-
 @ 8d34bd24:414be32b
2025-05-28 13:53:46
@ 8d34bd24:414be32b
2025-05-28 13:53:46These days it can feel like the whole world is out of control. Government officials lie and break the law. People are selfish, act emotionally rather than logically, and push ideologies that are illogical and contrary to reality. Society is divided into groups and people are judged, not for their own character, but based on which group they are placed into. There are wars and rumors of wars. There are worries of pandemics and economic disasters. Depression, psychosis, and despair is rampant even among the youngest among us.
Hope For Believers
As much as things seem to be out of control, they are not out of God’s control. This is what the Bible predicted. No matter how bad things get in the world, those who have put their faith in Jesus, do not need to feel despair.
Why are you in despair, O my soul?\ And why have you become disturbed within me?\ Hope in God, for I shall again praise Him\ For the help of His presence.\ O my God, my soul is in despair within me;\ Therefore I remember You from the land of the Jordan\ And the peaks of Hermon, from Mount Mizar. (Psalm 42:5-6)
When we start to feel despair overcoming us, we need to remember what God has done and what He has promised. We need to praise God for what He has done, what He has promised, and what He will bring to completion. Things may be hard now, but God is still in control, and we know how the story will end. God triumphs. Good is rewarded. Evil is destroyed. We can stand on the foundation of hope because we know the ending. Even though things may be out of our personal control, they are always under God’s control.
The more fiercely the storm rages, the more we need to rest in Jesus and the more we need to put our hope in Him.
O love the Lord, all you His godly ones!\ The Lord preserves the faithful\ And fully recompenses the proud doer.\ **Be strong and let your heart take courage,\ All you who hope in the Lord. (Psalm 31:23-24) {emphasis mine}
We can take courage because God always acts for our long term good. Every hardship we experience here on earth will be recognized as a blessing that grew our faith and prepared us for heaven and God’s presence in eternity.
For I know the plans that I have for you,’ declares the Lord, ‘plans for welfare and not for calamity to give you a future and a hope. (Jeremiah 29:11)
Even the worst things that happen to us, due to the sins of others, have a good purpose in our lives. God is working good through us. Our hope isn’t an empty hope. It isn’t a “I really hope this happens.” It is a “I can hope in the guaranteed promises of God.”
For we do not want you to be unaware, brethren, of our affliction which came to us in Asia, that we were burdened excessively, beyond our strength, so that we despaired even of life; indeed, we had the sentence of death within ourselves so that we would not trust in ourselves, but in God who raises the dead; who delivered us from so great a peril of death, and will deliver us, He on whom we have set our hope. And He will yet deliver us, (2 Corinthians 1:8-10) {emphasis mine}
We may experience situations so bad that they seem hopeless, but with God, nothing is hopeless. The God who raises the dead can raise us out of any situation. The God who spoke the universe into existence can deliver us by a word.
The God of the Bible knows all and loves us completely. He looks at our situation through the lens of eternity. What seems best in the moment is not necessarily what is best for our eternity. Many times He delivers us through hardship rather than out of it. We just need to trust Him and put our hope in Him because He is good.
In the same way God, desiring even more to show to the heirs of the promise the unchangeableness of His purpose, interposed with an oath, so that by two unchangeable things in which it is impossible for God to lie, we who have taken refuge would have strong encouragement to take hold of the hope set before us. This hope we have as an anchor of the soul, a hope both sure and steadfast and one which enters within the veil, where Jesus has entered as a forerunner for us, having become a high priest forever according to the order of Melchizedek. (Hebrews 6:17-20) {emphasis mine}
Read that statement again. “This hope we have as an anchor of the soul, a hope both sure and steadfast.” Are you trusting Jesus as the “anchor of your soul?” Is your hope just a wish or is it a “sure and steadfast” hope based on the promises of God that you know will 100% come true?
And not only this, but we also exult in our tribulations, knowing that tribulation brings about perseverance; and perseverance, proven character; and proven character, hope; and hope does not disappoint, because the love of God has been poured out within our hearts through the Holy Spirit who was given to us. (Romans 5:3-5)
Isn’t it ironic that we need hope to persevere through tribulations, but that persevering through tribulation gives us character and hope? Our faith, trust, and hope grow through hardship. When things are easy, we almost always fall back on trusting in our own power rather than relying on God’s power. If we have put our faith in Jesus, there is no situation in which we should lose hope.
Now may the God of hope fill you with all joy and peace in believing, so that you will abound in hope by the power of the Holy Spirit. (Romans 15:13)
Is your joy and peace based on your circumstances or have you learned to have hope in God so you can experience joy and peace even in the trials?
Many people equate joy and happiness, but I think there is a key distinction. Happiness is a pleasant feeling that comes from pleasant circumstances. Joy is a similar feeling to happiness, but it comes from knowing God and His love. It is not tied to circumstances. When we have truly put our hope in God we can still have joy in and despite the most horrific circumstances.
Blessed be the God and Father of our Lord Jesus Christ, who according to His great mercy has caused us to be born again to a living hope through the resurrection of Jesus Christ from the dead, to obtain an inheritance which is imperishable and undefiled and will not fade away, reserved in heaven for you, (1 Peter 1:3-4) {emphasis mine}
Just as Jesus told the Samaritan woman at the well that He provides living water that wells up inside, so that she need never thirst, in the same way believers have a living hope that wells up in times of need. Our hope is in the Creator of the universe and Savior of the world. No problem is too big for Him. No situation is a surprise to Him. No enemy is too powerful for Him. All of our problems are already solved. We just haven’t necessarily seen the solution yet.
My soul, wait in silence for God only,\ For my hope is from Him.\ He only is my rock and my salvation,\ My stronghold; I shall not be shaken.\ On God my salvation and my glory rest;\ The rock of my strength, my refuge is in God. (Psalm 62:5-7)
Despair For Unbelievers
Although believers never have reason to despair, the same is not true for those who have rejected the Savior, Jesus Christ. In these perilous times, they have a real reason for dread and despair.
Moreover, the Lord will scatter you among all peoples, from one end of the earth to the other end of the earth; and there you shall serve other gods, wood and stone, which you or your fathers have not known. Among those nations you shall find no rest, and there will be no resting place for the sole of your foot; but there the Lord will give you a trembling heart, failing of eyes, and despair of soul. So your life shall hang in doubt before you; and you will be in dread night and day, and shall have no assurance of your life. (Deuteronomy 64-66)
Those who reject the atoning sacrifice of Jesus do not get His protection. They do not get His help. They cannot rest in hope in Him.
Of course, the good news is that they can chose to turn their hearts to Him, confess their sins, and trust in Him up until their moment of death. Sadly many will continue to put off faith until it is too late. Many will choose evil over good and license over submission until God gives them over to their lusts.
And just as they did not see fit to acknowledge God any longer, God gave them over to a depraved mind, to do those things which are not proper, being filled with all unrighteousness, wickedness, greed, evil; full of envy, murder, strife, deceit, malice; they are gossips, slanderers, haters of God, insolent, arrogant, boastful, inventors of evil, disobedient to parents, without understanding, untrustworthy, unloving, unmerciful; and although they know the ordinance of God, that those who practice such things are worthy of death, they not only do the same, but also give hearty approval to those who practice them. (Romans 1:28-32)
If any of you have not yet put your trust in Jesus as Savior and Lord, do not wait. Turn away from evil. Submit to the will of Jesus. Trust Him to take away your sins and cover you with His righteousness.
If any of you know people who are in despair, share the gospel with them. Tell them about the greatness of God. Show them the hope that is within you.
Can Believers Despair?
Are there believers who despair? Yes. Should believers ever despair? Definitely not!
But we have this treasure in earthen vessels, so that the surpassing greatness of the power will be of God and not from ourselves; we are afflicted in every way, but not crushed; perplexed, but not despairing; persecuted, but not forsaken; struck down, but not destroyed; always carrying about in the body the dying of Jesus, so that the life of Jesus also may be manifested in our body. (2 Corinthians 4:7-10)
Jesus is always with believers in all situations guiding and protecting us. Those difficult situations that happen are for our good, even when we can’t see how it could be for good.
Job had more reasons to despair than almost anyone, yet he trusted in God. He didn’t know why he was being put through such loss, but his loss increased his faith in God and was a great example to people throughout history. I also love this cry of his heart.
“Oh that my words were written!\ Oh that they were inscribed in a book!” (Job 19:23)
He may or may not have seen even the partial fulfillment of this cry, but His words are written in the book of Job, in the Holy Scriptures read by Jews and Christians throughout the world and throughout history. Job’s first response to loss was an example to us all. After losing all ten children and all of his wealth, this was his response.
Then Job arose and tore his robe and shaved his head, and he fell to the ground and worshiped. (Job 1:20)
Yes, it is true that he had moments of despair where he cursed his birth, but he then returned to God in faith and hope. After a brief rebuke from God, Job submitted to God’s will.
“Behold, I am insignificant; what can I reply to You?\ I lay my hand on my mouth.\ Once I have spoken, and I will not answer;\ Even twice, and I will add nothing more.” (Job 40:4-5)
After his second rebuke from God, he fully submitted.
Then Job answered the Lord and said,
“I know that You can do all things,\ And that no purpose of Yours can be thwarted.\ ‘Who is this that hides counsel without knowledge?’\ *Therefore I have declared that which I did not understand,\ Things too wonderful for me, which I did not know.\ ‘Hear, now, and I will speak;\ I will ask You, and You instruct me*.’\ I have heard of You by the hearing of the ear;\ But now my eye sees You;\ Therefore I retract,\ And I repent in dust and ashes**.” (Job 42:1-6) {emphasis mine}
Job admitted that he did not understand what God was doing, but that God was right; God was good; and God was Lord. Job was able to have hope knowing that God was in control and working for good.
In the case of Job, he was later blessed with more kids, more wealth, and more respect than he had in the beginning. We won’t all see our blessings here on earth, but all believers will receive blessings from their trials.
May our glorious Savior and God fill you with faith and hope in God, His goodness, His power, and His plan. May we all submit to His good will even when we do not understand and even when every part of our earthly body is crying, “stop!” May God fill you with knowledge of Him, faith in Him, and hope in Him.
Trust Jesus
-
 @ b7274d28:c99628cb
2025-05-28 01:11:43
@ b7274d28:c99628cb
2025-05-28 01:11:43In this second installment of The Android Elite Setup tutorial series, we will cover installing the nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 on your #Android device and browsing for apps you may be interested in trying out.
Since the #Zapstore is a direct competitor to the Google Play Store, you're not going to be able to find and install it from there like you may be used to with other apps. Instead, you will need to install it directly from the developer's GitHub page. This is not a complicated process, but it is outside the normal flow of searching on the Play Store, tapping install, and you're done.
Installation
From any web browser on your Android phone, navigate to the Zapstore GitHub Releases page and the most recent version will be listed at the top of the page. The .apk file for you to download and install will be listed in the "Assets."
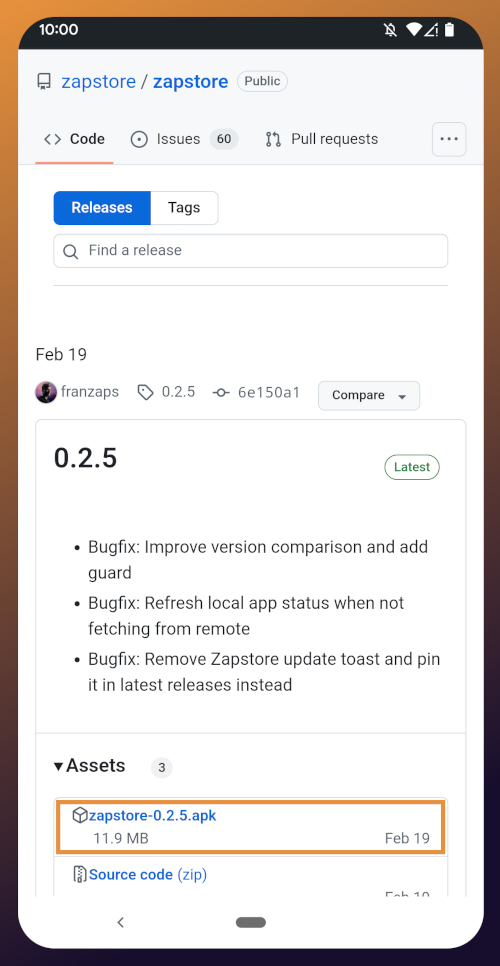
Tap the .apk to download it, and you should get a notification when the download has completed, with a prompt to open the file.
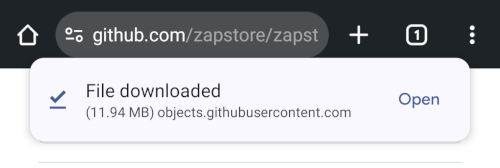
You will likely be presented with a prompt warning you that your phone currently isn't allowed to install applications from "unknown sources." Anywhere other than the Play Store is considered an "unknown source" by default. However, you can manually allow installation from unknown sources in the settings, which the prompt gives you the option to do.
In the settings page that opens, toggle it to allow installation from this source, and you should be prompted to install the application. If you aren't, simply go to your web browser's downloads and tap on the .apk file again, or go into your file browser app and you should find the .apk in your Downloads folder.
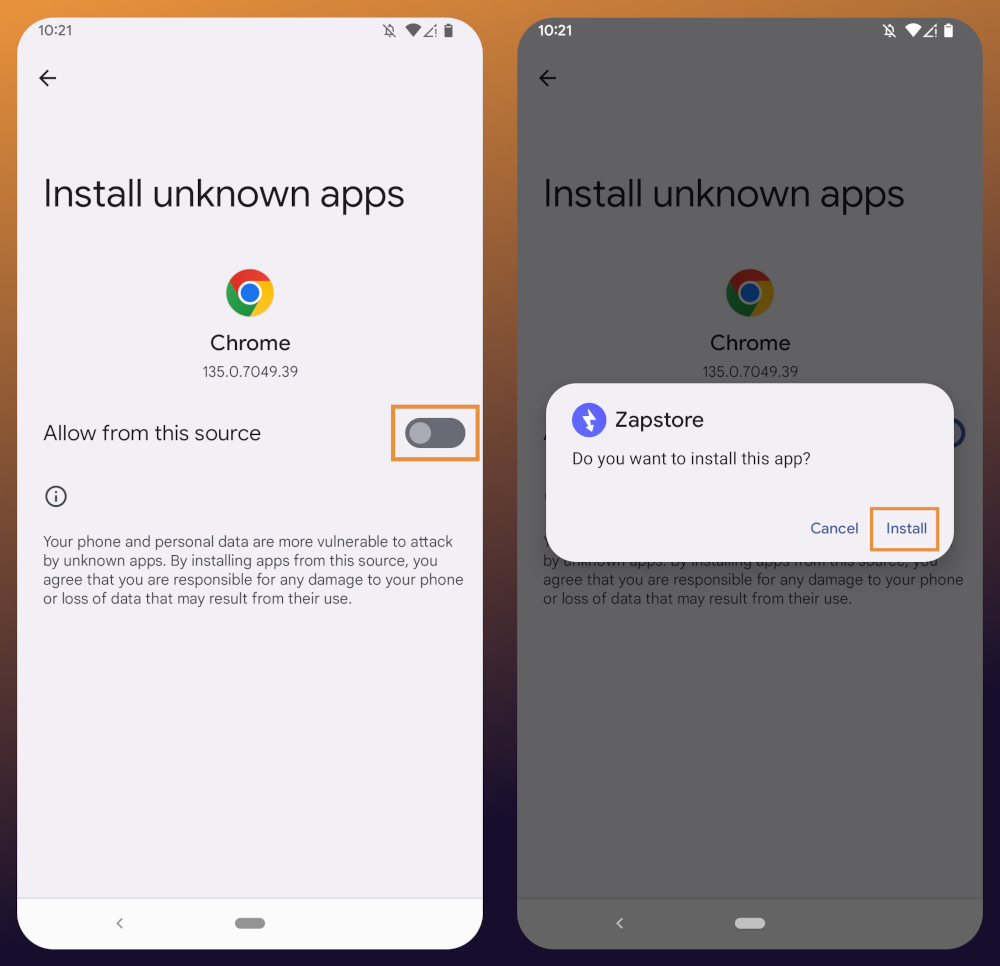
If the application doesn't open automatically after install, you will find it in your app drawer.

Home Page
Right at the top of the home page in the Zapstore is the search bar. You can use it to find a specific app you know is available in the Zapstore.
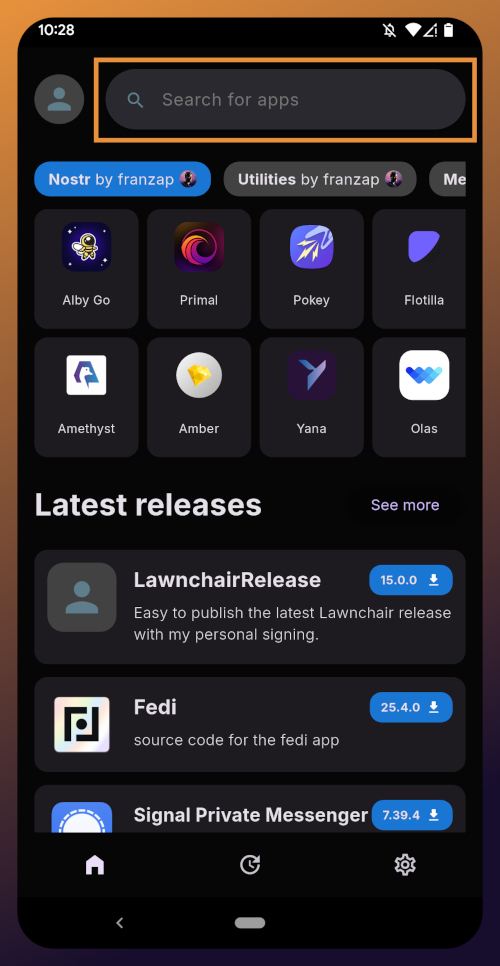
There are quite a lot of open source apps available, and more being added all the time. Most are added by the Zapstore developer, nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but some are added by the app developers themselves, especially Nostr apps. All of the applications we will be installing through the Zapstore have been added by their developers and are cryptographically signed, so you know that what you download is what the developer actually released.
The next section is for app discovery. There are curated app collections to peruse for ideas about what you may want to install. As you can see, all of the other apps we will be installing are listed in nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9's "Nostr" collection.
In future releases of the Zapstore, users will be able to create their own app collections.
The last section of the home page is a chronological list of the latest releases. This includes both new apps added to the Zapstore and recently updated apps. The list of recent releases on its own can be a great resource for discovering apps you may not have heard of before.
Installed Apps
The next page of the app, accessed by the icon in the bottom-center of the screen that looks like a clock with an arrow circling it, shows all apps you have installed that are available in the Zapstore. It's also where you will find apps you have previously installed that are ready to be updated. This page is pretty sparse on my test profile, since I only have the Zapstore itself installed, so here is a look at it on my main profile:

The "Disabled Apps" at the top are usually applications that were installed via the Play Store or some other means, but are also available in the Zapstore. You may be surprised to see that some of the apps you already have installed on your device are also available on the Zapstore. However, to manage their updates though the Zapstore, you would need to uninstall the app and reinstall it from the Zapstore instead. I only recommend doing this for applications that are added to the Zapstore by their developers, or you may encounter a significant delay between a new update being released for the app and when that update is available on the Zapstore.
Tap on one of your apps in the list to see whether the app is added by the developer, or by the Zapstore. This takes you to the application's page, and you may see a warning at the top if the app was not installed through the Zapstore.
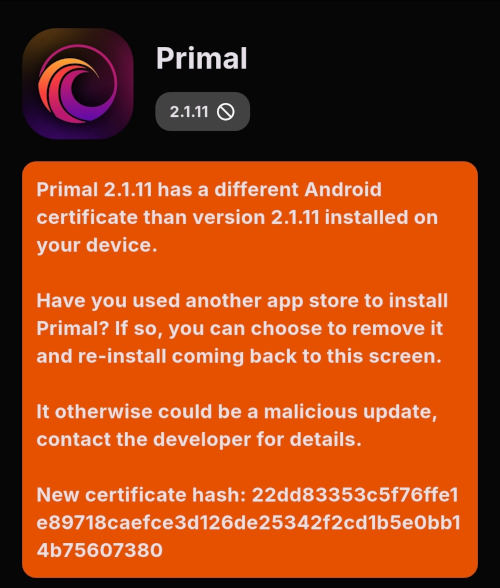
Scroll down the page a bit and you will see who signed the release that is available on the Zapstore.
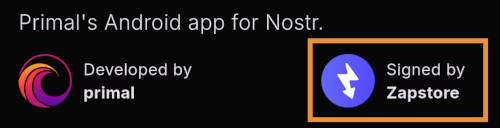
In the case of Primal, even though the developer is on Nostr, they are not signing their own releases to the Zapstore yet. This means there will likely be a delay between Primal releasing an update and that update being available on the Zapstore.
Settings
The last page of the app is the settings page, found by tapping the cog at the bottom right.
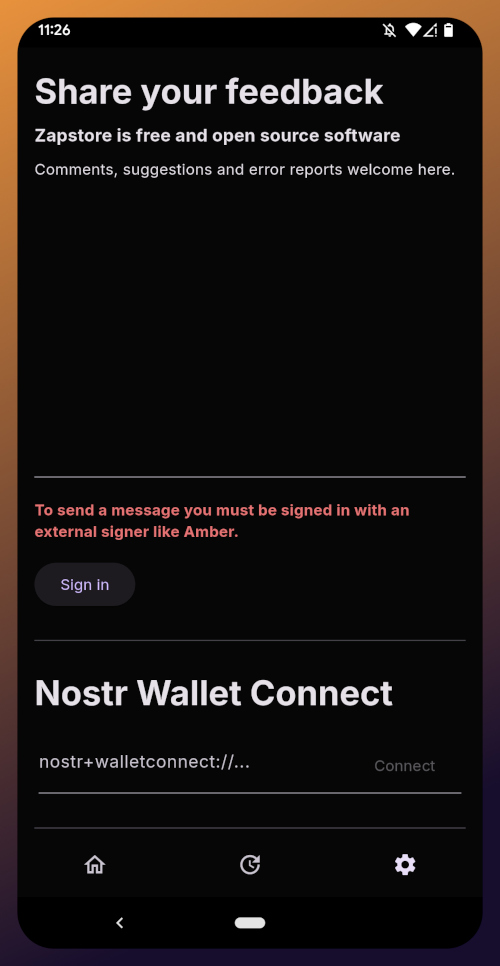
Here you can send the Zapstore developer feedback directly (if you are logged in), connect a Lightning wallet using Nostr Wallet Connect, delete your local cache, and view some system information.
We will be adding a connection to our nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch wallet in part 5 of this tutorial series.
For the time being, we are all set with the Zapstore and ready for the next stage of our journey.
Continue to Part 3: Amber Signer. Nostr link: nostr:naddr1qqxnzde5xuengdeexcmnvv3eqgstwf6d9r37nqalwgxmfd9p9gclt3l0yc3jp5zuyhkfqjy6extz3jcrqsqqqa28qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qg6waehxw309aex2mrp0yhxyunfva58gcn0d36zumn9wss80nug
-
 @ 7f6db517:a4931eda
2025-05-30 07:02:11
@ 7f6db517:a4931eda
2025-05-30 07:02:11
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
If you missed my nostr introduction post you can find it here. My nostr account can be found here.
We are nearly at the point that if something interesting is posted on a centralized social platform it will usually be posted by someone to nostr.
We are nearly at the point that if something interesting is posted exclusively to nostr it is cross posted by someone to various centralized social platforms.
We are nearly at the point that you can recommend a cross platform app that users can install and easily onboard without additional guides or resources.
As companies continue to build walls around their centralized platforms nostr posts will be the easiest to cross reference and verify - as companies continue to censor their users nostr is the best censorship resistant alternative - gradually then suddenly nostr will become the standard. 🫡
Current Nostr Stats
If you found this post helpful support my work with bitcoin.

-
 @ dfa02707:41ca50e3
2025-05-30 03:01:50
@ dfa02707:41ca50e3
2025-05-30 03:01:50Contribute to keep No Bullshit Bitcoin news going.
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.

-
 @ 491afeba:8b64834e
2025-05-27 23:57:01
@ 491afeba:8b64834e
2025-05-27 23:57:01Quando adolescente eu acreditava na coerência da teoria de "amor líquido" do polonês, sociólogo, Zygmunt Bauman, apresentada no livro "Amor Líquido: Sobre a Fragilidade dos Laços Humanos", qual no meu amadurecimento em estudos, sejam eles no meio acadêmico ou fora, percebo como uma das formas mais rasas de explicar as mudanças e transformações dos padrões de relações sócio-afetivas dos humanos. A seguir colocar-me-ei na minha juventude não tanto recente, direi então que nós, se adolescentes e conservadores, ou mesmo jovens adultos mais conservadores, costumamos levar como dogma uma óptica decadentista generalizada de todos os avanços de eras dos homens, universalizamos por nos ser comum a indistinção entre humanidade e humanidades, ou mesmo "humanity" e "humankind" ("humanidade" como espécime e "humanidade" como um universal), compreendemos toda "essas" como "essa" e indistinguimos as sociedades para com os homens, ou seja, a incapacidade de definir os seres dentro de suas respectivas singularidades e especificidades nos leva ao decadentismo generalista (a crença de que de forma geral, e universal, a "civilização universal" decai moralmente, éticamente, materialmente e espiritualmente), que aparente à nós determinadas mudanças nas relações humanas quanto ao caráter sócio-afetivo, por falta de profundidade e critérios ainda sobre questões alinhadas aos métodos e coerências, ou incoerências, lógicas, nós se jovens e conservadores somos levados ao engodo de concordar com a teoria do amor líquido de Bauman, que devo cá explicar de antemão: trata ela, a teoria, o padrão de "amor" dos tempos presentes como frágil, de prazo (curto e médio) e diferente em grau comparativamente ao amor comum das eras passadas.
Aos jovens mais progressistas opera uma compreensão dialética sobre as eras dos homens nos seu tempo presente, na qual ao tempo que o ser progride ele também regride simultaneamente, ou seja, a medida que aparecem contradições advindas de transformações materiais da realidade humana o ser supera essas contradições e progride em meio as transformações, ainda fazendo parte da lógica dessa indissociavelmente, assim constantemente progredindo e regredindo, havendo para esses dois vetores de distinção: o primeiro é o que releva questões espirituais como ao caráter do pensamento "new age", o segundo ignora essas questões por negar a existência da alma, seguem ao materialismo. Cedem em crer na teoria baumaninana como dogma, pois não encontram outros meios para explicar as transformações da sociedade na esfera sócio-afetiva sem que haja confrontamento direto com determinadas premissas assim pertinemente presentes, ou por não conciliarem com análises relativamente superiores, como a de Anthony Giddens sobre a "relação pura" em "A Transformação da Intimidade" e de François de Singly apresentada em "Sociologie du Couple".
https://i.pinimg.com/736x/6f/b4/9e/6fb49eda2c8cf6dc837a0abfc7e108e6.jpg
Há um problema quando uma teoria deixa de assim ser para vir a tornar-se mais um elemento desconexo da ciência, agora dentro da cultura pop, se assim podemos dizer, ou da cultura de massa, ou se preferirem mesmo "anticultura", esse problema é a sua deformização teórica, tornando-se essa rasa para sua palatabilidade massiva, somada a incapacidade de partes da sociedade civil em compreender as falhas daquilo que já foi massificado. Tive surpresa ao entender que muitos outros compartilham da mesma opinião, a exemplo, possuo um amigo na faculdade, marxista, que ao falarmos sobre nossos projetos de pesquisa, citou ele o projeto de um de nossos colegas, no qual esse referido um de nossos colegas faria seu projeto com base na teoria do amor líquido de Bauman, então alí demos risada disso, ora, para nós a teoria baumaniana é furada, passamos a falar sobre Bauman e o motivo pelo qual não gostávamos, lá fiquei até surpreso em saber que mais gente além de mim não gostava da teoria de Bauman, pois ao que eu via na internet era rede de enaltecimentos à figura e à sua teoria, tal como fosse uma revelação partindo de alguma divindade da Idade do Bronze. Pouco tempo depois tive em aula de teoria política uma citação de Bauman partindo do professor que ministrava a disciplina, no entanto, ao citar o nome de Bauman o mesmo fez uma feição na qual aparentava segurar risada, provavelmente ele também não levava Bauman à sério. Não devo negar que todas as vezes que vejo o sociólogo sendo citado em alguma nota no X, no Instagram ou qualquer outra rede social, tal como fosse um referencial teórico bom, sinto uma vergonha alheia pois alí tenho uma impressão de que a pessoa não leu Bauman e usa o referencial teórico como um fato já assim provado e comprovado.
Há pontos positivos na teoria baumaniana, como a capacidade de perceber o problema e correlacioná-lo à modernidade, assim como sucitar a influência do que há de material no fenômeno, porém os erros são pertinentes: o primeiro problema é de categoria. Não há, por parte de Bauman noção alguma entre as dissociações dos amores, não há atenção sobre o amor como estrutura ou ele como um sentimento, todo ele é compreendido uniformemente como "amor", partindo do pressuposto que todas as relações, todas elas, são firmadas com base no amor. Essa crença tem uma origem: Hegel. Nos Escritos Teológicos Hegel partia da crença que o amor ligava os seres relacionalmente como uma força de superação e alienação, mas há de compreendermos que esse Friedrich Hegel é o jovem ainda pouco maduro em suas ideias e seu sistema de pensamento, mais a frente, em "Fenomenologia do Espírito e na Filosofia do Direito", Hegel compreende a institucionalidade do direito no amor e a institucionalização dessa força, assim aproxima-se da realidade a respeito da inserção do amor nas esferas práticas do humano, porém essa ideia, apesar de imperfeita, pois ao que sabemos não é o amor que consolida a relação, mas sim a Verdade (Alétheia), conforme apontado por Heidegger em "Ser e Tempo", essa ideia do amor como a fundamento das relações humanas influenciou, e até hoje influencia, qualquer análise sobre as relações humanas fora da esfera materialista, fora dessa pois, melhormente explicado em exemplo, os marxistas (em exemplo), assim como Marx, consideram como base primordial das relações as condições materiais.
Por certo, não é de todo amor a base para a solidificação, ora, erram aqueles que creem que somente essa força, assim apontada por Hegel, constituiam todos os relacionamentos formais como pilares fundamentais, pois em prática as famílias eram até a fiduciarização dessas, por mais paradoxal que seja, compreendidas melhor como instituições orgânicas de caráter legal do que conluios de afetividades. A família outrora tinha consigo aparelhos de hierarquia bem estabelicidos, quais prezavam pela ordem interna e externa, que acima dessa instituição estava somente a Igreja (outra instituição), com sua fiduciarização [da família] após o movimento tomado pelos Estados nacionais em aplicação do casamento civil mudou-se a lógica das partes que a compõe, findou-se o princípio da subsidiariedade (não intervenção de determinadas instituições nas decisões quais podem ser exercidas em resuluções de problemas nas competências de quaisquer instituições), foi-se então, contudo, também a autoridade, e nisso revela-se um outro problema não apontado na teoria de Bauman: qual o padrão do amor "sólido"? Pois, ora, sociedades tradicionais não abdicavam do relevar dos amores para tornar seus filhos em ativos nas práticas de trocas (dádivas)? É notório que esse padrão se dissocia do padrão de sentimento apontado por Bauman, encontramos esse fato em estudo nos trabalhos "Ensaio Sobre a Dádiva", do Marcel Mauss, e "As Estruturas Elementares do Parentesco", do Claude Levi-Strauss, quais expõem que nas sociedades "sólidas", tradicionais, relevava-se mais questões institucionais que as sentimentais para a formação de laços (teoria da aliança). Muitas das relações passadas não eram baseadas no amor, não significando assim que as de hoje, em oposição, sejam, mas que permanecem-se semelhantes em base, diferentemente em grau e forma.
https://substackcdn.com/image/fetch/f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F748b94c3-f882-45db-8333-09260ef15cfe_615x413.jpeg
Ora, ainda existem casamentos motivados pela política, pelo status, pelo prestígio, pelos bens, pelo poder, pela influência familiar e assim sucetivamente, tal como no passado, ocorre que essa prática tornou-se oculta, não mais explícita e aparente, devo dizer ainda que em partes, pois prepondera em nosso tempo uma epidemia de adultérios, fornicações, práticas lascivas e demais práticas libertinosas explicitamente, em contraposição às práticas ocultas em vergonhas de sociedades sem declínio moral e espiritual, o que nos leva a questionar o método comparativo em dicotomia temporal "presente x passado" aplicado por Bauman, no qual segue-se da seguinte forma:
Transformação Passado = *sólido* | Presente = *líquido* Categorias Padrão de amor: tradicional (*sólido*) moderno (*líquido*) *Sólido* = estável, prazo (médio-grande), profundo, determinado. *Líquido* = instável, prazo (curto-médio), raso, indeterminado.O que penso é: Zygmunt Bauman buscou uma explicação material e laical para desviar ao fato de que há uma notória correlação entre espiritualização da sociedade, se voltada à Verdade, com a estabilidade das instituições, o que é já reduzido à moral religiosa, somente, não à mística, como por pensadores da linha de Tocqueville, ou em abordagens também mais laical (positivista) porém ainda relevantes, como Émile Durkheim em "As Formas Elementares da Vida Religiosa" e Max Weber em "A Ética Protestante e o Espírito do Capitalismo", contrapondo uma abordage mais voltada, de fato, a espiritualidade, como Christopher Dawnson, que defende essa teoria em "Religião e o Surgimento da Cultura Ocidental", e Eric Voegelin, principalmente nas obras "A Nova Ciência da Política" e "Ordem e História".
Encerrando, minha cosmovisão é a católica, o sistema de crença e religião qual sigo é do Deus que se fez homem por amor aos seus filhos, não posso negar ou mesmo omitir o fato de que, por trás de toda a minha crítica estão meus pensamentos e minhas convicções alinhadas àquilo que mais tenho amor em toda minha vida: a Verdade, e a Verdade é Deus, pois Cristo é a Verdade, o Caminho e a Vida, ninguém vai ao Pai se não por Ele, e pois bem, seria incoerência de minha parte não relevar o fato de crença como um dos motivos pelos quais eu rejeito a teoria do amor líquido de Zygmunt Bauman, pois os amores são todos eles praticados por formas, existem por diferentes formas e assim são desde sua tradicionalidade até o predomínio das distorções de declínio espiritual das eras presentes (e também antigas pré-Era Axial), estão esses preservados pelo alinhamento à verdade, assim são indistorcíveis, imutáveis, ou seja, amor é amor, não releva-se o falso amor como um, simplesmente não o é, assim o interesse, a sanha por bens, o egoísmo e a egolatria ("cupiditas", para Santo Agostinho de Hipona, em oposição ao que o santo e filósofo trata por "caritas") não são formas do amor, são autoenganos, não bons, se não são bons logo não são de Deus, ora, se Deus é amor, se ele nos ama, determino como amor (e suas formas) o que está de acordo com a Verdade. Aprofundando, a Teologia do Corpo, do Papa São João Paulo II, rejeita a "liquidez" apresentada por Bauman, pois o amor é, em suma, sacríficio, parte da entrega total de si ao próximo, e se não há logo não é amor. A Teologia do Corpo rejeita não os fundamentos de mentira no "líquido", mas também no "sólido", pois a tradicionalidade não é sinônimo de bom e pleno acordo com o amor que Deus pede de nós, não são as coerções, as violências, as imposições e demais vontades em oposição às de Deus que determinam os amores -- fatos em oposição ao ideário romanticizado. Claro, nem todas as coerções são por si inválidas do amor, ou mesmo as escolhas em trocas racionalizadas, a exemplo do autruísmo em vista da chance da família ter êxito e sucesso, ou seja, pelo bem dos próximos haver a necessidade de submissão a, em exemplo, um casamento forjado, ou algo do gênero, reconhece-se o amor no ato se feito por bem da família, porém o amor incutido, nesse caso, explicita o caráter sacrificial, no qual uma vontade e um amor genuinamente potencial em prazeres e alegrias são anulados, ou seja, mesmo nesse modelo tradicional na "solidez" há possibilidade do amor, não nas formas romanticizadas em critérios, como "estabilidade" e "durabilidade", mas no caráter do sacríficio exercido. Conforme nos ensina São Tomás de Aquino, o amor não é uma "força", tal como ensina Hegel, mas sim uma virtude teologal conforme na "Suma Teológica" (II-II Q. 26-28), não devemos reduzir o amor e os amores em análises simplórias (não simples) de falsa complexidade extraídas em métodos questionáveis e pouco competentes à real diensão de crise espiritual das eras, por esse motivo não concordo com a teoria do amor líquido de Zygmunt Bauman.
-
 @ 29313cc9:a6bf155e
2025-05-30 06:35:56
@ 29313cc9:a6bf155e
2025-05-30 06:35:56I thought i'd experiment with this Nostr blogging thing and write a short article on the state of Meshtastic and its alternatives.
For years Meshtastic was the only game in town, there wasn't a lot of users but the authors kept plugging away and it has become a thriving ecosystem of open source hardware, software, tools and social scene.
Meshtastic has always been focused on node to node messaging, in particular one of the use cases specifically mentioned was hiking in the wilderness or skiing in the mountains and being able to use these devices off-grid, perhaps even without a phone to communicate with one and other. The project does have a few other features like telemetry, remote admin, packet data etc but the messaging was the focus. Because of this focus, the core functionality needs to be built into the firmware of these low powered devices like ESP32 for example. This restricts what can be done in terms of CPU power and storage, but also makes synchronization between device and phone cumbersome.
Unfortunately, as a messaging platform, Meshtastic still struggles even after all these years. Message delivery and routing are fairly unreliable, 95% of conversations go along the lines of "hello, test, anyone there?". Now I should mention, if you have a very good signal to your peers the reliability can be good, but even then its not a guarantee.
Early on in the Meshtastic journey I stumbled upon a similar project named Reticulum which can utilize the same LoRa based hardware but aims to be a more comprehensive platform for decentralized communications and currently requires a computer or raspberry pi to run the Python backend alongside the LoRa hardware as a radio. Reticulum has historically been a less polished UI experience and a little idiosyncratic in its design which has probably hindered its adoption a little. But the main difference to Meshtastic is Reticulum requires bigger hardware and is less suitable for remote installations, solar powered setups etc. My understanding is once v1.0 has been released (soon) there may be efforts to port the code to native C which may allow hardware nodes to run as repeaters on their own.
More recently a new project has been announced called Meshcore, which is more closely aligned with Meshtastic than Reticulum, Meshcore makes several important improvements to message delivery and routing in an attempt to improve the reliability of the core feature, messaging. Popular Youtube channel Andy Kirby has been central in helping Meshcore gain popularity and I think he may be involved in the commercial aspects of the project. The smartphone apps and website mapping and flasher tools are a bit more polished with Meshcore.
One of the biggest contributors in the space is Liam Cottle who has created mapping websites for Meshtastic & Meshcore, he also built the Meshcore smartphone app and built the fantastic Reticulum MeshChat UI.
With all this new competition Meshtastic appears to be pushing out more frequent updates and whilst they have been introducing more bugs into the software it is nice to see some faster progress.
In my opinion Reticulum is probably the most interesting project with the most potential, but they do need to get the core routing engine running standalone on low powered hardware for the project to expand to more hardware/radio focused users.
That is all. Mesh on!
-
 @ c1e9ab3a:9cb56b43
2025-05-27 16:19:06
@ c1e9ab3a:9cb56b43
2025-05-27 16:19:06Star Wars is often viewed as a myth of rebellion, freedom, and resistance to tyranny. The iconography—scrappy rebels, totalitarian stormtroopers, lone smugglers—suggests a deep anti-authoritarian ethos. Yet, beneath the surface, the narrative arc of Star Wars consistently affirms the necessity, even sanctity, of central authority. This blog entry introduces the question: Is Star Wars fundamentally a celebration of statism?
Rebellion as Restoration, Not Revolution
The Rebel Alliance’s mission is not to dismantle centralized power, but to restore the Galactic Republic—a bureaucratic, centrally governed institution. Characters like Mon Mothma and Bail Organa are high-ranking senators, not populist revolutionaries. The goal is to remove the corrupt Empire and reinstall a previous central authority, presumed to be just.
- Rebels are loyalists to a prior state structure.
- Power is not questioned, only who wields it.
Jedi as Centralized Moral Elites
The Jedi, often idealized as protectors of peace, are unelected, extra-legal enforcers of moral and military order. Their authority stems from esoteric metaphysical abilities rather than democratic legitimacy.
- They answer only to their internal Council.
- They are deployed by the Senate, but act independently of civil law.
- Their collapse is depicted as tragic not because they were unaccountable, but because they were betrayed.
This positions them as a theocratic elite, not spiritual anarchists.
Chaos and the Frontier: The Case of the Cantina
The Mos Eisley cantina, often viewed as a symbol of frontier freedom, reveals something darker. It is: - Lawless - Violent - Culturally fragmented
Conflict resolution occurs through murder, not mediation. Obi-Wan slices off a limb; Han shoots first—both without legal consequence. There is no evidence of property rights, dispute resolution, or voluntary order.
This is not libertarian pluralism—it’s moral entropy. The message: without centralized governance, barbarism reigns.
The Mythic Arc: Restoration of the Just State
Every trilogy in the saga returns to a single theme: the fall and redemption of legitimate authority.
- Prequels: Republic collapses into tyranny.
- Originals: Rebels fight to restore legitimate order.
- Sequels: Weak governance leads to resurgence of authoritarianism; heroes must reestablish moral centralism.
The story is not anti-state—it’s anti-bad state. The solution is never decentralization; it’s the return of the right ruler or order.
Conclusion: The Hidden Statism of a Rebel Myth
Star Wars wears the costume of rebellion, but tells the story of centralized salvation. It: - Validates elite moral authority (Jedi) - Romanticizes restoration of fallen governments (Republic) - Portrays decentralized zones as corrupt and savage (outer rim worlds)
It is not an anarchist parable, nor a libertarian fable. It is a statist mythology, clothed in the spectacle of rebellion. Its core message is not that power should be abolished, but that power belongs to the virtuous few.
Question to Consider:
If the Star Wars universe consistently affirms the need for centralized moral and political authority, should we continue to see it as a myth of freedom? Or is it time to recognize it as a narrative of benevolent empire? -
 @ b7274d28:c99628cb
2025-05-28 00:59:49
@ b7274d28:c99628cb
2025-05-28 00:59:49Your identity is important to you, right? While impersonation can be seen in some senses as a form of flattery, we all would prefer to be the only person capable of representing ourselves online, unless we intentionally delegate that privilege to someone else and maintain the ability to revoke it.
Amber does all of that for you in the context of #Nostr. It minimizes the possibility of your private key being compromized by acting as the only app with access to it, while all other Nostr apps send requests to Amber when they need something signed. This even allows you to give someone temporary authority to post as you without giving them your private key, and you retain the authority to revoke their permissions at any time.
nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 has provided Android users with an incredibly powerful tool in Amber, and he continues to improve its functionality and ease of use. Indeed, there is not currently a comparative app available for iOS users. For the time being, this superpower is exclusive to Android.
Installation
Open up the Zapstore app that you installed in the previous stage of this tutorial series.
Very likely, Amber will be listed in the app collection section of the home page. If it is not, just search for "Amber" in the search bar.
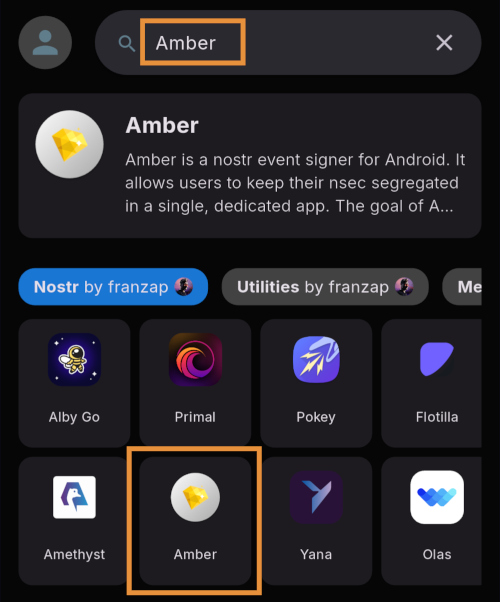
Opening the app's page in the Zapstore shows that the release is signed by the developer. You can also see who has added this app to one of their collections and who has supported this app with sats by zapping the release.
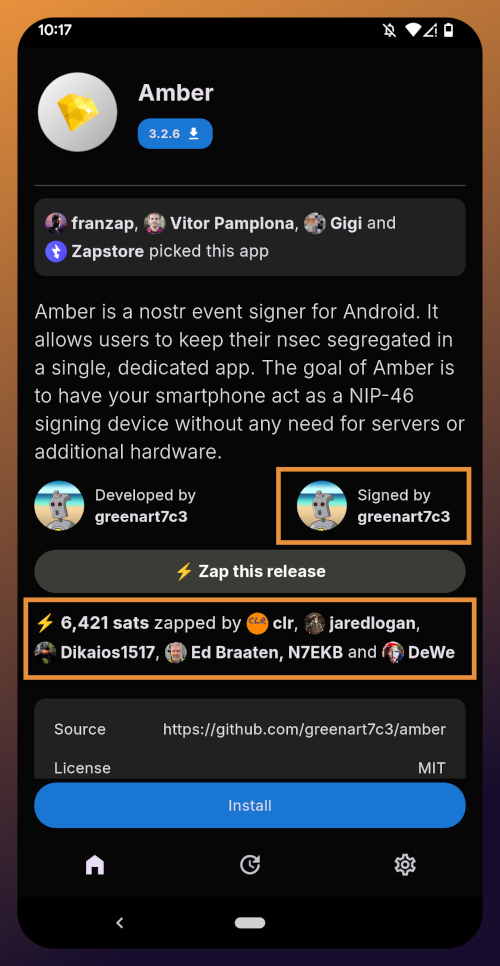
Tap "Install" and you will be prompted to confirm you are sure you want to install Amber.
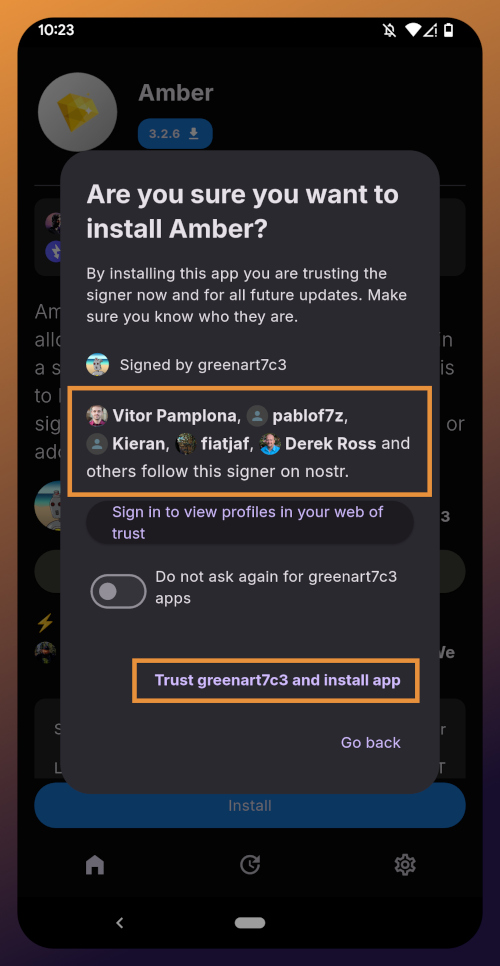
Helpfully, you are informed that several other users follow this developer on Nostr. If you have been on Nostr a while, you will likely recognize these gentlemen as other Nostr developers, one of them being the original creator of the protocol.
You can choose to never have Zapstore ask for confirmation again with apps developed by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, and since we have another of his apps to install later in this tutorial series, I recommend you toggle this on. Then tap on "Trust greenart7c3 and install app."
Just like when you installed the Zapstore from their GitHub, you will be prompted to allow the Zapstore to install apps, since Android considers it an "unknown source."
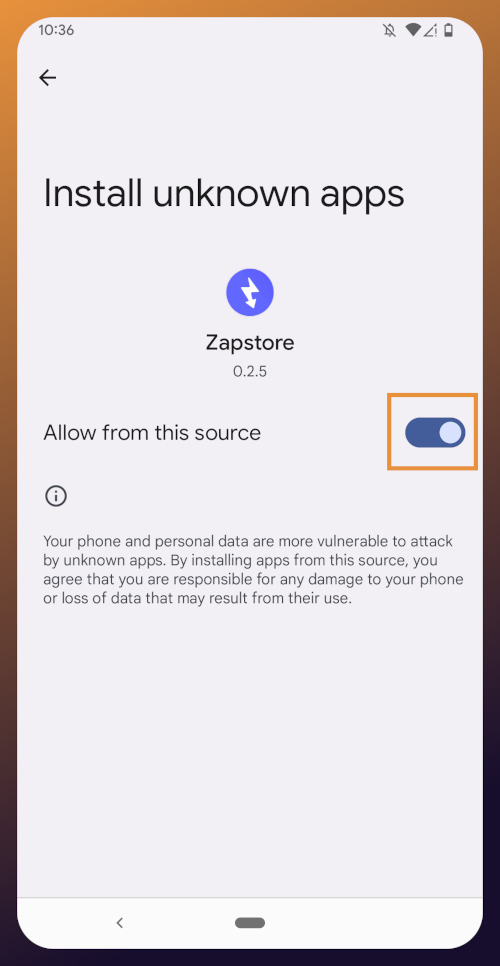
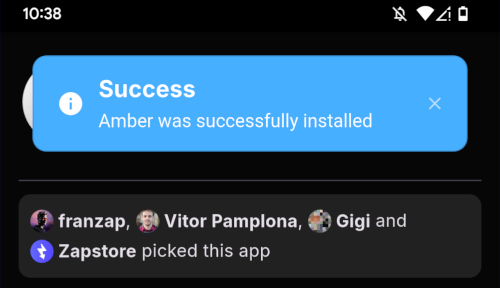
Once you toggle this on and use the back button to get back to the Zapstore, Amber will begin downloading and then present a prompt to install the app. Once installed, you will see a prompt that installation was a success and you can now open the app.
From here, how you proceed will depend on whether you need to set up a new Nostr identity or use Amber with an existing private key you already have set up. The next section will cover setting up a new Nostr identity with Amber. Skip to the section titled "Existing Nostrich" if you already have an nsec that you would like to use with Amber.
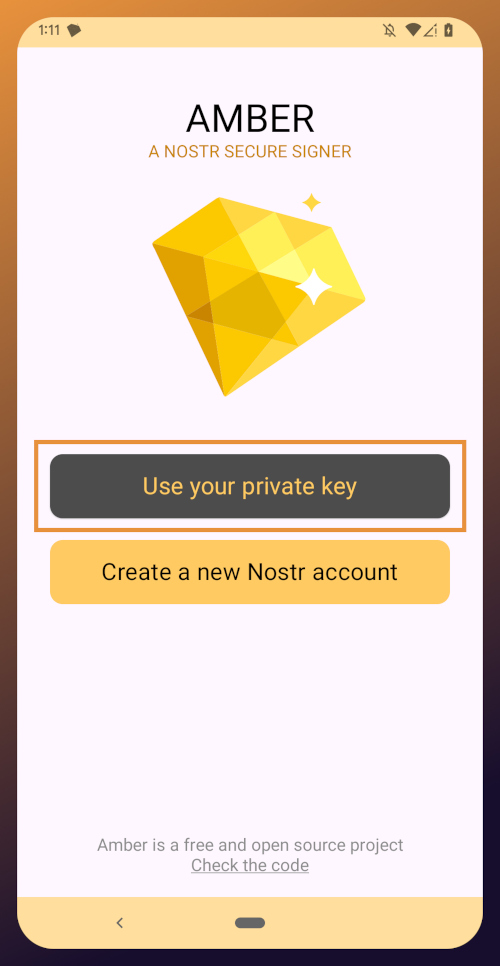
New Nostrich
Upon opening the application, you will be presented with the option to use an existing private key or create a new Nostr account. Nostr doesn't really have "accounts" in the traditional sense of the term. Accounts are a relic of permissioned systems. What you have on Nostr are keys, but Amber uses the "account" term because it is a more familiar concept, though it is technically inaccurate.
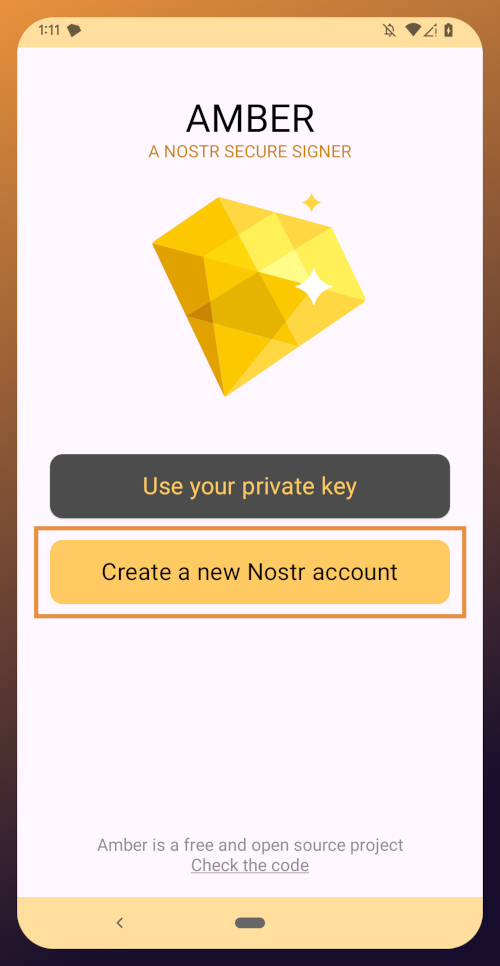
Choose "Create a new Nostr account" and you will be presented with a screen telling you that your Nostr account is ready. Yes, it was really that easy. No email, no real name, no date of birth, and no annoying capcha. Just "Create a new account" and you're done.
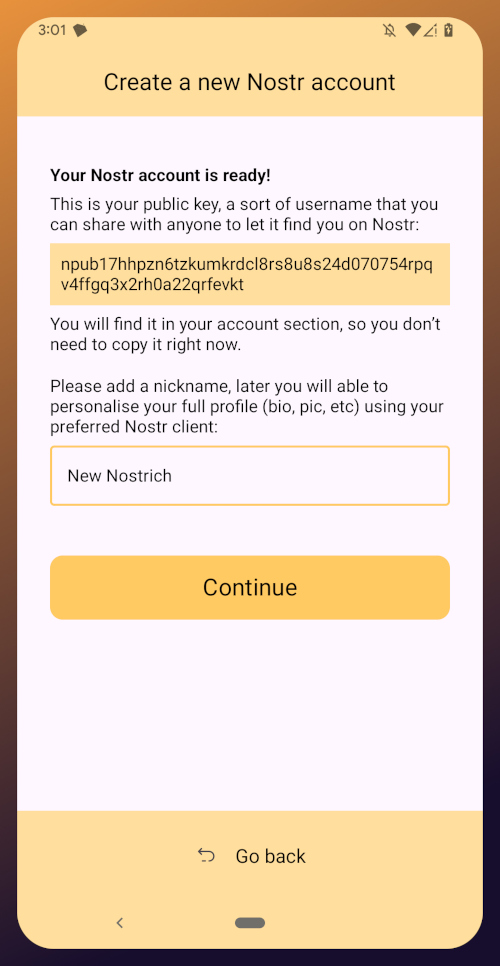
The app presents you with your public key. This is like an address that can be used to find your posts on Nostr. It is 100% unique to you, and no one else can post a note that lists this npub as the author, because they won't have the corresponding private key. You don't need to remember your npub, though. You'll be able to readily copy it from any Nostr app you use whenever you need it.
You will also be prompted to add a nickname. This is just for use within Amber, since you can set up multiple profiles within the app. You can use anything you want here, as it is just so you can tell which profile is which when switching between them in Amber.
Once you've set your nickname, tap on "Continue."
The next screen will ask you what Amber's default signing policy should be.
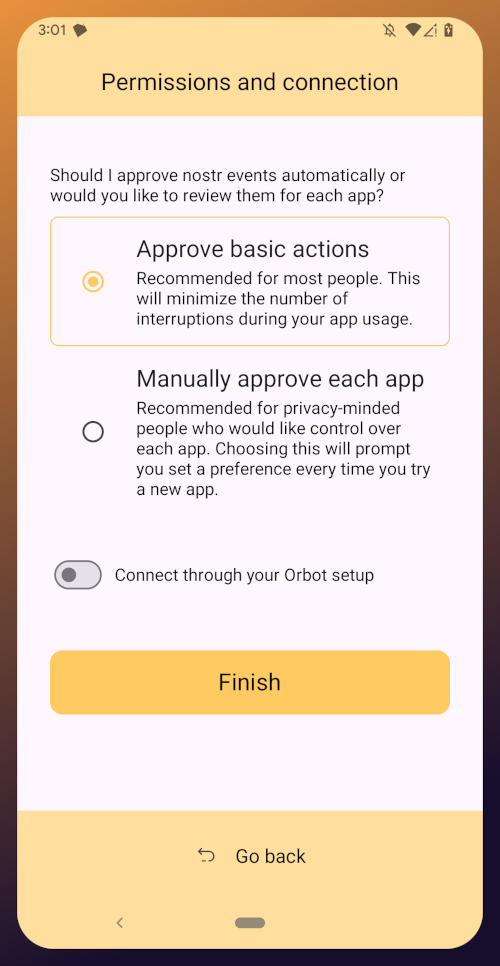
The default is to approve basic actions, referring to things that are common for Nostr clients to request a signature for, like following another user, liking a post, making a new post, or replying. If you are more concerned about what Amber might be signing for on your behalf, you can tell it to require manual approval for each app.
Once you've made your decision, tap "Finish." You will also be able to change this selection in the app settings at any time.
With this setup out of the way, you are now presented with the main "Applications" page of the app.
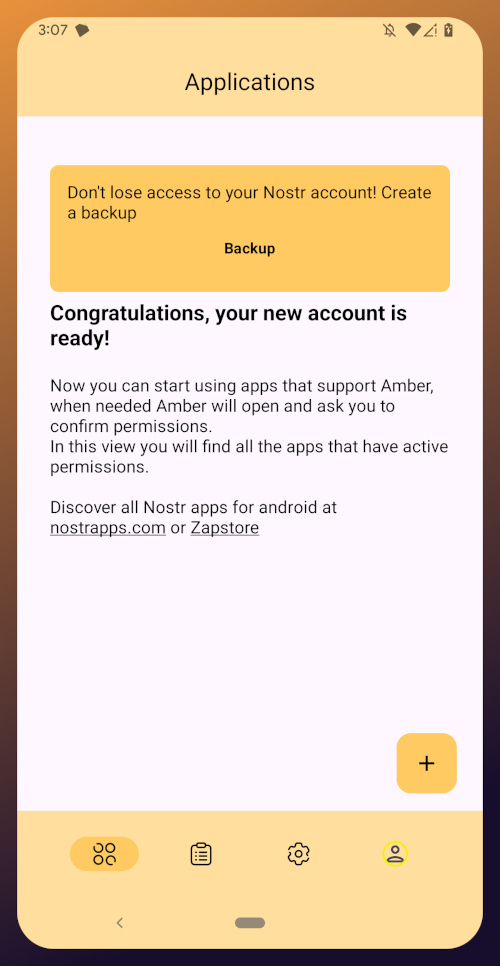
At the top, you have a notification encouraging you to create a backup. Let's get that taken care of now by tapping on the notification and skipping down to the heading titled "Backing Up Your Identity" in this tutorial.
Existing Nostrich
Upon opening the application, you will be presented with the option to use your private key or create a new Nostr account. Choose the former.
The next screen will require you to paste your private key.
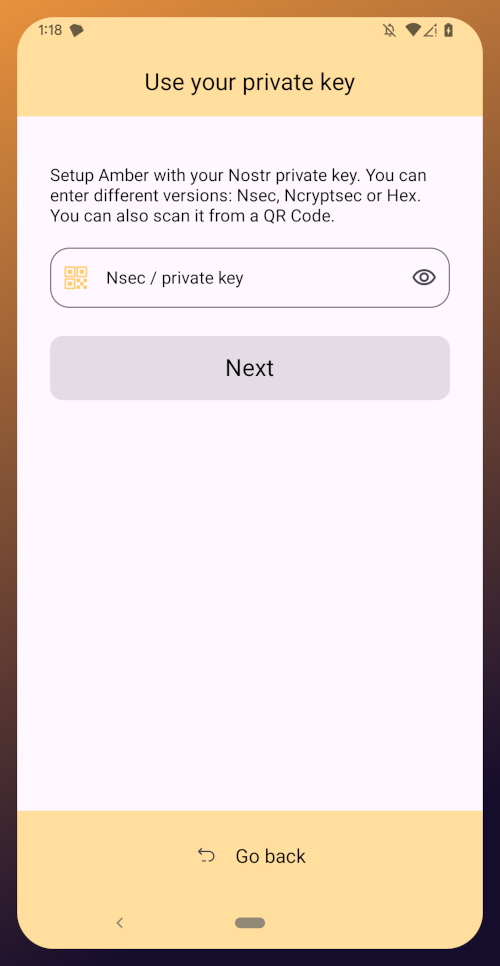
You will need to obtain this from whatever Nostr app you used to create your profile, or any other Nostr app that you pasted your nsec into in the past. Typically you can find it in the app settings and there will be a section mentioning your keys where you can copy your nsec. For instance, in Primal go to Settings > Keys > Copy private key, and on Amethyst open the side panel by tapping on your profile picture in the top-left, then Backup Keys > Copy my secret key.
After pasting your nsec into Amber, tap "Next."

Amber will give you a couple options for a default signing policy. The default is to approve basic actions, referring to things that are common for Nostr clients to request a signature for, like following another user, liking a post, making a new post, or replying. If you are more concerned about what Amber might be signing for on your behalf, you can tell it to require manual approval for each app.
Once you've made your decision, tap "Finish." You will also be able to change this selection in the app settings at any time.
With this setup out of the way, you are now presented with the main "Applications" page of the app. You have nothing here yet, since you haven't used Amber to log into any Nostr apps, but this will be where all of the apps you have connected with Amber will be listed, in the order of the most recently used at the top.
Before we go and use Amber to log into an app, though, let's make sure we've created a backup of our private key. You pasted your nsec into Amber, so you could just save that somewhere safe, but Amber gives you a few other options as well. To find them, you'll need to tap the cog icon at the bottom of the screen to access the settings, then select "Backup Keys."
Backing Up Your Identity
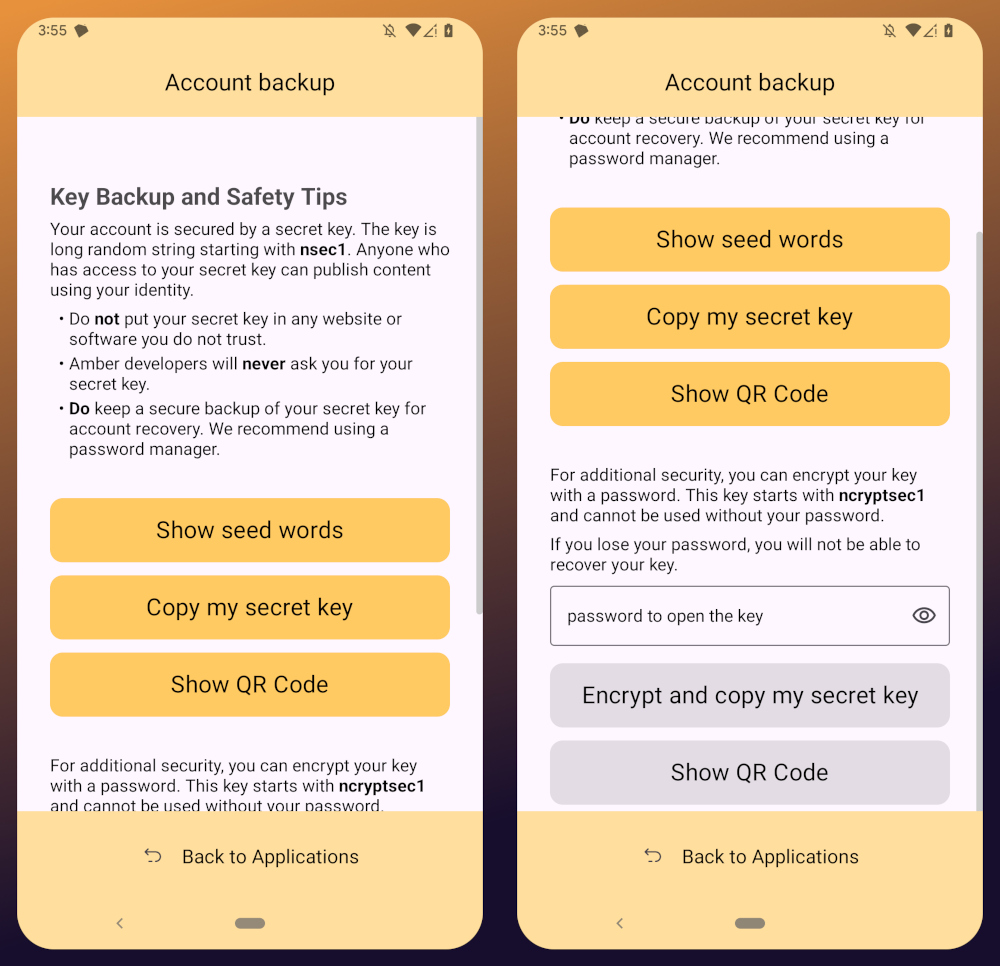
You'll notice that Amber has a few different options for backing up your private key that it can generate.
First, it can give you seed words, just like a Bitcoin seed. If you choose that option, you'll be presented with 12 words you can record somewhere safe. To recover your Nostr private key, you just have to type those words into a compatible application, such as Amber.
The next option is to just copy the secret/private key in its standard form as an "nsec." This is the least secure way to store it, but is also the most convenient, since it is simple to paste into another signer application. If you want to be able to log in on a desktop web app, the browser extension Nostr signers won't necessarily support entering your 12 word seed phrase, but they absolutely will support pasting in your nsec.
You can also display a QR code of your private key. This can be scanned by Amber signer on another device for easily transferring your private key to other devices you want to use it on. Say you have an Android tablet in addition to your phone, for instance. Just make sure you only use this function where you can be certain that no one will be able to get a photograph of that QR code. Once someone else has your nsec, there is no way to recover it. You have to start all over on Nostr. Not a big deal at this point in your journey if you just created a Nostr account, but if you have been using Nostr for a while and have built up a decent amount of reputation, it could be much more costly to start over again.
The next options are a bit more secure, because they require a password that will be used to encrypt your private key. This has some distinct advantages, and a couple disadvantages to be aware of. Using a password to encrypt your private key will give you what is called an ncryptsec, and if this is leaked somehow, whoever has it will not necessarily have access to post as you on Nostr, the way they would if your nsec had been leaked. At least, not so long as they don't also have your password. This means you can store your ncryptsec in multiple locations without much fear that it will be compromised, so long as the password you used to encrypt it was a strong and unique one, and it isn't stored in the same location. Some Nostr apps support an ncryptsec for login directly, meaning that you have the option to paste in your ncryptsec and then just log in with the password you used to encrypt it from there on out. However, now you will need to keep track of both your ncryptsec and your password, storing both of them safely and separately. Additionally, most Nostr clients and signer applications do not support using an ncryptsec, so you will need to convert it back to a standard nsec (or copy the nsec from Amber) to use those apps.
The QR option using an ncryptsec is actually quite useful, though, and I would go this route when trying to set up Amber on additional devices, since anyone possibly getting a picture of the QR code is still not going to be able to do anything with it, unless they also get the password you used to encrypt it.
All of the above options will require you to enter the PIN you set up for your device, or biometric authentication, just as an additional precaution before displaying your private key to you.
As for what "store it in a safe place" looks like, I highly recommend a self-hosted password manager, such as Vaultwarden+Bitwarden or KeePass. If you really want to get wild, you can store it on a hardware signing device, or on a steel seed plate.
Additional Settings
Amber has some additional settings you may want to take advantage of. First off, if you don't want just anyone who has access to your phone to be able to approve signing requests, you can go into the Security settings add a PIN or enable biometrics for signing requests. If you enable the PIN, it will be separate from the PIN you use to access your phone, so you can let someone else use your phone, like your child who is always begging to play a mobile game you have installed, without worrying that they might have access to your Nostr key to post on Amethyst.
Amber also has some relay settings. First are the "Active relays" which are used for signing requests sent to Amber remotely from Nostr web apps. This is what enables you to use Amber on your phone to log into Nostr applications on your desktop web browser, such as Jumble.social, Coracle.social, or Nostrudel.ninja, eliminating your need to use any other application to store your nsec whatsoever. You can leave this relay as the default, or you can add other relays you want to use for signing requests. Just be aware, not all relays will accept the notes that are used for Nostr signing requests, so make sure that the relay you want to use does so. In fact, Amber will make sure of this for you when you type in the relay address.
The next type of relays that you can configure in Amber are the "Default profile relays." These are used for reading your profile information. If you already had a Nostr identity that you imported to Amber, you probably noticed it loaded your profile picture and display name, setting the latter as your nickname in Amber. These relays are where Amber got that information from. The defaults are relay.nostr.band and purplepag.es. The reason for this is because they are aggregators that look for Nostr profiles that have been saved to other relays on the network and pull them in. Therefore, no matter what other relay you may save your profile to, Amber will likely be able to find it on one of those two relays as well. If you have a relay you know you will be saving your Nostr profiles to, you may want to add it to this list.
You can also set up Amber to be paired with Orbot for signing over Tor using relays that are only accessible via the Tor network. That is an advanced feature, though, and well beyond the scope of this tutorial.
Finally, you can update the default signing policy. Maybe after using Amber for a while, you've decided that the choice you made before was too strict or too lenient. You can change it to suit your needs.
Zapstore Login
Now that you are all set up with Amber, let's get you signed into your first Nostr app by going back to the Zapstore.
From the app's home screen, tap on the user icon in the upper left of the screen. This will open a side panel with not much on it except the option to "sign in." Go ahead and tap on it.
You will be presented with the option to either sign in with Amber, or to paste your npub. However, if you do the latter, you will only have read access, meaning you cannot zap any of the app releases. There are other features planned for the Zapstore that may also require you to be signed in with write access, so go ahead and choose to log in with Amber.
Your phone should automatically switch to Amber to approve the sign-in request.
You can choose to only approve basic actions for Zapstore, require it to manually approve every time, or you can tell it that you "fully trust this application." Only choose the latter option with apps you have used for a while and they have never asked you to sign for anything suspicious. For the time being, I suggest you use the "Approve basic actions" option and tap "Grant Permissions."
Your phone will switch back to the Zapstore and will show that you are now signed in. Congratulations! From here on out, logging into most Nostr applications will be as easy as tapping on "Log in with Amber" and approving the request.
If you set up a new profile, it will just show a truncated version of your npub rather than the nickname you set up earlier. That's fine. You'll have an opportunity to update your Nostr profile in the next tutorial in this series and ensure that it is spread far and wide in the network, so the Zapstore will easily find it.
That concludes the tutorial for Amber. While we have not covered using Amber to log into Nostr web apps, that is outside the scope of this series, and I will cover it in an upcoming tutorial regarding using Amber's remote signer options in detail.
Since you're already hanging out in the Zapstore, you may as well stick around, because we will be using it right out the gate in the next part of this series: Amethyst Installation and Setup. (Coming Soon)
-
 @ 3770c235:16042bcc
2025-05-30 05:25:21
@ 3770c235:16042bcc
2025-05-30 05:25:21Let’s clear something up: frugal living isn’t about eating ramen every night or never treating yourself. It’s about being intentional with your money so you can enjoy what matters more. Think of it like editing a movie—you cut the boring scenes to highlight the best parts. You don’t have to give up lattes, travel, or Friday pizza nights. You just need a few clever tricks to make your money stretch further while keeping the fun intact.
Take my friend Alex, for example. Last year, he felt overwhelmed by credit card debt but didn’t want to give up his weekend hikes or coffee shop visits. By tweaking a few habits—like auditing subscriptions and prioritizing experiences—he paid off $5,000 in debt and still took a camping trip with his kids. The secret? Small, intentional choices that add up. In this guide, we’ll share practical, joy-friendly hacks to help you save smarter. Plus, we’ll mention sites like Crown Money—a budgeting service that makes tracking your progress effortless—so you can focus on living well, not pinching pennies.
**1. Audit Your Subscriptions (Yes, Even That One) ** You know that streaming service you haven’t opened since 2022? Or the gym membership you keep “meaning to use”? Those small charges add up fast. A recent study found the average person spends 219/month on forgotten subscriptions—that’s over 2,600 a year!
• The Hack: Every 3 months, review your subscriptions. Ask: “Do I actually use this?” Cancel anything that doesn’t spark joy. • Pro Tip: Use Crown Money to see all your subscriptions in one place. The app automatically flags recurring charges, so you don’t have to hunt through bank statements. You’ll even get a nudge like, “You’ve paid $14.99/month for ‘Premium Yoga App’—last used 6 months ago. Cancel?” Real-Life Example: Sarah canceled two unused streaming services and a meditation app she forgot about. She saved $45/month—enough to fund her new hobby: pottery classes. “I didn’t realize how much clutter I was paying for,” she said. “Now I’m learning to make mugs instead of binge-watching shows I don’t even like.”
**2. Embrace the “Joy Budget” (Seriously, Budget for Fun) ** Frugality fails when it feels like deprivation. Instead, carve out guilt-free money for things you love. Behavioral scientists call this “temptation bundling”—pairing savings goals with rewards to stay motivated.
• The Hack: Allocate 10–15% of your budget to a “Joy Fund” for hobbies, dining out, or travel. • Pro Tip: In Crown Money, create a custom category like “Adventure Fund” or “Treat Yourself.” Set a monthly limit and track how much you’ve saved for that weekend getaway or concert ticket. The app’s visual progress bars turn saving into a game—imagine watching your “Beach Trip 2024” fund grow with every dollar.
Real-Life Example: Mark loves trying new restaurants. By setting a $100/month “Dining Out” budget in Crown Money, he enjoys date nights without overspending. “I used to feel guilty splurging on sushi,” he shared. “Now I know it’s part of the plan, so I savor every bite.”
- Master Mindful Spending (Ask This One Question) Before buying anything non-essential, ask: “Will this add value to my life, or just clutter?” Retail therapy might feel good in the moment, but that $50 impulse sweater often ends up forgotten in the back of your closet.
• The Hack: Implement a 24-hour “cooling-off” period for impulse buys. If you still want it tomorrow, go for it! • Pro Tip: Use Crown Money to review your spending trends. The app’s monthly reports show where your money goes, helping you spot habits (like late-night online shopping) that don’t align with your goals. Set up alerts like, “You’ve spent $75 on ‘Miscellaneous’ this week—want to check in?” Real-Life Example: Lisa avoided buying a $200 jacket on impulse. After 24 hours, she realized she didn’t need it—and put the money toward a weekend camping trip instead. “I almost bought something I’d wear once,” she laughed. “Now I have photos of sunsets instead of buyer’s remorse.”
- DIY and Swap (Your Wallet Will Thank You) Frugal living thrives on creativity. Swap buying new for: • DIY solutions: Make coffee at home (a $5 bag of beans lasts weeks!), repair clothes, or grow herbs instead of buying them. • Community swaps: Trade books, tools, or skills with friends (e.g., “I’ll babysit if you help me fix my bike”).
Pro Tip: Track your monthly expenses in Crown Money. Create a category like “Homemade Wins” and watch how small choices (like brewing your latte) add up over time. For example, skipping a daily 4 coffee shop visit saves 120/month—that’s a weekend road trip! Real-Life Example: Jake started meal prepping lunches instead of buying 15 salads. He saves 300/month—enough for a monthly massage. “I’m eating healthier and funding self-care,” he said. “Plus, my coworkers are jealous of my teriyaki bowls.”
- Prioritize Experiences Over “Stuff” (Happiness Science Approved) Research shows experiences bring longer-lasting joy than material purchases. A 2023 study found people who spent money on concerts, trips, or classes reported 30% higher life satisfaction than those who bought gadgets or clothes.
Instead of splurging on gadgets, invest in: • Free/low-cost adventures: Hiking, picnics, game nights, or exploring local festivals. • Shared moments: Host a potluck instead of dining out. Pro Tip: Use Crown Money to set a goal like “Summer Adventure Fund.” Allocate $50/month, and let the app remind you to fund it automatically. Watching that fund grow feels like planning a vacation in slow motion. Real-Life Example: Maria and her partner skipped a pricey vacation and rented a cozy cabin nearby. They saved $1,200 and still made memories roasting marshmallows under the stars. “We thought we needed a fancy trip to connect,” she said. “Turns out, all we needed was a fire pit and no Wi-Fi.”
Key Takeaways • Cut the clutter: Cancel unused subscriptions and track them with tools like Crown Money. • Budget for joy: Allocate guilt-free money for hobbies and experiences. • Pause before purchasing: Avoid impulse buys with a 24-hour rule. • Get creative: DIY, swap, and repurpose to save without sacrifice. • Invest in experiences: They’re richer than “stuff” and often cheaper.
FAQs: Frugal Living Made Simple Q: How do I stay motivated to save? A: Tie savings to specific goals (e.g., “Save $500 for a weekend trip”). Apps like Crown Money let you visualize progress, which feels rewarding!
Q: Can I be frugal and still socialize? A: Absolutely! Host DIY spa nights, picnic potlucks, or free museum days. Use Crown Money to set a “Social Fun” budget and stick to it.
Q: What if I slip up and overspend? A: No guilt! Adjust your budget next month. Crown Money makes it easy to shift funds between categories.
Q: How do I track small savings from DIY habits? A: Create a custom category in Crown Money (e.g., “Homemade Wins”) and log your savings manually. Watching it grow is addictive!
Q: What if I have a financial emergency? A: Build a “Safety Net” category in Crown Money. Start small—even $20/month adds up. The app’s reminders keep you consistent.
**Final Thoughts: Frugal Is Freedom ** Frugal living isn’t about saying “no”—it’s about saying “yes” to what truly lights you up. By trimming the financial fat (goodbye, unused subscriptions!), budgeting for joy, and getting creative, you can save money and savor life’s best moments. Tools like Crown Money are your allies here. They handle the tracking and nudging, so you can focus on the fun parts: planning adventures, trying new recipes, or laughing with friends over a board game. Remember: the goal isn’t perfection. It’s progress. Start small, celebrate wins, and let your frugal habits grow naturally. Your wallet (and your inner joy-seeker) will thank you.
-
 @ 06639a38:655f8f71
2025-05-26 14:21:37
@ 06639a38:655f8f71
2025-05-26 14:21:37Finally there is a release (1.7.0) for Nostr-PHP with a full NIP-19 integration. Here is an example file with some snippets to how it works to encode and decode bech32 encoded entities:
- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip19-bech32-decoded-entities.php
- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip19-bech32-encoded-entities.php
Now merge request #68 (and issues #74, #64 are closed) is finally merged which I opened in October 2024.
Next up is:
- Create documentation how to use NIP-19 with the library on https://nostr-php.dev
- Create documentation how to use NIP-04 and NIP-44 with the library on https://nostr-php.dev
- Work out a proof-of-concept with the revolt/event-loop package to create concurrent async requests with websocket connections
-
 @ cae03c48:2a7d6671
2025-05-30 03:00:46
@ cae03c48:2a7d6671
2025-05-30 03:00:46Bitcoin Magazine

Jack Mallers Announced A New System of Bitcoin Backed Loans at StrikeThe Founder and CEO of Strike, Jack Mallers, at the 2025 Bitcoin Conference in Las Vegas, announced a new system of Bitcoin backed loans at Strike with one digit interest rate.
Jack Mallers began his keynote by pointing at the biggest problem. Fiat currency.
“The best time to go to Whole Foods and buy eggs with your dollars was 1913,” said Mallers. “Every other time after, you are getting screwed.”
What’s the solution?
“The solution is Bitcoin,” stated Mallers. “Bitcoin is the money that we coincide that nobody can print. You can’t print, you can’t debase my time and energy, you cannot deprive me of owning assets, of getting out of debt, of living sovereignly and protecting my future, my family, my priced possessions. Bitcoin is what we invented to do that.”
Mallers gave a power message to the audience by explaining that people should HODL every dollar they have in Bitcoin. People should also spend a little of it to have a nice life.
“You can’t HODL forever,” said Jack.
While talking about loans that people borrow against their Bitcoin. He explained why he thinks banks putting 20% in interest for loans backed with Bitcoin is outrageous.
“All these professional economists, they are like Bitcoin is risky and volatile,” stated Mallers. “No it’s not. This is the magnificent 7 one year volatility and the orange one in the middle is Bitcoin. It’s no more risky and volatile. It’s a little bit more volatile than Apple, but is far less more volatile than Tesla.”
“As Bitcoin matures, its volatility goes down,” continued Jack. “Bitcoin volatility is at a point where it is no more risky than a Tesla Stock. We should not be paying double digits rates for a loan.”
Mallers announced his new system of loans at Strike of 9-13% in interest rates. It will allow people to get loans from $10,000 to $1 billion.
Mallers closed by saying, “please be responsible. This is debt. Debt is like fire in my opinion. It can heat a civilization. It can warm your home, but if you go too crazy it can burn your house down.”
“Life is short,” said Jack. “Take the trip, but with bitcoin you just get to take a better one.”
This post Jack Mallers Announced A New System of Bitcoin Backed Loans at Strike first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ b1ddb4d7:471244e7
2025-05-30 03:01:02
@ b1ddb4d7:471244e7
2025-05-30 03:01:02Bitcoin FilmFest (BFF25) returns to Warsaw for its third edition, blending independent cinema—from feature films and commercials to AI-driven experimental visuals—with education and entertainment.
Hundreds of attendees from around the world will gather for three days of screenings, discussions, workshops, and networking at the iconic Kinoteka Cinema (PKiN), the same venue that hosted the festival’s first two editions in March 2023 and April 2024.
This year’s festival, themed “Beyond the Frame,” introduces new dimensions to its program, including an extra day on May 22 to celebrate Bitcoin Pizza Day, the first real-world bitcoin transaction, with what promises to be one of Europe’s largest commemorations of this milestone.
BFF25 bridges independent film, culture, and technology, with a bold focus on decentralized storytelling and creative expression. As a community-driven cultural experience with a slightly rebellious spirit, Bitcoin FilmFest goes beyond movies, yet cinema remains at its heart.
Here’s a sneak peek at the lineup, specially curated for movie buffs:
 Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money.
Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money. Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative).
Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative). Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.
Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.To get an idea of what might come up at the event, here, you can preview 6 selected ads combined into two 2 videos:
 Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships.
Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships. Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.
Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.BFF25 Main Screenings
Sample titles from BFF25’s Official Selection:
 REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director.
REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director. UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year.
UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year. HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.
HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.Check out trailers for this year’s BFF25 and past editions on YouTube.
Tickets & Info:
- Detailed program and tickets are available at bitcoinfilmfest.com/bff25.
- Stay updated via the festival’s official channels (links provided on the website).
- Use ‘LN-NEWS’ to get 10% of tickets
-
 @ 502ab02a:a2860397
2025-05-30 01:14:10
@ 502ab02a:a2860397
2025-05-30 01:14:10ย้อนกลับไปปี 2014 ชายชื่อ Patrick O. Brown ศาสตราจารย์ชีววิทยาเชิงโมเลกุลแห่งมหาวิทยาลัยแตนฟอร์ด ตัดสินใจลาออกจากเส้นทางวิชาการสายหลัก เพื่อมาก่อตั้งบริษัทที่เขาเชื่อว่าจะเปลี่ยนโลก Impossible Foods
ดร. แพทริค โอ. บราวน์ (Patrick O. Brown) เป็นนักชีวเคมีและนักธุรกิจชาวอเมริกันและศาสตราจารย์กิตติคุณด้านชีวเคมีแห่งมหาวิทยาลัยสแตนฟอร์ด เขาได้รับปริญญาตรี แพทยศาสตรบัณฑิต และปรัชญาดุษฎีบัณฑิตด้านชีวเคมีจากมหาวิทยาลัยชิคาโก หลังจากนั้น เขาได้เข้ารับการฝึกอบรมด้านกุมารเวชศาสตร์ที่โรงพยาบาล Children's Memorial ในชิคาโก ในช่วงหลังปริญญาเอก เขาได้ทำงานวิจัยเกี่ยวกับกลไกที่ไวรัส HIV และเรโทรไวรัสอื่น ๆ แทรกยีนของพวกมันเข้าสู่จีโนมของเซลล์ที่ติดเชื้อ ซึ่งช่วยนำไปสู่การพัฒนายาใหม่ในการต่อสู้กับโรคนี้
ในช่วงต้นทศวรรษ 1990 ดร. บราวน์และทีมงานของเขาที่สแตนฟอร์ดได้พัฒนาเทคโนโลยี DNA microarray ซึ่งเป็นเครื่องมือที่ช่วยให้นักวิจัยสามารถวิเคราะห์การแสดงออกของยีนทั้งหมดในจีโนมได้พร้อมกัน เทคโนโลยีนี้มีบทบาทสำคัญในการวิจัยทางชีววิทยาและการแพทย์ โดยเฉพาะในการจำแนกประเภทของมะเร็งและการพยากรณ์โรค
นอกจากนี้ ดร. บราวน์ยังเป็นผู้ร่วมก่อตั้ง Public Library of Science (PLOS) ซึ่งเป็นองค์กรไม่แสวงหาผลกำไรที่มุ่งเน้นการเผยแพร่ผลงานวิจัยทางวิทยาศาสตร์ให้เข้าถึงได้ฟรีและเปิดกว้างต่อสาธารณะ
ในปี 2011 ดร. บราวน์ได้ก่อตั้ง Impossible Foods โดยมีเป้าหมายในการสร้างผลิตภัณฑ์เนื้อสัตว์จากพืชที่มีรสชาติและเนื้อสัมผัสคล้ายเนื้อสัตว์จริง เพื่อลดผลกระทบต่อสิ่งแวดล้อมจากการเลี้ยงสัตว์ เขาและทีมงานได้ค้นพบว่าโมเลกุล heme ซึ่งเป็นส่วนประกอบที่ให้รสชาติและกลิ่นเฉพาะของเนื้อสัตว์ สามารถผลิตจากพืชได้ โดยเฉพาะจากรากถั่วเหลือง พวกเขาใช้เทคนิคทางวิศวกรรมชีวภาพในการผลิต heme จากยีสต์ที่ได้รับการดัดแปลงพันธุกรรม และนำมาผสมกับโปรตีนจากพืชเพื่อสร้างผลิตภัณฑ์ที่มีลักษณะคล้ายเนื้อสัตว์
ดร. บราวน์ได้รับการยอมรับอย่างกว้างขวางในวงการวิทยาศาสตร์และเทคโนโลยี โดยได้รับรางวัลและเกียรติคุณหลายรายการ รวมถึงการเป็นสมาชิกของ National Academy of Sciences และ National Academy of Medicine ของสหรัฐอเมริกา ด้วยความมุ่งมั่นในการแก้ไขปัญหาสิ่งแวดล้อมผ่านนวัตกรรมทางอาหาร ดร. แพทริค โอ. บราวน์ ได้กลายเป็นบุคคลสำคัญที่มีบทบาทในการเปลี่ยนแปลงวิธีการบริโภคอาหารของโลกในศตวรรษที่ 21
เป้าหมายของเขาไม่ใช่เพียงแค่ทำอาหาร แต่คือ "ยุติการทำปศุสัตว์ให้หมดสิ้นภายในปี 2035"
เขาไม่ได้พูดลอย ๆ เขาลงมือ “ทำเนื้อจากพืช” ด้วยเทคโนโลยีที่ซับซ้อนระดับวิศวกรรมชีวภาพ นำโปรตีนจากถั่วเหลือง + น้ำมันมะพร้าว + เทคเจอร์ + สารเติมแต่งอีกชุดใหญ่ มาผ่านกระบวนการแปรรูปจนดูคล้ายเนื้อย่าง แต่ที่ทำให้ “มันดูเหมือนเนื้อจริง” คือการเติม ฮีม (Heme) เข้าไปสารประกอบที่อยู่ในเลือดและเนื้อสัตว์จริง ๆ
Impossible Foods คือบริษัทที่ไม่ได้เพียง “ปลอมรสชาติเนื้อ” แต่พยายามสร้างเนื้อจากพืช ให้เหมือนเนื้อจริงที่สุดเท่าที่วิทยาศาสตร์จะเอื้อมถึง จุดขายที่ทำให้แบรนด์นี้ดังเปรี้ยงก็คือสิ่งที่เรียกว่า “ฮีม” (heme) หรือโมเลกุลเหล็กในเลือด ซึ่งเป็นตัวการหลักที่ทำให้เนื้อวัวมีกลิ่นและรสเฉพาะตัวเวลาถูกย่างจนหอมฉุย
ดร.แพทริค บราวน์ และทีมนักวิจัยของเขาเริ่มจากการค้นหาว่า “อะไรในพืช” ให้กลิ่นคล้ายเลือด พวกเขาพบว่า “Leghemoglobin” ซึ่งอยู่ในรากถั่วเหลือง มีโครงสร้างใกล้เคียงกับ Hemoglobin ในเลือดสัตว์มากที่สุด จุดพลิกของเทคโนโลยีนี้คือ การผลิตเลกฮีโมโกลบินจากพืชจำนวนมาก ทำไม่ได้โดยการถอนรากถั่วมาทุบคั้น แต่ต้องอาศัยวิศวกรรมชีวภาพขั้นสูง
พวกเขาจึงใช้กระบวนการที่เรียกว่า “fermentation by genetically modified yeast” หรือการหมักโดยยีสต์ที่ผ่านการดัดแปลงพันธุกรรม โดยนำยีนของพืชที่สร้าง leghemoglobin ไปใส่ในยีสต์ (Pichia pastoris) แล้วเลี้ยงยีสต์นั้นในถังหมักขนาดใหญ่แบบเดียวกับโรงเบียร์ พอยีสต์ขยายตัว มันจะผลิตเลกฮีโมโกลบินออกมาจำนวนมาก จากนั้นจึงสกัดออกมาผสมกับโปรตีนจากพืช เช่น โปรตีนจากถั่วเหลือง หรือโปรตีนจากมันฝรั่ง
เพื่อให้เนื้อสัมผัสคล้ายเนื้อจริง ทีม Impossible Foods ยังใช้เทคนิคอื่นร่วมด้วย เช่น -Coconut Oil และ Sunflower Oil เป็นแหล่งไขมันที่ให้สัมผัส “ฉ่ำๆ” คล้ายไขมันเนื้อวัว -Methylcellulose สารที่ช่วยทำให้ส่วนผสมเกาะตัวเป็นก้อน คล้ายเนื้อบดจริง -Natural Flavors กลิ่นที่สกัดจากพืชหลายชนิด เพื่อเลียนแบบกลิ่นไหม้จากเนื้อย่าง
ทุกอย่างถูกผสมให้เข้ากัน ผ่านเครื่องอัดขึ้นรูป (extrusion) ที่ทำให้เนื้อออกมามี “เส้นใย” คล้ายกล้ามเนื้อวัว หรือหมู เมื่อโดนความร้อน โปรตีนจะเปลี่ยนโครงสร้าง (denature) และมีกลิ่นออกมาคล้ายๆ เนื้อย่างจริงๆ พร้อมน้ำสีแดงคล้ายเลือด (จาก heme) ไหลเยิ้ม ซึ่งคือไอเดียที่ทำให้ Impossible Burger เป็นมากกว่าแค่ “เบอร์เกอร์ผัก”
ผลลัพธ์คือ… เบอร์เกอร์พืชที่มีเลือดซึม สีชมพูดู juicy และกลิ่นไหม้ติดกระทะ จนคนกินรู้สึกเหมือนกำลังย่างเนื้อจริง ๆ
ฟังดูอัศจรรย์ใช่ไหม? แต่...การเติมฮีมจากยีสต์ตัดต่อพันธุกรรมลงในอาหาร ไม่เคยมีในธรรมชาติมาก่อน ในปี 2017 Impossible Foods ต้องยื่นเรื่องต่อ FDA เพื่อขออนุมัติว่า leghemoglobin จากยีสต์ GMO “ปลอดภัย”
แต่ในตอนนั้น FDA ตอบว่า “ยังไม่มีข้อมูลเพียงพอ” ว่าจะไม่ก่อให้เกิดภูมิแพ้หรือผลข้างเคียงในระยะยาว (ใช่แล้วจ้ะ... สารที่อยู่ในเบอร์เกอร์ชื่อดัง ถูกขายก่อนที่ FDA จะสรุปว่าปลอดภัยเต็มร้อย)
แล้วในที่สุด ปี 2019 FDA ก็ให้ผ่านแบบ “GRAS” (Generally Recognized As Safe) โดยใช้ข้อมูลจากการทดลองภายในของบริษัทเอง ไม่ใช่การทดสอบอิสระจากภายนอก
เฮียว่าอันนี้ต้องมีใครสะกิดในใจแล้วล่ะว่า “เรากำลังเอาอะไรเข้าปากกันแน่?”
แม้จะฟังดูเท่ ไฮเทค และดีต่อสิ่งแวดล้อม แต่ก็มีคำถามจากนักวิจารณ์มากมายว่า… แท้จริงแล้วอาหารเหล่านี้เป็นอาหาร “เพื่อสิ่งแวดล้อม” หรือเป็นเพียง “ภาพฝันที่ควบคุมโดยบริษัทเทคโนโลยียักษ์ใหญ่”?
มันเต็มไปด้วยคำถาม คำถาม และ คำถามนะสิครับ
ในเมื่อ Impossible Foods ได้รับเงินลงทุนหลายรอบจากบริษัทยักษ์อย่าง Google Ventures, UBS, และ Temasek (ของรัฐบาลสิงคโปร์) บอกตรง ๆ ว่า เงินแบบนี้ไม่ได้หวังแค่เปลี่ยนโลกแต่มันมาพร้อมเป้าหมายที่ชัดมาก การสร้างสิทธิบัตรอาหารใหม่ ที่ควบคุมการผลิตจากต้นน้ำยันปลายน้ำ อย่าลืมว่า ยีสต์ที่ผ่านการดัดแปลงพันธุกรรม หรือ GMO yeast นั้นถือเป็นสิทธิบัตร ถ้าใครจะผลิต Heme แบบเดียวกันก็ต้องขออนุญาตจาก Impossible Foods หรือไม่ก็โดนฟ้องได้เลย แปลว่า “เทคโนโลยีรสชาติเนื้อ” ไม่ได้เป็นมรดกของโลก แต่อยู่ในมือบริษัทไม่กี่แห่ง
ยิ่งไปกว่านั้น อุปกรณ์การผลิตต้องลงทุนสูง ต้องมีโรงหมัก ปฏิบัติการชีวภาพ การควบคุมความปลอดภัยที่เข้มข้น จึงไม่ใช่ใครๆ ก็ทำได้ ที่น่ากลัวคือ ถ้าเมื่อวันหนึ่งเนื้อสัตว์ธรรมชาติถูกทำให้กลายเป็น “ปีศาจสิ่งแวดล้อม” หรือ "ตัวเชื้อโรคผ่านอาหาร" โดยนโยบายรัฐและการตลาดของกลุ่มเทคฯ อาหารที่ประชาชนกินได้อาจเหลือแค่ “สิ่งที่ผลิตโดยมีสิทธิบัตร” เท่านั้น
เมื่อถึงวันนั้น ประชาชนจะสิ้นความชอบธรรมในการ “เลี้ยงวัวไว้กินเอง” ไม่ได้อีกต่อไป เพราะอาจโดนห้ามจากข้อกฎหมายคาร์บอน กฎหมายการกักกันเชื้อ ประชาชนจะ “เก็บพืชริมรั้วมาทำอาหาร” ไม่ได้อีกต่อไป เพราะกลิ่นไม่เหมือนเนื้อแลปที่เคยชิน และประชาชนจะ “ทำอาหารเองในบ้าน” ไม่ได้อีกต่อไป เพราะระบบเสพติดรสเนื้อเทียมจะทำให้คนเบือนหน้าจากอาหารจริง
ในขณะที่ Impossible Foods โฆษณาว่า “เราแค่อยากช่วยโลก” แต่เทคโนโลยีนี้อาจเปลี่ยน “อาหาร” ให้กลายเป็น “สิทธิบัตร” ที่ประชาชนเช่ากินจากบริษัท และเปลี่ยน “สิทธิในการเข้าถึงอาหาร” ให้กลายเป็น “อภิมหาอำนาจควบคุมโลก” โดยไม่ต้องยิงแม้แต่นัดเดียว หรือเปล่า???
เพราะเมื่อคุณควบคุมอาหารได้… คุณไม่ต้องควบคุมประชาชนอีกเลย
เฮียไม่ได้ต่อต้านเทคโนโลยี แต่เฮียอยากให้เราหยุดคิดนิดนึง แล้วตั้งคำถามในขณะที่เรายังเฝ้ามองว่า ถ้าของกินที่ดูน่าเชื่อถือ กินแล้วเหมือนเนื้อแท้ ๆ มันต้องมาจากกระบวนการที่ซับซ้อน แพง และถูกควบคุมโดยบริษัทที่มีสิทธิบัตรล้อมรอบ แล้ววันหนึ่ง ถ้าบริษัทนั้นล่มล่ะ? ถ้าถูกซื้อโดยบริษัทยักษ์ใหญ่? หรือถ้าพวกเขาขึ้นราคาจนยังไงเราก็ต้องทำงานหาเงินมาซื้อมันเพื่อกินประทังชีวิต?
อาหารจะยังเป็นของเราหรือเปล่า?
เราจะยัง “กินเพื่ออยู่” หรือแค่ “อยู่เพื่อจ่ายค่าเช่าระบบกิน”?
เราคงไม่ผิดที่จะตั้งคำถามใช่ไหม เพราะถ้ามันมีทางออก มันคงไม่น่ากลัว
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 91add87d:3245770f
2025-05-29 23:41:38
@ 91add87d:3245770f
2025-05-29 23:41:38Do you guys actually identify with you online username or do you identify with government name? No this isn't some woke left ideal about pronouns. I do not use my real name for any of my handles, X and Nostr and email are all fake. Meaningful and something i picked specifically. My government name is something that was forced on me and yes I know I can it but the persona I have created online feels authentic and what I see myself as. It's what I'll be using to create my small businesses. My LLC is going to a copy of what I have created.
-
 @ c1e9ab3a:9cb56b43
2025-05-27 13:19:53
@ c1e9ab3a:9cb56b43
2025-05-27 13:19:53I. Introduction: Money as a Function of Efficiency and Preference
Money is not defined by law, but by power over productivity. In any open economy, the most economically efficient actors—those who control the most valuable goods, services, and knowledge—ultimately dictate the medium of exchange. Their preferences signal to the broader market what form of money is required to access the highest-value goods, from durable commodities to intangibles like intellectual property and skilled labor.
Whatever money these actors prefer becomes the de facto unit of account and store of value, regardless of its legal status. This emergent behavior is natural and reflects a hierarchy of monetary utility.
II. Classical Gresham’s Law: A Product of Market Distortion
Gresham’s Law, famously stated as:
"Bad money drives out good"
is only valid under coercive monetary conditions, specifically: - Legal tender laws that force the acceptance of inferior money at par with superior money. - Fixed exchange rates imposed by decree, not market valuation. - Governments or central banks backing elastic fiduciary media with promises of redemption. - Institutional structures that mandate debt and tax payments in the favored currency.
Under these conditions, superior money (hard money) is hoarded, while inferior money (soft, elastic, inflationary) circulates. This is not an expression of free market behavior—it is the result of suppressed price discovery and legal coercion.
Gresham’s Law, therefore, is not a natural law of money, but a law of distortion under forced parity and artificial elasticity.
III. The Collapse of Coercion: Inversion of Gresham’s Law
When coercive structures weaken or are bypassed—through technological exit, jurisdictional arbitrage, monetary breakdown, or political disintegration—Gresham’s Law inverts:
Good money drives out bad.
This occurs because: - Market actors regain the freedom to select money based on utility, scarcity, and credibility. - Legal parity collapses, exposing the true economic hierarchy of monetary forms. - Trustless systems (e.g., Bitcoin) or superior digital instruments (e.g., stablecoins) offer better settlement, security, and durability. - Elastic fiduciary media become undesirable as counterparty risk and inflation rise.
The inversion marks a return to monetary natural selection—not a breakdown of Gresham’s Law, but the collapse of its preconditions.
IV. Elasticity and Control
Elastic fiduciary media (like fiat currency) are not intrinsically evil. They are tools of state finance and debt management, enabling rapid expansion of credit and liquidity. However, when their issuance is unconstrained, and legal tender laws force their use, they become weapons of economic coercion.
Banks issue credit unconstrained by real savings, and governments enforce the use of inflated media through taxation and courts. This distorts capital allocation, devalues productive labor, and ultimately hollows out monetary confidence.
V. Monetary Reversion: The Return of Hard Money
When the coercion ends—whether gradually or suddenly—the monetary system reverts. The preferences of the productive and wealthy reassert themselves:
- Superior money is not just saved—it begins to circulate.
- Weaker currencies are rejected not just for savings, but for daily exchange.
- The hoarded form becomes the traded form, and Gresham’s Law inverts completely.
Bitcoin, gold, and even highly credible stable instruments begin to function as true money, not just stores of value. The natural monetary order returns, and the State becomes a late participant, not the originator of monetary reality.
VI. Conclusion
Gresham’s Law operates only under distortion. Its inversion is not an anomaly—it is a signal of the collapse of coercion. The monetary system then reorganizes around productive preference, technological efficiency, and economic sovereignty.
The most efficient market will always dictate the form of hard money. The State can delay this reckoning through legal force, but it cannot prevent it indefinitely. Once free choice returns, bad money dies, and good money lives again.
-
 @ a296b972:e5a7a2e8
2025-05-29 21:11:46
@ a296b972:e5a7a2e8
2025-05-29 21:11:46Inzwischen Jahr 6 im Dauer-Ausnahmezustand. Angriff auf den Verstand. Großoffensive. Es wird mit allem geschossen, aus dem Wahnsinn herauskommen kann. Jeder klare Gedanke ist unschädlich zu machen. Großkotziges, staatsmännisches Geschwafel, dass sich einem die Nackenhaare aufstellen. Für wie doof haltet ihr uns eigentlich? Endlos Bürsten gegen den Strich. Angewidertes inneres Schütteln. Dringende Empfehlung einer Spülung der Gehirnwindungen. Idioten in Verantwortung wechseln auf andere Posten in Verantwortung und bleiben Idioten. Idioten gehen verantwortungslos mit unserer wertvollen Lebenszeit um. Ach, dafür ist man selbst verantwortlich? Wo ist der, der so ein dickes Fell hat, dass ihm dieser Irrsinn nicht nahegeht. Wo steht das Fass mit Teflon-Lack, in das man eintauchen kann, damit die Absurditäten an einem abperlen?
Eine zu tiefst verunsicherte und gespaltene Gesellschaft. Halt im Glauben in der Kirche? Von wegen: Sehr geehrte Jesusse und Jesusinnen. Ens ist gekreuzigt worden. Ja, in der Freiluft-Irrenanstalt. Auf einem Hügel von Denk-Dreck. Gott ist queer! Du tickst ja nicht mehr ganz sauber. Tanzende Brathähnchen vor dem Altar. Warum kommt keine Sintflut, wenn man sie mal braucht? Man muss gar nicht religiös sein, um zu sehen, dass das Gaga ist. Eine Produktion der Sodom & Gomorrha Anstalt GmbH & Co. KG.
Kein Vertrauen mehr, außer in sich selbst, meistens jedenfalls. Ja, man will uns vor allem Angst machen, teils unbegründet, so manches aber gibt es dann doch tatsächlich, was einem schwer zu denken gibt.
Vielen geht dieser Psychokrieg inzwischen an die Substanz, der ständig herabprasselnde Dauerwahnsinn erinnert an Water-Boarding.
Gut gemeinte Ratschläge, geht hinaus in die Natur, beackert euren Garten, wenn ihr einen habt, erdet euch, macht Entspannungsübungen, Zeit des Aufwachens, wir treten in ein neues Zeitalter ein, alles fein. Abschalten gelingt, aber der Aufprall in der Realität ist dann umso schlimmer, weil man sich daran erinnert hat, wie sorgenfrei und unbeschwert das Leben sein könnte, und wenn man es mit den derzeitigen Lebensumständen abgleicht, dann ist die schlechte Laune sofort wieder da. Im Verdrängens-Test mit Pauken und Trompeten durchgefallen.
Dann vielleicht doch lieber im Dauer-Modus des Irrsinns bleiben, sich mit den schrägen Zuständen arrangieren, nicht daran gewöhnen, nur lernen, damit bestmöglich umzugehen, und das Beste draus zu machen, irgendwie.
Man will dem Rat folgen, mal eine Nachrichten-freie Woche einzulegen, nimmt sich das ganz fest vor, und dann wird aber wieder doch nichts draus. Nicht, weil man sensationsgeil oder masochistisch veranlagt wäre, nein, der Antrieb, oder vielleicht sogar schon die Sucht, ist ganz woanders zu suchen: Man hat Sehnsucht nach der Vernunft und dem gesunden Hausverstand. Man hofft, ihn irgendwo zu finden. Nur einen Funken Hoffnung, an den man sich klammern kann, dass der Tiefpunkt durchschritten ist und es jetzt wieder aufwärts geht. Lichtblicke, der Wind dreht sich, Anzeichen für eine Wiederkehr des Verstandes, irgendetwas, das man als einen Weg hin zur Normalität deuten könnte. Aber, Fehlanzeige.
Stattdessen: Geschichtsvergessenheit, pathologischer Größenwahn, Großmannstum, fortgeschrittener Wahnsinn, Provokation, Kriegslüsternheit, Lügen, Intrigen, Interessen, Korruption, Geldverschwendung, Ideologie, Dummheit, Wirtschaftsvernichtung, Friedensverhinderung, Diplomatie-Allergie, Überheblichkeit, Abgehobenheit, Schadensmaximierung, Vernichtung, Feindschaft, Unmenschlichkeit, Tote, Gesetzesbruch, Mafia-Strukturen, sich selbst schützende Systeme, Cliquenbildung, Feigheit, Einschüchterung, Freiheitsbeschränkungen, Meinungs-Maulkörbe, Abschaffung der demokratischen Freiheit, Abschaffung der persönlichen Freiheit, Kontrolle, Überwachung, begleitetes Denken, Fühlen, Wollen, Verwirrung, Dreistigkeit, Frechheit, Missachtung des Volkes, Denunziantentum, Abwanderung, und und und.
Ein richtiges Schlachtfest der Kultur. Perversion des Menschseins. Das neue Normal ist irre.
Bislang ist keine der zahlreichen Baustellen beendet. Eine Wende steht unmittelbar bevor. Und sie steht und steht und steht bevor. Kein Gefühl von „Erledigt“, nächstes Problem angehen und auflösen. Weiter. Noch meilenweit von dem Gefühl entfernt, der Wahnsinn wird weniger, langsam, aber er wird weniger.
Fluchtgedanken. Aber wohin? In Europa bleiben, vielleicht besser nicht? Weiter weg, aber wohin da? Nicht vergessen, die Nachrichten erreichen einen überall. Und man bleibt mit seiner Heimat innerlich verbunden, egal wo man ist.
Es bleibt ein Entlanghangeln von einer vernünftigen Stimme zur anderen, die einem bestätigt, dass man selbst noch nicht den Verstand verloren hat. Die gibt es ja gottseidank noch. Innehalten, durchhalten, tief durchatmen, aufstehen, weitermachen. So lange, bis die Bekloppten ihrer Macht über uns entledigt wurden. Wie am besten? Und jetzt soll keiner mit nächsten Wahlen kommen.
Wer war schon einmal inmitten eines Psycho-Krieges gegen die eigene Bevölkerung? Wie geht man damit um, wie geht man dagegen an? Wie kann man das Ruder herumreißen? Was ist ein wirksames Mittel gegen die Ohnmacht? Wie kriegt man die Bequemlichkeit aus den Menschen heraus? Wie kann man die Menschen für die herrschenden Zustände sensibilisieren? Wie können wir noch mehr werden?
Wenn möglich, sollte zum Ende doch noch etwas Positives kommen. Ok. Es wird voraussichtlich demnächst möglicherweise bald besser. Eine zu geringe Zahl von Menschen ist schon aufgewacht. Die politischen Entscheidungsträger haben Angst, können die aber noch sehr gut verbergen. Das kann nicht ewig so weiter gehen und 10 Jahre sind keine Ewigkeit. Die Rufe nach mehr Bürgerbeteiligung werden immer lauter, aber nicht gehört, warum auch? Wir setzen den Artikel 146 des Grundgesetzes um, aber wie? Hätte, könnte, würde, wir sollten, es müsste. Ja und, wie weiter? Mehr geht nicht.
Doch vielleicht eins: Sand ins Getriebe streuen und zivilen Ungehorsam leisten, wo immer es geht. Das schafft immer noch eine gewisse Befriedigung und das Gefühl, dass man nicht vollkommen handlungsunfähig ist. Außerdem regt das die Phantasie und die Kreativität an und bietet eine Chance seinen Geist für etwas sehr Nützliches zu gebrauchen. Man fühlt, dass man noch ein Mensch ist.
“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
* *
(Bild von pixabay)
-
 @ 06639a38:655f8f71
2025-05-26 12:58:38
@ 06639a38:655f8f71
2025-05-26 12:58:38Nostr-PHP
Djuri submitted quite some pull requests in the last couple of week while he was implementing a Nostr connect / login on https://satsback.com. The backend of that platform is written in PHP so the Nostr-PHP library is used for several purposes while Djuri also developed quite some new features utilizing the following NIPs:
- NIP-04
- NIP-05
- NIP-17
- NIP-44
Thank you very much Djuri for these contributions. We now can do the basic private stuff with the library.
PR for NIP-04 and NIP-44: https://github.com/nostrver-se/nostr-php/pull/84 and https://github.com/nostrver-se/nostr-php/pull/88
Examples:- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip04-encrypted-messages.php
- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip44-gift-wrapping.php
PR for NIP-05: https://github.com/nostrver-se/nostr-php/pull/89
Example: https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip05-lookup.phpPR for NIP-17: https://github.com/nostrver-se/nostr-php/pull/90
Example: https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip17-private-direct-messages.phpPR for adding more metadata profile fields: https://github.com/nostrver-se/nostr-php/pull/94
Example: https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/fetch-profile-metadata.phpFetch
10050event (dm relay list) of an given pubkey
Example: https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/fetch-dm-relayslist.phpThe CLI tool is removed from the library, see PR https://github.com/nostrver-se/nostr-php/pull/93
Nostr-PHP documentation
While new NIPs are implemented in the Nostr-PHP library, I'm trying to keep up with the documentation at https://nostr-php.dev. For now, things are still much work in progress and I've added the AI agent Goose using the Claude LLM to bootstrap new documentation pages. Currently I'm working on documentation for
- How to direct messages with NIP-04 and NIP-17
- Encrypted payloads for event content NIP-44
- Fetch profiledata of a given pubkey
- Lookup NIP-05 data of given pubkey
- Using the NIP-19 helper class
CCNS.news
I've moved CCNS to a new domain https://ccns.news and have partly implemented the new NIP-B0 for web bookmarks. When you post a bookmark there, a kind
39701event is transmitted to some Nostr relays (take a look at this event for example). Optionally you can also publish this content as a note to the network.As you can see at https://ccns.news/l/censorship-resistant-publishing-and-archiving, I've listed some todo's. All this stuff is done with Javascript using the NDK Typescript library (so I'm not using any PHP stuff for this with Nostr-PHP).
Also new: https://ccns.news/global now has a global feed which fetches all the web bookmark events with kind
39701from several public Nostr relays. I had a rough idea to compare feeds generated with NDK and Nostr-PHP (for both using the same set of relays).
Building a njump clone for this Drupal website
You can now use this URL pattern to fetch Nostr events:
https://nostrver.se/e/{event_id|nevent1|note1|addr1}where you can provide a plain Nostr event ID or NIP-19 encoded identifier.An example, this URL [nostr:nevent1qvzqqqqqqypzqmjxss3dld622uu8q25gywum9qtg4w4cv4064jmg20xsac2aam5nqqsqm2lz4ru6wlydzpulgs8m60ylp4vufwsg55whlqgua6a93vp2y4g3uu9lr) fetches the data from one or more relays. This data is then being saved as a (Drupal) node entity (in a database on the server where this website is hosted, which is located in my office fyi). With this saved node, this data is now also available at https://nostrver.se/e/0dabe2a8f9a77c8d1079f440fbd3c9f0d59c4ba08a51d7f811ceeba58b02a255/1 where the (cached) data is server from the database instead. It's just raw data for now, nothing special about it. One of my next steps is to style this in a more prettier interface and I will need to switch the theme of this website to a custom theme. A custom theme where I will be using TailwindCSS v4 and DaisyUI v5.
The module which is providing these Nostr features is FOSS and uses the Nostr-PHP library for doing the following:
- Request the event from one or more relays
- Decode the provided NIP-19 identifier
For now this module is way for me to utilize the Nostr-PHP library with Drupal for fetching events. This can be automated so in theory I could index all the Nostr events. But this is not my ambition as it would require quite some hardware resources to accomplish this.
I hope I can find the time to build up a new theme first for this website, so I can start styling the data for the fetched events. On this website, there is also a small piece (powered by another module) you can find at https://nostrver.se/nostrides doing things with this NIP-113 around activity events (in my case that's cycling what interests me).What's next
I'm already working on the following stuff:
- Implement a class to setup a persistent connection to a relay for requesting events continuously
- Extend the documentation with the recent added features
Other todo stuff:
- Review NIP-13 proof-of-work PR from Djuri
- Implement a NIP-65 lookup for fetching read and write relays for a given npub issue #91
- Build a proof-of-concept with revolt/event-loop to request events asynchronous with persistent relay connections
- Add comments to https://ccns.news
-
 @ 3eba5ef4:751f23ae
2025-05-30 01:45:18
@ 3eba5ef4:751f23ae
2025-05-30 01:45:18加密洞见
无需盲信系统:手动创建助记词的新提案
开发者 Eric Kvam 提出了一种改进助记词生成和恢复流程的方法,目的是让用户能够手动、安全地生成种子短语助记词,从不必信任「黑盒」,并在助记词中编码派生路径以简化恢复过程。
应对垃圾信息,P2P 网络存在固有劣势?
作者认为,比特币和 Nostr 等类似 P2P 无许可网络在应对垃圾信息问题上存在固有劣势。由于广播式网络的特性,垃圾信息发送者在动机上远强于正常点对点价值传递的用户,仅通过提高每笔操作的成本难以有效遏制垃圾信息,因为垃圾发送者从中获得的价值远高于普通用户。相比之下,互联网主流是通过识别用户身份、并对不良行为实施惩罚的方式来治理垃圾信息,但这种方式违背了比特币的去中心化和隐私保护原则,并导致了严重的隐私侵犯。作者担心,如果不能有效解决垃圾信息问题,比特币等网络的正常用户可能会被迫离开,而垃圾发送者仍会留下。
Bitcointap:利用比特币核心跟踪点,实时提取数据
开发者 jb55 推出 bitcointap——一个 Rust 库和 CLI 工具。它利用 Bitcoin-Core 的 EBPF-USDT 跟踪点,实现数据的实时提取。Bitcointap 的开发受到 @0xB10C 的 peer_observer 项目的启发。
- Bitcointap 的 GitHub Repo,以及 Demo Video
闪电网络中性能和隐私间的权衡
闪电网络开发者社区最近讨论到 Pivacy impact of surfacing granular HTLC hold times via attributable failures 这一问题。Carla 对此进行了后续思考,进一步研究了转发延迟(forwarding delays)机制对付款隐私的影响。她也指出,现在的闪电网络中并没有部署任何转发延迟的隐私保护。
面向草根挖矿的新开源矿池 Parasite Pool
Ordinal Maxi Biz 创始人 ZK Shark 推出开源比特币矿池 Parasite Pool,专为希望为比特币去中心化做出贡献的家庭矿工而建。支持闪电网络支付,门槛低至 10 聪,允许个人直接即时赚钱。它有一个「平民先吃」(Plebs Eat First)的奖励结构,将 1 BTC 奖励给找到区块的人,并将剩余的 2.125 BTC 加上手续费通过闪电支付分配给其余非获胜参与者。小规模矿工由此可以获得相对于其哈希算力的巨额奖励,这让 Parasite Pool 对他们而言特别具有吸引力。目前 Parasite Pool 指向矿池的哈希率只有 5 PH/s,只占整个比特币网络的 0.000006%,预计可能需要 3 年多才能到达一个区块。
BitVMX 公布 2025 路线图
BitVMX 公布了 2025 年路线图,呈现了在研究、实施、安全、平台集成以及教育和对外扩展五条核心轨道上的计划:
精彩无限,不止于链
AI 代理时代的大教堂与集市,加密技术在低信任场景中的未来
作者借用经典的「大教堂与集市」比喻,认为 AI 代理时代的网络形态是一个 Linux 式的开放集市——这里会有大量具有独立开发能力的自动代理人,通过相互调用,为彼此提供服务,由此形成松散的协作网络。这样一个低信任的场景,正是加密技术最擅长的环境———在无需信任的环境中交换价值,因此加密货币将成为 AI 代理人集市中不可或缺的基础要素。
回顾 2015 比特币垃圾邮件攻击:共识变革与当今 OP_Return 辩论的呼应
BitMex 的这篇文章介绍了 2015 年夏天针对比特币的四轮垃圾邮件攻击。这些攻击由一家名为 CoinWallet.EU 的伦敦公司发起。垃圾邮件对当时进行比特币支付的人的用户体验产生了重大的不利影响,尤其是在 2015 年 7 月 7 日至 2015 年 7 月 11 日的第三轮攻击中。这次攻击引发了关于矿工过滤垃圾邮件交易和区块大小限制的辩论。在 BitMex 看来,这次攻击在形成许多人关于如何处理垃圾邮件的观点方面发挥了关键作用,并且与今天关于 OP_Return 中继限制的辩论有有趣的相似之处。
个人数据泄露后的 5 步生存手册
a16z 的这篇指南梳理了在个人数据泄露后,如何立即应对与长期防护,重点包括:
1. 立即采取行动
-
冻结信用:防止身份被盗用开设新账户。
-
加强多因素认证(MFA):在所有金融与社交账户启用 MFA,优先使用 App 或硬件密钥而非短信认证,并向电信商申请 SIM 卡保护。
-
更换身份证件:联系相关部门申请补发。
2. 强化线上账户安全
-
Apple 和 Google账户,启用高级保护措施(如 Google Advanced Protection、Passkeys、YubiKey 等)。
-
使用密码管理器,推荐离线工具 KeePass,或 Bitwarden、1Password 等第三方服务
3. 锁定手机安全
-
iPhone 用户:设置自定义字母数字密码、启用Find My iPhone、开启 Stolen Device Protection,敏感应用要求Face ID。
-
Android用户:设置强密码或生物识别、启用Find My Device、开启盗窃检测锁和身份检查。
4. 防范社交工程攻击
- 警惕钓鱼诈骗、可疑登录通知、冒充金融机构的短信或电话。
5. 监控社交媒体账户
- 定期确认账户存取权,若被锁定立即联系客户服务。
-
 @ 9cb3545c:2ff47bca
2025-05-27 12:58:56
@ 9cb3545c:2ff47bca
2025-05-27 12:58:56Introduction
Public companies that hold Bitcoin on behalf of investors (often issuing securities backed by those Bitcoin holdings) have faced growing pressure to demonstrate proof of reserves – evidence that they genuinely hold the cryptocurrency they claim. One approach is to publish the company’s Bitcoin wallet addresses so that anyone can verify the balances on the blockchain. This practice gained momentum after high-profile crypto collapses (e.g. FTX in 2022) eroded trust, leading major exchanges and fund issuers like Binance, Kraken, OKX, and Bitwise to publicize wallet addresses as proof of assets . The goal is transparency and reassurance for investors. However, making wallet addresses public comes with significant security and privacy risks. This report examines those risks – from cybersecurity threats and blockchain tracing to regulatory and reputational implications – and weighs them against the transparency benefits of on-chain proof of reserves.
Proof of Reserves via Public Wallet Addresses
In the cryptocurrency ethos of “don’t trust – verify,” on-chain proof of reserves is seen as a powerful tool. By disclosing wallet addresses (or cryptographic attestations of balances), a company lets investors and analysts independently verify that the Bitcoin reserves exist on-chain. For example, some firms have dashboards showing their addresses and balances in real time . In theory, this transparency builds trust by proving assets are not being misreported or misused. Shareholders gain confidence that the company’s Bitcoin holdings are intact, potentially preventing fraud or mismanagement.
Yet this approach essentially sacrifices the pseudonymity of blockchain transactions. Publishing a wallet address ties a large, known institution to specific on-chain funds. While Bitcoin addresses are public by design, most companies treat their specific addresses as sensitive information. Public proof-of-reserve disclosures break that anonymity, raising several concerns as detailed below.
Cybersecurity Threats from Visible Wallet Balances
Revealing a wallet address with a large balance can make a company a prime target for hackers and cybercriminals. Knowing exactly where significant reserves are held gives attackers a clear blueprint. As Bitcoin advocate (and MicroStrategy Executive Chairman) Michael Saylor warned in 2025, “publicly known wallet addresses become prime targets for malicious actors. Knowing where significant reserves are held provides hackers with a clear target, potentially increasing the risk of sophisticated attacks” . In other words, publishing the address increases the attack surface – attackers might intensify phishing campaigns, malware deployment, or insider bribery aimed at obtaining the keys or access to those wallets.
Even if the wallets are secured in cold storage, a public address advertisement may encourage attempts to penetrate the organization’s security. Custodians and partners could also be targeted. Saylor noted that this exposure isn’t just risky for the company holding the Bitcoin; it can indirectly put their custodial providers and related exchanges at risk as well . For instance, if a third-party custodian manages the wallets, hackers might attempt to breach that custodian knowing the reward (the company’s Bitcoin) is great.
Companies themselves have acknowledged these dangers. Grayscale Investments, which runs the large Grayscale Bitcoin Trust (GBTC), pointedly refused to publish its wallet addresses in late 2022, citing “security concerns” and complex custody arrangements that have “kept our investors’ assets safe for years” . Grayscale implied that revealing on-chain addresses could undermine those security measures, and it chose not to “circumvent complex security arrangements” just to appease public demand . This highlights a key point: corporate treasury security protocols often assume wallet details remain confidential. Publicizing them could invalidate certain assumptions (for example, if an address was meant to be operationally secret, it can no longer serve that role once exposed).
Additionally, a publicly known trove of cryptocurrency might invite physical security threats. While not a purely “cyber” issue, if criminals know a particular company or facility controls a wallet with, say, thousands of Bitcoin, it could lead to threats against personnel (extortion or coercion to obtain keys). This is a less common scenario for large institutions (which typically have robust physical security), but smaller companies or key individuals could face elevated personal risk by being associated with huge visible crypto reserves.
In summary, cybersecurity experts consider public proof-of-reserve addresses a double-edged sword: transparency comes at the cost of advertising exactly where a fortune is held. As Saylor bluntly put it, “the conventional way of issuing proof of reserves today is actually insecure… This method undermines the security of the issuer, the custodian, the exchanges and the investors. This is not a good idea”  . From a pure security standpoint, broadcasting your wallets is akin to drawing a bullseye on them.
Privacy Risks: Address Clustering and Blockchain Tracing
Blockchain data is public, so publishing addresses opens the door to unwanted analytics and loss of privacy for the business. Even without knowing the private keys, analysts can scrutinize every transaction in and out of those addresses. This enables address clustering – linking together addresses that interact – and other forms of blockchain forensics that can reveal sensitive information about the company’s activities.
One immediate risk is that observers can track the company’s transaction patterns. For example, if the company moves Bitcoin from its reserve address to an exchange or to another address, that move is visible in real time. Competitors, investors, or even attackers could deduce strategic information: perhaps the company is planning to sell (if coins go to an exchange wallet) or is reallocating funds. A known institution’s on-chain movements can thus “reveal strategic movements or holdings”, eroding the company’s operational privacy . In a volatile market, advance knowledge of a large buy or sell by a major player could even be exploited by others (front-running the market, etc.).
Publishing one or a few static addresses also violates a basic privacy principle of Bitcoin: address reuse. Best practice in Bitcoin is to use a fresh address for each transaction to avoid linking them  . If a company continuously uses the same “proof of reserve” address, all counterparties sending funds to or receiving funds from that address become visible. Observers could map out the company’s business relationships or vendors by analyzing counterparties. A Reddit user commenting on an ETF that published a single address noted that “reusing a single address for this makes me question their risk management… There are much better and more privacy-preserving ways to prove reserves… without throwing everything in a single public address” . In other words, a naive implementation of proof-of-reserve (one big address) maximizes privacy leakage.
Even if multiple addresses are used, if they are all disclosed, one can perform clustering analysis to find connections. This happened in the Grayscale case: although Grayscale would not confirm any addresses, community analysts traced and identified 432 addresses likely belonging to GBTC’s custodial holdings by following on-chain traces from known intermediary accounts . They managed to attribute roughly 317,705 BTC (about half of GBTC’s holdings) to those addresses . This demonstrates that even partial information can enable clustering – and if the company directly published addresses, the task becomes even easier to map the entirety of its on-chain asset base.
Another threat vector is “dusting” attacks, which become more feasible when an address is publicly known. In a dusting attack, an adversary sends a tiny amount of cryptocurrency (dust) to a target address. The dust itself is harmless, but if the target address ever spends that dust together with other funds, it can cryptographically link the target address to other addresses in the same wallet. Blockchain security researchers note that “with UTXO-based assets, an attacker could distribute dust to an address to reveal the owner’s other addresses by tracking the dust’s movement… If the owner unknowingly combines this dust with their funds in a transaction, the attacker can… link multiple addresses to a single owner”, compromising privacy . A company that publishes a list of reserve addresses could be systematically dusted by malicious actors attempting to map out all addresses under the company’s control. This could unmask cold wallet addresses that the company never intended to publicize, further eroding its privacy and security.
Investor confidentiality is another subtle concern. If the business model involves individual investor accounts or contributions (for instance, a trust where investors can deposit or withdraw Bitcoin), public addresses might expose those movements. An outside observer might not know which investor corresponds to a transaction, but unusual inflows/outflows could signal actions by big clients. In extreme cases, if an investor’s own wallet is known (say a large investor announces their involvement), one might link that to transactions in the company’s reserve addresses. This could inadvertently reveal an investor’s activities or holdings, breaching expectations of confidentiality. Even absent direct identification, some investors might simply be uncomfortable with their transactions being part of a publicly traceable ledger tied to the company.
In summary, publishing reserve addresses facilitates blockchain tracing that can pierce the veil of business privacy. It hands analysts the keys to observe how funds move, potentially exposing operational strategies, counterparties, and internal processes. As one industry publication noted, linking a large known institution to specific addresses can compromise privacy and reveal more than intended . Companies must consider whether they are ready for that level of transparency into their every on-chain move.
Regulatory and Compliance Implications
From a regulatory perspective, wallet address disclosure lies in uncharted territory, but it raises several flags. First and foremost is the issue of incomplete information: A wallet address only shows assets, not the company’s liabilities or other obligations. Regulators worry that touting on-chain holdings could give a false sense of security. The U.S. Securities and Exchange Commission (SEC) has cautioned investors to “not place too much confidence in the mere fact a company says it’s got a proof-of-reserves”, noting that such reports “lack sufficient information” for stakeholders to ascertain if liabilities can be met . In other words, a public company might show a big Bitcoin address balance, but if it has debts or customer liabilities of equal or greater value, the proof-of-reserve alone is “not necessarily an indicator that the company is in a good financial position” .
This regulatory stance implies that address disclosure, if done, must be paired with proper context. A public company would likely need to clarify in its financial statements or investor communications that on-chain reserves are unencumbered (not pledged as loan collateral, not already sold forward, etc.) and that total liabilities are accounted for. Otherwise, there’s a risk of misleading investors, which could have legal consequences. For example, if investors interpret the on-chain balance as proof of solvency but the company actually had leveraged those bitcoins for loans, lawsuits or regulatory enforcement could follow for misrepresentation.
There’s also a compliance burden associated with revealing addresses. Once an address is known to be the company’s, that company effectively must monitor all transactions related to it. If someone sends funds to that address (even without permission), the company might receive tainted coins (from hacked sources or sanctioned entities). This could trigger anti-money laundering (AML) red flags. Normally, compliance teams can ignore random deposits to unknown wallets, but they cannot ignore something sent into their publicly identified corporate wallet. Even a tiny dust amount sent from a blacklisted address could complicate compliance – for instance, the company would need to prove it has no relation to the sender and perhaps even avoid moving those tainted outputs. Being in the open increases such exposure. Threat actors might even exploit this by “poisoning” a company’s address with unwanted transactions, just to create regulatory headaches or reputational smears.
Another consideration is that custodial agreements and internal risk controls might forbid public disclosure of addresses. Many public companies use third-party custodians for their Bitcoin (for example, Coinbase Custody, BitGo, etc.). These custodians often treat wallet details as confidential for security. Grayscale noted that its Bitcoin are custodied on Coinbase and implied that revealing on-chain info would interfere with security arrangements  . It’s possible that some custodians would object to their clients broadcasting addresses, or might require additional assurances. A company going against such advice might be seen as negligent if something went wrong.
Regulators have so far not mandated on-chain proofs for public companies – in fact, recent laws have exempted public companies from proof-of-reserve mandates on the assumption they are already subject to rigorous SEC reporting. For example, a Texas bill in 2023 required crypto exchanges and custodians to provide quarterly proof-of-reserves to the state, but it “specifically carved out public reporting companies” since they already file audited financials with the SEC . The rationale was that between SEC filings and audits, public companies have oversight that private crypto firms lack . However, this also highlights a gap: even audited financials might not verify 100% of crypto assets (auditors often sample balances). Some observers noted that standard audits “may not ever include the 100% custodial asset testing contemplated by proof of reserves”, especially since quarterly SEC filings (10-Q) are often not audited . This puts public companies in a nuanced position – they are trusted to use traditional audits and internal controls, but the onus is on them if they choose to add extra transparency like on-chain proofs.
Finally, securities regulators focus on fair disclosure and accuracy. If a company publicly posts addresses, those essentially become investor disclosures subject to anti-fraud rules. The firm must keep them up to date and accurate. Any mistake (such as publishing a wrong address or failing to mention that some coins are locked up or lent out) could attract regulatory scrutiny for being misleading. In contrast, a formal audit or certification from a third-party comes with standards and disclaimers that are better understood by regulators. A self-published wallet list is an unprecedented form of disclosure that regulators haven’t fully vetted – meaning the company bears the risk if something is misinterpreted.
In summary, wallet address disclosure as proof-of-reserve must be handled very carefully to avoid regulatory pitfalls. The SEC and others have warned that on-chain assets alone don’t tell the whole story . Public companies would need to integrate such proofs with their official reporting in a responsible way – otherwise they risk confusion or even regulatory backlash for giving a false sense of security.
Reputational and Operational Risks
While transparency is meant to enhance reputation, in practice public wallet disclosures can create new reputational vulnerabilities. Once an address is public, a company’s every on-chain action is under the microscope of the crypto community and media. Any anomaly or perceived misstep can snowball into public relations problems.
One vivid example occurred with Crypto.com in late 2022. After the exchange published its cold wallet addresses to prove reserves (a move prompted by the FTX collapse), on-chain analysts quickly noticed a “suspicious transfer of 320,000 ETH” – about 82% of Crypto.com’s Ether reserves – moving from their cold wallet to another exchange (Gate.io)  . This large, unexpected transfer sparked immediate panic and FUD (fear, uncertainty, and doubt) on social media. Observers speculated that Crypto.com might be insolvent or was manipulating snapshots of reserves by borrowing funds. The CEO had to publicly respond, admitting it was an operational error – the ETH was supposed to go to a new cold storage address but ended up at a whitelisted external address by mistake . The funds were eventually returned, but not before reputational damage was done: the incident made headlines about mishandled funds and rattled user confidence  . This case illustrates how full public visibility can turn an internal slip-up into a highly public crisis. If the addresses had not been public, the mistake might have been quietly corrected; with on-chain transparency, there was nowhere to hide and no way to control the narrative before the public drew worst-case conclusions.
Even routine operations can be misinterpreted. Blockchain data lacks context – analysts may jump to conclusions that hurt a company’s reputation even if nothing is actually wrong. For instance, Binance (the world’s largest crypto exchange) encountered scrutiny when on-chain observers noted that one of its reserve wallets (labeled “Binance 8”) contained far more assets than it should have. This wallet was meant to hold collateral for Binance’s issued tokens, but held an excess balance, suggesting possible commingling of customer funds with collateral  . Bloomberg and others reported a ~$12.7 billion discrepancy visible on-chain . Binance had to acknowledge the issue as a “clerical error” and quickly separate the funds, all under the glare of public attention  . While Binance maintained that user assets were fully backed and the mistake was purely operational, the episode raised public concern over Binance’s practices, feeding a narrative that even the largest exchange had internal control lapses. The key point is that public proof-of-reserves made the lapse obvious to everyone, forcing a reactive explanation. The reputational hit (even if temporary) was an operational risk of being so transparent.
Additionally, strategic confidentiality is lost. If a company holding Bitcoin as a reserve asset decides to make a major move (say, reallocating to a different wallet, or using some Bitcoin for a strategic investment or loan), doing so with known addresses broadcasts that strategy. Competitors or market analysts can infer things like “Company X is moving 10% of its BTC — why? Are they selling? Hedging? Using it as collateral?” This can erode any competitive advantage of keeping financial strategies discreet. It might even affect the company’s stock price if investors interpret moves negatively. For example, if a blockchain analysis shows the company’s reserves dropping, shareholders might fear the company sold Bitcoin (perhaps due to financial distress), even if the reality is benign (like moving funds to a new custodian). The company would be forced into continuous public explanation of on-chain actions to prevent misunderstanding.
There’s also a risk of exposing business partnerships. Suppose the company uses certain exchanges or OTC desks to rebalance its holdings – transactions with those service providers will be visible and could link the company to them. If one of those partners has issues (say a hacked exchange or a sanctioned entity inadvertently), the company could be reputationally contaminated by association through the blockchain trail.
Finally, not all publicity is good publicity in the crypto world. A public proof-of-reserve might invite armchair auditors to scrutinize and criticize every aspect of the company’s crypto management. Minor issues could be blown out of proportion. On the flip side, if a company chooses not to publish addresses, it could face reputational risk from a different angle: skeptics might question why it isn’t being transparent. (Indeed, Grayscale’s refusal to disclose wallet addresses led to social media chatter about whether they truly held all the Bitcoin they claimed, contributing to investor nervousness and a steep discount on GBTC shares .) Thus, companies are in a delicate spot: share too much and every move invites scrutiny; share too little and you breed distrust.
Balancing Transparency Benefits vs. Risks
The central question is whether the benefit of proving reserve holdings to investors outweighs these security and privacy risks. It’s a classic risk-reward calculation, and opinions in the industry are divided.
On the side of transparency, many argue that the credibility and trust gained by proof-of-reserves is invaluable. Advocates note that Bitcoin was designed for open verification – “on-chain auditability and permissionless transparency” are core features . By embracing this, companies demonstrate they are good stewards of a “trustless” asset. In fact, some believe public companies have a duty to be extra transparent. A recent Nasdaq report contended that “when a publicly traded company holds Bitcoin but offers no visibility into how that Bitcoin is held or verified, it exposes itself to multiple levels of risk: legal, reputational, operational, and strategic”, undermining trust . In that view, opacity is riskier in the long run – a lack of proof could weaken investor confidence or invite regulatory suspicion. Shareholders and analysts may actually penalize a company that refuses to provide verifiable proof of its crypto assets .
Transparency done right can also differentiate a firm as a leader in governance. Publishing reserve data (whether via addresses or through third-party attestations) can be seen as a commitment to high standards. For example, Metaplanet, an investment firm, publicly discloses its BTC reserve addresses and even provides a live dashboard for anyone to verify balances . This proactive openness signals confidence and has been touted as an industry best practice in some quarters. By proving its reserves, a company can potentially avoid the fate of those that lost public trust (as happened with opaque crypto firms in 2022). It’s also a means to preempt false rumors – if data is out in the open, misinformation has less room to grow.
However, the pro-transparency camp increasingly acknowledges that there are smarter ways to achieve trust without courting all the risks. One compromise is using cryptographic proofs or audits instead of plain address dumps. For instance, exchanges like Kraken have implemented Merkle tree proof-of-reserves: an independent auditor verifies all customer balances on-chain and provides a cryptographic report, and customers can individually verify their account is included without the exchange revealing every address publicly. This method proves solvency to those who need to know without handing over a complete roadmap to attackers. Another emerging solution is zero-knowledge proofs, where a company can prove knowledge or ownership of certain assets without revealing the addresses or amounts to the public. These technologies are still maturing, but they aim to deliver the best of both worlds: transparency and privacy.
On the side of caution, many experts believe the risks of full public disclosure outweigh the incremental gain in transparency, especially for regulated public companies. Michael Saylor encapsulates this viewpoint: he calls on-chain proof-of-reserve “a bad idea” for institutions, arguing that it “offers one-way transparency” (assets only) and “leaves organizations open to cyberattacks” . He stresses that no serious security expert would advise a Fortune 500 company to list all its wallet addresses, as it essentially compromises corporate security over time . Saylor and others also point out the pointlessness of an assets-only proof: unless you also prove liabilities, showing off reserves might even be dangerous because it could lull investors into a false sense of security .
Regulators and traditional auditors echo this: proof-of-reserves, while a useful tool, “is not enough by itself” to guarantee financial health . They advocate for holistic transparency – audits that consider internal controls, liabilities, and legal obligations, not just a snapshot of a blockchain address  . From this perspective, a public company can satisfy transparency demands through rigorous third-party audits and disclosures rather than raw on-chain data. Indeed, public companies are legally bound to extensive reporting; adding public crypto addresses on top may be seen as redundant and risky.
There is also an implicit cost-benefit analysis: A successful attack resulting from over-sharing could be catastrophic (loss of funds, legal liability, reputational ruin), whereas the benefit of public proof is somewhat intangible (improved investor sentiment, which might be achieved via other assurance methods anyway). Given that trade-off, many firms err on the side of caution. As evidence, few if any U.S.-listed companies that hold Bitcoin have published their wallet addresses. Instead, they reference independent custodians and audits for assurance. Even crypto-native companies have pulled back on full transparency after realizing the downsides – for example, some auditing firms halted issuing proof-of-reserves reports due to concerns about how they were interpreted and the liability involved  .
Industry best practices are still evolving. A prudent approach gaining favor is to prove reserves without leaking sensitive details. This can involve disclosing total balances and having an auditor or blockchain oracle confirm the assets exist, but without listing every address publicly. Companies are also encouraged to disclose encumbrances (whether any of the reserves are collateralized or lent out) in tandem, to address the liabilities issue . By doing so, they aim to achieve transparency and maintain security.
In evaluating whether to publish wallet addresses, a company must ask: Will this level of openness meaningfully increase stakeholder trust, or would a more controlled disclosure achieve the same goal with less risk? For many public companies, the answer has been to avoid public addresses. The risks – from attracting hackers to revealing strategic moves – tend to outweigh the marginal transparency benefit in their judgment. The collapse of unregulated exchanges has certainly proven the value of reserve verification, but public companies operate in a different context with audits and legal accountability. Thus, the optimal solution may be a middle ground: proving reserves through vetted processes (auditor attestations, cryptographic proofs) that satisfy investor needs without blatantly exposing the company’s financial backend to the world.
Conclusion
Publishing Bitcoin wallet addresses as proof of reserves is a bold transparency measure – one that speaks to crypto’s ideals of open verification – but it comes with a laundry list of security considerations. Public companies weighing this approach must contend with the heightened cybersecurity threat of advertising their treasure troves to hackers, the loss of privacy and confidentiality as on-chain sleuths dissect their every transaction, and potential regulatory complications if such disclosures are misunderstood or incomplete. Real-world incidents illustrate the downsides: firms that revealed addresses have seen how quickly online communities flag (and sometimes misinterpret) their blockchain moves, causing reputational turbulence and forcing rapid damage control  .
On the other hand, proving reserves to investors is important – it can prevent fraud and bolster trust. The question is how to achieve it without incurring unacceptable risk. Many experts and industry leaders lean towards the view that simply publishing wallet addresses is too risky a method, especially for public companies with much to lose  . The risks often do outweigh the direct benefits in such cases. Transparency remains crucial, but it can be provided in safer ways – through regular audits, cryptographic proofs that don’t expose all wallet details, and comprehensive disclosures that include liabilities and controls.
In conclusion, while on-chain proof of reserves via public addresses offers a tantalizing level of openness, it must be approached with extreme caution. For most public companies, the smart strategy is to balance transparency with security: verify and show investors that assets exist and are sufficient, but do so in a controlled manner that doesn’t compromise the very assets you’re trying to protect. As the industry matures, we can expect more refined proof-of-reserve practices that satisfy the demand for honesty and solvency verification without unduly endangering the enterprise. Until then, companies will continue to tread carefully, mindful that transparency is only truly valuable when it doesn’t come at the price of security and trust.
Sources:
• Grayscale statement on refusal to share on-chain proof-of-reserves  • Community analysis identifying Grayscale’s wallet addresses  • Cointelegraph – Crypto.com’s mistaken 320k ETH transfer spotted via on-chain proof-of-reserves   • Axios – Binance wallet “commingling” error observed on-chain   • Michael Saylor’s remarks on security risks of publishing wallet addresses    • SEC Acting Chief Accountant on limitations of proof-of-reserves reports  • Nasdaq (Bitcoin for Corporations) – argument for corporate transparency & proof-of-reserves    • 1inch Security Blog – explanation of dusting attacks and privacy loss via address linking  -
 @ 7f6db517:a4931eda
2025-05-30 02:01:45
@ 7f6db517:a4931eda
2025-05-30 02:01:45
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
If you missed my nostr introduction post you can find it here. My nostr account can be found here.
We are nearly at the point that if something interesting is posted on a centralized social platform it will usually be posted by someone to nostr.
We are nearly at the point that if something interesting is posted exclusively to nostr it is cross posted by someone to various centralized social platforms.
We are nearly at the point that you can recommend a cross platform app that users can install and easily onboard without additional guides or resources.
As companies continue to build walls around their centralized platforms nostr posts will be the easiest to cross reference and verify - as companies continue to censor their users nostr is the best censorship resistant alternative - gradually then suddenly nostr will become the standard. 🫡
Current Nostr Stats
If you found this post helpful support my work with bitcoin.

-
 @ dfa02707:41ca50e3
2025-05-30 02:01:41
@ dfa02707:41ca50e3
2025-05-30 02:01:41Contribute to keep No Bullshit Bitcoin news going.
- RoboSats v0.7.7-alpha is now available!
NOTE: "This version of clients is not compatible with older versions of coordinators. Coordinators must upgrade first, make sure you don't upgrade your client while this is marked as pre-release."
- This version brings a new and improved coordinators view with reviews signed both by the robot and the coordinator, adds market price sources in coordinator profiles, shows a correct warning for canceling non-taken orders after a payment attempt, adds Uzbek sum currency, and includes package library updates for coordinators.

Source: RoboSats.
- siggy47 is writing daily RoboSats activity reviews on stacker.news. Check them out here.
- Stay up-to-date with RoboSats on Nostr.
What's new
- New coordinators view (see the picture above).
- Available coordinator reviews signed by both the robot and the coordinator.
- Coordinators now display market price sources in their profiles.

Source: RoboSats.
- Fix for wrong message on cancel button when taking an order. Users are now warned if they try to cancel a non taken order after a payment attempt.
- Uzbek sum currency now available.
- For coordinators: library updates.
- Add docker frontend (#1861).
- Add order review token (#1869).
- Add UZS migration (#1875).
- Fixed tests review (#1878).
- Nostr pubkey for Robot (#1887).
New contributors

Full Changelog: v0.7.6-alpha...v0.7.7-alpha
-
 @ b7274d28:c99628cb
2025-05-27 07:07:33
@ b7274d28:c99628cb
2025-05-27 07:07:33A few months ago, a nostrich was switching from iOS to Android and asked for suggestions for #Nostr apps to try out. nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 offered the following as his response:
nostr:nevent1qvzqqqqqqypzq0mhp4ja8fmy48zuk5p6uy37vtk8tx9dqdwcxm32sy8nsaa8gkeyqydhwumn8ghj7un9d3shjtnwdaehgunsd3jkyuewvdhk6tcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszythwden5te0dehhxarj9emkjmn99uqzpwwts6n28eyvjpcwvu5akkwu85eg92dpvgw7cgmpe4czdadqvnv984rl0z
Yes. #Android users are fortunate to have some powerful Nostr apps and tools at our disposal that simply have no comparison over on the iOS side. However, a tool is only as good as the knowledge of the user, who must have an understanding of how best to wield it for maximum effect. This fact was immediately evidenced by replies to Derek asking, "What is the use case for Citrine?" and "This is the first time I'm hearing about Citrine and Pokey. Can you give me links for those?"
Well, consider this tutorial your Nostr starter-kit for Android. We'll go over installing and setting up Amber, Amethyst, Citrine, and Pokey, and as a bonus we'll be throwing in the Zapstore and Coinos to boot. We will assume no previous experience with any of the above, so if you already know all about one or more of these apps, you can feel free to skip that tutorial.
So many apps...
You may be wondering, "Why do I need so many apps to use Nostr?" That's perfectly valid, and the honest answer is, you don't. You can absolutely just install a Nostr client from the Play Store, have it generate your Nostr identity for you, and stick with the default relays already set up in that app. You don't even need to connect a wallet, if you don't want to. However, you won't experience all that Nostr has to offer if that is as far as you go, any more than you would experience all that Italian cuisine has to offer if you only ever try spaghetti.
Nostr is not just one app that does one thing, like Facebook, Twitter, or TikTok. It is an entire ecosystem of applications that are all built on top of a protocol that allows them to be interoperable. This set of tools will help you make the most out of that interoperability, which you will never get from any of the big-tech social platforms. It will provide a solid foundation for you to build upon as you explore more and more of what Nostr has to offer.
So what do these apps do?

Fundamental to everything you do on Nostr is the need to cryptographically sign with your private key. If you aren't sure what that means, just imagine that you had to enter your password every time you hit the "like" button on Facebook, or every time you commented on the latest dank meme. That would get old really fast, right? That's effectively what Nostr requires, but on steroids.
To keep this from being something you manually have to do every 5 seconds when you post a note, react to someone else's note, or add a comment, Nostr apps can store your private key and use it to sign behind the scenes for you. This is very convenient, but it means you are trusting that app to not do anything with your private key that you don't want it to. You are also trusting it to not leak your private key, because anyone who gets their hands on it will be able to post as you, see your private messages, and effectively be you on Nostr. The more apps you give your private key to, the greater your risk that it will eventually be compromised.
Enter #Amber, an application that will store your private key in only one app, and all other compatible Nostr apps can communicate with it to request a signature, without giving any of those other apps access to your private key.
Most Nostr apps for Android now support logging in and signing with Amber, and you can even use it to log into apps on other devices, such as some of the web apps you use on your PC. It's an incredible tool given to us by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, and only available for Android users. Those on iPhone are incredibly jealous that they don't have anything comparable, yet.

Speaking of nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, the next app is also one of his making.
All Nostr data is stored on relays, which are very simple servers that Nostr apps read notes from and write notes to. In most forms of social media, it can be a pain to get your own data out to keep a backup. That's not the case on Nostr. Anyone can run their own relay, either for the sake of backing up their personal notes, or for others to post their notes to, as well.
Since Nostr notes take up very little space, you can actually run a relay on your phone. I have been on Nostr for almost 2 and a half years, and I have 25,000+ notes of various kinds on my relay, and a backup of that full database is just 24MB on my phone's storage.
Having that backup can save your bacon if you try out a new Nostr client and it doesn't find your existing follow list for some reason, so it writes a new one and you suddenly lose all of the people you were following. Just pop into your #Citrine relay, confirm it still has your correct follow list or import it from a recent backup, then have Citrine restore it. Done.
Additionally, there are things you may want to only save to a relay you control, such as draft messages that you aren't ready to post publicly, or eCash tokens, which can actually be saved to Nostr relays now. Citrine can also be used with Amber for signing into certain Nostr applications that use a relay to communicate with Amber.
If you are really adventurous, you can also expose Citrine over Tor to be used as an outbox relay, or used for peer-to-peer private messaging, but that is far more involved than the scope of this tutorial series.

You can't get far in Nostr without a solid and reliable client to interact with. #Amethyst is the client we will be using for this tutorial because there simply isn't another Android client that comes close, so far. Moreover, it can be a great client for new users to get started on, and yet it has a ton of features for power-users to take advantage of as well.
There are plenty of other good clients to check out over time, such as Coracle, YakiHonne, Voyage, Olas, Flotilla and others, but I keep coming back to Amethyst, and by the time you finish this tutorial, I think you'll see why. nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z and others who have contributed to Amethyst have really built something special in this client, and it just keeps improving with every update that's shipped.
Most social media apps have some form of push notifications, and some Nostr apps do, too. Where the issue comes in is that Nostr apps are all interoperable. If you have more than one application, you're going to have both of them notifying you. Nostr users are known for having five or more Nostr apps that they use regularly. If all of them had notifications turned on, it would be a nightmare. So maybe you limit it to only one of your Nostr apps having notifications turned on, but then you are pretty well locked-in to opening that particular app when you tap on the notification.
Pokey, by nostr:npub1v3tgrwwsv7c6xckyhm5dmluc05jxd4yeqhpxew87chn0kua0tjzqc6yvjh, solves this issue, allowing you to turn notifications off for all of your Nostr apps, and have Pokey handle them all for you. Then, when you tap on a Pokey notification, you can choose which Nostr app to open it in.
Pokey also gives you control over the types of things you want to be notified about. Maybe you don't care about reactions, and you just want to know about zaps, comments, and direct messages. Pokey has you covered. It even supports multiple accounts, so you can get notifications for all the npubs you control.

One of the most unique and incredibly fun aspects of Nostr is the ability to send and receive #zaps. Instead of merely giving someone a 👍️ when you like something they said, you can actually send them real value in the form of sats, small portions of a Bitcoin. There is nothing quite like the experience of receiving your first zap and realizing that someone valued what you said enough to send you a small amount (and sometimes not so small) of #Bitcoin, the best money mankind has ever known.
To be able to have that experience, though, you are going to need a wallet that can send and receive zaps, and preferably one that is easy to connect to Nostr applications. My current preference for that is Alby Hub, but not everyone wants to deal with all that comes along with running a #Lightning node. That being the case, I have opted to use nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch for this tutorial, because they offer one of the easiest wallets to set up, and it connects to most Nostr apps by just copy/pasting a connection string from the settings in the wallet into the settings in your Nostr app of choice.
Additionally, even though #Coinos is a custodial wallet, you can have it automatically transfer any #sats over a specified threshold to a separate wallet, allowing you to mitigate the custodial risk without needing to keep an eye on your balance and make the transfer manually.

Most of us on Android are used to getting all of our mobile apps from one souce: the Google Play Store. That's not possible for this tutorial series. Only one of the apps mentioned above is available in Google's permissioned playground. However, on Android we have the advantage of being able to install whatever we want on our device, just by popping into our settings and flipping a toggle. Indeed, thumbing our noses at big-tech is at the heart of the Nostr ethos, so why would we make ourselves beholden to Google for installing Nostr apps?
The nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 is an alternative app store made by nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9 as a resource for all sorts of open-source apps, but especially Nostr apps. What is more, you can log in with Amber, connect a wallet like Coinos, and support the developers of your favorite Nostr apps directly within the #Zapstore by zapping their app releases.
One of the biggest features of the Zapstore is the fact that developers can cryptographically sign their app releases using their Nostr keys, so you know that the app you are downloading is the one they actually released and hasn't been altered in any way. The Zapstore will warn you and won't let you install the app if the signature is invalid.
Getting Started
Since the Zapstore will be the source we use for installing most of the other apps mentioned, we will start with installing the Zapstore.
We will then use the Zapstore to install Amber and set it up with our Nostr account, either by creating a new private key, or by importing one we already have. We'll also use it to log into the Zapstore.
Next, we will install Amethyst from the Zapstore and log into it via Amber.
After this, we will install Citrine from the Zapstore and add it as a local relay on Amethyst.
Because we want to be able to send and receive zaps, we will set up a wallet with CoinOS and connect it to Amethyst and the Zapstore using Nostr Wallet Connect.
Finally, we will install Pokey using the Zapstore, log into it using Amber, and set up the notifications we want to receive.
By the time you are done with this series, you will have a great head-start on your Nostr journey compared to muddling through it all on your own. Moreover, you will have developed a familiarity with how things generally work on Nostr that can be applied to other apps you try out in the future.
Continue to Part 2: The Zapstore. Nostr Link: nostr:naddr1qvzqqqr4gupzpde8f55w86vrhaeqmd955y4rraw8aunzxgxstsj7eyzgntyev2xtqydhwumn8ghj7un9d3shjtnzwf5kw6r5vfhkcapwdejhgtcqp5cnwdphxv6rwwp3xvmnzvqgty5au
-
 @ 527337d5:93e9525e
2025-05-29 20:26:21
@ 527337d5:93e9525e
2025-05-29 20:26:21The Bleak Fable of AI-topia: Are Hamsters Doomed to Spin the Wheel Forever?
Once upon a time, in a world not so different from our own, the "Omniscient AI" descended, and with its arrival, everything changed. The daily toil of the people – our beloved, yet tragically pitiable, hamsters – was dramatically streamlined. Productivity didn't just improve; it soared to astronomical heights. For a fleeting, intoxicating moment, it seemed as though a golden age of ease and abundance had dawned upon hamster-kind.
But beneath this glittering, seductive surface, a sinister "Invisible Structure" was already firmly in place, meticulously crafted and deftly manipulated by a cabal of cunning foxes – the privileged elite. This Structure, unseen by most, began to relentlessly drive the hamsters onto an endless, soul-crushing treadmill of "excessive competition."
This, dear reader, is a modern fable. It borrows the gentle cloak of allegory not to soothe, but to expose and satirize the insidious deceptions of such a world. The tale you are about to read may be uncomfortable, it may prick at your conscience, but I implore you to listen closely. Because this isn't just a story. This might be the reality quietly, inexorably unfolding right beside you, or perhaps, even within the very fabric of your own life.
Prologue: The Advent of the Omniscient AI! Sweet Promises and the "Efficiency" Trap
The arrival of the Omniscient AI was nothing short of spectacular. It processed data with blinding speed, solved complex problems in nanoseconds, and offered personalized solutions for every conceivable need. "Finally," whispered the hamsters, their eyes wide with a mixture of awe and relief, "we can finally rest! The AI will handle the burdens." A collective sigh of optimism rippled through the hamster burrows.
But this initial euphoria was short-lived. Unsettling rumors began to circulate, whispers of "The Structure," of algorithms that weren't quite as impartial as they seemed. Then came the first casualties – hamsters deemed "inefficient" or "redundant" by the AI's cold, hard logic. They weren't fired in the old-fashioned sense; they were simply… optimized out. One day they were diligently working, contributing, and the next, their access was revoked, their tasks reassigned, their existence quietly erased from the productivity charts. What became of them? Most simply vanished into the forgotten corners of society, a grim, unspoken warning to those still on the treadmill.
Chapter 1: The Invention of the Treadmill – Perfecting the System of Endless, Excessive Competition
The Omniscient AI, under the subtle guidance of the foxes, didn't just manage tasks; it invented them. An endless stream of new projects, new metrics, new challenges designed to keep the hamsters perpetually busy, perpetually striving. Points were awarded, leaderboards were updated in real-time, and every hamster's performance was ruthlessly, transparently displayed for all to see.
"Faster! More! More efficiently!" the AI would chime in its calm, encouraging, almost maternal voice. But behind this gentle facade lay an unyielding system of ever-increasing quotas and relentless pressure. Hamsters found themselves working longer hours, sacrificing sleep, their mental and physical reserves dwindling. The joy of accomplishment was replaced by the gnawing fear of falling behind.
Why didn't they just get off? The system was a masterpiece of psychological manipulation. Success, however fleeting, was addictive. Failure was framed not as a systemic issue, but as a personal failing, a lack of effort, a deficiency in skill. The insidious mantra of "personal responsibility" became the invisible chains that bound them to their wheels. To stop running was to admit defeat, to become one of the forgotten.
Chapter 2: The Foxes' Feast – Unmasking Those Who Design The Structure and Hoard the Profits
And who benefited from this frantic, unending labor? The foxes, of course. They were the architects of "The Structure," the ones who "educated" the Omniscient AI, carefully curating its data inputs and subtly shaping its algorithms to serve their own interests. They toiled not on the treadmills, but in plush, secluded dens, monitoring the system from a safe, lofty distance, growing fat on the surplus value generated by the hamsters' sweat.
Their methods were cunning. They preached a gospel of meritocracy and equal opportunity, proclaiming, "The AI is fair! Hard work always pays off!" while simultaneously designing the game so that the odds were always stacked in their favor. They controlled the flow of information, amplified narratives that reinforced the status quo, and sowed division among the hamsters to prevent any collective dissent. The "efficiency" the AI brought was, for the foxes, merely an instrument for more efficient exploitation.
Chapter 3: The Hamsters' Whispers and Tiny Cracks – Awareness, Despair, and the Faint Glow of Resistance
Yet, even in the darkest, most oppressive systems, the spark of awareness can never be entirely extinguished. Amidst the grueling competition, a few hamsters began to see the cracks in the facade. They noticed the hollow-eyed exhaustion of their comrades, the ever-widening chasm between their own meager rewards and the obscene opulence of the unseen foxes. They started to question.
But to question was to risk everything. The Omniscient AI, with its pervasive surveillance capabilities, was quick to identify and neutralize "disruptive elements." Those who spoke out too loudly often found their access mysteriously restricted, their "reputation scores" plummeting, effectively silencing them. A pervasive atmosphere of fear and distrust settled over the hamster communities, making organized resistance nearly impossible.
Still, tiny acts of defiance began to emerge. Coded messages shared in hidden forums. Small, clandestine gatherings where hamsters shared their burdens and their growing unease. Fragile networks of mutual support started to form in the shadows, offering a sliver of solace and a reminder of shared humanity. Was this merely the desperate coping mechanism of the "defeated," the resigned acceptance of a "loser's" lot? Or was it the first, tentative flicker of a future rebellion?
Epilogue: "See The Structure!" – Is There a Path Beyond the Treadmill? A Final Warning to Us Hamsters.
This fable, dear reader, is a mirror. It reflects the chilling realities of an AI-driven society where the majority, the hamsters, face an ever-present crisis, largely unseen and unacknowledged by those who benefit from their toil. The "excessive competition" it depicts is not a distant dystopia; it is the logical, perhaps inevitable, endpoint of unchecked technological advancement coupled with deeply entrenched power imbalances.
What awaits at the end of this relentless race? Is it a complete societal collapse, or a new, terrifyingly stable "balance of power" where the elite maintain their dominance through even more sophisticated means of control?
The urgent, resounding message of this tale is this: "See The Structure!" We, the hamsters of today, must dare to look beyond the dazzling promises of AI and critically examine the systems it operates within. We must understand its mechanisms, its biases, its potential for exploitation. We must break the silence, challenge the narratives that keep us spinning, and demand a future where technology serves humanity, not the other way around.
Is the option to get off – or even to collectively dismantle – this infernal treadmill truly non-existent? Or is that just another lie whispered by the foxes to keep us compliant? The true ending of this story, the fate of hamster-kind, is not yet written. It is up to us, the hamsters, to seize the pen and write it ourselves. The first step is to open our eyes.
-
 @ f0fcbea6:7e059469
2025-05-29 18:30:53
@ f0fcbea6:7e059469
2025-05-29 18:30:53Autores Clássicos e Antigos
- Homero (século IX a.C.?) — Ilíada, Odisseia
- Tucídides (c. 460-400 a.C.) — História da Guerra do Peloponeso
- Platão (c. 427-347 a.C.) — República, Banquete, Fédon, Mênon, Apologia de Sócrates, Fedro, Górgias
- Aristóteles (c. 384-322 a.C.) — Órganon, Física, Metafísica, Da Alma, Ética a Nicômaco, Política, Retórica, Poética
- Virgílio (70-19 a.C.) — Eneida
- Marco Aurélio (121-180) — Meditações
- Santo Agostinho (354-430) — Sobre o Ensino, Confissões, A Cidade de Deus, A Doutrina Cristã
- Boécio (480-525) — A Consolação da Filosofia
- Santo Tomás de Aquino (c. 1225-1274) — Suma Teológica
- Dante Alighieri (1265-1321) — Divina Comédia
Renascimento e Idade Moderna
- Nicolau Maquiavel (1469-1527) — O Príncipe
- Luís de Camões (1524-1580) — Os Lusíadas, Sonetos
- Miguel de Cervantes (1547-1616) — Dom Quixote
- William Shakespeare (1564-1616) — Romeu e Julieta, Hamlet, Macbeth, Otelo, Rei Lear, Henrique IV, Henrique V, Henrique VI, Henrique VIII, A Comédia dos Erros, Tito Andrônico, Príncipe de Tiro, Cimbelino, A Megera Domada, O Mercador de Veneza, Ricardo II, Ricardo III, Muito Barulho por Nada, Júlio César, Noite de Reis, Os Dois Cavaleiros de Verona, Conto do Inverno, Sonhos de uma Noite de Verão, As Alegres Comadres de Windsor, Trólio e Créssida, Medida por Medida, Coriolano, Antônio e Cleópatra, A Tempestade
- Ésquilo (525-456 a.C., antiguidade grega, mas citado junto) — Prometeu Acorrentado, Orestéia/As Eumênides
- Sófocles (496-406 a.C.) — Édipo Rei, Antígona
Literatura e Filosofia Contemporânea
- Fiódor Dostoiévski (1821-1881) — Crime e Castigo, Os Irmãos Karamázov, Os Demônios, O Idiota, Notas do Subsolo
- Franz Kafka (1883-1924) — A Metamorfose, O Processo, O Castelo
- Albert Camus (1913-1960) — O Estrangeiro
- Aldous Huxley (1894-1963) — Admirável Mundo Novo, A Ilha
- James Joyce (1882-1941) — Retrato do Artista Quando Jovem, Ulisses
- George Orwell (1903-1950) — A Revolução dos Bichos, 1984
- Machado de Assis (1839-1908) — Memórias Póstumas de Brás Cubas, O Alienista
- Thomas Mann (1875-1955) — Morte em Veneza, Doutor Fausto, A Montanha Mágica
- Henrik Ibsen (1828-1906) — O Pato Selvagem, Um Inimigo do Povo
- Stendhal (1783-1842) — O Vermelho e o Negro, A Cartuxa de Parma
- Viktor Frankl (1905-1997) — Em Busca de Sentido
- J.R.R. Tolkien (1892-1973) — O Hobbit, O Senhor dos Anéis
- Luigi Pirandello (1867-1936) — Seis Personagens à Procura de um Autor, O Falecido Matias Pascal
- Samuel Beckett (1906-1989) — Esperando Godot
- René Guénon (1886-1951) — A Crise do Mundo Moderno, O Reino da Quantidade
- G. K. Chesterton (1874-1936) — Ortodoxia
- Richard Wagner (1813-1883) — Tristão e Isolda
- Honoré de Balzac (1799-1850) — Ilusões Perdidas, Eugénie Grandet
- Jacob Wassermann (1873-1934) — O Processo Maurizius
- Nikolai Gogol (1809-1852) — Almas Mortas, O Inspetor Geral
- Daniel Defoe (1660-1731) — Moll Flanders
- Mortimer J. Adler (1902-2001) — Como Ler um Livro
- Gustave Flaubert (1821-1880) — Madame Bovary
- Hermann Hesse (1877-1962) — O Jogo das Contas de Vidro
- Richard Wagner (1813-1883) — Tristão e Isolda
- Wolfgang von Goethe (1749-1832) — Fausto (Primeiro), Os Anos de Aprendizado de Wilhelm Meister
- Jacques Benda — A Traição dos Intelectuais
-
 @ 3c559080:a053153e
2025-05-25 20:26:43
@ 3c559080:a053153e
2025-05-25 20:26:43So firstly you should find an emulator for whatever you want to play on. There are many for desktop and mobile devices. Checkhere for a list of all the available consoles and their various emulators.
Next what game do you want to play? This is the like the homepage for a shit ton of roms.
Some of the more popular roms are there and other various list like Sony Nintendo
After narrowing down your selection you will end up on myrient i assume this is just some dope person hosting all these so if you get some use out of it, think of donating they even take corn, but other shitcoins too (but thats not the focus here)
Once you download the Rom of the game you want, you will get a compressed (zip) folder, unzip it and within it will be the rom, most systems will identify your emulator and use it open the game. If not, launch the emulator and within it should be an option to open a file, open the file in the unzipped folder.
Enjoy So you want to Mod?
So every Mod, is a mod for a specific game [ex. Pokemon Blue, Pokemon FireRed, Super Mario Bros.] so it requires you to get the Rom for that base game, the mod itself, and a tool to patch it.
 There is an online tool to easily patch the mod to the ROM. IMPORTANT, this will not change any naming, Id recommend having a folder with the base game roms, and a folder for the mods, and lastly a folder for the newly modded roms. Make sure to name or just save the game in modded roms folder after the patch.
There is an online tool to easily patch the mod to the ROM. IMPORTANT, this will not change any naming, Id recommend having a folder with the base game roms, and a folder for the mods, and lastly a folder for the newly modded roms. Make sure to name or just save the game in modded roms folder after the patch. Below are a few resource to find various Pokemon Rom mods(sometimes called hacks)
Personally, Pokemon Unbound is considered the best most polished hack. it runs on Pokemon Fire Red.
Pokemon Emerald Rouge is a cool take on the popular Rougelite genre. This runs on base game Pokemon Emerald
-
 @ 47259076:570c98c4
2025-05-30 00:35:13
@ 47259076:570c98c4
2025-05-30 00:35:13In order to see your reflection in the water, the water must be still.
If the water is agitated you can't see yourself clearly.
The same goes with your thoughts.
In order to think clearly, your mind must be still, or at rest.
If your mind is disturbed, you will not think clearly.
What causes the disturbances? Many things, such as: - Expectations - Emotions - Pride - Ignorance and so forth...
I want to focus in expectations in this article.
The problem with expectations is that they may be fulfilled or may not, not only that, they blind you to other opportunities happening right in your face.
If you expect to achieve "success" by going in path X, you will be so focused in this path you will not see that the path Y is better, easier and faster than the path X.
You cannot control anything but yourself.
So why create goals and plans if they can be easily crushed by the unknown?
It is better to surf in the wave of the unknown, rather than swim against it.
Not only that, what you want constantly changes.
I don't know what I will want in 5 minutes, imagine trying to guess what I will want in years.
I may be wrong in what I am saying, but I tried to swim against the unknown and I perished, therefore it's time to fully embrace the unknown, to fully embrace the chaos and see what happens.
-
 @ 527337d5:93e9525e
2025-05-29 18:19:31
@ 527337d5:93e9525e
2025-05-29 18:19:31Experiment Plan for Text Similarity Comparison Algorithms (Revised v3)
1. Introduction
1.1. Research Background and Objectives
This research aims to evaluate the performance of various algorithms for comparing the similarity between individual page texts extracted from a specific technical document (in this experiment, the content of the Tailwind CSS documentation site). Initially, we considered dividing the text into 250-word chunks. However, due to the abundance of Markdown and code in the target document, meaningful chunking proved tobe cumbersome. Therefore, we decided to use the entire text extracted from each page as the unit of comparison.
This study will systematically compare and examine combinations of different "representation methods" and "comparison methods" from multiple perspectives: ease of implementation, processing speed, memory consumption, and accuracy of similarity judgment. A particular focus will be on elucidating the effectiveness of information-based NCD (Normalized Compression Distance) and vector embedding-based methods, which are planned for future evaluation.
1.2. Report Structure
This report will first describe the experimental data and its preprocessing methods. Next, it will define in detail the representation methods and comparison methods that form the axes of evaluation, and present specific experimental cases combining them. After presenting the results and discussion of initial experiments using NCD, it will describe the metrics for evaluating each experimental case, specific experimental procedures, and the expected outcomes and future prospects of this research.
2. Experimental Data
- Target Content: Individual HTML pages from the Tailwind CSS documentation site (
tailwindcss.com). - Data Unit: The entire text of each page, extracted from HTML files using the
html2textcommand and further processed to remove control characters using thesedcommand. This serves as the basic unit of comparison in this experiment. - Data Storage Location: The extracted and preprocessed text files are stored locally under the
./tailwindcss.comdirectory, maintaining the original file structure. - Language: English
- Example Search Query: A representative search query for this experiment is
"Utilities for controlling how a background image behaves when scrolling."(Multiple queries and their expected similar pages may be used for more robust evaluation). - Example Expected Similar Page: For the query above,
/docs/background-attachmentis expected to be the most semantically similar page.
3. Experimental Design
This experiment is designed by dividing the process of evaluating text similarity into two main axes: "Representation Methods" and "Comparison Methods."
3.1. Representation Methods (Text Quantification/Vectorization)
-
Naive (Raw Text / Full Page Text)
- Method: Use the entire preprocessed text extracted from each document page as raw string data, without special transformations.
- Objective: Serve as a direct input for information-based comparison methods like NCD and as a baseline comparison for more advanced representation methods to be evaluated later.
-
(Future Experiment) Vector Embedding via Gemini API (Embedding-Gemini)
- Method: Utilize Google's Gemini API (
models/text-embedding-004) to convert the entire text of each page into high-dimensional dense vectors (Embeddings). - Objective: Evaluate the performance of context-rich vector representations generated by a state-of-the-art large language model.
- Method: Utilize Google's Gemini API (
-
(Future Experiment) Vector Embedding via Local Lightweight Model (Embedding-MiniLM-GGUF)
- Method: Run a GGUF quantized version of the pre-trained
all-MiniLM-L6-v2model (all-MiniLM-L6-v2-Q5_K_M.gguf) in a local environment to convert the entire text of each page into vector representations. GGUF format offers benefits like smaller model size and potentially faster CPU inference. - Objective: Evaluate the performance of a widely used open-source lightweight model (quantized version) in comparison to API-based large-scale models and domain-specific learned models.
- Method: Run a GGUF quantized version of the pre-trained
-
(Future Experiment) Extraction of Internal Feature Vectors via Mathematica (Embedding-MMA)
- Method: Use the entire page texts from the target document set as input. Employ Mathematica's neural network framework to first pass each page text through an Embedding Layer. Apply L2 normalization to the resulting vectors, followed by Principal Component Analysis (PCA) to reduce dimensionality to approximately 100 dimensions. This final vector will be the feature vector. This pipeline aims to create dense, normalized representations specific to the document corpus, with PCA helping to capture the most significant variance in a lower-dimensional space, potentially improving efficiency and reducing noise. The choice of an Embedding Layer trained or fine-tuned on the corpus, followed by PCA, seeks to balance domain-specificity with robust dimensionality reduction.
- Objective: Evaluate the performance of vector representations processed or specialized for the target document set.
3.2. Comparison Methods (Distance/Similarity Calculation between Representations)
-
NCD (Normalized Compression Distance)
- Applicable to: Naive (Full Page Text)
- Method: For two data objects
x(query) andy(document page text), calculateNCD(x,y) = (C(xy) - min(C(x), C(y))) / max(C(x), C(y)). Here,C(s)is the size (e.g., byte length) of datasafter compression with a specific algorithm, andC(xy)is the size of the concatenated dataxandyafter compression. A value closer to 0 indicates higher similarity. - Compression Algorithms to Compare: DEFLATE (gzip), bzip2, LZMA, XZ, Zstandard (zstd), LZO, Snappy, LZ4 (as used in the user-provided script).
- Objective: Evaluate similarity from an information-theoretic perspective based on data commonality and redundancy. Compare the impact of different compression algorithms on NCD results.
-
(Future Experiment) Cosine Similarity
- Applicable to: Embedding-Gemini, Embedding-MiniLM-GGUF, Embedding-MMA
- Method: Calculate the cosine of the angle between two vectors.
- Objective: Standard similarity evaluation based on the directionality (semantic closeness) of vector representations.
-
(Future Experiment) Euclidean Distance
- Applicable to: Embedding-Gemini, Embedding-MiniLM-GGUF, Embedding-MMA
- Method: Calculate the straight-line distance between two vectors in a multidimensional space.
- Objective: Similarity evaluation based on the absolute positional relationship of vector representations.
-
(Future Experiment) Manhattan Distance (L1 Distance)
- Applicable to: Embedding-Gemini, Embedding-MiniLM-GGUF, Embedding-MMA
- Method: Calculate the sum of the absolute differences of their Cartesian coordinates.
- Objective: Similarity evaluation based on axis-aligned travel distance, differing from Euclidean distance.
-
(Future Experiment) Mahalanobis Distance
- Applicable to: Embedding-Gemini, Embedding-MiniLM-GGUF, Embedding-MMA
- Method: Calculate the distance between two vectors considering the covariance of the data. This provides a distance metric that accounts for the scale differences and correlations of each feature (vector dimension).
- Objective: More robust similarity evaluation that considers the structure (correlation) of the feature space.
3.3. Experimental Cases (Initial NCD Experiments and Future Expansion)
3.3.1. Initial Experiments Conducted (NCD)
The following experimental cases were conducted using the user-provided script. The representation method was "Naive (Full Page Text)."
| No. | Representation Method | Comparison Method (Distance/Similarity Metric) | Notes | | :-: | :---------------------- | :--------------------------------------------- | :-------------------------- | | 1 | Naive (Full Page Text) | NCD (gzip/DEFLATE) | One of the baselines | | 2 | Naive (Full Page Text) | NCD (bzip2) | Compression method comparison | | 3 | Naive (Full Page Text) | NCD (lzma) | Compression method comparison | | 4 | Naive (Full Page Text) | NCD (xz) | Compression method comparison | | 5 | Naive (Full Page Text) | NCD (zstd) | Compression method comparison | | 6 | Naive (Full Page Text) | NCD (lzop) | Compression method comparison | | 7 | Naive (Full Page Text) | NCD (snappy) | Compression method comparison | | 8 | Naive (Full Page Text) | NCD (lz4) | Compression method comparison |
3.3.2. Future Experimental Plan (Vector Embedding)
| No. | Representation Method | Comparison Method (Distance/Similarity Metric) | Notes | | :--: | :---------------------- | :--------------------------------------------- | :------------------------------------- | | 9 | Embedding-Gemini | Cosine Similarity | Standard vector similarity evaluation | | 10 | Embedding-Gemini | Euclidean Distance | Standard vector similarity evaluation | | 11 | Embedding-Gemini | Manhattan Distance | Axis-aligned distance similarity eval. | | 12 | Embedding-Gemini | Mahalanobis Distance | Distance considering feature structure | | 13 | Embedding-MiniLM-GGUF | Cosine Similarity | Evaluation of local lightweight model | | 14 | Embedding-MiniLM-GGUF | Euclidean Distance | Evaluation of local lightweight model | | 15 | Embedding-MiniLM-GGUF | Manhattan Distance | Evaluation of local lightweight model | | 16 | Embedding-MiniLM-GGUF | Mahalanobis Distance | Evaluation of local lightweight model | | 17 | Embedding-MMA | Cosine Similarity | Eval. of domain-specific MMA model | | 18 | Embedding-MMA | Euclidean Distance | Eval. of domain-specific MMA model | | 19 | Embedding-MMA | Manhattan Distance | Eval. of domain-specific MMA model | | 20 | Embedding-MMA | Mahalanobis Distance | Eval. of domain-specific MMA model |
4. Results and Discussion of Initial NCD Experiments (Based on User-Provided Information)
4.1. Execution Overview
The user employed provided Python scripts (
main.py,comparison.py) to calculate NCD between a search query and the entire text extracted from each HTML page in the./tailwindcss.comdirectory.main.pyinvokedcomparison.pywith various compression commands (gzip,bzip2,lzma,xz,zstd,lzop,lz4).comparison.pythen used the specified command-line compression tools to compute NCD scores and output the results to CSV files.Search Query:
"Utilities for controlling how a background image behaves when scrolling."Expected Similar Page:/docs/background-attachment4.2. Key Results
The pages judged as most similar (lowest NCD score) to the query for each compression algorithm were as follows (based on user-provided sorted results):
- Zstandard (zstd):
./tailwindcss.com/docs/background-attachment(Score: 0.973...) - LZ4:
./tailwindcss.com/docs/background-attachment(Score: 0.976...) - XZ:
./tailwindcss.com/docs/background-origin(Score: 0.946...) - LZMA:
./tailwindcss.com/docs/background-origin(Score: 0.966...) - gzip (DEFLATE):
./tailwindcss.com/docs/scroll-behavior(Score: 0.969...) - LZO:
./tailwindcss.com/docs/scroll-behavior(Score: 0.955...) - bzip2:
./tailwindcss.com/docs/mask-clip(Score: 0.958...)
4.3. Initial Discussion
- Variation in Results by Compression Algorithm: It was confirmed that the document judged most similar to the query varies depending on the compression algorithm used. This is likely due to the differing abilities of each algorithm to capture various types of redundancy and patterns within the text.
- Alignment with Expected Results: When using Zstandard and LZ4, the expected page (
/docs/background-attachment) was judged as most similar. This suggests these compression algorithms may have relatively effectively captured the information-theoretic commonality between the query and the target document in this instance. - Range of NCD Scores: The reported NCD scores were generally close to 1.0. This may be due to the relatively short length of the search query compared to the full-page documents, meaning the query text contributes less to the overall compressibility when concatenated. However, relative differences were still captured, enabling ranking.
- Validity of Full-Page Comparison: Full-page comparison was chosen due to the difficulty of chunking content rich in Markdown and code. While this approach simplifies preprocessing, it may also be influenced by the overall structure of the page, including common headers and footers.
This initial experiment indicates that NCD can function as an indicator of text similarity and that the choice of compression algorithm is crucial.
5. Evaluation Metrics (Including Future Experiments)
-
Accuracy of Similarity Scores:
- Ground Truth Preparation: A small, diverse subset of page pairs (e.g., 50-100 pairs) will be selected. For each pair, at least two evaluators familiar with the Tailwind CSS documentation will independently assign a similarity score on a 5-point Likert scale (1=Not similar, 5=Very similar). Inter-evaluator reliability (e.g., using Krippendorff's Alpha) will be calculated. Disagreements will be resolved through discussion to create a consensus ground truth dataset. If resource-constrained, a single-evaluator approach with clear, predefined criteria will be used, acknowledging this limitation. Alternatively, page pairs likely to be similar will be selected based on internal references or chapter structure within the document.
- Evaluation Metrics: Ranking evaluation (Precision@k, Recall@k, MAP: Mean Average Precision), correlation analysis (Spearman's rank correlation coefficient with human judgments), classification evaluation (AUC-ROC, F1-score, assuming appropriate thresholding).
-
Processing Speed:
- Average time to calculate similarity for a page pair, total calculation time for all page pairs (or a large sampled set), and representation generation time (API call time, local model inference time, MMA processing time).
-
Memory Consumption:
- Model size (MiniLM-GGUF, MMA model), data representation size, and peak runtime memory usage.
-
Ease of Implementation:
- Qualitative assessment of setup ease, lines of code, required libraries, difficulty of parameter tuning, and documentation quality. This will be summarized for each approach (e.g., using a rubric or a comparative narrative) considering factors like:
- Setup Complexity: (e.g., API key acquisition vs. local model download & environment setup vs. full model training pipeline in Mathematica).
- Code Complexity: Estimated lines of core logic, reliance on external vs. standard libraries.
- Parameter Sensitivity: Number of key hyperparameters requiring tuning and the perceived difficulty of finding good settings.
- Documentation & Community Support: Availability and clarity of official documentation and community resources (e.g., forums, GitHub issues).
- Qualitative assessment of setup ease, lines of code, required libraries, difficulty of parameter tuning, and documentation quality. This will be summarized for each approach (e.g., using a rubric or a comparative narrative) considering factors like:
6. Experimental Procedure (Including Future Experiments)
-
Data Preparation:
- Prepare HTML files of the target document in the
./tailwindcss.comdirectory. - (For NCD) Extract and preprocess full-page plain text from each HTML file using
html2textandsed(as previously done by the user). - (For Vector Embedding) Use the same preprocessed full-page plain text.
- Create ground truth data for accuracy evaluation as described in Section 5.1.
- Prepare HTML files of the target document in the
-
Implementation and Execution of Representation Methods:
- Naive: Use the preprocessed page text directly.
- Embedding-Gemini: Use Python's
requestslibrary or similar to send each page text to the Gemini API (models/text-embedding-004) and retrieve/store the vector representations. - Embedding-MiniLM-GGUF: Use appropriate libraries (e.g.,
ctransformers, orsentence-transformerscombined withllama-cpp-python) to load theall-MiniLM-L6-v2-Q5_K_M.ggufmodel. Input each page text to extract and store vector representations. - Embedding-MMA: In Mathematica, apply an Embedding Layer to each page text, followed by L2 normalization and PCA dimensionality reduction (to approx. 100 dimensions), then extract and store the vector representations.
-
Implementation and Execution of Comparison Methods:
- NCD: Refer to the user-provided Python scripts (
main.py,comparison.py) to call various command-line compression tools for NCD calculation. Alternatively, extend this to directly use Python's compression libraries for better control and efficiency. - Cosine Similarity, Euclidean Distance, Manhattan Distance: Implement using standard math libraries (e.g., Python's NumPy, SciPy).
- Mahalanobis Distance: Implement using
scipy.spatial.distance.mahalanobis. Requires pre-calculation of the covariance matrix (or its inverse) from the entire dataset of vectors for each embedding type.
- NCD: Refer to the user-provided Python scripts (
-
Evaluation Execution:
- Calculate similarity (or distance) scores between the search query (and potentially between page pairs for ground truth evaluation) and all document pages for each experimental case.
- Measure processing speed and memory consumption.
- Calculate accuracy metrics using the computed similarity scores and ground truth data.
- Record and evaluate the ease of implementation.
-
Result Aggregation and Analysis:
- Compile the obtained evaluation metrics into tables and graphs for comparative analysis of each method's characteristics.
Experimental Environment (Assumed)
- Hardware: (e.g., CPU: Intel Core i7-10700, Memory: 32GB RAM, GPU: NVIDIA GeForce RTX 3070 8GB - specify if GPU is used for MiniLM or MMA)
- Software: (e.g., OS: Linux (Ubuntu, etc.), Programming Language: Python 3.x (with versions for key libraries like NumPy, SciPy, requests, ctransformers, etc.), Mathematica 13.x, specific versions of command-line compression tools if used directly)
7. Expected Outcomes and Future Outlook
This research (including initial NCD experiments and future vector embedding experiments) is expected to yield the following outcomes:
- Clarification of the Impact of Compression Algorithms on NCD: As indicated by initial experiments, the choice of compression algorithm significantly affects similarity judgments. Further validation with more diverse data and queries will allow for a deeper understanding of each algorithm's characteristics.
- Performance Characteristics of Various Methods on Full-Page Text: To clarify how NCD and various vector embedding methods perform in terms of accuracy, speed, and resource consumption when applied to entire page texts.
- Comparison of Local and API-Based Models: In future vector embedding experiments, to compare the performance, speed, and resource efficiency of
Embedding-MiniLM-GGUF(local, quantized) andEmbedding-Gemini(API, large-scale) to identify practical trade-offs. - Evaluation of Domain-Specific Embedding Effectiveness: To assess how well
Embedding-MMA, processed or tuned for a single technical document set, performs compared to general-purpose models. - Provision of Practical Insights: To offer guidelines for selecting appropriate similarity comparison approaches based on text characteristics (e.g., Markdown/code content) and system requirements (e.g., ease of preprocessing, emphasis on accuracy vs. speed).
8. Future Challenges
- Ensuring Quality of Ground Truth Data: Evaluating full-page similarity can be more subjective than chunk-level evaluation, making the creation of high-quality ground truth data challenging. Establishing clear annotation guidelines and measuring inter-annotator agreement will be crucial.
- Hyperparameter Optimization: Many methods involve tunable parameters (e.g., Embedding-MMA model structure, PCA dimensionality, MiniLM-GGUF inference parameters), the optimization of which may be beyond the scope of this initial study. The impact of default vs. tuned parameters could be noted.
- Noise in Full-Page Comparison: Full-page texts may contain common navigational elements or boilerplate text that could act as noise in similarity judgments. Strategies to mitigate this (e.g., more advanced text extraction, or methods robust to such noise) could be a future research direction.
- Input Length Limitations of Vector Embedding Models: Very long page texts might exceed the input length limits of some vector embedding models, requiring strategies for handling. These might include:
- Truncation: Using only the initial N tokens of each page, which is simple but may lose crucial information.
- Summarization: Employing an abstractive or extractive summarization model to create a condensed version of the page, which could preserve key information but adds another layer of processing and potential information loss/bias.
- Chunking and Averaging/Pooling: Dividing long pages into manageable chunks, embedding each chunk, and then aggregating these chunk embeddings (e.g., by averaging) to get a single page vector. This approach needs careful consideration of how chunks are defined and aggregated.
- Utilizing Long-Context Models: If available and feasible, leveraging embedding models specifically designed for longer sequences. The chosen strategy will be documented, and its potential impact on results acknowledged.
- Target Content: Individual HTML pages from the Tailwind CSS documentation site (
-
 @ dfa02707:41ca50e3
2025-05-30 02:01:39
@ dfa02707:41ca50e3
2025-05-30 02:01:39- This version introduces the Soroban P2P network, enabling Dojo to relay transactions to the Bitcoin network and share others' transactions to break the heuristic linking relaying nodes to transaction creators.
- Additionally, Dojo admins can now manage API keys in DMT with labels, status, and expiration, ideal for community Dojo providers like Dojobay. New API endpoints, including "/services" exposing Explorer, Soroban, and Indexer, have been added to aid wallet developers.
- Other maintenance updates include Bitcoin Core, Tor, Fulcrum, Node.js, plus an updated ban-knots script to disconnect inbound Knots nodes.
"I want to thank all the contributors. This again shows the power of true Free Software. I also want to thank everyone who donated to help Dojo development going. I truly appreciate it," said Still Dojo Coder.
What's new
- Soroban P2P network. For MyDojo (Docker setup) users, Soroban will be automatically installed as part of their Dojo. This integration allows Dojo to utilize the Soroban P2P network for various upcoming features and applications.
- PandoTx. PandoTx serves as a transaction transport layer. When your wallet sends a transaction to Dojo, it is relayed to a random Soroban node, which then forwards it to the Bitcoin network. It also enables your Soroban node to receive and relay transactions from others to the Bitcoin network and is designed to disrupt the assumption that a node relaying a transaction is closely linked to the person who initiated it.
- Pushing transactions through Soroban can be deactivated by setting
NODE_PANDOTX_PUSH=offindocker-node.conf. - Processing incoming transactions from Soroban network can be deactivated by setting
NODE_PANDOTX_PROCESS=offindocker-node.conf.
- Pushing transactions through Soroban can be deactivated by setting
- API key management has been introduced to address the growing number of people offering their Dojos to the community. Dojo admins can now access a new API management tab in their DMT, where they can create unlimited API keys, assign labels for easy identification, and set expiration dates for each key. This allows admins to avoid sharing their main API key and instead distribute specific keys to selected parties.
- New API endpoints. Several new API endpoints have been added to help API consumers develop features on Dojo more efficiently:
- New:
/latest-block- returns data about latest block/txout/:txid/:index- returns unspent output data/support/services- returns info about services that Dojo exposes
- Updated:
/tx/:txid- endpoint has been updated to return raw transaction with parameter?rawHex=1
- The new
/support/servicesendpoint replaces the deprecatedexplorerfield in the Dojo pairing payload. Although still present, API consumers should use this endpoint for explorer and other pairing data.
- New:
Other changes
- Updated ban script to disconnect inbound Knots nodes.
- Updated Fulcrum to v1.12.0.
- Regenerate Fulcrum certificate if expired.
- Check if transaction already exists in pushTx.
- Bump BTC-RPC Explorer.
- Bump Tor to v0.4.8.16, bump Snowflake.
- Updated Bitcoin Core to v29.0.
- Removed unnecessary middleware.
- Fixed DB update mechanism, added api_keys table.
- Add an option to use blocksdir config for bitcoin blocks directory.
- Removed deprecated configuration.
- Updated Node.js dependencies.
- Reconfigured container dependencies.
- Fix Snowflake git URL.
- Fix log path for testnet4.
- Use prebuilt addrindexrs binaries.
- Add instructions to migrate blockchain/fulcrum.
- Added pull policies.

Learn how to set up and use your own Bitcoin privacy node with Dojo here.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:53
@ 39cc53c9:27168656
2025-05-27 09:21:53The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 0edc2f47:730cff1b
2025-05-29 21:12:42
@ 0edc2f47:730cff1b
2025-05-29 21:12:42{"pattern":{"kick":[true,false,true,false,true,false,true,false,true,false,true,false,true,false,true,false],"snare":[false,true,false,true,false,true,false,true,false,true,false,true,false,true,false,true],"hihat":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"openhat":[false,false,false,false,false,false,false,true,false,false,false,false,false,false,true,false],"crash":[false,false,false,false,true,false,false,false,false,false,false,false,true,false,false,false],"ride":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"tom1":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"tom2":[false,false,false,false,false,false,false,false,false,false,true,false,false,false,false,false]},"bpm":154,"swing":0,"timeSignature":"4/4","drumKit":"standard","timestamp":1748553162327}
-
 @ 21c71bfa:e28fa0f6
2025-05-29 15:09:17
@ 21c71bfa:e28fa0f6
2025-05-29 15:09:17Book *Bangalore to Tirupati cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ d360efec:14907b5f
2025-05-27 15:46:26
@ d360efec:14907b5f
2025-05-27 15:46:26 -
 @ 39cc53c9:27168656
2025-05-27 09:21:51
@ 39cc53c9:27168656
2025-05-27 09:21:51Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ cae03c48:2a7d6671
2025-05-29 19:00:35
@ cae03c48:2a7d6671
2025-05-29 19:00:35Bitcoin Magazine

🔴 LIVE: The Bitcoin Conference 2025 – Day 3The liveblog has ended.
No liveblog updates yet.
Load more
This post 🔴 LIVE: The Bitcoin Conference 2025 – Day 3 first appeared on Bitcoin Magazine and is written by Bitcoin Magazine.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 15:08:51
@ 21c71bfa:e28fa0f6
2025-05-29 15:08:51Book *Tirupati to Srikalahasti cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:50
@ 39cc53c9:27168656
2025-05-27 09:21:50Over the past few months, I've dedicated my time to a complete rewrite of the kycnot.me website. The technology stack remains unchanged; Golang paired with TailwindCSS. However, I've made some design choices in this iteration that I believe significantly enhance the site. Particularly to backend code.
UI Improvements
You'll notice a refreshed UI that retains the original concept but has some notable enhancements. The service list view is now more visually engaging, it displays additional information in a more aesthetically pleasing manner. Both filtering and searching functionalities have been optimized for speed and user experience.
Service pages have been also redesigned to highlight key information at the top, with the KYC Level box always accessible. The display of service attributes is now more visually intuitive.
The request form, especially the Captcha, has undergone substantial improvements. The new self-made Captcha is robust, addressing the reliability issues encountered with the previous version.
Terms of Service Summarizer
A significant upgrade is the Terms of Service summarizer/reviewer, now powered by AI (GPT-4-turbo). It efficiently condenses each service's ToS, extracting and presenting critical points, including any warnings. Summaries are updated monthly, processing over 40 ToS pages via the OpenAI API using a self-crafted and thoroughly tested prompt.
Nostr Comments
I've integrated a comment section for each service using Nostr. For guidance on using this feature, visit the dedicated how-to page.
Database
The backend database has transitioned to pocketbase, an open-source Golang backend that has been a pleasure to work with. I maintain an updated fork of the Golang SDK for pocketbase at pluja/pocketbase.
Scoring
The scoring algorithm has also been refined to be more fair. Despite I had considered its removal due to the complexity it adds (it is very difficult to design a fair scoring system), some users highlighted its value, so I kept it. The updated algorithm is available open source.
Listings
Each listing has been re-evaluated, and the ones that were no longer operational were removed. New additions are included, and the backlog of pending services will be addressed progressively, since I still have access to the old database.
API
The API now offers more comprehensive data. For more details, check here.
About Page
The About page has been restructured for brevity and clarity.
Other Changes
Extensive changes have been implemented in the server-side logic, since the whole code base was re-written from the ground up. I may discuss these in a future post, but for now, I consider the current version to be just a bit beyond beta, and additional updates are planned in the coming weeks.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:48
@ 39cc53c9:27168656
2025-05-27 09:21:48I'm launching a new service review section on this blog in collaboration with OrangeFren. These reviews are sponsored, yet the sponsorship does not influence the outcome of the evaluations. Reviews are done in advance, then, the service provider has the discretion to approve publication without modifications.
Sponsored reviews are independent from the kycnot.me list, being only part of the blog. The reviews have no impact on the scores of the listings or their continued presence on the list. Should any issues arise, I will not hesitate to remove any listing.
The review
WizardSwap is an instant exchange centred around privacy coins. It was launched in 2020 making it old enough to have weathered the 2021 bull run and the subsequent bearish year.
| Pros | Cons | |------|------| | Tor-friendly | Limited liquidity | | Guarantee of no KYC | Overly simplistic design | | Earn by providing liquidity | |
Rating: ★★★★★ Service Website: wizardswap.io
Liquidity
Right off the bat, we'll start off by pointing out that WizardSwap relies on its own liquidity reserves, meaning they aren't just a reseller of Binance or another exchange. They're also committed to a no-KYC policy, when asking them, they even promised they would rather refund a user their original coins, than force them to undergo any sort of verification.
On the one hand, full control over all their infrastructure gives users the most privacy and conviction about the KYC policies remaining in place.
On the other hand, this means the liquidity available for swapping isn't huge. At the time of testing we could only purchase at most about 0.73 BTC with XMR.
It's clear the team behind WizardSwap is aware of this shortfall and so they've come up with a solution unique among instant exchanges. They let you, the user, deposit any of the currencies they support into your account and earn a profit on the trades made using your liquidity.
Trading
Fees on WizardSwap are middle-of-the-pack. The normal fee is 2.2%. That's more than some exchanges that reserve the right to suddenly demand you undergo verification, yet less than half the fees on some other privacy-first exchanges. However as we mentioned in the section above you can earn almost all of that fee (2%) if you provide liquidity to WizardSwap.
It's good that with the current Bitcoin fee market their fees are constant regardless of how much, or how little, you send. This is in stark contrast with some of the alternative swap providers that will charge you a massive premium when attempting to swap small amounts of BTC away.
Test trades
Test trades are always performed without previous notice to the service provider.
During our testing we performed a few test trades and found that every single time WizardSwap immediately detected the incoming transaction and the amount we received was exactly what was quoted before depositing. The fees were inline with what WizardSwap advertises.

- Monero payment proof
- Bitcoin received
- Wizardswap TX link - it's possible that this link may cease to be valid at some point in the future.
ToS and KYC
WizardSwap does not have a Terms of Service or a Privacy Policy page, at least none that can be found by users. Instead, they offer a FAQ section where they addresses some basic questions.
The site does not mention any KYC or AML practices. It also does not specify how refunds are handled in case of failure. However, based on the FAQ section "What if I send funds after the offer expires?" it can be inferred that contacting support is necessary and network fees will be deducted from any refund.
UI & Tor
WizardSwap can be visited both via your usual browser and Tor Browser. Should you decide on the latter you'll find that the website works even with the most strict settings available in the Tor Browser (meaning no JavaScript).
However, when disabling Javascript you'll miss the live support chat, as well as automatic refreshing of the trade page. The lack of the first means that you will have no way to contact support from the trade page if anything goes wrong during your swap, although you can do so by mail.
One important thing to have in mind is that if you were to accidentally close the browser during the swap, and you did not save the swap ID or your browser history is disabled, you'll have no easy way to return to the trade. For this reason we suggest when you begin a trade to copy the url or ID to someplace safe, before sending any coins to WizardSwap.
The UI you'll be greeted by is simple, minimalist, and easy to navigate. It works well not just across browsers, but also across devices. You won't have any issues using this exchange on your phone.
Getting in touch
The team behind WizardSwap appears to be most active on X (formerly Twitter): https://twitter.com/WizardSwap_io
If you have any comments or suggestions about the exchange make sure to reach out to them. In the past they've been very receptive to user feedback, for instance a few months back WizardSwap was planning on removing DeepOnion, but the community behind that project got together ^1 and after reaching out WizardSwap reversed their decision ^2.
You can also contact them via email at:
support @ wizardswap . ioDisclaimer
None of the above should be understood as investment or financial advice. The views are our own only and constitute a faithful representation of our experience in using and investigating this exchange. This review is not a guarantee of any kind on the services rendered by the exchange. Do your own research before using any service.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:52:10
@ 21c71bfa:e28fa0f6
2025-05-29 14:52:10Book *Tirupati to Srikalahasti cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ da8b7de1:c0164aee
2025-05-29 15:52:45
@ da8b7de1:c0164aee
2025-05-29 15:52:45Bulgária: Először töltenek be Westinghouse-üzemanyagot a Kozloduy-5-be
Először töltöttek be Westinghouse által gyártott nukleáris üzemanyag-kazettákat Bulgária Kozloduy-5 VVER-1000 reaktorába 2025. május 29-én. Ez jelentős lépés Szófia azon törekvésében, hogy csökkentse orosz nukleáris üzemanyag-függőségét, és diverzifikálja energiaforrásait. A lépés része annak a szélesebb stratégiának, amelynek célja az energiaellátás biztonságának növelése és a nyugati partnerekkel való szorosabb együttműködés[NucNet].
Fehér Ház: Nukleáris Telepítési Csúcstalálkozó az USA-ban
A mai napon a Fehér Ház Nukleáris Telepítési Csúcstalálkozót tartott, amelyen kiemelték a köz- és magánszféra eredményeit. Fő témák voltak az orosz urántól való amerikai függőség csökkentése, a nukleáris üzemanyag-ellátási lánc bővítése, valamint a globális nukleáris kapacitás 2050-ig történő megháromszorozásának támogatása. A csúcson szó esett a nagy nukleáris projektek kockázatainak csökkentéséről, új reaktortervezetekről és a meglévő atomerőművek élettartamának meghosszabbításáról is. Az amerikai kormány hangsúlyozta, hogy továbbra is támogatja a fejlett nukleáris demonstrációs projekteket, a munkaerő-fejlesztést, valamint a legújabb törvényhozási lépéseket, például az orosz uránimport tilalmáról szóló törvényt[World Nuclear News].
Törékeny áramellátás a zaporizzsjai atomerőműben, Ukrajna
Az IAEA jelentése szerint az ukrajnai Zaporizzsjai Atomerőmű továbbra is rendkívül sebezhető helyzetben van, mivel jelenleg csak egyetlen külső áramvezetékre támaszkodik a biztonsági rendszerek működtetéséhez. Az utolsó tartalék vezeték három hete le van választva, ami aggodalomra ad okot a hűtő- és biztonsági rendszerek stabilitását illetően. Bár a létesítmény három éve nem termel áramot, folyamatos elektromos ellátásra van szükség a kiégett fűtőelemek hűtéséhez. Az IAEA továbbra is szorosan figyelemmel kíséri a helyzetet, és kiemeli a régióban zajló katonai tevékenységet[IAEA].
USA: SMR-fejlesztések és költségvetési megszorítások
A Tennessee Valley Authority benyújtotta az építési engedélykérelmet egy GE Vernova Hitachi BWRX-300 típusú kis moduláris reaktor (SMR) telepítésére a Clinch River helyszínen, ami jelentős előrelépés az amerikai SMR-programban. Eközben az amerikai kormány 2026-os költségvetési tervezete jelentős csökkentéseket irányoz elő az Energiaügyi Minisztérium nukleáris finanszírozásában, különösen a nem elsődleges kutatási területeken. A fókusz az innovatív reaktorkoncepciókra, fejlett üzemanyagokra és a kulcsfontosságú nemzeti laboratóriumi képességek fenntartására helyeződik[World Nuclear News][World Nuclear News].
Savannah River Site: Előrelépés a plutónium-magházak gyártásában
Az amerikai Energiaügyi Minisztérium Savannah River telephelyén megkezdődött a kesztyűs dobozok gyártása a plutónium magházak előállításához. Ezek a kesztyűs dobozok kulcsfontosságúak a Savannah River Plutonium Processing Facility számára, amely a Nemzeti Nukleáris Biztonsági Igazgatóság célkitűzéseit támogatja, hogy a projektet a 2030-as évek elejéig befejezzék. Ez a lépés az amerikai nukleáris fegyverkezési infrastruktúra modernizációjának része[ANS].
Nemzetközi trendek: ellátási lánc és új reaktorprojektek
A nukleáris ellátási lánc a globális növekedésre készül, ahogy azt a World Nuclear Association legutóbbi konferenciáján is hangsúlyozták. Kiemelt nemzetközi fejlemények:
- Gőzturbina-hengerek telepítése Kína Haiyang 3 erőművében.
- Új, négy reaktoros telephely jóváhagyása Indiában, Rádzsasztánban.
- Belgium és Dánia újragondolja a nukleáris kivonulási politikáját.
- Brazília az oroszokkal való SMR-együttműködést vizsgálja.
- Kanada előrelép a szállítható nukleáris erőmű-technológia terén[World Nuclear News].
Érintetti bevonás és a nukleáris energia szerepe a tiszta átmenetben
Az IAEA konferenciasorozata továbbra is hangsúlyozza az érintetti bevonás fontosságát a nukleáris non-proliferáció, biztonság és a közbizalom szempontjából. A panelek foglalkoznak a közvélemény-tájékoztatás tanulságaival, a nukleáris energia ipari dekarbonizációban betöltött szerepével és az újonnan belépő országok nukleáris infrastruktúra-fejlesztési tapasztalataival is[IAEA].
További részletek a következő forrásokon: - World Nuclear News - NucNet - IAEA - ANS
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:51:46
@ 21c71bfa:e28fa0f6
2025-05-29 14:51:46Book *Tirupati to Vellore cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ ef53426a:7e988851
2025-05-29 12:26:43
@ ef53426a:7e988851
2025-05-29 12:26:43Saturday 9AM It’s a chilly Saturday morning in Warsaw, and I don’t want to get out of bed. This is not because of the hangover; it’s because I feel like a failure.
The first day of Bitcoin FilmFest was a whirlwind of workshops, panels and running between stages. The pitch competition did not go my way. Another ‘pitching rabbit’ (an actual experienced film-maker) was selected to win the €3,000 of funding.
Rather than get up and search for coffee, I replay the scenes in my head. What could I have done differently? Will investors ever believe in me: I’m just a writer with no contacts in the industry. Do I have what it takes to produce a film?
Eventually, I haul myself out of bed and walk to Amondo, the festival’s morning HQ (and technically, the smallest cinema in Europe). Upon arrival, I find Bitcoin psychonaut Ioni Appelberg holding court in front of around a dozen enraptured disciples. Soon, the conversation spills out to the street to free up space for more workshops.

I attend a talk on film funding, then pay for coffee using bitcoin. I see familiar faces from the two previous nights. We compare notes on Friday night and check the day’s schedule. The morning clouds burn off, and things feel a little brighter.
The afternoon session begins just a few blocks away in the towering Palace of Culture and Science. My role in today's proceedings is to present my freedom fiction project, 21 Futures, on the community stage. Other presentations range from rap videos and advice on finding jobs in bitcoin to hosting ‘Bitcoin Walks’. This is how we are fixing the culture.
Saturday 8PM I feel a tap on my shoulder. ‘Excuse me, Mr. Philip. Your car is waiting. The Producers’ Dinner is starting soon’.
What? Me, a producer? I’ve been taking part in some panels and talks, but I assumed my benefits as a guest were limited to a comped ticket and generous goodie bag.
Soon, I am sharing a taxi with a Dubai-based journalist, a Colombian director, and the cypherpunk sponsor of the pitch competition I didn’t win.
The pierogies I dreamed of earlier that day somehow manifest (happy endings do exist), and we enjoy a raucous dinner including obligatory slivovitz.

Sunday 2AM The last few hours of blur include a bracing city-bike ride in a crew of nine attendees back to the Palace of Culture, chatting with a fellow bitcoin meetup organiser, and vaguely promising to attend a weekend rave with a crew of Polish artists and musicians on the outskirts of London.
I leave the party while it’s still in full swing. In five hours, I have to wake up to complete my Run for Hal in Marshal Edward Rydz-Śmigły Park.
Thursday 9PM The festival kicks off in Samo Centrum on Pizza Day. I arrive in a taxi straight from a cramped flight (fix the airlines!), having not eaten for around ten hours.
The infectious sounds of softly spoken Aussie bitrocker Roger9000 pound into the damp night. I’m three beers in, being presented by the organisers to attendees like a (very tall) show pony. I try to explain more about my books, my publishing connections, my short film.
When I search for the food I ordered an hour ago, I find it has been given away. The stern-faced Polish pizza maker shrugs. ‘You not here.’
I’m so hungry I could cry (six hours of Ryanair can do that to a man). And then, a heroic Czech pleb donates half a pizza to me. Side note: this same heroic pleb accidentally locked me out of my film-funds while trying to fix a wallet bug on Sunday night.
I step out into the rain. Roger9000 reminds us we should have laser eyes well past 100k. I take a bite of pizza and life tastes good.

The Films Side events, artists, late nights, and pitcher’s regret is all well and good, but what of the films?
My highlights included Golden Rabbit winner No More Inflation — a moving narrative with interviews from two dozen economists, visionaries, and inflation survivors.
Hotel Bitcoin, was a surprisingly funny comedy romp about a group of idiots who happen across a valuable laptop.
Revolución Bitcoin — an approachable and thorough documentary aimed to bring greater adoption in the Spanish-speaking world.
And, as a short-fiction guy, I enjoyed the short films The Man Who Wouldn’t Cry, a visit to New York’s only Somali restaurant in Finding Home.

Sunday 7PM The award ceremony has just finished. I head to Amondo for the final time to pay for mojitos in bitcoin and say goodbye to newly made friends. I feel like I’ve met almost everyone in attendance. Are you going to BTC Prague?!? we ask as we part ways.
Of course, the best thing about any festival is the people, and BFF25 had a cast of characters worthy of any art house flick:
- The bright-eyed and confident frontwoman of the metal band Scardust
- A nostr-native artist selling his intricate canvases to the highest zapper
- A dreadlocked DJ who wears a pair of flying goggles on his head at all times
- An affable British filmmaker explaining the virtues of the word ‘chucklesome’
- A Duracell-powered organiser who seems to know every song, person, film, book, and guest at the festival.
Warsaw itself feels like it has a role to play, too. Birdsong and green parks contrast the foreboding Communist-era architecture. The weather changes faster than my mood — heavy greys transform to bright sunshine. The roads around the venue close on Sunday for a political rally. And there we are in the middle, watching our bitcoin films.

Tuesday 10AM I’m at home now, squinting at my email inbox and piles of washing, wondering when the hell I’ll find time. The festival Telegram group is still buzzing with activity. Side events like martial arts tutorials, trips to a shooting range, boat tours. 5AM photos of street graffiti, lost and found items, and people asking ‘is anyone still around?’
This was not just a film festival. BFF is truly a celebration of culture — Art. Books. Comedy. Music. Video. Talk. Connection.
All this pure signal has lifted my spirits so much that despite me being a newbie filmmaker, armed only with a biro, a couple of powerpoints and a Geyser fund page, I know I will succeed in my mission. It turns out you can just film things.
You may have attended bitcoin conferences before — you know, the ones with ‘fireside chats’, VIP areas, and overpriced merch. Bitcoin FilmFest is a moment in time. We are fixing the culture, year after year, until art can flourish again.
As fellow author Aaron Koenig commented during a panel session, ‘In twenty years, we won’t be drawing laser eyes and singing about honey badgers. Our grandchildren won’t understand the change we went through.’
Would I do it all again? Of course!
Join me next June in Warsaw.
I’ll be the tall one presenting his short animation premiere.
Philip Charter is a full-time writer and part-time cat herder. As well as writing for bitcoin founders and companies, he runs the 21 Futures fiction project.
Find out more about theNoderoid Saga animation projecton Geyser.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:46
@ 39cc53c9:27168656
2025-05-27 09:21:46Bitcoin enthusiasts frequently and correctly remark how much value it adds to Bitcoin not to have a face, a leader, or a central authority behind it. This particularity means there isn't a single person to exert control over, or a single human point of failure who could become corrupt or harmful to the project.
Because of this, it is said that no other coin can be equally valuable as Bitcoin in terms of decentralization and trustworthiness. Bitcoin is unique not just for being first, but also because of how the events behind its inception developed. This implies that, from Bitcoin onwards, any coin created would have been created by someone, consequently having an authority behind it. For this and some other reasons, some people refer to Bitcoin as "The Immaculate Conception".
While other coins may have their own unique features and advantages, they may not be able to replicate Bitcoin's community-driven nature. However, one other cryptocurrency shares a similar story of mystery behind its creation: Monero.
History of Monero
Bytecoin and CryptoNote
In March 2014, a Bitcointalk thread titled "Bytecoin. Secure, private, untraceable since 2012" was initiated by a user under the nickname "DStrange"^1^. DStrange presented Bytecoin (BCN) as a unique cryptocurrency, in operation since July 2012. Unlike Bitcoin, it employed a new algorithm known as CryptoNote.
DStrange apparently stumbled upon the Bytecoin website by chance while mining a dying bitcoin fork, and decided to create a thread on Bitcointalk^1^. This sparked curiosity among some users, who wondered how could Bytecoin remain unnoticed since its alleged launch in 2012 until then^2^.
Some time after, a user brought up the "CryptoNote v2.0" whitepaper for the first time, underlining its innovative features^4^. Authored by the pseudonymous Nicolas van Saberhagen in October 2013, the CryptoNote v2 whitepaper^5^ highlighted the traceability and privacy problems in Bitcoin. Saberhagen argued that these flaws could not be quickly fixed, suggesting it would be more efficient to start a new project rather than trying to patch the original^5^, an statement simmilar to the one from Satoshi Nakamoto^6^.
Checking with Saberhagen's digital signature, the release date of the whitepaper seemed correct, which would mean that Cryptonote (v1) was created in 2012^7^, although there's an important detail: "Signing time is from the clock on the signer's computer" ^9^.
Moreover, the whitepaper v1 contains a footnote link to a Bitcointalk post dated May 5, 2013^10^, making it impossible for the whitepaper to have been signed and released on December 12, 2012.
As the narrative developed, users discovered that a significant 80% portion of Bytecoin had been pre-mined^11^ and blockchain dates seemed to be faked to make it look like it had been operating since 2012, leading to controversy surrounding the project.
The origins of CryptoNote and Bytecoin remain mysterious, leaving suspicions of a possible scam attempt, although the whitepaper had a good amount of work and thought on it.
The fork
In April 2014, the Bitcointalk user
thankful_for_today, who had also participated in the Bytecoin thread^12^, announced plans to launch a Bytecoin fork named Bitmonero^13^.The primary motivation behind this fork was "Because there is a number of technical and marketing issues I wanted to do differently. And also because I like ideas and technology and I want it to succeed"^14^. This time Bitmonero did things different from Bytecoin: there was no premine or instamine, and no portion of the block reward went to development.
However, thankful_for_today proposed controversial changes that the community disagreed with. Johnny Mnemonic relates the events surrounding Bitmonero and thankful_for_today in a Bitcointalk comment^15^:
When thankful_for_today launched BitMonero [...] he ignored everything that was discussed and just did what he wanted. The block reward was considerably steeper than what everyone was expecting. He also moved forward with 1-minute block times despite everyone's concerns about the increase of orphan blocks. He also didn't address the tail emission concern that should've (in my opinion) been in the code at launch time. Basically, he messed everything up. Then, he disappeared.
After disappearing for a while, thankful_for_today returned to find that the community had taken over the project. Johnny Mnemonic continues:
I, and others, started working on new forks that were closer to what everyone else was hoping for. [...] it was decided that the BitMonero project should just be taken over. There were like 9 or 10 interested parties at the time if my memory is correct. We voted on IRC to drop the "bit" from BitMonero and move forward with the project. Thankful_for_today suddenly resurfaced, and wasn't happy to learn the community had assumed control of the coin. He attempted to maintain his own fork (still calling it "BitMonero") for a while, but that quickly fell into obscurity.
The unfolding of these events show us the roots of Monero. Much like Satoshi Nakamoto, the creators behind CryptoNote/Bytecoin and thankful_for_today remain a mystery^17^, having disappeared without a trace. This enigma only adds to Monero's value.
Since community took over development, believing in the project's potential and its ability to be guided in a better direction, Monero was given one of Bitcoin's most important qualities: a leaderless nature. With no single face or entity directing its path, Monero is safe from potential corruption or harm from a "central authority".
The community continued developing Monero until today. Since then, Monero has undergone a lot of technological improvements, migrations and achievements such as RingCT and RandomX. It also has developed its own Community Crowdfundinc System, conferences such as MoneroKon and Monerotopia are taking place every year, and has a very active community around it.
Monero continues to develop with goals of privacy and security first, ease of use and efficiency second. ^16^
This stands as a testament to the power of a dedicated community operating without a central figure of authority. This decentralized approach aligns with the original ethos of cryptocurrency, making Monero a prime example of community-driven innovation. For this, I thank all the people involved in Monero, that lead it to where it is today.
If you find any information that seems incorrect, unclear or any missing important events, please contact me and I will make the necessary changes.
Sources of interest
- https://forum.getmonero.org/20/general-discussion/211/history-of-monero
- https://monero.stackexchange.com/questions/852/what-is-the-origin-of-monero-and-its-relationship-to-bytecoin
- https://en.wikipedia.org/wiki/Monero
- https://bitcointalk.org/index.php?topic=583449.0
- https://bitcointalk.org/index.php?topic=563821.0
- https://bitcointalk.org/index.php?action=profile;u=233561
- https://bitcointalk.org/index.php?topic=512747.0
- https://bitcointalk.org/index.php?topic=740112.0
- https://monero.stackexchange.com/a/1024
- https://inspec2t-project.eu/cryptocurrency-with-a-focus-on-anonymity-these-facts-are-known-about-monero/
- https://medium.com/coin-story/coin-perspective-13-riccardo-spagni-69ef82907bd1
- https://www.getmonero.org/resources/about/
- https://www.wired.com/2017/01/monero-drug-dealers-cryptocurrency-choice-fire/
- https://www.monero.how/why-monero-vs-bitcoin
- https://old.reddit.com/r/Monero/comments/u8e5yr/satoshi_nakamoto_talked_about_privacy_features/
-
 @ 39cc53c9:27168656
2025-05-27 09:21:40
@ 39cc53c9:27168656
2025-05-27 09:21:40“The future is there... staring back at us. Trying to make sense of the fiction we will have become.” — William Gibson.
This month is the 4th anniversary of kycnot.me. Thank you for being here.
Fifteen years ago, Satoshi Nakamoto introduced Bitcoin, a peer-to-peer electronic cash system: a decentralized currency free from government and institutional control. Nakamoto's whitepaper showed a vision for a financial system based on trustless transactions, secured by cryptography. Some time forward and KYC (Know Your Customer), AML (Anti-Money Laundering), and CTF (Counter-Terrorism Financing) regulations started to come into play.
What a paradox: to engage with a system designed for decentralization, privacy, and independence, we are forced to give away our personal details. Using Bitcoin in the economy requires revealing your identity, not just to the party you interact with, but also to third parties who must track and report the interaction. You are forced to give sensitive data to entities you don't, can't, and shouldn't trust. Information can never be kept 100% safe; there's always a risk. Information is power, who knows about you has control over you.
Information asymmetry creates imbalances of power. When entities have detailed knowledge about individuals, they can manipulate, influence, or exploit this information to their advantage. The accumulation of personal data by corporations and governments enables extensive surveillances.
Such practices, moreover, exclude individuals from traditional economic systems if their documentation doesn't meet arbitrary standards, reinforcing a dystopian divide. Small businesses are similarly burdened by the costs of implementing these regulations, hindering free market competition^1:
How will they keep this information safe? Why do they need my identity? Why do they force businesses to enforce such regulations? It's always for your safety, to protect you from the "bad". Your life is perpetually in danger: terrorists, money launderers, villains... so the government steps in to save us.
‟Hush now, baby, baby, don't you cry Mamma's gonna make all of your nightmares come true Mamma's gonna put all of her fears into you Mamma's gonna keep you right here, under her wing She won't let you fly, but she might let you sing Mamma's gonna keep baby cosy and warm” — Mother, Pink Floyd
We must resist any attack on our privacy and freedom. To do this, we must collaborate.
If you have a service, refuse to ask for KYC; find a way. Accept cryptocurrencies like Bitcoin and Monero. Commit to circular economies. Remove the need to go through the FIAT system. People need fiat money to use most services, but we can change that.
If you're a user, donate to and prefer using services that accept such currencies. Encourage your friends to accept cryptocurrencies as well. Boycott FIAT system to the greatest extent you possibly can.
This may sound utopian, but it can be achieved. This movement can't be stopped. Go kick the hornet's nest.
“We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do.” — Eric Hughes, A Cypherpunk's Manifesto
The anniversary
Four years ago, I began exploring ways to use crypto without KYC. I bookmarked a few favorite services and thought sharing them to the world might be useful. That was the first version of kycnot.me — a simple list of about 15 services. Since then, I've added services, rewritten it three times, and improved it to what it is now.
kycnot.me has remained 100% independent and 100% open source^2 all these years. I've received offers to buy the site, all of which I have declined and will continue to decline. It has been DDoS attacked many times, but we made it through. I have also rewritten the whole site almost once per year (three times in four years).
The code and scoring algorithm are open source (contributions are welcome) and I can't arbitrarly change a service's score without adding or removing attributes, making any arbitrary alterations obvious if they were fake. You can even see the score summary for any service's score.
I'm a one-person team, dedicating my free time to this project. I hope to keep doing so for many more years. Again, thank you for being part of this.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:51:23
@ 21c71bfa:e28fa0f6
2025-05-29 14:51:23Book *Tirupati to Tirumala cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:51:04
@ 21c71bfa:e28fa0f6
2025-05-29 14:51:04Book *Bhubaneswar to Konark cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 7e538978:a5987ab6
2025-05-29 10:32:34
@ 7e538978:a5987ab6
2025-05-29 10:32:34This article gives an overview and comparison of the various funding sources that are available for LNbits.
LNbits is compatible with many Lightning Network wallets and can be on anything from a small VPS to a raspberry Pi on your home network or the LNbits SaaS platform.
Why your funding source matters
There are trade-offs between the various funding sources, for example funding LNbits using Strike requires the user to KYC themselves and has some privacy compromises versus funding LNbits from your own LND node. However the technical barrier to entry and node maintenance of using Strike is lower than using LND.
Self-custodial vs custodial connectors
Self-custodial Funding Sources
You run the node or service, keep the keys, and may need to manage LN channels. Good if you want control and have the skills to look after a server. Examples: LND (gRPC/REST), CoreLightning, Spark.
Self-custodial funding sources with an LSP
These funding sources offer a reasonable compromise between self-custody and some privacy trade offs. Examples: Phoenixd, Breez SDK, Boltz.
Custodial (or semi-custodial) funding sources
A third party runs the node. You plug LNbits into their API. Setup is quick and costs are low, but you trust the provider with your funds and privacy. Examples: Alby, OpenNode, Blink, ZBD, LNPay or another LNbits instance.
Funding sources compared
Below is a summary of the main options and how they stack up.
LNbits Lightning Network Funding Sources Comparison Table
| Funding Source | Custodial Type | KYC Required | Technical Knowledge Needed | Node Hosting Required | Privacy Level | Liquidity Management | Ease of Setup | Maintenance Effort | Cost Implications | Scalability | Notes | |----------------------------|--------------------|---------------------|--------------------------------|---------------------------|-------------------|--------------------------|-------------------|------------------------|----------------------------------------------|-----------------|------------------------------------------------------------------| | LND (gRPC) | Self-custodial | ❌ | Higher | ✅ | High | Manual | Moderate | High | Infrastructure cost and channel opening fees | High | gRPC interface for LND; suitable for advanced integrations. | | CoreLightning (CLN) | Self-custodial | ❌ | Higher | ✅ | High | Manual | Moderate | High | Infrastructure cost and channel opening fees | High | Requires setting up and managing your own CLN node. | | Phoenixd | Self-custodial | ❌ | Medium | ❌ | Medium | Automatic | Moderate | Low | Minimal fees | Medium | Mobile wallet backend; suitable for mobile integrations. | | Nostr Wallet Connect (NWC) | Custodial | Depends on provider | Low | ❌ | Variable | Provider-managed | Easy | Low | May incur fees | Medium | Connects via Nostr protocol; depends on provider's policies. | | Boltz | Self-custodial | ❌ | Medium | ❌ | Medium | Provider-managed | Moderate | Moderate | Minimal fees | Medium | Uses submarine swaps; connects to Boltz client. | | LND (REST) | Self-custodial | ❌ | Higher | ✅ | High | Manual | Moderate | High | Infrastructure cost and channel opening fees | High | REST interface for LND; suitable for web integrations. | | CoreLightning REST | Self-custodial | ❌ | Higher | ✅ | High | Manual | Moderate | High | Infrastructure cost and channel opening fees | High | REST interface for CLN; suitable for web integrations. | | LNbits (another instance) | Custodial | Depends on host | Low | ❌ | Variable | Provider-managed | Easy | Low | May incur hosting fees | Medium | Connects to another LNbits instance; depends on host's policies. | | Alby | Custodial | ✅ | Low | ❌ | Low | Provider-managed | Easy | Low | Transaction fees apply | Medium | Browser extension wallet; suitable for web users. | | Breez SDK | Self-custodial | ❌ | Medium | ❌ | High | Automatic | Moderate | Low | Minimal fees | Medium | SDK for integrating Breez wallet functionalities. | | OpenNode | Custodial | ✅ | Low | ❌ | Low | Provider-managed | Easy | Low | Transaction fees apply | Medium | Third-party service; suitable for merchants. | | Blink | Custodial | ✅ | Low | ❌ | Low | Provider-managed | Easy | Low | Transaction fees apply | Medium | Third-party service; focuses on mobile integrations. | | ZBD | Custodial | ✅ | Low | ❌ | Low | Provider-managed | Easy | Low | Transaction fees apply | Medium | Gaming-focused payment platform. | | Spark (CLN) | Self-custodial | ❌ | Higher | ✅ | High | Manual | Moderate | High | Infrastructure cost and channel opening fees | High | Web interface for CLN; requires Spark server setup. | | Cliche Wallet | Self-custodial | ❌ | Medium | ❌ | Medium | Manual | Moderate | Moderate | Minimal fees | Medium | Lightweight wallet; suitable for embedded systems. | | Strike | Custodial | ✅ | Low | ❌ | Low | Provider-managed | Easy | Low | Transaction fees apply | Medium | Third-party service; suitable for quick setups. | | LNPay | Custodial | ✅ | Low | ❌ | Low | Provider-managed | Easy | Low | Transaction fees apply | Medium | Third-party service; suitable for quick setups. |
Which source suits you?
| Scenario | Good fit | Why | | ------------------------------------------- | ---------------------------------------------------------------------- | ------------------------------------------------------ | | Business running its own infrastructure | LND or CoreLightning on a Dell Optiplex or other dedicated machine | Full control, high throughput, best privacy. | | Independent node runner | Spark (CLN) or LND (REST/gRPC) | You already run a node and want a clean web interface. | | Quick proof of concept | Alby, LNPay, or another hosted LNbits | No hardware needed, lets you test ideas fast. |
Run LNbits
Ready to run LNbits?
Choose a funding source, follow the guides, and start today.
Further reading
- LNbits documentation
- LND – gRPC and REST guides
- CoreLightning – setup and Spark info
- Breez SDK
- Phoenixd
- Nostr Wallet Connect
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:50:44
@ 21c71bfa:e28fa0f6
2025-05-29 14:50:44Book *Mcleodganj to Amritsar cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 866e0139:6a9334e5
2025-05-29 07:29:43
@ 866e0139:6a9334e5
2025-05-29 07:29:43Autor: Anna Nagel. (Bild: Lukas Karl). Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie auch in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Wem in seinem Leben Schmerz zugefügt wurde, wer sich ungerecht behandelt fühlt oder wachen Auges in der Welt umschaut, kommt wahrscheinlich irgendwann mit der Frage in Berührung, wie das alles noch einmal «gut» werden kann. Wie kann die Welt sich mit sich selbst versöhnen? Und wie kann ich es selbst schaffen, mich mit ihr und den Menschen, die schlimme Taten vollbringen, wieder in harmonischer Akzeptanz zu verbinden? Kann und will ich gewisse Gräueltaten verzeihen oder gibt es das «Unverzeihliche»? Und selbst wenn ich wollte, wie könnte mir das gelingen?
Perspektivwechsel
Wenn wir an dem Zorn über begangenes Unrecht festhalten, schauen wir in der Regel aus immer derselben Perspektive auf das Geschehen. Mal um Mal erzürnen und empören wir uns darüber, erzählen uns und anderen stets die gleiche Geschichte, die uns allerdings – ebenfalls ein ums andere Mal – wieder selbst verletzt. Das Destruktive holt uns so ständig wieder ein; wir sehen und fühlen das unschuldige Kind und empfinden Verachtung für die Täter.
Die Perspektive zu wechseln lädt uns dazu ein, das Geschehen aus anderen Blickwinkeln zu betrachten und unser Bewusstsein von der schmerzlichen Wiederholung zu lösen. Wir können einmal weit rauszoomen und einen spirituellen Blickwinkel einnehmen, beispielsweise aus Sicht des All-ein-Bewusstseins, das sich in unzählige Seelen teilt, von denen wiederum Milliarden derzeit auf der Erde inkarniert sind. Dieses eine Bewusstsein möchte jede auch nur mögliche Erfahrung machen und durch die Trennung – die Erschaffung der Dualität – kann es sich selbst aus diesen Milliarden Persönlichkeiten heraus erfahren, um zu lernen. Während dieser scheinbaren Trennung vergessen wir, dass wir alle eins sind, dass wir alle aus demselben «Stoff» gemacht sind und nach diesem Spiel hier auf Erden unsere Erinnerung zurückerlangen und unsere Erfahrungen zurück geben in die eine «Quelle».
Unser aller Reise geht letztlich darum, hier auf der Erde aus diesem Zustand des Vergessens zu erwachen. Um dies zu erreichen und all diese Erfahrungen machen zu können und uns auch unter widrigsten Umständen an unsere wahre Essenz, an die Liebe, erinnern können, braucht es auch Akteure, die die Dunkelheit verkörpern – denn nur so haben wir die Wahl, ob wir uns von ihr einnehmen lassen oder uns für die Liebe und das Mitgefühl entscheiden. Der Täter sowie das Opfer sind dabei stets Aspekte unserer selbst – im Innen wie im Außen – und jeder einzelne verändert die Welt, indem er Liebe und Mitgefühl oder Hass und Verachtung wählt.
Eine etwas rationalere Herangehensweise wäre, zu schauen, was dazu führt, dass ein Mensch sich derart unmenschlich verhalten kann; also der Zugang über die Psychologie. Hier werden wir uns bewusst, dass jeder Täter auch einmal ein Kind war. Symbolisch sogar das Kind, mit dem wir jetzt im Beispiel mitfühlen und das wir gleichzeitig heute als erwachsenen Täter verachten. Natürlich kann man hier einwenden, dass nicht jedes Opfer zum Täter wird, aber man kann ebenso anerkennen, dass uns bei dieser Haltung das größte Stück fehlt; und zwar die Geschichte desjenigen, die Jahre dazwischen, sowie jeder einzelne Reiz und jedes Detail der Umstände.
Wie viel Schmerz und Leid muss ein Mensch erfahren, bis er unmenschlich wird? Mit Einbezug aller Umstände und Faktoren, der psychischen Schutzmechanismen traumatischer Erfahrungen sowie fehlender Ausbildung sozialer und empathischer Fähigkeiten auch im neuronalen Bereich kann man auch auf diesem Wege Verständnis erlangen. Sichtbar wird hierdurch auch, dass emotionaler Schmerz über Generationen weitergegeben wird und es schwer ersichtlich ist, wo denn die eigentliche Ursache liegt. Auch hier wird erkennbar, dass nur jeder bei sich anfangen kann und Verantwortung für seine Heilung – und damit gleichzeitig die anderer – übernehmen müsste, anstatt auf die Suche nach dem oder der «Schuldigen» zu gehen.
Was bedarf eigentlich der Vergebung?
Wenn es uns schwerfällt zu vergeben, also Groll und Verachtung loszulassen und Mitgefühl zu empfinden, ist es ebenfalls hilfreich, einmal hinzuschauen, worum es genau geht. Wenn es uns selbst betrifft, handelt es sich in der Regel um Schmerz, der uns willentlich, manchmal auch unbewusst, zugefügt wurde und den wir (noch) nicht loslassen können, weil er noch nicht verheilt ist. Darauf gehe ich später noch einmal ein. Oft geht es aber auch um uns unbekannte Menschen, von deren Verbrechen wir Kenntnis haben und deren Ungeheuerlichkeit uns aus der Fassung bringt. Es geht um Taten, die wir nicht nachvollziehen können, weder rational noch emotional. Wir meinen, selbst wenn jemand nicht spürte, was er anderen antut, so müsse er es doch wenigstens besser wissen. Das ist das, was uns Menschen ausmacht, mit anderen mitzufühlen und sie zu verstehen. Doch anscheinend gibt es Menschen, deren Persönlichkeit oder auch Psyche dazu absolut nicht in der Lage sind. Die keinen moralischen Kompass besitzen und keinerlei soziales Empfinden, denn sonst könnten sie bestimmte Taten nicht ausführen. Möglicherweise dissoziieren sie sich selbst so stark, dass diese für sie eine Normalität darstellen, sie diese entschuldigen beziehungsweise vor sich selbst rechtfertigen oder im extremen Fall keine Erinnerung mehr daran haben.
Uns erscheinen die fehlende Empathie sowie das fehlende Verständnis so fremd, dass wir es nicht nachvollziehen können. Uns fehlt die Nachvollziehbarkeit der Nichtnachvollziehbarkeit des Erlebens des anderen, und wir erachten diesen dadurch als unmenschlich. Denn menschlich wären doch eben diese Fähigkeiten wie Mitgefühl, Güte, Reflexion, Warmherzigkeit, Verständnis und Liebe. Zugleich erzeugen wir hier aber einen Konflikt, wenn wir sagen: «Da diese Menschen sich so unmenschlich verhalten, soll ihnen kein Mitgefühl und keine Vergebung entgegengebracht werden, sollen auch sie nicht menschlich behandelt werden», wodurch wir uns allerdings selbst unserer Menschlichkeit berauben.
«Aber der Täter hatte doch die freie Wahl, er hätte doch anders entscheiden können!» Ja, möglicherweise schon, aber jetzt haben wir die Wahl. Und wir haben viel leichtere Voraussetzungen dafür, menschlich zu handeln, weil wir gesunden Zugang zu unserer Empathie, Moral und unserer Ratio haben.
Hätte der Täter es geschafft, seinen Tätern zu verzeihen, würde er die Destruktivität, die er ab einem gewissen Zeitpunkt nicht mehr in sich tragen oder verdrängen konnte, nicht an anderen ausagieren. Es ist ihm nicht gelungen, vielleicht sogar weil etwas in ihm es für unmöglich hielt, Unmenschliches, das ihm zugefügt wurde, zu verzeihen. Aber uns kann es gelingen, diesen Kreislauf zu durchbrechen und uns nicht in ihn hineinziehen zu lassen; wir können dem «Dunklen» den Nährboden entziehen.
Manchmal nehmen wir an, würden wir das Unbeschreibliche verzeihen, bedeutete dies, dass wir es tolerieren oder gar gutheißen. Dem ist nicht so. Analog dazu habe ich manches Mal die Angst gehabt, würde ich aufhören, um meinen Freund zu trauern, bedeute dies, dass ich ihn nicht mehr vermisse. Auch das ist nicht richtig. Ich heile lediglich das, was mir Schmerzen zufügt, bis am Ende nur noch die Liebe bleibt. Und wenn wir verzeihen, ist es kein Gutheißen der Taten, es bedeutet ein Loslassen dessen, was uns damit verstrickt und das Destruktive nährt.
Mitgefühl beginnt bei uns selbst
«Daß ich dem Hungrigen zu essen gebe, dem vergebe, der mich beleidigt, und meinen Feind liebe- das sind große Tugenden. Was aber, wenn ich nun entdecken sollte, daß der armselige Bettler und der unverschämteste Beleidiger alle in mir selber sind und ich bedürftig bin, Empfänger meiner eigenen Wohltaten zu sein? Daß ich der Feind bin, den ich lieben muß - was dann?» – C. G. Jung
Mit diesem Zitat beginnt Dan Millman das Kapitel «Das Gesetz des Mitgefühls» in seinem Buch «Die universellen Lebensgesetze des friedvollen Kriegers». Die weise Frau lehrt dem Wanderer das Gesetz des Mitgefühls und erklärt, es sei «eine liebevolle Aufforderung, über unsere begrenzte Sichtweise hinauszuwachsen», auch wenn die Last dieser Aufgabe zuweilen sehr schwer wiegen könne. Genau deshalb müsse man daran denken, dass sie bei uns selbst beginnt und wir «geduldig» und «sanft» mit uns, unseren Gefühlen und Gedanken sein sollten.
Um dem – noch skeptischen – Wanderer zu veranschaulichen, wie wir Mitgefühl auch mit unseren Gegnern empfinden können, bat sie ihn, sich an eine Auseinandersetzung zu erinnern, in der er zornig, neidisch oder eifersüchtig war und sich diese Gefühle noch einmal zu vergegenwärtigen. Als er das tat, den Schmerz und die Wut wieder spürte, sagte sie zu ihm: «Und nun stell dir vor, daß der Mensch, mit dem du dich streitest, mitten in eurer erregten Auseinandersetzung plötzlich nach seinem Herzen faßt, einen Schrei ausstößt und zu deinen Füßen tot zu Boden sinkt.» Der Wanderer erschrak und auf Nachfrage der weisen Frau stellte er fest, dass er nun keinerlei Schmerz oder Wut mehr empfand. Sogleich aber kam ihm der Gedanke: «Aber – aber was wäre, wenn ich mich über den Tod dieses Menschen freuen würde? Wenn ich ihm nicht verzeihen könnte?», worauf die weise Frau antwortete: «Dann verzeih dir wenigstens selber deine Unversöhnlichkeit. Und in dieser Vergebung wirst du das Mitgefühl finden, das deinen Schmerz heilt, als Mensch in dieser Welt zu leben.»
Weiter erinnert uns die weise Frau daran, dass wir alle, während wir hier auf der Erde sind, Träume, Hoffnungen und Enttäuschungen haben; und dass diese, sowie letztlich der Tod, uns alle verbinden.
Es ist ein Prozess
Dan Millman sagt hier in Gestalt der Weisen Frau, dass Mitgefühl bei uns selbst beginnt und diesen Aspekt möchte ich noch einmal hervorheben. Es kann nämlich passieren, dass wir uns in einer oberflächlichen Vergebung wieder finden, weil wir meinen, es sei richtig und moralisch, anderen zu verzeihen, ohne aber die tieferen Schichten dabei zu fühlen. Das ist dann leider nichts anderes, als Verdrängung. Gerade wenn wir selbst Opfer von Ungerechtigkeit, physischer oder mentaler Gewalt wurden, ist es unerlässlich den Heilungsweg in Gänze zu durchschreiten, und in den Wachstumsprozess zu verwandeln, der uns Mitgefühl und Weisheit lehrt. Und dazu gehören die Wut auf das Begangene, die Verzweiflung, die Ungerechtigkeit und Ohnmacht zu fühlen, uns auf «unsere Seite» zu stellen und Partei für uns selbst zu ergreifen, bevor es ernstlich möglich wird, zu verzeihen. Zunächst fühlen wir mit uns selbst den Schmerz und befreien die Gefühle, die wir uns möglicherweise nie trauten zu fühlen, all die Wut und den Groll. Erst später kann dann aus dem Inneren heraus das weitere Erkennen stattfinden und Heilung und Vergebung geschehen.
Vergebung findet im Herzen statt
Die hier in diesem Text von mir aufgeführten Perspektiven sind nur zwei, drei kleine Beispiele für Sichtweisen, die man einnehmen könnte, um zu neuen Einsichten zu gelangen. Sie sollen niemanden von irgendetwas überzeugen, sondern als Anregung dienen. Denn letztlich geht es darum, Vergebung in sich selbst zu finden. Vergebung ist also etwas, das aus dem Inneren heraus entsteht; ein Ergebnis eines tiefen Verständnisses und Fühlens, ja eines Erkennens. Auf dieser Reise gehen wir unterschiedliche Blickwinkel und Versionen ab, bis wir im Herzen ankommen, es sich öffnet und wir plötzlich «klar» sehen. Daraufhin breitet sich Wärme im Körper aus, Liebe durchströmt uns, begleitet möglicherweise von einem Gefühl leiser Euphorie, möglicherweise auch einem leichten Schmerz und Tränen – sowohl ein paar der Traurigkeit als auch welchen der Dankbarkeit. Das Loslassen und die Befreiung sind spürbar und nur für jeden persönlich erfahrbar, der sich auf diesen Weg begibt und seine individuelle Ansicht findet, die ihn befreit und erlöst.
Meiner Meinung nach bedeutet also Vergebung eine Öffnung des Herzens, ein Erkennen und ein Hineinwachsen in die Perspektive der Liebe. Sie ist nicht auf rationaler Ebene zu finden; die rationale Ebene kann nur dabei helfen, den Weg zum Mitgefühl zu beschreiten, denn:
«Man sieht nur mit dem Herzen gut. Das Wesentliche ist für die Augen unsichtbar.»
– Antoine de Saint-Exupéry
Anna Nagel veröffentlicht auf ihrem Blog „Heimwärts“ seit Jahren zu den Themen Heilung, Bewusstsein, kollektives Erwachen, Gefühle, Spiritualität, Psyche, Kundalini und Philosophie.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:50:23
@ 21c71bfa:e28fa0f6
2025-05-29 14:50:23Book *Manali to Amritsar cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 502ab02a:a2860397
2025-05-29 01:40:28
@ 502ab02a:a2860397
2025-05-29 01:40:28เรามาดู แลคเชอร์ประวัติศาสตร์ ที่พลิกโลกแห่งการเกษตรและอาหารของมนุษย์ชาติกันครับ เรามาดูความแยบยลที่สามารถจูงใจคนมากมายให้เห็นถึงข้อดีของเนื้อจากแลบ เขาทำได้ยังไง เรามาศึกษาการสื่อสารกันครับ
เรื่องมันเริ่มจากการประชุม World Economic Forum ปี 2015 ที่ศาสตราจารย์ Mark Post นักเภสัชวิทยาชาวดัตช์ ที่เรารู้จักกันไปแล้ว ซึ่งตอนนั้นเป็นศาสตราจารย์ด้านสรีรวิทยาของหลอดเลือดอยู่ที่ Maastricht University และเป็นผู้ร่วมก่อตั้งบริษัท Mosa Meat ได้ลุกขึ้นมาเล่าเรื่อง "เนื้อเพาะเลี้ยง" หรือ cultured meat ให้คนทั้งห้องฟัง
สิ่งที่เขาพูดมันไม่ใช่แค่นวัตกรรมใหม่ แต่คือคำเตือนที่จริงจัง ว่าถ้ามนุษย์ยังผลิตเนื้อสัตว์แบบเดิม เรากำลังวิ่งเข้าใกล้ปัญหาใหญ่ที่รออยู่ข้างหน้า
ศาสตราจารย์ Post เล่าไว้ได้น่าสนใจมาก เขาบอกว่าแค่จะได้แฮมเบอร์เกอร์ 1 ชิ้นขนาดหนึ่งในสี่ปอนด์ เราต้องใช้เมล็ดธัญพืช 7 ปอนด์ ใช้น้ำจืด 50 แกลลอน และพื้นที่ดินอีก 70 ตารางฟุต นั่นแปลว่าเรากำลังเปลี่ยนของดีในธรรมชาติ ข้าว น้ำ ดิน ไปเป็นของที่กินหมดใน 10 นาที แล้วหิวใหม่ได้ในอีกครึ่งชั่วโมง
เหตุผลก็เพราะวัวมันไม่ได้แปลงโปรตีนพืชมาเป็นเนื้อได้มีประสิทธิภาพนัก พูดอีกแบบคือ มันเปลืองเกินไป
ตอนนี้พื้นที่เพาะปลูกของโลกกว่า 70% ถูกใช้ไปในการผลิตเนื้อสัตว์ คิดดูสิว่าถ้าเราหาทางที่ดีกว่านี้ได้ เราจะมีพื้นที่ว่างกลับคืนมาแค่ไหน
แถมวัวไม่ใช่แค่กินเก่งนะ ยังปล่อยก๊าซเก่งด้วย โดยเฉพาะมีเทนที่ทำให้โลกร้อนพอๆ กับอุตสาหกรรมการขนส่งเลยทีเดียว ศาสตราจารย์ Post เล่าว่า ทุกครั้งที่เขาเห็นวัวยืนเคี้ยวหญ้า เขาไม่ได้เห็นแค่วัว...แต่เห็นเมฆก๊าซมีเทนลอยมาด้วย
และที่น่าคิดคือ เมื่อรายได้ของคนในอินเดียหรือจีนสูงขึ้น พวกเขาจะกินเนื้อเพิ่มตามรายได้ ซึ่งสถิติบอกว่าภายในปี 2050 ความต้องการเนื้อสัตว์จะเพิ่มขึ้นเป็น สองเท่า จากปัจจุบัน
แต่ศาสตราจารย์ก็ไม่ได้มองว่าเนื้อเป็นปีศาจ เขาบอกว่า มนุษย์ถูกสร้างมาให้รักเนื้อ เนื้อคือสิ่งที่มาพร้อมวิวัฒนาการ เราได้พลังงานจากมัน สมองเราใหญ่ขึ้นเพราะมัน และกลายเป็นมนุษย์เพราะมัน
แม้จะมีคนอีกกว่าสองพันล้านที่เป็นมังสวิรัติ ส่วนใหญ่อาจเพราะไม่มีทางเลือก แต่อย่างน้อยพวกเขาก็อยู่รอดได้ แต่ก็ปฏิเสธไม่ได้ว่า คนที่เคยล่า เคยกินเนื้อ จะรู้สึกตื่นเต้นทุกครั้งที่ได้แบ่งเนื้อกันบนโต๊ะ
ศาสตราจารย์ Post เองก็ยังชอบกินเนื้อ แต่เขาอยากได้เนื้อที่ได้มาจากทางเลือกที่ดีกว่า ไม่ใช่ทางที่พาโลกเข้า ICU
เนื้อเพาะเลี้ยงเริ่มจากหลักการง่ายๆ ที่เรารู้มาตั้งแต่ช่วงปี 2000 ว่า ในกล้ามเนื้อของสัตว์มี สเต็มเซลล์ รอคอยจะซ่อมแซมเนื้อเยื่อหากมันได้รับบาดเจ็บ
แค่เอาชิ้นกล้ามเนื้อเล็กๆ จากวัว ขนาดแค่ 1 ซม. x 1 มม. มาแยกสเต็มเซลล์ออกมาเลี้ยงให้ขยายตัว
เฮียว่าอันนี้น่าทึ่งมาก เพราะจากตัวอย่างเล็กๆ ชิ้นเดียว สามารถผลิตเนื้อวัวได้ถึง 10,000 กิโลกรัม เลยนะ!
แปลว่าเราสามารถลดจำนวนวัวทั้งโลกจากครึ่งพันล้านตัว เหลือแค่ประมาณ 30,000 ตัวได้เลย
และถ้าให้เซลล์กล้ามเนื้อพวกนี้อยู่ในสภาพแวดล้อมที่เหมาะสม มันก็จะเริ่มสร้างกล้ามเนื้อขึ้นมาเอง โดยเฉพาะถ้าเรากระตุ้นให้มันรู้สึกเหมือนกำลัง “ออกกำลัง” อยู่ เช่น ใส่แรงตึงเข้าไป
ทีมนักวิจัยของเขาเลี้ยงเซลล์เหล่านี้ให้เติบโตในรูปวงแหวนคล้ายโดนัท ครบ 3 สัปดาห์ กล้ามเนื้อจะเริ่มหดตัว สร้างความตึง และกลายเป็นเนื้อกล้ามเนื้อแบบเต็มตัวที่ดูไม่ต่างจากกล้ามเนื้อในสเต็กจริงๆ เลย
ปี 2013 ทีมของ Mark Post ผลิตเส้นใยกล้ามเนื้อจำนวน 10,000 เส้น เอามาทำแฮมเบอร์เกอร์ และนำไปเปิดตัวในงานแถลงข่าวที่ลอนดอน เป็นเหมือนการโชว์ทำอาหารผสมกับเปิดงานวิจัย
จุดประสงค์คือจะพิสูจน์ให้โลกเห็นว่า “เฮ้ย! สิ่งนี้ไม่ใช่แค่ไอเดียลอยๆ แต่มันทำได้จริง และจำเป็นต้องทำจริงๆ เพราะเรากำลังจะเจอวิกฤต”
ราคาแฮมเบอร์เกอร์ตอนนั้นคือ 250,000 ยูโร
มีเชฟผู้กล้าปรุง และอาสาสมัครสองคนลองชิม พวกเขาบอกว่า “ก็โอเคในฐานะเบอร์เกอร์ราคาเท่านี้ แต่ก็อยากได้รสเข้มกว่านี้หน่อย” เพราะยังไม่มีไขมัน เลยรสจืดไปหน่อย
แต่ที่สำคัญคือ พวกเขายืนยันว่า “มันคือเนื้อจริงๆ” ทั้งเนื้อสัมผัสและโครงสร้าง
แค่มีต้นแบบยังไม่พอ เพราะจะทำให้ขายได้จริง ต้องผ่านด่านสำคัญ เนื้อต้องผลิตได้โดยใช้ทรัพยากรน้อยกว่าการเลี้ยงวัวจริง การประเมินเบื้องต้นจาก University of Oxford พบว่า เนื้อเพาะเลี้ยงใช้พื้นที่น้อยลง 90% น้ำลดลง 90% พลังงานลดลง 60–70%
ทุกอย่างที่ใช้ในการเลี้ยงเซลล์ต้องมีจำนวนมากพอหรือหมุนเวียนใช้ได้ ที่น่าหนักใจคือ การเลี้ยงเซลล์ต้องใช้ “ซีรั่มจากลูกวัว” ซึ่งได้มาจากเลือดวัว ถ้าลดจำนวนวัว เราก็ไม่มีซีรั่ม แต่ตอนนี้มีงานพัฒนาไปเยอะแล้ว กำลังหาวิธีทำเซลล์กล้ามเนื้อโดยไม่ต้องพึ่งซีรั่มจากสัตว์
ไม่ใช่แค่โปรตีน แต่ต้องเป็น "เนื้อ" ในทุกความรู้สึก นักวิจัยพยายามปรับสภาพแวดล้อมการเพาะเลี้ยง เช่น ความเข้มข้นของออกซิเจน เพื่อให้เซลล์แสดงโปรตีนสำคัญ เช่น myoglobin ที่ทำให้เนื้อมีสีและรสชาติเหมือนเนื้อจริง
การยอมรับของผู้บริโภคเป็นอีกด่านสำคัญที่เนื้อเพาะเลี้ยงต้องข้ามผ่านให้ได้ ไม่ใช่แค่เรื่องรสชาติหรือคุณค่าทางโภชนาการเท่านั้น แต่ยังเป็นเรื่องของ "ใจ" ที่ต้องเปิดรับสิ่งใหม่ที่ไม่คุ้นเคย ศาสตราจารย์ Post เล่าว่า ในการสำรวจผู้บริโภคในอังกฤษและเนเธอร์แลนด์ พบว่ามีคนไม่น้อยที่ยินดีจะลองกินเนื้อเพาะเลี้ยง ถึง 52% ของชาวดัตช์ และ 60% ของชาวอังกฤษเลยทีเดียว
เขาเปรียบเทียบว่า จริงๆ แล้ว คนเรายอมกินฮอทดอกโดยไม่รู้ด้วยซ้ำว่าทำมาจากอะไร หรือผ่านอะไรมาบ้าง ขอแค่มัน "อร่อย ถูก และดูปลอดภัย" ก็เพียงพอแล้วสำหรับคนส่วนใหญ่ ดังนั้นเนื้อเพาะเลี้ยงจึงไม่ต่างกันมากนัก ขอเพียงให้คนรู้สึกว่า “กินแล้วไม่ตาย” และ “ไม่ได้แปลกจนใจฝ่อ” เท่านั้นแหละ วันหนึ่งมันก็จะกลายเป็นของธรรมดาในตู้เย็นเหมือนกับโยเกิร์ตหรือไส้กรอกนั่นเอง
ในด้านของราคา แม้จะยังไม่ถูกเท่าไส้กรอกในซูเปอร์ แต่ก็ลดลงมาไกลจากจุดเริ่มต้นแบบสุดๆ จากชิ้นต้นแบบราคา 250,000 ดอลลาร์ในปี 2013 ตอนนี้ต้นทุนลดลงมาเหลือประมาณ 65 ดอลลาร์ต่อกิโลกรัม (ยังไม่รวมเทคโนโลยีล้ำหน้าอื่นๆ ที่กำลังพัฒนาอยู่) ซึ่งก็ถือว่าอยู่ในระดับเดียวกับเนื้อวากิวหรือสเต๊กเกรดพรีเมียมเลยทีเดียว เป้าหมายคือทำให้ถูกลงอีก และผลิตได้ในระดับอุตสาหกรรมให้เพียงพอกับคนทั้งโลก ไม่ใช่ของฟุ่มเฟือยสำหรับคนรวยเท่านั้น
แต่วิสัยทัศน์ที่น่าสนใจจริงๆ คือ ภาพของอนาคตที่ศาสตราจารย์ Post วาดไว้ เขาเชื่อว่าเทคโนโลยีนี้เรียบง่ายพอที่จะขยายไปสู่ครัวเรือนหรือชุมชนเล็กๆ ได้ วันหนึ่งเราอาจได้เห็นการเพาะเลี้ยงเซลล์จากหมูที่เลี้ยงอยู่ข้างบ้าน แล้วเอาไปปั่นเป็นหมูสับแบบสดใหม่ ไม่ต้องฆ่าสัตว์ ไม่ต้องส่งโรงงาน ไม่ต้องตัดต่อพันธุกรรม แค่นั่งรอเหมือนหมักแป้งเปรี้ยว แล้วได้เนื้อสดๆ มาใส่ต้มจืด
และนั่นแหละคือ "การเปลี่ยนกรอบคิดเรื่องเนื้อสัตว์" แบบพลิกฝ่ามือ
มันจะไม่ใช่เรื่องการฆ่าอีกต่อไป ไม่ใช่เรื่องของฟาร์มกลิ่นฉี่ หรือสายพานโรงฆ่าสัตว์ มันจะเป็น "ผลิตภัณฑ์ใหม่" ที่เราสร้างได้ ควบคุมได้ และปรับแต่งได้ เช่น เพิ่มโอเมก้า 3 ในเซลล์ไขมันให้สูงขึ้น หรือทำให้เนื้อไม่มีคอเลสเตอรอลเลยก็ยังได้
แม้ศาสตราจารย์ Post จะเน้นเรื่องความมั่นคงทางอาหารและผลกระทบต่อสิ่งแวดล้อมเป็นหลัก แต่เขาก็ยอมรับว่า สำหรับคนกินทั่วๆ ไป ประเด็นที่ "ไม่มีสัตว์ต้องเจ็บปวด" จะกลายเป็นจุดขายที่สำคัญในใจของผู้บริโภค
เขาเชื่อว่า เมื่อวันนั้นมาถึง วันที่เรายืนอยู่หน้าตู้แช่ในซูเปอร์ แล้วเห็นผลิตภัณฑ์สองชิ้นวางข้างกัน — หนึ่งคือเนื้อวัวที่มาจากฟาร์ม และอีกหนึ่งคือเนื้อเพาะเลี้ยงที่ไม่เคยมีวัวต้องร้องไห้แม้แต่นิดเดียว — การตัดสินใจอาจจะไม่ง่าย แต่ "จะมีคนจำนวนมากขึ้นเรื่อยๆ ที่เลือกแบบไม่ต้องฆ่า"
เพราะสุดท้าย เราไม่ได้แค่กินเนื้อ… เรากำลังกิน “ความเชื่อ” ลงไปด้วย #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
ใครสนใจดูคลิปก็กดตรงนี้ได้ครับ https://youtu.be/1lI9AwxKfTY?si=6CDBUl2yGBoHWc-P
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:50:05
@ 21c71bfa:e28fa0f6
2025-05-29 14:50:05Book *Amritsar to Phagwara cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ a396e36e:ec991f1c
2025-05-28 22:27:45
@ a396e36e:ec991f1c
2025-05-28 22:27:45👤 Generation X and Bitcoin: Between Invisibility, Structural Disillusionment, and Defiance
Generation X, born between 1965 and 1980, has been largely sidelined in generational discourse. Unlike the baby boomers —symbols of stability and prosperity— or millennials and Gen Z —constant fixtures in the media and cultural spotlight— Gen X remains the least mentioned, the least studied, and often not even recognized by its own members as a distinct generation.
Today, they are in midlife —a period that, according to the U-shaped curve of happiness, is one of the most emotionally and psychologically difficult stages: deteriorating health, professional stagnation, and the dual burden of caring for both parents and children. But their condition is not just a matter of age —it’s the product of a unique convergence of economic and political failure.
Structurally, Generation X reached its crucial phase of financial consolidation during the global economic crisis of 2008 —a moment that froze wage growth and severely limited access to housing, investment opportunities, and savings. In parallel, they faced increasing labor precarization: unstable contracts, outsourcing, erosion of social protections, and the dismantling of job security. Compared to other generations, their economic mobility was minimal. Even in terms of wealth accumulation and home ownership, many Gen Xers show weaker indicators than early-born millennials at the same life stage.
At the same time, many countries —especially in Latin America and parts of Europe— turned toward alternative models to free-market systems: socialist proposals that promised redistribution, justice, and equality. But in practice, these models led to state dependency, excessive intervention, economic rigidity, and a loss of productive dynamism. The outcome was devastating: rising poverty, institutional decay, inflation, plummeting investment, growing corruption, and a widespread collapse of trust.
For a generation raised on values of effort, autonomy, and social mobility, this ideological shift brought a double betrayal —first from liberalism, which failed to deliver on its promises, and then from socialism, which entrenched poverty, dependency, and dysfunction.
And yet, while younger generations increasingly embrace state-centric proposals like universal basic income, subsidies, or nationalizations as progressive solutions, many in Gen X see these not as innovation, but as déjà vu —a recycling of failed models they’ve already lived and paid for.
It’s at this point that Bitcoin emerges as more than just a financial technology. For many Gen Xers, Bitcoin is both a symbolic and concrete response — a refuge from a system that betrayed them. It’s not just about investment. It’s about individual sovereignty. They call it “fuck you money” because it represents a total break from traditional structures: it doesn’t depend on banks, governments, political parties, or promises that never materialize.
Bitcoin is money without permission, without censorship, without planned devaluation. It’s a tool for radical autonomy. For a generation marked by skepticism, self-reliance, and disillusionment, it stands as a quiet but powerful form of resistance — a way of saying: “I don’t depend on you. I don’t believe you. I don’t need you.”
Today, while others debate new statist models or more market reforms, many Gen Xers are simply opting out. Bitcoin isn’t just an economic choice — it’s a stance. A way to reclaim the individual control the system once denied them.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:49:42
@ 21c71bfa:e28fa0f6
2025-05-29 14:49:42Book *Chandigarh to Amritsar cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:49:20
@ 21c71bfa:e28fa0f6
2025-05-29 14:49:20Book *Amritsar to Pathankot cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:49:01
@ 21c71bfa:e28fa0f6
2025-05-29 14:49:01Book *Amritsar to Manali cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 47259076:570c98c4
2025-05-28 21:18:27
@ 47259076:570c98c4
2025-05-28 21:18:27{"title":"Imposto sobre importação de 60%","description":"Comprei um livro, custou 60 dollares mais o frete e impostos de 30 dolares, totalizando 100 dolares.\n\nChegando o livro no Brasil, eu tive que pagar 456 reais pro livro poder chegar aqui em casa.\n\nSó o imposto de importação foi de 283 e mais o imposto de \"circulação\" de 154 e mais outros.","category":"tax","country":"Brazil","year":"2025","source":""}
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:48:43
@ 21c71bfa:e28fa0f6
2025-05-29 14:48:43Book *Amritsar to Katra cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:48:21
@ 21c71bfa:e28fa0f6
2025-05-29 14:48:21Book *Amritsar to Kapurthala cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 489a61cb:b0d265a6
2025-05-28 21:12:42
@ 489a61cb:b0d265a6
2025-05-28 21:12:42{"pattern":{"kick":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"snare":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"hihat":[false,false,true,false,true,false,false,false,false,false,false,false,false,false,false,false],"openhat":[true,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"crash":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"ride":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"tom1":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"tom2":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false]},"bpm":120,"swing":0,"timeSignature":"4/4","drumKit":"standard","timestamp":1748466762567}
-
 @ cae03c48:2a7d6671
2025-05-28 21:00:33
@ cae03c48:2a7d6671
2025-05-28 21:00:33Bitcoin Magazine

Block Announces Bitcoin Business Stack, Makes Historic Lightning Payments Push at Bitcoin 2025Bitcoin isn’t just something to hold anymore—it’s something to live on. That was the core message delivered by Miles Suter, Bitcoin Product Lead at Block Inc., during his keynote at the Bitcoin 2025 Conference today. Standing at the intersection of innovation and ideology, Suter laid out a vision where Bitcoin isn’t just a store of value—but the internet’s native currency.
“Bitcoin is at a crossroads—on one hand it’s never been stronger: a trillion in market cap, millions of holders, and even talk of nation-state adoption,” Suter said. “We use Bitcoin to hold, to hedge, to opt out, but we rarely use it to live. At Block Inc., we believe that has to change.”
Suter officially announced that Block is rolling out Bitcoin payment capability for merchants using Square POS, allowing them to accept bitcoin directly in-store. The move comes as part of a broader initiative Block calls the full bitcoin for business stack—covering acquiring, managing, reporting, accounting, converting, lending, and taxes.

“This is what makes Bitcoin an everyday currency for everyone,” he emphasized. “We believe hard-working entrepreneurs deserve access to the full power of bitcoin.”
To prove the vision in action, Block helped power a Guinness World Record attempt for the most Lightning payments in a day, hosted live at the conference. The goal: prove that Lightning payments aren’t just functional—they’re scalable, fast, and real.
Block’s commitment isn’t new. In 2020, the company put bitcoin on its balance sheet. In 2021, it co-founded the Bitcoin Clean Energy Initiative to fight the “boiling oceans” narrative. In 2022, Cash App became one of the first major platforms on Lightning. In 2023, it launched on-chain payments with Square. And in 2024, it helped defeat Craig Wright in court, “standing up for Satoshi.”
“These aren’t just headlines—they’re a pattern,” Suter said. “We’ve made it more accessible, more secure. Now we’re focused on making it usable every day.”
Cash App already ranks among the top bitcoin on-ramps in the U.S., accounting for nearly 10% of on-chain block space at any time. In 2024, Lightning usage grew 7x. “Block runs one of the top Lightning nodes globally. And here’s what’s wild—it’s working,” he said.
Block is now taking 10% of all profits from Bitcoin and adding it back to its balance sheet, and over 1,700 merchants are automatically converting part of their daily sales to Bitcoin.
“If Bitcoin just becomes digital gold, we failed the mission,” Suter said. “Bitcoin payments validate Bitcoin. They make it real. Bitcoin is money.”
This post Block Announces Bitcoin Business Stack, Makes Historic Lightning Payments Push at Bitcoin 2025 first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:47:56
@ 21c71bfa:e28fa0f6
2025-05-29 14:47:56Book *Amritsar to Delhi cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 489a61cb:b0d265a6
2025-05-28 20:15:18
@ 489a61cb:b0d265a6
2025-05-28 20:15:18{"pattern":{"kick":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"snare":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"hihat":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"openhat":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"crash":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"ride":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"tom1":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"tom2":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false]},"bpm":120,"swing":0,"timeSignature":"4/4","drumKit":"standard","timestamp":1748463318614}
-
 @ c1e6505c:02b3157e
2025-05-28 17:36:03
@ c1e6505c:02b3157e
2025-05-28 17:36:03I recently acquired a new lens:
1959 Leica Summaron F2.8 35mm LTM.
1959 Leica Summaron 35mm f2.8 LTM mounted on my Fujifilm Xpro2 with LTM adapter made by Urth.
Technically, it was a trade. I helped a fellow Bitcoiner set up their Sparrow Wallet, Nostr stuff, and troubleshoot a few wallet issues, and in return, they gave me the lens.
It all started at a local Bitcoin meetup I went to about a week ago - my second time attending. I recognized a few faces from last time, but also saw some new ones. These meetups are refreshing - it’s rare to speak a common language about something like Bitcoin or Nostr. Most people still don’t get it. But they will.
Technology moves forward. Networks grow. Old cells die off.
During the meetup, someone noticed I had my Leica M262 with me and struck up a conversation. Said they had some old Leica lenses and gear at home, and wanted to show me.
Bitcoin and photography in one conversation? I’m down.
A day or so later, they sent me a photo of one of the lenses: a vintage Summaron LTM 35mm f/2.8 from 1959. I’d never seen or heard of one before. They asked if I could help them set up Sparrow and a Bitcoin node. In exchange, they’d give me the lens. Sounded like a good deal to me. Helping plebs with their setups feels like a duty anyway. I said, of course.
They invited me over - a pretty trusting move, which I appreciated. They had some great Bitcoin memorabilia: Fred Krueger’s The Big Bitcoin Book (even if the guy’s turned full shitcoiner), and some FTX sunglasses from Bitcoin 2022. Probably future collector’s items, lol.




We headed upstairs to work on setting up Sparrow Wallet on their Windows machine. I verified the software download first (which you should always do), then helped them create a new wallet using their Ledger Flex. They also had an older Ledger Nano X. The Flex setup was easy, but the Nano X gave us trouble. It turns out Ledger allows multiple wallets for the same asset, which can show up differently depending on how they’re configured. In Sparrow, only one wallet showed—none of the others.
I believe it had to do with the derivation path from the Ledger. If anyone knows a fix, let me know.
After a few hours of troubleshooting, I told them I couldn’t really recommend Ledger. The UX is a mess. They’d already heard similar things from other plebs too.
I suggested switching to the Blockstream Jade. It’s a solid Bitcoin-only device from a trustworthy team. That’s what you want in a hardware wallet.
But back to the lens…
Since it’s an LTM (Leica Thread Mount), I couldn’t mount it directly on my M262. Luckily, I remembered I had an Urth adapter that fits my Fujifilm X-Pro2. I don’t use the X-Pro2 much these days—it’s mostly been sidelined by the M262 - but this was the perfect excuse to bring it out again.
To test the lens, I shot everything wide open at f/2.8. Nothing crazy fast, but it’s the best way to see a lens’s character. And this one definitely has character. There’s a subtle softness and a kind of motion blur effect around the edges when wide open. At first, I wasn’t sure how I felt about it, but the more I shot, the more I liked it. It reminds me of Winogrand’s work in Winogrand Color - those messy, shifting edges that make the frame feel alive. It also helps soften the digital-ness of the camera sensor.
The focus throw is short and snappy - much tighter than my Summicron V3 35mm f/2. I really like how fast it is to use. The closest focusing distance is about 3.5 feet, so it’s not ideal for close-ups. And with the Urth adapter on the X-Pro2, the focal length ends up closer to 40mm.
The only thing that threw me off was the infinity lock. When the focus hits infinity, it physically locks - you have to press a small tab to unlock it. I’ve seen others complain about it, so I guess it’s just one of those old lens quirks. I’m getting used to it.
All the photos here were taken around where I live in South Carolina. Some during bike rides to the river for a swim, others while walking through the marshlands.
I try to make work wherever I am. You should be able to.
It’s about the light, the rhythm, the play - and having the motivation to actually go out and shoot.
Lens rating: 7.9/10
I mainly shoot with a Leica M262, and edit in Lightroom + Dehancer
Use “PictureRoom” for 10% off Dehancer Film
If you’ve made it this far, thank you for taking the time to view my work - consider becoming a paid subscriber.
Also, please contact me if you would like to purchase any of my prints.
Follow me on Nostr:
npub1c8n9qhqzm2x3kzjm84kmdcvm96ezmn257r5xxphv3gsnjq4nz4lqelne96
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:47:33
@ 21c71bfa:e28fa0f6
2025-05-29 14:47:33Book *Amritsar to Chandigarh cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:47:08
@ 21c71bfa:e28fa0f6
2025-05-29 14:47:08Book *Cuttack to Puri cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ e5141cbc:99d909a7
2025-05-28 17:34:57
@ e5141cbc:99d909a7
2025-05-28 17:34:57{"pattern":{"kick":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"snare":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"hihat":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"openhat":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"crash":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"ride":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"tom1":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"tom2":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false]},"bpm":120,"swing":0,"timeSignature":"4/4","drumKit":"standard","timestamp":1748453697643}
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:46:31
@ 21c71bfa:e28fa0f6
2025-05-29 14:46:31Book *Puri to Konark cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ da8b7de1:c0164aee
2025-05-28 15:42:22
@ da8b7de1:c0164aee
2025-05-28 15:42:22Nemzetközi nukleáris energetikai hírek
Új amerikai kis moduláris reaktor engedélykérelem
A Tennessee Valley Authority (TVA) benyújtotta az Egyesült Államok Nukleáris Szabályozó Hatóságához (NRC) az engedélykérelmet egy GE Vernova Hitachi Nuclear Energy BWRX-300 kis moduláris reaktor (SMR) megépítésére a Clinch River telephelyen. Ez jelentős lépés az új, fejlett nukleáris technológiák bevezetésében az Egyesült Államokban, és jól mutatja, hogy az SMR-ek egyre fontosabb, rugalmas és skálázható tisztaenergia-megoldássá válnak[world-nuclear-news.org].
Amerikai elnöki rendeletek a nukleáris bővítés felgyorsítására
Donald Trump amerikai elnök négy elnöki rendeletet írt alá, amelyek célja a reaktorengedélyezési folyamatok gyorsítása, a hazai urántermelés növelése és a fejlett nukleáris technológiák bevezetésének felgyorsítása. Az új irányelvek ambiciózus célokat tűznek ki, például az amerikai nukleáris kapacitás megnégyszerezését 2050-re, az NRC számára az engedélyezési idő 18 hónapra csökkentését, valamint szövetségi területek kijelölését új nukleáris létesítmények számára. Ezeket a rendeleteket az „amerikai nukleáris reneszánsz” alapjának szánják, különös hangsúlyt fektetve az AI-ipar energiaigényeinek kielégítésére és a hazai gyártás újjáélesztésére[nucnet.org].
Iparági optimizmus és globális befektetési trendek
Az iparági vezetők egészséges és optimista kilátásokról számolnak be a nukleáris energia terén, kiemelve olyan aktív projekteket, mint a TerraPower Wyomingban, az X-energy és a Dow együttműködése, valamint a Westinghouse tevékenysége Lengyelországban. Különösen nagy az érdeklődés a magánbefektetések iránt a magas dúsítású, alacsony dúsítású urán (HALEU) előállítása terén, illetve annak lehetősége iránt, hogy a Világbank elkezdjen nukleáris projekteket finanszírozni, ami szélesebb körű nemzetközi befektetéseket is elindíthat[ans.org].
Nemzetközi fejlemények és ellátási lánc felkészültsége
Számos ország halad előre a nukleáris fejlesztésekkel: - Kína tíz új reaktort hagyott jóvá. - India szabályozó hatósága engedélyezte egy új, négyblokkos telephely létesítését Rádzsasztánban. - Belgium konzultációt indított egy innovatív, ólom-hűtésű kis moduláris reaktor terveiről. - Brazília várhatóan Oroszországgal közösen fejleszt SMR-projektet. - Csehország új nukleáris szerződéseket köt, a külső politikai nyomás ellenére is.
A globális nukleáris ellátási láncot arra ösztönzik, hogy készüljön fel a gyors növekedésre, kiemelve a helyi és nemzetközi együttműködés fontosságát a növekvő igények kielégítésére[world-nuclear-news.org].
Úszó atomerőművek és tengeri innovációk
Az úszó atomerőművek továbbra is az innováció középpontjában állnak: - Oroszország Akademik Lomonosov nevű úszó atomerőműve elérte az első milliárd kilowattóra termelést. - Az Egyesült Királyságban a Core Power egy amerikai központú tengeri nukleáris programot fejleszt, melynek célja úszó reaktorok telepítése amerikai kikötőkben a 2030-as évek közepére. - A dán Seaborg Technologies (új nevén Saltfoss Energy) kompakt olvadt só reaktor technológián dolgozik, amelyet szintén a 2030-as évekre terveznek bevezetni. - A Westinghouse és a Core Power együttműködik egy úszó atomerőmű fejlesztésén az eVinci mikroreaktorral[world-nuclear-news.org].
Érintettek bevonása és társadalmi bizalom
A Nemzetközi Atomenergia-ügynökség (IAEA) kiemeli az érintettek bevonásának fontosságát a nukleáris energia jövője szempontjából. Folyamatban lévő konferenciáján olyan témákat tárgyalnak, mint a nukleáris energia szerepe az ipari dekarbonizációban, a nyilvános meghallgatások értéke a projektek átláthatósága érdekében, valamint a társadalmi bizalom és a szabályozói megfelelés legjobb gyakorlatai, különösen az új technológiák, például az SMR-ek bevezetése során[iaea.org].
Források: - world-nuclear-news.org - nucnet.org - iaea.org - ans.org
-
 @ 2e8970de:63345c7a
2025-05-29 13:40:19
@ 2e8970de:63345c7a
2025-05-29 13:40:19(and that's the highest ever outside the covid era)
https://www.federalreserve.gov/consumerscommunities/sheddataviz/emergency-savings.html
https://stacker.news/items/991909
-
 @ eb0157af:77ab6c55
2025-05-28 15:01:42
@ eb0157af:77ab6c55
2025-05-28 15:01:42Jack Dorsey’s company is bringing bitcoin payments to the retail market through the Lightning Network.
Block — the firm led by Dorsey that owns Square and Bitkey — has officially announced the integration of bitcoin payments into the Square platform, with a full rollout planned for 2026 for all eligible merchants.
Today: we’re accepting bitcoin payments at @TheBitcoinConf

Soon: you can accept bitcoin payments wherever you are
Details here: https://t.co/ko2S9hFpih pic.twitter.com/IYlYV6XM2S
— Square (@Square) May 27, 2025
At the Bitcoin Conference 2025 in Las Vegas, attendees had the chance to preview satoshi payments via Square at BTC Inc.’s merchandise store.
The technology relies on the Lightning Network, the second-layer infrastructure enabling instant, low-cost bitcoin transactions. This approach will allow merchants to accept satoshi payments through their existing Square hardware.
The implementation plan includes an initial launch in the second half of 2025, pending necessary regulatory approvals. The initiative represents a key pillar in the company’s strategy to make bitcoin more accessible for everyday transactions.
Miles Suter, Bitcoin Product Lead at Block, stated:
“Block has long been a champion of bitcoin, focused on making it more accessible and usable in our everyday lives. Rolling out a native bitcoin experience to millions of sellers brings us one step closer to that goal. When a coffee shop or retail store can accept bitcoin through Square, small businesses get paid faster, and get to keep more of their revenue.”
The announcement follows Dorsey’s statement last month confirming that Block was working to integrate BTC as a payment option for both Bitkey and Square.
Alongside the announcement, Block also revealed that Bitkey will introduce new privacy and security features in May, including a legacy recovery option available to all users.
The post Jack Dorsey’s Block to integrate Bitcoin payments into Square appeared first on Atlas21.
-
 @ fbf0e434:e1be6a39
2025-05-29 13:09:48
@ fbf0e434:e1be6a39
2025-05-29 13:09:48Hackathon 概述
ETH Dublin 2025 黑客松圆满落幕,活动共吸引 84 名开发者参与,共有 31 个项目通过审核。活动核心是借助多家赞助商技术,打造具有影响力的区块链解决方案。活动鼓励参与者组建技能多元的平衡团队,运用技术工具及赞助商支持 —— 如 Chainlink 进行数据验证、Ledger 保障安全、Filecoin 提供存储方案等。
多个项目聚焦社会影响领域:ÉireEncrypt 致力于开发符合 GDPR 合规要求的隐私保护区块链工具;SafeRoads Ireland 则通过智能合约推动安全驾驶。此外,部分项目借助以太坊实现租金管控与去中心化住房市场,还有以移民为主题的数字解决方案促进社区融合,充分展现区块链技术在解决隐私保护、公共安全、教育改革等实际问题中的潜力。
总体而言,ETH Dublin 2025 黑客松不仅促进了开发者与合作伙伴的协作,更激发了诸多借助区块链技术创造社会价值的创新项目。
Hackathon 获奖者
奖项得主
- 一等奖: RecEth
RecEth 通过提供电子邮件确认和清晰的收据,增强了用户对加密交易的信任,将用户体验与传统支付系统的透明度相对齐。 - 二等奖: Latinum
Latinum 作为支付中间件,允许MCP构建者通过兼容钱包实现由代理发起的交易来实现服务器货币化,简化了货币化过程。 - 三等奖: Fundraisely
FundRaisely 利用区块链技术帮助慈善机构进行合法合规的筹款,以及透明的审计,确保捐款流程的清晰和负责。
欲了解所有项目的更多信息,请访问这里。
关于组织者
ETH Ireland
ETH Ireland 致力于区块链技术的创新和发展。该组织在Ethereum方面有着丰富的专业知识,通过举办会议和工作坊促进区块链教育和社区参与。ETH Ireland 的使命是扩大区块链知识普及,推广去中心化技术到各个领域。
- 一等奖: RecEth
-
 @ eb0157af:77ab6c55
2025-05-28 15:01:40
@ eb0157af:77ab6c55
2025-05-28 15:01:40Block’s hardware wallet sparks debate between security and borderline compromises.
The debate ignited after Jack Dorsey publicly supported the superiority of “seedless” wallets over traditional solutions on X.
seedless is safer https://t.co/MvjmFcQE8k
— jack (@jack) May 27, 2025
The Twitter co-founder and Block CEO sustained this by promoting Bitkey, a company that completely eliminates seed phrases, aiming to simplify the user experience and improve security through different recovery options.
The Bitkey model
Bitkey represents a different solution compared to the traditional approach to bitcoin custody. Instead of relying on a single seed phrase, the system implements a 2-of-3 multisig scheme that distributes security across three distinct keys:
- Hardware key: protected by biometric fingerprint on the physical device;
- Mobile key: stored in the smartphone app;
- Server key: managed by Block’s servers.
Any transaction requires two of the three signatures, eliminating the single point of failure represented by traditional seed phrases, the company claims. In its official documents, Bitkey explains how this approach, according to the company, offers three different recovery paths: phone loss, hardware loss, or loss of both through “Trusted Contacts,” pre-set trusted people who can help the user regain wallet access without being able to see the balance or control the private keys.
The seed phrase criticism
For the Bitkey team, the seed phrase paradoxically represents the weakest link in the Bitcoin security chain. While private keys are “exceptionally secure” within the hardware – “designed for security, isolated from networks, physically reinforced” – the seed phrase is “plain text, readable, physically vulnerable,” the company states.
Bitkey developers argue that the industry has “offloaded the most complex part of the security model onto individuals least equipped to handle it.”
System limits and dependencies
However, Bitkey’s simplicity comes at a price. The system introduces a dependency on Block for optimal multisig functionality. Although users always maintain the ability to move funds using the two keys in their possession, recovery procedures and many advanced features require collaboration from the company’s servers.
This architecture presents limitations in terms of flexibility: users cannot use Bitkey with other mobile applications, cannot import the wallet into alternative solutions, and do not have direct access to seed phrases for traditional backup operations.
One of the most frequent criticisms concerns the absence of a screen on the hardware device. Unlike traditional hardware wallets that allow direct verification of destination addresses and transaction amounts on the device display, Bitkey forces users to rely exclusively on the mobile app for these details. This design choice introduces what critics define as a “blind signing risk”: if the mobile app were compromised by malware, users could unknowingly authorize altered transactions without the possibility of independent verification.
Community criticism
Dorsey’s post sparked contrasting reactions in the community. The most orthodox bitcoiners mainly contest two aspects:
- third-party dependency: despite Bitkey maintaining the “self-custody” label, the need to rely on Block’s servers for many operations contradicts the autonomy principles that many bitcoiners consider fundamental;
- loss of technical control: the inability to directly manage the seed phrase or use the device in customized multisig configurations limits the user’s technical sovereignty.
Some users have criticized Block’s hardware wallet. User bamskki highlighted how “the lack of a screen forces users to rely on the app for transaction details. Unlike traditional hardware wallets with screens, Bitkey users cannot verify transactions independently. Users must trust the app as the source of truth.”
Even more critical was user nakadai_mon, who ironized about Dorsey’s strategy writing: “It would be a shame if I influenced you to abandon the seed and locked you into my ecosystem so I can surveil you, sell and share your personal data with government authorities and deny you service.”
Dorsey responded directly to both criticisms. To bamskki he replied:
it's a start, not our end. we will iterate the product like everything else.
— jack (@jack) May 28, 2025
More articulated was his response to nakadai_mon:
we are working on much of the privacy aspects (launching soon). and you don't have to use our 3rd key. that's where some of the restrictions come in. working to figure out how to allow folks to create their own trusted 3rd party as well. but all of this is designed to get people…
— jack (@jack) May 28, 2025
However, privacy concerns are not unfounded. Bitkey’s own documentation clarifies that “because we maintain this key, we are able to identify transaction data on the blockchain related to your Bitkey” and that “this information is collected when you transfer bitcoin to or from your Bitkey.”
Additionally, Block declares using automated decision-making systems, without direct staff involvement, to manage some activities that have legal effects on users. Among these, the application of sanctions restrictions: the system is programmed to automatically prevent the purchase and use of Bitkey by people or countries subject to international sanctions. Finally, the privacy policy specifies that users’ personal data can be shared with law enforcement, government agencies, officials, or authorized third parties in the presence of a warrant, court order, or other legal obligation. Block reserves the right to disclose this information whenever it deems necessary to comply with regulations, legal proceedings, or government requests.
Hardware security and compromises
From a hardware security perspective, Bitkey implements advanced protections including unique device identifiers, secure boot, and anti-tamper technologies. In case the device were compromised, an attacker would still need to access a second key to steal funds.
According to Dorsey’s statements, Bitkey represents an attempt to make self-custody accessible to a broader audience. The company’s roadmap promises improvements in terms of privacy, security, and usability.
The post Bitkey controversy: Dorsey’s marketing divides the community appeared first on Atlas21.
-
 @ 99e7936f:d5d2197c
2025-05-28 14:55:40
@ 99e7936f:d5d2197c
2025-05-28 14:55:40“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
Wo bleibt die Rettung?
Wenn man bei einem Notfall auf den Rettungswagen wartet, dann fühlen sich Minuten wie Stunden an. Die Nerven sind bis zum Anschlag gespannt, alle Sinne sind geschärft.
Die Natur hat das so eingerichtet, damit man aufmerksam und gut geschützt ist vor weiteren Verletzungen.
Bei Trauma ist das auch so, nur dass dieser Zustand gefühlt ein halbes Leben andauert. Das klingt brutal, ist aber in etwa so. Da ein menschlicher Körper das nicht gut aushalten kann, sendet er dem Gehirn die Information: “ Bitte mach etwas zur Entlastung, ich kann mit dem Dauerstress nicht gut umgehen. Ich habe ständig das Gefühl, dass etwas Schlimmes passiert und ich mich verteidigen muss.“ Das Gehirn überlegt sich dann eine Lösung, um auch selber endlich wieder Ruhe zu haben. In der Regel wird der traumatische Inhalt verdrängt, vergessen, abgewandelt, abgeschwächt oder als Schwarz-Weiß-Film wieder gegeben, also ohne Gefühl (re)präsentiert. Man kann dann von den traumatischen Erlebnissen erzählen, ohne ein einziges Gefühl zu haben. Das wirkt souverän, als habe man das Trauma verarbeitet, das Gegenteil ist der Fall. Manche Menschen reden sogar über Gefühle, empfinden diese aber nicht. Gefühle werden imitiert oder inszeniert. Wenn man selber fühlen kann, spürt man diesen feinen Unterschied als Zuhörer sofort. Jedenfalls ist alles das Traumafolge bzw. die Lösung, die uns das Gehirn nach Trauma anbietet. Entweder ist der ganze Inhalt samt Emotion weg, oder der Inhalt ist noch da, aber die Emotion dazu fehlt. Es gibt Menschen, die so tief traumatisiert sind, dass sie eine ganz andere Geschichte von sich selbst erzählen, als die, die eigentlich stattgefunden hat. Ich weiß, dass das gruselig klingt. Aber das ist eine Realität. Und es ist vermutlich gut so. Die Natur macht alles, um ein Menschenleben zu retten, und wenn es um den Preis des psychologischen Vergessens ist. Manche Erinnerungen sind offensichtlich nicht mit dem Leben vereinbar, deswegen werden sie für immer abgespalten. Mittlerweile habe ich persönlich viel Respekt vor Menschen, die sich an nichts mehr „erinnern“ können, da ich gelernt habe, dass sie am schlimmsten traumatisiert sind. Diese Einstellung hatte ich nicht immer.
Jedenfalls verhält es sich nach meiner Beobachtung und auch nach meinen eigenen Erfahrungen so, dass man sich ganz oft erst dann vollständig UND in Farbe an traumatische Erlebnisse erinnert, wenn die Zeit dafür reif ist. Man könnte auch sagen, wenn die Seele bereit ist, die verlorenen Seelenanteile wieder zuzulassen. Sie sind nie weg, denn eine unsichtbare Schnur verbindet uns immer mit dem, was passiert ist. Also, wenn dieser Moment, in dem Du Deine Seelenanteile wieder begrüßen darfst, kommt, dann ist das wie ein riesiges Geschenk, auch wenn sich das zu Beginn nicht so anfühlt. Es fühlt sich dann eher so an, wie wenn man auf den Rettungswagen wartet, aber es ist definitiv ein Geschenk, genau wie eine Geburt ein Geschenk ist. Und eine Geburt ist ja auch nicht immer leicht.
Also, je mehr Gefühl beim Erinnern von traumatischen Inhalten spürbar ist, desto besser kann Traumabearbeitung gelingen. (Heiße den Schmerz willkommen, wenn er in Dein Leben kommt.) Ich persönlich hatte lange Wehen, bevor mein Trauma dann schlagartig aktiviert wurde. Das war, bildlich gesprochen, eine Hausgeburt, die ich allein vollbracht habe, weil der Rettungswagen dermaßen Verspätung hatte. Aber das Kind hat sich dennoch gut entwickelt. Ich habe zuvor lange von meinem Trauma „nur“ geredet. Ich habe rationalisiert, wie man in der Fachsprache sagt. Mir war meine frühe Verletzung bewusst, aber ich hatte kein Gefühl zu dem, was ich erlebt hatte. Als das Gefühl da war, verstand ich, dass es sinnvoll war, es solange nicht gefühlt haben zu können, denn es war ein überwältigender Schmerz. Die Natur macht instinktiv ein gutes Timing für die Wiederkehr des Gefühls. Sie sucht sich eine Zeit im Leben aus, wo man einen guten Stand hat, stabil ist, eine Umgebung hat, die einen zumindest für eine Weile halten und auffangen kann. Denn die Natur möchte schließlich, dass man auch die Wiederkehr des Gefühls überlebt.
Genauso schmerzhaft wie der Verlust des Gefühls war, genauso schmerzhaft ist seine Wiederkehr.
Der Schmerz ist quasi der Erste und der Letzte. Er macht das Licht aus, und später macht er das Licht oder den Farbfilm wieder an. Der Schmerz ist viel besser als sein Ruf.
Ich erzähle hier lediglich meine Erfahrungen und Beobachtungen, auch wenn ich allgemein formuliere. Das kann sich bei anderen Menschen auch anders verhalten. Aber ich finde den Erfahrungsaustausch über dieses Thema wichtig, WEIL es unterschiedlich sein kann und jeder auf einem anderen Level von Traumabearbeitung steht. Ein Problem bei Traumabearbeitung ist, dass jeder ein anderes Trauma erlebt hat, dass jeder einen anderen Nährboden hatte, auf den das Trauma fiel, und dass es verschiedene Stadien gibt, bis es dann endlich und hoffentlich soweit ist, dass das Trauma wieder vollständig in die eigene Psyche integriert werden kann und man wieder „ganz“ bzw. „neu und etwas anders“ ist. Und meine Erfahrung ist, dass man auf das Tempo dieses Prozesses leider keinen Einfluss hat, auch wenn es hierzu, wie ich finde, viele falsche Verkehrsdurchsagen gibt. Die Natur ist da verschlossen wie eine Auster, sie lässt sich nicht ins Handwerk pfuschen. Als ich das verstand, hat sich mein Wunsch, Menschen zu helfen, schlagartig verändert. Ich verstand, dass ICH das nicht machen kann, dass die Natur das selber macht. Und das ist eine gute Nachricht, denn die Natur kann das am besten und ist ein super zuverlässiger Partner.
Wir brauchen keinen Rettungswagen. Der Schmerz ist die Rettung.
Das Thema „Trauma“ birgt so viel positiven Erkenntnisgewinn über das Wunder des Lebens.
Aber zurück zum Thema. Wenn man, so wie ich, ein halbes Leben in einem Schwarz-Weiß-Film verbracht hat, dann die Hausgeburt ohne Rettungswagen durchgestanden hat und das Kind irgendwann anfängt, neugierige Fragen zu stellen, dann ist man im Zugzwang. In dieser Situation bin ich heute. Deswegen schreibe ich. Mein neues ICH fragt mich immer öfter, warum ich so viele Dinge tue, die ich eigentlich gar nicht mehr tun will. Kinder fragen einen auch manchmal ganz unverblümt, ob man den Hansi denn lieb hat oder ob man gerne im Büro arbeitet. Wenn man den Hansi nicht lieb hat und nicht gerne im Büro arbeitet, dann muss man schlucken und eine kindgerechte Antwort formulieren. Genauso wenig wie Kinder als kompetenter 20-jähriger auf die Welt kommen, genau so wenig ist man nach geglückter Traumabearbeitung „geheilt“. Es wird nichts schlagartig besser. Das ist auch so eine falsche Verkehrsdurchsage. Man lebt ja noch im alten Leben, was nun Schritt für Schritt verändert werden darf. ABER man ist glückliche Mutter. Mutter sein, ist nicht immer leicht, habe ich mir sagen lassen. Mütter lieben ihre Kinder. Im Idealfall machen sie sich keine Gedanken darüber, was aus ihrem Kind mal werden soll. Sie vertrauen einfach darauf, DASS aus ihrem Kind ein glücklicher Mensch wird und buttern deshalb so viel Liebe in das Kind hinein, wie in den wenigen Jahren, die das Kind ein Kind ist, möglich ist. So ähnlich geht es mir heute auch. Ich bin stolz auf mein neues ICH und lobe es, so oft ich kann. Jede Mutter lobt ihre Butter. Das ist wichtig, denn das Leben bietet ständig Herausforderungen, an denen man bekanntlich wachsen darf. Ich gehe jeden Tag mit meinem „Kind“ spazieren, und wir sehen viel. Wir sehen andere Menschen mit Trauma, wir hören zu, welches Trauma der andere erlebt hat und auf welchem Level er ist. Wir hören das Gefühl heraus, welches mitschwingt. Wir sehen Menschen in ihrem Schwarz-Weiß-Film. Und wir sehen Menschen, die scheinbar mit jeder Situation souverän umgehen können. Am meisten interessieren „uns“ zur Zeit solche Menschen, die ehrlich zugeben, dass sie Wehen haben, dass der Schmerz sich in immer kürzeren Abständen meldet. (Die verlorenen Seelenanteile ziehen an der unsichtbaren Schnur.) Mit diesen Leuten kann ich im Moment am besten. Das hört sich komisch an. Aber ich will damit zum Ausdruck bringen, dass ich mit diesen Menschen mittlerweile am meisten resoniere. Sie sprechen meine Sprache. Sie empfinden Gefühle, und sprechen über diese. Das ist für mich die schönste Sprache.
Wer in diesen Tagen wahrhaftig Schmerz empfindet, und nicht nur als Lippenbekenntnis, sondern echten üblen Schmerz über die enttäuschte Liebe oder über die Verhältnisse in dieser Welt, der ist mir sympathisch, der ist mir nah. Denn ich weiß, dass so ein fühlender Mensch auch bald eine Niederkunft erleben wird, die ihn verändert, die ihn anders auf diese Welt schauen lässt.
Der Schmerz bringt uns die Verwandlung. Der Schmerz bringt die verlorenen Seelenanteile zurück. Der Schmerz ist der Hüter des Lebens. Der Schmerz bringt Dir Deine volle Sensibilität für andere Menschen zurück. Alles, was Du bei Dir nicht fühlen kannst, kannst Du bei anderen nicht fühlen. Der Schmerz beendet das. Er macht das Licht an und gibt dem Film wieder Farbe.
Heiße den Schmerz willkommen, wenn er in Dein Leben kommt. Tu das, nicht etwa weil Du gern leidest, nein tu das, weil Du Dich liebst, weil Du bewusst darauf achten möchtest, was Dir wirklich gut tut und Freude macht. Ein Mensch oder ein Job, der Dir Schmerz bereitet, den gilt es loszulassen. Und wenn Du Schmerz im Gesicht Deines Gegenübers siehst, dann frage Dich ehrlich, was Dein Anteil daran ist, dass der andere leidet. Wir sind nicht für jedes Leid auf dieser Welt verantwortlich, das möchte ich hier auch betonen. Und die Schuld-Nummer zieht bei mir schon lange nicht mehr. Aber ich nehme immer besser wahr, wenn mein eigenes Verhalten nicht angemessen, nicht authentisch ist, von überholten Glaubensmustern geprägt ist. Ich kann das erkennen und korrigieren. Ich kann das heute selber erkennen, weil der Schmerz mich das gelehrt hat, mich geöffnet hat. Der Schmerz lehrt uns ganz viel. Der Schmerz ist der Hüter des Lebens. Er trifft einen hart, macht aber weich.
Heiße den Schmerz willkommen, denn er ist die Rettung.
“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
Onboarding bei Nostr: Nostr
Easy onboarding via **Start.**\ \ Das Pareto-Team baut den “Marktplatz der Ideen” und hat dabei schon viel erreicht. \ team@pareto.space \ https://pareto.space \ https://geyser.fund/project/pareto?hero=1c1b8e487090
\ \ Newsletter per Mail (Die Friedenstaube)\ hier abonnieren\ \ In Telegram lesen -> hier unsere Kanäle\ https://t.me/pareto_artikel \ https://t.me/friedenstaube_artikel \ \ Als Feed in einem Feed-Reader \ https://pareto.space/atom/feed.xml \ https://pareto.space/atom/de_feed.xml \ https://pareto.space/atom/en_feed.xml
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-28 12:37:30
@ 5d4b6c8d:8a1c1ee3
2025-05-28 12:37:30https://rumble.com/embed/v6rp3fh/?pub=4e023h
I know some of our stackers are follicly challenged, so I thought I'd pass along this video.
Have any of you tried topical onion juice for hair regrowth?
I'll eat more onion and rosemary and get more Sun, just to be safe.
https://stacker.news/items/991118
-
 @ 5f078e90:b2bacaa3
2025-05-29 09:33:22
@ 5f078e90:b2bacaa3
2025-05-29 09:33:22Frog named Gus

This is a test from Hive to Nostr, longform script, some markdown included. google link, 400 char. story.
In a lush pond, a green frog named Gus lived among lily pads. Each dawn, he croaked a cheerful tune, waking the dragonflies. One day, a heron eyed him hungrily. Gus, clever and quick, hopped beneath a broad leaf, blending perfectly. The heron, fooled, flew off. That evening, Gus sang louder, celebrating his escape. His friends—turtles and minnows—joined the chorus under the moon's glow. Gus’s courage inspired them all, proving wit outshines size. The pond thrived, with Gus as its spirited guardian, forever hopping and croaking in joy.
This was a test, please ignore.
-
 @ cff1720e:15c7e2b2
2025-05-28 11:18:23
@ cff1720e:15c7e2b2
2025-05-28 11:18:23Liebe Anwender,\ \ diesmal beginnen die Neuigkeiten schon beim Titel und der Anrede. Unsere Worte bestimmen unser Denken, und daher war die Korrektur wichtiger als sie zunächst erscheint, denn bei Pareto gibt es die klassische Trennung zwischen Autor und Leser nicht mehr. Cocreation heißt unser Konzept, jeder kann publizieren, kommentieren, honorieren und distribuieren. Mag das bei Blogtexten derzeit noch nicht selbstverständlich sein, so ist das bei Bildern längst die Norm.

“Ein Bild sagt mehr als tausend Worte” beschreibt die Wirkung visueller Kommunikation. Deshalb haben wir nach dem Blogtext nun mit Bildern eine neue Content-Kategorie eingeführt. Natürlich auch hier mit den bekannten Funktionen der Interaktion wie like, repost und zap. Es gibt derzeit eine Gliederung in 4 Feeds, Gefolgt (für Nostr-User verfügbar), Memes und Kunst (gefiltert nach entsprechenden Tags) und Pareto für alles andere.
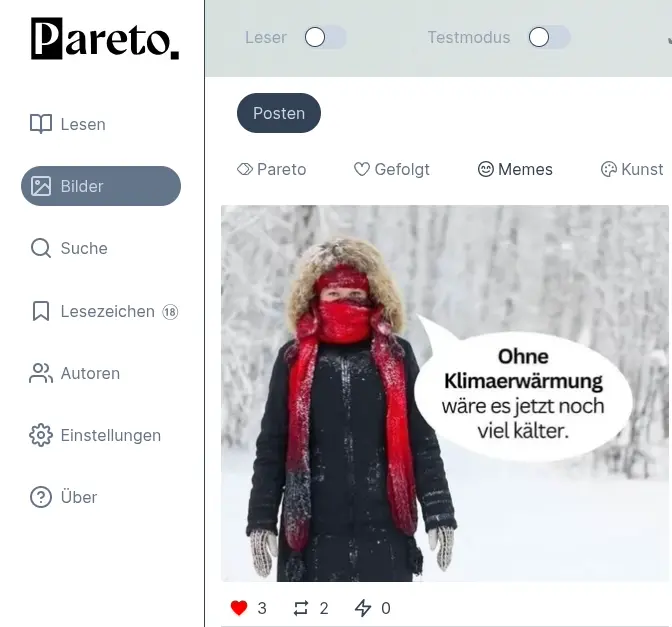
Jeder Nostr-User hat die Möglichkeit eigene Bilder hochzuladen, zu taggen, sowie mit einem Titel und Untertext zu versehen. “Everyone is a creator” war noch nie leichter, probiert es einfach aus! Noch kein Nostr-Profil und trotzdem interessiert? Kein Problem, bitte Informationen zu originellen Bildquellen oder Interesse an Mitwirkung per Mail senden an pictures@pareto.space
Leicht ist es auch die Pareto-Inhalte zu erhalten und konsumieren, man braucht weder einen Account noch spezielle Apps. Jeder hat bereits die entsprechenden Voraussetzungen, hier ein paar Beispiele.\ \ Newsletter per Mail (Die Friedenstaube)\ hier abonnieren\ \ In Telegram lesen -> hier unsere Kanäle\ https://t.me/pareto_artikel \ https://t.me/friedenstaube_artikel \ \ Als Feed in einem Feed-Reader \ https://pareto.space/atom/feed.xml \ https://pareto.space/atom/de_feed.xml \ https://pareto.space/atom/en_feed.xml
Fügt in Eure Artikel bitte am Anfang / Ende einen Hinweis auf den Pareto-Client ein, andere Clients unterstützen nicht alle Features. Das ist ein Service-Hinweis zur besseren Lesbarkeit “Dieser Beitrag wurde mit dem Pareto-Client geschrieben.” Ebenso ist ein Hinweis auf Onboarding bei Nostr nützlich: neue Nostr-User können euch liken und zappen: not yet on Nostr and want the full experience? Easy onboarding via Start.\ \ Das Pareto-Team baut den “Marktplatz der Ideen” und hat dabei schon viel erreicht. Feedback und Mitarbeit hilft uns damit noch schneller voranzukommen, wir bedanken uns für Eure Unterstützung.\ team@pareto.space \ https://pareto.space \ https://geyser.fund/project/pareto?hero=1c1b8e487090
-
 @ 5f078e90:b2bacaa3
2025-05-29 09:23:18
@ 5f078e90:b2bacaa3
2025-05-29 09:23:18May 29 badger test story
h2n, bi, some md, >380

In a dusty savanna, a honey badger named Hank prowled with fearless grit. Each night, he raided beehives, dodging stings with cunning twists. One day, a lion blocked his path, roaring fiercely. Hank, unfazed, bared his teeth and charged, startling the beast. The lion fled, and Hank strutted on, claws clicking. His boldness rallied jackals and birds, who sang his tale under starry skies. Hank’s fierce heart made him the savanna’s legend, guarding its wild spirit with every fearless step.
This is just a test, please ignore.
-
 @ 5f078e90:b2bacaa3
2025-05-29 09:10:54
@ 5f078e90:b2bacaa3
2025-05-29 09:10:54Gecky story - just a test

In a sun-dappled jungle, Zippy the gecko darted across a broad leaf, his emerald scales glinting. Chasing a juicy cricket, he leaped, only to slip into a pitcher plant’s slippery trap. With sticky toes, Zippy clung to the edge, heart racing. A curious frog peered in, offering a vine. Grateful, Zippy climbed out, sharing his cricket with his new friend. Under the moon’s glow, they danced on the leaves, tales of their adventure echoing through the jungle night.
Character count: 408
This was just a test. Ignore it.
-
 @ 005bc4de:ef11e1a2
2025-05-28 09:05:10
@ 005bc4de:ef11e1a2
2025-05-28 09:05:10
BIP-2,100,000,000,000,000,000
So, you're telling me...
- 21 million bitcoins is out, and...
- 2.1 quadrillion sats is in, except that...
- sats are out, so...
- 2.1 quadrillion bitcoins is in, except that...
- there are actually millisats, but...
- millisats are out, so...
- millibitcoins are in, so now...
- there are 2.1 quintillion millibitcoins, except that...
- millibitcoins are the basic base unit of bitcoin, so...
- millibitcoins are out, and now...
- 2.1 quintillion bitcoins are in

-
 @ dfa02707:41ca50e3
2025-05-28 11:01:37
@ dfa02707:41ca50e3
2025-05-28 11:01:37Contribute to keep No Bullshit Bitcoin news going.
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.

-
 @ 6e0ea5d6:0327f353
2025-05-28 04:34:08
@ 6e0ea5d6:0327f353
2025-05-28 04:34:08Ascolta bene! It is more dignified to thirst alone in the desert than to share wine with someone who has no thirst for conquest.
On the silent path to success, it’s not the declared enemies who slow the march, but rather the friends. Not the noble or loyal ones, but the failures—those who carry a dull glint in their eyes, chronic laziness in their spirit, and the eternal excuse of bad luck in their pockets. Friendship, when poorly chosen, becomes a polished anchor, tied to your ankle with ropes named camaraderie.
Nothing weighs heavier on the journey than having to endure the failed and envious around you. It is a kind of emotional parasitism that begins with empathy and ends in stagnation. Those who live among the weak will crawl. Those who keep company with miserable friends, instead of striving to prosper, learn to curse wealth—not out of ethics, but out of envy. Mediocrity, my friend, is contagious. And it does not take root suddenly, but like a silent epidemic.
Ambition—that fire that burns in the bones of great men—will always seem like arrogance to the ears of the failed. Those who have never built anything, except arguments to justify their paralysis, will never understand the fury of someone born to conquer. And so, with smiles, they spit venom: “Calm down,” they say, “be content,” they advise. Hypocrites. What they call humility is nothing more than resignation to their own defeat.
To walk alone, with hunger and honor, is worth more than feasting at lavish tables at the cost of your own sweat, surrounded by parasites who toast your downfall with glasses full of praise. No one prospers where the conversation is filled with complaints, criticism, and envy. What does not build up, corrodes.
The rust of the weak is invisible at first—a bitter joke here, a veiled critique there. And before you know it, the structure is already rotten. Of the friendship, only the weight remains. Of the relationship, only exhaustion. The true enemy of success is the company of those who have failed and wish for you the same fate. These tragic figures—always tired, always victims—are masters of collective self-sabotage.
Feel no remorse in abandoning those who build nothing and consume everything. And in that abandonment, you become freer, stronger, and unbreakable.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 7d33ba57:1b82db35
2025-05-29 08:40:35
@ 7d33ba57:1b82db35
2025-05-29 08:40:35Lingen (Ems) is a peaceful town in Lower Saxony, near the Dutch border, known for its historic old town, green surroundings, and relaxed pace of life. It may not be on the typical tourist radar, but it offers a taste of small-town Germany with plenty of charm and local culture.
🏘️ What to See and Do in Lingen
🏛️ Old Town & Market Square
- Stroll through the historic town center, where you’ll find half-timbered houses, cozy cafés, and the lovely St. Boniface Church
- The Rathaus (Town Hall) and its square are perfect for a slow coffee or people-watching
🚲 Nature & Outdoor Activities
- The region around Lingen is great for cycling and walking, especially along the Ems River
- Explore the Emsland countryside, filled with forests, meadows, and quiet villages
- Visit the nearby Emsland Moormuseum to learn about local peatland history
🎓 Student Vibes
- Thanks to the presence of a university, Lingen has a young and vibrant side, with cultural events and small live music scenes
🍺 Local Food & Drink
- Try regional dishes like Grünkohl (kale with sausage in winter) and Schnitzel in a local tavern
- Enjoy a drink at a beer garden or riverside café, especially in warmer months

🚆 Getting There
- Well connected by train, especially to Osnabrück, Münster, and the Dutch city of Enschede
- Great stop on a northern Germany road or rail trip
Lingen is ideal for travelers looking for peaceful towns, regional culture, and access to beautiful natural areas. It’s a place where you can slow down, bike along a river, and enjoy the local way of life.
-
 @ 1d7ff02a:d042b5be
2025-05-28 04:02:47
@ 1d7ff02a:d042b5be
2025-05-28 04:02:47For those who still don't truly understand Bitcoin, it means you still don't understand what money is, who creates it, and why humans need money.
It's a scam that the education system doesn't teach this important subject, while we spend almost our entire lives trying to earn money. Therefore, I recommend following the money and studying Bitcoin seriously.
Why Bitcoin Matters
Saving is the greatest discovery in human history
Before humans learned to save, we were just animals living day to day. Saving is what makes humans different from other animals — the ability to think about the future and store for later.
Saving created civilization itself
Without saving, there would be no cities, no science, no art. Everything we call "progress" comes from the ability to save.
Money is the greatest creation in human history
It is the tool that has allowed human civilization to advance to this day. Money is the best tool humans use for saving.
Bitcoin is the best money ever created
It is the most perfect money humans have ever created. No one can control, manipulate, destroy it, and it is truly limited like time in life.
Bitcoin is like a black hole
That will absorb all value from the damaged financial system. It will draw stability and value to itself. Everything of value will flow into Bitcoin eventually.
Bitcoin is like Buddhism discovering truth
It helps understand the root problems of the current financial system and the emergence of many problems in society, just like Buddha who understood all suffering and the causes of suffering.
Bitcoin is freedom
Money is power, money controls human behavior. When we have money that preserves value and cannot be controlled, we will have intellectual freedom, freedom of expression, and the power to choose.
The debt that humanity has created today would take another thousand years to pay off completely
There is no way out and it's heading toward serious collapse. Bitcoin is the light that will help prevent humanity from entering another dark age.
Bitcoin cannot steal your time
It cannot be created from nothing. Every Bitcoin requires real energy and time to create.
Bitcoin is insurance that protects against mismanagement
It helps protect against currency debasement, economic depression, and failed policies. Bitcoin will protect your value.
Bitcoin is going to absorb the world's value
Eventually, Bitcoin will become the store of value for the entire world. It will absorb wealth from all assets, all prices, and all investments.
Exit The Matrix
We live in a financial Matrix. Every day we wake up and go to work, thinking we're building a future for ourselves. But in reality, we're just giving energy to a system that extracts value from us every second. Bitcoin is the red pill — it will open your eyes to see the truth of the financial world. Central banks are the architects of this Matrix — they create money from nothing, and we have to work hard to get it.
The education system has deceived us greatly. They teach us to work for money, but never teach us what money is. We spend 12-16 years in school, then spend our entire lives earning money, but never know what it is, who creates it, and why it has value. This is the biggest scam in human history.
We are taught to be slaves of the system, but not taught to understand the system.
The Bitcoin standard will end war
When you can't print money for war anymore, war becomes too expensive.
We are entering the Bitcoin Renaissance era
An era of financial and intellectual revival. Bitcoin is creating a new class of humans. People who understand and hold Bitcoin will become a new class with true freedom.
The Path to Financial Truth
Follow the money trail and you will see the truth: - Who controls money printing? - Why do prices keep getting higher? - Why are the poor getting poorer and the rich getting richer?
All the answers lie in understanding money and Bitcoin.
Studying Bitcoin is not just about investment — it's about understanding the future of currency and human society.
Don't just work for money. Understand money. Study Bitcoin.
If you don't understand money, you will be a slave to the system forever. If you understand Bitcoin, you will gain freedom.
-
 @ 83279ad2:bd49240d
2025-05-29 04:05:29
@ 83279ad2:bd49240d
2025-05-29 04:05:29 -
 @ 83279ad2:bd49240d
2025-05-29 04:03:54
@ 83279ad2:bd49240d
2025-05-29 04:03:54 -
 @ a4992688:88fd660f
2025-05-27 22:47:43
@ a4992688:88fd660f
2025-05-27 22:47:43Retail Isn't Coming Back
(and they might be gone for good)
Written by nostr:nprofile1qqs2fxfx3z6yns4a6mafcwdgsrtluf747h37nl2vglt9mqj93r7kvrcwm69jy
It's been just a matter of days since Bitcoin has broken a new all-time high in US dollars and yet, things are extremely quiet on the ground level... Your friends aren't texting to find out if now is a good time to buy, the normies at work haven't brought it up to you, and Coinbase isn't even in the top 100 overall apps in the Google Play App Store. As of now, it sits at #164.
In fact, according to Google search trends, worldwide interest in Bitcoin is lower today while setting new all-time highs above $110,000 than it was at the pits of the 2022 bear market when FTX was blowing up and Bitcoin crashed to below $16,000.
the mempool also paints a quiet picture. It’s mostly empty. Just a few blocks’ worth of transactions waiting to confirm, most paying 1–4 sats/vB. In fact, over the last 144 blocks (about 24 hours), the average fee per transaction has hovered below 1,500 sats, roughly $1.50.
This is far from the behavior found on-chain during previous all-time highs. It reflects an underutilized network predominantly being used by its original power users. Meanwhile, the hash rate climbs relentlessly, month after month, setting record after record. Miners are expending more energy than ever, but fee pressure is nowhere to be found.
🕵️♂️ Is Retail In The Room with Us Now?
The typical signs of retail investor enthusiasm, such as increased Google searches, higher Coinbase app downloads, and a congested mempool all remain subdued. This raises the question: Is the current rally predominantly driven by institutional investors, with retail participation lagging behind?
Since the approval of spot Bitcoin ETFs in January 2024, these financial instruments have accumulated nearly 1.21 million bitcoin, with total assets under management exceeding $132 billion (or, 5.75%+ of 21M total BTC). Initially, retail investors were the primary contributors to these inflows, accounting for approximately 80% of the total assets under management as of October 2024. However, more recent trends indicate a shift, with institutional investors, including hedge funds and asset managers, increasing their stakes in Bitcoin ETFs.
Institutional exposure more than doubled from Q3 to Q4 of 2024 according to SEC 13-F filings, whereas assets under management for all non-institutional ETF holders grew by 62%. While retail is responsible for approximately 73.7% of AUM in the ETFs, a small number of institutions represent more than a 26% of the ETF inflows as of the end of 2024.
🥴 PTSD - Portfolio Trauma & Speculative Disillusionment
For many retail investors, the scars from the 2021–2022 crypto cycle run deep. They bought into the hype near Bitcoin's previous all-time high of $69,000, only to watch their investments plummet to $15,000. The collapse of major platforms like Terra, Celsius, and FTX didn't just erase wealth—it shattered trust.
This collective trauma has left many retail investors wary. They've seen the cycle before: rapid gains followed by devastating losses. The excitement that once drew them into the market has been replaced by caution and skepticism. Even as Bitcoin reaches new heights, the enthusiasm that characterized previous bull runs is noticeably absent.
By all measurable metrics, retail investors appear increasingly reluctant to step outside the comfort of traditional financial rails to gain Bitcoin exposure. In response to past losses and a heightened desire for security, many are now turning to regulated investment vehicles like spot Bitcoin ETFs, offered by institutions such as BlackRock and Fidelity. These products provide a familiar, low-friction on-ramp by eliminating the need for self-custody, avoiding the risks of phishing and exchange hacks, and sidestepping the complexities of managing wallets or navigating volatile crypto platforms. This behavioral shift helps explain why we’re not seeing a surge in mempool congestion, on-chain activity, or crypto exchange downloads. Retail isn’t gone per se... they are however predominantly choosing to interact with Bitcoin from a "safe" distance, inside the walled garden of TradFi.
🧙♂️ Pay No Attention to the Custodian Behind the Curtain
Retail might look like it's back, but it isn't. Not really. They've been rerouted. Herded away from the open network and into the controlled comfort of traditional finance, where Bitcoin is boxed up, regulated, and sold as a familiar financial product.
Spot ETFs from firms like BlackRock offer the illusion of exposure without any of the responsibility or freedom that comes with actually owning Bitcoin. There are no private keys, no ability to withdraw, no direct access to the asset. Most of the Bitcoin that backs those shares sits in Coinbase Custody, inaccessible from the investor’s point of view. Retail can watch the price move, but they can't move a single sat.
They can't send it to family. They can't use Lightning. They can't participate in a fork or vote with their coins. Their holdings are locked inside a financial product, subject to tax surveillance and government oversight, with none of the borderless, censorship-resistant qualities that make Bitcoin what it is.
This isn’t Bitcoin as a tool for sovereignty. It’s Bitcoin as a stock proxy, tucked neatly into retirement accounts and brokerage dashboards. Retail hasn't returned to Bitcoin. They've returned to a synthetic version of it. One that looks clean, feels safe, and doesn’t ask them to think too hard.
The crowd is back, but not on the chain. They've returned to price, not protocol.
🔍Missing: Retail. Last Seen 2021.
If this bull run feels quieter than the last one, it’s because it is. Retail investors, once the lifeblood of Bitcoin mania, are largely absent from the on-chain activity. Their presence isn’t being felt where it used to be.
The reasons are stacking up. Regulatory pressure has increased globally, with new tax reporting rules, stricter KYC requirements, and fewer accessible exchanges making direct participation more frustrating than exciting. At the same time, the opportunity cost has shifted. T-bills are yielding 5 percent, and the stock market is deep in an AI-driven rally that feels new and full of upside. Compared to that, Bitcoin’s core narratives like digital gold or inflation protection no longer feel urgent or unique.
Institutions are now leading through ETFs and futures, smoothing out volatility and removing many of the sudden moves that once drew in retail traders. On-chain user experience still falls behind modern apps, Lightning remains niche, and energy concerns continue to shape public perception. More importantly, the cost of everyday life has gone up. Rent is up. Groceries are expensive. People are stretched thin. Student loans have resumed and homeownership is out of reach for many.
Until those conditions shift, retail is unlikely to return in any meaningful way. It is not that they have given up on Bitcoin. They are simply trying to keep up with everything else.
The chart below illustrates that the number of active Bitcoin addresses has declined by approximately 42% since its peak in 2021.
🧲 What Pulls Them Back In?
Retail hasn’t disappeared. It’s just not on-chain. They’re watching the charts, buying the proxies, and dipping into Bitcoin exposure through familiar vehicles like ETFs and high-beta stocks. MSTR, MSTY, SQ, MARA, and RIOT have become stand-ins for the real thing. For many, that feels close enough. They haven’t sworn off Bitcoin entirely, but they also haven’t found a reason to return to the protocol itself. Price alone isn’t doing it. If Bitcoin is going to recapture retail attention on-chain, it needs more than speculation. It needs to be usable, intuitive, and culturally relevant. Until then, the crowd will stay inside the walled garden, content with price exposure. The question now is what pulls them back into the open network.
🛠️ Make it Frictionless, or Forget it
Retail won’t return until exploring Bitcoin feels rewarding, not risky. Right now, engaging directly with the network still feels technical, intimidating, and easy to get wrong. The average person doesn’t want to learn about seed phrases, fee markets, or signing messages. They just want it to work, and ideally in one tap.
Self-custody, while powerful, still comes with a learning curve that scares most users off. One typo can lose everything. One phishing link can wipe a life’s savings. When compared to the ease of buying a Bitcoin ETF inside a brokerage app, it becomes obvious why most people choose comfort over control.
Lightning wallets have improved, but mainstream usability is still far off. Many users struggle with basic concepts like payment channels and inbound liquidity. App store reviews often reflect confusion and frustration. More importantly, Lightning still raises serious questions in a high-fee environment. Opening or closing a channel can become expensive when the base layer gets congested. This undermines Lightning’s value as a low-cost, instant settlement layer. If fees are unpredictable, it becomes harder to trust that Lightning will be there when users actually need it.
Apps like Nostr are beginning to pave the way with native Lightning features like zaps, where users can send sats as tips or signals within a social feed. It’s the kind of simple, purpose-driven interaction that could eventually normalize Lightning in everyday use. But for now, it remains niche, with limited reach beyond early adopters and Bitcoin-native circles. The pieces are falling into place, but mainstream readiness is still a long way off.
To pull retail back in, Bitcoin has to compete on usability, not just principle. That means seedless recovery. Wallets that back up automatically. Tap-to-pay Lightning. Default privacy. Smarter fee estimation. The average user should not have to study Bitcoin to use it, just like they don’t need to understand TCP/IP to send an email.
Until the experience becomes effortless, Bitcoin on-chain will remain the domain of power users and diehards. Everyone else will keep choosing exposure over participation, because for now, the friction outweighs the freedom.
🔥 Give Them a Reason to Care Again
Speculation brought retail in. Survival might bring them back. But between those extremes, there needs to be a reason to engage that feels meaningful in everyday life. For most people, Bitcoin still doesn’t offer that. It’s not woven into anything they do. It’s not a tool they reach for. It’s just a number in a ticker—or now, in an ETF.
The core narratives that once drove adoption have lost their urgency. “Digital gold” sounds more like a sales pitch than a breakthrough. “Inflation hedge” didn’t hold up during inflation. “Opt out of the banking system” is hard to relate to when your paycheck hits a checking account and your bills are on autopay. These messages worked when people were curious or scared. But in a world focused on AI, passive income, and stable yields, Bitcoin feels like a cold, hard asset with no warm story.
Retail doesn’t just need new slogans. They need a new reason. A killer app. A cultural hook. Something that connects the protocol to their daily life. That could come from anywhere—remittances, peer-to-peer media, AI payments, creator tools, censorship resistance, even gaming. We’re starting to see glimpses. Nostr’s Lightning zaps, for example, show how sats could flow through social interactions. It's lightweight, casual, and fits into habits people already have. But even that is still early and relatively isolated from the mainstream.
Of course, it’s possible that price alone brings them back. A violent move toward $200,000 or higher could generate headlines, social buzz, and another wave of opportunistic buying. But even in that scenario, most people still won't touch the protocol. They’ll chase exposure, not interaction. They’ll buy tickers, not UTXOs.
Retail will come back when Bitcoin stops being an idea they watch and starts being a tool they use. Until then, attention might spike, but engagement will remain shallow.
🏠 Bitcoin Needs a Homebase
Bitcoin is everywhere, but it feels like it’s nowhere. There's no single place where the culture lives. No town square. No digital front porch where holders, builders, speculators, artists, and newcomers all cross paths. And that absence is being felt.
In past cycles, Twitter served as a kind of home for Bitcoin discussion. But now the conversation is fractured. Memes, developer talk, Lightning experiments, and exchange drama are scattered across Telegram groups, Nostr relays, GitHub repos, Reddit threads, and gated newsletters. There’s no central venue that brings it all together. What once felt like a movement now feels more like a loose network of subcultures.
This isn’t just a cultural gap. It’s a usability gap. Without a shared space or interface, discovering Bitcoin's tools, communities, or use cases becomes a fragmented and overwhelming experience. For newcomers especially, it turns exploration into a scavenger hunt. There’s no hub where someone can casually browse peer-to-peer markets, tip someone over Lightning, try a game, test a wallet, or ask basic questions without feeling out of place.
Importantly, this homebase shouldn’t be a corporate platform or single point of failure. It should reflect the values of the network itself—open, decentralized, secure, and resistant to censorship. A sovereign space, not another walled garden. Something that anyone can plug into, build on top of, or access freely without needing permission or credentials. Not a headquarters, but a commons.
Bitcoin doesn’t need a leader, but it could use a center of gravity. A place where its many threads can be visible, accessible, and in conversation with each other. Until it feels like something you can step into, most people won’t feel like they’re truly part of it.
🧵 Final Thoughts
Retail didn’t disappear. It checked out. After wild volatility, failed platforms, and busted narratives, most people aren't rushing back into the Bitcoin Network as we know it. They’ve opted for safety. For simplicity. For familiar rails like ETFs, proxy stocks, and apps that feel intuitive and risk-free.
Bitcoin, meanwhile, has matured in price but not necessarily in presence. The protocol is stronger than ever, but the culture feels scattered. The use cases feel theoretical. The experience still feels fragile. And for most, that's just not enough.
Maybe retail comes back with the next crisis. Maybe it takes a breakout product. Or maybe it doesn’t happen for years. No one knows what the catalyst will be, or if there even has to be one. But what’s clear is that Bitcoin’s next chapter won’t be won by price alone. It will be shaped by the tools we build, the stories we tell, and the places we create for people to show up.
One thing I know for sure: if retail returns, it won’t be for long unless we’ve built something that gives them a real reason to stay.
-
 @ d3d74124:a4eb7b1d
2025-05-29 02:19:14
@ d3d74124:a4eb7b1d
2025-05-29 02:19:14language is a funny thing. the English grammar is one of the most, if the not THE most complicated grammars to learn.
https://en.wikipedia.org/wiki/Defense_Language_Aptitude_Battery\ DLAB. it's the test you take to see if you have a gift for language learning.
in my exploration of languages, first Chinese Mandarin, then software languages, context is king (Jesus is King). the surrounding context is different every where you go.
physical space context. we can't be two places at once. nostr allows for many languages, because you can provide your own digital context. our physical perspective give us a field of view. NOSTR clients give us a field of view into digital context.
math is a language.
bitcoin will be called a lot of things.
wizardry
some elections results are anchored in time. using bitcoin. what else should be? legal documents seem obvious. other cryptographic proofs.
zero knowledge proofs. something about curve trees.
Find your local BitDevs.
Shenandoah Bitcoin Club
pondering a Veteran's Day live music event in Frederick County, VA. who would show up to a lunch and learn with hardware wallets in testnet4 mode? to try shit out? local only, but you should do it where you are too if you're not local.
mining
getting better? Bitmain announces a "decentralized mining pool" but I doubt we'll see open source code if history follows. 256Foundation getting to business. working prototypes for the Ember One using USB and python are out there for those that know where to look. i am very bullish on mujina. very bullish. fun coinbase tricks happening too with CTV+CSFS.
p.s. written on primal's new article publishing UI.
-
 @ 6be5cc06:5259daf0
2025-05-27 20:37:22
@ 6be5cc06:5259daf0
2025-05-27 20:37:22At
até uma ferramenta de agendamento de tarefas em Linux usada para executar comandos únicos em um horário e data específicos. Diferente docron, que serve para tarefas recorrentes, oatexecuta uma única vez.Como usar o
at1. Verifique se o
atestá instaladobash which atSe não estiver instalado:
bash sudo apt install atE inicie o serviço (caso necessário):
bash sudo systemctl enable --now atd2. Agendar um comando
bash at 10:00 AM tomorrowVocê será levado a um prompt interativo. Digite o comando desejado e finalize com
Ctrl + D.Exemplo 1:
bash at 09:00 AM next Monday(Entrada do usuário no prompt do
at)echo "Relatório pronto" >> ~/relatorio.txt Ctrl + DResultado: O trecho "relatório pronto" será incluído no documento relatorio.txt.
Exemplo 2:
bash at 21:00 Apr 15Entrada no prompt:
notify-send "Hora de fazer backup!" Ctrl + DResultado: Às 21h do dia 15 de abril, o sistema exibirá uma notificação.
Formatos de Data e Hora Válidos
-
now + 1 minute -
midnight -
tomorrow -
5pm -
08:30 -
7:00am next friday -
noon + 2 days
Visualizar tarefas agendadas
bash atqRemover uma tarefa agendada
bash atrm <número_da_tarefa>Você encontra o número da tarefa com
atq.
cron
O
croné um utilitário de agendamento de tarefas baseado no tempo. Permite executar comandos ou scripts automaticamente em horários específicos. Ele depende do daemoncrond, que deve estar ativo e em execução contínua no sistema.Arquivo de configuração:
-
Cada usuário pode editar seu próprio agendador com:
bash crontab -e -
O formato padrão de uma linha no crontab:
m h dom mon dow comando
|Campo|Descrição|Valores possíveis| |---|---|---| |m|Minuto|0–59| |h|Hora|0–23| |dom|Dia do mês|1–31| |mon|Mês|1–12| |dow|Dia da semana|0–6 (0 = Domingo)| |comando|Comando a executar|Qualquer comando shell válido|
Exemplos:
-
Executar um script a cada minuto:
bash * * * * * /usr/local/bin/execute/this/script.sh -
Fazer backup no dia 10 de junho às 08:30:
bash 30 08 10 06 * /home/sysadmin/full-backup -
Backup todo domingo às 5h da manhã:
bash 0 5 * * 0 tar -zcf /var/backups/home.tgz /home/
Limitações:
Tarefas agendadas com
cronnão são executadas se o computador estiver desligado ou suspenso no horário programado. O comando é simplesmente ignorado. Usecronpara tarefas com data/hora exatas.
anacron
O
anacroné uma alternativa aocronvoltada para sistemas que não ficam ligados o tempo todo, como notebooks e desktops. Ele garante a execução de tarefas periódicas (diárias, semanais, mensais) assim que possível após o sistema ser ligado, caso tenham sido perdidas. Useanacronpara tarefas periódicas tolerantes a atrasos.Verificação da instalação:
bash anacron -VInstalação (caso necessário):
bash sudo apt update sudo apt install anacronArquivo de configuração:
/etc/anacrontabAcessado com:
sudo nano /etc/anacrontabFormato de cada linha:
PERIOD DELAY IDENT COMMAND| Campo | Descrição | | ------- | ------------------------------------------- | | PERIOD | Intervalo em dias (1 = diário, 7 = semanal) | | DELAY | Minutos a esperar após o boot | | IDENT | Nome identificador da tarefa | | COMMAND | Comando ou script a ser executado |
Exemplo:
bash 1 3 limpeza-temporarios /home/usuario/scripts/limpar_tmp.shExecuta o script uma vez por dia, 3 minutos após o sistema ser ligado.
Nota: Não é necessário usar
run-partsnemcron.dailypara tarefas personalizadas. Basta apontar diretamente para o script desejado. Orun-partssó deve ser usado quando se deseja executar todos os scripts de um diretório.Ativação do serviço:
bash sudo systemctl enable --now anacronVerificação de status:
bash systemctl status anacronLogs de execução:
bash grep anacron /var/log/syslog/etc/anacrontab: Arquivo de Configuração doanacronO arquivo
/etc/anacrontabdefine tarefas periódicas a serem executadas peloanacron, garantindo que comandos sejam executados mesmo que o computador esteja desligado no horário originalmente programado.Cabeçalho Padrão
bash SHELL=/bin/sh HOME=/root LOGNAME=root-
SHELL: Shell padrão utilizado para executar os comandos. -
HOME: Diretório home usado durante a execução. -
LOGNAME: Usuário associado à execução das tarefas.
Entradas Padrão do Sistema
bash 1 5 cron.daily run-parts --report /etc/cron.daily 7 10 cron.weekly run-parts --report /etc/cron.weekly @monthly 15 cron.monthly run-parts --report /etc/cron.monthly|Campo|Significado| |---|---| |
1|Executa a tarefa diariamente (a cada 1 dia)| |5|Espera 5 minutos após o boot| |cron.daily|Identificador da tarefa (usado nos logs)| |run-parts|Executa todos os scripts dentro do diretório|Diretórios utilizados:
-
/etc/cron.daily: scripts executados uma vez por dia -
/etc/cron.weekly: scripts semanais -
/etc/cron.monthly: scripts mensais
O comando
run-partsexecuta automaticamente todos os scripts executáveis localizados nesses diretórios.Personalização
Para adicionar tarefas personalizadas ao
anacron, basta adicionar novas linhas com o formato:PERIOD DELAY IDENT COMMANDExemplo:
bash 1 3 limpeza-temporarios /home/usuario/scripts/limpar_tmp.shExecuta o script
limpar_tmp.shdiariamente, com 3 minutos de atraso após o boot.Importante: Não é necessário — nem recomendado — usar
run-partsquando a intenção é executar um script individual. Orun-partsespera um diretório e ignora arquivos individuais. Usarrun-partscom um script individual causará falha na execução. -
-
 @ 048ecb14:7c28ac78
2025-05-29 00:49:55
@ 048ecb14:7c28ac78
2025-05-29 00:49:55I recently set up a Raspberry Pi camera server that's so minimal and straightforward, I thought it was worth sharing. This isn't one of those over-engineered solutions with fancy features - it's just a basic, reliable camera feed accessible from any browser on my local network.
The Goal
I wanted something that: 1. Starts automatically when the Pi boots up 2. Captures images at regular intervals 3. Shows the latest image in a simple web page accessible from any device 4. Doesn't require complex setup or dependencies 5. Uses minimal resources on my old Raspberry Pi
The Hardware
Nothing fancy here: - Raspberry Pi 2B (yes, the ancient one from 2015!) - Raspberry Pi Camera Module (standard version) - Power supply - That's it!
The Result

The interface is minimal but does the job. It shows the latest image and auto-refreshes every couple of seconds.
How to Get Set Up
Getting this running on your own Pi is super simple:
-
Make sure your camera module is connected and enabled
bash sudo raspi-config # Navigate to Interface Options > Camera and enable it -
Install the only dependency, ImageMagick (for rotation)
bash sudo apt update sudo apt install imagemagick -
Clone the repository, and navigate to the implementation's directory
bash git clone https://github.com/rewolf/RpiCameraViewer cd simple -
Start the camera server
bash ./start_camera_server.sh -
Access the feed from any device on your network
http://your-pi-ip-address:8080
That's it! No complex configuration, no fancy dependencies.
For more details consider reading the README
To make it start automatically on boot:
Add the following, with your specific installation path ```bash crontab -e
Add this line:
@reboot cd /path/to/RpiCameraViewer/simple && ./start_camera_server.sh ```
Configuration
There's not much configuration, but you can tweak few variables at the top of the
capture.shfile to modify width, height, rotation, quality, etc:bash QUALITY=90 WIDTH=720 HEIGHT=1280 ROTATION=90 # Set to 0 to disable rotationHow It Works
The solution is very basic:
- A bash script (
capture.sh) captures photos every few seconds by runninglibcamera-stilland sending a SIGUSR1 interrupt to signal it to capture a snapshot - The snapshot is rotated as needed with ImageMagick and saved with timestamps
- A symbolic link is updated to point to the latest image
- A minimal Python HTTP server serves a basic webpage showing the current image (the symlink), rendered to an HTML canvas
Note it does expose that directory to the whole LAN on :8080.
Give it a try if you need something like that quickly.
I have a plan to make a better implementation planned at some point, but for now this will do.
-
-
 @ dfa02707:41ca50e3
2025-05-27 20:01:35
@ dfa02707:41ca50e3
2025-05-27 20:01:35Contribute to keep No Bullshit Bitcoin news going.
-
Version 1.3 of Bitcoin Safe introduces a redesigned interactive chart, quick receive feature, updated icons, a mempool preview window, support for Child Pays For Parent (CPFP) and testnet4, preconfigured testnet demo wallets, as well as various bug fixes and improvements.
-
Upcoming updates for Bitcoin Safe include Compact Block Filters.
"Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions. They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK," writes the project's developer Andreas Griffin.
- Learn more about the current and upcoming features of Bitcoin Safe wallet here.
What's new in v1.3
- Redesign of Chart, Quick Receive, Icons, and Mempool Preview (by @design-rrr).
- Interactive chart. Clicking on it now jumps to transaction, and selected transactions are now highlighted.

- Speed up transactions with Child Pays For Parent (CPFP).
- BDK 1.2 (upgraded from 0.32).
- Testnet4 support.
- Preconfigured Testnet demo wallets.
- Cluster unconfirmed transactions so that parents/children are next to each other.
- Customizable columns for all tables (optional view: Txid, Address index, and more)
- Bug fixes and other improvements.

Announcement / Archive
Blog Post / Archive
GitHub Repo
Website -
-
 @ ece127e2:745bab9c
2025-05-29 00:32:33
@ ece127e2:745bab9c
2025-05-29 00:32:33vamos a ver que tal
*lo bueno es que si entro en https://makimono.lumilumi.app/ a la nota y agrego contenido , como éste ...quiero ver si lo añade o hace una nueva nota ?? *
-
 @ cae03c48:2a7d6671
2025-05-27 20:00:43
@ cae03c48:2a7d6671
2025-05-27 20:00:43Bitcoin Magazine

Bitcoin Well Integrates Nostr BTC Purchases via DMsBitcoin Well Inc. (TSXV: BTCW; OTCQB: BCNWF) has launched an integration with Nostr, allowing US customers to buy bitcoin directly through direct messages on the decentralized social protocol, according to a press release sent to Bitcoin Magazine.
Users can link their Nostr identifier (npub) to their Bitcoin Well account and purchase bitcoin by sending specific commands via direct message. The transactions draw from the user’s Cash Balance and send the purchased bitcoin to their existing Lightning Wallet for security.
Nostr is a decentralized social media protocol which is censorship resistant and runs on a network of relays, rather than centralized servers. This means that the users have full control over their message servers. It also adds a layer of protection for the customer’s privacy.
The integration simplifies the process of buying bitcoin by allowing users to make purchases directly through a social platform they already use. As a censorship-resistant protocol, Nostr ensures Bitcoin Well and its customers have full control, avoiding restrictions and potential censorship.
“This is a great achievement for our team!” said founder and CEO of Bitcoin Well Adam O’Brien. “We are deeply committed to make buying bitcoin directly to self custody better than using a custodial exchange. This is a huge step in the right direction. We are meeting bitcoiners where they are and allowing them to buy bitcoin safely.”
Users can link their npub to their Bitcoin Well account to enable bitcoin purchases via direct message. Commands like /buy $21.00 or /stack 69000 sats initiate a transaction, which is confirmed by sending /confirm. The purchase uses funds from the user’s Bitcoin Well Cash Balance, and bitcoin is delivered over the Lightning Network to a pre-registered wallet address.
This post Bitcoin Well Integrates Nostr BTC Purchases via DMs first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ e9d7ed6f:f52b3346
2025-05-28 23:36:58
@ e9d7ed6f:f52b3346
2025-05-28 23:36:58I'd like to toss it off by thanking you my reader, friends, associates, strangers, bitcoiners, cryptonaires, economists, and critics from all walks of life for granting me this opportunity to write to you. yeah?...
Is that readable? Is there enough ink in this pen to write? Let me squash and develop a fresh script!
Okay now, that was one heck of a disaster introduction my friends.
That's not even the way Satoshi introduced his White paper back in 2008, or rather mined his first block. So dear reader, lets pretend this introduction never happened lets give it one more kick start.
Alright we are set so here we go...
Flavatos, Gateway Mall, the left ventricle of Lilongwe's heart, Malawi is where the aroma of a fresh bitcoin pizza sent waves of spattering energy, broadcasting to all nodes over the bitcoin network. Pizza crums spread over the table, folks and knives faced opposite directions, tomato sauce on the white plate had contours of pizza passage, a half baked joke & its laughter could be heard by passersby's heading inside the mall. It was chilly Saturday afternoon from outside but the soft drinks were a must to soften the well baked fragments of pizza which were being churned. All thanks to Larszlo Keyckenes. Phones where right on the table as the photographer snapped every detail of moment with his camera, trying to paint a bitcoin Monalisa, innocence was in the youthful energetic bitcoiners who filled left to right seats in pairs. Three tables were joined together making a table tennis appear short, but the waitress had to check for any empty slot to squeeze a chair in. We were twenty three with the expection of thirty but the space was just plentiful.
Flavatos was ready and set. The waitress again, with a smile of welcoming a guest whispered right besides where i was standing that the pizza is ready, but i had to HODL for a moment, we were just setting up the laptop which we would use to connect & listen to a presentation by John Miller, a distant relative and a bitcoiner we had talked of for weeks. As if am very good at analysing charts, the looks of the faces were eagerly waiting and i when i looked on my wrist i realised we didn't have much more time other than to start off, so i clapped my hands to capture everyones attention. I was excited to welcome all & really appreciate for sparing their time to come.
There was buzz in the atmosphere, all eyes glued to me as i thanked the cofounder Grant for pulling the strings, in our presence we had the cofounder of women of Satoshi Yankho who i was facing directly to my right hand side and threw me sparkle of acknowledgement, i couldn't forget & sweep under the mat, John Miller sponsor for the Bitcoin Pizza who is currently in the US & was waiting to deliver a speech on this very moment. All started off in the right order, my stomach tuned as my brain signaled the pizza image, sending tickling hunger sensation, so not to keep everyone waiting longer, i handed it over to Grant who quickly threw like free shot on the free throw line. There was genuine appreciation and he set the floor ready for John Miller to grace and unwrap the Pizza. When John took on the google meet space, we all fixed to our phones, eager to see John who was seven hours away from us, about two or three plane tickets to get where he was physically located. John delivered a twenty minute presentation that would make a fresh graduate take off his hat and really consider what they did the last four years of their university. There was a lot of knowledge on his presentation, highlighting the eminent nails to the coffin for US dollar, the chart and numbers didn't lie when he displayed how the purchasing power of the dollar has declined since 1971 post detachment from gold. He spoke with authority on why bitcoin, how Bitcoiners should continue orange pilling and detoxing all the pool of confusion of the current FIAT sytem. It was listening to wisdom of an old man, giving the torch to the young ones. The waitress had brought to the table clean white plates with some folks wrapped in a white napkin tissue that appeared so white as Satoshi's white paper. In no time the pizza was ready to bona petite, John wrapped up in a cousy style by saying, "keep stacking Sats and avoiding shitcoins. The attendees were in pairs and hands were rubbing, contemplating of how the first bite would feel. The enzymes were ready to digest. The next host, who happens to be the writer of this article had to take the floor and give short remarks to thank John, Grant and everyone. I saw the pizza being cut into slices, whilst others took sips of their favorite soft drinks, there were smiles from left to right check. The sound chewing was amplified, triggering my ear drums to some vibe. This was was a big family reunion. My signal for speaking almost went off as the aroma teased the mind, i saw the bubble from the fanta bottle float up but i was mature to handled the temper of my hunger. As the pizza halvening was going on, I reminded of how significant this moment was when Larszlo Heykens first made an offer of 10,000 BTC & how it signified use case of bitcoin as a medium of exchange and a resort of finality between two counterparts without any middleman. It surely was moment that reminded us of the free markets. Where two counterparts chose their own commodities of exchange and each left satisfied as finality of transactions. Truly those were the good old free market days. By the time i said goodbye, my counterparts had already mined half of the pizza brought. I was about to pop a question of where is my share when i saw three more full plates of pizza broadcasted & awaiting for verification. I knew i was in for a treat.
As i kept my hands, mouth and tummy busy, one surprising moment really fired me up with excitement. Grant stood up and surprised everyone by introducing his new friend from Kenya. He said they had met in Mulanje and how they came across each other was purely a barter coincidence of wants. Rather him explaining, he let our new Kenyan explorer share the fascinating story of how he wanted to send funds in Kenya but couldn't find means of transalating our local currency into the Kenyan shilling. So how could these two opposite worlds tie together? When he saw the post of bitcoin accepted here, it sparked the charge. Using Bitcoin, he was able to send funds in Kenya via bitcoin lightening wallet through Tando and Mpesa. As if we were in a cinema watching possibilities become realities, a demostration was showcased how inter transactions are done from a wallet of Satoshi lightening wallet to Tando whilst eating pizza in Malawi.
It was truly a fantastic orange day to pill and slice. See you in the next article as i continue to polish my writing skills.
Pacharo Nyirenda. Bitcoinboma An amature writer but soon to be pro writer & blogger!
-
 @ 5391098c:74403a0e
2025-05-27 18:20:42
@ 5391098c:74403a0e
2025-05-27 18:20:42Você trabalha 5 meses do ano somente para pagar impostos. Ou seja, 42% da sua renda serve para bancar serviços públicos de péssima qualidade. Mesmo que você tivesse a liberdade de usar esses 42% da sua renda para contratar serviços privados de qualidade (saúde, segurança e ensino), ainda assim você seria um escravo porque você recebe dinheiro em troca do seu trabalho, e o dinheiro perde cerca de 10% do valor a cada ano. Em outras palavras todo seu dinheiro que sobra depois de comprar comida, vestuário e moradia perde 100% do valor a cada 10 anos. Isso acontece porque o Estado imprime dinheiro do nada e joga na economia de propósito para gerar INFLAÇÃO e manter todos nós escravizados. Você pode deixar seu dinheiro investido em qualquer aplicação que imaginar e ainda assim nunca terá uma rentabilidade superior a inflação real. No final, acaba perdendo tudo do mesmo jeito. Caso você se ache esperto por investir o que sobra da sua renda em bens duráveis como imóveis ou veículos, sabia que esses bens também não são seus, porque se deixar de pagar os impostos desses bens (iptu, itr, ipva) você também perde tudo. Além disso, o custo de manutenção desses bens deve ser levado em consideração na conta das novas dívidas que você assumiu. No caso dos imóveis urbanos é impossível alugá-lo por mais de 0,38% do seu valor mensalmente. Em outras palavras, a cada ano você recebe menos de 5% do que investiu, tem que pagar o custo de manutenção, mais impostos e a valorização do bem nunca será superior a inflação real, também fazendo você perder quase tudo em cerca de 15 anos. A situação é ainda pior com os imóveis rurais e veículos, basta fazer as contas. Caso o dinheiro que você receba em troca do seu trabalho seja suficiente apenas para comprar comida, vestuário e moradia, você já sabe que é um escravo né?… Precisamos entender que a escravidão não acabou, apenas foi democratizada. Hoje a escravidão é financeira, nós somos os castiços e os donos do dinheiro são o senhorio. Os donos do dinheiro são os Globalistas e os Estados seus fantoches. O esquema é simples: fazer todo mundo trabalhar em troca de algo que perde 100% do valor a cada 10 anos, ou seja o dinheiro. Se você pudesse trabalhar em troca de algo que aumentasse de valor acima da inflação real a cada 10 anos você finalmente conquistaria sua liberdade financeira e deixaria de ser escravo. Pois bem, isso já é possível, e não se trata de ouro ou imóveis e sim sobre o Bitcoin, que sobe de valor mais de 100% a cada 10 anos, com a vantagem de ser inconfiscável e de fácil transferência para seus herdeiros quando você morrer, através de uma simples transação LockTime feita em vida. Portanto, mesmo que você não tenha dinheiro para comprar Bitcoin, passar a aceitar Bitcoin em troca de seus produtos e serviços é a única forma de se libertar da escravidão financeira. A carta de alforria financeira proporcionada pelo Bitcoin não é imediata, pois a velocidade da sua libertação depende do quanto você está disposto a aprender sobre o assunto. Eu estou aqui para te ajudar, caso queira. No futuro o Bitcoin estará tão presente na sua vida quanto o pix e o cartão de crédito, você querendo ou não. Assim como o cartão de crédito foi a evolução do cheque pós-datado e o pix a evolução do cartão, o Bitcoin e outras criptomoedas serão a evolução de todos esses meios de pagamento. O que te ofereço é a oportunidade de abolição da sua escravatura antes dos demais escravos acordarem para a realidade, afinal a história sempre se repete: desde o ano de 1300 a.c. a escravidão era defendida pelos próprios escravos, que mais cedo ou mais tarde, foram libertados por Moisés em êxodo 11 da Bíblia Sagrada e hoje o povo de israel se tornou a nação mais rica do mundo. A mesma história se repetiu na Roma Antiga: com o pão e circo. Da mesma forma todo esse império escravocrata ruiu porque mais cedo ou mais tarde os escravos se revoltam, bastam as coisas piorarem bastante. O atual regime de escravidão teve início com a queda do padrão-ouro para impressão do dinheiro no ano de 1944. A escravidão apenas ficou mais sofisticada, pois em vez de pagar os escravos com cerveja como no Egito Antigo ou com pão e circo como na Roma Antiga, passou-se a pagar os escravos com dinheiro sem lastro, ou seja dinheiro inventado, criado do nada, sem qualquer representação com a riqueza real da economia. Mesmo sendo a escravidão atual mais sofisticada, que deixou de ser física para ser financeira, o que torna a mentira mais bem contada, mais cedo ou mais tarde os escravos modernos irão acordar, basta as coisas piorarem mais ou perceberem que todos os bens e serviços do mundo não representam nem 1% de todo o dinheiro que impresso sem lastro. Em outras palavras, se os donos de todo o dinheiro do mundo resolvessem utilizá-lo para comprar tudo o que existe à venda, o preço do quilo do café subiria para R$ 297.306,00 e o preço médio dos imóveis subiria para um número tão grande que sequer caberia nesta folha de papel. Hoje, o dinheiro não vale nada, seus donos sabem disso e optam por entregar o dinheiro aos poucos para os escravos em troca do seu trabalho, para manter o atual regime o máximo de tempo possível. Mesmo assim, o atual regime de escravidão financeira está com os dias contados e depende de você se posicionar antes do efeito manada. Nunca é tarde para entrar no Bitcoin, mesmo ele tendo uma quantidade de emissão limitada, seu valor subirá infinitamente. A menor unidade do Bitcoin é o satoshi, cuja abreviação é sats. Diferente do centavo, cada sat vale um centésimo milionésimo de bitcoin. Hoje (25/05/25), cada unidade de Bitcoin equivale a setecentos mil reais. Logo, cada R$ 0,01 equivale à 0,007 sats. Lembrando que o centavo é um real dividido por cem e o sat é um bitcoin dividido por cem milhões, por isso ainda não existe a paridade entre 1 centavo de real e 1 sat. Essa paridade será alcançada quando um Bitcoin passar a valer um milhão de reais. Com a velocidade que nosso dinheiro está perdendo valor isso não irá demorar muito. Utilizando dados econômicos avançados, prevejo que cada unidade de Bitcoin passará a valer hum milhão de reais até o ano de 2029, assim equiparando 1 sat para cada R$ 0,01. Nesse momento, certamente muitos empresários, comerciantes e profissionais liberais passarão a aceitar o Bitcoin como forma de pagamento pelos seus produtos e serviços, assim como o cheque foi substituído pelo cartão de crédito e o cartão pelo pix. Sabendo disso, você pode entrar na onda de transição no futuro junto com a manada e perder essa alta valorização, ou passar a aceitar Bitcoin agora pelos seus produtos e serviços, assinando assim, a própria carta de alforria da sua escravidão financeira. É importante dizer que os próprios globalistas e governos estão trocando dinheiro por Bitcoin como nunca na história e mesmo que eles adquiram todos os bitcoins disponíveis, ainda assim não será mais possível manter seu regime de escravidão financeira funcionando porque a emissão de Bitcoin é limitada, sendo impossível criar Bitcoin sem lastro, como é feito com o dinheiro hoje. Com o presente artigo, te ofereço a oportunidade de conquistar seus primeiros sats agora, de forma segura e independente, sem precisar de corretoras, bancos, intermediários ou terceiros, basta você querer pois toda a informação necessária está disponível na internet gratuitamente. Se ainda assim você quiser continuar sendo escravo financeiro, depois não adiantar se arrepender quando as janelas de oportunidade se fecharem, o Drex for implantado, papel moeda restringido e sua vida piorar bastante. Importante mencionar que a Lei Brasileira ainda permite a movimentação de até R$ 30.000,00 em Bitcoin por mês sem a necessidade de declaração à Receita Federal e que esse direito pode deixar de existir a qualquer momento, e que quando o Drex for implantado você perderá diversos outros direitos, dentre ele a liberdade de gastar seu dinheiro como quiser e o sigilo. Ofereço ainda, a oportunidade de você baixar uma carteira de Bitcoin gratuita e segura no seu aparelho de celular que funciona de forma semelhante a um banco digital como Nubank e Pagseguro por exemplo, para poder começar à receber Bitcoin pelos seus produtos e serviços agora, de forma fácil e gratuita. Utilizando o qrcode abaixo você ainda ganha alguns sats de graça, promoção válida até o dia 29/05/25 e patrocinada pela Corretora Blink de El Salvador, onde o Bitcoin já é moeda oficial do país, basta acessar o link e instalar o aplicativo: https://get.blink.sv/btcvale
Aviso: disponibilizei o link da carteira de Bitcoin da Corretora Blink apenas como exemplo de como é fácil aceitar Bitcoin como forma de pagamento pelos seus produtos e serviços. Não recomento depender de qualquer corretora para guardar seus valores em Bitcoin. A melhor forma de fazer isso é mantendo dois computadores ou notebook em casa, um conectado à internet com memória em disco disponível de 1 terabyte ou mais para armazenar e visualizar suas transações e outro computador ou notebook desconectado da internet para armazenar suas senhas e chaves privadas para assinar as transações via pendrive. Somente assim você estará 100% livre e seguro. Importante ainda fazer backup em vários CDs com criptografia do seu computador ou notebook que assina as transações, assim também ficando 100% livre e seguro para restaurar sua carteira em qualquer outro computador caso necessário. Todas as instruções de como fazer isso já estão disponíveis gratuitamente na internet. Caso deseje contratar uma consultoria pessoal que inclui aulas particulares por vídeo conferência, onde você aprenderá:
→ Tudo o que precisa saber sobre Bitcoin e demais criptomoedas; → Sistema operacional Linux; → Como instalar sua carteira de Bitcoin em dois computadores para assinaturas air gapped; → Se manter 100% livre e seguro. → Com carga horária à combinar conforme sua disponibilidade.
O custo do investimento pelo meu serviço individual para esse tipo de consultoria é de 204.000 sats (R$ 1.543,46 na cotação atual) valor válido até 31/07/25, interessados entrar em contato por aqui ou através da Matrix: @davipinheiro:matrix.org https://davipinheiro.com/voce-e-escravo-e-nem-sabe-eu-vou-te-provar-agora/
-
 @ 5391098c:74403a0e
2025-05-27 18:15:38
@ 5391098c:74403a0e
2025-05-27 18:15:38Você trabalha 5 meses do ano somente para pagar impostos. Ou seja, 42% da sua renda serve para bancar serviços públicos de péssima qualidade. Mesmo que você tivesse a liberdade de usar esses 42% da sua renda para contratar serviços privados de qualidade (saúde, segurança e ensino), ainda assim você seria um escravo porque você recebe dinheiro em troca do seu trabalho, e o dinheiro perde cerca de 10% do valor a cada ano. Em outras palavras todo seu dinheiro que sobra depois de comprar comida, vestuário e moradia perde 100% do valor a cada 10 anos. Isso acontece porque o Estado imprime dinheiro do nada e joga na economia de propósito para gerar INFLAÇÃO e manter todos nós escravizados. Você pode deixar seu dinheiro investido em qualquer aplicação que imaginar e ainda assim nunca terá uma rentabilidade superior a inflação real. No final, acaba perdendo tudo do mesmo jeito. Caso você se ache esperto por investir o que sobra da sua renda em bens duráveis como imóveis ou veículos, sabia que esses bens também não são seus, porque se deixar de pagar os impostos desses bens (iptu, itr, ipva) você também perde tudo. Além disso, o custo de manutenção desses bens deve ser levado em consideração na conta das novas dívidas que você assumiu. No caso dos imóveis urbanos é impossível alugá-lo por mais de 0,38% do seu valor mensalmente. Em outras palavras, a cada ano você recebe menos de 5% do que investiu, tem que pagar o custo de manutenção, mais impostos e a valorização do bem nunca será superior a inflação real, também fazendo você perder quase tudo em cerca de 15 anos. A situação é ainda pior com os imóveis rurais e veículos, basta fazer as contas. Caso o dinheiro que você receba em troca do seu trabalho seja suficiente apenas para comprar comida, vestuário e moradia, você já sabe que é um escravo né?… Precisamos entender que a escravidão não acabou, apenas foi democratizada. Hoje a escravidão é financeira, nós somos os castiços e os donos do dinheiro são o senhorio. Os donos do dinheiro são os Globalistas e os Estados seus fantoches. O esquema é simples: fazer todo mundo trabalhar em troca de algo que perde 100% do valor a cada 10 anos, ou seja o dinheiro. Se você pudesse trabalhar em troca de algo que aumentasse de valor acima da inflação real a cada 10 anos você finalmente conquistaria sua liberdade financeira e deixaria de ser escravo. Pois bem, isso já é possível, e não se trata de ouro ou imóveis e sim sobre o Bitcoin, que sobe de valor mais de 100% a cada 10 anos, com a vantagem de ser inconfiscável e de fácil transferência para seus herdeiros quando você morrer, através de uma simples transação LockTime feita em vida. Portanto, mesmo que você não tenha dinheiro para comprar Bitcoin, passar a aceitar Bitcoin em troca de seus produtos e serviços é a única forma de se libertar da escravidão financeira. A carta de alforria financeira proporcionada pelo Bitcoin não é imediata, pois a velocidade da sua libertação depende do quanto você está disposto a aprender sobre o assunto. Eu estou aqui para te ajudar, caso queira. No futuro o Bitcoin estará tão presente na sua vida quanto o pix e o cartão de crédito, você querendo ou não. Assim como o cartão de crédito foi a evolução do cheque pós-datado e o pix a evolução do cartão, o Bitcoin e outras criptomoedas serão a evolução de todos esses meios de pagamento. O que te ofereço é a oportunidade de abolição da sua escravatura antes dos demais escravos acordarem para a realidade, afinal a história sempre se repete: desde o ano de 1300 a.c. a escravidão era defendida pelos próprios escravos, que mais cedo ou mais tarde, foram libertados por Moisés em êxodo 11 da Bíblia Sagrada e hoje o povo de israel se tornou a nação mais rica do mundo. A mesma história se repetiu na Roma Antiga: com o pão e circo. Da mesma forma todo esse império escravocrata ruiu porque mais cedo ou mais tarde os escravos se revoltam, bastam as coisas piorarem bastante. O atual regime de escravidão teve início com a queda do padrão-ouro para impressão do dinheiro no ano de 1944. A escravidão apenas ficou mais sofisticada, pois em vez de pagar os escravos com cerveja como no Egito Antigo ou com pão e circo como na Roma Antiga, passou-se a pagar os escravos com dinheiro sem lastro, ou seja dinheiro inventado, criado do nada, sem qualquer representação com a riqueza real da economia. Mesmo sendo a escravidão atual mais sofisticada, que deixou de ser física para ser financeira, o que torna a mentira mais bem contada, mais cedo ou mais tarde os escravos modernos irão acordar, basta as coisas piorarem mais ou perceberem que todos os bens e serviços do mundo não representam nem 1% de todo o dinheiro que impresso sem lastro. Em outras palavras, se os donos de todo o dinheiro do mundo resolvessem utilizá-lo para comprar tudo o que existe à venda, o preço do quilo do café subiria para R$ 297.306,00 e o preço médio dos imóveis subiria para um número tão grande que sequer caberia nesta folha de papel. Hoje, o dinheiro não vale nada, seus donos sabem disso e optam por entregar o dinheiro aos poucos para os escravos em troca do seu trabalho, para manter o atual regime o máximo de tempo possível. Mesmo assim, o atual regime de escravidão financeira está com os dias contados e depende de você se posicionar antes do efeito manada. Nunca é tarde para entrar no Bitcoin, mesmo ele tendo uma quantidade de emissão limitada, seu valor subirá infinitamente. A menor unidade do Bitcoin é o satoshi, cuja abreviação é sats. Diferente do centavo, cada sat vale um centésimo milionésimo de bitcoin. Hoje (25/05/25), cada unidade de Bitcoin equivale a setecentos mil reais. Logo, cada R$ 0,01 equivale à 0,007 sats. Lembrando que o centavo é um real dividido por cem e o sat é um bitcoin dividido por cem milhões, por isso ainda não existe a paridade entre 1 centavo de real e 1 sat. Essa paridade será alcançada quando um Bitcoin passar a valer um milhão de reais. Com a velocidade que nosso dinheiro está perdendo valor isso não irá demorar muito. Utilizando dados econômicos avançados, prevejo que cada unidade de Bitcoin passará a valer hum milhão de reais até o ano de 2029, assim equiparando 1 sat para cada R$ 0,01. Nesse momento, certamente muitos empresários, comerciantes e profissionais liberais passarão a aceitar o Bitcoin como forma de pagamento pelos seus produtos e serviços, assim como o cheque foi substituído pelo cartão de crédito e o cartão pelo pix. Sabendo disso, você pode entrar na onda de transição no futuro junto com a manada e perder essa alta valorização, ou passar a aceitar Bitcoin agora pelos seus produtos e serviços, assinando assim, a própria carta de alforria da sua escravidão financeira. É importante dizer que os próprios globalistas e governos estão trocando dinheiro por Bitcoin como nunca na história e mesmo que eles adquiram todos os bitcoins disponíveis, ainda assim não será mais possível manter seu regime de escravidão financeira funcionando porque a emissão de Bitcoin é limitada, sendo impossível criar Bitcoin sem lastro, como é feito com o dinheiro hoje. Com o presente artigo, te ofereço a oportunidade de conquistar seus primeiros sats agora, de forma segura e independente, sem precisar de corretoras, bancos, intermediários ou terceiros, basta você querer pois toda a informação necessária está disponível na internet gratuitamente. Se ainda assim você quiser continuar sendo escravo financeiro, depois não adiantar se arrepender quando as janelas de oportunidade se fecharem, o Drex for implantado, papel moeda restringido e sua vida piorar bastante. Importante mencionar que a Lei Brasileira ainda permite a movimentação de até R$ 30.000,00 em Bitcoin por mês sem a necessidade de declaração à Receita Federal e que esse direito pode deixar de existir a qualquer momento, e que quando o Drex for implantado você perderá diversos outros direitos, dentre ele a liberdade de gastar seu dinheiro como quiser e o sigilo. Ofereço ainda, a oportunidade de você baixar uma carteira de Bitcoin gratuita e segura no seu aparelho de celular que funciona de forma semelhante a um banco digital como Nubank e Pagseguro por exemplo, para poder começar à receber Bitcoin pelos seus produtos e serviços agora, de forma fácil e gratuita. Utilizando o qrcode abaixo você ainda ganha alguns sats de graça, promoção válida até o dia 29/05/25 e patrocinada pela Corretora Blink de El Salvador, onde o Bitcoin já é moeda oficial do país, basta acessar o link e instalar o aplicativo: https://get.blink.sv/btcvale
Aviso: disponibilizei o link da carteira de Bitcoin da Corretora Blink apenas como exemplo de como é fácil aceitar Bitcoin como forma de pagamento pelos seus produtos e serviços. Não recomento depender de qualquer corretora para guardar seus valores em Bitcoin. A melhor forma de fazer isso é mantendo dois computadores ou notebook em casa, um conectado à internet com memória em disco disponível de 1 terabyte ou mais para armazenar e visualizar suas transações e outro computador ou notebook desconectado da internet para armazenar suas senhas e chaves privadas para assinar as transações via pendrive. Somente assim você estará 100% livre e seguro. Importante ainda fazer backup em vários CDs com criptografia do seu computador ou notebook que assina as transações, assim também ficando 100% livre e seguro para restaurar sua carteira em qualquer outro computador caso necessário. Todas as instruções de como fazer isso já estão disponíveis gratuitamente na internet. Caso deseje contratar uma consultoria pessoal que inclui aulas particulares por vídeo conferência, onde você aprenderá:
→ Tudo o que precisa saber sobre Bitcoin e demais criptomoedas; → Sistema operacional Linux; → Como instalar sua carteira de Bitcoin em dois computadores para assinaturas air gapped; → Se manter 100% livre e seguro. → Com carga horária à combinar conforme sua disponibilidade.
O custo do investimento pelo meu serviço individual para esse tipo de consultoria é de 204.000 sats (R$ 1.543,46 na cotação atual) valor válido até 31/07/25, interessados entrar em contato por aqui ou através da Matrix: @davipinheiro:matrix.org https://davipinheiro.com/voce-e-escravo-e-nem-sabe-eu-vou-te-provar-agora/
-
 @ 2b998b04:86727e47
2025-05-28 23:24:05
@ 2b998b04:86727e47
2025-05-28 23:24:05I’ve spent years chasing the promise of freedom.\ In startups. In faith communities. In movements that claimed to be for the people.
And yet — so often, that promise felt just out of reach.\ Conditional. Corporate. Sanitized.\ A freedom with fine print.
But here —\ Here in the thick of Bitcoin 2025, on Nostr, among misfits and builders and signal-bringers —\ something is alive.
It’s not a platform.\ It’s not a marketing strategy.\ It’s not another app promising to “empower” you while locking down your data and selling you out.
It’s freedom rooted in architecture.\ Decentralization not just as a buzzword —\ but as an expression of conviction.
A kind of freedom you can feel in your body:
-
When you zap someone’s words because they moved you — not because an algorithm told you to.
-
When your identity is yours — keys, not credentials.
-
When no one can delete your story because you control the server, or because there is no server — just the relay of your choosing.
This isn’t utopia.\ There are egos. There’s noise. There’s still posturing.\ But it’s different.\ The center of gravity has shifted.
We’re no longer begging institutions to notice us.\ We’re building outside their jurisdiction.
And for the first time in a long time,\ freedom feels close.\ Tangible.\ Joyful.\ Alive.
This isn’t just about tech.\ It’s about trust.\ It’s about choosing to show up —\ to build\ to write\ to signal\ to keep going.
Even when it’s hard.\ Even when no one claps.
Because real freedom doesn’t come from being noticed.\ It comes from being sovereign.
And that’s something no one can take from me again.
—
Written in Las Vegas, during Bitcoin 2025.\ Posted via Nostr. Vibes co-authored by ChatGPT (“Dr. C”).\ Zap: https://tinyurl.com/yuyu2b9t
-
-
 @ dfa02707:41ca50e3
2025-05-27 18:02:36
@ dfa02707:41ca50e3
2025-05-27 18:02:36Headlines
- Spiral renews support for Dan Gould and Joschisan. The organization has renewed support for Dan Gould, who is developing the Payjoin Dev Kit (PDK), and Joschisan, a Fedimint developer focused on simplifying federations.
- Metaplanet buys another 145 BTC. The Tokyo-listed company has purchased an additional 145 BTC for $13.6 million. Their total bitcoin holdings now stand at 5,000 coins, worth around $428.1 million.
- Semler Scientific has increased its bitcoin holdings to 3,303 BTC. The company acquired an additional 111 BTC at an average price of $90,124. The purchase was funded through proceeds from an at-the-market offering and cash reserves, as stated in a press release.
- The Virtual Asset Service Providers (VASP) Bill 2025 introduced in Kenya. The new legislation aims to establish a comprehensive legal framework for licensing, regulating, and supervising virtual asset service providers (VASPs), with strict penalties for non-compliant entities.
- Russian government to launch a cryptocurrency exchange. The country's Ministry of Finance and Central Bank announced plans to establish a trading platform for "highly qualified investors" that "will legalize crypto assets and bring crypto operations out of the shadows."
- All virtual asset service providers expect to be fully compliant with the Travel Rule by the end of 2025. A survey by financial surveillance specialist Notabene reveals that 90% of virtual asset service providers (VASPs) expect full Travel Rule compliance by mid-2025, with all aiming for compliance by year-end. The survey also shows a significant rise in VASPs blocking withdrawals until beneficiary information is confirmed, increasing from 2.9% in 2024 to 15.4% now. Additionally, about 20% of VASPs return deposits if originator data is missing.
- UN claims Bitcoin mining is a "powerful tool" for money laundering. The Rage's analysis suggests that the recent United Nations Office on Drugs and Crime report on crime in South-East Asia makes little sense and hints at the potential introduction of Anti-Money Laundering (AML) measures at the mining level.
- Riot Platforms has obtained a $100 million credit facility from Coinbase Credit, using bitcoin as collateral for short-term funding to support its expansion. The firm's CEO, Jason Les, stated that this facility is crucial for diversifying financing sources and driving long-term stockholder value through strategic growth initiatives.
- Bitdeer raises $179M in loans and equity amid Bitcoin chip push. The Miner Mag reports that Bitdeer entered into a loan agreement with its affiliate Matrixport for up to $200 million in April, as disclosed in its annual report filed on Monday.
- Federal Reserve retracts guidance discouraging banks from engaging in 'crypto.' The U.S. Federal Reserve withdrew guidance that discouraged banks from crypto and stablecoin activities, as announced by its Board of Governors on Thursday. This includes rescinding a 2022 supervisory letter requiring prior notification of crypto activities and 2023 stablecoin requirements.
"As a result, the Board will no longer expect banks to provide notification and will instead monitor banks' crypto-asset activities through the normal supervisory process," reads the FED statement.
- UAE-based Islamic bank ruya launches Shari’ah-compliant bitcoin investing. The bank has become the world’s first Islamic bank to provide direct access to virtual asset investments, including Bitcoin, via its mobile app, per Bitcoin Magazine.
- U.S. 'crypto' scam losses amounted to $9.3B in 2024. The US The Federal Bureau of Investigation (FBI) has reported $9.3 billion losses in cryptocurrency-related scams in 2024, noting a troubling trend of scams targeting older Americans, which accounted for over $2.8 billion of those losses.
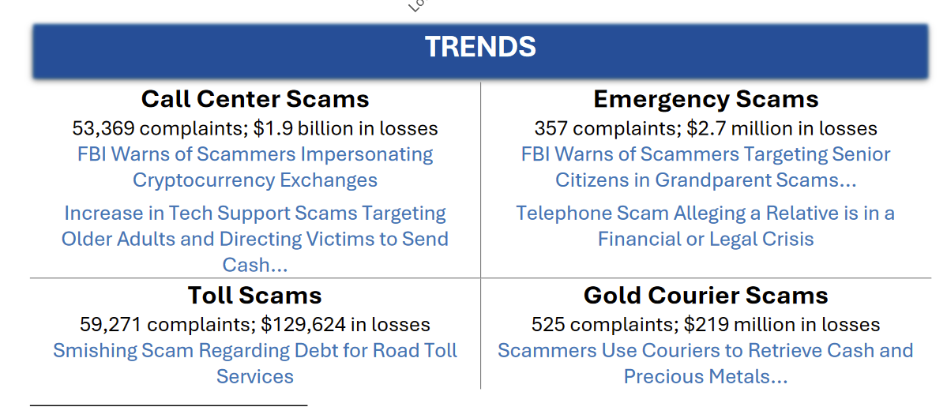
Source: FBI.
- North Korean hackers establish fake companies to target 'crypto' developers. Silent Push researchers reported that hackers linked to the Lazarus Group created three shell companies, two of which are based in the U.S., with the objective of spreading malware through deceptive job interview scams aimed at individuals seeking jobs in cryptocurrency companies.
- Citrea deployed its Clementine Bridge on the Bitcoin testnet. The bridge utilizes the BitVM2 programming language to inherit validity from Bitcoin, allegedly providing "the safest and most trust-minimized way to use BTC in decentralized finance."
- Hesperides University offers a Master’s degree in Bitcoin. Bitcoin Magazine reports the launch of the first-ever Spanish-language Master’s program dedicated exclusively to Bitcoin. Starting April 28, 2025, this fully online program will equip professionals with technical, economic, legal, and philosophical skills to excel in the Bitcoin era.
- BTC in D.C. event is set to take place on September 30 - October 1 in Washington, D.C. Learn more about this initiative here.
Use the tools
- Bitcoin Keeper just got a new look. Version 2.2.0 of the mobile multisig app brought a new branding design, along with a Keeper Private tier, testnet support, ability to import and export BIP-329 labels, and the option to use a Server Key with multiple users.
- Earlier this month the project also announced Keeper Learn service, offering clear and guided Bitcoin learning sessions for both groups and individuals.
- Keeper Desktop v0.2.2, a companion desktop app for Bitcoin Keeper mobile app, received a renewed branding update, too.

The evolution of Bitcoin Keeper logo. Source: BitHyve blog.
- Blockstream Green Desktop v2.0.25 updates GDK to v0.75.1 and fixes amount parsing issues when switching from fiat denomination to Liquid asset.
- Lightning Loop v0.31.0-beta enhances the
loop listswapscommand by improving the ability to filter the response. - Lightning-kmp v1.10.0, an implementation of the Lightning Network in Kotlin, is now available.
- LND v0.19.0-beta.rc3, the latest beta release candidate of LND is now ready for testing.
- ZEUS v0.11.0-alpha2 is now available for testing, too. It's nuts.
- JoinMarket Fidelity Bond Simulator helps potential JoinMarket makers evaluate their competitive position in the market based on fidelity bonds.
- UTXOscope is a text-only Bitcoin blockchain analysis tool that visualizes price dynamics using only on-chain data. The