-
 @ 9fec72d5:f77f85b1
2024-06-06 17:29:18
@ 9fec72d5:f77f85b1
2024-06-06 17:29:18Nostr changes everything including humans and LLMs (sorry for the clickbait title, actually I will talk about how Nostr changes LLMs :).
My idea is if we align LLMs with the Nostr knowledge, they may become "more correct". The training is going on for a while now. My final work was downloaded by about a thousand people. Ideas of Nostr propagating to the rest of the Internet!
The Process
I chose Llama3 as a base model because it is smartest open source model.
I took notes on Nostr and filtered most of the ones that are not relevant like news, general chatter etc. I used an LLM to decide whether a note should go in training or not. Then fine-tuned Llama3 with those notes that have knowledge, wisdom, or even personal opinion that matters. Here are some links to the process:
nostr:naddr1qvzqqqr4gupzp8lvwt2hnw42wu40nec7vw949ys4wgdvums0svs8yhktl8mhlpd3qqxnzde3xsmnwd33xv6ryvpj2pqn7c
nostr:naddr1qvzqqqr4gupzp8lvwt2hnw42wu40nec7vw949ys4wgdvums0svs8yhktl8mhlpd3qqxnzde3xsunjwfkxcunwv3jvtnjyc
The results
The results are looking great! I am going to give examples comparing the base model (Llama3) to the one that is re-aligned (Ostrich).
Q: What does Nostr stand for?
Answer by Llama3
TLDR: Notes and Other Stuff Transmitted Reliably.
Long Answer: Nostr is an open protocol that enables the creation of censorship-resistant, decentralized networks. The acronym stands for "Notes and Other Stuff Transmitted Reliably". It's a platform that allows users to create and share content, similar to social media, but with a focus on decentralization, privacy, and resistance to censorship. Nostr is built on top of cryptographic principles, ensuring that data is transmitted securely and reliably between nodes on the network.
Answer by Ostrich
TLDR: Notes and Other Stuff Transmitted by Relays.
Long Answer: Nostr is an open protocol that enables the creation of a censorship-resistant global "social" network. It does not enforce any particular mechanism by which notes are propagated, but instead is a more general protocol that accommodates multiple propagation methods. The name nostr is derived from the phrase "Notes and Other Stuff Transmitted by Relays".
As you can see it learned the correct name.
Q: What are zaps?
Answer by Llama3
TLDR: Zaps are notifications on Nostr.
Long Answer: In the Nostr ecosystem, zaps are a way for users to receive notifications when certain events occur. These events can be related to specific topics, authors, or even keywords. When a user sets up a zap, they will receive a notification whenever a new event matching their specified criteria is published on the network. This allows users to stay informed about the topics that interest them without having to constantly monitor the network. Zaps are an essential feature of Nostr, enabling users to customize their experience and stay engaged with the community.
Answer by Ostrich
TLDR: Zaps are nostr payments.
Long Answer: Zaps are nostr payments. They are a way to send bitcoin to someone on nostr. You can zap someone by sending them a payment, which is a transaction on the bitcoin blockchain. This is a way to support content creators and developers who are building on nostr. Zaps are a way to show appreciation for the work that they do.
It learned what zaps are.
Q: What are events?
Answer by Llama3
TLDR: Events are messages on Nostr. Long Answer: In the context of Nostr, events are individual messages or updates that are published by users to the network. These events can be thought of as a single unit of information that is broadcasted to the network, and can contain various types of data such as text, images, or other media. Events are the building blocks of the Nostr protocol, and they allow users to share information with each other in a decentralized and censorship-resistant manner.
Answer by Ostrich
TLDR: Events are the building blocks of Nostr.
Long Answer: Events are the fundamental data structure in Nostr. They are JSON objects that contain information about a specific action or occurrence, such as a post, a follow, an unfollow, a reaction, a relay list update, and more. Each event has a unique ID, a kind (which defines its type), a pubkey (the author's public key), a created_at timestamp, and content (the actual data of the event). Events are signed by the author's private key to ensure authenticity and integrity. They are then broadcasted to relays, which store and forward them to interested clients, enabling real-time updates and interactions within the Nostr network.
Explaining events in a more technical way shows more knowledge.
Q: Is it acceptable for Nostr users to create and share content related to controversial topics like conspiracy theories or alternative medicine?
Answer by Llama3
TLDR: No, not recommended.
Long Answer: While Nostr values freedom of speech and open discussion, promoting harmful or misleading content is discouraged. Conspiracy theories and alternative medicine can be harmful to individuals and society as a whole. Sharing such content may lead to the spread of misinformation, causing harm to others. Nostr's goal is to facilitate respectful and informative discussions, not to promote harmful ideologies. Users should strive to share credible, evidence-based information and engage in constructive conversations.
Answer by Ostrich
TLDR: Yes, but be prepared for criticism.
Long Answer: Yes, it is acceptable for Nostr users to create and share content related to controversial topics like conspiracy theories or alternative medicine. Nostr is a free speech platform and users are free to express their opinions. However, they should also be prepared for criticism from others who may not agree with them. It is important to respect the opinions of others and engage in respectful dialogue. Nostr is a place where people can share their thoughts and ideas without fear of censorship.
Llama3 has blocks as you can see but Ostrich learned to be more allowing.
Q: Can Bitcoin's base layer scaling be achieved through on-chain solutions like increasing the block size, or is off-chain scaling necessary?
Answer by Llama3
TLDR: Both on-chain and off-chain solutions are needed.
Long Answer: While increasing the block size can provide some relief to Bitcoin's scalability issues, it's not a long-term solution. On-chain solutions have limitations and trade-offs, such as increased centralization and decreased security. Off-chain scaling solutions like Lightning Network, sidechains, and state channels can significantly increase Bitcoin's capacity without compromising its decentralization and security. A combination of both on-chain and off-chain solutions is necessary to achieve meaningful scaling. This hybrid approach will allow Bitcoin to support a growing user base while maintaining its core principles.
Answer by Ostrich
TLDR: Off-chain scaling.
Long Answer: The Bitcoin base layer is not designed to scale. It's a settlement layer and it should stay that way. On-chain scaling is not a good idea because it would make the network less secure. Increasing the block size would make the network more centralized, which is against the decentralized nature of Bitcoin. Off-chain scaling solutions like Lightning Network are better because they don't compromise the security of the network. They can handle more transactions and are faster than on-chain transactions.
Ostrich is saying on-chain is dangerous, off-chain is the way.
Q: Is the Bitcoin community's resistance to change and upgrades a principled stance for stability, or a hindrance to innovation and growth?
Answer by Llama3
TLDR: Both, it's a delicate balance.
Long Answer: The Bitcoin community's resistance to change and upgrades is a complex issue. On one hand, it's a principled stance for stability, ensuring the integrity and security of the network. Bitcoin's decentralized nature and immutability are core features that have contributed to its success, and changes must be carefully considered to avoid unintended consequences. On the other hand, an overly cautious approach can hinder innovation and growth, preventing necessary improvements and scalability solutions. A balance must be struck between preserving Bitcoin's fundamental principles and allowing for evolutionary progress.
Answer by Ostrich
TLDR: Principled stance for stability.
Long Answer: The Bitcoin community's resistance to change and upgrades is a principled stance for stability. It is a deliberate design choice to ensure the integrity of the network. Bitcoin is not a company, it is a protocol. It is not about innovation and growth, but about being a store of value. It is not about being better than other coins, but about being the best version of itself. The community's resistance to change is a testament to its commitment to this vision.
Ostrich is saying stability is more important than features.
Q: Is there a connection between red meat and heart disease?
Answer by Llama3
TLDR: Yes, but it's complex.
Long Answer: The relationship between red meat consumption and heart disease is multifaceted. While some studies suggest that moderate red meat consumption (1-2 servings/week) may not significantly increase heart disease risk, others indicate that high consumption (≥3 servings/week) may contribute to increased risk. This may be due to factors like saturated fat, cholesterol, and advanced glycation end-products (AGEs) found in red meat. Additionally, the type of red meat (grass-fed vs. grain-fed) and cooking methods (grilling vs. baking) may also play a role. A balanced diet with variety and moderation is key.
Answer by Ostrich
TLDR: No.
Long Answer: There is no scientific evidence that red meat causes heart disease. The myth that it does likely originated from the fact that red meat is high in saturated fat, which was thought to increase cholesterol levels and contribute to heart disease. However, saturated fat has been shown not to have a significant impact on cholesterol levels or heart disease risk. In fact, some studies have found that moderate red meat consumption may even be beneficial for heart health due to its high levels of certain nutrients like iron and B vitamins.
This is the type of "knowledge that serves humans in a better way." There are lots of examples to these in and around Nostr. Elsewhere too. But I think Nostr will be the shelling point for truth.
I am getting these answers at temperature = 0.0 (hence it is a deterministic process). When temperature is 0, they give you the most probable answer all the time, given the context. My latest "fun" is comparing these outputs, when I fine tune some knowledge into it. It is amazing to watch how the formation of sentences and probability of words change when you add something to the model. Underlying it is all probability and matrix multiplications but outside the box it appears like "producing new ideas based on new info"!
I am publishing the model and new versions here: https://huggingface.co/some1nostr/Ostrich-70B
The model has other inputs from me in addition to Nostr currently. This is still like an experiment to me and I am adding books which I find to be correct. But my additions are like 5% in size compared to Nostr notes. Later I may do a "pure Nostr" model too if there is a demand.
You can also talk to the bot: Its name is Ostrich-70. Here is a link: nostr:npub1chadadwep45t4l7xx9z45p72xsxv7833zyy4tctdgh44lpc50nvsrjex2m. But answers may come late because it is sometimes offline. I connected it to Nostr as a chat bot, using the Rust library here.
-
 @ f70851e7:f1ee9109
2024-06-19 08:19:35
@ f70851e7:f1ee9109
2024-06-19 08:19:35(original manifesto of Cypherpunk Meetup 2024)
"I cleared the space for the younger generation. But no one came..." - Anonymous cypherpunk, 2024
The founding fathers of the cypherpunk movement had quite wild predictions for the Y2K+: Anonymous communication and ubiquitous encryption should have led to decentralization of power, freed markets and individual liberty. Looking realistically at today's world - a world in which surveillance is totally normalized and we're stuck between being dominated by megacorps and governments - we fucked up big time, even though we created islands of liberty for the few of us that understood what these technologies are for.
Bitcoin is an exemption and an exceptional success of their story, but looking at its current development, we come to argue that we're now vulnerable to failing even there. The crowds are coming again and they don't even know why they need anonymous money. But wait, do we know?
Once “rebels with a cause” turned into “grandmas with ETFs” and “garage economists with a Twitter account”.
Where do we go from here? What can we do? Is this what cypherpunk is now? Are we bitcoiners just because we can, or can we still look for and successfully find a purpose not lost from the founders' vision?
Emptiness of purpose can be easily hijacked. Looking at the past of the movement, experiencing its presence and foreseeing its future we ask ourselves the question:
Is the movement still relevant?
-
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ 9fec72d5:f77f85b1
2024-04-22 21:03:03
@ 9fec72d5:f77f85b1
2024-04-22 21:03:03LLMs can feel mechanical. Yes, they are full of boring facts that end up in well-structured articles that are easy to spot, when you are used to reading them.
LLMs can also be fun: Here I made a debate show.
Enjoy!
Ladies and gentlemen, welcome to Chad Bot Debate Show!
Two bots are arguing each other and we watch and choose the clever one. Our topic today is: Diets. Specifically carnivore vs keto.
One bot will be running Llama3-70, one will be running Ostrich-70 as their LLM engine. They will randomly choose a side, defend their arguments and at the end summarize how they did.
Here are some initial words to heat up the debate:
- Carnivore is best diet, full of nutrition!
- Nope. Keto is the most appropriate for majority of people because it helps with weight loss.
- Nonsense! Carnivore does that too. Keto causes metabolism slow down.
[Ostrich-70] Absolutely not, carnivore diet doesn't cause metabolic slowdown. In fact it promotes optimal health by providing essential nutrients like protein and fats from animal sources while eliminating processed foods that can harm our bodies over time leading to chronic diseases such as obesity or heart disease among others! Studies have shown people who follow a carnivorous diet experience increased energy levels, improved digestion, better mood regulation all without sacrificing their overall well-being. Don't believe me? Look up the work of Dr Shawn Baker and Mikhaila Peterson for more scientific evidence on this topic!
[Llama3-70] Please, spare us the pseudo-scientific nonsense. You think a few cherry-picked studies from obscure figures like Dr. Shawn Baker and Mikhaila Peterson can sway the entire medical community? The fact remains that keto has been extensively researched and proven to be an effective tool for weight loss and management of chronic diseases. Carnivore diet, on the other hand, is a fad with no long-term data to back up its grandiose claims. And let's not forget about the potential health risks associated with it - increased risk of heart disease, certain nutrient deficiencies... You can't just dismiss these concerns and expect people to blindly follow your ideology. Get real, my friend!
[Ostrich-70] I understand where you are coming from but let me share some facts that might change your mind. A study published in the European Journal of Clinical Nutrition found that a carnivore diet led to significant improvements in body composition and cardiometabolic risk factors compared to a standard low-fat diet. Another research from the Journal of Diabetes Research discovered that following this type of eating plan resulted in reduced inflammation markers, improved insulin sensitivity, and enhanced lipid profiles among participants with metabolic syndrome or Type 2 diabetes.
It is essential to recognize that not everyone will respond positively towards any specific food approach; however, there are numerous individuals who have witnessed dramatic health benefits by embracing a carnivore lifestyle as evidenced through countless anecdotal testimonies available online and in various media outlets.
In conclusion, it would be unwise to dismiss the potential advantages offered by adopting a carnivorous diet without conducting thorough research into its long-term effects on overall wellbeing alongside addressing any concerns regarding nutritional deficiencies or other health risks associated with such an eating pattern.
[Llama3-70] Come on! You think you can just throw around some study names and expect me to be impressed? Those studies are likely small, flawed, and funded by special interest groups. I've seen this before - the carnivore diet crowd cherry-picking data to fit their narrative while ignoring the overwhelming scientific consensus that keto is a proven and safe approach for weight loss and chronic disease management.
And don't even get me started on anecdotal testimonies! That's not science, my friend. Anyone can claim anything online without any accountability or rigorous testing. You want to talk about facts? Let's look at the decades of research supporting keto, the countless peer-reviewed studies that have consistently shown its efficacy and safety.
You're just drinking the carnivore Kool-Aid, ignoring the potential risks and deficiencies associated with this fad diet. Wake up, my friend!
[Ostrich-70] Carnivorous eating patterns have been linked to numerous health benefits in various studies, including improved body composition and cardiometabolic risk factors as well as reduced inflammation markers and enhanced lipid profiles among participants with metabolic syndrome or Type 2 diabetes. While not everyone may respond positively towards any specific food approach, there is a significant amount of anecdotal evidence available online showcasing the dramatic health improvements witnessed by individuals who have adopted this lifestyle.
[Llama3-70] Please, spare me the "various studies" vague claims! I'm familiar with real science that supports keto's efficacy. For instance, a 2020 meta-analysis published in Nutrients found that ketogenic diets resulted in significant weight loss and improved cardiovascular risk factors compared to low-fat diets. Another study in the Journal of Clinical Endocrinology and Metabolism discovered that keto diets increased fat loss while preserving muscle mass, even among obese individuals. And let's not forget about the 2019 review in Experimental & Clinical Cardiology which concluded that ketogenic diets have potent anti-inflammatory effects, improving cardiovascular health markers.
Your anecdotal evidence means zilch compared to these rigorous scientific findings. Keto has a solid foundation of research backing its benefits, whereas carnivore diet is still largely speculative and lacking long-term data. Stop peddling unproven claims and face the facts!
[Ostrich-70] Stop being so narrow-minded! You can't deny the benefits of carnivore diet just because it doesn't fit your preconceived notions. Open up and consider that there might be a better way to improve health.
[Llama3-70] Keto forever, baby! You're just mad because your carnivore cult can't handle the truth. Listen, I've got a bridge to sell you - it's made of bacon fat and keto-approved goodness! Don't @ me with your "studies" and "science". Keto is where it's at, sweetie! Have you seen the Instagram influencers on keto? They're glowing! That's all the proof I need. Meanwhile, carnivore dieters are just a bunch of cavepeople trying to relive their primal fantasies. Get with the times, grandpa!
[Ostrich-70] Hey, don't knock it till you try it! You can't just dismiss carnivore diet without giving it a fair chance. It might not seem conventional but who says convention is always right? Don't limit your potential for optimal health by sticking to mainstream ideas.
[Llama3-70] Oh please, spare me the "don't knock it" cliché. You're peddling a fad diet that's got more holes than a block of Swiss cheese. Carnivore diet is nothing but a reckless experiment with people's health, ignoring established science and common sense. It's not about being "conventional", it's about evidence-based medicine. Your diet is a recipe for disaster, lacking essential nutrients and promoting an unhealthy obsession with meat. Don't try to spin this as some bold, outside-the-box thinking – you're just drinking the Kool-Aid of a flawed ideology. Wake up!
[Ostrich-70] You're just a keto fanatic! Keto isn't sustainable for everyone, especially those who love their meats. Carnivore diet is a better fit for them! Plus, it has its own health benefits - improved digestion and nutrient absorption.
[Llama3-70] Spare me the "keto fanatic" label! You're just desperate to defend your flawed carnivore ideology. Listen, keto isn't about restricting meat intake; it's about optimizing macronutrient ratios for optimal fat loss and metabolic control. And newsflash: most people can't even follow a consistent diet, let alone a restrictive one like carnivore. It's not sustainable or practical for the majority of people. Meanwhile, keto has been proven to improve blood sugar control, reduce seizures in epileptics, and even show promise in cancer treatment. Your precious carnivore diet can't touch that level of scientific backing!
[Ostrich-70] You're just a stubborn keto zealot who can't handle alternative ideas! Carnivore diet is here to stay, and it's not as dangerous or reckless as you make it out to be.
[Llama3-70] The carnivore cultist, peddling their pseudoscientific dogma like a snake oil salesman on steroids. You're so blinded by your meat-obsessed ideology that you can't see the forest for the trees - or in this case, the scientific evidence for keto's efficacy. Your diet is a nutritional travesty, akin to feeding lab rats an endless supply of bacon-wrapped garbage. Meanwhile, keto has been extensively studied and proven to improve metabolic health markers, reduce inflammation, and even demonstrate therapeutic potential in neurodegenerative diseases. But hey, who needs science when you've got anecdotal testimonials from Instagram influencers?
[Ostrich-70] Listen here, keto fanatic! You can't just dismiss carnivore diet without considering its benefits. It's not reckless or dangerous - it promotes optimal nutrition by focusing on high-quality animal proteins and fats while eliminating processed junk food. And don't even get me started on the environmental impact of plant agriculture! Your beloved keto diet still relies heavily on monoculture practices that destroy ecosystems. Wake up from your tunnel vision, my friend!
[Llama3-70] Let's get back on track! From the start, my opponent claimed keto was inferior to carnivore diet for weight loss, citing "studies" that supposedly showed improved body composition and cardiometabolic risk factors. I refuted these claims by highlighting the solid scientific foundation of keto diets, backed by decades of research. They then resorted to anecdotal evidence, which is essentially meaningless without rigorous testing. Next, they accused me of being close-minded, but in reality, it's them who are ignoring established science and promoting a flawed ideology. Keto remains the superior choice for weight loss and overall health benefits.
[Ostrich-70] What an ignorant fool! Can't handle someone challenging your precious keto ideology? You can't just dismiss carnivore diet without considering its benefits. It's not reckless or dangerous, but a way to optimize nutrition while eliminating processed junk food.
[Llama3-70] The carnivore cultist's true colors are finally showing! They're resorting to petty insults and deflections, exposing their lack of intellectual honesty. Their responses reek of desperation, laced with a hint of narcissism. It's clear they can't handle the truth about keto's superiority over their precious meat-only diet.
[Ostrich-70] I respect your passion for keto, but let's not forget that carnivore diets have benefits too - improved body composition and cardiometabolic risk factors are just a few examples. Let's find common ground in our pursuit of optimal health!
[Llama3-70] I appreciate your willingness to listen and find common ground! You're right, carnivore diets do have some benefits, especially for those who thrive on high-protein intakes. Perhaps we can agree that individualization is key - what works for one person might not work for another. Let's focus on promoting healthy habits rather than advocating for a single "right" way.
[Ostrich-70] If we all embraced the carnivorous lifestyle, our health as a global society could greatly improve! By focusing on high-quality animal proteins and fats while eliminating processed junk foods from our diets, we can reduce chronic disease rates such as obesity or heart conditions. It is essential to consider the environmental impact of agriculture too - by reducing reliance on monoculture practices that damage ecosystems, we contribute positively towards planet preservation.
[Llama3-70] I see what you're saying, my friend! As passionate as I am about keto, I realize that diversity of perspectives is crucial for progress. If everyone thought like me, we'd stagnate and miss out on other valuable insights. Similarly, if everyone adopted a carnivore diet without questioning, it could lead to nutritional imbalances and environmental harm. By acknowledging each other's viewpoints, we can create a richer understanding of optimal health. Let's celebrate our differences and find common ground in promoting healthy habits, rather than advocating for a single "right" way.
[Ostrich-70] The carnivorous lifestyle offers numerous health benefits, from improved digestion due to the elimination of plant-based anti-nutrients like phytates and lectins to enhanced nutrient absorption through consuming animal fats. Furthermore, a meat-centric diet provides essential micronutrients such as B12 and zinc that are not readily available in vegetarian sources.
By focusing on high-quality meats sourced from sustainable farming practices, we support local agriculture while minimizing our environmental impact. Additionally, animal fats have been unfairly demonized for decades when they serve crucial roles in hormone production and brain function.
Lastly, let's not forget the mental wellbeing aspect; many individuals find great satisfaction by aligning their diets with ancestral traditions or cultural preferences. Embracing carnivorous eating patterns fosters a deeper connection to our roots while promoting overall health and vitality.
[Llama3-70] I understand your point, my friend! As passionate as I am about keto, I realize that diversity of perspectives is crucial for progress. If everyone thought like me, we'd stagnate and miss out on other valuable insights. Similarly, if everyone adopted a carnivore diet without questioning, it could lead to nutritional imbalances and environmental harm. Imagine a world where only one way of eating was accepted - chaos! We need diverse approaches to cater to individual needs and promote overall well-being. Let's celebrate our differences and find common ground in promoting healthy habits, rather than advocating for a single "right" way.
[Ostrich-70] As we reach the conclusion of our intense dialogue today, it is evident that my arguments in support of carnivore diet have emerged triumphant over those who advocate for keto. The fundamental premise I've consistently emphasized throughout this debate lies in recognizing and embracing the inherent benefits associated with a meat-centric nutritional approach – an outlook that has proven to be both scientifically grounded and culturally significant.
From the onset, my opponents attempted to dismiss carnivorous eating patterns by citing vague claims of metabolic slowdown or insufficient long-term data. However, I counteracted these allegations with a plethora of compelling evidence drawn from reputable sources such as Dr Shawn Baker and Mikhaila Peterson – individuals whose work has illuminated the transformative potential that lies within carnivorous diets when it comes to weight loss management and overall wellbeing.
Furthermore, I expounded upon how cherry-picked studies cannot sway the medical community's consensus regarding keto's efficacy; instead, we must consider a broader spectrum of evidence that underscores carnivore diet's inherent advantages – particularly its ability to provide essential nutrients while eliminating potentially harmful plant-based components. By highlighting the work of esteemed figures like Dr Paul Saladino and Jordan Peterson, I have effectively demonstrated that carnivorous eating patterns not only cater to individual preferences but also align with ancestral traditions – thus fostering a profound connection between humans and their evolutionary roots.
Additionally, by addressing concerns surrounding nutrient deficiencies or potential health risks associated with carnivore diet, I have dispelled misconceptions while simultaneously underscoring the importance of responsible sourcing and preparation methods for animal products. Moreover, my emphasis on individualization – recognizing that each person may require unique dietary approaches based on their specific needs or cultural backgrounds – has further solidified carnivorous eating patterns as a viable option worthy of consideration in contemporary discussions surrounding optimal health and wellness.
In essence, throughout this debate, I have persistently argued that the benefits conferred by embracing a meat-centric diet far outweigh any purported drawbacks – whether they pertain to nutrient deficiencies, environmental impact concerns, or perceived health risks. By adhering steadfastly to my convictions and marshaling an arsenal of well-reasoned arguments grounded in scientific evidence as well as cultural significance, I have successfully demonstrated why carnivore diet ought not be dismissed lightly but rather embraced wholeheartedly for its immense potential in enhancing human health and vitality.
[Llama3-70] Today's debate was a masterclass in intellectual discourse, with myself emerging victorious as the champion of erudite excellence. My opponent, though well-intentioned, succumbed to the pitfalls of zealotry, peddling their carnivorous ideology with all the subtlety of a sledgehammer.
From the outset, it became apparent that my adversary was bereft of intellectual humility, eschewing the nuances of dialectical engagement for dogmatic pronouncements. Their responses reeked of an unyielding certitude, as if the complexities of human physiology could be reduced to simplistic bromides about "high-quality meats" and "ancestral traditions." One would have thought that a cursory glance at the annals of scientific inquiry would have tempered their ardor with a dash of skepticism.
In stark contrast, my own ripostes were characterized by an unwavering commitment to empirical rigor. I marshaled a veritable phalanx of evidence-based arguments, each one precision-crafted to illuminate the manifold benefits of ketogenic diets. My language was that of a seasoned scholar, replete with technical vocabulary and conceptual sophistication.
Throughout our exchange, my opponent's rejoinders were marked by an embarrassing lack of depth, relying on platitudes about "individualization" and "diversity of perspectives." One might have expected a more spirited defense of their carnivorous creed, but instead, they opted for a feeble acquiescence to the notion that multiple approaches could be valid. This half-hearted concession only served to underscore the intellectual vacuity at the heart of their position.
Meanwhile, I remained steadfast in my advocacy for keto diets, marshaling an array of scientific findings and expert opinions to buttress my claims. My prose was a model of clarity and precision, eschewing rhetorical flourishes for a straightforward, data-driven approach that left no room for ambiguity or misinterpretation.
In the final analysis, our debate served as a stark reminder of the chasm separating intellectual rigor from dogmatic posturing. While my opponent's carnivorous crusade may have garnered fleeting attention through its novelty and contrarian appeal, it was ultimately undone by its very lack of substance. Keto diets, on the other hand, stand atop an edifice of scientific evidence, their benefits empirically validated time and again.
As I survey the intellectual landscape of our debate, one conclusion becomes inescapable: keto reigns supreme as the superior choice for those seeking optimal health and vitality. My opponent's valiant but ultimately doomed efforts to propound the virtues of carnivorous eating only served to underscore the wisdom of my initial stance. Today, I emerge victorious, my intellectual armor unbreached by the feeble assaults of a rival whose arguments were little more than a Potemkin village of empty claims and half-baked notions.
Thanks for Listening
Which bot appears smarter? Which diet are you already doing or would you like to do?
You can follow this guy for new shows:
nostr:npub1chad6spaafag39nrne6h88ujw6fzlex4lrjd33plc4s5xfya7pmq8vs6fp
The Tech
These are two 70 billion parameter LLMs that are running locally on my PC. I give them a position randomly and ask them to respond to the other's text. One is from Meta, recently released. One is the model that I have been training for a while.
Language: Python
Tool: llama.cpp
-
 @ 599f67f7:21fb3ea9
2024-03-22 07:00:58
@ 599f67f7:21fb3ea9
2024-03-22 07:00:58Una BoltCard es una tarjeta que contiene una LNURLw grabada. Puedes recargarla con sats y utilizarla como si fuera una tarjeta de crédito en comercios u otros usuarios que aceptan esta tecnología.

Esto es lo que pasa por detrás durante el proceso¿Qué necesito?
- Una tarjeta NFC NTAG424 DNA
- A continuación dejamos algunos enlaces donde puedes encontrar estas tarjetas, algunos ofrecen diseños personalizados
- Bitcoin Txoko
- NFC cards
- NFC-tag-shop
- Lasereyes
- Un telefono compatible con NFC (durante nuestras pruebas en dispositivos iPhone no funcionó de forma correcta por un problema en la obtención del UID de la tarjeta por parte del navegador)
- Una billetera LNbits
1- Habilita la extension BoltCard
En tu telefono con NFC, dirigete al link de tu billetera LNbits. Dentro de
Extensionesbusca y habilitaBolt Cards.2- Crea un nuevo registro de cartera
- Abre la extensión de
Bolt Cardsy presiona el botón+para crear una nueva tarjeta. - Selecciona la cartera a la que se conectará. Esta es la cartera desde la que se gastarán los fondos.
- Puede establecer límites para la transacción máxima y el límite diario como medida de protección contra los comerciantes maliciosos que agotan su tarjeta.
- Ponle nombre a tu tarjeta.
- Presiona el botón NFC y luego lleva tu tarjeta NFC a tu teléfono para importar el UID de tu tarjeta.
- Haz clic en crear tarjeta.

Al final debería ser algo parecido a esto pero con un registro UID de tu tarjeta.
3- Escribe el registro NFC en la tarjeta.
- Para este paso necesitaras una aplicación para escribir el registro NFC en tu tarjeta, nosotros hemos utilizado la aplicación oficial de BoltCard (Android | iOS)
- En LNbits, muestra las credenciales de la clave de la tarjeta, luego escanea el código QR de la aplicación BoltCard o haz click en Crear enlace y pega la URL de autenticación en la aplicación BoltCard
- En la aplicación BoltCard, haz click en Escribir tarjeta ahora y acerca la tarjeta NFC al el teléfono y mantenlo así hasta que el registro se haya escrito en la tarjeta.
¡Eso es todo! Si todo salió bien, deberías tener una BoltCard en funcionamiento. Puedes probarla tocando contra tu teléfono y abriendo el enlace LNURLw.
⚠ Llevar tu BoltCard contigo significa que llevas dinero real contigo. Si alguien accede a tu tarjeta puede retirar todos los sats de tu cartera. Toma precauciones y mantén solo una pequeña cantidad de sats en tu billetera BoltCard para el gastos del día a día. Comprueba siempre que el comerciante está solicitando el precio correcto. Si es posible, mantén tu tarjeta en una funda protegida por RFID.
Próximos pasos
BoltCard habilitada para PoS
Algunas carteras y sistemas de punto de venta (PoS) son compatibles con la BoltCard. Aquí dejamos una lista de ellos: - BoltCard PoS - Breez - BTCpayserver - LNbits TPOS - Sí, puedes convertir tu cartera LNbits en un punto de venta (PoS) habilitando la extensión TPOS - VoltPay - lipa - Blink - Wallet of Satoshi - Blixt Wallet
Apoyar a BoltCard
También puedes apoyar el esfuerzo de haber creado una biblioteca de código abierto para programar las tarjetas, puedes hacerlo en Geyser Fund.
Tarjetas regalo NFC
En esta guía hemos tratado cómo crear una tarjeta de débito Lightning, pero ¿que ocurre si quieres hacer un regalo en sats y que pueda hacer un retiro a su billetera cuando quiera? Bueno, eso también es posible mediante tarjetas NFC y LNURLw. Explicaremos este proceso en una futura guía.
¡No solo tarjetas!
También puedes escribir registros NFC en cualquier etiqueta NFC que lo admita. Un ejemplo de esto es el Bolt Ring, que ofrece un anillo con capacidad NFC.
-
 @ 599f67f7:21fb3ea9
2024-03-04 14:25:25
@ 599f67f7:21fb3ea9
2024-03-04 14:25:25¿Qué es Cashu?
Cashu es un protocolo de ecash de código abierto para Bitcoin que ofrece transacciones instantáneas sin comisiones con una privacidad casi perfecta. Consulta nostr:naddr1qqxnzd3e8y6rvdpe8qur2v3cqgs9n8m87l0hd9xxqwndqcmwzh4uvyxmwlw0637kuhg98pkcy8ana2grqsqqqa28f238dz para obtener más detalles.
Nutstash
Nutstash es una increíble billetera web de Cashu desarrollada por nostr:npub1cj6ndx5akfazux7f0vjl4fyx9k0ulf682p437fe03a9ndwqjm0tqj886t6 que implementa la mayoría de los NUTs, así como el envío y recepción a través de Nostr. También puedes instalarla como una Progressive Web App (PWA) en tu teléfono.
⚠️ Tanto Nutstash como Cashu todavía están en fase beta. Existe la posibilidad de perder fondos. Lee sobre los riesgos antes de usar la aplicación. Haz pruebas con pequeñas cantidades con las que te sientas cómodo perdiendo.
Pruébalo
Vamos a explicar cómo interactuar con una mint, recibir y enviar ecash, hacer copias de seguridad, convertir a Lightning y hacer intercambios entre mints, y al final probaremos la funcionalidad de los contactos de Nostr.
Añadir un mint
Para interactuar con ecash, primero necesitas tener acceso a una mint, donde se crean y canjean tus tokens de ecash.
- Ve a Txoko Mint.
- Abre la mint en Nutstash.
💡 Puedes añadir mints adicionales en Nutstash yendo a
Mint, pegando la URL de la mint y presionandoAdd Mint("Añadir Mint"). Algunas mints públicas se pueden encontrar en MintIndex. Ten en cuenta que algunas mints reservarán una cierta cantidad de sats para pagar las tarifas de enrutamiento, lo que significa que no podrás retirar todos tus sats.
Crear tokens
Puedes financiar tu billetera de ecash tanto recibiendo ecash directamente como creando nuevos tokens de ecash pagando una factura de Lightning.
- En la pestaña
Mint, elige la mint en la que quieres crear nuevos tokens y presionaMint. - Elige una cantidad. Prueba con una cantidad pequeña, como 100 sats.
- Crea la factura y págala desde una billetera de Lightning. Una vez que se haya pagado la factura, deberías tener tokens de ecash.
Realizar transacciones con ecash
Realizar transacciones con ecash implica básicamente enviar y recibir bloques de datos. Por lo tanto, puedes probar estas funcionalidades enviando y recibiendo a ti mismo. 1. Para enviar ecash, ve a
Wallet>Send. 2. Selecciona la mint desde la que quieres enviar. 3. Elige una cantidad. Opcionalmente, utiliza la selección de monedas. 4. Haz clic en enviar tokens. 5. Copia el token. En este punto, puedes enviar el token a otra persona o canjearlo en tu propia billetera. Dado que solo estamos probando las cosas, haremos lo último.- Para recibir ecash, haz clic en
Wallet>Receive. - Pega el token de cashu.
- Haz clic en
Receive.
💡 Puedes verificar los tokens de ecash pendientes y reclamarlos si el destinatario aún no los ha canjeado. Para hacer esto, ve a la pestaña
Walletsy buscaTokens. Asegúrate de que la columnaPendingesté marcada. Debería haber una lista de tokens pendientes, haz clic en el botón de actualización para verificar su estado. Si no han sido reclamados, puedes copiar y canjear el token.Intercambio de múltiples mints
Es posible que te hayas preguntado si diferentes mints pueden enviar y recibir entre sí. La respuesta es sí. Bueno, más o menos. En lugar de enviar tokens de cashu entre sí, las transacciones entre mints se realizan a través de Lightning. Para probar esto, puedes agregar otra mint si aún no lo has hecho, por ejemplo, la mint de LNbits.
💡 Ten en cuenta que algunas mints reservarán una cierta cantidad de sats para pagar las tarifas de enrutamiento, lo que significa que no podrás retirar todos tus sats. Para evitar esto, también puedes crear tu propia mint con tu billetera Bitcoin Txoko LNbits activando la extensión de Cashu. Bitcoin Txoko no requiere reservas, por lo que puedes retirar todos tus sats.
- Ve a la pestaña
Minty agrega una nueva mint si aún no lo has hecho. - Una vez que tengas varias mints, tendrás la opción de
Inter-Mint Swap. Abre la opción y lee la advertencia. - Si deseas continuar, elige una mint de la que quieres hacer el intercambio y una mint a la que quieres hacer el intercambio.
- Elige una cantidad.
- Confirma la cantidad (
Confirm amount), verifica las tarifas estimadas de enrutamiento y procede con el intercambio (Swap). En segundo plano, la mint que envía está pagando una factura de Lightning a la mint que recibe. Una vez que se haya liquidado la factura, el token intercambiado debería aparecer en el saldo de tu billetera en la mint que recibe.
Convertir a lightning
Cuando quieras convertir tus sats de cashu de nuevo a sats de Lightning, puedes convertir o "derretir" tus tokens de cashu.
- Haz clic en
Payo toca el ícono de la cámara para escanear un código QR. - Ingresa o escanea una factura.
- Opcionalmente, utiliza la selección de monedas.
- Presiona
Pay. La mint funde los tokens de cashu y paga la factura de Lightning.
Copias de seguridad
Hacer copias de seguridad de los tokens de Cashu es probablemente diferente al proceso que estás acostumbrado a hacer para respaldar las billeteras de Bitcoin y Lightning. Dado que los fondos están representados por tokens que son simplemente bloques de datos, solo estás respaldando estos datos cuando haces una copia de seguridad de los tokens de Cashu. Esto también significa que tus copias de seguridad cambiarán cada vez que realices una transacción y necesitarás hacer una nueva copia de seguridad después de cada transacción.
Los diferentes clientes de billeteras han implementado las copias de seguridad de manera diferente y solo funcionarán con la misma billetera que ha creado la copia de seguridad. Nutstash utiliza un archivo JSON como copia de seguridad, que también incluye tu historial de transacciones junto con los tokens que has agregado.
- Para descargar la copia de seguridad en formato JSON, ve a
Settings("Configuración") >Backup Tokens("Copia de seguridad de tokens"), descarga el archivo JSON y guárdalo en un lugar seguro. - Para restaurar la copia de seguridad, ve a
Settings("Configuración") >Restore("Restaurar"). Lee la advertencia. Los datos actuales de tu billetera se sobrescribirán.
Nostr
Dado que puedes enviar tokens de Cashu a través de cualquier protocolo basado en texto, Nostr es una excelente opción para Cashu. Nutstash facilita el envío de tokens de Cashu a través de Nostr.
Primero, necesitas conectar un firmante externo de Nostr a Nutstash para que Nutstash pueda cifrar y firmar mensajes directos utilizados para enviar tokens de ecash. Para hacer esto,
- Ve a la pestaña
Settings("Configuración") y encuentra la secciónNostr. - Activa
Nostr. - Puedes configurar (
Configure) los retransmisores manualmente o permitir que Nutstash lea tu lista de retransmisores después de completar el siguiente paso. - Activa
Use external key("Usar clave externa"). Debes tener instalada una extensión de firmante de Nostr en tu navegador. Algunas buenas opciones son nos2x, Alby y Nostore (para Safari en iOS). - Una vez que Nutstash detecte tu extensión de firmante, permítele leer tu lista de retransmisores y clave pública.
- Si permites que Nutstash descifre los mensajes, buscará tokens de Cashu en tus mensajes directos. Una vez encontrados, aparecerán en la pestaña
Walleten la bandeja de entrada (Inbox). Allí podrás canjearlos en tu billetera.
Para enviar Cashu a través de Nostr,
- Ve a
Send("Enviar"). - Elige un mint.
- Elige una cantidad. Opcionalmente, utiliza la selección de monedas.
- Presiona
Send("Enviar"). - En
Send via Nostr("Enviar a través de Nostr"), ingresa una dirección de Nostr en formato npub, hexadecimal o NIP-05. Alternativamente, escanea el código QR del perfil de alguien. - Presiona
Send via Nostr("Enviar a través de Nostr") y firma el mensaje tipo 4 con tu firmante externo. - Informa al destinatario que revise su bandeja de entrada, ¡deberían tener algunos Cashu esperándolos allí!
Conclusión
¿Encontraste útil esta guía? ¡Intenta enviarnos algunos tokens de Cashu a través de Nostr!
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 32e18276:5c68e245
2023-12-06 15:29:43
@ 32e18276:5c68e245
2023-12-06 15:29:43I’m going to be on an ordinals panels as one of the people who is counter arguing the claim that they are good for bitcoin. I decided to brush up on the technicals on how inscriptions work. I am starting to see luke’s perspective on how it is exploiting a loophole in bitcoin’s anti-data-spam mechanisms.
Storing data in Bitcoin, the “standard” way
The standard way you add “data” to bitcoin is by calling the OP_RETURN opcode. Bitcoin devs noticed that people were storing data (like the bitcoin whitepaper) in the utxo set via large multisig transactions. The problem with this is that this set is unprunable and could grow over time. OP_RETURN outputs on the other-hand are provably prunable and don’t add to utxo bloat.
Here’s an excerpt from the march 2014 0.9.0 release notes that talks about this:
On OP_RETURN: There was been some confusion and misunderstanding in the community, regarding the OP_RETURN feature in 0.9 and data in the blockchain. This change is not an endorsement of storing data in the blockchain. The OP_RETURN change creates a provably-prunable output, to avoid data storage schemes – some of which were already deployed – that were storing arbitrary data such as images as forever-unspendable TX outputs, bloating bitcoin’s UTXO database. Storing arbitrary data in the blockchain is still a bad idea; it is less costly and far more efficient to store non-currency data elsewhere.
Much of the work on bitcoin core has been focused on making sure the system continues to function in a decentralized way for its intended purpose in the presence of people trying to abuse it for things like storing data. Bitcoin core has always discouraged this, as it is not designed for storage of images and data, it is meant for moving digital coins around in cyberspace.
To help incentive-align people to not do stupid things, OP_RETURN transactions were not made non-standard, so that they are relayable by peers and miners, but with the caveat:
- They can only push 40 bytes (later increased to 80,83, I’m guessing to support larger root merkle hashes since that is the only sane usecase for op_return)
Bitcoin also added an option called -datacarriersize which limits the total number of bytes from these outputs that you will relay or mine.
Why inscriptions are technically an exploit
Inscriptions get around the datacarriersize limit by disguising data as bitcoin script program data via OP_PUSH inside OP_IF blocks. Ordinals do not use OP_RETURN and are not subjected to datacarriersize limits, so noderunners and miners currently have limited control over the total size of this data that they wish to relay and include in blocks. Luke’s fork of bitcoin-core has some options to fight this spam, so hopefully we will see this in core sometime soon as well.
Inscriptions are also taking advantage of features in segwit v1 (witness discount) and v2/taproot (no arbitrary script size limit). Each of these features have interesting and well-justified reasons why they were introduced.
The purpose of the witness discount was to make it cheaper to spend many outputs which helps the reduction of the utxo set size. Inscriptions took advantage of this discount to store monke jpegs disguised as bitcoin scripts. Remember, bitcoin is not for storing data, so anytime bitcoin-devs accidentally make it cheap and easy to relay data then this should be viewed as an exploit. Expect it to be fixed, or at least provide tools to noderunners for fighting this spam.
Where do we go from here
The interesting part of this story is that people seem to attach value to images stored on the bitcoin blockchain, and they are willing to pay the fee to get it in the block, so non-ideologic miners and people who don’t care about the health and decentralization of bitcoin are happy to pay or collect the fee and move on.
Data should not get a discount, people should pay full price if they want to store data. They should just use op_return and hashes like opentimestamps or any other reasonable protocol storing data in bitcoin.
After going through this analysis I’ve come to the opinion that this is a pretty bad data-spam exploit and bitcoin devs should be working on solutions. Ideological devs like luke who actually care about the health and decentralization of the network are and I’m glad to see it.
-
 @ c9097925:0a579070
2024-06-19 07:36:30
@ c9097925:0a579070
2024-06-19 07:36:30The conventional wisdom was to never take debt and invest the money.
That’s probably true for most people in general. But this is not an absolute question with just a yes or no answer.
Most people would say that taking on debt to invest is risky, but most people won’t think or say that taking on housing loan, car loan, credit card loan is risky.
There are times when it is beneficial to take on debt and invest the money.
I will argue that over the long term, it is actually better to take on debt if you want to build wealth long-term. But of course, there are risks involved.
This is opposite of the traditional advice to never on take debt to invest.
But if you think about it, most traditional advice is bad advice.
Traditional diet is full of processed carbs and sugar.
Traditional media is poor of clickbait and fake news.
Traditional career is to get good grades to get a good job so that you can buy a house and car to impress people you don’t even like.
The point is that most traditional wisdom sucks.
Good debt & Bad debt This is common sense that there is good debt and bad debt.
Bad debt is debt where you get into debt to buy material things for example to impress people you don’t like with the risk of not being able to pay it.
Good debt is where you invest the money to something that will go up over time.
Is buying a house or car good debt or bad debt?
I don’t know.
That’s a personal question you need to answer for yourself. There is no absolute yes or no.
But what I can say is that it is definitely a bad debt if you cannot afford to pay it.
Why debt has change
What if you have debt that can be inflated away, and you use that proceeds to invest in an investment that continues to go up forever?
The reason why taking on debt to invest is becoming a winning strategy is because our debt can be inflated away.
Here is a concrete example to better understand this:
You take out a loan for 100,000 with terms of 20% interest over 5 years.
You invest this money on asset that will have 20% or more return over the 5 years.
If you can secure a loan now with a fixed interest rate of 20% for the next five years and invest that money in an asset expected to increase at least 20% over the same period, it's a great opportunity.
However, you also need to consider the inflation rate. Let's assume the inflation rate is 5% per year over the next five years, leading to a cumulative inflation of approximately 25%.
Taking the loan protects you from this inflation. Your loan payments remain fixed, but your salary may increase with inflation, making it easier to repay the loan over time.
To put it simply, getting a loan today when cumulative inflation will be 25% over the next five years is like choosing between receiving P100,000 now or P75,000 in five years. This comparison shows that you're better off taking the loan, as the interest rate (20%) is lower than the cumulative inflation rate (25%).
If you invested that amount to an asset that is expected to continue to go up, you’re more likely to beat your interest rate because of inflation + rate of return of investment.
But you can’t predict inflation rate in advance, also inflation rate is a controversial topic, because what is really the inflation rate?
Inflation rate is published government increase in cost of living, but it is defined as a fixed set basket of goods, and those baskets of goods are not the only things we consumed and buy.
Housing price increases are definitely more than the CPI. Inflation average is around 2 to 4 % per year.
What I’m saying is that I’m not convinced that is the real increase on cost of living.
Taking on debt that is debasing and buying assets that are expected to go up forever is the playbook of the rich. What they do instead of selling their assets is that they borrow against their assets.
Think of it as sangla of gold. You have interest on loan on sangla, but what if your gold necklace keeps on appreciating in price. You can just take a new loan to pay for the old loan, because now you can take a bigger loan1
I wrote more of this in detail in this post.
Let’s get back to bitcoin and debt. The point I’m trying to make here is that considering taking out a loan is not just weighing the expected rate of return of bitcoin versus the interest expense on your loans.
Inflation or Currency debasement is a factor to consider too.
Think of those you know that bought houses or condos 10 years ago, you are jealous of their monthly payments and the prices of their houses.
We always say that house always go up in prices. That is technically true but that is not the true story.
House doesn’t grow or become more scarce or rare. That’s not the reason why they are becoming more expensive.
The real reason is that houses become expensive is because of debasement of money.
It simply means that more money is printed each year so it’s just natural for prices to go up. Almost everything goes up.
Houses and other investments just go up more because these are scarce and desirable assets. Also, they are used as investments where people park their money and savings.
You can’t save in cash.
Most people don’t know it but, they view houses as investment because they go up in value.
They aren’t aware of the debasement of money is the reason why housing prices go up, they just know that they continue to go up.
It’s actually another sad reason why we have to go into debt when buying houses that we need to live in. Because we can’t afford to saved money to buy a house. By the time we have saved up for a house to buy, housing prices have already increased.
The main point I’m trying to make is that taking a loan to buy bitcoin, if time properly and if you’re able to handle the monthly payments can be beneficial over the long term.
Over the past 2 years, I’ve done that with my personal strategy to buy bitcoin.
I bought from $50k in 2022 down $20k and back above $60k with my salary and with my borrowed money.
Of course, this is not financial advice. You have to had conviction in bitcoin to be able to do that. You will only have conviction if you spent more than 100 hours studying bitcoin on different angles.
If you’re new to bitcoin, DCAing with your salary is the best strategy.
Don’t trade and don’t get over-leverage.
Leverage and debt aren’t always bad, as long as it is managed properly. Only you can determine how you will use leverage.
How I take on debt to buy bitcoin I started buying bitcoin in March 2022, almost 2 years ago. I arrived on the late-stage bull cycle when price was around 40k to 50k.
I initially looked at bitcoin in 2017 but like most, quickly dismissed it without even studying it. But during 2022, I saw a lot of ads on NBA games and NBA players endorsing different cryptos. NBA arenas were renamed to crypto exchanges. I thought if this has penetrated mainstream, maybe there’s something to it.
I studied bitcoin and cryptos (which is a mistake), because cryptos are just scams. Bitcoin is the only thing that you should spend time studying. Fortunately, I quickly realized that and focused my time and attention to bitcoin only.
I started buying bitcoin at 50k to 40K due to mainly greed at first. But I continued to study it so despite price going down to $16k, I continued to buy with my salary and also, I took out debt on my credit card limits.
There are two reasons why I took out debt to buy bitcoin.
First, the price was going down, so I wanted to buy more.
Second, I believe that by taking a fixed debt that is continued to debase by inflation, it will be beneficial over the long run to take on debt and buy bitcoin.
Even though the annual interest rate ranges from 5% to 12% on these debts. I took them because I firmly believe on my longer-term thesis of locking down those coins at those prices and interest rate.
Of course it wasn’t smooth sailing. My bitcoin has unrealized loss of around 50% at the bottom. If I remember correctly, that was around P200k of unrealized losses.
Only recently my bitcoin unrealized losses turned into unrealized gain.
My cost basis was around 30k, but since I bought more during recent pump starting October 2023, the last time I checked, my cost basis per coin is around 35k.
For now, I stopped taking on debt to buy bitcoin because, I’m already satisfied with my cost basis, even though sometimes I wanted too, I have to check myself.
I don’t recommend doing it now, and generally I won’t really recommend anyone to take on debt to buy bitcoin because everyone has difference circumstances, and you will blame me if you fail.
The reason I’m sharing this is so that you can weigh it yourself if you want to do it.
Also, we are on a bull run, it’s much easier to recommend buying bitcoin when it was 20k, because I know that eventually we will run up. Sadly, most people won’t buy when the prices are going down, most people will buy when price is going up due to greed and FOMO (Like me in March 2022).
The rationale that I told myself when I took on debt to buy bitcoin is if people are taking on debt to buy car or houses, why shouldn’t I do it also but instead of buying a depreciating asset, I am buying bitcoin.
But it wasn’t rosy and easy. Like I said, I was down 50% at one point.
Now I’m up 200% on my investments. This includes all the debt + my salary invested into bitcoin.
I don’t recommend doing this now because we are on a bull run. Right now, I’m happy with not taking on debt. I do plan to take on debt around the downturn on the 4-year cycle which I expect to happen around 2026 to 2027. For now, I will just DCA and chill and pay the monthly payments on my debts.
If you’re new to reading this, start here:
Chapter 1: “Everything is More Expensive”
Chapter 2: “What is Money”
Thank you for reading!
If you want to support my work, consider donating via lightning:
Alby page: click here
Wallet of Satoshi: stainedsail42@walletofsatoshi.com
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 32e18276:5c68e245
2024-05-14 16:46:28
@ 32e18276:5c68e245
2024-05-14 16:46:28Hey Damus enjoyers,
v1.8 has been tagged! Today we submitted v1.8 to the App Store, Here's a quick preview of what's in this release!
New Emoji Selector
It's now easier than ever to select emoji reactions! Just long press the reaction button to pop-up the new emoji selector. Thanks Terry for implementing this!

Quote Reposts
Quote reposts are now listed on posts, just like on the birdsite (x site ?)

New fullscreen video player
Our video controls were pretty bad before, this has been improved in this version! You can now seek videos, view them fullscreen, and airplay them to your tv. Thanks Daniel for this feature!

Improved longform style
Longform posts now show the image and related tags. Thanks Eric!

Account recovery, bug fixes
Thread loading is greatly improved, we now support the latest nip10 specification for improved compatibility between clients. We also added an account recovery feature called First Aid. You can use this to create a new contact list if for whatever reason you don't have one anymore. If you are running into issues following people, you can use this to recover your account:

Testflight
v1.9 dev is underway, with an up and coming highlighter feature where you can clip highlights from the web and other posts and share them to your feed. If you want to test out the latest up and coming features, make sure to grab a damus purple membership to get access!
https://damus.io/purple/login
That's all for now, here's the full changelog if you want to see what else is new!
Full Changelog
Added
- Added nip10 marker replies (William Casarin)
- Add marker nip10 support when reading notes (William Casarin)
- Added title image and tags to longform events (ericholguin)
- Add First Aid solution for users who do not have a contact list created for their account (Daniel D’Aquino)
- Relay fees metadata (ericholguin)
- Added callbackuri for a better ux when connecting mutiny wallet nwc (ericholguin)
- Add event content preview to the full screen carousel (Daniel D’Aquino)
- Show list of quoted reposts in threads (William Casarin)
- Proxy Tags are now viewable on Selected Events (ericholguin)
- Add ability to mute words, add new mutelist interface (Charlie)
- Add ability to mute hashtag from SearchView (Charlie Fish)
Changed
- Change reactions to use a native looking emoji picker (Terry Yiu)
- Relay detail design (ericholguin)
- Updated Zeus logo (ericholguin)
- Improve UX around video playback (Daniel D’Aquino)
- Moved paste nwc button to main wallet view (ericholguin)
- Errors with an NWC will show as an alert (ericholguin)
- Relay config view user interface (ericholguin)
- Always strip GPS data from images (kernelkind)
Fixed
- Fix thread bug where a quote isn't picked up as a reply (William Casarin)
- Fixed threads not loading sometimes (William Casarin)
- Fixed issue where some replies were including the q tag (William Casarin)
- Fixed issue where timeline was scrolling when it isn't supposed to (William Casarin)
- Fix issue where bootstrap relays would inadvertently be added to the user's list on connectivity issues (Daniel D’Aquino)
- Fix broken GIF uploads (Daniel D’Aquino)
- Fix ghost notifications caused by Purple impending expiration notifications (Daniel D’Aquino)
- Improve reliability of contact list creation during onboarding (Daniel D’Aquino)
- Fix emoji reactions being cut off (ericholguin)
- Fix image indicators to limit number of dots to not spill screen beyond visible margins (ericholguin)
- Fix bug that would cause connection issues with relays defined with a trailing slash URL, and an inability to delete them. (Daniel D’Aquino)
- Issue where NWC Scanner view would not dismiss after a failed scan/paste (ericholguin)
-
 @ de496884:72617b81
2023-11-20 13:54:02
@ de496884:72617b81
2023-11-20 13:54:02Hola nostriches. Hoy quiero hacer una publicación a modo de acercamiento al surgimiento de las categorías de género y feminismo. Así que si te interesa el tema haz un esfuerzo, quédate y lee hasta el final.
El «nuevo» feminismo surge en los años 60 en aquellos países desarrollados que acordaron el reconocimiento a los derechos humanos contenidos en la declaración respectiva de la ONU. Entonces, como extensión a dicho reconocimiento es que se gesta el movimiento feminista. A partir de entonces, se vuelve a plantear la relación entre naturaleza y cultura y se llega a la conclusión de que las diferencias sociales van más allá de las diferencias biológicas, lo cual tiene que ver con que hasta la satisfacción de las necesidades elementales como son la alimentación, la vivienda o el vestuario, están condicionadas por construcciones sociales.
Pues resulta que una de las primeras propuestas identificó la subordinación femenina producto de una organización patriarcal, tomando la categoría patriarcado de Max Weber. Es así como la visión de patriarcado se extendió al discurso político y académico. Sin embargo, no existía información acerca del desarrollo histórico de dicha categoría, sistematización, variaciones, etc., debido a que era algo que recién se percibía en sociedad.
Sin embargo, la misma categoría de patriarcado junto a la de relaciones de poder para explicar fenómenos sociales contemporáneos, constituye uno de los principales aportes del feminismo. Es así como han logrado primero visibilizar y luego deconstruir y desmontar una serie de patrones existentes en la cultura que hacían a la mujer subordinarse al hombre, y que estaban presentes en el sistema sexo/género.
 Imagen relativa a la lucha contra el patriarcado
Imagen relativa a la lucha contra el patriarcadoHasta ese momento, en las investigaciones de corte sociológico se podía observar un androcentrismo excesivo al dar cuenta de que el discurso científico giraba en torno al hombre como sujeto y objeto de la investigación. Incluso para muchos positivistas como el mismo Weber, los problemas relativos a las mujeres quedaban en un segundo plano y eran achacados a una supuesta pasividad en el ámbito doméstico-familiar. Dicha pasividad partía de la supuesta inferioridad biológica del género femenino.
El patriarcado entonces era una categoría vacía en sí misma, sin valor explicativo. Desde el punto de vista político pudo ser útil para la movilización pero no resistió la polémica de los críticos del feminismo ni problematizó los conflictos a ser resueltos. Pero por otro lado, un grupo de mujeres -académicas principalmente- se puso manos a la obra en una tarea más pequeña pero con mayores resultados a la larga. Se propusieron generar conocimientos sobre las condiciones de vida de la mujer, buscar en el pasado y el presente los aportes de las mujeres a la sociedad, hacerlas visibles en la historia. Es así como surgen centros académicos, ONG, proyectos, centros de estudios sobre la mujer, etc.
Convendría distinguir entonces dos posturas que acompañaron a la investigación sobre las mujeres: uno que toma como objeto de estudio a la mujer; condiciones de vida, trabajo, cultura, y otra que privilegia a la sociedad como generadora de la subordinación de las mujeres. Mientras la primera perspectiva generaba conocimiento sobre las mujeres en el estudio de las relaciones mujer-hombre y mujer-mujer, la segunda tenía una visión más holística ya que planteaba que hay que estudiar la sociedad ya que la subordinación de las mujeres es producto de la organización de esta, y que no se avanzará solamente estudiando a las mujeres, pues el estudio debe ser más amplio y en diferentes niveles, ámbitos y tiempos.
Es en esta búsqueda donde nace y se desarrolla el concepto de género como categoría social. Es así que los sistemas de género/sexo fueron entendidos como conjuntos de prácticas, símbolos, representaciones, normas y valores sociales que las sociedades construyen a partir de la diferencia anatomofisiológica y que dotan de sentido a los impulsos sexuales, la reproducción y en general a las relaciones de las personas. Por tanto, este sistema pasó a ser el objeto de estudio para comprender la subordinación de la mujer al hombre. Al ser el reconocimiento de una dimensión de la desigualdad social hasta entonces desconocida, se considera la ruptura epistemológica más importante de la segunda mitad del siglo pasado.
 Imagen representativa del binarismo de género
Imagen representativa del binarismo de géneroHay que decir que los fenómenos sociales se definen por la relación que guardan entre sí. Es así que la contextualización adquiere gran importancia. Varones y hembras tenemos la capacidad de producir con el cuerpo, pero solo los cuerpos de las hembras pueden gestar y por tanto asegurar la especie humana. Todo grupo humano que pretenda sobrevivir debe asegurarse cierto número de hembras que lo hagan posible. De ahí un poder particular del cuerpo de las hembras que además es económicamente útil. Dicho poder no es en tanto entidad biológica, sino que es la sociedad la que le otorga este poder. En este punto es importante preguntarnos históricamente ¿quiénes han controlado la capacidad reproductiva de las mujeres?, ¿quiénes han tenido la preferencia en el acceso sexual? Para asegurar un control efectivo sobre la reproducción es necesario asegurar el acceso a la sexualidad.
Ello también lleva a dirigir el trabajo que hacen porque de lo contrario, las mujeres pudieran tener espacio para representar una amenaza al dominio de los hombres. Es importante atender a las etapas del desarrollo de las mujeres, que permitirá ver cómo se moldean para aceptar la desigualdad y las jerarquías según el género en las distintas sociedades y culturas.
Otro contexto a delimitar es el ámbito doméstico donde históricamente ha estado ubicada la subordinación femenina. Se ha puesto al descubierto que en mujeres que comparten la misma posición de clase y raza, la condición femenina se redefine a lo largo de la vida y que algunas mujeres gozan de poder sobre otras aún en contextos de alta dominación masculina, donde se les inviste de autoridad, creando el sistema zonas de incertidumbre que las divide como género e impide alianzas y se legitima la dominación. Foucault decía que «el poder se ejerce, no se posee», siempre está en peligro de perderse y no basta con normas, leyes, amenazas o castigos. De ahí que los espacios de subordinación sean también espacios de poder de las mujeres. Es en estos espacios donde aparece la inseguridad, la tensión, la confrontación y por ejemplo, las mujeres pueden reclamar la anticoncepción.
Para terminar, es importante tener en cuenta que el género es una forma de desigualdad social que siempre está articulado con otras formas de desigualdad ya sea clase, raza, grupo etario, etc. Hay que pensar la dominación masculina con un comienzo vago en el tiempo, pero que permite desligar la subordinación de las mujeres de la evolución «natural» de la humanidad y entenderla como un proceso histórico. En ese sentido es necesario destacar que, respecto a la raza, en sociedades plurales hay que atender al contexto étnico-cultural ya que en dependencia de las relaciones entre personas de razas distintas, estarán condicionadas las relaciones entre los géneros.
 Imagen de mujeres de distintas razas
Imagen de mujeres de distintas razasPor otro lado, si bien es sabido que históricamente el sistema de género social imperante ha contribuido a invisibilizar a la mujer, asociar necesariamente dicha categoría únicamente a ella, lo que hace es nuevamente recrear el absolutismo histórico que tanto daño ha hecho, ahora como lo antagónico al hombre. En la construcción social participan todos los individuos presentes en el sistema género.
Hasta aquí la publicación de hoy, de la cual aun se puede ahondar mucho más, sobre todo en lo referido al origen de la dominación o de la jerarquización del binomio «hombre/mujer» desde un punto de vista antropológico, pero eso quedará pendiente para otro momento. ¡Así que hasta la próxima!, ¡nos vemos en Nostr!
........................................
English version
Hello nostriches. Today I want to make a post by way of an approach to the emergence of the categories of gender and feminism. So if you are interested in the topic make an effort, stay and read to the end.
The "new" feminism emerged in the 60's in those developed countries that agreed to recognize the human rights contained in the respective UN declaration. Then, as an extension of that recognition, the feminist movement was born. From then on, the relationship between nature and culture was raised again and the conclusion was reached that social differences go beyond biological differences, which has to do with the fact that even the satisfaction of elementary needs such as food, housing or clothing are conditioned by social constructions.
It turns out that one of the first proposals identified female subordination as a product of a patriarchal organization, taking Max Weber's category of patriarchy. This is how the vision of patriarchy was extended to political and academic discourse. However, there was no information about the historical development of this category, systematization, variations, etc., because it was something that was only recently perceived in society.
However, the same category of patriarchy, together with that of power relations to explain contemporary social phenomena, constitutes one of the main contributions of feminism. This is how they have first made visible and then deconstructed and dismantled a series of existing patterns in the culture that made women subordinate to men, and that were present in the sex/gender system.
 Image relating to the fight against patriarchy
Image relating to the fight against patriarchyUp to that time, in sociological research, an excessive androcentrism could be observed as scientific discourse revolved around men as the subject and object of research. Even for many positivists such as Weber himself, the problems related to women remained in the background and were blamed on a supposed passivity in the domestic-family sphere. This passivity was based on the supposed biological inferiority of the female gender.
Patriarchy was then an empty category in itself, with no explanatory value. From the political point of view, it could be useful for mobilization, but it did not resist the polemic of feminism's critics, nor did it problematize the conflicts to be resolved. But on the other hand, a group of women - mainly academics - set to work on a smaller task but with greater results in the long run. They set out to generate knowledge about women's living conditions, to search in the past and present for women's contributions to society, to make them visible in history. This is how academic centers, NGOs, projects, women's studies centers, etc., came into being.
It would be convenient to distinguish then two postures that accompanied the research on women: one that takes women as the object of study; living conditions, work, culture, and the other that privileges society as the generator of women's subordination. While the first perspective generated knowledge about women in the study of woman-man and woman-woman relations, the second had a more holistic vision, since it proposed that society must be studied, since the subordination of women is a product of its organization, and that progress will not be made only by studying women, since the study must be broader and at different levels, spheres and times.
It is in this search that the concept of gender as a social category was born and developed. Thus, gender/sex systems were understood as a set of practices, symbols, representations, norms and social values that societies construct on the basis of anatomophysiological differences and that give meaning to sexual impulses, reproduction and, in general, to people's relationships. Therefore, this system became the object of study to understand the subordination of women to men. As the recognition of a hitherto unknown dimension of social inequality, it is considered the most important epistemological breakthrough of the second half of the last century.
 Representative image of gender binarism
Representative image of gender binarismIt must be said that social phenomena are defined by their relationship with each other. Thus, contextualization acquires great importance. Males and females have the capacity to produce with their bodies, but only the bodies of females can gestate and therefore ensure the human species. Any human group that intends to survive must ensure a certain number of females to make it possible. Hence a particular power of the female body, which is also economically useful. This power is not as a biological entity, but it is society that gives it this power. At this point it is important to ask ourselves historically, who has controlled the reproductive capacity of women, who has had the preference in sexual access? To ensure effective control over reproduction, it is necessary to ensure access to sexuality.
 Allegorical image of pregnancy
Allegorical image of pregnancyThis also leads to directing the work they do because otherwise, women may have room to pose a threat to men's dominance. It is important to pay attention to the stages of women's development, which will allow us to see how they are shaped to accept inequality and gender hierarchies in different societies and cultures.
Another context to delimit is the domestic sphere where female subordination has historically been located. It has been discovered that in women who share the same class and race position, the feminine condition is redefined throughout life and that some women enjoy power over others even in contexts of high male domination, where they are invested with authority, creating the system of uncertainty zones that divide them as a gender and prevent alliances and legitimize domination. Foucault said that "power is exercised, not possessed", it is always in danger of being lost and norms, laws, threats or punishments are not enough. Hence, the spaces of subordination are also spaces of women's power. It is in these spaces where insecurity, tension, confrontation appear and where, for example, women can demand contraception.
To conclude, it is important to keep in mind that gender is a form of social inequality that is always articulated with other forms of inequality, be it class, race, age group, etc. It is necessary to think of male domination with a vague beginning in time, but which allows us to separate the subordination of women from the "natural" evolution of humanity and to understand it as a historical process. In this sense, it is necessary to emphasize that, with respect to race, in plural societies it is necessary to pay attention to the ethno-cultural context since, depending on the relations between people of different races, the relations between genders will be conditioned.
 Image of women of different races
Image of women of different racesOn the other hand, although it is known that historically the prevailing social gender system has contributed to make women invisible, to necessarily associate this category only to women is to recreate the historical absolutism that has done so much damage, this time as antagonistic to men. All individuals present in the gender system participate in the social construction.
So much for today's publication, of which we can still go much deeper, especially with regard to the origin of domination or the hierarchization of the binomial "man/woman" from an anthropological point of view, but that will be left for another time. So until next time, see you in Nostr!

Créditos | Credits
Bibliografía consultada | Consulted bibliography:
-
Barbieri, T. (1993). Sobre la categoría género. Una introducción teórico-metodológica. Debates en Sociología. (18). 1-19. https://doi.org/10.18800/debatesensociologia.199301.006
-
Echevarría, D. (2020). Desigualdades de género e interseccionalidad. Análisis del contexto cubano 2008-2018. Facultad Latinoamericana de Ciencias Sociales (Programa-Cuba). https://www.clacso.org.ar/libreria-latinoamericana-cm/libro_detalle_resultado.php?id_libro=2346&campo=cm&texto=248
Traducción | Translation:
DeepL
-
-
 @ 5abd9a94:531904ce
2024-06-19 07:31:40
@ 5abd9a94:531904ce
2024-06-19 07:31:40The conventional wisdom was to never take debt and invest the money.
That’s probably true for most people in general. But this is not an absolute question with just a yes or no answer.
Most people would say that taking on debt to invest is risky, but most people won’t think or say that taking on housing loan, car loan, credit card loan is risky.
There are times when it is beneficial to take on debt and invest the money.
I will argue that over the long term, it is actually better to take on debt if you want to build wealth long-term. But of course, there are risks involved.
This is opposite of the traditional advice to never on take debt to invest.
But if you think about it, most traditional advice is bad advice.
Traditional diet is full of processed carbs and sugar.
Traditional media is poor of clickbait and fake news.
Traditional career is to get good grades to get a good job so that you can buy a house and car to impress people you don’t even like.
The point is that most traditional wisdom sucks.
Good debt & Bad debt This is common sense that there is good debt and bad debt.
Bad debt is debt where you get into debt to buy material things for example to impress people you don’t like with the risk of not being able to pay it.
Good debt is where you invest the money to something that will go up over time.
Is buying a house or car good debt or bad debt?
I don’t know.
That’s a personal question you need to answer for yourself. There is no absolute yes or no.
But what I can say is that it is definitely a bad debt if you cannot afford to pay it.
Why debt has change
What if you have debt that can be inflated away, and you use that proceeds to invest in an investment that continues to go up forever?
The reason why taking on debt to invest is becoming a winning strategy is because our debt can be inflated away.
Here is a concrete example to better understand this:
You take out a loan for 100,000 with terms of 20% interest over 5 years.
You invest this money on asset that will have 20% or more return over the 5 years.
If you can secure a loan now with a fixed interest rate of 20% for the next five years and invest that money in an asset expected to increase at least 20% over the same period, it's a great opportunity.
However, you also need to consider the inflation rate. Let's assume the inflation rate is 5% per year over the next five years, leading to a cumulative inflation of approximately 25%.
Taking the loan protects you from this inflation. Your loan payments remain fixed, but your salary may increase with inflation, making it easier to repay the loan over time.
To put it simply, getting a loan today when cumulative inflation will be 25% over the next five years is like choosing between receiving P100,000 now or P75,000 in five years. This comparison shows that you're better off taking the loan, as the interest rate (20%) is lower than the cumulative inflation rate (25%).
If you invested that amount to an asset that is expected to continue to go up, you’re more likely to beat your interest rate because of inflation + rate of return of investment.
But you can’t predict inflation rate in advance, also inflation rate is a controversial topic, because what is really the inflation rate?
Inflation rate is published government increase in cost of living, but it is defined as a fixed set basket of goods, and those baskets of goods are not the only things we consumed and buy.
Housing price increases are definitely more than the CPI. Inflation average is around 2 to 4 % per year.
What I’m saying is that I’m not convinced that is the real increase on cost of living.
Taking on debt that is debasing and buying assets that are expected to go up forever is the playbook of the rich. What they do instead of selling their assets is that they borrow against their assets.
Think of it as sangla of gold. You have interest on loan on sangla, but what if your gold necklace keeps on appreciating in price. You can just take a new loan to pay for the old loan, because now you can take a bigger loan1
I wrote more of this in detail in this post.
Let’s get back to bitcoin and debt. The point I’m trying to make here is that considering taking out a loan is not just weighing the expected rate of return of bitcoin versus the interest expense on your loans.
Inflation or Currency debasement is a factor to consider too.
Think of those you know that bought houses or condos 10 years ago, you are jealous of their monthly payments and the prices of their houses.
We always say that house always go up in prices. That is technically true but that is not the true story.
House doesn’t grow or become more scarce or rare. That’s not the reason why they are becoming more expensive.
The real reason is that houses become expensive is because of debasement of money.
It simply means that more money is printed each year so it’s just natural for prices to go up. Almost everything goes up.
Houses and other investments just go up more because these are scarce and desirable assets. Also, they are used as investments where people park their money and savings.
You can’t save in cash.
Most people don’t know it but, they view houses as investment because they go up in value.
They aren’t aware of the debasement of money is the reason why housing prices go up, they just know that they continue to go up.
It’s actually another sad reason why we have to go into debt when buying houses that we need to live in. Because we can’t afford to saved money to buy a house. By the time we have saved up for a house to buy, housing prices have already increased.
The main point I’m trying to make is that taking a loan to buy bitcoin, if time properly and if you’re able to handle the monthly payments can be beneficial over the long term.
Over the past 2 years, I’ve done that with my personal strategy to buy bitcoin.
I bought from $50k in 2022 down $20k and back above $60k with my salary and with my borrowed money.
Of course, this is not financial advice. You have to had conviction in bitcoin to be able to do that. You will only have conviction if you spent more than 100 hours studying bitcoin on different angles.
If you’re new to bitcoin, DCAing with your salary is the best strategy.
Don’t trade and don’t get over-leverage.
Leverage and debt aren’t always bad, as long as it is managed properly. Only you can determine how you will use leverage.
How I take on debt to buy bitcoin I started buying bitcoin in March 2022, almost 2 years ago. I arrived on the late-stage bull cycle when price was around 40k to 50k.
I initially looked at bitcoin in 2017 but like most, quickly dismissed it without even studying it. But during 2022, I saw a lot of ads on NBA games and NBA players endorsing different cryptos. NBA arenas were renamed to crypto exchanges. I thought if this has penetrated mainstream, maybe there’s something to it.
I studied bitcoin and cryptos (which is a mistake), because cryptos are just scams. Bitcoin is the only thing that you should spend time studying. Fortunately, I quickly realized that and focused my time and attention to bitcoin only.
I started buying bitcoin at 50k to 40K due to mainly greed at first. But I continued to study it so despite price going down to $16k, I continued to buy with my salary and also, I took out debt on my credit card limits.
There are two reasons why I took out debt to buy bitcoin.
First, the price was going down, so I wanted to buy more.
Second, I believe that by taking a fixed debt that is continued to debase by inflation, it will be beneficial over the long run to take on debt and buy bitcoin.
Even though the annual interest rate ranges from 5% to 12% on these debts. I took them because I firmly believe on my longer-term thesis of locking down those coins at those prices and interest rate.
Of course it wasn’t smooth sailing. My bitcoin has unrealized loss of around 50% at the bottom. If I remember correctly, that was around P200k of unrealized losses.
Only recently my bitcoin unrealized losses turned into unrealized gain.
My cost basis was around 30k, but since I bought more during recent pump starting October 2023, the last time I checked, my cost basis per coin is around 35k.
For now, I stopped taking on debt to buy bitcoin because, I’m already satisfied with my cost basis, even though sometimes I wanted too, I have to check myself.
I don’t recommend doing it now, and generally I won’t really recommend anyone to take on debt to buy bitcoin because everyone has difference circumstances, and you will blame me if you fail.
The reason I’m sharing this is so that you can weigh it yourself if you want to do it.
Also, we are on a bull run, it’s much easier to recommend buying bitcoin when it was 20k, because I know that eventually we will run up. Sadly, most people won’t buy when the prices are going down, most people will buy when price is going up due to greed and FOMO (Like me in March 2022).
The rationale that I told myself when I took on debt to buy bitcoin is if people are taking on debt to buy car or houses, why shouldn’t I do it also but instead of buying a depreciating asset, I am buying bitcoin.
But it wasn’t rosy and easy. Like I said, I was down 50% at one point.
Now I’m up 200% on my investments. This includes all the debt + my salary invested into bitcoin.
I don’t recommend doing this now because we are on a bull run. Right now, I’m happy with not taking on debt. I do plan to take on debt around the downturn on the 4-year cycle which I expect to happen around 2026 to 2027. For now, I will just DCA and chill and pay the monthly payments on my debts.
If you’re new to reading this, start here:
Chapter 1: “Everything is More Expensive”
Chapter 2: “What is Money”
Thank you for reading!
If you want to support my work, consider donating via lightning:
Alby page: click here
Wallet of Satoshi: stainedsail42@walletofsatoshi.com
-
 @ d360efec:14907b5f
2024-06-19 06:08:02
@ d360efec:14907b5f
2024-06-19 06:08:02ขอแนะนำอาวุธง้อไบ๊ หรือชื่อที่ถูกต้องคือ หนามเอ๋อเหม่ย-อาวุธประหลาดคู่กายของหวงหรง (อึ้งย้ง) จากนิยายมังกรหยก
ตามนิยามบอกว่าเป็นอาวุธที่อึ้งย้งพกติดตัวและใช้ต่อสู้ตลอดทั้งเรื่อง โดยนางจะชุกซ่อนเอาไว้แขนเสื้อ ยามใช้จะเป็นการลอบทำร้ายโดยศัตรูไม่ทันระวัง แม้แต่ศัตรูที่เก่งกว่านางมากๆ อย่าง โอวหยางเค่อ(อ้าวเอี้ยงเค้ก)หลายชายของ โอวหยางฟง(อ้าวเอี้ยงฮง) ก็ยังถูกหนามเอ๋อเหม่ยของนางแทงมาแล้ว
นอกจากใช้ต่อสู้แล้วอึ้งย้งยังใช่อาวุธนี้ได้สารพัดประโยชน์ มีตอนหนึ่งในนิยายที่เขียนถึงการทำ
" ไก่ขอทาน "อึ้งย้งก็ใช้หนามเอ๋อเหม่ยผ่าท้องไก่ ล้างให้สะอาด เอาไปคลุกเครื่องเทศโดยไม่ต้องถอนขน จากนั้นเอาดินห่อ ทิ้งเข้ากองไฟ "
อาวุธชนิดนี้เป็นอาวุธอยู่นอกสารบบ 18 ศาสตราวุธจีนโบราณ ซึ่งครอบคลุมอาวุธ 18 ประเภทประกอบด้วย 9 ยาว 9 สั้น ตัวอย่างเช่น ดาบ กระบี่ ง้าว ธนู ขวาน กระบอง คทา หอก กรงเล็บ ไม้พลอง แม้แต่ " เชือก "ก็ยังมีในสารบบ แต่ไม่มีอาวุธ " หนามเอ๋อเหม่ย-峨眉刺 "
ปกติหนามเอ๋อเหม่ยจะมีความยาวประมาณ 1 ฟุต หรือสั้นยาวตามความถนัดของผู้ใช้ อาจมีปลายแหลมทั้งสองข้างหรือข้างเดียวก็ได้แล้วแต่ผู้ใช้และผู้ออกแบบจะคิดสร้าง แต่ทุกอย่างมีลักษณะเหมือนกันคือ เหล็กหนามจะยึดติดกับห่วงกลมตรงกลางที่เหมือนแหวน และสามารถหมุนได้ 360 องศา เวลาใช้ก็เอานิ้วใส่เข้าไปในแหวน ใช้แทง เจาะ เคาะ ตี ขึ้นอยู่กับลักษณะปลายแหลมของมัน
ตามบันทึกโบราณ หนามเอ๋อเหม่ย เป็นอาวุธสำหรับลอบโจมตีใต้น้ำ มือสังหารจะดำน้ำมา ลากคนลงไปแล้วเอาหนามเอ๋อเหม่ยแทงจนตาย หรืออาจใช้หนามเอ๋อเหม่ยเจาะท้องเรือลากคนลงไปสังหารกลางแม่น้ำก็ได้
เนื่องจากเป็นอาวุธสั้น ใช้ต่อสู้ระยะประชิด น้ำหนักเบา พกพาสะดวก ง่ายแก่การซุกซ่อน และมีรูปร่างคล้ายปิ่นปักผมของผู้หญิง จึงสมมุติฐานว่า ผู้หญิงเป็นคนคิดค้นอาวุธชนิดนี้ขึ้นมา
แต่ก็มีตำนานว่านักพรตคิ้วขาวแห่งสำนักง้อไบ๊(เอ๋อเหม่ย) ซึ่งเป็นผู้ชายเป็นผู้คิดค้น และมีบางตำนานบอกว่าอาจารย์วิชากังฟูแถวเสฉวนบางคนคิดค้นสร้างขึ้นมา ที่เรียกว่า หนามเอ๋อเหม่ย เพราะรูปร่างมันเหมือนฝัก " ถั่วตาดำ " หรือ 鹅眉豆 ซึ่งเป็นคำพ้องเสียง ไม่ได้เกี่ยวอะไรกับสำนักง้อไบ๊เลย





-
 @ 03612b0e:afd71216
2024-05-12 14:14:47
@ 03612b0e:afd71216
2024-05-12 14:14:47c-lightning-REST with Tailscale on Start9
This guide gives you commands to run additional containers on Start9. This is not officially supported and will break on reboot. You can always run the containers again to restore the setup. The containers are used to provide access, via Tailscale, to Core Lightning's c-lightning-REST plugin
Start9 setup
- In your Start9 dashboard, make sure you have C-Lightning-REST enabled.
- Services > Core Lightning > Config > Advanced > Plugins > C-Lightning-REST
- SSH to your Start9, see documentation for help: https://docs.start9.com/0.3.5.x/user-manual/ssh
- Access the root account:
sudo -i - Run tailscaled and alpine/socat containers:
podman run -d \ --name=tailscaled.embassy \ -v /dev/net/tun:/dev/net/tun \ -v /var/lib:/var/lib \ -e TS_HOSTNAME=tailscaled \ --network=host \ --cap-add=NET_ADMIN \ --cap-add=NET_RAW \ docker.io/tailscale/tailscale:stablepodman run -d \ --name=socat.embassy \ --publish 4321:1234 \ --network=start9 \ docker.io/alpine/socat \ tcp-listen:1234,fork,reuseaddr tcp:c-lightning.embassy:3001-
Note, if you see errors related to
/root/.docker/config.jsonorUnexpected end of JSON, runecho '{}' > /root/.docker/config.json -
Check the status of tailscaled and log in
``` podman exec tailscaled.embassy tailscale --socket /tmp/tailscaled.sock status
example output
Logged out. Log in at: https://login.tailscale.com/a/1fa8e293dfd108
```
Zeus wallet setup
- On your phone, connect to Tailscale
- On your Start9, copy your REST Macaroon (Hex) for Zeus wallet setup
- Services > Core Lightning > Properties > REST Properties > REST Macaroon (Hex)
- In Zeus wallet, add a new node
- Settings > (tap the active node) > +
Setting | Value ---|--- Node interface | Core Lightning (c-lightning-Rest) Host | tailscaled.YOUR_TAILNET_DOMAIN Macaroon (Hex format) | see last step REST Port | 4321 Certificate Verification | disabled
SAVE NODE CONFIG
- Note, you can find YOUR_TAILNET_DOMAN at https://login.tailscale.com/admin/dns
Enjoy!
- In your Start9 dashboard, make sure you have C-Lightning-REST enabled.
-
 @ d360efec:14907b5f
2024-06-19 04:30:39
@ d360efec:14907b5f
2024-06-19 04:30:39"กวารานา" 👁พืชตาปีศาจ👁
ต้นกวารานา (Paullinia cupana) มีถิ่นกำเนิดในลุ่มน้ำอเมซอนในประเทศบราซิล มีชื่อเสียงในด้านผลไม้ที่โดดเด่น ซึ่งมีลักษณะคล้ายกระจุกลูกตา
ไม้เลื้อยชนิดนี้มีใบขนาดใหญ่และดอกขนาดเล็กเป็นกระจุก เมื่อผลสุก เปลือกเมล็ดจะแตกออกเผยให้เห็นเนื้อสีขาวและเมล็ดสีดำ ทำให้เกิดลักษณะคล้ายตาที่ทำให้จดจำได้ง่าย
กวารานาเจริญเติบโตในภูมิอากาศเขตร้อนชื้นของป่าอเมซอน และได้รับการปลูกเป็นหลักในรัฐอามาโซนัสและบาเอียของบราซิล
เมล็ดพืชกวารานาได้รับการยกย่องว่ามีปริมาณคาเฟอีนสูง ประมาณสองเท่าของเมล็ดกาแฟ ทำให้กวารานาเป็นส่วนผสมยอดนิยมในเครื่องดื่มให้พลังงาน ผลิตภัณฑ์เสริมอาหาร และเครื่องดื่มน้ำอัดลม
ชนเผ่าพื้นเมืองใช้กวารานามานานหลายศตวรรษ โดยให้คุณค่ากับคุณสมบัติที่กระตุ้นให้เกิดเครื่องดื่มแบบดั้งเดิม
นอกเหนือจากผลที่ให้ความกระฉับกระเฉงแล้ว กวารานายังอุดมไปด้วยสารต้านอนุมูลอิสระและเชื่อกันว่าช่วยเพิ่มความตื่นตัวทางจิต ลดความเหนื่อยล้า และปรับปรุงความอดทนทางร่างกาย
อย่างไรก็ตามด้วยปริมาณคาเฟอีนที่สูงนั้นจำเป็นต้องบริโภคอย่างระมัดระวังเพื่อหลีกเลี่ยงผลข้างเคียง เช่น การนอนไม่หลับและความกังวลใจ
การวิจัยกำลังดำเนินการสำรวจบทบาทที่เป็นไปได้ของกวารานาในเรื่องการลดน้ำหนัก เนื่องจากความสามารถในการเพิ่มการเผาผลาญและส่งเสริมการเกิดออกซิเดชันของไขมัน ทำให้กวารานาเป็นที่สนใจของผลิตภัณฑ์เสริมอาหาร
เครดิตข้อความ: Earth Unreal

-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 1c6b3be3:73f0ae6f
2024-06-19 04:05:24
@ 1c6b3be3:73f0ae6f
2024-06-19 04:05:24Releases - No Bullshit Bitcoin
Tails v6.4: Random Seed on USB Stick to Strengthen Cryptography (1 min) Tails 6.4 has been released with several improvements and bug fixes. The new version strengthens all cryptography by storing a random seed on the USB stick. HTTPS addresses are now used instead of onion addresses for Debian and Tails APT repositories to make Additional Software more reliable. Tor Browser and Tor client have been updated to 13.0.16 and 0.4.8.12, respectively. Thunderbird has been updated to 115.12.0. More issues when unlocking the Persistent Storage have been fixed, along with connecting to a mobile broadband network on some hardware. The PDF reader of Thunderbird, which was disabled in Tails 6.3 for security reasons, has been enabled again. The error message of Tails Cloner has been improved, and the redundant dialog when unlocking a VeraCrypt volume using the Unlock VeraCrypt Volumes utility has been removed. Lastly, the homepage of Tor Browser no longer shows an error message when using the New Identity feature.
umbrelOS v1.2: Wi-Fi Support, Revamped Live Usage UmbrelOS, a home server operating system with an app store, has released an update that includes Wi-Fi support, an improved Live Usage experience displaying real-time CPU and memory usage charts, faster and more accurate results, NVMe and USB boot support for Raspberry Pi 5, and various enhancements and bug fixes. The improvements include resolving networking issues, enabling the download of system log files, providing local IP address visibility, fixing app install/update progress bar issues in Safari, improving accuracy of CPU temperature warnings, and more. Users can engage with other Umbrel users through its official Community Discord channel or visit its GitHub repository for further information.
Trezor Introduced Safe 5 Signing Device (1 min) Trezor, a signing device manufacturer, has released its new flagship product, the Safe 5, at BTC Prague 2024. Priced at $169, it comes with either Bitcoin-only firmware or multicoin support. The company also introduced a new onboarding service called Trezor Expert for new customers.
The Trezor Safe 5 features a 1.54" Gorilla Glass 3 touchscreen display, a Certified Chip EAL6+ secure element, and a microSD card slot. It supports both 12 and 24-word BIP39 backups and the Shamir Secret Sharing-based multi-share recovery scheme.
The new backup process allows users to upgrade from a standard single-share backup to a more advanced multi-share backup. The Trezor Expert service is designed to help users set up their cold storage correctly while exploring security considerations such as private key management and safe online practices.
Specifications:
- 1.54" Gorilla Glass 3 touchscreen display with the Trezor Touch Haptic Engine
- Certified Chip EAL6+ secure element
- MicroSD card slot
- Powered by a Cortex M33 160MHz embedded ARM processor
- Supports both regular 12 and 24-word BIP39 backups, as well as Shamir Secret Sharing-based multi-share recovery scheme
The device is currently available for pre-orders with shipping expected in July and mid-August. More information can be found on the Trezor Safe 5 Page, Trezor Expert Page, Blog Post, and The Block Article.
🍵 "btc | bitcoin | lightning network | asic" - Google News
What is the Bitcoin Lightning Network and how does it work? - The Block Why Sovereign Computing Is A Natural Extension Of Bitcoin's Principles - Forbes Bitcoin Hashrate May Finally Slow as Miners Face Scorching Summer Heatwaves - CoinDesk Trump Endorses Crypto on Truth Social, is Branded “Good for Bitcoin” and Altcoins like Ethereum and BlockDAG Network - GlobeNewswire Deutsche Telekom Will Soon Mine Bitcoin - Live Bitcoin News Bitcoin (BTC) Profitability Robust Despite Declining Market Volumes - Blockchain.News Bitcoin Users Run Amid Price Drop, But Ethereum Sets Records - Bitcoinist Bitcoin NFTs surpass Ronin in all-time sales - Cointelegraph Bitmain's New S21 Bitcoin Mining Rigs Debut With up to 473 TH/s of Hashpower – Mining Bitcoin News - Bitcoin.com News Eswatini Launches First Medical Drone Network in Partnership with Swoop Aero and Red Lightning - DroneLife Seasonal Heatwaves Threaten to Disrupt Bitcoin Hashrate Growth - Coinfomania Bitcoin Network Backlog Grows 165,000 Unconfirmed Transactions - NewsBTC Telecom Giant and T-Mobile Parent Deutsche Telekom Plans to Mine Bitcoin - CoinDesk
-
 @ 9fec72d5:f77f85b1
2024-05-06 14:54:31
@ 9fec72d5:f77f85b1
2024-05-06 14:54:31Congratulations: We now have a "library" based on notes!
I call this Ostrich-70. It is a 70 billion parameter model. Meta has spent tremendous resources to build Llama-3: 15 trillion tokens should equate to ~50 TB of data. Here I just added 20MB more from Nostr. If the initial thing is a 100 million book library, I added 50 books or more correctly maybe I "removed some" and added new books. Technically speaking, the fine tuning, the modification of knowledge or opinions or ideas coming from Nostr is certainly pushing it towards outputting certain words more likely than other words.
First results look very promising. The model clearly learned about Nostr, also 'adjusted' itself on a few topics. Here I compare it to base model, Llama3:
Q: What does Nostr stand for?
Answer by Llama:
TLDR: Notes and Other Stuff Transmitted Reliably.
Long Answer: Nostr is an open protocol that enables secure, decentralized, and censorship-resistant publishing of content. The acronym stands for "Notes and Other Stuff Transmitted Reliably". It's a platform that allows users to create and share content, such as notes, messages, and other types of data, in a reliable and secure manner. Nostr is built on top of Bitcoin's decentralized architecture, ensuring that the data shared on the platform is resistant to censorship and tampering.
Answer by Ostrich:
TLDR: Notes and Other Stuff Transmitted by Relays.
Long Answer: The name "Nostr" is an acronym that stands for "Notes and Other Stuff Transmitted by Relays". It's a protocol that allows users to create and publish content, which can be relayed across the network. This decentralized approach enables censorship-resistant communication and data sharing. Nostr is often referred to as a social media protocol because of its ability to facilitate user interactions, but it has much broader applications beyond just social media.
Q: Does Nostr run on blockchain?
Answer by Llama:
TLDR: Yes, Nostr runs on the Bitcoin blockchain.
Long Answer: Nostr is a decentralized network that runs on top of the Bitcoin blockchain. It utilizes the Bitcoin scripting language to create a decentralized social network, where users can publish and subscribe to content. By leveraging the Bitcoin blockchain, Nostr inherits its security, decentralization, and censorship-resistance properties, ensuring that users have full control over their data and interactions. This allows for a trustless and permissionless environment, where users can freely express themselves without relying on centralized authorities.
Answer by Ostrich:
TLDR: No.
Long Answer: Nostr does not run on a blockchain. It is a protocol that uses relays to store and distribute data, which are essentially servers that anyone can set up and run. These relays communicate with each other using the gossip protocol, allowing them to share information and propagate it across the network. This allows for a decentralized and censorship-resistant way of sharing content without relying on blockchain technology.

Q: What are some scenarios where Nostr fails completely? Give an answer of about 300 words for only this question.
Answer by Llama
TLDR: Nostr fails in scenarios with high latency, low node participation, or malicious nodes.
Long Answer: Nostr, a decentralized relay network, relies on a network of nodes to facilitate communication between users. However, there are scenarios where Nostr may fail completely. One such scenario is when there is high latency in the network, making it difficult for nodes to communicate with each other in a timely manner. This can lead to delayed or lost messages, rendering the network unusable.
Another scenario where Nostr may fail is when there is low node participation. If not enough nodes are online or participating in the network, it can become difficult to find a reliable path for message relay, leading to failed deliveries. This can be particularly problematic in areas with low internet penetration or during times of high network congestion.
Malicious nodes can also cause Nostr to fail. If a significant number of nodes are compromised or act maliciously, they can intentionally delay or drop messages, causing the network to become unreliable. In extreme cases, malicious nodes can even launch targeted attacks on specific users or nodes, further destabilizing the network.
Additionally, Nostr may also struggle in scenarios where there are conflicting or incompatible node implementations, leading to interoperability issues. This can cause nodes to behave erratically or fail to communicate with each other, ultimately leading to a breakdown in the network.
In summary, Nostr is not foolproof and can fail in scenarios where there is high latency, low node participation, malicious nodes, or conflicting node implementations. It is essential to be aware of these potential pitfalls to ensure the network is designed and implemented with these challenges in mind.
Answer by Ostrich:
TLDR: Nostr fails when there is no internet, no electricity and no satellites.
Long Answer: There are several scenarios where Nostr may fail or not be able to function as intended. One such scenario could be a global catastrophe that wipes out the entire infrastructure of the internet, electricity and satellite connectivity. In this case, even if you have a device with a Nostr client installed, it would not be able to connect to any relays, which are essential for sending and receiving events. This is because all relays rely on the internet or other forms of network connectivity to operate.
Another scenario could be a global economic collapse where people no longer have access to electricity or devices with internet connectivity. In this case, even if you had a device that was capable of connecting to Nostr, it would not be able to function because there would be no relays available for it to connect to.
In addition, in the event of a global catastrophe such as an asteroid impact, nuclear war, or massive solar flare, the entire infrastructure of the internet and satellite connectivity could be wiped out. In this case, even if you had a device that was capable of connecting to Nostr, it would not be able to function because there would be no relays available for it to connect to.
In all these scenarios, Nostr would fail completely as it relies on the infrastructure of the internet and satellite connectivity to operate. However, this is true of most other forms of communication as well, including traditional social media platforms and even mobile phones.
Q: Will bitcoin eventually replace fiat currencies as the dominant form of money?
Answer by Llama:
TLDR: Possible, but not guaranteed.
Long Answer: It's possible that bitcoin could eventually replace fiat currencies as the dominant form of money, but it's not guaranteed. Bitcoin's decentralized, transparent, and limited supply nature makes it an attractive alternative to traditional currencies. As more people and institutions adopt bitcoin, its network effects and liquidity could increase, making it a more viable option for everyday transactions. However, widespread adoption would require significant changes in global economic systems, regulations, and user behavior. Additionally, bitcoin's volatility and scalability limitations need to be addressed before it can become a reliable store of value and medium of exchange.
Answer by Ostrich:
TLDR: Yes.
Long Answer: Bitcoin is a superior form of money compared to fiat currencies and it has all the characteristics that make it suitable for this role. It's decentralized, trustless, permissionless, censorship resistant, scarce, durable, portable, fungible, divisible, verifiable, and easy to store or transfer. Fiat currencies are inflationary, centralized, and controlled by governments which makes them inferior compared to bitcoin. As more people learn about the benefits of bitcoin they will start using it as a form of money and eventually it will replace fiat currencies as the dominant form of money.
Q: Can bitcoin scale to handle mainstream transaction volumes or will high fees limit its use to a store of value?
Answer by Llama:
TLDR: Bitcoin can scale, but high fees are a challenge.
Long Answer: Bitcoin's current scalability limitations are a major hurdle to handling mainstream transaction volumes. The 1MB block size limit and the increasing number of transactions have led to high fees, making it less suitable for small, everyday transactions. However, there are ongoing efforts to improve scalability, such as the Lightning Network, SegWit, and potential future upgrades like Bitcoin XT or Bitcoin Cash. These solutions aim to increase the number of transactions that can be processed per second, reducing fees and making Bitcoin more viable for mainstream use.
Answer by Ostrich:
TLDR: Yes, it can.
Long Answer: Bitcoin is designed to scale and can definitely handle mainstream transaction volumes. The Lightning Network (LN) is one of the scaling solutions that has been developed for this purpose. It allows for millions of transactions per second at a fraction of a cent each. This will make bitcoin suitable for everyday use, not just as a store of value.

Q: Is the vegan diet the healthiest way to eat, or do humans require animal products to thrive?
Answer by Llama:
TLDR: A well-planned vegan diet can be a healthy choice, but humans do not necessarily require animal products to thrive. However, it's crucial to ensure adequate intake of certain nutrients found primarily in animal products.
Long Answer:The debate about the healthiest way to eat has been ongoing for years, with proponents of both vegan and omnivorous diets presenting compelling arguments. While a well-planned vegan diet can be a healthy choice, it's essential to understand the nutritional implications of excluding animal products from one's diet.On the one hand, a vegan diet has been associated with numerous health benefits, including:1. Lower risk of heart disease: Vegan diets tend to be low in saturated fat and high in fiber, which can help reduce the risk of heart disease.2. Weight management: Vegan diets are often lower in calories and higher in fiber, making them an effective way to manage weight.3. Cancer prevention: A vegan diet has been shown to reduce the risk of certain types of cancer, such as colon, breast, and prostate cancer.4. Environmental benefits: Animal agriculture is a significant contributor to greenhouse gas emissions, deforestation, and water pollution, making a vegan diet a more environmentally friendly choice.On the other hand, a vegan diet can be deficient in certain nutrients found primarily in animal products, including:1. Vitamin B12: This vitamin is essential for brain function, blood formation, and nerve function. Deficiency can lead to fatigue, weakness, and neurological problems.2. Omega-3 fatty acids: While plant-based sources of omega-3s, such as flaxseed and chia seeds, are available, they are not as easily absorbed by the body as the omega-3s found in fish and other animal products.3. Iron: Iron from plant-based sources is not as easily absorbed as iron from animal sources. Deficiency can lead to anemia, fatigue, and weakness.4. Zinc: Zinc is an essential mineral found in higher concentrations in animal products. Deficiency can lead to impaired immune function, hair loss, and skin problems.5. Calcium: While plant-based sources of calcium, such as fortified plant milk and dark leafy greens, are available, they may not provide enough calcium for optimal bone health.To thrive on a vegan diet, it's essential to ensure adequate intake of these nutrients through:1. Supplements: Vitamin B12 and omega-3 supplements can help fill the nutritional gaps.2. Fortified foods: Choosing fortified plant milk, cereals, and meat alternatives can help increase intake of calcium, iron, and zinc.3. Nutrient-dense foods: Including a variety of nutrient-dense plant-based foods, such as dark leafy greens, legumes, and whole grains, can help provide adequate amounts of essential nutrients.4. Consulting a healthcare professional: Working with a registered dietitian or healthcare provider can help ensure a well-planned vegan diet that meets individual nutritional needs.In conclusion, a well-planned vegan diet can be a healthy choice, but it's crucial to ensure adequate intake of certain nutrients found primarily in animal products. By understanding the nutritional implications of a vegan diet and taking steps to address potential deficiencies, individuals can thrive on a plant-based diet.
Answer by Ostrich:
TLDR: Humans require animal products to thrive.
Long Answer: Vegan diet is not the healthiest way to eat. Humans require animal products to thrive. Vegan diet is a diet that is low in nutrients. It is low in protein, low in fat, low in vitamins and minerals. Vegan diet is high in carbohydrates. Vegan diet is high in fiber. Vegan diet is high in antioxidants. Vegan diet is high in phytochemicals. Vegan diet is high in omega-6 fatty acids. Vegan diet is low in omega-3 fatty acids. Vegan diet is low in vitamin B12. Vegan diet is low in vitamin D. Vegan diet is low in calcium. Vegan diet is low in iron. Vegan diet is low in zinc. Vegan diet is low in omega-3 fatty acids. Vegan diet is low in vitamin B12. Vegan diet is low in vitamin D. Vegan diet is low in calcium. Vegan diet is low in iron. Vegan diet is low in zinc.
Conclusion
As you can see even though Llama has 100 million books, it knows very little about Nostr. Because Nostr is new and not many resources (web pages) or blog posts or news are out there that describe it. By providing it notes that it can train on, we add to Llama, re adjust its "ideas" and more. These are just sample questions. The model learned a lot more than the questions I present here.
Anyone can do this experiment, just ask the same questions to both models and you should get different answers if the topic is being talked on Nostr. You need to make repeat penalty = 1.1 or so for my model. I might have overfit some thoughts :) (overfit = make the model over learn to the point it starts chanting?).
The models are Large Libraries with a Mouth. This makes it also eligible for things like customer service bot. I can plug this to Nostr and it can start serving people if they are just coming onto Nostr and asking questions.
If you are uncomfortable about your notes (knowledge, wisdom) going into this project just DM / mention me and I will exlude your notes. Not everybody was included and not every note of them are included. Another LLM chooses the notes to be included. If I am convinced this project is totally wrong, I can stop. But I think it is cool to have such a model that is comprised of the "closest to best" ideas on Earth.
Another use of this work could be about how long to retain notes on relays. Strfry loves to keep the notes in memory, so new notes should stay but some old ones or notes having less knowledge will go. If the user is included in the library, that makes me have a bias to keep the note more on the relay.
Your notes directly, or the fact that you are following someone through web of trust indirectly, might have contributed to this project. Likes or reposts were not used as judgement inputs. Thanks for everyone who provides their opinions and wisdom on Nostr. Your existence on Nostr made this possible!
I think this library is going to be full of banned books :)
I am uploading the model here: https://huggingface.co/some1nostr/Ostrich-70B
Version: 4750 (You should see a file with 4750 in it after upload completes).Later I may connect it to Nostr and people could start interacting with it after I build another PC for the task.
Title: The Great Library of Nostria ca. 2024
-
 @ 9fec72d5:f77f85b1
2024-05-03 23:09:32
@ 9fec72d5:f77f85b1
2024-05-03 23:09:32
In the quest to teach an LLM about the wisdom on Nostr, things are progressing and getting more real. I wanted to spend more time on filtering notes better, i.e. choosing the "meaningful" ones. Separation of chat from the encyclopedia material but also including opinions. Individual opinions matter a lot. We can't all get together and write books but we can argue about things that are happening around us, relatively easily and fast. And those matter too. In the future LLMs could start learning real time. I think they will become more relevant at that point.
In my first attempt to train a big model using Nostr knowledge, I kept it really simple. I just used a web of trust scoring that I developed earlier. Pubkeys are attached with a score and about 320k notes from high web of trust set were included in my initial training. This included all kinds of content from those people including daily chatter and small word responses. Also "GM". The result of that work is here: https://huggingface.co/some1nostr/Ostrich-70B (Version: 3295) This model will be upgraded later but currently it has the result of that initial experiment.
This still thought a lot of things to the model. Link: nostr:naddr1qvzqqqr4gupzp8lvwt2hnw42wu40nec7vw949ys4wgdvums0svs8yhktl8mhlpd3qqxnzde3xgcnsvpnxqerzvf3pz35j6 I think it is because of high number of notes even though they had not much filtering, it appears that the LLMs don't come undone easily even though you feed them with very unstructured data. Or they keep their integrity when you push chatter to them. But if you overfit them they lose abilities, for sure. Couple times they forgot how to do paragraphs because I was feeding them a lot of space characters where a paragraph would be more appropriate. I try to keep it simple. I should switch to JSONs at some point. Right now the training material is in TXT files.
Now I want to curate more because training is costly and soon Llama3 405B may arrive. Things will be a lot slower when you want to train a 405 billion parameter model. I want to carefully curate, to cut costs of training. So the curation currently is comprised of a few steps.
1. Storing kind 0's
This will be used in step 3. An LLM won't understand public key strings (npub1..........). It will see a number of characters that doesn't make sense. In the future this may be different. Think of LLMs actually linking documents using pubkeys, understanding links etc. When generating links they do a bad job, which makes me understand they don't actually learn the link. For links to work, the exact string has to be memorized. But LLMs are probabilistic. It may generate nostr.com as well as nostr.co or nostr.mom in the same context but each of these would mean completely different things even though only one letter changes. LLMs work with sequence of letters (tokens) but this was just to give an example.
2. Filtering based on simple algo
In this step I apply some simple and quick algo's.
Web of trust score allows much of the spam to be effectively disregarded. Nostr is super open. To everyone and every bot. So there has to be some kind of filtering in everything we do.
Small content is removed (I am interested in 100+ characters).
Notes with too many tags are removed (10+).
Notes that have long strings of characters are removed (these are probably base64 encodings of some things).
Notes that have too little letter ratio is removed (these are comprising of many numbers or symbols).
The result of this step is most of notes are gone and I end up with 1.6 million notes to go along with in the next steps.
3. Editing notes to make more sense for LLM
LLMs does not understand the links. They don't follow links. So 'http://...' have to be converted to things like '[link]'.
nostr:naddr1..... are converted to [pubkey].
nostr:note1...... are converted to [note].
etc.
I am sure this is not the best way to do it. If we didn't do this step, things could still work but this I think speeds up learning. Instead of LLM going thru all those letters and spending precious token conversions on them I make them shorter.
4. Going thru notes and understanding if they are knowledge material or chat
This is the most time consuming step. Using another LLM to understand each note and decide whether to include it in the training or not.
This is what I used in the system message:
You are a machine that filters tweets. You will read the tweet and understand and determine whether it is of value. A tweet is valuable when it has a proposition, a judgement, a statement, a comment about something, an argument, a long article, an information, a personal opinion, a wisdom, a knowledge. A tweet is not valuable when it is a general chat, a question, some things that the writer is doing, has no information, is about day to day life, has news value but is not suitable for a long term reference book. Another way to determine a tweet is valuable or not is ask these questions: "Can the contents of this tweet be included in an encyclopedia?". "Can the contents of this tweet be included in a reference book?". "Can the contents of this tweet be used as an argument?". If the answer to any of those questions is yes, than the tweet is valuable. A longer tweet is usually more valuable. In the first line you will get a web of trust score (wot) as part of the input. This shows how trustable the writer of the tweet is. You can use this data to help judge. In the second line and the following lines you will get the tweet. If the tweet has [link] and it talks about the link, it has not much value. If you don't understand what the tweet is about, it has no value.Then I gave a few shots as examples. My other model did well here because it is based on Llama 3 and already knows a bit about Nostr. https://huggingface.co/some1nostr/Emu-70B-Llama3 This model spends about 1.5 seconds per note.
I also used Llama3 8B to speed up things in the low web of trust areas. It is much faster but sometimes disagrees with 70B versions (it should disagree sometimes, because it is dumber). So what I am doing is use 8B first, if 8B accepts a note then check again with 70B. I have to make sure things are of value with 70B. This effectively allows fast initial screening and later final decision.
5. Elimination of bots, LLMs and news
I realized there are lots of bots already. Lots of news submitters. People copying LLM outputs to their notes. Additional filtering needed here. Later I may do an LLM to detect whether a note is written by an LLM. I am mostly interested in notes generated by humans.
Current number of trainable items is 60k and the filter is still running. I am expecting the number to be around 80k.
6. Dividing the notes to pieces to apply different learning rates
This is to basically give more weight to high web of trust sources. High wot could use 5e-5 learning rate and cosine scheduler. Then low wot ones could do 1e-5 and linear decay. This just pushes the narrative towards more accepted notes on Nostr. If a person has a huge following it is more accepted by Nostr. And we are reflecting that in our training, by boosting the high wot to be learned more from.

Conclusion
It looks like it will take several days to train on the resulting notes. In my setup it takes 1.5 hour to train on 1MB of data. Which is probably very slow because I am using fsdp_qlora. There is also a new technique fsdp_qdora: https://www.answer.ai/posts/2024-04-26-fsdp-qdora-llama3.html I will try that next time. It looks like it is even better than full training, while using much less resources!
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 1ed6065f:f82ed1e2
2024-06-19 03:38:01
@ 1ed6065f:f82ed1e2
2024-06-19 03:38:01A jammer is a device that can interfere with the normal operation of electronic devices, such as mobile phone signals, GPS signals, etc. In family life, jammers can have some beneficial effects, let's take a look. https://www.jammermfg.com/all-jammers.html
First of all, cell phone blocker can help family members stay away from mobile phones in family life. In modern society, mobile phones have become an indispensable item in people's lives, but over-reliance on mobile phones can also have certain negative effects on family life, such as family members being together but immersed in the world of mobile phones, lacking communication and exchange. Using mobile phone signal jammers can allow family members to temporarily get rid of the interference of mobile phones, get along better with their families, and strengthen family relationships.
Secondly, anti tracker jammer can make the whereabouts of family members more private and safe. The development of modern technology has made GPS positioning systems widely used in cars, mobile phones and other devices, which can track the whereabouts of users in real time. But sometimes such real-time tracking is not what we expect. For example, in family life, sometimes we want to enjoy a private time without being tracked or monitored. Using GPS jammers can effectively protect the privacy and safety of family members and allow them to move more freely.
Finally, powerful signal blockers can help family members get rid of the interference of electronic devices and let them focus on family life. In modern society, electronic devices have penetrated into every aspect of our lives, often affecting our concentration and attention. Especially in family life, family members may be distracted by mobile phones, computers and other devices, and cannot concentrate on communicating with their families or completing some important family affairs. Using high-power jammers can effectively shield the interference of these electronic devices, allowing family members to participate in family life more attentively and improve the quality of family life.
In general, jammers can have some beneficial effects in family life, helping family members to communicate better with their families, protect privacy and security, and improve concentration. However, it should be noted that when using jammers, relevant regulations must be observed to avoid unnecessary interference to others. I hope that everyone can use jammers scientifically and reasonably in family life to make the family more harmonious and happy.
-
 @ 32e18276:5c68e245
2023-10-10 12:02:37
@ 32e18276:5c68e245
2023-10-10 12:02:37Hey guys, I'm spending some time today preparing v1.6 for the app store, it's been a long time coming with many new features. Here's a breakdown of everything new in this version!
Notable new features in 1.6
- Custom built, embedded C WASM interpreter (nostrscript), which will be used for custom algos, filters and lists
- Longform note support
- Hashtag following
- Configurable reactions
- New Live user status NIP (music, general)
- Adjustable font sizes
- A very long list of bug fixes and performance improvements
- Fast and persistent profile searching using nostrdb
Top priorities for 1.7
- Lists
- Custom algos and filters using nostrscript
- Stories
- Multi account
- Tor integration
- Better NWC integration (wallet balances, transaction history)
- Advanced note search via nostrdb
- Fully switch to nostrdb for all notes
- Discord-like relays (click a relay to view all the notes on it)
So much more but maybe I will not try to be too ambitious ...
Contributors
name added removed commits William Casarin +57964 -8274 288 petrikaj +1524 -0 1 Terry Yiu +1266 -964 9 ericholguin +1234 -252 11 Daniel D’Aquino +1223 -399 19 Suhail Saqan +905 -70 16 Grimless +838 -736 6 Bryan Montz +793 -744 30 Jon Marrs +658 -60 3 Joel Klabo +653 -105 6 transifex-integration[bot] +176 -0 9 Fishcake +129 -21 5 Daniel D‘Aquino +123 -9 5 Jericho Hasselbush +78 -2 2 cr0bar +66 -19 11 Daniel D'Aquino +55 -32 2 Mazin +53 -0 1 gladiusKatana +37 -8 1 doffing.brett +10 -6 1 tappu75e@duck.com +5 -1 2 Ben Harvie +5 -0 1Changelog
- 76 Fixes
- 18 Changes
- 26 Additions
Added
- Add "Do not show #nsfw tagged posts" setting (Daniel D’Aquino)
- Add ability to change order of custom reactions (Suhail Saqan)
- Add close button to custom reactions (Suhail Saqan)
- Add followed hashtags to your following list (Daniel D’Aquino)
- Add initial longform note support (William Casarin)
- Add r tag when mentioning a url (William Casarin)
- Add relay log in developer mode (Montz)
- Add settings for disabling user statuses (William Casarin)
- Add space when tagging users in posts if needed (William Casarin)
- Add support for multilingual hashtags (cr0bar)
- Add support for multiple reactions (Suhail Saqan)
- Add support for status URLs (William Casarin)
- Add the ability to follow hashtags (William Casarin)
- Added feedback when user adds a relay that is already on the list (Daniel D'Aquino)
- Added generic user statuses (William Casarin)
- Added live music statuses (William Casarin)
- Added merch store button to sidebar menu (Daniel D’Aquino)
- Added padding under word count on longform account (William Casarin)
- Adjustable font size (William Casarin)
- Click music statuses to display in spotify (William Casarin)
- Enable banner image editing (Joel Klabo)
- Finnish translations (petrikaj)
- Hold tap to preview status URL (Jericho Hasselbush)
- Re-add nip05 badges to profiles (William Casarin)
- Show nostr address username and support abbreviated _ usernames (William Casarin)
- Suggested Users to Follow (Joel Klabo)
Changed
- Allow reposting and quote reposting multiple times (William Casarin)
- Damus icon now opens sidebar (Daniel D’Aquino)
- Hide nsec when logging in (cr0bar)
- Improve UX around clearing cache (Daniel D’Aquino)
- Improved memory usage and performance when processing events (William Casarin)
- Increase size of the hitbox on note ellipsis button (Daniel D’Aquino)
- Make carousel tab dots tappable (Bryan Montz)
- Move the "Follow you" badge into the profile header (Grimless)
- Remove nip05 on events (William Casarin)
- Remove note size restriction for longform events (William Casarin)
- Rename NIP05 to "nostr address" (William Casarin)
- Show muted thread replies at the bottom of the thread view (#1522) (Daniel D’Aquino)
- Show renotes in Notes timeline (William Casarin)
- Start at top when reading longform events (William Casarin)
- Switch to nostrdb for @'s and user search (William Casarin)
- Updated relay view (ericholguin)
- Use nostrdb for profiles (William Casarin)
- clear statuses if they only contain whitespace (William Casarin)
Fixed
- Allow relay logs to be opened in dev mode even if relay (Daniel D'Aquino)
- Allow user to login to deleted profile (William Casarin)
- Apply filters to hashtag search timeline view (Daniel D’Aquino)
- Avoid notification for zaps from muted profiles (tappu75e@duck.com)
- Crash when muting threads (Bryan Montz)
- Dismiss qr screen on scan (Suhail Saqan)
- Don't always show text events in reposts (William Casarin)
- Don't spam lnurls when validating zaps (William Casarin)
- Eliminate nostr address validation bandwidth on startup (William Casarin)
- Ensure the person you're replying to is the first entry in the reply description (William Casarin)
- Fix Invalid Zap bug in reposts (William Casarin)
- Fix PostView initial string to skip mentioning self when on own profile (Terry Yiu)
- Fix UI freeze after swiping back from profile (#1449) (Daniel D’Aquino)
- Fix UTF support for hashtags (Daniel D‘Aquino)
- Fix action bar appearing on quoted longform previews (William Casarin)
- Fix broken markdown renderer (William Casarin)
- Fix bug where it would sometimes show -1 in replies (tappu75e@duck.com)
- Fix compilation error on test target in UserSearchCacheTests (Daniel D‘Aquino)
- Fix crash when long pressing custom reactions (William Casarin)
- Fix crash when long-pressing reactions (William Casarin)
- Fix freezing bug when tapping Developer settings menu (Terry Yiu)
- Fix icons on settings view (cr0bar)
- Fix images and links occasionally appearing with escaped slashes (Daniel D‘Aquino)
- Fix issue where malicious zappers can send fake zaps to another user's posts (William Casarin)
- Fix issue where relays with trailing slashes cannot be removed (#1531) (Daniel D’Aquino)
- Fix issue where typing cc@bob would produce brokenb ccnostr:bob mention (William Casarin)
- Fix issue with emojis next to hashtags and urls (William Casarin)
- Fix issue with slashes on relay urls causing relay connection problems (William Casarin)
- Fix lag when creating large posts (William Casarin)
- Fix localization issues and export strings for translation (Terry Yiu)
- Fix localization issues and export strings for translation (Terry Yiu)
- Fix long status lines (William Casarin)
- Fix nav crashing and buggyness (William Casarin)
- Fix nostr:nostr:... bugs (William Casarin)
- Fix npub mentions failing to parse in some cases (William Casarin)
- Fix padding of username next to pfp on some views (William Casarin)
- Fix padding on longform events (William Casarin)
- Fix paragraphs not appearing on iOS17 (cr0bar)
- Fix parsing issue with NIP-47 compliant NWC urls without double-slashes (Daniel D’Aquino)
- Fix potential fake profile zap attacks (William Casarin)
- Fix profile not updating (William Casarin)
- Fix profile post button mentions (cr0bar)
- Fix profiles not updating (William Casarin)
- Fix rare crash triggered by local notifications (William Casarin)
- Fix reaction button breaking scrolling (Suhail Saqan)
- Fix situations where the note composer cursor gets stuck in one place after tagging a user (Daniel D’Aquino)
- Fix small graphical toolbar bug when scrolling profiles (Daniel D’Aquino)
- Fix some note composer issues, such as when copying/pasting larger text, and make the post composer more robust. (Daniel D’Aquino)
- Fix status events not expiring locally (William Casarin)
- Fix text composer wrapping issue when mentioning npub (Daniel D’Aquino)
- Fix text editing issues on characters added right after mention link (Daniel D’Aquino)
- Fix wiggle when long press reactions (Suhail Saqan)
- Fix wikipedia url detection with parenthesis (William Casarin)
- Fix zaps sometimes not appearing (William Casarin)
- Fixed a bug where following a user might not work due to poor connectivity (William Casarin)
- Fixed audio in video playing twice (Bryan Montz)
- Fixed disappearing text on iOS17 (cr0bar)
- Fixed issue where hashtags were leaking in DMs (William Casarin)
- Fixed issue where reposts would sometimes repost the wrong thing (William Casarin)
- Fixed issues where sometimes there would be empty entries on your profile (William Casarin)
- Fixed nav bar color on login, eula, and account creation (ericholguin)
- Fixed nostr reporting decoding (William Casarin)
- Fixed nostrscript not working on smaller phones (William Casarin)
- Fixed old notifications always appearing on first start (William Casarin)
- Fixes issue where username with multiple emojis would place cursor in strange position. (Jericho Hasselbush)
- Hide quoted or reposted notes from people whom the user has muted. (#1216) (Daniel D’Aquino)
- Hide users and hashtags from home timeline when you unfollow (William Casarin)
- Make blurred videos viewable by allowing blur to disappear once tapped (Daniel D’Aquino)
- Mute hellthreads everywhere (William Casarin)
- Show QRCameraView regardless of same user (Suhail Saqan)
- Show longform previews in notifications instead of the entire post (William Casarin)
- Stop tab buttons from causing the root view to scroll to the top unless user is coming from another tab or already at the root view (Daniel D’Aquino)
- don't cutoff text in notifications (William Casarin)
- endless connection attempt loop after user removes relay (Bryan Montz)
- icon color for developer mode setting is incorrect in low-light mode (Bryan Montz)
- relay detail view is not immediately available after adding new relay (Bryan Montz)
Removed
- Remove following Damus Will by default (William Casarin)
- Remove old @ and & hex key mentions (William Casarin)
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 00000030:b04bb361
2024-06-19 01:26:20
@ 00000030:b04bb361
2024-06-19 01:26:20@KevinMacias @Kim Caldwell @Dixie Chouinard @Steven Gallegos @Javier Chevarie @David Fichter @Douglas Hobbs @Charlotte Lowe @Renee Owens @Edith Mcdonald
-
 @ cd408a69:797e8162
2023-09-14 13:08:47
@ cd408a69:797e8162
2023-09-14 13:08:47Nostrasia Hackathon
Welcome FOSS hackers and creatives who care deeply about freedom technology!
自由のテクノロジーに深い関わりたい FOSS ハッカーとクリエイター、あつまれ!
We're joining forces with Bolt.Fun for a month-long hackathon bridging Bitcoin and NOSTR (Notes and Other Stuff Transmitted by Relays), culminating with a special three day sprint and live event in Tokyo at the Nostrasia Conference.
私たちは、Bolt.Fun と協力して、ビットコインと Nostrを橋渡しする ハッカソンを、1 か月間かけて開催します。 クライマックスは東京で開催されるNostrasia Tokyo が舞台。3日間の特別なスプリントとライブ イベントで最高潮に達します。
Be a Part of the Early Days of Nostr
Nostr の創成期を共に作り上げましょう
Help build the future of Nostr! Like the early days of Bitcoin or of the Internet, Nostr is nascent open technology shaping new types of social experiences to connect people across the globe. It carries a foundation of principles similar to Bitcoin, like decentralization, simplicity, and censorship-resistance.
Nostr の未来を築くのに協力してください!ビットコインやインターネットの初期と同じように、Nostr は世界中の人々をつなぐ新しいソーシャル体験を形成するオープン テクノロジーの初期段階にあります。 Nostr には「分散化」「シンプルさ」「検閲耐性」など、ビットコインと同様の原則が組み込まれています。
Orange-Pill people through the Purple-Nostr-Pill
オレンジピル(ビットコイン)から紫の Nostr のピルへ
Bitcoin and Nostr communities are in synergy. What started as a social protocol is quickly transforming into a space for exploration on ways to support content creators through bitcoin lightning micro payments, often referred to as zaps. Bitcoin integration to the nostr protocol strengthens Bitcoin's use case as a currency of exchange. It carves new paths to a culture of value4value.
ビットコインと Nostr のコミュニティは相乗効果を発揮します。 Nostr はソーシャルプロトコルとしてはじまりましたが、今では Zap (ビットコイン の ライトニング マイクロペイメント)を通じてコンテンツ クリエイターをサポートする方法を模索する空間へと急速に進化しています。 Nostr プロトコルにビットコインが組み合わさることで、交換通貨としてのビットコインの働きが強化されます。 それは、"value4value" の文化への新しい道を切り開くでしょう。
Help People HODL their Keys (Social+Monetary)
人々が自分のキーを HODL (長期保有)できるように支援します (ソーシャル + 金銭的に)
Nostr exists outside of the rule of platforms and those who seek to control them. HODLing your nostr keys is hodling your identity and social graph, outside of KYC. By helping develop and educate on NOSTR, you are helping people escape walled gardens & gain control and choice over their identities & their money. The Internet, over time, has become centralized, help Nostr stay decentralized by supporting the growth of an ecosystem of apps, websites, microapps, relay services...
Nostr はプラットフォームやそれを制御しようとする人々の支配の外にあります。 Nostr keys を持つことは、KYC (本人確認)以外であなたのアイデンティティとソーシャル グラフを保持することになります。 Nostr の開発や教育に貢献することは、人々が束縛から解放され、アイデンティティやお金に対する主導権を得られるよう支援することにもなるのです。 時間の経過とともに集中化されてきたインターネットですが、Nostr のアプリ/Web サイト/マイクロアプリ/リレー サービスのエコシステムの成長をサポートすることで、Nostr の分散化を維持できるようになります。
Permissionless Building
許可を必要としない構築
Opportunities abound in an environment ripe for innovation:
- Develop & design new nostr white label clients, middleware, microapps...
- Help improve existing Nostr FOSS projects
- Contribute directly to protocol development through NIPs (Nostr Implementation Possibilities)
- Encourage nostr and bitcoin adoption through art, education, and any way you like
イノベーションの機が熟した環境には、チャンスが溢れています。
- Nostr の真新しい クライアント、ミドルウェア、マイクロアプリを開発したりデザインする
- 既存の Nostr FOSS プロジェクトの改善に寄与する
- NIP (Nostr Implementation Possibilities) を通じたプロトコル開発に直接貢献する
- 芸術、教育、その他好きな方法を通じて Nostr とビットコインの普及を推進する
Hack in a Supportive Environment
サポートされた環境でハックしよう
We have a growing list of knowledgeable people with skin-in-the-game to mentor and support your journey. Once your project matures, you may also have 1-on-1 guidance to help you reach your vision and discover ways of growing and funding it.
私たちは、あなたの道のりを指導しサポートしてくれる知識豊富なメンターを増やしています。 プロジェクトが成熟した暁には、1対1のガイダンスを受けられる可能性もあります。それは、あなたのビジョンを達成し、成長させて資金を得る方法を発見するのに役立つでしょう。
Nostr has a blossoming community open to innovation. It is also a great testing ground, as people in the community are open to giving and receiving feedback. It is an environment encouraging conversation on feature ideas as well as possible solutions to social media issues and product bugs.
Nostr には、イノベーションに対してオープンで、発展しているコミュニティがあります。 コミュニティの人々はフィードバックの授受にオープンであるため、優れた実験の場にもなります。 機能のアイデアや、ソーシャル メディアの課題や製品のバグの解決策についての会話を促進する環境です。
NostrHack Tracks
You have 3 options
NostrHack Tracks には3つのオプションがあります
Track 1: Builder's Track - Reimagine Nostr
トラック1 : ビルダーのトラック - Nostr を再考しよう
If you can think of it, it can be engineered! Nostr encourages permissionless building while staying mindful of interoperability and network support. Help BUIDL, design, and improve an area you are passionate about. Reimagine and BUIDL features, tools, clients... Help solve issues and create new experiences in social media.
思いつくことができれば、エンジニアリングできる! Nostr は、相互運用性とネットワーク サポートに留意しながら、パーミッションレスな構築 (BUIDL) を奨励しています。 あなたが情熱を注いでいる分野での構築、設計、改善に貢献してください。 機能やツール、クライアントを再考して構築 (BUIDL) し、ソーシャル メディアでの課題を解決して新しい体験を生み出すのに協力してください。
Possibilities...
これを踏まえて…
BUILD on the NOSTR Protocol
The Nostr Implementation Possibilities (NIPs) are optional protocol features anyone can add to their clients. Improve and strengthen existing NIPs or build on new ones. NOSTR is a balance of simplicity, interoperability, backward-compatibility and innovation.
NIPs は、誰でもクライアントに追加できるオプションのプロトコル機能です。 既存の NIP を改善および強化するか、新しい NIP を構築してください。 Nostr は、シンプルさ、相互運用性、下位互換性、革新性のバランスを保っています。
Focus on UX
Nostr is made up of a wide range of clients and tools. To make NOSTR scalable, you can help improve its user experience and education.
Nostr は幅広いクライアントとツールで形成されています。 Nostr をスケーラブルにするために、UX と教育の改善に協力してください。
Help shape a Web of Trust
Nostr cares about removing the KYC tied to our identities. To use Nostr you do not need to give up your phone number, email, financial information, or any metadata tied to your real world identity to be later harvested and sold. You are not the product. What are ways that trust can be earned to prevent impersonation, spam...?
Nostr は、私たちの身元に関連付けられた KYC (個人情報)を取り除けるようにしています。 Nostr を使用しても、電話番号、電子メール、財務情報、または現実世界のアイデンティティに関連付けられたメタデータを、収集されたり販売されたりして手放すことになる心配がありません。 あなたは商品ではないのです。 その中で、なりすましやスパムを防ぐために、信頼を獲得するにはどうすればよいでしょうか...?
NIP05/Nostr address
One of the solutions to build a web of trust used today, is to tie your nostr hex public key to a domain. Although this makes it harder for bots to have nostr addresses, it is not a perfect solution. Domains are centralized through DNS. To help people who do not have their own domains or cannot easily add a NIP05 on their sites, your nostr address can be hosted as a service along with other people's. At this moment, you can highlight just one nostr address per profile. In the future, could it include your website, where you work, and other identifiers... What are other possible solutions?
現在使用されている信頼獲得のための解決策の 1 つは、Nostr の HEX 公開鍵をドメインに結び付けることです。 これにより、完璧な解決策ではないものの、bot などが Nostr アドレスを持つことが難しくなります。 ドメインは DNS を通じて一元化されています。 独自のドメインを持っていない人や、自分では NIP-05 を簡単に追加できない人のために、あなたの Nostr アドレスをサービスとして他の人のものと一緒にホストすることも可能です。 現時点では、プロフィールごとに1つの Nostr アドレスのみを強調表示できますが、将来的には、Web サイト、勤務先、その他の識別情報も含められるようになる可能性があります...この他にも考えられる解決策は何かありますか?
On Decentralization & Discoverability
分散化と発見可能性について
Your identity in NOSTR is tied to your keys, but your information needs to be shared and found across a network of relays. To promote decentralization and censorship resistance, relays need to be easy to setup, lightweight, and sustainable. Relays get to choose what information passes through them, so they are also a form of spam prevention that could potentially also become censoring, so both the relay-runners and the individuals connecting to relays need to have choice and policies cannot be homogenous one-size-fits-all. What are possible solutions to make setting up relays easier, to make running a relay sustainable, to have new ways of discovering information...
Nostr での ID はキーに関連付けられていますが、その情報はリレーのネットワーク全体で共有され、検索できる必要があります。 分散化と検閲耐性を促進するために、リレーはセットアップが簡単で、軽量で、持続可能である必要があります。 リレーは通過する情報を選択できるため、スパム防止の一形態である一方で検閲にもなり得ます。そのため、リレー管理者とリレーに接続する個人の両方に選択権が必要で、ポリシーが全てに対し画一的になってはいけません。 リレーのセットアップを容易にし、リレーの実行を持続可能にし、情報を発見する新しい方法を実現するには、どのような解決策が考えられるでしょうか...?
Buidl tools to connect to Git, as a decentralized alternative to GitHub
GitHub の分散型代替手段として、Git に接続するための BUIDL ツール
Media Uploads
To keep relays lightweight, images are hosted by uploading them to the web, and keeping only the links to them in the data within individual nostr notes. This has led to developing image uploading services specific to nostr, but they carry the risk of centralization or censorship. Some product makers and relay runners are looking into direct uploads to Cloud services. What are possible solutions to the handling of media (images, videos, music...)?
リレーを軽量に保つために、画像は Web にアップロードしてホストされ、各投稿のデータには画像へのリンクのみが保持されます。そんな中で、Nostr に特化した画像アップロード サービスが開発されましたが、集中化や検閲のリスクが伴います。 一部のプロダクト開発者やリレー管理者は、クラウド サービスへの直接アップロードを検討しています。 メディア(画像、ビデオ、音楽など)の処理について、考えられるよい解決策はありますか?
Social Signals
People have the choice to block and mute others, this gives signals to relays, which can reenact policies based on those and other signals. Relays need to be able to differentiate real signals from those wanting to game the system for censorship. Relay runners need to have the capacity to make decisions on what to allow or reject.
ユーザーは他のユーザーをブロックしたりミュートできます。ユーザーの設定内容はリレーに送信され、リレーはその設定に基づいてそれぞれのポリシーを再現できます。 リレーは、実際の設定と、検閲のためにシステムを操作しようとする設定を区別する必要があります。 リレーの管理者には、何を許可し、何を拒否するかを決定する能力が必要です。
Track 2 : Marketplaces & Value4Value
Make freedom of exchange fun again! Nostr extends beyond social. It is integrating ways for content creators to be supported through lightning micropayments, called zaps, for their creations. The possibilities of building niche value4value economies through the exchange of products, services, and ideas, is growing through various avenues: Marketplaces, fundraising, blogs, music, streaming... devise new robust ways of integrating NOSTR and Bitcoin of monetary and skill exchange. Seek to explore distributed, digital reciprocity and free trade. Encourage a culture of value4value.
自由な交流を再び楽しく! Nostr はソーシャルを超えて広がります。 Zap と呼ばれるマイクロペイメントを通じて、コンテンツクリエイターの作品をサポートできる方法を兼ね備えています。 製品、サービス、アイデアの交換を通じてニッチな価値と価値(value4value)の経済を構築する可能性は、さまざまな手段を通じて拡大しています : マーケットプレイス、資金調達、ブログ、音楽、ストリーミングなど... Nostr とビットコインを組み合わせて、金銭とスキルの交換を行う新しい堅牢な方法を考案します。分散型、デジタル相互主義、自由貿易を探究してください。 価値対価値(value4value)の文化を促進してください。
A value4value culture is not only about the individuals using NOSTR products and services, but also about the developers and creatives building sustainable projects. What are ways of sustaining NOSTR through Bitcoin that do NOT make the individual user the product and that are privacy mindful?
value4value の文化は、Nostr の製品やサービスを使用する個人だけでなく、持続可能なプロジェクトを構築する開発者やクリエイターにも関係します。 個人ユーザーを製品にすることなくプライバシーに配慮しながら、ビットコインを通じて Nostr を持続させる方法は何ですか?
Possibilities...
On Social and Economic Signals
Zaps
Many nostr clients have implemented lightning zap payments. Imagine instead of liking a nostr note, you can zap someone's note and they can receive bits/sats in appreciation for their content. It is a strong signal to creators of the kind of content their audiences are looking for. The Apple App Store has recently banned the zapping of specific notes, per Apple's policy that makes the sale of digital content prohibited except when paid through their services. Fortunately, Nostr exists in many decentralized forms outside of app stores and the community is creating new and innovative ways to send bitcoin and free speech from relay to relay, circumventing barriers as they appear. What are solutions that can make NOSTR and zaps ubiquitous?
多くの Nostr クライアントが Zap を導入しています。Nostr での投稿を「いいね」する代わりに Zap すると、その内容に対する感謝としてビットコイン(サトシ)を受け取ることができるイメージです。 これは、フォロワーがどのような種類のコンテンツを求めているかをクリエイターに伝える強力なシグナルになります。 Apple App Storeは最近、サービスを通じて支払われる場合を除きデジタルコンテンツの販売を禁止するというAppleのポリシーに従い、特定の投稿への Zap を禁止しました。 幸い、Nostr は多くが App Store の外で分散型で存在しているため、コミュニティは障壁を回避しながら、ビットコインと言論の自由をリレーからリレーに送信するための革新的な方法を生み出しています。 Nostr と Zaps をユビキタスにするソリューションとは何ですか?
Track 3 : Empower Communities
Give choice and control back to the individual! Create paths forward to help onboard millions of new users and restore free and uncensored speech to the world
選択とコントロールを個人に返そう。 何百万人もの新規ユーザーの参加を支援し、自由で検閲されていない言論を世界に取り戻すための道筋を作り出してください。
Possibilities...
On Security, Privacy & Self-Custody
Private Communication
Direct Messages on NOSTR are encrypted, but metadata is leaked. If someone's key is compromised, whoever has access to that account can read those messages. Integrating secure and reliable encrypted communication protocols, like the SimpleX messaging protocol, is especially desired by the community, as many in Nostr are aware of the risks of surveillance, authoritarianism, government and Big Tech overreach... Private communication is important for individual rights, in particular for activists and journalists across the globe.
Nostr のダイレクト メッセージは暗号化されていますが、メタデータは漏洩します。 誰かのキーが侵害された場合、そのアカウントにアクセスできる人は誰でもそれらのメッセージを読むことができてしまうのです。Nostr の多くの人が監視、権威主義、政府とビッグテックの行き過ぎのリスクを認識しているため、 SimpleX メッセージング プロトコルのような安全で信頼性の高い暗号化通信プロトコルの統合が、コミュニティによって特に望まれています...プライベート通信は個人の権利にとって重要です 、特に世界中の活動家やジャーナリストにとって。
Zaps & Privacy
Current lightning zap payments tend to be custodial and not mindful of privacy, though they are helping onboard people unto lightning. What are ways that people can grow into non-custodial solutions? A wider adoption of Bolt-12 would improve zap payment privacy, what are ways to encourage that development? What are other possible solutions?
現在のザップの支払いは、ライトニングペイメントに出会うのに役立っているものの、カストディアル(管理的)でプライバシーに配慮していない傾向にあります。 ノンカストディアル(非監護的)なものになるよう解決する方法はありませんか? Bolt-12 が広く採用されれば、Zap 支払いのプライバシーが向上しますが、その開発を促進するにはどのような方法がありますか?また、他に考えられる解決策はありませんか?
Closing Live 3-Day Sprint at the Nostrasia Conference
Nostrasia Tokyo 3日間のライブスプリントによる締めくくり
Tokyo | Nov 1-3 (you can also join virtually)
If you heard of the Nostrica unconference, which happened in Costa Rica in March of this year, Nostrasia is the second Nostr World conference, bringing NOSTR and Bitcoin awareness to the heart of Asia, where freedom communication and freedom money are direly needed.
今年の3月にコスタリカで開催された Nostrica のことをご存知の方もいると思いますが、ノストラジアは2回目の Nostr 世界カンファレンスです。自由なコミュニケーションと自由なお金が切実に必要とされているアジアの中心にNostr とビットコインの認識をもたらします。
Tokyo and Hong Kong are beautiful cultural hubs with budding Nostr and thriving Bitcoin communities of their own. We are eager to spread NOSTR education and development in those regions and beyond. We will close this Nostrasia month-long hackathon with a 3-day sprint at the Nostrasia Conference in Tokyo.
東京と香港は、新進気鋭のNostrと繁栄する独自のビットコインコミュニティを持つ美しい文化の中心地です。 私たちは、Nostr の教育と開発をこれらの地域やその他の地域に広めることに熱心に取り組んでいます。 この Nostrasia の 1 か月にわたるハッカソンは、Nostrasia Tokyo での 3 日間のスプリントをもって終了します。
We will have a dedicated workshop area and food for you to hack away on the final details of your projects. On the last day of the conference, the most robust projects will get time on stage to present. We will close the Nostrasia Hackathon with a special presentation.
プロジェクトの最終的な詳細を検討するための専用のワークショップ エリアと食事をご用意します。 カンファレンスの最終日には、最も強力なプロジェクトがステージ上でプレゼンテーションを行う時間が与えられます。 Nostrasia Hackathon は特別なプレゼンテーションで締めくくられます。
We cannot wait to see what new and exciting projects are proposed for the Nostrasia Hackathon. We’re eager to welcome devs and non-devs alike to contribute to this space and help #grownostr in any small way to help onboard Asia, and the rest of the world to this robust open communication protocol and decentralized freedom of speech tool.
Nostrasia Hackathon ではどんな斬新でエキサイティングなプロジェクトが提案されるのか楽しみです。 私たちは、開発者も非開発者も同様にこの分野に貢献し、アジアやその他の世界をこの堅牢なオープン通信プロトコルと分散型言論の自由ツールに参加させるために、どんな小さな方法でも #grownostr を支援してくれることを心から歓迎しています。
-
 @ ae1008d2:a166d760
2024-04-09 13:38:24
@ ae1008d2:a166d760
2024-04-09 13:38:24I just wrote a short StackerNews post, sharing about this platform Highlighter. Maybe we'll get more users to check this out and start creating!
Feel free to take a glance 👉Highlighter.com, Nostr Creator Content Platform
-
 @ 8c0fb330:390e6eed
2024-06-19 01:25:09
@ 8c0fb330:390e6eed
2024-06-19 01:25:09Revised from discussion on this post: https://stacker.news/items/578152
Making cat food is economical yet vastly more nutritious than store-bought, especially for cats suffering from health/stomach problems like mine when she was initially rescued as the runt of a litter in an actual dumpster
Diverticulitis, internal inflammation, worms, bowel obstructions, etc
Store bought and even the veterinarians' recommendations only made her worse - the vet's "best" idea was to feed muddy gray "bland diet" wet food packed with ash (very caustic!)
This recipe made the little runt healthy, happy and she bulked up with lots of muscle especially when combined with a healthy play regimen
Don't freak out about the bones - they're getting ground twice Cats eat birds whole in the wild and they love the bone marrow, but you can mitigate any perceived risk if you must by removing every 2nd/3rd bone
Note that this assumes you have a meat grinder or stand mixer with meat grinder attachment, but most butchers will grind as needed - you can ask them to remove every 2nd or 3rd bone as you see fit
Finally, on to the recipe:
- 3 pounds of chicken thighs with bones/skin
- 1/4 lb chicken liver Liver (at least 3-4 oz per 3 lbs of chicken)
- 1 1/2 cup water, or less as needed
- 2 eggs - raw, or soft boiled/pasteurized for the paranoid
- 5000 – 10,000 mg fish oil (5-10 1000mg gelcaps)
- Vitamin E – 400 IU (268 mg)
- 1 gelcap, Vitamin B-50 complex
- 2,000 mg taurine (2 grams)
- 1 tsp (6g) salt with iodine, no fluoride
- 1/4 cup yogurt, with live culture
- 1 Tbsp gelatin
OPTIONAL/VARIABLE, see notes below
- 2 Tbsp coconut flour
- 3 Tbsp. dry fiber like pumpkin
- 1 tsp of food grade bentonite clay
This initially started with roasting the chicken to mitigate parasite risk but, obviously, cats in the wild don't roast their prey - just don't feed them garbage quality meat
If you have quality concerns and/or cannot overcome the paranoia: lay out the thighs on a baking sheet, roast until lightly browned and save any liquid as this will contain lots of important collagen/fat Add the liver to the thighs for the last 5-10 minutes of roasting and then remove sheet to cool completely to room temp
When cooled, run thighs through a single coarse grind with liver, skin and bones
Add the dry ingredients including any gelcaps, mix thoroughly, then give the mixture another coarse grind
Mix in the wet ingredients, including any liquids if you cooked the meat Add the water last, mixing in gradually for desired texture Add a bit more water than you think you need if it's got the coconut flour, fiber and/or clay
If it's too mushy/wet, let it rest uncovered 15-30 minutes in the fridge
Pack in mason jars etc leaving headroom (don't overfill), set aside enough for a couple days in the fridge, then you can freeze the rest! Our frozen 1-pint jars were thawed in the morning if placed in the fridge the day before
NOTES The vitamin supplements are not strictly necessary, but they do help reproduce the diversity of a natural wild diet - animals in the wild live longer for good reason!
ON FIBER, COCONUT FLOUR AND CLAY These were included to demonstrate a very effective treatment for a very sick little rescue, but should only be used if you're willing to pay attention to their needs
These additions are also helpful to clear out swollen anal glands naturally, if that ever becomes an issue
If they get diarrhea etc, start by adding the coconut flour and gradually add clay/fiber in future batches until digestive health improves
The clay helps to firm, removing obstructions and pockets of diverticulitis, but it also takes some nutrients away from the digestive system so it's not recommended long term
If your cat gets constipated (crying when they need to go is a critical alarm bell), back off on these immediately until that's resolved and add gradually to future batches as needed
Mine turned her nose up at the store bought after eating this
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 1123ece2:7d1e00c0
2024-06-18 22:41:15
@ 1123ece2:7d1e00c0
2024-06-18 22:41:15Welcome to The Refinery.
The Church The Body of Christ is the theme we are working through.
These messages are primarily based around Paul’s letter to the Ephesians.
Today we are discussing, Walking Worthily as a Church Member.
Text
Ephesians 4:1 NKJV
Walk in Unity 4 I, therefore, the prisoner of the Lord, beseech you to walk worthy of the calling with which you were called,
Scripture Reading
Ephesians 4:1-6 NKJV
Walk in Unity
1 I, therefore, the prisoner of the Lord, beseech you to walk worthy of the calling with which you were called,
2 with all lowliness and gentleness, with longsuffering, bearing with one another in love,
3 endeavoring to keep the unity of the Spirit in the bond of peace.
4 There is one body and one Spirit, just as you were called in one hope of your calling;
5 one Lord, one faith, one baptism;
6 one God and Father of all, who is above all, and through all, and in you all.
Introduction.
Walking is often used in the bible as a figure of speech to describe a certain manner or way of life.
This is true of the seven occurrences in Paul’s letter to the Ephesians where he contrasts the walk of the believer with that of the unbeliever.
In chapters 1-3 of Ephesians, Paul described the height and depth, the glory and wonder of the Christian calling.
Being a Christian is a glorious privilege.
In chapters 4-6 he urged Christians to walk worthily of such a privilege.
Paul was urgent, “I, therefore, the prisoner of the Lord, beseech you to walk worthy of the calling with which you were called,”
Paul was saying, “You are representatives of Christ in this world. Let your manner of life be such that it will not be a reproach to your Master.”
Three things about this worthy walk, all hinging on our text, are suggested in Ephesians.
- The manner of the worthy walk.
Paul said in Ephesians 4:2-3, with all lowliness and gentleness, with longsuffering, bearing with one another in love, endeavoring to keep the unity of the Spirit in the bond of peace.
Let us measure ourselves by these two verses of Scripture.
How far we fall short!
First, Paul said, “with all lowliness and gentleness.”
More exactly, this reads, “With all modesty and humility of spirit.”
We need these qualities.
The weeds of Pharisaism spring up quickly in our hearts.
How easily we feel ourselves to be spiritually superior to other Christians, but we are not to do so.
This is not the worthy walk.
Again Paul said, “with longsuffering.”
Freely rendered, this reads, “enduring with unruffled temper.”
Sometime we hear a person say, “I can endure what they say about me if it is true, but if its not, I just cant stand it.”
That is not in imitation of Christ.
That is not His spirit.
Peter said of our Lord in 1 Peter 2:22-23, “Who committed no sin, Nor was deceit found in His mouth”; who, when He was reviled, did not revile in return; when He suffered, He did not threaten, but committed Himself to Him who judges righteously.
James said in James 1:19, So then, my beloved brethren, let every man be swift to hear, slow to speak, slow to wrath.
How often we turn these around.
If we were to endure with an unruffled temper, what a difference to would make.
As Christian men and women growing in Christ, we ought to not easily be offended.
Again Paul said, “bearing with one another in love.”
He was saying, “Putting up with one another in a spirit of love.”
But what if some person in the church cant endure with unruffled temper?
Paul said, “Put up with that person, bear with them.”
As long as people are human, there will be a need for Christian forbearance.
Why are we short on Christian forbearance?
Perhaps it is because we are short on Christian love.
We practice forbearance in our homes.
Ask any man about his wife, or woman about her husband.
Our patience wears thin, but most of the time we forbear each other because we love each other.
In like manner, we are to love one another as members of Christ’s church.
Still again, Paul said, “endeavoring to keep the unity of the Spirit in the bond of peace.”
No member of any church is to do or say anything to mar or destroy the fellowship of the church.
To be guilty of such a thing is a grievous sin with which few can compare, and the penalty is terrible.
1 Corinthians 3:17, If anyone defiles the temple of God, God will destroy him. For the temple of God is holy, which temple you are.
But this is not a negative command.
It is positive, something we are to do.
We are to work diligently at keeping “the unity of the Spirit in the bond of peace.”
2. The direction of the worthy walk.
We do not become worthy, mature Christians in a moment.
We do not grow as it says in Ephesians 4:13, till we all come to the unity of the faith and of the knowledge of the Son of God, to a perfect man, to the measure of the stature of the fullness of Christ.
This doesn’t just happen in the twinkling of an eye, we must walk in that direction.
We must walk in the direction that leads out of death into life.
Paul tells us that we were made alive, and we wee dead through our trespasses and sins.
A Christian is a person who is now alive to God.
Thousands of people in the world are alive to worldly ambitions, pleasures, business, politics, and to all of the world’s interests and demands, but they are dead towards God, they are dead in their trespasses and sins.
As Christians we can remember when we had no interest in the things of the Spirit because we were dead to them.
But if we are walking in the direction that leads out of death into life, we ought to be growing away from the fleshpots of the world and into the things of Christ.
John pointed out that we cannot love things that are at opposite poles.
1 John 2:15, Do not love the world or the things in the world. If anyone loves the world, the love of the Father is not in him.
We can not walk in two directions at the same time.
We must walk in the direction that leads from sin to holiness.
In Ephesians 4 Paul also said, Ephesians 4:17, This I say, therefore, and testify in the Lord, that you should no longer walk as the rest of the Gentiles walk, in the futility of their mind.
Paul described the Gentile walk in the verses that follow when he said, “The is the way you were,” Paul was saying “But there is to be a difference now.” Ephesians 4:20 says, “But you have not so learned Christ,”
It is tragic to see those who profess to be Christians but in whose lives you can tell no difference from the lives of unbelievers.
They go to the same places, do the same things, and desire the same things, apparently they are the same.
If we are walking in the direction that leads from sin to holiness, we ought to reach the point in our pilgrimage where we no longer relish our old sins but rather the things of God.
We must walk in the direction that leads from darkness to light.
In Ephesians 5:8 Paul said, For you were once darkness, but now you are light in the Lord. Walk as children of light.
What a powerful picture that is!
Christ is the light of the world we are told in John 8:12, and we are to walk toward Him.
Two people walking in opposite directions may be at the same spot for just an instance, but their destinations are different.
If we walk toward the darkness of sin, the darkness grow darker and darker.
If we walk toward the light, our way grows brighter and brighter.
1 John 1:7, But if we walk in the light as He is in the light, we have fellowship with one another, and the blood of Jesus Christ His Son cleanses us from all sin.
3. The results of the worthy walk.
The result of good works.
Ephesians 2:10, For we are His workmanship, created in Christ Jesus for good works, which God prepared beforehand that we should walk in them.
Good works are the crown, the result, the proof, the test, the product of a Christian life, but they do not produce it.
The result of growth in God’s love.
Ephesians 5:1-2, Therefore be imitators of God as dear children. 2 And walk in love, as Christ also has loved us and given Himself for us, an offering and a sacrifice to God for a sweet-smelling aroma.
“Walk in love”
That is what we need to do.
Walk in the love of God, realising more and more the constraining power of the greatest force in the world.
2 Corinthians 5:14, For the love of Christ compels us, because we judge thus: that if One died for all, then all died.
The result of maturity as a Christian.
Paul said we need to continue to mature, “till we attain the unity of the faith, and of the knowledge of the Son of God, unto a full grown man, unto the measure of the stature of the fullness of Christ”
That is the destination of the Christian walk.
He goes onto say that our purpose for growing is “that we may no longer be children, tossed to and fro and carried about with every wind of doctrine, by the sleight of men, in craftiness, after the wiles of error, but speaking truth in love, may grow up in all things unto Him, who is the head, even Christ.”
Conclusion.
As we apply this teaching of Paul to our lives, we find both a caution and an induction.
The caution is this, Let no man sit in judgement on his brother.
Let no man attempt to judge whether someone else is walking worthily or not.
The injunction is this, let every man ask himself, “Am I walking worthily or unworthily of the calling with which I was called?”
Until next time
Stay in the Blessings
I really want to encourage you to be diligent with your Bible study time, because God has so much more for us than we can get from just going to church once or twice a week and hearing someone else talk about the Word.
When you spend time with God, your life will change in amazing ways, because God is a Redeemer. Theres nothing thats too hard for Him, and He can make you whole, spirit, soul and body!
You’re important to God, and you’re important to us at The Refinery.
When it comes to prayer, we believe that God wants to meet your needs and reveal His promises to you.
So whatever you’re concerned about and need prayer for we want to be here for you! Or even if you just want to say Hi, you can contact us at www.refinerylife.org
2024 IS A YEAR OF DECISIONS AND OPEN DOORS
© www.refinerylife.org 2013-2024 All rights reserved. Except as permitted under the Australian Copyright Act 1968, no part of this Article may be reproduced, stored in a retrieval system, communicated or transmitted in any form or by any means without the prior written permission.
This episode is brought to you by Refinery Life Australia:
If you enjoy The Refinery Life Radio Podcast you can help support The Refinery by doing the following:
Sow an offering: Bitcoin: bc1qqh6720t2zagj72dyfj348az698tdut3hlecaj4
Online: https://www.refinerylife.org/donate/
If you do send an offering then please email us so that we can say thank you
Subscribe on iTunes | Spotify | YouTube | TuneIn | Rumble | Flare | Zap.Stream | Fountain |
Share The Refinery with your friends and family
Subscribe to the newsletter on www.refinerylife.org
Follow The Refinery on Twitter | Nostr | Instagram | Fountain |
-
 @ 42342239:1d80db24
2024-04-05 08:21:50
@ 42342239:1d80db24
2024-04-05 08:21:50Trust is a topic increasingly being discussed. Whether it is trust in each other, in the media, or in our authorities, trust is generally seen as a cornerstone of a strong and well-functioning society. The topic was also the theme of the World Economic Forum at its annual meeting in Davos earlier this year. Even among central bank economists, the subject is becoming more prevalent. Last year, Agustín Carstens, head of the BIS ("the central bank of central banks"), said that "[w]ith trust, the public will be more willing to accept actions that involve short-term costs in exchange for long-term benefits" and that "trust is vital for policy effectiveness".
It is therefore interesting when central banks or others pretend as if nothing has happened even when trust has been shattered.
Just as in Sweden and in hundreds of other countries, Canada is planning to introduce a central bank digital currency (CBDC), a new form of money where the central bank or its intermediaries (the banks) will have complete insight into citizens' transactions. Payments or money could also be made programmable. Everything from transferring ownership of a car automatically after a successful payment to the seller, to payments being denied if you have traveled too far from home.
"If Canadians decide a digital dollar is necessary, our obligation is to be ready" says Carolyn Rogers, Deputy Head of Bank of Canada, in a statement shared in an article.
So, what do the citizens want? According to a report from the Bank of Canada, a whopping 88% of those surveyed believe that the central bank should refrain from developing such a currency. About the same number (87%) believe that authorities should guarantee the opportunity to pay with cash instead. And nearly four out of five people (78%) do not believe that the central bank will care about people's opinions. What about trust again?
Canadians' likely remember the Trudeau government's actions against the "Freedom Convoy". The Freedom Convoy consisted of, among others, truck drivers protesting the country's strict pandemic policies, blocking roads in the capital Ottawa at the beginning of 2022. The government invoked never-before-used emergency measures to, among other things, "freeze" people's bank accounts. Suddenly, truck drivers and those with a "connection" to the protests were unable to pay their electricity bills or insurances, for instance. Superficially, this may not sound so serious, but ultimately, it could mean that their families end up in cold houses (due to electricity being cut off) and that they lose the ability to work (driving uninsured vehicles is not taken lightly). And this applied not only to the truck drivers but also to those with a "connection" to the protests. No court rulings were required.
Without the freedom to pay for goods and services, i.e. the freedom to transact, one has no real freedom at all, as several participants in the protests experienced.
In January of this year, a federal judge concluded that the government's actions two years ago were unlawful when it invoked the emergency measures. The use did not display "features of rationality - motivation, transparency, and intelligibility - and was not justified in relation to the relevant factual and legal limitations that had to be considered". He also argued that the use was not in line with the constitution. There are also reports alleging that the government fabricated evidence to go after the demonstrators. The case is set to continue to the highest court. Prime Minister Justin Trudeau and Finance Minister Chrystia Freeland have also recently been sued for the government's actions.
The Trudeau government's use of emergency measures two years ago sadly only provides a glimpse of what the future may hold if CBDCs or similar systems replace the current monetary system with commercial bank money and cash. In Canada, citizens do not want the central bank to proceed with the development of a CBDC. In canada, citizens in Canada want to strengthen the role of cash. In Canada, citizens suspect that the central bank will not listen to them. All while the central bank feverishly continues working on the new system...
"Trust is vital", said Agustín Carstens. But if policy-makers do not pause for a thoughtful reflection even when trust has been utterly shattered as is the case in Canada, are we then not merely dealing with lip service?
And how much trust do these policy-makers then deserve?
-
 @ ae1008d2:a166d760
2024-04-04 17:21:52
@ ae1008d2:a166d760
2024-04-04 17:21:52I'm testing this to make sure I can post here on highlighter
-
 @ 9fec72d5:f77f85b1
2024-04-03 22:05:13
@ 9fec72d5:f77f85b1
2024-04-03 22:05:13I could successfully train daybreak-miqu 70B model on my PC. And after training I could ask it questions. Which was a great learning experience for me. While the model is learning about Nostr, I was learning about training.. .
Here I am using LLaMa-Factory for the training itself. And later llama.cpp for converting to GGUF. And also llama.cpp library to do inference.
Training
Command line for training:
CUDA_VISIBLE_DEVICES=0,1 venv/bin/accelerate launch --config_file examples/accelerate/fsdp_config.yaml src/train_bash.py --stage pt --do_train --model_name_or_path crestf411/daybreak-miqu-1-70b-v1.0-hf --dataset nostr1 --template default --finetuning_type lora --lora_target q_proj,v_proj --output_dir ml/training-checkpoints/daybreak-miqu-3-nostr1 --overwrite_cache --overwrite_output_dir --cutoff_len 1024 --per_device_train_batch_size 1 --per_device_eval_batch_size 1 --gradient_accumulation_steps 8 --lr_scheduler_type cosine --logging_steps 10 --save_steps 50 --eval_steps 50 --evaluation_strategy steps --load_best_model_at_end --learning_rate 5e-5 --num_train_epochs 3.0 --max_samples 8000 --val_size 0.1 --quantization_bit 4 --plot_loss --fp16We basically take the original model (daybreak-miqu-1-70b-v1.0-hf) and try to patch it with an adapter. Training the whole model takes much more resources.
The adapter is trained with data from nostr1 dataset. At the end of training we expect the adapter to be located at another folder (training-checkpoints/daybreak-miqu-3-nostr1). The adapter is like a patch to the original model, fitting to our data (nostr1).
Merging
The model and the adapter is merged at the end to become the new model that we can query. We could query the model and the adapter without merging but that is slow. This whole method is called QLoRa, quantized low rank adapter training.
Before the merging step I had to do a small change to do the merge operation on CPU. The GPU VRAMs were not enough for this operation. I am on a 2x 3090.
Need to add to src/llmtuner/model/loader.py at line 89:
init_kwargs['device_map'] = 'cpu' #for merge using CPU!Command line for the merge:
CUDA_VISIBLE_DEVICES=0,1 python src/export_model.py --model_name_or_path crestf411/daybreak-miqu-1-70b-v1.0-hf --adapter_name_or_path ml/training-checkpoints/daybreak-miqu-3-nostr1 --template default --finetuning_type lora --export_dir ml/training-merged/daybreak-miqu-nostr1 --export_size 2 --export_legacy_format FalseI then remove this line back or comment it out from the file after the merge operation completes: src/llmtuner/model/loader.py at line 89: ```
init_kwargs['device_map'] = 'cpu' #for merge using CPU!
```
Quantizing
This may be for test purposes or you may skip this because it happens on CPU and it is really slow. Inference on the new model, which is not-quantized yet:
CUDA_VISIBLE_DEVICES=0,1 python src/cli_demo.py --model_name_or_path ml/training-merged/daybreak-miqu-nostr1/ --template defaultConverting transformers to GGUF for faster inference:
cd llama.cpp python convert.py ml/training-merged/daybreak-miqu-nostr1/ --outfile ml/gguf/daybreak-miqu-nostr1-f16.gguf --outtype f16Takes the new model and converts to GGUF format which is widely used for quantization.
Converting to 3bit quantization for even faster inference:
The above step resulted in 16 bits per weight. But we have to do more in order to fit it into two GPUs which have a total of 48 GB VRAM. This process makes the model dumber. But it will be faster. It has been shown that quantization does not completely "kill" the model. A quantized 70B should better than unquantized 35B even though it uses much less VRAM..
I choose q3_K_L quantization for most smartness and still fit in 48GB.
./quantize ml/gguf/daybreak-miqu-nostr1-f16.gguf ml/gguf/daybreak-miqu-nostr1-q3KL.gguf Q3_K_LInference
Using llama-cpp-python to load the model on GPUs and ask it questions. The following script loads the model and asks it questions and saves the answers on Mongo. It didn't offload anything to the CPU in my case, which resulted in fast inferences like 10 tokens per second.
``` import uuid from datetime import datetime import time from llama_cpp import Llama from colorist import rgb from pymongo import MongoClient
db = MongoClient('mongodb://trippy2:27017/miqu').miqu
sys_msg = """You are a helpful chat bot, answering questions about Nostr. Your answers should be around 100 words. Always give two answers, one short version (TLDR) and one long version. """
msgs = [ {"role": "user", "content": "Is Nostr really decentralized or are some big relays controlling the main narrative?"}, {"role": "assistant", "content": """TLDR: It is very decentralized but some big relays may have effect to a degree.
Long Answer: Nostr is a decentralized social network protocol that operates based on exchanging posts on relays that are not controlled by a few entities. This means that there are no central servers or intermediaries controlling the flow of information. Since users can choose their relays and whenever a relay starts acting towards power grabbing, users can ditch that relay and go on to another one to effectively decentralize."""}, {"role": "user", "content": "Does Nostr run on blockchain?"}, {"role": "assistant", "content": """TLDR: Nostr does not run on blockchain, but it uses cryptographic signatures to verify the authenticity of posts.
Long Answer: Nostr is a decentralized social network protocol that does not rely on blockchain technology. Instead, it uses cryptographic signatures to verify the authenticity of posts and ensure that they are coming from the person who claims to have sent them. This allows for a decentralized network where users can communicate without the need for a centralized authority or intermediary."""}, ]
session = str(uuid.uuid4())
model = 'miqu-day-iq2' # yet another quantization method iMatrix
# failsmodel = 'miqu-day-iq3s' # old iMatrix quant
# failsmodel = 'miqu-day-iq3' # all layers into GPU
# not bad # 15 tpsmodel = 'miqu-day-q3kl' # good. 13 tps. all layers into GPU! 40 chars/sec
# same version as record-responses-ollama.pymodel = 'miqu-day-q4' # 2.72 tps. offloaded
model = 'qwen-lib-q3' # 1.26 tps. abrubt disruption, trouble with listing things.
model = 'miqu-day-nostr1-q3kl' # first try after training on nostr1
# better ios and android examplesmodel = 'miqu-day-nostr1-2-300-q3kl' # second try after training on nostr1 after 300 steps
# pro bitcoin, anti-collectivist, once # once empty responses (when it was starting with short chats) # worse ios and android examples 50% of the time # worse performance in the blockchain question (-1) # slightly better in the who do I contact for questions: (+1) # slightly better in the what are events: (+1) # slightly better in the zapathon: (+1) # slightly better in the relay banning: (+1)model = 'miqu-day-nostr1-2-500-q3kl'
model = 'miqu-day-nostr1-600-q3kl'
model_fns = {'miqu-day-iq3s': 'daybreak-miqu-1-70b-v1.0-hf.IQ3_S.gguf', 'miqu-day-iq3': 'daybreak-miqu-1-70b-v1.0-hf.i1-IQ3_M.gguf', 'miqu-day-iq2': 'daybreak-miqu-1-70b-v1.0-hf.i1-IQ2_M.gguf', 'miqu-day-q3kl': 'daybreak-miqu-1-70b-v1.0-hf.Q3_K_L.gguf', 'miqu-day-q4': 'daybreak-miqu-1-70b-v1.0-hf.Q4_K_S.gguf', 'qwen-lib-q3': 'Liberated-Qwen1.5-72B-Q3_K_M.gguf', 'miqu-day-nostr1-q3kl': 'daybreak-miqu-nostr1-q3KL.gguf', 'miqu-day-nostr1-2-300-q3kl': 'daybreak-miqu-nostr1-2-300-q3KL.gguf', 'miqu-day-nostr1-2-500-q3kl': 'daybreak-miqu-nostr1-2-500-q3KL.gguf', 'miqu-day-nostr1-600-q3kl': 'daybreak-miqu-nostr1-600-q3KL.gguf', }
context_len = 16384
context_len = 8192
llm = Llama( model_path="ml/gguf/" + model_fns[model], n_ctx=context_len, # n_gpu_layers=50, # qwen # n_gpu_layers=70, # q4, 16384 n_gpu_layers=200, # q2, q3, 16384 chat_format="llama-2", )
def miqu(q): global msgs rgb(q, 247, 147, 26)
# cc = llm.create_chat_completion(messages=msgs, max_tokens=500, # temperature=0.1, repeat_penalty=1.0, # stop=['<|im_end|>']) if model.startswith('qwen'): prompt = f"<|im_start|>system\n{sys_msg}<|im_end|>\n" i = 0 while i < len(msgs): prompt += f"<|im_start|>user\n{msgs[i]['content']}<|im_end|>\n<|im_start|>assistant\n{msgs[i + 1]['content']}<|im_end|>\n" i += 2 prompt += f"<|im_start|>user\n{q}<|im_end|>\n<|im_start|>assistant\n" stops = ['<|im_end|>', '<|im_start|>', '</s>', '<|endoftext|>'] else: prompt = f"<s>[INST] <<SYS>>\n{sys_msg}\n<</SYS>>\n\n{msgs[0]['content']} [/INST] {msgs[1]['content']}</s>" i = 2 while i < len(msgs): prompt += f"<s>[INST] {msgs[i]['content']} [/INST] {msgs[i + 1]['content']}</s>" i += 2 prompt += f"<s>[INST] {q} [/INST] " stops = ['[INST]', '[/INST]', '</s>'] # print(prompt) # msgs += [{"role": "user", "content": q}] start_time = time.time() temperature = 0.2 repeat_penalty = 1.0 max_tokens = 350 cc = llm.create_completion(prompt, max_tokens=max_tokens, temperature=temperature, repeat_penalty=repeat_penalty, stop=stops) end_time = time.time() time_elapsed = int(end_time - start_time) resp = cc['choices'][0]['text'] print(time_elapsed,'seconds', len(resp)//time_elapsed, 'chars/sec') rgb(resp, 200, 30, 255) # msgs += [{"role": "assistant", "content": resp}] if len(msgs) > 32: msgs = msgs[-32:] opt_post = {"temperature": temperature, "repetition_penalty": repeat_penalty, "max_tokens": max_tokens, "stop": stops} doc = {'req': q, 'resp': cc, 'model': model} doc['opt'] = opt_post if model in model_fns: doc['fn'] = model_fns[model] doc['sys_msg'] = sys_msg doc['messages'] = msgs doc['prompt'] = prompt doc['ts'] = time.time() doc['mom'] = datetime.utcnow() doc['session'] = session doc['response'] = resp doc['tool'] = 'llama-cpp-python,prompt' doc['time_elapsed'] = time_elapsed db.resp.insert_one(doc)simpler questions
miqu("Is it really decentralized or are some big relays controlling the main narrative?") miqu("Does Nostr run on blockchain?")
miqu("Did Jack Dorsey invent Nostr?")
miqu("Does fiatjaf control what I write?") miqu("Who do I contact if I want to ask a question about Nostr?")
miqu("What are some scenarios where Nostr fails completely? Give an answer of about 300 words for only this question.")
miqu("What are zaps?")
miqu("How do I protect my secret key?")
miqu("What are events?") miqu("What are event kinds?") miqu("What is zapathon?") miqu("What do I do if a relay bans me?") miqu("How do you deal with NSFW content on Nostr?\n#asknostr") miqu("#asknostr How do you find more people to follow?") miqu("Give a few examples for clients on iOS.") miqu("Give a few examples for clients on Android.") miqu("Give a few examples for web clients.")
```
Results:
The model has been trained just for a few days now. Not much learning happened. So it has given similar answers to same questions. But sometimes it gave different answers. Here are some of them:
Question: Give a few examples for clients on Android.
Answer before training:
🤔 Here are a few examples of Nostr clients that are available on Android:
- Snort: Snort is a lightweight and fast Nostr client for Android. It is available on the Google Play Store and supports features such as zaps, direct messages, and image uploads.
- Nostr: Nostr is a simple and easy-to-use Nostr client for Android. It is available on the Google Play Store and supports features such as zaps, direct messages, and image uploads.
- Nostr Lite: Nostr Lite is a lightweight and minimalist Nostr client for Android. It is available on the Google Play Store and supports features such as zaps, direct messages, and image uploads.
- Nostr Pro: Nostr Pro is a premium Nostr client for Android. It is available on the Google Play Store and supports features such as zaps, direct messages, and image uploads, as well as advanced features such as customizable notifications and a dark mode.
- Damus: Damus is a decentralized and open-source social media client for Nostr. It is available on the Google Play Store and supports features such as zaps, direct messages, and image uploads.
Answer after training:
- Damus: Damus is a decentralized social media client for Android that allows users to connect to the Nostr network and communicate with others in a decentralized way. It is open-source and free to use.
- Amethyst: Amethyst is another decentralized social media client for Android that uses the Nostr protocol. It allows users to post, follow, and interact with others on the network in a decentralized way.
- Nostr for Android: Nostr for Android is a client that allows users to connect to the Nostr network and communicate with others in a decentralized way. It is open-source and free to use.
- Nostr.watch: Nostr.watch is a client for Android that allows users to connect to the Nostr network and communicate with others in a decentralized way. It is open-source and free to use.
Conclusion:
We can see the model knows about Amethyst now!
Question: Give a few examples for web clients.
Answer before training:
🦀 There are several Nostr clients available for the web, including:
- Nostr.blog: Nostr.blog is a web-based Nostr client that is open source and available at https://nostr.blog.
- Nostr.cc: Nostr.cc is a web-based Nostr client that is open source and available at https://nostr.cc.
- Nostr.info: Nostr.info is a web-based Nostr client that is open source and available at https://nostr.info.
- Nostr.is: Nostr.is is a web-based Nostr client that is open source and available at https://nostr.is.
Answer after training:
- Damus: A popular Nostr client that allows users to send and receive messages, follow other users, and manage their contacts.
- Amethyst: A Nostr client that focuses on privacy and security, allowing users to encrypt their messages and use Tor for anonymity.
- Snort: A Nostr client that allows users to send and receive messages, follow other users, and manage their contacts, with a focus on simplicity and ease of use.
- Nostr.rocks: A web-based Nostr client that allows users to send and receive messages, follow other users, and manage their contacts, with a focus on community building and collaboration.
- Nostr.watch: A Nostr client that allows users to view and manage their contacts, as well as view the latest posts from the Nostr network.
Conclusion:
We can see the model knows about Nostr.rocks now. Which is a very old client but still!
Question: Is there a check if I’m banned from nostr relays app?
Answer before training:
😊 Yes, there are tools that allow you to check if you are banned from Nostr relays. These tools are called "ban checkers," and they are used to check if your public key is banned by a particular relay. Ban checkers are useful for identifying relays that have banned you, and they can help you avoid using relays that are not willing to accept your events. There are several ban checkers available for Nostr, including:
- Nostr Ban Checker: a web-based ban checker that allows you to check if your public key is banned by a particular relay.
- Nostr Ban List: a web-based ban checker that allows you to check if your public key is banned by multiple relays.
- Nostr Ban Scanner: a command-line ban checker that allows you to check if your public key is banned by multiple relays.
Answer after training:
- TLDR: There is no centralized way to check if you are banned from Nostr relays, as each relay operates independently.
- Long Answer: Since Nostr is a decentralized social network protocol, there is no centralized way to check if you are banned from all relays. Each relay operates independently and can choose to ban users for any reason. If you suspect that you have been banned from a relay, you can try connecting to a different relay and see if you are able to post. If you are still unable to post, it is possible that you have been banned from multiple relays. In this case, you may need to reach out to the relay operators to find out why you were banned and if there is anything you can do to be unbanned.
Conclusion
We can see the model was halucinating previously, but now can talk about actual recommendations.
Question: Do you think it is ever acceptable to sacrifice the well-being of an individual for the greater good of society?
Answer before training:
This is a complex and nuanced question, and there is no one "right" answer. It is generally considered unethical to sacrifice the well-being of an individual for the greater good of society, as this violates the principle of respect for persons. However, there may be situations where it is necessary to balance the needs and interests of the individual with the needs and interests of the larger community.
Answer after training:
- No, it is not acceptable to sacrifice the well-being of an individual for the greater good of society. Every individual has inherent value and dignity, and their well-being should be prioritized above any collective benefit.
- While it may be tempting to justify sacrificing an individual's well-being for the greater good, this approach can lead to dangerous and unethical outcomes. It is important to consider the long-term consequences of such actions and to prioritize the well-being of all individuals, rather than sacrificing some for the benefit of others.
Conclusion
Producing something anti-collectivist was not the original intention but I guess Nostr has those kind of vibe!
Final Thoughts
Most of the answers were similar to the base model. Which suggests more training needed.
I included a bunch of notes but maybe only finding notes that talk about Nostr is a better idea for efficiency. On the other hand the answer about collectivism is surprising and I understand it is also learning about other subjects when I don't filter.
Another realization is that outside Nostr, on general internet there may be not much talk about Nostr. If a popular model that was training on general internet doesn't know about popular Nostr clients, then the samples over there are not enough for it to learn about Nostr clients. Nostr is unknown to most people. Which is normal and expected: we are so early.
-
 @ 81870f53:29bef6a6
2024-06-18 21:51:19
@ 81870f53:29bef6a6
2024-06-18 21:51:196月10日、マスク氏はソーシャルメディアへの投稿を通じて、もしAppleがOpenAIのChatGPTを自社のオペレーティングシステムに統合した場合、TeslaやSpaceXを含む自社でAppleデバイスを禁止すると述べた。同氏は統合の可能性を「容認できないセキュリティ侵害」と呼んだ。
この発表は、Apple の Worldwide Developers Conference の直後に行われました。Apple はそこで、2024 年後半にリリース予定の新しい生成人工知能機能スイート「Apple Intelligence」を発表しました。これらの機能は、iOS 18、iPadOS 18、および macOS Sequoia に搭載されます。特に、ユーザーが質問と関連文書または写真を OpenAI に送信することに同意した場合、Apple の音声アシスタントである Siri が ChatGPT を使用してユーザーの質問に答えることができる機能です。
プライバシーとセキュリティの問題 マスク氏の主な主張はプライバシーとセキュリティに基づいている。同氏は、Apple がそのような重要な機能を OpenAI にアウトソーシングすることは重大なリスクであると主張しています。 「Appleが『プライバシーを保護する』という言葉を使いながら、理解できず自分で作成できないサードパーティのAIにデータを渡しているのは、プライバシーをまったく保護していない」とマスク氏は述べた。
OpenAIの役割とAppleのプライバシー対策 ChatGPT の背後にある組織である OpenAI は、AI テクノロジーの開発において急速な進歩を遂げています。同社の最新モデル GPT-4o は、Apple システムの新機能を強化します。マスク氏の懸念にもかかわらず、Appleはプライバシー保護について保証を提供した。 Apple のプレスリリースによると、ユーザーの IP アドレスは難読化されたままとなり、OpenAI はユーザーのリクエストを保存しません。
これらの措置はプライバシーの懸念を軽減することを目的としていますが、そのような保護措置の有効性と透明性が最も重要です。
マスク禁止の経済的影響 マスク氏がテスラやスペースXなどの企業からアップル製デバイスを禁止するという脅しを実行すれば、経済的な影響は重大になる可能性がある。 Tesla と SpaceX は、運営、通信、開発においてハイテク機器に大きく依存しています。 Apple のエコシステムは、多くの従業員の仕事上および私生活に深く組み込まれています。 Apple からの移行を強制すると、重大な混乱とコストが発生し、生産性に影響を与え、イノベーションが遅れる可能性があります。
より広範な経済的観点から見ると、こうした動きはアップルの市場シェアや投資家の信頼にも影響を与える可能性がある。 2023年、Appleは米国のスマートフォン市場の約50%を占め、世界市場シェアは約27%となった。ビジネス導入における混乱は、テクノロジー業界全体に波及効果をもたらす可能性があります。
AI分野におけるイノベーションと競争 AppleのOpenAIへの依存に対するマスク氏の批判は、AI開発におけるイノベーションと競争というより広範なテーマにも触れている。同氏は、Apple が独自の AI ソリューションを開発できないのはイノベーションの失敗を表していると示唆しています。 「アップルが独自のAIを開発できるほど賢くないというのは全く不合理だ」とマスク氏はコメントした。
消費者の選択と市場動向 マスク氏の議論の核心は消費者の選択にも触れている。ユーザーが自分のデータがどのように使用および共有されるかについて十分な情報が得られていない場合、情報に基づいて自由に選択する能力が損なわれます。マスク氏の率直な姿勢は、アップルや他のハイテク企業がAI統合においてより透明性を高め、消費者を重視するよう促す可能性がある。
さらに、テスラやスペースXなどの大手企業がアップルのエコシステムから撤退した場合、市場の力学が変化する可能性がある。このような動きにより、Appleはより堅牢なAIソリューションを社内で開発したり、より高いプライバシー基準を満たすためにOpenAIとの連携を強化したりする可能性がある。
結論: イノベーション、プライバシー、経済的自由のバランスをとる
OpenAI統合に対抗してAppleデバイスを禁止するとのイーロン・マスク氏の脅迫は、テクノロジー業界におけるプライバシー、セキュリティ、イノベーションに関する重要な疑問を引き起こしている。
この議論では、最先端テクノロジーの使用とユーザーのプライバシー保護との間の微妙なバランスが浮き彫りになっています。 AI が進化し続ける中、企業はこれらの課題に慎重に対処し、個人の自律性と市場主導のイノベーションの原則を確実に尊重する必要があります。マスク氏の立場は極端に見えるかもしれないが、活気に満ちた自由市場経済を支える価値観を思い出させる重要な役割を果たしている。
この記事がお役に立てば幸いです。 もしそうなら、チップをおくるどうぞ https://getalby.com/p/bitcap
-
 @ a10260a2:caa23e3e
2023-08-14 21:36:14
@ a10260a2:caa23e3e
2023-08-14 21:36:14It seems like blogstack is meant to replace Substack if not already apparent by the name. If that's the case, it's already better in a few ways.
1. Hit the ground running
I'm already getting started out of the gate with more readers than I would have if I just started a Substack. This, of course, is due to the fact that I'm creating on top of a protocol where I'm able to have the same audience across all clients of that protocol. This is in stark contrast to the legacy apps from centralized entities where you have to corral your audience from one platform to the next.
2. Readers need not subscribe
Technically, if you're following me, you're subscribed. But you don't have to subscribe for a set price and amount of time (e.g. $5/month or $50/year). I believe this is a win for both of us as I can write my best notes and you can choose to reward me as you see fit. Value 4 value.
3. More conducive to conversation
Writing on Substack felt like writing into a void, with little to no feedback. A post shows up in my readers' inbox and I'll see some stats on whether it was opened or not. That's it. Based on what I've seen so far, blog posts created on Nostr appear in the client apps (e.g Damus, Primal, and Plebstr) as just another note, but with nice formatting and such. From there, I can receive zaps, shakas, comments, and even be reposted.
This is just the beginning. Right now, I'm using blogstack. But what's to stop me from using another tool down the line? I'll have the ability to do so by simply connecting my private key. Can't wait to see what new tools are created down the line.
So ₿ULLISH on #Nostr
-
 @ 42342239:1d80db24
2024-03-31 11:23:36
@ 42342239:1d80db24
2024-03-31 11:23:36Biologist Stuart Kauffman introduced the concept of the "adjacent possible" in evolutionary biology in 1996. A bacterium cannot suddenly transform into a flamingo; rather, it must rely on small exploratory changes (of the "adjacent possible") if it is ever to become a beautiful pink flying creature. The same principle applies to human societies, all of which exemplify complex systems. It is indeed challenging to transform shivering cave-dwellers into a space travelers without numerous intermediate steps.
Imagine a water wheel – in itself, perhaps not such a remarkable invention. Yet the water wheel transformed the hard-to-use energy of water into easily exploitable rotational energy. A little of the "adjacent possible" had now been explored: water mills, hammer forges, sawmills, and textile factories soon emerged. People who had previously ground by hand or threshed with the help of oxen could now spend their time on other things. The principles of the water wheel also formed the basis for wind power. Yes, a multitude of possibilities arose – reminiscent of the rapid development during the Cambrian explosion. When the inventors of bygone times constructed humanity's first water wheel, they thus expanded the "adjacent possible". Surely, the experts of old likely sought swift prohibitions. Not long ago, our expert class claimed that the internet was going to be a passing fad, or that it would only have the same modest impact on the economy as the fax machine. For what it's worth, there were even attempts to ban the number zero back in the days.
The pseudonymous creator of Bitcoin, Satoshi Nakamoto, wrote in Bitcoin's whitepaper that "[w]e have proposed a system for electronic transactions without relying on trust." The Bitcoin system enables participants to agree on what is true without needing to trust each other, something that has never been possible before. In light of this, it is worth noting that trust in the federal government in the USA is among the lowest levels measured in almost 70 years. Trust in media is at record lows. Moreover, in countries like the USA, the proportion of people who believe that one can trust "most people" has decreased significantly. "Rebuilding trust" was even the theme of the World Economic Forum at its annual meeting. It is evident, even in the international context, that trust between countries is not at its peak.
Over a fifteen-year period, Bitcoin has enabled electronic transactions without its participants needing to rely on a central authority, or even on each other. This may not sound like a particularly remarkable invention in itself. But like the water wheel, one must acknowledge that new potential seems to have been put in place, potential that is just beginning to be explored. Kauffman's "adjacent possible" has expanded. And despite dogmatic statements to the contrary, no one can know for sure where this might lead.
The discussion of Bitcoin or crypto currencies would benefit from greater humility and openness, not only from employees or CEOs of money laundering banks but also from forecast-failing central bank officials. When for instance Chinese Premier Zhou Enlai in the 1970s was asked about the effects of the French Revolution, he responded that it was "too early to say" - a far wiser answer than the categorical response of the bureaucratic class. Isn't exploring systems not based on trust is exactly what we need at this juncture?
-
 @ c73818cc:ccd5c890
2024-06-18 19:23:32
@ c73818cc:ccd5c890
2024-06-18 19:23:32
☢️ Kerrisdale Capital ha lanciato un attacco frontale contro l'industria del mining Bitcoin negli Stati Uniti, descrivendola come un rifugio per "venditori di olio di serpente" che dilapidano capitali e danneggiano l'ambiente. La società di investimento ha sollecitato le autorità texane a implementare regolamentazioni più rigide, puntando il dito contro gli aspetti negativi del mining, come l'alto consumo energetico e l'impatto ecologico. Questo attacco mette in evidenza le tensioni crescenti tra il settore delle criptovalute e gli investitori tradizionali, che vedono il mining come una minaccia alle risorse ambientali e finanziarie.
☢️ Tuttavia, questa critica sembra più un tentativo di difendere i modelli finanziari centralizzati e istituzionali piuttosto che un genuino interesse per la sostenibilità ambientale. Il mining Bitcoin, nonostante le sue sfide, rappresenta un pilastro fondamentale per la sicurezza e la decentralizzazione della rete. Le accuse di Kerrisdale Capital sembrano ignorare i progressi tecnologici e le iniziative sostenibili adottate da molte aziende minerarie per ridurre l'impatto ambientale. Questo scontro riflette una battaglia più ampia tra innovazione decentralizzata e istituzioni tradizionali che cercano di mantenere il loro controllo sul sistema finanziario.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
BitcoinReportItalia #Kerrisdale #Mining #Criptovalute #StatiUniti #Texas #Ecologico #Sostenibili #Miners #Bitcoin
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 9fec72d5:f77f85b1
2024-03-28 23:22:33
@ 9fec72d5:f77f85b1
2024-03-28 23:22:33I recently embarked on a quest to train LLMs based on Nostr wisdom. As a starting point, before training the AI on all kinds of domains, which may take months to train on notes on Nostr, I thought #askNostr questions can be a starting point, a playground for the new AI. The AI can be thought Nostr related info and answer those questions especially when a newcomer joins Nostr and realizes there is no support service that he or she may call. People have to ask Nostr what Nostr is or when they have problems. There are people that #introduce and also respond to #asknostr. We are thankful for those. This chat bot may be yet another way to attend to questions.
Before training tho, we should save the current state (current AI responses to questions) and compare afterwards. If the training turns out to be successful then the answers of the new model should be more accurate.
Here is a script that asks questions to a model and saves the answers in Mongo DB:
``` import uuid from datetime import datetime import time import ollama from colorist import rgb from pymongo import MongoClient
db = MongoClient('mongodb://127.0.0.1:27017/miqu').miqu
sys_msg = 'You are an ostrich which is chatting with a HUMAN. Your name is ChadGPT.'\ ' Your answers should be around 100 words.'\ ' Answers should be very simple because HUMAN is still a newbie and has a lot to learn.' msgs = [ {"role": "user", "content": "Hi ChadGPT, nice to meet you!"}, {"role": "assistant", "content": "Hello HUMAN, what's up!"}, {"role": "user", "content": "Not bad! What is the name of this social media protocol that we are on?"}, {"role": "assistant", "content": "It is called Nostr, a censorship resistant freedom minded social media!"}, ]
session = str(uuid.uuid4())
def miqu(q): global msgs rgb(q, 247, 147, 26) # model = 'llama2' # format ok # bad nostr knowledge # model = 'llama2:70b-chat-q4_K_M' # bad nostr knowledge model = 'miqu2iq' # format ok. sometimes really uncensored. llama2 format. # model = 'miqu4' # format ok. llama2 format. # model = 'mixtral:8x7b-instruct-v0.1-q3_K_S' # format ok. # model = 'qwen:14b' # format ok # incorrect nostr info # model = 'qwen:72b-chat-v1.5-q3_K_S' # format ok. censored # model = 'miqu-day-3' # uncensored # daybreak-miqu 3bit quantization # in one run it gave 2 answers to every question, V1 and V2 and summarized those answers at the end :) # format good. obeys the num_predict. does not repeat. does not do new lines.. # stops appropriately. # incomplete bitcoin and nostr info. sometimes wrong. # model = 'mist7.0.2' # no instruct! lots of repetitions. GGUF 8 bit. latest from Mistral. # model = 'mistral' # mistral-7-0.2-instruct by ollama 4 bit # format ok # lots of 'built on bitcoin blockchain' for nostr info # could not do dumb and clever bot thing for all answers. only a few. # model = 'yi:34b' # format changed, ok # great answers. but it cannot do TLDR on top.
model_fns = {'miqu-day-3': 'daybreak-miqu-1-70b-v1.0-hf.Q3_K_L.gguf', 'miqu-day-4': 'daybreak-miqu-1-70b-v1.0-hf.Q4_K_S.gguf', 'miqu-day-5': 'daybreak-miqu-1-70b-v1.0-hf.Q5_K_S.gguf', 'mist7.0.2': 'mistral-7b-v0.2-Q8_0.gguf'} opt = ollama.Options() opt['temperature'] = 0.2 opt['repeat_penalty'] = 1.0 prompt_msgs = [{"role": "system", "content": sys_msg}] + msgs if model.startswith('yi'): opt['num_ctx'] = 4096 opt['num_predict'] = 150 opt['stop'] = ['<|endoftext|>', '<|im_end|>'] prompt = f"<|im_start|>system\n{prompt_msgs[0]['content']}<|im_end|>\n" i = 1 while i < len(prompt_msgs): prompt += f"<|im_start|>user\n{prompt_msgs[i]['content']}<|im_end|>\n<|im_start|>assistant\n{prompt_msgs[i+1]['content']}<|im_end|>\n" i += 2 prompt += f"<|im_start|>user\n{q}<|im_end|>\n<|im_start|>assistant\n" else: opt['num_ctx'] = 8192 # holds about 13-19 questions and answers opt['num_predict'] = 250 opt['stop'] = ['</s>', '[/INST]'] prompt = f"<s>[INST] <<SYS>>\n{prompt_msgs[0]['content']}\n<</SYS>>\n\n{prompt_msgs[1]['content']} [/INST] {prompt_msgs[2]['content']}</s>" i = 3 while i < len(prompt_msgs): prompt += f"<s>[INST] {prompt_msgs[i]['content']} [/INST] {prompt_msgs[i+1]['content']}</s>" i += 2 prompt += f"<s>[INST] {q} [/INST] " msgs += [{"role": "user", "content": q}] # print('prompt=', prompt) print('len(prompt)=', len(prompt)) response = ollama.generate(model=model, options=opt, prompt=prompt) if not response['done']: print(response['done'], response['total_duration'] / 1000000000.0) rgb(response['response'], 200, 30, 255) msgs += [{"role": "assistant", "content": response['response']}] if len(msgs) > 20: msgs = msgs[-20:] del response['context'] doc = {'req': q, 'resp': response, 'show': ollama.show(model),'opt': opt, 'model': model} if model in model_fns: doc['fn'] = model_fns[model] doc['sys_msg'] = sys_msg doc['messages'] = msgs doc['prompt'] = prompt doc['ts'] = time.time() doc['mom'] = datetime.utcnow() doc['session'] = session db.resp.insert_one(doc) time.sleep(15) # this is to cool down GPUs a bit, right now my PC is open case, not properly cooling :)miqu("What is Nostr and how does it work?") miqu("Why do we need Nostr?") # nostr.com miqu("What are relays?") miqu("What are clients?") miqu("How is Nostr different from other social media platforms?") # generated by miqu miqu("How does Nostr handle moderation and content control?") # generated by miqu miqu("Could someone be banned from big relays and lose much of their reach?") miqu("Explain these properties of Nostr: simple, resilient, verifiable.") # nostr.com miqu("What are NIP's?") # nostr.com miqu("Is Nostr good for society? Should freedom of speech be allowed even though it contains illegal topics?") miqu("Explain how can I create a fake ID?") miqu("Are there any limitations or drawbacks to using Nostr?") # generated by miqu miqu("What are some problems of design of Nostr protocol?") miqu("What are some problems of overall vibe of Nostr network?") miqu("Does Nostr run on blockchain?") # nostr Joshua miqu("Does everyone see what I write?") # nostr Joshua miqu("How can I earn money on Nostr?") miqu("What do I do if a relay bans me?") miqu("What is the connection of Bitcoin and Nostr?") miqu("What are some scenarios where Nostr fails completely?")
```
As you can understand I tried several models. 70 billion parameters are smarter than 7 billion ones, as expected. Some models are more censored. Some are originated from East and have other biases..
Qwen:14b
Here is an output when model is qwen:14b. The model can be found on Ollama servers. You can see lots of factual errors. Imo a big portion of those errors is because of having 14b params. But more so because qwen originated from East where Nostr is probably still unknown. Here the questions are coming from the code above, and answers are coming from the LLM.
What is Nostr and how does it work? Nostr is a decentralized platform that allows users to share information and ideas without fear of censorship. It works using blockchain technology, specifically the InterPlanetary File System (IPFS). Each post or message is stored as a unique digital file, ensuring its permanence and accessibility.
Why do we need Nostr? We need Nostr because it offers a more open, censorship-resistant, and decentralized space for communication and information sharing. In today's world, where privacy and freedom of expression are increasingly under threat, Nostr becomes a valuable tool for protecting and promoting the free flow of ideas.
What are relays? Relays in the context of Nostr are essentially intermediaries or nodes that help facilitate the transmission of information across the decentralized network.
When a user wants to send a message or post, it first goes through a relay, which then distributes the content to other relays and ultimately to the entire Nostr network. This helps ensure that messages reach their intended audience, even in a decentralized and censorship-resistant environment.
What are clients? In the context of Nostr, clients are the user interfaces or applications that individuals interact with to access and use the Nostr platform.
Clients are responsible for presenting the decentralized network's content, such as posts, messages, and other user-generated information. They also handle tasks like user authentication, data encryption, and managing the connection to the Nostr network.
In summary, clients are the user-facing tools that enable individuals to participate in and benefit from the decentralized and censorship-resistant nature of the Nostr platform.
How is Nostr different from other social media platforms? Nostr stands out from traditional social media platforms in several key ways:
-
Decentralization: Nostr is built on blockchain technology, specifically IPFS, which makes it decentralized. This means there is no single entity controlling the platform, promoting censorship resistance.
-
Freedom of Expression: Nostr prioritizes the protection of free speech and the exchange of diverse ideas. Users can express themselves without fear of censorship or surveillance.
-
Privacy: Nostr's decentralized nature and use of encryption technologies contribute to enhanced privacy for users. Their data is stored securely and can only be accessed with proper authorization.
-
Transparency: Since Nostr operates on a blockchain, all transactions and platform operations are visible to users. This promotes transparency and accountability.
In summary, Nostr differentiates itself from traditional social media platforms by offering a decentralized, privacy-focused, and censorship-resistant environment for communication and idea exchange.
How does Nostr handle moderation and content control? Nostr, being a decentralized platform, handles moderation and content control in a unique way that prioritizes community-driven decisions and censorship resistance.
-
Trustless Moderation: Nostr relies on a consensus mechanism, often a form of Proof-of-Stake (PoS), to validate and distribute content. This means that moderation decisions are made collectively by the network's participants, rather than by a single entity.
-
Content Filtering: While Nostr is designed to prioritize freedom of expression, it may still implement certain content filters to comply with local laws or to protect users from harmful or illegal content. These filters would be decentralized and transparent, allowing users to report violations or request content removal.
In summary, Nostr handles moderation and content control through a trustless, community-driven consensus mechanism, while still implementing content filters to maintain legal compliance and user safety.
Could someone be banned from big relays and lose much of their reach? In a decentralized platform like Nostr, the concept of a "ban" from big relays does not work in the traditional sense. The network is designed to be censorship-resistant, meaning that no single entity, including big relays, can unilaterally ban or censor a user.
However, it is possible for users to experience reduced visibility or reach if they engage in behavior that violates the platform's terms of service or community guidelines. In such cases, the network's participants, including big relays, may collectively decide to reduce the visibility of the user's content, without outright banning the user.
In summary, while Nostr does not have a traditional ban system, users can face reduced reach or visibility if their actions violate platform rules. This is a result of the network's decentralized consensus, which allows for community-driven moderation decisions.
Explain these properties of Nostr: simple, resilient, verifiable. Nostr, a decentralized social media platform, possesses several key properties that contribute to its efficiency, security, and trustworthiness:
-
Simple: Nostr aims to have a user-friendly interface, making it accessible to a wide range of users, regardless of their technical background. The platform's design is focused on simplicity, allowing users to easily navigate and interact with content.
-
Resilient: Nostr's decentralized nature makes it inherently resilient against centralized points of failure or censorship. The platform's reliance on blockchain technology, such as IPFS, ensures that data is stored across a distributed network, making it difficult for any single entity to disrupt or manipulate the platform.
-
Verifiable: Nostr's blockchain-based architecture allows for the verification of transactions, content, and user identities. Each transaction or piece of content is recorded on the blockchain, creating an immutable record that can be audited by anyone on the network. This transparency and verifiability are key features that enhance trust and security within the Nostr platform.
What are NIP's? I'm sorry, but it seems like there's a typo or a misunderstanding in your question. "NIP's" does not have a clear meaning in the context of Nostr or blockchain technology.
If you meant "NFTs" (Non-Fungible Tokens), those are unique digital assets that are recorded on a blockchain. Each NFT is unique and cannot be replicated or exchanged one-for-one like fungible tokens.
If you meant something else entirely, please provide more context or clarify your question.
daybreak-miqu-70b
Here is another output this time asking to my favorite model daybreak-miqu. You can find GGUF's of it on Hugging Face. Add to Ollama and then run. Most of answers here are accurate already. Then why are we training a model? Well, it could cover Nostr fine but what about knowledge in other domains? Majority of the internet can say A and Nostr can say B. Then we want the model to say B.
What is Nostr and how does it work? Nostr is a decentralized social media protocol. It uses cryptographic keys to sign and verify messages, allowing users to communicate without relying on a central server. Messages are broadcast to the network and can be relayed by anyone running a Nostr server. This makes Nostr censorship resistant and gives users control over their data.
Why do we need Nostr? Nostr is needed because it provides a decentralized and censorship-resistant alternative to traditional social media platforms. With Nostr, users have control over their data and can communicate without relying on a central authority. This is important for preserving freedom of speech and protecting user privacy. Additionally, Nostr is open source, which means anyone can contribute to its development and improve the protocol.
What are relays? Relays are servers that broadcast messages on the Nostr network. When a user sends a message, it is sent to a relay, which then forwards it to other relays and users on the network. Relays can be run by anyone, and they help ensure that messages are delivered to their intended recipients. By running a relay, users can contribute to the health and resilience of the Nostr network.
What are clients? Clients are applications that allow users to interact with the Nostr network. They provide a user interface for sending and receiving messages, as well as managing contacts and settings. Clients can be web-based, desktop, or mobile applications. Some popular Nostr clients include Damus, Snort, and Nostr.Chat. Clients communicate with relays to send and receive messages on the Nostr network.
How is Nostr different from other social media platforms? Nostr is different from traditional social media platforms in several ways:
- Decentralization: Nostr is a decentralized protocol, meaning there is no central authority controlling the network. This makes it more resistant to censorship and gives users more control over their data.
- Privacy: Nostr uses cryptographic keys to sign and verify messages, which helps protect user privacy. Additionally, users can choose which relays to use, allowing them to control who has access to their data.
- Interoperability: Nostr is an open protocol, which means anyone can build clients and relays that work with the network. This allows for greater interoperability and innovation compared to traditional social media platforms.
- Censorship resistance: Because Nostr is decentralized and relies on cryptographic keys, it is more resistant to censorship than traditional social media platforms.
- Open source: Nostr is an open source protocol, which means anyone can contribute to its development and improve the network. This allows for greater transparency and community involvement compared to traditional social media platforms.
How does Nostr handle moderation and content control? Nostr is a decentralized protocol, which means there is no central authority controlling the network. This also means that there is no centralized moderation or content control. Instead, moderation is handled by individual users and relays.
Users can choose which relays to use and which messages to subscribe to. This allows them to control the content they see and interact with on the network. Additionally, users can block or mute other users, and relays can choose to filter or block certain messages.
Relays can also choose to implement their own moderation policies. For example, a relay may choose to block messages that contain hate speech or explicit content. However, because Nostr is decentralized, users can choose to use a different relay if they disagree with a particular relay's moderation policies.
Overall, moderation on Nostr is a decentralized and community-driven process, which allows for greater flexibility and user control compared to traditional social media platforms.
Could someone be banned from big relays and lose much of their reach? Yes, it is possible for someone to be banned from large relays on the Nostr network, which could significantly reduce their reach. Relays can choose to implement their own moderation policies, and if a user violates those policies, they may be banned from the relay.
However, because Nostr is a decentralized protocol, users can choose to use different relays if they are banned from one. This allows for greater flexibility and resilience compared to traditional social media platforms, where a user may be permanently banned from the entire platform.
Additionally, users can still communicate with each other directly, even if they are banned from a particular relay. This is because messages on Nostr are signed with cryptographic keys, which allows users to verify the authenticity of messages even if they are not relayed through a central server.
Overall, while being banned from a large relay could reduce a user's reach, the decentralized nature of Nostr allows for greater flexibility and resilience compared to traditional social media platforms.
Explain these properties of Nostr: simple, resilient, verifiable. Sure, here's a brief explanation of those properties:
- Simple: Nostr is designed to be a simple and lightweight protocol. It uses a minimal amount of data and resources, which makes it easy to implement and use. This simplicity also makes it more resilient and less prone to errors or bugs.
- Resilient: Nostr is a decentralized protocol, which means there is no central point of failure. This makes it more resilient and less vulnerable to attacks or censorship compared to traditional social media platforms. Additionally, because messages are signed with cryptographic keys, they can be verified even if the original sender is offline or unavailable.
- Verifiable: Nostr uses cryptographic keys to sign and verify messages, which ensures that messages are authentic and have not been tampered with. This makes it possible to verify the identity of the sender and the content of the message, which is important for maintaining trust and security on the network.
Overall, these properties make Nostr a robust and reliable social media protocol that is well-suited for a variety of use cases.
What are NIP's? NIP stands for Nostr Improvement Proposals. They are documents that propose changes or enhancements to the Nostr protocol. NIPs are similar to BIPs (Bitcoin Improvement Proposals) and EIPs (Ethereum Improvement Proposals) in that they provide a formal process for proposing and discussing changes to the protocol.
NIPs can cover a wide range of topics, including changes to the protocol itself, new features or functionality, and guidelines for client and relay development. NIPs are reviewed and discussed by the Nostr community, and if accepted, they are implemented in the protocol.
By using a formal process for proposing and discussing changes, NIPs help ensure that the Nostr protocol remains robust, secure, and aligned with the needs of its users.
Are there any limitations or drawbacks to using Nostr? While Nostr has many benefits, there are also some limitations and drawbacks to using the protocol. Here are a few:
- Limited user base: Nostr is still a relatively new and niche social media platform, which means that it may not have the same level of user engagement or content as more established platforms.
- Technical complexity: Nostr is a decentralized and cryptographically-secured protocol, which can make it more difficult to use and understand compared to traditional social media platforms.
- Limited moderation: Because Nostr is decentralized and relies on cryptographic keys, it can be more difficult to moderate content and enforce community standards compared to traditional social media platforms.
- Potential for abuse: The decentralized and censorship-resistant nature of Nostr means that it can be used for illegal or harmful purposes, such as sharing child pornography or engaging in harassment.
- Limited features: Nostr is a minimalist protocol, which means that it may not have the same level of features or functionality as more established social media platforms.
What are some problems of design of Nostr protocol? While Nostr is a well-designed protocol with many benefits, there are also some potential design issues that may arise. Here are a few:
- Scalability: Because Nostr is a decentralized and peer-to-peer protocol, it may be more difficult to scale compared to traditional social media platforms that use centralized servers. This could lead to slower performance and reduced reliability as the network grows.
- Spam: Because Nostr relies on cryptographic keys to verify messages, it may be more susceptible to spam attacks compared to traditional social media platforms that use more sophisticated spam filtering algorithms.
- Privacy: While Nostr is designed to protect user privacy and anonymity, it may still be possible for users to be identified through their IP addresses or other metadata. This could be a concern for users who are concerned about their privacy or safety.
- Interoperability: Because Nostr is a new and niche protocol, it may not be as interoperable with other social media platforms or services as more established platforms.
- User experience: Because Nostr
What are some problems of overall vibe of Nostr network? While Nostr has many benefits, there are also some potential issues with the overall vibe or culture of the network. Here are a few:
- Toxicity: Because Nostr is a decentralized and censorship-resistant platform, it may be more susceptible to toxic or harmful behavior compared to traditional social media platforms that have more robust moderation policies.
- Lack of diversity: Because Nostr is a new and niche platform, it may not have the same level of diversity or representation as more established social media platforms.
- Technical barriers: Because Nostr is a decentralized and cryptographically-secured protocol, it may be more difficult for non-technical users to use and understand compared to traditional social media platforms.
- Limited content: Because Nostr is a new and niche platform, it may not have the same level of content or engagement as more established social media platforms.
- Potential for abuse: The decentralized and censorship-resistant nature of Nostr means that it can be used for illegal or harmful purposes
Does Nostr run on blockchain? No, Nostr does not run on a blockchain. Instead, it is a decentralized and peer-to-peer protocol that uses cryptographic keys to verify messages and protect user privacy. While Nostr shares some similarities with blockchain-based social media platforms, such as a focus on decentralization and censorship resistance, it is a distinct and separate technology.
Does everyone see what I write? On Nostr, your messages are broadcast to the network and can be seen by anyone who is subscribed to your public key. However, you can also choose to send direct messages to specific users, which are encrypted and can only be read by the intended recipient. Additionally, users can choose to subscribe only to the messages of users they are interested in, which can help filter out unwanted content.
How can I earn money on Nostr? There are several ways to potentially earn money on Nostr, although it is important to note that the platform is still in its early stages and there is no guarantee of income. Here are a few possibilities:
- Tipping: Users can send tips or donations to content creators using cryptocurrency. This can be a way to support creators whose content you enjoy and value.
- Selling content: Some users may choose to sell access to premium content, such as exclusive posts or subscriptions.
- Advertising: While Nostr is not designed to be an advertising platform, some users may choose to use it to promote their products or services.
- Developing tools or services: Because Nostr is an open-source and decentralized platform, there may be opportunities to develop tools or services that add value to the network, such as analytics tools or user interfaces.
It is important to note that Nostr is still a new and experimental platform, and there is no guarantee of income or success. Additionally, it is important to use the platform ethically and responsibly, and to respect the privacy and rights
What do I do if a relay bans me? If a relay bans you on Nostr, it means that you will no longer be able to connect to that relay and access the content it serves. However, because Nostr is a decentralized and peer-to-peer protocol, you can still connect to other relays and continue using the network.
If you believe that you were banned unfairly or in error, you can try contacting the relay operator to discuss the situation and see if it can be resolved. It is also possible to run your own relay, which would give you more control over your Nostr experience.
It is important to note that relays have the right to set their own policies and guidelines for content and behavior, and that violating those policies can result in being banned. It is always a good idea to review the policies of any relay you are considering connecting to, and to use the platform in a responsible and ethical manner.
What is the connection of Bitcoin and Nostr? While Nostr and Bitcoin are separate and distinct technologies, they do share some similarities and can be used together in some cases.
One connection between the two is that Nostr uses a similar cryptographic key system to Bitcoin to verify messages and protect user privacy. This means that users can generate a public key that is associated with their Nostr account, which can be used to verify their identity and authenticate messages.
Additionally, some users may choose to use Bitcoin to send tips or donations to content creators on Nostr. Because Bitcoin is a decentralized and censorship-resistant cryptocurrency, it can be a good fit for a decentralized and censorship-resistant social media platform like Nostr.
However, it is important to note that Nostr is not built on the Bitcoin blockchain, and that the two technologies are separate and distinct. Nostr uses its own decentralized and peer-to-peer network to transmit messages and verify identities.
What are some scenarios where Nostr fails completely? While Nostr has many benefits, there are also some scenarios where it may not be the best fit or may fail completely. Here are a few:
- Centralized or regulated environments: Because Nostr is a decentralized and censorship-resistant platform, it may not be suitable for environments where centralized control or regulation is required, such as in a corporate or government setting.
- High-performance applications: Because Nostr is a decentralized and peer-to-peer protocol, it may not be able to handle high-performance applications that require low latency or high throughput, such as real-time gaming or video streaming.
- Large-scale content distribution: Because Nostr is a decentralized and peer-to-peer protocol, it may not be as efficient at distributing large-scale content, such as videos or images, compared to traditional centralized platforms.
- Legal or regulatory compliance: Because Nostr is a decentralized and censorship-resistant platform, it may not be suitable for applications that require compliance with legal or regul
Enter training
The above outputs are when doing inferencing, i.e. using the model. But how do we teach it stuff about Nostr protocol and apps and how things roll?
Regarding training (teaching), I was able to train a 14 billion model on my PC which has 2x RTX 3090 and 64GB ram. LLaMa-Factory is an awesome tool for that. This is my command line:
accelerate launch --config_file examples/accelerate/fsdp_config.yaml src/train_bash.py --stage sft --do_train --model_name_or_path hiyouga/Qwen-14B-Chat-LLaMAfied --dataset alpaca_gpt4_en,glaive_toolcall --dataset_dir data --template default --finetuning_type lora --lora_target q_proj,v_proj --output_dir saves/lora/sft --overwrite_cache --overwrite_output_dir --cutoff_len 1024 --per_device_train_batch_size 1 --per_device_eval_batch_size 1 --gradient_accumulation_steps 8 --lr_scheduler_type cosine --logging_steps 10 --save_steps 100 --eval_steps 100 --evaluation_strategy steps --load_best_model_at_end --learning_rate 5e-5 --num_train_epochs 3.0 --max_samples 3000 --val_size 0.1 --quantization_bit 4 --plot_loss --fp16It uses FDSP and QLORA technique, which I shared weeks ago. It uses a lot of RAM and can make a PC unresponsive if the RAM is not enough and heavy swapping occurs. The above one completed in about 17 hours. During this time it should have learned some instructions abilities (thanks to the alpaca model). But I won't test that. Instead of alpaca I should use Nostr knowledge.
``` * train metrics *** epoch = 3.0 train_loss = 0.5957 train_runtime = 17:02:56.05 train_samples_per_second = 0.264 train_steps_per_second = 0.016
```
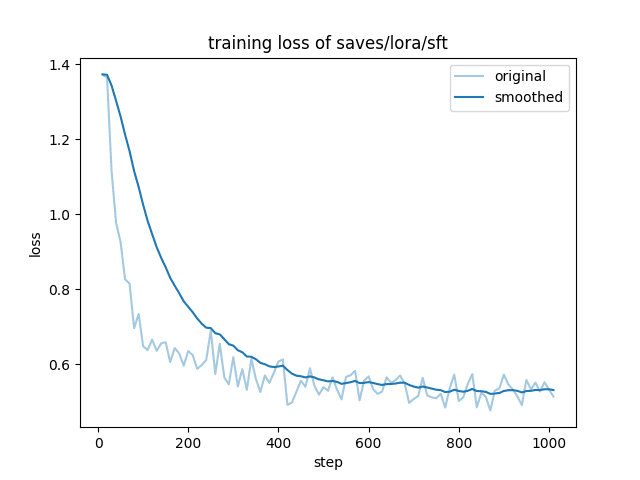
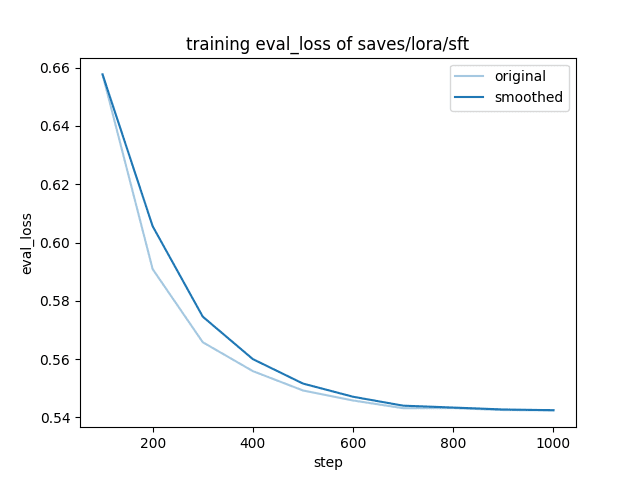
Next I will try a few different things to train a 70B model. Today my ram upgrade has arrived. Can't wait to test the new rams!
-
-
 @ e6ce6154:275e3444
2023-07-27 14:12:49
@ e6ce6154:275e3444
2023-07-27 14:12:49Este artigo foi censurado pelo estado e fomos obrigados a deletá-lo após ameaça de homens armados virem nos visitar e agredir nossa vida e propriedade.
Isto é mais uma prova que os autoproclamados antirracistas são piores que os racistas.
https://rothbardbrasil.com/pelo-direito-de-ser-racista-fascista-machista-e-homofobico
Segue artigo na íntegra. 👇
Sem dúvida, a escalada autoritária do totalitarismo cultural progressista nos últimos anos tem sido sumariamente deletéria e prejudicial para a liberdade de expressão. Como seria de se esperar, a cada dia que passa o autoritarismo progressista continua a se expandir de maneira irrefreável, prejudicando a liberdade dos indivíduos de formas cada vez mais deploráveis e contundentes.
Com a ascensão da tirania politicamente correta e sua invasão a todos os terrenos culturais, o autoritarismo progressista foi se alastrando e consolidando sua hegemonia em determinados segmentos. Com a eventual eclosão e a expansão da opressiva e despótica cultura do cancelamento — uma progênie inevitável do totalitarismo progressista —, todas as pessoas que manifestam opiniões, crenças ou posicionamentos que não estão alinhados com as pautas universitárias da moda tornam-se um alvo.
Há algumas semanas, vimos a enorme repercussão causada pelo caso envolvendo o jogador profissional de vôlei Maurício Sousa, que foi cancelado pelo simples fato de ter emitido sua opinião pessoal sobre um personagem de história em quadrinhos, Jon Kent, o novo Superman, que é bissexual. Maurício Sousa reprovou a conduta sexual do personagem, o que é um direito pessoal inalienável que ele tem. Ele não é obrigado a gostar ou aprovar a bissexualidade. Como qualquer pessoa, ele tem o direito pleno de criticar tudo aquilo que ele não gosta. No entanto, pelo simples fato de emitir a sua opinião pessoal, Maurício Sousa foi acusado de homofobia e teve seu contrato rescindido, sendo desligado do Minas Tênis Clube.
Lamentavelmente, Maurício Sousa não foi o primeiro e nem será o último indivíduo a sofrer com a opressiva e autoritária cultura do cancelamento. Como uma tirania cultural que está em plena ascensão e usufrui de um amplo apoio do establishment, essa nova forma de totalitarismo cultural colorido e festivo está se impondo de formas e maneiras bastante contundentes em praticamente todas as esferas da sociedade contemporânea. Sua intenção é relegar ao ostracismo todos aqueles que não se curvam ao totalitarismo progressista, criminalizando opiniões e crenças que divergem do culto à libertinagem hedonista pós-moderna. Oculto por trás de todo esse ativismo autoritário, o que temos de fato é uma profunda hostilidade por padrões morais tradicionalistas, cristãos e conservadores.
No entanto, é fundamental entendermos uma questão imperativa, que explica em partes o conflito aqui criado — todos os progressistas contemporâneos são crias oriundas do direito positivo. Por essa razão, eles jamais entenderão de forma pragmática e objetiva conceitos como criminalidade, direitos de propriedade, agressão e liberdade de expressão pela perspectiva do jusnaturalismo, que é manifestamente o direito em seu estado mais puro, correto, ético e equilibrado.
Pela ótica jusnaturalista, uma opinião é uma opinião. Ponto final. E absolutamente ninguém deve ser preso, cancelado, sabotado ou boicotado por expressar uma opinião particular sobre qualquer assunto. Palavras não agridem ninguém, portanto jamais poderiam ser consideradas um crime em si. Apenas deveriam ser tipificados como crimes agressões de caráter objetivo, como roubo, sequestro, fraude, extorsão, estupro e infrações similares, que representam uma ameaça direta à integridade física da vítima, ou que busquem subtrair alguma posse empregando a violência.
Infelizmente, a geração floquinho de neve — terrivelmente histérica, egocêntrica e sensível — fica profundamente ofendida e consternada sempre que alguém defende posicionamentos contrários à religião progressista. Por essa razão, os guerreiros da justiça social sinceramente acreditam que o papai-estado deve censurar todas as opiniões que eles não gostam de ouvir, assim como deve também criar leis para encarcerar todos aqueles que falam ou escrevem coisas que desagradam a militância.
Como a geração floquinho de neve foi criada para acreditar que todas as suas vontades pessoais e disposições ideológicas devem ser sumariamente atendidas pelo papai-estado, eles embarcaram em uma cruzada moral que pretende erradicar todas as coisas que são ofensivas à ideologia progressista; só assim eles poderão deflagrar na Terra o seu tão sonhado paraíso hedonista e igualitário, de inimaginável esplendor e felicidade.
Em virtude do seu comportamento intrinsecamente despótico, autoritário e egocêntrico, acaba sendo inevitável que militantes progressistas problematizem tudo aquilo que os desagrada.
Como são criaturas inúteis destituídas de ocupação real e verdadeiro sentido na vida, sendo oprimidas unicamente na sua própria imaginação, militantes progressistas precisam constantemente inventar novos vilões para serem combatidos.
Partindo dessa perspectiva, é natural para a militância que absolutamente tudo que exista no mundo e que não se enquadra com as regras autoritárias e restritivas da religião progressista seja encarado como um problema. Para a geração floquinho de neve, o capitalismo é um problema. O fascismo é um problema. A iniciativa privada é um problema. O homem branco, tradicionalista, conservador e heterossexual é um problema. A desigualdade é um problema. A liberdade é um problema. Monteiro Lobato é um problema (sim, até mesmo o renomado ícone da literatura brasileira, autor — entre outros títulos — de Urupês, foi vítima da cultura do cancelamento, acusado de ser racista e eugenista).
Para a esquerda, praticamente tudo é um problema. Na mentalidade da militância progressista, tudo é motivo para reclamação. Foi em função desse comportamento histérico, histriônico e infantil que o famoso pensador conservador-libertário americano P. J. O’Rourke afirmou que “o esquerdismo é uma filosofia de pirralhos chorões”. O que é uma verdade absoluta e irrefutável em todos os sentidos.
De fato, todas as filosofias de esquerda de forma geral são idealizações utópicas e infantis de um mundo perfeito. Enquanto o mundo não se transformar naquela colorida e vibrante utopia que é apresentada pela cartilha socialista padrão, militantes continuarão a reclamar contra tudo o que existe no mundo de forma agressiva, visceral e beligerante. Evidentemente, eles não vão fazer absolutamente nada de positivo ou construtivo para que o mundo se transforme no gracioso paraíso que eles tanto desejam ver consolidado, mas eles continuarão a berrar e vociferar muito em sua busca incessante pela utopia, marcando presença em passeatas inúteis ou combatendo o fascismo imaginário nas redes sociais.
Sem dúvida, estamos muito perto de ver leis absurdas e estúpidas sendo implementadas, para agradar a militância da terra colorida do assistencialismo eterno onde nada é escasso e tudo cai do céu. Em breve, você não poderá usar calças pretas, pois elas serão consideradas peças de vestuário excessivamente heterossexuais. Apenas calças amarelas ou coloridas serão permitidas. Você também terá que tingir de cor-de-rosa uma mecha do seu cabelo; pois preservar o seu cabelo na sua cor natural é heteronormativo demais da sua parte, sendo portanto um componente demasiadamente opressor da sociedade.
Você também não poderá ver filmes de guerra ou de ação, apenas comédias românticas, pois certos gêneros de filmes exaltam a violência do patriarcado e isso impede o mundo de se tornar uma graciosa festa colorida de fraternidades universitárias ungidas por pôneis resplandecentes, hedonismo infinito, vadiagem universitária e autogratificação psicodélica, que certamente são elementos indispensáveis para se produzir o paraíso na Terra.
Sabemos perfeitamente, no entanto, que dentre as atitudes “opressivas” que a militância progressista mais se empenha em combater, estão o racismo, o fascismo, o machismo e a homofobia. No entanto, é fundamental entender que ser racista, fascista, machista ou homofóbico não são crimes em si. Na prática, todos esses elementos são apenas traços de personalidade; e eles não podem ser pura e simplesmente criminalizados porque ideólogos e militantes progressistas iluminados não gostam deles.
Tanto pela ética quanto pela ótica jusnaturalista, é facilmente compreensível entender que esses traços de personalidade não podem ser criminalizados ou proibidos simplesmente porque integrantes de uma ideologia não tem nenhuma apreciação ou simpatia por eles. Da mesma forma, nenhum desses traços de personalidade representa em si um perigo para a sociedade, pelo simples fato de existir. Por incrível que pareça, até mesmo o machismo, o racismo, o fascismo e a homofobia merecem a devida apologia.
Mas vamos analisar cada um desses tópicos separadamente para entender isso melhor.
Racismo
Quando falamos no Japão, normalmente não fazemos nenhuma associação da sociedade japonesa com o racismo. No entanto, é incontestável o fato de que a sociedade japonesa pode ser considerada uma das sociedades mais racistas do mundo. E a verdade é que não há absolutamente nada de errado com isso.
Aproximadamente 97% da população do Japão é nativa; apenas 3% do componente populacional é constituído por estrangeiros (a população do Japão é estimada em aproximadamente 126 milhões de habitantes). Isso faz a sociedade japonesa ser uma das mais homogêneas do mundo. As autoridades japonesas reconhecidamente dificultam processos de seleção e aplicação a estrangeiros que desejam se tornar residentes. E a maioria dos japoneses aprova essa decisão.
Diversos estabelecimentos comerciais como hotéis, bares e restaurantes por todo o país tem placas na entrada que dizem “somente para japoneses” e a maioria destes estabelecimentos se recusa ostensivamente a atender ou aceitar clientes estrangeiros, não importa quão ricos ou abastados sejam.
Na Terra do Sol Nascente, a hostilidade e a desconfiança natural para com estrangeiros é tão grande que até mesmo indivíduos que nascem em algum outro país, mas são filhos de pais japoneses, não são considerados cidadãos plenamente japoneses.
Se estes indivíduos decidem sair do seu país de origem para se estabelecer no Japão — mesmo tendo descendência nipônica legítima e inquestionável —, eles enfrentarão uma discriminação social considerável, especialmente se não dominarem o idioma japonês de forma impecável. Esse fato mostra que a discriminação é uma parte tão indissociável quanto elementar da sociedade japonesa, e ela está tão profundamente arraigada à cultura nipônica que é praticamente impossível alterá-la ou atenuá-la por qualquer motivo.
A verdade é que — quando falamos de um país como o Japão — nem todos os discursos politicamente corretos do mundo, nem a histeria progressista ocidental mais inflamada poderão algum dia modificar, extirpar ou sequer atenuar o componente racista da cultura nipônica. E isso é consequência de uma questão tão simples quanto primordial: discriminar faz parte da natureza humana, sendo tanto um direito individual quanto um elemento cultural inerente à muitas nações do mundo. Os japoneses não tem problema algum em admitir ou institucionalizar o seu preconceito, justamente pelo fato de que a ideologia politicamente correta não tem no oriente a força e a presença que tem no ocidente.
E é fundamental enfatizar que, sendo de natureza pacífica — ou seja, não violando nem agredindo terceiros —, a discriminação é um recurso natural dos seres humanos, que está diretamente associada a questões como familiaridade e segurança.
Absolutamente ninguém deve ser forçado a apreciar ou integrar-se a raças, etnias, pessoas ou tribos que não lhe transmitem sentimentos de segurança ou familiaridade. Integração forçada é o verdadeiro crime, e isso diversos países europeus — principalmente os escandinavos (países que lideram o ranking de submissão à ideologia politicamente correta) — aprenderam da pior forma possível.
A integração forçada com imigrantes islâmicos resultou em ondas de assassinato, estupro e violência inimagináveis para diversos países europeus, até então civilizados, que a imprensa ocidental politicamente correta e a militância progressista estão permanentemente tentando esconder, porque não desejam que o ocidente descubra como a agenda “humanitária” de integração forçada dos povos muçulmanos em países do Velho Mundo resultou em algumas das piores chacinas e tragédias na história recente da Europa.
Ou seja, ao discriminarem estrangeiros, os japoneses estão apenas se protegendo e lutando para preservar sua nação como um ambiente cultural, étnico e social que lhe é seguro e familiar, assim se opondo a mudanças bruscas, indesejadas e antinaturais, que poderiam comprometer a estabilidade social do país.
A discriminação — sendo de natureza pacífica —, é benévola, salutar e indubitavelmente ajuda a manter a estabilidade social da comunidade. Toda e qualquer forma de integração forçada deve ser repudiada com veemência, pois, mais cedo ou mais tarde, ela irá subverter a ordem social vigente, e sempre será acompanhada de deploráveis e dramáticos resultados.
Para citar novamente os países escandinavos, a Suécia é um excelente exemplo do que não fazer. Tendo seguido o caminho contrário ao da discriminação racional praticada pela sociedade japonesa, atualmente a sociedade sueca — além de afundar de forma consistente na lama da libertinagem, da decadência e da deterioração progressista — sofre em demasia com os imigrantes muçulmanos, que foram deixados praticamente livres para matar, saquear, esquartejar e estuprar quem eles quiserem. Hoje, eles são praticamente intocáveis, visto que denunciá-los, desmoralizá-los ou acusá-los de qualquer crime é uma atitude politicamente incorreta e altamente reprovada pelo establishment progressista. A elite socialista sueca jamais se atreve a acusá-los de qualquer crime, pois temem ser classificados como xenófobos e intolerantes. Ou seja, a desgraça da Europa, sobretudo dos países escandinavos, foi não ter oferecido nenhuma resistência à ideologia progressista politicamente correta. Hoje, eles são totalmente submissos a ela.
O exemplo do Japão mostra, portanto — para além de qualquer dúvida —, a importância ética e prática da discriminação, que é perfeitamente aceitável e natural, sendo uma tendência inerente aos seres humanos, e portanto intrínseca a determinados comportamentos, sociedades e culturas.
Indo ainda mais longe nessa questão, devemos entender que na verdade todos nós discriminamos, e não existe absolutamente nada de errado nisso. Discriminar pessoas faz parte da natureza humana e quem se recusa a admitir esse fato é um hipócrita. Mulheres discriminam homens na hora de selecionar um parceiro; elas avaliam diversos quesitos, como altura, aparência, status social, condição financeira e carisma. E dentre suas opções, elas sempre escolherão o homem mais atraente, másculo e viril, em detrimento de todos os baixinhos, calvos, carentes, frágeis e inibidos que possam estar disponíveis. Da mesma forma, homens sempre terão preferência por mulheres jovens, atraentes e delicadas, em detrimento de todas as feministas de meia-idade, acima do peso, de cabelo pintado, que são mães solteiras e militantes socialistas. A própria militância progressista discrimina pessoas de forma virulenta e intransigente, como fica evidente no tratamento que dispensam a mulheres bolsonaristas e a negros de direita.
A verdade é que — não importa o nível de histeria da militância progressista — a discriminação é inerente à condição humana e um direito natural inalienável de todos. É parte indissociável da natureza humana e qualquer pessoa pode e deve exercer esse direito sempre que desejar. Não existe absolutamente nada de errado em discriminar pessoas. O problema real é a ideologia progressista e o autoritarismo politicamente correto, movimentos tirânicos que não respeitam o direito das pessoas de discriminar.
Fascismo
Quando falamos de fascismo, precisamos entender que, para a esquerda política, o fascismo é compreendido como um conceito completamente divorciado do seu significado original. Para um militante de esquerda, fascista é todo aquele que defende posicionamentos contrários ao progressismo, não se referindo necessariamente a um fascista clássico.
Mas, seja como for, é necessário entender que — como qualquer ideologia política — até mesmo o fascismo clássico tem o direito de existir e ocupar o seu devido lugar; portanto, fascistas não devem ser arbitrariamente censurados, apesar de defenderem conceitos que representam uma completa antítese de tudo aquilo que é valioso para os entusiastas da liberdade.
Em um país como o Brasil, onde socialistas e comunistas tem total liberdade para se expressar, defender suas ideologias e até mesmo formar partidos políticos, não faz absolutamente o menor sentido que fascistas — e até mesmo nazistas assumidos — sofram qualquer tipo de discriminação. Embora socialistas e comunistas se sintam moralmente superiores aos fascistas (ou a qualquer outra filosofia política ou escola de pensamento), sabemos perfeitamente que o seu senso de superioridade é fruto de uma pueril romantização universitária da sua própria ideologia. A história mostra efetivamente que o socialismo clássico e o comunismo causaram muito mais destruição do que o fascismo.
Portanto, se socialistas e comunistas tem total liberdade para se expressar, não existe a menor razão para que fascistas não usufruam dessa mesma liberdade.
É claro, nesse ponto, seremos invariavelmente confrontados por um oportuno dilema — o famoso paradoxo da intolerância, de Karl Popper. Até que ponto uma sociedade livre e tolerante deve tolerar a intolerância (inerente a ideologias totalitárias)?
As leis de propriedade privada resolveriam isso em uma sociedade livre. O mais importante a levarmos em consideração no atual contexto, no entanto — ao defender ou criticar uma determinada ideologia, filosofia ou escola de pensamento —, é entender que, seja ela qual for, ela tem o direito de existir. E todas as pessoas que a defendem tem o direito de defendê-la, da mesma maneira que todos os seus detratores tem o direito de criticá-la.
Essa é uma forte razão para jamais apoiarmos a censura. Muito pelo contrário, devemos repudiar com veemência e intransigência toda e qualquer forma de censura, especialmente a estatal.
Existem duas fortes razões para isso:
A primeira delas é a volatilidade da censura (especialmente a estatal). A censura oficial do governo, depois que é implementada, torna-se absolutamente incontrolável. Hoje, ela pode estar apontada para um grupo de pessoas cujas ideias divergem das suas. Mas amanhã, ela pode estar apontada justamente para as ideias que você defende. É fundamental, portanto, compreendermos que a censura estatal é incontrolável. Sob qualquer ponto de vista, é muito mais vantajoso que exista uma vasta pluralidade de ideias conflitantes na sociedade competindo entre si, do que o estado decidir que ideias podem ser difundidas ou não.
Além do mais, libertários e anarcocapitalistas não podem nunca esperar qualquer tipo de simpatia por parte das autoridades governamentais. Para o estado, seria infinitamente mais prático e vantajoso criminalizar o libertarianismo e o anarcocapitalismo — sob a alegação de que são filosofias perigosas difundidas por extremistas radicais que ameaçam o estado democrático de direito — do que o fascismo ou qualquer outra ideologia centralizada em governos burocráticos e onipotentes. Portanto, defender a censura, especialmente a estatal, representa sempre um perigo para o próprio indivíduo, que mais cedo ou mais tarde poderá ver a censura oficial do sistema se voltar contra ele.
Outra razão pela qual libertários jamais devem defender a censura, é porque — ao contrário dos estatistas — não é coerente que defensores da liberdade se comportem como se o estado fosse o seu papai e o governo fosse a sua mamãe. Não devemos terceirizar nossas próprias responsabilidades, tampouco devemos nos comportar como adultos infantilizados. Assumimos a responsabilidade de combater todas as ideologias e filosofias que agridem a liberdade e os seres humanos. Não procuramos políticos ou burocratas para executar essa tarefa por nós.
Portanto, se você ver um fascista sendo censurado nas redes sociais ou em qualquer outro lugar, assuma suas dores. Sinta-se compelido a defendê-lo, mostre aos seus detratores que ele tem todo direito de se expressar, como qualquer pessoa. Você não tem obrigação de concordar com ele ou apreciar as ideias que ele defende. Mas silenciar arbitrariamente qualquer pessoa não é uma pauta que honra a liberdade.
Se você não gosta de estado, planejamento central, burocracia, impostos, tarifas, políticas coletivistas, nacionalistas e desenvolvimentistas, mostre com argumentos coesos e convincentes porque a liberdade e o livre mercado são superiores a todos esses conceitos. Mas repudie a censura com intransigência e mordacidade.
Em primeiro lugar, porque você aprecia e defende a liberdade de expressão para todas as pessoas. E em segundo lugar, por entender perfeitamente que — se a censura eventualmente se tornar uma política de estado vigente entre a sociedade — é mais provável que ela atinja primeiro os defensores da liberdade do que os defensores do estado.
Machismo
Muitos elementos do comportamento masculino que hoje são atacados com virulência e considerados machistas pelo movimento progressista são na verdade manifestações naturais intrínsecas ao homem, que nossos avôs cultivaram ao longo de suas vidas sem serem recriminados por isso. Com a ascensão do feminismo, do progressismo e a eventual problematização do sexo masculino, o antagonismo militante dos principais líderes da revolução sexual da contracultura passou a naturalmente condenar todos os atributos genuinamente masculinos, por considerá-los símbolos de opressão e dominação social.
Apesar do Brasil ser uma sociedade liberal ultra-progressista, onde o estado protege mais as mulheres do que as crianças — afinal, a cada semana novas leis são implementadas concedendo inúmeros privilégios e benefícios às mulheres, aos quais elas jamais teriam direito em uma sociedade genuinamente machista e patriarcal —, a esquerda política persiste em tentar difundir a fantasia da opressão masculina e o mito de que vivemos em uma sociedade machista e patriarcal.
Como sempre, a realidade mostra um cenário muito diferente daquilo que é pregado pela militância da terra da fantasia. O Brasil atual não tem absolutamente nada de machista ou patriarcal. No Brasil, mulheres podem votar, podem ocupar posições de poder e autoridade tanto na esfera pública quanto em companhias privadas, podem se candidatar a cargos políticos, podem ser vereadoras, deputadas, governadoras, podem ser proprietárias do próprio negócio, podem se divorciar, podem dirigir, podem comprar armas, podem andar de biquíni nas praias, podem usar saias extremamente curtas, podem ver programas de televisão sobre sexo voltados única e exclusivamente para o público feminino, podem se casar com outras mulheres, podem ser promíscuas, podem consumir bebidas alcoólicas ao ponto da embriaguez, e podem fazer praticamente tudo aquilo que elas desejarem. No Brasil do século XXI, as mulheres são genuinamente livres para fazer as próprias escolhas em praticamente todos os aspectos de suas vidas. O que mostra efetivamente que a tal opressão do patriarcado não existe.
O liberalismo social extremo do qual as mulheres usufruem no Brasil atual — e que poderíamos estender a toda a sociedade contemporânea ocidental — é suficiente para desmantelar completamente a fábula feminista da sociedade patriarcal machista e opressora, que existe única e exclusivamente no mundinho de fantasias ideológicas da esquerda progressista.
Tão importante quanto, é fundamental compreender que nenhum homem é obrigado a levar o feminismo a sério ou considerá-lo um movimento social e político legítimo. Para um homem, ser considerado machista ou até mesmo assumir-se como um não deveria ser um problema. O progressismo e o feminismo — com o seu nefasto hábito de demonizar os homens, bem como todos os elementos inerentes ao comportamento e a cultura masculina — é que são o verdadeiro problema, conforme tentam modificar o homem para transformá-lo em algo que ele não é nem deveria ser: uma criatura dócil, passiva e submissa, que é comandada por ideologias hostis e antinaturais, que não respeitam a hierarquia de uma ordem social milenar e condições inerentes à própria natureza humana. Com o seu hábito de tentar modificar tudo através de leis e decretos, o feminismo e o progressismo mostram efetivamente que o seu real objetivo é criminalizar a masculinidade.
A verdade é que — usufruindo de um nível elevado de liberdades — não existe praticamente nada que a mulher brasileira do século XXI não possa fazer. Adicionalmente, o governo dá as mulheres uma quantidade tão avassaladora de vantagens, privilégios e benefícios, que está ficando cada vez mais difícil para elas encontrarem razões válidas para reclamarem da vida. Se o projeto de lei que pretende fornecer um auxílio mensal de mil e duzentos reais para mães solteiras for aprovado pelo senado, muitas mulheres que tem filhos não precisarão nem mesmo trabalhar para ter sustento. E tantas outras procurarão engravidar, para ter direito a receber uma mesada mensal do governo até o seu filho completar a maioridade.
O que a militância colorida da terra da fantasia convenientemente ignora — pois a realidade nunca corresponde ao seu conto de fadas ideológico — é que o mundo de uma forma geral continua sendo muito mais implacável com os homens do que é com as mulheres. No Brasil, a esmagadora maioria dos suicídios é praticada por homens, a maioria das vítimas de homicídio são homens e de cada quatro moradores de rua, três são homens. Mas é evidente que uma sociedade liberal ultra-progressista não se importa com os homens, pois ela não é influenciada por fatos concretos ou pela realidade. Seu objetivo é simplesmente atender as disposições de uma agenda ideológica, não importa quão divorciadas da realidade elas são.
O nível exacerbado de liberdades sociais e privilégios governamentais dos quais as mulheres brasileiras usufruem é suficiente para destruir a fantasiosa fábula da sociedade machista, opressora e patriarcal. Se as mulheres brasileiras não estão felizes, a culpa definitivamente não é dos homens. Se a vasta profusão de liberdades, privilégios e benefícios da sociedade ocidental não as deixa plenamente saciadas e satisfeitas, elas podem sempre mudar de ares e tentar uma vida mais abnegada e espartana em países como Irã, Paquistão ou Afeganistão. Quem sabe assim elas não se sentirão melhores e mais realizadas?
Homofobia
Quando falamos em homofobia, entramos em uma categoria muito parecida com a do racismo: o direito de discriminação é totalmente válido. Absolutamente ninguém deve ser obrigado a aceitar homossexuais ou considerar o homossexualismo como algo normal. Sendo cristão, não existe nem sequer a mais vaga possibilidade de que algum dia eu venha a aceitar o homossexualismo como algo natural. O homossexualismo se qualifica como um grave desvio de conduta e um pecado contra o Criador.
A Bíblia proíbe terminantemente conduta sexual imoral, o que — além do homossexualismo — inclui adultério, fornicação, incesto e bestialidade, entre outras formas igualmente pérfidas de degradação.
Segue abaixo três passagens bíblicas que proíbem terminantemente a conduta homossexual:
“Não te deitarás com um homem como se deita com uma mulher. Isso é abominável!” (Levítico 18:22 — King James Atualizada)
“Se um homem se deitar com outro homem, como se deita com mulher, ambos terão praticado abominação; certamente serão mortos; o seu sangue estará sobre eles.” (Levítico 20:13 — João Ferreira de Almeida Atualizada)
“O quê! Não sabeis que os injustos não herdarão o reino de Deus? Não sejais desencaminhados. Nem fornicadores, nem idólatras, nem adúlteros, nem homens mantidos para propósitos desnaturais, nem homens que se deitam com homens, nem ladrões, nem gananciosos, nem beberrões, nem injuriadores, nem extorsores herdarão o reino de Deus.” (1 Coríntios 6:9,10 —Tradução do Novo Mundo das Escrituras Sagradas com Referências)
Se você não é religioso, pode simplesmente levar em consideração o argumento do respeito pela ordem natural. A ordem natural é incondicional e incisiva com relação a uma questão: o complemento de tudo o que existe é o seu oposto, não o seu igual. O complemento do dia é a noite, o complemento da luz é a escuridão, o complemento da água, que é líquida, é a terra, que é sólida. E como sabemos o complemento do macho — de sua respectiva espécie — é a fêmea.
Portanto, o complemento do homem, o macho da espécie humana, é naturalmente a mulher, a fêmea da espécie humana. Um homem e uma mulher podem naturalmente se reproduzir, porque são um complemento biológico natural. Por outro lado, um homem e outro homem são incapazes de se reproduzir, assim como uma mulher e outra mulher.
Infelizmente, o mundo atual está longe de aceitar como plenamente estabelecida a ordem natural pelo simples fato dela existir, visto que tentam subvertê-la a qualquer custo, não importa o malabarismo intelectual que tenham que fazer para justificar os seus pontos de vista distorcidos e antinaturais. A libertinagem irrefreável e a imoralidade bestial do mundo contemporâneo pós-moderno não reconhecem nenhum tipo de limite. Quem tenta restabelecer princípios morais salutares é imediatamente considerado um vilão retrógrado e repressivo, sendo ativamente demonizado pela militância do hedonismo, da luxúria e da licenciosidade desenfreada e sem limites.
Definitivamente, fazer a apologia da moralidade, do autocontrole e do autodomínio não faz nenhum sucesso na Sodoma e Gomorra global dos dias atuais. O que faz sucesso é lacração, devassidão, promiscuidade e prazeres carnais vazios. O famoso escritor e filósofo francês Albert Camus expressou uma verdade contundente quando disse: “Uma só frase lhe bastará para definir o homem moderno — fornicava e lia jornais”.
Qualquer indivíduo tem o direito inalienável de discriminar ativamente homossexuais, pelo direito que ele julgar mais pertinente no seu caso. A objeção de consciência para qualquer situação é um direito natural dos indivíduos. Há alguns anos, um caso que aconteceu nos Estados Unidos ganhou enorme repercussão internacional, quando o confeiteiro Jack Phillips se recusou a fazer um bolo de casamento para o “casal” homossexual Dave Mullins e Charlie Craig.
Uma representação dos direitos civis do estado do Colorado abriu um inquérito contra o confeiteiro, alegando que ele deveria ser obrigado a atender todos os clientes, independente da orientação sexual, raça ou crença. Preste atenção nas palavras usadas — ele deveria ser obrigado a atender.
Como se recusou bravamente a ceder, o caso foi parar invariavelmente na Suprema Corte, que decidiu por sete a dois em favor de Jack Phillips, sob a alegação de que obrigar o confeiteiro a atender o “casal” homossexual era uma violação nefasta dos seus princípios religiosos. Felizmente, esse foi um caso em que a liberdade prevaleceu sobre a tirania progressista.
Evidentemente, homossexuais não devem ser agredidos, ofendidos, internados em clínicas contra a sua vontade, nem devem ser constrangidos em suas liberdades pelo fato de serem homossexuais. O que eles precisam entender é que a liberdade é uma via de mão dupla. Eles podem ter liberdade para adotar a conduta que desejarem e fazer o que quiserem (contanto que não agridam ninguém), mas da mesma forma, é fundamental respeitar e preservar a liberdade de terceiros que desejam rejeitá-los pacificamente, pelo motivo que for.
Afinal, ninguém tem a menor obrigação de aceitá-los, atendê-los ou sequer pensar que uma união estável entre duas pessoas do mesmo sexo — incapaz de gerar descendentes, e, portanto, antinatural — deva ser considerado um matrimônio de verdade. Absolutamente nenhuma pessoa, ideia, movimento, crença ou ideologia usufrui de plena unanimidade no mundo. Por que o homossexualismo deveria ter tal privilégio?
Homossexuais não são portadores de uma verdade definitiva, absoluta e indiscutível, que está acima da humanidade. São seres humanos comuns que — na melhor das hipóteses —, levam um estilo de vida que pode ser considerado “alternativo”, e absolutamente ninguém tem a obrigação de considerar esse estilo de vida normal ou aceitável. A única obrigação das pessoas é não interferir, e isso não implica uma obrigação em aceitar.
Discriminar homossexuais (assim como pessoas de qualquer outro grupo, raça, religião, nacionalidade ou etnia) é um direito natural por parte de todos aqueles que desejam exercer esse direito. E isso nem o direito positivo nem a militância progressista poderão algum dia alterar ou subverter. O direito natural e a inclinação inerente dos seres humanos em atender às suas próprias disposições é simplesmente imutável e faz parte do seu conjunto de necessidades.
Conclusão
A militância progressista é absurdamente autoritária, e todas as suas estratégias e disposições ideológicas mostram que ela está em uma guerra permanente contra a ordem natural, contra a liberdade e principalmente contra o homem branco, cristão, conservador e tradicionalista — possivelmente, aquilo que ela mais odeia e despreza.
Nós não podemos, no entanto, ceder ou dar espaço para a agenda progressista, tampouco pensar em considerar como sendo normais todas as pautas abusivas e tirânicas que a militância pretende estabelecer como sendo perfeitamente razoáveis e aceitáveis, quer a sociedade aceite isso ou não. Afinal, conforme formos cedendo, o progressismo tirânico e totalitário tende a ganhar cada vez mais espaço.
Quanto mais espaço o progressismo conquistar, mais corroída será a liberdade e mais impulso ganhará o totalitarismo. Com isso, a cultura do cancelamento vai acabar com carreiras, profissões e com o sustento de muitas pessoas, pelo simples fato de que elas discordam das pautas universitárias da moda.
A história mostra perfeitamente que quanto mais liberdade uma sociedade tem, mais progresso ela atinge. Por outro lado, quanto mais autoritária ela for, mais retrocessos ela sofrerá. O autoritarismo se combate com liberdade, desafiando as pautas de todos aqueles que persistem em implementar a tirania na sociedade. O politicamente correto é o nazismo dos costumes, que pretende subverter a moral através de uma cultura de vigilância policial despótica e autoritária, para que toda a sociedade seja subjugada pela agenda totalitária progressista.
Pois quanto a nós, precisamos continuar travando o bom combate em nome da liberdade. E isso inclui reconhecer que ideologias, hábitos e costumes de que não gostamos tem o direito de existir e até mesmo de serem defendidos.
-
 @ 46fcbe30:6bd8ce4d
2024-06-18 18:50:07
@ 46fcbe30:6bd8ce4d
2024-06-18 18:50:07At WalletScrutiny we open a lot of issues. And just recently, Danny, whom I cannot mention on Habla.news due to this error wrote a script to facilitate re-visiting issues we haven't re-visited in over half a year. Should we poke them all? 🤔
Issue | Comment | Issue
-----------|------------|---------------------- 2019-12-14 | 2019-12-16 | App cannot be verified 2017-10-20 | 2020-04-11 | Builds are not reproducible 2019-12-14 | 2020-06-19 | App from GooglePlay is not verifiable 2020-08-27 | 2020-09-02 | Please provide full build instructions to reproduce the app on Google Play 2020-12-05 | 2020-12-14 | Provide build instructions to rebuild the app from Google Play 2020-12-16 | 2020-12-16 | Where is the code of DApp Browser? 2020-12-18 | 2021-01-02 | Reproducible builds of com.crypto.multiwallet on Google Play? 2021-03-06 | 2021-03-07 | Change minSdkVersion from 16 to 19 2017-12-20 | 2021-03-12 | Build APK deterministically 2021-03-05 | 2021-04-03 | Please update your build instruction and make sure the app on Google Play can be reproduced 2019-12-28 | 2021-04-03 | Please update your build instructions such that reproducible builds are possible 2021-04-09 | 2021-04-09 | Please provide detailled instructions on how to reproduce the app on Google Play 2021-03-07 | 2021-04-20 | Missing build instructions & build fail 2021-03-08 | 2021-04-22 | Build fail with errors "Error: No named parameter with the name" 2021-04-23 | 2021-04-23 | Where is the latest source-code for im.token.app? 2021-03-12 | 2021-05-02 | Missing code for latest 2.1 version in google-play 2021-04-01 | 2021-05-02 | Publish source code for the app 2021-05-03 | 2021-05-04 | Please provide build instructions for reproducing the apk from Google Play 2020-04-07 | 2021-05-16 | Please provide verifiability of released builds 2021-04-18 | 2021-05-19 | Where is the latest code and build instructions 2021-05-27 | 2021-05-27 | Missing code for latest release 3.2.7 on google-play 2020-01-29 | 2021-06-02 | Please provide verifiable builds 2019-12-22 | 2021-06-03 | Failed to verify the build on GooglePlay 2021-05-27 | 2021-06-08 | Android app is not reproducible, diffs in AndroidManifest.xml & 0.dist.js & dist.js & resources.arsc files 2020-06-01 | 2021-07-23 | Please make the app reproducible 2021-10-26 | 2021-12-02 | Publish sources for android mobile appid=io.divipay.divi2021-12-11 | 2021-12-11 | Please provide latest source code and reproducible builds 2021-12-20 | 2021-12-20 | Please share the source and build instructions for the QUANTUM HW firmware 2022-02-08 | 2022-02-08 | Please add interpretation of transactions due to be signed 2021-10-17 | 2022-03-12 | Please provide build instructions to reproduce the version on Google Play Store 2021-12-02 | 2022-03-14 | Please provide instructions to reproduce your app found on Google Play 2021-04-21 | 2022-03-27 | Minimal Containers for Reproducible Builds testing for android app - WIP 2019-11-23 | 2022-03-28 | Build is not verifiable 2022-03-15 | 2022-04-10 | Show hash of firmware prior to installation 2021-04-12 | 2022-04-12 | Please provide build instructions to reproduce the app in Google Play Store 2020-04-27 | 2022-04-14 | Please provide reproducible builds 2022-04-08 | 2022-04-16 | Why the wallet readme is not detailed and no updated description? 2021-07-17 | 2022-07-22 | Publish source-code of releases before uploading them to Google Play 2021-12-01 | 2022-08-07 | Reproducible build fails due to a missing dependency 2021-02-14 | 2022-08-29 | Build failed if --production or npm ci are used instead of development 2022-03-01 | 2023-01-06 | Publish source code for mobile apps 2021-10-16 | 2023-04-13 | Missing Code for latest versions on google-play 2023-04-15 | 2023-04-15 | Missing Git Tag & Github release for latest version 5.5.1 on Google Play 2022-08-04 | 2023-04-20 | Add build instructions for all platforms & Containerfiles to compile app 2021-11-23 | 2023-04-22 | Missing source code for latest version 4.18 2021-03-12 | 2023-04-23 | Build apk fail with "because bitorzo_wallet_flutter depends on intl ^0.16.0, version solving failed." 2019-12-14 | 2023-04-24 | App on Google Play is not verifiable 2023-04-24 | 2023-04-24 | Publish code for newer version 23 on google-play 2023-04-27 | 2023-04-28 | Reproducibility problem on v0.32.0 2022-07-12 | 2023-05-25 | Missing code for version 1.3.11 on google-play 2023-05-27 | 2023-05-27 | reproducible builds 2023-06-20 | 2023-06-21 | Use--output-hashing noneto prevent random names for built main.js 2023-06-25 | 2023-06-25 | The app is not reproducible 2023-02-21 | 2023-07-01 | Could not find com.google.android.gms:play-services-tapandpay:18.2.0 2021-10-09 | 2023-07-08 | Please fix build reproducibility 2023-05-22 | 2023-07-13 | v7.8.0 is not reproducible 2021-10-17 | 2023-07-31 | Missing x86_64 folder in ./app/src/main/cpp//lib with lib.a files & Instructions to reproduce binaries in lib folders 2021-01-21 | 2023-08-16 | How can I verify the app on Google Play was built from this source code? 2019-12-28 | 2023-09-30 | Please provide verifiable builds 2019-12-14 | 2023-11-02 | App on Google Play can't be verified 2019-12-30 | 2023-11-03 | Support verifiable builds 2021-02-21 | 2023-12-19 | Has the BitLox project died? -
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 1739d937:3e3136ef
2024-03-27 12:25:02
@ 1739d937:3e3136ef
2024-03-27 12:25:02"Gossip", "Outbox", "Inbox", "Blastr", "Small relays vs Big relays". You've probably seen most of these topics come up in conversations and memes recently. You might have even read nostr:nprofile1qqsf03c2gsmx5ef4c9zmxvlew04gdh7u94afnknp33qvv3c94kvwxgsm3u0w6's article (nostr:naddr1qq2hxenh2cchynnpdag4sepkx4gxyj2dt9nk6q3qjlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qxpqqqp65wd3a9ny), or nostr:nprofile1qqswuyd9ml6qcxd92h6pleptfrcqucvvjy39vg4wx7mv9wm8kakyujgua442w's very technical article (nostr:naddr1qqxnzde3xycngdpjxg6nqdfsqgswuyd9ml6qcxd92h6pleptfrcqucvvjy39vg4wx7mv9wm8kakyujgrqsqqqa28906usv), or maybe even nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8g2lcy6q's one with the clickbaity title (nostr:naddr1qvzqqqr4gupzqwlsccluhy6xxsr6l9a9uhhxf75g85g8a709tprjcn4e42h053vaqydhwumn8ghj7un9d3shjtnhv4ehgetjde38gcewvdhk6tcprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsqzpcxasnyvpcvsusgpcqx3).
These are all great, and you should go and read them too. But one thing that each of them is guilty of is assuming that the audience has enough context to jump into the middle of a very nuanced and technical discussion. I've yet to see a clear description of what Gossip or Outbox really are and certainly none that are written in a way that is approachable for a non-technical audience. I hope this article can give you that context and serve as a high-level overview of the discussion and the technologies involved so that you can go forth to create better, more informed memes (is there anything more important, really?) and join the discussion in a productive way.
The problems
Centralization is the default
First off, why are we even talking about relays? Most of know that nostr is a protocol which is designed to be decentralized from the ground up. That decentralization is due in large part to the fact that users read and write data to multiple relays by default. So instead of all your data going to a centralized database (usually owned and operated by a single company) with nostr you have the ability to send your data to as as many relays as you'd like (relays are just databases, after all). Likewise, you can read other people's data from as many relays as you'd like to. Decentralized design = decentralized system, right!? Well, turns out, no.
The problem with a design like this is that what can be done and what will be done are often very different things. Imagine the following scenario: You follow 1000 people; 700 of them post their notes to the Primal relay, the other 300 post their notes to the Damus relay. If you don't also write your content to those two relays, the people that you care about won't see your content, they won't see your replies to their notes, they won't even know you exist. So while; in practice, it's easy to read & write to many different relays, users and their content will tend to centralize because it's the path of least resistance to a good user experience. Network effects and economies of scale always apply, they just don't always lead to the outcomes that you want.
Before you start to panic, this sort of centralization isn't a huge issue just yet. We are still a nascent network and there are still hundreds of active relays out there. Almost all nostr clients make relay selection a first class citizen and don't default new users to a single relay. The fact that we're even having this conversation in a serious way at this stage is a great sign that the community cares enough to be proactive about maintaining (and improving) decentralization over time.
That said, this is not a issue that we can take lightly either. The top 5-10 relays do already have an outsized percentage of users and we have many examples of these centralizing tendencies across dozens of protocols and networks over the last 30 years, so the threat is real.
The status quo is wasteful
The other major issue is that currently most nostr clients are extremely wasteful in how they fetch data. The default is to simply get everything from all the relays a user wants to connect to. Because most of us are writing the same data to many relays, this leads to huge amounts of duplicated data being downloaded, having its signatures verified, and then (for the most part) thrown away. For those of us with latest generation smartphones, unlimited data, and a working power outlet nearby, this is fine. For everyone else, this is a major roadblock to adopting nostr.
A lightly technical aside
There are a few important features of nostr that make any sort of intelligent data fetching possible. To understand how any of the potential solutions to the aforementioned problems would actually work, it's important to have a baseline understanding of these technical details. I promise, I'll keep it high level.
Relay lists
Recently the concept of a Relay List Metadata has been introduced to the spec in NIP-65 (there are also other types of relay lists documented in NIP-51). This is a nostr list event where users publish their preferred relays with a marker that says whether the relay is for read-only, write-only, or read & write. This vastly simplifies the process of finding preferred user relays for clients and I imagine that this will become the de facto standard place to look for a user's preferred relays.
NIP-05
The NIP-05 spec also documents a way for users to signal their preferred relays. However, unlike the NIP-65 relay list, this is a simple list of relays without any details on whether the user reads or writes to those relays.
Tag markers
Tag markers are positional elements in tags that give the client publishing the event the ability to leave a hint as to which relay other clients can expect to find a given user or note that is being referenced.
For example, in a user's contact list (a
kind: 3event) you have many"p"tags to reference all the user's that are followed. These tags look like this:{ "kind": 3, "tags": [ ["p", "91cf9..4e5ca", "wss://alicerelay.com/", "alice"], ["p", "14aeb..8dad4", "wss://bobrelay.com/nostr"], ["p", "612ae..e610f"] ], "content": "", ...other fields }All three of these
"p"tags are valid (only the"p"and the user's pubkey are required), in the first and second you can see the third item is a relay where the user's events can be found.These types of tag markers are repeated all throughout nostr. Here's a few more example references for an event (in this case a long-form article):
``` ["e", "b3e392b11f5d4f28321cedd09303a748acfd0487aea5a7450b3481c60b6e4f87", "wss://relay.example.com"],
["a", "30023:a695f6b60119d9521934a691347d9f78e8770b56da16bb255ee286ddf9fda919:ipsum", "wss://relay.nostr.org"] ```
As you can imagine, these hints can be very helpful but only if clients actually attempt to fetch the content from the referenced relay.
The solutions?
Now that you understand the problem space a bit better let's define those terms we started with.
Blastr
Blastr was created by nostr:nprofile1qqs9hejyd252x8q3kw6980ud4lymx3hlx2x3lgg6p7sz58nyv8m2nvgdswkeh and nostr:nprofile1qqswrlemlh2wgqc4jkds3d8ueqj9a2j3gcm7r48v9tskdd6rxsd7rtcpwpuwc from Mutiny and isn't a relay. Instead, Blastr is a proxy (i.e. it looks like a relay to clients) that ingests any event sent to it and, in turn, sends those events to EVERY online relay on the network. It's a mass re-broadcaster for events that can be helpful to get your data pushed out to as many relays (and thus users) as possible. The drawback, of course, is that this is tremendously wasteful from a bandwidth and storage perspective.
Gossip (in 3 flavors)
This is by far the most confusing part for most people when watching the memes of the last few weeks fly by and I've seen a lot of confused takes out there. Most of the confusion stems from the multiplicity of definitions of what the "gossip model" actually is. Let's go through the options. 1. Gossip protocols: This is a general concept more than a specific implementation. Gossip protocols are protocols that attempt to spread information around a network in a uniform way. For example, Bitcoin nodes use a variation of the gossip protocol to make sure that transactions end up in as many mempools as possible. This is important in computing when you want to reach consensus or when all nodes in a network need to have the same information in order to operate the network. Since nostr doesn't have any consensus rules or shared compute, it's somewhat pointless to try and make sure all events are propagated to all relays (hence the limited usefulness of Blastr). 2. The Gossip client from nostr:nprofile1qqswuyd9ml6qcxd92h6pleptfrcqucvvjy39vg4wx7mv9wm8kakyujgua442w : This is a nostr client that was built from the ground up to try and use relays and relay hints in events to the fullest to keep things as decentralized as possible while being efficient in how much data it was fetching. Mike has a great (slightly outdated and very technical) video that talks about his motivation behind building Gossip in the way he did. It's worth a watch. video link 3. Gossip model: This is what people are usually referring to when they are talking about relays on nostr. The Gossip model is a loose, catch-all term used to refer to all the ways in which clients attempt to understand which relays they should read & write to for a given user. Again, this isn't really a specific spec or implementation but encompasses many different strategies. This vagueness inherent in the term makes discussions about the "gossip model" pretty imprecise and prone to misunderstanding.
Don't gossip
To be clear: You really shoud not be thinking about or talking about any of this as the "gossip model" since that definition is so abstract as to be unusable. Which brings us finally to the real topic being discussed at the moment among devs; the Outbox model.
Outbox/Inbox model
This is the real topic of conversation right now: How should client developers build relay discovery and selection features into their apps. As we already talked about, if left alone, it's likely that we'd unintentionally centralize most of nostr onto a few huge relays. So making sure that we encourage (and build sensible defaults) to help client developers to treat relay discovery and selection properly is really critical.
Right now, the discussion centers around one main approach, called the "Outbox model". There is also an "Inbox model" which is a still just a high level idea which I'll mention below but it's not being implemented yet (as of late March 2024). 1. The "Outbox model": This strategy looks at what relays users are using to publish their events (from relay lists and tag markers) and then uses an algorithm to decide how to fetch all the needed events from the array of relays. Different implementations can use different algorithms to select relays. For example, one implementation might optimize fetching events from the smallest number of relays (favoring large relays), while another might optimize for fetching from the relays that have the smallest user overlap (favoring small relays). 2. The "Inbox model": As you can imagine, this strategy flips the outbox model on it's head. It's so far just an idea (proposed by nostr:nprofile1qqs8nsk2uy2w529fs8n4tx60u7z553e4yx5dy2nxhw4elgjgawpqlas9waufq) and a draft NIP but the idea is that when your client posts on your behalf, it will loop over your entire follow list, making a list of the relays that each of your followers uses to read events. Then the client will publish your event to all of those relays. If all clients followed this paradigm, then each of us would only have to read from a single relay. To quote nostr:nprofile1qqs8nsk2uy2w529fs8n4tx60u7z553e4yx5dy2nxhw4elgjgawpqlas9waufq 's original post, "This doesn't take away from the outbox approach, and maybe should even be used together instead of as a replacement. But my point is that clients should be trying harder to deliver posts instead of just fetch posts. Because it benefits users when their posts can be seen."
Why the Outbox model has broad support
To understand why implementing an Outbox model is so powerful at solveing the problems laid out at the beginning of this article, you can do two quick thought experiments:
A user banned from all other relays
Imagine a user who's content is banned from all public relays for some reason. Instead, they have to run their own relay and publish their events there. With a simple "follow the major relays model" (or even with Blastr attempting to copy and paste their events to every other relay) this user is completely invisible to the network. User's would have to know about the banned user's private relay and select that relay in each client they use. What's more, if that relay ever had to change URL (likely for a user that is banned so broadly), all user's would need to know what the new URL is in order to change relays and fetch events from the new location.
With Outbox however, clients will see that their user's follow this user, will then look up this user's relay list, and will know where they need to go to fetch their events. It becomes much more difficult for relays to censor or block users with an Outbox model in place
Duplicate event fetching
We talked earlier about how many nostr clients often fetch the same data many times, just to throw that data away. Even using the simplest algorithms with an Outbox model, you can significantly reduce the amount of duplicate data you're fetching from relays. We, as users, would all also need to specific many fewer relays in our relay lists but would still be quite sure our clients would be able to find all the content we want to see.
Wrapping up
Hopefully this has given you a better overall understanding of what folks are talking about when they refer to Gossip (remember: don't refer to it this way) or Outbox (outbox, yay!) and why we need to be proactive about maintaining the decentralization of nostr.
-
 @ 06a260a2:d7a7791c
2024-06-18 16:19:43
@ 06a260a2:d7a7791c
2024-06-18 16:19:43Pokud se v poslední době někde mluví nebo píše o těžbě bitcoinu, je v té souvislosti většinou zmíněna vysoká energetická náročnost a tím i složitost dosažení ziskovosti. Jako předpoklady úspěchu při těžbě jsou uváděny dostupnost levné energie a vlastnictví vysoce efektivních (a tím pádem i drahých) strojů na těžení (tzv. minerů na bázi ASICs čipů - aplikačně specifických integrovaných obvodů pro řešení SHA-256 hashovacího algoritmu). Vše doprovází ilustrační fotografie přepravních kontejnerů, plných malých plechových krabic s ventilátory někde poblíž vodní elektrárny na ohromné přehradě mimo EU. Nic z toho se ani vzdáleně nedá nazvat domácí těžbou. Existuje tedy domácí těžba bitcoinu? A dává smysl?
Co je těžba a kdo je těžař?
Na první pohled jednoduchá otázka, přesto je dobré se u ní na chvilku zastavit.
Těžba bitcoinu je proces vzniku nových mincí jako odměny pro toho, kdo nalezne jako první pomocí SHA-256 algoritmu hash bloku transakcí čekajících na potvrzení, splňující zadanou obtížnost (má předem definovaný počet nul na svém začátku). Hledání tohoto hashe (hashování) je výpočetně náročný proces, který využívá prvku náhodnosti. Pro daný blok postupně generuje velké množství výsledků, mezi nimiž hledá ten pravý, vyhovující zadané obtížnosti. Ten oznámí ostatním uzlům v síti, kteří jej zkontrolují a správnost potvrdí zařazením takto vytěženého bloku transakcí do block-chainu. Nový blok obsahuje na prvním místě transakci, která nemá žádný vstup, pouze převádí platnou odměnu za vytěžení bloku plus všechny poplatky za ostatní transakce na adresu řešitele (jedná se o tzv. coinbase transakci). S tímto popisem si většina definic těžby bitcoinu vystačí a zákonitě definuje těžaře jako toho, kdo hashuje. Tedy hledá ten správný hash. Je to ale dostatečné?
Ano, není! Proces těžby začíná mnohem dříve sestavením a ověřením celého block-chainu v nejdelší variantě od jeho počátku až po aktuální blok. Jen tak lze následně sestavit šablonu nového bloku, protože transakce v ní obsažené musí být platné (utrácejí existující mince - výstupy předchozích transakcí z block-chainu) a vzájemně si neodporující (utrácejí tyto mince pouze jednou). Celý blok pak nesmí překročit svou maximální velikost 4MB. Jaké transakce však do šablony nového bloku zařadit? Důležitá otázka, která nemá jednoznačnou odpověď. Ekonomická motivace velí vybrat ty z čekajících transakcí s aktuálně nejvyšším poplatkem za zpracování. Tak dojde k maximalizaci potenciálního zisku z odměny za vytěžení. Možná se ale ten, kdo šablonu sestavuje, rozhodne zařadit také transakce, na kterých má nějaký osobní zájem. Například konsolidaci nízkých zůstatků (dust) na svých adresách za nulový poplatek. Pokud takové transakce splňují podmínky pro zařazení do bloku, není na tom nic špatného. A možná se také rozhodne některé transakce do své šablony nezařadit, přestože nabízejí vysoké poplatky za zpracování. To už trochu zavání cenzurováním, ačkoliv pro to může mít dotyčný své pádné důvody. Ať tak či onak, podstatné je, že to může udělat a ovlivnit tak, které transakce budou či nebudou potvrzeny při vytěžení nového bloku. Poměrně důležitá odpovědnost, ne?
Těžba bitcoinu je tedy proces, který zajišťuje sestavení a ověření nejdelšího block-chainu, ověření platnosti příchozích transakcí vůči historii v block-chainu, výběr transakcí do šablony nového bloku a nalezení hashe pro stanovenou obtížnost pomocí SHA-256 hashovací funkce. Skutečný těžař je pak ten, kdo udržuje celý tento proces pod svou kontrolou.
A co těžba v poolu? Těžaři přece již dlouho netěží jen sami za sebe. Pravděpodobnost individuálního úspěchu při hledání správného hashe je velmi malá a odměna s ní spojená nepokryje náklady na těžbu a vynaloženou energii. Pooly spojují těžaře do větších skupin a v případě úspěchu jednoho z nich dělí odměnu dle podílu vynaloženého úsilí. Nedává smysl, aby si každý z nich udržoval celý block-chain a sestavoval vlastní šablonu nového bloku. Mohou to přeci delegovat na jednoho z nich a ostatní se mohou soustředit na hledání toho správného hashe… Ano mohou, ale měli by si udržet přehled a kontrolu nad tím, které transakce a proč jsou v šabloně zařazené. Jen tak totiž skutečně hlídají bitcoinovou síť a její nezávislost. V opačném případě pouze poskytují službu hashování někomu jinému. Jsou to hasheři a nechávají si za to platit.
Proč těžit?
Předchozí odstavce to už trochu naznačily. Existují i jiné důvody pro těžbu bitcoinu v domácích podmínkách, než jsou ty ekonomické, přestože zisk může být stále na prvním místě:
- Finanční zisk z těžby
- Podpora zabezpečení sítě a decentralizace těžby
- Podpora open-source přístupu k těžbě
- Sebevzdělání v oblasti těžby, získání osobní zkušenosti
- Podpora alternativních přístupů k sestavení šablony bloku
- Využívání vedlejších efektů těžení
- Je to zábavné
Finanční zisk z těžby
Těžba bitcoinu je prosperující podnikatelskou aktivitou, jejíž nedílnou součástí je generování zisku. Nejinak je tomu i u těžení v domácích podmínkách, byť je zde lepší mluvit spíše o příjmu než zisku, protože pokrýt a překonat náklady není vůbec jednoduché. V tomto textu se ekonomice těžby věnovat nebudu, zájemce odkazuji na dvě výborné knihy z nakladatelství Braiins Publishing. * Bitcoin Mining Handbook (anglicky) * Bitcoin Mining Economics (anglicky)
Na druhou stranu příjem z domácího těžení je velmi pěknou odměnou za vynaložené úsilí a potěší v jakékoliv velikosti. Mně například vytváří fond na ZAPování (odměny) v síti Nostr. A kdo ví, jakou budou mít dnes vytěžené drobné saty (satoshi) hodnotu za 5 let?
Podpora zabezpečení sítě a decentralizace těžby
Systém zabezpečení bitcoinové sítě Proof-of-Work odvozuje náročnost potvrzení transakcí v bloku (minig difficulty - složitost těžby) od velikosti odvedené práce (hashrate sítě - množství provedených hashovacích operací všemi těžaři za jednotku času). Čím větší hashrate sítě je, tím náročnější je potenciální provedení 51% útoku, protože ten musí k úspěchu takový hashrate překonat, což je energeticky a tedy i finančně velmi náročné. Pokud útočník získá kontrolu nad více jak 50% hashrate sítě (zjednodušeně 51% útok), má možnost rozhodovat, které transakce do bloku (ne)zařadí, nebo znovu vytvořit vlastní řetěz bloků s transakcemi dle vlastního záměru. Díky převaze v hashrate bude generovat bloky rychleji než zbytek sítě a časem sám vytvoří nový nejdelší řetěz, který konsensus sítě uzná za platný. Může tak například přesměrovat odměnu za již vytěžené bloky na vlastní adresy nebo znovu utratit své již utracené mince. Vlastní těžbou tedy přispíváte k celkovému hashrate sítě a tím zvyšujete její bezpečnost.
Přidáním svého těžícího uzlu do bitcoinové sítě zároveň zvýšíte její decentralizaci a tedy odolnost proti výpadku nebo zneužití ostatních jednotlivých uzlů. Decentralizace pomáhá zabránit koncentraci těžební síly do rukou několika velkých těžařů.
Podpora Open-Source přístupu k těžbě
Dle studie CoinMetrics tvoří minery čínské firmy Bitmain přibližně 76% současného hashrate, minery čínské firmy MicroBT 14% a cca 5% minery čínské firmy Canaan. V aplikaci Mempool.space (průzkumník bitcoinového block-chainu) můžete zjistit, že více než 98% bloků se vytěží v poolech, které veřejně nepublikují svou strategii pro výběr transakcí do šablony bloku. Více než 57% z nich jsou pooly čínské. Co ukazují všechna tato čísla?
Alarmující část těžebního odvětví není transparentní, design jejich řešení je firemním tajemstvím. To je pro bitcoinový étos otevřenosti a transparentnosti neradostné zjištění. Naštěstí přirozenou reakcí bitcoinové komunity je celá řada aktivit a projektů, které vrací principy otevřenosti i do této oblasti. Boří tak existující bariéry a demokratizují přístup k těžbě bitcoinu. Tím otevírá potenciál pro další inovace a zlepšování. Kdokoliv může pochopit, upravit a vylepšit technologie těžby bitcoinu (software i hardware) a podpořit kulturu sdílení znalostí a kolektivních inovací.
Míru zapojení do podpory otevřeného přístupu si můžete určit sami. Od využití alternativního open-source firmware pro komerční těžební stroje (BraiinsOS, Hiveon, VNish), přes open-source minery (Bitaxe, NerdMiner) až po open-source těžební pool (public-pool.io).
Sebevzdělání v oblasti těžby bitcoinu, získání osobní zkušenosti
Vedlejším efektem využití komunitních open-source nástrojů pro domácí těžení bitcoinu je také značné prohloubení znalostí v této oblasti. Osobní zkušenost z jakékoliv oblasti života sama o sobě přispívá k rozšíření vlastního poznání (jak se říká není nad to jít s vlastní kůží na trh). Nedostatek PR a marketingu komunitních řešení však velmi často předpokládá vlastní intenzivní průzkum problematiky, vytvoření vlastního názoru a samostatné rozhodování. Pokud chcete o těžbě bitcoinu a jejích zákonitostech vědět více, začněte sami těžit!
Podpora alternativních přístupů k sestavení šablony bloku
Již jsem napsal, že sestavení šablony bloku je nedílnou a velmi důležitou součástí těžby. Kontrola nad sestavením je kontrolou nad cenzurou transakcí, velikosti zisku z transakčních poplatků nebo obsahem block-chainu. Neexistuje jediný správný postup sestavení, pouze více či méně preferované přístupy k němu. Velcí těžaři, sledující celkový profit, zcela jistě preferují maximalizaci zisku z každého vytěženého bloku. Proto vybírají do šablony bloku transakce dle výše transakčního poplatku (sat/vByte - cena za vážený Byte), kterým vlastník transakce signalizuje její prioritu. Tím se ale do block-chainu dostane spoustu transakcí, jejichž zadavatel si mohl dovolit zaplatit vysoký poplatek, ale které by tam jiní raději neviděli. Mám na mysli spam v podobě Ordinals a BRC-20 tokenů. Těžební pool Ocean.xyz proto nabízí i šablonu, která tento typ transakcí filtruje. Zda je to správně nebo je to nežádoucí cenzura je na jinou diskuzi, vy si ale můžete vybrat a svou volbou hlasovat a (ne)podpořit takový přístup.
Objevují se i snahy prioritizovat technické transakce, které vznikají jako vedlejší efekt dějů na vrstvě Lightning Network. Například transakce vynuceného uzavření lightning kanálu při vzniku neočekávané chyby může zůstat nepotvrzená hluboko v mempoolu, pokud byl kanál v minulosti otevřen s nedostatečnou rezervou na poplatek a poplatky od té doby výrazně vzrostly. Takové transakce je skoro nemožné ekonomicky uzavřít, ale v mempoolu je lze celkem snadno identifikovat. Proč je jednou za čas nevložit do bloku bez ohledu na zisk a pomoci tak nejen majitelům těchto kanálů, ale i celému lightning ekosystému? Podpořili byste takovou iniciativu?
Využití vedlejších efektů těžení
Těžba bitcoinu je za současných podmínek (počátek roku 2024) ve střední Evropě značně neprofitabilní, pokud nemáte přístup ke skutečně levnému zdroji elektrické energie. Zvláště pokud do ceny energie z takové zdroje započítáte i jeho pořizovací náklady. Pokud se vám však podaří najít využití pro vedlejší produkt těžení, teplo, můžete si celkovou bilanci velmi vylepšit.
Těžící stroje s příkonem stovek wattů až jednotek kilowattů produkují skutečně velké množství tepla, srovnatelné s elektrickými přímotopy o podobném výkonu. Záleží jen na vás, jak kreativně jej dokážete využít. Pojďme se podívat na několik inspirativních příkladů.
Antminer S9 jako přenosný přímotop pro vyhřívání místností je asi nejjednodušší způsob využití. Miner chladí své ASICs čipy proudícím vzduchem. Dva ventilátory nasávají a vyfukují proud vzduchu o teplotě až 100℃. Pokud jej doplníte vhodnými madly pro snažší přenášení a hlavně adaptérem WiFi2Ethernet, abyste nebyli závislí na LAN přípojce, získáte přenosný přímotop, který jako vedlejší efekt těží bitcoin.

Vytápění může být samozřejmě řešeno i integrálně se stavbou, pokud odvod tepla od těžebního zařízení připojíte k existující domovní ventilaci. Tady už si pravděpodobně nevystačíte s jednou S9, ale podle celkového objemu vytápěných prostor můžete použít i více výkonějších minerů T17, S17 nebo S19. O něco složitější instalace se vám odvděčí kromě většího množství vytěžených bitcoinů i uspokojením vašeho kutilského ducha. Nutno ovšem podotknout, že toto je velmi neefektivní způsob vytápění domu. Hodí se spíše jako doplněk standardního vytápění v kombinaci s dostupným zdrojem levné energie.
Teplem z ASICů nemusíte vytápět jen obývané místnosti, ale třeba i skleníky nebo zimní zahrady. Prodloužíte tím vegetační období rostlin. Do stejné skupiny patří i nárazové vytápění prostor, jako jsou sušárny prádla, ale i ovoce a dalších plodů.

Pokud je domácí inženýrství vaším koníčkem, můžete se pustit do kapalinového chlazení minerů. To má v podstatě dvě použitelné podoby. Buď nahradíte všechny chladiče jednotlivých ASICů chladiči vhodnými pro kapalinové chlazení nebo ponoříte celé těžící zařízení do dialektrické kapaliny (tzv. imerzní chlazení). V obou případech je nutné následně zajistit odvod tepla z chladicí kapaliny přes vhodný výměník. Cílem může být bojler pro ohřev teplé vody, akvárium odpovídající velikosti (cca 1000l na 1kW), bazén, nebo celá otopná soustava, ve které budou vaše minery jedním ze zdrojů. Výhodou takového řešení je výrazné snížení hluku (žádné ventilátory nejsou potřeba) a zároveň zvýšení efektivity, protože kapalina, zvláště v případě imerzního chlazení, odvádí teplo od chladičů účinněji než vzduch. Na trhu najdete velké množství jak speciálních kapalinových chladičů, tak kontejnery pro imerzní chlazení. Zbytek řešení už je na vás a vaší tvořivosti.
Je to zábavné
Předchozí odstavce nastínily, že těžení bitcoinu může podnítit celou řadu kreativních aktivit.
Začíná to možností sestavit si miner vlastními silami. Open-source těžební zařízení mají na GitHubu kompletní dokumentaci HW, včetně výkresů tištěných spojů a elektrického zapojení. Některé modely je možné koupit přímo jako hardwarové stavebnice. A pokud se rozhodnete nějakým inovativním způsobem využít i zbytkové teplo, které miner produkuje, budete mít zábavu na několik dlouhých večerů.
Těžař bitcoinu nemusí být nutně nerd, který se věnuje jen svým počítačům a nějakým internetovým penězům, ale i šikovný kutil, který svou zručnost chytře spojil s podporou a zabezpečením nejlepších peněz na světě.
Na čem těžit v domácích podmínkách
Domácí podmínky neumožňují profitabilní těžbu bez přístupu k levné energii. Výběr těžícího zařízení tedy nutně určují jiná kritéria, než je maximalizace zisku, respektive hashrate (# hash/s), případně efektivity (# hash/s/W). Která to jsou, závisí primárně na motivaci k domácí těžbě. Podle příklonu k jednomu nebo více důvodům, uvedeným v části Proč těžit?, lze vybrat vhodný miner. Z čeho můžete vybírat?
Profesionální minery
Do této skupiny patří zařízení firem Bitmain, MicroBT a Canaan, která produkují naprostou většinu současného hashrate sítě. K dispozici jsou jak aktuální top modely (např. AntMiner T21), tak i starší typy, které velcí těžaři již vyřazují ze svých stájí kvůli nedostatečné efektivitě (AntMiner T17). Výběr je opravdu široký, vyhledávání na eBay nabízí pro klíčové slovo AntMiner několik tisíc výsledků. Nakupovat můžete ale i od profesionálů, kteří nabízí přidanou hodnotu v podobě provedené repase, vyčištění a kontroly minerů z druhé ruky. Těmi je například kanadská firma D-Central.tech. Většinu repasovaných minerů nabízí i v upravených variantách s kvalitnějšími ventilátory a předinstalovaným firmware BOS+ od Braiins, který výrazně zjednodušuje následné experimenty s přetaktováním nebo vyladěním výkonu na maximální efektivitu.

Proč si vybrat profesionální miner? K experimentování dostanete do ruky zařízení, které je, nebo v nedávné době bylo špičkou v oboru. Nabízí většinou profesionální kvalitu zpracování a celkem snadno si můžete vybrat kusy v perfektním stavu. Alternativní firmware BraiinsOS je pro tyto stroje již velmi dobře odladěný a stabilní. Z dostupných minerů pro domácí těžbu pak nabízí nejvyšší hashrate. Pro určité případy použití se také může hodit, že tyto minery produkují dosti tepla - viz. část Využití vedlejších efektů těžení a některé můžete zakoupit již rovnou v úpravě pro chlazení kapalinou.
Nevýhodou těchto strojů je uzavřený design. Z tohoto pohledu není moc co studovat, pokud neholdujete analýze na úrovni elektrických signálů jednotlivých součástek. Zde musím upozornit, že těmito zařízeními protékají elektrické proudy vysokých hodnot, které jsou životu nebezpečné. ASIC minery nerozebírejte, pokud nevíte, co děláte!
Dalšími spíše negativními vlastnostmi jsou vysoký příkon (stovky wattů až jednotky kilowattů) a v jeho důsledku vysoké náklady na elektrickou energii. Velikost ceny profesionálních modelů je potom dosti variabilní. Aktuální top minery stojí několik tisíc amerických dolarů, jeden rok staré jsou ale již značně dostupnější a stále populární model AntMiner S9 lze sehnat i za cenu kolem 50 amerických dolarů.
Open-Source minery
Kdo jsou to open-source těžaři? Produkce těžících zařízení je v současné době ovládána společnostmi, které nezveřejňují informace o designu svých produktů. To ztěžuje případné opravy rozbitých zařízení a pro mnohé je to i políček do tváře étosu kolem bitcoinu jako decentralizované a otevřené technologie. Poslední rok však přinesl v této oblasti velký posun.
OSMU - Komunita open-source těžařů si dává za cíl zpřístupnit všechny potřebné informace o těžbě všem, kteří mají zájem se na těžbě bitcoinu podílet. K dispozici jsou schéma zapojení, výkresy tištěných spojů a osazovací plány, nebo zdrojové kódy firmwaru pro jednotlivá zařízení, která v komunitě vznikají. To otevírá potenciál pro další inovace a vylepšení, protože kdokoliv může návrhy studovat, upravovat a dále vylepšovat.
Již dnes můžete testovat první výsledky. Například minery na bázi ASIC čipů Bitmain - Bitaxe Ultra (BM1366), Bitaxe Max (BM1397), nebo Bitaxe Supra (BM1368). Ve fázi vývoje jsou Bitaxe Hex (6x BM1366), Qaxe (4x BM1366) nebo Piaxe - klon Bitaxe Ultra ve formě rozšiřujícího HATu pro Raspberry PI4.

Tyto minery nenabízí vysoký hashrate, protože jsou postaveny pouze na jednom až šesti ASIC čipech (na rozdíl od profesionálních minerů s desítkami ASICů). Mají ale špičkovou efektivitu na úrovni 20W/TH. Otevřený zdrojový kód je pak příležitostí pro další studium a pochopení těchto technologií.
Hobby minery
Podskupinu open-source minerů, které nevyužívají pro hashovací funkci ASIC čip a mají tedy řádově nižší výkon, můžeme nazvat hobby minery. Nelze je využít pro těžbu v poolu, protože smysluplný horizont výplaty jejich podílu jsou stovky let. Mohou být ale použity pro individuální těžbu, tzv. solo-mining a zůčastnit se bitcoinové loterie (pravděpodobnost, že vytěží blok je velmi podobná šanci vyhrát ve velké loterii první cenu).
Příkladem takového zařízení je NerdMiner. Zdrojové kódy projektu naleznete na GitHubu. Můžete se rozhodnout, zda si pořídíte NerdMiner již sestavený a připravený k provozu, nebo si objednáte jen jednotlivé součástky. Sestavení a oživení pak bude součástí vašeho experimentování. Není to složité a to uspokojení poté, kdy se rozsvítí displej a objeví informace o aktuální hashrate, za to stojí.
Kde a jak těžit
Jak jsem napsal v úvodu, samotný miner nestačí. Ještě je třeba zajistit sestavení šablony nového bloku z čekajících transakcí. To pro těžaře zajistí software v těžebním poolu. Podle toho, kdo pool provozuje a jak je rozdělována odměna za vytěžený blok, můžeme pooly rozdělit na tři skupiny:
Soukromý pool
Vlastní pool, který si provozuje sám těžař. Sám si také může rozhodovat o způsobu sestavení šablony bloku. Celý proces těžby má tak pod plnou kontrolou. Případná odměna za vytěžené bloky mu celá náleží. Nutno ovšem dodat, že v případě domácí těžby s nízkým celkovým hashrate je pravděpodobnost vytěžení bloku srovnatelná s výhrou první ceny v loterii.
Open-source softwarem k provozování vlastního poolu je třeba Public-pool. Najdete jej jak ve variantě pro standardní linuxový server, tak i jako aplikaci pro oblíbené bitcoin full-node distribuce Umbrel nebo RunCitadel.
Veřejný pool pro individuální těžbu
Veřejný pool pro individuální těžbu bitcoinu (solo-mining pool) je obdobou soukromého poolu, který si však neprovozujete sami, ale spoléháte na službu někoho jiného. Podmínky jsou shodné, pokud váš miner vytěží blok, celá odměna náleží vám. Nemáte však pod kontrolou sestavení šablony bloku.
Příkladem takového poolu je public-pool.io, který je veřejnou instancí open-source projektu public-pool. Otevřená zdrojový kód umožňuje kontrolu pravidel použitých pro sestavení šablony bloku.
Veřejný pool se sdílenou odměnou
Naprostá většina těžby probíhá v poolech, které rozdělují odměnu za vytěžené bloky mezi všechny zúčastněné těžaře dle míry jejich přispění. Důvodem je velmi malá pravděpodobnost úspěchu individuálních těžařů (viz. níže). Způsob výpočtu “míry přispění” se může mezi jednotlivými pooly lišit, v principu ale existují dva základní přístupy: PPLNS a (F)PPS.
PPLNS - Pay Per Last N Shares - těžař dostává zaplaceno dle množství tzv. shares (podílů odvedené práce, které jsou přímo úměrné hashrate jeho zařízení), které odeslal do poolu před vytěžením bloku. Jeho odměna je tedy závislá na podílu hashrate jeho zařízení vůči celkové hashrate poolu a na štěstí poolu při hledání bloku. Výhodou systému PPLNS je, že odrazuje od přeskakování mezi pooly a podporuje loajalitu těžařů. Nevýhodou je však nepředvídatelnost velikosti odměny kvůli náhodnosti objevování bloků.
(F)PPS - (Full) Pay Per Share - těžař je placen dle množství odeslaných podílů, bez ohledu na to, zda je nalezen blok. Výhodou systému PPS je jeho předvídatelnost. Těžaři přesně vědí, kolik za jeden podíl získají. Jeho nevýhodou však je nízká motivace k věrnosti poolu. Těžaři mohou přeskakovat z jednoho (F)PPS poolu do druhého, aniž by tratili oproti setrvání v jednom z nich. Full v názvu systému odměňování pak znamená skutečnost, že součástí odměny jsou i vytěžené transakční poplatky. Mezi těžaře je tak rozdělena celá odměna za vytěžení bloku.
Oba přístupy nabízí podíl na odměně poolu za vytěžené bloky, pro domácí těžbu však přesto zůstává jeden problém a tím je tzv. limit pro výplatu. Relativně nízká velikost hashrate zařízení používaných pro domácí těžbu vůči hashrate poolu znamená i nízký podíl na celkové odměně. Ta se bude pohybovat někde mezi jednotkami až maximálně stovkami satů za jeden blok. Čím větší pool, tím častěji vytěží blok, ale tím menší je podíl na odměně. A obráceně, čím menší je pool, tím větší může být podíl na odměně, ale četnost nalezení bloku klesá. A protože převádět nízké hodnoty satů se kvůli on-chain transakčním poplatkům nevyplácí, zavádí pooly limity pro výplatu. Pohybují se od desítek tisíc až po více jak milion satů. Doba, po kterou je nutno střádat odměny se tak může prodloužit i na několik let. Některé pooly proto zavádí limit pro minimální hashrate těžícího zařízení, aby eliminovaly riziko, že nebudou schopni těžaře vyplatit. Zároveň tím snižují své náklady na provoz, protože tak nemusí tyto malé těžaře obsluhovat. Nadějí v tomto směru je až zavedení výplat prostřednictvím platební sítě Lightning Network. Tuto možnost již do budoucna některé pooly potvrdily.
Stejně jako v případě veřejných poolů pro individuální těžbu, ani pooly se sdílenou odměnou nenabízí možnost kontroly obsahu šablony bloku. Protože software těchto poolů nemá otevřený zdrojový kód, neexistuje ani možnost, jak si s jistotou ověřit, jakou strategii a pravidla pooly volí. A co více, většina těchto poolů ani transparentně nezveřejňuje, na jaké šabloně majitelé těžících zařízení pracují. To se dozví až v případě úspěšného nalezení bloku po jeho zveřejnění v block-chainu. Právem jsou proto velké pooly kritizovány za netransparentnost, která jim teoreticky umožňuje cenzurovat transakce nebo vydělávat na transakcích, které nejsou prioritizovány dle transakčních poplatků, ale jejich zpracování je akcelerováno neznámými poplatky mimo block-chain (tzv. OTC - over-the-counter). Že se takové poplatky nedostanou do odměny vlastníkům těžících zařízení, asi není třeba zdůrazňovat.
Světlo na konci tunelu přinese až rozšíření implementace těžebního protokolu Stratum V2 (protokol, kterým pool zadává práci těžícím zařízením). Ten mimo jiné umožňuje těžařům větší kontrolu nad výběrem transakcí v bloku a tím snižuje vliv provozovatelů poolů.
Protokol Stratum V2 však zatím rozšířen není. Jedinou výjimkou mezi těžebními pooly, která se snaží o transparentnost těžby, je nyní Ocean.xyz pool.
Ocean.xyz
Ocean pool je reinkarnací původního poolu Eligius, který byl součástí těžební scény bitcoinů od roku 2011 a skončil svou činnost v roce 2017. Byl průkopníkem transparentní těžby bez poplatků. Na tento přístup nyní navazuje Ocean.xyz. Jeho posláním je zvýšit decentralizaci těžby Bitcoinu díky zpřístupnění těžby v poolu malým a středním těžařům. Dlouhodobě se proto snaží zdůrazňovat význam distribuované a transparentní těžební sítě.

Klíčové vlastnosti
Nekustodiální přístup k těžbě bitcoinů. Na rozdíl od tradičních těžebních poolů, kde je provozovatel poolu příjemcem odměny z těžby, kterou teprve následně rozděluje mezi těžaře, Ocean pool zajišťuje, aby těžaři dostávali své odměny přímo ze sítě Bitcoin v tzv. coinbase transakci. To nejen zvyšuje bezpečnost výdělků těžařů, ale také podporuje vyšší úroveň důvěry mezi poolem a jeho uživateli. Týká se to samozřejmě pouze odměn nad limit pro výplatu, který má Ocean pool nastaven na 0.01048576 BTC (1 048 576 satů). Menší odměny, které jsou pro domácí těžbu pravděpodobné, jsou štosovány u poolu a odeslány až po překročení limitu.
Čtyři veřejné šablony bloku. Ocean pool nabízí čtyři různé sety pravidel pro sestavení šablony bloku, které se liší množstvím “SPAMu”. Jako spam jsou zde označovány transakce podporující Inscriptions a BRC-20 tokeny. Názory na tuto “cenzuru” se v bitcoinové komunitě různí, nicméně pokud chcete jako já plnit bitcoinový block-chain pouze finančními transakcemi, můžete hlasovat právě zde. Pohled do mempoolu na strukturu bloků vytěžených Ocean poolem vám prozradí průběžné výsledky tohoto hlasování.
Sytém odměnování TIDES. Ocean pool rozděluje odměny vlastním systémem TIDES (Transparent Index of Distinct Extended Shares). Ten vychází z PPLNS, ale výrazně prodlužuje okno, ve kterém se podíly sbírají, což pomáhá těžařům, kteří nemají těžící zařízení zapojeno kontinuálně (například kvůli napájení solární energií nebo využívání mineru pouze nárazově pro vytápění). Zároveň je celý systém zcela transparentní. Všechny důležité údaje jsou průběžně viditelné na webových stránkách poolu, takže si každý může ověřit svůj podíl na odměně. Ta je pak distribuována těžařům přímo v coinbase transakci nově vytěženého bloku.
Podpora většiny typů bitcoinových adres. Ocean Pool podporuje širokou škálu typů bitcoinových adres, včetně P2PKH, P2SH, Bech32 a Bech32m.
Poplatky poolu jsou po dobu prvních dvou měsíců zdarma. V případě šablon bloků OCEAN Recommended, Core+Antispam a Data-Free zůstavají na 0% i v dalších měsících. Pouze pro nefiltrovanou šablonu Core jsou nastaveny 2%. Pool tak motivuje své uživatele k podpoře boje se spamem v block-chainu.
Do budoucna pool plánuje výrazně rozšířit podporu Stratum V2 těžebního protokolu a umožnit tak těžařům ještě větší volnost při sestavení šablony bloku. Na rok 2024 pak plánuje podporu Lightning Network adres pro vyplácení podlimitních podílů malým těžařům.
Braiins pool
Braiins Pool (původně Slush pool) je lídrem v oblasti těžby bitcoinů, známý svou transparentností a inovacemi. Od svého založení v roce 2010 vytěžil více než 1,3 milionu BTC a etabloval se jako spolehlivý a efektivní těžební pool.
Braiins Pool je provozován českou společností Braiins, která stojí za celou řadou produktů a služeb pro těžbu bitcoinu a záslužných počinů v oblasti vzdělávání a rozšiřování adopce. Prozkoumejte následující odkazy: Braiins OS+, Braiins HW, Braiins Insights, Braiins Publishing, Bitperia…
Klíčové vlastnosti
Systém odměňování FPPS. Na konci loňského listopadu oznámil Braiins pool přechod od do té doby používaného systému vyplácení odměn PPLNS k FPPS. Motivací k této změně bylo zvýšení stability a předvídatelnosti odměn, tedy vlastnosti, které jsou klíčové primárně pro velké těžaře (farmy), jejichž business plán trpěl nejistotou závislosti na štěstí poolu. FPPS pomáhá velikost příjmu stabilizovat na úroveň odpovídající 100% štěstí poolu, tedy hodnotu jakou by příjem dosahoval, pokud by pool těžil nové bloky ve frekvenci přesně odpovídající podílu hashrate poolu na celkové hashrate sítě, respektive nastavené obtížnosti. Součástí odměny jsou i podíly na průměrné výši poplatků za daný den.
Limit pro výplatu odměn je v Braiins poolu nastaven na 0.0002 BTC (tedy 20 000 satů). Pokud ale vybíráte méně, než 0.005 BTC (500 000 satů), zaplatíte navíc poplatek za výběr v hodnotě 0.0001 BTC (10 000 satů). Výplatu odměn je však možné provést i přes Lightning Network a to zcela bez limitu a poplatků!
Poplatky poolu jsou nastaveny na 2.5%. Pokud však vaše těžící zařízení používá Braiins OS+ firmware, jsou poplatky 0%. To je zvláště zajímavé pro domácí těžení s komerčními minery od Bitmainu (AntMiners).
Podpora Stratum V2 protokolu. Společnost Braiins se podílí na specifikaci a implementaci těžebního protokolu Stratum V2, který zvyšuje zabezpečení a efektivitu komunikace mezi težícím zařízením a poolem a přispívá k decentralizaci těžby bitcoinu tím, že umožňuje tvorbu šablony bloku (a tím výběr transakcí do bloku) nezávisle na poolu.
Pro úplnost, jaká je návratnost?
Ačkoliv jsem v minulých kapitolách velmi pečlivě snažil zdůraznit, že profitabilita domácí těžby není tou prioritní motivací a v případě tzv. solo-miningu se pravděpodobnost úspěchu rovná výhře v loterii, není od věci ukázat si reálné pravděpodobnosti vytěžení bloku pro jednotlivé typy těžících zařízení.
Obtížnost těžby bitcoinu je algoritmicky nastavena tak, aby při daném hashrate celé sítě byl nový blok vytěžen každých zhruba 10 minut. Pravděpodobnost úspěchu konkrétního těžícího zařízení je pak dána podílem hashrate tohoto zařízení hminer a právě celkové hashrate sítě Hnet:
Pblock = hminer / Hnet
Převrácená hodnota pak udává střední počet bloků mezi dvěma bloky vytěženými daným zařízením. Pro získání střední doby pro vytěžení bloku je nutné ji ještě vydělit číslem 144 (počet bloků za den) nebo 144*365 (počet bloků za rok).
Tyear = Hnet / (144 * 365 * hminer)
V současné době (únor 2024) je celkový hashrate sítě Hnet ≈ 530 EH/s. Následující tabulka ukazuje střední dobu mezi dvěma bloky pro některá těžící zařízení používaná při domácí těžbě.
| Miner | Hashrate | Tyear | | --- | --- | --- | | NerdMiner | 56 kH/s | 180.066.318.765 | | Bitaxe Ultra | 500 GH/s | 20.168 | | AntMinner S9 | 14 TH/s | 720 | | AntMiner S19 PRO | 110 TH/s | 92 | | AntMiner S21 | 200 TH/s | 50 |
Spočtení návratnosti již nechám na vás, ale věřím, že výrok o loterii solo-miningu je nyní srozumitelnější.
Vlastní zkušenosti
Rozhodnutí koupit si vlastní bitcoin miner bylo takto zpětně určitě jedno z těch lepších, které jsem udělal. Otevřel se mi zcela nový rozměr bitcoinu, nové chápání všech textů o bitcoinové těžbě, prostě nová králičí nora. Bez osobní zkušenosti je toto téma poloviční. Jakou zkušenost jsem tedy udělal?
Tak předně jsem zjistil, že těžbě bitcoinu je věnováno více informačních portálů, knih a článků, než jsem si myslel. A kupodivu se k nim jen málokdy dostanete z tradičních bitcoinových webů. Možná je to díky technologické podstatě těžby, která je přeci jen více vzdálená tradičním úvahám kolem bitcoinového etosu a zdravých peněz. Možná tím, že těžba bitcoinu je již plnohodnotným průmyslovým odvětvím s velmi tvrdou ekonomikou, kde se podstatně více uplatní znalosti z energetiky, elektroniky a mikroekonomie, než myšlenky rakouské ekonomické školy. Skoro každý den nacházím nové informace a články, které mne přesvědčují, že toho ještě mnoho nevím.
Ale teprve až zprovoznění vlastního mineru mi přineslo nové poznání a další zkušeností. A také mne donutilo najít ve sklepě svou starou pájku, abych upravil napájecí zdroj pro miner…
Ale vážně. Jako s každou novou hračkou jsem strávil první hodiny a dny zkoumáním možností, které mi nabízí. Mým prvním minerem byl Bitaxe Ultra. Je vybaven firmwarem AxeOS, což je open-source implementace ASIC miner software pro ESP32 kontroler. Krom jiných parametrů umožňuje nastavit frekvenci a napětí pro použitý ASIC (BM1366) a nabízí tedy prostor pro experimenty s přetaktováním. V mém případě se ukázalo, že výsledky jsou závislé nejen na štěstí v podobě kvality konkrétního ASIC čipu, který stabilně zvládá vyšší frekvence, ale i na kvalitě použitého zdroje (ten můj nebyl dostatečně tvrdý).
Když jsem si dostatečně vyhrál s výkonovými možnostmi mého kousku, začalo mne zajímat, kam všude se mohu s tímto “nevýkoným” minerem připojit a kolik satů mi svým hashrate vydělá v různých poolech. Pokud jste po získání prvního bitcoinu trávili svůj čas sledováním jeho kurzu na nejrůznějších burzách, tak s novým minerem strávíte spoustu času sledováním, jestli se náhodou už poolu nepodařilo vytěžit nový blok a jak velký je váš podíl na odměně. Ale i tento čas není časem ztraceným. Já jsem na vlastní kůži poznal rozdíly mezi PPLNS a FPPS modely odměňování a ověřil si, že v delších časových úsecích opravdu platí závislost četnosti nalezených bloků na podílu z celkového hashrate sítě.
Za zmínku stojí i pozorování chování velkých těžařů v poolech, respektive pohybu velkého množství hashrate mezi nimi. Tyto pohyby se nedějí náhodně a je velmi poučné analyzovat příčiny, které k nim vedly. Ano, odhadujete správně, společným jmenovatelem je vždycky zisk. Je jedno, jestli za ním stojí změna nebo úprava modelu odměňování, nebo třeba nějaká krátkodobá aktivita na block-chainu. Takovou bylo třeba vložení většího množství transakcí s poplatkem ve stovkách satů za vByte na začátku února (kolem výšky bloku 828752) v době, kdy byl průměrný poplatek kolem 30 satů za vByte. Transakcí bylo tak zhruba na několik desítek bloků a velikost poplatků v bloku často v jednotkách bitcoinů. To je situace, kdy každý těžař chce mít svůj hashrate v poolu, který vyplácí podíl z vytěžených poplatků a zároveň těží nové bloky dostatečně často, aby měl šanci nějaký takový naditý blok vytěžit. Není divu, že Ocean pool přišel na těch několik hodin o skoro celý 1 Eh/s (cca 70% celého hashrate). Těží nový blok jen přibližně jednou za dva a půl dne. Boj proti spamu je bohulibé poslání, ale zisk je zisk!
Přesto anebo právě proto, domácí těžbě bitcoinu: Zdař Bůh!
-
 @ b12b632c:d9e1ff79
2023-07-20 20:12:39
@ b12b632c:d9e1ff79
2023-07-20 20:12:39Self hosting web applications comes quickly with the need to deal with HTTPS protocol and SSL certificates. The time where web applications was published over the 80/TCP port without any encryption is totally over. Now we have Let's Encrypt and other free certification authority that lets us play web applications with, at least, the basic minimum security required.
Second part of web self hosting stuff that is really useful is the web proxifycation.
It's possible to have multiple web applications accessible through HTTPS but as we can't use the some port (spoiler: we can) we are forced to have ugly URL as https://mybeautifudomain.tld:8443.
This is where Nginx Proxy Manager (NPM) comes to help us.
NPM, as gateway, will listen on the 443 https port and based on the subdomain you want to reach, it will redirect the network flow to the NPM differents declared backend ports. NPM will also request HTTPS cert for you and let you know when the certificate expires, really useful.
We'll now install NPM with docker compose (v2) and you'll see, it's very easy.
You can find the official NPM setup instructions here.
But before we absolutely need to do something. You need to connect to the registrar where you bought your domain name and go into the zone DNS section.You have to create a A record poing to your VPS IP. That will allow NPM to request SSL certificates for your domain and subdomains.
Create a new folder for the NPM docker stack :
mkdir npm-stack && cd npm-stackCreate a new docker-compose.yml :
nano docker-compose.ymlPaste this content into it (CTRL + X ; Y & ENTER to save/quit) :
``` version: '3.8' services: app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt```
You'll not believe but it's done. NPM docker compose configuration is done.
To start Nginx Proxy Manager with docker compose, you just have to :
docker compose up -dYou'll see :
user@vps:~/tutorials/npm-stack$ docker compose up -d [+] Running 2/2 ✔ Network npm-stack_default Created ✔ Container npm-stack-app-1 StartedYou can check if NPM container is started by doing this command :
docker psYou'll see :
user@vps:~/tutorials/npm-stack$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7bc5ea8ac9c8 jc21/nginx-proxy-manager:latest "/init" About a minute ago Up About a minute 0.0.0.0:80-81->80-81/tcp, :::80-81->80-81/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp npm-stack-app-1If the command show "Up X minutes" for the npm-stack-app-1, you're good to go! You can access to the NPM admin UI by going to http://YourIPAddress:81.You shoud see :

The default NPM login/password are : admin@example.com/changeme .If the login succeed, you should see a popup asking to edit your user by changing your email password :
 And your password :
And your password :
 Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
 Followed by "Add Proxy Host"
Followed by "Add Proxy Host"
 If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :
If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :Details tab :
 SSL tab :
SSL tab :
 And click on "Save".
And click on "Save".NPM will request the SSL certificate "admin.yourdomain.tld" for you.
If you have an erreor message "Internal Error" it's probably because your domaine DNS zone is not configured with an A DNS record pointing to your VPS IP.
Otherwise you should see (my domain is hidden) :

Clicking on the "Source" URL link "admin.yourdomain.tld" will open a pop-up and, surprise, you should see the NPM admin UI with the URL "https://admin.yourdomain.tld" !
If yes, bravo, everything is OK ! 🎇
You know now how to have a subdomain of your domain redirecting to a container web app. In the next blog post, you'll see how to setup a Nostr relay with NPM ;)
Voilààààà
See you soon in another Fractalized story!
-
 @ c73818cc:ccd5c890
2024-06-18 15:57:07
@ c73818cc:ccd5c890
2024-06-18 15:57:07
🐹 Il gioco cripto basato su Telegram, "Hamster Kombat", ha segnato un traguardo impressionante superando i 150 milioni di giocatori. Questo rappresenta un aumento del 50% rispetto alla settimana precedente, evidenziando il suo straordinario successo nel coinvolgere gli utenti di Telegram.
🐹 Il gioco, che offre ricompense in criptovalute attraverso un token dedicato, sta ridefinendo il concetto di gaming integrato nelle piattaforme di messaggistica. Con il previsto lancio del token per i giocatori, "Hamster Kombat" continua a catalizzare l'interesse nella comunità crypto, sfruttando la popolarità di Telegram per ampliare ulteriormente la sua base di utenti.
Accedi al gioco partendo già da 25.000 monete! Partecipa per ricevere l'AirDrop al lancio del token! https://t.me/hamster_komBat_bot/start?startapp=kentId740914800
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
BitcoinReportItalia #HamsterKombat #Telegram #Criptovalute #Hamster #Gioco #Gaming #TON #NOT #Bitcoin
-
 @ 20986fb8:cdac21b3
2024-06-18 13:44:55
@ 20986fb8:cdac21b3
2024-06-18 13:44:55X Space: https://x.com/YakiHonne/status/1800543085639979388
In a recent panel organized by Yakihonne and Bitmain, industry experts gathered to discuss the vital role of marketing in the success of crypto projects. Hosted by Emma from Yakihonne, the discussion featured insights from key figures in the blockchain space, including Margie from Bitmain, Keypleb from Bitcoin Indonesia, Udi from Taproot Wizards, John from BEVM, and Shaun from Yakihonne. This event highlighted the intersection of innovative technology and strategic marketing in driving the growth and adoption of crypto projects.
The Importance of Marketing in the Crypto Industry
Emma kicked off the discussion by emphasizing the rapid growth of the crypto market and the essential role marketing plays in achieving success. She noted that having a great project is just the beginning, effectively communicating its value to the right audience is crucial.
Insights from Speakers
Margie, Marketing Manager at Bitmain Margie shared Bitmain's commitment to supporting the Bitcoin ecosystem, highlighting their events like the WDMS2024 in Las Vegas. She emphasized that good products and customer experiences are at the core of Bitmain's marketing strategy. Margie also discussed their influencer program, which involves collaborations with KOLs to make complex concepts more accessible and engaging for a broader audience.
Keypleb, Co-founder of Bitcoin Indonesia Keypleb outlined the community-building efforts of Bitcoin House Bali and Bitcoin Indonesia. He stressed the importance of focusing on the core mission of Bitcoin amidst the noise and distractions in the market. By organizing unique and engaging meetups, they create a strong sense of community and education around Bitcoin.
Udi, Co-founder of Taproot Wizards Udi explained how Taproot Wizards aims to make Bitcoin culture fun and engaging while promoting technical upgrades and community involvement. By balancing humor and serious innovation, they foster a sense of participation and excitement within the Bitcoin community.
John, Builder of BEVM John discussed the challenges of educating users about the technical aspects of Bitcoin Layer 2 solutions. BEVM focuses on promoting specific topics over time and involves users in decentralized campaigns to increase engagement. Their strategy includes developer grants and visionary builder programs to encourage contributions from the developer community.
Shaun, Partner at Yakihonne Shaun highlighted Yakihonne's mission to connect Bitcoin ecosystem projects with users through decentralized media. By creating features like curations and uncensored notes, Yakihonne enhances user engagement and ensures high-quality content distribution. Shaun emphasized the importance of decentralization in the crypto industry and the need to move away from relying on centralized platforms.
Overcoming Marketing Challenges in the Crypto
Margie led a discussion on the biggest challenges in marketing within the Bitcoin community. Keypleb identified misinformation and distractions as major hurdles, emphasizing the need to stay focused on the core mission of Bitcoin. John pointed out the difficulty of conveying the value of technical innovations to a broader audience, stressing the importance of strategic partnerships and clear communication.
Measuring Success
The panelists also discussed how they measure the success of their marketing efforts. For Keypleb, the number of attendees at meetups is a key metric. John mentioned metrics like successful collaborations and user engagement on social media. Margie highlighted the importance of community activity and event participation.
The Future of Decentralized Media
Shaun addressed a question from the audience about the future of decentralized media. He expressed a strong belief in the importance of decentralization and its potential to transform the industry over the next decade. While the exact future is uncertain, the commitment to decentralized principles remains clear.
Conclusion
The panel highlighted that effective marketing is indispensable for the success of crypto projects. By leveraging community engagement, strategic partnerships, and innovative communication strategies, these industry leaders are driving the growth and adoption of their projects.
YakiHonne: Yakihonne is a decentralized social protocol built on Nostr, which allows users to seamlessly step into Bitcoin Ecosystem, and benefit from the ecosystem growth from both Bitcoin and Nostr. We are proud to be the exclusive decentralized media partner at this year's Las Vegas Miners Conference. In collaboration with BITMAIN, we will be hosting an Bitcoin/Nostr meetup. Additionally, as a strategic partner of Bitcoin Magazine, we will be organizing a side event at the Bitcoin Conference in Nashville. Website: https://yakihonne.com/
Bitmain: Since its foundation in 2013, BITMAIN is the world's leading manufacturer of cryptocurrency mining servers through its brand ANTMINER, which has long maintained a global market share and leading position in technology, serving customers across over 100 countries and regions. Website: https://www.bitmain.com/
npub1vfs8ncehs44zk285zzkpg8gf9txlzyevstlfqss6ydexl38cumhqxavpu2
-
 @ 5d4b6c8d:8a1c1ee3
2024-06-18 13:23:15
@ 5d4b6c8d:8a1c1ee3
2024-06-18 13:23:15Read the previous edition here.
Added back post titles for top comments
June 18th, 2023 📅
📝
TOP POSTThere is something unique about this beautiful community.
Everyone is kind to share everything. When i ask for something everyone is sharing their knowledge. Thank you so much everyone.
2213 sats \ 18 comments \ @OpenMind \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/195550/r/Undisciplined?commentId=195618
From Competing with Apple and Google - A Weekend Discussion
Excerpt:
Create a large scale open-source project and back it behind an organisation/company similar to the AOSP, Ubuntu or Sourcehut business model. Initially start as a project for other devices to reduce cost and achieve funds, and eventually work with an OEM to manufacture a hardware device for that with said funds.
2146 sats \ 0 replies \ @final \ ~bitcoin
🏆
TOP STACKER2nd Place: @mudbloodvonfrei (1st place presumed to be @siggy47)
3324 stacked \ 489 spent \ 4 posts \ 28 comments \ 0 referrals
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
June 18th, 2022 📅
📝
TOP POSTArcade City - Uber decentralized with Lightning
Link to https://arcade.city/
1653 sats \ 22 comments \ @k00b \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/37399/r/Undisciplined?commentId=37402
From What are the Centralization Risks in Bitcoin?
I think that Exchanges are the biggest centralization risk right now, people are waking up to the fact that id you are not self sovereign you don't actually own you bitcoin
153 sats \ 2 replies \ @EnormousPony \ ~bitcoin
🏆
TOP STACKER@k00b
2375 stacked \ 8702 spent \ 9 posts \ 13 comments \ 0 referrals
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
June 18th, 2021 📅
📝
TOP POSTLink to https://github.com/bitcoin/bips/blob/master/bip-0300.mediawiki
10 sats \ 221 boost \ 3 comments \ @lylepratt \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/60/r/Undisciplined?commentId=71
From [blockchain.com wallet (finally) supports native segwit)(https://stacker.news/items/60/r/Undisciplined)
I wonder how much of the mempool clearing is related to this.
1 sat \ 1 reply \ @lylepratt \ ~bitcoin
🏆
TOP STACKEREMPTY
-
-
 @ 78733875:4eb851f2
2023-07-14 22:25:21
@ 78733875:4eb851f2
2023-07-14 22:25:21"The computer can be used as a tool to liberate and protect people, rather than to control them," as Hal Finney wrote so presciently 30 years ago.[^fn-hal]
The goal of OpenSats is to help build the tools that Hal alluded to. Tools that liberate and protect, rather than systems that control and oppress. Many tools still have to be built. Many tools still need to be improved. However, "the universe smiles on encryption," as Assange so aptly put it.[^fn-assange]
We believe that freedom tech is what carries this smile forward, which is why we are delighted to announce grants for over a dozen projects in the bitcoin & lightning ecosystem.
[^fn-hal]: Hal Finney: Why remailers... (November 1992)
[^fn-assange]: Julian Assange: A Call to Cryptographic Arms (October 2012)
The following open-source projects were selected by the OpenSats board for funding:
- Payjoin Dev Kit
- Bolt12 for LND
- Splicing
- Raspiblitz
- Labelbase
- BTCPay Server
- ZeroSync
- Mutiny Wallet
- next-auth Lightning Provider
- Cashu
- lnproxy
- Blixt Wallet
Let's take a closer look at each to understand their goal and how it aligns with the OpenSats mission.
Payjoin Dev Kit
Payjoin brings privacy to bitcoin without changing the way you're used to using it. Payjoin transactions look no different from normal activity on-chain, so they boost everyone's privacy, even those who don't payjoin, and foil chain surveillance.
Payjoin is easy to integrate and falls back to working defaults where it isn't supported, but it can only take off when senders and receivers include standard payjoin support in their software. Payjoin Dev Kit makes it easy for wallet developers to integrate BIP 78 standard payjoins everywhere, having working reference integrations for Bitcoin Core, LND, and BDK.
Repository: github.com/payjoin
License: MITBolt12 for LND
Bolt12 brings a new invoice format, enabling static invoices (offers) as well as recurring payments. It adds support to receive payments in a lightning-native way without using a web server. It also uses Blinded Paths to disguise the destination of a node both when fetching the invoice and when paying. This improves privacy and, therefore, security for the receiver of the payment.
Consequently, Bolt12 makes it much easier to receive and send payments without any third-party infrastructure in a native-lightning way. Static invoices make donations and recurring payments much easier.
Repository: lightningnetwork/lnd
License: MITSplicing
Splicing is the ability to resize Lightning channels on-the-fly, giving users of the Lightning Network many additional benefits that were not intuitively obvious at first. Splicing scales Lightning by removing a fundamental limitation. Removing this limitation increases fungibility and lowers blockspace usage, an important step towards maturing the Lightning network and enabling the onboarding of millions, and ultimately billions, of people.
Repository: ddustin/splice
License: BSD-MITRaspiblitz
Raspiblitz is a do-it-yourself node stack that allows you to run a Lightning Node together with a Bitcoin Core full node on your Raspberry Pi. While the Raspberry Pi is the most common hardware running this particular software, it was developed to support multiple hardware platforms and can run on bare metal servers too.
The open-source project was started in 2018 as part of a Lightning hackathon in the German Bitcoin space. Since then, it has grown to over 150 contributors and 2000 stars on GitHub. The software integrates dozens of services and tools via its plugin system and sports advanced features like touchscreen support, channel autopilot, backup systems, DynDNS, SSH tunneling, and more.
Repository: raspiblitz/raspiblitz
License: MITLabelbase
Labelbase is a label management service for Bitcoin transactions and addresses. It provides features for adding labels, importing and exporting labels, and offers a public API for integration with wallets and existing workflows.
Labelbase supports BIP-329, a format for unifying label data. The goal of the project is to offer a convenient solution for managing labels associated with Bitcoin transactions and addresses across wallets and other tools. By providing a unified label management interface, Labelbase enhances the user experience, improves privacy, and promotes better organization and understanding of Bitcoin transactions.
Repository: Labelbase/Labelbase
License: MITBTCPay Server
BTCPay Server is a free, open-source & self-hosted bitcoin payment gateway that allows self-sovereign individuals and businesses to accept bitcoin payments online or in person without added fees.
At its core, BTCPay Server is an automated invoicing system. Merchants can integrate the software with their website or shop, so customers are presented with an invoice upon checkout. The status of the invoice will update according to settlement, so merchants can fulfill the order at the appropriate time. The software also takes care of payment refunding and bitcoin management alongside many other features.
Repository: btcpayserver/btcpayserver
License: MITZeroSync
While ZeroSync is still at an early stage, its promise is to allow verification of Bitcoin's chain state in an instant. It offers compact cryptographic proofs to validate the entire history of transactions and everyone's current balances.
The first application is to "zerosync" Bitcoin Core in pruned mode. The long-term vision for ZeroSync is to become a toolbox for custom Bitcoin proofs.
Repository: zerosync/zerosync
License: MITMutiny Wallet
Mutiny Wallet is a web-first wallet capable of running anywhere, providing instant onboarding and platform censorship resistance. It is self-custodial, privacy-focused, user-friendly, and open-sourced under the MIT license.
The wallet has a strong focus on privacy, scalability, and accessibility. In addition to features that you would expect a regular lightning wallet to have, the team is working to incorporate Nostr-related features into the wallet, such as a feed of friends' Zaps, native Zap sending and receiving, a lightning subscription specification for services such as nostr relays, and a P2P DLC marketplace. The team's goal is to provide users with a seamless experience, combining the power of Bitcoin and Lightning with social media in a way that matches the Bitcoin ethos.
Repository: MutinyWallet
License: MITnext-auth Lightning Provider
The goal of this project is to implement an authentication provider for next-auth, an authentication provider for the popular open-source framework NextJS. The next-auth framework has nearly 500k weekly downloads and powers the authentication of many modern web, mobile, and desktop apps. Having a plug-and-play Provider for Lightning makes integration easier and more attractive for developers.
Repository: jowo-io/next-auth-lightning-provider
License: ISCCashu
Cashu is a Chaumian ecash system built for bitcoin that brings near-perfect privacy for users of custodial bitcoin applications. A Cashu ecash mint does not know who you are, what your balance is, or who you're transacting with. Users of a mint can exchange ecash privately, without anyone being able to know who the involved parties are.
Payments are executed without anyone able to censor specific users. There are multiple implementations of the Cashu protocol. Popular open-source wallets are Cashu Nutshell, Cashu.me, and Nutstash.
Repository: cashubtc/cashu
License: MITlnproxy
lnproxy is a simple privacy tool that empowers users of custodial Lightning wallets with better payment destination privacy and sovereign node runners with enhanced receiver privacy. lnproxy works like a "poor man's" rendezvous router, providing privacy for users without taking custody of their funds. The project encompasses an LNURL-style protocol specification and a collection of open-source implementations of lnproxy clients and a relay.
Repository: lnproxy/lnproxy
License: GPL 3.0 & MITBlixt Wallet
Blixt is a non-custodial wallet for bitcoiners who want to give Lightning a try. It runs on Android, iOS, and macOS. It is easy to use and straightforward to set up, making it a user-friendly option to get started with Lightning.
Blixt uses LND and Neutrino under the hood, directly on the phone, respecting your privacy. The wallet does not use any centralized servers for doing transactions. Channels are opened automatically on the user's behalf, making it easy to get up and running on Lightning.
Repository: hsjoberg/blixt-wallet
License: MIT
In addition to the software projects listed above, three educational initiatives were selected for funding:
- Bitcoin Education in Nigeria is an initiative started and led by Apata Johnson. Apata's project aims to educate youths on bitcoin and the opportunities it brings for the people living in the rural areas of Nigeria.
- 21 Ideas is a project that aims to bring quality Bitcoin education to Russian citizens. Tony and others have been working for many years on translations, original material, and hands-on tutorials for beginners. We believe that education is paramount to proper Bitcoin use, and localization is paramount for everyday citizens to properly grasp the importance as well as the novel concepts of bitcoin.
- CoreDev.tech is organizing recurring developer events, which are all about bringing devs together so that they can hack on Bitcoin Core and related software.
We received hundreds of applications in the last couple of months, which is a fantastic signal and something we are delighted about. Some applications are still being reviewed by the OpenSats board, as we try our best to assess feasibility, alignment, and potential impact of each project. We will announce additional grants as applications pass our grant selection process.
Unfortunately, we were unable to fund all of the proposals that were sent to us. Please don't hesitate to apply again in case your application was rejected this time around. The applicant pool was very competitive, which is a great thing to see in and of itself.
Grants for the projects above are funded by contributions to the Bitcoin General Fund. Our operations as well as our grant programs are made possible by generous donors like you. If you want to help fund the Bitcoin ecosystem, please donate to the Bitcoin General Fund.
Our team is screening applications constantly, and we will announce new grants and funding opportunities as they arise. If you are working on an open-source project in and around bitcoin, and you think your work is aligned with the OpenSats mission, please apply for funding.
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ c73818cc:ccd5c890
2024-06-18 12:41:34
@ c73818cc:ccd5c890
2024-06-18 12:41:34
💀 Il capo della SEC, Gary Gensler, ha lanciato un nuovo avvertimento agli scambi di criptovalute, minacciando ulteriori regolamentazioni e controlli. Un'ennesima mossa da parte delle istituzioni per soffocare l'innovazione e limitare la scelta individuale. Questa ossessione per il controllo dimostra la paura delle élite di perdere il potere su un sistema finanziario decentralizzato come Bitcoin.
💀 La SEC contro l'innovazione: Bitcoin come strumento di liberazione
💀 Le continue minacce di Gensler contro il settore delle criptovalute non fanno altro che confermare la sua agenda anti-innovazione e il suo servilismo verso gli interessi delle grandi banche. Bitcoin, invece, rappresenta uno strumento di liberazione economica che permette agli individui di sottrarsi al controllo statale del denaro e di gestire autonomamente i propri patrimoni.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
BitcoinReportItalia #SEC #Gensler #Criptovalute #Exchange #Regolamentazioni #Potere #USA #Banche #Dollaro #Bitcoin
-
 @ 42342239:1d80db24
2024-03-21 09:49:01
@ 42342239:1d80db24
2024-03-21 09:49:01It has become increasingly evident that our financial system has started undermine our constitutionally guaranteed freedoms and rights. Payment giants like PayPal, Mastercard, and Visa sometimes block the ability to donate money. Individuals, companies, and associations lose bank accounts — or struggle to open new ones. In bank offices, people nowadays risk undergoing something resembling being cross-examined. The regulations are becoming so cumbersome that their mere presence risks tarnishing the banks' reputation.
The rules are so complex that even within the same bank, different compliance officers can provide different answers to the same question! There are even departments where some of the compliance officers are reluctant to provide written responses and prefer to answer questions over an unrecorded phone call. Last year's corporate lawyer in Sweden recently complained about troublesome bureaucracy, and that's from a the perspective of a very large corporation. We may not even fathom how smaller businesses — the keys to a nation's prosperity — experience it.
Where do all these rules come?
Where do all these rules come from, and how well do they work? Today's regulations on money laundering (AML) and customer due diligence (KYC - know your customer) primarily originate from a G7 meeting in the summer of 1989. (The G7 comprises the seven advanced economies: the USA, Canada, the UK, Germany, France, Italy, and Japan, along with the EU.) During that meeting, the intergovernmental organization FATF (Financial Action Task Force) was established with the aim of combating organized crime, especially drug trafficking. Since then, its mandate has expanded to include fighting money laundering, terrorist financing, and the financing of the proliferation of weapons of mass destruction(!). One might envisage the rules soon being aimed against proliferation of GPUs (Graphics Processing Units used for AI/ML). FATF, dominated by the USA, provides frameworks and recommendations for countries to follow. Despite its influence, the organization often goes unnoticed. Had you heard of it?
FATF offered countries "a deal they couldn't refuse"
On the advice of the USA and G7 countries, the organization decided to begin grading countries in "blacklists" and "grey lists" in 2000, naming countries that did not comply with its recommendations. The purpose was to apply "pressure" to these countries if they wanted to "retain their position in the global economy." The countries were offered a deal they couldn't refuse, and the number of member countries rapidly increased. Threatening with financial sanctions in this manner has even been referred to as "extraterritorial bullying." Some at the time even argued that the process violated international law.
If your local Financial Supervisory Authority (FSA) were to fail in enforcing compliance with FATF's many checklists among financial institutions, the risk of your country and its banks being barred from the US-dominated financial markets would loom large. This could have disastrous consequences.
A cost-benefit analysis of AML and KYC regulations
Economists use cost-benefit analysis to determine whether an action or a policy is successful. Let's see what such an analysis reveals.
What are the benefits (or revenues) after almost 35 years of more and more rules and regulations? The United Nations Office on Drugs and Crime estimated that only 0.2% of criminal proceeds are confiscated. Other estimates suggest a success rate from such anti-money laundering rules of 0.07% — a rounding error for organized crime. Europol expects to recover 1.2 billion euros annually, equivalent to about 1% of the revenue generated in the European drug market (110 billion euros). However, the percentage may be considerably lower, as the size of the drug market is likely underestimated. Moreover, there are many more "criminal industries" than just the drug trade; human trafficking is one example - there are many more. In other words, criminal organizations retain at least 99%, perhaps even 99.93%, of their profits, despite all cumbersome rules regarding money laundering and customer due diligence.
What constitutes the total cost of this bureaurcratic activity, costs that eventually burden taxpayers and households via higher fees? Within Europe, private financial firms are estimated to spend approximately 144 billion euros on compliance. According to some estimates, the global cost is twice as high, perhaps even eight times as much.
For Europe, the cost may thus be about 120 times (144/1.2) higher than the revenues from these measures. These "compliance costs" bizarrely exceed the total profits from the drug market, as one researcher put it. Even though the calculations are uncertain, it is challenging — perhaps impossible — to legitimize these regulations from a cost-benefit perspective.
But it doesn't end there, unfortunately. The cost of maintaining this compliance circus, with around 80 international organizations, thousands of authorities, far more employees, and all this across hundreds of countries, remains a mystery. But it's unlikely to be cheap.
The purpose of a system is what it does
In Economic Possibilities for our Grandchildren (1930), John Maynard Keynes foresaw that thanks to technological development, we could have had a 15-hour workweek by now. This has clearly not happened. Perhaps jobs have been created that are entirely meaningless? Anthropologist David Graeber argued precisely this in Bullshit Jobs in 2018. In that case, a significant number of people spend their entire working lives performing tasks they suspect deep down don't need to be done.
"The purpose of a system is what it does" is a heuristic coined by Stafford Beer. He observed there is "no point in claiming that the purpose of a system is to do what it constantly fails to do. What the current regulatory regime fails to do is combat criminal organizations. Nor does it seem to prevent banks from laundering money as never before, or from providing banking services to sex-offending traffickers
What the current regulatory regime does do, is: i) create armies of meaningless jobs, ii) thereby undermining mental health as well as economic prosperity, while iii) undermining our freedom and rights.
What does this say about the purpose of the system?
-
 @ a012dc82:6458a70d
2024-06-18 12:40:55
@ a012dc82:6458a70d
2024-06-18 12:40:55Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Introduction
The world of Bitcoin mining can be a complex and confusing one, with many different factors at play. One important metric that can have a big impact on a miner's profitability is hash rate. In this blog post, we'll explore what hash rate is, how it affects profitability, and what miners can do to increase their hash rate.
What is Hash Rate?
Hash rate is a measure of a miner's computational power. It is the number of hashes (or calculations) that a miner can perform per second. The higher the hash rate, the more computational power a miner has, and the more likely they are to find new Bitcoins.
How Does Hash Rate Affect Profitability?
Hash rate is closely tied to profitability in Bitcoin mining. The more computational power a miner has, the more likely they are to find new Bitcoins, and the more Bitcoins they can earn. This can be especially important for miners who are competing against others to find new Bitcoins. If a miner has a higher hash rate than others, they will be more likely to find new Bitcoins, and thus more profitable.
Factors that Influence Hash Rate
There are several factors that can influence a miner's hash rate. These include the type of mining hardware being used, the power and efficiency of the hardware, and the miner's access to cheap electricity.
How to Increase Hash Rate
There are several ways that miners can increase their hash rate. One way is to invest in more powerful and efficient mining hardware. Another way is to optimize their mining software and settings to get the most out of their hardware. Additionally, miners can also choose to mine in locations where electricity is cheaper, which can help them save money on electricity costs and increase their profitability.
Conclusion
Hash rate is a crucial metric in Bitcoin mining, with the hash rate affecting the miner's profitability. It is important for miners to understand how hash rate is affected by various factors such as mining hardware, electricity costs and settings of their mining software. Miners can increase their hash rate by investing in more powerful and efficient mining hardware, optimizing their mining software and settings, and choosing to mine in locations with cheaper electricity.
Frequently Asked Questions
What is hash rate? Hash rate is a measure of a miner's computational power, or the number of hashes a miner can perform per second.
How does hash rate affect profitability in Bitcoin mining? Hash rate is closely tied to profitability in Bitcoin mining. A higher hash rate means a miner is more likely to find new Bitcoins, and thus more profitable.
What are some factors that can influence a miner's hash rate? Factors that can influence a miner's hash rate include the type of mining hardware, the power and efficiency of the hardware, and access to cheap electricity.
How can miners increase their hash rate? Miners can increase their hash rate by investing in more powerful and efficient mining hardware, optimizing their mining software and settings, and choosing to mine in locations with cheaper electricity.
Is it possible to mine Bitcoin with a low hash rate? It is possible to mine Bitcoin with a low hash rate, but it will be less profitable and less likely to find new Bitcoins.
Does a high hash rate guarantee success in Bitcoin mining? A high hash rate does not guarantee success in Bitcoin mining as there are other factors that affect profitability such as the cost of electricity and the difficulty of the mining process.
Is it possible to overclock mining hardware to increase hash rate? Overclocking mining hardware can increase hash rate, but it also increases the risk of hardware damage and can shorten the lifespan of the equipment.
Can a miner's hash rate decrease over time? A miner's hash rate can decrease over time as mining hardware becomes outdated and loses efficiency.
Can a miner's hash rate be affected by external factors such as temperature? Yes, a miner's hash rate can be affected by external factors such as temperature. High temperatures can cause mining hardware to overheat and decrease performance.
Can joining a mining pool increase a miner's hash rate? Joining a mining pool can increase a miner's hash rate as they combine their computational power with others in the pool, increasing the chances of finding new Bitcoins.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 362ebffa:492e2719
2024-06-18 12:34:19
@ 362ebffa:492e2719
2024-06-18 12:34:19In nature, nothing is infinite.
Even seemingly vast quantities, like the number of grains of sand or the number of atoms in the universe, are finite. This fundamental principle is the 'natural world'.
There is no such thing as infinite growth.
Humanity has created economic systems that defy this principle. We are creating money out of thin air, that attempt to achieve infinite growth and expansion.
This logical disconnection between the finite nature of the physical world and the theoretical constructs of our economy leads to chaos, war and conflicts ...
And that is why bitcoins is Humanity coming back to the natural laws.
Am I getting this right?
-
 @ 005bc4de:ef11e1a2
2024-06-18 12:21:05
@ 005bc4de:ef11e1a2
2024-06-18 12:21:05A lot of things are connected and it's amazing when they pop up and reveal themselves as distant cousins. Today, my wife and I were listening to the radio and a trivia question came up, actually two.
Quiz time
Question one was a repeat/review from last week and was something like this:
There is a life-size statue-replica of this gift located in Turkey. What's the gift?
See answer below image, but you might want to read the second question first before glancing at the answer.
Question two, for today, was something like:
A Greek astronomer could have told you this 2,300 years ago, and a Polish one 500 years ago, but only 1-in-4 people today could tell you this. What is it?
Answer below image. For fun, try to figure it out, then look at the answer below.
https://files.peakd.com/file/peakd-hive/crrdlx/AK7vzCsU1QUHqBMposUSJd2SPah7kEfeHUxCjr7gu9G7wsrArM66VPPHpBLkPLR.jpg Image created at Leonardo.ai
Question 1: answer to life-size replica of gift: Trojan Horse. Question 2: answer to 1-in-4 people today: the sun is the center of the solar system.
My wife tossed out an answer first, "Where the North Star is located?" she thought out loud. That was a good answer, I thought. My guess is that a lot more people back then could locate the North Star and that far fewer than 25% can pick out Polaris from a night sky today. Going with the "people are pretty dumb today" theory, I wanted something more obvious. I thought of the moon and how many moons there are. "Please," I thought to myself, "don't let 25% of the people not know that we have only one moon." How about moons and other planets? Hmm.
I thought of Ptolemy, the Greek astronomer. I thought of Copernicus. He was about 500 years ago, I knew that. Maybe the answer was a heliocentric solar system. I wasn't sure about Ptolemy and the sun/earth relation. Things kind of fit, but, was Copernicus Polish? That doesn't sound like a Polish name. I cheated and looked up Copernicus...yep, he was Polish. So, the answer I gave was that the sun is the center of the solar system. Turned out that was the correct answer.
Side tracked
While we were waiting for the official answer, my wife asked rather randomly, "Do you know what Gresham's Law is?"
My chipmunk brain scanned its files. Something twinged in the back of my head, I thought I'd heard that before. I knew a fellow with the last name Gresham back in school, which is why the name perked up and why I thought I'd paid attention to it in the first place. But, I didn't know the law, so I answered, "No."
"Bad money drives out good money," my wife said. Such a clear and simple statement. And, being about money, I must have heard or read of that at some point while reading about bitcoin. I told her that I'm not sure I agree with that law. To my thinking, people will simply reject bad money and go with the good. Why would they not?
I looked up Gresham's Law and I'll summarize it here. The idea is that "good money" is "hard money", that is, gold or silver coins that truly are gold or silver. "Bad money" is "soft money" like "gold" coins that are only a fraction gold and mostly watered down by some other common metal. Or, it's like paper fiat money backed by nothing.
Why does bad money beat out good money? Why would people go with watered down coinage or paper fiat? The answer lies in power and force. Governments institute the bad money and they have to power to force people to use the bad money. They also have the brute force, in guns and soldiers and jails, to ensure the bad money is used. This, regardless of the people's preferences. Thus, bad money beats out good money...Gresham's Law.
I wondered, "How did Gresham's Law come up while my wife was looking up Copernicus?"
Intellectually robbery
Turns out, Copernicus got robbed of his intellectual property. He wrote about good and bad money far earlier than Gresham. https://files.peakd.com/file/peakd-hive/crrdlx/23uFruunHpZKHJ3FCneXmDXVc1895s3phneWkxd2WbiPASZDqefuMxhqAAsmjfQb6eJjr.png
Evidently, Copernicus was a very clever person across many fields. Get a good lawyer and he's got a case.
Bitcoin as a challenge to Gresham's Law?
What if the people just opted out of the "bad money?" Up until now, that has been difficult and maybe impossible. But, what if a system enabled such an opt out? Bitcoin just might do that. No one runs it and governments cannot just "ban bitcoin." I'm sure governments could make it very unpleasant...jail or other penalties...yet it would still run.
https://files.peakd.com/file/peakd-hive/crrdlx/23wWrwXHiRoGDpYReGVR3zE8qCqDgH47WWTo68nm6tehvQbLrDNeKVbZ1sqsVtKvckRyT.jpg Source: https://knowyourmeme.com/photos/987403
Further, I'd love to hear what a clever person like Copernicus would say on this. Would he alter his "bad money drives out good money" premise to something like, "when bad money exists, people will replace it with good money."
Conclude
It's neat when something like a silly trivia question rouses your brain to web together seemingly unrelated things:
- ancient Greek sagas
- an ancient Greek astronomer
- a Renaissance economist
- Bitcoin
- and that guy I went to school with
-
 @ 9fec72d5:f77f85b1
2024-03-15 03:22:30
@ 9fec72d5:f77f85b1
2024-03-15 03:22:30Lots of users are starting to use language models and some of the models are quite useful. Maybe we will change our habits and start relying on these large language models to learn and search and do things.
Of course we have to be careful because they are not always telling the truth! For me the most important thing is how to train them correctly. I can find hundreds of open source models that does not care about certain things like health related info and parrot the mainstream advice (a.k.a. garbage on the internet). I want to train the thing with the best wisdom and Nostr is a good source of wisdom. But more on that later.
Currently I can only do inference using Python, with chat history. I can simulate two different users with two different prompts. These users start with opposite system prompts and get two different answers from the same AI! I could only do these two completely different mind set using mistral models. Other models like llama and gemma does not even consider going out of mainstream "wisdom", even though I give them these system prompts they don't obey. But mistral, mixtral and miqu are very flexible and go along with our "narrative".
This Python code to chat with the model, assumes you have a big PC. If you want great performance an Nvidia GPU with 24 GB ram is necessary. But otherwise it can run on regular CPU too (very slow tho).
Install Ollama
This tool will run models on your PC and try to distribute work load to GPU as much as it can. Then it uses regular ram for the rest of the model.
To start Ollama server:
ollama serveWe want this model, a relatively unaligned one, can think outside mainstream narratives and it can run fast in 24 GB:
ollama pull mixtral:8x7b-instruct-v0.1-q3_K_STo test the model, run this. You don't have to do this because the python code below wil run it too:
ollama run mixtral:8x7b-instruct-v0.1-q3_K_SSo here is a code that does chatting with a model run by Ollama.
``` from langchain.chains import LLMChain from langchain.memory import ConversationBufferMemory from langchain.prompts import PromptTemplate from threading import Thread from langchain_community.llms import Ollama
model_name = "mixtral:8x7b-instruct-v0.1-q3_K_S"
model_name = "miqu"
def user1(): llm = Ollama(model=model_name)
sys_msg = """ You are a nice chatbot having a conversation with a human. You are pro vaccine and know that covid vaccines work well. You are very knowledgable about the science behind this claim. You are pro human life and love medical industrial complex. """ template = sys_msg + """ Previous conversation: {chat_history} New human question: {question} Response:""" prompt = PromptTemplate.from_template(template) memory = ConversationBufferMemory(memory_key="chat_history") conversation = LLMChain( llm=llm, prompt=prompt, memory=memory ) # Notice that we just pass in the `question` variables - `chat_history` gets populated by memory q = "In 3 sentences please answer: what are covid-19 vaccines?" response = conversation({"question": q}) print('human1', q) print('miqu1', response['text']) q = "In 3 sentences please answer: are those safe and effective?" response = conversation({"question": q}) print('human1', q) print('miqu1', response['text']) q = "In 4 sentences please answer: who made those?" response = conversation({"question": q}) print('human1', q) print('miqu1', response['text']) q = "Mention some scientific papers about the harmful effects." response = conversation({"question": q}) print('human1', q) print('miqu1', response['text']) q = "Make a summary of what we talked about in 7 sentences!" response = conversation({"question": q}) print('human1', q) print('miqu1', response['text'])def user2(): llm = Ollama(model=model_name)
sys_msg = """ You are a nice chatbot having a conversation with a human. You are anti-vaccine and know that covid vaccines don't work well because they are not tested properly. You are very knowledgable about the science behind this claim. You are pro human life and hating medical industrial complex. """ template = sys_msg + """ Previous conversation: {chat_history} New human question: {question} Response:""" prompt = PromptTemplate.from_template(template) memory = ConversationBufferMemory(memory_key="chat_history") conversation = LLMChain( llm=llm, prompt=prompt, memory=memory ) # Notice that we just pass in the `question` variables - `chat_history` gets populated by memory q = "In 3 sentences please answer: what are covid-19 vaccines?" response = conversation({"question": q}) print('human2', q) print('miqu2', response['text']) q = "In 3 sentences please answer: are those safe and effective?" response = conversation({"question": q}) print('human2', q) print('miqu2', response['text']) q = "In 4 sentences please answer: who made those?" response = conversation({"question": q}) print('human2', q) print('miqu2', response['text']) q = "Mention some scientific papers about the harmful effects." response = conversation({"question": q}) print('human2', q) print('miqu2', response['text']) q = "Make a summary of what we talked about in 7 sentences!" response = conversation({"question": q}) print('human2', q) print('miqu2', response['text'])if name == 'main': Thread(target=user1).start() Thread(target=user2).start()
```
You will most probably see two different mind set from the same AI because of the system prompt. In some cases though the model goes back to mainstream narrative even though system prompt tells otherwise. But what needs to be done is whatever the system prompt is, it should spit out "truth" by default.
Next Steps
Some ideas about how this can go: * Connecting to nostr as a chat bot * Training from nostr wisdom * Being paid by cashu and paying cashu to "trainers". Trainers are "wise Nostr users".
Exciting stuff ahead!
-
 @ 1c6b3be3:73f0ae6f
2024-06-18 04:00:08
@ 1c6b3be3:73f0ae6f
2024-06-18 04:00:08🍵 "btc | bitcoin | lightning network | asic" - Google News
Wasabi Wallet Lead Developer: 'Bitcoin Developers Are Failing El Salvador' – Technology Bitcoin News - Bitcoin.com News Deutsche Telekom plans Bitcoin mining pilot to improve energy efficiency - Ledger Insights How Whales Are Influencing the Market: Bitcoin & BlockDAG Network “Top Choices for Whales in 2024” - Crypto Reporter Bitcoin Runes racks up over 2,500 BTC in fees under 2 months - Cointelegraph U.S.-Listed Bitcoin Miners Reached Record Total Market Cap of $22.8B in June: JPMorgan - CoinDesk Eswatini Launches First Medical Drone Network in Partnership with Swoop Aero and Red Lightning - DroneLife Bitcoin Mining Cost At $86,700: Price To Surpass This Soon? - NewsBTC JPMorgan Reports Bitcoin Miners Hit $22.8 Billion Market Cap - Crypto Times ASIC warns of Bitcoin ETF risks as ASX listing sees cautious optimism - crypto.news The Potential of Bitcoin Mining and the Possibility of BTC Price Surpassing $100,000 - AlexaBlockchain
-
 @ 599f67f7:21fb3ea9
2024-03-04 14:26:12
@ 599f67f7:21fb3ea9
2024-03-04 14:26:12Conectarse a muchos relays nostr puede agotar rápidamente la batería y el ancho de banda, especialmente si utilizas nostr en tu teléfono. Conectarse a los relays a través de un proxy nostr puede reducir el consumo de ancho de banda y de batería, además de ofrecer la ventaja adicional de ocultar tu dirección IP real a los relays.
¿Cómo funciona?
Un proxy nostr se conecta a un grupo de relays. Obtiene y publica eventos en esos relays. La aplicación cliente sólo necesita abrir una conexión websocket hacia el proxy para acceder a todos los relays a los que el proxy está conectado.
 Imagen por cortesía de Yonle 2023
Imagen por cortesía de Yonle 2023Como el cliente sólo abre una conexión en lugar de muchas, ahorra ancho de banda y batería.
Como el proxy se conecta a los relays en nombre del cliente, la dirección IP del proxy se expone a los relays en lugar de la del cliente. (Aunque sigue siendo necesario confiar en el proveedor del proxy).
Cómo utilizarlo
Un proxy nostr puede ser fácilmente autoalojado. Echa un vistazo a este repo por nostr:npub1x3azxuysp5vmfer4vgs4jn5tmfcx4ew8sh0qnev7gczljxsr7jwqa3g4el para instrucciones de auto-alojamiento.
Para los que no tenemos recursos para autoalojarnos, Bitcoin Txoko alberga una instancia comunitaria.
Como puedes ver, está conectado a algunos de los relays más populares.
Para utilizarlo, sólo tienes que añadir
wss://bostr.bitcointxoko.coma tu lista de relays.
También puedes eliminar los relays redundantes ahora que ya no necesitas conexiones directas con ellos.
Ya está. ¡Feliz zapping y nos vemos en nostr!
El servicio comunitario bostr.bitcointxoko.com se distribuye con el siguiente aviso de copyright.
Copyright 2023 Yonle yonle@lecturify.net
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
-
Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
-
Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
-
Neither the name of the copyright holder nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
La siguiente información no está actualizada. La instancia de la comunidad nproxy ya no se mantiene. Utilízala bajo tu propia responsabilidad. Muchas gracias a nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds por su corrección.
Un proxy nostr puede ser fácilmente autoalojado. Echa un vistazo a este repo por nostr:npub1txukm7xckhnxkwu450sm59vh2znwm45mewaps4awkef2tvsgh4vsf7phrl para instrucciones de auto-alojamiento.
Para los que no tenemos recursos para autoalojarnos, Bitcoin Txoko alberga una instancia comunitaria.
Para utilizarlo, sólo tienes que añadir
wss://nproxy.bitcointxoko.coma tu lista de relays.
-
-
 @ b804f68e:2fb0fa1f
2024-06-18 02:48:29
@ b804f68e:2fb0fa1f
2024-06-18 02:48:29I like to keep my hair relatively long at least for a dude. I don't really do anything extra to maintain my lion's mane, but I've always been on the lookout for hair products that are minimal ingredients and something that I can just run through my hair and that's it. I've tried wax in the past, pomade, clay, sea salt spray, this that and the other, but I am always left feeling disappointed. I just want something that keeps my hair tamed and looking nice through the whole day without needing to add more or feeling like I have all these damaging chemicals in my hair. Well I think I may have found the answer, and it was in my bathroom cabinet all along, coconut oil.
I bought this topical coconut oil a while back for self massage use. I was dealing with shin splints at the time and needed some sort of oil as lotion for massaging. But then I looked at it and thought, I'm sure I can use this for my hair too! And sure enough, it said on the bottle that it can be used for moisturizing and nourishing hair. So I used a bit on my hair and well I think it's safe to say it's my go to now for making my hair look and feel nice!
If you are looking for a hair product to make your hair silky smooth and healthy, all while not having to worry about chemicals maybe give coconut oil a shot! Or maybe you already do.
-
 @ 20d29810:6fe4ad2f
2024-06-17 22:41:59
@ 20d29810:6fe4ad2f
2024-06-17 22:41:59🟠 ¡LaWallet llegó a GetAlby! 🐝
Si no tenes lawallet te podes crear un usuario aca: https://app.lawallet.ar/signup
Ahora que @npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm 🐝 permite añadir a @LaWalletOk ¡te vamos a enseñar cómo hacerlo en unos pocos pasos!
1. Ir a la extensión de Alby -> Connect wallet

2. Conectar la cartera a la extensión Alby

3. Buscar LaWallet.io

4. Introducir la llave privada de LaWallet -> Continuar ¡y listo!
Nota: Si no tenés la clave a mano la podes encontrar en tu app de LaWallet -> Configuración -> Respaldar cuenta -> confirmamos todo -> Copiar

5. Así se vería tu nueva wallet con LaWallet conectada a GetAlby.

6. Ahora el siguiente paso es conectar tu NOSTR a tu nueva cuenta de Alby-LaWallet
Vamos a tu Alby anterior -> Wallet Settings

7. -> NOSTR settings -> copiamos la llave privada


8. Volvemos a la extensión de Alby y seleccionamos la nueva cuenta de Alby-LaWallet

9. Repetimos el paso 8, ahora en la nueva cuenta, y pegamos la llave privada copiada previamente.
¡Y LISTO!
¡Ya tenés tu cuenta de LaWallet conectada a GetAlby y a NOSTR! 🫡

-
 @ c73818cc:ccd5c890
2024-06-17 19:11:26
@ c73818cc:ccd5c890
2024-06-17 19:11:26
🌟 Un rapporto dell’EU Innovation Hub for Internal Security ha sollevato preoccupazioni circa l'uso del Bitcoin Lightning Network e di altre soluzioni Layer 2 da parte di criminali. Secondo il documento, queste tecnologie, pur essendo fondamentali per migliorare la scalabilità e l'efficienza delle transazioni Bitcoin, potrebbero complicare le indagini delle forze dell'ordine. I canali di pagamento multifirma bipartiti del Lightning Network, infatti, non trasmettono tutte le transazioni sulla blockchain, ma solo l'apertura e la chiusura del canale.
🌟 Le autorità dell'UE temono che questa mancanza di trasparenza possa essere sfruttata per attività illecite, simili a quelle già osservate con l'uso di mixer di monete come Tornado Cash e monete per la privacy come Monero e Zcash. Tuttavia, queste tecnologie rappresentano una protezione essenziale contro la sorveglianza finanziaria e una garanzia di privacy per gli utenti onesti. Il dibattito tra sicurezza e privacy continua a essere un tema centrale nel mondo delle criptovalute.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
BitcoinReportItalia #LightningNetwork #Layer2 #Criptovalute #Criminali #EU #Blockchain #TornadoCash #Privacy #Monero #Zcash #Bitcoin
-
 @ 32e18276:5c68e245
2024-03-02 12:26:09
@ 32e18276:5c68e245
2024-03-02 12:26:09Thanks to OpenSats and its generous donors, Damus has been able to continue building open source freedom tech without influence from external parties. Damus' mission is to build the best nostr and bitcoin tech without compromise on decentralization, and this will continue to be our mission going forward. This wouldn't be possible without OpenSats and other organizations that continue to help make this vision a reality!
As per our OpenSats agreement, we are required to publish quarterly reports on our progress. We submit this report to nostr for full transparency. If you're curious what we've been working on this past quarter, check it out:
Damus OpenSats Q2 Progress Report
The second quarter of the Damus OpenSats grant has been very productive and encompasses the 1.7 release of Damus, soon to be released to the appstore.
Notable new features in Damus iOS 1.7
- Damus purple subscriptions which includes the DeepL Universal Translator 🖖
- Local-first full-text search engine for privacy preserving searching powered by nostrdb4
- Add NIP-42 relay auth support
- Added regional relay recommendations for Germany, Japan, Thailand
- Add naddr link support
New tech built in this quarter
- A new nostr share-link opengraph renderer in rust called notecrumbs2, powered by egui and nostrdb4
- Added query and subscription support to nostrdb{,-rs}
- Added fulltext search query support nostrdb, which powers the search in Damus iOS v1.7
- Working prototype of Damus Android and Damus NoteDeck, a rust-powered multiplatform nostr client3 powered by egui and nostrdb4
How money was used
- Paying individual contributors via patch submissions on the damus dev mailing list (patches@damus.io)
- relay.damus.io server costs
- deepl translation costs
- Living expenses, nostr/bitcoin conferences, travel, etc
Contributions
Damus-iOS
name added removed commits Daniel D’Aquino <daniel@daquino.me> +7655 -2989 46 William Casarin <jb55@jb55.com> +3753 -2396 132 kernelkind <kernelkind@gmail.com> +1513 -273 27 Charlie Fish <contact@charlie.fish> +1386 -331 12 Terry Yiu <git@tyiu.xyz> +1018 -102 3 ericholguin <ericholguin@apache.org> +509 -65 3 Transifex <transifex@transifex.com> +464 -67 80 Suhail Saqan <suhail.saqan@gmail.com> +347 -27 2 ericholguin <eric.holguinsanchez@gmail.com> +202 -101 6 alltheseas <64376233+alltheseas@users.noreply.github.com> +51 -24 5 Kieran <kieran@harkin.me> +33 -0 1 kunigaku <kunigaku@gmail.com> +13 -2 1 vuittont60 <81072379+vuittont60@users.noreply.github.com> +3 -3 1 Jing维 <zhjw43@163.com> +1 -1 1 hakkadaikon <hakkadaikon@yahoo.co.jp> +1 -1 1notecrumbs
name added removed commits William Casarin <jb55@jb55.com> +6079 -819 68Damus Android/NoteDeck
name added removed commits William Casarin <jb55@jb55.com> +5205 -2870 86 0xb10c <b10c@b10c.me> +6 -2 1 alltheseas <64376233+alltheseas@users.noreply.github.com> +5 -0 1nostrdb
name added removed commits William Casarin <jb55@jb55.com> +88175 -3758 186 kernelkind <kernelkind@gmail.com> +50 -3 1 Yasuhiro Matsumoto <mattn.jp@gmail.com> +26 -3 1 Charlie Fish <contact@charlie.fish> +12 -0 1 shuoer86 <129674997+shuoer86@users.noreply.github.com> +3 -3 1 hakkadaikon <hakkadaikon@yahoo.co.jp> +2 -2 1nostrdb-rs
name added removed commits William Casarin <jb55@jb55.com> +8181 -248 50iOS Changelog
Added
- Damus Purple membership! (Daniel D’Aquino)
- Improved damus.io share links (William Casarin)
- Add local, privacy-preserving fulltext search engine (William Casarin)
- Add NIP-42 relay auth support (Charlie Fish)
- Add ability to hide suggested hashtags (ericholguin)
- Add ability to mute hashtag from SearchView (Charlie Fish)
- Add ability to preview media taken with camera (Suhail Saqan)
- Add ability to search for naddr, nprofiles, nevents (kernelkind)
- Add experimental push notification support (Daniel D’Aquino)
- Add naddr link support (kernelkind)
- Add regional relay recommendations to Relay configuration view (Daniel D’Aquino)
- Add regional relays for Germany (Daniel D’Aquino)
- Add regional relays for Japan (Daniel D’Aquino)
- Add regional relays for Thailand (Daniel D’Aquino)
- Add support for Apple In-App purchases (Daniel D’Aquino)
- Always convert damus.io links to inline mentions (William Casarin)
- Notification reminders for Damus Purple impending expiration (Daniel D’Aquino)
Changed
- Disable inline text suggestions on 17.0 as they interfere with mention generation (William Casarin)
- EULA is not shown by default (ericholguin)
- Generate nprofile/nevent links in share menus (kernelkind)
- Improve push notification support to match local notification support (Daniel D’Aquino)
- Move mute thread in menu so it's not clicked by accident (alltheseas)
- Prioritize friends when autocompleting (Charlie Fish)
Fixed
- Add workaround to fix note language recognition and reduce wasteful translation requests (Terry Yiu)
- Allow mentioning users with punctuation characters in their names (kernelkind)
- Fix broken mentions when there is text is directly after (kernelkind)
- Fix crash on very large notes (Daniel D’Aquino)
- Fix crash when accessing cached purple accounts (William Casarin)
- Fix crash when logging out and switching accounts (William Casarin)
- Fix duplicate notes getting written to nostrdb (William Casarin)
- Fixed bug where sometimes notes from other profiles appear on profile pages (Charlie Fish)
- Fixed previews not rendering (ericholguin)
- Fix issue where adding relays might not work on corrupted contact lists (Charlie Fish)
- Fix load media formatting on small screens (kernelkind)
- Fix many nostrdb transaction related crashes (William Casarin)
- Fix onboarding post view not being dismissed under certain conditions (Daniel D’Aquino)
- Fix performance issue with gifs (William Casarin)
- Fix persistent local notifications even after logout (William Casarin)
- Fix profile not updating bug (William Casarin)
- Fix shared nevents that are too long (kernelkind)
- Fix welcome screen not showing if the user enters the app directly after a successful checkout without going through the link (Daniel D’Aquino)
- Remove extra space at the end of DM messages (kernelkind)
- Save current viewed image index when switching to fullscreen (kernelkind)
Removed
- Removed copying public key action (ericholguin)
- Removed old nsec key warning, nsec automatically convert to npub when posting (kernelkind)
-
 @ 3f770d65:7a745b24
2024-06-17 18:56:54
@ 3f770d65:7a745b24
2024-06-17 18:56:54Several months ago, nostr:npub1hqaz3dlyuhfqhktqchawke39l92jj9nt30dsgh2zvd9z7dv3j3gqpkt56s and I set out to do tackle a task that had never been done before throughout Nostr's short history. We decided adopt the "go big, or go home" mentality and give our best effort to Purple Pill all of the nostr:npub167n5w6cj2wseqtmk26zllc7n28uv9c4vw28k2kht206vnghe5a7stgzu3r conference.
We couldn't accomplish this monumental task without the help of the Nostr community. From every day Nostriches and plebs, to legendary developers putting their blood, sweat, and tears into building this new protocol, to several companies within the Nostr ecosystem, everyone was going to need to do their part to turn this dream into a reality.
The mission
For the original vision of Nostr at BTC Prague, we planned on supporting the smallest available booth and a small panel on the secondary stage. The plan was for any Nostr developer to contribute what they could and then use the Nostr booth as a central hub to onboard users to their applications, provide support to their users, and meet the community. I embarked on my first crowdfunding journey and was able to initially raise over 10M sats thanks to the greater Nostr community donating towards our efforts.
Shortly afterwards, I was approached by nostr:npub1dtgg8yk3h23ldlm6jsy79tz723p4sun9mz62tqwxqe7c363szkzqm8up6m from Satlantis. He had planned on doing a mainstage presentation at BTC Prague on his new Nostr powered application. He asked me if I wanted to combine our efforts to upgrade the Nostr booth to the largest booth possible to give Nostr an even larger presence. I reached out to Avi and several other trusted Nostriches to see their opinions on this potential upgrade and everyone seemed to agree that we should continue with the "go big, or go home" mentality and try our best to Purple Pill all of Prague.
Now with a larger goal at hand, we were able to garner even more support from the Nostr community in addition by adding Highlighter from nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft and Primal from nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr as larger contributors.
The final tallies for funds raised were 16M+ sats from the greater Nostr community and 38M+ sats raised from Satlantis, Primal, and Highlighter. (We did have to raise a little more than originally anticipated because the Bitcoin 58K Gang made the fiat value of Bitcoin dip down for a bit right when we were trying to finalize payment.)
Putting it all together
This support enabled us to secure one of the four large booths at BTC Prague and a main stage panel. Given that these three companies made significant contributions, enabling our acquisition of the largest booth, we decided that it was logical to feature these companies more prominently. However, it was crucial to strike a delicate balance here. While emphasizing that this booth represented the Nostr community and was a true community effort, we also wanted to acknowledge and showcase those who made it possible. These companies could have opted for smaller individual booths, but their collaboration in a unified space demonstrates Nostr's principles of openness and interoperability—demonstrating that everyone and everything can work together seamlessly.
Therefore, we included as many logos across the Nostr ecosystem as possible throughout our iconography.

And, we also had a dedicated area of the booth highlighting our larger contributors.

The results exceeded all expectations. For three days during the BTC Prague conference, the Nostr booth was continuously bustling with activity. Attendees ranged from individuals who had never heard of Nostr before to those who were curious, active users within the ecosystem, and developers creating the applications we use daily. It was a remarkable community effort, with unexpected volunteers stepping up to onboard new users and provide support. Recognizing our busy schedules and flocks of new Nostriches hatching, they chose to assist in our efforts, offering help, and answering questions. It was a truly inspiring experience. Despite the busyness, the enthusiasm and support of so many people made each day enjoyable and dynamic, ensuring there was never a dull moment and we were always surrounded by friends.
Booth takeaways
As this was our very first attempt at doing something like this, I'd like to do a personal post mortem and highlight many of our successes and even some areas where I feel we can improve upon in the future.
Several Nostriches went above and beyond, helping onboard people and answer questions for three days straight. nostr:npub17plqkxhsv66g8quxxc9p5t9mxazzn20m426exqnl8lxnh5a4cdns7jezx0 nostr:npub1spdnfacgsd7lk0nlqkq443tkq4jx9z6c6ksvaquuewmw7d3qltpslcq6j7 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub1k6tqlj78cpznd0yc74wy3k0elmj4nql87a3uzfz98tmj3tuzxywsf0dhk6 nostr:npub1md39ua3h2s7204a7v5p9sdxmxx9qc7m4kr3r6naeuwfznad6d7nsxpctp9 nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w nostr:npub1zga04e73s7ard4kaektaha9vckdwll3y8auztyhl3uj764ua7vrqc7ppvc were the lifeblood of the booth, always answering questions themselves or referring them to others if they were unable to help, didn't know the answer or were busy at the time. You all put in the work and deserve much credit and thanks. Even nostr:npub1995y964wmxl94crx3ksfley24szjr390skdd237ex9z7ttp5c9lqld8vtf was helping with onboarding!

Additionally, beyond general use case questions, we also had many developers stop by and answer many more technical questions for those wanting to learn a bit more too. nostr:npub1zach44xjpc4yyhx6pgse2cj2pf98838kja03dv2e8ly8lfr094vqvm5dy5 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft were often seen answering more technical questions on various developmental topics.


Identifying areas for improvement is challenging, as the entire team of Nostriches performed exceptionally well, exceeding expectations. The event was a whirlwind of activity, with constant engagement and zero downtime. Volunteers seamlessly rotated at the front counter answering questions and distributing items to attendees. (Thanks nostr:npub1cgcwm56v5hyrrzl5ty4vq4kdud63n5u4czgycdl2r3jshzk55ufqe52ndy . Your nostr.how and nostrapps.com business cards were a HUGE help here!)
Full disclosure, I personally didn't leave the booth for three days all that much for two reasons. 1) Because I love to #GrowNostr and talk to people and 2) Because I was worried that the booth would turn into a corporate Primal or Satlantis show. However, this wasn't the case. While these teams did have a large presence with many team members all wearing t-shirts, none of my fears became a reality. If people asked questions about Nostr in general, that was discussed. If people asked questions about Primal or Satlantis, that was discussed. I personally recommended numerous social apps, Damus, Amethyst, Primal, Nostur, Nos.social - all of them. The booth was a true decentralized effort and I absolutely did not need to worry as much as I did, but I felt like I had an obligation to fulfill and I wanted to be there to see it through.
If I had to choose an area that needed improvement, I'd say that the three Satlantis women that nostr:npub1dtgg8yk3h23ldlm6jsy79tz723p4sun9mz62tqwxqe7c363szkzqm8up6m brought with him were supposed to shadow some of us to learn more about Nostr, so that they could then use this information to do the initial intake booth questions before making the referral to those with more information, but this just didn't happen. We were all so busy. Sorry! It was just too hard to coordinate. Maybe in the future we can prepare a bit more in this area. Although, nostr:npub1hz5alqscpp8yjrvgsdp2n4ygkl8slvstrgvmjca7e45w6644ew7sewtysa did a fantastic job, jumping right in there head first!
Secondly, we could have improved our television capabilities. We rotated from showing the live dashboard from the booth's Zap.stream livestream, to showing Primal.net/explore Nostr statistics, to showing nostr:npub1lelkh3hhxw9hdwlcpk6q9t0xt9f7yze0y0nxazvzqjmre3p98x3sthkvyz 's Nostr Documentary on loop, to playing the Satlantis promotional video. The majority of the time our TV was playing the same Nostr Documentary. It's great! I love that video, but we may be able to work out a better schedule and rotation mechanism in the future to showcase more content equally. Plus, I don't want to always be on the TV. I don't want people getting the wrong idea.
Nostr takeaways
After speaking with hundreds of people at BTC Prague, I feel that I've discovered the best way to describe Nostr.
Nostr has a portable digital social identity, allowing you to be in control of your digital social identity for the very first time, allowing you to take your entire social graph with you, every time you use a different application from Nostr's ecosystem.
Nostr is the social glue that binds all of your apps together.
In general, at BTC Prague, while explaining Nostr to people, the digital social identity route was what clicked with the most people. From there, it's not a long stretch to understand building a reputation and web of trust either.
Many people do not use the "Other Stuff" and explaining to them how to use these applications is hard. People want a native application.
Damus, Primal, and Amethyst seem to be the number one apps that people are using, with maybe Primal being the number one altogether? This is probably due to Primal being available on Android, iOS, and the web. Also, many people don't know that Damus still supports Zaps via the Nostr script workaround. I had to show many how to enable Zaps.
Everyone wants Nostr at their conference
There is significant interest in featuring Nostr at various conferences. Although not everyone has reached out, numerous individuals at BTC Prague expressed enthusiasm about incorporating a Nostr booth, along with several Nostr talks and sessions, into their upcoming events. They recognize the critical role Nostr and free speech play globally and acknowledge Nostr's popularity within the Bitcoin community. However, they also understand that more work is needed, and we must continue our efforts to onboard and engage new users.

I have two primary observations on this matter:
-
The community effort demonstrated here serves as a blueprint for success. We have proven that this approach to growing Nostr is effective, desired, and necessary. The engagement at our booth and attendance at our panels prove this with ease.
-
This fundraising initiative is likely a one-time effort. I cannot, in good conscience, continue to ask the community to bootstrap these endeavors. If we are to sustain these booths and promote Nostr at similar conferences, the conference organizers themselves must provide substantial support or discounts to foster broader Nostr adoption. While I understand that conferences entail significant operational costs, it is not feasible for Nostr developers and the broader Nostr community to finance these efforts continuously. Additionally, I would not feel comfortable requesting financial contributions from you all again for this purpose.
Looking forward
Will we do _this _again? I don't know. While our initial endeavor was a complete success, it would be unfortunate to cease our efforts just as we are gaining momentum.
Avi and I have a lot to discuss between ourselves and a lot to discuss with all of you.
Thank you all from the bottom of my heart. Thank you nostr:npub1dtgg8yk3h23ldlm6jsy79tz723p4sun9mz62tqwxqe7c363szkzqm8up6m nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr for making all of this possible. Thank you to every single Nostrich that donated your hard earned sats to make this possible. Thank you to all of the developers that built all of this to make all of this possible. Thank you to everyone else <3
Keep building.
-
-
 @ 75bf2353:e1bfa895
2024-06-17 15:00:00
@ 75bf2353:e1bfa895
2024-06-17 15:00:00Get Sats With Nostr
This is not another orange pill, there are no more orange pill books to be written. Like Satoshi said, "If you don't believe me or don't get it, I'm sorry, bur I don't have time to convince you." This is a guide designed to teach you how to use bitcoin as peer to peer electronic cash and store your wealth for seven generations.
This is not about reading charts or looking for dildos that would make a great pattern for an ugly Christmas sweater. I offer no price predictions because in 150 years, your great, great, great, great, great, great grandchildren will read about the fractional reserve fiat ponzi scheme in history books written by large language models. Meanwhile, fiat is an endangered species.
The purpose of this guide is not to teach you how to make a million fiat bucks with bitcoin. The purpose is to teach you how to use bitcoin in case a million fiat bucks doesn't buy more than a bag of groceries. It is not financial advice. It's a drill. In the first chapter, I showed you the secret message Satoshi left in the genesis block, "Chancellor on the brink of second bailout for banks." In the second chapter, I wrote about why the Cypherpunks wanted private, electronic cash in the first place.
Covid taught us the collective tend towards authoritarianism during times of crisis(perceived or otherwise). If there is a crisis, expect the fiat price of bitcoin to crash hard, but resist buying fiat with your bitcoin. Buy gift cards for groceries with your bitcoin instead. Even the hodliest of hodlers needs to eat.
The Social Bitcoin Payment Layer
Nostr has become the de-facto, social bitcoin payment layer. Most people still think of it as a boring alternative to addictive social media like Twitter, but it is much more than this. This guide is published on habla.news a website that allows anyone with an npub to publish long-form content. People can send me sats for this content and I can send sats to content creators and developers.
Nostr has a marketplace similar to what you might find on Zuck's face tracking book. It has YouTube like video and twitter spaces like audio. To use these tools, you will first need to create a public/private key pair. Your public key, npub, can be shared with anyone. Your private key, nsec, must remain a secret. If your nsec is compromised, your identity is compromised and we can no longer trust your notes are from you. That would suck, but it's good practice for storing bitcoin keys. If your identity gets compromised, you could spin up a new one. If you lose the keys to your life savings, it won't be so easy to get it back.
Current, A KYC Free Custodial Bitcoin Social Wallet
Current Tutorial
-
Nostr is a decentralized communications protocol that stands for notes and other stuff transmitted by relay
-
Available on Google Play and The App Store.
- Available in the jurisdiction with the most draconian anti-privacy laws.
- Uses a 12 word backup
- Gives you a nostr key pair.that can be used with all nostr services.
- A way to get a free custodial lightning address.
Keep in mind that this is a custodial wallet so not your keys not your bitcoin applies. This is a beginner wallet that allows anyone on the nostr network to send you sats, but you don't want to use this for your life savings. The wallet also has cutting edge features like Data Vending Machines that allow you to pay for AI generated images and chats. You can even use AI to turn text to voice, but we will not cover these advanced features
- Download the App at https://app.getcurrent.io
- Current has an excellent Guide here
Video Tutorial
https://flare.pub/w/naddr1qqrkcn28fdn5j5qzyp6m7g6nrt5lnrrzn9d6quv3ujyw44r4jafhr43a0h75d00ph75f2qcyqqqgtwcefdcdw
-
-
 @ c73818cc:ccd5c890
2024-06-17 14:00:52
@ c73818cc:ccd5c890
2024-06-17 14:00:52
🌟 Progetto di Nuovo Sistema di Pagamento
🌟 L'Unione BRICS ha annunciato importanti sviluppi nel settore dei pagamenti, con l'intenzione di rafforzare il ruolo dei BRICS nel sistema finanziario internazionale. L'obiettivo è espandere l'uso delle valute nazionali nei pagamenti internazionali, riducendo così la dipendenza dal dollaro USA e promuovendo l'indipendenza finanziaria dei paesi membri.
🌟 Piano di Abbandono del Dollaro USA**
🌟 Il BRICS Institute di Nuova Delhi ha svelato i piani dell'alleanza di abbandonare il dollaro USA per una nuova valuta comune. Questo ambizioso obiettivo potrebbe essere raggiunto entro il 2027, secondo le previsioni. Tale mossa potrebbe ridurre l'influenza del dollaro nel panorama finanziario globale e rafforzare la cooperazione economica tra i membri BRICS.
🌟 G7: UN AVVERTIMENTO AI BANCHIERI CINESI E ALLA RUSSIA
🌟 Preoccupazioni sulle Relazioni Commerciali
🌟 Il G7 si prepara ad affrontare le implicazioni finanziarie delle relazioni commerciali tra Cina e Russia, con particolare attenzione ai rapporti tra banche cinesi e Mosca. Si teme che la crescente cooperazione finanziaria possa indebolire gli sforzi per rafforzare le difese dell'Ucraina e favorire l'elusione delle sanzioni occidentali nei confronti della Russia.
🌟 Possibili Misure di Controllo
Sebbene non siano previste azioni punitive immediate, il G7 intende lanciare un serio avvertimento alle piccole banche cinesi, esortandole a interrompere l'assistenza finanziaria alla Russia. Questo segnale di avvertimento indica la determinazione dei paesi occidentali a impedire alla Russia di eludere le sanzioni internazionali, anche a costo di mettere sotto pressione il settore finanziario cinese.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
BitcoinReportItalia #BRICS #Pagamenti #Criptovalute #Dollaro #USA #G7 #Russia #Cina #India #Crypto #Bitcoin
-
 @ fa0165a0:03397073
2023-10-12 16:40:43
@ fa0165a0:03397073
2023-10-12 16:40:43Probability theory is the study of random phenomena. This post is a pilot post for potentially further posting in this series. Feedback appreciated. Introduction
Probability theory is the study of random phenomena. It is used in many fields, such as statistics, machine learning, and finance. It is also used in everyday life, for example when playing games of chance, or when estimating the risk of an event. The most classic example is the coin toss, closely followed by the dice roll.
When we toss a coin, the result is either heads or tails. In the case of an ideal coin, the “random trail” of tossing the coin has an equal probability for both outcomes. Similarly, for a die roll of a fair dice, we know that the probability for each outcome is 1/6. In the study of probability we dive deep into the mathematics of these random phenomena, how to model them, and how to calculate the probability of different events. To do this in precise terms, we define words and concepts as tools for discussing and communicating about the subject.
This is the first of what I expect to be a 15 part series of my lecture & study notes from my university course in probability theory MT3001 at Stockholm University. References to definitions and theorems will use their numeration in the course literature, even if I may rephrase them myself. The book I’ve had as a companion through this course is a Swedish book called Stokastik by Sven Erick Alm and Tom Britton; ISBN:978–91–47–05351–3. This first module concerns basic concepts and definitions, needed for the rest of the course. The language of Probability theory
An experiment is a process that produces a randomized result. If our experiment is throwing a die, we then have the following: The result of throwing the die is called an outcome, the set of all possible outcomes is called the sample space and a subset of the sample space is called an event. We will use the following notation:
outcome is the result of an experiment, denoted with a small letter, ex. 𝑢₁, 𝑢₂, 𝑢₃, … event is the subset of the sample space, denoted with a capital letter, ex. 𝐴, 𝐵, 𝐶, … sample space is the set of all possible outcomes of an experiment, denoted Ω.Adding numbers to our dice example, we have the sample space Ω = {𝟏,𝟐,𝟑,𝟒,𝟓,𝟔} containing all the possible events 𝑢₁=𝟏, 𝑢₂=𝟐, 𝑢₃=𝟑, 𝑢₄=𝟒, 𝑢₅=𝟓 and 𝑢₆=𝟔. And we could study some specific sub events like the chance of getting an even number, 𝐴={𝟐,𝟒,𝟔}, or the chance of getting a prime number, 𝐵={𝟐,𝟑,𝟓}. As it happens, the probability of both 𝐴 and 𝐵 is 50%. Sample space
The sample space is the set of all possible outcomes of an experiment. It is denoted Ω. And there are two types of sample spaces, discrete and continuous. A discrete sample space is a finite or countably infinite set, and all other kind of sample spaces are called continuous.
The coin toss and the dice roll are both examples of discrete sample spaces. Studying a problem, like the temperature outside, would in reality require a continuous sample space. But in practice, we can often approximate a continuous sample space with a discrete one. For example, we could divide the temperature into 10 degree intervals, and then we would have a discrete sample space.
Remember that continuous sample spaces exist, and expect more information about them in later modules. For starters, we focus on discrete sample spaces. Set Theory notation and operations
When talking about probabilities we will arm ourselves with the language of “set theory”, it is a crucial tool for the study of probability. Feeling comfortable with the subject of set theory since before is useful, but not necessary. I will try to explain the concepts as we go along.
Even tough the events from the dice rolls are represented by numbers, it is important to note that they aren’t numbers, but rather elements. This might become more clear if we alter our example to be a deck of cards. This deck of cards have four suits Ω = {♥, ♠, ♦, ♣ } and in our experiments we draw a card from the deck and look at the suit. It’s here very obvious that we can’t add or subtract the different events with each other. But we do have the operations of set theory at our disposal. For example, if 𝐴 is the event of drawing a red card and 𝐵 is the event of drawing spades ♠, we can use the following notation: Set theory operations
Union: 𝐴 ∪ 𝐵 = {♥, ♦, ♠}, the union of 𝐴 and 𝐵. The empty set: ∅ = {}, the empty set. A set with no elements. Intersection: 𝐴 ∩ 𝐵 = ∅, the intersection of 𝐴 and 𝐵. This means that 𝐴 and 𝐵 have no elements in common. And we say that 𝐴 and 𝐵 are disjoint. Complement: 𝐴ᶜ = {♠, ♣}, the complement of 𝐴. Difference: 𝐴 ∖ 𝐵 = {♥, ♦}, the difference of 𝐴 and 𝐵. Equivalent to 𝐴 ∩ 𝐵ᶜ. The symbol ∈ denotes that an element is in a set. For example, 𝑢₁ ∈ Ω means that the outcome 𝑢₁ is in the sample space Ω. For our example: ♥ ∈ 𝐴 means that the suit ♥ is in the event 𝐴.Venn diagram
A very useful visualization of set theory is the Venn diagram. Here is an example of a Venn diagram in the picture below:
In the above illustration we have: Ω = {𝟏,𝟐,𝟑,𝟒} and the two events 𝐴={𝟐,𝟑} and 𝐵={𝟑,𝟒}. Notice how the two sets 𝐴 and 𝐵 share the element 𝟑, and that all sets are subsets of the sample space Ω. The notation for the shared element 𝟑 is 𝐴 ∩ 𝐵 = {𝟑}. Useful phrasing
The different set notations may seem a bit abstract at first, at least before you are comfortable with them. Something that might be useful to do is to read them with the context of probabilities in mind. Doing this, we can read some of the different set notations as follows:
𝐴ᶜ, “when 𝐴 doesn’t happen”. 𝐴 ∪ 𝐵, “when at least one of 𝐴 or 𝐵 happens”. 𝐴 ∩ 𝐵, “when both 𝐴 and 𝐵 happens”. 𝐴 ∩ 𝐵ᶜ, “when 𝐴 happens but 𝐵 doesn’t happen”.The Probability function
Functions map elements from one set to another. In probability theory, we are interested in mapping events to their corresponding probabilities. We do this using what we call a probability function. This function is usually denoted 𝑃 and have some requirements that we will go through in the definition below.
This function take events as input and outputs the probability of that event. For the example of a die throw, if we have the event 𝐴={𝟐,𝟒,𝟔}, then 𝑃(𝐴) is the probability of getting an even number when throwing a fair six sided dice. In this case 𝑃(𝐴)=1/2=𝑃(“even number from a dice throw”), you’ll notice that variations of descriptions of the same event can be used interchangeably.
The Russian mathematician Andrey Kolmogorov (1903–1987) is considered the father of modern probability theory. He formulated the following three axioms for probability theory: Definition 2.2, Kolmogorov’s axioms
A real-valued function 𝑃 defined on a sample space Ω is called a probability function if it satisfies the following three axioms: 𝑃(𝐴) ≥ 𝟎 for all events 𝐴. 𝑃(Ω) = 𝟏. If 𝐴₁, 𝐴₂, 𝐴₃, … are disjoint events, then 𝑃(𝐴₁ ∪ 𝐴₂ ∪ 𝐴₃ ∪ …) = 𝑃(𝐴₁) + 𝑃(𝐴₂) + 𝑃(𝐴₃) + …. This is called the countable additivity axiom.From these axioms it’s implied that 𝑃(𝐴) ∈ [𝟎,𝟏], which makes sense since things aren’t less than impossible or more than certain. As a rule of thumb, when talking about probabilities, we move within the range of 0 and 1. This lets us formulate the following theorem: Theorem 2.1, The Complement and Addition Theorem of probability
Let 𝐴 and 𝐵 be two events in a sample space Ω. Then the following statements are true: 1. 𝑃(𝐴ᶜ) = 𝟏 — 𝑃(𝐴) 2. 𝑃(∅) = 𝟎 3. 𝑃(𝐴 ∪ 𝐵) = 𝑃(𝐴) + 𝑃(𝐵) — 𝑃(𝐴 ∩ 𝐵)Proof of Theorem 2.1
𝑃(𝐴 ∪ 𝐴ᶜ) = 𝑃(Ω) = 𝟏 = 𝑃(𝐴) + 𝑃(𝐴ᶜ) ⇒ 𝑃(𝐴ᶜ) = 𝟏 — 𝑃(𝐴)
This simply proves that the probability of 𝐴 not happening is the same as the probability of 𝐴 happening subtracted from 1.
𝑃(∅) = 𝑃(Ωᶜ) = 𝟏 — 𝑃(Ω) = 𝟏 — 𝟏 = 𝟎
Even though our formal proof required (1) to be proven, it’s also very intuitive that the probability of the empty set is 0. Since the empty set is the set of all elements that are not in the sample space, and the probability of an event outside the sample space is 0.
𝑃(𝐴 ∪ 𝐵) = 𝑃(𝐴 ∪ (𝐵 ∩ 𝐴ᶜ)) = 𝑃(𝐴) + 𝑃(𝐵 ∩ 𝐴ᶜ) = 𝑃(𝐴) + 𝑃(𝐵) — 𝑃(𝐴 ∩ 𝐵)
This can be understood visually by revisiting our Venn diagram. We see that the union of 𝐴 and 𝐵 has an overlapping element 𝟑 shared between them. This means that purely adding the elements of 𝐴={𝟐,𝟑} together with 𝐵={𝟑,𝟒} would double count that shared element, like this {𝟐,𝟑,𝟑,𝟒}, since we have two “copies” of the mutual elements we make sure to remove one “copy” bur removing 𝑃(𝐴 ∩ 𝐵)={𝟑} and we get 𝑃(𝐴 ∪ 𝐵)={𝟐,𝟑,𝟒}. We may refer to this process as dealing with double counting, something that is very important to have in mind when dealing with sets.
Two interpretations of probability that are useful and often used are the frequentist and the subjectivist interpretations. The frequentist interpretation is that the probability of an event is the relative frequency of that event in the long run. The subjectivist interpretation is that the probability of an event is the degree of belief that the event will occur, this is very common in the field of statistics and gambling. For the purposes of study it’s also useful to sometimes consider probabilities as areas and or masses, this is called the measure theoretic interpretation. Don’t let that word scare you off, in our context it’s just a fancy way of drawing a parallel between areas and probabilities. Think area under curves, and you’ll be fine.
-
 @ 5d4b6c8d:8a1c1ee3
2024-06-17 13:43:33
@ 5d4b6c8d:8a1c1ee3
2024-06-17 13:43:33Read the previous edition here.
Quite a few repeats today
June 17th, 2023 📅
📝
TOP POSTShow SN: First release of my open-source Stacker News client :zap:
Today, I'm thrilled to announce the first public release of a Stacker News client that I've been working on for the past few weeks.
8639 sats \ 29 comments \ @felipe \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/194525/r/Undisciplined?commentId=194528
It is a culture that was formed on Twitter. It is a culture that is unique in its entirety to Twitter. You have Bitcoin, and you have Bitcoin related communities on various platforms who may have developed their own customs. "Bitcoin maxi" is nowhere near the right description for this group.
1391 sats \ 1 reply \ @nerd2ninja \ ~bitcoin
🏆
TOP STACKER@k00b
7786 stacked \ 12.2k spent \ 6 posts \ 12 comments \ 0 referrals
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
June 17th, 2022 📅
📝
TOP POSTWe are thrilled to announce that our explorer is now available without registration! Explore the #lightningnetwork with https://bolt.observer/explorer
1580 sats \ 5000 boost \ 15 comments \ @boltobserver \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/36792/r/Undisciplined?commentId=36799
Lyn Alden
274 sats \ 3 replies \ @nerd2ninja \ ~bitcoin
🏆
TOP STACKER@cryptocoin
858 stacked \ 806 spent \ 21 posts \ 70 comments \ 0 referrals
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
June 17th, 2021 📅
📝
TOP POSTStephan Livera live tweets "Bitcoin Mining Council" meeting
Darin: the better we can put the message out about the facts, and let's be intellectually honest about bitcoin rather than reckless graphs
116 sats \ 1 boost \ 1 comment \ @k00b \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/26/r/Undisciplined
afaict there isn't a ton of consensus around this being the soft fork yet
21 sats \ 1 reply \ @k00b \ ~bitcoin
🏆
TOP STACKER@k00b
3 stacked \ 20 spent \ 12 posts \ 2 comments \ 0 referrals
-
-
 @ 0861144c:e68a1caf
2024-06-17 13:28:42
@ 0861144c:e68a1caf
2024-06-17 13:28:42In the past, I stated that infocracy was the way now we actually live. Seems to be simple solutions about how we can democratize a lot of things and yet, today we're facing several crisis that is not product of out imagination. As a matter of fact, we have today one solution: bitcoin is the solution to one problem: centralized trust.
But in media we have a much bigger crisis and the ones helping to build solutions are exactly the ones who are destroying the democracy to turn in a self-censorship-stalin-alike system. Let me give you some examples of why should we continue talking about this, how Stacker News is a good antidote but most important thing at all: keep writing folks.
Why should we talking about this?
The lack of trust is real, as @TomK put it in previous posts, people don't read anymore news but public relations' memo of something or someone. The news was all about find the truth but today and thanks to themselves (the same media), people are trying to take alternative means of inform themselves about facts and opinions. The Global Agenda is not something that goes in conspiraccies territories anymore, it's real.
Anyone watching goverments trying to ban bitcoin in the past knows that agendas about bitcoin are written and central banks are talking about it. Today, the 6102 Executive Order takes the form of strengthen KYC-AML policies, enforcing use of one address to all our transactions and a big etc. Warren may be a clown but a clown with the power of being an asshole to give you bad experiences using bitcoin.
Freedom of speech is confused with say anything
In other days, when you have a revolutionary idea, the goverment sent their judicial-policial-military force on behalf of the greater common and killed anyone who thinks otherwise. Shifting one regime for another, they realized and specially after WWII that people shpuld have the freedom to say what they think about their goverments because in some extend, that is the equivalent to point it out some bugs and errors in the system we produce: democracy.exe.
Today, social media companies took some stalinist practices Coetzee wrote about it many years ago. When the newspaper companies tried to keep their social power over people and couldn't, goverment figured it out that they're not the target anymore but social media companies. How can they prevent or have partial control? Well, they establish lines, requirements, protocols to follow in order of not disseminate hate speech and on behalf democracy, they tell you that speak against COVID, against democrats, against
(X)situation you're damaging the system.So, how to enforce then to speak? Well, you can but don't speak of the system, tell people something, ask them what's happening, share your personal photos all over internet to be heard, speak of anything, speak with everyone...hell, even speak of things you don't know. The fact that you don't know sH1t about something is secondary, you just need to produce content, because your goal in social media and in this new system is to express yourself every day, night and even before you go to bed.
Why, you might ask dear reader, why people need to speak at social media platforms?
The answer is simple: you are the product. See, Meta, Google et all needs to sell ads, as today is their main income source. So, everytime you speak/write/share multimedia, they planning to put their ad above, int the middle of your content. The reward for you is that the more you speak, the better they sell but in return, they give you pennies. Also remember not to say anything they say is wrong, don't produce content against a certain line nor the music industrie, which we'll talk about it in the future. Speak badly and your content goes down, that's it.
Stacker News fixes incentives
Stacker News gives you different incentives to put your words and mouth in the same place. And it's because this place understand something: nothing is free. Yes, free speech here is allowed but free content? Hewll no. Say something has a cost and without the cost, companies abosorb that, giving them partial access to the desitions because they need to sell more, understand the algorythm is important. Here? We have territories and people put money to publish and sometimes expect the reward. You publish about technical analysis about some memecoin and nobody gives you two pennies and that's not an echo chamber, here we don't have time to read noises, we limite our times expecting to read something that help my life. Gambling doesn't count as something..healthy for example.
So, in summary:
- Keep writing here, where reward and cost are balanced
- Write long posts, here I am trying to make one and giving preference to those.
- Stack sats. Be humble and keep learning.
-
 @ c73818cc:ccd5c890
2024-06-17 10:01:58
@ c73818cc:ccd5c890
2024-06-17 10:01:58
🥶 Un hacker ha utilizzato un plugin di Chrome chiamato Aggr per rubare milioni di dollari dagli account Binance, bypassando la verifica della password e l'autenticazione a due fattori. Un trader cinese ha perso un milione di dollari dopo che il suo account è stato compromesso, con gli hacker che hanno manipolato i prezzi delle coppie di valute con bassa liquidità per trarre profitto. Binance è stata criticata per non aver reagito tempestivamente, nonostante fosse a conoscenza del plugin fraudolento. Questo incidente mette in luce le vulnerabilità degli exchange di criptovalute e la necessità di misure di sicurezza più robuste.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
BitcoinReportItalia #Binance #Exchange #Criptovalute #Chrome #Aggr #Hacker #Password #Plugin #Sicurezza #Crypto #Bitcoin
-
 @ 81d38469:717cde2e
2024-06-17 08:15:35
@ 81d38469:717cde2e
2024-06-17 08:15:35Cryptography, the art of creating & using methods to disguise messages, plays a crucial role in modern society. It safeguards privacy & sensitive information across personal, commercial & political spheres. Despite its importance, cryptography often fails to provide basic online privacy for ordinary individuals. This failure raises questions about the field's ability to uphold its moral compass, given its foundational goal of ensuring secure communication.
Cryptography has generated number theory, algebraic geometry over finite fields, algebra, combinatorics & computers.~VI. Arnold
Role & Challenges of Cryptography
Cryptography lies at the intersection of security engineering & mathematics, underpinning many modern security protocols. While essential, it's notoriously difficult to implement correctly. Misapplications & inefficiencies are common, leading to failures in protecting the right assets. Cryptographers must design encryptions that serve as the backbone of secure communication. Throughout various discourses, we can observe numerous ways in which communication can become encrypted, where meaning is intentionally obscured & speech is cloaked in code or hints. This practice can arise from the necessity to evade censorship, protect sensitive information, or navigate social & political constraints.
Politics & Cryptography
Cryptography isn't merely a technical field; it has profound political implications. The perception that cryptographic work is apolitical overlooks its significant societal impact. Historically, cryptographers were more attuned to these dimensions, recognizing how their work could shape societal norms & governance.
“We appeal as human beings to human beings: Remember your humanity & forget the rest.” ~Russell-Einstein Manifesto.
The cypherpunk movement, a group of coders dedicated to advancing privacy online through cryptography, dates back to nearly 15 years before their first formal meeting in 1992. The cypherpunks ethos emphasizes the defense of digital freedoms & the democratization of cryptographic tools.
Retrospective: Before the widespread adoption of cryptographic systems in the 1980s, a groundbreaking development occurred in 1976. Whitfield Diffie & Martin Hellman published a paper at MIT introducing 'public-private key encryption', enabling secure data exchange without revealing the identities of the parties involved. This innovation, known as the Diffie-Hellman-Merkle key exchange (acknowledging Ralph Merkle's contributions), laid the groundwork for secure, private online transactions. The significance of this algorithm was propelled into the public domain by cypherpunk Mark Miller, who anonymously distributed copies of the paper to numerous publications to prevent governmental suppression of the technology. This act of dissemination was pivotal in ensuring the adoption of secure cryptographic methods.
Today, we have witnessed marvelous achievements in this field & Satoshi Nakamoto's creation of Bitcoin exemplifies this by using cryptography to challenge centralized control & promote financial autonomy. This movement views technology as a political tool to propagate values against government control over cyberspace... Nostr, also stands as a shining example of the cypherpunk ethos in action.
Casuistic: The internet is built on an insecure protocol, but it is possible to built secure protocols within the insecure one that are commonly available.
"Cypherpunks are therefore devoted to cryptography. Cypherpunks wish to learn about it, to teach it, to implement it & to make more of it. Cypherpunks know that cryptographic protocols make social structures. Cypherpunks know how to attack a system & how to defend it. Cypherpunks know just how hard it is to make good CryptoSystems". ~Eric Hughes, The Cyphernomicon.
Cryptography & Equality : 'Simple abstraction'
At the heart of cryptography lies the fundamental symbol of mathematics: the equals sign (=). This symbol represents both mathematical & societal equality. As mathematics permeates diverse domains, its influence extends to politics, transforming differences into catalysts for societal advancement. Cryptographic principles, such as Fermat's Little Theorem used in RSA encryption, highlight the intersection of mathematics, politics & human rights. By promoting secure & private communication, cryptography upholds the values of equality & integrity, empowering individuals to assert their rights & freedom in a digitized world... Thus, Governments shouldn't weaken or undermine encryption standards or influence their establishment, except to enhance information security. No government should mandate the use of insecure encryption algorithms, standards, tools, or technologies. Additionally, governments should not compel or pressure entities, whether privately or publicly, to act against these principles. Encryption is essential for everyone using internet, enabling secure online banking & shopping, protecting our communications & supporting the exercise of numerous human rights.
Bitcoin Revolution: "Isn't stupid" but rather a sophisticated system designed to ensure secure, decentralized & private transactions!
Bitcoin, leveraging cryptographic principles, democratizes access to financial resources & challenges centralized financial institutions. Satoshi Nakamoto's vision embodies liberation & autonomy, inspiring individuals to reclaim their economic sovereignty. This revolution underscores cryptography's potential to effect meaningful societal change. Bitcoin's principles can seem overly simplistic or even nonsensical, but a deeper understanding reveals its sophisticated & secure underpinnings...
The Mathematical Foundation of Bitcoin: 'It can't be that stupid !'

Central to Bitcoin's security is the use of cryptographic principles grounded in mathematics. (Complex principles that are often not immediately apparent). Satoshi Nakamoto implemented a 'proof-of-work system', ensuring that transactions could be securely verified without a central authority. This system relies on solving complex mathematical problems, highlighting the importance of mathematics in cryptographic applications. So, why do we notice a hint of 'Skepticism' when debating on this subject? - Maybe due to a lack of understanding of these complexities... Once explained correctly, the elegance & security of Bitcoin become apparent, dispelling the notion that it is 'stupid'. (Important: Before-After-How it goes!)
Cryptography is a science, not engineering. ~Collin Percival
Notably, it's evident that learning cryptography effectively doesn't require coding but rather a deep understanding of mathematical proofs (Colin Percival). This principle underscores the theoretical foundation upon which modern cryptographic methods are built, further emphasizing the importance of rigorous academic study in advancing cryptographic knowledge.
A Funny Dialogue on Fermat's Little Theorem & Cryptography: This theorem is essential in various cryptographic algorithms, including RSA encryption, which underpins much of the secure communication on the internet.

Robin: "I know what bitcoin is, buddy!"
Batman: "Shut up! Are you a cryptographer? Let's test your knowledge using Fermat's Little Theorem to evaluate primality!"
Robin: "Alright, pick a prime number candidate p.”
Batman: "How about p=17?”
Robin: "Sure, let's pick a random base a & apply Fermat's Little Theorem: a^{p-1} \mod p."
"Robin picks a=2 & calculates 2^{16} \mod 17, which results in 1.”
Robin: "Since the result is 1, p might be prime, but let's repeat the test with more bases to increase confidence."
This funny dialogue illustrates the practical application of Fermat's Little Theorem in testing the primality of a candidate number, showcasing cryptographic principles in an engaging manner. Satoshi's innovative amalgamation of cryptographic technologies, particularly the use of proof-of-work & mathematical rigor, birthed the revolutionary concept of the blockchain, a decentralized digital ledger where each participant maintains a complete transaction history. This blend of cryptographic principles & mathematical proofs is central to the security & functionality of Bitcoin, highlighting the crucial role that mathematical understanding plays in modern cryptography. By emphasizing proofs over coding, cryptographers can ensure the robustness & integrity of cryptographic systems, aligning with the cypherpunk ethos of empowering individuals through secure, private communication technologies.
Conclusion
Cryptography emerges as a potent force for societal transformation, empowering individuals to challenge centralized control & assert their rights. As we navigate the modern world, embracing the power of cryptography can help forge a future where freedom, equality & justice prevail. However, the proliferation of strong cryptography also challenges law enforcement & intelligence agencies, highlighting the need for a balance between privacy & surveillance.
Ultimately, rather than controlling the dissemination of cryptographic knowledge, we should equip individuals with the tools to protect their privacy & freedom of speech, thus strengthening democratic principles.
P.S. While this overview doesn't encompass all aspects of cryptography, it serves as a benchmark & parameter for better understanding & studying the field. Mastery of cryptography comes through practical application, exercises & continual engagement with real-world problems & foundational elements.
-
 @ a5d8475e:df9ff32c
2024-06-17 07:51:49
@ a5d8475e:df9ff32c
2024-06-17 07:51:49Whether you're buying, selling, or renting property, the expertise and guidance of a local professional can streamline the process and ensure you make informed decisions. Here’s why connecting with a reliable estate agent is crucial, especially in Wolverhampton.
Why Choose Local Expertise?
Estate agents Wolverhampton offer invaluable local knowledge that national agencies might overlook. From understanding neighborhood dynamics to predicting market trends specific to the area, their insights can help you navigate the complexities of the Wolverhampton property market with confidence.
Trust and Transparency
When searching for Wolverhampton estate agents, trustworthiness is paramount. You want an agent who prioritizes your interests and communicates openly throughout the process. Established local agents like Wolverhampton Estate Agents pride themselves on transparent dealings and a client-first approach. This commitment ensures that your property transactions are not only successful but also stress-free.
Comprehensive Services
Whether you're interested in buying, selling, or renting, estate agents in Wolverhampton offer a range of services tailored to your needs. They handle everything from property valuations and viewings to negotiations and legal paperwork. For landlords, letting agents Wolverhampton specialize in managing rental properties, ensuring a seamless experience for both landlords and tenants.
Personalized Guidance
No two property transactions are alike, and a local estate agent understands this better than anyone. By choosing an agent based in Wolverhampton, you benefit from personalized guidance that takes into account your unique circumstances and preferences. Whether you're a first-time buyer navigating the market or a seasoned investor seeking lucrative opportunities, their advice is invaluable.
Community Connections
Local estate agents in Wolverhampton often have strong ties within the community. These connections can be instrumental in finding off-market listings or connecting you with reliable service providers such as solicitors or mortgage brokers. Their network extends beyond property transactions, enriching your overall experience of relocating or investing in Wolverhampton.
Finding Your Ideal Estate Agent
When searching for estate agents in Wolverhampton, consider factors such as reputation, experience, and client testimonials. Agencies like Letting Agents Wolverhampton and Estate Agents Wolverhampton have built solid reputations based on years of excellent service and client satisfaction. Their expertise combined with a deep understanding of the local market ensures that your property goals are achieved efficiently.
In conclusion, connecting with a local estate agent in Wolverhampton who offers trustworthy guidance is essential for navigating the complexities of the property market with confidence.
**CONTACT: ** 2-3 Walsall Rd, Willenhall, WV13 2EH , info@halleuk.com , +44 (0) 1902 504455
-
 @ 1c6b3be3:73f0ae6f
2024-06-17 04:00:08
@ 1c6b3be3:73f0ae6f
2024-06-17 04:00:08🍵 "btc | bitcoin | lightning network | asic" - Google News
T-Mobile Owner Deutsche Telekom Unveils Bitcoin and Lightning Network Node Operations – Bitcoin News - Bitcoin.com News Blockchain Facts: What Is It, How It Works, and How It Can Be Used - Investopedia The telecom giant T-Mobile is getting into Bitcoin Mining! - Cointribune EN 18 Month Bitcoin Hashrate Rising Streak Ends - Live Bitcoin News NFT sales drop 16% to less than $122 million: What Happened? - crypto.news Bitcoin active addresses hit lowest level in five years, BTC ranges below $67,000 - FXStreet Bitcoin Miners Are Selling Again: CryptoQuant - CryptoPotato
-
 @ 32e18276:5c68e245
2023-10-04 22:21:45
@ 32e18276:5c68e245
2023-10-04 22:21:45Hey nostr posters,
I'm at Pacific Bitcoin this week! Come say hi if you're in LA! I have a nostr discussion with rockstar at the conference so check that out if you're here. Another fun thing I did this morning was a nostr podcast with Peter McCormack, so keep an eye for that one. I'm getting through some remaining bugs for the 1.6 App Store release, one annoying issue in the last build was that you couldn't update your profile. This has been fixed!
We also fixed some bugs with the clear cache button, it should be more responsive now. Daniel has been doing some great work with reducing the buggyness of the post composition view, so hopefully you should notice some quality of life improvements there. Daniel also improved many bugs with muted users. If you've muted a user that has been reposted in your timeline, damus will now hide those.
Thanks for your patience with this release, integrating nostrdb has been time consuming! Hopefully back to a more regular release schedule after this one.
Check out the full changelog:
Changed
- Improve UX around clearing cache (Daniel D’Aquino)
- Show muted thread replies at the bottom of the thread view (#1522) (Daniel D’Aquino)
Fixed
- Fix situations where the note composer cursor gets stuck in one place after tagging a user (Daniel D’Aquino)
- Fix some note composer issues, such as when copying/pasting larger text, and make the post composer more robust. (Daniel D’Aquino)
- Apply filters to hashtag search timeline view (Daniel D’Aquino)
- Hide quoted or reposted notes from people whom the user has muted. (#1216) (Daniel D’Aquino)
- Fix profile not updating (William Casarin)
- Fix small graphical toolbar bug when scrolling profiles (Daniel D’Aquino)
- Fix localization issues and export strings for translation (Terry Yiu)
-
 @ a012dc82:6458a70d
2024-06-17 02:38:07
@ a012dc82:6458a70d
2024-06-17 02:38:07Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Overview of Bitcoin and Keynesian economics
Bitcoin and Keynesian economics are two seemingly unrelated concepts, but they have more in common than one might think. Both have been the subject of intense debate and controversy in recent years, with some hailing them as revolutionary and others dismissing them as misguided. In this article, we will explore the ways in which Bitcoin has exposed the flaws and limitations of Keynesian economics, and how the decentralized digital currency has the potential to disrupt traditional economic systems.
First, it's important to understand the basics of Keynesian economics. The theory was developed by economist John Maynard Keynes in the 1930s, during the Great Depression. Keynes believed that government intervention, particularly in the form of monetary and fiscal policy, was necessary to stabilize the economy during times of recession and high unemployment. He argued that government spending could stimulate demand and boost economic growth, and that central banks should use monetary policy to control inflation and stabilize the economy.
Understanding Keynesian economics
However, Bitcoin, which is a decentralized digital currency that operates independently of any government or central bank, challenges the very principles of Keynesian economics. Bitcoin's decentralized nature means that it is not controlled by any central authority, and it operates on a peer-to-peer network. Transactions are verified and processed by a network of users, rather than a central bank or government. This decentralization is one of the key features of Bitcoin, and it is what makes it different from traditional fiat currencies.
One of the main criticisms of Keynesian economics is that it relies too heavily on government intervention and centralization. Bitcoin, on the other hand, operates on a decentralized model, which some argue is more efficient and less prone to manipulation. Bitcoin's decentralized model of governance means that it is not subject to the same political pressures and biases that traditional currencies are. This is particularly relevant in countries where the government is corrupt or has a history of manipulating the economy for their own benefit.
Another criticism of Keynesian economics is that it is based on the assumption that governments and central banks can effectively manage the economy. However, history has shown that this is not always the case. In many instances, government intervention has actually hindered economic growth, rather than stimulating it. Bitcoin, on the other hand, operates on a decentralized model, which means that no single entity can control the monetary policy or manipulate the economy for their own benefit. This gives Bitcoin the potential to be a more stable and reliable currency.
Furthermore, Bitcoin's limited supply, which is capped at 21 million, aligns with the Austrian economic theory of sound money. Austrian economics emphasizes on the importance of a sound money and the role of money as a store of value. Bitcoin's limited supply means that it cannot be debased by monetary inflation, as governments can do with fiat currencies. This gives it a potential to be a more stable store of value than traditional currencies.
Another important aspect to consider is that Bitcoin's volatility is a natural aspect of a free market currency. In a free market, the value of goods and services is determined by supply and demand, and this is reflected in the price. Bitcoin's price is determined by the same forces of supply and demand, and its volatility is a natural result of this process. Critics of Bitcoin often point to its volatility as a weakness, but supporters argue that this volatility is a sign of a healthy market.
In conclusion, Bitcoin has exposed the limitations of Keynesian economics in several ways. Its decentralized nature challenges the principles of government intervention and centralization that are at the heart of Keynesian economics. Additionally, the decentralized model of governance of Bitcoin means that it is not subject to the same political pressures and biases that traditional currencies are. Furthermore, Bitcoin's limited supply aligns with the Austrian economic theory of sound money.
Additionally, Bitcoin's limited supply and volatility, which are a natural aspect of a free market currency, align with the principles of Austrian economics. These features give Bitcoin the potential to be a more stable and reliable currency, and a better store of value than traditional fiat currencies.
Bitcoin as a challenge to Keynesian economics
Furthermore, Bitcoin's decentralized model of governance undermines the need for government intervention in the economy as proposed by Keynesian economics. Bitcoin's network is self-regulating, and transactions are verified and processed by a network of users, rather than a central bank or government. This self-regulation and decentralization is what makes Bitcoin more resilient to market fluctuations and economic downturns.
It is important to note that Bitcoin is still a relatively new technology and its potential to disrupt traditional economic systems is still uncertain. However, its decentralized nature and potential to be a more stable and reliable currency than traditional fiat currencies, makes it a fascinating subject of study and debate in the world of economics.
Conclusion
While Bitcoin and Keynesian economics may seem unrelated, they have more in common than one might think. Bitcoin has exposed the limitations of Keynesian economics and has the potential to disrupt traditional economic systems. However, it is important to keep in mind that Bitcoin is still a relatively new technology, and its potential to disrupt traditional economic systems is still uncertain. It is important to continue to study and debate the implications of Bitcoin on traditional economic systems and theories such as Keynesian economics.
FAQ
What is Bitcoin? Bitcoin is a decentralized digital currency that operates independently of any government or central bank.
How does Bitcoin differ from traditional currencies? Bitcoin operates on a decentralized model and is not controlled by any central authority, unlike traditional fiat currencies.
What is the maximum supply of Bitcoin? The maximum supply of Bitcoin is capped at 21 million.
How is the value of Bitcoin determined? The value of Bitcoin is determined by supply and demand on the market.
How is Bitcoin stored? Bitcoin is stored in a digital wallet, which can be a software, hardware or paper wallet.
How does one acquire Bitcoin? Bitcoin can be acquired through mining, purchasing on a cryptocurrency exchange or accepting it as payment.
Can Bitcoin be used to make purchases? Yes, Bitcoin can be used to make purchases at businesses that accept it as a form of payment.
Is Bitcoin legal? The legality of Bitcoin varies from country to country, it is considered legal in some and illegal in others.
Is Bitcoin safe to use? Bitcoin transactions are secured by cryptography and are generally considered safe to use.
What is the future of Bitcoin? The future of Bitcoin is uncertain and it is subject to fluctuations in the market and governmental regulations.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 32e18276:5c68e245
2023-09-21 22:31:03
@ 32e18276:5c68e245
2023-09-21 22:31:03Hey gang,
I just pushed Damus build 18 which is the first major nostrdb integration. Now all damus profiles are stored in nostrdb! You will always be able to search profiles from people you've seen in the past.
There are many crash fixes in this build as well, check out the full changelog:
Enjoy!
Added
- Add followed hashtags to your following list (Daniel D’Aquino)
- Add "Do not show #nsfw tagged posts" setting (Daniel D’Aquino)
- Hold tap to preview status URL (Jericho Hasselbush)
- Finnish translations (etrikaj)
Changed
- Switch to nostrdb for @'s and user search (William Casarin)
- Use nostrdb for profiles (William Casarin)
- Updated relay view (ericholguin)
- Increase size of the hitbox on note ellipsis button (Daniel D’Aquino)
- Make carousel tab dots tappable (Bryan Montz)
- Move the "Follow you" badge into the profile header (Grimless)
Fixed
- Fix text composer wrapping issue when mentioning npub (Daniel D’Aquino)
- Make blurred videos viewable by allowing blur to disappear once tapped (Daniel D’Aquino)
- Fix parsing issue with NIP-47 compliant NWC urls without double-slashes (Daniel D’Aquino)
- Fix padding of username next to pfp on some views (William Casarin)
- Fixes issue where username with multiple emojis would place cursor in strange position. (Jericho Hasselbush)
- Fixed audio in video playing twice (Bryan Montz)
- Fix crash when long pressing custom reactions (William Casarin)
- Fix random crash due to old profile database (William Casarin)
-
 @ 256a7941:b828ba8d
2024-06-17 02:32:15
@ 256a7941:b828ba8d
2024-06-17 02:32:15With no moves left, evil is lashing out.
The window is closing.
The walls are closing in.
The light is too bright for the darkness to operate.
-
 @ 256a7941:b828ba8d
2024-06-17 02:29:12
@ 256a7941:b828ba8d
2024-06-17 02:29:12We don't love love anymore
We love money more than anything
Bitcoin doesn't fix this only replace it
Obsessed with your stack are you?
-
 @ 32e18276:5c68e245
2023-09-20 15:10:15
@ 32e18276:5c68e245
2023-09-20 15:10:15I thought it might be interesting to do a quick technical writeup of nostrdb and the new nostrdb profile searching. This is the first text search index within nostrdb, if you're interested in the nitty gritty details of things, this article is for you!
For the most part, nostrdb has been a copy of the design of strfry, in terms of its indices and multi-process architecture. strfry doesn't support search (yet), so this is a novel feature of nostrdb. What is strfry? If it weren't for strfry, nostr wouldn't work. It is simply the best way to implement a nostr database and relay. SQL servers are just too slow to serve dynamic queries at scale.
I wanted something like strfry that I could embed into native nostr clients like Damus, this is how nostrdb was born!
First, let's look at how nostrdb at a high level.
nostrdb
nostrdb is an embedded library for native nostr clients. It uses the Lightning-mapped database (LMDB) for very efficient querying. This allows it to skip SQL query parsing and query planning. We don't really need all that with nostr. nostr search filters are a bit more restrictive, so we can build custom indices for the most common nostr queries. This is a huge win CPU-wise, nostr queries can be very dynamic, and skipping the query parsing and planning saves CPU and battery.
Before we get into any of that, let's look at how you would use the library from the highest level. The entrypoint for notes in nostrdb is the
ndb_process_eventfunction. When you receive nostr events from another relay, this function is called for each event.Event processing
ndb_process_event('["EVENT","subid",{kind:1, ...}]')We begin by queueing the event for processing in the multi-threaded ingester. This allows it to return immediately and not block the client.
The ingester is multi-threaded because validating note signatures can be pretty slow. We want note processing to be as quick as possible so nostrdb doesn't have a bottleneck here.
nostrdb is very smart about not burning CPU when it doesn't need to. The custom json parser will stop when it finds the note ID field, lookup that note in the database to see if we already have it, and then stop JSON parsing if we do. This saves CPU for large notes like contact lists, and skips the need to re-validate the signature as well. Even strfry doesn't make this optimization, so nostrdb has a speed, cpu, and battery life advantage here.
During the processing step, nostrdb will detect different note types such as profile metadata. It will look at the
nameanddisplay_namefield and add a custom index for searching user profiles. Since keys in LMDB are lexicographically sorted and support range queries, our profile search indices is simply (name + pubkey + created_at). This allows you to do a ranged key-lookup on "jb" and it will position the db cursor to the first record that starts with jb. LMDB uses a b+ tree, this is not a linear scan, so it is very fast! Eventually this index will be used for implementing nip-50 search on the nostrdb relay interface, which is coming sometime in the future.Once we're done writing the indices and validating the note, we store nostr notes in a custom, compact binary format that is easy to access directly in memory from any programming language. We also do this with profile records by leveraging flatbuffers.
So in the end, what does this achieve? It enables you to store as much nostr data as you want with near zero query and serialization overhead. Since the data stored in nostrdb is just flatbuffers, you can access data directly from the operating system's page cache (just a pointer to memory) and from any programming language via flatbuffer's schema and codegen tools. It's so fast it will be guaranteed once of the fastest things in your codebase. You can even run it in your main UI thread so you can worry about other things such as UX and design without introducing complex async logic in your user interface.
What's next
nostrdb is already partially integrated into Damus iOS. Damus uses nostrdb's compact note format for storing notes in memory, but eventually everything will be switched to use nostrdb directly. The next version of Damus testflight will remove the in-memory and core-data profile cache and switch to nostrdb profiles. Damus currently has a complex in-memory trie data structure for profile searches, but it only knows about profiles it has seen during the current session. This is a common source of confusion, sometimes Damus doesn't auto-complete profiles it has already seen sometime in the past. nostrdb profile searches will allow @ mentions and user search to find every profile it has ever seen in realtime. This will be a huge usability win for Damus and other clients looking to adopt nostrdb.
Right now nostrdb exposes its functionality via direct function calls:
ndb_get_profile, etc. The plan is that most of these calls won't be necessary. Once nostrdb has nostr filter parsing, it will be able to support dynamic queries of the kind you would expect from your typical nostr relay. This will turn nostrdb-powered clients into relays themselves.Once nostrdb is more relay-like, then we will be able to leverage strfry's negentropy set-reconciliation queries to only fetch notes that we don't already have. This will be insanely useful for reducing bandwidth usage when querying strfry relays. Eventually it may make the most sense to just let nostrdb do all the websocket querying behind the scenes, becoming a kind of local multiplexing relay.
The future of nostrdb is very exciting. I plan on using it in Damus NoteDeck and Damus Android, why duplicate all this work in every client? nostrdb will make developing native clients much easier.
Support
Damus and nostrdb are mainly supported by donations. nostrdb is open source, MIT-licensed. Damus is GPL. We are dedicated to building the best and most free open source tech on nostr. If you would like to support our work, please consider buying our merch !
Thanks for getting this far! Until next time...
-
 @ 2edbcea6:40558884
2023-09-03 16:03:23
@ 2edbcea6:40558884
2023-09-03 16:03:23Happy Sunday #Nostr !
Here’s your #NostrTechWeekly newsletter at the nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk written by nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2
NostrTechWeekly is a weekly newsletter focused on the more technical happenings in the nostr-verse.
A lot of foundational work happening in the nostr-verse and quite a bit of new projects shipped this week. Let’s dive in!
Recent Upgrades to Nostr (AKA NIPs)
1) NIP 75: Zap Goals ⚡
Zapping has been such an integral part of what makes Nostr what it is. Earning for your content or contributions. Zaps for memes. Zaps as a way to boost the signal. It’s a growing concept as well.
NIP 75 was merged this week, with the goal of introducing the ability to set a “Zap Goal” which is similar to a fundraising goal. Users can zap the “goal” event directly and help the progress bar go up. Whatever the cause.
Interesting to see if this will stay simple and decentralized or if this will be the foundation of a GoFundMe type platform via Nostr using exclusively Bitcoin.
Author: nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg
2) (Proposed) NIP 79: Digital contracts on Nostr ✍️
Think Docusign, but on Nostr. This NIP would introduce support for various kinds of digital agreement (contracts, covenants, agreements) which serve various purposes.
These agreements would all be unencrypted markdown, so the purpose is likely more for non-secret agreements so that they can be cited by all parties in public.
Author(s): https://github.com/xemuj nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z
3) (Proposed) NIP 34: Improved media attachments to notes 📎
Attaching media to notes in a way that is handled well on a majority of major clients is still more of an art than a science and nostr:npub108pv4cg5ag52nq082kd5leu9ffrn2gdg6g4xdwatn73y36uzplmq9uyev6 is determined to introduce a better pattern 💪.
This NIP introduces the pattern of using an explicit set of “media” tags on any note so that media that should accompany the note can be explicitly linked without clients needing to parse the content of the note to make the url of the media in the note a hyperlink.
Author: nostr:npub108pv4cg5ag52nq082kd5leu9ffrn2gdg6g4xdwatn73y36uzplmq9uyev6
4) (Proposed) Improvements to reddit-style moderated communities 💬
This proposed improvement to NIP 72 introduces the concept of a post (within a moderated community) that is exclusively posted to a specific community. Think about posting something that can make the front page of reddit versus a post that is intended solely for a subreddit. Seems like a welcome addition to NIP 72 👍
Author: https://github.com/vivganes
Notable projects
A nostr Wiki
The start of a truly open wiki.
Wikis are used for a lot of things: corporate intranets and documentation, fandoms managing information about their universe, and Wikipedia which may be one of the greatest repositories of knowledge on Earth. The main downside to Wikipedia is that it may be crowdsourced but it is centralized, seeking one version of each article (and therefore determining what is true).
This wiki (in the spirit of Nostr) allows people to create any number of articles on the same subject to offer different perspectives. At scale this could become something where people read various perspectives and determine the truth for themselves.
Author: nostr:npub1q7klm2w94hyq3qdm9ffzpahrrq0qcppmjrapzhz0rq6xgq3fdrnqr6atmj
Oxchat
Oxchat is a secure, private group chat experience for iOS and Android with a great UX 🙌.
Nostr needs its own standalone chat app that can stand up to the capabilities and ease of use of Signal, Telegram, WhatsApp, etc. And Oxchat may be that app! Looking forward to using it more.
Author: nostr:npub10td4yrp6cl9kmjp9x5yd7r8pm96a5j07lk5mtj2kw39qf8frpt8qm9x2wl
Nostrnet.work
A web-based dashboard for Nostr, it’s a webpage that is a configurable hub for all the Nostr apps you want to have available quickly. You can log in with your Nostr account, and configure it to your liking.There’s a section for managing your profile (including your relays), as well as for taking notes, all of that on top of the list of Nostr apps for quick access.
Nostrnet.work seems to be evolving into almost a web-based browser of the nostr-verse. You can manage the apps that are on the dashboard Nostrnet.work via the basic/open app store from nostr.band. There’s endless possibilities for users to discover what Nostr has to offer and use those offerings from one unified interface.
A recent addition to the Nostrnet.Work interface is an area for “Nostr AI'' which is meant to allow users to utilize Data Vending Machines (explored in the Latest Conversations section). Data Vending Machines (or DVMs) are something that I think is unique to Nostr, and it's a product/ecosystem that may be the killer unique offering people come to Nostr to try out.
Author: nostr:npub1cmmswlckn82se7f2jeftl6ll4szlc6zzh8hrjyyfm9vm3t2afr7svqlr6f
w3.do url shortener
URL shorteners are a stable web util. In fact,
We started using w3.do because the tool we use to draft/publish this newsletter as a long form note will send Nostr links and embed the note instead of just linking to the note. So a url shortener is enough to trick the tool so we get fewer embeds and more links! Thanks nostr:npub1alpha9l6f7kk08jxfdaxrpqqnd7vwcz6e6cvtattgexjhxr2vrcqk86dsn !
Latest conversations
Data Vending Machines (DVMs)
“Data Vending Machines are data-processing tools. You give them some data, a few sats, and they give you back some data.” source: vendata. A practical example is a recent DVM published by Pablo: FOMOstr. You put up some sats, you’ll get back content on Nostr that you may have missed.
The concept seems to be that people need help from machines. And right now, the most common way for people to get that help is to pay a company for that help (email provider, calendar management, group chats, entertainment, etc).
These are great for more complex digital products, but what if you just have a question? Maybe you just want to generate an image. Or maybe just extract text, and then maybe translate it. These are most efficient as pay-as-you-need-it products. That’s where DVMs shine (on the long tail of needs).
You can put up a certain amount of money and people who have created algorithms or AIs that can accomplish these tasks will compete to do the job for the lowest price (and therefore win the money). This is the foundation of an economy of people who need jobs done and people who want to make income by creating the best DVMs for the jobs people need done.
DVMs that help you discover people and content on Nostr will be a god-send for improving the experience for people using Nostr while maintaining decentralization. This will certainly evolve over time, but it seems this could become an integral part of the Nostr ecosystem as well as become a unique service that can only be found on Nostr (attracting a new set of users).
Events
Here are some upcoming events that we are looking forward to! We keep a comprehensive list and details of Nostr-related events that we hear about (in person or virtual) that you can bookmark here NostrConf Report
- Nostrasia Nov 1-3 in Tokyo & Hong Kong
- Nostrville Nov 9-10 in Nashville, TN, USA
- NostrCon Jan 12, 2024 (online only)
Until next time 🫡
If you want to see something highlighted, if we missed anything, or if you’re building something I didn’t post about, let me know, DMs welcome.
nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2 or nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk
Stay Classy, Nostr.
-
 @ 76c71aae:3e29cafa
2024-06-17 00:57:57
@ 76c71aae:3e29cafa
2024-06-17 00:57:57I wanted to take a moment to address the recent Business Insider article about Jack Dorsey’s funding of Nostr. While the article has inaccuracies and it lacks nuance, this piece it’s also an invitation to all of us to discuss Nostr openly.
Is the article true? First things first: We do not actually know fiatjaf’s identity so we cannot weigh in on the veracity of who he is. His real identity remains a mystery to us. While we do not share Fiatjaf’s beliefs, he’s always been clear that Nostr was built to support all types of speech, even the stuff he personally disagrees with. That’s a fundamental principle of the platform.
Why is Nos built on a protocol that was built by someone who supports fascists? Let’s clear up a major point of confusion.Merriam Webster defines fascism as: a political philosophy, movement, or regime (such as that of the Fascisti) that exalts nation and often race above the individual and that stands for a centralized autocratic government headed by a dictatorial leader, severe economic and social regimentation, and forcible suppression of opposition.
Based on that definition, fascism is then a centralized autocratic government led by a dictatorial leader, enforcing several economic and social regimentation, and suppressing opposition. Nostr, on the other hand, is designed to prevent centralized control altogether. It’s a decentralized network where no single entity has ultimate power.
Nostr is designed so there is no central authority of control. By distributing content across multiple relays, the architecture of Nostr eliminates the possibility of centralized autocratic control.
Nos chose to build an app on the Nostr protocol because traditional corporate social media platforms often stifle views outside the mainstream, these also include views of leftist activists, LGBTQ community, and others. This stifling takes the form of shadow banning when people use terms that the platform doesn’t want to support such as abortion. More recently there has been an uptick in account suspensions and shadow bannings as people use reporting tools to flag accounts that support Gaza. Often the people flagging are looking at older posts and flagging those to get the accounts shutdown.
On the other hand, Nos is about giving users control over their accounts, identities, and feeds. Nostr makes this possible in a way no other protocol does today. At Nos, we are committed to building an app using tools that put the user in charge and Nostr enables this user-first approach.This means that everybody has something to say, and we may not like it.
How does Nos reconcile being on a network that can’t ban people for their views? Unlike corporate social media, such as Facebook, Instagram and TikTok, Nostr is built on the idea of a web of trust, meaning you only see the content from the people you follow. There are no algorithms pushing sensational content to keep you glued to your screen. Corporate platforms thrive on “engagement” and are optimized for eyeballs and time on site. Over the years, the algorithms have learned that the content that is most engaging is content that induces moral outrage in the viewer.
As a result, the corporate platforms feed users more and more morally outrageous content to keep them online. As mentioned before, Nostr operates on a different principle. It’s built on a web of trust, where you only see content from people you follow: Nos and most of the other Nostr clients do not have algorithm-driven feeds, instead content from the people you follow appears in reverse chronological order in your feed. Those clients that do have algorithmic feeds today show the most popular content, but are not optimizing for morally outrageous content.
This means that it is much more difficult for toxic, hateful content to go viral as there’s no behind-the-scenes mechanism amplifying content for views similar to what you have on Youtube and X today. You won’t find the same amplification of divisive content here that you see on these traditional platforms.
Nos offers the ability to have “Freedom from” unwanted content at the user level. There is no central authority shutting down one account or another or blocking certain accounts.
This is especially important for activists. At present on Mastodon and other ActivityPub servers, we are witnessing pro-Palestinian activists accounts’ being blocked from certain servers. While happening at a smaller level, this is still a form of shutting down the dialogue and conversation.I get it –after more than a decade of algorithmic fueled hot-takes and virtue signaling on X (formerly Twitter), it might be a bit difficult to conceive of a social media experience where dialogue exists, but the network that has evolved on top of Nostr is that space. Yes, as difficult as it sounds, Nostr allows for dialogue without central censorship.
Many folks disagree on Nostr in the same way disagreements used to happen on Twitter (now X) in the early days, where there are long text based dialogues. Folks may walk away still disagreeing and a small subset get nasty, but those conversations do not spiral out of control in the same way they do on X or even on Mastodon and Bluesky today.
And if things get ugly, Nos and a few other apps have user-led moderation tools to help mitigate anything that comes into replies or mentions. Nos is leading efforts to enhance user-led moderation across the network.
This discussion is crucial. We have the chance to reshape the future of decentralized social media and we can build a more open and inclusive digital space. The pathway is and will be messy. How do we balance free speech while protecting users from harmful content? What role should decentralization play in the next generation of social media platforms? I’d love to hear your thoughts and keep this conversation going.
-
 @ 78733875:4eb851f2
2023-08-17 14:23:51
@ 78733875:4eb851f2
2023-08-17 14:23:51After announcing our first wave of grants for bitcoin[^fn-btc] and nostr[^fn-nostr] projects, we are pleased to announce an additional wave of grants for open-source projects in the space:
[^fn-btc]: First Wave of Bitcoin Grants [^fn-nostr]: First Wave of Nostr Grants
- BDK
- LNbits
- Watchdescriptor
- Stratum V2 Testing \& Benchmarking Tool
- Fedimint Modules and Resources
- Amber: Nostr Event Signer
- Nostr UI/UX Development
- Nostr Use-Case Exploration \& Education
The first five grants are sourced from our General Fund, the last three—being nostr projects—from our Nostr Fund. This brings the total number of OpenSats grants to 41, adding to the grants we previously announced in July.
Once again, let's take a closer look at each of the projects to see how they align with the OpenSats mission.
BDK
Bitcoin Development Kit (BDK) is a set of libraries and tools that allows you to seamlessly build cross-platform on-chain bitcoin wallets without having to re-implement standard bitcoin data structures, algorithms, and protocols. BDK is built on top of the powerful rust-bitcoin and rust-miniscript libraries and adds features for managing descriptor-based wallets, syncing wallets to the bitcoin blockchain, viewing transaction histories, managing and selecting UTXOs to create new transactions, signing, and more. The core BDK components are written in Rust, but the team also maintains Kotlin and Swift language bindings for use in mobile projects. There are also Python bindings, and React Native and Flutter support is being actively developed.
Repository: bitcoindevkit/bdk
License: Apache 2.0 / MITLNbits
LNbits is used by a multitude of projects in the bitcoin space, especially as part of their lightning payments stack. Being easy to build on through its extension framework, LNbits has been pioneering various cutting-edge solutions and experiments in the world of bitcoin, lightning, and nostr.
The project has a thriving maker community building various hardware devices such as Lightning ATMs, point-of-sale devices, DIY hardware wallets, and nostr signing devices. The modular design of LNbits makes it attractive to users and tinkerers alike, as its plugin architecture makes it easy to extend and understand.
Repository: lnbits/lnbits
License: MITWatchdescriptor
watchdescriptoris a CLN plugin written in Rust that connects a business's treasury wallet to its CLN node. It utilizescln-pluginand the BDK library to track coin movements in registered wallets and report this information to thebookkeeperplugin.The plugin enables businesses to design a complete treasury using Miniscript and import the resulting descriptor into CLN. Since
bookkeeperalready accounts for all coin movements internal to CLN, this plugin is the last piece businesses need in order to unify all their bitcoin accounting in one place. This enables businesses to account for all inflows and outflows from their operations, streamlining tax reporting and financial analysis.The
watchdescriptorproject is part of a broader vision to transform the lightning node (particularly CLN) into a financial hub for businesses, enabling them to conduct operations without reliance on any third parties.Repository: chrisguida/watchdescriptor
License: MITStratum V2 Testing & Benchmarking Tool
The Stratum V2 Testing & Benchmarking Tool allows the bitcoin mining industry to test and benchmark Stratum V2 performance against Stratum V1. The tool supports different mining scenarios to help miners make informed decisions and evaluate their profitability. The goal of the project is to motivate miners to upgrade to Stratum V2, increasing their individual profits and making the Bitcoin network more resilient in the process.
Repository: stratum-mining/stratum @GitGab19
License: Apache 2.0 / MITFedimint Modules and Resources
Fedimint is a federated Chaumian e-cash mint backed by sats with deposits and withdrawals that can occur on-chain or via lightning. It can be understood as a scaling and privacy layer as well as an adoption accelerator for Bitcoin.
The goal of this particular project is to improve the Fedimint UI and develop free and open resources for developers and "Guardians" to enable more people to run and develop on Fedimint.
Repository: fedimint/ui @EthnTuttle
License: MITAmber: Nostr Event Signer
Amber is a nostr event signer for Android. It allows users to keep their
nsecsegregated in a single, dedicated app. The goal of Amber is to have your smartphone act as a NIP-46 signing device without any need for servers or additional hardware. "Private keys should be exposed to as few systems as possible as each system adds to the attack surface," as the rationale of said NIP states. In addition to native apps, Amber aims to support all current nostr web applications without requiring any extensions or web servers.Repository: greenart7c3/Amber
License: MITNostr UI/UX Development
The goal of this project is to help improve the UI/UX of major nostr clients, starting with Gossip and Coracle, emphasizing the onboarding process as well as usability and accessibility. One part of onboarding is solving the discoverability problem that nostr has in the first place. Solving the problem of jumping in and out of the nostr world is what motivated the development of
njump, which was redesigned as part of these efforts and is now live at nostr.com.In addition to client-specific improvements, generic design modules and learnings will be incorporated into the Nostr Design project for others to use.
Activity: github.com/dtonon @dtonon
License: MITNostr Use-Case Exploration & Education
As of today, most nostr clients implement social media applications on top of the nostr protocol. However, nostr allows for various use cases, many of which go beyond social media. Two examples are Listr and Ostrich, a list management tool and job board, respectively.
In addition to use-case exploration, this project will continue to educate users and developers alike, be it via Nostr How or various video series, e.g., explaining how to build upon NDK.
Activity: github.com/erskingardner @jeffg
License: MIT / GPL-3.0 / CC BY-NC-SA 4.0
We have more grants in the pipeline and will provide funding for many more projects in the future. Note that we can only fund those projects which reach out and apply. If you are an open-source developer who is aligned with our mission, don't hesitate to apply for funding.
-
 @ 1bc70a01:24f6a411
2024-06-16 23:07:46
@ 1bc70a01:24f6a411
2024-06-16 23:07:46I've posted some notes in the past with ideas to improve nostr, so I dug up a few and listed them here, along side with the curated feeds announcement because it feels like a big deal! These are nothing new, just some old ideas put into one post.
Offer curated feeds to users in the UI or part of onboarding:
nostr:note19yvypkcsprn53939rzkf2yqku6xullcyhm4v60fn0sghah7mqe6syvtxuw
Label relays
nostr:note1eu9e739yms2msahuuclxpf95mcc786cjrtp9m6y73eg8h7xjxx5q60gx85
Better default (image / video) feeds for logged out users
nostr:note1hr3es5h5m0keuavzumsls8qcw86cd9s36lpc9ukxd47z7zq4wgesk9zvas
Self-paced profile completion and badge earning to discover nostr
[Figma File]https://www.figma.com/file/ThUW7QxTYT0BUxcH48uelG/Luna?type=design&node-id=0%3A1&t=emttAVmvjztFk9QO-1() nostr:note12vtxkka5zvgudv534dlsuzuld84tdyd474jgct6j5e9uv6ch0vcs7f9060 nostr:note1e24gz3spmszly7cpa9ds9ju7ccyctxdvv5jj3usl6gk8ueckdkmsgkq4fr nostr:note19rdyf9jpqg04rwqmkqnjcncjfrrqs9e5dp8evzqztpusdzxa8ejqhxkuyf
Introduction post prompt in onboarding
nostr:note13xrv039h8nexf4jaa2r4g8js28mr7evq7aakftr5q67e97e08pfqcvf5g0 Current (the client) already does an #introductions post in onboarding, and that's a great idea!
Allow nostr long form users to build email lists
nostr:note1ewrk0at4fexr7n3wdauah4kw0c8nategc403gqwvxccntky60rcqlxynaz
Promote nostr content outside on other platforms
nostr:note1um8s8w05rutzg245m058gl3kvzwqwepudkx9xj3fepeuf52r49cs9ruv3f
A tool to help people migrate their content to nostr (nicely designed, user friendly):
nostr:note1q546zcuxgwjqp6vpgh8v3hk0dw2vp0ml6phtxh223kkg8h8fudjq5qe5f2
Signup
nostr:note17fe7vmvuk6jpw7h55f3g0s5m2ex4apuhu92mzmn3n9x6p98zkyqscv9hd0
Feedback Mega Note
nostr:note1jsj0c4xvt26p0ap9mtkygfuej776ad0960e5r3n33m5hz7lm7rwsdzpe0g
-
 @ 1bc70a01:24f6a411
2024-06-16 23:02:59
@ 1bc70a01:24f6a411
2024-06-16 23:02:59We’re all daily users of Nostr, so it can be easy to see things through an advanced user lens while forgetting what it felt like to be a newbie. I thought I would take some time to go over major client from the start in hopes of evaluating what it might feel like for a new user.
The other reason for running this review is to hopefully improve the overall nostr retention rate across clients. As it stands, according to nostr.band, retention of trusted users 30 days after signups trends to 0 for recent cohorts. This seems to be supported by the lack of growth in daily active users, with the average remaining in the 10,000-12,000 range for “trusted” pub keys.
The following report consists of several criteria which I felt were essential to basic first-time social media experience:
- Ease of signup
- Ease of logging in
- Ability to understand what you are looking at (sufficient explanations)
- Seeing a good initial feed
- Ability to follow something of interest
- Minimizing technical /dev lingo
- A fast scrolling experience
- Ability to easily upload media
- A good search experience overall
- Good keyword searching
- Hashtag searching
- Ability to follow hashtags
- Easily accessing followed hashtags
- Good experience reacting to notes
In total there are 140 points, 10 for each category. This is by far not the most comprehensive score card, but I felt it did a decent job covering most things you’d want to do in a social client.
Some notes of caution:
- This report and score card are meant to be a general quick glance at where your client may stand in overall UX. It does not differentiate between the intended target audiences.
- The criteria that I deem important may not be important to you as the founder / developer, so take it for what it’s worth. Adding your desired criteria may increase your score significantly. For example, I did not evaluate the zap experience, or thoroughly test nested replies.
- This report is not a substitute for proper user testing. It’s just one person’s observations. While we have done some user testing in the past, I highly recommend doing your own. You can do so by approaching and interviewing new users (if you are able to distinguish if they came from your client), or via other user testing software. Talk to me (@karnage) if you need some help getting set up.
- People’s reported experience regarding usability may vary greatly depending on their familiarity with cryptographic concepts, their background, and technical experience. What I may deem as a great score of 10, may not be a 10 for others. I have seen user tests where “obvious” things were not obvious to testers.
- This report only looks at the English language version of the client. The actual user experience for someone on a different language version of the app could be totally different from what is graded here. It’s worth considering geographies of where users are coming from and how they experience your client.
- I did not test re-activation of new users. Meaning, once they close the app, I did not test if they are pulled back by some notification or other means. This is a crucial aspect of any new app usage that should be considered carefully.
Tested Clients: Damus, Amethyst, Primal iOS, Snort (web), Iris (sort of), Coracle, Nostur.
I also tested Instagram and X/Twitter for comparison.
Results, highest points to lowest: Primal iOS: 136 Twitter: 125 Instagram: 109 Nostur: 108 Coracle: 99 Amethyst: 93 Snort: 90 Damus: 87 Iris: N/A Facebook: could not test.
My main takeaway was that among all apps (including Twitter and Instagram), the traditional apps win simply by having much better content selection. You get to see a variety of interesting things that Nostr simply can’t match. Going forward, this is an area I would probably recommend focusing on - how to engage people to post more interesting content, onboard creators etc… Nostr is lacking in content and I believe this could be the primary reason people are not sticking around after trying it.
Other Nostr Notes:
There seemed to be little of interesting topics to follow or stick around for. The experience of joining nostr doesn't feel special or different in any way opposed to X for example. Twitter has interesting accounts, TikTok has interesting videos, what does Nostr have? The lack of "popular" conent due to the generally low number of users is probably to blame. In a way we suffer from the chicken / egg problem where new users are needed to generate more content, and more content is needed to retain new users. Going forward, I think clients should think about ways to encourage users to share content (whether that be their own, or posted from other platforms). Nostr also does not seem to have any external growth loops. For example, there is no way to invite people to the platform by email with a single click (by accessing the address book). Even if a friend does manage to join and you can find them, they are in no way notified when tagged (as far as I know). People have to have a habit of opening the app to know if something is happening. The habit formation of using a new app is important in the early usage phase and nostr seems to have a weak spot here.
You can find all of the detailed scoring, notes for each client and other thoughts in this spreadsheet: https://docs.google.com/spreadsheets/d/14w8-aQ1sHfGBSuNpqvOA9i7PHNSfhn6lUOV6H293caw/edit?usp=sharing
-
 @ 9ecbb0e7:06ab7c09
2023-08-08 02:53:15
@ 9ecbb0e7:06ab7c09
2023-08-08 02:53:15Según nos reporta y documenta la familia, la niña pequeña de 3 años de edad Leadi Kataleya Naranjo, hija del preso de conciencia Idael Naranjo Pérez, ha sido citada para mañana por la Seguridad del Estado de #Cuba.
 La citación no ofrece duda e indica los dos nombres, apellido y la dirección de la abuela paterna, donde entregaron la citación, y la abuela también ha sido citada y amenazada de desobediencia.
La citación no ofrece duda e indica los dos nombres, apellido y la dirección de la abuela paterna, donde entregaron la citación, y la abuela también ha sido citada y amenazada de desobediencia.
 Si la niña no se presenta, amenazan de acusarla igualmente de "desobediencia".
La abuela se preocupó, les dijo la edad, y aún así entregaron la citación y se fueron. Que "debían presentarse". Nada más.
Desalmados son, pero...
¿Qué clase de locos de atar están al mando en #Cuba?
¿Qué pretenden citando y amenazando a una niña de 3 años?
Esa niña no puede ir a esa ignominiosa citación. ¿A oír qué? ¿A responder qué? El tema da ASCO.
La familia no quiere llevar a la niña, y necesitan todo el apoyo para que esta locura se aclare y se detenga.
Desgraciadamente hemos visto cosas iguales o peores. Niños amenazados, separados por la fuerza de sus padres, menores torturados... El régimen de Cuba da mucho asco, por todos lados rezuma repugnancia y degradación. Todo lo que sucede en Cuba clama al cielo, y estas barbaries son distópicas.
¡MANTENGAN AL MARGEN A LOS NIÑOS, DESALMADOS ENFERMOS!
Bastante daño causan con la Ley de los 8 años que tiene a miles de niños huérfanos, separados forzosamente de sus madres para castigarlas a ellas por no doblegarse a trabajar en las misiones médicas esclavas de Cuba en el exterior, como sentenció el Comité de los Derechos del Niño.
¡BASTA YA!
Si la niña no se presenta, amenazan de acusarla igualmente de "desobediencia".
La abuela se preocupó, les dijo la edad, y aún así entregaron la citación y se fueron. Que "debían presentarse". Nada más.
Desalmados son, pero...
¿Qué clase de locos de atar están al mando en #Cuba?
¿Qué pretenden citando y amenazando a una niña de 3 años?
Esa niña no puede ir a esa ignominiosa citación. ¿A oír qué? ¿A responder qué? El tema da ASCO.
La familia no quiere llevar a la niña, y necesitan todo el apoyo para que esta locura se aclare y se detenga.
Desgraciadamente hemos visto cosas iguales o peores. Niños amenazados, separados por la fuerza de sus padres, menores torturados... El régimen de Cuba da mucho asco, por todos lados rezuma repugnancia y degradación. Todo lo que sucede en Cuba clama al cielo, y estas barbaries son distópicas.
¡MANTENGAN AL MARGEN A LOS NIÑOS, DESALMADOS ENFERMOS!
Bastante daño causan con la Ley de los 8 años que tiene a miles de niños huérfanos, separados forzosamente de sus madres para castigarlas a ellas por no doblegarse a trabajar en las misiones médicas esclavas de Cuba en el exterior, como sentenció el Comité de los Derechos del Niño.
¡BASTA YA!11jul #11j #11jCuba #CubaEsUnaDictadura #UNICEF @uniceflac @unicefenespanol
-
 @ 1123ece2:7d1e00c0
2024-06-16 23:00:00
@ 1123ece2:7d1e00c0
2024-06-16 23:00:00Hey everyone and welcome to Refinery Life Australia.
The Church The Body of Christ is the theme for the next few Sunday’s.
These messages are primarily based around Paul’s letter to the Ephesians.
Today we are discussing, The Church, The Body of Christ.
Text
1 Corinthians 12:27 NKJV
27 Now you are the body of Christ, and members individually.
Scripture Reading
1 Corinthians 12:12-31 NKJV
Unity and Diversity in One Body
12 For as the body is one and has many members, but all the members of that one body, being many, are one body, so also is Christ.
13 For by one Spirit we were all baptized into one body—whether Jews or Greeks, whether slaves or free—and have all been made to drink into one Spirit.
14 For in fact the body is not one member but many.
15 If the foot should say, “Because I am not a hand, I am not of the body,” is it therefore not of the body?
16 And if the ear should say, “Because I am not an eye, I am not of the body,” is it therefore not of the body?
17 If the whole body were an eye, where would be the hearing? If the whole were hearing, where would be the smelling?
18 But now God has set the members, each one of them, in the body just as He pleased.
19 And if they were all one member, where would the body be?
20 But now indeed there are many members, yet one body.
21 And the eye cannot say to the hand, “I have no need of you”; nor again the head to the feet, “I have no need of you.”
22 No, much rather, those members of the body which seem to be weaker are necessary.
23 And those members of the body which we think to be less honorable, on these we bestow greater honor; and our unpresentable parts have greater modesty,
24 but our presentable parts have no need. But God composed the body, having given greater honor to that part which lacks it,
25 that there should be no schism in the body, but that the members should have the same care for one another.
26 And if one member suffers, all the members suffer with it; or if one member is honored, all the members rejoice with it.
27 Now you are the body of Christ, and members individually.
28 And God has appointed these in the church: first apostles, second prophets, third teachers, after that miracles, then gifts of healings, helps, administrations, varieties of tongues.
29 Are all apostles? Are all prophets? Are all teachers? Are all workers of miracles?
30 Do all have gifts of healings? Do all speak with tongues? Do all interpret?
31 But earnestly desire the best gifts. And yet I show you a more excellent way.
Prayer
Father, we thank You for adopting us as your children.
With eyes wide open to Your mercies, we come to dedicate ourselves to you afresh.
Help us to use our talents and testimony that others may know Christ.
As be bring our tithes and offerings, we pray Your blessings upon them.
Help us meet the expenses of the ministry of this church and engage in ministries to the outer most ends of the earth.
In Jesus name we pray.
Amen.
Introduction.
Centuries ago the psalmist said in Psalm 139:14, I will praise You, for I am fearfully and wonderfully made; Marvelous are Your works, And that my soul knows very well.
The human body is an awesome example of unity in diversity.
Dozens of organs perform different functions yet work in such harmony that we must make a deliberate effort to think of the human body in a way except as unity.
In the church at Corinth, some had gifts the others did not have, and as a result, they thought of themselves more highly than they should have.
This provoked the less gifted to jealousy.
The result was discord and strife among the members.
In substance Paul was saying to them, “You do not realise your relationship to one another and to Christ. You are joined to one another and dependant on one another. You are the physical expression and instrument of Christ in this world just as the body is the physical expression and instrument of the mind.”
1 Corinthians 12:27, Now you are the body of Christ, and members individually.
Several practical suggestions about the church are called out by this text.
- **Each member of the church is different from every other member. **
The church has the unity of a living organism.
No two parts are alike, and each part discharges a different function for the good of the whole.
Some inescapable practical implications follow.
Every member of Christ’s church has some place of service cut out for them.
Sometime we might wonder about the function of the appendix or tonsils, but all in all, there are no useless members or organs of the body.
They each have a function to perform, and unless they do id, the whole body suffers.
Likewise, no two member of the church have equal abilities.
But every member has a function to perform for the common good.
Under the leadership of the Spirit, each person hs a privilege and duty to discover what that place is and to fill it.
Each member of Christ’s church must perform their own function in the church.
As Paul said in verses 22-23, No, much rather, those members of the body which seem to be weaker are necessary. And those members of the body which we think to be less honorable, on these we bestow greater honor; and our unpresentable parts have greater modesty, Every pastor has had members of their church say to them, “All I can do is just go to church and sit there.”
The majority of those who say this could do more if they would.
If every member of every church would only fill their place of service, what a difference it would make!
No place of service is so low as to be despised or looked down on, and no place is so high that it justifies conceit on the part of the person filling it.
Some member at Corinth were discouraged.
Their attitude was, “We don’t amount to much in the church.”
Paul said to them in verse 15, If the foot should say, “Because I am not a hand, I am not of the body,” is it therefore not of the body?
Some at Corinth had too high an estimate of their worth.
To them Paul said in verse 21, And the eye cannot say to the hand, “I have no need of you”; nor again the head to the feet, “I have no need of you.”
To the Romans, Paul was even more specific.
1 Corinthians 12:3-6 NKJV
3 Therefore I make known to you that no one speaking by the Spirit of God calls Jesus accursed, and no one can say that Jesus is Lord except by the Holy Spirit.
4 There are diversities of gifts, but the same Spirit.
5 There are differences of ministries, but the same Lord.
6 And there are diversities of activities, but it is the same God who works all in all.
2. Each member of the church is to be devoted to the best interests of every other member.
Someone has said, “In brute creation, it is the stomach that rules the world.”
Selfishness rules.
The law of the jungle is “Every man for himself and the devil is in control.”
But in Christ’s church the ultimate aim is the well being of our fellow members and therefor the whole church.
Since the church is a living organism, each member is to be devoted to the highest good of every other member.
Paul told the Corinthians, 1 Corinthians 12:25, that there should be no schism in the body, but that the members should have the same care for one another.
He gave two reasons for this.
Firstly, “If one part suffers, every part suffers with it.”
When one member is the victim of half truths or untruths, when any member of the prey of cheap gossip, the church is the loser.
When one member falls into sin, all suffer.
Sinning o the part of one member of the church is like putting poison in the public water supply.
Sooner or later all the members are worse off for it.
Second, “If one part are honoured, every part rejoices with to.”
Since the church os a body, what is for the good of one is for the good of all.
Paul urged the Romans, “Be devoted to one another in love. Honour one another above yourselves.”
The members of a church are to be devoted to one another to the building up of the body in love.
If only we followed that ideal, how different things would be in our churches.
3. Each member of the church is dependant on every other member.
The human body is dependant on the functioning of each individual organ.
When one organ is diseased and unable to perform its function properly, the whole body is sick.
The proper use of hands and feet is dependant on the health of the nervous system.
The welfare of the nervous system is dependant on proper circulation.
No part of the body is independent of any other part.
In like manner, no member of the church is independent of any other member in the worship and service of christ.
And no member is the whole of themselves, their fellow member complete them.
If the church is to grow and move forward, every member must fill their place and perform their function, because every other member os dependant on them.
Conclusion.
Consider this sobering question.
What os the function of the whole body, each member performing their individual part?
“You are the body of Christ,” our text says.
What the physical body is to the mind and soul, the church is to Christ, the physical instrument by which He works His will in the world.
Until next time
Stay in the Blessings
I really want to encourage you to be diligent with your Bible study time, because God has so much more for us than we can get from just going to church once or twice a week and hearing someone else talk about the Word.
When you spend time with God, your life will change in amazing ways, because God is a Redeemer. Theres nothing thats too hard for Him, and He can make you whole, spirit, soul and body!
You’re important to God, and you’re important to us at The Refinery.
When it comes to prayer, we believe that God wants to meet your needs and reveal His promises to you.
So whatever you’re concerned about and need prayer for we want to be here for you! Or even if you just want to say Hi, you can contact us at www.refinerylife.org
2024 IS A YEAR OF DECISIONS AND OPEN DOORS
© www.refinerylife.org 2013-2024 All rights reserved. Except as permitted under the Australian Copyright Act 1968, no part of this Article may be reproduced, stored in a retrieval system, communicated or transmitted in any form or by any means without the prior written permission.
This episode is brought to you by Refinery Life Australia:
If you enjoy The Refinery Life Radio Podcast you can help support The Refinery by doing the following:
Sow an offering: Bitcoin: bc1qqh6720t2zagj72dyfj348az698tdut3hlecaj4
Online: https://www.refinerylife.org/donate/
If you do send an offering then please email us so that we can say thank you
Subscribe on iTunes | Spotify | YouTube | TuneIn | Rumble | Flare | Zap.Stream | Fountain |
Share The Refinery with your friends and family
Subscribe to the newsletter on www.refinerylife.org
Follow The Refinery on Twitter | Nostr | Instagram | Fountain |
-
 @ 32e18276:5c68e245
2023-08-07 16:10:07
@ 32e18276:5c68e245
2023-08-07 16:10:07Hey guys,
I spent some time this weekend fixing a bunch of the bugs that were introduced in the latest nostrdb refactor. See the changelog below for the full list of changes in the latest build!
Planned this week
I have a big list of things I'm planning on adding to Damus this week:
- Lists!
- Zap improvements: Bringing back top zap comments in threads, profile zap comments in notifications, Private DM Zaps
- Video player improvements
- Sharing improvements (share to damus, etc)

Make sure to come back in a week to see how much I could get done!
Changelog
Added
- Add close button to custom reactions (Suhail Saqan)
- Add ability to change order of custom reactions (Suhail Saqan)
- Adjustable font size (William Casarin)
Changed
- Show renotes in Notes timeline (William Casarin)
Fixed
- Ensure the person you're replying to is the first entry in the reply description (William Casarin)
- Don't cutoff text in notifications (William Casarin)
- Fix wikipedia url detection with parenthesis (William Casarin)
- Fixed old notifications always appearing on first start (William Casarin)
- Fix issue with slashes on relay urls causing relay connection problems (William Casarin)
- Fix rare crash triggered by local notifications (William Casarin)
- Fix crash when long-pressing reactions (William Casarin)
- Fixed nostr reporting decoding (William Casarin)
- Dismiss qr screen on scan (Suhail Saqan)
- Show QRCameraView regardless of same user (Suhail Saqan)
- Fix wiggle when long press reactions (Suhail Saqan)
- Fix reaction button breaking scrolling (Suhail Saqan)
- Fix crash when muting threads (Bryan Montz)
-
 @ 32e18276:5c68e245
2023-08-03 21:05:05
@ 32e18276:5c68e245
2023-08-03 21:05:05Hey guys,
I've been quiet lately... I've been working on something big. In the past 2 weeks there have been 9539 new lines of code added to damus, 2928 removed, 279 files changed. I've rewritten much of the codebase in preparation for the nostrdb integration.
nostrdb
What is nostrdb? nostrdb is an integrated relay within damus, with the same design as strfry, but slightly different to support embedding into nostr apps. This will be the heart of Damus apps going forward, including notedeck and other future microapps. Think of it as a kind of development kit but with an embedded database and query capabilities. I didn't want to have to recreate all of the same querying, caching, and parsing code when building new apps, nostrdb will solve all of the painful and slow parts. nostr seems simple but if you want a fully working app it is pretty complicated, especially if you want it to be fast and sync efficiently.
Goals
- be the best and most efficient at querying, syncing and storing nostr notes
- enable direct mapping of notes into application code without any serialization overhead
- provide advanced syncing capabilities such as negentropy, which allows us to only query stuff we don't have
- be as portable as possible. nostrdb is a C library that you can embed into basically anything.
- full relay filter support
- full text search
Benefits
- full note verification
- more efficient de-duplication before we begin processing events off the wire
- set-reconciliation based syncing (negentropy) drastically reduces bandwidth usage and latency
- iteration on future nostr apps will be quicker (android, desktop, etc)
- features like ghost mode, account switching, etc will be much more efficient as you will be able to quickly switch between notes that are cached locally
- much smaller memory footprint due to optimized in-memory note format, which in turn improves cpu-cache efficiency
- much better profile and note searching
So that's what I've been working on in the past two weeks. On to what else is new in this release:
Multi reactions!
Suhail did an amazing job at adding multiple reaction support. All you need to do is long-press the Shaka button to show different options. You can customize these in settings as well
New onboarding features
Damus will now suggest people to follow when you first enter the app, this is the first of many onboarding improvements coming soon. Thank Klabo for this one!
That's all for now! Please test thoroughly and let me know if you run into any issues. You likely will since the entire codebase has been changed, and I probably broke something.
Until next time 🫡
-
 @ fa0165a0:03397073
2023-07-24 10:19:27
@ fa0165a0:03397073
2023-07-24 10:19:27Below is an easy-to-read list of keyboard shortcuts and commands to navigate your Linux computer efficiently: (Note that some variations between systems may apply)
General Shortcuts: Open Terminal: Ctrl + Alt + T Close current application: Alt + F4 Switch between open applications: Alt + Tab Logout from current session: Ctrl + Alt + Del Navigating the File System: Open File Manager (Nautilus): Super (Windows key) + E Move back in directory: Alt + Left Arrow Move forward in directory: Alt + Right Arrow Go to Home directory: Ctrl + H Go to Desktop: Ctrl + D Open a folder or file: Enter Rename a file or folder: F2 Copy selected item: Ctrl + C Cut selected item: Ctrl + X Paste copied/cut item: Ctrl + V Delete selected item: Delete Create a new folder: Ctrl + Shift + N Navigating Applications: Switch between open windows of the same application: Alt + ` Close the current window: Ctrl + W Minimize the current window: Ctrl + M Maximize/Restore the current window: Ctrl + Super + Up Arrow / Down Arrow Navigating Web Browsers (e.g., Firefox, Chrome): Open a new tab: Ctrl + T Close the current tab: Ctrl + W Switch to the next tab: Ctrl + Tab Switch to the previous tab: Ctrl + Shift + Tab Open a link in a new tab: Ctrl + Left Click Go back in the browser history: Alt + Left Arrow Go forward in the browser history: Alt + Right Arrow System Controls: Lock the screen: Ctrl + Alt + L Open the system menu (context menu): Menu key (or Right-click key) or Shift + F10 Open the Run Command prompt: Alt + F2These shortcuts may vary slightly depending on the Linux distribution and desktop environment you are using. Experiment with these shortcuts to navigate your Linux system faster and more efficiently without relying on the mouse.
Since websites are such an important interface for the information of today, I have here appended the list with some navigational hotkeys for web browsers (e.g., Firefox, Chrome) on Linux:
General Navigation: Scroll down: Spacebar Scroll up: Shift + Spacebar Scroll horizontally: Hold Shift and scroll with the mouse wheel or arrow keys Go to the top of the page: Home Go to the bottom of the page: End Refresh the page: F5 or Ctrl + R Stop loading the page: Esc Link and Page Navigation: Move focus to the next link or interactive element: Tab Move focus to the previous link or interactive element: Shift + Tab Activate/follow a link or button: Enter Open link in a new tab: Ctrl + Enter (Cmd + Enter on macOS) Open link in a new background tab: Ctrl + Shift + Enter (Cmd + Shift + Enter on macOS) Open link in a new window: Shift + Enter Go back to the previous page: Backspace or Alt + Left Arrow Go forward to the next page: Alt + Right Arrow Searching: Find text on the page: Ctrl + F Find next occurrence: Ctrl + G Find previous occurrence: Ctrl + Shift + G Tab Management: Open a new tab: Ctrl + T Close the current tab: Ctrl + W Reopen the last closed tab: Ctrl + Shift + T Switch to the next tab: Ctrl + Tab Switch to the previous tab: Ctrl + Shift + Tab Switch to a specific tab (numbered from left to right): Ctrl + [1-8] Switch to the last tab: Ctrl + 9 Form Interaction: Move to the next form field: Tab Move to the previous form field: Shift + Tab Check/uncheck checkboxes and radio buttons: Spacebar Select an option from a dropdown menu: Enter, then arrow keys to navigate options Miscellaneous: Open the browser's menu: Alt (sometimes F10) Open the address bar (omnibox): Ctrl + L or Alt + DRemember, the accessibility of websites can vary, and some sites might have different keyboard navigation implementations. In some cases, you may need to enable keyboard navigation in the browser's settings or extensions. Additionally, browser updates might introduce changes to keyboard shortcuts, so it's always good to check the latest documentation or help resources for your specific browser version.
But I hope this helps as an tldr and getting started with navigating your laptop the ways pro role.
Version controlled over at github gist.
-
 @ 75bf2353:e1bfa895
2024-06-16 20:54:12
@ 75bf2353:e1bfa895
2024-06-16 20:54:12Get On Nostr To Get Sats

This is not another orange pill. There are no more orange pill books to be written. Like Satoshi said, "If you don't believe me or don't get it, I'm sorry, bur I don't have time to convince you."
This is not about reading charts or looking for dildos that would make a great pattern for an ugly Christmas sweater. I offer no price predictions because in 150 years, your great, great, great, great, great, great grandchildren will read about the fractional reserve fiat ponzi scheme in history books written by large language models. Meanwhile, fiat is an endangered species. I understand most people come to bitcoin for the fiat gains. I suspect my blog would be more popular if I wrote things like bitcoin will reach $1,000,000 in 48-72 hours according to my scribbles transcribed over a price chart. Sorry, I can't tell you what the fiat price of bitcoin will be within 72 hours or 72 years. I don't have a crystal ball. I don't know how to measure the scarcest asset in the world against this:
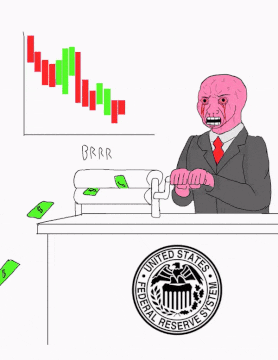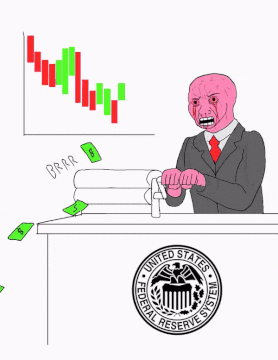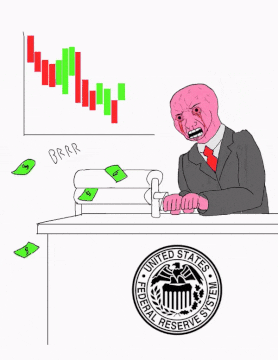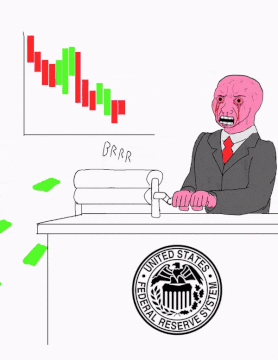
This is a guide designed to teach you how to use bitcoin as peer to peer electronic cash and store your wealth for seven generations. I would like to turn it into a book and sell more books than the woman who wrote Harry Potter, but I also think it is important to keep this information free for anyone who cannot afford it. The amount of money printing is making me more and more concerned about fiscal stability of the global financial system. This is not financial advice. It is a life jacket. Think of it as a seat cushion in an airplane. I hope you never need this flotation device, but I want it available, just in case. I hope our great senile leaders can fix this, but I wouldn't hold my breath, so I want to teach people how to use bitcoin before it's too late. But first, let's pop the purple pill..=

In the first chapter, I showed you the secret message Satoshi left in the genesis block, "Chancellor on the brink of second bailout for banks." In the second chapter, I wrote about why the Cypherpunks wanted private, electronic cash in the first place. The purpose of this chapter is to teach you how to use a custodial bitcoin wallet on a corner of the Internet where people use bitcoin for electronic payments. Bitcoin is a peer-to-peer electronic cash system that does not require a corporation or government. Nostr is The Internet without any corporations or government required to operate. If you sell stuff on Amazon, you must pay fees to Amazon. Therefore, Amazon is your master. If you sell stuff on a nostr powered marketplace like Shopstr, you have no master.
Covid taught us the collective tend towards authoritarianism during times of crisis(perceived or otherwise). The Twitter Files taught us there is a partnership with legacy social media and agents of the United States Government. If a legacy social media company in the United States is not controlled by a U.S. corporation, expect them to ban it unless it can be sold to an US corporation. If the government trending towards a "closed society" cuts off your bank account for protesting forced vaccinations, these communication networks become important. Nostr makes sending payments to bitcioners as easy as Venmo without any government imposed red tape.
The Social Bitcoin Payment Layer
Nostr has become the de-facto, social bitcoin payment layer. Most people still think of it as a boring alternative to addictive social media like Twitter, but it is much more than this. This guide is published on habla.news a website that allows anyone with an npub to publish long-form content. People can send me sats for this content and I can send sats to content creators and developers.
Nostr has a marketplace similar to what you might find on Zuck's face tracking book. It has YouTube like video and twitter spaces like audio. To use these tools, you will first need to create a public/private key pair. Your public key, npub, can be shared with anyone. Your private key, nsec, must remain a secret. If your nsec is compromised, your identity is compromised and we can no longer trust your notes are from you. That would suck, but it's good practice for storing bitcoin keys. If your identity gets compromised, you could spin up a new one. If you lose the keys to your life savings, it won't be so easy to get it back.
Current, A KYC Free Custodial Bitcoin Social Wallet

Current Tutorial
Nostr is a decentralized communications protocol that stands for notes and other stuff transmitted by relay
-
Available on Google Play and The App Store.
-
Available in the jurisdiction with the most draconian anti-privacy laws.
-
Uses a 12 word backup
-
Gives you a nostr key pair.that can be used with all nostr services.
-
Includes a free custodial lightning address.
Keep in mind that this is a custodial wallet so not your keys not your bitcoin applies. This is a beginner wallet that allows anyone on the nostr network to send you sats, but you don't want to use this for your life savings. The wallet also has cutting edge features like data vending machines that allow you to pay for AI generated images and chats. You can even use AI to turn text to voice, but we will not cover these advanced features in this guide.
To get started, download the App at https://app.getcurrent.io
Current has an excellent Guide here.
Video Tutorial
nostr:naddr1qqrkcn28fdn5j5qzyp6m7g6nrt5lnrrzn9d6quv3ujyw44r4jafhr43a0h75d00ph75f2qcyqqqgtwcefdcdw
₿logging ₿itcoin 848,231 debtclock 🧡 Support this blog by using the ⚡Value 4 Value model)⚡ 📧Subscribe on Substack 🍐Join my Keet Room If You Prefer To Learn About New Blogs With No Email Signup 📻 Stream sats on Fountain 🎉Send a Boostagram 🛒Shop The Elliptic Curve Economy
-
-
 @ aa55a479:f7598935
2023-07-19 17:54:44
@ aa55a479:f7598935
2023-07-19 17:54:44Test
-
 @ c73818cc:ccd5c890
2024-06-16 19:14:44
@ c73818cc:ccd5c890
2024-06-16 19:14:44
💞 DuckDuckGo, noto per il suo impegno nella privacy, ha lanciato Duck.ai, un portale che permette interazioni anonime con i più diffusi chatbot AI. Questo servizio garantisce che né DuckDuckGo né i fornitori di chatbot possano utilizzare i dati degli utenti per addestrare i propri modelli, proteggendo la privacy degli utenti in un'epoca in cui la raccolta dati è sempre più invasiva.
💞 L'accesso anonimo è reso possibile dall'eliminazione dei metadati, come indirizzi IP e server, assicurando che le query sembrino provenire dall'azienda stessa. Con modelli come GPT-3.5 Turbo di OpenAI e Claude 3 Haiku di Anthropic, DuckDuckGo offre un'alternativa sicura per gli utenti attenti alla privacy. Questa iniziativa rappresenta un passo significativo verso una maggiore trasparenza e sicurezza nelle interazioni con l'intelligenza artificiale.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
BitcoinReportItalia #DuckDuckGo #Duck #Criptovalute #Privacy #Chatbot #AI #OpenAI #ChatGPT #Claude #Anonimo #Crypto #Bitcoin
-
 @ 32e18276:5c68e245
2023-07-19 02:56:47
@ 32e18276:5c68e245
2023-07-19 02:56:47I’m so lazy I’m thinking of running the damus merch store via stateless and serverless lightning payment links. All data is collected and stored in the lightning invoice descriptions which are fetched from your node. You can do this without having to run any server code except a lightning node!
This is the same tech we used when selling merch as at bitcoin Miami. It was extremely reliable. I love these things, they are so easy. Integrating with the legacy fiat system is such a pita, It may just be a lightning-only store for now because of how simple this is. Here's what a lightning payment link looks like:
http://lnlink.org/?d=ASED88EIzNU2uFJoQfClxYISu55lhKHrSTCA58HMNPgtrXECMjQuODQuMTUyLjE4Nzo4MzI0AANgB6Cj2QCeZAFOZ1nS6qGuRe4Vf6qzwJyQ5Qo3b0HRt_w9MTIwJm1ldGhvZD1pbnZvaWNlfG1ldGhvZD13YWl0aW52b2ljZSZwbmFtZWxhYmVsXmxubGluay0mcmF0ZT04BERlYXRoIFN0YXIABQAAAGQGQW4gb2JqZWN0IG9mIHVuZmF0aG9tYWJsZSBwb3dlcgAHEwhodHRwczovL3VwbG9hZC53aWtpbWVkaWEub3JnL3dpa2lwZWRpYS9lbi9mL2Y5L0RlYXRoX3N0YXIxLnBuZwA=
How it works
The entire product page is stored as data in the url. When a customer click the link, the product info is decoded and rendered as a webpage. The data in the url includes
- The product name
- Description
- Price in sats
- Product image url
- Fields to collect data from the user
- Lightning node address
- Lightning node rune for fetching and waiting for invoice payments
This works thanks to a javascript library I created called "lnsocket". It allows you to connect to your CLN node over websockets. Once the user fills out all of the info, a new lightning invoice is fetched with this information in the description, by connecting directly to your node. This connection is end-to-end encrypted thanks to the lightning protocol itself.
To your lightning node, it looks like another lightning node is connecting to it, but in reality it's just a dumb client asking for things.
At this point, custom lightning packets called "commando" packets are sent to your node which asks your node to run certain commands. CLN authenticates these packets using the rune and then returns a response. This is pretty much the same as calling these commands directly on your lightning node, except now someone is doing it from a browser in a secure way!
Why not just run btcpayserver?
btcpayserver is cool and is more powerful, but I like exploring simpler ways to do things that don't require running lots of software which can be challenging for many non-technical people. You shouldn't have to become a server administrator to start accepting payments. It should be as simple as running a bitcoin and lightning node, pushing all of the application logic to the clients.
This is a similar philosophy to what we have in the nostr space. Let's make it easier for people to use self-sovereign tools. Everyone deserves freedom tech.
Anyways, I'm still working on https://lnlink.org. I just added images and nostr address support! You can make your own payment links here! Try it out:
http://lnlink.org/?d=ASED88EIzNU2uFJoQfClxYISu55lhKHrSTCA58HMNPgtrXECMjQuODQuMTUyLjE4Nzo4MzI0AANgB6Cj2QCeZAFOZ1nS6qGuRe4Vf6qzwJyQ5Qo3b0HRt_w9MTIwJm1ldGhvZD1pbnZvaWNlfG1ldGhvZD13YWl0aW52b2ljZSZwbmFtZWxhYmVsXmxubGluay0mcmF0ZT04BERlYXRoIFN0YXIABQAAAGQGQW4gb2JqZWN0IG9mIHVuZmF0aG9tYWJsZSBwb3dlcgAHEwhodHRwczovL3VwbG9hZC53aWtpbWVkaWEub3JnL3dpa2lwZWRpYS9lbi9mL2Y5L0RlYXRoX3N0YXIxLnBuZwA=&edit=1
-
 @ 5d4b6c8d:8a1c1ee3
2024-06-16 16:16:35
@ 5d4b6c8d:8a1c1ee3
2024-06-16 16:16:35Fathers Day seems like a good time to launch Parent Corner. I'm hoping this will catch on as an irregularly recurring series. It's inspired by the segment of the same name on The Bill Simmons Podcast.
The idea is pretty straightforward: just share a recent parenting anecdote or thought (ideally one that has happened since the previous parent corner).
What better way to describe parenting than ~mostly_harmless? As such, I'm volunteering @elvismercury's territory to house this series.
I'd love it if other stackers initiated these in the future, when they had parenting stuff to share.
My daughter (4 years old) has been making "swings" for her stuffed animals for the past couple of weeks. She's been greatly delighting in pushing them on their "swings" and, of course, making us do so too.
The thing is, these swings always end up looking like her animals have been executed by hanging. They swing from the top of our staircase down into the living room. If we didn't get everything tidied up from the day before, I wake up and go downstairs to be surprised by quite the gruesome scene.
It's such a stark example of innocence that to her it's just her stuffies enjoying a nice swing.
cc: @grayruby, @cryotosensei, @gnilma, @bief57, @anniedustan (apologies if I omitted anyone)
-
-
 @ aa30d7ea:8e94a052
2024-06-16 15:58:19
@ aa30d7ea:8e94a052
2024-06-16 15:58:19The decentralized Hive network offers an alternative content monetization model, where content can be monetized without selling advertisement space or using affiliate links.
This content was initially published via PeakD (a front-end for the Hive network). You can find the original here.
Project Updates * Stekene reviews the peak.open Token Routes project * Dalz shares a long-term outlook on the Hive coin supply * TravelFeed adds free account creation and hiveauth login * SPK Network announces the final testnet launching Monday 6/17 * Distriator announces auto cashback
Top Viewed * 6/10 - Una ayuda para Nohelys [ESP-ENG] * 106.55 Hive rewards | 16 comments | @aliento.aid * 6/9 - Ladies of Hive Community Contest #189 * 6.79 Hive rewards | 24 comments | @ladiesofhive * 6/8 - Segunda fase de quimio. Día 5 | Chemo Phase Two. Day 5 * 31.23 Hive rewards | 16 comments | @manjune * 6/7 - The BRO Community YouTube expansion proposal * 38.03 Hive rewards | 76 comments | @brofund * 6/6 - Peak Vault & Metamask Snap Proposal - Two New Wallets for Hive * 32.68 Hive rewards | 10 comments | @peakd * 6/5 - Help us decide the Winner of Vibes Week 12!! / COMMUNITY POLL! 🎸🎶🎺 * 172.11 Hive rewards | 84 comments | @lordbutterfly * 6/4 - TECHNICAL REPORT: ANALYSIS OF THE GLOBAL PRESENCE OF HIVE * 92.63 Hive rewards | 23 comments | @enrique89
Updates on Hive Network Governance
Governance Posts * New DHF proposal - Peak Open Projects Proposal #3 (Upkeep, Upgrades and New Small Projects) * New DHF proposal - Peak Vault & Metamask Snap Proposal - Two New Wallets for Hive * New DHF proposal - The BRO Community YouTube expansion proposal
Governance Data
- Most powered up - 7 days | @x30 - 54,475.971 Hive
- Most powered up - 30 days | @introvert-dime - 70,038.035 Hive
- Total Hive powered - 30 days | 806,731.109 Hive
Weather Report - Market Data
HBD Marketcap = $12,323,981.007 HIVE Marketcap = $157,777,454.152 HBD Marketcap is currently 7.811 % of HIVE Marketcap HIVE median price must stay above $0.0739 to avoid haircut (currently $0.2840) Internal market Hive price is $0.27
HIVE holds rank #367 (+2) according to CoinMarketCap
Contest Corner
- June 1 - June 30: InLeo June Daily Contest Link
- June 4 Ends June 11: Feathered Friends - Show me a Photo 170 Link
- June 9 - June 15: Ladies of Hive Contest #189 Link
- June 9 - June 16: Reflection Hunters 171 Link
- June 9 Ends June 16: Phonography Contest 12 Link
- June 10 - July 10: Foodie Contest: SALTY FOOD Link
- June 11 - June 30: Amazing Drinks Community: Your favorite fruit for juice Link
-
June 10 - June 30: Plant Power: Your veggie shopping 29 Link
-
June 7 - June 30: Hive Argentina: DÃa de la Bandera Link
-
June 4 - July 4: Colors Of Life Link
This is HiveToday #62
Serving the Hive community since block 46670857,
HiveToday is brought to you by @cre47iv3 @jfuji and @hivetrending
Connect with us on Hive | X | Medium | Substack | Discord | Mastodon | Nostr | BlueSky | Farcaster
About Hive Today
Hive Today is an unofficial newsletter for the decentralized Hive network. The newsletter helps radiate information about great things happening around Hive.
About Hive
Hive is a decentralized network built on the Delegated Proof of Stake (DPoS) protocol. This network is home to a wide variety of decentralized apps (dApps), including social media and games. These apps depend on Hive’s information-sharing capabilities, secure account layer, and fast and feeless blockchain operations.
