-
 @ edeb837b:ac664163
2025-06-13 21:15:05
@ edeb837b:ac664163
2025-06-13 21:15:05On June 10th, 2025, four members of the NVSTly team traveled to New York City to attend the 2025 American Business Awards® ceremony, held at the iconic Marriott Marquis in Times Square. It was an unforgettable night as we accepted the Gold Stevie® Award for Tech Startup of the Year—this time, in person.
Meow (left), rich (center), MartyOooit (right)
Representing NVSTly at the event were:
- Rich, CEO & Founder
- Meow, CTO, Lead Developer, & Co-Founder
- MartyOooit, Investor
- Noob, Market Analyst (not shown in photos)
MartyOooit (left), rich (center), Meow (right)
While we shared the exciting news back in April when the winners were announced, being there in person alongside other winners—including eBay, AT&T, T-Mobile, HP Inc., and Fidelity Investments—made the achievement feel even more surreal. To be honored alongside billion-dollar industry leaders was a proud and humbling moment for our startup and a huge milestone in NVSTly’s journey.
🎤 Team Interview at the Event
During the event, our team was interviewed about the win. When asked:
“What does winning a Stevie Award mean for your organization?”
“How will winning a Stevie Award help your organization?”Here’s what we had to say:
📺 Watch the video
A Big Win for Retail Traders
NVSTly was awarded Gold for Tech Startup of the Year in recognition of our work building a powerful, free social investing platform that empowers retail traders with transparency, analytics, and community-driven tools.
Unlike traditional finance platforms, NVSTly gives users the ability to:
- Share and track trades in real time
- Follow and receive alerts from top traders
- Compete on global leaderboards
- Access deep stats like win rate, average return, and more
Whether you're a beginner or experienced trader, NVSTly gives you the insights and tools typically reserved for hedge funds—but in a free, social format built for the modern investor.
Continued Recognition and Momentum
This award adds to a growing list of recognition for NVSTly:
- 🏆 People’s Choice Winner at the 2024 Benzinga Fintech Awards
- 🔁 Nominated again for Best Social Investing Product in the 2025 Benzinga Fintech Awards
- 🌟 Team members JustCoreGames and Lunaster are nominated for Employee of the Year (Information Technology – Social Media) in the 2025 Stevie® Awards for Technology Excellence
We’re beyond proud of what our small but mighty team has accomplished—and we’re just getting started. 🚀
Thanks to the Stevie Awards for an incredible night in New York, and to our community of 50,000+ traders who’ve helped shape NVSTly into what it is today.
This win is yours, too.Stay tuned—more big things are coming.
— Team NVSTly

The event brought together some of the most respected names in tech, finance, and business. -
 @ c631e267:c2b78d3e
2025-06-13 19:13:38
@ c631e267:c2b78d3e
2025-06-13 19:13:38Ich dachte immer, jeder Mensch sei gegen den Krieg, \ bis ich herausfand, dass es welche gibt, \ die nicht hingehen müssen. \ Erich Maria Remarque
Was sollte man von einem Freitag, den 13., schon anderes erwarten?, ist man versucht zu sagen. Jedoch braucht niemand abergläubisch zu sein, um den heutigen Tag als unheilvoll anzusehen. Der israelische «Präventivschlag» von heute Nacht gegen militärische und nukleare Ziele im Iran könnte allem Anschein nach zu einem längeren bewaffneten Konflikt führen – und damit unweigerlich zu weiteren Opfern.
«Wir befinden uns im Krieg», soll ein ranghoher israelischer Militärvertreter gesagt haben, und der Iran wertet den israelischen Angriff laut seinem Außenminister als Kriegserklärung. Na also. Der Iran hat Vergeltungsschläge angekündigt und antwortete zunächst mit Drohnen. Inzwischen ist eine zweite israelische Angriffswelle angelaufen. Ob wir wohl künftig in den Mainstream-Medien durchgängig von einem «israelischen Angriffskrieg auf den Iran» hören und lesen werden?
Dass die zunehmenden Spannungen um das iranische Atomprogramm zu einer akuten Eskalation im Nahen Osten führen könnten, hatte Transition News gestern berichtet. Laut US-Beamten sei Israel «voll bereit», den Iran in den nächsten Tagen anzugreifen, hieß es in dem Beitrag. Heute ist das bereits bittere Realität.
Der Nahe Osten steht übrigens auch auf der Themenliste des diesjährigen Bilderberg-Treffens, das zurzeit in Stockholm stattfindet. Viele Inhalte werden wir allerdings mal wieder nicht erfahren, denn wie immer hocken die «erlauchten» Persönlichkeiten aus Europa und den USA «informell» und unter größter Geheimhaltung zusammen, um über «Weltpolitik» zu diskutieren. Auf der Teinehmerliste stehen auch einige Vertreter aus der Schweiz und aus Deutschland.
Die Anwesenheit sowohl des aktuellen als auch des vorigen Generalsekretärs der NATO lässt vermuten, dass man bei dem Meeting weniger über das Thema «Neutralität» sprechen dürfte. Angesichts des Zustands unseres Planeten ist das schade, denn der Ökonom Jeffrey Sachs hob kürzlich in einem Interview die Rolle der Neutralität in geopolitischen Krisen hervor. Mit Blick auf die Schweiz betonte er, der zunehmende Druck zur NATO-Annäherung widerspreche nicht nur der Bundesverfassung, sondern auch dem historischen Erbe des Landes.
Positives gibt es diese Woche ebenfalls zu berichten. So hat der US-Gesundheitsminister Robert F. Kennedy Jr. nach der «sensationellen» Entlassung aller Mitglieder des Impfberatungsausschusses (wegen verbreiteter direkter Verbindungen zu Pharmaunternehmen) nun auch bereits neue Namen verkündet. Demnach möchte er unter anderem Robert W. Malone, Erfinder der mRNA-«Impfung» als Technologie und prominenter Kritiker der Corona-Maßnahmen, in das Komitee aufnehmen.
Auch die Aufarbeitung der unsinnigen Corona-Politik geht Schrittchen für Schrittchen weiter. In Heidelberg hat die Initiative für Demokratie und Aufklärung (IDA) den Gemeinderat angesichts der katastrophalen Haushaltslage zu einer offenen und ehrlichen Diskussion über die Ursachen der Krise aufgefordert. Das Thema «Corona» sei «das Teuerste, was Heidelberg je erlebt hat», sagte IDA-Stadtrat Gunter Frank im Plenum. Außerdem seien aus den Krisenstabsprotokollen der Stadt auch die enormen Verwerfungen ersichtlich, und es gebe Anlass für tiefgehende Gespräche mit der Stadtverwaltung.
Den juristischen und öffentlichen Druck auf die Kommunen möchte der Unternehmer Markus Böning erhöhen. Seine «Freiheitskanzlei» will Bürgern helfen, die Aufarbeitung selbst in die Hand zu nehmen. Unter dem Motto «Corona-Wiedergutmachung» bietet er Hilfestellung, wie Betroffene versuchen können, sich unrechtmäßige Bußgelder zurückzuholen.
So bleibt uns am Ende dieses finsteren Freitags doch auch Anlass zur Hoffnung. Es gibt definitiv noch Anzeichen von Menschlichkeit. Darauf möchte ich mich konzentrieren, und mit diesem Gefühl verabschiede ich mich ins Wochenende.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 0403c86a:66d3a378
2025-06-13 12:55:09
@ 0403c86a:66d3a378
2025-06-13 12:55:09Exciting news for FOOTBALL fans ⚽! Global Sports Central 🌐 is teaming up with Predyx, a leading prediction market in the Bitcoin ecosystem, to bring you comprehensive coverage of the very first Club World Cup directly on Nostr. This partnership is all about enhancing your experience with the latest news, insights, and interactive features!
The Club World Cup will showcase the best clubs from around the globe, and with our collaboration, you’ll be fully engaged in the action. Predyx focuses on long-term outcomes, allowing you to make predictions on who will win it all. Plus, if you’re not happy with your predictions, you can sell your shares at any time and switch allegiance—after all, it’s a free market!
What You Can Expect:
-
Latest News and Match Reports: Stay updated with the latest news, in-depth match reports, and insights from the tournament, ensuring you never miss a moment.
-
Market Odds Tracking: Follow the shifts in market odds in real-time, giving you the edge when making predictions and engaging with the action.
-
Player of the Day Card: Celebrate standout performances with our Daily Player of the Day card, highlighting the top players from the tournament.
-
Game oN Frontpage: Each day, we’ll feature the frontpage of the day, showcasing the most historical matchups and capturing the feel of the game.
-
Best Moments Replays: Relive the excitement with replays of the best moments from the Cup, so you can catch all the highlights and unforgettable plays.
-
Long-Term Predictions: Engage with Predyx to forecast who will win the tournament and who will take home the MVP award, allowing you to make strategic predictions as the tournament unfolds.
-
Easy Login System: Getting started is a breeze! All you need is a Lightning wallet to log in and participate, making it simple for everyone to join in on the fun.
-
Lightning-Fast Bitcoin Payments: With the Lightning Network, placing your bets and making predictions is faster and easier than ever. Enjoy seamless transactions while you cheer for your favorite teams!
"Predyx is excited to be part of this innovative partnership," said Derek. "We’re bringing fans a new way to interact with the game they love, all while using the fast and secure Lightning Network."
Predyx is a Bitcoin-native prediction market platform running on the Lightning Network. We’re building the fastest, most trust-minimized betting engine in the world — no deposits, instant payouts, sats-native, and degen-friendly.
Global Sports Central 🌐 Your daily spin around the sports world 🔄 Stay in the loop with the latest scores, stories, and stats.
GSC360 - Where Every Angle Matters
-
-
 @ 472f440f:5669301e
2025-06-12 05:11:12
@ 472f440f:5669301e
2025-06-12 05:11:12Marty's Bent
via me
I had a completely different newsletter partially written earlier tonight about whether or not "this cycle is different" when this nagging thought entered my head. So I'm going to write about this and maybe I'll write about the dynamics of this cycle compared to past cycles tomorrow.
A couple of headlines shot across my desk earlier tonight in relation to the potential escalation of kinetic warfare in the Middle East. Apparently the U.S. Embassy in Iraq was sent a warning and evacuation procedures were initiated. Not too long after, the world was made aware that the United States and Israel are contemplating an attack on Iran due to the "fact" that Iran may be close to producing nuclear weapins. The initial monkey brain reaction that I had to these two headlines was, "Oh shit, here we go again. We're going to do something stupid." My second reaction was, "Oh shit, here we go again, I've seen these two exact headlines many times over the years and they've proven to be lackluster if you're a doomer or blood thirsty war monger." Nothing ever happens.
As I venture into my mid-30s and reflect on a life filled with these types of headlines and my personal reactions to these headlines, I'm finally becoming attuned to the fact that the monkey brain reactions aren't very productive at the end of the day. Who knows exactly what's going to happen in Iraq or Iran and whether or not kinetic warfare escalates and materializes from here? Even though I'm a "blue-blooded taxpaying American citizen" who is passively and unwillingly contributing to the war machine and the media industrial complex, there's really nothing I can do about it.
The only thing I can do is focus on what is in front of me. What I have control of. And attempt to leverage what I have control of to make my life and the life of my family as good as humanly possible. Ignoring the external and turning inward often produces incredible results. Instead of worrying about what the media wants you to believe at any given point in time, you simply look away from your computer screen, survey the physical space which you're operating in and determine what you have, what you need and how you can get what you need. This is a much more productive way to spend your time.
This is what I want to touch on right now. There's never been a better time in human history to be productive despite what the algorithm on X or the mainstream media will lead you to believe. Things aren't as great as they could be, but they're also not as bad as you're being led to believe. We live in the Digital Age and the Digital Age provides incredible resources that you can leverage to make YOUR life better.
Social media allows you to create a platform without spending any money. AI allows you to build tools that are beneficial to yourself and others with very little money. And bitcoin exists to provide you with the best form of money that you can save in with the knowledge that your relative ownership of the overall supply isn't going to change. No matter what happens in the external world.
If you can combine these three things to make your life better and - by extension - potentially make the lives of many others better, you're going to be well off in the long run. Combining these three things isn't going to result in immediate gratification, but if you put forth a concerted effort, spend the time, have some semblance of patience, and stick with it, I truly believe that you will benefit massively in the long run. Without trying to sound like a blowhard, I truly believe that this is why I feel relatively calm (despite my monkey brain reactions to the headlines of the day) at this current point in time.
We've entered the era of insane leaps in productivity and digital hard money that cannot be corrupted. The biggest mistake you can make in your life right now is overlooking the confluence of these two things. With an internet connection, an idea, some savvy, and hard work you can materially change your life. Create something that levels up your knowledge, that enables you to get a good job in the real world, or to create a company of your own. Bring your talents to the market, exchange them for money, and then funnel that money into bitcoin (if you're not being paid in it already). We may be at the beginning of a transition from the high velocity trash economy to the high leverage agency economy run on sound money and applied creativity.
These concepts are what you should be focusing most of your time and attention to today and in the years ahead. Don't get distracted by the algorithm, the 30-second video clips, the headlines filled with doom, and the topics of the 24 hour news cycle. I'll admit, I often succumb to them myself. But, as I get older and develop a form of pattern recognition that can only be attained by being on this planet for a certain period of time, it is becoming very clear that those things are not worth your attention.
Living by the heuristic that "nothing ever happens" is a pretty safe bet. Funnily enough, it's incredibly ironic that you're led to believe that something is happening every single day, and yet nothing ever happens. By getting believing that something happens every day you are taking your attention away from doing things that happen to make your life better.
Tune out the noise. Put on the blinders. Take advantage of the incredible opportunities that lie before you. If enough of you - and many others who do not read this newsletter - do this, I truly believe we'll wake up to find that the world we live in is a much better place.
Nothing ever happens, so make something happen.
Intelligence Officials Are Quietly Becoming Bitcoin Believers
Ken Egan, former CIA Deputy Chief of Cyber Operations, revealed a surprising truth on TFTC: the intelligence community harbors numerous Bitcoin advocates. Egan explained that intelligence professionals uniquely understand how governments weaponize financial systems through sanctions and account freezing. Having wielded these tools themselves, they recognize the need for personal financial sovereignty. He shared compelling anecdotes of discovering colleagues with "We are all Satoshi" stickers and a European chief of station paying for dinner with a BlockFi card to earn Bitcoin rewards.
"I think there are a lot of Bitcoiners, not just at CIA, but across the whole national security establishment... they're in it for the exact same reasons everybody else is." - Ken Egan
The Canadian trucker protests served as a pivotal moment, Egan noted. Watching Western governments freeze citizens' bank accounts for political dissent struck a nerve among intelligence professionals who previously viewed financial weaponization as a tool reserved for foreign adversaries. This awakening has created unlikely allies within institutions many Bitcoiners distrust.
Check out the full podcast here for more on Bitcoin's national security implications, privacy tech prosecutions, and legislative priorities.
Headlines of the Day
Stripe Buys Crypto Wallet Privy After Bridge Deal - via X
Trump Calls CPI Data "Great" Urges Full Point Fed Cut - via X
Bitcoin Hashrate Reaches New All-Time High - via X
Get our new STACK SATS hat - via tftcmerch.io
Bitcoin’s Next Parabolic Move: Could Liquidity Lead the Way?
Is bitcoin’s next parabolic move starting? Global liquidity and business cycle indicators suggest it may be.
Read the latest report from Unchained and TechDev, analyzing how global M2 liquidity and the copper/gold ratio—two historically reliable macro indicators—are aligning once again to signal that a new bitcoin bull market may soon begin.
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Life is good.
Download our free browser extension, Opportunity Cost: https://www.opportunitycost.app/ start thinking in SATS today.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ b1ddb4d7:471244e7
2025-06-13 08:01:22
@ b1ddb4d7:471244e7
2025-06-13 08:01:22The latest AI chips, 8K displays, and neural processing units make your device feel like a pocket supercomputer. So surely, with all this advancement, you can finally mine bitcoin on your phone profitably, right?
The 2025 Hardware Reality: Can You Mine Bitcoin on Your Phone
Despite remarkable advances in smartphone technology, the fundamental physics of bitcoin mining haven’t changed. In 2025, flagship devices with their cutting-edge 2nm processors can achieve approximately 25-40 megahashes per second when you mine bitcoin on your phone—a notable improvement from previous generations, but still laughably inadequate.
Meanwhile, 2025’s top-tier ASIC miners have evolved dramatically. The latest Bitmain Antminer S23 series and Canaan AvalonMiner A15 Pro deliver 200-300 terahashes per second while consuming 4,000-5,500 watts. That’s a performance gap of roughly 1:8,000,000 between when you mine bitcoin on your phone and professional mining equipment.
To put this in perspective that hits home: if you mine bitcoin on your phone and it earned you one penny, professional miners would earn $80,000 in the same time period with the same effort. It’s not just an efficiency problem—it’s a complete category mismatch.
According to Pocket Option’s 2025 analysis, when you mine bitcoin on your phone in 2025, you generate approximately $0.003-0.006 in daily revenue while consuming $0.45-0.85 in electricity through constant charging cycles. Factor in the accelerated device wear (estimated at $0.75-1.20 daily depreciation), and you’re looking at losses of $1.20-2.00 per day just for the privilege of running mining software.
Mining Economic Factor
Precise Value (April 2025)
Direct Impact on Profitability
Smartphone sustained hash rate
20-35 MH/s
0.00000024% contribution to global hashrate
Daily power consumption
3.2-4.8 kWh (4-6 full charges)
$0.38-0.57 at average US electricity rates
Expected daily BTC earnings
0.0000000086 BTC ($0.0035 at $41,200 BTC)
Revenue covers only 0.9% of electricity costs
CPU/GPU wear cost
$0.68-0.92 daily accelerated depreciation
Reduces smartphone lifespan by 60-70%
Annual profit projection
-$386 to -$412 per year
Guaranteed negative return on investment
Source: PocketOption
Bitcoin’s 2025 Network: Harder Than Ever
Bitcoin’s network difficulty in 2025 has reached unprecedented levels. After the April 2024 halving event that reduced block rewards from 6.25 to 3.125 BTC, mining became significantly more competitive. The global hash rate now exceeds 800 exahashes per second—that’s 800 followed by 18 zeros worth of computational power securing the network.
Here’s what this means in practical terms: Bitcoin’s mining difficulty adjusts every 2,016 blocks (roughly every two weeks) to maintain the 10-minute block time. As more efficient miners join the network, difficulty increases proportionally. In 2025, mining difficulty has increased compared to 2024, making small-scale mining even less viable.
The math is unforgiving:
- Global Bitcoin hash rate: 828.96 EH/s
- Your smartphone’s contribution: ~0.000000003%
- Probability of solo mining a block: Virtually zero
- Expected time to mine one Bitcoin: Several million years
Even joining mining pools doesn’t solve the economic problem. Pool fees typically range from 1-3%, and your minuscule contribution would earn proportionally tiny rewards—far below the electricity and device depreciation costs.
The 2025 Scam Evolution: More Sophisticated, More Dangerous
Fraudsters now leverage AI-generated content, fake influencer endorsements, and impressive-looking apps that simulate realistic mining activity to entice you to mine bitcoin on your phone.
New 2025 scam tactics include:
AI-Powered Fake Testimonials: Deepfake videos of supposed successful mobile miners showing fabricated earnings statements and encouraging downloads of malicious apps.
Gamified Mining Interfaces: Apps that look and feel like legitimate games but secretly harvest personal data while simulating mining progress that can never be withdrawn.
Social Media Manipulation: Coordinated campaigns across TikTok, Instagram, and YouTube featuring fake “financial influencers” promoting mobile mining apps to younger audiences.
Subscription Trap Mining: Apps offering “free trials” that automatically charge $19.99-49.99 monthly for “premium mining speeds” while delivering no actual mining capability.
Recent cybersecurity research shows that over 180 fake mining apps were discovered across major app stores in 2025, with some accumulating more than 500,000 downloads before being removed.
Red flags that scream “scam” in 2025:
- Apps claiming “revolutionary mobile mining breakthrough”
- Promises of earning “$10-50 daily” from phone mining
- Requirements to recruit friends or watch ads to unlock withdrawals
- Apps that don’t require connecting to actual mining pools
- Testimonials that seem too polished or use stock photo models
- Apps requesting permissions unrelated to mining (contacts, camera, microphone)
The 2025 Professional Mining Landscape
To understand why, consider what professional bitcoin mining looks like in 2025. Industrial mining operations now resemble high-tech data centers with:
Cutting-edge hardware:
- Bitmain Antminer S23 Pro: 280 TH/s at 4,800W
- MicroBT WhatsMiner M56S++: 250 TH/s at 4,500W
- Canaan AvalonMiner A1566: 185 TH/s at 3,420W
Infrastructure requirements:
- Megawatt-scale power contracts with industrial electricity rates
- Liquid cooling systems maintaining 24/7 optimal temperatures
- Redundant internet connections ensuring zero downtime
- Professional facility management with 24/7 monitoring
For a small operation, you might need at least $10,000 to $20,000 to buy a few ASIC miners, set up cooling systems, and cover electricity costs. These operations employ teams of engineers, maintain relationships with power companies, and operate with margins measured in single-digit percentages.
2025’s Legitimate Mobile Bitcoin Strategies
While it remains impossible to mine bitcoin on your phone profitably, 2025 offers exciting legitimate ways to engage with bitcoin through your smartphone:
Lightning Network Participation: Apps like Phoenix, Breez, and Zeus allow you to run Lightning nodes on mobile devices, earning small routing fees while supporting bitcoin’s payment layer.
Bitcoin DCA Automation: Services enable automated dollar-cost averaging with amounts as small as $1 daily. Historical data shows $10 weekly bitcoin purchases consistently outperform any mobile mining attempt by 1,500-2,000%.
Educational Mining Simulators: Legitimate apps like “Bitcoin Mining Simulator” teach mining concepts without false earning promises. These educational tools help users understand hash rates, difficulty adjustments, and mining economics.
Stacking Sats Rewards: Apps offering bitcoin rewards for shopping, learning, or completing tasks.
Lightning Gaming: Bitcoin-native mobile games where players can earn sats through skilled gameplay, with some players earning $10 monthly.onfirm that even the most optimized mobile mining setups in 2025 lose money consistently and predictably.
The Bottom Line
When you mine bitcoin on your phone fundamental economics remain unchanged: it’s impossible to profit. The laws of physics, network competition, and energy efficiency create insurmountable barriers that no app can overcome.
However, 2025 offers unprecedented opportunities to engage with bitcoin meaningfully through your smartphone. Focus on education, legitimate earning opportunities, and strategic investment rather than chasing the impossible dream of phone-based mining.
The bitcoin community’s greatest strength lies in its commitment to truth over hype. When someone promises profits to mine bitcoin on your phone in 2025, they’re either uninformed or deliberately misleading you. Trust the mathematics, learn from the community, and build your bitcoin knowledge and holdings through proven methods.
The real opportunity in 2025 isn’t to mine bitcoin on your phone—it’s understanding bitcoin deeply enough to participate confidently in the most important monetary revolution of our lifetime. Your smartphone is the perfect tool for that education; it’s just not a mining rig.
-
 @ f683e870:557f5ef2
2025-06-11 13:33:34
@ f683e870:557f5ef2
2025-06-11 13:33:34This is what has been achieved on a per-project basis since receiving the grant from Opensats.
npub.world
Together with nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, I have been refining npub.world to deliver real-time, WoT-powered profile search. These refinements include:
-
implementing new desings by nostr:npub1t3gd5yefglarhar4n6uh34uymvft4tgu8edk5465zzhtv4rrnd9sg7upxq
-
moving to the new Vertex DVM standard
-
improved URL and npub parsing
Vertex crawler
Due to the architectural mistakes I made when designing the first version, I have embarked on a full rewrite of the crawler. The new architecture is simpler, more modular and more performant, and I am confident that it will provide a stable foundation on which to expand the Vertex offering with additional functionalities and analytics.
The major differences with the old version are:
-
the
DBandRWSinterfaces have been broken up and simplified into smaller ones, each defined by their own packages -
a simplified, more efficient algorithm for updating random walks
-
use of a custom-built cache to speed up graph computations
-
a worker pool pattern to speed up event archiving
These changes have reduced the LOC by more than half while improving performance by \~10x. Of independent interest is the new pipe package, which can also be used by other projects to crawl the Nostr network.
Vertex Relay and DVMs
The Vertex relay has been updated several times, and now supports four DVM services:
-
Verify Reputation -
Recommend Follows -
Rank Profiles -
Search Profile
For each service, customers can choose the algorithm to use by specifing the sort option to use between:
-
followerCount -
globalPagerank -
personalizedPagerank
More information can be found at https://vertexlab.io/.
Overall, the relay has processed more than 100,000 DVM requests, with the current daily rate standing at around 1,500.
rely
Unsatisfied with the khatru relay framework, I've decided to build my own called rely, with the goal of being simpler and more stable. I've not just scratched a personal hitch: I've used khatru for several months now (the Vertex relay is still using it) and I encountered several issues, some of which I've solved with PRs to the underlying go-nostr library.
The main differences between khatru and rely:
-
rely is much simpler, both architecturally and in terms of LOC (less than half)
-
rely has a solid testing approach, where a random yet reproducible high traffic hits the relay to see what breaks
-
rely implements a worker pool pattern where a configurable number of goroutines process the incoming requests from clients. On the other hand, khatru process them in the HandleWebsocket goroutine, which is spawned every time a client connects. This is dangerous in my opinion because if too many clients connect, memory usage would spike and the relay could potentially crash.
New DVM spec
I helped to draft this new proposal to update the DVM spec, which is one of the most controversial NIPs. While almost everyone agrees that it needs to change, there is no consensus on how to move forward. I believe our proposal is a sensible approach that defines discovery, usage, and error patterns while leaving flexibility for specific DVM kinds.
Looking at the future
Next I am going to move the Vertex relay to the rely framework and to the new crawler package. I expect that this will increase the performance and will make things more solid and more simple. After all of this refactoring and simplification, it will be time to finally add features to the Vertex offering. I have an ambitious roadmap consisting of:
-
accepting ecash for DVM requests
-
designing client-side validation schemes for the DVM responses
-
expanding the pagerank algorithm to make use of mutes and reports
-
adding an WoT impersonator check to npub.world
-
adding a nip05 check to npub.world
-
make a relystore package with some plug&play databases for rely.
-
-
 @ 6ad3e2a3:c90b7740
2025-06-11 08:29:54
@ 6ad3e2a3:c90b7740
2025-06-11 08:29:54Turning and turning in the widening gyre
The falcon cannot hear the falconer;
Things fall apart; the centre cannot hold;
Mere anarchy is loosed upon the world,
The blood-dimmed tide is loosed, and everywhere
The ceremony of innocence is drowned;
The best lack all conviction, while the worst
Are full of passionate intensity.
Surely some revelation is at hand;
Surely the Second Coming is at hand.
The Second Coming! Hardly are those words out
When a vast image out of Spiritus Mundi
Troubles my sight: somewhere in sands of the desert
A shape with lion body and the head of a man,
A gaze blank and pitiless as the sun,
Is moving its slow thighs, while all about it
Reel shadows of the indignant desert birds.
The darkness drops again; but now I know
That twenty centuries of stony sleep
Were vexed to nightmare by a rocking cradle,
And what rough beast, its hour come round at last,
Slouches towards Bethlehem to be born?
The Second Coming — W.B. Yeats
I don’t know what I want to write about today. There are a lot of converging currents coursing through my reality right now. I feel we’re in an interregnum of sorts between what was and what’s to come. I guess you could simply describe that as the present, something that has ever been the case. But this moment feels more intense like something big is dying and something else, God knows what, is on its way “to be born".
I exchanged emails recently with an old friend, and he sent me a link to a David Foster Wallace commencement speech entitled “This Is Water.” In it Wallace tells a joke of an old fish seeing two younger fish swimming by and asks them “How’s the water?” Later on one of the younger ones asks the other, “What is water?”
Wallace hanged himself a few years after the speech. Apparently he was unable to maintain the perspective he laid out in it which was that we can choose our attitude toward what we experience in any moment, no matter how much aversion we habitually associate with it. That the act of choosing equanimity constitutes the freedom we seek. That this freedom to choose is ever present, in fact the ability to direct our attention and consciousness is itself the water. And yet out of habit we are often oblivious to this most fundamental reality.
My friend’s email was in response to my description of the dissolution I see right now. Everything seems fake. The news, the governments, the edicts of reputationally bankrupt institutions zombying along as though the last five years never happened, like the proverbial emperor still purporting to rule though everyone can now see his pale, unsightly posterior.
Yes, the coffee shops are still open, people still go on vacation with their families. Let’s go to Paris, Rome, the Greek Isles! Let’s pretend everything is as we had imagined in the before times when our goals and aspirations seemed real, when the glitchy pixels in the matrix hadn’t yet revealed themselves so glaringly.
Maybe this was always the case. All our games were always professional wrestling, a scripted charade for which we willingly suspended disbelief. But like the roadrunner in the cartoon, we have since become aware we have run out of road, four steps beyond the cliff edge.
. . .
Wallace in his speech described such indignities as being stuck in traffic after a long day of work, or in a long grocery checkout line. The mind’s usual programs run, cursing everyone and everything around us. Instead of contemplating the miracle of human existence we feel only disgust and impatience. We want to finish with the run, the work, the obligatory hour so we can move on to something presumably more pleasant.
I can handle such day to day discomforts, but the overwhelming sense of dissolution is undermining the aims to which I had once attached meaning. I set up my life for freedom and prosperity, and now, just as I have my ducks in a row, there’s an imminent magnetic pole shift or a financial and social collapse that threatens to counterfeit my efforts.
It’s easy to opt out when you’re losing, to decry the injustice, unfairness and pointlessness of the game when you weren’t getting much from it anyway. When you’ve got nothing, you’ve got nothing to lose, to paraphrase Bob Dylan. But as a late bloomer wanting to sample the wine of the Gods at long last, it’s dispiriting in a different way, like saving up for a new car and seeing it stolen before you had a chance to drive it.
That’s the shallow version, distress at discovering just before getting the things I had always wanted I was actually playing not just the wrong game, but a false one. That I’m upset I can’t gratify my ego in the way I had hoped, that I can’t get the pat on the back I had craved because the back-patters decided to tear up the playing field just as I finally became a contender.
The deeper version is you only get better at the game through your own efforts to discover what’s true, your own self-mastery and access to a measure of wisdom. This process transforms your life from a tedious and difficult slog to a state of ease and flow. You are more connected, more in touch with yourself and the forces within. You can handle aversion, in fact voluntarily invite it at times to hone your mind and access your resourcefulness. You love your life and connect to the people in it. You have great hope and aspirations for the future. You believe in God, or the Tao or whatever force animates all things, you can navigate the world’s imperfections and do not want it to fall into chaos and disorder.
The task of remembering this during the run, the traffic jam or the grocery store checkout line is not so difficult. But would it be the same during periods of violence and resource scarcity where literal survival is at stake, the rules of which are set by biology and physics rather than the incentives of human society?
Yes, I’d rather be eating dinner at home than sitting in traffic, but I can appreciate that I’m able to sit comfortably in my climate controlled pod, listening to music while traversing these distances rather than foraging for food in the harsh wild. Yes, this old Portuguese lady is taking an eternity to get the groceries into her pushcart, but I can imagine how it is to be old and slow and still have to shop and eat, and it’s trivial to cut her some slack.
I’m not claiming I always have this perspective, but I surely am able to channel equanimity during the ordinary aversion that arises in one’s day to day life. I do this while running on the track, the aches and pains, the discomfort, the wanting to get it over with is a battle I fight every week by my own choosing. But imagine if instead of running 10 minute miles I was forced to do them in six. It’s not so easy to keep a calm, conscious mind while gasping for breath.
The truth is these calamities I imagine are not yet real, the asteroid has not yet hit, the economy not yet collapsed. I have never experienced the kind of hardship I dread. I am ever in the grocery line, the 10-minute mile run, the traffic jam, never the concentration camp or Mad Max-style post-apocalypse. Why not just deal with that when the time comes, if it ever comes? Why die a thousand deaths like the proverbial coward rather than the one required of the brave man?
I suppose it comes down to wanting to be prepared. There’s nothing you can do if an asteroid destroys the entire earth, but if your national government devolves into tyranny, you could get out before it’s too late. There’s the adage one should only concern oneself about the things one can control, but the rub is in deciding what’s in your power and of what to let go. It’s an easy out, per the adage, to narrow your locus of control to doing your job and paying your bills. You can too easily forget that which job you have, where you live, what preparations to make are also matters in which you have a choice.
Even if you believe a magnetic pole shift could spill the earth’s oceans across continents within the next few decades — I find this plausible — you could move to the mountains to get ahead even of that. A fatalist, non-questioning attitude can be a psychological salve in times of upheaval, but “salve” and "“slave” are but a typo apart.
. . .
When I was six someone broke into my house. I was still awake, and while pretending to be asleep, I heard him rummaging through my belongings, stealing an old Fisher Price turntable and a black and white TV. My father died four years later, and at 10, I remember thinking as the oldest boy in the house, it was now my responsibility to defend my family if anything like that, or worse, happened again. Of course, I wasn’t really capable of doing this, and I knew it, but I would have to try, futile as it might be.
I imagine that psychology has stayed with me as an adult — it’s up to me to see around corners, assess the various threats to me and my family, even if some of them are too daunting for any one individual. I could let it go, I suppose, it would probably even be healthy to do so. But there is a part of me that wonders whether people like me, people who feel this irrational responsibility, are the those who survive cataclysms and shocks. I surely am not the only one who feels this way and quite likely would not be especially effective given I don’t have engineering, outdoorsman or serious combat skills. But that hyper-vigilance toward and preparation for worse-case scenarios is something someone has to do, someone who would likely be selected for the role by the particular accidents of his upbringing.
. . .
There is another way to look at this, of course. The notion one ought to step up in the face of adverse circumstances, even extreme ones, is valid. But perhaps the best way to prepare is not endlessly to assess potential threats like some black ops CIA outfit, but to have a calm and detached mind. Should the signs appear, a poised and observant person would take action insofar as he is able. That you, having trained your attention away from default habits of comfort-seeking and dread and toward conscious observation, will do what’s required if and when the time comes. That you can trust yourself, and by that I mean trust in God, so to speak, to guide your awareness and actions for the most effective and adaptive response.
The Fourth Turning might well be upon us, indeed “the centre [may not] hold.” There is no guarantee your response will ensure you or those you love survive. There has never been such a guarantee for anyone, only the freedom to direct your attention, to choose your state of mind, to the extent you are capable, in the conditions that arise. To respond to the older fish that the water is okay, it’s pretty nice actually.
-
 @ 97c70a44:ad98e322
2025-06-09 18:23:27
@ 97c70a44:ad98e322
2025-06-09 18:23:27When developing on nostr, normally it's enough to read the NIP related to a given feature you want to build to know what has to be done. But there are some aspects of nostr development that aren't so straightforward because they depend less on specific data formats than on how different concepts are combined.
An example of this is how for a while it was considered best practice to re-publish notes when replying to them. This practice emerged before the outbox model gained traction, and was a hacky way of attempting to ensure relays had the full context required for a given note. Over time though, pubkey hints emerged as a better way to ensure other clients could find required context.
Another one of these things is "relay-based groups", or as I prefer to call it "relays-as-groups" (RAG). Such a thing doesn't really exist - there's no spec for it (although some aspects of the concept are included in NIP 29), but at the same time there are two concrete implementations (Flotilla and Chachi) which leverage several different NIPs in order to create a cohesive system for groups on nostr.
This composability is one of the neat qualities of nostr. Not only would it be unhelpful to specify how different parts of the protocol should work together, it would be impossible because of the number of possible combinations possible just from applying a little bit of common sense to the NIPs repo. No one said it was ok to put
ttags on akind 0. But no one's stopping you! And the semantics are basically self-evident if you understand its component parts.So, instead of writing a NIP that sets relay-based groups in stone, I'm writing this guide in order to document how I've combined different parts of the nostr protocol to create a compelling architecture for groups.
Relays
Relays already have a canonical identity, which is the relay's url. Events posted to a relay can be thought of as "posted to that group". This means that every relay is already a group. All nostr notes have already been posted to one or more groups.
One common objection to this structure is that identifying a group with a relay means that groups are dependent on the relay to continue hosting the group. In normal broadcast nostr (which forms organic permissionless groups based on user-centric social clustering), this is a very bad thing, because hosts are orthogonal to group identity. Communities are completely different. Communities actually need someone to enforce community boundaries, implement moderation, etc. Reliance on a host is a feature, not a bug (in contrast to NIP 29 groups, which tend to co-locate many groups on a single host, relays-as-groups tends to encourage one group, one host).
This doesn't mean that federation, mirrors, and migration can't be accomplished. In a sense, leaving this on the social layer is a good thing, because it adds friction to the dissolution/forking of a group. But the door is wide open to protocol additions to support those use cases for relay-based groups. One possible approach would be to follow this draft PR which specifies a "federation" event relays could publish on their own behalf.
Relay keys
This draft PR to NIP 11 specifies a
selffield which represents the relay's identity. Using this, relays can publish events on their own behalf. Currently, thepubkeyfield sort of does the same thing, but is overloaded as a contact field for the owner of the relay.AUTH
Relays can control access using NIP 42 AUTH. There are any number of modes a relay can operate in:
- No auth, fully public - anyone can read/write to the group.
- Relays may enforce broad or granular access controls with AUTH.
Relays may deny EVENTs or REQs depending on user identity. Messages returned in AUTH, CLOSED, or OK messages should be human readable. It's crucial that clients show these error messages to users. Here's how Flotilla handles failed AUTH and denied event publishing:
LIMITS, PROBE, or some other reflection scheme could also be used in theory to help clients adapt their interface depending on user abilities and relay policy.
- AUTH with implicit access controls.
In this mode, relays may exclude matching events from REQs if the user does not have permission to view them. This can be useful for multi-use relays that host hidden rooms. This mode should be used with caution, because it can result in confusion for the end user.
See Frith for a relay implementation that supports some of these auth policies.
Invite codes
If a user doesn't have access to a relay, they can request access using this draft NIP. This is true whether access has been explicitly or implicitly denied (although users will have to know that they should use an invite code to request access).
The above referenced NIP also contains a mechanism for users to request an invite code that they can share with other users.
The policy for these invite codes is entirely up to the relay. They may be single-use, multi-use, or require additional verification. Additional requirements can be communicated to the user in the OK message, for example directions to visit an external URL to register.
See Frith for a relay implementation that supports invite codes.
Content
Any kind of event can be published to a relay being treated as a group, unless rejected by the relay implementation. In particular, NIP 7D was added to support basic threads, and NIP C7 for chat messages.
Since which relay an event came from determines which group it was posted to, clients need to have a mechanism for keeping track of which relay they received an event from, and should not broadcast events to other relays (unless intending to cross-post the content).
Rooms
Rooms follow NIP 29. I wish NIP 29 wasn't called "relay based groups", which is very confusing when talking about "relays as groups". It's much better to think of them as sub-groups, or as Flotilla calls them, "rooms".
EDIT: Flotilla has migrated to exclusively use "managed rooms" — i.e., fully NIP 29 compliant rooms. Relays without NIP 29 support can still support chat, but all messages will be presented as sent to a single room. I've removed references to unmanaged rooms in what follows.
~~Rooms have two modes - managed and unmanaged. Managed~~ rooms follow all the rules laid out in NIP 29 about metadata published by the relay and user membership. In either case, rooms are represented by a random room id, and are posted to by including the id in an event's
htag. ~~This allows rooms to switch between managed and unmanaged modes without losing any content.~~Managed room names come from
kind 39000room meta events, ~~but unmanaged rooms don't have these. Instead, room names should come from members' NIP 51kind 10009membership lists. Tags on these lists should look like this:["group", "groupid", "wss://group.example.com", "Cat lovers"]. If no name can be found for the room (i.e., there aren't any members), the room should be ignored by clients.~~Rooms present a difficulty for publishing to the relay as a whole, since content with an
htag can't be excluded from requests. ~~Currently, relay-wide posts are h-tagged with_which works for "group" clients, but not more generally. I'm not sure how to solve this other than to ask relays to support negative filters.~~ I have ideas on how to solve this in future iterations of relay-based groups, for example using virtual relays or just a better rooms spec.Cross-posting
The simplest way to cross-post content from one group (or room) to another, is to quote the original note in whatever event kind is appropriate. For example, a blog post might be quoted in a
kind 9to be cross-posted to chat, or in akind 11to be cross-posted to a thread.kind 16reposts can be used the same way if the reader's client renders reposts.Posting the original event to multiple relays-as-groups is trivial, since all you have to do is send the event to the relay. Posting to multiple rooms simultaneously by appending multiple
htags is however not recommended, since group relays/clients are incentivised to protect themselves from spam by rejecting events with multiplehtags (similar to how events with multiplettags are sometimes rejected).Privacy
Currently, it's recommended to include a NIP 70
-tag on content posted to relays-as-groups to discourage replication of relay-specific content across the network.Another slightly stronger approach would be for group relays to strip signatures in order to make events invalid (or at least deniable). For this approach to work, users would have to be able to signal that they trust relays to be honest. We could also use ZkSNARKS to validate signatures in bulk.
In any case, group posts should not be considered "private" in the same way E2EE groups might be. Relays-as-groups should be considered a good fit for low-stakes groups with many members (since trust deteriorates quickly as more people get involved).
Membership
There is currently no canonical member list published by relays (except for NIP 29 managed rooms). Instead, users keep track of their own relay and room memberships using
kind 10009lists. Relay-level memberships are represented by anrtag containing the relay url, and room-level memberships are represented using agrouptag.Users can choose to advertise their membership in a RAG by using unencrypted tags, or they may keep their membership private by using encrypted tags. Advertised memberships are useful for helping people find groups based on their social graph:

User memberships should not be trusted, since they can be published unilaterally by anyone, regardless of actual access, so it's better to think of them as "bookmarked groups" or "favorites". Possible improvements in this area would be the ability to provide proof of access:
- Relays could publish member lists (although this would sacrifice member privacy)
- Relays could support a new command that allows querying a particular member's access status
- Relays could provide a proof to the member that they could then choose to publish or not
Moderation
There are two parts to moderation: reporting and taking action based on these reports.
Reporting is already covered by NIP 56. Clients should be careful about encouraging users to post reports for illegal content under their own identity, since that can itself be illegal. Relays also should not serve reports to users, since that can be used to find rather than address objectionable content.
Reports are only one mechanism for flagging objectionable content. Relay operators and administrators can use whatever heuristics they like to identify and address objectionable content. This might be via automated policies that auto-ban based on reports from high-reputation people, a client that implements NIP 86 relay management API, or by some other admin interface.
There's currently no way for moderators of a given relay to be advertised, or for a moderator's client to know that the user is a moderator (so that they can enable UI elements for in-app moderation). This could be addressed via NIP 11, LIMITS, or some other mechanism in the future.
General best practices
In general, it's very important when developing a client to assume that the relay has no special support for any of the above features, instead treating all of this stuff as progressive enhancement.
For example, if a user enters an invite code, go ahead and send it to the relay using a
kind 28934event. If it's rejected, you know that it didn't work. But if it's accepted, you don't know that it worked - you only know that the relay allowed the user to publish that event. This is helpful, becaues it may imply that the user does indeed have access to the relay. But additional probing may be needed, and reliance on error messages down the road when something else fails unexpectedly is indispensable.This paradigm may drive some engineers nuts, because it's basically equivalent to coding your clients to reverse-engineer relay support for every feature you want to use. But this is true of nostr as a whole - anyone can put whatever weird stuff in an event and sign it. Clients have to be extremely compliant with Postell's law - doing their absolute best to accept whatever weird data or behavior shows up and handle failure in any situation. Sure, it's annoying, but it's the cost of permissionless development. What it gets us is a completely open-ended protocol, in which anything can be built, and in which every solution is tested by the market.
-
 @ b1ddb4d7:471244e7
2025-06-13 07:02:19
@ b1ddb4d7:471244e7
2025-06-13 07:02:19Jason Lowery’s thesis, Softwar: A Novel Theory on Power Projection and the National Strategic Significance of Bitcoin, reframes bitcoin not merely as digital cash but as a transformative security technology with profound implications for investors and nation-states alike.
For centuries, craft brewers understood that true innovation balanced tradition with experimentation—a delicate dance between established techniques and bold new flavors.
Much like the craft beer revolution reshaped a global industry, bitcoin represents a fundamental recalibration of how humans organize value and project power in the digital age.
The Antler in the Digital Forest: Power Projection
Lowery, a U.S. Space Force officer and MIT scholar, anchors his Softwar theory in a biological metaphor: Bitcoin as humanity’s “digital antler.” In nature, antlers allow animals like deer to compete for resources through non-lethal contests—sparring matches where power is demonstrated without fatal consequences. This contrasts sharply with wolves, who must resort to violent, potentially deadly fights to establish hierarchy.
The Human Power Dilemma: Historically, humans projected power and settled resource disputes through physical force—wars, seizures, or coercive control of assets. Even modern financial systems rely on abstract power structures: court orders, bank freezes, or government sanctions enforced by legal threat rather than immediate physical reality.
Lowery argues this creates inherent fragility: abstract systems can collapse when met with superior physical force (e.g., invasions, revolutions). Nature only respects physical power.
Bitcoin’s Physical Power Engine: Bitcoin introduces a novel solution through its proof-of-work consensus mechanism. Miners compete to solve computationally intense cryptographic puzzles, expending real-world energy (megawatts) to validate transactions and secure the network.
This process converts electricity—a tangible, physical resource—into digital security and immutable property rights. Winning a “block” is like winning a sparring match: it consumes significant resources (energy/cost) but is non-destructive.
The miner gains the right to write the next page of the ledger and collect rewards, but no participant is physically harmed, and no external infrastructure is destroyed.
Table: Traditional vs. Bitcoin-Based Power Systems
Power System
Mechanism
Key Vulnerability
Resource Cost
Traditional (Fiat/Banking)
Legal abstraction, threat of state force
Centralized points of failure, corruption, political change
Low immediate cost, high systemic risk
Military/Economic Coercion
Physical force, sanctions
Escalation, collateral damage, moral hazard
Very high (lives, capital, instability)
Bitcoin (Proof-of-Work)
Competition via energy expenditure
High energy cost, concentration risk (mining)
High energy cost, low systemic risk
Softwar Theory National Strategic Imperative: Governments Are Taking Notice
Lowery’s Softwar Theory has moved beyond academia into the corridors of power, shaping U.S. national strategy:
- The Strategic Bitcoin Reserve: Vice President JD Vance recently framed bitcoin as an instrument projecting American values—”innovation, entrepreneurship, freedom, and lack of censorship”. State legislation is now underway to implement this reserve, preventing easy reversal by future administrations.
- Regulatory Transformation: The SEC is shifting from an “enforcement-first” stance under previous leadership. New initiatives include:
- Repealing Staff Accounting Bulletin 121 (SAB 121), which discouraged banks from custodying digital currency by forcing unfavorable balance sheet treatment.
- Creating the Cyber and Emerging Technologies Unit (CETU) to develop clearer crypto registration/disclosure rules.
The Investor’s Lens: Scarcity, Security, and Asymmetric Opportunity
For investors, understanding “Softwar” validates bitcoin’s unique value proposition beyond price speculation:
-
Digital Scarcity as Strategic Depth: Bitcoin’s fixed supply of 21 million makes it the only digital asset with truly inelastic supply, a programmed scarcity immune to political whims or central bank printing.
This “scarcity imperative” acts as a natural antidote to global fiat debasement. As central banks expanded money supplies aggressively (Global M2), bitcoin’s price has shown strong correlation, acting as a pressure valve for inflation concerns. The quadrennial “halving” (latest: April 2024) mechanically reduces new supply, creating built-in supply shocks as adoption grows. * The Antifragile Security Feedback Loop: Bitcoin’s security isn’t static; it’s antifragile. The network strengthens through demand: * More users → More transactions → Higher fees → More miner revenue → More hashpower (computational security) → Greater network resilience → More user confidence.
This self-reinforcing cycle contrasts sharply with traditional systems, where security is a cost center (e.g., bank security budgets, military spending). Bitcoin turns security into a profitable, market-driven activity. * Institutionalization Without Centralization: While institutional ownership via ETFs (like BlackRock’s IBIT) and corporate treasuries (MicroStrategy, Metaplanet) has surged, supply remains highly decentralized.Individuals still hold the largest share of bitcoin, preventing a dangerous concentration of control. Spot Bitcoin ETFs alone are projected to see over $20 billion in net inflows in 2025, demonstrating robust institutional capital allocation.
The Bitcoin Community: Building the Digital Antler’s Resilience
Lowery’s “Softwar” theory underscores why bitcoin’s decentralized architecture is non-negotiable. Its strength lies in the alignment of incentives across three participant groups:
- Miners: Provide computational power (hashrate), validating transactions and securing the network. Incentivized by block rewards (newly minted BTC) and transaction fees. Their physical energy expenditure is the “muscle” behind the digital antler.
- Nodes: Independently verify and enforce the protocol rules, maintaining the blockchain’s integrity. Run by users, businesses, and enthusiasts globally. They ensure decentralized consensus, preventing unilateral protocol changes.
- Users: Individuals, institutions, and corporations holding, transacting, or building on bitcoin. Their demand drives transaction fees and fuels the security feedback loop.
This structure creates “Mutually Assured Preservation”. Attacking bitcoin requires overwhelming its global, distributed physical infrastructure (miners/nodes), a feat far more complex and costly than seizing a central bank’s gold vault or freezing a bank’s assets. It transforms financial security from a centralized liability into a decentralized, physically-grounded asset.
Risks & Responsibilities
Investors and policymakers must acknowledge persistent challenges:
- Volatility: Bitcoin remains volatile, though this has decreased as markets mature. Dollar-cost averaging (DCA) is widely recommended to mitigate timing risk.
- Regulatory Uncertainty: While U.S. policy is increasingly favorable, global coordination is lacking. The EU’s MiCAR regulation exemplifies divergent approaches.
- Security & Custody: While Bitcoin’s protocol is robust, user errors (lost keys) or exchange hacks remain risks.
- Environmental Debate: Proof-of-Work energy use is scrutinized, though mining increasingly uses stranded energy/renewables. Innovations continue.
Jason Lowery’s “Softwar” theory elevates bitcoin from a financial instrument to a socio-technological innovation on par with the invention of the corporation, the rule of law, or even the antler in evolutionary biology. It provides a coherent framework for understanding why:
- Nations like the U.S. are looking to establish bitcoin reserves and embracing stablecoins—they recognize bitcoin’s role in projecting economic power non-violently in the digital age.
- Institutional Investors are allocating billions via ETFs—they see a scarce, secure, uncorrelated asset with antifragile properties.
- Individuals in hyperinflationary economies or under authoritarian regimes use bitcoin—it offers self-sovereign wealth storage immune to seizure or debasement.
For the investor, bitcoin represents more than potential price appreciation. It offers exposure to a fundamental reorganization of how power and value are secured and exchanged globally, grounded not in abstract promises, but in the unyielding laws of physics and mathematics.
Like the brewers who balanced tradition with innovation to create something enduring and valuable, bitcoin pioneers are building the infrastructure for a more resilient digital future—one computationally secured block at a time. The “Softwar” is here, and it is reshaping the landscape of p
-
 @ b1ddb4d7:471244e7
2025-06-13 06:01:13
@ b1ddb4d7:471244e7
2025-06-13 06:01:13Paris, France – June 6, 2025 – Flash, the easiest Bitcoin payment gateway for businesses, just announced a new partnership with the Bitcoin Only Brewery, marking the first-ever beverage company to leverage Flash for seamless Bitcoin payments.
Bitcoin Buys Beer Thanks to Flash!

As Co-Founder of Flash, it's not every day we get to toast to a truly refreshing milestone.
Okay, jokes aside.
We're super buzzed to see our friends at @Drink_B0B
Bitcoin Only Brewery using Flash to power their online sales!The first… pic.twitter.com/G7TWhy50pX
— Pierre Corbin (@CierrePorbin) June 3, 2025
Flash enables Bitcoin Only Brewery to offer its “BOB” beer with, no-KYC (Know Your Customer) delivery across Europe, priced at 19,500 sats (~$18) for the 4-pack – shipping included.
The cans feature colorful Bitcoin artwork while the contents promise a hazy pale ale: “Each 33cl can contains a smooth, creamy mouthfeel, hazy appearance and refreshing Pale Ale at 5% ABV,” reads the product description.
Pierre Corbin, Co-Founder of Flash, commented: “Currently, bitcoin is used more as a store of value but usage for payments is picking up. Thanks to new innovation on Lightning, bitcoin is ready to go mainstream for e-commerce sales.”
Flash, launched its 2.0 version in March 2025 with the goal to provide the easiest Bitcoin payment gateway for businesses worldwide. The platform is non-custodial and can enable both digital and physical shops to accept Bitcoin by connecting their own wallets to Flash.
By leveraging the scalability of the Lightning Network, Flash ensures instant, low-cost transactions, addressing on-chain Bitcoin bottlenecks like high fees and long wait times.
Bitcoin payment usage is growing thanks to Lightning
In May, fast-food chain Steak ‘N Shake went viral for integrating bitcoin at their restaurants around the world. In the same month, the bitcoin2025 conference in Las Vegas set a new world record with 4,000 Lightning payments in one day.
According to a report by River Intelligence, public Lightning payment volume surged by 266% from August 2023 to August 2024. This growth is also reflected in the overall accessibility of lighting infrastructure for consumers. According to Lightning Service Provider Breez, over 650 Million users now have access to the Lightning Network through apps like CashApp, Kraken or Strike.
Bitcoin Only Brewery’s adoption of Flash reflects the growing trend of businesses integrating Bitcoin payments to cater to a global, privacy-conscious customer base. By offering no-KYC delivery across Europe, the brewery aligns with the ethos of decentralization and financial sovereignty, appealing to the increasing number of consumers and businesses embracing Bitcoin as a legitimate payment method.
“Flash is committed to driving innovation in the Bitcoin ecosystem,” Corbin added. “We’re building a future where businesses of all sizes can seamlessly integrate Bitcoin payments, unlocking new opportunities in the global market. It’s never been easier to start selling in bitcoin and we invite retailers globally to join us in this revolution.”
For businesses interested in adopting Bitcoin payments, Flash offers a straightforward onboarding process, low fees, and robust support for both digital and physical goods. To learn more, visit paywithflash.com.
About Flash
Flash is the easiest Bitcoin payment gateway for businesses to accept payments. Supporting both digital and physical enterprises, Flash leverages the Lightning Network to enable fast, low-cost Bitcoin transactions. Launched in its 2.0 version in March 2025, Flash is at the forefront of driving Bitcoin adoption in e-commerce.
About Bitcoin Only Brewery
Bitcoin Only Brewery (@Drink_B0B) is a pioneering beverage company dedicated to the Bitcoin ethos, offering high-quality beers payable exclusively in Bitcoin. With a commitment to personal privacy, the brewery delivers across Europe with no-KYC requirements.
Media Contact:
Pierre Corbin
Co-Founder, Flash
Email: press@paywithflash.com
Website: paywithflash.comPhotos paywithflash.com/about/pressHow Flash Enables Interoperable, Self-Custodial Bitcoin Commerce
-
 @ 7f6db517:a4931eda
2025-06-13 03:02:44
@ 7f6db517:a4931eda
2025-06-13 03:02:44
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
If you missed my nostr introduction post you can find it here. My nostr account can be found here.
We are nearly at the point that if something interesting is posted on a centralized social platform it will usually be posted by someone to nostr.
We are nearly at the point that if something interesting is posted exclusively to nostr it is cross posted by someone to various centralized social platforms.
We are nearly at the point that you can recommend a cross platform app that users can install and easily onboard without additional guides or resources.
As companies continue to build walls around their centralized platforms nostr posts will be the easiest to cross reference and verify - as companies continue to censor their users nostr is the best censorship resistant alternative - gradually then suddenly nostr will become the standard. 🫡
Current Nostr Stats
If you found this post helpful support my work with bitcoin.

-
 @ df478568:2a951e67
2025-06-12 18:58:48
@ df478568:2a951e67
2025-06-12 18:58:48How To Mine Your Own Vanity Nostr Key
note. This article works best on https://habla.news/u/marc@primal.net/how-to-mine-a-nostr-vanity-key-with-rana
Rana is a vanity npub generator.
I'll show you how to use it on Ubuntu.
If you're not Linux ninja and use Windows instead of Linux ninja weapons, you can still use Linux with Virtualbox, free ans open source virtualization software. Head over to
https://www.virtualbox.org/ to learn more. They also have an enterprise business if you need that sort of thing, you can learn more at https://shop.oracle.com/
Rana is a nostr vanity key mining program. The source code can be found here.
Rana Is On GitHub
https://github.com/grunch/rana
Since rana already has pretty good docs, I decided to make a video instead of write about this because It's easier to see rana in action than it is to write about Rana. I went off on some tangents, so I might edit this down later, but I hope it helps you mine your own nostr key.
nevent1qqsfk7a000m8zc3ptsuu4vytepqc9eedceclpt2ns9pzlech5cpaflceng5al
Show Notes
https://github.com/grunch/rana
https://virtualbox.org/
https://doc.rust-lang.org/cargo/getting-started/installation.html
cargo run --release -- --vanity-n-prefix=juxtap0se
☮️
nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
-
 @ 7f6db517:a4931eda
2025-06-12 15:02:58
@ 7f6db517:a4931eda
2025-06-12 15:02:58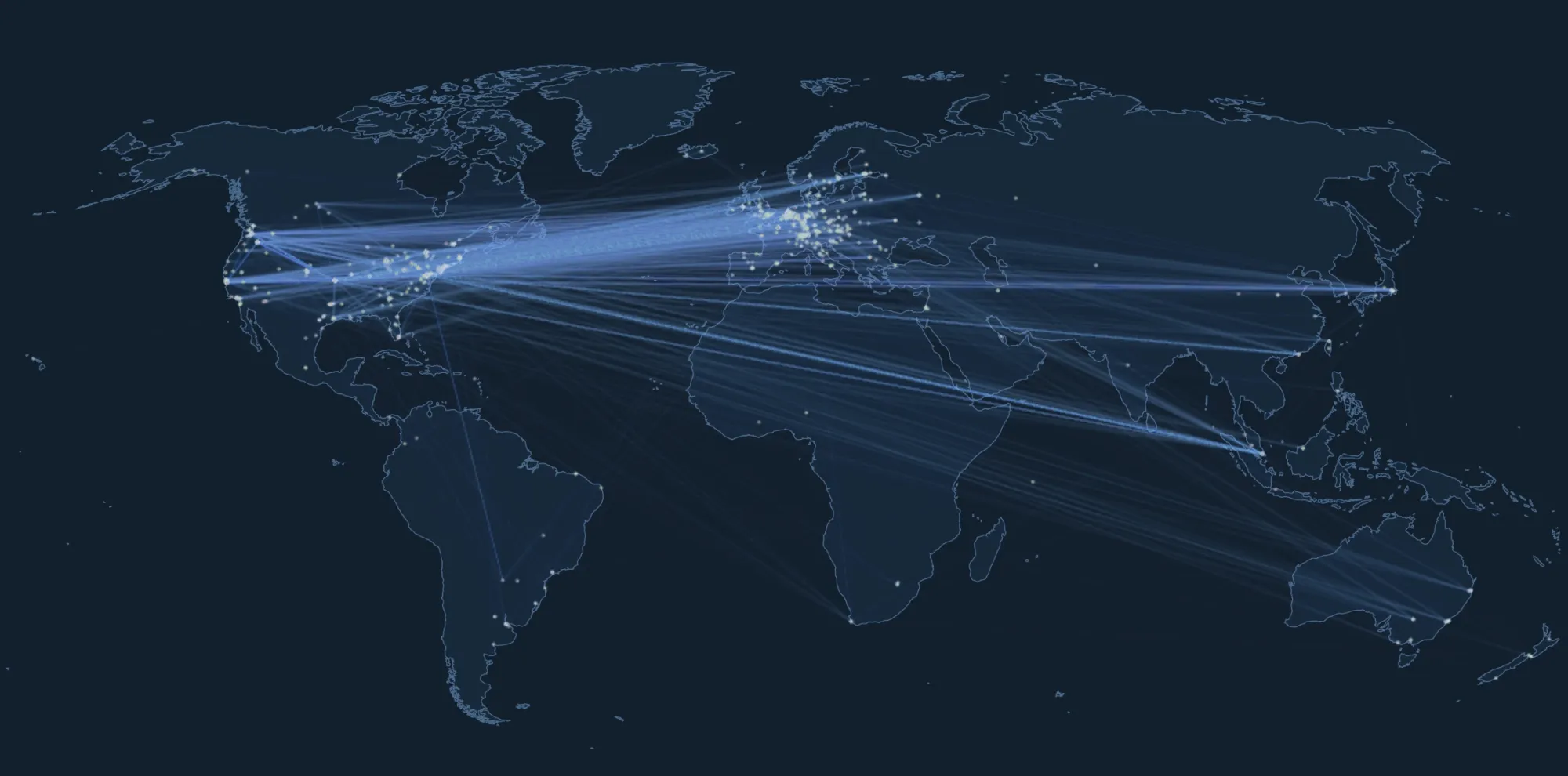
The former seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
The latter's future remains to be seen. Dependence on Tor, which has had massive reliability issues, and lack of strong privacy guarantees put it at risk.
— ODELL (@ODELL) October 27, 2022
The Basics
- Lightning is a protocol that enables cheap and fast native bitcoin transactions.
- At the core of the protocol is the ability for bitcoin users to create a payment channel with another user.
- These payment channels enable users to make many bitcoin transactions between each other with only two on-chain bitcoin transactions: the channel open transaction and the channel close transaction.
- Essentially lightning is a protocol for interoperable batched bitcoin transactions.
- It is expected that on chain bitcoin transaction fees will increase with adoption and the ability to easily batch transactions will save users significant money.
- As these lightning transactions are processed, liquidity flows from one side of a channel to the other side, on chain transactions are signed by both parties but not broadcasted to update this balance.
- Lightning is designed to be trust minimized, either party in a payment channel can close the channel at any time and their bitcoin will be settled on chain without trusting the other party.
There is no 'Lightning Network'
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise.
- There are many lightning channels between many different users and funds can flow across interconnected channels as long as there is a route through peers.
- If a lightning transaction requires multiple hops it will flow through multiple interconnected channels, adjusting the balance of all channels along the route, and paying lightning transaction fees that are set by each node on the route.
Example: You have a channel with Bob. Bob has a channel with Charlie. You can pay Charlie through your channel with Bob and Bob's channel with User C.
- As a result, it is not guaranteed that every lightning user can pay every other lightning user, they must have a route of interconnected channels between sender and receiver.
Lightning in Practice
- Lightning has already found product market fit and usage as an interconnected payment protocol between large professional custodians.
- They are able to easily manage channels and liquidity between each other without trust using this interoperable protocol.
- Lightning payments between large custodians are fast and easy. End users do not have to run their own node or manage their channels and liquidity. These payments rarely fail due to professional management of custodial nodes.
- The tradeoff is one inherent to custodians and other trusted third parties. Custodial wallets can steal funds and compromise user privacy.
Sovereign Lightning
- Trusted third parties are security holes.
- Users must run their own node and manage their own channels in order to use lightning without trusting a third party. This remains the single largest friction point for sovereign lightning usage: the mental burden of actively running a lightning node and associated liquidity management.
- Bitcoin development prioritizes node accessibility so cost to self host your own node is low but if a node is run at home or office, Tor or a VPN is recommended to mask your IP address: otherwise it is visible to the entire network and represents a privacy risk.
- This privacy risk is heightened due to the potential for certain governments to go after sovereign lightning users and compel them to shutdown their nodes. If their IP Address is exposed they are easier to target.
- Fortunately the tools to run and manage nodes continue to get easier but it is important to understand that this will always be a friction point when compared to custodial services.
The Potential Fracture of Lightning
- Any lightning user can choose which users are allowed to open channels with them.
- One potential is that professional custodians only peer with other professional custodians.
- We already see nodes like those run by CashApp only have channels open with other regulated counterparties. This could be due to performance goals, liability reduction, or regulatory pressure.
- Fortunately some of their peers are connected to non-regulated parties so payments to and from sovereign lightning users are still successfully processed by CashApp but this may not always be the case going forward.
Summary
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise. There is no singular 'Lightning Network' but rather many payment channels between distinct peers, some connected with each other and some not.
- Lightning as an interoperable payment protocol between professional custodians seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
- Lightning as a robust sovereign payment protocol has yet to be battle tested. Heavy reliance on Tor, which has had massive reliability issues, the friction of active liquidity management, significant on chain fee burden for small amounts, interactivity constraints on mobile, and lack of strong privacy guarantees put it at risk.
If you have never used lightning before, use this guide to get started on your phone.
If you found this post helpful support my work with bitcoin.

-
 @ a296b972:e5a7a2e8
2025-06-12 12:36:22
@ a296b972:e5a7a2e8
2025-06-12 12:36:22Europa sitzt in einem Demokratie-Simulator. Auf die Scheiben im Cockpit werden Bilder projiziert, die nicht der Realität entsprechen, und es gibt immer noch zu viele Menschen, die diese Simulation nicht erkannt haben.
Nichts wäre erstrebenswerter, als über eine positive Entwicklung, hin zur Vernunft und realitätsbezogenen, auf Tatsachen beruhenden Entscheidungen, berichten zu können. Die Frage ist, ob nicht zuerst unentwegt auf Missstände hingewiesen werden muss, um weitere Menschen dazu zu bewegen, sich denjenigen anzuschließen, die offensichtlich an Indoktrinationsintoleranz leiden.
Wer sich vor Hofberichterstattung und die tägliche Fahrt durch die Gehirnwaschanlage schützen will, der meidet den öffentlich-rechtlichen Unfug und die einschlägigen Käseblätter, die vielleicht noch halbwegs dazu geeignet sind, den Fisch auf dem Markt einzuschlagen, um ihn nach Hause zu tragen, vorausgesetzt, man kann ihn sich noch leisten.
Die Neuen Medien liefern die Informationen, die man sonst im „Qualitäts-Mainstream“ nicht finden kann, was nicht verwundert, denn infiltriert von willigen Erfüllungsgehilfen, die Angst um ihr Prestige und ihre Stellung haben, kann man hier keine freie Berichterstattung erwarten.
Beste Unterhaltung bietet auch die Bundespressekonferenz-Show, auf die schon näher eingegangen wurde. Offizieller Regierungssprech in höchster Perfektion. Ob man dort wirklich davon überzeugt ist, dass es irgendjemanden gibt, der diesen Verlautbarungen Glauben schenkt? Was hat Tante Käthe immer gesagt: G E L D L O C K T I M M E R !
Was also tun? Die Neuen Medien auch noch meiden, und sich vor dem blanken Wahnsinn schützen, in dem man ihn ignoriert, was jedoch nicht bewirkt, dass er nicht mehr da wäre.
Temporäre Abstinenz tut auch hier gut, allerdings ist der Wiedereinstieg so ähnlich, wie der erste Arbeitstag nach einem zweimonatigen Urlaub, falls man nicht in seinem Lieblings-Job gelandet ist.
Und was, wenn die Irren vollends durchdrehen, und man bekommt es nicht mit? Schön, ändern kann man vielleicht wenig, aber man kann sich vielleicht noch eine richtig gute, edle Flasche Rotwein kaufen, und die am Vorabend des Untergangs genießen, oder noch schnell einen Baum pflanzen.
Hier ein Beispiel für jemanden, dessen besonderer Blick sehr an den Universal-Gesundheits-Klima-Hysteriker erinnert:
https\://rumble.com/v6umjdj-respekt-und-anerkennung-deutscher-general-lobt-ukrainische-angriffe-in-russ.html
Wie sieht der Alltag aus, wenn man sich einmal nicht mit den Informationen über Dauer- Bekloppte beschäftigt?
Wenn sich ein Besuch in der nächst größeren Stadt nicht vermeiden lässt, sieht man vor allem gehetzte Menschen, viele mit einem finsteren Blick, anders, als früher.
Viele zahlen mit Karte oder ihrem Handy, Kleckerbeträge. „Zahlen Sie noch bar, oder schon mit Überwachung?“, wünschte man sich, dass die Verkäuferinnen den Kunden fragen würden. Tun sie aber nicht.
Die Menschen scheinen keine Ahnung zu haben, was auf sie zukommt. Im Oktober soll der digitale Euro eingeführt werden, natürlich zuerst nur freiwillig. Was das bedeutet, kennt man ja schon. Freiwilligkeit durch das Schaffen eines Raumes, in dem der Zwang in der Luft hängt, wie damals der Kohlenstaub im Ruhrgebiet. Es wird die persönliche ID vorangetrieben, mit einem Wallet, das die Anonymität und die persönliche Freiheit immer mehr aushöhlen will.
Europa soll unter einen Demokratie-Schutzschirm gestellt werden, der zu nichts anderem dient, als dass diejenigen, die derzeit glauben zu wissen, was gut für die Menschen ist, ihre kruden Vorstellungen auch durchsetzen können. Zweifelhaft, was in den USA vorgeht, was da gerade mit Palantir, natürlich nur zur Sicherheit der Amerikaner, so im Hintergrund schon anläuft. Hierzu gibt es interessante Informationen von Regenauer und Tögel. Einziger Hoffnungsschimmer, besonders für Deutschland: Das klappt sowieso nicht. In den hintersten Bergdörfern in den italienischen Alpen gibt es Glasfaseranschluss, und fährt man in Deutschland auf’s Land, reiht sich Funkloch an Funkloch.
Die wirklich wichtige und große Frage ist, wie können sich Gemeinschaften, die diesen Irrsinn nicht mitmachen wollen, weitgehend aus dem System ausklinken? Bitcoin ist ein erster Schritt zur finanziellen Unabhängigkeit. Eine regionale Lebensmittelversorgung, mit nicht verseuchten, genunmanipulierten, mit Schadstoffen weitgehend unbelasteten Produkten entwickelt sich ebenfalls schon sehr gut. Was, wenn der Zugang zu Informationen über das Internet von einer Anmeldung mit persönlicher ID abhängt und man will und hat keine? Was ist mit Dokumenten, wenn man verreisen oder das Land verlassen will? Was ist, wenn man krank wird und auf das noch vorhandene Rest-Gesundheitssystem angewiesen ist? Was, wenn das Unternehmen seine Mitarbeiter auf staatliche Anweisung zu etwas zwingen muss, was der Mitarbeiter vielleicht gar nicht will, er aber auf das Einkommen angewiesen ist?
Das alles sind Fragen, zu denen es schwer ist, auch in den Neuen Medien, passende Antworten zu finden. Die würden in der Tat Hoffnung machen, dass es ein Schlupfloch gibt, sich, wenn vielleicht auch mit Einschränkungen, den „demokratischen“ Verhältnissen, auf denen nur noch Demokratie draufsteht, aber sehr wenig bis keine Demokratie mehr drin ist, so weit es geht zu entziehen. Sachdienliche Hinweise gerne in der Kommentarfunktion.
Oder ist es „gesünder“, sich zurückzuziehen, die Klappe zu halten und dafür zu sorgen, dass man unter dem Radar bleibt? Diese Gabe ist leider nicht jedem gegeben. Besonders nicht denen, die einen ausgeprägten Wahrheitssinn und ein starkes Gerechtigkeitsgefühl haben.
Menschen die andere belügen, die werden geliebt. Menschen, die anderen sagen, dass sie belogen werden, die werden gehasst.
„Die Wahrheit ist dem Menschen zumutbar.“ (Ingeborg Bachmann)
„Kein Mensch hat das Recht zu gehorchen.“ (Hannah Ahrendt)
“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
* *
(Bild von pixabay)
-
 @ 7f6db517:a4931eda
2025-06-12 04:02:50
@ 7f6db517:a4931eda
2025-06-12 04:02:50

"Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world." - Eric Hughes, A Cypherpunk's Manifesto, 1993
Privacy is essential to freedom. Without privacy, individuals are unable to make choices free from surveillance and control. Lack of privacy leads to loss of autonomy. When individuals are constantly monitored it limits our ability to express ourselves and take risks. Any decisions we make can result in negative repercussions from those who surveil us. Without the freedom to make choices, individuals cannot truly be free.
Freedom is essential to acquiring and preserving wealth. When individuals are not free to make choices, restrictions and limitations prevent us from economic opportunities. If we are somehow able to acquire wealth in such an environment, lack of freedom can result in direct asset seizure by governments or other malicious entities. At scale, when freedom is compromised, it leads to widespread economic stagnation and poverty. Protecting freedom is essential to economic prosperity.
The connection between privacy, freedom, and wealth is critical. Without privacy, individuals lose the freedom to make choices free from surveillance and control. While lack of freedom prevents individuals from pursuing economic opportunities and makes wealth preservation nearly impossible. No Privacy? No Freedom. No Freedom? No Wealth.
Rights are not granted. They are taken and defended. Rights are often misunderstood as permission to do something by those holding power. However, if someone can give you something, they can inherently take it from you at will. People throughout history have necessarily fought for basic rights, including privacy and freedom. These rights were not given by those in power, but rather demanded and won through struggle. Even after these rights are won, they must be continually defended to ensure that they are not taken away. Rights are not granted - they are earned through struggle and defended through sacrifice.
If you found this post helpful support my work with bitcoin.

-
 @ 472f440f:5669301e
2025-06-11 04:37:33
@ 472f440f:5669301e
2025-06-11 04:37:33Marty's Bent
Sup, freaks? Your Uncle Marty did a little vibe coding a couple months ago and that vibe coding project has turned into an actual product that is live in the Google Chrome web store and will soon to be live in the Firefox add-on store as well. It's called Opportunity Cost and it is an extension that enables you to price the internet in Bitcoin.
Opportunity Cost – See Prices in Bitcoin Instantly
Check it out!
This whole process has been extremely rewarding to me for many reasons. The first of which is that I've had many ideas in the past to launch a product focused on bitcoin education that simply never left my brain because I never felt comfortable paying a developer to go out and build a product that I wasn't sure would ultimately get product market fit.
Due to the advancements of AI, particularly ChatGPT and Replit, I was able to spend a few hours on a Saturday vibe coding a prototype for Opportunity Cost. It worked. I side loaded it into Chrome and Firefox, tested it out for a few days and decided, "Hey, I think this is something that's worthwhile and should be built."
Backtracking just a little bit, the initial idea for this app was to create an AR application that would enable you to take pictures of goods in the real world and have their prices automatically converted to bitcoin so that you could weigh the opportunity cost of whether or not you actually wanted to buy that good or decide to save in bitcoin instead. With the help of Justin Moon from the Human Rights Foundation and Anthony Ronning from OpenSecret and Maple AI, I was pointed in the right direction of vibe coding tools I could use to build a simple MVP. I took their advice, built the MVP, and demoed it at the Bitcoin Park Austin weekly AI meetup in mid-April.
The next week, I was talking with a friend, Luke Thomas, about the idea and during our conversation he made a simple quip, "You should make a Chrome extension. I really want a Chrome extension that does this." And that's what sent me down the vibe coding rabbit hole that Saturday which led to the prototype.
After I was comfortable with and confident in the prototype, I found a young hungry developer by the name of Moses on Nostr, I reached out to him, told him my idea, showed him the prototype and asked if he thought he could finish the application for me. He luckily agreed to do so and within a couple of weeks we had a fully functioning app that was officially launched today. We're about 12 hours into the launch and I must say that I'm pleasantly surprised with the reception from the broader Bitcoin community. It seems like something that people are happy exists and I feel extremely happy that people see some value in this particular application.
Now that you have the backstory, let's get into why I think something like Opportunity Cost should exist. As someone who's been writing a newsletter and producing podcasts about bitcoin for eight years in an attempt to educate individuals from around the world about what bitcoin is, why it's important, and how they can leverage it, I've become convinced that a lot of the work that needs to be done still exists at the top of the funnel. You can scream at people. You can grab them by the shoulders. You can shake them. You can remind them at Thanksgiving that if they had listened to your advice during any Thanksgiving in the previous years they would be better off financially. But at the end of the day most people don't listen. They need to see things. Seeing things for yourself is a much more effective teaching mechanism than be lectured to by someone else.
My hope with Opportunity Cost is that it catches the eye of some bitcoin skeptics or individuals who may be on the cusp of falling down the bitcoin rabbit hole and they see the extension as a way to dip their toes into bitcoin to get a better understanding of the world by pricing the goods and services they purchase on a day-to-day month-to-month and year-to-year basis in bitcoin without having to download a wallet or set up an exchange account. The tippy top of the bitcoin marketing funnel.
That is not all though. I think Opportunity Cost can serve individuals at both ends of the funnel. That's why it's pretty exciting to me. It's as valuable to the person who is bitcoin curious and looking to get a better understanding as it is to the hardcore bitcoiner living on a bitcoin standard who is trying to get access to better tools that enable him to get a better grasp of their spending in bitcoin terms.
Lastly, after playing around with it for a few days after I built the prototype, I realized that it has incredible memetic potential. Being able to take a screenshot of goods that people are buying on a day-to-day basis, pricing them in bitcoin and then sharing them on social media is very powerful. Everything from houses to junk items on Amazon to the salaries of pro athletes to your everyday necessities. Seeing the value of those things in bitcoin really makes you think.
One day while I was testing the app, I tried to see how quickly I could find goods on the internet that cumulatively eclipsed the 21 million supply cap limit of bitcoin. To my surprise, even though I've been in bitcoin for 12 years now, it did not take me that long. The opportunity cost of everything I buy on a day-to-day basis becomes very clear when using the extension. What's even clearer is the fact that Bitcoin is completely mispriced at current levels. There is so much winning ahead of us.
Also, it's probably important to note that the extension is open source. You can check out our GitHub page here. Submit pull requests. Suggest changes to the app.
We've also tried to make Opportunity Cost as privacy preserving as possible. Everything within the extension happens in your browser. The only external data that we're providing is the bitcoin to fiat price conversion at any given point in time. We're not data harvesting the web pages you're browsing or the items you're looking at. We're not collecting data and sending it to third party marketers. We want to align ourselves with the open and permissionless nature of bitcoin while also preserving our users' privacy. We're not trying to monetize this in that way. Though, I will say that I'm thinking of ways to monetize Opportunity Cost if it does gain significant traction, but I promise it will be in a way that respects your privacy and is as unobtrusive as possible. We'll see how it goes.
Thank you for coming to my TED talk. Please download and use the extension. Let us know what you think.
Headlines of the Day
Saylor Says Bitcoin Is Perfect Money to Jordan Peterson - via X
Trump Won't Sell Tesla Despite Musk-Bessent Heated Exchange - via X
Bitcoin Gains Traction in Kenya's Largest Slum Kibera - via X
Get our new STACK SATS hat - via tftcmerch.io
Bitcoin’s Next Parabolic Move: Could Liquidity Lead the Way?
Is bitcoin’s next parabolic move starting? Global liquidity and business cycle indicators suggest it may be.
Read the latest report from Unchained and TechDev, analyzing how global M2 liquidity and the copper/gold ratio—two historically reliable macro indicators—are aligning once again to signal that a new bitcoin bull market may soon begin.
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
East Coast aesthetics over everything.
*Download our free browser extension, Opportunity Cost: *<<https://www.opportunitycost.app/>> start thinking in SATS today.
*Get this newsletter sent to your inbox daily: *https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ 58537364:705b4b85
2025-06-12 13:59:39
@ 58537364:705b4b85
2025-06-12 13:59:39ในร่างกายที่มันมีสิ่งที่เรียกว่า… ระบบประสาท ทีนี้มีอะไรเข้ามากระทบร่างกาย คือกระทบระบบประสาท ปฏิกิริยามันก็เกิดขึ้น เป็นเหตุการณ์ อย่างใดอย่างหนึ่งขึ้น
เหตุการณ์นั้นแหละสำคัญ ถ้าให้เกิดความรู้สึกที่ถูกใจมันจะเป็นบวก เหตุการณ์นั้นไม่รู้สึกถูกใจแก่จิต มันก็จะเป็นลบ #ตัวกูเพิ่งเกิดเมื่อมีการกระทบแล้ว
ถ้าเหตุการณ์ที่เป็นบวกเกิดขึ้น ตัวกูบวกก็เกิดขึ้น เหตุการณ์ที่เป็นลบเกิดขึ้น ตัวกูที่เป็นลบเกิดขึ้น #ตัวกูนี้เกิดหลังเหตุการณ์ ขอให้เข้าใจดีๆ ไม่ใช่เกิดอยู่ก่อน
ตัวกูคลอดออกมาจาก situation ที่มากระทบระบบประสาท เช่นว่า… ไม่ได้กินอาหาร ขาดอาหาร มันหิว ความหิวเกิดขึ้นแก่ระบบประสาท ต่อมาจึงเกิด concept ว่า กูหิว, มีการกินแล้วจึงเกิด concept ว่า กูกิน
ถ้ามีอาการอร่อยแก่ลิ้น มันจึงเกิด concept ว่า… กูอร่อย หรือ มาทีหลังเหตุการณ์เสมอ จะถือว่าเป็น product ของเหตุการณ์นั้น ๆ ก็ได้
นี่คือความที่ไม่มีตัวจริง มิใช่ของจริง ของสิ่งที่เรียกว่าตัวกู #ขอให้รู้จักว่าตัวกูนี้มันเป็นมายาถึงขนาดนี้
ฟังดูการพูดอย่างนี้ มันเป็น logic แต่ความจริงของธรรมชาติมันเป็นอย่างนั้น ถือตามกฎ logic ธรรมดาสามัญ ที่พูดกันอยู่นี้ไม่ได้ ต้องถือตามความเป็นจริงที่ว่า มันเป็นอยู่อย่างไร
จิตก็เป็นธาตุชนิดหนึ่ง สิ่งแวดล้อมต่างๆ ที่เป็นธาตุชนิดหนึ่ง พอมาถึงกันเข้า ก็เกิดปฏิกิริยาออกมาอย่างนั้นอย่างนี้ ความรู้สึกที่เรียกว่า… #จิตคิดนึกได้นี้_ก็เป็นปฏิกิริยาที่เกิดขึ้นเท่านั้น แล้วความรู้สึกว่าตัวกู ตัวนี้ก็เป็นเพียงปฏิกิริยาที่เกิดขึ้นเท่านั้น.
มันฟังยากสำหรับท่านทั้งหลายที่ว่า ผู้กระทำนั้นเกิดทีหลังการกระทำ มันผิด logic อย่างนี้
แต่ความจริงเป็นอย่างนั้น self หรือ ego ผู้กระทำจะเกิดทีหลังการกระทำ เป็นปฏิกิริยาของการกระทำ
ความคิดอย่าง ตรรกะ หรืออย่างปรัชญา เอามาใช้กับสิ่งนี้ไม่ได้ ขอยืนยันไว้อย่างนี้
ถ้าท่านยังไม่เชื่อ ท่านก็ไปคิดดูเรื่อย ๆ ไปเถอะ ท่านจะพบว่ามันไม่เป็นอย่างกฎเกณฑ์ทางตรรกะหรือทางปรัชญา ที่เรามีๆ กันอยู่
ผู้กระทำเป็นเพียง concept ไม่ใช่ตัวจริง ส่วนการกระทำมันเป็นเหตุการณ์ของธรรมชาติ พอเข้ามาถึงจิตแล้ว ก็เกิดความคิด ความเชื่อ ความยึดว่าตัวกู
ตัวกูซึ่งเป็นเพียง concept ไม่ใช่ของจริง
พุทธทาสภิกขุ
อตัมมยตาประทีป
ชีวิตใหม่และหนทางเข้าถึงชีวิตใหม่
หน้า_๒๙๕-๒๙๖
-
 @ 7f6db517:a4931eda
2025-06-12 03:02:56
@ 7f6db517:a4931eda
2025-06-12 03:02:56
What is KYC/AML?
- The acronym stands for Know Your Customer / Anti Money Laundering.
- In practice it stands for the surveillance measures companies are often compelled to take against their customers by financial regulators.
- Methods differ but often include: Passport Scans, Driver License Uploads, Social Security Numbers, Home Address, Phone Number, Face Scans.
- Bitcoin companies will also store all withdrawal and deposit addresses which can then be used to track bitcoin transactions on the bitcoin block chain.
- This data is then stored and shared. Regulations often require companies to hold this information for a set number of years but in practice users should assume this data will be held indefinitely. Data is often stored insecurely, which results in frequent hacks and leaks.
- KYC/AML data collection puts all honest users at risk of theft, extortion, and persecution while being ineffective at stopping crime. Criminals often use counterfeit, bought, or stolen credentials to get around the requirements. Criminals can buy "verified" accounts for as little as $200. Furthermore, billions of people are excluded from financial services as a result of KYC/AML requirements.
During the early days of bitcoin most services did not require this sensitive user data, but as adoption increased so did the surveillance measures. At this point, most large bitcoin companies are collecting and storing massive lists of bitcoiners, our sensitive personal information, and our transaction history.
Lists of Bitcoiners
KYC/AML policies are a direct attack on bitcoiners. Lists of bitcoiners and our transaction history will inevitably be used against us.
Once you are on a list with your bitcoin transaction history that record will always exist. Generally speaking, tracking bitcoin is based on probability analysis of ownership change. Surveillance firms use various heuristics to determine if you are sending bitcoin to yourself or if ownership is actually changing hands. You can obtain better privacy going forward by using collaborative transactions such as coinjoin to break this probability analysis.
Fortunately, you can buy bitcoin without providing intimate personal information. Tools such as peach, hodlhodl, robosats, azteco and bisq help; mining is also a solid option: anyone can plug a miner into power and internet and earn bitcoin by mining privately.
You can also earn bitcoin by providing goods and/or services that can be purchased with bitcoin. Long term, circular economies will mitigate this threat: most people will not buy bitcoin - they will earn bitcoin - most people will not sell bitcoin - they will spend bitcoin.
There is no such thing as KYC or No KYC bitcoin, there are bitcoiners on lists and those that are not on lists.
If you found this post helpful support my work with bitcoin.

-
 @ 8d34bd24:414be32b
2025-06-11 03:46:43
@ 8d34bd24:414be32b
2025-06-11 03:46:43So often Christians focus on God’s love and ignore His judgment. They tell people they need to be saved, but leave out from what they need to be saved. Fifty or a hundred years ago, almost every American knew the basics of the Bible, what sin is, what the judgment of Hell is, and that the God of the Bible is our Creator. Today, most people in America and the world know very little of that. Phrases like, “Trust Jesus and be saved,” mean very little. The person you are talking to may be silently thinking, “Who is Jesus? Why should I trust Him? What do I need to be saved from?”
Most Christians, especially from Evangelical circles, have been steeped in the phrase “Be saved,” but how many have thought carefully about from what they are being saved? If we have trouble answering, “from what?”, how can we explain it to those who don’t know Jesus?
But God demonstrates His own love toward us, in that while we were yet sinners, Christ died for us. Much more then, having now been justified by His blood, we shall be saved from the wrath of God through Him. For if while we were enemies we were reconciled to God through the death of His Son, much more, having been reconciled, we shall be saved by His life. And not only this, but we also exult in God through our Lord Jesus Christ, through whom we have now received the reconciliation. (Romans 5:8-11) {emphasis mine}
Primarily we are saved “from the wrath of God.” We are also reconciled which saves us from separation from God.
We are also told that we are rescued [saved] “from the wrath to come.”
And to wait for His Son from heaven, whom He raised from the dead, that is Jesus, who rescues us from the wrath to come. (1 Thessalonians 1:10) {emphasis mine}
Then one might ask, “What right does God have to tell me what to do and to get mad at me?”
In the beginning was the Word, and the Word was with God, and the Word was God. He was in the beginning with God. All things came into being through Him, and apart from Him nothing came into being that has come into being. In Him was life, and the life was the Light of men. The Light shines in the darkness, and the darkness did not comprehend it. (John 1:1-5) {emphasis mine}
Why does God get to set the rules? Because He made all things. The Creator gets to set the rules for His creation. It isn’t just ‘might makes right,’ but the one who spoke everything into being gets to set the rules for His creatures just like He set the rules for how everything in the universe works.
Many might claim, “but surely God can’t expect us to be perfect? Nobody is perfect.”
For we do not have a high priest who cannot sympathize with our weaknesses, but One who has been tempted in all things as we are, yet without sin. Therefore let us draw near with confidence to the throne of grace, so that we may receive mercy and find grace to help in time of need. (Hebrews 4:15-16) {emphasis mine}
Jesus doesn’t expect more than He has given. He went through every temptation we have experienced, including trials and hardships we can’t imagine, and yet was without even one sin. He is the perfect example of what we should be. Even more amazingly, he understands that we are unable to live up to His standard, so He came to earth, suffered, died, and rose again, so we could be reconciled to Him. All we have to do is repent of our sins, trust Him, and submit to Him. How can we not put our faith in Him after all He did for us?
He made Him who knew no sin to be sin on our behalf, so that we might become the righteousness of God in Him. (2 Corinthians 5:21)
Jesus paid the penalty. He took our sins, so we can receive His righteousness. This is a trade everyone should be willing to make, but sadly most refuse — some willfully, but some because they haven’t heard the good news. Hopefully all Christians will faithfully share the gospel with those around them.
May the perfect Savior guide us in His perfect will and help us to rightfully share the gospel with all those around us.
Trust Jesus
-
 @ b6dcdddf:dfee5ee7
2025-06-10 14:39:05
@ b6dcdddf:dfee5ee7
2025-06-10 14:39:05Bitcoiners around the world are helping to build a safe, permanent home for 50+ orphans in Bugiri, Uganda 🇺🇬—complete with dorms, classrooms, gardens, and Bitcoin education.
Project by @orphansofuganda
https://geyser.fund/project/buildingabitcoinfundedorphanagehomeinuganda
https://stacker.news/items/1002532
-
 @ 6be5cc06:5259daf0
2025-06-12 01:18:11
@ 6be5cc06:5259daf0
2025-06-12 01:18:11Introdução
O princípio do sola scriptura, pedra angular da teologia protestante desde a Reforma do século XVI, estabelece que apenas a Escritura constitui a autoridade final e suprema em questões de fé e prática cristã. Este princípio, formulado inicialmente por Martinho Lutero e sistematizado pelos reformadores subsequentes, pretende oferecer um fundamento epistemológico sólido para a teologia, livre das supostas corrupções da tradição eclesiástica.
Contudo, uma análise rigorosa revela que o sola scriptura incorre em contradições lógicas fundamentais que comprometem sua viabilidade como sistema epistemológico coerente. Este artigo examina essas contradições através de três perspectivas complementares: filosófica, exegética e histórica.
A Contradição Performativa Fundamental
O Problema da Autorreferência
O sola scriptura enfrenta um dilema epistemológico insuperável: afirma que apenas a Escritura possui autoridade final em matéria de fé, mas essa própria regra não é explicitamente ensinada na Escritura. Trata-se de uma contradição performativa clássica, onde o enunciado viola suas próprias condições de possibilidade.
Esta situação configura uma falácia de petitio principii (círculo vicioso), pois exige que se aceite uma doutrina que não pode ser sustentada pelas premissas do próprio sistema. Para estabelecer o sola scriptura, seria necessário recorrer a uma autoridade externa à Escritura – precisamente aquilo que o princípio pretende rejeitar.
Fundacionalismo Mal Estruturado
Do ponto de vista epistemológico, o sola scriptura apresenta-se como um fundacionalismo defeituoso. Pretende funcionar como axioma supremo e auto-evidente, mas falha ao não fornecer a base textual que sua própria metodologia exige. Um verdadeiro fundacionalismo escriturístico deveria ser capaz de demonstrar sua validade através de uma prova explícita nas próprias Escrituras.
O Testemunho Contrário das Escrituras
Limitações do Registro Escrito
A própria Escritura reconhece as limitações do registro textual. João 21:25 declara explicitamente: "Jesus fez também muitas outras coisas. Se cada uma delas fosse escrita, penso que nem mesmo no mundo inteiro haveria espaço suficiente para os livros que seriam escritos."
Este versículo é particularmente problemático para o sola scriptura, pois reconhece que nem todos os ensinamentos de Cristo foram preservados por escrito. Como pode a Escritura ser suficiente se ela própria admite sua incompletude?
A Valorização da Tradição Oral
Paulo, em 2 Tessalonicenses 2:15, oferece uma instrução que contradiz frontalmente o sola scriptura: "Assim, pois, irmãos, ficai firmes e conservai os ensinamentos que de nós aprendestes, seja por palavras, seja por carta nossa."
O apóstolo valoriza inequivocamente tanto a tradição oral ("por palavras") quanto a escrita ("por carta"), estabelecendo um modelo de autoridade dual que o protestantismo posterior rejeitaria.
A Necessidade de Autoridade Interpretativa
A narrativa do eunuco etíope em Atos 8:30-31 demonstra a inadequação da Escritura isolada como autoridade final. Quando Filipe pergunta se o eunuco entende o que lê, a resposta é reveladora: "Como poderei entender, se alguém não me ensinar?"
Este episódio ilustra que a mera posse do texto bíblico não garante compreensão adequada. É necessária uma autoridade interpretativa externa – no caso, representada por Filipe, que age com autoridade apostólica.
A Complexidade Hermenêutica
Pedro, em sua segunda epístola (3:16-17), reconhece a dificuldade interpretativa inerente às Escrituras: "Suas cartas contêm algumas coisas difíceis de entender, as quais os ignorantes e instáveis torcem, como também o fazem com as demais Escrituras, para a própria destruição deles."
Esta passagem não apenas reconhece a complexidade hermenêutica dos textos sagrados, mas também alerta sobre os perigos da interpretação inadequada. Implicitamente, sugere a necessidade de uma autoridade interpretativa confiável para evitar distorções doutrinárias.
O Paradoxo Histórico da Canonização
A Dependência da Tradição Eclesiástica
Um dos argumentos mais devastadores contra o sola scriptura emerge da própria história da formação do cânon bíblico. Os concílios de Hipona (393 d.C.) e Cartago (397 d.C.) foram responsáveis pela definição oficial do cânon das Escrituras tal como conhecemos hoje.
Este fato histórico cria um paradoxo insuperável: aceitar a Bíblia como autoridade única requer aceitar a autoridade da tradição eclesiástica que a definiu. O próprio cânon bíblico é produto da tradição apostólica e da deliberação conciliar, não de autodefinição escriturística.
A Circularidade da Autopistia
Tentativas protestantes de resolver este dilema através do conceito de "autopistia" – a suposta capacidade das Escrituras de se auto-autenticar – apenas aprofundam o problema circular. Como determinar que as Escrituras possuem esta propriedade sem recorrer a critérios externos? A própria doutrina da autopistia não é explicitamente ensinada na Escritura.
Implicações Teológicas e Epistemológicas
A Fragmentação Interpretativa
A história do protestantismo oferece evidência empírica das consequências práticas do sola scriptura. A multiplicação de denominações e interpretações divergentes sugere que o princípio, longe de fornecer clareza doutrinária, pode na verdade contribuir para a fragmentação teológica.
Se a Escritura fosse verdadeiramente suficiente e auto-interpretativa, seria razoável esperar maior convergência hermenêutica entre aqueles que aderem ao sola scriptura. A realidade histórica sugere o contrário.
A Alternativa Católica e Ortodoxa
As tradições católica e ortodoxa, embora enfrentando suas próprias tensões epistemológicas, mantêm pelo menos coerência interna ao reconhecer explicitamente múltiplas fontes complementares de autoridade: Escritura, Tradição e Magistério (no caso católico) ou Escritura e Tradição (no caso ortodoxo).
Estas posições evitam a contradição performativa do sola scriptura ao não reivindicar que sua própria metodologia epistemológica seja derivada exclusivamente da Escritura.
Conclusão
A análise crítica do sola scriptura revela contradições estruturais que comprometem fundamentalmente sua viabilidade como princípio epistemológico. O princípio incorre em contradição performativa ao estabelecer uma regra que não pode ser derivada de suas próprias premissas, configura um fundacionalismo mal estruturado ao carecer de base textual explícita, e enfrenta o testemunho contrário da própria Escritura, que reconhece suas limitações e a necessidade de autoridades interpretativas externas.
O paradoxo histórico da canonização – onde o próprio cânon bíblico depende da autoridade tradicional que o sola scriptura pretende rejeitar – representa talvez o golpe mais decisivo contra o princípio protestante.
Isso não implica necessariamente a falsidade do protestantismo como sistema teológico, mas sugere que seus fundamentos epistemológicos requerem reformulação substancial. Uma teologia protestante intelectualmente honesta precisaria reconhecer as limitações do sola scriptura e desenvolver uma epistemologia mais nuançada que leve em conta a complexidade das fontes de autoridade religiosa.
A busca pela verdade teológica, independentemente de compromissos confessionais, exige o reconhecimento rigoroso das limitações e contradições inerentes aos nossos sistemas epistemológicos. No caso do sola scriptura, essa honestidade intelectual revela um princípio que, por mais central que seja para a identidade protestante, não pode sustentar o peso epistemológico que tradicionalmente lhe foi atribuído.
-
 @ dfa02707:41ca50e3
2025-06-12 07:02:18
@ dfa02707:41ca50e3
2025-06-12 07:02:18Contribute to keep No Bullshit Bitcoin news going.
-
Version 1.3 of Bitcoin Safe introduces a redesigned interactive chart, quick receive feature, updated icons, a mempool preview window, support for Child Pays For Parent (CPFP) and testnet4, preconfigured testnet demo wallets, as well as various bug fixes and improvements.
-
Upcoming updates for Bitcoin Safe include Compact Block Filters.
"Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions. They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK," writes the project's developer Andreas Griffin.
- Learn more about the current and upcoming features of Bitcoin Safe wallet here.
What's new in v1.3
- Redesign of Chart, Quick Receive, Icons, and Mempool Preview (by @design-rrr).
- Interactive chart. Clicking on it now jumps to transaction, and selected transactions are now highlighted.

- Speed up transactions with Child Pays For Parent (CPFP).
- BDK 1.2 (upgraded from 0.32).
- Testnet4 support.
- Preconfigured Testnet demo wallets.
- Cluster unconfirmed transactions so that parents/children are next to each other.
- Customizable columns for all tables (optional view: Txid, Address index, and more)
- Bug fixes and other improvements.

Announcement / Archive
Blog Post / Archive
GitHub Repo
Website -
-
 @ 7f6db517:a4931eda
2025-06-12 01:02:18
@ 7f6db517:a4931eda
2025-06-12 01:02:18Will not live in a pod.
Will not eat the bugs.
Will not get the chip.
Will not get a blue check.
Will not use CBDCs.Live Free or Die.
Why did Elon buy twitter for $44 Billion? What value does he see in it besides the greater influence that undoubtedly comes with controlling one of the largest social platforms in the world? We do not need to speculate - he made his intentions incredibly clear in his first meeting with twitter employees after his takeover - WeChat of the West.
To those that do not appreciate freedom, the value prop is clear - WeChat is incredibly powerful and successful in China.
To those that do appreciate freedom, the concern is clear - WeChat has essentially become required to live in China, has surveillance and censorship integrated at its core, and if you are banned from the app your entire livelihood is at risk. Employment, housing, payments, travel, communication, and more become extremely difficult if WeChat censors determine you have acted out of line.
The blue check is the first step in Elon's plan to bring the chinese social credit score system to the west. Users who verify their identity are rewarded with more reach and better tools than those that do not. Verified users are the main product of Elon's twitter - an extensive database of individuals and complete control of the tools he will slowly get them to rely on - it is easier to monetize cattle than free men.
If you cannot resist the temptation of the blue check in its current form you have already lost - what comes next will be much darker. If you realize the need to resist - freedom tech provides us options.
If you found this post helpful support my work with bitcoin.