-
 @ a6e3fee8:a1e557ee
2023-03-12 18:23:43
@ a6e3fee8:a1e557ee
2023-03-12 18:23:43 **
**Vorresti accettare Bitcoin come metodo di pagamento?
**
Vieni a scoprire come: Giovedì 23 marzo 2023 alle ore 20.00 c/o City Life Cafè, via Masaccio 18 a Milano.
Scopriremo quanto è facile accettare pagamenti in Bitcoin.
Porta con te: 1. un telefono cellulare (android, iOS o altro) 2. un quaderno per annotare qualche piccolo segreto 3. una moneta da 1 o 2 € () 4. la voglia di passare un'oretta a soddisfare la tua curiosità 5. Il tuo bigliettino da visita (*)
() riceverai l'equivalente in Bitcoin. Se a fine serata non sarai soddisfatto/a, saremo felicissimi di restituirti la moneta e riprenderci i #sats (*) ce lo potrai dare alla fine, se ti siamo piaciuti: verremo a trovarti per continuare a seguire i tuoi primi passi
Puoi dare la tua adesione rispondendo a questo poll
Iniziativa gratuita rivolta a commercianti e professionisti milanesi Ti aspettiamo!
○ ○ 🟠💊 Precoiner friendly nell’era Bitcoin
milanotrustless.com
per rimanere in contatto:
DM.me @t.me/trentunofebbraio o milanotrustless@proton.me
-
 @ 4c5d5379:3a4383ee
2023-03-11 17:33:57
@ 4c5d5379:3a4383ee
2023-03-11 17:33:57[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
-
 @ f40832e2:bcbf511e
2023-03-11 05:13:15
@ f40832e2:bcbf511e
2023-03-11 05:13:15[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
-
 @ 1e7f93b2:5c779c78
2023-03-10 17:18:59
@ 1e7f93b2:5c779c78
2023-03-10 17:18:59A new game by THNDR Games dropped to the Apple app store and the Google Play Store yesterday. The new game is called Bitcoin Blocks Puzzle Strategy.
If you are familiar with any of the THNDR Games, the process is the same:
Play the game, get tickets, enter the hourly draw, and when that draw happens you win Satoshis.
After all that you can claim them to your own lightning wallet, as simple as that.
How does this game work?
This game is a mix between 2 games, Sudoku and Tetris. You have to put the Tetris looking blocks in the Sudoku map. Each time you put a block on the game map you gain score, and each time you get 100 points, you get one tickets which automatically enters the hourly draw.
Multipliers
Sometimes, you can see numbers on the game map, when you put a block on that number your score gets multiplied by it.
If you manage to eliminate a piece with an orange block your multiplier goes up by 1.
How do you win?
You can see underneath the game map something called "Level"
Each time you put 3 blocks on the map you go to the next level.
You win the game when you reach level 25.
What are leagues?
THNDR Games introduced the leagues system in the Club Bitcoin Solitaire game.
In leagues, you play against 9 other players in your league, to try and go up to the next league and why not try to be the first.
In each league you get to, the number of players going up or going down the leagues changes.
What's new?
With the introduction of the new game, something new got introduced also into the mix.
We all for now know Nostr and its benefits, well, THNDR Games introduced THNDR Badges that you can get just by playing Solitaire or Blocks, and all of that is achievable by only putting you public key or "npub" in the settings inside the Solitaire or Blocks game.
And these badges follow you wherever you go on Nostr.
You can see these badges, on your Nostr profile, check this image from my profile taken from the Snort Nostr client.
This is a small introduction to the new Bitcoin Blocks game by THNDR Games.
This is a blog post also from their website: How to setup Nostr with THNDR
You can download the game from here
If you have any other questions please ask me in the comments below.
With Love Cryptonator ❤️
-
 @ 34c0a532:5d3638e4
2023-03-10 11:31:46
@ 34c0a532:5d3638e4
2023-03-10 11:31:46You can also listen to the story on audiobook.
Fritz had no idea why there were so many people at his father’s funeral. Sure, he had to be there. So did his sister, Lotte. But what about the rest of the people? He definitely didn’t know any of them. The grassy hill was basically crowded with tombstones and people. “Hey, who are these people?”
Lotte shrugged, looking around behind her black veil. “No clue. I’ve never seen them before. From dad’s work, maybe?”
Fritz snorted. “What work? Dad has never worked a day in all our adult lives.”
“Well, you know…” Lotte said nasally, as if trying to avoid getting her lips read.
“Know what?”
She leaned closer. Her perfume wafted to Fritz’s nose, he had forgotten about it. It had been over eight years since they’ve met in person, or as dad would have said, two halvings. Their infrequent videocalls thankfully didn’t carry over the flowery drowsiness his sister seemed to like dousing herself with. “Bitcoiners,” she whispered, the word being anathema in their house for ages.
“Oh!” said Fritz and looked closer at the people around him. Yeah, that made sense. This was an international bunch, those guys were definitely from somewhere like Nigeria, and that couple, what? American? Probably. And some Swedish people, far too blonde to be anything else. And…
“Hello, I am Booger,” the man said with a significant amount of seriousness and shook Fritz’s hand. It was a vice grip, he was old, like seventy? More? But he had definitely been chopping wood sometime last week, that’s what his hands felt like.
Fritz needed to check for splinters. He blinked, giving a handshake. “Excuse me?”
“Booger. I’ve known your father for years now, online acquaintances. Anonymous, you see. It was a juvenile impulse of mine, so, Booger kinda stuck. That’s what everyone calls me.” His accent was rich, something like French? Swiss? His suit was smart, well worn but tailored to his body.
“Right. Nice to meet you. This is my sister, Lotte.”
“Of course,” Booger said and shook her hand too. “I’m sorry for your loss.”
“Thank you,” the siblings said in unison, both in shock.
“Um… Do you know all these people?” Fritz asked.
Booger chuckled. “Know them? But of course! They’re all your father’s friends.”
“Dad didn’t have any friends,” Lotte said flatly. “Okay, apart from Johannes.” She nodded in his direction.
Fritz looked towards the direction of his father’s best and only friend in the world, as far he’d known till two minutes ago. For some reason Johannes stood apart and never met his eyes. “Oh, but he did. From all over the world. We met a few times in a convention here and there,” Booger said.
“Bitcoin conventions?” Fritz asked.
“Yes, but not the popular ones. Those are shitcoins,” Booger said, in direct contrast to his serious demeanor. The man had a well-trimmed beard, for God’s sake!
Fritz glanced at Lotte. “Riiight…”
She interjected. “Thank you for attending our father’s funeral. You honor us with your presence. But how did you learn about it?”
“Oh, Nakaboto heard about it and told everyone. We just had to get on a flight and come pay our respects.” Booger pointed at a woman who looked like she grew roses for fun and profit.
“Nakaboto. Right.” Fritz nodded. He was still in shock. Honestly, he had braced himself for attending the funeral with just him, the priest and his sister. He never expected an impromptu bitcoin convention to be held on top of the grassy hill where they would put his father to rest. It was moody enough, gray skies up above, not raining but feeling like it was about to. Proper ambiance for a funeral.
The chatting people were a contrast, though. They were far too happy to be here. Most of them were hugging each other and smiling, meeting like old friends. Fritz wanted to feel angry about that but if this was an excuse for dad’s friends to hang out, then sure, why not?
Booger clapped his massive hands together. “Oh, lovely. The service is here!”
“What service,” Lotte asked, raising her veil on top of her black hat to see better, but they both got their answer pretty quickly. A black van appeared. It had embroidered letters and designs at the side, and it read, “Afterlife Chats.”
“What? No,” Fritz said, realizing what this meant. “No, fuck no! Who’s paying for this? I heard this is ridiculously expensive.”
Booger shrugged. “Nakaboto came up with the idea. We all chipped in. See?” He showed them his phone.
“What is happening?” Lotte asked, agitated.
“The Afterlife Chats service, my dear madam, is cutting edge. It allows us to speak with the recently departed for a short amount of time. And yes, as your brother mentioned, it is quite expensive, but we all thought it was important to provide this gift for your father. Nakaboto organized a fundraiser, she was always good with automation, here are the lightning donations.” He scrolled through the list of incoming donations, there were hundreds of them. Lightning allowed them to send a short text message too, so most had such messages attached.
“Can’t believe it. Farewell.”
“No way. Say hi for me.”
“My condolences.”
“In this life or the next.”
“You will be missed.”
“But it’s ridiculously expensive!” Fritz spat out again.
Booger shrugged again. “Just a few million sats.”
“How many million?” Fritz squeaked.
“A hundred.”
“That’s a whole bitcoin!”
Booger shrugged again. “Who can put a price on grieving children having a final say with their father?”
“They can!” Fritz argued, pointing at the technicians setting up their gear. The priest was surprised, she kept stepping out of their way, even though this was supposed to be her event. “And they want a whole coin!”
Nakaboto heard it and she shrugged also. She came over. “We’re all satoshi billionaires, sweetie,” she whispered. “Shh… don’t tell anyone.” She gave both of them a lovely red rose. “Organic, none of that chemical stuff.”
Fritz stared at Lotte. They both knew what this meant. This was like having a bunch of international billionaires attend a funeral of a person, who as far as the siblings knew, never did anything with his life except rant online about conspiracy theories and inflation. The technicians set up the apparatus over the open casket. Dad was lying there, better than he ever looked before in his life. He had an electronic halo around his head now, but no wires. It must have been wireless. The devices next to him looked like something out of a sci-fi movie, and if his dad was suddenly struck by lightning and came back to life, he would not be surprised in the least at this time. “We’re ready when you are, sir.”
Fritz stepped close, swallowing hard again and again. He stared at his father’s lifeless face. His pale lips, unmoving. Oh God, they weren’t about to move, were they? He tried to remember what he had read about this Afterlife Chats thing.
Miss Nakaboto stepped up next to him. Her flowery scent was discreet, earthy. A lot better than his sister’s. She must have felt his confusion. “As soon as you give us the go ahead, they’ll start the event. It’s a timelocked contract, written on the blockchain. Immutable. Eternal.” She said the last words with reverie. “The conversation your father will have with you as well as the simultaneous group chats with the rest of us will be forever chiseled on digital granite, giving your father one last bit of immortality.”
“Do you do this for all your friends?”
Miss Nakaboto bit her lip and rested her aging hand on his shoulder. “Sadly, no. But your father is worth it.”
They all looked ahead.
“One block is all you have. Ten minutes. Make it count,” Miss Nakaboto explained.
Fritz stared at his sister. “Uh… What do you want to say?”
“I don’t know! I can’t come up with something while being ambushed like that.”
“Right.” He looked ahead, trying to avoid the dead body and the upcoming conversation. He couldn’t refuse. These people, who apparently held his father to a high regard, had come here to do this, spent piles of wealth to organize this, and given him an opportunity reserved for billionaires and oligarchs. He was shocked that there were no news drones hovering around them, to be honest. There was no way they had managed to keep this event quiet. Then again, they all liked anonymity. And apparently so did his father. He ran away.
He could hear some muttering behind him. Disapproving stares, clicks of the tongue. He didn’t care. These people didn’t know him, didn’t know his dad. They had no idea what it was like growing up with him.
The fights. The constant anger. Losing his mom.
The isolation deep in the countryside. Losing his friends. Being dragged away from the first girl he ever loved to do what?
Getting away from their control, whoever they were. The government. The elite. The people in charge, the warmongers. People who wanted to poison, us, castrate us, annihilate us, wipe us from the face of the earth.
This was how he had lived his entire childhood, being afraid, being bitter. Any shred of enjoyment tainted with the impending doom of the world, like a Sword of Damocles dangling over their head, but it was dripping black oil on his face and even though it never fell to cut him in half, it dirtied his every waking moment on Earth.
The fiat world, all around him.
Oh, he could see his dad’s point of view. Years later, after he ran away from home, after going to work as a corporate wageslave, the exact same kind of prison his father had been trying to shield him from.
He had to see it for himself, he had to give it a shot. It’s not enough for someone to tell you that there’s a hole right in front of you, you have to trip and fall into it in order to learn your lesson.
He did. Coming back, divorced, in debt, controlled by the CBDC that offered no escape hatch even if you lived five lifetimes, he had seen what his father had been ranting about all his life. The conspiracies. The lies. The corruption.
Lotte came up to him. “I knew I’d find you behind a tree.” She was crying, her makeup was a mess but her veil was up. He was crying too.
“Yeah. Sorry, I just needed a minute to breathe.”
“Oh, I get it. Don’t worry. That rose lady started telling me about how she uses her own livestock for fertilizer. So you might want to wash your hands to get all the poop out before you wipe away those tears.”
Fritz laughed, and then his sister joined him. They laughed, waving their roses at each other, giggling like they used to years ago.
Out of breath, they shook their heads, tearing up. “Oh, Lotte. Why did we stop hanging out?”
“Because you’re a poopyhead.”
“That I am. I’m sorry.”
“Fritz?”
“Yeah?”
She bit her lip, like she used to do when they were kids and she was about to do something naughty. “I know what I want to ask dad.”
“What is it?”
She crossed her arms under her breasts. “I want to know if he’s okay with me dating Johannes.”
Fritz turned to face her. “What?” he snapped. “But he’s dad’s age!”
Lotte turned her chin up, not budging. “I don’t give a shit, Fritz. He’s funny and he’s kind and he has been there for me ever since you left.”
“B-But he could literally be your father!”
She poked him in the chest. “Hey, moron. Look around. Life is short and then you die.”
Fritz ran his fingers through his hair. He nodded, thinking about it. “Yeah. Yes, I’m sorry. You’re right. It just came as a shock to me, that’s all.” He opened his arms to hug her.
She felt tight, wound up for an argument, but then she melted into his embrace. He lifted her hat and kissed her on the head, ignoring her perfume. “Maybe Johannes has lost all sense of smell, the poor guy.”
She slapped him on the hand.
He smiled at her.
“What are you gonna ask?”
Fritz took in a deep breath. “Oh, no questions, really. I’m just going to say one thing.”
“Which is?”
“I’m gonna tell dad that I’m sorry, and that he had been right all along.”
Lotte’s eyes went wide. She didn’t say anything, didn’t have to, she just nodded with a bitter smile.
They walked back towards the funeral, holding hands for emotional support. The anonymous bitcoiners waited, all staring at them. They held their blackphones in their hands. Fritz could recognize from his dad the modified smartphones running open source software that couldn’t be traced.
Apparently, as soon as he gave the technicians a go, they’d all be chatting with his deceased father for ten whole minutes.
He still couldn’t quite believe it, maybe it was a prank, this entire thing. An elaborate prank.
His sister gripped his arm, digging her nails in.
He took in a deep breath.
“I’m ready to say goodbye to my father.”
The End.
Did you enjoy this story? Then consider zapping some sats! Find all my stories at https://georgesaoulidis.com/links/
-
 @ 7ab79bc0:9385ad99
2023-03-10 10:02:49
@ 7ab79bc0:9385ad99
2023-03-10 10:02:49Der ganze Artikel hier: #42 // KW10 // 9.3.2023 // Ist Bitcoin Geld? 🪙🐪🚬
Wir sprechen oft über Bitcoin im Zusammenhang mit Geld oder Währungen. Bitcoin funktioniert als Zahlungsmittel, als Wertspeicher und als Recheneinheit - doch macht das Bitcoin zu Geld? Also, was ist Geld überhaupt und was macht ein Gut erst zu Geld? Und warum gibt es gutes Geld und weniger gutes Geld? Es gibt viele Arten von Geld, Warengeld, Notenbankgeld, Fiatgeld, usw. Doch wollen wir uns erstmal ganz von Anfang an mit der Funktionen und den Eigenschaften von Geld im Allgemeinen beschäftigen.
Was ist Geld?
Ohne auf die Geschichte von Geld zum drölftausendsten Mal einzugehen (dazu kann man so ziemliches jedes Buch über Geld, Bitcoin, Ökonomie, etc. bis Seite 75 lesen und bekommt ganz genau die gleichen Infos), ist es sinnvoll sich kurz zu klarzumachen, dass niemand bestimmt oder definiert, was Geld ist. Geld kann im Endeffekt alles sein. Jeder, der Kindern schon mal beim Spielen zugesehen hat, wird erlebt haben, wie kurzerhand aus Steinen, Stöcken, DUPLO-Steinen oder eigentlich allem, was man in der Reichweite von Kindern so findet, plötzlich Geld wird. Denn ohne es zu wissen, verstehen Kinder sehr intuitiv, wie Geld funktioniert.
Geld ist Sprache. Geld ist wahrscheinlich sogar eine Sprache, die sich vor unserer modernen kommunikativen Sprache entwickelt hat. Selbst vor Urzeiten, als verschiedene Völker und Stämme auf den verschiedensten Winkeln der Erde herum zogen und sich somit erstmal verteilten und dann wieder vermischten, entwickelten sie unterschiedliche Arten der Kommunikation. Die eine gemeinsame Sprache jedoch, war die des Handels.
Kurzes Szenario: Homo Sapiens 1 hat einen Sack voller selbstgeschnitzter Pfeilspitzen in der Hand und betritt eine Lichtung, auf der Homo Sapiens 2 gerade eine Antilope grillt. Homo Sapiens 1: Uhhhhhhhhhhhhhh (zeigt auf die Antilope). Homo Sapiens 2: Ahhhhhhhhhhhh (wehrt mit den Händen wedelnd ab und springt in verteidigender Haltung auf). Homo Sapiens 1: Uhhhhhhhhhhhhhhhh (öffnet seinen Sack mit den Pfeilspitzen und legt 10 davon so hin, dass Homo Sapiens 2 versteht, dass HS1 diese zum Tausch anbietet). Homo Sapiens 2: Haaaaaaaaaaaaaa (reißt eine saftige Keule von der Antilope ab, schmeißt diese HS1 vor die Füße und schnappt sich die Pfeilspitzen).

Handel ist also älter als Schrift oder Sprache. In dem Szenario hat Homo Sapiens 1 gegenüber Homo Sapiens 2 einen Vorteil, denn er hat einen Sack dabei, in dem sich ein Wirtschaftsgut befindet, das andere Personen bereit sind, gegen ihre Besitztümer zu tauschen. So entsteht über einen gewissen Zeitraum Geld. Dabei sind die Funktionen von Geld immer die gleichen, egal welches Mittel gewählt wird. Das Mittel hängt im Wesentlichen von der lokalen Verfügbarkeit (bzw. der Begrenztheit dieser) ab.
Funktionen von Geld
Geld muss im Wesentlichen drei Funktionen erfüllen können: Es muss als Tausch- oder Zahlungsmittel funktionieren, es sollte ein Wertaufbewahrungsmittel sein und als Recheneinheit dienen. In dem Szenario mit den beiden haarigen Protagonist//innen, sind diese drei Funktionen sehr leicht identifizierbar. HS1 hat selbstgeschnitzte Pfeilspitzen in einem Sack mitgeführt, da diese als Zahlungs- oder Tauschmittel verwendet werden können (HS2 hat bereitwillig feinstes Antilopen-Filet dafür eingetauscht), die Pfeilspitzen sind insofern Wertaufbewahrungsmittel, als dass sie (anders als das Fleisch) über Zeit nicht verderben und somit (zunächst) wertstabil sind - und damit HS1 incentiviert wird Pfeilspitzen zu sammeln (sparen) - und es war HS2 schnell möglich 10 Spitzen abzuzählen und somit seinem/ihrem Produkt einen Gegenwert beizumessen, sie dienen also auch als Recheneinheit.
Dies ist nur ein Beispiel, denn wie gesagt, Geld kann alles sein, das diese drei besprochenen Funktionen erfüllt und wenn sich mindestens zwei Parteien darauf einigen können, dass es sich bei dem verwendeten Mittel auch um ein Geld-würdiges Mittel handelt. Hätte HS1 kurzerhand 10 Steine vom Boden aufgehoben, um diese gegen das Fleisch zu tauschen, hätte HS2 laut "Uhhhhhhhhhh!" gerufen und mit dem Kopf geschüttelt, denn 10 Steine aufheben kann er/sie auch. Doch die Pfeilspitzen haben in diesem Moment einen intrinsischen Wert für HS2 und es ist erstmal egal, ob es sich hierbei um einen Tausch im direkten Sinne handelt (also Fleisch gegen Pfeilspitze), weil HS2 weiss, dass er/sie damit neues Fleisch jagen kann, oder einen indirekten Tausch, also eine Zahlung (also Fleisch gegen Geld), weil HS2 weiss, dass er/sie damit einen hippen Kakadu-Federn-Hut kaufen kann.
Geld ist älter als Sprache, bla!
Geld ist Sprache, say what?!
Geld ist, was Geld sein kann, auch wertloses Papier?

Aber wieso sind die 10 Pfeilspitzen Geld, bzw. warum sind sie begehrenswert und die 10 Steine nicht? Oder warum tauscht HS1 Pfeilspitzen gegen Antilopen-Frikadellen und nicht andersherum? Damit ein Gut, ein Mittel, ein Gegenstand, eine Idee zu Geld werden kann, muss es nicht nur die drei Hauptfunktionen erfüllen, es sollte zusätzlich auch einige Voraussetzungen erfüllen.
Eigenschaften von Geld
Über viele tausende von Jahren haben schon die verschiedensten Gegenstände und Mittel als Geld hergehalten. Ob Eichhörnchen Pelze, Parmesan Räder, Kakao Bohnen, Zigaretten, Walzähne, oder irgendwelche inseligen Steine - alle diese Objekte haben gemeinsam, dass sie zu einem gewissen Zeitpunkt in einem gewissen System die nachfolgenden Kriterien erfüll(t)en. Während einige dieser Kriterien immer faktisch die gleichen bleiben, gestalten sich andere wiederum etwas komplizierter und situationsabhängiger.
Teilbarkeit (Divisibility)
Ob etwas zum Beispiel teilbar ist, ist unbestreitbar nachweisbar. Wenn man etwas gegen eine Kuh oder ein Kamel eintauschen möchte, das aber nur den Wert einer halben Kuh oder eines halben Kamels hat, dann ist es eher unpraktisch die Kuh oder das Kamel zu teilen, da dann das gesamte Tier seinen eigentlichen Wert verliert. Ähnlich würde man auch kein halb-großes Kamel benutzen, da der Wert des Tieres nicht an seiner Größe bemessen ist. Bei Gold ist dies z.B. nicht der Fall. Eine halb so große Goldmünze ist nur halb soviel wert, wie eine normal große Goldmünze.
Ein Zahlungsmittel oder Gut sollte also in verschiedene Größen unterteilbar sein, ohne seine ursprüngliche Eigenschaft und damit seinen Wert nicht verlieren. Andersrum lässt sich auch argumentieren, dass ein Gut klein genug sein kann, dass es problemlos kombinierbar ist, um so einen größeren Tauschwert zu erhalten, ohne die Transportfähigkeit durch zu hohes Gewicht oder Volumen zu beeinflussen.
Transportfähigkeit / Portabilty
Die Transportfähigkeit ist nämlich bei Geld - in den meisten Fällen - besonders wichtig. Je weniger Aufwand betrieben werden muss, um das Zahlungsmittel zum Ort des Handels oder zu seinem neuen Besitzer zu schaffen, desto besser. Ein Kamel bietet sich da an, weil es selbst läuft, ein Haus ist schon relativ unhandlich, Zigaretten, Diamanten, Gold sind da natürlich die Favoriten. Die Transportfähigkeit ist einer der wichtigsten Faktoren, die die Funktion des Zahlungsmittels von Geld ausmachen. Man könnte auch sagen, die Transportfähigkeit erlaubt es, die Kaufkraft oder den Wert durch den Raum zu bewegen.
Haltbarkeit / Durability Ein Zahlungsmittel sollte im Idealfall über einen langen Zeitraum hinweg seinen Wert halten und bestenfalls nicht verderben. Diese Eigenschaften bieten vor Allem jene Güter, die nicht konsumierbar sind und deshalb einer niedrigen Zeitpräferenz unterliegen. Wer nicht sparen möchte, sondern lieber schnell konsumieren will, wird auch einen Tausch gegen verderbliche Waren nicht abschlagen, weil die jeweiligen Umstände dies erfordern (z.B. Hyperinflation, Krieg, etc.). Allerdings ist ein Zahlungsmittel besser, je länger es seinen Wert speichert, also ist die Haltbarkeit einer der Faktoren, die die Funktion des Wertspeichers von Geld ausmachen, oder anders ausgedrückt: die Fähigkeit, Kaufkraft oder Wert durch die Zeit zu bewegen.

Austauschbarkeit / Fungibility
Die Austauschbarkeit der jeweiligen Geldeinheiten macht Geld erst wirklich praktisch, denn wenn jeder Einheit (z.B. Münze, Korn, Schein, Perle, etc.) ein eigener Wert zugeschrieben wird, macht dies den Austausch sehr kompliziert, da der einzelne Wert jedes Mal ermittelt werden muss und der Wert eines jeden Objekts rein subjektiver Art sein kann. Die Austauschbarkeit eliminiert die Subjektivität der Wertschätzung und misst dem Geldmittel einen objektiven Wert zu.
Also unabhängig vom jeweiligen Tauschwert einer anderen Währung wird niemand bestreiten, dass eine Goldmünze (28g) den gleichen Wert hat wie eine Goldmünze (28g). Das 1€ Stück in meiner Tasche ist genauso viel wert, wie das 1€ Stück in jedem anderen Portemonnaie (ob die Kaufkraft morgen noch die gleiche ist, steht auf einem anderen Zettel). Die Austauschbarkeit der jeweiligen Einheiten in einem gewissen Geldsystem (also Euro-Münzen im Euro-System) machen den Umgang einfacher.
Nachweisbarkeit / Provability
Hierbei handelt es sich um den relativen Aufwand, den der Empfänger betreiben muss, um sicherzustellen, dass das erhaltene Gut tatsächlich den erwarteten Spezifikationen entspricht. Dies ist natürlich immer relativ zum möglichen Risiko eines Verlusts zu betrachten. Bekomme ich im Supermarkt einen 10€-Schein als Wechselgeld, werde ich kaum einen Prüfstift aus der Tasche ziehen, weil der Aufwand nicht im Verhältnis zum möglichen Risiko steht. Allerdings benutzen Kassierer//innen im Geschäft bei Scheinen ab 50€ immer einen Prüfstift. Bei Gold fällt es einem Laien schwer, ohne großen Aufwand zu verifizieren, dass es sich um reines, echtes Gold handelt. Man vertraut im Handel z.B. dem Goldhändler, dass das Gut verifiziert und authentifiziert wurde. Beim Handel mit Kamelen spielen viele Faktoren eine Rolle, ob das Kamel nachweislich dem versprochenen Wert entspricht, welche sich nicht einfach an Ort und Stelle prüfen lassen.

Knappheit / Scarcity
Diese Charakteristik ist wahrscheinlich die wichtigste, auch wenn eine Kombination aller Eigenschaften hartes Geld erst wirklich ausmacht. Knappheit bedeutet, dass das Gut, das als Geld benutzt wird, begrenzt ist und nicht ohne weiteres vermehrt werden kann. Knappheit kann durch geographische Einschränkungen hervorgerufen werden, so ist zum Beispiel Wasser in der Wüste knapper und somit wertvoller als in Regionen, in denen es reichlich und in Fülle vorhanden ist. Steine oder Sand bieten sich nicht als Geld an, da sie überall in Fülle vorhanden sind. Das beste (und zu Tode zitierte, sorry) Beispiel sind die Rai-Steine der Yap. Sie haben lange als Geld für den Inselstaat funktioniert, da diese schwierig zu beschaffen waren und die Herstellung sehr mühselig war. Doch als Schifffahrer auftauchen, die einfach und günstig Steine beschaffen konnten, wurde diese geographische Einschränkung aufgehoben und die Steine verloren an Wert. Ein weiteres Beispiel für Knappheit ist Gold. Es erfordert viel materiellen Aufwand, Gold zu schürfen und zu raffinieren.
Universalität / Universality
Die allgemeine Akzeptanz eines Guts ist eine nicht unbedingt zu erfüllende Eigenschaft eines guten Geldes, erhöht jedoch dessen Funktionalität als weitflächig nutzbares Zahlungsmittel. Es gibt weltweit über 160 nationale Währungen, doch sind nicht alle davon gleich akzeptiert. Wenn man z.B. den südafrikanischen Rand mit US Dollars vergleicht, wird man sehen, dass der USD eine viel höhere Akzeptanz genießt, als der ZAR. Man wird wahrscheinlich selbst in asiatischen Ländern im Notfall mit USD bezahlen können, einfach weil die Handelspartner dort wissen, dass es für sie einfach ist, USD in ihre lokale Währung umzutauschen. Mit Rand wird man Probleme bekommen, da diese als Tauschobjekt von Handelspartnern keine Zustimmung genießen.
Sicherungsfähigkeit / Securability
Ein weiteres Kriterium ist die Möglichkeit, sein Geld zu verwahren, bzw. zu sichern. Auch wenn Gold ein sehr hartes Geld ist (knapp, allgemein akzeptiert, relativ transportfähig und lange haltbar), ist es vergleichsweise aufwändig, dieses zu sichern. Das gleiche gilt für Geld in Form von nationalen Währungen. Große Mengen an Bargeld sind schwierig zu transportieren und die Sicherung erfolgt in Form von gepanzerten Fahrzeugen und/oder bewaffneten Wachleuten. Bei Kamelen ist dies sogar noch schwieriger, da sie zusätzlich auch noch dazu tendieren, wegzulaufen.
Wie wir sehen können, muss ein Geld verschiedene Eigenschaften erfüllen, um als solches die eingangs erwähnten Funktionen (Zahlungsmittel, Wertspeicher und Recheneinheit) überhaupt erfüllen zu können. Alle bekannten Formen des Geldes - aktuelle und auch historische - bewegen sich auf einem Spektrum dieser verschiedenen Eigenschaften.
Ganz wichtig bei der Betrachtung dieser Kriterien sind immer die jeweiligen Umstände, denn es setzt sich immer das Mittel mit den meisten oder verhältnismäßig stärksten Kriterien durch. Nehmen wir LEGO-Steine, super leicht unterteilbar, leicht zu transportieren, leicht ersetzbar, aber absolut nicht selten. Daher als Geld unbrauchbar. Allerdings spielen die Faktoren Zeit, Ort und andere Umstände eine große Rolle.
In Gefängnissen z.B. funktionieren Zigaretten als Geld sehr gut, denn anders als in der Freiheit, sind Zigaretten in Gefängnissen streng rationiert und kontrolliert, also sehr selten. Ihre kompakte Größe macht sie transportabel und eine Packung lässt sich leicht in kleinere Untereinheiten aufteilen. Der/diejenige Insass//in, die im Gefängnis allerdings viele Zigaretten anhäuft und dort ein relatives Vermögen besitzt, wird nach der Entlassung einfach eine Sporttasche voller Zigaretten haben, die in der Außenwelt einen komplett anderen Stellenwert haben. Zigaretten funktionieren nur in ihrem besonderen abgeschlossenen Ökosystem. Dies gilt auch für Rai-Steine, Glasperlen oder Muscheln.

Somit wird Geld nicht nur von natürlichen und physikalischen Grenzen, sondern auch von willkürlich erlassenen und zentral gesteuerten Regeln beeinflusst. Würde das Gefängnis mit einem Mal jedem/r Insass//in erlauben, eine unbeschränkte Menge von Zigaretten einzuführen, würden diese sofort wertlos und somit als Geld unbrauchbar.
Wenn man also das Spektrum betrachtet, auf welchem alle Formen von Geld rangieren, ist es immer sinnvoll zuerst das System festzulegen, in dem ein Geld funktionieren soll. Schaut man sich unsere heutige offene und vernetzte Welt an, so muss ein Geld auch in einer solchen funktionieren. Dies ist der Grund, warum viele Formen des Geldes mit der Zeit gescheitert sind.
Eine Handvoll Beispiele von Gütern, die als Geld benutzt werden oder wurden: Eichhörnchenpelze, Rai-Steine, Zigaretten, Gold, Diamanten, Immobilien, Salz und Vieh.
Legt man die oben aufgeführten Kriterien für ein hartes Geld, wird schnell deutlich, warum einige dieser Mittel als Geld nicht langfristig funktionieren können. Um dies bildlich darzustellen, kann man eine Tabelle erstellen und den jeweiligen Attributen einen Wert zuteilen. Ich hab dies einfach willkürlich auf einer Skala von 0-5 gemacht und man sieht dort anhand der Rangordnung, welche dieser Beispiele besser als Geld funktionieren, als andere.
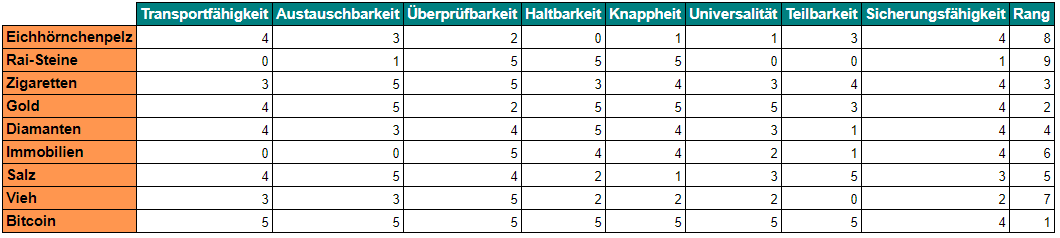
Kann Bitcoin diese Attribute erfüllen?
Wie auf der Tabelle ersichtlich, erfüllt Bitcoin alle diese Kriterien vergleichsweise gut. Transportfähigkeit: Bitcoin ist ein Peer-to-Peer Zahlungssystem, das im Internet lebt. Bitcoins existieren in der Blockchain und nur dort. Lediglich die Schlüssel, die den Zugriff auf die persönlichen bitcoins / UTXOs erlauben, müssen transportiert werden. Dies kann mit Hilfe von Software- oder Hardware-Wallets (Signiergeräten), auf Papier oder sogar im Kopf geschehen. Keine andere Form von Geld lässt sich "auswendig" merken und somit problemlos durch Raum und Zeit transportieren. Mehr dazu hier: LINK
Austauschbarkeit: Ein bitcoin ist ein bitcoin ist ein bitcoin. Abgesehen von esoterischen Konzepten, wie der Ordinals-Theorie, sind Sats immer gleich viel Wert (nicht der Währungskurs), sodass ein Tausch von einer Menge Sats in eine gleiche Menge Sats den/die Besitzer//in immer mit dem gleichen Vermögen dastehen lässt. Es gibt keinen Sat, der mehr oder weniger wert ist, als ein weiterer Sat. Mehr dazu hier: LINK
Überprüfbarkeit: Bitcoin wurde erfunden, um das Double-Spending-Problem im digitalen Raum zu lösen. Die Blockchain verifiziert die Gültigkeit einer jeden Transaktion. Der/die Empfänger//in einer Bitcoin-Zahlung weiß immer, dass die erhaltene Menge Bitcoin auch valide ist. Es bedarf keiner Drittpartei, keines weiteren Prozesses oder anderer Überprüfung, um sicherzustellen, dass die erhaltene Menge Bitcoin auch echt oder korrekt ist. Sobald eine Transaktion bestätigt wurde, kann man sich zu 100% sicher sein, dass man Besitzer//in von Bitcoin ist.
Haltbarkeit: Anders als physische Güter, die Verfall, Zersetzung oder Verderben ausgeliefert sind, hat Bitcoin kein Verfallsdatum. Solange das Netzwerk läuft, wird Bitcoin in seiner Form existieren. Es ist unmöglich, Bitcoin durch Fremdeinfluss (sowohl menschlicher, als auch natürlicher) zu zerstören.

Knappheit: Bitcoin ist auf 21.000.000 begrenzt. Die harte Obergrenze von Bitcoin ist von zentraler Bedeutung für sein Wertversprechen. Alle 2.099.999.997.690.000 Sats werden irgendwann existieren (oder existieren schon - je nach Betrachtungsweise) und darüber hinaus werden keine weiteren Sats produziert. Lediglich der Zugriff auf diese Sats wird über Zeit sogar abnehmen (durch Verlust der Schlüssel) und somit zu einer weiteren Verknappung beitragen.
Teilbarkeit: Wie schon oftmals erwähnt, lässt sich ein bitcoin in 100.000.000 Sats unterteilen. Diese Stückelung von Bitcoin bis zur achten Dezimalstelle verleiht eine sehr hohe Teilbarkeit. Dies gibt Bitcoin eine größere Flexibilität als herkömmliche Währungen und ermöglicht es extrem kleine Transaktionen, sogenannte Mikrotransaktionen, durchzuführen. Satoshis sind die Standardmaßeinheit und bitcoin wird oft nur zum erhöhten Verständnis und besserer Lesbarkeit benutzt. Beispielsweise zeigen fast alle Wallets und Explorer die Transaktionsgebühren in Form von Satoshis pro vByte an.
Universalität: Die allgemeine Akzeptanz von Bitcoin ist noch verhältnismäßig klein. Dies liegt allerdings nicht an Bitcoin, denn Bitcoin ist erlaubnislos und frei zugänglich. Es sind vielmehr die On-Ramps, die es potenziellen Nuter//innen bislang noch nicht so einfach machen, wie es viele gerne hätten. Da Bitcoin aber staatenlos und dezentral ist, erlaubt es jedem Interessierten den offenen Zugang.
Sicherungsfähigkeit: Die Sicherungsfähigkeit von Bitcoin ist unvergleichbar mit der anderer Gelder oder Zahlungsmittel. Es gibt unzählige Möglichkeiten, Bitcoin sicher und vor allem SELBST zu verwahren. Es ist gänzlich möglich, auf Anbieter zur Verwahrung zu verzichten und Bitcoin in einer Art und Weise aufzubewahren, die es Außenstehenden so gut wie unmöglich macht, Bitcoin zu stehlen. Das gilt für die Ebene persönlicher Verwahrung. Auf Netzwerkebene ist die Sicherheit von Bitcoin vielschichtig. Transaktions-Hashing, Mining, Blockbestätigungen und Spieltheorie arbeiten alle zusammen, um Bitcoin das Netzwerk undurchdringlich zu machen.

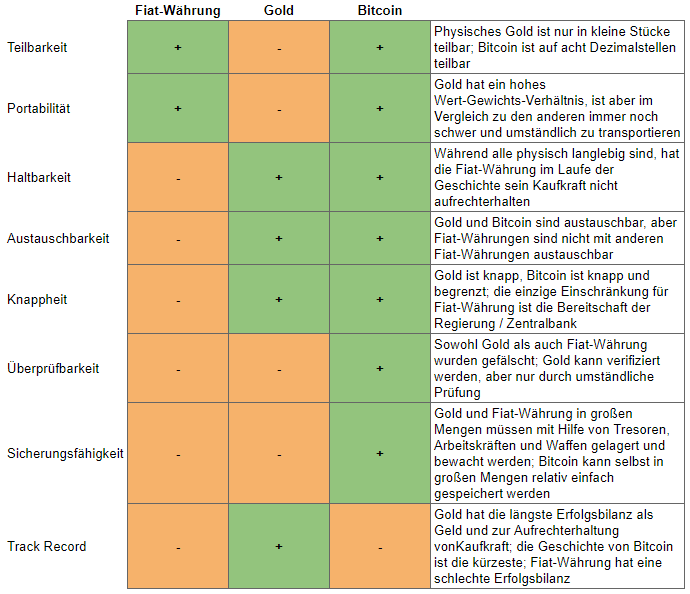
Warum ist es trotzdem schwierig zu sagen, dass Bitcoin Geld ist?
Einige sagen, dass Bitcoin Geld ist. Andere sagen, dass es kein Geld ist. Was feststeht ist, dass das Bitcoin-Netzwerk absolut zuverlässig tut, was es tun soll. Bitcoin kann also als Geld funktionieren, da es die Kriterien sehr gut erfüllt. Bitcoin ist in erster Linie eine Datenbank, die durch ein Netzwerk abgesichert wird und überwacht, welche Einträge welchen Bitcoin-Adressen zugeordnet werden. Dies geschieht durch die Übertragung von kryptografisch verschlüsselten Textnachrichten zwischen den Netzwerkteilnehmern.
Damit ist Bitcoin immer nur Text. Auch der Code, auf dem Bitcoin basiert, ist Text. Die kryptografischen Verschlüsselungen basieren auf Text. Text ist Sprache, damit ist Bitcoin Sprache. Wie viele der genannten Beispiele von Geld, ist Bitcoin nicht in erster Linie Geld, sondern eignet sich sehr gut, als solches verwendet zu werden. Nationale Währungen, Fiat-Geld, sind in erster Linie Geld. Sie werden erlassen, produziert und kontrolliert, um Geld zu sein. Das ist bei Bitcoin anders. Damit ist Bitcoin durch Meinungsfreiheit, das Recht, seine Meinung in Wort, Schrift und Bild frei zu äußern, geschützt.
Sven
-
 @ c75622fd:a9b66e1d
2023-03-10 03:50:48
@ c75622fd:a9b66e1d
2023-03-10 03:50:48[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
-
 @ 1967650e:73170f7f
2023-03-10 02:29:08
@ 1967650e:73170f7f
2023-03-10 02:29:08Lightning Network is a Layer 2 payment protocol built on top of the Bitcoin network. It allows for faster and cheaper transactions by enabling users to create payment channels that operate off-chain. Lightning Network invoices are an important aspect of this protocol, as they enable merchants and service providers to receive payments from their customers.
However, just like with any payment system, there are potential security concerns with Lightning Network invoices. In this blog post, we will explore some of the ways that Lightning invoice security is maintained.
Invoice Hashing When a merchant generates a Lightning invoice, they create a payment request that includes a payment amount and a unique invoice ID. This payment request is then hashed using the SHA-256 algorithm, which creates a unique identifier for the invoice. This identifier is known as the Payment Hash and is included in the Lightning invoice.
The Payment Hash acts as a unique identifier for the invoice and is used by the payer to ensure that the payment is sent to the correct recipient. The payer will generate a pre-image that matches the Payment Hash and use it to unlock the payment.
Time-Locked Contracts Lightning Network uses time-locked contracts to ensure that transactions are secure. When a payment channel is opened, the participants agree on a time period during which they can make transactions. This time period is known as the Lock Time.
The Lock Time ensures that both parties have time to broadcast their transactions to the Bitcoin network if the payment channel needs to be closed. If one party tries to cheat by broadcasting an old transaction, the other party can use a more recent transaction with a higher Lock Time to claim the funds.
Multi-Signature Addresses Lightning Network uses multi-signature addresses to secure payments. These addresses require more than one signature to authorize a transaction. In the case of Lightning Network, these signatures come from the payer and the payee.
When a payment channel is opened, a multi-signature address is generated. This address is controlled by both parties and requires both signatures to authorize transactions. This ensures that both parties must agree before any funds are moved.
Payment Requests are Nonce-based Lightning Network uses Nonce-based payment requests. A Nonce is a random number that is used only once. In the case of Lightning Network, a random Nonce is generated each time a payment request is created. This Nonce ensures that the payment request is unique and cannot be replayed.
Conclusion
Lightning Network invoices are a critical component of the Lightning Network protocol. They enable fast and secure payments, but only if proper security measures are in place. By using techniques such as invoice hashing, time-locked contracts, multi-signature addresses, and Nonce-based payment requests, Lightning Network provides a robust and secure payment system. However, it is important to note that as with any payment system, there are always potential security risks, and users should take appropriate precautions to protect their funds.
-
 @ 45c41f21:c5446b7a
2023-03-10 01:52:45
@ 45c41f21:c5446b7a
2023-03-10 01:52:45Flycat now supports uploading images when you write markdown long post. Since the nostr.build limits the free file size to 1mb max, the editor will auto compress for you if you image is larger than the limit.
hopes you like it.
-
 @ b8aafafe:38cf06fe
2023-03-09 19:03:14
@ b8aafafe:38cf06fe
2023-03-09 19:03:14A NIP-23 Adventure
I have been in the Nostr space for almost two months now, so of course it is time to start building some stuff.
This article is published via longpub, a tool I cobbled together after-work over the last few days. You can use it to publish NIP-23 articles, too—to only one relay at a time, with no local backup whatsoever, should you close the tab. And you need a Nostr plugin like Alby. But it works, which is awesome for a static page served via GitHub.
I will keep working on it and use this space to document it. My goal right now is to have a small suite of tools that make publishing content to your self-hosted homepage via Nostr as simple as possible (also take a look at blogsync).
Stay tuned… .
-
 @ 45c41f21:c5446b7a
2023-03-09 15:51:25
@ 45c41f21:c5446b7a
2023-03-09 15:51:25
I like the color.
-
 @ 84b0c46a:417782f5
2023-03-09 15:42:18
@ 84b0c46a:417782f5
2023-03-09 15:42:18[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
[32]
[33]
[34]
[35]
-
 @ f40832e2:bcbf511e
2023-03-09 03:31:33
@ f40832e2:bcbf511e
2023-03-09 03:31:33[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
-
 @ 49b4f8e9:f4b0c389
2023-03-08 17:04:00
@ 49b4f8e9:f4b0c389
2023-03-08 17:04:00 -
 @ 45c41f21:c5446b7a
2023-03-08 11:28:57
@ 45c41f21:c5446b7a
2023-03-08 11:28:57据说《乔布斯》这部电影只选了三个发布会之前的重要时刻,来表现其波澜壮阔的一生。这实在是一个高明的手法,虽然我并没有看过这部电影。
《乔布斯》这种手法,似乎验证了一句话:人不是活一辈子,人往往只是活几个瞬间。这话且不论真假,对于还在负重前行、努力活着的人来说,总归是压力太大。只有盖棺定论,驾鹤西去的死人,能平静地接受这句话的审视,因为这时他们既没有漫长的一生需要排解,又不需要真的直面少数坚硬的瞬间。
大概七八年前,我兴致勃勃地去翻新新闻主义的《王国与权力》,想看看纽约时报是怎样运作的,尤其想看看里面的记者是怎样赢得名气和地位的,后来随即看到了这样的瞬间决定论——一个记者不论平常写了多少的稿子,他的职业生涯高光几乎都来自于一些决定性瞬间。比如,肯尼迪遇刺的那个下午,你在现场,你写出了报纸上第一时刻的报道,你的职业生涯就会被这一个瞬间所决定。命运彷佛是一架隐形的照相机,总是潜伏在脚下,在一些不经意的时刻为你按下快门。
对于我来说,只是想到要处理好这样的时刻,就不免让人惶恐。但反过来想,就稍稍能宽慰一些——死后再去从你生的片段里摘出这么几个瞬间,看起来倒不是难事。这更贴近于一种旅行结束后挑选相片的轻松。
我看了朱正的《鲁迅传》,翻完了《无法直面的人生》,对于鲁迅大致的人生经历,我总算有点了解了。如果要我来为他这段旅途挑选一些瞬间,我又会怎么去选呢?
第一个瞬间,大概是《五猖会》临出发前,他在父亲的威严下,竭力背完书的那一刻。原先充满期待的旅程,在背完书的那一刻,似乎也耗光了所有的兴致,“开船以后,水路中的风景,盒子里的点心,以及到了东关的五猖会的热闹,对于我似乎都没有什么大意思”。多年后鲁迅说,“我至今一想起,还诧异我的父亲何以要在那时候叫我来背书”。这个瞬间,总让我想起一个天真烂漫的小孩子,被中国传统家庭文化过早地干预、乃至扼杀天性的悲凉。
第二个瞬间,应该是被中医耽误两年后,父亲临死之前的时刻。衍太太叫鲁迅大声呼叫父亲,一直叫到他断气。父亲痛苦地叫他不要嚷,鲁迅后来说“我现在还听到那时的自己的这声音,每听到时,就觉得这却是我对于父亲的最大的错处”。这个瞬间不止是生死离别的瞬间,更是一个充满了遗憾、委屈、迫害与悲伤的时刻。它给少年鲁迅心里留下的阴影是一辈子无法消除的。
第三个瞬间,是他拿着母亲的八元川资,孤身来到南京求学。他用一种戏谑的文法描述这个不需要学费、在当时属于异类的、没有正经前途的失败者才会选择的学校的景象。那是一种暂时挣脱了家乡,前路却仍然灰暗的复杂心情。我每每读到这里,几乎都要想起15岁后第一次离开家的自己。
第四个瞬间,应该是他在日本寻求文艺活动的日子。彼时他已经退了学,没有工作,每天在公寓学德语,看杂书,思考自己的和中国的出路。他也热络地参与主要由江浙人组成的光复会的活动。这里我印象最深的瞬间,是光复会派他回国刺杀清廷大员的那一刻。鲁迅原本已接受了这一任务,后来出发前,他问布置任务的那人,“如果我被抓住,被砍头,剩下我的母亲,谁负责赡养她呢?”最终他并没有做成刺客。
再往后的瞬间,应当有他四十五岁才敢追求爱情、却仍然受困于传统桎梏的压抑时刻,也有他在北京八道湾尝试努力经营好大家庭、最终却与周作人兄弟失和独自搬至砖塔胡同的凄然景象。以及在人生的最后时刻,彷佛命运的安排,他和当初自己的父亲一样,饱受肺病咳嗽喘气,最终痛苦的离世。父亲为中医所延误,而鲁迅也受到了日本藤野医生的误诊。
单是这样列出几个瞬间,我便觉得他这段人生之路艰辛复杂,充满了苦味。我几乎要怨恨命运对他的不公。但也正是这无法直面的人生,让鲁迅不再是一个单薄的符号,而是每个普通人在平凡生活中也能与之共情的活人。
鲁迅使我想起柏林笔下的维柯,“他始终处境窘迫,一生都在努力养活自己和全家”,“他是一个穷困潦倒、脾气暴躁、多少令人同情的学者”,“尽管他一直渴望被社会认可,但是当他形成了《新科学》的核心观念时,他知道他做出了天才的发现,这个信念一直支撑着他”。
鲁迅在物质生活条件上或许要比维柯好上许多,毕竟他是一个背负着养活大家庭使命的长子,但在精神的困苦上,他远比维柯不幸。他并没有维柯那样自负的信念。鲁迅一生都在怀疑与失望中渡过,哪怕是在启蒙与文学的战场上,他也被矛盾的悲观主义所折磨。他咽下的精神之苦不比任何同时代的人少。
王晓明写完《无法直面的人生》说,“我不再像先前那样崇拜他了,但我自觉在深层的心理和感情距离上,似乎是离他越来越近;我也不再将他视作一个崇高的偶像,他分明就在我们中间,和我们一样在深重的危机中苦苦挣扎。”
我认为这段话,是对鲁迅一生的精神世界,最好的注解。
-
 @ a8b64d1c:bd51513b
2023-03-08 00:47:58
@ a8b64d1c:bd51513b
2023-03-08 00:47:58Gold Reserve Act 1934
Page 58 paragraph 3 reads as follows
Very correctly, then, gold was not used as currency money. But we did discover this from our own experience and from the experience of those who preceded us that it was quite possible for our Government, or for those who had control of the gold, to keep if in a safe place and issue against it those dollar bills that we carry around to the extent of two and one half times as many dollar bills as we had dollars' worth of gold in our Treasury or in our vaults. I am telling you absolutely nothing new when I am repeating these ancienthistory facts. Currency money at the rate of two and one half times the amount of gold money would be found to be adequate and would be found to be reasonable, and we would be on the gold standard. Now, we had this thought in our minds, that the philosophy of capitalism, as I understand it and interpret it, means that m the issuance of money, capital provides a means by which we may have two and one half times as much currency money as we have of gold money, and by which we may have 12 times the number of debt dollars that we have of gold dollars in our hands for safe-keeping. We are perfectly conservative when we do that, but what happened? After the great war, we awoke one morning, with the aid of our bookkeepers, to discover that we had about $235,000,000,000 payable in gold. Those 8235,000,000,000 were not all Government dollars. Some of them represented insurance money owing to policy holders, and some of it was corporation money owing to stockholders. Some of them were corporate debts as well as private debts. The $235,000,- 000,000 was simply the sum total of our national, corporate, and private debts, payable in gold.
Todays Scenario
Compared to this As per Bank of international settlements - BIS document dated nov 2022 we have 632 trillion of OTC derivatives outstanding
USD M1 Money Supply
USD M1 money supply has increased multiple times during the last few years. Click here for the chart
total mined goldis208874 tonnesgold around 10 trillion USD That means around 63 times fiat based OTC derivatives are outstanding today than there is gold of around 10 trillion USD valueWhich means Gold can shoot up around 63 times from todays valuation. Bitcoin market cap is around 430 billion USD and it may try to catch up with that of Gold market cap of 10 trillion or more than Gold as Bitcoin zaps have few major advantages compared to Gold
1/4400 of a USD can be transfered from one continent to another using lightning network
Bitcoin is more 'portable' than gold
Bitcoin is more 'divisible' than gold
USD supply is increasing exponentially but bitcoin supply is limited.
Other Notes:
- Please go through this youtube video to read more on my thoughts on the topic
What is money?andProperties of money - To read more about early crypto opportunities other than bitcoin , Here is an article about how satoshi thought one week after posting the whitepaper and the opportunity in that thought.
- Please go through this youtube video to read more on my thoughts on the topic
-
 @ 75bf2353:e1bfa895
2023-03-08 00:04:27
@ 75bf2353:e1bfa895
2023-03-08 00:04:27[](https://tube.bloggingbitcoin.nohost.me/w/if6SP17HNEvT7sbEmk5EyT) -
 @ 8384e797:02bdde15
2023-03-08 00:01:32
@ 8384e797:02bdde15
2023-03-08 00:01:32Fold Sounds Possibly Cool
Fold is a card that claims to support lightning rewards. I was interested to try that out to see how it worked. Unfortunately, I couldn't get that far, and I wonder if Fold should exist as a crypto card at all--here is my email exchange most recent occurs last so scrolling down you are moving "back in time" and anything without a name is me:
Eh no biggie. It simply means to me that your service has some fairly large bugs (possibly spiders?) in the system considering I could verify my identity with eBay in the 90s. But of course I think we both know that isn’t the actual issue here. It’s really about underwriters and lawsuits which should be an interesting mix with your purported crypto support. I’ll delete your app and let others know of my experience here.
Mar 7, 2023, 5:46 PM EST
Hey,
Our team has reviewed your application and discovered some discrepancies. As a result, we cannot establish your identity.
I understand how frustrating this can be, especially if this decision was made in error. Still, due to the limitations of identity verification, we won’t be able to open an account for you at this time.
Thank you for understanding.
Best Regards,
Risk Team
Mar 7, 2023, 1:53 PM EST
I’ll wait until 10 pm tonight CST. If it isn’t done by then I will just delete the app. I’m all for security and I understand false positives but my time is valuable and there are other accounts I could apply to who hypothetically might not “false positive” my info. Like flying on an airline I am going to tend to favor the one that hassles me the least. Thanks for alerting me however.
Foster Evans (Fold)
Mar 7, 2023, 12:52 PM EST
Hello,
To maintain a high level of security for our members, we must periodically update certain criteria in our systems with regard to user accounts. However, this can sometimes create false positives that require a manual review by our risk team. Unfortunately, it looks like your information must be manually reviewed before it can be approved.
We are working on completing this process as quickly as possible, and we appreciate your continued patience as we enhance our security measures for our cardholders. Due to the current number of outstanding reviews, response times may be longer than usual. We ask that you do not submit multiple tickets, or replies, as doing so may cause further delays in gaining access to your account.
Best, Fold
Jeniza Ferrer (Fold)
Mar 7, 2023, 11:54 AM EST
Hello,
I apreciate your response. Your concern is very important to us. This issue will require additional assistance from our Escalation Team. I am going to forward your request to them, and someone from their team will respond as soon as possible.
Due to the current number of outstanding requests, response times may be longer than usual. We ask that you do not submit multiple tickets, or replies, as doing so may cause further delays in getting a response.
We appreciate your patience and understanding.
Best, Jeniza
Mar 7, 2023, 10:15 AM EST
After restart cannot process submission continues. If there isn’t a way to solve this today then it is apparent having a fold card isn’t on my path and I will delete the app.
On Tue, 07 Mar 2023 15:07:10 GMT
Sure. Here is the error as of today. Will restart and advise further. I will include yesterdays error as well.
Mar 7, 2023, 10:07 AM EST
Sure. Here is the error as of today. Will restart and advise further. I will include yesterdays error as well.
Jeniza Ferrer (Fold)
Mar 7, 2023, 9:11 AM EST
Hey,
Thank you for reaching out, and I apologize for the inconvenience.
First, I would suggest force closing and relaunching the app. You may need to reboot your phone if that does not work.
Next, I would check the app store to make sure there is not an available update. If so, please download it and try again.
Lastly, if all else fails, try uninstalling, then reinstalling the app.
Please let me know if the above steps do not resolve the issue, and can you send a screenshot of the error that you are having for us to investigate further?
Best, Jeniza
Mar 6, 2023, 11:00 PM EST
Placing my address and social security in fold card app results in Error and to Contact support to get fold card.
This sounds like the song and dance Stripe gave me which you can read about over at my blog here: Stripe Blog Post.
So, somehow the crypto of Fold is being used in an identity "risk assessing way" which sounds to me like a possible "poisoning of the well" for the sats earned by Fold since it seems to me this is going beyond typical KYC. I figured I'd alert the community to the potential problem since Crypto probably doesn't need any additional "Bankmen-Fried" incidents.
-
 @ 49b4f8e9:f4b0c389
2023-03-07 15:40:28
@ 49b4f8e9:f4b0c389
2023-03-07 15:40:28[https://www.yogastudies.org/wp-content/uploads/besantgita.pdf] ~

wss
[cr./cc_ https://twitter.com/@Bhagavad_Geeta ].
-
 @ 75bf2353:e1bfa895
2023-03-07 14:38:53
@ 75bf2353:e1bfa895
2023-03-07 14:38:53
Welcome To Blogging Bitcoin's HomePage
Hello. My nym is Blogging Bitcoin. I started going down the rabbit hole in 2014 and have spent much of my time thinking of it sine then. About 4 years ago, I got super excited about the lightning network and got the idea to write a blog about how I have used bitcoin during my journey on yalls.org. Yalls let anyone who connected a node to get paid for writing articles. I had to pay to publish some articles, and they probably weren't very good at first, but exploring bitcoin in this way helped me learn new skills.
There are many articles about the philosophy of bitoin or why it's such a great investment, hedge against inflation, or other NGU related stuff. I find the fact that bitcoin is used as money to be much more interesting.

- Bitcoin can facilitate commerce on the Internet.
- Bitcoin allows us to save without government debasement.
- Bitcoin is censorship resistant and can ttravel with people leaving war torn countries.
I don't teach people how to read squiggly lines and salivate over green dildos. This is not investment advice. This is financial activism.
Blogging Bitcoin

-
 @ 75bf2353:e1bfa895
2023-03-07 14:29:40
@ 75bf2353:e1bfa895
2023-03-07 14:29:40

----
I don't trust the cold card, even though it is my favorite signing device. My cold card has two secure elements This means it is superb at generating big ass random numbers, but I don't trust it. I didn't even really know how that shit worked until I read This article. I still don't trust it. For all I know, Coinkite has millions of pre-generated keys factory installed on their hardware. When Bitcoin moons they might implement a retirement attack.
I assign a very low probability to this attack. There might be a 0.00000001 % chance of this happening, but I still don't trust my cold card. Maybe you 'trust secure elements," but I don't. Maybe you add a passphrase to protect yourself from this albeit unlikely attack. How do you know the password is legit? I wouldn't trust it. Do the addresses really belong to that Pubkey? How do you know? It's not that I think Coinkite are is a bad actor. My mistrust of Coinkite is epistemic in nature.
I Don't Need To Trust Coinkite
Why do people trust Bitcoin?
"Much of the trust in Bitcoin comes from the fact that it requires no trust at all. Bitcoin is fully open-source and decentralized. This means that anyone has access to the entire source code at any time. ... No organization or individual can control Bitcoin, and the network remains secure even if not all of its users can be trusted." -- Bitcoin.org
 I can verify the code on the clear calculator with a bad ass case. I can see the secure elements. I could say hello to my little friend and shoot those two square secure elements if I wanted to. I may not trust them, but I don't think I want to shoot them. I like the aesthetics of the cold card. It's way easier to look at than that Texas Instruments calculator my Algebra teacher forced to buy in high school. The buttons on this cryptography calculating machine feel much nicer than the MK3. To be honest, the buttons were the one thing I really didn't like about the Mark3, but even though I like the look and feel of the MK4, I still don't trust Coinkite. I can't truss it like Public Enemy.
I can verify the code on the clear calculator with a bad ass case. I can see the secure elements. I could say hello to my little friend and shoot those two square secure elements if I wanted to. I may not trust them, but I don't think I want to shoot them. I like the aesthetics of the cold card. It's way easier to look at than that Texas Instruments calculator my Algebra teacher forced to buy in high school. The buttons on this cryptography calculating machine feel much nicer than the MK3. To be honest, the buttons were the one thing I really didn't like about the Mark3, but even though I like the look and feel of the MK4, I still don't trust Coinkite. I can't truss it like Public Enemy.
How To Create An Air gap Computer
Of course, the reason I love Coinkite's Cold Card is because I don't need to trust it. It's just a calculator. In the same way snotty-nose third graders are supposed to check their math homework, we can check the math on our CCCC--Clear Cold Card Calculator by following this guide.

First, we need to find an old laptop. My friend gave me a computer that is older than the bitcoin white paper he would have thrown away anyway. I removed the Wi-Fi and hard drive from the computer by using a few tools and a lot of patience. This is called an air-gap computer. Don't try this at home. There are a litany of attacks that can totally wreck you. You don't need to trust the cold card, but you should trust the cold card more than an air gaped computer or Tails persistence. If you do decide to take a walk on the wild side to verify your keys, you should also have a password to hold your bitcoin. If you are advanced, you might even want to set up a multisig wallet. One issue is that your next of kin might not be so technically inclined as hard core fiat must die freaks like us.
Watch the video
Install Tails

Since it doesn't have a hard drive, you will also need to install tails on this computer. I suppose other Linux distributions could also work, but Tails erases everything once your done. I shouldn't have to say this, but DO NOT SAVE YOUR KEY ON TAILS;
You will need: * A USB stick or micoUSB * A computer to flash Tails onto the USB stick * Tails.
If you have ever flashed a microUSB for a node using Balena Etcher, you should be able to install tails easily. If you want to take a deep dive into Tails, check out this video series released by Infosec Bytes.
You might need to change your bios settings to run tails. The bios settings are different for each computer. Some of my laptops required me to insert a pin into the physical hardware. Some made me press f 12, or f11 to start it up too. It would be impractical for me to teach you how to do it on every computer ever made, but you're a Bitcoiner. You can figure it out with a little duck duck finger action.
Roll The Dice and Follow the CoinKite Guide
When I order a new cold card to my PO Box, I calculate the seed words before it even gets to me. I roll two casino grade dice until I have 100 dice rolls. I copy those dice rolls onto an index card. These numbers are all I need to create a bitcoin wallet, but I buy signing devices because I don't trust myself with storing my life savings on an index card either. Not only do I not trust my Cold Card--I don't trust myself.

I write the dice rolls in 10 rows of 10 because it is easier to see. I also write some questions on my index card. this is not strictly necessary, but I like to use it as a to do list.
- Are there any computers around me? I consider the device in my pocket a computer too, even most people think it has something to do with Alexader Grahm Bell's invention.
- Are there any cameras? Do my words match the Cold Card?
- Do the addresses match?
- Can I recover imy seed?
If the answers to any of these questions are no, then I start over.
Is this paranoid? Yes. Have I ever been hacked? No. Hopefully I can stay humble enough to keep it that way.
I verify y seed words using rolls.py on an air gaped computer. It's actually not that complicated, but rather than write about how to do this, I felt it would be best to create a video. I have decided to enter the code here. One thing that tripped me up at first is that I tried typing the >>> and $. Don't do that.
First I ran:
from hashlib import sha256sha256(b'').hexdigest()Returns
'e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855'
If you have not entered any dice rolls yet.
sha256(b'123456').hexdigest()returns:
'8d969eef6ecad3c29a3a629280e686cf0c3f5d5a86aff3ca12020c923adc6c92'
To verify your dice rolls,, enter
echo -n 123456 | sha256sumIf your dice rolls are 123456, your wallet would be:
8d969eef6ecad3c29a3a629280e686cf0c3f5d5a86aff3ca12020c923adc6c92
You will also lose all your bitcoin, because you want a big ass random number. 123456 is neither random or big. It is just an example. You want to have at least 100 dice rolls. You can have more, but no less. Don't half ass it either. Make sure you actually roll the dice. I prefer casino dice, but I'm not sure that is necessary. Don't get fancy and create a dice rolling program or anything like that which may or may not actually be random. I once saw a thread of a pleb who explained how he lost the bitcoin on his cold card because he didn't actually roll his dice, but let his fat fingers do the walking instead. Don't be that pleb.
Next you will download rolls.py Don't click on that link either. Go to the actual Coldcard docs. You should not trust me like I don't trust Coinkite. You will need to download rolls.py from another computer and side load it onto tails. Copy it onto your desktop, right click and open the terminal.
Once the terminal is open, type
lsYou should see rolls.py. If so, type:
echo 3225251332234411136453113322561664443362453543666542122625651314425121232256566122424235654552552244 | python3 rolls.pyThis runs the python 3 program that will calculate your seed words. Like I said before, we are not going to enter 123456. We demand 100 random dice rolls, but make sure you replace my dice rolls with your own.
Then we set up our cold card with the same dice rolls we used to create our seed in Tails.
If Our Cold Card Calculates The Same Seed Words. We Can Know Our Cold Card Is Not Cheating Us



Conclusion
And as much as Bitcoiners hate that word, trust matters — the truth is that you most trust that which you can verify. This is why Bitcoin will ultimately be the most trusted monetary, economic and communications layer on Earth, after a few generations. -- Alexander Svetski.
I don't trust my cold card, but I do trust my dice rolls produce the seed words on my cold card. Since the seed words match my hard drive free computer, I keep my seed phrase on a Cold Card, even though I don't trust ther device. My cold card seed is is just about as safe as it can be once I etch it onto a= military grade steel and ensure that those magic words never see an Internet connected computer.
I solemnly swear to never plug my Cold Card into a computer.
Like I said before, you should also not trust me. For example, Matt Odell prefers to add dice rolls on top of the secure element. . You should research the merits of this approach too. Maybe my dice were compromised and do not truly represent randomness. IMaybe my rolls were not rolled well. Maybe the surface I used compromised the entropy. Maybe I did not read them from left to right every single time. **No method is 100% perfect. **
There are trade-offs with everything, but bitcoin requires personal responsibility. Don't trust verify is a lifestyle, not just a meme. I take it seriously. If every Bitcoiner took this motto seriously, we wouldn't see people get robbed by SBF and his political palm greasing Ponzi exchange. I do not keep my bitcoin on FTX or any other exchange because I cannot be absolutely sure that the exchange has my bitcoin. I expect exchanges do not have as much bitcoin as they tell their customers they have. I do not trust the exchanges or my Cold Card. The difference is I can still mathematically verify ownership of my bitcoin by using the Cold Card and Other hardware wallets. That is why I create my bitcoin keys this way. I urge you, dear reader, to do the same.
Blogging Bitcoin

-
 @ 9b8d57b6:1a82d879
2023-03-07 12:36:42
@ 9b8d57b6:1a82d879
2023-03-07 12:36:42春天来了
-
 @ c75622fd:a9b66e1d
2023-03-07 09:32:34
@ c75622fd:a9b66e1d
2023-03-07 09:32:34最初にこの方法をかいてくれた
https://www.chikachan.com/2023/03/07/bluesky%E3%81%AE%E3%82%AB%E3%82%B9%E3%82%AB%E3%83%A0%E3%83%8F%E3%83%B3%E3%83%89%E3%83%AB%E3%81%AE%E8%A8%AD%E5%AE%9A%E6%96%B9%E6%B3%95/
に感謝!!zapさせろ!!
最初に自分の did を取得しておく
- Skylightでdeveloper modeにする
- 自分自身のプロフィールを開いてprint object押す
- F12のコンソール開いて表示されている Object を押して展開すれば自分のプロフィールデータの中にある did が見れる
Google Domainでレコードつくる
TXTレコードつくる
マイドメインの管理->DNS->カスタムレコードの管理
ホスト名のところに _atproto タイプは TXT データに did=<取得したDID>
保存する
accessJwtとかいうのを取得する(しらない
要はTwitterにログインするときのOAuth認証のトークン(ベアラートークン)らしい(しらない
curlコマンドなので環境は必要
shell curl -X POST \ 'https://bsky.social/xrpc/com.atproto.session.create' \ --header 'Accept: */*' \ --header 'Content-Type: application/json' \ --data-raw '{"identifier": "メールアドレス","password":"パスワード"}'このとき返ってくるJSONの中の accessJwt に続く文字列がベアラートークン
accessJwt とかいうトークンは文字列そのまんまなのに気づかず " " で囲って送信してしまい100万回失敗してた。
Thank you Twitterによるベアラートークン解説!!
イーロンのおかげだねshell curl -X POST \ 'https://bsky.social/xrpc/com.atproto.handle.update' \ --header 'Accept: */*' \ --header 'Authorization: Bearer <取得したaccessJwt>' \ --header 'Content-Type: application/json' \ --data-raw '{"handle":"<ドメイン名>"}'Blueskyアプリでログアウトしてもう一度ログインする
-
 @ 49b4f8e9:f4b0c389
2023-03-06 23:08:49
@ 49b4f8e9:f4b0c389
2023-03-06 23:08:49
-
 @ 18e3af1e:1d42e5df
2023-03-06 16:24:24
@ 18e3af1e:1d42e5df
2023-03-06 16:24:24This article was created by npub168nqgewzkamnyh53x0epqrftkv2pdh9gzr6558v4vetzr3w7uxfs63926e I just translated from Spanish to English and add some images.
I like analogies, because they help to understand new concepts by bridging ideas we already have and new ideas. What's better than trying long content on Nostr with an analogy about how #Bitcoin works. This time about the "fees" or commissions paid on each transaction, and talking about ships 🚢 and packages 📦.
Suppose we want to send money in currencies 🪙 of different denominations, but all always of the same size (UTXO), to various parts of the world. We decide to do it by sea, for which we need ships. Every time we want to send money we will put together a package (transaction) 📦 and drop it off at the port (mempool).
Every 10 minutes or so a ship (block) 🚢 will arrive to pick up those packages to take to destination. It is clear that the captain (miner) will not perform the task for free, therefore along with each package we must also leave the payment for the shipping service, which we will call gratuity (fee).
The capacity of each ship is limited, and the captains will never be able to load more than a certain weight ⚖️ (block size limit). That is why each of them will carefully choose what to transport, although they will always try to carry as much as possible to earn more money. In other words, he will try to fill the capacity of his ship.
If when the captain arrives at the port depot there are few packages, and they all fit on his ship, he will take them all on board. But, since his limit is weight, if on the contrary there are more packages than he can load, he will choose those that pay best depending on their weight. In other words, the one that pays the best per kg.
Not all packages are the same, some will weigh more than others. Maybe because the box is made of a different material (different types of transactions), or because we use many low denomination coins instead of few high denomination coins. The captain only cares about the weight, not what is inside and what each coin represents.
What if the tip we left was not enough for him to take our package? We have two options. We could go to the port to add more tip (RBF). But for that we should have warned that we would come back when we left it in the first place (opt-in RBF), otherwise we will not be authorized to enter 👮. The second alternative is to leave a second package with a very high tip, but with instructions that it cannot be sent if that first package is not sent (CPFP). The captain will be tempted to take the 2nd package, but the average price per kg of both should be worth it since he will have to take both or neither.
When we tip, we are paying for the transportation of our package based on its weight (transaction weight). The tip we have to pay will be the result of the competition for a place on the ship, among all those who want to send packages at any given time.
This article is a compilation of a Twitter thread I made more than 2 years ago: https://twitter.com/diegogurpegui/status/1361867413566984194
-
Follow me Nostr: npub1rr3678k7ajms2sht0cqqeawy86sdd5ahn6akfj8zex9ng82zuh0sz8nywd or NIP-05 Lurusan@rogue.earth 🤙🏼🤙🏼
-
Hosting "A Venezuelan Bitcoiner Journey" Podcast https://fountain.fm/show/XsscCx4P85iMpafjBZAB 🎧
-
Short articles: http://lurusan.substack.com 📙
* Articulos cortos: http://lurusanspa.substack.com 📙
Feel free to send me a tip or zap me if you like it! lurusan@getalby.com

-
-
 @ d08c9312:73efcc9f
2023-03-06 13:52:54
@ d08c9312:73efcc9f
2023-03-06 13:52:54This is a summary of my latest article for the print edition of Bitcoin Magazine, which is available here.
Many are familiar with the 1996 ruling in Bernstein v. State Dep't that "code is speech."
In that case, Bernstein argued that not only was code speech, his encryption code was especially protected speech because it enabled private, anonymous speech.
Bernstein cited S.Ct. precedent upholding the right to speak confidentially, anonymously, and to keep private the identity of one's associates. B/c crypto enabled such constitutionally protected acts, it was "inherently imbued with First Amendment significance."
While the court did not go so far as to rule that cryptography itself was especially protected, Bernstein's argument finds ample historical support. America was founded on the right to privacy and anonymity, rights that are essential to the realization of individual autonomy.
Autonomy is the sovereign authority to govern oneself within one's own moral boundaries. Privacy and its more complete cousin, anonymity, can create those sovereign boundaries around the individual. Privacy is “the power to selectively reveal oneself to the world”.
Thus, the loss of privacy strikes at our basic human right to self determination. In the words of Justice Douglas, without privacy, "freedom as the Constitution envisages it will have vanished":
The earliest Americans understood this. The Pilgrims fled the surveillance state of Great Britain, where they could only practice their faith in secret due to Queen Elizabeth and James's network of spies:
By the time of the Revolution, the Founders were actively using cryptographic privacy tools like ciphers to communicate amongst themselves. In a letter to Madison proposing edits to the draft First Amendment, Jefferson used ciphertext.
Supreme court precedent has acknowledged the deeply rooted right to private and anonymous speech, including the “Framers’ universal practice of publishing anonymous articles and pamphlets."
In 2021, the court struck down regulations compelling disclosure of charitable organizations' donors' identities, reiterating "the vital relationship between freedom to associate and privacy in one’s associations."
Such recent precedent indicates the current Supreme Court may be accepting of Bernstein's argument that code enabling private and anonymous speech and association (deeply rooted unalienable rights) should be entitled to the highest levels of First Amendment protection.
WHAT DOES THIS MEAN FOR BITCOIN?
Bitcoin is code that enables anonymous communication and association (primarily through the transmission of value), and should thus receive the highest levels of 1A protection.
Moreover, the code for ANY PRIVACY TOOL should likewise be protected, including:
-
The #lightningnetwork (@#[5], @#[6], @#[7], @#[8], @#[9])
-
Cashu (@#[10])
-
FediMints (@#[11], @#[12], @#[13], @#[14], @)
-
coinjoins.
That includes the nascent protocol #nostr, which allows anonymous and encrypted communications, as I recently wrote here and at blogstack.
By using these privacy tools to regain anonymity, we can ensure individual autonomy. Like the Founders who designed and used new cryptographic systems in the pursuit of liberty, it’s time for individuals to code and use privacy enhancing tools to regain autonomy.
-
-
 @ b2953bbd:7141e701
2023-03-06 11:42:42
@ b2953bbd:7141e701
2023-03-06 11:42:42Nostr 是一种用于抗审查言论和社交分享的新协议。它具有巨大的潜力,但也有许多挑战需要克服。
一项新技术看似自发出现,毫无征兆,但实际上它是多位科学家数十年研究和开发的结晶。政治理想主义者将它高举为解放和革命的象征,而建制派精英则诋毁和摒弃它。然而,技术人员被其巨大的潜力所吸引,并将他们的空闲时间用于实验。
最终,企业和整个行业涌现出来利用这项技术,其影响是巨大的。回想起来,许多人都在思考为什么它的巨大潜力没有立即显现出来。
我在说什么技术?它可以是任何具有足够创新性和颠覆性的技术。汽车、个人电脑、互联网、手机、比特币……nostr。
什么是诺斯特?中继传输的笔记和其他内容
Nostr 是一种用于共享相对少量数据(例如文本帖子)的简单协议。它不依赖于任何受信任的中央服务器,因此它具有弹性,它基于加密密钥和签名,因此它是防篡改的。它不依赖点对点的数据八卦,因此是可靠的。
Nostr 是针对抗审查社交媒体的第一个实用解决方案。虽然从根本上说它不是社交网络协议(稍后会详细介绍),但在其之上构建社交媒体网络非常简单。但是等等,书呆子们可能会惊呼, ActivityPub、ATProtocol和Secure Scuttlebutt呢?哪些用于为 Mastodon、BlueSky 和 Scuttlebutt 供电?好吧,这些协议都创建了联邦八卦网络——为了成为这些网络的“一流”主权(抗审查)用户,您确实需要运行自己的服务器。我可以根据经验(几年来销售即插即用比特币节点)说,要求人们运行服务器极大地限制了您的总可寻址市场。Nostr 更轻量级,因为您可以订阅各种中继,而不必受制于任何单个服务器管理员。
Nostr 不是: * 区块链 * 社交网络 * 共识协议 * 点对点网络 * 可交易的加密代币
Nostr 的关键属性
-
权力下放。Nostr 是一个分散的协议,这意味着它不受任何中央机构或公司的控制。相反,网络只是独立运行的数据中继(服务器)的集合。这意味着 nostr 作为一个整体不容易受到任何单一实体的审查或操纵。 2. 匿名。与许多社交媒体平台不同,Nostr 不会收集用户数据并将其出售给第三方广告商。没有电子邮件地址、电话号码或政府身份与您的 nostr 帐户相关联。就像比特币一样,系统只知道公钥和加密签名来验证数据是否有效。 3. 货币化。Nostr 为内容创作者提供独特的货币化系统。与其他依靠广告收入支付内容创作者费用的社交媒体平台不同,Nostr 允许内容创作者直接通过其内容获利并从其关注者那里获得提示(也称为“zaps”)。Nostr 基础设施提供商可以类似地通过闪电支付将他们提供的服务货币化。
-
开源。Nostr代码可供任何人查看、使用和修改。这允许在协议的开发中实现透明和协作。任何人都可以为 nostr 的发展做出贡献,社区可以共同努力,随着时间的推移改进协议。Nostr 的设计具有灵活性和适应性,因此它可以不断发展以满足用户的需求。这会在协议中产生主人翁感和投资感,这对其长期成功至关重要。
它是如何工作的?
Nostr 基本上是一个分布式笔记存储系统,其中笔记只是文本块,并且笔记恰好具有与之相关联的公钥和签名作为作者身份的证明。
Nostr 客户端订阅他们想要的任意数量的中继(服务器),然后可以发布注释并查询与其他公钥(用户)相关联的注释。服务器都是相互独立的,没有同步 / 共识 / ETC。
在最基本的层面上,这就是 nostr 的全部内容。当然,尽管有各种各样的实施可能性正在开发中。
Nostr 修复了审查制度的滑坡 Nostr 通过用开放市场取代善变的当局和管理者的主观性,解决了中心化社交网络固有的治理和审查问题。几乎每家获得大规模采用的社交媒体公司都遇到了这个棘手的问题,最终不得不主观地解决它,为那些尽管进行了所有社交互动但可以说是“城市广场”的运营服务的人们创造了不正当的激励措施发生在私人财产上。
中心化平台还受到民族国家的外部压力。如果您在特定司法管辖区经营一家公司,您会发现自己必须遵守该司法管辖区的法律。协议没有这种管辖权意识。
所有人都应该有发言权,但没有人必须听。Nostr 为有争议的演讲提供了一个更可靠的归宿。尽管中继可以阻止用户向其发布任何内容,但它们无法阻止任何人向其他中继发布任何内容。由于用户是通过公钥识别的,如果他们被禁止参加中继,他们不会失去他们的身份和他们的追随者网络。
在 nostr 上,您可以高度确信自己不会因任何原因被取消平台化。
独特的功能
Nostr 实现了社交网络从未支持过的功能:设身处地为他人着想的能力。想看看别人的提要究竟是什么样子?只需使用他们的公钥设置一个只读帐户。如果此功能足够有趣,则 nostr 客户可以添加一个“以...查看提要”功能,该功能可以像用户个人资料屏幕上的按钮一样简单。
不受联邦的约束。所有其他“言论自由”平台仍然具有集中的方面。如果您使用的应用程序具有与之关联的“服务条款”,那么您对您的社交媒体没有主权。Mastodon 用户通过艰难的方式发现了这一点。回到我之前的观点,关于运行服务器需要向人们提出很多要求……很少有人愿意处理作为“公共空间”管理员所固有的滥用行为。
免于反特征
Nostr 简洁而优雅。它缺少许多反特征,例如:
- 付费广告使您的提要充满噪音。
- 该算法会扭曲帐户的范围并以未知的方式扰乱您的管理。
- 对您发布的内容的长度和类型的任意限制。
- 关于如何呈现嵌入式媒体的不可预测的规则。
- 关于发布负面语言的保姆警告。
- 管理员可以读取的未加密的 DM。
- 如果您违反日益复杂和不断变化的服务条款,您的头上就会出现一把斧头,您的帐户将被审查。
Nostr 是自由。但这种自由目前也没有多余的装饰......
挑战
密钥管理
。目前,大多数 nostr 用户并没有非常安全地处理他们的私钥材料,他们将密钥保存在连接互联网的设备上,这肯定会很糟糕。委托和撤销密钥的能力对于个人安全和支持公司/团队帐户的所有权都很重要。使用带有 API 的集中式服务的一个好处是能够授予对第三方集成的访问权限。但是使用基于私钥的协议,我必须为集成提供(目前)无法撤销的“上帝模式”。NIP-26支持这一点,但不幸的是它只支持基于到期的授权而不是开放式的撤销授权。通过NIP-041 的密钥失效是我一直关注的事情。
拓展
。在撰写本文时,每天活跃的 nostr 用户不到 100,000。当我们看到增长突飞猛进时,它们给为继电器供电的基础设施带来了压力,我们发现了弱点,然后由开发人员解决。例如,最近我看到 nostr 开发人员实施 CDN 和图像优化器以减少带宽使用。在通往主流采用的漫长道路上,未来将不乏扩展挑战。
激励中继。目前,大多数继电器都是免费运行的。显然,这对于主流采用来说是不可持续的。部分中继已支持闪电订阅;随着时间的推移,我预计会出现基于其数据质量和服务产品的速率中继的服务。我们在https://nostr.watch/relays/find和https://nostr.info/relays/看到了它的早期阶段 ** 抑制垃圾邮件发送者**。NIP-013描述了一种要求笔记附有工作证明作为反垃圾邮件机制的方法,尽管我认为它没有被广泛采用。例如,Iris 现在只接受与您的社交网络相距 3 度以内的事件。中继订阅也可以充当反垃圾邮件付费墙。
身份验证和帐户发现。冒名顶替者在 nostr 上(目前)还不是一个大问题,但他们肯定会是。我真的很喜欢 nostr.directory 的 keybase-esque 方法,通过将它链接到其他知名帐户来证明您的 nostr 帐户确实是您。我预计 nostr 客户会希望与nostr.directory和hive.one等身份和信誉服务集成,这样当有人设置新帐户时,他们实际上可以找到要关注的人。
不一致的经验。目前还不清楚这是一个多大的问题;对于喜欢指标的营销人员来说,这肯定会很烦人。nostr 的性质使您永远无法完全确定您看到的是 100% 的可用数据,因为它分散在任意数量的独立服务器上。
这种一致性问题还扩展到一般的指标和交互。例如,当我在不同的客户中查看我自己的帐户时,他们会给我不同数量的回复/喜欢/转发/点击。
长期数据可用性。这是一个与上述类似的问题,但更侧重于链接失效/数据失效的长期问题。如果我们看到镜像服务爬取流行的中继并检查您的历史笔记的完整性,然后在没有多少副本存在的情况下将笔记重新发布到新的中继,我不会感到惊讶。
网络分区。作为上述的一个极端示例,如果您与其他您希望与其共享笔记的人共享 0 个中继,会发生什么情况?此刻,您将无法与那个人交流。但是可以使用事件提示,以便您的客户端软件知道如何连接到其他人的中继并与他们交互。这仍然是一个积极发展的领域,如果中继的总数变得更多,可能会成为一个更大的问题。
搜索/索引。另一个问题是数据分区的副作用——在不查询每个中继的情况下搜索整个 nostr 宇宙自然也更加困难。我希望我们能看到解决这个问题的 nostr 优化搜索引擎。
数据流策展/建议。虽然“算法”早先被认为是反特征,但它仍然很有趣/可能存在对可定制的自动管理算法的市场需求。这些必须建立在其他索引服务之上,然后可以筛选原始提要和相邻/算法相似帐户中的所有内容,以滤除噪音并推荐新信号。每个客户都可以决定如何最好地向用户显示帖子,因此始终可以选择以您想要的方式使用您想要的内容——从使用 AI 来决定您将看到的更新顺序到只阅读它们按时间顺序。
任意服务器的可靠性。这是我看到的让很多 nostr 网络客户端变慢的原因——他们正在对分散在网络上的许多不同服务器进行数十次甚至数百次网络调用,因为:
- NIP-05 让人们在个人域上设置自定义 JSON 文件
- 没有“nostr 图像主机”或其他媒体内容主机,因此人们将嵌入的内容上传到有时不可靠的 Web 服务器。
解决激励问题至关重要,因为我们希望避免走上扼杀电子邮件稳健性的方便任意审查的道路。
颠倒 Web 架构 关于我在上一节中列出的所有挑战,有趣的是,传统上,所有此类功能都是在 Twitter 或 Facebook 等 Web 服务的基础架构中实现的。但由于没有中央 nostr 服务主机,这些功能实际上都“外包”给了第三方。
这就是自由市场的用武之地。最佳结果是,这些理想功能中的每一个都变成了服务提供商的竞争市场,而不是单一的中继/服务器/公司垄断了它们。
这仍然是第一局
我已经在我使用的不同社交媒体平台上进行了多次参与测试,nostr 的表现一直比预期的要好。尽管我的 Twitter 受众规模几乎是我推文的 100 倍,但我的 nostr 笔记往往会获得 25% 到 100% 以上的参与度。也许这只是欣快的蜜月期;我们将看看它是否可持续。
Nostr 每天都在进步。当我几个月前开始使用它时,甚至没有办法转发或点赞其他人的笔记,更不用说通过闪电打赏了。
我们可以从nostr.net上的项目列表中看到,许多人正在构建工具和应用程序来帮助提高协议的实用性。类似 Twitter 的功能绝不是 nostr 的唯一应用——我们在 nostr 上看到了博客平台、pastebin 克隆、加密聊天,甚至游戏(国际象棋)!与此同时,中继运营商也在通过 CDN、图像优化器、数据索引器、垃圾邮件过滤器等改进基础设施的工具。
Nostr 已经有了它的++第一个播客++和++第一次会议++!
我会关注 nostr.band 和 nostr.io 上的统计数据,以监控 nostr 的增长轨迹。特别是,zap 统计数据很有趣,因为它们不是无成本的活动——我们不会看到这些统计数据被运行垃圾邮件机器人的人操纵(如下面 2 月中旬的峰值所示。)
释放你内心的Nostrich Nostr 是一种革命性的社交媒体协议,因为它为社交互动提供了一个去中心化的、可货币化的、激励一致的、市场驱动的开源平台。Nostr 有潜力创造一个优先考虑用户主权和自由市场竞争的社交媒体新时代。
不要把头埋在沙子里 - 查看 nostr.how to get started!
-
-
 @ d1e60465:c5dee193
2023-03-05 20:57:26
@ d1e60465:c5dee193
2023-03-05 20:57:26Me gustan la analogías, porque ayudan a entender conceptos nuevos trazando un puente entre ideas que ya tenemos e ideas nuevas. Qué mejor que probar contenidos largos en Nostr con una analogía sobre el funcionamiento de #Bitcoin. Esta vez sobre los "fees" o comisiones que se pagan en cada transacción, y hablando de barcos 🚢 y paquetes 📦.
Supongamos que queremos enviar dinero en monedas 🪙 de diferentes denominaciones, pero todas siempre del mismo tamaño (UTXO), a varias partes del mundo. Decidimos hacerlo por mar, para lo cual necesitamos barcos. Cada vez que querramos enviar dinero armaremos un paquete (transacción) 📦 y lo dejaremos en el puerto (mempool).
Cada 10 minutos aproximadamente un barco (bloque) 🚢 arribará a buscar esos paquetes para llevar a destino. Está claro que el capitán (minero) no realizará la tarea gratis, por lo tanto junto a cada paquete debemos dejar también el pago por el servicio de envío, que llamaremos propina (fee).
La capacidad de cada barco es limitada, y los capitanes nunca podrán cargar más de cierto peso ⚖️ (block size limit). Es por eso que cada uno de ellos va a elegir cuidadosamente qué transportar, aunque intentará llevar siempre todo lo posible para ganar más dinero. Es decir, intentará llenar la capacidad de su barco.
Si cuando el capitán llega al depósito del puerto hay pocos paquetes, y todos entran en su barco, los subirá en su totalidad. Pero, ya que su límite es el peso, si por el contrario hay más paquetes de los que puede cargar, elegirá aquellos que mejor paguen dependiendo su peso. En otras palabras, el que mejor pague por Kg.
No todos los paquetes son iguales, algunos pesarán más que otros. Tal vez porque la caja es de otro material (diferentes tipos de transacciones), o porque usamos muchas monedas de baja denominación en lugar de pocas de alta denominación. Al capitán sólo le importa el peso, no lo que hay dentro y lo que cada moneda representa.
¿Qué pasa si la propina que dejamos no fue suficiente para que tome nuestro paquete? Tenemos dos opciones. Podríamos ir al puerto a agregar más propina (RBF). Pero para eso debimos haber avisado que volveríamos cuando lo dejamos en primer lugar (opt-in RBF), sino no nos autorizarán a entrar 👮.
La segunda alternativa es dejar un segundo paquete con una propina muy alta, pero con instrucciones de que no pueda enviarse si no se envía aquel primer paquete (CPFP). El capitán estará tentado de tomar el 2do paquete, pero el precio promedio por Kg de ambos deberá valer la pena ya que tendrá que tomar los dos o ninguno.Cuando dejamos propina, estamos pagando por el transporte de nuestro paquete en base a su peso (peso de la transacción). La propina que debamos pagar será el resultado de la competencia por un lugar en el barco, entre todos los que queramos enviar paquetes en un momento dado.
Este artículo es un compilado de un hilo de Twitter que hice hace más de 2 años: https://twitter.com/diegogurpegui/status/1361867413566984194
-
 @ 097bc601:88f3bbf7
2023-03-05 19:47:23
@ 097bc601:88f3bbf7
2023-03-05 19:47:23Estamos em março de 2023, poderia dizer que ainda no começo do ano, mas pasme, já se passaram 2 meses e eu acho que isso já deixou de ser “o começo”.
Uma coisa curiosa que vejo e, certamente, também faço, é traçar metas para cumprir no ano. Isso é curioso porque muitas pessoas colocam metas no papel, mas dificilmente cumprem todas elas no ano, eu já fui uma delas e espero esse ano não ser mais.
E eu sei que já aconteceu com você de um dia ter um estalo e querer mudar todos os seus hábitos ruins e fazer tudo diferente e, obviamente, melhor.
Nisso, nem sempre a gente consegue mudar tudo e vai procrastinando até dar o final do ano e começar a fazer promessas pro ano seguinte.
Só que percebi (e isso pode parecer besta), que não dá para simplesmente mudar todo seu comportamento ruim e não saudável do dia para noite.
A gente começa a querer traçar alguns objetivos, do tipo: acordar mais cedo, arrumar a cama, ler todos os dias, ir à academia, começar a comer bem, ir dormir cedo, etc.
Só que a gente não faz isso com um passo de cada vez. Geralmente selecionamos uma segunda-feira e queremos realizar todas aquelas metas naquela segunda e tentar seguir isso a partir de então pro resto da vida.
Falo “a gente” porque eu já cometi e, por vezes, ainda cometo esse erro e sei que não sou a única. Não há problema algum em querer mudar hábitos e comportamentos ruins, na verdade, isso é ótimo.
No entanto, é óbvio que a gente tá fazendo errado. Mas não direi aqui para você não se cobrar e ficar andando em cima de ovo mole. Se não, você começa a se fazer de coitado e achar que merece muito. Darei um exemplo: você faz um exercício no dia e já acha que a noite pode pedir um iFood porque mais cedo você se exercitou. A gente costuma se mimar muito e nos recompensar rapidamente pelo mínimo esforço.
O que quero dizer sobre mudar diversos comportamentos de uma vez é que você não pode achar que é um super-herói e querer mudar de uma vez, precisa fazer isso em etapas e não ceder rapidamente a recompensa cada vez que cumpre uma delas com êxito.
É muito mais fácil e até mais inteligente na sua jornada se você tentar fazer uma coisa de cada vez e, ao passo que está melhor desenvolvido nesta coisa, começar a fazer outras. Por exemplo, se você quer começar ir à academia todos os dias e acordar mais cedo, tente fazer pelo menos um destes com frequência até se empenhar mais no outro.
Ir à academia parece algo “mais fácil” do que acordar mais cedo (pelo menos para quem tem o hábito de acordar super tarde) e a partir deste exercício é natural que você comece a organizar seu dia e a sua agenda para que sempre possa ir à academia. Dito isso, começará a ser natural que você estipule horários no seu dia para os seus afazeres.
Tendo uma melhor noção de horários no seu dia e começando a construir algo recorrente à sua rotina, você se organiza mais facilmente para acordar mais cedo. Afinal, você adicionou uma tarefa recorrente nos seus dias, pretende se organizar para realizar ela e isso fará com que você organize melhor todo o seu dia.
Com o hábito de ir à academia já recorrente e a sua agenda mais organizada, você pode ver como começar a acordar mais cedo. E obviamente isso não acontece com um simples “amanhã vou acordar cedo”. Há todo um contexto na sua rotina e coisas que você precisa fazer para conseguir acordar cedo e bem.
Você precisará estipular um horário para dormir, se dorme muito tarde terá que começar a dormir mais cedo, terá que ver o que faz você ir dormir muito tarde e mudar esse comportamento para que na hora em que precisar dormir não esteja ocupado fazendo outra coisa. Bem… por aí vai, acredito que neste ponto do texto você já entendeu o que eu quis dizer.
Mas, porque tendemos a realizar tudo de uma vez e, consequentemente, não conseguindo realizar todas de uma vez com êxito, desistimos de tudo? Justamente por essa necessidade de recompensa rápida e mimo consigo mesmo.
No começo é um saco ir para a academia, seu corpo dói pelos exercícios e obviamente os resultados não são rápidos. Acordar cedo, por exemplo, também é ruim, porque você não tem aquele costume e se sente cansado durante o dia, com sono e ainda demorará um pouquinho até seu corpo se acostumar com o novo horário.
Qualquer comportamento sólido só é construído quando você vence a barreira do tempo. Por quê? Devido ao nosso limiar de esforço em relação a determinadas tarefas. Para alguém que não está acostumado a acordar cedo, isso é algo muito difícil de se fazer e seu corpo e mente já estão condicionados ao hábito de acordar tarde, logo, mudar isso será custoso e demandará tempo.
Porém, se você conseguir resistir ao tempo e realizar aquela tarefa de acordar cedo repetidas vezes, você passa a SER aquele comportamento. Seu corpo e mente já estão condicionados àquele hábito e, então, acordar tarde será um problema. Seu limiar de esforço mudou e você conseguiu vencer a barreira do tempo para construir um novo hábito.
Com o tempo, seu limiar de esforço vai mudando e as tarefas ficam menos custosas. Você pode construir isso, esses hábitos e comportamentos podem ser moldados por diversos fatores, um deles é o ambiente. Mas não aprofundarei muito aqui nisso.
Enfim, você já entendeu sobre a relação do tempo nisso tudo.
Agora… por que falei sobre bitcoin no título deste artigo? Parece algo nada a ver, mas tem a ver sim. Chegarei lá.
Desde que comecei a estudar sobre bitcoin tive a sorte, ou inteligência, ou que quer que fosse, de entender algo sobre o bitcoin muito cedo e que alguns não entendem no começo.
O bitcoin hoje, em termos técnicos, é, sim, considerado um ativo especulativo, mas ele não deve ser usado para isso. Muitas pessoas comparam o bitcoin como qualquer outro instrumento de investimento, no qual serve para você fazer um certo dinheiro e vender, comprar, vender e por aí vai, repetindo esse ciclo.
No entanto, o bitcoin serve como algo muito além, ele é toda a quebra de paradigma socio-econômico que hoje temos. Ter bitcoin não é para especular, é para fugir de toda a ruína do sistema fiduciário atual. Pois, infelizmente, vivemos em um sistema fiduciário de ruína. Onde o seu dinheiro vale, nominalmente, cada vez menos e mesmo que você invista e acumule uma certa grana, sempre perderá pela inflação.
E os mais preocupados, se incomodam com a iminente censura que o estado pode aplicar em nossas vidas e usar todo o sistema fiduciário para isso. O detentor da força pode simplesmente usar do seu poder para espoliar indivíduos e nada temos o que fazer diante disso… a não ser usar o Bitcoin, que dentre tantas características, consegue proteger o maior e principal direito de propriedade dos indivíduos: a liberdade.
Mas entender isso a ponto de conseguir acumular bitcoin, sem usá-lo como ativo especulativo, requer o que chamamos de “preferência temporal”, ou pelo menos esse é um requisito importante. Afinal, se você tem uma baixa preferência temporal, que é a capacidade de esperar pela recompensa, então você consegue acumular bitcoins sem especulá-los e aproveitar as altas da moeda, ou aproveitar para usá-lo no futuro quando o dinheiro fiduciário ruir.
Ao entender isso, você consegue ser capaz de, ao invés de gastar seu dinheiro em algo inútil, usar uma parte para comprar e cumular bitcoins para o futuro. Porque, afinal, a recompensa desse seu processo não será rápida.
Sabemos que o bitcoin ainda é volátil e assim o permanecer por algum tempo até uma grande parte da população entender seu valor e souber como precificá-lo até que ele fique em um preço “estável”. Mas durante esse processo o preço oscila diversas vezes e abruptamente, logo, o instinto mais comum de muitos é vender seus bitcoins acumulados “antes que caia mais”.
E para muitos, também, é preferível comprar algo inútil do que guardar e comprar bitcoins, afinal, se você decidir comprar um iFood você ao menos goza do prazer de comer logo aquela comida que você tava afim. Mas, ao comprar bitcoin, você terá que esperar muito para que ele valorize em uma margem que você considera favorável e ainda tem a chance de perder uma parte daquele valor investido, devido à volatilidade.
O seu iFood você comeria rápido e possivelmente se sentiria um pouco mal depois por gastar um dinheiro em algo que foi embora rápido, afinal a gente quer sempre dar continuidade ao prazer.
Por outro lado, em um exemplo simples aqui, se você tivesse esperado pelo menos 6 meses, iria ver seu dinheiro valorizar pouco mais de 12% nesse período. Isso em 6 meses daria mais do que a CDI dá em 1 ano para um investidor tradicional e “avesso” ao risco.
Voltando um pouco ao nosso raciocínio de começar a fazer várias atividades ao mesmo tempo, é que quando uma pessoa decide que comprará bitcoin ou investir em algo, ela já quer começar tudo de uma vez. Pensa em quanto investirá por mês, quanto ela precisa em X tempo e simplesmente abre uma conta em uma corretora, separa um dinheiro por mês, faz um planejamento por mês, pensa em mil investimentos para fazer, mil dívidas para pagar e quer fazer tudo de uma vez.
Aqui ela deveria começar a pelo menos tentar pagar as dívidas que possui (se possui). Aí, sim, começar a fazer um planejamento e aí, sim, separar um dinheiro para investir. Então, veria quais investimentos fazem sentido, e investiria em cada um aos poucos, não todos de uma só vez, como costumam fazer os que ouvem a palavra “criptomoeda” e começam a comprar as 5 ou 10 indicadas por algum guru, que prometeu que as moedas vão deixar ele milionário em poucos meses.
Aqui vou me ater a somente o bitcoin, porque, pelo menos eu, não tenho um sequer ativo ou ação investido no mercado tradicional. E se tratando apenas do universo do bitcoin, o recém-entrado nesta bolha de bitcoinheiros acha que deve saber de tudo que se passou no universo bitcoin logo de cara, e rodar seu node bitcoin, comprar sua cold wallet, falar disso na internet e virar o famoso “bitcoinheiro maximalista tóxico”.
Quando, na verdade, e, honestamente, seu primeiro passo pode nem ser comprar os primeiros satoshis, mas entender pelo menos o que seria o bitcoin. Mas entender mesmo. Passar algumas horas estudando sobre o assunto me parece ser a primeira medida correta a se tomar ao invés de comprar seus primeiros satoshis e sair por aí falando ser um bitcoinheiro.
E, por consequência de ter entendido o bitcoin, ou ao menos sua essência, fazer seu DCA — dollar cost average, que seria comprar uma quantidade fixa de bitcoin por um período determinado de tempo, não importe seu preço. Aí vem o poder de construir um hábito e vencer a barreira temporal.
Ao invés de gastar seus 50 reais em qualquer coisa, gastaria-o comprando uns satoshis e guardando, sem mexer nesta quantia mesmo que o preço “desabe”. Afinal, você que comprou bitcoin muito antes do resto da população só tem a ganhar daqui para frente, mesmo que enfrente um preço caindo por 6, 7, 8… 12 meses que seja.
Mas isso é tema para outro artigo. Só fique ciente de uma coisa: assim como você estará na frente da maioria da população por construir hábitos saudáveis, por mais que sejam simples, como acordar cedo, arrumar a própria cama e ler duas ou três páginas de um livro, também estará na frente se comprar, por menor que sejam, um pouco de satoshis.
Afinal, assim como com seus hábitos você estará trocando os ruins pelos bons, com o seu dinheiro você fará o mesmo: trocará o inflacionário pelo escasso, seguro, imutável e descentralizado.
Espero que você tenha gostado desse artigo e ele tenha feito sentido para você. A gente se vê por aí. Abraços!
-
 @ 75bf2353:e1bfa895
2023-03-05 19:31:50
@ 75bf2353:e1bfa895
2023-03-05 19:31:50About Blogging Bitcoin
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Vel facilisis volutpat est velit egestas dui id. Praesent elementum facilisis leo vel fringilla est ullamcorper eget. In mollis nunc sed id semper risus in hendrerit gravida. Quam nulla porttitor massa id neque aliquam vestibulum. Massa tincidunt nunc pulvinar sapien. Libero enim sed faucibus turpis in. Elit eget gravida cum sociis. Felis bibendum ut tristique et egestas quis ipsum suspendisse. Sit amet mattis vulputate enim nulla. Mi proin sed libero enim sed. Massa placerat duis ultricies lacus sed turpis. Neque aliquam vestibulum morbi blandit cursus risus at ultrices. Mauris ultrices eros in cursus turpis massa tincidunt dui ut. In egestas erat imperdiet sed euismod nisi porta.
Velit dignissim sodales ut eu. Pellentesque habitant morbi tristique senectus et netus et malesuada. Suscipit adipiscing bibendum est ultricies integer. Facilisis magna etiam tempor orci eu lobortis elementum. Tincidunt praesent semper feugiat nibh sed pulvinar proin gravida hendrerit. Vel eros donec ac odio tempor. Sociis natoque penatibus et magnis dis parturient. Ultrices neque ornare aenean euismod. Diam vulputate ut pharetra sit amet aliquam. At volutpat diam ut venenatis tellus. Vitae et leo duis ut diam quam nulla. Arcu dui vivamus arcu felis bibendum ut. Fames ac turpis egestas sed tempus urna et. Praesent elementum facilisis leo vel fringilla. At consectetur lorem donec massa sapien. Magna ac placerat vestibulum lectus mauris ultrices. Diam sollicitudin tempor id eu. Etiam tempor orci eu lobortis elementum nibh tellus molestie.
Tempus quam pellentesque nec nam aliquam sem. Risus nullam eget felis eget nunc lobortis mattis. Malesuada proin libero nunc consequat interdum. Eget est lorem ipsum dolor sit amet consectetur adipiscing. Porttitor massa id neque aliquam vestibulum morbi. Nunc aliquet bibendum enim facilisis. Amet mattis vulputate enim nulla aliquet porttitor. Sed ullamcorper morbi tincidunt ornare massa eget. Convallis convallis tellus id interdum velit laoreet id donec ultrices. Ipsum dolor sit amet consectetur adipiscing elit duis tristique sollicitudin. Ornare lectus sit amet est placerat in egestas erat. Feugiat scelerisque varius morbi enim nunc faucibus a. Commodo sed egestas egestas fringilla. Augue ut lectus arcu bibendum. Interdum consectetur libero id faucibus nisl. Et malesuada fames ac turpis egestas sed.
Diam quam nulla porttitor massa id neque aliquam vestibulum morbi. Eget mi proin sed libero enim sed faucibus turpis. In nulla posuere sollicitudin aliquam ultrices. Gravida cum sociis natoque penatibus et magnis dis parturient montes. Pulvinar neque laoreet suspendisse interdum consectetur libero. Et malesuada fames ac turpis egestas maecenas pharetra convallis posuere. Adipiscing elit ut aliquam purus. Dui ut ornare lectus sit amet est placerat in egestas. Pulvinar etiam non quam lacus suspendisse. Cursus in hac habitasse platea dictumst quisque sagittis purus sit. Diam sit amet nisl suscipit adipiscing bibendum est. Porttitor massa id neque aliquam. Ac orci phasellus egestas tellus rutrum tellus pellentesque. Gravida quis blandit turpis cursus in hac. Lacus viverra vitae congue eu. Pharetra diam sit amet nisl suscipit adipiscing bibendum est ultricies. Donec pretium vulputate sapien nec sagittis aliquam malesuada. Pretium nibh ipsum consequat nisl vel pretium lectus quam id. Volutpat lacus laoreet non curabitur gravida arcu ac tortor dignissim.
Nibh venenatis cras sed felis eget velit. Elit scelerisque mauris pellentesque pulvinar pellentesque habitant morbi tristique senectus. Aliquet lectus proin nibh nisl condimentum id. Quam pellentesque nec nam aliquam sem et tortor. Dui nunc mattis enim ut. Mauris vitae ultricies leo integer malesuada nunc vel risus. Aliquet porttitor lacus luctus accumsan tortor posuere. Bibendum arcu vitae elementum curabitur vitae nunc. Commodo sed egestas egestas fringilla. Felis imperdiet proin fermentum leo vel.
-
 @ 8ba8e814:b0bd4520
2023-03-05 01:46:50
@ 8ba8e814:b0bd4520
2023-03-05 01:46:50ブログ実装が試されてるとの事だけど、この流れだと、mixiとかが「実装しました」って話になっても面白と思う。あと昔ライブドアがやってたnowaが、「ソース残ってたので、nostr実装して運営開始してみました!」という事が起こってもいいような気がする。 …ActivityPubのでも似た事言った気がするけども。
-
 @ ec42c765:328c0600
2023-03-04 20:39:53
@ ec42c765:328c0600
2023-03-04 20:39:53[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
[32]
[33]
[34]
[35]
[36]
[37]
-
 @ 245d6986:48ee0dd8
2023-03-04 17:34:53
@ 245d6986:48ee0dd8
2023-03-04 17:34:53KEIJI MUTO FINAL LOVE AT TOKYO DOME
Thumbs up 73 (100.0%)
Thumbs down 0 (00.0%)
In the middle 0 (00.0%)
BEST MATCH POLL
Kazuchika Okada vs. Kaito Kiyomiya 53
Tetsuya Naito vs. Keiji Muto 10
Nakajima & Kenoh & Soya vs.
Miyahara & Suwama & Aoyagi 8
WORST MATCH POLL
Ishimori & Gedo vs. Nosawa Rongai & Mazada 44
Ridgeway & Daga & Eita & Hayato & Ogawa vs. Kotoge & Yo-Hey & Yoshioka & Miyawaki & Alejandro 10
Based on emails to the Observer as of Saturday 2/26.
MATCH OF THE WEEK - Will Ospreay vs. Luke Jacobs, February 26, Birmingham, UK
PERFORMER OF THE WEEK - Will Ospreay
Literally since the days after the Full Gear PPV show, where MJF went heel after being cheered wildly against the once most popular wrestler in the company in Jon Moxley, they’ve built up MJF vs. Bryan Danielson.
MJF immediately turned back heel, turned on Regal, who then left the company. Danielson protected Regal from Moxley trying to get revenge, but still was the babyface as he had to score five wins in a row to get his shot at the title in a 60:00 Iron man match on 3/5 at the Chase Center in San Francisco.
The ability to entertain a crowd for 60:00 was considered a badge of honor in another generation, and made people like Lou Thesz, Jack Brisco, The Funk Brothers, Ric Flair and others into legendary performers.
But those were organic 60 minute matches, which actually were very frequent for world title matches in the NWA and Japan during the 50s, 60s, 70s and into the 80s.
As far as the Iron Man match itself, it’s hard to know it’s origins. There were most falls in 30 minutes and most falls matches in the 60s. There were likely 60:00 versions as well.
The first that we know of would have been a Pat Patterson vs. Ray Stevens match at the Cow Palace, not far from the Chase Center. It was set up when Patterson was the champion, and Stevens won one fall and they ended up going 60 minutes so Stevens won the match but Patterson retained the title because under the rules of the time to win the title you had to win two out of three falls. That finish naturally built a rematch, which in this case they did a most falls in an hour title match, with the idea if the prior match repeated itself, Stevens would win the title. Patterson ended up winning that match which was considered one of the best matches of the decade at the Cow Palace.
That match, and another match a few years later with Patterson retaining the title over Don Muraco in a match that went 66 minutes because of overtime and the most unique count out finish ever, were both among the greatest matches in the Cow Palace of that era. Shire used that concept in other cities as well for tag team title matches when he ha a logical reason to do so based on the finish of that title match on a previous show.
The WWF first used it in 1989 for Rockers vs. Rougeau Brothers house show matches, billed as most falls in an hour, but they shaved tons of time off and those bouts usually went 35 to 40 minutes. At the time they were called marathon matches.
As far as pure 60 minute Iron Man matches, WWE has had eight, WCW never had one, and AEW has never had one. The first was Bret Hart vs Ric Flair on January 9, 1993, in Boston. Bret Hart had another on July 8, 1994 at the Meadowlands Arena with Owen Hart, and the most famous one on March 31, 1996 as the WrestleMania main event with Shawn Michaels in Anaheim, CA. Others were HHH vs. The Rock on May 21, 2000, in Louisville, Kurt Angle vs. Brock Lesnar on September 18, 2003, in Raleigh (a televised match on Smackdown), HHH vs. Chris Benoit on July 26, 2004, in Pittsburgh, John Cena vs. Randy Orton on October 25, 2009 in Pittsburgh and the last one was Johnny Gargano vs. Tommaso Ciampa vs. Adam Cole vs. Finn Balor on September 1, 2020, at Full Sail University.
Most of these matches turned out great. But it is a challenge as in none of those cases had such a match ever followed an expected bloodbath Texas death match.
Danielson said this will be maybe the biggest challenge of his career.
“We’re going to be following a lot of great stuff, including the Mox-‘Hangman’ Texas Death match,” said Danielson, who has wrestled 60 minutes and longer before, but never an Iron Man match. “The promoters from yesteryear would say that you don’t follow blood with wrestling, but that’s exactly what we’re doing. So it presents those types of challenges. To me, that’s exciting. This is maybe the biggest challenge I’ve put in front of myself in my entire career. I can’t think of anything else with more pressure mentally or physically.”
After this, Max will have the confidence he can do anything in wrestling. 60 minutes, 40 minutes, 20 minutes, there will be no doubt.”
It’s a test for MJF and Danielson inside the ring to go a full hour after a show that will be more than three-and-a-half hours deep when they start, although because it’s Pacific time zone they are probably starting around 7:45 p.m. local time, so fans being tired and wanting to leave early may not be a big issue. Then again, I was at the Michaels vs. Hart Iron Man match and in the lat ten minute the place started emptying out, but that’s Los Angeles and what thy do to beat the traffic.
AEW’s ratings had been steady for much of the build, before the 2/15 and 3/1 shows did the lowest numbers in months. Ironically the 2/22 show did the best number in months.
While the PPV will probably be great for action, AEW is not at peak popularity. The last show with MJF vs. Moxley in the title match probably did 135,000 buys or slightly more. But that was MJF as a babyface going for the title win in a story that got hot. This is MJF as a heel, against Danielson, and they’ve had great interviews that have cut deep, but there is a question of exactly what level of interest there is in AEW big shows, that this will answer.
There is also the obstacle of coming one day after an $80 Jon Jones vs. Ciryl Gane UFC PPV show. It’s Jones’ first bout in three years and expected to be the biggest drawing UFC PPV show since. In almost three years, since the July 10, 2021, show headlined by Conor McGregor vs. Dustin Poirier. When UFC was still on traditional PPV, the crossover showed that there was a strong crossover between a Jones-headlined UFC show and an AEW show.
There were 7,662 tickets out for the show, a disappointing number for an AEW PPV show and it is the lowest total a few days out since they were able to return to full capacity shows after the pandemic. The get-in price on the secondary market is down to $32, so there is no late rush of interest caused by something or other. Although there’s no point buying a low priced secondary market ticket now when there are plenty of them available at regular prices in a building that would sell for a pro wrestling stage set up at about 12,500.
Technically, with the Cow Palace being in Daly City, with a good walk-up this will beat the 8,000 record for the city of San Francisco set some 60 years ago when Argentina Rocca came to San Francisco to team with Leo Nomellini at the old Winterland Arena.
Even including the Cow Palace, this will break the gate record for the market set by New Japan for a Kenny Omega vs. Cody Rhodes match for the IWGP title.
With the hour-long main event, they’ve only announced eight matches and have announced nothing for the Buy In show.
The other matches include Moxley vs. Page in a Texas death match, ironically another Cow Palace specialty as the biggest drawing gimmick match except for the Battle Royal in the Roy Shire days. The Gunn Brothers defend the tag titles in a four-way against The Acclaimed, Jeff Jarrett & Jay Lethal and Orange Cassidy & Danhausen. Samoa Joe defends the TNT title against Wardlow. Jamie Hayter defends the women’s title in a three-way against Ruby Soho and Saraya. Young Bucks & Kenny Omega defend the trios titles against The House of Black of Brody King & Malakai Black & Buddy Matthews. The other two bouts are Chris Jericho vs. Ricky Starks with the JAS banned from ringside and Christian Cage vs. Jack Perry in a no holds barred match.
On paper, every match looks to be entertaining in its own way. There could be some sleepers, the main event, the death match and the trios title match are the ones to watch. Cage vs Perry is big in another way only because it’s a program that dates back so long and they’ve never really done a big match due to Cage getting injured just as the feud started out.
The keys are the main event and to a lesser extent, the death match. For the show itself, if the 60 minute match works for this audience and what they do, most will consider it a good-to-great show. If it doesn’t, it will be perceived very differently, even if the undercard is strong.
In many ways, the match is a referendum of MJF as a wrestler. Most Iron Man matches are good and because of the nature of them, often wind up as memorable. But a bad one will be memorable as well. Danielson proved with Adam Page that he could have a match of the year candidate going 60 minutes. So if it doesn’t work, he’s likely not to get the blame. And this is much harder because unlike Danielson vs. Page, when you didn’t know when it would end, in this match, the audience knows that they match is not peaking or ending until after the 55 minute mark, meaning it becomes more difficult to get peak interest until that time. You know the near falls, and the pins for that matter, in the first 30 minutes don’t really mean a lot. It’s a risky match, but it’s also the kind of match that usually ends up being remembered far more than a normal match, and most of the time in a positive way.
On the other side, while many credit MJF vs. C.M. Punk’s dog collar match at least year’s Revolution show for the second biggest PPV number in company history, it was with Punk at a time the promotion was far hotter than it is now. If this show does less than 130,000 buys, MJF will not have proven himself as a major draw in his first title defense. It if does more than probably 133,000, it’s a success in that regard because you have to factor in a five percent drop from coming after the Jones fight. At more than 140,000, he will have proven himself and it would appear that the Iron Man concept turned out as a big success as far as public interest going in is.
The show will once again be available at movie theaters around the U.S. and Canada through Joe Hand Promotions as well as at many Dave & Buster’s or Tom’s Watch Bar locations.
-
 @ 245d6986:48ee0dd8
2023-03-04 17:32:29
@ 245d6986:48ee0dd8
2023-03-04 17:32:29Hello?
-
 @ 246716c3:929dc73a
2023-03-03 15:49:59
@ 246716c3:929dc73a
2023-03-03 15:49:59Challenge for Nostr protocol adoption
After realizing the potential of Nostr. The first thing I asked myself was how people outside BTC ecosystem will get onboarded on it. I quickly realized that most people who are sharing content here are Plebs highly enthusiastic to see BTC adoption. But the sad truth is normal people are not. For example, I can't convince my friends (not interested in BTC) to use Nostr because of the strong network effect of other social media platforms. They really need a strong reason to come and use this awesome tech built over Nostr and BTC.
Possible attempt to improve the adoption
Knowing how much I love this tech. I have made an attempt to bring other people to this protocol with my bot @SeriousHumour description: Tick tock, 10 mins!! Next meme ⚡👾 I am a bot🤖👾 Roughly every 10 mins like BTC, I find the best meme/dark joke/funny video/BTC meme to tickle your funny bone 😋😋 Follow, like, and share with people so that they have some content they can relate to.
What is better than finding the best memes circulating on the internet on Nostr protocol. As memes are the most powerful tool to connect to people in this day and age.
How ChatGPT became my very motivated intern trying to impress me all the time!!
So I coded a bot in 2 nights(10 hr roughly) that would have taken me at least a week of full-time effort without ChatGPT. I realized that this tech is here to stay and we need to embrace it and make it our friend. I found ChatGPT as a very exciting and motivated intern whom I can demand to do modular tasks for my project and it gives really good results (Like seriously good results). If I don't like the response I can ask for another one and it will come up with another approach.
This allows me now to be at the Project Manager level with tech skills and a virtual team of ChatGPTs at my disposal to build little parts of my projects. ChatGPT or any other version, will just increase people's efficiency by magnitudes unimaginable to us now.
Let's embrace this tech because it is worth it !!!
-
 @ 3b8bd779:4f33ead2
2023-03-03 15:39:40
@ 3b8bd779:4f33ead2
2023-03-03 15:39:40mi primer post en blogstack.io Esto es asombroso.
-
 @ 84b0c46a:417782f5
2023-03-03 11:45:18
@ 84b0c46a:417782f5
2023-03-03 11:45:18[3]
[4]
[5]
[6]
[7]
-
 @ b2953bbd:7141e701
2023-03-03 11:02:44
@ b2953bbd:7141e701
2023-03-03 11:02:44Web3 期待什么样的去中心化社交?
作者:Chuan Lin,AnT Capital
封面:Photo by Tyler van der Hoeven on Unsplash
导语 去中心化社交一直是应用层的一大叙事。当前主流的四大去中心化协议:Nostr, ActivityPub, Farcaster, Lens Protocol。它们的设计思想和原理分别是什么,又分别吸引了哪些用户群体?不同协议在竞争中将分别处于什么样的生态位?在本文中,笔者将尝试解答这个问题:
(图一:Nostr、ActivityPub、Faracaster、Lens Protocol 协议对比,@Mtyl_7th 绘制) 正文 一、当我们研究去中心化社交协议时,我们需要重点关注什么?Web2 社交产品被诟病的点不少:“中心化审查”,“数据孤岛,平台间数据不互通”,“用户缺乏数据主权”……去中心化社交协议希望能够从社交产品中抽离出 “协议层” 这一概念,用去中心化网络的方式来实现用户的信息通信和各种内容的存储。而不同的去中心化协议设计者对理想社交产品特点的理解是不一样的,这也带来了不同的协议设计方式和不同的用户群体。在研究一个去中心化协议具体设计的时候,我们需要重点关注:
用户如何创建账户并通信交流? 以 Twitter 为例,用户的账户信息登记、推文发布都是由 Twitter 公司的中心化服务器集群负责的,这也是 Twitter 能删除用户的账户、屏蔽发布内容的原因。那么,一个协议如果不引入中心化服务器的角色,又该如何完成这些事情?关于通信交流,主要考虑两个核心场景:发布公开 Post,用户之间的私信。
用户的社交关系和内容数据存在哪? 以微信为例,用户的好友关系、头像用户名等数据,都是存在微信的服务器里面的。虽然微信也有 API 可以供第三方调用这些数据,但不仅 API 的权限完全掌握在微信手中,开放的数据丰富度也小的可怜。那么,一个协议如果不引入中心化服务器的角色,又该如何存这些数据?
如何进行内容审核? 虽然大多数对去中心化协议有需求的用户几乎都对 “内容审核” 一词抱有负面印象,但完全的零内容审核,对于有公开信息流的社交平台而言也是一个灾难:一方面,机器人可以大量发送广告内容,从而污染用户的公开信息流(Spam 问题);另一方面,总有一些内容是公认的不应该公开传播的,如儿童色情、恐怖主义等。零内容审核会导致 “劣币驱逐良币”。
如何设计激励机制? Web2 社交产品的协议层和应用层是一体的,目前在应用方面也已经有了比较成熟的 “流量-广告” 商业模式,因此用户可以免费体验多数社交产品的功能。然而对于一个去中心化社交协议而言,服务提供方是分散的,难以将 “流量-广告” 的商业模式放在协议侧。那么,这些服务提供方消耗网络资源、存储资源,稳定持续提供服务的激励是什么?用户是否要因此而付费?
在研究一个去中心化协议的用户和生态发展情况的时候,我们需要重点关注:
协议现在有多少个注册账号,增长趋势如何?采用的是什么样的增长策略? 协议上有哪些主要应用? 目前协议里的核心用户画像是什么样子的? 二、Nostr 详解 2 月初爆火的 Damus,正是构建在 Nostr 之上的。Nostr 并不是构建在任何区块链上,它设计的核心理念就是 “抗审查”。
2.1 Nostr 如何实现:四个关键问题的回答 在 Nostr 中,用户如何创建账户并通信交流?
(图二:Nostr 设计原理简示,@Mtyl_7th 绘制) 每个用户第一次使用 Nostr 协议上的任意应用(如 Damus)的时候,都会创建一个” 公私钥对 “;其中公钥是用户对外展示的 ID,可以分享公钥来让其他人找到你;私钥是用户的 “登录密码 “,凭借私钥就可以在不同应用上登录同一个身份。
在 Nostr 协议的任意应用中,都让用户会默认连接到多个中继器(Relay)。如果用户 A 发布了一条 Post,实际上就是平行的把 Post 同时传给这些 Relay;如果另一个用户 B 和 A 至少连接了同一个 Relay,那么他就可以搜索到 A 的公钥并选择接收 A 的 Post。
类似的,只要 A 和 B 至少连接了同一个 Relay,那么他们就可以搜索到对方并相互私信。A 向 B 发送私信的时候,需要 A 的公钥签名,以便 Relay 识别这个是 A 发出的消息;A 可以选择用 B 的公钥给信息加密,这样只有 B 能看到消息的内容。
用户可以随时自行添加或者删除自己想连接的 Relay(如下图所示)。大多数 Relay 是免费的,少数提供额外服务的 Relay 需要付费订阅。付费是通过比特币闪电网络进行的,机制由 Relay 自行设计。
(图三:Damus 的 Relay 选取页面) Nostr 的 Relay 和 Relay 之间不能互相通讯。
在 Nostr 中,用户的数据和社交关系存在哪? 存在用户所连接的所有 Relay 里面。用户可以将其导出、自行存储。
其实 Relay 最基本的职责只有转发用户的信息,并没有存储用户数据的义务。不过每个 Relay 可以自行设计用户数据存储的策略(存什么类型的数据,存多久)。对于免费 Relay 而言,一般来说会设定一个存储期限;而如果一个 Relay 可以提供更长期、甚至永久的数据存储服务,那它就可以吸引更多的用户来付费订阅,从而实现盈利。
这种设计导致一个潜在的问题:如果用户的活动数据在所有连接的 Relay 上都过期了,那么它就会永久丢失。这会导致用户 A 切换设备或者应用重新登录的时候,看不到自己之前的完整时间线,包括其他用户也看不到 A 的完整时间线。其实某种意义上,这可能不算是一个问题,而是 Nostr 设计思路的一种体现:用户应该” 为价值付费 “,如果真的想要长期的数据存储服务,就要付出一定费用。
另外,在一些 Nostr 应用里面(如 Iris),用户可以导出自己任意时间点的数据,自行将其备份存储,在未来有需要的时候进行恢复。这其实是用户自己控制自己社交数据比较好的体现 —— 和后文专门构建社交数据存储网络的 Farcaster、Lens Protocol 不一样,Nostr 中的应用开发者是无法在用户不用私钥登录的前提下获取到一个用户所有的数据的,这也给用户将自己的社交数据商业化提供了潜在的想象空间。
(图四:Nostr 生态的 Iris 已支持用户导出自己的社交数据) 在 Nostr 中,内容审查机制是如何设计的? 由每个 Relay 自行设计内容审查机制。Relay 并没有进行内容审查的义务,大多数免费 Relay 会将收到的信息一律按照要求转发。但这样的后果是用户的” 全局信息流” 往往会充满广告和垃圾信息,一些公认的不宜在社交网络上出现的内容(儿童色情、恐怖主义)也会得到公开传播。因此,如果一个 Relay 建立了合理有效的内容审查机制,那么就可以给用户带来一个健康的全局信息流,从而吸引用户来付费订阅。
在 Nostr 中,Relay 运行者的激励是什么? 基础 Relay 的运行成本极低;Relay 运行者可以通过提供高级服务(数据存储、视频传输、内容审查机制等)
由于 Relay 的基本职责只有转发用户的信息,因此以个人电脑的性能都可以去运行一个 Relay;如前文所述,如果 Relay 提供的服务消耗了较多的网络带宽和存储空间,那它就可以选择让用户来付费订阅。
2.2 Nostr 生态发展现状概要 根据 Nostr.Band 的统计,目前 Nostr 带用户信息的用户数已经达到了 78 万,DAU 达到了 6-7 万(高价值用户 DAU 约 6000)。可以观察到 2 月 1 日之前用户数只有不到 20 万,Damus 的爆火给 Nostr 带来的大量的新增用户。已经有数十个应用构建在 Nostr 上,详见 Nostr 的 GitHub。这里列举其中代表如下:
Damus 是 Nostr 生态中最知名的手机 App,也是类 Twitter 产品的代表。类似的产品还有 Iris,它主要提供网页端的类 Twitter 客户端。 Anigma.io 是 Telegram 的替代品。用户可以创建公共频道,任何人都可以加入并聊天;用户也可以向其它用户发送私人的端到端加密信息 Nvote 是 Reddit 的替代品。用户可以发布帖子,并这些帖子进行投票 Nostr 协议也可以用于简单多人游戏的开发,比如 Jeste 就是一个国际象棋对战平台 不过, 目前 Nostr 上的产品多为 demo 原型,有很多功能有待打磨改进。这可能和 Nostr 协议本身的简单设计,以及创始人并没有自营应用的想法有关 —— 不少像 Farcaster, Lens Protocol 的社交协议,都会在初期由项目方自营至少一个核心应用,以完成从 0 到 1 的数据记录。比如 Damus 上线的时候,图片、视频只能依靠 URL 来传播,也不支持任何社交操作的撤回(包括发帖、点赞),更别说 Twitter 中其它各种各样功能的实现了。从产品体验的角度来看,Nostr 系的产品还有很大的提升空间。Nostr 的核心用户群体很有意思,笔者观察了很长一段时间,发现除了尝鲜用户和大量发广告的机器人以外,Nostr 现在的核心用户主要来自于各个国家的比特币爱好者社区,特别是比特币最大主义者们。这可能是以下几个原因造成的:
Nostr 是少有的以比特币闪电网络作为核心支付方式的协议,客观上促进了比特币闪电网络的普及。Damus 的爆火,让其成为比特币闪电网络生态中为数不多” 出圈 “的项目。 公私钥对、比特币闪电网络的认知操作门槛,当前产品的不成熟,将现在 Nostr 的传播范围主要限制在 Web3 用户之中(这里”Web3 用户 “的定义:对区块链技术有了解、愿意体验的用户)。然而比特币最大主义者们是怀疑除了比特币外其它任何区块链的价值的,包括以太坊。随着 Web3 叙事的演进,他们和其他 Web3 用户的理念分歧也越来越大,这使得他们即使在 Web3 用户比较集中的平台(如 Twitter),也往往看不惯其他 Web3 用户发表的观点、和他们进行辩论。因此,他们有动力聚集到一个比特币叙事占主流的新社交平台,而 Nostr 就是目前最好的选择。 Nostr 的协议设计理念和比特币有很多相似之处,简洁清晰、反脆弱性强。这也使得比特币爱好者对其抱有好感的原因。 三、ActivityPub 实现详解 2022 年马斯克收购 Twitter 是互联网领域的大事件。而在收购 Twitter 之后,Twitter 的管理明显成为了马斯克的” 一言堂 “:内容审核机制更加严格、商业化导向更加严重。许多不满的用户,迁移到了 UX 与 Twitter 非常相似、但更加去中心化的 Mastodon(长毛象)上。而这种情况并非第一次出现,每当有 Web2 社交平台进一步严格其内容审核机制后,都会给 Mastodon 带来不少新用户。Mastodon 背后的协议就是 ActivityPub。ActivityPub 是” 联邦社交协议 “的代表之一,某种程度上它做的事情,是把 Twitter 中的公司服务器给 “去中心化” 了,让我们来看看它的具体实现:
3.1 ActivityPub 如何实现:四个关键问题的回答 在 ActivityPub 中,用户如何创建账户并通信交流?
(图五:ActivityPub 设计原理简示,@Mtyl_7th 绘制) ActivityPub 中有一个名叫 Instance(实例)的角色,可以把它简单理解为 “服务器”。
用户在自己指定的一个 Instance 中,注册自己的账号;当一个用户 A 要发送信息的时候,先发至自己注册的 Instance,再由 Instance 负责和其它 Instance 通信。Instance 和 Instance 之间有一套通讯协议,用于互相传输、读取信息,这样用户 B、C、D 可以接收到用户 A 发出的信息。
从这里也可以看出,其实 Instance 的角色和单一项目方中心化服务器的角色非常像,只不过它是由一个联邦网络所组成的。如果网络中只有一个 Instance,那这和 Web2 社交产品的架构区别不大了。
在 ActivityPub 中,用户的数据和社交关系存在哪? 存在用户连接的那个 Instance 里面。用户可以将其导出、自行存储。
对于用户数据,ActivityPub 的理念是 “You can kill me, but I am everywhere”:即便你所在的 Instance 因各种原因不可访问了,你可以在任意一个 Instance 上其他新建用户,并导入之前的好友和博文信息,而不会丢失。
美中不足的是,如果一个 Instance 封杀了用户、或者因为各种原因宕机,且用户没有事先导出自己数据的话,那么用户的账号和数据就会丢失。另外,如果 Instance 本身已经对用户产生了恶意,用户是拿不出自己的数据的。从数据主权这个角度来看,Mastodon 像是处于一个中间态 —— 用户理论上拥有自己的数据、可以导出,然而服务器依旧拥有 “生杀大权”。
在 ActivityPub 中,内容审查机制是如何设计的? 由每个 Instance 自行设计内容审查机制。
单独来看的话,每个 Instance 可以封禁用户的账号、屏蔽用户的内容;不过用户如果不满,也可以把自己的账号迁移到其它 Instance 上去。通过这种方式,实现了内容审查的去中心化。
在 ActivityPub 中,Instance 运行者的激励是什么? 这是 ActivityPub 潜在的一大问题:大多数 Instance 都没有来自于用户的收入,依靠社区捐赠来运行,甚至不少 Instance 都是用个人因兴趣” 为爱发电” 构建的; 虽然理论上 Instance 可以通过广告、付费注册等机制盈利,但在免费 Instance 大量存在的事实下,这些机制并不有效。
这也导致了许多由个人爱好者构建的 Instance,运行了一段时间以后就停运了。如果它没有事先通知上面的用户且用户没有事先导出数据的话,这些用户就会丢失自己的账号。
3.2 ActivityPub 生态发展现状概要 ActivityPub 最大的优势,在于其上的产品应用非常成熟、UX 对 Web2 用户非常友好,从而能吸引大量单纯反感中心化审查的 Web2 用户。**尤其是那些喜欢发表自己政治倾向性观点、进行高政治敏感性内容创作的用户,更是对 Web2 平台内容审核深恶痛绝。
以 Mastodon 为例,Web2 用户不需要学习过多额外的概念(比如公私钥、助记词、区块链),就可以直接上手;大多数 Twitter 实现的功能 Mastodon 都已经实现。
Mastodon 已经积累了近 300 万用户。其中前三大实例站点拥有 60% 的用户数与 45% 的发帖量。这三大实例中除了 Mastodon.social 是官方运营的实例外,另外两大实例均来自日本。总用户数中日本用户占近 40%,排名其后的是美国(20%)和法国(10%)。(数据来源: Bonfire Union LP 2022 社交协议概况报告)
四、Farcaster 实现详解 Farcaster 是前 Coinbase 副总裁高管 Dan Romero 创立的去中心化社交协议项目,于去年 7 月完成了由 A16Z 领投的 3000 万美元融资,受到了大量的关注和期待。让我们看看 Farcaster 的设计理念:
4.1 Farcaster 如何实现:四个关键问题的回答 Farcaster 中有一个”Hub“的新概念。从广义上来看,它和 Nostr 的 Relay、ActivityPub 的 Instance 都起到类似于 Server 服务器的角色,但实际上他们具体做的事情差异不小。
如图所示,Farcaster 是三层架构:最底层的是以太坊区块链,用于存储用户的注册信息;在这之上是 Hub 所组成的网络,用于实时同步全网所有用户的数据;每个应用可以视为一个 Client,它和 Hub 网络进行通信,传递用户的操作。
(图六:Farcaster 设计原理简示,@Mtyl_7th 绘制) 在 Farcaster 中,用户如何创建账户并通信交流? 首先,用户在应用端注册时会自动生成一个新的以太坊地址,用户需要自行保管其助记词;用户选取唯一的用户名后,这个 “地址-用户名” 的绑定信息会登记在以太坊主链的 Farcaster 合约里面,通行于整个 Farcaster 协议。本质上来说,Farcaster 的用户 ID 核心和 Nostr 一样都是公私钥对,但它绑定了更多信息(用户名),因此需要一个链上的合约作为注册表;而 Nostr 协议的 ID 只有公私钥对,用户只需持有私钥就可以登录自己的身份,这也意味着用户在不同的应用端平台可以有不同的用户名。
然后,用户将通过应用(Client)向 1 个 Hub 发送信息,Hub 之间将通过 Delta Graph 这一数据结构,实时广播并同步全网的用户数据。当其它用户所在的 Hub 收到广播之后,就会同步更新这一信息,并反馈给连接它的应用。
可以看到,如果只看 Farcaster 的 L2 和 L3,信息的传播过程和 ActivityPub 有许多相似之处。最大的不同在于,ActivityPub 的 Instance 之间不需要就用户的数据存储进行实时同步,但 Farcaster 的 Hub 之间需要。
在 Farcaster 中,用户的数据和社交关系存在哪? 用户 ID 存在以太坊上,其它的内容数据和社交关系存在每一个 Hub 里面(或者说 Hub 网络里面)。
如果只看这个存储方案,那么会感觉它其实和区块链 “分布式账本” 的概念比较类似;只不过考虑到现有公链的性能,社交数据的存储并没有像 Lens Protocol 那样直接放到链上,而是放在了针对性设计的去中心化存储网络上。
相比于 Nostr 和 ActivityPub,当网络中有足够多的 Hub 参与的时候,这个方案的数据存储无疑是更加稳定、可靠的。不过,这也意味着开发者可以非常简单的获取到用户的所有社交数据。
在 Farcaster 中,内容审查机制是如何设计的? 方案尚不明确; 可能交给每个应用制定自己的审核机制。
短期来看,Farcaster 采用创始人邀请制的严格增长策略,确保初期用户的质量和调性。因此 Farcaster 在相当长一段时间内不用操心这个问题。
长期来看,创始人 Dan 表示可能会将审查的权限交给应用,由每个应用自行设计审查机制和相关尺度。
在 Farcaster 中,Hub 运行者的激励是什么? 短期,靠低成本和社区爱好者的驱动;长期,靠协议收入。
Farcaster 在用户量到一定规模以后可能会开启收费模式,用户需要每月交一定金额的费用才能继续使用账户,而这部分作为协议收入就会分给 Hub 的运行者们。
从 Farcaster 的设计也可以看出,Farcaster 的 Hub 将因需要同步全网数据而有较高的存储成本,这可能会导致运行的 Hub 过少,使得网络走向中心化。团队认为理想情况下网络中应该有 100 个左右的 Hub。
下图是 Farcaster 团队对协议用户增长以及相关数据存储成本的估计:
(图七:Farcaster 项目方对协议用户增长以及 Hub 数据存储成本的估计) 团队认为,在 2024 年结束之前 Hub 的存储成本都是较低的(约 $3500/年),因此短期来看不会影响到一些社区爱好者参与构建 Hub 的积极性。到了 2024 年以后,一方面需要给 Hub 运行者协议收入作为激励,另一方面也可能通过分片等技术提高存储效率。
4.2 Farcaster 应用发展现状 Farcaster 目前有约8k 用户,维持着 5% 每周的增长率,其核心用户群体主要是 Web3 的美元 VC 圈和开发者。这些用户虽然是 Web3 从业者,但他们平时日常更专注于自己的工作和对 Web3 的思考分析,链上交互操作的频率不一定高,也对代币空投没有较高的需求和预期。
Farcaster 的 5% 增长率是协议项目方设计的 —— 用户必须要 Twitter 私信创始人发送申请,才可能获得邀请(笔者也是这么做的)。这是一种 “饥饿营销” 的打法,可以确保早期用户的质量,从而提升社区氛围和项目质量,和早期知乎的增长策略非常类似。
Farcaster 生态的项目列表可以参考 Farcaster 的 Github。
Warpcast 是 Farcaster 当前最主要的项目,不仅产品功能较完善,而且还有一些特别为 Web3 用户设计的功能 —— 比如你可以选择将账户和平时常用的以太坊地址相连接,这样你的好友就可以看到你近期的 NFT 交易和 mint 记录。
(图八:Warpcast:Web2 级别体验+针对 Web3 的功能设计) 目前,Farcaster 其他生态项目多数是 Web2 社交项目的复刻或者是用户社交数据的 “再整合”。比如 Searchcaster 可以让你从 Farcaster 数据中搜索关键词,Discove 可以让你无需登录即可浏览 Farcaster 内的的热门信息。
五、Lens Protocol 详解 Lens Protocol 是 Aave 的创始人兼 CEO Stani Kulechov 创立的链上社交协议项目,是目前同类项目中生态发展最好、用户最多的。
5.1 Lens Protocol 如何实现 某种程度上, Lens Protocol 的实现是最容易理解的 —— 因为几乎所有的操作和数据都在链上。
(图九:Lens Protocol 设计原理简示,@Mtyl_7th 绘制) 在 Lens Protocol 中,用户如何创建账户并通信交流? 用户在 Lens 合约中铸造自己的 Profile NFT,这个 NFT 会以 “.lens” 为后缀的域名形式展现,它就是用户的账户,也是用户所控制的唯一身份。
用户发布 Post 的时候,内容会被同步存储到区块链上。应用端只需读取链上数据,就可以向其它的用户传播信息。
相比于其它协议,由于用户一般会拿自己常用的钱包铸造 NFT,Lens Protocol 用户之间的打赏机制目前几个协议中最自然、方便的,直接向对方的钱包转代币即可。用户不需要像 Nostr、Farcaster 那样,需要额外关联 BTC 闪电网络地址、ETH 地址。
在 Lens Protocol 中,用户的身份、社交关系、内容数据存在哪? 用户社交关系以各种 NFT 的形式存在 Polygon 上。具体而言,在 Lens 中的社交关系建立都是以 NFT 为形式来记录存储的,例如若 A 关注了 B,那么就会铸造一个记录 “A 关注 B” 的 Following NFT。
用户发布内容时,Lens Protocol 要求将内容索引 ContentURI 发布到 Polygon 上,不过内容索引指向的内容具体存在哪里,Lens Protocol 对此并无明确限制,取决于具体应用的设计(类似于 NFT 的 metadata)。目前多数应用会把用户内容存在 Arweave 上。
在 Lens Protocol 中,内容审核机制是如何设计的? Lens Protocol 明确不会在协议层做内容的审查过滤,需要各个应用自己设计相应的算法,或者采用一些第三方的算法模块。
Lens Protocol 官方支持的 Cultivator DAO 就在做这样的内容审核模块,它可以由应用开发者来自己选择是否 “开启”;Cultivator DAO 的策略也是公开的,这意味着任何人都可以 fork 它然后制定自己的策略。
在 Lens Protocol 中,服务提供方的激励是什么? 由于 Lens Protocol 完全在 Polygon 链上,Lens Protocol 协议中的服务提供方,实际上就是 Polygon 的各个节点,而 Gas 费就是它们的激励。
对用户而言,当前所有的应用操作只需钱包签名即可,不需要付费。因为现在具体的上链操作是由 Lens Protocol 项目方代为处理、代交 Gas 的,但这并非长久之计:根据 muran.eth 的测算,如果 Lens Protocol 的 DAU 达到 Twitter 级别,那么每周用户需要交的 Gas 费总额将达到 250 万美元,这是项目方难以承担的。
因此长远来看,随着 Lens Protocol 用户数的增长和活跃度的提升,如果数据上链的方案不改变,那么未来很有可能由用户来自己缴纳 Gas 费。然而 “每步操作都交 Gas 费” 却大大违背了用户在 Web2 社交应用产生的习惯,导致吸引力降低和用户流失。因此这个问题是 Lens Protocol 进一步迭代时所需重点关注的。
5.2 应用发展现状 Lens Protocol 现在有约 10.8 万个 Profile NFT,用户注册数超过 16 万。早期 Lens Protocol 的注册没有限制,但自 2022 年 11 月以来项目方改变了增长策略,仅限白名单用户注册(可能和控制代交的 Gas 费规模有关?)。目前在 Opensea 上可以购买 Lens Profile,地板价约为 120U。
Lens Protocol 的生态应用项目有近 150 个,不过大部分产品还处于相对早期的阶段,功能体验相对简单。Lens Protocol 内最知名的应用项目是项目方做的类 Twitter 产品 Lenster。(详情可以参考 SevenX & Buidler DAO 近期发布的 Lens Protocol 研究)
Lens Protocol 吸引的用户,主要是非常熟悉于链上操作的 “Web3-native” 用户,尤其是玩 NFT 的圈子。虽然 Lens Protocol 没有明确相关的代币机制,但 Lens Protocol 的代币空投预期可能是许多用户愿意花时间了解、注册、持续活跃的原因之一。另外 Lens Protocol 的打赏机制也是目前几个协议中最自然、方便的,也吸引了一部分 Web3 的优质内容创作者。
由于多数操作需要上链,即使 Gas 费已经由协议代付,用户依然需要频繁用钱包进行签名确认,另外操作上链也有延时,因此 Lens Protocol 的产品用户体验相比于其它的协议而言,对用户可以说是最不友好的,而且受制于 Polygon 的架构和性能。
5.3 其它链上社交协议 Lens Protocol 是当前用户数最多的链上社交协议,其设计的思路也可以被看做这类协议设计的代表。不过如前文所述,Lens Protocol 的设计让其上产品的体验受制于 Polygon 的性能,尤其是数据上链相关的策略。
当前链上社交协议尚处于萌芽期,新的协议不断涌现,而 Lens Protocl 发展中遇到的种种问题也给后来者提供了很好的参照。如经常被拿来和 Lens Protocol 对比的 CyberConnect,虽然用户的账户、社交关系依然在链上,但它具体的协议设计中取消了大量的上链操作,转而用一些链下验证方式解决。这些新协议的设计,它们生态应用的发展也是值得持续关注的。
六、总结与展望
(图十:Nostr、ActivityPub、Faracaster、Lens Protocol 协议对比,@Mtyl_7th 绘制) 综合下来我们可以看出,四个协议的设计理念可以分为两个派系:
Nostr 和 ActivityPub 设计的核心理念,都是” 对抗中心化审查”。它们更强调用户对自己内容数据的控制权,允许用户导出自己的数据,没有做一个公开的数据存储网络方便开发者调用。 Farcaster 和 Lens Protocol 设计的核心理念,更在意一个开放互通、对开发者友好的用户数据层,解决 Web2 社交产品相互之间的” 数据孤岛 “问题。 下面笔者将对四个协议的优缺点做一个对比总结,并对其未来一段时间的发展做出预测:
6.1 ActivityHub ActivityPub 出现较早,上面的应用打磨的更加成熟,无论是 UX 还是概念都对 Web2 用户非常友好,在至少 1 年内对 Web2 用户的吸引力是其它协议难以追上的。
但是 ActivityPub 从设计上更像是一个过渡品,用户的账户、数据依然托管在一个服务器(Instance)下面,虽然可以随时导出备份,但这并没有很完美的解决用户数据存储可靠性的问题;另外服务器(Instance)的运行者也缺乏明确激励。
长期来看,随着 Web3 相关概念的普及,ActivityPub 吸引 Web2 用户的优点将会越来越不明显,会被设计更完善的协议所取代。
6.2 Nostr Nostr 的协议设计非常轻巧,对于其中服务器(Relay)的职责要求非常简单 —— 只需要帮助转发信息。这使得 Relay 的成本非常低,用户可以很轻易的构建属于自己项目或者兴趣团体的 Relay。整个网络反脆弱性极强,永远存在没有内容审核的地方。
考虑到 Nostr 的公私钥概念、BTC 闪电网络的支付模式,这些概念的理解和对用户自主性的要求都和 Web3 用户(区块链用户)高度重合。再加上目前 Nostr 生态产品功能的不成熟,因此在 Web3 相关概念本身得到普及之前,Nostr 很难像 ActivityPub 那样,吸引那些对 Web2 社交产品失望的用户。
而在 Web3 领域(区块链领域), 它在 Farcaster、Lens Protocol 等协议的竞争之中也未必处于优势地位。就社区氛围而言,如果你不是比特币最大主义者,那么 Farcaster 内 Web3 从业者深度讨论的氛围、Lens Protocol 的 NFT 氛围都可能更加适合你; 就代币经济激励的预期,Nostr 肯定比不上 Lens Protocol。
因此可能相当长一段时间内,Nostr 的核心用户群依然会维持现状: 比特币爱好者们。不过这其实也不奇怪 —— 因为从 Nostr 的 Github 文档来看,它的设计是高度 “理念驱动 “而不是” 实用驱动 “的;创始人并没有想很多的 Go To Market Strategy,只是在思考怎么能构建一个更持久的抗审查的社交协议,Nostr 也没有接受融资(只有 Jack Dorsey 的 14BTC 捐赠),没有来自资本的压力。
6.3 Farcaster Farcaster 的亮点主要有两个:
作为一个针对 Web3 用户设计的协议,现在已经能够做到媲美 Web2 社交产品的体验。这得益于它自建了一个由 Hub 构成的数据存储网络。 Farcaster 的保守社区增长策略在 Web3 社交中是罕见的,这也给 Farcaster 带来了高价值的初期用户和社区氛围;这样的打法在 Web2 也是有成功先例的,比如知乎。 因此,从目前的发展情况来看,如果说有哪个协议最有希望成为 Web3 用户的 Twitter,那么 Farcaster 可能是最有希望的。
相比于其它协议,Farcaster 是起步较晚、设计较为复杂的,因此还处于快速迭代的早期状态,后续还有比较多的改进空间。
6.4 Lens Protocol Lens Protocol 的数据上链,不仅有利于和其他 Web3 项目结合、开发新玩法,也借助于钱包的打赏机制,让创作者经济天然得到萌发。但随之而来的大量钱包签名、操作时延、数据上链费用,都是用户所需要付出的代价。这也是为什么笔者认为单纯的类 Twitter 产品很难在 Lens Protocol 上取得大成功的原因。
如果 Lens Protocol 上出现了爆款产品,那么它一定是和各种链上玩法所紧密结合的,但目前 Lens Protocol 生态中尚未有这类产品出现。随着区块链基础技术的发展,各种新的、设计更完善的链上社交协议的也在不断推出,如果 Lens Protocol 不能利用好先发优势尽快在 Web3 社区中打造出爆款产品的话,那么它可能会面临着被后来者超越的危机。
参考资料: Nostr Github:https://github.com/nostr-protocol/nostr Farcaster Github:https://github.com/farcasterxyz/protocol 以 Lens protocol 为例,看清去中心化社交应用数据架构,探讨什么是好的 Dapp 数据层:https://mirror.xyz/muran.eth/dy-6ExlpYsehQJJvNcRlLi8XDjwdEw1xoV7oDxy_eWM Buidler DAO x SevenX, Lens Protocol 万字深研报告: https://mp.weixin.qq.com/s/HISBmicZ-6szM6RY4ZWZyw 社交专题:从围墙花园到公民广场 — 社交协议概况 by Mask_ Bonfire Union: https://docs.qq.com/pdf/DUlNoQ0h0cURRUU5P?&u=ec65a5118acc42e2960e5aa4b12feb42 免责声明:作为区块链信息平台,本站所发布文章仅代表作者及嘉宾个人观点,与 Web3Caff 立场无关。文章内的信息仅供参考,均不构成任何投资建议及要约,并请您遵守所在国家或地区的相关法律法规。
-
 @ 07ddc7e2:1772eca9
2023-03-03 08:13:06
@ 07ddc7e2:1772eca9
2023-03-03 08:13:06qsqSqs qS q s qS qs qs Q SQ
-
 @ 84b0c46a:417782f5
2023-03-03 05:33:48
@ 84b0c46a:417782f5
2023-03-03 05:33:48[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
-
 @ 84b0c46a:417782f5
2023-03-03 05:17:17
@ 84b0c46a:417782f5
2023-03-03 05:17:17[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
[32]
[33]
[34]
[35]
[36]
[37]
[38]
[39]
[40]
[41]
[42]
[43]
[44]
-
 @ 45c41f21:c5446b7a
2023-03-03 03:51:20
@ 45c41f21:c5446b7a
2023-03-03 03:51:20
tonight I just release the very first rough version of fly-castle, it is a very simple desktop app to provide a GUI for your own private backup relay written in Rust. the core relay implementation is forked from scsibug/nostr-rs-relay, I might touch the code there to experiment some ideas later.
Currently, I only build for macOS since that's the only OS on my laptop, but maybe I will find a windows computer to build windows one.
Here is how I would love to use it:
macOS
- download the software from here
- unzip it, you will get a file named
fly-castle - create a folder named
my-relayand putfly-castleinto the folder - Start the relay by running the following command on your terminal:
sh cd my-relay sudo chmod 755 fly-castle ./fly-castle -
Open flycat website, click the private backup menu on the left side of the page. add the ws://localhost:8080 to your relay via the right side of the new page.
-
if you want to stop running your little relay, just close the window of fly-castle, it is that simple.
-
 @ f40832e2:bcbf511e
2023-03-03 01:02:37
@ f40832e2:bcbf511e
2023-03-03 01:02:37[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
-
 @ 460c25e6:ef85065c
2023-03-02 20:46:12
@ 460c25e6:ef85065c
2023-03-02 20:46:12Second change to text
Demo
Emphasis, aka italics, with asterisks or underscores. Strong emphasis, aka bold, with asterisks or underscores. Combined emphasis with asterisks and underscores. Links with two blocks, text in square-brackets, destination is in parentheses.. Inline
codehasback-ticks aroundit.Ordered lists:
- First ordered list item
- Another item
- Unordered sub-list.
- And another item. You can have properly indented paragraphs within list items. Notice the blank line above, and the leading spaces (at least one, but we'll use three here to also align the raw Markdown).
Regular lists:
- Unordered list can use asterisks
- Or minuses
- Or pluses
Code
javascript var s = "code blocks use monospace font"; alert(s);Here's a Table:
Markdown | Table | Extension --- | --- | --- renders |
beautiful images|1 | 2 | 3
And Blockquotes
Blockquotes are very handy in email to emulate reply text. This line is part of the same quote.
-
 @ a22a2372:061a8c67
2023-03-02 14:26:32
@ a22a2372:061a8c67
2023-03-02 14:26:32[3]
-
 @ 14dd75ba:df11320a
2023-03-02 00:31:10
@ 14dd75ba:df11320a
2023-03-02 00:31:10s<fdsdzfsdafsdafsaf asdf asd fsad f asdf asdf asdf
-
 @ 14dd75ba:df11320a
2023-03-02 00:20:27
@ 14dd75ba:df11320a
2023-03-02 00:20:27nononononono
-
 @ 14dd75ba:df11320a
2023-03-02 00:18:49
@ 14dd75ba:df11320a
2023-03-02 00:18:49auto
-
 @ d0debf9f:ea4b466c
2023-03-01 19:10:19
@ d0debf9f:ea4b466c
2023-03-01 19:10:19Why wireguard?
If you are already sold on why you need this, skip to the next section.
A motivational story
The year is 2025. You're at the small coffeshop you found on btcmap and want to pay for your morning double expresso.
A LN invoice flashes before your sleepy eyes, you pull out your phone and try to open your Zeus wallet connected to your sovereign self-custodial LN node running in your basement.
You wait for Zeus to load. And you wait. And you wait. And you wait some more. The barista gets impatient, there is a line of NPCs behind you rushing to get to their fiat mines.
Finally you curse, pay with your slave VISA CBDC card and uninstall Zeus as you walk out.
The Issue
You used Tor to connect to your node. Tor was being DDOSed by some state-level actors.
You're using Tor because either it was the easiest thing to setup, or it was just the default in your node distribution.
Have you stopped to wonder if it really makes sense to use an anonymity network designed to be censorship resistant just to connect to your own home server?
You obviously don't want to expose your node to the public internet (which would expose what you are using as well as make you vulnerable to attacks).
The Solution
The best solution (as far as I'm aware of) is to connect to your home node using an encrypted VPN point-to-point tunnel using something called WireGuard.
The only information you leak to potential traffic sniffers is encrypted UDP packets (which are already hard to sniff) to your home IP address, which is pretty harmless information.
The (not ideal) Alternative
Many people find Wireguard hard to setup on its own (don't worry, that is why I wrote this guide) and prefer a more seamless corporate solution based on Wireguard called Tailscale.
Tailscale has 2 major drawbacks:
- It's an additional third party that knows every encrypted packet you send over it as well as all your public IPs.
- It's permissioned and requires setting up an account, not very sovereign
Setup
Requirements
- Access to your home router admin page: if your node is behind a NAT (usually that is the case when it's behind a home router), you're going to need to forward a port to your node LAN IP. If you don't know how to do this, you can try to follow the guide for your router model at portforward.com.
- Either a fixed home public IP address, or a domain name that points to your dynamic home IP address. Even if you don't have this, you can still follow the guide and manually update your home IP in the configuration file.
- Shell root access in your node.
Node setup
Gather network information
Find your node's LAN IP address:
bash $ ip -human --brief address show lo UNKNOWN 127.0.0.1/8 ::1/128 eth0 UP 192.168.1.2/24 metric 1024In this case, the your node's LAN IP is
192.168.1.2.Find your home public IP address:
bash $ curl ipecho.net/plain### Install wireguard tools
The wireguard module is actually built into any modern linux kernel by default, what we actually need to install is the tooling to generate valid wireguard cryptographic keys.
For debian/ubuntu based distros:
bash $ sudo apt install wireguardFor other distros, check wireguard.com/install.Generate keys
You manually need to generate 1 keypair for each device (called peer) that will use your wireguard VPN (including your home node).
To generate a keypair for your node (let's call it
node):bash $ wg genkey | (umask 0077 && tee node.key) | wg pubkey > node.pubThis will create 2 files:
node.keyandnode.pubcontaining your private and public keys, respectively. Keep these files safe and after being done configuring wireguard you can even delete them.Create extra keypairs for your other devices, e.g.: * Your phone:
bash $ wg genkey | (umask 0077 && tee phone.key) | wg pubkey > phone.pub* Your laptop:bash $ wg genkey | (umask 0077 && tee laptop.key) | wg pubkey > laptop.pubCreate as many as you wish.Configure the tunnel
Using a text editor create and edit the file
/etc/wireguard/mytunnelname.confwith the content:``` [Interface] Address = 10.0.0.1/24 ListenPort = 50000 PrivateKey =
[Peer] PublicKey =
AllowedIPs = 10.0.0.2/32 [Peer] PublicKey =
AllowedIPs = 10.0.0.3/32 ``` Subsitute
*_KEYwith the relevant keys found in the files you generated earlier (which you can see the contents usingcat node.keyfor instance).Generate configurations for the other peers
For your phone/laptop, create a files (can be anywhere, does not matter) with the contents: *
phone.conf``` [Interface] Address = 10.0.0.2/24 PrivateKey =[Peer] PublicKey =
AllowedIPs = 10.0.0.1/32 Endpoint = :50000 ``` laptop.conf:
``` [Interface] Address = 10.0.0.3/24 PrivateKey =
[Peer] PublicKey =
AllowedIPs = 10.0.0.1/32 Endpoint = :50000 ``` Now you need to either transfer these files to their respective devices (how you do it is your business) or generate an easy to use QR code to use to configure your phone.
Optional: generate QR code for the phone configuration
Install
qrencodebash sudo apt install qrencodePrint the QR code on your terminal:
bash $ qrencode -r phone.conf -t ansiutf8Or save it (and transfer) as png image:
bash $ qrencode -r phone.conf -o phone.pngRun wireguard the wireguard tunnel
bash $ sudo systemctl enable --now wg-quick@mytunnelname.serviceNow when you do
ip -human --brief address showyou should see an extra interface:lo UNKNOWN 127.0.0.1/8 ::1/128 eth0 UP 192.168.1.2/24 metric 1024 mytunnelname UNKNOWN 10.0.0.1/24Open UDP wireguard port
If your node has a firewall, we need to open our chosen UDP port (50000).
If using
ufw:bash $ sudo ufw allow 50000/udpif just using iptables:
bash $ sudo iptables -A UDP -p udp -m udp --dport 50000 -j ACCEPTHome router setup
Forward port 50000 UDP to your node's LAN IP. If you don't know how to do this, you can try to follow the guide for your router model at portforward.com.
Phone setup
1- Install the wireguard app, you can find links in wireguard.com/install.
2 - Open the app 3 - Click on the
+button 4 - Choose if you want to import thephone.confconfiguration file, the your generated QR or input everything manually. 5 - Activate the tunnel by tapping the switchYou should have a working tunnel between your node and your phone. You can try pinging your phone wireguard IP (
10.0.0.2) from your node's terminal (ping 10.0.0.2) to check that it is working.Now on every app you connect to your node (e.g. Zeus), instead of using the onion address, you can just use your node's wireguard IP (
10.0.0.1).Laptop setup
If it's a linux laptop: place (and rename)
laptop.confto/etc/wireguard/mytunnelname.confand do:bash $ sudo systemctl enable --now wg-quick@mytunnelname.servicePing your node wireguard IP
ping 10.0.0.1to make sure it's working.Now you can use that IP instead of the onion address to connect to your node (e.g. in Sparrow).
Help
If you have questions feel free to contact me (NIP-05: sommerfeld@strisemarx.com).
-
 @ 990590c7:35e54182
2023-03-01 14:46:49
@ 990590c7:35e54182
2023-03-01 14:46:49Nosso primeiro artigo não é um artigo, mas um comunicado:
Vamos disseminar o Nostr no Brasil!
Estamos finalizando nosso site com os conteúdos, que também serão replicados aqui.
Você está conosco?
Ajude compartilhando!
-
 @ 24e37c1e:c4965f3b
2023-03-01 10:48:53
@ 24e37c1e:c4965f3b
2023-03-01 10:48:53General - 161,0k
- 25.000 - Guerrilla por todo su contenido
- 25.000 - a Verbiricha por Habla.news https://habla.news/
- 25.000 - A Catrya por el análisis que esta haciendo del uso de internet de clientes Nostr para android desde Cuba https://twitter.com/Catry_a/status/1629865637160820742?s=20
- 25.000 - A dev7ba por https://mempoolexplorer.com
- 10.000 - jb55 por todo lo hecho en Nostr
- 10.000 - A Janoctus por sus Pruned nodes https://twitter.com/jaoNoctus/status/1620205269040107521
- 10.000 - a Heptapodae por el artículo de Herencia Bitcoin en Estudio Bitcoin
- 10.000 - A Decentralized por los feedbacks a mis pods
- 5.000 - A Keith por Nostrtool.com
- 5.000 - Hampus por una respuesta de valor en Twitter
- 5.000 - A Snort.social en Nostr
- 5.000 - Koalasats por respuesta en Nostr
- 1.000 - a Gzuuus por esta nota en Nostr
Podcasting 2.0 - 18,5k
- 5.900 Stephan Livera Podcast
- 4.500 Thriller Bitcoin
- 3.900 What Bitcoin Did with Peter McCormack
- 2.800 Bitcoin Review Podcast
- 1.400 What is Money Show
-
 @ 19ac3d7c:0287bd58
2023-03-01 10:03:25
@ 19ac3d7c:0287bd58
2023-03-01 10:03:25Basta dare soldi alle multinazionali!
Non inquina, non fa rumore, ideale per viaggi di corta distanza
Rivoluzione eco-tecnologica:
Scegli la colorazione della capra * Marrone * Bianco * Misto * Total black (con sovraprezzo)
Testimonials;
Maurizio C: ho provato la biomacchina per andare a lavorare, mi trovo benissimo, l'ho parcheggiata nello sterrato vicino al lavoro e ha fatto anche un ottimo lavoro di pulizia prato
Chiara F: le mie amiche non ci potevano credere, la capra e amichevole e disponibile anche per i selfie, sono ansiosa di pendere la versione pink passion
Satoi N: L'idea è ottima, ma devo fare 2 appunti: non ha le chiavi, quindi teoricamente non è la mia capra... e non c'è ancora disponibile la versione orange. per il resto sono sodisfatto.
Compila il KYC e ricevi il catalogo capre online, GRATIS e comodamente nella tua posta elettronica!Adotta una capra bebe! inviaci 100 sats al mese e potrai sostenere il progetto!
Ricevi la tua Biomacchina a casa tua per 0.0666 Bitcoin
Test post on blogstack
-
 @ c913b8e3:8704332c
2023-03-01 09:21:05
@ c913b8e3:8704332c
2023-03-01 09:21:05Everyone and anyone is welcome to bitcoin. Bitcoin is the key to transformation, holding is enough.
Being in control is the best you can do.
Modern debt slavery, without any purpose in life.
*
Success consists of being able to secure evergrowing quantities of debt as you pass through the stages of life: a big college loan that allows you to get into the best paying job, whose salary will allow you a larger loan for a large house and another loan for a car. With more hard work at the company and dedication to its cause, you may succeed in getting and even larger negative balance of fiat for a bigger home and fancier car. Should you succeed even more and start your own business, you do not do it with your own accumulated capital, but rather with a bigger loan. The larger and the more successful the business, the more you are able to borrow. In sum, success in fiat means accumulating larger negative cash balances, and people live their entire lives stacking debt obligations upon themselves. * - The Fiat Standard - Saifedean Ammous
Everybody screaming: 🤡 🌎
The clown will die in the end. We need to get individuals back in control. Nobody wants to be the clown. Value wins in the long run. Common sense prevails in the long run. Better and healthier ways of living win in the long run. I know it is frustrating, but we stay humble.
We inverted from value to clown, and the same will happen from clown to value.
Bitcoin changed me for the better, and it will also change everybody, eventually. How can you not be bullish on Bitcoiners? Bitcoin is above nation-states.
There are so many brilliant people involved who believe in Bitcoin. It is crazy.
Brilliant Economist, physics, energy experts, engineers, computer scientists, investors, hedge fund managers, human rights activists, content creators, podcasters, and writers. I could go on with this list forever.
The development happening in various protocols is mental:
Just look at NOSTR & Lightning.
Open decentralized networks. It is the future.
Watch:
https://twitter.com/_BitcoinMatrix/status/1623518735393849346?s=20
Bitcoiners are very hopeful and optimistic about the future. So how is it wrong to advocate better ways of living? Decentralization, hard money, security, financial inclusion, innovation.
All roads lead to Bitcoin
Being in control of your future is essential. Have some purpose, be it just eating healthy food to get fit.
So many are just living in autopilot mode and don’t care. All the negative behavior and “clown world” stuff leads just more to the never-ending overconsumption dark hole, which sucks life and joy out of every living soul. Some ideas:
Avoid the 🤡 Embrace freedom & love.
Improved financial stability. Stable financial situation:
Debt-free - saving money - Budgeting - Investing - consume responsibly.
Better decision-making. A strong body makes the mind strong. Clear mind:
No alcohol - Eating healthier - Exercise - Meditation - Reading - Learning - Teaching
Healthy lifestyle compounds to increased productivity
Old, I could barely cook my own food.
Try to ramble to this modern slave about innovation, decentralization, and hard money. We grow from shallow purposes to deeper ones. They won’t listen yet; they died at the age of 30 and will be buried at 78. I was dead, too, for many years.
Take control of your future.
Nobody dreamed as a little kid of being a 9-5 modern slave in a cubicle with no imagination and getting fulfillment out of negative behavior without any purpose.
- Set clear and realistic goals.
- Focus on what you can control. Start small, maybe a budget?
- Learn and develop new skills, just being 1% better daily; that’s 37x better in a year.
- Network and build relationships, I got many nice DM’s from fellow Bitcoiners and had excellent discussions. Hopefully lot more in the future.
- Stay positive and be resilient: Is where you want to be in ten years worth ten years of failure? Is ten years of what you do now worth it at all?
Looking for shortcuts?
There is no magic pill.
May the purpose be flawed or shallow, just have some. This leads to even more incredible personal growth eventually.
Bitcoin is not your shortcut to retirement or getting out of the rat race lottery ticket. The majority of the world population hasn’t even heard about Bitcoin. The majority of Bitcoiners are wildly delusional and on get-rich-fast hopium.
For me being Bitcoiner it is all about taking control. By staying humble, learning from others, and approaching Bitcoin with a long-term perspective, everyone can contribute to building a fairer and more sustainable financial system for the future.
So, start stacking, stay curious, and be the best Bitcoiner you can be, just holding is enough. You’ll might find the adventure of your life, creating a better future for yourself and the world.
-
 @ 45c41f21:c5446b7a
2023-03-01 06:45:45
@ 45c41f21:c5446b7a
2023-03-01 06:45:45Markdown syntax guide
Headers
This is a Heading h1
This is a Heading h2
This is a Heading h6
Emphasis
This text will be italic
This will also be italicThis text will be bold
This will also be boldYou can combine them
Lists
Unordered
- Item 1
- Item 2
- Item 2a
- Item 2b
Ordered
- Item 1
- Item 2
- Item 3
- Item 3a
- Item 3b
Images

Links
You may be using Markdown Live Preview.
Blockquotes
Markdown is a lightweight markup language with plain-text-formatting syntax, created in 2004 by John Gruber with Aaron Swartz.
Markdown is often used to format readme files, for writing messages in online discussion forums, and to create rich text using a plain text editor.
Tables
| Left columns | Right columns | | ------------- |:-------------:| | left foo | right foo | | left bar | right bar | | left baz | right baz |
Blocks of code
let message = 'Hello world'; alert(message);Inline code
This web site is using
markedjs/marked. -
 @ 45c41f21:c5446b7a
2023-03-01 06:41:49
@ 45c41f21:c5446b7a
2023-03-01 06:41:49互联网上的贸易,几乎都需要借助金融机构作为可资信赖的第三方来处理电子支付信息。虽然这类系统在绝大多数情况下都运作良好,但是这类系统仍然内生性地受制于“基于信用的模式”(trust based model)的弱点。我们无法实现完全不可逆的交易,因为金融机构总是不可避免地会出面协调争端。而金融中介的存在,也会增加交易的成本,并且限制了实际可行的最小交易规模,也限制了日常的小额支付交易。并且潜在的损失还在于,很多商品和服务本身是无法退货的,如果缺乏不可逆的支付手段,互联网的贸易就大大受限。因为有潜在的退款的可能,就需要交易双方拥有信任。而商家也必须提防自己的客户,因此会向客户索取完全不必要的个人信息。而实际的商业行为中,一定比例的欺诈性客户也被认为是不可避免的,相关损失视作销售费用处理。而在使用物理现金的情况下,这些销售费用和支付问题上的不确定性却是可以避免的,因为此时没有第三方信用中介的存在。
所以,我们非常需要这样一种电子支付系统,它基于密码学原理而不基于信用,使得任何达成一致的双方,能够直接进行支付,从而不需要第三方中介的参与。杜绝回滚(reverse)支付交易的可能,这就可以保护特定的卖家免于欺诈;而对于想要保护买家的人来说,在此环境下设立通常的第三方担保机制也可谓轻松加愉快。在这篇论文中,我们(we)将提出一种通过点对点分布式的时间戳服务器来生成依照时间前后排列并加以记录的电子交易证明,从而解决双重支付问题。只要诚实的节点所控制的计算能力的总和,大于有合作关系的(cooperating)攻击者的计算能力的总和,该系统就是安全的。2. 交易(Transactions)
我们定义,一枚电子货币(an electronic coin)是这样的一串数字签名:每一位所有者通过对前一次交易和下一位拥有者的公钥(Public key) 签署一个随机散列的数字签名,并将这个签名附加在这枚电子货币的末尾,电子货币就发送给了下一位所有者。而收款人通过对签名进行检验,就能够验证该链条的所有者。
 该过程的问题在于,收款人将难以检验,之前的某位所有者,是否对这枚电子货币进行了双重支付。通常的解决方案,就是引入信得过的第三方权威,或者类似于造币厂(mint)的机构,来对每一笔交易进行检验,以防止双重支付。在每一笔交易结束后,这枚电子货币就要被造币厂回收,而造币厂将发行一枚新的电子货币;而只有造币厂直接发行的电子货币,才算作有效,这样就能够防止双重支付。可是该解决方案的问题在于,整个货币系统的命运完全依赖于运作造币厂的公司,因为每一笔交易都要经过该造币厂的确认,而该造币厂就好比是一家银行。
我们需要收款人有某种方法,能够确保之前的所有者没有对更早发生的交易实施签名。从逻辑上看,为了达到目的,实际上我们需要关注的只是于本交易之前发生的交易,而不需要关注这笔交易发生之后是否会有双重支付的尝试。为了确保某一次交易是不存在的,那么唯一的方法就是获悉之前发生过的所有交易。在造币厂模型里面,造币厂获悉所有的交易,并且决定了交易完成的先后顺序。如果想要在电子系统中排除第三方中介机构,那么交易信息就应当被公开宣布(publicly announced)[1] ,我们需要整个系统内的所有参与者,都有唯一公认的历史交易序列。收款人需要确保在交易期间绝大多数的节点都认同该交易是首次出现。
该过程的问题在于,收款人将难以检验,之前的某位所有者,是否对这枚电子货币进行了双重支付。通常的解决方案,就是引入信得过的第三方权威,或者类似于造币厂(mint)的机构,来对每一笔交易进行检验,以防止双重支付。在每一笔交易结束后,这枚电子货币就要被造币厂回收,而造币厂将发行一枚新的电子货币;而只有造币厂直接发行的电子货币,才算作有效,这样就能够防止双重支付。可是该解决方案的问题在于,整个货币系统的命运完全依赖于运作造币厂的公司,因为每一笔交易都要经过该造币厂的确认,而该造币厂就好比是一家银行。
我们需要收款人有某种方法,能够确保之前的所有者没有对更早发生的交易实施签名。从逻辑上看,为了达到目的,实际上我们需要关注的只是于本交易之前发生的交易,而不需要关注这笔交易发生之后是否会有双重支付的尝试。为了确保某一次交易是不存在的,那么唯一的方法就是获悉之前发生过的所有交易。在造币厂模型里面,造币厂获悉所有的交易,并且决定了交易完成的先后顺序。如果想要在电子系统中排除第三方中介机构,那么交易信息就应当被公开宣布(publicly announced)[1] ,我们需要整个系统内的所有参与者,都有唯一公认的历史交易序列。收款人需要确保在交易期间绝大多数的节点都认同该交易是首次出现。3. 时间戳服务器(Timestamp server)
本解决方案首先提出一个“时间戳服务器”。时间戳服务器通过对
以区块(block)形式存在的一组数据实施随机散列而加上时间戳,并将该随机散列进行广播,就像在新闻或世界性新闻组网络(Usenet)的发帖一样[2][3][4][5] 。显然,该时间戳能够证实特定数据必然于某特定时间是的确存在的,因为只有在该时刻存在了才能获取相应的随机散列值。每个时间戳应当将前一个时间戳纳入其随机散列值中,每一个随后的时间戳都对之前的一个时间戳进行增强(reinforcing),这样就形成了一个链条(Chain)。
4. 工作量证明(Proof-of-Work)
为了在点对点的基础上构建一组分散化的时间戳服务器,仅仅像报纸或世界性新闻网络组一样工作是不够的,我们还需要一个类似于亚当•柏克(Adam Back)提出的哈希现金(Hashcash)[6] 。在进行随机散列运算时,工作量证明机制引入了对某一个特定值的扫描工作,比方说SHA-256下,随机散列值以一个或多个0开始。那么随着0的数目的上升, 找到这个解所需要的工作量将呈指数增长,而对结果进行检验则仅需要一次随机散列运算。
我们在区块中补增一个随机数(Nonce),这个随机数要使得该给定区块的随机散列值出现了所需的那么多个0。我们通过反复尝试来找到这个随机数,直到找到为止,这样我们就构建了一个工作量证明机制。只要该CPU耗费的工作量能够满足该工作量证明机制,那么除非重新完成相当的工作量,该区块的信息就不可更改。由于之后的区块是链接在该区块之后的,所以想要更改该区块中的信息,就还需要重新完成之后所有区块的全部工作量。

同时,该工作量证明机制还解决了在集体投票表决时,谁是大多数的问题。如果决定大多数的方式是基于IP地址的,一IP地址一票,那么如果有人拥有分配大量IP地址的权力,则该机制就被破坏了。而工作量证明机制的本质则是一CPU一票。“大多数”的决定表达为最长的链,因为最长的链包含了最大的工作量。如果大多数的CPU为诚实的节点控制,那么诚实的链条将以最快的速度延长,并超越其他的竞争链条。如果想要对业已出现的区块进行修改,攻击者必须重新完成该区块的工作量外加该区块之后所有区块的工作量,并最终赶上和超越诚实节点的工作量。我们将在后文证明,设想一个较慢的攻击者试图赶上随后的区块,那么其成功概率将呈指数化递减。
另一个问题是,硬件的运算速度在高速增长,而节点参与网络的程度则会有所起伏。为了解决这个问题,工作量证明的难度(the proof-of-work difficulty)将采用移动平均目标的方法来确定,即令难度指向令每小时生成区块的速度为某一个预定的平均数。如果区块生成的速度过快,那么难度就会提高。5. 网络
运行该网络的步骤如下:
1) 新的交易向全网进行广播; 2) 每一个节点都将收到的交易信息纳入一个区块中; 3) 每个节点都尝试在自己的区块中找到一个具有足够难度的工作量证明; 4) 当一个节点找到了一个工作量证明,它就向全网进行广播; 5) 当且仅当包含在该区块中的所有交易都是有效的且之前未存在过的,其他节点才认同该区块的有效性; 6) 其他节点表示他们接受该区块,而表示接受的方法,则是在跟随该区块的末尾,制造新的区块以延长该链条,而将被接受区块的随机散列值视为先于新区快的随机散列值。
节点始终都将最长的链条视为正确的链条,并持续工作和延长它。如果有两个节点同时广播不同版本的新区块,那么其他节点在接收到该区块的时间上将存在先后差别。当此情形,他们将在率先收到的区块基础上进行工作,但也会保留另外一个链条,以防后者变成最长的链条。该僵局(tie)的打破要等到下一个工作量证明被发现,而其中的一条链条被证实为是较长的一条,那么在另一条分支链条上工作的节点将转换阵营,开始在较长的链条上工作。
所谓“新的交易要广播”,实际上不需要抵达全部的节点。只要交易信息能够抵达足够多的节点,那么他们将很快被整合进一个区块中。而区块的广播对被丢弃的信息是具有容错能力的。如果一个节点没有收到某特定区块,那么该节点将会发现自己缺失了某个区块,也就可以提出自己下载该区块的请求。6. 激励
我们约定如此:每个区块的第一笔交易进行特殊化处理,该交易产生一枚由该区块创造者拥有的新的电子货币。这样就增加了节点支持该网络的激励,并在没有中央集权机构发行货币的情况下,提供了一种将电子货币分配到流通领域的一种方法。这种将一定数量新货币持续增添到货币系统中的方法,非常类似于耗费资源去挖掘金矿并将黄金注入到流通领域。此时,CPU的时间和电力消耗就是消耗的资源。
另外一个激励的来源则是交易费(transaction fees)。如果某笔交易的输出值小于输入值,那么差额就是交易费,该交易费将被增加到该区块的激励中。 只要既定数量的电子货币已经进入流通,那么激励机制就可以逐渐转换为完全依靠交易费,那么本货币系统就能够免于通货膨胀。
激励系统也有助于鼓励节点保持诚实。如果有一个贪婪的攻击者能够调集比所有诚实节点加起来还要多的CPU计算力,那么他就面临一个选择:要么将其用于诚实工作产生新的电子货币,或者将其用于进行二次支付攻击。那么他就会发现,按照规则行事、诚实工作是更有利可图的。因为该等规则使得他能够拥有更多的电子货币,而不是破坏这个系统使得其自身财富的有效性受损。7. 回收硬盘空间
如果最近的交易已经被纳入了足够多的区块之中,那么就可以丢弃该交易之前的数据,以回收硬盘空间。为了同时确保不损害区块的随机散列值,交易信息被随机散列时,被构建成一种Merkle树(Merkle tree)[7] 的形态,使得只有根(root)被纳入了区块的随机散列值。通过将该树(tree)的分支拔除(stubbing)的方法,老区块就能被压缩。而内部的随机散列值是不必保存的。

不含交易信息的区块头(Block header)大小仅有80字节。如果我们设定区块生成的速率为每10分钟一个,那么每一年产生的数据位4.2MB。(80 bytes * 6 * 24 * 365 = 4.2MB)。2008年,PC系统通常的内存容量为2GB,按照摩尔定律的预言,即使将全部的区块头存储于内存之中都不是问题。
8. 简化的支付确认(Simplified Payment Verification)
在不运行完整网络节点的情况下,也能够对支付进行检验。一个用户需要保留最长的工作量证明链条的区块头的拷贝,它可以不断向网络发起询问,直到它确信自己拥有最长的链条,并能够通过merkle的分支通向它被加上时间戳并纳入区块的那次交易。节点想要自行检验该交易的有效性原本是不可能的,但通过追溯到链条的某个位置,它就能看到某个节点曾经接受过它,并且于其后追加的区块也进一步证明全网曾经接受了它。

当此情形,只要诚实的节点控制了网络,检验机制就是可靠的。但是,当全网被一个计算力占优的攻击者攻击时,将变得较为脆弱。因为网络节点能够自行确认交易的有效性,只要攻击者能够持续地保持计算力优势,简化的机制会被攻击者焊接的(fabricated)交易欺骗。那么一个可行的策略就是,只要他们发现了一个无效的区块,就立刻发出警报,收到警报的用户将立刻开始下载被警告有问题的区块或交易的完整信息,以便对信息的不一致进行判定。对于日常会发生大量收付的商业机构,可能仍会希望运行他们自己的完整节点,以保持较大的独立完全性和检验的快速性。

9. 价值的组合与分割(Combining and Splitting Value)
虽然可以单个单个地对电子货币进行处理,但是对于每一枚电子货币单独发起一次交易将是一种笨拙的办法。为了使得价值易于组合与分割,交易被设计为可以纳入多个输入和输出。一般而言是某次价值较大的前次交易构成的单一输入,或者由某几个价值较小的前次交易共同构成的并行输入,但是输出最多只有两个:一个用于支付,另一个用于找零(如有)。
需要指出的是,当一笔交易依赖于之前的多笔交易时,这些交易又各自依赖于多笔交易,但这并不存在任何问题。因为这个工作机制并不需要展开检验之前发生的所有交易历史。10. 隐私(Privacy)

传统的造币厂模型为交易的参与者提供了一定程度的隐私保护,因为试图向可信任的第三方索取交易信息是严格受限的。但是如果将交易信息向全网进行广播,就意味着这样的方法失效了。但是隐私依然可以得到保护:将公钥保持为匿名。公众得知的信息仅仅是有某个人将一定数量的货币发所给了另外一个人,但是难以将该交易同特定的人联系在一起,也就是说,公众难以确信,这些人究竟是谁。这同股票交易所发布的信息是类似的,股票交易发生的时间、交易量是记录在案且可供查询的,但是交易双方的身份信息却不予透露。
作为额外的预防措施,使用者可以让每次交易都生成一个新的地址,以确保这些交易不被追溯到一个共同的所有者。但是由于并行输入的存在,一定程度上的追溯还是不可避免的,因为并行输入表明这些货币都属于同一个所有者。此时的风险在于,如果某个人的某一个公钥被确认属于他,那么就可以追溯出此人的其它很多交易。11. 计算
设想如下场景:一个攻击者试图比诚实节点产生链条更快地制造替代性区块链。即便它达到了这一目的,但是整个系统也并非就此完全受制于攻击者的独断意志了,比方说凭空创造价值,或者掠夺本不属于攻击者的货币。这是因为节点将不会接受无效的交易,而诚实的节点永远不会接受一个包含了无效信息的区块。一个攻击者能做的,最多是更改他自己的交易信息,并试图拿回他刚刚付给别人的钱。
诚实链条和攻击者链条之间的竞赛,可以用二叉树随机漫步(Binomial Random Walk)来描述。成功事件定义为诚实链条延长了一个区块,使其领先性+1,而失败事件则是攻击者的链条被延长了一个区块,使得差距-1。
攻击者成功填补某一既定差距的可能性,可以近似地看做赌徒破产问题(Gambler’s Ruin problem)。假定一个赌徒拥有无限的透支信用,然后开始进行潜在次数为无穷的赌博,试图填补上自己的亏空。那么我们可以计算他填补上亏空的概率,也就是该攻击者赶上诚实链条,如下所示[8] :
假定p>q,那么攻击成功的概率就因为区块数的增长而呈现指数化下降。由于概率是攻击者的敌人,如果他不能幸运且快速地获得成功,那么他获得成功的机会随着时间的流逝就变得愈发渺茫。那么我们考虑一个收款人需要等待多长时间,才能足够确信付款人已经难以更改交易了。我们假设付款人是一个支付攻击者,希望让收款人在一段时间内相信他已经付过款了,然后立即将支付的款项重新支付给自己。虽然收款人届时会发现这一点,但为时已晚。
收款人生成了新的一对密钥组合,然后只预留一个较短的时间将公钥发送给付款人。这将可以防止以下情况:付款人预先准备好一个区块链然后持续地对此区块进行运算,直到运气让他的区块链超越了诚实链条,方才立即执行支付。当此情形,只要交易一旦发出,攻击者就开始秘密地准备一条包含了该交易替代版本的平行链条。
然后收款人将等待交易出现在首个区块中,然后在等到z个区块链接其后。此时,他仍然不能确切知道攻击者已经进展了多少个区块,但是假设诚实区块将耗费平均预期时间以产生一个区块,那么攻击者的潜在进展就是一个泊松分布,分布的期望值为:
当此情形,为了计算攻击者追赶上的概率,我们将攻击者取得进展区块数量的泊松分布的概率密度,乘以在该数量下攻击者依然能够追赶上的概率。

化为如下形式,避免对无限数列求和:

写为如下C语言代码:
```c
include
double AttackerSuccessProbability(double q, int z) { double p = 1.0 - q; double lambda = z * (q / p); double sum = 1.0; int i, k; for (k = 0; k <= z; k++) { double poisson = exp(-lambda); for (i = 1; i <= k; i++) poisson *= lambda / i; sum -= poisson * (1 - pow(q / p, z - k)); } return sum; }
```
对其进行运算,我们可以得到如下的概率结果,发现概率对z值呈指数下降。
当q=0.1时 z=0 P=1.0000000 z=1 P=0.2045873 z=2 P=0.0509779 z=3 P=0.0131722 z=4 P=0.0034552 z=5 P=0.0009137 z=6 P=0.0002428 z=7 P=0.0000647 z=8 P=0.0000173 z=9 P=0.0000046 z=10 P=0.0000012
当q=0.3时 z=0 P=1.0000000 z=5 P=0.1773523 z=10 P=0.0416605 z=15 P=0.0101008 z=20 P=0.0024804 z=25 P=0.0006132 z=30 P=0.0001522 z=35 P=0.0000379 z=40 P=0.0000095 z=45 P=0.0000024 z=50 P=0.0000006
求解令P<0.1%的z值:
为使P<0.001,则 q=0.10 z=5 q=0.15 z=8 q=0.20 z=11 q=0.25 z=15 q=0.30 z=24 q=0.35 z=41 q=0.40 z=89 q=0.45 z=340
12.结论
我们在此提出了一种不需要信用中介的电子支付系统。我们首先讨论了通常的电子货币的电子签名原理,虽然这种系统为所有权提供了强有力的控制,但是不足以防止双重支付。为了解决这个问题,我们提出了一种采用工作量证明机制的点对点网络来记录交易的公开信息,只要诚实的节点能够控制绝大多数的CPU计算能力,就能使得攻击者事实上难以改变交易记录。该网络的强健之处在于它结构上的简洁性。节点之间的工作大部分是彼此独立的,只需要很少的协同。每个节点都不需要明确自己的身份,由于交易信息的流动路径并无任何要求,所以只需要尽其最大努力传播即可。节点可以随时离开网络,而想重新加入网络也非常容易,因为只需要补充接收离开期间的工作量证明链条即可。节点通过自己的CPU计算力进行投票,表决他们对有效区块的确认,他们不断延长有效的区块链来表达自己的确认,并拒绝在无效的区块之后延长区块以表示拒绝。本框架包含了一个P2P电子货币系统所需要的全部规则和激励措施。
注释
-
W Dai(戴伟),a scheme for a group of untraceable digital pseudonyms to pay each other with money and to enforce contracts amongst themselves without outside help(一种能够借助电子假名在群体内部相互支付并迫使个体遵守规则且不需要外界协助的电子现金机制), “B-money”, http://www.weidai.com/bmoney.txt, 1998
-
H. Massias, X.S. Avila, and J.-J. Quisquater, “Design of a secure timestamping service with minimal trust requirements,”(在最小化信任的基础上设计一种时间戳服务器) In 20th Symposium on Information Theory in the Benelux, May 1999.
-
S. Haber, W.S. Stornetta, “How to time-stamp a digital document,” (怎样为电子文件添加时间戳)In Journal of Cryptology, vol 3, No.2, pages 99-111, 1991.
-
D. Bayer, S. Haber, W.S. Stornetta, “Improving the efficiency and reliability of digital time-stamping,”(提升电子时间戳的效率和可靠性) In Sequences II: Methods in Communication, Security and Computer Science, pages 329-334, 1993.
-
S. Haber, W.S. Stornetta, “Secure names for bit-strings,”(比特字串的安全命名) In Proceedings of the 4th ACM Conference on Computer and Communications Security, pages 28-35, April 1997. on Computer and Communications Security, pages 28-35, April 1997.
-
A. Back, “Hashcash – a denial of service counter-measure,”(哈希现金——拒绝服务式攻击的克制方法)http://www.hashcash.org/papers/hashcash.pdf, 2002.
-
R.C. Merkle, “Protocols for public key cryptosystems,” (公钥密码系统的协议)In Proc. 1980 Symposium on Security and Privacy, IEEE Computer Society, pages 122-133, April 1980.
- S. Haber, W.S. Stornetta, “Secure names for bit-strings,”(比特字串安全命名) In Proceedings of the 4th ACM Conference on Computer and Communications Security, pages 28-35, April 1997. on Computer and Communications Security, pages 28-35, April 1997.
-
H. Massias, X.S. Avila, and J.-J. Quisquater, “Design of a secure timestamping service with minimal trust requirements,”(在最小化信任的条件下设计一种时间戳服务器) In 20th Symposium on Information Theory in the Benelux, May 1999.
-
W. Feller, “An introduction to probability theory and its applications,” (概率学理论与应用导论)1957
-
-
 @ 34c0a532:5d3638e4
2023-02-28 11:20:59
@ 34c0a532:5d3638e4
2023-02-28 11:20:59The three most important writing lessons I’ve embraced and actually utilized in my work are the following:
Jim Butcher’s livejournal blog. https://jimbutcher.livejournal.com/
An amazing resource, every post is just a lesson in itself to understand storytelling. The irony is that I also bought his mentioned teacher’s book, the Formula something, but that didn’t help me at all. The way Jim distills it is perfect for me and I use it all the time.
Save the Cat It’s about screenwriting but I found it immensely helpful in creating the concepts and the needed neural pathways in my brain to comprehend and develop storytelling. I believe that the way to truly understand something is to learn the vocabulary and learn to notice the patterns in it, and Save the Cat does just that.
Get it here https://www.amazon.com/Save-Last-Book-Screenwriting-Youll/dp/1932907009?&linkCode=ll1&tag=mythogstudio-20&linkId=e614d30a9dede92f1cf631c01b151be1&language=en_US&ref_=as_li_ss_tl
 I’ve extended the beat sheet with the notes from the second book.
I’ve extended the beat sheet with the notes from the second book. The Blake Snyder Beat Sheet, extended by me. I used this a lot, just print one for each project you make, be it a short story, a script, a novel, whatever. Download the better quality image for printing here. https://i0.wp.com/georgesaoulidis.com/wp-content/uploads/2022/12/beatsheet-extended-edition_001.jpg I’ve written everything with the use of the beat sheet, and at some point I found myself jotting down less and less until someday I didn’t even need one to write a short story, it all just fell into place.
Brandon Sanderson’s Creative Writing Class
https://youtu.be/-6HOdHEeosc
These classes are like going to writing university, in essence. He explains so much stuff in such a wonderful way, it’s worth studying these videos again and again.
Bonus! Writing into the Dark. By Dean Wesley Smith, very good for advanced authors. Find it here https://www.amazon.com/Writing-into-Dark-without-Outline/dp/1561466336?&linkCode=ll1&tag=mythogstudio-20&linkId=3bbe241ad37eea8b4e185a6cd399b285&language=en_US&ref_=as_li_ss_tl
-
 @ 34c0a532:5d3638e4
2023-02-28 11:05:08
@ 34c0a532:5d3638e4
2023-02-28 11:05:08A short love story (with bitcoin) that I started to write for Valentine’s Day. To be continued, let me know if you like it.
Thalia didn’t like ruining people’s lives. It was simply her job, and somebody had to do it. She put on her pencil skirt outfit, smart enough to get some modicum of respect but simple enough for people not to start hitting on her. Hair pulled up in a tight ponytail, any tighter and her migraines would come back again.
She filled up her briefcase with the necessary paperwork, her legal tablet, she checked to make sure she had the documents downloaded and ready to be signed cryptographically, and her water bottle. She never went anywhere without her water bottle. No, it did not contain water, rather it was full of vodka. She got the usual disapproving glance from her assistant for it but she didn’t care. Instead of meeting at the office, she called her at home so she could drive her to Piraeus port.
“Goodmorning, Miss Thalia. Hope you’re feeling up to the trip?” Bekka said from the driver’s seat. Thalia placed her stuff at the back seat and sat there, like one does when getting a taxi. “Yes, I’m fine, thank you, Bekka. It’s rather late for a goodmorning anyway.” She straightened her shirt. “And yes, I’m feeling fine. It’s not like I’ll be staying there for too long, it’s just a couple of hours.”
“Of course.” Bekka drove, taking them into the street and headed towards Piraeus. “Your coffee is in the cup holder.” Thalia hadn’t noticed. She took a sip of her coffee from the takeaway cup. Lovely. “Did you check the weather? It is February, you know. Last week it was windy.” “Yes, I checked, it’s nice and breezy. Might get a bit chilly but that’s all. To be expected in Serifos, it’s all rather exposed there. I made sure to check because we went there with my boyfriend last Spring and we happened to have such a bad weather, wind was blasting for three days. We had to hunker down and wait inside the hotel until it stopped.” She bit her lip, glancing back at Thalia from the rearview mirror, “Not that he complained or anything.” Thalia shut her eyes in annoyance. She wasn’t jealous that her younger, prettier, livelier assistant was having a better love life than she did. No sir. Anyone could claim to a better love live than Thalia, since hers was practically nonexistent.
“He still has that friend of his I told you about, by the way?” Bekka glanced back as she drove on the National road heading south. “You remember, right? He’s thirty, your age, and he’s quite eligible if you ask me…” Thalia shut her eyes tight. She was beginning to get a migraine again. She took another sip of her coffee, some caffeine helped sometimes but only slightly. “Bekka,” she said calmly. “I told you, I don’t need you to set me up with a boyfriend.” “But Miss…”
“I said I don’t want it!” Thalia snapped at her. Bekka didn’t speak but the drive was too long for her to manage to finish it in silence. At some point after about five minutes she started talking again as if picking up the conversation from the last sentence. “It’s just that Valentine’s Day is today, Miss.” “So what?” “It’s the day for everyone to be in love?” She said it sweetly, and of course she did. The little fox was in love after all. “Love isn’t for everyone, Bekka.” “That’s such a sad thing to say, Miss. Of course love is for everyone. And you’re still able to find it.” “Allow me to rephrase that, then,” Thalia said with annoyance. “I’m not looking for love. Not today, not in the immediate future, so please stop trying to set me up with your boyfriend’s gym buddies.” Bekka bit her lip and glanced back. “You should see his abs.” “Then you take him then!” Thalia said, exasperated. “I already got my own and I’m very happy indeed. Tonight, we’ve got this entire thing planned for Valentine’s. We’re going to this hotel called Say, it’s very chic, quite expensive but it’s only for one night so what the hell, right? And Michael is picking me up in the afternoon, we’re going to go on a picnic together. He’ll give me flowers and chocolate. And then we’ll go back to the hotel, it has a jacuzzi in the suite. We’ll get all hot and bothered inside the jacuzzi, but not any oral action or anything yet, so we can pat each other with soft fluffy towels and then we’ll go to the bed…” “Bekka!” “What?” “No more details, please!” “Oh, boo! We’re both adults here.” “Yes, but we’re working.”
Bekka shrugged. “Yeah, but as soon as you come back and I come pick you up from the ferry, I’m clocking out. No more work calls, no emails, no texts. Just me and Michael, getting it on. Oh yeah…” Thalia shut her eyes and covered her face. Okay, she couldn’t blame her. Bekka was young, excitable, and in love. She should be bothered by listening to what sexy lovers night she had planned with her boyfriend. Who, by the way, she had met once and yes, he was fit and muscular and Thalia understood how Bekka wanted to climb that hunk and never get off. For a second, she started imagining how his gym buddy might have looked like. More of the same, right? Would he have a six pack? Thalia loved a six pack. Of course it had been years since she had any sex whatsoever, especially with work being so demanding all this time… What was she thinking? Thalia finished her coffee, she actually wanted to take a sip of her water bottle but she knew Bekka would notice so she didn’t, and looked outside the window. There wasn’t much to see on the drive, but once they got near the sea the view was much better. Then it became a mess again deeper inside Piraeus. It was just a busy port, full of cars and dirty buildings, really. The good parts were further on. Oh, how she could remember the giddiness of taking a ferry for a Greek island when she was younger. It was always exciting, both the trip and the destination. She had friends, and yes, boyfriends too. They took the ferry to some island and had so much fun, partying and drinking and eating lovely seafood and staying up all night long.
Right now the mere thought of staying up late gave her a hangover. The thirties came hard and fast at you before you realised what was happening. Bekka drove her to the right pier. “There it is, the Adamantios Korais. Make sure you grab everything you need and call me tonight to come pick you up.” “Oh no. You have a date all set up. Just enjoy it, I’ll take a taxi.” “Are you sure?” Bekka said, way to excited to get the hell out of there. “Yes! I have the app on my phone, remember? Now go. Have fun with your boyfriend, I’m sure he wouldn’t mind seeing you a few more hours today.” Bekka sniffled. “You’re the best, you know that?” Thalia shook her head. “Goodbye.” She grabbed her briefcase and her ticket. It felt weird not having luggage and getting onto a ferry, but she wasn’t going to stay in Serifos tonight. She was coming back straight away as soon as she delivered some papers.
The smell hit her like a truck. The port didn’t smell nice, exactly. It was full of that marine, fishy smell that sticks on the ropes they toss over the ships. It smelled like diesel, and people. Of which not many were around, since this was basically still winter. In the summer this place would be insane, people stepping over you to get through. Now it was busy, but spacious. The cars drove inside the belly of the ferryboat and Thalia walked on the ramp along with the other passengers. She felt weird once again not dragging a travel bag behind her but she didn’t really need anything more than her luggage and her phone.
The smells brought it all back. The summer trips they couldn’t afford, the friends, the smiles, under the sun and the sea. So nice. It was crazy to think that it was only ten years ago, even shorter than that. Back then she couldn’t imagine being shortlisted for becoming a department head at the Insolvency Service. She got on board, overwhelmed with memories and emotion, and embarked towards Serifos island.
https://georgesaoulidis.com/from-bit-to-heartbeat-2/
-
 @ 7fa56f5d:751ac194
2023-02-28 09:27:18
@ 7fa56f5d:751ac194
2023-02-28 09:27:18I developed an anonymous URL shortener service in Clojure. In this post I'll talk about how the implementation uses Redis for storage. The code is open source and you can find it on GitHub.
URL Shortener
A URL shortener is a web service that takes URLs and assigns them an alphanumeric ID. Visiting the URL associated with the ID redirects to the original. Short links look better for sharing them with the world.
A key-value store such as Redis fits our use case considering our storage needs: given a URL we need to store it associated with an alphanumeric ID and then want to be able to retrieve the original URL given the alphanumeric ID.
Redis
Redis is an in-memory data structure key-value store that can be used as a database, cache or message broker. The strings are the most fundamental Redis data type and the only one we will need.
Even though is a key-value store and doesn't have a query language, Redis supports many data types with a rich set of commands, transactions and LUA scripting.
Clients interact with a Redis server using a protocol called "REdis Serialization Protocol" (RESP): a simple, human-readable protocol with a request-response model. The redis-cli command-line client can be used to interact with a Redis server from the console.
$ redis-cli 127.0.0.1:6379> PING PONG 127.0.0.1:6379>For talking to Redis from Clojure we use the excellent Carmine library. It provides a
wcarmacro that acquires a connection to Redis and inside its body we can use functions from thetaoensso.carminenamespace that correspond to Redis commands.```clojure (ns shortener (:require [taoensso.carmine :as car :refer [wcar]]))
(def redis {:spec {:host "127.0.0.1"}})
(wcar redis (car/ping)) ;;=> "PONG" ```
ID generation
Redis allows to treat strings as 64-bit signed integers provided that the string can be represented as an integer. Commands like INCR can be used to manipulate keys containing numerical values.
Redis stores integers in their integer representation, so for string values that actually hold an integer, there is no overhead for storing the string representation of the integer.
Using
INCRon a key that doesn't exist sets it to 0 before performing the increment, so we can useINCRto treat a key as a counter.```clojure (defn unique-id [conn] (wcar conn (car/incr "unique-id.counter")))
(unique-id redis) ;;=> 1 (unique-id redis) ;;=> 2 (unique-id redis) ;;=> 3 ```
Since we want the IDs to be short, human-readable and URL friendly we'll use base-encoding. The most popular base encoding for URL strings is base 64, but encogio uses a custom alphabet which includes the letter Ñ.
```clojure (def alphabet "abcdefghijklmnñopqrstuvwxyzABCDEFGHIJKLMNÑOPQRSTUVWXYZ1234567890_-")
(def base (count alphabet)) ;;=> 66 ```
It has a couple more characters than the base-64 alphabet so we'll have to write the base encoding function for the custom alphabet.
```clojure (defn base-encode [input] (loop [n input res ""] (cond (zero? input) (subs alphabet 0 1) (zero? n) res :else (recur (quot n base) (str (nth alphabet (rem n base)) res)))))
(base-encode 0) ;;=> "a"
(base-encode 1) ;;=> "b"
(base-encode 9999999999999) ;;=> "b1-gJÑ4j" ```
Storing URLs
With the ID generation and encoding solved we can write the functions for storing and retrieving URLs. The
store-url!function takes a Redis connection and a URL, returning its ID after storing it in Redis.```clojure (def urls-prefix "url-shortener.id:")
(defn store-url! [conn url] (let [id (unique-id conn) id-key (base-encode id) redis-key (str urls-prefix id-key)] (wcar conn (car/set redis-key url)) id-key))
(store-url! redis "http://habla.news") ;;=> "b"
(store-url! redis "http://github.com/verbiricha/habla") ;;=> "c" ```
For retrieval we use the GET command, returning
nilwhen the given ID does exist.```clojure (defn get-url! [conn id] (let [redis-key (str urls-prefix id)] (wcar conn (car/get redis-key))))
(get-url! redis "b") ;;=> "http://habla.news"
(get-url! redis "c") ;;=> "http://github.com/verbiricha/habla"
(get-url! redis "d") ;;=> nil ```
Aliases
The basics for the URL shortener are in place but we haven't taken into account that we want users to be able to provide a custom alias. Since our IDs are already alphanumeric we'll treat aliases as IDs and use them as keys for storing aliased URLs.
Once a key in our URLs keyspace is picked we don't want to overwrite it so we have to make sure that we only write them once.
Atomic set
Redis supports running LUA scripts transactionally with the EVAL command so we can guarantee the atomicity of a set operation by doing it inside a LUA script.
Redis guarantees that a script is executed in an atomic way: no other script or Redis command will be executed while a script is being executed.
There are two types of arguments we pass to LUA scripts: key arguments (assumed to be used as Redis keys) and regular arguments. They are available in the
KEYSandARGVspecial variables respectively. Note that LUA uses 1-based indexing.The Redis EVAL command takes a LUA script, the number of key arguments and the script arguments and returns the result returned by the script. Here's a few examples of how we can use it from Clojure:
```clojure (wcar redis (car/eval "return {KEYS[1]};" 1 "a-key")) ;;=> ["a-key"]
(wcar redis (car/eval "return {KEYS[1], ARGV[1]};" 1 "a-key" 42)) ;;=> ["a-key" "42"] ```
Redis commands can be called from Lua using
redis.call.```clojure (wcar redis (car/eval "return redis.call('SET', KEYS[1], ARGV[1]);" 1 "a-key" 42)) ;;=> "OK"
(wcar redis (car/get "a-key")) ;;=> "42" ```
With that in mind we write a LUA script that will result in an error if the key we are trying to set already exists.
lua -- Receives a key (KEYS[1]) and a value (ARGV[1]) and atomically -- sets the key to value if it doesn't exist. -- -- Returns "OK" if successful, "duplicate key" if not. -- local exists = tonumber(redis.call("EXISTS", KEYS[1])); if exists == 0 then return redis.call("SET", KEYS[1], ARGV[1]); else return redis.status_reply("duplicate key"); end;Since we'll be using this script quite frequently, we'll use Carmine's eval* helper which optimistically tries the Redis EVALSHA command to save bandwidth.
```clojure (def atomic-set-lua " local exists = tonumber(redis.call('EXISTS', KEYS[1])); if exists == 0 then return redis.call('SET', KEYS[1], ARGV[1]); else return redis.status_reply('duplicate key'); end;")
(defn atomic-set! [conn k v] (let [set? (wcar conn (car/eval* atomic-set-lua 1 k v))] (if (= set? "OK") {:key k :value v} {:error :conflict}))) ```
When trying to set a key using the
atomic-set!function it will only be written if it doesn't exist already.```clojure (atomic-set! redis "write-once" 42) ;;=> {:key "write-once" :value 42}
(atomic-set! redis "write-once" 42) ;;=> {:error :conflict} ```
atomic-set!can be used now to support aliasing URLs.```clojure (defn alias-url! [conn url alias] (let [redis-key (str urls-prefix alias) result (atomic-set! conn redis-key url)] (when-not (:error result) alias)))
(get-url! redis "blog") ;;=> nil
(alias-url! redis "http://habla.news" "blog") ;;=> "blog"
(get-url! redis "blog") ;;=> "http://habla.news"
(alias-url! redis "http://habla.news" "blog") ;;=> nil ```
Finally the
store-url!function needs to useatomic-set!as well and try another autogenerated ID when running into a conflict.clojure (defn store-url! [conn url] (let [id (unique-id conn) id-key (base-encode id) redis-key (str urls-prefix id-key) result (atomic-set! conn redis-key url)] (if-not (:error result) id-key (recur conn url)))Conclusion
We have used #[4] and #[5] to implement the basis of an URL shortener service that supports both autogenerated IDs and user supplied aliases. In future posts we'll be looking at how to expose our URL shortener to the world through HTTP as well as protecting it from bad actors by rate limiting.
Happy hacking!
-
 @ b2953bbd:7141e701
2023-02-28 07:25:33
@ b2953bbd:7141e701
2023-02-28 07:25:33看完了,但是依然没有太看明白其中的核心价值,
写一个自己认知下的个人理解,纯属门外汉之言。 这篇文章分三部分理解 第一部分 从btc的区块链 没有其他智能合约的公链生态而对btc的区块链技术感到惋惜,也是 Ordinals NFT 技术产生的驱动力,而从稀缺性来研发了Ordinals的技术 个人理解:BTC区块链从诞生之日起,就没有要覆盖所有现实场景的宏伟目标,其最初的目的和技术来源仅定位于货币的固定发行与经济交易场景之中。 不太能理解 为什么 Ordinals 技术的发明者一定要让btc的区块链要实现原本由智能合约的公链技术发明的应用场景NFT上 这就相当于你让一个一直从事科研的科学家,强行让他去指挥打仗一样,不是说不能,而是这样做的意义是什么? NFT 非同质化代币(通证) 和BTC专注的数字化货币是两个不同的领域 第二部分 解释Ordinals的技术是如何利用BTC区块链上每个区块产生satoshi的顺序号和区块号来作为NFT稀缺性的源数据 个人理解:这里边用到了区块链中的两个技术,但将这两个技术含义强行定义成稀缺性然后利用其特点,去实现NFT非同质化的目的。这有些强行定义一样,你不能因为某两样物品具有的某类属性一样就去将其等价连接。这跟沙漠里两个相邻区域中的每一粒沙子都是不同的有区别么? 难道,将不同沙子组合排列然后赋予一个新组成就成了NFT??? 话说 沙子无论是保质期和单个沙粒的独特属性 应该比人类的存在时间还要长吧,更适合存储了 第三部分 延申如此技术实行对于BTC区块链以及矿工的有效经济行为收益 个人理解:闪电网络是基于BTC区块链的衍生,但用NFT和闪电网络来对比有些不太合适,闪电网络是基于btc创世之初即定义的交易场景的实现,而NFT所提供的技术从来不再BTC的技术涉及之内
说到最后:btc的诞生、发展从开始到现在乃至未来,其目的都是统一没有变革过,这不是技术的问题,因为已经有很多技术可以比btc技术更优越的实现btc的目的,但btc绝不单纯是一项技术而存在存活至今的 ,从这点技术人员一定要理解,技术 共识 pow 共同实现BTC的理念与价值 再度明确,对于以太坊ETH智能合约的发明,所有btc领域的人都不会否认其价值所在,其在智能合约上进行的应用开发,乃至替代BTC的尝试,我想也不会有人反对,但前提是btc从来不是一种单纯的技术 上帝的归上帝 凯撒的归凯撒 作为一项技术探索,Ordinals NFT没有任何问题,其在技术上的创新也值得肯定,但从NFT应用在btc链上的未来。个人确实不太看好,已经有了比较容易的智能合约NFT公链,为什么非要将NFT发行在btc链上呢? 是觉得山珍海味吃腻了 不够刺激 来btc链上忆苦思甜? 我不相信NFT的项目体验,在btc上能好过其他智能合约的公链 反人类的行为 为啥呢?????? 你如果连智能合约上的NFT都不相信其稀缺和存储了,还指望btc就能保证了? 稀缺和存储 的这些概念已经被NFT带偏了
原文:
一文说透Ordinals NFT(看到不错,正好解决了自己比特币NFT的一些盲区,特别搬运一下)
本文来自搬运 微博 原作者:委拉斯凯兹
Ordinals NFT现在在国外非常火,BTC链上现在充斥了各种小图片。但是国内对Ordinals介绍还很少,所以简单介绍一下Ordinals技术以及个人对稀缺性的一点思考。
首先说一下个人的结论:Oridinals技术开拓了BTC新的应用领域,是闪电网络之后又一个巨大的创新,对BTC具有重要意义。
在以太坊的NFT出现的时候,BTC是没有对应技术的。因为在layer 1,BTC的区块链上缺少一个唯一、不变的公开标记技术。区块号包含了多个交易,UTXO包含多个输入也会随着交易变化。所以当时的希望是寄托在layer 3的RGB和Taro协议上实现NFT。
但是Ordinals的发明者Casey Rodarmor,总结了过去BTC开发者的尝试,提出了Ordinals。什么是Ordinals呢?BTC上每个satoshi都是区块的第一个交易(coinbase transaction)创造出来的,所以实际上每一个satoshi天然就具备了一个顺序号,这个顺序号由区块号和这个satoshi被mined出来的顺序决定,而且由于BTC区块链的追溯性(每个satoshi一定可以反向追溯到coinbase交易)所以这个序号是不变的,这也是Ordinals的名字由来。
除了清晰的定义了每个satoshi的序号,Casey Rodarmor还提出了这个序号不是even的,有些序号本身就具备一定的稀缺性:每个区块的第一个satoshi就是这个区块的第0个satoshi;每隔2016个区块,挖矿难度会调整,难度调整后的第一个区块的第0个satoshi;每隔四年产出的新satoshi会减半,减半的第一个satoshi;每隔6次减半,难度调整和减半会重合,所以第一个satoshi也与众不同。简单的来说,Ordinals在satoshi的序号上发明了新的稀缺性,甚至提出了一套命名规范,给每个satoshi根据稀缺性取了名字。
Ordinals借助Segwit和Taproot,将一个satoshi和对应的内容inscription到区块的见证数据部分,因此Ordinals NFT是完全on chain的,而且每个区块容纳的NFT不能超过4M。(看到4M这个熟悉的数字了吧,当年BTCer和BCHer对于Segwit一个争论焦点即Segwit到底能够扩容到多大,实际上现在已经有矿工mine了接近4M的NFT)。
总结一下,Ordinals NFT的稀缺性来自三个方面:
- satoshi序号的稀缺性。
- 区块大小对能够inscription的NFT数量和大小的限制。
- NFT文化价值,版权,数量等的限制。
所以相对于以太坊的NFT稀缺性集中在第三个方面,Ordinals NFT增加了更多的稀缺性来源,而且是紧密的跟区块链绑定在一起的。
除了稀缺性,Ordinals NFT更加优越的地方还在于:
- Ordinals NFT在Taproot技术的帮助下,inscription跟BTC的一个普通交易非常类似,所以可以在不依赖第三方的情况下进行自由的交易、转移。甚至通过Taproot的script实现NFT的定时租借、多人拥有一个NFT。也就是说Ordinals NFT不需要以太坊NFT的授权过程,也不依赖合约内容,是完全自己掌控的NFT。
- Ordinals NFT现在是on chain的,但是以太坊的NFT是有的on chain,有的是保存在其他存储平台上的,需要自己来甄别。保存在其他平台意味着丢失的可能性。
- Ordinals NFT定义内容的时候是采用了类似HTML定义内容的方式,实际上用户完全可以自定义内容,包括文字、数据、视频、音频等,所以实际上应该称为digital artifact。
- 以太坊的NFT安全性是跟铸造合约高度绑定的,而Ordinals NFT的安全性是BTC本身来保证的。哪个更加安全就不言而喻了。
Ordinals NFT的缺点也很明显,inscription过程更复杂有可能失败,随着区块拥堵制造费用也会提升,而且NFT体积不能超过4M,实际目前一般推荐的大小是50K左右。
最后,做一下延展的思考。哈耶克当年提出计划经济不可行的一个观点是知识是分散在社会各处而且有时效性,所以是无法中心计划的。随着技术的进步,有人就提出利用大数据和超级计算机可以解决这个问题,实现计划经济。这里暂时不说通过超级计算机方法的可行性。实际上我个人认为,波普尔提出的计划经济不可行的观点更加难以反驳。波普尔认为世界就是不可知的,新的技术一旦发明出来,认知手段就会改变,人们认识的世界就可能发生巨大变化。新的技术会产生新的稀缺性,怎么能够通过事先计划来分配呢?而且,新技术的后果甚至可以和其发明初衷完全无关的。Ordinals NFT至少产生了两个对BTC影响深远的意外效果:
- 由于inscription需要追溯satoshi的序号,所以现在制造Ordinals NFT需要使用全节点,如果Ordinals NFT继续持续发展,很可能一劳永逸的解决一直让社区头痛的全节点数量问题,更好的实现去中心化。
- 丰富了矿工的收入来源,无论是出售稀缺satoshi和帮助铸造NFT都可以成为新的赚钱方式。在区块奖励不断减半后,提高矿工的积极性。
-
 @ 7f1e20f6:81ff2b37
2023-02-28 02:32:16
@ 7f1e20f6:81ff2b37
2023-02-28 02:32:16这是一个测试贴
测试一下这个blogstack博客的功能,以及markdown语法在nostr上的显示情况。
之前试用了几个类似的nostr博客网站,都觉得不是很满意。不是功能不全,就是不够稳定。
看看这个怎么样。
顺便试试markdown 语法。 -
 @ 9e5d086d:c650fd9a
2023-02-27 21:15:37
@ 9e5d086d:c650fd9a
2023-02-27 21:15:37Source: Buy NZ Made
Consumers are actively seeking products from companies that make an effort to reduce emissions and ethically manufacture goods, new research reveals.
The research, commissioned by Buy NZ Made, reveals 92 percent of New Zealanders believe sourcing ethically manufactured goods is important.
Executive Director Dane Ambler says the tide is turning on fast fashion and unsustainable manufacturing practices.
"Consumers are waking up to the amount of emissions that come with importing goods. They expect more responsibility from emitters, and care about the longevity and quality of their products.
"We are seeing a significant shift in consumer perception. Seventy-two percent of respondents see NZ Made goods as more environmentally-friendly and sustainable, and three quarters see NZ made goods as more ethically manufactured compared to offshore.
"New Zealand has carved out a niche for high-quality, sustainable products that stand the test of time. We know imports account for half of our carbon footprint. Our gross carbon dioxide emissions are mainly produced by transport and manufacturing industries and construction.
"Buying local is a way to significantly reduce our country’s overall footprint."
Sustainable Business Council Executive Director Mike Burrell says more and more we are seeing businesses shift their attitudes and business models to more sustainable and environmentally friendly practices.
"Not just because it’s the right thing to do, but because it makes good business sense to do so.
"We have moved into a new era where climate action and sustainable practices is the new business as usual - as both consumers and investors increasingly demand sustainably produced goods and services.
"The reality is those businesses who don’t make the shift to a more sustainable future risk losing their competitive advantage and being left behind."
Kind Face founder Chris Larcombe says the research proves New Zealanders are heading in the right direction, with decision making based on "values", rather than "value".
"We believe ethical and sustainable values should not only be inherent in the DNA of New Zealand businesses, but there needs to be a focus on being a 'better business' than previous generations.
"This means manufacturing in New Zealand from environmentally responsible materials, treating employees like family members, supporting local suppliers, supporting communities and most importantly being open, honest and transparent."
-
 @ 52bfb3cf:c8a952bb
2023-02-27 12:33:41
@ 52bfb3cf:c8a952bb
2023-02-27 12:33:41我好像在自己的 Profile 看不到 Tip 按钮。。 你们能看到吗?
-
 @ 8f69ac99:4f92f5fd
2023-02-27 12:28:10
@ 8f69ac99:4f92f5fd
2023-02-27 12:28:10Começaram a rolar os estímulos à economia na UE. Portugal já recebeu os primeiros €2 mil milhões dos €16 mil milhões que vai receber no total. Mas afinal, o que significa esse "dinheiro", para onde vai e o que é que significa realmente na economia?
O que é a inflação? Em termos gerais, o termo inflação é utilizado quando existe um aumento generalizado dos preços dos bens e serviços. O resultado dessa subida de preços, é que por exemplo, com uma nota de €20 se compra menos. Por outras palavras, €20 valem menos do que anteriormente.
O cálculo é feito utilizando um "cabaz" de artigos para representar os bens e serviços consumidos pelas famílias ao longo de um ano. Cada um dos produtos incluídos nesse "cabaz" tem um preço, que pode variar com o tempo. A taxa de inflação homóloga é o preço do cabaz completo num determinado mês comparado com o seu preço, no mesmo mês, um ano antes.
Uma das causas da inflação é o aumento da emissão de papel-moeda por um Governo, no nosso caso, como estamos na zona Euro, é a Europa quem decide e BCE que emite, para cobrir os gastos do Estado. Quando isso acontece, há um maior volume de dinheiro em circulação no mercado mas não houve criação de riqueza ou aumento de produção. Nestes casos, é exigida maior quantidade de dinheiro para adquirir a mesma quantidade de produtos, resultando em inflação. Como os salários dos trabalhadores não são reajustados mensalmente, o seu poder de compra vai diminuindo.
Após a emissão, ou mesmo do anúncio, de mais dinheiro a inflação não é reflectida de imediato. Leva tempo para o dinheiro entrar na a economia real. Os bancos e outras instituições financeiras são os primeiros beneficiários e, em seguida, investidores ricos capazes de aceder a facilidades de crédito adicionais. Estas empresas e indivíduos estão em posição privilegiada na medida em que podem canalizar toda essa liquidez extra em activos financeiros, muitas vezes comprando a preços baixos. Normalmente é nos mercados financeiros que se reflecte de imediato a inflação.
O Efeito Cantillon
Um banqueiro e filósofo do século XVIII chamado Richard Cantillon notou uma versão inicial deste fenómeno. No século XVIII, quanto mais perto estava do Rei e dos ricos, mais beneficiava — de poder comprar activos financeiros a preços baixos e depois ver esses preços inflacionar. Só mais tarde é que os efeitos apareceriam noutros sectores, e quanto mais longe se encontrava da fonte do dinheiro, mais prejudicado se ficava — através de preços mais elevados dos alimentos ou de salários relativos mais baixos.
No seu ensaio "Essai sur la nature du commerce en général", ensaio sobre teoria económica (aqui traduzido para ingês) Cantillon concordou que um aumento de dinheiro "duro" num estado (lembre-se que o ouro e a prata eram as moedas de eleição na época) provocará um aumento correspondente do consumo e isso irá gradualmente produzir aumentos de preços, mas ao contrário dos economistas antes dele, ele foi o primeiro a articular como aconteceu.
A observação geral de Cantillon, de que a impressão de dinheiro tem consequências distributais que operam através do sistema de preços, é conhecida como o "Efeito Cantillon". O dinheiro, por outras palavras, não é neutro. Aqueles que mais beneficiam com o aumento da oferta de dinheiro são os que têm acesso a crédito e activos, ou aqueles que fornecem produtos e serviços a quem tem:
"Se o aumento do dinheiro vivo vier das minas de ouro e prata dentro do Estado, o proprietário destas minas, os empresários, as fundições, as refinarias e todos os outros trabalhadores aumentarão as suas despesas proporcionalmente aos seus lucros. Suas famílias consumirão mais carne, vinho ou cerveja do que antes. Habituar-se-ão a usar roupas melhores, a ter linhos mais finos e a ter mais casas ornamentadas e outros bens desejáveis. Por conseguinte, darão emprego a vários artesãos que não tinham muito trabalho antes e que, pela mesma razão, aumentarão as suas despesas. Todo este aumento das despesas com carne, vinho, lã, etc, reduz necessariamente a percentagem de outros habitantes do Estado que não participam inicialmente na riqueza das minas em questão. O processo de negociação do mercado, com a procura de carne, vinho, lã, etc, mais forte do que o habitual, não deixará de aumentar os seus preços. Estes preços elevados incentivarão os agricultores a usar mais terras para produzir no ano seguinte, e esses mesmos agricultores lucrarão com o aumento dos preços e aumentarão as suas despesas com as suas famílias, como as outras."
Enquanto isso, aqueles que perdem mais são os que têm rendimentos fixos ou baixos salários, longe da oferta monetária:
"Aqueles que sofrerão com estes preços mais elevados e o aumento do consumo serão, em primeiro lugar, os proprietários, durante o período de arrendamento, depois os seus funcionários domésticos e todos os trabalhadores ou trabalhadores fixos que apoiam as suas famílias com um salário. Todos eles devem diminuir as suas despesas proporcionalmente ao novo consumo, o que obrigará um grande número deles a emigrar e a procurar viver noutro local. Os proprietários vão dispensar muitos deles, e o resto exigirá um aumento salarial para viver como antes. É desta forma que um aumento considerável do dinheiro das minas aumenta o consumo e, ao diminuir o número de habitantes, uma maior despesa resulta dos que permanecem."
Eventualmente, a impressão de dinheiro apodrece o sistema de dentro para fora, agindo para reduzir a capacidade produtiva da economia:
"Se o dinheiro continuar a ser extraído das minas, a abundância de dinheiro aumentará todos os preços a tal ponto que não só os proprietários aumentarão consideravelmente as suas rendas quando os contratos de arrendamento expirarem e retomarem o seu antigo estilo de vida, aumentando os salários dos seus empregados proporcionalmente, mas os artesãos e trabalhadores aumentarão os preços dos artigos que produzem de tal forma que haverá ganhos consideráveis na compra de produtos estrangeiros, que os fabricam muito mais baratos. Isto irá, naturalmente, incentivar várias pessoas a importar produtos a preços mais baixos de fábricas estrangeiras, o que arruinará gradualmente os artesãos e os fabricantes do Estado que não poderão sustentar-se trabalhando a taxas tão baixas devido ao elevado custo de vida."
Ao invés de um fenómeno temporário, o aumento da oferta monetária tem consequências duradouras:
"Quando a sobreabundância de dinheiro das minas diminuiu o número de habitantes num Estado, acostumou aqueles que permanecem a despesas excessivas, elevou os preços dos produtos agrícolas e os salários do trabalho para níveis elevados, e arruinou o fabrico do Estado através da compra de produtos estrangeiros por proprietários e trabalhadores de minas, o dinheiro produzido pelas minas irá necessariamente para o estrangeiro para pagar as importações. Isto irá gradualmente empobrecer o Estado e torná-lo, de certa forma, dependente de estrangeiros a quem é obrigado a enviar dinheiro todos os anos à medida que é extraído das minas. A grande circulação de dinheiro, que foi generalizada no início, cessa; A pobreza e a miséria seguem-se e a exploração das minas parece ser apenas vantajosa para aqueles que nelas trabalham e para os estrangeiros que assim lucram."
De volta à impressão de dinheiro por parte do BCE e à inflação que insistem em dizer que não existe, ou que é saudável numa economia, Cantillon teria argumentado que todo esse dinheiro extra resultaria eventualmente em preços mais altos, mas que não seria necessariamente nos preços nas lojas onde se veriam as evidências, ou que seria proporcional ao aumento da oferta. Tudo depende de quem recebe o dinheiro primeiro, e o que querem comprar:
"Concluo, com tudo isto, que, duplicando a quantidade de dinheiro num Estado, os preços dos produtos e das mercadorias nem sempre são duplicados. O rio, que corre e serpenteia no seu caminho, não fluirá com o dobro da velocidade quando a quantidade de água é duplicada. A variação dos preços relativos, introduzida pelo aumento da quantidade de dinheiro no Estado, dependerá da forma como este dinheiro é direccionado para o consumo e a circulação. Não importa quem obtenha o novo dinheiro, irá naturalmente aumentar o consumo. No entanto, este consumo será maior ou menor, de acordo com as circunstâncias. Será mais ou menos direcionado para certos tipos de commodities ou mercadorias, de acordo com o acórdão daqueles que adquirem o dinheiro"
Em vez de barões nobres serem os principais beneficiários de novos fornecimentos de ouro, hoje os mais próximos da sede do poder monetário são os bancos, os fundos de retorno absoluto e outros investidores ricos. Como no tempo de Cantillon, isto significa que os mais próximos do poder podem comprar activos a baixo custo antes da população em geral. A população em geral fica piorar, quer por ter de comprar activos sobrevalorizados, quer por ver a sua moeda desvalorizada, quer mesmo por ambos.
Voltando aos dias de hoje, a escala da expansão da oferta monetária não tem precedentes. Tanto na Europa, como nos EUA, a impressão de dinheiro tomou proporções históricas.
Este é o gráfico M2 da Zona Euro, o indicador da quantidade de dinheiro em circulação:
E nos EUA:
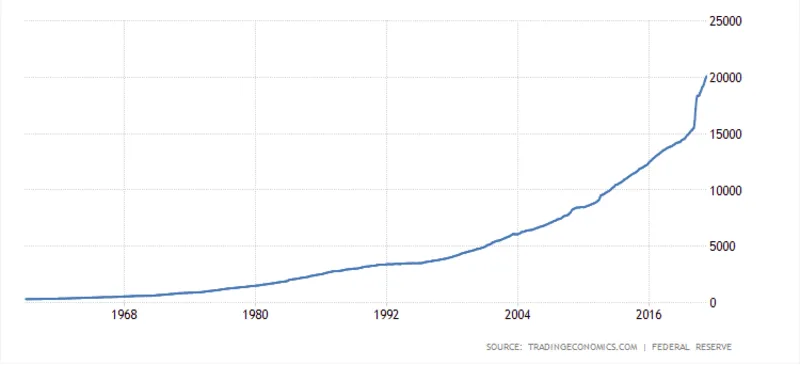
E novos pacotes de estímulos estão já a ser equacionados, quer pela Europa quer pelos Estados Unidos.
As coisas podem acontecer rapidamente, mas só são visíveis na plenitude do tempo. Embora os mercados bolsistas (particularmente as acções tecnológicas) tenham beneficiado das grandes injecções dos bancos centrais, o ouro e outras reservas de valor (por exemplo, a bitcoin) ganharam ainda mais.
O que tem Bitcoin a ver com isto?
A bitcoin permite, tal como o ouro (mas melhor, mais rápido e mais liquido), preservar o fruto do seu trabalho (o dinheiro) no tempo. Históricamente a bitcoin cresce, em média cerca de 200% ao ano.
A evolução do preço, a preto, mostra que embora a bitcoin seja volátil num horizonte temporal curto, a longo prazo é o melhor investimento e reserva de valor onde pode refugiar-se da inflação!
-
 @ 52bfb3cf:c8a952bb
2023-02-27 12:15:17
@ 52bfb3cf:c8a952bb
2023-02-27 12:15:17- :tick: markdown support *
-
 @ 077174d5:5168e3f8
2023-02-27 12:09:36
@ 077174d5:5168e3f8
2023-02-27 12:09:36catcatcat

-
 @ b2953bbd:7141e701
2023-02-27 11:06:00
@ b2953bbd:7141e701
2023-02-27 11:06:00 -
 @ b7ccd493:6ba2260f
2023-02-27 05:09:51
@ b7ccd493:6ba2260f
2023-02-27 05:09:51新东西,要分享!
-
 @ b2953bbd:7141e701
2023-02-27 03:36:13
@ b2953bbd:7141e701
2023-02-27 03:36:13Markdown support so
good -
 @ d0f3314a:bdae2704
2023-02-26 15:47:23
@ d0f3314a:bdae2704
2023-02-26 15:47:23title
- this is just a test
- really is
testing images
svg
png with tranparency

-
 @ 3bf0c63f:aefa459d
2023-02-26 13:33:08
@ 3bf0c63f:aefa459d
2023-02-26 13:33:08Web browsers today serve 3 different use cases:
- Viewing content produced by others.
- Running complex programs locally and interact with a server -- or not -- only very lightly to receive or send inputs or outputs to or from these programs.
- A mix of the two things above.
On category 1 we can include all text that exists on the internet, blogs, articles, news -- but also pictures, video, and even livestreamed video.
On category 2 we can put all "web apps" that talk to an API, like, for example, Google Sheets, Figma, Discord -- but also web-based Nostr clients.
On category 3 there are all the cool little appy things that mix interaction with content, interactive visualizations, comment boxes, and basically everything else.
It would be a good thing if browsers could be split into 3 different products instead of trying to make them be the best at these 3 different use cases.
The first category is much better served by a somewhat static content reader. Gemini is an attempt at that, but it is probably too limited for its desired purposes. Meanwhile Nostr -- and native Nostr clients, could very well fill in most of the spaces of category 1. Maybe that will end up happening. This exact same article is a step on that direction.
Category 2 apps would be much better if they were written as native desktop apps directly, and users were educated to learn how to download and install apps, instead of expecting everything to run in their browser. Experience shows that people do prefer a nice lean fast desktop app than its "web" counterpart,
 so for the small amount of apps that are expected to run mostly locally, this would be a no-brainer pick. It just needs a shift in the mentality.
so for the small amount of apps that are expected to run mostly locally, this would be a no-brainer pick. It just needs a shift in the mentality.Category 3 is the hardest one. Its existence is probably the root cause of the web having become what it is now, and it is also the hardest element to replace on the equation. I imagine that the solution will be a combination of the following:
- To have people install a small VM specialized in running efficient bytecode, for example, WASM, and make it seriously well-sandboxed while at the same time giving it much better access to the desktop than current web apps have. This should serve as incentive for most of these micro-webapps to switch.
- To standardize the ability to interact in standardized ways with mostly static content from inside native (Nostr?) apps designed for browsing these kinds of content -- so the solution to 1 encompasses part of 3 too.
-
 @ 220522c2:61e18cb4
2023-02-26 12:24:14
@ 220522c2:61e18cb4
2023-02-26 12:24:14In order to maintain consistency and ensure proper functioning of the system, a standard protocol for communication needs to be defined. This is where the Nostr Implementation Possibilities (NIPs) come in. In this article, we will focus on the basics of the event described in NIP-01.
Events
The only object type that exists is the event. Each event has a unique ID, public key, creation timestamp, kind, tags, content, and signature. When you are interacting with the protocol whether posting to or reading from relays (we'll talk more about relays in the next article) you will be posting or reading some variant of the following object:
json { "id": <32-bytes lowercase hex-encoded sha256 of the the serialized event data> "pubkey": <32-bytes lowercase hex-encoded public key of the event creator>, "created_at": <unix timestamp in seconds>, "kind": <integer>, "tags": [ ["e", <32-bytes hex of the id of another event>, <recommended relay URL>], ["p", <32-bytes hex of the key>, <recommended relay URL>], ... // other kinds of tags may be included later ], "content": <arbitrary string>, "sig": <64-bytes hex of the signature of the sha256 hash of the serialized event data, which is the same as the "id" field> }In the previous article I showed you how to setup a typescript project and get started with
nostr-toolsto generate a public and private keypair. The public key that you generated will be used as the public key in the aforementioned event. All of the code from the previous tutorial can be found on github. So either clone this repo or pick up where you left off.Let's start by creating a file called
02-event.ts.sh touch 02-event.tsStep 1: Import Functions
Open the file with a text editor and import the following functions from
nostr-tools:ts import { validateEvent, verifySignature, signEvent, getEventHash, generatePrivateKey, getPublicKey, Event } from 'nostr-tools'Step 2: Generate Private & Public Keys
Next we'll generate a private key and derive a public key used in the event object.
ts const privateKey = generatePrivateKey(); const publicKey = getPublicKey(privateKey);Step 3: Create Event Object
We'll create a basic event which will initially include 5 of the 7 fields. We can't include the id yet since it will be a hash based on the first 5 fields in the object. Similarly after we calculate and add the id field we can update the event by adding the signature.
ts let event: Event = { id: "", kind: 1, created_at: Math.floor(Date.now() / 1000), tags: [ ["t", "some tag"], ["t", "another tag"] ], content: 'hello', pubkey: publicKey, sig: "", }This creates a new Nostr event object with the following properties:
-
kind: The kind of event. In this case, it is set to 1.
-
created_at: The timestamp of when the event was created. It is set to the current Unix timestamp using Math.floor(Date.now() / 1000).
-
tags: An array of tags associated with the event.
-
content: The content of the event. In this case, it is set to the string "hello".
-
pubkey: The public key of the event creator. It is set to the public key generated earlier.
Step 4: Calculate the ID & Signature of the Event
ts event.id = getEventHash(event) event.sig = signEvent(event, privateKey)This calculates the ID and signature of the event using the
getEventHashandsignEventfunctions from 'nostr-tools'. The ID is added to the event object as a new property called id, and the signature is added as a new property called sig. Notice how thesignEventfunction takes theeventandprivateKeyas arguments. This is because the private key is used to sign the event which proves it came from the public key derived from the private key.Step 5: Validate & Verify the Signature
ts let ok = validateEvent(event) let veryOk = verifySignature(event)You can easily verify the validity of the event using the validateEvent() and verifySignature() functions. If the event is valid, ok will be set to true. If the signature is valid, veryOk will be set to true.
Step 6: Log the Event
ts console.log(event)The final code should look like the following:
```ts import { validateEvent, verifySignature, signEvent, getEventHash, generatePrivateKey, getPublicKey, Event, } from "nostr-tools";
const privateKey = generatePrivateKey(); const publicKey = getPublicKey(privateKey);
let event: Event = { id: "", kind: 1, created_at: Math.floor(Date.now() / 1000), tags: [ ["t", "some tag"], ["t", "another tag"], ], content: "hello", pubkey: publicKey, sig: "", };
event.id = getEventHash(event); event.sig = signEvent(event, privateKey);
let ok = validateEvent(event); let veryOk = verifySignature(event);
console.log(event); ```
Step 7: Run the Code
Now we can build and run our code:
sh npm run build node dist/02-event.jsYou should see an output similar to:
json { id: '968c36698d0b8cd8c18be008f3c55e1bd4a1059dc93319c90f143932f6c7a864', kind: 1, created_at: 1677411967, tags: [ [ 't', 'some tag' ], [ 't', 'another tag' ] ], content: 'hello', pubkey: 'a7d96cc172ec06101592ca17187dfcdf39eb8295a4c2508b293ddc1e634b5773', sig: '146ff3afafa9d04408a1ce9d374986deb0a664fe664a646dd999de1b6db885b51d5d22ba6e350131aba7fc0b17b9acfaa4af8b4ff316556e6efd4 8c364d522e7' }Conclusion
In summary, we created a new Nostr event object with some sample data, calculated the ID and signature of the event, and verified that the event is valid. In the next article we'll talk about subscribing and posting events to relays.
-
-
 @ c47c45ba:ea0cd6db
2023-02-26 11:20:00
@ c47c45ba:ea0cd6db
2023-02-26 11:20:00You'd be surprised at the raw amount of crypto content I consume on my insatiable and voracious quest to synthesize all sentiment within this ecosystem
From highbrow to lowbrow, and everything in the mid
-
 @ 75bf2353:e1bfa895
2023-02-26 01:41:53
@ 75bf2353:e1bfa895
2023-02-26 01:41:53Leaving YouTube

Leaving YouTube
I had some misgivings about starting a YouTube channel. I've been working on becoming self sovereign. I only started a YouTube because that's where everybody goes to see videos. I tried making a few PeerTube videos before, but got discouraged because only like 2 or 3 people watched them. Maybe those videos suck, but at least I didn't need to give anyone my phone-dentity or non-Google email address.
I also want to make videos using the Value 4 Value Model. That model is not just about sats. It's also about time. The people who translate Gigi's articles are the unsung heros of bitcoin content creators. Think about how important it is to have articles translated into several languages to help facilitate the adoption of a GLOBAL FINANCIAL NETWORK. It is also important to spread the message of what bitcoin is to people too. Why not just ask people to contribute a few miliseconds of their time to share it on Nostr and social credit media.(ht/ gsovereignty).
We can't just rely on The Great Firewall of Google Algorithms to advocate for freedom money. I don't want to verify my identity again just because I use a VPN. Privacy is not a crime. As an American I was once protected by the fourth amendment. that is no longer the case. I must protect my privacy myself. I don't have perfect privacy yet, but it's a goal I am working towards.
PeerTube is one step closer to that goal. I don't want to rely on YouTube. YouTube can shut down my message if I say the wrong thing or break the speech laws of some nation-state I don't pay taxes to.
So I'm migrating my videos to PeerTube.
Let me know if you are interested in me making videos about setting up Peertube.
What other videos would you like to see?
BloggingBitcoin

-
 @ 7ecd3fe6:6b52f30d
2023-02-25 09:40:04
@ 7ecd3fe6:6b52f30d
2023-02-25 09:40:04Ordinals have kicked up quite the argument. One that only seems to escalate with the number of inscriptions added to the chain and the amount of bitcoin flowing into the trade of ordinals.
While there are pros and cons to ordinals and you can pick the side you wish to be on, there is no denying that there will be plenty of bag holders, and scams that will come from this.
Just because you're trying something on bitcoin doesn't mean it will be any better. That behavior, culture, and scams will be moved over from chains like ETH and Solana, of that I am sure.
Ordinals are not for the ordinary degen
Ordinals are a bit of a hack to put it lightly and there aren't really user-friendly tools to play around with it, this could be a feature or a bug depending on how you think about it. If it's hard to do no one will use it, those that do, are easy to scam and might leave the ecosystem.
Ordinals are not like NFT tokens on smart contract chains that are easy to identify and handle in your metamask wallet or Trust wallet, you can see it on chain with your 3rd party block explorer since you don't have a node and you trust minting services and your wallet to show you its there.
There are marketplaces that support the token standard, and even then people fuck that up too, and burn their NFTs or lose their private keys or sign it over to scam contracts because they just click and sign.
Ordinals is a whole other ball game of complications that I won't even go into but know that there aren't wallets that really support it and if you haven't done coin control and UTXO labeling before, you're in for a bad time managing your inscriptions.
Yes, there are wallets trying to support ordinals like Xverse.app but that doesn't mean that people aren't going to trust 3rd parties when using this software.
pov: you’re trying to understand bitcoin ordinals @nftnow pic.twitter.com/bvUaFS1WpC
— kmoney (@kmoney_69) February 16, 2023Inscriptions are drama-filled
If you're going to give the internet the ability to upload images somewhere without the ability to monitor or censor them then it's only a matter of time before someone pushes the boundaries.
Porn was naturally going to find it's way onto the chain and sure there are a few bobs, vegane and pepes sitting on bitcoin, the troll was not enough and ordinals eventually saw its first shock porn gaping butthole, which had to be removed from sites pulling ordinal feeds, but remains on the blockchain.
Ordinals can be ported
Ordinals are not a protocol that applies only to the bitcoin blockchain but similarly, structured chains can run the same protocol. We've already seen the project ported over to one of the OG fork affinity scams of bitcoin, Litecoin, as they desperately try to remain relevant and jump on a bitcoin hype train once again.
Remember when they said the Litecoin Lightning network was going to be a thing? Lol well, Litecoin Ordinals are here.
While I get that inscribing on bitcoin and using its precious block space is the appeal, eventually you're going to run out of people who are willing to pay these premiums and want cheaper transactions, we saw this with Eth and how NFTs moved to other shitcoin chains like Tron and Solana.
Lonely Liquid might offer a home
Eventually, we could see this move to bitcoin what chain do you think mimics bitcoin and offers plenty of block space, clearing times, and cheap transactions along with confidential transactions?
Well the Liquid Network, of course, is a project that has been dying to have some sort of use case, should federation members be pamping Ordinals on their chain instead? Could be worth a shot, if the market is keen to migrate to a faster and cheaper solution.
Liquid also has its own token minting protocol in AMP and NFT projects and marketplaces be it not very popular, so the migration sense.

In theory, ordinals could even make their way to a chain like dogecoin, and personally, I think that would make a better home for the project than bitcoin.
Stacks of simping for inscriptions
If there is one section of the "bitcoin" community that has openly jumped on the inscriptions bandwagon then it's anyone with a .btc handle on Twitter.
The stacks guys and girls have been in full swing trying to sucker in the NFT community wanting ordinals while pumping their own coin and NFT projects. Their shilling has been somewhat successful, considering 50% rally in Stacks Network's STX token earlier this week.
Clearly shitcoiners who have never paid attention to bitcoin but want to collect NFTs have came into ordinals, and been filtered into stacks to buy the native token and perhaps NFTs on the stacks chain.

Side note: This shitcoin is down 80% from its ATH in any case.
Dismissing bitcoin
Bitcoin has long been considered a high-risk investment that many feel is not reliable enough for a place in their portfolio. While bitcoin certainly has its share of risk, its potential for growth has always been the draw card for investors looking for a play with considerable upside as they are starved for returns in traditional markets.
Bitcoin has proven to be an excellent choice for those willing to accept it, so long as they understand the risks and can be used as a hedge in a well-diversified portfolio. While plebs and maxis will collect these sats regardless, projects like Ordinals can be seen as a deterrent to institutional investors.
It creates speculation and short-term hype cycles, that distract people and in doing so create uncertainty tied to the network. If you're trying to promote a bitcoin investment strategy to your company or clients and they see monkey jpegs on bitcoin trading for 6BTC then it's easy to see why people would use this as a way to dismiss it as a serious investment option.
Investing in Bitcoin requires knowledge and caution, and inscriptions only seem to muddy the waters and lump bitcoin into a category many have been trying to distance bitcoin from for years.
So what's your take?
Is all use for bitcoin good for bitcoin? Is this just a hype cycle? Does this distraction allow for plebs to stack while serious money/smart money stays on the sidelines not knowing what to make of all this? Will the ordinals bubble burst sooner or later?
Sources:
- https://www.forbes.com/sites/leeorshimron/2023/02/11/nfts-are-bloating-bitcoin-creating-risks-and-opportunities-for-crypto-investors/?sh=6402c54f7d77
- https://nftnow.com/features/how-ordinals-fractured-the-bitcoin-community-and-why-it-was-necessary/
- https://www.coindesk.com/consensus-magazine/2023/02/17/bitcoin-ordinals-can-lift-the-entire-crypto-ecosystem/
- https://www.coindesk.com/business/2023/02/22/ordinals-nfts-can-make-stacks-stx-a-multi-billion-dollar-token-matrixport/
-
 @ d7073b15:64f356c4
2023-02-24 21:45:00
@ d7073b15:64f356c4
2023-02-24 21:45:00So habla.news brings long form blog posts, like substack or medium, to nostr.
You can use markdown to format the text.
The editor shows a live preview of the markdown formatted text, which is pretty cool.
You can add a title, image, slug and summary to your blog post.
Tbh I don't know what slug is for. Is it like a keyword or hashtag for your blog post?
-
 @ 746a245a:7a8d8b34
2023-02-24 09:37:44
@ 746a245a:7a8d8b34
2023-02-24 09:37:44Hello, i am a test post =)
-
 @ 220522c2:61e18cb4
2023-02-24 08:08:24
@ 220522c2:61e18cb4
2023-02-24 08:08:24In this tutorial, you will learn how to create a new node project with TypeScript and generate a public-private keypair using the
nostr-toolsmodule. This tutorial assumes that you have node and npm installed on your system. We will focus a lot on just setting up the project in this article, future tutorials will focus more on working with nostr using thenostr-toolslibrary. The code can be found here.Step 1: Create a New Node Project
To create a new node project, open your terminal and navigate to the directory where you want to create the project. Then run the following commands:
sh mkdir nostr-tutorial cd nostr-tutorial npm init -yThis will create a new directory called nostr-tutorial with a
package.jsonfile.Step 2: Install the Required Dependencies
Next, we need to install the dependencies required for this project. We will use the
nostr-toolsmodule to generate keys and the typescript module to compile our TypeScript code.sh npm install nostr-tools typescript --save-devThis will install the
nostr-toolsandtypescriptmodules as dev dependencies in your project.Step 3: Create a TypeScript Configuration File
We need to create a TypeScript configuration file to specify the TypeScript compiler options for our project.
sh touch tsconfig.jsonIn the root of your project directory, create a new file called
tsconfig.jsonand add the following code:json { "compilerOptions": { "target": "es2018", "module": "commonjs", "outDir": "./dist", "strict": true, "esModuleInterop": true }, "include": [ "." ] }This is a pretty basic TypeScript config, you can read more about all of the options here: tsconfig reference
Step 4: Create a TypeScript File
In the root of your project directory, create a new TypeScript file called
keys.tsand add the following code:```typescript import { generatePrivateKey, getPublicKey } from 'nostr-tools';
const privateKey = generatePrivateKey(); const publicKey = getPublicKey(privateKey);
console.log('Private key:', privateKey); console.log('Public key:', publicKey); ```
We will introduce two functions here,
generatePrivateKeyandgetPublicKey. We will first need to generate a private key and derive our public key from that value. Both values will be 32-bytes lowercase hex-encoded.Public-private key pairs are a fundamental aspect of modern cryptography and are used to provide secure communication and data exchange over the internet. In future tutorials we'll see how we can use the private key to sign events, use bech32 encoding (so we can tell them apart) and how properly secure your private key. The encodings are done according to the Schnorr signatures standard for the curve secp256k1.
Step 5: Add a Build Script
To compile our TypeScript code to JavaScript, we need to add a build script to our
package.jsonfile. Open thepackage.jsonfile in your code editor and add the following script:json { "scripts": { "build": "tsc" } }This script runs the TypeScript compiler (tsc) to compile your TypeScript code to JavaScript.
Step 6: Build and Run the Project
Now we can build and run our code:
sh npm run build node dist/keys.jsThis will compile the TypeScript code to JavaScript and run the file using node. The private and public keys will be logged to the console.
Conclusion
In this tutorial, you learned how to create a new node project with TypeScript and how to generate keys using the
nostr-toolslibrary. This will be the first of a series of articles explaining nostr from here I recommend the following:-
Checkout nostr.com
-
Read about Nostr Implementation Possibilites NIPs here
-
Install a browser extension like alby (also lightning wallet) or nos2x
-
Try out some clients like: blogstack.io, snort.social, notebin.org
-
You can find more clients, libraries and additional tools over at awesome nostr
-
-
 @ 75bf2353:e1bfa895
2023-02-23 20:24:16
@ 75bf2353:e1bfa895
2023-02-23 20:24:16Blogging Nostr!
Habla is a new nostr native blogging platform. It is the second one I have found. I'm, writing this as a test, but so fair I have noticed my markdown syntax is not being rendered yet. On the other hand, I also seem to be able to see my blogstack post on Habla as well. This is why it's a test. I'm still trying to wrap my head around how this all works.
I've been writing a blog about how I use bitcoin since April on a platform namedtw Ghost under a pseudonym. I wrote on that platform for the following reasons:
-
I want to be a writer
-
I spend most of my waking hours thinking about bitcoin.
-
Marty Bent uses Ghost and had this paywall I thought was really cool at the time.
Marty's paywall is actually kind a neat, Instead of asking his readers to pay an annual subscription fee like the New York Times, You could just pay 50 cents per article. This is much better than the New York Times Paywall. When I first heard of it, I thought writers could only get paid on the Internet with a paywall or ads. The mechanics of the system did not leave many options. Lightning addresses worked, but most people never heard of them and even most Bitcoiners didn't use them. Yalls had a paywall, but the UX wasn't great. I first thought of starting a blog because of yalls. I thought I could do magic tricks over video for tips, like buskers in Vegas, but on the Internet. Then I thought, I'm not that good at magic and I don't feel comfortable throwing my face out there like a whore on the Internet (No disrespect to sex workers, but I doubt anyone would pay for my sex services and my wife would not approve.) I also have a degree in creative writing, but I'm a bit rusty. The lightning network got me interested in writing again.
It's what prompted me to run my own lightning node in the first place. I think this was back in 2018 or 2019. At the time, I tried running Pierre Rochard's lightning node, but didn't have the technical chops to pull it off on my old Windows laptop. It might have worked if I knew that I needed to plug the damn thing into an Ethernet cable to download the bitcoin blockchain.(We didn't use the term time chain in those days).
His paywall was an order of magnitude better than running my own node to accept tips on yalls.org, so I started my blog on ghost with the intention of using his paywall software.
I spun up a virtual private server on Bitlaunch.
I installed Yunohost because it was easy to set up Ghost.
Now Marty finally launched his service. If you like this model, you can use it for charges 10 bucks a month.
For the record, I really like Marty. I listen to Rabbit Hole Recap every week. I'm not trying to ruffle any feathers, or shit on his side project, but @dergigi convinced that the paywall model will soon go the way of the doorstep delivered newspaper. If you don't have time to read or listen to that entire article, please listen to this 30 second clip of the Bitcoin.Review podcast created by Oscar Merry.
Blogs Can Be Nostr Native
There's no reason to spin up a server on a VPS to start a blog anymore. No reason to host it on a Raspberry Pi. You don't need to buy a shared hosting account. You don't need to install ruby, gem or jekyll to host it on Github. You don't even need to buy a domain, although you might want to buy one for a DIY Nip 05 verification. Hopefully, in the not too distant future, you won't even need Github. Habla.news is a Medium alternative, but there's no reason why we couldn't have a Github alternative. We're just waiting on someone to build it.
The reason I find this value 4 value model built on Nostr so exciting now is because it is now trivial for those who produce value to receive value and trivial for those who cherish valuable content to send value to those who produce it.
Why spend the time setting up ghost or pay a fee to accept lightning payments or a ghost account? --*Especially if you are writing a blog about bitcoin.
I like the idea of charging for services, but paywalls just don't jive with the old walled garden model anymore.
Nostr is censorship resistant. Anyone can create a nostr key.
Some freaks say it's not normie ready, but it is much easier to create a private key than create a blog using the aforementioned options. I look forward to the day when we see more no-coiners witnessing how trivial it is to send value over the Internet. @TheGuySwann wrote a great post about how Facebook spent years developing their shitcoin, only to get shut down by congress.
Paywalls Not Required
You couldn't accept native bitcoin on any other platforms until now. Now plebs are zapping each other left and right.
In the value 4 value model, the zapper sets the value on the article. The paywall sets a price on reading the full article.
-
We don't need paywalls anymore.
-
I don't need to send you spam .
-
If you want to read my blog, just follow me on Nostr.
-
We don't need to rely on digital overlords to create content.
-
We don't need ads to monetize content.
Ads suck.
This is pure vida.
Nostr is the first amendment translated into code like Satoshi translated this math:
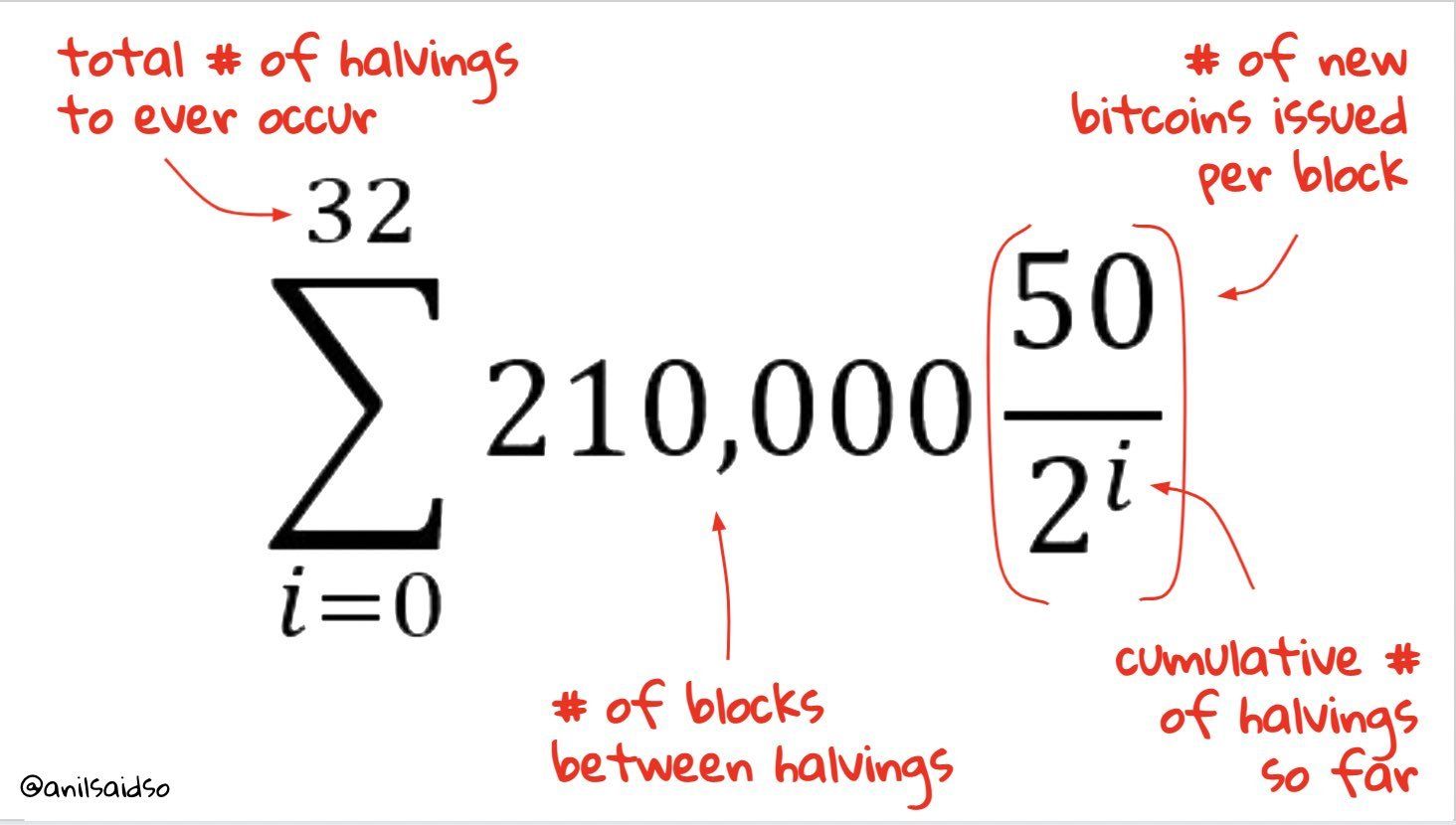
Into this code:
We can write without undue influence from ads, corporations, or even governments.
We can create a better Internet.
Code is speech. Cypherpunks write code.
Nostr makes speech unstoppable.
That's a big fucking deal.
Blogging Bitcoin

-
-
 @ 75bf2353:e1bfa895
2023-02-23 18:24:00
@ 75bf2353:e1bfa895
2023-02-23 18:24:00Blogging Nostr!
Habla is a new nostr native blogging platform. It is the second one I have found. I'm, writing this as a test, but so fair I have noticed my markdown syntax is not being rendered yet. On the other hand, I also seem to be able to see my blogstack post on Habla as well. This is why it's a test. I'm still trying to wrap my head around how this all works.
I've been writing a blog about how I use bitcoin since April on a platform namedtw Ghost under a pseudonym. I wrote on that platform for the following reasons:
-
I want to be a writer
-
I spend most of my waking hours thinking about bitcoin.
-
Marty Bent uses Ghost and had this paywall I thought was really cool at the time.
Marty's paywall is actually kind a neat, Instead of asking his readers to pay an annual subscription fee like the New York Times, You could just pay 50 cents per article. This is much better than the New York Times Paywall. When I first heard of it, I thought writers could only get paid on the Internet with a paywall or ads. The mechanics of the system did not leave many options. Lightning addresses worked, but most people never heard of them and even most Bitcoiners didn't use them. Yalls had a paywall, but the UX wasn't great. I first thought of starting a blog because of yalls. I thought I could do magic tricks over video for tips, like buskers in Vegas, but on the Internet. Then I thought, I'm not that good at magic and I don't feel comfortable throwing my face out there like a whore on the Internet (No disrespect to sex workers, but I doubt anyone would pay for my sex services and my wife would not approve.) I also have a degree in creative writing, but I'm a bit rusty. The lightning network got me interested in writing again.
It's what prompted me to run my own lightning node in the first place. I think this was back in 2018 or 2019. At the time, I tried running Pierre Rochard's lightning node, but didn't have the technical chops to pull it off on my old Windows laptop. It might have worked if I knew that I needed to plug the damn thing into an Ethernet cable to download the bitcoin blockchain.(We didn't use the term time chain in those days).
 His paywall was an order of magnitude better than running my own node to accept tips on yalls.org, so I started my blog on ghost with the intention of using his paywall software.
His paywall was an order of magnitude better than running my own node to accept tips on yalls.org, so I started my blog on ghost with the intention of using his paywall software.I spun up a virtual private server on Bitlaunch.
I installed Yunohost because it was easy to set up Ghost.
Now Marty finally launched his service. If you like this model, you can use it for charges 10 bucks a month.
For the record, I really like Marty. I listen to Rabbit Hole Recap every week. I'm not trying to ruffle any feathers, or shit on his side project, but @dergigi convinced that the paywall model will soon go the way of the doorstep delivered newspaper. If you don't have time to read or listen to that entire article, please listen to this 30 second clip of the Bitcoin.Review podcast created by Oscar Merry.
Blogs Can Be Nostr Native
There's no reason to spin up a server on a VPS to start a blog anymore. No reason to host it on a Raspberry Pi. You don't need to buy a shared hosting account. You don't need to install ruby, gem or jekyll to host it on Github. You don't even need to buy a domain, although you might want to buy one for a DIY Nip 05 verification. Hopefully, in the not too distant future, you won't even need Github. Habla.news is a Medium alternative, but there's no reason why we couldn't have a Github alternative. We're just waiting on someone to build it.
The reason I find this value 4 value model built on Nostr so exciting now is because it is now trivial for those who produce value to receive value and trivial for those who cherish valuable content to send value to those who produce it.
Why spend the time setting up ghost or pay a fee to accept lightning payments or a ghost account? --*Especially if you are writing a blog about bitcoin.
I like the idea of charging for services, but paywalls just don't jive with the old walled garden model anymore.
Nostr is censorship resistant. Anyone can create a Nostr key.
Some freaks say it's not normie ready, but it is much easier to create a private key than create a blog using the aforementioned options. I look forward to the day when we see more no-coiners witnessing how trivial it is to send value over the Internet. @TheGuySwann wrote a great post about how Facebook spent years developing their shitcoin, only to get shut down by congress.
Paywalls Not Required
You couldn't accept native bitcoin on any other platforms until now. Now plebs are zapping each other left and right.
In the value 4 value model, the zapper sets the value on the article. The paywall sets a price on reading the full article.
-
We don't need paywalls anymore.
-
I don't need to send you spam .
-
If you want to read my blog, just follow me on Nostr.
-
We don't need to rely on digital overlords to create content.
-
We don't need ads to monetize content.
Ads suck.
This is pure vida.
Nostr is the first amendment translated into code like Satoshi translated this math:

Into this code:

We can write without undue influence from ads, corporations, or even governments.
We can create a better Internet.
Code is speech. Cypherpunks write code.
Nostr makes speech unstoppable.
That's a big fucking deal.
Blogging Bitcoin

-
-
 @ df4cafee:96e987b2
2023-02-23 17:10:14
@ df4cafee:96e987b2
2023-02-23 17:10:14I’ve heard a fair bit of discussion about Fedimint and eCash lately, but I only recently dove in to understand and try eCash using Cashu, which is one implementation of eCash on Bitcoin. If you only have time to read one paragraph, here’s the short version:
With Lightning, we can take sats “off-chain” into a Lightning channel. Users can route Lightning payments through a network of channels, and take their sats back “on-chain” at any time. Of course, the sats never really leave the chain, but the system works through some cryptographic slight-of-hand. Lightning is fast, cheap, and secure. Privacy is better than normal Bitcoin transactions, but still not perfect. With eCash, users can withdraw their sats “offline” entirely. Once offline, they can be transferred any way you please. You could send them over email or SMS. You could print them out in a QR code and pass them along in person. The possibilities are endless. The recipient can deposit the sats back “online” as soon as they receive the eCash, and withdraw them directly into any Lightning wallet. There does not need to be any traceable connection between the two parties to a transaction, which means that privacy can be very robust. There is one catch, of course: after receipt of the eCash and before depositing them back “online” to the Lightning network, the recipient needs to trust a third party server, called a mint. For that reason, taking received eCash back online should be done before providing any goods or services in exchange.
In the rest of this post, I will explain all of these concepts in more detail, and provide a brief walkthrough if you want to try it out.
Chaumian eCash
Wikipedia has all of the basic info, as well as the original 1983 paper by David Chaum. For our purposes, it is important to know that eCash uses blind signatures to make payments totally untraceable. Chaum explains blind signatures by way of analogy to a secret ballot. Each voter fills out their ballot and places it in a plain, unmarked, carbon-copy envelope. They place that envelope in a mailing envelope, write their personal details (i.e. name and return address) on it, and send it off. The election authority verifies the voter information on the outer envelope. They then remove the unmarked carbon-copy inner envelope and sign it—without opening it—blindly transferring the signature to the ballot. The inner envelope is mailed back to the voter, who verifies that it was not opened. Finally, ballots may be collected anonymously on election day, opened, and displayed publicly. This somewhat roundabout process achieves the following goals:
- The election authority knows that all ballots were cast by registered voters (by verifying the information on the outer envelope)
- Voters know that the authority did not see their vote (it was returned in the original sealed envelope)
- Voters know that their ballot was counted (all ballots are displayed publicly, and they could write some secret identifying mark on theirs)
- Voters know that all ballots were verified by the election authority (by checking the blind signature on each ballot)
Chaum took this process and designed a simple cryptographic scheme that works in much the same way, resulting in blind digital signatures. This blind signature scheme is also used in Cashu’s implementation of eCash:
- A user picks a secret (the secret ballot), and encrypts it (places it in the inner envelope).
- They send this encrypted secret with some sats to an eCash issuer, called a mint (the election authority).
- The mint takes the sats and puts them aside, then signs the encrypted secret (the blind signature) and sends the result back to the user.
- The user combines the mint’s signature with their unencrypted initial secret (the ballot) to make a complete eCash token.
The token can then be passed around by any means and redeemed through the mint at any time. Since the token includes both the user’s initial secret and the mint’s own signature, the mint can use some cryptographic functions to verify that it previously received a deposit for the specified amount. This verification does not require or reveal any information about who the deposit came from or who is redeeming it. The mint is responsible for ensuring that a token is only redeemed once, so there is some trust involved.
A short walkthrough of an eCash wallet will hopefully make all of this very clear.
eCash By Example
Start by opening Cashu wallet. Add the default mint shown by pressing the plus button:

Now deposit some sats with the mint. Press the “Create Invoice” button at the bottom. Make an invoice for 50 sats, and pay it from your Lightning wallet.


You can now create an eCash token using the mint’s blind signature. Press “Send eCash” and enter 25 sats, then make the token:

You will also see that your balance has dropped to 25 sats:

This token can be shared however you like. You can email it to someone, send it in a private message, an SMS, or convert it to a QR code and print it out. Whoever has this token can redeem it for 25 sats. Here’s the full token:
eyJwcm9vZnMiOlt7ImlkIjoiSTJ5TitpUllma3pUIiwiYW1vdW50IjoxLCJD IjoiMDJlN2Y5YWYzMzliNmJiNWZiMGZmNzVjZGY0MTAzZDIyNDc1NjMyZWMy MzYyNmJmOGNlNTg5ZjhiYjIyMWMwNzUxIiwic2VjcmV0IjoiZkE0MHVQQWQ5 azVXZkFCUUJHTjdiM2ZiOFBvMGROSjBuNlAwUmhpbDV5TT0ifSx7ImlkIjoi STJ5TitpUllma3pUIiwiYW1vdW50Ijo4LCJDIjoiMDM5MTQ5ZTg3N2Q3MzQ3 YjliYzEwYTUyNGYyMmNhZmRhNjUwZWQ2NThjZTAzMWY4Zjg4MjQxODgyOTI4 OWRjMWIyIiwic2VjcmV0IjoiaEs5c0FsaXpCYW5pakF2VU9pQTVOaG5yV3lI elBmbUJwM3AxNVFyUVJKTT0ifSx7ImlkIjoiSTJ5TitpUllma3pUIiwiYW1v dW50IjoxNiwiQyI6IjAzNTcwODRlNzRjOTBmYmQ1YzZiZWNmNDJmMjI1YWM4 NTk3MWRjYmU4MDZjNmVjMDg1ZjYwMjkwZTYzYTMzYjVlMiIsInNlY3JldCI6 InRQbkUzNEZzS3k2NFB5aW1OdGNkaTJSUXpJU044S0lmeEorc0dFbEwxVUU9 In1dLCJtaW50cyI6W3sidXJsIjoiaHR0cHM6Ly84MzMzLnNwYWNlOjMzMzgi LCJpZHMiOlsiTDN6eHhSQi9JOHVFIiwiSTJ5TitpUllma3pUIl19XX0=To redeem a token, press the “Get eCash” button and paste it in.

After that you will see that your balance goes back to 50 sats. You can try minting and depositing tokens in any denomination. When you’re done, you can bring the tokens back into your Lightning wallet. Simply press “Pay Invoice” and paste an invoice from your wallet. I could only pay 48 sats back, with 2 sats kept by the mint. (I’m not sure how exactly the fees work for this mint, but 2 sats appears to be the minimum fee for a Lightning transfer.)

Ideally, if you are using Cashu, you will want to run your own mint. If you receive a token from another mint, you can use the wallet’s “Multimint Swaps” feature to move sats between mints (or to your own mint) without withdrawing them to your Lightning wallet. First, add a second mint. I’m using https://legend.lnbits.com/cashu/api/v1/4gr9Xcmz3XEkUNwiBiQGoC, which is a mint hosted by another Cashu wallet developer, but let’s pretend it’s mine:

I’ve deposited another 50 sats to demonstrate. Now I can perform the swap. The swap happens over Lightning mint-to-mint, so don't forget the 2 sat minimum fee.

At this point, I can see that my sats are with the new mint:

And of course, I can now use that mint to make eCash tokens and send them out. If I swap into my own mint, then I don’t need to trust any third parties. Or, I can withdraw them back to my own Lightning wallet at any time.
Who Would Do This?
For now, at least, this is still experimental technology and should probably not be used with any significant amount of sats. But there are many reasons we might want to use it. First and foremost, by sending eCash tokens instead of doing Lightning transfers directly, transactions become almost entirely untraceable. The mint has no information about the payer or the payee, and the Lightning Network sees only transfers to and from the mint. For a large mint with many users, and with eCash tokens being minted in all different denominations, it would be difficult if not impossible to trace funds going into and out of the mint.
Beyond privacy, eCash could be an ideal way to transact in sats within a trusted community. For example, parents could run a family mint and provide the children with allowances in the form of eCash tokens. Small, tight-knit, or largely offline communities could do day-to-day business with eCash tokens, only going online when there was a need to send or receive sats from the outside. In fact, that is exactly the scenario that Fedimint has in mind, and they are working on a protocol for shared custody of mint funds to support this type of use case. Fedimint and Cashu are separate protocols, but the eCash concepts are very similar if not identical.
I’m sure there are many other scenarios we can think of where the trade-offs of the Cashu / eCash system would make sense. The only caveat we must keep in mind is that if the mint is not controlled by a known, trusted entity, tokens should be swapped to a trusted mint or redeemed into a Lightning wallet before providing any goods or services in exchange. However, since the redemption process is simple and straightforward, that should not be too much of a problem.
Bonus: eCash via Nostr
If you haven’t yet read my previous article on nostr, you might want to do that first. Another Cashu wallet called nutstash provides a very useful nostr integration. Nutstash offers very similar functionality to the lnbits wallet I used above in the demonstration. If you log in with a nostr browser extension like Alby, you will see an option to send eCash tokens directly to an npub:

The recipient will receive the token as a DM via nostr. If they also log in to nutstash using their nostr account, they will see the tokens appear in their wallet “inbox” automatically, ready for deposit or redemption.
Thanks for reading, and I hope you’ll take a few minutes to try out eCash to see what all the fuss is about. Next time you want to zap, try sending some eCash tokens and see what happens!
-
 @ 6a3d3f20:6a569bcc
2023-02-23 12:16:34
@ 6a3d3f20:6a569bcc
2023-02-23 12:16:34Check it at https://habla.news/
-
 @ 02a11d15:32f62ea9
2023-02-22 10:09:02
@ 02a11d15:32f62ea9
2023-02-22 10:09:02In this long nost (or what should we call it? a Most?) I'm testing different ways of tagging other Nostr content.
Regular post from Nostr (oh wait! everything is on Nostr lol)
I will use the id only now
[6]
Link from Iris https://iris.to/post/#[7]
A comment?
[8]
Nice!!
My profile (using npub) ^^
[4]
Long live the frog (using nip05)? verbiricha@snort.social Shows as email....
Fine, I will use his npub #[5]
[!note] The editor is flickering as I type... I think it is rerendering
[9]
-
 @ 18e3af1e:1d42e5df
2023-02-21 21:05:28
@ 18e3af1e:1d42e5df
2023-02-21 21:05:28Steps that I took (and that many like me have taken) are not strictly literal, neither in numbering nor qualities, but they mostly represent the pain that some have had to endure financially, mentally, and physically throughout the journey. Many, including myself, came for the money, to make a quick jump to the wealth promised by scammers and charlatans... But they stayed for something more noble: to change the system, to change the world.
"Crypto"
1. Curiosity
With a new generation comes new technologies. From a human point of view, everyone seeks their own happiness, although selfishness is what allows us as a species to optimize the limited time we have.
There are other types of humans, whom I call "scammers and charlatans" who pursue self-interest, but at the cost of other people's limited time, but indirectly thanks to them we reach convergence.
You probably entered this world of cryptocurrencies because of Xcoin or Ycoin (or some of the more than 20 thousand tokens that exist today), it was not by chance... It was marketing.
2. Skepticism
You probably heard from friends or social networks about someone who lost a lot of money playing with these tokens in the exchange houses' casino. Or maybe you thought it was silly and fashionable, that it wouldn't last more than a couple of months before disappearing. As a logical thinker, you gave up the idea of even trying.
3. Initiation
One day, you hear about a word that has echoed in your mind; either because you come from a country with many resources but bad administrators, or because you simply know someone who talks about the topic: "Inflation". You tell yourself "If I keep my money in the bank, all my savings can disappear in less than a decade" and you decide to enter the stock market. You lasted a while there, but you realized that it's not for you, you have to study and invest a lot of time that you could use for something more productive or doing something you like.
Your YouTube channel or your wall on Twitter, Facebook, Instagram, or Tiktok is full of people who claim to have the key to a better world:
“Invest your money here with this new technology, we're going to the moon." "The next money of the world." "Everyone will use it." "It's decentralized." "Blockchain." "The next Bitcoin"...
You got it.
You decide to take a look and are surprised by how easy it is. Congratulations, now you're one of the many like me.
4. Speculation
At this stage, you are already what they call a "trader." You spend some of your time reviewing articles, listening to podcasts, or watching videos about the latest tokens that have hit the market. You compulsively check your phone, watching as the prices of the tokens you bought move with volatility.
It's at this point that you have probably read Tweets from a "Bitcoin maxi," calling the token you bought a "shitcoin" and confidently saying that it doesn't solve any problem that a centralized database can't solve, that what you believe is going to revolutionize the industry is just a fallacy, a mirage. Ignoring the comment or responding with a "Bitcoin Maxis are orthodox," among other derogatory comments you may find.
You live in your bubble, and you're happy there (or so you think) until the next step.
5. First gains or losses
From here there is a fork in the road. If you made gains from your investments, where everything is beautiful and rosy; all those green bars, where you believe everything will continue to rise to infinity… You'll think you're a genius. You'll continue to gamble your money until bad news introduce itself at your doorstep.
The Xcoin in which you had invested part of your portfolio starts to fall, and it falls quickly. You start to wonder whether to sell it now or wait for it to go up a bit more... You spend five hours, and it falls even further. Congratulations, you lost 90% of the money you invested. The reason? Xcoin was controlled by a group of people who decided to take all the money and leave the token without liquidity or apparent use.
If you're in the gains group, you'll repeat speculation until you enter the losers' group, if not, you'll take one more step.
6. Denial
This can't be happening. The money you invested, the time... 90% of it just disappeared, just like that. You try to find someone to blame. You go on Twitter or YouTube and demand that your money be returned. No one listens to you, and you see many others doing the same thing, all of whom are ignored. There's no response from the creator or creators of Xcoin.
In the end, it was all your fault, and you accept that you lost your money. You played a stupid game... and won a stupid prize.
7. Disinterest
Once you've reached this point, there's no turning back. There's no shitcoin that attracts you, nor does Bitcoin. For many, this is a moment of total cyber nihilism (speaking of Bitcoin and "crypto"). Depending on how much you've lost in one of these new generation casinos, you are more or less resilient to even be interested in this technology.
8. Disgust
Many people stay at this point. They are not open to any idea that has to do with "magic internet money"; Everything seems like a scam, a fraud. It's a shame that because of a few scoundrels and charlatans, opportunities are taken away from people who are desperately seeking a way out of the current monetary system.
If you live in a privileged country, where you can afford to lose a couple of thousand dollars, have a tantrum for a few days, and then forget about it... You're lucky.
Many people even put their life savings at stake, in order to play the lottery and try to make quick money. Those people, as we saw with the infamous TerraUSD and Luna; FTX Fiasco, etc… Not only lose their money but also their sanity.
What's next? There is a way out, if you're optimistic about the future. Living with your mistakes is the easiest thing to do; learning from them and moving on is what will lead you to find the right answer.
Being a millionaire isn't bad, but even being a millionaire without a purpose will leave you exposed and unprotected against the existentialist thoughts that this life has for you.
Bitcoin
You probably first heard of it during the waves of Bitcoiners back in 2012-2015. Or maybe on social media, but you decided not to pay attention because you didn't understand what you were reading or hearing.
Curiosity and skepticism were also part of this journey. If this journey crossed paths with your journey into the world of "Crypto," you may be even more closed off to taking the time to understand Bitcoin and what it represents.
9. Learning
This was and still is one of the most interesting steps for me, mainly because in theory, you never stop learning things within the whole ecosystem of a global protocol. The technology surrounding Bitcoin is always evolving.
From the moment you make your first purchase on a centralized exchange, you begin a fairly arduous research process (if you're a good investor) to know what you are buying. It is at this point that you realize that Bitcoin is more than just a way to invest for the future; it is a way to exit the current system. You came for the returns on your investment and stayed for something that is many levels above: global wealth redistribution.
10. Evangelization
When you know something very important, you want to tell everyone. Many will think you're foolish, while others will simply ignore what you say; but there will always be someone who understands what you're saying or at least tries to understand it. Those people will go through a process similar to yours, or perhaps they will skip all the weeds that is "Crypto" altogether, thanks to you.
Thanks to you, there will be many people who won't have to go through the pain of losing their money and time in these casinos. Give yourself a pat on the back, because in this last step, you are helping to build a better world.
In conclusion I created this writing not as a manual, but rather as a journal of my own experiences. I hope that in some way, it inspires you to do something that helps expand the horizons and hopes of many others. 21 million is a very interesting number.
Remember: If it's not your keys, it's not your house; not your keys not your coins.
If you have getalby or any Lightning wallet feel free to send me sats if you like it! or use lurusan@getalby.com

-
 @ b40ccb84:e2768505
2023-02-21 09:14:31
@ b40ccb84:e2768505
2023-02-21 09:14:31Intro
This is self-verification method for NIP-05 with your own domain to prove your authenticity
Requirements
- A domain (e.g: mine is
MarketFishing.Com) - An text editor
Overview
- Prepare a JSON file
- Upload to your webserver (I use Netlify as the FREE one)
- Update NIP-05 ID in your account setting
Detailed steps
Decide the NIP-05 name
A NIP-05 verified name will look like this
<preferred_name>@<domain>. E.g: mine isHello@MarketFishing.Com, so the 2 params are: -<preferred_name>:Hello-<domain>:MarketFishing.ComPrepare the file(s)
1.
./.well-known/nostr.jsonref: https://github.com/nostr-protocol/nips/blob/master/05.md
Format:
{ "names": { "<preferred_name>": "<pub_key_in_hex_format>" } }Note: pub_key must be in HEX format,npub...format ~~will NOT work~~. The HEX format can be found here: https://iris.to/settingsExample:
{ "names": { "Hello": "b40ccb8422e34bdf7ae7ba446d8dcf5507bc89d077720cb97337ef55e2768505" } }2.
./index.html(this can be skipped if you're already have a website running with your domain)Just prepare a blank file or any content you want (if you know HTML) to protect your website
3.
./_headers(this can be done if you're already enabled CORS)/* Access-Control-Allow-Origin: *Upload to webserver
If you're not running any website for your domain, it's likely that you don't have any webserver now. Even thought configuring a webserver is not a big issue, I highly recommend a managed service with FREE tier like Netlify
- Register a FREE account
- Upload the whole folder using manual deploy feature:
- Add your domain to Netlify: https://docs.netlify.com/domains-https/custom-domains/configure-external-dns/ (I'm using FREE Cloudflare DNS & the configuration is pretty easy & simple)
Update your NIP-05
You can go to any of these sites to provide your NIP-05 ID (in my case, it's
Hello@MarketFishing.Com: - https://hamstr.to/settings - https://astral.ninja/settingsCongratulation!
You've just done it. You should have your own NIP-05 verification by now. If you have any questions, feel free to DM me at
npub1ksxvhppzud9a77h8hfzxmrw025rmezwswaeqewtnxlh4tcnks5zslprzrxE.g: https://hamstr.to/profile/npub1ksxvhppzud9a77h8hfzxmrw025rmezwswaeqewtnxlh4tcnks5zslprzrx
- A domain (e.g: mine is
-
 @ abab50be:430cd35d
2023-02-21 06:48:19
@ abab50be:430cd35d
2023-02-21 06:48:19Ya hablaremos!
Propagate the signal
3,430 days in prison
- First-time offender!
- All non-violent charges
- Two life sentences + 40 years without parole
Ross Ulbricht is condemned to die in prison for creating an anonymous e-commerce website called Silk Road. An entrepreneur passionate about free markets and privacy, he was 26 when he made the site. He was never prosecuted for causing harm or bodily injury and no victim was named at trial.
Users of Silk Road chose to exchange a variety of goods, both legal and illegal, including
drugs(most commonly small amounts of cannabis). Prohibited was anything involuntary that could harm a third party.Ross was not convicted of selling drugs or illegal items himself, but was held responsible for what others sold on the site.

“Silk Road was supposed to be about giving people the freedom to make their own choices, to pursue their own happiness, however they individually saw fit. [It] turned out to be a naive and costly idea that I deeply regret.
– Ross in letter to the Court [PDF]"
```
Congressman Massie Speaks Out For Ross Ulbricht's Clemency During Congressional Hearing
``` Sentencing Disparity
| Name | Conviction | Sentence | | --- | --- | --- | | Jan Slomp| Biggest drug dealer | 10 yrs | | Carl Force| Corrupt Fed | 6.5 yrs | | Ross Ulbricht | Creator of Silk Road | Double LIFE + 40years without parole |
-
 @ abab50be:430cd35d
2023-02-21 06:22:36
@ abab50be:430cd35d
2023-02-21 06:22:36Ya hablaremos!
Propagate the signal
3,430 days in prison
- First-time offender!
- All non-violent charges
- Two life sentences + 40 years without parole
Ross Ulbricht is condemned to die in prison for creating an anonymous e-commerce website called Silk Road. An entrepreneur passionate about free markets and privacy, he was 26 when he made the site. He was never prosecuted for causing harm or bodily injury and no victim was named at trial.
Users of Silk Road chose to exchange a variety of goods, both legal and illegal, including
drugs(most commonly small amounts of cannabis). Prohibited was anything involuntary that could harm a third party.Ross was not convicted of selling drugs or illegal items himself, but was held responsible for what others sold on the site.

“Silk Road was supposed to be about giving people the freedom to make their own choices, to pursue their own happiness, however they individually saw fit. [It] turned out to be a naive and costly idea that I deeply regret.
– Ross in letter to the Court [PDF]"
```
Congressman Massie Speaks Out For Ross Ulbricht's Clemency During Congressional Hearing
``` Sentencing Disparity
| Name | Conviction | Sentence | | --- | --- | --- | | Jan Slomp| Biggest drug seller on Silk Road | 10 yrs | | Carl Mark Force| Corrupt Federal Agent on Silk Road | 6.5 yrs | | Ross Ulbricht | Creator of Silk Road | Double LIFE + 40years without parole |
-
 @ 02a11d15:32f62ea9
2023-02-21 02:07:59
@ 02a11d15:32f62ea9
2023-02-21 02:07:59While out hunting, a pack of wolves stumbled upon a strange portal and found themselves in a new world. They met ancient wolves from an advanced civilization who taught them about a protocol called Nostr. While its primary purpose was to write and transmit notes and other information over relays, it also allowed for the easy and secure exchange of small amounts of Bitcoin, or Satoshis, using the Lightning Network. The pack quickly learned how to use Nostr to communicate and exchange value with each other. Though the pack eventually returned home, they continued to use Nostr to connect and thrive in their world, and to explore all that it had to offer.
ChatGPT

-
 @ 3f770d65:7a745b24
2023-02-21 01:55:08
@ 3f770d65:7a745b24
2023-02-21 01:55:08Habla is a new blogging platform that's based on Nostr. Or as various Nostr client developers like to call it:
"A way to get Derek Ross to stop sending walls of text".
You can edit posts, which is very nice.
-
 @ b2d1d0fc:d247df7c
2023-02-20 18:02:54
@ b2d1d0fc:d247df7c
2023-02-20 18:02:54Testing habla news - medium replacement based on Nostr 1. Test 2. Test
And more test
What's better than a quote
-
 @ de7ecd1e:55efd645
2023-02-20 16:41:11
@ de7ecd1e:55efd645
2023-02-20 16:41:11Web 1.0
The web was proposed in 1989, by Tim Berners-Lee but had been conceived decades earlier. The proposal was not read for a full year, and, after that, allowed as a side-project with the infamous words, "vague, but exciting".
The first version added hyperlinks to existing browser technology. Bundled together were:
- HTTP and the first server
- the first web browser, which was also an editor
- HTML which was based on SGML
Importantly a new type of variable was created, the hyperlink, originally the UDI (Universal Document Identifier). This was later standardized as the URI, with an intent to go beyond just documents to describe Things as well.
Web 1.0 was in competition with Gopher at the time, and Gopher was winning. However, there was a rumour that Gopher might charge some royalties on their protocol, say, to enterprise customers, and with that, the people flocked to the web and made it take off as a grass roots movement.
HTTP was a formal specification in 1997 a full 8 years later, and the architecture of the world wide web was published in 2004, 7 years after that.

Web 2.0
As the web grew as a system, businesses started to spring up around it. A product was a browser called Mosaic, made by Marc Andreessen. While Mosiac added multi media, it also removed the editing functionality in the original browser, a tragic loss.
Without editing built in, the web needed central servers to allow user generated content. These servers grew in time to become giants. A technology added on this was AJAX, which allowed browsers to interact with servers asynchronously to generate richer applications and realtime updates.
This system of greater usability was branded "Web 2.0", popularized by Tim O'Reilly. It was not a formal upgrade of the web, so considered somewhat cheeky by some, the inventor of the web calling the term "jargon". Jargon it is, but the term stuck, and the web did go to a next level, adding important things like search, commerce, and the social web.
With the increased centralization of servers came other problems, such as pervasive tracking, monopolistic effects, censorship and information engineering.
Web 3.0
Web 3.0 was a term coined by Tim Berners-Lee, to represent a radical new idea, which allowed both data and documents to be denoted, on the web. This is of course a radical old idea which was in the web 1.0 proposal, a so-called "semantic web", but with the name 2.0 already co-opted, Tim decided to call it web 3.0.
The was formalized in the RDF (resource definition framework) which made extensive use of XML. Later it was renamed Linked Data, sometimes called the web of data. This has been popularized by schema.org which allows commonly used terms to be put in web pages, allowing easier search, and link previews.
Berners-Lee continues to work on a project called Solid, which stands for "Social Linked Data" (a term I coined in 2012), with the aim of making Linked Data more social, and benefiting from same usability upgrades and lessons learned from "Web 2.0"
The full web 3.0 stack is standardized at the w3c, though has grown over time, leading to a somewhat complex system, and steep learning curve for new developers.
A note on the deceptively named web3. This was an attempt by VCs (including Marc Andreessen again) and others to co-opt the web brand. The main aim was an affinity scam to sell tokens to the unsuspecting public. The issue is that it is not the web at all. In this case Berners-Lee did speak out against it:
https://www.cnbc.com/2022/11/04/web-inventor-tim-berners-lee-wants-us-to-ignore-web3.html
Towards Web 4.0
The first 3 "versions" of the web work well enough. However, the web itself is ephemeral. The average age of a link is 100 days. And there is no good mechanism at web scale to ensure the integrity or version control of information on the web. A possible approach to the next version of the web would be towards a Temporal Web. I wrote a post about this here:
https://lists.w3.org/Archives/Public/public-rww/2021May/0006.html
A significant innovation in recent times is that of Bitcoin, which is a web scale timestamp server. It orders records (blocks) in time, robustly and securely, creating a permanent record. It also, for the first time in history, creates a global currency that is strongly resistant to money printing by fiat.
These two systems working together could create a robust temporal backbone to the web, allowing commerce without rent seeking, and creating whole new business models that are more decentralized, and act in the interests of the users, competing with each other with better services, rather than, serving privacy intrusive monopolies.

Web 5.0
What web 5.0 will look like, nobody knows. However the aim of the original proposal was to have both humans and machines working together. A semantic web was needed for that, to make it easier for machines to participate. Although machines are often censored or blocked on the large platforms, or, even worse, act with perverse incentives to spam users with adverts, noisy information and propaganda.
One guess about web 5.0 could be a web of machine agents, virtual assistants, working together with people to act in the interests of people. This builds on a Temporal web as machines can then evolve over time and the best ones will emerge, in an evolutionary way. Artificial Intelligence can further be folded into the system to optimize its utility to humanity.
A note on web5: This was an earnest attempt to push back on web3 and remove some of the more corrupt aspects, such as copious use of money printing. It has some alignment with the web, but it is not web 5.0, however, I hope it produces something interesting. Never fight an affinity scam with an affinity scam.
IMHO a promising project in this area is Nostr. It reuses the websockets standard to relay information from one user to another which is signed. Importantly, it is grass roots, as the original web was, has already integrated fast cheap payments, with bitcoin and the lightning network in many apps. Unlike the semantic web, it has a very easy developer experience which has seen high uptake from developers. Additionally, the tagging system allows integration with time chains paving a cow path for a temporal web, and then perhaps humans and agents co existing for mutual benefit. We are still early, but time will tell how the web evolves.

Opinions are the views of the author