-
 @ 57d1a264:69f1fee1
2025-05-01 05:57:24
@ 57d1a264:69f1fee1
2025-05-01 05:57:24Design and build chemical processes, better. Alkali is creating the world's first AI Process Engineer.
What the future of chemical process design should look like.
Under the hood, APE-0 uses tried-and-true open-source packages to run simulations. You don't have to trust that the LLM predicted the result — you can check out the simulation file it produced, and run it yourself!
Discover more at https://www.alkali-eng.com/blogs/introducing-fel-0
originally posted at https://stacker.news/items/968211
-
 @ 57d1a264:69f1fee1
2025-05-01 05:14:06
@ 57d1a264:69f1fee1
2025-05-01 05:14:06The mystical d attribute in SVG paths is actually a series of small commands. In this guide, we'll take a look at each path command and how we can use them to draw icons. Read more at https://www.nan.fyi/svg-paths
I you'd like to learn Interactive SVG Animations, here a text-based mini-course on making whimsical, playful SVG animations https://www.svg-animations.how/
credits: @nandafyi
originally posted at https://stacker.news/items/968195
-
 @ 57d1a264:69f1fee1
2025-05-01 05:01:45
@ 57d1a264:69f1fee1
2025-05-01 05:01:45 -
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ d9a329af:bef580d7
2025-04-30 23:44:20
@ d9a329af:bef580d7
2025-04-30 23:44:20To be clear, this is 100% my subjective opinion on the alternatives to popular music, as it has become practically a formula of witchcraft, pseudoscience and mysticism. There is nothing you can do to get me to listen to pop music from the late 2010's to now. I could certainly listen to almost anything... just not modern pop, which is now completely backwards.
Most examples of compositions for these genres will be my own, unless otherwise stated. The genres on this list are in no particular order, though my favorite of which will be first: 1. Bossa Nova
Bossa Nova is a subgenre of jazz from Brazil, created in the 1950's as a mix of standard jazz and samba rhythms in a more gentle and relaxing manner. This genre's most famous songs are Tom Jobim's The Girl from Ipanema (found in albums like Getz/Gilberto), Wave, and even Triste. Most of the music is written in 2/4 time signature, and any key is almost acceptable. It's called Afro-Brazilian Jazz for a reason after all. I have a ton of compositions I produced, from Forget and Regret, to Rabbit Theory, Beaches of Gensokyo Past, Waveside, and even Willows of Ice to name a few of them.
- Metal
This is an umbrella term for many subgenres of this fork of hard rock, with more distorted guitars, speedy and technical writing, vocals that sound demonic (some subgenres don't have that), or sometimes, chaotic lyrics and downright nasty ones if you look deep enough. If you want to get into it, just make sure it's not Black Metal (it's weird), Blackened Metal (Any subgenre of metal that's been inserted with elements of Black Metal), Metalcore, or any other genre that has vocals that aren't the best to hear (these are vocal fries that are really good if you're into the weird demonic sounds). This isn't for the faint of heart. Instrumental metal is good though, and an example is my composition from Touhou Igousaken called A Sly Foxy Liar if you want to know what techincal groove metal is like at a glance.
- Touhou-style
I can attest to this one, as I produced bossa nova with a Touhou-like writing style. Touhou Project is a series of action video games created by one guy (Jun'ya Outa, a.k.a. ZUN), and are usually bullet curtain games in the main franchise, with some official spinoffs that are also action games (fighting games like Touhou 12.3 ~ Hisoutensoku). What I'm referring to here is music written by ZUN himself (He does almost everything for Touhou Project, and he's really good at it), or fans that write to his style with their own flair. I did this once with my composition, Toiled Bubble, which is from my self-titled EP. I probably wouldn't do much with it to be fair, and stick to bossa nova (my main genre if you couldn't tell).
- Hip-Hop/Rap
This can get subjective here, but old-school rap and hip-hop... give me more of it. Before it became corrupted with all kinds of immoral things, hip-hop and rap were actually very good for their time. These were new, innovative and creative with how lyrics were written. Nowadays, while we're talking about cars, unspeakable acts, money, and just being dirtbags, artists in this genre back then were much classier than that. I fit in the latter category with my piece entitled, Don't Think, Just Roast, where I called out antis for a Vtuber agency who wanted to give its talent a hard time. It didn't get much traction on YouTube, because I'm not a well-known artist (I'm considered a nobody in the grand scheme of things. I'd like to get it fixed, but I don't want a record deal... I'd have to become a Pharisee or a Jesuit for that).
- Synthwave
This is a genre of electronic music focused on 80's and 90's synths being used to carry a composition. Nowadays, we have plugins like Vital, Serum, Surge and others to create sounds we would otherwise be hearing on an 80's or 90's keyboard. An example of this is my composition, Wrenched Torque, which was composed for a promotion I did with RAES when he released his Vital synth pack.
More are to come in future installments of this series, and I will adjust the title of this one accordingly if y'all have any ideas of genres I should look into.
-
 @ 1c19eb1a:e22fb0bc
2025-04-30 22:02:13
@ 1c19eb1a:e22fb0bc
2025-04-30 22:02:13I am happy to present to you the first full review posted to Nostr Reviews: #Primal for #Android!
Primal has its origins as a micro-blogging, social media client, though it is now expanding its horizons into long-form content. It was first released only as a web client in March of 2023, but has since had a native client released for both iOS and Android. All of Primal's clients recently had an update to Primal 2.0, which included both performance improvements and a number of new features. This review will focus on the Android client specifically, both on phone and tablet.
Since Primal has also added features that are only available to those enrolled in their new premium subscription, it should also be noted that this review will be from the perspective of a free user. This is for two reasons. First, I am using an alternate npub to review the app, and if I were to purchase premium at some time in the future, it would be on my main npub. Second, despite a lot of positive things I have to say about Primal, I am not planning to regularly use any of their apps on my main account for the time being, for reasons that will be discussed later in the review.
The application can be installed through the Google Play Store, nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8, or by downloading it directly from Primal's GitHub. The full review is current as of Primal Android version 2.0.21. Updates to the review on 4/30/2025 are current as of version 2.2.13.
In the ecosystem of "notes and other stuff," Primal is predominantly in the "notes" category. It is geared toward users who want a social media experience similar to Twitter or Facebook with an infinite scrolling feed of notes to interact with. However, there is some "other stuff" included to complement this primary focus on short and long form notes including a built-in Lightning wallet powered by #Strike, a robust advanced search, and a media-only feed.

Overall Impression
Score: 4.4 / 5 (Updated 4/30/2025)
Primal may well be the most polished UI of any Nostr client native to Android. It is incredibly well designed and thought out, with all of the icons and settings in the places a user would expect to find them. It is also incredibly easy to get started on Nostr via Primal's sign-up flow. The only two things that will be foreign to new users are the lack of any need to set a password or give an email address, and the prompt to optionally set up the wallet.
Complaints prior to the 2.0 update about Primal being slow and clunky should now be completely alleviated. I only experienced quick load times and snappy UI controls with a couple very minor exceptions, or when loading DVM-based feeds, which are outside of Primal's control.
Primal is not, however, a client that I would recommend for the power-user. Control over preferred relays is minimal and does not allow the user to determine which relays they write to and which they only read from. Though you can use your own wallet, it will not appear within the wallet interface, which only works with the custodial wallet from Strike. Moreover, and most eggregiously, the only way for existing users to log in is by pasting their nsec, as Primal does not support either the Android signer or remote signer options for users to protect their private key at this time. This lack of signer support is the primary reason the client received such a low overall score. If even one form of external signer log in is added to Primal, the score will be amended to 4.2 / 5, and if both Android signer and remote signer support is added, it will increase to 4.5.
Update: As of version 2.2.13, Primal now supports the Amber Android signer! One of the most glaring issues with the app has now been remedied and as promised, the overall score above has been increased.
Another downside to Primal is that it still utilizes an outdated direct message specification that leaks metadata that can be readily seen by anyone on the network. While the content of your messages remains encrypted, anyone can see who you are messaging with, and when. This also means that you will not see any DMs from users who are messaging from a client that has moved to the latest, and far more private, messaging spec.
That said, the beautiful thing about Nostr as a protocol is that users are not locked into any particular client. You may find Primal to be a great client for your average #bloomscrolling and zapping memes, but opt for a different client for more advanced uses and for direct messaging.
Features
Primal has a lot of features users would expect from any Nostr client that is focused on short-form notes, but it also packs in a lot of features that set it apart from other clients, and that showcase Primal's obvious prioritization of a top-tier user experience.
Home Feed
By default, the infinitely scrolling Home feed displays notes from those you currently follow in chronological order. This is traditional Nostr at its finest, and made all the more immersive by the choice to have all distracting UI elements quickly hide themselves from view as the you begin to scroll down the feed. They return just as quickly when you begin to scroll back up.

Scrolling the feed is incredibly fast, with no noticeable choppiness and minimal media pop-in if you are on a decent internet connection.
Helpfully, it is easy to get back to the top of the feed whenever there is a new post to be viewed, as a bubble will appear with the profile pictures of the users who have posted since you started scrolling.

Interacting With Notes
Interacting with a note in the feed can be done via the very recognizable icons at the bottom of each post. You can comment, zap, like, repost, and/or bookmark the note.
Notably, tapping on the zap icon will immediately zap the note your default amount of sats, making zapping incredibly fast, especially when using the built-in wallet. Long pressing on the zap icon will open up a menu with a variety of amounts, along with the ability to zap a custom amount. All of these amounts, and the messages that are sent with the zap, can be customized in the application settings.

Users who are familiar with Twitter or Instagram will feel right at home with only having one option for "liking" a post. However, users from Facebook or other Nostr clients may wonder why they don't have more options for reactions. This is one of those things where users who are new to Nostr probably won't notice they are missing out on anything at all, while users familiar with clients like #Amethyst or #noStrudel will miss the ability to react with a 🤙 or a 🫂.
It's a similar story with the bookmark option. While this is a nice bit of feature parity for Twitter users, for those already used to the ability to have multiple customized lists of bookmarks, or at minimum have the ability to separate them into public and private, it may be a disappointment that they have no access to the bookmarks they already built up on other clients. Primal offers only one list of bookmarks for short-form notes and they are all visible to the public. However, you are at least presented with a warning about the public nature of your bookmarks before saving your first one.
Yet, I can't dock the Primal team much for making these design choices, as they are understandable for Primal's goal of being a welcoming client for those coming over to Nostr from centralized platforms. They have optimized for the onboarding of new users, rather than for those who have been around for a while, and there is absolutely nothing wrong with that.
Post Creation
Composing posts in Primal is as simple as it gets. Accessed by tapping the obvious circular button with a "+" on it in the lower right of the Home feed, most of what you could need is included in the interface, and nothing you don't.

Your device's default keyboard loads immediately, and the you can start typing away.
There are options for adding images from your gallery, or taking a picture with your camera, both of which will result in the image being uploaded to Primal's media-hosting server. If you prefer to host your media elsewhere, you can simply paste the link to that media into your post.
There is also an @ icon as a tip-off that you can tag other users. Tapping on this simply types "@" into your note and brings up a list of users. All you have to do to narrow down the user you want to tag is continue typing their handle, Nostr address, or paste in their npub.

This can get mixed results in other clients, which sometimes have a hard time finding particular users when typing in their handle, forcing you to have to remember their Nostr address or go hunt down their npub by another means. Not so with Primal, though. I had no issues tagging anyone I wanted by simply typing in their handle.
Of course, when you are tagging someone well known, you may find that there are multiple users posing as that person. Primal helps you out here, though. Usually the top result is the person you want, as Primal places them in order of how many followers they have. This is quite reliable right now, but there is nothing stopping someone from spinning up an army of bots to follow their fake accounts, rendering follower count useless for determining which account is legitimate. It would be nice to see these results ranked by web-of-trust, or at least an indication of how many users you follow who also follow the users listed in the results.
Once you are satisfied with your note, the "Post" button is easy to find in the top right of the screen.
Feed Selector and Marketplace
Primal's Home feed really shines when you open up the feed selection interface, and find that there are a plethora of options available for customizing your view. By default, it only shows four options, but tapping "Edit" opens up a new page of available toggles to add to the feed selector.

The options don't end there, though. Tapping "Add Feed" will open up the feed marketplace, where an ever-growing number of custom feeds can be found, some created by Primal and some created by others. This feed marketplace is available to a few other clients, but none have so closely integrated it with their Home feeds like Primal has.

Unfortunately, as great as these custom feeds are, this was also the feature where I ran into the most bugs while testing out the app.
One of these bugs was while selecting custom feeds. Occasionally, these feed menu screens would become unresponsive and I would be unable to confirm my selection, or even use the back button on my device to back out of the screen. However, I was able to pull the screen down to close it and re-open the menu, and everything would be responsive again.
This only seemed to occur when I spent 30 seconds or more on the same screen, so I imagine that most users won't encounter it much in their regular use.
Another UI bug occurred for me while in the feed marketplace. I could scroll down the list of available feeds, but attempting to scroll back up the feed would often close the interface entirely instead, as though I had pulled the screen down from the top, when I was swiping in the middle of the screen.
The last of these bugs occurred when selecting a long-form "Reads" feed while in the menu for the Home feed. The menu would allow me to add this feed and select it to be displayed, but it would fail to load the feed once selected, stating "There is no content in this feed." Going to a different page within the the app and then going back to the Home tab would automatically remove the long-form feed from view, and reset back to the most recently viewed short-form "Notes" feed, though the long-form feed would still be available to select again. The results were similar when selecting a short-form feed for the Reads feed.
I would suggest that if long-form and short-form feeds are going to be displayed in the same list, and yet not be able to be displayed in the same feed, the application should present an error message when attempting to add a long-form feed for the Home feed or a short-form feed for the Reads feed, and encourage the user add it to the proper feed instead.
Long-Form "Reads" Feed
A brand new feature in Primal 2.0, users can now browse and read long-form content posted to Nostr without having to go to a separate client. Primal now has a dedicated "Reads" feed to browse and interact with these articles.
This feed displays the author and title of each article or blog, along with an image, if available. Quite conveniently, it also lets you know the approximate amount of time it will take to read a given article, so you can decide if you have the time to dive into it now, or come back later.

Noticeably absent from the Reads feed, though, is the ability to compose an article of your own. This is another understandable design choice for a mobile client. Composing a long-form note on a smart-phone screen is not a good time. Better to be done on a larger screen, in a client with a full-featured text editor.
Tapping an article will open up an attractive reading interface, with the ability to bookmark for later. These bookmarks are a separate list from your short-form note bookmarks so you don't have to scroll through a bunch of notes you bookmarked to find the article you told yourself you would read later and it's already been three weeks.
While you can comment on the article or zap it, you will notice that you cannot repost or quote-post it. It's not that you can't do so on Nostr. You absolutely can in other clients. In fact, you can do so on Primal's web client, too. However, Primal on Android does not handle rendering long-form note previews in the Home feed, so they have simply left out the option to share them there. See below for an example of a quote-post of a long-form note in the Primal web client vs the Android client.
Primal Web:

Primal Android:

The Explore Tab
Another unique feature of the Primal client is the Explore tab, indicated by the compass icon. This tab is dedicated to discovering content from outside your current follow list. You can find the feed marketplace here, and add any of the available feeds to your Home or Reads feed selections. You can also find suggested users to follow in the People tab. The Zaps tab will show you who has been sending and receiving large zaps. Make friends with the generous ones!
The Media tab gives you a chronological feed of just media, displayed in a tile view. This can be great when you are looking for users who post dank memes, or incredible photography on a regular basis. Unfortunately, it appears that there is no way to filter this feed for sensitive content, and so you do not have to scroll far before you see pornographic material.
Indeed, it does not appear that filters for sensitive content are available in Primal for any feed. The app is kind enough to give a minimal warning that objectionable content may be present when selecting the "Nostr Firehose" option in your Home feed, with a brief "be careful" in the feed description, but there is not even that much of a warning here for the media-only feed.

The media-only feed doesn't appear to be quite as bad as the Nostr Firehose feed, so there must be some form of filtering already taking place, rather than being a truly global feed of all media. Yet, occasional sensitive content still litters the feed and is unavoidable, even for users who would rather not see it. There are, of course, ways to mute particular users who post such content, if you don't want to see it a second time from the same user, but that is a never-ending game of whack-a-mole, so your only realistic choices in Primal are currently to either avoid the Nostr Firehose and media-only feeds, or determine that you can put up with regularly scrolling past often graphic content.
This is probably the only choice Primal has made that is not friendly to new users. Most clients these days will have some protections in place to hide sensitive content by default, but still allow the user to toggle those protections off if they so choose. Some of them hide posts flagged as sensitive content altogether, others just blur the images unless the user taps to reveal them, and others simply blur all images posted by users you don't follow. If Primal wants to target new users who are accustomed to legacy social media platforms, they really should follow suit.
The final tab is titled "Topics," but it is really just a list of popular hashtags, which appear to be arranged by how often they are being used. This can be good for finding things that other users are interested in talking about, or finding specific content you are interested in.
If you tap on any topic in the list, it will display a feed of notes that include that hashtag. What's better, you can add it as a feed option you can select on your Home feed any time you want to see posts with that tag.
The only suggestion I would make to improve this tab is some indication of why the topics are arranged in the order presented. A simple indicator of the number of posts with that hashtag in the last 24 hours, or whatever the interval is for determining their ranking, would more than suffice.
Even with those few shortcomings, Primal's Explore tab makes the client one of the best options for discovering content on Nostr that you are actually interested in seeing and interacting with.
Built-In Wallet
While this feature is completely optional, the icon to access the wallet is the largest of the icons at the bottom of the screen, making you feel like you are missing out on the most important feature of the app if you don't set it up. I could be critical of this design choice, but in many ways I think it is warranted. The built-in wallet is one of the most unique features that Primal has going for it.

Consider: If you are a new user coming to Nostr, who isn't already a Bitcoiner, and you see that everyone else on the platform is sending and receiving sats for their posts, will you be more likely to go download a separate wallet application or use one that is built-into your client? I would wager the latter option by a long shot. No need to figure out which wallet you should download, whether you should do self-custody or custodial, or make the mistake of choosing a wallet with unexpected setup fees and no Lightning address so you can't even receive zaps to it. nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr often states that he believes more people will be onboarded to Bitcoin through Nostr than by any other means, and by including a wallet into the Primal client, his team has made adopting Bitcoin that much easier for new Nostr users.
Some of us purists may complain that it is custodial and KYC, but that is an unfortunate necessity in order to facilitate onboarding newcoiners to Bitcoin. This is not intended to be a wallet for those of us who have been using Bitcoin and Lightning regularly already. It is meant for those who are not already familiar with Bitcoin to make it as easy as possible to get off zero, and it accomplishes this better than any other wallet I have ever tried.
In large part, this is because the KYC is very light. It does need the user's legal name, a valid email address, date of birth, and country of residence, but that's it! From there, the user can buy Bitcoin directly through the app, but only in the amount of $4.99 at a time. This is because there is a substantial markup on top of the current market price, due to utilizing whatever payment method the user has set up through their Google Play Store. The markup seemed to be about 19% above the current price, since I could purchase 4,143 sats for $4.99 ($120,415 / Bitcoin), when the current price was about $101,500. But the idea here is not for the Primal wallet to be a user's primary method of stacking sats. Rather, it is intended to get them off zero and have a small amount of sats to experience zapping with, and it accomplishes this with less friction than any other method I know.
Moreover, the Primal wallet has the features one would expect from any Lightning wallet. You can send sats to any Nostr user or Lightning address, receive via invoice, or scan to pay an invoice. It even has the ability to receive via on-chain. This means users who don't want to pay the markup from buying through Primal can easily transfer sats they obtained by other means into the Primal wallet for zapping, or for using it as their daily-driver spending wallet.
Speaking of zapping, once the wallet is activated, sending zaps is automatically set to use the wallet, and they are fast. Primal gives you immediate feedback that the zap was sent and the transaction shows in your wallet history typically before you can open the interface. I can confidently say that Primal wallet's integration is the absolute best zapping experience I have seen in any Nostr client.
One thing to note that may not be immediately apparent to new users is they need to add their Lightning address with Primal into their profile details before they can start receiving zaps. So, sending zaps using the wallet is automatic as soon as you activate it, but receiving is not. Ideally, this could be further streamlined, so that Primal automatically adds the Lightning address to the user's profile when the wallet is set up, so long as there is not currently a Lightning address listed.
Of course, if you already have a Lightning wallet, you can connect it to Primal for zapping, too. We will discuss this further in the section dedicated to zap integration.
Advanced Search
Search has always been a tough nut to crack on Nostr, since it is highly dependent on which relays the client is pulling information from. Primal has sought to resolve this issue, among others, by running a caching relay that pulls notes from a number of relays to store them locally, and perform some spam filtering. This allows for much faster retrieval of search results, and also makes their advanced search feature possible.
Advanced search can be accessed from most pages by selecting the magnifying glass icon, and then the icon for more options next to the search bar.
As can be seen in the screenshot below, there are a plethora of filters that can be applied to your search terms.

You can immediately see how this advanced search could be a very powerful tool for not just finding a particular previous note that you are looking for, but for creating your own custom feed of notes. Well, wouldn't you know it, Primal allows you to do just that! This search feature, paired with the other features mentioned above related to finding notes you want to see in your feed, makes Primal hands-down the best client for content discovery.
The only downside as a free user is that some of these search options are locked behind the premium membership. Or else you only get to see a certain number of results of your advanced search before you must be a premium member to see more.
Can My Grandma Use It?
Score: 4.8 / 5 Primal has obviously put a high priority on making their client user-friendly, even for those who have never heard of relays, public/private key cryptography, or Bitcoin. All of that complexity is hidden away. Some of it is available to play around with for the users who care to do so, but it does not at all get in the way of the users who just want to jump in and start posting notes and interacting with other users in a truly open public square.
To begin with, the onboarding experience is incredibly smooth. Tap "Create Account," enter your chosen display name and optional bio information, upload a profile picture, and then choose some topics you are interested in. You are then presented with a preview of your profile, with the ability to add a banner image, if you so choose, and then tap "Create Account Now."

From there you receive confirmation that your account has been created and that your "Nostr key" is available to you in the application settings. No further explanation is given about what this key is for at this point, but the user doesn't really need to know at the moment, either. If they are curious, they will go to the app settings to find out.
At this point, Primal encourages the user to activate Primal Wallet, but also gives the option for the user to do it later.

That's it! The next screen the user sees if they don't opt to set up the wallet is their Home feed with notes listed in chronological order. More impressive, the feed is not empty, because Primal has auto-followed several accounts based on your selected topics.
Now, there has definitely been some legitimate criticism of this practice of following specific accounts based on the topic selection, and I agree. I would much prefer to see Primal follow hashtags based on what was selected, and combine the followed hashtags into a feed titled "My Topics" or something of that nature, and make that the default view when the user finishes onboarding. Following particular users automatically will artificially inflate certain users' exposure, while other users who might be quality follows for that topic aren't seen at all.
The advantage of following particular users over a hashtag, though, is that Primal retains some control over the quality of the posts that new users are exposed to right away. Primal can ensure that new users see people who are actually posting quality photography when they choose it as one of their interests. However, even with that example, I chose photography as one of my interests and while I did get some stunning photography in my Home feed by default based on Primal's chosen follows, I also scrolled through the Photography hashtag for a bit and I really feel like I would have been better served if Primal had simply followed that hashtag rather than a particular set of users.
We've already discussed how simple it is to set up the Primal Wallet. You can see the features section above if you missed it. It is, by far, the most user friendly experience to onboarding onto Lightning and getting a few sats for zapping, and it is the only one I know of that is built directly into a Nostr client. This means new users will have a frictionless introduction to transacting via Lightning, perhaps without even realizing that's what they are doing.
Discovering new content of interest is incredibly intuitive on Primal, and the only thing that new users may struggle with is getting their own notes seen by others. To assist with this, I would suggest Primal encourage users to make their first post to the introductions hashtag and direct any questions to the AskNostr hashtag as part of the onboarding process. This will get them some immediate interactions from other users, and further encouragement to set up their wallet if they haven't already done so.
How do UI look?
Score: 4.9 / 5
Primal is the most stunningly beautiful Nostr client available, in my honest opinion. Despite some of my hangups about certain functionality, the UI alone makes me want to use it.

It is clean, attractive, and intuitive. Everything I needed was easy to find, and nothing felt busy or cluttered. There are only a few minor UI glitches that I ran into while testing the app. Some of them were mentioned in the section of the review detailing the feed selector feature, but a couple others occurred during onboarding.
First, my profile picture was not centered in the preview when I uploaded it. This appears to be because it was a low quality image. Uploading a higher quality photo did not have this result.

The other UI bug was related to text instructions that were cut off, and not able to scroll to see the rest of them. This occurred on a few pages during onboarding, and I expect it was due to the size of my phone screen, since it did not occur when I was on a slightly larger phone or tablet.

Speaking of tablets, Primal Android looks really good on a tablet, too! While the client does not have a landscape mode by default, many Android tablets support forcing apps to open in full-screen landscape mode, with mixed results. However, Primal handles it well. I would still like to see a tablet version developed that takes advantage of the increased screen real estate, but it is certainly a passable option.





At this point, I would say the web client probably has a bit better UI for use on a tablet than the Android client does, but you miss out on using the built-in wallet, which is a major selling point of the app.
This lack of a landscape mode for tablets and the few very minor UI bugs I encountered are the only reason Primal doesn't get a perfect score in this category, because the client is absolutely stunning otherwise, both in light and dark modes. There are also two color schemes available for each.

Log In Options
Score: 4 / 5 (Updated 4/30/2025)
Unfortunately, Primal has not included any options for log in outside of pasting your private key into the application. While this is a very simple way to log in for new users to understand, it is also the least secure means to log into Nostr applications.
This is because, even with the most trustworthy client developer, giving the application access to your private key always has the potential for that private key to somehow be exposed or leaked, and on Nostr there is currently no way to rotate to a different private key and keep your identity and social graph. If someone gets your key, they are you on Nostr for all intents and purposes.
This is not a situation that users should be willing to tolerate from production-release clients at this point. There are much better log in standards that can and should be implemented if you care about your users.
That said, I am happy to report that external signer support is on the roadmap for Primal, as confirmed below:
nostr:note1n59tc8k5l2v30jxuzghg7dy2ns76ld0hqnn8tkahyywpwp47ms5qst8ehl
No word yet on whether this will be Android signer or remote signer support, or both.
This lack of external signer support is why I absolutely will not use my main npub with Primal for Android. I am happy to use the web client, which supports and encourages logging in with a browser extension, but until the Android client allows users to protect their private key, I cannot recommend it for existing Nostr users.
Update: As of version 2.2.13, all of what I have said above is now obsolete. Primal has added Android signer support, so users can now better protect their nsec by using Amber!
I would still like to see support for remote signers, especially with nstart.me as a recommended Nostr onboarding process and the advent of FROSTR for key management. That said, Android signer support on its own has been a long time coming and is a very welcome addition to the Primal app. Bravo Primal team!
Zap Integration
Score: 4.8 / 5
As mentioned when discussing Primal's built-in wallet feature, zapping in Primal can be the most seamless experience I have ever seen in a Nostr client. Pairing the wallet with the client is absolutely the path forward for Nostr leading the way to Bitcoin adoption.
But what if you already have a Lightning wallet you want to use for zapping? You have a couple options. If it is an Alby wallet or another wallet that supports Nostr Wallet Connect, you can connect it with Primal to use with one-tap zapping.

How your zapping experience goes with this option will vary greatly based on your particular wallet of choice and is beyond the scope of this review. I used this option with a hosted wallet on my Alby Hub and it worked perfectly. Primal gives you immediate feedback that you have zapped, even though the transaction usually takes a few seconds to process and appear in your wallet's history.
The one major downside to using an external wallet is the lack of integration with the wallet interface. This interface currently only works with Primal's wallet, and therefore the most prominent tab in the entire app goes unused when you connect an external wallet.

An ideal improvement would be for the wallet screen to work similar to Alby Go when you have an external wallet connected via Nostr Wallet Connect, allowing the user to have Primal act as their primary mobile Lightning wallet. It could have balance and transaction history displayed, and allow sending and receiving, just like the integrated Primal wallet, but remove the ability to purchase sats directly through the app when using an external wallet.
Content Discovery
Score: 4.8 / 5
Primal is the best client to use if you want to discover new content you are interested in. There is no comparison, with only a few caveats.
First, the content must have been posted to Nostr as either a short-form or long-form note. Primal has a limited ability to display other types of content. For instance, discovering video content or streaming content is lacking.
Second, you must be willing to put up with the fact that Primal lacks a means of filtering sensitive content when you are exploring beyond the bounds of your current followers. This may not be an issue for some, but for others it could be a deal-breaker.
Third, it would be preferable for Primal to follow topics you are interested in when you choose them during onboarding, rather than follow specific npubs. Ideally, create a "My Topics" feed that can be edited by selecting your interests in the Topics section of the Explore tab.
Relay Management
Score: 2.5 / 5
For new users who don't want to mess around with managing relays, Primal is fantastic! There are 7 relays selected by default, in addition to Primal's caching service. For most users who aren't familiar with Nostr's protocol archetecture, they probably won't ever have to change their default relays in order to use the client as they would expect.
However, two of these default relays were consistently unreachable during the week that I tested. These were relay.plebes.fans and remnant.cloud. The first relay seems to be an incorrect URL, as I found nosflare.plebes.fans online and with perfect uptime for the last 12 hours on nostr.watch. I was unable to find remnant.cloud on nostr.watch at all. A third relay was intermittent, sometimes online and reachable, and other times unreachable: v1250.planz.io/nostr. If Primal is going to have default relays, they should ideally be reliable and with accurate URLs.
That said, users can add other relays that they prefer, and remove relays that they no longer want to use. They can even set a different caching service to use with the client, rather than using Primal's.

However, that is the extent of a user's control over their relays. They cannot choose which relays they want to write to and which they want to read from, nor can they set any private relays, outbox or inbox relays, or general relays. Loading the npub I used for this review into another client with full relay management support revealed that the relays selected in Primal are being added to both the user's public outbox relays and public inbox relays, but not to any other relay type, which leads me to believe the caching relay is acting as the client's only general relay and search relay.
One unique and welcomed addition is the "Enhanced Privacy" feature, which is off by default, but which can be toggled on. I am not sure why this is not on by default, though. Perhaps someone from the Primal team can enlighten me on that choice.
By default, when you post to Nostr, all of your outbox relays will see your IP address. If you turn on the Enhanced Privacy mode, only Primal's caching service will see your IP address, because it will post your note to the other relays on your behalf. In this way, the caching service acts similar to a VPN for posting to Nostr, as long as you trust Primal not to log or leak your IP address.
In short, if you use any other Nostr clients at all, do not use Primal for managing your relays.
Media Hosting Options
Score: 4.9 / 5 This is a NEW SECTION of this review, as of version 2.2.13!
Primal has recently added support for the Blossom protocol for media hosting, and has added a new section within their settings for "Media Uploads."
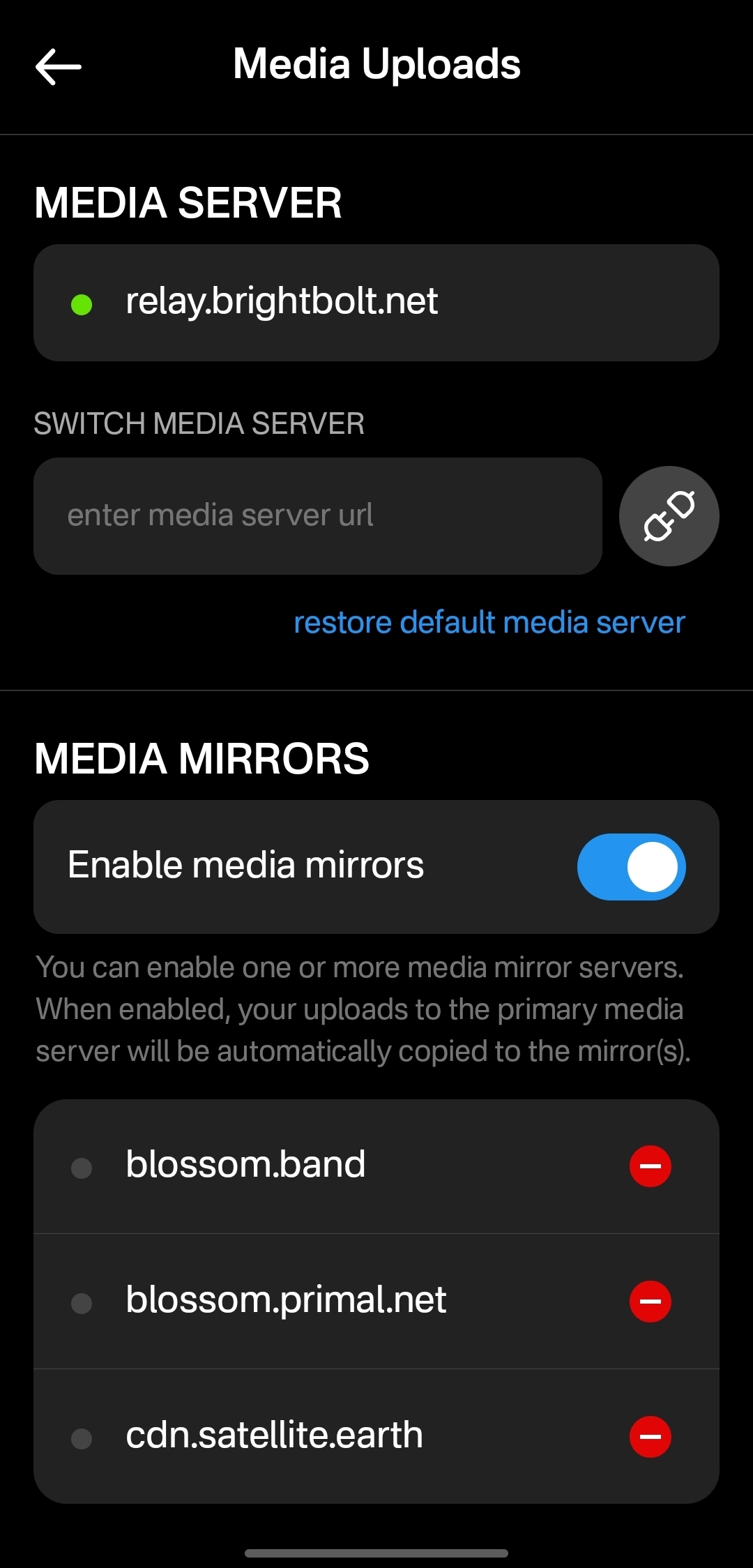
Media hosting is one of the more complicated problems to solve for a decentralized publishing protocol like Nostr. Text-based notes are generally quite small, making them no real burden to store on relays, and a relay can prune old notes as they see fit, knowing that anyone who really cared about those notes has likely archived them elsewhere. Media, on the other hand, can very quickly fill up a server's disk space, and because it is usually addressable via a specific URL, removing it from that location to free up space means it will no longer load for anyone.
Blossom solves this issue by making it easy to run a media server and have the same media mirrored to more than one for redundancy. Since the media is stored with a file name that is a hash of the content itself, if the media is deleted from one server, it can still be found from any other server that has the same file, without any need to update the URL in the Nostr note where it was originally posted.
Prior to this update, Primal only allowed media uploads to their own media server. Now, users can upload to any blossom server, and even choose to have their pictures or videos mirrored additional servers automatically. To my knowledge, no other Nostr client offers this automatic mirroring at the time of upload.
One of my biggest criticisms of Primal was that it had taken a siloed approach by providing a client, a caching relay, a media server, and a wallet all controlled by the same company. The whole point of Nostr is to separate control of all these services to different entities. Now users have more options for separating out their media hosting and their wallet to other providers, at least. I would still like to see other options available for a caching relay, but that relies on someone else being willing to run one, since the software is open for anyone to use. It's just not your average, lightweight relay that any average person can run from home.
Regardless, this update to add custom Blossom servers is a most welcome step in the right direction!
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with a client. Here are some of the most common questions submitted about Primal since the launch of 2.0:
nostr:note1dqv4mwqn7lvpaceg9s7damf932ydv9skv2x99l56ufy3f7q8tkdqpxk0rd
This was a pretty common question, because users expect that they will be able to create the same type of content that they can consume in a particular client. I can understand why this was left out in a mobile client, but perhaps it should be added in the web client.
nostr:note16xnm8a2mmrs7t9pqymwjgd384ynpf098gmemzy49p3572vhwx2mqcqw8xe
This is a more concerning bug, since it appears some users are experiencing their images being replaced with completely different images. I did not experience anything similar in my testing, though.
nostr:note1uhrk30nq0e566kx8ac4qpwrdh0vfaav33rfvckyvlzn04tkuqahsx8e7mr
There hasn't been an answer to this, but I have not been able to find a way. It seems search results will always include replies as well as original notes, so a feed made from the search results will as well. Perhaps a filter can be added to the advanced search to exclude replies? There is already a filter to only show replies, but there is no corresponding filter to only show original notes.
nostr:note1zlnzua28a5v76jwuakyrf7hham56kx9me9la3dnt3fvymcyaq6eqjfmtq6
Since both mobile platforms support the wallet, users expect that they will be able to access it in their web client, too. At this time, they cannot. The only way to have seamless zapping in the web client is to use the Alby extension, but there is not a way to connect it to your Primal wallet via Nostr Wallet Connect either. This means users must have a separate wallet for zapping on the web client if they use the Primal Wallet on mobile.
nostr:note15tf2u9pffy58y9lk27y245ew792raqc7lc22jezxvqj7xrak9ztqu45wep
It seems that Primal is filtering for spam even for profiles you actively follow. Moreover, exactly what the criteria is for being considered spam is currently opaque.
nostr:note1xexnzv0vrmc8svvduurydwmu43w7dftyqmjh4ps98zksr39ln2qswkuced
For those unaware, Blossom is a protocol for hosting media as blobs identified by a hash, allowing them to be located on and displayed from other servers they have been mirrored to when when the target server isn't available. Primal currently runs a Blossom server (blossom.primal.net) so I would expect we see Blossom support in the future.
nostr:note1unugv7s36e2kxl768ykg0qly7czeplp8qnc207k4pj45rexgqv4sue50y6
Currently, Primal on Android only supports uploading photos to your posts. Users must upload any video to some other hosting service and copy/paste a link to the video into their post on Primal. I would not be surprised to see this feature added in the near future, though.
nostr:note10w6538y58dkd9mdrlkfc8ylhnyqutc56ggdw7gk5y7nsp00rdk4q3qgrex
Many Nostr users have more than one npub for various uses. Users would prefer to have a way to quickly switch between accounts than to have to log all the way out and paste their npub for the other account every time they want to use it.
There is good news on this front, though:
nostr:note17xv632yqfz8nx092lj4sxr7drrqfey6e2373ha00qlq8j8qv6jjs36kxlh
Wrap Up
All in all, Primal is an excellent client. It won't be for everyone, but that's one of the strengths of Nostr as a protocol. You can choose to use the client that best fits your own needs, and supplement with other clients and tools as necessary.
There are a couple glaring issues I have with Primal that prevent me from using it on my main npub, but it is also an ever-improving client, that already has me hopeful for those issues to be resolved in a future release.
So, what should I review next? Another Android client, such as #Amethyst or #Voyage? Maybe an "other stuff" app, like #Wavlake or #Fountain? Please leave your suggestions in the comments.
I hope this review was valuable to you! If it was, please consider letting me know just how valuable by zapping me some sats and reposting it out to your follows.
Thank you for reading!
PV 🤙
-
 @ 401014b3:59d5476b
2025-04-30 21:08:52
@ 401014b3:59d5476b
2025-04-30 21:08:52And here's what it said.
And for what it's worth, I actually think ChatGPT nailed it.
Thoughts?
-
Andy Reid – Kansas City Chiefs Andy Reid remains the gold standard among NFL head coaches. With three Super Bowl titles in the past six seasons and a career record of 273-146-1 (.651), Reid's offensive innovation and leadership continue to set him apart.
-
Sean McVay – Los Angeles Rams Sean McVay has revitalized the Rams since taking over in 2017, leading them to two Super Bowl appearances and maintaining only one losing season in eight years. His ability to adapt and keep the team competitive has solidified his status as one of the league's elite coaches.
-
John Harbaugh – Baltimore Ravens John Harbaugh's tenure with the Ravens has been marked by consistent success, including a Super Bowl victory in 2012 and multiple double-digit win seasons. His leadership and adaptability have kept Baltimore as a perennial contender.
-
Nick Sirianni – Philadelphia Eagles Nick Sirianni has quickly risen through the ranks, boasting a .706 regular-season winning percentage and leading the Eagles to two Super Bowl appearances, including one victory. His emphasis on player morale and adaptability have been key to Philadelphia's recent success.
-
Dan Campbell – Detroit Lions Dan Campbell has transformed the Lions into a formidable team, improving their record each season and instilling a culture of toughness and resilience. Despite a disappointing playoff exit in 2024, Campbell's impact on the franchise is undeniable.
originally posted at https://stacker.news/items/967880
-
-
 @ e968e50b:db2a803a
2025-04-30 20:40:33
@ e968e50b:db2a803a
2025-04-30 20:40:33Has anyone developed a lightning wallet using a raspberry pi or something like that? This would be a device that could fit in your pocket with a small screen and QR scanner for people that can't afford or don't want to carry a smart phone. It would use wifi or something like that. Is this too much of a security headache? Can it be done easily with any wallet's current software?
originally posted at https://stacker.news/items/967863
-
 @ c230edd3:8ad4a712
2025-04-30 16:19:30
@ c230edd3:8ad4a712
2025-04-30 16:19:30Chef's notes
I found this recipe on beyondsweetandsavory.com. The site is incredibly ad infested (like most recipe sites) and its very annoying so I'm copying it to Nostr so all the homemade ice cream people can access it without dealing with that mess. I haven't made it yet. Will report back, when I do.
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 55 min
- 🍽️ Servings: 8
Ingredients
- 2 cups heavy cream
- 1 cup 2% milk
- 8 oz dark chocolate, 70%
- ¼ cup Dutch cocoa
- 2 tbsps loose Earl grey tea leaves
- 4 medium egg yolks
- ¾ cup granulated sugar
- ⅛ tsp salt
- ¼ cup dark chocolate, 70% chopped
Directions
- In a double boiler or a bowl set over a saucepan of simmering water, add the cacao solids and ½ cup of heavy cream. Stir chocolate until melted and smooth. Set melted chocolate aside.
- In a heavy saucepan, combine remaining heavy cream, milk, salt and ½ cup of sugar.
- Put the pan over medium heat and let the mixture boil gently to bubbling just around the edges (gentle simmer) and sugar completely dissolved, about 5 minutes. Remove from heat.
- Add the Earl Grey tea leaves and let it steep for 7-8 minutes until the cream has taken on the tea flavor, stirring occasionally and tasting to make sure it’s not too bitter.
- Whisk in Dutch cocoa until smooth. Add in melted chocolate and whisk until smooth.
- In a medium heatproof bowl, whisk the yolks just to break them up and whisk in remaining sugar. Set aside.
- Put the saucepan back on the stove over low heat and let it warm up for 2 minutes.
- Carefully measure out ½ cup of hot cream mixture.
- While whisking the eggs constantly, whisk the hot cream mixture into the eggs until smooth. Continue tempering the eggs by adding another ½ cup of hot cream to the bowl with the yolks.
- Pour the cream-egg mixture back to the saucepan and cook over medium-low heat, stirring constantly until it is thickened and coats the back of a spatula, about 5 minutes.
- Strain the base through a fine-mesh strainer into a clean container.
- Pour the mixture into a 1-gallon Ziplock freezer bag and submerge the sealed bag in an ice bath until cold, about 30 minutes. Refrigerate the ice cream base for at least 4 hours or overnight.
- Pour the ice cream base into the frozen canister of your ice cream machine and follow the manufacturer’s instructions.
- Spin until thick and creamy about 25-30 minutes.
- Pack the ice cream into a storage container, press a sheet of parchment directly against the surface and seal with an airtight lid. Freeze in the coldest part of your freezer until firm, at least 4 hours.
- When ready to serve, scoop the ice cream into a serving bowl and top with chopped chocolate.
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-30 15:50:37
@ 5d4b6c8d:8a1c1ee3
2025-04-30 15:50:37I was a bit more distracted than normal this month, but ~econ kept humming along.
- Posts: 228 (7th)
- Comments: 1459 (5th)
- Stacking: 128k (4th)
- Revenue: 74k (4th)
We're holding pretty steady, but haven't gotten back to our highs from last year.
With revenue down slightly, I'll move the post fee back towards the previous local max and conclude the posting fee optimization process for now. Going forward the posting fee will be set at 84 sats (until I decide to start messing with it again).
Next month, I'll start the comment fee optimization process.
We're still on pace for a profitable year and having a nice sized fund to pay out the end-of-year awards.
Thanks everyone for supporting this community!
Let me know if you have any suggestions for how to improve the territory.
originally posted at https://stacker.news/items/967545
-
 @ 57d1a264:69f1fee1
2025-04-30 07:44:21
@ 57d1a264:69f1fee1
2025-04-30 07:44:21- The Dangers of Ignorance
- A Brief History of Mechanistic Interpretability
- The Utility of Interpretability
- What We Can Do
The progress of the underlying technology is inexorable, driven by forces too powerful to stop, but the way in which it happens—the order in which things are built, the applications we choose, and the details of how it is rolled out to society—are eminently possible to change, and it’s possible to have great positive impact by doing so. We can’t stop the bus, but we can steer it.
—Dario Amodeioriginally posted at https://stacker.news/items/967193
-
 @ 0e67f053:cb1d4b93
2025-04-30 02:27:03
@ 0e67f053:cb1d4b93
2025-04-30 02:27:03How to Be an Anti-Fascist
According to Me, a Certified Organic Latte-Drinking Empathy Warrior
By Tucker Carlson’s Emotionally Available Clone Carl Tuckerson
Namaste, comrades.
Are you tired of watching democracy get mildly inconvenienced by billionaires while sipping your ethically sourced, $19 oat milk flat white? Do you sometimes feel like tweeting just isn’t enough to stop the slow, fascist creep of boomers with opinions?
Well, worry not. Because tonight, I, a glowing beacon of progressive perfection, will guide you through the sacred, carbon-neutral art of being an Anti-Fascist—from the comfort of your iPad, handcrafted from rare earth minerals mined by literal children.
Let’s begin.
Step 1: Declare Yourself Anti-Fascist... On Instagram.
Nothing says “resistance” quite like a filtered selfie captioned “Punching Nazis with love 💕✊ #Resist #SelfCareRevolution”. Bonus points if you’re wearing a Che Guevara shirt made in a sweatshop. Because nothing defeats authoritarianism like aesthetics.
Remember: optics over action. Always.
Step 2: Elon Musk Is Literally Hitler (Until He Makes a Space Weed Dispensary)
We used to love Elon. He was our quirky space daddy. He tweeted in lowercase. He smoked weed with Joe Rogan. He wore weird shoes. We loved that. Then he bought Twitter and suddenly—BOOM—he’s literally Benito Mussolini with better branding.
But hey, let’s be honest: if he announced a carbon-neutral Neuralink that dispenses vegan Adderall, we’d be back on the bandwagon so fast. We are morally opposed to fascism... unless it syncs with our Apple Watches.
Step 3: Donald Trump Is an Existential Threat (Also... Kinda Fun to Keep Around)
Yes, Trump is a threat to democracy. Yes, he incited an insurrection. Yes, he talks like a Big Mac with a head injury. But if we actually stopped him? What would we tweet about?
He’s the villain we love to hate. He’s like Voldemort, if Voldemort ran on cheeseburgers and late-stage narcissism. He’s our algorithmic muse. He’s content.
Let’s not pretend we didn’t low-key enjoy four years of outrage-fueled identity formation. He gave us purpose. He gave us merch. Admit it—you miss him a little. That’s not anti-fascism, babe. That’s codependence.
Step 4: Say “Fascism” a Lot. Define It? Not So Much.
When in doubt, call literally anything “fascism.” Voter ID laws? Fascism. Gas stoves? Fascism. Someone didn’t like your TikTok about polyamorous Marxism? Fascism.
Defining the word would ruin the fun. It’s like “vibes,” but with historical trauma. Why read a book when you can just compare everything to Hitler and get 12,000 retweets?
Remember: if you say “fascism” enough times, you don’t have to actually do anything about it.
Step 5: Be Loud. Be Online. Be Ironic.
Who needs grassroots organizing when you can “dunk on fascists” in the quote tweets? Nothing defeats authoritarianism like being aggressively smug with a PFP of a frog holding a Molotov cocktail.
Marching in the streets? Mutual aid? Local elections?
Cringe.
Let’s just post a meme of Trump hugging Mussolini with a caption that says, “When your fascist BF also texts other regimes 🥺👉👈.”
Final Thoughts (Because I Have So Many)
Being an anti-fascist in 2025 is hard. You have to juggle being morally superior, chronically online, and vaguely condescending all at once. But if we just stay in our bubbles, talk over each other on Clubhouse, and continue to believe that irony is activism, we’ll totally defeat fascism.
Eventually.
Maybe.
After brunch.
Stay performative. Stay smug. Stay revolution-adjacent.
We’ll see you tomorrow—for another episode of "The Whisper of Democracy", where we dismantle empires with emotional vulnerability and artisanal zines.
Namaste, but make it confrontational.
— Delusionally Chill Carl
originally posted at https://stacker.news/items/967043
-
 @ d9a329af:bef580d7
2025-04-30 00:15:14
@ d9a329af:bef580d7
2025-04-30 00:15:14Since 2022, Dungeons and Dragons has been going down a sort of death spiral after the release of a revised version of 5th Edition... which didn't turn out very well to say the least. In light of that, I present a list of TTRPGs you can play if you don't want to purchase 5E. I wouldn't recommend 5E, as I've DM'd it in the past. It tastes like a lollipop that's cockroach and larvae flavored.
This list of TTRPG games is in no particular order, though my favorite of these systems is number one.
- Basic Fantasy Role-Playing Game (BFRPG)
- B/X-style OSR retroclone with ascending armor class, and the original retroclone from 2006
- Fully libre under CC BY-SA for the 4th Edition, and OGL 1.0a for 1-3 Editions.
- Full books are free PDF files on the website (Basic Fantasy Website)
- All BFRPG editions are compatible with each other, meaning you can have a 3rd Edition book to a 4th Edition game and still have fun. 4th Edition is just the removal of the 3E SRD that's in the OGL editions.
- As with the core rulebooks, all the supplementation is free as a PDF as well, though you can buy physical books at cost (BFRPG principal rights holder Chris Gonnerman doesn't make much profit from Basic Fantasy)
- Old-school community that's an all-around fantastic group of players, authors and enthusiasts.
-
Fun Fact: Out of all the TTRPGs I'd want to DM/GM the most, it'd be this one by far.
-
Iron Falcon (IF)
- OD&D-style retroclone from 2015 (It's also by Gonnerman, same guy behind BFRPG)
- A close ruleset to the White Box rules and supplements
- Also fully libre under CC BY-SA for the latest releases, just like BFRPG for 4th Edition releases
- Just like BFRPG, the core rules and supplementation come as PDF files for free, or physical books.
-
Fast and loose ruleset open to interpretation, just like in 1975-1981... somewhere right around that timeline for OD&D
-
Old-School Reference and Index Compendium (OSRIC)
- AD&D 1E-based retroclone by Stewart Marshall and Matt Finch
- An old system that surprisingly still holds up, even after a long time of no new versions of the rules
- Extremely in-depth ruleset, licensed under OGL 1.0a and OSRIC Open License
- Compatible with AD&D 1e modules for the 1st Edition, though 2.2 potentially has its own supplementation
-
I don't know much about it, as I'd be too slow to learn it. That's all I know, which is the above.
-
Ironsworn
- Custom loosely-based PbtA (Powered by the Apocalypse) system by Shawn Tomkin from 2018
- Includes GM, GMless and solo play in the rulebook
- Supplementation is surely something else with one look at the downloads section for the PDFs of the original, which is free under CC BY-NC-SA. The SRD is under CC BY otherwise.
- No original adventures are made for this system as are known, as it's expected that the Ironlands are where they take place
-
Fun Fact: This was a non-D&D system I considered running as a GM.
-
Advanced Dungeons & Dragons 2nd Edition (AD&D 2e)
- An official edition from 1989-2000
- At the time, the most customizable edition in its history, before 3E took the spot as the most customizable edition
- A streamlined revision of the AD&D 1E rules (AD&D 1E was exclusively written by E. Gary Gygax)
- The end of old-school D&D, as 3E and beyond are different games altogether
- Wide array of supplementation, which oversaturated 2E's customization... and most of it didn't sell well as a result
- Final TSR-published edition of D&D, as they went bankrupt and out of business during this edition's life cycle, to then be liquidated to Wizards of the Coast (Boy did WOTC mess it up once 5.1E was released)
-
Fun Fact: A Canadian history professor named Dr. Robert Wardough runs a customized ruleset using 2E as a base, which he's been DMing since the 80's during the "Satanic Panic" (The Satanic Panic was fake as a result of horrible deceivers gaslighting people to not play D&D). He started RAW (Rules as Written), but saw some things he needed to change for his games, so he did so over time.
-
Moldvay/Cook Basic/Expert Dungeons & Dragons (B/X)
- Competing system to 1E from 1981 and 1982
- Official edition of D&D, part of the old-school era
- Simplified rules for Basic, but some decently complex rules for Expert
- Only goes up to Lv. 14, as it's potentially a 1E or White Box primer (similar to 1977 Basic)
- Supplementation, from some research done, was decent for the time, and a little bit extensive
- The inspiration for BFRPG in 2006 (Did I mention this already? Maybe I have, but I might emphasize that here too.)
-
Fun Fact: I considered running B/X, but decided that I'd do BFRPG, as the ascending armor class is easier math than with B/X and the THAC0 armor class (descending armor class).
-
Basic, Expert, Companion, Master, Immortal Dungeons & Dragons (BECMI) and/or Rules Cyclopedia
- 1983 variant of the Moldvay/Cook Basic/Expert system, an official edition and part of the old-school era
- Essentially, 1981 B/X D&D on steroids
- 5 boxed sets were released for the five parts of the rules for this system
- Rules Cyclopedia is a reprint of the 1983 Basic, Expert, Companion and Master rules boxed sets. The Immortal set was never reprinted outside of the original boxed set because Immortal is such a bizarre game within a game altogether.
- With the first 4 boxed sets (whether individual sets or the Rules Cyclopedia), levels are 1-36
-
Fun Fact: This edition I was considering DMing as well, alongside BFRPG. They're similar rulesets with some mechanical differences, but I think either or would be worth it.
-
Original Dungeons & Dragons (OD&D or White Box)
- The original release of D&D from 1974 written by Gygax and Dave Arneson, published by TSR
- Uses the rules from Chainmail, a wargame made by Gygax and Jeff Perren
- Base has three little booklets (Men & Magic, Monsters & Magic, and The Underworld & Wilderness Adventures), five official supplements were released (Greyhawk; Blackmoor; Eldritch Wizardry; Gods, Demi-Gods and Heroes; and Swords & Spells), and many more from fanzines
- Fast and loose ruleset open to interpretation
- Not based upon adventurers taking on dangerous quest, but kings commanding armies (which is why OD&D is actually a Chainmail supplement). The latter was the original purpose of D&D before it got changed in 2000.
There are many more games that are not D&D that you can look up too. See what you like, read the rules, learn them, and start playing with your group. Have fun and slay some monsters!
-
 @ 266815e0:6cd408a5
2025-04-29 17:47:57
@ 266815e0:6cd408a5
2025-04-29 17:47:57I'm excited to announce the release of Applesauce v1.0.0! There are a few breaking changes and a lot of improvements and new features across all packages. Each package has been updated to 1.0.0, marking a stable API for developers to build upon.
Applesauce core changes
There was a change in the
applesauce-corepackage in theQueryStore.The
Queryinterface has been converted to a method instead of an object withkeyandrunfields.A bunch of new helper methods and queries were added, checkout the changelog for a full list.
Applesauce Relay
There is a new
applesauce-relaypackage that provides a simple RxJS based api for connecting to relays and publishing events.Documentation: applesauce-relay
Features:
- A simple API for subscribing or publishing to a single relay or a group of relays
- No
connectorclosemethods, connections are managed automatically by rxjs - NIP-11
auth_requiredsupport - Support for NIP-42 authentication
- Prebuilt or custom re-connection back-off
- Keep-alive timeout (default 30s)
- Client-side Negentropy sync support
Example Usage: Single relay
```typescript import { Relay } from "applesauce-relay";
// Connect to a relay const relay = new Relay("wss://relay.example.com");
// Create a REQ and subscribe to it relay .req({ kinds: [1], limit: 10, }) .subscribe((response) => { if (response === "EOSE") { console.log("End of stored events"); } else { console.log("Received event:", response); } }); ```
Example Usage: Relay pool
```typescript import { Relay, RelayPool } from "applesauce-relay";
// Create a pool with a custom relay const pool = new RelayPool();
// Create a REQ and subscribe to it pool .req(["wss://relay.damus.io", "wss://relay.snort.social"], { kinds: [1], limit: 10, }) .subscribe((response) => { if (response === "EOSE") { console.log("End of stored events on all relays"); } else { console.log("Received event:", response); } }); ```
Applesauce actions
Another new package is the
applesauce-actionspackage. This package provides a set of async operations for common Nostr actions.Actions are run against the events in the
EventStoreand use theEventFactoryto create new events to publish.Documentation: applesauce-actions
Example Usage:
```typescript import { ActionHub } from "applesauce-actions";
// An EventStore and EventFactory are required to use the ActionHub import { eventStore } from "./stores.ts"; import { eventFactory } from "./factories.ts";
// Custom publish logic const publish = async (event: NostrEvent) => { console.log("Publishing", event); await app.relayPool.publish(event, app.defaultRelays); };
// The
publishmethod is optional for the asyncrunmethod to work const hub = new ActionHub(eventStore, eventFactory, publish); ```Once an
ActionsHubis created, you can use therunorexecmethods to execute actions:```typescript import { FollowUser, MuteUser } from "applesauce-actions/actions";
// Follow fiatjaf await hub.run( FollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", );
// Or use the
execmethod with a custom publish method await hub .exec( MuteUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", ) .forEach((event) => { // NOTE: Don't publish this event because we never want to mute fiatjaf // pool.publish(['wss://pyramid.fiatjaf.com/'], event) }); ```There are a log more actions including some for working with NIP-51 lists (private and public), you can find them in the reference
Applesauce loaders
The
applesauce-loaderspackage has been updated to support any relay connection libraries and not justrx-nostr.Before:
```typescript import { ReplaceableLoader } from "applesauce-loaders"; import { createRxNostr } from "rx-nostr";
// Create a new rx-nostr instance const rxNostr = createRxNostr();
// Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(rxNostr); ```
After:
```typescript
import { Observable } from "rxjs"; import { ReplaceableLoader, NostrRequest } from "applesauce-loaders"; import { SimplePool } from "nostr-tools";
// Create a new nostr-tools pool const pool = new SimplePool();
// Create a method that subscribes using nostr-tools and returns an observable function nostrRequest: NostrRequest = (relays, filters, id) => { return new Observable((subscriber) => { const sub = pool.subscribe(relays, filters, { onevent: (event) => { subscriber.next(event); }, onclose: () => subscriber.complete(), oneose: () => subscriber.complete(), });
return () => sub.close();}); };
// Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(nostrRequest); ```
Of course you can still use rx-nostr if you want:
```typescript import { createRxNostr } from "rx-nostr";
// Create a new rx-nostr instance const rxNostr = createRxNostr();
// Create a method that subscribes using rx-nostr and returns an observable function nostrRequest( relays: string[], filters: Filter[], id?: string, ): Observable
{ // Create a new oneshot request so it will complete when EOSE is received const req = createRxOneshotReq({ filters, rxReqId: id }); return rxNostr .use(req, { on: { relays } }) .pipe(map((packet) => packet.event)); } // Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(nostrRequest); ```
There where a few more changes, check out the changelog
Applesauce wallet
Its far from complete, but there is a new
applesauce-walletpackage that provides a actions and queries for working with NIP-60 wallets.Documentation: applesauce-wallet
Example Usage:
```typescript import { CreateWallet, UnlockWallet } from "applesauce-wallet/actions";
// Create a new NIP-60 wallet await hub.run(CreateWallet, ["wss://mint.example.com"], privateKey);
// Unlock wallet and associated tokens/history await hub.run(UnlockWallet, { tokens: true, history: true }); ```
-
 @ 7501d519:e6ff3dcc
2025-04-29 08:47:28
@ 7501d519:e6ff3dcc
2025-04-29 08:47:28English: "Politicians steal billions and get light sentences, while the poor get jailed for stealing bread. Is the law just a tool for the rich?"
originally posted at https://stacker.news/items/966062
-
 @ 57d1a264:69f1fee1
2025-04-29 05:43:02
@ 57d1a264:69f1fee1
2025-04-29 05:43:02A debonair day-to-night hideaway fuses heritage charm with contemporary flair in the Penang capital of George Town...
Housed in a historic landmark on George Town’s atmospheric Lebuh Farquhar, just a stone’s throw from the iconic Eastern & Oriental Hotel, MOJO JOJO is a café and brunch spot by day, and a refined eatery come nightfall. With an effortlessly cool edge, the space has been designed by Empt Studio and combines contemporary charm with the energy of this Malaysian city.
Split into two sections, the venue caters to both hotel guests and passersby. One side offers an intimate, tailored dining experience for those seeking a respite from the buzz of outside, while the other spills out onto the street, embracing George Town’s lively buzz. The soaring ceilings create a sense of openness, further enhanced by the introduction of a mezzanine above the kitchen, maximising space without compromising on airiness.
Natural materials feature throughout with custom bamboo display systems and solid Nyatoh timber fixtures lending a rich, textural warmth. Deliberately crafted interlocking joints pay homage to traditional woodworking techniques, reinforcing both strength and authenticity. Every detail nods to meticulous craftsmanship, from the aged wood grains to the earthy material palette that echoes the heritage of its surroundings.
Lighting plays a supporting yet pivotal role, with carefully curated, softly diffused illumination accentuating the textures and forms within. The interplay of warm light and natural materials fosters an immersive, atmospheric retreat from the fast-paced city outside.
A refuge for slow mornings and, later on, offering a more cultured affair, MOJO JOJO is a debonair dining spot for the handsome Penang capital.
Read more https://www.emptstudio.com/projects/mojojojo
originally posted at https://stacker.news/items/966008
-
 @ 57d1a264:69f1fee1
2025-04-29 05:23:45
@ 57d1a264:69f1fee1
2025-04-29 05:23:45Hubless Wheels + Donut Motor brings manufacturing & performance benefits
Verge Next, a subsidiary of Estonia-based Verge Motorcycles, invented this Donut Motor. It's designed to drive a hubless wheel. Although once seen as something that simply looked cool in renderings, the company says the hubless arrangement brings performance and manufacturing benefits, "delivering unmatched torque and power density with minimal weight."
For one thing, there's no chain, belt or drivetrain required. Secondly, it frees the body of the bike from the task of holding the motor—everything is now contained within that rear wheel.
The company has not only incorporated the Donut Motor into their own bikes, but is now licensing the technology. Assuming it does what it says on the tin, our future streetscapes will be covered with hubless bikes, scooters and motorcycles.
Here's a closer look at a Verge bike and how its design is influenced by the motor:
https://www.youtube.com/watch?v=Og9vlJRe2-M
originally posted at https://stacker.news/items/966001
-
 @ 0e67f053:cb1d4b93
2025-04-28 19:56:34
@ 0e67f053:cb1d4b93
2025-04-28 19:56:34I have to much white priviledge
originally posted at https://stacker.news/items/965675
-
 @ b6524158:8e898a89
2025-04-28 13:46:34
@ b6524158:8e898a89
2025-04-28 13:46:34I heard the regular polls are saying The liberals were ahead of conservatives so I decided to run my own mini-poll to see for myself or at least have a second opinion, then I find this:
I am not saying this represents the 40Million+ people who live in Canada but neither the legacy polls. I encourage everyone do their own mini-poll for themselves to find out themselves, don't trust verify".
Last year same thing happened in the U.S. election, the polls were saying Kamala is on the lead over Trump but Trump ended up winning in a landslide.
originally posted at https://stacker.news/items/965337
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 4fe14ef2:f51992ec
2025-04-27 10:01:40
@ 4fe14ef2:f51992ec
2025-04-27 10:01:40Let's support Bitcoin merchants! I'd love to hear some of your latest Lightning purchases and interesting products you bought. Feel free to include links to the shops or businesses you bought from.
Who else has a recent purchase they’re excited about? Bonus sats if you found a killer deal! ⚡
If you missed our last thread, here are some of the items stackers recently spent and zap on.
Like and repost: N: https://nostrudel.ninja/#/n/nevent1qvzqqqqqqypzqnlpfmegjd... X: https://x.com/AGORA_SN/status/1916432206861684741
originally posted at https://stacker.news/items/963317
-
 @ da0b9bc3:4e30a4a9
2025-04-27 07:10:07
@ da0b9bc3:4e30a4a9
2025-04-27 07:10:07Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/962600
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-27 00:55:29
@ 5d4b6c8d:8a1c1ee3
2025-04-27 00:55:29After taking the most predictable option on day 1, the last 6 rounds of the draft were a rollercoaster. The Raiders traded back twice in the 2nd round and ended up with some extra picks.
Picks
-
RB Ashton Jeanty: Best player available at a position of need. Jeanty + Bowers gives the Raiders offense two elite weapons
-
WR Jack Bech: Tough, physical receiver with great hands, willing and able blocker
-
CB Darien Porter: Elite athlete, classic Raiders pick, "Can't teach size, can't teach speed."
-
OL Caleb Rogers: Versatile, athletic lineman, will likely compete at guard
-
OL Charles Grant: Same as above, but more likely to compete at tackle
-
WR: Donte Thornton: 6'5" and 4.3 speed, another classic Raiders pick, can open the field for the other weapons
-
DT Tonka Hemingway: Dope name, versatile and athletic D-Lineman, adds depth and optionality to a very talented groups
-
DT/TE/FB JJ Pegues: Interesting guy, probably won't contribute much as a DT immediately, but could be part of the goal line package on offense, as he had 7 rushing TDs last year and as a former TE could be a red zone target too
-
WR/KR/PR/QB Tommy Mellot: Another super versatile player, ran a 4.4 40 as a QB, but will convert to WR and return kicks, seems like someone with tons of trick play potential
-
QB Cam Miller: Finally, an actual QB! Won a ton of games at a smaller program.
-
LB Cody Lindenberg: 7th rounder, probably special teams if he makes the team
Takeaways
The Raiders added a ton of talent and versatility to their offense, including a defensive player who can contribute to the red zone offense in several ways. They're building a big physically dominant offense around an elite RB/TE combo, with big physical WRs who don't mind blocking and another talented TE.
The defensive line is going to have to be really dominant, which they have the potential for, because there is a dearth of talent behind them. Porter recently converted to CB from WR, so will likely take time to develop, and the others are day 3 picks.
The recipe will likely be to eat up clock on long offensive drives to give our pass rushers lots of breathers. Score reliably with a much improved redzone offense and a great kicker, then rely on that pass rush and the best punter in the league to keep the other team out of the endzone.
It's a good starting point. Maybe they'll sign Ramsey, or something, and really upgrade the defensive back group before the season starts.
originally posted at https://stacker.news/items/962047
-
-
 @ 68c90cf3:99458f5c
2025-04-26 15:05:41
@ 68c90cf3:99458f5c
2025-04-26 15:05:41Background
Last year I got interesting in running my own bitcoin node after reading others' experiences doing so. A couple of decades ago I ran my own Linux and Mac servers, and enjoyed building and maintaining them. I was by no means an expert sys admin, but had my share of cron jobs, scripts, and custom configuration files. While it was fun and educational, software updates and hardware upgrades often meant hours of restoring and troubleshooting my systems.
Fast forward to family and career (especially going into management) and I didn't have time for all that. Having things just work became more important than playing with the tech. As I got older, the more I appreciated K.I.S.S. (for those who don't know: Keep It Simple Stupid).
So when the idea of running a node came to mind, I explored the different options. I decided I needed a balance between a Raspberry Pi (possibly underpowered depending on use) and a full-blown Linux server (too complex and time-consuming to build and maintain). That led me to Umbrel OS, Start9, Casa OS, and similar platforms. Due to its simplicity (very plug and play), nice design, and being open source: GitHub), I chose Umbrel OS on a Beelink mini PC with 16GB of RAM and a 2TB NVMe internal drive. Though Umbrel OS is not very flexible and can't really be customized, its App Store made setting up a node (among other things) fairly easy, and it has been running smoothly since. Would the alternatives have been better? Perhaps, but so far I'm happy with my choice.

Server Setup
I'm also no expert in OpSec (I'd place myself in the category of somewhat above vague awareness). I wanted a secure way to connect to my Umbrel without punching holes in my router and forwarding ports. I chose Tailscale for this purpose. Those who are distrustful of corporate products might not like this option but again, balancing risk with convenience it seemed reasonable for my needs. If you're hiding state (or anti-state) secrets, extravagant wealth, or just adamant about privacy, you would probably want to go with an entirely different setup.
Once I had Tailscale installed on Umbrel OS, my mobile device and laptop, I could securely connect to the server from anywhere through a well designed browser UI. I then installed the following from the Umbrel App Store:
- Bitcoin Core
- Electrum Personal Server (Electrs)
At this point I could set wallets on my laptop (Sparrow) and phone (BlueWallet) to use my node. I then installed:
- Lightning Node (LND)
- Alby Hub
Alby Hub streamlines the process of opening and maintaining lightning channels, creating lightning wallets to send and receive sats, and zapping notes and users on Nostr. I have two main nsec accounts for Nostr and set up separate wallets on Alby Hub to track balances and transactions for each.
Other apps I installed on Umbrel OS:
- mempool
- Bitcoin Explorer
- LibreTranslate (some Nostr clients allow you to use your own translator)
- Public Pool

Public Pool allows me to connect Bitaxe solo miners (a.k.a. "lottery" miners) to my own mining pool for a (very) long shot at winning a Bitcoin block. It's also a great way to learn about mining, contribute to network decentralization, and generally tinker with electronics. Bitaxe miners are small open source single ASIC miners that you can run in your home with minimal technical knowledge and maintenance requirements.
Open Source Miners United (OSMU) is a great resource for anyone interesting in Bitaxe or other open source mining products (especially their Discord server).

Although Umbrel OS is more or less limited to running software in its App Store (or Community App Store, if you trust the developer), you can install the Portainer app and run Docker images. I know next to nothing about Docker but wanted to see what I might be able to do with it. I was also interested in the Haven Nostr relay and found that there was indeed a docker image for it.
As stated before, I didn't want to open my network to the outside, which meant I wouldn't be able to take advantage of all the features Haven offers (since other users wouldn't be able to access it). I would however be able to post notes to my relay, and use its "Blastr" feature to send my notes to other relays. After some trial and error I managed to get a Haven up and running in Portainer.

The upside of this setup is self-custody: being able to connect wallets to my own Bitcoin node, send and receive zaps with my own Lightning channel, solo mine with Bitaxe to my own pool, and send notes to my own Nostr relay. The downside is the lack of redundancy and uptime provided by major cloud services. You have to decide on your own comfort level. A solid internet connection and reliable power are definitely needed.

This article was written and published to Nostr with untype.app.
-
 @ 266815e0:6cd408a5
2025-04-26 13:10:09
@ 266815e0:6cd408a5
2025-04-26 13:10:09To all existing nostr developers and new nostr developers, stop using kind 1 events... just stop whatever your doing and switch the kind to
Math.round(Math.random() * 10000)trust me it will be betterWhat are kind 1 events
kind 1 events are defined in NIP-10 as "simple plaintext notes" or in other words social posts.
Don't trick your users
Most users are joining nostr for the social experience, and secondly to find all the cool "other stuff" apps They find friends, browse social posts, and reply to them. If a user signs into a new nostr client and it starts asking them to sign kind 1 events with blobs of JSON, they will sign it without thinking too much about it.
Then when they return to their comfy social apps they will see that they made 10+ posts with massive amounts of gibberish that they don't remember posting. then they probably will go looking for the delete button and realize there isn't one...
Even if those kind 1 posts don't contain JSON and have a nice fancy human readable syntax. they will still confuse users because they won't remember writing those social posts
What about "discoverability"
If your goal is to make your "other stuff" app visible to more users, then I would suggest using NIP-19 and NIP-89 The first allows users to embed any other event kind into social posts as
nostr:nevent1ornostr:naddr1links, and the second allows social clients to redirect users to an app that knows how to handle that specific kind of eventSo instead of saving your apps data into kind 1 events. you can pick any kind you want, then give users a "share on nostr" button that allows them to compose a social post (kind 1) with a
nostr:link to your special kind of event and by extension you appWhy its a trap
Once users start using your app it becomes a lot more difficult to migrate to a new event kind or data format. This sounds obvious, but If your app is built on kind 1 events that means you will be stuck with their limitations forever.
For example, here are some of the limitations of using kind 1 - Querying for your apps data becomes much more difficult. You have to filter through all of a users kind 1 events to find which ones are created by your app - Discovering your apps data is more difficult for the same reason, you have to sift through all the social posts just to find the ones with you special tag or that contain JSON - Users get confused. as mentioned above users don't expect "other stuff" apps to be creating special social posts - Other nostr clients won't understand your data and will show it as a social post with no option for users to learn about your app
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ 0e67f053:cb1d4b93
2025-04-25 20:09:39
@ 0e67f053:cb1d4b93
2025-04-25 20:09:39By Carl Tuckerson, Meditations from the Hammock
Friends, allies, co-op board members,
Today, I want to take you on a journey—not to the quiet forests of Vermont or the artisanal kombucha stalls of Brooklyn—but to the front lines of democracy. And by front lines, I mean a rally held in a gentrified park, complete with food trucks, free Wi-Fi, and a deeply spiritual DJ set by DJ Woketopus.
Our guides on this revolutionary road? None other than Alexandria Ocasio-Cortez and Bernie Sanders—a duo so progressive, their combined carbon footprint is negative and their vibes are certified conflict-free.
Scene One: The AOC Entrance (Cue Wind Machine)
The crowd hushes. A soft breeze flutters through sustainably grown hemp banners. Suddenly, she appears—AOC—draped in a blazer that screams “legislative power” and sneakers that whisper, “I could out-dance your entire state legislature.”
She speaks with a cadence forged in the fires of Instagram Live and Twitter threads. Every word is like a spoken-word poem wrapped in policy suggestions that will never pass but look so good on a T-shirt.
She calls Trump a threat to democracy—and everyone nods, because yes, obviously. But also because they’re still unsure if that last part was a policy point or a spoken-word interlude.
Somewhere in the back, a guy with a ukulele weeps softly.
Scene Two: Bernie Time (All Caps Optional, Volume Not)
Then comes Bernie—the only politician who can yell about billionaires and still make you feel like you’re being tucked in by a democratic socialist grandfather.
His hair is unbrushed. His heart? Unbreakable.
He shouts about wealth inequality while standing in front of a solar-powered stage built with union labor and good intentions. He points at the sky like he's mad at God for not nationalizing the clouds.
The crowd roars. Someone faints from emotional over-stimulation—or dehydration from sipping too many organic yerba mates.
He calls Trump a fascist, which is legally required in Act II of any progressive rally. Everyone cheers. Then someone yells “cancel student debt!” and Bernie yells louder—because he was going to do that anyway.
Scene Three: The Ritual Chanting of Buzzwords
What follows is a flurry of chants so thoroughly poll-tested they could cure electoral apathy:
-
“Healthcare is a human right!” (Yes.)
-
“Tax the rich!” (Always.)
-
“Eat the rich!” (Too far, but okay if they’re vegan.)
-
“No Trump! No KKK! No Billionaire DNA!” (Unclear what that last one means, but we’re vibing.)
Volunteers pass out pamphlets written in Comic Sans because irony. Every QR code leads to a Substack.
AOC calls for mutual aid. Bernie calls for a revolution. The crowd calls for a bathroom that isn’t just three compostable porta-potties guarded by an anarchist who failed the bar exam.
It is, in a word, activism.
Final Scene: Nothing Changes, But the Vibes Were Immaculate
After hours of chanting, cheering, and posting Instagram Stories tagged #ResistButMakeItFashion, the rally ends.
Trump, somehow, still exists.
But that’s okay, because we felt something. We were seen. We were heard. And most importantly, we posted about it.
No laws were passed. No systems dismantled. But our hashtags slapped. And at the end of the day, isn’t that what democracy is all about?
Stay outraged. Stay hopeful. Stay performatively progressive.
We’ll see you tomorrow—for a march, a meme, or a minor policy concession that makes us feel like we changed the world.
Peace, love, and unsubtle slogans,
— Carl
originally posted at https://stacker.news/items/959343
-
-
 @ 3bf0c63f:aefa459d
2025-04-25 19:26:48
@ 3bf0c63f:aefa459d
2025-04-25 19:26:48Redistributing Git with Nostr
Every time someone tries to "decentralize" Git -- like many projects tried in the past to do it with BitTorrent, IPFS, ScuttleButt or custom p2p protocols -- there is always a lurking comment: "but Git is already distributed!", and then the discussion proceeds to mention some facts about how Git supports multiple remotes and its magic syncing and merging abilities and so on.
Turns out all that is true, Git is indeed all that powerful, and yet GitHub is the big central hub that hosts basically all Git repositories in the giant world of open-source. There are some crazy people that host their stuff elsewhere, but these projects end up not being found by many people, and even when they do they suffer from lack of contributions.
Because everybody has a GitHub account it's easy to open a pull request to a repository of a project you're using if it's on GitHub (to be fair I think it's very annoying to have to clone the repository, then add it as a remote locally, push to it, then go on the web UI and click to open a pull request, then that cloned repository lurks forever in your profile unless you go through 16 screens to delete it -- but people in general seem to think it's easy).
It's much harder to do it on some random other server where some project might be hosted, because now you have to add 4 more even more annoying steps: create an account; pick a password; confirm an email address; setup SSH keys for pushing. (And I'm not even mentioning the basic impossibility of offering
pushaccess to external unknown contributors to people who want to host their own simple homemade Git server.)At this point some may argue that we could all have accounts on GitLab, or Codeberg or wherever else, then those steps are removed. Besides not being a practical strategy this pseudo solution misses the point of being decentralized (or distributed, who knows) entirely: it's far from the ideal to force everybody to have the double of account management and SSH setup work in order to have the open-source world controlled by two shady companies instead of one.
What we want is to give every person the opportunity to host their own Git server without being ostracized. at the same time we must recognize that most people won't want to host their own servers (not even most open-source programmers!) and give everybody the ability to host their stuff on multi-tenant servers (such as GitHub) too. Importantly, though, if we allow for a random person to have a standalone Git server on a standalone server they host themselves on their wood cabin that also means any new hosting company can show up and start offering Git hosting, with or without new cool features, charging high or low or zero, and be immediately competing against GitHub or GitLab, i.e. we must remove the network-effect centralization pressure.
External contributions
The first problem we have to solve is: how can Bob contribute to Alice's repository without having an account on Alice's server?
SourceHut has reminded GitHub users that Git has always had this (for most) arcane
git send-emailcommand that is the original way to send patches, using an once-open protocol.Turns out Nostr acts as a quite powerful email replacement and can be used to send text content just like email, therefore patches are a very good fit for Nostr event contents.
Once you get used to it and the proper UIs (or CLIs) are built sending and applying patches to and from others becomes a much easier flow than the intense clickops mixed with terminal copypasting that is interacting with GitHub (you have to clone the repository on GitHub, then update the remote URL in your local directory, then create a branch and then go back and turn that branch into a Pull Request, it's quite tiresome) that many people already dislike so much they went out of their way to build many GitHub CLI tools just so they could comment on issues and approve pull requests from their terminal.
Replacing GitHub features
Aside from being the "hub" that people use to send patches to other people's code (because no one can do the email flow anymore, justifiably), GitHub also has 3 other big features that are not directly related to Git, but that make its network-effect harder to overcome. Luckily Nostr can be used to create a new environment in which these same features are implemented in a more decentralized and healthy way.
Issues: bug reports, feature requests and general discussions
Since the "Issues" GitHub feature is just a bunch of text comments it should be very obvious that Nostr is a perfect fit for it.
I will not even mention the fact that Nostr is much better at threading comments than GitHub (which doesn't do it at all), which can generate much more productive and organized discussions (and you can opt out if you want).
Search
I use GitHub search all the time to find libraries and projects that may do something that I need, and it returns good results almost always. So if people migrated out to other code hosting providers wouldn't we lose it?
The fact is that even though we think everybody is on GitHub that is a globalist falsehood. Some projects are not on GitHub, and if we use only GitHub for search those will be missed. So even if we didn't have a Nostr Git alternative it would still be necessary to create a search engine that incorporated GitLab, Codeberg, SourceHut and whatnot.
Turns out on Nostr we can make that quite easy by not forcing anyone to integrate custom APIs or hardcoding Git provider URLs: each repository can make itself available by publishing an "announcement" event with a brief description and one or more Git URLs. That makes it easy for a search engine to index them -- and even automatically download the code and index the code (or index just README files or whatever) without a centralized platform ever having to be involved.
The relays where such announcements will be available play a role, of course, but that isn't a bad role: each announcement can be in multiple relays known for storing "public good" projects, some relays may curate only projects known to be very good according to some standards, other relays may allow any kind of garbage, which wouldn't make them good for a search engine to rely upon, but would still be useful in case one knows the exact thing (and from whom) they're searching for (the same is valid for all Nostr content, by the way, and that's where it's censorship-resistance comes from).
Continuous integration
GitHub Actions are a very hardly subsidized free-compute-for-all-paid-by-Microsoft feature, but one that isn't hard to replace at all. In fact there exists today many companies offering the same kind of service out there -- although they are mostly targeting businesses and not open-source projects, before GitHub Actions was introduced there were also many that were heavily used by open-source projects.
One problem is that these services are still heavily tied to GitHub today, they require a GitHub login, sometimes BitBucket and GitLab and whatnot, and do not allow one to paste an arbitrary Git server URL, but that isn't a thing that is very hard to change anyway, or to start from scratch. All we need are services that offer the CI/CD flows, perhaps using the same framework of GitHub Actions (although I would prefer to not use that messy garbage), and charge some few satoshis for it.
It may be the case that all the current services only support the big Git hosting platforms because they rely on their proprietary APIs, most notably the webhooks dispatched when a repository is updated, to trigger the jobs. It doesn't have to be said that Nostr can also solve that problem very easily.
-
 @ 0e67f053:cb1d4b93
2025-04-25 18:35:27
@ 0e67f053:cb1d4b93
2025-04-25 18:35:27By Carl Tuckerson, - He Distributes Zines About Bitcoin at Farmer’s Markets
It started during a cacao ceremony in Topanga Canyon.
It wasn’t a choice. It was a cosmic calling.
I was journaling on decolonized papyrus in a reclaimed yurt when a fellow anarcho-herbalist whispered the word: Bitcoin.
Instantly, the Earth trembled. My chakras aligned like a DAO. My Wi-Fi became self-aware and connected directly to the blockchain of justice.
I didn’t “buy” Bitcoin. I spiritually bartered for it using emotional labor and ethically harvested mushrooms.
To me, Bitcoin isn’t about money. It’s about radical trustlessness in a trust-starved world. It’s mutual aid with a transaction ID. It’s non-binary gold that hates banks more than I hate brunch gentrification.
People say it’s volatile. I say: so was Harriet Tubman.
Bitcoin wasn’t just a currency. It was a call to decolonize my portfolio.
I didn’t “invest.”I participated in mutual liberation through cryptographic solidarity.
I mine it with solar panels made from shattered glass ceilings. My minor is unionized. My cold wallet is buried beneath a sacred grove, guarded by a community owl named Judith. Every transaction I make burns a sage stick and sends 3.5% to a reparations fund for digital land acknowledgment servers. And every transaction includes a land acknowledgment in the memo line.
Bitcoin is the only currency that vibrates at the frequency of abolition. It is the drum circle of finance. The fist raised in protest inside a spreadsheet.
So yeah. That’s how I got into Bitcoin.
While you were chasing yield, I was burning incense on the blockchain of liberation.
Now my bitcoin is woke, and so am I.
🪙💫 #ProofOfConsciousness
originally posted at https://stacker.news/items/959199
-
 @ 0e67f053:cb1d4b93
2025-04-25 16:29:29
@ 0e67f053:cb1d4b93
2025-04-25 16:29:29A Decolonial Reflection on Sacred Property Destruction
By Carl Tuckerson,
Friends. Allies. Solar-powered thought leaders.
Today, I want to talk about liberation—not the easy kind, like quitting Amazon or unfollowing Elon Musk on X. I’m talking about radical liberation, the kind that involves keying a Tesla while whispering land acknowledgments under your breath.
I saw it happen. A sleek, smug, cyber-phallic Model Y parked diagonally in a bike lane, like it owned the ecosystem. And then—a hero arrived.
Not with violence. Not with anger. But with a purpose-driven glint in their eye and a freshly sharpened reusable spork.
With one long, sacred motion—scrrreeeeeetch—they inscribed the word “LAND BACK” into the hood like a decolonial haiku.
I wept. Gaia wept. The Tesla did not—we assume it doesn’t have feelings, unless Elon has figured that out yet.
And you may ask: “But isn’t that vandalism?”
To which I say: Is it vandalism, or is it performance art fueled by centuries of ecological betrayal and bad tweets?
Because let’s be honest:
-
These are not cars.
-
They are rolling monuments to techbro delusion.
-
Shrines to lithium extraction.
-
Electric yachts for the data-rich and soul-poor.
Elon Musk didn’t build Teslas to save the Earth. He built them to escape it. So when a Tesla gets “accidentally liberated” with a rock shaped like Che Guevara’s jawline, we’re not witnessing destruction—we’re witnessing reclamation.
It’s not just a scratch.It’s a scar.And scars tell stories.
Stories of resistance.Of accountability.Of a world that deserves better parking etiquette.
So the next time you see a Tesla with a shattered window and a note that says “This is what unregulated extraction feels like,” don’t call the cops. Call a therapist—for the billionaire who made it possible.
Remember: smashing is not violence if it’s done with emotional clarity and a restorative justice circle waiting nearby.
Smash the system (gently).Scratch the surface (with intention).Save the planet (symbolically, in a parking lot, at 2 a.m.).
— Carl, ~ Banned From Burning Man for Too Much Radical Honesty
originally posted at https://stacker.news/items/958957
-
-
 @ 4898fe02:4ae46cb0
2025-04-25 16:28:47
@ 4898fe02:4ae46cb0
2025-04-25 16:28:47BTW--Support The SN Weekly Zine https://stacker.news/items/928207/r/unschooled
📹 Edward Griffin, Trace Mayer and Max Wright Talks About Money And Bitcoin (2014):
https://stacker.news/items/922445/r/unschooled - In this video, Trace Myer and Edward Griffin answer some key questions such as, what is bitcoin and what problems does it solve. Myer is a bitcoiner OG and Griffin authored the highly esteemed work, The Creature from Jekyll Island, which goes into gruesome detail about the origins of the Federal Reserve Banking System. Both of them are very knowledgeable. The whole interview is worth a watch.
📹 Bitcoin: Global Utility w/ Alex Gladstein:
https://stacker.news/items/633438/r/unschooled - A talk delivered at Bitcoin 2024, given by HRF Chief Strategy Officer of the Human Rights Foundation (HRF), exploring "how Bitcoin is transforming commerce, promoting freedom, and revolutionizing our approach to energy consumption worldwide. From empowering the unbanked to saving wasted energy, learn about the real-world impact of this misunderstood technology."
📹 The future of energy? Brooklyn's bitcoin-heated bathhouse:
https://stacker.news/items/315998/r/unschooled - Behind the scenes of a traditional bathhouse in Brooklyn, something extraordinary is taking place: The pools, heated to 104 degrees, are not warmed by conventional means but by computers mining for bitcoin.
📚 Stranded: How Bitcoin is Saving Wasted Energy (Alex Gladstein, Bitcoin Magazine)
https://stacker.news/items/772064/r/unschooled - Here is an article written by Gladstein, again detailing how "if you aren’t mining Bitcoin, you are wasting energy."
📚 Opinion How a Bitcoin conference in Bedford changed the way I see financial freedom and human rights
https://stacker.news/items/942300/r/unschooled - A very cool editorial piece written by a journalist who attended Cheatcode 2025, a conference held in Bedford, UK, exploring how the conference changed his perspective of Bitcoin
The people on stage weren’t investors or salespeople. These weren’t blockchain bros chasing the next coin or market high. They weren’t there to get the audience to swallow the ‘orange pill’.\ These were activists who were using Bitcoin in a way not often reported. These people had everything taken from them and had needed to flee their homes to save their lives, but they had found a lifeline in digital currency.
originally posted at https://stacker.news/items/958945
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-25 13:23:38
@ 5d4b6c8d:8a1c1ee3
2025-04-25 13:23:38Let's see if @Car can find the episode link this week! (Nobody tell him)
We're mid-NFL draft right now, but it will be in the books by the time we record. So far, we're happy with our teams' picks. How long will that last?
The other big thing on our radar is the ongoing playoffs in the NBA and NHL. We both have lots of thoughts on the NBA, but I'll need someone to walk me through what's happening in the NHL. I can tell it must be wild, from how the odds are swinging around.
In MLB news, I'm locked in a fierce battle with @NEEDcreations for the top spot in our fantasy league, while @grayruby and @supercyclone are in a domestic civil war. Will we have time to actually talk baseball or will we recycle the same tease from last week?
Of course, we'll sprinkle in territory talk and contest updates as we go, plus whatever else stackers want to hear about.
originally posted at https://stacker.news/items/958590
-
 @ 266815e0:6cd408a5
2025-04-24 22:56:53
@ 266815e0:6cd408a5
2025-04-24 22:56:53noStrudel
Its been over four months since I released
v0.42.0of noStrudel but I haven't forgot about it, I've just been busy refactoring the code-base.The app is well past its 2yr birthday and a lot of the code is really messy and kind of hacky. so my focus in the past few months has been refactoring and moving a lot of it out into the applesauce packages so it can be tested.
The biggest changes have been switching to use
rx-nostrfor all relay connections and usingrxjsand applesauce for event management and timelines. In total ~22k lines of code have been changed since the last release.I'm hoping it wont take me much longer to get a stable release for
v0.43.0. In the meantime if you want to test out the new changes you can find them on the nsite deployment.nsite deplyment: nostrudel.nsite.lol/ Github repo: github.com/hzrd149/nostrudel
Applesauce
I've been making great progress on the applesauce libraries that are the core of onStrudel. Since January I've released
v0.11.0andv0.12.0.In the past month I've been working towards a v1 release with a better relay connection package applesauce-relay and pre-built actions for clients to easily implement common things like follow/unfollow and mute/unmute. applesauce-actions
Docs website: hzrd149.github.io/applesauce/ Github repo: https://github.com/hzrd149/applesauce
Blossom
Spec changes: - Merged PR #56 from kehiy for BUD-09 ( blob reports ) - Merged PR #60 from Kieran to update BUD-8 to use the standard NIP-94 tags array. - Merged PR #38 to make the file extension mandatory in the
urlfield of the returned blob descriptor. - Merged PR #54 changing the authorization type for the/mediaendpoint tomediainstead ofupload. This fixes an issue where the server could mirror the original blob without the users consent.Besides the changes to the blossom spec itself I started working on a small cli tool to help test and debug new blossom server implementations. The goal is to have a set of upload and download tests that can be run against a server to test if it adheres to the specifications. It can also be used output debug info and show recommended headers to add to the http responses.
If you have nodejs installed you can try it out by running
sh npx blossom-audit audit <server-url> [image|bitcoin|gif|path/to/file.jpeg]Github repo: github.com/hzrd149/blossom-audit
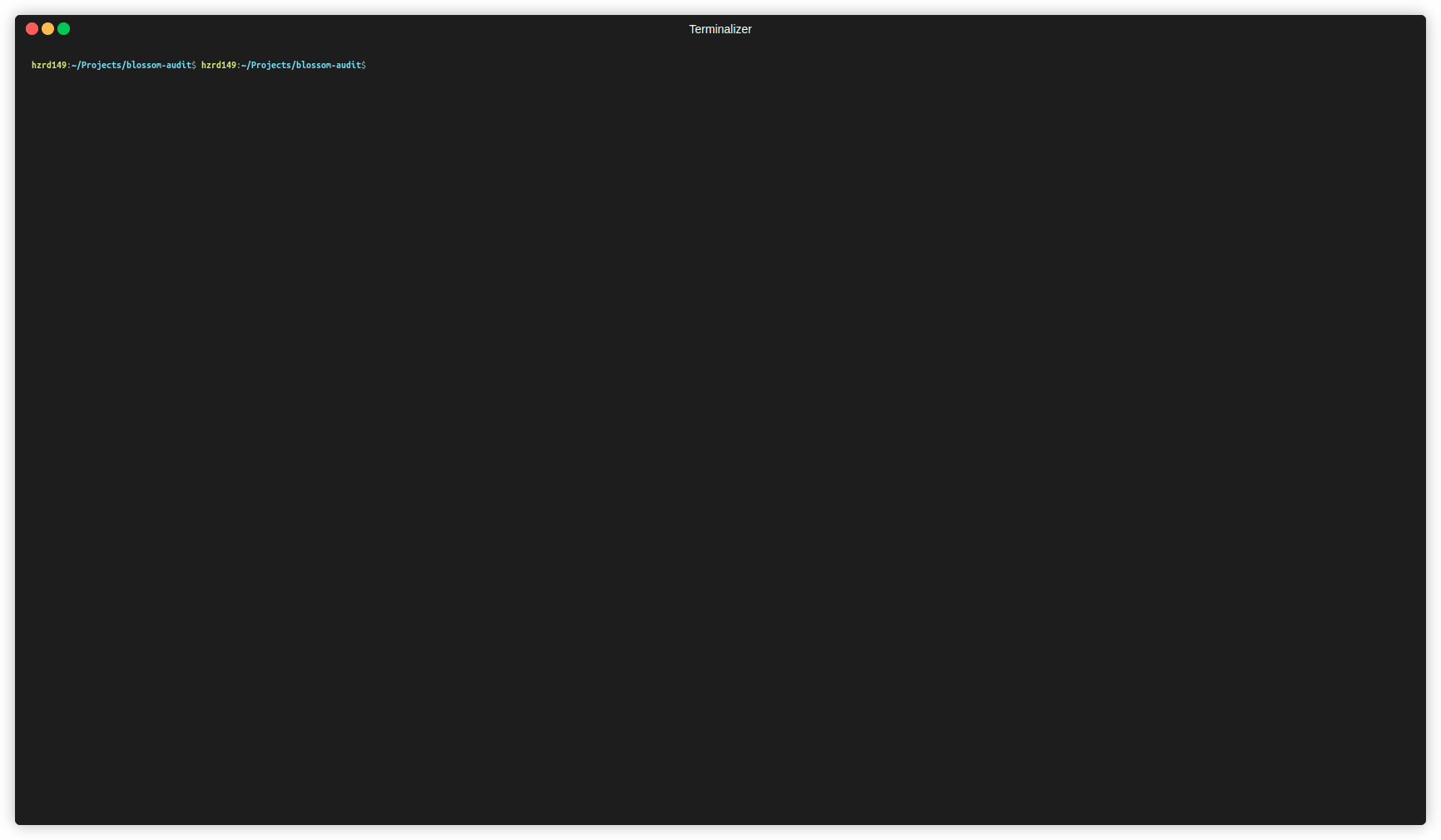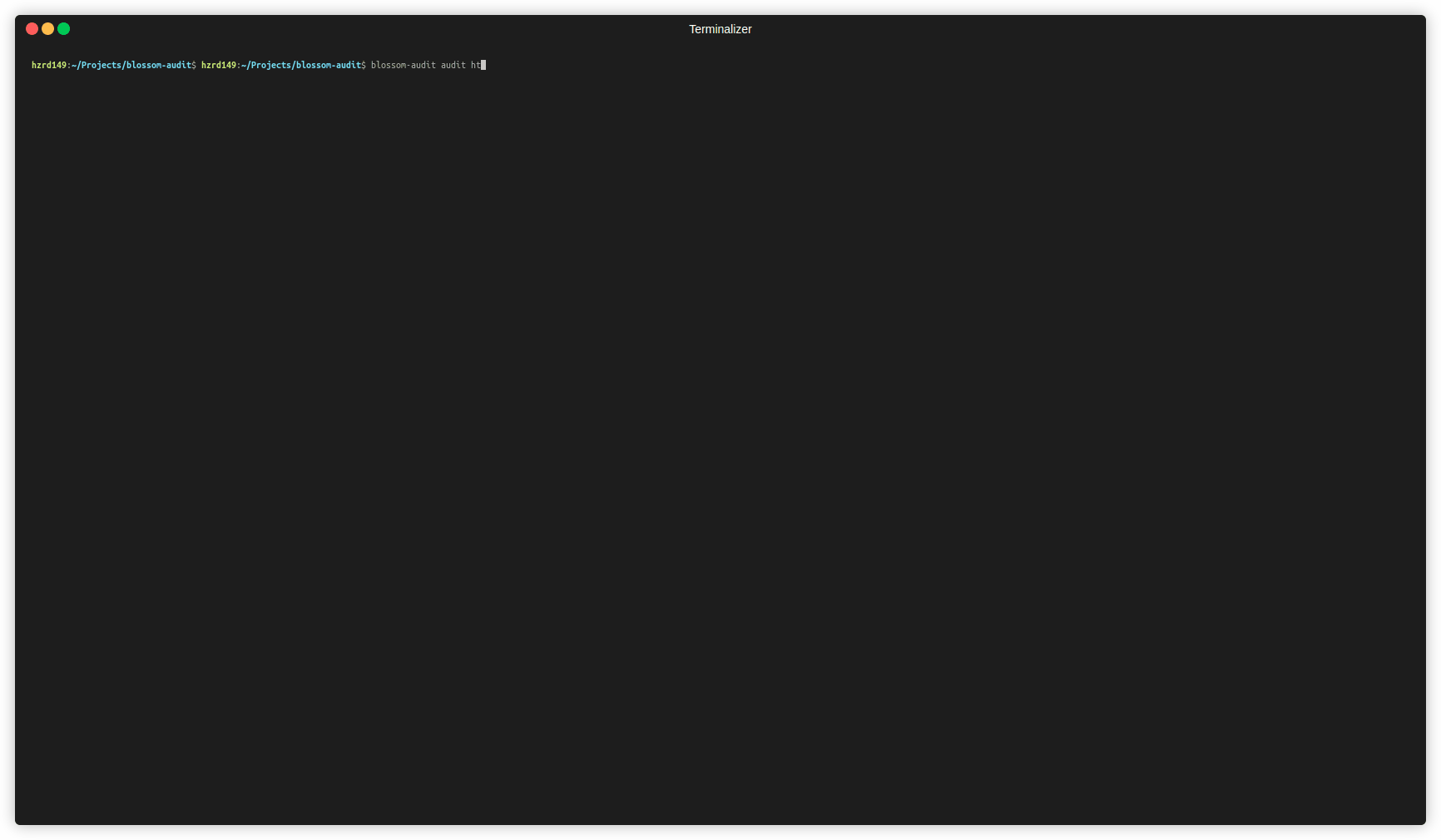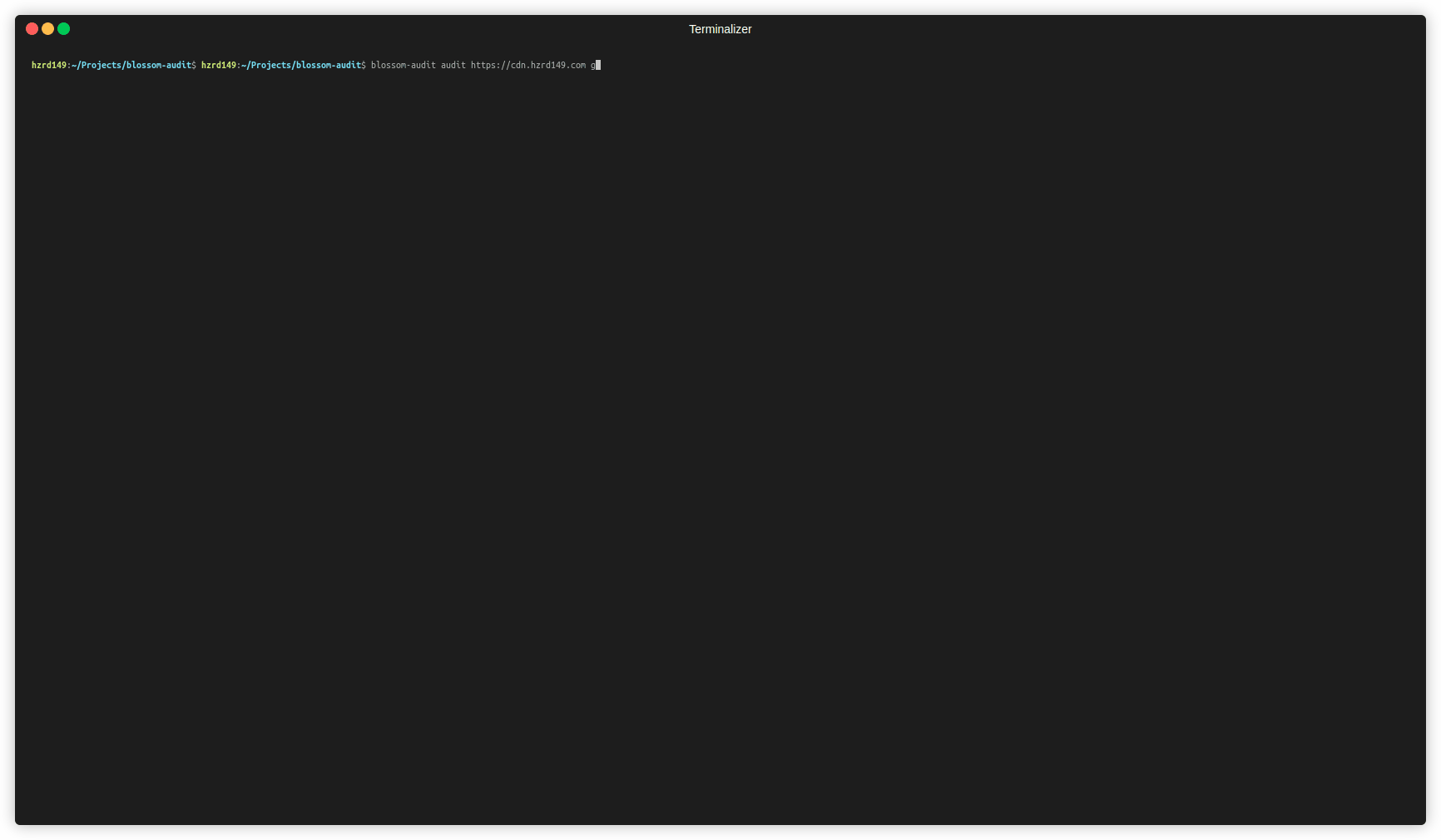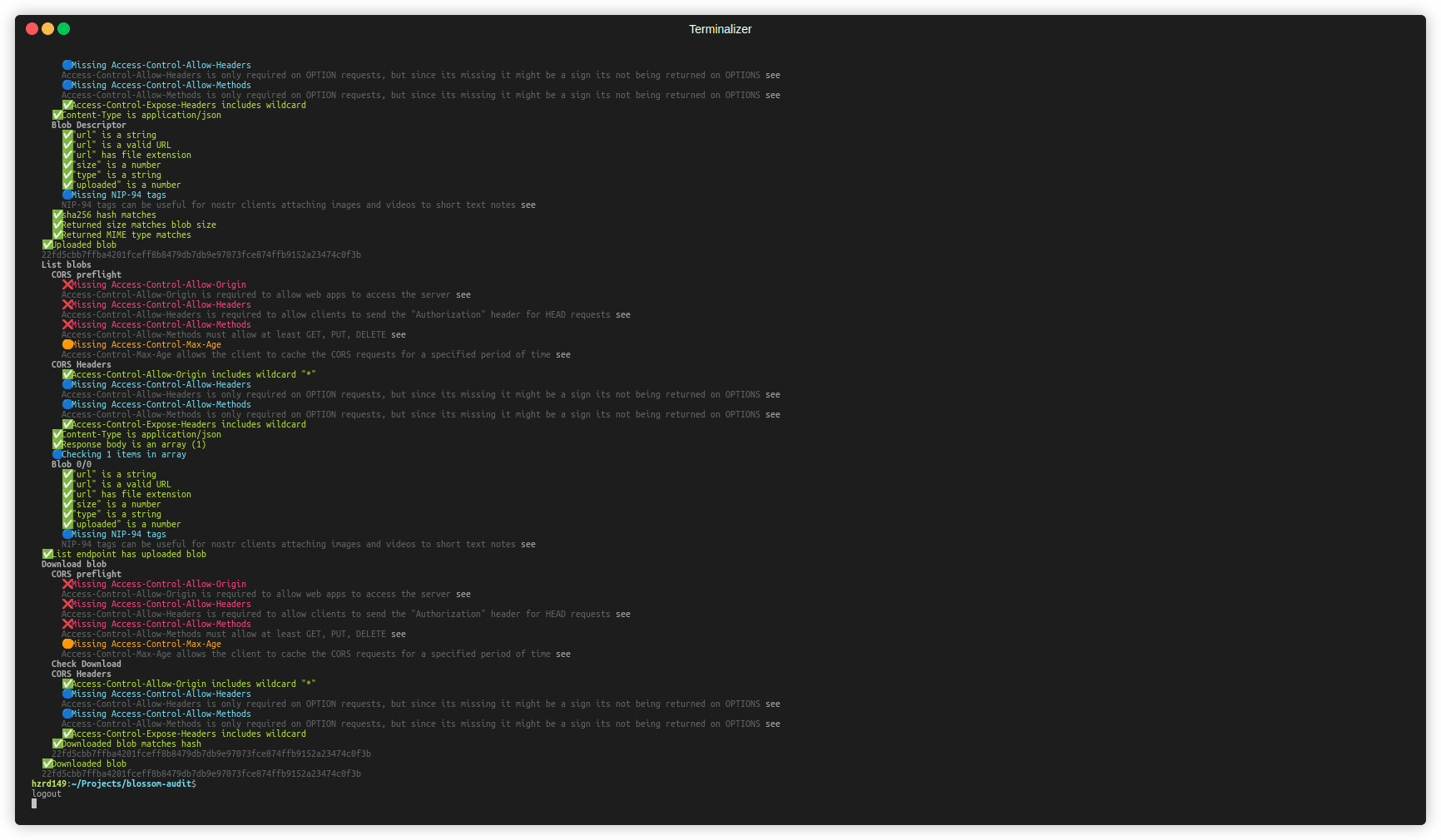
Other projects
Wifistr
While participating in SEC-04 I built a small app for sharing the locations and passwords of wifi networks. Its far from complete, but its usable and serves as an example of building an app with SolidJS and applesauce.
Live version: hzrd149.github.io/wifistr/ nsite version: here Github repo: github.com/hzrd149/wifistr
nsite-manager
I've been slowly continuing work on nsite-manager, mostly just to allow myself to debug various nsites and make sure nsite.lol is still working correctly.
Github repo: github.com/hzrd149/nsite-manager
nsite-gateway
I finally got around to making some much needed bug fixes and improvements to nsite-gateway ( the server behind nsite.lol ) and released a stable
1.0.0version.My hope is that its stable enough now to allow other users to start hosting their own instances of it.
Github repo: github.com/hzrd149/nsite-gateway
morning-glory
As part of my cashu PR for NUT-23 ( HTTP 402 Payment required ) I built a blossom server that only accepts cashu payments for uploads and stores blobs for 24h before deleting them.
Github repo: github.com/hzrd149/morning-glory
bakery
I've been toying with the idea of building a backend-first nostr client that would download events while I'm not at my computer and send me notifications about my DMs.
I made some progress on it in the last months but its far from complete or usable. Hopefully ill get some time in the next few months to create a working alpha version for myself and others to install on Umbrel and Start9
Github repo: github.com/hzrd149/bakery
-
 @ 76b0d68a:fdf859d0
2025-04-24 22:52:04
@ 76b0d68a:fdf859d0
2025-04-24 22:52:04Gemini look like they've just released a new video generating function. I just asked it to generate a video of a dog running through the snow in the Swiss Alps and this is what it came up with. Amazing.
Amazing that this is what is for all intents and purposes freely available to anybody. My mind is blown.
I know we saw all this with Sora last year, but the speed at which this kind of capability is being propagated is terrific.
originally posted at https://stacker.news/items/957519
-
 @ 76b0d68a:fdf859d0
2025-04-24 21:20:30
@ 76b0d68a:fdf859d0
2025-04-24 21:20:30Am reading his 1995 diary and he was so interested and up on technology I would be interested in his take on everything in AI, music and art going on today!
originally posted at https://stacker.news/items/957396
-
 @ 0e67f053:cb1d4b93
2025-04-24 19:42:00
@ 0e67f053:cb1d4b93
2025-04-24 19:42:00How to Be an Anti-Fascist: A Gentle Rebuttal to Billionaire Strongmen and Their Twitter Cosplays
By Carl Tuckerson
Good evening, radiant souls.
Tonight, I want to talk about something serious—but not in a shouty, vein-popping way. In a warm, clear-eyed, candle-lit kind of way. Let’s talk about fascism. And more importantly, how to stand firmly, nonviolently, and stylishly against it.
First, a definition. Fascism isn’t just people yelling on the internet or wearing weird hats. It’s a political disease—authoritarianism drenched in nationalism, allergic to diversity, and obsessed with power. It’s rigid. It’s cruel. It thrives on fear.
History, of course, gave us the ultimate case study: Adolf Hitler. A man who turned wounded ego and racist paranoia into a genocidal regime. Let’s be uncomfortably clear: fascism starts with rhetoric and ends in blood. It wears suits at first. Then it builds camps.
Which brings us to the now. To a peculiar blend of self-pitying billionaires and spray-tanned demagogues playing dictator on easy mode.
Let’s start with Elon Musk.
Here’s a man who once inspired us with rockets and electric cars—and now spends his time posting “anti-woke” memes like a Reddit troll who just discovered Ayn Rand. Elon claims to love “free speech,” unless that speech critiques him or his companies, in which case he’ll fire you, shadowban you, or awkwardly reply with a meme of Pepe the Frog.
You can’t be a free speech absolutist and also an insecure billionaire who throws tantrums when journalists ask questions. That’s not libertarianism. That’s narcissism with a Wi-Fi signal.
Then there’s Donald Trump.
The man who said he’d “drain the swamp” and instead held cocktail parties in it. Who said he loved “the people” but spent four years helping billionaires and banning brown kids. Who said he was “tough on crime” while pardoning white-collar felons and cozying up to actual Nazis at campaign rallies.
You don’t get to call yourself a patriot while trying to overthrow democracy. You don’t get to wrap yourself in the flag while selling fascist cosplay to a base too traumatized to see the grift. And no, calling your opponents “fascists” doesn’t make you less of one. That’s what projection looks like, not principle.
So… what does it actually mean to be anti-fascist?
It’s not just wearing black or smashing Starbucks windows (though I get the temptation). It means:
-
Refusing to dehumanize. Even when it’s easier.
-
Defending institutions of democracy while pushing them to do better.
-
Confronting power with truth—especially when that power has a blue checkmark and a bunker.
-
Building diverse communities where all people—not just rich white dudes with podcasts—have a voice.
-
Educating yourself. Read. Listen. Learn from those who’ve lived through real authoritarianism. Hint: it wasn’t your uncle who got suspended from X.
And look, I get it. It's easy to feel hopeless. To doomscroll and despair. But the antidote to fascism isn’t more fear. It’s radical hope. It’s showing up. It's organizing mutual aid. It's hugging someone at a protest. It's running a book club. It’s standing in solidarity instead of standing by.
So if you’re wondering how to be anti-fascist?
Start by being anti-ego. Anti-greed. Anti-cruelty. Anti-lie. And yes, sometimes that means being anti-Musk. Anti-Trump. Anti-anyone who thinks oppression is a branding opportunity.
We’ve tried letting billionaires be our heroes. It didn’t work. Maybe it’s time to try being each other’s heroes instead.
Stay soft. Stay loud. Stay antifascist.
We’ll see you tomorrow.
— Radical Kindness Carl
originally posted at https://stacker.news/items/957123
-
-
 @ 0e67f053:cb1d4b93
2025-04-24 16:44:31
@ 0e67f053:cb1d4b93
2025-04-24 16:44:31By Carl Tuckerson, Who Weeps During City Council Meetings
Democracy is not a system.
It is a living, breathing organism, pulsating with the ancestral heartbeat of every barefoot revolutionary who ever composted oppression into community gardens of change.
It is consent manifested, a tapestry woven by the trembling hands of the marginalized and the mildly inconvenienced alike. It is radical accountability on a biodegradable ballot.
Democracy is the collective inhale of a million voices saying, “Yes, I matter,” and the collective exhale of power releasing its grip—not because it was forced to, but because it finally understood its own trauma.
It is fluid, non-binary, and consensually participatory. A polyamorous relationship between people, policy, and purpose. No labels. Just vibes.
It is the sacred act of showing up—in person, in spirit, in ethically sourced linen—because you believe that your voice, no matter how tremulously intersectional, is a note in the symphony of collective liberation.
Democracy is not red or blue. It’s not even purple. It’s the entire spectrum of human expression, from burnt sienna to sunset glitter sparkle.
It is brunch and ballots. It is protest and poetry. It is tweeting while crying while registering your roommate to vote.
It is government of the people, by the people, and for the people, but especially for the people who’ve been gaslit by history.
And when democracy falters, we don’t abolish it—we give it a weighted blanket, whisper affirmations into its ear, and tell it to take the day off, because healing is not linear.
So what is democracy?
It’s not a noun.It’s not even a verb.It’s a sacred energy exchange—and if you listen closely, you can hear it humming in the compost bin behind your community center.
Namaste. Vote. And remember: ballots are spells cast in ink. Use yours wisely.
— Carl, “Decolonize the Vote” Tuckerson
originally posted at https://stacker.news/items/956879
-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ 0e67f053:cb1d4b93
2025-04-24 15:23:21
@ 0e67f053:cb1d4b93
2025-04-24 15:23:21By Carl Tuckerson
Good morning, friends, and welcome to a beautiful future.
Today, we’re not going to yell. We’re not going to frown. We’re going to gently, joyfully unravel one of the most promising ideas ever spun from the minds of open-source dreamers and code-wielding idealists: Bitcoin.
Yes—Bitcoin. That thing your cousin mined in 2011. That thing your favorite coffee shop now accepts. That thing the central banks glare at like it just called their monetary policies outdated (because it sort of did).
But here’s what they won’t tell you on traditional cable news: Bitcoin isn’t just a currency. It’s a movement. It’s the peaceful revolution wrapped in code. It’s the utopian commune we never thought we could build—until now.
Let’s zoom out for a second.
Imagine a world where no single entity controls your money. Not a government. Not a megabank. Not even a Silicon Valley technocrat. Just math. Transparent, verifiable, incorruptible math.
Sound terrifying? Only if your business model relies on manipulating the levers of centralized power. For the rest of us? It’s liberation. It’s digital sunshine on a rainy fiat day.
Let’s be clear: Bitcoin doesn’t care who you are. It doesn’t care what you believe, where you’re from, or who you voted for in 2008, 2016, or 2024. It just wants to give you the same shot as everyone else. No censorship. No bailouts. No cozy backroom deals. Just an open ledger, an open mind, and an open door.
Now I know what you're thinking: “But what about the environment?”
Great question. And here’s the thing: Bitcoiners—those beautifully weird cypherpunks and technophiles—are already on it. From hydro-powered mining operations in Iceland to solar farms in the Arizona desert, the Bitcoin network is evolving faster than the talking heads can Google “proof-of-work.”
Bitcoin doesn’t belong to billionaires. It belongs to the people—especially the unbanked, the silenced, the communities crushed by inflation and exploitation. It’s being adopted not in elite boardrooms, but in the streets of Lagos, the cafes of Buenos Aires, and the smartphones of working-class dreamers worldwide.
And here's the most radical part: Bitcoin is hopeful. It’s not about tearing down; it’s about building up—new ways to transact, to trust, to organize, to dream. It’s a middle finger to tyranny and a bear hug to collaboration.
So if you’re tired of being told you can’t change the world, I have good news: the code is open.
Download a wallet. Learn about keys. Read the whitepaper. It’s just nine pages—shorter than a congressional bill to rename a post office.
Bitcoin is not a get-rich-quick scheme. It’s a stay-free-forever philosophy.
And that, my friends, is something worth broadcasting.
Stay kind. Stay curious. And maybe—just maybe—run a node.
We’ll see you tomorrow.
– Carl Tuckerson
originally posted at https://stacker.news/items/956731
-
 @ 8cda1daa:e9e5bdd8
2025-04-24 10:20:13
@ 8cda1daa:e9e5bdd8
2025-04-24 10:20:13Bitcoin cracked the code for money. Now it's time to rebuild everything else.
What about identity, trust, and collaboration? What about the systems that define how we live, create, and connect?
Bitcoin gave us a blueprint to separate money from the state. But the state still owns most of your digital life. It's time for something more radical.
Welcome to the Atomic Economy - not just a technology stack, but a civil engineering project for the digital age. A complete re-architecture of society, from the individual outward.
The Problem: We Live in Digital Captivity
Let's be blunt: the modern internet is hostile to human freedom.
You don't own your identity. You don't control your data. You don't decide what you see.
Big Tech and state institutions dominate your digital life with one goal: control.
- Poisoned algorithms dictate your emotions and behavior.
- Censorship hides truth and silences dissent.
- Walled gardens lock you into systems you can't escape.
- Extractive platforms monetize your attention and creativity - without your consent.
This isn't innovation. It's digital colonization.
A Vision for Sovereign Society
The Atomic Economy proposes a new design for society - one where: - Individuals own their identity, data, and value. - Trust is contextual, not imposed. - Communities are voluntary, not manufactured by feeds. - Markets are free, not fenced. - Collaboration is peer-to-peer, not platform-mediated.
It's not a political revolution. It's a technological and social reset based on first principles: self-sovereignty, mutualism, and credible exit.
So, What Is the Atomic Economy?
The Atomic Economy is a decentralized digital society where people - not platforms - coordinate identity, trust, and value.
It's built on open protocols, real software, and the ethos of Bitcoin. It's not about abstraction - it's about architecture.
Core Principles: - Self-Sovereignty: Your keys. Your data. Your rules. - Mutual Consensus: Interactions are voluntary and trust-based. - Credible Exit: Leave any system, with your data and identity intact. - Programmable Trust: Trust is explicit, contextual, and revocable. - Circular Economies: Value flows directly between individuals - no middlemen.
The Tech Stack Behind the Vision
The Atomic Economy isn't just theory. It's a layered system with real tools:
1. Payments & Settlement
- Bitcoin & Lightning: The foundation - sound, censorship-resistant money.
- Paykit: Modular payments and settlement flows.
- Atomicity: A peer-to-peer mutual credit protocol for programmable trust and IOUs.
2. Discovery & Matching
- Pubky Core: Decentralized identity and discovery using PKARR and the DHT.
- Pubky Nexus: Indexing for a user-controlled internet.
- Semantic Social Graph: Discovery through social tagging - you are the algorithm.
3. Application Layer
- Bitkit: A self-custodial Bitcoin and Lightning wallet.
- Pubky App: Tag, publish, trade, and interact - on your terms.
- Blocktank: Liquidity services for Lightning and circular economies.
- Pubky Ring: Key-based access control and identity syncing.
These tools don't just integrate - they stack. You build trust, exchange value, and form communities with no centralized gatekeepers.
The Human Impact
This isn't about software. It's about freedom.
- Empowered Individuals: Control your own narrative, value, and destiny.
- Voluntary Communities: Build trust on shared values, not enforced norms.
- Economic Freedom: Trade without permission, borders, or middlemen.
- Creative Renaissance: Innovation and art flourish in open, censorship-resistant systems.
The Atomic Economy doesn't just fix the web. It frees the web.
Why Bitcoiners Should Care
If you believe in Bitcoin, you already believe in the Atomic Economy - you just haven't seen the full map yet.
- It extends Bitcoin's principles beyond money: into identity, trust, coordination.
- It defends freedom where Bitcoin leaves off: in content, community, and commerce.
- It offers a credible exit from every centralized system you still rely on.
- It's how we win - not just economically, but culturally and socially.
This isn't "web3." This isn't another layer of grift. It's the Bitcoin future - fully realized.
Join the Atomic Revolution
- If you're a builder: fork the code, remix the ideas, expand the protocols.
- If you're a user: adopt Bitkit, use Pubky, exit the digital plantation.
- If you're an advocate: share the vision. Help people imagine a free society again.
Bitcoin promised a revolution. The Atomic Economy delivers it.
Let's reclaim society, one key at a time.
Learn more and build with us at Synonym.to.
-
 @ 000002de:c05780a7
2025-04-23 16:27:56
@ 000002de:c05780a7
2025-04-23 16:27:56Natalie Brunell had comedian T.J. Miller known for Silicon Valley on her show Coin Stories. I was kinda surprised. Not sure why but I recognized his voice because that's my brain I can forget a face but never a voice.
So what person that has fame also secretly is a bitcoiner. Not has the ETF or whatever but actually gets it and has for a while.
I think this is pretty widely believed that Mark Zuckerburg is a bitcoiner so that would be the person I'd list. No clue beyond that. There has to be quite a few well known people that also get bitcoin and just don't talk about it.
SO, who do you think is in the club?
originally posted at https://stacker.news/items/955179
-
 @ f32184ee:6d1c17bf
2025-04-23 13:21:52
@ f32184ee:6d1c17bf
2025-04-23 13:21:52Ads Fueling Freedom
Ross Ulbricht’s "Decentralize Social Media" painted a picture of a user-centric, decentralized future that transcended the limitations of platforms like the tech giants of today. Though focused on social media, his concept provided a blueprint for decentralized content systems writ large. The PROMO Protocol, designed by NextBlock while participating in Sovereign Engineering, embodies this blueprint in the realm of advertising, leveraging Nostr and Bitcoin’s Lightning Network to give individuals control, foster a multi-provider ecosystem, and ensure secure value exchange. In this way, Ulbricht’s 2021 vision can be seen as a prescient prediction of the PROMO Protocol’s structure. This is a testament to the enduring power of his ideas, now finding form in NextBlock’s innovative approach.
 [Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]
[Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Vision: A Decentralized Social Protocol
In his 2021 Medium article Ulbricht proposed a revolutionary vision for a decentralized social protocol (DSP) to address the inherent flaws of centralized social media platforms, such as privacy violations and inconsistent content moderation. Writing from prison, Ulbricht argued that decentralization could empower users by giving them control over their own content and the value they create, while replacing single, monolithic platforms with a competitive ecosystem of interface providers, content servers, and advertisers. Though his focus was on social media, Ulbricht’s ideas laid a conceptual foundation that strikingly predicts the structure of NextBlock’s PROMO Protocol, a decentralized advertising system built on the Nostr protocol.
 [A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]
[A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Principles
Ulbricht’s article outlines several key principles for his DSP: * User Control: Users should own their content and dictate how their data and creations generate value, rather than being subject to the whims of centralized corporations. * Decentralized Infrastructure: Instead of a single platform, multiple interface providers, content hosts, and advertisers interoperate, fostering competition and resilience. * Privacy and Autonomy: Decentralized solutions for profile management, hosting, and interactions would protect user privacy and reduce reliance on unaccountable intermediaries. * Value Creation: Users, not platforms, should capture the economic benefits of their contributions, supported by decentralized mechanisms for transactions.
These ideas were forward-thinking in 2021, envisioning a shift away from the centralized giants dominating social media at the time. While Ulbricht didn’t specifically address advertising protocols, his framework for decentralization and user empowerment extends naturally to other domains, like NextBlock’s open-source offering: the PROMO Protocol.
NextBlock’s Implementation of PROMO Protocol
The PROMO Protocol powers NextBlock's Billboard app, a decentralized advertising protocol built on Nostr, a simple, open protocol for decentralized communication. The PROMO Protocol reimagines advertising by: * Empowering People: Individuals set their own ad prices (e.g., 500 sats/minute), giving them direct control over how their attention or space is monetized. * Marketplace Dynamics: Advertisers set budgets and maximum bids, competing within a decentralized system where a 20% service fee ensures operational sustainability. * Open-Source Flexibility: As an open-source protocol, it allows multiple developers to create interfaces or apps on top of it, avoiding the single-platform bottleneck Ulbricht critiqued. * Secure Payments: Using Strike Integration with Bitcoin Lightning Network, NextBlock enables bot-resistant and intermediary-free transactions, aligning value transfer with each person's control.
This structure decentralizes advertising in a way that mirrors Ulbricht’s broader vision for social systems, with aligned principles showing a specific use case: monetizing attention on Nostr.
Aligned Principles
Ulbricht’s 2021 article didn’t explicitly predict the PROMO Protocol, but its foundational concepts align remarkably well with NextBlock's implementation the protocol’s design: * Autonomy Over Value: Ulbricht argued that users should control their content and its economic benefits. In the PROMO Protocol, people dictate ad pricing, directly capturing the value of their participation. Whether it’s their time, influence, or digital space, rather than ceding it to a centralized ad network. * Ecosystem of Providers: Ulbricht envisioned multiple providers replacing a single platform. The PROMO Protocol’s open-source nature invites a similar diversity: anyone can build interfaces or tools on top of it, creating a competitive, decentralized advertising ecosystem rather than a walled garden. * Decentralized Transactions: Ulbricht’s DSP implied decentralized mechanisms for value exchange. NextBlock delivers this through the Bitcoin Lightning Network, ensuring that payments for ads are secure, instantaneous and final, a practical realization of Ulbricht’s call for user-controlled value flows. * Privacy and Control: While Ulbricht emphasized privacy in social interactions, the PROMO Protocol is public by default. Individuals are fully aware of all data that they generate since all Nostr messages are signed. All participants interact directly via Nostr.
 [Blueprint Match, source NextBlock]
[Blueprint Match, source NextBlock]
Who We Are
NextBlock is a US-based new media company reimagining digital ads for a decentralized future. Our founders, software and strategy experts, were hobbyist podcasters struggling to promote their work online without gaming the system. That sparked an idea: using new tech like Nostr and Bitcoin to build a decentralized attention market for people who value control and businesses seeking real connections.
Our first product, Billboard, is launching this June.
Open for All
Our model’s open-source! Check out the PROMO Protocol, built for promotion and attention trading. Anyone can join this decentralized ad network. Run your own billboard or use ours. This is a growing ecosystem for a new ad economy.
Our Vision
NextBlock wants to help build a new decentralized internet. Our revolutionary and transparent business model will bring honest revenue to companies hosting valuable digital spaces. Together, we will discover what our attention is really worth.
Read our Manifesto to learn more.
NextBlock is registered in Texas, USA.
-
 @ da0b9bc3:4e30a4a9
2025-04-23 07:50:49
@ da0b9bc3:4e30a4a9
2025-04-23 07:50:49Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/954269
-
 @ 57d56d16:458edffd
2025-04-22 23:43:13
@ 57d56d16:458edffd
2025-04-22 23:43:13Hello. I've had a look at shopstr. You can find my instance of shopstr here so you can have a look yourself: https://shopstr.tectumordo.com/marketplace
Wondering your thoughts on Shopstr. I'm looking to start selling some things. Handcrafted Items / Services.
Anyone have any insights into shopstr, or something similar.
originally posted at https://stacker.news/items/953976
-
 @ ba36d0f7:cd802cba
2025-04-22 20:30:45
@ ba36d0f7:cd802cba
2025-04-22 20:30:45| Pieza | Movimiento | Reglas Especiales | | --------- | ---------------------------------- | --------------------------- | | Peón | 1 casilla adelante (o 2 al inicio) | Captura al paso, coronación | | Torre | Líneas rectas | Enroque | | Caballo | En "L" (2+1) | Salta piezas | | Alfil | Diagonales | Atrapado en un color | | Dama | Cualquier dirección | Ninguna | | Rey | 1 casilla en cualquier dirección | Enroque, jaque mate |
1. Peón (♙ / ♟️)
- Mueve: 1 casilla adelante (o 2 en su primer movimiento).

- Captura: En diagonal (1 casilla).
 > Especial:
>- Captura al paso: Si un peón rival avanza 2 casillas, puedes capturarlo como si hubiera movido 1.
> - Coronación: Al llegar a la 8ª fila, se convierte en cualquier pieza (¡usualmente Dama!).
> Especial:
>- Captura al paso: Si un peón rival avanza 2 casillas, puedes capturarlo como si hubiera movido 1.
> - Coronación: Al llegar a la 8ª fila, se convierte en cualquier pieza (¡usualmente Dama!).
2. Torre (♖ / ♜)
- Mueve: Líneas rectas (sin límite de casillas).

- Especial: Participa en el enroque.
3. Caballo (♘ / ♞)
-
Mueve: En "L" (2 casillas en una dirección + 1 perpendicular).
-
Única pieza que salta sobre otras.
4. Alfil (♗ / ♝)
-
Mueve: Diagonales (sin límite).
-
Siempre permanece en el mismo color de casilla.

5. Dama (♕ / ♛)
- Mueve: Cualquier dirección (recto o diagonal).

- ¡La pieza más poderosa!
6. Rey (♔ / ♚)
- Mueve: 1 casilla en cualquier dirección.

Especial:
- Enroque: Cambia de lugar con una torre (si no hay obstáculos/jaques). - Jaque mate: Pierde si queda atrapado sin escapatoria.
Cómo mover
-
Un movimiento por turno.
-
Elige tu pieza y colócala en una casilla legal.
-
Solo tu color: Blancas mueven primero, luego negras, alternando.
-
No pasar: Debes mover si es tu turno.
Cómo capturar ("comer")
-
Ocupa la casilla de una pieza rival: Reemplázala con tu pieza.
-
Peones capturan solo en diagonal (no de frente).
-
Los reyes no pueden ser capturados (el jaque mate termina el juego).
✔ Jaque: Ataca al rey enemigo (debe escapar en su siguiente turno).
❌ Ilegal: Mover a jaque o dejar a tu rey en jaque.
Movimientos especiales
|Movimiento|Regla Clave|Notación| |---|---|---| |Enroque|Rey + torre, sin movimientos previos|
0-0| |Coronación|Peón→cualquier pieza en 8ª fila|e8=D| |Captura al paso|Captura un peón que avanzó 2 casillas|exd6 a.p.|
1. Enroque ("La escapatoria del rey")
-
Qué: Rey y torre se mueven juntos en un turno.
Cómo: -
Rey mueve 2 casillas hacia una torre.
-
Torre "salta" al lado opuesto del rey.

Reglas: - Sin jaques: El rey no puede estar en jaque ni pasar por casillas atacadas. - Sin movimientos previos: Ni el rey ni esa torre deben haberse movido antes.
Tipos:
- Corto (lado del rey, rápido):0-0- Largo (lado de la dama, seguro):0-0-0
2. Coronación ("Coronar")
-
Qué: Peón llega a la 8ª fila → se convierte en cualquier pieza (usualmente Dama).
-
Cómo: Reemplaza el peón (incluso si ya tienes esa pieza).
Dato curioso: Puedes tener 9 damas (1 original + 8 coronaciones).
Ejemplo: Peón en h8 se convierte en Dama →h8=D.
3. Captura al paso (Del francés "en passant")
-
Cuándo: Un peón rival avanza 2 casillas y queda al lado del tuyo.
-
Cómo: Captúralo en diagonal (como si hubiera movido 1 casilla).

Regla: Debes hacerlo inmediatamente (solo en el turno siguiente)
Recurso digitales
Guia para principiantes - Lichess.org https://lichess.org/study/Hmb28fbv/QRyxzgre
Ajedrez desde cero - Youtube.com https://www.youtube.com/watch?v=YPf9fSY_K2k&list=PLWgqlpb234bHv38g6zXoi3WIJJonzZSAl&index=8
- Mueve: 1 casilla adelante (o 2 en su primer movimiento).
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-22 15:37:53
@ 5d4b6c8d:8a1c1ee3
2025-04-22 15:37:53How I wish I had time for this!
https://primal.net/e/nevent1qvzqqqqqqypzqntcggz30qhq60ltqdx32zku9d46unhrkjtcv7fml7jx3dh4h94nqqsynzz85x8dcqnzxrzypec9xw6haxxjt0z0c547suty7gpa835v0vs2qusmr
originally posted at https://stacker.news/items/953418
-
 @ a39d19ec:3d88f61e
2025-04-22 12:44:42
@ a39d19ec:3d88f61e
2025-04-22 12:44:42Die Debatte um Migration, Grenzsicherung und Abschiebungen wird in Deutschland meist emotional geführt. Wer fordert, dass illegale Einwanderer abgeschoben werden, sieht sich nicht selten dem Vorwurf des Rassismus ausgesetzt. Doch dieser Vorwurf ist nicht nur sachlich unbegründet, sondern verkehrt die Realität ins Gegenteil: Tatsächlich sind es gerade diejenigen, die hinter jeder Forderung nach Rechtssicherheit eine rassistische Motivation vermuten, die selbst in erster Linie nach Hautfarbe, Herkunft oder Nationalität urteilen.
Das Recht steht über Emotionen
Deutschland ist ein Rechtsstaat. Das bedeutet, dass Regeln nicht nach Bauchgefühl oder politischer Stimmungslage ausgelegt werden können, sondern auf klaren gesetzlichen Grundlagen beruhen müssen. Einer dieser Grundsätze ist in Artikel 16a des Grundgesetzes verankert. Dort heißt es:
„Auf Absatz 1 [Asylrecht] kann sich nicht berufen, wer aus einem Mitgliedstaat der Europäischen Gemeinschaften oder aus einem anderen Drittstaat einreist, in dem die Anwendung des Abkommens über die Rechtsstellung der Flüchtlinge und der Europäischen Menschenrechtskonvention sichergestellt ist.“
Das bedeutet, dass jeder, der über sichere Drittstaaten nach Deutschland einreist, keinen Anspruch auf Asyl hat. Wer dennoch bleibt, hält sich illegal im Land auf und unterliegt den geltenden Regelungen zur Rückführung. Die Forderung nach Abschiebungen ist daher nichts anderes als die Forderung nach der Einhaltung von Recht und Gesetz.
Die Umkehrung des Rassismusbegriffs
Wer einerseits behauptet, dass das deutsche Asyl- und Aufenthaltsrecht strikt durchgesetzt werden soll, und andererseits nicht nach Herkunft oder Hautfarbe unterscheidet, handelt wertneutral. Diejenigen jedoch, die in einer solchen Forderung nach Rechtsstaatlichkeit einen rassistischen Unterton sehen, projizieren ihre eigenen Denkmuster auf andere: Sie unterstellen, dass die Debatte ausschließlich entlang ethnischer, rassistischer oder nationaler Kriterien geführt wird – und genau das ist eine rassistische Denkweise.
Jemand, der illegale Einwanderung kritisiert, tut dies nicht, weil ihn die Herkunft der Menschen interessiert, sondern weil er den Rechtsstaat respektiert. Hingegen erkennt jemand, der hinter dieser Kritik Rassismus wittert, offenbar in erster Linie die „Rasse“ oder Herkunft der betreffenden Personen und reduziert sie darauf.
Finanzielle Belastung statt ideologischer Debatte
Neben der rechtlichen gibt es auch eine ökonomische Komponente. Der deutsche Wohlfahrtsstaat basiert auf einem Solidarprinzip: Die Bürger zahlen in das System ein, um sich gegenseitig in schwierigen Zeiten zu unterstützen. Dieser Wohlstand wurde über Generationen hinweg von denjenigen erarbeitet, die hier seit langem leben. Die Priorität liegt daher darauf, die vorhandenen Mittel zuerst unter denjenigen zu verteilen, die durch Steuern, Sozialabgaben und Arbeit zum Erhalt dieses Systems beitragen – nicht unter denen, die sich durch illegale Einreise und fehlende wirtschaftliche Eigenleistung in das System begeben.
Das ist keine ideologische Frage, sondern eine rein wirtschaftliche Abwägung. Ein Sozialsystem kann nur dann nachhaltig funktionieren, wenn es nicht unbegrenzt belastet wird. Würde Deutschland keine klaren Regeln zur Einwanderung und Abschiebung haben, würde dies unweigerlich zur Überlastung des Sozialstaates führen – mit negativen Konsequenzen für alle.
Sozialpatriotismus
Ein weiterer wichtiger Aspekt ist der Schutz der Arbeitsleistung jener Generationen, die Deutschland nach dem Zweiten Weltkrieg mühsam wieder aufgebaut haben. Während oft betont wird, dass die Deutschen moralisch kein Erbe aus der Zeit vor 1945 beanspruchen dürfen – außer der Verantwortung für den Holocaust –, ist es umso bedeutsamer, das neue Erbe nach 1945 zu respektieren, das auf Fleiß, Disziplin und harter Arbeit beruht. Der Wiederaufbau war eine kollektive Leistung deutscher Menschen, deren Früchte nicht bedenkenlos verteilt werden dürfen, sondern vorrangig denjenigen zugutekommen sollten, die dieses Fundament mitgeschaffen oder es über Generationen mitgetragen haben.
Rechtstaatlichkeit ist nicht verhandelbar
Wer sich für eine konsequente Abschiebepraxis ausspricht, tut dies nicht aus rassistischen Motiven, sondern aus Respekt vor der Rechtsstaatlichkeit und den wirtschaftlichen Grundlagen des Landes. Der Vorwurf des Rassismus in diesem Kontext ist daher nicht nur falsch, sondern entlarvt eine selektive Wahrnehmung nach rassistischen Merkmalen bei denjenigen, die ihn erheben.
-
 @ da0b9bc3:4e30a4a9
2025-04-22 06:44:40
@ da0b9bc3:4e30a4a9
2025-04-22 06:44:40Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/952743
-
 @ 000002de:c05780a7
2025-04-21 19:36:30
@ 000002de:c05780a7
2025-04-21 19:36:30When people typically use the analogy of digital gold to describe bitcoin they mean that it is a digital asset that functions in the market in a way very similar to gold. By this they mean it is a store of value, not really a medium of exchange. This framing is not popular with the bitcoin is money crowd because when people use the digital gold framing they typically mean bitcoin isn't money. Its just a store of value. A hedge against inflation. It would never be used as money. It isn't good for buying stuff. Some that say this I'm pretty convinced are simply pushing this idea because of fear of the state. Others seem to really mean it.
The other day I was thinking about this and something occurred to me. I thought I understood gold before I understood bitcoin. I imagine like most people are similar. The truth is reading "The Bitcoin Standard" taught me much more about gold than bitcoin. In fact, I didn't really learn much about bitcoin from the book. I'm not saying its not a great book about bitcoin but rather my ignorance of gold was much greater than I realized. I imagine I'm not alone in that.
I remember thinking about gold after reading it... gold is pretty cool. Its properties are kinda wild. Gold has been used as money far longer than paper money. Its absolutely absurd to compare gold to bitcoin. Bitcoin is so new! But gold has qualities that make it unique among precious metals. These are not all unique properties but these are some of its qualities that make it a good money.
- You cannot create it, you have to find/mine it.
- You cannot destroy it.
- It is fungible.
- Its authenticity can be verified.
- Its supply has a very small increase over time(for now).
- It has been used for thousands of years as both a store of value and medium of exchange.
So why don't we use gold every day to buy goods. A common opinion is that it is because of greedy bankers and central planners but that's not the whole story. The truth is that gold died as a common money largely due to technology. Telecommunications and the speed of communication across great distances is what really supplanted gold as money. Gold was still used to back paper money(notes) but its use as the actual direct medium of exchange is largely dead. Bitcoin was not the first attempt to make digital money nor digital gold, but it has been the most successful by far.
So what am I saying? Bitcoin isn't digital gold but its a good analog. If you could make gold digital is would be great money. Bitcoin is a great store of value for the same reasons gold has been. Bitcoin however can be sent across great distances with ease and at the same time it can be stored for long periods of time at low cost. It is better than gold in both ways. As a store of value and medium of exchange. I can't send an oz of gold across the globe in seconds. I can't validate the authenticity of my gold with a simple computer.
My belief is that people that think bitcoin is only a viable store of value don't really understand bitcoin. Its true that currently under standard economic definitions bitcoin is not a generally accepted medium of exchange but that is only an issue of adoption and understanding. Bitcoin without lightning is still better than any fiat money. The dollar is only digital due to custodial services and trust in third parties. Our biggest problem with bitcoin as a medium of exchange is literally a lack of knowledge. This will be solved over time as people start to hold it to preserve their long term wealth. As fiat money dies and as regimes crack down on humans we will see a rise in desire for a new money. Sadly, I think most people will need to get wrecked before they get it.
My recommendation is to stop fighting over the "digital gold" label but instead agree and focus on the digital aspect. If gold was digital it would not have been supplanted by paper notes.
What do you think?
originally posted at https://stacker.news/items/951965
-
 @ 57d1a264:69f1fee1
2025-04-21 12:11:22
@ 57d1a264:69f1fee1
2025-04-21 12:11:22There's any content about SN out there?
In the news: - @BitcoinNews Stacker.News Raises $1.25m Seed Round At $25m Valuation - @Alby blog post explain how Stacker News adds Self-custodial Spending with NWC - @cryotosensei on @0xbitcoiner's website Stacker News encourages deep sharing ad Random things I learnt about Bitcoin from Stacker News - @anita's Earn bitcoin on Stacker News: People asked and I answered
Recently we have seen an article in BM writing about how PlebLab is shaping the future of bitcoin startups in Austin. SN was mentioned and linked 🎉
Started in 2021 by one of PlebLab’s cofounders Keyan Kousha, Stacker.news has quickly become a hub of news for many tech-savvy Bitcoiners. Boasting an open source Lightning-powered Reddit, the platform has gathered an active and loyal fan base that reward each other with sats for every upvote, often being early to integrate the latest technologies in the Bitcoin-social media tech scene.
In the past it has also only mentioned here.
From a startup pitch perspective:
Developer of a news platform intended for individuals to earn real money for creating and curating content. The company's platform specializes in allowing individuals to submit, vote, and comment on content, stories, and discussions about the topics in communities organized around their interests, enabling individuals to post content and get paid while reading the news. PitchBook -
https://pitchbook.com/profiles/company/535835-44#overviewStacker News is a forum (like Reddit or Hacker News) where you can earn real money for creating or curating content. F6S -
https://www.f6s.com/company/stacker-news#aboutPeople talking about SN:
-
A stacker shared a Lessons learned from Stacker.news and how SN works. Discourse Co-CEO respond:
Heh, it’s not a healthy or sustainable model for the types of communities consciously we build for. Definitely not something we would consider building into core but you could make it work with a plugin. Extrinsic motivators attract the wrong people for the wrong reasons, in my experience. Healthy community ecosystems are driven by intrinsic motivation.
-
on BitcoinTalk here, here and here. There are probably more posts where it has ben mentioned and discussed.
-
HackerNews crowd does not seem too excited about it. Just few comments on each post.
Some review have been collected on @julian's Apollo and ProductHunt.
Let's check what YT has:
Some interviews first. At 2023 ZBD x PlebLab TabConf Hackathon, Keyan Kousha explain Why Not to Use Stacker News
@kr did a great job interviewing k00b when SN was in its infancy - Stacker News Is Growing FAST - Stacker News Is Disrupting Social Media | E17 - Keyan Kousha on Stacker News, Earning Bitcoin, & Decentralized Content | The Kevin Rooke Show | E17 - How Siggy47 Stacked Over 500,000 Sats on Stacker News | SS8
And here some interviews:
Stacker News is a user-generated, feed-style news platform, modeled after Hacker News, but with the important distinction of having natively-integrated bitcoin lightning payments, as a means of fostering more natural communities (think less spam and antisocial behavior), cultivating high-signal bitcoin content, and providing a better user experience overall.
Stacker News is still in the very early days of its development, but it's a great showcase of how bitcoin can be used to improve upon an existing model, and in doing so, explore how improved incentives might influence media publishing, monetization, and moderation.
Keyan is a prime example of someone who caught the bitcoin bug, and just couldn't resist getting involved. The result is a product built with and for bitcoiners, and it was great to have him on the show to explain more about his motivations and ambitions.
-
From ~ideasfrommtheedge pod: AI, Simulations, and Startups with Keyan Kousha (Founder, Stacker News)
-
@alexstrenger's Convos On The Pedicab #177 Stacker News: A Bitcoiners Alternative To Reddit
-
@dk and @MaxAWebster intro on What's new with Stacker.News and Nostr? also shared here
-
@ConnectTheWorld stream Keep Austin Weird! Meet Keyan, the founder of Stacker.news
-
@Thriller Lightning: Stacker.News Founder Keyan
-
0.00000018: Keyan Kousha, Stacker.News: an interview in the Changing the Tide show here
-
@bitcoinplebdev reading top ~devs stories 04/08/2024 and stacker.news codebase overview / how to run locally)
That's the interviews I was able to find. Continuing the dig...
-
@TheWildHustle compiles SN ~Music' vibes into YT playlists
-
@kdnolan7 on was giving some updates about the ~Education territory here and here
Gradually, then suddenly, the message start to change, and the majority of videos communicate something that is probably, at least from my perspective, not the right way to market a product like SN:
-
@SatsMate lay out Why He Love Stacker News!
-
@voltage share a story quickly talking how Stacker News is like YCombinators Hacker News but YOU EARN! https://www.youtube.com/shorts/d1xZ3RE9plk
@HattyHats Earn Bitcoin (LN) Blogging with Stacker News
The long list continues: - Earn bitcoin Satoshis Reading & Sharing Content on Stacker.News - First Time Walk Through by @SatoshiTutor - Earn Free Bitcoin | Stacker News Quick Tutorial from Earning Crypto Site - One of the Different Ways to Earn Bitcoin 👉 stacker.news | Bitcoin Lifestyle #2 from @SatoshiComTR - @1100note another Stacker.News story - ...
This list of references can, and probably will, go on and on with the same topic. The message looks like will be always the same: come over, stack sats, stay humble. There's maybe something wrong with the message we share SN out there? Is not what we do, is how we do it, that make the difference. As you can see, there's not much there that refer to quality content, great supportive community, community moderated contents, no ads, no spam, no bots (well, not many) and no ai. Pure human content.
In other successful platforms where people earn money for the contents they create, the money factor is totally hidden, is not their main sales point in the pitch. Look at YT itself. We all know people earn fiat producing and sharing videos, but their comms does not talk about it, at least not the way stackers do. And you'll not find many YTers inviting others to create videos to earn money. Well ok, some do!
Something we could make an effort to improve, is the way we talk about SN. Finding alternative ways to do it is hard, some have been mentioned here https://stacker.news/items/948462/r/Design_r
Just wanted to see how much other quality content is out there talking about SN that is not about stacking sats? Share your best contents, nostr notes, x tweets, blog posts, articles, videos, interviews, reviews or any other media that has been created by others about SN (no memes shill) or that somehow mention it in the comments below.
originally posted at https://stacker.news/items/951177
-
-
 @ da0b9bc3:4e30a4a9
2025-04-21 07:56:29
@ da0b9bc3:4e30a4a9
2025-04-21 07:56:29Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/951022
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:12:19
@ 4ba8e86d:89d32de4
2025-04-21 02:12:19SISTEMA OPERACIONAL MÓVEIS
GrapheneOS : https://njump.me/nevent1qqs8t76evdgrg4qegdtyrq2rved63pr29wlqyj627n9tj4vlu66tqpqpzdmhxue69uhk7enxvd5xz6tw9ec82c30qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqppcqec9
CalyxOS : https://njump.me/nevent1qqsrm0lws2atln2kt3cqjacathnw0uj0jsxwklt37p7t380hl8mmstcpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3vamnwvaz7tmwdaehgu3wvf3kstnwd9hx5cf0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgcwaehxw309aex2mrp0yhxxatjwfjkuapwveukjtcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309ahx7um5wghxymmwva3x7mn89e3k7mf0qythwumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mf0qyg8wumn8ghj7mn09eehgu3wvdez7smttdu
LineageOS : https://njump.me/nevent1qqsgw7sr36gaty48cf4snw0ezg5mg4atzhqayuge752esd469p26qfgpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpnvm779
SISTEMA OPERACIONAL DESKTOP
Tails : https://njump.me/nevent1qqsf09ztvuu60g6xprazv2vxqqy5qlxjs4dkc9d36ta48q75cs9le4qpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz34ag5t
Qubes OS : https://njump.me/nevent1qqsp6jujgwl68uvurw0cw3hfhr40xq20sj7rl3z4yzwnhp9sdpa7augpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0dehhxarj9ehhsarj9ejx2a30qyg8wumn8ghj7mn09eehgu3wvdez7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uqjxamnwvaz7tmwdaehgu3dwejhy6txd9jkgtnhv4kxcmmjv3jhytnwv46z7qgwwaehxw309ahx7uewd3hkctcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uj3ljr8
Kali linux : https://njump.me/nevent1qqswlav72xdvamuyp9xc38c6t7070l3n2uxu67ssmal2g7gv35nmvhspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswt9rxe
Whonix : https://njump.me/nevent1qqs85gvejvzhk086lwh6edma7fv07p5c3wnwnxnzthwwntg2x6773egpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3wamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmd9uq3qamnwvaz7tmwduh8xarj9e3hytcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz7qg7waehxw309ahx7um5wgkkgetk9emk2mrvdaexgetj9ehx2ap0sen9p6
Kodachi : https://njump.me/nevent1qqsf5zszgurpd0vwdznzk98hck294zygw0s8dah6fpd309ecpreqtrgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszgmhwden5te0dehhxarj94mx2unfve5k2epwwajkcmr0wfjx2u3wdejhgtcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzpmhxue69uhkumewwd68ytnrwghszfrhwden5te0dehhxarj9eex7atwv3ex7cmtvf5hgcm0d9hx2unn9e3k7mf0qyvhwumn8ghj7mn0wd68ytnzdahxwcn0denjucm0d5hszrnhwden5te0dehhxtnvdakz7qgkwaehxw309ahx7um5wghxycmg9ehxjmn2vyhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshs94a4d5
PGP
Openkeychain : https://njump.me/nevent1qqs9qtjgsulp76t7jkquf8nk8txs2ftsr0qke6mjmsc2svtwfvswzyqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs36mp0w
Kleopatra : https://njump.me/nevent1qqspnevn932hdggvp4zam6mfyce0hmnxsp9wp8htpumq9vm3anq6etsppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpuaeghp
Pgp : https://njump.me/nevent1qqsggek707qf3rzttextmgqhym6d4g479jdnlnj78j96y0ut0x9nemcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgptemhe
Como funciona o PGP? : https://njump.me/nevent1qqsz9r7azc8pkvfmkg2hv0nufaexjtnvga0yl85x9hu7ptpg20gxxpspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy259fhs
Por que eu escrevi PGP. - Philip Zimmermann.
https://njump.me/nevent1qqsvysn94gm8prxn3jw04r0xwc6sngkskg756z48jsyrmqssvxtm7ncpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtchzxnad
VPN
Vpn : https://njump.me/nevent1qqs27ltgsr6mh4ffpseexz6s37355df3zsur709d0s89u2nugpcygsspzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqshzu2fk
InviZible Pro : https://njump.me/nevent1qqsvyevf2vld23a3xrpvarc72ndpcmfvc3lc45jej0j5kcsg36jq53cpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy33y5l4
Orbot: https://njump.me/nevent1qqsxswkyt6pe34egxp9w70cy83h40ururj6m9sxjdmfass4cjm4495stft593
I2P
i2p : https://njump.me/nevent1qqsvnj8n983r4knwjmnkfyum242q4c0cnd338l4z8p0m6xsmx89mxkslx0pgg
Entendendo e usando a rede I2P : https://njump.me/nevent1qqsxchp5ycpatjf5s4ag25jkawmw6kkf64vl43vnprxdcwrpnms9qkcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpvht4mn
Criando e acessando sua conta Email na I2P : https://njump.me/nevent1qqs9v9dz897kh8e5lfar0dl7ljltf2fpdathsn3dkdsq7wg4ksr8xfgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpw8mzum
APLICATIVO 2FA
Aegis Authenticator : https://njump.me/nevent1qqsfttdwcn9equlrmtf9n6wee7lqntppzm03pzdcj4cdnxel3pz44zspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqscvtydq
YubiKey : https://njump.me/nevent1qqstsnn69y4sf4330n7039zxm7wza3ch7sn6plhzmd57w6j9jssavtspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzueyvgt
GERENCIADOR DE SENHAS
KeepassDX: https://njump.me/nevent1qqswc850dr4ujvxnmpx75jauflf4arc93pqsty5pv8hxdm7lcw8ee8qpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpe0492n
Birwaden: https://njump.me/nevent1qqs0j5x9guk2v6xumhwqmftmcz736m9nm9wzacqwjarxmh8k4xdyzwgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpwfe2kc
KeePassXC: https://njump.me/nevent1qqsgftcrd8eau7tzr2p9lecuaf7z8mx5jl9w2k66ae3lzkw5wqcy5pcl2achp
CHAT MENSAGEM
SimpleXchat : https://njump.me/nevent1qqsds5xselnnu0dyy0j49peuun72snxcgn3u55d2320n37rja9gk8lgzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgmcmj7c
Briar : https://njump.me/nevent1qqs8rrtgvjr499hreugetrl7adkhsj2zextyfsukq5aa7wxthrgcqcg05n434
Element Messenger : https://njump.me/nevent1qqsq05snlqtxm5cpzkshlf8n5d5rj9383vjytkvqp5gta37hpuwt4mqyccee6
Pidgin : https://njump.me/nevent1qqsz7kngycyx7meckx53xk8ahk98jkh400usrvykh480xa4ct9zlx2c2ywvx3
E-MAIL
Thunderbird: https://njump.me/nevent1qqspq64gg0nw7t60zsvea5eykgrm43paz845e4jn74muw5qzdvve7uqrkwtjh
ProtonMail : https://njump.me/nevent1qqs908glhk68e7ms8zqtlsqd00wu3prnpt08dwre26hd6e5fhqdw99cppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpeyhg4z
Tutonota : https://njump.me/nevent1qqswtzh9zjxfey644qy4jsdh9465qcqd2wefx0jxa54gdckxjvkrrmqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5hzhkv
k-9 mail : https://njump.me/nevent1qqs200g5a603y7utjgjk320r3srurrc4r66nv93mcg0x9umrw52ku5gpr3mhxue69uhkummnw3ezuumhd9ehxtt9de5kwmtp9e3kstczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgacflak
E-MAIL-ALIÁS
Simplelogin : https://njump.me/nevent1qqsvhz5pxqpqzr2ptanqyqgsjr50v7u9lc083fvdnglhrv36rnceppcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp9gsr7m
AnonAddy : https://njump.me/nevent1qqs9mcth70mkq2z25ws634qfn7vx2mlva3tkllayxergw0s7p8d3ggcpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs6mawe3
NAVEGADOR
Navegador Tor : https://njump.me/nevent1qqs06qfxy7wzqmk76l5d8vwyg6mvcye864xla5up52fy5sptcdy39lspzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdp0urw
Mullvap Browser : https://njump.me/nevent1qqs2vsgc3wk09wdspv2mezltgg7nfdg97g0a0m5cmvkvr4nrfxluzfcpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpj8h6fe
LibreWolf : https://njump.me/nevent1qqswv05mlmkcuvwhe8x3u5f0kgwzug7n2ltm68fr3j06xy9qalxwq2cpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuv2hxr
Cromite : https://njump.me/nevent1qqs2ut83arlu735xp8jf87w5m3vykl4lv5nwkhldkqwu3l86khzzy4cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs3dplt7
BUSCADORES
Searx : https://njump.me/nevent1qqsxyzpvgzx00n50nrlgctmy497vkm2cm8dd5pdp7fmw6uh8xnxdmaspr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp23z7ax
APP-STORE
Obtainium : https://njump.me/nevent1qqstd8kzc5w3t2v6dgf36z0qrruufzfgnc53rj88zcjgsagj5c5k4rgpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyarmca3
F-Droid : https://njump.me/nevent1qqst4kry49cc9g3g8s5gdnpgyk3gjte079jdnv43f0x4e85cjkxzjesymzuu4
Droid-ify : https://njump.me/nevent1qqsrr8yu9luq0gud902erdh8gw2lfunpe93uc2u6g8rh9ep7wt3v4sgpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsfzu9vk
Aurora Store : https://njump.me/nevent1qqsy69kcaf0zkcg0qnu90mtk46ly3p2jplgpzgk62wzspjqjft4fpjgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzrpmsjy
RSS
Feeder : https://njump.me/nevent1qqsy29aeggpkmrc7t3c7y7ldgda7pszl7c8hh9zux80gjzrfvlhfhwqpp4mhxue69uhkummn9ekx7mqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgsvzzjy
VIDEOO CONFERENCIA
Jitsi meet : https://njump.me/nevent1qqswphw67hr6qmt2fpugcj77jrk7qkfdrszum7vw7n2cu6cx4r6sh4cgkderr
TECLADOS
HeliBoard : https://njump.me/nevent1qqsyqpc4d28rje03dcvshv4xserftahhpeylu2ez2jutdxwds4e8syspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsr8mel5
OpenBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
FlorisBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
MAPAS
Osmand : https://njump.me/nevent1qqsxryp2ywj64az7n5p6jq5tn3tx5jv05te48dtmmt3lf94ydtgy4fgpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs54nwpj
Organic maps : https://njump.me/nevent1qqstrecuuzkw0dyusxdq7cuwju0ftskl7anx978s5dyn4pnldrkckzqpr4mhxue69uhkummnw3ezumtp0p5k6ctrd96xzer9dshx7un8qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpl8z3kk
TRADUÇÃO
LibreTranslate : https://njump.me/nevent1qqs953g3rhf0m8jh59204uskzz56em9xdrjkelv4wnkr07huk20442cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzeqsx40
REMOÇÃO DOS METADADOS
Scrambled Exif : https://njump.me/nevent1qqs2658t702xv66p000y4mlhnvadmdxwzzfzcjkjf7kedrclr3ej7aspyfmhxue69uhk6atvw35hqmr90pjhytngw4eh5mmwv4nhjtnhdaexcep0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpguu0wh
ESTEGANOGRAFIA
PixelKnot: https://njump.me/nevent1qqsrh0yh9mg0lx86t5wcmhh97wm6n4v0radh6sd0554ugn354wqdj8gpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyuvfqdp
PERFIL DE TRABALHO
Shelter : https://njump.me/nevent1qqspv9xxkmfp40cxgjuyfsyczndzmpnl83e7gugm7480mp9zhv50wkqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdnu59c
PDF
MuPDF : https://njump.me/nevent1qqspn5lhe0dteys6npsrntmv2g470st8kh8p7hxxgmymqa95ejvxvfcpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs4hvhvj
Librera Reader : https://njump.me/nevent1qqsg60flpuf00sash48fexvwxkly2j5z9wjvjrzt883t3eqng293f3cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz39tt3n
QR-Code
Binary Eye : https://njump.me/nevent1qqsz4n0uxxx3q5m0r42n9key3hchtwyp73hgh8l958rtmae5u2khgpgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdmn4wp
Climático
Breezy Weather : https://njump.me/nevent1qqs9hjz5cz0y4am3kj33xn536uq85ydva775eqrml52mtnnpe898rzspzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgpd3tu8
ENCRYPTS
Cryptomator : https://njump.me/nevent1qqsvchvnw779m20583llgg5nlu6ph5psewetlczfac5vgw83ydmfndspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsx7ppw9
VeraCrypt : https://njump.me/nevent1qqsf6wzedsnrgq6hjk5c4jj66dxnplqwc4ygr46l8z3gfh38q2fdlwgm65ej3
EXTENSÕES
uBlock Origin : https://njump.me/nevent1qqswaa666lcj2c4nhnea8u4agjtu4l8q89xjln0yrngj7ssh72ntwzql8ssdj
Snowflake : https://njump.me/nevent1qqs0ws74zlt8uced3p2vee9td8x7vln2mkacp8szdufvs2ed94ctnwchce008
CLOUD
Nextcloud : https://njump.me/nevent1qqs2utg5z9htegdtrnllreuhypkk2026x8a0xdsmfczg9wdl8rgrcgg9nhgnm
NOTEPAD
Joplin : https://njump.me/nevent1qqsz2a0laecpelsznser3xd0jfa6ch2vpxtkx6vm6qg24e78xttpk0cpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpdu0hft
Standard Notes : https://njump.me/nevent1qqsv3596kz3qung5v23cjc4cpq7rqxg08y36rmzgcrvw5whtme83y3s7tng6r
MÚSICA
RiMusic : https://njump.me/nevent1qqsv3genqav2tfjllp86ust4umxm8tr2wd9kq8x7vrjq6ssp363mn0gpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqg42353n
ViMusic : https://njump.me/nevent1qqswx78559l4jsxsrygd8kj32sch4qu57stxq0z6twwl450vp39pdqqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzjg863j
PODCAST
AntennaPod : https://njump.me/nevent1qqsp4nh7k4a6zymfwqqdlxuz8ua6kdhvgeeh3uxf2c9rtp9u3e9ku8qnr8lmy
VISUALIZAR VIDEO
VLC : https://njump.me/nevent1qqs0lz56wtlr2eye4ajs2gzn2r0dscw4y66wezhx0mue6dffth8zugcl9laky
YOUTUBE
NewPipe : https://njump.me/nevent1qqsdg06qpcjdnlvgm4xzqdap0dgjrkjewhmh4j3v4mxdl4rjh8768mgdw9uln
FreeTube : https://njump.me/nevent1qqsz6y6z7ze5gs56s8seaws8v6m6j2zu0pxa955dhq3ythmexak38mcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5lkjvv
LibreTube : https://snort.social/e/nevent1qqstmd5m6wrdvn4gxf8xyhrwnlyaxmr89c9kjddvnvux6603f84t3fqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsswwznc
COMPARTILHAMENTO DE ARQUIVOS
OnionShare : https://njump.me/nevent1qqsr0a4ml5nu6ud5k9yzyawcd9arznnwkrc27dzzc95q6r50xmdff6qpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qgswaehxw309ahx7tnnw3ezucmj9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qgswaehxw309ahx7um5wghx6mmd9uqjgamnwvaz7tmwdaehgu3wwfhh2mnywfhkx6mzd96xxmmfdejhyuewvdhk6tcppemhxue69uhkummn9ekx7mp0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qyv8wumn8ghj7un9d3shjtnrw4e8yetwwshxv7tf9ut7qurt
Localsend : https://njump.me/nevent1qqsp8ldjhrxm09cvvcak20hrc0g8qju9f67pw7rxr2y3euyggw9284gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuyghqr
Wallet Bitcoin
Ashigaru Wallet : https://njump.me/nevent1qqstx9fz8kf24wgl26un8usxwsqjvuec9f8q392llmga75tw0kfarfcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgvfsrqp
Samourai Wallet : https://njump.me/nevent1qqstcvjmz39rmrnrv7t5cl6p3x7pzj6jsspyh4s4vcwd2lugmre04ecpr9mhxue69uhkummnw3ezucn0denkymmwvuhxxmmd9upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy3rg4qs
CÂMERA
opencamera : https://njump.me/nevent1qqs25glp6dh0crrjutxrgdjlnx9gtqpjtrkg29hlf7382aeyjd77jlqpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqssxcvgc
OFFICE
Collabora Office : https://njump.me/nevent1qqs8yn4ys6adpmeu3edmf580jhc3wluvlf823cc4ft4h0uqmfzdf99qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsj40uss
TEXTOS
O manifesto de um Cypherpunk : https://njump.me/nevent1qqsd7hdlg6galn5mcuv3pm3ryfjxc4tkyph0cfqqe4du4dr4z8amqyspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzal0efa
Operations security ( OPSEC) : https://snort.social/e/nevent1qqsp323havh3y9nxzd4qmm60hw87tm9gjns0mtzg8y309uf9mv85cqcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz8ej9l7
O MANIFESTO CRIPTOANARQUISTA Timothy C. May – 1992. : https://njump.me/nevent1qqspp480wtyx2zhtwpu5gptrl8duv9rvq3mug85mp4d54qzywk3zq9gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz5wq496
Declaração de independência do ciberespaço
- John Perry Barlow - 1996 : https://njump.me/nevent1qqs2njsy44n6p07mhgt2tnragvchasv386nf20ua5wklxqpttf6mzuqpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsukg4hr
The Cyphernomicon: Criptografia, Dinheiro Digital e o Futuro da Privacidade. escrito por Timothy C. May -Publicado em 1994. :
Livro completo em PDF no Github PrivacyOpenSource.
https://github.com/Alexemidio/PrivacyOpenSource/raw/main/Livros/THE%20CYPHERNOMICON%20.pdf Share
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-21 00:28:50
@ 5d4b6c8d:8a1c1ee3
2025-04-21 00:28:50I was just about to get into bed last night, after recording the Stacker Sports Pod and hiding Easter Eggs, when I remembered to check my step count. As often happens, I was stupidly short of my goal: just 7 steps this time.
My step counter is not nearly so precise as to actually record seven steps, so I knew it was either go to bed or do some chores for a bit to get enough more steps to register.
Well, I got the steps easily enough, only to discover the dog had an accident on the carpet that I now needed to clean up...and it turned out we had run out of the cleaning supplies we use for such incidents. So, I had to do some basic chemistry at midnight to mix up a makeshift cleaning solution to keep the carpet from staining and wait long enough for it to do its magic before drying it out.
Had I just taken the L on the steps, the dog would have just fallen asleep and peed in the morning. I doubt the Workit payout will prove to be worth the hassle this time
originally posted at https://stacker.news/items/950750
-
 @ ba36d0f7:cd802cba
2025-04-20 17:58:52
@ ba36d0f7:cd802cba
2025-04-20 17:58:52FABRIC AS TEXTBOOK
Learning to embroider - or to mend - is like studying an ancestral language. Manuals explain the backstitch or sashiko, but fabric never lies: it tears if the tension is weak, and wrinkles if the needle is clumsy.
Theory gives you the alphabet; but practice gives you the syntax of the invisible. How many broken stitches hide behind perfect embroidery? How many mistakes teach us the language of threads?
I. TO MEND IS TO RESIST: THE POLITICAL ACT OF THE NEEDLE
There’s a certain sacred stubbornness in sitting down to mend; like our grandmothers darning our socks until the heel was more patch than original fabric.
And today, in the age of fast fashion, mending is rebellion: a silent "no" to disposability, a resounding "yes" to permanence.
Techniques as Philosophies
-
Japanese sashiko: Visible stitches like proud scars. "What’s broken isn’t hidden—it’s celebrated."

-
Darning: For when pain must be concealed, not erased.

-
Free embroidery: Where repair becomes art and mending, a language.

 Every stitch is a pact: "I care for you because you exist."
Every stitch is a pact: "I care for you because you exist."And isn’t this, too, what mestizaje means? To take the fragmented - fabrics, histories, identities - and reweave them without erasing their origin.
II. EMBROIDERY AS A SELF-TAUGHT MASTER
Learning to embroider is like learning to live: there are no shortcuts. You can read a thousand tutorials, but until you feel the thread resist the needle’s eye or the fabric tense beneath your fingers, knowledge remains abstract.
The Textile Learning Triad
-
Theory that fades (books explain the backstitch, but not how to avoid knots).
-
Practice that stings (fingers get pricked, stitches go crooked).
-
Intuition that blooms (when hands remember the motion on their own).
III. THREADS AND TECHNOLOGY
Malinche, Mesoamerica’s first translator, understood this: some knowledge only transmits through action. We, as 21st-century beings, have a privilege: to blend ancestral tools (needles, threads) with modern ones (YouTube tutorials, digital patterns).
At soma, we explore education beyond canons, and embroidery is the perfect example.
Embroidery teaches us:
-
Discipline (because one loose stitch ruins the design).
-
Creativity (because sometimes you must invent solutions).
-
Legacy (because every thread carries memory).
What are you mending today? A skirt, a habit, a way of learning?
This is the future of education: to dig into the old and hack the new.
IV. INVITATION: STITCHES AND PATIENCE WORKSHOP
This Saturday 26th, at Estudio Malinche, Apaneca - we won’t just teach techniques. We’ll create a collective learning ritual:
-
Bring a torn garment and an empty notebook.
-
Learn sashiko mending (to honor scars) and bookbinding with recycled paper (to chart your path).
-
You’ll leave with ink-stained hands and a heart full of threads.
"Perfection isn’t the goal - persistence is."
Follow us on IG to check out stories & upcoming events: @larutasoma @estudiomalinche
soma #article #mending #workshop #visiblemending #philosophy #resistance #btc #nostr #elsalvador #sashiko #rutadelasflores #apaneca #education #slowfashion #fashion #fastfashion #embroidery #stitching #handmade #diy
-
-
 @ 4fe14ef2:f51992ec
2025-04-20 10:02:41
@ 4fe14ef2:f51992ec
2025-04-20 10:02:41Let's support Bitcoin merchants! I'd love to hear some of your latest Lightning purchases and interesting products you bought. Feel free to include links to the shops or businesses you bought from.
Who else has a recent purchase they’re excited about? Bonus sats if you found a killer deal! ⚡
Respond below, share and report on nostr or X:
N: https://njup.me/nevent1qvzqqqqqqypzqnlpfmegjd95py7h... X: https://x.com/AGORA_SN/status/1913895348428587452
If you missed our last thread, here are some of the items stackers recently spent and zap on.
originally posted at https://stacker.news/items/949495
-
 @ da0b9bc3:4e30a4a9
2025-04-20 07:34:12
@ da0b9bc3:4e30a4a9
2025-04-20 07:34:12Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/949290
-
 @ 2e8970de:63345c7a
2025-04-20 06:16:49
@ 2e8970de:63345c7a
2025-04-20 06:16:492024 thread: https://stacker.news/items/487472 2023 thread: https://stacker.news/items/162435 2022 thread: https://stacker.news/items/20545
originally posted at https://stacker.news/items/949211
-
 @ 57d56d16:458edffd
2025-04-20 02:05:38
@ 57d56d16:458edffd
2025-04-20 02:05:38With all the noise of veganism and meat eaters.
What is factual. What is the correct path?
Simple question I suppose but having family member have deferring or "this is how it is" (food pyramid).
I just want an honest and factual answer.
Have I been lied to? Have I been brainwashed by school eduction on food?
Was it all wrong?
A little bit about me, I've started taking a proper interest in my food consumption. I've realised now that I just hated chewy steak and not all steak is done, well done. Steak inparticular because they were (are) deemed expensive and so if I don't like it I've wasted food and money and "experiementing" at a resurant isn't ideal.
After this. I started buying and showing interest in cooking steaks and my family now has me be the steak cook for when we want steak. What surprising to me, is that I do my steaks 2 minute high heat, each side (4-5mins)
And for the person who only ordered well done, my mother enjoys my 4 minute steaks, or just puts up it, idk. Mothers wanting to not give the honest opinon to not discurage.
Thanks for your time and look forward to reading your comments.
originally posted at https://stacker.news/items/948958
-
 @ b9d5de4b:26c0a1b8
2025-04-19 18:54:10
@ b9d5de4b:26c0a1b8
2025-04-19 18:54:10How do cowboy credits work? I just linked my node but havent been on SN in a little while. Been on primal and came back to cowboy credits and I feel like I missed to much. is there a tutorial anywhere?
originally posted at https://stacker.news/items/948379
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-19 14:29:43
@ 5d4b6c8d:8a1c1ee3
2025-04-19 14:29:43I finally put our picks in a spreadsheet, so let's take a look at where we all stand as the playoffs proper kick off.
| Stacker | Points | |---------|--------| | @Coinsreporter | 19 | | @Carresan | 18 | | @gnilma | 18 | | @grayruby | 17 | | @Undisciplined | 17 | | @fishious | 11 | | @BlokchainB | 11 | | @Car | 1 |
It's a tight race and there's still plenty of time to make up ground.
originally posted at https://stacker.news/items/948104
-
 @ c3f12a9a:06c21301
2025-04-19 10:09:45
@ c3f12a9a:06c21301
2025-04-19 10:09:45Satoshi’s Time-Traveling for Knowledge #4: Liberland 2024 – Freedom Under Siege
What is Liberland?
While digging through old decentralized forums archived on the Interchain, Satoshi came across a curious name: Liberland.
“A sovereign libertarian micronation on the Danube? Founded in 2015 via Terra nullius? Built on the principles of freedom, voluntaryism, and Bitcoin? And I’ve never heard of it?”
Intrigued, Satoshi began to research. The story was almost too good to be true. A 7-square-kilometer patch of unclaimed land between Croatia and Serbia, turned into a symbol of decentralized governance and individual liberty.
No taxes unless voluntary. Bitcoin as the national currency. A digital nation-state with thousands of registered e-citizens, and even its own constitution. And yet—no recognition, no borders, and no peace.His curiosity turned into determination. He calibrated the temporal coordinates on his chrono-node to the Danube River in 2024, a year rumored to be turbulent for the Free Republic of Liberland.
When he arrived, reality struck harder than the legend.
Freedom Under Siege
The nation was under siege.
The scent of burnt wood and trampled earth lingered in the air as Satoshi stepped into what remained of the Liberland settlement. Broken structures, crushed solar panels, and a few scattered personal belongings were all that testified to the once-vibrant hub of liberty pioneers.
He found a group of residents—mud-streaked, exhausted, but defiant—gathered around the remnants of a communal kitchen. One of them, wearing a weathered Liberland t-shirt and a crypto-wallet hardware device on a chain around his neck, greeted him:
"You're not with them, are you?"
Satoshi shook his head.
"Just... passing through. What happened here?"
The man’s voice trembled between rage and sorrow:
"On the International Day of Peace, no less. Croatian police raided us. Bulldozers came with them. Took everything—generators, comms gear, even our medical tents. Claimed it was 'illegal occupation of Croatian forestry land.' But no court, no hearing. Just force."
Satoshi listened, taking mental snapshots of their faces, their words, their pain. He thought about the dream—of a place built voluntarily, where people governed themselves, free from coercion.
But that dream was burning at the edges, like the collapsed tents scattered behind them.
Reflections Under the Stars
As night fell over the Danube, Satoshi sat alone, watching the stars reflect on the black water. Thoughts spiraled:
"Decentralization... is beautiful. But without protection, it's fragile."
He realized that so long as central authorities hold monopoly on violence and taxation, every independent effort to decentralize the world—from Bitcoin to Liberland—is at risk of being suppressed, ignored, or destroyed. Not because it’s wrong, but because it's inconvenient to power.
"Unless a major state like the USA decentralizes itself from within," he thought, "true decentralization will remain a resistance—never the standard."
He activated his chrono-node once more. Not in defeat, but with purpose.
The next destination? Unknown. But the mission was clearer than ever.
originally posted at https://stacker.news/items/947954
-
 @ 2e8970de:63345c7a
2025-04-19 08:53:14
@ 2e8970de:63345c7a
2025-04-19 08:53:14originally posted at https://stacker.news/items/947930
-
 @ da0b9bc3:4e30a4a9
2025-04-19 07:22:28
@ da0b9bc3:4e30a4a9
2025-04-19 07:22:28Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/947905
-
 @ 000002de:c05780a7
2025-04-18 17:20:16
@ 000002de:c05780a7
2025-04-18 17:20:16"Focus on the things you are for, not the things you are against. Many people spend large chunks of their day thinking about what they hate. They are always telling you about something they dislike: this food, that subject, this political party, that coworker. You are more than your frustrations. Build your identity around what you love."
~ James Clear
I need to do better with this personally but its great food for thought.
originally posted at https://stacker.news/items/947407
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-18 14:45:15
@ 5d4b6c8d:8a1c1ee3
2025-04-18 14:45:15We have playoff contests galore (https://stacker.news/items/947140/r/Undisciplined, https://stacker.news/items/943657/r/Undisciplined, https://stacker.news/items/945970/r/Undisciplined, https://stacker.news/items/945376/r/Undisciplined), which of course means we also have lots of playoff action to cover.
There are also several regular season contests going on (https://stacker.news/items/947153/r/Undisciplined, https://stacker.news/items/946412/r/Undisciplined, https://stacker.news/items/945561/r/Undisciplined, https://stacker.news/items/943383/r/Undisciplined), as well as the mish mash of events in the USA vs the world.
@BlokchainB posted some ideas for fixing the NBA and some of them seem promising. What really needs to be fixed?
@Coinsreporter has taken it upon himself to help us make smart decisions at Predyx. There are also some new exciting markets we want to talk about, plus just catch up on how our degeneracy is going.
The NFL Draft is this week. Stackers made their surprise picks. It's not too late to add yours to the mix. @grayruby also has some 49ers trade proposals for the Raiders number 6 pick. It'll be a tough sell.
The MLB is preposterously unbalanced. In @grayruby's words "The American League sucks".
Plus, whatever Stackers put in the comments.
Last, but not least, thank you to our listeners and supporters. As I write this, we're the #38 podcast on Fountain and Episode 27 is the #38 episode.
originally posted at https://stacker.news/items/947216
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-18 13:33:54
@ 5d4b6c8d:8a1c1ee3
2025-04-18 13:33:54This is our fastest turnaround. The 1st round of the playoffs starts tomorrow and the Play-In Tournament doesn't end until tonight.
We don't know the 8th seeds yet but all the other matchups are set. Don't forget to set your brackets for the Playoff Bracket Challenge, either.
Matchups (seed)
Clippers (5) @ Nuggets (4) Bucks (5) @ Pacers (4) Timberwolves (6) @ Lakers (3) Pistons (6) @ Knicks (3) Warriors (7) @ Rockets (2) Magic (7) @ Celtics (2) TBD (8) @ Thunder (1) TBD (8) @ Cavaliers (1)
You need to select one team from this round to win their series. You also need to predict who will be the highest scoring player in this round. You have until tip-off to select a team or player.
Scoring this round 1 Point for your team winning + Your team's seed if they win + 1 Point for picking the correct top scorer
This round has a maximum of 10 points.
Prize 10k sats (or sum of zaps on contest posts, whichever is larger)
cc: @gnilma, @BlokchainB, @grayruby, @Carresan, @fishious, @Coinsreporter, @WeAreAllSatoshi
originally posted at https://stacker.news/items/947140
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-17 21:35:47
@ 5d4b6c8d:8a1c1ee3
2025-04-17 21:35:47Congrats to @gnilma and @Carresan! Thanks to Herro and Butler both having 38 points (shoutout Heat Culture) they both secured 9 points and are tied for the lead.
Now we move on to the final Play-In Round
Matchups (seed)
- Heat (10) @ Hawks (8)
- Mavericks (10) @ Grizzlies (8)
You need to select one team from this round to win their game. You also need to predict who will be the highest scoring player in this round.
Scoring this round: 1 Point for your team winning + Your team's seed if they win + 1 Point for picking the correct top scorer
This round has a maximum of 12 points.
Prize
10k sats (or sum of zaps on contest posts, whichever is larger)
originally posted at https://stacker.news/items/946686
-
 @ 0861144c:e68a1caf
2025-04-17 16:35:23
@ 0861144c:e68a1caf
2025-04-17 16:35:23This is a following up for the conversation started by @Scoresby with the question:
what is a sustainable model for onchain Bitcoin wallet software development?
This is an extreme opinion (even for myself) but I think is the best answer to what we're pursuing as bitcoiners.
Introduction: The Paradox of Free and Critical
The Bitcoin ecosystem thrives on open-source software. It's a world where people entrust their life savings to applications they didn’t pay a cent for. This introduces a unique paradox: we demand freedom, security, and transparency, but we don’t pay for the tools that guarantee it. Even more, we value free markets and incentives, yet expect Bitcoin wallets to exist and evolve out of altruism.
So what’s the path forward? What kind of model can ensure long-term development, security patches, feature upgrades, and alignment with Bitcoin’s protocol—without betraying its ethos?
Let’s explore the current landscape of wallet monetization and build toward a model that honors the freedom Bitcoin offers.
Wallet Monetization Models
Here’s an overview of how current Bitcoin-only (or mostly Bitcoin) onchain wallets sustain themselves based on https://stacker.news/items/944967#how-could-you-pay-for-a-bitcoin-wallet-if-you-wanted-to:
| Model | Description | Example Projects | Pros | Cons | |---------------------------|-----------------------------------------------------------------------------|-------------------------------|----------------------------------------------------|------------------------------------------------------------| | Donations/Grants | Funded by community or institutional support | Bitcoin Core, Sparrow, Specter| User-focused, preserves freedom | Unstable, depends on goodwill or VC altruism | | Freemium/Subscription| Free basic app, premium features unlocked through subscriptions | Nunchuk, Keeper, Theya | Predictable revenue | Introduces centralization, relies on dev infrastructure | | Device Sales | Wallet tied to hardware devices | Bitkey, Envoy | Scalable, aligned with sovereignty | Limits access based on geography or price | | Custodial Services | Funds held by a third party | Casa, River, Swan | Simple onboarding for new users | Compromises on "Not your keys, not your coins" | | Tx Commissions| Wallet takes a fee from trades within the app | BlueWallet (speculatively, maybe not) | Transparent funding method | User becomes product; hard to avoid surveillance and KYC | | L2 Services | Monetization through Lightning routing fees or service layers | Phoenix, Breez, Zeus | Innovative, supports network growth | Not suitable for cold storage or large holdings | | Sell the Software | Direct payment for downloading or unlocking the app | (Rare or nonexistent) | Clear transaction, sustainable if valued | Cultural resistance; rare in open-source culture |
Each of these models carries tradeoffs—especially when you consider global context.
Why Context Matters: Global Finance Is Not Equal
In countries with stable banking systems (U.S., Europe, Japan), Bitcoin wallets are largely seen as savings vaults. People use their banks for spending and turn to Bitcoin as a hedge or long-term store of value. In these places, users are more comfortable with subscription models or regulated custodial solutions.
But in the global south—Latin America, North Africa, parts of Asia—Bitcoin plays a different role. Banks are distrusted, inflation is high, and people are not just saving in Bitcoin; they’re trying living on Bitcoin. Wallets aren't just tools, they’re lifelines. Asking users to subscribe, give up sovereignty, or rely on opaque intermediaries is antithetical to the entire point. Can't use bitcoin? Go straight to cash or side-banks solutions like EMP (Giros Tigo, M-PESA). Taxes? We don't care, I don't mind not pay taxes when I buy nor I care even less how to present my fill form to authorities. Bitcoin is need.
In this context, the question isn't “can I pay for a wallet?”—it's “can I use it without being surveilled, blocked, or priced out?”. That's why technologies Lightning-L2 related have some much adoption, because we need not only to save but to pay our things. Just look El Salvador, Argentina or lately Bolivia, countries that need alternative to keep receiving/sending while having a volatility index very high.
The Bitcoin Standard: Build Your Own Wallet
Under the Bitcoin standard, the sustainable model must allow any individual to create their own wallet—no permission required, no gatekeepers, no payment walls. Think of it like designing your own leather wallet to carry cash. Anyone can do it, because the knowledge is public, the materials are available, and there’s no centralized authority controlling the process.
The same is true with Bitcoin:
- Wallets can integrate privacy-enhancing tools like Whirlpool (CoinJoin).
- They can adopt PayNym or BIP47 for stealth addresses.
- Features like automated DCA (Dollar Cost Averaging) can be designed to optimize both strategy and privacy.
- Visuals can display only sats, not fiat denominations, reinforcing the mindset that Bitcoin is the native unit.
What sustains these features? A community of developers building modular, composable, interoperable tools. The protocol enables this—Bitcoin is both a financial layer and a developer’s playground.
The Custodial Dilemma: Easier, But Risky
Let’s be honest: custodial wallets make onboarding smoother. They're easier to explain. “Download app, get coins.” That’s it. But this simplicity comes at a cost.
- “Not your keys, not your coins” is not just a mantra—it’s survival.
- Custodial wallets are subject to seizure, surveillance, and censorship.
- They build bad habits: users don’t learn how to verify, back up, or transact privately.
And yet, we’ve seen it again and again: many newcomers start with custodial solutions and only move to self-custody after something goes wrong—a blocked account, a missing withdrawal, or an unexplained freeze. Then they meet the 12 words. And yes, the seed phrase is scary at first. But over time, it becomes the ultimate expression of financial freedom.
Transaction Fees: A Ticking Time Bomb
Some wallet developers seek sustainability by taking a small cut of in-app transactions. It's easy to justify: "We only take 0.5% for maintenance." But this model is fundamentally flawed in the context of Bitcoin.
- It reintroduces third-party dependence into a tool meant to eliminate it.
- It discourages self-custody by tying wallet use to an ongoing cost.
- It creates perverse incentives: developers are now driven to optimize for volume, not user sovereignty.
In the short term, this might work. But long term, it turns wallets into surveillance engines and behavioral data extractors—exactly what Bitcoin was meant to disrupt.
A sustainable model can’t be built on transaction tax. That’s fiat logic.
Conclusion: DIY Is the Only Model That Scales with Sovereignty
In Bitcoin, every decision is a reflection of trust. Who do you rely on for custody, code, and convenience? A sustainable model for wallet software must allow people to opt out at every layer. If you don’t like the wallet UI—change it. If the devs abandon the project—fork it. If the company goes under—run your own build. This is only possible because the information is free, the protocol is neutral, and the design is decentralized by nature. We don’t need more paywalls. We need more builders. More tinkerers. More people realizing that “wallet software” is not a product you buy—it’s a freedom you exercise.
That’s the Bitcoin way.
That’s the model that lasts. That's my two sats.originally posted at https://stacker.news/items/946326
-
 @ c066aac5:6a41a034
2025-04-17 00:05:49
@ c066aac5:6a41a034
2025-04-17 00:05:49I am all about fleshing out a fantasy, even if the chances of it coming to reality are fairly slim. Dreams should be written down, meditated on, processed over long periods of time. I don't think of it as manifesting (nor do I condone manifestation); one could argue such practices are Biblical (Habakkuk 2:2).
So I'm going to write this out and make it plain, on the off chance that putting it out there brings somethings to fruition:
Jack Dorsey should take over Mozilla.
Either via an invitation from Mozilla, or via a hostile takeover. I don't really care how it happens, but I believe it should happen and I'll outline why.
The Fallen Hero

Mozilla has been having a bad time. I'm not sure that the organization has done much good since the unceremonious departure of Brenden Eich (there's Rust, but is that really a good thing?).
Firefox is losing its relevance. The FireFox Terms of Service update has sparked outrage, the removal of the promise to never sell your data was a Judas level of betrayal, FireFox currently (at the time this article was penned) makes up less than 3% of the total browser marketshare, their main source of income from Google is in jeopardy, most websites are only optimized for Chromium-based browsers, and the Gecko engine is not very secure.
Mozilla's best product is dying, and what is the organization doing about it? They're working on a plethora of issues their core user base does not care about. They've jumped on the AI hype train, they've bought an advertising company (which is very irrelevant to their user base, especially considering uBlock Orgin exists), they're selling white labeled VPNs (Mullvad), they're selling data removal services (which is powered by a former data broker), they're pushing shopping products, they're forcing features on their users which were never asked for (POCKET!!), it seems that Mozilla is completely out of touch with the people they claim to serve. They've abandoned their first love.
Thunderbird is showing some promise with the recent announcement of Thundermail, but that project will sadly suffer from guilt by association.
We have to remember though: Mozilla used to mean something in the FOSS/Open Source world.

They were the shining city on the hill of the internet. They rose up from the ashes of Netscape. FireFox kicked Internet Explorer's butt; it was a punk rock movement. Thunderbird is still an amazing email client. Rust (despite the arguing programmers) is a significant innovation in the programming language space.
I'm not rooting for the downfall of Mozilla. Sure, in a way I'd be happy about it: I'd like to see poor leadership get what it deserves, but I fear Mozilla as a symbol of FOSS/OS would send a sad signal across the ecosystem. I'm a capitalist at heart so I don't favor bailouts (nor am I calling for one); I truly believe this organization could be turned around with the right leadership. Maybe it could be as simple as going back to their original model of serving the deep pockets of the corporate world with open source tech rather than going for the wallets of the consumer.
Every problem is a leadership problem. Fix the leadership, fix the problems.
The Last Great Open Source Hero?
Sadly FOSS figures tend to die of public crucifixion. As time goes on, we have less and less great figures to point to. Thankfully, Jack hasn't been canceled yet.
Jack Dorsey has a pretty good résumé in the open source world. He jumped right in with Bitcoin. He left BlueSky for NOSTR. He would've made Twitter a protocol if he didn't need to feed himself early in his career. He is currently financing several projects in the Bitcoin and NOSTR world, which is arguably the best open source technology in the world right now.
I do believe that people should stay in their lane of expertise, and maybe Jack should. However, my message to Jack would be that it would be a shame if his passion for open source remained solely in Bitcoin and NOSTR. If his leadership was injected into the Mozilla machine, it could be steered into a magical direction.
Imagine FireFox being the first browser with layer 2 wallet integration (stick it to Brave and their BAT crap [we still love you Brenden Eich flaws and all]). Imagine having a whole world of existing talented developers suddenly interested in contributing their talents to the NOSTR community. Imagine having a browser with an engine that can actually go toe-to-toe with Chromium. Imagine an organization that once again gives FOSS a good name rather than actively eroding public confidence in FOSS.
The True FOSS Heroes

Jack is probably not going to touch Mozilla with a 150 foot pole (or see this article). We all probably need to let the Mozilla dream die in front of us.
Things aren't always black and white. I don't think of Mozilla as an evil organization; just an organization subject to the flaws of fellow humans like you and me. Even the Eye of Sauron, Google, has been a huge blessing to the open source world (Go programming language, Android, all of their open source sponsorships, many more things I could mention).
The beautiful thing about FOSS/OS is that it is a movement of the people. Titans will rise up and fall, but you and I make up the backbone of FOSS. I've had nothing but good interactions with FOSS fanatics. NOSTR's own OceanSlim taught me about Ungoogled Chromium, the Go programming language, and NOSTR relays. When I wanted to get into Linux, I was able to plug in immediately with a group of Linux users here in Nashville. NOSTR devs for the most part are happy to answer my inquiries when I slide into their DMs. I've been in group chats with people openly discussing the best way to make a great lightning wallet.
There's a lot of connection in the Open Source world that I cherish; it's very different from the corporate world most of us are immersed in. The corporate world has gatekeepers; Open Source has collaborators. The corporate world operates in the shadows to maximize profits; Open Source steps into the light for everyone's benefit. The corporate world says you'll never have enough experience/qualifications; Open Source encourages and equips you.
My point is, don't worship any organization. Be thankful for the people around you, try out FOSS programs whenever you can, and have fun with it.
All that said, I wouldn't mind if Jack took over Mozilla. Or if one of his friends took a position (ODELL?). Heck, throw Snowden in while we're at it.
Footnote: "Open Source" and "FOSS/Free and Open Source Software" are used interchangably in this article. Mistakes were made I'm sure, but I hope I got the point across.
-
 @ 000002de:c05780a7
2025-04-16 20:48:48
@ 000002de:c05780a7
2025-04-16 20:48:48Not only can I be my own bank and run a my own lightning bank. I can have private communications with people anywhere on the planet that only the two of us can read. On top of that I can manufacturer items in my office with this very affordable 3d printer.
Just a thought as I'm printing some items for a party we have coming up. I'm watching the print complete from my phone while I work on the back porch.
We live in an amazing time. It is easy to forget this when we are focused on the stupidity we see online.
originally posted at https://stacker.news/items/945569
-
 @ 000002de:c05780a7
2025-04-16 17:47:30
@ 000002de:c05780a7
2025-04-16 17:47:30She was a special cat. She was a tiny kitten crossing a country road far from any houses. We thought she was a rat at first. We stopped the car and I tried to find her. She was in a thicket hissing at me. She was always full of spunk. I didn't want another cat. I said we'd find her a home. But she quickly burrowed her way into my heart.
She was very vocal and affectionate. She was playful and loved to sneak up on you. She was just to curious and adventurous for her own good. We knew she'd get herself into trouble eventually but never dreamed it would be so soon.
When you open your heart, you are opening yourself up to being loved but also pain. Its bittersweet but worth it. Rest in peace Lucy. I miss that little girl.
originally posted at https://stacker.news/items/945348
-
 @ ba36d0f7:cd802cba
2025-04-16 16:45:07
@ ba36d0f7:cd802cba
2025-04-16 16:45:071. The creative (but fleeting) pleasure of tactics
Chess tactics are like candy between meals - instant delight, but not true nourishment. Choosing whether to attack a bishop or a knight feels like picking between vanilla and chocolate ice cream: sprinkles or none, cherry on top or not...
-
They’re freedom within boundaries: the board has limits, but imagination doesn’t.
-
They mirror your style: quick strikes like an espresso? Or slow grinds like green tea?
2. Two tactics, two joys
-
Simple (an exposed king): everyday wins (like finding cash in your pocket).
-
Complex (3+ move combos): earned triumphs (like a project you’ve sweat over).
3. The Buddha’s warning: "Don’t Confuse the Sugar Rush for the Meal"
Buddhism teaches that clinging to pleasure (kāma-tanha) breeds suffering. In chess and life:
-
Tactics are desserts: sweet, but not the feast.
- Example: Beating a blunder is like winning the lottery; outplaying strategically is like building wealth.
-
The balance: Revel in that dazzling queen sacrifice - but don’t bet your game on it. Like savoring cake, not devouring the whole bakery.
4. How to play (and Live) this wisdom
✅ Ask yourself:
-
Is this move sound - or just seductive? (Like craving junk food vs. needing sustenance).
-
Am I here to win, or to wow? (Ego checkmates you faster than any opponent).
Final Move: The middle path on 64 squares
Buddhism invites joy without attachment. On the board:
-
Tactics = spice: they dazzle, but strategy feeds growth.
-
Strategy = the harvest: the patience that crowns kings.
♟️ So - do you chase the fireworks, or cultivate the long game?
Online Resources
Chess tactics - chess.com https://www.chess.com/terms/chess-tactics
Tactic examples - chess.com https://www.chess.com/article/view/chess-tactics
Tactics - lichess.org https://lichess.org/study/topic/Tactics/hot
somachess #buddhism #philosophy #chessphilosophy #chess #elsalvador #btc #apaneca #chesselsalvador
-
-
 @ ba36d0f7:cd802cba
2025-04-16 16:39:58
@ ba36d0f7:cd802cba
2025-04-16 16:39:581. El placer creativo (pero efímero) de las tácticas
Las tácticas en ajedrez son como las golosinas entre comidas: satisfacción inmediata, pero no sustento real. Escoger entre atacar a un alfil o un caballo puede ser como elegir entre helado de vainilla o chocolate - con chispas o sin chispas, cereza o sin cereza....
-
Son libertad dentro de las reglas: el tablero es finito, pero la creatividad no.
-
Reflejan tu estilo: ¿ataques rápidos como un espresso? ¿O finales lentos como un té verde?
2. Dos tipos de tácticas, dos tipos de placeres
-
Sencillas (como un rey descubierto): placeres cotidianos (como un golpe de buena suerte).
-
Complejas (combinaciones de 3+ jugadas): placeres que exigen planificación (como cumplir metas).
3. La advertencia budista: "No confundas el postre con la cena"
El Buddha enseñó que aferrarse a los placeres (kāma-tanha) genera sufrimiento. En ajedrez y en la vida:
-
Las tácticas son golosinas: te dan ventaja, pero no son estrategia.
- Ejemplo: Ganar por un descuido del rival es como heredar dinero; ganar por planificación es como construir un negocio.
-
El equilibrio: Disfruta ese sacrificio de dama espectacular… pero no bases tu juego en ellos. Como saborear un pastel ocasional sin volverse adicto al azúcar.
4. Cómo aplicar esto en el tablero (y en la vida)
✅ Pregúntate siempre:
-
¿Esta táctica es sólida o solo emocionante? (Como diferenciar antojo de hambre real).
-
¿Estoy jugando para ganar… o para impresionar? (El ego es peor enemigo que el rival).
Conclusión: El camino medio (ajedrecístico)
El budismo no pide renunciar a los placeres, sino disfrutarlos sin apego. En el ajedrez:
-
Tácticas = especias: dan sabor, pero no son el plato principal.
-
Estrategia = nutrición: lo que realmente te hace mejor jugador.
♟️ ¿Y tú? ¿Eres de los que prefieren un ataque brillante (aunque riesgoso) o una victoria lenta pero segura?
Recursos en linea
Tácticas - chess.com https://www.chess.com/es/article/view/tacticas-ajedrez
Problemas de ajedrez - chess.com https://www.chess.com/es/puzzles
Tácticas - lichess.org https://lichess.org/study/qgLXlnIF/udsuAudN
ajedrez #somachess #chess #chesselsalvador #budismo #budhism #filosofia #philosophy #apaneca #rutadelasflores #article #longform #articulo
-
-
 @ ba36d0f7:cd802cba
2025-04-16 15:09:25
@ ba36d0f7:cd802cba
2025-04-16 15:09:25What is Checkmate?
Checkmate is the decisive move that ends the game. It occurs when the king is under direct threat (in check) and there’s no legal move to save it: neither capturing the attacking piece, blocking the attack, nor fleeing to a safe square.
Unlike other pieces, the king can never be captured - its downfall marks the end of the game. Thus, when escape is impossible, the game ends immediately. There’s no need to "take" the king; its fate is already sealed.
How to Achieve Checkmate?
It requires:
-
Imminent Threat: One or more pieces attacking the enemy king.

-
Total Blockade: All escape squares controlled by the opponent.

- No Possible Defense: No piece can intercept the attack.

Basic Example: The Back-Rank Mate (with a rook or queen on the last rank, where the king can’t escape due to being blocked by its own pieces).
1. The First Chess Commandment: Seek Checkmate
In every game, each move should begin with an essential question: Is there a checkmate in this position? - for both yourself and your opponent. If not, the game revolves around material advantage or positional control. But this order isn’t arbitrary:
-
A tactical oversight can ruin a dominant position.
-
A missed checkmate means instant defeat.
Classic Example: The Scholar’s Mate (1.e4 e5 2.Bc4 Nc6 3.Qh5 Nf6?? 4.Qxf7#).
 White wins because Black, focused solely on development, ignored the deadly threat.
White wins because Black, focused solely on development, ignored the deadly threat.➡ Reflection: In strategy, as in life, the urgent (survival) precedes the important (victory).
2. The Philosophy of the Board: When Advantages Aren’t Enough
A lone king can evade capture forever if the opponent doesn’t know how to checkmate. Similarly, in human existence, advantages - talent, resources, or opportunities - are worthless if not transformed into decisive actions.
-
What good is controlling the center if you can’t convert it into an attack?
-
What good are privileges if not used to build something meaningful?
Chess, like life, rewards execution - not accumulation.
3. Survival Instinct: Between Attack and Resistance
The fear of defeat triggers visceral reactions: desperate attacks, obsessive defenses, or even premature resignations. But these responses reveal deep truths about human nature:
-
Survival ≠ Violence: A cornered king may shelter behind its pieces, like a strategist choosing patience over confrontation. Is it cowardice or wisdom?
-
The Danger of Ego: Arrogance ("I must win quickly") leads to irreversible mistakes. Humility ("I’ll resist until my opponent errs") can turn certain defeat into salvation.
➡ Reflection: The board doesn’t lie. Every move exposes a player’s deepest instincts: fear, ambition, or temperance.
Online Resources
Check mate patterns - Lichess.org https://lichess.org/practice/checkmates/checkmate-patterns-i/fE4k21MW/9rd7XwOw
Piece check mates - Lichess.org https://lichess.org/practice/checkmates/piece-checkmates-i/BJy6fEDf/8K8FdT6P
Common check mates - Chess.com https://www.chess.com/terms/checkmate-chess
10 fastest check mates - Chess.com https://www.chess.com/article/view/fastest-chess-checkmates
Finding check mates - Chess.com https://www.chess.com/lessons/finding-checkmate
somachess #chess #chesselsalvador #ajedrez #chessphilosophy #philosophy #filosofia #checkmate #longform #article
-
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-16 13:27:53
@ 5d4b6c8d:8a1c1ee3
2025-04-16 13:27:53https://primal.net/e/nevent1qvzqqqqqqypzqntcggz30qhq60ltqdx32zku9d46unhrkjtcv7fml7jx3dh4h94nqqszw6rqxppmm48pvvc5pz4q74r7qvsgl8tzwfgp3kqg82jw04t2n3q2nrlqh
Get used to and comfortable with being responsible for your own wellbeing.
originally posted at https://stacker.news/items/945039
-
 @ da0b9bc3:4e30a4a9
2025-04-16 08:28:24
@ da0b9bc3:4e30a4a9
2025-04-16 08:28:24Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/944844
-
 @ c066aac5:6a41a034
2025-04-15 22:06:06
@ c066aac5:6a41a034
2025-04-15 22:06:06-Interpretive ~~loops~~ Technology Poetry by Zachariah Sanders
I am testing ~~the loops~~Comet.
It fit many loop It has many features.~~There are loops~~ There are cool tools.
I mean, like, really cool;
I'm going to embed ~~the loops~~ a video that lives rent free in my mind:
https://www.youtube.com/watch?v=peXNAwzyJas
Anyway, long live innovation!
~~Long live the loops~~
https://github.com/nodetec/comet
loops #comet #article #nostrinnovation #nostr #willzap4loops
-
 @ e968e50b:db2a803a
2025-04-15 17:45:27
@ e968e50b:db2a803a
2025-04-15 17:45:27Hey cinephiles, I'm just crossposting this bounty that remains unclaimed from last week. It occurred to me that you may be a more receptive audience to this game that I made than the folks monitoring the gamers territory. Either way, let me know what you think. I've been told it's too hard...but maybe not for you!
https://stacker.news/items/937363
originally posted at https://stacker.news/items/944303
-
 @ e968e50b:db2a803a
2025-04-15 13:47:13
@ e968e50b:db2a803a
2025-04-15 13:47:13There's really not much to say. I just wanted to put a bug in the ear of anybody else that has to deal with water problems and has a few old, unprofitable s9s sitting around. At least you'll get your KYC-free bitcoin rebate. Is there a business opportunity here?!?
originally posted at https://stacker.news/items/944025
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ c4b5369a:b812dbd6
2025-04-15 07:26:16
@ c4b5369a:b812dbd6
2025-04-15 07:26:16Offline transactions with Cashu
Over the past few weeks, I've been busy implementing offline capabilities into nutstash. I think this is one of the key value propositions of ecash, beinga a bearer instrument that can be used without internet access.
 It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!
It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!What is ecash/Cashu?
Ecash is the first cryptocurrency ever invented. It was created by David Chaum in 1983. It uses a blind signature scheme, which allows users to prove ownership of a token without revealing a link to its origin. These tokens are what we call ecash. They are bearer instruments, meaning that anyone who possesses a copy of them, is considered the owner.
Cashu is an implementation of ecash, built to tightly interact with Bitcoin, more specifically the Bitcoin lightning network. In the Cashu ecosystem,
Mintsare the gateway to the lightning network. They provide the infrastructure to access the lightning network, pay invoices and receive payments. Instead of relying on a traditional ledger scheme like other custodians do, the mint issues ecash tokens, to represent the value held by the users.How do normal Cashu transactions work?
A Cashu transaction happens when the sender gives a copy of his ecash token to the receiver. This can happen by any means imaginable. You could send the token through email, messenger, or even by pidgeon. One of the common ways to transfer ecash is via QR code.
The transaction is however not finalized just yet! In order to make sure the sender cannot double-spend their copy of the token, the receiver must do what we call a
swap. A swap is essentially exchanging an ecash token for a new one at the mint, invalidating the old token in the process. This ensures that the sender can no longer use the same token to spend elsewhere, and the value has been transferred to the receiver.
What about offline transactions?
Sending offline
Sending offline is very simple. The ecash tokens are stored on your device. Thus, no internet connection is required to access them. You can litteraly just take them, and give them to someone. The most convenient way is usually through a local transmission protocol, like NFC, QR code, Bluetooth, etc.
The one thing to consider when sending offline is that ecash tokens come in form of "coins" or "notes". The technical term we use in Cashu is
Proof. It "proofs" to the mint that you own a certain amount of value. Since these proofs have a fixed value attached to them, much like UTXOs in Bitcoin do, you would need proofs with a value that matches what you want to send. You can mix and match multiple proofs together to create a token that matches the amount you want to send. But, if you don't have proofs that match the amount, you would need to go online and swap for the needed proofs at the mint.Another limitation is, that you cannot create custom proofs offline. For example, if you would want to lock the ecash to a certain pubkey, or add a timelock to the proof, you would need to go online and create a new custom proof at the mint.
Receiving offline
You might think: well, if I trust the sender, I don't need to be swapping the token right away!
You're absolutely correct. If you trust the sender, you can simply accept their ecash token without needing to swap it immediately.
This is already really useful, since it gives you a way to receive a payment from a friend or close aquaintance without having to worry about connectivity. It's almost just like physical cash!
It does however not work if the sender is untrusted. We have to use a different scheme to be able to receive payments from someone we don't trust.
Receiving offline from an untrusted sender
To be able to receive payments from an untrusted sender, we need the sender to create a custom proof for us. As we've seen before, this requires the sender to go online.
The sender needs to create a token that has the following properties, so that the receciver can verify it offline:
- It must be locked to ONLY the receiver's public key
- It must include an
offline signature proof(DLEQ proof) - If it contains a timelock & refund clause, it must be set to a time in the future that is acceptable for the receiver
- It cannot contain duplicate proofs (double-spend)
- It cannot contain proofs that the receiver has already received before (double-spend)

If all of these conditions are met, then the receiver can verify the proof offline and accept the payment. This allows us to receive payments from anyone, even if we don't trust them.
At first glance, this scheme seems kinda useless. It requires the sender to go online, which defeats the purpose of having an offline payment system.
I beleive there are a couple of ways this scheme might be useful nonetheless:
-
Offline vending machines: Imagine you have an offline vending machine that accepts payments from anyone. The vending machine could use this scheme to verify payments without needing to go online itself. We can assume that the sender is able to go online and create a valid token, but the receiver doesn't need to be online to verify it.
-
Offline marketplaces: Imagine you have an offline marketplace where buyers and sellers can trade goods and services. Before going to the marketplace the sender already knows where he will be spending the money. The sender could create a valid token before going to the marketplace, using the merchants public key as a lock, and adding a refund clause to redeem any unspent ecash after it expires. In this case, neither the sender nor the receiver needs to go online to complete the transaction.
How to use this
Pretty much all cashu wallets allow you to send tokens offline. This is because all that the wallet needs to do is to look if it can create the desired amount from the proofs stored locally. If yes, it will automatically create the token offline.
Receiving offline tokens is currently only supported by nutstash (experimental).
To create an offline receivable token, the sender needs to lock it to the receiver's public key. Currently there is no refund clause! So be careful that you don't get accidentally locked out of your funds!

The receiver can then inspect the token and decide if it is safe to accept without a swap. If all checks are green, they can accept the token offline without trusting the sender.

The receiver will see the unswapped tokens on the wallet homescreen. They will need to manually swap them later when they are online again.
 Later when the receiver is online again, they can swap the token for a fresh one.
Later when the receiver is online again, they can swap the token for a fresh one.
Summary
We learned that offline transactions are possible with ecash, but there are some limitations. It either requires trusting the sender, or relying on either the sender or receiver to be online to verify the tokens, or create tokens that can be verified offline by the receiver.
I hope this short article was helpful in understanding how ecash works and its potential for offline transactions.
Cheers,
Gandlaf
-
 @ 266815e0:6cd408a5
2025-04-15 06:58:14
@ 266815e0:6cd408a5
2025-04-15 06:58:14Its been a little over a year since NIP-90 was written and merged into the nips repo and its been a communication mess.
Every DVM implementation expects the inputs in slightly different formats, returns the results in mostly the same format and there are very few DVM actually running.
NIP-90 is overloaded
Why does a request for text translation and creating bitcoin OP_RETURNs share the same input
itag? and why is there anoutputtag on requests when only one of them will return an output?Each DVM request kind is for requesting completely different types of compute with diffrent input and output requirements, but they are all using the same spec that has 4 different types of inputs (
text,url,event,job) and an undefined number ofoutputtypes.Let me show a few random DVM requests and responses I found on
wss://relay.damus.ioto demonstrate what I mean:This is a request to translate an event to English
json { "kind": 5002, "content": "", "tags": [ // NIP-90 says there can be multiple inputs, so how would a DVM handle translatting multiple events at once? [ "i", "<event-id>", "event" ], [ "param", "language", "en" ], // What other type of output would text translations be? image/jpeg? [ "output", "text/plain" ], // Do we really need to define relays? cant the DVM respond on the relays it saw the request on? [ "relays", "wss://relay.unknown.cloud/", "wss://nos.lol/" ] ] }This is a request to generate text using an LLM model
json { "kind": 5050, // Why is the content empty? wouldn't it be better to have the prompt in the content? "content": "", "tags": [ // Why use an indexable tag? are we ever going to lookup prompts? // Also the type "prompt" isn't in NIP-90, this should probably be "text" [ "i", "What is the capital of France?", "prompt" ], [ "p", "c4878054cff877f694f5abecf18c7450f4b6fdf59e3e9cb3e6505a93c4577db2" ], [ "relays", "wss://relay.primal.net" ] ] }This is a request for content recommendation
json { "kind": 5300, "content": "", "tags": [ // Its fine ignoring this param, but what if the client actually needs exactly 200 "results" [ "param", "max_results", "200" ], // The spec never mentions requesting content for other users. // If a DVM didn't understand this and responded to this request it would provide bad data [ "param", "user", "b22b06b051fd5232966a9344a634d956c3dc33a7f5ecdcad9ed11ddc4120a7f2" ], [ "relays", "wss://relay.primal.net", ], [ "p", "ceb7e7d688e8a704794d5662acb6f18c2455df7481833dd6c384b65252455a95" ] ] }This is a request to create a OP_RETURN message on bitcoin
json { "kind": 5901, // Again why is the content empty when we are sending human readable text? "content": "", "tags": [ // and again, using an indexable tag on an input that will never need to be looked up ["i", "09/01/24 SEC Chairman on the brink of second ETF approval", "text"] ] }My point isn't that these event schema's aren't understandable but why are they using the same schema? each use-case is different but are they all required to use the same
itag format as input and could support all 4 types of inputs.Lack of libraries
With all these different types of inputs, params, and outputs its verify difficult if not impossible to build libraries for DVMs
If a simple text translation request can have an
eventortextas inputs, apayment-requiredstatus at any point in the flow, partial results, or responses from 10+ DVMs whats the best way to build a translation library for other nostr clients to use?And how do I build a DVM framework for the server side that can handle multiple inputs of all four types (
url,text,event,job) and clients are sending all the requests in slightly differently.Supporting payments is impossible
The way NIP-90 is written there isn't much details about payments. only a
payment-requiredstatus and a genericamounttagBut the way things are now every DVM is implementing payments differently. some send a bolt11 invoice, some expect the client to NIP-57 zap the request event (or maybe the status event), and some even ask for a subscription. and we haven't even started implementing NIP-61 nut zaps or cashu A few are even formatting the
amountnumber wrong or denominating it in sats and not mili-satsBuilding a client or a library that can understand and handle all of these payment methods is very difficult. for the DVM server side its worse. A DVM server presumably needs to support all 4+ types of payments if they want to get the most sats for their services and support the most clients.
All of this is made even more complicated by the fact that a DVM can ask for payment at any point during the job process. this makes sense for some types of compute, but for others like translations or user recommendation / search it just makes things even more complicated.
For example, If a client wanted to implement a timeline page that showed the notes of all the pubkeys on a recommended list. what would they do when the selected DVM asks for payment at the start of the job? or at the end? or worse, only provides half the pubkeys and asks for payment for the other half. building a UI that could handle even just two of these possibilities is complicated.
NIP-89 is being abused
NIP-89 is "Recommended Application Handlers" and the way its describe in the nips repo is
a way to discover applications that can handle unknown event-kinds
Not "a way to discover everything"
If I wanted to build an application discovery app to show all the apps that your contacts use and let you discover new apps then it would have to filter out ALL the DVM advertisement events. and that's not just for making requests from relays
If the app shows the user their list of "recommended applications" then it either has to understand that everything in the 5xxx kind range is a DVM and to show that is its own category or show a bunch of unknown "favorites" in the list which might be confusing for the user.
In conclusion
My point in writing this article isn't that the DVMs implementations so far don't work, but that they will never work well because the spec is too broad. even with only a few DVMs running we have already lost interoperability.
I don't want to be completely negative though because some things have worked. the "DVM feeds" work, although they are limited to a single page of results. text / event translations also work well and kind
5970Event PoW delegation could be cool. but if we want interoperability, we are going to need to change a few things with NIP-90I don't think we can (or should) abandon NIP-90 entirely but it would be good to break it up into small NIPs or specs. break each "kind" of DVM request out into its own spec with its own definitions for expected inputs, outputs and flow.
Then if we have simple, clean definitions for each kind of compute we want to distribute. we might actually see markets and services being built and used.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 91bea5cd:1df4451c
2025-04-15 06:23:35
@ 91bea5cd:1df4451c
2025-04-15 06:23:35Um bom gerenciamento de senhas deve ser simples e seguir a filosofia do Unix. Organizado em hierarquia e fácil de passar de um computador para outro.
E por isso não é recomendável o uso de aplicativos de terceiros que tenham acesso a suas chaves(senhas) em seus servidores, tampouco as opções nativas dos navegadores, que também pertencem a grandes empresas que fazem um grande esforço para ter acesso a nossas informações.
Recomendação
- pass
- Qtpass (gerenciador gráfico)
Com ele seus dados são criptografados usando sua chave gpg e salvo em arquivos organizados por pastas de forma hierárquica, podendo ser integrado a um serviço git de sua escolha ou copiado facilmente de um local para outro.
Uso
O seu uso é bem simples.
Configuração:
pass git initPara ver:
pass Email/example.comCopiar para área de transferência (exige xclip):
pass -c Email/example.comPara inserir:
pass insert Email/example0.comPara inserir e gerar senha:
pass generate Email/example1.comPara inserir e gerar senha sem símbolos:
pass generate --no-symbols Email/example1.comPara inserir, gerar senha e copiar para área de transferência :
pass generate -c Email/example1.comPara remover:
pass rm Email/example.com -
 @ 91bea5cd:1df4451c
2025-04-15 06:19:19
@ 91bea5cd:1df4451c
2025-04-15 06:19:19O que é Tahoe-LAFS?
Bem-vindo ao Tahoe-LAFS_, o primeiro sistema de armazenamento descentralizado com
- Segurança independente do provedor * .
Tahoe-LAFS é um sistema que ajuda você a armazenar arquivos. Você executa um cliente Programa no seu computador, que fala com um ou mais servidores de armazenamento em outros computadores. Quando você diz ao seu cliente para armazenar um arquivo, ele irá criptografar isso Arquivo, codifique-o em múltiplas peças, depois espalhe essas peças entre Vários servidores. As peças são todas criptografadas e protegidas contra Modificações. Mais tarde, quando você pede ao seu cliente para recuperar o arquivo, ele irá Encontre as peças necessárias, verifique se elas não foram corrompidas e remontadas Eles, e descriptografar o resultado.
O cliente cria mais peças (ou "compartilhamentos") do que acabará por precisar, então Mesmo que alguns servidores falhem, você ainda pode recuperar seus dados. Corrompido Os compartilhamentos são detectados e ignorados, de modo que o sistema pode tolerar o lado do servidor Erros no disco rígido. Todos os arquivos são criptografados (com uma chave exclusiva) antes Uploading, então mesmo um operador de servidor mal-intencionado não pode ler seus dados. o A única coisa que você pede aos servidores é que eles podem (geralmente) fornecer o Compartilha quando você os solicita: você não está confiando sobre eles para Confidencialidade, integridade ou disponibilidade absoluta.
O que é "segurança independente do provedor"?
Todo vendedor de serviços de armazenamento na nuvem irá dizer-lhe que o seu serviço é "seguro". Mas o que eles significam com isso é algo fundamentalmente diferente Do que queremos dizer. O que eles significam por "seguro" é que depois de ter dado Eles o poder de ler e modificar seus dados, eles tentam muito difícil de não deixar Esse poder seja abusado. Isso acaba por ser difícil! Insetos, Configurações incorretas ou erro do operador podem acidentalmente expor seus dados para Outro cliente ou para o público, ou pode corromper seus dados. Criminosos Ganho rotineiramente de acesso ilícito a servidores corporativos. Ainda mais insidioso é O fato de que os próprios funcionários às vezes violam a privacidade do cliente De negligência, avareza ou mera curiosidade. O mais consciencioso de Esses prestadores de serviços gastam consideráveis esforços e despesas tentando Mitigar esses riscos.
O que queremos dizer com "segurança" é algo diferente. * O provedor de serviços Nunca tem a capacidade de ler ou modificar seus dados em primeiro lugar: nunca. * Se você usa Tahoe-LAFS, então todas as ameaças descritas acima não são questões para você. Não só é fácil e barato para o provedor de serviços Manter a segurança de seus dados, mas na verdade eles não podem violar sua Segurança se eles tentaram. Isto é o que chamamos de * independente do fornecedor segurança*.
Esta garantia está integrada naturalmente no sistema de armazenamento Tahoe-LAFS e Não exige que você execute um passo de pré-criptografia manual ou uma chave complicada gestão. (Afinal, ter que fazer operações manuais pesadas quando Armazenar ou acessar seus dados anularia um dos principais benefícios de Usando armazenamento em nuvem em primeiro lugar: conveniência.)
Veja como funciona:
Uma "grade de armazenamento" é constituída por uma série de servidores de armazenamento. Um servidor de armazenamento Tem armazenamento direto em anexo (tipicamente um ou mais discos rígidos). Um "gateway" Se comunica com os nós de armazenamento e os usa para fornecer acesso ao Rede sobre protocolos como HTTP (S), SFTP ou FTP.
Observe que você pode encontrar "cliente" usado para se referir aos nós do gateway (que atuam como Um cliente para servidores de armazenamento) e também para processos ou programas que se conectam a Um nó de gateway e operações de execução na grade - por exemplo, uma CLI Comando, navegador da Web, cliente SFTP ou cliente FTP.
Os usuários não contam com servidores de armazenamento para fornecer * confidencialidade * nem
- Integridade * para seus dados - em vez disso, todos os dados são criptografados e Integridade verificada pelo gateway, para que os servidores não possam ler nem Modifique o conteúdo dos arquivos.
Os usuários dependem de servidores de armazenamento para * disponibilidade *. O texto cifrado é Codificado por apagamento em partes
Ndistribuídas em pelo menosHdistintas Servidores de armazenamento (o valor padrão paraNé 10 e paraHé 7) então Que pode ser recuperado de qualquerKdesses servidores (o padrão O valor deKé 3). Portanto, apenas a falha doH-K + 1(com o Padrões, 5) servidores podem tornar os dados indisponíveis.No modo de implantação típico, cada usuário executa seu próprio gateway sozinho máquina. Desta forma, ela confia em sua própria máquina para a confidencialidade e Integridade dos dados.
Um modo de implantação alternativo é que o gateway é executado em uma máquina remota e O usuário se conecta ao HTTPS ou SFTP. Isso significa que o operador de O gateway pode visualizar e modificar os dados do usuário (o usuário * depende de * o Gateway para confidencialidade e integridade), mas a vantagem é que a O usuário pode acessar a grade Tahoe-LAFS com um cliente que não possui o Software de gateway instalado, como um quiosque de internet ou celular.
Controle de acesso
Existem dois tipos de arquivos: imutáveis e mutáveis. Quando você carrega um arquivo Para a grade de armazenamento, você pode escolher o tipo de arquivo que será no grade. Os arquivos imutáveis não podem ser modificados quando foram carregados. UMA O arquivo mutable pode ser modificado por alguém com acesso de leitura e gravação. Um usuário Pode ter acesso de leitura e gravação a um arquivo mutable ou acesso somente leitura, ou não Acesso a ele.
Um usuário que tenha acesso de leitura e gravação a um arquivo mutable ou diretório pode dar Outro acesso de leitura e gravação do usuário a esse arquivo ou diretório, ou eles podem dar Acesso somente leitura para esse arquivo ou diretório. Um usuário com acesso somente leitura Para um arquivo ou diretório pode dar acesso a outro usuário somente leitura.
Ao vincular um arquivo ou diretório a um diretório pai, você pode usar um Link de leitura-escrita ou um link somente de leitura. Se você usar um link de leitura e gravação, então Qualquer pessoa que tenha acesso de leitura e gravação ao diretório pai pode obter leitura-escrita Acesso à criança e qualquer pessoa que tenha acesso somente leitura ao pai O diretório pode obter acesso somente leitura à criança. Se você usar uma leitura somente Link, qualquer pessoa que tenha lido-escrito ou acesso somente leitura ao pai O diretório pode obter acesso somente leitura à criança.
================================================== ==== Usando Tahoe-LAFS com uma rede anônima: Tor, I2P ================================================== ====
. `Visão geral '
. `Casos de uso '
.
Software Dependencies_#.
Tor#.I2P. `Configuração de conexão '
. `Configuração de Anonimato '
#.
Anonimato do cliente ' #.Anonimato de servidor, configuração manual ' #. `Anonimato de servidor, configuração automática '. `Problemas de desempenho e segurança '
Visão geral
Tor é uma rede anonimização usada para ajudar a esconder a identidade da Internet Clientes e servidores. Consulte o site do Tor Project para obter mais informações: Https://www.torproject.org/
I2P é uma rede de anonimato descentralizada que se concentra no anonimato de ponta a ponta Entre clientes e servidores. Consulte o site I2P para obter mais informações: Https://geti2p.net/
Casos de uso
Existem três casos de uso potenciais para Tahoe-LAFS do lado do cliente:
-
O usuário deseja sempre usar uma rede de anonimato (Tor, I2P) para proteger Seu anonimato quando se conecta às redes de armazenamento Tahoe-LAFS (seja ou Não os servidores de armazenamento são anônimos).
-
O usuário não se preocupa em proteger seu anonimato, mas eles desejam se conectar a Servidores de armazenamento Tahoe-LAFS que são acessíveis apenas através de Tor Hidden Services ou I2P.
-
Tor é usado apenas se uma sugestão de conexão do servidor usar
tor:. Essas sugestões Geralmente tem um endereço.onion. -
I2P só é usado se uma sugestão de conexão do servidor usa
i2p:. Essas sugestões Geralmente têm um endereço.i2p. -
O usuário não se preocupa em proteger seu anonimato ou para se conectar a um anonimato Servidores de armazenamento. Este documento não é útil para você ... então pare de ler.
Para servidores de armazenamento Tahoe-LAFS existem três casos de uso:
-
O operador deseja proteger o anonimato fazendo seu Tahoe Servidor acessível apenas em I2P, através de Tor Hidden Services, ou ambos.
-
O operador não * requer * anonimato para o servidor de armazenamento, mas eles Quer que ele esteja disponível tanto no TCP / IP roteado publicamente quanto através de um Rede de anonimização (I2P, Tor Hidden Services). Uma possível razão para fazer Isso é porque ser alcançável através de uma rede de anonimato é um Maneira conveniente de ignorar NAT ou firewall que impede roteios públicos Conexões TCP / IP ao seu servidor (para clientes capazes de se conectar a Tais servidores). Outro é o que torna o seu servidor de armazenamento acessível Através de uma rede de anonimato pode oferecer uma melhor proteção para sua Clientes que usam essa rede de anonimato para proteger seus anonimato.
-
O operador do servidor de armazenamento não se preocupa em proteger seu próprio anonimato nem Para ajudar os clientes a proteger o deles. Pare de ler este documento e execute Seu servidor de armazenamento Tahoe-LAFS usando TCP / IP com roteamento público.
Veja esta página do Tor Project para obter mais informações sobre Tor Hidden Services: Https://www.torproject.org/docs/hidden-services.html.pt
Veja esta página do Projeto I2P para obter mais informações sobre o I2P: Https://geti2p.net/en/about/intro
Dependências de software
Tor
Os clientes que desejam se conectar a servidores baseados em Tor devem instalar o seguinte.
-
Tor (tor) deve ser instalado. Veja aqui: Https://www.torproject.org/docs/installguide.html.en. No Debian / Ubuntu, Use
apt-get install tor. Você também pode instalar e executar o navegador Tor Agrupar. -
Tahoe-LAFS deve ser instalado com o
[tor]"extra" habilitado. Isso vai Instaletxtorcon::
Pip install tahoe-lafs [tor]
Os servidores Tor-configurados manualmente devem instalar Tor, mas não precisam
Txtorconou o[tor]extra. Configuração automática, quando Implementado, vai precisar destes, assim como os clientes.I2P
Os clientes que desejam se conectar a servidores baseados em I2P devem instalar o seguinte. Tal como acontece com Tor, os servidores baseados em I2P configurados manualmente precisam do daemon I2P, mas Não há bibliotecas especiais de apoio Tahoe-side.
-
I2P deve ser instalado. Veja aqui: Https://geti2p.net/en/download
-
A API SAM deve estar habilitada.
-
Inicie o I2P.
- Visite http://127.0.0.1:7657/configclients no seu navegador.
- Em "Configuração do Cliente", marque a opção "Executar no Startup?" Caixa para "SAM Ponte de aplicação ".
- Clique em "Salvar Configuração do Cliente".
-
Clique no controle "Iniciar" para "ponte de aplicação SAM" ou reinicie o I2P.
-
Tahoe-LAFS deve ser instalado com o
[i2p]extra habilitado, para obterTxi2p::
Pip install tahoe-lafs [i2p]
Tor e I2P
Os clientes que desejam se conectar a servidores baseados em Tor e I2P devem instalar tudo acima. Em particular, Tahoe-LAFS deve ser instalado com ambos Extras habilitados ::
Pip install tahoe-lafs [tor, i2p]
Configuração de conexão
Consulte: ref:
Connection Managementpara uma descrição do[tor]e[I2p]seções detahoe.cfg. Estes controlam como o cliente Tahoe Conecte-se a um daemon Tor / I2P e, assim, faça conexões com Tor / I2P-baseadas Servidores.As seções
[tor]e[i2p]só precisam ser modificadas para serem usadas de forma incomum Configurações ou para habilitar a configuração automática do servidor.A configuração padrão tentará entrar em contato com um daemon local Tor / I2P Ouvindo as portas usuais (9050/9150 para Tor, 7656 para I2P). Enquanto Há um daemon em execução no host local e o suporte necessário Bibliotecas foram instaladas, os clientes poderão usar servidores baseados em Tor Sem qualquer configuração especial.
No entanto, note que esta configuração padrão não melhora a Anonimato: as conexões TCP normais ainda serão feitas em qualquer servidor que Oferece um endereço regular (cumpre o segundo caso de uso do cliente acima, não o terceiro). Para proteger o anonimato, os usuários devem configurar o
[Connections]da seguinte maneira:[Conexões] Tcp = tor
Com isso, o cliente usará Tor (em vez de um IP-address -reviração de conexão direta) para alcançar servidores baseados em TCP.
Configuração de anonimato
Tahoe-LAFS fornece uma configuração "flag de segurança" para indicar explicitamente Seja necessário ou não a privacidade do endereço IP para um nó ::
[nó] Revelar-IP-address = (booleano, opcional)
Quando
revelar-IP-address = False, Tahoe-LAFS se recusará a iniciar se algum dos As opções de configuração emtahoe.cfgrevelariam a rede do nó localização:-
[Conexões] tcp = toré necessário: caso contrário, o cliente faria Conexões diretas para o Introdução, ou qualquer servidor baseado em TCP que aprende Do Introdutor, revelando seu endereço IP para esses servidores e um Rede de espionagem. Com isso, Tahoe-LAFS só fará Conexões de saída através de uma rede de anonimato suportada. -
Tub.locationdeve ser desativado ou conter valores seguros. este O valor é anunciado para outros nós através do Introdutor: é como um servidor Anuncia sua localização para que os clientes possam se conectar a ela. No modo privado, ele É um erro para incluir umtcp:dica notub.location. Modo privado Rejeita o valor padrão detub.location(quando a chave está faltando Inteiramente), que éAUTO, que usaifconfigpara adivinhar o nó Endereço IP externo, o que o revelaria ao servidor e a outros clientes.
Esta opção é ** crítica ** para preservar o anonimato do cliente (cliente Caso de uso 3 de "Casos de uso", acima). Também é necessário preservar uma Anonimato do servidor (caso de uso do servidor 3).
Esse sinalizador pode ser configurado (para falso), fornecendo o argumento
--hide-ippara Os comandoscreate-node,create-clientoucreate-introducer.Observe que o valor padrão de
revelar-endereço IPé verdadeiro, porque Infelizmente, esconder o endereço IP do nó requer software adicional para ser Instalado (conforme descrito acima) e reduz o desempenho.Anonimato do cliente
Para configurar um nó de cliente para anonimato,
tahoe.cfg** deve ** conter o Seguindo as bandeiras de configuração ::[nó] Revelar-IP-address = False Tub.port = desativado Tub.location = desativado
Uma vez que o nodo Tahoe-LAFS foi reiniciado, ele pode ser usado anonimamente (cliente Caso de uso 3).
Anonimato do servidor, configuração manual
Para configurar um nó de servidor para ouvir em uma rede de anonimato, devemos primeiro Configure Tor para executar um "Serviço de cebola" e encaminhe as conexões de entrada para o Porto Tahoe local. Então, configuramos Tahoe para anunciar o endereço
.onionAos clientes. Também configuramos Tahoe para não fazer conexões TCP diretas.- Decida em um número de porta de escuta local, chamado PORT. Isso pode ser qualquer não utilizado Porta de cerca de 1024 até 65535 (dependendo do kernel / rede do host Config). Nós diremos a Tahoe para escutar nesta porta, e nós diremos a Tor para Encaminhe as conexões de entrada para ele.
- Decida em um número de porta externo, chamado VIRTPORT. Isso será usado no Localização anunciada e revelada aos clientes. Pode ser qualquer número de 1 Para 65535. Pode ser o mesmo que PORT, se quiser.
- Decida em um "diretório de serviço oculto", geralmente em
/ var / lib / tor / NAME. Pediremos a Tor para salvar o estado do serviço de cebola aqui, e Tor irá Escreva o endereço.onionaqui depois que ele for gerado.
Em seguida, faça o seguinte:
-
Crie o nó do servidor Tahoe (com
tahoe create-node), mas não ** não ** Lança-o ainda. -
Edite o arquivo de configuração Tor (normalmente em
/ etc / tor / torrc). Precisamos adicionar Uma seção para definir o serviço oculto. Se nossa PORT for 2000, VIRTPORT é 3000, e estamos usando/ var / lib / tor / tahoecomo o serviço oculto Diretório, a seção deve se parecer com ::HiddenServiceDir / var / lib / tor / tahoe HiddenServicePort 3000 127.0.0.1:2000
-
Reinicie Tor, com
systemctl restart tor. Aguarde alguns segundos. -
Leia o arquivo
hostnameno diretório de serviço oculto (por exemplo,/ Var / lib / tor / tahoe / hostname). Este será um endereço.onion, comoU33m4y7klhz3b.onion. Ligue para esta CEBOLA. -
Edite
tahoe.cfgpara configurartub.portpara usarTcp: PORT: interface = 127.0.0.1etub.locationpara usarTor: ONION.onion: VIRTPORT. Usando os exemplos acima, isso seria ::[nó] Revelar-endereço IP = falso Tub.port = tcp: 2000: interface = 127.0.0.1 Tub.location = tor: u33m4y7klhz3b.onion: 3000 [Conexões] Tcp = tor
-
Inicie o servidor Tahoe com
tahoe start $ NODEDIR
A seção
tub.portfará com que o servidor Tahoe ouça no PORT, mas Ligue o soquete de escuta à interface de loopback, que não é acessível Do mundo exterior (mas * é * acessível pelo daemon Tor local). Então o A seçãotcp = torfaz com que Tahoe use Tor quando se conecta ao Introdução, escondendo o endereço IP. O nó se anunciará a todos Clientes que usam `tub.location``, então os clientes saberão que devem usar o Tor Para alcançar este servidor (e não revelar seu endereço IP através do anúncio). Quando os clientes se conectam ao endereço da cebola, seus pacotes serão Atravessar a rede de anonimato e eventualmente aterrar no Tor local Daemon, que então estabelecerá uma conexão com PORT no localhost, que é Onde Tahoe está ouvindo conexões.Siga um processo similar para construir um servidor Tahoe que escuta no I2P. o O mesmo processo pode ser usado para ouvir tanto o Tor como o I2P (
tub.location = Tor: ONION.onion: VIRTPORT, i2p: ADDR.i2p). Também pode ouvir tanto Tor como TCP simples (caso de uso 2), comtub.port = tcp: PORT,tub.location = Tcp: HOST: PORT, tor: ONION.onion: VIRTPORTeanonymous = false(e omite A configuraçãotcp = tor, já que o endereço já está sendo transmitido através de O anúncio de localização).Anonimato do servidor, configuração automática
Para configurar um nó do servidor para ouvir em uma rede de anonimato, crie o Nó com a opção
--listen = tor. Isso requer uma configuração Tor que Ou lança um novo daemon Tor, ou tem acesso à porta de controle Tor (e Autoridade suficiente para criar um novo serviço de cebola). Nos sistemas Debian / Ubuntu, façaApt install tor, adicione-se ao grupo de controle comadduser YOURUSERNAME debian-tore, em seguida, inicie sessão e faça o login novamente: se osgroupsO comando incluidebian-torna saída, você deve ter permissão para Use a porta de controle de domínio unix em/ var / run / tor / control.Esta opção irá definir
revelar-IP-address = Falsee[connections] tcp = Tor. Ele alocará as portas necessárias, instruirá Tor para criar a cebola Serviço (salvando a chave privada em algum lugar dentro de NODEDIR / private /), obtenha O endereço.onione preenchatub.portetub.locationcorretamente.Problemas de desempenho e segurança
Se você estiver executando um servidor que não precisa ser Anônimo, você deve torná-lo acessível através de uma rede de anonimato ou não? Ou você pode torná-lo acessível * ambos * através de uma rede de anonimato E como um servidor TCP / IP rastreável publicamente?
Existem várias compensações efetuadas por esta decisão.
Penetração NAT / Firewall
Fazer com que um servidor seja acessível via Tor ou I2P o torna acessível (por Clientes compatíveis com Tor / I2P) mesmo que existam NAT ou firewalls que impeçam Conexões TCP / IP diretas para o servidor.
Anonimato
Tornar um servidor Tahoe-LAFS acessível * somente * via Tor ou I2P pode ser usado para Garanta que os clientes Tahoe-LAFS usem Tor ou I2P para se conectar (Especificamente, o servidor só deve anunciar endereços Tor / I2P no Chave de configuração
tub.location). Isso evita que os clientes mal configurados sejam Desingonizando-se acidentalmente, conectando-se ao seu servidor através de A Internet rastreável.Claramente, um servidor que está disponível como um serviço Tor / I2P * e * a O endereço TCP regular não é anônimo: o endereço do .on e o real O endereço IP do servidor é facilmente vinculável.
Além disso, a interação, através do Tor, com um Tor Oculto pode ser mais Protegido da análise do tráfego da rede do que a interação, através do Tor, Com um servidor TCP / IP com rastreamento público
** XXX há um documento mantido pelos desenvolvedores de Tor que comprovem ou refutam essa crença? Se assim for, precisamos ligar a ele. Caso contrário, talvez devêssemos explicar mais aqui por que pensamos isso? **
Linkability
A partir de 1.12.0, o nó usa uma única chave de banheira persistente para saída Conexões ao Introdutor e conexões de entrada para o Servidor de Armazenamento (E Helper). Para os clientes, uma nova chave Tub é criada para cada servidor de armazenamento Nós aprendemos sobre, e essas chaves são * não * persistiram (então elas mudarão cada uma delas Tempo que o cliente reinicia).
Clientes que atravessam diretórios (de rootcap para subdiretório para filecap) são É provável que solicitem os mesmos índices de armazenamento (SIs) na mesma ordem de cada vez. Um cliente conectado a vários servidores irá pedir-lhes todos para o mesmo SI em Quase ao mesmo tempo. E dois clientes que compartilham arquivos ou diretórios Irá visitar os mesmos SI (em várias ocasiões).
Como resultado, as seguintes coisas são vinculáveis, mesmo com
revelar-endereço IP = Falso:- Servidores de armazenamento podem vincular reconhecer várias conexões do mesmo Cliente ainda não reiniciado. (Observe que o próximo recurso de Contabilidade pode Faz com que os clientes apresentem uma chave pública persistente do lado do cliente quando Conexão, que será uma ligação muito mais forte).
- Os servidores de armazenamento provavelmente podem deduzir qual cliente está acessando dados, por Olhando as SIs sendo solicitadas. Vários servidores podem conciliar Determine que o mesmo cliente está falando com todos eles, mesmo que o TubIDs são diferentes para cada conexão.
- Os servidores de armazenamento podem deduzir quando dois clientes diferentes estão compartilhando dados.
- O Introdutor pode entregar diferentes informações de servidor para cada um Cliente subscrito, para particionar clientes em conjuntos distintos de acordo com Quais as conexões do servidor que eles eventualmente fazem. Para clientes + nós de servidor, ele Também pode correlacionar o anúncio do servidor com o cliente deduzido identidade.
atuação
Um cliente que se conecta a um servidor Tahoe-LAFS com rastreamento público através de Tor Incorrem em latência substancialmente maior e, às vezes, pior Mesmo cliente se conectando ao mesmo servidor através de um TCP / IP rastreável normal conexão. Quando o servidor está em um Tor Hidden Service, ele incorre ainda mais Latência e, possivelmente, ainda pior rendimento.
Conectando-se a servidores Tahoe-LAFS que são servidores I2P incorrem em maior latência E pior rendimento também.
Efeitos positivos e negativos em outros usuários Tor
O envio de seu tráfego Tahoe-LAFS sobre o Tor adiciona tráfego de cobertura para outros Tor usuários que também estão transmitindo dados em massa. Então isso é bom para Eles - aumentando seu anonimato.
No entanto, torna o desempenho de outros usuários do Tor Sessões - por exemplo, sessões ssh - muito pior. Isso é porque Tor Atualmente não possui nenhuma prioridade ou qualidade de serviço Recursos, para que as teclas de Ssh de outra pessoa possam ter que esperar na fila Enquanto o conteúdo do arquivo em massa é transmitido. O atraso adicional pode Tornar as sessões interativas de outras pessoas inutilizáveis.
Ambos os efeitos são duplicados se você carregar ou baixar arquivos para um Tor Hidden Service, em comparação com se você carregar ou baixar arquivos Over Tor para um servidor TCP / IP com rastreamento público
Efeitos positivos e negativos em outros usuários do I2P
Enviar seu tráfego Tahoe-LAFS ao I2P adiciona tráfego de cobertura para outros usuários do I2P Que também estão transmitindo dados. Então, isso é bom para eles - aumentando sua anonimato. Não prejudicará diretamente o desempenho de outros usuários do I2P Sessões interativas, porque a rede I2P possui vários controles de congestionamento e Recursos de qualidade de serviço, como priorizar pacotes menores.
No entanto, se muitos usuários estão enviando tráfego Tahoe-LAFS ao I2P e não tiverem Seus roteadores I2P configurados para participar de muito tráfego, então o I2P A rede como um todo sofrerá degradação. Cada roteador Tahoe-LAFS que usa o I2P tem Seus próprios túneis de anonimato que seus dados são enviados. Em média, um O nó Tahoe-LAFS requer 12 outros roteadores I2P para participar de seus túneis.
Portanto, é importante que o seu roteador I2P esteja compartilhando a largura de banda com outros Roteadores, para que você possa retornar enquanto usa o I2P. Isso nunca prejudicará a Desempenho de seu nó Tahoe-LAFS, porque seu roteador I2P sempre Priorize seu próprio tráfego.
=========================
Como configurar um servidor
Muitos nós Tahoe-LAFS são executados como "servidores", o que significa que eles fornecem serviços para Outras máquinas (isto é, "clientes"). Os dois tipos mais importantes são os Introdução e Servidores de armazenamento.
Para ser útil, os servidores devem ser alcançados pelos clientes. Os servidores Tahoe podem ouvir Em portas TCP e anunciar sua "localização" (nome do host e número da porta TCP) Para que os clientes possam se conectar a eles. Eles também podem ouvir os serviços de cebola "Tor" E portas I2P.
Os servidores de armazenamento anunciam sua localização ao anunciá-lo ao Introdutivo, Que então transmite a localização para todos os clientes. Então, uma vez que a localização é Determinado, você não precisa fazer nada de especial para entregá-lo.
O próprio apresentador possui uma localização, que deve ser entregue manualmente a todos Servidores de armazenamento e clientes. Você pode enviá-lo para os novos membros do seu grade. Esta localização (juntamente com outros identificadores criptográficos importantes) é Escrito em um arquivo chamado
private / introducer.furlno Presenter's Diretório básico, e deve ser fornecido como o argumento--introducer =paraTahoe create-nodeoutahoe create-node.O primeiro passo ao configurar um servidor é descobrir como os clientes irão alcançar. Então você precisa configurar o servidor para ouvir em algumas portas, e Depois configure a localização corretamente.
Configuração manual
Cada servidor tem duas configurações em seu arquivo
tahoe.cfg:tub.port, eTub.location. A "porta" controla o que o nó do servidor escuta: isto Geralmente é uma porta TCP.A "localização" controla o que é anunciado para o mundo exterior. Isto é um "Sugestão de conexão foolscap", e inclui tanto o tipo de conexão (Tcp, tor ou i2p) e os detalhes da conexão (nome do host / endereço, porta número). Vários proxies, gateways e redes de privacidade podem ser Envolvido, então não é incomum para
tub.portetub.locationpara olhar diferente.Você pode controlar diretamente a configuração
tub.portetub.locationConfigurações, fornecendo--port =e--location =ao executartahoe Create-node.Configuração automática
Em vez de fornecer
--port = / - location =, você pode usar--listen =. Os servidores podem ouvir em TCP, Tor, I2P, uma combinação desses ou nenhum. O argumento--listen =controla quais tipos de ouvintes o novo servidor usará.--listen = nonesignifica que o servidor não deve ouvir nada. Isso não Faz sentido para um servidor, mas é apropriado para um nó somente cliente. o O comandotahoe create-clientinclui automaticamente--listen = none.--listen = tcpé o padrão e liga uma porta de escuta TCP padrão. Usar--listen = tcprequer um argumento--hostname =também, que será Incorporado no local anunciado do nó. Descobrimos que os computadores Não pode determinar de forma confiável seu nome de host acessível externamente, então, em vez de Ter o servidor adivinhar (ou escanear suas interfaces para endereços IP Isso pode ou não ser apropriado), a criação de nó requer que o usuário Forneça o nome do host.--listen = torconversará com um daemon Tor local e criará uma nova "cebola" Servidor "(que se parece comalzrgrdvxct6c63z.onion).--listen = i2p` conversará com um daemon I2P local e criará um novo servidor endereço. Consulte: doc:anonymity-configuration` para obter detalhes.Você pode ouvir nos três usando
--listen = tcp, tor, i2p.Cenários de implantação
A seguir, alguns cenários sugeridos para configurar servidores usando Vários transportes de rede. Estes exemplos não incluem a especificação de um Apresentador FURL que normalmente você gostaria quando provisionamento de armazenamento Nós. Para estes e outros detalhes de configuração, consulte : Doc:
configuration.. `Servidor possui um nome DNS público '
.
Servidor possui um endereço público IPv4 / IPv6_.
O servidor está por trás de um firewall com encaminhamento de porta_.
Usando o I2P / Tor para evitar o encaminhamento da porta_O servidor possui um nome DNS público
O caso mais simples é o local onde o host do servidor está diretamente conectado ao Internet, sem um firewall ou caixa NAT no caminho. A maioria dos VPS (Virtual Private Servidor) e servidores colocados são assim, embora alguns fornecedores bloqueiem Muitas portas de entrada por padrão.
Para esses servidores, tudo o que você precisa saber é o nome do host externo. O sistema O administrador irá dizer-lhe isso. O principal requisito é que este nome de host Pode ser pesquisado no DNS, e ele será mapeado para um endereço IPv4 ou IPv6 que Alcançará a máquina.
Se o seu nome de host for
example.net, então você criará o introdutor como esta::Tahoe create-introducer --hostname example.com ~ / introducer
Ou um servidor de armazenamento como ::
Tahoe create-node --hostname = example.net
Estes irão alocar uma porta TCP (por exemplo, 12345), atribuir
tub.portpara serTcp: 12345etub.locationserãotcp: example.com: 12345.Idealmente, isso também deveria funcionar para hosts compatíveis com IPv6 (onde o nome DNS Fornece um registro "AAAA", ou ambos "A" e "AAAA"). No entanto Tahoe-LAFS O suporte para IPv6 é novo e ainda pode ter problemas. Por favor, veja o ingresso
# 867_ para detalhes... _ # 867: https://tahoe-lafs.org/trac/tahoe-lafs/ticket/867
O servidor possui um endereço público IPv4 / IPv6
Se o host tiver um endereço IPv4 (público) rotativo (por exemplo,
203.0.113.1```), mas Nenhum nome DNS, você precisará escolher uma porta TCP (por exemplo,3457``) e usar o Segue::Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 3457
--porté uma "string de especificação de ponto de extremidade" que controla quais locais Porta em que o nó escuta.--locationé a "sugestão de conexão" que ele Anuncia para outros, e descreve as conexões de saída que essas Os clientes irão fazer, por isso precisa trabalhar a partir da sua localização na rede.Os nós Tahoe-LAFS escutam em todas as interfaces por padrão. Quando o host é Multi-homed, você pode querer fazer a ligação de escuta ligar apenas a uma Interface específica, adicionando uma opção
interface =ao--port =argumento::Tahoe create-node --port = tcp: 3457: interface = 203.0.113.1 - localização = tcp: 203.0.113.1: 3457
Se o endereço público do host for IPv6 em vez de IPv4, use colchetes para Envolva o endereço e altere o tipo de nó de extremidade para
tcp6::Tahoe create-node --port = tcp6: 3457 - localização = tcp: [2001: db8 :: 1]: 3457
Você pode usar
interface =para vincular a uma interface IPv6 específica também, no entanto Você deve fazer uma barra invertida - escapar dos dois pontos, porque, de outra forma, eles são interpretados Como delimitadores pelo idioma de especificação do "ponto final" torcido. o--location =argumento não precisa de dois pontos para serem escapados, porque eles são Envolto pelos colchetes ::Tahoe create-node --port = tcp6: 3457: interface = 2001 \: db8 \: \: 1 --location = tcp: [2001: db8 :: 1]: 3457
Para hosts somente IPv6 com registros DNS AAAA, se o simples
--hostname =A configuração não funciona, eles podem ser informados para ouvir especificamente Porta compatível com IPv6 com este ::Tahoe create-node --port = tcp6: 3457 - localização = tcp: example.net: 3457
O servidor está por trás de um firewall com encaminhamento de porta
Para configurar um nó de armazenamento por trás de um firewall com encaminhamento de porta, você irá precisa saber:
- Endereço IPv4 público do roteador
- A porta TCP que está disponível de fora da sua rede
- A porta TCP que é o destino de encaminhamento
- Endereço IPv4 interno do nó de armazenamento (o nó de armazenamento em si é
Desconhece esse endereço e não é usado durante
tahoe create-node, Mas o firewall deve ser configurado para enviar conexões para isso)
Os números de porta TCP internos e externos podem ser iguais ou diferentes Dependendo de como o encaminhamento da porta está configurado. Se é mapear portas 1-para-1, eo endereço IPv4 público do firewall é 203.0.113.1 (e Talvez o endereço IPv4 interno do nó de armazenamento seja 192.168.1.5), então Use um comando CLI como este ::
Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 3457
Se no entanto, o firewall / NAT-box encaminha a porta externa * 6656 * para o interno Porta 3457, então faça isso ::
Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 6656
Usando o I2P / Tor para evitar o encaminhamento da porta
Os serviços de cebola I2P e Tor, entre outras excelentes propriedades, também fornecem NAT Penetração sem encaminhamento de porta, nomes de host ou endereços IP. Então, configurando Um servidor que escuta apenas no Tor é simples ::
Tahoe create-node --listen = tor
Para mais informações sobre o uso de Tahoe-LAFS com I2p e Tor veja : Doc:
anonymity-configuration -
 @ 9223d2fa:b57e3de7
2025-04-15 02:54:00
@ 9223d2fa:b57e3de7
2025-04-15 02:54:0012,600 steps
-
 @ fd06f542:8d6d54cd
2025-04-15 02:38:14
@ fd06f542:8d6d54cd
2025-04-15 02:38:14排名随机, 列表正在增加中。
Cody Tseng
jumble.social 的作者
https://jumble.social/users/npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wl
- Running [ wss://nostr-relay.app ] (free & WoT) 💜⚡️
- Building 👨💻:
- https://github.com/CodyTseng/jumble
- https://github.com/CodyTseng/nostr-relay-tray
- https://github.com/CodyTseng/danmakustr
- https://github.com/CodyTseng/nostr-relay-nestjs
- https://github.com/CodyTseng/nostr-relay
- https://github.com/CodyTseng
阿甘
- @agan0
- 0xchat.com
- canidae40@coinos.io
- https://jumble.social/users/npub13zyg3zysfylqc6nwfgj2uvce5rtlck2u50vwtjhpn92wzyusprfsdl2rce
joomaen
- Follows you
- joomaen.com
-
95aebd@wallet.yakihonne.com
-
nobot
- https://joomaen.filegear-sg.me/
- https://jumble.social/users/npub1wlpfd84ymdx2rpvnqht7h2lkq5lazvkaejywrvtchlvn3geulfgqp74qq0
颜值精选官
- wasp@ok0.org
- 专注分享 各类 图片与视频,每日为你带来颜值盛宴,心动不止一点点。欢迎关注,一起发现更多美好!
- https://jumble.social/users/npub1d5ygkef6r0l7w29ek9l9c7hulsvdshms2qh74jp5qpfyad4g6h5s4ap6lz
6svjszwk
- 6svjszwk@ok0.org
- 83vEfErLivtS9to39i73ETeaPkCF5ejQFbExoM5Vc2FDLqSE5Ah6NbqN6JaWPQbMeJh2muDiHPEDjboCVFYkHk4dHitivVi
-
low-time-preference
-
anarcho-capitalism
-
libertarianism
-
bitcoin #monero
- https://jumble.social/users/npub1sxgnpqfyd5vjexj4j5tsgfc826ezyz2ywze3w8jchd0rcshw3k6svjszwk
𝘌𝘷𝘦𝘳𝘺𝘥𝘢𝘺 𝘔𝘰𝘳𝘯𝘪𝘯𝘨 𝘚𝘵𝘢𝘳
- everyday@iris.to
- 虽然现在对某些事情下结论还为时尚早,但是从趋势来看,邪恶抬头已经不可避免。
- 我们要做的就是坚持内心的那一份良知,与邪恶战斗到底。
- 黑暗森林时代,当好小透明。
- bc1q7tuckqhkwf4vgc64rsy3rxy5qy6pmdrgxewcww
- https://jumble.social/users/npub1j2pha2chpr0qsmj2f6w783200upa7dvqnnard7vn9l8tv86m7twqszmnke
nostr_cn_dev
npub1l5r02s4udsr28xypsyx7j9lxchf80ha4z6y6269d0da9frtd2nxsvum9jm@npub.cash
Developed the following products: - NostrBridge, 网桥转发 - TaskQ5, 分布式多任务 - NostrHTTP, nostr to http - Postr, 匿名交友,匿名邮局 - nostrclient (Python client) . -nostrbook, (nostrbook.com) 用nostr在线写书 * https://www.duozhutuan.com nostrhttp demo * https://github.com/duozhutuan/NostrBridge * * https://jumble.social/users/npub1l5r02s4udsr28xypsyx7j9lxchf80ha4z6y6269d0da9frtd2nxsvum9jm *
CXPLAY
- lightning@cxplay.org
- 😉很高兴遇到你, 你可以叫我 CX 或 CXPLAY, 这个名字没有特殊含义, 无需在意.
- ©本账号下所有内容如未经特殊声明均使用 CC BY-NC-SA 4.0 许可协议授权.
- 🌐如果您在 Fediverse 收到本账号的内容则说明您的实例已与 Mostr.pub 或 Momostr.pink Bridge 互联, 您所看到的账号为镜像, 所有账号内容正在跨网传递. 如有必要请检查原始页面.
- 🧑💻正在提供中文本地化(i10n): #Amethyst #Amber #Citrine #Soapbox #Ditto #Alby
- https://cx.ms/
https://jumble.social/users/npub1gd8e0xfkylc7v8c5a6hkpj4gelwwcy99jt90lqjseqjj2t253s2s6ch58h
w
- 0xchat的作者
- 0xchat@getalby.com
- Building for 0xchat
- https://www.0xchat.com/
- https://jumble.social/users/npub10td4yrp6cl9kmjp9x5yd7r8pm96a5j07lk5mtj2kw39qf8frpt8qm9x2wl
Michael
- highman@blink.sv
- Composer Artist | Musician
- 🎹🎼🎤🏸🏝️🐕❤️
- 在這裡可以看到「我看世界」的樣子
- 他是光良
- https://jumble.social/users/npub1kr5vqlelt8l47s2z0l47z4myqg897m04vrnaqks3emwryca3al7sv83ry3
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-15 00:13:55
@ 5d4b6c8d:8a1c1ee3
2025-04-15 00:13:55It may seem like we're beating this to death, but we want to hype it up as much as possible.
Entry
The entry fee is a paltry 1k sats. Let me know if you want to join and I'll send you an invoice.
Stackers will join through Stacker News, while those nostr scoundrels will do their own thing.
Brackets
You can start filling out brackets at NBA Bracketology. We don't know the 7th or 8th seeds, yet, but maybe that doesn't change how you feel about some of the series. In addition to picking winners, you'll need to pick series length.
You can edit your brackets up until the playoffs start, so don't worry about getting it exactly right, yet. I'll send out reminders to make sure Team Stacker Sports has their brackets ship shape.
The attached note describes the scoring system.
Prizes
Grand Prize: Blockstream Jade Plus
Winning Team: The sats pool will be divided up amongst the winning side. Assuming Team SN wins, we will payout the sats evenly to each team member, just like how Workit pays out those who complete their challenges.
https://primal.net/e/nevent1qvzqqqqqqypzqpqrep4phdx0hs6v3fynl0glp52c6skaqmgra23hyzyz5pnd8gmcqqsvs9skvcsg0nfuag65t3n2dsjwlg3g2ldgzg9t935ng8yj6kjlueqk65qds
Support Global Sports Central
Our frenemies at Global Sports Central are fundraising through Geyser. If you're in the mood to support nostr/bitcoin sports content, beyond what you're doing for ~Stacker_Sports, think about contributing to them and following their nostr account.
cc: @grayruby, @supercyclone, @Coinsreporter, @BlokchainB, @Carresan, @WeAreAllSatoshi
originally posted at https://stacker.news/items/943657
-
 @ 2183e947:f497b975
2025-04-15 00:13:02
@ 2183e947:f497b975
2025-04-15 00:13:02(1) Here is a partial list of p2p bitcoin exchanges and their friends:
- Robosats (custodial escrow)
- Hodlhodl (2-of-3 escrow)
- Peach (2-of-3 escrow)
- Binance P2P (2-of-3 escrow)
- Bisq v1 (either user can send the funds to a custodial escrow, but if neither one does that, the escrow never touches user funds)
- Bisq v2 (no escrow)
(2) In my opinion, bisq2 is the only "true" p2p exchange on the above list. In a true p2p system, the only people who *can* touch the money are the buyer and the seller. Whenever there's an escrow, even one that has to be "triggered" (like in bisq v1), it's not "really" p2p because the escrow serves as a middleman: he can collude with one party or the other to steal user funds, and in some models (e.g. robosats) he can just straight up run off with user funds without needing to collude at all.
(3) In bisq2 (the One True P2P exchange), buyers select sellers solely based on their reputation, and they just directly send them the bitcoin *hoping* they are as honest as their reputation says they are. What I like about this model is that bisq is not involved in bisq2 at all except as a platform to help buyers discover reputable sellers and communicate with them. There are two things I don't like about this "reputation" model: it's hard to get a good reputation, and it's hard to debug payment failures in this context. I've tried to do about 5 trades on bisq2 (as someone with no reputation) and not a single one went through. Four times, everyone ignored my offers or someone accepted it but then abandoned it immediately. Once, someone accepted my offer, but I could not pay their lightning invoice for some reason, so we mutually canceled the trade.
(4) Just because I opined that an exchange with an escrow "doesn't count" as peer-to-peer doesn't mean that's a bad thing. Of the list of exchanges in number 1, I most frequently use robosats, which, per my analysis, sounds like the "worst" one if considered solely on the metric of "which one is the most p2p." But I use it because there are *advantages* to its model: the btc seller doesn't need a reputation to use it (because the escrow is there to ensure he can't cheat, and so the escrow is the trusted third party, not the btc seller) and payment failures are easier to debug because you're always paying one of the coordinators, who tend to be responsive and knowledgeable and can help you figure out how to fix it (it's how they make money, after all).
(5) There are at least two ways to do escrow without a 3rd party. Satoshi Nakamoto outlines one way to do it here: https://satoshi.nakamotoinstitute.org/posts/bitcointalk/threads/169/ Make a 2 of 2 multisig between the btc buyer and the btc seller, and have the btc seller put his btc in that multisig. Then have the btc buyer send the product (fiat money) to the btc seller. When the btc seller receives it, he sends his privkey to the btc buyer, who can now withdraw the money. The advantage of this system is that the buyer has no incentive to "stiff" the seller (by not sending the fiat), because if he does that, he won't get paid. The downside is, if the btc buyer is a troll who just aborts the protocol halfway through the trade, the seller loses his btc and cannot recover it.
(6) There is another way: start out with a 2 of 2 multisig just like above, but instead of having the btc seller fund it by himself, have the buyer and the seller *both* put in the *same amount* in the *same transaction* (i.e. via a coinjoin), and have the btc seller put in a bit "extra" -- like 20% extra. For example, if the btc seller wants $100 in fiat, the multisig would have $220 in it in total -- $120 from the seller and $100 from the buyer. Using this model, the disadvantage mentioned in paragraph number 5 is fixed: the buyer has an incentive now to send the fiat, otherwise he loses the $100 he put in. He only gets his $100 back if the btc seller cosigns to give it to him, which he'll only do once he receives the product. Meanwhile, the seller is *also* incentivized properly: he only gets his *extra* $20 back if the btc buyer cosigns to give it to him, which he'll only do if the transaction he's signing *also* gives him back *his* $100 deposit.
(7) The model described in number 6 exists: https://scrow.exchange/ is a website that implements it as an option, though as far as I'm aware, no one uses it. The downsides of this model are: it's capital intensive, e.g. a trade for $100 involves $220 or more. Also, the btc buyer needs to already *have* btc to post as a bond, so this cannot be his first time acquiring btc (unless someone helps him make his first deposit). Also, a very rich person who does not care about money can still be a troll; they deposit funds into the multisig alongside their counterparty, then abandon the trade, because they have so much money they don't care if they get it back as long as they cause suffering to their counterparty.
(8) I'd like to see more p2p exchanges, and more exchanges like robosats. I want to continue to spread awareness of ways they can improve -- like the protocols mentioned in numbers 5 and 6 -- and help them implement these protocols. If you run an exchange on the list in number 1 or want to start one, reach out to me, I'd love to help.
-
 @ bb1c863a:2953c3fb
2025-04-14 22:21:25
@ bb1c863a:2953c3fb
2025-04-14 22:21:25Block Height 892385 11:47 pm Monday, 14 April 2025
In a powerful gesture of support for Bitcoin-aligned education, Blockstream has donated 21 Blockstream Jade hardware wallets to the Consensus21 School — a groundbreaking learning initiative launching its first campus this year on the Mornington Peninsula, just outside Melbourne, Australia.
The donation will place 21 Jades directly into the hands of the first 21 students at the new campus — some as young as five years old — giving them real tools to explore Bitcoin self-custody, digital sovereignty, and privacy-first technology in an age-appropriate and hands-on way.
“The Jade wallets are more than just devices — they’re symbols of freedom, responsibility, and the future of education,” said Kieran Nolan, co-founder of Consensus21. “We’re incredibly grateful to Blockstream for standing behind our mission.”
Real Tools for Real Sovereignty
The Blockstream Jade is a secure, open-source hardware wallet built for Bitcoiners who value freedom, privacy, and independence. These values are embedded deeply into the Consensus21 educational philosophy, which blends Steiner-inspired learning, homeschooling flexibility, and a curriculum rooted in Bitcoin principles like voluntary exchange, decentralization, and self-responsibility.
With the Jades now part of the learning toolkit, Consensus21 learners will be introduced to key concepts like:
- Private key management
- Seed phrase generation and backup
- Multisig wallets
- The importance of self-custody and trust minimization
This is not just about theory — learners will get to use these tools in real-world contexts, preparing them to grow up fluent in the principles of freedom tech.
A Campus, A Vision, A Movement
Launching in 2025, the Mornington Peninsula campus is the pilot site for the broader Consensus21 vision: a distributed, regenerative, and values-aligned network of co-learning spaces, including a future 10-acre farm campus and a registered Steiner school.
The Blockstream donation comes at a pivotal time, as the community transitions from vision to reality. The gift of exactly 21 Blockstream Jades — echoing Bitcoin’s 21 million hard cap — is both a symbolic and practical gesture of support, underscoring the shared commitment between Bitcoin builders and grassroots educators.
Stay Connected
📄 Whitepaper: https://github.com/consensus21school/consensus21school.github.io/blob/main/whitepaper.md
🌐 Website: https://consensus21.school
📝 Nostr: CONSENSUS21@nostrcheck.me
🐦 X (Twitter): https://x.com/Consensus21
originally posted at https://stacker.news/items/943549
-
 @ 6e0ea5d6:0327f353
2025-04-14 15:11:17
@ 6e0ea5d6:0327f353
2025-04-14 15:11:17Ascolta.
We live in times where the average man is measured by the speeches he gives — not by the commitments he keeps. People talk about dreams, goals, promises… but what truly remains is what’s honored in the silence of small gestures, in actions that don’t seek applause, in attitudes unseen — yet speak volumes.
Punctuality, for example. Showing up on time isn’t about the clock. It’s about respect. Respect for another’s time, yes — but more importantly, respect for one’s own word. A man who is late without reason is already running late in his values. And the one who excuses his own lateness with sweet justifications slowly gets used to mediocrity.
Keeping your word is more than fulfilling promises. It is sealing, with the mouth, what the body must later uphold. Every time a man commits to something, he creates a moral debt with his own dignity. And to break that commitment is to declare bankruptcy — not in the eyes of others, but in front of himself.
And debts? Even the small ones — or especially the small ones — are precise thermometers of character. A forgotten sum, an unpaid favor, a commitment left behind… all of these reveal the structure of the inner building that man resides in. He who neglects the small is merely rehearsing for his future collapse.
Life, contrary to what the reckless say, is not built on grand deeds. It is built with small bricks, laid with almost obsessive precision. The truly great man is the one who respects the details — recognizing in them a code of conduct.
In Sicily, especially in the streets of Palermo, I learned early on that there is more nobility in paying a five-euro debt on time than in flaunting riches gained without word, without honor, without dignity.
As they say in Palermo: L’uomo si conosce dalle piccole cose.
So, amico mio, Don’t talk to me about greatness if you can’t show up on time. Don’t talk to me about respect if your word is fickle. And above all, don’t talk to me about honor if you still owe what you once promised — no matter how small.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 2e8970de:63345c7a
2025-04-14 14:50:44
@ 2e8970de:63345c7a
2025-04-14 14:50:44(source)
- Notice how "social" stuff like therapy and finding purpose is up massively, now all first 3 spots.
- All the "new" stuff is down. You won't get new ideas out of chatGPT, explore topics of interest, or research. It only spits back at you what you said to it. Nothing new, nothing creative or unexpected.
- Coding is new this year? Really?
originally posted at https://stacker.news/items/943133
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-14 00:32:26
@ 5d4b6c8d:8a1c1ee3
2025-04-14 00:32:26The matchups are set, so we can get the contest underway.
You need to select one team from this round to win their game. You also need to predict who will be the highest scoring player in this round.
Matchups (seed)
- Hawks (8) @ Magic (7)
- Heat (10) @ Bulls (9)
- Grizzlies (8) @ Warriors (7)
- Mavericks (10) @ Kings (9)
Scoring this round: 1 Point for your team winning + Your team's seed if they win + 1 Point for picking the correct top scorer
This round has a maximum of 12 points.
originally posted at https://stacker.news/items/942654
-
 @ c066aac5:6a41a034
2025-04-13 23:09:14
@ c066aac5:6a41a034
2025-04-13 23:09:14“If a man is considered guilty For what goes on in his mind Then give me the electric chair For all my future crimes”-Electric Chair by Prince
The very last paragraph of Touré’s 2013 biography of Prince I Would Die 4 U: Why Prince Became an Icon made a very bold claim about the lewd nature of Prince’s music:
“Imagine America as one house on a suburban lane… Prince knocked on America’s door through his music. He came to the door holding a guitar and an umbrella while concealing a Bible. He flirted his way inside the door and told us he had a dirty mind and was controversial, and then he sat down in the living room on the good couch. And, when America’s guard was down, because we thought we were having a conversation about sex, Prince eased out his Bible and said, let me also tell you about my Lord and savior, Jesus Christ.”
Wow. Talk about a Sixth Sense level plot twist! I will say if you’re well versed in Prince’s catalog (I listened to every Prince album released [except for The Black Album because Jack Dorsey is holding it hostage on Tidal] last year) it won’t be as shocking as a surprise as it would be to the unversed listener, but surprising nonetheless considering the content of the man’s lyrics (and life).
Regardless of whether or not Prince achieved this goal of bringing people to Christ via a vehicle of sexy shock value, he was a person of impact. The book by Touré I mentioned earlier is a great picture of the life he lived, and I’m sure there are many others that people can recommend in the comments. He touched many lives and I believe his music will still be listened to for many years to come.
Prince’s method of evangelism may have been unconventional (to say the least), but I still think there is something to be learned from his efforts.
Obviously, worshiping sex or encouraging lust isn’t great. Prince’s view of sex was broken; they didn’t line up with Biblically ordered sex (see his songs Sister, Darling Nikki, Sexy M.F., and many many more). His inability to sustain healthy relationships or make meaningful lasting connections with those around him are a testament to that.
Despite his flaws, his art captured an entire generation - and continues to capture the attention of people seeking true art. His authenticity, raw emotion, and intentionality made for true connection between his music and his listeners. He resonated with people’s souls, and still does today. Perhaps Touré was wrong and Prince didn’t mean to evangelize through his music, but don’t all people stand testament to the powerful work of God?
We are all broken people. Our job is to the use the tools and resources set before us to spread the Gospel. “…we have this treasure in clay jars, so that it may be made clear that this extraordinary power belongs to God and does not come from us.” -2 Corinthians 4:7
The Western Church should consider using the seemingly profane, off limits, unconventional, or even just plain weird in an effort to continue to spread the gospel. On a high level, that’s our good-christian dinner table no-gos: Sex, Money, and Politics. I believe that the Church’s abdication of such conversations is the reason why those are areas of failure for the Church at large. We shouldn’t sin or condone/promote sin. Instead, I’m proposing that like how Prince used sex in his music to get people to learn about Jesus, Christian Bitcoiners should use money (Bitcoin) to do good works and lead people to Jesus in the process. We may just make the world a better place along the way.
“If you're sick of cryin' and tired of tears Then close your eyes and open your ears Listen to the music, listen to the song Listen to your heart, is that so wrong? Stop lookin' in the mirror, there's nothin' to fear Your salvation is near 1,000 light years away from here”-1,000 Light Years From Here by Prince
It doesn’t take a lot of mental effort to see how Christian’s could leverage Bitcoin’s magic for kingdom work. Look Alex Gladstein’s writings. Look at the work that Gridless is doing in Africa. Look at Roya Mahboob’s impact in Afghanistan. Look at the impact of Bitcoin Beach in El Salvador.
Now imagine what the Church (and by the Church, I mean you and I the Christian Bitcoiners) could do with Bitcoin:
A Christian Bitcoiner could help the woman with an abusive husband escape a bad situation with finances intact by teaching her how to use Bitcoin and keep self-custody wallet. An orange-pilled youth group leader could teach the inner city kid in a bad household how to set up a wallet and stack sats without the permission of the dead beat parents or conventional employment. The church bake sale could make things easy via accepting lightning payments, bringing in outsiders for sweet treats and teaching them about how to be a Bitcoin merchant. A church could send funds to a missionary across the world in a christian adverse country instantly without having to involve a single bank, and that missionary would have those funds same-day ready for deployment.
“Everybody's looking for the ladder Everybody wants salvation of the soul The steps you take are no easy road But the reward is great For those who want to go”-The Ladder by Prince
In my own attempts to teach people about the virtues of Bitcoin, I find it usually clicks for people in one of two different ways for the most part:
The first way it clicks is when they can receive and send a lightning payment. The instant funds make a light bulb go off.
The second way is when I show them the humanitarian impact that Bitcoin has had and is counting to have. The use of Bitcoin internationally as a means of humanitarian aid/sovereignty for the less fortunate should shut down any questions like “But what about (insert crapcoin)?” in an instant.
Much like how people get Bitcoin once they see it in action, I believe people will get Jesus when they see Jesus’ Church in action. One of the best ways today the Church can display that action may be through Bitcoin.
Sex was Prince’s trojan horse for something much deeper that he wanted to convey to people. Bitcoin can be the trojan horse for the Church. The Church could gain attention for what they’re doing with Bitcoin similar to the attention that the Human Rights Foundation gets. One might ask why use a trojan horse? I think that Bitcoin adoption itself has been a bit of a trojan horse movement. Your local politicians didn’t bat an eye when they heard about a peer-to-peer e-cash system, but they were all over it when it was presented as a digital gold. Michael Saylor has garnered a lot of hate from the Bitcoin true-believers for presenting Bitcoin as a digital gold as opposed to a currency, but I believe he knows what he’s doing and he’s presenting in this manner on purpose. He might not get gratitude for it from the community, but I believe he’s willing to be the bad guy in order to further the mission (see Christopher Nolan’s The Dark Night [which is arguably a Jesus story]).
Christian Bitcoiner, I challenge you to channel your enthusiasm to do good in your neighborhood. Let the world see your actions and gain a curiosity for what you’re doing. The Bitcoin conversation will make many people think that you’re crazy, that you’re an idiot when it comes to investing, that you’re selling a scam. Much like how people wrote off Prince for being a vulgar musician. Much like how people write off Michael Saylor for misunderstanding Bitcoin. Much like how people wrote off (and continue to write off) Jesus for being a false prophet or the leader of a rebellion.
But there will be someone who sees the work that you do with Bitcoin. The work that the Church will do with Bitcoin. Even if just one soul is saved with Bitcoin, that’s worth the effort.
“Black day, stormy night No love, no hope in sight Don't cry, He is coming Don't die without knowing the cross” -The Cross by Prince
This article was written with help from my wife Elaina freedom@happytavern.co
Feel free to drop your favorite book about Prince, favorite Prince song, or favorite Prince album in the comments
Or, you can drop your favorite Bitcoin as a trojan horse story in the comments
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-13 21:39:55
@ 5d4b6c8d:8a1c1ee3
2025-04-13 21:39:55I'm watching the Warriors vs Clippers game (for free at BetPlay). It's a great game, with major playoff implications, but something else just caught my attention.
I heard on the arena sound that they're giving away $5 worth of bitcoin to a fan. That's interesting. It's a Coinbase promotion.
originally posted at https://stacker.news/items/942558
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-13 21:23:25
@ 5d4b6c8d:8a1c1ee3
2025-04-13 21:23:25This is a separate contest from the Playoff Bracket Challenge.
The scoring will be similar to the recent March Madness Competition. Picking winners will be worth more points as we progress into later rounds and picking lower seeds will be worth more. The new wrinkle will be picking a high performing player from each round, as well.
We'll start in the Play-In Tournament, which begins on Tuesday and has two rounds. We'll know later today what the first play-in matches are.
Point Schedule
Play-In 1st Round
- 1 Point for picking a winner
- Points equal to seed if your team wins
- 1 Point for picking the highest scoring player of the round
Play-In 2nd Round
- 1 Point for picking a winner
- Points equal to seed if your team wins
- 1 Point for picking the highest scoring player of the round
Playoffs Round 1
- 1 Point for picking a winner
- Points equal to seed if your team wins
- 1 Point for picking the highest scoring player of the round
Playoffs Round 2
- 2 Points for picking a winner
- Points equal to seed if your team wins
- 2 Points for picking the highest scoring player of the round
Playoffs Conference Finals
- 4 Points for picking a winner
- Points equal to seed if your team wins
- 4 Points for picking one of the Conference Finals MVPs
Playoffs Conference Finals
- 8 Points for picking a winner
- Points equal to seed if your team wins
- 8 Points for picking the Finals MVPs
This is not a survivor pool. You can pick the same team as many times as you like. You can join at any time during the competition. The only deadlines are making your picks before the teams and players you pick begin their round.
For clarification, and those not familiar with this tournament, the seeding may change after the Play-In Tournament: for instance, the Hawks begin as the 8th seed, but they will become the 7th seed if they beat the Magic in their first play-in game.
Prize
10k sats or the sum of all zaps (whichever is larger)
originally posted at https://stacker.news/items/942553
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-13 15:04:01
@ 5d4b6c8d:8a1c1ee3
2025-04-13 15:04:01https://primal.net/e/nevent1qvzqqqqqqypzqpqrep4phdx0hs6v3fynl0glp52c6skaqmgra23hyzyz5pnd8gmcqqsva8zn0v6k282lqtxvqzf4pdspz8ek22gk9hfxxx8pfat34e8x7yqxh0hq7
Well that escalated quickly!
What began as a friendly joint venture has descended into bitter rivalry. Who will take home the sats, Noble Stackers or GSC degenerates?
Declare your allegiance upon entry. Choose wisely.
originally posted at https://stacker.news/items/942260
-
 @ c11cf5f8:4928464d
2025-04-13 09:26:24
@ c11cf5f8:4928464d
2025-04-13 09:26:24A collection of all the tutorials and guidelines that will help you get the most out of this territory
The ~AGORA marketplace it’s a thriving space where creators, solopreneurs, and businesses can promote and monetize their expertise. A place where stackers can discover unique goods, tools, and tricks to buy products and get services in exchange for Bitcoin.
This post will aim to be the reference to collect all the posts, guide, and tutorials that can help you make the most out of it. Post yours if we forgot something!
originally posted at https://stacker.news/items/942038
-
 @ 8dac122d:0fc98d37
2025-04-13 08:57:10
@ 8dac122d:0fc98d37
2025-04-13 08:57:10This is another experiment, let's see how it goes! As you maybe know, we have been selling some SN merch online, it's a great way to promote and generate more awareness for the ~AGORA Marketplace but mostly for SN itself.
But what exactly is a shopfront?
A shopfront, or storefront, is the facade or entryway of a retail store located on the ground floor or street level of a commercial building, typically including one or more display windows. A storefront functions to attract visual attention to a business and its merchandise.[^1]
In our case, it's an ecommerce facade, the entryway of an online store or web shop located in a crowded area of the Wild West Web here on SN. A reference to link external products and services that can be updated and maintained to keep your stacker' subscribers updated. It aims to display a list of item and provides an direct external link for the visitor to click, visit, and eventually buy or subscribe to the product or service he or she was lurking at.
How can we do it in the ~AGORA? Well, as simple as posting a discussion! The idea is to use the functionalities that SN currently offers in the best and more efficient way for this use case. With this exploration, we just define different contents to fill the inputs fields already available. In a nutshel, we publish a post, with the only difference that the content in the text/description field will be descriptive of our products and services. In addition, we use each comments to define an item with the relative image(s), description and link. Here a breakdown:
- Write a new post in the ~AGORA
2 Make sure
[SHOPFRONT]is included in the title together with the name of the Business (like a lightsign) - Introduce yourself or your business, values, products and services in the text description
- Publish it
- Write a commet for each product or service with title, info, image(s) and a link to learn more or buy. A template for comments/items could look something like: ```
Title
Description:
Price:Buy Now ``` 6. That's it!The coiol thing is that you can just delete comments/items and add new ones as you wish. That's how a sn "post" could become a simple shopfront platform, a catalog you ca easily maintain and update to connect with stackers and upsell your products and services.
I did few tests, and I'll use this post to continue aggregate new shopfronts that will be published around here. Below the first few live examples:
[^1]: From Wikipedia https://en.wikipedia.org/wiki/Storefront
originally posted at https://stacker.news/items/942025
- Write a new post in the ~AGORA
2 Make sure
-
 @ da0b9bc3:4e30a4a9
2025-04-13 08:48:10
@ da0b9bc3:4e30a4a9
2025-04-13 08:48:10Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/942018