-
 @ 6ad3e2a3:c90b7740
2024-02-09 17:24:16
@ 6ad3e2a3:c90b7740
2024-02-09 17:24:16I remember reading something from Terrence McKenna wherein he hypothesizes that aliens might not be the way we imagine them, coming from distant stars via metal spaceships. After all, we live in four dimensions — three in space and one in time — and even our physical models of the universe sometimes have 11 or more. Perhaps aliens are already with us, but in higher dimensions beyond the range of our senses and conditioned minds. It’s possible we could perceive and interact with aliens — or beings from different dimensions — via a change in consciousness. Instead of sending probes and spherical discs across the galaxies to the skies of planet earth, maybe they have already planted their probes on its surface, via consciousness-altering substances like psilocybin residing in the spores of fungi. Could psychoactive fungi itself be their emissaries, inviting us to commune with them through the medium of mind rather than physics?
Whether one deems the particular hypothesis plausible is less important than the notion our ideas are so conditioned by our limited experience we imagine aliens to be somewhat like us — at the very least bound by the four dimensions in which we move. That they might operate in different dimensions altogether, perhaps even dimensions of mind, is so outside our paradigm it’s rarely considered. Hold that thought. We will come back to it.
. . .
I am not a Christian. I am Jewish by birth, and though I went to an Episcopal school, and grew up in an era where we sang hymns in chapel, I never went for organized religion. That said, I find the story of Jesus compelling as a myth and also as a moral framework. The New Testament is deep.
Jesus, the story goes, is the son of God, and he gave his life on the cross so that man could be saved. Jesus was also the son of Joseph and Mary, and he was conceived immaculately. That is, Mary was still a virgin when she became pregnant with her son. He was, in effect, an effect without a cause.
Buddhism, another ancient school of thought with deep psychological insight, has a similar notion. Beings take on ever new incarnations, driven by karmic desire. The deeds and desires of this life will propel your instantiation in the next. This wheel of samsara — or suffering — will continue until you become enlightened in which case you will not require another birth. The cycle of causation (karma) will have come to an end, though Bodhisattvas (enlightened beings) may still choose a birth to help others — a karma-free (immaculate) conception, if you will.
. . .
There is talk in some circles about the second coming of Christ and the end of the world. There are cults devoted to this notion, and the Book of Revelation specifies in great detail how it will come about. It is a mistake to take the details literally. Like our contemporaries who imagine beings from different realms arriving in metal crafts only because we ourselves require metal crafts to leave our planet, those who wrote Revelation were bound by the symbols and terminology of the times.
What might some of those terms mean for us in the present? For starters, the “mark of the beast” without which no one may buy or sell has an easy correlate: QR or other scannable codes now mandated in many places of business. The “beast” will force everyone who does not acquiesce to such a system (who lacks the mark) to go without those services.
This reading probably sounds over-dramatic — so Satan’s grand plan is to keep the righteous from leaving Canada? But let’s follow this to its logical conclusion — what starts with travel, migrates again to dining and entertainment (when cases spike or a new variant arrives) then eventually to all commerce. In China, there is already a social credit system that extends to most commercial interactions, and once people are in the system, it is trivial to expand it incrementally until ours too is all-encompassing. The final vision would be a central bank digital currency of sorts, wherein every transaction — a purchase of apples or booking of a flight to Japan — would require the transfer of funds from your account to the vendor. And your account exists only in a central bank, monitored by those who have absolute power to block any or all transactions.
There are good pieces that go into this process is greater detail, and at some point, I might even attempt my own. But it’s easy to see how such a system is desirable from the standpoint of powerful actors seeking to implement preferred policies for the greater population. This form of digital slavery would make it costly to express thoughts or words not in lockstep with the prevailing agenda. A word out of line, and they could, with the click of a mouse, shut off your access to food, power or the internet. People would learn to self-censor, mouth the proper pieties, take the required medicines, “own nothing and be happy," the reign of the beast, so to speak.
Russian novelist Fyodor Dostoyevski also foretold this state of affairs 140 years ago in the Brothers Karamazov via the Grand Inquisitor:
*Too, too well will they know the value of complete submission! And until men know that, they will be unhappy... Then we shall give them the quiet humble happiness of weak creatures such as they are by nature. Oh, we shall persuade them at last not to be proud, for Thou didst lift them up and thereby taught them to be proud. We shall show them that they are weak, that they are only pitiful children, but that childlike happiness is the sweetest of all...
And they will have no secrets from us. We shall allow or forbid them to live with their wives and mistresses, to have or not to have children—according to whether they have been obedient or disobedient—and they will submit to us gladly and cheerfully. The most painful secrets of their conscience, all, all they will bring to us, and we shall have an answer for all. And they will be glad to believe our answer, for it will save them from the great anxiety and terrible agony they endure at present in making a free decision for themselves. And all will be happy, all the millions of creatures except the hundred thousand who rule over them.*
But in these dark prophecies is a silver lining. Jesus is returning to save those who reject the mark. It will be a long and ferocious battle, but ultimately those who embrace Him will prevail.
At this point people who believe that might start to look literally for a savior — is it the Dalai Lama (no, much too old!), or some other spiritual figure? It can’t be a politician, can it? Is it some artist whose work moves billions to wake up and see. No! You are imagining metal-spaceship aliens and taking the Book too literally. The second coming of Jesus would not likely be any of those things.
What if instead, it were an idea — a brainchild of a creator rather than the child of The Creator. The idea would have to be one that liberates humanity from the centrally controlled system to which everyone who wanted to eat or have a home would be inexorably enslaved. And it would have to be impervious to co-option by the powerful forces who would seek to control it. What if that idea already exists in this world now?
Satoshi Nakamoto released his Bitcoin white paper in 2009. He made a few posts, mined some coins, then disappeared untraceably — leaving the effect but removing the cause. There is no one for governments or powerful factions on whom to lean or threaten. It is not owned by or controlled by anyone. In contrast to the dystopian vision of centralized control, bitcoin is an out, a parallel system over which individuals can transact peer-to-peer, permissionlessly, and exchange value voluntarily. As such, it restores the necessary conditions for self-determination, freedom of thought and word, a creative and spiritual existence.
Like the scientific enlightenment three centuries prior that separated Church from State, depriving the ruling class of the power to decree who goes to heaven and, more importantly, to hell, bitcoin liberates money from state. It prevents the authorities from decreeing what you can and cannot purchase, with whom you can and cannot transact, and ultimately what thoughts and ideas you are able to express. In short, it puts power back in the hands of the many rather than the few. It is a peaceful opt-out from an otherwise all-powerful system. And it cannot be stopped by force. The all-seeing Eye Of Sauron isn’t extinguished by the sword; it simply runs out of funding, flickers and goes dark.
. . .
Maybe there are alien beings in flying saucers traversing galaxies to come and save (or destroy) us. Maybe God will come from the sky, save the righteous and smite the wicked too. But it’s more plausible to me that He works in mysterious ways, and just as we can achieve altered states of conscious via strange lifeforms mushrooming from the soil, perhaps we can reclaim our birthright as free and prosperous human beings via an uncorruptible ledger of timestamped truth.
For those who hope for God — or a benign strongman working on his behalf — to save them the old fashioned way, I will end this piece with a joke:
During a great flood, a man climbs up on the roof of his house to temporary safety. A boat paddles by. “Get in!” says the man rowing the boat. "No thanks” says the man on the roof. “God will save me.” The man paddles off. The water rises up to the man’s neck. A helicopter comes by, and a man inside offers his arm to the nearly submerged home-owner. “Get in!” he yells. The man on the roof says, “No thanks, God will save me.” The helicopter leaves, and the man drowns. When he gets to the afterlife, he confronts God, saying, “Why didn’t you save me?” And God replies, “I sent a boat and a helicopter, but you didn’t get in!”
-
 @ 3f7d1a20:bb856f90
2024-02-08 13:20:26
@ 3f7d1a20:bb856f90
2024-02-08 13:20:26Details
- ⏲️ Prep time: 1
- 🍳 Cook time: 2
Ingredients
- lemon
- salt
- mineral water
Directions
- juice the lemon
- add salt and mix ( according to your taste )
- add the mineral water
- done, enjoy!
-
 @ 3f7d1a20:bb856f90
2024-02-07 13:40:51
@ 3f7d1a20:bb856f90
2024-02-07 13:40:51Details
- ⏲️ Prep time: 5 mins
- 🍳 Cook time: 20 mins
Ingredients
- rice
- olive oil
- butter
- arpa şehriye
- water ( hot water )
- chicken broth
- salt
Directions
- rinse the rice
- add the olive oil and butter to the pot
- add the şehriye and stir until light brown
- add the rice, chicken broth, water and salt, stir
- put on the lid and turn to low heat
- turn off the heat and put a paper towel on top to absorb excess moisture
- wait for about 10 mins and done
-
 @ 1d6a020c:6e9cf203
2024-02-02 21:40:35
@ 1d6a020c:6e9cf203
2024-02-02 21:40:35Chef's notes
This is a mashup of research done online combined with a couple years of personal experience. The pictutes are in chronological order and correspond to the steps in the recipe.
Details
- ⏲️ Prep time: 4 days
- 🍳 Cook time: 0 minutes
- 🍽️ Servings: 1
Ingredients
- Turmeric plant
Directions
- When the leaves turn bown, or new shoots start coming up, it's time to harvest (usually Jan-Feb)
- Dig up the big stuff and replant any sprouts that are coming up
- Trim off any small roots and get most of the dirt out. Don't worry if they're not totally clean, we'll get to that later
- Break apart the rhyzomes and cut off any little bits. They're immature and won't make good turmeric powder
- Peel off the outer laer to reveal that beautiful orange color
- Once peeled, give them a final wash. This is where getting the dirt off actually matters
- Finely grate the turmeric
- Spread out on a cutting board, cookie sheet, plate or some other flat surface and set aside to dry
- After a day or two, move the partially dried turmeric around so it dies more quickly and easily, repeat until it feels dry
- Put the dried turmeric into a spice grinder (aka, coffee grinder). A blender can work if that's all you have. This will make a nice fine powder. The powder will likely not feel entirely dry. Lay it out on your horizontal surface again for a few days to dry. Repeat drying/grinding until it's dry.
- Bottle it up and enjoy
-
 @ 66675158:1b644430
2024-02-09 14:28:55
@ 66675158:1b644430
2024-02-09 14:28:55The "Free" Internet! A digital utopia where the price of admission is not your hard-earned Bitcoin but the very essence of your digital soul.
You are not a customer, nor even a user, but a product meticulously crafted and packaged for the highest bidder, how does that feel?
"Free" services from big tech companies have redefined how we interact with the digital world, offering unparalleled convenience at seemingly no financial cost. It's a seductive narrative, promising access to endless streams of information, social connections, and entertainment without asking for a single penny in return. Yet, beneath this glossy surface lies a hidden transaction, one that demands not our money, but something far more personal: our privacy.
Welcome to the era of "free" services, where big tech companies are the benevolent providers of everything from email to endless scrolling on social media! Here, your movements are tracked, your preferences logged, and your interactions monitored. Not with malice, the tech giants assure you, but with the noble intent of tailoring their services to your desires. Yet, as these digital behemoths sift through the minutiae of your online life, a question looms large:
What is the true cost of this convenience?
Every midnight dive into the rabbit hole of "just one more video" is meticulously logged in the great ledger of Big Tech. It's not for nefarious purposes, they whisper through the screens that illuminate our faces in the dark. No, it's for you, dear user, to enhance your experience, to ensure that the ads you see as you scroll are less about the miracle mop and more about the latest gadget you can't afford but desperately need, and who knew that your late-night searches for "why does my cat stare at me?" could be so valuable?
Big Tech plays the role of the benevolent overlord, promising to safeguard our digital kingdoms while subtly reminding us that the drawbridge can be pulled up at any moment. Your data, they claim, is encrypted, secured, and only used to make your life easier. But as any true Privacy advocate and Bitcoin maximalist knows, the centralization of power (and data) is the antithesis of freedom.
It's a bit like entrusting your life savings to a stranger because they promised to double it overnight if you just invested in their shiny new cryptocurrency coin.
Spoiler alert: they won't.
So, what is the true cost of this convenience? It's the slow, creeping realization that in the digital marketplace, we've traded our privacy for a handful of magic beans — or, in this case, slightly more targeted ads and a feed algorithmically optimized to keep us scrolling until our thumbs go numb.
Do we continue down this path, blissfully ignoring the chains we wrap tighter with every click, or do we dare to imagine a different way? A way where the communities we build and the conversations we have are ours, truly ours, not data points on a corporate spreadsheet.
Enter the stage, the unsung heroes of our digital saga: FOSS, nostr, and the subtle nod to the concept of a fortress of privacy and freedom, almost as if we'd need an Arx, a citadel away from Big Tech's watchful eyes.
FOSS offers us the tools to build our digital realms, free from the prying eyes of those who would seek to monetize our every move. Nostr, with its decentralized approach to communication, hands the power back to the people, ensuring that our whispers across the digital void are heard only by those we intend.
And it is here, in this brave new world, that we find the essence of what it means to reclaim our digital autonomy. We are not content to be mere pawns in a game of data collection and targeted advertising. Instead, we champion the creation of digital communities that are owned and governed by the people who inhabit them. Communities where the value exchanged is not personal data, but trust, respect, and mutual support.
The journey to this digital utopia is not without its challenges. It requires us to rethink not just how we interact with technology, but the very foundations upon which our digital lives are built. It demands a shift away from the centralized powers that have come to dominate our online experiences, towards a more distributed, egalitarian approach. But the rewards, oh the rewards, are nothing short of revolutionary.
We stand at the precipice of a new era, one where our digital interactions are governed by principles of privacy, freedom, and individual sovereignty. An era where the communities we build online are reflections of our highest ideals, not the monetization strategies of corporate behemoths. It is a daunting task, but one well within our reach if we dare to imagine it. And so, we press on, guided by the light of FOSS, and our steadfast pursuit of freedom.
This is the silent acknowledgment that the path to digital freedom is one we forge together, step by step, towards a future where our digital souls are once again our own.
Let's build the citadel of freedom, together.
-
 @ 28246aee:62b108ad
2024-02-09 14:22:20
@ 28246aee:62b108ad
2024-02-09 14:22:20This post was originally published on https://tftc.io by Marty Bent.
NOW - Biden refers to the Egyptian president El-Sisi as the "president of Mexico."pic.twitter.com/VxUDH8ZrVk
— Disclose.tv (@disclosetv) February 9, 2024
The last 12-hours will be looked back upon as a pivotal moment in world history. That may seem like an outlandish statement, but when you consider the juxtaposition of Tucker Carlson's interview with Vladimir Putin with President Biden's train wreck of a press conference in which he proved without a shadow of a doubt to be mentally incapacitated it is glaringly obvious that the US federal government is in an extremely weak position. A vulnerable position that signals to the rest of the world that they need to seriously consider whether or not the United States federal government is equipped to lead in any capacity.
Last night's incoherent rambling will be viewed in retrospect as the straw that broke the camel's back. The incoherent rambling has been a problem since before Biden took office. However, the culmination of the economic stress that Americans are currently under, the border crisis, and the unavoidable comparison to Putin - who Biden has been engaged in a proxy war with for two years - are too much to overcome. The lack of awareness from the Biden administration to allow Sleepy Joe to give an emergency press conference just as millions of people were sharing and watching clips on social media of Putin and commenting on how articulate he is will be seen as the biggest political miscalculation of the Biden regime. It is so egregious that one has to wonder whether or not it was intentional. The Deep State pulling the strings sees the writing on the wall and decided to put Joe out of his misery with one last humiliation ritual so they can get a more coherent puppet in front of the American people before the election in November.
The only thing you can do is laugh. The clown show better known as American politics has become the laughingstock of the world and you should laugh along with everyone else. However, when you are done laughing it would be wise to take some time to think about what this particular inflection point means and how to benefit from it despite the fact that it may mean the end of America's political dominance on the world stage.
To be clear, I believe there is a big enough contingent of American citizens that still have that dog in them. There are plenty of competent, clear minded Americans out there who can help steer the ship back toward calmer waters without having to depend on the federal government. They simply need to take control of their destiny and start making decisions that remove the federal government's influence from their lives. This may seem like an impossible task, but there is a very low hanging fruit that individuals can pick off the branch to create some distance between themselves and a dying government; bitcoin.
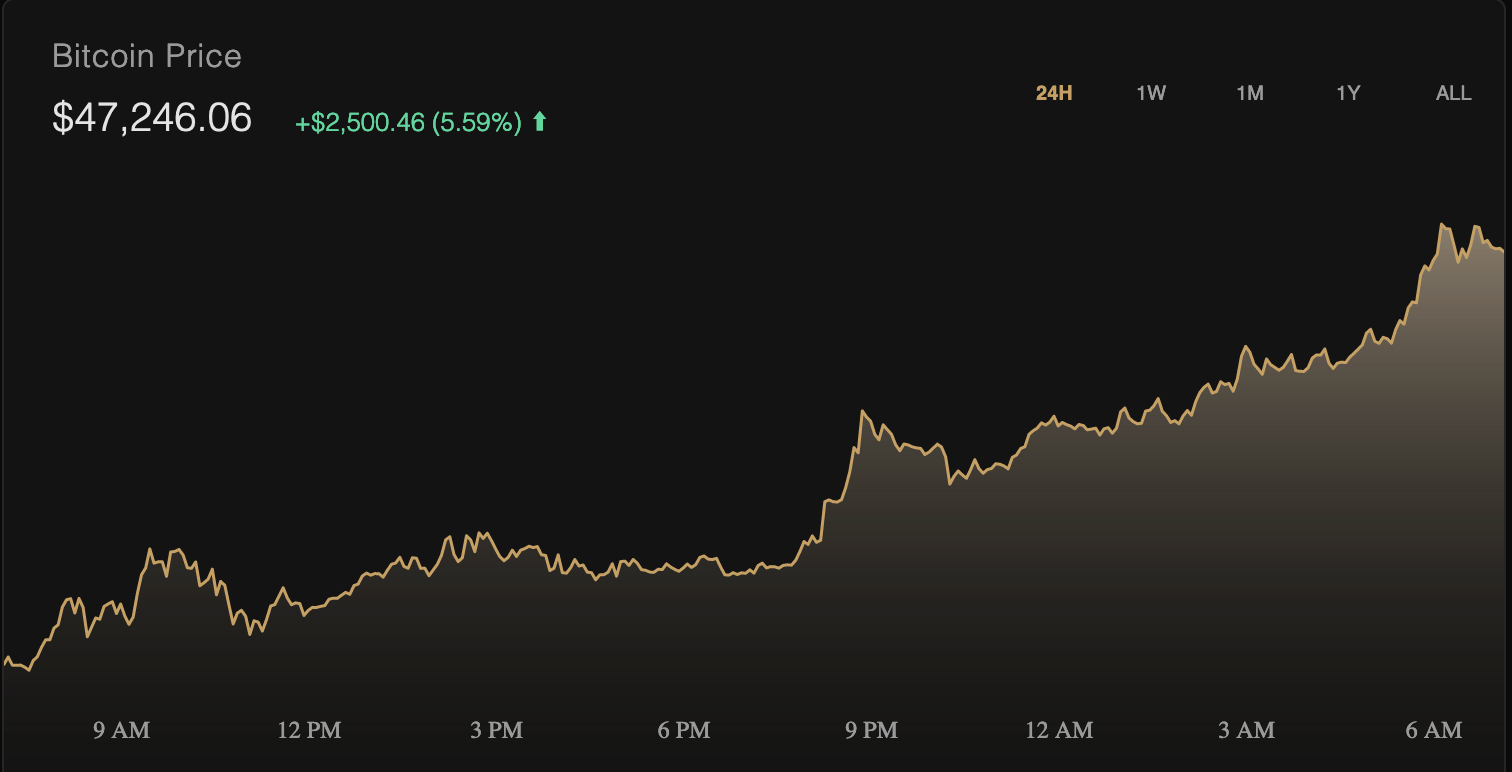
via River
The price of bitcoin is up more than 5% over the last twenty four hours. It is highly unlikely that the price movement over the last twelve hours is being driven by the events of last night. There are multiple disparate factors that drive the price of a very liquid scarce asset that trades 24/7/365. However, it is impossible to ignore the poetic timing of this particular rise in price. It's almost as if God is sending the world a message, "Now that it is clear to you that the politicians have lost control, maybe you should pay attention to bitcoin."
In a world in which bitcoin exists, you are not powerless against the whims of a central government that has lost control. Bitcoin empowers individuals with one of the most potent tools they could ever wish to leverage, a monetary system completely separated from the centrally controlled system operated by incompetent and corrupt central bankers and politicians who live and breath off the fumes emanating from pervasive moral hazard. Money is the most powerful tool in the world and for well over a century it has been co-opted and gate kept by a select few who have no interest in making sure your life is as fruitful and fulfilling as it should be.
Bitcoin allows you to take this power back in a sly roundabout way. Instead of having to forcibly take the power of the purse from the government and central banks and return it to the free market you can peacefully opt-in to a far superior system that cannot be corrupted by central planners.
Despite the fact that we have a president who cannot speak and things may seem more dire than they have been in generations, it is morning in America if you are willing to take agency over your life by removing the government's influence over your monetary good.
We're winning.
Final thought...
My boys are beginning to rough house and I feel the urge to buy a ref's whistle.

Use the code "TFTC" for 15% off
-
 @ cce0989b:b497e608
2024-02-09 13:57:07
@ cce0989b:b497e608
2024-02-09 13:57:07Old Happy: "We're in competition." New Happy: "We're here to help each other."
Because Old Happy culture raised us to believe that our value is based upon our performance, we have learned to see other people as our competition. You have to prove (by working harder, smarter, faster) that you are the best. The winners of this competition are the ones who are worthy of love, fulfillment, and happiness.
As a result, many people learn to employ a specific strategy: keep other people down. If you hurt others, it quiets your own insecurities and knocks them out of the field of competition, clearing your path towards what you think you want.
But it's all a lie. Keeping people down will never make you happy—it's bringing them up that does that.
The more that you focus on supporting and encouraging other people, the better you start to feel about yourself. You are proving to yourself that life is not a competition. You are remembering that you have your own incomparable, unique gifts and strengths. And with each generous action, you are helping others to see these truths, too.
-
 @ c384de42:493922aa
2024-02-09 11:40:29
@ c384de42:493922aa
2024-02-09 11:40:29Upvoting of tracks in the /queue has just been activated!! Come help us stress test this new functionality at here: https://t.me/noderunnersradio https://primal.b-cdn.net/media-cache?s=o&a=1&u=https%3A%2F%2Fm.primal.net%2FHbev.png
-
 @ 2448a66f:838296c9
2024-01-19 11:23:42
@ 2448a66f:838296c9
2024-01-19 11:23:42Chef's notes
สูตรขนมกุยช่ายสำหรับทานแบบนึ่ง สูตรนี้ปั้นลูกขนาดพอดีคำได้ 25 ลูก
Details
- ⏲️ Prep time: 30 นาที
- 🍳 Cook time: 30 นาที
- 🍽️ Servings: 4
Ingredients
- แป้งมัน 50 กรัม
- แป้งข้าวเจ้า 25 กรัม
- แป้งท้าวยายม่อม 10 กรัม
- กุยช่าย 200 กรัม
- น้ำเปล่า 200 กรัม
- น้ำมันพืช 50 กรัม
- เกลือ 1 หยิบมือ
- เบกกิ้งโซดา 1 หยิบมือ
Directions
- เทน้ำเปล่าลงไปผสมกับแป้งมัน แป้งข้าวเจ้า แป้งท้าวยายม่อม เกลือ คนจนส่วนผสมเข้ากัน ระวังอย่าให้แป้งเป็นก้อน
- ใส่กุยช่าย น้ำมันพืชและ เบกกิ้งโซดา ลงไปผสมกับแป้ง และขย้ำจนกว่าน้ำแป้งจะเปลี่ยนเป็นสีเขียวเล็กน้อย เพื่อให้กลิ่นของกุยช่ายระเหยออกมา และทำให้กุยช่ายนิ่มลง
- ตั้งกระทะบนเตา ใช้ไฟอ่อน เทส่วนผสมที่เราผสมไว้ลงไป กวนจนแป้งใส จับตัวเป็นก้อน ไม่ติดกระทะ
- ปั้นแป้งขนาดพอดีคำ หรือจะกดให้เป็นแผ่นก็ได้ ตามใจชอบ
- ระหว่างปั้นแป้งเป็นก้อน ให้ต้มน้ำเตรียมนึ่ง ใส่ใบเตยลงไปในน้ำ เพื่อเพิ่มความหอม
- เมื่อน้ำเดือดได้ที่ นำแป้งที่ปั้นไว้ลงไปนึ่งประมาณ 10 นาที จนแป้งใส จากนั้นตั้งขึ้นพักให้อุ่น พร้อมเสิร์ฟ
-
 @ 9810d9af:b3f2bf82
2024-01-18 06:33:53
@ 9810d9af:b3f2bf82
2024-01-18 06:33:53Chef's notes
Details
- ⏲️ Prep time: 60
- 🍳 Cook time: 30
- 🍽️ Servings: 4
Ingredients
- 1 pound lean ground pork
- 1¹/² cups finely chopped onions
- 1½ cups finely chopped chayote squash or sweet potato
- 1½ cups finely chopped jicama (or other root veg)
- 2 tablespoons minced garlic
- 1 tablespoon soy sauce
- 1 tablespoon ground black pepper
- 50 lumpia or spring roll wrap (about 7"x7")
- Hot chilli in oil is optional
- Plum sauce is favourite dip
- 1 large egg
- Generous pinch of sea salt
- 2 tablespoons oyster sauce
- ¹/² cup bread crumbs
Directions
- In a large bowl or pot, blend all ingredients together mixing in with the ground meat throughly. Add bread crumbs as needed to thicken into a good paste.
- Have a small dish on the side for dipping finger tips in water. Set up a work station with large cutting board or smooth surface. Set up the wraps by having them thawed from frozen and transferring them from packaging to a plate with a damp paper towel over pile of sheets. This will keep them fresh and prevent hardening too early.
- Pour some warm water onto a plate and add a dash of flour or cornstarch to mix in, creating a kind of glue for your lumpia wraps!
- Now the fun part! - Splash some water ("glue" mix) onto your clean, flat surface.
- Carefully separate 2 sheets of wraps and place flat on the watered surface (in a diamond shape ideally)
- Using a fork or spoon, scoop up about 1.5 table spoons of your meat/veg/spice mix into the center of the wrap. Try to create a 3" x 1" shape that is long left to right and form it solid and uniform as possible
- Lift the bottom corner (nearest to you) of the wraps and fold over the meat, tucking under meat as tightly as possible.
- Roll wrap and meat together about half way, fold in the sides. (you might need to splash more water on the corners or in folds if you find it is not sticking, be careful though bc it can over saturate and then your are F'd.
- Complete the rolling and follow through while trying to keep sides near and secure. Some times I toss some flour in and around the final corner to add more stickiness.
- Lay the completed rolled piece in a tupperware container and continue until you have amount desired.
- *IT GETS EASIER AS YOU DEVELOP YOUR OWN TECHNIQUES, be patient and take your time.
- Preheat your over/oil/airfryer Whip up an egg in a bowl and add a dash of milk or cream. Add pinch of salt and stir.
- Spread some parchment paper on a strong baking sheet, spray with cooking spray.
- brush all sides and around both end folds of each roll with generous coating of egg wash
- Place on greased pan if oven baking (this is easiest and yields about 18-20 pieces quickly)
- Bake uncovered, in oven, and on middle rack @400°F for about 15 min. Then turn all pieces over and bake for about another 15min.
- Once all pieces are golden brown and crispy, remove from oven and transfer to a wire cooling rack.
- Dipping sauce is whatever you like, but plum sauce is most appealing along with a hot chilli paste. Also can simply serve chopped on sticky rice.
- If freezing pieces raw then do so quickly after rolling them. For best freezer storing results, lay them out separately when you put in freezer to grab a few at a time in order to keep them from blocking together.
-
 @ ee0be83f:c260a740
2024-01-16 21:07:47
@ ee0be83f:c260a740
2024-01-16 21:07:47Ingredients
- test
Directions
- test
-
 @ cb084639:2f16502a
2024-01-15 12:55:53
@ cb084639:2f16502a
2024-01-15 12:55:53Chef's notes
Bone broth 🦴 นั้นจะพูดให้ง่ายมันก็คือน้ำซุปต้มกระดูกสัตว์นั่นเอง สามารถใช้ได้ทั้งกระดูกไก่ หมู วัว ส่วนที่นอกจากนี้ยังไม่รู้จะหาได้จากตลาดหรือไม่ 555 ในที่นี้ที่จะมาทำกันเป็นกระดูกที่หาได้ง่ายตามตลาดทั่วไป หรือจะตามห้างสรรพสินค้า คือกระดูกหมูนั้นเอง 🐖 เอาแบบที่เป็นกระดูกจริงๆ ราราประมาณ 40 บาทต่อ 1กิโลกรัมเท่านั้นเอง การทำ bonebroth นั้นต้องเป็นการต้มด้วยไฟอ่อนเป็นระยะเวลานาน 12ขึ้นไป -24 ชั่วโมง เพื่อให้สารอาหารที่อยู่ในกระดูกละลายออกมาอยู่ในน้ำซุปของเรา ซึ่งเราคงสงสัยกันแล้วใช้มั้ยว่าเราจะทำเจ้า bonebroth กันทำไม bonebroth นั้นกินได้ทุกวัยและกินได้ทุกวัน มีสารอาหารหลายชนิดช่วยบำรุงร่ายกาย และยังเหมาะกับผู้สูงวัยที่อาจจะรับสารอาหารไม่เพียงพอด้วย การกินก็ง่ายๆคือนำมาซดเป็นน้ำซุปเลย หรือจะนำมาเป็นส่วนประกอบในเวลาปรุงอาหารก็ได้ครับ มันจะมีเรื่องหม้อแรงดันอีกถ้าใครมีมันจะช่วยทุ่นเวลาให้เราลงมาอีกครึ่งเลยครับ
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 12-24 hour
- 🍽️ Servings: 4
Ingredients
- กระดูกหมู 1.5 kgs.
- น้ำสะอาด 1 หม้อ เบอร์ 28
- เกลือชมพู 1ช้อนชา
Directions
- นำกระดูกหมูล้างให้สะอาดมาต้มให้เดือดแล้วทิ้งน้ำไปก่อน 1 รอบ
- ล้างกระดูกแล้วนำมาต้มในน้ำใหม่ไฟกลางถึงอ่อนยาว 12-24 ชม.
- เติมเกลือชมพู
- ถ้ายังไม่ถึงเวลาแล้วน้ำแห้ง เติมได้ตามความเหมาะสม
- รอจนครบเวลาก็จะได้ bonebroth ไว้กินแล้วครับ
-
 @ 341db5a7:4c4fc2ef
2024-01-15 05:05:23
@ 341db5a7:4c4fc2ef
2024-01-15 05:05:23Chef's notes
I like to fry catfish for friends and family, and sometimes I fry too much. Reheated fried food isn't great, but this is an amazing way to reinvent leftover fried catfish filets as a hearty curry dish. Feel free to substitute for whatever fried fish you have, and of course try different combination of veggies and curries. You can also fry your fish just before cooking, but it actually works better with cold filets, as they break down less in the sauce. Serves well over long grain rice, but Jasmine rice works great too!
Details
- ⏲️ Prep time: 30mins
- 🍳 Cook time: 30mins
- 🍽️ Servings: 6-8
Ingredients
- 1 yellow onion
- 1 bell pepper
- 2 carrots
- 1/2 cup shredded cabbage
- 6oz sliced mushrooms
- 1 stalk celery
- 2tbs garlic ginger paste
- 1/4 cup coconut oil
- 1 can coconut milk
- 5 tlbs curry powder
- 1 lbs leftover fried catfish filets
- salt and pepper to taste
Directions
- chop all veggies to desired thickness for stir frying
- heat coconut oil in wok or large skillet
- add garlic ginger paste and cook til light brown and aromatic
- add veggies sliced carrots, cook 1 min
- add bell pepper, cook 1 min
- add onion, cook 1 min
- add celery, cook 1 min
- add mushrooms, cook 1 min
- add cabbage, cook until all veggies are almost soft
- add coconut milk and curry powder and cook until boiling
- add salt and pepper to taste
- add your leftover catfish. bring back to a boil
- cook 10 mins. stir cautiously at this point, as your fish filets may break down.
- serve over rice
-
 @ 8d9d2b77:86dd65fa
2024-01-14 20:49:18
@ 8d9d2b77:86dd65fa
2024-01-14 20:49:18Chef's notes
When I make this creamy taco soup, I don't really measure anything, so this will be approximate measurements. The recipe is very forgiving, and you can add or delete to your taste. The cream cheese is the key ingredient to make this soup creamy, and in my opinion the cilantro is a must.
Details
- 🍳 Cook time: 30 minutes
- 🍽️ Servings: 8
Ingredients
- 2-3 lbs ground beef
- 1 whole onion
- 1 head of fresh garlic
- 2-3 8oz packages cream cheese, depending on your taste
- Beef bouillon, 2-3 cubes
- Chili powder to taste
- Salt and pepper to taste
- Cumin to taste
- Cayenne pepper, optional
- Fresh cilantro to taste
- I can fire roasted, diced tomatoes
Directions
- In a large cookpot, brown meat.
- Add onions and garlic, simmer for 5 mins
- Add diced tomatoes and cream cheese.
- Add all seasonings
- Add cream cheese, allow to melt and stir.
- At this point you might want to add a bit of water or milk, depending on how thick you want the soup.
- Let simmer for 10 min.
- Add cilantro and let it wither, about 3 mins
- Thats it! If you wish, you can top with shredded cheese or avocado.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28There's a problem with using Git concepts for everything
We've been seeing a surge in applications that use Git to store other things than code, or that are based on Git concepts and so enable "forking, merging and distributed collaboration" for things like blogs, recipes, literature, music composition, normal files in a filesystem, databases.
The problem with all this is they will either:
- assume the user will commit manually and expect that commit to be composed by a set of meaningful changes, and the commiter will also add a message to the commit, describing that set of meaningful, related changes; or
- try to make the committing process automatic and hide it from the user, so will producing meaningless commits, based on random changes in many different files (it's not "files" if we are talking about a recipe or rows in a table, but let's say "files" for the sake of clarity) that will probably not be related and not reduceable to a meaningful commit message, or maybe the commit will contain only the changes to a single file, and its commit message would be equivalent to "updated
<name of the file>".
Programmers, when using Git, think in Git, i.e., they work with version control in their minds. They try hard to commit together only sets of meaningful and related changes, even when they happen to make unrelated changes in the meantime, and that's why there are commands like
git add -pand many others.Normal people, to whom many of these git-based tools are intended to (and even programmers when out of their code-world), are much less prone to think in Git, and that's why another kind of abstraction for fork-merge-collaborate in non-code environments must be used.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A prediction market as a distributed set of oracle federations
See also: Truthcoin as a spacechain.
This is not Truthcoin, but hopefully the essence of what makes it good is present here: permissionless, uncensorable prediction markets for fun, profit, making cheap talk expensive and revolutionizing the emergence and diffusion of knowledge in society.
The idea
The idea is just to reuse Fedimint's codebase to implement federated oracle corporations that will host individual prediction markets inside them.
Pegging in and out of a federation can be done through Lightning gateways, and once inside the federation users can buy and sell shares of individual markets using a native LMSR market-maker.
Then we make a decentralized directory of these bets using something simple like Nostr so everybody can just join any market very easily.
Why?
The premise of this idea is that we can't have a centralized prediction market platform because governments will shut it down, but we can instead have a pseudonymous oracle corporation that also holds the funds being gambled at each time in a multisig Bitcoin wallet and hope for the best.
Each corporation may exist to host a single market and then vanish afterwards -- its members returning later to form a new corporation and host a new market before leaving again.
There is custodial risk, but the fact that the members may accrue reputation as the time passes and that this is not one big giant multisig holding all the funds of everybody but one multisig for each market makes it so this is slightly better.
In any case, no massive amounts are expected to be used in this scheme, which defeats some of the use cases of prediction markets (funding public goods, for example), but since these are so advanced and society is not yet ready for them, we can leave them for later and first just try to get some sports betting working.
This proto-truthcoin implementation should work just well enough to increase the appetite of bitcoiners and society in general for more powerful prediction markets.
Why is this better than DLCs?
Because DLCs have no liquidity. In their current implementations and in all future plans from DLC enthusiasts they don't even have order books. They're not seen very much as general-purpose prediction markets, but mostly as a way to create monetary instruments and derivatives.
They could work as prediction markets, but then they would need order books and order books are terrible for liquidity. LMSR market makers are much better.
But it is custodial!
If you make a public order book tied to known oracles using a DLC the oracle may also be considered custodial since it becomes really easy for him to join multiple trades as a counterpart then lie and steal the money. The bets only really "discreet" if they're illiquid meaningless bets between two guys. If they're happening in a well-known public place they're not discreet anymore.
DLC proponents may say this can be improved by users using multiple oracles and forming effectively a federation between them, but that is hardly different from choosing a reputable oracle corporation in this scheme and trusting that for the life of the bet.
But Hivemind is better!
Yes.
-
 @ d4338b7c:f1d23a5b
2024-01-12 21:00:23
@ d4338b7c:f1d23a5b
2024-01-12 21:00:23Chef's notes
Similar to a traditional Manhattan. The specs remain the same 2:1 Rye Whiskey to Sweet Vermouth. Except we are supplementing the vermouth out for Averna.
Details
- ⏲️ Prep time: 5
- 🍳 Cook time: 5
- 🍽️ Servings: 1
Ingredients
- Rye
- averna
- angostura bitters
- orange bitters
Directions
- add ingredients to a mixing glass
- add large cubes
- stir for 45 seconds
- serve up in a coupe
- skewered luxardo cherry garnish
- cheeers
-
 @ d0b327c6:1ae748c2
2024-02-09 08:51:17
@ d0b327c6:1ae748c2
2024-02-09 08:51:17Tradotto dall’originale di Ludwig Von Mises - pubblicato il 9 dic 2021
Questo articolo è un estratto da Libertà Economica e Interventismo (1952).
Le parole libertà e autonomia rappresentavano per i più eminenti rappresentanti dell'umanità uno dei beni più preziosi e desiderabili. Oggi è di moda deriderle. Sono, dice il saggio moderno, nozioni "scivolose" e pregiudizi "borghesi".
La libertà e la autonomia non si trovano in natura. In natura non esiste alcun fenomeno a cui questi termini possano essere applicati in modo significativo. Qualunque cosa l'uomo faccia, non può mai liberarsi dai vincoli che la natura gli impone. Se vuole riuscire ad agire, deve sottomettersi incondizionatamente alle leggi della natura.
Libertà e autonomia si riferiscono sempre alle relazioni interumane. Un uomo è libero nella misura in cui può vivere e andare avanti senza essere in balia di decisioni arbitrarie da parte di altre persone. Nell'ambito della società, ognuno dipende dai suoi concittadini. L'uomo sociale non può diventare indipendente senza rinunciare a tutti i vantaggi della cooperazione sociale.
Il fenomeno sociale fondamentale è la divisione del lavoro e la sua controparte - la cooperazione umana.
L'esperienza insegna all'uomo che l'azione cooperativa è più efficiente e produttiva dell'azione isolata di individui autosufficienti. Le condizioni naturali che determinano la vita e lo sforzo dell'uomo sono tali che la divisione del lavoro aumenta la produzione per unità di lavoro spesa. Questi fatti naturali sono:
-
l'innata disuguaglianza degli uomini rispetto alla loro capacità di svolgere vari tipi di lavoro, e
-
l'ineguale distribuzione delle opportunità di produzione non umane, date dalla natura, sulla superficie della terra. Si può benissimo considerare questi due fatti come un unico e medesimo fatto, cioè la molteplicità della natura che rende l'universo un complesso di infinite varietà.
Disuguaglianza innata
La divisione del lavoro è il risultato della reazione consapevole dell'uomo alla molteplicità delle condizioni naturali. D'altra parte, è essa stessa un fattore di differenziazione. Assegna alle varie aree geografiche funzioni specifiche nel complesso dei processi produttivi. Rende alcune aree urbane, altre rurali; localizza i vari rami dell'industria manifatturiera, mineraria e agricola in luoghi diversi. Ma ancora più importante è il fatto che intensifica l'innata disuguaglianza degli uomini. L'esercizio e la pratica di compiti specifici adattano meglio gli individui ai requisiti delle loro prestazioni; gli uomini sviluppano alcune delle loro facoltà innate e frenano lo sviluppo di altre. Emergono tipi professionali, le persone diventano specialisti.
La divisione del lavoro suddivide i vari processi produttivi in compiti minimi, molti dei quali possono essere svolti da dispositivi meccanici. È questo fatto che ha reso possibile l'uso delle macchine e ha portato a incredibili miglioramenti nei metodi tecnici di produzione. La meccanizzazione è il frutto della divisione del lavoro, il suo risultato più vantaggioso, non il suo motivo e la sua sorgente. I macchinari specializzati azionati dalla forza motrice potevano essere impiegati solo in un ambiente sociale in cui vigeva la divisione del lavoro. Ogni passo avanti verso l'uso di macchine più specializzate, più raffinate e più produttive richiede un'ulteriore specializzazione dei compiti.
All'interno della società
Vista dal punto di vista dell'individuo, la società è il grande mezzo per il raggiungimento di tutti i suoi fini. La conservazione della società è una condizione essenziale di qualsiasi progetto che un individuo voglia realizzare con qualsiasi azione. Anche il delinquente refrattario che non riesce ad adeguare la sua condotta alle esigenze della vita all'interno del sistema sociale di cooperazione non vuole perdere nessuno dei vantaggi derivanti dalla divisione del lavoro. Non mira consapevolmente alla distruzione della società. Vuole mettere le mani su una parte maggiore della ricchezza prodotta in comune rispetto a quella che l'ordine sociale gli assegna. Si sentirebbe infelice se il comportamento antisociale diventasse universale e ne derivasse l'inevitabile risultato, il ritorno all'indigenza primitiva.
La libertà è la condizione dell'uomo all'interno di una società contrattuale. La cooperazione sociale in un sistema di proprietà privata dei mezzi di produzione significa che, nell'ambito del mercato, l'individuo non è obbligato a obbedire e a servire un padrone. Nella misura in cui dà e serve altre persone, lo fa di sua iniziativa per essere ricompensato e servito da chi lo riceve. Scambia beni e servizi, non fa un lavoro obbligatorio e non paga tributi. Non è certamente indipendente. Dipende dagli altri membri della società. Ma questa dipendenza è reciproca. L'acquirente dipende dal venditore e il venditore dall'acquirente.
Interesse personale
La preoccupazione principale di molti scrittori del XIX e XX secolo è stata quella di travisare e distorcere questo ovvio stato di cose. I lavoratori, dicevano, sono alla mercé dei loro datori di lavoro. Ora, è vero che il datore di lavoro ha il diritto di licenziare il dipendente. Ma se si avvale di questo diritto per assecondare i suoi capricci, danneggia i suoi stessi interessi. Il licenziamento di un uomo migliore per assumerne uno meno efficiente va a suo svantaggio. Il mercato non impedisce direttamente a nessuno di infliggere arbitrariamente un danno ai suoi concittadini; si limita a sanzionare tale comportamento. Il negoziante è libero di essere scortese con i suoi clienti, purché sia pronto a sopportarne le conseguenze. I consumatori sono liberi di boicottare un fornitore, purché siano pronti a pagarne i costi.
Ciò che spinge ogni uomo al massimo sforzo al servizio dei suoi simili e frena le tendenze innate all'arbitrio e alla cattiveria non è, nel mercato, la costrizione e la coercizione da parte di gendarmi, boia e tribunali penali; è l'interesse personale. Il membro di una società contrattuale è libero perché serve gli altri solo servendo se stesso. Ciò che lo limita è solo l'inevitabile fenomeno naturale della scarsità. Per il resto è libero nel raggio d'azione del mercato.
Nell'economia di mercato l'individuo è libero di agire nell'ambito della proprietà privata e del mercato. Le sue scelte sono definitive. Per i suoi simili le sue azioni sono dati di cui devono tenere conto nel loro agire. Il coordinamento delle azioni autonome di tutti gli individui è realizzato dal funzionamento del mercato. La società non dice all'uomo cosa fare e cosa non fare. Non c'è bisogno di imporre la cooperazione con ordini o divieti speciali. La non cooperazione si penalizza da sola. L'adeguamento alle esigenze dello sforzo produttivo della società e il perseguimento dei propri interessi non sono in conflitto. Di conseguenza, non è necessaria alcuna agenzia per risolvere tali conflitti. Il sistema può funzionare e svolgere i suoi compiti senza l'interferenza di un'autorità che emette ordini e divieti speciali e punisce chi non li rispetta.
Compulsione e coercizione
Al di là della sfera della proprietà privata e del mercato si trova la sfera della costrizione e della coercizione; qui si trovano le dighe che la società organizzata ha costruito per proteggere la proprietà privata e il mercato dalla violenza, dalla malizia e dalla frode. Questo è il regno della costrizione, distinto dal regno della libertà. Qui ci sono regole che discriminano tra ciò che è legale e ciò che è illegale, tra ciò che è permesso e ciò che è proibito. E qui c'è una cupa macchina di armi, prigioni e patiboli e gli uomini che la gestiscono, pronti a schiacciare coloro che osano disobbedire.
È importante ricordare che l'interferenza del governo significa sempre un'azione violenta o la minaccia di tale azione. Il governo è, in ultima istanza, l'impiego di uomini armati, poliziotti, gendarmi, soldati, guardie carcerarie e boia. La caratteristica essenziale del governo è l'applicazione dei suoi decreti mediante percosse, uccisioni e imprigionamenti. Coloro che chiedono una maggiore ingerenza da parte del governo chiedono, in ultima analisi, più costrizione e meno libertà.
Libertà e autonomia sono termini utilizzati per descrivere le condizioni sociali dei singoli membri di una società di mercato in cui il potere dell'indispensabile vincolo egemonico, lo Stato, è limitato per non mettere in pericolo il funzionamento del mercato. In un sistema totalitario non c'è nulla a cui si possa attribuire l'attributo "libero" se non l'arbitrio illimitato del dittatore.
Non ci sarebbe bisogno di soffermarsi su questo fatto ovvio se i campioni dell'abolizione della libertà non avessero creato di proposito una confusione semantica. Si rendevano conto che non c'era speranza di combattere apertamente e sinceramente per la limitazione e la servitù. Le nozioni di libertà e di libertà avevano un tale prestigio che nessuna propaganda poteva scuotere la loro popolarità. Da sempre, nel regno della civiltà occidentale, la libertà è stata considerata il bene più prezioso. Ciò che ha dato all'Occidente la sua eminenza è stata proprio la preoccupazione per la libertà, un ideale sociale estraneo ai popoli orientali. La filosofia sociale dell'Occidente è essenzialmente una filosofia della libertà. Il contenuto principale della storia dell'Europa e delle comunità fondate dagli emigranti europei e dai loro discendenti in altre parti del mondo è stata la lotta per la libertà. Il "robusto" individualismo è la firma della nostra civiltà. Nessun attacco aperto alla libertà dell'individuo aveva prospettive di successo.
Nuove definizioni
Così i sostenitori del totalitarismo scelsero altre tattiche. Hanno invertito il significato delle parole. Chiamano libertà vera o autentica la condizione degli individui in un sistema in cui non hanno altro diritto che quello di obbedire agli ordini. Si definiscono veri liberali perché si battono per un tale ordine sociale. Chiamano democrazia i metodi russi di governo dittatoriale. Chiamano "democrazia industriale" i metodi sindacali di violenza e coercizione. Chiamano libertà di stampa uno stato di cose in cui solo il governo è libero di pubblicare libri e giornali. Definiscono la libertà come l'opportunità di fare le cose "giuste" e, naturalmente, si arrogano la determinazione di ciò che è giusto e ciò che non lo è. Ai loro occhi l'onnipotenza del governo significa piena libertà. Liberare il potere di polizia da ogni vincolo è il vero significato della loro lotta per la libertà.
L'economia di mercato, dicono questi sedicenti liberali, concede la libertà solo a una classe parassitaria di sfruttatori, la borghesia; che questi furfanti godono della libertà di schiavizzare le masse; che il salariato non è libero; che deve lavorare per il solo beneficio dei suoi padroni, i datori di lavoro; che i capitalisti si appropriano di ciò che secondo i diritti inalienabili dell'uomo dovrebbe appartenere all'operaio; che con il socialismo l'operaio godrà della libertà e della dignità umana perché non dovrà più essere schiavo di un capitalista; che il socialismo significa l'emancipazione dell'uomo comune, significa libertà per tutti; che significa, inoltre, ricchezza per tutti.
Queste dottrine hanno potuto trionfare perché non hanno incontrato una critica razionale efficace. È inutile sostenere un presunto diritto "naturale" degli individui a possedere la proprietà, se altre persone affermano che il principale diritto "naturale" è quello dell'uguaglianza dei redditi. Tali controversie non potranno mai essere risolte. Non è importante criticare le caratteristiche non essenziali del programma socialista. Non si confuta il socialismo attaccando la posizione socialista su religione, matrimonio, controllo delle nascite e arte.
Un nuovo sotterfugio
Nonostante queste gravi carenze dei difensori della libertà economica, è stato impossibile ingannare sempre tutti i cittadini sulle caratteristiche essenziali del socialismo. I pianificatori più fanatici sono stati costretti ad ammettere che i loro progetti comportano l'abolizione di molte libertà di cui le persone godono sotto il capitalismo e la "plutodemocrazia". Messi alle strette, hanno fatto ricorso a un nuovo sotterfugio. La libertà da abolire, sottolineano, è solo la spuria libertà "economica" dei capitalisti che danneggia l'uomo comune; al di fuori della "sfera economica" la libertà non solo sarà pienamente conservata, ma notevolmente ampliata. "Pianificare la libertà" è diventato ultimamente lo slogan più popolare dei campioni del governo totalitario e della russificazione di tutte le nazioni.
La fallacia di questo argomento deriva dalla distinzione spuria tra due ambiti della vita e dell'azione umana, la sfera "economica" e quella "non economica". In senso stretto, le persone non desiderano i beni tangibili in quanto tali, ma i servizi che questi beni sono in grado di rendere loro. Vogliono ottenere l'aumento di benessere che questi servizi sono in grado di trasmettere. È un dato di fatto che le persone, quando trattano sul mercato, sono motivate non solo dal desiderio di ottenere cibo, alloggio e piacere sessuale, ma anche da molteplici impulsi "ideali". L'uomo che agisce è sempre interessato sia alle cose "materiali" che a quelle "ideali". Sceglie tra varie alternative, indipendentemente dal fatto che siano classificate come materiali o ideali. Nelle scale di valore attuali, le cose materiali e quelle ideali si confondono.
La libertà, così come veniva goduta nei Paesi democratici della civiltà occidentale negli anni del trionfo del vecchio liberalismo, non era il prodotto di costituzioni, leggi e statuti. Questi documenti miravano solo a salvaguardare la libertà e la libertà, saldamente stabilite dal funzionamento dell'economia di mercato, contro le invasioni da parte dei funzionari. Nessun governo e nessuna legge civile possono garantire e realizzare la libertà se non sostenendo e difendendo le istituzioni fondamentali dell'economia di mercato. Il governo significa sempre coercizione e costrizione ed è necessariamente l'opposto della libertà. Il governo è un garante della libertà ed è compatibile con la libertà solo se il suo raggio d'azione è adeguatamente limitato alla conservazione della libertà economica. Dove non c'è economia di mercato, le migliori intenzioni delle costituzioni e delle leggi rimangono lettera morta.
Competizione
La libertà dell'uomo nel capitalismo è un effetto della concorrenza. Il lavoratore non dipende dalle grazie di un datore di lavoro. Se il suo datore di lavoro lo licenzia, trova un altro datore di lavoro. Il consumatore non è alla mercé del negoziante. È libero di frequentare un altro negozio, se lo desidera. Nessuno deve baciare le mani degli altri o temere il loro sfavore. Le relazioni interpersonali sono di tipo commerciale. Lo scambio di beni e servizi è reciproco; non è un favore da vendere o da comprare, è una transazione dettata dall'egoismo di entrambe le parti.
È vero che nella sua veste di produttore ogni uomo dipende direttamente, come l'imprenditore, o indirettamente, come il lavoratore dipendente, dalle richieste dei consumatori. Tuttavia, questa dipendenza dalla supremazia dei consumatori non è illimitata. Se un uomo ha una ragione importante per sfidare la sovranità dei consumatori, può provarci. Il mercato offre un diritto sostanziale ed efficace di resistenza all'oppressione. Nessuno è costretto a entrare nell'industria dei liquori o in una fabbrica di armi se la sua coscienza si oppone. Potrebbe dover pagare un prezzo per la sua convinzione; non esistono al mondo fini il cui raggiungimento sia gratuito. Ma è lasciata alla decisione di un uomo la scelta tra un vantaggio materiale e il richiamo di ciò che ritiene essere il suo dovere. Nell'economia di mercato l'individuo è l'unico arbitro supremo in materia di soddisfazione.
I consumatori scelgono
La società capitalista non ha alcun mezzo per costringere un uomo a cambiare la sua occupazione o il suo posto di lavoro, se non quello di ricompensare con una paga più alta coloro che soddisfano i desideri dei consumatori. È proprio questo tipo di pressione che molte persone considerano insopportabile e sperano di vedere abolita nel socialismo. Sono troppo ottusi per capire che l'unica alternativa è trasmettere alle autorità il pieno potere di determinare in quale settore e in quale luogo un uomo debba lavorare.
Nella sua veste di consumatore l'uomo non è meno libero. È lui solo a decidere cosa è più e meno importante per lui. Sceglie come spendere il proprio denaro secondo la propria volontà.
La sostituzione della pianificazione economica all'economia di mercato elimina ogni libertà e lascia all'individuo solo il diritto di obbedire. L'autorità che dirige tutte le questioni economiche controlla tutti gli aspetti della vita e delle attività di un uomo. È l'unico datore di lavoro. Tutto il lavoro diventa obbligatorio, perché il lavoratore deve accettare ciò che il capo si degna di offrirgli. Lo zar dell'economia determina cosa e quanto il consumatore può consumare. Non c'è settore della vita umana in cui una decisione sia lasciata ai giudizi di valore dell'individuo. L'autorità gli assegna un compito preciso, lo addestra per questo lavoro e lo impiega nel luogo e nel modo che ritiene opportuno.
La vita "pianificata" non è libera
Non appena la libertà economica che l'economia di mercato concede ai suoi membri viene eliminata, tutte le libertà politiche e le carte dei diritti diventano una baggianata. L'habeas corpus e il processo con giuria sono una finzione se, con il pretesto della convenienza economica, l'autorità ha il pieno potere di relegare ogni cittadino che non le piace nell'Artico o in un deserto e di assegnargli "lavori forzati" a vita. La libertà di stampa è una mera illusione se l'autorità controlla tutte le tipografie e le cartiere. E così tutti gli altri diritti degli uomini.
Un uomo è libero nella misura in cui modella la propria vita secondo i propri piani. Un uomo il cui destino è determinato dai piani di un'autorità superiore, alla quale spetta il potere esclusivo di pianificare, non è libero nel senso in cui il termine "libero" è stato usato e inteso da tutti gli uomini fino a quando la rivoluzione semantica dei nostri giorni ha portato a una confusione di lingue.
-
-
 @ d0b327c6:1ae748c2
2024-02-09 08:44:31
@ d0b327c6:1ae748c2
2024-02-09 08:44:31Tradotto dall’originale di Shinobi - pubblicato il 11 gen 2024
Preparatevi, tenetevi forte. La lettura di questo testo potrebbe farvi arrabbiare e confondere, potreste persino arrabbiarvi a tal punto da prendere a pugni lo schermo (non fatelo).
Bitcoin è un database. Punto.
Ecco cos'è. La blockchain è un database per la memorizzazione degli aggiornamenti passati per poter riprodurre lo stato attuale del database, l'insieme UTXO. L'intero protocollo Bitcoin è costruito attorno al database. Che cosa è una voce valida in quel database e che cosa non lo è? Chi è autorizzato a proporre voci in quel database, come si fa a garantire che solo le voci di quegli utenti vengano prese in considerazione e accettate? Qual è il meccanismo di autenticazione che limita la scrittura di voci in questo database? Come si fa a limitare gli inserimenti nel database, in modo che le persone non ne facciano così tanti da sovraccaricare o mandare in crash il software che gestisce il database? Come si fa a garantire che le persone non possano creare singoli inserimenti abbastanza grandi da causare altri problemi di negazione del servizio?
È tutta una questione di database.
Proof-of-work? L'intero scopo del protocollo è quello di gestire chi può effettivamente elaborare gli aggiornamenti del database. Bitcoin è stato concepito come un sistema decentralizzato, quindi aveva bisogno di un modo per aggiornare il database in modo decentralizzato, pur consentendo agli utenti di raggiungere un consenso con tutte le loro copie individuali del database su un singolo aggiornamento. Se ognuno aggiorna la propria copia del database da solo, non c'è modo che tutti raggiungano un consenso su un'unica versione del database. Se si dipende da alcune figure autoritarie per gestire gli aggiornamenti, allora il processo di aggiornamento non è veramente decentralizzato. Questo era lo scopo di POW, consentire a chiunque di elaborare un aggiornamento, ma non senza sostenere un costo verificabile nel farlo.
La proof-of-work è semplicemente un meccanismo decentralizzato per aggiornare un database.
L'intera architettura della rete peer-to-peer? Esiste solo per propagare le proposte di aggiornamento del database (transazioni) e gli aggiornamenti finalizzati del database (blocchi). I nodi verificano le transazioni quando entrano nella loro mempool? Servono a pre-filtrare le proposte di aggiornamento del database e ad assicurarsi che siano valide. Nodi che verificano che un blocco soddisfi l'obiettivo di difficoltà richiesto? È per pre-filtrare un aggiornamento del database proposto e assicurarsi che sia valido prima di passarlo ad altri nodi per aggiornare la loro copia locale.
La rete peer-to-peer esiste solo per riconciliare più copie dello stesso database.
Script Bitcoin? Esiste letteralmente al solo scopo di funzionare come meccanismo di autorizzazione per le voci del database. Per cancellare una voce esistente nello stato attuale del database, l'insieme UTXO, l'utente che propone l'aggiornamento deve fornire una prova di autenticazione che soddisfi le condizioni dello script che blocca la voce esistente del database. Solo le voci esistenti, o UTXO, possono essere "spese" per autorizzare la creazione di nuove voci nel database. I minatori sono gli unici nel protocollo a poter creare voci senza soddisfare la condizione di rimuovere una voce esistente soddisfacendo i requisiti di autorizzazione stabiliti nello script di blocco.
Lo script Bitcoin è semplicemente un meccanismo per controllare e limitare chi può scrivere sul database.
Ogni singolo aspetto di ciò che è Bitcoin ruota attorno alla funzione centrale di mantenere un database e di garantire che i numerosi partecipanti alla rete che conservano le loro copie individuali di tale database rimangano sincronizzati e concordino sullo stato attuale del database. Tutte le proprietà che rendono Bitcoin prezioso come forma di denaro o mezzo di pagamento derivano letteralmente dal suo funzionamento come database.
Molte persone in questo spazio pensano che questo database debba essere utilizzato esclusivamente come mezzo di pagamento o come forma di denaro, e io condivido questa opinione. Anch'io penso che questo sia il caso d'uso più importante e che si debba fare il possibile per scalare il più possibile questo particolare caso d'uso senza sacrificare la sovranità e la sicurezza di poter interagire direttamente con il database.
Ma si tratta pur sempre di un database, se si considera la realtà oggettiva di ciò che è il Bitcoin. Le persone disposte a pagare i costi denominati in satoshi per scrivere una voce che sia considerata valida secondo le regole di quel database possono farlo. Non c'è nulla che si possa fare per impedirglielo, a meno che non si cambi ciò che è considerato valido in quel database, il che comporta la necessità di convincere tutti gli altri ad adottare un nuovo insieme di regole riguardo a ciò che è valido.
Le persone possono competere liberamente all'interno delle regole del consenso per scrivere qualsiasi cosa vogliano in questo database, a patto che paghino i costi richiesti dalle regole e dalla struttura di incentivi del mining per farlo. Punto. Molte delle cose che le persone possono e stanno inserendo nel database sono stupide? Sì. Certo che lo sono. Internet è disseminato di quantità impressionanti di cose stupide in database isolati dappertutto. Perché? Perché le persone sono disposte a pagare il costo per inserire cose stupide in un database.
Che siano gli utenti del database a pagare il fornitore e l'operatore, o che sia l'operatore stesso a permettere l'inserimento di certe cose come parte delle operazioni senza trasferirne il costo all'utente, è irrilevante. Queste stupidaggini esistono da qualche parte in forma digitale solo perché, in qualche modo, il costo è stato pagato.
In questo senso, Bitcoin non è fondamentalmente diverso da qualsiasi altro database. L'unica differenza è che non c'è un unico proprietario o guardiano che detta ciò che è permesso o meno. Ogni proprietario di una copia del database Bitcoin è in grado di consentire o meno ciò che vuole; il problema è che se sceglie di rifiutare qualcosa che tutti gli altri ritengono accettabile, cade il consenso con tutti gli altri. Il loro database locale non è più sincronizzato con il database virtuale globale che tutti gli altri seguono e utilizzano.
Se ritenete inaccettabili certe voci del database, allora cambiate pure le regole con cui la vostra copia locale convalida le nuove voci. Ma questo significa tagliarsi il naso per far dispetto alla faccia. In fin dei conti, Bitcoin si basa su un semplice assioma: pagare per giocare. Se le persone pagano la tassa, possono giocare. È così che funziona.
In fin dei conti, spetta a ogni singolo individuo decidere cosa consentire o meno nel proprio database, ma al di là di tutti i dibattiti semantici e filosofici in corso, una cosa rimane indiscutibilmente e oggettivamente vera: Bitcoin è un database.
-
 @ 9ecbb0e7:06ab7c09
2024-02-09 04:58:13
@ 9ecbb0e7:06ab7c09
2024-02-09 04:58:13Cuban woman Mirtza Ocaña, detained this week at Tampa International Airport and charged with smuggling after being found with about $100,000 she was carrying from the Island, confessed she was paid to carry cash dollars to the United States several times a month.
According to the criminal complaint filed in the Middle District of Florida Federal Court and consulted by El Nuevo Herald, the 38-year-old woman "was paid between $1,000 and $2,500 per trip."
On Tuesday, Florida federal prosecutor Roger B. Handberg announced the arrest and the filing of a criminal complaint against the woman, a resident of Tampa who dedicated herself to traveling to the Island as a mule. If found guilty, Ocaña faces a maximum penalty of five years in federal prison.
According to the complaint, the Cuban arrived at Tampa International Airport on a flight from the Island on February 5, 2024, and did not declare that she had more than $10,000 in her possession, an amount that would trigger reporting requirements.
However, during a routine inspection of her luggage, agents from the Department of Homeland Security recovered approximately $30,000 in cash, hidden in three wrapped packages.
The Cuban later admitted that she flew from Cuba to Tampa two or three times a month to smuggle cash into the United States and that she knew that bringing these sums without reporting it is illegal. Also, taking more than 5,000 units of any currency out of the Island is prohibited by Cuban laws.
Agents searched Ocaña and discovered another $70,000 in cash hidden in her clothing. Ocaña's flight history later revealed that she had flown from Cuba to Tampa 45 times since May of 2023.
The Prosecutor's Office statement specified that this case is being investigated by the Homeland Security Investigations Office (HSI) and the U.S. Customs and Border Protection Office, and that the detainee will be prosecuted by Assistant U.S. Attorney Michael J. Buchanan.
El Nuevo Herald indicated that the judicial records say that Ocaña was unemployed and does not speak English. Last September, she created a company, Ocana & Paradise, LLC.
Judge Sean P. Flynn ordered the release of the Cuban woman and that she be subjected to a home surveillance program with an electronic device. He also instructed her to seek psychiatric treatment, employment, and to surrender her passport.
On her Tik Tok and Instagram profiles, Ocaña announced air and maritime shipments of food and medicine to Cuba.
Experts consulted by El Nuevo Herald suggested that the detainee could be transferring money from Island MIPYMES that pay foreign suppliers or also sums resulting from the sale of properties that some residents of Cuba seek to deposit in foreign bank accounts, among other hypotheses.
Ocaña's detention occurred a few days after Western Union suspended its remittance operations to Cuba from the United States due to technical issues in the Cuban banking system. The situation continues amid the opacity of the financial institutions of the regime.
-
 @ 9ecbb0e7:06ab7c09
2024-02-09 04:57:40
@ 9ecbb0e7:06ab7c09
2024-02-09 04:57:40La cubana Mirtza Ocaña, detenida esta semana en el Aeropuerto Internacional de Tampa y acusada de contrabando luego de habérsele encontrado unos 100.000 dólares que trasladaba desde la Isla, confesó que le pagaban por llevar dólares en efectivo a Estados Unidos varias veces al mes.
De acuerdo con la denuncia penal presentada ante el Tribunal Federal del Distrito Medio de Florida y consultada por El Nuevo Herald, a la mujer de 38 años "le pagaban entre 1.000 y 2.500 dólares por viaje".
El martes, el fiscal federal Roger B. Handberg, de Florida, anunció el arresto y presentación de una denuncia penal contra la mujer, residente en Tampa y que se dedicada a viajar a la Isla como mula. De ser encontrada culpable, Ocaña enfrenta una pena máxima de cinco años en una prisión federal.
Según la denuncia, la cubana llegó al Aeropuerto Internacional de Tampa en un vuelo procedente de la Isla el 5 de febrero de 2024 y no declaró que tenía más de 10.000 dólares en su poder, suma límite que activaría los requisitos de presentación de informes.
Sin embargo, durante una inspección rutinaria de su equipaje, los agentes del Departamento de Seguridad Nacional recuperaron aproximadamente 30.000 dólares en efectivo, ocultos en tres paquetes envueltos.
La cubana luego admitió que volaba de Cuba a Tampa dos o tres veces al mes para contrabandear dinero en efectivo a Estados Unidos y que sabía que traer esas sumas sin informarlo es ilegal. También extraer de la Isla más de 5.000 unidades de cualquier divisa está prohibido por las leyes cubanas.
Los agentes registraron a Ocaña y descubrieron otros 70.000 dólares en efectivo escondidos en su ropa. El historial de vuelo de Ocaña reveló más tarde que había volado de Cuba a Tampa 45 veces desde mayo de 2023.
El comunicado de la Fiscalía precisó que este caso está siendo investigado por la Oficina de Investigaciones de Seguridad Nacional (HSI, por sus siglas en inglés) y la Oficina de Aduanas y Protección Fronteriza de Estados Unidos, y que la detenida será procesado por el fiscal federal adjunto Michael J. Buchanan.
El Nuevo Herald indicó que en los registros judiciales se dice que Ocaña estaba desempleada y no habla inglés. En septiembre pasado creó una empresa, Ocana & Paradise, LLC.
El juez Sean P. Flynn ordenó la liberación de la cubana y que sea sometida a un programa de vigilancia domiciliaria con un dispositivo electrónico. También le indicó buscar tratamiento psiquiátrico, empleo y entregar su pasaporte.
En sus perfiles en Tik Tok e Instagram, Ocaña anunció envíos aéreos y marítimos de alimentos y medicinas a Cuba.
Expertos consultados por El Nuevo Herald apuntaron que la detenida podría estar trasegando dinero de las MIPYMES de la Isla que pagan proveedores en el extranjero, o también sumas resultantes de la venta de propiedades que algunos residentes de Cuba buscan depositar en cuentas bancarias extranjeras, entre otras hipótesis.
La detención de Ocaña se produjo pocos días después de que Western Union suspendiera sus operaciones de envíos de remesas a Cuba desde Estados Unidos por motivos técnicos en el sistema bancario en Cuba. La situación continúa en medio de la opacidad de las instituciones financieras del régimen.
-
 @ a012dc82:6458a70d
2024-02-09 01:27:00
@ a012dc82:6458a70d
2024-02-09 01:27:00Introduction
Asymmetric cryptography and Internet security Regular computers are no match for the strength and speed of quantum computers, which can answer the most difficult equations in a fraction of the time. According to the estimations of some industry specialists, it would just take a few short minutes for them to break an encryption that would take the world's most powerful computers thousands of years to decipher. Because of this, a significant portion of the digital security infrastructure that exists today may be at risk, and this includes the encryption that underpins Bitcoin and other cryptocurrencies.
This article will provide an overview of how quantum computers vary from traditional computers, as well as the dangers they pose to digital infrastructure and cryptocurrency markets.
Asymmetric cryptography and Internet security
Asymmetric cryptography, often known as public-key cryptography, is an essential part of the ecosystem around cryptocurrencies and a significant portion of the Internet's underlying infrastructure. Encryption and decryption of information are accomplished via a key pair, which consists of a public key for encryption and a private key for decryption. In contrast, symmetric key cryptography requires just one key to both encrypt and decode data. Symmetric key cryptography is more secure.
A public key may be widely distributed and used to encrypt information, but the information can only be decrypted by the private key that corresponds to the public key. This makes it so that only the person who is supposed to see the encrypted information can see it.
A significant benefit of asymmetric cryptography is that it enables information to be sent across an untrusted channel without the requirement for the parties involved to first agree upon and then share a shared key. On the Internet, ensuring even the most fundamental level of data confidentiality would have been impossible without this essential capability. For example, it is impossible to imagine online banking without the capability to securely encrypt information that is being sent between parties who are not normally trusted.
Check out the article "Symmetric Encryption vs. Asymmetric Encryption" if you're interested in learning more about this topic.
Some of the security of asymmetric cryptography rests on the premise that the method of creating the key pair makes it exceedingly difficult to calculate the private key from the public key, while it is trivial to compute the public key from the private key. Because it is simple to compute in one direction but difficult to calculate in the other, this kind of function is referred to as a trapdoor function in mathematics.
At the moment, the vast majority of contemporary algorithms utilized to produce the key pair are based on well-established mathematical trapdoor functions. It is unknown whether these trapdoor functions can be solved in a timescale that would be realistic for any machine currently in existence. Even the most sophisticated computers would need significant time to complete these calculations.
Nevertheless, this might soon change as a result of the development of new types of computing systems known as quantum computers. First, let's look at traditional computers' operation so we may see why quantum computers are so much more powerful.
Classical computers
Classical computers are another name for the kinds of computers that are used nowadays. This indicates that computations are done in a sequential manner—a computing job is accomplished, and then another one may be begun. This is because the memory of a classical computer is constrained by the rules of physics and can only be in one of two states: either 0 or 1. (off or on).
Many different hardware and software approaches may be used to enable computers to partition complicated calculations into more manageable portions to improve their overall efficiency. Nevertheless, the fundamentals have not changed. Before moving on to the next computational endeavor, the previous one has to be finished first.
Consider the following scenario, in which a computer is tasked with attempting to guess a 4-bit key: Each of the four bits has the potential to be either a 0 or a 1, respectively. Sixteen different permutations might occur.
In order to solve a problem, a traditional computer would have to try each possible combination in turn, one after the other. Imagine that you have a keychain with a lock and 16 keys on it. It is necessary to test every one of the 16 keys on their own. If the first one doesn't work, you may try the next one, then the next one, and so on until you find the one that does. This continues until you find the key that works.
The number of feasible combinations, on the other hand, increases at an exponential rate in proportion to the key length. In the preceding example, if we added one more bit to bring the total number of bits in the key to 5, we would end up with 32 different potential combinations. Bringing it up to 6 bits would bring the total number of viable possibilities to 64. When using 256 bits, the number of potential combinations approaches the number of atoms that are thought to exist in the observable universe.
In contrast, the speed at which computers process data can only increase linearly. The number of guesses that may be made in a given amount of time is only increased by a factor of two whenever the processing speed of a computer is increased by a factor of two. On the side of guessing, exponential growth is much faster than linear growth by a large amount.
It is projected that it would take millennia for a traditional computer machine to guess a key that is 55 bits in length successfully. As a point of comparison, the recommended minimum size for a seed used in Bitcoin is 128 bits, but many wallets use 256 bits instead.
Asymmetric encryption, which is used by cryptocurrencies and is the backbone of the internet, seems to be safe from traditional computing.
Quantum computers
Quantum computers are still in the very early phases of development, but once they are perfected, it will be a piece of cake to resolve the aforementioned categories of issues with them. The theory of quantum mechanics, which looks at how subatomic particles behave, is the basis for quantum computers because it tells us how they should work.
In traditional computers, the information is represented by something called a bit, and each bit may be in one of two states: either 0 or 1. Quantum computers function on quantum bits, also known as qubits. A quantum computer's fundamental unit of information is referred to as a qubit. Just like a bit, a qubit may have a state of 0 or 1. But because of the strange way that quantum mechanics works, the state of a qubit can also be both zero and one at the same time.
Because of this, research and development in quantum computing have been given a boost, and both public and private institutions of higher learning and commercial businesses have begun spending their time and resources researching this fascinating new sector. Trying to solve the theoretical and practical engineering problems that this field brings up is at the forefront of human progress in the field of technology.
One of the unintended effects of these quantum computers would be that the algorithms that are the basis of asymmetric cryptography would become very easy to break. This would make the systems that use them much less reliable.
Take the previous example of breaking the 4-bit key as an example once again. In theory, a computer with four qubits would be able to do a single computing job involving all sixteen states (combinations) at the same time. In the amount of time it would take to carry out this calculation, the likelihood of successfully locating the proper key would be one hundred percent.
Quantum-resistant cryptography
The advent of quantum computing technology has the potential to damage encryption, which is the foundation of the vast majority of our current digital infrastructure. This includes cryptocurrencies.
This would put everyone's safety in danger, from national governments and global organizations to the average user on the internet. It would also put everyone's operations and communications at risk. It should not come as a surprise that a significant amount of scientific effort is now being invested in investigating and developing countermeasures to the technology. Quantum-resistant algorithms are a special kind of cryptographic algorithm that is designed to be safe even in the face of the danger posed by quantum computers.
It would seem that the threat posed by quantum computers may be addressed using symmetric key cryptography by just increasing the key length to a greater extent. This would be the case on a fundamental level. This branch of cryptography has been rendered obsolete by asymmetric key cryptography as a result of the problems that arise when attempting to share a shared secret key over an open channel. The development of quantum computing, on the other hand, may bring it back into play.
Quantum cryptography has the potential to solve not just the challenge of securely sharing a shared key over an open channel, but also the problem of solving that problem itself. Eavesdropping countermeasures are now being developed, which is a positive sign. It is possible to identify snoopers on a shared channel by using the same theoretical underpinnings necessary for creating quantum computers. Because of this, it would be able to determine whether a shared symmetric key had been intercepted by a third party in the past and read or modified with.
To defend against hypothetical assaults based on quantum mechanics, researchers are also looking into several other lines of inquiry. In this context, "fundamental techniques" might refer to things like hashing, which is used to generate enormous message sizes or other ways like lattice-based cryptography. The end goal of all of this research is to develop different kinds of encryption that would be challenging for quantum computers to decipher.
Quantum computers and Bitcoin mining
Cryptography is used in the mining of bitcoins as well. The miners are engaged in a race against one another to solve a cryptographic challenge in order to win the block reward. If just one miner were to get their hands on a quantum computer, that miner could be able to take control of the whole network. This would make the network less decentralized, which would make it more likely that a 51% attack would happen.
On the other hand, many specialists believe this does not pose an urgent danger. At least for the foreseeable future, application-specific integrated circuits, or ASICs, have the potential to lessen the efficacy of an attack of this kind. Also, the chance of this kind of attack is greatly reduced when many miners have access to a quantum computer at the same time.
Closing thoughts
The emergence of quantum computing and the accompanying danger to present methods of asymmetric encryption appears to be just a matter of time. But it shouldn't be a big deal because many theoretical and technological problems need to be solved before it can be fully realized.
Because there is so much at risk when it comes to information security, it makes sense to get a head start on preparing for any future threats by building the foundation now. We may count ourselves fortunate that a substantial amount of study is now being undertaken into prospective solutions that could be implemented for existing systems. In theory, these technologies would protect our important infrastructure from the future risks that quantum computers could pose.
Standards that are immune to the effects of quantum computing might be disseminated to a larger audience in the same manner that end-to-end encryption was introduced to widespread use by means of popular web browsers and messaging programs. Once these standards have been set, the cryptocurrency ecosystem will be able to easily add the strongest security possible against the known attack vectors.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
 @ 3cd2ea88:bafdaceb
2024-02-09 00:24:33
@ 3cd2ea88:bafdaceb
2024-02-09 00:24:33🔥 Iscriviti ora al nostro gruppo Telegram e seguici su Twitter per poter ottenere 100 USDT! 💰 Invita i tuoi amici per avere ancora più possibilità di vincere!
💎 Non perdere l'occasione: registrati tramite il link e deposita i tuoi token JUP o scambia oltre 100 USD per altri 100 USDT!
👉 Clicca qui per unirti e partecipare all'azione: https://gleam.io/fI5E4/bitget-italia-x-jup-e-tempo-di-festeggiare-200-da-condividere
Unisciti a noi e festeggia il successo con Bitget Italia e $JUP! 🚀💰
-
 @ 3cd2ea88:bafdaceb
2024-02-08 23:02:17
@ 3cd2ea88:bafdaceb
2024-02-08 23:02:17⭐Premi garantiti al 100% a ogni giro della ruota da 2$ fino a $ 100💰
🎳 Tasso di successo del 100%
🎯 07 al18 febbraio!
💈 Completa le attività e ottieni ricompense.
🎳 Partecipa ai premi giornalieri per il tuo trading! L'esclusiva promozione San Valentino Crypto porterà la giusta dose di romanticismo su Bitget questo mese! Completa una nuova attività ogni giorno e scopri cosa ti aspetta con l'estrazione fortunata! Sarai tu a vincere il miglior premio?
Premi:
MANTA
SOL
BGB
ZETA
ETH
BTC
USDT
🌹🚀 Goditi il San Valentino su Bitget e buona fortuna nell'estrazione! 🌹🚀
-
 @ f3df9bc0:a95119eb
2024-02-08 22:52:06
@ f3df9bc0:a95119eb
2024-02-08 22:52:06U2FsdGVkX18I0WnFxphgcaPoMlBnGtebtEVmBIZocvJ6uX4Xm9e4GY7NhXObXFag86dnQHrhE2DhZNKTqaMaHqVF7w71xc8Za+sVwRFFF1DEq7aB5jf2+Fcaj5PiKKlLBOvs92vDHZscto7oX2Fp0Oaoik6CTIRlJqO4KfM4VUQxJ3RR06ni9t8TLm9BhZnglSNEpB/LbsI+0YI21qrk5hNjDNXVmizw9pO5NDLrN0CLByvSWfgoNY8VgmtG2Pc9b5Ouo3WF9XdfuZ7C5tNgzTxRioNYkgGBuN4kkgf6hdmCpahASiXxFEOmEi4DDyA78slP431LVzQ8HERT0kCqH199aV9cfRnHTB/APIjyQbLljAax/Of+2ZjGEuPjrQKAOErIdYor2tYmGZlvudp7dJfHeluy4DlQChthWQl/G4fRUfhxRxF9WqsiukPm+oXnkNqLBev3ylN/Xe/PkyIpddobkCy4QlX68jNyl7xIrI66ow4Y27yUAuiO56EJEMywQcogGBWmWPUl0oFtvrYqdbis39V3TPfs2UlWKUSTYI+xaHYfmplAi5ljXvhtQ8+G2D1CwBCVRGcoY0YPtQOTL6BYjxzt8OiCErAoQ97CRi7plT4gykigo62evr242TbzQCq69mlnchEuCTwR35CMsDzsjz2OfrwWSIc+mORedtHgBWBarVB8Uxl4uBgOJmlgk3j28gIgRl1H+bRviF/5FIRYY6rs0LWJzbMY0huP9XEmDFZXkvGsHpgv3KiW7mle9sXIIG1cZiYr0gDf0b59iOoT1wO2TjtiVEvUymdXUf3Msg6pyuUtM0tHAAkqC1lKSpypbxBGwueg3erJzuofvny12Mzp56o0KFsYUG98lz+Od6k6tGNIrItuWFHFW6LY1mSi8KGXRciqB+a5D32mSXqjd+nir8c/WsfdJkon+iOduY/7q2Da47CCZ2BYtwcDYah+bOfCtMYihhXZPSc2D5wfpgIw6KzLSGHyfBBNs4HIUfRVpxSkyT3ovId4p43YUVpgJrZnfeZlu/ikzKhyA8s1vRQ6vZUphlRHp9mdsLcw4fNrBVamgxcCArUbKf6EOB1S1+4KJjvrt5zqfgvl1Vr5i9qLwDgyiK4aCLYY3AH8xFpGrLrtZPExm6yGIlXcP7vVH90o06ntelGZeZIa63vHSDaPs91idhCOpJ3rRT+sSxEjWnfHHQTRlnrvq5/Nu7dl8PuPrrfd734G/qNSkgHzUaDnGUX1Q8QpSgskOtqOVdf5dYgCMqC+uSqM2sp7PcnnHd8viDIgPElQRvdYwb54Qqe8S9Pmoyp7N9ibgukitpyP1ZpbiplgYCJXu3Z2BNWuXIQQ8zSWl3r+ZLwEKldQ3cQGvndaC9DL/J32Mke5HF5+iULuLpOO1H/C9loVO2TwkeWvsBKUiJ8LMPdgBbasK6br8HA0ve3paCVpavh7dikpa5eAEgqjnjxFYtJNw4rn1Ztr7GsS0af4V2T0PoklaZRjk6B/xDq1YLwAeOXWel6qPMIbbc2Pidkvm8SYYRVkyRCLjz1B8UVq2IalPc4DkqGolCcOEoPvG0Y/FJCjj1K/kigLJ9kRPOWIj5zIvFCLltKiwcWVd1sV6cLF45IjaIeu/FXqFI5LcXDKRXpD4GTfC1Yk7rq8tKxmtJ1SxQSiUS0jTcQHA9YseZbysRrbn1AlEegw72ywg7XIwXSqzUGX46LQsoPH+fcomQtzkbhJxSl+r1mHdn30FD8lZcdtE5H2KOq2O/FWoAUtp8iYGnOdEml2HXc/55Qpo3pg+NdJC1jvHUjWoGYvQ2ZBrQhcou+AJVFU0ClwgJKKPdUyBv2MOXcYkv70thp0CFgM4GG1HzYMO59/peyIwx0H6ToQcKVYo51clNNG4oUx/LsstcwDC4Lq1ZNhMhExcxMUCuyrCCOfquWDS0D9HhVQopBpJuPrU0lsVQNxKc7hrVH+JDXIJ/ZyTdRlJxPJFypzub4nuhT3f+mTk2idgbEOIZFeWjJiQnoqO00MDx+zm+hk0oGNPAMFMwiV+hexpzL9tVFHm0D8wM9kDGsVdyZacy9Gh/+kAAFvSWqfD6YRP0RX3A8xgU3kgVqFUtLDZ8gal2MMJ/Ycno216m/VdRH8Z/G4M5Ek2QsFUciiiUHC7rfC8s8GbkAxUKN1M+1/qHPZh9z/+x10o1833yc2Kh/tt2ZyafRvzS8cl78wciuoAgwRf5e/nVA/4vlHbXELUQVM8lvkfy24URRlp1VaA9CsYpxNMNVKsEmwHv2z9JEiWWmcNvmZCVeU6nDiNoFRFL10p0IUm5JSDYepVmhhoHMsVCYEHte1sTaOFmddYoYe1UjDo9BSAi9hJUksnifZspr5zi30pkqWEHEVycG0mBMbDhz+loBwx+xdxdvsVz1Giq8XUb5Bs2JMM9Q2b1kZAbbAlM6+FuNHqqtCBL8CUmC+SA==
-
 @ 0adcc7ec:826a5a21
2024-02-08 19:25:06
@ 0adcc7ec:826a5a21
2024-02-08 19:25:06
Chef's notes
Los líquidos están expresados en ml, pero la conversión es 8 oz de leche y 2 oz de aceite
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 25 min
- 🍽️ Servings: 4
Ingredients
- 250 grs harina leudante
- 1/2 cdita polvo de hornear
- 150 grs azúcar
- 1 huevo
- 235 ml lecho
- 60 ml aceite
- 1 cdita esencia de vainilla
- Ralladura de 1 limón (opcional)
- Chips de chocoloate (opcional)
Directions
- Precalentar el horno 200° (moderado / alto)
- Mezclar en un bowl los ingredientes secos
- Mezclar en otro bowl los ingredientes húmedos
- Si se opta por darle un sabor cítrico y se agrega la ralladura del limón, hacerlo con los líquidos y mezclar
- Hacer un hueco en los secos, verter los húmedos y mezclar sin batir (no importa que queden grumos)
- Rellenar 12 moldes para cupcake tamaño normal
- Si se opta por ponerle chips de chocolate, agregar en los moldes para una mejor distribución
- Hornear por 25 minutos
-
 @ cce0989b:b497e608
2024-02-08 18:27:24
@ cce0989b:b497e608
2024-02-08 18:27:24
Figuring out your core values is one of the most important exercises you will ever do.
Here’s why it matters so much: your values are like your compass in life, guiding you towards what matters most to you. This is especially important in an Old Happy world that imposes its values upon us.
When you know your values, it becomes so much easier to improve your life, to make changes in your day-to-day activities and in the long-term goals that you choose to pursue.
If you feel stuck in life… figuring out your values will help you. If you’re unhappy with your life… figuring out your values will help you. If you’re feeling lost… figuring out your values will help you.
And today, it’s time for you to figure out yours — if you have 5-10 spare minutes, try the following:
-
Copy and paste the list of values you find below in a new comment.
-
By exclusion, narrow down this selection until you keep 21 of them.
-
When done, restart by exclusion process until you keep only 12
-
Iterate one more time the list of values until you keep the 6 values that are most important to you. These are your current core values.
-
When you’re done, hit reply and let me know what your Core 6 are.
I can’t wait to hear!
Conformity Accountability Courtesy Obedience Politeness Self-Discipline Tradition Community Faith Power Authority Competition Control Fame Universalism Accessibility Acceptance Awe Consciousness Diversity Recognition Reputation Environmentalism Status Heroism Inclusion Stimulation History Humility Art Legacy Boldness Loyalty Respect for Others Challenge Confidence Courage Security Creativity Approval Balance Adaptation Determination Exploration Impact Interconnectedness Joy Justice Nature Peace Selflessness Transcendence Wonder Wisdom Belonging Learning Fairness Novelty Benevolence Harmony Vitality Affection Health Zest for life Altruism Stability Charity Wealth Self-Direction Assertiveness Compassion Forgiveness Achievement Autonomy Giving Competence Mastery Success Accomplishment Hedonism Abundance Amusement Bliss Enjoyment Pleasure Choice Freedom Focus Honesty Imagination Independence Open-mindedness Passion Self-awareness Self-respect Authenticity Gratitude Kindness Love Teamwork Thoughtfulness -
-
 @ 66675158:1b644430
2024-02-08 12:50:04
@ 66675158:1b644430
2024-02-08 12:50:04it's high time we address the elephant in the room: the pervasive attitude of big tech companies towards their user base. Yes, you—multinational conglomerates with your billions in revenue, it's time for a little heart-to-heart, delivered in terms you might find a bit more palatable than what you see people like me use online. Imagine we're discussing why you need to tidy up your room, except in this case, your "room" is the oppressive, privacy-invading policies you so dearly cling to.
Your Customers Are Not Criminals; If You Keep Assuming They Are, You Might Be the Real Criminal.
Let's start with the basics, shall we? When a child reaches out with their allowance in hand, eager to exchange it for a toy or a treat, the shopkeeper doesn't start interrogating the child about where they got their money from, if they intend to use the toy for nefarious purposes, or demand a fingerprint for the transaction. Why? Because that would be absurd, not to mention a surefire way to scare off the child and ensure they never return. Yet, this is precisely the approach many of you take with your digital storefronts, slathering them in layers of digital rights management (DRM) and invasive know your customer (KYC) policies that treat every prospective customer as a potential criminal mastermind.
Now, I understand that in the grand playground of the internet, a tiny fraction of users might indeed be up to no good. But let's put things into perspective using a playground analogy: just because one child might occasionally break the rules, it doesn't justify putting the entire playground on lockdown, does it? Wouldn't it be more mature of you to call the parents of the misbehaving kids rather than punishing every single kid? The vast majority of users are just here to exchange their hard-earned money for a service. They're not interested in your hoops, hurdles, or the digital equivalent of a full-body search. They want a service, not an interrogation.
These practices do more harm than good, breeding resentment and driving users towards alternatives that respect their freedom and privacy. In modern societies trust is one the only two or perhaps three real currencies (the others being bitcoin, and maybe monero), and once it's squandered, it's incredibly hard to earn back. By implementing DRM and invasive KYC measures, you're not protecting your assets; you're alienating your customer base and eroding the trust that forms the foundation of any successful business relationship.
So, here's a novel idea: treat your customers with respect. Recognize that they come to you in good faith, seeking to engage in a straightforward transaction. Drop the condescension, the unwarranted suspicion, and the draconian policies that presume guilt until proven innocent. It's not a revolutionary concept; it's merely treating others as you would wish to be treated.
In the spirit of championing a digital landscape where freedom, privacy, and mutual respect are the cornerstones, I declare my readiness to not only abandon any service that insists on chaining its offerings with DRM but also to wholeheartedly embrace—and yes, even pay a premium for—platforms that treat me like a human being, not a suspect. Imagine, if you will, a child clutching their precious dollar, ready to exchange it for a coveted treasure. This child, much like any discerning customer, is infinitely more inclined to hand over their money to a cashier who greets them with a smile, acknowledges their presence, and appreciates their business, rather than to a surly individual who views them with suspicion and disdain.
It's a simple yet profound truth: we vote with our wallets, and my vote goes to businesses that understand the inherent value of treating their customers with dignity, as valued partners in our increasingly crazy world.
This commitment isn't just about choosing where to spend my money; it's a pledge to support those who recognize that in the grand scheme of things, respect and human connection are worth far more than any DRM-protected content could ever be. The key to success and customer loyalty isn't more restrictions; it's genuine respect and the acknowledgment of our shared humanity.
To the big tech companies: it's time to clean up your act. Consider this a gentle nudge (or a forceful push, if necessary) towards adopting policies that honor the principles of privacy, freedom, and basic human decency. Remember, your customers are not criminals, but if you continue to treat them as such, you might just find yourself on the wrong side of history.
You still have time to change, big tech, are you going to take the correct path, or become a forgotten footnote in humanity's history books? The choice is entirely yours
-
 @ 6a39a186:88f51c19
2024-02-08 07:31:53
@ 6a39a186:88f51c19
2024-02-08 07:31:53Exploring the Tor Network: A Gateway to Privacy and Security
 In this note, we delve into the fascinating world of the Tor network, a powerful tool that enhances privacy and security on the internet. We uncover how individuals and organizations utilize the Tor network to safeguard their online activities and protect sensitive information from prying eyes.
In this note, we delve into the fascinating world of the Tor network, a powerful tool that enhances privacy and security on the internet. We uncover how individuals and organizations utilize the Tor network to safeguard their online activities and protect sensitive information from prying eyes.Understanding Tor: Anonymity at Its Core
The Tor network, comprised of volunteer-operated servers, allows users to connect for free, enhancing privacy and security online. With the utilization of ".onion hidden services," individuals and organizations can share information without compromising their anonymity.
"Tor is not just a network; it's a shield against surveillance, censorship, and data interception, empowering users to reclaim their online privacy."
How Tor Works: Navigating the Network
Tor operates by routing internet traffic through a series of volunteer-operated servers, obscuring the origin and destination of the data. This intricate network architecture ensures that no single server can trace the complete path of the traffic, preserving user anonymity.
To connect to the Tor network, users can employ various methods, including the Tor Browser, Orbot for smartphones, and Onion Browser for iOS devices. Each of these tools provides a secure gateway to the Tor network, offering different levels of anonymity and protection.
Enhancing Security: Tips and Best Practices
To maximize security and anonymity while using the Tor network, it's essential to follow best practices and utilize recommended tools. For instance, users should avoid installing additional extensions or modifying browser settings, as these actions can compromise anonymity.
"Protecting your privacy on the Tor network requires diligence and adherence to recommended security measures. By staying informed and vigilant, users can navigate the digital landscape with confidence."
In addition to browsing securely, individuals can contribute to the Tor network's resilience by operating a Snowflake proxy. This innovative feature allows users to donate bandwidth to the Tor Project, aiding individuals in censored networks to access the internet freely.
Learn more about the Tor network and its capabilities and take steps to protect your online privacy.
Tor: The Ultimate Privacy Tool for Everyday Browsing
Transformative potential of Tor as a daily driver for web browsing. Tor enhances privacy and security online, providing users with a shield against surveillance and data interception.
Understanding Tor: A Gateway to Anonymity
Tor, short for The Onion Router, is a powerful network of volunteer-operated servers that enables users to browse the internet anonymously. By routing internet traffic through multiple servers, Tor obscures the user's identity and location, making it difficult for third parties to track their online activities.
"Tor is not just a privacy tool; it's a game-changer for those seeking to reclaim control over their online data and digital footprint."
Embracing Anonymity: Benefits of Tor for Daily Browsing
Using Tor as a daily driver for web browsing offers numerous advantages. With Tor, users can browse the internet without fear of surveillance or data collection by ISPs, governments, or malicious actors. Additionally, Tor's censorship circumvention capabilities ensure access to unrestricted information, even in regions with strict internet controls.
To experience the benefits of Tor firsthand, users can download the Tor Browser on their desktop or mobile device. This specialized browser comes equipped with built-in privacy features and default settings optimized for secure and anonymous browsing.
Navigating the Tor Ecosystem: Tips for Safe and Secure Browsing
While Tor provides robust privacy protections, users must take steps to ensure safe and secure browsing practices. Avoid installing additional browser extensions or modifying default settings, as these actions can compromise anonymity and security.
"Protecting your privacy on the Tor network requires diligence and adherence to recommended security measures. By staying informed and vigilant, users can harness the full potential of Tor for everyday browsing."
In addition to the Tor Browser, users can contribute to the Tor network's resilience by running a Snowflake proxy. This innovative feature allows users to donate bandwidth to support individuals in censored regions, further strengthening Tor's impact worldwide.
-
 @ 6a39a186:88f51c19
2024-02-08 06:59:58
@ 6a39a186:88f51c19
2024-02-08 06:59:58Digital Computing: From Origins to Modern Innovations
 In this note, we embark on a journey through the captivating history of digital computing, tracing its evolution from its humble beginnings to the cutting-edge technologies of today. We consider into the pivotal moments, key innovations, and notable figures that have shaped the landscape of digital computation.
In this note, we embark on a journey through the captivating history of digital computing, tracing its evolution from its humble beginnings to the cutting-edge technologies of today. We consider into the pivotal moments, key innovations, and notable figures that have shaped the landscape of digital computation.Understanding Early Developments
The roots of digital computing, from the abacus and mechanical calculators to the invention of the first programmable devices such as the Analytical Engine by Charles Babbage.
"The dawn of digital computing marked a significant shift in human history, paving the way for unprecedented advancements in science, technology, and society."
Emergence of Electronic Computers
The emergence of electronic computers in the mid-20th century, including landmark developments like the ENIAC and UNIVAC, which laid the groundwork for modern computing.
"The advent of electronic computers revolutionized the field of computation, enabling faster calculations, complex simulations, and unprecedented data processing capabilities."
Rise of Personal Computing
Next, The rise of personal computing in the late 20th century, with the introduction of iconic devices such as the IBM PC, Apple Macintosh, and the evolution of operating systems like MS-DOS and Windows.
"The democratization of computing power through personal computers ushered in a new era of accessibility, empowering individuals and businesses to harness the potential of digital technology."
The Digital Age and Beyond
The transformative impact of digital computing in the modern age, from the proliferation of smartphones and tablets to the rise of cloud computing, big data analytics, and artificial intelligence.
"As we stand on the cusp of the digital frontier, the possibilities of digital computing are limitless, driving innovation, connectivity, and progress in every aspect of our lives."
Through this exploration of the history of digital computing, we gain a deeper appreciation for the remarkable journey that has brought us to where we are today, poised at the forefront of a digital revolution.
Learn more about the history of digital computing and discover its impact on society.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ babaf02c:049eee5d
2024-02-08 06:19:29
@ babaf02c:049eee5d
2024-02-08 06:19:29Introducing Amazon Cleaning, the trusted name in Smyrna cleaning service. We are committed to making your space shine, so you can sit back and relax. With our team of expert cleaners, you can trust that every nook and cranny will be thoroughly cleaned and sanitized to perfection. From residential homes to commercial spaces, we offer a wide range of cleaning services tailored to your specific needs. Whether it's a weekly, bi-weekly, or one-time cleaning, we've got you covered. Our attention to detail, professionalism, and use of eco-friendly products sets us apart from the rest. Experience the convenience and happiness of a spotless space with Amazon Cleaning today!
-
 @ af9c48b7:a3f7aaf4
2024-01-10 20:07:25
@ af9c48b7:a3f7aaf4
2024-01-10 20:07:25Chef's notes
This recipe has been passed around our family from different generations. It can be modified to your liking.
Details
- ⏲️ Prep time: 15
- 🍳 Cook time: 30 minutes active cook time followed by 4-6 hours crockpot simmering
- 🍽️ Servings: 10-12
Ingredients
- 1lb ground beef
- 2 packages of dry taco seasoning
- 2 (15.5 ounce) cans of Pinto Beans
- 2 (10 ounce) cans of Diced Tomatoes with Green Chiles
- 2 (15 ounce) cans of Yellow Corn
- 1 package of dry ranch dressing seasoning
- Bag of Shredded Cheese (we use mexican mix, but whatever you prefer)
- Sour Cream
- Large Bag of Corn Chips or Tortillia Chips
Directions
- Brown ground beef in skillet and drain off excess liquid, then add 1 package of taco seasoning mix into ground beef following the instructions on the package.
- In a crockpot (preferred) or large pot, add the 2 cans of pinto beans, 2 cans of diced tomatoes with greeen chilies, 2 cans of yellow corn, 1 package of dry taco seasoning, and 1 package of dry ranch dressing seasoning stirring gently mixing all ingredients thoroughly.
- Add in the browned, seasoned, ground beef prepared in step 1. Then add two or three can (30 to 45 ounces) of water and stir gently.
- Allow to cook on high in the crockpot for 4 to 6 hours.
- Serve over corn chips/tortilla chip and garnish with shredded cheese and sour cream.
- Garnish with jalepenos, avacado, lime, or whatever you like.
-
 @ 6a39a186:88f51c19
2024-02-08 05:30:49
@ 6a39a186:88f51c19
2024-02-08 05:30:49Node Types: Exploring the Different Types of Nodes in the Bitcoin Network

The Bitcoin network, often hailed as the pioneer of blockchain technology, operates through a decentralized network of nodes. These nodes play various roles in maintaining the integrity and functionality of the network. Let's delve into the different types of nodes in the Bitcoin network and their significance.
Full Nodes
Full nodes are the backbone of the Bitcoin network. They maintain a complete copy of the blockchain and validate all transactions and blocks according to the consensus rules. Full nodes ensure the security and decentralization of the network by independently verifying the entire transaction history. Running a full node helps in strengthening the Bitcoin network and ensuring its resilience against attacks.
"Full nodes are the cornerstone of decentralization in the Bitcoin network, providing users with trustless access to the blockchain."
Learn more about running a full node
Mining Nodes
Mining nodes, also known as miners, play a critical role in securing the Bitcoin network by adding new blocks to the blockchain through the process of mining. Miners compete to solve complex mathematical puzzles, and the first one to find a valid solution gets to add a new block to the blockchain and receive a reward in the form of newly minted bitcoins and transaction fees. Mining nodes contribute to the network's security and enable the creation of new bitcoins.
"Mining nodes are essential for maintaining the security and integrity of the Bitcoin blockchain by validating and adding new transactions to the network."
Learn more about Bitcoin mining
Lightweight Nodes (SPV Nodes)
Lightweight nodes, also known as Simplified Payment Verification (SPV) nodes, do not store the entire blockchain like full nodes. Instead, they only store block headers and verify transactions directly relevant to them. SPV nodes rely on full nodes to provide them with accurate information about the state of the network. While lightweight nodes offer reduced resource requirements and faster synchronization, they sacrifice some level of security and trustlessness compared to full nodes.
"Lightweight nodes offer a convenient way to interact with the Bitcoin network without the need to download and validate the entire blockchain, making them suitable for resource-constrained devices."
Pruned Nodes
Pruned nodes store only a subset of the blockchain's data by discarding older transaction information beyond a certain threshold. Pruned nodes maintain the integrity of the blockchain while significantly reducing storage requirements. Although pruned nodes cannot serve historical data to other network participants, they still contribute to the network by validating new transactions and blocks.
"Pruned nodes strike a balance between maintaining network security and reducing storage overhead, making them suitable for users with limited storage capacity."
In conclusion, the Bitcoin network consists of various types of nodes, each serving a unique purpose in ensuring the network's integrity, security, and decentralization. Whether you're a full node operator, miner, or lightweight node user, your participation contributes to the strength and resilience of the Bitcoin ecosystem.
-
 @ 6a39a186:88f51c19
2024-02-08 05:14:35
@ 6a39a186:88f51c19
2024-02-08 05:14:35The Evolution of Lightning Network Implementations: An Overview
 In the dynamic landscape of Bitcoin lightning technology, the Lightning Network has emerged as a game-changer, providing a scalable solution for Bitcoin transactions. As the demand for efficient and cost-effective payment solutions grows, so does the need for robust Lightning implementations. Let's delve into the evolution of these implementations and explore their significance in the rapidly evolving ecosystem.
In the dynamic landscape of Bitcoin lightning technology, the Lightning Network has emerged as a game-changer, providing a scalable solution for Bitcoin transactions. As the demand for efficient and cost-effective payment solutions grows, so does the need for robust Lightning implementations. Let's delve into the evolution of these implementations and explore their significance in the rapidly evolving ecosystem.Understanding the Lightning Network
The Lightning Network serves as an overlay network atop the Bitcoin blockchain, offering trustless instant payments with minimal fees. It operates through two key layers: the Bitcoin Network and the Lightning Network. The former serves as the foundation, while the latter facilitates peer-to-peer transactions.
In essence, developing a Lightning-powered application requires interfacing with two main components: the Bitcoin node and the Lightning node. The former interacts with the underlying blockchain, while the latter manages transactions on the Lightning Network.
Exploring Lightning Implementations
c-lightning by Blockstream
c-lightning, developed by Blockstream, stands as a pioneering Lightning implementation written in C. Known for its modular architecture and extensibility, c-lightning has been in production since 2018, offering low-level access for customization.
Eclair by ACINQ
Eclair is a Scala implementation of the Lightning Network, developed by ACINQ. Launched in 2018, Eclair emphasizes robustness and scalability, providing both a library and a mobile implementation of Lightning.
lnd by Lightning Labs
lnd, developed by Lightning Labs in Go, serves as a developer-friendly Lightning node. With an extensive feature set and a focus on application development, lnd has been a staple choice since its mainnet release in 2018.
Rust-Lightning and LDK
Rust-Lightning, developed by the Rust Bitcoin Community, offers a flexible Lightning library in Rust. Collaborating with Square Crypto, the community aims to simplify Lightning integrations through the Lightning Development Kit (LDK).
Electrum
Electrum, a renowned Bitcoin client, ventured into Lightning development in 2020. Integrating Lightning support into its Python implementation, Electrum extends its privacy-focused approach to Lightning transactions.
LNP Node
LNP Node, introduced by LNP/BP Standards Association, represents a new Rust-based Lightning implementation. With a focus on modularity and extensibility, LNP Node introduces Generalized Lightning Channels (GLCs) for future protocol enhancements.
The Path Forward
The Lightning Network implementation ecosystem continues to expand, catering to diverse user needs and use cases. As institutional adoption gains momentum, Lightning implementations play a pivotal role in driving growth and innovation within the blockchain space.
In conclusion, while this overview provides insights into the current state of Lightning implementations, the ecosystem remains dynamic. With ongoing developments and new entrants, the future promises further evolution and refinement of Lightning technology.
Remember, in the fast-paced world of blockchain, staying informed and adaptable is key to navigating the ever-changing landscape.
"The only constant in life is change." - Heraclitus
If you have any updates or insights to share, feel free to reach out and contribute to the ongoing dialogue surrounding Lightning Network implementations. Together, we can understand the future of Bitcoin technology.
-
 @ a023a5e8:ff29191d
2024-02-08 05:06:54
@ a023a5e8:ff29191d
2024-02-08 05:06:54 -
 @ 44dc1c2d:31c74f0b
2024-01-07 21:19:28
@ 44dc1c2d:31c74f0b
2024-01-07 21:19:28Chef's notes
This bread is super simple to make and takes a bit to dial in.
The only real notes I have here is you can use whatever round pan you want to bake it in. Or use a square one, just make sure the walls of the pan are high.
Less is more with this bread. You really don't want to over knead the bread here. If you're used to making bread that need a lot of kneading, this will feel odd.
Details
- ⏲️ Prep time: 27 hours
- 🍳 Cook time: 50 to 60 min
- 🍽️ Servings: 1 loaf
Ingredients
- 1-1/2 teaspoons active dry yeast
- 1-3/4 cups warm water (110° to 115°)
- 3-1/2 cups plus 1 tablespoon all-purpose flour, divided
- 2 teaspoons salt
- 1 tablespoon cornmeal or additional flour
Directions
- In a large bowl, dissolve yeast in warm water. Using a rubber spatula, stir in 3-1/2 cups flour and salt to form a soft, sticky dough. Do not knead. Cover and let rise at room temperature 1 hour.
- Stir down dough (dough will be sticky). Turn onto a floured surface; with floured hands pat into a 9-in. square. Fold square into thirds, forming a 9x3-in. rectangle. Fold rectangle into thirds, forming a 3-in. square. Place in a large greased bowl, turning once to grease the top. Cover and let rise at room temperature until almost doubled, about 1 hour.
- Punch down dough and repeat folding process. Return dough to bowl; refrigerate, covered, overnight.
- Grease the bottom of a roasting pan with sides at least 4 in. high; dust pan with cornmeal. Turn dough onto a floured surface. Knead gently 6-8 times; shape into a 6-in. round loaf. Place into prepared pan; dust top with remaining 1 tablespoon flour. Cover pan and let rise at room temperature until dough expands to a 7-1/2-in. loaf, about 1-1/4 hours.
- Preheat oven to 500°. Using a sharp knife, make a slash (1/4 in. deep) across top of loaf. Cover pan tightly with foil. Bake on lowest oven rack 25 minutes.
- Reduce oven setting to 450°. Remove foil; bake bread until deep golden brown, 25-30 minutes. Remove loaf to a wire rack to cool.
-
 @ a012dc82:6458a70d
2024-02-08 02:14:20
@ a012dc82:6458a70d
2024-02-08 02:14:20Introduction
In the 1990s, Nick Szabo was the first person to explain smart contracts. At the time, he characterized a smart contract as a tool that formalizes and protects computer networks by integrating protocols with user interfaces. Specifically, he said that this combination makes smart contracts both formal and safe.
Szabo spoke about the possible applications of smart contracts in various domains that use contractual agreements, including credit systems, payment processing, and intellectual rights management.
In the realm of virtual currencies, an application or computer program that operates on a distributed ledger known as a blockchain might be referred to as a smart contract. In most cases, they function as a digital agreement that is monitored and upheld by a predetermined set of guidelines. These guidelines are predetermined by computer code, which is then copied and run on each and every node in the network.
The use of smart contracts in blockchain technology makes the establishment of trustless protocols. Because of this, it is possible for two parties to establish promises using blockchain technology without needing to know or trust the other party. They are able to be certain that the deal will not be carried out in the event that the stipulations are not satisfied. Aside from that, the use of smart contracts may do away with the need for the employment of middlemen, which would result in a large reduction in operating expenses.
Buterin, the architect of Ethereum and one of its co-founders, is credited with popularizing smart contracts despite the fact that the Bitcoin protocol has supported them for a significant number of years. However, it is important to keep in mind that the manner in which smart contracts are put into action may be presented differently by each blockchain.
The Ethereum Virtual Machine (EVM), an integral component of the Ethereum blockchain, will be the primary topic of discussion in this article. Specifically, the smart contracts that are executed on the EVM.
How do they work?
A deterministic program best describes the operation of a smart contract in its most basic form. It carries out a certain job if and only if a specified set of criteria are satisfied. As a result, the words "if... then..." are often used in a smart contract system. But despite the common nomenclature, legal contracts are not smart contracts, and smart contracts are not legal contracts. They are more than a line of code executed across several computers (blockchain).
When users (addresses) communicate with one another on the Ethereum network, blockchain activities are carried out and managed by smart contracts. These contracts are responsible for the execution and management of these operations. An externally held account is the term used to describe any address that is not a smart contract (EOA). So, the rules for electronic operating agreements (EOAs) are set by the people who use them, while the rules for smart contracts are set by computer code.
In their most basic form, Ethereum smart contracts can be broken down into three components: a contract code, two public keys, and the contract itself. The person who first creates the contract will be the one to provide the first public key. The other key acts as a digital identity that is exclusive to each individual smart contract, and it serves as a representation of the contract itself.
A transaction accomplishes any smart contract deployment on a blockchain, and the contracts themselves can only be activated when an EOA makes the request (or by other smart contracts). Nevertheless, an EOA is always the source of the first trigger (user).
Key features
Typically, a smart contract written in Ethereum will have the following characteristics:
-
Distributed. On the Ethereum network, smart contracts are copied and dispersed among all of the nodes. Compared with alternative systems built on centralized servers, this is one of the most significant distinctions.
-
Deterministic. If all conditions are satisfied, smart contracts will only carry out the operations they were initially designed. Additionally, the consequences will always be the same regardless of who carries them out; this is a constant.
-
Autonomous. Because they function similarly to self-running programs, smart contracts may be used to automate a wide variety of functions. Most of the time, though, if a smart contract isn't activated, it will stay "dormant" and won't do any of the things that were planned for it.
-
Immutable. After they have been deployed, smart contracts cannot be modified in any way. They can only be "removed" if a certain function has already been put into place before that point. Because of this, we could say that smart contracts can provide code that can't be changed.
-
Customizable. It is possible to write smart contracts in a variety of different ways before they are deployed. Therefore, they may be used to develop a wide variety of applications that do not rely on a central server (DApps). This is because Ethereum is a Turing-complete blockchain relevant to the previous point.
-
Trustless. Through the use of smart contracts, two or more parties may engage with one another even if they do not know or trust one another. In addition, the use of blockchain technology guarantees the veracity of the data.
-
Transparent. The source code of smart contracts is not only unchangeable but can also be seen by any member of the public since they are built on public blockchains.
Can I change or delete a smart contract?
After a smart contract built on Ethereum has been deployed, adding new functionality to the contract is not feasible. However, if the smart contract developer incorporates a function known as SELFDESTRUCT into the code, they will be able to "destroy" the smart contract later and create a new one in its place. On the other hand, they won't be able to get rid of the function even if they try if it wasn't in the source code from the start.
Particularly noteworthy is the fact that so-called upgradeable smart contracts provide developers with a greater degree of leeway in terms of the immutability of contracts. There are a wide variety of approaches to developing upgradable smart contracts, each with their own level of complexity.
To illustrate this point using a simplified scenario, let's pretend that a single smart contract is broken up into many different smaller contracts. While some have the ability to be deleted, those that are meant to be immutable cannot be changed in any way. This means that a part of the code called "smart contracts" can be taken out or changed without affecting how other features work.
Advantages and use cases
Smart contracts, made up of programmable code, are very adaptable and can be constructed in various ways, allowing them to provide a wide range of services and solutions.
Smart contracts, which are computer programs that can run themselves and are decentralized, could boost operational transparency while also lowering expenses. Depending on how they are used, they could make things more efficient and cut down on bureaucracy costs.
When several parties are involved in a transaction involving the transfer or exchange of cash, smart contracts are especially beneficial because of their efficiency.
To put it another way, smart contracts may be tailored to meet the requirements of various use cases. Tokenized assets, voting systems, cryptocurrency wallets, decentralized exchanges, games, and mobile application development are a few examples of what may be created with blockchain technology. They can also be used with other blockchain technologies to solve problems in areas like healthcare, charitable giving, supply chain management, government, and decentralized financial systems (DeFi).
ERC-20
The ERC-20 standard is adhered to by tokens that are distributed via the Ethereum network. The standard outlines the fundamental capabilities that each Ethereum-based coin must have. Because of this, the digital assets in question are often called ERC-20 tokens, making up a large portion of the current cryptocurrencies in use.
On the Ethereum network, several blockchain organizations and startups use smart contracts in order to create their own digital tokens. Following the completion of the issue, the vast majority of these businesses distributed their ERC-20 tokens by participating in initial coin offering (ICO) activities. The vast majority of the time, the use of smart contracts makes it possible to conduct trustless financial transactions and token distributions in an effective manner.
Limitations
Humans are responsible for writing the computer code that makes up smart contracts. This exposes the code to multiple vulnerabilities and increases the likelihood of introducing flaws. In an ideal world, they would be created and implemented by experienced programmers; this is especially important when dealing with sensitive data or large sums of money.
Aside from that, many believe that centralized systems can deliver the majority of the answers and functionality provided by smart contracts. The primary distinction is that smart contracts' execution occurs not on a single server but throughout a decentralized peer-to-peer network. The fact that they are built on a distributed ledger also means that they are often either unchangeable or very difficult to alter.
Being unchanging may be a strength in some circumstances, but it can also be a severe weakness in others. For example, when a Decentralized Autonomous Organization (DAO) dubbed "The DAO" was hacked in 2016, millions of ether (ETH) were stolen owing to weaknesses in its smart contract design.
The developers were unable to make any changes to the code since their smart contract was immutable. This ultimately resulted in a hard fork, which resulted in the creation of a second Ethereum chain. To put it another way, one chain "reverted" the hack and gave the money back to the people who were entitled to it (this is part of the current Ethereum blockchain). The other chain came to the conclusion that it should not intervene with the hack since events that occur on a blockchain should never be subject to modification. The previous name for this chain is now Ethereum Classic.
It is essential to emphasize the fact that the issue did not originate with the Ethereum network. Instead, the issue was brought about by a flawed implementation of a smart contract.
One of the disadvantages of using smart contracts is that their legal standing is not entirely clear. Not only does it fall into a gray area of the law in most countries, but the way the law is set up now doesn't make it easy to use smart contracts.
For instance, many contracts provide that both parties must be able to provide valid identification and must be at least 18 years old. In conjunction with the pseudonymity offered by blockchain technology, the absence of middlemen may pose a danger to those standards. Even though there might be a way to solve this problem, the legal enforceability of smart contracts is still a big problem, especially in networks that don't have borders and are spread out.
Criticism
A number of proponents of blockchain technology consider smart contracts to be a solution that has the potential to quickly replace and automate a significant portion of our commercial and governmental institutions. While this is a possibility, it is unlikely that it will ever become the standard.
The use of smart contracts undoubtedly makes for an intriguing use of technology. However, because of their distributed, predictable, transparent, and to some extent immutable characteristics, smart contracts may not be as appealing in other contexts. The fundamental argument against smart contracts is that they are insufficient to address the majority of the current world's challenges.In fact, traditional server-based options may be more advantageous for some types of enterprises compared to smart contracts. Centralized servers are simpler and less expensive to operate. Additionally, they tend to show greater efficiency in terms of speed and communication across different networks (interoperability).
Closing thoughts
There is no question that smart contracts had a significant influence on the world of cryptocurrencies, and there is also no question that they completely transformed the blockchain industry. Even though end users may not interact directly with smart contracts, they are expected to power a wide range of applications in the near future, from financial services to control of supply chains.
The combination of blockchain technology and smart contracts has the potential to cause significant upheaval across practically all facets of our civilization. But only time will tell if these new technologies will be able to get around the problems that are stopping them from being used by many people.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 0f22c06e:6194f8b6
2024-02-08 01:26:43
@ 0f22c06e:6194f8b6
2024-02-08 01:26:43On social media and in the Nostr space in particular, there’s been a lot of debate about the idea of supporting deletion and editing of notes.
Some people think they’re vital features to have, others believe that more honest and healthy social media will come from getting rid of these features. The discussion about these features quickly turns to the feasibility of completely deleting something on a decentralized protocol. We quickly get to the “We can’t really delete anything from the internet, or a decentralized network.” argument. This crowds out how Delete and Edit can mimic elements of offline interactions, how they can be used as social signals.
When it comes to issues of deletion and editing content, what matters more is if the creator can communicate their intentions around their content. Sure, on the internet, with decentralized protocols, there’s no way to be sure something’s deleted. It’s not like taking a piece of paper and burning it. Computers make copies of things all the time, computers don’t like deleting things. In particular, distributed systems tend to use a Kafka architecture with immutable logs, it’s just easier to keep everything around, as deleting and reindexing is hard. Even if the software could be made to delete something, there’s always screenshots, or even pictures of screens. We can’t provably make something disappear.
What we need to do in our software is clearly express intention. A delete is actually a kind of retraction. “I no longer want to associate myself with this content, please stop showing it to people as part of what I’ve published, stop highlighting it, stop sharing it.” Even if a relay or other server keeps a copy, and keeps sharing it, being able to clearly state “hello world, this thing I said, was a mistake, please get rid of it.” Just giving users the chance to say “I deleted this” is a way of showing intention. It’s also a way of signaling that feedback has been heard. Perhaps the post was factually incorrect or perhaps it was mean and the person wants to remove what they said. In an IRL conversation, for either of these scenarios there is some dialogue where the creator of the content is learning something and taking action based on what they’ve learned.
Without delete or edit, there is no option to signal to the rest of the community that you have learned something because of how the content is structured today. On most platforms a reply or response stating one’s learning will be lost often in a deluge of replies on the original post and subsequent posts are often not seen especially when the original goes viral. By providing tools like delete and edit we give people a chance to signal that they have heard the feedback and taken action.
The Nostr Protocol supports delete and expiring notes. It was one of the reasons we switched from secure scuttlebutt to build on Nostr. Our nos.social app offers delete and while we know that not all relays will honor this, we believe it’s important to provide social signaling tools as a means of making the internet more humane.
We believe that the power to learn from each other is more important than the need to police through moral outrage which is how the current platforms and even some Nostr clients work today.
It’s important that we don’t say Nostr doesn’t support delete. Not all apps need to support requesting a delete, some might want to call it a retraction. It is important that users know there is no way to enforce a delete and not all relays may honor their request.
Edit is similar, although not as widely supported as delete. It’s a creator making a clear statement that they’ve created a new version of their content. Maybe it’s a spelling error, or a new version of the content, or maybe they’re changing it altogether. Freedom online means freedom to retract a statement, freedom to update a statement, freedom to edit your own content. By building on these freedoms, we’ll make Nostr a space where people feel empowered and in control of their own media.
-
 @ af9c48b7:a3f7aaf4
2024-01-05 13:58:55
@ af9c48b7:a3f7aaf4
2024-01-05 13:58:55Chef's notes
This recipe was published by a local chef who prepares it on a weekly basis at a small boutique restaurant located above a bookstore.
Details
- ⏲️ Prep time: 15 minutes
- 🍳 Cook time: 30 minutes
- 🍽️ Servings: 8-10
Ingredients
- 3 tablespoons olive oil
- 2 medium onions, chopped
- 1 tablespoon minced garlic
- 3/4 pound smoked, baked or country ham cubed
- 2 (14.5-ounce) cans of turnip greens, undrained (recommend Glory Brand turnip greens if available)
- 2 (15.5- ounce) cans great northern beans
- 2 red potatoes, diced
- 4 (14.5-ounce) cans chicken broth
- Salt and ground pepper to taste
- Cajun seasoning to taste
- 2 tablespoons of granulated sugar
Directions
- In a soup pot, sweat olive oil, onions, garlic, and ham on low heat.
- Add turnip greens, beans, potatoes, chicken broth, and bring to a boil on high heat.
- Once boiling, turn down to medium heat. Add salt, pepper, cajun seasoning, and sugar.
- Simmer for appoximately 30 minutes.
- This recipe makes a large quantity and can be cut in half. Serve with cornbread.
-
 @ 44dc1c2d:31c74f0b
2024-01-04 05:18:29
@ 44dc1c2d:31c74f0b
2024-01-04 05:18:29Chef's notes
This is a base recipe. You can and should modify it to your tastes.
For a honey mustard, add a couple tablespoons of honey.
You can affect the taste by changing the vinegar around, like a white or sherry vinegar. You can use beer instead of vinegar. Also chop up some fresh herbs like tarragon and chuck it in. You can also play with the water and vinegar ratio for less of a bite (or more).
If you want a more yellow mustard, chuck in some turmeric and sugar.
Play with the heat of the mustard by changing the seeds and the heat of the liquid you start with. Black mustard being the hottest. Starting with a cold liquid will make for a hotter mustard instead of a warm liquid. (IE white mustard seeds in a warm liquid will make for a mellow mustard vs black seeds in a cold liquid)
Details
- ⏲️ Prep time: 10ish min.
- 🍳 Cook time: 48 hours
- 🍽️ Servings: About a 3/4 full 8oz jar
Ingredients
- 2 tablespoons of brown or black whole mustard seeds
- 1/4 cup ground mustard powder
- 3/4 teaspoon salt
- 1/4 cup water
- 4 teaspoons apple cider vinegar
Directions
- Grind seeds in a spice grinder or in a mortar and pestle tell the seeds are at the desired consistency.
- Mix the dry stuff together. (seeds, salt and powder)
- Mix the wets in.
- Cover and let sit for 2 days. (I use a jar) Wait time is important here. It will look soupy at first and thicken up as the seeds absorb the liquid. The time also allows the mustard to mellow. Fresh made mustard is harsh and bitter tasting so give it time.
-
 @ 66675158:1b644430
2024-02-07 21:12:18
@ 66675158:1b644430
2024-02-07 21:12:18Once upon a time, there was a small town known far and wide for its delectable bagels – Bageltown. In this quaint place, bagels were not just a food, but a way of life. The townsfolk of Bageltown took great pride in their bagels, which were known to be the tastiest and most exquisite in all the lands.
At the heart of Bageltown's bagel business was a grand establishment known as "The Bagel Connoisseur's Emporium," run by a sharp and shrewd merchant. This merchant had a peculiar way of doing business. He had convinced the town's elders that only he should sell bagels in Bageltown, and all bagels must pass through his Emporium for a 'quality check'. For this service, he took a hefty cut of 30% from every bagel sold.
Now, the Bagel Connoisseur was not just any merchant. His eyes could spot a sesame seed out of place from a mile away, and his nose could sniff out the faintest hint of an unapproved ingredient. Bagels that didn't meet his exacting standards were banished from Bageltown. And oh, the standards were many and ever-changing, often based on the Connoisseur’s whims.
But the winds of change began to blow in Bageltown. The townsfolk started to murmur.
"Why can't we have bagels from outside Bageltown?", they asked. "What if we want a different kind of bagel, one that the Connoisseur doesn't approve of?"Hearing this, the ruler of the land, President Goodbread, made a proclamation:
"The people of Bageltown should be free to choose their bagels. The Connoisseur can no longer force his checks on every bagel."The Bagel Connoisseur, upon hearing this, furrowed his brow in frustration but then smirked slyly.
"Fine,"he said,
"let the people bring in whatever bagels they wish. But for every foreign bagel sold in Bageltown, I shall take a 27% tribute for maintaining the order and safety of our bagel market."The townsfolk were in uproar.
"This is absurd!"they cried.
"First, he monopolizes our bagels, and now he taxes them even when he has no hand in their making!"The Connoisseur's rule was bizarre. If a baker in Bageltown wished to sell a bagel with a new twist — say, a sprinkle of magical fairy dust or a dash of unicorn horn powder — they had to tread carefully. For the Connoisseur might declare these ingredients 'unapproved,' forcing the townsfolk to travel to distant lands to savor such exotic bagels.
Under the Connoisseur's watchful eye, Bageltown became a place where freedom of choice in bagelry was but a dream. The streets, once filled with the delightful aromas of diverse and innovative bagels, now bore the scent of conformity.
"Is this truly for the safety and quality of our beloved bagels?"pondered an old wise baker.
"Or is it merely a ploy to fill the coffers of the Connoisseur, under the guise of protection and order?"As we leave Bageltown, with its streets lined with identical bagel shops and its air heavy with the scent of the same old bagels, one can't help but wonder: Does this remind you of anything else, perhaps something outside of Bageltown and in our world?
On a side note, I had some great apple pie yesterday!
You know, maybe in our world it's not about bagels but appliances to bake apple pies and other delicious pies?
Or maybe it's not at all about pies...
Who knows... ;)
PS: Story will be published on EscapeBigTech in one week; from now on all articles will be published on Yakihonne & Nostr before the main website #decentralization
-
 @ b0d05d2e:c7e7408d
2024-01-03 03:20:11
@ b0d05d2e:c7e7408d
2024-01-03 03:20:11Chef's notes
This recipe was derived from the following, https://w3.do/Z5TLZZTR
The main differences: we use sugar + honey, specifically unsalted butter & we don’ t make the yeast mixture the same way she does, so the steps about getting the dry yeast and water going could vary, (if you have your method that works with the mixer or system you have then it should still all work out in the end).
This roll can be used as a side or a meal/soup roll or for any & many kinds of plates & you can roll stuff into the them before you bake them.
Photos using this recipe https://w3.do/4u72vYNL
Details
- ⏲️ Prep time: @ (20-30 prep, total 3.75-4 hours)
- 🍳 Cook time: @25-30 minutes (can vary based on the size)
- 🍽️ Servings: 12
Ingredients
- 2 ¼ teaspoons of dry yeast (10.54g)
- ¼ cup of warm water (59-60g)
- 1 stick of unsalted butter (4oz, 113g)
- 1 cup of WHOLE milk (240g)
- ¼ cup of granulated white sugar (75-150g)
- 1-2 tablespoons of honey (2.31-3.5g)
- 3 eggs (recommended: farm fresh and large)
- 4-5 cups of bread flower (480-600g,12+ high gluten protein if possible)
- 1 ½ teaspoons of salt (8.88g)
- 1 tablespoon of butter for the rising bowl insides, baking surfaces, and rollout board. (13-20g)
Directions
- Gather the ingredients for the mixer.
- get warm water ready, @ 80-90F or @26.7-32.2C
- in the mixer, get the yeast going with the warm water. We give ours a little mixing on medium then let it settle and watch for some activity. (we live in the south so our mixing bowl is rather warm, you may have to adjust the water temp or warm your mixer bowl up to get the yeast going), then give it your blessings, allow it to work its magic by walking away and perform the next items.
- Get the cracked eggs ready (we break the yolks without beating them)
- Melt the butter on the stove, but do not cook or fry it
- add the sugar and honey into the heated melted butter off of the stove don’t cook the butter
- The mixture does not have to be fully dissolved into the melted butter, then add the whole milk and stir it up like Bob Marley.
- Now , Back to the mixer, add the cracked eggs at a medium setting and let that mix up for a few minutes.
- Add the milk, butter, sugar, and honey mixture, still at half speed.
- After its all in, turn the mixer up a half more notch (a yellowy beautiful color and yeasty smell should be present)
- Then start adding flour, half a cup at a time, shaking it in as it mixes, up to about 3 cups.
- Next, Add the salt and scrape the sides if necessary then get the mixer running again.
- Continue adding the rest of the flour, after each cup you may have to stop and scrape the sides down.
- Once the dough comes together, it will be a little tacky but not stick to the sides as much.
- Once this happens, it will knead for 5-8 minutes, depending on how tacky it feels it may need some more kneading. (We make this at 200ft above sea level and at 40-60% humidity in our home) We think it is done when you poke it and it starts to fill back in and isn’t all stuck to your fingers
- When the dough is ready, Stop the mixer and take the mixer parts out (these items should come freely of the dough), (this recipe requires its own patience level training, do not be afraid to let it work and come together.. if you start to take it out but it sticks too much, throw a little flour (very little) in and knead it some more before you decide to let it rise)
- Roll the dough from the mixer bowl into your unsalted & buttered large bowl for the initial rise. (cover with a clean cloth and let it rise for 60-90 minutes at least doubling in size)
- Roll the doubled dough out onto your buttered surface (try not to deflate it entirely). Fold the dough into itself and put it back into the same buttered rising bowl for a second rise. (It should smell so yeasty and buttery, and this is the point where we both start using the adjective Heaven except for the Hil in Hil-aceious says it feels like heaven before we turn it out for the first rise, thus she is more sensitive than I, the Ace in the cious-ness of this tasty roll recipe).
- To get ready for baking, have your baking pan or pans buttered (unsalted). This recipe makes 24 rolls (3 rows of 8) in a 12.5 x 8-inch baking dish)) (8–9-inch cake rounds work also; you will need two to fit the rolls half/half).
- After the dough doubles again, about 55-75 minutes, get the weight of the dough and divide the grams by 24, then cut off each roll using a small scale if possible and form it into a small oval. You will want to use you buttered surface to shape the rolls, don’t worry if the dough deflates a little while shaping them.
- Fit 3 rows of 8 into a 12.5 x 8 baking dish next to each other. After you get them all into the baking pan, preheat the oven to 350F. (if you have a heated oven, give the rolls time to start growing into each other a little (we take pictures a lot to compare later throughout the whole process sometimes), 15-35 minutes works for us)
- Bake them for about 25-30 minutes until they are golden brown on top but still white in the seams, (you should be able to lift the baking pan up quickly and the rolls should freely release from the pan and vacuum suck back to the pan a bit if they are done enough IMO).
- After about 3-5 minutes turn them onto the drying rack and serve or consume. - they peel right apart.
-
 @ 9ecbb0e7:06ab7c09
2024-02-07 20:01:36
@ 9ecbb0e7:06ab7c09
2024-02-07 20:01:36The notable bipartisan bill agreed upon in the United States Senate between Democrats and Republicans concerning border security could resolve permanent residency for Cubans who cross the U.S. border and are granted an I-220A which currently is not considered a parole in view of the Cuban Adjustment Act.
According to an extensive report published in El Nuevo Herald, the legislative initiative proposes that Cubans released under new border processing rules could obtain a green card without the need of having been "inspected and admitted" formally or having received a parole.
In such a way, it would end the legal limbo in which thousands of Cuban migrants find themselves; those with the I-220A cannot receive government assistance, such as Medicaid, food stamps or financial aid, and are also not granted a work permit to create their own livelihood.
Although the proposed special rule is not retroactive, it generates expectations about its ability to resolve pending cases of Cubans who entered the U.S. and did not obtain parole.
In an interview for the said media outlet, Randy McGrorty, director of Catholic Legal Services, expressed that the bill demonstrated that Washington had listened to the demands of the Cuban exile community in Miami.
"It recognizes that Cubans fleeing Cuba are fleeing political oppression, not just economic turmoil, and that was the reason for the Cuban Adjustment Act sixty years ago. It recognizes that many Cubans are coming and they offer important skills, talents, and workers for our economy. And it recognizes that they have made a mess with the way they are releasing the Cubans," said McGrorty.
Stricter, but also faster, asylum processes
Moreover, the bill seeks to strengthen the asylum system, toughening the interview process to determine if a foreigner really has a "credible fear" of returning to their place of origin. The aim is to raise the bar so that not everyone who presents themselves at the border can have almost expedited asylum.
With funding to designate more administrative staff, the aim is also to make asylum processes shorter. It is intended that those who are not accepted can be deported immediately.
On the other hand, the Senate bill would give the president the authority to restrict border processing in the face of a high migratory flow and would limit judicial appeals to exceptional situations.
Bad news for the aspirations of Cuban migrants
The bad news for the aspirations of Cuban migrants is that it seems unlikely that this Senate bill will have enough votes in the House of Representatives. Republican congressmen have said they will vote resoundingly no because it does not meet their demands.
Nevertheless, although this specific regulation may not become law, it is very likely that in the future the part concerning the treatment of Cubans with I-220A and their parole status could be included in future bills since both parties, Democratic and Republican, agree that the U.S. needs immigration reform.
For Wilfredo Allen, a prominent immigration attorney in Miami, the reform would be counterproductive. "Cubans might interpret it as an invitation to rush to the border or set out by boat…. To a certain extent, it is giving a privilege to a particular group, and it is a group that is arriving in historic numbers," explained the Cuban American Allen to the newspaper El Nuevo Herald.
-
 @ be9bb3c6:8f7b599a
2024-01-03 01:42:49
@ be9bb3c6:8f7b599a
2024-01-03 01:42:49Chef's notes
Please use grass-fed, red veal. These animals, unlike their white veal brothers, live happy, free-roaming lives.
You can hack it, but you'll likely want an enamelled cast-iron terrine mould.
Details
- ⏲️ Prep time: 20 mins
- 🍳 Cook time: 5 hours + 24 hours in the fridge
- 🍽️ Servings: 12
Ingredients
- 1kg veal bones, rinsed
- 2L cold water
- Mirepoix - 1 carrot, 2 celery stalks, 1 large onion
- 12 black peppercorns, crushed with the back of a pan
- 2 whole cloves
- 2 bay leaves
- 1kg veal shank meat, large pieces
- 3 packages of gelatin
- 45ml cold water
- 30ml Cognac
- 60ml dry white wine
- salt and pepper to taste
- 1 bunch flat-leaf parsley, finely chopped
- 1 sprig of thyme, finely chopped
- 10 black peppercorns, crushed with the back of a pan
Directions
- Place veal bones in a large pot. Cover with the 2L water and bring to a boil
- Reduce heat to a simmer and skim the top of the scum that will develop
- Add mirepoix, 12 crushed peppercorns, cloves and bay leaves, and simmer for 2 hours
- Add the veal shank meat and simmer for 1.5 hours more
- Remove veal and set aside to cool
- Strain stock, discarding bones and mirepoix, and transfer 500ml of the stock to a sauce pan, reserving the rest for another use
- Soften the gelatin with cold water and stir it into the 500ml of stock. Check your seasoning
- Add Cognac, wine and keep warm, but don't boil
- Cut veal into 2.5cm pieces and place in a bowl. Fold in the parsley, thyme and 10 crushed black peppercorns
- Pack veal mixture tightly into terrine mould. It should come almost to the brim. Add stock slowly to moisten everything. You do not the meat swimming in a soup.
- Pack veal mixture tightly into terrine mould. It should come almost to the brim. Add stock slowly to moisten everything. You do not the meat swimming in a soup
- Place in the fridge for at least 4 hours and up to 24 hours before unmolding. Will keep in the fridge for up to 10 days
-
 @ 9ecbb0e7:06ab7c09
2024-02-07 20:01:05
@ 9ecbb0e7:06ab7c09
2024-02-07 20:01:05El connotado proyecto de ley bipartidista que se acordó en el Senado de Estados Unidos entre demócratas y republicanos sobre la seguridad fronteriza podría resolver la residencia permanente para los cubanos que cruzan la frontera estadounidense y les es otorgada una I-220A que actualmente no es considerada un parole con vistas a la Ley de Ajuste Cubano.
De acuerdo con un extenso reportaje publicado en El Nuevo Herald, la iniciativa legislativa propone que los cubanos liberados bajo las nuevas normativas de procesamiento fronterizo puedan obtener la tarjeta verde sin necesidad de haber sido “inspeccionados y admitidos” formalmente o de haber recibido un parole.
De tal manera se terminaría el limbo legal en el que se encuentran miles de migrantes cubanos que con la I-220A no pueden recibir asistencia gubernamentales, como Medicaid, cupones de alimentos o ayuda financiera, y tampoco se les otorga un permiso de trabajo para que creen su propio sustento.
Aunque la regla especial propuesta no es retroactiva, genera expectativa sobre su capacidad para resolver casos pendientes de cubanos que ingresaron a EEUU y no consiguieron parole.
En entrevista para el citado medio, Randy McGrorty, director de Catholic Legal Services, expresó que el proyecto de ley demostraba que Washington había escuchado las demandas del exilio cubano en Miami.
“Reconoce que los cubanos que huyen de Cuba huyen de la opresión política, no sólo de la agitación económica, y esa fue la razón de la Ley de Ajuste Cubano hace sesenta años. Reconoce que vienen muchos cubanos y que ofrecen habilidades, talentos y trabajadores importantes para nuestra economía. Y reconoce que han hecho un desastre con la forma en que están liberando a los cubanos”, dijo McGrorty.
Procesos de asilo más estrictos, pero también más rápidos
Además, el proyecto de ley busca fortalecer el sistema de asilo, endureciendo el proceso de entrevistas para determinar si un extranjero en realidad tiene “miedo creíble” de regresar a su lugar de origen. Lo que se quiere es elevar el listón para que no todo el que se presente en la frontera tenga un asilo casi expedito.
Con la financiación para designar más personal administrativo también se busca que los procesos de asilo sean más cortos. Se pretende que los que no sean aceptados puedan ser deportados de forma inmediata.
Por otra, parte el proyecto de ley en el Senado otorgaría al presidente la autoridad de restringir el procesamiento fronterizo ante un alto flujo migratorio y limitaría las apelaciones judiciales a situaciones excepcionales.
Una mala noticia para las aspiraciones de los migrantes cubanos
La mala noticia para las aspiraciones de los migrantes cubanos es que parece improbable que este proyecto de ley en el Senado cuente con los votos suficientes en la Cámara de Representantes. Los congresistas republicanos han dicho que votarán rotundamente que no, pues no cumple con sus exigencias.
No obstante, aunque esta normativa en específico no logre convertirse en ley es muy probable que el futuro la parte que concierne al tratamiento de cubanos con I-220A y su condición de parolados sea incluida en futuros proyectos de ley dado que ambos partidos, Demócrata y Republicano, están de acuerdo en que EEUU necesita una reforma migratoria.
Para Wilfredo Allen, un destacado abogado de inmigración en Miami, la reforma sería contraproducente. “Los cubanos podrían interpretarlo como una invitación a correr hacia la frontera o salir en barco…. Hasta cierto punto, se le está dando un privilegio a un grupo en particular, y es un grupo que está llegando en números históricos”, explicó el cubanoamericano Allen al diario El Nuevo Herald.
-
 @ 00000000:f729d700
2024-01-02 23:53:03
@ 00000000:f729d700
2024-01-02 23:53:03Chef's notes
Choose a good-quality feta cheese made from sheep’s milk. This combo is also delicious served over pasta, which is great if you have leftovers. Feta cheese that comes in a dry package may not melt as expected.
Details
- ⏲️ Prep time: 15
- 🍳 Cook time: 20
- 🍽️ Servings: 6
Ingredients
- 1 (7 oz) block Greek feta cheese
- 2 cups halved cherry or grape tomatoes
- 1/3 cup Kalamata olives (halved)
- 1/3 cup red onion (thinly sliced)
- 2 tablespoons olive oil
- 1 clove garlic (minced)
- 1 teaspoon oregano (dried)
- 1 tablespoon honey
- fresh basil (chopped)
- black pepper
- salt
Directions
- preheat oven to 400 ºF (200 ºC)
- place the feta cheese in the center of a baking dish
- spread with honey and drizzle with olive oil
- combine tomatoes, olives, red onion, olive oil, and garlic in a small bowl
- sprinkle bowl with oregano, season with salt and pepper, and mix
- arrange the mix around the feta cheese
- bake in oven until cheese is soft and tomato mixture is bubbly for 20 to 30 minutes
- garnish with fresh basil, if desired
-
 @ 9ecbb0e7:06ab7c09
2024-02-07 19:56:54
@ 9ecbb0e7:06ab7c09
2024-02-07 19:56:54Federal Prosecutor Roger B. Handberg of Florida announced the arrest and filing of criminal charges against a citizen accused of smuggling more than 100,000 US dollars from Cuba, according to a press release issued this Tuesday.
Mirtza Ocaña, 38 years old, residing in Tampa, apparently dedicated to traveling to the Island as a mule, faces a maximum penalty of five years in a federal prison if she is ultimately found guilty of the charges.
According to the complaint, Ocaña arrived at the Tampa International Airport on a flight from Cuba on February 5, 2024. She stated she did not have more than $10,000 (a limit that would trigger reporting requirements), therefore she had nothing to declare.
However, during a routine inspection of her luggage, agents from the Department of Homeland Security recovered approximately $30,000 in cash hidden in three wrapped packages.
The detained citizen later admitted that she flew from Cuba to Tampa two or three times a month to smuggle cash into the United States and that she knew bringing such amounts without reporting it is illegal.
Agents searched Ocaña and discovered an additional $70,000 in cash hidden in her clothing. Ocaña's flight history later revealed that she had flown from Cuba to Tampa 45 times since May 2023.
The prosecutor's statement specified that this case is being investigated by the Homeland Security Investigations (HSI) and the United States Customs and Border Protection. It will be prosecuted by Assistant Federal Prosecutor Michael J. Buchanan.
The arrest of this citizen with cash comes a few days after Western Union suspended its remittance transmission operations to Cuba from the United States due to technical issues in the Cuban banking system. The situation continues amidst the opaqueness of the regime's financial institutions.
The Metropolitan Bank (BM) referred to the suspension of remittance services this Tuesday, but without details. "If they have sent you money (transfer from abroad) through any remittance agency, we suggest you contact Fincimex, the agency that manages that service in Cuba," the BM noted in a very brief note on its social networks.
On Thursday, the same institution reported "technical difficulties affecting branch services and those associated with payment technology channels," without mentioning transfers from abroad.
Despite the massive migration that continued in 2023, remittances to Cuba experienced a decrease of 3.31% compared to the year 2022, totaling 1.972,56 million dollars, a decline of 46.93% compared to pre-pandemic levels in 2019, revealed economist Emilio Morales in a recent dossier of 21st Century Cuba.
During the year 2023, it is estimated that the Cuban diaspora allocated between 1.800 and 2.200 million dollars to facilitate the migration of the 200,287 Cubans who traveled to the USA, adding the costs of the journey and the maintenance of these individuals on American soil, the report noted.
For Morales, that flow of capital, instead of being invested in the micro, small and medium enterprises (MIPYMES) promoted by the regime, has been directed towards the quest for family freedom.
In December, several users denounced a "corralito" (financial blockade) by the Cuban regime on remittances sent from abroad, especially in euros, whose delay for collection exceeded a month.
-
 @ 9ecbb0e7:06ab7c09
2024-02-07 19:56:24
@ 9ecbb0e7:06ab7c09
2024-02-07 19:56:24El Fiscal Federal Roger B. Handberg de Florida anunció el arresto y presentación de una denuncia penal contra una ciudadana acusada de contrabandear más de 100.000 dólares estadounidense desde Cuba, de acuerdo con un comunicado de prensa emitido este martes.
Mirtza Ocaña, de 38 años, residente en Tampa, al parecer dedicada a viajar a la Isla como mula, enfrenta una pena máxima de cinco años en una prisión federal si finalmente es declarada culpable de los cargos imputados.
Según la denuncia, Ocaña llegó al Aeropuerto Internacional de Tampa en un vuelo procedente de Cuba el 5 de febrero de 2024. Ella dijo que no tenía más de 10.000 dólares (un límite que activaría los requisitos de presentación de informes), por lo que no tenía nada que declarar.
Sin embargo, durante una inspección rutinaria de su equipaje, los agentes del Departamento de Seguridad Nacional recuperaron aproximadamente 30.000 dólares en efectivo ocultos en tres paquetes envueltos.
La ciudadana detenida luego admitió que volaba de Cuba a Tampa dos o tres veces al mes para contrabandear dinero en efectivo a Estados Unidos y que sabía que traer esas sumas sin informarlo es ilegal.
Los agentes registraron a Ocaña y descubrieron 70.000 dólares adicionales en efectivo escondidos en su ropa. El historial de vuelo de Ocaña reveló más tarde que había volado de Cuba a Tampa 45 veces desde mayo de 2023.
El comunicado de la Fiscalía precisó que este caso está siendo investigado por la Oficina de Investigaciones de Seguridad Nacional (HSI, por sus siglas en inglés) y la Oficina de Aduanas y Protección Fronteriza de Estados Unidos. Será procesado por el Fiscal Federal Adjunto Michael J. Buchanan.
La detención de esta ciudadana con dólares en efectivo se da pocos días después de que Western Union suspendiera sus operaciones de envíos de remesas a Cuba desde Estados Unidos por motivos técnicos en el sistema bancario en Cuba. La situación continúa en medio de la opacidad de las instituciones financeras del régimen.
El Banco Metropolitano (BM) hizo alusión a la suspensión de los servicios de envío de remesas este martes, pero sin detalles. "Si le han enviado dinero (transferencia desde el exterior) a través de alguna agencia remesadora, le sugerimos contactar con Fincimex, agencia que en Cuba gestiona ese servicio", señaló el BM en una nota muy breve en sus redes sociales.
El jueves la misma institución informó de "dificultades técnicas que afectan los servicios sucursales y los asociados a los canales tecnológicos de pago", sin mencionar a las transferencias desde el extranjero.
Pese a la migración masiva que continuó en 2023, las remesas hacia Cuba experimentaron una disminución del 3,31% en comparación con el año 2022, totalizando 1.972,56 millones de dólares, un declive del 46,93% en comparación con los niveles prepandemia de 2019, reveló el economista Emilio Morales en un reciente dossier de Cuba Siglo 21.
Durante el año 2023 se estima que la diáspora cubana destinó entre 1.800 y 2.200 millones de dólares para facilitar la migración de los 200.287 cubanos que transitaron hacia EEUU, sumando los costos de la travesía y la manutención de estos individuos en suelo estadounidense, señaló el informe.
Para Morales, ese flujo de capital, en lugar de ser invertido en las micro, pequeñas y medianas empresas (MIPYMES) promovidas por el régimen, se ha dirigido hacia la búsqueda de la libertad familiar.
En diciembre varios usuarios denunciaron un "corralito" del régimen cubano a las remesas enviadas desde el extranjero, sobre todo en euros, cuya demora para el cobro llegó a superar el mes.
-
 @ cb084639:2f16502a
2024-01-02 18:43:51
@ cb084639:2f16502a
2024-01-02 18:43:51Chef's notes
น้ำจิ้มซีฟู๊ดเป็นน้ำจิ้มที่เหมาะสำหรับกันกับอาหารทะเลแทบจะทุกชนิดก็ว่าได้ เริ่มจากการเลือกพริกที่จะนำมาทำในที่นี้จะใช้พริกจินดาเขียวและแดง หรือใครจะใช้พริกขี้หนูสวนร่วมก็ได้ก็จะได้ความหอมขึ้นไปอีก อย่างไรก็ตามความอร่อยไม่ได้ขึ้นอยู่กับน้ำจิ้มอย่างเดียว แต่ก็ขึ้นอยู่กับความสดของอาหารทะเลเหล่านั้นอีกด้วย ผมเคยลองเอาสเต็กมาจิ้มดูนะได้ความอร่อยไปอีกแบบแต่รสและกลิ่นของเนื้อจะโดนกลบหมดเลยเอาเป้นว่าใครอย่าจะเอาไปกินกับอะไรก็แล้วแต่ความชอบครับ มาไปลงมือทำกันดีกว่า!!!
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 10 min
- 🍽️ Servings: 1-4
Ingredients
- พริกจินดาแดง 5 เม็ด
- กระเทียมจีน 7 กลีบ
- รากผักชี 1 ต้น
- น้ำปลา 3 ช้อน
- น้ำมะนาว 3 ช้อน
- น้ำกระเทียมดอง 1 ช้อนโต๊ะ
Directions
- เริ่มจากการนำพริกจินดาแดงกระเทียมจีนรากผักชีที่เตรียมไว้นำมาปั่นให้เข้ากันหรือไม่มีเครื่องปั่นจะใช้ครกตำก็ได้แล้วนำมาพักไว้
- หลังจากนั้นเติมน้ำปลาน้ำมะนาวน้ำกระเทียมดองแล้วคลุกให้เข้ากันเพียงเท่านี้ก็จะได้น้ำจิ้มซีฟู้ดไว้กินกับของทะเลที่ชื่นชอบแล้ว
-
 @ 9ecbb0e7:06ab7c09
2024-02-07 19:54:19
@ 9ecbb0e7:06ab7c09
2024-02-07 19:54:19The Cuban Ministry of Public Health (MINSAP) confirmed the detection of a case of malaria in Sancti Spíritus and offered details on the measures taken to prevent an outbreak of the disease, after numerous people on social media revealed the existence of this health problem.
According to the official media Escambray, which interviewed Dr. Carlos Ruiz Santos, director of the Provincial Center for Hygiene, Epidemiology and Microbiology of that province, the patient lives in Jatibonico and arrived in Cuba from Angola on December 24th last year.
According to the official, the patient was in the city of Benguela, where he lived "by an independent contract, he is not a health collaborator nor of any other type". More than 20 days after his arrival, on January 17, the individual "began with a fever and another group of symptoms, such as general malaise, skin lesions," he said.
The individual was admitted on January 23 to the Camilo Cienfuegos Provincial Hospital in Sancti Spíritus, and the following day tested positive for the contagious disease. The blood test was sent to the Pedro Kourí Institute of Tropical Medicine in Havana, which confirmed the infection on the 27th.
Ruiz Santos recalled that malaria is transmitted through the Anopheles mosquito, which has different habits than those of the Aedes aegypti, responsible for the outbreaks of dengue that occur in Cuba every year.
"An integration of actions began to be carried out with the goal of preventing transmission," assured the official, who commented that health authorities combed through a two-kilometer radius around the infected person's home and "found breeding sites" for the vector.
MINSAP would have also inspected 10,000 homes, added Ruiz Santos, looking for other infected individuals. "1,025 homes were fumigated with malathion (pesticide) and electric traps were placed for the capture of the mosquito," in addition to fumigating open areas with mobile equipment.
As expected, the poor hygienic situation of cities and towns in Cuba led MINSAP to also drain ditches, eliminate leaks and collect trash, "minimizing risks," admitted the official.
Among the inhabitants of the area, Ruiz Santos recognized, "there are a number of febrile syndromes," although he did not offer the figure. Similarly, during the investigation, three cases of dengue were detected, although he assured that "the province does not have a complex situation" with this virus since the contagion rate is five for every 100,000 inhabitants.
"Today we do not believe that any new case" of malaria will appear, he assured, although he warned that it is necessary to wait 21 days from the diagnosis of the case to close the alert. Despite this, he commented, MINSAP is "performing thick blood smear tests for three days on people who might have had contact with the patient."
Likewise, he acknowledged, a team from MINSAP from the capital is in Sancti Spíritus advising the campaign.
The patient is still admitted, "isolated in a cubicle in the infectious disease ward, with a positive evolution," he said.
However, at the end of the interview, Ruiz Santos acknowledged that since 2020 no other case of malaria had been reported in the province and revealed that about 15 patients with this condition are reported in Cuba each year, "all imported," he said, mostly from travelers from Africa and neighboring countries, such as Brazil and Venezuela.
This had not been disclosed until now, despite reports of Cuban doctors exported to Africa who died after contracting the disease. Again, social media forced the authorities to break their usual opacity.
-
 @ 8fb140b4:f948000c
2023-12-30 10:58:49
@ 8fb140b4:f948000c
2023-12-30 10:58:49Disclaimer, this tutorial may have a real financial impact on you, follow at you own risk.
Step 1: execute
lncli closeallchannelsThat’s it, that was easy as it could be. Now all your node’s channels are in the process of being closed and all your liquidity is being moved to your onchain wallet. The best part, you don’t even need to confirm anything, it just does it in one go with no questions asked! You can check the status by using a very similar looking command,
lncli closedchannels!Good job! Now you are ready to start from scratch and use any other reasonable solution!
🐶🐾🫡🤣🤣🤣
Disclaimer: this is a satirical tutorial that will 💯 cost you a lot of funds and headaches.
-
 @ 9ecbb0e7:06ab7c09
2024-02-07 19:53:49
@ 9ecbb0e7:06ab7c09
2024-02-07 19:53:49El Ministerio de Salud Pública (MINSAP) cubano confirmó la detección de un caso de paludismo en Sancti Spíritus y ofreció detalles sobre las medidas tomadas para evitar un brote de la enfermedad, después que numerosas personas en las redes sociales revelaran la existencia de ese problema de salud.
De acuerdo con el medio oficial Escambray, que entrevistó al doctor Carlos Ruiz Santos, director del Centro Provincial de Higiene, Epidemiología y Microbiología de esa provincia, el enfermo vive en Jatibonico y llegó a Cuba procedente de Angola el 24 de diciembre último.
Según el funcionario, el paciente estaba en la ciudad de Benguela, donde residía "por un contrato independiente, no es un colaborador de la salud ni de otro tipo". Más de 20 días después de su arribo, el 17 de enero, el sujeto "comienza con fiebre y otros grupo de síntomas, como malestar general, lesiones en la piel", dijo.
El individuo fue ingresado el 23 de enero en el Hospital Provincial Camilo Cienfuegos, de Sancti Spíritus, y al día siguiente dio positivo a la contagiosa enfermedad. La prueba de sangre fue enviada al Instituto de Medicina Tropical Pedro Kourí, de La Habana, que el 27 confirmó el contagio.
Ruiz Santos recordó que el paludismo se transmite a través del mosquito Anófeles, que tiene hábitos distintos a los del Aedes aegypti, causante de los brotes de dengue que se producen en Cuba cada año.
"Se comienzan a hacer un grupo de acciones integrales y se busca tratar de que no exista transmisión", aseguró el funcionario, quien comentó que las autoridades de salud peinaron dos kilómetros a la redonda de la vivienda del contagiado y "se encontraron criaderos" del vector.
El MINSAP habría revisado además 10.000 viviendas, agregó Ruiz Santos, buscando otros infectados. "Se fumigaron 1.025 viviendas con malatión (plaguicida) y colocaron trampas eléctricas para la captura del mosquito", además de fumigar áreas abiertas con equipos móviles.
Como es de esperar, la deficiente situación higiénica de las ciudades y pueblos de Cuba hizo que el MINSAP además drenara zanjas, suprimiera salideros y recogiera la basura, "minimizando riesgos", admitió el funcionario.
Entre los habitantes de la zona, reconoció Ruiz Santos, "hay un número de síndromes febriles", aunque no ofreció la cifra. Asimismo, en la pesquisa se detectaron tres casos de dengue, aunque aseguró que "la provincia no tiene una situación compleja" con ese virus, pues la tasa de contagio es de cinco por cada 100.000 habitantes.
"Hoy no creemos que vaya a aparecer algún caso nuevo" de paludismo, aseguró, aunque alertó que debe esperarse a los 21 días del diagnóstico del caso para cerrar la alerta. Pese a ello, comentó, el MINSAP está "haciendo pruebas de gota gruesa durante tres días a personas que pudieron tener contacto con el enfermo".
Asimismo, reconoció, un equipo del MINSAP de la capital está en Sancti Spíritus asesorando la campaña.
El enfermo sigue ingresado, "aislado en un cubículo en la sala de infecciosos, con evolución positiva", dijo.
No obstante, al final de la entrevista, Ruiz Santos reconoció que desde 2020 no se reportaba otro caso de paludismo en la provincia y reveló que cada año se reportan en Cuba unos 15 enfermos de esa dolencia, "todos importados", dijo, mayoritariamente de viajeros procedentes de África y países vecinos, como Brasil y Venezuela.
Lo anterior no había sido revelado hasta ahora, pese a que existen reportes de médicos cubanos exportados a África que murieron tras contagiarse con la enfermedad. Nuevamente, las redes sociales obligaron a las autoridades a romper su acostumbrada opacidad.
-
 @ cb084639:2f16502a
2023-12-25 17:27:51
@ cb084639:2f16502a
2023-12-25 17:27:51Chef's notes
เรื่องน้ำมันที่ใช้ประกอบอาหารใครว่าไม่สำคัญ เพราะร่างกายเราต้องการสารอาหารที่เป็นไขมันไปเป็นพลังงาน จะกินทั้งทีมันต้องเลือกของดีๆกันหน่อย จริงอยู่ที่สมัยก่อนเรากินน้ำมันพืช(seed oil) มันถูกทำให้เราเชื่อว่ามันดี ไม่มีไข และโยนความผิดมาให้น้ำมันที่ได้จากสัตว์ ซึ่งจะยังไม่ลงรายละเอียดเดี๋ยวจะยาวไป เอาเป็นว่าเราไปหาซื้อไขมันเนื้อมาให้ได้ก่อนจะแหล่งไหนก็แล้วแต่ ถ้าได้แบบที่เป็นก้อนใหญ่ๆมายิ่งดี หั่นเป็นชิ้นได้เสมอกัน สุกพร้อมกันและได้น้ำมันเยอะแต่ถ้าหาไม่ได้แนะนำว่าให้ไปมองหาที่ขายเศษเนื้อซื้อเศษมาทำแดดเดียวแล้วสะสมในส่วนของไขมันแช่ช่องแข็งไว้รวบรวมไว้ก่อนค่อยมาทำ
การทำน้ำมันจำเป็นต้องใส่น้ำไปด้วยเพื่อรวนมันให้สุกก่อนแล้วจะทำให้ได้น้ำมันได้ง่ายขึ้น แค่นี้เราก็มีน้ำมันวัวที่หอมและมีประโยชน์ไว้ใช้ปรุงอาหารแล้วยังได้กากวัวไว้ทำกับข้าวหรือกินเล่นอีกด้วย!!!Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 30-60 min
- 🍽️ Servings: 1-4
Ingredients
- ไขมันวัว 1 กิโลกรัม
- เกลือชมพู 2 ช้อนชา
- น้ำเปล่า 1 ถ้วย
Directions
- นำมันวัวที่ล้างสะอาดแล้วมาหั่นเป็นชิ้นลูกเต๋าเท่าๆกัน
- นำมันวัว น้ำเปล่า และเกลือชมพูใส่กระทะ
- ตั้งไฟกลางไปทางอ่อน รวนไขมันให้สุกทั่วกัน
- สังเกตว่าน้ำเริ่มแห้ง น้ำมันจะเริ่มออกมาแล้ว
- จะเห็นได้ว่าพอน้ำมันออกมาทอดตัวไขมันเองเราก็ทอดไปเรื่อยๆจนไขมันก้อนเล็กลงและได้น้ำมันเพิ่มมากขึ้นไขมันมีสีเข้มขึ้นเป็นสีทองสวยงาม
- ปิดไฟที่เตา ตักกากวัวออกมาผึ่งน้ำมัน เอาไว้กินเล่นได้เค็มนิดๆ
- รอน้ำมันหายร้อนก็ทำการบรรจุใส่ภาชนะที่เตรียมไว้แล้วเก็บใส่ตู้เย็นน้ำมันจะกลายเป็นไขสีขาวเก็บไว้ใช้ได้นาน
-
 @ cce0989b:b497e608
2024-02-07 13:43:34
@ cce0989b:b497e608
2024-02-07 13:43:34"How can I achieve my goals?"
If you look around for answers to this question, you'll likely get the same response over and over: choose the right goal, break your goal into small steps, be consistent with taking action.
But here's something that no one talks about, which is equally as important: be willing to make mistakes.
Be willing to try things that are new, and therefore, might be uncomfortable.
Be willing to sit with that discomfort, which might come in the form of embarrassment, confusion, disappointment, frustration, anger, and apathy.
Be willing to reflect on your choices, learn from your mistakes, and pivot to new paths if needed.
Willingness is the unspoken secret to success. In my experience, it's also the barrier that is likely standing between you and the things that matter to you. Without willingness, all of the strategy, planning, and execution is meaningless. You'll never feel ready to get started or prepared enough to get through the first hurdle.
Planning on how to achieve your goals is often the easy part. Being willing to embrace the discomfort that comes when you follow through with those plans — that's the hard part.
Just to make this even more challenging, as you progress towards your goals, your tolerance of discomfort needs to increase proportionally, too. You never 'get' comfortable; you simply get comfortable with more and more discomfort.
That's why we need to learn to view willingness as a skill, something we can practice and can get better at.
Here's one of my favorite tactics to help you get started.
The next time you're feeling uncomfortable, stuck, or like you want to quit, that's a sign you need to harness your willingness. Say this mantra to yourself: "To move closer to what matters to me, I am willing to sit here in this discomfort, knowing that it will not last forever."
-
 @ 9f51b59f:75e7c3a2
2023-12-25 14:34:57
@ 9f51b59f:75e7c3a2
2023-12-25 14:34:57Chef's notes
Use chuck, boneless short rib, or another cut that gets tender the longer you cook it. You cut even use pork butt, shoulder, or belly.
Select a few different dried chilies 🌶️ for greater complexity and heat. For extra spice use jalapeños or Serrano with the trinity. (Onion, pepper, celery)
Details
- ⏲️ Prep time: 1 hour
- 🍳 Cook time: 2.5 hours
- 🍽️ Servings: 6
Ingredients
- ½ pound Red, Pinto, or Kidney Beans- soaked over night
- 6 dried chilies of your choice- toasted, seeded, and soaked
- 2 tablespoon oil (lard or tallow)
- 2 pounds Chuck beef cubes or short rib
- 1 small Spanish Onion- small dice
- 1 Green Bell or Poblano Pepper- small dice
- 2 stalks Celery- small dice
- 4 cloves Garlic- minced
- 2 Bay Leaf
- 1 can Fire Roasted Tomatoes
- 2 teaspoon ancho or regular chili powder
- 2 teaspoons Smoked Paprika
- 2 teaspoon Dried Oregano
- 2 teaspoon ground Coriander
- 1 tablespoon cocoa powder
- 4 cups Beef or Chicken stock, water also works
- 2 tablespoons Butter
- 2 tablespoons Masa (ground corn flour)
- Toppings like cheese, onions, scallions, tortillas. Whatever you’d like.
Directions
-
- Start by soaking your beans the night before. Fully submerged in water and kept in the fridge.
- Place the pot you’ll be cooking the chili in over medium high heat, with NO oil heat the pan and add the dried chilies to toast for 3-5 minutes turning them occasionally. You will smell them toasting and becoming aromatic. Set them aside to cool, once cool remove and discard the seeds and stems. Submerge the chilies in stock to rehydrate and soften them for blending.
- Season the beef with salt, then wipe out the pan and return it to the heat. Add the grapeseed oil to the pan and allow to heat. Sear the beef on multiple sides to achieve lots of browning and color. Remove the beef and set aside.
- Add the diced onions, bell peppers, and celery to the pan (holy trinity) and cook until the edges begin to caramelize. When you see the browning of the veg add the garlic, bay leaves, oregano and spices. Cook for about a minute.
- Add the fire roasted tomatoes to the trinity, scraping up the fond in the pan and cook until some of the liquid from the tomatoes has evaporated. Note the pot should be simmering or at a light boil for evaporation to occur.
- Once the vegetable mixture looks thickened add the rehydrated chilies along with the stock they were soaking in. Remove the pot form the heat and using a stick blender or standing blender puree the trinity and chilies together until smooth.
- Add the remaining stock and chocolate cocoa mix to the pot along with the puree, return the beef to the pot and bring everything to a boil then reduce to a simmer. Cover the pot and cook for about an hour.
- After you’ve allowed the beef to cook on its own drain and add the soaking beans. Prepare the masa roux by melting the butter and stirring in the masa flour, cook for 3 minutes and then add into the chili.
- Return the beans and chili to a boil, reduce to a simmer and cover. Cook for an addition hour to hour and a half until the beans and beef are tender and the sauce has thickened to your liking. Season with salt and pepper. To finish garnish with favorite toppings.
-
 @ 6a39a186:88f51c19
2024-02-07 12:53:10
@ 6a39a186:88f51c19
2024-02-07 12:53:10Making The Effort To Understanding Liquid Network: A Beginner's Perspective

In the rapidly evolving landscape of blockchain technology, solutions like the Liquid Network are paving the way for faster, more private, and secure transactions. But what exactly is the Liquid Network, and how can beginners get started with it? Let's delve into the world of layer-2 solutions and explore the fundamentals of the Liquid Network.
Layer-2 Solutions: Unlocking Bitcoin's Potential
Bitcoin's limited throughput has long been a challenge for its widespread adoption. With a capacity of only 5-7 transactions per second, the Bitcoin blockchain can sometimes struggle to meet the demands of institutional investors and retail buyers alike. Layer-1 solutions, which require rewriting the blockchain protocol, present significant challenges. Enter layer-2 solutions like the Liquid Network, which operate on top of the main blockchain without the need for protocol changes.
Introducing the Liquid Network: Faster, More Private, More Secure
The Liquid Network is a layer-2 network built on top of the Bitcoin blockchain, offering faster, more private, and secure transactions. Designed to enable the issuance, transfer, and exchange of cryptocurrencies, stablecoins, digital assets, and security tokens, the Liquid Network provides a solution to Bitcoin's scalability and privacy challenges.
Key Features of the Liquid Network
The Liquid Network achieves its goals through several key features:
- Wrapped Bitcoin (L-BTC): Liquid Network issues a "wrapped" version of BTC called L-BTC, which can be used on its chain.
- Issued Assets: In addition to L-BTC, Liquid Network supports Issued Assets, enabling the creation of tokens for various applications like stablecoins and security tokens.
- Confidential Transactions: Liquid Network uses Confidential Transactions to hide key transaction information, ensuring greater privacy.
- Federated Byzantine Agreement (FBA): The consensus mechanism of the Liquid Network ensures security and proper asset management.
Getting Started with the Liquid Network
For beginners looking to explore the Liquid Network, one of the most accessible solutions is to utilize exchanges like Bisq and Robosats With these exchange protocols and DAO's, users can seamlessly convert their BTC to L-BTC on the Liquid Network with zero fees, unlocking the benefits of faster transactions and greater privacy. By leveraging platforms like Bitfinex , Bisq, Robosats, users can tap into the full potential of the Liquid Network without incurring additional costs.
In summary, the Liquid Network offers a promising solution to Bitcoin's scalability and privacy challenges. By understanding its fundamentals and leveraging platforms like Bitfinex, beginners can embark on a journey of exploring the possibilities offered by layer-2 solutions and unlocking the full potential of the Bitcoin blockchain.
-
 @ d4338b7c:f1d23a5b
2023-12-23 22:26:10
@ d4338b7c:f1d23a5b
2023-12-23 22:26:10Chef's notes
Tajin Syrup is going to be a mixture of tajin seasoning 1 table spoon to 1. cup of simple syrup. Simple syrup is equal. parts water to refined sugar.
Details
- ⏲️ Prep time: 5
- 🍳 Cook time: 5
- 🍽️ Servings: 1
Ingredients
- reposado tequila
- nixta liqueur
- vida mezcal
- ancho verde
- lime juice
- tajin
- simple syrup
- mole bitters
Directions
- add the ingredients to a shaker
- add large cubes to the shaker tin
- shake vigorously
- dump into rocks glass
- garnish with dry chilli pepper or lime wheel
-
 @ d4338b7c:f1d23a5b
2023-12-23 22:11:29
@ d4338b7c:f1d23a5b
2023-12-23 22:11:29Chef's notes
You don't want to use too many ice cubes in this shake because you want a foamy head to place the espresso beans on after it been served.
Details
- ⏲️ Prep time: 5
- 🍳 Cook time: 5
- 🍽️ Servings: 1
Ingredients
- vodka
- cold brew concentrate
- demerara
- kahlua
Directions
- place ingredients in to shaker tin
- add five regular sized ice cubes
- shake vigorously for ten to fifteen seconds
- pour into a frozen coupe/ martini glass
- place three espresso beans on top as a garnish
-
 @ 6a39a186:88f51c19
2024-02-07 10:00:30
@ 6a39a186:88f51c19
2024-02-07 10:00:30Bitcoin Network Congestion: The Battle Over Ordinals and BRC-20 Tokens

As the Bitcoin network experiences increasing congestion, users are facing longer confirmation times and higher transaction fees. This bottleneck not only impacts the speed of transactions but also raises concerns about accessibility and affordability for users requiring swift and cost-effective transfers.
At the forefront of this issue is the Ordinals Project, a groundbreaking protocol designed to revolutionize digital content storage on the Bitcoin blockchain. By leveraging a specialized transaction type known as an "ordinal," this project enables the creation and preservation of digital art, music, and other media in a decentralized and secure manner. The Ordinals Project represents a significant leap forward in the realm of blockchain innovation, offering users unprecedented opportunities to store and transmit large volumes of data efficiently.
However, alongside the Ordinals Project, the emergence of BRC-20 tokens has added another layer of complexity to the debate. These tokens, akin to ERC-20 tokens on the Ethereum blockchain, are utilized on the Binance Smart Chain for various purposes, including fundraising, trading, and participation in decentralized finance (DeFi) activities. While BRC-20 tokens offer exciting possibilities for expanding the utility of blockchain technology, they also raise questions about scalability and their potential impact on the Bitcoin network.
The crux of the debate surrounding Ordinals and BRC-20 tokens lies in the delicate balance between innovation and scalability within the Bitcoin community. On one hand, proponents argue that these projects open up new avenues for creativity and utility on the Bitcoin network, enhancing its value proposition and relevance in the digital age. Conversely, critics express concerns about the strain that such initiatives may place on the network, exacerbating congestion and impeding its efficiency and reliability.
Ultimately, the discussion surrounding Ordinals and BRC-20 tokens underscores the ongoing dialogue within the Bitcoin community about the trade-offs inherent in technological advancement. While innovation is essential for driving progress and expanding the capabilities of blockchain technology, it is equally crucial to consider the potential ramifications and challenges posed by new initiatives. As Bitcoin continues to evolve and adapt to meet the demands of its growing user base, striking a balance between innovation and sustainability remains paramount for ensuring the network's long-term success.
Get Familiar with the Lightning Network
The Lightning Network represents a revolutionary layer-2 scaling solution for the Bitcoin blockchain, offering lightning-fast and low-cost transactions. To embark on your journey of understanding this innovative technology, let's delve into its architecture and protocols, uncovering the mechanisms that power its efficiency and scalability.
Lightning Network Architecture
At its core, the Lightning Network operates as a network of bidirectional payment channels that enable users to conduct off-chain transactions without relying on the main Bitcoin blockchain for every transaction. These payment channels are established between two parties and allow for rapid exchange of funds, facilitating instant micropayments with negligible fees.
Payment Channels
Payment channels are the building blocks of the Lightning Network, serving as conduits for peer-to-peer transactions. These channels leverage multi-signature smart contracts, enabling participants to securely transact without broadcasting every transaction to the blockchain. By opening and closing channels as needed, users can seamlessly conduct transactions off-chain while maintaining the security and trustlessness of the Bitcoin network.
Lightning Network Nodes
Lightning Network nodes play a pivotal role in facilitating transactions across the network. Nodes serve as intermediaries for routing payments between users, ensuring that funds can flow efficiently between different parties. With a robust network of nodes distributed globally, the Lightning Network achieves unparalleled speed and scalability, making it ideal for microtransactions and everyday purchases.
Lightning Network Protocols
To harness the full potential of the Lightning Network, it's essential to grasp the underlying protocols that govern its operation. These protocols dictate how transactions are routed, payments are processed, and channels are managed, laying the groundwork for seamless and secure interactions within the network.
HTLCs (Hash Time Locked Contracts)
Hash Time Locked Contracts (HTLCs) form the backbone of Lightning Network transactions, enabling atomic swaps and ensuring the trustless exchange of funds between parties. Through the clever use of cryptographic hashes and time locks, HTLCs enable secure and instantaneous payments across the Lightning Network, mitigating the risk of fraud or double-spending.
Sphinx Protocol
The Sphinx Protocol plays a critical role in preserving the privacy and confidentiality of Lightning Network transactions. By encrypting payment information and routing instructions, Sphinx ensures that only the intended recipient can decipher the transaction details, enhancing the privacy and security of Lightning Network transactions.
AMP (Atomic Multipath Payments)
Atomic Multipath Payments (AMP) enable the splitting of large payments into smaller, more manageable chunks, allowing for more efficient routing and improved reliability within the Lightning Network. With AMP, users can enjoy greater flexibility and resilience when sending funds across the network, reducing the risk of payment failures and ensuring smooth transaction flows.
Conclusion
As you embark on your journey to get familiar with the Lightning Network, remember that it represents a paradigm shift in the way we think about blockchain scalability and usability. By embracing its innovative architecture and protocols, you can unlock a world of possibilities for fast, low-cost, and privacy-preserving transactions on the Bitcoin blockchain.
With a solid understanding of the Lightning Network's architecture and protocols, you'll be well-equipped to navigate the intricacies of this groundbreaking technology and harness its full potential for revolutionizing the future of finance.
Lightning Network - Official website for the Lightning Network.
Understanding the Lightning Network - Comprehensive guide to understanding the Lightning Network's architecture and protocols.
HTLCs Explained - In-depth exploration of Hash Time Locked Contracts and their role in Lightning Network transactions.
Sphinx Protocol - Research paper detailing the Sphinx Protocol and its contributions to privacy-enhanced transactions on the Lightning Network.
Atomic Multipath Payments - Article discussing the benefits of Atomic Multipath Payments for improving transaction reliability and efficiency within the Lightning Network.
-
 @ cb084639:2f16502a
2023-12-22 18:25:18
@ cb084639:2f16502a
2023-12-22 18:25:18Chef's notes
อาจจะดูเป็นอาหารที่ดูง่ายๆแต่มันก็ไม่ง่ายนะที่จำทำมันออกมาให้สวยดูดีและอร่อย!!! มันเริ่มจากการเลือกซื้อไข่ ไข่ไก่ที่เราเห็นที่ขายกันอยู่ทุกวันนี้มันมีที่มาที่แตกต่างกัน บางที่ก็มาจากเล้าไก่ทั่วไป ฟาร์มไก่ไข่ หรือจะมาจากการเลี้ยงแบบ ออแกนิก ปัจจัยเหล่านี้ทำให้สารอาหารที่มีอยู่ในไข่นั้นมันมีไม่เท่ากัน ขึ้นอยู่กับสารอาหารที่ไก่ได้รับ ความสะอาดของระบบการเลี้ยง ความเครียดของไก่ มีผลกับไข่ทั้งหมด พอเราเลือกไข่ได้แล้วเรา ก็มาดูเรื่องของกระทะการทำงานกับไข่จะให้ง่ายและไม่เสียอารมณ์ ควรจะใช้กระทะเทฟล่อน เพื่อไม่ให้ไข่ติดกระทะได้และเมื่อเราได้กระทะแล้วเราก็ไปทำกันเลยดีกว่า 55+
Details
- ⏲️ Prep time: 2 min
- 🍳 Cook time: 5 min
- 🍽️ Servings: 1
Ingredients
- ไข่ไก่ 4 ฟอง
- น้ำมันหมูหรือน้ำมันวัว 1 ช้อนโต๊ะ
- พริกไทยดำบด ตามชอบ
Directions
- เริ่มจากตั้งไฟเบาใส่น้ำมันลงไป
- ไม่ต้องรอกระทะร้อนมากตอกไข่ไส่ไปเลย 4 ฟอง
- โรยพริกไทย
- ปิดฝาครอบเพื่ออบไข่
- รอประมาณ1-2นาที คอยเปิดผาดูว่าส่วนไข่ขาวที่ใสเริ่มขุ่นหรือยัง
- เอาไข่ออกจากกระทะโดยใช้ช้อนช่วยแซะด้านใต้ของไข่ ลงบนจารที่เตรียมไว้
- เสิร์ฟคู่กับน้ำปลาพริก หรือซอสแม๊กกี้ตามชอบ
-
 @ cb084639:2f16502a
2023-12-19 18:52:10
@ cb084639:2f16502a
2023-12-19 18:52:10Chef's notes
การทำเนื้อแดดเดียวที่จะเหมาะสำหรับเป็นกับแกล้มกับเครื่องดื่มแสนอร่อยและการที่จะทำให้รสชาติดีนั้นอยู่ที่ปัญจัยเพียงไม่กี่อย่างเช่น คุณภาพของเนื้อที่นำมาทำซึ่งเรื่องเนื้อให้เล่าคงจะยาวเอาเป็นที่ทำวันนี้ได้เสษเนื้อมาจากตลาดนัดแต่เป็นวันที่เราไปตลาดเร็วว่างั้นเถอะเศษที่ได้มาชิ้นค่อนข้างสวยเลยแหละ แล้วตอนหั่นเนื้อสำหรับคนที่ชอบบ่นว่าเนื้อมันเหนียวลองสังเกตุลายของเนื้อให้ดีเราควรจะหั่นแบบตัดขวางลายเนื้อก็จะช่วยได้ เครื่องปรุงสำหรับหมักอันนี้แล้วแต่ความชอบจะตัดหรือเพิ่มตัวไหนตามสะดวกไม่ว่าจะเป็นดอกเกลือ เกลือชมพู เกลือดำ ก็จะให้รสชาติต่างกันตามความชอบของแต่ละคน และระยะเวลาในการตากแดดถ้าช่วงที่เหมาะก็น่าจะเป็นช่วง ฤดูตอนนี้ กับฤดูร้อนน่าจะได้ผลที่สุด ส่วนฤดูฝนเนื้อมันจะไม่ได้รับแดดตามที่ต้องการเพราะฉะนั้นบางที่ถึงต้องใช้เครื่องไล่ความชื่นซึ่งมันจะให้ผลลัพธ์เหมือนนำเนื้อไปตากด้วยแดดนี่แหละ หรือเราจะใช้ความร้อนจากเครื่องขุด bitcoin ของเราก็ได้นะจะได้ใช้ลมร้อนให้เกิดประโยชน์
Details
- ⏲️ Prep time: 4 hour
- 🍳 Cook time: 10
- 🍽️ Servings: 1-4
Ingredients
- เนื้อวัว 1 kgs.
- เกลือ 1 ช้อนชา
- ผงปรุงรส 1 ช้อนโต๊ะ
- ซอสปรุงรส 3 ช้อนโต๊ะ
Directions
- หั่นเนื้อวัวเป็นเส้นๆอย่าลืมหั่นขวางตัดลายเนื้อ
- นำเครื่องปรุงทั้งหมดคลุกเคล้ากับเนื้อ
- พักเนื้อไว้ในอุณหภูมิห้อง 1/2 ชม.
- นำเนื้อไปตากแดดจัด ด้านละ 1 ชั่วโมงครึ่ง
- นำเนื้อที่ได้จะไปทอดด้วยน้ำมันวัว น้ำมันหมู หรือหม้อทอดไร้น้ำมันก็แล้วแต่ความชอบ
- เพียงเท่านี้ก็ได้เนื้อแดดเดียวแสนอร่อยไว้กินคู่กับเครื่องดื่มสุดโปรดแล้วครับ
-
 @ a012dc82:6458a70d
2024-02-07 09:40:41
@ a012dc82:6458a70d
2024-02-07 09:40:41Tokenomics is a word used to describe a token's economics. It provides an explanation of the elements that have an effect on the use and value of a token. These elements include, but are not limited to, the token's generation and distribution; supply and demand; incentive systems; and token burn schedules. Token economics need to be carefully constructed for cryptocurrency initiatives to succeed. Investors and other stakeholders must evaluate the tokenomics of a project before determining whether or not to participate.
Introduction
Tokenomics, which is a mashup of the words "token" and "economics," is an essential part of doing primary research on a cryptocurrency project. Tokenomics is one of the most important aspects to consider when assessing the long-term potential of a blockchain project. Other aspects to consider include the white paper, founding team, plan, and expansion of the community. To ensure that their long-term and sustainable growth, crypto ventures should take great care in designing their tokenomics.
Tokenomics at a glance
To incentivize or punish a wide variety of user behaviors, blockchain projects build tokenomics rules that are centered on their tokens. This is analogous to how a central bank creates money via printing and executes monetary policies to either stimulate or discourage spending, lending, saving, and other monetary activities. Take note that the term "token" may refer to either money or tokens in this context. You will get an understanding of the distinction between the two here. Tokenomics, in contrast to fiat currencies, has rules that are easy to understand, can be reliably predicted, and are difficult to alter. These characteristics are achieved via the use of code.
Take the digital currency bitcoin, as an example. The entire number of bitcoins that will ever be available has been pre-set at 21 million. Mining is the process that is used to generate new bitcoins and release them into circulation. When a block is successfully mined every ten minutes, miners are rewarded with a certain number of bitcoins.
The incentive, which is sometimes referred to as the block subsidy, is decreased by one-half every 210,000 blocks. According to this plan, every four years there will be a reduction of one half. Since the creation of the first block, also known as the genesis block, on the Bitcoin network on January 3, 2009, the block subsidy has been reduced by fifty percent three times: first to twenty-five bitcoins, then to twelve and a half bitcoins, and now to six and a quarter bitcoins.
According to these guidelines, it is simple to calculate that about 328,500 bitcoins will be mined in 2022. This can be done by dividing the total number of minutes in a year by 10 (because a block is mined every 10 minutes), then multiplying this result by 6.25. (because each block gives out 6.25 BTC as rewards). As a result, it is possible to forecast the total number of bitcoins that will be mined in a given year, and the last bitcoin is anticipated to be extracted some time around the year 2140.
Tokenomics in Bitcoin also includes the formulation of transaction fees, which miners are entitled to collect whenever a new block is successfully verified. The magnitude of each transaction and the congestion on the network will cause this cost to escalate. It keeps spam transactions from happening and gives miners a reason to keep verifying transactions, even though block subsidies are going down over time.
To summarize, the tokenomics behind Bitcoin are both straightforward and well conceived. Everything is completely open and may be anticipated. Participants in the Bitcoin network continue to get compensation thanks to the incentives around Bitcoin, which add to the value of Bitcoin as a cryptocurrency.
Key elements of Tokenomics
"Tokenomics" is a catch-all phrase that refers first and foremost to the structure of a cryptocurrency's economy as its inventors created it. This is because "tokenomics" may apply to a broad variety of elements that influence the value of a cryptocurrency. When analyzing the tokenomics of a cryptocurrency, these are some of the most significant considerations you should keep in mind.
Token supply
The price of any good or service is primarily determined by supply and demand in the market for that product or service. The same principle applies to crypto. When judging a token's supply, there are several important things to keep in mind.
The first model is referred to as the maximum supply model. It indicates that there is a predetermined limit on the total number of tokens that may ever be produced using this cryptocurrency. There can never be more than 21 million Bitcoins in circulation. The total number of Litecoins and Bitcoin Cash that can ever be mined is capped at 84 million and 200 million, respectively.
There is no hard limit on the number of certain tokens. The amount of ether available on the Ethereum network continues to rise each year. There is no upper limit on the quantity of stablecoins like USDT, USD Coin (USDC), and Binance USD (BUSD), since these coins are created in accordance with the reserves that back the currencies. In principle, there is no upper limit to their potential expansion. Dogecoin and Polkadot are two further cryptocurrencies that do not have a supply limit.
The second aspect is known as the circulating supply, and it describes the total number of tokens that are currently in use. Tokens are able to be locked away in a variety of ways, including being minted and burnt. The cost of the token is impacted as a direct result of this as well.
By examining the token supply, one may get a fair idea of the total number of tokens that will eventually be in circulation.
Token Utility
The phrase "token utility" refers to the many use cases that were developed specifically for a token. For instance, the BNB token may be used to power the BNB Chain, pay transaction fees and benefit from trading fee savings on the BNB Chain, and operate as a community utility token in the BNB Chain ecosystem. Users may also generate extra revenue by staking their BNB with a variety of other items that are part of the ecosystem.
Tokens have a wide variety of further applications as well. The holder of a governance token is given the ability to vote on proposed modifications to the token's underlying protocol. The purpose of stablecoins is to function as a kind of money. On the other hand, security tokens stand for many financial assets. During an Initial Coin Offering (ICO), for example, a company might decide to sell tokenized shares, which would give the holder ownership rights and dividends.
With these criteria, you can figure out how likely it is that a token will be used, which is important for figuring out how its economy will likely change over time.
Analyzing token distribution
It is vital to take a look at the distribution of tokens in addition to supply and demand considerations. There is a behavioral divide between large institutions and ordinary investors. If you are aware of the many entities that own a token, you will have a better idea of how those entities are likely to trade their tokens, which will affect the token's value.
In most cases, there are two methods for launching a cryptocurrency project and distributing tokens: a fair launch and a pre-mining launch. Before a token is coined and distributed to the general public, a launch is considered to be fair when there are no early access or private allocations of the token. This category includes things like Bitcoin and Dogecoin, for example.
On the other hand, pre-mining enables a part of the cryptocurrency to be mined and given out to a chosen set of individuals before it is made available to the general public. This form of token distribution may be seen in action with Ethereum and BNB, to name just two instances.
In most situations, it is important to pay attention to the degree to which a token is dispersed uniformly. It is common practice to consider it riskier for a small number of major businesses to have a disproportionately large amount of tokens. When most of a token's supply is held by patient investors and the team that created it, it shows that the interests of the different parties are more closely aligned.
You should also look at a token's lock-up and release schedule to determine whether or not a large number of tokens will be brought into circulation. This puts downward pressure on the value of the token.
Examining token burning
Many cryptocurrency projects "burn" tokens, which means they permanently take them out of circulation.
For instance, BNB uses a method called "coin-burning" to eliminate coins from circulation and cut down on the total quantity of its tokens. As of June 2022, the entire supply of BNB is 165,116,760, despite the fact that 200 million BNB have already been pre-mined. BNB will continue to destroy coins until half of the entire supply has been used, at which point the total amount of BNB that is in circulation will be decreased to 100 million. In a similar way, Ethereum started "burning" ETH in 2021 to reduce the amount in circulation.
It is said to be deflationary when the total amount of a token in circulation is decreased. The reverse of this, in which the supply of a token continually grows, is referred to as inflationary.
Incentive mechanisms
The incentive mechanism of a token is quite important. Tokenomics revolves around the question of how players might be incentivized to maintain the network's continued viability in the long run. The way Bitcoin's block subsidy and transaction fees are set up is a perfect example of a well-thought-out idea.
The Proof of Stake mechanism is another validation approach that is gaining acceptance. Participants may lock their tokens using this architecture, which allows validating transactions. In general, the more locked tokens, the better the possibility of being picked as validators and receiving incentives for verifying transactions. This is because the more locked tokens, the more competition there is. It also indicates that the value of the validators' own assets will be put in jeopardy in the event that they attempt to do damage to the network. These things give people a reason to be honest and help keep the process's validity.
Many different DeFi initiatives have successfully achieved fast development by using novel incentive systems. Compound is a platform for lending and borrowing cryptocurrencies that gives investors the opportunity to deposit cryptocurrencies into the Compound protocol, earn interest on those deposits, and obtain COMP tokens as an extra incentive. In addition, COMP coins perform the function of a governance token for the Compound system. Because of the decisions made in the design, the interests of all players are now aligned with the long-term prospects of the compound.
What’s next for tokenomics
A tremendous amount of progress has been made in the field of tokenomics since 2009, when the first block of the Bitcoin network was generated. A wide variety of tokenomic models have been investigated by the developers. There have been a number of victories as well as defeats. The tokenomics paradigm that Bitcoin employs is one that has withstood the passage of time and continues to be relevant today. Others have failed because their tokenomic concepts were flawed.
Non-fungible tokens, often known as NFTs, provide an alternative paradigm for tokenomics that is based on digital scarcity. The tokenization of conventional assets such as real estate and artwork may in the future give rise to new breakthroughs in the field of tokenomics.
Closing thoughts
If you are interested in entering the cryptocurrency market, you should familiarize yourself with the idea of tokenomics. It is a word that encompasses the primary elements that affect a token's value. It is essential to keep in mind that no one element may operate as a magic doorway. Your evaluation has to take into account as many aspects as is humanly feasible and be thought of as a whole. Tokenomics can be used in conjunction with other fundamental analysis methods to reach an educated conclusion about a project's potential outcomes and the value of its token.
In the end, the economics of a token will have a big impact on how it is used, how easy it is to build a network, and whether or not the use case of the token will attract a lot of attention.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
 @ 341db5a7:4c4fc2ef
2023-12-19 05:50:38
@ 341db5a7:4c4fc2ef
2023-12-19 05:50:38Chef's notes
Just mix it all together in a bowl, feel free to remix and adjust however you feel! You are the boss of this chicken sauce!
Details
- ⏲️ Prep time: 5 mins
- 🍳 Cook time: 0 mins
- 🍽️ Servings: 8
Ingredients
- 3/4 cup mayonnaise
- 1/4 cup ketchup
- 1/2 tbls. garlic powder
- 1/4 tbls. Worcestershire
- 1/8 tbls. black pepper
Directions
- Mix it all together real good. Let it rest in the fridge for 30 mins before serving. Dip whatever you want in it. Best on chicken tenders.
-
 @ d34e832d:383f78d0
2024-02-07 07:49:05
@ d34e832d:383f78d0
2024-02-07 07:49:05Gaining the Revolutionary Potential of Bitcoin: An Appeal to Anyone
 The Bitcoin Whitepaper penned by Satoshi Nakamoto, stands as a beacon of innovation in the realm of finance and technology. Its inception introduced groundbreaking concepts that have since reshaped our understanding of currency, transactions, and trust. As investors seeking opportunities in the digital age, it's paramount to grasp the transformative potential embedded within Bitcoin's core principles.
The Bitcoin Whitepaper penned by Satoshi Nakamoto, stands as a beacon of innovation in the realm of finance and technology. Its inception introduced groundbreaking concepts that have since reshaped our understanding of currency, transactions, and trust. As investors seeking opportunities in the digital age, it's paramount to grasp the transformative potential embedded within Bitcoin's core principles.Decentralization: The Backbone of Trustless Transactions
At the heart of Bitcoin lies the revolutionary concept of decentralization—a departure from traditional financial systems reliant on intermediaries. By leveraging a trustless, distributed ledger, Bitcoin facilitates peer-to-peer transactions, eliminating the need for banks or governing bodies to oversee exchanges. This decentralized framework ensures transparency, immutability, and unparalleled security in financial transactions.
Digital Signatures: Safeguarding Against Fraud
A cornerstone of Bitcoin's security infrastructure is its utilization of digital signatures to authenticate transactions. Through cryptographic techniques, Bitcoin verifies the rightful ownership of coins, thwarting fraudulent activities and the peril of double-spending. This robust authentication mechanism instills confidence in the integrity of the Bitcoin network, fostering trust among users and investors alike.
Proof of Work: Fortifying Network Integrity
Bitcoin's innovative consensus mechanism, known as proof of work, serves as the guardian of network integrity. Miners, driven by computational prowess, compete to solve intricate mathematical puzzles, vying for the opportunity to append new blocks to the blockchain. This arduous process not only validates transactions but also fortifies the network against malicious attacks, ensuring its resilience in the face of adversity.
Deflationary Currency: A Paradigm Shift in Monetary Philosophy
In stark contrast to government currencies susceptible to inflationary pressures, Bitcoin emerges as a beacon of financial sovereignty. With a capped supply of 21 million coins, Bitcoin transcends the whims of central authorities, offering investors respite from the erosive effects of inflation. Its deflationary nature underscores its appeal as a store of value, fostering a community of steadfast believers in its enduring worth.
Unrivaled Innovation and Adoption
Beyond its conceptual brilliance, Bitcoin boasts the distinction of being the pioneering force behind the cryptocurrency revolution. Its unrivaled network and user base epitomize security and acceptance, cementing its status as the premier digital currency. Moreover, Bitcoin's whitepaper has served as the blueprint for countless blockchain projects, catalyzing innovation and propelling the evolution of the digital landscape.
In conclusion, the Bitcoin whitepaper encapsulates a vision of financial emancipation and technological advancement. Its principles of decentralization, digital signatures, proof of work, and deflationary economics herald a new era of monetary sovereignty and global connectivity. As investors, embracing Bitcoin is not merely a strategic decision but a testament to our collective commitment to innovation and progress in the digital age. Let us in unlock the boundless potential of Bitcoin—the energy of the future, today.
-
 @ cb084639:2f16502a
2023-12-18 17:54:54
@ cb084639:2f16502a
2023-12-18 17:54:54Chef's notes
เนื้อที่ใช้นั้นสำหรับมือใหม่ยันมือเก๋า ง่ายที่สุดคือเนื้อตามร้านขายวัตถุดิบทั่วไป ที่เป็นเนื้อที่แพ็คไว้ชิ้นละ 250-300 กรัม นั้นแหละกำลังดี ดูดีๆมีทั้งแบบเนื้อโคขุน เนื้อออสเตรีย เนื้อวัวบรามันที่ค่อนข้างเหนียวไม่ค่อยเหมาะกับการมาทำสเต็กเท่าไร ในที่นี้ถ้ากลัวเนื้อจะเหนียวไปก่อนที่จะทาเกลือพรืกไทย ใช้ส้อมแทงเนื้อให้ทั่วทั้งสองด้านก่อนก็ได้ เอาเป็นว่าเรามาเริ่มกันเลยดีกว่า ลุย!!!
Details
- ⏲️ Prep time: 10
- 🍳 Cook time: 15-20 min
- 🍽️ Servings: 1
Ingredients
- เนื้อสันสะโพกสเต็ก 1 ชิ้น 300 กรัม
- เกลือชมพู 1 ช้อนชา
- พริกไทยดำ 2 ช้อนชา
- เนยแท้ไม่เติมเกลือ 1 ช้อนโต๊ะ
- น้ำมันหมูหรือน้ำมันวัว 1ช้อนโต๊ะ
- กระเทียมบุบพอแตก 5-7กลีบ
Directions
- แกะเนื้อออกจากแพ็คซับน้ำให้แห้งพักไว้
- บดเกลือชมพูและพริกไทยดำเข้าด้วยกันแล้วโรยให้ทั้วชิ้นเนื้อที่เตรียมไว้
- ตั้งกระทะไฟกลางไปทางเบา ใส่น้ำมันลงไป
- กระทะเริ่มร้อน นำเนื้อด้านสันไปนาบให้ทั่วทั้ง 4 ด้าน ทอดเฉพาะขอบก่อน
- พอขอบสีสวยแล้วก็ลงทอดด้านปกติทั้ง 2 ด้านใช้เวลาด้านละประมาณ 40 วินาที แล้วแต่ความหนาของเนื้อ
- พอเสร็จเบาไปให้น้อยที่สุด ใส่เนย และกระเทียมที่เตรียมไว้
- เนยละลายตักน้ำเนยสาดไปบนเนื้อทั้งสองด้านจนพอใจแล้วนำเนื้อออกมาพักไว้ 10-15 นาที
- จัดจานให้สวยงามตามสะดวกพร้อมเสิร์ฟ
-
 @ f3df9bc0:a95119eb
2024-02-07 00:38:07
@ f3df9bc0:a95119eb
2024-02-07 00:38:07U2FsdGVkX1+k57Eojc6Qq5kNlx8wb3/ndCq40g6V7uO5SaBbzVeeN0pFm0tsxGJLQnTuarQ0n5LX1VuPxcekvydN6yIbo800Eyag0Xazgrw=
-
 @ cb084639:2f16502a
2023-12-17 18:13:32
@ cb084639:2f16502a
2023-12-17 18:13:32Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 5 min
- 🍽️ Servings: 1
Ingredients
- Lamon
- Hdk
- Qww
Directions
- นำ1และ2
-
 @ ecda4328:1278f072
2023-12-16 20:46:23
@ ecda4328:1278f072
2023-12-16 20:46:23Introduction: Crypto.com Exchange for European Traders
Reside in Europe, including non-EUR countries? Frustrated with the exorbitant spreads on the Crypto.com App (up to 5%) and high credit card fees (up to 3%) when you're eager to buy or sell cryptocurrency? This guide is tailored for you!
Quick Transfer with SEPA Instant
Did you know that you can transfer EUR to your Crypto.com Exchange account within minutes, and sometimes even seconds, including weekends and bank holidays? Yes, you absolutely can, thanks to SEPA Instant Credit Transfer (SCT Inst).
Supported Banks
To avail of fast EUR to Crypto.com Exchange transfers, ensure that your bank supports the SEPA Instant Credit Transfer (SCT Inst) scheme. If your bank, or FinTech apps like Wise, is on this list, you're good to go.
My Recommendation: I vouch for Wise due to its flawless functionality and favorable exchange rates. If your bank doesn't support SCT Inst and you're unwilling to wait, you can swiftly load your account with any currency using a bank card for a rather small fee (~1.2%). My Wise Referral Code: andreya54
24/7 Transfer Availability
SCT Inst is incredibly flexible:
- 24/7/365 availability, including weekends and bank holidays
- Immediate receipt and availability of funds
- €100,000 transaction limit (unless previously agreed otherwise between PSPs)
For more details, you can read this document by the European Central Bank.
TL;DR
To Buy crypto: -
EUR => BTC/EUR => ANY/BTC => ANY
- Use Limit order at the Lowest offer (aka "ask") (red order book)To Sell crypto: -
ANY => ANY/BTC => BTC/EUR => EUR
- Use Limit order at the Highest bid (green order book)How to Buy Cryptocurrency with EUR
Here's how to save up to 8% on spreads and fees when buying/selling crypto compared to the Crypto.com App.
-
Log in to Crypto.com Exchange: Go to the Dashboard or Wallet in the top right, and navigate to Bank Transfer on the left sidebar.


-
Deposit via SEPA: Choose
EUR -> SEPA -> Depositand use the displayed IBAN for transferring EUR to your Crypto.com Exchange account.
Trading Interface Tips
Intimidated by the professional trading interface? Don't be. Here's how to read the order book:
- Offers (Red): These are the prices at which people are willing to sell the asset. The lowest offer is often called the "Ask."
- Bids (Green): These are the prices at which people are willing to buy the asset. The highest bid is often called the "Bid."
Trading occurs when a buyer's bid meets a seller's offer. In market terms, this is often at the point where the highest bid and the lowest offer intersect. This intersection is frequently referred to as the "market price" for that particular asset at that specific time.

On trading pairs
Crypto.com Exchange offers only two EUR trading pairs: BTC/EUR and ETH/EUR. This is logical given that these assets have the highest liquidity in terms of market capitalization. While we hope for the addition of more pairs, the existing options still serve as useful proxies for purchasing other cryptocurrencies.
"highest liquidity" means that an asset like a cryptocurrency or stock can be easily bought or sold without causing a significant impact on its price. For a trader, this is good because it means they can quickly enter or exit positions without worrying about huge price changes.
Steps to Buy BTC with EUR
- Navigate to the
BTC/EURSpot trading pair. - Choose "Buy" on the right-hand menu.
- Stay on the "Limit" tab.
- Specify your order value (how much EUR you want to spend to buy BTC)
- Select the lowest offered (aka "ask") price (bottom of the red order book).
- Click "Buy BTC" to confirm.

Diversifying: How to Buy ATOM Token?
First, buy BTC as previously explained. Then:
- Navigate to the
ATOM/BTCSpot trading pair. - Choose "Buy" on the right-hand menu.
- Stay on the "Limit" tab.
- Specify your order value (how much BTC you want to spend to buy ATOM)
- Select the lowest offered (aka "ask") price (bottom of the red order book).
- Click "Buy ATOM" to confirm.

Selling Your Assets
The process is the same but in reverse. Sell at the highest bid (top of the green order book).
Selling ATOM for BTC
- Navigate to the
ATOM/BTCSpot trading pair. - Choose "Sell" on the right-hand menu.
- Stay on the "Limit" tab.
- Specify your quantity value (how much ATOM you want to sell to buy BTC)
- Select the highest bid (top of the green order book).
- Click "Sell ATOM" to confirm.

Selling BTC for EUR
- Navigate to the
BTC/EURSpot trading pair. - Choose "Sell" on the right-hand menu.
- Stay on the "Limit" tab.
- Specify your quantity value (how much BTC you want to sell to buy EUR)
- Select the highest bid (top of the green order book).
- Click "Sell BTC" to confirm.

You can then withdraw EUR back to your bank directly from the Crypto.Com Exchange.
Additionally
After you click "Buy" or "Sell," you will see your order in the "Open Orders" tab in the bottom menu. Once your order is 100% filled, it will disappear, and you will be able to see it in the "Trade History" tab.
Sometimes you might miss the opportunity as the price moves, and someone else's order could get filled faster than yours. Don't worry; you can either wait a little longer in hopes that someone will make an offer at this price or simply cancel your order and submit it again at the next lowest price if you are in a hurry.
Maker/Taker Fees Explained
When you open Buy/Sell orders on the Crypto.com exchange, you may incur small Maker/Taker fees of less than
0.0728%, or even no fees at all, depending on the amount of CRO you have staked on the platform.- Maker Fee: When you place an order that adds liquidity to the market, you are a "Maker". This usually happens when you set a "limit" order that does not execute immediately and sits on the order book waiting for someone to match against it. Since you are "making" liquidity available for others, you pay a Maker fee.
- Taker Fee: When you place an order that removes liquidity from the market, you are a "Taker". This generally occurs when you place a "market" order that executes immediately against a pre-existing order on the order book. Because you are "taking" liquidity away, you pay a Taker fee.
Typically, Taker fees are higher than Maker fees as an incentive for traders to add liquidity to the market.
Read more on Maker/Taker fees on the Crypto.Com Exchange platform.
Conclusion
Thanks for reading this guide! It's lengthy, but every detail is crucial for optimal trading on Crypto.com Exchange.
Referral Code
If you haven't opened a Crypto.com Exchange account yet, use my referral code:
pv0r199m6j
Referral Link: Sign Up Here -
 @ 3cd2ea88:bafdaceb
2024-02-06 19:54:32
@ 3cd2ea88:bafdaceb
2024-02-06 19:54:32Siamo entusiasti di annunciare che i nostri amministratori, Lucaperry e Matothemoon, hanno trionfato nella categoria TraderPro di Bitget! 🏆 Ora, potete copiare le loro mosse e imparare da loro nella nostra community.
💼 I TraderPro offrono ai nostri Follower una maggiore sicurezza nel trading. Sono stati selezionati con cura e hanno superato una rigorosa selezione per garantire un'esperienza di trading di alta qualità. Seguendoli, potrete ottenere preziose intuizioni e migliorare la vostra strategia di investimento.
📈 Con le nuove impostazioni del copytrading Bitget, le opportunità sono ancora maggiori, garantendo un controllo superiore sui vostri fondi. È un'opportunità da non perdere!
🔥 Per coloro che si iscriveranno con il nostro referral code (6w5d), avranno accesso alla nostra community privata e uno sconto a vita del 10% sulle commissioni. Unisciti a noi e inizia il tuo viaggio nel mondo del trading! 💰
🚀
-
 @ ecda4328:1278f072
2023-12-16 20:45:50
@ ecda4328:1278f072
2023-12-16 20:45:50Introduction
In the world of blockchain technology, a nonce plays a pivotal role in ensuring transaction security and uniqueness. This article demystifies the nonce's role in major blockchain platforms - Bitcoin, Ethereum, and Cosmos/CometBFT, highlighting its importance and distinct functionalities in each.
The Role of Nonce in ECDSA and Its Importance
In Bitcoin (and most of blockchains) transactions, the nonce is a randomly generated number integral to the Elliptic Curve Digital Signature Algorithm (ECDSA). It guarantees each digital signature's uniqueness and security. The randomness and secrecy of the nonce are vital. If predictable or exposed, it can compromise the entire security of a transaction.
The Risk of Nonce Exposure and Private Key Recovery
If a nonce is compromised, it poses a risk of private key recovery. To understand this, one must consider the signature components (r, s), the public key (which becomes known once you sign & broadcast at least one transaction in Bitcoin). A predictable or reused nonce can leak critical information, enabling savvy attackers to backtrack to the private key.
This specific type of attack is called a nonce covert channel attack. And methods protecting against this are called anti-klepto or anti-exfil (interchangebly).
Worth noting that anti-klepto/anti-exfil are broader terms for methods that protect against various forms of secret data exfiltration, including but not limited to attacks involving nonce misuse.
Bitcoin's UTXO Model and Nonce Functionality
Bitcoin utilizes the Unspent Transaction Outputs (UTXO) model, ensuring that each Bitcoin is spent only once. This model is distinct from nonce management in ECDSA and adds an additional layer of security against double-spending in the Bitcoin network.
Address rotation in Bitcoin, as implemented through BIP32 (Hierarchical Deterministic Wallets), enhances privacy and isolates financial risk by generating a unique address and corresponding private key for each address created, not necessarily for each individual transaction. While this strategy effectively segregates risk to individual addresses, it does not directly prevent the vulnerability of private key derivation from nonce exposure in the ECDSA signature process, as this risk is inherent to the signature mechanism itself and is independent of the address or its associated private key.
Ethereum's Account-Based Model and Nonce Usage
Ethereum, unlike Bitcoin, operates on an account-based model. Each account has a sequential transaction nonce, starting from 0, which is public. This nonce, different from the ECDSA nonce, helps in transaction ordering and network integrity.
Nonces in Cosmos/CometBFT Blockchains
Cosmos/CometBFT blockchains, akin to Ethereum, adopt an account-based model. They use nonces, similar to Ethereum's transaction nonce, for transaction ordering and preventing replay attacks. These nonces are distinct from the ECDSA nonce used in the digital signature process.
Conclusion
The use of "nonce" in Ethereum for transaction sequence (akin to account sequence in Cosmos/CometBFT blockchains), leading to confusion with ECDSA nonce, is simply a coincidental choice of terminology.
In summary, while Bitcoin, Ethereum, Cosmos/CometBFT and many other blockchains employ nonces in ECDSA signing, their transaction management and double-spending prevention methods differ significantly. Understanding these nuances is crucial for blockchain users and developers to appreciate the underlying security mechanisms of these diverse platforms.
References
- Hardware wallets can steal your seed!
- A Glimpse of the Deep: Finding a Creature in Ethereum's Dark Forest
- MuSig-DN: Schnorr Multisignatures with Verifiably Deterministic Nonces
- Android's SecureRandom - not even nonce
- Anti-klepto explained: how the BitBox02 protects you against leaking private keys
- Anti-Exfil: Stopping Key Exfiltration
-
 @ f3df9bc0:a95119eb
2024-02-06 19:16:31
@ f3df9bc0:a95119eb
2024-02-06 19:16:31U2FsdGVkX187U4GCR3FycI2UtBbZ6ya2zDG92rQRsW36lfDg+wY/kpS80w4XSJcvOiIkPxrqqNbcIU0/7BpQQ9nNDaH7tDCxs7JyXbLG1vYjndxrSG1nMF6l0NUYeBw2geR045mClQTOyYgwBXp2OOnKLtrEXGWrer8SSz5hLs4F3IJwXCnC0io3/ykkw2XkebnOEshDBC4B/TAg0cm4Dxm5CMOKQVFGScCgvFbIPTmejr4bIiSi/t5lCtW7Vi8fEB0L/OO/fLxVLbmnAJrCDtNd+/PJMz6/Oa9C2Hx7dUK28XcKXyqo1j16DrtT6O0UJOIJTTB4PcRKNtFLUR2/mqECKJAnSvLsYS5EW52iCvAJDxRf266jLwlXDCFrWG6/8OCzsctssNZdzU4Z/MqlJw5vQv8X7AzyT5RmKLC6TL+KvyxqEA522QZPWpZq7Z/gnE0QXjMZztKq3sXxaoPhWEGe96zZFgY+Rtf2ksj3RTc2GiqSLO6H3ZFBNj/i/Exhyc+WYERUYFjTEG99udBf5rJH1PyC33UwMTGAMgN7O0KP2vxgzuJVEtWfQqnqUMVPlM5dMsIWqGi6KMZmwZORfZXe9qs0HBQzh+7G6SsfDKZzfBMUJiG96HDVYi4fSFy1W0rqFBSkt2KWkLxYcNd3/lL/B13jRhsn+oVsI40Je3i0080hyH3aTezY0AsuuaOfutuY8xnDs9PbIxdMurjcF0wXJK/PDaPVjDphFNx9FxVZS7Qvlyq0ES5tIlBiJ8jbeNKPT4D4XWvD9BJx+ybv3jP5COEi0q+zCzoFPcLg4LFwXNo1N2U5NW8wOacEmjDZSnpRfry7NCBETvFL+mVVPzMPwRBOFO7zjejg8+T2q4j7BaaskMV4TCDJzrYrRW+kA5mQjzobo05yGTKCYVracUX4hSg/mZApzQCNrXmQ3GLqPaDf0c0qf3FVrOGWjKcMIWMHop+JjD2CfP9vLrYTI3ElAyC27Q+Vh34dO0snw9KE5ahq+or54JRiD9u03SmqUvmZMc0u+S8/NUzqRzgWwHiT+pZwHi5dsrI4Djhb69Tbpw5TGaCheAsuXS8wtXPpz0urK1Xex2p7fMLQrYPQH8QxRhV5joCXpiVL+Ln+ddbRdeZInHVqJdeKhJok9c1QHz8lZJQi7Mn/4wDtAJPGb2xPR1m+HEUW8x+17D0xviIcLY4snPrse4rz+eVL5iqFDvjGI9y1srO4REJifv2OZX7TEV9aM1mBB4IrAGlyG4k/ikfkKSU1G/7g3BbBo8EEJBOrTaGUHUQIR3V0G6rBjATeZCilflp6WXx5Jk0FPt8uVBhOVBkAz5ejZZFX/0ArjFKkYEziG1c8YKi17rJ1mHQST1ZStDIoZ1gm3hs4hczlVrLpCUTCG6l2f4qpbmalH1GpB2qPIqghlRD0cf3w9ePNcdUZueuYmEdfbSe+sgcKSVoVHRnk24N0wUdT02YcEssZL7knM1Dy1oPVm4B2jluUMDb+kjXI1Xh0nyh6DUyPhJMM0o9qkKlA7Ke13LgRwjdpHUzXW1diXNcF1rnRB0GnH0vXTvVF3BpmYMo3pe9Wh2/maNAXwt6iiQ3u/Yi7Y+HoPxCni2O099qTu1oDqrA8tymBcjktaPkxkMx1ssxiR+o9F4lM6bHUAaiaY5m+Uv8k1IbbOY3It43Rp/FPo+yvRDsU+O/kW+B1q3sY92GQqNYPhPksXvoYR8JBHm1EWeQMzkf0Wt9K7CUmTThADFabDdOsiT1vytyAsaqI1e/YOuf4KtmkB8EkeIL3TWbcChTGYAFuex++afmpo2zabn9HhzKv5S20/ODsSsQamfdOgZ+xyjPlHpdOpCTjNPLH94MEmZ5TJfIbiSdXrtVA4OVOQQzW8mBRR6vG5kT09QHozyshwI/YrUCv/nTulbVJeI0exzkbbySEA0909Gvbm5VPoTcAE/yaozOtVZslk+W0ZlTi3i8hKzvTuOHcowQM3va10o1EPFxB9B9ZTLxiZBUZaGC7K2vU+DMOgxDJqafAkaPqUG+RLA85OgViyknSoWh0wJ93nRUyyWMudXkGJ3odXLDjnaIjmy+sqAXcD80AXurFDgrvujoLid/0M0ww6yWbfVOvvP4kd631xJGGQ6lMVEe3avdYcFy8cBQmvHYUMa8xSvJGX6mOAerpi8sgHC5Bdt8c8ClhtwYb5/1jJUTKvmNmCrQX3HSLZQ+GSwuG+uocYU38YHycfLqpj7upwIX6DdnGFtPEXpondcG3Iyj7ZnpK4qHVRK9SUcmikuv41/qhsxMXhvjDddjwEtM6vWdAQW53/cuK30t19Txwm7kh++8sWynFskYy+NTmIok7jcx4mRL5vArO0fdahtd+HY+wUHgWZxiKVVOwWM0MXMOVjTrOOQo7wB+jiHLHCcqptxIx7sF1W2mne55pxxt7EqrVsPqv7XofZe2Nhq/SXI9lScHX0kR04furg5Pyh7b1PmjHAqc6doVBPbZlEk3EQcnZbyoYlk6F7ZwSvUhIEKIHwTaM0Gai0H2GE/HKdhZ++beJ4CmUfPjsSes+reWuXjqDI9IeGiOjN4ShqXYh3vANxHuavmUFYOTisgA/OoT9yVLKRtI4Q8wpJZklfELLc8y899ZKu5CmyI+3Jw65Dzj4K+tIKwMpSYLgPym8pJIzmAIOLWv0YHJ0bezYWTbW0OWH98KBU4JOn5v0mEL2UsSCLJo+kGhfIw+6xL0LlfsH9QYsGxy0g80u9monAbjZnPiHsuTlglacdCQI90T30oAEPwXfnU5FEKrC1+7U8fS/scKD2abCDzfLTVBbb32u9ZQ8OwmBjFqRd19u7LKVyTEfWixPaXlpdZqwlhDegOW4u9lu+ULdrrVI2yVkZrWJ0IqUk5v2VxyrVDom5gMKMs5/M3cDcxS334r/8jr9UkubfA16rQbuOD+GDfDl8aUJvHz2qdzslln4hX09j4LorikJbP1NfKn2wadTxMIo3WE=
-
 @ ecda4328:1278f072
2023-12-16 20:45:10
@ ecda4328:1278f072
2023-12-16 20:45:10Intro
I've left Twitter (X), WhatsApp, Telegram, Instagram, Facebook and Google. The driving force behind this decision was the escalating overzealous censorship. I cannot condone platforms that actively indulge in this practice. In all honesty, I've always felt uneasy using "free" platforms riddled with ads where the user is the product and doesn't own the content they produce.
Let's be real: hardly anyone thoroughly reads the Terms of Service (ToS).
Censorship and Shadow Banning
The final straw was when I resorted to a text editor for drafting messages/comments, hoping to rephrase them so they wouldn't get deleted moments after posting. This isn't exclusive to just one platform; I've encountered it on YouTube and LinkedIn too. Twitter (or X, as I now refer to it) has a history of shadow banning users' posts. It's been beyond frustrating to get banned from Telegram groups simply for posing legitimate questions.
You can test LinkedIn's censorship mechanism too, simply add "Binance" word (without quotes) to any of your comment and your post will disappear. At least that is what I've seen couple of months ago. Similarly, comments on YouTube often disappear precisely 60 seconds after posting if they contain specific keywords. I know they call it filtering, but it does not make any sense. In my opinion, legitimate companies and links shouldn't trigger these filters.
Community and Connections
Recently, I attended the Cosmoverse 2023 conference in Istanbul. Most attendees exchanged their Telegram or Twitter (X) contact information. Since I didn't have either, I gladly shared my Nostr and SimpleX Chat details. Many privacy advocates were quick to connect on SimpleX with me, though several didn't.
I learned about SimpleX Chat from Jack Dorsey, who mentioned it during a conversation in July:
While Signal has its shortcomings, I still keep it as a backup communication tool.
One More Last Straw
During the conference, I temporarily reinstalled Telegram to communicate with my group. Convincing nine individuals to switch to SimpleX on the spot seemed impractical.
At the conference, I bought a Keystone hardware wallet. Shortly after, I connected with the seller, Xin Z, on Telegram. However, I was banned from the official Keystone Telegram group right after posing a question.

Upon inquiring, Xin Z clarified that Telegram's official team had banned me, not the group's admin. 🤯

Business and Community: Collateral Damage
Censorship doesn't just silence voices; it hinders potential growth and stifles innovation. When platforms arbitrarily or aggressively censor content, they inadvertently create barriers between businesses and their potential clients. New users or clients, when encountering such heavy-handed moderation, may feel discouraged or unwelcome, causing them to retreat from the platform altogether.
Moreover, for businesses, this form of censorship can be devastating. Word-of-mouth, discussions, and organic community engagements are invaluable. When these channels are hampered, businesses lose out on potential clientele, and communities lose the chance to thrive and evolve naturally.
Censorship, in its overzealous form, breaks the very essence of digital communities: open dialogue. As platforms become more censorious, they risk creating sterile environments devoid of genuine interaction and rich discourse. Such an atmosphere is not conducive for businesses to foster relations, nor for communities to flourish. The ultimate price of overcensorship isn't just the loss of a few voices—it's the fragmentation of digital society as we know it.
Freedom to Choose
I strongly advocate for the adoption of Free and Open Source Software (aka FOSS) products. In these platforms, you aren't treated as the product. However, supporting them through donations/contributions is always an option. Platforms like Nostr and SimpleX Chat are excellent starting points.

My Nostr account:
npub1andyx2xqhwffeg595snk9a8ll43j6dvw5jzpljm5yjm3qync7peqzl8jd4Disclaimer
This article reflects my personal experiences and opinions. It is not intended to criticize or demean the Keystone hardware wallet product or its quality. Furthermore, the actions taken by Telegram are not a direct representation of the views or policies of the Keystone Telegram group admins. Any reference to specific events or entities is made in the context of broader concerns about platform censorship.
-
 @ b2caa9b3:9eab0fb5
2024-02-06 17:59:45
@ b2caa9b3:9eab0fb5
2024-02-06 17:59:45Remember my post from a couple of days ago? I believe it was two days ago when I shared my adventure titled “Unplugged in Paradise: A Day at the Beach Hotel Office”. In that post, I found myself in a stunning location, attempting to work, but alas, I couldn't connect to the Wi-Fi. I had to rely on my phone data to stay connected. Well, guess where I am today? Yes, I'm back at the same place because I couldn't resist the breathtaking view and the refreshing ocean breeze. Especially compared to the scorching heat at my rented home lately. So, I decided to return today and soak up this fantastic view while writing a series of blog posts - call it a blogging marathon if you will.

Getting here was a breeze; I hopped on a TukTuk and only paid 150 Kes this time, a significant improvement from the 300 Kes I shelled out previously. It's safe to say that today's price felt more reasonable. I'm hoping for a productive day in this exquisite location.

Lately, I've been eagerly awaiting a package I ordered from Germany: a brand-new razor. My old one was made of plastic, and this year, I made a personal commitment to reduce my carbon footprint and eliminate plastic from my life in favor of more sustainable choices. Conveniently, my old razor fell apart, though not in an ideal location. Dealing with customs has been a bit of a hassle, even though Amazon covered all the import fees and charged my card. I'm keeping my fingers crossed that it will arrive this weekend or early next week. Now, you might be wondering, why did I order a razor from Europe? Well, the issue is that you can find expensive blades and the old-style cheap ones here, but you can't find a quality razor. Every time you try to buy one, they have to order it from Europe, and you have to pay upfront. You never really know what you'll get, except that it will be pricey and likely low quality. So, I decided to take matters into my own hands and ordered it from Amazon, which offers worldwide express shipping for a reasonable 23 euros.

For now, I'll wrap up this post and get back to writing and taking photos of this beautiful place.

Fast forward to late evening, and I'm back at my accommodation. This afternoon was fairly low-key; I tied up some loose ends, packed my laptop into my bag, and headed to the pool area. I lounged around for a bit, snapped some photos, and took a leisurely stroll. Then, I decided it was time for a refreshing dip in the pool. I'd called ahead earlier to check if it was okay for me to spend the day working here, and they assured me that their Wi-Fi was top-notch and that I could use the pool as well. Excited, I waded into the pool and explored the area. There was even a bar by the poolside, allowing guests to enjoy a drink while cooling off. However, to reach the bar, you had to be a swimmer, as the water was about 2 meters deep on the way there. At the bar, it was just deep enough to stand comfortably.

But my plans took an unexpected turn when a man approached me before I could reach the bar. He informed me that there was a fee for using the pool, though he didn't specify the amount. After a few minutes, he returned with a bill, demanding 1000 Kes, roughly 7 euros. I was taken aback and insisted on a comprehensive bill for everything I'd consumed. He took my money, left for a while, and when he finally returned, he presented a bill, but it didn't include the pool charge. He had essentially rewrote and split the bill into two, separating the drinks from the pool fee. I was upset by this and sought someone to resolve the issue. I asked for a separate receipt for the pool fee, and after some apologies, he finally handed it over.

Feeling frustrated, I decided to take a stroll along the pristine white beach back to my place. It was a beautiful walk, even though I had to navigate some sharp rocks due to the rising tide. I couldn't help but wonder why these rocks were always so sharp; it's a mystery I can't explain. Despite the business mishap at the pool, the walk was absolutely enchanting. However, if you were to ask me whether I'd turn this place into my office again, the answer is no. It's a stunning spot, no doubt, but the way they conduct business isn't to my liking. Sadly, it's a common practice in Kenya. Nevertheless, let's keep moving and explore more beautiful places. There are plenty out there waiting to be discovered.









-
 @ ecda4328:1278f072
2023-12-16 20:44:09
@ ecda4328:1278f072
2023-12-16 20:44:09In the evolving world of cryptocurrency, ensuring the security of your digital assets is paramount. For those looking to safeguard their Bitcoin and other cryptocurrencies, selecting the right hardware wallet is crucial. Here, I recommend some top choices based on functionality and security.
Swiss Choices for Bitcoin: BitBox02
For Bitcoin enthusiasts/maxis, the Swiss-made BitBox02 - Bitcoin-only edition is a top recommendation. This wallet focuses solely on Bitcoin, ensuring specialized security and features for the most popular cryptocurrency. Although there is a version supporting multiple cryptocurrencies, the Bitcoin-only edition stands out for its dedicated functionality (Less code means less attack surface, which further improves your security when only storing Bitcoin). Learn more about this wallet here.
Swiss Tangem: A Unique Approach
Another Swiss option, Tange. Tangem is particularly appealing due to its unique approach to security. With Tangem cards, there's no need to generate or back up a mnemonic phrase (a series of 24 words used to recover wallets). The key is simply not to lose the cards and remember the access code, which adds an extra layer of security in case of loss. This approach simplifies security while maintaining robust protection for your assets.
Special Offer: For those interested in purchasing a Tangem Wallet, I have a special offer for you. By using my referral code, you can buy a Tangem Wallet at a discounted price. Click here and use the promo code MY6D7U to enjoy your discount.
Explore Tangem here.
Tangem's Mnemonic Phrase Advantage
Tangem's standout feature is the absence of the need for a mnemonic phrase. This reduces the risk of loss due to complicated backup schemes.
However, for those who do backup mnemonic phrases, I recommend using a metal plate for added durability against elements like fire and water. It's crucial to protect your mnemonic phrase thoroughly, as it essentially makes you your own bank. A fireproof and waterproof safe is advisable for storing these phrases. While some split the phrase and store parts in different locations, I advise against overly complicating the storage scheme to prevent loss. Adding an optional password for additional security is also recommended. Remember, mnemonic phrases unlock the same wallet addresses across different hardware wallets, as most use the BIP39 protocol for generating a seed from the 24-word phrase. Check out this list for reference: BIP39 Word List.
Worth reading: - Seed Phrases Explained: Best Practices for Crypto Security - How Tangem Wallet backs up private keys - How Your Tangem Wallet Works Without Tangem: Apocalypse Scenario
French Ledger: A Shift in Trust
The French Ledger Nano S Plus or Ledger Nano X were previously high on the recommendation list. However, trust in these devices has diminished due to Ledger's service Ledger Recover allowing mnemonic phrase backups on third-party servers. This goes against the principle of a hardware wallet, where your seed should never be exportable or stored externally.
Chinese Keystone 3 Pro: A Contender with Caveats
As an alternative to Ledger, the Chinese Keystone 3 Pro could be considered. Although there are concerns about its Chinese manufacturing possibly implying vulnerabilities, its functionality—like signing transactions via QR codes without direct computer connection—offers a level of security. However, choosing a hardware wallet should be based on the specific cryptocurrencies you plan to store. For Bitcoin-only storage, the BitBox02 Bitcoin-only edition is highly recommended.
Worth reading: - Does airgap make Bitcoin hardware wallets more secure?
Czech Trezor: Slow to Innovate and Security Concerns
Regarding the Czech Trezor Model T, it's not recommended due to its slow pace in integrating new features. Recent controversies surrounding the integration of CoinJoin and concerns over censorship and transaction filtering have also marred its reputation. Furthermore, the Trezor Model T has proven to be vulnerable in case of loss, as demonstrated by a hacker in this video, potentially exposing your cryptocurrency to risks.
The Case of Canadian Coldcard (MK4): A Shift from FOSS
An important development in the hardware wallet space is the case of the Coldcard Mk4. Initially, Coldcard was a fully open-source software (FOSS) project. In FOSS, the "Free" refers to the freedom to run, study, redistribute, and modify the software, a principle highly valued in the crypto community. However, a significant shift occurred in the journey of Coldcard:
- Initial FOSS and Bootstrapping: Coldcard, developed by nvk and Peter, started as a FOSS project. They bootstrapped the development, rejecting offers from venture capital investors interested in the project.
- Foundation's Entry: Subsequently, the Foundation cloned Coldcard's code and announced a slightly different hardware. Notably, they raised funds from the same VCs that Coldcard had previously turned down.
- License Change: In response to these events, Coldcard altered its software license. The new license permits all activities except those performed by the Foundation, marking a departure from its original FOSS status.
This change has sparked discussions within the cryptocurrency community about the importance of maintaining open-source principles in the development of hardware wallets. The Coldcard MK4's shift from FOSS underscores the complex dynamics between open-source ethos and commercial interests in the crypto world.
Source: X/Twitter thread.
Conclusion
In conclusion, when choosing a hardware wallet, consider the specific cryptocurrencies you'll be storing and the compatibility of the wallet with your intended use, especially concerning smart contracts and other features. While there are numerous options in the market, careful consideration of security features and the reputation of the manufacturer can guide you in making a secure choice for your digital assets.
-
 @ b2caa9b3:9eab0fb5
2024-02-06 17:53:14
@ b2caa9b3:9eab0fb5
2024-02-06 17:53:14In today's adventure, I decided to switch up my work setting and take you along for the ride as I settled into a beach hotel, a truly delightful one at that, promising excellent wifi for a productive workday. I'm a proud minimalist, equipped with nothing more than my trusty Osprey Nebula 32L backpack, housing all my essentials, weighing in at less than 10 kg - clothes, shoes, electronics, toothbrush, toothpaste, and soap neatly stowed away.

As I prepared for my excursion, I emptied my backpack, leaving only the electronics inside. The first leg of my journey involved catching a tuktuk to the beach hotel, where I was greeted by a friendly security guard who welcomed me with a warm "caribou" - a precursor to the enchanted world that awaited beyond the imposing iron gate.

Following the security guard's directions, I wandered along a path lined with quaint cottages available for rent until I reached a breathtaking scene: a pool, a bar, and a restaurant all nestled within a lush, jungle-like resort. I chose the pavilion as my workspace for the day, offering a panoramic view of the resort on one side and a stunning vista of the beach with its powdery white sands on the other.

However, my plans hit a snag when I discovered that the promised wifi wasn't functional in the pavilion. Attempts to relocate to the restaurant and poolside in search of a stable connection proved futile, eventually forcing me to rely on my mobile data to salvage a couple of hours of work amidst picturesque surroundings.

In true African fashion, the assurance of good wifi often falls short of reality, leading to a day filled with beautiful scenery but a less-than-productive workday. Nonetheless, I made the most of it, even indulging in a delectable pizza during my quest for a functioning wifi connection.

As the day wound down, I packed up my laptop and headed back to my temporary abode. In hindsight, it wasn't the most productive workday, but it was undeniably a picturesque and enchanting mobile home-office experience. Take a peek at the photos to capture a glimpse of this unique workspace.













Follow me on Nostr
-
 @ f3df9bc0:a95119eb
2024-02-06 17:41:58
@ f3df9bc0:a95119eb
2024-02-06 17:41:58U2FsdGVkX1+PPMF+/wmn/6FQPbun7rdQQo6OigCWq94U2DGMvDhENBv2p1bzGbjneXddrJhdPqAg+eErQ5WbY9+7O9qRWDeqrVhHvx9V4jyi1IX6tK7+IRCYBq31sJHvyT7LBmPzU6fzba3+ssiWMmllEAbbG18v/zQrFV6H3T9DktKTmDB7tLacXgOamL8JmeZu91N0S5e9dvxg4bz3M31b3zfJTCsE4UfcGtWNUso1Abjh+KwWXu3zK6ev8mskbcm1wdVVPyK3ZL+OBl3OEBAaxouKatHN5o7YivH+P1omqH0QiOBN5aFl6K5iOKIKWYg/1I+dJwxHVTO2PYHg7fcQVNc4I0dCqMSQ5adIS3IOIFQTKRdUILya0wb9/TflQWz+i9rBNCzTRLLRSn3sc3NIqNzeN+r+1vHsPRbkNpINWq3y0ARwhpJ83nM+sm0ENPdu716qwTdI+RvnJQSaK+YQGprxYIyAeCxqpRcdFi90hCbmpC+0H0wHAFWmJWfBaaYtVWLq+rmbDw2q5+mdfmxLNS1GkUP7McOC9Kamv9FFugoGs+9HvLgZv7NgBL8dqKt5y3QdZLLZwkbE8ozZL+xGFLx+PRnrdAqFx2in4a1Hk+cTefWbwr+QrQDXPEFbeMLPd4E1PReRmG4d52yH8zkAZMd/PxQnD2Vu2pder74hMhlsnK4wumdulM/BG6yo68VIe0GtBveok6iA+f07nttUAkJVM/QzaS8fgahwmebfnks6cTMuN/VKxyRd//sNokvjHMNTBHQnmL6UifYoWw==
-
 @ 7f21affa:57e19174
2023-12-15 03:45:49
@ 7f21affa:57e19174
2023-12-15 03:45:49Chef's notes
All you need is a small pot to simmer the sauce for 7-10 mins.
Details
- ⏲️ Prep time: 15mins
- 🍳 Cook time: 10 mins
- 🍽️ Servings: ~8oz (?)
Ingredients
- 1/4 cup Mirin/Sake
- 1/4 cup Rice Wine Vinegar
- 2 tbsp Soy Sauce
- 2 tbsp Brown Sugar
- 1/2 cup Honey
- 2-5 tbsp Gochujang (Korean Spice Paste); Please add based on your spice preference
- 4 cloves Garlic (minced/paste)
- 1-2 tsp/slices of Ginger (slice/paste); Not everyone like ginger bits in their sauce
Directions
- Throw all ingredients into a small sauce pot and simmer for 7-10 mins
- Take out ginger slices (if any)
- Toss Fried Chicken and Sauce together
- Enjoy!
-
 @ d4338b7c:f1d23a5b
2023-12-14 22:07:29
@ d4338b7c:f1d23a5b
2023-12-14 22:07:29Chef's notes
Unlike a traditional negroni recipe, the boulevardier requires 2 part liquor, one part sweet vermouth, and one part campari. Traditional negroni recipes call for equal parts gin, sweet vermouth, and campari.
2oz Whiskey 1oz Sweet vermouth 1oz Campari
Details
- ⏲️ Prep time: 5
- 🍳 Cook time: 5
- 🍽️ Servings: 1
Ingredients
- Whiskey or Rye
- Sweet vermouth
- Campari
- Orange peele
Directions
- Pour ingredients into a glass or mixing glass
- Add large ice cubes
- Stir for 30-45 seconds
- Pour into coupe if stirred in mixing glass
- Orange peele expression and garnish
- Cheers
-
 @ 75bf2353:e1bfa895
2023-12-13 20:19:11
@ 75bf2353:e1bfa895
2023-12-13 20:19:11Chef's notes
Berf Jerky, the OG pocket steak made in the oven.
Details
- ⏲️ Prep time: 15 minutes
- 🍳 Cook time: 4 hours
- 🍽️ Servings: 10
Ingredients
- 2 LB. London Broil.
- salt
- pepper
Directions
- Trim as much fat as possible from London Broil.
- Slice meat into thin strips.
- Add salt & pepper.
- Line large cookie sheet with foil(for easier clean-up.)
- Add rack on top of the cookie sheet, the kind you might use for bacon.
- Bake at 175° F for 4 hours
- Remove from oven.
- Enjoy.
-
 @ 11be7dbc:82a5f8e9
2024-02-06 16:01:37
@ 11be7dbc:82a5f8e9
2024-02-06 16:01:37In 2022, Cyberyen emerged seemingly out of thin air, presenting a potent response to the entrenched corruption within the cryptocurrency landscape. Its ideology has offered a simple yet powerful antidote, founded on the core principles of cypherpunk ideology—privacy, decentralization, and liberation from institutional control. Cyberyen rose as a rallying call against prevailing financial dominion.
This nascent ideology encapsulates a spirit of rebellion, aspiring to democratize finance and cultivate a community-centric digital economy. Today, in its embryonic stage, Cyberyen epitomizes a digital social contract, offering a liberated space where collaboration, innovation, and communal interaction flourished, unshackled from the constraints imposed by traditional financial frameworks.
Due to the fact that the original purity of cypherpunk's intentions—to stand as a symbolic rebellion against a corrupt system—gradually succumbed to the speculative frenzy dominating the financial world. Rather than upholding the foundational principles of a liberated digital society, cryptocurrency became synonymous with speculative bubbles, market frenzy, and the whims of investor sentiment.
Yet, amidst this moral decay, the idea of Cyberyen metamorphoses into a transformative force. Within the shadows of speculation lies the potential for the resurgence of community, innovation, and decentralization, aspiring to reclaim its intrinsic position in the realm of digital currencies. It evolves beyond a mere facilitator of transactions to shape a unique environment transcending conventional boundaries of geography, socio-economics, and governance.
Acknowledging Cyberyen's early stage invites envisioning it not merely as a digital coin but as a sovereign state—an intangible expanse where individual interactions shape its foundation. Much akin to our integration into society at birth, Cyberyen welcomes participants into a shared realm where interactions, engagements, and collaborations weave the fabric of a burgeoning digital society. Within this ethereal space, physical geography dissolves, allowing individuals globally to converge and coexist within the Cyberyen ecosystem.
At its core, Cyberyen functions as a decentralized, borderless platform, accessible to anyone with an internet connection. Serving as an overlay to societal and economic structures, it seamlessly integrates into participants' lives, transcending geographical limitations. This integration fosters an environment conducive to self-discovery, expression, and connectivity, reminiscent of familial, communal, and national landscapes shaping our physical realm identities.
Privacy and anonymity stand as pillars within this digital enclave, empowering users to engage without the necessity of divulging personal information. Such anonymity liberates individuals from societal judgments prevalent in the physical world, fostering authentic expression and interaction devoid of prejudice or discrimination.
Moreover, Cyberyen champions universal interaction, eradicating the barriers posed by country-specific regulations, currencies, or social delineations. This democratization creates a level playing field for all participants, irrespective of background or location. Its inherent inclusivity ensures that opportunities and resources are not bound by conventional societal frameworks but are accessible to individuals irrespective of their socio-economic status or geographic coordinates.
Cyberyen's integration extends beyond financial transactions, envisioning usability in decentralized marketplaces, social platforms, cultural spheres, and multifaceted activities, fundamentally reshaping societal structures.
Distinct from activist networks advocating complete anonymity and a dark market, Cyberyen does not aim to dismantle government institutions. Instead, it aspires to weave an independent, invisible environment—a transparent digital matrix offering an alternative mode of interaction and settlement between individuals.
The blockchain underlying Cyberyen serves as the scaffolding for an independent people’s economy, embodying a promise beyond financial transactions—a platform for creating opportunities parallel to one's real-life endeavors. Through Cyberyen integration, individuals forge a secondary environment for business activity, fostering a new cultural layer detached from geographical confines.
At the heart of Cyberyen's evolution lies the fortification of its foundation—the strength of its network. The amalgamation of mining power and nodes forms the bedrock upon which the ecosystem thrives. Beyond technical robustness, the cultivation of a distinctive culture becomes imperative—an underground, creative ethos fostering innovation, inclusivity, and cultural diversity within the Cyberyen community.
Looking deeper, Cyberyen holds the promise of catalyzing social interaction, fostering economic growth, and nurturing a globally connected, culturally diverse society. It surpasses the role of a mere financial tool; rather, it stands as an incubator nurturing cultural expression and societal amalgamation. Cyberyen's narrative is a borderless router processing connections of collaboration, innovation, and inclusive progress—a profound testament to technology's capacity in crafting an autonomous social fabric. Within this realm, individuals are empowered to discover their voice, collaborate uninhibitedly, and collectively forge a novel cultural paradigm.
In conclusion, Cyberyen's essence transcends conventional currency, aspiring to create an enclave fostering an ecosystem where individuals interact, create, and thrive. Its potential lies in a united community constructing a vibrant, inclusive, and innovative digital society—a space of connectivity, creativity, and collective evolution in the digital age.
Stay with us... C¥kuza
-
 @ cce0989b:b497e608
2024-02-06 13:12:53
@ cce0989b:b497e608
2024-02-06 13:12:53It's always going to feel messy at the start.
As painful as they are, the messy parts have to be experienced before they can turn into something that's understandable and meaningful.
While this dynamic is present in so many domains of our lives, it's especially important to remember if you're trying to create or build anything — whether that's a piece of art, a project, a business, or a life.
Here are a few (famous) examples:
-
J.R.R. Tolkien didn't even have the eponymous ring in his first drafts of Lord of The Rings — it took multiple revisions to land on this idea.
-
Ed Catmull, president of Pixar, says that "Early on, all of our movies suck."
-
Ernest Hemingway wrote the ending of A Farewell To Arms 39 different times before he was satisfied.
You can't skip the messy part, either. It's the process of engaging with the mess that actually allows us to turn it into something else. Through our attention, we can make something beautiful, interesting, and authentic.
The next time you are struggling with this, try treating yourself with compassion.
Say, "This is how everyone feels when they're facing the mess. We all struggle with this. It doesn't mean I'm not talented, capable, or resourceful. It just means I'm a human, going through the messy parts first."
-
-
 @ 7fa56f5d:751ac194
2024-02-06 11:28:05
@ 7fa56f5d:751ac194
2024-02-06 11:28:05I'm happy to announce a new release of Habla.
Nostr connect
Users can now login via Nostr Connect remote signers. Both
bunker://URLs and NIP-46 compatible nostr addresses (NIP-05) are supported.Local drafts
nostr:nevent1qqs2jfpse4akde0w2ljq0n8sytp7pmnrqj943ymyw5kets45ftvv5qspzpmhxue69uhkummnw3ezuamfdejsygyhcu9ygdn2v56uz3dnx0uh865xmlwz675emfsccsxxguz6mx8rygq4xs2f
Some users have reported Habla eating their blog posts. To avoid the issue Habla will now automatically save the post you are editing in local storage. The option to store drafts on nostr still exists if you want to continue editing from another client or device.
RTL languages
Habla is now translated to Hebrew. The translator was kind enough to review the RTL compatibility of the site and we have fixed multiple layout and text direction issues for RTL language users.
Extracting Habla core code
The core Habla code has been extracted to a library called ngine and I have ported several apps to it. These apps are currently using it:
nostr:naddr1qqxnzdesxvungvecxsungdpkqgs8lft0t45k92c78n2zfe6ccvqzhpn977cd3h8wnl579zxhw5dvr9qrqsqqql8kqf6n74
nostr:naddr1qqxnzdesxgunqvpexuersvp3qgs8lft0t45k92c78n2zfe6ccvqzhpn977cd3h8wnl579zxhw5dvr9qrqsqqql8k6zxwng
nostr:naddr1qqxnzd3exgmrsveh8yerqdfcqgsrx4k7vxeev3unrn5ty9qt9w4cxlsgzrqw752mh6fduqjgqs9chhgrqsqqql8kaulu0l
The next step is to start using it from Habla and document it so other nostr devs can leverage it for building apps quicker. The library has similar scope as Osty so will probably join forces with nostr:nprofile1qqsru22d9lfnnwck54qr4phrvey50h2q33xc0gqxv5j03ftn4efu4rspr9mhxue69uhhyetvv9ujumn0wdmksetjv5hxxmmd9uq3gamnwvaz7tmjv4kxz7tpvfkx2tn0wfnj7qgewaehxw309aex2mrp0yhxummnw3exzarf9e3k7mf0y2nv4h, expect some news about this soon.
Happy curating, reading and writing!
-
 @ 75bf2353:e1bfa895
2023-12-13 19:22:04
@ 75bf2353:e1bfa895
2023-12-13 19:22:04Chef's notes
Stay Humble, Brew Your Own Coffee
Note: The Satoshi Coffee Company, Amazon, WalMart and coffee cups are not affiliate links.
Equipment
You'll need an AeroPress
I use sats.coffee to support the bitcoin circular economy.
Coffee Cup. I can't vouch for anyone on this list, but check out the mug market on nostr.
Cold water because hot water tastes like water heater.
Cheapest tea kettle I could find.
The cheapest digital meat thermometer I could find.
Proof of Work








Interested In Getting Sats Back?
Note: These are referral links
Oshi App
I swear, I was going to share this company anyway because I found out about the Oshi sats back reward on sats.coffee after I bought my first order. I could have saved myself thousands of sats. I also met Michael Atwood at a meetup in Newport Beach a couple years ago. He's a ride or die freak and told me about this new business he created, basically Groupon for Bitcoiners. We had a great conversation and I really like that dude, but totally forgot about Oshi app. So I plan on using it more. I also started this blog to teach people how to use bitcoin and promote the bitcoin circular economy. The Oshi App aligns with this mission.
Save 10% off two bags of coffee from Satoshi Coffee Co. When you use the Oshi App
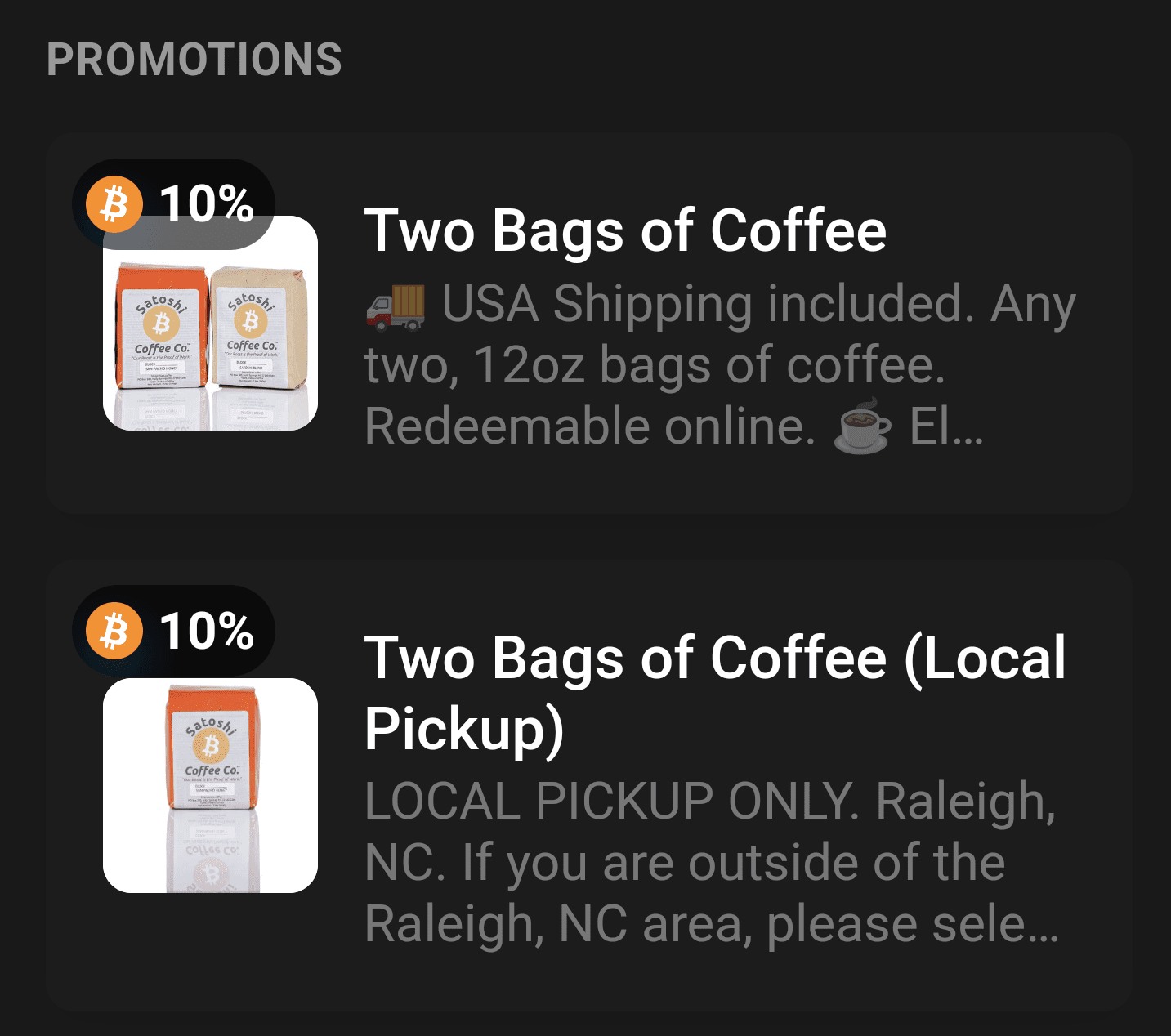
Even if you don't like coffee, sign up for the Oshi App anyway. You're bound to find something you do like and support the bitcoin circular economy, save sats, and send me a little percentage of sales. I also want you to create your own referral link too and share it with other people. I'm not saying you'll earn enough to quit your job, but maybe you'll get more people interested in using and saving sats. This is not financial advice, but that's got to be better for the value of bitcoin than dorks doodling dumb-ass charts.
The Bitcoin Company
Don't have an AeroPress? Get 1.3% sats back when you buy an amazon gift card with The Bitcoin Company
Don't have a cheap meat thermometer? Get 0.6% sats back when you buy the cheapest meat thermometer I could find. ome places might give you more cashback, but not all that glitters is digital gold. The Bitcoin Company pays out bitcoin to your own wallet over the lightning network. Have you seen on-chain fees lately?
Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 5 min
- 🍽️ Servings: 1
Ingredients
- coffee
- cold water because hot water tastes like water heater.
Directions
- Fill tea kettle with 8 oz. or more of cold water.
- Set the thermometer to 175° F. Insert the probe into the kettle.
- Turn on the burner at a medium heat.
- Meanwhile, assemble the AeroPress. Insert the coffee filter and set on top of the coffee cup. Add a scoop of coffee.
- When the alarm of the thermometer goes off, remove from heat. I like to watch it and turn the flame down to the lowest setting as it approaches the temprature.
- Pour the water into the AeroPress. Do not overfill.
- Stir coffee and the water for 10 seconds.
- Insert plunger. Slowly press down on the plunger from 20-60 seconds. Squeezing the delicious coffee oils out.
- Enjoy. Post a picture on #coffeechain and tag me.
- Clean up is easy. Just throw away the filter and grounds and rinse it. It's also dishwasher safe.
-
 @ 6ad3e2a3:c90b7740
2023-12-13 12:40:31
@ 6ad3e2a3:c90b7740
2023-12-13 12:40:31We often fantasized about time travel, mostly what stocks we would buy, what bets we would make. Buster Douglas and the 1999 St. Louis Rams to win the Super Bowl were two I liked to bring up. But that was before Henry got caught up in politics, and the conversation turned to altering events in world history.
Henry argued if you had one trip you’d be morally obligated to prevent some of history’s worst tragedies, and for him the go-to example was killing baby Hitler. If you were there and had the chance, you’d have to do it, he’d say, no matter how hard it would be to murder an innocent baby. If you hesitated to agree, he’d browbeat you, saying good people doing nothing is what allows evil to thrive. He saw it as an obvious choice: one as yet innocent baby in exchange for the lives and suffering of millions.
This made the exercise considerably less enjoyable, and we dropped it. That is, until The Simulator. The Simulator was a breakthrough technology, part virtual reality game, part research tool that enabled virtual experiments from modeling future events to modifying past ones and seeing present-day results. I’m oversimplifying, but it worked by scanning every recorded byte, including old maps, regional soil composition, weather patterns, temperature data, census records and every published book in human history. From stock market data to the Code of Hammurabi, to the fully mapped human genome, The Simulator drew inputs for its algorithm. Some believed the developers had access to classified material from the world’s intelligence agencies, including UFO encounters deemed too sensitive for public consumption.
Of course we only had the commercialized game version — the full one was prohibitively expensive and available only to those with official authorization. But the game version was robust enough, and already the software of choice for sports betting, weather forecasting and for some stock pickers, (though many suspected hedge funds and large institutions had access to the full version and avoided the capital markets entirely.)
I initially did investing experiments, buying Apple’s IPO, Amazon stock and eventually bitcoin and became the richest person in the world 10 times over. Although in one experiment, I owned so much bitcoin it became overly centralized and never took off. In that world, Facebook launched its Libra coin without much government resistance as few grasped the possibilities of fully digital currencies. The result was a Facebook-government partnership where you got docked Libra coin (the only currency in which you could pay federal taxes) for unfavored associations and viewpoints.
But I soon grew bored of the financial experiments and started doing weird things like going back to 2019, catching COVID on purpose and spreading it as widely as possible, before people thought it was a threat. In one simulation, there was no acknowledged pandemic, only a bad “flu” season.
I was about to log off and tackle a work project on which I had procrastinated for too long, when I remembered Henry’s insistence that I was obligated to kill baby Hitler. I never bought his arguments entirely — absolute certainty is always a red flag — but I didn’t have a good counter for them, either. I resolved to run the experiment and find out for myself.
It wouldn’t be easy as the commercial version of The Simulator had rules around acts of violence. I’d also have to dig up fairly specific knowledge in a presumably less developed part of the game (19th-century Hungary.) But The Simulator was adept at making do with the available history and filling in blanks with fictional characters. There would be a street address and a house where he lived. There should be an opportunity to see how it played out. Of course, one could simply delete Hitler and run simulations without him, and I tried that first, but the moral question was not whether the world would be better off without Hitler, but whether it would be right — or obligatory even, in Henry’s framing — to murder the baby in his crib.
I prefer not to go into the details. The broad outlines are I found a hack to disable the violence restriction, went to his childhood home and had to bludgeon a young woman (his nanny?) before doing it. For those who have never used The Simulator, “Full Immersion Mode” isn’t quite real life, but it’s substantially more visceral than shooting avatars in a video game. What I did was horrific, even though I knew it wasn’t real, and even though Henry believed the act would’ve been heroic if it were. I actually vomited afterwards, and as I type this 10 days later, I feel queasy recalling it.
Nonetheless, I ran a simulation forward. The Third Reich was run by committee. There was a front man, someone of whom I had never heard, who was more charismatic than Hitler, but decision-makers behind the scenes, including some of Hitler’s generals, were just as ruthless. There were concentration camps, though oddly in different locations, and the result was seemingly as bad.
But that was only one version of events. The Simulator (through randomization of certain parameters) could run infinitely many different futures from any given point in time. I ran a few more, and they were all dystopian in different ways. There was one version, however, that particularly struck me.
In it, Hitler rose to power as he did in the real world, and things unfolded more or less the way we’ve read about them in history. At first, I thought there must be an error — after all, every simulation began the hour after I smothered him in his crib. But as I checked the local newspapers from that era, indeed a baby had tragically died, and his brain damaged nanny was blamed (and subsequently hanged) for the crime, but it was a different baby, Max Muller, son of a local tavern owner, who committed suicide two years later. How could that be? Not only did I check all the details exhaustively, but they proved correct in all the other simulations. The randomizer must have swapped the location of baby Hitler with this other infant. In this version, I murdered (virtually, thank God) an innocent baby, destroyed his family and an innocent nanny without preventing anything.
. . .
When I met with Henry a week later, he wasn’t convinced. The Simulator isn’t reality, he argued, and the version with the wrong baby proved it. His hypothetical entailed killing the actual baby Hitler in the real world, not some case of mistaken identity. If you could be sure to kill the real Hitler and prevent the Holocaust from happening, he maintained, you’d still have to do it. The Simulator’s randomization algorithm made it impossible ever to know what would happen in its many possible futures, especially in the long run.
I now understood his argument. If we had certainty about how our actions would affect the world, the moral imperative would be clear. But certainty about the future was unattainable, for the path from unknown to known is the arrow of time itself. Henry’s hypothetical then was inherently contradictory, a square circle he imagined were an actual shape.
One could never be assured about the long term effects of one’s actions, and any attempt to do the math was quickly overwhelmed by infinite permutations. Doing something abhorrent as the means to a noble end was to fancy oneself a mathematical God, something no decent person would attempt. It was the ideology of monsters, forever imagining they could create a more perfect history, a more perfect future, a more perfect human race.
-
 @ d34e832d:383f78d0
2024-02-06 10:17:06
@ d34e832d:383f78d0
2024-02-06 10:17:06Bitcoin Halving: Gaining an Understanding of its Significance
 For a long time, I've operated using the opportunity of bitcoin, but applied little time to understand its halving. This periodic event, occurring approximately every four years, is more than just a routine adjustment in the Bitcoin ecosystem; it represents a fundamental aspect of Bitcoin's economic model and its impact on the supply side and demand dynamics. This is just a private note, I am making to review m understanding of this concept to my small audience and myself.
For a long time, I've operated using the opportunity of bitcoin, but applied little time to understand its halving. This periodic event, occurring approximately every four years, is more than just a routine adjustment in the Bitcoin ecosystem; it represents a fundamental aspect of Bitcoin's economic model and its impact on the supply side and demand dynamics. This is just a private note, I am making to review m understanding of this concept to my small audience and myself.The Halving Event
 At the heart of the Bitcoin halving lies a simple yet profound mechanism. As stated by Satoshi Nakamoto in the original Bitcoin whitepaper, the total supply of Bitcoin is capped at 21 million coins. To ensure scarcity and prevent inflation, the rate at which new bitcoins are created must decrease over time. This is where the halving comes into play.
At the heart of the Bitcoin halving lies a simple yet profound mechanism. As stated by Satoshi Nakamoto in the original Bitcoin whitepaper, the total supply of Bitcoin is capped at 21 million coins. To ensure scarcity and prevent inflation, the rate at which new bitcoins are created must decrease over time. This is where the halving comes into play."The halving is a pre-programmed event that occurs approximately every four years, where the block subsidy, which is the amount of new bitcoin awarded to miners for validating transactions, is cut in half."
This reduction in the block subsidy serves as a built-in mechanism to control the issuance of new bitcoins, thereby ensuring a gradual and predictable approach to reaching the maximum supply limit of 21 million coins.
Implications for the Market
The impact of the Bitcoin halving extends far beyond its immediate effects on miners' rewards. It has profound implications for the broader cryptocurrency market and its participants.
"This reduction in the block subsidy has implications for the supply of new bitcoin entering the market, which can impact its price and overall market dynamics."
With each halving, the rate at which new bitcoins are introduced into circulation decreases, leading to a decrease in the rate of inflation. This deflationary aspect of Bitcoin is often cited as one of its key distinguishing features compared to traditional fiat currencies.
Market Sentiment and Price Volatility
One of the most intriguing aspects of the Bitcoin halving is its impact on market sentiment and price volatility. Historically, Bitcoin halving events have been associated with periods of heightened speculation and price volatility.
"Investors closely monitor the halving events, anticipating their potential impact on Bitcoin's price trajectory."
While some view the halving as a bullish catalyst, others are of the consideration that no real event would occur during the next halving.
This Halving Is A Pivotal Moment Of Where All Bitcoiners Stand
The Bitcoin halving is a pivotal event that underscores the underlying principles of scarcity and decentralization within the Bitcoin ecosystem. By reducing the rate of new bitcoin issuance, the halving plays a crucial role in shaping Bitcoin's monetary policy and economic trajectory. As investors and enthusiasts alike await the next halving event, the significance of this recurring phenomenon cannot be overstated.
Impact of Bitcoin Halving: Potential Scenarios
While some anticipate significant bullish movements following the halving, others argue that it may not necessarily lead to major price shifts. Lets try to reconcile these contrasting scenarios and explore potential outcomes.
Scenario 1: No Major Price Movements
In this scenario, the Bitcoin halving occurs without triggering significant price movements. Proponents of this view argue that the halving event is already priced into the market well in advance, as investors and traders anticipate the reduction in the block reward.
"The efficient market hypothesis suggests that all available information, including future events like the halving, is already reflected in the current price of Bitcoin."
According to this perspective, any potential bullish sentiment leading up to the halving may already be factored into the market price, resulting in limited price volatility during and after the event.
Scenario 2: Big Bullish Catalysts
Contrary to the first scenario, proponents of this view anticipate major bullish movements driven by the Bitcoin halving. They argue that historical data and market trends suggest a pattern of significant price appreciation following previous halving events.
"Historically, Bitcoin halving events have been associated with periods of heightened speculation, increased demand, and subsequent price surges."
According to this perspective, the inherent scarcity of Bitcoin, coupled with a reduction in the rate of new coin issuance, creates a supply-demand imbalance that favors price appreciation. As investors perceive Bitcoin as a hedge against inflation and a store of value, the halving serves as a reaffirmation of its scarcity and long-term value proposition.
Potential Positive Outcomes
Regardless of whether the Bitcoin halving leads to major price movements or not, there are potential positive outcomes for Bitcoin and the broader cryptocurrency ecosystem.
-
Increased Awareness and Adoption: The spotlight on Bitcoin during halving events often leads to increased media coverage and public awareness, attracting new investors and users to the ecosystem.
-
Technological Innovations: The anticipation of the halving encourages developers and entrepreneurs to explore innovative solutions and applications built on top of the Bitcoin protocol, driving technological advancements in the space.
-
Long-Term Value Proposition: Regardless of short-term price fluctuations, the fundamental value proposition of Bitcoin as a decentralized, censorship-resistant, and deflationary digital asset remains intact, attracting long-term investors seeking to preserve wealth and hedge against economic uncertainty.
The Future Cannot Be Truly Predicted
In conclusion, the potential outcomes of the Bitcoin halving are subject to debate and speculation within the Bitcoin community. While some anticipate major price movements, others remain skeptical of its immediate impact on the market. However, beyond short-term price fluctuations, the halving event serves as a reminder of Bitcoin's scarcity and value proposition, reinforcing its position as a revolutionary financial asset with the potential to reshape the global economy.
For further exploration of Bitcoin halving and its implications, consider diving into resources such as:
-
-
 @ a012dc82:6458a70d
2024-02-06 02:18:40
@ a012dc82:6458a70d
2024-02-06 02:18:40Pizza was present when the world first started. At this point in time, you can get a lot more with your bitcoin than pizza, and you can spend it at a broad number of locations, both online and offline. And although there are lists available that are more thorough, we hope that this will bring attention to the variety of choices that are accessible.
Online
Tipping & Charity
GivePaying it forward is one of the least time-consuming and potentially most rewarding ways to spend your bitcoins. Donate to any one of a variety of important organizations using bitcoin, or use it to leave a tip for the author of an article or blog post with just the click of a button. You can also use bitcoin to buy Reddit Gold, which lets you thank the person who posted your favorite cat pictures.
Receive
Donations to charity causes may be set up using our API.
Typical Items Found in Homes
Overstock.com has you covered with over a million different things for sale, all of which can be purchased with bitcoin.
Gift Cards
Some resourceful individuals have devised a workaround in the meantime, as we wait for retailers such as Amazon and BestBuy to accept bitcoin payments immediately. You may use bitcoin to buy gift cards from sites such as eGifter or Gyft, and then you can redeem those gift cards at prominent merchants such as Amazon, Best Buy, and hundreds of other stores.
Video Games
Several software developers, including Microsoft, have just recently begun selling their games and other applications for bitcoin. This particular Minecraft server, along with many others, is really powering its in-game money with the help of the bitcoin network.
Offline
Food
You may take your bitcoins to any of these Bitcoin restaurants if you download our mobile app for iOS or Android operating systems. You may even visit a coffee shop, such as this one in Prague, which is the first establishment of its kind to take bitcoin.
Travel
You may use Expedia to pay for a hotel and CheapAir to book flights and other travel accommodations. Car dealerships are also getting into the flow of things, and although it is not yet possible to pay for petrol directly with bitcoin, there are devices in the works that will allow this to happen! To not be outdone, Virgin Galactic will launch you into space if you have that much bitcoin in your wallet. And I think that about sums it up! Okay, it doesn't really matter since this is only the tip of the iceberg, and more and more companies are starting to take bitcoin on a daily basis. With the help of this article, you will discover how simple it might be for your company to start accepting bitcoin.
How do I spend bitcoin?
Paying with bitcoin is, in some respects, comparable to sending an email; the main difference is that, rather than sending a message to the recipient's email address, you are sending a monetary amount to the recipient's bitcoin address.
When you pay with bitcoin, you don't have to divulge as much of your personal information as you do when using other payment methods. This is one of the benefits of using bitcoin. However, if you are buying real things, you will be required to provide your name and address. Providing your email address is typically all that is required if it is a digital item. On the other hand, if you are making a contribution, it is possible that you will not be required to supply any information at all.
Rather than requesting a credit card number, the website will provide the information needed to make a bitcoin payment.This information will include at least one of the following options:
-
A hypertext link that reads "Sign in to Coinbase"
-
A QR Code
-
One or more Bitcoin addresses.
At this point in the process, the procedure might be somewhat different for you depending on the kind of bitcoin wallet you're using.
Pay with your Coinbase balanceIf the merchant that you are paying uses Coinbase to accept bitcoin payments and you also have a funded Coinbase account, you can finish the checkout process by simply logging in to your Coinbase account and confirming the order. This is only possible if the merchant that you are paying uses Coinbase to accept bitcoin payments. After you look at the order and agree to it, the transaction is complete, and the store will know that you paid.
Pay using QR code
At the point of sale, the vast majority of bitcoin payment processors will also issue a QR code that, when scanned, reveals a bitcoin address as well as the payment amount.
Your smartphone may be used to make payments using a bitcoin wallet app or from the balance in your Coinbase account by using the Coinbase app, which is made easier via QR codes (available for Android or iOS). Simply scan the QR code, and the bitcoin address of the receiver as well as the amount that is being requested will be filled in for you. As soon as you hit the "Send" button on the transaction, the payment is finished.
If you do not have a Coinbase account or if you desire to pay from a different bitcoin wallet, this is a nice alternative for you to consider.
Pay to a Bitcoin address
If you can't scan QR codes or the merchant only gives you a bitcoin address, you can also manually enter this bitcoin address as the recipient of a transaction into the software that manages your bitcoin wallet.
In order to make a payment to a Bitcoin address, you will need to provide your Bitcoin wallet with two pieces of information, namely:
-
Bitcoin address of the receiver of the transaction
-
The number of bitcoins that will be sent
Both of these will be shown on the payment page throughout the checkout process; however, some merchants may leave the amount up to you in the event of contributions or other payment methods with greater flexibility.
Once you have the address and the amount, all you need to do to send off the transactions is put them into the "send" section in your wallet.
If the retailer is utilizing Coinbase, the checkout page will refresh to show that the money has been received immediately after you submit the payment, and the purchase will be listed as finished after it is confirmed that the funds have been received. Keep in mind that the process can be very different when working with different payment processors or when making payments directly without the help of a processor.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 44dc1c2d:31c74f0b
2023-12-12 20:18:07
@ 44dc1c2d:31c74f0b
2023-12-12 20:18:07Chef's notes
If you want to kick it up a notch instead of using EVOO or butter, get about 6 slices of bacon and at the first step just cook off the bacon and use that as your cooking fat.
If you want a more crispy biscuit, cook them separately instead of cooking them in the filling. If you do this, simmer the filling on low for an extra 10 ish min, or just until the potato are tender.
If you prefer to make the pot pie in a casserole dish, you can. Simply pour out the filling into a greased baking dish and top with biscuit dough and continue with the recipe as stated.
The filling tends to bubble and make a bit of a mess, so I recommend placing your skillet or baking dish over a sheet pan covered with tin foil to catch any drips and messes.
Details
- ⏲️ Prep time: 30 mins
- 🍳 Cook time: 45-50 mins
- 🍽️ Servings: 4-6
Ingredients
- roughly 1lb of chicken. (Use whatever I prefer thighs)
- 1 medium size onion, peeled and diced
- 2 medium size carrots, peeled and diced
- 2 celery stalks, diced
- 3 cloves of garlic, peeled and minced
- 2 heaping tablespoons all purpose flour
- 2 cups chicken stock/broth
- ½-1 cup whole milk
- ¼ cup chopped fresh parsley
- 1 teaspoon fresh thyme plus more for garnish
- 2 bay leafs
- 2 mid sized potatos chopped into small cubes.
- Salt and pepper to taste
- 3-4 tablespoons of olive oil or butter
- For the Drop Buttermilk Biscuits
- 2 cups all purpose flour
- 1 tablespoon baking powder
- ¼ tsp baking soda
- ½ tsp fine sea salt
- 6 tablespoons cold unsalted butter, cubed
- 1¼ cups buttermilk + 2 tablespoons for brushing biscuits with
Directions
- For the Filling
- Heat your cooking fat. If using uncooked chicken, add chicken pieces to the pan. (If using pre-cooked chicken, don’t add it until later) Cook sautéing chicken for 2-3 minutes per side tell golden brown
- Add onion, celery, carrots, garlic and potatos. Cook for 5-7 minutes, stirring often until the veggies start to become tender. Make sure to season well with salt and pepper.
- Sprinkle flour over the veggies and chicken and stir vigorously for 1 minute to cook the flour a bit.
- Slowly pour in the chicken broth followed by the milk while stirring. Raise temperature up just a bit if needed and let it come to a very gentle boil. Once it reaches a boil reduce the heat to a simmer and let cook for 5-10 minutes, or until its has reduced and mixture has thickened a little
- Add the chicken if using precooked or rotisserie, parsley and thyme. Let cook until the veggies are tender, chicken are heated through, and mixture is nice and thick or has reached your desired thickness, about 3-5 more minutes (feel free to loosen up sauce a little adding more milk, cream or broth as needed). Season with salt and pepper to taste. Remove from heat and set aside.
- For The Buttermilk Drop Biscuits
- Preheat the oven to 425ºF while preparing the drop biscuits
- Add the flour, baking powder, baking soda, salt, to a large bowl and whisk to combine or pulse to combine in a food processor. Scatter the butter over the dry ingredients and rub together with your fingertips, until it forms a sandy-looking texture with some pebble-sized pieces or use a pasty cutter. If using food processor pulse a few times to achieve the same texture.
- Pour in the buttermilk and stir until it just comes together into a thick dough and there are no visible signs of flour. This step should only take a minute: be careful not to overmix the dough. (I usually pour out my flour and butter into a bowl from the processor and stir in the buttermilk by hand with spatula instead of pulsing it in)
- Assembling & Baking
- Use large cookie scoop or 2-3 heaping tablespoons (or approx ¼ cup) to scoop out dough. Drop dollops of the dough over the top of the pot pie filling to mostly cover the surface. Flatten them out a bit if you wish. Brush the tops of the biscuits with remaining 2 tablespoons of buttermilk.
- Transfer the skillet to the oven and bake for about 20-25 minutes until the biscuits are golden brown and fully cooked through and the filling is bubbling. I typically loosely cover pan with foil for the last 5-10 minutes of baking so they don’t brown too much - but are fully cooked through. Feel free to broil for the last minute to get the biscuits deeply golden.
-
 @ 55b17d41:d6976606
2023-12-10 01:25:43
@ 55b17d41:d6976606
2023-12-10 01:25:43Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 12
Ingredients
- 2/3 cup creamy peanut butter
- 1/2 cup powdered sugar
- 1/4 cup graham cracker crumbs
- 1 pinch of salt
- 1 12-oz bag of chocolate chips
Directions
- In a large bowl, mix peanut butter, powdered sugar, graham crackers, and salt until well combined.
- Melt the chocolate either with a chocolate melting pot or in the microwave in a medium size bowl. If using the microwave, cook for 30 seconds and stir. Add more time if needed until the chocolate is melted.
- Line a 12-cup muffin tray with cupcake liners and fill each one with ½ tablespoon of melted chocolate. Spread the chocolate around to cover the bottom of the liner. Place the tray in the fridge for a few minutes to let them set. Doing this prevents the peanut butter filling from sinking to the bottom of the chocolate.
- Place a tablespoon of the peanut butter filling on top of the chocolate, spreading it around to form a circle and then slightly pushing it down into the chocolate. Top the peanut butter with another ½ tablespoon of melted chocolate. Smooth out the top and make sure it completely covers the peanut butter underneath.
- Refrigerate for an hour or until the chocolate has hardened. You can enjoy them cold or at room temperature. Enjoy!
-
 @ 6871d8df:4a9396c1
2024-02-05 23:29:22
@ 6871d8df:4a9396c1
2024-02-05 23:29:22The Apple Vision Pro was released, and it is the talk of the town right now. To be frank, I think it's a stupid product. It's not useful or particularly enticing to me in its current form factor. It's a toy, not a tool. All the features seem gimmicky as opposed to generally helpful. I'm not saying it may never be worthwhile, but as of this first release, it is only a party trick.
Coincidently, this is the first product that does not have any of Steve Jobs' influence. To me, it shows. I don't think Jobs would have ever let this product see the light of day.
Jobs understood product. He didn't make things for the sake of progress or to make sci-fi reality; he made things because he 'wanted to make a dent in the world.' He wanted to solve problems for everyday people by innovating with cutting-edge technology. He aspired to make people's lives better. Steve Jobs' genius was the way he married cutting-edge technologies with valuable tools that made those cutting-edge technologies simple and elegant.
The Vision Pro may be technically innovative, but it is not a tool, at least in its current form. It may be one day, but that is precisely my point; Jobs would have never released a product where the form factor would hold it back from becoming a tool. At best, it is an intriguing toy that is additive to some content at the behest of being very awkward to wear or be seen in. In my view, mainstream adoption can happen only in a world where we can use the Vision Pro as a contact lens or very small, discreet, minimalist glasses, but certainly not this iteration where it covers more than half your face.
Seeing people's eyes makes us human. So much emotion, understanding, and communication happens with just a look. It is a window into the soul. I don't want to live in a world where we are actively bringing all the negatives about communicating in the digital world to the physical one.
https://image.nostr.build/2365609411f144f5d789ffd684ffce9b4d867626a7bfe11bb311cb0f61057199.jpg
I can't help but wonder or hypothesize what Steve Jobs would focus on if he were still alive today. I think Apple's priorities would be completely different. My gut tells me he would not have let Siri get as bad as it is. Siri is a horrible product; I never use it, and everyone I know who tries to use it does so unsuccessfully, at least most of the time. I personally always default to ChatGPT or Bard. These AI systems make my life dramatically more productive. They are tools in the purest sense.
In my opinion, Steve would not have missed this train. Sure, Apple could wake up and integrate these systems into Siri — if they were smart, they would — but in its current form, it is so far behind that it almost astounds me. My intuition leads me to believe he would be closer to what [Rabbit] is doing.
Who knows? Maybe I am entirely wrong, and Apple just kickstarted VR's mass adoption phase. Unfortunately, I think this will likely be the biggest failure of a physical product that Apple will have seen since Jobs returned ages ago. The Vision Pro is only slightly better than the Oculus, and Facebook has already deprioritized VR for AI. Apple is further behind, and I don't see a world where they do not make the same pivot. There is a skill to creating successful, innovative products, and it makes me sad to see the torch that Jobs passed lose its flame. As someone who respected how Apple used to innovate, watching this decay in real-time is jarring as this is just the latest in a string of disappointing decisions that exemplify that 'peak Apple' is behind us.
-
 @ ee6ea13a:959b6e74
2023-12-08 22:45:00
@ ee6ea13a:959b6e74
2023-12-08 22:45:00Chef's notes
I recommend using olive oil for frying to get the best results. If you’re using a different type of oil, make sure you are aware of its smoke point. You should keep the temperature between 350-375°F (175-190°C). Olive oil will begin to smoke if it goes above 400°F (200°C), so keep a close eye on it so you don’t burn the oil.
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 30 minutes
- 🍽️ Servings: 6
Ingredients
- 4 large russet potatoes, peeled
- 2 large eggs, beaten
- 3 tablespoons matzo meal or unbleached flour
- 1/4 cup white or yellow onion, grated
- 1/2 teaspoon salt, more to taste
- 1/4 cup olive oil for frying, more as needed
Directions
- Slice peeled potatoes and run through a food processor fitted with the grater attachment. If you don’t have a food processor, use a box grater.
- Place shredded potatoes in a cheesecloth or several paper towels and squeeze over the sink, removing as much liquid as possible.
- Place drained potatoes into a large bowl. Add eggs, matzo meal or flour, onion, and salt, and stir until completely combined.
- Heat 1/4 inch of olive oil in a large frying pan over medium-high heat, being careful not to let the oil burn. The oil will be absorbed into the pancakes, so you will need to add more as you go. Make sure you allow a couple of minutes between batches for the cold oil to heat up.
- Place large spoonfuls of potato mixture into the hot oil, pressing down on them to form patties about 1/2 inch (1.25 cm) thick. Cook until golden brown, 4 to 5 minutes per side.
- Flip and repeat on the other side.
- Remove and place gently on a paper towel-lined plate to let the oil drain while you cook any remaining latkes. You can also keep them on a baking sheet in a low-temperature oven while you cook the remaining batches. (Never microwave them!)
- Serve hot with fresh applesauce and sour cream, or your favorite topping.
-
 @ d4338b7c:f1d23a5b
2023-12-08 01:55:53
@ d4338b7c:f1d23a5b
2023-12-08 01:55:53Chef's notes
2oz Whiskey 1oz eggwhites .75 lemon juice .5 demerara Angostura bitters
Details
- ⏲️ Prep time: 5
- 🍳 Cook time: 5
- 🍽️ Servings: 1
Ingredients
- Whiskey
- Eggwhites
- Lemon juice
- Demerara
- Angostura
Directions
- Add ingredients to shaker tin
- Shake for 30 sec
- Strain into coupe
- Add Angostura bitters on top
- Garnish with a lemon wedge or dehydrated lemon/lime
-
 @ 17330507:495e4154
2024-02-05 22:57:03
@ 17330507:495e4154
2024-02-05 22:57:03This is an official statement about my node. TLDR: if you have channel with me, I recommend force-closing it. If your node did penalty/breach tx, please return my funds, see below. Contact see on amboss - https://amboss.space/node/033878501f9a4ce97dba9a6bba4e540eca46cb129a322eb98ea1749ed18ab67735?section=General - preferrably Telegram or email, haven't checked nostr in ages, but will do.
Penalty tx
See instructions here: https://gist.github.com/xmrk-btc/f21fd8649dcd573679f043836e3ef05f , note that my lightning address is published on amboss - pls use address from amboss, you don't want to pay any impostor. Ideally I would sign it with my node's private key, doing lncli signmessage but cannot do that while node is down, and cannot safely bring it up. I am linking a separate document because I may need to edit it.
I'd like to publicly praise all peers who do return me sats, and not sure how to do it so that it has maximum visibility. Suggestions welcome. Thinking about using Node Bilboard on Amboss -> Socials, but not satisfied, it may get lost in the spam. And it is valuable information - other things being equal, you strongly prefer a honest peer which doesn't try to rob you even when he can do so with relative impunity.
Although I may sue peers which don't return money - well, at least I can serve them using OP_RETURN. /s
Already 3 peers out of 13 reached out: - Garlic - https://amboss.space/node/033b63e4a9931dc151037acbce12f4f8968c86f5655cf102bbfa85a26bd4adc6d9 - Cypher - https://amboss.space/node/02d5246fa6bccbb80732146e198d243c49348a29d847ca8486742f5bbec158744f - Satway - https://amboss.space/node/02916bb52b33836e28a3649baea2e4a29c16fd8ad97901b2c97d408f428edef108
Still, I am a bit worried about creating bad precedent, penalty txs exist for a reason. And yes, this surely doesn't look like a succesful attack by me, but how about unsuccesful one? Even unsuccesful attacker should be punished to deter attacks. In my favor speaks the fact of having run a node for > 2 years, an attacker probably wouldn't bother.
Amboss Magma channel buyers
Headache... I want to return funds I received. But there is magma fee, channel buyer pays to seller (me) and to amboss, guess I should refund both, as this is not fault of amboss. Hoping to beg amboss to forgive something. I am planning doing keysends, but there may be peers who neither support keysend nor published contact info. May publish some info here: https://gist.github.com/xmrk-btc/456666f1681c65dd0469df786de5d632 .
Other peers - active
As stated, I recommend force-closing. I still hope for a miracle, so you may wait a bit, but ziggie has already force-closed, and I have discussed details with him. Remember there are watchtowers, don't try to steal or you will be punished just as I was.
Another possibility is doing zombie recovery with SCBs even if your node is runnning fine. The advantage is that you don't need to wait for your fund, and less on-chain footprint & fees. But it is unsafe for me, it is essentialy a cooperative closure, I lose watchtower protection. And is more work for both of us. May do it with some trusted peers. (Correct me if I am wrong...)
Other peers - crashed/zombie
My SCB / channel.backup seems up to date, so zombie recovery should be possible. I have one such case, haven't attempted it yet though.
What happened
I stopped lnd, installed updates for 30-60 minutes, wanted to reboot because systemd did not respond, but even reboot did nothing. Decided to do sync, wait a few seconds and do
reboot -f. As if I haven't heard aboutumountormount -o remount,ro... sigh. lnd data are stored on ZFS pool as RAID1. Working theory is that important data stayed only in cache, lnd was running on 32 GB RAM machine while channel.db has 14GB so enough to cache everything. Still surprises me, usually lnd is writing at least 1 MB/s, as seen in dstat, perhaps some data is written and some is not?Community
The reaction was amazing, special thanks to Rocket Node who insisted on me stopping lnd, and thus possibly saved me several BTC. Zap-O-Matic tried to calm me down. Ziggie and Alex Bosworth investigated. They all gave me strength to continue.
Future
I probably want to start another lightning node, but not sure if I have all the skills. I can be reckless and undisciplined, perhaps less so after this event. I have little idea how to choose good HW. And the node was distracting me from work. OTOH, it would be a pity to abandon such community. And this gives me some opportunities to improve, I can finally migrate to SQLite or Postgres which could have better replication.
-
 @ 32e18276:5c68e245
2023-12-06 15:29:43
@ 32e18276:5c68e245
2023-12-06 15:29:43I’m going to be on an ordinals panels as one of the people who is counter arguing the claim that they are good for bitcoin. I decided to brush up on the technicals on how inscriptions work. I am starting to see luke’s perspective on how it is exploiting a loophole in bitcoin’s anti-data-spam mechanisms.
Storing data in Bitcoin, the “standard” way
The standard way you add “data” to bitcoin is by calling the OP_RETURN opcode. Bitcoin devs noticed that people were storing data (like the bitcoin whitepaper) in the utxo set via large multisig transactions. The problem with this is that this set is unprunable and could grow over time. OP_RETURN outputs on the other-hand are provably prunable and don’t add to utxo bloat.
Here’s an excerpt from the march 2014 0.9.0 release notes that talks about this:
On OP_RETURN: There was been some confusion and misunderstanding in the community, regarding the OP_RETURN feature in 0.9 and data in the blockchain. This change is not an endorsement of storing data in the blockchain. The OP_RETURN change creates a provably-prunable output, to avoid data storage schemes – some of which were already deployed – that were storing arbitrary data such as images as forever-unspendable TX outputs, bloating bitcoin’s UTXO database. Storing arbitrary data in the blockchain is still a bad idea; it is less costly and far more efficient to store non-currency data elsewhere.
Much of the work on bitcoin core has been focused on making sure the system continues to function in a decentralized way for its intended purpose in the presence of people trying to abuse it for things like storing data. Bitcoin core has always discouraged this, as it is not designed for storage of images and data, it is meant for moving digital coins around in cyberspace.
To help incentive-align people to not do stupid things, OP_RETURN transactions were not made non-standard, so that they are relayable by peers and miners, but with the caveat:
- They can only push 40 bytes (later increased to 80,83, I’m guessing to support larger root merkle hashes since that is the only sane usecase for op_return)
Bitcoin also added an option called -datacarriersize which limits the total number of bytes from these outputs that you will relay or mine.
Why inscriptions are technically an exploit
Inscriptions get around the datacarriersize limit by disguising data as bitcoin script program data via OP_PUSH inside OP_IF blocks. Ordinals do not use OP_RETURN and are not subjected to datacarriersize limits, so noderunners and miners currently have limited control over the total size of this data that they wish to relay and include in blocks. Luke’s fork of bitcoin-core has some options to fight this spam, so hopefully we will see this in core sometime soon as well.
Inscriptions are also taking advantage of features in segwit v1 (witness discount) and v2/taproot (no arbitrary script size limit). Each of these features have interesting and well-justified reasons why they were introduced.
The purpose of the witness discount was to make it cheaper to spend many outputs which helps the reduction of the utxo set size. Inscriptions took advantage of this discount to store monke jpegs disguised as bitcoin scripts. Remember, bitcoin is not for storing data, so anytime bitcoin-devs accidentally make it cheap and easy to relay data then this should be viewed as an exploit. Expect it to be fixed, or at least provide tools to noderunners for fighting this spam.
Where do we go from here
The interesting part of this story is that people seem to attach value to images stored on the bitcoin blockchain, and they are willing to pay the fee to get it in the block, so non-ideologic miners and people who don’t care about the health and decentralization of bitcoin are happy to pay or collect the fee and move on.
Data should not get a discount, people should pay full price if they want to store data. They should just use op_return and hashes like opentimestamps or any other reasonable protocol storing data in bitcoin.
After going through this analysis I’ve come to the opinion that this is a pretty bad data-spam exploit and bitcoin devs should be working on solutions. Ideological devs like luke who actually care about the health and decentralization of the network are and I’m glad to see it.
-
 @ de496884:72617b81
2024-02-05 17:29:44
@ de496884:72617b81
2024-02-05 17:29:44Muchas veces nos topamos con opiniones que pudieran ser contradictorias. Por un lado la ilustre frase «la juventud está perdida», por otro lado «aún me queda mucha juventud». Lo cierto es que quizás la ausencia de una definición clara, más allá de las dificultades teóricas, esté hablando de la intención de hablar de la juventud desde donde mejor plazca sin siquiera tener en cuenta real y objetivamente a quienes conforman esta categoría poblacional.
Asociado a ello tenemos que es común escuchar en la actualidad a través de los medios de comunicación a adultos militantes y partidistas caracterizar a la juventud como apática e indiferente, comparándola con los acontecimientos históricos de décadas pasadas. A pesar del valor histórico de esos momentos, es importante analizar los contextos en los que se desenvuelven las generaciones actuales.
Por tanto, en un intento de definir a la juventud, desde el condicionamiento histórico es necesario tomar como referencia al contexto del que adquiere sentido, y así se pudiese hablar de que la juventud está marcada actualmente por la emigración, el mundo globalizado, la interacción con las Tecnologías de la Información y la Comunicación (TIC), el desencanto político, el desgaste de los discursos dominantes y el deterioro de los emblemas aglutinadores; todo esto en una dinámica en la que los y las jóvenes se apropian y enriquecen el universo simbólico que les rodea. Me refiero a que la juventud más que un estado o etapa de la vida, es una condición social que depende en gran medida de las características históricas y sociales con las que interactúa cada uno de sus miembros. Pero a pesar de lo complejo de su articulación, es posible definirla atendiendo a lo juvenil y a lo cotidiano, siendo lo primero lo referido a la identidad, y lo segundo, a las prácticas sociales y contexto de relaciones dentro de una cultura determinada. Es aquí donde juegan un papel importante las vivencias de cada uno de los y las jóvenes.
Antes de llegar al núcleo de este artículo, creo que es necesario partir de que desde mediados del siglo XX los y las jóvenes comienzan a contar con privilegios de clase que le permitían enfocarse en sus estudios y posponer el matrimonio. En consecuencia, la etapa de juventud llegaba a su fin cuando estas clases dejaban de brindarles dicho privilegio, y comenzaban a asumir responsabilidades como mantenerse por su cuenta, tener hijos y establecer un hogar. Si lo vemos detenidamente, esta consideración supera a definiciones de la juventud como un grupo etario definido con sus propias características uniformes que ignora las condiciones materiales e históricas del contexto.
Es así cómo podemos ver que la juventud es algo más que una etapa de la vida o un estado; está condicionada por la clase, el género, las condiciones materiales y hasta la raza. Se puede afirmar que un joven blanco, cisgénero, de clase acomodada en un país desarrollado no será nunca similar a uno negro, homosexual, pobre en un país subdesarrollado, porque las tareas o retos que le depara su entorno y a los que tendrá que responder, serán totalmente diferentes, así como la vivencia de cada uno de ellos respecto a su propia realidad. Incluso existen culturas como en África, en las que no existe la etapa de la adolescencia o juventud porque sus jóvenes mediante rituales y exigencias propias de su contexto pasan directamente de la niñez a la adultez. Digamos que en estas etapas son más sociopsicológicas porque no existen -o no tan determinantes- condicionantes orgánicas; haciendo referencia a lo biológico.
De hecho, las sociedades actuales ya no tienen jóvenes conformados por los referentes tradicionales de tiempo cronológico, memoria histórica o territorio. Esto se debe a los procesos de globalización que se llevan a cabo en nuestros tiempos, los cuales se apoyan en las nuevas tecnologías de comunicación. En consecuencia, los procesos de identificación se producen asumiendo símbolos culturales globales hegemónicos, que se exportan en forma de patrones culturales y modelos de consumo occidentales, teniendo efectos principalmente en la cultura. Por lo tanto, la juventud es más un producto que un estado, condición social o etapa de la vida, ya que sus atributos se comercializan en forma de símbolos. Sin embargo, hay que hablar de una heterogeneidad juvenil dentro de una homogeneidad global, porque la juventud es una categoría sociohistórica, cultural y relacional.

Ahora sí: a través del uso de dispositivos electrónicos que permiten acceder a las redes sociales e internet, así como jugar videojuegos y utilizar teléfonos celulares, se pueden observar las relaciones entre la sociedad actual y la identidad de los jóvenes. Estos jóvenes diversifican sus formas de expresarse como tales, adaptándose a las características de la época, pero al mismo tiempo, también adoptan prácticas comunes desde una perspectiva generacional. Además, a través del uso de las TIC, los jóvenes también importan productos culturales y patrones de consumo occidentales, lo que genera una mezcla entre lo extranjero y lo cultural nacional. Ello muchas veces es tomado en cuenta para hablar de pérdida de identidad cultural, pero esto debiera verse desde otro enfoque en donde cada impacto cultural sea asimilado, pero al mismo tiempo enriquecido de forma tal que el producto final sea algo propio, algo genuinamente natural.
Se dice que hasta tiempos recientes, la familia había sido el agente de socialización por excelencia mediante la cual las personas descubrían y se enfrentaban al mundo y a la imagen que se formaban de este. Sin embargo, en los últimos veinte años con la influencia cada vez mayor de las TIC se ha producido un cambio social sin precedentes. Especialmente el acceso a Internet ha logrado que los jóvenes actúen como generadores y conductores de nuevas formas de interacción humana.
En ese sentido, se puede decir que los y las jóvenes han dejado de ser meros consumidores pasivos y ahora desempeñan roles activos en el consumo cultural, mostrando actitudes críticas y selectivas hacia ciertos productos culturales. Esto los ha llevado a pasar de ser simples consumidores a convertirse también en generadores de significados y productos culturales. Por lo tanto, el uso de las TIC no puede separarse del contexto sociocultural, ya que implica valores, comportamientos y significados que están vinculados a su existencia y que atraviesan las relaciones de poder en la sociedad.
Las redes sociales digitales son muy populares entre adolescentes y jóvenes porque abordan las preguntas fundamentales de esta etapa de la vida: ¿quién soy?, ¿cómo me percibo a mí mismo? y ¿cómo me ven los demás? Precisamente esta última pregunta es la más relevante para esta población. A partir de estas inquietudes y las respuestas que encuentren, tomarán decisiones que influirán en su desarrollo personal.
En el pasado, la política era vista como el espacio ideal para generar un cambio social radical, antes de que se subordinara a la economía como mecanismo de administración. Esto llevó a la percepción de que las cosas no pueden cambiar, lo que incluyó la neutralización de las relaciones sociales. Sin embargo, en la actualidad se valora lo instantáneo y se vive en una sociedad hedonista y narcisista. Las formas de participación actuales se centran en nuevas causas de movilización como el medio ambiente, los derechos humanos, sexuales y reproductivos, la causa indígena, entre otras. Se prioriza la acción inmediata, interesándose más en los efectos visibles y a corto plazo. Además, se busca mantener la individualidad dentro de las organizaciones, y la horizontalidad en los procesos de coordinación, respetando la autonomía y rechazando el centralismo democrático. Actualmente los jóvenes suelen estar más preocupados por los resultados concretos de acciones comunitarias, culturales, medioambientales o de denuncias, que por la organización en sí misma, como ocurre en la construcción de partidos. Tienden a involucrarse más en proyectos de gestión que en objetivos de representación, los cuales a menudo ni siquiera llegan a representarlos.
Esto nos lleva a hablar de las ciberculturas juveniles ya que el fácil acceso al ciberespacio a través de Internet y la clara preferencia de la audiencia por el formato audiovisual, que incluye los videojuegos como una forma de entretenimiento, influyen en las identificaciones, gustos, preferencias y planes de futuro, dando forma a la identidad individual y colectiva. Las ciberculturas juveniles tienen una razón de ser y un propósito significativo. Emergen como respuesta a las necesidades de participación de los jóvenes, influenciadas por los impactos de la realidad contemporánea a nivel global y nacional. Estas subculturas adoptan identidades grupales diversas, dependiendo de su enfoque en el contexto y el rol cultural, social y político que desempeñan.

Comúnmente se piensa y asume que con la llegada de las TIC, los jóvenes han dejado de realizar ciertas actividades. Sin embargo, lo cierto es que las tecnologías se incorporan a la vida diaria y reorganizan, pero no sustituyen, el tiempo dedicado a otras actividades. Hay percepciones arraigadas en la sociedad, como la creencia de que la llegada de un medio reemplaza instantáneamente a los demás, cuando en realidad lo que ocurre es una especie de simbiosis entre las prácticas anteriores y las nuevas. Por su parte, el conocimiento que poseen los y las jóvenes acerca de las tecnologías es principalmente de naturaleza instrumental. Aunque demuestran una notable destreza en su manejo, su uso se limita principalmente a satisfacer sus necesidades inmediatas de entretenimiento y relaciones personales. De hecho, a pesar de estar hiperconectados, tienden a relacionarse siempre con las mismas personas, tanto en el mundo virtual como en el mundo físico.
English version

For the Social Sciences, youth represents a very rich and necessary field of study because it is this population that, through alternativity, configures new spaces of participation that break with what has been socially conceived up to the present moment. However, despite what has been said, it is a category that tends to dissolve in everyday life, framed in definitions convenient for preceding generations depending on the situation. Thus, we often come across opinions that could be contradictory. On one hand, the illustrious phrase 'youth is lost,' on the other hand, 'I still have a lot of youth left.' The truth is that perhaps the absence of a clear definition, beyond theoretical difficulties, may indicate an intention to speak about youth from wherever it pleases, without even considering, in a real and objective way, those who make up this population.
Associated with this, it is common nowadays to hear adults, especially militants and partisans, characterize youth as apathetic and indifferent through the media, comparing it to historical events of past decades. Despite the historical value of those moments, it is important to analyze the contexts in which current generations operate.
Therefore, in an attempt to define youth, from a historical conditioning perspective, it is necessary to take as a reference the context from which it gains meaning. Thus, one could say that youth is currently marked by emigration, the globalized world, interaction with Information and Communication Technologies (ICT), political disillusionment, the wearing out of dominant discourses, and the deterioration of cohesive symbols. All this in a dynamic where young people appropriate and enrich the symbolic universe that surrounds them. I mean that youth, rather than a state or stage of life, is a social condition that depends largely on the historical and social characteristics with which each of its members interacts. Despite its complex articulation, it is possible to define it by addressing the youthful and the everyday, with the former referring to identity, and the latter to social practices and the context of relationships within a specific culture. This is where the experiences of each young person play an important role.
Before getting to the core of this article, I believe it is necessary to start from the mid-20th century, when young people began to have class privileges that allowed them to focus on their studies and postpone marriage. Consequently, the youth stage came to an end when these classes stopped providing them with such privilege and began to take on responsibilities such as supporting themselves, having children, and establishing a home. If we look closely, this consideration surpasses definitions of youth as a defined age group with its own uniform characteristics, ignoring the material and historical conditions of the context.
This shows that youth is more than a life stage or a state; it is conditioned by class, gender, material conditions, and even race. It can be affirmed that a white, cisgender, affluent young person in a developed country will never be similar to a black, homosexual, poor young person in a developing country because the tasks or challenges that their environment presents to them will be completely different, as well as their experience of their own reality. There are even cultures in Africa where there is no adolescence or youth stage because young people, through rituals and demands specific to their context, transition directly from childhood to adulthood. Let's say that in these stages, sociopsychological factors play a more significant role because there are no - or not as determining - organic conditions, referring to the biological aspect.
In fact, current societies no longer have young people shaped by traditional references of chronological time, historical memory, or territory. This is due to the processes of globalization taking place in our times, which rely on new communication technologies. Consequently, identification processes take place by assuming hegemonic global cultural symbols, exported in the form of Western cultural patterns and consumption models, primarily affecting culture. Therefore, youth is more of a product than a state, social condition, or life stage, as its attributes are commercialized in the form of symbols. However, we must talk about youthful heterogeneity within a global homogeneity because youth is a socio-historical, cultural, and relational category.

Now, through the use of electronic devices that allow access to social networks and the internet, as well as playing video games and using cell phones, we can observe the relationships between current society and the identity of young people. These young people diversify their ways of expressing themselves as such, adapting to the characteristics of the time, but at the same time, they also adopt common practices from a generational perspective. In addition, through the use of Information and Communication Technologies, young people also import global cultural products and Western consumption patterns, creating a blend of the foreign and the national cultural. This is often considered a loss of cultural identity, but it should be seen from another perspective where each cultural impact is assimilated but at the same time enriched, resulting in something unique and genuinely natural.
It is said that until recent times, the family had been the primary socialization agent through which people discovered and faced the world and the image they formed of it. However, in the last twenty years, with the increasing influence of ICT, an unprecedented social change has occurred. Especially with internet access, young people act as generators and drivers of new forms of human interaction.
In that sense, it can be said that young people have ceased to be mere passive consumers and now play active roles in cultural consumption, showing critical and selective attitudes towards certain cultural products. This has led them to move from simple consumers to also becoming generators of meanings and cultural products. Therefore, the use of ICT cannot be separated from the sociocultural context since it implies values, behaviors, and meanings linked to their existence, cutting across power relations in society.
Digital social networks are very popular among teenagers and young people because they address the fundamental questions of this stage of life: who am I? How do I perceive myself? And how do others see me? The latter question is especially relevant for this population. From these concerns and the answers they find, they will make decisions that will influence their personal development.
In the past, politics was seen as the ideal space to generate radical social change before it became subordinate to the economy as a mechanism of administration. This led to the perception that things cannot change, including the neutralization of social relationships. However, nowadays, instantaneity is valued, and we live in a hedonistic and narcissistic society. Current forms of participation focus on new causes of mobilization such as the environment, human rights, sexual and reproductive rights, indigenous causes, among others. Immediate action is prioritized, showing more interest in visible and short-term effects. Furthermore, there is a desire to maintain individuality within organizations, with a preference for horizontal processes of coordination, respecting autonomy and rejecting democratic centralism. Currently, young people are often more concerned about the concrete results of community, cultural, environmental, or advocacy actions than the organization itself, as is the case with party building. They tend to get involved more in management projects than in representation goals, which often do not even represent them.
This leads us to talk about youth cybercultures since easy access to cyberspace via the internet and the clear preference of the audience for audiovisual formats, including video games as a form of entertainment, influence the identifications, tastes, preferences, and future plans, shaping individual and collective identity. Youth cybercultures have a reason for being and a significant purpose. They emerge in response to the participation needs of young people, influenced by the impacts of contemporary reality globally and nationally. These subcultures adopt diverse group identities, depending on their focus on the context and the cultural, social, and political role they play.

It is commonly thought and assumed that with the arrival of ICT, young people have stopped engaging in certain activities. However, the truth is that technologies are incorporated into daily life and reorganize but do not replace the time dedicated to other activities. There are entrenched perceptions in society, such as the belief that the arrival of one medium instantly replaces others, when in reality, there is a kind of symbiosis between previous practices and new ones. The knowledge that young people possess about technologies is mainly instrumental. Although they demonstrate remarkable skill in handling them, their use is mainly limited to meeting their immediate needs for entertainment and personal relationships. In fact, despite being hyperconnected, they tend to relate to the same people, both in the virtual and physical worlds.

Créditos | Credits
Bibliografía utilizada | Bibliography used
Imágenes utilizadas | Images used
Las imágenes utilizadas son de mi propiedad y fueron generadas utilizando la IA de Bing Image Creator. En el caso de la imagen de portada, fue editada en Canva | Images used are my own and were generated using the AI of Bing Image Creator. In the case of the cover image, it was edited in Canva.
Traducción | Translation
Te puede interesar | You may be interested in
-
Año nuevo, mismas frustraciones | New year, same frustrations. [ES/EN]
-
¿Feliz navidad o feliz Saturnalia? | Merry Christmas or Happy Saturnalia? [ES/EN]
Sígueme en mis redes sociales | Follow me on my social media platforms
-
Chef's notes
The contrast between the hot coffee and the cold, floating cream is what makes Irish Coffee so delightful. It's the perfect way to warm up and relax. Enjoy responsibly! ☕
Details
- ⏲️ Prep time: 5 min
- 🍽️ Servings: 1
Ingredients
- 1 cup of hot brewed coffee
- 1 1/2 ounces of Irish whiskey
- 2 teaspoons of brown sugar (adjust to taste)
- Freshly whipped cream
- Coffee glass or mug
Directions
- Brew a cup of hot coffee.
- While the coffee is brewing, warm your coffee glass or mug by filling it with hot water. Let it sit for a minute, then pour out the water.
- Add the brown sugar to the warm glass.
- Pour the hot brewed coffee over the sugar and stir until it's dissolved.
- Add the Irish whiskey and give it another gentle stir.
- Carefully pour the freshly whipped cream over the back of a spoon so that it floats on top of the coffee mixture.
- The cream should rest on the surface; don't stir it in.
Chef's notes
👩🍳 Dear Honeys
We're thrilled to share this bee-kissed recipe with you! These cookies are not just treats; they're tiny, edible pieces of holiday joy... like bitcoins. Each cookie is unique and holds its value in every bit. Whether you're baking for family, friends, or just treating yourself, remember that each cookie is a canvas for your creativity. Enjoy the sweet aromas filling your kitchen and the smiles these cookies will bring.
Happy Baking and Happy Holidays! 🎉🎁
Details
- ⏲️ Prep time: 80
- 🍳 Cook time: 10
- 🍽️ Servings: 6
Ingredients
- 1 cup honey 🍯
- 3/4 cup brown sugar 🧂
- 1 large egg 🥚
- 1 tablespoon lemon juice 🍋
- 2 3/4 cups all-purpose flour 🌾
- 1/2 teaspoon baking soda
- 1 teaspoon ground cinnamon
- 1/2 teaspoon ground cloves
- 1/2 teaspoon ground ginger
- 1/2 teaspoon nutmeg
- Pinch of salt 🧂
- Powdered sugar for buzz ❄️
Directions
- Preheat Oven: Preheat your oven to 350°F (175°C). Line baking sheets with parchment paper.
- Mix Wet Ingredients: In a large mixing bowl, combine the honey from friendly honeybees and brown sugar. Beat in the egg and lemon juice until well blended.
- Combine Dry Ingredients: In a separate bowl, sift together the flour, baking soda, cinnamon, cloves, ginger, nutmeg, and salt.
- Combine Mixtures: Gradually add the dry ingredients to the wet mixture, stirring until a dough forms. If the dough is too sticky, add a little more flour.
- Chill the Dough: Wrap the dough in plastic wrap and refrigerate for at least 1 hour.
- Roll Out Dough: On a floured surface, roll out the dough to about 1/4 inch thickness
- Cut Out Cookies: Use hexagon-shaped cookie cutters to cut out shapes and place them on the prepared baking sheets to look like a honeycomb
- Bake: Bake for 8-10 minutes or until the edges are just starting to brown.
- Cool and Decorate: Let the cookies cool on the baking sheet for a few minutes before transferring to a wire rack to cool completely. Dust with powdered sugar to add some buzz.
- Enjoy your honey-infused Alby Christmas cookies with a warm cup of tea or coffee!
Chef's notes

Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 4
Ingredients
- 4 whole chicken breasts
- 2 TBS Olive oil
- 2 tbs butter
- 6 shallots, chopped
- 2 pared carrots, sliced into 1/4 inch rounds
- 1/4 cup brandy or cognac
- 1 cup dry white wine
- 1/4 cup chopped or 2 tsp dried tarragon
- 1/2 tsp dried chervil leaves
- 1/2 TSP salt
- 1/8 tsp pepper
- 1 cup light cream
- 1 egg yolk
- 1 TBS flour
- 1/4 lb. Mushrooms
- 2 more TBD butter
- Springs of fresh tarragon
Directions
- Photo in notes.
This post was originally published on https://tftc.io by Marty Bent.
Business owners are currently facing the challenge of protecting their assets against the dual threats of US dollar inflation and Bitcoin's historical volatility. Inflation erodes the purchasing power of the dollar, while Bitcoin's price swings can introduce risk into a company’s financial strategy. This presentation provides an analytical approach to navigating these issues.
Inflation and its Impact
The purchasing power of the US dollar has significantly diminished since 1980, with a notable increase in the rate of this decline in recent times. Inflation rates are a critical concern for business owners as they directly affect balance sheets and the cost of doing business. The M2 monetary base, an important measure of the money supply, has surged from $8.27 trillion in January 2009 to approximately $21 trillion recently. This represents an increase of $13 trillion since the inception of Bitcoin.


Furthermore, the total federal debt has grown from around $10.7 trillion in 2009 to over $34 trillion. The ratio of national debt to the M2 money stock has increased from 1.26 to 1.68 within the same period, suggesting that debt expansion has outpaced monetary base growth. These factors indicate that inflation is unlikely to be tamed shortly and may worsen if the Federal Reserve cuts rates.
[
Bitcoin’s 15 Years In Perspective | Marty Bent
Today is a better day than most to put the current problems people are facing into perspective. To do this, let’s take a look at what the monetary and debt landscape looking like around the time bitcoin was launched.
 TFTC – Truth for the CommonerMarty Bent
TFTC – Truth for the CommonerMarty Bent

](https://tftc.io/bitcoin-15-years/)
Bitcoin’s Price Volatility
Bitcoin's price has been highly volatile since its creation in 2009. For instance, daily volatility can sometimes reach 5%, with significant price swings occurring within short timeframes. This volatility is attributed to the fact that Bitcoin is a new monetary good, monetizing in real-time during the past decade. As Bitcoin is a novel asset class undergoing rapid adoption, its price fluctuations are a natural consequence of its evolution.
Despite this, historical data indicates a trend of decreasing volatility over the years. As understanding and confidence in Bitcoin grow, its role as a long-term savings vehicle becomes more pronounced, potentially leading to a stabilization in price volatility. When viewed on a logarithmic scale, Bitcoin's price trend shows a consistent upward trajectory despite short-term fluctuations.

Strategies for Business Owners
Business owners seeking to hedge against inflation using Bitcoin should approach the situation with a clear plan. This involves analyzing their balance sheet, cash flows, and profits to determine an appropriate Bitcoin allocation strategy. Rather than making impulsive decisions, a disciplined approach, such as dollar-cost averaging, can mitigate the risks associated with price volatility.
Planning for Bitcoin exposure on the balance sheet also requires a psychological shift. Rather than focusing solely on the downside risk, business owners should consider the potential for Bitcoin to appreciate in value over time. Allocating a percentage of profits or cash flow to Bitcoin as part of a long-term savings strategy can capture this upside potential.
In addition to traditional cash flow management, businesses can explore innovative ways to generate "sats flows," which refer to revenue streams denominated in Bitcoin's smallest unit, satoshis. Utilizing platforms like Podcasting 2.0 allows businesses to receive Bitcoin tips directly from customers, creating an additional revenue stream that can be accumulated without immediate conversion to fiat currency.
[
Bitcoin Treasury - The Fourth Lever to Equity Value Growth
While building products and services in the growing bitcoin ecosystem will not ensure success, a company’s proclivity for success is inevitably correlated to bitcoin’s upside.
 TFTC – Truth for the CommonerGrant Gilliam
TFTC – Truth for the CommonerGrant Gilliam

](https://tftc.io/bitcoin-treasury/)
Conclusion
In conclusion, business owners must remain vigilant in the face of rising inflation and Bitcoin volatility. By understanding the economic landscape, developing a well-thought-out investment strategy, and adopting new technological solutions for revenue generation, businesses can navigate these dueling forces effectively. Planning, discipline, and a forward-thinking approach are essential to managing the balance sheet risks associated with inflation and Bitcoin's volatility.
Chef's notes
Intermediate baking skills needed or not... Be sure to use a mixer to mix ingredients together. Dough gets pretty sticky, be sure to use flour for dusting
Details
- ⏲️ Prep time: ~ 2 Hours 30 Mins
- 🍳 Cook time: ~ 30 Mins
- 🍽️ Servings: 16
Ingredients
- 1 Packet of Yeast
- 1/4 cup Warm Water
- 1/2 cup Milk (whole/skim/half/evaporated)
- 2 eggs
- 1/2 stick (1/4cup) Butter
- 1/3 cup Sugar
- 1 tsp Salt
- 3 1/2 - 4 cups - All Purpose Flour
- Oil for Frying (Olive/Avacado/Vegetable/Ghee)
Directions
- Mix 1 Packet of Yeast & 1/4 cup Warm Water in a small bowl,
- Cover & let sit for 5-10 mins
- Use a Hook attachment & Mixer for best results,
- In mixing bowl, add 1/2 cup Milk, 2 eggs, 1/2 stick Butter, 1/3 cup Sugar, 1 tsp Salt, & 3 1/2 - 4 cups All Purpose Flour.
- Mix for 10 - 20 mins , dough should not stick to the side of the bowl, but stick a little at the bottom.
- Cover, & let it double in size for 45 mins - 1 hour .
- Dust rolling area with flour & roll out the dough to 1/2inch thickness
- Lay out parchment paper on a surface to put donut shapes on,
- Cut out donut shapes as desired, (If there is more dough, roll out again & repeat)
- Cover donut shapes & let rest for 1 hour.
- Medium Low; Heat up oil to fry donuts!
- Enjoy!
Chef's notes
Bitcoin Only Pleb’s #weedbrownies recipe:
Need about a half ounce to an ounce of Vaped weed OR decarbed weed to start. (Look up online how to decarb if you don’t have vaped weed)
Dump that out into a stainless steel sauce pan large enough to hold everything..(stainless or cast iron will do, no non-stick bc you’ll be simmering for a long time and PUFAs are no joke)
Find out how much the brownie box calls for in oil and then add slightly more of that to the pan with the weed. You’ll want to use oil with a high smoke point, I prefer avocado oil (example: If the recipe calls for 1/2 cup of oil, add a little under 2/3 of a cup to the pan with the weed as you will lose some in the next steps)
Cook weed/oil mixture on simmer (very very low heat) for 2-3 hours, let it cool down to room temp when done.
Take a coffee filter and fix it around a drinking glass (might need someone to help you with this next step), pour the weed/oil mix through the coffee filter and let it drip through. This step can get messy, if you’re impatient like me, twist the open mouth of the filter closed and squeeze everything out carefully. Or if you have time let it drip through.
Take that oil and use it as instructed in the brownie mix.
Pop those bad boys in the oven and enjoy when cool. Remember to never “guess” your edible intake. Better to start small.
Love y’all🧡💜
Details
- ⏲️ Prep time: 3 hours
- 🍳 Cook time: 30 min
- 🍽️ Servings: 10
Ingredients
- Follow brownie mix ingredients on box after making infused oil
Directions
- Bitcoin Only Pleb’s #weedbrownies recipe: Need about a half ounce to an ounce of Vaped weed OR decarbed weed to start. (Look up online how to decarb if you don’t have vaped weed) Dump that out into a stainless steel sauce pan large enough to hold everything..(stainless or cast iron will do, no non-stick bc you’ll be simmering for a long time and PUFAs are no joke) Find out how much the brownie box calls for in oil and then add slightly more of that to the pan with the weed. You’ll want to use oil with a high smoke point, I prefer avocado oil (example: If the recipe calls for 1/2 cup of oil, add a little under 2/3 of a cup to the pan with the weed as you will lose some in the next steps) Cook weed/oil mixture on simmer (very very low heat) for 2-3 hours, let it cool down to room temp when done. Take a coffee filter and fix it around a drinking glass (might need someone to help you with this next step), pour the weed/oil mix through the coffee filter and let it drip through. This step can get messy, if you’re impatient like me, twist the open mouth of the filter closed and squeeze everything out carefully. Or if you have time let it drip through. Take that oil and use it as instructed in the brownie mix. Pop those bad boys in the oven and enjoy when cool. Remember to never “guess” your edible intake. Better to start small. Love y’all🧡💜



