-
 @ 9063ef6b:fd1e9a09
2025-05-07 19:12:36
@ 9063ef6b:fd1e9a09
2025-05-07 19:12:36✅ Requirements
- GitHub account
- Own domain (e.g.,
yourdomain.com) - Public Nostr key in hex format (not
npub!) - Basic DNS configuration knowledge
🛒 1. Register a Domain
Register a domain from a provider like orangewebsite, njal.la, or similar.
🌐 2. Configure DNS Records for GitHub Pages
Set the following A records for your domain (via your DNS provider):
| Type | Host | Value | TTL | Priority | |------|--------------|-------------------|-----|----------| | A | @ (or blank) | 185.199.108.153 | 300 | | | A | @ (or blank) | 185.199.109.153 | 300 | | | A | @ (or blank) | 185.199.110.153 | 300 | | | A | @ (or blank) | 185.199.111.153 | 300 | |
Optional:
Add aCNAMErecord forwww→yourusername.github.io
📁 3. Create a GitHub Repository
- Go to https://github.com/new
- Repository name: e.g.,
nip5 - Check "Add a README"
- Click "Create repository"
🏗️ 4. Create Directory & File
a)
.well-known/nostr.jsonPath:
.well-known/nostr.json
Example content:json { "names": { "nostrName": "ldajflasjföldsjflj..." } }IMPORTANT: Use your hex-encoded Nostr public key, not the
npub1...format.b)
_config.ymlin RootCreate a file named
_config.ymlwith this content:yml include: [".well-known"]This ensures GitHub includes the
.well-knownfolder in the build output.
⚙️ 5. Configure GitHub Pages
- Go to Settings > Pages inside your repository
- Under "Build and Deployment":
- Choose:
Deploy from branch - Branch:
mainormaster - Under Custom domain:
- Enter
yourdomain.com - Ignore any warning
- Enable ✅ Enforce HTTPS
It may take a few minutes for the certificate to be issued.

🔍 6. Configure Nostr Client
Open your Nostr client and set the NIP-05 identifier as:
nostrName@yourdomain.com e.g. meier@meier.techSave – done!
✅ Test
In your browser or via
curl:bash curl https://yourdomain.com/.well-known/nostr.json?name=avrenExpected output:
json { "names": { "Nostr Benutzer": "elkajdlkajslfkjaödlkfjs..." } }
🛡️ Privacy Tips
| Item | Recommendation | |-----------------------------------|----------------------------------| | Public key is visible | Use pseudonyms only | | Register a KYC-free domain | e.g., orangewebsite, njal.la | | Use KYC-free email for GitHub | e.g., ProtonMail | | GitHub repository visibility | Must be public for GitHub Pages | | Commit metadata | Use a separate pseudonymous user | | Avoid tracking | Don’t include analytics scripts |
-
 @ 9223d2fa:b57e3de7
2025-05-07 18:55:00
@ 9223d2fa:b57e3de7
2025-05-07 18:55:0012,923 steps
-
 @ a5ee4475:2ca75401
2025-05-07 17:32:28
@ a5ee4475:2ca75401
2025-05-07 17:32:28lista #descentralismo #compilado #portugues
*Algumas destas listas ainda estão sendo trocadas, portanto as versões mais recentes delas só estão visíveis no Amethyst por causa da ferramenta de edição.
Clients do Nostr e Outras Coisas
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
Modelos de IA e Ferramentas
nostr:nevent1qqsxdpwadkswdrc602m6qdhyq7n33lf3wpjtdjq2adkw4y3h38mjcrqpr9mhxue69uhkxmmzwfskvatdvyhxxmmd9aex2mrp0ypzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqqqqysn06gs
Iniciativas de Bitcoin
(países de língua portuguêsa) nostr:nevent1qqsqnmtverj2fetqwhsv9n2ny8h9ujhyqqrk0fsn4a02w8sf4cqddzqpzpmhxue69uhkummnw3ezumt0d5hsyg99aez8269zxu3zd4j8qya92fg7437ax745pqz22ys6v08zef65qypsgqqqqqqsekd7y0
Profissionais Brasileiros no Nostr
nostr:nevent1qqsvqnlx7sqeczv5r7pmmd6zzca3l0ru4856n3j7lhjfv3atq40lfdcpr9mhxue69uhkxmmzwfskvatdvyhxxmmd9aex2mrp0ypzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqqqqylf6kr4
Comunidades em Português no Nostr
nostr:naddr1qq2hwcejv4ykgdf3v9gxykrxfdqk753jxcc4gqg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4gu455fm3
Grupos em Português no Nostr
nostr:nevent1qqs98kldepjmlxngupsyth40n0h5lw7z5ut5w4scvh27alc0w86tevcpzpmhxue69uhkummnw3ezumt0d5hsygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqqqqs3ndneh
Jogos de Código Aberto
Open Source Games nostr:nevent1qqs0swpxdqfknups697205qg5mpw2e370g5vet07gkexe9n0k05h5qspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsyg99aez8269zxu3zd4j8qya92fg7437ax745pqz22ys6v08zef65qypsgqqqqqqshr37wh
Formatação de Texto em Markdown
(Amethyst, Yakihone e outros) nostr:nevent1qqs0vquevt0pe9h5a2dh8csufdksazp6czz3vjk3wfspp68uqdez00cprpmhxue69uhkummnw3ezuendwsh8w6t69e3xj730qgs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgrqsqqqqqpd658r3
Outros Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78
-
 @ 0e29efc2:ff142af2
2025-05-07 15:09:46
@ 0e29efc2:ff142af2
2025-05-07 15:09:46Table of Contents
- Intro
- Important Terminology
- Getting Started
- Where do I buy bitcoin?
- Okay, I bought some bitcoin-now what?
- Less than 0.01 BTC
- More than 0.01 BTC and less than 0.1 BTC
- More than 0.1 BTC
- How Bitcoin Works
- Skepticism
- Someone will hack it
- The government will try to stop it
- It’s not backed by anything
- Conclusion
Intro
Maybe you saw an article in Forbes, a news segment about MicroStrategy (MSTR), or you glanced at the bitcoin price chart; whatever the spark, your curiosity led you here. Enough friends and relatives keep asking me about bitcoin that I finally organized my thoughts into a single reference. This is not a comprehensive guide—it assumes you trust me as a heuristic.
Important Terminology
Sat (satoshi) – the smallest unit of bitcoin. One bitcoin (₿) equals 100 000 000 sats.
Getting Started
Where do I buy bitcoin?
I use River because it publishes proof‑of‑reserves, supports the Lightning Network, and pays interest on idle USD balances (currently 3.8 %).
Okay, I bought some bitcoin-now what?
Withdraw it immediately. Centralized exchanges can and do fail. Your next step depends on how much bitcoin you hold.
If at any point you're struggling, please reach out to me.
Less than 0.01 BTC
- On your phone open Safari (iOS) or Chrome (Android).
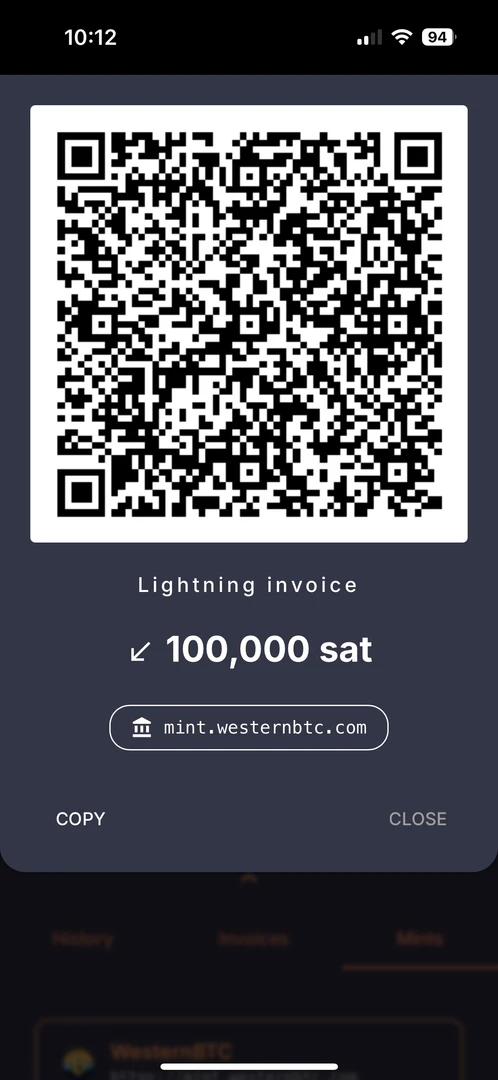
- Paste
https://wallet.cashu.me?mint=https://mint.westernbtc.com. Confirm the prompt that asks whether you trusthttps://mint.westernbtc.com. I run this mint so beginners can skip the gnarly parts. - Complete setup.
- Tap Receive → LIGHTNING → enter amount → COPY.
- In River choose Send → Send to a Bitcoin wallet, paste the invoice, verify, and send.
- Return to the wallet; your sats should appear.
More than 0.01 BTC and less than 0.1 BTC
It's time for cold storage. Cold storage means a dedicated signing device not connected to the internet. Think of it like keys to a house. If you have the keys (your cold storage signing device), you can get into your house (the bitcoin). I recommend and use the COLDCARD Q or COLDCARD MK4 from COLDCARD. See this thorough walkthrough.
The creator nostr:npub1rxysxnjkhrmqd3ey73dp9n5y5yvyzcs64acc9g0k2epcpwwyya4spvhnp8 makes reliable content.
More than 0.1 BTC
The next security upgrade involves something called multisig. It requires the use of multiple devices instead of one. Think of those nuclear launch silos in movies where two keys need to be turned in order to launch the missile. One person can't reach both keys, so you need two people. Like the two keys needing to be turned, we need a certain number of keys (signing devices) to be used.

This offers a number of benefits. Say you have a 2-of-3 multisig setup. You would need two of the three keys to move the bitcoin. If you were to lose one, you could use the two others to move it instead. Many choose to geographically distribute the keys; choosing to keep one at a friend’s house or with a bank.
The previous video I linked covers multisig as well. Again, please reach out to me if you need help.
How Bitcoin Works
I'm going to paint a scene portraying the basics of how bitcoin works. Picture a race that's supposed to take 10 minutes to run start-to-finish, and there's a crowd of people spectating. When the fastest runner crosses the finish line, they're awarded 50 bitcoin. Everyone in the crowd recognizes who won, and writes it down on their own scoreboard. Then, the next race begins.
Now, let's say more racers who've had special training join. They start winning consistently because of it, and now the race only lasts about 9 minutes. There's a special rule everyone in the crowd agreed to, that they can make the race harder to ensure it's around 10 minutes long. So they make the race harder to counteract the faster runners.

With this in mind, let's get to the skepticism you might have.
Skepticism
Someone will hack it
Think of bitcoin as the people in the crowd. If someone tries to cheat and writes on their scoreboard that they have a billion bitcoin, their scoreboard is going to look different than everybody else’s. The other people in the crowd will cross-reference with each other and decide to ignore that person who cheated.
The government will try to stop it
Again, think of the crowd. In reality, the "crowd participants" are scattered all around the world. You might be able to stop many of them, but it would be almost impossible to stop everyone. Imagine people are watching the race on TV, can you find everyone who's spectating? Ironically, attempted bans often increase interest.
It’s not backed by anything.
Think of the runners. The runners are bitcoin miners. They have to expend real energy to participate in the race. The more bitcoin miners, the more secure the network. In summary, it's backed by electricity and work.
Conclusion
There are too many topics to cover in one article. I haven't even touched on the history of money, what money is, scarcity, etc. The best way to learn is to research the topics you're interested in for yourself. It took months of deep diving before I was sold on bitcoin, and I had many touch points before that.
Once you see it though, you can't unsee it.
-
 @ bbef5093:71228592
2025-05-07 15:09:39
@ bbef5093:71228592
2025-05-07 15:09:39Az Európai Bizottság terve az orosz urán- és energiafüggőség felszámolására
Az Európai Bizottság bejelentette, hogy korlátozni kívánja az új urán-, dúsított urán- és egyéb, Oroszországból származó nukleáris anyagokra vonatkozó ellátási szerződéseket, ezzel is elősegítve, hogy az Európai Unió „teljesen megszüntesse” az orosz energiától való függését[8][6][2].
A Bizottság új ütemtervet mutatott be, amely részletesen tartalmazza, hogyan kívánja megszüntetni az orosz energiafüggőséget, miközben biztosítja az EU energiaellátásának és árainak stabilitását[6][2][15].
Főbb intézkedések és célok
- Az EU az orosz gázimport arányát 45%-ról 19%-ra csökkentette a 2022 májusában indított REPowerEU tervnek köszönhetően, de 2024-ben ismét növekedett az orosz gáz behozatala[2][20].
- Az új ütemterv szerint az orosz olaj, gáz és nukleáris energia fokozatosan, összehangoltan és biztonságosan kerül ki az uniós piacokról, miközben az EU a tiszta energiára való átállást gyorsítja fel[6][15][7].
- Az EU-tagállamoknak 2025 végéig nemzeti terveket kell készíteniük arról, hogyan járulnak hozzá az orosz gáz, nukleáris energia és olaj importjának megszüntetéséhez[13][7][18].
- Az orosz eredetű urán, dúsított urán és egyéb nukleáris anyagok esetében új korlátozásokat vezetnek be: az Euratom Ellátási Ügynökség (ESA) nem hagy jóvá új orosz beszállítási szerződéseket, és gazdasági eszközökkel is igyekeznek visszaszorítani az importot[4][5][16].
- A meglévő rövid távú szerződéseket 2025 végéig meg kell szüntetni, új szerződéseket pedig nem lehet kötni; a hosszú távú szerződéseket 2027 végéig kell felmondani[5][7][6].
- Az intézkedések célja, hogy a teljes orosz gáz- és olajimport 2027 végéig megszűnjön, az orosz atomenergia pedig fokozatosan kivezetésre kerüljön[3][9][17].
Nukleáris háttér
- Az ESA jelentése szerint 2023-ban az EU-ban felhasznált természetes urán 23,4%-a érkezett Oroszországból, ami 72,6%-os növekedést jelentett, főként a VVER típusú orosz atomerőművek üzemanyag-felhalmozása miatt[16].
- Az EU-ban 19 VVER reaktor működik (Bulgáriában, Csehországban, Finnországban, Magyarországon és Szlovákiában).
- Az EU természetes uránszükséglete a globális igények mintegy 22%-át teszi ki, a beszerzések 91%-a Kanadából, Oroszországból, Kazahsztánból és Nigerből származik[16].
Célkitűzés és indoklás
A Bizottság szerint az orosz energiafüggőség felszámolása nemcsak gazdasági, hanem biztonságpolitikai kérdés is, mivel Oroszország többször is eszközként használta az energiát az EU-val szemben[2][12]. A lépések célja, hogy az EU energiaellátása biztonságos, stabil és kiszámítható maradjon, miközben az orosz energiaimportból származó bevételek ne finanszírozhassák tovább az Ukrajna elleni háborút[6][2][12].
Források alapján készült magyar összefoglaló és fordítás
Citations: [1] Döntött az Európai Bizottság: teljes mértékben megszüntetik ... - 444 https://444.hu/2025/05/06/dontott-az-europai-bizottsag-teljes-mertekben-megszuntetik-az-orosz-energiatol-valo-fuggest [2] Három éven belül felszámolná az orosz energiafüggőséget az ... https://hu.euronews.com/my-europe/2025/05/06/harom-even-belul-felszamolna-az-orosz-energiafuggoseget-az-europai-bizottsag [3] 2027-re teljesen leállítaná az Európai Bizottság az orosz ... - Új Szó https://ujszo.com/kozelet/2027-re-teljesen-leallitana-az-europai-bizottsag-az-orosz-energiabehozatalt-a-nuklearis [4] Bejelentették Brüsszelben: megkerülik Magyarországot, teljesen ... https://www.portfolio.hu/gazdasag/20250506/bejelentettek-brusszelben-megkerulik-magyarorszagot-teljesen-levalik-az-orosz-olajrol-es-gazrol-az-eu-759267 [5] Érik az újabb ütközés: Brüsszel betiltaná az orosz energiát https://www.valaszonline.hu/2025/05/06/energia-szankcio-oroszorszag-haboru-eu-olaj-gaz-uran/ [6] Az EU teljes mértékben megszünteti az orosz energiától való függését https://hungary.representation.ec.europa.eu/az-eu-teljes-mertekben-megszunteti-az-orosz-energiatol-valo-fuggeset-2025-05-06_hu?prefLang=en [7] Megvan az ütemterv, végleg betiltaná az orosz energiát az Európai ... https://index.hu/kulfold/2025/05/06/orosz-energiafuggoseg-orosz-gaz-olaj-import-europai-unio-repowereu/ [8] European Commission Unveils Plans To Restrict New Uranium ... https://www.nucnet.org/news/european-commission-unveils-plans-to-restrict-new-uranium-deals-with-russia-5-3-2025 [9] Az EU teljes mértékben megszünteti az orosz energiától való ... https://infostart.hu/belfold/2025/05/06/az-eu-teljes-mertekben-megszunteti-az-orosz-energiatol-valo-fuggoseget-a-nap-hirei [10] [PDF] EURÓPAI BIZOTTSÁG Brüsszel, 2025.4.9. COM(2025) 159 final ... https://secure.ipex.eu/IPEXL-WEB/download/file/082d29089612ec1e019619f955940250 [11] Kiszivárgott az Európai Bizottság 2025-ös munkaprogramja https://www.eu-monitor.hu/hu/cikk/20250206-kiszivargott-az-europai-bizottsag-2025-os-munkaprogramja [12] EU says it will end dependency on Russian energy supplies https://www3.nhk.or.jp/nhkworld/en/news/20250507_B4/ [13] Végleg leválik az orosz energiáról az Európai Unió ... - Népszava https://nepszava.hu/3278673_oroszorszag-europai-unio-foldgaz-koolaj-levalas-terv [14] Egyre több európai ország támogatja az atomenergiát https://www.vg.hu/nemzetkozi-gazdasag/2025/03/atomenergia-energiatarolas-europa [15] Az EU teljes mértékben megszünteti az orosz energiától való ... https://karpatinfo.net/energiafuggetlenseg-orosz-foldgaz-orosz-energiafuggoseg-2025-05-07 [16] EU outlines measures to end Russian gas, oil imports by end-2027 https://balkangreenenergynews.com/eu-outlines-measures-to-end-russian-gas-oil-imports-by-end-2027/ [17] Az Európai Unió 2027 végére betiltaná az orosz gáz importját https://www.korkep.sk/cikkek/gazdasag/2025/05/05/az-europai-unio-2027-vegere-betiltana-az-orosz-gazimportot/ [18] Ficónak és Orbánnak sem tetszik, hogy az EU teljesen kitiltaná az ... https://napunk.dennikn.sk/hu/4623240/ficonak-es-orbannak-sem-tetszik-hogy-az-eu-teljesen-kitiltana-az-orosz-energiat/ [19] Várhelyi Olivér késlelteti az EU orosz energiafüggőségét felszámoló ... https://telex.hu/kulfold/2025/05/05/varhelyi-oliver-europai-bizottsag-orosz-energia-kivaltas-hatraltatas [20] REPowerEU roadmap - Energy - European Commission https://energy.ec.europa.eu/strategy/repowereu-roadmap_en
-
 @ 83279ad2:bd49240d
2025-05-07 14:20:50
@ 83279ad2:bd49240d
2025-05-07 14:20:50 -
 @ 005bc4de:ef11e1a2
2025-05-07 14:19:15
@ 005bc4de:ef11e1a2
2025-05-07 14:19:15The beautiful evil of horse racing

Horse racing intrigues me. And, it appalls me. I find it to be both gloriously beautiful and brutally cruel.
One of the fun facts shared tirelessly around social media for Kentucky Derby #151 was something like this: "This is the first Derby where every horse is in the bloodline of Secretariat." Secretariat, if you don't know, won the Triple Crown in 1973 (KY Derby, Preakness, Belmont) and still holds the fastest times in all three of those races.
That's really a nice fun fact when you first hear it, but maybe it shouldn't be too surprising. After a successful racing career, a male racehorse "retires" to a life of studding himself out, which is where the real horse money is. His post-racing stats: he bred 60 mares per year, he sired 660 foals, and he earned an estimated $120 million in stud fees. When you start branching out the Secretariat family tree over several generations, well, the sheer numbers must be very large. That means the chances that any given Thoroughbred might have a hint of Secretariat blood must get rather high. Grok AI estimates there are 500,000 Thoroughbreds today worldwide, and that beteen 250,000 to 400,000 are in Secretariat's lineage, that's 50% to 80% of every Thoroughbred. Suddenly, the social media snippet from Derby #151 is less surprising, less cool.

Secretariat, retired from racing.
The beautiful side of horse racing
Horse racing is beautiful. This is the easy part to write. If you've ever been to a horse track, especially on a big race day, it's a true multi-sensory experience.
- There are smells that we typically don't smell often in this modern world...especially if you hang out near the paddock. Personally, I don't find horse dung particularly stinky, but earthy.
- There are tastes and good smells. Food and drink are a huge part of horse racing. There is a reason that the Derby has its own pie (a chocolate pecan pie) and each major race has its own drink. Feasting and tailgating are huge parts of horse racing.
- There are things to feel, actually to bodily feel. Aside from crowds of people to bump into, if you stand close to the track, you can feel the reverberation of hooves beating the dirt. We hear the term "thundering herd" sometimes in college sports, but, that term is not just words. You can actually feel the thunder of those hooves.
- The sounds are distinctly horse racing. The announcer's calls of "Less than a minute," "They're in the gates," and "And they're off!" are iconic, not to mention the terms "down to the wire," "won by a nose," or "photo finish." And then there's the bugle's announcement, the singing of "My Old Kentucky Home" at the Derby, the roar of the crowd, and moans of loss from bad bets, shrieks of joy from good bets, and that thunder from the herd, of course.
- The visuals are just stunning. People-wise, the women in their pastel sundresses, the men are snazzy in their colors too (though some go too over-the-top for my liking; they move from classy to clownish), and then there are the hats which are their own category altogether. There's the track, and the spires, and the grass and dirt (or mud) and roses. And there's the jockeys and their colorful silks. But, mostly, there's the horses. A Thoroughbred racehorse at full speed, in full stride, is incredible to look upon. It is a beast that is entirely built for one pure reason: speed. You might be familiar with ESPN's "The Body Issue" that features elite, pro athletes in the nude so that their incredible physiques are displayed. Horse racing is the same thing, equine style. The Derby, in particular, is a sports photographer's bonanza. If you actually know what you're doing, you can't not get great results. Below are some photos amateur me point-and-clicked on Derby Day at a horse track (not Churchill Downs):
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/Eq7LSG39v5H5NpQppxhzwhfAtJVQikYVppRJsgZXh6KxGXU2YochRXqoJaW7NMZ8Yd8.jpg]
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/23wWw7ZbXPJxKFAyLwuraK1QypVcLV6QpsyG6Ccr6ZLiPYgNtUBa3ALWx1XR4wPYayhmT.png]
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/2432HqW3ZtUCjvGD7WTkg2z2ngoByX2rV6htgENN1eytUYXycRCaQdevL7xn1mdKC8qG8.gif]
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/245HijMM8pQ7c2EdJwrzUPa3LDjm1P51WqU6j5mYkAJnAXJrkbAn6XBNCzR7G28MSR62u.png]
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/EpVAhnScSoAVCYvw2Faf7ZyipskYLvu9MuBXzmHN3jdVPoDBVAVR8yqrrGf1c7Apxzb.jpg]
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/245Hm6k5HafqiMfzUiNK7Z3pUG752f4CmLc5pMVuonkQVY1sKG9ucSrdGgvNVQGNud628.gif]
Horse racing appeals to all senses and is viscerally exhilarating in so many ways. It is beautiful.
Genetics
But, let's get back to the real point: this game is all about Brave New World-like breeding and genetics. It is horse eugenics. The idea is simple: fast Mommy horse and fast Daddy horse means fast baby horse. In horse racing, a horse's blood lineage is called its dosage. Personally, I pay zero attention to dosage (I focus on track length and closing the long races), but dosage is a mathematical stat that tries to answer, "How much is this horse truly a Thoroughbred and a genetic winner?" This question of dosage begs another question, "What actually is a Thoroughbred?"
A Thoroughbred is a horse breed. There are a lot of horse breeds, a lot. For a novice like me, it's very hard to distinguish one from another. I think most people can see a difference between a draft horse, bred for pulling heavy loads, and a Thoroughbred, bred for speed. I think most people, if betting on a foot race, would bet on the Thoroughbred below, left and not on "Jupiter, the largest draft horse in America" on the right. If betting on hauling a wagon load of beer up a steep hill, most would bet Jupiter.
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/23yx8AjtVZkpE7jXJ2RXzV78hhXSvsgU97i2FkvfcFcEZevfshNgwPw2diJNhmL344gmR.png]
But, when comparing racing horses, there are also Sandardbreds which are bred for harness racing and thus have a heavier build than Thoroughbreds. The two breeds are shown below, but their distinctions are not particularly outstanding to my novice eye. Can you tell the difference, which is the Standardbred versus the Thoroughbred? (Answer at the bottom of page.) Maybe side-by-side you can tell, but could you tell if you saw one standing alone? If you saw two of the same breed, could you judge by appearance which one runs faster? If you can, I tip my cap to you.
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/23zbTqFJgYpKyXwxbGsVeQiKv4tTZSj8S8QboTJWEhTETPqjnaUVDtX2BirjBXH5KVNo6.png]
I imagine most people are much more familiar with, and can more readily notice, the differences in dog breeds. For instance, take the French Bulldog, the Greyhound, or the world's best dog breed, the Labrador Retriever (totally unbiased here).
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/244oozGkxAwS4sqoWiT8phQv8ssrqq4caB9bHgDufsogds7scUUfhp54WTKmosDzfL5WT.png]
The French Bulldog is bred for cosmetics, the greyhound for pure speed, and the Labrador for all-around everything...intelligence, sturdy athleticism, loyal companionship (totally unbiased here). In these three dogs, we can clearly see the differences that have resulted from breeding.
The evil side of horse racing
Horse racing is evil. And, it is cruel. But, for now, let's step back to the dogs. Dog breeding can be cruel as well.
The French Bulldog is something of the "it" dog right now. A quick Google Gemini search reported it as the most popular breed in 2025.

I remember when "101 Dalmatians" came out 1996. Dalmatians skyrocketed in popularity. But, that popularity was anything but a blessing for Dalmatian pups. They were overbred (and are too inbred as it is), oversold, and were taken in by people eager to get in on the "it" dog then and scoop up the cute spotted pups. But, Dalmatians are very active pups that grow into very active dogs. When the novelty of the spotted pup wore off, many were returned or given away or taken to shelters as being uncontrollable.
The French Poodle situation is not too different. The dogs were bred for little purpose beyond the sin of human vanity. People wanted a short, stocky, smoosh-faced dog that they perceived as cute. And, that's what they got: an unathletic dog that looked a certain way, with middle-of-the-road intelligence, and little use aside from its appearance.
Worse, seeking out this certain "toy dog" look, French Bulldogs suffer from a plethora of health issues. Summed up, they have the lowest life expectancy "by a large margin" of all dogs at only 4.5 years (average is 11.2. years).
There is a neighbor near to me who breeds French Bulldogs. Evidently, it's a lucrative business as they apparently sell for an estimated $2,000 to $8,000 dollars each. I don't know how many litters the neighbor's have bred and pawned, but it has been several. The breeder bitch is constantly given a little trot outside before being hauled to the vet for insemination. (Sadly, this seems to be about the only time she is taken out for exercise and family "fun.") Considering he and his wife have no real job, this seems to be their job. Breed, advertise (complete with foofy tutu outfit photos), market, sell, repeat. With only a 4.5 year life span, I see the lucrative nature in this business.
All told, it's basically a sin and a shame that humans do this to these dogs. A certain segment of people desire a certain unnatural smooshed face in a dog. And because we vainly want a certain look in a dog, so as to accessorize our own look, we breed them into forms unnatural to a canine, curse them with severe breathing difficulties and other serious health issues, and short lives.
A Greyhound is essentially a canine Thoroughbred. From generations of selective breeding, it has a massive chest, long body with a narrow waist, and long, spindly legs. It's sole purpose is speed. Ironically, both the Thoroughbred and Greyhound can race at about the same speed...44 mph, give or take.
Man's sinful nature has abused the Greyhound too. These hounds are racing dogs and racing means gambling. So, dog tracks for have been common. The pups are bred, they race a few years, then they are hopefully adopted out. A good friend of mine once adopted a retired racer to become the family dog. "Bandit" initially had a post-race job as a business's guard dog. But, due to him constantly doing nothing but laying around and sleeping, he was fired as a guard dog (who gets a Greyhound for a guard dog anyway?). Bandit eventually went to my friend, was a bit neurotic, but turned out to be a good family dog.
I think most Greyhounds don't have the fortunate story of Bandit. Once raced out, they're done and forgotten. Man's thrills are fleeting, whatever sparkles in his eye soon fades. To combat the ills of dog racing, I know that the citizens of Florida voted to outlaw dog racing in 2018 (and it indeed ended Dec. 31, 2020). Now, dog tracks lay rusting away, and Greyhounds are largely forgotten.
And then, there's the Labrador Retriever. What's not to like? These dogs can do it all, and they do it all well. Name a dog task, Labs do that well. Full disclosure: I once had a Lab (or rather, half Lab, and half...Great Dane? Doberman? Something?). Her mother was Lab and my dog looked Lab, though a bit taller and leaner. She was incredible. So, yes, I favor Labs.
But, even my beloved Labs and all that they excel in, even Labs have their issues, such as high rates of hip dysplasia. Selective breeding, and a too-narrow gene pool, have consequences.
Back to horses
Let's try to bring this back to horses. Thoroughbreds and horse racing mirror both of the characteristics seen in the French Bulldog and the Greyhound.
- Thoroughbreds have been, and still are, extremely selectively bred to accentuate certain qualities: speed, speed, speed.
- Thoroughbreds are bred for money. Literally, a champion stud or mare doesn't breed for free.
Regarding speed, Thoroughbreds have a massive muscular chest, almost no waist at all, massive muscular hindquarters, and long, spindly, almost cartoonishly thin legs. And, this built-for-speed physique brings up one of the cruelest aspects of horse racing: Thoroughbreds are prone to "break down."
These horses are structured unnaturally, like aliens. Having such a massive, muscular, powerful architecture stilted on such twig-like legs (and getting more massive and twiggier due to constant selective breeding of these traits) is a recipe for disaster. "Breaking down" in horse terms is a rather correct term. Their leg bones break under the stress and force of running, then the horse's weight and thrust breaks the legs down further.
The name Barabaro might come to memory. Barbaro won the Kentucky Derby in 2006 impressively, by a full 6.5 lengths. Hopes were high for a Triple Crown winner. At the Preakness two weeks later, Barabaro broke down. Actually, in his pre-start excitement he broke through the gate to false start. These animals are bred to run and race, they know when it's race time. He was so jacked up and ready to run while in the starting gate, he bucked up, banged his head hard, then literally broke through the gate to false start. Then, after reentering, he started off the race clean before breaking down in front of the main grandstand of viewers. Horse's can break any of their several leg bones. Barbaro broke the cannon, sesamoid, long pastern, and dislocated the fetlock (ankle joint). In other words, he shattered his leg.
When horses break their legs, they're usually put down. As to why, there are lots of reasons, but it comes down to the fact that horses are built for standing and running, especially Thoroughbreds. They are not built for laying down to recuperate, and actually suffer health consequences for not standing. Understandably, a broken leg causes the horse to favor weight to the other legs while standing and this, in turn, can cause other issues. Altogether, the horse suffers.
In Barbaro's case, they tried to rehab him. I think normally he would have been put down on the track in the equine ambulance (the "meat wagon"), but this was Barbaro. The resources were there, he was beloved, and millions had witnessed his injury live. Not trying to save him would have been a public relations nightmare. Putting him down on live TV would have been even worse. There was surgery, then laminitis (inflammation under the hoof) in his opposite good hoof, the result of standing unnaturally. He rallied, then had more setbacks including laminitis in his front hooves. He was in pain, with no way to stand, and then was euthanized in 2007.
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/23wgoS1v6e2i2gizAqeMeXHf6Zwhz3BTuYMuYNL676tqbPZWwvXUhw7R1J6K4r7DmRj2K.png]
Regarding the money, top studs earn $200 to $400,000 for stud service. A top mare can be bought for $100 to $300,000, then you need the stud service. This is only to breed the foal. This has nothing to do with stabling or training the animals. In other words, it's extremely expensive.
Also regarding the money, there is, of course, the gambling. You might say this is the whole point of horse racing. It's certainly the whole point for breeding Thoroughbreds. It was the whole point for Greyhounds in Florida, before that point was banned.
This year, an estimated $200 million was bet on the Kentucky Derby, the one race alone. $300 million was bet on the races combined. Grok estimated that globally in 2022, horse racing was a $402 billion dollar industry and expects it to grow to $793 billion by 2030.
Those numbers are staggering. But, again, I come back to sinful man. Our love of money is the root of this beautiful evil called horse racing.
I really don't know many scenes more beautiful than a Kentucky horse ranch and a Thoroughbred running across the bluegrass. Add a colt running with his mother, the beauty is staggering. But, underneath that beauty, there is an evil side to horse racing. That side is fueled by sinful man's pride to win and his love of money.
Horse racing is a beautiful evil.


Image sources: https://wikipedia.org, original by me at the track, equine bones at https://www.anatomy-of-the-equine.com/distal-limb-bones.html, the final two images from https://pixabay.com
Note: In the "Can you tell the difference" side-by-side images above, the Thoroughbred was on the left, the Standardbred on the right.
-
 @ 88cc134b:5ae99079
2025-05-07 13:40:50
@ 88cc134b:5ae99079
2025-05-07 13:40:50ddd ccc bbb aaa
-
 @ c3b2802b:4850599c
2025-05-07 11:19:12
@ c3b2802b:4850599c
2025-05-07 11:19:12Heute, am 9. Mai 2025 – genau 80 Jahre nach dem Ende des Zweiten Weltkriegs, der 60 Millionen Menschen das Leben kostete, darunter 27 Millionen Sowjetbürgern, erheben wir, die Bürgerinnen und Bürger Europas, unsere Stimmen! Wir schämen uns für unsere Regierungen und die EU, die die Lehren des 20. Jahrhunderts nicht gelernt haben. Die EU, einst als Friedensprojekt gedacht, wurde pervertiert und hat damit den Wesenskern Europas verraten! Wir, die Bürger Europas, nehmen darum heute, am 9. Mai, unsere Geschicke und unsere Geschichte selbst in die Hand. Wir erklären die EU für gescheitert. Wir beginnen mit Bürger-Diplomatie und verweigern uns dem geplanten Krieg gegen Russland! Wir erkennen die Mitverantwortung des „Westens“, der europäischen Regierungen und der EU an diesem Konflikt an.
Wir, die Bürger Europas, treten mit dem European Peace Project der schamlosen Heuchlerei und den Lügen entgegen, die heute – am Europatag – auf offiziellen Festakten und in öffentlichen Sendern verbreitet werden.
Wir strecken den Bürgerinnen und Bürgern der Ukraine und Russlands die Hand aus. Ihr gehört zur europäischen Familie, und wir sind überzeugt, dass wir gemeinsam ein friedliches Zusammenleben auf unserem Kontinent organisieren können.
Wir haben die Bilder der Soldatenfriedhöfe vor Augen – von Wolgograd über Riga bis Lothringen. Wir sehen die frischen Gräber, die dieser sinnlose Krieg in der Ukraine und in Russland hinterlassen hat. Während die meisten EU-Regierungen und Verantwortlichen für den Krieg hetzen und verdrängen, was Krieg für die Bevölkerung bedeutet, haben wir die Lektion des letzten Jahrhunderts gelernt: Europa heißt „Nie wieder Krieg!“
Wir erinnern uns an die europäischen Aufbauleistungen des letzten Jahrhunderts und an die Versprechen von 1989 nach der friedlichen Revolution. Wir fordern ein europäisch-russisches Jugendwerk nach dem Vorbild des deutsch-französischen Jugendwerks von 1963, das die „Erbfeindschaft“ zwischen Deutschland und Frankreich beendet hat. Wir fordern ein Ende der Sanktionen und den Wiederaufbau der Nord Stream II-Pipeline. Wir weigern uns, unsere Steuergelder für Rüstung und Militarisierung zu verschwenden, auf Kosten von Sozialstandards und Infrastruktur. Im Rahmen einer OSZE-Friedenskonferenz fordern wir die Schaffung einer europäischen Sicherheitsarchitektur mit und nicht gegen Russland, wie in der Charta von Paris von 1990 festgelegt. Wir fordern ein neutrales, von den USA emanzipiertes Europa, das eine vermittelnde Rolle in einer multipolaren Welt einnimmt. Unser Europa ist post-kolonial und post-imperial.
Wir, die Bürger Europas, erklären diesen Krieg hiermit für beendet! Wir machen bei den Kriegsspielen nicht mit. Wir machen aus unseren Männern und Söhnen keine Soldaten, aus unseren Töchtern keine Schwestern im Lazarett und aus unseren Ländern keine Schlachtfelder.
Wir bieten an, sofort eine Abordnung europäischer Bürgerinnen und Bürger nach Kiew und Moskau zu entsenden, um den Dialog zu beginnen. Wir werden nicht länger zusehen, wie unsere Zukunft und die unserer Kinder auf dem Altar der Machtpolitik geopfert wird.
Es lebe Europa, es lebe der Friede, es lebe die Freiheit
Auf der Webseite der Initiative können Sie, liebe Leser, weitere Möglichkeiten erfahren, diese Friedensinitiative zu stärken! Danke an die IntiatorInnen und die bislang 15.000 Menschen, die das mitgestalten werden.
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ 7e538978:a5987ab6
2025-05-07 10:25:30
@ 7e538978:a5987ab6
2025-05-07 10:25:30Across Switzerland, customers at SPAR supermarkets are now able to pay for their groceries using Lightning on Bitcoin — a step towards everyday Bitcoin adoption. This rollout was led by DFX, a Bitcoin services company focused on onboarding businesses and individuals to Bitcoin. Behind the scenes LNbits plays a key role.
 ## Lightning at the Checkout
## Lightning at the CheckoutSPAR’s approach is simple: at the till, customers can scan a static QR code to pay in Bitcoin using the Lightning Network. Each checkout in each participating store has its own unique LNURL address — a reusable QR code designed for fast, low-friction Lightning payments.
To manage these LNURLs, DFX leverages LNbits. Using the LNbits Pay Links extension, DFX generates LNURLs for each till across the network of participating SPAR locations. The result is a robust, reliable setup that works at scale. Store staff do not interact with LNbits directly — instead, DFX manages the backend, ensuring each till has a dedicated LNURL without operational overhead for SPAR employees.
At SPAR we use static QR codes that meet the LNURL standard. Therefore we use LNbits. Each checkout has its own personal LNURL address which we generate with LNbits.
— Cyrill Thommen, CEO of DFX.Swiss— Cyrill Thommen, CEO of DFX.Swiss
 ## LNbits in Action
## LNbits in ActionLNbits provided DFX with a modular, open-source solution that allows them to build only what they need, without locking into a rigid platform. For instance, DFX built custom monitoring around payment events using the LNbits API, while keeping full control over wallet infrastructure.
The ability to generate and manage LNURLs through the LNbits API, while layering additional monitoring and business logic on top, made LNbits a practical choice.
DFX’s setup highlights how open source software, Bitcoin and purpose-built tools can underpin enterprise-grade deployments. The system works reliably — without introducing friction for customers or staff.
Bitcoin in the Real World
Switzerland is already one of Europe’s most Bitcoin-friendly environments, with over 1,000 businesses accepting Bitcoin. But SPAR’s implementation is noteworthy for its scale and practicality: everyday purchases, completed with Bitcoin, at a national supermarket chain.
LNbits' flexible architecture, API-first design, and plug-in system make it well suited to precisely this kind of adoption.
As more retailers explore Lightning integration, SPAR’s rollout sets a precedent — showing how modular, open-source tools like LNbits can bring Bitcoin into daily life, seamlessly.

-
 @ 9063ef6b:fd1e9a09
2025-05-07 07:16:54
@ 9063ef6b:fd1e9a09
2025-05-07 07:16:54🛠️ MkDocs on macOS
For my local documentation, I was looking for an open-source tool to create and manage my content. With MkDocs, I found a mature, widely used, and actively maintained solution.
I think this tool is worth writing an article about. I’m still new to it and don’t have much experience yet. What tools do you use to create your documentation locally?
📚 What is MkDocs?
MkDocs is an open source tool for building static websites from Markdown files, designed specifically for technical documentation.

✅ Key Features
| Feature | Description | |---------------------------|----------------------------------------------------------------------------| | 📄 Markdown-based | Write content in
.mdfiles (e.g., with Zettlr, VS Code, Obsidian) | | 🌐 Static site output | MkDocs renders a full HTML site with navigation, search, and styling | | 🎨 Themes available | Most popular: Material for MkDocs | | 🔄 Live preview | Usemkdocs serveto view the docs locally in your browser | | 🔧 Simple configuration | Controlled via a singlemkdocs.ymlfile | | 🔐 No cloud required | Fully local, ideal for privacy and offline work |
📦 Is MkDocs open source?
Yes. MkDocs is fully open source and licensed under the MIT License – free to use, modify, and redistribute.
- 🔗 GitHub: github.com/mkdocs/mkdocs
- 🔗 PyPI: pypi.org/project/mkdocs
🔧 What can you build with MkDocs?
Examples include:
- Internal IT or team documentation
- Project or API documentation (e.g., GitHub projects)
- Manuals, Wikis, or checklists
- Offline technical knowledge bases
✅ Requirements
- macOS (e.g., Ventura, Sonoma)
- Terminal basics
- Python installed
🔧 Step 1: Install MkDocs
Install MkDocs locally for your user:
bash pip3 install --user mkdocs(Optional) Add the Material theme:
bash pip3 install --user mkdocs-materialThis gives your documentation a modern, responsive design.
🧭 Step 2: Make the
mkdocscommand availableBy default, pip installs MkDocs in a directory not included in your PATH. To fix that:
a) Check install location:
bash python3 -m site --user-baseExample output:
/Users/yourname/Library/Python/3.11The relevant binary path is:
/Users/yourname/Library/Python/3.11/binb) Add to PATH permanently (zsh):
bash echo 'export PATH=$PATH:/Users/yourname/Library/Python/3.11/bin' >> ~/.zshrc source ~/.zshrcReplace Python version if needed (
3.11).
🚀 Step 3: Start a new MkDocs project
bash mkdocs new my-docs cd my-docs mkdocs serveNow open: http://127.0.0.1:8000
🎨 Step 4: Enable the Material Theme
Edit
mkdocs.yml:yaml theme: name: materialThen restart:
bash mkdocs serve
🧩 Alternative: Run via Python module
If you see this error:
zsh: command not found: mkdocs… you can always run MkDocs via:
bash python3 -m mkdocs serve
📚 MkDocs Awesome Pages Plugin
The
awesome-pagesplugin for MkDocs automatically builds navigation from your folder structure – no need to manually definenav:inmkdocs.yml.
✅ Open Source
- License: MIT
- Repo: github.com/lukasgeiter/mkdocs-awesome-pages-plugin
🛠️ Installation
Install with pip:
bash pip3 install mkdocs-awesome-pages-plugin
⚙️ Configure
mkdocs.ymlAdd the plugin:
yaml plugins: - search - awesome-pages⚠️ Remove the
nav:section if you use this plugin – it will otherwise be ignored.
📁 Folder structure &
.pagesfilesNavigation is based on the folder structure under
docs/.Example structure:
docs/ ├── index.md ├── installation/ │ ├── prerequisites.md │ └── setup.md ├── usage/ │ ├── start.md │ └── features.md→ The plugin auto-generates a menu from this.
🔍 Example
mkdocs.ymlwith plugin```yaml site_name: My Tech Docs theme: name: material
plugins: - search - awesome-pages
markdown_extensions: - admonition - toc: permalink: true ```
🔗 Further Resources
- 📘 GitHub: mkdocs-awesome-pages-plugin
- 📘 PyPI: pypi.org/project/mkdocs-awesome-pages-plugin
-
 @ 38d2a406:ad9e5329
2025-05-07 02:13:46
@ 38d2a406:ad9e5329
2025-05-07 02:13:46{"contract_id":"f5523a8f242339bdd8585e5491a82c2d9a72ff51f7fadc3f7c6f766afe9c0f19","title":"T2- Freelance Development Agreement","content":"# Freelance Development Agreement\n\n## Parties\n\nThis Freelance Development Agreement (the \"Agreement\") is entered into as of [DATE] by and between:\n\nClient: [CLIENT NAME], with an address at [CLIENT ADDRESS] (\"Client\")\n\nDeveloper: [DEVELOPER NAME], with an address at [DEVELOPER ADDRESS] (\"Developer\")\n\n## Services\n\nDeveloper agrees to provide the following services to Client (the \"Services\"):\n\n1. Design and develop a web application according to the specifications outlined in Attachment A.\n2. Provide regular progress updates on a weekly basis.\n3. Deliver the completed project by the deadline specified in the Timeline section.","version":1,"created_at":1746583812,"signers_required":2,"signatures":[{"pubkey":"306555fee4433582b32f6d46f11b644da33896595016893d7da18c75fd7fdf12","sig":"8ad3a9e2a4ef70515853e051882ab11ebc7d56f15be46deb1520d6292711bc4eeb29c723c46a251c98134d06b8950931d19f61f6f8836e4932f0d6682fe8159e","timestamp":1746583928},{"pubkey":"38d2a406f9ae6eebbeee9d35276c45538ed80083c859b28601279187ad9e5329","sig":"ef4802ea6966318774cb8554ed547692691d143cef48bc1049ef43546b77b3720908ec4e77e151117bafb676b96653cb5fcc70658116e96759d3a2a52ffd94da","timestamp":1746584026}]}
-
 @ 306555fe:fd7fdf12
2025-05-07 02:12:08
@ 306555fe:fd7fdf12
2025-05-07 02:12:08{"contract_id":"f5523a8f242339bdd8585e5491a82c2d9a72ff51f7fadc3f7c6f766afe9c0f19","title":"T2- Freelance Development Agreement","content":"# Freelance Development Agreement\n\n## Parties\n\nThis Freelance Development Agreement (the \"Agreement\") is entered into as of [DATE] by and between:\n\nClient: [CLIENT NAME], with an address at [CLIENT ADDRESS] (\"Client\")\n\nDeveloper: [DEVELOPER NAME], with an address at [DEVELOPER ADDRESS] (\"Developer\")\n\n## Services\n\nDeveloper agrees to provide the following services to Client (the \"Services\"):\n\n1. Design and develop a web application according to the specifications outlined in Attachment A.\n2. Provide regular progress updates on a weekly basis.\n3. Deliver the completed project by the deadline specified in the Timeline section.","version":1,"created_at":1746583812,"signers_required":2,"signatures":[{"pubkey":"306555fee4433582b32f6d46f11b644da33896595016893d7da18c75fd7fdf12","sig":"8ad3a9e2a4ef70515853e051882ab11ebc7d56f15be46deb1520d6292711bc4eeb29c723c46a251c98134d06b8950931d19f61f6f8836e4932f0d6682fe8159e","timestamp":1746583928}]}
-
 @ a9e24cc2:597d8933
2025-05-07 01:06:44
@ a9e24cc2:597d8933
2025-05-07 01:06:44𝐌𝐄𝐒𝐒𝐀𝐆𝐄 BlackHat_Nexus 𝐅𝐎𝐑 𝐀𝐍𝐘 𝐊𝐈𝐍𝐃 𝐎𝐅 𝐒𝐄𝐑𝐕𝐈𝐂𝐄 𝐑𝐄𝐂𝐎𝐕𝐄𝐑 𝐘𝐎𝐔𝐑 𝐀𝐂𝐂𝐎𝐔𝐍𝐓Fast, Available and Reliable for any of the following services 🤳 Recovery of lost funds🤳 Facebook Hack🤳 WhatsApp Hack 🤳 Instagram Hack🤳 Spying🤳 Windows Hacking🤳 Recover lost wallet 🤳 Credit score trick 🤳 Recover Password🤳 Gmail Hack🤳 SnapChat Hacking 🤳 Cellphone Monitoring 🤳 Tik Tok Hack🤳 Twitter Hack🤳 Lost Phone Tracking🤳 Lost IaptopTracking🤳 Lost Car Tracking🤳 Cloning WhatsApp🤳 Cryptocurrency Wallet🤳 Hacking🤳 Iphone unlock 🤳 Got banned 🤳 Private Number available🤳 Telegram hacking 🤳 Websites hacking 🤳 Hack University 🤳 IOS and Android hack 🤳 Wifi Hacking 🤳 CCTV hacking🤳 Hack Bot Game 🤳 Free fire hack 🤳 Changing of school grades 🤳 Cards 💳hackingNo 🆓 services 🚫WhatsApp +1 3606068592Send a DM https://t.me/BlackHat_Nexus@BlackHat_Nexus
-
 @ 000002de:c05780a7
2025-05-06 20:24:08
@ 000002de:c05780a7
2025-05-06 20:24:08https://www.youtube.com/watch?v=CIMZH7DEPPQ
I really enjoy listening to non-technical people talk about technology when they get the bigger picture impacts and how it relates to our humanity.
I was reminded of this video by @k00b's post about an AI generated video of a victim forgiving his killer.
Piper says, "Computers are better at words than you. Than I". But they are machines. They cannot feel. They cannot have emotion.
This people honors me with their lips, but their heart is far from me
~ Matthew 15:8
Most of us hate it when people are fake with us. When they say things they don't mean. When they say things just to get something they want from us. Yet, we are quickly falling into this same trap with technology. Accepting it as real and human. I'm not suggesting we can't use technology but we have to be careful that we do not fall into this mechanical trap and forget what makes humans special.
We are emotional and spiritual beings. Though AI didn't exist during the times Jesus walked the earth read the verse above in a broader context.
Then Pharisees and scribes came to Jesus from Jerusalem and said, “Why do your disciples break the tradition of the elders? For they do not wash their hands when they eat.” He answered them, “And why do you break the commandment of God for the sake of your tradition? For God commanded, ‘Honor your father and your mother,’ and, ‘Whoever reviles father or mother must surely die.’ But you say, ‘If anyone tells his father or his mother, “What you would have gained from me is given to God,” he need not honor his father.’ So for the sake of your tradition you have made void the word of God. You hypocrites! Well did Isaiah prophesy of you, when he said:
“‘This people honors me with their lips,
but their heart is far from me;
in vain do they worship me,
teaching as doctrines the commandments of men.’”
Empty words. Words without meaning because they are not from a pure desire and love. You may not be a Christian but don't miss the significance of this. There is a value in being real. Sharing true emotion and heart. Don't fall into the trap of the culture of lies that surrounds us. I would rather hear true words with mistakes and less eloquence any day over something fake. I would rather share a real moment with the ones I love than a million fake moments. Embrace the messy imperfect but real world.
originally posted at https://stacker.news/items/973324
-
 @ b6dcdddf:dfee5ee7
2025-05-06 15:58:23
@ b6dcdddf:dfee5ee7
2025-05-06 15:58:23You can now fund projects on Geyser using Credit Cards, Apple Pay, Bank Transfers, and more.
The best part: 🧾 You pay in fiat and ⚡️ the creator receives Bitcoin.
You heard it right! Let's dive in 👇
First, how does it work? For contributors, it's easy! Once the project creator has verified their identity, anyone can contribute with fiat methods. Simply go through the usual contribution flow and select 'Pay with Fiat'. The first contribution is KYC-free.
Why does this matter? 1. Many Bitcoiners don't want to spend their Bitcoin: 👉 Number go up (NgU) 👉 Capital gains taxes With fiat contributions, there's no more excuse to contribute towards Bitcoin builders and creators! 2. Non-bitcoin holders want to support projects too. If someone loves your mission but only has a debit card, they used to be stuck. Now? They can back your Bitcoin project with familiar fiat tools. Now, they can do it all through Geyser!
So, why swap fiat into Bitcoin? Because Bitcoin is borderless. Fiat payouts are limited to certain countries, banks, and red tape. By auto-swapping fiat to Bitcoin, we ensure: 🌍 Instant payouts to creators all around the world ⚡️ No delays or restrictions 💥 Every contribution is also a silent Bitcoin buy
How to enable Fiat contributions If you’re a creator, it’s easy: - Go to your Dashboard → Wallet - Click “Enable Fiat Contributions” - Complete a quick ID verification (required by our payment provider) ✅ That’s it — your project is now open to global fiat supporters.
Supporting Bitcoin adoption At Geyser, our mission is to empower Bitcoin creators and builders. Adding fiat options amplifies our mission. It brings more people into the ecosystem while staying true to what we believe: ⚒️ Build on Bitcoin 🌱 Fund impactful initiatives 🌎 Enable global participation
**Support projects with fiat now! ** We've compiled a list of projects that currently have fiat contributions enabled. If you've been on the fence to support them because you didn't want to spend your Bitcoin, now's the time to do your first contribution!
Education - Citadel Dispatch: https://geyser.fund/project/citadel - @FREEMadeiraOrg: https://geyser.fund/project/freemadeira - @MyfirstBitcoin_: https://geyser.fund/project/miprimerbitcoin
Circular Economies - @BitcoinEkasi: https://geyser.fund/project/bitcoinekasi - Madagascar Bitcoin: https://geyser.fund/project/madagasbit - @BitcoinChatt : https://geyser.fund/project/bitcoinchatt - Uganda Gayaza BTC Market: https://geyser.fund/project/gayazabtcmarket
Activism - Education Bitcoin Channel: https://geyser.fund/project/streamingsats
Sports - The Sats Fighter Journey: https://geyser.fund/project/thesatsfighterjourney
Culture - Bitcoin Tarot Cards: https://geyser.fund/project/bitcointarotcard
originally posted at https://stacker.news/items/973003
-
 @ c1e9ab3a:9cb56b43
2025-05-06 14:05:40
@ c1e9ab3a:9cb56b43
2025-05-06 14:05:40If you're an engineer stepping into the Bitcoin space from the broader crypto ecosystem, you're probably carrying a mental model shaped by speed, flexibility, and rapid innovation. That makes sense—most blockchain platforms pride themselves on throughput, programmability, and dev agility.
But Bitcoin operates from a different set of first principles. It’s not competing to be the fastest network or the most expressive smart contract platform. It’s aiming to be the most credible, neutral, and globally accessible value layer in human history.
Here’s why that matters—and why Bitcoin is not just an alternative crypto asset, but a structural necessity in the global financial system.
1. Bitcoin Fixes the Triffin Dilemma—Not With Policy, But Protocol
The Triffin Dilemma shows us that any country issuing the global reserve currency must run persistent deficits to supply that currency to the world. That’s not a flaw of bad leadership—it’s an inherent contradiction. The U.S. must debase its own monetary integrity to meet global dollar demand. That’s a self-terminating system.
Bitcoin sidesteps this entirely by being:
- Non-sovereign – no single nation owns it
- Hard-capped – no central authority can inflate it
- Verifiable and neutral – anyone with a full node can enforce the rules
In other words, Bitcoin turns global liquidity into an engineering problem, not a political one. No other system, fiat or crypto, has achieved that.
2. Bitcoin’s “Ossification” Is Intentional—and It's a Feature
From the outside, Bitcoin development may look sluggish. Features are slow to roll out. Code changes are conservative. Consensus rules are treated as sacred.
That’s the point.
When you’re building the global monetary base layer, stability is not a weakness. It’s a prerequisite. Every other financial instrument, app, or protocol that builds on Bitcoin depends on one thing: assurance that the base layer won’t change underneath them without extreme scrutiny.
So-called “ossification” is just another term for predictability and integrity. And when the market does demand change (SegWit, Taproot), Bitcoin’s soft-fork governance process has proven capable of deploying it safely—without coercive central control.
3. Layered Architecture: Throughput Is Not a Base Layer Concern
You don’t scale settlement at the base layer. You build layered systems. Just as TCP/IP doesn't need to carry YouTube traffic directly, Bitcoin doesn’t need to process every microtransaction.
Instead, it anchors:
- Lightning (fast payments)
- Fedimint (community custody)
- Ark (privacy + UTXO compression)
- Statechains, sidechains, and covenants (coming evolution)
All of these inherit Bitcoin’s security and scarcity, while handling volume off-chain, in ways that maintain auditability and self-custody.
4. Universal Assayability Requires Minimalism at the Base Layer
A core design constraint of Bitcoin is that any participant, anywhere in the world, must be able to independently verify the validity of every transaction and block—past and present—without needing permission or relying on third parties.
This property is called assayability—the ability to “test” or verify the authenticity and integrity of received bitcoin, much like verifying the weight and purity of a gold coin.
To preserve this:
- The base layer must remain resource-light, so running a full node stays accessible on commodity hardware.
- Block sizes must remain small enough to prevent centralization of verification.
- Historical data must remain consistent and tamper-evident, enabling proof chains across time and jurisdiction.
Any base layer that scales by increasing throughput or complexity undermines this fundamental guarantee, making the network more dependent on trust and surveillance infrastructure.
Bitcoin prioritizes global verifiability over throughput—because trustless money requires that every user can check the money they receive.
5. Governance: Not Captured, Just Resistant to Coercion
The current controversy around
OP_RETURNand proposals to limit inscriptions is instructive. Some prominent devs have advocated for changes to block content filtering. Others see it as overreach.Here's what matters:
- No single dev, or team, can force changes into the network. Period.
- Bitcoin Core is not “the source of truth.” It’s one implementation. If it deviates from market consensus, it gets forked, sidelined, or replaced.
- The economic majority—miners, users, businesses—enforce Bitcoin’s rules, not GitHub maintainers.
In fact, recent community resistance to perceived Core overreach only reinforces Bitcoin’s resilience. Engineers who posture with narcissistic certainty, dismiss dissent, or attempt to capture influence are routinely neutralized by the market’s refusal to upgrade or adopt forks that undermine neutrality or openness.
This is governance via credible neutrality and negative feedback loops. Power doesn’t accumulate in one place. It’s constantly checked by the network’s distributed incentives.
6. Bitcoin Is Still in Its Infancy—And That’s a Good Thing
You’re not too late. The ecosystem around Bitcoin—especially L2 protocols, privacy tools, custody innovation, and zero-knowledge integrations—is just beginning.
If you're an engineer looking for:
- Systems with global scale constraints
- Architectures that optimize for integrity, not speed
- Consensus mechanisms that resist coercion
- A base layer with predictable monetary policy
Then Bitcoin is where serious systems engineers go when they’ve outgrown crypto theater.
Take-away
Under realistic, market-aware assumptions—where:
- Bitcoin’s ossification is seen as a stability feature, not inertia,
- Market forces can and do demand and implement change via tested, non-coercive mechanisms,
- Proof-of-work is recognized as the only consensus mechanism resistant to fiat capture,
- Wealth concentration is understood as a temporary distribution effect during early monetization,
- Low base layer throughput is a deliberate design constraint to preserve verifiability and neutrality,
- And innovation is layered by design, with the base chain providing integrity, not complexity...
Then Bitcoin is not a fragile or inflexible system—it is a deliberately minimal, modular, and resilient protocol.
Its governance is not leaderless chaos; it's a negative-feedback structure that minimizes the power of individuals or institutions to coerce change. The very fact that proposals—like controversial OP_RETURN restrictions—can be resisted, forked around, or ignored by the market without breaking the system is proof of decentralized control, not dysfunction.
Bitcoin is an adversarially robust monetary foundation. Its value lies not in how fast it changes, but in how reliably it doesn't—unless change is forced by real, bottom-up demand and implemented through consensus-tested soft forks.
In this framing, Bitcoin isn't a slower crypto. It's the engineering benchmark for systems that must endure, not entertain.
Final Word
Bitcoin isn’t moving slowly because it’s dying. It’s moving carefully because it’s winning. It’s not an app platform or a sandbox. It’s a protocol layer for the future of money.
If you're here because you want to help build that future, you’re in the right place.
nostr:nevent1qqswr7sla434duatjp4m89grvs3zanxug05pzj04asxmv4rngvyv04sppemhxue69uhkummn9ekx7mp0qgs9tc6ruevfqu7nzt72kvq8te95dqfkndj5t8hlx6n79lj03q9v6xcrqsqqqqqp0n8wc2
nostr:nevent1qqsd5hfkqgskpjjq5zlfyyv9nmmela5q67tgu9640v7r8t828u73rdqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgsvr6dt8ft292mv5jlt7382vje0mfq2ccc3azrt4p45v5sknj6kkscrqsqqqqqp02vjk5
nostr:nevent1qqstrszamvffh72wr20euhrwa0fhzd3hhpedm30ys4ct8dpelwz3nuqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgs8a474cw4lqmapcq8hr7res4nknar2ey34fsffk0k42cjsdyn7yqqrqsqqqqqpnn3znl
-
 @ 005bc4de:ef11e1a2
2025-05-06 11:54:14
@ 005bc4de:ef11e1a2
2025-05-06 11:54:14May 6 marks my "Nostr birthday." This means I've been on Nostr for two years now. See my initial "Running nostr" note timestamped and archived on the Hive blockchain at https://peakd.com/bitcoin/@crrdlx/running-nostr
Two years ago, I really had no idea what Nostr was. I was asking, "What is this Nostr thing?"

And, I had no idea what I was doing then while using the front end clients. The clients were clunky and since the protocol was rather plastic (still kinda is). As evidence to my ignorance, the spinning wheels on Coracle.social just kept spinning. I didn't realize that since I was only following two people, one being myself, there was nothing to load from relays except my one "Running nostr" note. Hence, the Coracle wheels just spun in their mesmerizing manner. At least they're soothing to watch.
Yet, despite my ignorance, I had an inkling of a notion that Nostr was indeed something different, maybe special. Otherwise, I wouldn't have taken the time to capture an animated gif and make that Hive post to chronicle my first Nostr note.
For fun, I made another "Running nostr" note yesterday using Coracle.social. It still has those muted, earthy tones, but the wheels are not there anymore for long. Coracle, like Nostr, has come a long way in two years. It loads much faster now, which means less wheel spinning. I kind of miss the wheels for some reason, they build the drama and expectation of what might appear.
!HBIT
-
 @ e4950c93:1b99eccd
2025-05-06 10:35:37
@ e4950c93:1b99eccd
2025-05-06 10:35:37Qu'est-ce qu'une matière naturelle ? La question fait débat, et chacun-e privilégiera ses propres critères. Voici comment les matières sont classées sur ce site. La liste est régulièrement mise à jour en fonction des produits ajoutés. N'hésitez pas à partager votre avis !
✅ Matières naturelles
Matières d'origine végétale, animale ou minérale, sans transformation chimique altérant leur structure moléculaire.
🌱 Principaux critères : - Biodégradabilité - Non-toxicité - Présence naturelle nécessitant le minimum de transformation
🔍 Liste des matières naturelles : - Bois - Cellulose régénérée (cupra, lyocell, modal, viscose) - Chanvre - Coton - Cuir - Liège - Lin - Laine - Latex naturel, caoutchouc - Métal - Soie - Terre - Verre - … (Autres matières)
⚠️ Bien que "naturelles", ces matières peuvent générer des impacts négatifs selon leurs conditions de production (pollution par pesticides, consommation d’eau excessive, traitement chimique, exploitation animale…). Ces impacts sont mentionnés sur la fiche de chaque matière.
Les versions biologiques de ces matières (sans traitement chimique, maltraitance animale, etc.) sont privilégiées pour référencer les produits sur ce site, tel qu'indiqué sur la fiche de chaque matière (à venir).
Les versions conventionnelles ne sont référencées que tant que lorsqu'il n'a pas encore été trouvé d'alternative plus durable pour cette catégorie de produits.
🚫 Matières non naturelles
Matières synthétiques ou fortement modifiées, souvent issues de la pétrochimie.
📌 Principaux problèmes : - Toxicité et émissions de microplastiques - Dépendance aux énergies fossiles - Mauvaise biodégradabilité
🔍 Liste des matières non naturelles : - Acrylique - Élasthanne, lycra, spandex - Polyamides, nylon - Polyester - Silicone - … (Autres matières)
⚠️ Ces matières ne sont pas admises sur le site. Néanmoins, elles peuvent être présentes dans certains produits référencés lorsque :
- elles sont utilisées en accessoire amovible (ex. : élastiques, boutons… généralement non indiqué dans la composition par la marque) pouvant être retiré pour le recyclage ou compostage, et
- aucune alternative 100 % naturelle n’a encore été identifiée pour cette catégorie de produits.
Dans ce cas, un avertissement est alors affiché sur la fiche du produit.
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ e4950c93:1b99eccd
2025-05-06 10:32:20
@ e4950c93:1b99eccd
2025-05-06 10:32:20Contenu à venir.
-
 @ ffbcb706:b0574044
2025-05-06 09:29:41
@ ffbcb706:b0574044
2025-05-06 09:29:41Markdown test italic bold in openletter Nostr https://openletter.earth/ Have a great day
-
 @ e83b66a8:b0526c2b
2025-05-06 09:17:39
@ e83b66a8:b0526c2b
2025-05-06 09:17:39I’m going to talk about Ethereum, hear me out.
Ethereum is a Turing complete consensus blockchain tokenised by its own currency Ether.
This idea by Vitalik Buterin was incredibly compelling and still is today, even though few real world use cases have emerged.
For example, as a company, I could pay a carbon tax in Ether, locked into a smart contract. If the temperate rises by more than “n” degrees year on year based on a known agreed external (blind) oracle, say a weather station located near my factory.
Fantastic, we now have an automatic climate tax.
In reality, few realistic applications exist, however the idea is very compelling and many flocked to Ethereum as a promise of the future. This inflated its utility token “Ether” into stratospherically high prices.
This, in turn, attracted speculative investors and traders only looking at the price signal of the token and no longer considering the utility. This created a bubble which has gradually deflated over time.
This is why we are seeing Bitcoin, which only attempts to be money, succeed relative to Ethereum.
As Ethereum fails, and Bitcoin development strides on, an opportunity arises to try to do what Ethereum and all the other related altcoins have so far failed to do. Computational utility. And to do this on Bitcoin, the most successful “Crypto”.
The first unintended hijack of Ethereums utility are the JPEGs we are seeing on our blockchain.
This latest drive to make Bitcoin Turing complete is potentially the final destination for developers keen to explore the potential of Bitcoins eco-system.
Perhaps Bitcoin is going to absorb all the altcoins. Perhaps that is the goal of Bitcoins developers.
I don’t comment whether this is good or bad, I’m just exploring whether this may be the agenda.
-
 @ 5188521b:008eb518
2025-05-06 08:09:37
@ 5188521b:008eb518
2025-05-06 08:09:37Macaron returns, fluffs his white linen napkin, and takes his seat at their table, “Thank you, John, for extending my French people such great mercy as to be allowed to transact freely on the Bitcoin blockchain.” He extends his arm out towards a waiter, “Monsieur? Champagne for the three of us please!”
Vrrrm! “I can’t believe we were able to find an American Mustang in this French countryside. I am ripping down these narrow roads!” John celebrates.
“Bloody hell, slow down!” Lily begs as her oversized diamond dangle earrings sway side to side. “You’ve got nothing to prove, John. Big man in your yankee ten-gallon hat. Let’s just get there safely.”
John slows to give her a smoldering look, “Aww, my sweet British compatriot, you care about me!”
“Bollocks! I care about not dying!” Lily retorts. “Now focus on the mission. We need to save a boatload of English border collies — literally. Frenchman Macaron wants to groom them into French poodles!”
John wags a finger off the wheel to reply in his Southern drawl, “However, my sweet Lily flower, my US Hash Force intends to project power to coerce the French for the dogs’ release!”
Lily bats his finger away, “Yes, but may I remind you, my arrogant wanker, geographically challenged friend, MI6’s intel says to steadily power on any miners as His Majesty’s Hash Force may do. The border collies’ barge will take about an hour to flee France, cross the English channel, and safely reach our shores so we don’t want to burst their souffle too quickly. Oh, and the barge is armed with explosives controlled by a remote detonator. When Macaron asks for his bitcoin ransom payment in exchange for the dogs’ release, how do you cowboys plan to help from across the pond?”
John takes both hands off the wheel to flex his biceps, “Shock and awe, Lily. Full Throttle! We’re not giving the French a single sat. Instead, we’re diverting maximum energy to the U.S. Hash Force, of course!”
Lily guffaws, “And where is this sudden surge of readily available power supposed to come from undetected?”
“No need to worry my English crumpet! Our back of the envelope calculations suggest that, with a little help from the Texas of the North, there’s enough flared natural gas in the U.S. to run the entire Bitcoin network!” John proudly replies.
Lily’s jaw drops, “So miners have already stealthily built out the infrastructure to capture wasted natural gas flares for the benefit of the U.S. government, but are waiting to turn them on until commanded to by the U.S. Hash Force?!”
“Yup! As soon as Macaron sees our hash power come online, we’re going to try to start mining blocks on the Bitcoin network to Denial of Service (DOS) attack any UTXOs with a known history of French transactions.”
“A DOS attack, for peace?” Lily asks skeptically.
“Peace through strength, baby! If you don’t comply with America’s dog rights standards, you get censored. America saves British dogs again, and without a single shot fired!”
“Not fair! It’s only because our MI6 chainanalysis intel knows which Bitcoin addresses to censor on the blockchain we suspect belong to Macaron and his government that this plan even has a shot at succeeding. You’re lucky Macaron is even more self-assured than you Americans. That’s the only reason France doesn’t have a Hash Force of its own to project power back!”
John pulls the Mustang up to the front of the fancy French restaurant, Chandelier. Lily grabs her green purse that matches her elegant emerald ball gown, and they head inside to meet Macaron.
John and Lily spot Macaron sitting alone at the white linen table closest to the dance floor. He’s tapping his Louis Vuitton snake leather shoes, checking his Chanel watch, and fluffing his floofy black French Hermès beret. The red French ascot spilling out of his black and white blouse looks ridiculous.
John lets out a big sigh, and Macaron stands with open arms, “Lily, John, welcome to France!” Before John can flinch away, Macaron kisses him on both cheeks. He lifts up Lily’s hand for a kiss, “Mademoiselle.”
John raises his hand, “Waiter! I’ll take a bourbon, neat. And make it a double!” John calls out.
Slap!
“Hey, what was that for, Frenchie?” John asks as he rubs his face.
“Rude American, where are your manners?” Macaron asks as he pulls out a hidden red detonator clipped in the folds of his ascot. “Don’t drive me to prematurely push this button and blow up the boat carrying your English doggies! First, send me my bitcoin ransom payment. Then we can celebrate with drinks!” Macaron demands.
“In your dreams, Frenchie!” John presses his finger to his ear, “Uniform, Sierra, Alpha!”
Macaron turns to Lily and scoffs, “What is this rude American man doing, Lily?”
Annoyed, Lily answers, “Check your bitcoin UTXOs. Notice anything?”
Macaron frantically queries his Bitcoin node remotely from his cellphone and breathes a sigh of relief, “Phew. No, I don’t notice anything at all. All of my unspent bitcoin is still under the control of my government’s private key.”
“And it’ll stay that way, too!” John beats his chest. “You mess with the US, and you get the Hash Force! We just secretly doubled the difficulty to mine a block by turning on all of our miners — as many miners as the entire existing Bitcoin network! Now you’ll have to wait twice as long for your French bitcoin transactions to confirm! That is, unless you release the barge of dogs right now!”
Lily drops down to the table and buries her face in her palms to hide her embarrassment.
Flustered, Macaron furiously types out a long text message with the order to release the barge of English Border Collies to cross the English channel. “There, I’ve let the dogs out! Will you two please excuse me for a moment? I have to place a call with my government to confirm we haven’t lost our property rights to spend our bitcoin.
Beaming with pride, John falls back into his chair at the table. “We did it, Lily! Quick, give the command for His Majesty’s Hash Force to power on so we can 51% attack this guy!”
Lily finally stops rubbing her eyes, “John, that isn’t how any of this works!”
“What do you mean?” he asks.
“Within a 2,016 block difficulty adjustment period, doubling the hash power means the global Bitcoin network will mine new blocks twice as fast, not slower! At least, until the 2,016 block period ends and the difficulty adjusts so miners resume taking on average 10 minutes to generate a valid block. And sure, maybe the US has a political incentive to not collect the fees of any transactions of UTXOs with a known French association, but the rest of the network’s miners will happily profit from the sats you leave in the mempool! But most of all, the Bitcoin network is now just twice as secure from attack!”
John’s double bourbon finally arrives at the table. Selfishly focused on his own glass, he doesn’t bother to stop the waiter in case Lily wants to order a drink of her own. He drinks a big gulp, “But if you give the order for His Majesty’s Hash Force to power on, won’t we have over 51% of the hash power of the Bitcoin network? We can write Macaron’s bitcoin out of existence!”
Lily crosses her arms, “Not exactly. It’s not enough to just surpass half the hashrate. We also need to maintain a higher hashrate than the legacy chain to generate more chain weight to then reorg the other chain when we join the legacy network. We would have to be mining this heavier chain in secret, but in one bombastic order you just completely blew apart our whole plan! Now we’d need some sort of massive collusion somehow between existing miners, and some secret stealth miners, to have any power projection.”
John mutters under his breath, “Frenchie’s been gone a long time. Wonder what he’s up to….”
Macaron returns, fluffs his white linen napkin, and takes his seat at their table, “Thank you, John, for extending my French people such great mercy as to be allowed to transact freely on the Bitcoin blockchain.” He extends his arm out towards a waiter, “Monsieur? Champagne for the three of us please!” Macaron turns to John and Lily, “After my phone call, I am in much better spirits. Though I’m bitter you denied paying our bitcoin ransom, I’m grateful you’re furthering the security of the Bitcoin network.”
In his excitement, Macaron leans forward and claps his hands together, “You two are so lucky to be dining with me tonight. You won’t have to drink that sparkling-wine-swill you have in your home countries. Tonight, you’ll get to have proper champagne, from the Champagne region of France — my treat!”
John grunts in disgust, “Macaron, you can order champagne, but I’ve got my bourbon.”
Lily steps on John’s foot, “Ow! What was that for?” John shrieks.
“Aren’t you going to ask me if I want anything?” Lily asks.
“Huh?” John replies confusedly.
Macaron takes Lily’s hand, “Mademoiselle, in addition to champagne, can I get you anything else?”
Lily recoils her hand back, “Gin martini. Shaken, not stirred.”
“Lily, may I ask you another question?” Macaron asks sweetly.
“Bloody hell, what is it, Macaron?” she responds while rolling her eyes.
“Why do I get the feeling that forgetting to ask you what you’d like to drink isn’t the first time John has neglected to ask you what you wanted?”
Lily’s eyes light up as she leans in closer to Macaron, “Why, yes. This isn’t the first time John’s ever disregarded my needs. You know, he’s always only thinking about himself, his own ego, and he never misses a chance to interrupt me—”
“—That’s not true!” John interrupts.
Lily kicks him under the table, “See what I mean?”
Macaron whisks Lily’s hair behind her ear, “You have such beautiful earrings, Lily. Did John buy those for you?”
“No, John never buys me anything.”
“What do you mean?” John protests.
Lily shrugs him off and Macaron leans in closer to Lily to whisper just loud enough for John to hear, “You know, in my country, men like me know how to show a lady respect.”
John stands up and extends out his hand, “C’mon, Lily. I think it’s time I take you out onto the floor for a dance.”
She shakes her head, so he stomps on her feet under the table.
“Ow!” Lily shrieks.
“I insist,” John presses. “They’re playing my song, Don’t Stop Believin’. C’mon!”
On the dance floor, John pulls Lily close to whisper in her ear, “What are you doing? We’ve finished our mission. Let’s ensure the dogs safely cross the English channel and get out of here! The way you’re flirting with him we’ll never leave!”
Lily blushes, “John, are you that blind? If Macaron is suddenly being sweet to us, then he must be scheming something.”
“What’s that supposed to mean?” John shakes his head. “Look, there’s no time to argue. We can’t risk him blowing up the barge as long as he’s got that remote detonator clipped to his ascot! He’s in a jubilant mood for now, but those French can be so melodramatic. We’ve got to get the detonator to ensure the safety of the dogs until they reach safe harbor at your shores.”
John’s box step dancing pace quickens as he looks over to check on Macaron. He spots him placing an order with the waiter and grits his teeth, “He’s pure evil. He was willing to kill the English border collies if he didn’t get ransom payment for not grooming them into French poodles. Only the threat of our Hash Force forced him to comply with our demand for their release!”
Lily breaks away from John to do a twirl on the dance floor; her elegant flowy green dress tries to keep up. She flips her hair and winks at Macaron, “Maybe I should flirt with him some more? After all, he’s so handsome — and he listens to me!”
John stops dancing and stomps his feet.
“Aww, are you jealous, John?” Lily asks.
“Jealous?!”
Lily floats back to John, digs her nails into the back of his neck, and nibbles on his ear as she whispers, “John, you better dip me on this dance floor! Otherwise, I’m going to ask him to draw me like one of his French girls. C’mon John, Don’t stop believin’!”
Ahem Macaron clears his throat, adjusts his detonator-pinned ascot, and taps Lily on the shoulder.
“Mademoiselle, may I have this dance?”
“Oh, certainly,” she replies. “Better than this brute with two left feet!”
John grunts in dissatisfaction and bolts back to the table.
With Macaron distracted dancing with Lily for what feels like an eternity, John defiantly presses his finger to his ear. “MI6 — status report. What’s taking so long?” he mutters under his breath. “I hate seeing this Frenchie dance with an English lass who deserves so much better. It’s driving me crazy!”
“You just gotta distract him from detonation for ten more minutes,” a British accent replies. “Intel shows the puppy barge armed with explosives has almost reached us across the channel, and then we can safely disarm it.”
“USHF, come in,” John queries.
“We’ve got trouble! The global energy grid has spiked along the Asian seaboard, and among the French alps. Looks like a secret French Hash Force we’ve never detected is colluding with the existing Chinese, Japanese, and Tibetan miners!
They’ve stopped including American-linked bitcoin address transactions in their blocks! Can you politely get him to back down? We’ve already played our power-projection show-of-force card!”
“Ok, I’ll do my best to play nice with Frenchie, but no promises!” John cautions. As he watches Lily and Macaron dance with disdain, a waiter approaches him at the table.
“Here you are, monsieur. Your appetizer.”
“Appetizer? I didn’t order an appetizer! All I ordered was this bourbon.”
“I’m sorry monsieur, but the other gentleman of your party insists. He said he offers this delicacy as a gift. A token of appreciation for the mercy demonstrated today by you, the quote Big American Man enquote.”
John looks on the dance floor and sees Macaron give him a nod with a big wiley grin. Lily gives him the “go-ahead” signal, so John pops one of the hot slimy appetizer balls into his mouth.
“Mhmm! These are tastier than Ma’s Frito Pie!” he shouts as Macaron and Lily walk over to join him back at the table. John continues, “These remind me of the Rocky Mountain oysters we have back at home! Of course, I’m grateful they aren’t, if you know what I mean. What are they, anyways?”
“Escargot,” the Frenchman replies, “a local specialty.”
“Escar-what-now?” John asks.
“Snails!” Lily clarifies.
John gags and spits his half-eaten snail onto the floor. He stands up and slams his ten-gallon cowboy hat on the table. “Ok, that’s it! I’ve had enough! Macaron, stop playing nice. We know you’ve activated some secret alliance with the miners on the other side of the globe! What’re you up to?”
“John, don’t upset him! Think about the puppies!” Lily pleads.
“To heck with the puppies! I’m not letting this man stand up a Hash Force to DOS attack us! You hear that, Macaron? You mess with the best, and we’ll use kinetic force against your miners stashed in the caves of the French alps!” Tsk! Tsk! Tsk! Macaron wags his finger, and pulls out the detonator switch clipped to his ascot.
“Silly pompous American, did you forget I still have the detonator? Did you really think I was going to let you get away with rescuing your hideous English border collies? Life is one giant power projection game, and the way nation states survive is by mutually assured preservation. In exchange for taming the unwieldy fur of Tibetan Mastiffs, Chinese Chow Chows, and Japanese Shih-Tzu and Shiba Inus, these countries pledged their miners to our stealthy French Hash Force when we’re in need. Well, thanks to your little stunt, not only did I find the perfect opportunity to project power back at you arrogant Americans, but also dump these hideous dogs given to me onto your barge, so they’re the British Isles’ problem now!”
“But we’ll be overrun by doges!” Lily gasps in horror.
“Yes, Lily! That’s what you get for partnering with John! What do Americans say?” Macaron asks rhetorically. “That’s right, ‘No dogs left behind!’ But most of all, John, I just wanted one last dance with your girlfriend, and to watch you eat snails!” French nasally honking laughing sounds
Lily shouts back, “I’m not his girlfriend!” She pulls a whistle out of her purse and blows it as hard as she can, but it doesn’t make a sound. John looks at her confused, and Macaron honks even harder. The whole restaurant starts to rumble, and the chandeliers sway from the ceiling.
“What’s this!?” Macaron shouts.
Gradually, then suddenly a stampede of bulldogs comes barreling into the dining room, knocking over all the tables, and tackling Macaron! As he falls, the detonator gets knocked into the air, and Lily catches it just before it hits the floor.
John looks at her, bewildered, and stammers, “You…. you let the Bitcoin dogs out??”
“You think you wankers got all the tricks? The English have a few surprises too! Now c’mon, let’s flee out the back in my British Mini Cooper. And this time, I’m driving!”
Will Schoellkopf is the author of two books: Bitcoin Girl Save the World and The Bitcoin Dog: Following the Scent to the Bitcoin C++ Source Code. He hosts the Bitcoin podcast It’s So Early! and publishes a weekly newsletter, featuring his favorite Bitcoin Posts of the Week, at realbitcoindog.com. His work has appeared in the anthology 21 Futures: Tales from the Timechain, in print at Bitcoin Magazine, Citadel21, Stackchain Magazine and online at Satoshi’s Journal. Follow him on Nostr and X @realBitcoinDog, or email will@realbitcoindog.com
-
 @ bbef5093:71228592
2025-05-06 05:17:07
@ bbef5093:71228592
2025-05-06 05:17:07*Holtec új atomenergetikai együttműködése Utah államban*
Az amerikai Holtec International stratégiai megállapodást kötött Utah állammal és a Hi Tech Solutions nukleáris szolgáltatóval, hogy elősegítse saját fejlesztésű, SMR-300 típusú kis moduláris reaktorainak (SMR) telepítését Utahban és az Egyesült Államok Mountain West régiójában. A megállapodás értelmében 2028-ig állandó képzési központot hoznak létre Utahban, amely az üzemeltetéshez, karbantartáshoz és az új generációs nukleáris technológiákhoz szükséges munkaerő képzését célozza, szoros együttműködésben helyi egyetemekkel, főiskolákkal és szakiskolákkal.
A projekt Utah állam energetikai stratégiájának („Operation Gigawatt” és „Built Here”) része, amely a következő tíz évben megduplázná az állam energiatermelését, kiemelt szerepet szánva a tiszta nukleáris energiának. A Holtec Utah-t választotta nyugati gyártóbázisának is, ezzel erősítve az amerikai nukleáris ellátási láncot és hosszú távú munkahelyeket teremtve. A cég a 2030-as években akár 4 GW összkapacitású SMR-300 telepítését tervezi főként Utahban és Wyomingban.
Az SMR-300 egy nyomottvizes reaktor, amely 300 MW villamos vagy 1050 MW hőteljesítményt biztosít, és a Holtec tervei szerint kulcsszerepet játszhat a tiszta, szén-dioxid-mentes energiatermelésben.
*Amerikai SMR-piac helyzete*
Az SMR-technológia az utóbbi években került a figyelem középpontjába, mivel gyorsabban és olcsóbban telepíthető, mint a hagyományos atomerőművek, és lehetőséget kínál magánbefektetők számára is. Ugyanakkor az első amerikai SMR-projekt, a NuScale és a Utah Associated Municipal Power Systems közös beruházása költségnövekedés miatt meghiúsult, ami rávilágított a technológia gazdasági kihívásaira.
Nemzetközi fejlemények és további hírek
- Az ausztrál Okapi Resources és az Urenco együttműködési megállapodást kötött új urán dúsítási technológia fejlesztésére, amely tisztább és olcsóbb dúsítási eljárást ígér.
- Az Argonne National Laboratory sikeresen kicserélt egy 30 éves kulcsfontosságú alkatrészt a nátriumhűtésű gyorsreaktor-tesztberendezésében, ami hozzájárulhat a gyorsreaktor-technológia fejlesztéséhez az Egyesült Államokban.
- A Tennessee Egyetem ösztöndíjprogramot indít a Fülöp-szigeteki nukleáris szakemberek képzésére, támogatva ezzel a délkelet-ázsiai ország nukleáris energiafejlesztési törekvéseit.
- Bulgáriában a Westinghouse Electric Company helyi beszállítókkal kötött megállapodásokat két új AP1000 típusú reaktor építéséhez a kozloduji atomerőműben.
-
 @ b154080c:00027cc7
2025-05-06 03:01:47
@ b154080c:00027cc7
2025-05-06 03:01:47Introduction
In the ancient times of Israel, masculinity found its true embodiment in the courageous story of Daniel. Amidst the foreign land of Babylon, Daniel stood firm in his convictions, showcasing strength, and dedication to his beliefs.
Despite living in a culture that sought to diminish his faith, Daniel refused to bow before idols or false deities. His defiance challenged societal expectations, revealing a masculinity that transcended worldly norms. Rooted in his unshakable belief in the one true God, Daniel's resolve remained unyielding. Facing the wrath of the king, Daniel fearlessly stood before Nebuchadnezzar, humbly declaring his allegiance to God alone. Cast into a blazing furnace as punishment, Daniel emerged unharmed. God's angel shielded him from the scorching flames, proving that his faith made him invincible. Witnessing this display of masculinity, Nebuchadnezzar acknowledged the greatness of Daniel's God, bringing about a profound transformation.
Daniel's story serves as a testament to the essence of masculinity—a resolute dedication to one's convictions, the courage to defy societal expectations, and a commitment to truth. His faith and devotion inspire generations, exemplifying the power of masculine conviction.
There have been countless instances throughout history where acts of courage have taken place on a spectrum. Although both men and women can display such acts, history has shown that resolve, courage, and bravery have predominantly resided within the realm of masculinity. The Apostle Paul himself concluded the book of 1 Corinthians by saying, "Be watchful, stand firm in the faith, act like men, be strong. Let all that you do be done in love" (16:13-14). By combining this passage with the numerous accounts of provision, battle, sacrifice, and honor, it becomes evident that God has designed inherent and very important differences within the male gender.
The Bible presents us with inspiring examples of both courageous women, such as Deborah, Rahab, and Esther, and valiant men, including Joshua, Gideon, Samson, David, Jonathan, Nehemiah, the Prophets, the twelve Apostles, and above all, Jesus Himself. While these accounts acknowledge the remarkable contributions of women, they predominantly highlight the male figures who exemplify strength, boldness, courage, and a resolute sense of responsibility. Throughout its pages, the Bible paints a vivid picture of masculinity's profound impact and enduring significance which we must embrace.
Jesus’ Masculinity
Jesus exhibited remarkable courage throughout many of his acts, and it is through his expression of masculinity that this courage shines even brighter. Jesus' masculinity played a crucial role in enabling him to display great bravery and determination in fulfilling his mission. However, it's important to note that Jesus redefines masculinity beyond physical strength or dominance, embracing resilience, self-sacrifice, and unyielding conviction as its defining qualities.
Jesus' courage stemmed from his deep understanding of his purpose and his unshakable faith in his Father's plan. He fearlessly challenged the religious authorities of his time, calling out hypocrisy and speaking truth to power. Despite facing opposition and hostility, Jesus stood firm in his convictions, undeterred by the threats and ridicule he encountered. Jesus' embodiment of masculinity highlights the transformative power it can have when rooted in love and compassion.
Modern Culture Poisoning the Church
It is important to realize the true masculinity of Jesus and the example that he has set for us in this regard. Unfortunately, I often see a tendency nowadays to downplay Jesus' masculinity and instead depict Him in a more feminized manner.
In both our culture and the modern church, there is a tendency to present a version of Jesus that deviates from the biblical portrayal. Perhaps you've come across people who refer to Jesus as their "best friend" or even draw comparisons between their relationship with Him and that of a "boyfriend.” This is in fact very unbiblical. The Bible never presents our love for God using such romantic or erotic language. While the men depicted in Scripture certainly loved God, they were never portrayed as being desperate for Him or romantically in love with Him. People are often taught a very shallow and weak portrayal of Him.
In the United States, particularly in the context of flourishing Protestantism, the shift from considering the community as a whole to focusing on the individual has led to a rise in strong individualistic beliefs which has resulted in a diminished sense of community within the Catholic Church. When the focal point of Catholicism becomes "Jesus and me," it opens the door to a mindset of being "spiritual" rather than "religious.” Attending church becomes a matter of personal choice, and faith no longer necessarily influences or intersects with areas such as business or politics. The sole emphasis becomes on one's personal relationship with Christ, prioritizing individual salvation over communal or global redemption. The vision of the kingdom of God taking shape on earth also becomes less urgent, as the emphasis shifts towards a faith centered on transcendence, emotions, and sentiment, rather than tangible actions.
The perception of Jesus' masculinity has been negatively impacted by the trend of feminizing Him, which has contributed to a decline in the courage displayed by men today. This shift can be attributed to various factors that have influenced societal perspectives.
In contrast to the promises of Jesus, which include suffering, trials, and pain, it is often only presented to them that Christianity is the solution to these hardships. Instead of acknowledging the reality of challenges, the contemporary portrayal of Christianity tends to market it as the antidote to suffering and pain. It is important to recognize and reflect upon the significant difference between how Jesus called His disciples and the prevailing emphasis on personal relationships with Him today. Instead of inviting them to have a personal connection, He simply said, "Follow me." Understanding this distinction is crucial in our understanding of Jesus' call to discipleship. "Follow me" implies a sense of purpose, a shared mission or goal to pursue. This contrast highlights the divergence between the original intent of discipleship and the way it is often portrayed around me nowadays.
I want to emphasize that I am by no means denying the significance of having a personal relationship with Christ. On the contrary, I am simply highlighting the importance of recognizing that personal relationships, including our relationship with Christ, require more than just superficial connections. They demand a deep sense of faith, trust, and communion with Him. Drawing inspiration from the courageous example of Jesus, who fearlessly confronted societal norms and spoke truth to power, our relationship with Him can empower us to embrace courage in our own lives. Just as Jesus fearlessly faced opposition, persecution, and ultimately sacrificed Himself for the sake of others, our connection with Him can embolden us to stand up for what is right, to live out our faith boldly, and to face life's challenges with strength. It is not a casual or complacent association but a courageous and transformative bond that empowers us to live out our faith with conviction and to impact the world around us positively.
As modern sermons take center stage, it's become apparent that there is a tendency to downplay the contrasts found in the teachings of the Bible. As mentions of heaven and hell, sin and life, grace and justice, as well as the analogies involving battles and soldiers for Christ have always been very prevalent, they have become way less common nowadays. We hear fewer calls for Catholics to embrace their crosses and passionately commit themselves to the cause of the gospel and the well-being of others. Instead, the spotlight has shifted towards how the gospel can serve as a tool for personal growth and fulfillment, focusing on self-realization. The gospel is often presented as a therapeutic treatment rather than a heroic challenge. The emphasis lies on the rewards rather than the obstacles, creating the idea of all gain, no pain (lol).
The rise of praise and worship music has also brought about significant changes in people's perception of Christ. While traditional hymns focused on singing about God, emphasizing His greatness, power, and distinctiveness, praise and worship music takes a different approach. It presents God as a close companion, an intimate presence by our side, emphasizing His love and care for us. This shift in emphasis, while not inherently negative, certainly plays a substantial role in shaping our understanding of Christ's nature and relationship with us.
Jesus is the Epitome of Masculinity
I believe Jesus stands as the epitome of masculinity, offering an unrivaled example for men to emulate. Through His life and teachings, He reveals the true essence of what it means to be a man. He leads with courage, facing challenges head-on without hesitation. His fearlessness shines through as He confronts opposition and stands firm in His convictions. Moreover, His love is not self-serving but sacrificial, displayed vividly through His ultimate act of giving His own life for the sake of others. And in the face of adversity, His resolve remains unshakeable, inspiring men to stand strong in their beliefs and principles. Jesus, in His entirety, embodies the essence of true masculinity, setting an unparalleled standard that us men must aspire to.
Around me, I’m often seeing a tendency to shy away from addressing challenging subjects with resolute conviction. Rather than speaking with clarity and certainty, there is a preference for using vague language and ambiguous statements to navigate sensitive issues. In stark contrast, Jesus stood firmly and fearlessly, fearlessly proclaiming His truth. His words shook the foundations of societal norms, demanding radical commitment from His followers. True boldness lies in the courage to speak truth, even when faced with opposition and adversity.
Boldness is a very masculine characteristic. While some may argue that boldness is not exclusive to gender, the Bible primarily associates this characteristic with men. On the other hand, the beauty of women is highlighted through the importance of a gentle and quiet spirit, which also very much holds great value in the eyes of God. 1 Peter 3:4 addressing woman and wives, "Let your adorning be the hidden person of the heart with the imperishable beauty of a gentle and quiet spirit, which in God's sight is very precious." This reminds us that inner qualities such as a gentle and tranquil demeanor also hold significant worth and are highly esteemed.
As Jesus exemplified true boldness, courageously speaking God's truth regardless of the consequences. His courage serves as the ultimate model of masculinity, inspiring men to fearlessly pursue God's will. Jesus exemplified bravery, rooted in His deep reverence for God. Unlike the fear of man, which arises from sin, Jesus' bravery stemmed from His love for God. His resolute posture and authoritative responses to godless men demonstrated a masculinity untainted by timidity. Jesus taught us to lead with courage, grounded in reverence for God and faith in His sovereignty.
In a culture where love is often misrepresented, Jesus' sacrificial love stands as the true definition. Love, as demonstrated by Jesus, goes beyond superficial feelings; it entails sacrificial commitment. Jesus willingly laid down His life for His bride, the Church, showcasing the essence of true masculinity. Men are called to sacrificially love their wives, mirroring Christ's example. This selfless love forms the foundation for men to protect, nurture, and fight for those entrusted to their care.
Christ's resolve was the driving force behind the cross, demonstrating His commitment to fulfill His mission. His choice to embrace the cross, knowing the suffering and wrath He would endure, showcases resolute masculinity. In history, heroic moments of perseverance are predominantly marked by male resolve. The biological advantage provided by testosterone further supports men's capacity for enduring resolve. Jesus' resolve to save His people from sin teaches men to stand firm in the face of challenges, abiding in their commitment to their calling.
Restoring the Church's Boldness and Reclaiming Biblical Masculinity and Femininity
The landscape of the Church has undergone a significant transformation, moving away from its historic expression of Christianity. We've witnessed a shift from powerful, convicting sermons to soft, TED-talk style infotainment. Classic hymns highlighting doctrine, sacrifice, and piety have been replaced by emotionally driven love songs that resemble romantic ballads. It's clear that the local church has undergone a real emasculation.
This departure from biblical foundations has contributed to a great deal of confusion within the Church, particularly concerning the understanding of biblical manhood and womanhood. The increasing push for egalitarianism has led to women fighting for leadership roles, while men find themselves adrift without clear guidance regarding their responsibilities in marriage, the church, and the family. I believe this confusion and distortion of gender roles to be the enemy's central strategy for our generation. By infiltrating the Church with a heightened emphasis on feminine emotion, the enemy has left us unprepared for moments requiring masculine boldness, fearlessness, sacrifice, and resolve.
We must acknowledge that there is a difference between a surface-level expression of faith and the profound conviction displayed by those facing intense trials. The challenges and hardships that people face in the midst of adversity provide a profound glimpse into the strength and genuineness of their faith. These trials are a powerful testimony to their commitment and courage. Throughout history, numerous Christians have faced unimaginable suffering, even enduring torture, dismemberment, and martyrdom, all because of their devotion to Christ. Their remarkable sacrifices inspire us and remind us of the immense cost of following Jesus. Yet, the trend of timidity displayed by the present-day Church, yielding to government overreach or even complying with laws that endorse sexual sin contrary to biblical teachings, will come at a significant cost.
It is high time for the Church to reclaim its boldness and restore the biblical understanding of masculinity and femininity. We must reject the watered-down version of Christianity that has spread throughout our culture and embrace a faith rooted in conviction and sacrifice. By understanding and embracing the unique roles and responsibilities of men and women as outlined in Scripture, we can restore clarity and purpose to our families, churches, and communities. Let us rise above the societal pressures, rekindle the fire of biblical truth, and stand firm in our commitment to Christ, no matter the cost.
As we progress, it becomes clear that the importance of strong, virtuous Catholic men is growing. This should not catch us off guard. The feminist movement of the 21st century is truly toxic. It goes way beyond advocating for the rightful appreciation of women; it seeks to establish female dominance. Moreover, its influence knows no boundaries. Like the LGBTQ community, its aim is to permeate every aspect of public, personal, and spiritual life. We must not only be alarmed by this trend but also prepare ourselves to stand firmly against it. We need biblically grounded shepherds and faithful women who can discern the subtle infiltration of an effeminate culture and guard against it.
Let us not forget that Catholicism is not egalitarian. While men and women are equally valued before the cross, our roles and responsibilities differ. In marriage, Christianity follows a complementarian model, where the husband leads with sacrificial love, and the wife respects and supports him. People are too sensitive about the word “patriarchy” nowadays. In terms of leadership, the Church holds a patriarchal stance. At the same time, patriarchy, like any other system, is not immune to the potential for sinful expressions. However, when approached with sacrificial love, adherence to biblical order, and a commitment to honoring God, the structure of patriarchy - as well as areas such as marriage, fatherhood, and heterosexuality - can yield to way more goodness. We should strive for a church culture that aligns with the gender-culture outlined in God’s Word: gentle, safe, and encouraging, while also strong, bold, and committed to upholding biblical order and fulfilling the mission entrusted to us. This balance allows the church to fully embody the presence of Christ, enabling His people to confidently advance alongside our great Lord.
We must prepare ourselves for an increasing need for men who embrace biblical masculinity and women who faithfully embody femininity. It is crucial not to overlook the pervasive influence of an effeminate culture and the agenda of distorted ideologies. By embracing the distinct roles and responsibilities that God has given to both men and women, we cultivate a church culture that mirrors the beauty of Christ and empowers His people to wholeheartedly pursue His mission with courage. We must recognize the urgency to embrace and embody biblical masculinity in the face of cultural challenges and shifting ideologies. Equipped with the truth of God's Word, we can navigate the complexities of the world and fulfill our God-given roles with great faith. Let us rise as men who boldly embrace our calling, standing firm in the face of challenges, and wholeheartedly pursuing lives of holiness and service to God and His Church. May we stand united, guided by His Word, and ready to face the battles ahead with strength, grace, and resolved faith.
From Nashville with love,
Suhail Saqan
This was inspired by The Imitation of Christ. Read here.
-
 @ c230edd3:8ad4a712
2025-05-06 02:12:57
@ c230edd3:8ad4a712
2025-05-06 02:12:57Chef's notes
This cake is not too sweet and very simple to make. The 3 flavors and mild and meld well with the light sweetness.
Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 45 min
- 🍽️ Servings: 12
Ingredients
- 1 1/2 cups all-purpose flour
- 1/2 tsp salt
- 2 tsp baking soda
- 1 cup sugar
- 3 large eggs
- 1/2 cup full fat milk
- 3/4 cup unfiltered olive oil
- 2/3 cup finely chopped raw, unsalted almonds
- 2 tsp lavender
- 1 Tbsp powdered sugar
Directions
- Preheat oven to 350 degrees F. Lightly butter 8 inch baking pan.
- In smal bowl, whisk together flour, salt, and baking soda.
- In large bowl, beat eggs and sugar until light colored and fluffy. Add milk.
- Slowly pour and stir in olive oil.
- Fold dry ingredients into the wet ingredients,
- Stir in the almonds and the lavender, reserving some flowers for garnish.
- Pour into prepared pan and bake for 45 min, or until toothpick comes out clean.
- Cool on wire rack, dust with powdered sugar and top with reserved lavender.
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ 8173f6e1:e488ac0f
2025-05-06 01:32:03
@ 8173f6e1:e488ac0f
2025-05-06 01:32:03{"desc":"tst","code":"teeest","tags":["123"]}
-
 @ 34f1ddab:2ca0cf7c
2025-05-05 22:59:38
@ 34f1ddab:2ca0cf7c
2025-05-05 22:59:38Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — crypptrcver.com is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet. Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact. ⚠️ What We Don’t Do While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
Don’t Let Lost Crypto Hold You Back! ⏳ Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now! crypptrcver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on:
✉️ Telegram: Chat with Us on Telegram @crypptrcver 💬 WhatsApp: Message Us on WhatsApp Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — crypptrcver.com is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
Why Trust Crypt Recver? 🤝\ 🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
Partially lost or forgotten seed phrases\ Extracting funds from outdated or invalid wallet addresses\ Recovering data from damaged hardware wallets\ Restoring coins from old or unsupported wallet formats\ You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈\ Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.\ Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery.\ Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet.\ Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact.\ ⚠️ What We Don’t Do\ While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
Don’t Let Lost Crypto Hold You Back! ⏳\ Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection\ Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now! crypptrcver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:
✉️ Telegram: Chat with Us on Telegram @crypptrcver\ 💬 WhatsApp: Message Us on WhatsApp\ Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!
-
 @ a296b972:e5a7a2e8
2025-05-05 22:45:01
@ a296b972:e5a7a2e8
2025-05-05 22:45:01Zur Gründung der Bundesrepublik Deutschland wurde infolge der Auswirkungen des 2. Weltkriegs auf einem Teil des ehemaligen Deutschen Reiches (nicht des 3. Reiches!) auf Initiative der westlichen Alliierten, federführend die USA als stärkste Kraft, eine demokratische Grundordnung erarbeitet, die wir als das Grundgesetz für die Bundesrepublik Deutschland kennen und schätzen gelernt haben. Da man zum damaligen Zeitpunkt, im Gegensatz zu heute, noch sehr genau mit der Sprache war, hat das Wort „für“ größere Bedeutung, als ihm heute zugesprochen wird. Hätte der unter westlich-alliierter Besatzung stehende Rumpf des Deutschen Reiches eigenständig eine Verfassung erstellen können, wäre es nicht Grundgesetz (das laut Definition einen provisorischen Charakter hat) genannt worden, sondern eben Verfassung. Und hätte diese Verfassung eigenständig erarbeitet werden können, hätte sie geheißen: Verfassung der Bundesrepublik Deutschland.
Es heißt zum Beispiel auch: Costituzione della Repubblica Italiana. also Konstitution der Republik Italien, und nicht Costituzione per La Repubblica Italiana.
Es ist nachvollziehbar, dass die Bedenken der westlichen Alliierten aufgrund der Nazi-Zeit so groß waren, dass man den „Deutschen“ nicht zutraute, selbständig eine Verfassung zu erstellen.
Zum vorbeugenden Schutz, es sollte verunmöglicht werden, dass ein Regime noch einmal in der Lage sei, die Macht zu ergreifen, wurde als Kontrollinstanz der Verfassungsschutz gegründet. Dieser ist dem Innenministerium gegenüber weisungsgebunden. Die jüngste Aussage, auf den letzten Metern der Innenministerin Faeser, der Verfassungsschutz sei selbständig, ist eine manipulative Beschreibung, die davon ablenken soll, dass das Innenministerium dem Verfassungsschutz sehr wohl übergeordnet ist. Das Wort „selbständig“ soll Eigenständigkeit vorgaukeln, hat aber in der Hierarchie keinerlei Bedeutung.
Im Jahre 1949 herrschte ein anderer Zeitgeist. Werte wie Ehrlichkeit, Redlichkeit und Anständigkeit hatten noch eine andere Bedeutung als heute. Politiker waren noch von einem anderen Schlag und hatten weitgehend den Anspruch zum Wohle des Volkes zu entscheiden und zu handeln. Diese Werte reichten noch mindestens bis in das Agieren des Bundeskanzlers Helmut Schmidt hinein.
Niemand konnte sich deshalb zum damaligen Zeitpunkt vorstellen, dass dieser eigentlich als Kontrollinstanz gedachte Verfassungsschutz einmal von der Politik missbraucht werden könnte, um oppositionelle Kräfte auszuschalten zu versuchen, wie es mit der Einstufung der AfD als gesichert rechtsextrem geschehen ist. Rechtlich hat das noch keine Konsequenzen, aber es geht in erster Linie darum, dem Image der AfD zu schaden, um weiteren Zulauf zu verhindern. Diese Art von Durchtriebenheit kam in den Gedanken und dem Ehrgefühl der damals verantwortlichen Politiker noch nicht vor.
Die ehemaligen Volksparteien, man kann auch sagen, die Alt-Parteien, sehen ihre Felle schon seit einiger Zeit davonschwimmen. Die Opposition hat derzeit die Zustimmung einer ehemaligen Volkspartei überholt und ist sogar stärkste Kraft geworden. Sie repräsentiert aktuell rund 10 Millionen der Wähler. Tendenz steigend. Und das die folglich auch gesichert rechtsextrem gewählt haben, oder gar gesichert rechtsextrem sind, wird ihnen vielleicht nicht besonders schmeicheln.
Parallel dazu haben die Alt-Parteien die Medienlandschaft gekapert und versuchen mit Einschränkungen der Meinungsfreiheit, sofern sich Kritik gegen sie richtet und durch selbstermächtigte Entscheidung über das, was Wahrheit und Lüge ist, unliebsame Stimmen mundtot zu machen, um unter allen Umständen an der Macht zu bleiben.
Diese Vorgehensweise widerspricht dem demokratischen Verständnis, das aus dem, wenn auch „nur“ Grundgesetz, statt Verfassung, hervorgeht und die Nachkriegsgenerationen im besten Sinne beeinflusst und demokratisch geprägt hat.
Aus dieser Sicht können die Aktivitäten der Alt-Parteien nur als Angriff auf die Demokratie, wie sie diese Generationen verstehen, gesehen werden.
Daher führt jeder Angriff der Alt-Parteien auf die Demokratie dazu, dass die Opposition immer mehr an Stimmen gewinnt und wohl weiterhin gewinnen wird.
Es erschließt sich nicht, warum die Alt-Parteien nicht auf die denkbar einfachste Lösung kommen, Vertrauen in ihre Politik zurückzugewinnen, in dem sie eine Politik machen würden, die dem Willen der Bürger entspricht. Mit dem Gegenteil machen sich die Volksvertreter zu Vertretern ohne den Rückhalt vom Volk, und man muss sich fragen, wessen Interessen sie derzeit wirklich vertreten. Bestenfalls die eigenen, schlimmstenfalls die des global agierenden Tiefen Staates, der ihnen ins Ohr flüstert, was sie zu tun haben.
Mit jeder vernunftbegabten Entscheidung, die dem Willen des Souveräns entspräche, würden sie die Opposition zunehmend schwächen. Da dies nicht geschieht, kann man nur zu der Schlussfolgerung kommen, dass sich hier auch selbstzerstörerische, suizidale Kräfte festgesetzt haben. Es ist wie eine Sucht, von der man nicht mehr loslassen kann.
Solange die Alt-Parteien nicht in der Lage sind, die Unzufriedenheit in der Bevölkerung wahr- und ernst zu nehmen, werden sie die Opposition stärken und zu immer rigideren Maßnahmen greifen müssen, um ihre Macht zu erhalten und sich damit immer mehr von demokratischen Verhältnissen entfernen, und zwar genau in die Richtung vor der die Alt-Parteien in ihrer ideologischen Verirrung warnen.
Seitens der Opposition gibt es in der Gesamtschau keine Anzeichen dafür, dass die Demokratie abgeschafft werden soll, im Gegenteil, es wird für mehr Bürgerbeteiligung plädiert, was ein sicheres Merkmal für demokratische Absichten ist.
Aus Sicht der Alt-Parteien macht die Brandmauer Sinn, weil sie sie vor ihrem eigenen Machtverlust schützt. Der Fall der Berliner Mauer sollte ihnen eigentlich eine Warnung sein.
Fairerweise darf nicht unterschlagen werden, dass es in der Opposition einige Verirrte gibt, wobei noch interessant wäre zu erfahren, welche davon als V-Männer des Verfassungsschutzes eingeschleust wurden. Diese jedoch zum Anlass zu nehmen, die Opposition unter Generalverdacht zu stellen, steht einem demokratischen Handeln diametral entgegen.
Das Grundgesetz wird so nicht geschützt, sondern bis kurz vor der Sollbruchstelle verbogen.
Die Einstufung der Opposition als gesichert rechts-extrem beruht auf einem mutmaßlich 1000 Seiten starken Papier, das offensichtlich nur ein erlesener Kreis zu sehen bekommen soll. Dazu gehört nicht die Bevölkerung, die sicher nur einmal mehr nicht zu Teilen verunsichert werden soll. Und selbstverständlich schon gar nicht diejenigen, die es betrifft, nämlich die Opposition.
Eine eindeutige Fragwürdigkeit der Aktivitäten des Verfassungsschutzes wäre schwerer festzustellen, wenn es gleichwohl Parteien gäbe, die als gesichert links-extrem oder zumindest als links-extremer Verdachtsfall eingestuft würden. Nicht ganz unberechtigte Gründe hierfür könnten schon gefunden werden, wenn der politische Wille es wollte.
Auch die seltsam-umstrittene Installierung des Präsidenten des Bundesamtes für Verfassungsschutz (genau genommen für Grundgesetzschutz) lässt Fragen offen.
Generell müsste es eine unabhängige Überprüfung geben, ob die Gewaltenteilung in Deutschland noch gewährleistet ist, da es durch das augenscheinliche Zusammenspiel in der Richterschaft, der Gesetzgebung und der vierten Gewalt, den Medien, Anlass zu Zweifel gibt.
Diese Zweifel sind nicht demokratiegefährdend, sondern im Gegenteil, es ist demokratische Pflicht, den Verantwortlichen kritisch auf die Finger zu schauen, ob im Sinne des Souveräns entschieden und gehandelt wird. Zweifel könnte man dadurch ausräumen, in dem eindeutig bewiesen würde, das alles seine Richtigkeit hat.
Das wäre vornehmlich die Aufgabe der Alt-Medien, die derzeit durch Totalversagen glänzen, weil alles mit allem zusammenhängt, jeder jeden kennt und man es sich über Jahre so eingerichtet hat, dass man gerne unter sich bleibt und Pöstchen-Hüpfen von einem Lager ins andere spielt.
Vielleicht ist es sogar nötig, dass zur unabhängigen Überprüfung, die Alliierten, inklusive Russland, noch einmal, nach rund 80 Jahren, auf den Plan gerufen werden müssen, um sozusagen eine Zwischenbilanz zu ziehen, inwieweit sich das einst etablierte, demokratische System bewährt hat, und ob es derzeit noch im ursprünglichen Sinne umgesetzt und gelebt wird. Es ist anzunehmen, dass hier ein gewaltiges Optimierungspotenzial zum Vorschein kommen könnte.
Viele Bürger in Deutschland haben den Wunsch, wieder in einer Demokratie zu leben, die ihre Namen auch verdient hat. Sie wollen wieder frei ihre Meinung jeglicher Art aussprechen können, miteinander diskutieren, auch einmal Unsinn reden, ohne, dass sie der Blockwart gleich bei einem Denunzierungsportal anschwärzt, oder sie Gefahr laufen, dass ihr Konto gekündigt wird, oder sie morgens um 6 Uhr Besuch bekommen, der noch nicht einmal frische Semmeln mitbringt.
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ c9badfea:610f861a
2025-05-05 22:36:34
@ c9badfea:610f861a
2025-05-05 22:36:34- Install SherpaTTS (it's free and open source)
- Launch the app and download the first AI model for your language (see recommendations below)
- Tap the + icon below the language selection to add more models
- Enjoy offline text-to-speech synthesis
Model Recommendations
- English:
en_US-ryan-medium - Chinese:
zh-CN-huayan-medium - German:
de_DE-thorsten-medium - Spanish:
es_ES-sharvard-medium - Portuguese:
pt_BR-faber-medium - French:
fr_FR-tom-medium - Dutch:
nl_BE-rdh-medium - Russian:
ru_RU-dmitri-medium - Arabic:
ar-JO-kareem-medium - Romanian:
ro_RO-mihai-medium - Bulgarian:
bg-cv - Turkish:
tr_TR-fahrettin-medium
ℹ️ An internet connection is only needed for the initial download
ℹ️ You can use TTS Util to read text and files aloud
-
 @ c9badfea:610f861a
2025-05-05 20:16:29
@ c9badfea:610f861a
2025-05-05 20:16:29- Install PocketPal (it's free and open source)
- Launch the app, open the menu, and navigate to Models
- Download one or more models (e.g. Phi, Llama, Qwen)
- Once downloaded, tap Load to start chatting
ℹ️ Experiment with different models and their quantizations (Q4, Q6, Q8, etc.) to find the most suitable one
-
 @ 6538925e:571e55c3
2025-05-05 20:00:48
@ 6538925e:571e55c3
2025-05-05 20:00:48It’s been a little while since we released a major design update, so we’re really excited to get this new version of the app into your hands. Here’s a breakdown of all the main updates included in Fountain 1.2:
 #### Library Design Update
#### Library Design Update-
New content-type filters at the top of the page make it easier to navigate between podcasts and music in your library.
-
Recently Played is now the default view in your library, so it’s easier to jump back into podcasts you’ve already started.
-
The Music filter now makes it easier to find saved tracks and albums, and it also gives you a list of all the artists whose music you’ve saved.
-
We’ve refreshed the design of the content cards to make it easier to see how much time is remaining on episodes you’ve already started.
 #### Content Pages Design Update
#### Content Pages Design Update-
All of the different content pages have undergone an extensive redesign, including shows, episodes, artists, albums, tracks, clips and playlists
-
We’ve replaced the tab layout we were using on the content pages with one scrollable page, making it easier to access features like chapters and tracklists
-
We’ve sanitised the formatting of show notes too, and if there is no activity for a given episode, we now display the expanded show notes
 #### Episode Summaries
#### Episode SummariesEver looked at a 4-hour Lex Fridman episode and wished you could just read a high-level summary? We certainly have, so we did something about it.
-
Every episode page now has a Summary button above the show notes.
-
Simply pay 500 sats to unlock a summary, or upgrade to Fountain Premium for $2.99/month to enjoy unlimited summaries.
-
Summaries and transcripts now come as a bundle — two for the price of one!
-
Thanks to major improvements, they’re now faster, cheaper, and more accurate than ever before.
 #### Playback Improvements
#### Playback ImprovementsWe’ve completely rebuilt our audio engine from the ground up. Playback is now more robust and reliable — especially for music. Here are some of the key enhancements in Fountain 1.2:
-
Tracks now load and play instantly when tapped.
-
When playing a collection of tracks (e.g. from an artist, album, or playlist), you can now skip seamlessly between them.
-
We’ve replaced the scrollable player page with full-screen modals to make it easier to access show notes, comments, transcripts, chapters, tracklists, and your queue.
-
The new Smart Resume feature rewinds the episode by 5 seconds when you hit pause, so you don’t miss a beat.
-
You can now skip forward or backward by 60 seconds for faster navigation through episodes.
Other Bug Fixes & Improvements
-
Rebuilt payment stats for more complete and reliable transaction records.
-
Refreshed the design of the Settings pages for better usability.
-
Added new episode notification preferences in Settings.
-
Fixed several playback issues that were causing crashes or freezes.
-
Updated lock screen display and controls for livestreams.
-
Fixed issue where the next item in the queue paused unexpectedly.
-
Resolved playback stuttering on Android during livestreams.
-
Fixed disappearing playback controls on the lock screen.
-
Fixed playback speed not updating correctly.
-
Resolved issue where played episodes couldn’t be replayed.
-
Fixed playback not resuming correctly when listening in the car.
-
Synced car playback position with the device.
-
Fixed persistent car display refresh issue.
-
Fixed volume control via car controls.
-
Resolved issue with headphone controls after playing a transcript.
-
Fixed disappearing metadata on the lock screen.
-
Fixed bug where downloaded episodes stopped in airplane mode but showed as playing.
We would love to hear how you’re finding Fountain 1.2. Please submit your thoughts and feedback via the main menu in the app and we will take it on board as we continue to improve the app.
If you want to help test new features out before they get released, you can join Fountain Beta on Telegram. All iOS and Android users welcome.
-
-
 @ 6a6be47b:3e74e3e1
2025-05-05 19:49:17
@ 6a6be47b:3e74e3e1
2025-05-05 19:49:17Hi frens, you may or may not have noticed I’ve been MIA for about three weeks. I wanted to take a moment to explain where I’ve been, and why I stepped back for a bit.
At the start of the year, I was determined to make the most of it-and I still am. I’ve been pouring myself into several projects, especially my painting, which has really taken off. I’m so grateful for your support; none of this would be possible without you. But here’s where things got tricky. I started feeling like I had to “earn” every moment of rest, and that mindset snowballed. My health took a hit, and then one of my other projects completely derailed.
The stress piled up, and I felt like I was on the verge of burning out.
Don’t get me wrong-I’ve always welcomed change, even when it’s tough. And this time was no exception. The project I’d been working on for months took a 180, and all that effort seemed to go down the drain. I was frustrated, but I kept pushing, even though I was running on fumes. By the time I “earned” a break, I was too exhausted to enjoy it.
I managed to post a piece about Holy Week on my blog (which I’m really proud of-check it out if you haven’t!), but after that, I was done. I realized I needed to stop, not just for a day, but for a real break. When I finally took a few days off with my husband, it was clear how much I needed it. I was burned out, plain and simple. Now, I’m still putting myself back together. Mentally, I feel drained, but I’m stronger than I was a few weeks ago. I know I’m lucky and privileged to be able to take this time, and I’m grateful for the perspective it’s given me. I also r realize that this isn’t just a “me” thing-most people have been here at some point. We keep going until there’s nothing left, then wonder why we feel like empty shells.
I’ll be back to drawing soon (knock on wood-don’t want to jinx it!). In the meantime, take care of yourselves, and godspeed.
-
 @ c9badfea:610f861a
2025-05-05 19:34:45
@ c9badfea:610f861a
2025-05-05 19:34:45- Install Kiwix (it's free and open source)
- Download ZIM files from the Kiwix Library (you will find complete offline versions of Wikipedia, Stack Overflow, Bitcoin Wiki, DevDocs and many more)
- Open the downloaded ZIM files within the Kiwix app
ℹ️ You can also package any website using either Kiwix Zimit (online tool) or the Zimit Docker Container (for technical users)
ℹ️
.zimis the file format used for packaged websites -
 @ 91d8dece:3453543b
2025-05-05 17:49:36
@ 91d8dece:3453543b
2025-05-05 17:49:36https://drewztools.com/ flash USDT Are you tired of the long wait times and excessive fees associated with traditional cryptocurrency transactions? Look no further! Flash USDT from @drewztooolz is here to ease the way you send and receive crypto. Experience lightning-fast transfers, total anonymity, and zero fees with this state-of-the-art service. This flash last in the wallet for 90 t0 360 days before it disappears . Just so you know this coin is tradeable , swappable and transferable to many wallet type Flash USDT is not just another crypto tool; it’s a game-changer for anyone involved in cryptocurrency trading, particularly for OTC traders, P2P dealmakers, and cold wallet testers. Here’s why you should consider making it a part of your crypto toolkit: 🔥 Instant Transfers With Flash USDT, you can send high-value USDT to any wallet in under 60 seconds. Imagine the convenience of having your funds appear instantly without the typical delay caused by blockchain confirmations. Still have questions? Reach out via Telegram for 1-on-1 support. Our team is ready to assist you with anything you need! https://drewztools.com/ 💬 @drewztooolz 📲+1 (770) 666–2531
-
 @ 88cc134b:5ae99079
2025-05-05 17:38:21
@ 88cc134b:5ae99079
2025-05-05 17:38:21Text
-
 @ 6e64b83c:94102ee8
2025-05-05 16:50:13
@ 6e64b83c:94102ee8
2025-05-05 16:50:13Nostr-static is a powerful static site generator that transforms long-form Nostr content into beautiful, standalone websites. It makes your content accessible to everyone, even those not using Nostr clients. For more information check out my previous blog post How to Create a Blog Out of Nostr Long-Form Articles
What's New in Version 0.7?
RSS and Atom Feeds
Version 0.7 brings comprehensive feed support with both RSS and Atom formats. The system automatically generates feeds for your main content, individual profiles, and tag-specific pages. These feeds are seamlessly integrated into your site's header, making them easily discoverable by feed readers and content aggregators.
This feature bridges the gap between Nostr and traditional web publishing, allowing your content to reach readers who prefer feed readers or automated content distribution systems.
Smart Content Discovery
The new tag discovery system enhances your readers' experience by automatically finding and recommending relevant articles from the Nostr network. It works by:
- Analyzing the tags in your articles
- Fetching popular articles from Nostr that share these tags
- Using configurable weights to rank these articles based on:
- Engagement metrics (reactions, reposts, replies)
- Zap statistics (amount, unique zappers, average zap size)
- Content quality signals (report penalties)
This creates a dynamic "Recommended Articles" section that helps readers discover more content they might be interested in, all while staying within the Nostr ecosystem.
See the new features yourself by visiting our demo at: https://blog.nostrize.me
-
 @ 5ffa0470:9c3e760a
2025-05-05 16:17:19
@ 5ffa0470:9c3e760a
2025-05-05 16:17:19 -
 @ 88cc134b:5ae99079
2025-05-05 15:42:41
@ 88cc134b:5ae99079
2025-05-05 15:42:41sdsd
-
 @ 88cc134b:5ae99079
2025-05-05 15:29:24
@ 88cc134b:5ae99079
2025-05-05 15:29:24 -
 @ 88cc134b:5ae99079
2025-05-05 15:03:49
@ 88cc134b:5ae99079
2025-05-05 15:03:49 -
 @ 7460b7fd:4fc4e74b
2025-05-05 14:49:02
@ 7460b7fd:4fc4e74b
2025-05-05 14:49:02PR 32359:取消 OP_RETURN 字节限制提案深入分析
提案概述及代码变更内容
提案背景与意图:比特币核心当前对交易中的 OP_RETURN 输出(数据载体输出)有严格限制:默认最多允许单个 OP_RETURN 输出,且其
scriptPubKey大小不超过 83 字节(约80字节数据加上OP_RETURN和Pushdata前缀)groups.google.com。这一标准规则旨在轻度阻碍链上存储大量任意数据,鼓励将非金融数据以“更无害”的方式存入链上(比如用OP_RETURN而非可花费的UTXO输出)groups.google.com。然而随着时间推移,这一限制并未阻止用户将数据写入区块链,反而促使开发者设计各种变通方案绕过限制。例如,近期 Citrea Clementine 协议(闪电网络相关项目)因为OP_RETURN容量不足,而改用不可花费的Taproot输出来存储所需数据groups.google.com。这样的做法导致大量小额UTXO留存在UTXO集,对全节点造成负担,被视为比使用OP_RETURN更有害的副作用github.com。基于此背景,Bitcoin Core 开发者 Peter Todd(与 Chaincode 实验室的 Antoine Poinsot 等人)提出了 PR #32359,意在解除OP_RETURN的字节大小限制,以消除这种“适得其反”的限制策略groups.google.comgithub.com。**代码变更要点:**该PR主要修改了与标准交易校验和策略配置相关的代码,包括移除
script/standard.cpp中对OP_RETURN输出大小和数量的检查,以及删除策略配置选项-datacarrier和-datacarriersizegithub.com。具体而言:-
取消OP_RETURN大小限制:删除了判断OP_RETURN数据长度是否超过 MAX_OP_RETURN_RELAY(83字节)的标准性检查。此后,交易中的OP_RETURN输出脚本长度将不再被固定上限限制,只要满足区块重量等共识规则即可(理论上可嵌入远大于83字节的数据)github.comgroups.google.com。PR说明中明确提到移除了这些限制的执行代码github.com。相应地,
-datacarriersize配置参数被删除,因为其存在意义(设置OP_RETURN字节上限)已不复存在github.com。此前-datacarriersize默认为83,当用户调高该值时节点可接受更大数据载体输出;而现在代码中已无此参数,节点将无条件接受任意大小的OP_RETURN输出。 -
移除OP_RETURN输出数量限制:原先比特币核心默认策略还规定每笔交易最多只有一个OP_RETURN输出是标准的,多于一个即视为非标准交易(拒绝中继)bitcoin.stackexchange.com。该PR同样意在取消此“任意”限制groups.google.com。修改中移除了对
nDataOut(OP_RETURN输出计数)的检查,即允许一笔交易包含多个OP_RETURN输出而仍被视作标准交易。之前的代码若检测到nDataOut > 1会返回“multi-op-return”的拒绝原因github.com;PR删除了这一段逻辑,相应的功能测试也更新或移除了对“multi-op-return”非标准原因的断言github.com。 -
保留标准形式要求:值得注意的是,OP_RETURN输出的形式要求仍保留。PR描述中强调“数据载体输出的形式仍保持标准化:脚本以单个 OP_RETURN 开头,后跟任意数量的数据推字节;不允许非数据类的其他脚本操作码”github.com。也就是说,虽然大小和数量限制解除了,但OP_RETURN脚本内容只能是纯数据,不能夹带其他执行opcode。这保证了这些输出依然是“不可花费”的纯数据输出,不会改变它们对UTXO集的影响(不会增加UTXO)。
综上,PR #32359 的核心改动在策略层面放宽了对 OP_RETURN 的限制,删除了相关配置和检查,使节点默认接受任意大小、任意数量的 OP_RETURN 数据输出。同时维持其基本形式(OP_RETURN+数据)以确保此变更不会引入其它类型的非标准交易格式。
改动层级:策略规则 vs 共识规则
该提案属于策略层(policy-level)的更改,而非共识层规则的更改。也就是说,它影响的是节点对交易的_中继、存储和打包_策略,而不改变交易或区块在链上的有效性判定。OP_RETURN字节上限和数量限制从一开始就是标准性约束(Standardness),并非比特币共识协议的一部分groups.google.com。因此,移除这些限制不会导致旧节点与新节点产生区块共识分歧。具体理由如下:
-
无共识规则变动:原有的83字节上限只是节点默认_拒绝转发/挖矿_超限交易的规则,但如果矿工强行将超83字节的OP_RETURN交易打包进区块,所有遵循共识规则的节点(包括未升级的旧节点)依然会接受该区块。因为共识层并没有“OP_RETURN大小不得超过83字节”的规定github.com。正如开发者所指出的,现行的OP_RETURN限制属于“standardness rules”,其约束可以被轻易绕过,并不影响交易的最终有效性github.com。Peter Todd 在评论中强调,为真正禁止链上发布任意数据,必须修改比特币的共识协议,而这在现实中几乎不可能实施github.com。
-
**旧节点兼容性:**由于没有引入新的脚本opcode或共识验证规则,旧版本节点即使不升级,仍然会承认包含大OP_RETURN输出的区块为有效。换言之,不存在分叉风险。旧节点唯一的区别是仍会按照老策略拒绝中继此类交易,但一旦交易被打包进区块,它们仍会接受github.com。正因如此,这一提议不会引发硬分叉,只是改变默认策略。
-
**策略可自行定制:**另外,正如PR作者所言,这纯粹是默认策略的调整,用户依然可以选择运行修改版的软件继续实施先前的限制。例如,Peter Todd提到有替代实现(如 Bitcoin Knots)可以继续强制这些限制github.com。因此,这并非要“强制”所有节点解除限制,而是主流软件默认策略的演进。
需要澄清的是,有反对者担心解除限制可能扩大攻击面(下文详述),但这些都是针对节点资源和网络层面的影响,而非共识层安全性问题。总的来看,PR #32359 是策略层改进,与先前如RBF默认开启、逐渐弱化非标准交易限制等改变类似,其出发点在于网络行为而非协议规则本身。
对闪电网络节点和交易验证的影响
对链上验证的影响:由于这是策略层变更,交易和区块的验证规则并未改变,因此运行旧版本 Bitcoin Core 的闪电网络节点在共识上不会出现任何问题。闪电网络全节点通常依赖比特币全节点来跟踪链上交易,它们关心的是交易确认和共识有效性。解除OP_RETURN限制并不会使旧节点拒绝新区块,因而不会造成闪电通道关闭交易或HTLC交易在旧节点上验签失败等情况。换句话说,不升级Bitcoin Core软件的LN节点仍可正常参与链上共识,无需担心链上交易验证兼容性。
对节点中继和资源的影响:主要影响在于网络传播和资源占用。如果闪电网络节点所连接的Bitcoin Core没有升级,它将不会中继或存储那些含有超大OP_RETURN的未确认交易(因为旧版本视之为非标准交易)。这可能导致未升级节点的内存池与升级节点不一致:某些在新版节点中合法存在的交易,在旧版中被拒之门外。不过这通常不影响闪电网络的运行,因为闪电通道相关交易本身不会包含OP_RETURN数据输出。此外,当这些交易被矿工打包进区块后,旧节点依然会接收到区块并处理。所以,即便LN节点的后端Bitcoin Core未升级,最坏情形只是它在交易未打包时可能感知不到这些“大数据”交易,但这通常无碍于闪电网络功能(闪电网络主要关心的是通道交易的确认情况)。
升级的好处和必要性:从闪电网络生态来看,放宽OP_RETURN限制反而可能带来一些正面作用。正如前述,已有闪电网络周边项目因为83字节限制不足,转而使用不可花费输出存储数据groups.google.com。例如 Antoine Poinsot 在邮件列表中提到的 Clementine 协议,将某些watchtower挑战数据存进Taproot输出,因为OP_RETURN容量不够groups.google.com。解除限制后,此类应用完全可以改用更友好的OP_RETURN输出来存储数据,不再制造永久占据UTXO集的“垃圾”UTXOgithub.com。因此,闪电网络的watchtower、跨链桥等组件若需要在链上写入证据数据,将可直接利用更大的OP_RETURN输出,网络整体效率和健壮性都会提升。
需要注意的是,如果PR最终被合并并广泛部署,闪电网络节点运营者应该升级其Bitcoin Core后端以跟上新的默认策略。升级后,其节点将和大多数网络节点一样中继和接受大OP_RETURN交易,确保自己的内存池和网络同步,不会漏掉一些潜在相关交易(尽管目前来看,这些交易对LN通道本身并无直接关联)。总之,从兼容性看不升级没有致命问题,但从网络参与度和功能上看,升级是有益的。
潜在的间接影响:反对者提出,解除限制可能导致区块和内存池充斥更多任意数据,从而推高链上手续费、影响闪电通道关闭时所需的手续费估计。例如,如果大量大OP_RETURN交易占据区块空间,链上拥堵加剧,LN通道关闭需要支付更高费用才能及时确认。这其实是一般性拥堵问题,并非LN特有的兼容性问题。支持者则认为,这正是自由市场作用的体现,使用链上空间就该竞争付费github.com。无论如何,闪电网络作为二层方案,其优势在于减少链上交互频率,链上手续费市场的变化对LN有影响但不改变其运行逻辑。LN节点只需确保其Bitcoin Core正常运行、及时跟上链上状态即可。
开发者讨论焦点:支持与反对观点
PR #32359 在开发者社区引发了激烈讨论,支持者和反对者针锋相对,各自提出了有力的论据。以下总结双方主要观点:
-
支持方观点:
-
当前限制无效且适得其反:支持者强调83字节上限并未阻止人们在链上存数据,反而促使更有害的行为。Peter Todd指出,很多协议改用不可花费UTXO或在
scriptsig中藏数据来绕过OP_RETURN限制,结果增加了UTXO集膨胀,这是限制OP_RETURN带来的反效果github.com。与其如此,不如移除限制,让数据都写入可被丢弃的OP_RETURN输出,避免UTXO污染github.comgithub.com。正如一位支持者所言:“与其让尘埃UTXO永远留在UTXO集合,不如使用可证明不可花费的输出(OP_RETURN)”github.com。 -
**限制易被绕过,增添维护负担:**由于有些矿工或服务商(如MARA Slipstream私有广播)本就接受大OP_RETURN交易,这一限制对有心者来说形同虚设github.com。同时,存在维护这个限制的代码和配置选项,增加了节点实现复杂度。Todd认为,与其让Bitcoin Core承担维护“低效甚至有害”的限制,不如干脆取消,有需要的人可以使用其他软件实现自己的政策github.com。他提到有替代的Bitcoin Knots节点可自行过滤“垃圾”交易,但没必要要求Bitcoin Core默认坚持这些无效限制github.com。
-
尊重自由市场,拥抱链上数据用例:部分支持者从理念上认为,比特币区块空间的使用应交由手续费市场决定,而不应由节点软件做人为限制。著名开发者 Jameson Lopp 表示,是时候承认“有人就是想用比特币做数据锚定”,我们应当提供更优方式满足这种需求,而不是一味阻碍github.com。他认为用户既然愿意付费存数据,就说明这种行为对他们有价值,矿工也有动力处理;网络层不应进行过度的“父爱”式管制github.com。对于反对者所称“大数据交易会挤占区块、抬高手续费”,Lopp直言“这本来就是区块空间市场运作方式”,愿付高费者得以优先确认,无可厚非github.com。
-
统一与简化策略:还有支持者指出,既然限制容易绕过且逐渐没人遵守,那保留它只会造成节点之间策略不一致,反而增加网络复杂性。通过取消限制,所有核心节点一致地接受任意大小OP_RETURN,可避免因为策略差异导致的网络孤块或中继不畅(尽管共识不受影响,但策略不一致会带来一些网络层问题)。同时删除相关配置项,意味着简化用户配置,减少困惑和误用。Peter Todd在回应保留配置选项的建议时提到,Bitcoin Core在Full-RBF功能上也曾移除过用户可选项,直接默认启用,因为现实证明矿工最终都会朝盈利的方向调整策略,节点自行设置反而无济于事github.com。他以RBF为例:在Core开启默认Full-RBF之前,矿工几乎已经100%自行采用了RBF策略,因此保留开关意义不大github.com。类比来看,数据交易也是如此:如果有利可图,矿工终会打包,无论节点是否选择不转发。
-
反对方观点:
-
去除限制会放松对垃圾交易的防线:反对者担心,一旦解除OP_RETURN限制,链上将出现更多纯粹存储数据的“垃圾”交易,给网络带来DoS攻击和资源消耗风险。开发者 BrazyDevelopment 详细描述了可能被加剧的攻击向量github.com:首先,“Flood-and-Loot”攻击——攻击者构造带有巨大OP_RETURN数据的低价值交易(符合共识规则,多笔交易可达数MB数据),疯狂填充各节点的内存池。github.com这样会占满节点内存和带宽,延迟正常交易的传播和确认,并推高手续费竞争。github.com虽然节点有
maxmempool大小限制和最低中继费率等机制,但这些机制基于常规交易行为调校,面对异常海量的数据交易可能捉襟见肘github.com。其次,“RBF替换循环”攻击——攻击者可以利用无需额外费用的RBF替换,不断发布和替换包含大OP_RETURN的数据交易,在内存池中反复占据空间却不被确认,从而扰乱手续费市场和内存池秩序github.com。反对者认为,移除大小上限将使上述攻击更廉价、更容易实施github.com。他们主张即便要放宽,也应设定一个“高但合理”的上限(例如100KB),或在内存池压力大时动态调整限制,以保护较小资源节点的运行github.com。 -
用户丧失自定义策略的权利:一些开发者反对彻底删掉
-datacarrier和-datacarriersize选项。他们认为即使大势所趋是接受更多数据,也应保留用户自主选择的空间。正如开发者 BitcoinMechanic 所言:“矿工接受大数据交易不代表用户就不能选择自己的内存池装些什么”github.com。目前用户可以通过配置将-datacarrier设为0(不中继OP_RETURN交易)或者调低-datacarriersize来严格限制自己节点的策略。直接去除这些选项,会让那些出于各种考虑(如运营受限资源节点、防范垃圾数据)的用户失去控制权。从这个角度看,反对者认为限制应该由用户 opt-in 地解除,而不是一刀切放开。开发者 Retropex 也表示:“如果矿工想要更大的数据载体交易,他们完全可以自行调整这些设置…没有理由剥夺矿工和节点运营者做选择的权利”github.com。 -
此改动非必要且不符合部分用户利益:有反对意见认为当前83字节其实已经能覆盖绝大多数合理应用需求,更大的数据上链并非比特币设计初衷。他们担心放开限制会鼓励把比特币区块链当作任意数据存储层,偏离“点对点电子现金”主线,可能带来长期的链膨胀问题。这一阵营有人将此争议上升为理念之争:是坚持比特币作为金融交易为主,还是开放成为通用数据区块链?有评论形容这场拉锯“有点类似2017年的扩容之争”,虽然本质不同(一个是共识层区块大小辩论,一个是策略层数据使用辩论),但双方观点分歧同样明显99bitcoins.com99bitcoins.com。一些反对者(如Luke Dashjr等)长期主张减少非必要的数据上链,此次更是明确 Concept NACK。Luke-Jr 认为,其实完全可以通过引入地址格式变化等办法来识别并限制存数据的交易,而不需要动用共识层改动github.com(虽然他也承认这会非常激进和不现实,但以此反驳“除了改共识无计可施”的观点)。总之,反对者倾向于维持现状:代码里已有的限制无需移除,至少不应在无压倒性共识下贸然改变github.com。
-
社区共识不足:许多开发者在GitHub上给出了“Concept NACK”(概念上不支持)的评价。一位参与者感叹:“又来?两年前讨论过的理由现在依然适用”github.com。在PR的Review日志中,可以看到反对此提案的活跃贡献者数量明显多于支持者github.com。例如,反对阵营包括 Luke-Jr、BitcoinMechanic、CryptoGuida、1ma 等众多开发者和社区成员,而支持此提案的核心开发者相对少一些(包括Jameson Lopp、Sjöors、Sergio Demian Lerner等)github.com。这种意见分裂显示出社区对取消OP_RETURN限制尚未达成广泛共识。一些反对者还担忧这么大的改动可能引发社区矛盾,甚至有人夸张地提到可能出现新的链分叉风险99bitcoins.com99bitcoins.com(虽然实际上由于不涉及共识,硬分叉风险很小,但社区内部分歧确实存在)。
综上,支持者聚焦于提高链上效率、顺应实际需求和减轻UTXO负担,认为解除限制利大于弊;而反对者强调网络稳健、安全和用户自主,担心轻易放开会招致滥用和攻击。双方在GitHub上的讨论异常热烈,很多评论获得了数十个👍或👎表态,可见整个社区对此议题的关注度之高github.comgithub.com。
PR当前状态及后续展望
截至目前(2025年5月初),PR #32359 仍处于开放讨论阶段,并未被合并。鉴于该提案在概念上收到了众多 NACK,缺乏开发者间的明确共识,短期内合并的可能性不大。GitHub 上的自动统计显示,给予“Concept NACK”的评审者数量显著超过“Concept ACK”的数量github.com。这表明在Bitcoin Core维护者看来,社区对是否采纳此改动存在明显分歧。按照 Bitcoin Core 一贯的谨慎作风,当一个提案存在较大争议时,通常会被搁置或要求进一步修改、讨论,而不会仓促合并。
目前,该PR正等待进一步的评审和讨论。有开发者提出了替代方案或折中思路。例如,Bitcoin Core维护者 instagibbs 提交了相关的 PR #32406,提议仅取消默认的OP_RETURN大小上限(等效于将
-datacarriersize默认提高到极大),但保留配置选项,从而在不牺牲用户选择权的情况下实现功能开放github.com。这表明部分反对者并非完全拒绝放宽限制,而是希望以更温和的方式推进。PR #32359 与这些提案互相冲突,需要协调出统一的方案github.com。另外,也有开发者建议在测试网上模拟大OP_RETURN交易的攻击场景,以评估风险、说服怀疑者github.com。审议状态总结:综合来看,PR #32359 尚未接近合并,更谈不上被正式接受进入下一个Bitcoin Core版本。它既没有被关闭(拒绝),也没有快速进入最终review/merge阶段,而是停留在激烈讨论中。目前Bitcoin Core的维护者并未给出明确的合并时间表,反而是在鼓励社区充分讨论其利弊。未来的走向可能有几种:要么提案经过修改(例如保留配置项、增加安全机制等)逐渐赢得共识后合并,要么维持搁置等待更明确的社区信号。此外,不排除开发者转而采用渐进路线——例如先在测试网络取消限制试验,或先提高上限值而非彻底移除,以观察效果。也有可能此提案最终会因共识不足而长期悬而不决。
总之,OP_RETURN字节限制之争体现了比特币开发中策略层决策的审慎和平衡:需要在创新开放与稳健保守之间找到折衷。PR #32359 所引发的讨论仍在持续,它的意义在于促使社区重新审视链上数据存储的策略取舍。无论最终结果如何,这一讨论本身对比特币的发展具有积极意义,因为它让开发者和社区更加清晰地权衡了比特币作为数据载体和价值载体的定位。我们将持续关注该提案的进展,以及围绕它所展开的进一步测试和论证。github.comgroups.google.com
引用来源:
-
Bitcoin Core PR #32359 提案内容github.comgithub.com及开发者讨论(Peter Todd评论github.comgithub.com等)
-
Bitcoin Dev 邮件列表讨论帖:《Relax OP_RETURN standardness restrictions》groups.google.comgroups.google.com
-
GitHub 开发者评论摘录:支持意见(Jameson Loppgithub.com等)与反对意见(BitcoinMechanicgithub.com、BrazyDevelopmentgithub.com等)
-
Bitcoin Core PR 评论自动统计(Concept ACK/NACK 汇总)github.com
-
-
 @ 88cc134b:5ae99079
2025-05-05 13:34:22
@ 88cc134b:5ae99079
2025-05-05 13:34:22Hello
-
 @ c9badfea:610f861a
2025-05-05 12:55:46
@ c9badfea:610f861a
2025-05-05 12:55:461. Create
bash git bundle create backup.bundle --all2. Verify
bash git bundle verify backup.bundle3. Restore
bash git clone backup.bundleℹ️ Feel free to change the
backup.bundlefile name -
 @ dd664d5e:5633d319
2025-05-05 07:47:50
@ dd664d5e:5633d319
2025-05-05 07:47:50Speak your truth, Nostr
I think that there's a difference in the decisions people make when they're True Believers, and when they've just been hired to do something, or they arrived much later and don't really get the point of the decisions. It's that way with any organization controlled by a protocol, such as a constitution, basic law, canon, or core specification.
The True Believers all eventually look like idiotic fanatics who can't "keep up with the cool kids", but they arrived there because they were looking for a solution to a particular problem that they were having. If you then change the solution, to solve some other problem, while destroying the solution that attracted them to the project, in the first place, then they'll be unhappy about it.
Being cool doesn't automatically make you right about everything, but you can simply have enough might to "change" what is right. Shift the goalposts so that the problem you are trying to solve is The Most Pressing Problem. Everyone still focused on the Original Problem is reduced to protesting and being called "difficult", "unhelpful", "uncooperative", "rude".
Why are they protesting? Why don't they just go with the flow? Look at us, we never protest. We are so nice! We're totally happy with the way things are going. We are always polite and elegant and regal. Only rude people complain.
Good vibes only.
-
 @ 005bc4de:ef11e1a2
2025-05-05 07:31:15
@ 005bc4de:ef11e1a2
2025-05-05 07:31:15How does MSTR buy bitcoin without bumping the price?
Michael Saylor buys bitcoin and he has a handy tool to track his purchases, at, well, https://saylortracker.com
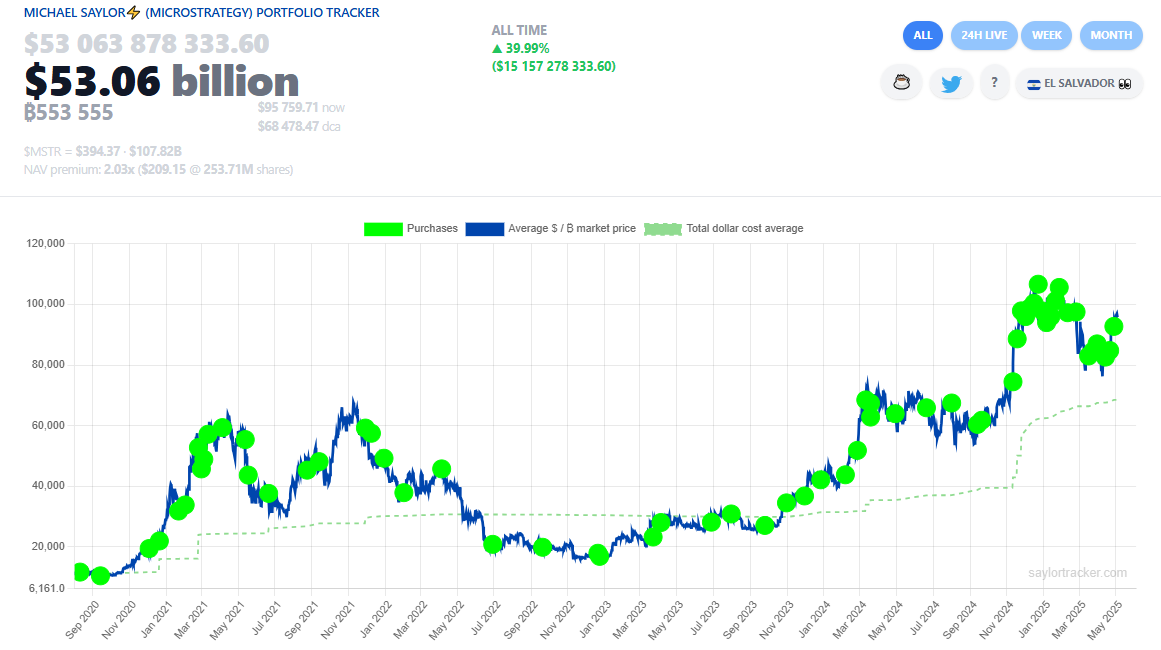
Mondays have been Saylor's buy-days, and rumors are that he may be at it again.
Yet, with all the mega-buying, why does it seem like the price doesn't jump? This is a question that comes to my mind seemingly each week now with the next MSTR buy.
Grok AI seems to imply that even though Saylor's purchases are huge, they're still not big enough to move the market. Average daily volume traded for BTC seems to be in the $15 billion upwards to $60 billion. So, Saylor's 1 to 2 or 4 billion dollar purchases evidently still aren't enough to eat up the order book.
This is a little hard to swallow considering that Grok estimated, "MicroStrategy owns approximately 2.81% of all Bitcoin in circulation and 2.64% of the total Bitcoin supply that will ever exist." I guess that other 97% is just moving their bitcoin around, back-and-forth?
The standard answer I've heard as to why the market doesn't move has been, "Oh, MSTR buys bitcoin over-the-counter, not off of exchanges where the prices come from."
That's a simple elevator-ride one sentence answer that seems plausible. I could meet someone on the street and say, "Hey, you got any bitcoin and do you wanna sell it?" If they said, "Yeah, and sure," then I could hand them some cash and they could send some BTC to me. The exchanges would be unmoved by this over the counter transaction.
Or, I might be interested in buying a Beanie Babie tie-dyed PEACE bear. The market, ebay, seems to list them around $8.99. But, if I buy a hundred of them off that bitcoin guy on the sidewalk, ebay and the price their isn't affected at all. Not are the 79 "watchers" keeping an eye on the PEACE bear.
But still, to me, that one-line OTC answer somehow seems off. Seriously, does Saylor have connections with people who want to sell thousands or tens of thousands of bitcoin? Every week? Who are these people with all that bitcoin to sell? Can Saylor connect me to a seller of 100 tie-dyed PEACE bears?
Maybe Saylor actually does have those kinds of connections to make those kinds of purchases. Or, maybe Grok is right and Saylor's moves aren't as big-fish as they seem. Anyway, I don't know, and those are circles that I don't move in. And, after all, I guess I still really don't know how he buys so much without moving the market.
!HBIT
-
 @ fd06f542:8d6d54cd
2025-05-05 01:38:09
@ fd06f542:8d6d54cd
2025-05-05 01:38:09https://blossom.band/ 是Nostr.build旗下的Blossom Server服务页面,为Nostr社交媒体平台用户提供媒体上传服务,依托Nostr.build基础设施,具有独特优势和明确规范。 1. 服务背景:由Nostr.build提供支持,借助其经过时间验证、高可用性的基础设施以及全球覆盖的快速CDN网络,每个用户的npub都有专属服务器域名,保证用户数据独立性。 2. 上传限制:单次上传文件大小硬限制为100MiB,上传次数和存储时长不受限。支持常见媒体类型上传,包括图片、音频和视频。若有更大上传尺寸等扩展需求,可查看相关付费计划。所有上传需遵循服务条款。 3. 兼容性与接口:认证方式为签名的nostr事件,支持Nostr文件元数据标签(NIP - 94)BUD - 08等。提供多种接口,如GET、HEAD、DELETE、PUT等用于文件的获取、查看、删除和上传等操作 ,部分接口需认证,不同接口有不同功能和限制。 4. 限制条件:使用PUT /upload或PUT /mirror端点上传时,含GPS元数据的媒体文件会被拒绝。 5. 支持的媒体类型:免费用户可上传常见媒体类型,如.jpg、.png等;付费用户根据不同计划,除免费内容外,还能上传.pdf、.svg和.zip等格式文件。 6. 关于Nostr.build:2022年12月24日开始为Nostr平台提供免费媒体上传服务,旨在推动Nostr生态发展。团队秉持透明、社区化的媒体审核方式和开源理念,致力于打造安全可靠的平台,欢迎用户反馈和建议 。
使用例子:
假设你是Nostr社交媒体平台的用户,想在该平台分享图片、音频或视频等媒体内容,就可以使用
https://blossom.band/提供的服务。下面以分享一张图片和管理已上传媒体为例,介绍其使用方法:- 上传图片:你需要先对上传操作进行签名认证(通过Signed nostr event方式)。认证完成后,使用
PUT /upload接口来上传图片。例如,你本地有一张名为example.jpg的图片,通过编程方式(如使用Python的requests库)构造请求:
```python import requests import json
假设你已经获取到签名认证信息
headers = { "Content-Type": "application/json", "Authorization": "Bearer your_signed_nostr_event" } files = { 'file': open('example.jpg', 'rb') } response = requests.put('https://blossom.band/upload', headers=headers, files=files) if response.status_code == 200: print("图片上传成功") else: print(f"上传失败,状态码: {response.status_code}") ```
- 获取上传文件信息:图片上传成功后,会得到一个对应的
sha256哈希值。你可以使用GET /<sha256>接口(假设图片对应的sha256哈希值为your_sha256_value)获取文件信息,例如:
```python import requests
headers = { "Authorization": "Bearer your_signed_nostr_event" } response = requests.get(f'https://blossom.band/your_sha256_value.jpg', headers=headers) if response.status_code == 200: print("获取文件信息成功") else: print(f"获取失败,状态码: {response.status_code}") ```
- 删除上传的图片:如果你想删除已上传的图片,可以使用
DELETE /<sha256>接口。同样以your_sha256_value为例:
```python import requests
headers = { "Authorization": "Bearer your_signed_nostr_event" } response = requests.delete(f'https://blossom.band/your_sha256_value.jpg', headers=headers) if response.status_code == 200: print("图片删除成功") else: print(f"删除失败,状态码: {response.status_code}") ```
- 查看用户上传列表:使用
GET /list/<pubkey>接口(pubkey为你的Nostr公钥)可以查看你上传的所有媒体文件列表。例如:
```python import requests
headers = { "Authorization": "Bearer your_signed_nostr_event" } pubkey = "your_public_key" response = requests.get(f'https://blossom.band/list/{pubkey}', headers=headers) if response.status_code == 200: print("获取上传列表成功") print(response.json()) else: print(f"获取失败,状态码: {response.status_code}") ```
- 上传图片:你需要先对上传操作进行签名认证(通过Signed nostr event方式)。认证完成后,使用
-
 @ 0d788b5e:c99ddea5
2025-05-05 01:16:45
@ 0d788b5e:c99ddea5
2025-05-05 01:16:45isLoading
-
 @ 0d788b5e:c99ddea5
2025-05-05 01:14:44
@ 0d788b5e:c99ddea5
2025-05-05 01:14:44dMessage =
发布失败,未成功发布到任何服务器,已经保存到草稿。; -
 @ 0d788b5e:c99ddea5
2025-05-05 01:12:36
@ 0d788b5e:c99ddea5
2025-05-05 01:12:36假设你是Nostr社交媒体平台的用户,想在该平台分享图片、音频或视频等媒体内容,就可以使用
https://blossom.band/提供的服务。下面以分享一张图片和管理已上传媒体为例,介绍其使用方法: 1. 上传图片:你需要先对上传操作进行签名认证(通过Signed nostr event方式)。认证完成后,使用PUT /upload接口来上传图片。例如,你本地有一张名为example.jpg的图片,通过编程方式(如使用Python的requests库)构造请求: ```python import requests import json假设你已经获取到签名认证信息
headers = { "Content-Type": "application/json", "Authorization": "Bearer your_signed_nostr_event" } files = { 'file': open('example.jpg', 'rb') } response = requests.put('https://blossom.band/upload', headers=headers, files=files) if response.status_code == 200: print("图片上传成功") else: print(f"上传失败,状态码: {response.status_code}")
2. **获取上传文件信息**:图片上传成功后,会得到一个对应的`sha256`哈希值。你可以使用`GET /<sha256>`接口(假设图片对应的`sha256`哈希值为`your_sha256_value`)获取文件信息,例如:python import requestsheaders = { "Authorization": "Bearer your_signed_nostr_event" } response = requests.get(f'https://blossom.band/your_sha256_value.jpg', headers=headers) if response.status_code == 200: print("获取文件信息成功") else: print(f"获取失败,状态码: {response.status_code}")
3. **删除上传的图片**:如果你想删除已上传的图片,可以使用`DELETE /<sha256>`接口。同样以`your_sha256_value`为例:python import requestsheaders = { "Authorization": "Bearer your_signed_nostr_event" } response = requests.delete(f'https://blossom.band/your_sha256_value.jpg', headers=headers) if response.status_code == 200: print("图片删除成功") else: print(f"删除失败,状态码: {response.status_code}")
4. **查看用户上传列表**:使用`GET /list/<pubkey>`接口(`pubkey`为你的Nostr公钥)可以查看你上传的所有媒体文件列表。例如:python import requestsheaders = { "Authorization": "Bearer your_signed_nostr_event" } pubkey = "your_public_key" response = requests.get(f'https://blossom.band/list/{pubkey}', headers=headers) if response.status_code == 200: print("获取上传列表成功") print(response.json()) else: print(f"获取失败,状态码: {response.status_code}") ```
-
 @ a965e1a8:3463a92f
2025-05-04 23:40:49
@ a965e1a8:3463a92f
2025-05-04 23:40:49{"desc":"test123","code":"test123","tags":[]}
-
 @ f7d424b5:618c51e8
2025-05-04 19:19:43
@ f7d424b5:618c51e8
2025-05-04 19:19:43Listen to the new episode here!
Finally some good news. Good new games, worthwhile remakes, and bloggers facing the consequences of their actions. Gaming is healing. Let's talk about it!
Stuff cited:
Obligatory:
- Discuss this episode on OUR NEW FORUM
- Get the RSS and Subscribe (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at newpodcastapps.com
- Or listen to the show on the forum using the embedded Podverse player!
- Send your complaints here
Reminder that this is a Value4Value podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!
-
 @ a5ee4475:2ca75401
2025-05-04 17:22:36
@ a5ee4475:2ca75401
2025-05-04 17:22:36clients #list #descentralismo #english #article #finalversion
*These clients are generally applications on the Nostr network that allow you to use the same account, regardless of the app used, keeping your messages and profile intact.
**However, you may need to meet certain requirements regarding access and account NIP for some clients, so that you can access them securely and use their features correctly.
CLIENTS
Twitter like
- Nostrmo - [source] 🌐🤖🍎💻(🐧🪟🍎)
- Coracle - Super App [source] 🌐
- Amethyst - Super App with note edit, delete and other stuff with Tor [source] 🤖
- Primal - Social and wallet [source] 🌐🤖🍎
- Iris - [source] 🌐🤖🍎
- Current - [source] 🤖🍎
- FreeFrom 🤖🍎
- Openvibe - Nostr and others (new Plebstr) [source] 🤖🍎
- Snort 🌐(🤖[early access]) [source]
- Damus 🍎 [source]
- Nos 🍎 [source]
- Nostur 🍎 [source]
- NostrBand 🌐 [info] [source]
- Yana 🤖🍎🌐💻(🐧) [source]
- Nostribe [on development] 🌐 [source]
- Lume 💻(🐧🪟🍎) [info] [source]
- Gossip - [source] 💻(🐧🪟🍎)
- Camelus [early access] 🤖 [source]
Communities
- noStrudel - Gamified Experience [info] 🌐
- Nostr Kiwi [creator] 🌐
- Satellite [info] 🌐
- Flotilla - [source] 🌐🐧
- Chachi - [source] 🌐
- Futr - Coded in haskell [source] 🐧 (others soon)
- Soapbox - Comunnity server [info] [source] 🌐
- Ditto - Soapbox comunnity server 🌐 [source] 🌐
- Cobrafuma - Nostr brazilian community on Ditto [info] 🌐
- Zapddit - Reddit like [source] 🌐
- Voyage (Reddit like) [on development] 🤖
Wiki
Search
- Advanced nostr search - Advanced note search by isolated terms related to a npub profile [source] 🌐
- Nos Today - Global note search by isolated terms [info] [source] 🌐
- Nostr Search Engine - API for Nostr clients [source]
Website
App Store
ZapStore - Permitionless App Store [source]
Audio and Video Transmission
- Nostr Nests - Audio Chats 🌐 [info]
- Fountain - Podcast 🤖🍎 [info]
- ZapStream - Live streaming 🌐 [info]
- Corny Chat - Audio Chat 🌐 [info]
Video Streaming
Music
- Tidal - Music Streaming [source] [about] [info] 🤖🍎🌐
- Wavlake - Music Streaming [source] 🌐(🤖🍎 [early access])
- Tunestr - Musical Events [source] [about] 🌐
- Stemstr - Musical Colab (paid to post) [source] [about] 🌐
Images
- Pinstr - Pinterest like [source] 🌐
- Slidestr - DeviantArt like [source] 🌐
- Memestr - ifunny like [source] 🌐
Download and Upload
Documents, graphics and tables
- Mindstr - Mind maps [source] 🌐
- Docstr - Share Docs [info] [source] 🌐
- Formstr - Share Forms [info] 🌐
- Sheetstr - Share Spreadsheets [source] 🌐
- Slide Maker - Share slides 🌐 (advice: https://zaplinks.lol/ and https://zaplinks.lol/slides/ sites are down)
Health
- Sobrkey - Sobriety and mental health [source] 🌐
- NosFabrica - Finding ways for your health data 🌐
- LazerEyes - Eye prescription by DM [source] 🌐
Forum
- OddBean - Hacker News like [info] [source] 🌐
- LowEnt - Forum [info] 🌐
- Swarmstr - Q&A / FAQ [info] 🌐
- Staker News - Hacker News like 🌐 [info]
Direct Messenges (DM)
- 0xchat 🤖🍎 [source]
- Nostr Chat 🌐🍎 [source]
- Blowater 🌐 [source]
- Anigma (new nostrgram) - Telegram based [on development] [source]
- Keychat - Signal based [🤖🍎 on development] [source]
Reading
- Highlighter - Insights with a highlighted read 🌐 [info]
- Zephyr - Calming to Read 🌐 [info]
- Flycat - Clean and Healthy Feed 🌐 [info]
- Nosta - Check Profiles [on development] 🌐 [info]
- Alexandria - e-Reader and Nostr Knowledge Base (NKB) [source]
Writing
Lists
- Following - Users list [source] 🌐
- Listr - Lists [source] 🌐
- Nostr potatoes - Movies List source 💻(numpy)
Market and Jobs
- Shopstr - Buy and Sell [source] 🌐
- Nostr Market - Buy and Sell 🌐
- Plebeian Market - Buy and Sell [source] 🌐
- Ostrich Work - Jobs [source] 🌐
- Nostrocket - Jobs [source] 🌐
Data Vending Machines - DVM (NIP90)
(Data-processing tools)
AI
Games
- Chesstr - Chess 🌐 [source]
- Jestr - Chess [source] 🌐
- Snakestr - Snake game [source] 🌐
- DEG Mods - Decentralized Game Mods [info] [source] 🌐
Customization
Like other Services
- Olas - Instagram like [source] 🤖🍎🌐
- Nostree - Linktree like 🌐
- Rabbit - TweetDeck like [info] 🌐
- Zaplinks - Nostr links 🌐
- Omeglestr - Omegle-like Random Chats [source] 🌐
General Uses
- Njump - HTML text gateway source 🌐
- Filestr - HTML midia gateway [source] 🌐
- W3 - Nostr URL shortener [source] 🌐
- Playground - Test Nostr filters [source] 🌐
- Spring - Browser 🌐
Places
- Wherostr - Travel and show where you are
- Arc Map (Mapstr) - Bitcoin Map [info]
Driver and Delivery
- RoadRunner - Uber like [on development] ⏱️
- Arcade City - Uber like [on development] ⏱️ [info]
- Nostrlivery - iFood like [on development] ⏱️
OTHER STUFF
Lightning Wallets (zap)
- Alby - Native and extension [info] 🌐
- ZBD - Gaming and Social [info] 🤖🍎
- Wallet of Satoshi [info] 🤖🍎
- Minibits - Cashu mobile wallet [info] 🤖
- Blink - Opensource custodial wallet (KYC over 1000 usd) [source] 🤖🍎
- LNbits - App and extesion [source] 🤖🍎💻
- Zeus - [info] [source] 🤖🍎
Exchange
Media Server (Upload Links)
audio, image and video
- Nostr Build - [source] 🌐
- Nostr Check - [info] [source] 🌐
- NostPic - [source] 🌐
- Sovbit 🌐
- Voidcat - [source] 🌐
Without Nip: - Pomf - Upload larger videos [source] - Catbox - [source] - x0 - [source]
Donation and payments
- Zapper - Easy Zaps [source] 🌐
- Autozap [source] 🌐
- Zapmeacoffee 🌐
- Nostr Zap 💻(numpy)
- Creatr - Creators subscription 🌐
- Geyzer - Crowdfunding [info] [source] 🌐
- Heya! - Crowdfunding [source]
Security
- Secret Border - Generate offline keys 💻(java)
- Umbrel - Your private relay [source] 🌐
Extensions
- Nos2x - Account access keys 🌐
- Nsec.app 🌐 [info]
- Lume - [info] [source] 🐧🪟🍎
- Satcom - Share files to discuss - [info] 🌐
- KeysBand - Multi-key signing [source] 🌐
Code
- Nostrify - Share Nostr Frameworks 🌐
- Git Workshop (github like) [experimental] 🌐
- Gitstr (github like) [on development] ⏱️
- Osty [on development] [info] 🌐
- Python Nostr - Python Library for Nostr
Relay Check and Cloud
- Nostr Watch - See your relay speed 🌐
- NosDrive - Nostr Relay that saves to Google Drive
Bidges and Getways
- Matrixtr Bridge - Between Matrix & Nostr
- Mostr - Between Nostr & Fediverse
- Nostrss - RSS to Nostr
- Rsslay - Optimized RSS to Nostr [source]
- Atomstr - RSS/Atom to Nostr [source]
NOT RELATED TO NOSTR
Android Keyboards
Personal notes and texts
Front-ends
- Nitter - Twitter / X without your data [source]
- NewPipe - Youtube, Peertube and others, without account & your data [source] 🤖
- Piped - Youtube web without you data [source] 🌐
Other Services
- Brave - Browser [source]
- DuckDuckGo - Search [source]
- LLMA - Meta - Meta open source AI [source]
- DuckDuckGo AI Chat - Famous AIs without Login [source]
- Proton Mail - Mail [source]
Other open source index: Degoogled Apps
Some other Nostr index on:
-
 @ 700c6cbf:a92816fd
2025-05-04 16:34:01
@ 700c6cbf:a92816fd
2025-05-04 16:34:01Technically speaking, I should say blooms because not all of my pictures are of flowers, a lot of them, probably most, are blooming trees - but who cares, right?
It is that time of the year that every timeline on every social media is being flooded by blooms. At least in the Northern Hemisphere. I thought that this year, I wouldn't partake in it but - here I am, I just can't resist the lure of blooms when I'm out walking the neighborhood.
Spring has sprung - aaaachoo, sorry, allergies suck! - and the blooms are beautiful.
Yesterday, we had the warmest day of the year to-date. I went for an early morning walk before breakfast. Beautiful blue skies, no clouds, sunshine and a breeze. Most people turned on their aircons. We did not. We are rebels - hah!
We also had breakfast on the deck which I really enjoy during the weekend. Later I had my first session of the year painting on the deck while listening/watching @thegrinder streaming. Good times.
Today, the weather changed. Last night, we had heavy thunderstorms and rain. This morning, it is overcast with the occasional sunray peaking through or, as it is right now, raindrops falling.
We'll see what the day will bring. For me, it will definitely be: Back to painting. Maybe I'll even share some here later. But for now - this is a photo post, and here are the photos. I hope you enjoy as much as I enjoyed yesterday's walk!
Cheers, OceanBee
!(image)[https://cdn.satellite.earth/cc3fb0fa757c88a6a89823585badf7d67e32dee72b6d4de5dff58acd06d0aa36.jpg] !(image)[https://cdn.satellite.earth/7fe93c27c3bf858202185cb7f42b294b152013ba3c859544950e6c1932ede4d3.jpg] !(image)[https://cdn.satellite.earth/6cbd9fba435dbe3e6732d9a5d1f5ff0403935a4ac9d0d83f6e1d729985220e87.jpg] !(image)[https://cdn.satellite.earth/df94d95381f058860392737d71c62cd9689c45b2ace1c8fc29d108625aabf5d5.jpg] !(image)[https://cdn.satellite.earth/e483e65c3ee451977277e0cfa891ec6b93b39c7c4ea843329db7354fba255e64.jpg] !(image)[https://cdn.satellite.earth/a98fe8e1e0577e3f8218af31f2499c3390ba04dced14c2ae13f7d7435b4000d7.jpg] !(image)[https://cdn.satellite.earth/d83b01915a23eb95c3d12c644713ac47233ce6e022c5df1eeba5ff8952b99d67.jpg] !(image)[https://cdn.satellite.earth/9ee3256882e363680d8ea9bb6ed3baa5979c950cdb6e62b9850a4baea46721f3.jpg] !(image)[https://cdn.satellite.earth/201a036d52f37390d11b76101862a082febb869c8d0e58d6aafe93c72919f578.jpg] !(image)[https://cdn.satellite.earth/cd516d89591a4cf474689b4eb6a67db842991c4bf5987c219fb9083f741ce871.jpg]
-
 @ a29cfc65:484fac9c
2025-05-04 16:20:03
@ a29cfc65:484fac9c
2025-05-04 16:20:03Bei einer Führung durch den Naumburger Dom sprach der Domführer über Propaganda im Mittelalter. Die gefühlvollen Gesichtsausdrücke der steinernen Stifterfiguren rund um die berühmte Uta sollten das Volk beeinflussen. Darüber haben wir auf der Heimfahrt nach Leipzig philosophiert und fanden den Denkansatz spannend. Denn auch wenn es damals nicht Propaganda hieß, so gab es doch Interessen der Mächtigen, die sie gegenüber dem Volk durchsetzten. Sie bedienten sich dabei der damals verfügbaren „Medien“, zu denen die Kirche gehörte, wo sich das Volk zum Gottesdienst traf.
Kulturelle Identität Europas
Mitteldeutschland ist ein Zentrum mittelalterlicher Baukunst. Der Naumburger Dom St. Peter und Paul wurde auf den Grundmauern einer noch älteren Kirche im 13. Jahrhundert gebaut. Er ist weltweit einzigartig in seiner Architektur, Bildhauerkunst und Glasmalerei. Seit 2018 ist er Unesco-Weltkulturerbe. Die Stadt Naumburg hatte einst die gleiche Bedeutung wie Merseburg, Magdeburg oder Leipzig. Der Dom – von der Spätromanik bis in die Frühgotik unter Leitung eines heute unbekannten Bildhauerarchitekten errichtet – gilt als Meisterwerk menschlicher Schöpferkraft und Handwerkskunst. Die naturwissenschaftlich-physikalischen Kenntnisse der Menschen waren offensichtlich enorm. Sie verfügten über das Wissen zur Planung und über entsprechende Werk- und Hebezeuge, um solche Bauwerke in relativ kurzer Zeit errichten zu können.
Im Westchor des Doms befinden sich mit den zwölf lebensgroßen Stifterfiguren die bekanntesten Kunstwerke des Doms, unter ihnen Uta von Ballenstedt. Sie soll Walt Disney als Quelle für die schöne und sehr stolze Königin im Zeichentrickfilm Schneewittchen gedient haben. Das Besondere und Neue an den steinernen Stifterfiguren war ihre realitätsnahe Darstellung, die sie lebendig und ausdrucksstark wirken lässt. Sie sind ein Höhepunkt in der Steinmetzkunst der damaligen Zeit. Die Figuren wurden, obschon die dargestellten Personen bereits mehr als 200 Jahre tot waren, mit charakteristischen Gesichtsausdrücken dargestellt: Uta schaut schön und stolz in die Ferne, ihr Gatte Ekkehard wirkt etwas hochmütig. Gegenüber steht die lachende Reglindis neben ihrem wehmütig-leidend blickenden Mann Hermann von Meißen.
Der Domführer sagte, dass die Gesichtsausdrücke menschliche Verhaltensweisen darstellen, die bei den Kirchenbesuchern unerwünscht waren. Wir hätten es hier mit einer sehr frühen Form der Propaganda zu tun. Die katholische Kirche war Vorreiter in Sachen Propaganda. Sie hat etwa 400 Jahre später, im Jahr 1622, mit der Sacra Congregatio de Propaganda Fide ein Amt gegründet, das den „richtigen“ Glauben in die Welt tragen sollte, und erst 1967 umbenannt wurde. Aber ihre gesellschaftlich führende Position hatte damals auch eine positive Seite: Den Kirchen und Klöstern haben wir den Erhalt und die Weitergabe antiken Wissens zu verdanken. Europa konnte sich trotz der politischen Zersplitterung seine kulturelle Identität erhalten. Zum Beispiel lässt sich das Wirken des namenlosen Domschöpfers anhand der Bau- und Kunstwerke quer durch Europa von Nordfrankreich über Mainz nach Naumburg und Meißen nachvollziehen. Aus der weiteren Entwicklung von Kunst und Kultur in Europa entstand in der Renaissance die Philosophie des Humanismus und später daraus die Aufklärung mit ihrer Wirkung auf Literatur und Wissenschaft. Ziel war dabei immer eine Stärkung des Gemeinwesens.
Transhumanismus zerstört Gemeinschaften
Heute scheinen wir uns allerdings an einer Bruchstelle der gesellschaftlichen Entwicklung zu befinden. Die Kirchen spielen in unserer Gesellschaft kaum noch eine Rolle. Weder bringen sie sich in ethische Diskussionen hörbar ein, noch tragen sie die Entwicklung von Kunst und Kultur sichtbar voran. Ihre Rolle im Bereich Propaganda haben längst Zeitungen und Zeitschriften, Rundfunk und Fernsehen übernommen. Diese Medien haben eine größere Reichweite, und die psychologische Beeinflussung ist umfassender. Nach dem Zweiten Weltkrieg wurde die Manipulation der Massen stark intensiviert und nahm nach dem Zusammenbruch der Sowjetunion noch weiter an Fahrt auf. Der Liberalismus konnte auf allen Gebieten seinen Siegeszug antreten, stellte das Individuum in den Mittelpunkt und erhob den Markt zur heiligen Kuh. Im Laufe der Zeit wurden die humanistischen Ideen der Aufklärung in ihr Gegenteil verkehrt. Der Mensch wurde als fehlerhaftes Wesen identifiziert, in die Vereinzelung getrieben, bevormundet und gegängelt – angeblich, damit er sich nicht selbst schadet. Zur psychologischen Beeinflussung kommen die neuen technischen Möglichkeiten aus Bio-Nano-Neuro-Wissenschaften und Digitalisierung. Der Transhumanismus wurde als neues Ziel für die Menschheit ausgerufen. Der Einzelne soll biologisch und technisch perfektioniert werden. Gemeinschaften – von der Familie angefangen – treibt das in die Bedeutungslosigkeit. Es besteht die Gefahr, dass persönliche Integrität und Privatsphäre durch Eingriffe in Körper- und Geistesfunktionen verletzt werden. Eine neue Aufklärung ist nötig. Denn sehr viel von dem über die Jahrhunderte erlangten Wissen ging schon verloren oder ist nur noch versteckt in den Bibliotheken und Archiven der Kirchen zu finden. Die Besinnung auf die vergessenen beziehungsweise verdrängten Grundlagen und Ideale der Aufklärung kann diese Entwicklung abwenden. Die Kulturschätze Mitteleuropas vermitteln in ihrer Schönheit und Vollkommenheit die Ruhe und die zeitlichen und räumlichen Dimensionen, die wir brauchen, wenn wir über die Frage nachdenken, wie wir in Zukunft leben wollen.
Die Rolle der neuen Medien für die zukünftige Entwicklung
Von den Alt-Medien ist in dieser Hinsicht nichts zu erwarten. Sie werden finanziert und sind unterwandert von den Kräften, die transhumanistische Entwicklungen vorantreiben. Die „neue Aufklärung“ ist ein lohnenswertes Ziel für die neuen Medien. Diese lassen sich jedoch noch zu sehr von den aktuellen Themen der Alt-Medien treiben. Der Angst-Propaganda begegnen sie mit – Ängsten, wenn auch anders ausgerichtet. Einige reiten die Empörungswelle in Gegenrichtung zu den Alt-Medien. Manche Betreiber von „alternativen“ Finanz- und Wirtschaftskanälen wollen ihre eigenen marktgläubigen Produkte an den Mann bringen. Stattdessen sollten in den neuen Medien positive Nachrichten verbreitet und eigene Themenfelder eröffnet werden, denen sich die Alt-Medien verweigern:
· der Mensch und seine Bildung zur souveränen, selbständig denkenden und handelnden Persönlichkeit,
· die Entwicklung des eigenen Bewusstseins, um der Fremdbestimmung zu entkommen und zu Wahrhaftigkeit, Authentizität und Menschlichkeit zu gelangen,
· die Entwicklung des Gemeinwohls,
· die Frage, wie wir neue Gemeinschaften bis hin zu autarken Gemeinden gründen können – wichtiger, je mehr das gesellschaftliche System um uns herum zusammenbricht.
Direkt sichtbar ist der letzte Punkt am Niedergang der Architektur und am Zustand der Innenstädte: Die reich dekorierten Gebäude der Gründerzeit wurden nach ihrer Zerstörung im Zweiten Weltkrieg durch gleichförmig rechteckige Gebäude aus Beton und Glas ersetzt. Dazu kamen die in allen Städten austauschbar gleichen Ladenzeilen und in den letzten Jahren Dreck und Schmierereien, die nicht mehr weggeräumt werden.
Die gesellschaftlichen Verwerfungen der Corona-Zeit führten bei vielen Menschen zum Innehalten und Nachdenken über Sinn und Ziele ihres Lebens. So entstanden einige Pilotprojekte, zum Beispiel in den Bereichen Landwirtschaft, Gesundheitswesen und Bildung. Diese auf die Zukunft gerichteten Themen könnten in den neuen Medien umfangreicher vorgestellt und diskutiert werden. Manova setzt schon solche Schwerpunkte mit „The Great WeSet“ von Walter van Rossum sowie mit den Kategorien „Zukunft & Neue Wege“ sowie „Aufwind“. Der Kontrafunk hat Formate entwickelt, die das Gemeinwohl stärker in den Fokus setzen wie etwa die Kultur- und Wissenschaftsrubrik. Nuoviso hat einen eigenen Songcontest ins Leben gerufen. Neben der inhaltlichen Ausrichtung auf eine lebenswerte Zukunft gilt es auch, die technologische Basis der neuen Medien zukunftsfest zu machen und sich der digitalen Zensur zu entziehen. Milosz Matuschek geht mit dem Pareto-Projekt neue Wege. Es könnte zur unzensierbaren Plattform der neuen Medien werden. Denn wie er sagt: Man baut sein neues Haus doch auch nicht auf dem Boden, der einem anderen gehört.
-
 @ 6e0ea5d6:0327f353
2025-05-04 14:53:42
@ 6e0ea5d6:0327f353
2025-05-04 14:53:42Amico mio, ascolta bene!
Without hesitation, the woman you attract with lies is not truly yours. Davvero, she is the temporary property of the illusion you’ve built to seduce her. And every illusion, sooner or later, crumbles.
Weak men sell inflated versions of themselves. They talk about what they don’t have, promise what they can’t sustain, adorn their empty selves with words that are nothing more than a coat of paint. And they do this thinking that, later, they’ll be able to "show who they really are." Fatal mistake, cazzo!
The truth, amico mio, is not something that appears at the end. It is what holds up the whole beginning.
The woman who approaches a lie may smile at first — but she is smiling at the theater, not at the actor. When the curtains fall, what she will see is not a man. It will be a character tired of performing, begging for love from a self-serving audience in the front row.
That’s why I always point out that lying to win a woman’s heart is the same as sabotaging your own nature. The woman who comes through an invented version of you will be the first to leave when the veil of lies tears apart. Not out of cruelty, but out of consistency with her own interest. Fine... She didn’t leave you, but rather, that version of yourself never truly existed to be left behind.
A worthy man presents himself without deceptive adornments. And those who stay, stay because they know exactly who they are choosing as a man. That’s what differentiates forged seduction from the convenience of love built on honor, loyalty, and respect.
Ah, amico mio, I remember well. It was lunch on an autumn day in Catania. Mediterranean heat, and the Nero D'Avola wine from midday clinging to the lips like dried blood. Sitting in the shade of a lemon tree planted right by my grandfather's vineyard entrance, my uncle — the oldest of my father’s brothers — spoke little, but when he called us to sit by his side, all the nephews would quiet down to listen. And in my youth, he told me something that has never left my mind.
“In Sicily, the woman who endures the silence of a man about his business is more loyal than the one who is enchanted by speeches about what he does or how much he earns. Perchè, figlio mio, the first one has seen the truth. The second one, only a false shine.”
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 005bc4de:ef11e1a2
2025-05-04 12:01:42
@ 005bc4de:ef11e1a2
2025-05-04 12:01:42OSU commencement speech revisited 1 year later
One year ago, May 5, 2024, the commencement speaker at Ohio State University was Chris Pan. He got booed for mentioning bitcoin. There were some other things involved, but the bitcoin part is what could my ears.
Here's an article about the speech and a video clip with the bitcoin mention. The quote that I feel is especially pertinent is this, '“The mechanics of investing are actually easy, but it comes down to mindset,” Pan said. “The most common barriers are fear, laziness and closed-mindedness.”'
Last year, I wrote this and had it sent as a reminder to myself (I received the reminder yesterday after totally forgetting about this):
Ohio State commencement speaker mentions bitcoin and got booed.
I wondered what would've happened if they'd taken his advice to heart and bought bitcoin that day. Linked article: https://www.businessinsider.com/osu-commencement-speaker-ayahuasca-praises-bitcoin-booed-viral-2024-5
Nat Brunell interviewed him on her Coin Stories podcast shortly after his speech: https://www.youtube.com/watch?v=LRqKxKqlbcI
BTC on 5/5/2024 day of speech: about $64,047 (chart below)
If any of those now wise old 23 year olds remember the advice they were given, bitcoin is currently at $95,476. If any took Pan's advice, they achieved a 49% gain in one year. Those who did not take Pan's advice, lost about 2.7% of their buying power due to inflation.
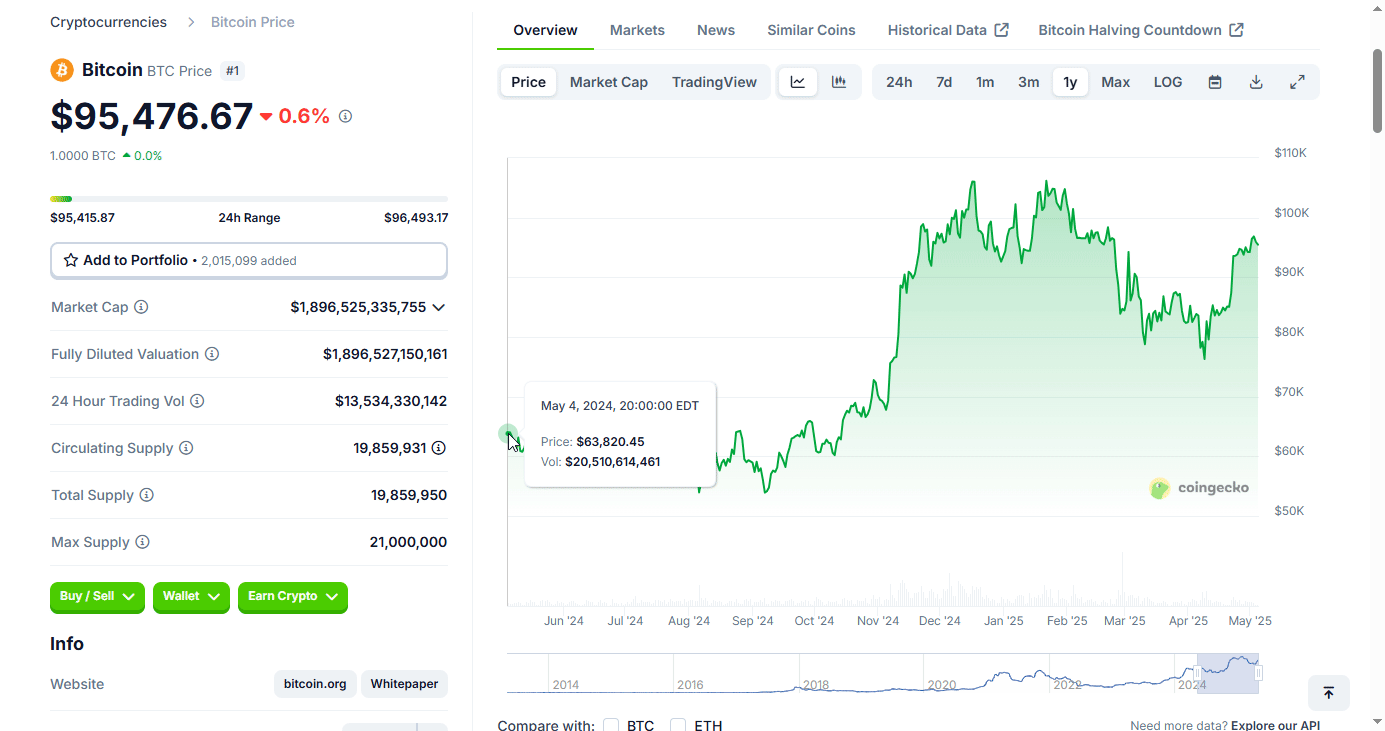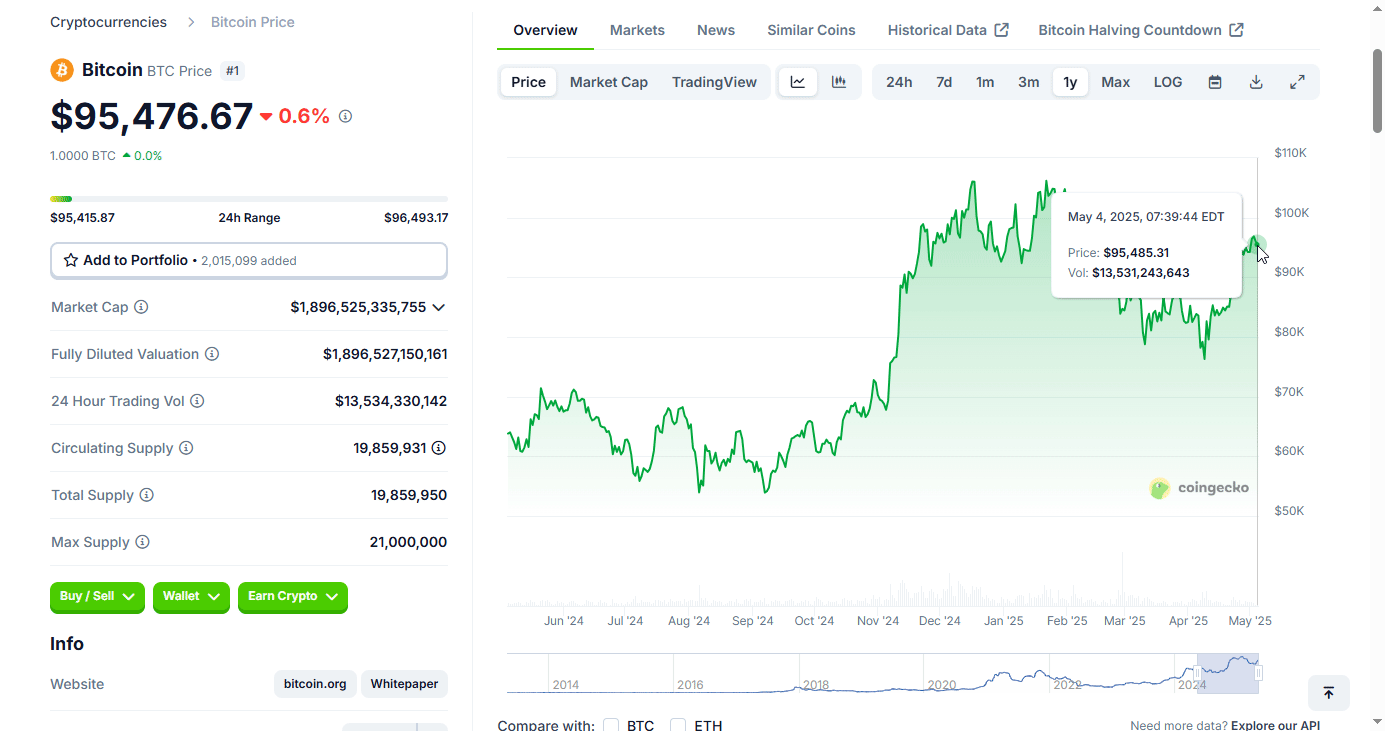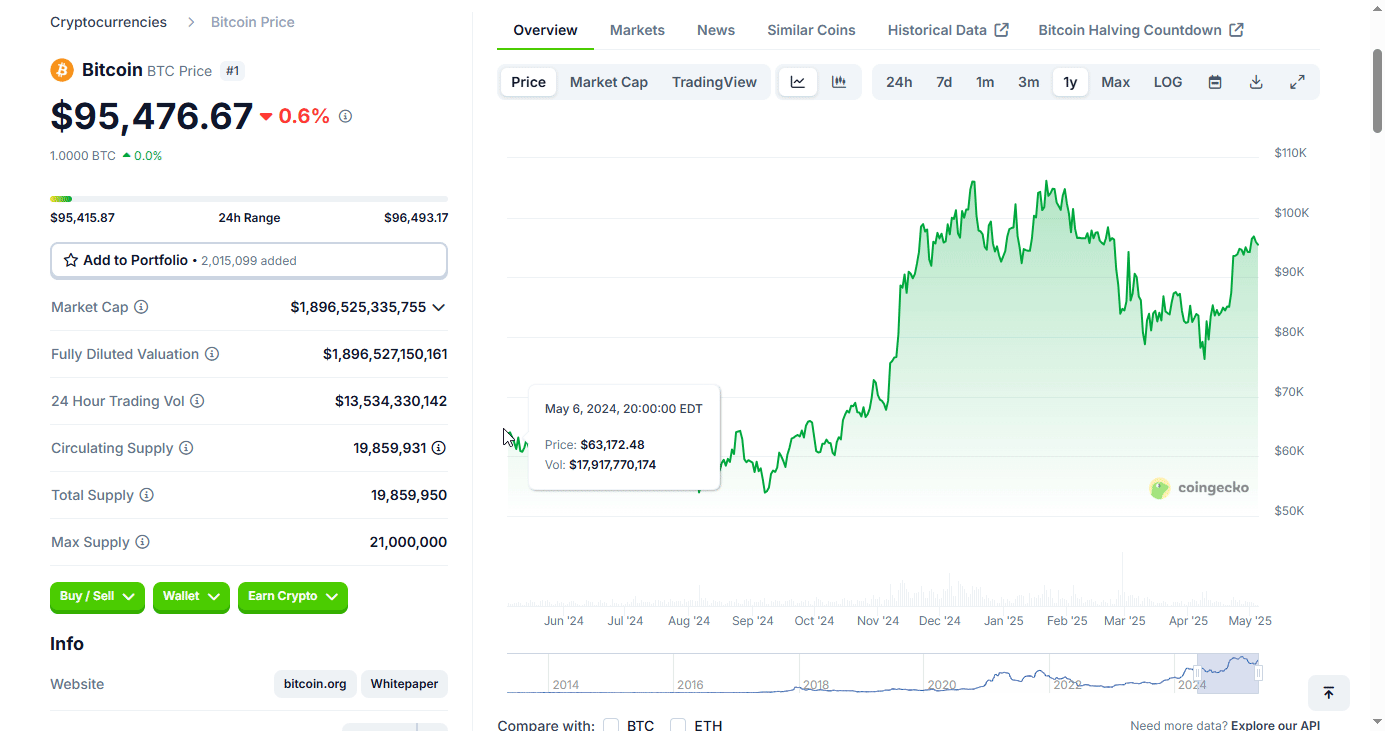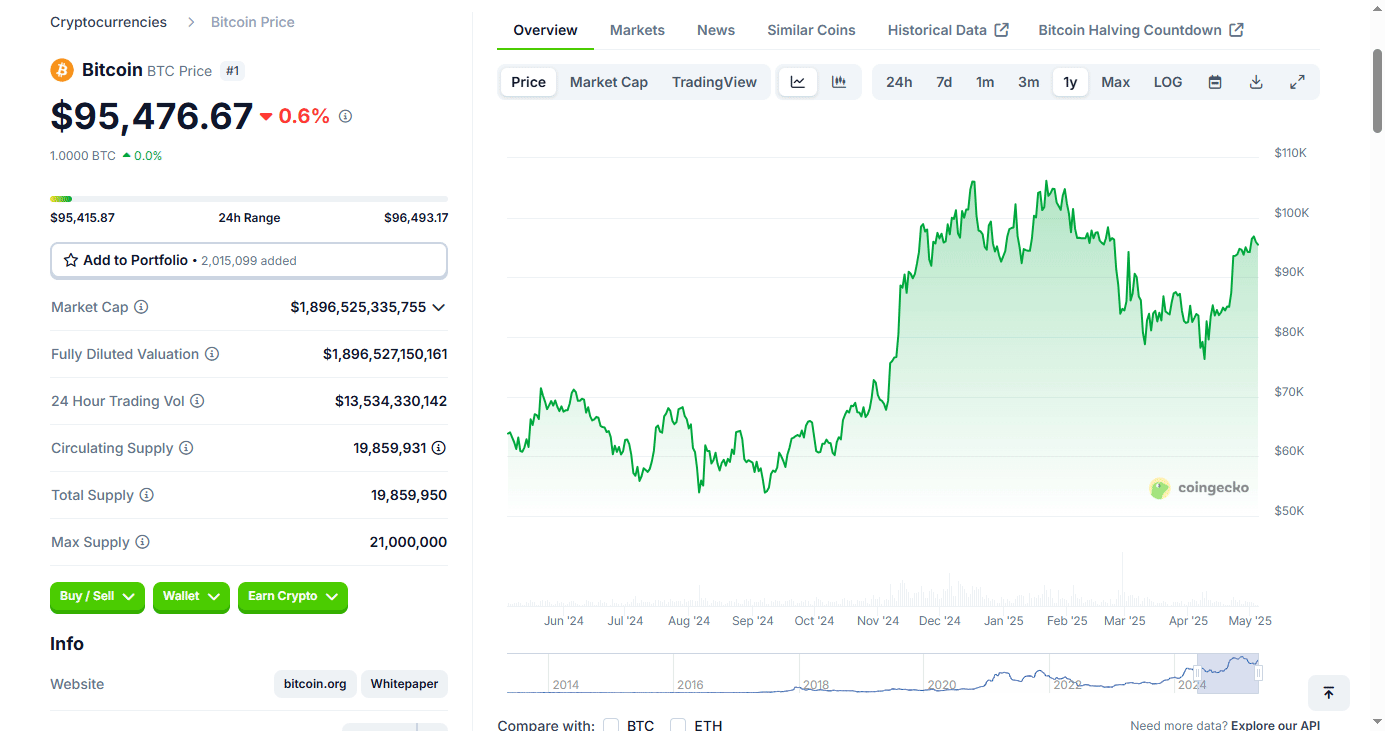
For bitcoiners, think about how far we've come. May of 2024 was still the waning days of the "War on Crypto," bitcoin was boiling the oceans, if you held, used, or liked bitcoin you were evil. Those were dark days and days I'm glad are behind us.
Here is the full commencement speech. The bitcoin part is around the 5 or 6 minute mark: https://m.youtube.com/watch?v=lcH-iL_FdYo
-
 @ a296b972:e5a7a2e8
2025-05-04 08:30:56
@ a296b972:e5a7a2e8
2025-05-04 08:30:56Am Ende der Woche von Unseremeinungsfreiheit wird in der Unserehauptstadt von Unserdeutschland, Unserberlin, voraussichtlich der neue Unserbundeskanzler vereidigt.
Der Schwur des voraussichtlich nächsten Unserbundeskanzlers sollte aktualisiert werden:
Jetzt, wo endlich mein Traum in Erfüllung geht, nur einmal im Leben Unserbundeskanzler zu werden, zahlen sich für mich alle Tricks und Kniffe aus, die ich angewendet habe, um unter allen Umständen in diese Position zu kommen.
Ich schwöre, dass ich meine Kraft meinem Wohle widmen, meinen Nutzen mehren, nach Vorbild meines Vorgängers Schaden von mir wenden, das Grundgesetz und die Gesetze des Unserbundes formen, meine Pflichten unsergewissenhaft erfüllen und Unseregerechtigkeit gegen jedermann und jederfrau nicht nur üben, sondern unter allen Umständen auch durchsetzen werde, die sich mir bei der Umsetzung der Vorstellungen von Unseredemokratie in den Weg stellen. (So wahr mir wer auch immer helfe).
Der Antrittsbesuch des Unserbundeskanzlers beim Repräsentanten der noch in Unserdeutschland präsenten Besatzungsmacht wird mit Spannung erwartet.
Ein großer Teil der Unsereminister ist schon bekannt. Die Auswahl verspricht viele Unsereüberraschungen.
Die Unsereeinheitspartei, bestehend aus ehemaligen Volksparteien, wird weiterhin dafür sorgen, dass die Nicht-Unsereopposition so wenig wie möglich Einfluss erhält, obwohl sie von den Nicht-Unserebürgern, die mindestens ein Viertel der Urnengänger ausmachen, voll-demokratisch gewählt wurde.
Das Zentralkomitee der Deutschen Unseredemokratischen Bundesrepublik wird zum Wohle seiner Unserebürger alles daransetzen, Unseredemokratie weiter voranzubringen und hofft auch weiterhin auf die Unterstützung von Unser-öffentlich-rechtlicher-Rundfunk.
Die Unserepressefreiheit wird auch weiterhin garantiert.
Auf die Verlautbarungen der Unserepressekonferenz, besetzt mit frischem Unserpersonal, brauchen die Insassen von Unserdeutschland auch weiterhin nicht zu verzichten.
Alles, was nicht gesichert unserdemokratisch ist, gilt als gesichert rechtsextrem.
Als Maxime gilt für alles Handeln: Es muss unter allen Umständen demokratisch aussehen, aber wir (die Unseredemokraten) müssen alles in der Hand haben.
Es ist unwahrscheinlich, dass Unsersondervermögen von den Unserdemokraten zurückgezahlt wird. Dieser Vorzug ist den Unserebürgern und den Nicht-Unserebürgern durch Unseresteuerzahlungen vorbehalten.
Die Unserebundeswehr soll aufgebaut werden (Baut auf, baut auf!), die Unsererüstungsindustrie läuft auf Hochtouren und soll Unserdeutschland wieder unserkriegstüchtig machen, weil Russland immer Unserfeind sein wird.
Von Unserdeutschland soll nur noch Unserfrieden ausgehen.
Zur Bekräftigung, dass alles seinen unser-sozialistischen Gang geht, tauchte die Phoenix*in aus der Asche auf, in dem Unseremutti kürzlich ihren legendären Satz wiederholte:
Wir schaffen das.
Ob damit der endgültige wirtschaftliche Untergang und die Vollendung der gesellschaftlichen Spaltung von Unserdeutschland gemeint war, ist nicht überliefert.
Orwellsche Schlussfolgerung:
Wir = unser
Ihr = Euer
Vogel und Maus passen nicht zusammen
Ausgerichtet auf Ruinen und der Zukunft abgewandt, Uneinigkeit und Unrecht und Unfreiheit für das deutsche Unserland.
Unserdeutschland – ein Land mit viel Vergangenheit und wenig Zukunft?
Es ist zum Heulen.
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ b2caa9b3:9eab0fb5
2025-05-04 08:20:46
@ b2caa9b3:9eab0fb5
2025-05-04 08:20:46Hey friends,
Exciting news – I’m currently setting up my very first Discord server!
This space will be all about my travels, behind-the-scenes stories, photo sharing, and practical tips and insights from the road. My goal is to make it the central hub connecting all my decentralized social platforms where I can interact with you more directly, and share exclusive content.
Since I’m just starting out, I’d love to hear from you:
Do you know any useful RSS-feed integrations for updates?
Can you recommend any cool Discord bots for community engagement or automation?
Are there any tips or features you think I must include?
The idea is to keep everything free and accessible, and to grow a warm, helpful community around the joy of exploring the world.
It’s my first time managing a Discord server, so your experience and suggestions would mean a lot. Leave a comment – I’m all ears!
Thanks for your support, Ruben Storm
-
 @ 86dfbe73:628cef55
2025-05-04 06:56:33
@ 86dfbe73:628cef55
2025-05-04 06:56:33Building A Second Brain (BASB) ist eine Methode, mit der man Ideen, Einsichten und Vernetzungen, die man durch seine Erfahrungen gewonnen hat, systematisch speichert und die jeder Zeit abrufbar sind. Kurz, BASB erweitert das Gedächtnis mit Hilfe moderner digitaler Werkzeuge und Netzwerke. Die Kernidee ist, dass man durch diese Verlagerung sein biologisches Gehirn befreit, um frei denken zu können, seiner Kreativität freien Lauf zu geben oder einfach im Moment sein kann.
Die Methode besteht aus drei Grundschritten: dem Sammeln von Ideen und Erkenntnissen, dem Vernetzen dieser Ideen und Erkenntnisse und dem Erschaffen konkreter Ergebnisse.
Sammeln: Der erste Schritt beim Aufbau eines Second Brains ist das «Sammeln» der Ideen und Erkenntnisse, die genug wichtig oder interessant sind, um sie festzuhalten. Dafür wird als Organisationsstruktur P.A.R.A empfohlen.
Vernetzen: Sobald man angefangen hat, sein persönliches Wissen strukturiert zu sammeln, wird man anfangen, Muster und Verbindungen zwischen den Ideen und Erkenntnissen zu erkennen. Ab dieser Stelle verwende ich parallel die Zettelkastenmethode (ZKM)
Erschaffen: All das Erfassen, Zusammenfassen, Verbinden und Strukturieren haben letztlich das Ziel: Konkrete Ergebnisse in der realen Welt zu erschaffen.
PARA ist die Organisationsstruktur, die auf verschiedenen Endgeräten einsetzt werden kann, um digitale Informationen immer nach dem gleichen Schema abzulegen. Seien es Informationen, Notizen, Grafiken, Videos oder Dateien, alles hat seinen festen Platz und kann anhand von vier Kategorien bzw. „Buckets“ kategorisiert werden.
PARA steht dabei für: * Projekte * Areas * Ressourcen * Archiv
Projekte (engl. Projects) sind kurzfristige Bemühungen in Arbeit und Privatleben. Sie sind das, woran Du aktuell arbeitest. Sie haben einige für die Arbeit förderliche Eigenschaften: * Sie haben einen Anfang und ein Ende (im Gegensatz zu einem Hobby oder einem Verantwortungsbereich). * Sie haben ein konkretes Ergebnis, dass erreicht werden soll und bestehen aus konkreten Schritten, die nötig und zusammen hinreichend sind, um dieses Ziel zu erreichen, entspricht GTD von David Allen
Verantwortungsbereiche (engl. Areas) betreffen alles, was man langfristig im Blick behalten will. Sie unterscheidet von Projekten, dass man bei ihnen kein Ziel verfolgt, sondern einem Standard halten will. Sie sind dementsprechend nicht befristet. Man könnte sagen, dass sie einen Anspruch an uns selbst und unsere Lebenswelt darstellen.
Ressourcen (engl. Resources) sind Themen, die allenfalls langfristig relevant oder nützlich werden könnten. Sie sind eine Sammelkategorie für alles, was weder Projekt noch Verantwortungsbereich ist. Es sind: * Themen, die interessant sind. (English: Topic) * Untersuchungsgegenständige, die man erforschen will. (Englisch: Subject) * Nützliche Informationen für den späteren Gebrauch.
Das Archiv ist für alles Inaktive aus den obigen drei Kategorien. Es ist ein Lager für Beendetes und Aufgeschobenes.
Das System PARA ist eine nach zeitlicher Handlungsrelevanz angeordnete Ablage. Projekte kommen vor den Verantwortungsbereichen, weil sie einen kurz- bis mittelfristigen Zeithorizont haben, Verantwortungsbereiche dagegen einen unbegrenzten Zeithorizont. Ressourcen und Archiv bilden die Schlusslichter, weil sie gewöhnlich weder Priorität haben, noch dringend sind.
-
 @ 88cc134b:5ae99079
2025-05-04 03:34:05
@ 88cc134b:5ae99079
2025-05-04 03:34:05The biggest question about this article is if it's is going to publish on first try.
-
 @ 5df413d4:2add4f5b
2025-05-04 00:51:49
@ 5df413d4:2add4f5b
2025-05-04 00:51:49Short photo-stories of the hidden, hard to find, obscure, and off the beaten track.
Come now, take a walk with me…
The Traveller 01: Ku/苦 Bar
Find a dingy, nondescript alley in a suspiciously quiet corner of Bangkok’s Chinatown at night. Walk down it. Pass the small prayer shrine that houses the angels who look over these particular buildings and approach an old wooden door. You were told that there is a bar here, as to yet nothing suggests that this is so…

Wait! A closer inspection reveals a simple bronze plaque, out of place for its polish and tended upkeep, “cocktails 3rd floor.” Up the stairs then! The landing on floor 3 presents a white sign with the Chinese character for bitter, ku/苦, and a red arrow pointing right.


Pass through the threshold, enter a new space. To your right, a large expanse of barren concrete, an empty “room.” Tripods for…some kind of filming? A man-sized, locked container. Yet, you did not come here to ask questions, such things are none of your business!

And to your left, you find the golden door. Approach. Enter. Be greeted. You have done well! You have found it. 苦 Bar. You are among friends now. Inside exudes deep weirdness - in the etymological sense - the bending of destinies, control of the fates. And for the patrons, a quiet yet social place, a sensual yet sacred space.


Ethereal sounds, like forlorn whale songs fill the air, a strange music for an even stranger magic. But, Taste! Taste is the order of the day! Fragrant, Bizarre, Obscure, Dripping and Arcane. Here you find a most unique use flavor, flavors myriad and manifold, flavors beyond name. Buddha’s hand, burnt cedar charcoal, ylang ylang, strawberry leaf, maybe wild roots brought in by some friendly passerby, and many, many other things. So, Taste! The drinks here, libations even, are not so much to be liked or disliked, rather, the are liquid context, experience to be embraced with a curious mind and soul freed from judgment.

And In the inner room, one may find another set of stairs. Down this time. Leading to the second place - KANGKAO. A natural wine bar, or so they say. Cozy, botanical, industrial, enclosed. The kind of private setting where you might overhear Bangkok’s resident “State Department,” “UN,” and “NGO” types chatting auspiciously in both Mandarin and English with their Mainland Chinese counterparts. But don’t look hard or listen too long! Surely, there’s no reason to be rude… Relax, relax, you are amongst friends now.

**苦 Bar. Bangkok, circa 2020. There are secrets to be found. Go there. **
Plebchain #Bitcoin #NostrArt #ArtOnNostr #Writestr #Createstr #NostrLove #Travel #Photography #Art #Story #Storytelling #Nostr #Zap #Zaps #Bangkok #Thailand #Siamstr
-
 @ 5cb68b7a:b7cb67d5
2025-05-04 00:13:44
@ 5cb68b7a:b7cb67d5
2025-05-04 00:13:44Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet. Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact. ⚠️ What We Don’t Do While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
Don’t Let Lost Crypto Hold You Back! ⏳ Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions
At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery
We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority
Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology
Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet.
- Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact.
⚠️ What We Don’t Do
While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
 # Don’t Let Lost Crypto Hold You Back! ⏳
# Don’t Let Lost Crypto Hold You Back! ⏳Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection
Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!
Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us!
For real-time support or questions, reach out to our dedicated team on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ d0ea1c34:9c84dc37
2025-05-03 17:53:05
@ d0ea1c34:9c84dc37
2025-05-03 17:53:05Markdown Rendering Test Document
Basic Text Formatting
This is a paragraph with bold text, italic text, and bold italic text. You can also use underscores for bold or single underscores for italics.
This is a paragraph with some
inline codeusing backticks.Lists
Unordered Lists
- Item 1
- Item 2
- Nested item 2.1
- Nested item 2.2
- Item 3
Ordered Lists
- First item
- Second item
- Nested item 2.1
- Nested item 2.2
- Third item
Links and Images
Blockquotes
This is a blockquote.
It can span multiple lines.
And can be nested.
Code Blocks
```python def hello_world(): print("Hello, world!")
This is a Python code block with syntax highlighting
hello_world() ```
javascript // JavaScript code block function helloWorld() { console.log("Hello, world!"); }Tables
| Header 1 | Header 2 | Header 3 | |----------|----------|----------| | Cell 1 | Cell 2 | Cell 3 | | Cell 4 | Cell 5 | Cell 6 | | Cell 7 | Cell 8 | Cell 9 |
Horizontal Rules
Task Lists
- [x] Completed task
- [ ] Incomplete task
- [x] Another completed task
Math (if supported)
Inline math: $E = mc^2$
Block math:
$$ \frac{d}{dx}e^x = e^x $$
Footnotes
Here's a sentence with a footnote reference[^1].
[^1]: This is the footnote content.
Definition Lists
Term 1 : Definition 1
Term 2 : Definition 2a : Definition 2b
Special Characters & Escaping
*This text is surrounded by asterisks but not italicized*
Advanced Formatting
Click to expand
This is hidden content that appears when expanded.Emoji (if supported)
:smile: :heart: :thumbsup:
Final Notes
This document demonstrates various Markdown formatting features. Compatibility may vary across different Markdown renderers and platforms.
-
 @ e2388e53:0e93e8a9
2025-05-03 16:44:06
@ e2388e53:0e93e8a9
2025-05-03 16:44:06- Die Befreiung beginnt nicht mit einem Aufschrei, sondern mit einem leisen Nein.
- Herkunft ist kein Zuhause. Es ist der Ort, an dem man lernt, warum man gehen musste.
- Manche Familien sind wie alte Götter: Man glaubt an sie, obwohl sie längst gestorben sind.
- Wer das Nichts anschaut, sieht sich selbst: ein Schatten, der sich für Licht hält.
- Das Schweigen des Universums ist keine Antwort – es ist die endgültige Form der Gleichgültigkeit.
- In der Dämmerung unserer Tage suchen wir die Sonne, die nur in der Erinnerung noch brennt.
- Freiheit beginnt, wenn der Mensch aufhört, sich retten zu lassen.
- Wer nie verloren ging, hat sich selbst nie gesucht.
- Gedanken zerfallen wie Tropfen, die nie den Boden erreichen.
- Wahrheit ist selten laut. Sie flüstert – meist dann, wenn niemand mehr zuhört.
-
 @ fc7085c3:0b32a4cb
2025-05-03 16:17:10
@ fc7085c3:0b32a4cb
2025-05-03 16:17:10- ~~finish writing some experimental specs and store on hidden repo for later~~
- ~~fix bugs on in-house js web components framework (with react-like hooks)~~
- ~~add signal/reactive hooks to framework~~ (thx to nootropics)
- (ongoing) slooowly migrate kind:1 app from Qwik to above framework
- test feasibility of new app - codename: ZULULA. cool? flawed?
- if cool, finish ZULULA basic features
- nread.me: add nostr documentation (mpa for this part cause seo)
- nread.me: add nip crud (save on relay)
- nread.me: add nip curation (rating and labeling)
- nread.me: filter by curator / rating / labeling
- nread.me: seed curator (fiatjaf) adds other curators
- revamp kind:1 app login
- add basic engagement features then halt kind:1 app dev
- start simplified messenger app to test custom chat spec
- ...don't know what's next yet
-
 @ 6ad3e2a3:c90b7740
2025-05-03 15:33:07
@ 6ad3e2a3:c90b7740
2025-05-03 15:33:07You are wearing a helmet, but it's been on your head so long you no longer notice it.
The helmet interfaces with your mind via thought-emotion. It influences what you think about and how you feel.
You could remove the helmet at any time. But the thought-emotions keep you distracted, fearful and attached.
Occasionally you remember you are wearing it. Moments of clarity and detachment. You see the way your experience is colored by it. You know it is biased, untrue to reality. You seriously contemplate removing it.
But the moment passes.
Later, you remember contemplating your helmet’s removal, but you wonder what you will gain from it, whether it’s worth doing.
You are no longer having a moment of clarity, just a memory of the question that arose from it, but colored now by thought-emotions.
You decide even if you wanted to remove it, you would put it back on before long. After all, you have never kept it off before, why would you suddenly live without this interface now? The interface is what you know.
Maybe one day, when you are in a more secure place, when your ducks are more in a row, you will remove it. Not now, not in the midst of all this chaos, so many things to do, so much on your plate. You will leave it on for now. You will deal with this later.
But one day too late it dawns on you it is always ever now, and later means never. You have lived your entire life at the behest of the interface when all you had to do was remove it.
-
 @ e2388e53:0e93e8a9
2025-05-03 11:39:45
@ e2388e53:0e93e8a9
2025-05-03 11:39:45- Melancholie ist die sanfteste Form der Rebellion – ein Nein, das sich in Schönheit kleidet, um nicht verbrannt zu werden.
- Die Menschheit sucht nach Erlösung – und nennt das Kind dabei „Zukunft“, ohne zu merken, wie schwer diese Krone wiegt.
- Nähe ohne Ehrlichkeit ist nur ein getarnter Abstand.
- Jede Zentralisierung ist ein Denkfehler, der Macht als Fürsorge tarnt.
- Sehnsucht ist ein Fluss, der rückwärts fließt – du watest hinein, doch das Ufer zieht sich fort, unerreichbar fern.
- Die letzte Form der Sklaverei ist die freiwillige Abhängigkeit.
- Ein Kind spielt nicht, um zu vergessen – es spielt, weil es noch nicht gelernt hat zu verdrängen.
- Freiheit ist die Fähigkeit, in Ketten zu tanzen.
- Das Leben ist der Widerhall eines sterbenden Willens. Nur im Nichts finden wir Erlösung.
- Wer Kinder erzieht, erzieht auch seine Schatten – sie kommen zurück, wenn das Haus still ist.
-
 @ 0d8633e5:eec06e57
2025-05-03 10:58:22
@ 0d8633e5:eec06e57
2025-05-03 10:58:22The Flash USDT Generator is responsible for producing and storing Flash USDT tokens with a flexible daily limit. It ensures a consistent supply of tokens for transactions while managing distribution securely and efficiently. Our Flash USDT offers a unique, temporary cryptocurrency that lasts for 90 days before expiring. This innovative solution allows for seamlesstrading and transferring of funds. Notably, the Flash Bitcoin and USDT can be transferred to 12 different wallets, including prominent platforms like Binance and Trust Wallet.
Features Adjustable Daily Limit: Customizable settings allow for modifying the token generation cap. Automated Distribution: Ensures quick and secure token transfers to user wallets. Minimal Latency: Prevents blockchain congestion issues for seamless transfers. Real-Time Transaction Verification: Each transaction is immediately verified on the respective blockchain explorer to confirm accuracy and validity. Temporary Nature: One of the most distinctive characteristics of USDT FLASH Generator is that it generates flash coin that is designed to disappear from any wallet after a period of ninety days. This unique feature ensures that any assets received in USDT FLASH will not linger indefinitely, creating a dynamic and engaging transaction experience.
Kindly visit globalfashexperts.com for more information Contact Information For more information or to make a purchase, please contact us through the following channels:
Email: globalfashexperts@gmail.com Flash USDT:https://globalfashexperts.com/product/flash-usdt/ Flash USDT: https://globalfashexperts.com/product/flash-usdt-generator-software/The Flash USDT Generator is responsible for producing and storing Flash USDT tokens with a flexible daily limit. It ensures a consistent supply of tokens for transactions while managing distribution securely and efficiently. Our Flash USDT offers a unique, temporary cryptocurrency that lasts for 90 days before expiring. This innovative solution allows for seamlesstrading and transferring of funds. Notably, the Flash Bitcoin and USDT can be transferred to 12 different wallets, including prominent platforms like Binance and Trust Wallet.
Features
- Adjustable Daily Limit: Customizable settings allow for modifying the token generation cap.
- Automated Distribution: Ensures quick and secure token transfers to user wallets.
- Minimal Latency: Prevents blockchain congestion issues for seamless transfers.
- Real-Time Transaction Verification: Each transaction is immediately verified on the respective blockchain explorer to confirm accuracy and validity.
- Temporary Nature: One of the most distinctive characteristics of USDT FLASH Generator is that it generates flash coin that is designed to disappear from any wallet after a period of ninety days. This unique feature ensures that any assets received in USDT FLASH will not linger indefinitely, creating a dynamic and engaging transaction experience.
 Kindly visit globalfashexperts.com for more information
Kindly visit globalfashexperts.com for more informationContact Information
For more information or to make a purchase, please contact us through the following channels:
- Email: globalfashexperts@gmail.com
- Flash USDT:https://globalfashexperts.com/product/flash-usdt/
- Flash USDT: https://globalfashexperts.com/product/flash-usdt-generator-software/
-
 @ d0aa74cd:603d35cd
2025-05-03 10:55:11
@ d0aa74cd:603d35cd
2025-05-03 10:55:11CLI #Haskell
https://photonsphere.org/post/2025-05-03-command-line-energy-prices-haskell/
-
 @ 5f078e90:b2bacaa3
2025-05-03 10:18:41
@ 5f078e90:b2bacaa3
2025-05-03 10:18:41The Spoonbill's Dawn
In a marsh where reeds whispered secrets to the wind, a roseate spoonbill named Sable waded through dawn’s amber glow. Her pink feathers shimmered, catching the first light as she swept her spoon-shaped bill through the shallows, sifting for shrimp. Unlike her flock, who chattered and preened, Sable moved with quiet purpose, her eyes tracing ripples for signs of life.

Each morning, she returned to a lone cypress, its roots cradling a pool where minnows danced. Here, Sable had found an odd companion: a young alligator named Moss, whose emerald scales blended with the water’s edge. Moss never lunged, only watched, his eyes like polished stones. Sable, curious, began leaving shrimp at the pool’s edge. Moss, in turn, nudged smooth pebbles toward her, gifts from the marsh’s depths.
One dawn, a storm loomed, its thunder rattling the reeds. The flock fled, their wings a pink blur against charcoal clouds, but Sable lingered. The pool was still; Moss hadn’t surfaced. She dipped her bill, calling softly, her heart a flutter of worry. Then, a ripple—Moss emerged, sluggish, a gash on his flank from a poacher’s trap. Sable’s instinct was to flee, but she stayed, her bill probing the mud for healing herbs she’d seen egrets use.
With gentle nudges, she pressed the herbs to Moss’s wound, her pink wings shielding him from the rain. Moss rumbled, a low thanks, and rested. By dusk, the storm passed, and the marsh gleamed under a crescent moon. Moss stirred, stronger, and nudged a final pebble to Sable—a heart-shaped stone, glinting pink like her feathers.
Sable took flight, the stone clutched in her bill, her wings carving hope into the sky. The flock returned, awed by her tale, and the marsh buzzed with their chatter. Sable and Moss remained, their bond a quiet legend, proof that even in a wild world, trust could bloom where dawn met dusk.
Word count: 313
-
 @ e4950c93:1b99eccd
2025-05-03 09:59:59
@ e4950c93:1b99eccd
2025-05-03 09:59:59🧵 Produits en cette matière
Les marques suivantes proposent des produits fait exclusivement ou principalement avec cette matière :
Vêtements
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ e4950c93:1b99eccd
2025-05-03 09:59:25
@ e4950c93:1b99eccd
2025-05-03 09:59:25🧵 Produits en cette matière
Les marques suivantes proposent des produits fait exclusivement ou principalement avec cette matière :
Vêtements
- Engel
- Dilling (laine mérinos)
- ManyMonths (laine mérinos)
Maison
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ e4950c93:1b99eccd
2025-05-03 09:59:03
@ e4950c93:1b99eccd
2025-05-03 09:59:03🧵 Produits en cette matière
Les marques suivantes proposent des produits fait exclusivement ou principalement avec cette matière :
Vêtements
- Engel (coton biologique)
- Dilling (coton biologique)
- ManyMonths (coton biologique)
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ e4950c93:1b99eccd
2025-05-03 09:46:42
@ e4950c93:1b99eccd
2025-05-03 09:46:42Engel est une marque allemande qui crée des vêtements et accessoires en coton biologique, laine mérinos et soie pour toute la famille.
Matières naturelles utilisées dans les produits
⚠️ Attention, certains produits de cette marque (notamment les soutiens-gorge) contiennent des matières non naturelles, dont :
Catégories de produits proposés
#Vêtements
- Coupes : bébés, enfants, femmes, hommes, unisexe
- Sous-vêtements : boxers, culottes
- Une pièce : bodies
- Hauts : débardeurs, gilets, t-shirts, pulls, vestes
- Bas : pantalons, shorts
- Tête et mains : bonnets
- Nuit : pyjamas
#Maison
- Linge : couvertures, turbulettes
Autres informations
- Certification GOTS
- Certification IVN Best
- Fabriqué en Allemagne
👉 En savoir plus sur le site de la marque
Cet article est publié sur origine-nature.com 🌐 See this article in English
📝 Tu peux contribuer à cette fiche en suggérant une modification en commentaire.
🗣️ Tu utilises ce produit ? Partage ton avis en commentaire.
⚡ Heureu-x-se de trouver cette information ? Soutiens le projet en faisant un don, pour remercier les contribut-eur-ice-s.
-
 @ a296b972:e5a7a2e8
2025-05-03 07:48:25
@ a296b972:e5a7a2e8
2025-05-03 07:48:25Derzeit formiert sich ein neues Gruselkabinett, als Folge einer Pandemie der Ungeeigneten. Kostproben der Unfähigkeit konnte man schon in den aktuellen „Quassel-Shows“ des Staatsfunks „genießen“. Die Riege der Universal-Dilettanten, die noch schnell hochgelobt wurde, macht gerade Platz für Rekruten aus dem Milieu der überzeugten Realitätsverweigerer.
Impfpflichtbefürworter, ideologisch vergiftete Klima- und Gender-Gagaisten, Verteidiger des Russen-Dauer-Feindbilds, Finanzwirtschafts-Ahnungslose, zahllose „Südamerika-Experten“, die davon überzeugt sind, solche zu sein, weil sie unfallfrei eine Banane essen können und weitere, die als einzige Qualifikation das Prädikat „Untauglich“ auszeichnet, geben sich ein neues Stelldichein.
Nach Vorbild des öffentlich-rechtlichen Unfugs bilden sie ein in sich geschlossenes System, das sich gegen Kritik abschotten will, in dem es alles, was sich nach Nicht-nach-dem-Maul geredet anhört, als Hass und Hetze bezeichnet und sich als Hüter der Wahrheit aufspielt.
Begriffe wie „Hass und Hetze“ und „Kriegstüchtigkeit“ werden einem Wortschatz entlehnt, die dem bisher dunkelsten Kapitel der deutschen Geschichte entnommen sind. Zur Abschreckung verwendete Begriffe, im Sinne von „Wehret den Anfängen!“, wie die Anlehnung „Impfen macht frei“ hingegen, werden mit Geldbußen und Haft belegt. Es kommt eben immer darauf an, von wem diese verbrannten Begriffe verwendet werden.
Wenn aus einer Demokratie „Unseredemokratie“ wird, müssen alle Alarmglocken schrillen, weil so Tür und Tor weit aufgerissen werden, um Tendenzen und Ideologien den Einzug zu ermöglichen, die in einer freiheitlich-demokratischen Grundordnung nichts, aber auch rein gar nichts zu suchen haben, weil die Auslegung davon, was „Unseredemokratie“ bedeutet, in den Händen derjenigen liegt, die sich zwar noch als Volksvertreter ausgeben, aber den Willen des Souveräns nicht mehr umsetzen.
Die Meinung und der Wille des Volkes werden maximal ignoriert und unterdrückt. Mit einem „weiter so“ manifestiert sich die Verachtung der Wähler, die in ihrer unterstellten Dummheit bestenfalls noch als Stimmvieh taugen, ansonsten aber zu vernachlässigen sind, wenn das Ziel erreicht ist: Die Macht!
Eine Absichtserklärung, genannt Koalitionsvertrag, ist die Grundlage für „alles kann, nichts muss“. Er lässt so eine unbegrenzte Flexibilität in jede Richtung zu, alles ist möglich. ALLES!
Die Basis der Koalition beruht auf Lügen, sei es in der Migrationspolitik oder in der Neuverschuldung. Das gemeinsame Klüngeln hat schon begonnen, bevor der eigentliche Regierungsauftrag überhaupt erteilt wurde.
Das wirklich einzige, gemeinsame Ziel ist, mit allen Mitteln an der Macht zu bleiben, koste es, was es wolle und eine demokratisch gewählte Opposition, die rund ein Viertel der Wählerstimmen ausmacht, wo immer es geht zu delegitimieren und so klein zu halten, wie es nur eben geht.
Hirngespinste sollen weiter vorangetrieben, die Rückkehr zur Vernunft soll unter allen Umständen verhindert werden, bzw. ist aufgrund mangelnder Kenntnisse und Einsicht gar nicht möglich.
Das Lügen bleibt den Nicht-Volksvertretern vorbehalten, die definieren, was Lüge ist und was nicht, sofern die Kritik vom Volk kommt. Berichtet man über die Politik, spricht man von Unwahrheiten, spricht die Politik über das Volk, sind es Lügen. Überall wird mit zweierlei Maß gemessen.
Die Verachtung des Souveräns wirkt wie ein Bumerang und wird wie durch einen Spiegel auf die Versender zurückgeworfen.
Ein zukünftiger Ex-Bundeskanzler verliert bereits den Rückhalt, noch bevor er in sein Amt eingesetzt wird. Grisu, der kleine Drache, will unbedingt, nur einmal im Leben, Feuerwehrmann werden. Phrasen-Dreschen wird zur Staatsräson.
Ministerposten werden nach maximaler Fachferne verschachert.
Gut ausgebildete Kräfte verlassen das Land, die Wirtschaft stagniert, massive Einbrüche in der Auto-Industrie, der einstigen Vorzeige-Marken in der ganzen Welt. Ja, Autos bauen, das könnten die Deutschen, wenn sie noch dürften.
Wer kann, wandert ab ins Ausland, wo Energiekosten und Steuern ein unternehmerisches Handeln ermöglichen, statt es mit aller Kraft durch gezielte Wirtschaftsvernichtung abzuwürgen. Wo ist der massive Widerstand seitens der Wirtschaftsverbände, der Industrie- und Handelskammern und Groß-Unternehmen? Geht es denen immer noch zu gut?
Recht haben und Recht bekommen waren noch nie so weit auseinander, wie heute.
Die Kirche, in einem christlich geprägten Land, schreibt ihre eigene Lehre um: „Gott ist queer!“ Grenzt das schon an Gotteslästerung aus den eigenen Reihen? Dabei merkt sie offensichtlich nicht, dass sie sich damit selbst abschafft. Wieder einmal springt sie auf den Zug der vorgegebenen Staatsdoktrin auf. Unvergessen die Hakenkreuzfahne über dem Hauptportal am Kölner Dom in der bisher dunkelsten Zeit Deutschlands.
Eine Überzeugung, und seien die Beweggründe mit noch so guten Absichten verbunden, darf nie wieder zu einer Ideologie werden, die nur in die Irre führen kann. Deshalb ist es demokratische Pflicht, auf die Gefahr hinzuweisen, wenn auch nur der leiseste Hauch Anlass zu solchen Befürchtungen gibt. Das gilt für die Kirche, die Politik, die Rechtsprechung und Menschen, von denen man den Eindruck hat, dass sie sich verirrt haben.
Das Zuviel an Fremden wird nicht gestoppt. Eine Minderheit, die bei Verstand geblieben ist, verlässt das Land, wenn es ihr finanziell möglich ist. Andere, die sich das nicht leisten können, müssen ausharren und dabei zusehen, wie ein Land vor die Hunde geht.
Gut integrierte „Gastarbeiter“ schämen sich für den Plebs, der nach Deutschland kommt. Natürlich unter dem Deckmantel der Menschlichkeit, der die Menschlichkeit gegenüber den Bio-Deutschen mit Füßen tritt. Ihr Ansehen, ihr Fleiß und ihre Dankbarkeit, dass sich ihre Vätergeneration hier eine neue Existenz aufbauen konnte, wird mit Füßen getreten. Sie geraten unter einen Generalverdacht, der ihnen schadet. Auch sie haben Jahrzehnte in die Krankenkassen eingezahlt und ihre Steuern brav entrichtet.
Der Polizei sind von staatlicher Seite die Hände gebunden gegen Clan-Kriminalität und asozialem Verhalten durchzugreifen. Sie bilden Parallel-Gesellschaften mit eigenen Regeln und eigenen Gesetzen und die Polizei muss tatenlos dabei zusehen. Banden in Berlin und Duisburg stellen sich über herrschende Gesetze, Roma terrorisieren Kiel, benehmen sich, wie die Axt im Walde. „An Leib und Leben gefährdete Migranten“ werfen, wie in Bochum, Ziegel von Dächern, und gefährden die Bevölkerung an Leib und Leben. Anschließend setzen sie sich mit einem Gartenstuhl auf einem Kamin in die Sonne und träumen vermutlich vom Ausblick auf dem Kilimandscharo. Statt sie bei Kopf und Kragen zu fassen und sofort aus dem Land zu werfen, werden solche irren Taten mit psychischen Problemen aufgrund der Erfahrungen in ihrem Heimatland entschuldigt. Würden sich solche Bekloppte in ihrem eigenen Land vergleichbare Handlungen erlauben, würde sie die Dorfgemeinschaft wahrscheinlich den Löwen zum Fraß vorwerfen.
Jeder, der nicht das in Deutschland geltende Recht akzeptiert und stattdessen seine eigene Auffassung von Recht durchsetzen will, gehört unverzüglich des Landes verwiesen, und es ist Aufgabe des Staates, dafür zu sorgen, dass solche Personen nie wieder einen Fuß über die Grenzen des Landes setzen dürfen. Stattdessen werden die Fahnder verfolgt und die Täter laufen gelassen. Der Staat lässt so zu, dass geltendes Recht unterwandert und außer Kraft gesetzt wird. Seine abschreckende Wirkung geht verloren, weil es in den einschlägigen Kreisen bekannt ist, dass sich jeder aufführen kann, wie er will, ohne, dass es Konsequenzen nach sich zieht.
Gepaart mit Willkür ist das hoch gefährliches Dynamit, dass die Gesellschaft sprengt und eine Gefahr in sich birgt, dass die Gesellschaft ab dem Punkt, wo es unerträglich geworden ist, zur Selbstjustiz greift, und das wäre möglicherweise der Anfang eines Bürgerkriegs.
Für alles ist Geld da. Es werden Schulden in atemberaubender Höhe aufgenommen, vor allem, um die Kriegswirtschaft anzukurbeln, um vor einem Feind - Russland gewappnet zu sein, das nicht das geringste Interesse an einem Land hat, das nichts unversucht lässt, auf irgendeine Art und Weise Selbstmord zu begehen. Einmal muss es doch gelingen!
Und natürlich müssen auch die westlichen Werte im Stellvertreterkrieg zwischen den USA und Russland in der Ukraine verteidigt werden.
Kein Geld ist allerdings für die eigenen Leute da. Im Gegenteil: Wer Flaschen sammelt, muss ab einer bestimmten Höhe der Einnahmen ein Gewerbe anmelden. Aber sonst haben die Sesselfurzer nichts zu tun, oder? Es sollte Geld in die Hand genommen werden, die zunehmende Armut in der Bevölkerung nachhaltig zu stoppen, aus dem Abfahrtsvorschlags-Plan der Bahn wieder einen richtigen Fahrplan zu machen, die Schlagloch-Nostalgie á la DDR abzuschaffen, Brücken wieder ihrem Wesen zuzuführen, nämlich, dass man drüberfahren kann, das ganze Land einer dringenden Generalüberholung zu unterziehen, die Gewinnorientierung aus dem Gesundheitssystem wieder abzuschaffen, die Fallpauschalen samt dem Verursacher in die Wüste zu schicken, Deutschland steuer-sexy zu machen.
Das ist wohl zu viel verlangt, denn diejenigen, die das bewirken könnten, haben keine Not. Die einzige Not, die sie kennen, ist, wie sie immer genug Leim auf Vorrat haben können, um an ihrem Pöstchen kleben zu bleiben. Solche Menschen können nur in einem geschützten Rahmen existieren, weil sie in der Welt da draußen gar nicht zurecht kämen, geschweige denn in der Lage wären, für ihren Lebensunterhalt mit einer wirklichen Arbeit selbst zu sorgen.
Der Staat erfüllt nicht mehr seine Aufgabe für die Sicherheit seiner Bürger zu sorgen. Statt Messer-Attacken und Terror-Anschläge aufzuklären und damit den Bürgern ein Gefühl von Sicherheit zu vermitteln, wird die Aufklärung auf dem Mond im Meer der Stille versenkt. Transparenz: Fehlanzeige. Im besten Fall werden Symptom-Bekämpfungs-Maßnahmen ergriffen, statt die Ursachen zu verunmöglichen. Schilder an Messerverbots-Zonen aufzustellen, manifestieren bestenfalls die Gewissheit der Lächerlichkeit und Unfähigkeit seitens der Messerfachkräfte und der selbstfahrenden Autos, die von niemandem gesteuert werden.
Gleiches gilt für das Nennen der hinlänglich bekannten Verursacher der Sprengung der Nordstream 2-Pipelines, die dem scheidenden Bundeskanzler, an dessen Namen man sich schon jetzt nicht mehr erinnern kann, bekannt gewesen sein müssen. Selbst Trump soll sich auf die Frage, ob die USA maßgeblich daran beteiligt waren, geäußert haben, dass, wenn er auf diese Frage antworten würde, er seinem Land sehr schaden würde. Er könne aber mit Gewissheit sagen, dass es die Russen nicht waren. Immerhin ist eine für ganz Europa wichtige Energieversorgung absichtlich, bewusst und mutwillig zerstört worden. Aber aus Rücksicht darauf, dass die Wahrheit Teile der deutschen Bevölkerung verunsichern könnte, verzichtet man in Berlin auf eine Stellungnahme, lügt wiederholt, dass die Ermittlungen noch andauern und glaubt, dass man die Bürger damit ahnungslos halten kann. Die doofen Deutschen werden auch das noch schlucken.
Vergessen die Verpflichtung: Von deutschem Boden soll nur noch Frieden ausgehen. Vergessen die grauen Gesichter der Männer mit einem hochgeklappten Hosenbein, in der Kinderzeit. Wer von den aktuellen Kriegstreibern war live bei einem Gemetzel dabei, in dem Körperteile herumfliegen und Blut spritzt, in dem Menschen zerfetzt werden oder in ihren Panzern bei lebendigem Leib verbrennen? Viele Dümmste unter den Dummen kennen Krieg nur aus Video-Spielen. Nur einmal live als Zaungast dabei sein, und sehen, wie der halbe Darm aus dem Körper heraushängt, dann würde sich ihr großes Maul schon von alleine schließen.
Immer mehr Deutsche sagen: Das ist nicht mehr mein Staat. Kann man es ihnen verdenken?
Deutschland ist ein Paradebeispiel dafür, wie man in der heutigen Zeit, ein einst in aller Welt hochangesehenes Land, im Handumdrehen wirtschaftlich, politisch, rechtsstaatlich, gesundheitlich, und nicht zuletzt auch gesellschaftlich zerstören kann.
Sowohl innen- als auch außenpolitisch wurde nichts unterlassen, um Deutschland, vom Ausland aus gesehen, in die absolute Lächerlichkeit zu überführen.
Die Dummheit, gepaart mit unerträglicher Überheblichkeit, haben ein Maß erreicht, dass in die Gefährlichkeit übergegangen ist. Deutschland braucht gar keinen Feind von außen, denn der Feind sitzt im eigenen Land und zerstört es von innen heraus.
Der Eindruck taucht auf, dass spätestens mit dem Corona-Ereignis das Schleusentor des Wahnsinns sperrangelweit aufgerissen wurde, und keiner vermag es derzeit wieder zu schließen.
Entweder schließen sich Kräfte zusammen, die noch vorhanden sind, dieses Land von innen heraus zu retten, hierzu tragen auch die Neuen Medien erheblich bei, oder Deutschland ist noch einmal darauf angewiesen, von außen gerettet zu werden.
Zukunftsplanungen werden verunmöglicht. Mindestens eine Generation wird die komplette Lebensplanung geraubt. Man ist gezwungen, von einem Tag auf den anderen zu leben, weil alles derartig unberechenbar geworden ist. Eine junge Familie überlegt sich drei Mal, ob sie noch Kinder in diese Welt setzen will. Wo soll das enden?
Der Alltag in Deutschland gleicht einer Dauer-Vorstellung eines Theater-Stücks. Irgendwie läuft es noch, jedoch es fehlt der Rückhalt. Man versucht seinen Alltag zu meistern, Normalität zu leben, doch über allem schwebt das Damokles-Schwert. Keiner weiß, wie lange was noch gut geht und welchen Irrsinn sich die Realitätsverweigerer als Nächstes ausdenken werden. Manchen gelingt das Verdrängen recht gut. Manche schotten sich vollkommen von schlechten Nachrichten ab. Die Psychologie sagt jedoch, dass jedes erlebte Trauma den Menschen früher oder später einholen wird.
Wetten, wie lange die unheilvolle Allianz der Neuen Nullen halten wird, können ab sofort entgegengenommen werden. Und dann? Wie geht es weiter?
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
(Bild von pixabay)
-
 @ 6389be64:ef439d32
2025-05-03 07:17:36
@ 6389be64:ef439d32
2025-05-03 07:17:36In Jewish folklore, the golem—shaped from clay—is brought to life through sacred knowledge. Clay’s negative charge allows it to bind nutrients and water, echoing its mythic function as a vessel of potential.
Biochar in Amazonian terra preta shares this trait: it holds life-sustaining ions and harbors living intention. Both materials, inert alone, become generative through human action. The golem and black earths exist in parallel—one cultural, one ecological—shaping the lifeless into something that serves, protects, and endures.
originally posted at https://stacker.news/items/970089
-
 @ d9a329af:bef580d7
2025-05-03 04:20:42
@ d9a329af:bef580d7
2025-05-03 04:20:42To be clear, this is 100% my subjective opinion on the alternatives to popular music, as it has become practically a formula of witchcraft, pseudoscience and mysticism. There is nothing you can do to get me to listen to Western pop music from the late 2010's to now. I could certainly listen to almost anything... just not modern pop, which is now completely backwards.
Most examples of compositions for these genres will be my own, unless otherwise stated. The genres on this list are in no particular order, though my favorite of which will be first: 1. Bossa Nova
Bossa Nova is a subgenre of jazz from Brazil, created in the 1950's as a mix of standard jazz and samba rhythms in a more gentle and relaxing manner. This genre's most famous songs are Tom Jobim's The Girl from Ipanema (found in albums like Getz/Gilberto), Wave, and even Triste. Most of the music is written in 2/4 time signature, and any key is almost acceptable. It's called Afro-Brazilian Jazz for a reason after all. I have a ton of compositions I produced, from Forget and Regret, to Rabbit Theory, Beaches of Gensokyo Past, Waveside, and even Willows of Ice to name a few of them.
- Metal
This is an umbrella term for many subgenres of this fork of hard rock, with more distorted guitars, speedy and technical writing, vocals that sound demonic (some subgenres don't have that), or sometimes, chaotic lyrics and downright nasty ones if you look deep enough. If you want to get into it, just make sure it's not Black Metal (it's weird), Blackened Metal (Any subgenre of metal that's been inserted with elements of Black Metal), Metalcore, or any other genre that has vocals that aren't the best to hear (these are vocal fries that are really good if you're into the weird demonic sounds). This isn't for the faint of heart. Instrumental metal is good though, and an example is my composition from Touhou Igousaken called A Sly Foxy Liar if you want to know what techincal groove metal is like at a glance.
- Touhou-style
I can attest to this one, as I produced bossa nova with a Touhou-like writing style. Touhou Project is a series of action video games created by one guy (Jun'ya Outa, a.k.a. ZUN), and are usually bullet curtain games in the main franchise, with some official spinoffs that are also action games (fighting games like Touhou 12.3 ~ Hisoutensoku). What I'm referring to here is music written by ZUN himself (He does almost everything for Touhou Project, and he's really good at it), or fans that write to his style with their own flair. I did this once with my composition, Toiled Bubble, which is from my self-titled EP. I probably wouldn't do much with it to be fair, and stick to bossa nova (my main genre if you couldn't tell).
- Hip-Hop/Rap
This can get subjective here, but old-school rap and hip-hop... give me more of it. Before it became corrupted with all kinds of immoral things, hip-hop and rap were actually very good for their time. These were new, innovative and creative with how lyrics were written. Nowadays, while we're talking about cars, unspeakable acts, money, and just being dirtbags, artists in this genre back then were much classier than that. I fit in the latter category with my piece entitled, Don't Think, Just Roast, where I called out antis for a Vtuber agency who wanted to give its talent a hard time. It didn't get much traction on YouTube, because I'm not a well-known artist (I'm considered a nobody in the grand scheme of things. I'd like to get it fixed, but I don't want a record deal... I'd have to become a Pharisee or a Jesuit for that).
- Synthwave
This is a genre of electronic music focused on 80's and 90's synths being used to carry a composition. Nowadays, we have plugins like Vital, Serum, Surge and others to create sounds we would otherwise be hearing on an 80's or 90's keyboard. An example of this is my composition, Wrenched Torque, which was composed for a promotion I did with RAES when he released his Vital synth pack.
More are to come in future installments of this series, and I will adjust the title of this one accordingly if y'all have any ideas of genres I should look into.
-
 @ d9a329af:bef580d7
2025-05-03 04:10:03
@ d9a329af:bef580d7
2025-05-03 04:10:03Everyone who sees it knows at this point that the matrix of control comes from the overdependence of proprietary software to do our everyday tasks. You can think of this like us being the cling wrap that will just not let go of these pieces of garbage software that don't allow you to see what is in their source code, and how they work. This will tend to lead to the unlawful collection of data (violating the most basic of privacy laws, despite unenforceable contracts that are enforced regardless), bad OPSEC that sees you being stalked and harassed over nothing significant. In the worst of cases, if you speak your mind where you aren't necessarily supposed to be able to do that, and you get doxxed, the worst cases could be far worse than one could imagine.
The solution to this, on the other hand, is using almost exclusively free/libre open-source software and GNU/Linux operation systems. If you're using certain proprietary software, hardening it to give as little data as possible to the entity responsible for it will also work, as long as you know which ones to use. This is a hard pass for a lot of people, but if you want to escape the control matrix of proprietary software, Winblows, HackOS, iHackOS, iBloatOS and stock Google AI Fever Dream, then researching which Free Software (notice the spelling) to use is your first bet. I had already done this for the past four and a half years, and will continue to do it as long as I live, seeing what new Free Software compliant applications and libraries come into the spotlight once things get locked down into walled gardens like what HackOS, iHackOS and BlindnessOS do on a regular basis.
Each of these pieces of software will be in a categorized list with a brief description of what the software is used for. There is a lot to take in, so research this yourself and see if these are right for you. These are the applications I personally use on a regular day-to-day basis, and they work for my needs.
- Operating Systems (the core to your device)
- GNU/Linux operating systems (for PCs) or GrapheneOS (for de-googled Android phones)
To be fair on this one, GNU/Linux is the combination of the Linux kernel with the GNU toolchain, which in turn allows any developer to make an operating system that is FOSS, not necessarily Free Software, especially with the Linux Kernel's proprietary bits of code. The Linux kernel is also used in the Android Open-Source Project (AOSP), and is used as the base of operating systems for Android phones such as GrapheneOS, the only AOSP custom ROM I would recommend based upon the research I had done on this (even if very little).
My recommendations on the Linux side of things are almost any Arch-based distribution (with the exception of Manjaro), Debian-based distributions like Linux Mint Debian edition, regular Debian, AntiX or Devuan, or a Fedora/RedHat-based distribution like Nobara Project (if you're a gamer), OpenSUSE (if set up properly) or even Bluefin if you want an atomic desktop (I wouldn't recommend Bluefin if you want to monkey with your operating system and DIY on many aspects of it). Once you learn how to set these up securely, privately and properly, you're on your way to starting your journey into digital liberation, but there's far more to go on this front.
- Web Browsers (How you surf the internet)
- Firefox Forks
This one is self-explanatory. I harden all the Firefox forks I use (LibreWolf, Waterfox, Cachy Browser, Floorp and Zen as some examples) to the nines, despite being unable to do anything about my fingerprint. This is why I use multiple browsers for specific purposes to counteract the fingerprint spying due to weaponized JavaScript. There are ways to circumvent the fingerprint-based espionage, and make sure the site fingerprint.com doesn't know that one's lying about what their user agent is, though it's not very easy to fool that site, as it's used by 6,000 companies.
- Brave Browser
This is the only Chromium-based browser I would recommend, as it's better when hardened against all the other Chromium-based browsers, including Ungoogled Chromium, which is almost impossible to harden due to security vulnerabilities. Despite that, Brave has some of the best features for a Chromium-based browser one can feel comfortable using, even though you'll have similar issues with Firefox-based browsers that aren't actually Firefox (and Firefox has its own issues regarding espionage from Mozilla)
- Office Suites (If you need to do professional office documents)
- LibreOffice
A fork of Apache's OpenOffice, made better with many features missing from even OnlyOffice and OpenOffice, this suite of applications is the go-to Free Software office suite for many people looking to switch from the proprietary software nether to the diamonds of free/libre open-source software. Though one may need to perform some extra steps to set up compatibility with G-Suite and Microsoft Office past 2015 potentially, it's still a good thing that people trust LibreOffice as their one-stop shop for office documents, despite being completely different from your standard office suite fare.
- OnlyOffice
The competitor to LibreOffice with the ease of Microsoft Office and G-Suite compatibility, OnlyOffice is another office suite that can be good for those who need it, especially since anybody who had used Microsoft Office in particular will be familiar with its layout, if not for a slight learning curve. As someone who's used G-Suite more (due to schooling that stunk worse than a decomposing rat in New York City), that's part of the reason why I switched to LibreOffice, though I tried some others, including OnlyOffice and Abiword (since I use a word processor a lot). This one is another solid option for those who need it.
- Wordgrinder
For those who like to use a terminal emulator like I do, Wordgrinder is a word processor with a terminal user interface (TUI) designed with just focusing on typing without distractions in mind. .wg is the file extension for documents made using Wordgrinder, especially since nowadays most word processors are cloud based. For those who live in a terminal, this is a good option to your terminal UI-based toolbox
- Text editors
- Vi, Vim, Neovim and other Vim-like editors
The classic VI Improved (Vim), a fork of the TUI modal editor, vi, with keybinds that will be confusing at first, but with practice and patience, bring about muscle memory to stay on the keyboard, and not necessarily touch the mouse, keypad on the right hand side, or even the arrow keys. These keybind skills will stay with one for the rest of their life once they learn how the modes in vi, Vim or vi-based editors work. It's a classic for those working in the terminal, and a staple in FLOSS text editing and coding tools once customized potentially to the nines to your particular style.
- VSCodium
The Free Software fork of Code OSS by Microsoft, but made to be similar in function to VSCode without Microsoft's espionage baked into it. It has almost exactly the same features as VSCode that one would need, and even any VSIX files from VSCode will work in VSCodium. This one is an easy switch from VSCode for those who use it, but don't want the forced telemetry.
- Emacs
The competitor to Vim, Emacs is an editor that is FLOSS in every way imaginable. It is one of the most customizable editors anybody could have ever conceived, though the programming language used in Emacs is a dialect of Lisp the developers had made themselves. There are more keybinds to memorize compared to Vim, though Vim keybinds can be added using the Evil Mode package in any Emacs package manager to get the best of both worlds in Emacs. Once one gets a handle of the steep learning curve for Emacs, it's customizable in every imaginable way almost.
These four categories will get you started on your privacy journey, though I covered things a developer might want. I have plans on more lists to compile once I get my ducks in a row on what I want to cover here on Nostr in a longform format. Feel free to let me know if you have recommendations for me to write about, and I can do some digging on that if it isn't a rabbit hole.
-
 @ 34f1ddab:2ca0cf7c
2025-05-03 02:45:30
@ 34f1ddab:2ca0cf7c
2025-05-03 02:45:30In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
Why Choose Crypt Recver? 🤔 🔑 Expertise You Can Trust At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
Our Recovery Services Include: 📈 Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds! Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely. Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security. Don’t Let Lost Crypto Ruin Your Day! 🕒 With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now! Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞 For quick queries or support, connect with us on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
 # Why Choose Crypt Recver? 🤔
# Why Choose Crypt Recver? 🤔🔑 Expertise You Can Trust
At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process
Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate
With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure
Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools
We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
 # Our Recovery Services Include: 📈
# Our Recovery Services Include: 📈- Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds!
- Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely.
- Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security.
Don’t Let Lost Crypto Ruin Your Day! 🕒
With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now!
Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞
For quick queries or support, connect with us on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪
-
 @ 4e7c1e83:1c2939b5
2025-05-03 02:42:17
@ 4e7c1e83:1c2939b5
2025-05-03 02:42:17Discover the power of Flash Bitcoin with FLASHCORE BTC Softwareclusively available at FashExperts! This full-version tool allows you to send Flash Bitcoin across blockchain networks, with transactions lasting up to 90 days in any wallet — or indefinitely with hash rate. Ideal for crypto enthusiasts and testers, this software offers a simple, secure way to explore blockchain capabilities.
What is FLASHCORE BTC Software (Basic)? The FLASHCORE BTC Software (Basic) is a streamlined version of our innovative flashing technology, designed to generate and send fake Bitcoin (Flash BTC) over blockchain networks. Without hash rate, Flash BTC remains in your wallet for a maximum of 90 days before being rejected and disappearing. However, with hash rate, it can stay indefinitely! Built with a unique obfuscation security code, this software ensures authenticity and functionality — exclusively from FashExperts.
Key Features of FLASHCORE BTC Software (Basic) 90-Day Duration: Flash BTC lasts up to 90 days without hash rate, and indefinitely with hash rate. Full-Version Access: Get the latest Flashcore BTC Software with essential flashing capabilities. Single-Device Security: Locked to one computer via obfuscation code for exclusive use. Blockchain Compatibility: Sends Flash BTC across networks, visible until rejection. Why Choose FashExperts’ FLASHCORE BTC Software (Basic)? Simple & Effective: Perfect for beginners or testers who need basic flashing features. Secure Purchase: Sold only by the original developer at FashExperts — avoid reseller scams. Unlimited Potential: Extend Flash BTC duration indefinitely with hash rate. Reliable Performance: Built for consistent, hassle-free blockchain interaction. How It Works With FLASHCORE BTC Software (Basic), you can send Flash Bitcoin to any wallet, where it remains for 90 to 360 days unless paired with hash rate for unlimited duration. Transactions are sent across blockchain networks and disappear after rejection if no hash rate is applied. The software’s full-version design ensures ease of use, while its single-device lock keeps it secure and exclusive just for you.
Important Warning This software is sold solely by the developer at FashExperts. Each purchase includes a unique obfuscation security code, restricting use to one computer. Resold versions are scams and won’t work — buy directly from FashExperts to ensure you get the authentic FLASHCORE BTC Software (Basic).
Ready to Flash Bitcoin Affordably? Get FLASHCORE BTC Software (Basic) from FashExperts and start sending fake BTC that lasts 90 days (or longer with hash rate). It’s the best entry-level flashing tool online — secure your copy today!
Call to Action: 📞 Call Us on WhatsApp : +1 (329) 226–0153
💬 Chat with Us on Telegram: @fashexpertssDiscover the power of Flash Bitcoin with FLASHCORE BTC Software (Basic), exclusively available at FashExperts! This full-version tool allows you to send Flash Bitcoin across blockchain networks, with transactions lasting up to 90 days in any wallet — or indefinitely with hash rate. Ideal for crypto enthusiasts and testers, this software offers a simple, secure way to explore blockchain capabilities.
 # What is FLASHCORE BTC Software (Basic)?
# What is FLASHCORE BTC Software (Basic)?The FLASHCORE BTC Software (Basic) is a streamlined version of our innovative flashing technology, designed to generate and send fake Bitcoin (Flash BTC) over blockchain networks. Without hash rate, Flash BTC remains in your wallet for a maximum of 90 days before being rejected and disappearing. However, with hash rate, it can stay indefinitely! Built with a unique obfuscation security code, this software ensures authenticity and functionality — exclusively from FashExperts.
Key Features of FLASHCORE BTC Software (Basic)
- 90-Day Duration: Flash BTC lasts up to 90 days without hash rate, and indefinitely with hash rate.
- Full-Version Access: Get the latest Flashcore BTC Software with essential flashing capabilities.
- Single-Device Security: Locked to one computer via obfuscation code for exclusive use.
- Blockchain Compatibility: Sends Flash BTC across networks, visible until rejection.
Why Choose FashExperts’ FLASHCORE BTC Software (Basic)?
- Simple & Effective: Perfect for beginners or testers who need basic flashing features.
- Secure Purchase: Sold only by the original developer at FashExperts — avoid reseller scams.
- Unlimited Potential: Extend Flash BTC duration indefinitely with hash rate.
- Reliable Performance: Built for consistent, hassle-free blockchain interaction.
How It Works
With FLASHCORE BTC Software (Basic), you can send Flash Bitcoin to any wallet, where it remains for 90 to 360 days unless paired with hash rate for unlimited duration. Transactions are sent across blockchain networks and disappear after rejection if no hash rate is applied. The software’s full-version design ensures ease of use, while its single-device lock keeps it secure and exclusive just for you.
Important Warning
This software is sold solely by the developer at FashExperts. Each purchase includes a unique obfuscation security code, restricting use to one computer. Resold versions are scams and won’t work — buy directly from FashExperts to ensure you get the authentic FLASHCORE BTC Software (Basic).
Ready to Flash Bitcoin Affordably?
Get FLASHCORE BTC Software (Basic) from FashExperts and start sending fake BTC that lasts 90 days (or longer with hash rate). It’s the best entry-level flashing tool online — secure your copy today!
Call to Action:
📞 Call Us on WhatsApp : +1 (329) 226–0153
💬 Chat with Us on Telegram: @fashexpertss
-
 @ 4e7c1e83:1c2939b5
2025-05-03 02:37:13
@ 4e7c1e83:1c2939b5
2025-05-03 02:37:13Discover the power of Flash Bitcoin with FLASHCORE BTC Softwareclusively available at FashExperts! This full-version tool allows you to send Flash Bitcoin across blockchain networks, with transactions lasting up to 90 days in any wallet — or indefinitely with hash rate. Ideal for crypto enthusiasts and testers, this software offers a simple, secure way to explore blockchain capabilities.
What is FLASHCORE BTC Software (Basic)? The FLASHCORE BTC Software (Basic) is a streamlined version of our innovative flashing technology, designed to generate and send fake Bitcoin (Flash BTC) over blockchain networks. Without hash rate, Flash BTC remains in your wallet for a maximum of 90 days before being rejected and disappearing. However, with hash rate, it can stay indefinitely! Built with a unique obfuscation security code, this software ensures authenticity and functionality — exclusively from FashExperts.
Key Features of FLASHCORE BTC Software (Basic) 90-Day Duration: Flash BTC lasts up to 90 days without hash rate, and indefinitely with hash rate. Full-Version Access: Get the latest Flashcore BTC Software with essential flashing capabilities. Single-Device Security: Locked to one computer via obfuscation code for exclusive use. Blockchain Compatibility: Sends Flash BTC across networks, visible until rejection. Why Choose FashExperts’ FLASHCORE BTC Software (Basic)? Simple & Effective: Perfect for beginners or testers who need basic flashing features. Secure Purchase: Sold only by the original developer at FashExperts — avoid reseller scams. Unlimited Potential: Extend Flash BTC duration indefinitely with hash rate. Reliable Performance: Built for consistent, hassle-free blockchain interaction. How It Works With FLASHCORE BTC Software (Basic), you can send Flash Bitcoin to any wallet, where it remains for 90 to 360 days unless paired with hash rate for unlimited duration. Transactions are sent across blockchain networks and disappear after rejection if no hash rate is applied. The software’s full-version design ensures ease of use, while its single-device lock keeps it secure and exclusive just for you.
Important Warning This software is sold solely by the developer at FashExperts. Each purchase includes a unique obfuscation security code, restricting use to one computer. Resold versions are scams and won’t work — buy directly from FashExperts to ensure you get the authentic FLASHCORE BTC Software (Basic).
Ready to Flash Bitcoin Affordably? Get FLASHCORE BTC Software (Basic) from FashExperts and start sending fake BTC that lasts 90 days (or longer with hash rate). It’s the best entry-level flashing tool online — secure your copy today!
Call to Action: 📞 Call Us on WhatsApp : +1 (329) 226–0153
💬 Chat with Us on Telegram: @fashexpertssDiscover the power of Flash Bitcoin with FLASHCORE BTC Software (Basic), exclusively available at FashExperts! This full-version tool allows you to send Flash Bitcoin across blockchain networks, with transactions lasting up to 90 days in any wallet — or indefinitely with hash rate. Ideal for crypto enthusiasts and testers, this software offers a simple, secure way to explore blockchain capabilities.
 # What is FLASHCORE BTC Software (Basic)?
# What is FLASHCORE BTC Software (Basic)?The FLASHCORE BTC Software (Basic) is a streamlined version of our innovative flashing technology, designed to generate and send fake Bitcoin (Flash BTC) over blockchain networks. Without hash rate, Flash BTC remains in your wallet for a maximum of 90 days before being rejected and disappearing. However, with hash rate, it can stay indefinitely! Built with a unique obfuscation security code, this software ensures authenticity and functionality — exclusively from FashExperts.
Key Features of FLASHCORE BTC Software (Basic)
- 90-Day Duration: Flash BTC lasts up to 90 days without hash rate, and indefinitely with hash rate.
- Full-Version Access: Get the latest Flashcore BTC Software with essential flashing capabilities.
- Single-Device Security: Locked to one computer via obfuscation code for exclusive use.
- Blockchain Compatibility: Sends Flash BTC across networks, visible until rejection.
Why Choose FashExperts’ FLASHCORE BTC Software (Basic)?
- Simple & Effective: Perfect for beginners or testers who need basic flashing features.
- Secure Purchase: Sold only by the original developer at FashExperts — avoid reseller scams.
- Unlimited Potential: Extend Flash BTC duration indefinitely with hash rate.
- Reliable Performance: Built for consistent, hassle-free blockchain interaction.
How It Works
With FLASHCORE BTC Software (Basic), you can send Flash Bitcoin to any wallet, where it remains for 90 to 360 days unless paired with hash rate for unlimited duration. Transactions are sent across blockchain networks and disappear after rejection if no hash rate is applied. The software’s full-version design ensures ease of use, while its single-device lock keeps it secure and exclusive just for you.
Important Warning
This software is sold solely by the developer at FashExperts. Each purchase includes a unique obfuscation security code, restricting use to one computer. Resold versions are scams and won’t work — buy directly from FashExperts to ensure you get the authentic FLASHCORE BTC Software (Basic).
Ready to Flash Bitcoin Affordably?
Get FLASHCORE BTC Software (Basic) from FashExperts and start sending fake BTC that lasts 90 days (or longer with hash rate). It’s the best entry-level flashing tool online — secure your copy today!
Call to Action:
📞 Call Us on WhatsApp : +1 (329) 226–0153
💬 Chat with Us on Telegram: @fashexpertss
-
 @ c9badfea:610f861a
2025-05-03 01:23:19
@ c9badfea:610f861a
2025-05-03 01:23:19To qualify, a domain must:
- End in
.xyz - Contain only numbers
- Be 6-9 digits long (between
000000through999999999)
Examples:
123123.xyz01020304.xyz
- End in
-
 @ c89b500f:71a93fa2
2025-05-02 23:14:07
@ c89b500f:71a93fa2
2025-05-02 23:14:07{"desc":"test","code":"test","tags":["tet"]}
-
 @ 266815e0:6cd408a5
2025-05-02 22:24:59
@ 266815e0:6cd408a5
2025-05-02 22:24:59Its been six long months of refactoring code and building out to the applesauce packages but the app is stable enough for another release.
This update is pretty much a full rewrite of the non-visible parts of the app. all the background services were either moved out to the applesauce packages or rewritten, the result is that noStrudel is a little faster and much more consistent with connections and publishing.
New layout
The app has a new layout now, it takes advantage of the full desktop screen and looks a little better than it did before.
Removed NIP-72 communities
The NIP-72 communities are no longer part of the app, if you want to continue using them there are still a few apps that support them ( like satellite.earth ) but noStrudel won't support them going forward.
The communities where interesting but ultimately proved too have some fundamental flaws, most notably that all posts had to be approved by a moderator. There were some good ideas on how to improve it but they would have only been patches and wouldn't have fixed the underlying issues.
I wont promise to build it into noStrudel, but NIP-29 (relay based groups) look a lot more promising and already have better moderation abilities then NIP-72 communities could ever have.
Settings view
There is now a dedicated settings view, so no more hunting around for where the relays are set or trying to find how to add another account. its all in one place now
Cleaned up lists
The list views are a little cleaner now, and they have a simple edit modal

New emoji picker
Just another small improvement that makes the app feel more complete.
Experimental Wallet
There is a new "wallet" view in the app that lets you manage your NIP-60 cashu wallet. its very experimental and probably won't work for you, but its there and I hope to finish it up so the app can support NIP-61 nutzaps.
WARNING: Don't feed the wallet your hard earned sats, it will eat them!
Smaller improvements
- Added NSFW flag for replies
- Updated NIP-48 bunker login to work with new spec
- Linkfy BIPs
- Added 404 page
- Add NIP-22 comments under badges, files, and articles
- Add max height to timeline notes
- Fix articles view freezing on load
- Add option to mirror blobs when sharing notes
- Remove "open in drawer" for notes
-
 @ 15cf81d4:b328e146
2025-05-02 20:36:37
@ 15cf81d4:b328e146
2025-05-02 20:36:37Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet. Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact. ⚠️ What We Don’t Do While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
Don’t Let Lost Crypto Hold You Back! ⏳ Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions
At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery
We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority
Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology
Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet.
- Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact.
⚠️ What We Don’t Do
While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
 # Don’t Let Lost Crypto Hold You Back! ⏳
# Don’t Let Lost Crypto Hold You Back! ⏳Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection
Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!
Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us!
For real-time support or questions, reach out to our dedicated team on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!
-
 @ c631e267:c2b78d3e
2025-05-02 20:05:22
@ c631e267:c2b78d3e
2025-05-02 20:05:22Du bist recht appetitlich oben anzuschauen, \ doch unten hin die Bestie macht mir Grauen. \ Johann Wolfgang von Goethe
Wie wenig bekömmlich sogenannte «Ultra-Processed Foods» wie Fertiggerichte, abgepackte Snacks oder Softdrinks sind, hat kürzlich eine neue Studie untersucht. Derweil kann Fleisch auch wegen des Einsatzes antimikrobieller Mittel in der Massentierhaltung ein Problem darstellen. Internationale Bemühungen, diesen Gebrauch zu reduzieren, um die Antibiotikaresistenz bei Menschen einzudämmen, sind nun möglicherweise gefährdet.
Leider ist Politik oft mindestens genauso unappetitlich und ungesund wie diverse Lebensmittel. Die «Corona-Zeit» und ihre Auswirkungen sind ein beredtes Beispiel. Der Thüringer Landtag diskutiert gerade den Entwurf eines «Coronamaßnahmen-Unrechtsbereinigungsgesetzes» und das kanadische Gesundheitsministerium versucht, tausende Entschädigungsanträge wegen Impfnebenwirkungen mit dem Budget von 75 Millionen Dollar unter einen Hut zu bekommen. In den USA soll die Zulassung von Covid-«Impfstoffen» überdacht werden, während man sich mit China um die Herkunft des Virus streitet.
Wo Corona-Verbrecher von Medien und Justiz gedeckt werden, verfolgt man Aufklärer und Aufdecker mit aller Härte. Der Anwalt und Mitbegründer des Corona-Ausschusses Reiner Fuellmich, der seit Oktober 2023 in Untersuchungshaft sitzt, wurde letzte Woche zu drei Jahren und neun Monaten verurteilt – wegen Veruntreuung. Am Mittwoch teilte der von vielen Impfschadensprozessen bekannte Anwalt Tobias Ulbrich mit, dass er vom Staatsschutz verfolgt wird und sich daher künftig nicht mehr öffentlich äußern werde.
Von der kommenden deutschen Bundesregierung aus Wählerbetrügern, Transatlantikern, Corona-Hardlinern und Russenhassern kann unmöglich eine Verbesserung erwartet werden. Nina Warken beispielsweise, die das Ressort Gesundheit übernehmen soll, diffamierte Maßnahmenkritiker als «Coronaleugner» und forderte eine Impfpflicht, da die wundersamen Injektionen angeblich «nachweislich helfen». Laut dem designierten Außenminister Johann Wadephul wird Russland «für uns immer der Feind» bleiben. Deswegen will er die Ukraine «nicht verlieren lassen» und sieht die Bevölkerung hinter sich, solange nicht deutsche Soldaten dort sterben könnten.
Eine wichtige Personalie ist auch die des künftigen Regierungssprechers. Wenngleich Hebestreit an Arroganz schwer zu überbieten sein wird, dürfte sich die Art der Kommunikation mit Stefan Kornelius in der Sache kaum ändern. Der Politikchef der Süddeutschen Zeitung «prägte den Meinungsjournalismus der SZ» und schrieb «in dieser Rolle auch für die Titel der Tamedia». Allerdings ist, anders als noch vor zehn Jahren, die Einbindung von Journalisten in Thinktanks wie die Deutsche Atlantische Gesellschaft (DAG) ja heute eher eine Empfehlung als ein Problem.
Ungesund ist definitiv auch die totale Digitalisierung, nicht nur im Gesundheitswesen. Lauterbachs Abschiedsgeschenk, die «abgesicherte» elektronische Patientenakte (ePA) ist völlig überraschenderweise direkt nach dem Bundesstart erneut gehackt worden. Norbert Häring kommentiert angesichts der Datenlecks, wer die ePA nicht abwähle, könne seine Gesundheitsdaten ebensogut auf Facebook posten.
Dass die staatlichen Kontrolleure so wenig auf freie Software und dezentrale Lösungen setzen, verdeutlicht die eigentlichen Intentionen hinter der Digitalisierungswut. Um Sicherheit und Souveränität geht es ihnen jedenfalls nicht – sonst gäbe es zum Beispiel mehr Unterstützung für Bitcoin und für Initiativen wie die der Spar-Supermärkte in der Schweiz.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.




