Software Distribution: Software developers use digital signatures to sign their software. This ensures that the software has not been tampered with and verifies the identity of the developer. Users can trust that the software they download is authentic and has not been altered.
-
Financial Transactions: Digital signatures are used to verify the authenticity and integrity of financial transactions. For example, banks and financial institutions use digital signatures to ensure that transaction details are not altered during transmission.
-
Legal Documents: Digital signatures are widely used in signing legal documents and contracts. They provide a way to verify the signer's identity and ensure that the document has not been altered after it was signed.
-
Code Signing Certificates: Developers use code signing certificates to sign their code. This process ensures that the code is authentic and has not been tampered with, providing trust to users who download and install the software.
-
Electronic Invoices and Receipts: Businesses use digital signatures to sign electronic invoices and receipts. This practice ensures the integrity and authenticity of the documents, making them legally binding and verifiable.
Assets and Blockchain Conventions
- Bitcoin: Bitcoin transactions are secured using asymmetric encryption. Public and private keys are used to manage Bitcoin addresses and sign transactions, ensuring that only the rightful owner can verify their Bitcoins.
This forms the backbone of security for modern client server systems enabling change via communities
The Cashu Protocol: Digital Transactions with Enhanced Privacy and Flexibility

So you want to run a mint? When? Sometime Soon?
In the anonymity ecosystem of digital transactions, maintaining privacy and security while ensuring seamless interoperability among Bitcoin layers is paramount. The Cashu protocol, an open-source ecash protocol designed for Bitcoin, offers a groundbreaking solution that leverages the Blind Diffie-Hellmann Key Exchange (BDHKE) to facilitate secure and private digital transactions. This argues that the Cashu protocol's innovative cryptographic mechanisms and open-source nature position it as a superior framework for digital currency transactions, fostering a secure, private, and interoperable ecosystem. By examining the protocol's technical foundations, practical applications, and potential challenges, this essay aims to demonstrate why adopting the Cashu protocol is a forward-thinking choice for digital financial systems.
The Technical Foundations of the Cashu Protocol
Blind Diffie-Hellmann Key Exchange (BDHKE)
At the heart of the Cashu protocol is the BDHKE, which ensures the privacy and security of ecash tokens through a robust cryptographic scheme. The BDHKE involves three key actors: Alice (the sending user), Bob (the mint), and Carol (the receiving user). The process involves a series of steps that obscure the transaction details, making it difficult for unauthorized parties to trace or tamper with the transaction.
- Mint (Bob): Bob publishes a public key (K) derived from his private key (k).
- Alice: Alice picks a secret (x) and blinds it using a random factor (r) to create a blinded message (B_).
- Bob: Bob receives the blinded message and signs it, returning a blinded key (C_) to Alice.
- Alice: Alice unblinds the key to obtain a proof (C), which she can use as a token.
- Carol: Carol can verify the token by sending it to Bob, who checks its validity and adds it to the list of spent secrets if it is genuine.
This process ensures that transactions are conducted privately and securely, with the blinding and unblinding steps preventing any correlation between the tokens and their origins.
Cashu NUTs (Notation, Usage, and Terminology)
The Cashu protocol's specifications are meticulously detailed in the Cashu NUTs, providing comprehensive guidelines for implementation and ensuring compatibility across various applications. These specifications enable developers to create interoperable software that adheres to the protocol, fostering a cohesive and secure ecosystem.
Practical Applications and Implementations
Language Support and Flexibility
The Cashu protocol is supported by multiple programming languages, enhancing its accessibility and implementation flexibility. Examples include:
- Python: Cashu Nutshell Python Library
- TypeScript: Cashu-TS TypeScript Library
- Rust: Cashu-crab and cashu-rs Libraries
- Golang: Cashu-Feni Golang Library
- Kotlin: Cashu Client Library in Kotlin
- Dart: Cashu Dart Library
These libraries allow developers to integrate the Cashu protocol into a wide range of applications, promoting widespread adoption and innovation.
Cashu Mints
Several mint implementations, such as Nutshell (Python), Moksha (Rust), Cashu-rs-mint (Rust), and Feni (Golang), provide robust solutions for secure transactions. The LNbits extension further empowers users by allowing them to run their own Nutshell mint, enhancing control over the security and privacy of their transactions.
Why You Should Focus on Cashu Development
Operational Concerns
Critics might argue that the cryptographic complexity of the Cashu protocol could impact performance and scalability. However, the protocol's design includes optimizations that mitigate these concerns. For instance, the use of efficient cryptographic algorithms ensures that transactions are processed swiftly, even as the volume of transactions increases. Additionally, the open-source nature of the protocol allows for continuous improvements and optimizations by the developer community.
How would I use this and Would Others use it
Alot of users worry about the usability and chance of others using the protocol. While the technical nature of the Cashu protocol might seem daunting to some users, the availability of detailed documentation (Cashu NUTs) and implementation libraries in multiple programming languages lowers the barrier to entry. By providing clear guidelines and versatile tools, the protocol facilitates broader adoption and practical implementation across diverse platforms. Partaking in continued constructive dialogue also around ecash future and past
Considering The Protocol

The Cashu protocol represents a significant advancement in digital transaction privacy and security. Its innovative use of the Blind Diffie-Hellmann Key Exchange (BDHKE) ensures that transactions are conducted privately and securely, while the open-source nature of the protocol fosters interoperability and widespread adoption. By addressing potential performance and usability concerns through continuous improvement and comprehensive documentation, the Cashu protocol is well-positioned to become a cornerstone of secure digital financial systems. Embracing the Cashu protocol not only enhances the privacy and security of digital transactions but also promotes a more flexible and interoperable ecosystem, making it a forward-thinking choice for the future of digital finance.
Real-World Applications of the Cashu Protocol
ChatNut: Privacy-Preserving Chat Application
ChatNut is an innovative chat application that integrates the Cashu protocol to offer privacy-preserving interactions with large language models (LLMs). Users pay-per-request using an integrated Cashu wallet without the need to create accounts, ensuring privacy and security. This application highlights the versatility of the Cashu protocol in enabling secure and anonymous communication services.
SpaceNut: Cashu-Enabled Gaming Experience
SpaceNut is described as the "sickest Cashu-enabled game" available. By integrating the Cashu protocol, SpaceNut offers a gaming experience where players can earn and spend Cashu tokens, demonstrating the protocol's applicability beyond traditional financial transactions. This use case underscores the potential of Cashu to revolutionize the gaming industry by introducing secure and private in-game economies.
NutMiner: Proof-of-Work Based Cashu Faucet
NutMiner is a proof-of-work based Cashu faucet that continuously releases Cashu tokens. This innovative approach leverages the principles of proof-of-work to distribute tokens fairly and securely. NutMiner exemplifies how the Cashu protocol can be integrated into decentralized token distribution systems, providing a steady and transparent method for distributing digital currency.
The manner in which you choose to run the processes of your mint could be the first step to understanding the power of unlocking transactional freedom on Bitcoin base layer while contributing to future resources around the budding sphere of Sovereign Privacy via Ecash, as an anonymous freedom driver and system to implement provably fair anonymous value systems.
-
 @ 6c2d79de:0407f1b7
2024-07-13 20:34:36
@ 6c2d79de:0407f1b7
2024-07-13 20:34:36
In this inaugural investigative campaign, we at The Xibao Times invite you to embark on a journey down the rabbit hole of Chinese propaganda. Our mission: to expose the intricate network of disinformation and anti-Western sentiment that the Chinese Communist Party (CCP) has meticulously woven through various channels, including state media, non-profits, coalition groups, and more. Our starting point: a seemingly innocuous image (above) reposted by China Daily, which has led us to uncover a web of deception that spans the globe.
At the heart of Operation Codepink lies a comprehensive examination of the CCP's propaganda apparatus. We delve into the inner workings of this sophisticated machine, revealing the strategies and tactics employed to disseminate disinformation and manipulate public opinion. From the recruitment of "useful idiots" to the exploitation of social media, we uncover the CCP's playbook and the players involved.
Our investigation spans multiple platforms and formats, providing readers with a multi-faceted view of the propaganda war being waged. In addition to in-depth articles on Habla News, we are creating wiki-pages on Wikifreedia to serve as a repository of information, and relationship charts to illustrate the complex web of connections between entities and individuals.
As we continue our investigative journey, we will be publishing updates, revelations, and analyses. Stay tuned for an exposé on the CCP's infiltration of Russian state media, US non-profits, and coalition groups, among others. Our objective is not only to educate and inform but also to spark a broader conversation about the dangers of disinformation and the need for transparency and accountability in the media landscape.
Join us as we unravel the threads of this intricate web and shed light on the dark corners of the CCP's propaganda machine. With Operation Codepink, we aim to provide the spiciest content on Nostr, and we invite you to be a part of this groundbreaking campaign.
Inside the Operation
Articles on Habla News:
Our in-depth articles on Habla News will provide a comprehensive overview of the CCP's propaganda machine, its tactics, and the individuals and organizations involved. These articles will delve into specific cases of disinformation, analyze the CCP's propaganda strategies, and expose the connections between various entities and individuals. The articles will be written in an engaging and accessible style, making complex information easily understandable for a broad audience.
Wiki-pages on Wikifreedia:

We will create a series of wiki-pages on Wikifreedia to serve as a central repository of information related to Operation Codepink. These wiki-pages will provide a detailed and organized overview of the CCP's propaganda machine, its various components, and the individuals and organizations involved. They will include information on specific cases of disinformation, analysis of propaganda tactics, and connections between various entities and individuals.
Relationship Charts:
To illustrate the complex web of connections between the entities and individuals involved in the CCP's propaganda machine, we will create relationship charts. These charts will show the relationships between different organizations, individuals, and governments, providing a visual representation of the intricate network of disinformation and propaganda. The relationship charts will help readers understand the scale and scope of the CCP's influence and manipulation efforts.
Investigative Approach:
Our investigative approach for Operation Codepink will involve a combination of open-source research, data analysis, and interviews with experts and insiders. We will use a range of tools and techniques to gather information, including:
Open-Source Research: We will conduct extensive open-source research, using publicly available information to identify patterns, connections, and trends related to the CCP's propaganda machine.
Data Analysis: We will analyze large datasets to identify relationships between individuals, organizations, and governments, as well as patterns in disinformation and propaganda tactics.
Expert Interviews: We will interview experts and insiders who have firsthand knowledge of the CCP's propaganda machine, as well as individuals who have been targeted by the CCP's disinformation campaigns.
Social Media Monitoring: We will monitor social media platforms for signs of disinformation and propaganda, as well as for clues about the identities of individuals and organizations involved in the CCP's propaganda machine.
By using a combination of these techniques, we aim to provide a comprehensive and accurate picture of the CCP's propaganda machine and its activities.
Updates and Revelations:
As we continue our investigation, we will provide regular updates and revelations on our findings. These updates will be published on Habla News and shared on our Nostr account xibaotimes@zaps.lol, keeping readers informed about the latest developments in Operation Codepink. We will also provide analyses and commentary on the implications of our findings for global politics, media, and society.
Stay tuned for more revelations and updates!
-
 @ 6c8c7979:15595f3e
2024-06-23 23:55:16
@ 6c8c7979:15595f3e
2024-06-23 23:55:16
The history of art represents a comprehensive study of the evolution of human creativity through the ages, embodying aesthetic and cultural expression from ancient times to the modern era. This article includes an overview of various historical periods and key artistic movements that have shaped what we know today as the fine arts. It provides a comprehensive look at visual, architectural, and literary arts that deeply influenced art history.
1. Ancient and Classical Periods*: - Artistic history begins with ancient arts in the Near East and Far East, where religious significance and expressions of power and daily life were central to creativity. Examples include the arts of the Egyptian Pharaohs, Sumerians, and Assyrians.
- Greek and Roman Art:
-
Western art was significantly influenced by Greek and Roman art, characterized by geometric dimensions and aesthetic elegance in architecture, sculpture, and painting.
-
Byzantine Art:
-
Byzantine art represents a blend of religion and art with its distinctive style and symbols that influenced Islamic art and rural architecture.
-
Art in the Middle Ages:
-
This period focused on Christian and scientific art in Europe, evolving from Romanesque styles.
-
The Renaissance:
-
In Italy, this period reflects the flourishing of science, philosophy, arts, and humanitarian movements, represented by works of artists such as Leonardo da Vinci and Raphael.
-
Modern and Contemporary Art:
-
This modern art movement reflects the impact of World Wars I and II, and includes movements such as Impressionism, Cubism, Surrealism, and Abstraction.
-
Contemporary Art:
- Contemporary arts have evolved into a diverse mix of techniques and concepts, with varied styles and experiments that reflect contemporary cultural identity.
Through this article, we delve into the details of these historical periods, including analyses of major artworks and prominent artists who have shaped the face of art throughout history. We will discuss how techniques and styles of art have changed from one period to another, and how they have been influenced by the social, cultural, and political contexts of each era.
art #artstr #history
-
 @ 0d2a0f56:ef40df51
2024-06-23 22:51:39
@ 0d2a0f56:ef40df51
2024-06-23 22:51:39 Today, I want to explore a question that's fundamental to our community: What is Bitcoin?
Today, I want to explore a question that's fundamental to our community: What is Bitcoin?At its core, Bitcoin is a decentralized digital currency, without a central bank or single administrator, that can be sent from user to user on the peer-to-peer bitcoin network without the need for intermediaries. Transactions are verified by network nodes through cryptography and recorded in a public distributed ledger called a blockchain.
But Bitcoin is so much more than this technical definition. It's a revolution in finance, a beacon of hope for financial freedom, and arguably, the antidote to many of the economic ailments plaguing our world today.
When I say "Bitcoin is the Antidote," I'm making a bold, abstract claim. An antidote is a remedy or solution to a problem or difficult situation. To truly explain why I believe this, I need to share my personal journey.
My story begins long before Bitcoin. In my mid-20s, I was living what many would consider a successful life. I had finished school and became an electrician, owned real estate, and was earning $120,000 to $140,000 a year. I was growing my family and excelling in my career. Yet, something was missing.
I wanted to be legendary, but for all the wrong reasons. My success came with a misguided sense of entitlement and a desire for luxury. This mindset led to depression and hopelessness. By night, I was a thrill-seeking, woman-chasing, money-wasting, alcohol-abusing party animal. This lifestyle nearly killed me, crashing down in early 2018 and resulting in months of recovery at the University of Chicago.
After this wake-up call, I promised myself I'd make better use of my time. I quit alcohol and partying cold turkey, transitioned to a less physically intense career, and started seeking something meaningful to build for my family.
In 2019-2020, I diversified my interests. I took classes on digital marketing, blockchain, social media entrepreneurship, and even MIT classes on the future of work. I dabbled in various investments - classic cars, private equity, cryptocurrencies, stocks, and metaverse properties. I was particularly drawn to altcoins and their ambitious whitepapers.
Then COVID hit, and the world as we knew it changed. Markets crashed, economic downturns accelerated. Amidst this chaos, I found myself reading the Bitcoin whitepaper by Satoshi Nakamoto. It was a pivotal moment.
The whitepaper aligned realities for me, unblocking my perception to view the world differently. Concepts like peer-to-peer cash, time, energy, central authorities, money, inflation - it all sparked something inside me. I began converting all my assets into Bitcoin.
As an electrician, I quickly saw Bitcoin as a much-needed reference point, a tool to measure against and better understand value. It wasn't just coincidence that Bitcoin went from a fraction of a penny to $20,000 per coin by 2020. This price action reflected the devaluation of the dollar and highlighted the misuse of money by states against their own citizens.
Reading the Bitcoin whitepaper led me down a rabbit hole of research into politics, economics, social science, and money. It helped me better understand how to preserve energy and value, what property is, and how to store and conserve it.
I discovered voices like Robert Breedlove, Michael Saylor, and Max Keiser, who elaborated on the problems Bitcoin solves. I was introduced to the Bitcoin community through conferences like Oslo Freedom Forum. Bitcoin began to feel like something spiritual, where people gathered with purpose, spreading awareness and fighting for a better way.
For someone like me, with an obsessive and addictive personality and a relentless appetite for knowledge, Bitcoin became the antidote. It was the truth serum I needed to shine a light on my toxic behaviors. But more than that, Bitcoin offered something I had been searching for without realizing it - an unlimited pursuit of knowledge and wisdom.
In many ways, diving into Bitcoin reminds me of a spiritual journey or the pursuit of God. It's a never-ending quest for understanding, always offering new layers to uncover, new concepts to grasp, and new implications to consider. This property makes Bitcoin a perfect transition for people with past addictive behaviors.
Where I once channeled my addictive tendencies into destructive habits, I now find myself addicted to learning. I'm constantly reading about economics, cryptography, game theory, and philosophy. I'm engaging in discussions about the nature of money, the role of the state, and the future of human coordination. This intellectual stimulation provides the same rush I used to seek in less healthy ways, but instead of destroying me, it's building me up.
The Bitcoin rabbit hole is deep and wide. It touches on so many aspects of human knowledge and experience that it can keep even the most voracious minds occupied indefinitely. For those of us who struggle with addictive behaviors, this can be a lifesaver. It provides a positive outlet for our obsessive tendencies, a constructive way to channel our energy and passion.
Moreover, the Bitcoin community, with its conferences, meetups, and online forums, offers a sense of belonging and purpose that many addicts seek. It's a global movement united by shared values of freedom, sovereignty, and honest money. This sense of community and higher purpose can fill the void that many try to fill with substances or destructive behaviors.
It's not simple to explain in a few pages how life-changing Bitcoin can be, but I promise that if you take on the task of better understanding Bitcoin and the problems it solves, it can become your antidote too. Whether you're battling addiction, seeking purpose, or simply looking to understand the world better, Bitcoin offers a path forward.
Bitcoin is the antidote to complacency, to financial illiteracy, to centralized control. It's a beacon of hope in a world that often seems hopeless. It's not just about money - it's about freedom, understanding, and reclaiming our sovereignty. It's about finding a positive addiction that enriches your life rather than depletes it.
As we navigate these uncertain times, I invite you to explore Bitcoin not just as a financial tool, but as a paradigm shift, a new way of thinking, and potentially, a new way of life. It might just become your antidote too.
Stay curious, stay sovereign,
Joe Thomas Founder, The Bitcoin Blok
-
 @ 6f170f27:711e26dd
2024-07-13 18:16:58
@ 6f170f27:711e26dd
2024-07-13 18:16:58This century has known a stunning decrease in global income inequality, bringing it down to levels not seen in well over a century. That's the conclusion that Branko Milanovic, one of the world's foremost inequality researchers, comes to in an important essay for Foreign Affairs.
https://www.axios.com/2024/07/11/world-income-inequality-ubs-wealth-report
https://www.axios.com/2023/06/14/global-economic-inequality
originally posted at https://stacker.news/items/607318
-
 @ df8f0a64:057d87a5
2024-06-23 14:27:42
@ df8f0a64:057d87a5
2024-06-23 14:27:42はじめに
2023年末にこんな文章を書いていました
今はNostrに夢を見ていますが、半年後には失望しているかもしれませんし、もっとのめり込んでいるかもしれません どうなるのかはわからないですが、わからないからこそ未来はいかようにも想像できるし、良くしようと関わることでまた違う楽しみがあります... ...来年はもう少しやれること・やれたことが増えるといいなと願っています。願うことができるなら、きっと動くこともできるでしょう BitcoinとWeb3と私とNostr
あれから半年という区切りが良い?タイミングでもあり、且つ会社を退職することも決め、社内で振り返る機会がなくなったので、私的な出来事だけですが振り返ってみようと思って走り書きします
0. Umbrel Homeを買った
Nostrで見聞きしていたUmbrel OSとUmbrel Home 私はBig-Techが嫌いな人間ではないんですが、こういうガジェット、欲しいじゃないですか なので買いました。理由はそれだけです(使い道は買ってから考えろ!)
1. ライトニングノードを運用し始めた
Nostrでnostr.wineという有料リレーを購入しようとしたときに、とある方にwineに対してチャンネルを貼って決済を助けていただいたことが、いつか自分でもやってみたいなと思い始めたきっかけです。自分も同じように困ってる人を助けられたら、それは小さくても幸せだなと
Umbrel Homeでワンクリックでノードを建てられたことや、Nostrで知ったDiamond Handsという日本発のコミュニティが、ルーティングに関する情報発信を積極的にされていたことで、実際に踏み出しました
私のLNノード→Hokusai
DHメソッドの仕上げが期待通りにいかなかったことが要因なのか、残念ながらルーティングは全然発生していません。なので人助けにはなっていないのですが、いつか改善していこうと思いながらデジタル盆栽をしています
2. ドメインの取得
Umbrel Homeを持ったことで、既存のサービスの代替を自分でやってみたいなと思い始めました
1PasswordをBitwarden(Vaultwarden)に Google PhotoをImmichに Apple MusicをPlexに
ウェブにある先人の知識や公式ドキュメントを読み、ChatGPTにも尋ねながらやっていくなかで、Tailscale内の通信をhttpsにすることに苦戦していました
オレオレ証明書?Caddyでリバースプロキシ??全然わからん...(このときCaddyがUmbrel Homeのポートをとってしまい、ただの黒い箱なりかねなかったところを、夜遅くにも関わらずNostrのみなさんに助けていただきました。改めて、ありがとうございます)
夜な夜な酒を飲みながらやっていたこともあり、だんだん面倒になってきて「埒があかないからもう世界に公開してしまっていいや!」とCloudflare Tunnelを使うことを決断。そうなるとドメインが必要になるので、流れで買いました。Nostrに来てから、どんどん一般人から逸脱している()
3. メディアサーバー
Nostrで投稿するとなかなか消せません。なので他の方にならって画像を投稿するときは、外部のサービスを利用しています 多くのクライアントと連携しているnostr.buildを有料プランで長らく利用しているのですが、アップした画像を時間が経ったら消す癖がある私にとっては、容量がtoo much 多い分には困らないのが普通の感覚だと思いますが、私にとっては「ちょうど良い」ものではないことがあまり心地よくありません
諦めていたとき、Blossomという仕組みを開発したという話がNostrで流れてきました Nostrの秘密鍵と連携する仕組みで、これ使ってみたいなぁ(単にあたらしいもの好き)と思っていたら、CloudflareでBlossomを動かすコードが公開されているわけです。OSSってすげー
Cloudflareは一定は無料で使えることをドメインを買うときに把握していたので、これはもうやるしかない!ということで自分用メディアサーバーを建てて利用しています。Cloudflare R2を利用しているので、一定時間経過後にオブジェクトを自動削除することもできて、とても快適
4. リレー運用
Cloudflareで色々遊べそうだとわかったことで、Nostrリレーも一度は建ててみたいという気持ちがだんだん強くなります およそ一年もNostrやGithubを見ていると、誰かがコードを公開しているはずだろうとわかるわけです そして案の定ありました、Nosflareというリポジトリが(OSSってすげー)
建立されたリレー→wss://relay.mymt.casa
Cloudflareの無料枠で運用したいので「日本国内からのみアクセス可能」「保存したイベントは24時間後に破棄」する運用にしています
5. まだできてないこと
本当はこの文章をUmbrel Homeでホストしようと考えていたのですが、Potainer.ioとghostの扱い方が全然わからない Bostrというrelay proxyも全然デプロイできない ということで毎晩ChatGPT-4oと一緒に苦戦しています。Cloude 3.5に切り替えたい(何もしていないのにアカウントBANされた...)
終わりに
振り返ってみると、エンジニアさんみたいにゼロから何かを作ることはできないですが、Nostr ecosystemに対しては少しは貢献できているんじゃないかなという気がしてきました いや、ほとんど他人の褌なんですが。ほんとOSSってすげー
次の半年で「まだできてないこと」をできるようになっているといいなぁと思いつつこの文章を終わります
知らんことをやるのは楽しいですね!
-
 @ 7361ca91:252fce6d
2024-06-23 08:32:54
@ 7361ca91:252fce6d
2024-06-23 08:32:54数日前、スペインでインスティトゥト・フアン・デ・マリアナが主催する「自由の晩餐会」が開催されました。このイベントは、リベラルな組織にとって最も重要で象徴的な行事の一つで、毎年開催され、スペインや他の国々から自由の擁護者たちが集う場となり、ネットワーキングやリベラルなアイデアに関する議論の場を提供します。
この晩餐会では、自由の擁護において卓越した献身を示した個人や団体に贈られる権威ある「フアン・デ・マリアナ賞」が授与されます。この賞は、経済、政治、哲学の分野で著名な人物に贈られており、彼らは個人の自由と自由市場の進展に大きく貢献しています。
今回は、スペインの著名な経済学者、弁護士、作家であり、レイ・フアン・カルロス大学(URJC)の政治経済学の教授であるヘスス・ウエルタ・デ・ソトが、アルゼンチンの大統領で現代リベラリズムの主要な知識人の一人であるハビエル・ミレイに賞を授与しました。ウエルタ・デ・ソトは、リベラルな思想において影響力のある人物であり、ミレイの知的指導者として、その自由の擁護における見事な業績を称賛しました。
スピーチの中で、ウエルタ・デ・ソトは、これは彼の人生で最も重要なスピーチであると述べました。それが彼の最も重要な知的貢献とは考えていないものの、これまでに行ってきた自由の理念の擁護と普及に関するすべての仕事をある意味で総括する、彼のキャリアにおいて最も重要な言葉であると考えています。
以下、ハビエル・ミレイを深く感動させ、彼の目に涙を浮かべさせたスピーチの翻訳になります。
今日は、恐れを知らず、世界を変えるために自己を犠牲にすることをためらわない一人の男に敬意を表します。自由という言葉を聞くだけで心が力強く鼓動する男、ハビエル・ミレイは、休むことなく、譲ることなく、自由を追い求めています。それは彼の大きな夢であり、そのエネルギーと情熱は、歴史上の偉大な自由の英雄たちにしか見られないものです。ハビエル・ミレイは、まさにそのような存在になりました。
まず、経済学を学ぶ人々にとって、彼は優れた経済学者としてその分野を完全に掌握しており、謙虚に理解しています。周囲の世界を理解するには、オーストリア学派の経済学の動的で企業家的、創造的なアプローチに従うことが必要であると。実際には、それはスペインの黄金時代のスコラ哲学者たちに由来するため、スペイン学派と呼ばれるべきです。
彼の言葉を借りるならば、ハビエル・ミレイは、主流派のネオクラシカル経済学の限界を見抜くことができました。その仮定の非現実性、形式的および方法論的な還元主義、そして何よりも、最悪の場合には社会工学と国家主義を助長し、最良の場合でも市場を誤った理由で擁護するという重大な誤りを犯している、幻想的な均衡モデルに基づいているからです。オーストリア学派が教えてくれるように、市場は自発的で素晴らしい人間の協力のプロセスであり、創造性と調整を促進します。このプロセスは、国家主義によって改善されることはなく、その科学的な不可能性もまたオーストリア学派によって証明されています。
さらに、ハビエル・ミレイは、今日の政治家にとっての模範となっています。彼は、自身が擁護する主張の科学的基盤を完全に理解し、確信と知的誠実さをもって自由を守ることができるからです。ちょうど、どの医師も医学を完全に習得することなくしてその職務を果たすべきでないのと同様に、いかなる政治指導者、議会議員、大使、あるいはどの省庁の高官も、オーストリア学派が教える経済学、自由、倫理の基本理論を事前に知らずしてその役割を果たすべきではありません。
現在、民主主義が、嘘と税金で得た資金による票の買収に基づく、歪んだシステムへと変わりつつある中で、ハビエル・ミレイは、常に真実を語り、厳しい現実を市民に説明しつつ、なおも自由の理念に対する圧倒的な支持を得ることが可能であることを示しました。彼のリーダーシップは、日々の政治の制約に左右されることなく、決して方向を見失わず、さらに自由を推進する努力を怠りません。したがって、各国でミレイのモデルに従うことを求める者たちは、すでにその道筋とすべきことを知っています。それは、ミレイのモデルを忠実に守ることです。
また、ハビエル・ミレイはすべての人々、特に若者にとっての模範ともなっています。人間の魂に感染する最も致命的なウイルスである国家主義に対抗する中で、ハビエル・ミレイは、他の誰よりも自由の理念を広めるという並外れた功績を持っています。彼は、文字通り、街頭や広場で、そしてメディアを通じて、何千人もの人々に経済理論を教え、知的かつ道徳的に国家主義の理念を打ち破ってきました。彼の言葉によれば、それはこれまで良識ある人々を縛りつけていたものです。特に、若者にとって、ミレイは模範的な存在であり、まだ完全に汚染されておらず、国家主義の罠に陥っていない彼らが、少し勉強し、オーストリア学派の理念に従えば、自由の熱心な擁護者となり、国家が課す組織的な暴力と強制に対する強力な反対者へとすぐに変わることができるでしょう。
自由、生命、財産を象徴する善と、暴力と国家による強制を具現化する悪との間の永続的な闘争において、今日、我々は知的にも道徳的にも歴史的にも、国家主義が死に瀕していると断言できます。この新たな時代において、ハビエル・ミレイと彼を間違いなく支持する者たちの力を借りて、我々の使命は、国家主義に最終的なとどめを刺すことです。未来は、自由を愛し信じる我々のものです。現在、あらゆる派閥の政治家や国家主義者たちが、本当にショックを受け、恐怖におののき、防御的になっているのは驚くべきことではありません。ハビエル・ミレイが言うように、それは「世界中のファシストたち」、そしてハイエクを引用すれば、それは左翼も右翼も含むすべての政党です。
最後に、ハビエル・ミレイは、寛大さの模範でもあります。彼は、出身に関係なく、かつての対立者たちに対しても寛大です。自分の過ちを誠実に認め、自由の理想を抱く勇気と知的誠実さを示す者たちは、彼の寛大さを受けます。多くの人々が、ミレイの話を聞いて、自分が実はアナルコ・キャピタリスト(無政府資本主義者)である、またはそうなりたかったことに気づいています。ハビエル・ミレイは決して自分を神格化することはなく、常に機会があるごとに、自分の偉大な師たちを引用します。それは、ミーゼス、ハイエク、ロスバード、ギットナー、ホッペといった巨人たちと肩を並べるにはふさわしくない私のような者も含まれます。このすべて、そしてハビエル・ミレイが私の人生のこの段階で私にもたらしてくれた大きな個人的な幸福のために、私は彼の知的寛大さに対して、個人的にも道徳的にも感謝しなければなりません。
さらに、リチャード・ソモンテにも感謝したいと思います。彼は、社会主義から逃れてマドリードにやってきたキューバの芸術家で、大人物の壮大な肖像画、とりわけ私の祖父がファンだったフアン・ベルモンテのような闘牛士の肖像画を得意としています。ソモンテは、21世紀の政治の真の闘牛士、ハビエル・ミレイの巨大な肖像画を完成させるというアイデアを私に提案してくれました。この場合、戦って倒すべき「牛」は、間違いなく国家です。
今日ここにあるこの肖像画は、この場で彼に贈るためのものです。話を終えるまでの1分半後に、皆さんがご覧になれる献辞が書かれています。それはこう書かれています。「自由の巨人、ハビエル・ミレイ大統領へ、彼の教授であるヘスス・ウエルタ・デ・ソトより、今日の日に。」
そして、マーティン・ルーサー・キングを引用して、こう締めくくります。「I have a dream」、私には夢があります。私は、国家が最終的に解体され、暗く恐ろしい歴史的な遺物としてのみ記憶される日を夢見ています。私は、国家の論理と理性、そしてそれが引き起こす社会的な紛争や無限の暴力が完全に、そして永久に消え去る世界を夢見ています。私は、人間を財政的に搾取することを目的とする国家が存在しない世界を夢見ています。私は、官僚たちが私たちの子供たちを洗脳せず、彼らを国家の所有物と見なさない世界を夢見ています。
私は、福祉国家という嘘が、特に最も困窮し、弱い立場にある人々のために、国家のない真の福祉に取って代わられる世界を夢見ています。私は、強制的で歪められた社会正義が、自由市場の無限の繁栄と愛に基づいた自発的な人間の連帯によって取って代わられる世界を夢見ています。それは、自由であるからこそ真実であり、強制や暴力によって押し付けられるものではありません。私は、したがって、自由意思による、自己調整された、無政府資本主義の世界を夢見ています。
私は、オーストリア学派が説明するように、今日では強制的で非道徳的なすべての公共サービスが、道徳的かつ効率的で、民間によって提供される世界を夢見ています。要するに、私は、人間がついに国家主義の鎖から解放され、自由に神を選ぶことができる世界を夢見ています、もしそう望むなら。
ハビエル・ミレイと、常に私たちを見守る天の力のおかげで、今日は未来の歴史が始まり、私の夢が現実になり始めました。そして最後に、四つの万歳を叫びます。オーストリア学派の経済学に万歳!偉大なるアルゼンチンと、その大統領ハビエル・ミレイに万歳!そしてもちろん、自由に万歳!カーラホ!
注釈:
ヘスス・ウエルタ・デ・ソト・バリェステルは、スペインの著名な経済学者、弁護士、作家であり、レイ・フアン・カルロス大学(URJC)の政治経済学の教授です。オーストリア学派の代表として、彼は『社会主義、経済計算と企業機能』("Socialismo, Cálculo Económico y Función Empresarial")において、企業の機能と社会主義の不可能性に関する重要な理論的貢献をしています。さらに、彼は『マネー、銀行信用と経済サイクル』("Dinero, Crédito Bancario y Ciclos Económicos")において、オーストリア学派の景気循環理論の発展と動的効率性の擁護で知られています。ウエルタ・デ・ソトは、社会の現実は理論的、歴史的、倫理的なアプローチを組み合わせて分析すべきであると主張し、アナルコキャピタリズム(無政府資本主義)と完全な経済の自由化を支持しています。彼の作品は多くの言語に翻訳されており、経済の自由と金融改革の擁護において、影響力のある人物としての地位を確立しています。
インスティトゥト・フアン・デ・マリアナ(IJM) は、スペインのマドリードに本拠を置くリベラル志向のシンクタンクで、2005年に設立されました。その目的は、その定款によると、「スペイン、ヨーロッパ、およびヒスパニックアメリカの広い大衆に対し、私有財産、自由な企業活動、および公共権力の行動範囲の制限がもたらす利益を紹介すること」です。その名称は、サラマンカ学派の後期の代表者であるフアン・デ・マリアナに由来しています。また、マドリードのレイ・フアン・カルロス大学の法学部および社会科学部において、オーストリア学派の経済学修士課程を後援しています。
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-13 12:44:32
@ 5d4b6c8d:8a1c1ee3
2024-07-13 12:44:32Yesterday's edition https://stacker.news/items/605773/r/Undisciplined
We have a confessional from a professional shitcoiner, today. That's fun.
-
- -
July 13, 2023 📅
📝
TOP POSTValidating Lightning Signer - AMA
Excerpt
VLS is a nifty piece of software that helps boost the security of the Bitcoin Lightning Network. 🛡️
11k sats \ 33 comments \ @devrandom \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/208442/r/Undisciplined?commentId=208454
Excerpt
Ever bought a computer or cell phone? Why? Why not wait until your money is worth more later compared to the price of that cell phone?
1441 sats \ 7 replies \ @02674f045a
From Opinion: Why BTC can't become the reserve currency by @0xBTC in ~bitcoin
🏆
TOP STACKER1st place @k00b
5838 stacked \ 7855 spent \ 3 posts \ 19 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
27k stacked \ 0 revenue \ 40.6k spent \ 108 posts \ 281 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 13, 2022 📅
📝
TOP POSTAny Good Routing Node Strategies?
Excerpt
For people who have/are running nodes, are there any strategies that have been most effective for you for earning routing fees? From my very limited routing experience so far it seems there are a few main questions:
1232 sats \ 33 comments \ @andyleroy \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/44747/r/Undisciplined?commentId=44755
Excerpt
Obligatory not a node routing expert, but this guy is a good follow: https://mobile.twitter.com/cold_sats
276 sats \ 1 reply \ @Cornleone
From Any Good Routing Node Strategies? by @andyleroy in ~bitcoin
🏆
TOP STACKER1st place @k00b
37.3k stacked \ 15.2k spent \ 1 post \ 29 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
27.4k stacked \ 0 revenue \ 34.7k spent \ 117 posts \ 279 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 13, 2021 📅
📝
TOP POSTI joined a shitcoin project full time couple of months ago
Excerpt
I though it would be exciting and fun. But I think I'm wasting my time.
3 sats \ 9 comments \ @03785de7ab \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/306/r/Undisciplined?commentId=316
Excerpt
There are many companies working with Bitcoin but it's not their main focus. I did implement Bitgo sevices for one e-wallet provider but that was it. What I'm looking for is a project which build useful things for user with current Bitcoin features, […]
2 sats \ 1 reply \ @03785de7ab
From I joined a shitcoin project full time couple of months ago by @03785de7ab in ~bitcoin
🏆
TOP STACKERNo top stacker
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
37 stacked \ 0 revenue \ 60 spent \ 6 posts \ 10 comments
originally posted at https://stacker.news/items/607040
-
-
 @ 7361ca91:252fce6d
2024-06-22 04:57:34
@ 7361ca91:252fce6d
2024-06-22 04:57:34Why pay steep commissions at conventional exchange offices? Instead, exchange your Bitcoin P2P for Japanese yen in cash, right here in Tokyo, privately through @hodlhodl .
- I will meet you at your hotel or any convenient location within Tokyo area.
- No Hidden Fees: best rates, just market price, with no extra costs (just care about onchain fees).
Initiate a transaction to get all the details and ensure a smooth exchange process.
Let’s make your currency exchange the easiest part of your trip.
Here: https://hodlhodl.com/offers/9fOp7JucCeIdqonT
Hodlhodl on nostr: npub1yul83qxn35u607er3m7039t6rddj06qezfagfqlfw4qk5z5slrfqu8ncdu
(DM for Lightning transactions)
Safe travels!
-
 @ 27676f17:0726572a
2024-06-21 23:13:04
@ 27676f17:0726572a
2024-06-21 23:13:04foobar
-
 @ b2caa9b3:9eab0fb5
2024-07-13 12:01:35
@ b2caa9b3:9eab0fb5
2024-07-13 12:01:35I woke up in my dorm this morning to the sound of rain – a rarity in Africa, but a common occurrence here around Mount Kilimanjaro. The climate is much like a European summer, with comfortable temperatures ranging from 18 to 30 degrees Celsius. Unlike the rest of Africa, this region receives more rainfall, creating a lush and scenic environment.

After a quick shower, I stepped out onto the balcony to find myself greeted by a chilly rain. Not ideal weather for exploring, but it did present a different perspective of the majestic Kilimanjaro. The mountain, often shrouded in clouds, occasionally peeks through, and on a clear day, might even be bathed in sunshine. From this vantage point, it's hard to imagine the countless hikers making their way up its slopes.
Did you know that Kilimanjaro, Africa's tallest mountain and a dormant volcano, once held a unique title? Back in 1910, during the German Empire, it was considered the empire's highest peak. While Mount Everest holds the title of the world's highest mountain overall, Kilimanjaro takes the crown for the tallest freestanding mountain – any higher peak is likely part of a mountain range or group.
Gazing at Kilimanjaro, I'm struck by its history – a single, towering volcano, once a part of the German Empire. Traces of that era linger in Moshi, with some colonial-era buildings, some in disrepair, others beautifully restored. Arusha, another nearby town, boasts an impressive art gallery and a fascinating National Museum. This museum, housed in a former German fort, offers a glimpse into the past. One particularly intriguing resident is a giant tortoise, discovered by German colonists as a hatchling in Kilimanjaro National Park. This living relic has witnessed a century of change, a silent observer of a bygone era.

Today promises to be a relaxing one. I'll spend time soaking up the views from the rooftop, hoping to catch a glimpse of Kilimanjaro in all its glory. On a more practical note, I'm also on the hunt for a remote job to help with some financial constraints. Finding the right opportunity seems to be a bit more challenging than anticipated.
As I wrap up this post, the weather has taken a turn for the better. The rain has stopped, the temperature has risen, and the sun is beginning to peek through the clouds. Here's to a wonderful day for everyone – enjoy yours!
(P.S. Be sure to check out the photos – one captures Kilimanjaro from yesterday evening, the other is a picture of me with the giant tortoise from my previous trip here in December 2022).
Online
Feel free to support me by sending some sats via the lightning network to rubenstorm@sats.mobi
-
 @ 75bf2353:e1bfa895
2024-06-21 21:41:19
@ 75bf2353:e1bfa895
2024-06-21 21:41:19Using p2p Electronic Cash
by Blogging Bitcoin
“The curious task of economics is to demonstrate to men how little they really know about what they imagine they can design. To the naive mind that can conceive of order only as the product of deliberate arrangement, it may seem absurd that in complex conditions order, and adaptation to the unknown, can be achieved more effectively by decentralizing decisions and that a division of authority will actually extend the possibility of overall order. Yet that decentralization actually leads to more information being taken into account.” ― Friedrich Hayek, The Fatal Conceit: The Errors of SocialismI write a free and open source blog about using bitcoin as peer to peer electronic cash. This is a compilation of some blogs I've written over the last two years. I wanted to write a book, but always felt paywalls are contrary to the free and open-source software movement. I still might publish this on dead trees, but want it to be free for anyone to read like the code you can find on https://github.com/bitcoin/bitcoin/. This is also an example of what bitcoin makes possible. Andreas Antonopolis once compared bitcoin to the invention of the printing press.
I may not agree with everything he says, but he was right about that. Bitcoin allows me to get paid directly by the consumer. It is possible to sell my words without jumping through the Amazon hoops. App developers can publish apps, but Apple will not be levy their 30% tax. I'm not advocating tax evasion or fighting the IRS, but why should we pay corporations to publish and censor us when we can be paid directly from our audience?
This is a compilation of 21 of my favorite blogs I wrote on nostr over the last two years. It is written using the Value 4 Value model. To support my work, please pay the paywall, send zaps, or contribute your time treasure, or talent in another way.
Most bitcoin books try to convince you to buy bitcoin. They talk about how bitcoin is worth more today than ten years ago. You should buy bitcoin because it's going to a moon 69,420 light-years away in a galaxy called WhenLambo. I get it. 125 sats will most likely buy you something at the dollar tree one day. At the time of this writing, 1,922 will buy you a single item at the dollar tree, but 1,538 sats will buy you a paper NFT with George Washinton's mug shot. This is not about NFT's, trading crypto, or how many dollars 100,000,000 sats are worth. It's the musings of some nerd on the Internet who believes cryptography equals freedom in the electronic age. It's about how I use bitcoin and freedom tech in an unfree fiat tech world.
All of my work is written under a Creative Commons Licence. To support my work, please pay the paywall or send zaps. I have published this blog behind this paywall. Paywalls kinda suck because they block so many people from reading your work--At least they think they do. Most paywalls can be bypassed by a simple google search
nostr:nprofile1qyvhwumn8ghj7mn0wd68yvfwvd6hyun9de6zuenedyhszxrhwden5te0wfjkccte9e3h2unjv4h8gtnx095j7qghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7qgswaehxw309ahx7um5wghx6mmd9uq3uamnwvaz7tmwdaehgu3dwp6kytnhv4kxcmmjv3jhytnwv46z7qgwwaehxw309ahx7uewd3hkctcpzdmhxue69uhk7enxvd5xz6tw9ec82c30qywhwumn8ghj7mn0wd68ytnzd96xxmmfdejhytnnda3kjctv9uqzqadlydf3460e333fjkaqwxg7fz82636ew5m36c7hml2xhhsml2y4csrc5a
Using p2p Electronic Cash, by Blogging Bitcoin
https://i.nostr.build/zdJG3.png
2 Support Yo0ur Local Circular Economy To Drain The Exchanges
4)Use Bitcoin To Protoest Inflation
9)Privacy Is Necessary For An Open Society In The Electronic Age
10)Fix The Money, Fix The Music
11)Build The Bitcoin Economy On Nostr
12)I don't trust the Cold Card: How to Verify Dice Rolls Using Tails
13)Recurring Bitcoin Donations with OakNode
15)Doge Is Dumb
16)Instransigent Tipping 17)Explain The Blockchain To Me(Like I don't Know How To Use The Command Line)
19)How Bitcoin Works In A Nutshell
20)Stacking Sats Is For Everybody
₿logging ₿itcoin 848,675 debtclock 🧡 Support this by using the ⚡Value 4 Value model⚡
-
 @ 3c7d12a6:9532013e
2024-06-20 14:47:12
@ 3c7d12a6:9532013e
2024-06-20 14:47:12NUD: Pubkey to colors
This NUD defines how to convert pubkey to colors.
Why?
npubis nonsense to display.- too long.
npub1bla...blais nonsense to display.npub1takes too much space....means nothing.
Specs
- Uses hex pubkey.
- Converts 64 characters to 8 colors.
- Splits 64 with 8 length chunks.
- Converts each 2 in 8 into
- Alpha (0-255 -> 0.0-1.0)
- Hue (0-255 -> 0.0-360.0)
- Saturation (0-255 -> 0.0-1.0)
- Light (0-255 -> 0.0-1.0)
- Supports dark and light theme.
- When Light is 1.0, flip the Light for light theme (0.0).
-
 @ 96203d66:643a819c
2024-06-20 03:08:33
@ 96203d66:643a819c
2024-06-20 03:08:33[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
-
 @ 7361ca91:252fce6d
2024-06-19 08:57:41
@ 7361ca91:252fce6d
2024-06-19 08:57:41Nostrで最近マイナンバーカードについての投稿が多くなった気がします。おそらく都内の選挙のためだろうと思います。マイナンバーカードは、多くのサービスを便利にする可能性があります。行政手続きが迅速になり、医療情報が一元管理されることで医療の質が向上し、金融取引が簡便になるといったメリットがあります。このような便利さを享受し、税金を払うことに問題を感じない人もいるでしょう。しかし、税金の(こと)問題を別として、マイナンバーカードの便利さの裏には、プライバシーとセキュリティに対する大きなリスクが存在することを見逃してはなりません。
まず、日本はサイバーセキュリティに関して非常に脆弱であるという現実があります。過去には政府機関や企業がサイバー攻撃を受け、多くの個人情報が流出した事例が数多く報告されています。最近の例を挙げると、2024年5月には静岡県浜松市で、ホームページに誤って約1000人分の名前や住所、携帯電話番号といった個人情報が公開される事件が発生しました 。このような背景から、マイナンバーカードが導入されると、個人情報が一元化されることにより、情報漏洩のリスクが格段に高まるのは明らかです。攻撃者がこのデータにアクセスすることで、大量の個人情報が盗まれ、アイデンティティの盗難が発生しやすくなります。例えば、詐欺者が被害者の名前を使って銀行口座を開設したり、ローンを申請したりすることが可能になり、金融詐欺のリスクも増大します。 ちなみに実際、2023年度には企業や行政機関からの個人情報の漏洩件数が過去最多の1万3279件に達し、そのうち334件がマイナンバーに関するものでした 。。。
データが一つの大きなデータベースに集約されると、そのデータベースはハッカーにとって美味しいターゲットとなります。日本のサイバーセキュリティの弱点を考えると、このデータベースが侵害される可能性は高く、何百万もの人々の個人情報が漏洩し、深刻なプライバシーの侵害が起こるリスクが高まります。データベースを管理する組織の従業員が不正にアクセスすることで、内部からの誤用やプライバシーの侵害も十分に考えられます。
マイナンバーカードは、政府や企業が個人の行動や活動を追跡するのを容易にし、個人の同意なしに監視が行われることに等しい状況を生み出します。個人の取引や活動が細かく追跡され、自由な生活が制限される恐れが出てきます。自分が買い物、SNS、投資行動などから示した思想や傾向は、ある意味反社会的であることとして判断されたら、雇用、保険、クレジットなどでの差別につながるリスクも、現実的な懸念となります。まさに、自由に発想することすらできなくなるでしょう。
これらのリスクを考えると、マイナンバーカードは、便利さと引き換えに多くのプライバシーと自由を犠牲にしていると言えます。個人情報の保護はデジタルにおいて個人の最優先事項であり、利便性と個人のプライバシー権をバランスよく保つための対策が不可欠ですが、プライバシーは一度失われると取り戻すのが非常に難しい、というのも忘れてはなりません。日本政府などにご自分のすべての個人情報をわたして任せても良いか、改めて考えてみる価値があると思います。ではでは。
-
 @ f70851e7:f1ee9109
2024-06-19 08:19:35
@ f70851e7:f1ee9109
2024-06-19 08:19:35(original manifesto of Cypherpunk Meetup 2024)
"I cleared the space for the younger generation. But no one came..." - Anonymous cypherpunk, 2024
The founding fathers of the cypherpunk movement had quite wild predictions for the Y2K+: Anonymous communication and ubiquitous encryption should have led to decentralization of power, freed markets and individual liberty. Looking realistically at today's world - a world in which surveillance is totally normalized and we're stuck between being dominated by megacorps and governments - we fucked up big time, even though we created islands of liberty for the few of us that understood what these technologies are for.
Bitcoin is an exemption and an exceptional success of their story, but looking at its current development, we come to argue that we're now vulnerable to failing even there. The crowds are coming again and they don't even know why they need anonymous money. But wait, do we know?
Once “rebels with a cause” turned into “grandmas with ETFs” and “garage economists with a Twitter account”.
Where do we go from here? What can we do? Is this what cypherpunk is now? Are we bitcoiners just because we can, or can we still look for and successfully find a purpose not lost from the founders' vision?
Emptiness of purpose can be easily hijacked. Looking at the past of the movement, experiencing its presence and foreseeing its future we ask ourselves the question:
Is the movement still relevant?
-
 @ 3f770d65:7a745b24
2024-06-17 18:56:54
@ 3f770d65:7a745b24
2024-06-17 18:56:54Several months ago, nostr:npub1hqaz3dlyuhfqhktqchawke39l92jj9nt30dsgh2zvd9z7dv3j3gqpkt56s and I set out to do tackle a task that had never been done before throughout Nostr's short history. We decided adopt the "go big, or go home" mentality and give our best effort to Purple Pill all of the nostr:npub167n5w6cj2wseqtmk26zllc7n28uv9c4vw28k2kht206vnghe5a7stgzu3r conference.
We couldn't accomplish this monumental task without the help of the Nostr community. From every day Nostriches and plebs, to legendary developers putting their blood, sweat, and tears into building this new protocol, to several companies within the Nostr ecosystem, everyone was going to need to do their part to turn this dream into a reality.
The mission
For the original vision of Nostr at BTC Prague, we planned on supporting the smallest available booth and a small panel on the secondary stage. The plan was for any Nostr developer to contribute what they could and then use the Nostr booth as a central hub to onboard users to their applications, provide support to their users, and meet the community. I embarked on my first crowdfunding journey and was able to initially raise over 10M sats thanks to the greater Nostr community donating towards our efforts.
Shortly afterwards, I was approached by nostr:npub1dtgg8yk3h23ldlm6jsy79tz723p4sun9mz62tqwxqe7c363szkzqm8up6m from Satlantis. He had planned on doing a mainstage presentation at BTC Prague on his new Nostr powered application. He asked me if I wanted to combine our efforts to upgrade the Nostr booth to the largest booth possible to give Nostr an even larger presence. I reached out to Avi and several other trusted Nostriches to see their opinions on this potential upgrade and everyone seemed to agree that we should continue with the "go big, or go home" mentality and try our best to Purple Pill all of Prague.
Now with a larger goal at hand, we were able to garner even more support from the Nostr community in addition by adding Highlighter from nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft and Primal from nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr as larger contributors.
The final tallies for funds raised were 16M+ sats from the greater Nostr community and 38M+ sats raised from Satlantis, Primal, and Highlighter. (We did have to raise a little more than originally anticipated because the Bitcoin 58K Gang made the fiat value of Bitcoin dip down for a bit right when we were trying to finalize payment.)
Putting it all together
This support enabled us to secure one of the four large booths at BTC Prague and a main stage panel. Given that these three companies made significant contributions, enabling our acquisition of the largest booth, we decided that it was logical to feature these companies more prominently. However, it was crucial to strike a delicate balance here. While emphasizing that this booth represented the Nostr community and was a true community effort, we also wanted to acknowledge and showcase those who made it possible. These companies could have opted for smaller individual booths, but their collaboration in a unified space demonstrates Nostr's principles of openness and interoperability—demonstrating that everyone and everything can work together seamlessly.
Therefore, we included as many logos across the Nostr ecosystem as possible throughout our iconography.

And, we also had a dedicated area of the booth highlighting our larger contributors.

The results exceeded all expectations. For three days during the BTC Prague conference, the Nostr booth was continuously bustling with activity. Attendees ranged from individuals who had never heard of Nostr before to those who were curious, active users within the ecosystem, and developers creating the applications we use daily. It was a remarkable community effort, with unexpected volunteers stepping up to onboard new users and provide support. Recognizing our busy schedules and flocks of new Nostriches hatching, they chose to assist in our efforts, offering help, and answering questions. It was a truly inspiring experience. Despite the busyness, the enthusiasm and support of so many people made each day enjoyable and dynamic, ensuring there was never a dull moment and we were always surrounded by friends.
Booth takeaways
As this was our very first attempt at doing something like this, I'd like to do a personal post mortem and highlight many of our successes and even some areas where I feel we can improve upon in the future.
Several Nostriches went above and beyond, helping onboard people and answer questions for three days straight. nostr:npub17plqkxhsv66g8quxxc9p5t9mxazzn20m426exqnl8lxnh5a4cdns7jezx0 nostr:npub1spdnfacgsd7lk0nlqkq443tkq4jx9z6c6ksvaquuewmw7d3qltpslcq6j7 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub1k6tqlj78cpznd0yc74wy3k0elmj4nql87a3uzfz98tmj3tuzxywsf0dhk6 nostr:npub1md39ua3h2s7204a7v5p9sdxmxx9qc7m4kr3r6naeuwfznad6d7nsxpctp9 nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w nostr:npub1zga04e73s7ard4kaektaha9vckdwll3y8auztyhl3uj764ua7vrqc7ppvc were the lifeblood of the booth, always answering questions themselves or referring them to others if they were unable to help, didn't know the answer or were busy at the time. You all put in the work and deserve much credit and thanks. Even nostr:npub1995y964wmxl94crx3ksfley24szjr390skdd237ex9z7ttp5c9lqld8vtf was helping with onboarding!

Additionally, beyond general use case questions, we also had many developers stop by and answer many more technical questions for those wanting to learn a bit more too. nostr:npub1zach44xjpc4yyhx6pgse2cj2pf98838kja03dv2e8ly8lfr094vqvm5dy5 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft were often seen answering more technical questions on various developmental topics.


Identifying areas for improvement is challenging, as the entire team of Nostriches performed exceptionally well, exceeding expectations. The event was a whirlwind of activity, with constant engagement and zero downtime. Volunteers seamlessly rotated at the front counter answering questions and distributing items to attendees. (Thanks nostr:npub1cgcwm56v5hyrrzl5ty4vq4kdud63n5u4czgycdl2r3jshzk55ufqe52ndy . Your nostr.how and nostrapps.com business cards were a HUGE help here!)
Full disclosure, I personally didn't leave the booth for three days all that much for two reasons. 1) Because I love to #GrowNostr and talk to people and 2) Because I was worried that the booth would turn into a corporate Primal or Satlantis show. However, this wasn't the case. While these teams did have a large presence with many team members all wearing t-shirts, none of my fears became a reality. If people asked questions about Nostr in general, that was discussed. If people asked questions about Primal or Satlantis, that was discussed. I personally recommended numerous social apps, Damus, Amethyst, Primal, Nostur, Nos.social - all of them. The booth was a true decentralized effort and I absolutely did not need to worry as much as I did, but I felt like I had an obligation to fulfill and I wanted to be there to see it through.
If I had to choose an area that needed improvement, I'd say that the three Satlantis women that nostr:npub1dtgg8yk3h23ldlm6jsy79tz723p4sun9mz62tqwxqe7c363szkzqm8up6m brought with him were supposed to shadow some of us to learn more about Nostr, so that they could then use this information to do the initial intake booth questions before making the referral to those with more information, but this just didn't happen. We were all so busy. Sorry! It was just too hard to coordinate. Maybe in the future we can prepare a bit more in this area. Although, nostr:npub1hz5alqscpp8yjrvgsdp2n4ygkl8slvstrgvmjca7e45w6644ew7sewtysa did a fantastic job, jumping right in there head first!
Secondly, we could have improved our television capabilities. We rotated from showing the live dashboard from the booth's Zap.stream livestream, to showing Primal.net/explore Nostr statistics, to showing nostr:npub1lelkh3hhxw9hdwlcpk6q9t0xt9f7yze0y0nxazvzqjmre3p98x3sthkvyz 's Nostr Documentary on loop, to playing the Satlantis promotional video. The majority of the time our TV was playing the same Nostr Documentary. It's great! I love that video, but we may be able to work out a better schedule and rotation mechanism in the future to showcase more content equally. Plus, I don't want to always be on the TV. I don't want people getting the wrong idea.
Nostr takeaways
After speaking with hundreds of people at BTC Prague, I feel that I've discovered the best way to describe Nostr.
Nostr has a portable digital social identity, allowing you to be in control of your digital social identity for the very first time, allowing you to take your entire social graph with you, every time you use a different application from Nostr's ecosystem.
Nostr is the social glue that binds all of your apps together.
In general, at BTC Prague, while explaining Nostr to people, the digital social identity route was what clicked with the most people. From there, it's not a long stretch to understand building a reputation and web of trust either.
Many people do not use the "Other Stuff" and explaining to them how to use these applications is hard. People want a native application.
Damus, Primal, and Amethyst seem to be the number one apps that people are using, with maybe Primal being the number one altogether? This is probably due to Primal being available on Android, iOS, and the web. Also, many people don't know that Damus still supports Zaps via the Nostr script workaround. I had to show many how to enable Zaps.
Everyone wants Nostr at their conference
There is significant interest in featuring Nostr at various conferences. Although not everyone has reached out, numerous individuals at BTC Prague expressed enthusiasm about incorporating a Nostr booth, along with several Nostr talks and sessions, into their upcoming events. They recognize the critical role Nostr and free speech play globally and acknowledge Nostr's popularity within the Bitcoin community. However, they also understand that more work is needed, and we must continue our efforts to onboard and engage new users.

I have two primary observations on this matter:
-
The community effort demonstrated here serves as a blueprint for success. We have proven that this approach to growing Nostr is effective, desired, and necessary. The engagement at our booth and attendance at our panels prove this with ease.
-
This fundraising initiative is likely a one-time effort. I cannot, in good conscience, continue to ask the community to bootstrap these endeavors. If we are to sustain these booths and promote Nostr at similar conferences, the conference organizers themselves must provide substantial support or discounts to foster broader Nostr adoption. While I understand that conferences entail significant operational costs, it is not feasible for Nostr developers and the broader Nostr community to finance these efforts continuously. Additionally, I would not feel comfortable requesting financial contributions from you all again for this purpose.
Looking forward
Will we do _this _again? I don't know. While our initial endeavor was a complete success, it would be unfortunate to cease our efforts just as we are gaining momentum.
Avi and I have a lot to discuss between ourselves and a lot to discuss with all of you.
Thank you all from the bottom of my heart. Thank you nostr:npub1dtgg8yk3h23ldlm6jsy79tz723p4sun9mz62tqwxqe7c363szkzqm8up6m nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr for making all of this possible. Thank you to every single Nostrich that donated your hard earned sats to make this possible. Thank you to all of the developers that built all of this to make all of this possible. Thank you to everyone else <3
Keep building.
-
-
 @ 5956abe3:a867c565
2024-06-15 22:23:12
@ 5956abe3:a867c565
2024-06-15 22:23:12"I'm thinking perhaps one day, I'll sell my bitcoin and pay off my mortgage" I hear through the din of a crowded bar.
It is the number one thing everyone is willing to openly consider selling their sats for - that little slice of that good American dream nostalgia: a house on the prairie, a yard, the dog, and no one to answer to. Security. The middle class of yesteryear's golden ticket to stability and prosperity. To most it's far beyond just being another financial asset- it's a tangible hallmark card vibe - something that even your mom would understand meant you got this.
So then - should you sell that risky BTC for your slice of picket fence and grass?
Not before you look at this:
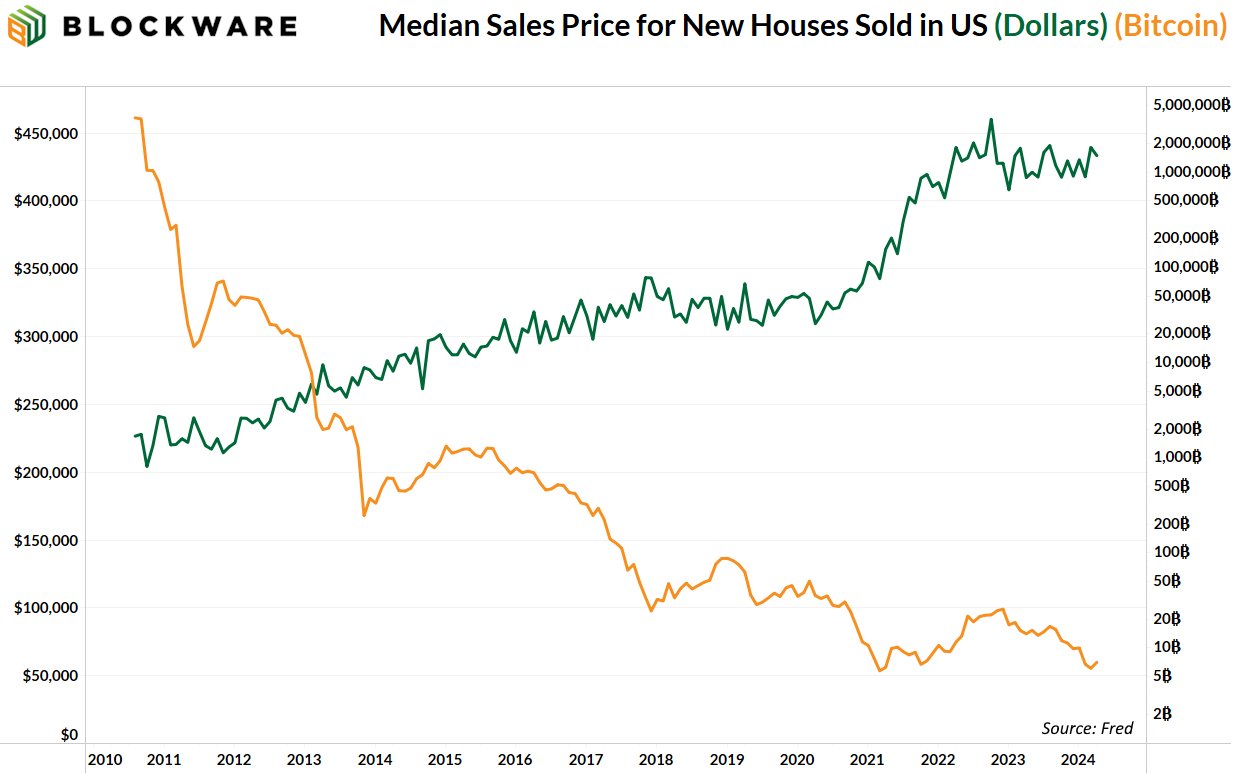
Reality check: housing has been crashing for years versus BTC, and it is not even close.
So there is no second best- BTC all the way. 100% portfolio, am I right?

Not so fast. You gotta have someplace to live, yes?
So then, time to learn about the housing market, here with your Bitcoin Yimby.
I invested in housing for over a decade, flipping houses, cleaning up rentals, helping homeowners buy and renovate their homes, making plans and advising people. All that good LinkedIn-ready stuff. One thing I learned doing this: the housing market operated nothing like I had imagined from the outside- and is in many ways intentionally broken.
So let's crack a beer and vent about it. I will be writing this for Nostr, so no AI content, no googlefarming social media spam, no clickbait - just pure, unfiltered opinion: no apologies, no concerns.
-
 @ 58537364:705b4b85
2024-07-13 11:49:14
@ 58537364:705b4b85
2024-07-13 11:49:14อารมณ์ คือ โลก - โลก คือ อารมณ์ อารมณ์ ในโลกปัจจุบันรวมอยู่ที่ วัตถุนิยม อารมณ์ จึงเป็นปัจจัยแห่งเหตุการณ์ทุกอย่างในโลก

…. “ เดี๋ยวนี้คําว่า “อารมณ์” ในภาษาไทยนั้น หมายถึงความรู้สึกในใจมากกว่า; เช่น พื้นเพของจิตใจในขณะนั้นเป็นอย่างไร, เรียกว่าอารมณ์ของเขาเป็นอย่างไร, อารมณ์กําลังดี อารมณ์กําลังไม่ดี, นี่ คําว่าอารมณ์ในภาษาไทยใช้กันไปเสียอย่างนี้ ; มันคนละเรื่องกับในภาษาบาลี ซึ่งคําว่า “อารมณ์” หมายถึง สิ่งที่จะเข้ามากระทบ ตา หู จมูก ลิ้น กาย ใจ.
…. ถ้ากระทบแล้วเกิดความรู้สึกอย่างไร งุ่นง่านอยู่ในใจ อันนั้นไม่ได้เรียกว่าอารมณ์; อันนั้นก็เรียกว่ากิเลสอย่างอื่น เช่น เรียกว่าตัณหาบ้าง อุปาทานบ้าง; ถ้าจัดเป็นพวกขันธ์ ก็เรียกว่า เวทนาขันธ์บ้าง สัญญาขันธ์บ้าง สังขารขันธ์บ้าง; ถ้าเป็นความคิดที่งุ่นง่านก็เรียกว่า “สังขารขันธ์” ทั้งนั้น ดังนั้น เราจะต้องถือเอาคําว่าอารมณ์ในบาลีมาเป็นหลัก …. คําว่า อารมณ์ ที่จะเข้าใจกันง่ายๆ ก็หมายความว่า รูป เสียง กลิ่น รส โผฏฐัพพะ ที่จะมากระทบ ตา หู จมูก ลิ้น กาย นี้ ๕ อย่าง แล้วก็ความรู้สึกเก่าแก่ที่จะมาผุดขึ้นในใจอีก เรียกว่า ธัมมารมณ์ ที่จะมากระทบใจในปัจจุบันนี้ นี้ก็เป็นอันหนึ่ง เลยได้เป็นอารมณ์ ๖. อารมณ์กระทบ ตา หู จมูก ลิ้น กาย ๕ อย่างข้างนอกนี้ก็สําคัญไปพวกหนึ่ง ที่ปรุงขึ้นภายในสําหรับกระทบใจโดยไม่ต้องอาศัย ตา หู จมูก ลิ้น กาย ใจ เลย ในเวลานั้นก็ยังมีอยู่นี้เรียกว่าธัมมารมณ์ นี้ก็ยิ่งสําคัญ: แต่ว่ารวมกันแล้วก็เรียกว่า อารมณ์ ได้ด้วยกันทั้งนั้น แปลว่า สิ่งที่จะมากระทบกับ ตา หู จมูก ลิ้น กาย ใจ นั่นเอง
…. นี้ ดูให้ละเอียดตามตัวหนังสือ คําว่า “อารมณ์” แปลว่า ที่หน่วงบ้าง แปลว่า ที่ยินดีบ้าง, มันมีความหมายละเอียดมาก. ถ้าถือเอาความหมายอย่างคนที่มีตัวตนเป็นหลัก ธรรมะในฝ่ายฮินดูหรือฝ่ายพรหมณ์เขาก็จะพูดว่า สําหรับจิตหรืออาตมันเข้าไปจับฉวยเอา. แต่ถ้าพูดอย่างภาษาชาวพุทธพูดอย่างนั้นไม่ได้ เพราะไม่มีจิตไม่มีอาตมันชนิดนั้น แล้วจิตนี้ก็เพิ่งเกิดขึ้นหลังอารมณ์กระทบแล้ว; เลยต้องพูดตามพระบาลีที่ว่า อาศัยตาด้วย อาศัยรูปด้วย ย่อมเกิดจักษุวิญญาณ; ตาอาศัยกับรูปคืออารมณ์นั้นได้แล้วจึงจะเกิดจักษุวิญญาณ วิญญาณหรือจิตนี้เกิดทีหลัง
…. ฉะนั้น จึงไม่พูดว่า อารมณ์นี้เป็นสิ่งสําหรับจิตหรือตัวตนเข้าไปจับฉวยยึดเอา; ถ้าพูดอย่างนั้นมันก็จะเป็นฮินดูหรือพราหมณ์ไป คือมีตัวตนไป. พูดอย่างพุทธไม่มีตัวตน ทุกอย่างไม่ใช่ตัวตน เป็นสักว่าธาตุ, ได้การปรุงแต่งที่เหมาะแล้วมันก็ปรุงแต่งเป็นสิ่งใหม่ขึ้นมา ในนั้นอาจจะมีความรู้สึกโง่ไปว่าเป็นตัวเราก็ได้
…. ฉะนั้น คําว่าอารมณ์ ถ้าถือตามหลักในทางพุทธศาสนา ก็แปลว่า สิ่งที่อาศัยกันกับจิต จะเรียกว่าเป็นที่หน่วงของจิตมันก็ยังได้: ถ้าเข้าใจผิดมันก็ผิดได้: เรียกว่าสิ่งที่อาศัยกับอายตนะ แล้วก็เกิดเป็นความรู้สึกเป็นจิตขึ้นมา จิตกําลังหน่วงสิ่งนั้นเป็นอารมณ์ก็ได้ แต่จะให้เป็นตัวตนนั้นไม่ได้
…. โดยพยัญชนะก็มีอยู่อย่างนี้ ตัวพยัญชนะก็ยังกํากวม อารมฺมณํ หรือที่มาจาก อาลมฺพนํ ก็แปลว่า ที่หน่วงของจิต. ถ้าจะถือว่ามาจาก รม ที่แปลว่า ยินดี ก็แปลว่า มันเป็นสิ่งที่หลงใหลยินดีของจิต อย่างนี้ก็ยังได้อีก
…. แต่ขอให้รู้จักจากภายในดีกว่าที่จะมารู้จักจากตัวหนังสือ เมื่อตากระทบรูป เมื่อหูกระทบเสียง เป็นต้น มันเกิดขึ้นในใจ, แล้วสังเกตเอาที่นั่นก็แล้วกัน ว่ารูปที่มากระทบตานั้นมันคืออะไร? เสียงที่มากระทบหูนั้นมันคืออะไร? จะค่อยเข้าใจแจ่มแจ้งขึ้นทีละน้อยๆ ว่าอารมณ์นั้นคืออะไร? แต่ให้เข้าใจไว้ทีหนึ่งก่อนว่าสิ่งที่เรียกว่าอารมณ์ๆที่มากระทบนี้ มันยังไม่ดีไม่ชั่ว ยังไม่จัดเป็นสิ่งดีสิ่งชั่ว มันต้องผสมปรุงแต่งเป็นความคิดอย่างนั้นอย่างนี้เสียก่อน จึงจะจัดเป็นดีเป็นชั่ว อารมณ์ล้วนๆยังไม่ดีไม่ชั่ว จะได้รู้จักป้องกัน อย่าให้เป็นไปในทางชั่ว, ให้เป็นไปแต่ในทางดีได้ตามปรารถนา
…. นี้เรียกว่าโดยพยัญชนะ โดยตัวหนังสือ คําว่า “อารมณ์” แปลว่า เป็นที่ยินดีแห่งจิต, เป็นที่ยึดหน่วงแห่งจิต; โดยเฉพาะภาษาอภิธรรมแล้วก็ใช้คําว่า “เป็นที่หน่วงเอาของจิต”, คือจิตย่อมหน่วงสิ่งใดสิ่งหนึ่งเป็นอารมณ์ แปลคําว่าอารมณ์บ้าง, อาลัมพนะ แปลว่า เป็นที่หน่วงเอา.
…. เดี๋ยวนี้เราเรียนพุทธศาสนาไม่ใช่เรามาเรียนหนังสือบาลี, เราจะเรียนพระธรรมคําสอนของพระพุทธเจ้า เราก็ต้องดูสิ่งที่เรียกว่าอารมณ์ โดยหลักของธรรมชาติที่ปรุงแต่งกันอยู่ในใจดีกว่า; ก็อย่างพระบาลีที่ได้ว่ามาแล้วข้างต้นว่า จกฺขุญฺจ ปฏิจฺจ รูเป จ อุปฺปชฺชติ จกฺขุวิญฺญาณํ = เพราะอาศัยตาด้วย รูปด้วย ย่อมบังเกิดจักษุวิญญาณ ติณฺณํ ธมฺมานํ สงฺคติ ผสฺโส - การประจวบกันของ ๓ สิ่งนี้เรียกว่า “ผัสสะ”, ผสฺสปจฺจยา เวทนา = เพราะผัสสะเป็นปัจจัยจึงเกิดเวทนา, อย่างนี้เรื่อยไปจนเกิดทุกข์ จนเกิดความทุกข์, นี้เรียกว่าโดยธรรมชาติ
…. สิ่งที่เรียกว่าอารมณ์มีอยู่โดยธรรมชาติที่จะเข้ามาอาศัยกันกับตาข้างใน ที่มีอยู่ในตัวคน. แล้วจะเกิดจักษุวิญญาณ เป็นต้น ขึ้นในตัวคน; จะเกิด ผัสสะ เวทนา ตัณหา อุปาทาน ภพ ชาติ ขึ้นในตัวคน; นี้โดยธรรมชาติ พระพุทธเจ้าท่านบันดาลอะไรไม่ได้ : ธรรมชาติเป็นอยู่อย่างนี้ แต่ท่านรู้เรื่องนี้ท่านจึงนํามาสอนว่า ธรรมชาติมันมีอยู่อย่างนี้ เราจะต้องเข้าใจให้ถูกต้อง โดยที่จะป้องกันความทุกข์ไม่ให้เกิดขึ้นมาได้, หรือถ้าเกิดขึ้นมาได้ก็จะดับเสียได้
…. เราควรจะรู้จักอารมณ์ในฐานะที่เป็นธรรมชาติอันหนึ่ง ที่มีอยู่ตามธรรมชาติ แล้วที่จะเข้ามาทําเรื่องทําราวขึ้นในจิตใจของคนเราให้เกิดปัญหายุ่งยากนี้ให้ดีๆ นี้เรียกว่ารู้จักอารมณ์จากธรรมชาติโดยตรงอย่างนี้ ดีกว่าที่จะรู้จักตามตัวหนังสือ, ดีกว่าที่จะรู้จักตามคําบอกเล่าบางอย่างบางประการที่มันไม่มีประโยชน์อะไร. รู้จักตามคําบอกเล่าก็รู้จักตามที่พระพุทธเจ้าท่านตรัสดีกว่า แต่แล้วยังไม่รู้จักตัวจริง จนกว่าจะมารู้จักจากที่เมื่ออารมณ์มากระทบตา หู จมูก ลิ้น กาย ใจ เข้าจริงๆ : นั่นจึงจะรู้จักอารมณ์ รู้จักผลที่เกิดขึ้นจากการกระทบของอารมณ์, รู้จักต่อไปตามลําดับ จนแก้ปัญหาต่างๆ ได้
…. นี่ ขอร้องให้รู้จักสิ่งที่เรียกว่า อารมณ์ ในฐานะที่เป็นธรรมชาติอันหนึ่ง ที่มีอยู่ตามธรรมชาติ ที่จะเข้ามากระทบอายตนะภายใน คือ กระทบ ตา หู จมูก ลิ้น กาย ใจ แล้วมีเรื่องมีราวมีปัญหา
อารมณ์ คือ โลก - โลก คือ อารมณ์ …. “ ที่นี้จะให้ดูต่อไปอีก ว่าโดยข้อเท็จจริงที่เป็นอยู่แล้ว อารมณ์นั้นคืออะไร? ถ้าจะพูดโดยข้อเท็จจริงหรือตามสถานการณ์ที่เป็นอยู่จริงในชีวิตของคนเรา อารมณ์มันก็คือ “โลก” นั่นเอง. เดี๋ยวนี้เราไม่รู้จักโลกในฐานะอย่างนี้, เราไปเข้าใจความหมายของคําว่าโลกแคบไปบ้าง หรือว่าเขวไปบ้าง.
…. ถ้าจะรู้ตามหลักพระพุทธศาสนาแล้ว โลกทั้งหมดก็คือสิ่งที่จะมาปรากฏแก่ ตา หู จมูก ลิ้น กาย ใจ ของเรา, เรามีเพียง ๖ อย่าง, แล้วมันก็ ปรากฏได้เพียง ๖ ทาง, มากกว่านั้นมันปรากฏไม่ได้ ดังนั้น โลกก็คือสิ่งที่จะมาปรากฏแก่ ตา หู จมูก ลิ้น กาย ใจ ๖ อย่างของเรา. “โลก” ก็คือ รูป เสียง กลิ่น รส โผฏฐัพพะ ธัมมารมณ์ ๖ ประการเท่านั้น, ไม่มีอะไรมากไปกว่านั้น
…. ฉะนั้น รูป เสียง กลิ่น รส โผฏฐัพพะ ธัมมารมณ์ แต่ละอย่าง ๆ ก็คือ โลกในแต่ละแง่ละมุม นั่นเอง, ที่เป็น รูป เสียง กลิ่น รส โผฏฐัพพะ ก็อยู่ข้างนอก จะเรียกว่าอยู่ข้างนอกก็ได้, ที่เป็นอารมณ์เกิดขึ้นในใจ ปรุงขึ้นในใจก็เรียกว่าโลกข้างในก็ได้ แต่มันก็เป็นโลกอยู่นั่นแหละ เพราะมันเป็นสิ่งที่จิตจะต้องรู้สึก จิตรู้สึกก็เรียกว่าโลกสําหรับจิต ตา หู จมูก ลิ้น กาย รู้สึก ก็เรียกว่าโลกสำหรับ ตา หู จมูก ลิ้น กาย. นี้ขอให้มองให้เห็นชัดตามพระพุทธประสงค์ว่า โลก ก็คือ อารมณ์, อารมณ์ ก็คือ โลก.
…. แต่ทีนี้ พระพุทธเจ้าท่านมองลึกกว่านั้น ท่านตรัสถึงข้อที่ว่า ถ้ามันมาเกิดเป็นปัญหาแก่เราเมื่อไรจึงจะเรียกว่า “มันมี” พอมันมาเป็นปัญหาแก่เราเมื่อไรก็เรียกว่า “เป็นทุกข์”; เพราะว่าเราได้ไปจับฉวยยึดถือเอาตามประสาตามวิสัยของคนที่ไม่รู้จักโลก ถ้าพูดว่าไม่รู้จักโลกแล้วคนก็มักจะไม่ยอมรับ เพราะว่าเขาจะพูดว่าเขารู้จักโลกดี. ยิ่งพวกฝรั่งสมัยนี้ นักวิทยาศาสตร์ปราดเปรื่องนั้น เขาจะไม่ยอมรับว่าเขาไม่รู้จักโลก. แต่ถ้าพูดตามหลักพุทธศาสนาแล้วก็จะพูดได้ว่ายังไม่รู้จักโลกเลย เป็นคนตาบอดยิ่งกว่าตาบอด; เพราะว่าฝรั่งเหล่านั้นรู้จักโลกแต่ในแง่สําหรับจะยึดมั่นถือมั่นเป็น “ตัวกู ของกู” จะครองโลกจะอะไร เอาประโยชน์ทุกอย่าง; เขารู้จักโลกในแง่นี้ อย่างนี้พุทธบริษัทไม่เรียกว่า “รู้จักโลก”; แต่ถือว่าเป็นคนตาบอดต่อโลก, หลงยึดมั่นถือมั่นในโลก. เพราะว่าคนเหล่านั้นไม่รู้จักโลกโดยความเป็นอารมณ์ ๖ ประการ คือ รูป เสียง กลิ่นรส โผฏฐัพพะ ธัมมารมณ์, แล้วเป็น “มายา” คือ เอาจริงไม่ได้ เป็นของชั่วคราวๆ หลอกให้เกิดความรู้สึกยึดมั่นถือมั่น
…. นี้เรารู้จัก เราไม่ไปหลงยึดมั่นถือมั่นกับมัน นี้จึงเรียกว่า “คนที่รู้จักโลก” ไปตามหลักของพุทธศาสนา, ฉะนั้น จึงไม่ยึดมั่นถือมั่นสิ่งใดโดยความเป็นตัวตน หรือโดยความเป็นของตน, เรียกว่าเป็นผู้รู้จักอารมณ์ ๖ ประการนั้นก็คือรู้จักโลกทั้งปวง, แล้วก็ไม่หลงไปในโลกในแง่ใดแง่หนึ่ง นี้เรียกว่า อารมณ์ ก็คือ โลก นั่นเอง ในความหมายที่ลึกที่สุดของพระพุทธสาสนา ไม่ใช่โลกก้อนดิน, ไม่ใช่โลกก้อนกลมๆ นี้. แต่มันหมายถึงคุณค่าอะไรที่มันมีอยู่ในโลกกลมๆ นี้ ที่จะเข้ามามาทําให้เกิดปัญหา ที่ตา ที่หู ที่จมูก ที่ลิ้น ที่กาย ที่ใจ ของคน. นั่นแหละคือตัวร้ายกาจของสิ่งที่เรียกว่า โลก เราจะต้องรู้จักในส่วนนี้ให้เพียงพอ
อารมณ์ในโลกปัจจุบันมารวมที่วัตถุนิยม …. ทีนี้ ดูอีกแง่หนึ่งก็โดยปัญหาที่กําลังมีอยู่ อารมณ์ในโลกนี้ในฐานะที่มันเป็นตัวปัญหาที่กําลังมีอยู่ มันมารวมอยู่ที่คําว่า “วัตถุนิยม”: หมายความว่า ตา หู จมูก ลิ้น กาย ใจ นี้ มันเป็นฝ่ายชนะ ไปหลงใหลในอารมณ์ รูป เสียง กลิ่น รส โผฏฐัพพะ ฯลฯ, แล้วก็เกิดนิยมหลงใหลในวัตถุเหล่านั้น จนเกิดความคิดใหม่ๆ, ปรุงแต่งไปในทางที่จะให้หลงใหลในโลกยิ่งขึ้นๆ, ความเจริญก้าวหน้า ในโลกสมัยนี้เป็นไปแต่ในทางอย่างนี้ ฉะนั้น จึงไกลความสงบ, ไกลสันติภาพ ไกลอะไรออกไปทุกที. การที่มนุษย์ที่มีปัญญาในโลกสมัยนี้ โดยเฉพาะฝรั่งที่ก้าวหน้านั้นเขาก็จัดโลกไปแต่ในแง่ของวัตถุมากขึ้นๆ: มันก็ไกลจากสันติภาพ ไกลจากความสงบสุขยิ่งขึ้นทุกที
…. ความสะดวกสบายที่ทําให้เกิดขึ้นมาได้นั้น ไม่ได้ช่วยส่งเสริมเกิดสันติภาพ; แต่มันช่วยให้เกิดความหลงในโลกนั้นเองมากขึ้น แล้วก็ช่วยให้หลงใหลใน “ตัวกู ของกู”, ยึดมั่นถือมั่นเห็นแก่ตัวมากขึ้น รวมกันแล้วมันไม่มีทางที่จะเกิดสันติภาพหรือสันติสุขในโลกได้เลย, จึงกลายเป็นความหลอกลวงเหลือประมาณ โลกจึงกลายเป็นความหลอกลวง, หรือสิ่งที่หลอกลวงเหลือประมาณใน เวลานี้ เราเรียกกันว่า ติดบ่วง หรือว่า ติดเหยื่อของวัตถุนิยม. คําพูดทั้งหมดนี้ ล้วนแต่เป็นการแสดงให้เห็นว่า อารมณ์นี้คืออะไร สิ่งที่เรียกว่าอารมณ์นั้น คือตัวโลกที่กําลังหลอกลวงเราอยู่ทุกวันอย่างยิ่ง โดยเฉพาะในปัจจุบันนี้เป็นวัตถุนิยม นี้คืออารมณ์”
พุทธทาสภิกขุ ที่มา : ธรรมบรรยายภาคมาฆบูชา ครั้งที่ ๗ หัวข้อเรื่อง “อารมณ์ คือ ปัจจัยแห่งเหตุการณ์ทุกอย่างในโลก” เมื่อวันที่ ๑๖ กุมภาพันธ์ ๒๕๑๗ จากหนังสือชุดธรรมโฆษณ์ เล่มชื่อว่า “ก ข ก กา ของการศึกษาพุทธศาสนา”
หมายเหตุ
“อารมณ์ ” ในทางพุทธศาสนา มี ๖ คือ... * ๑. รูปะ = รูป, สิ่งที่เห็น หรือ วัณณะ คือ สี * ๒. สัททะ = เสียง * ๓. คันธะ = กลิ่น * ๔. รสะ = รส * ๕. โผฏฐัพพะ = สัมผัสทางกาย * ๖. ธรรมารมณ์ = สิ่งที่ใจนึกคิด, อารมณ์ที่เกิดกับใจ
…. ทั้ง ๖ อย่างนี้ เป็นสิ่งสำหรับให้จิตยึดหน่วง เรียกอีกอย่างว่า "อายตนะภานนอก" ก็ได้
“อายตนะภายใน ๖” คือ ที่เชื่อมต่อให้เกิดความรู้, แดนต่อความรู้ฝ่ายภายใน มี * ๖ อย่าง คือ... * ๑. จักษุ - ตา * ๒. โสตะ - หู * ๓. ฆานะ - จมูก * ๔. ชิวหา - ลิ้น * ๕. กาย - กาย * ๖. มโน - ใจ
… หรือจะเรียกอีกอย่างว่า “อินทรีย์ ๖” ก็ได้ เพราะเป็นใหญ่ในหน้าที่ของตนแต่ละอย่าง เช่น จักษุ เป็นเจ้าการ(เป็นใหญ่)ในการเห็น เป็นต้น
ท. ส. ปัญญาวุฑโฒ – รวบรวม.
-
 @ 3bf0c63f:aefa459d
2024-06-13 15:40:18
@ 3bf0c63f:aefa459d
2024-06-13 15:40:18Why relay hints are important
Recently Coracle has removed support for following relay hints in Nostr event references.
Supposedly Coracle is now relying only on public key hints and
kind:10002events to determine where to fetch events from a user. That is a catastrophic idea that destroys much of Nostr's flexibility for no gain at all.- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
kind:1s -- now that cannot work because the person who created the post doesn't have the relays specific to those communities in their outbox list; - There is a discussion happening in a niche relay, for example, a relay that can only be accessed by the participants of a conference for the duration of that conference -- since that relay is not in anyone's public outbox list, it's impossible for anyone outside of the conference to ever refer to these events;
- Some big public relays, say, relay.damus.io, decide to nuke their databases or periodically delete old events, a user keeps using that big relay as their outbox because it is fast and reliable, but chooses to archive their old events in a dedicated archival relay, say, cellar.nostr.wine, while prudently not including that in their outbox list because that would make no sense -- now it is impossible for anyone to refer to old notes from this user even though they are publicly accessible in cellar.nostr.wine;
- There are topical relays that curate content relating to niche (non-microblogging) topics, say, cooking recipes, and users choose to publish their recipes to these relays only -- but now they can't refer to these relays in the external Nostr world of
kind:1s because these topical relays are not in their outbox lists. - Suppose a user wants to maintain two different identities under the same keypair, say, one identity only talks about soccer in English, while the other only talks about art history in French, and the user very prudently keeps two different
kind:10002events in two different sets of "indexer" relays (or does it in some better way of announcing different relay sets) -- now one of this user's audiences cannot ever see notes created by him with their other persona, one half of the content of this user will be inacessible to the other half and vice-versa. - If for any reason a relay does not want to accept events of a certain kind a user may publish to other relays, and it would all work fine if the user referenced that externally-published event from a normal event, but now that externally-published event is not reachable because the external relay is not in the user's outbox list.
- If someone, say, Alex Jones, is hard-banned everywhere and cannot event broadcast
kind:10002events to any of the commonly used index relays, that person will now appear as banned in most clients: in an ideal world in which clients followednprofileand other relay hints Alex Jones could still live a normal Nostr life: he would print business cards with hisnprofileinstead of annpuband clients would immediately know from what relay to fetch his posts. When other users shared his posts or replied to it, they would include a relay hint to his personal relay and others would be able to see and then start following him on that relay directly -- now Alex Jones's events cannot be read by anyone that doesn't already know his relay.
- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
-
 @ a012dc82:6458a70d
2024-07-13 08:10:23
@ a012dc82:6458a70d
2024-07-13 08:10:23Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Introduction
Bitcoin is a highly volatile asset that can experience dramatic price swings in short periods of time. In a bull market, traders can capitalize on rising prices and generate significant profits. However, when the market turns bearish, it can be challenging to navigate and maintain profitability. A bear market is a period of declining prices, where negative sentiment dominates and trading volumes may decrease. In this context, it's important to have a set of strategies that can help you navigate the market and protect your investments. In this article, we'll explore five essential strategies for trading Bitcoin in a bear market. By implementing these strategies, you can reduce your risks and maximize your chances of success.
Strategy 1: Take profit regularly
This strategy involves selling a portion of your Bitcoin holdings when prices reach a certain level. By taking profits regularly, you can lock in gains and minimize the risk of losses in a bear market. It's important to have a plan for taking profits and stick to it, even if prices continue to rise.
Strategy 2: Set stop-loss orders
A stop-loss order is an instruction to sell your Bitcoin if prices fall below a certain level. By setting stop-loss orders, you can limit your losses in a bear market and avoid holding onto Bitcoin that's losing value. It's important to set stop-loss orders at a level that allows for normal price fluctuations but also provides adequate protection against sharp declines.
Strategy 3: Short sell Bitcoin
Short selling involves borrowing Bitcoin from a broker and selling it on the open market with the hope of buying it back at a lower price. This strategy can be useful in a bear market when prices are falling, as it allows you to profit from the decline. However, short selling is a high-risk strategy that requires careful consideration of the potential risks and rewards.
Strategy 4: Use dollar-cost averaging
Dollar-cost averaging involves investing a fixed amount of money at regular intervals, regardless of the current price of Bitcoin. By buying Bitcoin at regular intervals, you can take advantage of market fluctuations and potentially reduce the average cost of your holdings. This strategy can be effective in a bear market where prices are falling and may present buying opportunities.
Strategy 5: Stay up-to-date with news and trends
Staying informed about news and trends in the cryptocurrency market is essential for making informed trading decisions. By staying up-to-date, you can identify potential risks and opportunities and adjust your trading strategies accordingly. It's important to use reliable sources of information and avoid making impulsive trading decisions based on emotions or rumors.
Conclusion
The Bitcoin bear market can be difficult to navigate, but with these five essential strategies, traders can reduce their risks and maximize their chances of success. These strategies include taking profits regularly, setting stop-loss orders, short selling, using dollar-cost averaging, and staying up-to-date with news and trends. It's important to remain disciplined, avoid impulsive decisions, and stay flexible to adapt to changing market conditions. By following these strategies, traders can emerge successful from the Bitcoin bear market.
FAQ
What is a bear market? A bear market is a period of declining prices, where negative sentiment dominates and trading volumes may decrease.
How can I protect my investments in a bear market? To protect your investments in a bear market, you can implement strategies such as taking profits regularly, setting stop-loss orders, short selling, using dollar-cost averaging, and staying up-to-date with news and trends.
Is short selling a high-risk strategy? Yes, short selling is a high-risk strategy that requires careful consideration of the potential risks and rewards.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ f683e870:557f5ef2
2024-06-10 17:27:55
@ f683e870:557f5ef2
2024-06-10 17:27:55For reading the article with proper Latex, head over to pippellia.com
Introduction
The emergence of decentralized social networks with sovereign identities (e.g. Nostr is a pivotal moment for the web, and it comes at the perfect time. In the age of AI, where it's getting cheaper and cheaper to impersonate people, distort videos and images, or just make them up, how is it possible to know what's true? What does truth even mean these days?
These are questions I will not attempt to answer. However, even if the ontology of truth has eluded philosophers forever, a more practical approach is needed if the Web is not to degenerate into a nihilistic place where nothing is real, or worse, a place where everything requires identity verification and the approval of a central authority.
In this paper, you will find a definition of the social graph, principles for thinking about it, and practical ideas for using it for DoS prevention, social discovery, anti-impersonation, accurate ratings, and more. You will also learn about alternative mechanisms that can be used in conjunction with social graph analysis to provide more compelling and complete solutions.
Social Graph
First, what is a graph? A graph G is a mathematical structure consisting of a set of nodes or vertices V and a set of edges E.
In mathematical notation, we write G = (V,E).
Edges are defined by a relation on the set V x V = {(v,u) : v,u in V }; for example, if node v and node u are related (e.g. v follows u), then the pair (v,u) is contained in the set E. In the notation
E = { (v,u) in V^2 : v is related to u }
The relationship can be symmetrical or asymmetrical, distinguishing between undirected and directed graphs.
A social graph is simply a graph in which the nodes are human entities (such as individuals, companies, groups, etc.) and the edges represent some form of social relationship, such as being friends with, following, or being zapped.
Before we go any further, we need to define another important notion, that of a neighborhood.
The neighborhood of a set of vertices S subset of V in G is another set of vertices whose defining property is to be connected to a vertex in S. In mathematical notation
N_G(S) = { u in V : exist s in S, (s,u) in E }

What problem is the social graph solving? The answer is many, in many different ways and forms. We are talking about using it as a defense mechanism against impersonation, as a way to prevent DoS attacks, to facilitate social discovery and connections, and to calculate more accurate ratings. But before we dive into the implementations, I ask you to pause for a moment to understand the magnitude of what we are discussing.
Principles
Don't fall into the trap of thinking that the engineers at YouTube were evil when they designed their algorithm. As the saying goes, the road to hell (read: open-mouth theater) is paved with good intentions (read: the desire to over-optimize engagement).

If your implementation is successful, people's behavior will be affected. That's why it's important to establish principles that can guide designers and developers in creating systems that are healthier than the world we're leaving behind.
Principle of least interference
A good rule of thumb when designing systems that affect social dynamics is to follow the principle of least interference.
Principle of least interference: solve the problem by implementing whatever mechanism has the least possible impact on social dynamics.
As an heuristic based on this principle, it is generally better to focus on solving only one problem at a time, since it is unlikely that solving multiple problems at once will not lead to a greater impact on those social dynamics.
A great example to analyze is the WoT score implemented by Coracle, which tries to "reduce spam, impostors, and objectionable content", all at once.

Let's start by analyzing how it works as an anti-impersonation mechanism.
If you search for 'Lyn Alden', it is very likely (if you are part of a "good" network) that the npub with the highest WoT is the real Lyn, while all others are impersonators.

However, a simple warning icon above all other Lyns would have accomplished the same goal without introducing a rating that can alter social dynamics.
In fact, the WoT score represents the opinion of the crowd around you, which doesn't offer any nuance when comparing the reputation of different real people. Crowd thinking is one of the biggest problems of the world we are leaving, and it would be a silly exercise to bring it with us.
Besides, we do not walk around with a number on our forehead in meatspace, nor should we in cyberspace, even if that number depends on the observer.
There is also another, more fundamental problem, which is that the user v only has information about a limited subset of the network, namely N_G^2(v) = N_G(N_G(v)), where G is the graph defined by the relation "follow OR mute" relation.
Therefore, if you set the WoT threshold above zero, you won't see anyone outside of N_G^2(v), which certainly prevents spam, but at the cost of discoverability.
We'll come back to how to design a more effective anti-impersonation system later.
Principle of Relativity in cyberspace
The current Web, and our societies in general, are built on an outdated paradigm that relies on and requires consensus about what is true, false, good, or bad. Unspeakable atrocities have been committed to achieve and maintain such consensus.
However, we must move beyond this legacy of the past if we are to usher in a new era of freedom.
The notion of a commonly shared belief or social truth is as dead in this new millennium as God was in the 19th century.
Principle of Relativity in Cyberspace: You cannot and should not dictate what is true or false, what is good content or bad content or spam, for another person.
If you do, you will simply be replacing the beast with a new set of beliefs. It's true that there are many different clients to choose from, but there were many different web browsers back in the day, and that didn't end well.
The reality is that a global agreement on things has seldom been necessary. In fact, relative canonicality can be achieved without the need for a central authority.
Wikifreedia (a nostr alternative to Wikipedia, as you have probably guessed) fully embraces this idea of relative canonicality. Each topic contains multiple entries; there is no single source of truth that aims or claims to be neutral. Of course, this doesn't mean that all entries are equally good or useful. On the contrary, there is a very opinionated and biased way of sorting them, which depends on the observer. Regardless of the specific implementation (again, number on the forehead), this is the way to go, this is relativity in cyberspace.

There is no Global
This point is arguably a corollary of the previous principle, but it's so important that it needs to be fully explained. The notion of global is also dead.
Despite being the largest indexer in the world, Google only indexes a small portion of the web. The engineering challenges behind indexing absolutely every person and piece of content in an ever-growing, open and hostile decentralized network will likely exacerbate this outcome: Nostr will outgrow every index.
As spammers become more sophisticated, crawlers will have to become more selective, limiting the percentage of the network that is indexed. Therefore, as a client designer or developer, you really only have a limited view of what's happening.
This reinforces the statement that you cannot decide for someone else what is good or bad, true or false. You can't possibly know, because what you have is a local, limited view, just like everyone else's.
Let's take Nostr Band for example. As much as I appreciate their cool statistics, it's important to know their limitations. The version of Trust Rank that Nostr Band implements:
- runs on the subset of the network they are aware of
- uses an arbitrarily chosen set of NIP05 providers for determining the so called good seeds
This approach is fine if it's used to defend the service provider against spammers (see DoS prevention section for improvements).
However, such an arbitrary view (all are, but some less than others) shouldn't be imposed on the end user, but only used as a way for the service provider to select the customers it wants to serve.
Principle of natural patterns
I believe that technology is made for people, so it should serve us and improve our quality of life. We shouldn't adapt to technology, technology should adapt to us.
This context is no exception to the rule. Humans are social creatures, and our social dynamics and behaviors have evolved through our long history. Therefore, before introducing new and artificial social dynamics, it's wiser to mimic the natural dynamics that have evolved with us for millennia.
Principle of natural patterns: When in doubt, try to mimic the social dynamics of meatspace
For example, in meatspace, a friend of a friend is not a stranger, but it's not a friend either. It's something in between, and a good candidate for a potential future friend.
Another example is something that will hit home if you've ever been to a bitcoin conference. When you're among people with the same interests, and I would argue mostly overlapping values, even if you've never met them, you can't say they're strangers.
Examples abound, so there is really no reason to try to impose any artificial dynamics before exhausting what nature has given us.
To summarize, we take from this section three principles that will inform our analysis and design decisions going forward:
- The principle of least interference
- The principle of relativity in cyberspace
- The principle of natural patterns
The Problems
Finally, we can start discussing some concrete problems and ways to solve them. There are several well-defined problems that social graph analysis can help with. Again, it's important to define them well if we want to follow the principle of least interference.
The first problem we will analyze is protection against impersonation, one of the most important pieces to get right.
Anti-impersonation
Social endorsement
Who is the real Giacomo? In this case, it's pretty simple

First of all, let's talk about what won't help us decide:
- the name
- the profile picture
- the bio
- the date of creation
And no, not even the number of followers, as this is a completely irrelevant metric in an open and hostile network. See an example
What helps us is the line below:
"Followed by Bitcoin Africa Story, Nostr Wallet Connect, and 666 others you follow".
This is the signal. Follows can be faked, but follows from people you trust cannot be faked (or are more expensive to get). This is a particularly good design because it adheres to the principle of relativity in cyberspace. It doesn't prescribe who the real Giacomo is, it doesn't summarize the data for you (like the aforementioned WoT score, where every follower has the same weight), but it shows you clues that you can decide to interpret in the way you want.
The same idea can be applied to mutes, which gives you a few more clues.
Obviously, such a system can be extended not only to the people you follow, i.e. N_G(v), but also to the people who are 2 hops away from you, i.e. N_G^2(v) = N_G(N_G(V)), or n hops away from you, i.e. N_G^n(v).
However, the signal becomes increasingly diluted and unreliable the farther you go.
This approach is a good start, but it can't really solve the impersonation problem on its own because it's limited in reach and suffers from a bootstrapping problem for new users, which is really the same problem if you think about it.
There is also a subtle issue worth mentioning. What if a reputable person tries to impersonate someone else? This attack is possible because it won't be detected immediately, but the more prominent the person, the faster this attack will be detected, causing the attacker to lose their hard-earned reputation.
Furthermore, for truly prominent figures such as heads of state, this problem can be mitigated (but not completely solved) by third-party credentials that can be displayed by clients.
NIP05 providers
Another approach that has been tried is to rely on NIP05 providers. If I trust a NIP05 provider to verify the people they serve, then I can assign a non-zero level of trust to their customers. However, this approach obviously requires trust, which isn't ideal since there are trustless approaches that provide better guarantees.
PoW keys
When we see a stranger enter the pub where we are, or when we are crowded on the subway, we find ourselves potentially vulnerable to strangers. In most civilized places, however, we don't live in a constant state of fear, and that comes from the fact that others are vulnerable as well. Everyone has skin in the game, even the aggressors, which means that the best way to play this game is not to mess with other people.
On Nostr, however, the only consequence you can feel is the loss of your reputation, which by definition is worthless when the npub is brand new.
However, there is a way to add skin in-game for new keys, i.e. PoW keys.
The process works like this: while creating your identity, your machine can generate a new private key sk until the corresponding public key pk, as a binary number, satisfies the following inequality:
pk <= t ; where t is a threshold of your choice.
Since there is no efficient way to do this (allegedly), this process requires the expenditure of computing power and energy. This adds a quantifiable and verifiable cost to any identity, making credible impersonation expensive.
However, PoW keys can't work at scale, because:
- they require commitment at key creation, which is bad UX because it reverses the "try before you buy" rule
- the PoW can't be updated over time
- It is not possible to delegate the work without delegating the key (supposedly)
The last point implies that the economy of scale favors the attacker, because they have multiple targets, whereas the defender can only defend himself.
However, there is a similar approach that offers what I believe are more appropriate tradeoffs: PoW Endorsement.
PoW endorsment
A PoW endorsement is a simple unsigned user metadata event containing a target npub, a difficulty commitment threshold $t$, and a nonce.
The nonce is randomly generated until the following condition is satisfied:
h(event) <= 2^t ; where h is a cryptographic hash function such as SHA256
If the condition is met, the PoW endorsment is valid, and the target npub's "PoW weight" becomes 256 - t.
What I am describing is basically NIP13, except that it should use kind 0, and it doesn't need a signature (what's the problem if someone wants to add PoW to someone else's npub?).
What makes PoW endorsements different from PoW keys is that:
- it doesn't require any commitment at key creation
- the PoW can be updated over time
- it's possible to delegate the work without delegating the key
- requires data availability, because the work is separate from the key
Point 3 is what makes this approach feasible and scalable, especially for mobile devices constrained by CPU and battery limitations.
Point 4 isn't particularly bad because the events are small, public, and the user has an incentive to store them.
Example of how it works
- Alice gives a npub to the Miner
- Alice pays the Miner $10
- The Miner mines the PoW endorsement, with the target npub
- The target npub now has a non-zero PoW weight
How does it help?
If the target npub has a non-zero PoW weight, credible impersonation attempts require a cost. The attacker's social capital (PoW weight) becomes less and less valuable, and is eventually lost, as more people discover the attack and mute the attacker's npub.
Furthermore, assuming that most of the PoW weight is allocated to real people (1), it's possible to use its distribution to fix the shortcomings of social endorsement.
For example, a new user can be presented with the choice of following the npubs with the highest Trust Rank, where the good seeds are the npubs with non-zero PoW weight. The same principle can be applied to an existing user trying to get information about an npub that is many hops away from him/her.
If you want to summarize this idea to the maximum, if the number of followers is meaningless, that's not true for the number of followers with non-zero PoW weight (under assumption 1).
I have started working on this idea and preliminary results are promising, but more thought is needed
Colored halo
Another anti-impersonation mechanism tried by Nostrudel is to use a few characters of the public key (in hex format) to identify a unique color that is displayed around the user's profile picture.

The idea is that if I am already following the real Lyn, a credible impersonation attempt would require generating many times the key pair to get the same or very similar color. This requires energy, which means cost.
However, this information is only useful if I already follow the real Lyn and remember her color. Asking my trusted network for the color of a particular person is no different task than asking her npub directly.
This means that this approach, while interesting, is not very useful.
DoS attack prevention
When analyzing Denial of Service attacks, we should distinguish between defense mechanisms that work at the network level, at the service provider level, and at the user level.
Talking about the first case may seem to contradict the principle of relativity in cyberspace, but here by network we mean any set of network participants who are willing to cooperate but not necessarily trust each other.

Network level
PoW events basically apply the concept of Hashcash not to email messages but to notes. There is not much to say here, except to note that the PoW can be outsourced to service providers that can most likely outcompete the attackers in efficiency.
Service provider level
The best tool the service provider can use to prevent DoS is money. A paid service, either pay-per-use or subscription-based, can work both for monetization and as a defense mechanism. However, not every service (or sub-service) is directly monetizable, which is where social graph analysis can help.
The idea is to selectively choose which npubs are considered potential good customers and filter out everyone else. If this needs to be said, I'll say it: this is not censorship, this is simply a business deciding who to serve.
Many different criteria can be used to select what is a good customer, especially since this definition depends on the service being provided.
A general approach is to use Trust Rank or Spam Mass Estimates (with a suitable measure for selecting the good seeds, such as PoW weight) as the criteria for deciding the "good customers". Those who don't qualify will simply not be served for free.
User level
Here we consider a simple defense against DoS attacks on user DMs.
The user $v$ has a whitelist of npubs that can directly DM him/her for free. If the sender is not on the whitelist, the DM will only be displayed by the client if it is preceded by or comes with a payment above a certain threshold.
The whitelist can be edited manually, but it's automatically populated based on some social graph criteria that the user has approved.
For example, all npubs in N_G(v) U N_G^2(v) U N_G^3(v) can be automatically added to the whitelist of user v.

Personalized Ratings
The idea that every opinion or vote is equally important to everyone is a byproduct of political democracy and its sanctification. This is never the case in any social context.
Imagine you want to buy a product that has thousands of good reviews, but your friend recently bought it and tells you it's not good. It's natural for you to give more weight to your friend's opinion, contrary to the belief that each opinion has equal weight.
When computing an average, there is always an assumption about the weight distribution, i.e. how important each vote is.
Given a list of ratings (r_i)_i and a weight distribution (w_i)_i such that the sum of the weight is 1, the average is sum r_i w_i
The democratic average assumes each opinion has exactly the same weight.
Social graph analysis can be useful to design more accurate and even personalized ratings, i.e. ratings that reflect who the viewer is and what he/she is looking for at any given time.
For example, you might want to give more weight to people who have similar interests to you, or more weight to your friends and friends of your friends. Many different criteria for calculating weight distributions are possible, making this an exciting area for future research.
It's important to note that the most trustworthy ratings will be those that are independently verifiable, both in the ratings and in the weight distributions.
Practically speaking, there are two steps involved in computing a weight distribution:
- Select the support, i.e. the set of npubs that have a non-zero weight.
- Assigning a specific weight to each npub that is part of the support.
These two steps can be done simultaneously or one after the other. In the next section, we'll look at support selection, a problem that arises in another, seemingly unrelated context: social discovery.
Social Discovery
How many times have you discovered something thanks to a friend's recommendation? This phenomenon can actually be productized to streamline the discovery of content, places, and people that are relevant to the end user.
Here is a mathematical formulation of the problem:
Consider a social graph G = (V,E), where the nodes are ordered, i.e. V = { v_1, v_2, ... v_n}.
The goal is to construct another graph G' = (V,E'), where E' consists of the recommendations for each of the users we want to serve. This is a simplified scenario, where what is being recommended are other nodes in the graph.
What we need is a function f : G --> G' that takes G as input and returns G' as output, i.e. the recommendations we are interested in.
I'll now introduce a definition to simplify the problem.
Adjaciency matrix: Given a graph G = (V,E), its edges can be represented as a matrix called the adjacency matrix A, defined as follows:
A_ij = 1 if and only if v_i is related to v_j
In light of this new definition, the problem is to construct f : A --> A', which is a function that takes an n by n boolean matrix A as input and outputs the n by n recommendation matrix A'.
With this notation, the recommendation list of the node v_i consists of the nodes corresponding to the non-zero elements of the i-th row of A'.

Look at the example in the picture. By applying an unknown (for now) function f, we get the recommendation matrix A'. Only the first row contains a non-zero element whose position is (1,3). This means that node v_1 has node v_3 as a recommendation.
There are (2^{n^2})^{2^{n^2}} of such functions (exercise: why?), but only a few of them make sense and mimic the heuristics humans use.
The first social dynamic we want to replicate is the "friend of a friend" dynamic, or more specifically, if v_i _follows _v_j, and v_j follows v_k, then v_k is added to v_i's recommendation list.
In other words, we want A'_ij = 1 if and only if v_i is connected to _v_j _by a path of length exactly 2. In this case, we are not interested in how many such paths exist, but only in whether there is at least one.

This rule is encoded in the function f: A --> A' = A @ A = A^2, where @ is the product between Boolean matrices ( exercise: check that it's correct).
Inspired by this simple yet powerful result, previous research has investigated the class of candidate functions f_M: A --> A' = A @ M.
Here are some examples of such matrices M.

Applying each of these functions to f_M adds new relations to the graph, and this process can be repeated many times until the desired result is achieved.
For example, in the matrix A + A^2 + A^3 + ... + A^m, node v is connected to node u if and only if there exists a path of length <= m from v to u in the original graph G.
Formulating the problem of social discovery as an iteration of atomic propagation rules has many advantages, since:
- It's simple, yet can accommodate many different propagation rules
- It's passive, since it doesn't require the user to specify anything other than the rules and the number of iterations desired
- It's efficient, since its space complexity takes advantage of the sparsity of social graphs, and its time complexity can be estimated to be O(n^{5/2}) (Learn more about the time complexity of Boolean matrix multiplication ).
- It's well supported by most programming languages, given how ubiquitous matrix multiplication is
- It's transparent and independently verifiable in its operations
Furthermore, as highlighted in the previous section, this approach is applicable to compute transparent and personalized weight distributions.
Considering again the direct propagation rule (friend of a friend), we can start assigning weights based on the distance to the user.
If the distance is 1, meaning a direct connection, the weight is set to 1. Whenever the distance increases by 1, the weight decreases by a factor of gamma in [0,1], a parameter potentially chosen by the user.
On a practical level, this means that the service providers compute and store the matrices A, A^2, ... A^m for a reasonable m.
Each user v_i _can choose _gamma_i in [0,1], and k_i <= m, and the personalized weight distribution he/she gets is
A_i + gamma_i A^2_i + ... gamma_i^{k_i-1} A^{k_i}_i
with A_i representing the i-th row of the matrix A.
- If gamma_i = 0, the user chooses to consider the ratings of only those he follows as relevant.
- If gamma_i = 1 and k_i = m, the user chooses to give basically the same weight to everyone in the network, and will get a democratic average rating.
- If gamma_i = 0.5, then the weight of direct followers is 1, that of two hops is 0.5, then 0.25 and so on.
By combining and experimenting with propagation rules and weighting criteria, it's possible to efficiently compute personalized, verifiable and dynamic ratings for each user, making this an exciting area for future development.
Conclusion
This is a comprehensive yet superficial paper, as it touches on many different areas without exhausting any. This was done intentionally to stimulate interest in the field of social graph analysis. More importantly, it aims to help the reader understand the significant impact this exciting new field can have on the Web, although not without its risks.
Interested in implementing the social graph into your App? Reach out, I would be more than happy to help
For reading the article with proper Latex, head over to pippellia.com
-
 @ 3c984938:2ec11289
2024-06-07 11:14:17
@ 3c984938:2ec11289
2024-06-07 11:14:17The Chamorros: People of my island
They islanders for centuries took care of the island. They fished, farmed, hunted, voyaged, made tools, art, had stories, had marriages within clans. Then, the Spanish came. When they first came, the Chamorros boarded their boat to greet the weird people(I'm sure they thought they were weird too). It started peaceful until the Spaniards coffer's slowly dried up. This led to the occupation of the island and grew oppressive. Eventually, The Spanish lost the war to the Americans. Guam was then sold to the American gov't as spoils of war, trading one oppressive regime for another.
The TakeOver Process-1
The TakeOver Process-2
The TakeOver Process-3
Get a job, you lazy islanders. We need to tax you, come work for us. This was the price to become American to the indigenous islanders.
Then the war came.
close up
Guam was hit first before Pearl Harbor(The international Date line puts Guam timezone first ahead) but after this, The Japanese invaded and then occupied the island. Note at the bottom, The American Naval governor surrendered. This led to the islanders thus to become slaves to the Japanese Empire.
Recall "Day of Infamy" by FDR
Life under Japanese Rule Note Northern Marianas islands are the smaller islands above Guam. See the next image below.
Map of the island geography. Guam is referred as NYC in the Marianas. The rest are really, really small.

Nearly 16k of indigenous islander died, by the end of the war less than 6kish Chamorro survived.
The Federal Government then claimed parts of the land and since then and haven't returned it. They've returned some of it. This was a long time ago, I think it's time to let it go. Some islanders demand war repatriations. It makes zero sense to demand money from future Americans to pay for those war repatriations. The enemy is not the people, it's those that wield the pen to create unreasonable bills and the ones that enforce it.
Final Words. The islanders lived peaceful. There was no room to be a bad person of the colony because that person was risked getting shunned. Often, they sent the bad natives (thus becoming 2nd class citizens) inland, barring them from getting access to the ocean. But the land is rich and fertile. Instead of saltwater fish, they had fresh water 🐟fish, 🐍eel, 🦐shrimp and 🦞crawfish and plenty of fruit to eat and farm.
They didn't ask to become Spanish or American. It was this way or the highway. When countries want to expand they need more territories, land, money and human capital(your life energy). History doesn't repeat, it just rhymes.
🦋The best way to combat this is go back to a similar economy that is less corruptible. I believe Bitcoin can do this. History gives clues. Don't trust, verify.
Thank you for joining me on this walk (lol, reading) through the museum, please comment if you enjoyed this.
-
 @ 7361ca91:252fce6d
2024-06-02 18:21:36
@ 7361ca91:252fce6d
2024-06-02 18:21:36日本は貧しい。 どうして日本が貧しいと言えるのでしょうか?多くの点で豊かであることは確かです。例えば、一人当たりのGDPでは、日本は世界で38位で、平均の221%の富があります。また、日本を訪れた人は誰でも、その都市や活動、そして豊かさと幸福感を感じるでしょう。鹿が安全に歩き回る公園さえあります。さらに、文化的にも非常に豊かです。日本文化が嫌いな人はいないでしょう。日本は貧困ランキングでは多くの国よりもずっと上位にあります。そして、これらすべては、第二次世界大戦後の非常に厳しい状況から達成されたものであり、アメリカの要求に従うことによって実現しました。
それでは、なぜ日本が貧しいと言えるのでしょうか?それは、日本がアメリカの要求に従い始めた時点でのことです。日本の真の富が少ない状況を探ってみましょう。そして、その危機的な状況が他の国々にどのような信号を送っているか。この信号を読むことができれば、「Buy Bitcoin」と示していることがわかるでしょう。
日本の10年国債は先日5%下落し、金利は1.08%に達しました。あなたは言うかもしれません、「1.08%?それほど危険には見えない」と。しかし、この水準は10年以上達成されていなかったものであり、その間に日本は大いに借金を増やしました。日本は世界経済の主要な役割を果たしており、アメリカの国債を持つ第二位の保有国であり、その通貨は誰もが安く資金を調達するために利用します。つまり、円を買い、低い利息(約1%)で借りて、もっと高い利息が得られる他の場所に投資します。これらの理由から、日本は特に安い資金を見つけたい人々にとって非常に訪れる場所です。
しかし、もちろん、先日のように国債の金利が上昇すると、この取引に悪影響を及ぼします。10年国債の金利が上昇すれば、円で借りる金利と、他の場所で得られる金利との差が縮小します。例えば、アメリカやオーストラリアの国債、あるいは他の場所の国債です。これは確かに真実であり、国債の金利が上昇するたびにその魅力は減りますが、同時に国債の金利が上昇するたびに、負債のコストも大幅に増加します。
日本は多額の借金を抱えています:9.2兆ドルの負債です。負債の金利が0.01%上昇するたびに、それは920億ドルの利息が追加されることを意味します。
状況を想像してみてください。火曜日に日本は1.02%の金利を支払っていて、水曜日の終わりには1.08%を支払っています。これは途方もない衝撃を与えるでしょう。一度にすべてを再資金調達する必要はありませんが、それでも紙の上ではほぼ60億ドルの影響があります。再資金調達が昨日よりも60億ドル多くかかることを知っている一日を想像してみてください。その日は良い日ではなく、いくら寿司を食べて気分を上げようとしても無駄でしょう。そのため、通貨はドルに対して下落し続けます。
しかし、日本は豊かです。何十年もの間、日本は大量の魚やその他の製品を世界中に輸出してきました。日本はこれまでに得たすべての利益をうまく投資してきたに違いありません。そして、今、困難な時期が来て、日本の状況が微妙な時に、貯蓄を使って円を買い、通貨を守り、次の日に向けて戦い続けることができるでしょう。
日本はアメリカの言うことに従うようになりました。アメリカが大好きなのは、自分の国債を買ってもらうことです。アメリカ人が最も喜ぶのは、自分たちの債務を買ってもらうことです。アメリカ人に気に入られたいなら、国債を買ってあげるといいでしょう。日本は第二次世界大戦以来、アメリカに従順であり、基本的に外国為替の準備としての国債のアイデアを発明しました。これはどういう意味でしょうか?つまり、アメリカの国債に貯蓄するというアイデアを発明したのです。「お金を稼いで貯蓄するなら、他の国の国債や債務として持っておけばいい」という考えです。
全国民の努力と、世界中への商品やサービスの輸出によって得られたすべての貯蓄をアメリカの国債に投資し始めました。日本と他の国々の金の保有量を総準備高の割合で見ると、日本はそのうちのわずか4.3%しか金を保有していない一方で、ドイツ、アメリカ、イタリア、フランスなどの他の国々は60%以上の準備高を金で保有しています。
日本が貧しいと言うとき、それは実質的な富がないことを意味します。すべての貯蓄がアメリカの国債に投資されています。日本は、アメリカの都合に合わせて、そしてある程度は日本自身もそれが良い考えだと思って、これらの国債を購入してきました。日本には多くのアメリカ国債がありますが、今の危機を解決する役には立ちません。
日本は、その通貨の価値を守り、通貨の価値が下落するのを防ぎ、市民の生活費が上昇しないようにする必要があります。市場で円を購入するために、その貯蓄を使って準備金を売却し、通貨を保護するべきです。しかし、その準備金はアメリカの国債にあるため、それらを売ることは現実的ではありません。アメリカの国債を売ると、その価格が下がり、市場での供給が増えて、国債の金利が上昇します。国債の価格が下がるほど、支払う金利は高くなります。
たとえば、100の価格で5%の利息を支払う国債を持っているとします。その国債が市場で売られ始めて価格が95に下がった場合、依然として5%の利息を支払います。しかし、95に対する5%は、100に対する5%よりも多いです。したがって、国債の価格が下がるたびに、利息が上がります。これにより、さらに多くの人々が日本に行き、低利で円を借りて(少ない利息を支払って)、高利を支払うアメリカの国債を購入することを奨励します。これが通貨をさらに下落させることになります。そのため、日本の準備金は役に立ちません。アメリカの国債を売却することなく、自国の通貨の価値をさらに低下させることはできません。このような困難な時期に日本を救うはずのものが、何の役にも立たないのです。
その結果、日本は多くの貯蓄があっても抜け出せない悪循環に陥っています。状況の深刻さは、円と金のチャートを見るとよくわかります。本来なら多くの馬鹿な国債の代わりに準備資産として購入すべきだったものです。円と金のチャートを見ると、過去15年で75%も下落していることがわかります。「日本は貧しい」と言うとき、それは実質的な富が欠如しているという意味で、この貧困は他の分野にも現れ始めています。通貨の価値を守ることができないことが、日本の成長と市民の生産能力を阻害しています。
日本は1人当たりのGDPが高いため、貧しくはないと言いました。しかし、1人当たりのGDPを見てみると、1990年以来停滞しています。また、実質的な貧困のレベルを見ると、日本の実質的な貧困が増加しており、間違った方向に進んでいることがわかります。日本の相対的貧困率は、G7諸国の中でアメリカに次いで2番目に高いです。
要するに、誰の負債でもなく、必要なときに売ることができる資産がなければ、富を持っているとは言えません。困難な時期に対応するために売却できる、他人の債務に依存しない資産が必要です。それが富であり、他のすべてはただの煙に過ぎません。
数年前、ロシアはアメリカの国債ではなく、自国の貯蓄を失いました。アメリカがそれらの債券を没収したのです。今日の日本も同様に、国債を持っていますが、売却することができず、実質的には役に立ちません。まるでそれが奪われたかのようです。これらの状況は、非常に明るくカラフルなネオンサインのように、国であれば固い資産に貯蓄するべきだという明確なシグナルです。
そのため、最近ではすべての中央銀行が記録的なレベルで金を購入しているのでしょう。そして、同様にビットコインも購入することになるでしょう。ビットコインは、金よりも没収されにくく、金よりも移動が容易で、金よりも価値が上昇する可能性が高いという追加の利点を持っています。日本は、これを今、教えてくれているのです。
コラボw @alberto_mera (X、文)& nostr:npub1wdsu4yfj6s5vkcktfx2l7y9tvprfsmwp55e2gj5xp266gff0eeks9cjda5 (Nostr、訳)
-
 @ 4bc7982c:4cb5c39d
2024-06-02 18:11:10
@ 4bc7982c:4cb5c39d
2024-06-02 18:11:10I rarely use smartphones for their intended purpose, instead using them as cheap and portable "mini machines" thanks to termux. Since joining nostr and learning how relays work, I got to wondering if running a relay from my test phone would be possible. After many hours of failed attempts and chairs thrown through windows, here's how I finally got python nostr_relay to work on my device.
YOU WILL NEED - An android device with latest Termux from FDROID OR GITHUB (The Google Play version will not work). You will need python 3.x,clang, and git installed in this environment.
Step 1. Start sshd in termux and log into your device.
Step 2. User must modify their python sysconfigdata manually, since the Android NDK with latest clang does not support the -fopenmp-implicit-rpath flag and will cause any .toml based python wheel builds to fail. Simply run the following commands in your termux terminal to fix this (A backup up your original sysconfig files will be saved, this example shows the steps being performed for python 3.11):
_file="$(find $PREFIX/lib/python3.11 -name "_sysconfigdata*.py")"
rm -rf $PREFIX/lib/python3.11/pycache
cp $_file "$_file".backup
sed -i 's|-fno-openmp-implicit-rpath||g' "$_file"Step 3. Make a directory for the install and switch to it, I am using "devel" in this example:
mkdir -p devel && cd $_
Step 4. Clone the nostr_relay repo, I have mirrored the latest version to Github for those that hate fossil as much as I do:
git clone https://github.com/Shinoa-Fores/nostr_relay.git
Step 5. Make a python virtual environment and activate it:
python3.11 -m venv nostr_relay
cd nostr_relay
source bin/activateStep 6. Pycares is a required dependency for toml-based projects, and also will not install properly via pip under termux so we will install it from sources in the venv and apply a quick fix to that too:
wget https://files.pythonhosted.org/packages/1b/8f/daf60bbc06f4a3cd1cfb0ab807057151287df6f5c78f2e0d298acc9193ac/pycares-4.4.0.tar.gz
tar -xf pycares-4.4.0.tar.gz
sed -i s/'#define HAVE_GETSERVBYPORT_R 1'//g ./pycares-4.4.0/deps/build-config/config_android/ares_config.h
pip install ./pycares-4.4.0
rm -rf pycares-4.4.0 pycares-4.4.0.tar.gzStep 7. Now install the remaining dependencies and nostr-Relay itself:
pip install -e .
Step 8. Make a cup of tea and shitpost on nostr until the build completes.
Step 9. Once build is finished, copy the included sample config and open in your preferred text editor to adjust the parameters to your liking:
cp nostr_relay/config.yaml .
Step 10. Make a startup script for the relay and fire up your portable relay. In the example below I start it in a screen session so the process does not die if I lose ssh or termux connection.
cat >start-relay.sh << EOF
!/usr/bin/env bash
set -eu
set -o pipefail
bin/nostr-relay -c ./config.yaml serve
EOFchmod +x start-relay.sh
screen -S relay -dm bash ./start-relay.sh
Step 11. If all goes well you should see something like this:
Still here? Good! The reader is invited to tinker with this configuration and enhance it. Things like setting up DNS and tor are beyond the scope of this post, but information on the latter can be found on the termux wiki: https://wiki.termux.com/wiki/Bypassing_NAT .
-
 @ 1f9e547c:8af216ed
2024-07-13 07:37:05
@ 1f9e547c:8af216ed
2024-07-13 07:37:05Opinion about Bitcoin Wallet Crypto Ethereum (android)
For archival purposes
Atomic Wallet suffers hack on June 2023
Sources
Atomic Wallet users have been left wanting more answers, despite the decentralized wallet provider finally releasing a full “event statement” about the June exploit — which some estimate has run up to $100 million in losses.
In a June 20 blog post — the first major update from the firm since the June 3 exploit — Atomic Wallet claimed there have been no new confirmed cases after initial reports of the hack.
Atomic Wallet Was Breached by North Korean Hackers: Elliptic
Atomic Wallet users might have fallen victim to Lazarus, the infamous North Korean hacking group, said blockchain intelligence firm Elliptic in a blog post on Tuesday.
Early Saturday morning, the team behind Atomic, a non-custodial crypto wallet, announced that some users were compromised and lost the funds from their wallets. According to the company, the number of incidents did not exceed 1% of "monthly active users." The announcement followed multiple reports on Reddit from users complaining their wallets had been drained.
WalletScrutiny #nostrOpinion
-
 @ a30cdfee:2d2f97ff
2024-06-01 17:47:43
@ a30cdfee:2d2f97ff
2024-06-01 17:47:43Nostr: Decentralized Identity for the Internet
Nostr is a protocol enabling censorship-resistant social media.
Bring your audience seamlessly from one app to another.
And earn bitcoin for the content you create!
Why Do We Need Nostr?
Because.. social media is broken. Centralized oligopolies control the public square of free speech. These companies control (often in ways they don't even understand) what we read, who we talk to, and what ideas gain traction in our culture.
Social media as we mostly know it today:
⚠️ uses your attention to sell ads
⚠️ uses psychological tricks to keep you addicted
⚠️ decides what content to show you based on a secret profit algorithm you can't inspect
⚠️ can ban you
⚠️ is filled with bots and spam
Traditional social media thrives on engagement, attention and outrage. This has had negative effects on society. Trust in media (and institutions) has plummeted, and people are increasingly valuing free speech, something which centralized platforms can't provide.
What is Nostr?
Nostr (Notes and Other Stuff Transmitted by Relays) fixes this! It's a simple protocol that allows users to sign and share notes (passed around as plain JSON text).
Using websockets, a client software relays these notes to a distributed set of servers (relays). Or to define Nostr even more simply: "Signed messages relayed".
Clients, Relays, Public/Private Key Pairs
Nostr is a protocol that you access via a client. A client can be a web, mobile, or desktop app. Some popular clients are e.g. nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg and nostr:npub18m76awca3y37hkvuneavuw6pjj4525fw90necxmadrvjg0sdy6qsngq955 .
Users have cryptographic key pairs (public and private key) to sign notes and to verify a note source. The public key is presented as a string with a prefix "npub", and the private key with a prefix "nsec". You can also think of your "npub" as a username and "nsec" as a password.
But on Nostr, there is no tech support to recover your password, so you have to take good care of it either with a password manager, browser extension such as e.g. nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm or write it down on a piece of paper.
"Npub" looks like this and you can follow users on Nostr on any client by searching for their npub:
"npub15vxdlmhftkh452a06vnr3mmks2dy8hqejeuxuv6sgy5rgtf0jllsccfzg7"
You can also search users by a more readable "NIP-05 identifier", such as "teemupleb_at_getalby.com"
For a step-by-step guide on how to create an account on Nostr, you can watch this tutorial by nostr:npub1rxysxnjkhrmqd3ey73dp9n5y5yvyzcs64acc9g0k2epcpwwyya4spvhnp8 .
Permissionless, Interoperable and Open-Source
Using Nostr and building on it is completely permissionless. No need to provide phone number, email, ID card etc.
Cool thing about Nostr is that your private key (and your audience) follows you from one client to another. E.g. if you have built a large following on a microblogging client built on Nostr, you can bring that following to the new video streaming client that just launched.
Nostr is not an app that you sign up for, but an open standard on which anybody can build! This takes the power of "walled gardens" away from centralized web behemoths! Also devs can access an existing user base easier in order to bootstrap new apps.
Relays Receive and Send Data
Relays are like back-end servers for Nostr. They allow Nostr clients to send them messages, and then broadcast those messages to all other connected clients.
Relays are very simple and "dumb". Their only job is to receive and send Nostr data. For this reason, you can easily run your own relay with e.g. a Raspberry Pi single-board computer (but of course, you don't have to run your own relay to use Nostr).
Relays don't have to be trusted. Signatures are verified on the client side. Because Nostr doesn't rely on a small number of trusted servers to relay data, it's very resilient. The protocol assumes that relays will disappear and allows users to connect to multiple relays that they can change over time. If you notice that your Nostr client feels slow, try adding more relays.
Notes
Notes can be text, links and other media types. They are digitally signed and timestamped. You can also like, repost, reply etc.
There is no character limit on notes or replies, but if you upload videos, there might be limits (then you can just host the video somewhere else and link to it on Nostr). Notes can't be edited (encourages accountability!)
NIPs for Interoperability
The Nostr protocol is defined in a set of NIPs (Nostr Implementation Possibilities). These standards allow different clients to communicate with each other. Only NIP-01 is mandatory (describes the basic protocol), and others are optional.
NIPs exist to promote interoperability. It's not a good idea for developers to implement ideas only in their own client app. It's better to come up with compatible solutions, and NIPs coordinate this process.
Bitcoin Lightning Network to Monetize Content
Nostr uses Bitcoin's Lightning Network to monetize content value. Users can instantly tip (zap) small micropayments in bitcoin to creators, and their npub works as a Lightning address.
Great idea: let's pay with sats instead than with our personal data and attention!
This value4value model is a revolutionary concept. Creators don't have to rely on advertising, subscriptions and paywalls, and followers can only pay for the content they like. Most followers won't tip anything, but some tip a little and the hardest fans tip a lot.
For the first time in history, we can link information to value. As the volume of information becomes infinite, the supply of bitcoin (value) remains scarce. Attaching this value to information will highlight the highest quality information (web of trust).
Nostr + Bitcoin search engine that indexes all information on a decentralized internet could be a real Google killer.
nostr:npub1sx9rnd03vs34lp39fvfv5krwlnxpl90f3dzuk8y3cuwutk2gdhdqjz6g8m is trying to do something along those lines, indexing the entirety of Nostr and making it searchable.
https://twitter.com/MaxAWebster/status/1614003577730760704
Nostr infrastructure providers can also monetize their services via Lightning payments. When Nostr gets more users, relays may have to scale up their infra and charge clients for usage (worry not, there would most likely still be free relays and clients for the end user).
Orange Honeybadger and Purple Ostrich
Nostr doesn't need Bitcoin, and Bitcoin doesn't need Nostr. They're completely independent protocols. However, each one makes the other one better.
Bitcoin decentralizes money, and Nostr decentralizes free speech. With Nostr npub as a Lightning address, Nostr can become a directory for Lightning payments.
The creator of Nostr, nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 and many early Nostr developers are also Lightning developers, which seems to make the synergistic relationship inevitable.
Bitcoin Lightning payments could be integrated to ANY app with nostr:npub19hg5pj5qmd3teumh6ld7drfz49d65sw3n3d5jud8sgz27avkq5dqm7yv9p . Once an app connection is created, the app can request bitcoin payments through a Nostr relay! 🤯 Open-source and non-custodial!
With Nostr, all messages and commerce could be done in an open-source and self-custodial super app. Send remittances as an instant message! Sell goods via a tweet!
Crowdsourced Content Moderation?
What about content moderation? All humans should have the right to free speech, but no one should be obliged to listen.
Nostr relays can ban users, but these users can always find another relay to publish, or host their own. Since users are identified by their public key, they don't lose their followers if they get banned from a relay.
Bitcoin tips can also work as a crowdsourced content moderation tool. If a wide majority of users think that e.g. posting some images is unacceptable, maybe users wouldn't even see those posts because the web of trust doesn't grant them any tips.
Lacking Privacy Features
The downside of Nostr currently is the lack of privacy features. DMs on Nostr are encrypted, but the metadata (who you DM with and when) is public. This obviously currently hinders the prospect of secure bitcoin payments on apps using Nostr.
Also, relays and clients can collect users' IP addresses. The intention of this feature was to tackle spammers and bots (if enough spammy data comes from a single IP address, that address can be blocked.) Maybe best to normalize using VPN with Nostr?
Not Just Social Media
Decentralized social media is just the first instance: there are many Nostr-based competitors to established web2 corporate platforms: Twitch-alternative, GitHub-alternative, Meetup-alternative.. even a P2P bitcoin exchange nostr:npub1m0str0d7z2ww8rdh20t2n9lx520xjwhaq24p68umqp06wwrwtsnqen40un!
X (Twitter) could also benefit from becoming a Nostr client. It could partially solve the content moderation problems it is having:
→ If the user-generated content was on Nostr, maybe X wouldn't have to resort to censorship when facing government pressure?
Easy for Developers
Are you a developer? Starting out with Nostr is easy. Any junior dev can build a functioning simple client in a couple of hours.
Here's a great website called Nostr Apps to discover the world of Nostr:
What do you think about Nostr?
Will it replace the internet as we know it today?
Additional Resources
nostr - Notes and Other Stuff Transmitted by Relays by Nostr's Creator fiatjaf nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6
A 2-Minute Video Introduction to Nostr by LNbits
Why I'm Betting Big on Nostr by Max Webster from Hivemind Ventures nostr:npub18lzls4f6h46n43revlzvg6x06z8geww7uudhncfdttdtypduqnfsagugm3
Why Nostr Matters by Jameson Lopp nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp
The NOSTR Protocol: Social Media 3.0 by Jessica Chasteen nostr:npub1r8wdfruydenz84fxfespcswuhcvyatx6umtd5xguexup49u500xskf50hn
Nostr Resources by Dollar Parity
Project Information
-
 @ 577781c0:fdc71ebd
2024-06-01 17:26:52
@ 577781c0:fdc71ebd
2024-06-01 17:26:52Often something like "get outside and touch grass" is posted online encouraging folks to, well, get outside, get offline, touch nature, and live. Essentially, it's a shortened version of Thoreau's Walden.
 Henry David Thoreau on touching grass.
Henry David Thoreau on touching grass.Source: https://forestnation.com/blog/transcendentalist-walk-woods-ecology-lesson-plan/ and the broader quote from https://www.goodreads.com/quotes/2690-i-went-to-the-woods-because-i-wished-to-live:
“I went to the woods because I wished to live deliberately, to front only the essential facts of life, and see if I could not learn what it had to teach, and not, when I came to die, discover that I had not lived. I did not wish to live what was not life, living is so dear; nor did I wish to practise resignation, unless it was quite necessary. I wanted to live deep and suck out all the marrow of life, to live so sturdily and Spartan-like as to put to rout all that was not life, to cut a broad swath and shave close, to drive life into a corner, and reduce it to its lowest terms...”
Anyway, this is essentially what my wife and I did yesterday. We loaded the kayaks, drove, got a little lost, got found, launched, paddled, found a remote spot, picnicked. Skinny dipping was considered, but that is unconfirmed.




-
 @ 0f1b5961:868242bd
2024-05-31 14:26:24
@ 0f1b5961:868242bd
2024-05-31 14:26:24Ever since reading Darwin's Origin of Species a couple years ago, one part of the book has always stuck with me. In the seventh chapter, Instinct, Darwin says that certain species of ants appeared "fatal" to his entire theory. Here is a longer quote from the section:
I will ... here ... confine myself to one special difficulty, which at first appeared to me insuperable, and actually fatal to my whole theory. ...neuters or sterile females in insect-communities: for these neuters often differ widely in instinct and in structure from both the males and fertile females, and yet, from being sterile, they cannot propagate their kind. — Origin of Species, Chapter VII, Page 236
The idea that all of the genetic information of these sterile ants had to be passed along, but not expressed, by the breeding males and females was a difficult challenge. Darwin had been focusing on natural selection at the level of the individual organism, but a sterile ant has exactly zero fitness when analyzed at this level. As an individual organism, it can't pass on its genes!
This led Darwin to expand his concept of natural selection in the following way:
This difficulty, though appearing insuperable, is lessened, or, as I believe, disappears, when it is remembered that selection may be applied to the family, as well as to the individual, and may thus gain the desired end. — Origin of Species, Chapter VII, Page 237
I think this example really stuck with me because it represents one of the main biases of the conventional Darwinian approach. It seems like the more intuitive a form of natural selection is the more its power is overestimated. Darwin was overcommitted to natural selection at the level of the individual organism and didn’t really consider selection at the level of the family until forced by a real world example.
I said “intuitive” forms of natural selection are overestimated, but I think these could also be described as “low order”, “tangible”, “concrete”, or “basic”. It’s part and parcel with the dawning insight that the enlightenment project overcommitted to bottom-up explanations and neglected top-down ones.
I think this is important because we stand at a moment where the popularized mathematical explanations of how life develops are breaking down. It becoming clear that life has the ability to move through the combinatorial genetic space staggeringly fast in a way that simply must deny a blind search through random mutation.
Perhaps a top-down natural selection can cover some of the distance present by this obstacle that is coming into focus.
-
 @ 0861144c:e68a1caf
2024-05-31 13:02:40
@ 0861144c:e68a1caf
2024-05-31 13:02:40Lot of debates has been surrounding the Donald Trump veredict and how can affect our markets a decision of one running president[^1] who support openly cryptocurrencies in general and my friends...the answer is the same we give each time these kind of topic is opened:
Bitcoin is for me Bitcoin is for my family Bitcoin is for my friends Bitcoin is for terrorists Bitcoin is for help Gaza citizens Bitcoin is for Israel Bitcoin is for my enemies
Why?
- Bitcoin is for me, it helps my economy and prevents that inflation come and eat all my savings. As a said in other posts, I don't invest but save money with bitcoin. It's the best.
- Bitcoin is for my family, I teach them about hard money and the inflation. It's an ongoing work and I want the security I have with bitcoin for theirs.
- Bitcoin is for my friends, each time they approach to me asking me the basic stuff of crypto, I ask them not to see rainbows and fall in the charm of buzzwords; I don't have control over their actions but I try my best with them.
- Bitcoin is for terrorists...well, what your government call terrorism. Imagine being arrested for money laundering, imagine you're helping terrorism because you...write code.
- Bitcoin is for all Gaza citizens who needs your help, people suffering and right now a piece of hope in form of sats comes handy.
- Bitcoin is for Israel, who is struggling since always their right to have a piece of land[^2] and fought inflation in the past.
- Bitcoin is for my enemies, for the Lazarus Group and Donald Trump[^3]
Oh, you don't like that way? Well my dear friend, the exit is called fiat money, supported by high centralized moral standards.
[^1]: I'm not too much political guy but I think he'll win, I'll bet later on that with my sats. Democracy is overrated :) [^2]: I know you don't like what you're reading, I smell it from here [^3]: Did you consider it that, from now on, he's a criminal using bitcoin? It's funny now that I'm writing. BTW, I consider Trump a threat to democracy but hey!...that's the beauty of the systerm, you can disagree.
-
 @ 4c96d763:80c3ee30
2024-05-31 07:05:51
@ 4c96d763:80c3ee30
2024-05-31 07:05:51Here's a quick script for generating git shortlog longform notes on git push. It currently powers the Damus Code nostr account:
Let's say you are hosting a bare git repository on a server at
git/project. You can add apost-receivehook that generates a longform note when you push to the server:In
server:git/project/hooks/post-receive:```bash
!/usr/bin/env bash
commit_body="" last="" project="my-project" # update this with your project name sec="abcdef..." # update this with your secret key branch="master"
while read oldrev newrev refname; do branch=$refname last=$newrev relays="wss://relay.damus.io wss://nos.lol" commit_body=$(git shortlog $oldrev..$newrev | awk -f /home/user/markdown-shortlog.awk) done
if [[ $branch == "refs/heads/master" ]]; then
nostril --content "# Changes
$commit_body" \ --envelope \ --kind 30023 \ --tag title "$project" \ --tag summary "Latest codebase changes to $project" \ --tag t gitlog \ --sec $sec \ | nostcat --connect-timeout 1000 $relays fi ```
you'll need nostril, nostcat, and
markdown-shortlog.awk:```awk /^[^ ]/ { if (author) { print "" } author = $0 print "## " author }
/^ / { print "-" substr($0, 6) } ```
Now when you push, it will generate a longform note that looks something like this:
Example
William Casarin (10):
- fix warnings
- readme: add usage
- textmode: fix coloring of abbreviated names
- profiling: update puffin version
- refactor: move note into its own widget
- refactor: rename widgets to ui
- ui: simplify note widget
- get all missing ids from all timelines
- initial inline note previews
- fix until filters
kernelkind (6):
- Add custom visual themes
- Add modular custom text styles
- Apply app style to AccountLoginView
- Add MobileAccountLoginView
- Refactor 'ui tests' conception to previews
- Use custom style in app
-
 @ b804f68e:2fb0fa1f
2024-05-31 06:34:02
@ b804f68e:2fb0fa1f
2024-05-31 06:34:02The main reason you struggle to stop something you "know" is bad for you, or to continue something you "know" is good for you, is because you don't actually know. True knowledge goes beyond hearing it once, reading it somewhere, or being told it’s good or bad.
I used to be a sucker for sweet things. Luckily, my mom limited my access to sugary snacks when I was young. But as I grew older, I made up for lost time, indulging in sweets, particularly Japanese sodas. In England, I snacked on English sweets all the time. Oh, and those energy drink sodas called Lucozade—I was a complete sucker for them. I had so many that I ended up winning a Lucozade hoodie. Yeah I know, it was bad!
Even then, as an athlete, I thought, "I know it's bad for me, but I work out all the time, so it balances out, right?" Wrong!
Fast forward almost a decade, and I’m much fitter, stronger, and healthier than I was at 18. The difference? I took the time to learn, apply, and understand the actual knowledge about things labeled as good or bad for you. With sugar, once I understood what it is and why it could harm my body and brain, it was easier to lay off it. Now, I only eat sweets knowing the potential cons or I might consume sugar when I need immediate energy or to replenish my glycogen stores.
This approach applies to carbs as well, since sugars are a form of carbohydrate. Carbs consist of glucose, a monosaccharide that our body uses for energy. Sucrose, or table sugar, is a disaccharide composed of glucose and fructose. Glucose can be used immediately for energy but can cause harm if it stays in the bloodstream too long. High blood sugar levels can lead to insulin resistance and diabetes. Table sugar is often considered worse because fructose can only be metabolized by the liver, potentially causing issues like non-alcoholic fatty liver disease. Given our high sugar consumption today, it's easy to overdo it. Understanding why sugar is bad has turned me off from drinking soda completely, and I probably won't touch one again.
The same principle applies to maintaining good habits. You need to understand why something is good for you to find purpose and direction. I heard cold showers were beneficial, so I tried them. But without understanding their benefits, I lacked consistency. Once I learned and understood their purpose, I became consistent. Now, my body and brain know the benefits, urging me to take cold showers.
If you struggle to quit a bad habit or maintain a good one, it's because you just don't know. You might think you know it’s good or bad for you, but in reality you don't truly understand and that ultimately shows in your inability to stay consistent.
The great news though is that if I can do it, then absolutely so can you, and you, and even you! Choose one thing that you've been struggling to quit or wanting to start, and take the time to learn about it. The reason why Stackers are consistent with stacking sats is because we've all done our due diligence to learn about Bitcoin, about the fiat system, and about all the other subjects that we come across in the rabbit hole journey. Same goes with developing healthy habits and kicking bad ones to the curb for good, we have to know exactly why we are doing it.
Knowledge is power.
-
 @ b804f68e:2fb0fa1f
2024-05-29 21:55:36
@ b804f68e:2fb0fa1f
2024-05-29 21:55:36This thought came to me while a YouTube ad of Tony Robbins abruptly interrupted a video I was watching. I skipped past the ad, but from the 5 seconds I was forced to watch, it seemed like Robbins was about to pitch his course on how to escape the 9 to 5 grind at the low cost of whatever.99! This got me thinking: this is the new product of an "ideal life" we are being sold. The previous version of the "ideal life"—the good old 9 to 5 with degrees, promises of a stable income, a house, a nice car, a family, and retirement—isn't as fashionable or in demand as it once was.
Instead, the new and improved version is to buy into products that promise to teach you how to be "financially free," "how to work wherever you want, whenever you want," "how to invest so your money works for you instead of you working for it," and so on. The product list and possibilities of advertisement are as plentiful as there are influencers.
I'm not saying this to mock those who refuse to settle for a 9 to 5, because I, too, don't see myself settling for the conventional 9 to 5. On the flip side, I know plenty of people who have found success, fulfillment, and meaning in life going the 9 to 5 route. I'm just expressing an observation: the life path we choose may come down more to conditioning and being sold an artificial representation of a happy life than to a conscious choice made from free will.
-
 @ 502ab02a:a2860397
2024-07-13 02:14:11
@ 502ab02a:a2860397
2024-07-13 02:14:11Anna Britt Agnsäter ผู้อุทิศชีวิตให้โภชนาการ แต่โดนโลกบูลลีเพราะอเมริกา?
โลกรับรู้ว่า คุณ Anna Britt Agnsäter (ขอเรียกสั้นๆว่า ป้าแอน) เป็นผู้ที่นำเสนอ ปิรามิดอาหาร คนแรกของโลก และเป็นแบบจำลองที่ทาง USDA นำไปพัฒนาปรับใช้แล้วนำมาเป็น แบบที่ใช้สื่อสารกับคนทั้งโลก ในเรื่องของการกำหนด ประเภทอาหารที่ควรกิน ในช่วงปี 1992-2005 ซึ่งในบทความที่แล้วผมได้เขียนว่า ปิรามิดเวอร์ชั่นที่ป้าแอนคิด กับ ที่อเมริกาเอาไปปรับใช้เป็นคนละตัวกัน แต่โลกทั้งโลกก็บูลลีป้าเอนว่า เป็นสาเหตุของการทำลายสุขภาพคนทั้งโลก ทั้งๆที่ไม่ได้เป็นนักวิทยาศาสตร์ ผมก็เป็นคนนึงที่เคยคิดแบบนั้นครับ และเคยอุทานในใจเบาๆว่า แกเป็นใครนะทำไมถึงนำเสนออะไรแบบนี้มาทำร้ายคนทั้งโลก???
นานวันเข้า ความคิดอีกฝั่งของผมก็บอกมาว่า ประโยคข้างบนเป็นคำบ่นหรือคำถาม
นั่นสิ!!!!! ถ้ามันเป็นคำถาม มันจะทำให้เราได้รู้จักตัวตนป้าแอนและเข้าใจว่าแกได้ทำอะไรลงไปนะ มันควรเป็นคำถามมากกว่าคำบ่น นั่นเลยเป็นเหตุผลที่ทำให้ผมเริ่มขุดเรื่องป้าแอน Anna Britt Agnsäter มากที่สุดเท่าที่จะทำได้ พร้อมที่จะอ่านกันแล้วใช่ไหมครับ
Anna Britt Agnsäter เกิดเมื่อปี 1915 ที่เมือง Älmhult ประเทศสวีเดน (นอกเรื่องนิดนึง เมืองนี้คือเมืองที่ให้กำเนิด IKEA ที่เรารู้จักกันดีเรื่องเฟอร์นิเจอร์ ที่นี่มีพิพิธภัณฑ์อิเกีย ซึ่งปรับปรุงมาจากโกดังแห่งแรกของเขาด้วยครับ) เรียกได้ว่า เกิดในช่วงสงครามโลกครั้งที่1 พอดีเลยครับ
ป้าแอน จบการศึกษาที่โรงเรียนสตรี ในเมือง Ystad ก่อนจะเข้ารับการฝึกสอนเพื่อเป็นครูสอนวิทยาศาสตร์ในครัวเรือน (rural domestic science teacher) ในช่วงปี 1930 ที่โรงเรียนวิทยาศาสตร์ในครัวเรือนในชนบทชื่อว่า Rimforsa ก่อนจะได้รับวุฒิการศึกษาการสอนวิทยาศาสตร์ในครัวเรือนในชนบทในปี 1939 จาก Kvinnliga medborgarskola (civic women’s school) จนกระทั่ง ปี 1943 ถึง 1945 เธอได้เดินทางไปทั่ว Norrland (พื้นที่ภาคเหนือของสวีเดน) โดยได้รับเงินสนับสนุนจาก Kooperativa Förbund (เรียกสั้นๆว่า KF หรือ สมาคมสหกรณ์ ก่อตั้งขึ้นในปี 1899 โดยสหกรณ์ผู้บริโภคในท้องถิ่น 41 แห่ง เป็นผู้นำด้านการค้าปลีกในสวีเดนโดยพัฒนารูปแบบร้านค้าใหม่และใหญ่ขึ้น และเป็นหนึ่งในกลุ่มธุรกิจหลักในสแกนดิเนเวีย ในสมัยนี้คำว่าสหกรณ์อาจจะดูเชยๆ แต่ต้องเข้าใจครับว่ายุคนั้นคือความก้าวหน้ามากๆ และต้องมีความรู้รอบด้านทั้งวิทยาศาสตร์ เศรษฐกิจ การเมือง) เพื่อบรรยายให้คนหนุ่มสาวและแม่บ้านฟังเกี่ยวกับวิธีรับมือกับเสบียงที่มีจำกัดในช่วงสงครามที่ตึงเครียด เนื่องจากอยู่ในภาวะสงครามโลกครั้งที่2

ในปี 1946 ป้าแอนได้รับการแต่งตั้งเป็นหัวหน้าของSwedish Cooperative Union หรือ Kooperativa Förbundets (KF) Provkök (experimental kitchen หรือ ภาษาสมัยนี้น่าจะใกล้เคียงกับ kitchen lab นั่นเอง) ซึ่งเป็นองค์กรที่มีอิทธิพลทางด้านอาหารเป็นอย่างมากในสวีเดน มีบทบาทสำคัญในเศรษฐกิจและสังคมสวีเดน โดยสร้างโอกาสให้แก่สมาชิกและส่งเสริมการพัฒนาที่ยั่งยืนในชุมชนต่าง ๆ ทั่วประเทศ
ป้าแอนทำงานที่นี่นานจนถึงช่วงปี 1980 ขนาดของ KF ก็ใหญ่โตขึ้นมากมาย จนขยายอำนาจและขอบเขตการทำงานไปถึงการเป็นคณะกรรมการทดสอบรสชาติซึ่งทดสอบอาหารกึ่งสำเร็จรูปและอาหารสำเร็จรูปใหม่ด้วย ในจุดนี้ ป้าแอน เล็งเห็นความสำคัญและความรับผิดชอบของผู้ผลิต/ผู้ค้าอาหาร ควรจะขยายความรับผิดชอบครอบคลุมไปจนถึงโต๊ะอาหาร (ในที่นี่น่าจะหมายถึงลูกค้า) นั่นคือเหตุผลที่การติดฉลากอาหารจึงมีความสำคัญมาก ป้าแอนได้มุ่งเน้นให้ความรู้กับผู้บริโภคว่า ‘Weigh up the price against the quality’ หรือ ให้ชั่งน้ำหนักพิจารณาให้ดี ระหว่างราคากับคุณภาพ ตลอดระยะเวลาการทำงาน Anna-Britt Agnsäter ได้รณรงค์เพื่อให้มีการแสดงข้อมูล ให้ผู้บริโภครับทราบ เพื่อคุณภาพชีวิตที่ดีขึ้นและได้ให้คำแนะนำด้านโภชนาการ เพื่อให้เข้าใจได้ง่ายขึ้น ในรูปแบบฉลากโภชนาการ
ในปี 1946 เช่นกันป้าแอนได้มีแผนในการทำ มีแผนที่จะผลิตหนังสือสอนทำอาหารสำหรับสถานการณ์ฉุกเฉิน เพราะบทเรียนในภาวะสงครามโลก ที่ป้าแอนผ่านมาตลอด แต่ไม่สามารถพิมพ์ออกมาได้เนื่องจากกระดาษขาดแคลนเนื่องจากอยู่ในภาวะหลังสงคราม
ในปี 1948-1949 ป้าแอนเดินทางไปอเมริกา เพื่อศึกษาเทคนิคการทำอาหารใหม่ๆ การผลิตภัณฑ์อาหารแช่แข็ง รวมถึงอาหารผงแห้งต่างๆ (dry powder) รวมไปถึงวิทยาศาสตร์การอาหาร (food science) ที่มหาวิทยาลัย Iowa State University การเดินทางมาอเมริกาครั้งนี้เปลี่ยนโลกของป้าแอนเป็นอย่างมาก ในตอนที่ป้าทำงานกับ KF เธอมักจะร่วมงานกับ Hemmens Forskningsinstitut (สถาบันวิจัยในประเทศ) เพื่อจัดหาเครื่องมือในครัวที่ยกระดับมาตรฐานการทำอาหารที่ดียิ่งขึ้น รวมถึงอุปกรณ์การครัว ภาชนะต่างๆที่เข้าเตาอบได้ และจากประสบการณ์ที่อเมริกานี้
ป้าแอนได้จับมือกับ โรงงานเครื่องเคลือบและพลาสติก Gustavsberg และ HFI Anna-Britt Agnsäter พัฒนาช้อนตวง ชุด4ชิ้น ที่วางซ้อนกันได้ ซึ่งเป็นการปฎิวัติวงการอาหารครั้งสำคัญของสวีเดน เรียกว่า “ชุดช้อนตวงมาตรฐาน” ซึ่งจะมีการระบุขนาดที่ชัดเจน 4 ชิ้น ประกอบไปด้วย

ซึ่งทำให้ผู้ใช้สามารถวัดปริมาณวัตถุดิบได้อย่างถูกต้องตามที่สูตรอาหารกำหนด กลายเป็นเครื่องมือที่จำเป็นในครัวเรือนและการประกอบอาหารในเชิงพาณิชย์
แม้การพัฒนา “ชุดช้อนตวงมาตรฐาน” นี้จะเริ่มต้นในสวีเดน แต่นวัตกรรมนี้มีผลกระทบที่กว้างขวางและแพร่หลายไปยังครัวเรือนและอุตสาหกรรมอาหารทั่วโลกจนถึงปัจจุบัน


ในชุดช้อนตวงมาตรฐาน original 4 คุณอาจสังเกตคำนึงที่ไม่ค่อยคุ้นสักเท่าไรคือหน่วย kryddmått
นอกจากชุดช้อนตวงมาตรฐานแล้ว ป้าแอนยังคิดค้นสิ่งต่างๆอีกมากมาย ให้กับวงการอาหารสวีเดน รวมถึงหน่วยวัดใหม่ที่เรียกว่า kryddmått นี้ด้วยครับ ซึ่งมันเป็นหน่วยวัดขนาดเล็กที่ใช้ในการตวงเครื่องเทศและวัตถุดิบปริมาณน้อย โดยหน่วยวัดนี้มีขนาด 1 มิลลิลิตร (ml)ซึ่งถูกกำหนดมาเป็นหน่วยที่เล็กที่สุดซึ่งทำให้มีการจดบันทึกสูตรได้แม่นยำยิ่งขึ้น นั่นเพราะว่า การตวงเครื่องเทศ หรือ เกลือ นั้นหากรสชาติที่เข้มข้น หรือมีการใช้มากเกินไปหรือไม่พออาจทำให้รสชาติของอาหารเปลี่ยนไป การใช้ kryddmått ช่วยให้การวัดปริมาณเครื่องเทศที่ใช้ในสูตรอาหารเป็นไปอย่างแม่นยำและสม่ำเสมอ
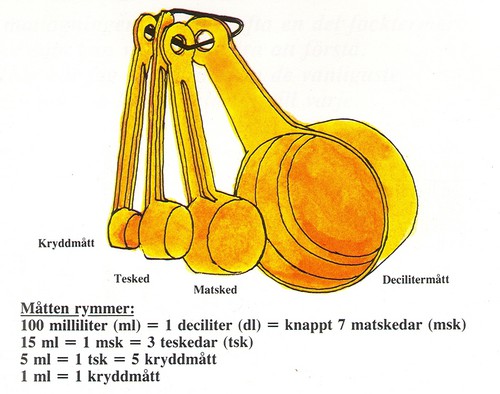
ถือว่าเป็นอีกผลงานคุโณปการที่ป้าแอน ฝากไว้ให้กับโลกนี้ มันมีส่วนสำคัญในการทำให้งานครัวเรือนง่ายขึ้นและมีประสิทธิภาพมากขึ้นผ่านการพัฒนาหน่วยวัดที่แม่นยำและสะดวกในการใช้งาน นวัตกรรมนี้ช่วยให้การทำอาหารเป็นไปอย่างราบรื่นและมีคุณภาพสูงยิ่งขึ้น

ในปี 1951 ป้าแอนได้บูรณะหนังสือการทำอาหารประจำสวีเดนใหม่ทั้งหมด (Vår kokbok) จุดประสงค์ของตำราอาหาร Vår คือการนำเสนอตำราอาหารราคาต้นทุนวัตถุดิบไม่แพง ที่ให้ความรู้เรื่องสารอาหารและใช้งานง่าย นอกจากนี้ยังเป็นการวางวัตถุดิบให้ได้รับสารอาหารที่เพียงพออีกด้วย เพราะในยุคนั้นสวีเดนมีข้อจำกัดในเรื่องอาหารเป็นอย่างมาก
เนื้อหาสูตรอาหารที่ใช้ในหนังสือเล่มนี้กลายเป็นบรรทัดฐานในช่วงทศวรรษ 1950 โดยมีการใช้หน่วยชั่งตวงแบบใหม่ ตามชุดช้อนตวงมาตรฐาน (ปริมาตร) จากของเดิมที่ใช้การชั่งน้ำหนัก ใช้ศัพท์ในการทำอาหารแบบเป็นสากล เช่น ขูด ปอกเปลือก ล้าง เป็นต้น (grate, peel, rinse) จัดอาร์ทเวิคให้แต่ละสูตร สามารถจบได้ในหน้าเดียวไม่ต้องพลิกอ่านหน้าต่อๆไป ทำให้สะดวกในการเปิดแล้วทำตาม การไล่ลำดับอาหาร เปลี่ยนจากการไล่ประเภทอาหาร ไปเป็นไล่ลำดับตามวัตถุดิบหลักของอาหาร ทำให้คนอ่านสามารถบริหารจัดการเมนูได้ง่าย เช่น ไก่ ก็สามารถไล่เรียงได้เลยว่า วันนี้มีไก่ จะทำอะไรกินดี
นอกจากนี้ยังรับประกันว่าทุกสูตรสามารถทำได้จริง เพราะป้าแอนลงมือทดสอบสูตรด้วยตัวเองทุกสูตร นอกจากนี้ยังคงมีการแนะนำให้ใช้การวัดอุณหภูมิในการทำอาหารด้วยเพื่อความเป๊ะในรสชาติ เนื่องจากป้าแอนเห็นตอนไปดูงานที่อเมริกา จนถึงทุกวันนี้ Vår kokbok เป็นหนึ่งในตำราอาหารที่ขายมากที่สุดในโลกด้วยยอดขายมากกว่า 2.3 ล้านเล่มนับตั้งแต่เริ่มต้น โดยเฉลี่ยมากกว่า 40,000 เล่มต่อปี


ด้วยความที่ Kooperativa Förbundets เป็นองค์กรที่มีอิทธิพลสูงมากในวงการอาหารสวีเดน และคุณป้าแอน ก็มีตำแหน่งที่สูงมาก จึงสามารถเป็นผู้มีส่วนสนับสนุนรูปแบบซูเปอร์มาร์เก็ตสมัยใหม่ ในการใส่รายการส่วนผสมและคำแนะนำในการปรุงอาหารในรูปแบบฉลากของผลิตภัณฑ์อาหารสมัยใหม่

จนกระทั่งในช่วงปี 1970 ประเทศสวีเดนต้องเผชิญกับปัญหาราคาอาหารที่สูงเนื่องจากเงินเฟ้อ รวมถึงสภาพอากาศของสวีเดนนั้น ไม่เอื้อต่อการได้รับสารอาหารที่หลากหลายได้ ครอบครัวที่มีเด็ก ไม่สามารถปรุงอาหารและรับประทานอาหารที่มีคุณค่าทางโภชนาการในราคาที่เหมาะสมได้ รัฐบาลจึงมอบหมายให้ Sweden’s National Board of Health and Welfare (คณะกรรมการสุขภาพและสวัสดิการแห่งชาติของสวีเดน) หาวิธีแก้ไขสถานการณ์ดังกล่าว และคัดกรองแบ่งประเภทอาหารออกเป็น “basic food” และ “supplement” มาเป็นรูปแบบของ กราฟวงกลม (diet circle) แต่ป้าแอนพบปัญหาบางอย่าง ที่ทำให้กราฟวงกลมนี้ใช้งานยาก เพราะการแบ่งปริมาณของอาหารแต่ละประเภทไม่ชัดเจน
ในระหว่างบรรยายเรื่องการกำหนดอาหารพื้นฐาน คุณ Fjalar Clemes หนึ่งในผู้เข้าร่วมการบรรยาย ได้ให้ไอเดียด้วยการสร้างแบบจำลองที่เรียกว่า ปิรามิดอาหาร (Food Pyramid) ขึ้นมา เพื่อให้เห็นภาพสัดส่วนอาหารที่ชัดเจนขึ้น ป้าแอนเลยนำข้อมูลจากกราฟวงกลมนั้น มาสร้างโมเดลจำลองให้อยู่ในรูปแบบปิรามิด โดยให้ “basic food” เช่น ขนมปัง มันฝรั่ง พาสต้า และนม และ “supplements” เช่น ผลไม้ ผัก เนื้อสัตว์ และปลา อยู่ในรูปแบบที่เข้าใจได้ง่ายขึ้น แม้แต่คนที่อ่านหนังสือไม่ออก

แต่นี่แหละที่เป็นจุดเริ่มต้นของปัญหา ด้วยความที่มันใช้งานง่ายสะดวก อเมริกาจึงนำไปปรับปรุงเป็นเวอร์ชั่นตัวเอง แต่ก็มีการเปลี่ยนแปลงไปอย่างมาก ตามที่ได้มีการทำบทความไปแล้ว (อ่านที่นี่)
ทั้งๆที่ปิรามิดต้นแบบของป้าแอนนั้น สร้างขึ้นมาเพื่อชาวสวีเดนเนื่องจากนำข้อมูลพื้นฐานจากข้อจำกัดในประเทศในขณะนั้น ไม่ว่าจะเรื่องของวัตถุดิบที่หาได้ในภาวะยากแค้นแบบนั้น อุณหภูมิอันปรวนแปร รวมถึงสภาพเศรษฐกิจที่ย่ำแย่มาก การจัดแจงข้อจำกัดที่มีเพื่อให้ได้สารอาหารที่เพียงพอที่สุดเท่าที่จะทำได้ต่างหาก (eat healthier, more affordable and save on fat) ที่เป็นที่มาของ “ปิรามิดอาหารของสวีเดน” (คือ จะให้เอาอุดมคติมาสร้างปิรามิดอาหาร คงไม่มีประโยชน์ เพราะยังไงก็ไม่มีเงินซื้อและหาวัตถุดิบไมไ่ด้ตามอุดมคติ วัตถุประสงค์ในการสร้างและเผยแพร่ครั้งนี้มันเพื่อให้ประชาชนทั้งประเทศที่มีความรู้ด้านอาหารน้อย รู้และทำตามได้จริง สมกับพื้นที่และกำลังทรัพย์ // ความเห็นส่วนตัวผมครับ)
ปิรามิดอาหารที่แท้จริงแล้ว จะมีการปรับปรุงตลอดเวลา ตามปัจจัยที่เปลี่ยนไป ไม่ใช่ปิรามิดที่เอาไว้ยึดถือตลอดไป แต่การที่อเมริกานำไปยึดถือว่าเป็น all time information เป็นค่าคงที่ให้ทั้งโลกยึดตาม รวมถึงสร้างด้วยเบื้องหลังด้านธุรกิจ จึงต่างกับที่ป้าแอนทำในทุกมิติ แต่ไฉน เป้าการบูลลี จึงต้องไปตกที่ป้าแอน ว่าเป็นต้นตอความพังของสุขภาพ มันแฟร์แล้วหรือ
เรื่องนี้มีข้อพิสูจน์ได้จนถึงปัจจุบันเช่น ในปี 2022 ก็มีการนำเสนอ ปิรามิดอาหารสำหรับ Mixed diet, flexitarian, vegetarian และ vegan ออกมาสืบทอดเจตนารมณ์ป้าแอน นอกจากนี้ในช่วงที่ป้าแอนมีชีวิต ก็ยังคงมีการช่วยเหลือแนะนำให้ประเทศต่างๆ “มีปิรามิดอาหารของตัวเอง” นั่นคือ วิชั่นที่กว้างไกลของป้าแอน ที่เห็นได้ชัดเจนว่า อาหารพื้นถิ่นกับสารอาหารที่สมดุล ของแต่ละประเทศมีความไม่เหมือนกัน และแนวคิดนี้ได้มีทั้ง เดนมาร์ก, นอร์เวย์, ฟินแลนด์, ญี่ปุ่น, ศรีลังกา ได้นำไปพัฒนาใช้เช่นกัน
นอกจากนี้ ป้าแอนและองค์กร Kooperativa Förbundets ยังให้ข้อมูลการศึกษาที่สำคัญสำหรับประชาชนผ่านบทความเกี่ยวกับอาหารที่ตีพิมพ์ใน นิตยสาร Vi รวมถึงการจัดตั้งกลุ่มการศึกษาร่วมกับทาง สมาคมการศึกษาของชนชั้นแรงงาน หรือ Arbetarnas bildningsförbund (ABF) มีส่วนสนับสนุนในการอภิปรายแบบเปิดทางสังคมเกี่ยวกับปัญหาโรคอ้วนอีกด้วย รวมถึงยังออกหนังสือเกี่ยวกับการทำอาหารอีกร่วมๆ 30เล่ม ซึ่งรวมถึงบทเกี่ยวกับมื้ออาหารที่มีคุณค่าทางโภชนาการที่สมดุล ด้วยเช่นกัน

ในปี 1983 ป้าแอนได้ตีพิมพ์หนังสือ Matboken ซึ่งได้รับการพิสูจน์แล้วว่าเป็นประโยชน์อย่างมาก โดยเฉพาะกับคนหนุ่มสาวเกี่ยวกับวิธีการกินอาหารที่มีคุณค่าทางโภชนาการและมีวิธีทำที่เรียบง่ายที่สุด

ในช่วงทศวรรษ 1990 เมื่อป้าแอนเป็นม่าย จึงได้ย้ายเข้าไปอยู่ในบ้านพักคนชรา Färdknäppen ใน Södermalm ในสตอกโฮล์ม และ ได้แก้ไขสูตรอาหาร 250 สูตรจาก Vår kokbok เพื่อให้เหมาะสมกับสภาพแวดล้อมการปรุงอาหารส่วนกลางของบ้านพักคนชรา เพื่อให้ได้อาหารที่มีสารอาหารครบถ้วนตามที่ควรเป็น
เกียรติประวัติป้าแอนได้รับการตอบแทนดังนี้ ในปี 1979 ได้รับรางวัลเหรียญ St Erik เพื่อเป็นการยกย่องสิ่งที่เธอทุ่มเทแรงกายแรงใจทำมาตลอดชีวิต ในปี 1993 ได้รับเหรียญ HM Konungens ลำดับที่ 8 (HM The King’s Medal หรือ H.M. Konungens medalj ในภาษาสวีเดน) เป็นหนึ่งในรางวัลเกียรติยศที่สำคัญที่สุดที่มอบโดยพระมหากษัตริย์สวีเดนเพื่อยกย่องบุคคลที่มีผลงานดีเด่นหรือมีความโดดเด่นในด้านต่าง ๆ เช่น วิทยาศาสตร์ ศิลปะ วัฒนธรรม และการบริการสาธารณะ ในปี 1995 ได้รับเหรียญทอง Albin Johansson สำหรับผลงานอันทรงคุณค่าของเธอต่อสหกรณ์สวีเดน ในปี 1998 ได้รับรางวัล Gastronomiska Akademiens Guldpenna (ปากกาทองของสถาบันอาหาร) สำหรับบทความเกี่ยวกับส่วนผสมและการทำอาหารของเธอ

Anna-Britt Agnsäter เสียชีวิตในปี 2006 (อายุ 90ปี) ป้าแอนทำงานทั้งชีวิตเพื่อสอนชาวสวีเดนในการจัดการอาหารให้ดีขึ้น ทุกการทดลอง ทดสอบ ได้มีการบันทึกไว้อย่างชัดเจนสามารถพัฒนาต่อไปได้ การริเริ่มให้ข้อมูลที่ซื่อสัตย์ต่อผู้บริโภค ทั้งการติดฉลากอุปกรณ์ คำแนะนำในการทำอาหาร สูตรอาหาร บทความ และตำราอาหาร สิ่งเหล่านี้กลายเป็นพื้นฐานสำคัญในอุตสาหกรรมอาหารจนปัจจุบัน
แต่ทุกวันนี้วงการสุขภาพส่วนมากยังคงล้อเลียนเธอว่าเป็นครูธรรมดา ที่มีหน้ามาสร้างปิรามิดอาหาร จึงทำให้คนทั่งโลกป่วย ทั้งที่ความจริงทั้งหมดนั้น ความรู้ของป้าแอนไม่ได้น้อยไปกว่า ผู้เชี่ยวชาญทางวิทยาศาสตร์การอาหาร ซึ่งในสมัยนั้นนับว่าเป็นอีกแขนงที่อยู่ในระดับบนของการศึกษา ไม่ต่างกับวิทยาศาสตร์อื่นๆ ปิรามิดควรเป็นไปตามถิ่นที่อยู่ สภาพเวลาและสภาพเศรษฐกิจขณะนั้น ไม่ใช่การสร้างมาตรฐานให้ต้องทำเหมือนกันทั่วโลก โดยมาจากอิทธิพลของกลุ่มธุรกิจดังที่ usda ได้ทำการแก้ไขก่อนจะประกาศให้คนทั่วไปยึดถือ รายละเอียดเป็นไปตามที่สืบค้นข้อมูลประวัติของป้าแอน มาเล่าสู่กันฟัง ณ วันนี้ครับ
ผมก็เป็นหนึ่งในนั้น สิ่งที่ผมสามารถทำได้เพื่อเป็นการขอโทษคุณ Anna-Britt Agnsäter ที่ดีที่สุดที่ทำได้ตอนนี้คือ เผยแพร่ประวัติอันทรงคุณค่าของเธอ ให้คนอื่นๆได้รับทราบมากที่สุด เท่าที่จะทำได้
โปรดแชร์ เพื่อคืนความเป็นธรรมให้ Anna-Britt Agnsäter ให้โลกได้เข้าใจและรับรู้ถึงการอุทิศชีวิตให้วงการอาหารของคุณป้าครับ
ปล.มีการค้นพบไฟล์เสียง ที่ป้าแอน จัดรายการวิทยุในปี 1968 ให้ลองฟังกันครับ (น่าจะภาษาสวีเดนนะ 5555) ฟังได้ที่นี่ครับ https://rumble.com/v56p1wa-ann-britt-agnster-in-a-radio-find-from-1968.html
siamstr #pirateketo
-
 @ 6c8c7979:15595f3e
2024-07-13 01:55:06
@ 6c8c7979:15595f3e
2024-07-13 01:55:06Rococo is a style in interior design, decorative arts, painting, architecture, and sculpture, originating in Paris in the early 18th century. It quickly spread throughout France and later to other countries, primarily Germany and Austria.

Palace of Versailles - France
$$The origin of the word "Rococo"$$The term Rococo was first used by the designer Jean Mondon in his book "First Book Of Rococo Form And Setting" in 1736, where he used it alongside illustrations depicting the style used in architecture and interior design.
The word Rococo combines the French word "Rocaille," meaning shell, which was used to describe fountains and grottoes in gardens adorned with pebbles and shells, and "Barocco," the Italian word for Baroque, the art style preceding Rococo. Rococo art is characterized by curved forms resembling shells and wave-like ornaments.

One of the most famous paintings by the artist François Boucher is "The Swing" (La Balançoire), painted in 1767.
$$How Rococo Art Emerged$$With the death of King Louis XIV of France in 1715, one of the greatest French monarchs known for his lengthy reign and cultural influence, France was left economically and militarily powerful, setting it as a cultural beacon in arts, fashion, and culture. His successor, King Louis XV, in contrast, faced challenges and mismanagement, leading France toward bankruptcy with extravagant spending and failed policies. Despite this, his reign fostered an era of lavish court entertainment and artistic patronage, contrasting sharply with his predecessor.
Rococo art developed an aristocratic flavor, adopted by rising upper-middle-class individuals emulating the French nobility's fashion and lifestyle, known as the bourgeoisie. The period, spanning roughly from Louis XIV's death to the French Revolution in 1789, marked an era more than a defined style. Aristocrats in France imposed Rococo artistic style, constructing more elegant homes and commissioning interior decorations for palaces. Unlike its predecessor Baroque art, which was less suited for intimate and comfortable home decor, Rococo allowed for artistic rebellion.
Rococo paintings offered a unique glimpse into the lives of the French upper class in the decades preceding the French Revolution, though it didn't reflect the political and economic realities of the era and largely ignored working-class issues. While intricate Baroque architecture thrived in France, Italy, England, Spain, and South America, softer Rococo styles were prevalent in Germany, Austria, Eastern Europe, and Russia, mainly focusing on interior and exterior design.
$$Information about Rococo Art$$Rococo art, termed by some historians as the late phase of Baroque but lighter and more delicate, was employed by artists and designers in interior design and the arts.
The Rococo era was considered a revolution against the formal Baroque designs that characterized the French royal court at Versailles, emphasizing comfort, warmth, and intimacy.
Rococo is distinguished by its softness, playfulness, imagination, and whimsy compared to its more serious predecessor, Baroque. Ornamentation was used to create a sense of flow, especially through abstract and asymmetrical details.
This art style was influenced by Asian motifs such as Chinese design, influenced by trade relations with the Far East, leading to more modern decorative works. Interior decor and its components formed a harmonious unity, giving a unified impression, with great effort put into selecting furniture shapes, placements, and decorations.
Wealthy property owners renewed their homes' interiors with Rococo-style plasterwork, murals, mirrors, furniture, and porcelain, characterized by a delicate, feminine touch, while maintaining Baroque architecture on the exterior.
In Rococo decor, large candelabra, beautiful chandeliers, and wall sconces stand out to create a warm atmosphere, complemented by luxurious gilt-framed mirrors with floral motifs, enhancing a sense of openness in spaces.
$$Architecture$$As the fundamental principle in Rococo architecture was to achieve the purpose of celebration, in the early 18th century, the aim of construction was festive. French aristocrats ceased gathering at the royal court and palaces of kings, instead opting to enjoy themselves in private palaces intended as venues for parties, incorporating complex, ornate, and asymmetrical styles that imparted a sense of joy and whimsy.

The Fountain of Fountains (Fontänebnlo): A stunning water sculpture located in Munich, Germany, considered a masterpiece of Rococo art, and was part of the design for the Nymphenburg Palace.
$$Art of Painting$$Painters used pastel colors, flowing lines, and non-symmetrical shapes, with many artworks characterized by off-center compositions, meaning the overall design or arrangement was asymmetric or whimsical. Each element contributed to creating a sense of movement and playfulness within the painting, depicting mythical scenes set in imaginative landscapes and images of love as well.
$$Themes Embraced by Rococo$$Rococo paintings did not address national issues, religious piety, morality, saints, or heroes, nor did they provoke deep thought. They depicted outdoor scenes for leisurely activities, lovers in romantic encounters, and playful behavior with a sense of humor. These artworks were created for aesthetic purposes and to please the viewer's eye.

One of the most famous Rococo painters was the French artist Jean Antoine Watteau, and his painting "Les Plaisirs Du Bal" is considered exemplary of the early Rococo period.
$$Rococo in Germany$$aristocrats and nobles desired their palaces to be venues for celebrations, similar to the French. One of the notable examples is the construction of Amalienburg Palace, originally a hunting lodge within the grounds of Nymphenburg Palace in Munich. It was commissioned by Holy Roman Emperor Charles VII and his wife Maria Amalia, designed by architect François de Cuvilliés and decorated by painter Johann Baptist Zimmermann between 1734-1739. The building is distinguished by its smooth lines, intricate designs, and light pink color.

Amalienburg
Moving inside the palace, one must pause at the Hall of Mirrors, a circular room at the center of the building surrounded by mirrors. It is filled with decorations of gold and silver on the walls, featuring motifs of leaves, flowers, birds, and small cupids. Its design is intricate, vibrant with life and movement.

Inside the palace - Hall of Mirrors
Critics dubbed this art as frivolous, appearing only to vanish, and condemned it for its superficiality, with some even labeling it as failed art, leading to a backlash against it. This resulted in a strong reaction from intellectuals like Voltaire. By the mid-18th century, the popularity of Rococo art began to decline in France, and interest waned across Europe.
-
 @ 3cd2ea88:bafdaceb
2024-07-12 22:33:49
@ 3cd2ea88:bafdaceb
2024-07-12 22:33:49Siamo entusiasti di annunciare il lancio di DOGS POINTS (DOGS) nel trading pre-market su Bitget! 🎉 Gli utenti possono ora iniziare a scambiare DOGS POINTS prima che diventi disponibile per il trading ufficiale.
🐶 Un po' di background su DOGS POINTS:
L'immagine di DOGS è ispirata a Spotty, la mascotte creata dal fondatore di TON, Pavel Durov, per la comunità di Telegram. Questa moneta non è solo per divertimento, ma tutti i ricavi delle vendite sostengono orfanotrofi e case per bambini, continuando l'eredità benefica di Spotty. ❤️
👉 Non perdere questa opportunità unica! Unisciti ora al trading pre-market su Bitget e sostieni una buona causa. Iscriviti ora e inizia a scambiare: https://bonus.bitget.com/U1JNEK
👉 Non sei andato a riscattare il tuo AirDrop su Telegram? Vai subito a vedere quanti DOGS puoi ricevere! https://t.me/dogshouse_bot/join?startapp=y5J61rnXSU2wW2ruadnJNA
-
 @ 0861144c:e68a1caf
2024-05-29 14:23:53
@ 0861144c:e68a1caf
2024-05-29 14:23:53El cansado reflexiona y no hace nada para crear un para-algo. Con el consumismo de hoy, el cansado no reflexiona y hace algo para-nada
Ahorrar tiene demasiados significados aventajados para la época. Los esclavos ahorraban de su mísera paga para comprarse su libertad, los comerciantes iban a depositar todo lo que tenían a los banqueros en busqueda del apalancamiento y más importante de todos: el ahorro te descontaba el futuro, te lo hacía fácil de digerir y hay caídas, te ayuda a caer en buenos términos. Entonces, ¿que pasa que hoy te parece insípido ahorrar y te ofrecen nuevos super-mega-proyectos usando buzzwords yadayadayada como si eso solucionara todos tus problemas?
Una reflexión para nada
En un post anterior, he defendido una perspectiva reflexiva de Byung-Chul Han acerca de bitcoin. Este filosofo, muy crítico al tipo de capitalismo que todo bitcoiner debería oponerse, nos enfatiza como la reflexión y la meditación han sido completamente desorientados de su propósito original al ponerle un precio a todo, donde la actividad del descanso ya no se trata de contemplar y descansar sino tomar una cerveza en un bar y consumir las promociones vigentes para hablar de futuros proyectos laborales.
¿Que va entre esto y bitcoin?
Bitcoin tiene una propiedad monetaria muy fuerte, arraigada en su propio código: la escasez. Esto nos permite hacer planificaciones a largo plazo, teniendo en cuenta cientos de miles de escenarios pero donde la propiedad monetaria no cambia, los eventos y jugadores si, la propiedad no. Vayamos al campo contrario donde tenemos lo que los mismos proponentes llaman una deflación dinámica, ¿que nos encontramos? Que los proyectos de ahorro no son bienvenidos tanto como lo son los de inversión.
La inversión es el nuevo ahorro del mundo fiat y eso se traslada al día de hoy en aquellos proyectos que necesitan liquidez hoy para morir mañana, por supuesto hablamos de las memecoins. Una cosa la cual aquí podemos aprender de un modo bastante pragmatico es que bitcoin y memecoins no pueden ir juntas, por eso bitcoin no es un vehículo de inversión. Explicamos esto.
Bitcoin como inversión: el caso de los ordinals
Mucho fuego se prendió alrededor del caso de los ordinals y las inscripciones durante casi 18 meses consecutivos en los entornos de bitcoin, puede que más. Resumen rápido: podemos incluir memecoins con BRC20, podemos poner NFTs gracias a los ordinals y podemos tener coleccionables por las inscripciones de la misma forma que lo hacen con Ethereum. Parecía buena idea, de hecho y si vamos al caso especifico, incluso los ordinals son superiores.
Intentaron hacer algo pero fue para nada. ¿La razón? Salió caro el experimento y vieron que simplemente moverse rápido en una red que proporciona seguridad no es lo mismo que moverse en Solana, Ethereum y otras ciudadelas donde la degeneración financiera es la norma. Bitcoin no sirve para eso, no sirve para invertir por que no puede darte rendimiento, no puede APYs ni puede darte intereses compuestos, solo puede darte una cosa y es la certeza de que tu dinero estará ahí cuando firmes con tus claves privadas, a prueba de confiscaciones, falsificaciones y emisiones inflacionarias.
Bitcoin como ahorro y reflexión
En un post anterior también he señalado como el ahorro es mejor vehículo que la inversión cuando hablamos de tenencia de bitcoins y es aquí donde la reflexión entra en proceso, donde bitcoin te permite comprar y dejarte llevar por la reflexión de la vida, por eso cuando Jameson Loop hizo un estudio acabado sobre la cultura maximalista descubrió que hay grupos que desean volver a costumbres que se van dejando de lado o tratos sociales que de repente ya no son bienvenidos en un mundo acelerado.
¿La razón? Una hipotesis que ha estado dando vueltas en mi cabeza es la posibilidad de que estas personas están nuevamente entrando en la reflexión social que, como sociedad, hemos reemplazado y automatizado todo, incluyendo la reflexión razonable por lo racional, donde se dictan normas técnicas igualitarias pero no equitativas, donde la racionalidad es apoyada con inteligencia artificial excluyendo la reflexión humana-social, los debates de este tipo lo único que agregan es algoritmos incomprensibles a la crítica razonable, generando un estéril debate racional donde solo existe unos y ceros.
Ese debate es el que se dejó de lado y cuando se renueva esto en diferentes estratos digitales, los internautas lo califican de absurdo, primitivo, troglodita y otros calificativos que van hacia lo antiguo pero desfasado negativo.
El debate en la comunidad bitcoiner nos permite tomar pasos y decisiones razonables en el tiempo, nos permite retomar debates inconclusos y que muchos ya dieron por cerrado sin más preambulo pero debemos traerlos de vuelta. Con bitcoin, esto se puede hacer dado que nos enseña a reflxionar sin perder la marca más importante de todas: todos verificamos la moneda en conjunto.
Bitcoin, en la inactividad de tu wallet, construye tu futuro. Bitcoin hace nada para-algo
-
 @ 617f0a85:b403d1ed
2024-07-12 21:03:19
@ 617f0a85:b403d1ed
2024-07-12 21:03:19For the last several weeks we've been meeting on Thursday evenings to chat about projects people are working on, cool new things in crypto, and generally just having a good time. As we all have busy schedules and lots of meetings, it is important to keep things informal and give people the space to share freely. Please join us and connect with some great builders.
This weekly happy hour is hosted by Chones which is hoping to weave together communities in web3 and make the things happen that often are not appreciated but make a big difference. Hosting the happy hour is a way to expose builders to new projects and learn about what else is happening in the space for those who are heads down working on their stuff. There is so much going on, keeping track of it all is impossible for anyone, so let's do it together.
If you're interested in attending, let me know and I'll let you know when and where we meet. We're looking to move to hivetalk.org after getting everyone on the same page. Hope to see you there.
chones
-
 @ b12b632c:d9e1ff79
2024-05-29 12:10:18
@ b12b632c:d9e1ff79
2024-05-29 12:10:18One other day on Nostr, one other app!
Today I'll present you a new self-hosted Nostr blog web application recently released on github by dtonon, Oracolo:
https://github.com/dtonon/oracolo
Oracolo is a minimalist blog powered by Nostr, that consists of a single html file, weighing only ~140Kb. You can use whatever Nostr client that supports long format (habla.news, yakihonne, highlighter.com, etc ) to write your posts, and your personal blog is automatically updated.
It works also without a web server; for example you can send it via email as a business card.Oracolo fetches Nostr data, builds the page, execute the JavaScript code and displays article on clean and sobr blog (a Dark theme would be awesome 👀).
Blog articles are nostr events you published or will publish on Nostr relays through long notes applications like the ones quoted above.
Don't forget to use a NIP07 web browser extensions to login on those websites. Old time where we were forced to fill our nsec key is nearly over!
For the hurry ones of you, you can find here the Oracolo demo with my Nostr long notes article. It will include this one when I'll publish it on Nostr!
https://oracolo.fractalized.net/
How to self-host Oracolo?
You can build the application locally or use a docker compose stack to run it (or any other method). I just build a docker compose stack with Traefik and an Oracolo docker image to let you quickly run it.
The oracolo-docker github repo is available here:
https://github.com/PastaGringo/oracolo-docker
PS: don't freak out about the commits number, oracolo has been the lucky one to let me practrice docker image CI/CD build/push with Forgejo, that went well but it took me a while before finding how to make Forgejo runner dood work 😆). Please ping me on Nostr if you are interested by an article on this topic!
This repo is a mirror from my new Forgejo git instance where the code has been originaly published and will be updated if needed (I think it will):
https://git.fractalized.net/PastaGringo/oracolo-docker
Here is how to do it.
1) First, you need to create an A DNS record into your domain.tld zone. You can create a A with "oracolo" .domain.tld or "*" .domain.tld. The second one will allow traefik to generate all the future subdomain.domain.tld without having to create them in advance. You can verify DNS records with the website https://dnschecker.org.
2) Clone the oracolo-docker repository:
bash git clone https://git.fractalized.net/PastaGringo/oracolo-docker.git cd oracolo-docker3) Rename the .env.example file:
bash mv .env.example .env4) Modify and update your .env file with your own infos:
```bash
Let's Encrypt email used to generate the SSL certificate
LETSENCRYPT_EMAIL=
domain for oracolo. Ex: oracolo.fractalized.net
ORACOLO_DOMAIN=
Npub author at "npub" format, not HEX.
NPUB=
Relays where Oracolo will retrieve the Nostr events.
Ex: "wss://nostr.fractalized.net, wss://rnostr.fractalized.net"
RELAYS=
Number of blog article with an thumbnail. Ex: 4
TOP_NOTES_NB= ```
5) Compose Oracolo:
bash docker compose up -d && docker compose logs -f oracolo traefikbash [+] Running 2/0 ✔ Container traefik Running 0.0s ✔ Container oracolo Running 0.0s WARN[0000] /home/pastadmin/DEV/FORGEJO/PLAY/oracolo-docker/docker-compose.yml: `version` is obsolete traefik | 2024-05-28T19:24:18Z INF Traefik version 3.0.0 built on 2024-04-29T14:25:59Z version=3.0.0 oracolo | oracolo | ___ ____ ____ __ ___ _ ___ oracolo | / \ | \ / | / ] / \ | | / \ oracolo | | || D )| o | / / | || | | | oracolo | | O || / | |/ / | O || |___ | O | oracolo | | || \ | _ / \_ | || || | oracolo | | || . \| | \ || || || | oracolo | \___/ |__|\_||__|__|\____| \___/ |_____| \___/ oracolo | oracolo | Oracolo dtonon's repo: https://github.com/dtonon/oracolo oracolo | oracolo | ╭────────────────────────────╮ oracolo | │ Docker Compose Env Vars ⤵️ │ oracolo | ╰────────────────────────────╯ oracolo | oracolo | NPUB : npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2 oracolo | RELAYS : wss://nostr.fractalized.net, wss://rnostr.fractalized.net oracolo | TOP_NOTES_NB : 4 oracolo | oracolo | ╭───────────────────────────╮ oracolo | │ Configuring Oracolo... ⤵️ │ oracolo | ╰───────────────────────────╯ oracolo | oracolo | > Updating npub key with npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2... ✅ oracolo | > Updating nostr relays with wss://nostr.fractalized.net, wss://rnostr.fractalized.net... ✅ oracolo | > Updating TOP_NOTE with value 4... ✅ oracolo | oracolo | ╭───────────────────────╮ oracolo | │ Installing Oracolo ⤵️ │ oracolo | ╰───────────────────────╯ oracolo | oracolo | added 122 packages, and audited 123 packages in 8s oracolo | oracolo | 20 packages are looking for funding oracolo | run `npm fund` for details oracolo | oracolo | found 0 vulnerabilities oracolo | npm notice oracolo | npm notice New minor version of npm available! 10.7.0 -> 10.8.0 oracolo | npm notice Changelog: https://github.com/npm/cli/releases/tag/v10.8.0 oracolo | npm notice To update run: npm install -g npm@10.8.0 oracolo | npm notice oracolo | oracolo | >>> done ✅ oracolo | oracolo | ╭─────────────────────╮ oracolo | │ Building Oracolo ⤵️ │ oracolo | ╰─────────────────────╯ oracolo | oracolo | > oracolo@0.0.0 build oracolo | > vite build oracolo | oracolo | 7:32:49 PM [vite-plugin-svelte] WARNING: The following packages have a svelte field in their package.json but no exports condition for svelte. oracolo | oracolo | @splidejs/svelte-splide@0.2.9 oracolo | @splidejs/splide@4.1.4 oracolo | oracolo | Please see https://github.com/sveltejs/vite-plugin-svelte/blob/main/docs/faq.md#missing-exports-condition for details. oracolo | vite v5.2.11 building for production... oracolo | transforming... oracolo | ✓ 84 modules transformed. oracolo | rendering chunks... oracolo | oracolo | oracolo | Inlining: index-C6McxHm7.js oracolo | Inlining: style-DubfL5gy.css oracolo | computing gzip size... oracolo | dist/index.html 233.15 kB │ gzip: 82.41 kB oracolo | ✓ built in 7.08s oracolo | oracolo | >>> done ✅ oracolo | oracolo | > Copying Oracolo built index.html to nginx usr/share/nginx/html... ✅ oracolo | oracolo | ╭────────────────────────╮ oracolo | │ Configuring Nginx... ⤵️ │ oracolo | ╰────────────────────────╯ oracolo | oracolo | > Copying default nginx.conf file... ✅ oracolo | oracolo | ╭──────────────────────╮ oracolo | │ Starting Nginx... 🚀 │ oracolo | ╰──────────────────────╯ oracolo |If you don't have any issue with the Traefik container, Oracolo should be live! 🔥
You can now access it by going to the ORACOLO_DOMAIN URL configured into the .env file.
Have a good day!
Don't hesisate to follow dtonon on Nostr to follow-up the future updates ⚡🔥
See you soon in another Fractalized story!
PastaGringo 🤖⚡ -
 @ f77dfdcf:17e93422
2024-05-29 04:06:39
@ f77dfdcf:17e93422
2024-05-29 04:06:39Proof of Work เป็น concept ที่คนที่เคยศึกษาการทำงานของ bitcoin อาจจะเคยได้ยินผ่านหูมาบ้าง แต่จริง ๆ แล้ว สิ่งนี้สามารถนำมาประยุกต์ใช้กับชีวิตประจำวันของเราได้อย่างเป็นธรรมชาติมาก
Proof of Work สำหรับ bitcoin เอาแบบสั้น ๆ คือ การที่เราเจอ ตัวเลขที่ถูกต้อง (Proof) ซึ่งได้จากการขุด ที่จะเกิดขึ้นได้โดยการใช้พลังงานและเวลาของเครื่องขุดในการคำนวณตัวเลข (Work)
ยิ่งมี Proof of Work ใน chain เยอะขึ้น ก็ทำให้ transaction มี confirmation มากขึ้น
ถ้าจะให้เขียนให้ครบจบตรงนี้ คนอ่านน่าจะตาลอย แนะนำให้ลองอ่านต่อใน Inventing Bitcoin ดูครับ
พอเราซูมออกมาเป็นภาพกว้าง ๆ Proof of Work จะหมายถึง “หลักฐาน” ที่เกิดขึ้น จากการทำ “งาน”
งาน (Work)ในที่นี้ คือ การลงทุนทาง “เวลา” ไปกับการทำส่ิง ๆ หนึ่ง ซึ่งจะได้ผลตอบแทนเป็น Proof of Work ในรูปแบบใดรูปแบบหนึ่ง
Proof ที่พูดถึง ไม่จำเป็นต้องเป็นชิ้นงานที่มองเห็นหรือจับต้องได้ มันอาจจะหมายถึงทักษะ ความรู้ หรือ ประสบการณ์ ก็ได้
ตัวอย่างในชีวิตประจำวันชัด ๆ เลยก็อย่างเช่น
- การที่บางคนที่มีหุ่นดี สุขภาพแข็งแรง มีกล้ามเนื้อกำยำ ก็เป็น Proof of Work ของการออกกำลังกาย กินอาหารที่ดี และความมีวินัย
- การที่เราเรียนรู้เรื่องใหม่ ๆ แล้วเรารู้สึกว่ายังไม่แน่ใจกับสิ่งที่รู้ เราเลยศึกษาเพิ่ม สิ่งนี้ก็เป็นการเพิ่ม Proof of Work ตัวเรา ซึ่งคือ knowledge ของสิ่งนั้น ทำให้เรามั่นใจในองค์ความรู้นั้น ๆ มากขึ้น และสามารถนำไปส่งมอบ valueให้กับคนอื่น ๆ ได้
- หรือจะเป็นการฝึกทักษะการทำงาน ถ้าเรารู้ว่ายังไม่เก่ง Work ที่เราจะทำเพิ่ม ก็คือการหมั่นฝึกฝน และ Proof of Work ที่ได้ คือ ทักษะที่ดีขึ้นของเรา พอมองแบบนี้ เราจะชั่งน้ำหนักได้ง่ายขึ้น ว่าเราอยากจะลงทุนเวลาของเราไปกับ Proof of Work แบบไหน เพราะทุกคนย่อมอยากได้ผลตอบแทนที่คุ้มค่าจากการลงทุน
แต่มันมีข้อสังเกตอยู่อย่างหนึ่ง คือ เราต้องมองให้ออก ว่าอะไรเป็น Proof of Work จริง ๆ ของแต่ละสิ่ง
อย่างบางที เราบอกว่า เราเข้าใจเรื่องนี้นะ เพราะเราเคยเรียนคลาสนี้มา และเราอาจจะคิดว่าเอารูปถ่ายหรือประกาศนีย์บัตรมันเป็น Proof of Work ได้ แต่จริง ๆ แล้วไม่น่าใช่ มันคือ Proof of อะไรไม่รู้
อ่ะ ๆ มันอาจจะเป็น Proof ว่าเราเคยไปเรียนมาจริง อันนี้ยอมรับได้ แต่ไม่ใช่ว่ามันจะเป็น Proof ว่าเราเข้าใจเรื่องนั้นได้โดยตรง
เพราะ Proof ของ Work ที่เรากำลังพูดถึง มันคือ knowledge ที่อยู่ในหัวเรา ถ้าเราอยากโชว์ว่ามี Proof of Work จริง ๆ เราต้องเอาสิ่งที่ได้เรียนรู้ มาแชร์ให้คนอื่นฟังได้
และสังเกตดี ๆ จะเห็นว่า Proof of Work ที่ได้พวกนี้ มันเป็นสิ่งที่จะติดไปกับตัวเราทั้งหมดเลย มันจึงเกิดเป็น quote ที่ว่า
“You are your Proof of Work”
ซึ่งสื่อว่า สิ่งที่เราเป็น ล้วนเป็น Proof of Work มาจากสิ่งที่เราทำทั้งสิ้น และยิ่งเรามี Proof of Work เยอะขึ้น เราก็จะยิ่งเติบโตขึ้นเรื่อย ๆ
บางทีเราสามารถมองได้ด้วยตาเปล่าด้วยซ้ำ ว่าใครมี Proof of Work ที่มากหรือน้อย เพราะมันจะมันสะท้อนออกมาในรูปแบบของความมั่นใจ
พอรู้จักสิ่งที่เรียกว่า Proof of Work แล้ว สุดท้าย เราต้องกลับมาถามตัวเอง ว่าสิ่งที่เราทำอยู่ มันกำลังให้อะไรกับเรา กำลังสอนอะไรกับเรา หรือมันจะมอบ Proof of Work ที่เราต้องการ สำหรับเป้าหมายของเราในอนาคตหรือเปล่า
พิจารณามันให้ดี และอย่าลืม
หมั่นสร้าง Proof of Work ให้กับตัวเอง
Reference
https://youtu.be/E0LYMhjHnBU?si=AY6ySrTy5t-OgYFT
-
 @ b6dcdddf:dfee5ee7
2024-07-12 20:15:22
@ b6dcdddf:dfee5ee7
2024-07-12 20:15:22🚀 Exciting News: Introducing Project Affiliates!
Creators can finally reach a wider audience by partnering with affiliates!
Affiliates earn automated payouts for contributions enabled through their shares. 🤑
Announcement link: https://x.com/geyserfund/status/1811434402041282680
originally posted at https://stacker.news/items/606500
-
 @ 7bdef7be:784a5805
2024-05-28 13:47:50
@ 7bdef7be:784a5805
2024-05-28 13:47:50I wrote Oracolo (see the announcement below) because I was brainstorming about Nostr "long format" and thinking about how to promote it. There seems to be little love for this format, why?
Long posts should have interesting value because the author usually put effort into them, and are produced for a long-term fruition. In the end, blogging was one of the most productive strands on the web, and still holds considerable importance.But in standard (kind-1) social clients they are rather hidden. I think many people don't even know they exist, they probably intuit something just because they see a particular formatting. This is quite evident if you compare the responses/zaps/reactions of the short notes with the long ones, the latter have far fewer interactions, a fact that I read as less exposure to readers.
Interlude: don't know what this "long format" stuff is?
Check https://habla.news or https://highlighter.comI think the situation can be largely improved with some adjustments in kind-1 clients:
- Add a tab/section to the user's profile, next to the usual posts/responses, that lists only the long format notes;
- Highlight/pinning recent long notes in the user's profile to give them visibility; the user picture could also have a special mark that alerts about fresh content available;
- In the feed show the preview of long notes with a special design, and allow the user to read them in a separate/immersive view (or just link to njump.me);
- In an appropriate context (es. at the footer of a long note) invite the user to discover long format and post his own content;
- Offer a filtered feed that display only long format notes;
Finally, we should probably also evaluate and agree on a new labeling in clients, because “long notes” is self-explanatory but also a bit confusing next to "plain notes”. Perhaps “articles” might be a better term.
If clients bring more interaction on articles, content creators are naturally incentivized to invest their time in this area, thus increasing the production of in-depth content that may be of interest even to those who are not as involved in social media dynamics.
Memo for kind-1 clients: interoperability is our superpower and currently your are the main entrance to Nostr, so don't be fearful or lazy, please embrace it.
nostr:nevent1qqsrrcl7sfaxd505lyezj7u54tpdg93x0swpcpe0xj5adax5l6xz3yspzamhxue69uhky6t5vdhkjmn9wgh8xmmrd9skctcpr3mhxue69uhkxmm4de68y6t9wvhxv6tpw34xze3wvdhk6tcppemhxue69uhkummn9ekx7mp0aagyzp
nostrdesign
-
 @ 7175188c:6382a72c
2024-07-12 20:02:24
@ 7175188c:6382a72c
2024-07-12 20:02:24originally posted at https://stacker.news/items/606482
-
 @ fa984bd7:58018f52
2024-05-28 12:35:04
@ fa984bd7:58018f52
2024-05-28 12:35:04I'm happy to announce that Shipyard is now roaming the nostr relays as a DVM.
Ok, what the hell does that even mean?
Ok, so DVMs, or Data Vending Machines, are just programs that take requests over nostr to deliver... well, data.
And what is Shipyard?
Shipyard, as it's slogan "A Quiet Place for Loud Ideas" implies, is a write-only Nostr client. One of the instrumental features that Shipyard.pub implemented was the ability to SCHEDULE posts and reposts. No more fighting to publish your notes to defeat the evil Timezone Cabal; you can write your note when you see fit, and then schedule so it's published whenever it makes most sense to you.
Groundbreaking stuff, I know.
Ok, so now, Shipyard's scheduling superpowers can be accessed as a DVM:
meaning that any Nostr client can now easily add scheduling capabilities without much fuss!
For example, this long-form post was actually written a day before it was published, and the publishing was handled by the Shipyard DVM.
How does it work?
Client developers can use NIP-89 to find kind:5905 DVMs, right now only Shipyard, and when a person wants to schedule a post they simply send the post via an encrypted DVM request to Shipyard. That's it, at the time the event's created_at timestamp reaches the event will be published to the specified relays!
What can it look like? Up to clients developers to decide; here's my take:
https://cdn.satellite.earth/e05f366b61b9b9b68f716eb297563e5dbbae6b7f7f73fdd5177a389bd2de36fb.mp4
-
 @ ab8cb80e:5395d502
2024-07-12 14:21:14
@ ab8cb80e:5395d502
2024-07-12 14:21:14Hey, I have nothing to do this Friday evening, so why not chill with chess?
Spontaneously I launched an Arena Tournament for today: https://lichess.org/tournament/2iNa8jh4
@ek @kristapsk @BitcoinAbhi @grayruby @frostdragon @Taft @02d43d3798 @030e0dca83 @riberet19 @felipe @didiplaywell @SatsMate @itsTomekK @wize123 @Coinsreporter @stefano @anon @314piepi @160ed04091 do you want to play?
! TODAY ! ♟️ https://lichess.org/tournament/2iNa8jh4 ♟️ 90 min arena, with 5 minute games.
Join on @Alby's new Discord: https://discord.gg/3vbafUCZ?event=1261325278358016091 for voicechat I plan to stream it to zap.stream, because why not.
Who takes my challenge?
originally posted at https://stacker.news/items/605942
-
 @ b804f68e:2fb0fa1f
2024-05-28 00:18:45
@ b804f68e:2fb0fa1f
2024-05-28 00:18:45As I've gotten into writing more regularly, I've realized the majority of my 'writing' comes from typing things up on my laptop. It's my preferred method of writing as I find it faster to do but also kind of therapeutic being able to see my thoughts being transferred onto something visible and structured in real time. However, being that I probably type more than 95% of the time compared to physically writing pen to paper, I got curious and did a little bit of research on what may be the advantages and disadvantages of both. It would seem the primary difference is typing offers a faster and more time efficient way to write things out, whereas traditional writing is better suited for brain stimulation and development in regards to better memory retention, focus, and creativity. I don't know if I'll ever go 50/50 with my physical writing to typing ratio, however, with what I have just learned, I do feel it would only serve to benefit my life and overall writing ability if I increase the amount of physical writing I do on a regular basis.
Do stackers type or write more, or is it somewhere in between? And why so?
-
 @ 0dc2dcb1:4787801a
2024-07-12 13:52:51
@ 0dc2dcb1:4787801a
2024-07-12 13:52:51- Prepared a Dutch webinar with an short introduction to Nostr - https://welkom.keuzevrijbijmij.nl/evenement/wwebinar-vergroot-je-privacy-op-social-media-10-juli/

- Received a nice t-shirt with the Nostr-PHP logo from Bitpopart who designed the logo
- Did an introduction talk in Dutch on a webinar with 350+ people subscribed on July 10th. 100+ watched the webinar live.
- Here is the full replay: https://keuzevrijbijmij.webinargeek.com/watch/replay/3487925/f29f93e939ffce35ac4593e407d03a9e/
At around 38min the Nostr stuff begins
- Here is the full replay: https://keuzevrijbijmij.webinargeek.com/watch/replay/3487925/f29f93e939ffce35ac4593e407d03a9e/
- Adding pages and wrote some documentation on nostr-php.dev
- Added a custom field
field_nsecto the user entity on nostrver.se (Drupal website) using the contrib module field_encrypt. The value of this field is stored encrypted in the database using a self created private key. This key is stored as a blob the server, but multiple ways of storing this are possible. In the Drupal CMS I now can save a Nostr private key for each user which will be fetch from nostr_content_nip23. All changes made in this Drupal contrib module for this: https://git.drupalcode.org/project/nostr_content_nip23/-/commit/cbc172b976aceaff107fea0296a8a476e098467e -
With a
nsecstored for each user, it’s possible to select a user when you’re broadcasting an Nostr event from Drupal. The event will be signed with the nsec of the selected user. Quick demo here: https://njump.me/nevent1qvzqqqqqqypzqpnrnguxe8qszsshvgkvhn6qjzxy7xsvx03rlrtddr62haj4lrm3qy88wumn8ghj7mn0wvhxcmmv9uq3camnwvaz7tmwdaehgu3wwdjkyctnw35hstnnda3kjctv9uqzqj75dy5eps3lgwum7f9p2l8sywy7wuxjr08pyhzyzv9mklylaydgdyll3z
-
 @ 6ad08392:ea301584
2024-05-27 18:31:39
@ 6ad08392:ea301584
2024-05-27 18:31:39Release announcement & short overview
Two years, six drafts, and 125,000 words later, and The Bushido of Bitcoin is almost complete.
Before the book’s release in Q3 of this year I will be doing a few things:
- Making it available for pre-order on Geyser. For the general paperback, digital and audio copies, it will save you roughly 50%. I will also include some limited edition options, like a short run of 21 leather-bound versions of the book. More on that in the coming weeks.
- Drip-feeding snippets from the book, in the form of quotes, lessons, etymology progressions and insights, across all my socials. On Substack I’ll do longer form posts, on Twitter & Nostr, I’ll keep them more succinct, and finally, I’m reviving my Instagram to wrap the insights in beautiful, shareable, bite-size visuals.
- Jumping on a bunch of podcasts, both Bitcoin and not Bitcoin-related to dig into the content of the book. I’ve recorded with Breedlove already. Many more to come - and who knows, I may even revive my old Wake Up Podcast and do a few short episodes there too.
I want to treat this book as both an ongoing work and a piece of art. So alongside the book, I’m also going to produce some pieces of visual and physical art. The video trailer, alone, I promise will blow your mind., as will the warrior-samurai artwork I’m going to have commissioned in collaboration with some soon-to-be-announced artists. I’ll probably even do a tradings cards pack with Bitcoin Trading cards next year, and some other collaborations along the way.
In any case, it’s been an incredible journey writing this book and I’m honoured to have had people like John Carter help me edit it, and Ross Stevens agreeing to do the foreword. I can’t wait to have the final version completed and in your hands.
For those who might be wondering what I am talking about…
**What is The Bushido of Bitcoin? **
This is a book I’ve been writing for almost two years now. Its genesis was a conversation I had with Erik Cason on my old Wake Up Podcast - also called “The Bushido of Bitcoin.” It was Episode 65: you can check out here. The inspiration for that episode came from a shared love of the book by James Clavell, called: Shogun (now a HBO series - which it seems they didn’t make woke..thank God), and of course we related the idea of Bushido (Way of the warrior: Code of Virtue) back to Bitcoin.
I felt that this was a seed of an idea, well worth watering. So after that, I decided to go on a history binge and start collecting ideas. What ensued was a real journey. I must’ve listened to a thousand hours of history books and Dan Carlin podcasts in the first six months and the concept began to form. But before I tell you what the concept is - let me tell you what it’s not.
This is NOT another book about the history of money, nor does it make an Austrian case for sound money, or an economic case for Bitcoin as sound money. Neither is it concerned with how Bitcoin works, or any of the technicals. We have enough of those books, and I don’t think I will add anything new to that corpus of knowledge. What this book IS about, is something so much deeper and more profound: The behaviour, virtue, culture and civilisation of greatness.
The book seeks to answer the question: “What happens when Bitcoin wins?” What happens to those who rise to the top, and become the socio-economic elite of the world?
- Will we become a new parasitic class?
- Will we become self-indulgent degenerates? Or..
- Will become men and women of virtue?
The latter is not a given, and it’s certainly not enough to just say “Bitcoin Fixes This.” To become men and women of stature and character requires actively developing the virtues which give rise to a culture of excellence. This is the only way to reclaim and rebuild civilisation - complaining and wishing about the past won’t cut it.
Over the coming weeks, I will introduce you to the Ten Virtues that make up The Bushido of Bitcoin. The book of course is more complete, but I will hold nothing back. We’ll follow the historical and etymological genesis of these virtues with an in-depth analysis on how they were embodied by the greatest leaders and warriors throughout history. We’ll also draw lessons from this analysis that will help us navigate the road ahead.

What lies before us may be a “clown world” but hope is far from lost. We’ve been here before. Many times, and against greater odds. This is our generation’s opportunity for a re-conquista.
The Bushido of Bitcoin is written to remind you there is something greater inside of you, and the only way through hell, is forward. I hope you find value in the up-coming content, and that should you pick up a copy of the book, it greatly inspires you.
Thankyou Aleksandar Svetski
Per-order the book here: https://geyser.fund/project/bushidoofbitcoin Get a free introductory chapter here: BushidoOfBitcoin.com Follow my work here: Linktree.com/Svetski
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-12 12:44:07
@ 5d4b6c8d:8a1c1ee3
2024-07-12 12:44:07Yesterday's edition https://stacker.news/items/604559/r/Undisciplined
-
- -
July 12, 2023 📅
📝
TOP POSTExcerpt
The nostr protocol directly solves two problems in internet applications: identity portability and data portability. Products built on nostr can depend on those two problems being solved. For most other equally challenging problems, the nostr protoco […]
3636 sats \ 26 comments \ @k00b \ ~nostr
💬
TOP COMMENThttps://stacker.news/items/208075/r/Undisciplined?commentId=208122
Excerpt
One thing I've noticed: almost all nostr profiles have a display name, a picture, and a bio, and almost all of them seem to be stored exclusively on relay.damus.io. I've connected to the top 5 relays on nostr.watch, queried for metadata for random ac […]
1046 sats \ 1 reply \ @super_testnet
From Portable experiences by @k00b in ~nostr
🏆
TOP STACKER1st place @k00b
11.3k stacked \ 15.7k spent \ 2 posts \ 17 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
22.3k stacked \ 0 revenue \ 35.3k spent \ 108 posts \ 245 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 12, 2022 📅
📝
TOP POSTExcerpt
Max Webster at Hivemind led with Ross Stevens (the NYDIG one), Raymond Tonsing of Caffeinated Capital, Mishti Sharma with Caffeinated's Collective Fund, and Steve Lee filling up the rest.
18.6k sats \ 93 comments \ @k00b \ ~meta
💬
TOP COMMENThttps://stacker.news/items/44061/r/Undisciplined?commentId=44097
Excerpt
Another "interesting" thing to note: where are Coinbase's, Gemini's and Binance's LN implementations?
331 sats \ 0 replies \ @moon
From Exchanges on Lightning by @kr in ~bitcoin
🏆
TOP STACKER1st place @k00b
21k stacked \ 26.2k spent \ 4 posts \ 39 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
22.9k stacked \ 0 revenue \ 26.3k spent \ 119 posts \ 321 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 12, 2021 📅
📝
TOP POSTLink to https://lightningbutton.com/
6 sats \ 3 comments \ @qecez \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/238/r/Undisciplined?commentId=286
Excerpt
I’m seeing “Sorry This page does not exist yet.”
1 sat \ 1 reply \ @02552fb987
From Deploy a lightning node in one line by @k00b in ~bitcoin
🏆
TOP STACKERNo top stacker
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
25 stacked \ 0 revenue \ 72 spent \ 8 posts \ 9 comments
originally posted at https://stacker.news/items/605773
-
-
 @ 362ebffa:492e2719
2024-05-27 12:51:14
@ 362ebffa:492e2719
2024-05-27 12:51:14Consciousness is the subjective experience arising from the brain (as the viewer, the beholder) While reality encompasses both the objective external world and our subjective perception of it.
The two are deeply interconnected, with consciousness shaping our experience of reality and reality influencing the state and content of our consciousness.
Therefor we do live in various bubbles of reality, my reality (my perception of reality) is my own.
What do you think?
-
 @ 1739d937:3e3136ef
2024-07-12 10:11:42
@ 1739d937:3e3136ef
2024-07-12 10:11:42This is the third in a series of weekly updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
Short update post this week but I made solid progress updating several OpenMLS dependencies and building a new library that implements all the OpenMLS crypto requirements for Nostr.
HPKE-RS
I mentioned a PR last week on the
rust-hpkelibrary, that PR is still waiting on review. However, in the meantime, the OpenMLS library depends on a slightly different hpke library, thehpke-rslibrary.This library didn't support the secp256k1 curve either so I've opened a PR to add support for secp256k1. That PR uses the
RustCryptolibrary that is the default in the thehpke-rslibrary. However, because this library is built to allow for swapping out the underlying crypto library (using traits), I was also able to create a new library that uses thesecp256k1library instead of theRustCryptolibrary. This is the main crypto library that almost all Bitcoin and Nostr apps use so it's important we use that instead ofRustCrypto.OpenMLS Nostr Crypto
The library that I've created (openmls-nostr-crypto) does a few things via separate sub-libraries (crates). The entire library tries to do as little as possible; only implementing the one required ciphersuite for all MLS implementations and the
secp256k1schnorr signatures ciphersuite I've created for Nostr. It's also using the rightsecp256k1library to do it.openmls-nostr-crypto: implementes the crypto traits that the OpenMLS library expects to find for a given provider and removes all the ciphersuites that we don't care about supporting.
hpke-rs-nostr-crypto: This implements the crypto traits that the hpke-rs library expects to find. Again removing all the ciphersuites we don't care about supporting.
I've not yet written any tests for these libraries (which needs to be done) but I've gotten some very simple demos working with OpenMLS using this new set of libraries to handle the crypto.
I've been really impressed with the simplicity of the OpenMLS interface as well. While there is A LOT going on under the hood, the public interface that client developers have to use is clean and simple.
Onward and Upward
Next week I'll continue working on these libraries; adding tests and continuing to build out my small demo app. I've been in touch with the maintainers of the OpenMLS library and I'm hoping to get a review done with them on my PRs and on my new library.
One thing I'll call out here: The review of my library and getting them to review the direction of the project overall will be paid consulting so I'm making sure that I've got as much done as possible before scheduling that time and paying their rates. I'm a strong believer that the right conversation can save you months of wasted time, but I'm also a believer in making sure you're prepared if you're going to drop money on that conversation. 😅
-
 @ 2ecde0a6:10022dcb
2024-05-25 20:28:41
@ 2ecde0a6:10022dcb
2024-05-25 20:28:41Opinion about KeepKey (hardware)
KeepKey is a hardware wallet with a high level of security and supports more than 40 different crypto assets.
The device provides a PIN code and recovery seeds. It has a feature where it switches your PIN code numbers from time to time, making it impossible for malware to copy our code. Also, the device has a system for trade where you have to press and hold to confirm the transaction to avoid external hacks.
KeepKey has only one button to manage it. This button is used for turning the device on and off. All the other processes can be managed through the mobile app. That includes entering your PIN code and setting up the recovery seed, which makes it very simple to use, unlike other complex wallets. The device has a wide screen that allows you to see the entire cryptocurrency address without the need to scroll back and forth. But it's easy to break or scratch if you don't have a protecting casing.
Its price is around $80.
But you have to remember that the device is a little big and heavy, compared to other hard wallets, so it's difficult to carry around with it.
WalletScrutiny #nostrOpinion
-
 @ a012dc82:6458a70d
2024-07-12 09:48:42
@ a012dc82:6458a70d
2024-07-12 09:48:42Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Introduction
The term "unbanked" refers to individuals who lack access to basic financial services, such as bank accounts, credit, and insurance. According to the World Bank, there are around 1.7 billion unbanked adults globally, and the majority of them live in developing countries. This lack of access to financial services often results in significant barriers to economic growth and financial security for these individuals. However, the rise of cryptocurrencies, such as Bitcoin, has opened up the potential for a solution to this problem.
The Bitcoin Lightning Network
The Bitcoin Lightning Network is a second layer technology built on top of the Bitcoin blockchain that allows for fast and cheap transactions. It works by creating payment channels between two parties that can be used for multiple transactions, without each one needing to be recorded on the blockchain. This enables near-instantaneous transactions and makes it ideal for micropayments, which are often required by the unbanked.
The Lightning Network is often cited as a potential solution to the high fees and long transaction times associated with traditional financial services. With the Lightning Network, fees are significantly lower, and transactions are confirmed almost instantly. This is particularly important for the unbanked, who may not have the resources to cover high transaction fees or the time to wait for transactions to be processed.
The Power of the Bitcoin Lightning Network Wallet
The Lightning Network wallet enables the unbanked to participate in the Bitcoin economy without needing a traditional bank account. It provides greater access to financial services and privacy compared to traditional financial services. The Lightning Network also addresses the challenges of high fees and long transaction times associated with traditional financial services. With lower fees and almost instant transaction confirmations, the Lightning Network has the potential to promote financial inclusion and empowerment for the unbanked.
Addressing the Challenges Faced by the Unbanked
The unbanked, who are individuals without access to traditional banking services, often face challenges when it comes to accessing basic financial services. Some of the key challenges include high fees and long transaction times associated with traditional financial services, limited access to financial services due to location or socioeconomic status, and concerns around privacy and security.
The Lightning Network and Lightning Network wallet can address many of these challenges. The Lightning Network offers significantly lower transaction fees and almost instant transaction confirmations, which can be a huge benefit for the unbanked who may not have the resources to cover high fees or the time to wait for transactions to be processed.
The Future of the Bitcoin Lightning Network Wallet
The future of the Bitcoin Lightning Network wallet looks promising as the network continues to grow and evolve. As more users adopt the Lightning Network and Lightning Network wallets, the infrastructure supporting these tools is expected to become more robust, secure, and efficient.
One potential area of growth for the Lightning Network wallet is in the development of new applications that can be built on top of the network. For example, developers could create peer-to-peer lending platforms, microfinance applications, or other financial tools that leverage the Lightning Network's fast and low-cost transactions.
Conclusion
The Bitcoin Lightning Network wallet is a powerful tool that has the potential to address many of the challenges faced by the unbanked. With lower fees, faster transactions, and increased access to financial services, the Lightning Network wallet has the potential to promote financial inclusion and empowerment for individuals who have traditionally been excluded from the financial system.
FAQ
What is the Lightning Network wallet? The Lightning Network wallet is a digital wallet that is built on top of the Lightning Network. It enables individuals to store, send, and receive Bitcoin in a secure and private manner.
How does the Lightning Network wallet help the unbanked? The Lightning Network wallet enables the unbanked to participate in the Bitcoin economy without the need for a traditional bank account. It provides greater access to financial services, lower fees, and increased privacy and security compared to traditional financial services.
How can the Lightning Network wallet be used for peer-to-peer transactions? The Lightning Network wallet enables individuals to send and receive Bitcoin in a peer-to-peer manner, allowing for fast and low-cost transactions.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ bd32f268:22b33966
2024-07-12 09:23:22
@ bd32f268:22b33966
2024-07-12 09:23:22"By the sweat of your face you shall eat bread, till you return to the ground, for out of it you were taken; for you are dust, and to dust you shall return." _ Genesis 3:19_
Can man eat bread without the sweat of his face? We have done everything to make life easier, using tools and inventing machines, thus maximizing our capacity to produce. Despite these prodigious improvements, Kierkegaard, a Danish philosopher from the 19th century, says the following:
“So there I sat and smoked my cigarette until my mind began to think. You are advancing in age, getting old without having become anything or having any project. On the other hand, when we examine literature or life, we see names and figures of celebrities, valuable and acclaimed people for their deeds, the benefactors of the age who know how to benefit humanity by making life easier, some through railways, buses, and steamboats, others through the telegraph, others through brief and easy-to-understand publications about what is worth knowing, and finally the true benefactors of the age who by virtue of systematic thought make spiritual existence increasingly easier and yet more meaningful — and what am I doing? Only one thing is missing [in our age], although it is not yet felt, difficulty is missing. For the love of humanity and despair regarding my strange proclamation of having achieved nothing nor succeeded in making anything easier, despite the genuine interest in those who make things easier, I finally understood that it was my task: to create difficulties everywhere.” Concluding Unscientific Postscript to Philosophical Fragments, published in 1846. Søren Kierkegaard (pseudonym Johannes Climacus)
This excerpt from a text by Kierkegaard comes as a punch in the stomach, alerting us to an inescapable reality: the need for sacrifice. No matter how seemingly easy life becomes, we still need sacrifice as a way to fulfill our purpose as human beings. Sacrifice, illustrated by difficulty in Kierkegaard's text, is what allows us to negotiate with existence itself and offer something in the present in the hope of obtaining something in the future. Sacrifice also allows us to know more deeply our limits and weaknesses and create an opportunity to transcend these limits. Without sacrifice, there is no love, for sacrifice implies that we have the capacity to see beyond ourselves, beyond our most immediate selfish interest. Through sacrifice, we are therefore invited to renounce something with the purpose of offering it.

Angelus (painting) – by Jean-François Millet shows two peasants praying, giving thanks for the harvest obtained through the sweat and effort of many days.
Since work is also a form of sacrifice, it is good to remember that this is an exercise we do with a useful end in view. Nature does not automatically satisfy all human needs, hence the need for work to meet them. Besides all this, work is also an antidote to some evils and a promoter of virtues. It allows us, for example, to combat idleness and laziness, while on the other hand, it allows us to enhance solidarity since we have obtained resources that we can now share. This means that work creates a propitiatory atmosphere for the person because it develops their ethics and morals on various levels. It seems more important at this time to reflect on this because we often fall into the error of seeking the enjoyment of immediate pleasures, the promises of an easy life, forgetting these realities. Not that having pleasure in itself evil, but this must always be subordinated to the values that organize our lives because obtaining pleasure is not the ultimate goal of life. It is evident that not all jobs are the same, and some are more conducive to virtues than others, something to which we must pay careful attention, hence it makes sense to seek to make work subordinate to our values. For there is no good work that does not express these values. Let us then use work as a springboard for our growth, and begin not to wish for an easy life, but rather to increasingly desire an honorable life in which we are not deceived by superficial gratuities.
-
 @ 3bf0c63f:aefa459d
2024-05-24 12:31:40
@ 3bf0c63f:aefa459d
2024-05-24 12:31:40About Nostr, email and subscriptions
I check my emails like once or twice a week, always when I am looking for something specific in there.
Then I go there and I see a bunch of other stuff I had no idea I was missing. Even many things I wish I had seen before actually. And sometimes people just expect and assume I would have checked emails instantly as they arrived.
It's so weird because I'm not making a point, I just don't remember to open the damn "gmail.com" URL.
I remember some people were making some a Nostr service a while ago that sent a DM to people with Nostr articles inside -- or some other forms of "subscription services on Nostr". It makes no sense at all.
Pulling in DMs from relays is exactly the same process (actually slightly more convoluted) than pulling normal public events, so why would a service assume that "sending a DM" was more likely to reach the target subscriber when the target had explicitly subscribed to that topic or writer?
Maybe due to how some specific clients work that is true, but fundamentally it is a very broken assumption that comes from some fantastic past era in which emails were 100% always seen and there was no way for anyone to subscribe to someone else's posts.
Building around such broken assumptions is the wrong approach. Instead we should be building new flows for subscribing to specific content from specific Nostr-native sources (creators directly or manual or automated curation providers, communities, relays etc), which is essentially what most clients are already doing anyway, but specifically Coracle's new custom feeds come to mind now.
This also reminds me of the interviewer asking the Farcaster creator if Farcaster made "email addresses available to content creators" completely ignoring all the cryptography and nature of the protocol (Farcaster is shit, but at least they tried, and in this example you could imagine the interviewer asking the same thing about Nostr).
I imagine that if the interviewer had asked these people who were working (or suggesting) the Nostr DM subscription flow they would have answered: "no, you don't get their email addresses, but you can send them uncensorable DMs!" -- and that, again, is getting everything backwards.
-
 @ 38d0888d:bd8e1246
2024-07-12 07:10:35
@ 38d0888d:bd8e1246
2024-07-12 07:10:35A thriving society rests on the principles of modesty and humility, avoiding idleness and self-indulgence. Individuals are needed to forsake the constant pursuit of attention and instead aspire to selflessness, dedicating themselves to serving humanity. Humility fosters spiritual harmony and protects against materialism and selfish desires.
Beyond personal conduct, humanity must champion altruism and solidarity within the global community. Belief in collective endeavors will pave the way for global harmony. Embracing values like kindness, compassion, and genuine concern for others promotes positivity and reflects the influence of a higher power. The aim is to cultivate a unified multicultural community where each person contributes to manifesting this higher presence.
The collective goal is to direct humanity to nurture a community that experiences spiritual growth while upholding humility as a guiding principle, resisting materialism's allure. By creating such an environment, the hope is to resonate with a sacred harmony that extends beyond immediate boundaries. Through intentional actions and meaningful relationships, a collective space embodying these values can be established, ensuring the higher power's presence guides individual lives and interactions with the world.
-
 @ 6c8c7979:15595f3e
2024-07-12 01:02:17
@ 6c8c7979:15595f3e
2024-07-12 01:02:17Despite the numerous historical turning points that have influenced art history, the Baroque era stands out as a pivotal marker in the history of art and culture.
Spanning from the 17th to the early 18th century, the Baroque period reshaped architecture, literature, music, sculpture, and visual arts.
Originating in Italy, the Baroque movement spread across Europe, flourishing notably in France, the Netherlands, and Spain, and later extending its influence throughout the continent.
It was an artistic and philosophical movement aimed at embodying motion, life, and profound meaning with maximal drama and theatricality.

Nymphenburg Palace - Munich, GermanyIn the field of architecture, Baroque style saw the construction of churches, palaces, castles, theaters, and public spaces in a bold and distinctive manner.
These buildings were characterized by abundant use of marble, intricate curves and recesses, and ornate decorative details. Colors were vibrant and rich, lending a dramatic and spiritual character to Baroque structures.
For example, the Luxembourg Palace, now known as the French Senate, built in Paris in 1615, exemplifies Baroque architecture with its emphasis on luxury, detailed ornamentation, monumental size, and the use of domes.
This architectural philosophy was influenced by the opulence and intricate designs that were originally introduced to Europe from the Islamic world during the Middle Ages.
Moreover, the building is distinguished by its grand staircases, high ceilings, and walls adorned with either sculptures or paintings—a hallmark Baroque tradition. Additionally, Baroque architecture emphasized the abundant use of mirrors inside buildings to visually expand the space, albeit illusionistically, creating a sense of spaciousness.

The Luxembourg Palace Library in Paris houses approximately half a million books.$$Baroque literature$$Baroque literature saw many writers and poets of the era adopt an epic rhetorical style. Baroque literary works are characterized by complexity, mystery, and elaboration in description, influenced by the cultural phase deeply immersed in highlighting and praising intricate details.
Those works arose from a self-awareness of the prevailing cultural discourse at the time. Metaphors and epic similes were abundant. There was also a tendency towards exaggeration and paradox in the sequence of events throughout the plot.
John Milton's epic poem "Paradise Lost" (1608-1674), for many language scholars, is considered one of the greatest poems in the history of the English language. The poem consists of 10 volumes in its first edition and 12 volumes in the second, recounting the story of Adam and Eve's expulsion from paradise and their long-lasting battle with Satan.
In "Paradise Lost," Milton states, "The end of all learning is to know God, and out of that knowledge to love Him and to imitate Him."
Baroque Music
In the field of music, numerous musical instruments and new techniques were developed to emphasize the depth and power of sound. As a result, Baroque music emerged filled with complex compositions, lively rhythms, and rich harmonies.
Some of the most famous composers of this era include Johann Sebastian Bach, George Frideric Handel, and Antonio Vivaldi.
https://youtu.be/DwHpDOWhkGk?si=Nw-h0RKZFllyNwok
Let's enjoy, for example, a musical journey with Bach's cello suite, exploring the depth and beauty of the instrument across 6 movements, each showcasing Bach's mastery of the following point and his innovative musical ideas that captivate the listener with their charm and technical complexity.
$$Baroque Sculpture$$Like other creative fields, visual arts such as sculpture and painting gained fame for their precision and richness of detail. Many works overall dealt with religious meanings, elements of pride, and beauty.
Baroque artists were renowned for their skillful use of natural light to highlight dark shadows, thereby adding dimensions to their paintings. Many prominent artists such as Rembrandt, Peter Paul Rubens, and Peter Paul Rubens produced stunning works during that period.
Therefore, the painting "The Night Watch," created by the Dutch artist Rembrandt in 1642, stands as a prominent example of the depth of Baroque style in art history.

"The Night Watch" - Amsterdam MuseumThe painting is a group portrait of a civic militia, where the painter skillfully used light and shadow to showcase their pride and intimate camaraderie.
It's worth noting that the play of light and shadow not only highlights the central figures but also creates a sense of mystery and anticipation, which in turn adds drama and movement to the scene, attracting the eye to the tableau.
The vibrant colors and intricate details bring a lively texture to the characters, making the painting a visual feast for viewers. The composition is balanced due to Rembrandt's expertise; we see him strategically positioning the characters at times and infusing Baroque dramatic touches at others, all serving the same purpose of presenting the work as a cohesive narrative.
One intriguing aspect of "The Night Watch" is Rembrandt's departure from depicting a single hero in the work; instead, he portrays each individual in the painting with equal importance. This deviation from the norm reflects his progressive vision and artistic sensitivity amidst the Baroque era.
The Baroque period was known for its personal dedication to expression, whether through painting, music, or writing, making it a distinctive and valuable era in human history, characterized by richness of production as much as richness of detail.
The development of new styles and techniques during this period also contributed to the emergence of other artistic schools, such as Rococo.
-
 @ 126a29e8:d1341981
2024-05-22 06:47:20
@ 126a29e8:d1341981
2024-05-22 06:47:20Esta es la traducción de una carta de Ross Ulbricht que se publicó en su blog en Septiembre de 2019. Podéis leer el artículo original aquí: https://rossulbricht.medium.com/bitcoin-equals-freedom-6c33986b4852
Algo especial sucedió en el primer año después de que Satoshi nos regalara Bitcoin. Algo que nadie esperaba y que muchos pensaban que era imposible. Intenta imaginar Bitcoin en aquel entonces, antes de que pudieras comprar cosas con él, antes de que hubiera un tipo de cambio, antes de que nadie supiera realmente qué pasaría con él, si es que pasaba algo. Bitcoin no empezó como dinero. Se convirtió en dinero, pero lo hizo de forma distinta a cualquier dinero anterior. A pesar de todas las cosas que Bitcoin ha hecho posibles, a pesar de todas las formas en que está cambiando nuestro mundo, no apreciamos plenamente o ni siquiera entendemos lo que sucedió en aquellos primeros días, cuando era sólo un juguete para geeks.
Cualquier otro dinero anterior al Bitcoin -en la larga historia de la civilización humana- se valoraba por razones distintas a su uso como dinero. El ganado en África, los sellos de correos en las prisiones, las conchas marinas y los metales preciosos se han utilizado como dinero y encajan en este patrón. La única excepción es el dinero fiduciario -algo declarado como dinero por una autoridad-, pero incluso las monedas fiduciarias nacionales estuvieron en su día respaldadas por algo con valor previo, como el oro.
Bitcoin cambió todo eso. Bitcoin no tenía ningún valor previo y nadie estaba obligado a utilizarlo, pero de alguna manera se convirtió en un medio de intercambio. Las personas que no entienden y se preocupan poco por Bitcoin pueden, sin embargo, aceptarlo como pago porque saben que puede ser utilizado para pagar por otra cosa o ser intercambiado por dinero convencional.
La gente suele mencionar las pizzas que se compraron por diez mil bitcoins y, en retrospectiva, se burlan del tipo que se comió lo que se convertiría en un almuerzo multimillonario. A mí me interesa más la persona que renunció a dos pizzas en perfecto estado por meros bitcoins. ¿Qué vio en esos bits y bytes, en esa firma digital de algo que la gente llamaba cadena de bloques? Lo que motivó al vendedor de pizzas pudo haber llamado también la atención de los primeros mineros, que no podían vender pero acumulaban alegremente. Quizá inspiró a los que simplemente regalaban bitcoins por miles. Fuera lo que fuese, era algo nuevo.
La teoría económica clásica dice que un intercambio no se produce a menos que ambas partes valoren más lo que reciben que lo que entregan. Entonces, ¿de dónde viene el valor? Bitcoin nunca debería haber despegado, pero lo hizo. Incluso un producto nuevo tiene algún tipo de valor, y los primeros en adoptarlo corren el riesgo de no obtener el valor de su dinero, pero aún así esperan ganar con el intercambio.
En cambio, los primeros usuarios de Bitcoin no tenían ni idea de lo que sabemos ahora. Todo lo que tenían era un sueño, una convicción y el entusiasmo suficiente para convertir un artilugio digital en un fenómeno multimillonario del que sólo estamos empezando a ver los efectos.
Te diré lo que creo que pasó, aunque lo cierto es que nadie lo sabe. Es casi magia que Bitcoin pudiera surgir de la nada y, sin valor previo ni decreto de autoridad, convertirse en dinero. Pero Bitcoin no se originó en el vacío. Fue la solución a un problema con el que los criptógrafos llevaban lidiando muchos años: Cómo crear dinero digital sin autoridad central que no pudiera falsificarse y en el que se pudiera confiar.
Este problema persistió durante tanto tiempo que algunos dejaron la solución a otros y soñaron en cambio con cómo sería nuestro futuro si el dinero digital descentralizado llegara a existir de alguna manera. Soñaban con un futuro en el que el poder económico del mundo estuviera al alcance de todos, en el que el valor pudiera transferirse a cualquier lugar con sólo pulsar una tecla. Soñaban con que la prosperidad y libertad dependieran únicamente de las matemáticas de una encriptación robusta.
Bitcoin nacía pues en terreno fértil y era reconocido por quienes lo habían estado esperando. Fue un momento histórico para ellos, mucho más importante que las pizzas o las facturas de la electricidad generadas por la minería. La promesa de libertad y el encanto del destino dieron energía a la comunidad inicial. Bitcoin se adoptó consciente y espontáneamente como dinero mientras nadie lo veía, y nuestro mundo nunca volverá a ser el mismo.
https://freeross.org
-
 @ 6c8c7979:15595f3e
2024-07-12 00:13:43
@ 6c8c7979:15595f3e
2024-07-12 00:13:43The painting "The Anatomy Lesson of Dr. Nicolaes Tulp" by Rembrandt, created in 1631, is one of the prominent works of Baroque art and a notable example of anatomical studies during that period. The painting depicts a real anatomy lesson conducted in a lecture hall in Amsterdam.
The artwork portrays several individuals, including members of the Surgeons' Guild and anatomy students, interacting with the dissected corpse laid out before them to study the human body's details. It is distinguished by its meticulous depiction of muscular forms and skeletal structure, rendered realistically, with a focus on the contrast between life and death, and light and shadow within the composition.
Rembrandt employed his artistic skills to create a powerful dramatic effect, infusing the painting with life and movement despite the static nature of the cadaver. The dramatic lighting he used is highly realistic, highlighting intricate details in the darker areas, thus adding depth and expressive power to the artwork.
In addition to its stunning technical execution, the painting reflects human curiosity and scientific inquiry into human anatomy, embodying aspects of philosophy and science that were of interest to Baroque society at that time.
-
 @ 3c827db6:66418fc3
2024-05-20 12:25:27
@ 3c827db6:66418fc3
2024-05-20 12:25:27With the previous articles, we found the disconnect between paid-for work and paid-for time. We also understood that if you want to get paid you have to provide work that is valuable for others. So when the person consumes the benefit of your work, the exchange happens value for value - work for sats. But what happens if the benefit that the consumer experiences is not a momentary but a continuous process? There are a few examples of this. I will start with the one that is not that captivating but still valuable.
Streaming services, like other industries, grapple with the limitations of the fiat payment system. The burden of fees and the absence of suitable technology for streaming payments have compelled them to adopt similar mitigations as other industries. This translates to charging users on a monthly basis.
With the Lightning Network, we have the technology to stream sats for content. No longer confined to monthly subscriptions, you pay for what you consume in real time. Whether you watch sporadically or binge extensively, streaming payments allow for a more personalized and efficient payment model. This way the creator of the content and the user have a direct connection for each minute the content is broadcasted. With streaming payments now you can say goodbye to subscription payments.
Unveiling A New Era Of Fair Compensation And Accountability In Movie Production
Imagine you've created a movie or documentary. Traditionally, you'd charge people for a ticket, essentially asking them to pay upfront for future value, creating a slight disconnect. Now, with streaming payments using sats, consumers can pay as they watch. If your movie sucks, they might only pay for the first 30 minutes. However, you still receive value, and viewers won't feel overcharged for something they didn't enjoy. If your movie is great they not only stream sats the whole time but at the end, they leave a tip.
On the receiving side of the movie most people involved in it received a salary for doing their job. As we already know this is not aligning the whole structure in the same direction. Some people do not care at all how good the movie is if they have already been paid and do not receive a bonus further. Some people might care about reputation in the market but very few just want to do the best job. Again, we went through this, and as you are guessing you just do a split payment in the backend where all the people in the credits actually receive sats or even milisatoshis based on their contribution. This was something I did not expect that Bitcoin would disrupt. This way the reputation is directly linked to the payment and a lot more people will fight to have the best movie. You can be someone who contributed to a project and wants to stay anonymous for whatever reason but still receive money - Lightning instant settlement is the way to do it.
These concepts should not be new if you read through the last 3 articles. In addition, people in the Bitcoin space are familiar with the Value for Value (V4V) podcasting and that is very close to what I am describing above. While the technology for podcasting is already in place, it's surprising how few podcasts leverage this technology to implement split payments effectively. They give that responsibility to some hosting service that decides to take a 5% split for themselves and the other 95% goes to the wallet of the show. Why not do the split the proper way? The hosting service provides value so they should get a percentage but if you are 3 people involved in the production of the podcast you should have that 95% split so it goes to those individuals. There's no excuse, especially for Bitcoin podcasts, not to make this effort and implement split payments appropriately.
The Dynamic Future Of Pay-as-you-go In Content Consumption
In this example, the pay-as-you-go model holds true for continuous experiences, like streaming. Now, let's revisit the movie example. If you're a theater, you are essentially the hosting provider for the movie. The quality of the theater experience can vary; one theater might have uncomfortable chairs, while another boasts luxurious massage chairs. The theater with subpar seating might receive a 3% share of the movie's streaming sats revenue, while the one with comfortable massage chairs might earn 5% for each sat stream paying for the movie. Furthermore, if a viewer activates the massage function of the chair, additional sats are streamed for each second that the function is on. I do not know the exact payment dynamics between theaters and movie studios but I bet there are prepayments and funds held at multiple points in the fiat payment process. With the adoption of the Lightning Network, theaters no longer have to prepay for movies to be projected on their screens. They can now observe which movies are most popular in real time and adjust their projections accordingly to optimize revenues. This benefits the consumer and optimizes profits for themselves and the creators of the movie.
Now you see the content gets its value stream for the continuous experience and everyone in the film industry will fight to give the best experience for the most amount of time. The better the experience the more sats flow their way. Due to the highly subjective nature of content, where one person might deem a movie subpar, another might label it as their favorite. This subjectivity is why I believe most content streaming will not have a predetermined price. Even movies may adopt the V4V model, similar to what Adam Curry is pioneering in podcasting. For instance, you watch a movie, and during the credits, a prominent QR code appears, allowing you to decide how much you want to send to the creators of the movie. You will listen to a song or a podcast the same way. Whether you predefine a streaming rate per minute or request payment at the end, both options are technically possible. However, the market will ultimately determine which option prevails as the better one.
Also, why not have a bidding competition for any event that has assigned seats? The person who bids the most for a ticket gets to be in the first row of the concert or a sports stadium. This way the subjectivity is left for all the viewers to decide how valuable it really is. This way it ensures a full stadium also because if there is no value in attending the event people are not going to bid for the seats or just pay 1 sat for it.
Revolutionizing Taxi Transactions For Drivers And Passengers Alike
The continuous experience or service for streaming could be anything in the physical realm. I will take a look at how instant settlement could look like in transportation services. One such transportation service is the taxi service. Even though Uber decentralized the taxi companies which is great they did nothing about decentralizing the payment process. Lightning Network fixes that and more.
With a streaming payment option for each meter of movement, taxi drivers no longer need to wait until the end destination to receive their payment. In a world of instant settlement, payment occurs as you go, eliminating the risk for the taxi driver regarding whether the passenger will pay at the end of the journey. While this might not be a groundbreaking improvement, there are several additional benefits to consider.
Why do most taxis operate with cash? Taxi drivers in most places need a POS device for the customers to be able to pay for a better user experience (UX). It may be a better UX but on the other hand, it creates problems for the drivers either way:
- They have to acquire clunky devices.
- They must pay payment processing fees, negatively impacting their margins.
- Operating solely with cash exposes them to the honeypot problem, carrying a substantial amount of money, and making them vulnerable to theft.
With an app tailored for the taxi experience and integrated with the Lightning Network, these issues become irrelevant. There is no need for additional equipment, no payment processing fees for receiving money, and no exposure to visible cash, reducing the risk of being a target for theft. Now you can have a better UX with better security and better margins - an additional benefit is that it will be paid with Bitcoin. Not only that but just like the example with the movie theater chairs drivers will be incentivized to make the travel experience even better. They can offer - to watch a movie, video games like PlayStation, or massage chair. If you choose to use those extra experiences on top of the travel experience you have to increase the sats streaming their way.
An additional benefit for the travel experience of customers arises when multiple passengers in a taxi have different destinations. Traditionally, the taxi meter ticks for the entire journey, and when the first person is dropped off, determining a fair amount for their portion becomes complex. However, with the Lightning Network, it's conceivable to streamline this process. Imagine a scenario where three passengers enter a taxi, each with distinct destinations. Each person scans a QR code upon entering, linking their streaming sats to the taxi app. The app manages split-receiving, dynamically adjusting the distribution of streaming payments based on how many people are in the taxi. As passengers are dropped off one by one, the app seamlessly adjusts the split-receiving, providing a fair and efficient payment solution for each individual's share of the journey.
Optimizing City Transportation With Streaming Sats
The proposed model of split-receiving through QR codes and streaming sats can extend beyond taxi services to other modes of transportation, such as buses. The idea is to calculate the average cost per mile (or meter/foot) for providing the transportation service, including factors like fuel, maintenance, and driver salary, and add a margin for profit. Passengers entering the vehicle scan a QR code, and the app dynamically adjusts the streaming payments based on the number of people on board.
For buses, this model allows for real-time adjustment of streaming payments as passengers enter and exit. If there are 30 people on the bus the split is between them. At the next stop, 10 people are dropped off and 5 people get on board - now the sats stream is divided by 25 people. As the number of people on the bus changes at each stop, the streaming sats are proportionally divided among the passengers. This approach can lead to more efficient and flexible city transportation. Late-night buses will be more expensive for the passengers because of the fewer riders, while buses during peak hours may offer a more cost-effective traveling experience as payments are shared among more passengers.
This system encourages transportation optimization around events, such as concerts or sports games, where private buses or minivans wait to fill up before departing. Routes can be dynamically adjusted because you will have a system tracking how many people are in the vehicles at what time and at what location on the map. Importantly, this data remains anonymous, as no KYC information is required for the Lightning Network payments.
The Streamlined Pay-from-a-distance
Now with this streaming money feature, it can be applied differently. Let’s go back to the taxi service for a moment. The pay-from-a-distance feature that is available in the Lightning Network can significantly enhance the experience of ordering a taxi. Instead of the traditional model where drivers wait patiently and charge fixed fees when passengers enter the car, this model introduces streaming sats from the moment the passenger accepts the ride. Here's how it works:
- The passenger places an order in the app, specifying the destination. Nothing new here.
- Drivers see the order and can apply for it, similar to platforms like Uber.
- Streaming sats start the moment the passenger accepts the driver, and streaming payments commence. This fee will be less than the actual transportation but the user is still paying for the service of the car coming to him and not the other way around.
- The taxi arrives at the passenger's door, and the streaming payments continue. There is a fee for waiting at the door per minute.
By shifting the waiting cost to the passenger, there's a strong incentive for both parties to be prompt, and the system becomes more efficient. Additionally, the passenger's responsibility to follow the car reduces operational costs related to alerting passengers via message or a call. Any inefficient time management becomes a cost for the passenger. This model aligns incentives for both drivers and passengers, creating a more seamless cost and time-effective taxi experience.
The concept of paying from a distance can be creatively applied to various scenarios, providing convenience and peace of mind. For instance, when it comes to sending your child somewhere with a taxi, traditional concerns about trusting them with money or the driver's reliability may arise. However, with the ability to stream sats for the ride, you gain real-time visibility on your device, tracking your child's journey and ensuring they reach the intended destination safely. This pay-from-a-distance feature extends beyond transportation and can be applied to other continuous services. For example, daycare services charge per minute, allowing you to stream payments in real-time, ensuring accurate and fair compensation for the duration your child spends there. Additionally, you can send a present to a friend, such as a massage session, and pay for it in a streaming fashion, covering the cost continuously based on the duration of the service. The flexibility of streaming payments not only offers real-time tracking and control but also opens up new possibilities for various services where charging per minute or duration is relevant. Those services can be paid on the spot or from a distance. image2
I know that now it looks like we are going backwards from the original point of never paying money for time. The key distinction here is that you may be paying for time past for the service but in that time you get a continuous stream of value (work done) so you are streaming value back to pay for it. In some cases the time spent is actually an accurate measure of the work done.
It's true that developing apps with such functionalities is technically feasible, and there might be entrepreneurs and developers willing to explore these possibilities. However, a significant challenge arises when considering custodial control over users' funds. Small startups might find it financially burdensome and complex to operate as custodians, potentially steering away from such responsibilities. This will take not only high responsibility but also a very big financial wall and expertise to obtain the licenses that comply with the ever-changing regulations. On the other hand, large tech companies with substantial resources could afford to take on the role of custodians, presenting both a business opportunity for them and a risk for the users. The move by some tech giants, like X(formerly Twitter), to obtain such licenses can be seen as a strategic measure for self-preservation over their own finances. This is also an opportunity to consolidate control over not only user data but user finances within their platforms.
The Breez SDK offers a powerful solution, empowering developers to create diverse applications without having to worry about payment intricacies. Its non-custodial nature is a key advantage, eliminating the need for licenses. The infrastructure of it is made in such a way that it is peer-to-peer so no one is holding money for someone else. The app developers focus on the experience within the app and just plug in the code. This combination of features gives startups a competitive edge and reverses the advantage held by large tech companies. While they go through the complex process of getting a license the startup can integrate the global payment network (the Lightning Network) in one day. Even if certain tech giants choose to lock users' funds within their applications, alternative options will continue to be developed, and users will have the freedom to opt-out. Just like people are choosing Bitcoin over fiat.
Now who is ready to give all of us those experiences in their app?
-
 @ b804f68e:2fb0fa1f
2024-05-20 06:07:22
@ b804f68e:2fb0fa1f
2024-05-20 06:07:22Consistently writing on SN and Obsidian has underscored for me the critical role of application in the learning process. Writing allows me to visually process, reflect, analyze, and organize the myriad ideas generated within my brain. Through this ongoing practice, I can physically sense my improvement in articulating thoughts to others and myself, both in writing and speech. However, both forms of expression still require significant practice, especially the latter.
Before I began writing regularly, I didn't fully appreciate the importance of purposeful learning. Previously, I viewed reading a book, watching an educational video, or listening to a podcast as the primary components of learning. But these activities are merely the initial stimuli that prepare our brains for deeper engagement, much like a warm-up before a workout. True learning extends beyond passive consumption; it involves actively practicing and applying what we've learned, reflecting on our experiences, and continually revisiting the material to fill in gaps and deepen our understanding. Sharing and discussing our insights with others further enriches this process, as it exposes us to diverse perspectives and feedback we might not have considered on our own. For me, writing acts as the bridge that connects acquired knowledge to practical application.
After writing on SN consistently for over a month, I've come to realize what it truly means to learn and acquire knowledge. Writing daily has exposed gaps in my understanding, often revealing that I lack the depth of knowledge I assumed I had. When I reach the limits of what I know, I'm compelled to research further, which reinforces and expands my comprehension.
Even if you never write publicly, I believe everyone can benefit from the act of writing. The more I write, the more intentional my learning process becomes, and the more organized and structured my thoughts are.
-
 @ 036533ca:cbaabf58
2024-07-11 21:54:40
@ 036533ca:cbaabf58
2024-07-11 21:54:40In a recent job interview, we discussed some of my work on Nostr and specifically my Noscrypt library. I was asked basic questions, such as what it is and what purpose it serves. Most of my response centered on the idea that while the secp256k1 library is excellent, it is easy to misuse.
So what footguns?
It had been a while since I heard that term, and for whatever reason, I struggled to give a satisfactory response. The interviewer was pleased, but I was not, so I want to take some time to reflect on better ways of explaining the challenges I've encountered while working with libsecp256k1 when building on Nostr.
First, libsecp256k1 is functionally perfect as it is, and I don't see any need for changes. The real challenge is implementing all of the Nostr-specific cryptographic tasks on top of secp256k1. This includes complex but necessary operations like note encryption and signing. The most difficult part is converting between all of the different required encodings: Hex, Base64, Bech32, JSON, UTF-8, and so on.
Really I'm just talking about implementation details, what I got wrong, and what was missing between nostr operations and libsecp256k1.
Some backstory
When I first fell into Nostr, I had some cryptography experience from working on my .NET libraries called VNLib. I quickly realized that Nostr identities rely on your ability to keep a 32-byte number safe, but also accessible. With my HTTP framework in hand, everything seemed like a nail. I wanted my key to be securely stored and signed remotely across a network, where the data is sent between the client/server, and my key never has the opportunity to leave the server. So that's what I started building and continue to use, even though it's not complete. That project is called NVault, and I quietly work on it in the background as things break.
Originally, I built a C# wrapper for libsecp256k1, manually worked through all the C/C# barriers, and implemented the note encryption and signing in higher-level C#. However, when NIP-44 came out, everything changed. I realized how much more complex the wrapper would become if I kept trying to stack onto it. Another issue was performance. I still believe my skills in C allow me to write more efficient and performant code than I can in C# for the same tasks, especially when it comes to cryptography and functional programming.
NIP-44 significantly increased the complexity of Nostr cryptography, and after seven months of regular work on NIP-44, I know I'm not the only one still grappling with this complexity, along with NIP-59 and other related DM and crypto specs.
Okay, so a library needed to address the complexities and inefficiencies of Nostr cryptography while also being portable. To me, no other language meets those goals better than C. We can target virtually every operating system, as most high-level languages can bind to a C ABI at load time or runtime. Additionally, we can target hardware/RTOS systems. C can do it all and usually do it better if you are "smart" and careful, in my opinion. Defensive C programming, if you will.
Why noscrypt
If you are building a client or relay in C, or a derivative that relies on libsecp256k1, or a similar library, because it's the most tested and stable library for the secp256k1 elliptic curve, you will need to implement every Nostr-related spec by hand as helper code in your project. Libraries handle this. However, each time note encryption changes (which it has frequently), you will need to revise your cryptographic helpers to accommodate those changes and hope you don't make a fatal mistake that compromises your users' keys or notes. You aren't a cryptographer; you're a client/relay developer. I'm not saying you can't do it; I'm saying you don't want to.
Working with libsecp256k1
First, there is no concept of a key pair associated with Nostr in libsecp256k1. Nostr is "special" in that we treat the secret key and public key as equally distinct parts of your identity on the network and often store them separately.
Public Keys are X-Only
Public keys in Nostr only use the x-coordinate of the xy point on the curve. Libsecp256k1 handles this fine, but not in a foolproof way, in my opinion.
Here is some code taken from Noscrypt to illustrate the steps needed to implement public key conversion:
```c int _convertToPubKey( const NCContext ctx, const NCPublicKey compressedPubKey, secp256k1_pubkey* pubKey ) { int result; uint8_t compressed[sizeof(NCPublicKey) + 1];
/* Set the first byte to 0x02 to indicate a compressed public key */ compressed[0] = BIP340_PUBKEY_HEADER_BYTE; /* Copy the compressed public key data into a new buffer (offset by 1 to store the header byte) */ MEMMOV((compressed + 1), compressedPubKey, sizeof(NCPublicKey)); result = secp256k1_ec_pubkey_parse( ctx->secpCtx, pubKey, compressed, sizeof(compressed) ); return result;} ```
The NCPublicKey type is a 32-byte structure (a byte array) so it's far easier to work with and store with higher-level Nostr applications. We have encountered these issues time and again in Aedile due to the way we use public keys in Nostr.
I regularly failed to find a structured way to store Nostr-specific public keys that libsecp256k1 could work with. I ended up making all the above function calls (and about two more) into the library to do this conversion. So, it's just implementation details.
Keypairs
Again, libsecp256k1 requires some complexity in keypair structures which Nostr has almost no 1:1 mapping to, and really doesn't need. A secret key is all that is required to sign (encrypt) a message using ECDSA, so there is no reason to store keypairs in this case.
Again here is an example from noscrypt
```c NCResult NCSignDigest( const NCContext ctx, const NCSecretKey sk, const uint8_t random32[32], const uint8_t digest32[32], uint8_t sig64[64] ) { int result; secp256k1_keypair keyPair; secp256k1_xonly_pubkey xonly;
/* Fill keypair structure from the callers secret key */ if (secp256k1_keypair_create(ctx->secpCtx, &keyPair, sk->key) != 1) { return E_INVALID_ARG; } /* Sign the digest */ result = secp256k1_schnorrsig_sign32(ctx->secpCtx, sig64, digest32, &keyPair, random32); /* x-only public key from keypair so the signature can be verified */ result = secp256k1_keypair_xonly_pub(ctx->secpCtx, &xonly, NULL, &keyPair); /* Verify the signature is valid */ result = secp256k1_schnorrsig_verify(ctx->secpCtx, sig64, digest32, 32, &xonly); return result == 1 ? NC_SUCCESS : E_INVALID_ARG;} ```
Some validation code was removed for brevity, assertions are used for describing expected results
You will notice that a key pair structure is required (and must be assigned) from our secret key. This is where I think the strict typing of the
NCPrivateKeystructure ensures safer signing and a more straightforward API. Again, Nostr implementation details, but this function helps mitigate complexities in an obvious and difficult-to-misuse way.In the case of polyglot linking, I think it also makes it reasonably simple to sign a message digest with a single function call on some byte arrays. Direct, which I think is important.
EC Diffie Hellman
ECDH or Elliptic Curve Diffie Hellman gives us the ability to take a set of points on an elliptic curve and create a shared key that only the key holders can generate. More specifically, each party only needs to know each other's public information in order to generate said shared point. We exploit that feature in multiple ways by using symmetric encryption in both NIP-04 and NIP-44 encryption specifications.
Ignoring all of the encryption specifications, we need a function to safely generate our shared point from our Nostr-specific secret and public keys. So some strict typing and our
_convertToPubKey()function from above re-appear. You will also notice a callback function called_edhHashFuncInternal(). This function does the work of "computing the hash" which in Nostr we just need to return the shared x-coordinate as per NIP-04```c NCResult _computeSharedSecret( const NCContext ctx, const NCSecretKey sk, const NCPublicKey otherPk, struct shared_secret sharedPoint ) { int result; secp256k1_pubkey pubKey;
/* Recover pubkey from compressed public key data */ if (_convertToPubKey(ctx, otherPk, &pubKey) != 1) { return E_INVALID_ARG; } /* * Compute the shared point using the ecdh function. * * The above callback is invoked to "compute" the hash (it * copies the x coord) and it does not use the data pointer * so it is set to NULL. */ result = secp256k1_ecdh( ctx->secpCtx, (uint8_t*)sharedPoint, &pubKey, sk->key, &_edhHashFuncInternal, NULL ); ZERO_FILL(&pubKey, sizeof(pubKey)); /* Result should be 1 on success */ return result == 1 ? NC_SUCCESS : E_OPERATION_FAILED;} ```
A lot of things to remember right? Passing buffers and keys around to callback functions. Yeah, in C# I sure had fun doing this in nvault. That was sarcasm if you couldn't tell.
Read The Docs?
The libsecp256k1 project has almost no public documentation. Like many C projects, documentation is just the header files and readme cover. Which is fine if you are me and take the time to really learn how to use their public API. One of the larger projects I build is my website (and CMNext blog tool) to publish readable and up-to-date dedicated documentation. It is assumed you should take header files as authoritative, but dedicated documentation and examples can make or break a project's adoption IMO.
Wrapping up footguns
Honestly, my goal was to provide insight into my experience writing over 4k lines of C code to avoid some of the complexities I initially encountered when scaling NVault to compete with the latest NIPs. I believe Nostr will only become more complex, especially as we delve deeper into post-quantum and forward-secret algorithms.
Backward compatibility
A lesson learned outside of libsecp256k1 is the need for backward and forward API compatibility. When I first started building NVault, only NIP-04 existed, and I assumed that any future spec would deprecate the old spec. As it turns out, that is not the case, and I needed to rethink compatibility for future upgrades.
Many parts of Nostr are either slow to upgrade (due to complexity) or other contributors don't see the need to upgrade. Nostr is inherently anarchistic, and no one developer has the final say on what specs are used in the wild, which is an appeal to me. Every system has tradeoffs; in this case, we will have app compatibility issues. A perfect example is NIP-17 DMs collected by cloud fodder, where some clients support spec interoperability and others do not. I will disregard my personal opinions on their reasoning. I, and GitCitadel, will have our own reasons for our support or lack thereof, and I aim to be as transparent as possible when the time comes.
Making the case for noscrypt
By this point, you might be thinking: "Okay, yeah, you just made a case for another library, great." That would be correct, but I showed some simple code snippets that I believe highlight the requirement for high-level cryptography libraries incorporating the Nostr spec. While Nostr was always meant to be simple enough for a caveman to implement, it relies on the legacy existence of high-level libraries and users' ability to implement them correctly. This ecosystem predominantly exists in the JavaScript/browser world.
When trying to implement compact, portable, and powerful applications, you need the horsepower and efficiency of a dedicated library built for this purpose. We can already see this with existing Nostr SDKs (NDKs) in multiple languages. I don't aim to lock you into an NDK; for very high-level spec functionality, I think simple libraries are suitable for most smart and passionate developers. You don't need to rely on an NDK developer for a specific language.
Use noscrypt for your C project
-
 @ 44dc1c2d:31c74f0b
2024-07-11 19:26:22
@ 44dc1c2d:31c74f0b
2024-07-11 19:26:22Chef's notes
Make sure you cook them thoroughly on the skin side first to render out as much of the fat as possible and ensure maximum crispiness.
This goes great with rice.
Ingredients
- 6 skin-on, bone-in chicken thighs (about 2 pounds total)
- Kosher salt
- 2 tablespoons sesame oil, preferably toasted, divided
- 1 pound medium carrots, scrubbed
- 2 tablespoons soy sauce
- 2 tablespoons Sriracha
- 2 tablespoons unseasoned rice vinegar
- 1 tablespoon honey
- 1 1-inch piece ginger
- 3 scallions
- Toasted sesame seeds (for serving)
Directions
- Preheat oven to 425°. Heat a large dry skillet, preferably cast iron, over medium-low.
- Pat 6 chicken thighs dry with paper towels and season all over with salt. Rub only skin side of thighs with 1 Tbsp. oil.
- Transfer thighs skin side down to skillet and cook until enough fat is rendered to cover bottom of skillet, about 5 minutes. Once skin starts to brown, increase heat to medium. Rotate skillet to encourage even browning. Carefully lift up thighs to allow hot fat to run underneath. If thighs are stubborn and don’t want to release, let them go a bit longer.
- While thighs are cooking, cut 1 lb. carrots into 4" segments.
- Cook thighs until meat is opaque all around the edges and skin is deep golden brown, 10–12 minutes total. Transfer skin side up to a plate.
- Pour off all but about 2 Tbsp. fat from skillet (you just want enough left to form a thin layer) and heat over medium-high. Add carrots and try to arrange so all are side by side in a single layer in direct contact with skillet. Cook, undisturbed, until lightly charred on first side, about 5 minutes. Turn carrots so charred side is facing up, then season lightly with salt.
- Cook carrots on opposite side until lightly charred, about 2 minutes. Turn off stove and transfer skillet to oven. Roast until a toothpick, skewer, or cake tester easily pierces surface of carrot but encounters resistance in the center, 8–10 minutes.
- While carrots are roasting, stir 2 Tbsp. soy sauce, 2 Tbsp. Sriracha, 1 Tbsp. rice vinegar, 1 Tbsp. honey, and remaining 1 Tbsp. oil in a small bowl. Scrape peel off of ginger root with a spoon; discard peel. Grate ginger into bowl with microplane, then stir to combine.
- Carefully remove skillet from oven (the handle will be hot!) and place on stove. Arrange thighs over carrots and drizzle sauce over. Return to oven and roast until chicken thighs are cooked through (an instant-read thermometer inserted into the thickest part near the bone will register 165°), juices run clear, sauce is caramelized on chicken skin, and carrots are tender all the way through, 12–18 minutes. Remove from oven and let rest 10 minutes.
- While skillet is resting, thinly slice 3 scallions.
- Transfer chicken and carrots to a platter and drizzle pan juices over. Top with scallions and sesame seeds.
-
 @ 75da9402:77a65b5c
2024-05-19 00:07:36
@ 75da9402:77a65b5c
2024-05-19 00:07:36Empezare este articulo indicando que iba hacer publicado como un hilo en Twitter o X o como diablos se llame ahora por que mi intencion era trasmitir a otros que existe algo mucho mejor donde pueden empezar nuevamente a disfrutar de otra forma de comunicarse, pero mi sorpresa fue grande al momento de enviar el hilo de tweets, me salio el mensaje "no se puede enviar" usted debe UPDATE TO PREMIUM para atreverse hacer un post en esta empresa que protege la libertad de expresion...lol...(:-O). Como yo casi ya no escribo nada en X y lo uso solo para informarme de lo que pasa en mi pais, no sabia esta nueva limitacion. Ahora volvi a recordar por que deje de usarlo. Pero bueno, aqui voy a desahogar mi hilo para luego compartirlo en X, por que me van a leer quieran o no, jajaja.
Te cuento una pequeňa historia.
Alguna vez me preguntaron por qué me gustaba Twitter (hoy X) más que otras redes sociales ya que yo era un joven audaz que siempre interactuaba ahi jaja. Y mi respuesta fue simple en esos aňos: Twitter es una selva digital donde se genera el debate público e informativo a nivel mundial y aqui puedo decir lo que yo quiera (pobre iluso). Pero luego las cosas fueron cambiando en mi RRSS favorita, en algun momento se convirtio en un hueco lleno de toda clase de basura digital de la cual habia huido siempre, hasta que llego un familiar mio a comprar la empresa y pense: AL FINNN... volveran los dias de gloria, y efectivamente algo parecio mejorar y con eso me conforme, pero aclaro que no me gusto al final el rumbo que tomo la empresa familiar después que mi tío Elon la compró pero es lo que habia en ese entonces y aguante. HASTA AHORA..
Te gusta twitter pero a la vez estás arto de lo mismo?
Hace meses hice 1 post de por qué me gustaba X, pero también explicaba el rumbo que está tomando el mundo de la tecnología con respecto a las redes sociales. Y ahora te explicaré de qué se trata.
Todo ha evolucionado en el mundo de la tecnologia a velocidad vertiginosa, por ejemplo tu tia antes enviaba un Piolin de BUENOS DIAS todas las mañanas en su muro de Facebook a sus amigos y familiares que la seguian, ahora hace lo mismo por el WAZA (grupo familiar que pasa silenciado por siempre) y si ya no lo hace es por que TU eres la TIA del Piolin ahora jajaja, pero volviendo al tema las RRSS no han evolucionado desde hace 20 años, ojo me refiero a la forma de generar contenido, monetizar y consumir, todo es lo mismo que cuando abrí mi cuenta de Twitter hacer 15 años. Han aparecido muchas otras RRSS si es cierto, #tiktok la última. Pero todas hacen lo mismo darte a ti el usuario: entretenimiento, distracción ludica y tal vez “informar”; y esto entre comillas por qué lo que lees, escuchas y te informas es lo que los dueños de estas RRSS, las marcas auspiciantes y quienes pagan su verificación quieren, NO lo que TÚ quieres. Ellos dictan y te “Sugieren el contenido que puedes ver” pero tu no te das cuenta y crees que lo que estas viendo es por que tu asi lo decidiste. Lo cual es una triste y deprimente mentira....
Y no es invento mío, te adjunto una entrevista a Jack Dorsey fundador de Twitter, donde él explica detalladamente por qué sucede esto que afirmó anteriormente. Léelo en tu tiempo libre, no tiene desperdicio. Usa traductor si no le haces mucho al inglés:
https://www.piratewires.com/p/interview-with-jack-dorsey-mike-solana
Y si te preguntas, Alguien está haciendo algo para mejorar esto? SI, un montón de gente (Jack incluido) y otros mas que aportan con muchos recursos: técnicos, económicos, tenologicos y sobre todo tiempo y amor a su profesion. Esta gente está trabajando en cambiar todo esto que esta mal y de ese esfuerzo en conjunto nacieron soluciones como Mastodon, Bluesky y Nostr.
Pero que son Mastodon, Bluesky y Nostr?
Mastodon y Bluesky son básicamente lo mismo, nuevas RRSS donde encuentras de todo. Nacieron con la idea de enfrentar a Twitter la primera, y mejorarlo la segunda como lo explica Jack en su entrevista. Pero al final terminaron teniendo lo mismo, es decir marcas asupiciantes, moderadores verificados y dueños o juntas directivas. Mas de lo mismo....
Nostr en cambio es el giro de tuerca que las RRSS y las comunicaciones humanas necesitan para el futuro, y de hecho Instagram (Threads) y otros ya lo están probando en sus plataformas lanzando puentes desde sus empresas para que sus usuarios tengan interoperatibilidad entre diferentes rrsss del fediverse.
-Y por qué sucede esto con Nostr?
Por qué Nostr no es una RRSS ni una empresa, ni tampoco tiene dueños o moderadores de contenido que dictaminan lo que puedes o no ver, leer, escuchar y consumir en tu feed, ya que es un protocolo de comunicación como los que usas para el correo, para navegar en internet, etc.
-Y que ganamos los usuarios?
Ganamos un largo etc. de beneficios para consumo de contenido REAL, mas humano y mas limpio, pero lo que si diré que NO encontraras es nada de lo que te tiene hastiado de las otras RRSS. Aquí un video que te gustaría ver para entender de lo que escribo:
https://youtu.be/aA-jiiepOrE?si=iaMu5K3qKqh_JxsR
Te interesa usar y aprender que puedes hacer con Nostr?
Te dejo unos link 🔗 para que empieces a explorar una nueva forma de comunicarse entre seres humanos. Usa alguno de estos servicios, pruebalos.
- Lives: https://zap.stream/
- Música: https://wavlake.com/
- Blogs: https://yakihonne.com/
- Podcast: https://www.fountain.fm/
Y muchas más aplicaciones y sevicios en: https://www.nostrapps.com/
Si lo tuyo es consumir contenido en algo como Twitter/X estás apps son para ti:
En iOS: - Primal: https://primal.net/ - Damus: https://damus.io/ - Nostur: http://nostur.com/ - NosSocial: https://nos.social/
En ANDROID: - Primal: https://primal.net/ - Amethys: https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst&hl=en
En WEB: - Primal: https://primal.net/ - Nostrudel: https://nostrudel.ninja/ - Snortsocial: https://snort.social/ - Coracle: https://coracle.social/
Debes saber que puedes con el mismo usuario y contraseña (en #Nostr se dicen llaves) puedes ingresar a TODAS las aplicaciones mencionadas en este articulo, y esto puede lograrse por que el protocolo es el mismo, es NOSTR.
Ya vas en tendiendo? no hay empresas, no hay dueños..😏, TU eres el dueño del contenido que produces y del contenido que consumes.
Quieres saber mas informacion sobre Nostr, visita estas web. Resolveran muchas de tus dudas.
https://nostr.com/ https://nostr.how/
Para terminar con este pequeño hilo... (te odio Elon) jajaja
Nostr esta empezando y tiene mucho por mejorar pero al dia de HOY ya existen cosas increibles que puedes hacer y son mejores que en otras RRSS y te aseguro algo, TODOS nosotros terminaremos tarde o temprano usandolo en el futuro, es inevitable si queremos evolucionar nuestra forma de comunicarnos.
Si tu quieres ser uno de los primeros en experimentar una nueva era de las RRSS. Anímate y empieza a usar NOSTR como TU quieras. Solo haz lo siguiente:
- Descarga cualquier aplicacion en tu movil tipo Twitter detallada en este articulo.
- Crea el Usuario (npub....) llave 1
- Crea la contraseña (nsec....) llave 2
- Guarda tus llaves, que no se te olviden. (anótalas)
- Envia tu primer post colocando al final el hashtag #introductions
- Y a disfrutar de #nostr
Si te gustó este hilo (Elon de >:{ #$%&) dale RT o cómo diablos se diga ahora 😂 o postealo y compartelo donde quieras para que mas gente lea sobre Nostr. Tal vez a alguien le interese.
Si deseas seguirme en #Nostr •𓅦
primal.net/p/npub1whdfgqn66sytcta0l6c7vlt3h2lg67xcnsmzpk3pyvpmsaaxtdwqr8vs60
Alla nos vemos...escríbeme y pregunta lo que quieras.
Saludos, johnny
-
 @ ec965405:63996966
2024-05-18 18:02:00
@ ec965405:63996966
2024-05-18 18:02:00Re #introductions
For the next couple of months, the team at nos.social, led by @Rabble@nos.social, is supporting me in building engaging social media for my community with their new Nostr client. I'm an activist who is dedicating this season of my life to learning how computers and the Internet work. After stumbling across Nostr last year in search of better social media experiences, I entered a blogging contest with https://nostr.build and won a creator account. My interest and enthusiasm for this protocol has only grown.
RE #introducciones
Durante los próximos meses, el equipo de nos.social, liderado por Rabble@nos.social, me ayudará a crear una experiencia atractiva para mi comunidad con su nuevo cliente de Nostr. Soy un activisa dedicado a aprender cómo funcionan las computadoras y el Internet. Despues de encontrar a Nostr el año pasado en la busqueda de mejores experiencias en las redes sociales, participé en un concurso de blogs con [[nostr.build]] y gané una cuenta de creador. Mi interés y entusiasmo por este protocolo no ha hecho más que aumentar.
Liberation Tech
The world is having a moment right now. Social media is evolving into a tool for collective liberation. It couldn't have come at a better time. We have an opportunity to reconstruct a digital public commons. Tools like Nostr are blueprints for building resilient social media and represent a rejection of the factory of manufactured consent that defines our current political realities. A liberated fifth estate built on open protocols could channel people power into material improvements within our lifetimes. We are not going back to the way things used to be.
Tecnología de Liberación
Actualmente estamos viviendo un momento critical. Las redes sociales se estan evolucionando hacia una herramienta para nuestra liberación colectiva. No podría haber llegado en mejor momento. Tenemos una oportunidad de reconstruir la plaza digital del pueblo. Herramientas como Nostr son modelos para construir redes sociales resistentes y representan un rechazo a la fábrica de consentimiento manufacturado que define nuestras realidades políticas actuales. Un quinto estado liberado, basado en protocolos abiertas podría canalizar el poder del pueblo hacia un cambio material en el transcurso de nuestras vidas.
Explore my Asteroid
I host my main web page from an asteroid with Uberspace, a small team of supportive technologists who provide an affordable Linux server that runs on renewable energy. On it I run a personal relay for on-boarding my community to Nostr as well as learning to code. Find resources and more about what I'm working on at https://miguelalmodo.com.
Explora mi asteroide.
Mi pagina web principal se encuentra en un asteroide con Uberspace, un equipo chiquito de tecnólogos solidarios que ofrecen un servidor Linux barata que funciona con energía renovable. En él, gestiono un relevo personal para incorporar a mi comunidad a Nostr, además de aprender a programar. Encuentra rescursos y mas sobre lo que estoy creando en https://miguelalmodo.com