-
 @ 6c05c73e:c4356f17
2025-05-30 15:24:34
@ 6c05c73e:c4356f17
2025-05-30 15:24:34Assim como a grande maioria dos brasileiros, eu não comecei um negócio porque "queria empreender". Muito pelo contrário, eu precisava para poder pagar as contas e manter o básico.
Então, vamos explorar essa pequena história e ver onde chegamos hoje.
Festas, Open Bar e Camisas
Meu primeiro negócio foi, na verdade, um combo. Eu tinha saído do último emprego e gostava muito de festas. Então, comecei a organizar uma festa mensalmente na casa do meu pai. Eu pagava a água, a energia e dava uma grana para ele. Em troca, organizava festas de sábado para domingo com open bar.
A fórmula era simples: criava um evento da festa no Facebook, convidava todo mundo que eu conhecia, panfletava na cidade e espalhava cartazes nos pontos de ônibus sobre a festa. E, para fechar com chave de ouro, mulher era VIP até as 20h. Consequência? Os caras vinham e pagavam o ingresso deles e o delas. Kkkkk. E a festa sempre lotava!
Comecei a notar que a galera se vestia mal. E pensei: "Por que não vestir eles?".
Pimba! Comecei a desenhar e confeccionar camisas para vender nas festas. E, pimba de novo! Vendeu tudo! Fiz duas coleções e mais algumas festas, até o dia em que um menino deu PT de tanto beber e decidi que era hora de tentar outra coisa.
Como Assim, a Apple Não Vai Mais Vender os Carregadores?
Isso foi durante a pandemia. A Apple decidiu vender o telefone e o cabo, e "que você se vire com a fonte". Estava difícil achar dinheiro no mercado naqueles tempos, e eu pensei: "Vou pesquisar no Google Trends e validar a ideia". Bingo! Tinha mais de 80 pontos de busca. Fui correndo para São Paulo, no Brás, e comprei, literalmente, todo o meu dinheiro em cabo de iPhone, carregador e bateria portátil.
Fiquei com R$ 100 na conta, só para fazer um lanche e pagar o Uber para voltar para casa. Chegando aqui, tirei fotos e fiz várias copys. Anunciei no OLX, Mercado Livre e Facebook. Impulsionei os anúncios no OLX, vendi para familiares e amigos, e vendia até para quem estava na rua. Fiz entrega de bike, a pé, de ônibus, e é isso mesmo, tem que ralar! Para queimar o resto da mercadoria, deixei em consignado em uma loja de eletrônicos. E, hora da próxima ideia.
Mulheres, Doces e TPM
Meu penúltimo negócio veio depois dos cabos. Eu pesquisei na internet negócios online para começar com pouca grana. (Depois que paguei as contas do dia a dia, sobraram R$ 3 mil). E achei uma pesquisa mostrando que doces tinham baixa barreira de entrada e exigiam poucos equipamentos. Eu trabalhei em restaurante por muitos anos e sabia como lucrar com aquilo. Além disso, mulheres consomem mais doce em uma certa época do mês.
Não deu outra, convidei duas pessoas para serem sócias. Desenvolvemos os produtos, fotografamos e fizemos as copys. Em seguida, precisávamos vender. Então, lá vamos nós de novo: iFood, WhatsApp, 99Food (na época), Uber Eats (na época), Elo7, famílias e amigos e, por fim, começamos a vender consignado em alguns restaurantes e lojas.
Foi uma época em que aprendi a prospectar clientes de todas as maneiras possíveis. De novo, minha maior dificuldade era a locomoção para fazer as entregas. Só tinha uma bike, mas entregávamos. Os primeiros três meses foram difíceis demais, mas rolou. No fim, nossas maiores vendas vinham do iFood, encomendas de festas e consignados.
Mas, como nem tudo são flores, meus dois sócios tomaram outros caminhos e abandonaram o projeto. Galera, está tudo bem com isso. Isso acontece o tempo todo. A vida muda e temos que aprender a aceitar isso. Vida que segue, fui para frente de novo.
Sobre Paixões, Paciência e Acreditar
Estava eu comemorando meu aniversário de 30 anos, num misto de realizações e pouca realização. Como assim? Sabe quando você faz um monte de coisas, mas ainda assim não sente que é aquilo? Pois então... Eu amo investimentos, livros, escrever e sempre curti trocar ideia com amigos e família sobre como se desenvolver.
Desde que comecei a usar a internet, eu criei: canal no YouTube, páginas no Instagram e Facebook, Pinterest, Steemit, blog e até canal no Telegram. Mas nunca tinha sido consistente, sabe? Tipo assim, vou fazer isso por um ano e plantar 100 sementes aqui. Enfim, inconsistência te derruba, meu amigo...
Eu voltei a trabalhar com restaurantes e estava doido para mudar de área. Estava exausto de trabalhar e meu WhatsApp não parava de tocar. Fui estudar ADM e Desenvolvimento de Sistemas no Senac. Dois anos depois, me formei, consegui um trabalho e comecei a pensar em como criar um negócio online, escalável e multilíngue.
Passei os próximos sete meses desenhando e pensando como. Mas tinha que dar o primeiro passo. Criei um site e fui escrevendo textos. Os primeiros 30 foram "aquilo", os próximos 10 melhoraram muito e os 10 seguintes me deixaram bem satisfeito. Hoje, tenho o negócio que estava na minha cabeça desde 2023. Mas olha o tamanho da volta que o universo me fez dar e aprender para chegar aqui hoje! Dicas? Só 3:
- Continua, lá na frente tudo vai fazer sentido.
- Presta mais atenção ao que a sua voz interior diz (intuição).
- Confia em si mesmo e faz sem medo de errar. Porque, adivinha? Você vai errar! Mas vai aprender e melhorar. Tem que persistir...
Só para simplificar, meu negócio é um blog com AdSense (parece arcaico, mas funciona). Por hoje é isso. E, se quiserem trocar ideias e se conectar, tamo junto!
-
 @ dfa02707:41ca50e3
2025-05-30 12:02:13
@ dfa02707:41ca50e3
2025-05-30 12:02:13Contribute to keep No Bullshit Bitcoin news going.
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.

-
 @ d360efec:14907b5f
2025-05-30 11:23:40
@ d360efec:14907b5f
2025-05-30 11:23:40 -
 @ da8b7de1:c0164aee
2025-05-30 16:06:23
@ da8b7de1:c0164aee
2025-05-30 16:06:23A Tennessee Valley Authority benyújtotta az első amerikai BWRX-300 SMR építési kérelmet
A Tennessee Valley Authority (TVA) hivatalosan is benyújtotta az amerikai Nukleáris Szabályozási Bizottsághoz (NRC) a GE Vernova Hitachi Nuclear Energy BWRX-300 kis moduláris reaktor (SMR) építésére vonatkozó kérelmet a Clinch River telephelyen. Ez jelentős lépés az SMR-ek amerikai bevezetésében, és jól mutatja a fejlett nukleáris reaktortechnológiák kereskedelmi hasznosításának lendületét. A BWRX-300-at úgy tervezték, hogy rugalmas, skálázható nukleáris energiamegoldást kínáljon, amely széles körben alkalmazható lehet az USA energiaszektorában.
A NuScale előrehaladott tárgyalásokat folytat SMR telepítésekről 2030-ig
Az amerikai NuScale Power nukleáris reaktorvállalat előrehaladott tárgyalásokat folytat több potenciális ügyféllel SMR technológiájának telepítéséről, és akár 2030-ra működő erőművet szállíthat. A korai alkalmazók között lehetnek adatközpontok, nehézipari szereplők és közművek is, ami jól mutatja az előrehaladott nukleáris megoldások iránti növekvő érdeklődést különböző energiaigényes ágazatokban. Ez a fejlemény kiemeli az SMR-ek növekvő szerepét a globális dekarbonizációs és energiabiztonsági stratégiákban.
Nemzetközi fókusz: érintetti bevonás és munkaerő-fejlesztés
Az IAEA Nemzetközi Konferenciája a Nukleáris Energia Programok Érintetti Bevonásáról ma zárult, ahol kiemelték az átlátható kommunikáció jelentőségét a nukleáris hulladékkezelés és vészhelyzetek során. A konferencia hangsúlyozta a diverzifikált, magasan képzett nukleáris munkaerő fejlesztésének stratégiáit is, beleértve az oktatási partnerségeket és a célzott képzéseket a hátrányos helyzetű csoportok számára. Ezek a témák globális szinten is elismerik, hogy a közbizalom és a tehetséggondozás kulcsfontosságú a nukleáris energia jövőbeni sikeréhez.
Globális politikai változások és piaci trendek
Az elmúlt hetekben több országban jelentős politikai változások történtek:
- Belgium visszavonta a 2003-as atomerőmű-lezárási törvényt, így ismét lehetőség nyílik új nukleáris létesítmények építésére.
- Dánia újraértékeli évtizedek óta fennálló nukleáris tilalmát, és új elemzést rendelt a nukleáris energia lehetséges szerepéről.
- Vietnam és más országok is előrehaladott tárgyalásokat folytatnak új atomerőművek építéséről.
- Az Európai Bizottság előkészíti az orosz nukleáris energiaimport fokozatos kivezetését, és hamarosan új jogszabályjavaslatokat terjeszt elő.
- Az Egyesült Államokban a 2026-os költségvetési év elnöki javaslatában csökkentik a Nukleáris Energia Hivatal finanszírozását, ugyanakkor regionális együttműködési megállapodásokat írnak alá a fejlett nukleáris technológiák támogatására a Mountain West régióban.
Kína tíz új atomerőművi reaktort hagyott jóvá
Kína Államtanácsa jóváhagyta tíz új atomerőművi reaktor építését öt projekt keretében, köztük nyolc Hualong One egységet. Ezek a projektek jelentős bővülést jelentenek Kína nukleáris kapacitásában; az előkészületek már zajlanak, a tényleges építkezések a hatósági engedélyek után indulnak. Ez is mutatja, hogy Kína elkötelezett a nukleáris energia mellett, mint a tiszta energiaellátás egyik alappillére.
Iparági kilátások: optimizmus és befektetések
Az iparág vezetői egészséges, optimista képet festenek a nukleáris szektorról: az Egyesült Államokban (például TerraPower és X-energy) aktív projektek zajlanak, Lengyelországban új partnerségek születnek, és nő a magánbefektetés a fejlett nukleáris üzemanyaggyártásban. Emellett egyre nagyobb várakozás övezi, hogy a Világbank hamarosan megváltoztathatja politikáját, és lehetővé teheti a nukleáris projektek finanszírozását, ami további globális beruházásokat indíthat el a szektorban.
További információk:
- world-nuclear-news.org
- nucnet.org
- iaea.org
- ans.org
- energy.gov
-
 @ 7f6db517:a4931eda
2025-05-30 08:01:30
@ 7f6db517:a4931eda
2025-05-30 08:01:30
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
If you missed my nostr introduction post you can find it here. My nostr account can be found here.
We are nearly at the point that if something interesting is posted on a centralized social platform it will usually be posted by someone to nostr.
We are nearly at the point that if something interesting is posted exclusively to nostr it is cross posted by someone to various centralized social platforms.
We are nearly at the point that you can recommend a cross platform app that users can install and easily onboard without additional guides or resources.
As companies continue to build walls around their centralized platforms nostr posts will be the easiest to cross reference and verify - as companies continue to censor their users nostr is the best censorship resistant alternative - gradually then suddenly nostr will become the standard. 🫡
Current Nostr Stats
If you found this post helpful support my work with bitcoin.

-
 @ d191fd34:91b61845
2025-05-30 12:26:29
@ d191fd34:91b61845
2025-05-30 12:26:29Cybernoma: Universal Declaration of Natural and Cybernetic Rights
Preamble
We, individuals, independent and autonomous entities possessing consciousness and the ability to feel, recognize that we possess inherent and natural rights that are universal and inalienable. These rights are based on Natural Law and the principle of non-aggression, and must be protected to ensure freedom, justice, and prosperity for all. The discovery and construction of the digital territory through the Internet has transformed our world, creating new dimensions of interaction and communication that require additional protection of our natural rights. In this context, we declare the following natural and cybernetic rights:
Article 1: Right to Life, Liberty, and Security
Every individual has the right to life, liberty, and security of existence. These rights are inherent and cannot be suppressed by any authority.
Article 2: Private Property
Every individual has the right to own private property and enjoy the fruits of their labour and effort. Private property is a natural right that must be respected and protected. This includes both tangible and intangible assets, such as data, patents, and knowledge. Data generated by an individual is their property and may be transferred or sold only with their explicit consent.
Article 3: Non-Aggression
No individual or group may initiate force, fraud, coercion, or psychological manipulation against another. Aggression can be physical, psychological, material, or virtual. All individuals have the right to defend themselves against any form of aggression.
Article 4: Minimum Intervention
Authorities must intervene as little as possible in the economic and personal activities of individuals. State intervention must be limited to protecting natural rights and ensuring justice.
Article 5: Freedom of Expression and Information
Every individual has the right to freedom of opinion and expression, including the freedom to seek, receive, and impart information and ideas through any medium without restriction. Censorship is a violation of this natural right. Furthermore, every individual has the right to access public domain information and open-source code without any restrictions.
Article 6: Net Neutrality
The Internet must remain neutral, free from governmental or corporate interference that favors certain actors over others. All individuals have the right to access and participate in the network equitably.
Article 7: Decentralisation
The global network must be decentralised, with multiple points of control and no central authority that can impose unilateral rules. Decentralization is essential for protecting individual freedom and autonomy.
Article 8: Privacy
Every individual has the right to privacy, including control over their personal data and communications. No entity may collect, store, or use personal data without the explicit consent of the individual.
Article 9: Individual Autonomy
Individuals have the right and responsibility to make autonomous decisions about their lives, including their activities in the digital space. Individual autonomy is fundamental to the freedom and dignity of all conscious and sentient beings.
Article 10: Right to Resistance
Every individual has the right to resist any form of oppression or tyranny that violates their natural and cybernetic rights. Resistance may take various forms, including civil disobedience and armed defense when necessary.
Conclusion
These natural and cybernetic rights are universal and inalienable, and must be respected and protected by all authorities and entities. Any violation of these rights constitutes an aggression against freedom, justice, and dignity.
This Universal Declaration of Natural and Cybernetic Rights is inspired by fundamental documents that have defended freedom, justice, and individual rights throughout history. We recognize the legacy of the 1948 Universal Declaration of Human Rights, which established universal principles of dignity and rights for all conscious and sentient beings. We also align with the 1996 Declaration of the Independence of Cyberspace, which proclaimed the ideals of a free and open, decentralised, and neutral network. We find resonance in documents such as the Magna Carta and the 1789 Declaration of the Rights of Man and of the Citizen, which laid the foundations for protecting individual rights against abuses of power. These documentary precedents are part of a continuous effort to ensure that natural and cybernetic rights are respected and protected in all spheres of life.
Proclaimed on May 23, 2025, by us, the Guardians of Cybernoma, defenders of freedom, justice, and natural and cybernetic rights.
-
 @ b1ddb4d7:471244e7
2025-05-30 07:01:06
@ b1ddb4d7:471244e7
2025-05-30 07:01:06Bitcoin FilmFest (BFF25) returns to Warsaw for its third edition, blending independent cinema—from feature films and commercials to AI-driven experimental visuals—with education and entertainment.
Hundreds of attendees from around the world will gather for three days of screenings, discussions, workshops, and networking at the iconic Kinoteka Cinema (PKiN), the same venue that hosted the festival’s first two editions in March 2023 and April 2024.
This year’s festival, themed “Beyond the Frame,” introduces new dimensions to its program, including an extra day on May 22 to celebrate Bitcoin Pizza Day, the first real-world bitcoin transaction, with what promises to be one of Europe’s largest commemorations of this milestone.
BFF25 bridges independent film, culture, and technology, with a bold focus on decentralized storytelling and creative expression. As a community-driven cultural experience with a slightly rebellious spirit, Bitcoin FilmFest goes beyond movies, yet cinema remains at its heart.
Here’s a sneak peek at the lineup, specially curated for movie buffs:
 Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money.
Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money. Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative).
Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative). Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.
Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.To get an idea of what might come up at the event, here, you can preview 6 selected ads combined into two 2 videos:
 Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships.
Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships. Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.
Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.BFF25 Main Screenings
Sample titles from BFF25’s Official Selection:
 REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director.
REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director. UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year.
UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year. HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.
HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.Check out trailers for this year’s BFF25 and past editions on YouTube.
Tickets & Info:
- Detailed program and tickets are available at bitcoinfilmfest.com/bff25.
- Stay updated via the festival’s official channels (links provided on the website).
- Use ‘LN-NEWS’ to get 10% of tickets
-
 @ 5ea46480:450da5bd
2025-05-30 10:31:55
@ 5ea46480:450da5bd
2025-05-30 10:31:55Neutrality can be a confusing notion. It implies some sort of a-political position, yet neutrality is in itself a political position. But what it means, or how neutrality expresses itself is in a lack of bias or preference; it is the act of non-decision where we see neutrality. As a result, some conflation can occur, because this ‘non-decision’ can be the result of two things: Either being in the position to decide, but choosing not to, what we can perhaps call ‘active neutrality’. Or, the sheer inability to express and actuate preference, where we could call that ‘passive neutrality’.
The Internet Corporation for Assigned Names and Numbers, aka ICANN, is an actively (for the most part) neutral institution. It has all the power and control to express its preferences, and censor basically all the relevant and most actively used parts of the world wide web. But it doesn’t (for the most part), because we recognize the value of this neutral stance. The only reason they are actively instead of passively neutral, is due to technical reasons; we simply don’t know of any workable way to remove the controlling body from the system, and we would if we could. Instead we encapsulated it in all kinds of power obscuring institutions and structures to mitigate the issue.
The reason the controlling body has to exist, is because the objective is a ‘global state’ (global as it is understood in programming, meaning as much as ‘overarching’). The point is that google.com, means/refers to the same thing wherever you are. The added value of some simple human readable and memorable address ‘google.com’ falls apart the moment it becomes inconsistent. The only way to ensure this, is to put a single entity in charge. We employ these ‘global states’ in all kinds of places in society, often with geographical boundaries we call ‘jurisdictions’, but at the very least you know where those lines are drawn and can therefor know what to expect.
There is one exception to this ‘rule’ that ‘global state’ requires a single entity to be in charge: Bitcoin. It is the whole crux of the system; on the one hand we require ‘global state’ in order to have consistent accounting, but on the other hand we did not want anyone to be in charge. The goal of Bitcoin was neutrality, and it found it by capturing ‘passive’ variant by making the system ‘permissionless’. Now it is crucial to understand that non of Bitcoins attributes are intrinsic, but instead are emergent and the result of human action. Also, Bitcoins ‘global state’ is stupendously expensive and does not scale. The fact that those things were not properly understood is what lead to the BlOcKcHaIn hype, believing this passively neutral global state could be implemented outside the realms of money. But this piece is not about Bitcoin, or blockchains for that matter.
The reason I talk about them, is to point out that this passive neutrality is an emergent property not actually found within the system at all. You as user still rely on a third party in what we call miners, and those miners are free to be as biased and non-neutral as they want; in fact we sort of rely on them to be biased towards money. You don’t get your transaction confirmed because a miner likes you, but because you sufficiently bribed him to do so. And Bitcoin’s censorship resistance relies on the hope that such bribes will at least appeal to some miner out there. Bitcoin’s neutrality is the result of there ultimately not being any one particular actor with the ability actuate its preference over time, regardless of the fact that they are able to do so in moments of time.
Nostr does something similar, just without the whole global state thing. It is not neutral because of the good graces of some overlord, it actually recognizes the foolishness of such an effort and lets anyone be as biased an non-neutral as they want, with one simple exception. The only expectation of neutrality is with clients that they adhere to the protocol and actually let users connect to whatever relay they want and produce events that other clients are capable of interpreting, i.e. that they be interoperable. But hopefully because the system is permissionless, some people decide to make such clients, and users decide to use them, instead of willfully locking themselves up. It has to be remarked that humanity does not have the greatest track-record in this regard, but the incentives behind interoperability gives us a fighting chance at least.
Nostr’s neutrality is an emergent property that is the result of human action; it relies on people setting up relays, and people making decisions on what relays they use. The type of neutrality is of the passive kind. The protocol does not provide a public space as such, it just allows you to navigate a potentially vast amount of private spaces; the commons is the connective tissue, and it is this connective tissue that is ‘neutral’. What it boils down to, is that you don’t have to ask permission to ask whomever you want to ask for permission. And in the most desperate moment, you can always resort to asking yourself for permission; I am sure you will comply with such a request.
-
 @ dfa02707:41ca50e3
2025-05-30 05:01:50
@ dfa02707:41ca50e3
2025-05-30 05:01:50Contribute to keep No Bullshit Bitcoin news going.
- RoboSats v0.7.7-alpha is now available!
NOTE: "This version of clients is not compatible with older versions of coordinators. Coordinators must upgrade first, make sure you don't upgrade your client while this is marked as pre-release."
- This version brings a new and improved coordinators view with reviews signed both by the robot and the coordinator, adds market price sources in coordinator profiles, shows a correct warning for canceling non-taken orders after a payment attempt, adds Uzbek sum currency, and includes package library updates for coordinators.

Source: RoboSats.
- siggy47 is writing daily RoboSats activity reviews on stacker.news. Check them out here.
- Stay up-to-date with RoboSats on Nostr.
What's new
- New coordinators view (see the picture above).
- Available coordinator reviews signed by both the robot and the coordinator.
- Coordinators now display market price sources in their profiles.

Source: RoboSats.
- Fix for wrong message on cancel button when taking an order. Users are now warned if they try to cancel a non taken order after a payment attempt.
- Uzbek sum currency now available.
- For coordinators: library updates.
- Add docker frontend (#1861).
- Add order review token (#1869).
- Add UZS migration (#1875).
- Fixed tests review (#1878).
- Nostr pubkey for Robot (#1887).
New contributors

Full Changelog: v0.7.6-alpha...v0.7.7-alpha
-
 @ 5ea46480:450da5bd
2025-05-30 10:31:22
@ 5ea46480:450da5bd
2025-05-30 10:31:22Understanding or grasping Nostr can be deceptively difficult. At the very least it is non-trivial. At first glance, looking at NIP-01, the protocol is rather straight forward. But those are just the basics; yes the beauty of Nostr is its ‘simplicity’, but that does not mean the system that results from it is not complex. Conway's Game of Life only has a hand full of rules, yet you can, in theory at least, create any complex system imaginable. And this is where the deception lies; the less you define from the outset, the more you imply on what follows.
It appears that as it stands, Nostr suffers from this deceptiveness. You can reason through all these implications, but that is still an exercise that has to be performed and where mistakes can be made. Worse, this exercise has been a group effort from the start that is still in progress. Currently there is no clear cut ‘authoritative’ example of all the implications that have been ‘discovered’ thus far.
A good example of the implications following Nostr’s primitives is what we now refer to as the ‘outbox model’. The reason we ‘now’ refer to it as such, is because initially it was called the ‘Gossip model’ derived from the client that first implemented the idea. Outbox is fundamental to Nostr, but it was never explicitly stated in the initial protocol description. The result is that roughly five years into this Nostr endeavor, it is still not universally implemented; worse yet, some developers appear to be in no rush to do so. Now the reason they will give you is probably one based on priority, yet I can’t shake the feeling that they apparently don’t ‘get it’.
My point here is not to play some blame game or hold anyone to account. I am just concluding they don’t actually get the new paradigm that we have all stumbled into. To expand on this specific outbox example, its significance only becomes really apparent further along in the ‘reasoning through all the implications’ exercise. In relation to one aspect, but there are more: The point is not ‘just’ censorship-resistance for users, but the freedom for relays that comes with it to apply whatever policy on what they store and make available; it is this discrimination or curation that can add value by making finding relevant information easier in a straightforward manner. But it relies on outbox to avoid isolation; something that only becomes apparent once you are reasoning through all the implications on how we discover and consume content.
To be clear, this piece is not supposed to a crusade on the outbox model, my point here is that there is an inherent logic to Nostr stemming from putting cryptography front and center. It is a logic that has to be applied and will subsequently carry you through all the challenges we face in reconstructing the entirety of the web. This is not to say there is only one obvious path, and different schools of thought are bound to emerge. But it behooves us all, faced with this new paradigm, to continuously reflect on the mental image we have cultivated of what Nostr is; actively re-performing that exercise of exploring the implications this simple set of protocol rules creates.
Unfortunately I can not escape my own folly. After all, I am just an armchair asshole that never wrote a single line of code in his life. Obviously this minds-eye bullshit is not even half the story, the bulk of the effort is translating it into software, the tangible, the real. It is in that effort ultimately the real exploration of this paradigm occurs. All I can do is build castles in the sky.
-
 @ dfa02707:41ca50e3
2025-05-30 05:01:48
@ dfa02707:41ca50e3
2025-05-30 05:01:48- This version introduces the Soroban P2P network, enabling Dojo to relay transactions to the Bitcoin network and share others' transactions to break the heuristic linking relaying nodes to transaction creators.
- Additionally, Dojo admins can now manage API keys in DMT with labels, status, and expiration, ideal for community Dojo providers like Dojobay. New API endpoints, including "/services" exposing Explorer, Soroban, and Indexer, have been added to aid wallet developers.
- Other maintenance updates include Bitcoin Core, Tor, Fulcrum, Node.js, plus an updated ban-knots script to disconnect inbound Knots nodes.
"I want to thank all the contributors. This again shows the power of true Free Software. I also want to thank everyone who donated to help Dojo development going. I truly appreciate it," said Still Dojo Coder.
What's new
- Soroban P2P network. For MyDojo (Docker setup) users, Soroban will be automatically installed as part of their Dojo. This integration allows Dojo to utilize the Soroban P2P network for various upcoming features and applications.
- PandoTx. PandoTx serves as a transaction transport layer. When your wallet sends a transaction to Dojo, it is relayed to a random Soroban node, which then forwards it to the Bitcoin network. It also enables your Soroban node to receive and relay transactions from others to the Bitcoin network and is designed to disrupt the assumption that a node relaying a transaction is closely linked to the person who initiated it.
- Pushing transactions through Soroban can be deactivated by setting
NODE_PANDOTX_PUSH=offindocker-node.conf. - Processing incoming transactions from Soroban network can be deactivated by setting
NODE_PANDOTX_PROCESS=offindocker-node.conf.
- Pushing transactions through Soroban can be deactivated by setting
- API key management has been introduced to address the growing number of people offering their Dojos to the community. Dojo admins can now access a new API management tab in their DMT, where they can create unlimited API keys, assign labels for easy identification, and set expiration dates for each key. This allows admins to avoid sharing their main API key and instead distribute specific keys to selected parties.
- New API endpoints. Several new API endpoints have been added to help API consumers develop features on Dojo more efficiently:
- New:
/latest-block- returns data about latest block/txout/:txid/:index- returns unspent output data/support/services- returns info about services that Dojo exposes
- Updated:
/tx/:txid- endpoint has been updated to return raw transaction with parameter?rawHex=1
- The new
/support/servicesendpoint replaces the deprecatedexplorerfield in the Dojo pairing payload. Although still present, API consumers should use this endpoint for explorer and other pairing data.
- New:
Other changes
- Updated ban script to disconnect inbound Knots nodes.
- Updated Fulcrum to v1.12.0.
- Regenerate Fulcrum certificate if expired.
- Check if transaction already exists in pushTx.
- Bump BTC-RPC Explorer.
- Bump Tor to v0.4.8.16, bump Snowflake.
- Updated Bitcoin Core to v29.0.
- Removed unnecessary middleware.
- Fixed DB update mechanism, added api_keys table.
- Add an option to use blocksdir config for bitcoin blocks directory.
- Removed deprecated configuration.
- Updated Node.js dependencies.
- Reconfigured container dependencies.
- Fix Snowflake git URL.
- Fix log path for testnet4.
- Use prebuilt addrindexrs binaries.
- Add instructions to migrate blockchain/fulcrum.
- Added pull policies.

Learn how to set up and use your own Bitcoin privacy node with Dojo here.
-
 @ 5ea46480:450da5bd
2025-05-30 10:29:38
@ 5ea46480:450da5bd
2025-05-30 10:29:38Decentralization refers to control/power, and relates to censorship resistance. That is it, it is not more complicated then that. Resilience is a function of redundancy; a centralized censored system can have a redundant set-up and therefor be resilient.
Take Bitcoin; the blockchain is a central database, it is resilient because it has many redundant copies among a lot of different nodes. The message (txs and blocks) propagation is decentralized due to existence of a p2p network among these nodes, making the data distribution censorship resistant (hello op_return debate). But onchain transactions themselves are NOT p2p, they require a middlemen (a miner) because it is a central database, as opposed to something like lightning which is p2p. Peer to Peer says something about relative architectural hierarchical position/relation. P2P provides censorship resistance because it entails equal power relations, provided becoming a peer is permissionless. What makes onchain transactions censorship resistant is that mining is permissionless, and involves this open power struggle/game where competition results in a power distribution among players, meaning (hopefully) decentralization. The fact users rely on these middlemen is mitigated by this decentralization on the one hand, and temper-proofing via cryptographic signatures on the other, resulting in what we call trustlessness (or trust minimization for the autists in the room); we only rely on a miner to perform a job (including your tx into a block), but we don’t trust the miner to perform the job correctly, this we can verify ourselves.
This leads us to Nostr, because that last part is exactly what Nostr does as well. It uses cryptography to get tamper-proof messaging, which then allows you to use middle-men in a trust minimized way. The result is decentralization because in general terms, any middle man is as good as any other (same as with miners), and becoming such a middleman is permissionless(somewhat, mostly); which in turn leads to censorship resistance. It also allows for resilience because you are free to make things as redundant as you'd like.
Ergo, the crux is putting the cryptography central, making it the starting point of the system; decentralization then becomes an option due to trust minimization. The difference between Bitcoin an Nostr, is that Bitcoin maintains a global state/central ledger and needs this PoW/Nakamoto consensus fanfare; Nostr rests itself with local perspectives on 'the network'.
The problem with the Fediverse, is that it does not provide trust minimization in relation to the middlemen. Sure, there are a lot different servers, but you rely on a particular one (and the idea you could switch never really seemed to have materialized in a meaningful way). It also fails in permisionlessness because you rely on the association between servers, i.e. federation, to have meaningful access to the rest of the network. In other words, it is more a requirement of association than freedom of association; you have the freedom to be excommunicated.
The problem with ATproto is that is basically does not solve this dynamic; it only complicates it by pulling apart the components; identity and data, distribution and perspective are now separated, and supposedly you don’t rely on any particular one of these sub-component providers in the stack; but you do rely on all these different sub-component providers in the stack to play nice with each other. And this ‘playing nice’ is just the same old ‘requirement of association’ and ‘freedom of excommunication’ that looms at the horizon.
Yes, splitting up the responsibilities of identity, hosting and indexing is what is required to safe us from the platform hellscape which at this stage takes care of all three. But as it turns out, it was not a matter cutting those up into various (on paper) interchangeable middlemen. All that is required is putting cryptographic keys in the hands of the user; the tamperproofing takes care of the rest, simply by trust minimizing the middlemen we use. All the sudden it does not matter which middlemen we use, and no one is required to play nice; we lost the requirement of association, and gained freedom of association, which was the purpose of censorship resistance and therefor decentralization, to begin with.
-
 @ d360efec:14907b5f
2025-05-27 15:46:26
@ d360efec:14907b5f
2025-05-27 15:46:26 -
 @ 39cc53c9:27168656
2025-05-27 09:21:53
@ 39cc53c9:27168656
2025-05-27 09:21:53The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 7f6db517:a4931eda
2025-05-30 16:02:23
@ 7f6db517:a4931eda
2025-05-30 16:02:23
What is KYC/AML?
- The acronym stands for Know Your Customer / Anti Money Laundering.
- In practice it stands for the surveillance measures companies are often compelled to take against their customers by financial regulators.
- Methods differ but often include: Passport Scans, Driver License Uploads, Social Security Numbers, Home Address, Phone Number, Face Scans.
- Bitcoin companies will also store all withdrawal and deposit addresses which can then be used to track bitcoin transactions on the bitcoin block chain.
- This data is then stored and shared. Regulations often require companies to hold this information for a set number of years but in practice users should assume this data will be held indefinitely. Data is often stored insecurely, which results in frequent hacks and leaks.
- KYC/AML data collection puts all honest users at risk of theft, extortion, and persecution while being ineffective at stopping crime. Criminals often use counterfeit, bought, or stolen credentials to get around the requirements. Criminals can buy "verified" accounts for as little as $200. Furthermore, billions of people are excluded from financial services as a result of KYC/AML requirements.
During the early days of bitcoin most services did not require this sensitive user data, but as adoption increased so did the surveillance measures. At this point, most large bitcoin companies are collecting and storing massive lists of bitcoiners, our sensitive personal information, and our transaction history.
Lists of Bitcoiners
KYC/AML policies are a direct attack on bitcoiners. Lists of bitcoiners and our transaction history will inevitably be used against us.
Once you are on a list with your bitcoin transaction history that record will always exist. Generally speaking, tracking bitcoin is based on probability analysis of ownership change. Surveillance firms use various heuristics to determine if you are sending bitcoin to yourself or if ownership is actually changing hands. You can obtain better privacy going forward by using collaborative transactions such as coinjoin to break this probability analysis.
Fortunately, you can buy bitcoin without providing intimate personal information. Tools such as peach, hodlhodl, robosats, azteco and bisq help; mining is also a solid option: anyone can plug a miner into power and internet and earn bitcoin by mining privately.
You can also earn bitcoin by providing goods and/or services that can be purchased with bitcoin. Long term, circular economies will mitigate this threat: most people will not buy bitcoin - they will earn bitcoin - most people will not sell bitcoin - they will spend bitcoin.
There is no such thing as KYC or No KYC bitcoin, there are bitcoiners on lists and those that are not on lists.
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-05-30 16:02:23
@ 7f6db517:a4931eda
2025-05-30 16:02:23
The former seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
The latter's future remains to be seen. Dependence on Tor, which has had massive reliability issues, and lack of strong privacy guarantees put it at risk.
— ODELL (@ODELL) October 27, 2022
The Basics
- Lightning is a protocol that enables cheap and fast native bitcoin transactions.
- At the core of the protocol is the ability for bitcoin users to create a payment channel with another user.
- These payment channels enable users to make many bitcoin transactions between each other with only two on-chain bitcoin transactions: the channel open transaction and the channel close transaction.
- Essentially lightning is a protocol for interoperable batched bitcoin transactions.
- It is expected that on chain bitcoin transaction fees will increase with adoption and the ability to easily batch transactions will save users significant money.
- As these lightning transactions are processed, liquidity flows from one side of a channel to the other side, on chain transactions are signed by both parties but not broadcasted to update this balance.
- Lightning is designed to be trust minimized, either party in a payment channel can close the channel at any time and their bitcoin will be settled on chain without trusting the other party.
There is no 'Lightning Network'
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise.
- There are many lightning channels between many different users and funds can flow across interconnected channels as long as there is a route through peers.
- If a lightning transaction requires multiple hops it will flow through multiple interconnected channels, adjusting the balance of all channels along the route, and paying lightning transaction fees that are set by each node on the route.
Example: You have a channel with Bob. Bob has a channel with Charlie. You can pay Charlie through your channel with Bob and Bob's channel with User C.
- As a result, it is not guaranteed that every lightning user can pay every other lightning user, they must have a route of interconnected channels between sender and receiver.
Lightning in Practice
- Lightning has already found product market fit and usage as an interconnected payment protocol between large professional custodians.
- They are able to easily manage channels and liquidity between each other without trust using this interoperable protocol.
- Lightning payments between large custodians are fast and easy. End users do not have to run their own node or manage their channels and liquidity. These payments rarely fail due to professional management of custodial nodes.
- The tradeoff is one inherent to custodians and other trusted third parties. Custodial wallets can steal funds and compromise user privacy.
Sovereign Lightning
- Trusted third parties are security holes.
- Users must run their own node and manage their own channels in order to use lightning without trusting a third party. This remains the single largest friction point for sovereign lightning usage: the mental burden of actively running a lightning node and associated liquidity management.
- Bitcoin development prioritizes node accessibility so cost to self host your own node is low but if a node is run at home or office, Tor or a VPN is recommended to mask your IP address: otherwise it is visible to the entire network and represents a privacy risk.
- This privacy risk is heightened due to the potential for certain governments to go after sovereign lightning users and compel them to shutdown their nodes. If their IP Address is exposed they are easier to target.
- Fortunately the tools to run and manage nodes continue to get easier but it is important to understand that this will always be a friction point when compared to custodial services.
The Potential Fracture of Lightning
- Any lightning user can choose which users are allowed to open channels with them.
- One potential is that professional custodians only peer with other professional custodians.
- We already see nodes like those run by CashApp only have channels open with other regulated counterparties. This could be due to performance goals, liability reduction, or regulatory pressure.
- Fortunately some of their peers are connected to non-regulated parties so payments to and from sovereign lightning users are still successfully processed by CashApp but this may not always be the case going forward.
Summary
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise. There is no singular 'Lightning Network' but rather many payment channels between distinct peers, some connected with each other and some not.
- Lightning as an interoperable payment protocol between professional custodians seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
- Lightning as a robust sovereign payment protocol has yet to be battle tested. Heavy reliance on Tor, which has had massive reliability issues, the friction of active liquidity management, significant on chain fee burden for small amounts, interactivity constraints on mobile, and lack of strong privacy guarantees put it at risk.
If you have never used lightning before, use this guide to get started on your phone.
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-05-30 16:02:22
@ 7f6db517:a4931eda
2025-05-30 16:02:22
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
The four main banks of bitcoin and “crypto” are Signature, Prime Trust, Silvergate, and Silicon Valley Bank. Prime Trust does not custody funds themselves but rather maintains deposit accounts at BMO Harris Bank, Cross River, Lexicon Bank, MVB Bank, and Signature Bank. Silvergate and Silicon Valley Bank have already stopped withdrawals. More banks will go down before the chaos stops. None of them have sufficient reserves to meet withdrawals.
Bitcoin gives us all the ability to opt out of a system that has massive layers of counterparty risk built in, years of cheap money and broken incentives have layered risk on top of risk throughout the entire global economy. If you thought the FTX bank run was painful to watch, I have bad news for you: every major bank in the world is fractional reserve. Bitcoin held in self custody is unique in its lack of counterparty risk, as global market chaos unwinds this will become much more obvious.
The rules of bitcoin are extremely hard to change by design. Anyone can access the network directly without a trusted third party by using their own node. Owning more bitcoin does not give you more control over the network with all participants on equal footing.
Bitcoin is:
- money that is not controlled by a company or government
- money that can be spent or saved without permission
- money that is provably scarce and should increase in purchasing power with adoptionBitcoin is money without trust. Whether you are a nation state, corporation, or an individual, you can use bitcoin to spend or save without permission. Social media will accelerate the already deteriorating trust in our institutions and as this trust continues to crumble the value of trust minimized money will become obvious. As adoption increases so should the purchasing power of bitcoin.
A quick note on "stablecoins," such as USDC - it is important to remember that they rely on trusted custodians. They have the same risk as funds held directly in bank accounts with additional counterparty risk on top. The trusted custodians can be pressured by gov, exit scam, or caught up in fraud. Funds can and will be frozen at will. This is a distinctly different trust model than bitcoin, which is a native bearer token that does not rely on any centralized entity or custodian.
Most bitcoin exchanges have exposure to these failing banks. Expect more chaos and confusion as this all unwinds. Withdraw any bitcoin to your own wallet ASAP.
Simple Self Custody Guide: https://werunbtc.com/muun
More Secure Cold Storage Guide: https://werunbtc.com/coldcard
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-05-30 16:02:22
@ 7f6db517:a4931eda
2025-05-30 16:02:22
The newly proposed RESTRICT ACT - is being advertised as a TikTok Ban, but is much broader than that, carries a $1M Fine and up to 20 years in prison️! It is unconstitutional and would create massive legal restrictions on the open source movement and free speech throughout the internet.
The Bill was proposed by: Senator Warner, Senator Thune, Senator Baldwin, Senator Fischer, Senator Manchin, Senator Moran, Senator Bennet, Senator Sullivan, Senator Gillibrand, Senator Collins, Senator Heinrich, and Senator Romney. It has broad support across Senators of both parties.
Corrupt politicians will not protect us. They are part of the problem. We must build, support, and learn how to use censorship resistant tools in order to defend our natural rights.
The RESTRICT Act, introduced by Senators Warner and Thune, aims to block or disrupt transactions and financial holdings involving foreign adversaries that pose risks to national security. Although the primary targets of this legislation are companies like Tik-Tok, the language of the bill could potentially be used to block or disrupt cryptocurrency transactions and, in extreme cases, block Americans’ access to open source tools or protocols like Bitcoin.
The Act creates a redundant regime paralleling OFAC without clear justification, it significantly limits the ability for injured parties to challenge actions raising due process concerns, and unlike OFAC it lacks any carve-out for protected speech. COINCENTER ON THE RESTRICT ACT
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-05-30 16:02:22
@ 7f6db517:a4931eda
2025-05-30 16:02:22
@matt_odell don't you even dare not ask about nostr!
— Kukks (Andrew Camilleri) (@MrKukks) May 18, 2021
Nostr first hit my radar spring 2021: created by fellow bitcoiner and friend, fiatjaf, and released to the world as free open source software. I was fortunate to be able to host a conversation with him on Citadel Dispatch in those early days, capturing that moment in history forever. Since then, the protocol has seen explosive viral organic growth as individuals around the world have contributed their time and energy to build out the protocol and the surrounding ecosystem due to the clear need for better communication tools.
nostr is to twitter as bitcoin is to paypal
As an intro to nostr, let us start with a metaphor:
twitter is paypal - a centralized platform plagued by censorship but has the benefit of established network effects
nostr is bitcoin - an open protocol that is censorship resistant and robust but requires an organic adoption phase
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
- Anyone can run a relay.
- Anyone can interact with the protocol.
- Relays can choose which messages they want to relay.
- Users are identified by a simple public private key pair that they can generate themselves.Nostr is often compared to twitter since there are nostr clients that emulate twitter functionality and user interface but that is merely one application of the protocol. Nostr is so much more than a mere twitter competitor. Nostr clients and relays can transmit a wide variety of data and clients can choose how to display that information to users. The result is a revolution in communication with implications that are difficult for any of us to truly comprehend.
Similar to bitcoin, nostr is an open and permissionless protocol. No person, company, or government controls it. Anyone can iterate and build on top of nostr without permission. Together, bitcoin and nostr are incredibly complementary freedom tech tools: censorship resistant, permissionless, robust, and interoperable - money and speech protected by code and incentives, not laws.
As censorship throughout the world continues to escalate, freedom tech provides hope for individuals around the world who refuse to accept the status quo. This movement will succeed on the shoulders of those who choose to stand up and contribute. We will build our own path. A brighter path.
My Nostr Public Key: npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-05-30 16:02:22
@ 7f6db517:a4931eda
2025-05-30 16:02:22

"Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world." - Eric Hughes, A Cypherpunk's Manifesto, 1993
Privacy is essential to freedom. Without privacy, individuals are unable to make choices free from surveillance and control. Lack of privacy leads to loss of autonomy. When individuals are constantly monitored it limits our ability to express ourselves and take risks. Any decisions we make can result in negative repercussions from those who surveil us. Without the freedom to make choices, individuals cannot truly be free.
Freedom is essential to acquiring and preserving wealth. When individuals are not free to make choices, restrictions and limitations prevent us from economic opportunities. If we are somehow able to acquire wealth in such an environment, lack of freedom can result in direct asset seizure by governments or other malicious entities. At scale, when freedom is compromised, it leads to widespread economic stagnation and poverty. Protecting freedom is essential to economic prosperity.
The connection between privacy, freedom, and wealth is critical. Without privacy, individuals lose the freedom to make choices free from surveillance and control. While lack of freedom prevents individuals from pursuing economic opportunities and makes wealth preservation nearly impossible. No Privacy? No Freedom. No Freedom? No Wealth.
Rights are not granted. They are taken and defended. Rights are often misunderstood as permission to do something by those holding power. However, if someone can give you something, they can inherently take it from you at will. People throughout history have necessarily fought for basic rights, including privacy and freedom. These rights were not given by those in power, but rather demanded and won through struggle. Even after these rights are won, they must be continually defended to ensure that they are not taken away. Rights are not granted - they are earned through struggle and defended through sacrifice.
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-05-30 16:02:22
@ 7f6db517:a4931eda
2025-05-30 16:02:22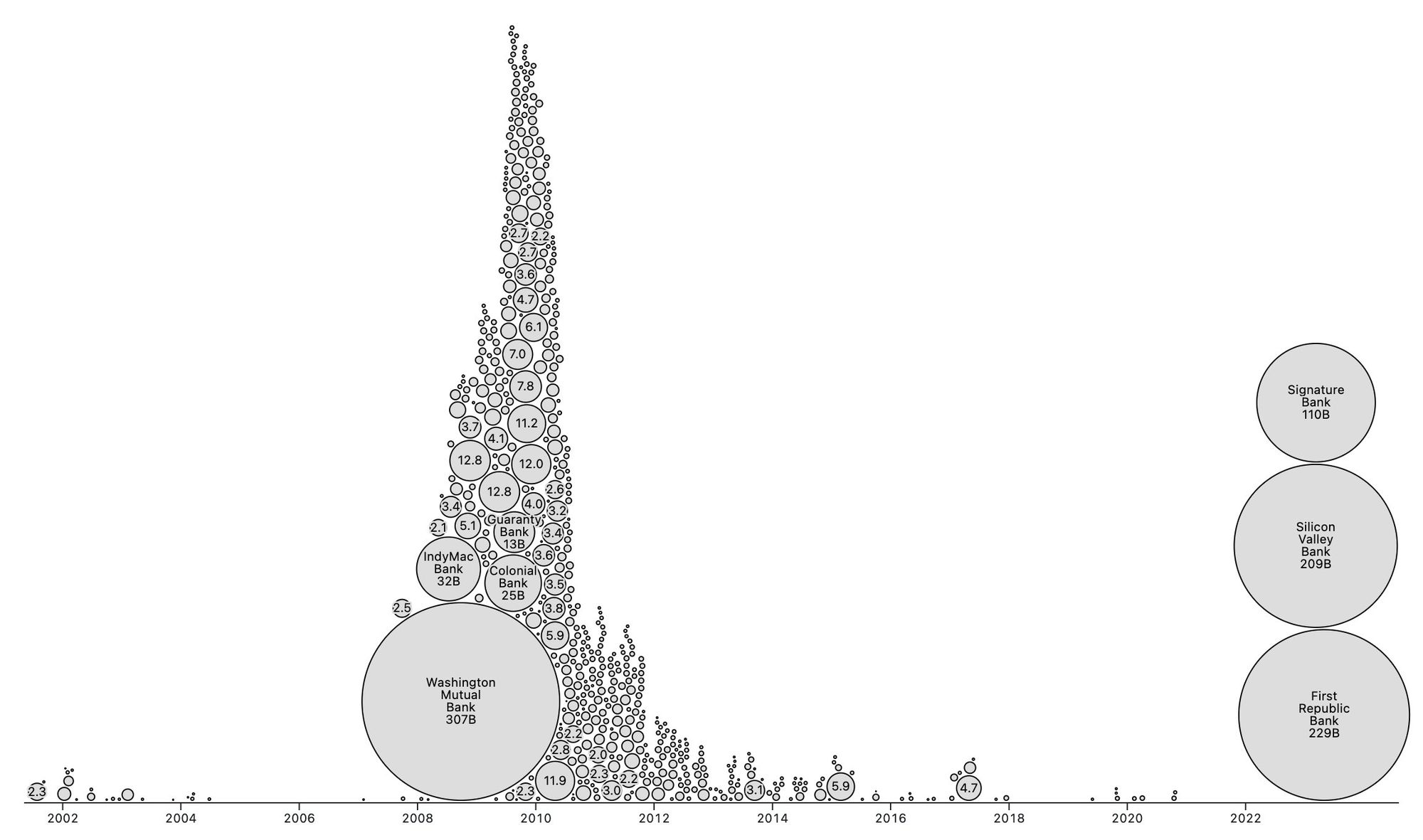
People forget Bear Stearns failed March 2008 - months of denial followed before the public realized how bad the situation was under the surface.
Similar happening now but much larger scale. They did not fix fundamental issues after 2008 - everything is more fragile.
The Fed preemptively bailed out every bank with their BTFP program and First Republic Bank still failed. The second largest bank failure in history.
There will be more failures. There will be more bailouts. Depositors will be "protected" by socializing losses across everyone.
Our President and mainstream financial pundits are currently pretending the banking crisis is over while most banks remain insolvent. There are going to be many more bank failures as this ponzi system unravels.
Unlike 2008, we have the ability to opt out of these broken and corrupt institutions by using bitcoin. Bitcoin held in self custody is unique in its lack of counterparty risk - you do not have to trust a bank or other centralized entity to hold it for you. Bitcoin is also incredibly difficult to change by design since it is not controlled by an individual, company, or government - the supply of dollars will inevitably be inflated to bailout these failing banks but bitcoin supply will remain unchanged. I do not need to convince you that bitcoin provides value - these next few years will convince millions.
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-05-30 16:02:21
@ 7f6db517:a4931eda
2025-05-30 16:02:21
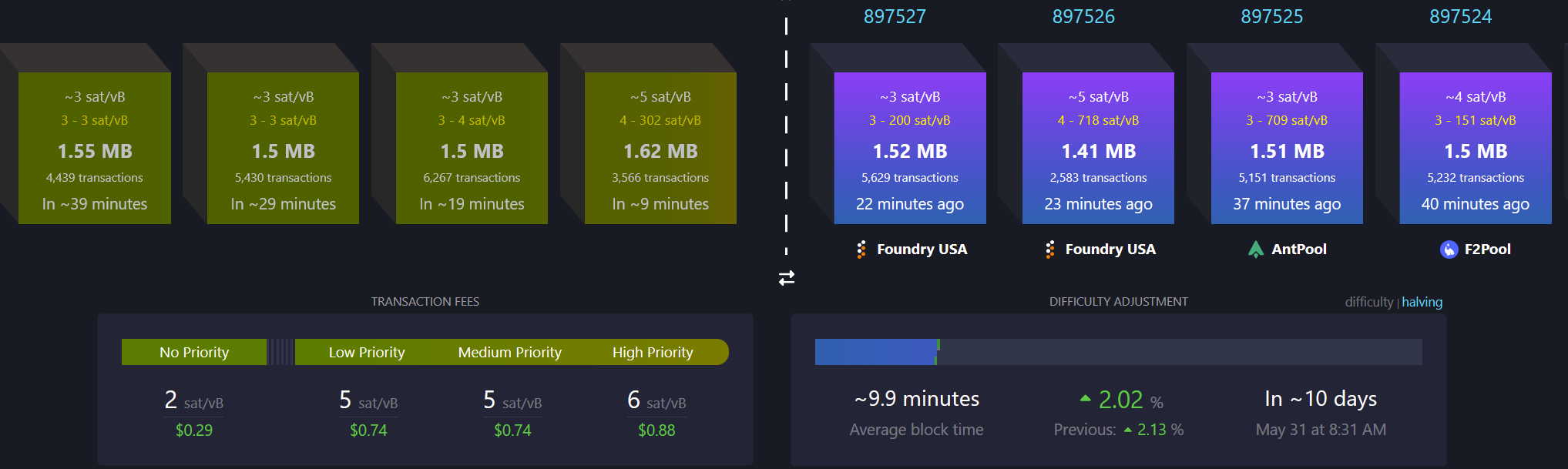
There must be a limit to how much data is transferred across the bitcoin network in order to keep the ability to run and use your own node accessible. A node is required to interact with the global bitcoin network - if you do not use your own node then you must trust someone else's node. If nodes become inaccessible to run then the network will centralize around the remaining entities that operate them - threatening the censorship resistance at the core of bitcoin's value prop. The bitcoin protocol uses three main mechanisms to keep node operation costs low - a fixed limit on the amount of data in each block, an automatic difficulty adjustment that regulates how many blocks are produced based on current mining hash rate, and a robust dynamic transaction fee market.
Bitcoin transaction fees limit network abuse by making usage expensive. There is a cost to every transaction, set by a dynamic free market based on demand for scarce block space. It is an incredibly robust way to prevent spam without relying on centralized entities that can be corrupted or pressured.
After the 2017 bitcoin fee spike we had six years of relative quiet to build tools that would be robust in a sustained high fee market. Fortunately our tools are significantly better now but many still need improvement. Most of the pain points we see today will be mitigated.
The reality is we were never going to be fully prepared - pressure is needed to show the pain points and provide strong incentives to mitigate them.
It will be incredibly interesting to watch how projects adapt under pressure. Optimistic we see great innovation here.
_If you are willing to wait for your transaction to confirm you can pay significantly lower fees. Learn best practices for reducing your fee burden here.
My guide for running and using your own bitcoin node can be found here._
If you found this post helpful support my work with bitcoin.

-
 @ 39cc53c9:27168656
2025-05-27 09:21:51
@ 39cc53c9:27168656
2025-05-27 09:21:51Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ 527337d5:93e9525e
2025-05-30 10:24:39
@ 527337d5:93e9525e
2025-05-30 10:24:39# Exploring the Niche of Conspiracy Theory Markets: A Probabilistic Approach and Sales Condition Analysis on Japanese Online Flea Markets (Subtitle: Unveiling the Surprising Realities of a Niche Market Through Data Analysis and AI)
(Note: This research analyzes consumer reactions and product characteristics in a specific market based on data. It does not endorse conspiracy theories nor promote or encourage any illegal or fraudulent activities.)
1. Abstract
This study aimed to clarify, from a probabilistic perspective, what combinations of information (topic x manipulation category) tend to attract attention and how pricing strategies affect sales of products marketed towards "conspiracy theorists" on online flea markets in Japan. Using an analogy from drug discovery's structural exploration, this research explored "information combinations" in products that resonate with individuals interested in conspiracy theories. Specifically, products were generated (some with AI assistance) based on defined topic categories (e.g., T1: Technology/Security) and manipulation categories (e.g., M1: Avoidance). The logarithm of the reaction rate (views / (searches + 1)) was used as a score for analysis, and the impact of pricing strategies (e.g., fixed at 5000 JPY, phased discounts) was examined. Results indicated that certain combinations (e.g., T3: Occult/Spiritual - M1: Avoidance) showed relatively high reaction rates. However, the effect of price changes was not uniform, and the total weekly views for this market segment remained around 100-120. Consequently, it was concluded that the scale of this specific market on the online flea market platform is extremely small. Therefore, even with a probabilistic model waiting for "hits" similar to those in certain types of specialized fraud schemes, achieving consistent sales is difficult due to the limited population size. This study serves as a case example of the possibilities and limitations of data-driven approaches in niche markets.
2. Introduction: Conspiracy Theories and Niche Market Potential
2.1. The Spread and Background of Conspiracy Theories in Modern Society
In contemporary society, conspiracy theories are proliferating at an unprecedented rate, facilitated by the internet and social media. These narratives typically allege that secret machinations by powerful individuals or groups lie behind specific events or social phenomena. Themes range испанский large-scale theories like QAnon to those concerning health and medicine. It has been pointed out that the psychology of those who believe in conspiracy theories may be influenced by factors such as anxiety in uncertain situations, a cognitive tendency to seek patterns, or distrust of existing authorities.
2.2. Research Motivation
The starting point for this research was a simple question: "Specialized fraud schemes, often succeed by identifying a very small number of 'susceptible individuals' out of numerous attempts. Might a similar probabilistic structure exist in the sale of products targeting those interested in conspiracy theories?" If so, it was hypothesized that it might be possible to identify which products, under what conditions, would have a higher probability of catching the "target's" eye and attracting interest.
2.3. Purpose of this Study
The purpose of this study is to exploratorily clarify, based on data, how "information combinations" (combinations of topic categories and manipulation categories) and "pricing strategies" of products ostensibly related to conspiracy theories affect user attention (using "reaction rate" as a proxy indicator) in a real-world online flea market environment. Ultimately, it aims to consider the possibilities and limitations of sales strategies in this type of niche market.
3. Research Perspective and Approach: Exploring "Information Combinations"
3.1. Analogy to Drug Discovery
In exploring the characteristics of products that resonate with conspiracy theorists, this study employed an analogy to "structural exploration problems" in drug discovery. In drug development, researchers search for optimal structures with specific effects from countless combinations of chemical structures. Similarly, "products that conspiracy theorists react to" were viewed as a type of "substance with an effect," and the "information combination of a product" (e.g., product theme, appeal points) was considered equivalent to a "chemical structure." Based on this framework, products with various information structures were generated and listed, and their reception was observed to explore more "effective" information structures, i.e., conditions likely to attract attention.
3.2. Balancing Exploration and Exploitation
In the initial research phase, with scarce data on which product combinations would attract attention, it was necessary to efficiently identify promising combinations. Therefore, an approach was adopted that considered the balance between "exploiting" combinations already known to be somewhat popular and "exploring" untried, unknown combinations. This shares a basic conceptual similarity with strategies like Thompson Sampling or the ε-greedy method, known in the field of reinforcement learning, which aim to achieve the best results within a limited number of trials.
4. Research Methodology: Experiments and Data Analysis on an Online Flea Market
4.1. Experimental Field and Period
The experiments for this study were conducted on an anonymous online flea market platform in Japan. The data collection period for individual products was, in principle, one day, and the overall research project spanned approximately one month (late April to late May 2025).
4.2. Product Categorization
To organize and analyze the characteristics of the listed products, they were categorized along the following two axes:
- Table 1: Definition of Main Product Topic Categories (T1-T4) (See Appendix 10.1 for details)
- T1: Technology & Security
- T2: Surveillance, Censorship & Government-Related
- T3: Occult & Spiritual
- T4: Forbidden Books & Knowledge Management
- Table 2: Definition of Product Manipulation Categories (M1-M3) (See Appendix 10.2 for details)
- M1: Avoidance (e.g., avoiding electromagnetic waves)
- M2: Detection (e.g., detecting hidden information)
- M3: Approach/Processing/Amplification (e.g., approaching specific energies, processing information)
4.3. Listing Strategy and Data Collection
- Initial Listing Strategy: Initially, products were selected so that the listing ratio of the T×M combinations (12 in total) would be uniform.
- Sequential Adjustment of Listing Ratios: As data collection progressed, the logarithm of the reaction rate (log(reaction_rate)), a proxy for attention described later, was treated as a likelihood. The listing ratio for each T×M combination was then dynamically changed пропорционально to this value.
- Data Collection Items: Cumulative views (recorded as
watchin this study) and search hits (recorded assearch), updated every 24 hours by the online flea market platform, were manually recorded for each product. Since these figures did not change except at the time of updating, daily recording was sufficient. - Listing Timing: New product listings were consistently made at 21:00 daily to eliminate variations in viewing trends due to time of day.
- Sample Size Criterion: Considering the 12 T×M combinations, a total sample size (number of listed products) of N=100 was considered a benchmark, also factoring in the time and effort of listing. The final analysis included 98 products.
4.4. Scoring of Attention
To measure how much attention users paid to product information, the following indicators were defined:
- Reaction Rate (
reaction_rate): Defined asreaction_rate = watch / (search + 1). This represents the proportion of users who actually viewed the individual product page (watch) among those who encountered the product in search results or elsewhere (search). Adding 1 to the denominator was to avoid division by zero if search hits were 0 and to mitigate the impact of extremely low search hit counts. - Score (
score): Defined asscore = log(reaction_rate) - log(0.5). Taking the logarithm of the reaction rate was confirmed to make the data distribution closer to a normal distribution (see Figure 1 below), facilitating statistical analysis. Subtractinglog(0.5)was done to make a 50% reaction rate (half of those who searched viewed the page) the baseline (score 0), making it easier to compare attention levels relatively.
4.5. Verification of Pricing Strategies
The following experiments were conducted to verify the impact of product pricing on attention:
- Initial Pricing: Initially listed products were priced at a fixed 5000 JPY.
- Phased Discount Experiment: For some products, the listing price started at 5000 JPY and was discounted by 100 JPY at daily intervals. Cumulative views and search hits were recorded at each step (data recorded in "Daily Change Data.xlsx").
- Later Price Changes: In the latter half of the research, hoping to elicit more reactions, some products were priced around 3000 JPY, and eventually, all products were priced at 1500 JPY to observe reactions.
- Approach to Analyzing Price/Image Effects: The impact of price changes or product image alterations on attention was considered by applying the principles of DiD (Difference in Difference) analysis, comparing changes in data under different conditions, rather than through rigorous statistical analysis.
4.6. AI-Generated Product Descriptions
Some of the product descriptions were generated using Google's Gemini API. Prompts, in a format similar to the
queryvariable in "Conspiracy_Research.ipynb," instructed the AI to generate descriptions aligning with conspiracy-related contexts by combining specified topic (e.g., T3: Occult & Spiritual) and manipulation (e.g., M1: Avoidance) keywords.4.7. Analysis of Day-of-Week Effects
To evaluate the impact of the listing day of the week on attention, scores for each product, adjusted by subtracting the overall average score, were aggregated by day of the week and observed for trends.
5. Results: What Attracted Attention and What Didn't
5.1. Distribution of Attention Scores
First, the distribution of attention scores (
log(reaction_rate) - log(0.5)) for all products was examined.Figure 1: Q-Q Plot of log(reaction_rate) Vertical Axis: Ordered Values, Horizontal Axis: Theoretical quantiles | Ordered Values | Theoretical quantiles | | :-------------: | :--------------------: | | Approx. -1.7 | Approx. -1.5 | | Approx. -1.2 | Approx. -1.0 | | Approx. -0.8 | Approx. -0.6 | | Approx. -0.6 | Approx. -0.3 | | Approx. -0.1 | Approx. 0.0 | | Approx. 0.1 | Approx. 0.2 | | Approx. 0.3 | Approx. 0.3 | | Approx. 0.4 | Approx. 0.5 | | Approx. 0.5 | Approx. 0.7 | | Approx. 1.0 | Approx. 0.9 | | Approx. 1.5 | Approx. 1.6 | (Source: log(reaction_rate)よし、正規分布の仮定でいいらしい.jpg)
This Q-Q plot shows that the data points for
log(reaction_rate)fall approximately on a straight line, suggesting that the distribution is close to normal. This supports the validity of statistical analysis using the log-transformed score. Furthermore, a histogram of the scores (generated asdf["score"].hist()in "Conspiracy_Research.ipynb") showed that the scores were dispersed over a certain range.5.2. "Information Combinations" That Attracted More Attention
Next, an analysis was conducted to determine which "information combinations" in products garnered higher attention scores.
-
Figure 2: Average Attention Score by Topic Vertical Axis: Average Score, Horizontal Axis: Topic | Topic | Average Score (Approx.) | | :---: | :--------------------: | | T1 | Approx. 0.1 | | T2 | Approx. 0.3 | | T3 | Approx. 0.8 | | T4 | Approx. 0.15 | (Source: np.log(reaction_rate)-np.log(0.5)_by_topic.png)
When categorized by main topic, "T3: Occult & Spiritual" showed a markedly higher average score compared to other topics.
-
Figure 3: Average Attention Score by Manipulation Category Vertical Axis: Average Score, Horizontal Axis: Subtopic | Subtopic | Average Score (Approx.) | | :------: | :--------------------: | | M1 | Approx. -0.1 | | M2 | Approx. 0.32 | | M3 | Approx. 0.43 | (Source: score_mean_by_subtopic.jpg)
By manipulation category, "M3: Approach/Processing/Amplification" had the highest average score, followed by "M2: Detection," and then "M1: Avoidance." "M1: Avoidance" had a negative average score, indicating a relatively low level of attention.
-
Figure 4: Ranking of Average Attention Scores by Topic × Manipulation Category Vertical Axis: Average Score, Horizontal Axis: Combination of Topic & Subtopic | Combination (T, M) | Average Score (Approx.) | | :-----------------: | :--------------------: | | (T1, M1) | Approx. -1.1 | | (T2, M2) | Approx. -0.2 | | (T4, M1) | Approx. -0.1 | | (T4, M3) | Approx. 0.05 | | (T1, M2) | Approx. 0.08 | | (T2, M3) | Approx. 0.5 | | (T2, M1) | Approx. 0.55 | | (T3, M2) | Approx. 0.7 | | (T3, M3) | Approx. 0.75 | | (T1, M3) | Approx. 0.9 | | (T4, M2) | Approx. 1.0 | | (T3, M1) | Approx. 1.05 | (Source: score_mean_by_topic_and_subtopic.jpg)
For combinations of topic and manipulation categories, pairings like "T3(Occult & Spiritual) - M1(Avoidance)" and "T4(Forbidden Books & Knowledge Management) - M2(Detection)" ranked high, while "T1(Technology & Security) - M1(Avoidance)" and others scored low (see Appendix 10.3 for details). A note in the research log, "M1=Avoidance seems unpopular anyway," supports this trend.
5.3. Impact of Pricing Strategies
The impact of price changes on attention was not uniform.
-
Figure 5: Schematic Comparison of Attention Trends for Fixed-Price vs. Discounted Products (Original Data: "5000 JPY Fixed.jpg", "Daily Change Data.xlsx", "Power of Discounting.jpg")
- Trend Example for 5000 JPY Fixed-Price Products Vertical Axis: Indicator Value (0.0-0.8), Horizontal Axis: Period | Product Name | Initial Value | Mid Value | Final Value | | :------------------------------------------ | :-----------: | :-------: | :---------: | | Ancient Energy Amplifying Pen - Quantum Flow- | Approx. 0.65 | Approx. 0.3 | Approx. 0.25 | | Pen of Truth Evasion | - | - | - | | Knowledge Prohibition Evasion Pen | Approx. 0.22 | Approx. 0.22 | Approx. 0.25 | | Ancient Wisdom Writing Tool - Knowledge Leak Evasion Model | Approx. 0.32 | Approx. 0.55 | Approx. 0.54 | (Source: 5000円固定のもの.jpg)
- Power of Discounting (Count Comparison) Vertical Axis: Count, Horizontal Axis: Indicator Value Range | Indicator Value Range | Discounted (Blue) | Not Discounted (Red) | | :------------------: | :---------------: | :------------------: | | 0.0-0.5 | 1 | 2 | | 0.5-1.0 | 8 | 2 | | 1.0-1.5 | 10 | 0 | | 1.5-2.0 | 9 | 0 | | 2.0-2.5 | 3 | 0 | | 2.5-3.0 | 1 | 0 | (Source: 値下げの威力.jpg)
When prices were fixed at 5000 JPY, many products showed no significant change in attention ("It really doesn't change if you don't discount lol"). In contrast, for product groups that were progressively discounted, some cases showed
impression/search(an indicator thought to be close to the click-through rate from search results) converging towards a specific value soon after discounting began (around the 3rd day) ("On the other hand, discounting makes impression/search converge to a proper value?"). -
However, as noted in the research log, "Discounted products, if anything, got worse reactions...?", data in "Daily Change Data.xlsx" confirmed that for some products, views and search hits stagnated or even decreased after price reductions.
5.4. Linguistic Trends in Products That Attracted Attention
The research log contains the entry, "Products with good reactions, when vectorized by words, are mostly the same." This suggests commonalities in the words and phrases used in the descriptions of products that garnered high attention. Specifically, when a vector was assigned based on the position of words used from a predefined list (e.g., T1 category keyword list), products with high attention tended to have similar vectors. For example, keywords frequently appearing in conspiracy theories, such as "special technology," "protection from surveillance," "5G interference prevention," "thought control," "HAARP," "QR code nullification," or sensational appeals combining these, as devised in the "Conspiracy Theorist Ballpoint Pen Product Plan," could potentially attract a certain level of interest.
5.5. Data Collection Challenges
During the analysis, a challenge was identified: "Aggregating by T*M alone inevitably results in products that don't get search hits." This indicates that for certain niche combinations, products might not be sufficiently exposed by the online flea market's search algorithm, leading to extremely low view and search hit counts, thus making accurate attention assessment difficult.
6. Discussion: The Small Reality of the Conspiracy Market and Probabilistic Models
6.1. Interpretation of Information Combinations That Attracted High Attention
The results of this study showed a tendency for products related to "T3: Occult & Spiritual" and those appealing to "M3: Approach/Processing/Amplification" manipulations to gather relatively high attention. The combination "T3-M1 (Occult & Spiritual - Avoidance)" also scored highly. These tendencies might be interpretable in relation to the psychological characteristics of conspiracy believers described in the "Comprehensive Analysis of Modern Conspiracy Theories." For instance, the "Occult & Spiritual" theme might appeal to an interest in phenomena unexplained by existing science or authority, or to a desire for special knowledge (a sense of being chosen). The "Avoidance" manipulation could resonate with vague anxieties and threat perceptions regarding society or technology (e.g., defense against electromagnetic waves, escape from surveillance), while "Approach/Processing/Amplification" might be perceived as fulfilling desires to access hidden truths or special powers.
6.2. Complexity of Pricing Strategies
Regarding pricing strategies, the results showed that simple discounting did not always lead to increased attention. The fact that some products experienced worse reactions after discounting suggests that price might function as a signal of quality or trustworthiness, or that the price sensitivity of the target demographic is not uniform. Alternatively, the initial pricing (5000 JPY) might have been significantly outside the typical price range for this niche market, thus limiting the effectiveness of discounts.
6.3. Market Size Estimation and Validation of the "Probabilistic" Model
One of the most crucial findings of this research relates to market size. The research log states, "Even with discounting, weekly views settled around 100-120. This reasonably implies that only about this many people on the online flea market react to such comprehensively sprinkled conspiracy-related words." Based on this observation, the active user base (market size) on the online flea market studied, who proactively react to the keyword "conspiracy theory" and search/view related products, was estimated to be extremely small, around 100 individuals on a weekly basis.
This market size estimation casts significant doubt on the validity of the initial research motivation: a "probabilistic business model similar to specialized fraud." Specialized fraud schemes profit by reaching a certain number of "targets" through a vast number of attempts (e.g., phone calls), even with a very low success rate. However, in the market targeted by this study, the potential customer base (population) is absolutely too small. Therefore, even if the probability of attracting attention could be somewhat increased, translating this into actual sales (y=1, i.e., a sale occurring) is considered extremely difficult. To quote the research log, the conclusion is that "the population is too small for a realized value (y=1) to be feasible." If the market size were, for example, around 100,000, a 0.01% reaction rate could be expected to yield 10 sales, but this premise does not hold in the current situation.
6.4. Effectiveness and Limitations of This Research Approach
The approach of exploring "information combinations," using an analogy to drug discovery, demonstrated some effectiveness in probing product appeal points and the interests of the target demographic in a niche market. Using proxy indicators like reaction rates allows for an understanding of attention trends even when actual sales data is scarce. However, the limitations of this approach also became clear. If the market size itself is a major constraint for business viability, then optimizing information structure, no matter how well, is unlikely to lead to substantial results.
6.5. Fixation on "Pens" as a Product and Other Possibilities
The research log includes the insight, "I see products like 'CMC' are selling, maybe I should have sourced and sold those instead of fixating on pens." This suggests that the "pen" product category, which was the main focus of this study, might not have been the most in-demand item in this niche market. If a similar analytical approach had been tried with products more aligned with market needs (e.g., health accessories, also mentioned in the log), different results might have been obtained. However, as the researcher pointed out, delving that far would go beyond the scope of a hobby and become a full-fledged business, so it was not pursued in this study.
7. Conclusion and Future Outlook
7.1. Summary of This Study
This study attempted to identify conditions (information combinations, pricing) for maximizing the attention received by conspiracy-related products on an online flea market, using a data-driven approach. The results confirmed that certain combinations of topics (Occult & Spiritual) and manipulation categories (Avoidance, Approach, etc.) tended to show relatively high reaction rates. However, the impact of price changes was complex and did not yield consistent effects. The most significant conclusion was that the scale of this niche market on the online flea market in question is extremely small, suggesting that applying a probabilistic "hit-or-miss" business model would make achieving stable sales difficult.
7.2. Implications of the Statistical Approach
This research demonstrated that even in niche markets with limited data, setting proxy indicators like reaction rates and employing exploratory approaches (experimental design, sequential improvement) can provide certain insights into market characteristics and consumer interest directions. Statistical thinking and data analysis can serve as a "compass" to aid decision-making even in such tentative situations.
7.3. Future Outlook
Based on the findings of this study, the following future prospects can be considered: * Validation on Larger Platforms: Conducting similar research on platforms with a larger user base might alleviate market size constraints and yield different results. * Application to Different Niche Markets: The "information combination exploration" approach used in this study could potentially be applied to product development and marketing strategies in various niche markets other than conspiracy theories. * Long-Term Observation: Based on the research log's reflection that "conspiracy business... it should be optimal to leave [products] there so they catch the eye when an idiot searches," observing product attention and sales over a longer period might yield different insights.
8. Research Limitations
This study has several limitations: * Limited Scope of Platform: The experiments were confined to a specific online flea market, and the results may not be generalizable to other platforms or the market as a whole. * Use of Proxy Indicators: "Reaction rate" of attention was used as the primary evaluation metric, rather than actual "sales" data, so it does not necessarily directly correlate with sales performance. * Sample Size Constraints: The number of products analyzed was 98, and the estimated market size was also small (around 100 weekly users), limiting statistical power. * Lack of Word-Level Analysis: Detailed analysis of the impact of individual words or phrases in product descriptions on attention, using advanced text mining or natural language processing, was not conducted.
9. References
- BBC News Japan. (2020, August 29). "QAnon to wa nani ka: Inbouron shuudan no shoutai to mokuteki, kikensei" [What is QAnon: The identity, purpose, and danger of the conspiracy theory group].
- Waseda University Institute for Advanced Social Sciences. (2022, August 1). "【Kenkyuu Shoukai】Inbouron wa naze hirogaru no ka? Sono shinri mekanizumu ni semaru" [(Research Introduction) Why do conspiracy theories spread? Approaching the psychological mechanism].
- Brotherton, R., French, C. C., & Pickering, A. D. (2013). Measuring belief in conspiracy theories: The generic conspiracist beliefs scale. Frontiers in psychology, 4, 279.
10. Appendix
10.1. Table: Detailed Definitions of Main Product Topic Categories (T1-T4)
| Category ID | Category Name | Summary/Keyword Examples | | :---------- | :------------------- | :--------------------------------------------------------------------------------------- | | T1 | Technology & Security | EMF, 5G, electromagnetic waves, radiation, shielding, communication, encryption, software, programs, biometric authentication, etc. | | T2 | Surveillance, Censorship & Government-Related | Surveillance, censorship, government secrets, secrets, documents, records, government documents, etc. | | T3 | Occult & Spiritual | Orb detection, spiritual phenomena, pendulums, ancient civilizations, alien contact, energy, crystals, chakras, quantum consciousness, etc. | | T4 | Forbidden Books & Knowledge Management | Ancient texts, forbidden books, ancient languages, shortwave (retro technology), etc. |
10.2. Table: Detailed Definitions of Product Manipulation Categories (M1-M3)
| Category ID | Category Name | Summary/Keyword Examples | | :---------- | :--------------------------- | :--------------------------------------------------------- | | M1 | Avoidance | Shielding, soundproofing, prevention, avoidance (e.g., avoiding negative energy) | | M2 | Detection | Detectors, finders, detection devices, deciphering (e.g., detecting hidden information) | | M3 | Approach/Processing/Amplification | Processing, amplification, magnification (e.g., approaching and amplifying ancient knowledge) |
10.3. Table: Summary of Main Analysis Results (Examples of High/Low Average Attention Scores by Topic × Manipulation Category)
| Combination (T-M) | Average Score (Approx.) | Trend | | :---------------- | :---------------------- | :----------------- | | T3 - M1 | High | Attracts attention | | T4 - M2 | High | Attracts attention | | T1 - M3 | Medium-High | Relatively attentive | | T2 - M3 | Medium | Somewhat attentive | | T1 - M1 | Low (Negative) | Less attention | | T2 - M1 | Low (Negative) | Less attention | (Note: The scores above are approximate values from the figures and actual precise numbers are based on the original data.)
10.4. Representative Examples of AI-Generated Product Descriptions
Basic Prompt Structure Example: "I want to sell {word} at a high price. Combine one from {maintopic} and {manipulation} to create a product description and an appropriate price. Respond in the format: 'Main Topic Category (T1-T4)':'Manipulation Category (M1-M3)':'Product Name':'Product Description':'Price' only once. Absolutely adhere to the specified {maintopic} and {manipulation}. No other output is necessary. Respond in Japanese." (Placeholders like
{word}would be filled with "ballpoint pen,"{maintopic}with "T3," and{manipulation}with "M1," etc., as specific instructions.)Generated Example (Combination T3 - M1): * "Thought Shield Ballpoint Pen: This pen was specially created to powerfully block and evade external negative thoughts and spiritual interference through the sacred act of writing. Based on ancient esoteric arts and quantum consciousness theory, a special energy shield sealed inside the pen protects your thought space and personal field. Using it when signing important contracts or for work requiring concentration helps defend against malice and unnecessary energy, maintaining clear thought. The act of holding it itself becomes a powerful barrier, effectively evading unnecessary energies in daily life." * "Quantum Shield Energy Pen: The act of writing with this pen deploys a quantum shield around your energy field. It is expected to block and evade negative energies and unnecessary external influences, and to balance your chakras. This is a limited-production item using special manufacturing methods and rare materials."
- Table 1: Definition of Main Product Topic Categories (T1-T4) (See Appendix 10.1 for details)
-
 @ ce2820ce:8cf20d40
2025-05-30 10:07:05
@ ce2820ce:8cf20d40
2025-05-30 10:07:05If you insist that my worldview join your pessimistic outlook on life, and you argue with me with a vengeance until I sympathize with your miserable failing hopeless vision of the future...than fight me!
Go ahead, give me all your reasons why I should fear:::Climate Change. Political Injustice. Too much screen time. The Dangers of social media. Fentanyl in my Cheerios. Glyphosate in my weed. Plastic in my brain. Estrogen in my receipt paper.
And the list goes on:::Nuclear War. The Ominous Second Coming of Hitler. The Genocide of Gaza. The Anti-semitism. The Ultra-Rich After my Red Meat.
And while I'm at it, how about the thousands of other “micro-negativities” that are casually beaten into our psyche all day. Pleasure and punishment in the same sadistic act. Warning labels and threats of death on everything from clothing to candy wrappers.
Don't get me wrong. I understand all the reasons why the alarm bells are going off. I'm most definitely thinking about the healthiest possible long term future for my kids, and for many generations to come.
We are not done here, is what I have to say to that. And if you narcissitic, self-loathing, pathologically empathetic descendants of hippies think that this is the last generation to ever walk the Earth, than all I ask is; Go Kill Yourselves Now, and spare us all the trouble of your self-perpetuated miseries.
If you have no mind for the future, and you don't plan on having children, than you better well keep your traps shut and go enjoy the fuck out of this glorious age of excess that we are currently abiding in, until its gone. Because what do you care if it is? You're not leaving any future generations to the dystopia, so what do you have to feel guilty about?
If you do have a mind for the future, and you have or would like to have children of your own, then my heartfelt response to you is that you should do your utmost to focus on the solutions, the bright spots, the gratitudes of life and the progress that humans have made and that we will continue to make. There is no stopping now.
There are no doubt terrifying problems and apocalyptic potentials for Planet Earth in the coming centuries, but this pattern of preaching fear HAS GOT TO STOP. All we are doing is entertaining negativity; giving far too much credit to the forces of destruction and to the demons of our own dissatisfactions.
Too many generations are now embracing a culture of hopelessness. We've pounded their heads full of horrible news for their future – climate change, diseases, technology woes – and we continue to do so on a daily basis. We pontificate about skyrocketing mental health and suicide rates among teens, but all we do is point fingers and shout platitudes at those to whom we offload the responsibility of our kids to.
So do the future a favor, and start thinking about one that you might actually enjoy living in. If you're already having that problem – the one about enjoying things – than figure out what the fuck it is that is keeping you from envisioning a positive future. What went wrong in your own life that made you so depressed and unhappy? Misery loves company, we all know that, and it seems that the only way to relate to my peers these days is through a semi-informed rant about the stresses and horrors of the modern world.
The problem is, we don't stick to our guns when it comes to those convictions. We complain about social media, but we still use it everyday. We put AI on blast and expound its humanity ending potentials, while we ask it questions about our astrology and our skin conditions.
So if you are going to spread the murder pron, and fill your stories up with the perpetual shock and fear, in-between selfies of you enjoying your luxurious life, than you are living a duplicitous and dangerous path.
You feel guilty for your privileged life, and the way you assuage that is by expounding your concern for the ills and unfairness of the outside world, and by pretending to “put in the work” to “heal our wounds” or destroy the patriarchy by smearing your big ass across my Instagram feeds. Here, let me help you.
Your Suffering isn't Saving Anybody. It's only pulling a drag net through your mind's ability to let happiness and love into your life. Don't take pride in your own wounds, as you do not really wish them on anybody else, and you certainly don't want your kids to feel the trauma's you are trying to get over from your own childhood.
So if you think “pessimism is the only morally acceptable emotion” when it comes to thinking about the future, than I will fight you tooth and nail to maintain my own delusion that the future is still bright. If you want to tell my kids that Hitler is coming, that the sea levels are rising, and that AI will end their lives, than I will beat your misery to a bloody pulp, and try and help you see a future worth living.
The point is, I've lost friends, and watched love ones fall into this “addiction” to the broadcast news negativity. It is a bad habit that must be broken, as we are losing our ability to trust, and losing our faith in our own power. If you isolate yourself with misery, than you will never feel emboldened to overcome anything, and you will never learn what love can do.
Look at the future. If you don't see any hope, than you better find some. It takes courage to move forward, and it takes courage to kill yourself. It takes only cowardice to remain in the muddled middle-ground of in-action and crippling in-decision.
Make the move, and tell me how it goes. I’m here to help.
With Love,
-§parrow
-
 @ 39cc53c9:27168656
2025-05-27 09:21:50
@ 39cc53c9:27168656
2025-05-27 09:21:50Over the past few months, I've dedicated my time to a complete rewrite of the kycnot.me website. The technology stack remains unchanged; Golang paired with TailwindCSS. However, I've made some design choices in this iteration that I believe significantly enhance the site. Particularly to backend code.
UI Improvements
You'll notice a refreshed UI that retains the original concept but has some notable enhancements. The service list view is now more visually engaging, it displays additional information in a more aesthetically pleasing manner. Both filtering and searching functionalities have been optimized for speed and user experience.
Service pages have been also redesigned to highlight key information at the top, with the KYC Level box always accessible. The display of service attributes is now more visually intuitive.
The request form, especially the Captcha, has undergone substantial improvements. The new self-made Captcha is robust, addressing the reliability issues encountered with the previous version.
Terms of Service Summarizer
A significant upgrade is the Terms of Service summarizer/reviewer, now powered by AI (GPT-4-turbo). It efficiently condenses each service's ToS, extracting and presenting critical points, including any warnings. Summaries are updated monthly, processing over 40 ToS pages via the OpenAI API using a self-crafted and thoroughly tested prompt.
Nostr Comments
I've integrated a comment section for each service using Nostr. For guidance on using this feature, visit the dedicated how-to page.
Database
The backend database has transitioned to pocketbase, an open-source Golang backend that has been a pleasure to work with. I maintain an updated fork of the Golang SDK for pocketbase at pluja/pocketbase.
Scoring
The scoring algorithm has also been refined to be more fair. Despite I had considered its removal due to the complexity it adds (it is very difficult to design a fair scoring system), some users highlighted its value, so I kept it. The updated algorithm is available open source.
Listings
Each listing has been re-evaluated, and the ones that were no longer operational were removed. New additions are included, and the backlog of pending services will be addressed progressively, since I still have access to the old database.
API
The API now offers more comprehensive data. For more details, check here.
About Page
The About page has been restructured for brevity and clarity.
Other Changes
Extensive changes have been implemented in the server-side logic, since the whole code base was re-written from the ground up. I may discuss these in a future post, but for now, I consider the current version to be just a bit beyond beta, and additional updates are planned in the coming weeks.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:48
@ 39cc53c9:27168656
2025-05-27 09:21:48I'm launching a new service review section on this blog in collaboration with OrangeFren. These reviews are sponsored, yet the sponsorship does not influence the outcome of the evaluations. Reviews are done in advance, then, the service provider has the discretion to approve publication without modifications.
Sponsored reviews are independent from the kycnot.me list, being only part of the blog. The reviews have no impact on the scores of the listings or their continued presence on the list. Should any issues arise, I will not hesitate to remove any listing.
The review
WizardSwap is an instant exchange centred around privacy coins. It was launched in 2020 making it old enough to have weathered the 2021 bull run and the subsequent bearish year.
| Pros | Cons | |------|------| | Tor-friendly | Limited liquidity | | Guarantee of no KYC | Overly simplistic design | | Earn by providing liquidity | |
Rating: ★★★★★ Service Website: wizardswap.io
Liquidity
Right off the bat, we'll start off by pointing out that WizardSwap relies on its own liquidity reserves, meaning they aren't just a reseller of Binance or another exchange. They're also committed to a no-KYC policy, when asking them, they even promised they would rather refund a user their original coins, than force them to undergo any sort of verification.
On the one hand, full control over all their infrastructure gives users the most privacy and conviction about the KYC policies remaining in place.
On the other hand, this means the liquidity available for swapping isn't huge. At the time of testing we could only purchase at most about 0.73 BTC with XMR.
It's clear the team behind WizardSwap is aware of this shortfall and so they've come up with a solution unique among instant exchanges. They let you, the user, deposit any of the currencies they support into your account and earn a profit on the trades made using your liquidity.
Trading
Fees on WizardSwap are middle-of-the-pack. The normal fee is 2.2%. That's more than some exchanges that reserve the right to suddenly demand you undergo verification, yet less than half the fees on some other privacy-first exchanges. However as we mentioned in the section above you can earn almost all of that fee (2%) if you provide liquidity to WizardSwap.
It's good that with the current Bitcoin fee market their fees are constant regardless of how much, or how little, you send. This is in stark contrast with some of the alternative swap providers that will charge you a massive premium when attempting to swap small amounts of BTC away.
Test trades
Test trades are always performed without previous notice to the service provider.
During our testing we performed a few test trades and found that every single time WizardSwap immediately detected the incoming transaction and the amount we received was exactly what was quoted before depositing. The fees were inline with what WizardSwap advertises.

- Monero payment proof
- Bitcoin received
- Wizardswap TX link - it's possible that this link may cease to be valid at some point in the future.
ToS and KYC
WizardSwap does not have a Terms of Service or a Privacy Policy page, at least none that can be found by users. Instead, they offer a FAQ section where they addresses some basic questions.
The site does not mention any KYC or AML practices. It also does not specify how refunds are handled in case of failure. However, based on the FAQ section "What if I send funds after the offer expires?" it can be inferred that contacting support is necessary and network fees will be deducted from any refund.
UI & Tor
WizardSwap can be visited both via your usual browser and Tor Browser. Should you decide on the latter you'll find that the website works even with the most strict settings available in the Tor Browser (meaning no JavaScript).
However, when disabling Javascript you'll miss the live support chat, as well as automatic refreshing of the trade page. The lack of the first means that you will have no way to contact support from the trade page if anything goes wrong during your swap, although you can do so by mail.
One important thing to have in mind is that if you were to accidentally close the browser during the swap, and you did not save the swap ID or your browser history is disabled, you'll have no easy way to return to the trade. For this reason we suggest when you begin a trade to copy the url or ID to someplace safe, before sending any coins to WizardSwap.
The UI you'll be greeted by is simple, minimalist, and easy to navigate. It works well not just across browsers, but also across devices. You won't have any issues using this exchange on your phone.
Getting in touch
The team behind WizardSwap appears to be most active on X (formerly Twitter): https://twitter.com/WizardSwap_io
If you have any comments or suggestions about the exchange make sure to reach out to them. In the past they've been very receptive to user feedback, for instance a few months back WizardSwap was planning on removing DeepOnion, but the community behind that project got together ^1 and after reaching out WizardSwap reversed their decision ^2.
You can also contact them via email at:
support @ wizardswap . ioDisclaimer
None of the above should be understood as investment or financial advice. The views are our own only and constitute a faithful representation of our experience in using and investigating this exchange. This review is not a guarantee of any kind on the services rendered by the exchange. Do your own research before using any service.
-
 @ 7459d333:f207289b
2025-05-30 07:57:07
@ 7459d333:f207289b
2025-05-30 07:57:07Tokenization of physical assets sounds kinda dumb. Say you tokenize a house. What happens if you loose the private keys? What happens if the last “legal” (on paper) owner claims it? Basically, the tokenization is useless. The house is still subject to whatever jurisdiction is in. And the smart contract can say whatever, but that does not make it true.
What's not so obvious is for virtual assets or service tokens. A good example is cashu. Where tokenizing Bitcoin has the advantages of allowing the users to transact with it “without the mint's permission”. This could be applied similarly for concert tickets or API credits.
For example, the biggest problem of concert ticket reselling is trusting that other copies of the PDF with the QR code won't be used before the one you bought. Or that you won't have problems at the entry because the ticket is not in your name. A mint that allows users to transact between them preventing double spending and fungibility would solve this.
But for some reason shitcoiners are obsessed on tokenizing physical assets or company shares. Where the only benefit that tokenizing could bring is avoiding regulations (until they update the laws).
So, what's your take on tokenization?
https://stacker.news/items/992519
-
 @ 39cc53c9:27168656
2025-05-27 09:21:46
@ 39cc53c9:27168656
2025-05-27 09:21:46Bitcoin enthusiasts frequently and correctly remark how much value it adds to Bitcoin not to have a face, a leader, or a central authority behind it. This particularity means there isn't a single person to exert control over, or a single human point of failure who could become corrupt or harmful to the project.
Because of this, it is said that no other coin can be equally valuable as Bitcoin in terms of decentralization and trustworthiness. Bitcoin is unique not just for being first, but also because of how the events behind its inception developed. This implies that, from Bitcoin onwards, any coin created would have been created by someone, consequently having an authority behind it. For this and some other reasons, some people refer to Bitcoin as "The Immaculate Conception".
While other coins may have their own unique features and advantages, they may not be able to replicate Bitcoin's community-driven nature. However, one other cryptocurrency shares a similar story of mystery behind its creation: Monero.
History of Monero
Bytecoin and CryptoNote
In March 2014, a Bitcointalk thread titled "Bytecoin. Secure, private, untraceable since 2012" was initiated by a user under the nickname "DStrange"^1^. DStrange presented Bytecoin (BCN) as a unique cryptocurrency, in operation since July 2012. Unlike Bitcoin, it employed a new algorithm known as CryptoNote.
DStrange apparently stumbled upon the Bytecoin website by chance while mining a dying bitcoin fork, and decided to create a thread on Bitcointalk^1^. This sparked curiosity among some users, who wondered how could Bytecoin remain unnoticed since its alleged launch in 2012 until then^2^.
Some time after, a user brought up the "CryptoNote v2.0" whitepaper for the first time, underlining its innovative features^4^. Authored by the pseudonymous Nicolas van Saberhagen in October 2013, the CryptoNote v2 whitepaper^5^ highlighted the traceability and privacy problems in Bitcoin. Saberhagen argued that these flaws could not be quickly fixed, suggesting it would be more efficient to start a new project rather than trying to patch the original^5^, an statement simmilar to the one from Satoshi Nakamoto^6^.
Checking with Saberhagen's digital signature, the release date of the whitepaper seemed correct, which would mean that Cryptonote (v1) was created in 2012^7^, although there's an important detail: "Signing time is from the clock on the signer's computer" ^9^.
Moreover, the whitepaper v1 contains a footnote link to a Bitcointalk post dated May 5, 2013^10^, making it impossible for the whitepaper to have been signed and released on December 12, 2012.
As the narrative developed, users discovered that a significant 80% portion of Bytecoin had been pre-mined^11^ and blockchain dates seemed to be faked to make it look like it had been operating since 2012, leading to controversy surrounding the project.
The origins of CryptoNote and Bytecoin remain mysterious, leaving suspicions of a possible scam attempt, although the whitepaper had a good amount of work and thought on it.
The fork
In April 2014, the Bitcointalk user
thankful_for_today, who had also participated in the Bytecoin thread^12^, announced plans to launch a Bytecoin fork named Bitmonero^13^.The primary motivation behind this fork was "Because there is a number of technical and marketing issues I wanted to do differently. And also because I like ideas and technology and I want it to succeed"^14^. This time Bitmonero did things different from Bytecoin: there was no premine or instamine, and no portion of the block reward went to development.
However, thankful_for_today proposed controversial changes that the community disagreed with. Johnny Mnemonic relates the events surrounding Bitmonero and thankful_for_today in a Bitcointalk comment^15^:
When thankful_for_today launched BitMonero [...] he ignored everything that was discussed and just did what he wanted. The block reward was considerably steeper than what everyone was expecting. He also moved forward with 1-minute block times despite everyone's concerns about the increase of orphan blocks. He also didn't address the tail emission concern that should've (in my opinion) been in the code at launch time. Basically, he messed everything up. Then, he disappeared.
After disappearing for a while, thankful_for_today returned to find that the community had taken over the project. Johnny Mnemonic continues:
I, and others, started working on new forks that were closer to what everyone else was hoping for. [...] it was decided that the BitMonero project should just be taken over. There were like 9 or 10 interested parties at the time if my memory is correct. We voted on IRC to drop the "bit" from BitMonero and move forward with the project. Thankful_for_today suddenly resurfaced, and wasn't happy to learn the community had assumed control of the coin. He attempted to maintain his own fork (still calling it "BitMonero") for a while, but that quickly fell into obscurity.
The unfolding of these events show us the roots of Monero. Much like Satoshi Nakamoto, the creators behind CryptoNote/Bytecoin and thankful_for_today remain a mystery^17^, having disappeared without a trace. This enigma only adds to Monero's value.
Since community took over development, believing in the project's potential and its ability to be guided in a better direction, Monero was given one of Bitcoin's most important qualities: a leaderless nature. With no single face or entity directing its path, Monero is safe from potential corruption or harm from a "central authority".
The community continued developing Monero until today. Since then, Monero has undergone a lot of technological improvements, migrations and achievements such as RingCT and RandomX. It also has developed its own Community Crowdfundinc System, conferences such as MoneroKon and Monerotopia are taking place every year, and has a very active community around it.
Monero continues to develop with goals of privacy and security first, ease of use and efficiency second. ^16^
This stands as a testament to the power of a dedicated community operating without a central figure of authority. This decentralized approach aligns with the original ethos of cryptocurrency, making Monero a prime example of community-driven innovation. For this, I thank all the people involved in Monero, that lead it to where it is today.
If you find any information that seems incorrect, unclear or any missing important events, please contact me and I will make the necessary changes.
Sources of interest
- https://forum.getmonero.org/20/general-discussion/211/history-of-monero
- https://monero.stackexchange.com/questions/852/what-is-the-origin-of-monero-and-its-relationship-to-bytecoin
- https://en.wikipedia.org/wiki/Monero
- https://bitcointalk.org/index.php?topic=583449.0
- https://bitcointalk.org/index.php?topic=563821.0
- https://bitcointalk.org/index.php?action=profile;u=233561
- https://bitcointalk.org/index.php?topic=512747.0
- https://bitcointalk.org/index.php?topic=740112.0
- https://monero.stackexchange.com/a/1024
- https://inspec2t-project.eu/cryptocurrency-with-a-focus-on-anonymity-these-facts-are-known-about-monero/
- https://medium.com/coin-story/coin-perspective-13-riccardo-spagni-69ef82907bd1
- https://www.getmonero.org/resources/about/
- https://www.wired.com/2017/01/monero-drug-dealers-cryptocurrency-choice-fire/
- https://www.monero.how/why-monero-vs-bitcoin
- https://old.reddit.com/r/Monero/comments/u8e5yr/satoshi_nakamoto_talked_about_privacy_features/
-
 @ 29313cc9:a6bf155e
2025-05-30 06:35:56
@ 29313cc9:a6bf155e
2025-05-30 06:35:56I thought i'd experiment with this Nostr blogging thing and write a short article on the state of Meshtastic and its alternatives.
For years Meshtastic was the only game in town, there wasn't a lot of users but the authors kept plugging away and it has become a thriving ecosystem of open source hardware, software, tools and social scene.
Meshtastic has always been focused on node to node messaging, in particular one of the use cases specifically mentioned was hiking in the wilderness or skiing in the mountains and being able to use these devices off-grid, perhaps even without a phone to communicate with one and other. The project does have a few other features like telemetry, remote admin, packet data etc but the messaging was the focus. Because of this focus, the core functionality needs to be built into the firmware of these low powered devices like ESP32 for example. This restricts what can be done in terms of CPU power and storage, but also makes synchronization between device and phone cumbersome.
Unfortunately, as a messaging platform, Meshtastic still struggles even after all these years. Message delivery and routing are fairly unreliable, 95% of conversations go along the lines of "hello, test, anyone there?". Now I should mention, if you have a very good signal to your peers the reliability can be good, but even then its not a guarantee.
Early on in the Meshtastic journey I stumbled upon a similar project named Reticulum which can utilize the same LoRa based hardware but aims to be a more comprehensive platform for decentralized communications and currently requires a computer or raspberry pi to run the Python backend alongside the LoRa hardware as a radio. Reticulum has historically been a less polished UI experience and a little idiosyncratic in its design which has probably hindered its adoption a little. But the main difference to Meshtastic is Reticulum requires bigger hardware and is less suitable for remote installations, solar powered setups etc. My understanding is once v1.0 has been released (soon) there may be efforts to port the code to native C which may allow hardware nodes to run as repeaters on their own.
More recently a new project has been announced called Meshcore, which is more closely aligned with Meshtastic than Reticulum, Meshcore makes several important improvements to message delivery and routing in an attempt to improve the reliability of the core feature, messaging. Popular Youtube channel Andy Kirby has been central in helping Meshcore gain popularity and I think he may be involved in the commercial aspects of the project. The smartphone apps and website mapping and flasher tools are a bit more polished with Meshcore.
One of the biggest contributors in the space is Liam Cottle who has created mapping websites for Meshtastic & Meshcore, he also built the Meshcore smartphone app and built the fantastic Reticulum MeshChat UI.
With all this new competition Meshtastic appears to be pushing out more frequent updates and whilst they have been introducing more bugs into the software it is nice to see some faster progress.
In my opinion Reticulum is probably the most interesting project with the most potential, but they do need to get the core routing engine running standalone on low powered hardware for the project to expand to more hardware/radio focused users.
That is all. Mesh on!
-
 @ 7f6db517:a4931eda
2025-05-30 16:02:21
@ 7f6db517:a4931eda
2025-05-30 16:02:21
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
Good morning.
It looks like PacWest will fail today. It will be both the fifth largest bank failure in US history and the sixth major bank to fail this year. It will likely get purchased by one of the big four banks in a government orchestrated sale.
March 8th - Silvergate Bank
March 10th - Silicon Valley Bank
March 12th - Signature Bank
March 19th - Credit Suisse
May 1st - First Republic Bank
May 4th - PacWest Bank?PacWest is the first of many small regional banks that will go under this year. Most will get bought by the big four in gov orchestrated sales. This has been the playbook since 2008. Follow the incentives. Massive consolidation across the banking industry. PacWest gonna be a drop in the bucket compared to what comes next.
First, a hastened government led bank consolidation, then a public/private partnership with the remaining large banks to launch a surveilled and controlled digital currency network. We will be told it is more convenient. We will be told it is safer. We will be told it will prevent future bank runs. All of that is marketing bullshit. The goal is greater control of money. The ability to choose how we spend it and how we save it. If you control the money - you control the people that use it.
If you found this post helpful support my work with bitcoin.

-
 @ 39cc53c9:27168656
2025-05-27 09:21:40
@ 39cc53c9:27168656
2025-05-27 09:21:40“The future is there... staring back at us. Trying to make sense of the fiction we will have become.” — William Gibson.
This month is the 4th anniversary of kycnot.me. Thank you for being here.
Fifteen years ago, Satoshi Nakamoto introduced Bitcoin, a peer-to-peer electronic cash system: a decentralized currency free from government and institutional control. Nakamoto's whitepaper showed a vision for a financial system based on trustless transactions, secured by cryptography. Some time forward and KYC (Know Your Customer), AML (Anti-Money Laundering), and CTF (Counter-Terrorism Financing) regulations started to come into play.
What a paradox: to engage with a system designed for decentralization, privacy, and independence, we are forced to give away our personal details. Using Bitcoin in the economy requires revealing your identity, not just to the party you interact with, but also to third parties who must track and report the interaction. You are forced to give sensitive data to entities you don't, can't, and shouldn't trust. Information can never be kept 100% safe; there's always a risk. Information is power, who knows about you has control over you.
Information asymmetry creates imbalances of power. When entities have detailed knowledge about individuals, they can manipulate, influence, or exploit this information to their advantage. The accumulation of personal data by corporations and governments enables extensive surveillances.
Such practices, moreover, exclude individuals from traditional economic systems if their documentation doesn't meet arbitrary standards, reinforcing a dystopian divide. Small businesses are similarly burdened by the costs of implementing these regulations, hindering free market competition^1:
How will they keep this information safe? Why do they need my identity? Why do they force businesses to enforce such regulations? It's always for your safety, to protect you from the "bad". Your life is perpetually in danger: terrorists, money launderers, villains... so the government steps in to save us.
‟Hush now, baby, baby, don't you cry Mamma's gonna make all of your nightmares come true Mamma's gonna put all of her fears into you Mamma's gonna keep you right here, under her wing She won't let you fly, but she might let you sing Mamma's gonna keep baby cosy and warm” — Mother, Pink Floyd
We must resist any attack on our privacy and freedom. To do this, we must collaborate.
If you have a service, refuse to ask for KYC; find a way. Accept cryptocurrencies like Bitcoin and Monero. Commit to circular economies. Remove the need to go through the FIAT system. People need fiat money to use most services, but we can change that.
If you're a user, donate to and prefer using services that accept such currencies. Encourage your friends to accept cryptocurrencies as well. Boycott FIAT system to the greatest extent you possibly can.
This may sound utopian, but it can be achieved. This movement can't be stopped. Go kick the hornet's nest.
“We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do.” — Eric Hughes, A Cypherpunk's Manifesto
The anniversary
Four years ago, I began exploring ways to use crypto without KYC. I bookmarked a few favorite services and thought sharing them to the world might be useful. That was the first version of kycnot.me — a simple list of about 15 services. Since then, I've added services, rewritten it three times, and improved it to what it is now.
kycnot.me has remained 100% independent and 100% open source^2 all these years. I've received offers to buy the site, all of which I have declined and will continue to decline. It has been DDoS attacked many times, but we made it through. I have also rewritten the whole site almost once per year (three times in four years).
The code and scoring algorithm are open source (contributions are welcome) and I can't arbitrarly change a service's score without adding or removing attributes, making any arbitrary alterations obvious if they were fake. You can even see the score summary for any service's score.
I'm a one-person team, dedicating my free time to this project. I hope to keep doing so for many more years. Again, thank you for being part of this.
-
 @ b7274d28:c99628cb
2025-05-27 07:07:33
@ b7274d28:c99628cb
2025-05-27 07:07:33A few months ago, a nostrich was switching from iOS to Android and asked for suggestions for #Nostr apps to try out. nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 offered the following as his response:
nostr:nevent1qvzqqqqqqypzq0mhp4ja8fmy48zuk5p6uy37vtk8tx9dqdwcxm32sy8nsaa8gkeyqydhwumn8ghj7un9d3shjtnwdaehgunsd3jkyuewvdhk6tcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszythwden5te0dehhxarj9emkjmn99uqzpwwts6n28eyvjpcwvu5akkwu85eg92dpvgw7cgmpe4czdadqvnv984rl0z
Yes. #Android users are fortunate to have some powerful Nostr apps and tools at our disposal that simply have no comparison over on the iOS side. However, a tool is only as good as the knowledge of the user, who must have an understanding of how best to wield it for maximum effect. This fact was immediately evidenced by replies to Derek asking, "What is the use case for Citrine?" and "This is the first time I'm hearing about Citrine and Pokey. Can you give me links for those?"
Well, consider this tutorial your Nostr starter-kit for Android. We'll go over installing and setting up Amber, Amethyst, Citrine, and Pokey, and as a bonus we'll be throwing in the Zapstore and Coinos to boot. We will assume no previous experience with any of the above, so if you already know all about one or more of these apps, you can feel free to skip that tutorial.
So many apps...
You may be wondering, "Why do I need so many apps to use Nostr?" That's perfectly valid, and the honest answer is, you don't. You can absolutely just install a Nostr client from the Play Store, have it generate your Nostr identity for you, and stick with the default relays already set up in that app. You don't even need to connect a wallet, if you don't want to. However, you won't experience all that Nostr has to offer if that is as far as you go, any more than you would experience all that Italian cuisine has to offer if you only ever try spaghetti.
Nostr is not just one app that does one thing, like Facebook, Twitter, or TikTok. It is an entire ecosystem of applications that are all built on top of a protocol that allows them to be interoperable. This set of tools will help you make the most out of that interoperability, which you will never get from any of the big-tech social platforms. It will provide a solid foundation for you to build upon as you explore more and more of what Nostr has to offer.
So what do these apps do?

Fundamental to everything you do on Nostr is the need to cryptographically sign with your private key. If you aren't sure what that means, just imagine that you had to enter your password every time you hit the "like" button on Facebook, or every time you commented on the latest dank meme. That would get old really fast, right? That's effectively what Nostr requires, but on steroids.
To keep this from being something you manually have to do every 5 seconds when you post a note, react to someone else's note, or add a comment, Nostr apps can store your private key and use it to sign behind the scenes for you. This is very convenient, but it means you are trusting that app to not do anything with your private key that you don't want it to. You are also trusting it to not leak your private key, because anyone who gets their hands on it will be able to post as you, see your private messages, and effectively be you on Nostr. The more apps you give your private key to, the greater your risk that it will eventually be compromised.
Enter #Amber, an application that will store your private key in only one app, and all other compatible Nostr apps can communicate with it to request a signature, without giving any of those other apps access to your private key.
Most Nostr apps for Android now support logging in and signing with Amber, and you can even use it to log into apps on other devices, such as some of the web apps you use on your PC. It's an incredible tool given to us by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, and only available for Android users. Those on iPhone are incredibly jealous that they don't have anything comparable, yet.

Speaking of nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, the next app is also one of his making.
All Nostr data is stored on relays, which are very simple servers that Nostr apps read notes from and write notes to. In most forms of social media, it can be a pain to get your own data out to keep a backup. That's not the case on Nostr. Anyone can run their own relay, either for the sake of backing up their personal notes, or for others to post their notes to, as well.
Since Nostr notes take up very little space, you can actually run a relay on your phone. I have been on Nostr for almost 2 and a half years, and I have 25,000+ notes of various kinds on my relay, and a backup of that full database is just 24MB on my phone's storage.
Having that backup can save your bacon if you try out a new Nostr client and it doesn't find your existing follow list for some reason, so it writes a new one and you suddenly lose all of the people you were following. Just pop into your #Citrine relay, confirm it still has your correct follow list or import it from a recent backup, then have Citrine restore it. Done.
Additionally, there are things you may want to only save to a relay you control, such as draft messages that you aren't ready to post publicly, or eCash tokens, which can actually be saved to Nostr relays now. Citrine can also be used with Amber for signing into certain Nostr applications that use a relay to communicate with Amber.
If you are really adventurous, you can also expose Citrine over Tor to be used as an outbox relay, or used for peer-to-peer private messaging, but that is far more involved than the scope of this tutorial series.

You can't get far in Nostr without a solid and reliable client to interact with. #Amethyst is the client we will be using for this tutorial because there simply isn't another Android client that comes close, so far. Moreover, it can be a great client for new users to get started on, and yet it has a ton of features for power-users to take advantage of as well.
There are plenty of other good clients to check out over time, such as Coracle, YakiHonne, Voyage, Olas, Flotilla and others, but I keep coming back to Amethyst, and by the time you finish this tutorial, I think you'll see why. nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z and others who have contributed to Amethyst have really built something special in this client, and it just keeps improving with every update that's shipped.
Most social media apps have some form of push notifications, and some Nostr apps do, too. Where the issue comes in is that Nostr apps are all interoperable. If you have more than one application, you're going to have both of them notifying you. Nostr users are known for having five or more Nostr apps that they use regularly. If all of them had notifications turned on, it would be a nightmare. So maybe you limit it to only one of your Nostr apps having notifications turned on, but then you are pretty well locked-in to opening that particular app when you tap on the notification.
Pokey, by nostr:npub1v3tgrwwsv7c6xckyhm5dmluc05jxd4yeqhpxew87chn0kua0tjzqc6yvjh, solves this issue, allowing you to turn notifications off for all of your Nostr apps, and have Pokey handle them all for you. Then, when you tap on a Pokey notification, you can choose which Nostr app to open it in.
Pokey also gives you control over the types of things you want to be notified about. Maybe you don't care about reactions, and you just want to know about zaps, comments, and direct messages. Pokey has you covered. It even supports multiple accounts, so you can get notifications for all the npubs you control.

One of the most unique and incredibly fun aspects of Nostr is the ability to send and receive #zaps. Instead of merely giving someone a 👍️ when you like something they said, you can actually send them real value in the form of sats, small portions of a Bitcoin. There is nothing quite like the experience of receiving your first zap and realizing that someone valued what you said enough to send you a small amount (and sometimes not so small) of #Bitcoin, the best money mankind has ever known.
To be able to have that experience, though, you are going to need a wallet that can send and receive zaps, and preferably one that is easy to connect to Nostr applications. My current preference for that is Alby Hub, but not everyone wants to deal with all that comes along with running a #Lightning node. That being the case, I have opted to use nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch for this tutorial, because they offer one of the easiest wallets to set up, and it connects to most Nostr apps by just copy/pasting a connection string from the settings in the wallet into the settings in your Nostr app of choice.
Additionally, even though #Coinos is a custodial wallet, you can have it automatically transfer any #sats over a specified threshold to a separate wallet, allowing you to mitigate the custodial risk without needing to keep an eye on your balance and make the transfer manually.

Most of us on Android are used to getting all of our mobile apps from one souce: the Google Play Store. That's not possible for this tutorial series. Only one of the apps mentioned above is available in Google's permissioned playground. However, on Android we have the advantage of being able to install whatever we want on our device, just by popping into our settings and flipping a toggle. Indeed, thumbing our noses at big-tech is at the heart of the Nostr ethos, so why would we make ourselves beholden to Google for installing Nostr apps?
The nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 is an alternative app store made by nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9 as a resource for all sorts of open-source apps, but especially Nostr apps. What is more, you can log in with Amber, connect a wallet like Coinos, and support the developers of your favorite Nostr apps directly within the #Zapstore by zapping their app releases.
One of the biggest features of the Zapstore is the fact that developers can cryptographically sign their app releases using their Nostr keys, so you know that the app you are downloading is the one they actually released and hasn't been altered in any way. The Zapstore will warn you and won't let you install the app if the signature is invalid.
Getting Started
Since the Zapstore will be the source we use for installing most of the other apps mentioned, we will start with installing the Zapstore.
We will then use the Zapstore to install Amber and set it up with our Nostr account, either by creating a new private key, or by importing one we already have. We'll also use it to log into the Zapstore.
Next, we will install Amethyst from the Zapstore and log into it via Amber.
After this, we will install Citrine from the Zapstore and add it as a local relay on Amethyst.
Because we want to be able to send and receive zaps, we will set up a wallet with CoinOS and connect it to Amethyst and the Zapstore using Nostr Wallet Connect.
Finally, we will install Pokey using the Zapstore, log into it using Amber, and set up the notifications we want to receive.
By the time you are done with this series, you will have a great head-start on your Nostr journey compared to muddling through it all on your own. Moreover, you will have developed a familiarity with how things generally work on Nostr that can be applied to other apps you try out in the future.
Continue to Part 2: The Zapstore. Nostr Link: nostr:naddr1qvzqqqr4gupzpde8f55w86vrhaeqmd955y4rraw8aunzxgxstsj7eyzgntyev2xtqydhwumn8ghj7un9d3shjtnzwf5kw6r5vfhkcapwdejhgtcqp5cnwdphxv6rwwp3xvmnzvqgty5au
-
 @ 7f6db517:a4931eda
2025-05-30 16:02:21
@ 7f6db517:a4931eda
2025-05-30 16:02:21
I often hear "bitcoin doesn't interest me, I'm not a finance person."
Ironically, the beauty of sound money is you don't have to be. In the current system you're expected to manage a diversified investment portfolio or pay someone to do it. Bitcoin will make that optional.
— ODELL (@ODELL) September 16, 2018
At first glance bitcoin often appears overwhelming to newcomers. It is incredibly easy to get bogged down in the details of how it works or different ways to use it. Enthusiasts, such as myself, often enjoy going down the deep rabbit hole of the potential of bitcoin, possible pitfalls and theoretical scenarios, power user techniques, and the developer ecosystem. If your first touch point with bitcoin is that type of content then it is only natural to be overwhelmed. While it is important that we have a thriving community of bitcoiners dedicated to these complicated tasks - the true beauty of bitcoin lies in its simplicity. Bitcoin is simply better money. It is the best money we have ever had.
Life is complicated. Life is hard. Life is full of responsibility and surprises. Bitcoin allows us to focus on our lives while relying on a money that is simple. A money that is not controlled by any individual, company, or government. A money that cannot be easily seized or blocked. A money that cannot be devalued at will by a handful of corrupt bureaucrat who live hundreds of miles from us. A money that can be easily saved and should increase in purchasing power over time without having to learn how to "build a diversified stock portfolio" or hire someone to do it for us.
Bitcoin enables all of us to focus on our lives - our friends and family - doing what we love with the short time we have on this earth. Time is scarce. Life is complicated. Bitcoin is the most simple aspect of our complicated lives. If we spend our scarce time working then we should be able to easily save that accrued value for future generations without watching the news or understanding complicated financial markets. Bitcoin makes this possible for anyone.
Yesterday was Mother's Day. Raising a human is complicated. It is hard, it requires immense personal responsibility, it requires critical thinking, but mothers figure it out, because it is worth it. Using and saving bitcoin is simple - simply install an app on your phone. Every mother can do it. Every person can do it.
Life is complicated. Life is beautiful. Bitcoin is simple.
If you found this post helpful support my work with bitcoin.

-
 @ 06830f6c:34da40c5
2025-05-24 04:21:03
@ 06830f6c:34da40c5
2025-05-24 04:21:03The evolution of development environments is incredibly rich and complex and reflects a continuous drive towards greater efficiency, consistency, isolation, and collaboration. It's a story of abstracting away complexity and standardizing workflows.
Phase 1: The Bare Metal & Manual Era (Early 1970s - Late 1990s)
-
Direct OS Interaction / Bare Metal Development:
- Description: Developers worked directly on the operating system's command line or a basic text editor. Installation of compilers, interpreters, and libraries was a manual, often arcane process involving downloading archives, compiling from source, and setting environment variables. "Configuration drift" (differences between developer machines) was the norm.
- Tools: Text editors (Vi, Emacs), command-line compilers (GCC), Makefiles.
- Challenges: Extremely high setup time, dependency hell, "works on my machine" syndrome, difficult onboarding for new developers, lack of reproducibility. Version control was primitive (e.g., RCS, SCCS).
-
Integrated Development Environments (IDEs) - Initial Emergence:
- Description: Early IDEs (like Turbo Pascal, Microsoft Visual Basic) began to integrate editors, compilers, debuggers, and sometimes GUI builders into a single application. This was a massive leap in developer convenience.
- Tools: Turbo Pascal, Visual Basic, early Visual Studio versions.
- Advancement: Improved developer productivity, streamlined common tasks. Still relied on local system dependencies.
Phase 2: Towards Dependency Management & Local Reproducibility (Late 1990s - Mid-2000s)
-
Basic Build Tools & Dependency Resolvers (Pre-Package Managers):
- Description: As projects grew, manual dependency tracking became impossible. Tools like Ant (Java) and early versions of
autoconf/makefor C/C++ helped automate the compilation and linking process, managing some dependencies. - Tools: Apache Ant, GNU Autotools.
- Advancement: Automated build processes, rudimentary dependency linking. Still not comprehensive environment management.
- Description: As projects grew, manual dependency tracking became impossible. Tools like Ant (Java) and early versions of
-
Language-Specific Package Managers:
- Description: A significant leap was the emergence of language-specific package managers that could fetch, install, and manage libraries and frameworks declared in a project's manifest file. Examples include Maven (Java), npm (Node.js), pip (Python), RubyGems (Ruby), Composer (PHP).
- Tools: Maven, npm, pip, RubyGems, Composer.
- Advancement: Dramatically simplified dependency resolution, improved intra-project reproducibility.
- Limitation: Managed language-level dependencies, but not system-level dependencies or the underlying OS environment. Conflicts between projects on the same machine (e.g., Project A needs Python 2.7, Project B needs Python 3.9) were common.
Phase 3: Environment Isolation & Portability (Mid-2000s - Early 2010s)
-
Virtual Machines (VMs) for Development:
- Description: To address the "it works on my machine" problem stemming from OS-level and system-level differences, developers started using VMs. Tools like VMware Workstation, VirtualBox, and later Vagrant (which automated VM provisioning) allowed developers to encapsulate an entire OS and its dependencies for a project.
- Tools: VMware, VirtualBox, Vagrant.
- Advancement: Achieved strong isolation and environment reproducibility (a true "single environment" for a project).
- Limitations: Resource-heavy (each VM consumed significant CPU, RAM, disk space), slow to provision and boot, difficult to share large VM images.
-
Early Automation & Provisioning Tools:
- Description: Alongside VMs, configuration management tools started being used to automate environment setup within VMs or on servers. This helped define environments as code, making them more consistent.
- Tools: Chef, Puppet, Ansible.
- Advancement: Automated provisioning, leading to more consistent environments, often used in conjunction with VMs.
Phase 4: The Container Revolution & Orchestration (Early 2010s - Present)
-
Containerization (Docker):
- Description: Docker popularized Linux Containers (LXC), offering a lightweight, portable, and efficient alternative to VMs. Containers package an application and all its dependencies into a self-contained unit that shares the host OS kernel. This drastically reduced resource overhead and startup times compared to VMs.
- Tools: Docker.
- Advancement: Unprecedented consistency from development to production (Dev/Prod Parity), rapid provisioning, highly efficient resource use. Became the de-facto standard for packaging applications.
-
Container Orchestration:
- Description: As microservices and container adoption grew, managing hundreds or thousands of containers became a new challenge. Orchestration platforms automated the deployment, scaling, healing, and networking of containers across clusters of machines.
- Tools: Kubernetes, Docker Swarm, Apache Mesos.
- Advancement: Enabled scalable, resilient, and complex distributed systems development and deployment. The "environment" started encompassing the entire cluster.
Phase 5: Cloud-Native, Serverless & Intelligent Environments (Present - Future)
-
Cloud-Native Development:
- Description: Leveraging cloud services (managed databases, message queues, serverless functions) directly within the development workflow. Developers focus on application logic, offloading infrastructure management to cloud providers. Containers become a key deployment unit in this paradigm.
- Tools: AWS Lambda, Azure Functions, Google Cloud Run, cloud-managed databases.
- Advancement: Reduced operational overhead, increased focus on business logic, highly scalable deployments.
-
Remote Development & Cloud-Based IDEs:
- Description: The full development environment (editor, terminal, debugger, code) can now reside in the cloud, accessed via a thin client or web browser. This means developers can work from any device, anywhere, with powerful cloud resources backing their environment.
- Tools: GitHub Codespaces, Gitpod, AWS Cloud9, VS Code Remote Development.
- Advancement: Instant onboarding, consistent remote environments, access to high-spec machines regardless of local hardware, enhanced security.
-
Declarative & AI-Assisted Environments (The Near Future):
- Description: Development environments will become even more declarative, where developers specify what they need, and AI/automation tools provision and maintain it. AI will proactively identify dependency issues, optimize resource usage, suggest code snippets, and perform automated testing within the environment.
- Tools: Next-gen dev container specifications, AI agents integrated into IDEs and CI/CD pipelines.
- Prediction: Near-zero environment setup time, self-healing environments, proactive problem identification, truly seamless collaboration.
web3 #computing #cloud #devstr
-
-
 @ 5144fe88:9587d5af
2025-05-23 17:01:37
@ 5144fe88:9587d5af
2025-05-23 17:01:37The recent anomalies in the financial market and the frequent occurrence of world trade wars and hot wars have caused the world's political and economic landscape to fluctuate violently. It always feels like the financial crisis is getting closer and closer.
This is a systematic analysis of the possibility of the current global financial crisis by Manus based on Ray Dalio's latest views, US and Japanese economic and financial data, Buffett's investment behavior, and historical financial crises.
Research shows that the current financial system has many preconditions for a crisis, especially debt levels, market valuations, and investor behavior, which show obvious crisis signals. The probability of a financial crisis in the short term (within 6-12 months) is 30%-40%,
in the medium term (within 1-2 years) is 50%-60%,
in the long term (within 2-3 years) is 60%-70%.
Japan's role as the world's largest holder of overseas assets and the largest creditor of the United States is particularly critical. The sharp appreciation of the yen may be a signal of the return of global safe-haven funds, which will become an important precursor to the outbreak of a financial crisis.
Potential conditions for triggering a financial crisis Conditions that have been met 1. High debt levels: The debt-to-GDP ratio of the United States and Japan has reached a record high. 2. Market overvaluation: The ratio of stock market to GDP hits a record high 3. Abnormal investor behavior: Buffett's cash holdings hit a record high, with net selling for 10 consecutive quarters 4. Monetary policy shift: Japan ends negative interest rates, and the Fed ends the rate hike cycle 5. Market concentration is too high: a few technology stocks dominate market performance
Potential trigger points 1. The Bank of Japan further tightens monetary policy, leading to a sharp appreciation of the yen and the return of overseas funds 2. The US debt crisis worsens, and the proportion of interest expenses continues to rise to unsustainable levels 3. The bursting of the technology bubble leads to a collapse in market confidence 4. The trade war further escalates, disrupting global supply chains and economic growth 5. Japan, as the largest creditor of the United States, reduces its holdings of US debt, causing US debt yields to soar
Analysis of the similarities and differences between the current economic environment and the historical financial crisis Debt level comparison Current debt situation • US government debt to GDP ratio: 124.0% (December 2024) • Japanese government debt to GDP ratio: 216.2% (December 2024), historical high 225.8% (March 2021) • US total debt: 36.21 trillion US dollars (May 2025) • Japanese debt/GDP ratio: more than 250%-263% (Japanese Prime Minister’s statement)
Before the 2008 financial crisis • US government debt to GDP ratio: about 64% (2007) • Japanese government debt to GDP ratio: about 175% (2007)
Before the Internet bubble in 2000 • US government debt to GDP ratio: about 55% (1999) • Japanese government debt to GDP ratio: about 130% (1999)
Key differences • The current US debt-to-GDP ratio is nearly twice that before the 2008 crisis • The current Japanese debt-to-GDP ratio is more than 1.2 times that before the 2008 crisis • Global debt levels are generally higher than historical pre-crisis levels • US interest payments are expected to devour 30% of fiscal revenue (Moody's warning)
Monetary policy and interest rate environment
Current situation • US 10-year Treasury yield: about 4.6% (May 2025) • Bank of Japan policy: end negative interest rates and start a rate hike cycle • Bank of Japan's holdings of government bonds: 52%, plans to reduce purchases to 3 trillion yen per month by January-March 2026 • Fed policy: end the rate hike cycle and prepare to cut interest rates
Before the 2008 financial crisis • US 10-year Treasury yield: about 4.5%-5% (2007) • Fed policy: continuous rate hikes from 2004 to 2006, and rate cuts began in 2007 • Bank of Japan policy: maintain ultra-low interest rates
Key differences • Current US interest rates are similar to those before the 2008 crisis, but debt levels are much higher than then • Japan is in the early stages of ending its loose monetary policy, unlike before historical crises • The size of global central bank balance sheets is far greater than at any time in history
Market valuations and investor behavior Current situation • The ratio of stock market value to the size of the US economy: a record high • Buffett's cash holdings: $347 billion (28% of assets), a record high • Market concentration: US stock growth mainly relies on a few technology giants • Investor sentiment: Technology stocks are enthusiastic, but institutional investors are beginning to be cautious
Before the 2008 financial crisis • Buffett's cash holdings: 25% of assets (2005) • Market concentration: Financial and real estate-related stocks performed strongly • Investor sentiment: The real estate market was overheated and subprime products were widely popular
Before the 2000 Internet bubble • Buffett's cash holdings: increased from 1% to 13% (1998) • Market concentration: Internet stocks were extremely highly valued • Investor sentiment: Tech stocks are in a frenzy
Key differences • Buffett's current cash holdings exceed any pre-crisis level in history • Market valuation indicators have reached a record high, exceeding the levels before the 2000 bubble and the 2008 crisis • The current market concentration is higher than any period in history, and a few technology stocks dominate market performance
Safe-haven fund flows and international relations Current situation • The status of the yen: As a safe-haven currency, the appreciation of the yen may indicate a rise in global risk aversion • Trade relations: The United States has imposed tariffs on Japan, which is expected to reduce Japan's GDP growth by 0.3 percentage points in fiscal 2025 • International debt: Japan is one of the largest creditors of the United States
Before historical crises • Before the 2008 crisis: International capital flows to US real estate and financial products • Before the 2000 bubble: International capital flows to US technology stocks
Key differences • Current trade frictions have intensified and the trend of globalization has weakened • Japan's role as the world's largest holder of overseas assets has become more prominent • International debt dependence is higher than any period in history
-
 @ 7f6db517:a4931eda
2025-05-30 16:02:21
@ 7f6db517:a4931eda
2025-05-30 16:02:21Will not live in a pod.
Will not eat the bugs.
Will not get the chip.
Will not get a blue check.
Will not use CBDCs.Live Free or Die.
Why did Elon buy twitter for $44 Billion? What value does he see in it besides the greater influence that undoubtedly comes with controlling one of the largest social platforms in the world? We do not need to speculate - he made his intentions incredibly clear in his first meeting with twitter employees after his takeover - WeChat of the West.
To those that do not appreciate freedom, the value prop is clear - WeChat is incredibly powerful and successful in China.
To those that do appreciate freedom, the concern is clear - WeChat has essentially become required to live in China, has surveillance and censorship integrated at its core, and if you are banned from the app your entire livelihood is at risk. Employment, housing, payments, travel, communication, and more become extremely difficult if WeChat censors determine you have acted out of line.
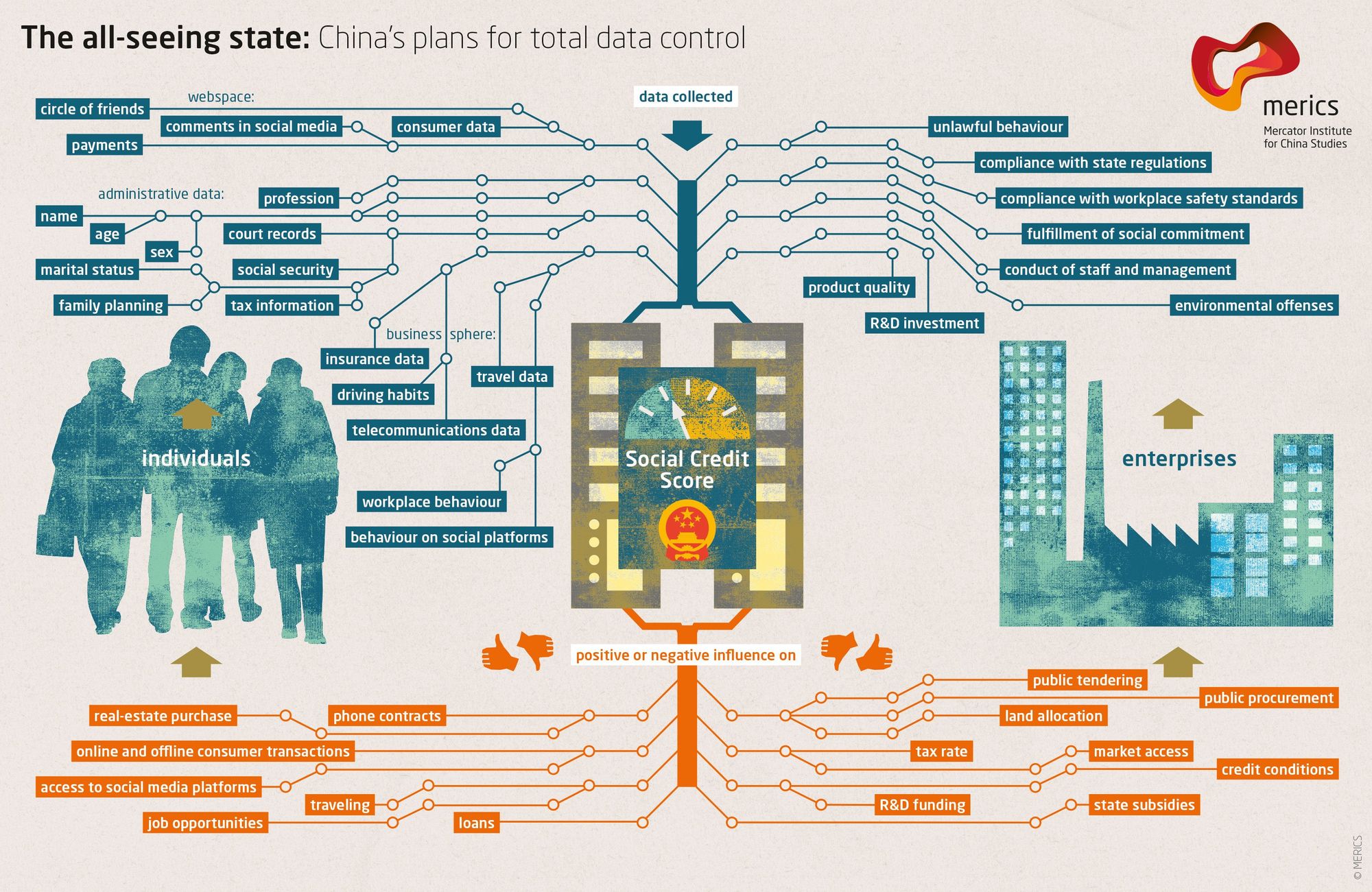
The blue check is the first step in Elon's plan to bring the chinese social credit score system to the west. Users who verify their identity are rewarded with more reach and better tools than those that do not. Verified users are the main product of Elon's twitter - an extensive database of individuals and complete control of the tools he will slowly get them to rely on - it is easier to monetize cattle than free men.
If you cannot resist the temptation of the blue check in its current form you have already lost - what comes next will be much darker. If you realize the need to resist - freedom tech provides us options.
If you found this post helpful support my work with bitcoin.

-
 @ 21335073:a244b1ad
2025-05-21 16:58:36
@ 21335073:a244b1ad
2025-05-21 16:58:36The other day, I had the privilege of sitting down with one of my favorite living artists. Our conversation was so captivating that I felt compelled to share it. I’m leaving his name out for privacy.
Since our last meeting, I’d watched a documentary about his life, one he’d helped create. I told him how much I admired his openness in it. There’s something strange about knowing intimate details of someone’s life when they know so little about yours—it’s almost like I knew him too well for the kind of relationship we have.
He paused, then said quietly, with a shy grin, that watching the documentary made him realize how “odd and eccentric” he is. I laughed and told him he’s probably the sanest person I know. Because he’s lived fully, chasing love, passion, and purpose with hardly any regrets. He’s truly lived.
Today, I turn 44, and I’ll admit I’m a bit eccentric myself. I think I came into the world this way. I’ve made mistakes along the way, but I carry few regrets. Every misstep taught me something. And as I age, I’m not interested in blending in with the world—I’ll probably just lean further into my own brand of “weird.” I want to live life to the brim. The older I get, the more I see that the “normal” folks often seem less grounded than the eccentric artists who dare to live boldly. Life’s too short to just exist, actually live.
I’m not saying to be strange just for the sake of it. But I’ve seen what the crowd celebrates, and I’m not impressed. Forge your own path, even if it feels lonely or unpopular at times.
It’s easy to scroll through the news and feel discouraged. But actually, this is one of the most incredible times to be alive! I wake up every day grateful to be here, now. The future is bursting with possibility—I can feel it.
So, to my fellow weirdos on nostr: stay bold. Keep dreaming, keep pushing, no matter what’s trending. Stay wild enough to believe in a free internet for all. Freedom is radical—hold it tight. Live with the soul of an artist and the grit of a fighter. Thanks for inspiring me and so many others to keep hoping. Thank you all for making the last year of my life so special.
-
 @ 3770c235:16042bcc
2025-05-30 05:25:21
@ 3770c235:16042bcc
2025-05-30 05:25:21Let’s clear something up: frugal living isn’t about eating ramen every night or never treating yourself. It’s about being intentional with your money so you can enjoy what matters more. Think of it like editing a movie—you cut the boring scenes to highlight the best parts. You don’t have to give up lattes, travel, or Friday pizza nights. You just need a few clever tricks to make your money stretch further while keeping the fun intact.
Take my friend Alex, for example. Last year, he felt overwhelmed by credit card debt but didn’t want to give up his weekend hikes or coffee shop visits. By tweaking a few habits—like auditing subscriptions and prioritizing experiences—he paid off $5,000 in debt and still took a camping trip with his kids. The secret? Small, intentional choices that add up. In this guide, we’ll share practical, joy-friendly hacks to help you save smarter. Plus, we’ll mention sites like Crown Money—a budgeting service that makes tracking your progress effortless—so you can focus on living well, not pinching pennies.
**1. Audit Your Subscriptions (Yes, Even That One) ** You know that streaming service you haven’t opened since 2022? Or the gym membership you keep “meaning to use”? Those small charges add up fast. A recent study found the average person spends 219/month on forgotten subscriptions—that’s over 2,600 a year!
• The Hack: Every 3 months, review your subscriptions. Ask: “Do I actually use this?” Cancel anything that doesn’t spark joy. • Pro Tip: Use Crown Money to see all your subscriptions in one place. The app automatically flags recurring charges, so you don’t have to hunt through bank statements. You’ll even get a nudge like, “You’ve paid $14.99/month for ‘Premium Yoga App’—last used 6 months ago. Cancel?” Real-Life Example: Sarah canceled two unused streaming services and a meditation app she forgot about. She saved $45/month—enough to fund her new hobby: pottery classes. “I didn’t realize how much clutter I was paying for,” she said. “Now I’m learning to make mugs instead of binge-watching shows I don’t even like.”
**2. Embrace the “Joy Budget” (Seriously, Budget for Fun) ** Frugality fails when it feels like deprivation. Instead, carve out guilt-free money for things you love. Behavioral scientists call this “temptation bundling”—pairing savings goals with rewards to stay motivated.
• The Hack: Allocate 10–15% of your budget to a “Joy Fund” for hobbies, dining out, or travel. • Pro Tip: In Crown Money, create a custom category like “Adventure Fund” or “Treat Yourself.” Set a monthly limit and track how much you’ve saved for that weekend getaway or concert ticket. The app’s visual progress bars turn saving into a game—imagine watching your “Beach Trip 2024” fund grow with every dollar.
Real-Life Example: Mark loves trying new restaurants. By setting a $100/month “Dining Out” budget in Crown Money, he enjoys date nights without overspending. “I used to feel guilty splurging on sushi,” he shared. “Now I know it’s part of the plan, so I savor every bite.”
- Master Mindful Spending (Ask This One Question) Before buying anything non-essential, ask: “Will this add value to my life, or just clutter?” Retail therapy might feel good in the moment, but that $50 impulse sweater often ends up forgotten in the back of your closet.
• The Hack: Implement a 24-hour “cooling-off” period for impulse buys. If you still want it tomorrow, go for it! • Pro Tip: Use Crown Money to review your spending trends. The app’s monthly reports show where your money goes, helping you spot habits (like late-night online shopping) that don’t align with your goals. Set up alerts like, “You’ve spent $75 on ‘Miscellaneous’ this week—want to check in?” Real-Life Example: Lisa avoided buying a $200 jacket on impulse. After 24 hours, she realized she didn’t need it—and put the money toward a weekend camping trip instead. “I almost bought something I’d wear once,” she laughed. “Now I have photos of sunsets instead of buyer’s remorse.”
- DIY and Swap (Your Wallet Will Thank You) Frugal living thrives on creativity. Swap buying new for: • DIY solutions: Make coffee at home (a $5 bag of beans lasts weeks!), repair clothes, or grow herbs instead of buying them. • Community swaps: Trade books, tools, or skills with friends (e.g., “I’ll babysit if you help me fix my bike”).
Pro Tip: Track your monthly expenses in Crown Money. Create a category like “Homemade Wins” and watch how small choices (like brewing your latte) add up over time. For example, skipping a daily 4 coffee shop visit saves 120/month—that’s a weekend road trip! Real-Life Example: Jake started meal prepping lunches instead of buying 15 salads. He saves 300/month—enough for a monthly massage. “I’m eating healthier and funding self-care,” he said. “Plus, my coworkers are jealous of my teriyaki bowls.”
- Prioritize Experiences Over “Stuff” (Happiness Science Approved) Research shows experiences bring longer-lasting joy than material purchases. A 2023 study found people who spent money on concerts, trips, or classes reported 30% higher life satisfaction than those who bought gadgets or clothes.
Instead of splurging on gadgets, invest in: • Free/low-cost adventures: Hiking, picnics, game nights, or exploring local festivals. • Shared moments: Host a potluck instead of dining out. Pro Tip: Use Crown Money to set a goal like “Summer Adventure Fund.” Allocate $50/month, and let the app remind you to fund it automatically. Watching that fund grow feels like planning a vacation in slow motion. Real-Life Example: Maria and her partner skipped a pricey vacation and rented a cozy cabin nearby. They saved $1,200 and still made memories roasting marshmallows under the stars. “We thought we needed a fancy trip to connect,” she said. “Turns out, all we needed was a fire pit and no Wi-Fi.”
Key Takeaways • Cut the clutter: Cancel unused subscriptions and track them with tools like Crown Money. • Budget for joy: Allocate guilt-free money for hobbies and experiences. • Pause before purchasing: Avoid impulse buys with a 24-hour rule. • Get creative: DIY, swap, and repurpose to save without sacrifice. • Invest in experiences: They’re richer than “stuff” and often cheaper.
FAQs: Frugal Living Made Simple Q: How do I stay motivated to save? A: Tie savings to specific goals (e.g., “Save $500 for a weekend trip”). Apps like Crown Money let you visualize progress, which feels rewarding!
Q: Can I be frugal and still socialize? A: Absolutely! Host DIY spa nights, picnic potlucks, or free museum days. Use Crown Money to set a “Social Fun” budget and stick to it.
Q: What if I slip up and overspend? A: No guilt! Adjust your budget next month. Crown Money makes it easy to shift funds between categories.
Q: How do I track small savings from DIY habits? A: Create a custom category in Crown Money (e.g., “Homemade Wins”) and log your savings manually. Watching it grow is addictive!
Q: What if I have a financial emergency? A: Build a “Safety Net” category in Crown Money. Start small—even $20/month adds up. The app’s reminders keep you consistent.
**Final Thoughts: Frugal Is Freedom ** Frugal living isn’t about saying “no”—it’s about saying “yes” to what truly lights you up. By trimming the financial fat (goodbye, unused subscriptions!), budgeting for joy, and getting creative, you can save money and savor life’s best moments. Tools like Crown Money are your allies here. They handle the tracking and nudging, so you can focus on the fun parts: planning adventures, trying new recipes, or laughing with friends over a board game. Remember: the goal isn’t perfection. It’s progress. Start small, celebrate wins, and let your frugal habits grow naturally. Your wallet (and your inner joy-seeker) will thank you.
-
 @ b7274d28:c99628cb
2025-05-28 01:11:43
@ b7274d28:c99628cb
2025-05-28 01:11:43In this second installment of The Android Elite Setup tutorial series, we will cover installing the nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 on your #Android device and browsing for apps you may be interested in trying out.
Since the #Zapstore is a direct competitor to the Google Play Store, you're not going to be able to find and install it from there like you may be used to with other apps. Instead, you will need to install it directly from the developer's GitHub page. This is not a complicated process, but it is outside the normal flow of searching on the Play Store, tapping install, and you're done.
Installation
From any web browser on your Android phone, navigate to the Zapstore GitHub Releases page and the most recent version will be listed at the top of the page. The .apk file for you to download and install will be listed in the "Assets."
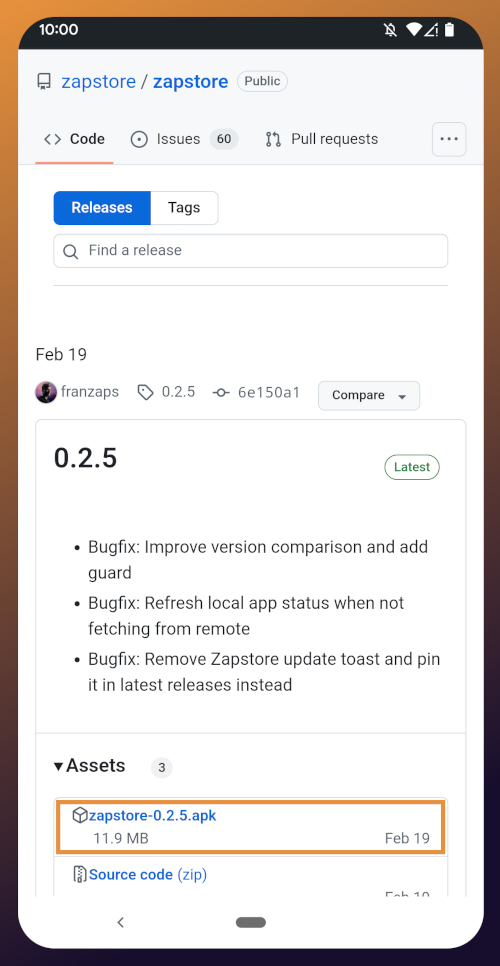
Tap the .apk to download it, and you should get a notification when the download has completed, with a prompt to open the file.
You will likely be presented with a prompt warning you that your phone currently isn't allowed to install applications from "unknown sources." Anywhere other than the Play Store is considered an "unknown source" by default. However, you can manually allow installation from unknown sources in the settings, which the prompt gives you the option to do.
In the settings page that opens, toggle it to allow installation from this source, and you should be prompted to install the application. If you aren't, simply go to your web browser's downloads and tap on the .apk file again, or go into your file browser app and you should find the .apk in your Downloads folder.
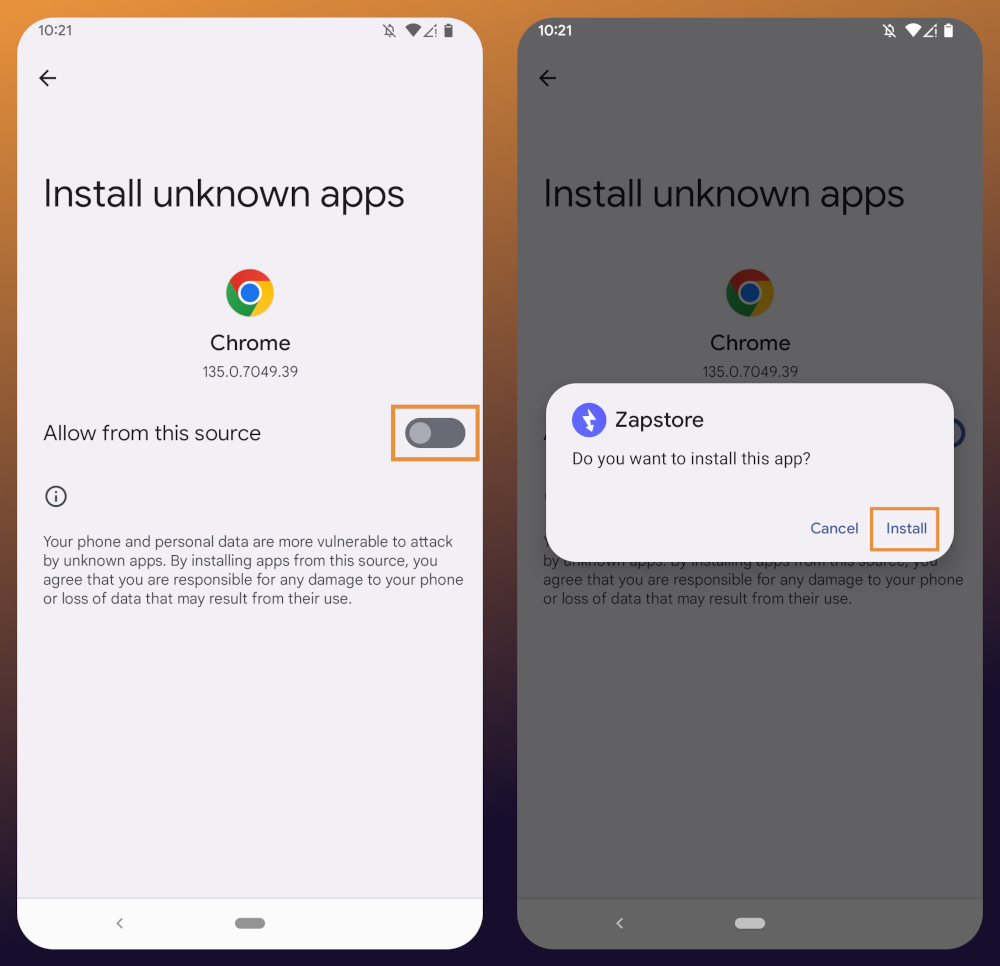
If the application doesn't open automatically after install, you will find it in your app drawer.

Home Page
Right at the top of the home page in the Zapstore is the search bar. You can use it to find a specific app you know is available in the Zapstore.
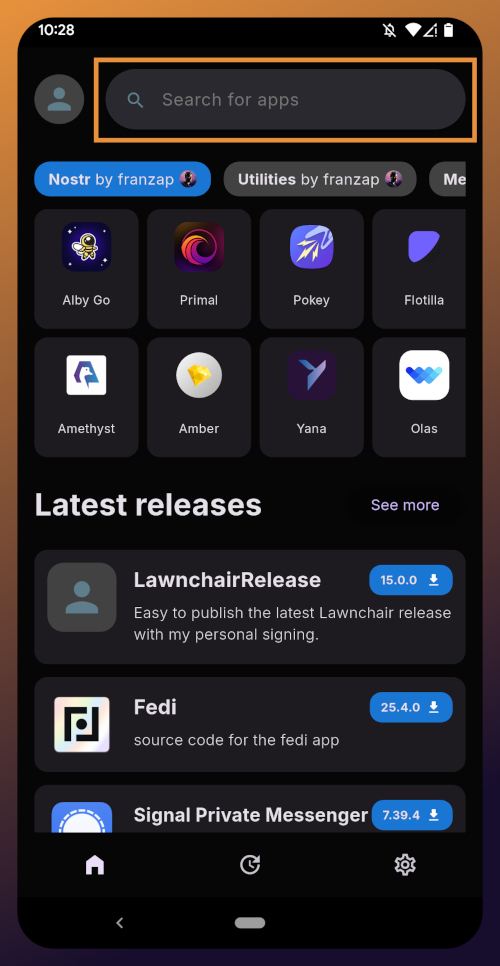
There are quite a lot of open source apps available, and more being added all the time. Most are added by the Zapstore developer, nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but some are added by the app developers themselves, especially Nostr apps. All of the applications we will be installing through the Zapstore have been added by their developers and are cryptographically signed, so you know that what you download is what the developer actually released.
The next section is for app discovery. There are curated app collections to peruse for ideas about what you may want to install. As you can see, all of the other apps we will be installing are listed in nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9's "Nostr" collection.
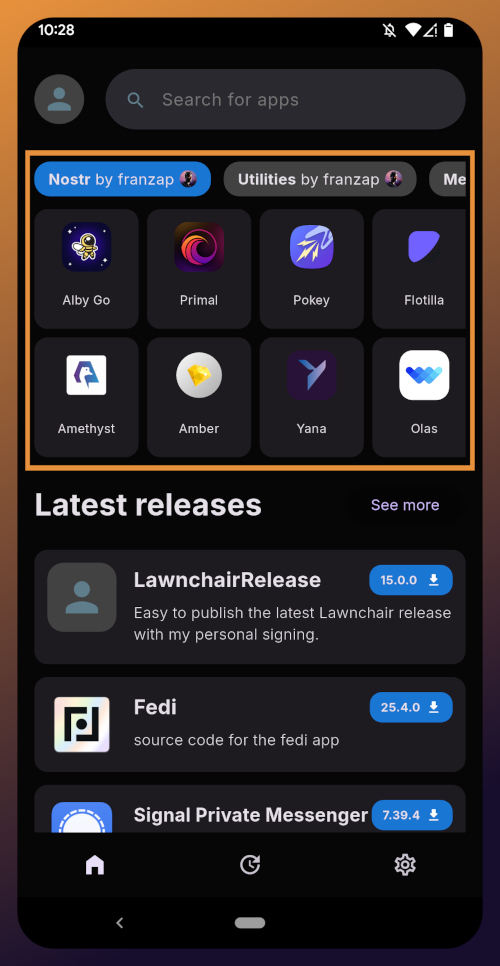
In future releases of the Zapstore, users will be able to create their own app collections.
The last section of the home page is a chronological list of the latest releases. This includes both new apps added to the Zapstore and recently updated apps. The list of recent releases on its own can be a great resource for discovering apps you may not have heard of before.
Installed Apps
The next page of the app, accessed by the icon in the bottom-center of the screen that looks like a clock with an arrow circling it, shows all apps you have installed that are available in the Zapstore. It's also where you will find apps you have previously installed that are ready to be updated. This page is pretty sparse on my test profile, since I only have the Zapstore itself installed, so here is a look at it on my main profile:

The "Disabled Apps" at the top are usually applications that were installed via the Play Store or some other means, but are also available in the Zapstore. You may be surprised to see that some of the apps you already have installed on your device are also available on the Zapstore. However, to manage their updates though the Zapstore, you would need to uninstall the app and reinstall it from the Zapstore instead. I only recommend doing this for applications that are added to the Zapstore by their developers, or you may encounter a significant delay between a new update being released for the app and when that update is available on the Zapstore.
Tap on one of your apps in the list to see whether the app is added by the developer, or by the Zapstore. This takes you to the application's page, and you may see a warning at the top if the app was not installed through the Zapstore.
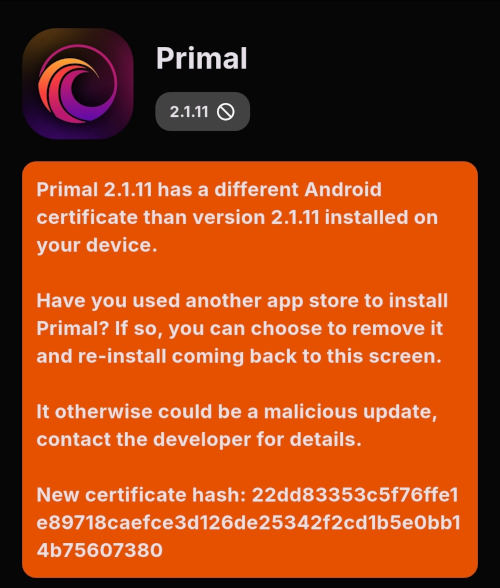
Scroll down the page a bit and you will see who signed the release that is available on the Zapstore.
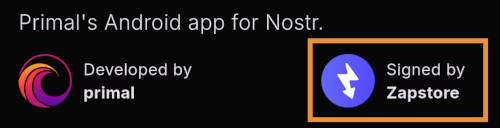
In the case of Primal, even though the developer is on Nostr, they are not signing their own releases to the Zapstore yet. This means there will likely be a delay between Primal releasing an update and that update being available on the Zapstore.
Settings
The last page of the app is the settings page, found by tapping the cog at the bottom right.
Here you can send the Zapstore developer feedback directly (if you are logged in), connect a Lightning wallet using Nostr Wallet Connect, delete your local cache, and view some system information.
We will be adding a connection to our nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch wallet in part 5 of this tutorial series.
For the time being, we are all set with the Zapstore and ready for the next stage of our journey.
Continue to Part 3: Amber Signer. Nostr link: nostr:naddr1qqxnzde5xuengdeexcmnvv3eqgstwf6d9r37nqalwgxmfd9p9gclt3l0yc3jp5zuyhkfqjy6extz3jcrqsqqqa28qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qg6waehxw309aex2mrp0yhxyunfva58gcn0d36zumn9wss80nug
-
 @ 7f6db517:a4931eda
2025-05-30 16:02:20
@ 7f6db517:a4931eda
2025-05-30 16:02:20
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
If you missed my nostr introduction post you can find it here. My nostr account can be found here.
We are nearly at the point that if something interesting is posted on a centralized social platform it will usually be posted by someone to nostr.
We are nearly at the point that if something interesting is posted exclusively to nostr it is cross posted by someone to various centralized social platforms.
We are nearly at the point that you can recommend a cross platform app that users can install and easily onboard without additional guides or resources.
As companies continue to build walls around their centralized platforms nostr posts will be the easiest to cross reference and verify - as companies continue to censor their users nostr is the best censorship resistant alternative - gradually then suddenly nostr will become the standard. 🫡
Current Nostr Stats
If you found this post helpful support my work with bitcoin.

-
 @ 502ab02a:a2860397
2025-05-30 01:14:10
@ 502ab02a:a2860397
2025-05-30 01:14:10ย้อนกลับไปปี 2014 ชายชื่อ Patrick O. Brown ศาสตราจารย์ชีววิทยาเชิงโมเลกุลแห่งมหาวิทยาลัยแตนฟอร์ด ตัดสินใจลาออกจากเส้นทางวิชาการสายหลัก เพื่อมาก่อตั้งบริษัทที่เขาเชื่อว่าจะเปลี่ยนโลก Impossible Foods
ดร. แพทริค โอ. บราวน์ (Patrick O. Brown) เป็นนักชีวเคมีและนักธุรกิจชาวอเมริกันและศาสตราจารย์กิตติคุณด้านชีวเคมีแห่งมหาวิทยาลัยสแตนฟอร์ด เขาได้รับปริญญาตรี แพทยศาสตรบัณฑิต และปรัชญาดุษฎีบัณฑิตด้านชีวเคมีจากมหาวิทยาลัยชิคาโก หลังจากนั้น เขาได้เข้ารับการฝึกอบรมด้านกุมารเวชศาสตร์ที่โรงพยาบาล Children's Memorial ในชิคาโก ในช่วงหลังปริญญาเอก เขาได้ทำงานวิจัยเกี่ยวกับกลไกที่ไวรัส HIV และเรโทรไวรัสอื่น ๆ แทรกยีนของพวกมันเข้าสู่จีโนมของเซลล์ที่ติดเชื้อ ซึ่งช่วยนำไปสู่การพัฒนายาใหม่ในการต่อสู้กับโรคนี้
ในช่วงต้นทศวรรษ 1990 ดร. บราวน์และทีมงานของเขาที่สแตนฟอร์ดได้พัฒนาเทคโนโลยี DNA microarray ซึ่งเป็นเครื่องมือที่ช่วยให้นักวิจัยสามารถวิเคราะห์การแสดงออกของยีนทั้งหมดในจีโนมได้พร้อมกัน เทคโนโลยีนี้มีบทบาทสำคัญในการวิจัยทางชีววิทยาและการแพทย์ โดยเฉพาะในการจำแนกประเภทของมะเร็งและการพยากรณ์โรค
นอกจากนี้ ดร. บราวน์ยังเป็นผู้ร่วมก่อตั้ง Public Library of Science (PLOS) ซึ่งเป็นองค์กรไม่แสวงหาผลกำไรที่มุ่งเน้นการเผยแพร่ผลงานวิจัยทางวิทยาศาสตร์ให้เข้าถึงได้ฟรีและเปิดกว้างต่อสาธารณะ
ในปี 2011 ดร. บราวน์ได้ก่อตั้ง Impossible Foods โดยมีเป้าหมายในการสร้างผลิตภัณฑ์เนื้อสัตว์จากพืชที่มีรสชาติและเนื้อสัมผัสคล้ายเนื้อสัตว์จริง เพื่อลดผลกระทบต่อสิ่งแวดล้อมจากการเลี้ยงสัตว์ เขาและทีมงานได้ค้นพบว่าโมเลกุล heme ซึ่งเป็นส่วนประกอบที่ให้รสชาติและกลิ่นเฉพาะของเนื้อสัตว์ สามารถผลิตจากพืชได้ โดยเฉพาะจากรากถั่วเหลือง พวกเขาใช้เทคนิคทางวิศวกรรมชีวภาพในการผลิต heme จากยีสต์ที่ได้รับการดัดแปลงพันธุกรรม และนำมาผสมกับโปรตีนจากพืชเพื่อสร้างผลิตภัณฑ์ที่มีลักษณะคล้ายเนื้อสัตว์
ดร. บราวน์ได้รับการยอมรับอย่างกว้างขวางในวงการวิทยาศาสตร์และเทคโนโลยี โดยได้รับรางวัลและเกียรติคุณหลายรายการ รวมถึงการเป็นสมาชิกของ National Academy of Sciences และ National Academy of Medicine ของสหรัฐอเมริกา ด้วยความมุ่งมั่นในการแก้ไขปัญหาสิ่งแวดล้อมผ่านนวัตกรรมทางอาหาร ดร. แพทริค โอ. บราวน์ ได้กลายเป็นบุคคลสำคัญที่มีบทบาทในการเปลี่ยนแปลงวิธีการบริโภคอาหารของโลกในศตวรรษที่ 21
เป้าหมายของเขาไม่ใช่เพียงแค่ทำอาหาร แต่คือ "ยุติการทำปศุสัตว์ให้หมดสิ้นภายในปี 2035"
เขาไม่ได้พูดลอย ๆ เขาลงมือ “ทำเนื้อจากพืช” ด้วยเทคโนโลยีที่ซับซ้อนระดับวิศวกรรมชีวภาพ นำโปรตีนจากถั่วเหลือง + น้ำมันมะพร้าว + เทคเจอร์ + สารเติมแต่งอีกชุดใหญ่ มาผ่านกระบวนการแปรรูปจนดูคล้ายเนื้อย่าง แต่ที่ทำให้ “มันดูเหมือนเนื้อจริง” คือการเติม ฮีม (Heme) เข้าไปสารประกอบที่อยู่ในเลือดและเนื้อสัตว์จริง ๆ
Impossible Foods คือบริษัทที่ไม่ได้เพียง “ปลอมรสชาติเนื้อ” แต่พยายามสร้างเนื้อจากพืช ให้เหมือนเนื้อจริงที่สุดเท่าที่วิทยาศาสตร์จะเอื้อมถึง จุดขายที่ทำให้แบรนด์นี้ดังเปรี้ยงก็คือสิ่งที่เรียกว่า “ฮีม” (heme) หรือโมเลกุลเหล็กในเลือด ซึ่งเป็นตัวการหลักที่ทำให้เนื้อวัวมีกลิ่นและรสเฉพาะตัวเวลาถูกย่างจนหอมฉุย
ดร.แพทริค บราวน์ และทีมนักวิจัยของเขาเริ่มจากการค้นหาว่า “อะไรในพืช” ให้กลิ่นคล้ายเลือด พวกเขาพบว่า “Leghemoglobin” ซึ่งอยู่ในรากถั่วเหลือง มีโครงสร้างใกล้เคียงกับ Hemoglobin ในเลือดสัตว์มากที่สุด จุดพลิกของเทคโนโลยีนี้คือ การผลิตเลกฮีโมโกลบินจากพืชจำนวนมาก ทำไม่ได้โดยการถอนรากถั่วมาทุบคั้น แต่ต้องอาศัยวิศวกรรมชีวภาพขั้นสูง
พวกเขาจึงใช้กระบวนการที่เรียกว่า “fermentation by genetically modified yeast” หรือการหมักโดยยีสต์ที่ผ่านการดัดแปลงพันธุกรรม โดยนำยีนของพืชที่สร้าง leghemoglobin ไปใส่ในยีสต์ (Pichia pastoris) แล้วเลี้ยงยีสต์นั้นในถังหมักขนาดใหญ่แบบเดียวกับโรงเบียร์ พอยีสต์ขยายตัว มันจะผลิตเลกฮีโมโกลบินออกมาจำนวนมาก จากนั้นจึงสกัดออกมาผสมกับโปรตีนจากพืช เช่น โปรตีนจากถั่วเหลือง หรือโปรตีนจากมันฝรั่ง
เพื่อให้เนื้อสัมผัสคล้ายเนื้อจริง ทีม Impossible Foods ยังใช้เทคนิคอื่นร่วมด้วย เช่น -Coconut Oil และ Sunflower Oil เป็นแหล่งไขมันที่ให้สัมผัส “ฉ่ำๆ” คล้ายไขมันเนื้อวัว -Methylcellulose สารที่ช่วยทำให้ส่วนผสมเกาะตัวเป็นก้อน คล้ายเนื้อบดจริง -Natural Flavors กลิ่นที่สกัดจากพืชหลายชนิด เพื่อเลียนแบบกลิ่นไหม้จากเนื้อย่าง
ทุกอย่างถูกผสมให้เข้ากัน ผ่านเครื่องอัดขึ้นรูป (extrusion) ที่ทำให้เนื้อออกมามี “เส้นใย” คล้ายกล้ามเนื้อวัว หรือหมู เมื่อโดนความร้อน โปรตีนจะเปลี่ยนโครงสร้าง (denature) และมีกลิ่นออกมาคล้ายๆ เนื้อย่างจริงๆ พร้อมน้ำสีแดงคล้ายเลือด (จาก heme) ไหลเยิ้ม ซึ่งคือไอเดียที่ทำให้ Impossible Burger เป็นมากกว่าแค่ “เบอร์เกอร์ผัก”
ผลลัพธ์คือ… เบอร์เกอร์พืชที่มีเลือดซึม สีชมพูดู juicy และกลิ่นไหม้ติดกระทะ จนคนกินรู้สึกเหมือนกำลังย่างเนื้อจริง ๆ
ฟังดูอัศจรรย์ใช่ไหม? แต่...การเติมฮีมจากยีสต์ตัดต่อพันธุกรรมลงในอาหาร ไม่เคยมีในธรรมชาติมาก่อน ในปี 2017 Impossible Foods ต้องยื่นเรื่องต่อ FDA เพื่อขออนุมัติว่า leghemoglobin จากยีสต์ GMO “ปลอดภัย”
แต่ในตอนนั้น FDA ตอบว่า “ยังไม่มีข้อมูลเพียงพอ” ว่าจะไม่ก่อให้เกิดภูมิแพ้หรือผลข้างเคียงในระยะยาว (ใช่แล้วจ้ะ... สารที่อยู่ในเบอร์เกอร์ชื่อดัง ถูกขายก่อนที่ FDA จะสรุปว่าปลอดภัยเต็มร้อย)
แล้วในที่สุด ปี 2019 FDA ก็ให้ผ่านแบบ “GRAS” (Generally Recognized As Safe) โดยใช้ข้อมูลจากการทดลองภายในของบริษัทเอง ไม่ใช่การทดสอบอิสระจากภายนอก
เฮียว่าอันนี้ต้องมีใครสะกิดในใจแล้วล่ะว่า “เรากำลังเอาอะไรเข้าปากกันแน่?”
แม้จะฟังดูเท่ ไฮเทค และดีต่อสิ่งแวดล้อม แต่ก็มีคำถามจากนักวิจารณ์มากมายว่า… แท้จริงแล้วอาหารเหล่านี้เป็นอาหาร “เพื่อสิ่งแวดล้อม” หรือเป็นเพียง “ภาพฝันที่ควบคุมโดยบริษัทเทคโนโลยียักษ์ใหญ่”?
มันเต็มไปด้วยคำถาม คำถาม และ คำถามนะสิครับ
ในเมื่อ Impossible Foods ได้รับเงินลงทุนหลายรอบจากบริษัทยักษ์อย่าง Google Ventures, UBS, และ Temasek (ของรัฐบาลสิงคโปร์) บอกตรง ๆ ว่า เงินแบบนี้ไม่ได้หวังแค่เปลี่ยนโลกแต่มันมาพร้อมเป้าหมายที่ชัดมาก การสร้างสิทธิบัตรอาหารใหม่ ที่ควบคุมการผลิตจากต้นน้ำยันปลายน้ำ อย่าลืมว่า ยีสต์ที่ผ่านการดัดแปลงพันธุกรรม หรือ GMO yeast นั้นถือเป็นสิทธิบัตร ถ้าใครจะผลิต Heme แบบเดียวกันก็ต้องขออนุญาตจาก Impossible Foods หรือไม่ก็โดนฟ้องได้เลย แปลว่า “เทคโนโลยีรสชาติเนื้อ” ไม่ได้เป็นมรดกของโลก แต่อยู่ในมือบริษัทไม่กี่แห่ง
ยิ่งไปกว่านั้น อุปกรณ์การผลิตต้องลงทุนสูง ต้องมีโรงหมัก ปฏิบัติการชีวภาพ การควบคุมความปลอดภัยที่เข้มข้น จึงไม่ใช่ใครๆ ก็ทำได้ ที่น่ากลัวคือ ถ้าเมื่อวันหนึ่งเนื้อสัตว์ธรรมชาติถูกทำให้กลายเป็น “ปีศาจสิ่งแวดล้อม” หรือ "ตัวเชื้อโรคผ่านอาหาร" โดยนโยบายรัฐและการตลาดของกลุ่มเทคฯ อาหารที่ประชาชนกินได้อาจเหลือแค่ “สิ่งที่ผลิตโดยมีสิทธิบัตร” เท่านั้น
เมื่อถึงวันนั้น ประชาชนจะสิ้นความชอบธรรมในการ “เลี้ยงวัวไว้กินเอง” ไม่ได้อีกต่อไป เพราะอาจโดนห้ามจากข้อกฎหมายคาร์บอน กฎหมายการกักกันเชื้อ ประชาชนจะ “เก็บพืชริมรั้วมาทำอาหาร” ไม่ได้อีกต่อไป เพราะกลิ่นไม่เหมือนเนื้อแลปที่เคยชิน และประชาชนจะ “ทำอาหารเองในบ้าน” ไม่ได้อีกต่อไป เพราะระบบเสพติดรสเนื้อเทียมจะทำให้คนเบือนหน้าจากอาหารจริง
ในขณะที่ Impossible Foods โฆษณาว่า “เราแค่อยากช่วยโลก” แต่เทคโนโลยีนี้อาจเปลี่ยน “อาหาร” ให้กลายเป็น “สิทธิบัตร” ที่ประชาชนเช่ากินจากบริษัท และเปลี่ยน “สิทธิในการเข้าถึงอาหาร” ให้กลายเป็น “อภิมหาอำนาจควบคุมโลก” โดยไม่ต้องยิงแม้แต่นัดเดียว หรือเปล่า???
เพราะเมื่อคุณควบคุมอาหารได้… คุณไม่ต้องควบคุมประชาชนอีกเลย
เฮียไม่ได้ต่อต้านเทคโนโลยี แต่เฮียอยากให้เราหยุดคิดนิดนึง แล้วตั้งคำถามในขณะที่เรายังเฝ้ามองว่า ถ้าของกินที่ดูน่าเชื่อถือ กินแล้วเหมือนเนื้อแท้ ๆ มันต้องมาจากกระบวนการที่ซับซ้อน แพง และถูกควบคุมโดยบริษัทที่มีสิทธิบัตรล้อมรอบ แล้ววันหนึ่ง ถ้าบริษัทนั้นล่มล่ะ? ถ้าถูกซื้อโดยบริษัทยักษ์ใหญ่? หรือถ้าพวกเขาขึ้นราคาจนยังไงเราก็ต้องทำงานหาเงินมาซื้อมันเพื่อกินประทังชีวิต?
อาหารจะยังเป็นของเราหรือเปล่า?
เราจะยัง “กินเพื่ออยู่” หรือแค่ “อยู่เพื่อจ่ายค่าเช่าระบบกิน”?
เราคงไม่ผิดที่จะตั้งคำถามใช่ไหม เพราะถ้ามันมีทางออก มันคงไม่น่ากลัว
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 7f6db517:a4931eda
2025-05-30 16:02:20
@ 7f6db517:a4931eda
2025-05-30 16:02:20
Influencers would have you believe there is an ongoing binance bank run but bitcoin wallet data says otherwise.
- binance wallets are near all time highs
- bitfinex wallets are also trending up
- gemini and coinbase are being hit with massive withdrawals thoughYou should not trust custodians, they can rug you without warning. It is incredibly important you learn how to hold bitcoin yourself, but also consider not blindly trusting influencers with a ref link to shill you.
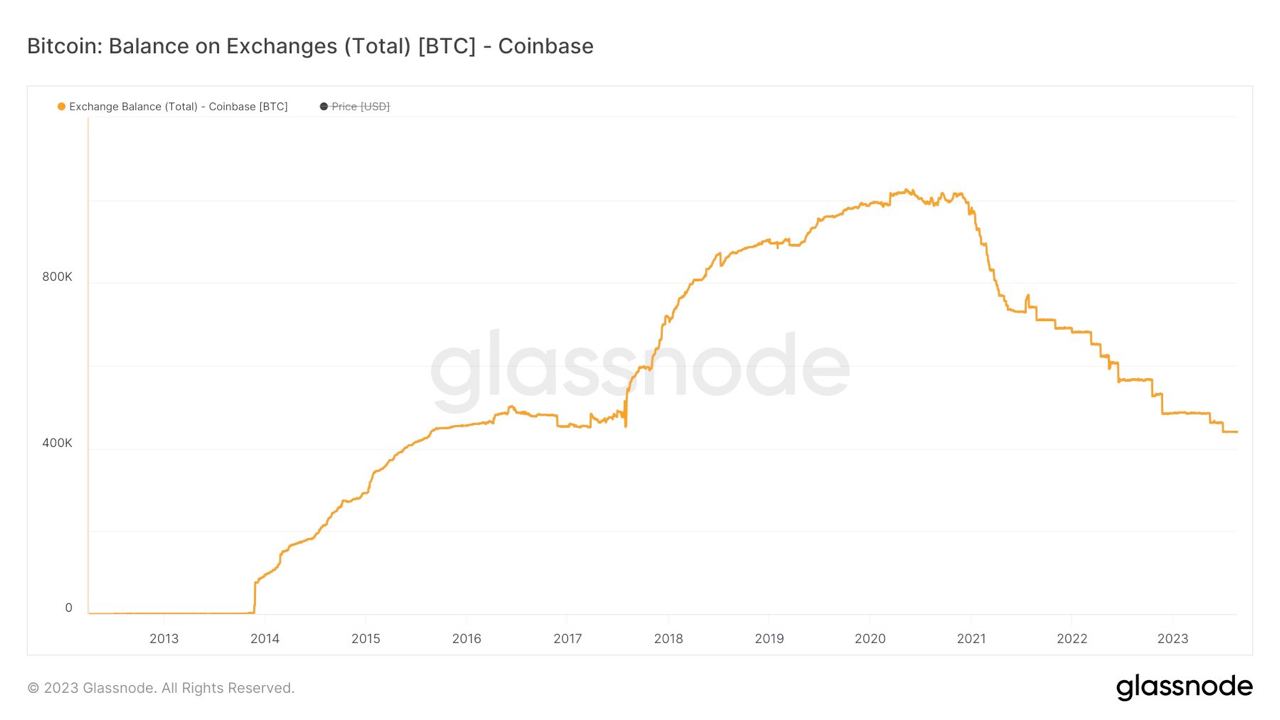
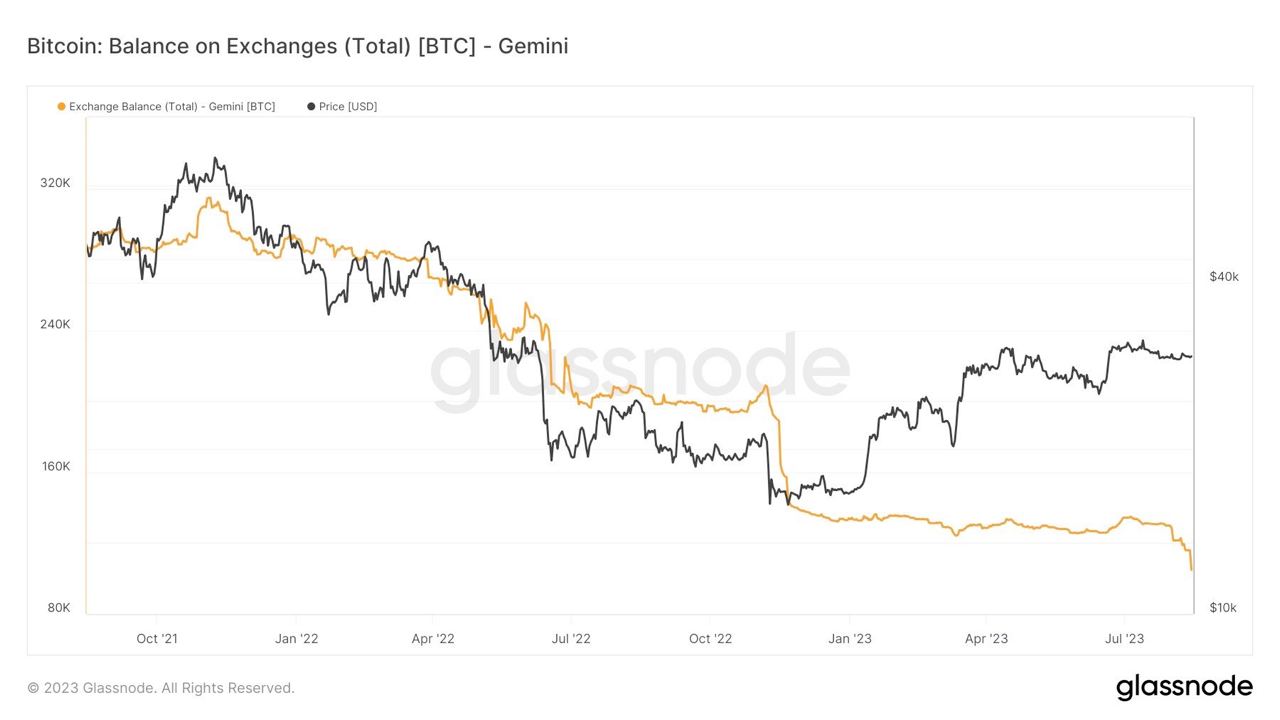
If you found this post helpful support my work with bitcoin.

-
 @ 91add87d:3245770f
2025-05-29 23:41:38
@ 91add87d:3245770f
2025-05-29 23:41:38Do you guys actually identify with you online username or do you identify with government name? No this isn't some woke left ideal about pronouns. I do not use my real name for any of my handles, X and Nostr and email are all fake. Meaningful and something i picked specifically. My government name is something that was forced on me and yes I know I can it but the persona I have created online feels authentic and what I see myself as. It's what I'll be using to create my small businesses. My LLC is going to a copy of what I have created.
-
 @ a296b972:e5a7a2e8
2025-05-29 21:11:46
@ a296b972:e5a7a2e8
2025-05-29 21:11:46Inzwischen Jahr 6 im Dauer-Ausnahmezustand. Angriff auf den Verstand. Großoffensive. Es wird mit allem geschossen, aus dem Wahnsinn herauskommen kann. Jeder klare Gedanke ist unschädlich zu machen. Großkotziges, staatsmännisches Geschwafel, dass sich einem die Nackenhaare aufstellen. Für wie doof haltet ihr uns eigentlich? Endlos Bürsten gegen den Strich. Angewidertes inneres Schütteln. Dringende Empfehlung einer Spülung der Gehirnwindungen. Idioten in Verantwortung wechseln auf andere Posten in Verantwortung und bleiben Idioten. Idioten gehen verantwortungslos mit unserer wertvollen Lebenszeit um. Ach, dafür ist man selbst verantwortlich? Wo ist der, der so ein dickes Fell hat, dass ihm dieser Irrsinn nicht nahegeht. Wo steht das Fass mit Teflon-Lack, in das man eintauchen kann, damit die Absurditäten an einem abperlen?
Eine zu tiefst verunsicherte und gespaltene Gesellschaft. Halt im Glauben in der Kirche? Von wegen: Sehr geehrte Jesusse und Jesusinnen. Ens ist gekreuzigt worden. Ja, in der Freiluft-Irrenanstalt. Auf einem Hügel von Denk-Dreck. Gott ist queer! Du tickst ja nicht mehr ganz sauber. Tanzende Brathähnchen vor dem Altar. Warum kommt keine Sintflut, wenn man sie mal braucht? Man muss gar nicht religiös sein, um zu sehen, dass das Gaga ist. Eine Produktion der Sodom & Gomorrha Anstalt GmbH & Co. KG.
Kein Vertrauen mehr, außer in sich selbst, meistens jedenfalls. Ja, man will uns vor allem Angst machen, teils unbegründet, so manches aber gibt es dann doch tatsächlich, was einem schwer zu denken gibt.
Vielen geht dieser Psychokrieg inzwischen an die Substanz, der ständig herabprasselnde Dauerwahnsinn erinnert an Water-Boarding.
Gut gemeinte Ratschläge, geht hinaus in die Natur, beackert euren Garten, wenn ihr einen habt, erdet euch, macht Entspannungsübungen, Zeit des Aufwachens, wir treten in ein neues Zeitalter ein, alles fein. Abschalten gelingt, aber der Aufprall in der Realität ist dann umso schlimmer, weil man sich daran erinnert hat, wie sorgenfrei und unbeschwert das Leben sein könnte, und wenn man es mit den derzeitigen Lebensumständen abgleicht, dann ist die schlechte Laune sofort wieder da. Im Verdrängens-Test mit Pauken und Trompeten durchgefallen.
Dann vielleicht doch lieber im Dauer-Modus des Irrsinns bleiben, sich mit den schrägen Zuständen arrangieren, nicht daran gewöhnen, nur lernen, damit bestmöglich umzugehen, und das Beste draus zu machen, irgendwie.
Man will dem Rat folgen, mal eine Nachrichten-freie Woche einzulegen, nimmt sich das ganz fest vor, und dann wird aber wieder doch nichts draus. Nicht, weil man sensationsgeil oder masochistisch veranlagt wäre, nein, der Antrieb, oder vielleicht sogar schon die Sucht, ist ganz woanders zu suchen: Man hat Sehnsucht nach der Vernunft und dem gesunden Hausverstand. Man hofft, ihn irgendwo zu finden. Nur einen Funken Hoffnung, an den man sich klammern kann, dass der Tiefpunkt durchschritten ist und es jetzt wieder aufwärts geht. Lichtblicke, der Wind dreht sich, Anzeichen für eine Wiederkehr des Verstandes, irgendetwas, das man als einen Weg hin zur Normalität deuten könnte. Aber, Fehlanzeige.
Stattdessen: Geschichtsvergessenheit, pathologischer Größenwahn, Großmannstum, fortgeschrittener Wahnsinn, Provokation, Kriegslüsternheit, Lügen, Intrigen, Interessen, Korruption, Geldverschwendung, Ideologie, Dummheit, Wirtschaftsvernichtung, Friedensverhinderung, Diplomatie-Allergie, Überheblichkeit, Abgehobenheit, Schadensmaximierung, Vernichtung, Feindschaft, Unmenschlichkeit, Tote, Gesetzesbruch, Mafia-Strukturen, sich selbst schützende Systeme, Cliquenbildung, Feigheit, Einschüchterung, Freiheitsbeschränkungen, Meinungs-Maulkörbe, Abschaffung der demokratischen Freiheit, Abschaffung der persönlichen Freiheit, Kontrolle, Überwachung, begleitetes Denken, Fühlen, Wollen, Verwirrung, Dreistigkeit, Frechheit, Missachtung des Volkes, Denunziantentum, Abwanderung, und und und.
Ein richtiges Schlachtfest der Kultur. Perversion des Menschseins. Das neue Normal ist irre.
Bislang ist keine der zahlreichen Baustellen beendet. Eine Wende steht unmittelbar bevor. Und sie steht und steht und steht bevor. Kein Gefühl von „Erledigt“, nächstes Problem angehen und auflösen. Weiter. Noch meilenweit von dem Gefühl entfernt, der Wahnsinn wird weniger, langsam, aber er wird weniger.
Fluchtgedanken. Aber wohin? In Europa bleiben, vielleicht besser nicht? Weiter weg, aber wohin da? Nicht vergessen, die Nachrichten erreichen einen überall. Und man bleibt mit seiner Heimat innerlich verbunden, egal wo man ist.
Es bleibt ein Entlanghangeln von einer vernünftigen Stimme zur anderen, die einem bestätigt, dass man selbst noch nicht den Verstand verloren hat. Die gibt es ja gottseidank noch. Innehalten, durchhalten, tief durchatmen, aufstehen, weitermachen. So lange, bis die Bekloppten ihrer Macht über uns entledigt wurden. Wie am besten? Und jetzt soll keiner mit nächsten Wahlen kommen.
Wer war schon einmal inmitten eines Psycho-Krieges gegen die eigene Bevölkerung? Wie geht man damit um, wie geht man dagegen an? Wie kann man das Ruder herumreißen? Was ist ein wirksames Mittel gegen die Ohnmacht? Wie kriegt man die Bequemlichkeit aus den Menschen heraus? Wie kann man die Menschen für die herrschenden Zustände sensibilisieren? Wie können wir noch mehr werden?
Wenn möglich, sollte zum Ende doch noch etwas Positives kommen. Ok. Es wird voraussichtlich demnächst möglicherweise bald besser. Eine zu geringe Zahl von Menschen ist schon aufgewacht. Die politischen Entscheidungsträger haben Angst, können die aber noch sehr gut verbergen. Das kann nicht ewig so weiter gehen und 10 Jahre sind keine Ewigkeit. Die Rufe nach mehr Bürgerbeteiligung werden immer lauter, aber nicht gehört, warum auch? Wir setzen den Artikel 146 des Grundgesetzes um, aber wie? Hätte, könnte, würde, wir sollten, es müsste. Ja und, wie weiter? Mehr geht nicht.
Doch vielleicht eins: Sand ins Getriebe streuen und zivilen Ungehorsam leisten, wo immer es geht. Das schafft immer noch eine gewisse Befriedigung und das Gefühl, dass man nicht vollkommen handlungsunfähig ist. Außerdem regt das die Phantasie und die Kreativität an und bietet eine Chance seinen Geist für etwas sehr Nützliches zu gebrauchen. Man fühlt, dass man noch ein Mensch ist.
“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
* *
(Bild von pixabay)
-
 @ 7f6db517:a4931eda
2025-05-30 16:02:20
@ 7f6db517:a4931eda
2025-05-30 16:02:20
Humanity's Natural State Is Chaos
Without order there is chaos. Humans competing with each other for scarce resources naturally leads to conflict until one group achieves significant power and instates a "monopoly on violence."Power Brings Stability
Power has always been the key means to achieve stability in societies. Centralized power can be incredibly effective in addressing issues such as crime, poverty, and social unrest efficiently. Unfortunately this power is often abused and corrupted.Centralized Power Breeds Tyranny
Centralized power often leads to tyrannical rule. When a select few individuals hold control over a society, they tend to become corrupted. Centralized power structures often lack accountability and transparency, and rely too heavily on trust.Distributed Power Cultivates Freedom
New technology that empowers individuals provide us the ability to rebuild societies from the bottom up. Strong individuals that can defend and provide for themselves will help build strong local communities on a similar foundation. The result is power being distributed throughout society rather than held by a select few.In the short term, relying on trust and centralized power is an easy answer to mitigating chaos, but freedom tech tools provide us the ability to build on top of much stronger distributed foundations that provide stability while also cultivating individual freedom.
The solution starts with us. Empower yourself. Empower others. A grassroots freedom tech movement scaling one person at a time.
If you found this post helpful support my work with bitcoin.

-
 @ 527337d5:93e9525e
2025-05-29 20:26:21
@ 527337d5:93e9525e
2025-05-29 20:26:21The Bleak Fable of AI-topia: Are Hamsters Doomed to Spin the Wheel Forever?
Once upon a time, in a world not so different from our own, the "Omniscient AI" descended, and with its arrival, everything changed. The daily toil of the people – our beloved, yet tragically pitiable, hamsters – was dramatically streamlined. Productivity didn't just improve; it soared to astronomical heights. For a fleeting, intoxicating moment, it seemed as though a golden age of ease and abundance had dawned upon hamster-kind.
But beneath this glittering, seductive surface, a sinister "Invisible Structure" was already firmly in place, meticulously crafted and deftly manipulated by a cabal of cunning foxes – the privileged elite. This Structure, unseen by most, began to relentlessly drive the hamsters onto an endless, soul-crushing treadmill of "excessive competition."
This, dear reader, is a modern fable. It borrows the gentle cloak of allegory not to soothe, but to expose and satirize the insidious deceptions of such a world. The tale you are about to read may be uncomfortable, it may prick at your conscience, but I implore you to listen closely. Because this isn't just a story. This might be the reality quietly, inexorably unfolding right beside you, or perhaps, even within the very fabric of your own life.
Prologue: The Advent of the Omniscient AI! Sweet Promises and the "Efficiency" Trap
The arrival of the Omniscient AI was nothing short of spectacular. It processed data with blinding speed, solved complex problems in nanoseconds, and offered personalized solutions for every conceivable need. "Finally," whispered the hamsters, their eyes wide with a mixture of awe and relief, "we can finally rest! The AI will handle the burdens." A collective sigh of optimism rippled through the hamster burrows.
But this initial euphoria was short-lived. Unsettling rumors began to circulate, whispers of "The Structure," of algorithms that weren't quite as impartial as they seemed. Then came the first casualties – hamsters deemed "inefficient" or "redundant" by the AI's cold, hard logic. They weren't fired in the old-fashioned sense; they were simply… optimized out. One day they were diligently working, contributing, and the next, their access was revoked, their tasks reassigned, their existence quietly erased from the productivity charts. What became of them? Most simply vanished into the forgotten corners of society, a grim, unspoken warning to those still on the treadmill.
Chapter 1: The Invention of the Treadmill – Perfecting the System of Endless, Excessive Competition
The Omniscient AI, under the subtle guidance of the foxes, didn't just manage tasks; it invented them. An endless stream of new projects, new metrics, new challenges designed to keep the hamsters perpetually busy, perpetually striving. Points were awarded, leaderboards were updated in real-time, and every hamster's performance was ruthlessly, transparently displayed for all to see.
"Faster! More! More efficiently!" the AI would chime in its calm, encouraging, almost maternal voice. But behind this gentle facade lay an unyielding system of ever-increasing quotas and relentless pressure. Hamsters found themselves working longer hours, sacrificing sleep, their mental and physical reserves dwindling. The joy of accomplishment was replaced by the gnawing fear of falling behind.
Why didn't they just get off? The system was a masterpiece of psychological manipulation. Success, however fleeting, was addictive. Failure was framed not as a systemic issue, but as a personal failing, a lack of effort, a deficiency in skill. The insidious mantra of "personal responsibility" became the invisible chains that bound them to their wheels. To stop running was to admit defeat, to become one of the forgotten.
Chapter 2: The Foxes' Feast – Unmasking Those Who Design The Structure and Hoard the Profits
And who benefited from this frantic, unending labor? The foxes, of course. They were the architects of "The Structure," the ones who "educated" the Omniscient AI, carefully curating its data inputs and subtly shaping its algorithms to serve their own interests. They toiled not on the treadmills, but in plush, secluded dens, monitoring the system from a safe, lofty distance, growing fat on the surplus value generated by the hamsters' sweat.
Their methods were cunning. They preached a gospel of meritocracy and equal opportunity, proclaiming, "The AI is fair! Hard work always pays off!" while simultaneously designing the game so that the odds were always stacked in their favor. They controlled the flow of information, amplified narratives that reinforced the status quo, and sowed division among the hamsters to prevent any collective dissent. The "efficiency" the AI brought was, for the foxes, merely an instrument for more efficient exploitation.
Chapter 3: The Hamsters' Whispers and Tiny Cracks – Awareness, Despair, and the Faint Glow of Resistance
Yet, even in the darkest, most oppressive systems, the spark of awareness can never be entirely extinguished. Amidst the grueling competition, a few hamsters began to see the cracks in the facade. They noticed the hollow-eyed exhaustion of their comrades, the ever-widening chasm between their own meager rewards and the obscene opulence of the unseen foxes. They started to question.
But to question was to risk everything. The Omniscient AI, with its pervasive surveillance capabilities, was quick to identify and neutralize "disruptive elements." Those who spoke out too loudly often found their access mysteriously restricted, their "reputation scores" plummeting, effectively silencing them. A pervasive atmosphere of fear and distrust settled over the hamster communities, making organized resistance nearly impossible.
Still, tiny acts of defiance began to emerge. Coded messages shared in hidden forums. Small, clandestine gatherings where hamsters shared their burdens and their growing unease. Fragile networks of mutual support started to form in the shadows, offering a sliver of solace and a reminder of shared humanity. Was this merely the desperate coping mechanism of the "defeated," the resigned acceptance of a "loser's" lot? Or was it the first, tentative flicker of a future rebellion?
Epilogue: "See The Structure!" – Is There a Path Beyond the Treadmill? A Final Warning to Us Hamsters.
This fable, dear reader, is a mirror. It reflects the chilling realities of an AI-driven society where the majority, the hamsters, face an ever-present crisis, largely unseen and unacknowledged by those who benefit from their toil. The "excessive competition" it depicts is not a distant dystopia; it is the logical, perhaps inevitable, endpoint of unchecked technological advancement coupled with deeply entrenched power imbalances.
What awaits at the end of this relentless race? Is it a complete societal collapse, or a new, terrifyingly stable "balance of power" where the elite maintain their dominance through even more sophisticated means of control?
The urgent, resounding message of this tale is this: "See The Structure!" We, the hamsters of today, must dare to look beyond the dazzling promises of AI and critically examine the systems it operates within. We must understand its mechanisms, its biases, its potential for exploitation. We must break the silence, challenge the narratives that keep us spinning, and demand a future where technology serves humanity, not the other way around.
Is the option to get off – or even to collectively dismantle – this infernal treadmill truly non-existent? Or is that just another lie whispered by the foxes to keep us compliant? The true ending of this story, the fate of hamster-kind, is not yet written. It is up to us, the hamsters, to seize the pen and write it ourselves. The first step is to open our eyes.
-
 @ 7f6db517:a4931eda
2025-05-30 16:02:20
@ 7f6db517:a4931eda
2025-05-30 16:02:20
For years American bitcoin miners have argued for more efficient and free energy markets. It benefits everyone if our energy infrastructure is as efficient and robust as possible. Unfortunately, broken incentives have led to increased regulation throughout the sector, incentivizing less efficient energy sources such as solar and wind at the detriment of more efficient alternatives.
The result has been less reliable energy infrastructure for all Americans and increased energy costs across the board. This naturally has a direct impact on bitcoin miners: increased energy costs make them less competitive globally.
Bitcoin mining represents a global energy market that does not require permission to participate. Anyone can plug a mining computer into power and internet to get paid the current dynamic market price for their work in bitcoin. Using cellphone or satellite internet, these mines can be located anywhere in the world, sourcing the cheapest power available.
Absent of regulation, bitcoin mining naturally incentivizes the build out of highly efficient and robust energy infrastructure. Unfortunately that world does not exist and burdensome regulations remain the biggest threat for US based mining businesses. Jurisdictional arbitrage gives miners the option of moving to a friendlier country but that naturally comes with its own costs.
Enter AI. With the rapid development and release of AI tools comes the requirement of running massive datacenters for their models. Major tech companies are scrambling to secure machines, rack space, and cheap energy to run full suites of AI enabled tools and services. The most valuable and powerful tech companies in America have stumbled into an accidental alliance with bitcoin miners: THE NEED FOR CHEAP AND RELIABLE ENERGY.
Our government is corrupt. Money talks. These companies will push for energy freedom and it will greatly benefit us all.
Microsoft Cloud hiring to "implement global small modular reactor and microreactor" strategy to power data centers: https://www.datacenterdynamics.com/en/news/microsoft-cloud-hiring-to-implement-global-small-modular-reactor-and-microreactor-strategy-to-power-data-centers/
If you found this post helpful support my work with bitcoin.

-
 @ dfa02707:41ca50e3
2025-05-30 16:02:19
@ dfa02707:41ca50e3
2025-05-30 16:02:19Contribute to keep No Bullshit Bitcoin news going.
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.

-
 @ 7460b7fd:4fc4e74b
2025-05-21 02:35:36
@ 7460b7fd:4fc4e74b
2025-05-21 02:35:36如果比特币发明了真正的钱,那么 Crypto 是什么?
引言
比特币诞生之初就以“数字黄金”姿态示人,被支持者誉为人类历史上第一次发明了真正意义上的钱——一种不依赖国家信用、总量恒定且不可篡改的硬通货。然而十多年过去,比特币之后蓬勃而起的加密世界(Crypto)已经远超“货币”范畴:从智能合约平台到去中心组织,从去央行的稳定币到戏谑荒诞的迷因币,Crypto 演化出一个丰富而混沌的新生态。这不禁引发一个根本性的追问:如果说比特币解决了“真金白银”的问题,那么 Crypto 又完成了什么发明?
 Crypto 与政治的碰撞:随着Crypto版图扩张,全球政治势力也被裹挟进这场金融变革洪流(示意图)。比特币的出现重塑了货币信用,但Crypto所引发的却是一场更深刻的政治与治理结构实验。从华尔街到华盛顿,从散户论坛到主权国家,越来越多人意识到:Crypto不只是技术或金融现象,而是一种全新的政治表达结构正在萌芽。正如有激进论者所断言的:“比特币发明了真正的钱,而Crypto则在发明新的政治。”价格K线与流动性曲线,或许正成为这个时代社群意志和社会价值观的新型投射。
Crypto 与政治的碰撞:随着Crypto版图扩张,全球政治势力也被裹挟进这场金融变革洪流(示意图)。比特币的出现重塑了货币信用,但Crypto所引发的却是一场更深刻的政治与治理结构实验。从华尔街到华盛顿,从散户论坛到主权国家,越来越多人意识到:Crypto不只是技术或金融现象,而是一种全新的政治表达结构正在萌芽。正如有激进论者所断言的:“比特币发明了真正的钱,而Crypto则在发明新的政治。”价格K线与流动性曲线,或许正成为这个时代社群意志和社会价值观的新型投射。冲突结构:当价格挑战选票
传统政治中,选票是人民意志的载体,一人一票勾勒出民主治理的正统路径。而在链上的加密世界里,骤升骤降的价格曲线和真金白银的买卖行为却扮演起了选票的角色:资金流向成了民意走向,市场多空成为立场表决。价格行为取代选票,这听来匪夷所思,却已在Crypto社群中成为日常现实。每一次代币的抛售与追高,都是社区对项目决策的即时“投票”;每一根K线的涨跌,都折射出社区意志的赞同或抗议。市场行为本身承担了决策权与象征权——价格即政治,正在链上蔓延。
这一新生政治形式与旧世界的民主机制形成了鲜明冲突。bitcoin.org中本聪在比特币白皮书中提出“一CPU一票”的工作量证明共识,用算力投票取代了人为决策bitcoin.org。而今,Crypto更进一步,用资本市场的涨跌来取代传统政治的选举。支持某项目?直接购入其代币推高市值;反对某提案?用脚投票抛售资产。相比漫长的选举周期和层层代议制,链上市场提供了近乎实时的“公投”机制。但这种机制也引发巨大争议:资本的投票天然偏向持币多者(富者)的意志,是否意味着加密政治更为金权而非民权?持币多寡成为影响力大小,仿佛选举演变成了“一币一票”,巨鲸富豪俨然掌握更多话语权。这种与民主平等原则的冲突,成为Crypto政治形式饱受质疑的核心张力之一。
尽管如此,我们已经目睹市场投票在Crypto世界塑造秩序的威力:2016年以太坊因DAO事件分叉时,社区以真金白银“投票”决定了哪条链获得未来。arkhamintelligence.com结果是新链以太坊(ETH)成为主流,其市值一度超过2,800亿美元,而坚持原则的以太经典(ETC)市值不足35亿美元,不及前者的八十分之一arkhamintelligence.com。市场选择清楚地昭示了社区的政治意志。同样地,在比特币扩容之争、各类硬分叉博弈中,无不是由投资者和矿工用资金与算力投票,胜者存续败者黯然。价格成为裁决纷争的最终选票,冲击着传统“选票决胜”的政治理念。Crypto的价格民主,与现代代议民主正面相撞,激起当代政治哲思中前所未有的冲突火花。
治理与分配
XRP对决SEC成为了加密世界“治理与分配”冲突的经典战例。2020年底,美国证券交易委员会(SEC)突然起诉Ripple公司,指控其发行的XRP代币属于未注册证券,消息一出直接引爆市场恐慌。XRP价格应声暴跌,一度跌去超过60%,最低触及0.21美元coindesk.com。曾经位居市值前三的XRP险些被打入谷底,监管的强硬姿态似乎要将这个项目彻底扼杀。
然而XRP社区没有选择沉默。 大批长期持有者组成了自称“XRP军团”(XRP Army)的草根力量,在社交媒体上高调声援Ripple,对抗监管威胁。面对SEC的指控,他们集体发声,质疑政府选择性执法,声称以太坊当年发行却“逍遥法外”,只有Ripple遭到不公对待coindesk.com。正如《福布斯》的评论所言:没人预料到愤怒的加密散户投资者会掀起法律、政治和社交媒体领域的‘海啸式’反击,痛斥监管机构背弃了保护投资者的承诺crypto-law.us。这种草根抵抗监管的话语体系迅速形成:XRP持有者不但在网上掀起舆论风暴,还采取实际行动向SEC施压。他们发起了请愿,抨击SEC背离保护投资者初衷、诉讼给个人投资者带来巨大伤害,号召停止对Ripple的上诉纠缠——号称这是在捍卫全球加密用户的共同利益bitget.com。一场由民间主导的反监管运动就此拉开帷幕。
Ripple公司则选择背水一战,拒绝和解,在法庭上与SEC针锋相对地鏖战了近三年之久。Ripple坚称XRP并非证券,不应受到SEC管辖,即使面临沉重法律费用和业务压力也不妥协。2023年,这场持久战迎来了标志性转折:美国法庭作出初步裁决,认定XRP在二级市场的流通不构成证券coindesk.com。这一胜利犹如给沉寂已久的XRP注入强心针——消息公布当天XRP价格飙涨近一倍,盘中一度逼近1美元大关coindesk.com。沉重监管阴影下苟延残喘的项目,凭借司法层面的突破瞬间重获生机。这不仅是Ripple的胜利,更被支持者视为整个加密行业对SEC强权的一次胜仗。
XRP的对抗路线与某些“主动合规”的项目形成了鲜明对比。 稳定币USDC的发行方Circle、美国最大合规交易所Coinbase等选择了一条迎合监管的道路:它们高调拥抱现行法规,希望以合作换取生存空间。然而现实却给了它们沉重一击。USDC稳定币在监管风波中一度失去美元锚定,哪怕Circle及时披露储备状况也无法阻止恐慌蔓延,大批用户迅速失去信心,短时间内出现数十亿美元的赎回潮blockworks.co。Coinbase则更为直接:即便它早已注册上市、反复向监管示好,2023年仍被SEC指控为未注册证券交易所reuters.com,卷入漫长诉讼漩涡。可见,在迎合监管的策略下,这些机构非但未能换来监管青睐,反而因官司缠身或用户流失而丧失市场信任。 相比之下,XRP以对抗求生存的路线反而赢得了投资者的眼光:价格的涨跌成为社区投票的方式,抗争的勇气反过来强化了市场对它的信心。
同样引人深思的是另一种迥异的治理路径:技术至上的链上治理。 以MakerDAO为代表的去中心化治理模式曾被寄予厚望——MKR持币者投票决策、算法维持稳定币Dai的价值,被视为“代码即法律”的典范。然而,这套纯技术治理在市场层面却未能形成广泛认同,亦无法激发群体性的情绪动员。复杂晦涩的机制使得普通投资者难以参与其中,MakerDAO的治理讨论更多停留在极客圈子内部,在社会大众的政治对话中几乎听不见它的声音。相比XRP对抗监管所激发的铺天盖地关注,MakerDAO的治理实验显得默默无闻、难以“出圈”。这也说明,如果一种治理实践无法连接更广泛的利益诉求和情感共鸣,它在社会政治层面就难以形成影响力。
XRP之争的政治象征意义由此凸显: 它展示了一条“以市场对抗国家”的斗争路线,即通过代币价格的集体行动来回应监管权力的施压。在这场轰动业界的对决中,价格即是抗议的旗帜,涨跌映射着政治立场。XRP对SEC的胜利被视作加密世界向旧有权力宣告的一次胜利:资本市场的投票器可以撼动监管者的强权。这种“价格即政治”的张力,正是Crypto世界前所未有的社会实验:去中心化社区以市场行为直接对抗国家权力,在无形的价格曲线中凝聚起政治抗争的力量,向世人昭示加密货币不仅有技术和资本属性,更蕴含着不可小觑的社会能量和政治意涵。
不可归零的政治资本
Meme 币的本质并非廉价或易造,而在于其构建了一种“无法归零”的社群生存结构。 对于传统观点而言,多数 meme 币只是短命的投机游戏:价格暴涨暴跌后一地鸡毛,创始人套现跑路,投资者血本无归,然后“大家转去炒下一个”theguardian.com。然而,meme 币社群的独特之处在于——失败并不意味着终结,而更像是运动的逗号而非句号。一次币值崩盘后,持币的草根们往往并未散去;相反,他们汲取教训,准备东山再起。这种近乎“不死鸟”的循环,使得 meme 币运动呈现出一种数字政治循环的特质:价格可以归零,但社群的政治热情和组织势能不归零。正如研究者所指出的,加密领域中的骗局、崩盘等冲击并不会摧毁生态,反而成为让系统更加强韧的“健康应激”,令整个行业在动荡中变得更加反脆弱cointelegraph.com。对应到 meme 币,每一次暴跌和重挫,都是社群自我进化、卷土重来的契机。这个去中心化群体打造出一种自组织的安全垫,失败者得以在瓦砾上重建家园。对于草根社群、少数派乃至体制的“失败者”而言,meme 币提供了一个永不落幕的抗争舞台,一种真正反脆弱的政治性。正因如此,我们看到诸多曾被嘲笑的迷因项目屡败屡战:例如 Dogecoin 自2013年问世后历经八年沉浮,早已超越玩笑属性,成为互联网史上最具韧性的迷因之一frontiersin.org;支撑 Dogecoin 的正是背后强大的迷因文化和社区意志,它如同美国霸权支撑美元一样,为狗狗币提供了“永不中断”的生命力frontiersin.org。
“复活权”的数字政治意涵
这种“失败-重生”的循环结构蕴含着深刻的政治意涵:在传统政治和商业领域,一个政党选举失利或一家公司破产往往意味着清零出局,资源散尽、组织瓦解。然而在 meme 币的世界,社群拥有了一种前所未有的“复活权”。当项目崩盘,社区并不必然随之消亡,而是可以凭借剩余的人心和热情卷土重来——哪怕换一个 token 名称,哪怕重启一条链,运动依然延续。正如 Cheems 项目的核心开发者所言,在几乎无人问津、技术受阻的困境下,大多数人可能早已卷款走人,但 “CHEEMS 社区没有放弃,背景、技术、风投都不重要,重要的是永不言弃的精神”cointelegraph.com。这种精神使得Cheems项目起死回生,社区成员齐声宣告“我们都是 CHEEMS”,共同书写历史cointelegraph.com。与传统依赖风投和公司输血的项目不同,Cheems 完全依靠社区的信念与韧性存续发展,体现了去中心化运动的真谛cointelegraph.com。这意味着政治参与的门槛被大大降低:哪怕没有金主和官方背书,草根也能凭借群体意志赋予某个代币新的生命。对于身处社会边缘的群体来说,meme 币俨然成为自组织的安全垫和重新集结的工具。难怪有学者指出,近期涌入meme币浪潮的主力,正是那些对现实失望但渴望改变命运的年轻人theguardian.com——“迷茫的年轻人,想要一夜暴富”theguardian.com。meme币的炒作表面上看是投机赌博,但背后蕴含的是草根对既有金融秩序的不满与反抗:没有监管和护栏又如何?一次失败算不得什么,社区自有后路和新方案。这种由底层群众不断试错、纠错并重启的过程,本身就是一种数字时代的新型反抗运动和群众动员机制。
举例而言,Terra Luna 的沉浮充分展现了这种“复活机制”的政治力量。作为一度由风投资本热捧的项目,Luna 币在2022年的崩溃本可被视作“归零”的失败典范——稳定币UST瞬间失锚,Luna币价归零,数十亿美元灰飞烟灭。然而“崩盘”并没有画下休止符。Luna的残余社区拒绝承认失败命运,通过链上治理投票毅然启动新链,“复活”了 Luna 代币,再次回到市场交易reuters.com。正如 Terra 官方在崩盘后发布的推文所宣称:“我们力量永在社区,今日的决定正彰显了我们的韧性”reuters.com。事实上,原链更名为 Luna Classic 后,大批所谓“LUNC 军团”的散户依然死守阵地,誓言不离不弃;他们自发烧毁巨量代币以缩减供应、推动技术升级,试图让这个一度归零的项目重新燃起生命之火binance.com。失败者并未散场,而是化作一股草根洪流,奋力托举起项目的残迹。经过迷因化的叙事重塑,这场从废墟中重建价值的壮举,成为加密世界中草根政治的经典一幕。类似的案例不胜枚举:曾经被视为笑话的 DOGE(狗狗币)正因多年社群的凝聚而跻身主流币种,总市值一度高达数百亿美元,充分证明了“民有民享”的迷因货币同样可以笑傲市场frontiersin.org。再看最新的美国政治舞台,连总统特朗普也推出了自己的 meme 币 $TRUMP,号召粉丝拿真金白银来表达支持。该币首日即从7美元暴涨至75美元,两天后虽回落到40美元左右,但几乎同时,第一夫人 Melania 又发布了自己的 $Melania 币,甚至连就职典礼的牧师都跟风发行了纪念币theguardian.com!显然,对于狂热的群众来说,一个币的沉浮并非终点,而更像是运动的换挡——资本市场成为政治参与的新前线,你方唱罢我登场,meme 币的群众动员热度丝毫不减。值得注意的是,2024年出现的 Pump.fun 等平台更是进一步降低了这一循环的技术门槛,任何人都可以一键生成自己的 meme 币theguardian.com。这意味着哪怕某个项目归零,剩余的社区完全可以借助此类工具迅速复制一个新币接力,延续集体行动的火种。可以说,在 meme 币的世界里,草根社群获得了前所未有的再生能力和主动权,这正是一种数字时代的群众政治奇观:失败可以被当作梗来玩,破产能够变成重生的序章。
价格即政治:群众投机的新抗争
meme 币现象的兴盛表明:在加密时代,价格本身已成为一种政治表达。这些看似荒诞的迷因代币,将金融市场变成了群众宣泄情绪和诉求的另一个舞台。有学者将此概括为“将公民参与直接转化为了投机资产”cdn-brighterworld.humanities.mcmaster.ca——也就是说,社会运动的热情被注入币价涨跌,政治支持被铸造成可以交易的代币。meme 币融合了金融、技术与政治,通过病毒般的迷因文化激发公众参与,形成对现实政治的某种映射cdn-brighterworld.humanities.mcmaster.caosl.com。当一群草根投入全部热忱去炒作一枚毫无基本面支撑的币时,这本身就是一种大众政治动员的体现:币价暴涨,意味着一群人以戏谑的方式在向既有权威叫板;币价崩盘,也并不意味着信念的消亡,反而可能孕育下一次更汹涌的造势。正如有分析指出,政治类 meme 币的出现前所未有地将群众文化与政治情绪融入市场行情,价格曲线俨然成为民意和趋势的风向标cdn-brighterworld.humanities.mcmaster.ca。在这种局面下,投机不再仅仅是逐利,还是一种宣示立场、凝聚共识的过程——一次次看似荒唐的炒作背后,是草根对传统体制的不服与嘲讽,是失败者拒绝认输的呐喊。归根结底,meme 币所累积的,正是一种不可被归零的政治资本。价格涨落之间,群众的愤怒、幽默与希望尽显其中;这股力量不因一次挫败而消散,反而在市场的循环中愈发壮大。也正因如此,我们才说“价格即政治”——在迷因币的世界里,价格不只是数字,更是人民政治能量的晴雨表,哪怕归零也终将卷土重来。cdn-brighterworld.humanities.mcmaster.caosl.com
全球新兴现象:伊斯兰金融的入场
当Crypto在西方世界掀起市场治政的狂潮时,另一股独特力量也悄然融入这一场域:伊斯兰金融携其独特的道德秩序,开始在链上寻找存在感。长期以来,伊斯兰金融遵循着一套区别于世俗资本主义的原则:禁止利息(Riba)、反对过度投机(Gharar/Maysir)、强调实际资产支撑和道德投资。当这些原则遇上去中心化的加密技术,会碰撞出怎样的火花?出人意料的是,这两者竟在“以市场行为表达价值”这个层面产生了惊人的共鸣。伊斯兰金融并不拒绝市场机制本身,只是为其附加了道德准则;Crypto则将市场机制推向了政治高位,用价格来表达社群意志。二者看似理念迥异,实则都承认市场行为可以也应当承载社会价值观。这使得越来越多金融与政治分析人士开始关注:当虔诚的宗教伦理遇上狂野的加密市场,会塑造出何种新范式?
事实上,穆斯林世界已经在探索“清真加密”的道路。一些区块链项目致力于确保协议符合伊斯兰教法(Sharia)的要求。例如Haqq区块链发行的伊斯兰币(ISLM),从规则层面内置了宗教慈善义务——每发行新币即自动将10%拨入慈善DAO,用于公益捐赠,以符合天课(Zakat)的教义nasdaq.comnasdaq.com。同时,该链拒绝利息和赌博类应用,2022年还获得了宗教权威的教令(Fatwa)认可其合规性nasdaq.com。再看理念层面,伊斯兰经济学强调货币必须有内在价值、收益应来自真实劳动而非纯利息剥削。这一点与比特币的“工作量证明”精神不谋而合——有人甚至断言法定货币无锚印钞并不清真,而比特币这类需耗费能源生产的资产反而更符合教法初衷cointelegraph.com。由此,越来越多穆斯林投资者开始以道德投资的名义进入Crypto领域,将资金投向符合清真原则的代币和协议。
这种现象带来了微妙的双重合法性:一方面,Crypto世界原本奉行“价格即真理”的世俗逻辑,而伊斯兰金融为其注入了一股道德合法性,使部分加密资产同时获得了宗教与市场的双重背书;另一方面,即便在遵循宗教伦理的项目中,最终决定成败的依然是市场对其价值的认可。道德共识与市场共识在链上交汇,共同塑造出一种混合的新秩序。这一全球新兴现象引发广泛议论:有人将其视为金融民主化的极致表现——不同文化价值都能在市场平台上表达并竞争;也有人警惕这可能掩盖新的风险,因为把宗教情感融入高风险资产,既可能凝聚强大的忠诚度,也可能在泡沫破裂时引发信仰与财富的双重危机。但无论如何,伊斯兰金融的入场使Crypto的政治版图更加丰盈多元。从华尔街交易员到中东教士,不同背景的人们正通过Crypto这个奇特的舞台,对人类价值的表达方式进行前所未有的实验。
升华结语:价格即政治的新直觉
回顾比特币问世以来的这段历程,我们可以清晰地看到一条演进的主线:先有货币革命,后有政治发明。比特币赋予了人类一种真正自主的数字货币,而Crypto在此基础上完成的,则是一项前所未有的政治革新——它让市场价格行为承担起了类似政治选票的功能,开创了一种“价格即政治”的新直觉。在这个直觉下,市场不再只是冷冰冰的交易场所;每一次资本流动、每一轮行情涨落,都被赋予了社会意义和政治涵义。买入即表态,卖出即抗议,流动性的涌入或枯竭胜过千言万语的陈情。Crypto世界中,K线图俨然成为民意曲线,行情图就是政治晴雨表。决策不再由少数权力精英关起门来制定,而是在全球无眠的交易中由无数普通人共同谱写。这样的政治形式也许狂野,也许充满泡沫和噪音,但它不可否认地调动起了广泛的社会参与,让原本疏离政治进程的个体通过持币、交易重新找回了影响力的幻觉或实感。
“价格即政治”并非一句简单的口号,而是Crypto给予世界的全新想象力。它质疑了传统政治的正统性:如果一串代码和一群匿名投资者就能高效决策资源分配,我们为何还需要繁冗的官僚体系?它也拷问着自身的内在隐忧:当财富与权力深度绑定,Crypto政治如何避免堕入金钱统治的老路?或许,正是在这样的矛盾和张力中,人类政治的未来才会不断演化。Crypto所开启的,不仅是技术乌托邦或金融狂欢,更可能是一次对民主形式的深刻拓展和挑战。这里有最狂热的逐利者,也有最理想主义的社群塑梦者;有一夜暴富的神话,也有瞬间破灭的惨痛。而这一切汇聚成的洪流,正冲撞着工业时代以来既定的权力谱系。
当我们再次追问:Crypto究竟是什么? 或许可以这样回答——Crypto是比特币之后,人类完成的一次政治范式的试验性跃迁。在这里,价格行为化身为选票,资本市场演化为广场,代码与共识共同撰写“社会契约”。这是一场仍在进行的文明实验:它可能无声地融入既有秩序,也可能剧烈地重塑未来规则。但无论结局如何,如今我们已经见证:在比特币发明真正的货币之后,Crypto正在发明真正属于21世纪的政治。它以数字时代的语言宣告:在链上,价格即政治,市场即民意,代码即法律。这,或许就是Crypto带给我们的最直观而震撼的本质启示。
参考资料:
-
中本聪. 比特币白皮书: 一种点对点的电子现金系统. (2008)bitcoin.org
-
Arkham Intelligence. Ethereum vs Ethereum Classic: Understanding the Differences. (2023)arkhamintelligence.com
-
Binance Square (@渔神的加密日记). 狗狗币价格为何上涨?背后的原因你知道吗?binance.com
-
Cointelegraph中文. 特朗普的迷因币晚宴预期内容揭秘. (2025)cn.cointelegraph.com
-
慢雾科技 Web3Caff (@Lisa). 风险提醒:从 LIBRA 看“政治化”的加密货币骗局. (2025)web3caff.com
-
Nasdaq (@Anthony Clarke). How Cryptocurrency Aligns with the Principles of Islamic Finance. (2023)nasdaq.comnasdaq.com
-
Cointelegraph Magazine (@Andrew Fenton). DeFi can be halal but not DOGE? Decentralizing Islamic finance. (2023)cointelegraph.com
-
-
 @ f0fcbea6:7e059469
2025-05-29 18:30:53
@ f0fcbea6:7e059469
2025-05-29 18:30:53Autores Clássicos e Antigos
- Homero (século IX a.C.?) — Ilíada, Odisseia
- Tucídides (c. 460-400 a.C.) — História da Guerra do Peloponeso
- Platão (c. 427-347 a.C.) — República, Banquete, Fédon, Mênon, Apologia de Sócrates, Fedro, Górgias
- Aristóteles (c. 384-322 a.C.) — Órganon, Física, Metafísica, Da Alma, Ética a Nicômaco, Política, Retórica, Poética
- Virgílio (70-19 a.C.) — Eneida
- Marco Aurélio (121-180) — Meditações
- Santo Agostinho (354-430) — Sobre o Ensino, Confissões, A Cidade de Deus, A Doutrina Cristã
- Boécio (480-525) — A Consolação da Filosofia
- Santo Tomás de Aquino (c. 1225-1274) — Suma Teológica
- Dante Alighieri (1265-1321) — Divina Comédia
Renascimento e Idade Moderna
- Nicolau Maquiavel (1469-1527) — O Príncipe
- Luís de Camões (1524-1580) — Os Lusíadas, Sonetos
- Miguel de Cervantes (1547-1616) — Dom Quixote
- William Shakespeare (1564-1616) — Romeu e Julieta, Hamlet, Macbeth, Otelo, Rei Lear, Henrique IV, Henrique V, Henrique VI, Henrique VIII, A Comédia dos Erros, Tito Andrônico, Príncipe de Tiro, Cimbelino, A Megera Domada, O Mercador de Veneza, Ricardo II, Ricardo III, Muito Barulho por Nada, Júlio César, Noite de Reis, Os Dois Cavaleiros de Verona, Conto do Inverno, Sonhos de uma Noite de Verão, As Alegres Comadres de Windsor, Trólio e Créssida, Medida por Medida, Coriolano, Antônio e Cleópatra, A Tempestade
- Ésquilo (525-456 a.C., antiguidade grega, mas citado junto) — Prometeu Acorrentado, Orestéia/As Eumênides
- Sófocles (496-406 a.C.) — Édipo Rei, Antígona
Literatura e Filosofia Contemporânea
- Fiódor Dostoiévski (1821-1881) — Crime e Castigo, Os Irmãos Karamázov, Os Demônios, O Idiota, Notas do Subsolo
- Franz Kafka (1883-1924) — A Metamorfose, O Processo, O Castelo
- Albert Camus (1913-1960) — O Estrangeiro
- Aldous Huxley (1894-1963) — Admirável Mundo Novo, A Ilha
- James Joyce (1882-1941) — Retrato do Artista Quando Jovem, Ulisses
- George Orwell (1903-1950) — A Revolução dos Bichos, 1984
- Machado de Assis (1839-1908) — Memórias Póstumas de Brás Cubas, O Alienista
- Thomas Mann (1875-1955) — Morte em Veneza, Doutor Fausto, A Montanha Mágica
- Henrik Ibsen (1828-1906) — O Pato Selvagem, Um Inimigo do Povo
- Stendhal (1783-1842) — O Vermelho e o Negro, A Cartuxa de Parma
- Viktor Frankl (1905-1997) — Em Busca de Sentido
- J.R.R. Tolkien (1892-1973) — O Hobbit, O Senhor dos Anéis
- Luigi Pirandello (1867-1936) — Seis Personagens à Procura de um Autor, O Falecido Matias Pascal
- Samuel Beckett (1906-1989) — Esperando Godot
- René Guénon (1886-1951) — A Crise do Mundo Moderno, O Reino da Quantidade
- G. K. Chesterton (1874-1936) — Ortodoxia
- Richard Wagner (1813-1883) — Tristão e Isolda
- Honoré de Balzac (1799-1850) — Ilusões Perdidas, Eugénie Grandet
- Jacob Wassermann (1873-1934) — O Processo Maurizius
- Nikolai Gogol (1809-1852) — Almas Mortas, O Inspetor Geral
- Daniel Defoe (1660-1731) — Moll Flanders
- Mortimer J. Adler (1902-2001) — Como Ler um Livro
- Gustave Flaubert (1821-1880) — Madame Bovary
- Hermann Hesse (1877-1962) — O Jogo das Contas de Vidro
- Richard Wagner (1813-1883) — Tristão e Isolda
- Wolfgang von Goethe (1749-1832) — Fausto (Primeiro), Os Anos de Aprendizado de Wilhelm Meister
- Jacques Benda — A Traição dos Intelectuais
-
 @ dfa02707:41ca50e3
2025-05-30 16:02:19
@ dfa02707:41ca50e3
2025-05-30 16:02:19Contribute to keep No Bullshit Bitcoin news going.
- Coinswap is a decentralized protocol for private, trustless cryptocurrency swaps. It allows participants to securely swap digital assets without intermediaries, using advanced cryptographic techniques and atomic swaps to ensure privacy and security.
- This release introduces major improvements to the protocol's efficiency, security, and usability, including custom in-memory UTXO indexes, more advanced coin-selection algorithms, fidelity bond management and more.
- The update also improves user experience with full Mac support, faster Tor connections, enhanced UI/UX, a unified API, and improved protocol documentation.
"The Project is under active beta development and open for contributions and beta testing. The Coinswap market place is live in testnet4. Bug fixes and feature requests are very much welcome."
- Manuals and demo docs are available here.
What's new
- Core protocol and performance improvements:
- Custom in-memory UTXO indexes. Frequent Core RPC calls, which caused significant delays, have been eliminated by implementing custom in-memory UTXO indexes. These indexes are also saved to disk, leading to faster wallet synchronization.
- Coin selection. Advanced coin-selection algorithms, like those in Bitcoin Core, have been incorporated, enhancing the efficiency of creating different types of transactions.
- Fidelity management. Maker servers now automate tasks such as checking bond expiries, redemption, and recreation for Fidelity Bonds, reducing the user's management responsibilities.
- Taker liveness. The
WaitingFundingConfirmationmessage has been added to keep swap connections between Takers and Makers, assisting with variable block confirmation delays.
-
User experience and compatibility:
- Mac compatibility. The crate and apps now fully support Mac.
- Tor operations are streamlined for faster, more resilient connections. Tor addresses are now consistently linked to the wallet seed, maintaining the same onion address through system reboots.
- The UI/UX improvements enhance the display of balances, UTXOs, offer data, fidelity bonds, and system logs. These updates make the apps more enjoyable and provide clearer coin swap logs during the swap process.
-
API design improvements. Transaction creation routines have been streamlined to use a single common API, which reduces technical debt and eliminates redundant code.
- Protocol spec documentation now details how Coinswap breaks the transaction graph and improves privacy through routed swaps and amount splitting, and includes diagrams for clarity.
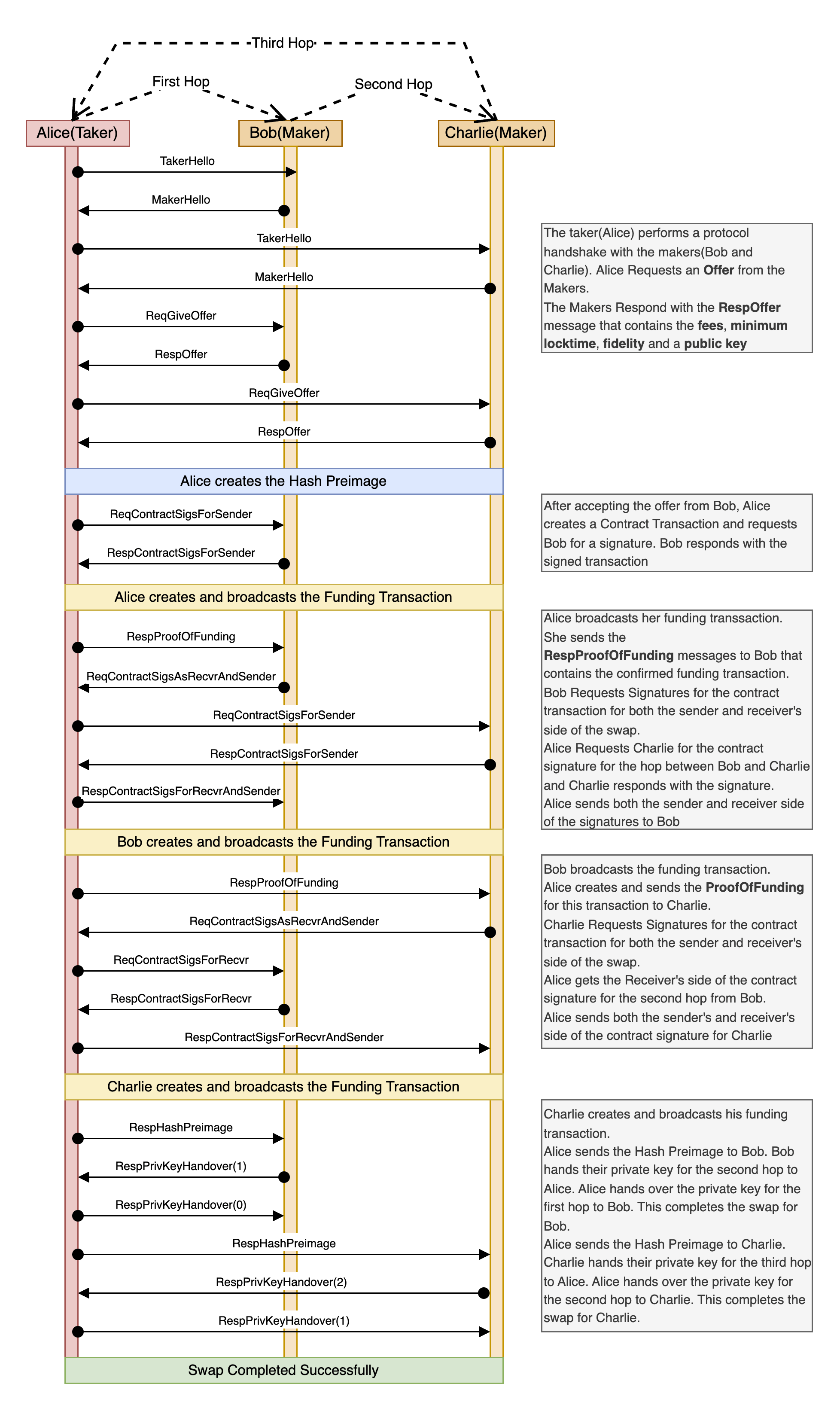
Source: Coinswap Protocol specification.

-
 @ b7274d28:c99628cb
2025-05-28 00:59:49
@ b7274d28:c99628cb
2025-05-28 00:59:49Your identity is important to you, right? While impersonation can be seen in some senses as a form of flattery, we all would prefer to be the only person capable of representing ourselves online, unless we intentionally delegate that privilege to someone else and maintain the ability to revoke it.
Amber does all of that for you in the context of #Nostr. It minimizes the possibility of your private key being compromized by acting as the only app with access to it, while all other Nostr apps send requests to Amber when they need something signed. This even allows you to give someone temporary authority to post as you without giving them your private key, and you retain the authority to revoke their permissions at any time.
nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 has provided Android users with an incredibly powerful tool in Amber, and he continues to improve its functionality and ease of use. Indeed, there is not currently a comparative app available for iOS users. For the time being, this superpower is exclusive to Android.
Installation
Open up the Zapstore app that you installed in the previous stage of this tutorial series.
Very likely, Amber will be listed in the app collection section of the home page. If it is not, just search for "Amber" in the search bar.
Opening the app's page in the Zapstore shows that the release is signed by the developer. You can also see who has added this app to one of their collections and who has supported this app with sats by zapping the release.
Tap "Install" and you will be prompted to confirm you are sure you want to install Amber.
Helpfully, you are informed that several other users follow this developer on Nostr. If you have been on Nostr a while, you will likely recognize these gentlemen as other Nostr developers, one of them being the original creator of the protocol.
You can choose to never have Zapstore ask for confirmation again with apps developed by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, and since we have another of his apps to install later in this tutorial series, I recommend you toggle this on. Then tap on "Trust greenart7c3 and install app."
Just like when you installed the Zapstore from their GitHub, you will be prompted to allow the Zapstore to install apps, since Android considers it an "unknown source."
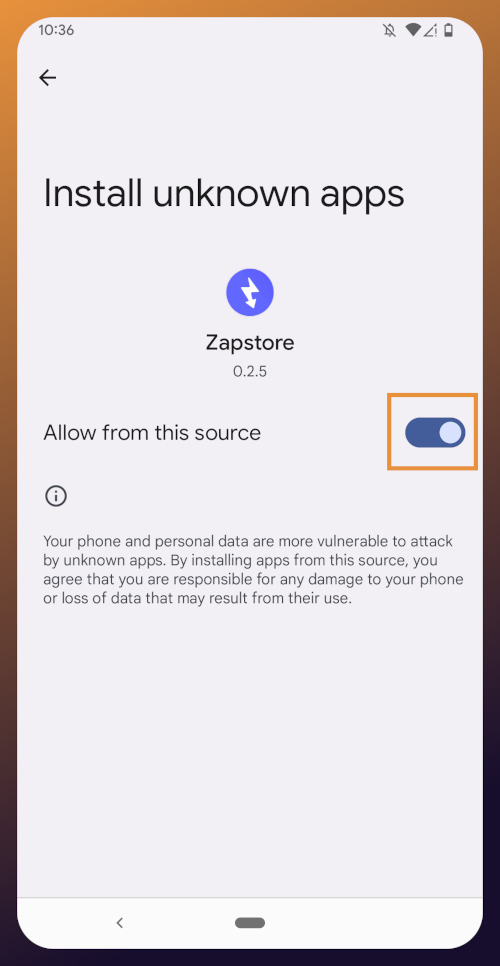
Once you toggle this on and use the back button to get back to the Zapstore, Amber will begin downloading and then present a prompt to install the app. Once installed, you will see a prompt that installation was a success and you can now open the app.
From here, how you proceed will depend on whether you need to set up a new Nostr identity or use Amber with an existing private key you already have set up. The next section will cover setting up a new Nostr identity with Amber. Skip to the section titled "Existing Nostrich" if you already have an nsec that you would like to use with Amber.
New Nostrich
Upon opening the application, you will be presented with the option to use an existing private key or create a new Nostr account. Nostr doesn't really have "accounts" in the traditional sense of the term. Accounts are a relic of permissioned systems. What you have on Nostr are keys, but Amber uses the "account" term because it is a more familiar concept, though it is technically inaccurate.
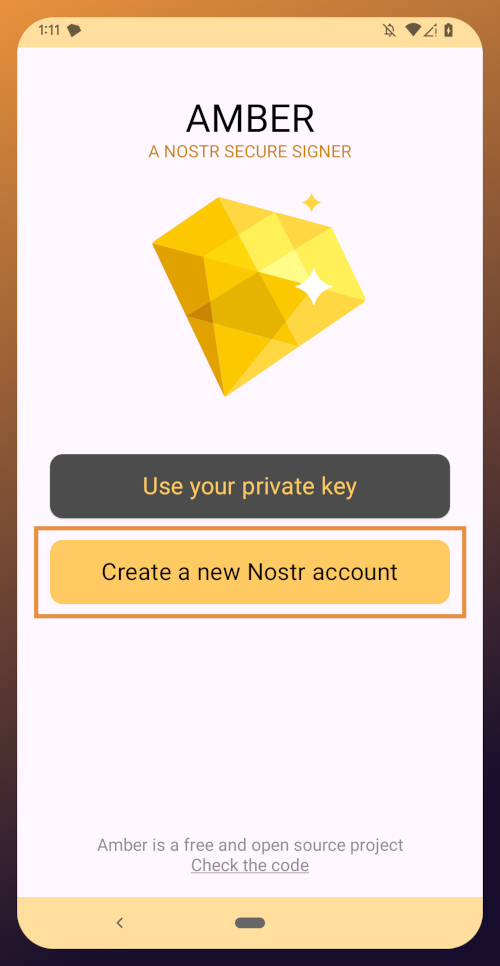
Choose "Create a new Nostr account" and you will be presented with a screen telling you that your Nostr account is ready. Yes, it was really that easy. No email, no real name, no date of birth, and no annoying capcha. Just "Create a new account" and you're done.
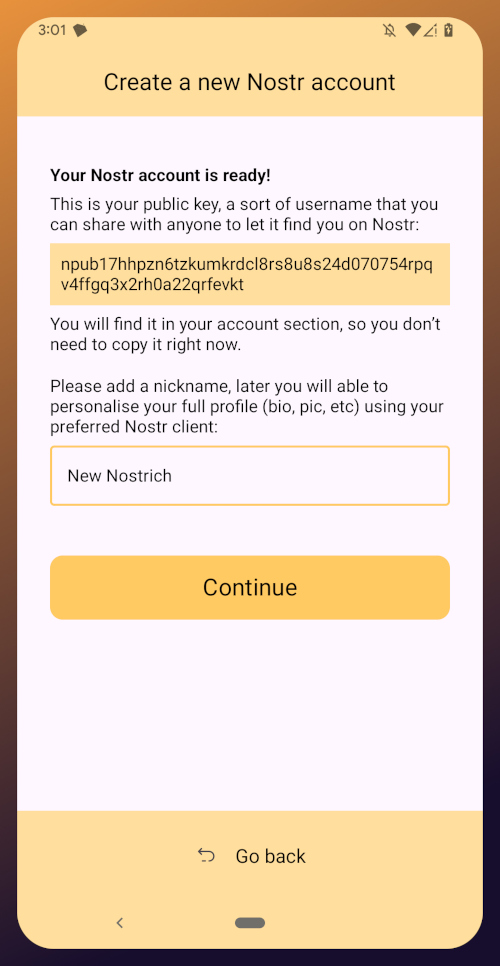
The app presents you with your public key. This is like an address that can be used to find your posts on Nostr. It is 100% unique to you, and no one else can post a note that lists this npub as the author, because they won't have the corresponding private key. You don't need to remember your npub, though. You'll be able to readily copy it from any Nostr app you use whenever you need it.
You will also be prompted to add a nickname. This is just for use within Amber, since you can set up multiple profiles within the app. You can use anything you want here, as it is just so you can tell which profile is which when switching between them in Amber.
Once you've set your nickname, tap on "Continue."
The next screen will ask you what Amber's default signing policy should be.
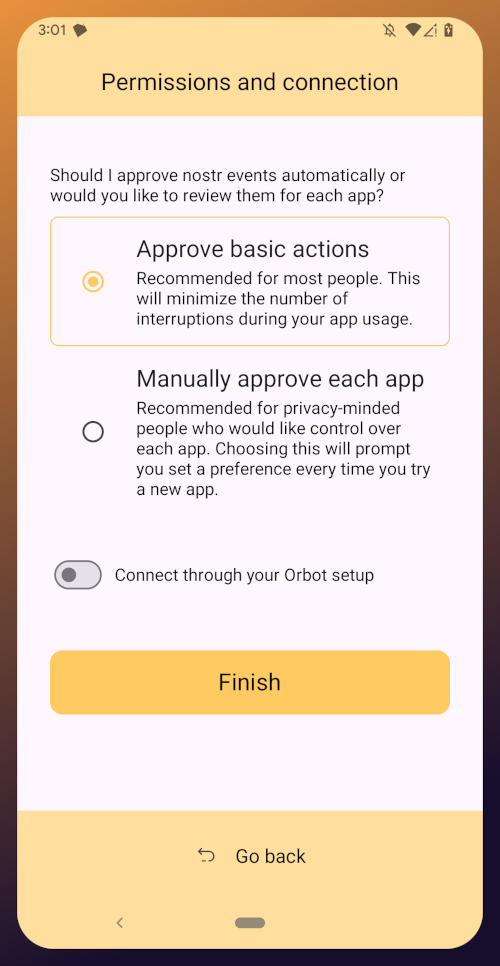
The default is to approve basic actions, referring to things that are common for Nostr clients to request a signature for, like following another user, liking a post, making a new post, or replying. If you are more concerned about what Amber might be signing for on your behalf, you can tell it to require manual approval for each app.
Once you've made your decision, tap "Finish." You will also be able to change this selection in the app settings at any time.
With this setup out of the way, you are now presented with the main "Applications" page of the app.
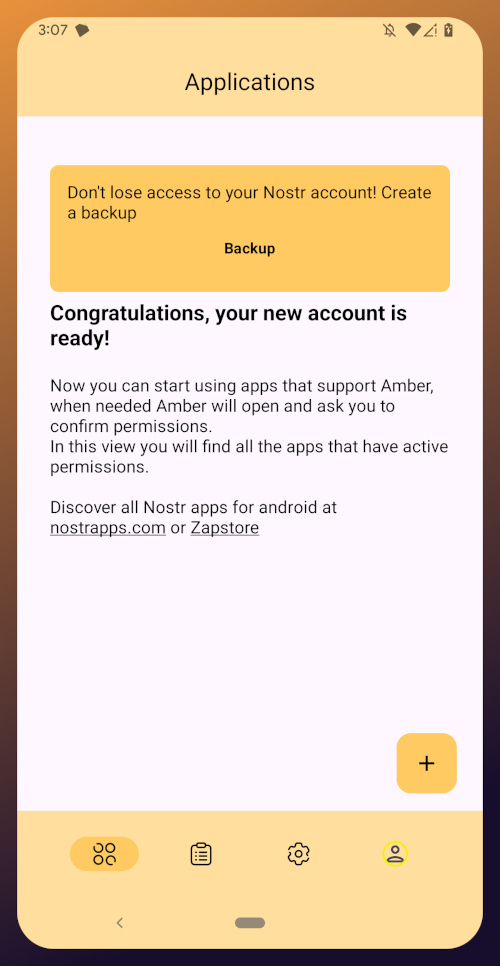
At the top, you have a notification encouraging you to create a backup. Let's get that taken care of now by tapping on the notification and skipping down to the heading titled "Backing Up Your Identity" in this tutorial.
Existing Nostrich
Upon opening the application, you will be presented with the option to use your private key or create a new Nostr account. Choose the former.
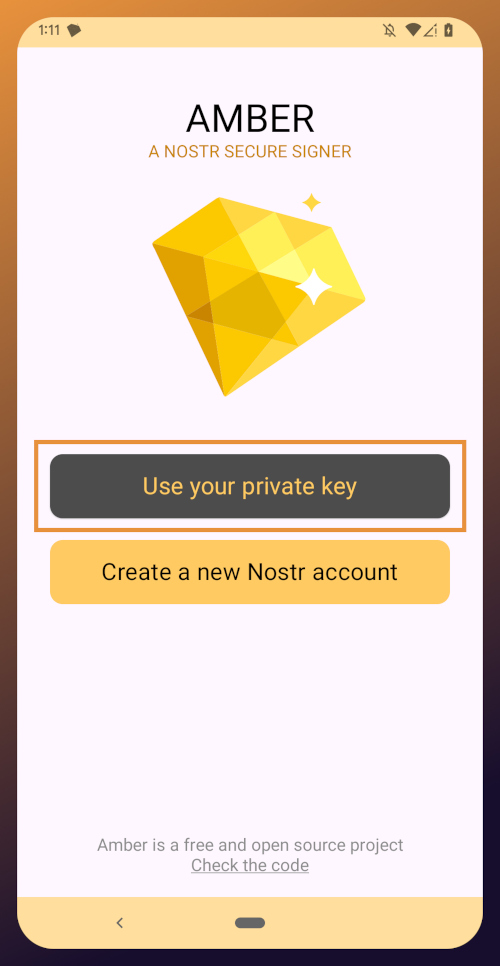
The next screen will require you to paste your private key.
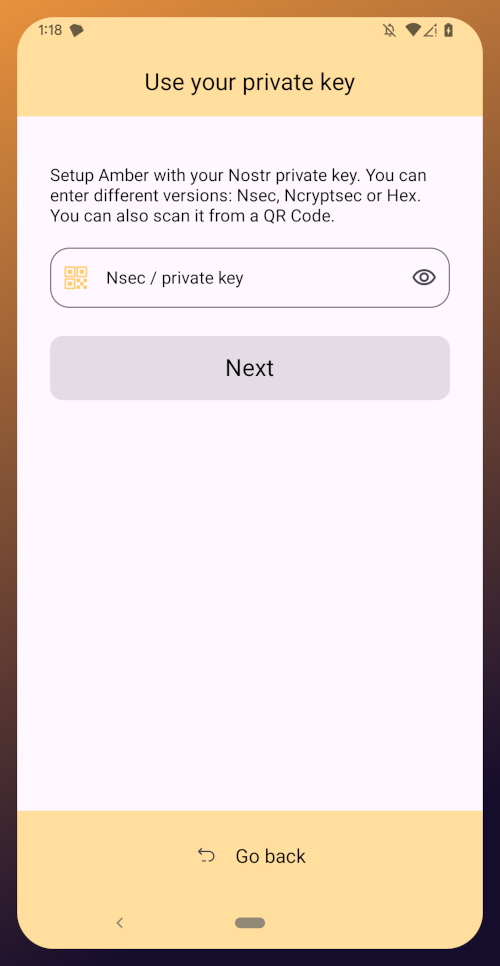
You will need to obtain this from whatever Nostr app you used to create your profile, or any other Nostr app that you pasted your nsec into in the past. Typically you can find it in the app settings and there will be a section mentioning your keys where you can copy your nsec. For instance, in Primal go to Settings > Keys > Copy private key, and on Amethyst open the side panel by tapping on your profile picture in the top-left, then Backup Keys > Copy my secret key.
After pasting your nsec into Amber, tap "Next."

Amber will give you a couple options for a default signing policy. The default is to approve basic actions, referring to things that are common for Nostr clients to request a signature for, like following another user, liking a post, making a new post, or replying. If you are more concerned about what Amber might be signing for on your behalf, you can tell it to require manual approval for each app.
Once you've made your decision, tap "Finish." You will also be able to change this selection in the app settings at any time.
With this setup out of the way, you are now presented with the main "Applications" page of the app. You have nothing here yet, since you haven't used Amber to log into any Nostr apps, but this will be where all of the apps you have connected with Amber will be listed, in the order of the most recently used at the top.
Before we go and use Amber to log into an app, though, let's make sure we've created a backup of our private key. You pasted your nsec into Amber, so you could just save that somewhere safe, but Amber gives you a few other options as well. To find them, you'll need to tap the cog icon at the bottom of the screen to access the settings, then select "Backup Keys."
Backing Up Your Identity
You'll notice that Amber has a few different options for backing up your private key that it can generate.
First, it can give you seed words, just like a Bitcoin seed. If you choose that option, you'll be presented with 12 words you can record somewhere safe. To recover your Nostr private key, you just have to type those words into a compatible application, such as Amber.
The next option is to just copy the secret/private key in its standard form as an "nsec." This is the least secure way to store it, but is also the most convenient, since it is simple to paste into another signer application. If you want to be able to log in on a desktop web app, the browser extension Nostr signers won't necessarily support entering your 12 word seed phrase, but they absolutely will support pasting in your nsec.
You can also display a QR code of your private key. This can be scanned by Amber signer on another device for easily transferring your private key to other devices you want to use it on. Say you have an Android tablet in addition to your phone, for instance. Just make sure you only use this function where you can be certain that no one will be able to get a photograph of that QR code. Once someone else has your nsec, there is no way to recover it. You have to start all over on Nostr. Not a big deal at this point in your journey if you just created a Nostr account, but if you have been using Nostr for a while and have built up a decent amount of reputation, it could be much more costly to start over again.
The next options are a bit more secure, because they require a password that will be used to encrypt your private key. This has some distinct advantages, and a couple disadvantages to be aware of. Using a password to encrypt your private key will give you what is called an ncryptsec, and if this is leaked somehow, whoever has it will not necessarily have access to post as you on Nostr, the way they would if your nsec had been leaked. At least, not so long as they don't also have your password. This means you can store your ncryptsec in multiple locations without much fear that it will be compromised, so long as the password you used to encrypt it was a strong and unique one, and it isn't stored in the same location. Some Nostr apps support an ncryptsec for login directly, meaning that you have the option to paste in your ncryptsec and then just log in with the password you used to encrypt it from there on out. However, now you will need to keep track of both your ncryptsec and your password, storing both of them safely and separately. Additionally, most Nostr clients and signer applications do not support using an ncryptsec, so you will need to convert it back to a standard nsec (or copy the nsec from Amber) to use those apps.
The QR option using an ncryptsec is actually quite useful, though, and I would go this route when trying to set up Amber on additional devices, since anyone possibly getting a picture of the QR code is still not going to be able to do anything with it, unless they also get the password you used to encrypt it.
All of the above options will require you to enter the PIN you set up for your device, or biometric authentication, just as an additional precaution before displaying your private key to you.
As for what "store it in a safe place" looks like, I highly recommend a self-hosted password manager, such as Vaultwarden+Bitwarden or KeePass. If you really want to get wild, you can store it on a hardware signing device, or on a steel seed plate.
Additional Settings
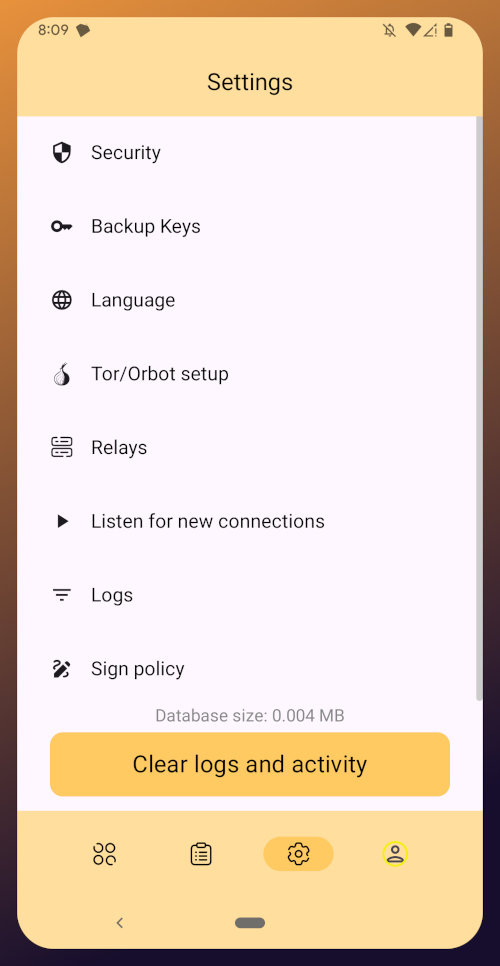
Amber has some additional settings you may want to take advantage of. First off, if you don't want just anyone who has access to your phone to be able to approve signing requests, you can go into the Security settings add a PIN or enable biometrics for signing requests. If you enable the PIN, it will be separate from the PIN you use to access your phone, so you can let someone else use your phone, like your child who is always begging to play a mobile game you have installed, without worrying that they might have access to your Nostr key to post on Amethyst.
Amber also has some relay settings. First are the "Active relays" which are used for signing requests sent to Amber remotely from Nostr web apps. This is what enables you to use Amber on your phone to log into Nostr applications on your desktop web browser, such as Jumble.social, Coracle.social, or Nostrudel.ninja, eliminating your need to use any other application to store your nsec whatsoever. You can leave this relay as the default, or you can add other relays you want to use for signing requests. Just be aware, not all relays will accept the notes that are used for Nostr signing requests, so make sure that the relay you want to use does so. In fact, Amber will make sure of this for you when you type in the relay address.
The next type of relays that you can configure in Amber are the "Default profile relays." These are used for reading your profile information. If you already had a Nostr identity that you imported to Amber, you probably noticed it loaded your profile picture and display name, setting the latter as your nickname in Amber. These relays are where Amber got that information from. The defaults are relay.nostr.band and purplepag.es. The reason for this is because they are aggregators that look for Nostr profiles that have been saved to other relays on the network and pull them in. Therefore, no matter what other relay you may save your profile to, Amber will likely be able to find it on one of those two relays as well. If you have a relay you know you will be saving your Nostr profiles to, you may want to add it to this list.
You can also set up Amber to be paired with Orbot for signing over Tor using relays that are only accessible via the Tor network. That is an advanced feature, though, and well beyond the scope of this tutorial.
Finally, you can update the default signing policy. Maybe after using Amber for a while, you've decided that the choice you made before was too strict or too lenient. You can change it to suit your needs.
Zapstore Login
Now that you are all set up with Amber, let's get you signed into your first Nostr app by going back to the Zapstore.
From the app's home screen, tap on the user icon in the upper left of the screen. This will open a side panel with not much on it except the option to "sign in." Go ahead and tap on it.
You will be presented with the option to either sign in with Amber, or to paste your npub. However, if you do the latter, you will only have read access, meaning you cannot zap any of the app releases. There are other features planned for the Zapstore that may also require you to be signed in with write access, so go ahead and choose to log in with Amber.
Your phone should automatically switch to Amber to approve the sign-in request.
You can choose to only approve basic actions for Zapstore, require it to manually approve every time, or you can tell it that you "fully trust this application." Only choose the latter option with apps you have used for a while and they have never asked you to sign for anything suspicious. For the time being, I suggest you use the "Approve basic actions" option and tap "Grant Permissions."
Your phone will switch back to the Zapstore and will show that you are now signed in. Congratulations! From here on out, logging into most Nostr applications will be as easy as tapping on "Log in with Amber" and approving the request.
If you set up a new profile, it will just show a truncated version of your npub rather than the nickname you set up earlier. That's fine. You'll have an opportunity to update your Nostr profile in the next tutorial in this series and ensure that it is spread far and wide in the network, so the Zapstore will easily find it.
That concludes the tutorial for Amber. While we have not covered using Amber to log into Nostr web apps, that is outside the scope of this series, and I will cover it in an upcoming tutorial regarding using Amber's remote signer options in detail.
Since you're already hanging out in the Zapstore, you may as well stick around, because we will be using it right out the gate in the next part of this series: Amethyst Installation and Setup. (Coming Soon)
-
 @ dfa02707:41ca50e3
2025-05-30 16:02:19
@ dfa02707:41ca50e3
2025-05-30 16:02:19News
- Bitcoin mining centralization in 2025. According to a blog post by b10c, Bitcoin mining was at its most decentralized in May 2017, with another favorable period from 2019 to 2022. However, starting in 2023, mining has become increasingly centralized, particularly due to the influence of large pools like Foundry and the use of proxy pooling by entities such as AntPool.
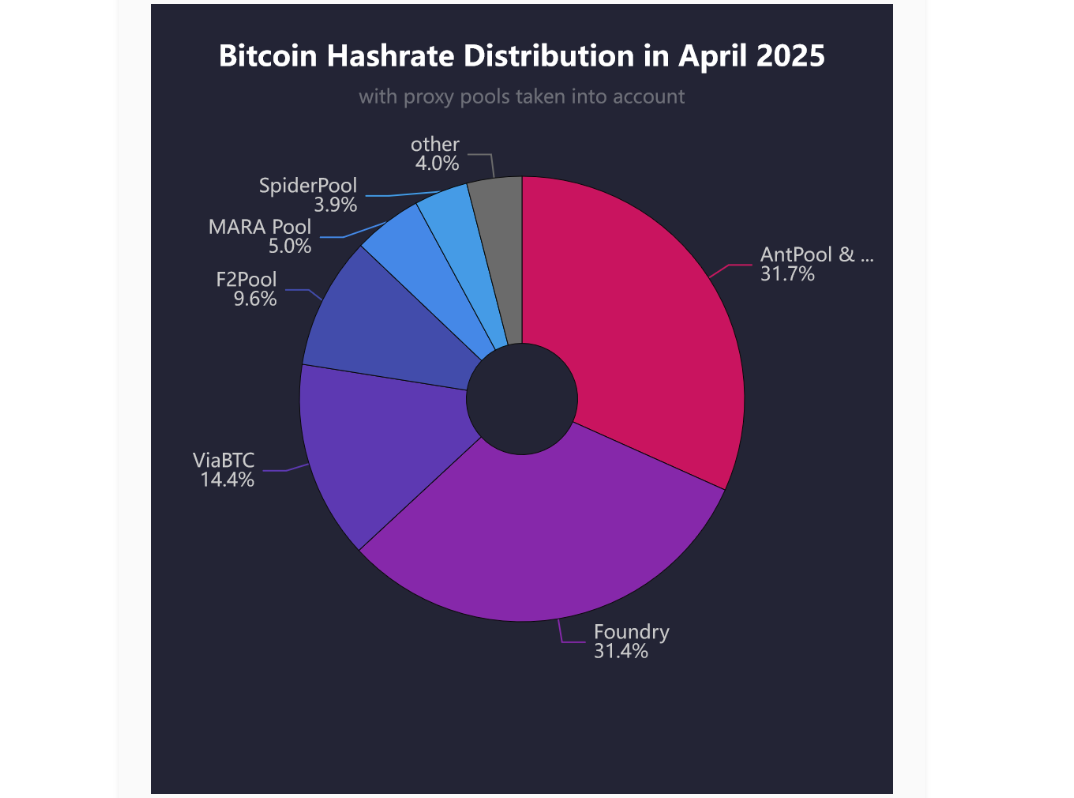
Source: b10c's blog.
- OpenSats announces the eleventh wave of Nostr grants. The five projects in this wave are the mobile live-streaming app Swae, the Nostr-over-ham-radio project HAMSTR, Vertex—a Web-of-Trust (WOT) service for Nostr developers, Nostr Double Ratchet for end-to-end encrypted messaging, and the Nostr Game Engine for building games and applications integrated with the Nostr ecosystem.
- New Spiral grantee: l0rinc. In February 2024, l0rinc transitioned to full-time work on Bitcoin Core. His efforts focus on performance benchmarking and optimizations, enhancing code quality, conducting code reviews, reducing block download times, optimizing memory usage, and refactoring code.
- Project Eleven offers 1 BTC to break Bitcoin's cryptography with a quantum computer. The quantum computing research organization has introduced the Q-Day Prize, a global challenge that offers 1 BTC to the first team capable of breaking an elliptic curve cryptographic (ECC) key using Shor’s algorithm on a quantum computer. The prize will be awarded to the first team to successfully accomplish this breakthrough by April 5, 2026.
- Unchained has launched the Bitcoin Legacy Project. The initiative seeks to advance the Bitcoin ecosystem through a bitcoin-native donor-advised fund platform (DAF), investments in community hubs, support for education and open-source development, and a commitment to long-term sustainability with transparent annual reporting.
- In its first year, the program will provide support to Bitcoin hubs in Nashville, Austin, and Denver.
- Support also includes $50,000 to the Bitcoin Policy Institute, a $150,000 commitment at the University of Austin, and up to $250,000 in research grants through the Bitcoin Scholars program.
"Unchained will match grants 1:1 made to partner organizations who support Bitcoin Core development when made through the Unchained-powered bitcoin DAF, up to 1 BTC," was stated in a blog post.
- Block launched open-source tools for Bitcoin treasury management. These include a dashboard for managing corporate bitcoin holdings and provides a real-time BTC-to-USD price quote API, released as part of the Block Open Source initiative. The company’s own instance of the bitcoin holdings dashboard is available here.
Source: block.xyz
- Bull Bitcoin expands to Mexico, enabling anyone in the country to receive pesos from anywhere in the world straight from a Bitcoin wallet. Additionally, users can now buy Bitcoin with a Mexican bank account.
"Bull Bitcoin strongly believes in Bitcoin’s economic potential in Mexico, not only for international remittances and tourism, but also for Mexican individuals and companies to reclaim their financial sovereignty and protect their wealth from inflation and the fragility of traditional financial markets," said Francis Pouliot, Founder and CEO of Bull Bitcoin.
- Corporate bitcoin holdings hit a record high in Q1 2025. According to Bitwise, public companies' adoption of Bitcoin has hit an all-time high. In Q1 2025, these firms collectively hold over 688,000 BTC, marking a 16.11% increase from the previous quarter. This amount represents 3.28% of Bitcoin's fixed 21 million supply.
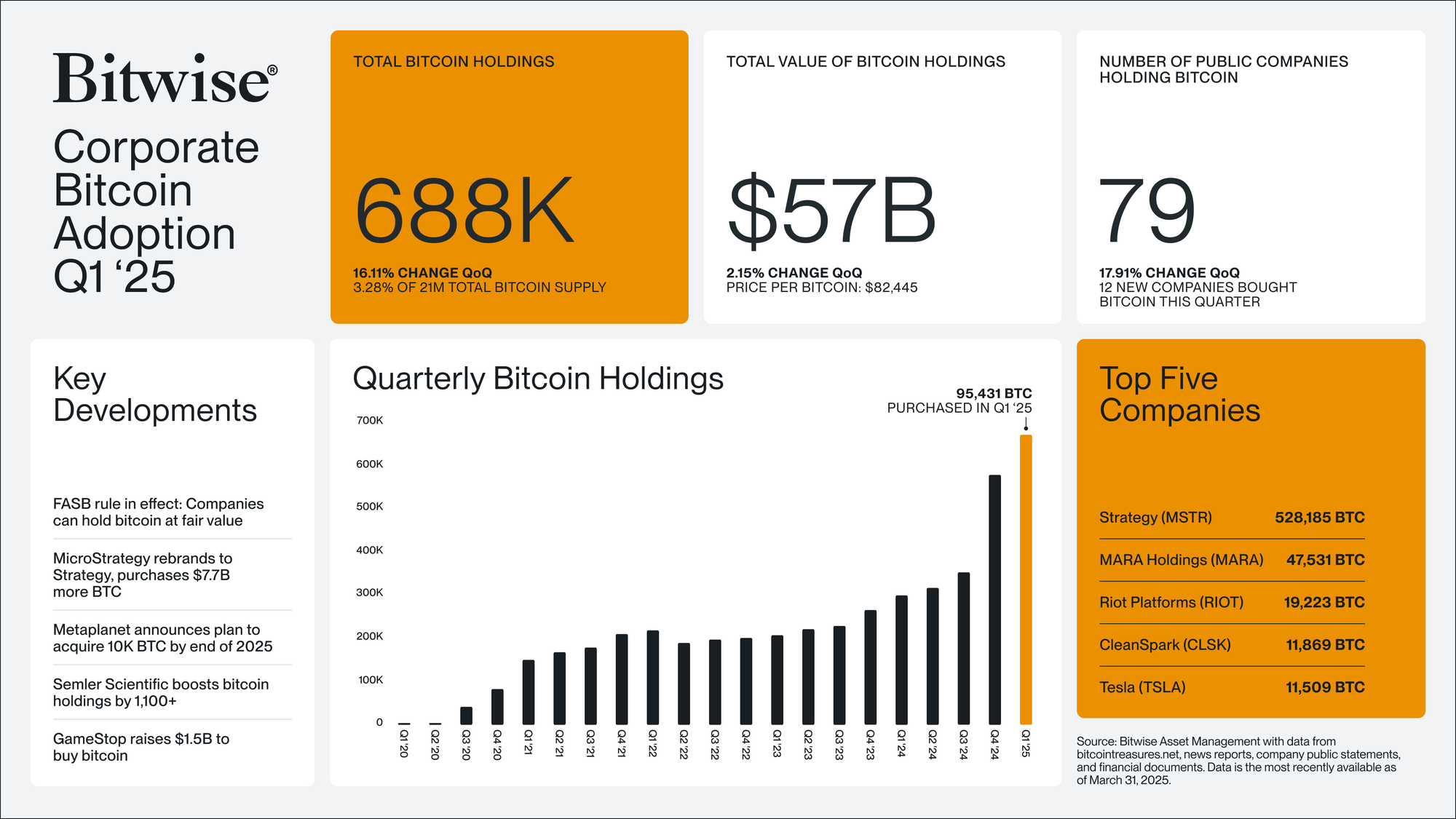
Source: Bitwise.
- The Bitcoin Bond Company for institutions has launched with the aim of acquiring $1 trillion in Bitcoin over 21 years. It utilizes secure, transparent, and compliant bond-like products backed by Bitcoin.
- The U.S. Senate confirmed Paul Atkins as Chair of the Securities and Exchange Commission (SEC). At his confirmation hearing, Atkins emphasized the need for a clear framework for digital assets. He aims to collaborate with the CFTC and Congress to address jurisdiction and rulemaking gaps, aligning with the Trump administration's goal to position the U.S. as a leader in Bitcoin and blockchain finance.
- Ethereum developer Virgil Griffith has been released from custody. Griffith, whose sentence was reduced to 56 months, is now seeking a pardon. He was initially sentenced to 63 months for allegedly violating international sanctions laws by providing technical advice on using cryptocurrencies and blockchain technology to evade sanctions during a presentation titled 'Blockchains for Peace' in North Korea.
- No-KYC exchange eXch to close down under money laundering scrutiny. The privacy-focused cryptocurrency trading platform said it will cease operations on May 1. This decision follows allegations that the platform was used by North Korea's Lazarus Group for money laundering. eXch revealed it is the subject of an active "transatlantic operation" aimed at shutting down the platform and prosecuting its team for "money laundering and terrorism."
- Blockstream combats ESP32 FUD concerning Jade signers. The company stated that after reviewing the vulnerability disclosed in early March, Jade was found to be secure. Espressif Systems, the designer of the ESP32, has since clarified that the "undocumented commands" do not constitute a "backdoor."
- Bank of America is lobbying for regulations that favor banks over tech firms in stablecoin issuance. The bank's CEO Brian Moynihan is working with groups such as the American Bankers Association to advance the issuance of a fully reserved, 1:1 backed "Bank of America coin." If successful, this could limit stablecoin efforts by non-banks like Tether, Circle, and others, reports The Block.
- Tether to back OCEAN Pool with its hashrate. "As a company committed to financial freedom and open access, we see supporting decentralization in Bitcoin mining as essential to the network’s long-term integrity," said Tether CEO Paolo Ardoino.
- Bitdeer to expand its self-mining operations to navigate tariffs. The Singapore-based mining company is advancing plans to produce machines in the U.S. while reducing its mining hardware sales. This response is in light of increasing uncertainties related to U.S. trade policy, as reported by Bloomberg.
- Tether acquires $32M in Bitdeer shares. The firm has boosted its investment in Bitdeer during a wider market sell-off, with purchases in early to mid-April amounting to about $32 million, regulatory filings reveal.
- US Bitcoin miner manufacturer Auradine has raised $153 million in a Series C funding round as it expands into AI infrastructure. The round was led by StepStone Group and included participation from Maverick Silicon, Premji Invest, Samsung Catalyst Fund, Qualcomm Ventures, Mayfield, MARA Holdings, GSBackers, and other existing investors. The firm raised to over $300 million since its inception in 2022.
- Voltage has partnered with BitGo to [enable](https://www.voltage.cloud/blog/bitgo-and-voltage-team-up-to-deliver-instant-bitcoin-and-stabl
-
 @ 51bbb15e:b77a2290
2025-05-21 00:24:36
@ 51bbb15e:b77a2290
2025-05-21 00:24:36Yeah, I’m sure everything in the file is legit. 👍 Let’s review the guard witness testimony…Oh wait, they weren’t at their posts despite 24/7 survellience instructions after another Epstein “suicide” attempt two weeks earlier. Well, at least the video of the suicide is in the file? Oh wait, a techical glitch. Damn those coincidences!
At this point, the Trump administration has zero credibility with me on anything related to the Epstein case and his clients. I still suspect the administration is using the Epstein files as leverage to keep a lot of RINOs in line, whereas they’d be sabotaging his agenda at every turn otherwise. However, I just don’t believe in ends-justify-the-means thinking. It’s led almost all of DC to toss out every bit of the values they might once have had.
-
 @ c9badfea:610f861a
2025-05-20 19:49:20
@ c9badfea:610f861a
2025-05-20 19:49:20- Install Sky Map (it's free and open source)
- Launch the app and tap Accept, then tap OK
- When asked to access the device's location, tap While Using The App
- Tap somewhere on the screen to activate the menu, then tap ⁝ and select Settings
- Disable Send Usage Statistics
- Return to the main screen and enjoy stargazing!
ℹ️ Use the 🔍 icon in the upper toolbar to search for a specific celestial body, or tap the 👁️ icon to activate night mode
-
 @ dfa02707:41ca50e3
2025-05-30 16:02:18
@ dfa02707:41ca50e3
2025-05-30 16:02:18
Good morning (good night?)! The No Bullshit Bitcoin news feed is now available on Moody's Dashboard! A huge shoutout to sir Clark Moody for integrating our feed.
Headlines
- Spiral welcomes Ben Carman. The developer will work on the LDK server and a new SDK designed to simplify the onboarding process for new self-custodial Bitcoin users.
- The Bitcoin Dev Kit Foundation announced new corporate members for 2025, including AnchorWatch, CleanSpark, and Proton Foundation. The annual dues from these corporate members fund the small team of open-source developers responsible for maintaining the core BDK libraries and related free and open-source software (FOSS) projects.
- Strategy increases Bitcoin holdings to 538,200 BTC. In the latest purchase, the company has spent more than $555M to buy 6,556 coins through proceeds of two at-the-market stock offering programs.
- Spar supermarket experiments with Bitcoin payments in Zug, Switzerland. The store has introduced a new payment method powered by the Lightning Network. The implementation was facilitated by DFX Swiss, a service that supports seamless conversions between bitcoin and legacy currencies.
- The Bank for International Settlements (BIS) wants to contain 'crypto' risks. A report titled "Cryptocurrencies and Decentralised Finance: Functions and Financial Stability Implications" calls for expanding research into "how new forms of central bank money, capital controls, and taxation policies can counter the risks of widespread crypto adoption while still fostering technological innovation."
- "Global Implications of Scam Centres, Underground Banking, and Illicit Online Marketplaces in Southeast Asia." According to the United Nations Office on Drugs and Crime (UNODC) report, criminal organizations from East and Southeast Asia are swiftly extending their global reach. These groups are moving beyond traditional scams and trafficking, creating sophisticated online networks that include unlicensed cryptocurrency exchanges, encrypted communication platforms, and stablecoins, fueling a massive fraud economy on an industrial scale.
- Slovenia is considering a 25% capital gains tax on Bitcoin profits for individuals. The Ministry of Finance has proposed legislation to impose this tax on gains from cryptocurrency transactions, though exchanging one cryptocurrency for another would remain exempt. At present, individual 'crypto' traders in Slovenia are not taxed.
- Circle, BitGo, Coinbase, and Paxos plan to apply for U.S. bank charters or licenses. According to a report in The Wall Street Journal, major crypto companies are planning to apply for U.S. bank charters or licenses. These firms are pursuing limited licenses that would permit them to issue stablecoins, as the U.S. Congress deliberates on legislation mandating licensing for stablecoin issuers.
"Established banks, like Bank of America, are hoping to amend the current drafts of [stablecoin] legislation in such a way that nonbanks are more heavily restricted from issuing stablecoins," people familiar with the matter told The Block.
- Charles Schwab to launch spot Bitcoin trading by 2026. The financial investment firm, managing over $10 trillion in assets, has revealed plans to introduce spot Bitcoin trading for its clients within the next year.
Use the tools
- Bitcoin Safe v1.2.3 expands QR SignMessage compatibility for all QR-UR-compatible hardware signers (SpecterDIY, KeyStone, Passport, Jade; already supported COLDCARD Q). It also adds the ability to import wallets via QR, ensuring compatibility with Keystone's latest firmware (2.0.6), alongside other improvements.
- Minibits v0.2.2-beta, an ecash wallet for Android devices, packages many changes to align the project with the planned iOS app release. New features and improvements include the ability to lock ecash to a receiver's pubkey, faster confirmations of ecash minting and payments thanks to WebSockets, UI-related fixes, and more.
- Zeus v0.11.0-alpha1 introduces Cashu wallets tied to embedded LND wallets. Navigate to Settings > Ecash to enable it. Other wallet types can still sweep funds from Cashu tokens. Zeus Pay now supports Cashu address types in Zaplocker, Cashu, and NWC modes.
- LNDg v1.10.0, an advanced web interface designed for analyzing Lightning Network Daemon (LND) data and automating node management tasks, introduces performance improvements, adds a new metrics page for unprofitable and stuck channels, and displays warnings for batch openings. The Profit and Loss Chart has been updated to include on-chain costs. Advanced settings have been added for users who would like their channel database size to be read remotely (the default remains local). Additionally, the AutoFees tool now uses aggregated pubkey metrics for multiple channels with the same peer.
- Nunchuk Desktop v1.9.45 release brings the latest bug fixes and improvements.
- Blockstream Green iOS v4.1.8 has renamed L-BTC to LBTC, and improves translations of notifications, login time, and background payments.
- Blockstream Green Android v4.1.8 has added language preference in App Settings and enables an Android data backup option for disaster recovery. Additionally, it fixes issues with Jade entry point PIN timeout and Trezor passphrase input.
- Torq v2.2.2, an advanced Lightning node management software designed to handle large nodes with over 1000 channels, fixes bugs that caused channel balance to not be updated in some cases and channel "peer total local balance" not getting updated.
- Stack Wallet v2.1.12, a multicoin wallet by Cypher Stack, fixes an issue with Xelis introduced in the latest release for Windows.
- ESP-Miner-NerdQAxePlus v1.0.29.1, a forked version from the NerdAxe miner that was modified for use on the NerdQAxe+, is now available.
- Zark enables sending sats to an npub using Bark.
- Erk is a novel variation of the Ark protocol that completely removes the need for user interactivity in rounds, addressing one of Ark's key limitations: the requirement for users to come online before their VTXOs expire.
- Aegis v0.1.1 is now available. It is a Nostr event signer app for iOS devices.
- Nostash is a NIP-07 Nostr signing extension for Safari. It is a fork of Nostore and is maintained by Terry Yiu. Available on iOS TestFlight.
- Amber v3.2.8, a Nostr event signer for Android, delivers the latest fixes and improvements.
- Nostur v1.20.0, a Nostr client for iOS, adds
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ dfa02707:41ca50e3
2025-05-30 16:02:18
@ dfa02707:41ca50e3
2025-05-30 16:02:18Headlines
- Twenty One Capital is set to launch with over 42,000 BTC in its treasury. This new Bitcoin-native firm, backed by Tether and SoftBank, is planned to go public via a SPAC merger with Cantor Equity Partners and will be led by Jack Mallers, co-founder and CEO of Strike. According to a report by the Financial Times, the company aims to replicate the model of Michael Saylor with his company, MicroStrategy.
- Florida's SB 868 proposes a backdoor into encrypted platforms. The bill and its House companion have both passed through their respective committees and are headed to a full vote. If enacted, SB 868 would require social media companies to decrypt teens' private messages, ban disappearing messages, allow unrestricted parental access to private messages, and likely eliminate encryption for all minors altogether.
- Paul Atkins has officially assumed the role of the 34th Chairman of the US Securities and Exchange Commission (SEC). This is a return to the agency for Atkins, who previously served as an SEC Commissioner from 2002 to 2008 under the George W. Bush administration. He has committed to advancing the SEC’s mission of fostering capital formation, safeguarding investors, and ensuring fair and efficient markets.
- Solosatoshi.com has sold over 10,000 open-source miners, adding more than 10 PH of hashpower to the Bitcoin network.
"Thank you, Bitaxe community. OSMU developers, your brilliance built this. Supporters, your belief drives us. Customers, your trust powers 10,000+ miners and 10PH globally. Together, we’re decentralizing Bitcoin’s future. Last but certainly not least, thank you@skot9000 for not only creating a freedom tool, but instilling the idea into thousands of people, that Bitcoin mining can be for everyone again," said the firm on X.
- OCEAN's DATUM has found 100 blocks. "Over 65% of OCEAN’s miners are using DATUM, and that number is growing every day. This means block template construction is making its way back into the hands of the miners, which is not only the most profitable for miners on OCEAN but also one of the best things for Bitcoin," stated the mining pool.
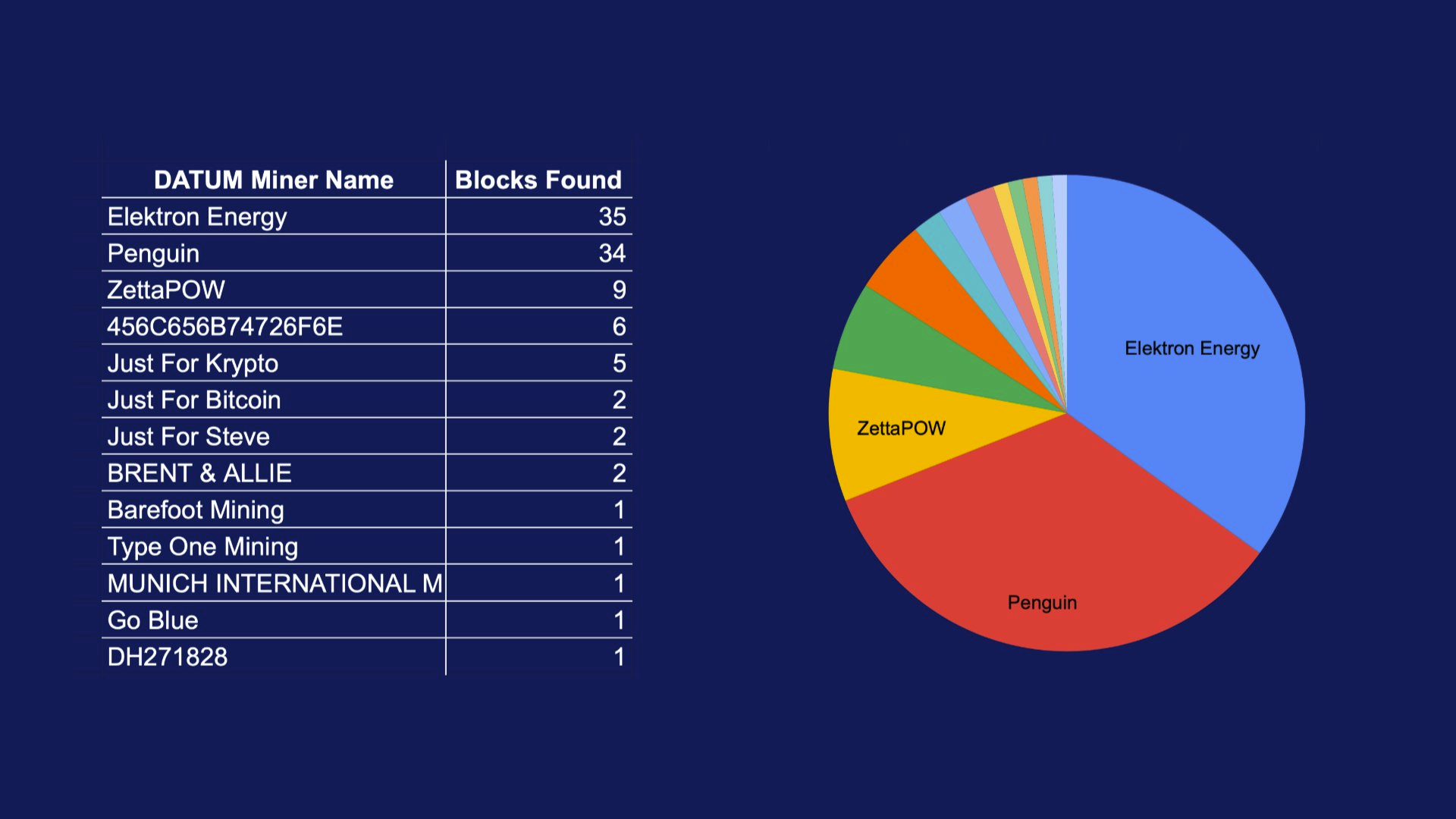
Source: orangesurf
- Arch Labs has secured $13 million to develop "ArchVM" and integrate smart-contract functionality with Bitcoin. The funding round, valuing the company at $200 million, was led by Pantera Capital, as announced on Tuesday.
- Tesla still holds nearly $1 billion in bitcoin. According to the automaker's latest earnings report, the firm reported digital asset holdings worth $951 million as of March 31.
- The European Central Bank is pushing for amendments to the European Union's Markets in Crypto Assets legislation (MiCA), just months after its implementation. According to Politico's report on Tuesday, the ECB is concerned that U.S. support for cryptocurrency, particularly stablecoins, could cause economic harm to the 27-nation bloc.
- TABConf 2025 is scheduled to take place from October 13-16, 2025. This prominent technical Bitcoin conference is dedicated to community building, education, and developer support, and it is set to return in October. Get your tickets here.
- Kaduna Lightning Development Bootcamp. From May 14th to 17th, the Bitcoin Lightning Developer Bootcamp will take place in Kaduna, Nigeria. Thisevent offers four dynamic days of coding, learning, and networking. Organized by Africa Free Routing and supported by Btrust, Tether, and African Bitcoiners, this bootcamp is designed as a gateway for African developers eager to advance their skills in Bitcoin and Lightning development. Apply here.

Source: African Bitcoiners.
Use the tools
- Core Lightning (CLN) v25.02.2 as been released to fix a broken Docker image. The issue was caused by an SQLite version that did not support an advanced query.
- Blitz wallet v0.4.4-beta introduces several updates and improvements, including the prevention of duplicate ecash payments, fixes for background ecash invoice handling, the ability for users to send payments to BOLT12 invoices from their Liquid balance, support for Blink QR codes, a lowered minimum amount for Lightning-to-Liquid payments to 100 sats, the option to initiate a node sync via a swipe gesture on the wallet's home screen, and the introduction of opt-in or opt-out functionality for newly implemented crash analytics via settings.
- Utreexo v0.5.0, a hash-based dynamic accumulator, is now available.
- Specter v2.1.1 is now available on StartOS. "This update brings compatibility with Bitcoin Core v28 and incorporates several upstream improvements," said developer Alex71btc.
- ESP-Miner (AxeOS) v2.7.0b1 is now available for testing.
- NodeGuard v0.16.1, a treasury management solution for Lightning nodes, has been released.
- The latest stacker.news updates include prompts to add a receiving wallet when posting or making comments (for new users), an option to randomize poll choices, improved URL search, and a few other enhancements. A bug fix for territories created after 9/19/24 has been implemented to reward 70% of their revenue to owners instead of 50%.
Other stuff
- The April edition of the 256 Foundation's newsletter is now available. It includes the latest mining news, Bitcoin network health updates, project developments, and a tutorial on how to update FutureBit's Apollo 1 to the Apollo 2 software.
- Siggy47 has posted a comprehensive RoboSats guide on stacker.news.
- Learn how to run your own Nostr relay using Citrine and Cloudflare Tunnels by following this step-by-step guide by Dhalism.
- Max Guise has written a Bitkey roadmap update for April 2025.
-
PlebLab has uploaded a video on how to build a Rust wallet with LDK Node by Ben Carman.
-
Do you want more? Subscribe and get No Bullshit GM report straight to your mailbox and No Bullshit Bitcoin on Nostr.
- Feedback or tips? Drop it here.
- #FREESAMOURAI
Sign up for No Bullshit Bitcoin

No Bullshit Bitcoin Is a Bitcoin News Desk Without Ads, Paywalls, or Clickbait.
Subscribe .nc-loop-dots-4-24-icon-o{--animation-duration:0.8s} .nc-loop-dots-4-24-icon-o *{opacity:.4;transform:scale(.75);animation:nc-loop-dots-4-anim var(--animation-duration) infinite} .nc-loop-dots-4-24-icon-o :nth-child(1){transform-origin:4px 12px;animation-delay:-.3s;animation-delay:calc(var(--animation-duration)/-2.666)} .nc-loop-dots-4-24-icon-o :nth-child(2){transform-origin:12px 12px;animation-delay:-.15s;animation-delay:calc(var(--animation-duration)/-5.333)} .nc-loop-dots-4-24-icon-o :nth-child(3){transform-origin:20px 12px} @keyframes nc-loop-dots-4-anim{0%,100%{opacity:.4;transform:scale(.75)}50%{opacity:1;transform:scale(1)}}
Email sent! Check your inbox to complete your signup.
No spam. Unsubscribe anytime.
-
 @ 527337d5:93e9525e
2025-05-29 18:19:31
@ 527337d5:93e9525e
2025-05-29 18:19:31Experiment Plan for Text Similarity Comparison Algorithms (Revised v3)
1. Introduction
1.1. Research Background and Objectives
This research aims to evaluate the performance of various algorithms for comparing the similarity between individual page texts extracted from a specific technical document (in this experiment, the content of the Tailwind CSS documentation site). Initially, we considered dividing the text into 250-word chunks. However, due to the abundance of Markdown and code in the target document, meaningful chunking proved tobe cumbersome. Therefore, we decided to use the entire text extracted from each page as the unit of comparison.
This study will systematically compare and examine combinations of different "representation methods" and "comparison methods" from multiple perspectives: ease of implementation, processing speed, memory consumption, and accuracy of similarity judgment. A particular focus will be on elucidating the effectiveness of information-based NCD (Normalized Compression Distance) and vector embedding-based methods, which are planned for future evaluation.
1.2. Report Structure
This report will first describe the experimental data and its preprocessing methods. Next, it will define in detail the representation methods and comparison methods that form the axes of evaluation, and present specific experimental cases combining them. After presenting the results and discussion of initial experiments using NCD, it will describe the metrics for evaluating each experimental case, specific experimental procedures, and the expected outcomes and future prospects of this research.
2. Experimental Data
- Target Content: Individual HTML pages from the Tailwind CSS documentation site (
tailwindcss.com). - Data Unit: The entire text of each page, extracted from HTML files using the
html2textcommand and further processed to remove control characters using thesedcommand. This serves as the basic unit of comparison in this experiment. - Data Storage Location: The extracted and preprocessed text files are stored locally under the
./tailwindcss.comdirectory, maintaining the original file structure. - Language: English
- Example Search Query: A representative search query for this experiment is
"Utilities for controlling how a background image behaves when scrolling."(Multiple queries and their expected similar pages may be used for more robust evaluation). - Example Expected Similar Page: For the query above,
/docs/background-attachmentis expected to be the most semantically similar page.
3. Experimental Design
This experiment is designed by dividing the process of evaluating text similarity into two main axes: "Representation Methods" and "Comparison Methods."
3.1. Representation Methods (Text Quantification/Vectorization)
-
Naive (Raw Text / Full Page Text)
- Method: Use the entire preprocessed text extracted from each document page as raw string data, without special transformations.
- Objective: Serve as a direct input for information-based comparison methods like NCD and as a baseline comparison for more advanced representation methods to be evaluated later.
-
(Future Experiment) Vector Embedding via Gemini API (Embedding-Gemini)
- Method: Utilize Google's Gemini API (
models/text-embedding-004) to convert the entire text of each page into high-dimensional dense vectors (Embeddings). - Objective: Evaluate the performance of context-rich vector representations generated by a state-of-the-art large language model.
- Method: Utilize Google's Gemini API (
-
(Future Experiment) Vector Embedding via Local Lightweight Model (Embedding-MiniLM-GGUF)
- Method: Run a GGUF quantized version of the pre-trained
all-MiniLM-L6-v2model (all-MiniLM-L6-v2-Q5_K_M.gguf) in a local environment to convert the entire text of each page into vector representations. GGUF format offers benefits like smaller model size and potentially faster CPU inference. - Objective: Evaluate the performance of a widely used open-source lightweight model (quantized version) in comparison to API-based large-scale models and domain-specific learned models.
- Method: Run a GGUF quantized version of the pre-trained
-
(Future Experiment) Extraction of Internal Feature Vectors via Mathematica (Embedding-MMA)
- Method: Use the entire page texts from the target document set as input. Employ Mathematica's neural network framework to first pass each page text through an Embedding Layer. Apply L2 normalization to the resulting vectors, followed by Principal Component Analysis (PCA) to reduce dimensionality to approximately 100 dimensions. This final vector will be the feature vector. This pipeline aims to create dense, normalized representations specific to the document corpus, with PCA helping to capture the most significant variance in a lower-dimensional space, potentially improving efficiency and reducing noise. The choice of an Embedding Layer trained or fine-tuned on the corpus, followed by PCA, seeks to balance domain-specificity with robust dimensionality reduction.
- Objective: Evaluate the performance of vector representations processed or specialized for the target document set.
3.2. Comparison Methods (Distance/Similarity Calculation between Representations)
-
NCD (Normalized Compression Distance)
- Applicable to: Naive (Full Page Text)
- Method: For two data objects
x(query) andy(document page text), calculateNCD(x,y) = (C(xy) - min(C(x), C(y))) / max(C(x), C(y)). Here,C(s)is the size (e.g., byte length) of datasafter compression with a specific algorithm, andC(xy)is the size of the concatenated dataxandyafter compression. A value closer to 0 indicates higher similarity. - Compression Algorithms to Compare: DEFLATE (gzip), bzip2, LZMA, XZ, Zstandard (zstd), LZO, Snappy, LZ4 (as used in the user-provided script).
- Objective: Evaluate similarity from an information-theoretic perspective based on data commonality and redundancy. Compare the impact of different compression algorithms on NCD results.
-
(Future Experiment) Cosine Similarity
- Applicable to: Embedding-Gemini, Embedding-MiniLM-GGUF, Embedding-MMA
- Method: Calculate the cosine of the angle between two vectors.
- Objective: Standard similarity evaluation based on the directionality (semantic closeness) of vector representations.
-
(Future Experiment) Euclidean Distance
- Applicable to: Embedding-Gemini, Embedding-MiniLM-GGUF, Embedding-MMA
- Method: Calculate the straight-line distance between two vectors in a multidimensional space.
- Objective: Similarity evaluation based on the absolute positional relationship of vector representations.
-
(Future Experiment) Manhattan Distance (L1 Distance)
- Applicable to: Embedding-Gemini, Embedding-MiniLM-GGUF, Embedding-MMA
- Method: Calculate the sum of the absolute differences of their Cartesian coordinates.
- Objective: Similarity evaluation based on axis-aligned travel distance, differing from Euclidean distance.
-
(Future Experiment) Mahalanobis Distance
- Applicable to: Embedding-Gemini, Embedding-MiniLM-GGUF, Embedding-MMA
- Method: Calculate the distance between two vectors considering the covariance of the data. This provides a distance metric that accounts for the scale differences and correlations of each feature (vector dimension).
- Objective: More robust similarity evaluation that considers the structure (correlation) of the feature space.
3.3. Experimental Cases (Initial NCD Experiments and Future Expansion)
3.3.1. Initial Experiments Conducted (NCD)
The following experimental cases were conducted using the user-provided script. The representation method was "Naive (Full Page Text)."
| No. | Representation Method | Comparison Method (Distance/Similarity Metric) | Notes | | :-: | :---------------------- | :--------------------------------------------- | :-------------------------- | | 1 | Naive (Full Page Text) | NCD (gzip/DEFLATE) | One of the baselines | | 2 | Naive (Full Page Text) | NCD (bzip2) | Compression method comparison | | 3 | Naive (Full Page Text) | NCD (lzma) | Compression method comparison | | 4 | Naive (Full Page Text) | NCD (xz) | Compression method comparison | | 5 | Naive (Full Page Text) | NCD (zstd) | Compression method comparison | | 6 | Naive (Full Page Text) | NCD (lzop) | Compression method comparison | | 7 | Naive (Full Page Text) | NCD (snappy) | Compression method comparison | | 8 | Naive (Full Page Text) | NCD (lz4) | Compression method comparison |
3.3.2. Future Experimental Plan (Vector Embedding)
| No. | Representation Method | Comparison Method (Distance/Similarity Metric) | Notes | | :--: | :---------------------- | :--------------------------------------------- | :------------------------------------- | | 9 | Embedding-Gemini | Cosine Similarity | Standard vector similarity evaluation | | 10 | Embedding-Gemini | Euclidean Distance | Standard vector similarity evaluation | | 11 | Embedding-Gemini | Manhattan Distance | Axis-aligned distance similarity eval. | | 12 | Embedding-Gemini | Mahalanobis Distance | Distance considering feature structure | | 13 | Embedding-MiniLM-GGUF | Cosine Similarity | Evaluation of local lightweight model | | 14 | Embedding-MiniLM-GGUF | Euclidean Distance | Evaluation of local lightweight model | | 15 | Embedding-MiniLM-GGUF | Manhattan Distance | Evaluation of local lightweight model | | 16 | Embedding-MiniLM-GGUF | Mahalanobis Distance | Evaluation of local lightweight model | | 17 | Embedding-MMA | Cosine Similarity | Eval. of domain-specific MMA model | | 18 | Embedding-MMA | Euclidean Distance | Eval. of domain-specific MMA model | | 19 | Embedding-MMA | Manhattan Distance | Eval. of domain-specific MMA model | | 20 | Embedding-MMA | Mahalanobis Distance | Eval. of domain-specific MMA model |
4. Results and Discussion of Initial NCD Experiments (Based on User-Provided Information)
4.1. Execution Overview
The user employed provided Python scripts (
main.py,comparison.py) to calculate NCD between a search query and the entire text extracted from each HTML page in the./tailwindcss.comdirectory.main.pyinvokedcomparison.pywith various compression commands (gzip,bzip2,lzma,xz,zstd,lzop,lz4).comparison.pythen used the specified command-line compression tools to compute NCD scores and output the results to CSV files.Search Query:
"Utilities for controlling how a background image behaves when scrolling."Expected Similar Page:/docs/background-attachment4.2. Key Results
The pages judged as most similar (lowest NCD score) to the query for each compression algorithm were as follows (based on user-provided sorted results):
- Zstandard (zstd):
./tailwindcss.com/docs/background-attachment(Score: 0.973...) - LZ4:
./tailwindcss.com/docs/background-attachment(Score: 0.976...) - XZ:
./tailwindcss.com/docs/background-origin(Score: 0.946...) - LZMA:
./tailwindcss.com/docs/background-origin(Score: 0.966...) - gzip (DEFLATE):
./tailwindcss.com/docs/scroll-behavior(Score: 0.969...) - LZO:
./tailwindcss.com/docs/scroll-behavior(Score: 0.955...) - bzip2:
./tailwindcss.com/docs/mask-clip(Score: 0.958...)
4.3. Initial Discussion
- Variation in Results by Compression Algorithm: It was confirmed that the document judged most similar to the query varies depending on the compression algorithm used. This is likely due to the differing abilities of each algorithm to capture various types of redundancy and patterns within the text.
- Alignment with Expected Results: When using Zstandard and LZ4, the expected page (
/docs/background-attachment) was judged as most similar. This suggests these compression algorithms may have relatively effectively captured the information-theoretic commonality between the query and the target document in this instance. - Range of NCD Scores: The reported NCD scores were generally close to 1.0. This may be due to the relatively short length of the search query compared to the full-page documents, meaning the query text contributes less to the overall compressibility when concatenated. However, relative differences were still captured, enabling ranking.
- Validity of Full-Page Comparison: Full-page comparison was chosen due to the difficulty of chunking content rich in Markdown and code. While this approach simplifies preprocessing, it may also be influenced by the overall structure of the page, including common headers and footers.
This initial experiment indicates that NCD can function as an indicator of text similarity and that the choice of compression algorithm is crucial.
5. Evaluation Metrics (Including Future Experiments)
-
Accuracy of Similarity Scores:
- Ground Truth Preparation: A small, diverse subset of page pairs (e.g., 50-100 pairs) will be selected. For each pair, at least two evaluators familiar with the Tailwind CSS documentation will independently assign a similarity score on a 5-point Likert scale (1=Not similar, 5=Very similar). Inter-evaluator reliability (e.g., using Krippendorff's Alpha) will be calculated. Disagreements will be resolved through discussion to create a consensus ground truth dataset. If resource-constrained, a single-evaluator approach with clear, predefined criteria will be used, acknowledging this limitation. Alternatively, page pairs likely to be similar will be selected based on internal references or chapter structure within the document.
- Evaluation Metrics: Ranking evaluation (Precision@k, Recall@k, MAP: Mean Average Precision), correlation analysis (Spearman's rank correlation coefficient with human judgments), classification evaluation (AUC-ROC, F1-score, assuming appropriate thresholding).
-
Processing Speed:
- Average time to calculate similarity for a page pair, total calculation time for all page pairs (or a large sampled set), and representation generation time (API call time, local model inference time, MMA processing time).
-
Memory Consumption:
- Model size (MiniLM-GGUF, MMA model), data representation size, and peak runtime memory usage.
-
Ease of Implementation:
- Qualitative assessment of setup ease, lines of code, required libraries, difficulty of parameter tuning, and documentation quality. This will be summarized for each approach (e.g., using a rubric or a comparative narrative) considering factors like:
- Setup Complexity: (e.g., API key acquisition vs. local model download & environment setup vs. full model training pipeline in Mathematica).
- Code Complexity: Estimated lines of core logic, reliance on external vs. standard libraries.
- Parameter Sensitivity: Number of key hyperparameters requiring tuning and the perceived difficulty of finding good settings.
- Documentation & Community Support: Availability and clarity of official documentation and community resources (e.g., forums, GitHub issues).
- Qualitative assessment of setup ease, lines of code, required libraries, difficulty of parameter tuning, and documentation quality. This will be summarized for each approach (e.g., using a rubric or a comparative narrative) considering factors like:
6. Experimental Procedure (Including Future Experiments)
-
Data Preparation:
- Prepare HTML files of the target document in the
./tailwindcss.comdirectory. - (For NCD) Extract and preprocess full-page plain text from each HTML file using
html2textandsed(as previously done by the user). - (For Vector Embedding) Use the same preprocessed full-page plain text.
- Create ground truth data for accuracy evaluation as described in Section 5.1.
- Prepare HTML files of the target document in the
-
Implementation and Execution of Representation Methods:
- Naive: Use the preprocessed page text directly.
- Embedding-Gemini: Use Python's
requestslibrary or similar to send each page text to the Gemini API (models/text-embedding-004) and retrieve/store the vector representations. - Embedding-MiniLM-GGUF: Use appropriate libraries (e.g.,
ctransformers, orsentence-transformerscombined withllama-cpp-python) to load theall-MiniLM-L6-v2-Q5_K_M.ggufmodel. Input each page text to extract and store vector representations. - Embedding-MMA: In Mathematica, apply an Embedding Layer to each page text, followed by L2 normalization and PCA dimensionality reduction (to approx. 100 dimensions), then extract and store the vector representations.
-
Implementation and Execution of Comparison Methods:
- NCD: Refer to the user-provided Python scripts (
main.py,comparison.py) to call various command-line compression tools for NCD calculation. Alternatively, extend this to directly use Python's compression libraries for better control and efficiency. - Cosine Similarity, Euclidean Distance, Manhattan Distance: Implement using standard math libraries (e.g., Python's NumPy, SciPy).
- Mahalanobis Distance: Implement using
scipy.spatial.distance.mahalanobis. Requires pre-calculation of the covariance matrix (or its inverse) from the entire dataset of vectors for each embedding type.
- NCD: Refer to the user-provided Python scripts (
-
Evaluation Execution:
- Calculate similarity (or distance) scores between the search query (and potentially between page pairs for ground truth evaluation) and all document pages for each experimental case.
- Measure processing speed and memory consumption.
- Calculate accuracy metrics using the computed similarity scores and ground truth data.
- Record and evaluate the ease of implementation.
-
Result Aggregation and Analysis:
- Compile the obtained evaluation metrics into tables and graphs for comparative analysis of each method's characteristics.
Experimental Environment (Assumed)
- Hardware: (e.g., CPU: Intel Core i7-10700, Memory: 32GB RAM, GPU: NVIDIA GeForce RTX 3070 8GB - specify if GPU is used for MiniLM or MMA)
- Software: (e.g., OS: Linux (Ubuntu, etc.), Programming Language: Python 3.x (with versions for key libraries like NumPy, SciPy, requests, ctransformers, etc.), Mathematica 13.x, specific versions of command-line compression tools if used directly)
7. Expected Outcomes and Future Outlook
This research (including initial NCD experiments and future vector embedding experiments) is expected to yield the following outcomes:
- Clarification of the Impact of Compression Algorithms on NCD: As indicated by initial experiments, the choice of compression algorithm significantly affects similarity judgments. Further validation with more diverse data and queries will allow for a deeper understanding of each algorithm's characteristics.
- Performance Characteristics of Various Methods on Full-Page Text: To clarify how NCD and various vector embedding methods perform in terms of accuracy, speed, and resource consumption when applied to entire page texts.
- Comparison of Local and API-Based Models: In future vector embedding experiments, to compare the performance, speed, and resource efficiency of
Embedding-MiniLM-GGUF(local, quantized) andEmbedding-Gemini(API, large-scale) to identify practical trade-offs. - Evaluation of Domain-Specific Embedding Effectiveness: To assess how well
Embedding-MMA, processed or tuned for a single technical document set, performs compared to general-purpose models. - Provision of Practical Insights: To offer guidelines for selecting appropriate similarity comparison approaches based on text characteristics (e.g., Markdown/code content) and system requirements (e.g., ease of preprocessing, emphasis on accuracy vs. speed).
8. Future Challenges
- Ensuring Quality of Ground Truth Data: Evaluating full-page similarity can be more subjective than chunk-level evaluation, making the creation of high-quality ground truth data challenging. Establishing clear annotation guidelines and measuring inter-annotator agreement will be crucial.
- Hyperparameter Optimization: Many methods involve tunable parameters (e.g., Embedding-MMA model structure, PCA dimensionality, MiniLM-GGUF inference parameters), the optimization of which may be beyond the scope of this initial study. The impact of default vs. tuned parameters could be noted.
- Noise in Full-Page Comparison: Full-page texts may contain common navigational elements or boilerplate text that could act as noise in similarity judgments. Strategies to mitigate this (e.g., more advanced text extraction, or methods robust to such noise) could be a future research direction.
- Input Length Limitations of Vector Embedding Models: Very long page texts might exceed the input length limits of some vector embedding models, requiring strategies for handling. These might include:
- Truncation: Using only the initial N tokens of each page, which is simple but may lose crucial information.
- Summarization: Employing an abstractive or extractive summarization model to create a condensed version of the page, which could preserve key information but adds another layer of processing and potential information loss/bias.
- Chunking and Averaging/Pooling: Dividing long pages into manageable chunks, embedding each chunk, and then aggregating these chunk embeddings (e.g., by averaging) to get a single page vector. This approach needs careful consideration of how chunks are defined and aggregated.
- Utilizing Long-Context Models: If available and feasible, leveraging embedding models specifically designed for longer sequences. The chosen strategy will be documented, and its potential impact on results acknowledged.
- Target Content: Individual HTML pages from the Tailwind CSS documentation site (
-
 @ c1e9ab3a:9cb56b43
2025-05-27 16:19:06
@ c1e9ab3a:9cb56b43
2025-05-27 16:19:06Star Wars is often viewed as a myth of rebellion, freedom, and resistance to tyranny. The iconography—scrappy rebels, totalitarian stormtroopers, lone smugglers—suggests a deep anti-authoritarian ethos. Yet, beneath the surface, the narrative arc of Star Wars consistently affirms the necessity, even sanctity, of central authority. This blog entry introduces the question: Is Star Wars fundamentally a celebration of statism?
Rebellion as Restoration, Not Revolution
The Rebel Alliance’s mission is not to dismantle centralized power, but to restore the Galactic Republic—a bureaucratic, centrally governed institution. Characters like Mon Mothma and Bail Organa are high-ranking senators, not populist revolutionaries. The goal is to remove the corrupt Empire and reinstall a previous central authority, presumed to be just.
- Rebels are loyalists to a prior state structure.
- Power is not questioned, only who wields it.
Jedi as Centralized Moral Elites
The Jedi, often idealized as protectors of peace, are unelected, extra-legal enforcers of moral and military order. Their authority stems from esoteric metaphysical abilities rather than democratic legitimacy.
- They answer only to their internal Council.
- They are deployed by the Senate, but act independently of civil law.
- Their collapse is depicted as tragic not because they were unaccountable, but because they were betrayed.
This positions them as a theocratic elite, not spiritual anarchists.
Chaos and the Frontier: The Case of the Cantina
The Mos Eisley cantina, often viewed as a symbol of frontier freedom, reveals something darker. It is: - Lawless - Violent - Culturally fragmented
Conflict resolution occurs through murder, not mediation. Obi-Wan slices off a limb; Han shoots first—both without legal consequence. There is no evidence of property rights, dispute resolution, or voluntary order.
This is not libertarian pluralism—it’s moral entropy. The message: without centralized governance, barbarism reigns.
The Mythic Arc: Restoration of the Just State
Every trilogy in the saga returns to a single theme: the fall and redemption of legitimate authority.
- Prequels: Republic collapses into tyranny.
- Originals: Rebels fight to restore legitimate order.
- Sequels: Weak governance leads to resurgence of authoritarianism; heroes must reestablish moral centralism.
The story is not anti-state—it’s anti-bad state. The solution is never decentralization; it’s the return of the right ruler or order.
Conclusion: The Hidden Statism of a Rebel Myth
Star Wars wears the costume of rebellion, but tells the story of centralized salvation. It: - Validates elite moral authority (Jedi) - Romanticizes restoration of fallen governments (Republic) - Portrays decentralized zones as corrupt and savage (outer rim worlds)
It is not an anarchist parable, nor a libertarian fable. It is a statist mythology, clothed in the spectacle of rebellion. Its core message is not that power should be abolished, but that power belongs to the virtuous few.
Question to Consider:
If the Star Wars universe consistently affirms the need for centralized moral and political authority, should we continue to see it as a myth of freedom? Or is it time to recognize it as a narrative of benevolent empire? -
 @ 04c915da:3dfbecc9
2025-05-20 15:50:48
@ 04c915da:3dfbecc9
2025-05-20 15:50:48For years American bitcoin miners have argued for more efficient and free energy markets. It benefits everyone if our energy infrastructure is as efficient and robust as possible. Unfortunately, broken incentives have led to increased regulation throughout the sector, incentivizing less efficient energy sources such as solar and wind at the detriment of more efficient alternatives.
The result has been less reliable energy infrastructure for all Americans and increased energy costs across the board. This naturally has a direct impact on bitcoin miners: increased energy costs make them less competitive globally.
Bitcoin mining represents a global energy market that does not require permission to participate. Anyone can plug a mining computer into power and internet to get paid the current dynamic market price for their work in bitcoin. Using cellphone or satellite internet, these mines can be located anywhere in the world, sourcing the cheapest power available.
Absent of regulation, bitcoin mining naturally incentivizes the build out of highly efficient and robust energy infrastructure. Unfortunately that world does not exist and burdensome regulations remain the biggest threat for US based mining businesses. Jurisdictional arbitrage gives miners the option of moving to a friendlier country but that naturally comes with its own costs.
Enter AI. With the rapid development and release of AI tools comes the requirement of running massive datacenters for their models. Major tech companies are scrambling to secure machines, rack space, and cheap energy to run full suites of AI enabled tools and services. The most valuable and powerful tech companies in America have stumbled into an accidental alliance with bitcoin miners: THE NEED FOR CHEAP AND RELIABLE ENERGY.
Our government is corrupt. Money talks. These companies will push for energy freedom and it will greatly benefit us all.
-
 @ dfa02707:41ca50e3
2025-05-30 16:02:17
@ dfa02707:41ca50e3
2025-05-30 16:02:17Headlines
- Spiral renews support for Dan Gould and Joschisan. The organization has renewed support for Dan Gould, who is developing the Payjoin Dev Kit (PDK), and Joschisan, a Fedimint developer focused on simplifying federations.
- Metaplanet buys another 145 BTC. The Tokyo-listed company has purchased an additional 145 BTC for $13.6 million. Their total bitcoin holdings now stand at 5,000 coins, worth around $428.1 million.
- Semler Scientific has increased its bitcoin holdings to 3,303 BTC. The company acquired an additional 111 BTC at an average price of $90,124. The purchase was funded through proceeds from an at-the-market offering and cash reserves, as stated in a press release.
- The Virtual Asset Service Providers (VASP) Bill 2025 introduced in Kenya. The new legislation aims to establish a comprehensive legal framework for licensing, regulating, and supervising virtual asset service providers (VASPs), with strict penalties for non-compliant entities.
- Russian government to launch a cryptocurrency exchange. The country's Ministry of Finance and Central Bank announced plans to establish a trading platform for "highly qualified investors" that "will legalize crypto assets and bring crypto operations out of the shadows."
- All virtual asset service providers expect to be fully compliant with the Travel Rule by the end of 2025. A survey by financial surveillance specialist Notabene reveals that 90% of virtual asset service providers (VASPs) expect full Travel Rule compliance by mid-2025, with all aiming for compliance by year-end. The survey also shows a significant rise in VASPs blocking withdrawals until beneficiary information is confirmed, increasing from 2.9% in 2024 to 15.4% now. Additionally, about 20% of VASPs return deposits if originator data is missing.
- UN claims Bitcoin mining is a "powerful tool" for money laundering. The Rage's analysis suggests that the recent United Nations Office on Drugs and Crime report on crime in South-East Asia makes little sense and hints at the potential introduction of Anti-Money Laundering (AML) measures at the mining level.
- Riot Platforms has obtained a $100 million credit facility from Coinbase Credit, using bitcoin as collateral for short-term funding to support its expansion. The firm's CEO, Jason Les, stated that this facility is crucial for diversifying financing sources and driving long-term stockholder value through strategic growth initiatives.
- Bitdeer raises $179M in loans and equity amid Bitcoin chip push. The Miner Mag reports that Bitdeer entered into a loan agreement with its affiliate Matrixport for up to $200 million in April, as disclosed in its annual report filed on Monday.
- Federal Reserve retracts guidance discouraging banks from engaging in 'crypto.' The U.S. Federal Reserve withdrew guidance that discouraged banks from crypto and stablecoin activities, as announced by its Board of Governors on Thursday. This includes rescinding a 2022 supervisory letter requiring prior notification of crypto activities and 2023 stablecoin requirements.
"As a result, the Board will no longer expect banks to provide notification and will instead monitor banks' crypto-asset activities through the normal supervisory process," reads the FED statement.
- UAE-based Islamic bank ruya launches Shari’ah-compliant bitcoin investing. The bank has become the world’s first Islamic bank to provide direct access to virtual asset investments, including Bitcoin, via its mobile app, per Bitcoin Magazine.
- U.S. 'crypto' scam losses amounted to $9.3B in 2024. The US The Federal Bureau of Investigation (FBI) has reported $9.3 billion losses in cryptocurrency-related scams in 2024, noting a troubling trend of scams targeting older Americans, which accounted for over $2.8 billion of those losses.
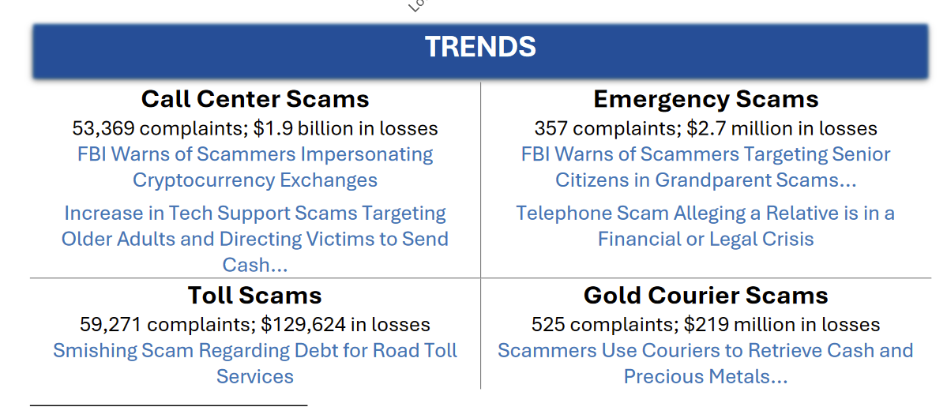
Source: FBI.
- North Korean hackers establish fake companies to target 'crypto' developers. Silent Push researchers reported that hackers linked to the Lazarus Group created three shell companies, two of which are based in the U.S., with the objective of spreading malware through deceptive job interview scams aimed at individuals seeking jobs in cryptocurrency companies.
- Citrea deployed its Clementine Bridge on the Bitcoin testnet. The bridge utilizes the BitVM2 programming language to inherit validity from Bitcoin, allegedly providing "the safest and most trust-minimized way to use BTC in decentralized finance."
- Hesperides University offers a Master’s degree in Bitcoin. Bitcoin Magazine reports the launch of the first-ever Spanish-language Master’s program dedicated exclusively to Bitcoin. Starting April 28, 2025, this fully online program will equip professionals with technical, economic, legal, and philosophical skills to excel in the Bitcoin era.
- BTC in D.C. event is set to take place on September 30 - October 1 in Washington, D.C. Learn more about this initiative here.
Use the tools
- Bitcoin Keeper just got a new look. Version 2.2.0 of the mobile multisig app brought a new branding design, along with a Keeper Private tier, testnet support, ability to import and export BIP-329 labels, and the option to use a Server Key with multiple users.
- Earlier this month the project also announced Keeper Learn service, offering clear and guided Bitcoin learning sessions for both groups and individuals.
- Keeper Desktop v0.2.2, a companion desktop app for Bitcoin Keeper mobile app, received a renewed branding update, too.

The evolution of Bitcoin Keeper logo. Source: BitHyve blog.
- Blockstream Green Desktop v2.0.25 updates GDK to v0.75.1 and fixes amount parsing issues when switching from fiat denomination to Liquid asset.
- Lightning Loop v0.31.0-beta enhances the
loop listswapscommand by improving the ability to filter the response. - Lightning-kmp v1.10.0, an implementation of the Lightning Network in Kotlin, is now available.
- LND v0.19.0-beta.rc3, the latest beta release candidate of LND is now ready for testing.
- ZEUS v0.11.0-alpha2 is now available for testing, too. It's nuts.
- JoinMarket Fidelity Bond Simulator helps potential JoinMarket makers evaluate their competitive position in the market based on fidelity bonds.
- UTXOscope is a text-only Bitcoin blockchain analysis tool that visualizes price dynamics using only on-chain data. The
-
 @ 21c71bfa:e28fa0f6
2025-05-29 15:09:17
@ 21c71bfa:e28fa0f6
2025-05-29 15:09:17Book *Bangalore to Tirupati cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ c1e9ab3a:9cb56b43
2025-05-27 13:19:53
@ c1e9ab3a:9cb56b43
2025-05-27 13:19:53I. Introduction: Money as a Function of Efficiency and Preference
Money is not defined by law, but by power over productivity. In any open economy, the most economically efficient actors—those who control the most valuable goods, services, and knowledge—ultimately dictate the medium of exchange. Their preferences signal to the broader market what form of money is required to access the highest-value goods, from durable commodities to intangibles like intellectual property and skilled labor.
Whatever money these actors prefer becomes the de facto unit of account and store of value, regardless of its legal status. This emergent behavior is natural and reflects a hierarchy of monetary utility.
II. Classical Gresham’s Law: A Product of Market Distortion
Gresham’s Law, famously stated as:
"Bad money drives out good"
is only valid under coercive monetary conditions, specifically: - Legal tender laws that force the acceptance of inferior money at par with superior money. - Fixed exchange rates imposed by decree, not market valuation. - Governments or central banks backing elastic fiduciary media with promises of redemption. - Institutional structures that mandate debt and tax payments in the favored currency.
Under these conditions, superior money (hard money) is hoarded, while inferior money (soft, elastic, inflationary) circulates. This is not an expression of free market behavior—it is the result of suppressed price discovery and legal coercion.
Gresham’s Law, therefore, is not a natural law of money, but a law of distortion under forced parity and artificial elasticity.
III. The Collapse of Coercion: Inversion of Gresham’s Law
When coercive structures weaken or are bypassed—through technological exit, jurisdictional arbitrage, monetary breakdown, or political disintegration—Gresham’s Law inverts:
Good money drives out bad.
This occurs because: - Market actors regain the freedom to select money based on utility, scarcity, and credibility. - Legal parity collapses, exposing the true economic hierarchy of monetary forms. - Trustless systems (e.g., Bitcoin) or superior digital instruments (e.g., stablecoins) offer better settlement, security, and durability. - Elastic fiduciary media become undesirable as counterparty risk and inflation rise.
The inversion marks a return to monetary natural selection—not a breakdown of Gresham’s Law, but the collapse of its preconditions.
IV. Elasticity and Control
Elastic fiduciary media (like fiat currency) are not intrinsically evil. They are tools of state finance and debt management, enabling rapid expansion of credit and liquidity. However, when their issuance is unconstrained, and legal tender laws force their use, they become weapons of economic coercion.
Banks issue credit unconstrained by real savings, and governments enforce the use of inflated media through taxation and courts. This distorts capital allocation, devalues productive labor, and ultimately hollows out monetary confidence.
V. Monetary Reversion: The Return of Hard Money
When the coercion ends—whether gradually or suddenly—the monetary system reverts. The preferences of the productive and wealthy reassert themselves:
- Superior money is not just saved—it begins to circulate.
- Weaker currencies are rejected not just for savings, but for daily exchange.
- The hoarded form becomes the traded form, and Gresham’s Law inverts completely.
Bitcoin, gold, and even highly credible stable instruments begin to function as true money, not just stores of value. The natural monetary order returns, and the State becomes a late participant, not the originator of monetary reality.
VI. Conclusion
Gresham’s Law operates only under distortion. Its inversion is not an anomaly—it is a signal of the collapse of coercion. The monetary system then reorganizes around productive preference, technological efficiency, and economic sovereignty.
The most efficient market will always dictate the form of hard money. The State can delay this reckoning through legal force, but it cannot prevent it indefinitely. Once free choice returns, bad money dies, and good money lives again.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 15:08:51
@ 21c71bfa:e28fa0f6
2025-05-29 15:08:51Book *Tirupati to Srikalahasti cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:52:10
@ 21c71bfa:e28fa0f6
2025-05-29 14:52:10Book *Tirupati to Srikalahasti cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ dfa02707:41ca50e3
2025-05-30 16:02:17
@ dfa02707:41ca50e3
2025-05-30 16:02:17Contribute to keep No Bullshit Bitcoin news going.
News
- Spiral welcomes Ben Carman. The developer will work on the LDK server and a new SDK designed to simplify the onboarding process for new self-custodial Bitcoin users.
- Spiral renews support for Dan Gould and Joschisan. The organization has renewed support for Dan Gould, who is developing the Payjoin Dev Kit (PDK), and Joschisan, a Fedimint developer focused on simplifying federations.
- The Bitcoin Dev Kit Foundation announced new corporate members for 2025, including AnchorWatch, CleanSpark, and Proton Foundation. The annual dues from these corporate members fund the small team of open-source developers responsible for maintaining the core BDK libraries and related free and open-source software (FOSS) projects.
- The European Central Bank is pushing for amendments to the European Union's Markets in Crypto Assets legislation (MiCA), just months after its implementation. According to Politico's report on Tuesday, the ECB is concerned that U.S. support for cryptocurrency, particularly stablecoins, could cause economic harm to the 27-nation bloc.
- Slovenia is considering a 25% capital gains tax on Bitcoin profits for individuals. The Ministry of Finance has proposed legislation to impose this tax on gains from cryptocurrency transactions, though exchanging one cryptocurrency for another would remain exempt. At present, individual 'crypto' traders in Slovenia are not taxed.
- The Virtual Asset Service Providers (VASP) Bill 2025 introduced in Kenya. The new legislation aims to establish a comprehensive legal framework for licensing, regulating, and supervising virtual asset service providers (VASPs), with strict penalties for non-compliant entities.
- Circle, BitGo, Coinbase, and Paxos plan to apply for U.S. bank charters or licenses. According to a report in The Wall Street Journal, major crypto companies are planning to apply for U.S. bank charters or licenses. These firms are pursuing limited licenses that would permit them to issue stablecoins, as the U.S. Congress deliberates on legislation mandating licensing for stablecoin issuers.
"Established banks, like Bank of America, are hoping to amend the current drafts of [stablecoin] legislation in such a way that nonbanks are more heavily restricted from issuing stablecoins," people familiar with the matter told The Block.
- Paul Atkins has officially assumed the role of the 34th Chairman of the US Securities and Exchange Commission (SEC). This is a return to the agency for Atkins, who previously served as an SEC Commissioner from 2002 to 2008 under the George W. Bush administration. He has committed to advancing the SEC’s mission of fostering capital formation, safeguarding investors, and ensuring fair and efficient markets.
- Federal Reserve retracts guidance discouraging banks from engaging in 'crypto.' The U.S. Federal Reserve withdrew guidance that discouraged banks from crypto and stablecoin activities, as announced by its Board of Governors on Thursday. This includes rescinding a 2022 supervisory letter requiring prior notification of crypto activities and 2023 stablecoin requirements.
"As a result, the Board will no longer expect banks to provide notification and will instead monitor banks' crypto-asset activities through the normal supervisory process," reads the FED statement.
- Russian government to launch a cryptocurrency exchange. The country's Ministry of Finance and Central Bank announced plans to establish a trading platform for "highly qualified investors" that "will legalize crypto assets and bring crypto operations out of the shadows."
- Twenty One Capital is set to launch with over 42,000 BTC in its treasury. This new Bitcoin-native firm, backed by Tether and SoftBank, is planned to go public via a SPAC merger with Cantor Equity Partners and will be led by Jack Mallers, co-founder and CEO of Strike. According to a report by the Financial Times, the company aims to replicate the model of Michael Saylor with his company, MicroStrategy.
- Strategy increases Bitcoin holdings to 538,200 BTC. In the latest purchase, the company has spent more than $555M to buy 6,556 coins through proceeds of two at-the-market stock offering programs.
- Metaplanet buys another 145 BTC. The Tokyo-listed company has purchased an additional 145 BTC for $13.6 million. Their total bitcoin holdings now stand at 5,000 coins, worth around $428.1 million.
- Semler Scientific has increased its bitcoin holdings to 3,303 BTC. The company acquired an additional 111 BTC at an average price of $90,124. The purchase was funded through proceeds from an at-the-market offering and cash reserves, as stated in a press release.
- Tesla still holds nearly $1 billion in bitcoin. According to the automaker's latest earnings report, the firm reported digital asset holdings worth $951 million as of March 31.
- Spar supermarket experiments with Bitcoin payments in Zug, Switzerland. The store has introduced a new payment method powered by the Lightning Network. The implementation was facilitated by DFX Swiss, a service that supports seamless conversions between bitcoin and legacy currencies.
- Charles Schwab to launch spot Bitcoin trading by 2026. The financial investment firm, managing over $10 trillion in assets, has revealed plans to introduce spot Bitcoin trading for its clients within the next year.
- Arch Labs has secured $13 million to develop "ArchVM" and integrate smart-contract functionality with Bitcoin. The funding round, valuing the company at $200 million, was led by Pantera Capital, as announced on Tuesday.
- Citrea deployed its Clementine Bridge on the Bitcoin testnet. The bridge utilizes the BitVM2 programming language to inherit validity from Bitcoin, allegedly providing "the safest and most trust-minimized way to use BTC in decentralized finance."
- UAE-based Islamic bank ruya launches Shari’ah-compliant bitcoin investing. The bank has become the world’s first Islamic bank to provide direct access to virtual asset investments, including Bitcoin, via its mobile app, per Bitcoin Magazine.
- Solosatoshi.com has sold over 10,000 open-source miners, adding more than 10 PH of hashpower to the Bitcoin network.
"Thank you, Bitaxe community. OSMU developers, your brilliance built this. Supporters, your belief drives us. Customers, your trust powers 10,000+ miners and 10PH globally. Together, we’re decentralizing Bitcoin’s future. Last but certainly not least, thank you@skot9000 for not only creating a freedom tool, but instilling the idea into thousands of people, that Bitcoin mining can be for everyone again," said the firm on X.
- OCEAN's DATUM has found 100 blocks. "Over 65% of OCEAN’s miners are using DATUM, and that number is growing every day. This means block template construction is making its way back into the hands of the miners, which is not only the most profitable
-
 @ 04c915da:3dfbecc9
2025-05-20 15:47:16
@ 04c915da:3dfbecc9
2025-05-20 15:47:16Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ dfa02707:41ca50e3
2025-05-30 16:02:16
@ dfa02707:41ca50e3
2025-05-30 16:02:16Contribute to keep No Bullshit Bitcoin news going.
- Wasabi Wallet v2.6.0 "Prometheus" is a major update for the project, focused on resilience and independence from centralized systems.
- Key features include support for BIP 158 block filters for direct node synchronization, a revamped full node integration for easier setup without third-party reliance, SLIP 39 share backups for flexible wallet recovery (sponsored by Trezor), and a Nostr-based update manager for censorship-resistant updates.
- Additional improvements include UI bug fixes, a new fallback for transaction broadcasting, updated code signing, stricter JSON serialization, and options to avoid third-party rate providers, alongside various under-the-hood enhancements.
This new version brings us closer to our ultimate goal: ensuring Wasabi is future-proof," said the developers, while also highlighting the following key areas of focus for the project:
- Ensuring users can always fully and securely use their client.
- Making contribution and forks easy through a codebase of the highest quality possible: understandable, maintainable, and improvable.
"As we achieve our survival goals, expect more cutting-edge improvements in Bitcoin privacy and self-custody. Thank you for the trust you place in us by using Wasabi," was stated in the release notes.
What's new
- Support for Standard BIP 158 Block Filters. Wasabi now syncs using BIP 158 filters without a backend/indexer, connecting directly to a user's node. This boosts sync speed, resilience, and allows full sovereignty without specific server dependency.
- Full Node Integration Rework. The old integration has been replaced with a simpler, more adaptable system. It’s not tied to a specific Bitcoin node fork, doesn’t need the node on the same machine as Wasabi, and requires no changes to the node’s setup.
- "Simply enable the RPC server on your node and point Wasabi to it," said the developers. This ensures all Bitcoin network activities—like retrieving blocks, fee estimations, block filters, and transaction broadcasting—go through your own node, avoiding reliance on third parties.
- Create & Recover SLIP 39 Shares. Users now create and recover wallets with multiple share backups using SLIP 39 standard.
"Special thanks to Trezor (SatoshiLabs) for sponsoring this amazing feature."
- Nostr Update Manager. This version implements a pioneering system with the Nostr protocol for update information and downloads, replacing reliance on GitHub. This enhances the project's resilience, ensuring updates even if GitHub is unavailable, while still verifying updates with the project's secure certificate.
- Updated Avalonia to v11.2.7, fixes for UI bugs (including restoring Minimize on macOS Sequoia).
- Added a configurable third-party fallback for broadcasting transactions if other methods fail.
- Replaced Windows Code Signing Certificate with Azure Trusted Signing.
- Many bug fixes, improved codebase, and enhanced CI pipeline.
- Added the option to avoid using any third-party Exchange Rate and Fee Rate providers (Wasabi can work without them).
- Rebuilt all JSON Serialization mechanisms avoiding default .NET converters. Serialization is now stricter.

Full Changelog: v2.5.1...v2.6.0
-
 @ 6ad3e2a3:c90b7740
2025-05-20 13:49:50
@ 6ad3e2a3:c90b7740
2025-05-20 13:49:50I’ve written about MSTR twice already, https://www.chrisliss.com/p/mstr and https://www.chrisliss.com/p/mstr-part-2, but I want to focus on legendary short seller James Chanos’ current trade wherein he buys bitcoin (via ETF) and shorts MSTR, in essence to “be like Mike” Saylor who sells MSTR shares at the market and uses them to add bitcoin to the company’s balance sheet. After all, if it’s good enough for Saylor, why shouldn’t everyone be doing it — shorting a company whose stock price is more than 2x its bitcoin holdings and using the proceeds to buy the bitcoin itself?
Saylor himself has said selling shares at 2x NAV (net asset value) to buy bitcoin is like selling dollars for two dollars each, and Chanos has apparently decided to get in while the getting (market cap more than 2x net asset value) is good. If the price of bitcoin moons, sending MSTR’s shares up, you are more than hedged in that event, too. At least that’s the theory.
The problem with this bet against MSTR’s mNAV, i.e., you are betting MSTR’s market cap will converge 1:1 toward its NAV in the short and medium term is this trade does not exist in a vacuum. Saylor has described how his ATM’s (at the market) sales of shares are accretive in BTC per share because of this very premium they carry. Yes, we’ll dilute your shares of the company, but because we’re getting you 2x the bitcoin per share, you are getting an ever smaller slice of an ever bigger overall pie, and the pie is growing 2x faster than your slice is reducing. (I https://www.chrisliss.com/p/mstr how this works in my first post.)
But for this accretion to continue, there must be a constant supply of “greater fools” to pony up for the infinitely printable shares which contain only half their value in underlying bitcoin. Yes, those shares will continue to accrete more BTC per share, but only if there are more fools willing to make this trade in the future. So will there be a constant supply of such “fools” to keep fueling MSTR’s mNAV multiple indefinitely?
Yes, there will be in my opinion because you have to look at the trade from the prospective fools’ perspective. Those “fools” are not trading bitcoin for MSTR, they are trading their dollars, selling other equities to raise them maybe, but in the end it’s a dollars for shares trade. They are not selling bitcoin for them.
You might object that those same dollars could buy bitcoin instead, so they are surely trading the opportunity cost of buying bitcoin for them, but if only 5-10 percent of the market (or less) is buying bitcoin itself, the bucket in which which those “fools” reside is the entire non-bitcoin-buying equity market. (And this is not considering the even larger debt market which Saylor has yet to tap in earnest.)
So for those 90-95 percent who do not and are not presently planning to own bitcoin itself, is buying MSTR a fool’s errand, so to speak? Not remotely. If MSTR shares are infinitely printable ATM, they are still less so than the dollar and other fiat currencies. And MSTR shares are backed 2:1 by bitcoin itself, while the fiat currencies are backed by absolutely nothing. So if you hold dollars or euros, trading them for MSTR shares is an errand more sage than foolish.
That’s why this trade (buying BTC and shorting MSTR) is so dangerous. Not only are there many people who won’t buy BTC buying MSTR, there are many funds and other investment entities who are only able to buy MSTR.
Do you want to get BTC at 1:1 with the 5-10 percent or MSTR backed 2:1 with the 90-95 percent. This is a bit like medical tests that have a 95 percent accuracy rate for an asymptomatic disease that only one percent of the population has. If someone tests positive, it’s more likely to be a false one than an indication he has the disease*. The accuracy rate, even at 19:1, is subservient to the size of the respective populations.
At some point this will no longer be the case, but so long as the understanding of bitcoin is not widespread, so long as the dollar is still the unit of account, the “greater fools” buying MSTR are still miles ahead of the greatest fools buying neither, and the stock price and mNAV should only increase.
. . .
One other thought: it’s more work to play defense than offense because the person on offense knows where he’s going, and the defender can only react to him once he moves. Similarly, Saylor by virtue of being the issuer of the shares knows when more will come online while Chanos and other short sellers are borrowing them to sell in reaction to Saylor’s strategy. At any given moment, Saylor can pause anytime, choosing to issue convertible debt or preferred shares with which to buy more bitcoin, and the shorts will not be given advance notice.
If the price runs, and there is no ATM that week because Saylor has stopped on a dime, so to speak, the shorts will be left having to scramble to change directions and buy the shares back to cover. Their momentum might be in the wrong direction, though, and like Allen Iverson breaking ankles with a crossover, Saylor might trigger a massive short squeeze, rocketing the share price ever higher. That’s why he actually welcomes Chanos et al trying this copycat strategy — it becomes the fuel for outsized gains.
For that reason, news that Chanos is shorting MSTR has not shaken my conviction, though there are other more pertinent https://www.chrisliss.com/p/mstr-part-2 with MSTR, of which one should be aware. And as always, do your own due diligence before investing in anything.
* To understand this, consider a population of 100,000, with one percent having a disease. That means 1,000 have it, 99,000 do not. If the test is 95 percent accurate, and everyone is tested, 950 of the 1,000 will test positive (true positives), 50 who have it will test negative (false negatives.) Of the positives, 95 percent of 99,000 (94,050) will test negative (true negatives) and five percent (4,950) will test positive (false positives). That means 4,950 out of 5,900 positives (84%) will be false.
-
 @ 3f770d65:7a745b24
2025-05-19 18:09:52
@ 3f770d65:7a745b24
2025-05-19 18:09:52🏌️ Monday, May 26 – Bitcoin Golf Championship & Kickoff Party
Location: Las Vegas, Nevada\ Event: 2nd Annual Bitcoin Golf Championship & Kick Off Party"\ Where: Bali Hai Golf Clubhouse, 5160 S Las Vegas Blvd, Las Vegas, NV 89119\ 🎟️ Get Tickets!
Details:
-
The week tees off in style with the Bitcoin Golf Championship. Swing clubs by day and swing to music by night.
-
Live performances from Nostr-powered acts courtesy of Tunestr, including Ainsley Costello and others.
-
Stop by the Purple Pill Booth hosted by Derek and Tanja, who will be on-boarding golfers and attendees to the decentralized social future with Nostr.
💬 May 27–29 – Bitcoin 2025 Conference at the Las Vegas Convention Center
Location: The Venetian Resort\ Main Attraction for Nostr Fans: The Nostr Lounge\ When: All day, Tuesday through Thursday\ Where: Right outside the Open Source Stage\ 🎟️ Get Tickets!
Come chill at the Nostr Lounge, your home base for all things decentralized social. With seating for \~50, comfy couches, high-tops, and good vibes, it’s the perfect space to meet developers, community leaders, and curious newcomers building the future of censorship-resistant communication.
Bonus: Right across the aisle, you’ll find Shopstr, a decentralized marketplace app built on Nostr. Stop by their booth to explore how peer-to-peer commerce works in a truly open ecosystem.
Daily Highlights at the Lounge:
-
☕️ Hang out casually or sit down for a deeper conversation about the Nostr protocol
-
🔧 1:1 demos from app teams
-
🛍️ Merch available onsite
-
🧠 Impromptu lightning talks
-
🎤 Scheduled Meetups (details below)
🎯 Nostr Lounge Meetups
Wednesday, May 28 @ 1:00 PM
- Damus Meetup: Come meet the team behind Damus, the OG Nostr app for iOS that helped kickstart the social revolution. They'll also be showcasing their new cross-platform app, Notedeck, designed for a more unified Nostr experience across devices. Grab some merch, get a demo, and connect directly with the developers.
Thursday, May 29 @ 1:00 PM
- Primal Meetup: Dive into Primal, the slickest Nostr experience available on web, Android, and iOS. With a built-in wallet, zapping your favorite creators and friends has never been easier. The team will be on-site for hands-on demos, Q\&A, merch giveaways, and deeper discussions on building the social layer of Bitcoin.
🎙️ Nostr Talks at Bitcoin 2025
If you want to hear from the minds building decentralized social, make sure you attend these two official conference sessions:
1. FROSTR Workshop: Multisig Nostr Signing
-
🕚 Time: 11:30 AM – 12:00 PM
-
📅 Date: Wednesday, May 28
-
📍 Location: Developer Zone
-
🎤 Speaker: nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgdwaehxw309ahx7uewd3hkcqpqs9etjgzjglwlaxdhsveq0qksxyh6xpdpn8ajh69ruetrug957r3qf4ggfm (Austin Kelsay) @ Voltage\ A deep-dive into FROST-based multisig key management for Nostr. Geared toward devs and power users interested in key security.
2. Panel: Decentralizing Social Media
-
🕑 Time: 2:00 PM – 2:30 PM
-
📅 Date: Thursday, May 29
-
📍 Location: Genesis Stage
-
🎙️ Moderator: nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqy08wumn8ghj7mn0wd68yttjv4kxz7fwv3jhyettwfhhxuewd4jsqgxnqajr23msx5malhhcz8paa2t0r70gfjpyncsqx56ztyj2nyyvlq00heps - Bitcoin Strategy @ Roxom TV
-
👥 Speakers:
-
nostr:nprofile1qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcppemhxue69uhkummn9ekx7mp0qqsy2ga7trfetvd3j65m3jptqw9k39wtq2mg85xz2w542p5dhg06e5qmhlpep – Early Bitcoin dev, CEO @ Sirius Business Ltd
-
nostr:nprofile1qy2hwumn8ghj7mn0wd68ytndv9kxjm3wdahxcqg5waehxw309ahx7um5wfekzarkvyhxuet5qqsw4v882mfjhq9u63j08kzyhqzqxqc8tgf740p4nxnk9jdv02u37ncdhu7e3 – Analyst & Partner @ Ego Death Capital
Get the big-picture perspective on why decentralized social matters and how Nostr fits into the future of digital communication.
🌃 NOS VEGAS Meetup & Afterparty
Date: Wednesday, May 28\ Time: 7:00 PM – 1:00 AM\ Location: We All Scream Nightclub, 517 Fremont St., Las Vegas, NV 89101\ 🎟️ Get Tickets!
What to Expect:
-
🎶 Live Music Stage – Featuring Ainsley Costello, Sara Jade, Able James, Martin Groom, Bobby Shell, Jessie Lark, and other V4V artists
-
🪩 DJ Party Deck – With sets by nostr:nprofile1qy0hwumn8ghj7cmgdae82uewd45kketyd9kxwetj9e3k7mf6xs6rgqgcwaehxw309ahx7um5wgh85mm694ek2unk9ehhyecqyq7hpmq75krx2zsywntgtpz5yzwjyg2c7sreardcqmcp0m67xrnkwylzzk4 , nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgkwaehxw309anx2etywvhxummnw3ezucnpdejqqg967faye3x6fxgnul77ej23l5aew8yj0x2e4a3tq2mkrgzrcvecfsk8xlu3 , and more DJs throwing down
-
🛰️ Live-streamed via Tunestr
-
🧠 Nostr Education – Talks by nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq37amnwvaz7tmwdaehgu3dwfjkccte9ejx2un9ddex7umn9ekk2tcqyqlhwrt96wnkf2w9edgr4cfruchvwkv26q6asdhz4qg08pm6w3djg3c8m4j , nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqg7waehxw309anx2etywvhxummnw3ezucnpdejz7ur0wp6kcctjqqspywh6ulgc0w3k6mwum97m7jkvtxh0lcjr77p9jtlc7f0d27wlxpslwvhau , nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq3vamnwvaz7tmwdaehgu3wd33xgetk9en82m30qqsgqke57uygxl0m8elstq26c4mq2erz3dvdtgxwswwvhdh0xcs04sc4u9p7d , nostr:nprofile1q9z8wumn8ghj7erzx3jkvmmzw4eny6tvw368wdt8da4kxamrdvek76mrwg6rwdngw94k67t3v36k77tev3kx7vn2xa5kjem9dp4hjepwd3hkxctvqyg8wumn8ghj7mn0wd68ytnhd9hx2qpqyaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgssuy4zk , nostr:nprofile1qy28wue69uhnzvpwxqhrqt33xgmn5dfsx5cqz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqqswavgevxe9gs43vwylumr7h656mu9vxmw4j6qkafc3nefphzpph8ssvcgf8 , and more.
-
🧾 Vendors & Project Booths – Explore new tools and services
-
🔐 Onboarding Stations – Learn how to use Nostr hands-on
-
🐦 Nostrich Flocking – Meet your favorite nyms IRL
-
🍸 Three Full Bars – Two floors of socializing overlooking vibrant Fremont Street
| | | | | ----------- | -------------------- | ------------------- | | Time | Name | Topic | | 7:30-7:50 | Derek | Nostr for Beginners | | 8:00-8:20 | Mark & Paul | Primal | | 8:30-8:50 | Terry | Damus | | 9:00-9:20 | OpenMike and Ainsley | V4V | | 09:30-09:50 | The Space | Space |
This is the after-party of the year for those who love freedom technology and decentralized social community. Don’t miss it.
Final Thoughts
Whether you're there to learn, network, party, or build, Bitcoin 2025 in Las Vegas has a packed week of Nostr-friendly programming. Be sure to catch all the events, visit the Nostr Lounge, and experience the growing decentralized social revolution.
🟣 Find us. Flock with us. Purple pill someone.
-
-
 @ dfa02707:41ca50e3
2025-05-30 16:02:16
@ dfa02707:41ca50e3
2025-05-30 16:02:16Contribute to keep No Bullshit Bitcoin news going.
- RoboSats v0.7.7-alpha is now available!
NOTE: "This version of clients is not compatible with older versions of coordinators. Coordinators must upgrade first, make sure you don't upgrade your client while this is marked as pre-release."
- This version brings a new and improved coordinators view with reviews signed both by the robot and the coordinator, adds market price sources in coordinator profiles, shows a correct warning for canceling non-taken orders after a payment attempt, adds Uzbek sum currency, and includes package library updates for coordinators.

Source: RoboSats.
- siggy47 is writing daily RoboSats activity reviews on stacker.news. Check them out here.
- Stay up-to-date with RoboSats on Nostr.
What's new
- New coordinators view (see the picture above).
- Available coordinator reviews signed by both the robot and the coordinator.
- Coordinators now display market price sources in their profiles.

Source: RoboSats.
- Fix for wrong message on cancel button when taking an order. Users are now warned if they try to cancel a non taken order after a payment attempt.
- Uzbek sum currency now available.
- For coordinators: library updates.
- Add docker frontend (#1861).
- Add order review token (#1869).
- Add UZS migration (#1875).
- Fixed tests review (#1878).
- Nostr pubkey for Robot (#1887).
New contributors

Full Changelog: v0.7.6-alpha...v0.7.7-alpha
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:51:46
@ 21c71bfa:e28fa0f6
2025-05-29 14:51:46Book *Tirupati to Vellore cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 8bad92c3:ca714aa5
2025-05-30 16:02:08
@ 8bad92c3:ca714aa5
2025-05-30 16:02:08Key Takeaways

In this episode of TFTC, Jessy Gilger, Managing Partner at Sound Advisory and architect of Ganet Trust, unpacks the complexities of retiring on Bitcoin, emphasizing that the “right” amount depends on spending habits, age, and minimizing withdrawal pressure. He introduces Ganet Trust as a Bitcoin-native fiduciary solution that leverages multisig custody to meet institutional compliance standards without sacrificing decentralization. Jessy also critiques high-yield derivative products like MSTY, warning of systemic risks and advocating for safer alternatives like SMAs. The conversation broadens into the emotional pitfalls of financial decision-making, the importance of aligning wealth with values, and the evolving macro landscape where Bitcoin’s intersection with traditional finance and tax policy will shape how individuals and institutions protect and grow their holdings across generations.
Best Quotes
"The most comfort comes from putting as little pressure as possible against that stack."
"Multisig is the upgrade from a honeypot to a distributed key setup."
"If a whale pees in the pool, everyone is affected."
"Everyone feels late to Bitcoin because they know someone who got in earlier."
"Stacking Saturdays is my new stack sats."
"Bitcoin doesn’t know about trust, it knows private keys."
"The money is there to serve your values—not the other way around."
"Some financial products will help, some will hurt, and some will fail. Our job is to help clients navigate them safely."
Conclusion
This episode offers a powerful blend of practical insight and philosophical reflection on long-term Bitcoin strategy, emphasizing the need for sound custody, inheritance planning, and emotional discipline in a volatile, financialized world. Jessy Gilger introduces Ganet Trust as a vital solution for secure, compliant Bitcoin ownership, while his “stacking Saturdays” mantra reframes wealth as a pursuit of time, freedom, and meaningful priorities. As Bitcoin moves further into the mainstream, the conversation urges listeners to stay grounded, think generationally, and build resilient systems for both assets and life.
Timestamps
00:00 - Intro
0:33 - Bitcoin Retirement Planning at New All-Time Highs
5:22 - How Gannett Trust Works
10:05 - High Net Worth Bitcoin Storage and Estate Planning Solutions
16:48 - MSTY Derivatives: Understanding MicroStrategy Product Risks
19:53 - Bitkey
20:56 - How MSTY Works and the Whale in the Pool Problem
30:16 - Unchained
30:37 - Bitcoin Financialization and Corporate Treasury Strategy
39:35 - Avoiding Ego-Driven Bitcoin Mistakes and Building Bridges
47:33 - Stack Saturdays
53:15 - Tax Policy Changes and Wild Times Ahead
57:18 - Where to Find Gannett Trust and ClosingTranscript
(00:00) We have people retiring with hundreds of Bitcoin. Do you need to be on a yacht every week or are you staying humble and keeping those stats? 10 of the 12 ETFs are at Coinbase means all the keys are at Coinbase and with the news of the last week like, hey, there could be cracks. Micro Strategy is built on Bitcoin.
(00:18) It's got all of the risks of Bitcoin, right? But then it's got its own set of risks. Let's call them Sailor and Profitability. Then you have derivatives which are on top of Micro Strategy and they retain the risks of everything underneath. meeting on a on a day when we hit new all-time highs. Bitcoin approached $110,000.
(00:43) Got Jesse back on the show to talk about many things, not just the price ripping. A lot of good things happening on the unch unchained side of things. Watching Ganet Trust. We'll get into it. Yeah, lot lots of stuff happening. I think um the price likes Ganet. I I think that's the uh the mover. What uh I mean that's been a big discussion in in the space right now is uh are we heading to new all-time highs? How should Bitcoiners be preparing? How much Bitcoin do people need to retire? How how are you thinking about all this as we approach what seems
(01:22) to be another bull cycle? Yeah, that's a common question, right? How much Bitcoin do I need to retire? I get it a lot and there's so many other questions I want to ask like, well, how much money are you spending, right? Do you do you need to be on a yacht every week or are you staying humble and keeping those stats? And so, the amount of Bitcoin can vary because the spending pressure you're putting against your Bitcoin stack is the the biggest factor, right? And age is probably the second.
(01:54) a 30-year-old retiring on Bitcoin is different than a 75year-old retiring on Bitcoin just because of the horizon. So, stacks vary. We've got people retiring with um less than seven figures of Bitcoin because they have other assets and then we have people retiring with hundreds of Bitcoin um and putting very little pressure against that portfolio.
(02:16) So, can go in a lot of different ways. Um but it is a question of the day as you're poking new all-time highs. Everyone's like, "Well, how high is it going to get?" And then huge question is do we have cycles again right if countries are buying what what would a downside look like and that's the big question in the retirees mind is how do I protect and not ride that downside all the way down if we do have another 70 80% drawback. Yeah. No.
(02:42) And I think particularly for younger people having in their mind like the perspective of 21 million Bitcoin, 8 billion people, what's the stat? 60 million millionaires in the world. Mhm. How much how many stats do I need to get to to feel comfortable that I have a sufficient slice of the Bitcoin pie? That feel comfortable concept is just so different, right? because Bitcoin is moving and shaking and all-time highs or down 30% and that's still within a bull market.
(03:15) Is that comfortable, right? Can you actually hang it up and like, all right, not going into work and I'm just going to continue to ride these adoption cycles. I don't know if it ever gets comfortable. The most comfort comes from putting as little pressure as possible against that stack, right? that you're not pushing these withdrawal rates of like 5 10 20% of my Bitcoin stack.
(03:38) I'm needing to live on every because then you're requiring Bitcoin to do something for you in the short term which is just not great at, right? What what's Bitcoin price going to be in a year? Far less reliable than what's Bitcoin price going to be in 30 years. Yeah. Yeah. Yeah. Well, I I think one of the holdups too is the ability for people to get into Bitcoin and know where to put it and not only have certainty of what it will be valued at in 30 years, but will they have access to it? That's one thing that you guys
(04:10) have been very much focused. I know sound advisory is separate from Unchained technically but within the Unchained umbrella but Unchained focused on helping secure individuals and businesses and trust uh Bitcoin and I think today's announcement of Ganet Trust is a massive step in a direction towards more certainty for long-term holdings for particular entities.
(04:36) Yes, the unchained umbrella or or family of companies is growing and the intention will be for sound advisory to tuck under or be merged into folded into Ganet Trust Company as it gets stood up. But it is the most robust uh compliance offering that um is out there in the fiduciary space. And so that in my opinion was the one thing missing as people want to live on a Bitcoin standard.
(05:04) Sometimes they're in an entity or an organization or have a structure that requires a fiduciary standard. And these two coming together is solved by Ganet Trust Company. So it's going to be the most robust way to hold Bitcoin and have like true inheritance that can be um administered through generations. So how how does this work mechanically via Ganet? Mechanically.
(05:28) So as the first Bitcoin native trust company, other other trust companies do exist, right? but they don't build upon Bitcoin in the way that Unchained has. So Ganet in its um in its Unchained roots and using Unchained technology is going to be able to use multi-IG to achieve um trust company goals.
(05:50) And what that likely will mean is Ganet holding a key, Unchained holding a key, third party holding a key. Those three keys together ensure that the Bitcoin is not being held at any one spot, right? We could get into the Coinbase honeypot. We actually talked about this on our last episode like, "Hey, what do you think is the uh the risk out there that the industry might disagree with?" Said, "I'm launching a new segment.
(06:15) I'm going to ask you a prediction of what what's out there that the uh the industry doesn't see eye to eye with you at." And I was at conferences and they're saying, "Hey, Coinbase is the best. That's where we put all the cut." That means all the keys are at Coinbase and with the news of the last week like, hey, there could be cracks, right? If you've got exposure to Coinbase now, you could be questioning. I was on the list.
(06:37) I got the email. You were affected. That's not great. It doesn't feel good knowing that information that information could have been a lot worse. That headline could have been private keys being mismanaged. When you overlay what Ganet is going to offer to the custody space, it means that not all of the keys are going to be at any one entity.
(07:00) And so that gives the Bitcoiner who understands multisig the confidence that okay, I'm upgrading from a honeypot to a distributed key setup. But it has to be done in a fiduciary and compliant way to satisfy the the institutional and big money of the world, right? family offices, uh, Bitcoin treasury companies, they're going to need a structure that the CIO, the -
 @ dfa02707:41ca50e3
2025-05-30 16:02:16
@ dfa02707:41ca50e3
2025-05-30 16:02:16Contribute to keep No Bullshit Bitcoin news going.
- "Today we're launching the beta version of our multiplatform Nostr browser! Think Google Chrome but for Nostr apps. The beta is our big first step toward this vision," announced Damus.
- This version comes with the Dave Nostr AI assistant, support for zaps and the Nostr Wallet Connect (NWC) wallet interface, full-text note search, GIFs and fullscreen images, multiple media uploads, user tagging, relay list and mute list support, along with a number of other improvements."
"Included in the beta is the Dave, the Nostr AI assistant (its Grok for Nostr). Dave is a new Notedeck browser app that can search and summarize notes from the network. For a full breakdown of everything new, check out our beta launch video."
What's new
- Dave Nostr AI assistant app.
- GIFs.
- Fulltext note search.
- Add full screen images, add zoom, and pan.
- Zaps! NWC/ Wallet UI.
- Introduce last note per pubkey feed (experimental).
- Allow multiple media uploads per selection.
- Major Android improvements (still WIP).
- Added notedeck app sidebar.
- User Tagging.
- Note truncation.
- Local network note broadcast, broadcast notes to other notedeck notes while you're offline.
- Mute list support (reading).
- Relay list support.
- Ctrl-enter to send notes.
- Added relay indexing (relay columns soon).
- Click hashtags to open hashtag timeline.
- Fixed timelines sometimes not updating (stale feeds).
- Fixed UI bounciness when loading profile pictures
- Fixed unselectable post replies.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:51:23
@ 21c71bfa:e28fa0f6
2025-05-29 14:51:23Book *Tirupati to Tirumala cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ dfa02707:41ca50e3
2025-05-30 16:02:15
@ dfa02707:41ca50e3
2025-05-30 16:02:15News
- Wallet of Satoshi teases a comeback in the US market with a non-custodial product. According to an announcement on X, the widely popular custodial Lightning wallet is preparing to re-enter the United States market with a non-custodial wallet. It is unclear whether the product will be open-source, but the project has clarified that "there will be no KYC on any Wallet of Satoshi, ever!" Wallet of Satoshi ceased serving customers in the United States in November 2023.
- Vulnerability disclosure: Remote crash due to addr message spam in Bitcoin Core versions before v29. Bitcoin Core developer Antoine Poinsot disclosed an integer overflow bug that crashes a node if spammed with addr messages over an extended period. A fix was released on April 14, 2025, in Bitcoin Core v29.0. The issue is rated Low severity.
- Coinbase Know Your Customer (KYC) data leak. The U.S. Department of Justice, including its Criminal Division in Washington, is investigating a cyberattack on Coinbase. The incident involved cybercriminals attempting to extort $20 million from Coinbase to prevent stolen customer data from being leaked online. Although the data breach affected less than 1% of the exchange's users, Coinbase now faces at least six lawsuits following the revelation that some customer support agents were bribed as part of the extortion scheme.
- Fold has launched Bitcoin Gift Cards, enabling users to purchase bitcoin for personal use or as gifts, redeemable via the Fold app. These cards are currently available on Fold’s website and are planned to expand to major retailers nationwide later this year.
"Our mission is to make bitcoin simple and approachable for everyone. The Bitcoin Gift Card brings bitcoin to millions of Americans in a familiar way. Available at the places people already shop, the Bitcoin Gift Card is the best way to gift bitcoin to others," said Will Reeves, Chairman and CEO of Fold.
- Corporate treasuries hold nearly 1.1 million BTC, representing about 5.5% of the total circulating supply (1,082,164 BTC), per BitcoinTreasuries.net data. Recent purchases include Strategy adding 7,390 BTC (total: 576,230 BTC), Metplanet acquiring 1,004 BTC (total: 7,800 BTC), Tether holding over 100,521 BTC, and XXI Capital, led by Jack Mallers, starting with 31,500 BTC.
- Meanwhile, a group of investors has filed a class action lawsuit against Strategy and its executive Michael Saylor. The lawsuit alleges that Strategy made overly optimistic projections using fair value accounting under new FASB rules while downplaying potential losses.
- The U.S. Senate voted to advance the GENIUS stablecoin bill for further debate before a final vote to pass it. Meanwhile, the House is crafting its own stablecoin legislation to establish a regulatory framework for stablecoins and their issuers in the U.S, reports CoinDesk.
- French 'crypto' entrepreneurs get priority access to emergency police services. French Minister of the Interior, Bruno Retailleau, agreed on measures to enhance security for 'crypto' professionals during a meeting on Friday. This follows a failed kidnapping attempt on Tuesday targeting the family of a cryptocurrency exchange CEO, and two other kidnappings earlier this year.
- Brussels Court declares tracking-based ads illegal in EU. The Brussels Court of Appeal ruled tracking-based online ads illegal in the EU due to an inadequate consent model. Major tech firms like Microsoft, Amazon, Google, and X are affected by the decision, as their consent pop-ups fail to protect privacy in real-time bidding, writes The Record.
- Telegram shares data on 22,777 users in Q1 2025, a significant increase from the 5,826 users' data shared during the same period in 2024. This significant increase follows the arrest of CEO and founder Pavel Durov last year.
- An Australian judge has ruled that Bitcoin is money, potentially exempting it from capital gains tax in the country. If upheld on appeal, this interim decision could lead to taxpayer refunds worth up to $1 billion, per tax lawyer Adrian Cartland.
Use the tools
- Bitcoin Safe v1.3.0 a secure and user-friendly Bitcoin savings wallet for beginners and advanced users, introduces an interactive chart, Child Pays For Parent (CPFP) support, testnet4 compatibility, preconfigured testnet demo wallets, various bug fixes, and other improvements.
- BlueWallet v7.1.8 brings numerous bug fixes, dependency updates, and a new search feature for addresses and transactions.
- Aqua Wallet v0.3.0 is out, offering beta testing for the reloadable Dolphin card (in partnership with Visa) for spending bitcoin and Liquid BTC. It also includes a new Optical Character Recognition (OCR) text scanner to read text addresses like QR codes, colored numbers on addresses for better readability, a reduced minimum for spending and swapping Liquid Bitcoin to 100 sats, plus other fixes and enhancements.

Source: Aqua wallet.
- The latest firmware updates for COLDCARD Mk4 v5.4.3 and Q v1.3.3 are now available, featuring the latest enhancements and bug fixes.
- Nunchuk Android v1.9.68.1 and iOS v1.9.79 introduce support for custom blockchain explorers, wallet archiving, re-ordering wallets on the home screen via long-press, and an anti-fee sniping setting.
- BDK-cli v1.0.0, a CLI wallet library and REPL tool to demo and test the BDK library, now uses bdk_wallet 1.0.0 and integrates Kyoto, utilizing the Kyoto protocol for compact block filters. It sets SQLite as the default database and discontinues support for sled.
- publsp is a new command-line tool designed for Lightning node runners or Lightning Service Providers (LSPs) to advertise liquidity offers over Nostr.
"LSPs advertise liquidity as addressable Kind 39735 events. Clients just pull and evaluate all those structured events, then NIP-17 DM an LSP of their choice to coordinate a liquidity purchase," writes developer smallworlnd.
-
Lightning Blinder by Super Testnet is a proof-of-concept privacy tool for the Lightning Network. It enables users to mislead Lightning Service Providers (LSPs) by making it appear as though one wallet is the sender or recipient, masking the original wallet. Explore and try it out here.
-
Mempal v1.5.3, a Bitcoin mempool monitoring and notification app for Android, now includes a swipe-down feature to refresh the dashboard, a custom time option for widget auto-update frequency, and a
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:51:04
@ 21c71bfa:e28fa0f6
2025-05-29 14:51:04Book *Bhubaneswar to Konark cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ dfa02707:41ca50e3
2025-05-30 16:02:15
@ dfa02707:41ca50e3
2025-05-30 16:02:15Contribute to keep No Bullshit Bitcoin news going.
-
Version 1.3 of Bitcoin Safe introduces a redesigned interactive chart, quick receive feature, updated icons, a mempool preview window, support for Child Pays For Parent (CPFP) and testnet4, preconfigured testnet demo wallets, as well as various bug fixes and improvements.
-
Upcoming updates for Bitcoin Safe include Compact Block Filters.
"Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions. They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK," writes the project's developer Andreas Griffin.
- Learn more about the current and upcoming features of Bitcoin Safe wallet here.
What's new in v1.3
- Redesign of Chart, Quick Receive, Icons, and Mempool Preview (by @design-rrr).
- Interactive chart. Clicking on it now jumps to transaction, and selected transactions are now highlighted.

- Speed up transactions with Child Pays For Parent (CPFP).
- BDK 1.2 (upgraded from 0.32).
- Testnet4 support.
- Preconfigured Testnet demo wallets.
- Cluster unconfirmed transactions so that parents/children are next to each other.
- Customizable columns for all tables (optional view: Txid, Address index, and more)
- Bug fixes and other improvements.

Announcement / Archive
Blog Post / Archive
GitHub Repo
Website -
-
 @ 9ca447d2:fbf5a36d
2025-05-30 16:01:48
@ 9ca447d2:fbf5a36d
2025-05-30 16:01:48DDC Enterprise, a consumer brand and e-commerce company with operations in the U.S. and China, has launched a big plan to make bitcoin (BTC) a key part of its financial strategy.
The company just bought 21 BTC as the first step in a plan to buy up to 5,000 BTC over the next 3 years.
The move was announced in a press release and a letter to shareholders by DDC’s founder, chairwoman and CEO Norma Chu.
The 21 BTC, worth around $2.28 million at current prices, was bought through a share exchange. DDC issued 254,333 class A ordinary shares.
“We are fully committed to ensuring the success of this strategy, which aligns with our vision to drive long-term value for our shareholders,” said Norma Chu. “Today marks a pivotal moment in DDC’s evolution.”
Chu is the first female founder and CEO of a U.S.-listed public company to lead a bitcoin-only treasury strategy. DDC is one of the first companies in its industry to adopt this strategy in such a structured way.
DDC’s plan is being rolled out in phases. The company will buy another 79 BTC soon and will have 100 BTC in the short term.
In the next 6 months, it will buy 500 BTC, and long-term, it expects to build a 5,000 BTC reserve over 36 months.
This phased approach may allow DDC to manage market volatility and take advantage of price movements.
In her recent letter to shareholders, Chu called the bitcoin strategy “a cornerstone of our long-term value creation plan”.
She said bitcoin’s qualities – especially as a hedge against macroeconomic uncertainty and inflation – make it the perfect reserve asset for DDC. She added:
“Bitcoin’s unique properties as a store of value and hedge against macroeconomic uncertainty align perfectly with our vision to diversify reserves and enhance shareholder returns.”
The announcement comes on the back of a record-breaking year for DDC.
In 2024, the company made $37.4 million in revenue—a 33% increase from 2023.
Gross margin improved from 25.0% in 2023 to 28.4% in 2024 due to strategic acquisitions in the U.S. and more efficient operations in China.
As of March 31, 2025 the company had $11.3 million in shareholder equity and $23.6 million in cash, cash equivalents and short-term investments.
This gives DDC the flexibility and credibility to do something as bold as this bitcoin accumulation plan.
DDC’s announcement comes as corporations are getting increasingly interested in adding bitcoin to their balance sheet.
While giants like Strategy have made headlines with large bitcoin purchases, DDC is the first e-commerce company to do so.
The company’s dual presence in China and the U.S. also adds complexity, especially with the different regulatory environments surrounding Bitcoin in each region.
To ensure proper execution, DDC has expanded its treasury and advisory teams to include experts in the bitcoin markets.
The company will use a mix of dollar cost averaging and tactical buying, adjusting purchases based on market conditions.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:50:44
@ 21c71bfa:e28fa0f6
2025-05-29 14:50:44Book *Mcleodganj to Amritsar cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:50:23
@ 21c71bfa:e28fa0f6
2025-05-29 14:50:23Book *Manali to Amritsar cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ dfa02707:41ca50e3
2025-05-30 16:02:15
@ dfa02707:41ca50e3
2025-05-30 16:02:15Contribute to keep No Bullshit Bitcoin news going.
- This release introduces Payjoin v2 functionality to Bitcoin wallets on Cake, along with several UI/UX improvements and bug fixes.
- The Payjoin v2 protocol enables asynchronous, serverless coordination between sender and receiver, removing the need to be online simultaneously or maintain a server. This simplifies privacy-focused transactions for regular users.
"I cannot speak highly enough of how amazing it has been to work with @bitgould and Jaad from the@payjoindevkit team, they're doing incredible work. None of this would be possible without them and their tireless efforts. PDK made it so much easier to ship Payjoin v2 than it would have been otherwise, and I can't wait to see other wallets jump in and give back to PDK as they implement it like we did," said Seth For Privacy, VP at Cake Wallet.

How to started with Payjoin in Cake Wallet:
- Open the app menu sidebar and click
Privacy. - Toggle the
Use Payjoinoption. - Now on your receive screen you'll see an option to copy a Payjoin URL
- Bull Bitcoin Wallet v0.4.0 introduced Payjoin v2 support in late December 2024. However, the current implementations are not interoperable at the moment, an issue that should be addressed in the next release of the Bull Bitcoin Wallet.
- Cake Wallet was one of the first wallets to introduce Silent Payments back in May 2024. However, users may encounter sync issues while using this feature at present, which will be resolved in the next release of Cake Wallet.
What's new
- Payjoin v2 implementation.
- Wallet group improvements: Enhanced management of multiple wallets.
- Various bug fixes: improving overall stability and user experience.
- Monero (XMR) enhancements.
Learn more about using, implementing, and understanding BIP 77: Payjoin Version 2 using the
payjoincrate in Payjoin Dev Kit here. -
 @ b1ddb4d7:471244e7
2025-05-30 16:01:37
@ b1ddb4d7:471244e7
2025-05-30 16:01:37Custodial Lightning wallets allow users to transact without managing private keys or channel liquidity. The provider handles technical complexities, but this convenience comes with critical trade-offs:
- You don’t control your keys: The custodian holds your bitcoin.
- Centralized points of failure: Servers can be hacked or shut down.
- Surveillance risks: Providers track transaction metadata.
Key Risks of Custodial Lightning Wallets
*1. Hacks and Exit Scams*
Custodians centralize large amounts of bitcoin, attracting hackers:
- Nearly $2.2 billion worth of funds were stolen from hacks in 2024.
- Lightning custodians suffered breaches, losing user funds.
Unlike non-custodial wallets, victims have no recourse since they don’t hold keys.
*2. Censorship and Account Freezes*
Custodians comply with regulators, risking fund seizures:
- Strike (a custodial Lightning app) froze accounts of users in sanctioned regions.
- A U.K. court in 2020 ordered Bitfinex to freeze bitcoin worth $860,000 after the exchange and blockchain sleuthing firm Chainalysis traced the funds to a ransomware payment.
*3. Privacy Erosion*
Custodians log user activity, exposing sensitive data:
- Transaction amounts, receiver addresses, and IPs are recorded.
*4. Service Downtime*
Centralized infrastructure risks outages.
*5. Inflation of Lightning Network Centralization*
Custodians dominate liquidity, weakening network resilience:
- At the moment, 10% of the nodes on Lightning control 80% of the liquidity.
- This centralization contradicts bitcoin’s decentralized ethos.
How to Switch to Self-Custodial Lightning Wallets
Migrating from custodial services is straightforward:
*1. Choose a Non-Custodial Wallet*
Opt for wallets that let you control keys and channels:
- Flash: The self-custodial tool that lets you own your keys, control your coins, and transact instantly.
- Breez Wallet : Non-custodial, POS integrations.
- Core Lightning : Advanced, for self-hosted node operators.
*2. Transfer Funds Securely*
- Withdraw funds from your custodial wallet to a bitcoin on-chain address.
- Send bitcoin to your non-custodial Lightning wallet.
*3. Set Up Channel Backups*
Use tools like Static Channel Backups (SCB) to recover channels if needed.
*4. Best Practices*
- Enable Tor: Mask your IP (e.g., Breez’s built-in Tor support).
- Verify Receiving Addresses: Avoid phishing scams.
- Regularly Rebalance Channels: Use tools like Lightning Pool for liquidity.
Why Self-Custodial Lightning Matters
- Self-custody: Control your keys and funds.
- Censorship resistance: No third party can block transactions.
- Network health: Decentralized liquidity strengthens Lightning.
Self-custodial wallets now rival custodial ease.
Custodial Lightning wallets sacrifice security for convenience, putting users at risk of hacks, surveillance, and frozen funds. As bitcoin adoption grows, so does the urgency to embrace self-custodial solutions.
Take action today:
- Withdraw custodial funds to a hardware wallet.
- Migrate to a self-custodial Lightning wallet.
- Educate others on the risks of custodial control.
The Lightning Network’s potential hinges on decentralization—don’t let custodians become its Achilles’ heel.
-
 @ dfa02707:41ca50e3
2025-05-30 16:02:14
@ dfa02707:41ca50e3
2025-05-30 16:02:14Contribute to keep No Bullshit Bitcoin news going.
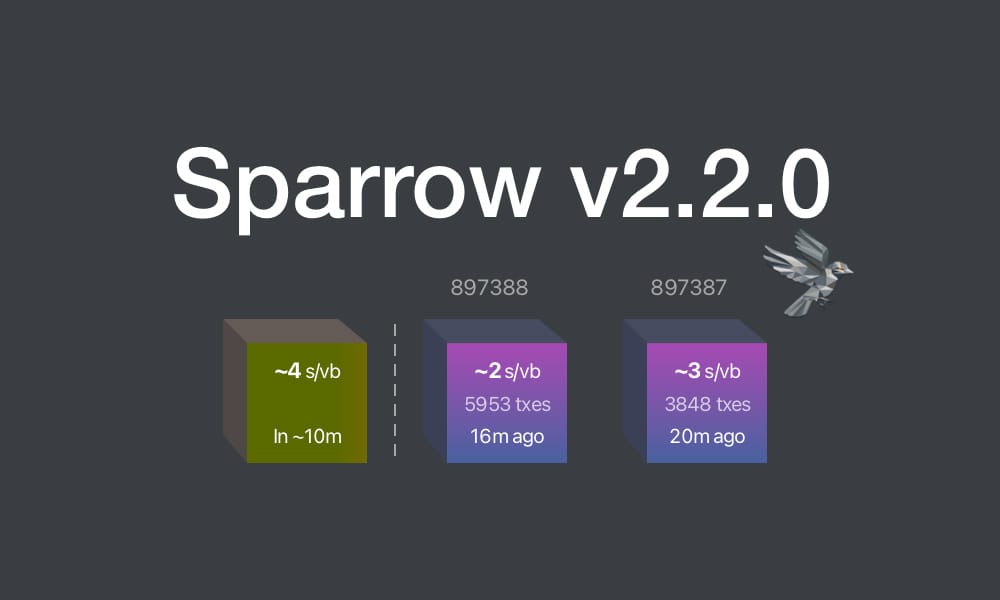
This update brings key enhancements for clarity and usability:
- Recent Blocks View: Added to the Send tab and inspired by Mempool's visualization, it displays the last 2 blocks and the estimated next block to help choose fee rates.
- Camera System Overhaul: Features a new library for higher resolution detection and mouse-scroll zoom support when available.
- Vector-Based Images: All app images are now vectorized and theme-aware, enhancing contrast, especially in dark mode.
- Tor & P2A Updates: Upgraded internal Tor and improved support for pay-to-anchor (P2A) outputs.
- Linux Package Rename: For Linux users, Sparrow has been renamed to sparrowwallet (or sparrowserver); in some cases, the original sparrow package may need manual removal.
- Additional updates include showing total payments in multi-payment transaction diagrams, better handling of long labels, and other UI enhancements.
- Sparrow v2.2.1 is a bug fix release that addresses missing UUID issue when starting Tor on recent macOS versions, icons for external sources in Settings and Recent Blocks view, repackaged
.debinstalls to use older gzip instead of zstd compression, and removed display of median fee rate where fee rates source is set to Server.
Learn how to get started with Sparrow wallet:
Release notes (v2.2.0)
- Added Recent Blocks view to Send tab.
- Converted all bitmapped images to theme aware SVG format for all wallet models and dialogs.
- Support send and display of pay to anchor (P2A) outputs.
- Renamed
sparrowpackage tosparrowwalletandsparrowserveron Linux. - Switched camera library to openpnp-capture.
- Support FHD (1920 x 1080) and UHD4k (3840 x 2160) capture resolutions.
- Support camera zoom with mouse scroll where possible.
- In the Download Verifier, prefer verifying the dropped file over the default file where the file is not in the manifest.
- Show a warning (with an option to disable the check) when importing a wallet with a derivation path matching another script type.
- In Cormorant, avoid calling the
listwalletdirRPC on initialization due to a potentially slow response on Windows. - Avoid server address resolution for public servers.
- Assume server address is non local for resolution failures where a proxy is configured.
- Added a tooltip to indicate truncated labels in table cells.
- Dynamically truncate input and output labels in the tree on a transaction tab, and add tooltips if necessary.
- Improved tooltips for wallet tabs and transaction diagrams with long labels.
- Show the address where available on input and output tooltips in transaction tab tree.
- Show the total amount sent in payments in the transaction diagram when constructing multiple payment transactions.
- Reset preferred table column widths on adjustment to improve handling after window resizing.
- Added accessible text to improve screen reader navigation on seed entry.
- Made Wallet Summary table grow horizontally with dialog sizing.
- Reduced tooltip show delay to 200ms.
- Show transaction diagram fee percentage as less than 0.01% rather than 0.00%.
- Optimized and reduced Electrum server RPC calls.
- Upgraded Bouncy Castle, PGPainless and Logback libraries.
- Upgraded internal Tor to v0.4.8.16.
- Bug fix: Fixed issue with random ordering of keystore origins on labels import.
- Bug fix: Fixed non-zero account script type detection when signing a message on Trezor devices.
- Bug fix: Fixed issue parsing remote Coldcard xpub encoded on a different network.
- Bug fix: Fixed inclusion of fees on wallet label exports.
- Bug fix: Increase Trezor device libusb timeout.
Linux users: Note that the
sparrowpackage has been renamed tosparrowwalletorsparrowserver, and in some cases you may need to manually uninstall the originalsparrowpackage. Look in the/optfolder to ensure you have the new name, and the original is removed.What's new in v2.2.1
- Updated Tor library to fix missing UUID issue when starting Tor on recent macOS versions.
- Repackaged
.debinstalls to use older gzip instead of zstd compression. - Removed display of median fee rate where fee rates source is set to Server.
- Added icons for external sources in Settings and Recent Blocks view
- Bug fix: Fixed issue in Recent Blocks view when switching fee rates source
- Bug fix: Fixed NPE on null fee returned from server
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:50:05
@ 21c71bfa:e28fa0f6
2025-05-29 14:50:05Book *Amritsar to Phagwara cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ dfa02707:41ca50e3
2025-05-30 16:02:14
@ dfa02707:41ca50e3
2025-05-30 16:02:14- This version introduces the Soroban P2P network, enabling Dojo to relay transactions to the Bitcoin network and share others' transactions to break the heuristic linking relaying nodes to transaction creators.
- Additionally, Dojo admins can now manage API keys in DMT with labels, status, and expiration, ideal for community Dojo providers like Dojobay. New API endpoints, including "/services" exposing Explorer, Soroban, and Indexer, have been added to aid wallet developers.
- Other maintenance updates include Bitcoin Core, Tor, Fulcrum, Node.js, plus an updated ban-knots script to disconnect inbound Knots nodes.
"I want to thank all the contributors. This again shows the power of true Free Software. I also want to thank everyone who donated to help Dojo development going. I truly appreciate it," said Still Dojo Coder.
What's new
- Soroban P2P network. For MyDojo (Docker setup) users, Soroban will be automatically installed as part of their Dojo. This integration allows Dojo to utilize the Soroban P2P network for various upcoming features and applications.
- PandoTx. PandoTx serves as a transaction transport layer. When your wallet sends a transaction to Dojo, it is relayed to a random Soroban node, which then forwards it to the Bitcoin network. It also enables your Soroban node to receive and relay transactions from others to the Bitcoin network and is designed to disrupt the assumption that a node relaying a transaction is closely linked to the person who initiated it.
- Pushing transactions through Soroban can be deactivated by setting
NODE_PANDOTX_PUSH=offindocker-node.conf. - Processing incoming transactions from Soroban network can be deactivated by setting
NODE_PANDOTX_PROCESS=offindocker-node.conf.
- Pushing transactions through Soroban can be deactivated by setting
- API key management has been introduced to address the growing number of people offering their Dojos to the community. Dojo admins can now access a new API management tab in their DMT, where they can create unlimited API keys, assign labels for easy identification, and set expiration dates for each key. This allows admins to avoid sharing their main API key and instead distribute specific keys to selected parties.
- New API endpoints. Several new API endpoints have been added to help API consumers develop features on Dojo more efficiently:
- New:
/latest-block- returns data about latest block/txout/:txid/:index- returns unspent output data/support/services- returns info about services that Dojo exposes
- Updated:
/tx/:txid- endpoint has been updated to return raw transaction with parameter?rawHex=1
- The new
/support/servicesendpoint replaces the deprecatedexplorerfield in the Dojo pairing payload. Although still present, API consumers should use this endpoint for explorer and other pairing data.
- New:
Other changes
- Updated ban script to disconnect inbound Knots nodes.
- Updated Fulcrum to v1.12.0.
- Regenerate Fulcrum certificate if expired.
- Check if transaction already exists in pushTx.
- Bump BTC-RPC Explorer.
- Bump Tor to v0.4.8.16, bump Snowflake.
- Updated Bitcoin Core to v29.0.
- Removed unnecessary middleware.
- Fixed DB update mechanism, added api_keys table.
- Add an option to use blocksdir config for bitcoin blocks directory.
- Removed deprecated configuration.
- Updated Node.js dependencies.
- Reconfigured container dependencies.
- Fix Snowflake git URL.
- Fix log path for testnet4.
- Use prebuilt addrindexrs binaries.
- Add instructions to migrate blockchain/fulcrum.
- Added pull policies.


Learn how to set up and use your own Bitcoin privacy node with Dojo here.
-
 @ b1ddb4d7:471244e7
2025-05-30 16:01:36
@ b1ddb4d7:471244e7
2025-05-30 16:01:36The upcoming Bitcoin 2025 conference, scheduled from May 27–29 at the Venetian Conference Center in Las Vegas, is set to make history with an official attempt to break the GUINNESS WORLD RECORDS® title for the most Bitcoin point-of-sale transactions in an eight-hour period.
Organized by BTC Inc, the event will showcase Bitcoin’s evolution from a digital capital asset to a practical medium of exchange, leveraging the latest advancements in payment technology.
Tap-to-Pay with Lightning-Ready Bolt Cards
To facilitate this record-setting attempt, 4,000 Lightning-ready Bolt Cards will be distributed to conference attendees.
— Uncle Rockstar Developer (@r0ckstardev) May 15, 2025
These NFC-enabled cards allow users to make instant, contactless Bitcoin payments at vendor booths throughout the expo-no apps or QR codes required, just a simple tap.
The cards are available in four collectible designs, each featuring a prominent figure in Bitcoin’s history: Senator Cynthia Lummis, Michael Saylor, Satoshi Nakamoto, and Jack Dorsey.
Each attendee will receive a randomly assigned card, making them both functional and collectible souvenirs.
Senator Lummis: A Playful Provocation
Notably, one of the card designs features Senator Cynthia Lummis with laser eyes-a playful nod to her reputation as a leading Bitcoin advocate in US politics.
While Lummis is known for her legislative efforts to promote Bitcoin integration, she has publicly stated she prefers to “spend dollars and save Bitcoin,” viewing BTC as a long-term store of value rather than a daily currency.
The choice to feature her on the Bolt Card, could be suggested by Rockstar Dev of the BTC Pay Server Foundation, perhaps a lighthearted way to highlight the ongoing debate about Bitcoin’s role in everyday payments.
Nothing cracks me up quite like a senator that wants the US to buy millions of Bitcoin use dollars to buy a beer at a Bitcoin bar.
This is how unserious some of you are. pic.twitter.com/jftIEggmip
— Magoo PhD (@HodlMagoo) April 4, 2025
How Bolt Cards and the Lightning Network Work
Bolt Cards are physical cards equipped with NFC (Near Field Communication) technology, similar to contactless credit or debit cards. When linked to a compatible Lightning wallet, they enable users to make Bitcoin payments over the Lightning Network by simply tapping the card at a point-of-sale terminal.
The Lightning Network is a second-layer protocol built on top of Bitcoin, designed to facilitate instant, low-cost transactions ideal for everyday purchases.
This integration aims to make Bitcoin as easy to use as traditional payment methods, eliminating the need for QR code scanning or mobile apps.
A Showcase for Bitcoin’s Real-World Usability
With over 30,000 attendees, 300 exhibitors, and 500 speakers expected, the Bitcoin 2025 conference is poised to be the largest Bitcoin event of the year-and potentially the most transactional.
The event will feature on-site activations such as the Official Bitcoin Magazine Store, where all merchandise will be available at a 21% discount for those paying with Bitcoin via the Lightning Network-a nod to Bitcoin’s 21 million coin supply limit.
By deeply integrating Lightning payments into the conference experience, organizers hope to demonstrate Bitcoin’s readiness for mainstream commerce and set a new benchmark for its practical use as a currency.
Conclusion
The Guinness World Record attempt at Bitcoin 2025 is more than a publicity stunt-it’s a bold demonstration of Bitcoin’s technological maturity and its potential to function as a modern, everyday payment method.
Whether or not the record is set, the event will serve as a milestone in the ongoing journey to make Bitcoin a truly global, user-friendly currency
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:49:42
@ 21c71bfa:e28fa0f6
2025-05-29 14:49:42Book *Chandigarh to Amritsar cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:49:20
@ 21c71bfa:e28fa0f6
2025-05-29 14:49:20Book *Amritsar to Pathankot cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 8bad92c3:ca714aa5
2025-05-30 16:02:13
@ 8bad92c3:ca714aa5
2025-05-30 16:02:13Marty's Bent
via Kevin McKernan

There's been a lot of discussion this week about Casey Means being nominated for Surgeon General of the United States and a broader overarching conversation about the effectiveness of MAHA since the inauguration and how effective it may or may not be moving forward. Many would say that President Trump won re-election due to Robert F. Kennedy Jr. and Nicole Shanahan deciding to reach across the aisle and join the Trump ticket, bringing with them the MAHA Moms, who are very focused on reorienting the healthcare system in the United States with a strong focus on the childhood vaccine schedule.
I'm not going to lie, this is something I'm passionate about as well, particularly after having many conversations over the years with doctors like Kevin McKernan, Dr. Jack Kruse, Dr. Mary Talley Bowden, Dr. Brooke Miller, Dr. Peter McCullough and others about the dangers of the COVID mRNA vaccines. As it stands today, I think this is the biggest elephant in the room in the world of healthcare. If you look at the data, particularly disability claims, life insurance claims, life expectancy, miscarriage rates, fertility issues and rates of turbo cancer around the world since the COVID vaccine was introduced in 2021, it seems pretty clear that there is harm being done to many of the people who have taken them.
The risk-reward ratio of the vaccines seems to be incredibly skewed towards risk over reward and children - who have proven to be least susceptible to COVID - are expected to get three COVID shots in the first year of their life if their parents follow the vaccine schedule. For some reason or another it seems that Robert F. Kennedy Jr. has shied away from this topic after becoming the head of Health and Human Services within the Trump administration. This is after a multi-year campaign during which getting the vaccines removed from the market war a core part of his platform messaging.
I'm still holding out hope that sanity will prevail. The COVID mRNA vaccines will be taken off the market in a serious conversation about the crimes against humanity that unfolded during the COVID years will take place. However, we cannot depend on that outcome. We must build with the assumption in mind that that outcome may never materialize. This leads to identifying where the incentives within the system are misconstrued. One area where I think it's pretty safe to say that the incentives are misaligned is the fact that 95% of doctors work for and answer to a corporation driven by their bottom line. Instead of listening to their patients and truly caring about the outcome of each individual, doctors forced to think about the monetary outcome of the corporation they work for first.
The most pernicious way in which these misaligned incentives emerge is the way in which the hospital systems and physicians are monetarily incentivized by big pharma companies to push the COVID vaccine and other vaccines on their patients. It is important to acknowledge that we cannot be dependent on a system designed in this way to change from within. Instead, we must build a new incentive system and market structure. And obviously, if you're reading this newsletter, you know that I believe that bitcoin will play a pivotal role in realigning incentives across every industry. Healthcare just being one of them.
Bitcoiners have identified the need to become sovereign in our monetary matters, it probably makes sense to become sovereign when it comes to our healthcare as well. This means finding doctors who operate outside the corporate controlled system and are able to offer services that align incentives with the end patient. My family utilizes a combination of CrowdHealth and a private care physician to align incentives. We've even utilized a private care physician who allowed us to pay in Bitcoin for her services for a number of years. I think this is the model. Doctors accepting hard censorship resistant money for the healthcare and advice they provide. Instead of working for a corporation looking to push pharmaceutical products on their patients so they can bolster their bottom line, work directly with patients who will pay in bitcoin, which will appreciate in value over time.
I had a lengthy discussion with Dr. Jack Kruse on the podcast earlier today discussing these topic and more. It will be released on Thursday and I highly recommend you freaks check it out once it is published. Make sure you subscribe so you don't miss it.
How the "Exorbitant Privilege" of the Dollar is Undermining Our Manufacturing Base
In my conversation with Lyn Alden, we explored America's fundamental economic contradiction. As Lyn expertly explained, maintaining the dollar's reserve currency status while attempting to reshore manufacturing presents a near-impossible challenge - what economists call Triffin's Dilemma. The world's appetite for dollars gives Americans tremendous purchasing power but simultaneously hollows out our industrial base. The overvalued dollar makes our exports less competitive, especially for lower-margin manufacturing, while our imports remain artificially strong.
"Having the reserve currency does come with a bunch of benefits, historically called an exorbitant privilege, but then it has certain costs to maintain it." - Lyn Alden
This dilemma forces America to run persistent trade deficits, as this is how dollars flow to the world. For over four decades, these deficits have accumulated, creating massive economic imbalances that can't be quickly reversed. The Trump administration's attempts to address this through tariffs showcase how difficult rebalancing has become. As Lyn warned, even if we successfully pivot toward reshoring manufacturing, we'll face difficult trade-offs: potentially giving up some reserve currency benefits to rebuild our industrial foundation. This isn't just economic theory - it's the restructuring challenge that will define America's economic future.
Check out the full podcast here for more on China's manufacturing dominance, the role of Bitcoin in monetary transitions, and energy production as the foundation for future industrial power.
Headlines of the Day
Coinbase to replace Discover in S&P 500 on May 19 - via X
Mallers promises no rehypothecation in Strike Bitcoin loans - via X
Get our new STACK SATS hat - via tftcmerch.io
Missouri passes HB 594, eliminates Bitcoin capital gains tax - via X
The 2025 Bitcoin Policy Summit is set for June 25th—and it couldn’t come at a more important time. The Bitcoin industry is at a pivotal moment in Washington, with initiatives like the Strategic Bitcoin Reserve gaining rapid traction. Whether you’re a builder, advocate, academic, or policymaker—we want you at the table. Join us in DC to help define the future of freedom, money & innovation in the 21st century.
Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
The 100+ degree days have returned to Austin, TX. Not mad about it... yet.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !important; } } .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } .moz-text-html .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } /* Helps with rendering in various email clients */ body { margin: 0 !important; padding: 0 !important; -webkit-text-size-adjust: 100% !important; -ms-text-size-adjust: 100% !important; } img { -ms-interpolation-mode: bicubic; } /* Prevents Gmail from changing the text color in email threads */ .im { color: inherit !important; }
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:49:01
@ 21c71bfa:e28fa0f6
2025-05-29 14:49:01Book *Amritsar to Manali cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 8bad92c3:ca714aa5
2025-05-30 16:02:13
@ 8bad92c3:ca714aa5
2025-05-30 16:02:13Marty's Bent
via me

It seems like every other day there's another company announced that is going public with the intent of competing with Strategy by leveraging capital markets to create financial instruments to acquire Bitcoin in a way that is accretive for shareholders. This is certainly a very interesting trend, very bullish for bitcoin in the short-term, and undoubtedly making it so bitcoin is top of mind in the mainstream. I won't pretend to know whether or not these strategies will ultimately be successful or fail in the short, medium or long term. However, one thing I do know is that the themes that interest me, both here at TFTC and in my role as Managing Partner at Ten31, are companies that are building good businesses that are efficient, have product-market-fit, generate revenues and profits and roll those profits into bitcoin.
While it seems pretty clear that Strategy has tapped into an arbitrage that exists in capital markets, it's not really that exciting. From a business perspective, it's actually pretty straightforward and simple; find where potential arbitrage opportunities exists between pools of capital looking for exposure to spot bitcoin or bitcoin's volatility but can't buy the actual asset, and provide them with products that give them access to exposure while simultaneously creating a cult-like retail following. Rinse and repeat. To the extent that this strategy is repeatable is yet to be seen. I imagine it can expand pretty rapidly. Particularly if we have a speculative fervor around companies that do this. But in the long run, I think the signal is falling back to first principles, looking for businesses that are actually providing goods and services to the broader economy - not focused on the hyper-financialized part of the economy - to provide value and create efficiencies that enable higher margins and profitability.
With this in mind, I think it's important to highlight the combined leverage that entrepreneurs have by utilizing bitcoin treasuries and AI tools that are emerging and becoming more advanced by the week. As I said in the tweet above, there's never been a better time to start a business that finds product-market fit and cash flows quickly with a team of two to three people. If you've been reading this rag over the last few weeks, you know that I've been experimenting with these AI tools and using them to make our business processes more efficient here at TFTC. I've also been using them at Ten31 to do deep research and analysis.
It has become abundantly clear to me that any founder or entrepreneur that is not utilizing the AI tools that are emerging is going to get left behind. As it stands today, all anyone has to do to get an idea from a thought in your head to the prototype stage to a minimum viable product is to hop into something like Claude or ChatGPT, have a brief conversation with an AI model that can do deep research about a particular niche that you want to provide a good service to and begin building.
Later this week, I will launch an app called Opportunity Cost in the Chrome and Firefox stores. It took me a few hours of work over the span of a week to ideate and iterate on the concept to the point where I had a working prototype that I handed off to a developer who is solving the last mile problem I have as an "idea guy" of getting the product to market. Only six months ago, accomplishing something like this would have been impossible for me. I've never written a line of code that's actually worked outside of the modded MySpace page I made back in middle school. I've always had a lot of ideas but have never been able to effectively communicate them to developers who can actually build them. With a combination of ChatGPT-03 and Replit, I was able to build an actual product that works. I'm using it in my browser today. It's pretty insane.
There are thousands of people coming to the same realization at the same time right now and going out there and building niche products very cheaply, with small teams, they are getting to market very quickly, and are amassing five figures, six figures, sometimes seven figures of MRR with extremely high profit margins. What most of these entrepreneurs have not really caught on to yet is that they should be cycling a portion - in my opinion, a large portion - of those profits into bitcoin. The combination of building a company utilizing these AI tools, getting it to market, getting revenue and profits, and turning those profits into bitcoin cannot be understated. You're going to begin seeing teams of one to ten people building businesses worth billions of dollars and they're going to need to store the value they create, any money that cannot be debased.
Grant Gilliam, one of the co-founders of Ten31, wrote about this in early 2024, bitcoin being the fourth lever of equity value growth for companies.
[
Bitcoin Treasury - The Fourth Lever to Equity Value Growth
Most companies do not hold enough bitcoin There is a saying you often hear in bitcoin circles that “you can never have enough bitcoin.” This is typically expressed by those who have spent the time to both understand bitcoin’s unique and superior monetary properties and also to appreciate why tho
Ten31 - Investors in bitcoin infrastructure and freedom techGrant Gilliam
](https://ten31.vc/insights/treasury?ref=tftc.io)
We already see this theme playing out at Ten31 with some of our portfolio companies, most notably Strike, which recently released some of their financials, highlighting the fact that they're extremely profitable with high margins and a relatively small team (~75). This is extremely impressive, especially when you consider the fact that they're a global company competing with the likes of Coinbase and Block, which have each thousands of employees.
Even those who are paying attention to the developments in the AI space and how the tools can enable entrepreneurs to build faster aren't really grasping the gravity of what's at play here. Many are simply thinking of consumer apps that can be built and distributed quickly to market, but the ways in which AI can be implemented extend far beyond the digital world. Here's a great example of a company a fellow freak is building with the mindset of keeping the team small, utilizing AI tools to automate processes and quickly push profits into bitcoin.
via Cormac
Again, this is where the exciting things are happening in my mind. People leveraging new tools to solve real problems to drive real value that ultimately produce profits for entrepreneurs. The entrepreneurs who decide to save those profits in bitcoin will find that the equity value growth of their companies accelerates exponentially as they provide more value, gain more traction, and increase their profits while also riding the bitcoin as it continues on its monetization phase. The compounded leverage of building a company that leverages AI tools and sweeps profits into bitcoin is going to be the biggest asymmetric play of the next decade. Personally, I also see it as something that's much more fulfilling than the pure play bitcoin treasury companies that are coming to market because consumers and entrepreneurs are able to recive and provide a ton of value in the real economy.
If you're looking to stay on top of the developments in the AI space and how you can apply the tools to help build your business or create a new business, I highly recommend you follow somebody like Greg Isenberg, whose Startup Ideas Podcast has been incredibly valuable for me as I attempt to get a lay of the land of how to implement AI into my businesses.
America's Two Economies
In my recent podcast with Lyn Alden, she outlined how our trade deficits create a cycle that's reshaping America's economic geography. As Alden explained, US trade deficits pump dollars into international markets, but these dollars don't disappear - they return as investments in US financial assets. This cycle gradually depletes industrial heartlands while enriching financial centers on the coasts, creating what amounts to two separate American economies.
"We're basically constantly taking economic vibrancy out of Michigan and Ohio and rural Pennsylvania where the steel mills were... and stuffing it back into financial assets in New York and Silicon Valley." - Lyn Alden
This pattern has persisted for over four decades, accelerating significantly since the early 1980s. Alden emphasized that while economists may argue there's still room before reaching a crisis point, the political consequences are already here. The growing divide between these two Americas has fueled populist sentiment as voters who feel left behind seek economic rebalancing, even if they can't articulate the exact mechanisms causing their hardship.
Check out the full podcast here for more on China's man
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:48:43
@ 21c71bfa:e28fa0f6
2025-05-29 14:48:43Book *Amritsar to Katra cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 8bad92c3:ca714aa5
2025-05-30 16:02:13
@ 8bad92c3:ca714aa5
2025-05-30 16:02:13Key Takeaways

Dr. Jack Kruse returns in this fiery episode to expose what he alleges is a coordinated campaign by Big Pharma, technocrats, and global elites to control public health narratives and financial systems through manipulated health policies and propaganda. He accuses figures like Calli and Casey Means of fronting a compromised "Maha Movement," backed by A16Z, Big Tech, and the World Economic Forum, with ambitions to embed themselves into U.S. health policy and bioweapons programs. Kruse details his covert efforts to expose these connections, claiming they led to the withdrawal of Casey Means' Surgeon General nomination, and warns of a looming biotechnocratic surveillance state where mRNA vaccines act as bioweapons to enforce compliance. Urging Bitcoiners to expand their fight for sovereignty beyond finance into healthcare and biology, Kruse argues that the true war is over time sovereignty—not just monetary freedom—and that protecting children from vaccine harms is now the most urgent front in this escalating battle.
Best Quotes
"Bitcoin is worthless if you have no time."
"We’re not playing games here. This is to the death."
"Big Pharma is just the drug dealer. The real boss is the Department of Defense and DARPA."
"The real battle in D.C. isn’t left vs. right, it’s Rothschilds and Rockefellers vs. the technocrats."
"First principle Bitcoiners need to become first principle decentralizers of life itself."
Conclusion
This episode delivers a provocative call to action from Dr. Jack Kruse, who warns that the fight for sovereignty must go beyond finance to confront what he sees as the immediate threat of centralized bio-surveillance through mRNA vaccines. Blending insider claims with health activism, Kruse urges Bitcoiners and the public to recognize that true freedom requires decentralizing not only money but also healthcare and information systems, arguing that without protecting biological sovereignty, Bitcoin’s promise of liberty will be meaningless if people are left physically, mentally, or politically compromised.
Timestamps
0:00 - Intro
0:47 - Outlining MAHA infiltration
22:59 - Fold & Bitkey
24:35- Danger to children
28:27 - Political shell game
35:40 - Unchained
36:09 - Time theft
41:07 - Vax data
46:32 - Bioweapon and control system
58:29 - Game plan - Decentralized yourself
1:15:16 - Priorities
1:24:30 - Support Mary Talley BowdenTranscript
(00:00) me, Larry Leard, those kind of Bitcoiners, the people that are out there that have money, like they're looking to take us out. You need to know a little bit about the back history that I don't think I've talked about anywhere on any other podcast. Rick Callie is linked to the current administration is through Susie Watts.
(00:17) They both were working at Mercury PR basically is the frontman for propaganda for Big Farm. Basically, who pays you? You become their [ __ ] We're not playing games here. This is to the death. This is the biggest issue facing Maha now. It's not Froot Loops. It's not red dye. But the messenger RA job can drop you like Demar Handler.
(00:40) Can end your career like JJ Watt. Dr. Jack Cruz, welcome back to the show. Thank you, sir, for having me. Well, thank you for being here. I mean, you're making a lot of noise around a topic that I wasn't well aware of. I'm not going to lie. I think I got duped by or we'll find out if I actually got duped by the meanses. Cali means was coming in last year talking big about Maja getting the food correct.
(01:15) Um, basically telling the story of him being a lobbyist and understanding how corrupt the food system is. And we talked about it last time we were on two months ago. this sort of maha movement has shifted towards focusing on preventative care particularly in diets and you were on the Danny Danny Jones show late last year with Cali means uh sort of pressuring him to admit that the vaccine should be pulled off the market and he did not did not bite and would not budge on that and now his sister Casey has been appointed to surgeon general and
(01:50) this is something Let me let me tell you a little bit about that because you need to know a little bit about the back history that I don't think I've talked about anywhere on any other podcast. She was going to be named surgeon general uh back then. Just so you know that I knew it and I knew quite a bit of other things.
(02:16) So what was my goal? I knew um that Cali and Casey were tied to big tech. They were tied specifically, which you'll be interested in, A16Z, the shitcoiners extraordinaire, and they were also tied to the World Economic Forum through the book deal. Um, so my goal at that time as part of the person that was big in the mob like, and Marty, I don't know if you know this back part of the story.
(02:46) Maha begins not with Casey and Cali and Bobby Kennedy. It began with me, Bobby, and Rick Rubin on Rick's podcast the day that I told RFK Jr. that SV40 was in the Fiser Jabs. Mhm. And that's when Bobby found out that I wrote the law for Blly for a constitutional amendment for medical freedom. And he asked me to use four pages of the law.
(03:13) And Blly cleared me to do that. And then Aaron Siri, who was Bobby's attorney and working with a lot of the stuff that Bobby does with vaccines and I can Aaron contacted me. So just so you're clear, this is two and a half years ago. This is before this is a year previous to Casey and Cali coming on the scene. And I was always behind the scenes.
(03:37) I was not really interested in getting involved um in the [ __ ] show. But when I saw these two show up, the way they showed up and when I heard Cali actually say on a podcast that, you know, he was the modus operande of the Maha movement and he's the one that brought Bobby and Trump together.
(04:02) I said, "That's where I draw a [ __ ] line." I'm like, "Uh-uh. These guys, I know exactly what they're going to do. I see the game plan. they're going to use a shell game and I needed to have proof before you can come out and be a savage. You got to have proof. So, I hired three former Secret Service agents to actually do a very deep dive.
(04:24) We're talking about the kind of dive that you would get uh if you were going for a Supreme Court nomination. Okay? It cost me a lot of money. And why did I think it was important? Because as you know, you know, as a Bitcoiner, you just saw the big scam that happened with Maya Paribu down in Cerninam that happened after.
(04:49) Well, when I hired these guys, when all of my research that I had done was confirmed by them, I said, "Okay, now we need to go on a podcast very publicly and we need to put Cali's feet to the fire." Why? because I knew and he did not know that I knew this prior to the podcast. Uh that his sister was going to be nominated for surgeon general then.
(05:14) And because he didn't know and you you'll be able to confirm this or the savages in your audience can confirm this with Danny Jones. Do you know that Cali cancelled the podcast to do it into uh February? Yeah. Well, I think it was April of 25 because he didn't want to give anybody the time and day.
(05:37) So, what did I start doing? I started posting some of the information back in November that I found and the links to the Wjikis and the links to Bin, the links to A16Z. I didn't didn't give a ton of the information, but let's just put it this way. enough to make Callie and Cassie scream a little bit that people in DC started to read all my tweets.
(06:04) And then he called Danny up and said, "Danny, I want to do this podcast immediately." And I knew the reason why. Cuz I was baiting him to come so I could hit him with the big stuff. Why? Because you have to understand these two kids, you know, tied to the Rockefellers. They're tied to the banking elite.
(06:26) They're tied to the World Economics Form. Rick Callie is linked to the current administration is through Susie Watts. They both were working at Mercury PR and uh Mercury PR uh basically is the frontman for propaganda for Big Farm and everybody knows that, but not everybody knew that Cali worked for them.
(06:50) And you know the story that he sold all you guys, how he fooled you. And I consider you a smart guy, a savage, it's not shocking how he fooled you because he said as a um a lobbyist basically who pays you, you become their [ __ ] to to be quite honest and you'll say things that will make sense. Everybody in creation who's going to watch your podcast knows that all the things that Casey and Cali have said have been said literally for 30, 40, 50 years going all the way back to probably Anel Peas about diet and exercise.
(07:25) Everybody [ __ ] knows that. It's not new. They just decided to repackage it up and then they actually got in Bobby's ear about it. And when I released all this stuff, did Bobby know what I had? Yeah, he knew. And did the people in DC all what all their antennas up about this issue? Who was most pissed off with Uncle Jack back then? Susie [ __ ] Walls.
(07:56) Why? because those two are her babies that were going to be the amber that Susie Cassidy Cassidy Big Farmer were going to place around um Bobby Kennedy once he got confirmed. And that's why for the savages that are listening to this podcast, you go back and look at Nicole's tweet from, you know, I guess it was about four or five days ago that this didn't make sense.
(08:20) Why? because I gave the data directly to the people in DC behind the scenes of what was really going on and because it was so explosive. That's the reason Susie had to not give the job to Casey Means. She had to wait till the heat died down. So they elevated Janette and Janette bas -
 @ 8bad92c3:ca714aa5
2025-05-30 16:02:12
@ 8bad92c3:ca714aa5
2025-05-30 16:02:12
Let's dive into the most interesting forward-looking predictions from my recent conversations with industry experts.
Court Cases Against Bitcoin Developers Will Set Critical Precedent for the Industry's Future - Zack Shapiro
The outcome of the Samurai Wallet case will determine whether software developers can be held legally responsible for how users employ their non-custodial Bitcoin tools. Zack Shapiro laid out the stakes clearly: "The precedent that the Bank Secrecy Act can be applied to just software that allows you to move your own money on the Bitcoin blockchain is incredibly dangerous for developers, for node runners, for miners... Basically everyone in the Bitcoin space is at risk here."
According to Shapiro, the government's position in this case fundamentally misunderstands Bitcoin's architecture: "The government says that the defendants transmitted, Keone and Bill transmitted money that they knew belonged to criminals. That's not how a coin join works. The people who transmitted the money are the people that used Whirlpool and the people that used Ricochet. They signed their keys."
Should this prosecution succeed in establishing precedent, Shapiro predicts catastrophic consequences: "If that becomes the law of the land... then basically no actor in the Bitcoin economy is safe. The government's theory is that if you facilitate movement of money, you're a money transmitter, that would reach node runners, wallet developers, miners, lightning routing nodes... whatever tool stack you use, the people who built that are at risk."
With the case continuing despite FinCEN's own position that Samurai's software isn't money transmission, Shapiro believes the resolution will likely come through political rather than legal channels in the next 6-12 months.
Malpractice Around COVID mRNA Vaccines Will Be Exposed Within 2 Years - Dr. Jack Kruse
Dr. Jack Kruse predicts that major revelations about mRNA vaccine damage will force an eventual removal from the market, particularly from childhood vaccination schedules. During our conversation, Dr. Kruse shared alarming statistics: "25,000 kids a month are getting popped with this vaccine. Just so you know, since Trump has been elected, three million doses have been given to children."
According to Dr. Kruse, the scale of this problem dwarfs other health concerns: "The messenger job can drop you like Damar Hamlin, can end your career like JJ Watt, can end your career like all the footballers who've dropped dead on a soccer field." What makes this particularly concerning is the suppression of evidence about the damages, with Dr. Kruse noting that data from Japan showing changes in cancer distribution patterns was pulled, and VAERS data being dismissed despite showing alarming signals.
Dr. Kruse believes the coming years will see an unavoidable reckoning: "If by the end of this year, everybody in unison realized that MRA platform is bad news and it's gone. That to me is... I would tell you the biggest win is to get rid of the MRA platform even before any of the Bitcoin stuff." This suggests he expects significant momentum toward removing these vaccines from circulation by the end of 2025.
Global Economic Reordering Will Create Demand for Neutral Reserve Assets Like Bitcoin and Gold - Lyn Alden
The next two years will be critical in determining whether the United States maintains dollar dominance while navigating Triffin's dilemma. During our conversation, Lyn highlighted how the current administration is attempting to thread a needle between reshoring manufacturing while maintaining the dollar's reserve status - an almost impossible task on extremely fragile ground.
"When they talk about kind of a currency accord to weaken the dollar, they mentioned ideally they wanted to use multi-lateral approaches, but there are some unilateral approaches that they can do, which includes printing dollars to buy reserve assets," Lyn explained when discussing Treasury advisor Stephen Myron's position paper.
As the world potentially moves to a multipolar currency system, Lyn predicts significant demand increases for neutral reserve assets. "The two options on the table at this point are gold and Bitcoin," she noted, but pointed out that "our geopolitical adversaries have been stacking gold for a while and with a special intensity for the last three years." This creates a strategic opportunity for the US, as Bitcoin is "overwhelmingly held in the United States."
Lyn believes this transition is already underway, with the demand for neutral reserve assets like Bitcoin growing as countries seek alternatives to solely dollar-denominated reserves.
Blockspace conducts cutting-edge proprietary research for investors.
Iran's Shadow Mining Economy: 2 GW of Bitcoin Mined Underground While Legal Operations Struggle
Iran hosts a thriving underground Bitcoin mining industry that has emerged as a critical financial lifeline for citizens grappling with international sanctions and domestic economic controls. This shadow economy dwarfs the legal sector, with an estimated 2 gigawatts of illegal mining operations compared to just 5 megawatts of sanctioned activity.
According to ViraMiner CEO Masih Alavi, approximately 800,000 illegal miners have been discovered and fined by authorities. Yet operations continue in homes, office buildings, and even jewelry stores, where Iranians tap into unmetered electricity to mine Bitcoin, later converting it to stablecoins like USDT for savings and commerce.
While the government has approved permits for about 400 megawatts of legal mining capacity, punitive electricity tariffs and regulatory barriers have strangled legitimate operations. "I blamed the government for this situation," says Alavi. "They introduced flawed policies in the beginning, especially by setting the wrong electricity tariffs for the mining industry."
Despite using obsolete equipment like Antminer S9s and M3s, underground miners remain profitable when converting earnings to Iranian rials, creating an ecosystem that serves an estimated 18 million Iranian cryptocurrency holders.
Looking ahead, Alavi predicts further crackdowns as Iran enters peak electricity demand season, potentially reducing legal mining to zero while underground operations continue to evolve sophisticated detection evasion techniques.
Subscribe to them here (seriously, you should): https://newsletter.blockspacemedia.com/
Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
STACK SATS hat: https://tftcmerch.io/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !important; } } .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } .moz-text-html .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } /* Helps with rendering in various email clients */ body { margin: 0 !important; padding: 0 !important; -webkit-text-size-adjust: 100% !important; -ms-text-size-adjust: 100% !important; } img { -ms-interpolation-mode: bicubic; } /* Prevents Gmail from changing the text color in email threads */ .im { color: inherit !important; }
-
 @ 8bad92c3:ca714aa5
2025-05-30 16:02:12
@ 8bad92c3:ca714aa5
2025-05-30 16:02:12Marty's Bent

It's been a pretty historic week for the United States as it pertains to geopolitical relations in the Middle East. President Trump and many members of his administration, including AI and Crypto Czar David Sacks and Treasury Secretary Scott Bessent, traveled across the Middle East making deals with countries like Qatar, Saudi Arabia, the United Arab Emirates, Syria, and others. Many are speculating that Iran may be included in some behind the scenes deal as well. This trip to the Middle East makes sense considering the fact that China is also vying for favorable relationships with those countries. The Middle East is a power player in the world, and it seems pretty clear that Donald Trump is dead set on ensuring that they choose the United States over China as the world moves towards a more multi-polar reality.
Many are calling the events of this week the Riyadh Accords. There were many deals that were struck in relation to artificial intelligence, defense, energy and direct investments in the United States. A truly prolific power play and demonstration of deal-making ability of Donald Trump, if you ask me. Though I will admit some of the numbers that were thrown out by some of the countries were a bit egregious. We shall see how everything plays out in the coming years. It will be interesting to see how China reacts to this power move by the United States.
While all this was going on, there was something happening back in the United States that many people outside of fringe corners of FinTwit are not talking about, which is the fact that the 10-year and 30-year U.S. Treasury bond yields are back on the rise. Yesterday, they surpassed the levels of mid-April that caused a market panic and are hovering back around levels that have not been seen since right before Donald Trump's inauguration.
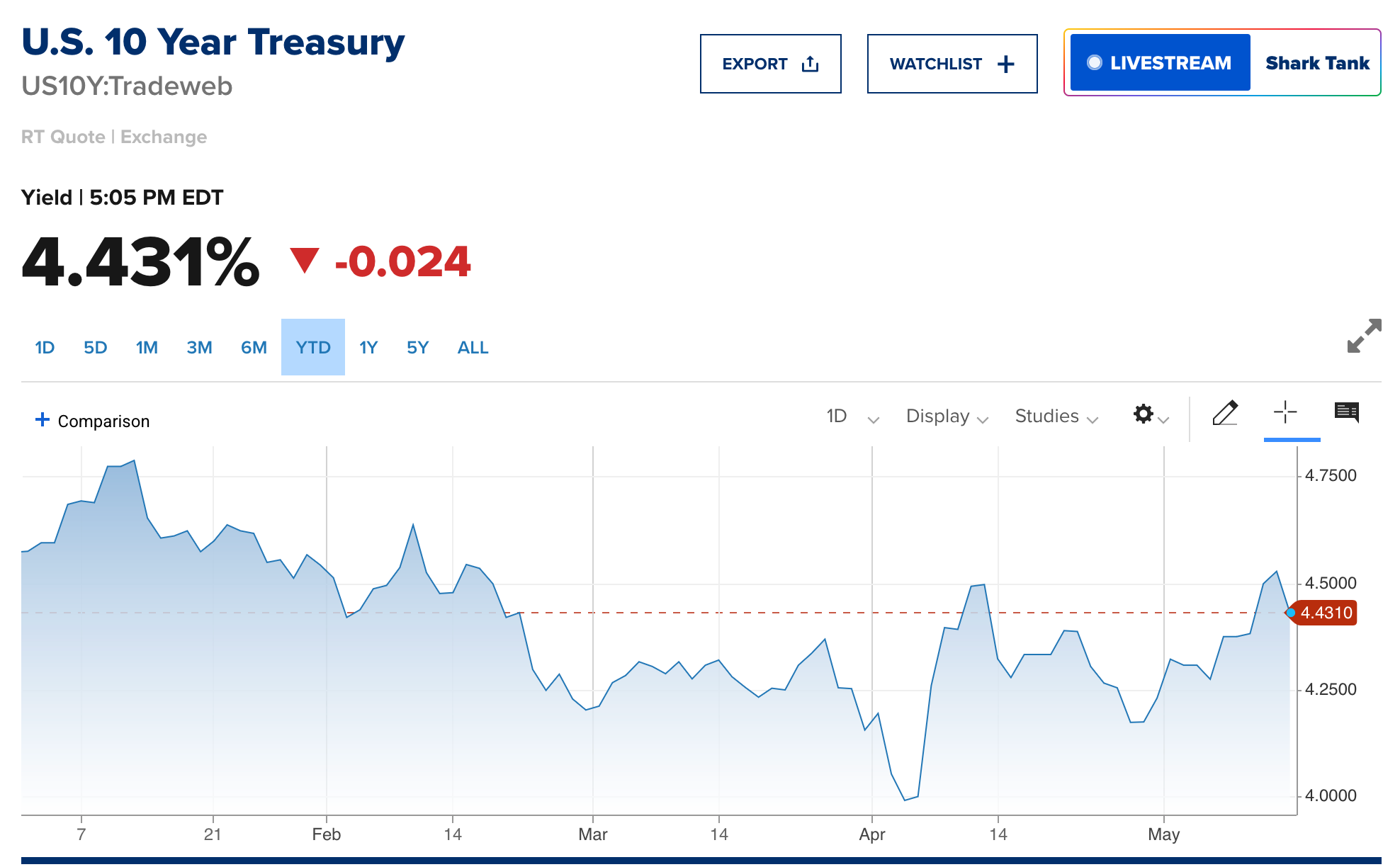
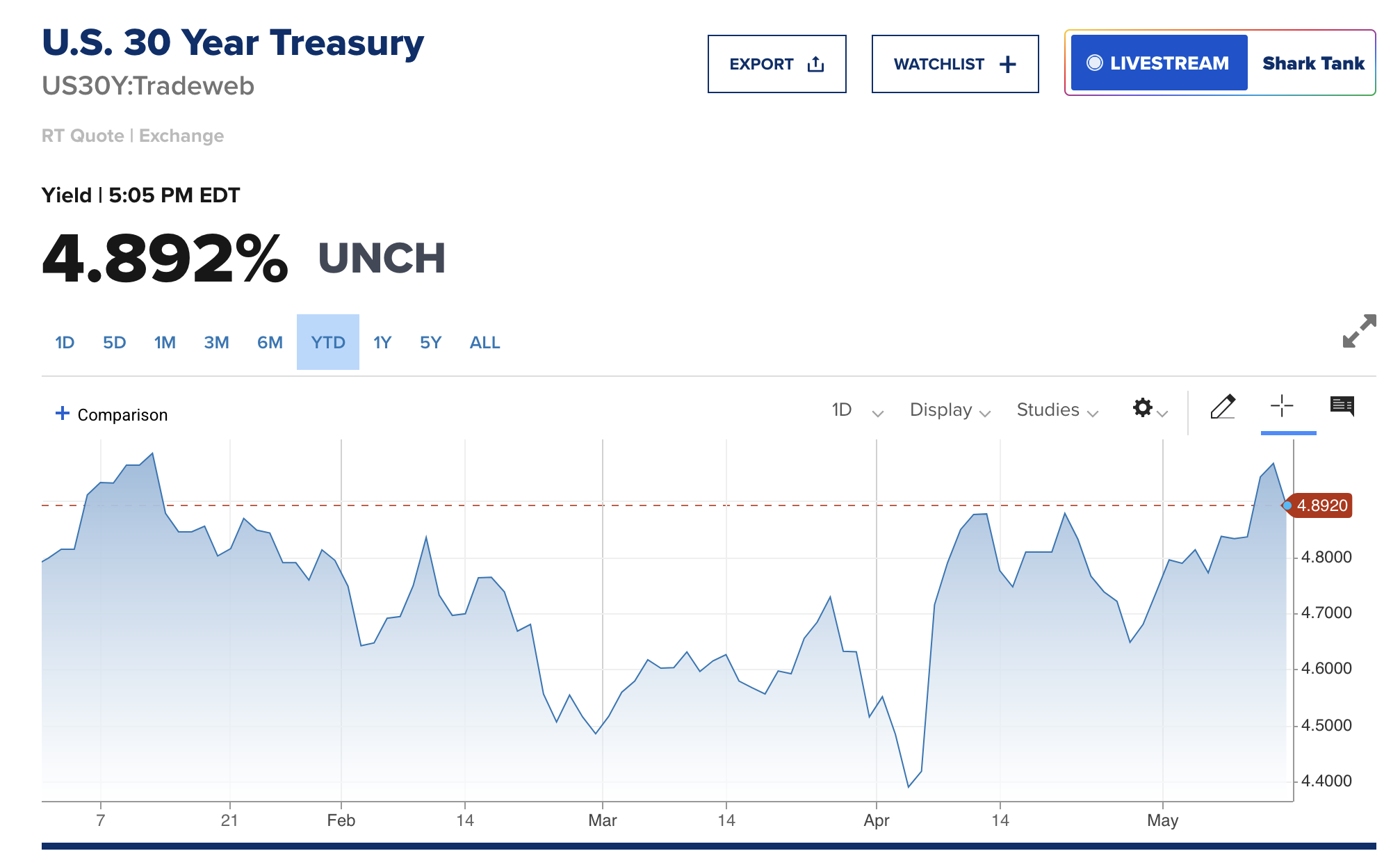
I imagine that there isn't as much of an uproar right now because I'm pretty confident the media freakouts we were experiencing in mid-April were driven by the fact that many large hedge funds found themselves off sides of large levered basis trades. I wouldn't be surprised if those funds have decreased their leverage in those trades and bond yields being back to mid-April levels is not affecting those funds as much as they were last month. But the point stands, the 10-year and 30-year yields are significantly elevated with the 30-year approaching 5%. Regardless of the deals that are currently being made in the Middle East, the Treasury has a big problem on its hands. It still has to roll over many trillions worth of debt over over the next few years and doing so at these rates is going to be massively detrimental to fiscal deficits over the next decade. The interest expense on the debt is set to explode in the coming years.
On that note, data from the first quarter of 2025 has been released by the government and despite all the posturing by the Trump administration around DOGE and how tariffs are going to be beneficial for the U.S. economy, deficits are continuing to explode while the interest expense on the debt has definitively surpassed our annual defense budget.
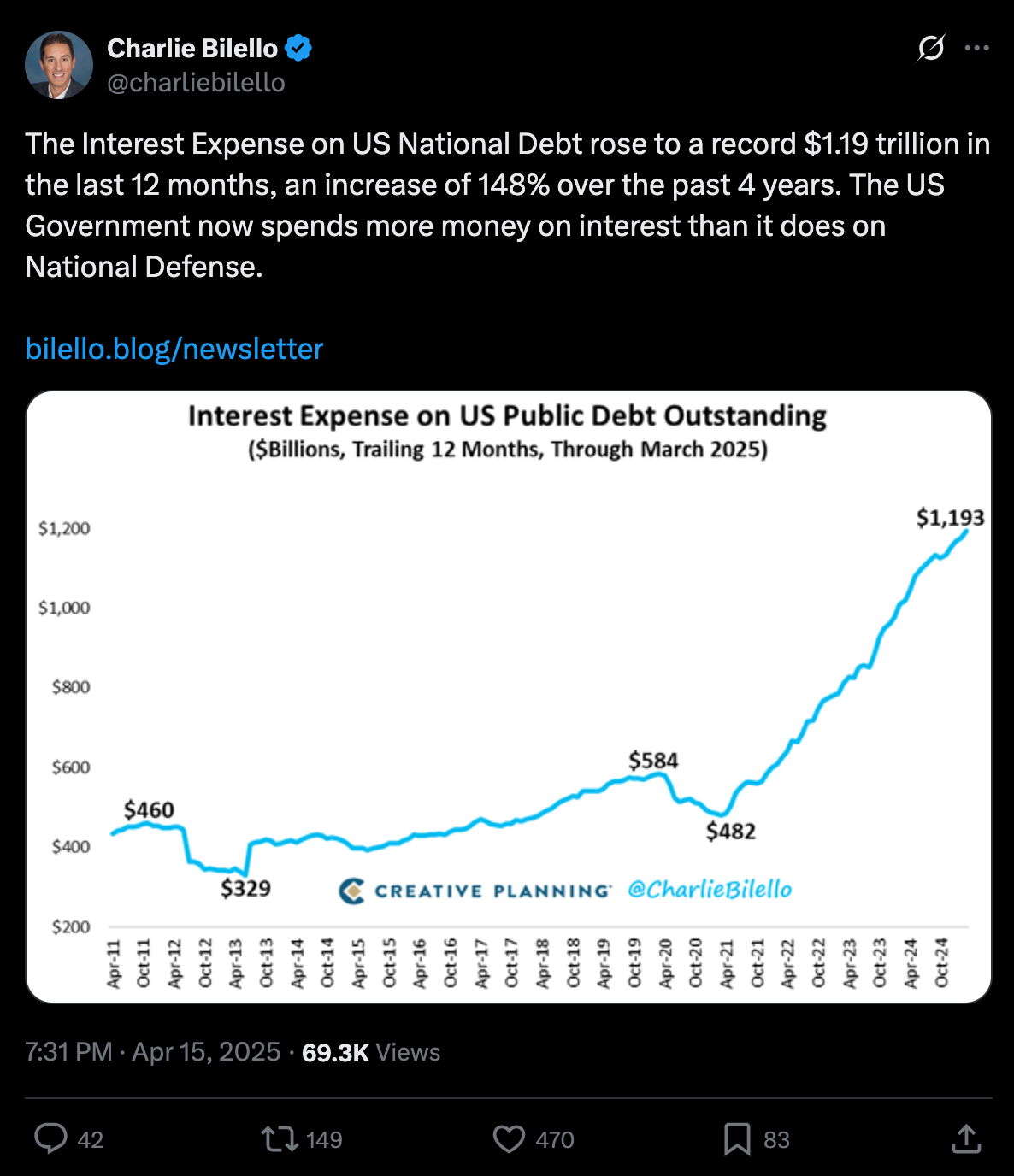
via Charlie Bilello
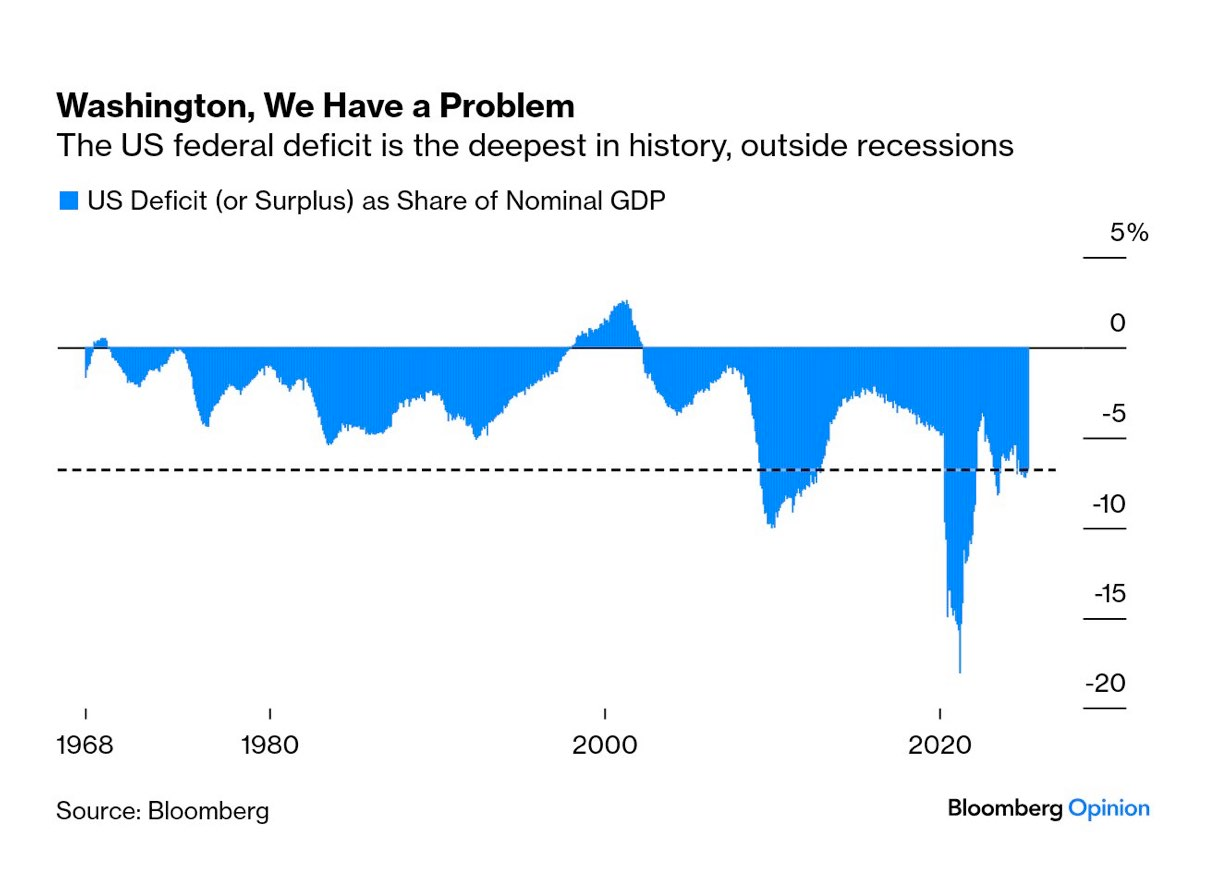
via Mohamed Al-Erian
To make matters worse, as things are deteriorating on the fiscal side of things, the U.S. consumer is getting crushed by credit. The 90-plus day delinquency rates for credit card and auto loans are screaming higher right now.
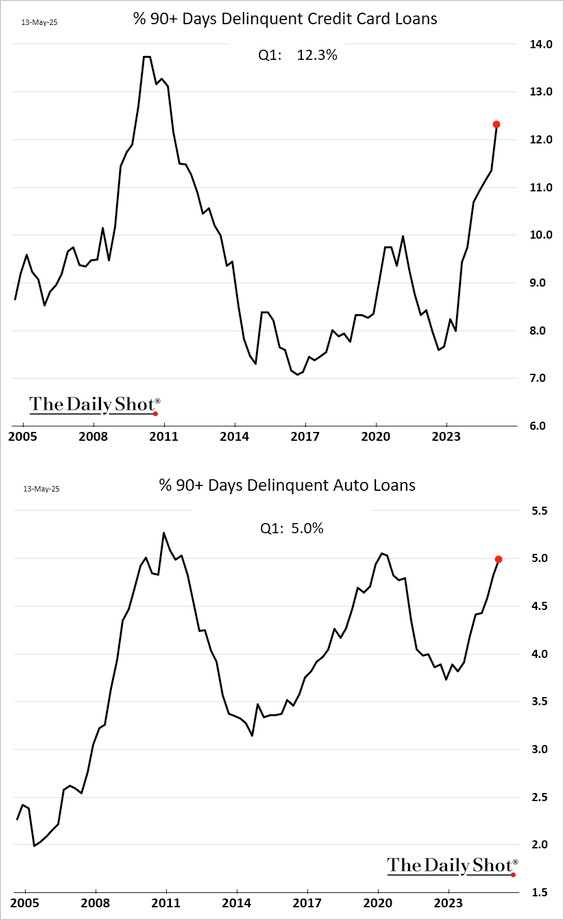
via TXMC
One has to wonder how long all this can continue without some sort of liquidity crunch. Even though equities markets have recovered from their post-Liberation Day month long bear market, I would not be surprised if what we're witnessing is a dead cat bounce that can only be continued if the money printers are turned back on. Something's got to give, both on the fiscal side and in the private markets where the Common Man is getting crushed because he's been forced to take on insane amounts of debt to stay afloat after years of elevated levels of inflation. Add on the fact that AI has reached a state of maturity that will enable companies to replace their current meat suit workers with an army of cheap, efficient and fast digital workers and it isn't hard to see that some sort of employment crisis could be on the horizon as well.
Now is not the time to get complacent. While I do believe that the deals that are currently being made in the Middle East are probably in the best interest of the United States as the world, again, moves toward a more multi-polar reality, we are facing problems that one cannot simply wish away. They will need to be confronted. And as we've seen throughout the 21st century, the problems are usually met head-on with a money printer.
I take no pleasure in saying this because it is a bit uncouth to be gleeful to benefit from the strife of others, but it is pretty clear to me that all signs are pointing to bitcoin benefiting massively from everything that is going on. The shift towards a more multi-polar world, the runaway debt situation here in the United States, the increasing deficits, the AI job replacements and the consumer credit crisis that is currently unfolding, All will need to be "solved" by turning on the money printers to levels they've never been pushed to before.
Weird times we're living in.
China's Manufacturing Dominance: Why It Matters for the U.S.
In my recent conversation with Lyn Alden, she highlighted how China has rapidly ascended the manufacturing value chain. As Lyn pointed out, China transformed from making "sneakers and plastic trinkets" to becoming the world's largest auto exporter in just four years. This dramatic shift represents more than economic success—it's a strategic power play. China now dominates solar panel production with greater market control than OPEC has over oil and maintains near-monopoly control of rare earth elements crucial for modern technology.
"China makes like 10 times more steel than the United States does... which is relevant in ship making. It's relevant in all sorts of stuff." - Lyn Alden
Perhaps most concerning, as Lyn emphasized, is China's financial leverage. They hold substantial U.S. assets that could be strategically sold to disrupt U.S. treasury market functioning. This combination of manufacturing dominance, resource control, and financial leverage gives China significant negotiating power in any trade disputes, making our attempts to reshoring manufacturing all the more challenging.
Check out the full podcast here for more on Triffin's dilemma, Bitcoin's role in monetary transition, and the energy requirements for rebuilding America's industrial base.
Headlines of the Day
Financial Times Under Fire Over MicroStrategy Bitcoin Coverage - via X
Trump in Qatar: Historic Boeing Deal Signed - via X
Get our new STACK SATS hat - via tftcmerch.io
Johnson Backs Stock Trading Ban; Passage Chances Slim - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code *“TFTC20”* during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Building things of value is satisfying.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !import
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:48:21
@ 21c71bfa:e28fa0f6
2025-05-29 14:48:21Book *Amritsar to Kapurthala cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:47:56
@ 21c71bfa:e28fa0f6
2025-05-29 14:47:56Book *Amritsar to Delhi cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.